Bug ID
int64 961
1.91M
| Comment ID
int64 3.98k
17.1M
| Author
stringlengths 8
48
| Comment Text
stringlengths 1
64.3k
⌀ |
|---|---|---|---|
1,684,459 | 15,197,012 |
**[Affected versions]:**
- Firefox Nightly 86.0a1, BuildID 20201228205313
- Firefox Beta 85.0b4, BuildID 20201220193140
**[Affected Platforms]:**
- Windows 10
- macOS 10.15
- Linux MX 4.19
**[Prerequisites]:**
- Have a new Firefox profile.
- Have the `browser.newtabpage.activity-stream.newNewtabExperience.enabled` pref set to `true`.
**[Steps to reproduce]:**
1. Open the browser with the profile from prerequisites and open a new tab.
2. Hover the "Personalize" button and observe the bahavior.
3. Click and hold the "Personalize" button and observe the behavior.
**[Expected results]:**
- Light theme:
- Step 2: The button has a dark gray hover effect.
- Step 3: The button becomes darker.
- Dark theme:
- Step 2: The button has a light gray hover effect.
- Step 3: The button becomes even lighter.
**[Actual results]:**
- Light theme:
- Step 2: The button has a dark gray hover effect.
- Step 3: The button becomes lighter.
- Dark theme:
- Step 2: The button has a light gray hover effect.
- Step 3: The button becomes darker.
**[Additional notes]:**
- The issue is also reproducible on the Light theme, but it's much more noticeable on Dark theme.
- Attached a screen recording of the issue.
|
|
1,684,967 | 15,201,419 |
From github: https://github.com/mozilla-mobile/fenix/issues/16748.
> [comment]: # (Please do your best to search for duplicate issues before filing a new issue so we can keep our issue board clean)
> [comment]: # (Every issue should have the exact bug and steps to reproduce described in it. Please do not file feedback list tickets as it is difficult to parse them and address their individual points)
> [comment]: # (Read https://github.com/mozilla-mobile/fenix#i-want-to-file-an-issue for more information)
>
> ## Steps to reproduce
>
> 1. open https://bbs.kafan.cn/forum.php?mobile=no
>
> 2. type something in the search box, then press the enter key on the keyboard, not a button on the web page, it will pop up a blank page
> 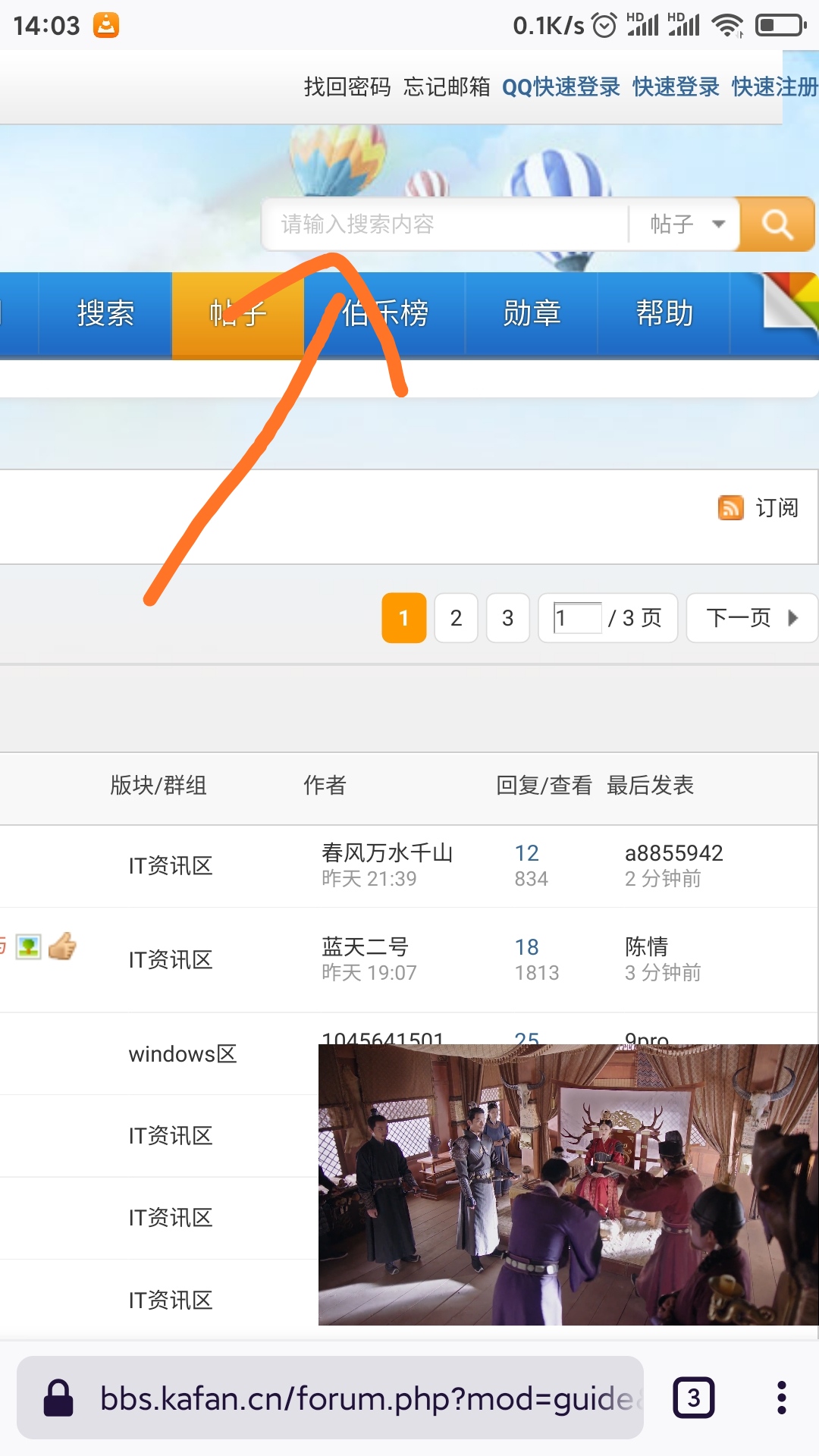
>
> 3. the first page died
>
>
> ### Expected behavior
>
>
> ### Actual behavior
>
>
> ### Device information
>
> * Android device: ?
> * Fenix version: ?
> Nightly 201123 17:01 (Build #2015777355)
> AC: 68.0.20201122190139, 52be4ca37
> GV: 85.0a1-20201122093438
> AS: 67.0.0
>
Change performed by the [Move to Bugzilla add-on](https://addons.mozilla.org/en-US/firefox/addon/move-to-bugzilla/).
|
|
1,685,925 | 15,208,839 |
The following testcase crashes on mozilla-central revision 20210108-1c7597ab79cc (opt build, run with --fuzzing-safe --ion-offthread-compile=off --baseline-warmup-threshold=0):
var realToString = toString;
function tryItOut(code) {
try {
f = new Function(code);
} catch (exc) {}
try { f(); } catch(exc) {}
delete this.toString;
this.toString = realToString;
}
t0 = new Uint8ClampedArray();
Object.defineProperty(this, 'g0', {
get: function() {
return o1.length;
}
});
o1={};
tryItOut(`g0`);
g0;
tryItOut("}");
tryItOut("}");
tryItOut("}")
tryItOut("}");
o1 = new Uint32Array();
tryItOut("}");
o1= Object.create(t0);
Array.p([g0]);
Backtrace:
received signal SIGSEGV, Segmentation fault.
0x0000022f2b6aa609 in ?? ()
#0 0x0000022f2b6aa609 in ?? ()
#1 0xfffe01b4d1800900 in ?? ()
#2 0xfffe170f1be96400 in ?? ()
#3 0xfff9800000000000 in ?? ()
#4 0x0000000000000000 in ?? ()
rax 0x1b4d1800930 1876120570160
rbx 0x2f2f2f2fffff 51879701643263
rcx 0xffffaf2f2f2f2f2f -88857786765521
rdx 0x7fffffffc360 140737488339808
rsi 0x0 0
rdi 0x7ffff6023000 140737320726528
rbp 0x7fffffffc118 140737488339224
rsp 0x7fffffffc0b8 140737488339128
r8 0x7ffff6023030 140737320726576
r9 0x7ffff6023000 140737320726528
r10 0x7fffffffb708 140737488336648
r11 0x1ffff 131071
r12 0x0 0
r13 0x0 0
r14 0x1043 4163
r15 0x7ffff6023000 140737320726528
rip 0x22f2b6aa609 2401615128073
=> 0x22f2b6aa609: cmpl $0x1,-0x17(%rbx)
0x22f2b6aa60d: jne 0x22f2b6aa63b
Marking s-s because the crash address has a 0x2f pattern and a debug build crashes with a dangerous-looking trap.
|
|
1,686,002 | 15,210,692 |
From https://github.com/mozilla-mobile/fenix/issues/17108
Steps to reproduce:
1. Go to bing.com
2. Search for something
3. Click on IMAGE to search for images
Expected:
-> IMAGES page should load
Actual:
-> Keyboard opens up for a split second then the whole GeckoView locks up, touch events not doing anything.
Reproduced in Fenix and GeckoView Example.
|
|
1,686,494 | 15,214,498 |
Created attachment 9196842
LongWaitTime.gif
**Affected versions**
* Firefox 86.0a1 (BuildId:20210113100240)
* Firefox 85.0b8 (BuildId:20210112185508)
**Affected platforms**
* Windows 10 64bit
* Ubuntu 20.04 64bit
* macOS 10.14
**Steps to reproduce**
1. Launch Firefox.
2. Open the following [webpage](https://www.stmarys-ca.edu/sites/default/files/attachments/files/Faust.pdf)
3. Hit Ctrl + P
4. Select from the page range to print the first page.
5. Click print.
**Expected result**
* The print job is successfully started.
**Actual result**
* The status remains blocked in “printing” but no actual print job is initiated.
**Regression Range**
* This seems to be a regression:
* Pushlog : https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=4489f33bf6521cdc4ecc915063d8733f5daa0814&tochange=f831fe50e3baa7ec892cb7112ccff5b4cb30ae53
* Potential Regressor: Bug 1661868
**Notes**
* For further information regarding this issue please observe the attached screencast.
* Tentatively tracking this for [print2020_v86]
|
|
1,686,611 | 15,215,235 |
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:86.0) Gecko/20100101 Firefox/86.0
Steps to reproduce:
Try to load ipchicken.com or forums.mozillazine.org on nightly, with network.dns.upgrade_with_https_rr=true (enabled by default now) and TRR enabled.
Actual results:
ipchicken.com first displays a page telling the site cannot be found, on refresh the site loads correctly.
forums.mozillazine.org doesn't load, or only partially (keeps loading forever)
Note that it seems to need uBlock Origin for the issue to be reproduced.
Sometimes the load is finished, but the banner image is missing : disabling then enabling it again in the CSS (devtools) triggers the request.
Looking at network requests in devtools doesn't show anything specific.
The IP addresses are resolved in about:networking#dns (sometimes there are up to 5 lines for the same hostname).
On about:networking#dnslookuptool, both hostnames show NS_ERROR_UNKNOWN_HOST for HTTP RR, but many other sites have this and don't fail.
|
|
1,678,906 | 15,143,137 |
[Tracking Requested - why for this release]: ux broken
Reproducible: always.
Steps to reproduce:
1. Start Firefox with new profile
2. Open sidebar
3. Move sidebar to right from dropdown of sidebar header
4. Try resize the sidebar with mouse dragging
Actual results:
The sidebar resizes in the opposite direction to the mouse drag
Expected results:
The sidebar should resize in the same direction as the mouse drag.
Regression window:
https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=2109cb4b5529c4a82279f6fc73bc40eccc06f132&tochange=d26e05828f37b8229ae9eb88fed03c61ed389ef1
|
|
1,678,987 | 15,144,972 |
User Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:83.0) Gecko/20100101 Firefox/83.0
Steps to reproduce:
Press Alt key on any site with alternative stylesheets (e.g. https://iichan.hk/b/).
Choose View -> Page Style. You can't select alternative stylesheets - there aren't any.
It's a regression due to removing disabled stylesheets from document.styleSheets for consistency with weird Blink/Webkit behavior. (https://github.com/whatwg/html/issues/3840) But this menu relies on the assumption that document.styleSheets contains all available stylesheets on the page.
Actual results:
The menu displays only currently selected stylesheet and No Style.
Expected results:
The menu should display all alternative stylesheets.
|
|
1,679,414 | 15,147,917 |
Just noticed that the MarionetteCommand actor creates an instance of the `DialogObserver` within `actorCreated`, and registers for all the following observer notifications:
> Services.obs.addObserver(this, "common-dialog-loaded");
> Services.obs.addObserver(this, "tabmodal-dialog-loaded");
> Services.obs.addObserver(this, "toplevel-window-ready");
Sadly we do not remove those listeners in `didDestroy`, and as such these are going to leak.
As result I see tons of `toplevel-window-ready` notifications for `TestClickCloseContext.test_click_close_window` when running all tests in that file.
|
|
1,679,641 | 15,149,565 |
Created attachment 9190111
screencast_of_issue.mov
Nightly 85.0a1 (2020-11-28) (64-Bit)
MacOS 10.15.7
Steps to reproduce:
1.) type google into the Address Bar
2.) arrow down until you focus the new Google Search Button
3.) press Enter to clean up the Result List
4.) now type e.g. mozilla
5.) press Enter
Actual: Google Search page opens with "mozilla" results, but the Address Bar keeps still focus.
Expected: The Address Bar should not have focus. The Page should have focus instead.
A screencast is attached.
This is a regression in latest Tring. Works fine in latest Firefox Stable.
Thanks for checking.
|
|
1,680,177 | 15,155,041 |
User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.11; rv:78.0) Gecko/20100101 Firefox/78.0
Steps to reproduce:
Click menu Bookmarks > cmd-click on any bookmark.
Actual results:
Bookmark replaces content of current tab.
Expected results:
Bookmark opens in new tab.
|
|
1,681,292 | 15,165,231 |
Created attachment 9191928
Submenu.mp4
[Affected versions]
85.0a1 (2020-12-08)
[Affected platforms]
MacOsX
[Preconditions]
Have VoiceOver enabled on MacOS (Command + F5)
[Steps to reproduce]
1. Open the Firefox browser and reach a tab's Context Menu (CTRL+Option+Shift+M)
2. Reach the Close multiple Tabs submenu.
3. Reach any of the Options (Close Other tabs / Close Tabs to the Right)
[Expected result]
The User should be able to reach the Close Multiple tabs submenu.
[Actual result]
The Submenus from the tab's Context menu are not indicated by VoiceOver.
|
|
1,636,722 | 14,806,528 |
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:76.0) Gecko/20100101 Firefox/76.0
Steps to reproduce:
1. Open firefox using the taskbar icon with no valid audio device (all audio devices disabled)
2. Open a youtube video
3. Connect an usb audio device (mine's a multilaser's ph144 warrior)
4. Update the page and play the video
5. Video still won't have audio (i always did this on prior versions and it worked as expected)
OBS: win10 x64 version 1909 build 18363.815, firefox x64 76.
I'm not an english speaker, if there is anything you can't understand, feel free to contact me.
Actual results:
The video still won't have audio after connecting a valid audio device and updating the page, even though this always worked on prior versions.
Expected results:
The video should've audio after connecting a valid audio device and updating the page as it always happened.
|
|
1,636,769 | 14,806,792 |
*Thank you for helping make Firefox better. If you are reporting a defect, please complete the following:*
## What were you doing?
I was debugging bug 1636366 comment 0 - loading the page while clearing the cache several times (ctrl-shift-delete), then looking at the network responses.
I was going up and down through network requests, using the Up and Down keyboard keys, then decided to use PgUp/PgDn
## What happened?
Netmonitor became white, and this was printed in the browser console:
```
TypeError: "can't access property "setOption", cm is undefined"
setOption resource://devtools/client/shared/sourceeditor/editor.js:1299
setMode resource://devtools/client/shared/sourceeditor/editor.js:557
updateEditor resource://devtools/client/netmonitor/src/components/previews/SourcePreview.js:92
componentDidUpdate resource://devtools/client/netmonitor/src/components/previews/SourcePreview.js:53
React 36
bootstrap resource://devtools/client/netmonitor/src/app.js:77
open resource://devtools/client/netmonitor/panel.js:20
onLoad resource://devtools/client/framework/toolbox.js:2522
react-dom.js:12769:13
TypeError: can't access property "setOption", cm is undefined
editor.js:1299:7
```
|
|
1,636,771 | 14,806,817 |
Created attachment 9147106
chacha20_oob_read.cpp
User Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0
Steps to reproduce:
Recent NSS checkout compiled on 64 bit Linux using:
./build.sh --clang --enable-fips --static --asan --disable-tests --fuzz=oss
Then compile and run the attached C++ file.
Actual results:
out-of-bounds read
=================================================================
==20341==ERROR: AddressSanitizer: global-buffer-overflow on address 0x00000085a697 at pc 0x00000063ca9c bp 0x7ffdb7d48510 sp 0x7ffdb7d48508
READ of size 1 at 0x00000085a697 thread T0
#0 0x63ca9b in Hacl_Chacha20Poly1305_256_aead_decrypt /mnt/2tb/cf-nss/sandbox/nss/out/Debug/../../lib/freebl/verified/Hacl_Chacha20Poly1305_256.c:1167:64
#1 0x58fedf in ChaCha20Poly1305_Open /mnt/2tb/cf-nss/sandbox/nss/out/Debug/../../lib/freebl/chacha20poly1305.c:267:19
#2 0x7ef031 in sftk_ChaCha20Poly1305_Decrypt /mnt/2tb/cf-nss/sandbox/nss/out/Debug/../../lib/softoken/pkcs11c.c:705:12
#3 0x7f1383 in NSC_Decrypt /mnt/2tb/cf-nss/sandbox/nss/out/Debug/../../lib/softoken/pkcs11c.c:1813:10
#4 0x6eadfd in PK11_Decrypt /mnt/2tb/cf-nss/sandbox/nss/out/Debug/../../lib/pk11wrap/pk11obj.c:933:11
#5 0x5192a8 in main /mnt/2tb/cf-nss/cryptofuzz/modules/nss/poc.cpp:46:5
#6 0x7f503c413b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#7 0x41c6e9 in _start (/mnt/2tb/cf-nss/cryptofuzz/modules/nss/poc+0x41c6e9)
I have not yet checked if Firefox via TLS or WebCrypt might be affected.
Expected results:
no memory violations
|
|
1,638,030 | 14,820,099 | null |
|
1,638,297 | 14,822,649 |
Created attachment 9149348
Recording of the issue
**Tested on:**
Windows 10
MacOS
**Affected builds:**
Nightly 78.0a1 (2020-05-14)
Beta 77.0b7
**Steps to reproduce:**
1. Go on a register form, ex: [Wikipedia](https://en.wikipedia.org/w/index.php?title=Special:CreateAccount&returnto=Main+Page)
2. Click on the Password field and select Use a Securely Generated password
**the generated password will be filled in the Password (unmasked) and Confirm password field as well (masked)
3. Edit the generated password (in the Password field) and focus out of the field
**Expected:**
The "Password Saved!" toast should be displayed and edits autosaved.
