id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
197k
| cpes
listlengths 0
4.89k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2019-15058 | stb_image.h (aka the stb image loader) 2.23 has a heap-based buffer over-read in stbi__tga_load, leading to Information Disclosure or Denial of Service. | [
"cpe:2.3:a:stb_project:stb:2.23:*:*:*:*:*:*:*"
]
| null | null | 9.1 | 6.4 |
|
CVE-2020-8801 | SuiteCRM through 7.11.11 allows PHAR Deserialization. | [
"cpe:2.3:a:salesagility:suitecrm:*:*:*:*:*:*:*:*"
]
| null | 7.2 | null | 6.5 |
|
GHSA-5x35-9r35-66x7 | Quick Emulator (Qemu) built with the Virtio GPU Device emulator support is vulnerable to a memory leakage issue. It could occur while destroying gpu resource object in 'virtio_gpu_resource_destroy'. A guest user/process could use this flaw to leak host memory bytes, resulting in DoS for a host. | []
| null | 6.5 | null | null |
|
GHSA-pvmx-mjmh-jfcx | Concrete CMS affected by a stored XSS in Folder Function.The "Add Folder" functionality | Concrete CMS versions 9.0.0 through 9.3.9 are affected by a stored XSS in Folder Function.The "Add Folder" functionality lacks input sanitization, allowing a rogue admin to inject XSS payloads as folder names. The Concrete CMS security team gave this vulnerability a CVSS 4.0 Score of 4.8 with vector: CVSS:4.0/AV:N/AC:L/AT:N/PR:H/UI:P/VC:L/VI:N/VA:N/SC:L/SI:N/SA:N. Versions below 9 are not affected. Thanks, Alfin Joseph for reporting. | []
| 4.8 | null | null | null |
GHSA-6qp6-2ggr-xv6x | A memory corruption issue was addressed with improved state management. This issue is fixed in iOS 12.5.4. Processing maliciously crafted web content may lead to arbitrary code execution. Apple is aware of a report that this issue may have been actively exploited.. | []
| null | 8.8 | null | null |
|
CVE-2022-26205 | Marky commit 3686565726c65756e was discovered to contain a remote code execution (RCE) vulnerability via the Display text fields. This vulnerability allows attackers to execute arbitrary code via injection of a crafted payload. | [
"cpe:2.3:a:marky_project:marky:-:*:*:*:*:*:*:*"
]
| null | 9.8 | null | 7.5 |
|
CVE-2024-23316 | PingAccess HTTP Request Desynchronization Weakness | HTTP request desynchronization in Ping Identity PingAccess, all versions prior to 8.0.1 affected allows an attacker to send specially crafted http header requests to create a request smuggling condition for proxied requests. | [
"cpe:2.3:a:pingidentity:pingaccess:*:*:*:*:*:*:*:*"
]
| 8.8 | null | null | null |
GHSA-p6xf-x5px-f2vq | A vulnerability in the CLI of Cisco AsyncOS for Secure Web Appliance could allow an authenticated, local attacker to execute arbitrary commands and elevate privileges to root.This vulnerability is due to insufficient validation of user-supplied input for the CLI. An attacker could exploit this vulnerability by authenticating to the system and executing a crafted command on the affected device. A successful exploit could allow the attacker to execute arbitrary commands on the underlying operating system and elevate privileges to root. To successfully exploit this vulnerability, an attacker would need at least guest credentials. | []
| null | 8.8 | null | null |
|
GHSA-852q-xxj4-x2rx | SQL Injection in SimpleSAMLphp | The proxystatistics module before 3.1.0 for SimpleSAMLphp allows SQL Injection in lib/Auth/Process/DatabaseCommand.php. | []
| null | null | 9.8 | null |
CVE-2022-27546 | HCL iNotes is susceptible to a Reflected Cross-site Scripting (XSS) vulnerability | HCL iNotes is susceptible to a Reflected Cross-site Scripting (XSS) vulnerability caused by improper validation of user-supplied input supplied with a form POST request. A remote attacker could exploit this vulnerability using a specially-crafted URL to execute script in a victim's web browser within the security context of the hosting web site and/or steal the victim's cookie-based authentication credentials. | [
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_10:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_6:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_7:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_8:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:9.0.1:fixpack_9:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_1:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_2:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_6:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_7:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:10.0.1:fixpack_8:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:fixpack_1:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:fixpack_2:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:11.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:12.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:12.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:hcl_inotes:12.0.1:fixpack_1:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_10:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_6:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_7:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_8:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:9.0.1:fixpack_9:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_1:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_2:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_6:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_7:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:10.0.1:fixpack_8:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:fixpack_1:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:fixpack_2:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:fixpack_3:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:fixpack_4:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:11.0.1:fixpack_5:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:12.0:*:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:12.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:hcltech:domino:12.0.1:fixpack_1:*:*:*:*:*:*"
]
| null | 8.3 | null | null |
CVE-2022-47432 | WordPress Shortcode IMDB Plugin <= 6.0.8 is vulnerable to SQL Injection | Improper Neutralization of Special Elements used in an SQL Command ('SQL Injection') vulnerability in Kemal YAZICI - PluginPress Shortcode IMDB allows SQL Injection.This issue affects Shortcode IMDB: from n/a through 6.0.8.
