Datasets:
id
stringlengths 7
14
| text
stringlengths 1
106k
|
|---|---|
13899_0 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_1 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_2 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_3 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_4 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_5 | public AbstractBackendMessage decode(DecoderInputStream input, boolean block) throws IOException {
// If mark is not support and we can't block, throw an exception
if (!input.markSupported() && !block) {
throw new IllegalArgumentException("Non-blocking decoding requires an InputStream that supports marking");
}
// TODO This should be the max packet size - make this configurable
input.mark(Integer.MAX_VALUE);
AbstractBackendMessage message = null;
try {
message = doDecode(input, block);
} finally {
if (message == null) {
input.reset();
}
}
return message;
} |
13899_6 | @Override
public int read() throws IOException {
int i = in.read();
if (i >= 0) {
limit--;
}
assertLimit();
return i;
} |
13899_7 | public String readString(Charset charset) throws IOException {
// TODO: Add support for UTF-16
byte[] buffer = new byte[getLimit()];
int pos = 0;
int c;
while ((c = read()) > 0) {
buffer[pos++] = (byte)c;
}
return new String(buffer, 0, pos, charset);
} |
13899_8 | public static int safeRead(InputStream in) throws IOException {
int i = in.read();
if (i < 0) {
throw new EOFException();
}
return i;
} |
13899_9 | public static int readShort(InputStream in) throws IOException {
int b0 = safeRead(in);
int b1 = safeRead(in);
int i = b1 << 8 | b0;
if ((b1 & 0x80) == 0x80) {
i |= 0xffff0000;
}
return i;
} |
32578_0 | public List<LabelValue> getAllRoles() {
List<Role> roles = dao.getRoles();
List<LabelValue> list = new ArrayList<LabelValue>();
for (Role role1 : roles) {
list.add(new LabelValue(role1.getName(), role1.getName()));
}
return list;
} |
32578_1 | public User getUser(String userId) {
return userDao.get(new Long(userId));
} |
32578_2 | public User saveUser(User user) throws UserExistsException {
if (user.getVersion() == null) {
// if new user, lowercase userId
user.setUsername(user.getUsername().toLowerCase());
}
// Get and prepare password management-related artifacts
boolean passwordChanged = false;
if (passwordEncoder != null) {
// Check whether we have to encrypt (or re-encrypt) the password
if (user.getVersion() == null) {
// New user, always encrypt
passwordChanged = true;
} else {
// Existing user, check password in DB
String currentPassword = userDao.getUserPassword(user.getUsername());
if (currentPassword == null) {
passwordChanged = true;
} else {
if (!currentPassword.equals(user.getPassword())) {
passwordChanged = true;
}
}
}
// If password was changed (or new user), encrypt it
if (passwordChanged) {
user.setPassword(passwordEncoder.encodePassword(user.getPassword(), null));
}
} else {
log.warn("PasswordEncoder not set, skipping password encryption...");
}
try {
return userDao.saveUser(user);
} catch (DataIntegrityViolationException e) {
//e.printStackTrace();
log.warn(e.getMessage());
throw new UserExistsException("User '" + user.getUsername() + "' already exists!");
} catch (JpaSystemException e) { // needed for JPA
//e.printStackTrace();
log.warn(e.getMessage());
throw new UserExistsException("User '" + user.getUsername() + "' already exists!");
}
} |
32578_3 | public User saveUser(User user) throws UserExistsException {
if (user.getVersion() == null) {
// if new user, lowercase userId
user.setUsername(user.getUsername().toLowerCase());
}
// Get and prepare password management-related artifacts
boolean passwordChanged = false;
if (passwordEncoder != null) {
// Check whether we have to encrypt (or re-encrypt) the password
if (user.getVersion() == null) {
// New user, always encrypt
passwordChanged = true;
} else {
// Existing user, check password in DB
String currentPassword = userDao.getUserPassword(user.getUsername());
if (currentPassword == null) {
passwordChanged = true;
} else {
if (!currentPassword.equals(user.getPassword())) {
passwordChanged = true;
}
}
}
// If password was changed (or new user), encrypt it
if (passwordChanged) {
user.setPassword(passwordEncoder.encodePassword(user.getPassword(), null));
}
} else {
log.warn("PasswordEncoder not set, skipping password encryption...");
}
try {
return userDao.saveUser(user);
} catch (DataIntegrityViolationException e) {
//e.printStackTrace();
log.warn(e.getMessage());
throw new UserExistsException("User '" + user.getUsername() + "' already exists!");
} catch (JpaSystemException e) { // needed for JPA
//e.printStackTrace();
log.warn(e.getMessage());
throw new UserExistsException("User '" + user.getUsername() + "' already exists!");
}
} |
32578_4 | public void send(SimpleMailMessage msg) throws MailException {
try {
mailSender.send(msg);
} catch (MailException ex) {
log.error(ex.getMessage());
throw ex;
}
} |
32578_5 | public void sendMessage(SimpleMailMessage msg, String templateName, Map model) {
String result = null;
try {
result =
VelocityEngineUtils.mergeTemplateIntoString(velocityEngine,
templateName, model);
} catch (VelocityException e) {
e.printStackTrace();
log.error(e.getMessage());
}
msg.setText(result);
send(msg);
} |
56670_0 | protected String getPackage() {
return pkg;
} |
56670_1 | public Set<String> getClasses() throws IOException {
Set<String> classes = new HashSet<String>();
