id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
197k
| cpes
listlengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2022-22321 | IBM MQ Appliance 9.2 CD and 9.2 LTS local messaging users stored with a password hash that provides insufficient protection. IBM X-Force ID: 218368. | [
"cpe:2.3:a:ibm:mq:*:*:*:*:lts:*:*:*",
"cpe:2.3:a:ibm:mq:*:*:*:*:continuous_delivery:*:*:*"
]
| null | null | 5.1 | null |
|
CVE-2024-41125 | Out-of-bounds read in SNMP when decoding a string in Contiki-NG | Contiki-NG is an open-source, cross-platform operating system for IoT devices. An out-of-bounds read of 1 byte can be triggered when sending a packet to a device running the Contiki-NG operating system with SNMP enabled. The SNMP module is disabled in the default Contiki-NG configuration. The vulnerability exists in the os/net/app-layer/snmp/snmp-ber.c module, where the function snmp_ber_decode_string_len_buffer decodes the string length from a received SNMP packet. In one place, one byte is read from the buffer, without checking that the buffer has another byte available, leading to a possible out-of-bounds read. The problem has been patched in Contiki-NG pull request #2936. It will be included in the next release of Contiki-NG. Users are advised to apply the patch manually or to wait for the next release. A workaround is to disable the SNMP module in the Contiki-NG build configuration. | [
"cpe:2.3:o:contiki-ng:contiki-ng:-:*:*:*:*:*:*:*"
]
| null | 8.4 | null | null |
GHSA-39rp-fmqv-8wr2 | A vulnerability, which was classified as critical, has been found in Wanhu ezOFFICE 11.1.0. This issue affects some unknown processing of the file defaultroot/platform/bpm/work_flow/operate/wf_printnum.jsp. The manipulation of the argument recordId leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier VDB-252281 was assigned to this vulnerability. | []
| null | 6.3 | null | null |
|
GHSA-5v46-5c9p-j4mg | redhat-certification does not properly restrict files that can be download through the /download page. A remote attacker may download any file accessible by the user running httpd. | []
| null | null | 7.5 | null |
|
CVE-2020-35797 | NETGEAR NMS300 devices before 1.6.0.27 are affected by command injection by an unauthenticated attacker. | [
"cpe:2.3:o:netgear:nms300_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:nms300:-:*:*:*:*:*:*:*"
]
| null | 9.8 | null | null |
|
CVE-2014-3596 | The getCN function in Apache Axis 1.4 and earlier does not properly verify that the server hostname matches a domain name in the subject's Common Name (CN) or subjectAltName field of the X.509 certificate, which allows man-in-the-middle attackers to spoof SSL servers via a certificate with a subject that specifies a common name in a field that is not the CN field. NOTE: this issue exists because of an incomplete fix for CVE-2012-5784. | [
"cpe:2.3:a:apache:axis:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.1:beta:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.1:rc1:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.1:rc2:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:alpha:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:beta1:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:beta2:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:beta3:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:rc1:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:rc2:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2:rc3:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:axis:1.3:*:*:*:*:*:*:*"
]
| null | null | null | 5.8 |
|
CVE-2020-24514 | Improper authentication in some Intel(R) RealSense(TM) IDs may allow an unauthenticated user to potentially enable escalation of privilege via physical access. | [
"cpe:2.3:o:intel:realsense_id_f450_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:realsense_id_f450:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:realsense_id_f455_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:realsense_id_f455:-:*:*:*:*:*:*:*"
]
| null | 6.8 | null | 4.6 |
|
GHSA-jp7c-8h7v-c764 | Multiple vulnerabilities exist in the Link Layer Discovery Protocol (LLDP) implementation for Cisco Small Business RV Series Routers. An unauthenticated, adjacent attacker could execute arbitrary code or cause an affected router to leak system memory or reload. A memory leak or device reload would cause a denial of service (DoS) condition on an affected device. For more information about these vulnerabilities, see the Details section of this advisory. Note: LLDP is a Layer 2 protocol. To exploit these vulnerabilities, an attacker must be in the same broadcast domain as the affected device (Layer 2 adjacent). | []
| null | 7.4 | null | null |
|
GHSA-wcm9-qmw5-8964 | Payments Director in IBM Financial Transaction Manager (FTM) for ACH Services, Check Services, and Corporate Payment Services (CPS) 3.0.0.x before fp0015 and 3.0.1.0 before iFix0002 allows remote authenticated users to conduct clickjacking attacks via a crafted web site. | []
| null | null | 5.7 | null |
|
CVE-2024-0077 | CVE | NVIDIA Virtual GPU Manager contains a vulnerability in the vGPU plugin, where it allows a guest OS to allocate resources for which the guest OS is not authorized. A successful exploit of this vulnerability may lead to code execution, denial of service, escalation of privileges, information disclosure, and data tampering. | [
"cpe:2.3:a:nvidia:virtual_gpu_manager:*:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
CVE-2018-0316 | A vulnerability in the Session Initiation Protocol (SIP) call-handling functionality of Cisco IP Phone 6800, 7800, and 8800 Series Phones with Multiplatform Firmware could allow an unauthenticated, remote attacker to cause an affected phone to reload unexpectedly, resulting in a temporary denial of service (DoS) condition. The vulnerability exists because the firmware of an affected phone incorrectly handles errors that could occur when an incoming phone call is not answered. An attacker could exploit this vulnerability by sending a set of maliciously crafted SIP packets to an affected phone. A successful exploit could allow the attacker to cause the affected phone to reload unexpectedly, resulting in a temporary DoS condition. This vulnerability affects Cisco IP Phone 6800, 7800, and 8800 Series Phones with Multiplatform Firmware if they are running a Multiplatform Firmware release prior to Release 11.1(2). Cisco Bug IDs: CSCvi24718. | [
"cpe:2.3:o:cisco:ip_phone_firmware:11.1\\(2\\):*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_6841:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_6851:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_7811:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_7821:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_7841:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_7861:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8811:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8841:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8845:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8851:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8861:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:ip_phone_8865:-:*:*:*:*:*:*:*"
]
| null | null | 7.5 | 7.8 |
|
GHSA-6539-3m2g-57x4 | libde265 v1.0.10 was discovered to contain a NULL pointer dereference in the put_weighted_pred_8_fallback function at fallback-motion.cc. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted input file. | []
| null | 5.5 | null | null |
|
CVE-2019-8553 | A memory corruption issue was addressed with improved validation. This issue is fixed in iOS 12.2, tvOS 12.2, watchOS 5.2. Clicking a malicious SMS link may lead to arbitrary code execution. | [
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:tvos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:watchos:*:*:*:*:*:*:*:*"
]
| null | 8.8 | null | 6.8 |
|
CVE-2024-38575 | wifi: brcmfmac: pcie: handle randbuf allocation failure | In the Linux kernel, the following vulnerability has been resolved:
wifi: brcmfmac: pcie: handle randbuf allocation failure
The kzalloc() in brcmf_pcie_download_fw_nvram() will return null
if the physical memory has run out. As a result, if we use
get_random_bytes() to generate random bytes in the randbuf, the
null pointer dereference bug will happen.