| [
"cpe:2.3:a:kemalyazici:shortcode_imdb:*:*:*:*:*:wordpress:*:*"
]
| null | 9.8 | null | null |
CVE-2025-24571 | WordPress WP Fast Total Search plugin <= 1.78.258 - Broken Access Control vulnerability | Missing Authorization vulnerability in Epsiloncool WP Fast Total Search allows Exploiting Incorrectly Configured Access Control Security Levels. This issue affects WP Fast Total Search: from n/a through 1.78.258. | []
| null | 5.4 | null | null |
CVE-2017-0854 | An information disclosure vulnerability in the Android media framework (n/a). Product: Android. Versions: 7.0, 7.1.1, 7.1.2, 8.0. Android ID: A-63873837. | [
"cpe:2.3:o:google:android:6.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:6.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:7.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:7.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:7.1.2:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:8.0:*:*:*:*:*:*:*"
]
| null | null | 9.1 | 8.5 |
|
GHSA-g4f8-m87g-59mw | The Form Fill feature in Firefox before 1.0.1 allows remote attackers to steal potentially sensitive information via an input control that monitors the values that are generated by the autocomplete capability. | []
| null | null | null | null |
|
CVE-2005-4406 | SQL injection vulnerability in index.cfm in Mercury CMS 4.0 and earlier allows remote attackers to execute arbitrary SQL commands via the page parameter. | [
"cpe:2.3:a:tmc_visionpool:mercury_cms:*:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
GHSA-666r-c2v5-8x54 | The installer in MyBB before 1.8.13 allows remote attackers to execute arbitrary code by writing to the configuration file. | []
| null | null | 9.8 | null |
|
CVE-2024-36175 | Adobe Experience Manager | Cross-site Scripting (Stored XSS) (CWE-79) | Adobe Experience Manager versions 6.5.20 and earlier are affected by a stored Cross-Site Scripting (XSS) vulnerability that could be abused by an attacker to inject malicious scripts into vulnerable form fields. Malicious JavaScript may be executed in a victim’s browser when they browse to the page containing the vulnerable field. | [
"cpe:2.3:a:adobe:experience_manager:*:*:*:*:*:*:*:*",
"cpe:2.3:a:adobe:experience_manager:*:*:*:*:aem_cloud_service:*:*:*"
]
| null | 5.4 | null | null |
CVE-2014-7818 | Directory traversal vulnerability in actionpack/lib/action_dispatch/middleware/static.rb in Action Pack in Ruby on Rails 3.x before 3.2.20, 4.0.x before 4.0.11, 4.1.x before 4.1.7, and 4.2.x before 4.2.0.beta3, when serve_static_assets is enabled, allows remote attackers to determine the existence of files outside the application root via a /..%2F sequence. | [
"cpe:2.3:a:rubyonrails:rails:3.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:beta2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:beta3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:beta4:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:rc:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.1:pre:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.2:pre:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.4:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.5:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.6:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.6:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.7:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.7:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.8:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.8:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.8:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.8:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.8:rc4:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:rc4:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.9:rc5:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.10:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.10:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.11:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.12:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.12:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.13:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.13:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.14:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.16:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.17:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.18:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.19:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.0.20:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:beta1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc4:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc5:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc6:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc7:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.0:rc8:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.1:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.1:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.1:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.2:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.2:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.4:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.5:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.6:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.7:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.8:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.9:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.1.10:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.2:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.2:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.3:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.3:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.3:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.4:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.4:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.5:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.6:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.7:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.8:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.10:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.11:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.12:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.13:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.13:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.15:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.16:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.17:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:3.2.18:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.0:-:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.0:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.1:-:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.1:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.1:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.1:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.1:rc4:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.6:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.6:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.6:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.7:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.8:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.9:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.10:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.0.10:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.0:-:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.0:beta1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.2:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.2:rc2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.2:rc3:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.6:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.1.6:rc1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.2.0:beta1:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:rails:4.2.0:beta2:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:ruby_on_rails:3.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:rubyonrails:ruby_on_rails:3.2.19:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:opensuse:12.3:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:opensuse:13.1:*:*:*:*:*:*:*",
"cpe:2.3:o:opensuse:opensuse:13.2:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2019-11699 | A malicious page can briefly cause the wrong name to be highlighted as the domain name in the addressbar during page navigations. This could result in user confusion of which site is currently loaded for spoofing attacks. This vulnerability affects Firefox < 67. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*"
]
| null | null | 6.5 | 4.3 |
|
GHSA-h897-v8rp-9crr | Missing Authorization vulnerability in CoCart Headless, LLC CoCart – Headless ecommerce allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects CoCart – Headless ecommerce: from n/a through 3.11.2. | []
| null | 5.3 | null | null |
|