Enumeration<URL> resources = getClassLoader().getResources(pkg + "/");
if (resources != null) {
while (resources.hasMoreElements()) {
String path = sanitizeURL(resources.nextElement().getFile());
if ((path != null) && (path.trim().length() > 0))
classes.addAll(
isJARPath(path) ? getClassesFromJAR(path) : getClassesFromDirectory(path)
);
}
}
return classes;
} |
56904_0 | public static String camelize(String s) {
StringBuffer name = new StringBuffer();
for (String part : s.split(" |_")) {
name.append(Inflector.capitalize(part));
}
return name.toString();
} |
56904_1 | public static String camelize(String s) {
StringBuffer name = new StringBuffer();
for (String part : s.split(" |_")) {
name.append(Inflector.capitalize(part));
}
return name.toString();
} |
56904_2 | public static String camelize(String s) {
StringBuffer name = new StringBuffer();
for (String part : s.split(" |_")) {
name.append(Inflector.capitalize(part));
}
return name.toString();
} |
56904_3 | public static String camelize(String s) {
StringBuffer name = new StringBuffer();
for (String part : s.split(" |_")) {
name.append(Inflector.capitalize(part));
}
return name.toString();
} |
56904_4 | public static String humanize(String camelCased) {
List<String> parts = Inflector.split(camelCased);
for (int i = 0; i < parts.size(); i++) {
parts.set(i, Inflector.capitalize(parts.get(i).toLowerCase()));
}
return Join.space(parts);
} |
56904_5 | public static String humanize(String camelCased) {
List<String> parts = Inflector.split(camelCased);
for (int i = 0; i < parts.size(); i++) {
parts.set(i, Inflector.capitalize(parts.get(i).toLowerCase()));
}
return Join.space(parts);
} |
56904_6 | public static String underscore(String camelCased) {
List<String> parts = Inflector.split(camelCased);
for (int i = 0; i < parts.size(); i++) {
parts.set(i, parts.get(i).toLowerCase());
}
return Join.underscore(parts);
} |
56904_7 | public static String humanize(String camelCased) {
List<String> parts = Inflector.split(camelCased);
for (int i = 0; i < parts.size(); i++) {
parts.set(i, Inflector.capitalize(parts.get(i).toLowerCase()));
}
return Join.space(parts);
} |
56904_8 | public static String string(String message, Object... args) {
for (Object arg : args) {
int i = message.indexOf("{}");
if (i != -1) {
message = message.substring(0, i) + String.valueOf(arg) + message.substring(i + 2);
}
}
return message;
} |
56904_9 | public static String string(String message, Object... args) {
for (Object arg : args) {
int i = message.indexOf("{}");
if (i != -1) {
message = message.substring(0, i) + String.valueOf(arg) + message.substring(i + 2);
}
}
return message;
} |
74217_0 | public List<Class> locate(URL url, String packageName) {
return locate(url, Pattern.compile(packageName));
} |
74217_1 | @Override
public ObjectMapping find(Class domainClass) {
if (getObjectMappingCount() == 0) {
initializeObjectMappings();
}
return super.find(domainClass);
} |
74217_2 | @Override
public ObjectMapping find(Class domainClass) {
if (getObjectMappingCount() == 0) {
initializeObjectMappings();
}
return super.find(domainClass);
} |
74217_3 | public List<Class<?>> scan(List<String> packages) {
List<Class<?>> classes = new ArrayList<Class<?>>();
for (String packageName : packages) {
for (Class clazz : findClassesInPackage(packageName)) {
if (hasRecordAnnoation(clazz))
classes.add(clazz);
}
}
return classes;
} |
74217_4 | public List<Class<?>> scan(List<String> packages) {
List<Class<?>> classes = new ArrayList<Class<?>>();
for (String packageName : packages) {
for (Class clazz : findClassesInPackage(packageName)) {
if (hasRecordAnnoation(clazz))
classes.add(clazz);
}
}
return classes;
} |
74217_5 | public List<Class<?>> scan(List<String> packages) {
List<Class<?>> classes = new ArrayList<Class<?>>();
for (String packageName : packages) {
for (Class clazz : findClassesInPackage(packageName)) {
if (hasRecordAnnoation(clazz))
classes.add(clazz);
}
}
return classes;
} |
74217_6 | public List<Class<?>> scan(List<String> packages) {
List<Class<?>> classes = new ArrayList<Class<?>>();
for (String packageName : packages) {
for (Class clazz : findClassesInPackage(packageName)) {
if (hasRecordAnnoation(clazz))
classes.add(clazz);
}
}
return classes;
} |
74217_7 | public ReflectionField locateById(Class<?> clazz, String id) {
for (java.lang.reflect.Field field : locateAnnotated(clazz, Field.class)) {
String annotationValue = field.getAnnotation(Field.class).value();
if (!isEmpty(annotationValue) && id.equals(annotationValue)) {
return new ReflectionField(field);
} else if (isEmpty(annotationValue) && (field.getName().equals(id) || field.getName().equals(convertIdIntoJavaFieldName(id)))) {
return new ReflectionField(field);
}
}
return null;
} |
74217_8 | public ReflectionField locateById(Class<?> clazz, String id) {
for (java.lang.reflect.Field field : locateAnnotated(clazz, Field.class)) {
String annotationValue = field.getAnnotation(Field.class).value();
if (!isEmpty(annotationValue) && id.equals(annotationValue)) {
return new ReflectionField(field);
} else if (isEmpty(annotationValue) && (field.getName().equals(id) || field.getName().equals(convertIdIntoJavaFieldName(id)))) {
return new ReflectionField(field);
}
}
return null;
} |
74217_9 | public ReflectionField locateById(Class<?> clazz, String id) {
for (java.lang.reflect.Field field : locateAnnotated(clazz, Field.class)) {