**Actual result:**
The toast is not displayed and edits are not auto-saved.
**Notes:**
Only the edits for the Confirm password field are auto-saved. Maybe the edits of the second field are captured as it is seen as the last field that was autofilled with a generated password?
**Regression-range:**
This seems to be because of Bug 1576490 , as now we also autofill the second password field with the generated password.
On Release 76 (where we don't have the above functionality) the edits are saved on the fly correctly for both fields.
|
|
1,638,568 | 14,825,382 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:76.0) Gecko/20100101 Firefox/76.0
Steps to reproduce:
Open this page with Firefox 75.0 or 76.0:
https://sergeyext.github.io/sergeyext/firefox_gluniform3fv_test.html
Then open console (F12)
Actual results:
There are two errors in console:
1) WebGL warning: uniform setter: `values` length (4) must be a positive integer multiple of size of <enum 0x8b51>.
2) GL error state is set to GL_INVALID_VALUE.
Expected results:
Should be no errors.
Some renderers control their shader features with shader source modification and/or glsl preprocessor macros. Such shader design can cause some uniforms to be optimized out. In this case getUniformLocation returns null, and it should be perfectly OK to pass null or undefined to uniform setter functions. It is similar to passing -1 as uniform location in GL ES3, in which case the passed in values are silently ignored.
When passing null or undefined to glUniform3fv in FF 75 or 76, it warns that array length should be multiple of sizeof<enum 0x8b51> (i.e. sizeof vec3, 12 bytes), which is completely irrelevant, as the same call with valid uniform location object does not have such requirement.
Also, gl error state is set to GL_INVALID_VALUE, which seems to be irrelevant too, as in ES3 this error is only generated when count is less than 0.
|
|
1,639,165 | 14,830,395 |
**Steps to reproduce**
1. Go to https://nchevobbe.github.io/demo/console-test-app.html
1. Open the multiprocess browser toolbox
1. In the content page, click on the "Exception" button
**Expected results**
An error is displayed in the browser toolbox
**Actual results**
2 errors are displayed in the browser toolbox.
---
After some investigation, I was able to see that those messages are coming from different targets.
The first one is from the content process target, and the second one from the parent process one.
I think the second message is coming from [xpcom/base/nsConsoleService.cpp#162](https://searchfox.org/mozilla-central/rev/9193635dca8cfdcb68f114306194ffc860456044/xpcom/base/nsConsoleService.cpp#162), where nsIScriptError from the content processes are forwarded to the parent process.
We should return early in `MaybeForwardScriptError` if `devtools.browsertoolbox.fission` is set to `true`.
|
|
1,625,791 | 14,721,962 |
User Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:74.0) Gecko/20100101 Firefox/74.0
Steps to reproduce:
Thunderbird 68.4.1 (and some versions before, too), Ubuntu 18.04. I'm not sure which NSS version is used, but it's the one used by the TB binaries from Ubuntu. apt doesn't show any dependency on nss, so it's probably compiled in.
I have a smartcard set up which which holds my signing certificates for S/MIME. Right after insertion of the card, signing works. But after some time (say, hours), the card seems to become kind of stale (it may well be a problem of its PKCS#11 driver, or just the card being old (5+ years)). When I'm composing a message and TB tries to save a draft, which triggers signing, I get a complete hang of TB. The same happens when sending the message before draft is saved (but again, only when the card gets into this stale state).
Maybe this is a regression/consequence of https://bugzilla.mozilla.org/show_bug.cgi?id=1381784 ?
Actual results:
This is the stack trace of thread #1, which is the stuck one:
#0 0x00007fec266bc10d in __lll_lock_wait () at ../sysdeps/unix/sysv/linux/x86_64/lowlevellock.S:135
#1 0x00007fec266b5154 in __GI___pthread_mutex_lock (mutex=0x7fec07efd660) at ../nptl/pthread_mutex_lock.c:133
#2 0x00007fec24ea5cf9 in PR_Lock (lock=0x7fec07efd660) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/nsprpub/pr/src/pthreads/ptsynch.c:171
#3 0x00007fec23dbc02c in nssTrustDomain_RemoveTokenCertsFromCache (td=0x7fec088cf830, token=0x7fec088d2830)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/tdcache.c:428
#4 0x00007fec23db2f8e in nssSlot_IsTokenPresent (slot=0x7fec088d3030) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/dev/devslot.c:240
#5 0x00007fec23db301c in nssSlot_GetToken (slot=0x7fec088d3030) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/dev/devslot.c:285
#6 0x00007fec23dbd875 in nssTrustDomain_FindTrustForCertificate (td=0x7fec088cf830, c=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/trustdomain.c:1059
#7 0x00007fec23db825d in nssTrust_GetCERTCertTrustForCert (c=0x7febef3210c0, cc=0x7febef322020)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/pki3hack.c:613
#8 0x00007fec23db8ab3 in fill_CERTCertificateFields (c=<optimized out>, cc=<optimized out>, forced=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/pki3hack.c:819
#9 0x00007fec23db8ab3 in stan_GetCERTCertificate (c=0x7febef3210c0, forceUpdate=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/pki3hack.c:893
#10 0x00007fec23db6e79 in nssCertificate_GetDecoding (c=0x7febef3210c0) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/certificate.c:266
#11 0x00007fec23db6e79 in nssCertificate_SubjectListSort (v1=0x7febef3210c0, v2=0x7febee6d60c0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/certificate.c:699
#12 0x00007fec23db18ff in nsslist_add_element (list=0x7febee6d8830, data=0x7febef3210c0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/base/list.c:194
#13 0x00007fec23db1a0c in nssList_AddUnique (list=0x7febee6d8830, data=0x7febef3210c0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/base/list.c:241
#14 0x00007fec23dbc573 in add_subject_entry (arena=0x7febf19bcf70, cache=0x7fec088d0030, cert=<optimized out>, nickname=<optimized out>, subjectList=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/tdcache.c:523
#15 0x00007fec23dbc573 in add_cert_to_cache (td=0x7fec088cf830, cert=0x7febef3210c0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/tdcache.c:752
#16 0x00007fec23dbc573 in nssTrustDomain_AddCertsToCache (td=0x7fec088cf830, certs=<optimized out>, numCerts=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/tdcache.c:841
#17 0x00007fec23dbab20 in cert_createObject (o=0x7febef321030) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/pkibase.c:1023
#18 0x00007fec23dba826 in nssPKIObjectCollection_AddInstanceAsObject (collection=0x7febeba4a830, instance=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/pkibase.c:927
#19 0x00007fec23db4f74 in nssToken_TraverseCertificates (token=0x7fec088d1830, sessionOpt=<optimized out>, searchType=<optimized out>, callback=
0x7fec23dbd7d0 <collector>, arg=0x7febeba4a830) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/dev/devtoken.c:1531
#20 0x00007fec23dbd760 in NSSTrustDomain_TraverseCertificates (td=<optimized out>, callback=0x7fec23d9fa70 <CollectNicknames>, arg=0x7febeb868820)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/pki/trustdomain.c:1019
#21 0x00007fec23d9f849 in CERT_GetCertNicknames (handle=0x7fec088cf830, what=2, wincx=0x7febec10ee90)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/security/nss/lib/certhigh/certhigh.c:485
#22 0x00007fec1380d1fc in nsMsgComposeSecure::MimeCryptoHackCerts(char const*, nsIMsgSendReport*, bool, bool, nsIMsgIdentity*) (this=0x7febf32db8a0, aRecipients=0x7febec2b1820 "*REDACTED*", sendReport=0x7febeef18e70, aEncrypt=<optimized out>, aSign=<optimized out>, aIdentity=0x7fec07683a60)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/extensions/smime/src/nsMsgComposeSecure.cpp:811
#23 0x00007fec1380cf71 in nsMsgComposeSecure::BeginCryptoEncapsulation(nsIOutputStream*, char const*, nsIMsgCompFields*, nsIMsgIdentity*, nsIMsgSendReport*, bool) (this=0x7febf32db8a0, aStream=0x7febe9747268, aRecipients=0x7febec2b1820 "*REDACTED*", aCompFields=<optimized out>, aIdentity=0x7fec07683a60, sendReport=0x7febeef18e70, aIsDraft=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/extensions/smime/src/nsMsgComposeSecure.cpp:359
#24 0x00007fec137c0757 in nsMsgComposeAndSend::BeginCryptoEncapsulation() (this=0x7febe6e39ff0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSend.cpp:1065
#25 0x00007fec137d0cc6 in nsMsgSendPart::Write() (this=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSendPart.cpp:448
#26 0x00007fec137bf54e in nsMsgComposeAndSend::GatherMimeAttachments() (this=0x7febe6e39ff0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSend.cpp:836
#27 0x00007fec137c5a2b in nsMsgComposeAndSend::HackAttachments(nsIArray*, nsIArray*) (this=0x7febe6e39ff0, attachments=0x0, preloadedAttachments=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSend.cpp:2266
#28 0x00007fec137c7387 in nsMsgComposeAndSend::Init(nsIMsgIdentity*, char const*, nsMsgCompFields*, nsIFile*, bool, bool, int, nsIMsgDBHdr*, char const*, nsTSubstring<char> const&, nsIArray*, nsIArray*, nsTSubstring<char16_t> const&, nsTSubstring<char> const&, int) (this=0x7febe6e39ff0, aUserIdentity=0x7fec07683a60, aAccountKey=<optimized out>, fields=0x7febe6afd580, sendFile=0x0, digest_p=false, dont_deliver_p=false, mode=4, msgToReplace=0x0, attachment1_type=0x7fec17ed0639 "text/html", attachment1_body=..., attachments=0x0, preloaded_attachments=0x0, password=..., aOriginalMsgURI=..., aType=2)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSend.cpp:2793
#29 0x00007fec137cb1ef in nsMsgComposeAndSend::CreateAndSendMessage(nsIEditor*, nsIMsgIdentity*, char const*, nsIMsgCompFields*, bool, bool, int, nsIMsgDBHdr*, char const*, nsTSubstring<char> const&, nsIArray*, nsIArray*, mozIDOMWindowProxy*, nsIMsgProgress*, nsIMsgSendListener*, nsTSubstring<char16_t> const&, nsTSubstring<char> const&, int) (this=0x7febe6e39ff0, aEditor=0x7febe98c4c00, aUserIdentity=0x7fec07683a60, aAccountKey=0x7febec10e630 "account3", fields=0x7febe6afd580, digest_p=<optimized out>, dont_deliver_p=<optimized out>, mode=<optimized out>, msgToReplace=<optimized out>, attachment1_type=<optimized out>, attachment1_body=..., attachments=<optimized out>, preloaded_attachments=<optimized out>, parentWindow=<optimized out>, progress=<optimized out>, aListener=<optimized out>, password=..., aOriginalMsgURI=..., aType=<optimized out>) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgSend.cpp:3717
#30 0x00007fec137a7da4 in nsMsgCompose::SendMsgToServer(int, nsIMsgIdentity*, char const*) (this=0x7fec10920f60, deliverMode=4, identity=0x7fec07683a60, accountKey=0x7febec10e630 "account3") at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgCompose.cpp:1186
#31 0x00007fec137a89c9 in nsMsgCompose::SendMsg(int, nsIMsgIdentity*, char const*, nsIMsgWindow*, nsIMsgProgress*) (this=0x7fec10920f60, deliverMode=<optimized out>, identity=0x7fec07683a60, accountKey=0x7febec10e630 "account3", aMsgWindow=0x7febe8ecb880, progress=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mailnews/compose/src/nsMsgCompose.cpp:1378
#32 0x00007fec13a84082 in NS_InvokeByIndex () at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/xpcom/reflect/xptcall/md/unix/xptcinvoke_asm_x86_64_unix.S:106
#33 0x00007fec1421ab7b in CallMethodHelper::Invoke() (this=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/xpconnect/src/XPCWrappedNative.cpp:1650
#34 0x00007fec1421ab7b in CallMethodHelper::Call() (this=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/xpconnect/src/XPCWrappedNative.cpp:1191
#35 0x00007fec1421ab7b in XPCWrappedNative::CallMethod(XPCCallContext&, XPCWrappedNative::CallMode) (ccx=..., mode=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/xpconnect/src/XPCWrappedNative.cpp:1157
#36 0x00007fec1421c0fb in XPC_WN_CallMethod(JSContext*, unsigned int, JS::Value*) (cx=0x7fec0af23000, argc=<optimized out>, vp=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/xpconnect/src/XPCWrappedNativeJSOps.cpp:946
#37 0x00007fec16f26890 in CallJSNative(JSContext*, bool (*)(JSContext*, unsigned int, JS::Value*), JS::CallArgs const&) (cx=<optimized out>, native=
0x7fec1421bee0 <XPC_WN_CallMethod(JSContext*, unsigned int, JS::Value*)>, args=...)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:443
#38 0x00007fec16f26890 in js::InternalCallOrConstruct(JSContext*, JS::CallArgs const&, js::MaybeConstruct) (cx=0x7fec0af23000, args=..., construct=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:535
#39 0x00007fec16f20182 in js::CallFromStack(JSContext*, JS::CallArgs const&) (cx=<optimized out>, args=...)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:594
#40 0x00007fec16f20182 in Interpret(JSContext*, js::RunState&) (cx=<optimized out>, state=...)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:3082
#41 0x00007fec16f16361 in js::RunScript(JSContext*, js::RunState&) (cx=0x7fec0af23000, state=...)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:423
#42 0x00007fec16f26b7d in js::InternalCallOrConstruct(JSContext*, JS::CallArgs const&, js::MaybeConstruct) (cx=0x7fec0af23000, args=..., construct=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:563
#43 0x00007fec16f27036 in js::Call(JSContext*, JS::Handle<JS::Value>, JS::Handle<JS::Value>, js::AnyInvokeArgs const&, JS::MutableHandle<JS::Value>) (cx=0x7fec07efd660, fval=..., thisv=..., args=..., rval=...) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/vm/Interpreter.cpp:606
#44 0x00007fec1727e280 in JS::Call(JSContext*, JS::Handle<JS::Value>, JS::Handle<JS::Value>, JS::HandleValueArray const&, JS::MutableHandle<JS::Value>) (cx=0x7fec0af23000, thisv=..., fval=..., args=..., rval=...) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/js/src/jsapi.cpp:2673
#45 0x00007fec1511e43c in mozilla::dom::Function::Call(JSContext*, JS::Handle<JS::Value>, nsTArray<JS::Value> const&, JS::MutableHandle<JS::Value>, mozilla::ErrorResult&) (this=0x7febeb153540, cx=<optimized out>, aThisVal=..., arguments=..., aRetVal=..., aRv=...) at FunctionBinding.cpp:41
#46 0x00007fec148618e3 in mozilla::dom::Function::Call<nsCOMPtr<nsISupports> >(nsCOMPtr<nsISupports> const&, nsTArray<JS::Value> const&, JS::MutableHandle<JS::Value>, mozilla::ErrorResult&, char const*, mozilla::dom::CallbackObject::ExceptionHandling, JS::Realm*) (this=0x7febeb153540, thisVal=..., arguments=..., aRetVal=..., aRv=..., aExecutionReason=<optimized out>, aExceptionHandling=mozilla::dom::CallbackObject::eReportExceptions, aRealm=0x0)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/obj-x86_64-linux-gnu/dist/include/mozilla/dom/FunctionBinding.h:73
#47 0x00007fec148613b8 in nsGlobalWindowInner::RunTimeoutHandler(mozilla::dom::Timeout*, nsIScriptContext*) (this=
0x7febe78e8000, aTimeout=0x7febf95e6c80, aScx=<optimized out>) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/dom/base/nsGlobalWindowInner.cpp:5695
#48 0x00007fec14962348 in mozilla::dom::TimeoutManager::RunTimeout(mozilla::TimeStamp const&, mozilla::TimeStamp const&, bool) (this=0x7febe99fc030, aNow=..., aTargetDeadline=..., aProcessIdle=<optimized out>) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/dom/base/TimeoutManager.cpp:971
#49 0x00007fec1495e774 in mozilla::dom::TimeoutExecutor::MaybeExecute() (this=0x7febe65c3280)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/dom/base/TimeoutExecutor.cpp:177
#50 0x00007fec1495e774 in mozilla::dom::TimeoutExecutor::Notify(nsITimer*) (this=0x7febe65c3280, aTimer=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/dom/base/TimeoutExecutor.cpp:244
#51 0x00007fec1495e7aa in non-virtual thunk to mozilla::dom::TimeoutExecutor::Notify(nsITimer*) ()
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/dom/base/TimeoutBudgetManager.cpp:34
#52 0x00007fec13a71c2e in nsTimerImpl::Fire(int) (this=0x7febfc6dda60, aGeneration=13)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/xpcom/threads/nsTimerImpl.cpp:564
#53 0x00007fec13a7194d in nsTimerEvent::Run() (this=0x7fec0287a3e0) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/xpcom/threads/TimerThread.cpp:260
#54 0x00007fec13a77ae6 in nsThread::ProcessNextEvent(bool, bool*) (this=0x7fec109d6b80, aMayWait=<optimized out>, aResult=0x7ffe6d0eaba7)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/xpcom/threads/nsThread.cpp:1175
#55 0x00007fec13a797a6 in NS_ProcessNextEvent(nsIThread*, bool) (aThread=0x7fec07efd660, aMayWait=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/xpcom/threads/nsThreadUtils.cpp:486
#56 0x00007fec13f15edd in mozilla::ipc::MessagePump::Run(base::MessagePump::Delegate*) (this=0x7fec10934800, aDelegate=0x7fec25558200)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/ipc/glue/MessagePump.cpp:110
#57 0x00007fec13ee0048 in MessageLoop::RunInternal() (this=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/ipc/chromium/src/base/message_loop.cc:315
#58 0x00007fec13ee0048 in MessageLoop::RunHandler() (this=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/ipc/chromium/src/base/message_loop.cc:308
#59 0x00007fec13ee0048 in MessageLoop::Run() (this=0x80) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/ipc/chromium/src/base/message_loop.cc:290
#60 0x00007fec15d2f5a6 in nsBaseAppShell::Run() (this=0x7fec0fa80a00) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/widget/nsBaseAppShell.cpp:137
#61 0x00007fec16d7422b in nsAppStartup::Run() (this=0x7fec0fb83920)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/toolkit/components/startup/nsAppStartup.cpp:276
#62 0x00007fec16e461d0 in XREMain::XRE_mainRun() (this=0x7ffe6d0eaea0) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/toolkit/xre/nsAppRunner.cpp:4616
#63 0x00007fec16e46949 in XREMain::XRE_main(int, char**, mozilla::BootstrapConfig const&) (this=0x7ffe6d0eaea0, argc=<optimized out>, argv=<optimized out>, aConfig=...) at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/toolkit/xre/nsAppRunner.cpp:4750
#64 0x00007fec16e46e15 in XRE_main(int, char**, mozilla::BootstrapConfig const&) (argc=128, argv=0xb, aConfig=...)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/toolkit/xre/nsAppRunner.cpp:4831
#65 0x000056021b0d361c in do_main(int, char**, char**) (argc=128, argv=<optimized out>, envp=<optimized out>)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mail/app/nsMailApp.cpp:216
#66 0x000056021b0d361c in main(int, char**, char**) (argc=<optimized out>, argv=<optimized out>, envp=0x7ffe6d0ec138)
at /build/thunderbird-ThyQ3Z/thunderbird-68.4.1+build1/comm/mail/app/nsMailApp.cpp:291
|
|
1,633,270 | 14,778,760 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Steps to reproduce:
1. In about:preferences#general -> Applications, make sure the Action for PDFs is "Preview in Firefox
2. click the Download button on e.g. https://github.com/trailofbits/publications/blob/master/reviews/hegic-summary.pdf
Actual results:
The download is immediately started, without a confirmation popup. Given that this is unexpected, the *file downloaded* animation is easy to miss.