In order to prevent allocation failure, this patch adds a separate
function using buffer on kernel stack to generate random bytes in
the randbuf, which could prevent the kernel stack from overflow. | []
| null | 5.5 | null | null |
CVE-2018-11495 | OpenCart through 3.0.2.0 allows directory traversal in the editDownload function in admin\model\catalog\download.php via admin/index.php?route=catalog/download/edit, related to the download_id. For example, an attacker can download ../../config.php. | [
"cpe:2.3:a:opencart:opencart:*:*:*:*:*:*:*:*"
]
| null | null | 4.9 | 4 |
|
CVE-2025-1561 | AppPresser – Mobile App Framework <= 4.4.10 - Unauthenticated Stored Cross-Site Scripting | The AppPresser – Mobile App Framework plugin for WordPress is vulnerable to Stored Cross-Site Scripting via the 'title' parameter in all versions up to, and including, 4.4.10 due to insufficient input sanitization and output escaping. This makes it possible for unauthenticated attackers to inject arbitrary web scripts in pages when logging is enabled that will execute whenever a user accesses an injected page. | []
| null | 7.2 | null | null |
CVE-2002-0165 | LogWatch 2.5 allows local users to gain root privileges via a symlink attack, a different vulnerability than CVE-2002-0162. | [
"cpe:2.3:a:logwatch:logwatch:2.5:*:*:*:*:*:*:*"
]
| null | null | null | 7.2 |
|
CVE-2009-0923 | Unspecified vulnerability in Kerberos Incremental Propagation in Solaris 10 and OpenSolaris snv_01 through snv_110 allows remote attackers to cause a denial of service (loss of incremental propagation requests to slave KDC servers) via unknown vectors related to the master Key Distribution Center (KDC) server. | [
"cpe:2.3:o:sun:opensolaris:snv_01:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_02:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_03:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_04:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_05:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_06:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_07:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_08:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_09:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_10:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_11:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_12:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_13:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_14:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_15:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_16:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_17:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_18:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_19:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_20:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_21:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_22:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_23:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_24:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_25:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_26:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_27:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_28:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_29:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_30:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_31:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_32:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_33:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_34:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_35:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_36:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_37:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_38:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_39:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_40:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_41:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_42:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_43:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_44:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_45:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_46:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_47:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_48:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_49:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_50:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_51:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_52:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_53:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_54:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_55:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_56:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_57:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_58:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_59:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_60:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_61:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_62:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_63:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_64:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_65:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_66:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_67:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_68:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_69:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_70:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_71:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_72:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_73:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_74:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_75:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_76:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_77:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_78:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_79:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_80:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_81:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_82:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_83:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_84:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_85:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_86:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_87:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_88:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_89:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_90:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_91:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_92:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_93:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_94:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_95:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_96:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_97:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_98:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_99:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_100:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_101:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_102:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_103:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_104:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_105:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_106:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_107:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_108:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_109:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_110:*:sparc:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_01:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_02:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_03:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_04:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_05:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_06:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_07:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_08:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_09:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_10:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_11:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_12:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_13:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_14:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_15:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_16:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_17:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_18:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_19:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_20:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_21:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_22:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_23:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_24:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_25:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_26:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_27:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_28:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_29:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_30:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_31:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_32:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_33:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_34:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_35:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_36:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_37:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_38:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_39:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_40:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_41:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_42:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_43:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_44:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_45:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_46:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_47:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_48:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_49:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_50:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_51:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_52:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_53:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_54:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_55:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_56:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_57:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_58:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_59:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_60:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_61:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_62:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_63:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_64:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_65:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_66:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_67:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_68:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_69:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_70:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_71:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_72:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_73:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_74:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_75:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_76:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_77:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_78:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_79:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_80:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_81:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_82:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_83:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_84:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_85:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_86:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_87:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_88:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_89:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_90:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_91:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_92:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_93:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_94:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_95:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_96:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_97:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_98:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_99:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_100:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_101:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_102:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_103:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_104:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_105:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_106:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_107:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_108:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_109:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:opensolaris:snv_110:*:x86:*:*:*:*:*",
"cpe:2.3:o:sun:solaris:10.0:*:sparc:*:*:*:*:*"
]
| null | null | null | 7.8 |
|
GHSA-4cmp-m2j4-4727 | A SQL Injection vulnerability in Nagios XI 2024R1.2.2 allows a remote attacker to execute SQL injection via a crafted payload in the History Tab component. | []
| null | 6.5 | null | null |
|
GHSA-7m6v-q233-q9j9 | Minio Operator uses Kubernetes apiserver audience for AssumeRoleWithWebIdentity STS | Prevent token leakage / privilege escalationMinIO Operator STS: A Quick OverviewMinIO Operator STS is a native IAM Authentication for Kubernetes. MinIO Operator offers support for [Secure Tokens](https://min.io/docs/minio/linux/developers/security-token-service.html?ref=op-gh) (a.k.a. STS) which are a form of temporary access credentials for your MinIO Tenant. In essence, this allows you to control access to your MinIO tenant from your applications without having to explicitly create credentials for each application.For an application to gain access into a MinIO Tenant, a `PolicyBinding` resource is required, granting explicit access to the applications by validating the kubernetes [Service Account](https://kubernetes.io/docs/concepts/security/service-accounts/) authorization token.The service account token is validated as follows:The application calls `AssumeRoleWithWebIdentity` API MinIO Operator provides.MinIO Operator verifies the Service Account token agains the kubernetes API using the [TokenReview API](https://kubernetes.io/docs/reference/kubernetes-api/authentication-resources/token-review-v1/)MinIO Operator reviews the TokenReviewResult confirms if the token is a valid token and the user is authenticated.MinIO Operator validates the service account has `PolicyBinding` in the Tenant namespace.MinIO Operator gets the PolicyBindingMinIO Operator calls the AssumeRole API in the MinIO TenantMinIO Operator obtains temporary credentials (STS).MinIO Operator return temporary Credentials to the requester application.The applicaiton consumes Object Storage using the temporary credentials.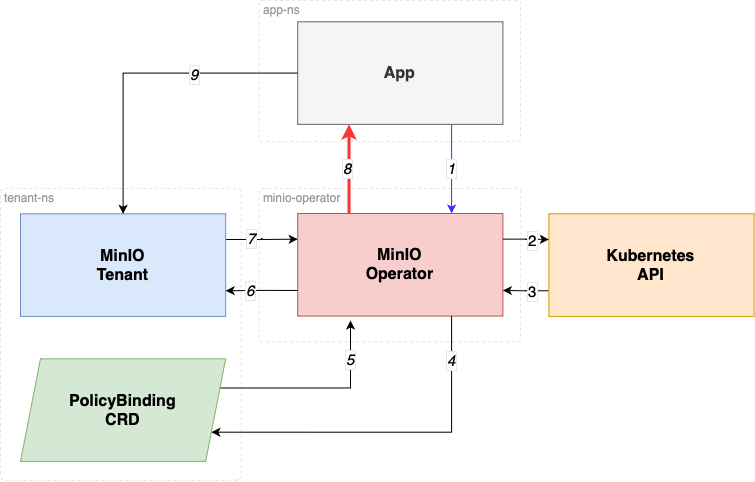Understanding Audiences in Kubernetes TokenReviewIn step 2 the `TokenReview` API call attempts to authenticate a token to a known user, TokenReviewStatus is the result of the `TokenReview` request.Audiences are audience identifiers chosen by the authenticator that are compatible with both the TokenReview and token.An identifier is any identifier in the intersection of the TokenReviewSpec audiences and the token's audiences.A client of the TokenReview API that sets the `spec.audiences` field should validate that a compatible audience identifier is returned in the status.audiences field to ensure that the TokenReview server is audience aware.