CVE-2021-46900 | Sympa before 6.2.62 relies on a cookie parameter for certain security objectives, but does not ensure that this parameter exists and has an unpredictable value. Specifically, the cookie parameter is both a salt for stored passwords and an XSS protection mechanism. | [
"cpe:2.3:a:sympa:sympa:*:*:*:*:*:*:*:*"
]
| null | 7.5 | null | null |
|
CVE-2023-48755 | WordPress teachPress Plugin <= 9.0.4 is vulnerable to Cross Site Request Forgery (CSRF) | Cross-Site Request Forgery (CSRF) vulnerability in Michael Winkler teachPress.This issue affects teachPress: from n/a through 9.0.4.
| [
"cpe:2.3:a:teachpress_project:teachpress:*:*:*:*:*:wordpress:*:*"
]
| null | 4.3 | null | null |
CVE-2017-20124 | Online Hotel Booking System Pro Plugin roomtype-details.php sql injection | A vulnerability classified as critical has been found in Online Hotel Booking System Pro Plugin 1.0. Affected is an unknown function of the file /front/roomtype-details.php. The manipulation of the argument tid leads to sql injection. It is possible to launch the attack remotely. The exploit has been disclosed to the public and may be used. | [
"cpe:2.3:a:bestsoftinc:online_hotel_booking_system:1.0:*:*:*:pro:wordpress:*:*"
]
| null | 6.3 | null | null |
GHSA-pqg5-m5v9-4mx6 | Vulnerability in the Oracle iStore component of Oracle E-Business Suite (subcomponent: Shopping Cart). Supported versions that are affected are 12.1.1, 12.1.2, 12.1.3, 12.2.3, 12.2.4, 12.2.5, 12.2.6 and 12.2.7. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle iStore. Successful attacks of this vulnerability can result in unauthorized read access to a subset of Oracle iStore accessible data. CVSS 3.0 Base Score 5.3 (Confidentiality impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:L/I:N/A:N). | []
| null | null | 5.3 | null |
|
CVE-2015-1348 | Heap-based buffer overflow in Aruba Instant (IAP) with firmware before 4.0.0.7 and 4.1.x before 4.1.1.2 allows remote attackers to cause a denial of service (crash or reset to factory default) via a malformed frame to the wireless interface. | [
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:4.1.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:4.1.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:4.1.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:4.1.1:*:*:*:*:*:*:*",
"cpe:2.3:o:arubanetworks:instant_access_point_firmware:4.1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:h:arubanetworks:instant_access_point:-:*:*:*:*:*:*:*"
]
| null | null | null | 7.8 |
|
GHSA-72pq-mjrc-rjh9 | Cross-site scripting (XSS) vulnerability in IBM Rational Engineering Lifecycle Manager 3.0 before 3.0.1.6 iFix7 Interim Fix 1, 4.0 before 4.0.7 iFix10, 5.0 before 5.0.2 iFix15, and 6.0 before 6.0.1 iFix4 allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. IBM X-Force ID: 108633. | []
| null | null | 5.4 | null |
|
GHSA-xvcg-ff9f-p7x7 | SQL injection vulnerability in home.html in Xpoze Pro 4.10 allows remote attackers to execute arbitrary SQL commands via the menu parameter. | []
| null | null | null | null |
|
CVE-2002-1675 | Format string vulnerability in the Cio_PrintF function of cio_main.c in Unreal IRCd 3.1.1 allows remote attackers to cause a denial of service (crash) and possibly execute arbitrary code via format string specifiers. | [
"cpe:2.3:a:unreal:unrealircd:3.1.1:*:*:*:*:*:*:*"
]
| null | null | null | 6.4 |
|
GHSA-h5xv-9vpq-r4gm | Jama Connect 8.44.0 has XSS via the "Import File and Destination" tab on the "Data import wizard" screen. | []
| null | null | null | null |
|
GHSA-6mw3-wxm8-6f87 | Cross-Site Request Forgery (CSRF) vulnerability in Alexey Trofimov's Access Code Feeder plugin <= 1.0.3 at WordPress. | []
| null | 8 | null | null |
|
CVE-2003-1580 | The Apache HTTP Server 2.0.44, when DNS resolution is enabled for client IP addresses, uses a logging format that does not identify whether a dotted quad represents an unresolved IP address, which allows remote attackers to spoof IP addresses via crafted DNS responses containing numerical top-level domains, as demonstrated by a forged 123.123.123.123 domain name, related to an "Inverse Lookup Log Corruption (ILLC)" issue. | [
"cpe:2.3:a:apache:http_server:2.0.44:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
GHSA-598w-rp37-8cpg | Multiple cross-site scripting (XSS) vulnerabilities in Mobotix IP Network Cameras M1 1.9.4.7 and M10 2.0.5.2, and other versions before 2.2.3.18 for M10/D10 and 3.0.3.31 for M22, allow remote attackers to inject arbitrary web script or HTML via URL-encoded values in (1) the query string to help/help, (2) the get_image_info_abspath parameter to control/eventplayer, and (3) the source_ip parameter to events.tar. | []
| null | null | null | null |
|
GHSA-mf3r-3pfj-4w6f | Adobe Acrobat and Reader versions 2019.010.20069 and earlier, 2019.010.20069 and earlier, 2017.011.30113 and earlier version, and 2015.006.30464 and earlier have an out-of-bounds write vulnerability. Successful exploitation could lead to arbitrary code execution . | []
| null | null | null | null |
|
CVE-2011-1662 | Cross-site scripting (XSS) vulnerability in Translation Management module 6.x before 6.x-1.21 for Drupal allows remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta1:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta2:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta3:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta4:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta5:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta6:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.0:beta7:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.2:beta1:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.3:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.4:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.5:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.6:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.7:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.8:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.9:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.20:*:*:*:*:*:*:*",
"cpe:2.3:a:icanlocalize:translation_management:6.x-1.x:dev:*:*:*:*:*:*",
"cpe:2.3:a:drupal:drupal:*:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2024-41775 | IBM Cognos Controller information disclosure | IBM Cognos Controller 11.0.0 and 11.0.1 uses weaker than expected cryptographic algorithms that could allow an attacker to decrypt highly sensitive information. | [
"cpe:2.3:a:ibm:cognos_controller:11.0.0:*:*:*:*:*:*:*",
"cpe:2.3:a:ibm:cognos_controller:11.0.1:*:*:*:*:*:*:*"
]
| null | 5.9 | null | null |
CVE-2024-10078 | WP Easy Post Types <= 1.4.4 - Authenticated (Subscriber+) Missing Authorization via Multiple Functions | The WP Easy Post Types plugin for WordPress is vulnerable to unauthorized access, modification, and loss of data due to a missing capability check on multiple functions in all versions up to, and including, 1.4.4. This makes it possible for authenticated attackers, with subscriber-level access and above, to add, modify, or delete plugin options and posts. | [
"cpe:2.3:a:wp_easy_post_types_project:wp_easy_post_types:*:-:-:*:-:wordpress:*:*",
"cpe:2.3:a:newsignature:wp_easy_post_types:*:*:*:*:*:wordpress:*:*"
]
| null | 7.3 | null | null |
GHSA-cc8q-rrgm-f274 | Cesanta MJS v2.20.0 was discovered to contain a SEGV vulnerability via exec_expr at src/mjs_exec.c. This vulnerability can lead to a Denial of Service (DoS). | []
| null | null | null | null |
|
GHSA-gwmc-7qc2-284q | Multiple PHP remote file inclusion vulnerabilities in Soholaunch Pro Edition 4.9 r46 and earlier, when register_globals is enabled, allow remote attackers to execute arbitrary PHP code via a URL in the _SESSION[docroot_path] parameter to (1) includes/shared_functions.php or (2) client_files/shopping_cart/pgm-shopping_css.inc.php. | []
| null | null | null | null |
|
GHSA-rv94-849j-v27x | In DA, there is a possible out of bounds read due to a missing bounds check. This could lead to local information disclosure, if an attacker has physical access to the device, if a malicious actor has already obtained the System privilege. User interaction is needed for exploitation. Patch ID: ALPS09291146; Issue ID: MSV-2056. | []
| null | 5.7 | null | null |
|
RHSA-2020:4542 | Red Hat Security Advisory: cryptsetup security, bug fix, and enhancement update | cryptsetup: Out-of-bounds write when validating segments | [
"cpe:/a:redhat:enterprise_linux:8::appstream",
"cpe:/o:redhat:enterprise_linux:8::baseos"
]
| null | 7.8 | null | null |
GHSA-9pqr-jpg7-8j32 | Stack-based buffer overflow in the HTTP server in Rhino Software Serv-U Web Client 9.0.0.5 allows remote attackers to cause a denial of service (server crash) or execute arbitrary code via a long Session cookie. | []
| null | null | null | null |
|
CVE-2015-7018 | FontParser in Apple iOS before 9.1 and OS X before 10.11.1 allows remote attackers to execute arbitrary code or cause a denial of service (memory corruption) via a crafted font file, a different vulnerability than CVE-2015-6976, CVE-2015-6977, CVE-2015-6978, CVE-2015-6990, CVE-2015-6991, CVE-2015-6993, CVE-2015-7008, CVE-2015-7009, and CVE-2015-7010. | [