Expected results:
Either:
- the pdf should have been previewed with pdf.js
Or:
- the download confirmation popup should have been displayed
Note: I've found a similar Bug, but I belive this to be a different issue:
- Bug 1231127 - "Open with" option missing for files sent as Content-Type: application/octet-stream
|
|
1,633,880 | 14,784,907 |
**Filed by:** nbeleuzu [at] mozilla.com
**Parsed log:** https://treeherder.mozilla.org/logviewer.html#?job_id=299839709&repo=autoland
**Full log:** https://firefox-ci-tc.services.mozilla.com/api/queue/v1/task/NXuwz04MTzGpuWJMXmLtOg/runs/0/artifacts/public/logs/live_backing.log
---
[task 2020-04-28T19:31:18.611Z] 19:31:18 INFO - PID 4148 | Write of size 8 at 0x7f2c1893cd18 by main thread:
[task 2020-04-28T19:31:18.611Z] 19:31:18 INFO - PID 4148 | #0 AssignAssumingAddRef /builds/worker/workspace/obj-build/dist/include/mozilla/StaticPtr.h:171:13 (libxul.so+0x3912542)
[task 2020-04-28T19:31:18.611Z] 19:31:18 INFO - PID 4148 | #1 AssignWithAddref /builds/worker/workspace/obj-build/dist/include/mozilla/StaticPtr.h:166:5 (libxul.so+0x3912542)
[task 2020-04-28T19:31:18.611Z] 19:31:18 INFO - PID 4148 | #2 operator= /builds/worker/workspace/obj-build/dist/include/mozilla/StaticPtr.h:120:5 (libxul.so+0x3912542)
[task 2020-04-28T19:31:18.612Z] 19:31:18 INFO - PID 4148 | #3 mozilla::dom::IPCBlobInputStreamStorage::Observe(nsISupports*, char const*, char16_t const*) /builds/worker/checkouts/gecko/dom/file/ipc/IPCBlobInputStreamStorage.cpp:64:14 (libxul.so+0x3912542)
[task 2020-04-28T19:31:18.612Z] 19:31:18 INFO - PID 4148 | #4 nsObserverList::NotifyObservers(nsISupports*, char const*, char16_t const*) /builds/worker/checkouts/gecko/xpcom/ds/nsObserverList.cpp:65:19 (libxul.so+0xa4dbd3)
[task 2020-04-28T19:31:18.612Z] 19:31:18 INFO - PID 4148 | #5 nsObserverService::NotifyObservers(nsISupports*, char const*, char16_t const*) /builds/worker/checkouts/gecko/xpcom/ds/nsObserverService.cpp:288:19 (libxul.so+0xa50a0c)
[task 2020-04-28T19:31:18.613Z] 19:31:18 INFO - PID 4148 | #6 mozilla::ShutdownXPCOM(nsIServiceManager*) /builds/worker/checkouts/gecko/xpcom/build/XPCOMInit.cpp:618:26 (libxul.so+0xb13c22)
[task 2020-04-28T19:31:18.613Z] 19:31:18 INFO - PID 4148 | #7 NS_ShutdownXPCOM /builds/worker/checkouts/gecko/xpcom/build/XPCOMInit.cpp:565:10 (libxul.so+0xb13ae5)
[task 2020-04-28T19:31:18.614Z] 19:31:18 INFO - PID 4148 | #8 XRE_XPCShellMain(int, char**, char**, XREShellData const*) /builds/worker/checkouts/gecko/js/xpconnect/src/XPCShellImpl.cpp:1383:8 (libxul.so+0x1923f85)
[task 2020-04-28T19:31:18.614Z] 19:31:18 INFO - PID 4148 | #9 mozilla::BootstrapImpl::XRE_XPCShellMain(int, char**, char**, XREShellData const*) /builds/worker/checkouts/gecko/toolkit/xre/Bootstrap.cpp:54:12 (libxul.so+0x63a26ab)
[task 2020-04-28T19:31:18.614Z] 19:31:18 INFO - PID 4148 | #10 main /builds/worker/checkouts/gecko/js/xpconnect/shell/xpcshell.cpp:66:27 (xpcshell+0xc8b86)
-------------------------------------------------------
[task 2020-04-28T19:31:18.648Z] 19:31:18 INFO - PID 4148 | #65 XRE_XPCShellMain(int, char**, char**, XREShellData const*) /builds/worker/checkouts/gecko/js/xpconnect/src/XPCShellImpl.cpp:1353:14 (libxul.so+0x1924634)
[task 2020-04-28T19:31:18.649Z] 19:31:18 INFO - PID 4148 | #66 mozilla::BootstrapImpl::XRE_XPCShellMain(int, char**, char**, XREShellData const*) /builds/worker/checkouts/gecko/toolkit/xre/Bootstrap.cpp:54:12 (libxul.so+0x63a26ab)
[task 2020-04-28T19:31:18.649Z] 19:31:18 INFO - PID 4148 | #67 main /builds/worker/checkouts/gecko/js/xpconnect/shell/xpcshell.cpp:66:27 (xpcshell+0xc8b86)
[task 2020-04-28T19:31:18.649Z] 19:31:18 INFO - PID 4148 | SUMMARY: ThreadSanitizer: data race /builds/worker/workspace/obj-build/dist/include/mozilla/StaticPtr.h:171:13 in AssignAssumingAddRef
|
|
1,634,090 | 14,786,557 |
This bug is for crash report bp-6f44326d-0797-4ccc-b1d1-dbb220200428.
```
Top 10 frames of crashing thread:
0 fcagff64.dll fcagff64.dll@0x3774b9
1 fcagff64.dll fcagff64.dll@0xc7354
2 fcagff64.dll fcagff64.dll@0xd35b8
3 fcagff64.dll fcagff64.dll@0x201be
4 mozglue.dll arena_t::GetNonFullBinRun memory/build/mozjemalloc.cpp:2715
5 mozglue.dll static Allocator<MozJemallocBase>::malloc memory/build/malloc_decls.h:51
6 mozglue.dll static Allocator<MozJemallocBase>::malloc memory/build/malloc_decls.h:51
7 mozglue.dll replace_malloc memory/replace/phc/PHC.cpp:1122
8 mozglue.dll moz_xmalloc memory/mozalloc/mozalloc.cpp:52
9 @0x24162f4257f
```
Crashes starting with Nightly build 20200415215103 in some DLL from McAfee. Bug 1420872 also reported similar crashes in that DLL a while ago. Not sure if this is actionable.
|
|
1,634,386 | 14,788,614 |
Created attachment 9144668
linux.png
**[Affected versions]:**
- Firefox Nightly 77.0a1 Build ID 20200429215539;
**[Affected Platforms]:**
- Linux Ubuntu 18.04;
**[Prerequisites]:**
- Have at least a pair of credentials saved in latest Chrome (i.e for Facebook)
- In Firefox set “signon.showAutoCompleteImport” pref to “import”
**[Steps to reproduce]:**
1. Open the browser with the profile from prerequisites.
2. Open in Firefox the site foe which you saved the credentials.
3. Click on the username field.
4. The password autocomplete import suggestion is displayed.
**[Expected result]:**
- Nothing should be displayed, because importing passwords is not possible while using Linux.
**[Actual result]:**
- The Password Import Autocomplete option is displayed, and the import wizard can be triggered.
**[Notes}:**
- Finalizing the wizard will have no effect, and the import suggestion will be re-displayed.
- The wizard options are correct - don’t contain password options to be imported.
|
|
1,635,106 | 14,795,712 |
STR
1. Start Firefox
2. Use it without closing for 3-4 days
3. Copy some information from a web page
4. Try to paste to any editable element (textarea, input, etc) with context menu
5. Try to get a spelling suggestion for any word highlighted as spelt incorrectly.
Expected result
1. Option to paste in context menu
2. List of potential words to replace incorrectly spelt word.
Actual result
1. Varies sometimes context menu shows things like:
Copy, Select All, Search Google for "<paste content>", Inspect Element
or:
Navigation icons, Save Page As..., etc
It seems to depend on the last context menu outside of an editable element
2. As for 1.
Workaround:
Keyboard shortcuts still work for pasting.
Also to note:
Context menu still works correctly in browser's address bar, search and other UI dialogs.
|
|
1,635,490 | 14,798,155 |
User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:78.0) Gecko/20100101 Firefox/78.0
Steps to reproduce:
1. Install Reddit Enhancement Suite
2. Browsed Reddit on an account with "New Reddit" disabled to get the classic view
3. Scrolled down to bottom of page
This problem started on either the 3rd or 4th of May nightly builds and has been tested with both Linux and macOS based systems with the same results. Older versions of Firefox still work as expected showing this is not a regression in the extension itself (though it has been reported to them also - https://www.reddit.com/r/RESissues/comments/gdu62a/could_not_load_the_next_page_page_loaded_was_not/ )
Actual results:
Neverending reddit fails with "Could not load the next page: Page loaded was not for current user"
Expected results:
Next page should have loaded
|
|
1,627,427 | 14,734,799 |
Created attachment 9138237
screen.png
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0
Steps to reproduce:
Open this PDF file in FireFox.
https://gongu.copyright.or.kr/gongu/wrt/cmmn/wrtFileDownload.do?wrtSn=9002094&fileSn=1&wrtFileTy=01
If the direct download link does not work, go to https://gongu.copyright.or.kr/gongu/wrt/wrt/view.do?wrtSn=9002094&menuNo=200030
and click the big teal download button at the centre of the page.
Select the first sentence, and right click it.
Actual results:
"새쵨하게 흐린 펈이 눈이 씬 듯하더니 눈은 아니 씤고 얼다가 만 비가 추윁추윁 내리는 꾠이었다." is copied. See the attached screenshot. Top is FireFox, and bottom is Chrome.
Expected results:
"새침하게 흐린 품이 눈이 올 듯하더니 눈은 아니 오고 얼다가 만 비가 추
적추적 내리는 날이었다." should be copied, as is when doing the same thing in Chrome.
|
|
1,627,667 | 14,738,072 |
This bug is for crash report bp-a786feaf-ea57-4075-970f-8fceb0200404.
```
Top 10 frames of crashing thread:
0 ucrtbase.dll strlen
1 xul.dll std::basic_string<char, std::char_traits<char>, std::allocator<char> >::assign vs2017_15.8.4/VC/include/xstring:2676
2 xul.dll mozilla::WebGLContext::GetString const dom/canvas/WebGLContext.cpp
3 xul.dll mozilla::RunOn<mozilla::Maybe<std::basic_string<char, std::char_traits<char>, std::allocator<char> > > dom/canvas/ClientWebGLContext.cpp:372
4 xul.dll mozilla::ClientWebGLContext::GetParameter dom/canvas/ClientWebGLContext.cpp:1907
5 xul.dll mozilla::dom::WebGLRenderingContext_Binding::getParameter dom/bindings/WebGLRenderingContextBinding.cpp:18104
6 xul.dll mozilla::dom::binding_detail::GenericMethod<mozilla::dom::binding_detail::NormalThisPolicy, mozilla::dom::binding_detail::ThrowExceptions> dom/bindings/BindingUtils.cpp:3205
7 xul.dll js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:581
8 xul.dll Interpret js/src/vm/Interpreter.cpp:3040
9 xul.dll js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:616
```
This is a `NULL` pointer access that started with 74.0. Disregard all crashes for older versions as they're unrelated and have different stacks. The stacks are consistent across versions and the oldest crash I could find is for 74.0 nightly with buildid 20200116214549.
|
|
1,629,783 | 14,753,436 |
Created attachment 9140343
canvasFF75.html
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:75.0) Gecko/20100101 Firefox/75.0
Steps to reproduce:
In Firefox version 75, webgl canvas contents are lost when setting the size to an unchanged value. This does not happen in Firefox version 74 and earlier or chrome.
Attached is a minimal reproduction sample. The green square disappears in version 75 and newer.
Actual results:
canvas contents are lost. I'm not sure if this behavior is technically allowed by the spec, but it looks like an unintended regression to me.
Expected results:
The contents of the canvas should be preserved when setting the canvas size to an unchanged value.
|
|
1,563,236 | 14,212,919 |
User Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:67.0) Gecko/20100101 Firefox/67.0
Steps to reproduce:
The unwrapKey method does not support AES-KW wrapped key:
window.crypto.subtle.unwrapKey(
'raw',
wrappedKey, // AES-KW wrapped key
wrappingKey, // AES-KW wrapping key
'AES-KW',
{ name: 'AES-KW', length: 256 },
true,
['wrapKey', 'unwrapKey']
)
Actual results:
An error is returned: DOMException: "Operation is not supported".
Expected results:
The AES-KW key should be unwrapped, as it is a valid key algorithm according to the documentation:
https://developer.mozilla.org/en-US/docs/Web/API/SubtleCrypto/unwrapKey
I assume this is because "WEBCRYPTO_ALG_AES_KW" is missing here: https://dxr.mozilla.org/mozilla-central/source/dom/crypto/WebCryptoTask.cpp#3410-3414
|
|
1,639,173 | 14,830,414 |
Created attachment 9150102
info button is not reachable with keyboard only navigation.gif
**[Affected versions]:**
- Firefox Nightly 78.0a1, BuildID 20200518214824
- Firefox Beta 77.0b7, BuildID 20200515125749
**[Affected Platforms]:**
- All Windows
- All Mac
**[Prerequisites]:**
- Have a clean new profile with no saved or imported logins.
- Have the following prefs set to the following values:
- `signon.showAutoCompleteImport` set to `import`
- Have a couple of logins saved in either Chrome or Edge (chromium)
**[Steps to reproduce]:**
1. Open the browser with the profile from prerequisites and navigate to a website that has a saved login in Chrome/Edge.
2. Focus the username filed.
3. Press the `Down Arrow` key twice.
4. Press the `Enter` key and observe the behavior.
**[Expected results]:**
- The `https://support.mozilla.org/en-US/kb/import-data-another-browser?as=u&utm_source=inproduct` page is opened.
**[Actual results]:**
- The `about:logins` page is opened.
**[Additional Notes]:**
- Attached a screen recording of the issue.
|
|
1,639,816 | 14,835,210 |
Created attachment 9150700
printProblem .gif
**Affected versions**
* Firefox 76.0.1 (BuildId:20200507114007)
* Firefox 77.0b8 (BuildId:20200519220135)
* Firefox 78.0a1 (BuildId:20200520213050)
**Unaffected versions**
* Firefox 68.8.0esr (BuildId:20200429190206)
**Affected platforms**
* Windows 10 64bit
* Ubuntu 18.04 64bit
**Unaffected platforms**
* macOS 10.14
**Steps to reproduce**
1. Launch Firefox.
2. Access the about:support page.
3. Press CTRL + P in order to open the Print Menu.
4. Click on Print.
5. Redo Steps 3 & 4.
**Expected result**
* The about:support page is successfully printed.
**Actual result**
* Step 3: Nothing happens (for both print to file/pdf or starting an actual print job).
* Step 5: The following error is shown: `Some printing functionality is not currently available`.
**Regression Range**
This seems to be a regression
* Pushlog:https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=40ca68bfea62e27f6934d4327f1ff88df9c17828&tochange=4c92802939c15a2356c587d247577e07cfb52ff7
* Regressed by: Bug 1552966
**Notes**
* macOS has a different behavior See Bug 1639823
* Printing the page via print preview seems to work as expected.
* After triggering this issue navigation from about:support to any other local page (about:cache,etc) seems to no longer work. A workaround for this is opening another tab and accessing the local page or from within the same broken tab accessing a remote website and then a local page.
* The Browser Console outputs the following error: `In Printing:Print:Done handler, got unexpected rv 2147746065. 2 PrintingChild.jsm:403`
* At first try it will not print and the error is displayed, at second try (in a new tab or after accessing a remote page and going back) it will print but printing again after a successful print seems to no longer work again.
|
|
1,639,901 | 14,835,735 |
[initiatorType](https://searchfox.org/mozilla-central/rev/a40ef31fc9af34a99ceda6d65cdc4573d52b83d2/netwerk/base/nsITimedChannel.idl#73)
Example how this is [set for images](https://searchfox.org/mozilla-central/rev/a40ef31fc9af34a99ceda6d65cdc4573d52b83d2/dom/base/Document.cpp#11360).
All resource types we support preload for should properly set the initiatorType to either "link" or "preload" or "link-preload". Personal pref is "preload".
|
|
1,639,972 | 14,836,187 |
Created attachment 9150841
ff vs chrome table.mov
[Affected versions]
Release 76.0 (64-bit)
Beta 77.0b8 (64-bit)
Firefox Nightly 78.0a1 (2020-05-21) (64-bit)
[Affected platforms]
( macOS 10.14 (Mojave))
(Ubuntu 18.04 x64)
[Steps to reproduce]
1- Launch the Firefox Browser and visit https://en.wikipedia.org/wiki/Game_of_Thrones or https://www.w3schools.com/html/html_tables.asp
2- Open https://docs.google.com/document
3- Select two rows from table from step 1 and copy
4- Paste it in the word tab from step 2
5- Data is pasted as a text paragraph.
6- Launch Chrome and open link from step 2
7- Paste your selection
8- Table format is kept.
Also, if pasting table from one window to a different window,it is also pasted correctly (for example from nightly to release/beta), the problem is when pasting table from another tab of the **same** window.
[Expected result]
FF should keep the table's format when pasting in an online editor.
[Actual result]
Format is lost when pasting.
|
|
1,640,091 | 14,837,062 |
User Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:78.0) Gecko/20100101 Firefox/78.0
Steps to reproduce:
Within the last few Nightly updates, it appears that the behaviour of synchronous `dnsResolve()` has changed.