String annotationValue = field.getAnnotation(Field.class).value();
if (!isEmpty(annotationValue) && id.equals(annotationValue)) {
return new ReflectionField(field);
} else if (isEmpty(annotationValue) && (field.getName().equals(id) || field.getName().equals(convertIdIntoJavaFieldName(id)))) {
return new ReflectionField(field);
}
}
return null;
} |
88960_0 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_1 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_2 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_3 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_4 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_5 | public List<File> files() throws IOException {
if (!sourceDirectory.exists()) {
return ImmutableList.of();
}
String includesStr = StringUtils.join(includes.iterator(), ",");
String excludesStr = StringUtils.join(excludes.iterator(), ",");
return FileUtils.getFiles(sourceDirectory, includesStr, excludesStr);
} |
88960_6 | public void execute() throws MojoExecutionException, MojoFailureException {
if (skip) {
getLog().info("skipping JSLint");
return;
}
JSLint jsLint = applyJSlintSource();
applyDefaults();
applyOptions(jsLint);
List<File> files = getFilesToProcess();
int failures = 0;
ReportWriter reporter = makeReportWriter();
try {
reporter.open();
for (File file : files) {
JSLintResult result = lintFile(jsLint, file);
failures += result.getIssues().size();
logIssues(result, reporter);
}
} finally {
reporter.close();
}
if (failures > 0) {
String message = "JSLint found " + failures + " problems in " + files.size() + " files";
if (failOnError) {
throw new MojoFailureException(message);
} else {
getLog().info(message);
}
}
} |
88960_7 | @VisibleForTesting
String getEncoding() {
return encoding;
} |
88960_8 | public void execute() throws MojoExecutionException, MojoFailureException {
if (skip) {
getLog().info("skipping JSLint");
return;
}
JSLint jsLint = applyJSlintSource();
applyDefaults();
applyOptions(jsLint);
List<File> files = getFilesToProcess();
int failures = 0;
ReportWriter reporter = makeReportWriter();
try {
reporter.open();
for (File file : files) {
JSLintResult result = lintFile(jsLint, file);
failures += result.getIssues().size();
logIssues(result, reporter);
}
} finally {
reporter.close();
}
if (failures > 0) {
String message = "JSLint found " + failures + " problems in " + files.size() + " files";
if (failOnError) {
throw new MojoFailureException(message);
} else {
getLog().info(message);
}
}
} |
88960_9 | public void execute() throws MojoExecutionException, MojoFailureException {
if (skip) {
getLog().info("skipping JSLint");
return;
}
JSLint jsLint = applyJSlintSource();
applyDefaults();
applyOptions(jsLint);
List<File> files = getFilesToProcess();
int failures = 0;
ReportWriter reporter = makeReportWriter();
try {
reporter.open();
for (File file : files) {
JSLintResult result = lintFile(jsLint, file);
failures += result.getIssues().size();
logIssues(result, reporter);
}
} finally {
reporter.close();
}
if (failures > 0) {
String message = "JSLint found " + failures + " problems in " + files.size() + " files";
if (failOnError) {
throw new MojoFailureException(message);
} else {
getLog().info(message);
}
}
} |
97620_0 | public String get() {
return this.fullClassNameWithGenerics;
} |
103035_0 | public static Document stringToDoc(String str) throws IOException {
if (StringUtils.isNotEmpty(str)) {
try {
Reader reader = new StringReader(str);
DocumentBuilder db = DocumentBuilderFactory.newInstance()
.newDocumentBuilder();
Document doc = db.parse(new InputSource(reader));
reader.close();
return doc;
} catch (Exception ex) {
log.debug("String: {}", str);
throw new IOException(String.format("Error converting from string to doc %s", ex.getMessage()));
}
} else {
throw new IOException("Error - could not convert empty string to doc");
}
} |
103035_1 | public static String docToString(Document dom) {
return XMLUtils.docToString1(dom);
} |
103035_2 | public static String docToString1(Document dom) {
StringWriter sw = new StringWriter();
DOM2Writer.serializeAsXML(dom, sw);
return sw.toString();
} |
103035_3 | public static String docToString2(Document domDoc) throws IOException {
try {
TransformerFactory transFact = TransformerFactory.newInstance();
Transformer trans = transFact.newTransformer();
trans.setOutputProperty(OutputKeys.INDENT, "no");
StringWriter sw = new StringWriter();
Result result = new StreamResult(sw);
trans.transform(new DOMSource(domDoc), result);
return sw.toString();
} catch (Exception ex) {
throw new IOException(String.format("Error converting from doc to string %s", ex.getMessage()));
}
} |
103035_4 | public byte[] computeMac() {
Mac hm = null;
byte[] result = null;
if (log.isDebugEnabled()) {
log.debug("Key data: {}", byteArrayToHex(keyBytes));
log.debug("Hash data: {}", byteArrayToHex(dataBytes));
log.debug("Algorithm: {}", ALGORITHM_ID);
}
try {
hm = Mac.getInstance(ALGORITHM_ID);
Key k1 = new SecretKeySpec(keyBytes, 0, keyBytes.length, ALGORITHM_ID);
hm.init(k1);
result = hm.doFinal(dataBytes);
} catch (Exception e) {
log.warn("Bad algorithm or crypto library problem", e);
}
return result;
} |
103035_5 | public void init() {
//environmental var holder
HashMap<String, Object> env = null;
if (enableRmiAdapter) {
// Create an RMI connector server
log.debug("Create an RMI connector server");
// bind the rmi hostname for systems with nat and multiple binded addresses !