**If no audiences are provided, the audience will default to the audience of the Kubernetes apiserver.**Solution: Properly Issuing and Using Audience-Specific ServiceAccount TokensThis PR ensures the Operator STS service request the Service Account JWT to belong to the audience`sts.min.io` in the TokenReviewRequest.This PR ensures the examples and documentation provided guides in how to create Service accounts with "disabled auto mount services tokens", by doing this the pods where the service account is used no longer mounts the service account automatically in the path `/var/run/secrets/kubernetes.io/serviceaccount`.For illustrative purposes, here is how you disable auto mount of service account tokens at the service account level.Additionally documentation and examples show how to request an audience-specific token with audience `sts.min.io`, by asking for an ServiceAccount Token to be audience specific.For illustrative purposes, here is how you request an audience specific service account token in a pod:How this prevent a token leakage or possible privilege escalation?.This setup prevents privilege escalation and token leakage by combining multiple defense-in-depth mechanisms that ensure service account tokens are only usable by their intended audience, short-lived, and not exposed unnecessarily.Audience restriction (aud: sts.min.io)**Problem**: A ServiceAccount token is often valid for multiple audiences (e.g., the default Kubernetes API server). Without scoping, it can be replayed to other internal systems, which may unintentionally trust it.**Mitigation**: Now we enforce that tokens are explicitly created for the sts.min.io audience using the Kubernetes TokenRequest API, and the MinIO Operator:Sends audiences: ["sts.min.io"] in the TokenReview.Verifies that the token was issued with this audience via status.audiences.**Effect**: Even if a token is stolen or misused, it will fail validation if used outside the sts.min.io STS endpoint (e.g., reused at the API server or another service).Token Leakage MitigationDisabling auto-mounted service account tokens**Problem**: By default, Kubernetes mounts long-lived service account tokens into all pods at `/var/run/secrets/kubernetes.io/serviceaccount`, making them vulnerable to theft if the container is compromised.**Mitigation**: No we guide users to set `automountServiceAccountToken: false` in their ServiceAccount definitions.**Effect**: Prevents automatic token injection into all pods, reducing the attack surface.Requesting short-lived, audience-specific tokens via serviceAccountToken projection**Problem**: Long-lived tokens can be reused indefinitely if leaked.
**Mitigation**: You use projected service account tokens with:audience: "sts.min.io"A short expirationSeconds (e.g., 86400 = 24 hours, or even shorter)**Effect**: Even if the token is leaked, it is:Only usable for sts.min.ioShort-lived and expires soonRevocable by disabling the SA or STS accessAffected Versions and Risk AssessmentThe issue affects MinIO Operator versions v5.0.x and above, when the STS feature was first introduced.In v5.0.x, STS was introduced as v1alpha1 and disabled by default. It required explicit API calls to be used.In v6.0.x, STS graduated to v1beta1 and was enabled by default, but still requires explicit calls to the STS API for token usage.The risk is minimal, as:The Operator does not persist the token (neither in memory nor on disk).The Operator only uses the token for a single validation and does not reuse it for any other purpose.ReleaseFix released in [v7.1.0](https://github.com/minio/operator/releases/tag/v7.1.0) | []
| 6.9 | null | null | null |
CVE-2024-10536 | FancyPost – Best Ultimate Post Block, Post Grid, Layouts, Carousel, Slider For Gutenberg & Elementor <= 6.0.0 - Missing Authorization to Authenticated (Subscriber+) Shortcode Export | The FancyPost – Best Ultimate Post Block, Post Grid, Layouts, Carousel, Slider For Gutenberg & Elementor plugin for WordPress is vulnerable to unauthorized access of data due to a missing capability check on the handle_block_shortcode_export() function in all versions up to, and including, 6.0.0. This makes it possible for authenticated attackers, with Subscriber-level access and above, to export shortcodes. | []
| null | 4.3 | null | null |
CVE-2010-1157 | Apache Tomcat 5.5.0 through 5.5.29 and 6.0.0 through 6.0.26 might allow remote attackers to discover the server's hostname or IP address by sending a request for a resource that requires (1) BASIC or (2) DIGEST authentication, and then reading the realm field in the WWW-Authenticate header in the reply. | [
"cpe:2.3:a:apache:tomcat:5.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.3:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.4:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.5:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.6:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.7:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.8:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.9:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.10:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.11:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.12:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.13:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.14:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.15:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.16:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.17:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.18:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.19:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.20:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.21:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.22:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.23:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.24:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.25:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.26:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.27:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.28:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:5.5.29:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.8:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.9:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.10:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.11:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.12:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.13:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.14:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.15:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.16:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.17:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.18:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.19:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.20:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.24:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat:6.0.26:*:*:*:*:*:*:*"
]
| null | null | null | 2.6 |
|
GHSA-hcgg-293c-27px | The NonManagedConnectionFactory in JBoss Enterprise Application Platform (EAP) 5.1.2 and 5.2.0, Web Platform (EWP) 5.1.2 and 5.2.0, and BRMS Platform before 5.3.1 logs the username and password in cleartext when an exception is thrown, which allows local users to obtain sensitive information by reading the log file. | []
| null | null | null | null |
|
CVE-2019-17338 | TIBCO Patterns - Search Exposes Cross Site Scripting Vulnerabilities | The user interface component of TIBCO Software Inc.'s TIBCO Patterns - Search contains multiple vulnerabilities that theoretically allow authenticated users to perform persistent cross-site scripting (XSS) attacks. Affected releases are TIBCO Software Inc.'s TIBCO Patterns - Search: versions 5.4.0 and below. | [
"cpe:2.3:a:tibco:patterns_-_search:*:*:*:*:*:*:*:*"
]
| null | null | 7.3 | null |
GHSA-4crj-f4f5-7mhf | A vulnerability has been identified in SINEMA Remote Connect Server (All versions < V3.2 HF1). Affected applications are vulnerable to command injection due to missing server side input sanitation when loading VxLAN configurations. This could allow an authenticated attacker to execute arbitrary code with root privileges. | []
| 8.7 | 8.8 | null | null |
|
GHSA-373c-56rw-r5q5 | Race condition occurs while calling user space ioctl from two different threads can results to use after free issue in video in Snapdragon Auto, Snapdragon Compute, Snapdragon Connectivity, Snapdragon Industrial IOT, Snapdragon Mobile, Snapdragon Wearables | []
| null | null | null | null |
|
CVE-2012-2360 | Cross-site scripting (XSS) vulnerability in the Wiki subsystem in Moodle 2.0.x before 2.0.9, 2.1.x before 2.1.6, and 2.2.x before 2.2.3 allows remote authenticated users to inject arbitrary web script or HTML via a crafted string that is inserted into a page title. | [