`dnsResolve()` seems to get the value from DNS cache and thus fails on un-cached DNS.
If the DNS has been previously cached by Firefox, it synchronously returns the value but if not, it actually stops the PAC from functioning.
It might be that the behaviour has become asynchronous which breaks the synchronous PAC.
|
|
1,640,490 | 14,839,467 |
Bug 1591469 broke something for login protected sites. Since this change the reader mode will just contain a "readable" version of the login form, instead of the blog post after login. I can reproduce this on [removed], but I obviously can't share that password.
12:03.66 INFO: Last good revision: c060bcf8ea7a089333bfd0d99f096ef797ceb390
12:03.66 INFO: First bad revision: 217394da44ac9b55df2f91bf639944ea47949b3d
12:03.66 INFO: Pushlog:
https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=c060bcf8ea7a089333bfd0d99f096ef797ceb390&tochange=217394da44ac9b55df2f91bf639944ea47949b3d
|
|
1,640,607 | 14,841,763 |
Created attachment 9151462
aboutsupport (2).txt
Note:
360 Video stutters on 4k monitor(resolution: 20560x2048). The same problem happens with webrender on and off.
Affected versions:
Nightly v78.0a1
Affected platforms:
Windows 10
Steps to reproduce:
1. Open Nightly 78.0a1
2. Go to https://www.youtube.com/watch?v=JtYa0rb_jGQ&list=FLQDozCIKe1FJdThFLX-YWLg&index=4
3. Click on Full-screen button
4. Move the camera up/down/right side/left side
Expected result
360 Video should be properly displayed.
Actual result
360 Video stutters on 4k monitor
|
|
1,641,487 | 14,848,880 |
University of Birmingham Vulnerability Report - Firefox Browser - Download Site Obscured from User
About this Document
-------------------
This document details a vulnerability identified by the University of Birmingham in the Firefox Web Browser.
University of Birmingham Contact Information
--------------------------------------------
The researchers, Richard Thomas and Tom Chothia can be contacted at {r.j.thomas,t.p.chothia}@cs.bham.ac.uk. Please contact us for our PGP key.
Crediting the University of Birmingham
--------------------------------------
The University of Birmingham would appreciate credit to the researchers and the University for any advisories which you may publish about this issue.
Please inform the researchers via their contact email addresses should you:
- confirm that this is a security issue
- allocate the issue a CVE identifier
- determine a date to release a patch
- determine a date to publish advisories
University of Birmingham Disclosure Policy
------------------------------------------
The University of Birmingham follows a responsible, coordinated disclosure approach with affected parties. We do not publicly disclose vulnerabilities without consulting the vendor.
The University of Birmingham recognises that vendors need a reasonable amount of time to mitigate a vulnerability, understand the impact to customers, triage other vulnerability reports and implement resolutions in coordination with others and its customers. The researchers are happy to discuss how such disclosures may take place.
If the researchers believe a vendor is not making appropriate progress with the resolution of this vulnerability, we may, following discussion with the vendor, choose to share details with the UK National Cyber Security Centre to protect UK interests.
Summary
-------
A User Interface (UI) Misrepresentation of Critical Information issue exists on the Download UI process on the Firefox browser, and has been tested on Firefox 76.0.1 for Windows, MacOS and Linux (Kali Repositories). This can be exploited by an adversary exploiting an Open Redirect (CWE-601) on a trusted device to display the source of the download in the Download List UI as the trusted device, and not the true download site.
If a user is tricked into downloading and running a malicious file by making the trusted host appear in the downloads list, they will be more likely to run the malware.
These vulnerabilities have a Severity Score of 7.1 and a High Severity rating (based on the Common Vulnerability Scoring System v3.1).
CVSS
----
This vulnerability has a Severity Score of 7.1 and a High Severity rating (the CVSS Vector is AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:L).
The Common Weakness Enumeration ID is CWE-451: User Interface (UI) Misrepresentation of Critical Information.
Details
-------
The Firefox browser is one of a number of cross-platform browsers which commonly used by end-users. Where an Open Redirect vulnerability (CWE-601) exists on a device that is trusted by the user, the response to a user request may redirect the user to untrusted content which was not initially requested. In Firefox, given an Open Redirect using the HTTP POST method, upon receipt of the HTTP 302 Redirect from the trusted device, the browser may start a download of a malicious file from the adversary. Where Firefox displays a dialog box for the user to select whether to Open or Save the file, the adversary host is displayed as the source, however, upon completion of the download, the Download UI on Firefox displays the trusted device as the source of the download in the list. Where the user has previously configured Firefox to automatically save files of a particular type, the user would see the trusted device as the download host, not the adversary's host.
On MacOS, if the user attempts to execute an installer downloaded via the Open Redirect, MacOS Gatekeeper will confirm that Firefox downloaded the file from the trusted device, and not the true download site.
This issue has been tested on Firefox 76.0.1. on Windows 10 Enterprise N (Version 1709), MacOS 10.15 Catalina and Kali Linux 2019.4.
Steps to reproduce:
- Submit a HTTP POST request to a trusted device, which will issue a HTTP 302 Redirect to another site, hosting a download.
- If a download prompt is displayed, the site should be shown as the one indicated in the 302 Redirect. Click Save.
- Once the download has completed, click the Download UI Button, and the file should show there. No host is displayed. Click 'Show All Downloads' and the downloaded file will show in the list with the host shown as the trusted device, not the true download site.
PoC code is given at the bottom of this report.
Mitigation
----------
Firefox should display the name of the host that the file was downloaded from in teh download list (i.e. the host stated in the download dialog), not the name of the host that issued the redirect.
Note
----
This issue was identified during the assessment of an Open Redirect Vulnerability using POST, which is undergoing responsible disclosure with the Vendor.
A minimal example demonstrating this behaviour is given below:
1. Trusted Page simulating Open Redirect form behaviour (test.html)
<!DOCTYPE html>
<html>
<body>
<form action="index.php" method="POST">
<input type="submit" value="Submit">
</form>
<p>If you click the "Submit" button, the form-data will be sent to a page called "/index.php".</p>
</body>
</html>
2. PHP (on server) to trigger the download and force this behaviour
<?php
Header("HTTP/1.1 302 Object Moved" );
Header("Content-Type: text/html; charset=UTF-8");
Header("Cache-Control: no-cache");
Header("Pragma: no-cache");
Header("Expires: 0");
Header("Location: //<Download Page>");
Header("Content-Length: 0");
Header("Connection: close");
exit();
?>
|
|
1,642,059 | 14,852,823 |
Created attachment 9152910
NIghtly autofill (filling a form with a saved card).mov
CC autofill dropdown should appear once the user clicks in the field
Steps to reproduce:
- Visit BestBuy.com
- In the checkout form, click credit card/ debit card field
Expected result:
See the cc drop down menu
Actual result:
Don't see the cc dropdown menu until the 2nd click
|
|
1,642,067 | 14,852,870 |
Created attachment 9152916
test-case.html
Noticed that Firefox is way slower than other browsers performing some fractal calculations.
While investigating, it has been found that prepending a try-catch block anywhere before the heavy calculations would make FF compete with others.
Running `test-case.html` on my machine, I get
> no try catch: > 1000ms
> with try catch: < 200ms
This is a regression, and searching for a range I found this [pushlog][1] which is linked to bug 1607986.
Ps: Note that for simplicity the attached test case builds the Functions on the fly, but whatever the execution context the same would happen (original case is more complicated and running in multiple Web-Workers).
[1]: https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=ad033cfda3900e2602ff7bb39a242011b61962eb&tochange=987c2ef0a10c0829875cfe889e35b0bda2d225c1
|
|
1,642,201 | 14,853,548 |
## What were you doing?
With a new profile on any page use the Edit-and-Resend functionality.
## What happened?
The editable request headers look like this:
```
undefined
Host: [hostname removed]
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:78.0) Gecko/20100101 Firefox/78.0
Accept: image/webp,*/*
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
```
This does not seem to affect the actually sent headers though.
## What should have happened?
`undefined` and empty newlines should not be there if they were not in the original request.
|
|
1,642,267 | 14,853,853 | null |
|
1,642,449 | 14,856,569 |
I suspect that this addition was uneccessary and caused build errors when compiling against macOS 10.15 SDK.
|
|
1,650,751 | 14,920,469 |
This bug is for crash report bp-6a35a53f-6e3a-4529-ba85-33f9f0200703.
Top 10 frames of crashing thread:
```
0 libc.so.6 __fcntl64_nocancel_adjusted /build/glibc-YYA7BZ/glibc-2.31/io/../sysdeps/unix/sysv/linux/fcntl_nocancel.c:64
1 libc.so.6 __libc_fcntl64 /build/glibc-YYA7BZ/glibc-2.31/io/../sysdeps/unix/sysv/linux/fcntl64.c:51
2 libglib-2.0.so.0 <name omitted> ../../../glib/glib-unix.c:177
3 libgio-2.0.so.0 g_socket_constructed ./debian/build/deb/../../../gio/gsocket.c:709
4 libgobject-2.0.so.0 g_object_new_internal ../../../gobject/gobject.c:1977
5 libgobject-2.0.so.0 <name omitted> ../../../gobject/gobject.c:2262
6 libgio-2.0.so.0 g_initable_new_valist ./debian/build/deb/../../../gio/ginitable.c:244
7 libgio-2.0.so.0 g_initable_new ./debian/build/deb/../../../gio/ginitable.c:162
8 libgio-2.0.so.0 g_socket_new ./debian/build/deb/../../../gio/gsocket.c:1290
9 libgio-2.0.so.0 create_socket ./debian/build/deb/../../../gio/gsocketclient.c:136
```
This is happening in recent Linux distros, mostly Arch and Ubuntu 20.04. The crash starts in `nsLookAndFeel::EnsureInit()` which calls `gtk_settings_get_for_display()` and through a long and winding stack lands here:
https://github.com/GNOME/glib/blob/1ee22d0ae9145f0557fc9d1fc649ae22fd4c4f6f/gio/gsocket.c#L709
Which is implemented like so:
https://github.com/GNOME/glib/blob/mainline/glib/glib-unix.c#L177
None of this code is new, so I had to dig into glibc to figure out what's going and the chase led me to this change in glibc:
https://sourceware.org/git/?p=glibc.git;a=commit;h=bc2eb9321ec0d17d41596933617b2522c9aa5e0b
It's the only recent change that altered the syscall-calling code that appears in this stack. Unfortunately I have no clue what the change does :-|
|
|
1,650,872 | 14,921,445 |
When running Browsertime against recent Fenix production builds, the following error is seen:
"ERROR: InvalidArgumentError: setWindowRect is only supported in Firefox desktop"
I believe that the following Marionette capabilities test is failing:
https://searchfox.org/mozilla-central/rev/91d82d7cbf05a71954dfa49d0e43824c7c973e62/testing/marionette/capabilities.js#548
Perhaps the name of Fenix has changed and so `appinfo.name != "firefox"` ?
This is an example Fenix binary where I'm seeing this issue:
https://firefox-ci-tc.services.mozilla.com/api/index/v1/task/project.mobile.fenix.v2.fennec-production.2020.07.03.latest/artifacts/public/build/arm64-v8a/geckoBeta/target.apk
More logs: https://paste.rs/GlK
Depending on the root issue, this bug may be in the wrong component.
|
|
1,651,186 | 14,923,854 |
We may want to make this change in the future for bug 1625391 but we would want to do more to ease the transition. For now let's not regress the previous behaviour unintentionally (since `LoginHelper.getLoginOrigin` would be inconsistent with the new behaviour in `LoginManagerParent`).
See bug 1625391 comment 8.
|
|
1,651,682 | 14,927,494 |
Found this thanks to @dcicas and @bmaris. Sometimes, when the network goes up, we don't re-run heuristics.
The reason is that we receive a signal that the network link is up, but captive portal state is unknown, so we don't run heuristics. Later, we never receive a captive portal state change event. This implies that the observer notification `ipc:network:captive-portal-set-state` which is used by the captive portal web extension API is unreliable. However, I verified that `network:captive-portal-connectivity` IS sent, so that one should work.
We should change the captive portal handler to use onConnectivityAvailable rather than onStateChanged, at least for now. Once bug 1603779 lands we should solve this network handling issue once and for all.
I'll attach a patch specifically for beta - this bug does not manifest the same way in Nightly and I'd rather solve it in central after bug 1603779 lands.
|
|
1,652,032 | 14,929,939 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0
Steps to reproduce:
I'm currently working on cross-compiling LibreOffice from Windows x86_64 to arm64. One of the dependencies is NSS / NSPR, which fails to build in my setup.
I also had a look into the repo, but couldn't find any patch looking like a fix.
Actual results:
Compilation failed.
Expected results:
Compilation works.
|
|
1,652,244 | 14,931,266 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:80.0) Gecko/20100101 Firefox/80.0
Steps to reproduce:
Login to Wordpress account
Visit https://mozillagfx.wordpress.com/2020/07/10/moz-gfx-newsletter-54/
Click 'Like'
Actual results:
Click on 'Like' opens a popup window but the change is not reflected.
The Re-blog button is missing
Expected results:
Click on 'like' button should reflect change on the webpage.
Reblog button should not be missing
Setting network.cookie.cookieBehavior to 4 fixes the issue
|
|
1,652,487 | 14,934,574 |
I opened the global JS console and see the following error:
```
SyntaxError: Element.closest: '#widget:[addonid]@jetpack-[widgetid]' is not a valid selector BrowserUsageTelemetry.jsm:900
_getWidgetID resource:///modules/BrowserUsageTelemetry.jsm:900
_recordCommand resource:///modules/BrowserUsageTelemetry.jsm:1032
_addUsageListeners resource:///modules/BrowserUsageTelemetry.jsm:1047
```
The code here in [browser/modules/BrowserUsageTelemetry.jsm](https://searchfox.org/mozilla-central/rev/89814940895946b48b4c04c702efd2c676ec8e7e/browser/modules/BrowserUsageTelemetry.jsm#888,901) assumes that the input ID is a valid CSS selector. IDs do not have to be a valid CSS selector, to fix this `CSS.escape` should be used first.
This ID is somehow present in my xulstore.json, and originates from a Jetpack add-on that used the sdk/widget module - https://github.com/mozilla/addon-sdk/blob/e5ce4a3c956327c25e48d49754e09bac95b0897d/lib/sdk/widget.js#L701-L702
|
|
1,652,492 | 14,934,602 |
The following testcase crashes on mozilla-central revision 20200712-22f5f7e91444 (debug build, run with --fuzzing-safe --no-threads):
function f1() {
arr = f2;
var p = arr[(gczeal(9))|0];
}
f2 = f1;
f2();
try {
function allocObj() { return {}; }
{
let obj = allocObj();
wr = new WeakRef(obj);
}
clearKeptObjects();
(new obj);
} catch(exc) {}
let obj = allocObj();
wr = new WeakRef(obj);
Backtrace:
received signal SIGSEGV, Segmentation fault.
#0 0x00005555558126cf in JSObject::writeBarrierPost(void*, JSObject*, JSObject*) ()
#1 0x0000555555f1ab67 in mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>::HashMapEntry(mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>&&) ()
#2 0x0000555555f1aa74 in void mozilla::detail::EntrySlot<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector> >::setLive<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector> >(unsigned int, mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>&&) ()
#3 0x0000555555f1a673 in void mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::forEachSlot<mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::changeTableSize(unsigned int, mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::FailureBehavior)::{lambda(mozilla::detail::EntrySlot<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector> >&)#1}>(char*, unsigned int, mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::changeTableSize(unsigned int, mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::FailureBehavior)::{lambda(mozilla::detail::EntrySlot<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector> >&)#1}&&) ()
#4 0x0000555555f1a537 in mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::changeTableSize(unsigned int, mozilla::detail::HashTable<mozilla::HashMapEntry<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector>, mozilla::HashMap<js::HeapPtr<JSObject*>, js::WeakRefHeapPtrVector, js::MovableCellHasher<js::HeapPtr<JSObject*> >, js::ZoneAllocPolicy>::MapHashPolicy, js::ZoneAllocPolicy>::FailureBehavior) ()
#5 0x0000555555ed6bc8 in js::WeakRefMap::sweep() ()
#6 0x0000555556237780 in js::gc::GCRuntime::sweepWeakRefs() ()
#7 0x0000555556269e0c in AutoRunParallelTask::run() ()
#8 0x000055555625403c in js::GCParallelTask::runTask() ()
#9 0x0000555556237a0a in js::gc::GCRuntime::startTask(js::GCParallelTask&, js::gcstats::PhaseKind, js::AutoLockHelperThreadState&) ()
#10 0x00005555562393b3 in js::gc::GCRuntime::beginSweepingSweepGroup(JSFreeOp*, js::SliceBudget&) ()
#11 0x000055555627ce01 in sweepaction::SweepActionSequence::run(js::gc::SweepAction::Args&) ()
#12 0x000055555626b4b7 in sweepaction::SweepActionForEach<js::gc::SweepGroupsIter, JSRuntime*>::run(js::gc::SweepAction::Args&) ()
#13 0x000055555623e249 in js::gc::GCRuntime::performSweepActions(js::SliceBudget&) ()
#14 0x000055555624320a in js::gc::GCRuntime::incrementalSlice(js::SliceBudget&, mozilla::Maybe<JSGCInvocationKind> const&, JS::GCReason, js::gc::AutoGCSession&) ()
#15 0x000055555624608b in js::gc::GCRuntime::gcCycle(bool, js::SliceBudget, mozilla::Maybe<JSGCInvocationKind> const&, JS::GCReason) ()
#16 0x0000555556247d10 in js::gc::GCRuntime::collect(bool, js::SliceBudget, mozilla::Maybe<JSGCInvocationKind> const&, JS::GCReason) ()
#17 0x000055555620eb8d in js::gc::GCRuntime::finishGC(JS::GCReason) ()
#18 0x00005555562167dc in js::gc::FinishGC(JSContext*, JS::GCReason) ()
#19 0x00005555557c301b in mozilla::ScopeExit<main::$_5>::~ScopeExit() ()
#20 0x00005555557bad07 in main ()
rax 0x555556fcc147 93825019986247
rbx 0x7ffff572c488 140737311327368
rcx 0x5555583ca840 93825040951360
rdx 0x0 0
rsi 0x7ffff6abd770 140737331844976
rdi 0x7ffff6abc540 140737331840320
rbp 0x7fffffffce30 140737488342576
rsp 0x7fffffffce10 140737488342544
r8 0x7ffff6abd770 140737331844976
r9 0x7ffff7fe3d40 140737354022208
r10 0x58 88
r11 0x7ffff67647a0 140737328334752
r12 0x20 32
r13 0x7ffff4e4f380 140737302033280
r14 0x7ffff571a9f0 140737311255024
r15 0x7ffff4e4f380 140737302033280
rip 0x5555558126cf <JSObject::writeBarrierPost(void*, JSObject*, JSObject*)+255>
=> 0x5555558126cf <_ZN8JSObject16writeBarrierPostEPvPS_S1_+255>: movl $0x18d,0x0
0x5555558126da <_ZN8JSObject16writeBarrierPostEPvPS_S1_+266>: callq 0x5555558492fe <abort>
Signature and test are different to that in bug 1652425, so filing this separately.
|
|
1,652,720 | 14,936,290 |
Created attachment 9163466
Recording of the issue
**Affected versions**
Nightly 80 - since V2 doorhanger functionality landed with Bug 1641415
**Tested on**
Windows 10 x64
**Steps to reproduce**
- Launch Firefox
- Go to Facebook Sign up page or Reddit
- Fill in all the required fields and open the dismissed doorhanger
- Click on the arrow from the username field to open the suggestions dropdown
- Focus out of the doorhanger
- Focus the password field and clear it out to toggle the autocomplete dropdown
**Expected result**
The autocomplete dropdown should be displayed correctly by showing only the Password Generation option and "View Saved Logins" footer
**Actual Result**
The autocomplete dropdown becomes scrollable and displays one of the suggested username at the bottom of it.