System.setProperty("java.rmi.server.hostname", rmiAdapterHost);
try {
Registry r = null;
try {
//lookup the registry
r = LocateRegistry.getRegistry(Integer
.valueOf(rmiAdapterPort));
//ensure we are not already registered with the registry
for (String regName : r.list()) {
if (regName.equals("red5")) {
//unbind connector from rmi registry
r.unbind("red5");
}
}
} catch (RemoteException re) {
log.info("RMI Registry server was not found on port "
+ rmiAdapterPort);
//if we didnt find the registry and the user wants it created
if (startRegistry) {
log.info("Starting an internal RMI registry");
r = LocateRegistry.createRegistry(Integer
.valueOf(rmiAdapterPort));
}
}
JMXServiceURL url = null;
// Configure the remote objects exported port for firewalls !!
if (StringUtils.isNotEmpty(rmiAdapterRemotePort)) {
url = new JMXServiceURL("service:jmx:rmi://"
+ rmiAdapterHost + ":" + rmiAdapterRemotePort + "/jndi/rmi://" + rmiAdapterHost + ":" + rmiAdapterPort + "/red5");
} else {
url = new JMXServiceURL(
"service:jmx:rmi:///jndi/rmi://:" + rmiAdapterPort
+ "/red5");
}
log.info("JMXServiceUrl is: {}", url);
//if SSL is requested to secure rmi connections
if (enableSsl) {
// Setup keystore for SSL transparently
System.setProperty("javax.net.ssl.keyStore", remoteSSLKeystore);
System.setProperty("javax.net.ssl.keyStorePassword", remoteSSLKeystorePass);
// Environment map
log.debug("Initialize the environment map");
env = new HashMap<String, Object>();
// Provide SSL-based RMI socket factories
SslRMIClientSocketFactory csf = new SslRMIClientSocketFactory();
SslRMIServerSocketFactory ssf = new SslRMIServerSocketFactory();
env
.put(
RMIConnectorServer.RMI_CLIENT_SOCKET_FACTORY_ATTRIBUTE,
csf);
env
.put(
RMIConnectorServer.RMI_SERVER_SOCKET_FACTORY_ATTRIBUTE,
ssf);
}
//if authentication is requested
if (StringUtils.isNotBlank(remoteAccessProperties)) {
//if ssl is not used this will be null
if (null == env) {
env = new HashMap<String, Object>();
}
//check the existance of the files
//in the war version the full path is needed
File file = new File(remoteAccessProperties);
if (!file.exists() && remoteAccessProperties.indexOf(System.getProperty("red5.config_root")) != 0) {
log.debug("Access file was not found on path, will prepend config_root");
//pre-pend the system property set in war startup
remoteAccessProperties = System
.getProperty("red5.config_root")
+ '/' + remoteAccessProperties;
remotePasswordProperties = System
.getProperty("red5.config_root")
+ '/' + remotePasswordProperties;
}
env.put("jmx.remote.x.access.file", remoteAccessProperties);
env.put("jmx.remote.x.password.file",
remotePasswordProperties);
}
// create the connector server
cs = JMXConnectorServerFactory.newJMXConnectorServer(url, env, mbs);
// add a listener for shutdown
cs.addNotificationListener(this, null, null);
// Start the RMI connector server
log.debug("Start the RMI connector server");
cs.start();
log.info("JMX RMI connector server successfully started");
} catch (ConnectException e) {
log
.warn("Could not establish RMI connection to port "
+ rmiAdapterPort
+ ", please make sure \"rmiregistry\" is running and configured to listen on this port.");
} catch (IOException e) {
String errMsg = e.getMessage();
if (errMsg.indexOf("NameAlreadyBoundException") != -1) {
log
.error("JMX connector (red5) already registered, you will need to restart your rmiregistry");
} else {
log.error("{}", e);
}
} catch (Exception e) {
log.error("Error in setup of JMX subsystem (RMI connector)", e);
}
} else {
log.info("JMX RMI adapter was not enabled");
}
} |
103035_6 | public static boolean unregisterMBean(ObjectName oName) {
boolean unregistered = false;
if (null != oName) {
try {
if (mbs.isRegistered(oName)) {
log.debug("Mbean is registered");
mbs.unregisterMBean(oName);
//set flag based on registration status
unregistered = !mbs.isRegistered(oName);
} else {
log.debug("Mbean is not currently registered");
}
} catch (Exception e) {
log.warn("Exception unregistering mbean {}", e);
}
}
log.debug("leaving unregisterMBean...");
return unregistered;
} |
103035_7 | public static ObjectName createMBean(String className, String attributes) {
log.info("Create the {} MBean within the MBeanServer", className);
ObjectName objectName = null;
try {
StringBuilder objectNameStr = new StringBuilder(domain);
objectNameStr.append(":type=");
objectNameStr.append(className
.substring(className.lastIndexOf(".") + 1));
objectNameStr.append(",");
objectNameStr.append(attributes);
log.info("ObjectName = {}", objectNameStr);
objectName = new ObjectName(objectNameStr.toString());
if (!mbs.isRegistered(objectName)) {
mbs.createMBean(className, objectName);
} else {
log.debug("MBean has already been created: {}", objectName);
}
} catch (Exception e) {
log.error("Could not create the {} MBean. {}", className, e);
}
return objectName;
} |
103035_8 | public static ObjectName createSimpleMBean(String className,
String objectNameStr) {
log.info("Create the {} MBean within the MBeanServer", className);
log.info("ObjectName = {}", objectNameStr);
try {
ObjectName objectName = ObjectName.getInstance(objectNameStr);
if (!mbs.isRegistered(objectName)) {
mbs.createMBean(className, objectName);
} else {
