id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
197k
| cpes
listlengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2015-1363 | Cross-site scripting (XSS) vulnerability in Free Reprintables ArticleFR 3.0.5 allows remote attackers to inject arbitrary web script or HTML via the q parameter to search/v/. | [
"cpe:2.3:a:freereprintables:articlefr:3.0.5:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2017-15749 | IrfanView 4.50 - 64bit with CADImage plugin version 12.0.0.5 allows attackers to cause a denial of service or possibly have unspecified other impact via a crafted .dwg file, related to "Data from Faulting Address controls Branch Selection starting at CADIMAGE+0x00000000000348b9." | [
"cpe:2.3:a:irfanview:irfanview:4.50:*:*:*:*:x64:*:*",
"cpe:2.3:a:irfanview:cadimage:12.0.0.5:*:*:*:*:*:*:*"
]
| null | null | 7.8 | 6.8 |
|
GHSA-7pm2-436m-jff6 | A sandboxing issue in Odoo Community 15.0 and earlier and Odoo Enterprise 15.0 and earlier allows authenticated administrators to read and write local files on the server. | []
| null | null | 8.7 | null |
|
GHSA-5xmm-chg9-ppmr | In the Linux kernel, the following vulnerability has been resolved:nfs: fix UAF in direct writesIn production we have been hitting the following warning consistently------------[ cut here ]------------
refcount_t: underflow; use-after-free.
WARNING: CPU: 17 PID: 1800359 at lib/refcount.c:28 refcount_warn_saturate+0x9c/0xe0
Workqueue: nfsiod nfs_direct_write_schedule_work [nfs]
RIP: 0010:refcount_warn_saturate+0x9c/0xe0
PKRU: 55555554
Call Trace:
<TASK>
? __warn+0x9f/0x130
? refcount_warn_saturate+0x9c/0xe0
? report_bug+0xcc/0x150
? handle_bug+0x3d/0x70
? exc_invalid_op+0x16/0x40
? asm_exc_invalid_op+0x16/0x20
? refcount_warn_saturate+0x9c/0xe0
nfs_direct_write_schedule_work+0x237/0x250 [nfs]
process_one_work+0x12f/0x4a0
worker_thread+0x14e/0x3b0
? ZSTD_getCParams_internal+0x220/0x220
kthread+0xdc/0x120
? __btf_name_valid+0xa0/0xa0
ret_from_fork+0x1f/0x30This is because we're completing the nfs_direct_request twice in a row.The source of this is when we have our commit requests to submit, we
process them and send them off, and then in the completion path for the
commit requests we haveif (nfs_commit_end(cinfo.mds))
nfs_direct_write_complete(dreq);However since we're submitting asynchronous requests we sometimes have
one that completes before we submit the next one, so we end up calling
complete on the nfs_direct_request twice.The only other place we use nfs_generic_commit_list() is in
__nfs_commit_inode, which wraps this call in anfs_commit_begin();
nfs_commit_end();Which is a common pattern for this style of completion handling, one
that is also repeated in the direct code with get_dreq()/put_dreq()
calls around where we process events as well as in the completion paths.Fix this by using the same pattern for the commit requests.Before with my 200 node rocksdb stress running this warning would pop
every 10ish minutes. With my patch the stress test has been running for
several hours without popping. | []
| null | 7.8 | null | null |
|
GHSA-vq74-9583-hrm4 | Publify vulnerable to DoS attack | Publify before 8.0.1 is vulnerable to a Denial of Service attack | []
| null | 7.5 | null | null |
CVE-2019-14790 | The limb-gallery (aka Limb Gallery) plugin 1.4.0 for WordPress has XSS via the wp-admin/admin-ajax.php?action=grsGalleryAjax&grsAction=shortcode task parameter, | [
"cpe:2.3:a:limbcode:limb-gallery:*:*:*:*:*:wordpress:*:*"
]
| null | null | 6.1 | 4.3 |
|
GHSA-qjm5-rcr7-wvhh | Unspecified vulnerability in the SQLJ component in Oracle Database Server 11.1.0.7, 11.2.0.3, 11.2.0.4, 12.1.0.1, and 12.1.0.2 allows remote authenticated users to affect confidentiality via unknown vectors, a different vulnerability than CVE-2014-4298, CVE-2014-4299, CVE-2014-4300, CVE-2014-6454, and CVE-2014-6542. | []
| null | null | null | null |
|
GHSA-fg4r-8mvv-vm28 | rpc.ypupdated (NIS) allows remote users to execute arbitrary commands. | []
| null | null | null | null |
|
GHSA-hgmm-hq8f-f7pc | The Linux Foundation Magma <= 1.8.0 (fixed in v1.9 commit 08472ba98b8321f802e95f5622fa90fec2dea486) was discovered to contain a buffer overflow in the decode_pdn_address function at /nas/ies/PdnAddress.cpp. This vulnerability allows attackers to cause a Denial of Service (DoS) via a crafted NAS packet. | []
| null | 7.5 | null | null |
|
PYSEC-2023-158 | null | The session fixation vulnerability allowed the authenticated user to continue accessing Airflow webserver even after the password of the user has been reset by the admin - up until the expiry of the session of the user. Other than manually cleaning the session database (for database session backend), or changing the secure_key and restarting the webserver, there were no mechanisms to force-logout the user (and all other users with that).
With this fix implemented, when using the database session backend, the existing sessions of the user are invalidated when the password of the user is reset. When using the securecookie session backend, the sessions are NOT invalidated and still require changing the secure key and restarting the webserver (and logging out all other users), but the user resetting the password is informed about it with a flash message warning displayed in the UI. Documentation is also updated explaining this behaviour.
Users of Apache Airflow are advised to upgrade to version 2.7.0 or newer to mitigate the risk associated with this vulnerability.