**Regression-range**
Not a regression as it can be reproduced in the very first day when Bug 1641415 enabled this new functionality.
**Notes**
Attached screen recording and log for refference. It can be intermittent but always involves the password field.
|
|
1,652,925 | 14,938,002 |
Created attachment 9163705
memory-report.json.gz
This may or may not be a bug in the extension in question (uBlock origin) but I was surprised to discover that this behavior was possible at all.
I have uBlock origin enabled for my profile and generally don't have any trouble with it. While glancing through about:memory I discovered a tab I left open for a day or so was now using about 2 gigabytes of memory (almost entirely due to ads and trackers), so I closed it. After Firefox spent a few seconds recovering from this, I fired off GC/CC manually to see whether anything would fail to get flushed out. After doing this, I noticed that the WebExtensions process was using over 2GB of memory, most of it under the 'strings' 'malloc-heap' for uBlock origin. I've attached an anonymized memory report. When I expanded the little summary view before anonymizing erased everything, I didn't see any particularly large string objects, so it seems like it somehow managed to allocate and retain a truly ridiculous number of string objects.
There may be some reasons why this is necessary that I'm not aware of, but I'm surprised that the webextensions process as a whole - or even a single extension - is allowed to use this much memory. I couldn't find any way to knock over this specific extension or restart it even though I know it's not performing any ongoing work, and the GC/CC buttons don't seem to free up any of the memory it's using.
This extension memory usage is *also* not visible in about:performance at all. According to about:performance my Firefox session is slim and happy, which is very much not the case.
|
|
1,653,186 | 14,939,822 |
Created attachment 9163952
Capture 2020-07-16 14-43-58.webm
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:80.0) Gecko/20100101 Firefox/80.0
Steps to reproduce:
1. Pick an element from `about:addons`
Actual results:
Highlighter did not appear.
|
|
1,644,924 | 14,875,307 |
This is a regression of bug 1642455.
|
|
1,645,777 | 14,882,702 |
This bug is for crash report bp-550e15ac-c709-4c8f-af9e-97ac00200614.
Top 10 frames of crashing thread:
```
0 XUL mozilla::PermissionManager::GetKeyForPrincipal extensions/permissions/PermissionManager.cpp:3069
1 XUL mozilla::ContentBlocking::UpdateAllowAccessOnParentProcess toolkit/components/antitracking/ContentBlocking.cpp:791
2 XUL mozilla::ContentBlocking::SaveAccessForOriginOnParentProcess toolkit/components/antitracking/ContentBlocking.cpp:618
3 XUL mozilla::ContentBlocking::CompleteAllowAccessFor const toolkit/components/antitracking/ContentBlocking.cpp:509
4 XUL mozilla::ContentBlocking::CompleteAllowAccessFor toolkit/components/antitracking/ContentBlocking.cpp:564
5 XUL mozilla::dom::ContentParent::RecvCompleteAllowAccessFor dom/ipc/ContentParent.cpp:6004
6 XUL mozilla::dom::PContentParent::OnMessageReceived ipc/ipdl/PContentParent.cpp:11218
7 XUL mozilla::ipc::MessageChannel::DispatchMessage ipc/glue/MessageChannel.cpp:2166
8 XUL mozilla::ipc::MessageChannel::MessageTask::Run ipc/glue/MessageChannel.cpp:1969
9 XUL nsThread::ProcessNextEvent xpcom/threads/nsThread.cpp:1238
```
There is 1 crash in nightly 79 with buildid 20200613214137. In analyzing the backtrace, the regression may have been introduced by patch [1] to fix bug 1643115.
[1] https://hg.mozilla.org/mozilla-central/rev?node=c9b9111c017f
|
|
1,646,940 | 14,890,579 |
This is created to temporarily fix Bug 1644275 in 78.
### Reasons
In the fix for Bug 1644275 we use `WeakRef` which gets enabled on 79, so we cannot uplift that patch to 78.
### Goal
The main goal of this is to temporarily fix 78, so the expectation is land this on 79, uplift to 78 and then remove this from 79.
|
|
1,646,955 | 14,890,706 |
Created attachment 9157903
Additional separator
**Affected versions**
- Firefox 78.0b9
**Affected platforms**
- Ubuntu 20.04 & 18.04
**Steps to reproduce**
1. Launch Firefox
2. Access about:logins
3. Click on the three dots in the upper right part of the screen
**Expected result**
- The dropdown has no additional separator if no Import/Export options are listed in it.
**Actual result**
- The dropdown has an additional separator.
**Regression range**
- Will see for one if this is not intended. It seems that for example that Firefox 76.0b5 does not have that additional separator.
**Additional notes**
- This may be intended, as I saw that in nightly, there is a feature for Ubuntu to add export logins option.
|
|
1,646,958 | 14,890,763 |
Created attachment 9157908
the text is not visible with high contrast theme.png
**Note**
* When the user activates high contrast and shares his screen in a conference, he will notice that the text on the Global Sharing Overlay is not being displayed.
**Affected versions**
* Nightly v79.0a1
* Beta v78.0b9 shows this behavior: bug 1643012
**Affected platforms**
* Windows 10
* Windows 7
**Steps to reproduce**
1. Make sure prefs
privacy.webrtc.allowSilencingNotifications = true
privacy.webrtc.legacyGlobalIndicator = false
2. Apply a high contrast theme from OS settings.
3. Engage in a video conference on ant WebRTC web-app.
4. Share a screen or a window.
5. Observe the Global Sharing Overlay.
**Expected result**
* The Global Sharing Overlay is correctly displayed.
**Actual result**
* The text displayed on the Global Sharing Overlay is improperly displayed.
**Regression range**
* This is an issue with the newly implemented design seen in Nightly v79.0a1.
**Additional notes**
* The text will be displayed on yellow, green or not visible at all, based on the High Contrast theme applied.
|
|
1,646,974 | 14,890,846 |
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:78.0) Gecko/20100101 Firefox/78.0
Steps to reproduce:
Open Netmonitor, then load this page:
http://adobkin.name/firefox/unstyled-flash-bug.html
Actual results:
2 requests are listed (the HTML page, and the favicon)
Expected results:
3 requests should be listed (a css/php file)
I came across this problem while debugging something else. The similarity between my situation and the above page is that the css file is getting added using document.write.
The problem is in Firefox Nightly, and 78. It is not in 77.
|
|
1,647,293 | 14,894,028 |
When running the following script
```
function foo() {
let v3 = 0;
while (v3 != 10000) {
const v6 = typeof v3 === "number";
if (v6) {
} else {
const v7 = v3 || 8;
}
const v8 = v3 + 1;
v3 = arguments;
v3 = v8;
}
}
function main() {
foo();
}
main();
gc();
```
Spidermonkey fails on the following assertion:
`Assertion failure: !IsMagicType(ins->type()) in js/src/jit/IonBuilder.cpp:2625`
`jit::AnalyzeArgumentsUsage` correctly determines that the arguments object is not needed and can be optimized out, which means that the TypeSet for `v3` is the union of types `int` and `MagicOptimizedArguments`. It seems that the compiler tries to optimize the typeof compare and propagate the type information to the branches. If the typeof compare is true, `v3` has to be a number in the true branch, which means that v3 has to be of type `MagicOptimizedArguments` in the false branch.
It does not seem to be a security issue as the false branch is always dead code but if the bug is observable in a branch taken at runtime, it might be a security issue like shown in https://bugs.chromium.org/p/project-zero/issues/detail?id=1794, which is why I am reporting this as a security issue. I tried to bisect the bug but failed to do so as I had troubles building spidermonkey versions pre 2017. It does trigger on builds from early 2017 to the latest commit as of now (3d39d3b7dd1b2be30692d4541ea681614e34c786) on the github mirror.
|
|
1,647,652 | 14,895,923 |
Created attachment 9158449
Recording of the issue
**Affected version:**
All - if CC specific prefs are enabled
**Tested on:**
Windows 10
**Steps to reproduce:**
1. Have a CC entry saved in storage with: CC number(362339320726338), Exp Date (08/2020)
2. Fill in a form with: CC number (362339320726338), Exp Date (04/2024), Name
3. Submit the form and chose to save the Credit Card in the Save CC doorhanger
**Expected results:**
1. The profiles should be merged since they have the same CC number, based on: https://mozilla.invisionapp.com/share/56E59T04Q#/screens
**Actual results:**
1. The CC entries are not merged.
**Notes:**
Scenario based on point 3 from https://bugzilla.mozilla.org/show_bug.cgi?id=1402963#c20
|
|
1,647,699 | 14,896,348 |
Created attachment 9158513
distribution.7z
**Suggested severity**
* S2
**Affected versions**
* Firefox 78.0
**Affected platforms**
* Windows 10 x64
* Windows 7 x64
**Prerequisites**
* Install the old version of firefox (< 72.0.2), but do not start it, change update channel to release-localtest with the locale "pl".
* Unpack the attached file and place them inside the Firefox install folder (ex: Firefox/distribution)
* Start CMD as admin and input the following comands to remove all profile data:
rd /s /q %userprofile%\AppData\Roaming\Mozilla
rd /s /q %userprofile%\AppData\Local\Mozilla
rd /s /q %userprofile%\AppData\LocalLow\Mozilla
**Steps to reproduce**
1. Start Firefox with the default profile.
2. Update Firefox to the latest version.
3. Perform a search from the URL bar.
**Expected result**
* The search is performed with Bing.
**Actual result**
* The search is performed with Google.
**Regression range**
* I can't a regression, because I can't control to which build the update is last performed to.
**Additional notes**
* This issue is reproducing on other locales, too (e.g. ru).
* This changes happen only after the build is updated from 72.0.2 to the latest build.
|
|
1,656,388 | 14,964,900 |
With the refactor to use the resource watcher in Bug 1625909 . We left out sending the `packet.response.waitingTime` to the netmonitor frontend
|
|
1,656,477 | 14,965,411 |
Created attachment 9167288
no-changes-collected-regression.mp4
CSS changes should be collected in the background and displayed when the Changes panel is visible.
Mozregression points to [this pushlog](https://hg.mozilla.org/integration/autoland/pushloghtml?fromchange=676e1c3e21e655604d885ef299f577c959b5d152&tochange=e860655e21e7afac7575014c6e974e0de47288ed).
Bug 1625957 has regressed this functionality.
~~Now, the Changes panel must have been invoked at least once before changes are collected in the background.
Most likely, the corresponding ChangesActor is not created on Inspector init. Actors are lazy. If not explicitly invoked, they are not instantiated.~~
EDIT: The changes do get collected in the background. They're erroneously cleared as soon as the Changes panel is first focused.
This happens because the Changes panel reacts to cached `DOCUMENT_EVENT` resources from resource watcher (which is also watching for `CSS_CHANGE` resources) leading it to mistakenly believe that the document is refreshing, thus clearing the list of changes.
**Steps to reproduce**
- Run the following in the URL bar:
```
data:text/html,<style>body {color: red}</style>TEST
```
- Open DevTools > Inspector
- **Ensure the Changes panel is NOT active**; if it is, switch to another panel, close DevTools, refresh the page and start over.
- In the Rules view, change the value of `color: red` to `color: blue`
- Switch to the Changes panel
**Expected result**
The Changes panel shows a diff view of the changed CSS declaration
**Actual result**
The Changes panel behaves as if no changes have happened.
|
|
1,656,697 | 14,967,113 |
The attached testcase crashes on mozilla-central revision 20200801-750bc4c5c4ad (tsan build).
For detailed crash information, see attachment.
To reproduce the issue, perform the following steps:
1. Download the attached testcase, save as "test.bin".
2a. Build with --enable-fuzzing (requires Clang and TSan, also build gtests using `./mach gtest dontruntests`).
2b. Alternatively you can download builds from TC using `python -mfuzzfetch --tsan --fuzzing --gtest` (see https://github.com/MozillaSecurity/fuzzfetch).
3. Run FUZZER=NetworkHttp2ProxyHttp2 objdir/dist/bin/firefox -runs=2 test.bin
(See also the new documentation on the fuzzing interface for further pointers about builds and reproducing: https://firefox-source-docs.mozilla.org/tools/fuzzing/fuzzing_interface.html#fuzzing-interface)
Initially this was reported by AddressSanitizer as a heap-use-after-free, I will add the corresponding trace in the follow-up comment.
|
|
1,656,991 | 14,970,222 |
This bug is for crash report bp-6095e611-20c0-480a-9cfd-271130200803.
Top 10 frames of crashing thread:
```
0 xul.dll MapSrcDest gfx/thebes/gfxUtils.cpp:107
1 xul.dll static gfxUtils::PremultiplyDataSurface gfx/thebes/gfxUtils.cpp:160
2 xul.dll mozilla::ClientWebGLContext::GetFrontBufferSnapshot dom/canvas/ClientWebGLContext.cpp:903
3 xul.dll mozilla::layers::CanvasRenderer::BorrowSnapshot const gfx/layers/CanvasRenderer.cpp:62
4 xul.dll mozilla::layers::BasicCanvasLayer::Paint gfx/layers/basic/BasicCanvasLayer.cpp:38
5 xul.dll mozilla::layers::BasicLayerManager::PaintSelfOrChildren gfx/layers/basic/BasicLayerManager.cpp:703
6 xul.dll mozilla::layers::BasicLayerManager::PaintLayer gfx/layers/basic/BasicLayerManager.cpp
7 xul.dll mozilla::layers::BasicLayerManager::EndTransactionInternal gfx/layers/basic/BasicLayerManager.cpp:609
8 xul.dll mozilla::FrameLayerBuilder::PaintItems layout/painting/FrameLayerBuilder.cpp:7043
9 xul.dll static mozilla::FrameLayerBuilder::DrawPaintedLayer layout/painting/FrameLayerBuilder.cpp:7251
```
this content crash signature is newly showing up in firefox 79 and is looking related to the changes from bug 1632249.
the crash seems to primarily hit russian users on 32bit versions of the browser - all submitted urls in reports point towards yandex live wether maps (e.g. https://yandex.ru/pogoda/yurev-polskiy/maps/nowcast?via=mmapw&le_Lightning=1) as the source of the crash.
|
|
1,657,149 | 14,971,607 |
User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_5) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.105 Safari/537.36
Steps to reproduce:
Went to https://www.webaim.org. Turned on VoiceOver on MacOS Catalina version 10.15.5 (19F101). Navigated to the Search bar and started typing.
Actual results:
Nothing.
Expected results:
VoiceOver should have announced each letter I typed as I typed it.
|
|
1,657,246 | 14,972,756 |
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0
Steps to reproduce:
If I establish an audio path using the Web Audio API, if I put the computer into sleep and wake it up, the audio stops working (mute). I am not sure if it is an intended behaviour or not, but one thing I am sure of is that it worked on FireFox just up until several months ago.
1. Put the HTML and a video file on a web server.
2. Load the page
3. Play the video.
4. Click the "Test" button to create an audio Path.
5. Pause the video
6. Put the computer into sleep mode
7. Wake it up.
8. Resume the video.
Actual results:
No sound.
Expected results:
Sound. I tried the same thing with Chrome and Edge (the non-Chromium one), and they both played the audio. Tested on Windows 10.
|
|
1,657,256 | 14,972,833 |
From https://github.com/mozilla-mobile/fenix/issues/13208.
### Environment
- Firefox 81 (2020-08-04) on Windows 10
- Fenix Nightly
### Steps to reproduce
1. Open a website with selectable text, e.g. https://www.mozilla.org/en-GB/mission/
2. Select some text
3. Scroll down while still keeping the selected part in your viewport
4. Drag the lower selection cursor down
### Expected behavior
The lower selection cursor follows the touch pointer.
###Actual behavior
The lower selection cursor jumps below the context menu and now has an offset to the touch pointer.
### Notes
This also occurs on Windows too. So it isn't related to GeckoView. I guess that this issue is accessibility caret.
|
|
1,657,306 | 14,973,164 |
User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:80.0) Gecko/20100101 Firefox/80.0
Steps to reproduce:
Ensure 'recommended by pocket' is unchecked in Firefox home content preferences. Update Firefox Beta to 80.0b4 (64-bit), open new tab.
Actual results:
Where I had previously configured only top sites to show, now a "recommended by pocket" section appears also. Preferences continue to show that recommended pocket is unchecked.
Expected results:
Preferences should be followed and unchecked sections should not appear
|
|
1,657,343 | 14,973,386 |
**[Affected versions]:**
- Firefox Beta 80.0b3, Build ID 20200803045446
- Firefox Nightly 81.0a1, Build ID 20200803094100
**[Affected Platforms]:**
- Windows 10
- macOS 10.15
- Linux MX 4.19
**[Steps to reproduce]:**
1. Open a new Firefox Beta profile with the `--jsconsole` argument.
2. Observe the Browser Console.
3. Navigate through all the slides and observe the Browser Console.
4. Refresh the page and observe the Browser Console.
5. Refresh the page a second time and observe the Browser Console.
**[Expected results]:**
- No errors are displayed.
**[Actual results]:**
- Step 2: Two `Error: Can't find profile directory.` errors and a `can't convert null to object` error are displayed.
- Step 3: Multiple `Error: Can't find profile directory.` errors are displayed.