"cpe:2.3:o:apple:iphone_os:*:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:*:*:*:*:*:*:*:*"
]
| null | null | null | 6.8 |
|
GHSA-p4qc-734h-4fcp | ASUS Router RT-AX3000 Firmware versions prior to 3.0.0.4.388.23403 uses sensitive cookies without 'Secure' attribute. When an attacker is in a position to be able to mount a man-in-the-middle attack, and a user is tricked to log into the affected device through an unencrypted ('http') connection, the user's session may be hijacked. | []
| null | 5.3 | null | null |
|
GHSA-4h5r-vjx5-6qc2 | mpg321 0.2.10 allows remote attackers to overwrite memory and possibly execute arbitrary code via an mp3 file that passes certain strings to the printf function, possibly triggering a format string vulnerability. | []
| null | null | null | null |
|
CVE-2023-0058 | Tiempo.com <= 0.1.2 - Stored XSS via CSRF | The Tiempo.com WordPress plugin through 0.1.2 does not have CSRF check when creating and editing its shortcode, and is missing sanitisation as well as escaping, which could allow attackers to make logged in admin add Stored XSS payloads via a CSRF attack | [
"cpe:2.3:a:tiempo:tiempo:*:*:*:*:*:wordpress:*:*"
]
| null | 6.1 | null | null |
ICSMA-17-250-01 | i-SENS, Inc. SmartLog Diabetes Management Software | An uncontrolled search path element vulnerability has been identified which could be exploited by placing a specially crafted DLL file in the search path. If the malicious DLL is loaded prior to the valid DLL, an attacker could execute arbitrary code on the system. This vulnerability does not affect the connected blood glucose monitor and would not impact delivery of therapy to the patient. CVE-2017-13993 been assigned to this vulnerability. A CVSS v3 base score of 7.3 has been assigned; the CVSS vector string is (AV:L/AC:L/PR:L/UI:R/S:U/C:H/I:H/A:H). | []
| null | null | 7.3 | null |
CVE-2023-23577 | Uncontrolled search path element for some ITE Tech consumer infrared drivers before version 5.5.2.1 for Intel(R) NUC may allow an authenticated user to potentially enable escalation of privilege via local access. | [
"cpe:2.3:a:ite_tech_consumer_infared_drivers_for_intel_nuc:ite_tech_consumer_infared_drivers_for_intel_nuc:*:*:*:*:*:*:*:*",
"cpe:2.3:a:intel:ite_tech_consumer_infrared_driver:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:nuc_11_enthusiast_kit_nuc11phki7c:-:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:nuc_11_enthusiast_mini_pc_nuc11phki7caa:-:*:*:*:*:*:*:*"
]
| null | 6.7 | null | null |
|
GHSA-w697-crqq-q58c | Memory corruption in system firmware for Intel(R) NUC may allow a privileged user to potentially enable escalation of privilege, denial of service and/or information disclosure via local access. | []
| null | 7.8 | null | null |
|
CVE-2023-38467 | In urild service, there is a possible out of bounds write due to a missing bounds check. This could lead to local denial of service with System execution privileges needed | [
"cpe:2.3:o:google:android:11.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:12.0:*:*:*:*:*:*:*",
"cpe:2.3:o:google:android:13.0:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:s8000:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc7731e:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc9832e:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:sc9863a:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t310:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t606:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t610:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t612:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t616:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t618:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t760:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t770:-:*:*:*:*:*:*:*",
"cpe:2.3:h:unisoc:t820:-:*:*:*:*:*:*:*"
]
| null | 4.4 | null | null |
|
CVE-2021-20760 | Improper input validation vulnerability in User Profile of Cybozu Garoon 4.0.0 to 5.0.2 allows a remote authenticated attacker to alter the data of User Profile without the appropriate privilege. | [
"cpe:2.3:a:cybozu:garoon:*:*:*:*:*:*:*:*"
]
| null | 4.3 | null | 4 |
|
CVE-2010-3531 | Unspecified vulnerability in the PeopleSoft Enterprise FMS ESA - RM component in Oracle PeopleSoft and JDEdwards Suite 8.9 Bundle #38, 9.0 Bundle #31, and 9.1 Bundle #6 allows remote authenticated users to affect confidentiality and integrity via unknown vectors. | [
"cpe:2.3:a:oracle:peoplesoft_and_jdedwards_product_suite:8.9:bundle38:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_and_jdedwards_product_suite:9.0:bundle31:*:*:*:*:*:*",
"cpe:2.3:a:oracle:peoplesoft_and_jdedwards_product_suite:9.1:bundle6:*:*:*:*:*:*"
]
| null | null | null | 5.5 |
|
GHSA-49q8-f85j-7fq7 | Junos Pulse Secure Access Service (IVE) 7.1 before 7.1r5, 7.2 before 7.2r10, 7.3 before 7.3r6, and 7.4 before 7.4r3 and Junos Pulse Access Control Service (UAC) 4.1 before 4.1r8.1, 4.2 before 4.2r5, 4.3 before 4.3r6 and 4.4 before 4.4r3, when a hardware SSL acceleration card is enabled, allows remote attackers to cause a denial of service (device hang) via a crafted packet. | []
| null | null | null | null |
|
CVE-2023-2181 | An issue has been discovered in GitLab affecting all versions before 15.9.8, 15.10.0 before 15.10.7, and 15.11.0 before 15.11.3. A malicious developer could use a git feature called refs/replace to smuggle content into a merge request which would not be visible during review in the UI. | [
"cpe:2.3:a:gitlab:gitlab:*:*:*:*:*:*:*:*"
]
| null | 6.3 | null | null |
|
CVE-2020-9609 | Adobe Acrobat and Reader versions 2020.006.20042 and earlier, 2017.011.30166 and earlier, 2017.011.30166 and earlier, and 2015.006.30518 and earlier have an out-of-bounds read vulnerability. Successful exploitation could lead to information disclosure. | [
"cpe:2.3:a:adobe:acrobat_dc:*:*:*:*:classic:*:*:*",
"cpe:2.3:a:adobe:acrobat_dc:*:*:*:*:continuous:*:*:*",
"cpe:2.3:a:adobe:acrobat_reader_dc:*:*:*:*:classic:*:*:*",
"cpe:2.3:a:adobe:acrobat_reader_dc:*:*:*:*:continuous:*:*:*",
"cpe:2.3:o:apple:macos:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
]
| null | 5.5 | null | 4.3 |
|
RHSA-2013:1083 | Red Hat Security Advisory: openstack-keystone security update | openstack-keystone: Authentication bypass when using LDAP backend | [
"cpe:/a:redhat:openstack:2::el6"
]
| null | null | null | null |
CVE-2019-5748 | In Traccar Server version 4.2, protocol/SpotProtocolDecoder.java might allow XXE attacks. | [
"cpe:2.3:a:traccar:server:4.2:*:*:*:*:*:*:*"
]
| null | null | 9.8 | 7.5 |
|
RHSA-2012:1556 | Red Hat Security Advisory: openstack-keystone security, bug fix, and enhancement update | OpenStack: Keystone /etc/keystone/ec2rc secret key exposure OpenStack: Keystone EC2-style credentials invalidation issue | [
"cpe:/a:redhat:openstack:1::el6"
]
| null | null | null | null |
GHSA-jvmw-m6j5-52p7 | An out-of-bounds read was addressed with improved input validation. This issue affected versions prior to iOS 12.1, macOS Mojave 10.14.1, tvOS 12.1, watchOS 5.1. | []
| null | null | 7.8 | null |
|
CVE-2021-1451 | Cisco IOS XE Software Easy Virtual Switching System Arbitrary Code Execution Vulnerability | A vulnerability in the Easy Virtual Switching System (VSS) feature of Cisco IOS XE Software for Cisco Catalyst 4500 Series Switches and Cisco Catalyst 4500-X Series Switches could allow an unauthenticated, remote attacker to execute arbitrary code on the underlying Linux operating system of an affected device. The vulnerability is due to incorrect boundary checks of certain values in Easy VSS protocol packets that are destined for an affected device. An attacker could exploit this vulnerability by sending crafted Easy VSS protocol packets to UDP port 5500 while the affected device is in a specific state. When the crafted packet is processed, a buffer overflow condition may occur. A successful exploit could allow the attacker to trigger a denial of service (DoS) condition or execute arbitrary code with root privileges on the underlying Linux operating system of the affected device. | [