log.debug("MBean has already been created: {}", objectName);
}
return objectName;
} catch (Exception e) {
log.error("Could not create the {} MBean. {}", className, e);
}
return null;
} |
103035_9 | public static String getDefaultDomain() {
return domain;
} |
116547_0 | String allCucumberArgs() {
List<String> allCucumberArgs = new ArrayList<String>();
if (cucumberArgs != null)
allCucumberArgs.addAll(cucumberArgs);
if (extraCucumberArgs != null)
allCucumberArgs.add(extraCucumberArgs);
allCucumberArgs.add(features);
return Utils.join(allCucumberArgs.toArray(), " ");
} |
116547_1 | String allCucumberArgs() {
List<String> allCucumberArgs = new ArrayList<String>();
if (cucumberArgs != null)
allCucumberArgs.addAll(cucumberArgs);
if (extraCucumberArgs != null)
allCucumberArgs.add(extraCucumberArgs);
allCucumberArgs.add(features);
return Utils.join(allCucumberArgs.toArray(), " ");
} |
116547_2 | String allCucumberArgs() {
List<String> allCucumberArgs = new ArrayList<String>();
if (cucumberArgs != null)
allCucumberArgs.addAll(cucumberArgs);
if (extraCucumberArgs != null)
allCucumberArgs.add(extraCucumberArgs);
allCucumberArgs.add(features);
return Utils.join(allCucumberArgs.toArray(), " ");
} |
116547_3 | public CucumberTask cucumber(String args) throws MojoExecutionException {
CucumberTask cucumber = new CucumberTask();
cucumber.setProject(getProject());
for (String jvmArg : getJvmArgs()) {
if (jvmArg != null) {
Commandline.Argument arg = cucumber.createJvmarg();
arg.setValue(jvmArg);
}
}
cucumber.setArgs(args);
return cucumber;
} |
116547_4 | public String format(Method method) {
String signature = method.toGenericString();
Matcher matcher = METHOD_PATTERN.matcher(signature);
if (matcher.find()) {
String M = matcher.group(1);
String r = matcher.group(2);
String qc = matcher.group(3);
String m = matcher.group(4);
String qa = matcher.group(5);
String qe = matcher.group(6);
String c = qc.replaceAll(PACKAGE_PATTERN, "");
String a = qa.replaceAll(PACKAGE_PATTERN, "");
String e = qe.replaceAll(PACKAGE_PATTERN, "");
return format.format(new Object[]{
M,
r,
qc,
m,
qa,
qe,
c,
a,
e
});
} else {
throw new RuntimeException("Cuke4Duke bug: Couldn't format " + signature);
}
} |
116547_5 | public String format(Method method) {
String signature = method.toGenericString();
Matcher matcher = METHOD_PATTERN.matcher(signature);
if (matcher.find()) {
String M = matcher.group(1);
String r = matcher.group(2);
String qc = matcher.group(3);
String m = matcher.group(4);
String qa = matcher.group(5);
String qe = matcher.group(6);
String c = qc.replaceAll(PACKAGE_PATTERN, "");
String a = qa.replaceAll(PACKAGE_PATTERN, "");
String e = qe.replaceAll(PACKAGE_PATTERN, "");
return format.format(new Object[]{
M,
r,
qc,
m,
qa,
qe,
c,
a,
e
});
} else {
throw new RuntimeException("Cuke4Duke bug: Couldn't format " + signature);
}
} |
116547_6 | public Object invoke(Method method, Object target, Object[] javaArgs) throws Throwable {
try {
if (method.isAnnotationPresent(Pending.class)) {
throw exceptionFactory.cucumberPending(method.getAnnotation(Pending.class).value());
} else {
return method.invoke(target, javaArgs);
}
} catch (IllegalArgumentException e) {
String m = "Couldn't invokeWithArgs " + method.toGenericString() + " with " + cuke4duke.internal.Utils.join(javaArgs, ",");
throw exceptionFactory.cucumberArityMismatchError(m);
} catch (InvocationTargetException e) {
throw e.getTargetException();
}
} |
116547_7 | @Override
public void load_code_file(String classFile) throws Throwable {
Class<?> clazz = loadClass(classFile);
addClass(clazz);
} |
116547_8 | @Override
public void load_code_file(String classFile) throws Throwable {
Class<?> clazz = loadClass(classFile);
addClass(clazz);
} |
116547_9 | public static Locale localeFor(String isoString) {
String[] languageAndCountry = isoString.split("-");
if (languageAndCountry.length == 1) {
return new Locale(isoString);
} else {
return new Locale(languageAndCountry[0], languageAndCountry[1]);
}
} |
121672_0 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_1 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_2 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_3 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_4 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_5 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_6 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_7 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_8 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
121672_9 | @Override
blic String apply( Visibility visibility, Object value )
{
if( value == null )
return null;
URI uri;
if( value instanceof URI )
{
uri = (URI) value;
}
else
{
try
{
uri = URI.create( encode( value.toString() ) );
}
catch( IllegalArgumentException exception )
{
LOG.warn( "failed to parse uri: {}, message: {}", value, exception.getMessage() );
LOG.debug( "failed to parse uri: {}", value, exception );
if( Boolean.parseBoolean( System.getProperty( FAILURE_MODE_PASS_THROUGH ) ) )
{
LOG.warn( "ignoring uri sanitizer failures, returning unsanitized value, property '{}' set to true", FAILURE_MODE_PASS_THROUGH );
return value.toString();
}
// return an empty string, to avoid the leakage of sensitive information.