- Step 4: A `this._store is undefined` and multiple `Error: Can't find profile directory.` errors are displayed
- Step 5: An `InvalidStateError: An attempt was made to use an object that is not, or is no longer, usable`, a `this._store is undefined`, and multiple `Error: Can't find profile directory.` errors are displayed
**[Notes]:**
- At first start-up there are also a few more errors, such as
- `[Exception... "Component returned failure code: 0x80520001 (NS_ERROR_FILE_UNRECOGNIZED_PATH) [nsIXPCComponents_Utils.readUTF8URI]" nsresult: "0x80520001 (NS_ERROR_FILE_UNRECOGNIZED_PATH)" location: "JS frame :: resource://gre/modules/L10nRegistry.jsm :: L10nRegistry.loadSync :: line 684" data: no]`
- `SearchCache: _readCacheFile: Error reading cache file:
Object { operation: "open", path: "C:\\Users\\work\\AppData\\Roaming\\Mozilla\\Firefox\\Profiles\\yi9khhlb.9\\search.json.mozlz4", winLastError: 2, stack: "", fileName: "(unknown module)", lineNumber: undefined }`
- `Win error 2 during operation copy on file C:\Users\work\AppData\Roaming\Mozilla\Firefox\Profiles\yi9khhlb.9\logins-backup.json (The system cannot find the file specified.)`
but I'm not sure if those are related to the start-up mechanism or the about:welcome page.
- Attached a screen recording of the issue.
- Attached the [output of the Browser Console](https://drive.google.com/file/d/1-d7bTE5tlsVjKPRwW0Ft4KX7wIUa3RyO/view?usp=sharing).
|
|
1,657,909 | 14,977,728 |
Created attachment 9168776
fields_modified.gif
[Affected versions]:
- Nightly 81.0a1;
- Beta 80.0b5;
[Affected Platforms]:
- All Windows;
- All macOS;
- All Linux;
[Prerequisites]:
- Have a Firefox profile with the following prefs set:
- Have the "extensions.formautofill.creditCards.available" pref set to "true";
- Have the "extensions.formautofill.creditCards.enabled " pref set to "true";
[Steps to reproduce]:
1. Open the Firefox browser and navigate to https://luke-chang.github.io/autofill-demo/basic_cc.html
2. Complete only the Card Number field with valid information.
3. Click the "Submit" button.
4. Click the "Save" button from the doorhanger.
5. Navigate to "about:telemetry#events-tab" page.
6. Search for the {"category:creditcard", "method:submitted") event.
7. Observe the "extra" column.
[Expected result]:
- The "field_modified" contain the number of the modified fields: 1 since only the number card was filled.
[Actual result]:
- The "field_modified" has the value "4" even if only one field was completed.
[Notes]:
- We are also not sure if the "field_modified" should or should not count the new manually entered information as a field modified. However, I considered that this is intended since initially, the field is blank and then it is modified by adding new information. Please correct me if I'm wrong.
- Attached a screen recording with the issue.
|
|
1,658,165 | 14,979,713 |
Created attachment 9169005
printesc.gif
**Affected versions**
* 81.0a1 (BuildId:20200804215246)
**Affected platforms**
* Windows 10 64bit
* macOS 10.14
**Unaffected platforms**
* Ubuntu 18.04 64bit (will confirm this on Monday)
**Steps to reproduce**
1. Launch Firefox.
2. Open two tabs containing two different webpages.
3. Open the print preview on both tabs.
4. Press the escape keyboard button in one tab.
5. Observe the second tab.
**Expected result**
* Only the print preview for the tab where the esc keyboard button was pressed gets dismissed.
**Actual result**
* The print preview gets dismissed for all tabs.
**Regression Range**
* I don’t think that this is a regression.
**Notes**
* Please observe the attached screencast for further information regarding this issue.
* There seems to be a difference between dismissing the print preview via escape keyboard button and the “Cancel” button (from the print preview). It seems that clicking the cancel button dismisses only the print preview from the tab where this action was performed (not affecting print preview on other tabs) but pressing the escape button affects the print preview for other tabs as well.
|
|
1,648,064 | 14,898,781 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:77.0) Gecko/20100101 Firefox/77.0
Steps to reproduce:
Open a site which has images with native lazy loading (using loading="lazy" on the img elements) out of the immediately visible area and send the page to print.
Actual results:
Only the images which have been scrolled to are printed.
Expected results:
This is tricky question: Firefox is doing exactly what the user asked to do. However, because the rest of the content, which is not under loading=lazy is printed, the images with loading=lazy should also be printer - at least this would be the logical outcome.
|
|
1,648,683 | 14,903,228 |
1) Goto https://www.w3schools.com/tags/tryit.asp?filename=tryhtml_select
2) "right click" (two finger tap) anywhere on the iframe on the right.
Pretty often (~25% of the time) I get a very large context menu.
Bisected to bug 1592416.
macOS 10.15.5, I'm running 2019 16" macbook pro with an external (non-retina) monitor connected. The issue only seems to happen on the built-in retina screen.
|
|
1,648,854 | 14,904,839 |
Telemetry Logging can be turned on by setting `toolkit.telemetry.log.level` to a log level (e.g. `Trace`). You can get it to pipe to console by setting `toolkit.telemetry.log.dump` to the boolean `true`.
This isn't working with latest mozilla-central, but reverting the two patches from bug 1645862 (and the one from bug 1648178 first so it doesn't complain about merge conflicts) makes it work again.
My only guess is the logger is configured someplace in TelemetryController and I missed that it was no longer called in the review.
|
|
1,649,056 | 14,906,053 |
Setting low priority&severity because I've only experienced this locally, I cannot reproduce it on Try.
While running profiler gtests, I'm getting the following deadlock:
1. Start profiling, capture profile.
2. On main thread (MT), the profiler locks its mutex.
3. MT: `StreamMetaJSCustomObject()` does [`do_GetService(NS_NETWORK_PROTOCOL_CONTRACTID_PREFIX "http", &res);`](https://searchfox.org/mozilla-central/rev/21f2b48e01f2e14a94e8d39a665b56fcc08ecbdb/tools/profiler/core/platform.cpp#2379-2380)
4. MT: In that `do_GetService`, `mozilla::ipc::GetIPCLauncher()` [creates a new thread "IPC Launch"](https://searchfox.org/mozilla-central/rev/21f2b48e01f2e14a94e8d39a665b56fcc08ecbdb/ipc/glue/GeckoChildProcessHost.cpp#927-928).
5. MT: `nsThread::Init()` [blocks until the new thread completes its initialization](https://searchfox.org/mozilla-central/rev/21f2b48e01f2e14a94e8d39a665b56fcc08ecbdb/xpcom/threads/nsThread.cpp#674-676) (which is when an initial `startup` event is handled).
6. In IPC Launch (IL), `nsThread::ThreadFunc()` [calls `profiler_register_thread()`](https://searchfox.org/mozilla-central/rev/21f2b48e01f2e14a94e8d39a665b56fcc08ecbdb/xpcom/threads/nsThread.cpp#430) before starting the event loop that would handle the startup event.
7. IL: `profiler_register_thread()` tries to lock the profiler thread, which was taken on the MT at step 2, but won't be released because the MT is waiting for IL here to finish its startup.
I think the solution here is to move all `do_GetService` calls before the profiler-locked scope.
|
|
1,649,347 | 14,909,575 |
*Push:* https://treeherder.mozilla.org/#/jobs?repo=mozilla-central&group_state=expanded&selectedTaskRun=DhSWcVhJRkqkUEiLq8qAzA.0&revision=79d69f36a2202fadd572b0243b618e100d29b525&searchStr=linux%2C18.04%2Cx64%2Casan%2Copt%2Cweb%2Cplatform%2Ctests%2Ctest-linux1804-64-asan%2Fopt-web-platform-tests-e10s-22%2Cw%28wpt22%29
*Failure log:* https://treeherder.mozilla.org/logviewer.html#/jobs?job_id=307971535&repo=mozilla-central&lineNumber=4999
>[task 2020-06-30T02:54:12.761Z] 02:54:12 ERROR - PID 10594 | ==10907==ERROR: AddressSanitizer: heap-use-after-free on address 0x611000222bc0 at pc 0x7f8f9987ee60 bp 0x7f8f8769dce0 sp 0x7f8f8769dcd8
[task 2020-06-30T02:54:12.761Z] 02:54:12 INFO - PID 10594 | WRITE of size 4 at 0x611000222bc0 thread T23 (DOM Worker)
[task 2020-06-30T02:54:13.342Z] 02:54:13 INFO - PID 10594 | #0 0x7f8f9987ee5f in fetch_add /builds/worker/fetches/clang/bin/../lib/gcc/x86_64-unknown-linux-gnu/7.4.0/../../../../include/c++/7.4.0/bits/atomic_base.h:514:16
[task 2020-06-30T02:54:13.342Z] 02:54:13 INFO - PID 10594 | #1 0x7f8f9987ee5f in AddRef /builds/worker/checkouts/gecko/xpcom/string/nsSubstring.cpp:169:17
[task 2020-06-30T02:54:13.342Z] 02:54:13 INFO - PID 10594 | #2 0x7f8f9987ee5f in nsTSubstring<char>::Assign(nsTSubstring<char> const&, std::nothrow_t const&) /builds/worker/checkouts/gecko/xpcom/string/nsTSubstring.cpp:490:44
[task 2020-06-30T02:54:13.343Z] 02:54:13 INFO - PID 10594 | #3 0x7f8f99873f74 in nsTSubstring<char>::Assign(nsTSubstring<char> const&) /builds/worker/checkouts/gecko/xpcom/string/nsTSubstring.cpp:456:8
[task 2020-06-30T02:54:13.360Z] 02:54:13 INFO - PID 10594 | #4 0x7f8f9e87775b in nsTString /builds/worker/workspace/obj-build/dist/include/nsTString.h:101:11
[task 2020-06-30T02:54:13.361Z] 02:54:13 INFO - PID 10594 | #5 0x7f8f9e87775b in DOMExceptionInfo /builds/worker/checkouts/gecko/dom/bindings/BindingUtils.cpp:373:9
[task 2020-06-30T02:54:13.362Z] 02:54:13 INFO - PID 10594 | #6 0x7f8f9e87775b in mozilla::binding_danger::TErrorResult<mozilla::binding_danger::AssertAndSuppressCleanupPolicy>::ThrowDOMException(nsresult, nsTSubstring<char> const&) /builds/worker/checkouts/gecko/dom/bindings/BindingUtils.cpp:422:28
[task 2020-06-30T02:54:13.378Z] 02:54:13 INFO - PID 10594 | #7 0x7f8f9cd21f11 in ThrowDataCloneError /builds/worker/workspace/obj-build/dist/include/mozilla/dom/DOMExceptionNames.h:42:1
[task 2020-06-30T02:54:13.380Z] 02:54:13 INFO - PID 10594 | #8 0x7f8f9cd21f11 in mozilla::dom::StructuredCloneHolder::ReadFromBuffer(nsIGlobalObject*, JSContext*, JSStructuredCloneData&, unsigned int, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/base/StructuredCloneHolder.cpp:382:9
[task 2020-06-30T02:54:13.381Z] 02:54:13 INFO - PID 10594 | #9 0x7f8f9cd21d28 in mozilla::dom::StructuredCloneHolder::ReadFromBuffer(nsIGlobalObject*, JSContext*, JSStructuredCloneData&, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/base/StructuredCloneHolder.cpp:365:3
[task 2020-06-30T02:54:13.389Z] 02:54:13 INFO - PID 10594 | #10 0x7f8fa057d31f in mozilla::dom::ipc::StructuredCloneData::Read(JSContext*, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/ipc/StructuredCloneData.cpp:117:3
[task 2020-06-30T02:54:13.391Z] 02:54:13 INFO - PID 10594 | #11 0x7f8fa057cf10 in mozilla::dom::SharedMessageBody::Read(JSContext*, JS::MutableHandle<JS::Value>, mozilla::dom::RefMessageBodyService*, mozilla::dom::SharedMessageBody::ReadMethod, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/ipc/SharedMessageBody.cpp
[task 2020-06-30T02:54:13.392Z] 02:54:13 INFO - PID 10594 | #12 0x7f8fa069b801 in mozilla::dom::BroadcastChannel::MessageReceived(mozilla::dom::MessageData const&) /builds/worker/checkouts/gecko/dom/broadcastchannel/BroadcastChannel.cpp:417:9
[task 2020-06-30T02:54:13.393Z] 02:54:13 INFO - PID 10594 | #13 0x7f8fa069c574 in mozilla::dom::BroadcastChannelChild::RecvNotify(mozilla::dom::MessageData const&) /builds/worker/checkouts/gecko/dom/broadcastchannel/BroadcastChannelChild.cpp:28:8
[task 2020-06-30T02:54:13.396Z] 02:54:13 INFO - PID 10594 | #14 0x7f8f9b2f585a in mozilla::dom::PBroadcastChannelChild::OnMessageReceived(IPC::Message const&) /builds/worker/workspace/obj-build/ipc/ipdl/PBroadcastChannelChild.cpp:142:28
[task 2020-06-30T02:54:13.404Z] 02:54:13 INFO - PID 10594 | #15 0x7f8f9af47fb0 in mozilla::ipc::PBackgroundChild::OnMessageReceived(IPC::Message const&) /builds/worker/workspace/obj-build/ipc/ipdl/PBackgroundChild.cpp:6080:32
[task 2020-06-30T02:54:13.421Z] 02:54:13 INFO - PID 10594 | #16 0x7f8f9abcceec in mozilla::ipc::MessageChannel::DispatchAsyncMessage(mozilla::ipc::ActorLifecycleProxy*, IPC::Message const&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:2169:25
[task 2020-06-30T02:54:13.422Z] 02:54:13 INFO - PID 10594 | #17 0x7f8f9abc9a2c in mozilla::ipc::MessageChannel::DispatchMessage(IPC::Message&&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:2093:9
[task 2020-06-30T02:54:13.424Z] 02:54:13 INFO - PID 10594 | #18 0x7f8f9abcb04f in mozilla::ipc::MessageChannel::RunMessage(mozilla::ipc::MessageChannel::MessageTask&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:1941:3
[task 2020-06-30T02:54:13.425Z] 02:54:13 INFO - PID 10594 | #19 0x7f8f9abcb85e in mozilla::ipc::MessageChannel::MessageTask::Run() /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:1972:13
[task 2020-06-30T02:54:13.441Z] 02:54:13 INFO - PID 10594 | #20 0x7f8f99ac8809 in nsThread::ProcessNextEvent(bool, bool*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:1234:14
[task 2020-06-30T02:54:13.443Z] 02:54:13 INFO - PID 10594 | #21 0x7f8f99ad30dc in NS_ProcessNextEvent(nsIThread*, bool) /builds/worker/checkouts/gecko/xpcom/threads/nsThreadUtils.cpp:504:10
[task 2020-06-30T02:54:13.459Z] 02:54:13 INFO - PID 10594 | #22 0x7f8fa0616c4a in mozilla::dom::WorkerPrivate::DoRunLoop(JSContext*) /builds/worker/checkouts/gecko/dom/workers/WorkerPrivate.cpp:2981:7
[task 2020-06-30T02:54:13.476Z] 02:54:13 INFO - PID 10594 | #23 0x7f8fa05dde67 in mozilla::dom::workerinternals::(anonymous namespace)::WorkerThreadPrimaryRunnable::Run() /builds/worker/checkouts/gecko/dom/workers/RuntimeService.cpp:2216:40
[task 2020-06-30T02:54:13.478Z] 02:54:13 INFO - PID 10594 | #24 0x7f8f99ac8809 in nsThread::ProcessNextEvent(bool, bool*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:1234:14
[task 2020-06-30T02:54:13.479Z] 02:54:13 INFO - PID 10594 | #25 0x7f8f99ad30dc in NS_ProcessNextEvent(nsIThread*, bool) /builds/worker/checkouts/gecko/xpcom/threads/nsThreadUtils.cpp:504:10
[task 2020-06-30T02:54:13.480Z] 02:54:13 INFO - PID 10594 | #26 0x7f8f9abd59d9 in mozilla::ipc::MessagePumpForNonMainThreads::Run(base::MessagePump::Delegate*) /builds/worker/checkouts/gecko/ipc/glue/MessagePump.cpp:332:5
[task 2020-06-30T02:54:13.482Z] 02:54:13 INFO - PID 10594 | #27 0x7f8f9aaf1fc7 in RunInternal /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:316:10
[task 2020-06-30T02:54:13.483Z] 02:54:13 INFO - PID 10594 | #28 0x7f8f9aaf1fc7 in RunHandler /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:309:3
[task 2020-06-30T02:54:13.484Z] 02:54:13 INFO - PID 10594 | #29 0x7f8f9aaf1fc7 in MessageLoop::Run() /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:291:3
[task 2020-06-30T02:54:13.486Z] 02:54:13 INFO - PID 10594 | #30 0x7f8f99ac177a in nsThread::ThreadFunc(void*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:447:10
[task 2020-06-30T02:54:13.487Z] 02:54:13 INFO - PID 10594 | #31 0x7f8fb6fd8d3e in _pt_root /builds/worker/checkouts/gecko/nsprpub/pr/src/pthreads/ptthread.c:201:5
[task 2020-06-30T02:54:13.488Z] 02:54:13 INFO - PID 10594 | #32 0x7f8fbad986da in start_thread (/lib/x86_64-linux-gnu/libpthread.so.0+0x76da)
[task 2020-06-30T02:54:13.561Z] 02:54:13 INFO - PID 10594 | #33 0x7f8fb9d7688e in clone /build/glibc-OTsEL5/glibc-2.27/misc/../sysdeps/unix/sysv/linux/x86_64/clone.S:95
[task 2020-06-30T02:54:13.561Z] 02:54:13 INFO - PID 10594 | 0x611000222bc0 is located 0 bytes inside of 256-byte region [0x611000222bc0,0x611000222cc0)
[task 2020-06-30T02:54:13.561Z] 02:54:13 INFO - PID 10594 | freed by thread T22 (DOM Worker) here:
[task 2020-06-30T02:54:13.561Z] 02:54:13 INFO - PID 10594 | #0 0x562df4bef0fd in free /builds/worker/fetches/llvm-project/llvm/projects/compiler-rt/lib/asan/asan_malloc_linux.cc:123:3
[task 2020-06-30T02:54:13.563Z] 02:54:13 INFO - PID 10594 | #1 0x7f8f99888e2f in ReleaseData /builds/worker/checkouts/gecko/xpcom/string/nsSubstring.cpp
[task 2020-06-30T02:54:13.563Z] 02:54:13 INFO - PID 10594 | #2 0x7f8f99888e2f in nsTSubstring<char>::Truncate() /builds/worker/checkouts/gecko/xpcom/string/nsTSubstring.cpp:949:3
[task 2020-06-30T02:54:13.563Z] 02:54:13 INFO - PID 10594 | #3 0x7f8f9cd21f64 in operator() /builds/worker/checkouts/gecko/dom/base/StructuredCloneHolder.cpp:376:62