| []
| null | 8 | null | null |
GHSA-x863-gchp-57m3 | An issue in Texas Instruments Fusion Digital Power Designer v.7.10.1 allows a local attacker to obtain sensitive information via the plaintext storage of credentials | []
| null | 6.6 | null | null |
|
GHSA-84fv-prrc-5ggr | Route Validation Bypass in call | Affected versions of `call` do not validate empty parameters, which may result in a bypass of route validation rules.Proof of ConceptRouting Scheme:Triggering Request Path:RecommendationUpdate to version 3.0.2 or later. | []
| null | null | null | null |
CVE-2014-5331 | Cross-site scripting (XSS) vulnerability in Aflax allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [
"cpe:2.3:a:aptana:aflax:1.0:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2006-2421 | Stack-based buffer overflow in Pragma FortressSSH 4.0.7.20 allows remote attackers to execute arbitrary code via long SSH_MSG_KEXINIT messages, which may cause an overflow when being logged. NOTE: the provenance of this information is unknown; the details are obtained solely from third party information. | [
"cpe:2.3:a:pragma_systems:fortressssh:*:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
CVE-2018-19226 | An issue was discovered in LAOBANCMS 2.0. It allows remote attackers to list .txt files via a direct request for the /data/0/admin.txt URI. | [
"cpe:2.3:a:laobancms:laobancms:2.0:*:*:*:*:*:*:*"
]
| null | null | 5.3 | 5 |
|
CVE-2020-3869 | An issue existed in the handling of the local user's self-view. The issue was corrected with improved logic. This issue is fixed in iOS 13.3.1 and iPadOS 13.3.1. A remote FaceTime user may be able to cause the local user's camera self-view to display the incorrect camera. | [
"cpe:2.3:o:apple:ipados:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*"
]
| null | 5.3 | null | 5 |
|
CVE-2007-2699 | The Administration Console in BEA WebLogic Express and WebLogic Server 9.0 and 9.1 does not properly enforce certain Domain Security Policies, which allows remote administrative users in the Deployer role to upload arbitrary files. | [
"cpe:2.3:a:bea:weblogic_server:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:bea:weblogic_server:9.0:*:express:*:*:*:*:*",
"cpe:2.3:a:bea:weblogic_server:9.1:*:*:*:*:*:*:*",
"cpe:2.3:a:bea:weblogic_server:9.1:*:express:*:*:*:*:*"
]
| null | null | null | 7.1 |
|
GHSA-c6j2-5m6p-g3q5 | Cross-site scripting (XSS) vulnerability in IBM 10x, as used in Multi-Enterprise Integration Gateway 1.x through 1.0.0.1 and B2B Advanced Communications before 1.0.0.5_2, allows remote authenticated users to inject arbitrary web script or HTML via unspecified vectors. | []
| null | null | 5.4 | null |
|
GHSA-5pw6-cwq7-cw23 | When a user opens manipulated Computer Graphics Metafile (.cgm, CgmCore.dll) files received from untrusted sources in SAP 3D Visual Enterprise Viewer, the application crashes and becomes temporarily unavailable to the user until restart of the application. | []
| null | 5.5 | null | null |
|
GHSA-69j5-58xf-9g4v | System command injection in formAliasIp in TOTOLINK A3002RU version 1.0.8 allows attackers to execute system commands via the "ipAddr" POST parameter. | []
| null | null | 9.8 | null |
|
GHSA-hqc8-j86x-2764 | Off-by-one error in simple-slab | An issue was discovered in the simple-slab crate before 0.3.3 for Rust. remove() has an off-by-one error, causing memory leakage and a drop of uninitialized memory. | []
| null | 7.5 | null | null |
GHSA-rp8c-wjjp-xgv9 | Hycus CMS 1.0.4 allows Authentication Bypass via "'=' 'OR'" credentials. | []
| null | null | 9.8 | null |
|
CVE-2017-15029 | Open-Xchange GmbH OX App Suite 7.8.4 and earlier is affected by: SSRF. | [
"cpe:2.3:a:open-xchange:open-xchange_appsuite:*:*:*:*:*:*:*:*"
]
| null | null | 4.3 | 4 |
|
GHSA-6hjp-gc44-j7vr | Vulnerability in the Oracle GlassFish Server component of Oracle Fusion Middleware (subcomponent: Security). Supported versions that are affected are 2.1.1, 3.0.1 and 3.1.2. Easily exploitable vulnerability allows unauthenticated attacker with network access via LDAP to compromise Oracle GlassFish Server. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle GlassFish Server accessible data as well as unauthorized read access to a subset of Oracle GlassFish Server accessible data and unauthorized ability to cause a partial denial of service (partial DOS) of Oracle GlassFish Server. CVSS v3.0 Base Score 7.3 (Confidentiality, Integrity and Availability impacts). | []
| null | null | 7.3 | null |
|
CVE-2023-5291 | The Blog Filter plugin for WordPress is vulnerable to Stored Cross-Site Scripting via 'AWL-BlogFilter' shortcode in versions up to, and including, 1.5.3 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | [
"cpe:2.3:a:awplife:blog_filter:*:*:*:*:*:wordpress:*:*"
]
| null | 6.4 | null | null |
|
CVE-2023-5135 | The Simple Cloudflare Turnstile plugin for WordPress is vulnerable to Stored Cross-Site Scripting via 'gravity-simple-turnstile' shortcode in versions up to, and including, 1.23.1 due to insufficient input sanitization and output escaping on user supplied attributes. This makes it possible for authenticated attackers with contributor-level and above permissions to inject arbitrary web scripts in pages that will execute whenever a user accesses an injected page. | [
"cpe:2.3:a:replywp:simple_cloudfare_turnstile:*:*:*:*:*:wordpress:*:*"
]
| null | 6.4 | null | null |
|
GHSA-w2wp-3764-9qmf | Vulnerability in the Oracle Demantra Demand Management component of Oracle Supply Chain Products Suite (subcomponent: Product Security). Supported versions that are affected are 7.3.5 and 12.2. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Demantra Demand Management. Successful attacks require human interaction from a person other than the attacker. Successful attacks of this vulnerability can result in unauthorized update, insert or delete access to some of Oracle Demantra Demand Management accessible data. CVSS 3.0 Base Score 4.3 (Integrity impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:L/A:N). | []
| null | null | 4.3 | null |
|
GHSA-hq87-h4jg-vxfw | Jenkins temporary uploaded file created with insecure permissions | In Jenkins 2.423 and earlier, LTS 2.414.1 and earlier, uploaded files processed via the Stapler web framework and the Jenkins API `MultipartFormDataParser` create temporary files in the system temporary directory with the default permissions for newly created files.If these permissions are overly permissive, attackers with access to the system temporary directory may be able to read and write the file before it is used.This vulnerability only affects operating systems using a shared temporary directory for all users (typically Linux). Additionally, the default permissions for newly created files generally only allow attackers to read the temporary file, but not write to it.
Jenkins 2.424, LTS 2.414.2 creates the temporary files in a subdirectory with more restrictive permissions.As a workaround, you can change your default temporary-file directory using the Java system property `java.io.tmpdir`, if you’re concerned about this issue but unable to immediately update Jenkins. | []
| null | 3.6 | null | null |
GHSA-f3cr-v9p6-f6x2 | Stack-based buffer overflow in Foxit Advanced PDF Editor 3 before 3.04 might allow remote attackers to execute arbitrary code via a crafted document containing instructions that reconstruct a certain security cookie. | []
| null | null | null | null |
|