"cpe:2.3:a:moodle:moodle:2.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.0.8:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:moodle:moodle:2.2.2:*:*:*:*:*:*:*"
]
| null | null | null | 3.5 |
|
CVE-2024-47795 | Uncontrolled search path for some Intel(R) oneAPI DPC++/C++ Compiler software before version 2025.0.0 may allow an authenticated user to potentially enable escalation of privilege via local access. | []
| 5.4 | 6.7 | null | null |
|
CVE-2025-41646 | RevPi Webstatus application is vulnerable to an authentication bypass | An unauthorized remote attacker can bypass the authentication of the affected software package by misusing an incorrect type conversion. This leads to full compromise of the device | []
| null | 9.8 | null | null |
CVE-2017-11127 | Bolt CMS 3.2.14 allows stored XSS by uploading an SVG document with a "Content-Type: image/svg+xml" header. | [
"cpe:2.3:a:bolt:bolt_cms:3.2.14:*:*:*:*:*:*:*"
]
| null | null | 5.4 | 3.5 |
|
ICSA-16-021-01 | CAREL PlantVisor Enhanced Authentication Bypass Vulnerability | CAREL PlantVisorEnhanced allows remote attackers to bypass intended access restrictions via a direct file request. | []
| null | null | 7.5 | null |
CVE-2021-41849 | An issue was discovered in Luna Simo PPR1.180610.011/202001031830. It sends the following Personally Identifiable Information (PII) in plaintext using HTTP to servers located in China: user's list of installed apps and device International Mobile Equipment Identity (IMEI). This PII is transmitted to log.skyroam.com.cn using HTTP, independent of whether the user uses the Simo software. | [
"cpe:2.3:o:bluproducts:g90_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:bluproducts:g90:-:*:*:*:*:*:*:*",
"cpe:2.3:o:bluproducts:g9_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:bluproducts:g9:-:*:*:*:*:*:*:*",
"cpe:2.3:o:wikomobile:tommy_3_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:wikomobile:tommy_3:-:*:*:*:*:*:*:*",
"cpe:2.3:o:wikomobile:tommy_3_plus_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:wikomobile:tommy_3_plus:-:*:*:*:*:*:*:*",
"cpe:2.3:o:luna:simo_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:luna:simo:-:*:*:*:*:*:*:*"
]
| null | 5.5 | null | 2.1 |
|
CVE-2021-41220 | Use after free in `CollectiveReduceV2` | TensorFlow is an open source platform for machine learning. In affected versions the async implementation of `CollectiveReduceV2` suffers from a memory leak and a use after free. This occurs due to the asynchronous computation and the fact that objects that have been `std::move()`d from are still accessed. The fix will be included in TensorFlow 2.7.0. We will also cherrypick this commit on TensorFlow 2.6.1, as this version is the only one that is also affected. | [
"cpe:2.3:a:google:tensorflow:*:*:*:*:*:*:*:*",
"cpe:2.3:a:google:tensorflow:2.7.0:rc0:*:*:*:*:*:*",
"cpe:2.3:a:google:tensorflow:2.7.0:rc1:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
ICSA-24-193-14 | Siemens SIPROTEC | The affected devices are supporting weak ciphers on several ports (443/tcp for web, 4443/tcp for DIGSI 5 and configurable port for syslog over TLS).
This could allow an unauthorized attacker in a man-in-the-middle position to decrypt any data passed over to and from those ports. | []
| null | 5.9 | null | null |
GHSA-74x9-89m7-944x | A tampering vulnerability exists when Git for Visual Studio improperly handles virtual drive paths, aka 'Git for Visual Studio Tampering Vulnerability'. | []
| null | null | null | null |
|
GHSA-c6qp-cg3c-4g5h | Windows Remote Access Elevation of Privilege Vulnerability This CVE ID is unique from CVE-2020-17025, CVE-2020-17026, CVE-2020-17027, CVE-2020-17028, CVE-2020-17031, CVE-2020-17033, CVE-2020-17034, CVE-2020-17043, CVE-2020-17044, CVE-2020-17055. | []
| null | 7.8 | null | null |
|
CVE-2024-43861 | net: usb: qmi_wwan: fix memory leak for not ip packets | In the Linux kernel, the following vulnerability has been resolved:
net: usb: qmi_wwan: fix memory leak for not ip packets
Free the unused skb when not ip packets arrive. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.11:rc2:*:*:*:*:*:*"
]
| null | 5.5 | null | null |
CVE-2011-4754 | Multiple cross-site scripting (XSS) vulnerabilities in Parallels Plesk Small Business Panel 10.2.0 allow remote attackers to inject arbitrary web script or HTML via crafted input to a PHP script, as demonstrated by smb/app/available/id/apscatalog/ and certain other files. | [
"cpe:2.3:a:parallels:parallels_plesk_small_business_panel:10.2.0:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
GHSA-6x8q-mcvj-v6v9 | A vulnerability classified as critical has been found in RainyGao DocSys 2.02.37. This affects an unknown part of the component ZIP File Decompression Handler. The manipulation leads to path traversal: '../filedir'. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-215271. | []
| null | 7.2 | null | null |
|
GHSA-8p3w-97vg-66h2 | CRLF injection vulnerability in IBM WebSphere Application Server (WAS) 7.0 before 7.0.0.43, 8.0 before 8.0.0.13, 8.5 Full before 8.5.5.10, and 8.5 Liberty before Liberty Fix Pack 16.0.0.2 allows remote attackers to inject arbitrary HTTP headers and conduct HTTP response splitting attacks via a crafted URL. | []
| null | null | 6.1 | null |
|
CVE-2007-1911 | Multiple unspecified vulnerabilities in Microsoft Word 2007 allow remote attackers to cause a denial of service (CPU consumption) via crafted documents, as demonstrated by (1) file798-1.doc and (2) file613-1.doc, possibly related to a buffer overflow. | [
"cpe:2.3:a:microsoft:word:2007:*:*:*:*:*:*:*"
]
| null | null | null | 7.1 |
|
CVE-2006-6745 | Multiple unspecified vulnerabilities in Sun Java Development Kit (JDK) and Java Runtime Environment (JRE) 5.0 Update 7 and earlier, and Java System Development Kit (SDK) and JRE 1.4.2_12 and earlier 1.4.x versions, allow attackers to develop Java applets or applications that are able to gain privileges, related to serialization in JRE. | [
"cpe:2.3:a:sun:j2se:1.4:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.1:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_01:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_02:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_03:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_04:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_05:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_06:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_07:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_08:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_09:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_10:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_11:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:1.4.2_12:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update1:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update2:*:sdk:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update3:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update4:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update5:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update6:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:j2se:5.0_update7:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_1:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_2:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_3:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_4:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_5:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_6:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_7:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_8:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_9:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_10:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_11:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_12:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.4.2_13:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update1:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update2:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update3:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update4:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update5:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update6:*:*:*:*:*:*",
"cpe:2.3:a:sun:jre:1.5.0:update7:*:*:*:*:*:*"
]
| null | null | null | 9.3 |
|
GHSA-62jr-gjr6-pf9v | Smarty before 3.0.0 RC3 does not properly handle an on value of the asp_tags option in the php.ini file, which has unspecified impact and remote attack vectors. | []
| null | null | null | null |
|
RHSA-2016:0561 | Red Hat Security Advisory: Red Hat Enterprise Linux 5 One-Year Retirement Notice | This is the One-Year notification for the retirement of Red Hat Enterprise
Linux 5. This notification applies only to those customers subscribed to
the channel for Red Hat Enterprise Linux 5.