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #4 0x7f8f9cd21f64 in ~ScopeExit /builds/worker/workspace/obj-build/dist/include/mozilla/ScopeExit.h:111:7
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #5 0x7f8f9cd21f64 in mozilla::dom::StructuredCloneHolder::ReadFromBuffer(nsIGlobalObject*, JSContext*, JSStructuredCloneData&, unsigned int, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/base/StructuredCloneHolder.cpp:385:1
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #6 0x7f8f9cd21d28 in mozilla::dom::StructuredCloneHolder::ReadFromBuffer(nsIGlobalObject*, JSContext*, JSStructuredCloneData&, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/base/StructuredCloneHolder.cpp:365:3
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #7 0x7f8fa057d31f in mozilla::dom::ipc::StructuredCloneData::Read(JSContext*, JS::MutableHandle<JS::Value>, JS::CloneDataPolicy const&, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/ipc/StructuredCloneData.cpp:117:3
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #8 0x7f8fa057cf10 in mozilla::dom::SharedMessageBody::Read(JSContext*, JS::MutableHandle<JS::Value>, mozilla::dom::RefMessageBodyService*, mozilla::dom::SharedMessageBody::ReadMethod, mozilla::ErrorResult&) /builds/worker/checkouts/gecko/dom/ipc/SharedMessageBody.cpp
[task 2020-06-30T02:54:13.566Z] 02:54:13 INFO - PID 10594 | #9 0x7f8fa069b801 in mozilla::dom::BroadcastChannel::MessageReceived(mozilla::dom::MessageData const&) /builds/worker/checkouts/gecko/dom/broadcastchannel/BroadcastChannel.cpp:417:9
[task 2020-06-30T02:54:13.567Z] 02:54:13 INFO - PID 10594 | #10 0x7f8fa069c574 in mozilla::dom::BroadcastChannelChild::RecvNotify(mozilla::dom::MessageData const&) /builds/worker/checkouts/gecko/dom/broadcastchannel/BroadcastChannelChild.cpp:28:8
[task 2020-06-30T02:54:13.569Z] 02:54:13 INFO - PID 10594 | #11 0x7f8f9b2f585a in mozilla::dom::PBroadcastChannelChild::OnMessageReceived(IPC::Message const&) /builds/worker/workspace/obj-build/ipc/ipdl/PBroadcastChannelChild.cpp:142:28
[task 2020-06-30T02:54:13.577Z] 02:54:13 INFO - PID 10594 | #12 0x7f8f9af47fb0 in mozilla::ipc::PBackgroundChild::OnMessageReceived(IPC::Message const&) /builds/worker/workspace/obj-build/ipc/ipdl/PBackgroundChild.cpp:6080:32
[task 2020-06-30T02:54:13.579Z] 02:54:13 INFO - PID 10594 | #13 0x7f8f9abcceec in mozilla::ipc::MessageChannel::DispatchAsyncMessage(mozilla::ipc::ActorLifecycleProxy*, IPC::Message const&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:2169:25
[task 2020-06-30T02:54:13.580Z] 02:54:13 INFO - PID 10594 | #14 0x7f8f9abc9a2c in mozilla::ipc::MessageChannel::DispatchMessage(IPC::Message&&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:2093:9
[task 2020-06-30T02:54:13.585Z] 02:54:13 INFO - PID 10594 | #15 0x7f8f9abcb04f in mozilla::ipc::MessageChannel::RunMessage(mozilla::ipc::MessageChannel::MessageTask&) /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:1941:3
[task 2020-06-30T02:54:13.586Z] 02:54:13 INFO - PID 10594 | #16 0x7f8f9abcb85e in mozilla::ipc::MessageChannel::MessageTask::Run() /builds/worker/checkouts/gecko/ipc/glue/MessageChannel.cpp:1972:13
[task 2020-06-30T02:54:13.587Z] 02:54:13 INFO - PID 10594 | #17 0x7f8f99ac8809 in nsThread::ProcessNextEvent(bool, bool*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:1234:14
[task 2020-06-30T02:54:13.588Z] 02:54:13 INFO - PID 10594 | #18 0x7f8f99ad30dc in NS_ProcessNextEvent(nsIThread*, bool) /builds/worker/checkouts/gecko/xpcom/threads/nsThreadUtils.cpp:504:10
[task 2020-06-30T02:54:13.589Z] 02:54:13 INFO - PID 10594 | #19 0x7f8fa0616c4a in mozilla::dom::WorkerPrivate::DoRunLoop(JSContext*) /builds/worker/checkouts/gecko/dom/workers/WorkerPrivate.cpp:2981:7
[task 2020-06-30T02:54:13.590Z] 02:54:13 INFO - PID 10594 | #20 0x7f8fa05dde67 in mozilla::dom::workerinternals::(anonymous namespace)::WorkerThreadPrimaryRunnable::Run() /builds/worker/checkouts/gecko/dom/workers/RuntimeService.cpp:2216:40
[task 2020-06-30T02:54:13.591Z] 02:54:13 INFO - PID 10594 | #21 0x7f8f99ac8809 in nsThread::ProcessNextEvent(bool, bool*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:1234:14
[task 2020-06-30T02:54:13.592Z] 02:54:13 INFO - PID 10594 | #22 0x7f8f99ad30dc in NS_ProcessNextEvent(nsIThread*, bool) /builds/worker/checkouts/gecko/xpcom/threads/nsThreadUtils.cpp:504:10
[task 2020-06-30T02:54:13.593Z] 02:54:13 INFO - PID 10594 | #23 0x7f8f9abd5879 in mozilla::ipc::MessagePumpForNonMainThreads::Run(base::MessagePump::Delegate*) /builds/worker/checkouts/gecko/ipc/glue/MessagePump.cpp:302:20
[task 2020-06-30T02:54:13.597Z] 02:54:13 INFO - PID 10594 | #24 0x7f8f9aaf1fc7 in RunInternal /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:316:10
[task 2020-06-30T02:54:13.598Z] 02:54:13 INFO - PID 10594 | #25 0x7f8f9aaf1fc7 in RunHandler /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:309:3
[task 2020-06-30T02:54:13.599Z] 02:54:13 INFO - PID 10594 | #26 0x7f8f9aaf1fc7 in MessageLoop::Run() /builds/worker/checkouts/gecko/ipc/chromium/src/base/message_loop.cc:291:3
[task 2020-06-30T02:54:13.600Z] 02:54:13 INFO - PID 10594 | #27 0x7f8f99ac177a in nsThread::ThreadFunc(void*) /builds/worker/checkouts/gecko/xpcom/threads/nsThread.cpp:447:10
[task 2020-06-30T02:54:13.601Z] 02:54:13 INFO - PID 10594 | #28 0x7f8fb6fd8d3e in _pt_root /builds/worker/checkouts/gecko/nsprpub/pr/src/pthreads/ptthread.c:201:5
[task 2020-06-30T02:54:13.601Z] 02:54:13 INFO - PID 10594 | #29 0x7f8fbad986da in start_thread (/lib/x86_64-linux-gnu/libpthread.so.0+0x76da)
[..]
[task 2020-06-30T02:54:14.044Z] 02:54:14 INFO - PID 10594 | SUMMARY: AddressSanitizer: heap-use-after-free /builds/worker/fetches/clang/bin/../lib/gcc/x86_64-unknown-linux-gnu/7.4.0/../../../../include/c++/7.4.0/bits/atomic_base.h:514:16 in fetch_add
[task 2020-06-30T02:54:14.045Z] 02:54:14 INFO - PID 10594 | Shadow bytes around the buggy address:
[task 2020-06-30T02:54:14.045Z] 02:54:14 INFO - PID 10594 | 0x0c228003c520: fa fa fa fa fa fa fa fa 00 00 00 00 00 00 00 00
[task 2020-06-30T02:54:14.046Z] 02:54:14 INFO - PID 10594 | 0x0c228003c530: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
[task 2020-06-30T02:54:14.046Z] 02:54:14 INFO - PID 10594 | 0x0c228003c540: 00 00 00 00 00 00 00 fa fa fa fa fa fa fa fa fa
[task 2020-06-30T02:54:14.047Z] 02:54:14 INFO - PID 10594 | 0x0c228003c550: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
[task 2020-06-30T02:54:14.047Z] 02:54:14 INFO - PID 10594 | 0x0c228003c560: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
[task 2020-06-30T02:54:14.048Z] 02:54:14 INFO - PID 10594 | =>0x0c228003c570: fa fa fa fa fa fa fa fa[fd]fd fd fd fd fd fd fd
[task 2020-06-30T02:54:14.048Z] 02:54:14 INFO - PID 10594 | 0x0c228003c580: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
[task 2020-06-30T02:54:14.048Z] 02:54:14 INFO - PID 10594 | 0x0c228003c590: fd fd fd fd fd fd fd fd fa fa fa fa fa fa fa fa
[task 2020-06-30T02:54:14.048Z] 02:54:14 INFO - PID 10594 | 0x0c228003c5a0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
[task 2020-06-30T02:54:14.049Z] 02:54:14 INFO - PID 10594 | 0x0c228003c5b0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
[task 2020-06-30T02:54:14.049Z] 02:54:14 INFO - PID 10594 | 0x0c228003c5c0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
[task 2020-06-30T02:54:14.049Z] 02:54:14 INFO - PID 10594 | Shadow byte legend (one shadow byte represents 8 application bytes):
[task 2020-06-30T02:54:14.050Z] 02:54:14 INFO - PID 10594 | Addressable: 00
[task 2020-06-30T02:54:14.050Z] 02:54:14 INFO - PID 10594 | Partially addressable: 01 02 03 04 05 06 07
[task 2020-06-30T02:54:14.050Z] 02:54:14 INFO - PID 10594 | Heap left redzone: fa
[task 2020-06-30T02:54:14.051Z] 02:54:14 INFO - PID 10594 | Freed heap region: fd
[task 2020-06-30T02:54:14.051Z] 02:54:14 INFO - PID 10594 | Stack left redzone: f1
[task 2020-06-30T02:54:14.051Z] 02:54:14 INFO - PID 10594 | Stack mid redzone: f2
[task 2020-06-30T02:54:14.052Z] 02:54:14 INFO - PID 10594 | Stack right redzone: f3
[task 2020-06-30T02:54:14.052Z] 02:54:14 INFO - PID 10594 | Stack after return: f5
[task 2020-06-30T02:54:14.053Z] 02:54:14 INFO - PID 10594 | Stack use after scope: f8
[task 2020-06-30T02:54:14.055Z] 02:54:14 INFO - PID 10594 | Global redzone: f9
[task 2020-06-30T02:54:14.056Z] 02:54:14 INFO - PID 10594 | Global init order: f6
[task 2020-06-30T02:54:14.056Z] 02:54:14 INFO - PID 10594 | Poisoned by user: f7
[task 2020-06-30T02:54:14.056Z] 02:54:14 INFO - PID 10594 | Container overflow: fc
[task 2020-06-30T02:54:14.057Z] 02:54:14 INFO - PID 10594 | Array cookie: ac
[task 2020-06-30T02:54:14.058Z] 02:54:14 INFO - PID 10594 | Intra object redzone: bb
[task 2020-06-30T02:54:14.058Z] 02:54:14 INFO - PID 10594 | ASan internal: fe
[task 2020-06-30T02:54:14.059Z] 02:54:14 INFO - PID 10594 | Left alloca redzone: ca
[task 2020-06-30T02:54:14.059Z] 02:54:14 INFO - PID 10594 | Right alloca redzone: cb
[task 2020-06-30T02:54:14.060Z] 02:54:14 INFO - PID 10594 | Shadow gap: cc
[task 2020-06-30T02:54:14.060Z] 02:54:14 INFO - PID 10594 | ==10907==ABORTING
|
|
1,649,407 | 14,910,000 |
Created attachment 9160329
The zap svg covers "Firefox" word from the "welcome-text"
**[Notes]**:
- There is not enough distance between the zap image and the “welcome-text” on the other “about:welcome” slides.
**[Affected Versions]:**
- Firefox Beta 79.0a1 (Build ID: 20200629224419)
- Firefox Nightly 80.0a1 (Build ID: 20200629154604)
**[Affected Platforms]:**
- Windows 10 (x64)
**[Prerequisites]:**
- Have a new profile created.
- Have the value of the `browser.aboutwelcome.overrideContent` pref set to `{"id": "multi-stage-welcome-importable-theme","template": "multistage","screens": [{"id": "AW_GET_STARTED","order": 0,"content": {"zap": true,"title": { "string_id": "onboarding-multistage-welcome-header" }, "subtitle": "The fast, safe, and private browser that's backed by a non-profit.", "primary_button": {"label": "Start Setup","action":{"navigate": true}}, "secondary_button": {"text": "Have an account?", "label": "Sign in","position": "top", "action":{"type": "OPEN_URL","addFlowParams": true, "data":{"args": "https://accounts.firefox.com/?service=sync&action=email&context=fx_desktop_v3&entrypoint=activity-stream-firstrun&style=trailhead","where": "current"}}}}},{"id": "AW_IMPORT_SETTINGS","order": 1,"content": {"zap": true,"title": "Import your passwords, bookmarks,\u00a0and more","subtitle": "Coming from another browser? It's easy to bring everything to Firefox.","tiles": {"type": "topsites"}, "primary_button": {"label": "Start Import", "action":{"type": "SHOW_MIGRATION_WIZARD","navigate": true}},"secondary_button": {"label": "Not now","action":{"navigate": true}}}},{"id": "AW_CHOOSE_THEME","order": 2,"content": {"zap": true, "title": "Choose a look","subtitle": "Personalize Firefox with a theme.","tiles": {"type": "theme","action": {"theme": "<event>"}, "data": [{"theme": "light", "label": "Light"}, {"theme": "dark", "label": "Dark"}]}, "primary_button": {"label": "Save Theme", "action":{"navigate": true}},"secondary_button": {"label": "Not now","action":{"theme": "default","navigate": true}}}}]}`.
**[Steps to reproduce]:**
1. Start the Firefox Browser with the profile from prerequisites.
2. Navigate to the “about:welcome” page.
3. Click the “Start Setup” button and observe the string underneath the zap image.
**[Expected results]:**
- The zap image does not cover the “welcome-text” string.
**[Actual results]:**
- The zap image partially covers the “Firefox” word from the “welcome-text” string.
**[Additional Notes]:**
- The issue is not reproducible for the following displays:
- MacBook Pro Retina, 13”, early 2015.
- iMac, 21.5”, late 2013.
- Ubuntu Linux 18.04 (x64) actual machine as well as a VM.
- Linux MX 4.19 (VM) (x64).
- Attached a screen-shot with the issue.
|
|
1,649,487 | 14,910,594 |
Created attachment 9160417
secvfy.patch
User Agent: Mozilla/5.0 (X11; Fedora; Linux x86_64; rv:77.0) Gecko/20100101 Firefox/77.0
Steps to reproduce:
JSS upstream test suite is failing with sandboxed build of NSS. This fails within our SSLEngine code due to suboptimal verification of certificates.
This manifests as the following:
2020-06-25T22:50:11.0913044Z FINE: - CN=localhost,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0913171Z FINE: parent: CN=CACert,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0913404Z FINE: - CN=CACert,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0913530Z FINE: child: CN=localhost,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0913801Z FINE: JSSTrustManager: - CN=CACert,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0914077Z FINE: JSSTrustManager: - CN=localhost,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0914212Z FINE: JSSTrustManager: getAcceptedIssuers():
2020-06-25T22:50:11.0914478Z FINE: JSSTrustManager: - CN=CACert,OU=JSS Testing50,O=Mozilla,C=US
2020-06-25T22:50:11.0914749Z FINE: JSSTrustManager: - CN=CACert,OU=JSS Testing40,O=Mozilla,C=US
2020-06-25T22:50:11.0915018Z FINE: JSSTrustManager: - CN=CACert,OU=JSS Testing30,O=Mozilla,C=US
2020-06-25T22:50:11.0915286Z FINE: JSSTrustManager: - CN=CACert,OU=JSS Testing20,O=Mozilla,C=US
2020-06-25T22:50:11.0915399Z FINE: JSSTrustManager: checkCert(CN=CACert,OU=JSS Testing20,O=Mozilla,C=US):
2020-06-25T22:50:11.0915529Z FINE: JSSTrustManager: cert AKI: null
2020-06-25T22:50:11.0915656Z FINE: JSSTrustManager: SKI of CN=CACert,OU=JSS Testing50,O=Mozilla,C=US: null
2020-06-25T22:50:11.0915940Z Assertion failure: cx->hashAlg == hashid, at ../../lib/cryptohi/secvfy.c:691
2020-06-25T22:50:11.0916026Z
In particular, because recoverPKCS1DigestInfo() can fail, the assert immediately following it is invalid. This should only be checked when rv == SECSuccess.
See attached patch. Perhaps the assert should be removed?
Actual results:
secvfy caused NSS + JSS to crash.
Expected results:
secvfy should succeed and NSS + JSS shouldn't crash.
|
|
1,649,494 | 14,910,635 |
First report for this bug is 6/15, so either something we or AC did recently.
This bug is for crash report bp-140bf268-ae89-4d3b-b210-5eafa0200630.
Top 10 frames of crashing thread:
```
0 libxul.so mozilla::widget::AndroidAlerts::ShowPersistentNotification widget/android/AndroidAlerts.cpp:86
1 libxul.so nsAlertsService::ShowPersistentNotification toolkit/components/alerts/nsAlertsService.cpp:222
2 libxul.so nsAlertsService::ShowAlertNotification toolkit/components/alerts/nsAlertsService.cpp:193
3 libxul.so NS_InvokeByIndex xpcom/reflect/xptcall/md/unix/xptcinvoke_arm.cpp:167
4 libxul.so XPCWrappedNative::CallMethod js/xpconnect/src/XPCWrappedNative.cpp:1140
5 libxul.so XPC_WN_CallMethod js/xpconnect/src/XPCWrappedNativeJSOps.cpp:946
6 libxul.so js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:576
7 libxul.so Interpret js/src/vm/Interpreter.cpp:639
8 libxul.so js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:611
9 libxul.so js::jit::DoCallFallback js/src/jit/BaselineIC.cpp:2992
```
|
|
1,649,883 | 14,913,340 |
Created attachment 9160768
Firefox78Pocket.png
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.116 Safari/537.36 Edg/83.0.478.56
Steps to reproduce:
1) Go to Firefox settings -> Home
2) Uncheck Recommended by Pocket
3) Restart browser
4) Go into Firefox settings -> Home
Actual results:
Recommended by Pocket is no longer an option to enable/disable and is completely gone
Expected results:
Recommended by Pocket should still be present, allowing the user to enable the option if they want in future.
|
|
1,650,107 | 14,914,684 |
User Agent: Mozilla/5.0 (X11; Linux x86_64; rv:79.0) Gecko/20100101 Firefox/79.0
Steps to reproduce:
Press F1 on the 'will-change' property in the 'Computed' tab in the Inspector.
Actual results:
DevTools opens the URL 'https://developer.mozilla.org/CSS/will-change' which currently gives a 404 error page.
For most CSS properties there are redirects set up on MDN, e.g. https://developer.mozilla.org/CSS/background redirects to https://developer.mozilla.org/en-US/docs/Web/CSS/background.
Newer properties do not seem to have such redirects set up. Examples: 'will-change', 'line-break', 'justify-self', 'justify-items'.