GHSA-x9r7-5gw2-pphx | In version 3.5 and prior of Cambium Networks ePMP firmware, a lack of input sanitation for certain parameters on the web management console allows any authenticated user (including the otherwise low-privilege readonly user) to inject shell meta-characters as part of a specially-crafted POST request to the get_chart function and run OS-level commands, effectively as root. | []
| null | null | 8.8 | null |
|
GHSA-2g92-xwm3-3x93 | Missing Authorization vulnerability in AddonMaster Load More Anything.This issue affects Load More Anything: from n/a through 3.3.3. | []
| null | 5.4 | null | null |
|
CVE-2017-15694 | When an Apache Geode server versions 1.0.0 to 1.8.0 is operating in secure mode, a user with write permissions for specific data regions can modify internal cluster metadata. A malicious user could modify this data in a way that affects the operation of the cluster. | [
"cpe:2.3:a:apache:geode:*:*:*:*:*:*:*:*"
]
| null | null | 6.5 | 4 |
|
GHSA-q67f-3jq4-mww2 | Cross-site Scripting in Pimcore | Pimcore version 10.3.2 and prior is vulnerable to stored cross-site scripting. A patch is available and anticipated to be part of version 10.3.3. | []
| null | 5.4 | null | null |
GHSA-w25r-fmpr-8r73 | In Wireshark 2.2.0, the Bluetooth L2CAP dissector could crash, triggered by packet injection or a malformed capture file. This was addressed in epan/dissectors/packet-btl2cap.c by avoiding use of a seven-byte memcmp for potentially shorter strings. | []
| null | null | 7.5 | null |
|
GHSA-6w8c-6jrg-qwj2 | Radicale regex metacharacters injection in the user name | Radicale before 1.1 allows remote authenticated users to bypass `owner_write` and `owner_only` limitations via regex metacharacters in the user name, as demonstrated by `.*`. | []
| null | null | 5.3 | null |
RHSA-2019:3467 | Red Hat Security Advisory: dovecot security and bug fix update | dovecot: Improper certificate validation | [
"cpe:/a:redhat:enterprise_linux:8::appstream",
"cpe:/a:redhat:enterprise_linux:8::crb"
]
| null | null | 7.7 | null |
GHSA-gjr7-99gv-frxx | CWE-200: Exposure of Sensitive Information to an Unauthorized Actor vulnerability exists that
could cause exposure of credentials when attacker has access to application on network over
http | []
| null | 9.8 | null | null |
|
CVE-2016-0808 | Integer overflow in the getCoverageFormat12 function in CmapCoverage.cpp in the Minikin library in Android 5.x before 5.1.1 LMY49G and 6.x before 2016-02-01 allows attackers to cause a denial of service (continuous rebooting) via an application that triggers loading of a crafted TTF font, aka internal bug 25645298. | [
"cpe:2.3:o:google:android:5.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:5.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:5.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:5.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:5.1.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:5.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:6.0.1:*:*:*:*:*:*:*"
]
| null | null | 6.2 | 4.9 |
|
CVE-2024-0293 | Totolink LR1200GB cstecgi.cgi setUploadSetting os command injection | A vulnerability classified as critical was found in Totolink LR1200GB 9.1.0u.6619_B20230130. Affected by this vulnerability is the function setUploadSetting of the file /cgi-bin/cstecgi.cgi. The manipulation of the argument FileName leads to os command injection. The attack can be launched remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-249859. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | [
"cpe:2.3:o:totolink:lr1200gb_firmware:9.1.0u.6619_b20230130:*:*:*:*:*:*:*",
"cpe:2.3:h:totolink:lr1200gb:-:*:*:*:*:*:*:*"
]
| null | 6.3 | 6.3 | 6.5 |
GHSA-gpg4-32f3-j9f3 | system\errors\404.php in HongCMS 3.0.0 has XSS via crafted input that triggers a 404 HTTP status code. | []
| null | null | 6.1 | null |
|
GHSA-rvfc-9rrp-jw6f | Heap-based buffer overflow in libavformat/rtmppkt.c in FFmpeg before 2.8.10, 3.0.x before 3.0.5, 3.1.x before 3.1.6, and 3.2.x before 3.2.2 allows remote attackers to execute arbitrary code by leveraging failure to check for RTMP packet size mismatches. | []
| null | null | 9.8 | null |
|
CVE-2025-39365 | WordPress wProject theme < 5.8.0 - Reflected Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Rocket Apps wProject allows Reflected XSS.This issue affects wProject: from n/a before 5.8.0. | []
| null | 7.1 | null | null |
CVE-2025-23163 | net: vlan: don't propagate flags on open | In the Linux kernel, the following vulnerability has been resolved:
net: vlan: don't propagate flags on open
With the device instance lock, there is now a possibility of a deadlock:
[ 1.211455] ============================================
[ 1.211571] WARNING: possible recursive locking detected
[ 1.211687] 6.14.0-rc5-01215-g032756b4ca7a-dirty #5 Not tainted
[ 1.211823] --------------------------------------------
[ 1.211936] ip/184 is trying to acquire lock:
[ 1.212032] ffff8881024a4c30 (&dev->lock){+.+.}-{4:4}, at: dev_set_allmulti+0x4e/0xb0
[ 1.212207]
[ 1.212207] but task is already holding lock:
[ 1.212332] ffff8881024a4c30 (&dev->lock){+.+.}-{4:4}, at: dev_open+0x50/0xb0
[ 1.212487]
[ 1.212487] other info that might help us debug this:
[ 1.212626] Possible unsafe locking scenario:
[ 1.212626]
[ 1.212751] CPU0
[ 1.212815] ----
[ 1.212871] lock(&dev->lock);
[ 1.212944] lock(&dev->lock);
[ 1.213016]
[ 1.213016] *** DEADLOCK ***
[ 1.213016]
[ 1.213143] May be due to missing lock nesting notation
[ 1.213143]
[ 1.213294] 3 locks held by ip/184:
[ 1.213371] #0: ffffffff838b53e0 (rtnl_mutex){+.+.}-{4:4}, at: rtnl_nets_lock+0x1b/0xa0
[ 1.213543] #1: ffffffff84e5fc70 (&net->rtnl_mutex){+.+.}-{4:4}, at: rtnl_nets_lock+0x37/0xa0
[ 1.213727] #2: ffff8881024a4c30 (&dev->lock){+.+.}-{4:4}, at: dev_open+0x50/0xb0
[ 1.213895]
[ 1.213895] stack backtrace:
[ 1.213991] CPU: 0 UID: 0 PID: 184 Comm: ip Not tainted 6.14.0-rc5-01215-g032756b4ca7a-dirty #5
[ 1.213993] Hardware name: QEMU Standard PC (i440FX + PIIX, 1996), BIOS Arch Linux 1.16.3-1-1 04/01/2014
[ 1.213994] Call Trace:
[ 1.213995] <TASK>
[ 1.213996] dump_stack_lvl+0x8e/0xd0
[ 1.214000] print_deadlock_bug+0x28b/0x2a0
[ 1.214020] lock_acquire+0xea/0x2a0
[ 1.214027] __mutex_lock+0xbf/0xd40
[ 1.214038] dev_set_allmulti+0x4e/0xb0 # real_dev->flags & IFF_ALLMULTI
[ 1.214040] vlan_dev_open+0xa5/0x170 # ndo_open on vlandev
[ 1.214042] __dev_open+0x145/0x270
[ 1.214046] __dev_change_flags+0xb0/0x1e0
[ 1.214051] netif_change_flags+0x22/0x60 # IFF_UP vlandev
[ 1.214053] dev_change_flags+0x61/0xb0 # for each device in group from dev->vlan_info
[ 1.214055] vlan_device_event+0x766/0x7c0 # on netdevsim0
[ 1.214058] notifier_call_chain+0x78/0x120
[ 1.214062] netif_open+0x6d/0x90
[ 1.214064] dev_open+0x5b/0xb0 # locks netdevsim0
[ 1.214066] bond_enslave+0x64c/0x1230
[ 1.214075] do_set_master+0x175/0x1e0 # on netdevsim0
[ 1.214077] do_setlink+0x516/0x13b0
[ 1.214094] rtnl_newlink+0xaba/0xb80
[ 1.214132] rtnetlink_rcv_msg+0x440/0x490
[ 1.214144] netlink_rcv_skb+0xeb/0x120
[ 1.214150] netlink_unicast+0x1f9/0x320
[ 1.214153] netlink_sendmsg+0x346/0x3f0
[ 1.214157] __sock_sendmsg+0x86/0xb0
[ 1.214160] ____sys_sendmsg+0x1c8/0x220
[ 1.214164] ___sys_sendmsg+0x28f/0x2d0
[ 1.214179] __x64_sys_sendmsg+0xef/0x140
[ 1.214184] do_syscall_64+0xec/0x1d0
[ 1.214190] entry_SYSCALL_64_after_hwframe+0x77/0x7f
[ 1.214191] RIP: 0033:0x7f2d1b4a7e56
Device setup:
netdevsim0 (down)
^ ^
bond netdevsim1.100@netdevsim1 allmulticast=on (down)
When we enslave the lower device (netdevsim0) which has a vlan, we
propagate vlan's allmuti/promisc flags during ndo_open. This causes
(re)locking on of the real_dev.