LOG.info( "set property: '{}', to true to return unsanitized value, returning empty string", FAILURE_MODE_PASS_THROUGH );
return "";
}
}
if( uri.isOpaque() )
{
switch( visibility )
{
case PRIVATE:
return value.toString();
case PROTECTED:
case PUBLIC:
return uri.getScheme() + ":";
}
}
StringBuilder buffer = new StringBuilder();
if( uri.getPath() != null ) // can happen according to the javadoc
buffer.append( uri.getPath() );
if( ( visibility == Visibility.PROTECTED || visibility == Visibility.PRIVATE ) && uri.getQuery() != null )
buffer.append( "?" ).append( sanitizeQuery( uri.getQuery() ) );
if( visibility == Visibility.PRIVATE )
{
String currentString = buffer.toString(); // preserve before creating a new instance
buffer = new StringBuilder();
if( uri.getScheme() != null )
buffer.append( uri.getScheme() ).append( "://" );
if( uri.getAuthority() != null )
buffer.append( uri.getAuthority() );
buffer.append( currentString );
}
return buffer.toString();
} |
123235_0 | static String encodeHex(byte[] bytes) {
final char[] hex = new char[bytes.length * 2];
int i = 0;
for (byte b : bytes) {
hex[i++] = HEX_DIGITS[(b >> 4) & 0x0f];
hex[i++] = HEX_DIGITS[b & 0x0f];
}
return String.valueOf(hex);
} |
123235_1 | static String encodeHex(byte[] bytes) {
final char[] hex = new char[bytes.length * 2];
int i = 0;
for (byte b : bytes) {
hex[i++] = HEX_DIGITS[(b >> 4) & 0x0f];
hex[i++] = HEX_DIGITS[b & 0x0f];
}
return String.valueOf(hex);
} |
123235_2 | static String getOidFromPkcs8Encoded(byte[] encoded) throws NoSuchAlgorithmException {
if (encoded == null) {
throw new NoSuchAlgorithmException("encoding is null");
}
try {
SimpleDERReader reader = new SimpleDERReader(encoded);
reader.resetInput(reader.readSequenceAsByteArray());
reader.readInt();
reader.resetInput(reader.readSequenceAsByteArray());
return reader.readOid();
} catch (IOException e) {
Log.w(TAG, "Could not read OID", e);
throw new NoSuchAlgorithmException("Could not read key", e);
}
} |
123235_3 | static String getOidFromPkcs8Encoded(byte[] encoded) throws NoSuchAlgorithmException {
if (encoded == null) {
throw new NoSuchAlgorithmException("encoding is null");
}
try {
SimpleDERReader reader = new SimpleDERReader(encoded);
reader.resetInput(reader.readSequenceAsByteArray());
reader.readInt();
reader.resetInput(reader.readSequenceAsByteArray());
return reader.readOid();
} catch (IOException e) {
Log.w(TAG, "Could not read OID", e);
throw new NoSuchAlgorithmException("Could not read key", e);
}
} |
123235_4 | static String getOidFromPkcs8Encoded(byte[] encoded) throws NoSuchAlgorithmException {
if (encoded == null) {
throw new NoSuchAlgorithmException("encoding is null");
}
try {
SimpleDERReader reader = new SimpleDERReader(encoded);
reader.resetInput(reader.readSequenceAsByteArray());
reader.readInt();
reader.resetInput(reader.readSequenceAsByteArray());
return reader.readOid();
} catch (IOException e) {
Log.w(TAG, "Could not read OID", e);
throw new NoSuchAlgorithmException("Could not read key", e);
}
} |
123235_5 | static String getOidFromPkcs8Encoded(byte[] encoded) throws NoSuchAlgorithmException {
if (encoded == null) {
throw new NoSuchAlgorithmException("encoding is null");
}
try {
SimpleDERReader reader = new SimpleDERReader(encoded);
reader.resetInput(reader.readSequenceAsByteArray());
reader.readInt();
reader.resetInput(reader.readSequenceAsByteArray());
return reader.readOid();
} catch (IOException e) {
Log.w(TAG, "Could not read OID", e);
throw new NoSuchAlgorithmException("Could not read key", e);
}
} |
123235_6 | static String getOidFromPkcs8Encoded(byte[] encoded) throws NoSuchAlgorithmException {
if (encoded == null) {
throw new NoSuchAlgorithmException("encoding is null");
}
try {
SimpleDERReader reader = new SimpleDERReader(encoded);
reader.resetInput(reader.readSequenceAsByteArray());
reader.readInt();
reader.resetInput(reader.readSequenceAsByteArray());
return reader.readOid();
} catch (IOException e) {
Log.w(TAG, "Could not read OID", e);
throw new NoSuchAlgorithmException("Could not read key", e);
}
} |
123235_7 | static String getAlgorithmForOid(String oid) throws NoSuchAlgorithmException {
if ("1.2.840.10045.2.1".equals(oid)) {
return "EC";
} else if ("1.2.840.113549.1.1.1".equals(oid)) {
return "RSA";
} else if ("1.2.840.10040.4.1".equals(oid)) {
return "DSA";
} else {
throw new NoSuchAlgorithmException("Unknown algorithm OID " + oid);
}
} |
123235_8 | static String getAlgorithmForOid(String oid) throws NoSuchAlgorithmException {
if ("1.2.840.10045.2.1".equals(oid)) {
return "EC";
} else if ("1.2.840.113549.1.1.1".equals(oid)) {
return "RSA";
} else if ("1.2.840.10040.4.1".equals(oid)) {
return "DSA";
} else {
throw new NoSuchAlgorithmException("Unknown algorithm OID " + oid);
}
} |
123235_9 | static String getAlgorithmForOid(String oid) throws NoSuchAlgorithmException {