"cpe:2.3:o:cisco:ios_xe:3.6.0be:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.3e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.4e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.5ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.5be:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.5e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.6e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.7e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.8e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.9e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.6.10e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.3e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.4e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.7.5e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.3e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.4e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.5ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.5e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.6e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.7e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.8e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.9e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.8.10e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.9.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.9.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.9.2be:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.9.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.0ce:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.1ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.1se:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.10.3e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.0e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.1ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.1e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.2ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.2e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.3ae:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:3.11.3e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:15.2\\(7\\)e:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:16.11.2:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:16.12.5a:*:*:*:*:*:*:*",
"cpe:2.3:o:cisco:ios_xe:17.3.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:-:*:*:*:*:*:*:*"
]
| null | 8.1 | null | null |
GHSA-f499-jv47-9wxf | Directory Traversal in desafio | Affected versions of `desafio` resolve relative file paths, resulting in a directory traversal vulnerability. A malicious actor can use this vulnerability to access files outside of the intended directory root, which may result in the disclosure of private files on the vulnerable system.**Example request:**Recommendationno patch is available for this vulnerability.It is recommended that the package is only used for local development, and if the functionality is needed for production, a different package is used instead. | []
| null | null | null | null |
GHSA-2fqf-gfm4-v7pw | MiniTool Power Data Recovery 11.6 contains an insecure installation process that allows attackers to achieve remote code execution through a man in the middle attack. | []
| null | 8.1 | null | null |
|
GHSA-63fv-xmh7-4xvc | Uncontrolled search path in the Intel Unite(R) Client for Windows before version 4.2.25031 may allow an authenticated user to potentially enable an escalation of privilege via local access. | []
| null | null | null | null |
|
CVE-2017-9413 | Multiple cross-site request forgery (CSRF) vulnerabilities in the Podcast feature in Subsonic 6.1.1 allow remote attackers to hijack the authentication of users for requests that (1) subscribe to a podcast via the add parameter to podcastReceiverAdmin.view or (2) update Internet Radio Settings via the urlRedirectCustomUrl parameter to networkSettings.view. NOTE: These vulnerabilities can be exploited to conduct server-side request forgery (SSRF) attacks. | [
"cpe:2.3:a:subsonic:subsonic:6.1.1:*:*:*:*:*:*:*"
]
| null | null | 8.8 | 6.8 |
|
GHSA-w8jf-75vm-vj9w | There is an unvalidated redirect vulnerability in Esri Portal for ArcGIS 11.0 and 10.9.1 that may allow a remote, unauthenticated attacker to craft a URL that could redirect a victim to an arbitrary website, simplifying phishing attacks. | []
| null | 6.1 | null | null |
|
RHSA-2019:2169 | Red Hat Security Advisory: linux-firmware security, bug fix, and enhancement update | kernel: Bluetooth implementations may not sufficiently validate elliptic curve parameters during Diffie-Hellman key exchange | [
"cpe:/o:redhat:enterprise_linux:7::client",
"cpe:/o:redhat:enterprise_linux:7::computenode",
"cpe:/o:redhat:enterprise_linux:7::server",
"cpe:/o:redhat:enterprise_linux:7::workstation"
]
| null | null | 7.1 | null |
GHSA-wxg9-35f2-vw25 | Buffer overflow in portmir for AIX 4.3.0 allows local users to corrupt lock files and gain root privileges via the echo_error routine. | []
| null | null | null | null |
|
CVE-2007-2456 | Multiple PHP remote file inclusion vulnerabilities in FireFly 1.1.01 allow remote attackers to execute arbitrary PHP code via a URL in the doc_root parameter to (1) localize.php or (2) config.php in modules/admin/include/. | [
"cpe:2.3:a:firefly:firefly:1.1.01:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
GHSA-47jx-2m6r-9jxq | The phones have the heap overflow, out-of-bounds read, and null pointer vulnerabilities in the fingerprint trusted application (TA).Successful exploitation of this vulnerability may affect the fingerprint service. | []
| null | 3.4 | null | null |
|
RHSA-2022:6634 | Red Hat Security Advisory: webkit2gtk3 security update | webkitgtk: processing maliciously crafted web content may lead to arbitrary code execution | [
"cpe:/a:redhat:enterprise_linux:9::appstream"
]
| null | 8.8 | null | null |
CVE-2023-46387 | LOYTEC electronics GmbH LINX-212 and LINX-151 devices (all versions) are vulnerable to Incorrect Access Control via dpal_config.zml file. This vulnerability allows remote attackers to disclose sensitive information on Loytec device data point configuration. | [
"cpe:2.3:o:loytec:linx-212_firmware:6.2.4:*:*:*:*:*:*:*",
"cpe:2.3:h:loytec:linx-212:-:*:*:*:*:*:*:*",
"cpe:2.3:o:loytec:linx-151_firmware:7.2.4:*:*:*:*:*:*:*",
"cpe:2.3:h:loytec:linx-151:-:*:*:*:*:*:*:*"
]
| null | 7.5 | null | null |
|
GHSA-4g42-gqrg-4633 | Apache Struts vulnerable to memory exhaustion | Denial of service via out of memory (OOM) owing to no sanity limit on normal form fields in multipart forms. When a Multipart request has non-file normal form fields, Struts used to bring them into memory as Strings without checking their sizes. This could lead to an OOM if developer has set struts.multipart.maxSize to a value equal or greater than the available memory.Upgrade to Struts 2.5.31 or 6.1.2.1 or greater | []
| null | 7.5 | null | null |
CVE-2019-18845 | The MsIo64.sys and MsIo32.sys drivers in Patriot Viper RGB before 1.1 allow local users (including low integrity processes) to read and write to arbitrary memory locations, and consequently gain NT AUTHORITY\SYSTEM privileges, by mapping \Device\PhysicalMemory into the calling process via ZwOpenSection and ZwMapViewOfSection. | [
"cpe:2.3:o:patriotmemory:viper_rgb_firmware:1.0:*:*:*:*:*:*:*",
"cpe:2.3:h:patriotmemory:viper_rgb:-:*:*:*:*:*:*:*"
]
| null | 7.1 | null | 3.6 |
|
GHSA-p5h8-cwcq-q5g2 | An attacker could have injected CSS into stylesheets accessible via internal URIs, such as resource:, and in doing so bypass a page's Content Security Policy. This vulnerability affects Firefox ESR < 91.11, Thunderbird < 102, Thunderbird < 91.11, and Firefox < 101. | []
| null | 6.5 | null | null |
|
CVE-2024-1600 | Local File Inclusion in parisneo/lollms-webui | A Local File Inclusion (LFI) vulnerability exists in the parisneo/lollms-webui application, specifically within the `/personalities` route. An attacker can exploit this vulnerability by crafting a URL that includes directory traversal sequences (`../../`) followed by the desired system file path, URL encoded. Successful exploitation allows the attacker to read any file on the filesystem accessible by the web server. This issue arises due to improper control of filename for include/require statement in the application. | [
"cpe:2.3:a:parisneo:lollms-webui:*:*:*:*:*:*:*:*"
]
| null | null | 9.3 | null |
GHSA-76cw-59x8-rvfm | A vulnerability, which was classified as problematic, has been found in SourceCodester Human Resource Management System 1.0. This issue affects some unknown processing of the component Add Employee Handler. The manipulation of the argument First Name/Middle Name/Last Name leads to cross site scripting. The attack may be initiated remotely. The identifier VDB-210773 was assigned to this vulnerability. | []
| null | 5.4 | null | null |
|
CVE-2021-21963 | An information disclosure vulnerability exists in the Web Server functionality of Sealevel Systems, Inc. SeaConnect 370W v1.3.34. A specially-crafted man-in-the-middle attack can lead to a disclosure of sensitive information. An attacker can perform a man-in-the-middle attack to trigger this vulnerability. | [
"cpe:2.3:o:sealevel:seaconnect_370w_firmware:1.3.34:*:*:*:*:*:*:*",
"cpe:2.3:h:sealevel:seaconnect_370w:-:*:*:*:*:*:*:*"
]
| null | null | 7.4 | null |
|
CVE-2021-31637 | An issue found in UwAmp v.1.1, 1.2, 1.3, 2.0, 2.1, 2.2, 2.2.1, 3.0.0, 3.0.1, 3.0.2 allows a remote attacker to execute arbitrary code via a crafted DLL. | [
"cpe:2.3:a:uwamp_project:uwamp:*:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
|
cisco-sa-snort-dos-s2R7W9UU | Multiple Cisco Products Snort Memory Leak Denial of Service Vulnerability | Multiple Cisco products are affected by a vulnerability in the way the Snort detection engine processes ICMP traffic that could allow an unauthenticated, remote attacker to cause a denial of service (DoS) condition on an affected device.