Propagate allmulti/promisc on flags change, not on the open. There
is a slight semantics change that vlans that are down now propagate
the flags, but this seems unlikely to result in the real issues.
Reproducer:
echo 0 1 > /sys/bus/netdevsim/new_device
dev_path=$(ls -d /sys/bus/netdevsim/devices/netdevsim0/net/*)
dev=$(echo $dev_path | rev | cut -d/ -f1 | rev)
ip link set dev $dev name netdevsim0
ip link set dev netdevsim0 up
ip link add link netdevsim0 name netdevsim0.100 type vlan id 100
ip link set dev netdevsim0.100 allm
---truncated--- | []
| null | null | null | null |
CVE-2024-46809 | drm/amd/display: Check BIOS images before it is used | In the Linux kernel, the following vulnerability has been resolved:
drm/amd/display: Check BIOS images before it is used
BIOS images may fail to load and null checks are added before they are
used.
This fixes 6 NULL_RETURNS issues reported by Coverity. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*"
]
| null | 5.5 | null | null |
GHSA-v9x5-7566-775w | The WAN configuration page "wan.htm" on D-Link DIR-615 devices with firmware 20.06 can be accessed directly without authentication which can lead to disclose the information about WAN settings and also leverage attacker to modify the data fields of page. | []
| null | 9.8 | null | null |
|
CVE-2021-44648 | GNOME gdk-pixbuf 2.42.6 is vulnerable to a heap-buffer overflow vulnerability when decoding the lzw compressed stream of image data in GIF files with lzw minimum code size equals to 12. | [
"cpe:2.3:a:gnome:gdkpixbuf:2.42.6:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:35:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*"
]
| null | 8.8 | null | 6.8 |
|
CVE-2024-7473 | IDOR Vulnerability in lunary-ai/lunary | An IDOR vulnerability exists in the 'Evaluations' function of the 'umgws datasets' section in lunary-ai/lunary versions 1.3.2. This vulnerability allows an authenticated user to update other users' prompts by manipulating the 'id' parameter in the request. The issue is fixed in version 1.4.3. | [
"cpe:2.3:a:lunary-ai:lunary:*:*:*:*:*:*:*:*",
"cpe:2.3:a:lunary:lunary:1.3.2:*:*:*:*:*:*:*"
]
| null | null | 7.5 | null |
GHSA-hg34-rgjg-w968 | SearchBlox before 8.2 allows remote attackers to obtain sensitive information via a pretty=true action to the _cluster/health URI. | []
| null | null | null | null |
|
GHSA-7jr2-g9j6-qc7j | Microsoft Edge in Microsoft Windows 10 1607, 1703, and Windows Server 2016 allows an attacker to execute arbitrary code in the context of the current user, due to the way that Microsoft browser JavaScript engines render content when handling objects in memory, aka "Scripting Engine Memory Corruption Vulnerability". This CVE ID is unique from CVE-2017-8660, CVE-2017-8729, CVE-2017-8738, CVE-2017-8740, CVE-2017-8741, CVE-2017-8748, CVE-2017-8752, CVE-2017-8753, CVE-2017-8755, CVE-2017-8756, and CVE-2017-11764. | []
| null | null | 7.5 | null |
|
CVE-2017-15360 | PRTG Network Monitor version 17.3.33.2830 is vulnerable to stored Cross-Site Scripting on all group names created, related to incorrect error handling for an HTML encoded script. | [
"cpe:2.3:a:paessler:prtg_network_monitor:17.3.33.2830:*:*:*:*:*:*:*"
]
| null | null | 5.4 | 3.5 |
|
GHSA-q99w-j4mj-7hj8 | Contao Information Disclosure via Access Control Flaws | Contao 3.x before 3.5.37, 4.4.x before 4.4.31 and 4.6.x before 4.6.11 has Incorrect Access Control. | []
| null | null | 6.5 | null |
CVE-2025-43697 | Improper Preservation of Permissions vulnerability in Salesforce OmniStudio (DataMapper) allows exposure of encrypted data.
This impacts OmniStudio: before Spring 2025 | []
| null | 7.5 | null | null |
|
CVE-2006-4254 | Unspecified vulnerability in setlocale in IBM AIX 5.1.0 through 5.3.0 allows local users to gain privileges via unspecified vectors. | [
"cpe:2.3:o:ibm:aix:5.1:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:aix:5.2:*:*:*:*:*:*:*",
"cpe:2.3:o:ibm:aix:5.3:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
CVE-2023-21768 | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability | [
"cpe:2.3:o:microsoft:windows_11:21h2:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_11:21h2:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_11:22h2:*:*:*:*:*:arm64:*",
"cpe:2.3:o:microsoft:windows_11:22h2:*:*:*:*:*:x64:*",
"cpe:2.3:o:microsoft:windows_server_2022:-:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
GHSA-hhh4-9fpj-93rw | Improper access control in GitLab CE/EE versions 12.4 to 14.5.4, 14.5 to 14.6.4, and 12.6 to 14.7.1 allows project non-members to retrieve the service desk email address | []
| null | 4.3 | null | null |
|
CVE-2023-48201 | Cross Site Scripting (XSS) vulnerability in Sunlight CMS v.8.0.1, allows remote authenticated attackers to execute arbitrary code and escalate privileges via a crafted script to the Content text editor component. | [
"cpe:2.3:a:sunlight-cms:sunlight_cms:8.0.1:*:*:*:*:*:*:*"
]
| null | 5.4 | null | null |
|
GHSA-5mx2-ppx6-jrqv | The mm_init function in kernel/fork.c in the Linux kernel before 4.12.10 does not clear the ->exe_file member of a new process's mm_struct, allowing a local attacker to achieve a use-after-free or possibly have unspecified other impact by running a specially crafted program. | []
| null | null | 7.8 | null |
|
GHSA-cvhm-27fr-568j | An issue was discovered in GPAC version 0.8.0 and 0.9.0-development-20191109. There is a NULL pointer dereference in the function gf_isom_box_del() in isomedia/box_funcs.c. | []
| null | null | null | null |
|
CVE-2006-1306 | Microsoft Excel 2000 through 2004 allows user-assisted attackers to execute arbitrary code via a .xls file with a crafted BIFF record with an attacker-controlled array index that is used for a function pointer, aka "Malformed OBJECT record Vulnerability." | [
"cpe:2.3:a:microsoft:excel:2000:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2000:sp2:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2000:sp3:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2000:sr1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2002:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2002:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2002:sp2:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2002:sp3:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2003:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2003:sp1:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:2004:*:mac_os_x:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel:x:*:mac_os_x:*:*:*:*:*",
"cpe:2.3:a:microsoft:excel_viewer:2003:*:*:*:*:*:*:*"
]
| null | null | null | 9.3 |
|
CVE-2007-5378 | Buffer overflow in the FileReadGIF function in tkImgGIF.c for Tk Toolkit 8.4.12 and earlier, and 8.3.5 and earlier, allows user-assisted attackers to cause a denial of service (segmentation fault) via an animated GIF in which the first subimage is smaller than a subsequent subimage, which triggers the overflow in the ReadImage function, a different vulnerability than CVE-2007-5137. | [
"cpe:2.3:a:tcl_tk:tk_toolkit:*:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
RHSA-2016:0370 | Red Hat Security Advisory: nss-util security update | nss: Heap buffer overflow vulnerability in ASN1 certificate parsing (MFSA 2016-35) | [
"cpe:/o:redhat:enterprise_linux:6::client",
"cpe:/o:redhat:enterprise_linux:6::computenode",
"cpe:/o:redhat:enterprise_linux:6::server",
"cpe:/o:redhat:enterprise_linux:6::workstation",
"cpe:/o:redhat:enterprise_linux:7::client",
"cpe:/o:redhat:enterprise_linux:7::computenode",
"cpe:/o:redhat:enterprise_linux:7::server",
"cpe:/o:redhat:enterprise_linux:7::workstation"
]
| null | null | null | null |
GHSA-rx94-q7ch-5ww2 | A vulnerability in the web-based management interface of Cisco PI and Cisco EPNM could allow an authenticated, remote attacker to conduct a path traversal attack on an affected device. To exploit this vulnerability, the attacker must have valid credentials on the system.This vulnerability is due to insufficient input validation of the HTTPS URL by the web-based management interface. An attacker could exploit this vulnerability by sending a crafted request that contains directory traversal character sequences to an affected device. A successful exploit could allow the attacker to write arbitrary files to the host system.