if ("1.2.840.10045.2.1".equals(oid)) {
return "EC";
} else if ("1.2.840.113549.1.1.1".equals(oid)) {
return "RSA";
} else if ("1.2.840.10040.4.1".equals(oid)) {
return "DSA";
} else {
throw new NoSuchAlgorithmException("Unknown algorithm OID " + oid);
}
} |
135867_0 | public String getApplicationContextFile() {
return _appContextFile;
} |
135867_1 | public <T> T getBean(String beanName) {
if (beanName == null) {
throw new IllegalArgumentException("Argument 'beanName' is null");
}
return (T) _beanFactory.getBean(beanName);
} |
135867_2 | public String[] getRoles() {
return copyArray(_roles);
} |
135867_3 | public boolean hasRole(String role) {
for (String r : _roles) {
if (r.equalsIgnoreCase(role)) {
return true;
}
}
return false;
} |
135867_4 | public boolean hasOneRoleOf(String[] roles) {
for (String r : roles) {
if (hasRole(r)) {
return true;
}
}
return false;
} |
135867_5 | @SuppressWarnings("unchecked")
public ModelAndView logIn(HttpServletRequest request, HttpServletResponse response, LoginCommand login,
BindException errors) throws Exception {
// Checking whether logged in
ApplicationState state = getApplicationState(request);
LOG.debug("logIn() state=" + state);
if (state.getCurrentUser() != null) {
return redirectAfterLogin(request, response);
}
if (!errors.hasErrors()) {
User user = authenticate(login.getUsername(), login.getPassword(), errors);
if (user != null) {
state.setCurrentUser(user);
if (login.isAutoLogin()) {
// set autoLogin
setAutoLoginCookie(response, user.getToken());
}
setSingleLoginCookie(response, user.getToken());
String prevAction = state.getPreviousAction();
LOG.debug("logIn() prevAction=" + prevAction);
if (prevAction == null) {
return redirectAfterLogin(request, response);
} else {
state.setPreviousAction(null);
return new ModelAndView(new RedirectView(prevAction));
}
}
}
Map model = errors.getModel();
model.put("login", login);
BPMS_DESCRIPTOR_PARSER.addBpmsBuildVersionsPropertiesToMap(model);
return new ModelAndView(Constants.LOGIN_VIEW, model);
} |
135867_6 | @SuppressWarnings("unchecked")
public ModelAndView logIn(HttpServletRequest request, HttpServletResponse response, LoginCommand login,
BindException errors) throws Exception {
// Checking whether logged in
ApplicationState state = getApplicationState(request);
LOG.debug("logIn() state=" + state);
if (state.getCurrentUser() != null) {
return redirectAfterLogin(request, response);
}
if (!errors.hasErrors()) {
User user = authenticate(login.getUsername(), login.getPassword(), errors);
if (user != null) {
state.setCurrentUser(user);
if (login.isAutoLogin()) {
// set autoLogin
setAutoLoginCookie(response, user.getToken());
}
setSingleLoginCookie(response, user.getToken());
String prevAction = state.getPreviousAction();
LOG.debug("logIn() prevAction=" + prevAction);
if (prevAction == null) {
return redirectAfterLogin(request, response);
} else {
state.setPreviousAction(null);
return new ModelAndView(new RedirectView(prevAction));
}
}
}
Map model = errors.getModel();
model.put("login", login);
BPMS_DESCRIPTOR_PARSER.addBpmsBuildVersionsPropertiesToMap(model);
return new ModelAndView(Constants.LOGIN_VIEW, model);
} |
135867_7 | @SuppressWarnings("unchecked")
public ModelAndView logIn(HttpServletRequest request, HttpServletResponse response, LoginCommand login,
BindException errors) throws Exception {
// Checking whether logged in
ApplicationState state = getApplicationState(request);
LOG.debug("logIn() state=" + state);
if (state.getCurrentUser() != null) {
return redirectAfterLogin(request, response);
}
if (!errors.hasErrors()) {
User user = authenticate(login.getUsername(), login.getPassword(), errors);
if (user != null) {
state.setCurrentUser(user);
if (login.isAutoLogin()) {
// set autoLogin
setAutoLoginCookie(response, user.getToken());
}
setSingleLoginCookie(response, user.getToken());
String prevAction = state.getPreviousAction();
LOG.debug("logIn() prevAction=" + prevAction);
if (prevAction == null) {
return redirectAfterLogin(request, response);
} else {
state.setPreviousAction(null);
return new ModelAndView(new RedirectView(prevAction));
}
}
}
Map model = errors.getModel();
model.put("login", login);
BPMS_DESCRIPTOR_PARSER.addBpmsBuildVersionsPropertiesToMap(model);
return new ModelAndView(Constants.LOGIN_VIEW, model);
} |
135867_8 | public ModelAndView logOut(HttpServletRequest request, HttpServletResponse response, LoginCommand login,
BindException errors) throws Exception {
ApplicationState state = getApplicationState(request);
if (state != null) {
if (state.getCurrentUser() != null){
String userName = state.getCurrentUser().getName();
LOG.debug("Logout: user=" + userName);
}
state.setCurrentUser(null);
state.setPreviousAction(null);
clearAutoLogin(response);