The vulnerability is due to improper memory resource management while the Snort detection engine is processing ICMP packets. An attacker could exploit this vulnerability by sending a series of ICMP packets through an affected device. A successful exploit could allow the attacker to exhaust resources on the affected device, causing the device to reload.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is part of the October 2021 release of the Cisco ASA, FTD, and FMC Security Advisory Bundled publication. For a complete list of the advisories and links to them, see Cisco Event Response: October 2021 Cisco ASA, FMC, and FTD Software Security Advisory Bundled Publication ["https://sec.cloudapps.cisco.com/security/center/viewErp.x?alertId=ERP-74773"]. | []
| null | 6.8 | null | null |
CVE-2017-7815 | On pages containing an iframe, the "data:" protocol can be used to create a modal dialog through Javascript that will have an arbitrary domains as the dialog's location, spoofing of the origin of the modal dialog from the user view. Note: This attack only affects installations with e10 multiprocess turned off. Installations with e10s turned on do not support the modal dialog functionality. This vulnerability affects Firefox < 56. | [
"cpe:2.3:a:mozilla:firefox:*:*:*:*:*:*:*:*"
]
| null | null | 5.3 | 5 |
|
GHSA-mfxv-hqxp-fr38 | The method PVRSRVBridgeTLDiscoverStreams allocates puiStreamsInt on the heap, fills the contents of the buffer via TLServerDiscoverStreamsKM, and then copies the buffer to userspace. The method TLServerDiscoverStreamsKM may fail for several reasons including invalid sizes. If this method fails the buffer will be left uninitialized and despite the error will still be copied to userspace. Kernel leak of uninitialized heap data with no privs required.Product: AndroidVersions: Android SoCAndroid ID: A-236838960 | []
| null | 7.5 | null | null |
|
CVE-2022-32351 | Hospital's Patient Records Management System v1.0 is vulnerable to SQL Injection via /hprms/classes/Master.php?f=delete_message. | [
"cpe:2.3:a:hospital\\'s_patient_records_management_system_project:hospital\\'s_patient_records_management_system:1.0:*:*:*:*:*:*:*"
]
| null | 7.2 | null | 6.5 |
|
CVE-2025-31777 | WordPress Clockinator Lite plugin <= 1.0.7 - Broken Access Control vulnerability | Missing Authorization vulnerability in BeastThemes Clockinator Lite allows Exploiting Incorrectly Configured Access Control Security Levels. This issue affects Clockinator Lite: from n/a through 1.0.7. | []
| null | 5.3 | null | null |
CVE-2018-1649 | IBM QRadar Incident Forensics 7.2 and 7.3 could allow a remote attacker to traverse directories on the system. An attacker could send a specially-crafted URL request containing "dot dot" sequences (/../) to view arbitrary files on the system. IBM X-Force ID: 144655. | [
"cpe:2.3:a:ibm:qradar_incident_forensics:7.2.8:patch1:*:*:*:*:*:*",
"cpe:2.3:a:ibm:qradar_incident_forensics:7.2.8:patch13:*:*:*:*:*:*",
"cpe:2.3:a:ibm:qradar_incident_forensics:7.2.8:patch8:*:*:*:*:*:*",
"cpe:2.3:a:ibm:qradar_incident_forensics:7.3.1:patch3:*:*:*:*:*:*",
"cpe:2.3:a:ibm:qradar_incident_forensics:7.3.1:patch4:*:*:*:*:*:*",
"cpe:2.3:a:ibm:qradar_incident_forensics:*:*:*:*:*:*:*:*"
]
| null | null | 7.7 | null |
|