Cisco has released software updates that address these vulnerabilities. There are no workarounds that address these vulnerabilities. | []
| null | 6.5 | null | null |
|
GHSA-9852-4hhr-q2m8 | A Remote Authentication Restriction Bypass vulnerability in HPE Intelligent Management Center (iMC) PLAT version 7.3 E0504P4 was found. | []
| null | null | 7.5 | null |
|
GHSA-p978-563h-q2jg | A command injection vulnerability in the function setUpgradeFW of TOTOLINK Technology router T6 V3_Firmware T6_V3_V4.1.5cu.748_B20211015 allows attackers to execute arbitrary commands via a crafted MQTT packet. | []
| null | null | null | null |
|
CVE-2019-5889 | An log-management directory traversal issue was discovered in OverIT Geocall 6.3 before build 2:346977. | [
"cpe:2.3:a:overit:geocall:6.3:*:*:*:*:*:*:*"
]
| null | 7.5 | null | 5 |
|
CVE-2021-41836 | Fathom Analytics <= 3.0.4 Authenticated Stored Cross-Site Scripting | The Fathom Analytics WordPress plugin is vulnerable to Stored Cross-Site Scripting due to insufficient input validation and escaping via the $site_id parameter found in the ~/fathom-analytics.php file which allowed attackers with administrative user access to inject arbitrary web scripts, in versions up to and including 3.0.4. This affects multi-site installations where unfiltered_html is disabled for administrators, and sites where unfiltered_html is disabled. | [
"cpe:2.3:a:conva:fathom_analytics:*:*:*:*:*:wordpress:*:*"
]
| null | 4.8 | null | null |
RHSA-2025:0166 | Red Hat Security Advisory: thunderbird security update | firefox: thunderbird: WebChannel APIs susceptible to confused deputy attack firefox: thunderbird: Use-after-free when breaking lines in text firefox: Alt-Svc ALPN validation failure when redirected firefox: Compartment mismatch when parsing JavaScript JSON module firefox: Memory corruption when using JavaScript Text Segmentation firefox: thunderbird: Memory safety bugs fixed in Firefox 134, Thunderbird 134, Firefox ESR 115.19, Firefox ESR 128.6, Thunderbird 115.19, and Thunderbird 128.6 firefox: thunderbird: Memory safety bugs fixed in Firefox 134, Thunderbird 134, Firefox ESR 128.6, and Thunderbird 128.6 | [
"cpe:/a:redhat:rhel_eus:9.4::appstream"
]
| null | 7.5 | null | null |
CVE-2024-41809 | OpenObserve Cross-site Scripting (XSS) vulnerability in `openobserve/web/src/views/MemberSubscription.vue` | OpenObserve is an open-source observability platform. Starting in version 0.4.4 and prior to version 0.10.0, OpenObserve contains a cross-site scripting vulnerability in line 32 of `openobserve/web/src/views/MemberSubscription.vue`. Version 0.10.0 sanitizes incoming html. | [
"cpe:2.3:a:openobserve:openobserve:*:*:*:*:*:*:*:*"
]
| null | 7.2 | null | null |
CVE-2017-4978 | EMC RSA Adaptive Authentication (On-Premise) versions prior to 7.3 P2 (exclusive) contains a fix for a cross-site scripting vulnerability that could potentially be exploited by malicious users to compromise the affected system. | [
"cpe:2.3:a:rsa:adaptive_authentication_\\(on_premise\\):*:*:*:*:*:*:*:*"
]
| null | null | 5.4 | 3.5 |
|
CVE-2020-12401 | During ECDSA signature generation, padding applied in the nonce designed to ensure constant-time scalar multiplication was removed, resulting in variable-time execution dependent on secret data. This vulnerability affects Firefox < 80 and Firefox for Android < 80. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:android:*:*"
]
| null | 4.7 | null | 1.9 |
|
CVE-2018-20881 | cPanel before 74.0.8 allows self stored XSS on the Security Questions login page (SEC-446). | [
"cpe:2.3:a:cpanel:cpanel:*:*:*:*:*:*:*:*"
]
| null | null | 5.4 | 3.5 |
|
CVE-2024-12248 | Out-of-bounds Write vulnerability in Contec Health CMS8000 Patient Monitor | Contec Health CMS8000 Patient Monitor is vulnerable to an out-of-bounds write, which could allow an attacker to send specially formatted UDP requests in order to write arbitrary data. This could result in remote code execution. | []
| 9.3 | 9.8 | null | null |
CVE-2024-36141 | Adobe Experience Manager | Cross-site Scripting (Stored XSS) (CWE-79) | Adobe Experience Manager versions 6.5.20 and earlier are affected by a stored Cross-Site Scripting (XSS) vulnerability that could be abused by a low-privileged attacker to inject malicious scripts into vulnerable form fields. Malicious JavaScript may be executed in a victim’s browser when they browse to the page containing the vulnerable field. | [
"cpe:2.3:a:adobe:experience_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:adobe:experience_manager:*:*:*:*:aem_cloud_service:*:*:*"
]
| null | 5.4 | null | null |
GHSA-9jrh-xg5p-v2qr | Stack-based buffer overflow in the DtbClsLogin function in Yosemite Backup 8.7 allows remote attackers to (1) execute arbitrary code on a Linux platform, related to libytlindtb.so; or (2) cause a denial of service (application crash) and possibly execute arbitrary code on a Windows platform, related to ytwindtb.dll; via a long username field during authentication. | []
| null | null | null | null |
|
GHSA-4859-rv5m-vcjv | In fastboot, there is a possible secure boot bypass due to a configuration error. This could lead to local escalation of privilege with no additional execution privileges needed. User interaction is not needed for exploitation. Product: Android Versions: Android SoC Android ID: A-202018701 | []
| null | null | null | null |
|
CVE-2023-28386 | Snap One OvrC Pro devices versions 7.2 and prior do not validate firmware updates correctly. The device only calculates the MD5 hash of the firmware and does not check using a private-public key mechanism. The lack of complete PKI system firmware signature could allow attackers to upload arbitrary firmware updates, resulting in code execution. | [
"cpe:2.3:a:snapone:orvc:*:*:*:*:*:pro:*:*",
"cpe:2.3:h:control4:ca-1:-:*:*:*:*:*:*:*",
"cpe:2.3:h:control4:ca-10:-:*:*:*:*:*:*:*",
"cpe:2.3:h:control4:ea-1:-:*:*:*:*:*:*:*",
"cpe:2.3:h:control4:ea-3:-:*:*:*:*:*:*:*",
"cpe:2.3:h:control4:ea-5:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:an-110-rt-2l1w:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:an-110-rt-2l1w-wifi:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:an-310-rt-4l2w:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:ovrc-300-pro:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:pakedge_rk-1:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:pakedge_rt-3100:-:*:*:*:*:*:*:*",
"cpe:2.3:h:snapone:pakedge_wr-1:-:*:*:*:*:*:*:*"
]
| null | 8.6 | null | null |
|
CVE-2016-5161 | The EditingStyle::mergeStyle function in WebKit/Source/core/editing/EditingStyle.cpp in Blink, as used in Google Chrome before 53.0.2785.89 on Windows and OS X and before 53.0.2785.92 on Linux, mishandles custom properties, which allows remote attackers to cause a denial of service or possibly have unspecified other impact via a crafted web site that leverages "type confusion" in the StylePropertySerializer class. | [
"cpe:2.3:a:google:chrome:*:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:leap:42.1:*:*:*:*:*:*:*"
]
| null | null | 8.8 | 6.8 |
|
CVE-2023-0036 | platform_callback_stub in misc subsystem has an authentication bypass vulnerability which allows an "SA relay attack". | platform_callback_stub in misc subsystem within OpenHarmony-v3.0.5 and prior versions has an authentication bypass vulnerability which allows an "SA relay attack".Local attackers can bypass authentication and attack other SAs with high privilege.