Expected results:
I would expect DevTools to open the URL 'https://developer.mozilla.org/docs/Web/CSS/will-change'.
The URL is specified here in the code: https://github.com/mozilla/gecko-dev/blob/c350ad5bd6718e368dccba0e559493cb7d8e8230/devtools/client/inspector/computed/computed.js#L936
The URL I would expect is used other places in the code, for instance here: https://github.com/mozilla/gecko-dev/blob/5c78a8e3de57fac8b966eabee4bbbbecceb89e90/devtools/client/shared/widgets/tooltip/inactive-css-tooltip-helper.js#L86
|
|
1,650,281 | 14,916,107 |
User Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:78.0) Gecko/20100101 Firefox/78.0
Steps to reproduce:
Add this to user.js:
user_pref("browser.privatebrowsing.forceMediaMemoryCache", true);
user_pref("media.memory_cache_max_size", 393216); // Optional
Then go to https://www.kindgirls.com/ (yeah I know)
Click on Videos at the top right
Click on the first video (it's a link to an mp4 and a webm)
Let it play for 5 seconds
Click BACK and pick another video
Repeat this process a few times
Actual results:
Usually, after opening the third video, we get an error instead of the video, saying there are no mime types for this media. I usually get it after the 3rd one, but sometimes I get it on the second try, sometimes on the 4th; I cannot start playing more than a few videos until none will play. And mind you, I do not have to play them much, just a few seconds before trying out another one...
Expected results:
As you can see I tried increasing the size of the RAM cache, but it makes no difference. Yeah I know, pr0n site, but it's good for testing because it does not use a custom player, it's just pure links to small mp4 videos. I am guessing this might be an uplift from Tor? Tor will soon be using the new ESR and might then be affected too (for now it is not affected, it's still based on v68).
|
|
1,650,654 | 14,918,441 |
This bug is for crash report bp-802f5a47-ae5b-445f-ba81-295a30200705.
Top 10 frames of crashing thread:
```
0 nss3.dll PK11_TraverseCertsInSlot security/nss/lib/pk11wrap/pk11cert.c:2353
1 nss3.dll PK11_ListCertsInSlot security/nss/lib/pk11wrap/pk11cert.c:2893
2 xul.dll IntermediatePreloadingHealerCallback security/manager/ssl/nsNSSComponent.cpp:2186
3 xul.dll nsTimerImpl::Fire xpcom/threads/nsTimerImpl.cpp:562
4 xul.dll nsTimerEvent::Run xpcom/threads/TimerThread.cpp:251
5 xul.dll mozilla::TaskQueue::Runner::Run xpcom/threads/TaskQueue.cpp:158
6 xul.dll nsThreadPool::Run xpcom/threads/nsThreadPool.cpp:299
7 xul.dll nsThread::ProcessNextEvent xpcom/threads/nsThread.cpp:1234
8 xul.dll NS_ProcessNextEvent xpcom/threads/nsThreadUtils.cpp:504
9 xul.dll mozilla::ipc::MessagePumpForNonMainThreads::Run ipc/glue/MessagePump.cpp:332
```
this crash signature is starting to show up in the 79.0b cycle and looks related to the changes from bug 1630434.
|
|
1,642,570 | 14,857,505 |
User Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_3) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36
Steps to reproduce:
Autofill isn't saved when an input DOM node has `node.defaultValue === node.value` when submitted.
Any ReactJS app that uses controlled inputs,
Here is an example: https://codesandbox.io/embed/material-demo-y5mlt
Here is another example with plain HTML and 3 line of JS code that updates the `node.defaultValue`: https://codesandbox.io/s/naughty-feather-vwl6v?file=/index.html (over-simplification of what ReactJS does under the hood on user type)
The relevant issue in ReactJS repo: https://github.com/facebook/react/issues/18986
Actual results:
All ReactJS applications that use "controlled inputs" are affected. ReactJS updates the input DOM node's `defaultValue` to be equal to `value` as the user types. When the form is submitted, Firefox doesn't keep/save the form values for autocomplete/autofill.
In ReactJS web apps, this is an issue because it ruins user experience. ReactJS does this for "controlled inputs" so when a form is reset, it won't make all fields blank. Also, as far as I know, Firefox doesn't trigger events on inputs when form is reset, so it's still an issue and the best workaround still seems to be to do `node.defaultValue = node.value` so the state isn't out of sync with the form. However, this workaround introduces a new problem that _only_ happens in Firefox, it bails out of saving input values for autofill/autocomplete.
Expected results:
Submitting a form where input DOM nodes have `input.defaultValue === input.value` should still save them for autofill.
Why? because the `defaultValue` of an input may have come from a different source other than autocomplete.
For instance, a user profile was saved in Google Chrome, but the user opened it in Firefox and tried to modify their profile in Firefox (all fields with `defaultValue`). In this case, Firefox would only save one field for autofill/autocomplete rather than all of them. Chrome would offer autocomplete for all fields but Firefox only for one of them which is pretty confusing. If this same form was written in ReactJS with "controlled inputs", Firefox wouldn't offer autofill at all.
|
|
1,642,919 | 14,860,024 |
This bug is for crash report bp-8108293f-cd72-4afe-8143-740e30200603.
Top 10 frames of crashing thread:
```
0 xul.dll static mozilla::ContentBlockingNotifier::OnEvent toolkit/components/antitracking/ContentBlockingNotifier.cpp:505
1 xul.dll static mozilla::ContentBlocking::OnAllowAccessFor toolkit/components/antitracking/ContentBlocking.cpp:578
2 xul.dll mozilla::ContentBlocking::AllowAccessFor::<unnamed-tag>::operator const toolkit/components/antitracking/ContentBlocking.cpp:368
3 xul.dll mozilla::MozPromise<mozilla::Maybe<mozilla::ContentBlocking::StorageAccessPromptChoices>, mozilla::ipc::ResponseRejectReason, 1>::ThenValue<`lambda at /builds/worker/checkouts/gecko/toolkit/components/antitracking/ContentBlocking.cpp:358:14'>::DoResolveOrRejectInternal xpcom/threads/MozPromise.h:798
4 xul.dll mozilla::MozPromise<CopyableTArray<bool>, nsresult, 0>::ThenValueBase::ResolveOrRejectRunnable::Run xpcom/threads/MozPromise.h:405
5 xul.dll nsThread::ProcessNextEvent xpcom/threads/nsThread.cpp:1200
6 xul.dll NS_ProcessNextEvent xpcom/threads/nsThreadUtils.cpp:481
7 xul.dll mozilla::ipc::MessagePump::Run ipc/glue/MessagePump.cpp:87
8 xul.dll MessageLoop::RunHandler ipc/chromium/src/base/message_loop.cc:308
9 xul.dll MessageLoop::Run ipc/chromium/src/base/message_loop.cc:290
```
this crash signature is starting to show up in firefox 77 on windows - most of the time it's the content process that's crashing.
|
|
1,643,264 | 14,862,293 | null |
|
1,643,503 | 14,864,085 |
Created attachment 9154378
MeetOverlap.png
Unfortunate placement.
|
|
1,643,528 | 14,864,316 |
Created attachment 9154405
nss-3.53-strict-proto-fix.patch
Description of problem:
The latest upgrade of nss broke compilation with -Werror=strict-prototypes
Version-Release number of selected component (if applicable):
How reproducible:
Deterministic
Steps to Reproduce:
1. dnf install -y gcc nss-devel
2. cat >test.c <<EOF
#include <nss.h>
#include <sechash.h>
#include <pk11func.h>
EOF
3. gcc `pkg-config --cflags nss` -c -Wstrict-prototypes -Werror=strict-prototypes test.c
Actual results:
sh-5.0$ gcc `pkg-config --cflags nss` -c -Wstrict-prototypes -Werror=strict-prototypes test.c
In file included from /usr/include/nss3/pk11func.h:12,
from test.c:3:
/usr/include/nss3/pk11pub.h:951:1: error: function declaration isn’t a prototype [-Werror=strict-prototypes]
951 | int SECMOD_GetSystemFIPSEnabled();
| ^~~
cc1: some warnings being treated as errors
sh-5.0$ echo $?
1
Expected results:
sh-5.0$ gcc `pkg-config --cflags nss` -c -Wstrict-prototypes -Werror=strict-prototypes test.c
sh-5.0$ echo $?
0
Additional info:
Looks like it was newly added function.
sh-5.0$ grep -RniI SECMOD_GetSystemFIPSEnabled /usr/include/
sh-5.0$ rpm -q nss-devel
nss-devel-3.52.0-2.fc33.x86_64
And simple workaround is to run following command as root
sed -e '/SECMOD_GetSystemFIPSEnabled/s/();/(void);/' -i /usr/include/nss3/pk11pub.h
|
|
1,643,687 | 14,865,256 |
Created attachment 9154564
adress_bar_0.gif
*Affected versions*
* 78.0b3 (20200604213430)
* 79.0a1 (20200604220012)
*Affected platforms*
* macOS 10.12
* Windows 10x64
*Steps to reproduce*
1. Open Firefox and about:config and set devtools.chrome.enabled:true.
2. Open browser console and type `(async function() { let { ProfileAge } = ChromeUtils.import("resource://gre/modules/ProfileAge.jsm"); let age = await ProfileAge(); age._times = { firstUse: 1368255600000, created: 1368255600000 }; await age.writeTimes(); })();`.
3. Restart the browser and copy a random string in the clipboard (e.g `firefox`).
4. Open a new tab and select Paste and go from the context menu option into the address bar.
*Expected result*
* The copied string is successfully pasted and searched.
*Actual result*
* Nothing happens. Nightly shows [this error](https://drive.google.com/file/d/1BbOOwLPsttLhbQsytK0cevDQJW8fuq9x/view?usp=sharing) in console/ Beta shows [this error](https://drive.google.com/file/d/1gmb8j3J-1hBmkeYhR3nNlOVoHOWZjnip/view?usp=sharing) in console.
*Regression range*
* Firefox 77.0.1 (20200602222727) is not affected. I tried searching for one but I don’t know how to trigger the search tip in mozregression. It seems that it doesn't work by following the above steps. I will search for one manually ASAP.
*Notes*
* Attached a screen recording with the issue.
|
|
1,643,935 | 14,866,768 |
Created attachment 9154778
Correct at top - Wrong at bottom.png
User Agent: Mozilla/5.0 (Windows NT 6.1; rv:77.0) Gecko/20100101 Firefox/77.0
Steps to reproduce:
Press F11.
Hover over the top.
Actual results:
The #restore-button is not displayed correctly due to the following rule added in FF 77.
```
#restore-button > .toolbarbutton-icon:-moz-locale-dir(rtl) {
transform: scaleX(-1);
}
```
Regardless, I don't understand why the button should be transformed.
In Windows programs (e.g. Notepad) the top "window" in that button is on the left.
Actually, transforming the restore-button when NOT in full-screen would be better (I don't think this is really important either).
|
|
1,644,208 | 14,870,069 |
This bug is for crash report bp-28ccdc4b-5ce9-463a-b2fa-0c7ba0200606.
Top 10 frames of crashing thread:
```
0 @0x7bf474
1 xul.dll mozilla::detail::RunnableMethodImpl<mozilla::layers::CanvasDrawEventRecorder*, void xpcom/threads/nsThreadUtils.h:1212
2 xul.dll nsThread::ProcessNextEvent xpcom/threads/nsThread.cpp:1218
3 xul.dll mozilla::ipc::MessagePump::Run ipc/glue/MessagePump.cpp:87
4 xul.dll MessageLoop::RunHandler ipc/chromium/src/base/message_loop.cc:308
5 xul.dll MessageLoop::Run ipc/chromium/src/base/message_loop.cc:290
6 xul.dll nsBaseAppShell::Run widget/nsBaseAppShell.cpp:137
7 xul.dll nsAppShell::Run widget/windows/nsAppShell.cpp:430
8 xul.dll XRE_RunAppShell toolkit/xre/nsEmbedFunctions.cpp:913
9 xul.dll mozilla::ipc::MessagePumpForChildProcess::Run ipc/glue/MessagePump.cpp:237
```
|
|
1,644,237 | 14,870,351 |
This bug is for crash report bp-081cbcce-d503-40d3-9e2a-9e4a40200608.
Top 10 frames of crashing thread:
```
0 xul.dll mozilla::net::BackgroundFileSaver::GetWorkerThreadAttention netwerk/base/BackgroundFileSaver.cpp:290
1 xul.dll mozilla::net::BackgroundFileSaver::Finish netwerk/base/BackgroundFileSaver.cpp:212
2 xul.dll NS_InvokeByIndex
3 xul.dll static XPCWrappedNative::CallMethod js/xpconnect/src/XPCWrappedNative.cpp:1140
4 xul.dll XPC_WN_CallMethod js/xpconnect/src/XPCWrappedNativeJSOps.cpp:946
5 xul.dll js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:585
6 xul.dll Interpret js/src/vm/Interpreter.cpp:3312
7 xul.dll js::InternalCallOrConstruct js/src/vm/Interpreter.cpp:620
8 xul.dll JS_CallFunctionValue js/src/jsapi.cpp:2777
9 xul.dll nsXPCWrappedJS::CallMethod js/xpconnect/src/XPCWrappedJSClass.cpp:963
```
this crash signature is newly appearing in firefox 78, somewhat more common for 32bit builds - presumably the change from bug 1620366 triggered this.
|
|
1,644,240 | 14,870,373 |
This bug is for crash report bp-4bfad432-82b8-4f0e-923a-df4ec0200608.
Top 4 frames of crashing thread:
```
0 @0x7ffbbba00ffa
1 winmm.dll mciwindow
2 kernel32.dll BaseThreadInitThunk
3 ntdll.dll RtlUserThreadStart
```
this crash signature started appearing in late april and s constantly increasing in volume since then - correlations show the presence of a dll by kaspersky hooking into the browser process:
> (100.0% in signature vs 02.29% overall) Module "klsihk64.dll" = true
judging by locale and user comments this seems to primarily hit users in brazil.
|
|
1,653,899 | 14,946,037 |
Created attachment 9164643
immagine.png
This is the current Italian translation
```
onboarding-multistage-import-header = Importa password, segnalibri e <span data-l10n-name="zap">altro ancora</span>
```
Notice how the `zap` doesn't follow on the second line.
I can work around it by adding a non-breaking space, but I think it should be fixed on the code side. I tried adding a `white-space: nowrap`, and turns out the highlight it's too short for 2 words, although they're not very long.
|
|
1,653,945 | 14,946,234 |
Created attachment 9164664
Recording of the issue
**Affected Versions**
Nightly 80.0a1 (2020-07-19) (64-bit)
**Tested on**
Windows 10 x64
**Steps to reproduce**
**1. Have a profile with MP and saved credentials on Facebook**
2. Go to Facebook, dismiss the MP prompt when it appears
3. Fill in the username and start to fill in the password field
**Expected**
The Primary Password prompt should be displayed after the user unfocuses the field
**Actual**
Primary Password prompt appears right after typing in the first character and the rest of the password input is continued from the password field into the primary password prompt
**Regression-Range**
Did not perform mozregression yet, but looking at Bug 1612258 as the regressor since the dismissed doorhanger key appears right after typing in 1 character instead of unfocusing the password field. In Beta builds (where Bug 1612258 is absent) the primary password prompt appears after unfocusing the password field -at the time when the dismissed doorhanger key is displayed.
**Note**
See attached recording for Nightly and Beta comparison. Marking this as a regression of Bug 1612258 for now.
Can be reproduced only by following Step 1 scenario. Can't be reproduced if there are no credentials already saved on the site and Primary Password dismissed.
|
|
1,653,981 | 14,946,515 |
This bug is for crash report bp-8440ef13-d122-46d4-a2a2-43b2e0200720.
Top 10 frames of crashing thread:
```
0 XUL nsPrintJob::ReflowPrintObject layout/printing/nsPrintJob.cpp:2003
1 XUL nsPrintJob::ReflowDocList layout/printing/nsPrintJob.cpp:1648
2 XUL nsPrintJob::InitPrintDocConstruction layout/printing/nsPrintJob.cpp:1674
3 XUL nsPrintJob::Observe layout/printing/nsPrintJob.cpp:2907
4 XUL mozilla::embedding::PrintProgressDialogChild::RecvDialogOpened toolkit/components/printingui/ipc/PrintProgressDialogChild.cpp:37
5 XUL mozilla::embedding::PPrintProgressDialogChild::OnMessageReceived ipc/ipdl/PPrintProgressDialogChild.cpp:228
6 XUL mozilla::dom::PContentChild::OnMessageReceived ipc/ipdl/PContentChild.cpp:8424
7 XUL mozilla::ipc::MessageChannel::DispatchMessage ipc/glue/MessageChannel.cpp:2150
8 XUL mozilla::ipc::MessageChannel::MessageTask::Run ipc/glue/MessageChannel.cpp:1953
9 XUL mozilla::TaskController::DoExecuteNextTaskOnlyMainThreadInternal xpcom/threads/TaskController.cpp:242
```
It seems that trying to print a specific xml element selection leads to tab crash
**Affected versions**
* 80.0a1 (BuildId:20200720094507)
* 79.0b9 (BuildId:20200717001501)
* 78.0.2 (BuilId:20200708170202)
* 68.10.0esr (BuildId:20200622191537)
* 78.0.2esr (BuildId:20200708170510)
**Affected platforms**
* Windows 10 64bit
* Ubuntu 18.04 64bit
* macOS 10.14
**Steps to reproduce**
1. Launch Firefox.
2. Access the following [link](https://www.w3schools.com/xml/cd_catalog.xml).
3. Select <COUNTRY>USA</COUNTRY>
4. Hit CTRL+P or CMD+P (on macOS)
5. Select the “Selection” on Windows or “Print Selection Only” option on macOS.
6. Click the Ok/Print button.
**Expected result**
* Firefox is stable and the selection is successfully printed.
**Actual result**
* Tab Crash.
**Regression Range**
* This seems to be an old regression:
* Pushlog: https://hg.mozilla.org/mozilla-central/pushloghtml?fromchange=c2248f85346939d3e0b01f57276c440ccb2d16a1&tochange=18a9cb5cb32d0e8031d0a80901b199d5e9827d83
* Possible Regressor: Since this is reproducible on older builds, unfortunately, mozregression keeps skipping builds.
|
|
1,654,064 | 14,947,320 |
Created attachment 9164848
Screen Shot 2020-07-20 at 3.46.23 PM.png
**Steps to reproduce:**
1. Open https://app.plex.tv/desktop in recent Nightly desktop
3. Click "Sign in" on the top right.
4. After "Sign in" page is displayed, click on "Continue with Google".
5. Sign in to your Google account and after returning to the site observe the behaviour
**Expected Behavior:**
Signed in to the site
**Actual Behavior:**
Button is stuck in loading state
The issue is not reproducible if I turn off ETP. Also reproducible on mobile.
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.