clearSingleLogin(response);
clearSecureRandom(response);
clearRootCookie(response);
clearOtherCookie(response,JSESSION,UI_FW);
clearOtherCookie(response,JSESSION,MONITORING);
clearOtherCookie(response,JSESSION,BPMS_CONSOLE);
}
Map model = new HashMap();
model.put("login", new LoginCommand());
BPMS_DESCRIPTOR_PARSER.addBpmsBuildVersionsPropertiesToMap(model);
return new ModelAndView(Constants.LOGIN_VIEW, model);
} |
135867_9 | @SuppressWarnings("unchecked")
public ModelAndView logIn(HttpServletRequest request, HttpServletResponse response, LoginCommand login,
BindException errors) throws Exception {
// Checking whether logged in
ApplicationState state = getApplicationState(request);
LOG.debug("logIn() state=" + state);
if (state.getCurrentUser() != null) {
return redirectAfterLogin(request, response);
}
if (!errors.hasErrors()) {
User user = authenticate(login.getUsername(), login.getPassword(), errors);
if (user != null) {
state.setCurrentUser(user);
if (login.isAutoLogin()) {
// set autoLogin
setAutoLoginCookie(response, user.getToken());
}
setSingleLoginCookie(response, user.getToken());
String prevAction = state.getPreviousAction();
LOG.debug("logIn() prevAction=" + prevAction);
if (prevAction == null) {
return redirectAfterLogin(request, response);
} else {
state.setPreviousAction(null);
return new ModelAndView(new RedirectView(prevAction));
}
}
}
Map model = errors.getModel();
model.put("login", login);
BPMS_DESCRIPTOR_PARSER.addBpmsBuildVersionsPropertiesToMap(model);
return new ModelAndView(Constants.LOGIN_VIEW, model);
} |
13899_10 | public static int readUnsignedShort(InputStream in) throws IOException {
int b0 = safeRead(in);
int b1 = safeRead(in);
return b1 << 8 | b0;
} |
Dataset Description
Microsoft created the methods2test dataset, consisting of Java Junit test cases with its corresponding focal methods. It contains 780k pairs of JUnit test cases and focal methods which were extracted from a total of 91K Java open source project hosted on GitHub.
This is an assembled version of the methods2test dataset. It provides convenient access to the different context levels based on the raw source code (e.g. newlines are preserved). The test cases and associated classes are also made available.
The mapping between test case and focal methods are based heuristics rules and Java developer's best practice.
More information could be found here:
Dataset Schema
t: <TEST_CASE>
t_tc: <TEST_CASE> <TEST_CLASS_NAME>
fm: <FOCAL_METHOD>
fm_fc: <FOCAL_CLASS_NAME> <FOCAL_METHOD>
fm_fc_c: <FOCAL_CLASS_NAME> <FOCAL_METHOD> <CONTRSUCTORS>
fm_fc_c_m: <FOCAL_CLASS_NAME> <FOCAL_METHOD> <CONTRSUCTORS> <METHOD_SIGNATURES>
fm_fc_c_m_f: <FOCAL_CLASS_NAME> <FOCAL_METHOD> <CONTRSUCTORS> <METHOD_SIGNATURES> <FIELDS>
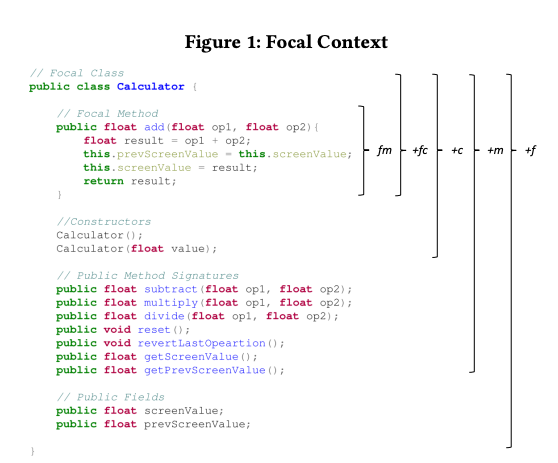
Focal Context
- fm: this representation incorporates exclusively the source code of the focal method. Intuitively, this contains the most important information for generating accurate test cases for the given method.
- fm+fc: this representations adds the focal class name, which can provide meaningful semantic information to the model.
- fm+fc+c: this representation adds the signatures of the constructor methods of the focal class. The idea behind this augmentation is that the test case may require instantiating an object of the focal class in order to properly test the focal method.
- fm+fc+c+m: this representation adds the signatures of the other public methods in the focal class. The rationale which motivated this inclusion is that the test case may need to invoke other auxiliary methods within the class (e.g., getters, setters) to set up or tear down the testing environment.
- fm+fc+c+m+f : this representation adds the public fields of the focal class. The motivation is that test cases may need to inspect the status of the public fields to properly test a focal method.
The different levels of focal contexts are the following:
T: test case
T_TC: test case + test class name
FM: focal method
FM_FC: focal method + focal class name
FM_FC_C: focal method + focal class name + constructor signatures
FM_FC_C_M: focal method + focal class name + constructor signatures + public method signatures
FM_FC_C_M_F: focal method + focal class name + constructor signatures + public method signatures + public fields
Limitations
The original authors validate the heuristics by inspecting a statistically significant sample (confidence level of 95% within 10% margin of error) of 97 samples from the training set. Two authors independently evaluated the sample, then met to discuss the disagreements. We found that 90.72% of the samples have a correct link between the test case and the corresponding focal method
Contribution
All thanks to the original authors.
- Downloads last month
- 17,809