| [
"cpe:2.3:o:openatom:openharmony:*:*:*:*:lts:*:*:*"
]
| null | 6.5 | null | null |
CVE-2017-1359 | IBM RELM 4.0, 5.0, and 6.0 is vulnerable to cross-site scripting. This vulnerability allows users to embed arbitrary JavaScript code in the Web UI thus altering the intended functionality potentially leading to credentials disclosure within a trusted session. IBM X-Force ID: 126686. | [
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:4.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:4.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:4.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:4.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:4.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:5.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:5.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:5.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:6.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:6.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:6.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:6.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:rational_engineering_lifecycle_manager:6.0.4:*:*:*:*:*:*:*"
]
| null | null | 5.4 | 3.5 |
|
CVE-2006-3579 | Cross-site scripting (XSS) vulnerability in Fujitsu ServerView 2.50 up to 3.60L98 and 4.10L11 up to 4.11L81 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [
"cpe:2.3:a:fujitsu:serverview:2.50:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:serverview:3.60l98:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:serverview:4.10l11:*:*:*:*:*:*:*",
"cpe:2.3:a:fujitsu:serverview:4.10l81:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
GHSA-5wg4-7x93-v266 | An issue was discovered in Amazon AWS VPN Client 2.0.0. It is possible to include a UNC path in the OpenVPN configuration file when referencing file paths for parameters (such as auth-user-pass). When this file is imported and the client attempts to validate the file path, it performs an open operation on the path and leaks the user's Net-NTLMv2 hash to an external server. This could be exploited by having a user open a crafted malicious ovpn configuration file. | []
| null | 5 | null | null |
|
CVE-2024-51567 | upgrademysqlstatus in databases/views.py in CyberPanel (aka Cyber Panel) before 5b08cd6 allows remote attackers to bypass authentication and execute arbitrary commands via /dataBases/upgrademysqlstatus by bypassing secMiddleware (which is only for a POST request) and using shell metacharacters in the statusfile property, as exploited in the wild in October 2024 by PSAUX. Versions through 2.3.6 and (unpatched) 2.3.7 are affected. | [
"cpe:2.3:a:cyberpanel:cyberpanel:*:*:*:*:*:*:*:*"
]
| null | 10 | null | null |
|
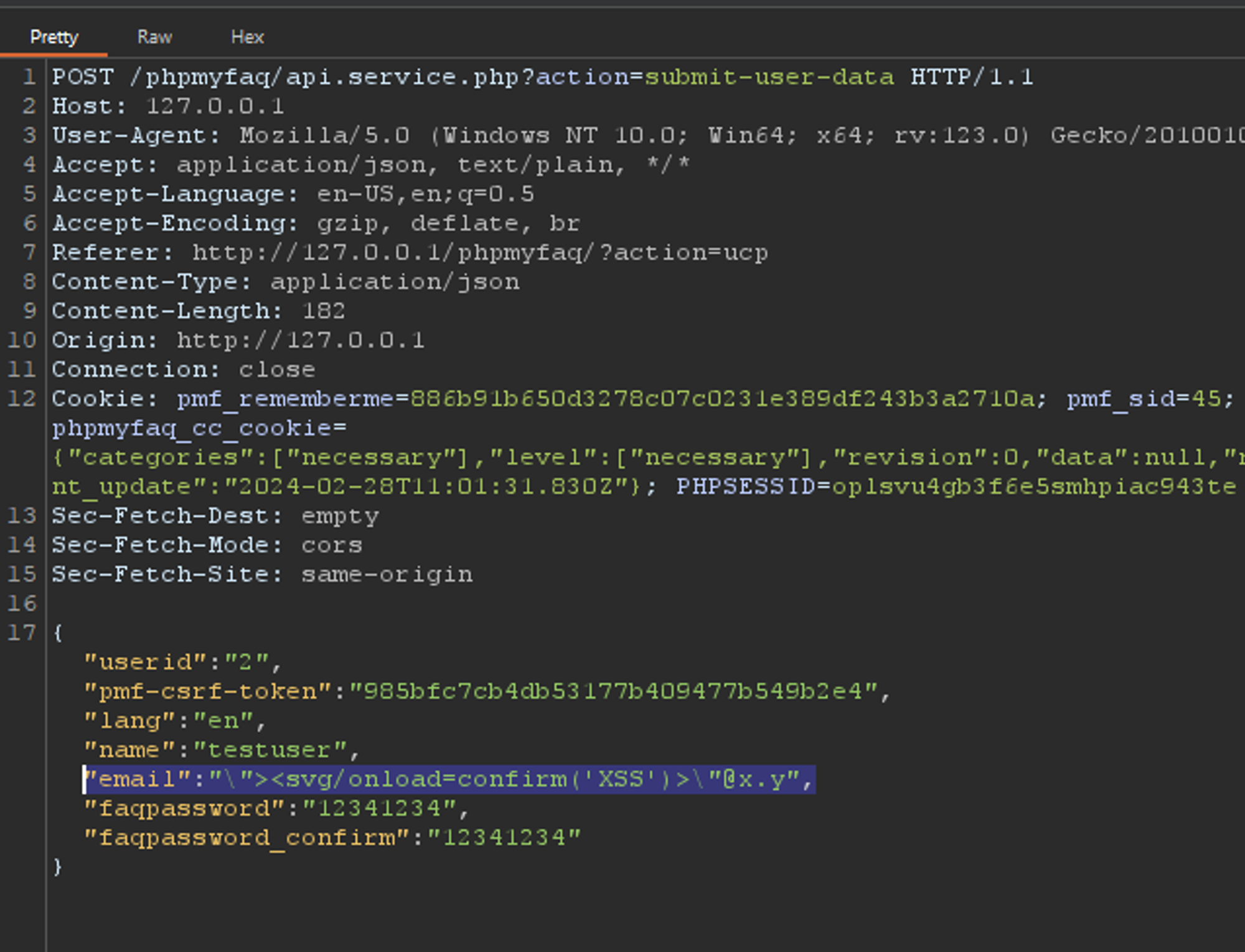
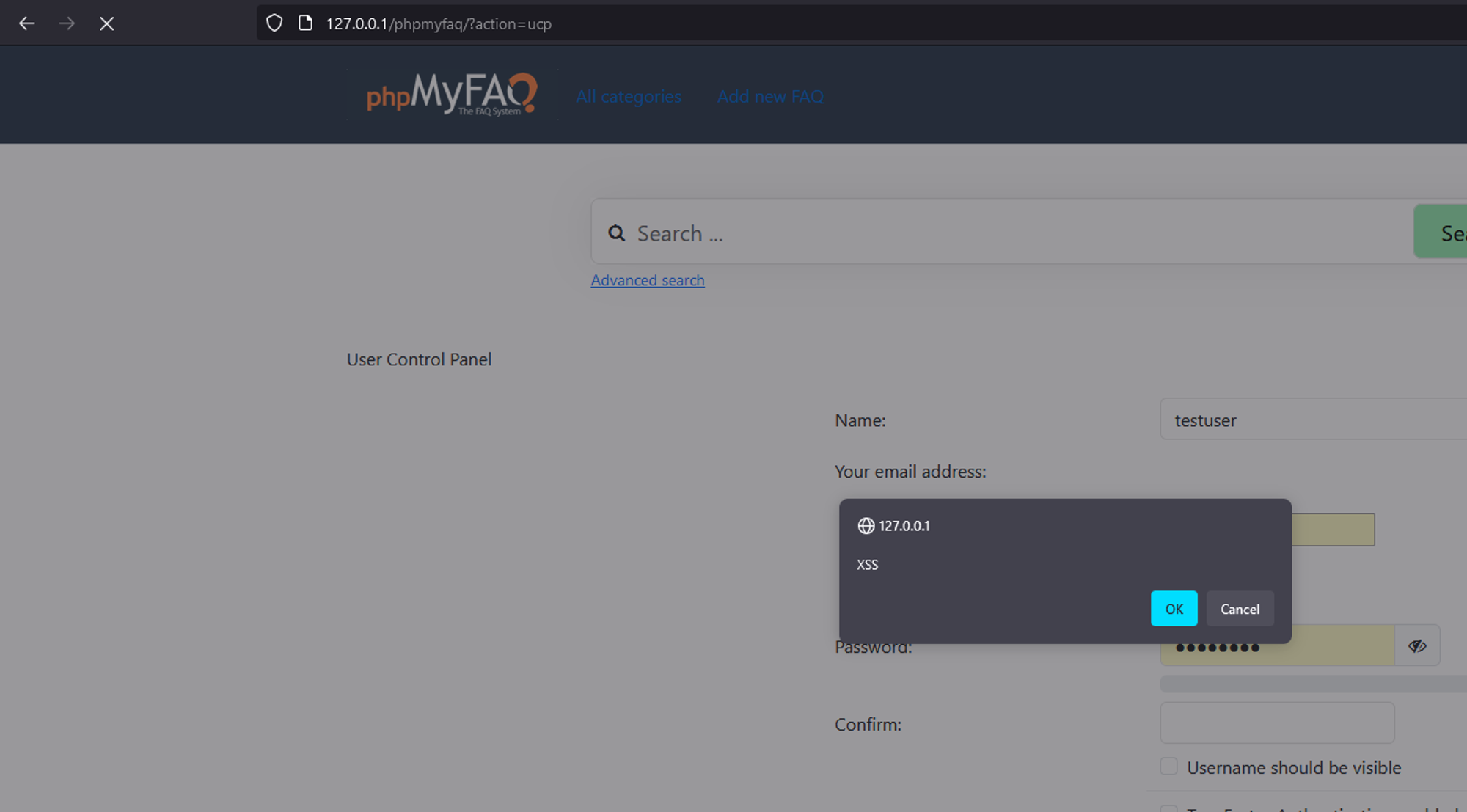
GHSA-q7g6-xfh2-vhpx | phpMyFAQ stored Cross-site Scripting at user email | SummaryThe `email` field in phpMyFAQ's user control panel page is vulnerable to stored XSS attacks due to the inadequacy of PHP's `FILTER_VALIDATE_EMAIL` function, which only validates the email format, not its content. This vulnerability enables an attacker to execute arbitrary client-side JavaScript within the context of another user's phpMyFAQ session.DetailsDespite using PHP's `FILTER_VALIDATE_EMAIL` function, the email field does not adequately validate the content of the email address. This means that malicious input, such as JavaScript code, can be accepted and stored in the database without being detected. When the stored data is retrieved and displayed on web pages, it is not properly sanitized to remove or neutralize any potentially harmful content, such as JavaScript code which leads to Stored XSS.PoCLogin as any user, go to the user control panel, change email to any valid email and intercept the request.Modify the request’s email parameter to the following payload: `"><svg/onload=confirm('XSS')>"@x.y`