GHSA-q655-3pj8-9fxq | Sidekiq vulnerable to a Reflected XSS in Queues Web Page | Description:During the source Code Review of the metrics.erb view of the Sidekiq Web UI, A reflected XSS vulnerability is discovered. The value of substr parameter is reflected in the response without any encoding, allowing an attacker to inject Javascript code into the response of the application.This vulnerability can be exploited to target the users of the application, and users of other applications deployed on the same domain or website as that of the Sidekiq website. Successful exploit results may result in compromise of user accounts and user data.Impact:The impact of this vulnerability can be severe. An attacker could exploit it to target users of the Sidekiq Web UI. Moreover, if other applications are deployed on the same domain or website as Sidekiq, users of those applications could also be affected, leading to a broader scope of compromise. Potentially compromising their accounts, forcing the users to perform sensitive actions, stealing sensitive data, performing CORS attacks, defacement of the web application, etc.Mitigation:Encode all output data before rendering it in the response to prevent XSS attacks.Steps to Reproduce:Go to the following URL of the sidekiq Web UI:
https://{host}/sidekiq/metrics?substr=beret%22%3E%3Cscript%20src=%22https://cheemahq.vercel.app/a.js%22%20/%3EXSS payload will be executed, causing a popup.Evidence: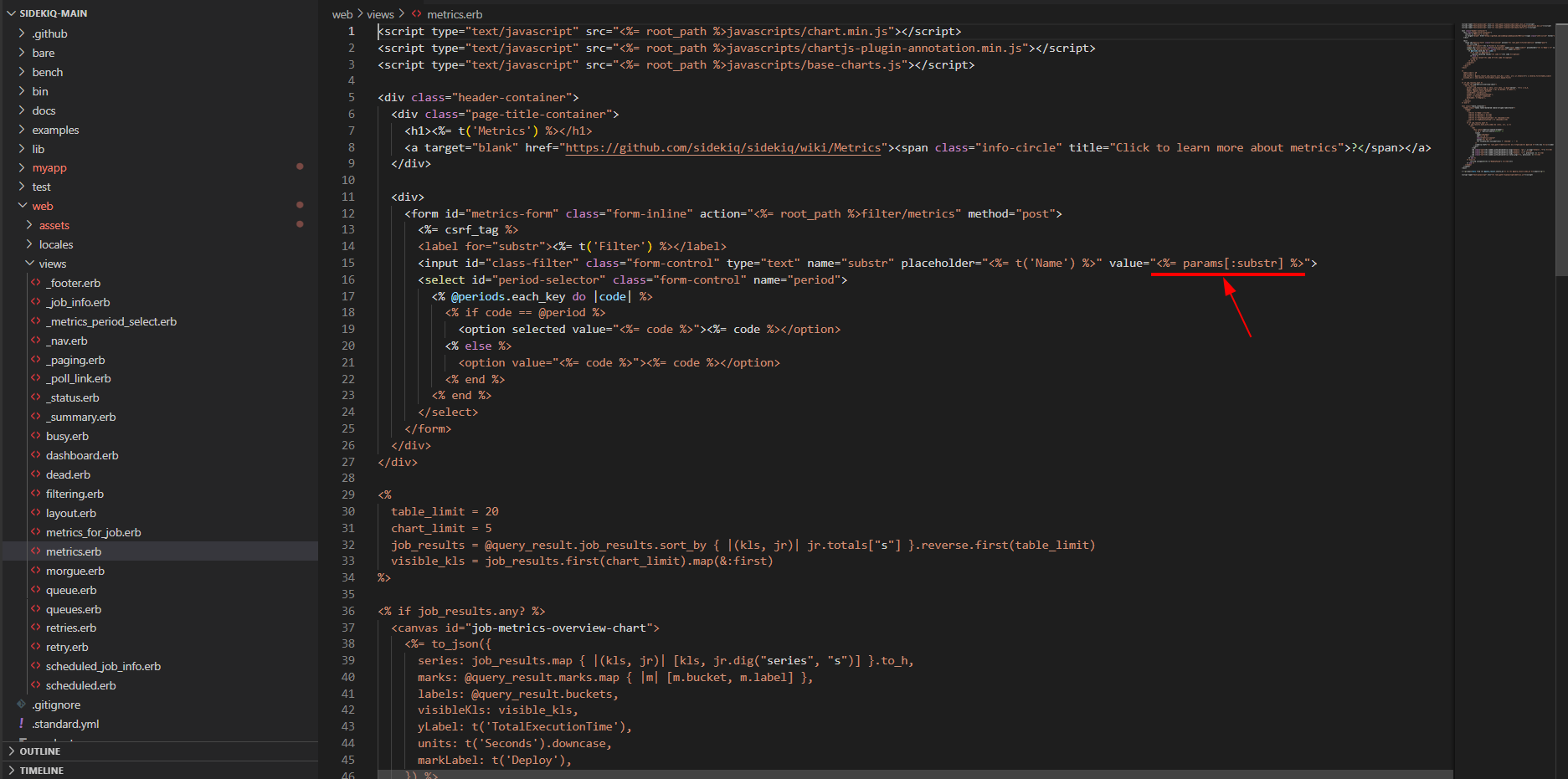
Figure 1: Source Code Vulnerable to XSS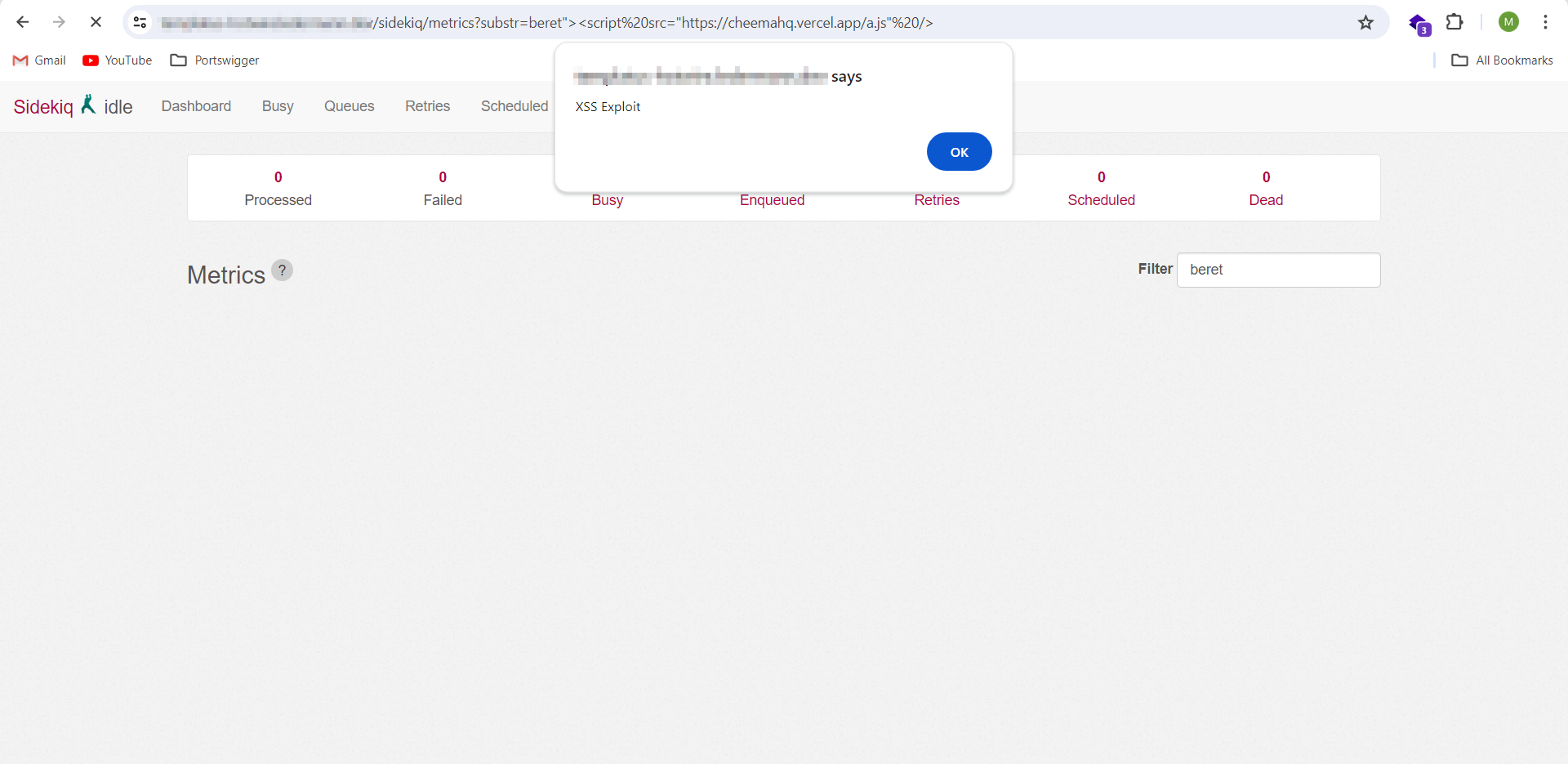
Figure 2: XSS payload triggered | []
| null | 5.5 | null | null |
CVE-2023-30676 | Improper access control vulnerability in Samsung Pass prior to version 4.2.03.1 allows physical attackers to access data of Samsung Pass. | [
"cpe:2.3:a:samsung:pass:*:*:*:*:*:*:*:*"
]
| null | 4.6 | null | null |
|
GHSA-xjmr-f49m-496p | A remote code execution vulnerability exists when the Microsoft Office Access Connectivity Engine improperly handles objects in memory, aka 'Microsoft Office Access Connectivity Engine Remote Code Execution Vulnerability'. This CVE ID is unique from CVE-2019-0945, CVE-2019-0946. | []
| null | null | 7.8 | null |
|
CVE-2024-2851 | Tenda AC15 setsambacfg formSetSambaConf os command injection | A vulnerability was found in Tenda AC15 15.03.05.18/15.03.20_multi. It has been classified as critical. This affects the function formSetSambaConf of the file /goform/setsambacfg. The manipulation of the argument usbName leads to os command injection. It is possible to initiate the attack remotely. The exploit has been disclosed to the public and may be used. The associated identifier of this vulnerability is VDB-257775. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | [
"cpe:2.3:o:tenda:ac15_firmware:15.03.05.18:*:*:*:*:*:*:*",
"cpe:2.3:o:tenda:ac15_firmware:15.03.05.20_multi:*:*:*:*:*:*:*",
"cpe:2.3:o:tenda:ac15_firmware:15.03.20_multi:*:*:*:*:*:*:*",
"cpe:2.3:h:tenda:ac15:-:*:*:*:*:*:*:*"
]
| null | 6.3 | 6.3 | 6.5 |
cisco-sa-20180905-tetration-vulns | Cisco Tetration Analytics Cross-Site Request Forgery Vulnerability | A vulnerability in the web-based management interface of Cisco Tetration Analytics could allow an authenticated, remote attacker to conduct a cross-site request forgery (CSRF) attack and perform arbitrary actions on an affected device.