[Updated 19 April 2016]
This advisory has been updated with a corrected list of architectures
supported with the RHEL 5 Extended Life Cycle Support (ELS) Add-On. | [
"cpe:/o:redhat:enterprise_linux:5::client",
"cpe:/o:redhat:enterprise_linux:5::server"
]
| null | null | null | null |
CVE-2022-45347 | Apache ShardingSphere-Proxy: MySQL authentication bypass | Apache ShardingSphere-Proxy prior to 5.3.0 when using MySQL as database backend didn't cleanup the database session completely after client authentication failed, which allowed an attacker to execute normal commands by constructing a special MySQL client. This vulnerability has been fixed in Apache ShardingSphere 5.3.0. | [
"cpe:2.3:a:apache:shardingsphere:*:*:*:*:*:*:*:*"
]
| null | 9.8 | null | null |
RHSA-2007:0873 | Red Hat Security Advisory: star security update | star directory traversal vulnerability | [
"cpe:/o:redhat:enterprise_linux:3::as",
"cpe:/o:redhat:enterprise_linux:3::desktop",
"cpe:/o:redhat:enterprise_linux:3::es",
"cpe:/o:redhat:enterprise_linux:3::ws",
"cpe:/o:redhat:enterprise_linux:4::as",
"cpe:/o:redhat:enterprise_linux:4::desktop",
"cpe:/o:redhat:enterprise_linux:4::es",
"cpe:/o:redhat:enterprise_linux:4::ws",
"cpe:/o:redhat:enterprise_linux:5::client",
"cpe:/o:redhat:enterprise_linux:5::server"
]
| null | null | null | null |
GHSA-jjw8-r4h6-8x47 | In the Linux kernel, the following vulnerability has been resolved:drm/amd/display: Send DTBCLK disable message on first commit[Why]
Previous patch to allow DTBCLK disable didn't address boot case. Driver
thinks DTBCLK is disabled by default, so we don't send disable message to
PMFW. DTBCLK is then enabled at idle desktop on boot, burning power.[How]
Set dtbclk_en to true on boot so that disable message is sent during first
commit. | []
| null | null | null | null |
|
CVE-2010-3488 | Directory traversal vulnerability in QuickShare 1.0 allows remote attackers to read arbitrary files via a ... (triple dot) in the URL. | [
"cpe:2.3:a:houbysoft:quickshare:1.0:*:*:*:*:*:*:*"
]
| null | null | null | 5 |
|
GHSA-w7cr-2ppg-3833 | Memory corruption in WLAN due to use after free | []
| null | 7.8 | null | null |
|
CVE-2021-41544 | A vulnerability has been identified in Siemens Software Center (All versions < V3.0). A DLL Hijacking vulnerability could allow a local attacker to execute code with elevated privileges by placing a malicious DLL in one of the directories on the DLL search path. | [
"cpe:2.3:a:siemens:software_center:*:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
|
GHSA-7r7x-g5gw-9rgv | The ConvolveHorizontally function in Skia, as used in Mozilla Firefox before 31.0, Firefox ESR 24.x before 24.7, and Thunderbird before 24.7, does not properly handle the discarding of image data during function execution, which allows remote attackers to execute arbitrary code by triggering prolonged image scaling, as demonstrated by scaling of a high-quality image. | []
| null | null | null | null |
|
GHSA-rqwm-chmc-r5vg | Microsoft Edge (Chromium-based) Spoofing Vulnerability | []
| null | 6.1 | null | null |
|
GHSA-fmhc-m7qr-cvhx | genfilt in the AIX Packet Filtering Module does not properly filter traffic to destination ports greater than 32767. | []
| null | null | null | null |
|
RHSA-2007:0559 | Red Hat Security Advisory: cman security update | possible buffer overflow could cause local DoS by crashing cman | [
"cpe:/o:redhat:enterprise_linux:5::client",
"cpe:/o:redhat:enterprise_linux:5::client_workstation",
"cpe:/o:redhat:enterprise_linux:5::server"
]
| null | null | null | null |
CVE-2024-38061 | DCOM Remote Cross-Session Activation Elevation of Privilege Vulnerability | DCOM Remote Cross-Session Activation Elevation of Privilege Vulnerability | [
"cpe:2.3:o:microsoft:windows_10_1507:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10_1607:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10_1809:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10_21h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10_22h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_21h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_22h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_11_23h2:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:sp1:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2012:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2022:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2022_23h2:*:*:*:*:*:*:*:*"
]
| null | 7.5 | null | null |
GHSA-q8hx-4ph9-479g | PHP remote file inclusion vulnerability in include/html/config.php in ModernGigabyte ModernBill 1.6 allows remote attackers to execute arbitrary PHP code via a URL in the DIR parameter. | []
| null | null | null | null |
|
CVE-2014-5461 | Buffer overflow in the vararg functions in ldo.c in Lua 5.1 through 5.2.x before 5.2.3 allows context-dependent attackers to cause a denial of service (crash) via a small number of arguments to a function with a large number of fixed arguments. | [
"cpe:2.3:o:opensuse:opensuse:12.3:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:opensuse:13.1:*:*:*:*:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:12.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:canonical:ubuntu_linux:14.04:*:*:*:lts:*:*:*",
"cpe:2.3:o:debian:debian_linux:7.0:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lua:lua:5.2.2:*:*:*:*:*:*:*",
"cpe:2.3:o:mageia:mageia:3.0:*:*:*:*:*:*:*",
"cpe:2.3:o:mageia:mageia:4.0:*:*:*:*:*:*:*"
]
| null | null | null | 5 |
|
CVE-1999-0376 | Local users in Windows NT can obtain administrator privileges by changing the KnownDLLs list to reference malicious programs. | [
"cpe:2.3:o:microsoft:windows_nt:3.5.1:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_nt:4.0:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_nt:4.0:sp1:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_nt:4.0:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_nt:4.0:sp3:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_nt:4.0:sp4:*:*:*:*:*:*"
]
| null | null | null | 4.6 |
|
GHSA-mhx2-29jj-rxfr | A race condition was addressed with improved state handling. This issue is fixed in iOS 14.7, macOS Big Sur 11.5. Opening a maliciously crafted PDF file may lead to an unexpected application termination or arbitrary code execution. | []
| null | null | null | null |
|
CVE-2021-27040 | A maliciously crafted DWG file can be forced to read beyond allocated boundaries when parsing the DWG file. This vulnerability can be exploited to execute arbitrary code. | [
"cpe:2.3:a:autodesk:advance_steel:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_architecture:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_electrical:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_lt:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_map_3d:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_mechanical:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_mep:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:autocad_plant_3d:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:civil_3d:*:*:*:*:*:*:*:*",