Send the request and see that the XSS is triggered in the user control panel page.
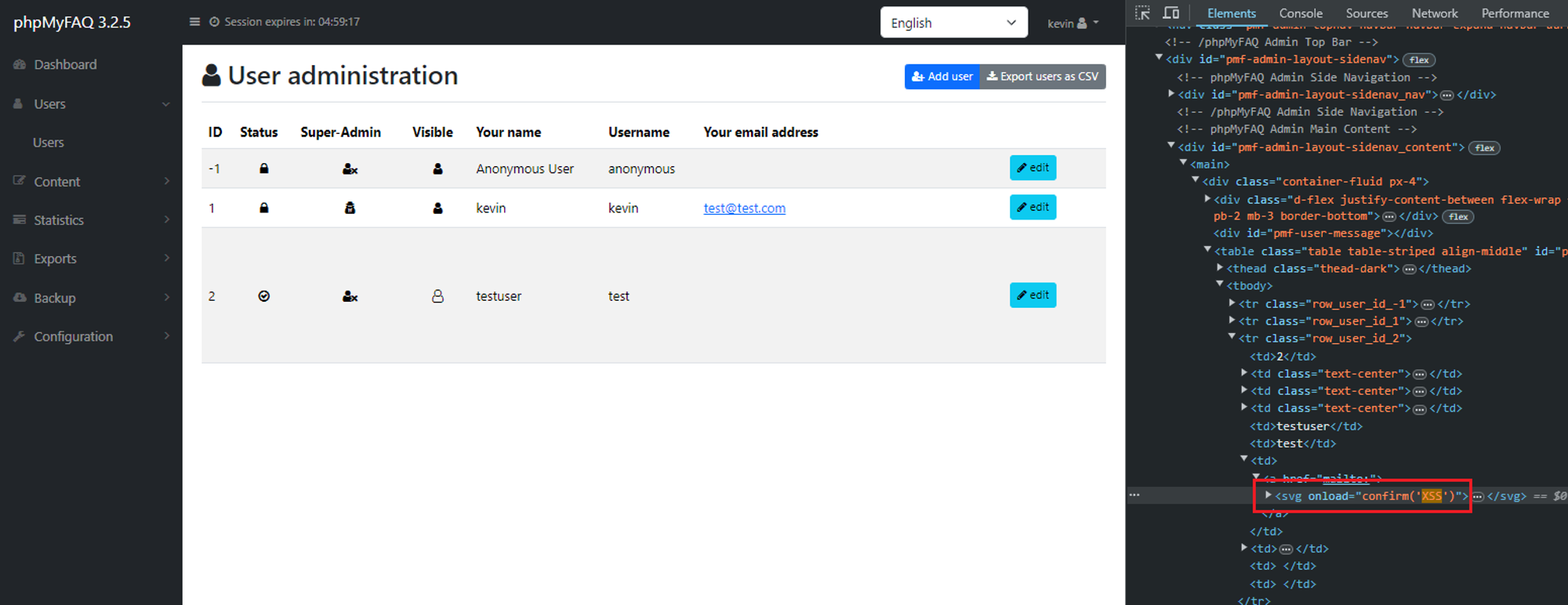
Also affects any user who browse to "../admin/?action=user&user_action=listallusers"
ImpactThis allows an attacker to execute arbitrary client side JavaScript within the context of another user's phpMyFAQ session. | []
| null | 5.5 | null | null |
GHSA-7cc7-6j4x-2w54 | A denial-of-service issue existed in one of modules that was incorporated in Kaspersky Anti-Virus products for home and Kaspersky Endpoint Security. A local user could cause Windows crash by running a specially crafted binary module. The fix was delivered automatically. Credits: (Straghkov Denis, Kurmangaleev Shamil, Fedotov Andrey, Kuts Daniil, Mishechkin Maxim, Akolzin Vitaliy) @ ISPRAS | []
| null | 5.5 | null | null |
|
CVE-2018-13130 | Bitotal (TFUND) is a smart contract running on Ethereum. The mintTokens function has an integer overflow that allows minted tokens to be arbitrarily retrieved by the contract owner. | [
"cpe:2.3:a:bitotal:bitotal:-:*:*:*:*:*:*:*"
]
| null | null | 7.5 | 5 |
|
GHSA-v25h-fv6g-fmcg | A vulnerability was found in code-projects Inventory Management System 1.0 and classified as critical. Affected by this issue is some unknown functionality of the file /php_action/createProduct.php. The manipulation of the argument productName leads to sql injection. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. | []
| 5.5 | 7.3 | null | null |
|
GHSA-2366-559p-m86q | In the Linux kernel, the following vulnerability has been resolved:tpm_tis_spi: Account for SPI header when allocating TPM SPI xfer bufferThe TPM SPI transfer mechanism uses MAX_SPI_FRAMESIZE for computing the
maximum transfer length and the size of the transfer buffer. As such, it
does not account for the 4 bytes of header that prepends the SPI data
frame. This can result in out-of-bounds accesses and was confirmed with
KASAN.Introduce SPI_HDRSIZE to account for the header and use to allocate the
transfer buffer. | []
| null | 7.8 | null | null |
|
PYSEC-2021-238 | null | TensorFlow is an end-to-end open source platform for machine learning. The TFLite implementation of concatenation is vulnerable to an integer overflow issue(https://github.com/tensorflow/tensorflow/blob/7b7352a724b690b11bfaae2cd54bc3907daf6285/tensorflow/lite/kernels/concatenation.cc#L70-L76). An attacker can craft a model such that the dimensions of one of the concatenation input overflow the values of `int`. TFLite uses `int` to represent tensor dimensions, whereas TF uses `int64`. Hence, valid TF models can trigger an integer overflow when converted to TFLite format. The fix will be included in TensorFlow 2.5.0. We will also cherrypick this commit on TensorFlow 2.4.2, TensorFlow 2.3.3, TensorFlow 2.2.3 and TensorFlow 2.1.4, as these are also affected and still in supported range. | []
| null | null | null | null |
CVE-2022-34459 |
Dell Command | Update, Dell Update, and Alienware Update versions prior to 4.7 contain a improper verification of cryptographic signature in get applicable driver component. A local malicious user could potentially exploit this vulnerability leading to malicious payload execution.
| [
"cpe:2.3:a:dell:alienware_update:*:*:*:*:*:*:*:*",
"cpe:2.3:a:dell:command_update:*:*:*:*:*:*:*:*",