The vulnerability is due to insufficient CSRF protections for the web-based management interface of an affected device. An attacker could exploit this vulnerability by persuading a user of the interface to follow a customized link. A successful exploit could allow the attacker to perform arbitrary actions on an affected device by using a web browser and with the privileges of the user.
There are no workarounds that address this vulnerability.
This advisory is available at the following link:
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-tetration-vulns ["https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180905-tetration-vulns"] | []
| null | null | 4.6 | null |
GHSA-gvjx-cgxf-v27v | Information exposure in Micro Focus Content Manager, versions 9.1, 9.2 and 9.3. This vulnerability when configured to use an Oracle database, allows valid system users to gain access to a limited subset of records they would not normally be able to access when the system is in an undisclosed abnormal state. | []
| null | null | null | null |
|
CVE-2020-15733 | URL Spoofing Vulnerability in Bitdefender SafePay (VA-8958) | An Origin Validation Error vulnerability in the SafePay component of Bitdefender Antivirus Plus allows a web resource to misrepresent itself in the URL bar. This issue affects: Bitdefender Antivirus Plus versions prior to 25.0.7.29. | [
"cpe:2.3:a:bitdefender:antivirus_plus:*:*:*:*:*:*:*:*"
]
| null | 6.5 | null | null |
GHSA-3gjx-4mvg-m9pc | Vulnerability in the Oracle Hospitality Simphony component of Oracle Hospitality Applications (subcomponent: Enterprise Management Console). Supported versions that are affected are 2.8, 2.9 and 2.10. Easily exploitable vulnerability allows low privileged attacker with network access via HTTP to compromise Oracle Hospitality Simphony. While the vulnerability is in Oracle Hospitality Simphony, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle Hospitality Simphony accessible data. CVSS 3.0 Base Score 7.7 (Confidentiality impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:C/C:H/I:N/A:N). | []
| null | null | 7.7 | null |
|
GHSA-6g3x-hhx6-885v | An issue was discovered by Elastic whereby sensitive information may be recorded in Kibana logs in the event of an error or in the event where debug level logging is enabled in Kibana. Elastic has released Kibana 8.11.2 which resolves this issue. The messages recorded in the log may contain Account credentials for the kibana_system user, API Keys, and credentials of Kibana end-users, Elastic Security package policy objects which can contain private keys, bearer token, and sessions of 3rd-party integrations and finally Authorization headers, client secrets, local file paths, and stack traces. The issue may occur in any Kibana instance running an affected version that could potentially receive an unexpected error when communicating to Elasticsearch causing it to include sensitive data into Kibana error logs. It could also occur under specific circumstances when debug level logging is enabled in Kibana. Note: It was found that the fix for ESA-2023-25 in Kibana 8.11.1 for a similar issue was incomplete. | []
| null | 8 | null | null |
|
GHSA-7j9g-3hxp-5wwv | The Imagination Technologies driver for Chrome OS before R74-11895.B, R75 before R75-12105.B, and R76 before R76-12208.0.0 allows attackers to trigger an Integer Overflow and gain privileges via a malicious application. This occurs because of intentional access for the GPU process to /dev/dri/card1 and the PowerVR ioctl handler, as demonstrated by PVRSRVBridgeSyncPrimOpCreate. | []
| null | 7.8 | null | null |
|
GHSA-mj8r-pwcx-74cf | Directory traversal vulnerability in the iJoomla News Portal (com_news_portal) component 1.5.x for Joomla! allows remote attackers to read arbitrary files via a .. (dot dot) in the controller parameter to index.php. | []
| null | null | null | null |
|
CVE-2015-2323 | FortiOS 5.0.x before 5.0.12 and 5.2.x before 5.2.4 supports anonymous, export, RC4, and possibly other weak ciphers when using TLS to connect to FortiGuard servers, which allows man-in-the-middle attackers to spoof TLS content by modifying packets. | [
"cpe:2.3:o:fortinet:fortios:5.0.0:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.3:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.4:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.5:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.6:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.7:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.8:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.9:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.10:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.0.11:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.2.0:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.2.1:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.2.2:*:*:*:*:*:*:*",
"cpe:2.3:o:fortinet:fortios:5.2.3:*:*:*:*:*:*:*"
]
| null | null | null | 6.4 |
|
CVE-2011-2744 | Directory traversal vulnerability in Chyrp 2.1 and earlier allows remote attackers to include and execute arbitrary local files via a ..%2F (encoded dot dot slash) in the action parameter to the default URI. | [
"cpe:2.3:a:chyrp:chyrp:*:*:*:*:*:*:*:*",
"cpe:2.3:a:chyrp:chyrp:2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:chyrp:chyrp:2.1:beta1:*:*:*:*:*:*",
"cpe:2.3:a:chyrp:chyrp:2.1:beta2:*:*:*:*:*:*",
"cpe:2.3:a:chyrp:chyrp:2.1:rc:*:*:*:*:*:*"
]
| null | null | null | 6.8 |
|
CVE-2007-4473 | Gesytec Easylon OPC Server before 2.3.44 does not properly validate server handles, which allows remote attackers to execute arbitrary code or cause a denial of service via unspecified network traffic to the OLE for Process Control (OPC) interface, probably related to free operations on arbitrary memory addresses through certain Remove functions, and read and write operations on arbitrary memory addresses through certain Set, Read, and Write functions. | [
"cpe:2.3:a:gesytec_easylon:opc_server:2.30.32:*:*:*:*:*:*:*"
]
| null | null | null | 10 |
|
GHSA-fmjx-hmcg-x6hg | FactoryTalk Linx versions 6.00, 6.10, and 6.11, RSLinx Classic v4.11.00 and prior,Connected Components Workbench: Version 12 and prior, ControlFLASH: Version 14 and later, ControlFLASH Plus: Version 1 and later, FactoryTalk Asset Centre: Version 9 and later, FactoryTalk Linx CommDTM: Version 1 and later, Studio 5000 Launcher: Version 31 and later Stud, 5000 Logix Designer software: Version 32 and prior is vulnerable. An exposed API call allows users to provide files to be processed without sanitation. This may allow an attacker to use specially crafted requests to traverse the file system and expose sensitive data on the local hard drive. | []
| null | null | null | null |
|
GHSA-4wrx-2682-w227 | resend command in Majordomo allows local users to gain privileges via shell metacharacters. | []
| null | null | null | null |
|
CVE-2022-1920 | Integer overflow in matroskademux element in gst_matroska_demux_add_wvpk_header function which allows a heap overwrite while parsing matroska files. Potential for arbitrary code execution through heap overwrite. | [
"cpe:2.3:a:gstreamer_project:gstreamer:*:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:11.0:*:*:*:*:*:*:*"
]
| null | 7.8 | null | null |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.