"cpe:2.3:a:autodesk:dwg_trueview:*:*:*:*:*:*:*:*",
"cpe:2.3:a:iconics:genesis64:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mitsubishielectric:mc_works64:*:*:*:*:*:*:*:*"
]
| null | 3.3 | null | 4.3 |
|
GHSA-3v49-294p-4c7w | The application is vulnerable to an unauthenticated parameter
manipulation that allows an attacker to set the credentials to blank
giving her access to the admin panel. Also vulnerable to account
takeover and arbitrary password change. | []
| null | 7.5 | null | null |
|
GHSA-rp7w-4xxf-cq5w | In Omron PLC CJ series, all versions, and Omron PLC CS series, all versions, an attacker could monitor traffic between the PLC and the controller and replay requests that could result in the opening and closing of industrial valves. | []
| null | null | null | null |
|
CVE-2006-5457 | Multiple cross-site scripting (XSS) vulnerabilities in the registration form in Casinosoft Casino Script (Masvet) 3.2 allow remote attackers to inject arbitrary web script or HTML via the (1) name or (2) surname field. | [
"cpe:2.3:a:casinosoft:casino_script:3.2:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2020-20289 | Sql injection vulnerability in the yccms 3.3 project. The no_top function's improper judgment of the request parameters, triggers a sql injection vulnerability. | [
"cpe:2.3:a:yccms:yccms:3.3:*:*:*:*:*:*:*"
]
| null | 9.8 | null | 7.5 |
|
GHSA-vpmj-9973-3qg4 | WordPress 3.4.2 does not invalidate a wordpress_sec session cookie upon an administrator's logout action, which makes it easier for remote attackers to discover valid session identifiers via a brute-force attack, or modify data via a replay attack. | []
| null | null | null | null |
|
GHSA-4xpq-qfh7-r9h2 | The hardware emulation in the of_dpa_cmd_add_l2_flood of rocker device model in QEMU, as used in 7.0.0 and earlier, allows remote attackers to crash the host qemu and potentially execute code on the host via execute a malformed program in the guest OS. | []
| null | 10 | null | null |
|
GHSA-pg65-86gh-q227 | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Survey Maker team Survey Maker allows Stored XSS. This issue affects Survey Maker: from n/a through 5.1.3.5. | []
| null | 5.9 | null | null |
|
GHSA-hph5-qh8m-x8v8 | Mozilla Firefox 2.x before 2.0.0.19 allows remote attackers to run arbitrary JavaScript with chrome privileges via vectors related to the feed preview, a different vulnerability than CVE-2008-3836. | []
| null | null | null | null |
|
GHSA-998j-j6v9-5846 | Apache Solr UpdateRequestHandler for XML resolves XML External Entities | The UpdateRequestHandler for XML in Apache Solr before 4.1 allows remote attackers to have an unspecified impact via XML data containing an external entity declaration in conjunction with an entity reference, related to an XML External Entity (XXE) issue. | []
| null | null | null | null |
RHSA-2016:1551 | Red Hat Security Advisory: firefox security update | Mozilla: Favicon network connection persists when page is closed (MFSA 2016-62) Mozilla: Miscellaneous memory safety hazards (rv:45.3) (MFSA 2016-62) Mozilla: Buffer overflow in ClearKey Content Decryption Module (CDM) during video playback (MFSA 2016-77) Mozilla: Buffer overflow rendering SVG with bidirectional content (MFSA 2016-64) Mozilla: Stack underflow during 2D graphics rendering (MFSA 2016-67) Mozilla: Use-after-free when using alt key and toplevel menus (MFSA 2016-70) Mozilla: Use-after-free in DTLS during WebRTC session shutdown (MFSA 2016-72) Mozilla: Use-after-free in service workers with nested sync events (MFSA 2016-73) Mozilla: Scripts on marquee tag can execute in sandboxed iframes (MFSA 2016-76) Mozilla: Type confusion in display transformation (MFSA 2016-78) Mozilla: Use-after-free when applying SVG effects (MFSA 2016-79) Mozilla: Same-origin policy violation using local HTML file and saved shortcut file (MFSA 2016-80) | [
"cpe:/o:redhat:enterprise_linux:5::client",
"cpe:/o:redhat:enterprise_linux:5::server",
"cpe:/o:redhat:enterprise_linux:6::client",
"cpe:/o:redhat:enterprise_linux:6::computenode",
"cpe:/o:redhat:enterprise_linux:6::server",
"cpe:/o:redhat:enterprise_linux:6::workstation",
"cpe:/o:redhat:enterprise_linux:7::client",
"cpe:/o:redhat:enterprise_linux:7::server",
"cpe:/o:redhat:enterprise_linux:7::workstation"
]
| null | null | 5.3 | null |
CVE-2016-10414 | In Android before 2018-04-05 or earlier security patch level on Qualcomm Small Cell SoC, Snapdragon Automobile, Snapdragon Mobile, and Snapdragon Wear FSM9055, IPQ4019, MDM9206, MDM9607, MDM9625, MDM9635M, MDM9640, MDM9645, MDM9650, MDM9655, MSM8909W, SD 210/SD 212/SD 205, SD 400, SD 410/12, SD 425, SD 430, SD 450, SD 615/16/SD 415, SD 617, SD 625, SD 650/52, SD 800, SD 808, SD 810, SD 820, SD 820A, SD 835, SD 845, SD 850, and SDX20, when a hash is passed with zero datalength, the code returns an error, even though zero data length is valid. | [
"cpe:2.3:o:qualcomm:mdm9206_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9206:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9607_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9607:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9625_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9625:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9635m_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9635m:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9640_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9640:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9645_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9645:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9650_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9650:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:mdm9655_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:mdm9655:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:msm8909w_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:msm8909w:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_210_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_210:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_212_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_212:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_205_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_205:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_400_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_400:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_410_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_410:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_412_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_412:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_425_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_425:