"cpe:2.3:a:dell:update:*:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
|
GHSA-gp69-8v27-vccw | ktsuss versions 1.4 and prior has the uid set to root and does not drop privileges prior to executing user specified commands, which can result in command execution with root privileges. | []
| null | 9.8 | null | null |
|
GHSA-m784-gw3f-67r6 | Unspecified vulnerability in the PeopleSoft Enterprise PeopleTools component in Oracle PeopleSoft Products 8.52 allows remote attackers to affect integrity via unknown vectors related to Security. | []
| null | null | null | null |
|
GHSA-8gpf-qj7v-hp3f | In the Linux kernel, the following vulnerability has been resolved:ovl: relax WARN_ON in ovl_verify_area()syzbot hit an assertion in copy up data loop which looks like it is
the result of a lower file whose size is being changed underneath
overlayfs.This type of use case is documented to cause undefined behavior, so
returning EIO error for the copy up makes sense, but it should not be
causing a WARN_ON assertion. | []
| null | null | null | null |
|
GHSA-rhv5-x75f-g9rj | ZyXEL Prestige routers, including P-660, P-661, and P-662 models with firmware 3.40(AGD.2) through 3.40(AHQ.3), allow remote authenticated users to obtain ISP and Dynamic DNS credentials by sending a direct request for (1) WAN.html, (2) wzPPPOE.html, and (3) rpDyDNS.html, and then reading the HTML source. | []
| null | null | null | null |
|
GHSA-g4wc-2gqq-5g7v | TCMAN GIM does not perform an authorization check when trying to access determined resources. A remote attacker could exploit this vulnerability to access URL that require privileges without having them. The exploitation of this vulnerability might allow a remote attacker to obtain sensible information. | []
| null | 7.2 | null | null |
|
CVE-2022-30922 | H3C Magic R100 R100V100R005 was discovered to contain a stack overflow vulnerability via the EditWlanMacList parameter at /goform/aspForm. | [
"cpe:2.3:o:h3c:magic_r100_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:h3c:magic_r100:-:*:*:*:*:*:*:*"
]
| null | 9.8 | null | 10 |
|
CVE-2000-0851 | Buffer overflow in the Still Image Service in Windows 2000 allows local users to gain additional privileges via a long WM_USER message, aka the "Still Image Service Privilege Escalation" vulnerability. | [
"cpe:2.3:o:microsoft:windows_2000:*:*:*:*:*:*:*:*"
]
| null | null | null | 4.6 |
|
GHSA-73j8-52vp-m475 | Cross-site scripting (XSS) vulnerability in includes/decorators/global-translations.jsp in Atlassian JIRA before 7.2.2 allows remote attackers to inject arbitrary web script or HTML via the HTTP Host header. | []
| null | null | 6.1 | null |
|
RHSA-2010:0475 | Red Hat Security Advisory: sudo security update | sudo: insufficient environment sanitization issue | [
"cpe:/o:redhat:enterprise_linux:5::client",
"cpe:/o:redhat:enterprise_linux:5::server"
]
| null | null | null | null |
CVE-2018-13757 | The mintToken function of a smart contract implementation for Coinquer, an Ethereum token, has an integer overflow that allows the owner of the contract to set the balance of an arbitrary user to any value. | [
"cpe:2.3:a:coinquer_project:coinquer:-:*:*:*:*:*:*:*"
]
| null | null | 7.5 | 5 |
|
GHSA-c3q6-58wx-x6rx | Invensys Wonderware Win-XML Exporter 1522.148.0.0 allows remote attackers to read arbitrary files, send HTTP requests to intranet servers, or cause a denial of service (CPU and memory consumption) via an XML external entity declaration in conjunction with an entity reference. | []
| null | null | null | null |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.