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_430_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_430:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_450_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_450:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_615_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_615:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_616_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_616:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_415_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_415:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_617_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_617:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_625_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_625:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_650_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_650:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_652_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_652:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_800_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_800:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_808_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_808:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_810_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_810:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_820_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_820:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_835_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_835:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_845_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_845:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sdx20_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sdx20:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_850_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_850:-:*:*:*:*:*:*:*",
"cpe:2.3:o:qualcomm:sd_820a_firmware:-:*:*:*:*:*:*:*",
"cpe:2.3:h:qualcomm:sd_820a:-:*:*:*:*:*:*:*"
]
| null | null | 9.8 | 10 |
|
CVE-2017-9489 | The Comcast firmware on Cisco DPC3939B (firmware version dpc3939b-v303r204217-150321a-CMCST) devices allows configuration changes via CSRF. | [
"cpe:2.3:o:cisco:dpc3939b_firmware:dpc3939b-v303r204217-150321a-cmcst:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:dpc3939b:-:*:*:*:*:*:*:*",
"cpe:2.3:o:commscope:arris_tg1682g_firmware:10.0.132.sip.pc20.ct:*:*:*:*:*:*:*",
"cpe:2.3:o:commscope:arris_tg1682g_firmware:tg1682_2.2p7s2_prod_sey:*:*:*:*:*:*:*",
"cpe:2.3:h:commscope:arris_tg1682g:-:*:*:*:*:*:*:*"
]
| null | 8.8 | null | 6.8 |
|
GHSA-j5mc-p7q3-p89m | Dell ECS versions prior to 3.8.1.5/ ObjectScale version 4.0.0.0 contains an Insertion of Sensitive Information into Log File vulnerability. A low privileged attacker with local access could potentially exploit this vulnerability, leading to Information disclosure. | []
| null | 5.5 | null | null |
|
CVE-2024-52601 | iTop portal Insecure Direct Object Reference vulnerability | iTop is an web based IT Service Management tool. Prior to versions 2.7.12, 3.1.3, and 3.2.1, anyone with an account having portal access can have read access to objects they're not allowed to see by querying an unprotected route. Versions 2.7.12, 3.1.3, and 3.2.1 contain a fix for the issue. | []
| null | 6.5 | null | null |
GHSA-q7gh-gv4p-hr7v | PrestaShop 1.6.x before 1.6.1.23 and 1.7.x before 1.7.4.4 on Windows allows remote attackers to write to arbitrary image files. | []
| null | null | 7.5 | null |
|
GHSA-q6h5-p9q5-mw7q | In all Android releases from CAF using the Linux kernel, the Hypervisor API could be misused to bypass authentication. | []
| null | null | 7.8 | null |
|
GHSA-99cg-2qhp-jx7g | Basic B2B Script allows SQL Injection via the product_view1.php pid or id parameter. | []
| null | null | 9.8 | null |
|
GHSA-523f-pwgc-24f9 | In Weidmueller Industrial WLAN devices in multiple versions an exploitable use of hard-coded credentials vulnerability exists in multiple iw_* utilities. The device operating system contains an undocumented encryption password, allowing for the creation of custom diagnostic scripts. An attacker can send diagnostic scripts while authenticated as a low privilege user to trigger this vulnerability. | []
| null | null | null | null |
|
GHSA-x67c-8vp2-26mr | A vulnerability in WhatsApp Desktop versions prior to 0.3.9309 when paired with WhatsApp for iPhone versions prior to 2.20.10 allows cross-site scripting and local file reading. Exploiting the vulnerability requires the victim to click a link preview from a specially crafted text message. | []
| null | 8.2 | null | null |
|
GHSA-xccw-hfwg-4hr9 | The Print-O-Matic WordPress plugin before 2.0.3 does not escape some of its settings before outputting them in attribute, which could allow high privilege users to perform Cross-Site Scripting attacks even when the unfiltered_html capability is disallowed. | []
| null | null | null | null |
|
RHSA-2015:0125 | Red Hat Security Advisory: Red Hat JBoss Web Framework Kit 2.7.0 update | CXF: SSL hostname verification bypass, incomplete CVE-2012-5783 fix RESTEasy: XXE via parameter entities Validator: JSM bypass via ReflectionHelper CXF: SSL hostname verification bypass, incomplete CVE-2012-6153 fix | [
"cpe:/a:redhat:jboss_enterprise_web_framework:2.7.0"
]
| null | null | 4.8 | null |
GHSA-9r82-f7g4-qf37 | In the Linux kernel, the following vulnerability has been resolved:io_uring: fix link timeout refsWARNING: CPU: 0 PID: 10242 at lib/refcount.c:28 refcount_warn_saturate+0x15b/0x1a0 lib/refcount.c:28
RIP: 0010:refcount_warn_saturate+0x15b/0x1a0 lib/refcount.c:28
Call Trace:
__refcount_sub_and_test include/linux/refcount.h:283 [inline]
__refcount_dec_and_test include/linux/refcount.h:315 [inline]
refcount_dec_and_test include/linux/refcount.h:333 [inline]
io_put_req fs/io_uring.c:2140 [inline]
io_queue_linked_timeout fs/io_uring.c:6300 [inline]
__io_queue_sqe+0xbef/0xec0 fs/io_uring.c:6354
io_submit_sqe fs/io_uring.c:6534 [inline]
io_submit_sqes+0x2bbd/0x7c50 fs/io_uring.c:6660
__do_sys_io_uring_enter fs/io_uring.c:9240 [inline]
__se_sys_io_uring_enter+0x256/0x1d60 fs/io_uring.c:9182io_link_timeout_fn() should put only one reference of the linked timeout
request, however in case of racing with the master request's completion
first io_req_complete() puts one and then io_put_req_deferred() is
called. | []
| null | 5.5 | null | null |
|
CVE-2022-49844 | can: dev: fix skb drop check | In the Linux kernel, the following vulnerability has been resolved:
can: dev: fix skb drop check
In commit a6d190f8c767 ("can: skb: drop tx skb if in listen only
mode") the priv->ctrlmode element is read even on virtual CAN
interfaces that do not create the struct can_priv at startup. This
out-of-bounds read may lead to CAN frame drops for virtual CAN
interfaces like vcan and vxcan.
This patch mainly reverts the original commit and adds a new helper
for CAN interface drivers that provide the required information in
struct can_priv.
[mkl: patch pch_can, too] | []
| null | 7.1 | null | null |
CVE-2000-0641 | Savant web server allows remote attackers to execute arbitrary commands via a long GET request. | [
"cpe:2.3:a:michael_lamont:savant_webserver:2.1:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
CVE-2015-7987 | Multiple buffer overflows in mDNSResponder before 625.41.2 allow remote attackers to read or write to out-of-bounds memory locations via vectors involving the (1) GetValueForIPv4Addr, (2) GetValueForMACAddr, (3) rfc3110_import, or (4) CopyNSEC3ResourceRecord function. | [
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:watchos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:airport_base_station_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:apple:airport_base_station:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:mdnsresponder:*:*:*:*:*:*:*:*"
]
| null | null | 9.8 | 6.8 |
|
GHSA-rvmh-678c-2f4f | A Use Of Less Trusted Source [CWE-348] vulnerability in Fortinet FortiPortal version 7.0.0 through 7.0.6 and version 7.2.0 through 7.2.1 allows an unauthenticated attack to bypass IP protection through crafted HTTP or HTTPS packets. | []
| null | 7.5 | null | null |
|
GHSA-7q6c-727m-8m74 | Multiple cross-site scripting (XSS) vulnerabilities in HydroBB 1.0.0 Beta 2 allow remote attackers to inject arbitrary web script or HTML via the s parameter to (1) search.php, (2) members.php, (3) stats.php, (4) viewforum.php, (5) register.php, (6) usercp.php, (7) groups.php, (8) pms.php, and (9) calendar.php. | []
| null | null | null | null |
|
CVE-2024-10797 | Full Screen Menu for Elementor <= 1.0.7 - Authenticated (Contributor+) Post Disclosure | The Full Screen Menu for Elementor plugin for WordPress is vulnerable to Information Exposure in all versions up to, and including, 1.0.7 via the Full Screen Menu Elementor Widget due to insufficient restrictions on which posts can be included. This makes it possible for authenticated attackers, with contributor-level access and above, to extract data from private or draft posts created with Elementor that they should not have access to. | []
| null | 4.3 | null | null |
CVE-2024-50328 | SQL injection in Ivanti Endpoint Manager before 2024 November Security Update or 2022 SU6 November Security Update allows a remote authenticated attacker with admin privileges to achieve remote code execution. | [
"cpe:2.3:a:ivanti:endpoint_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:-:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:su1:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:su2:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:su3:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:su4:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2022:su5:*:*:*:*:*:*",
"cpe:2.3:a:ivanti:endpoint_manager:2024:-:*:*:*:*:*:*"
]
| null | 7.2 | null | null |
|
CVE-2024-52959 | iota C.ai Conversational Platform - Improper Control of Generation of Code ('Code Injection') | A Improper Control of Generation of Code ('Code Injection') vulnerability in plugin management in iota C.ai Conversational Platform from 1.0.0 through 2.1.3 allows remote authenticated users to perform arbitrary system commands via a DLL file. | [
"cpe:2.3:a:galaxy_software_services_corporation:iota_c.ai_conversational_platform:*:*:*:*:*:*:*:*"
]
| 9.3 | null | null | null |
GHSA-c98m-pvjv-v9r2 | arclib.dll before 7.3.0.9 in CA Anti-Virus (formerly eTrust Antivirus) 8 and certain other CA products allows remote attackers to cause a denial of service (infinite loop and loss of antivirus functionality) via an invalid "previous listing chunk number" field in a CHM file. | []
| null | null | null | null |
|
CVE-2023-48967 | Ssolon <= 2.6.0 and <=2.5.12 is vulnerable to Deserialization of Untrusted Data. | [
"cpe:2.3:a:noear:solon:*:*:*:*:*:*:*:*",
"cpe:2.3:a:noear:solon:2.6.0:*:*:*:*:*:*:*"
]
| null | 9.8 | null | null |
|
GHSA-6fvf-gg5c-754m | Buffer overflows in GazTek ghttpd 1.4 allows a remote attacker to execute arbitrary code via long arguments that are passed to (1) the Log function in util.c, or (2) serveconnection in protocol.c. | []
| null | null | null | null |
|
GHSA-88j9-xvhv-gwc6 | Under certain circumstances, invalid authentication credentials could be sent to the login endpoint of Johnson Controls Metasys NAE55, SNE, and SNC engines prior to version 12.0.4 and Facility Explorer F4-SNC engines prior to versions 11.0.6 and 12.0.4 to cause denial-of-service. | []
| null | 7.5 | null | null |
|
CVE-2012-0559 | Unspecified vulnerability in the PeopleSoft Enterprise SCM component in Oracle PeopleSoft Products 9.0 and 9.1 allows remote authenticated users to affect confidentiality via unknown vectors related to Billing. | [
"cpe:2.3:a:oracle:peoplesoft_products:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_products:9.1:*:*:*:*:*:*:*"
]
| null | null | null | 4 |
|
CVE-2019-12220 | An issue was discovered in libSDL2.a in Simple DirectMedia Layer (SDL) 2.0.9 when used in conjunction with libSDL2_image.a in SDL2_image 2.0.4. There is an out-of-bounds read in the SDL function SDL_FreePalette_REAL at video/SDL_pixels.c. | [
"cpe:2.3:a:libsdl:sdl2_image:2.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:libsdl:simple_directmedia_layer:2.0.9:*:*:*:*:*:*:*"
]
| null | null | 6.5 | 4.3 |
|
RHSA-2019:4023 | Red Hat Security Advisory: samba security and bug fix update | samba: Combination of parameters and permissions can allow user to escape from the share path definition | [
"cpe:/a:redhat:storage:3.5:samba:el6"
]
| null | null | 6.5 | null |
GHSA-jj4r-pv4x-x3jw | Vulnerability in the Oracle Solaris product of Oracle Systems (component: Remote Administration Daemon). The supported version that is affected is 11. Easily exploitable vulnerability allows unauthenticated attacker with network access via multiple protocols to compromise Oracle Solaris. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Oracle Solaris. CVSS 3.1 Base Score 7.5 (Availability impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H). | []
| null | 7.5 | null | null |
|
GHSA-7wf3-fr96-gq58 | A maliciously crafted RCS file, when parsed through Autodesk Revit, can force an Out-of-Bounds Write vulnerability. A malicious actor may leverage this vulnerability to cause a crash, cause data corruption, or execute arbitrary code in the context of the current process. | []
| null | 7.8 | null | null |
|
GHSA-9hh7-vmjp-g84v | Multiple buffer overflows in Cray UNICOS 9.0.2.2 might allow local users to gain privileges by (1) invoking /usr/bin/script with a long command line argument or (2) setting the -c option of /etc/nu to the name of a file containing a long line. | []
| null | null | null | null |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.